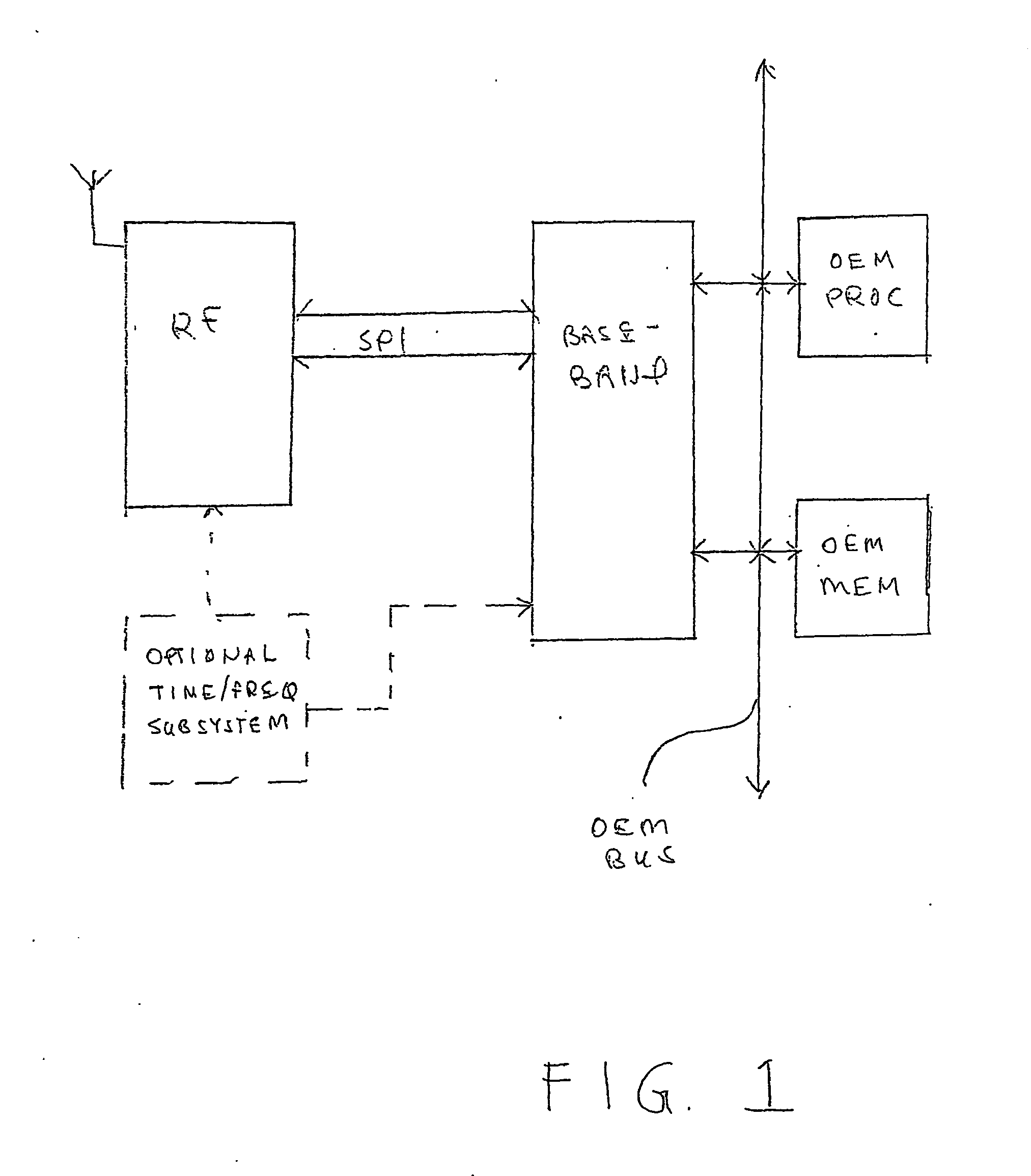
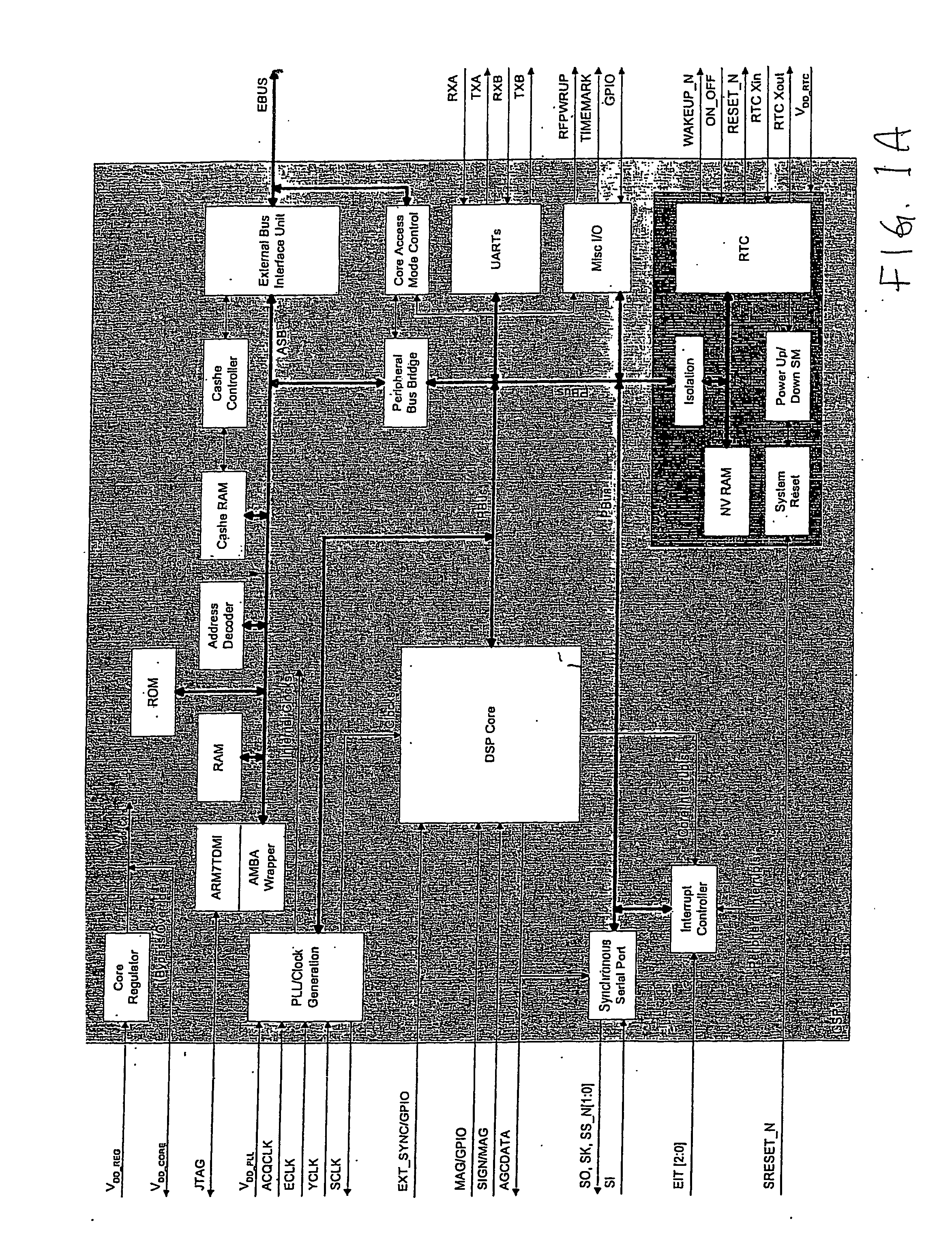
Patents
Literature
4135 results about "System configuration" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
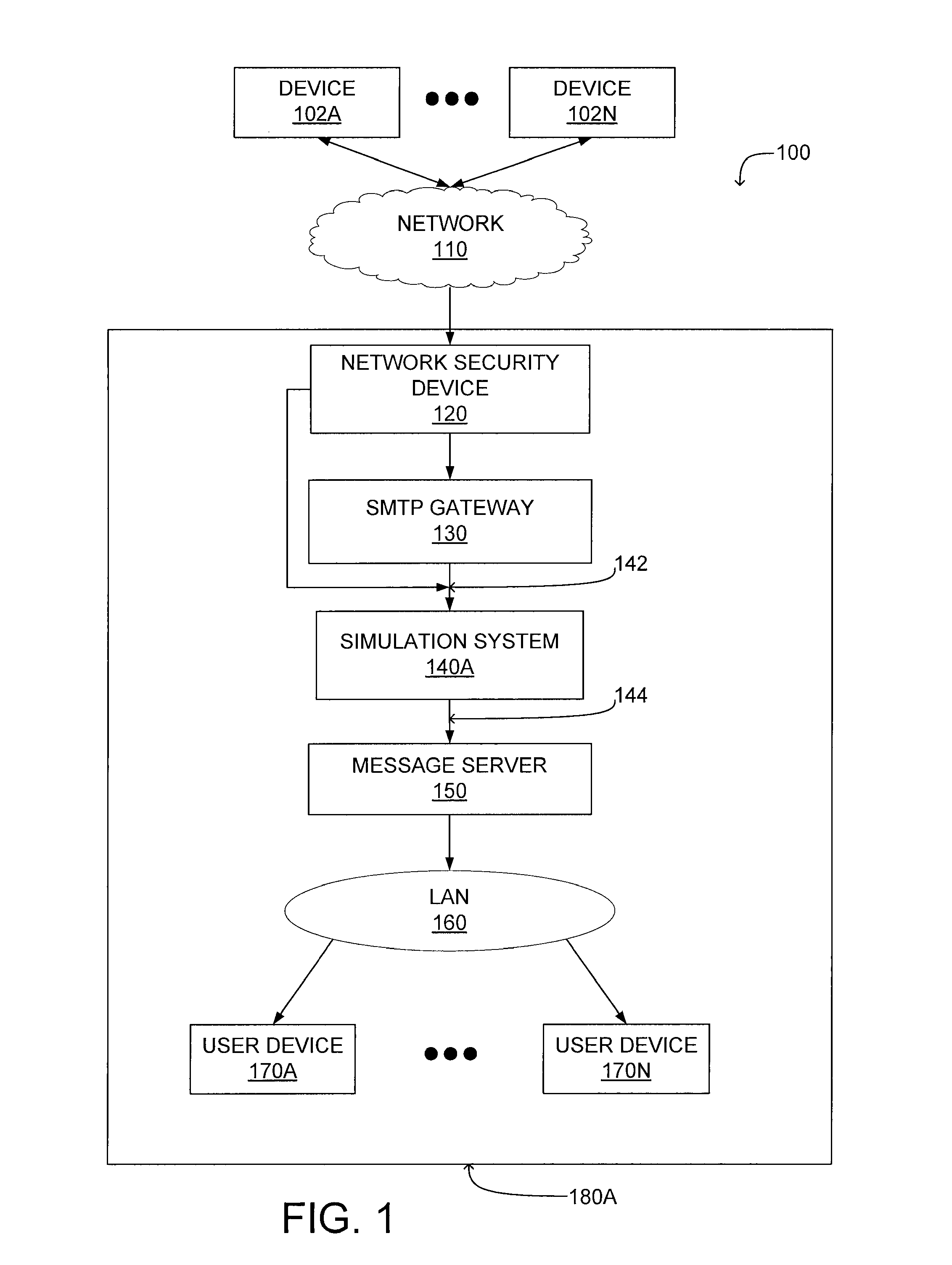
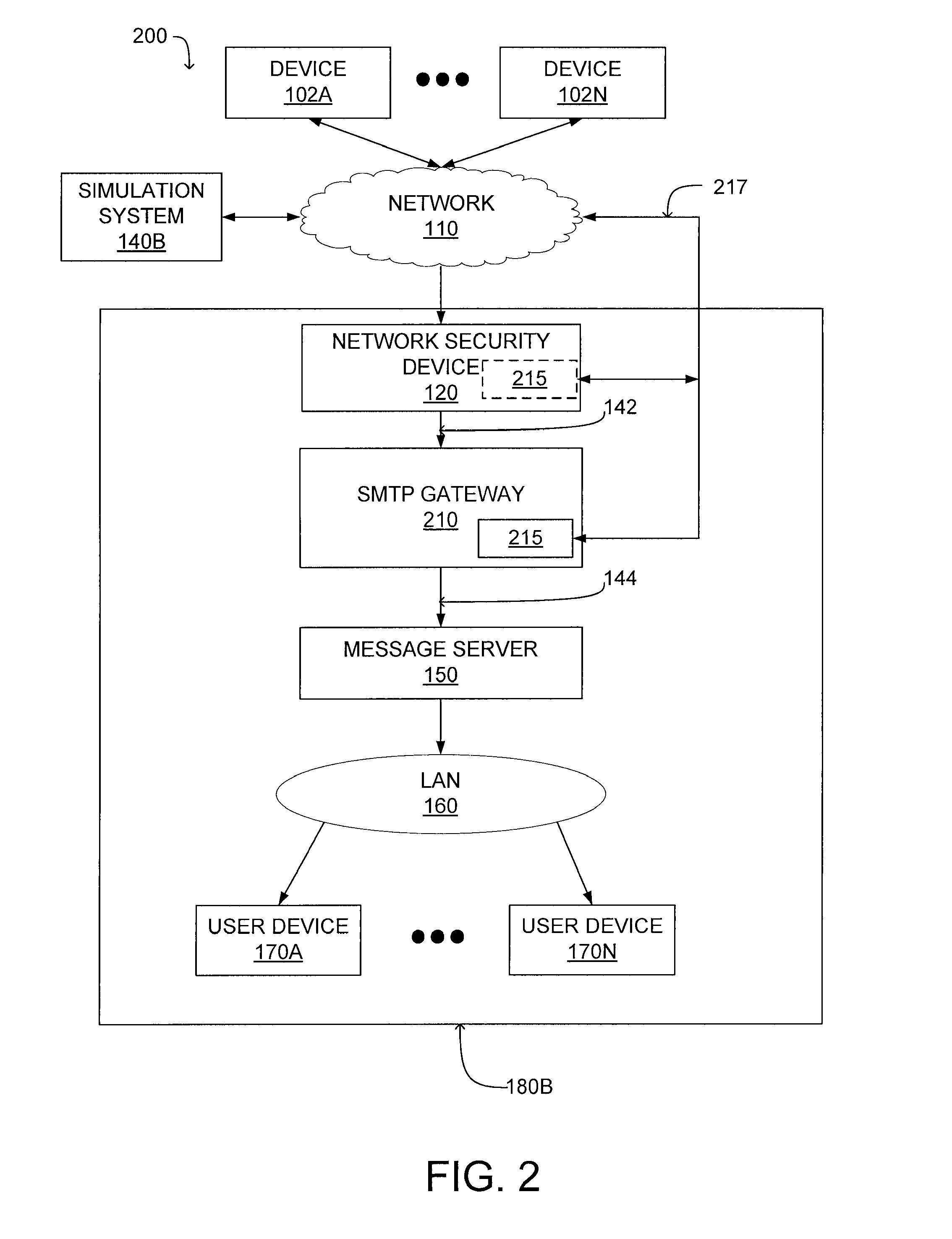
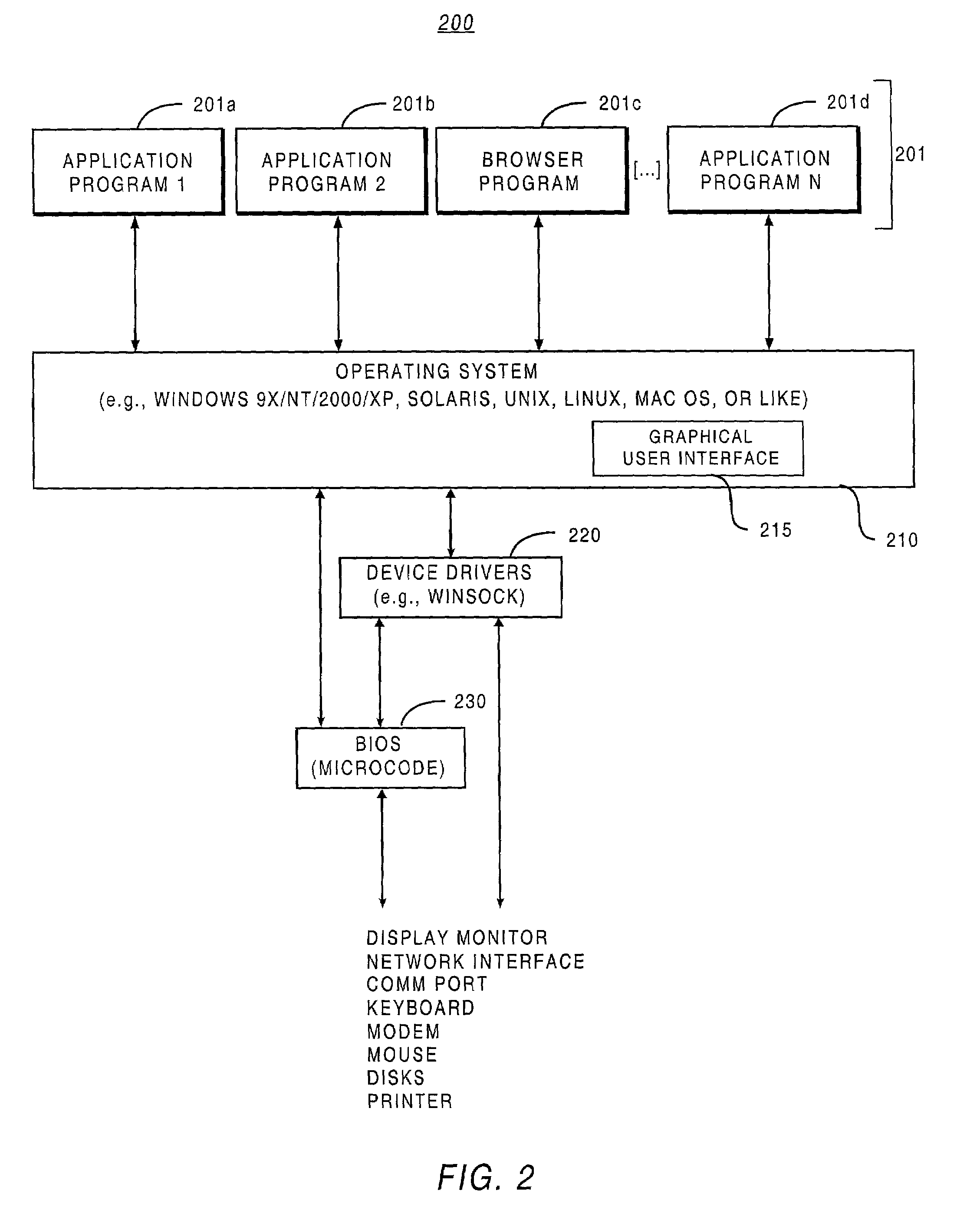
A system configuration (SC) in systems engineering defines the computers, processes, and devices that compose the system and its boundary. More generally, the system configuration is the specific definition of the elements that define and/or prescribe what a system is composed of.
System and Method for Distributed Denial of Service Identification and Prevention
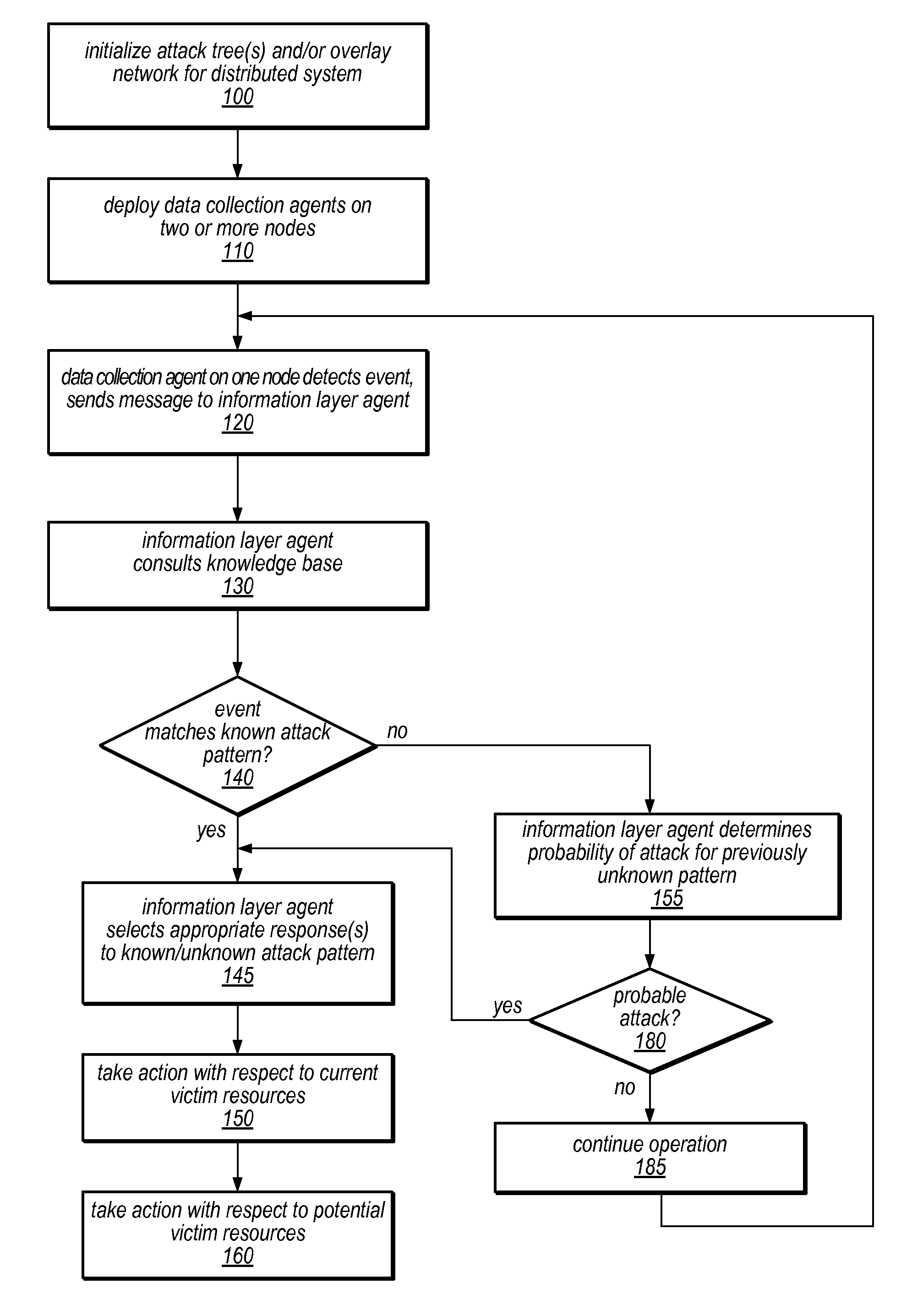
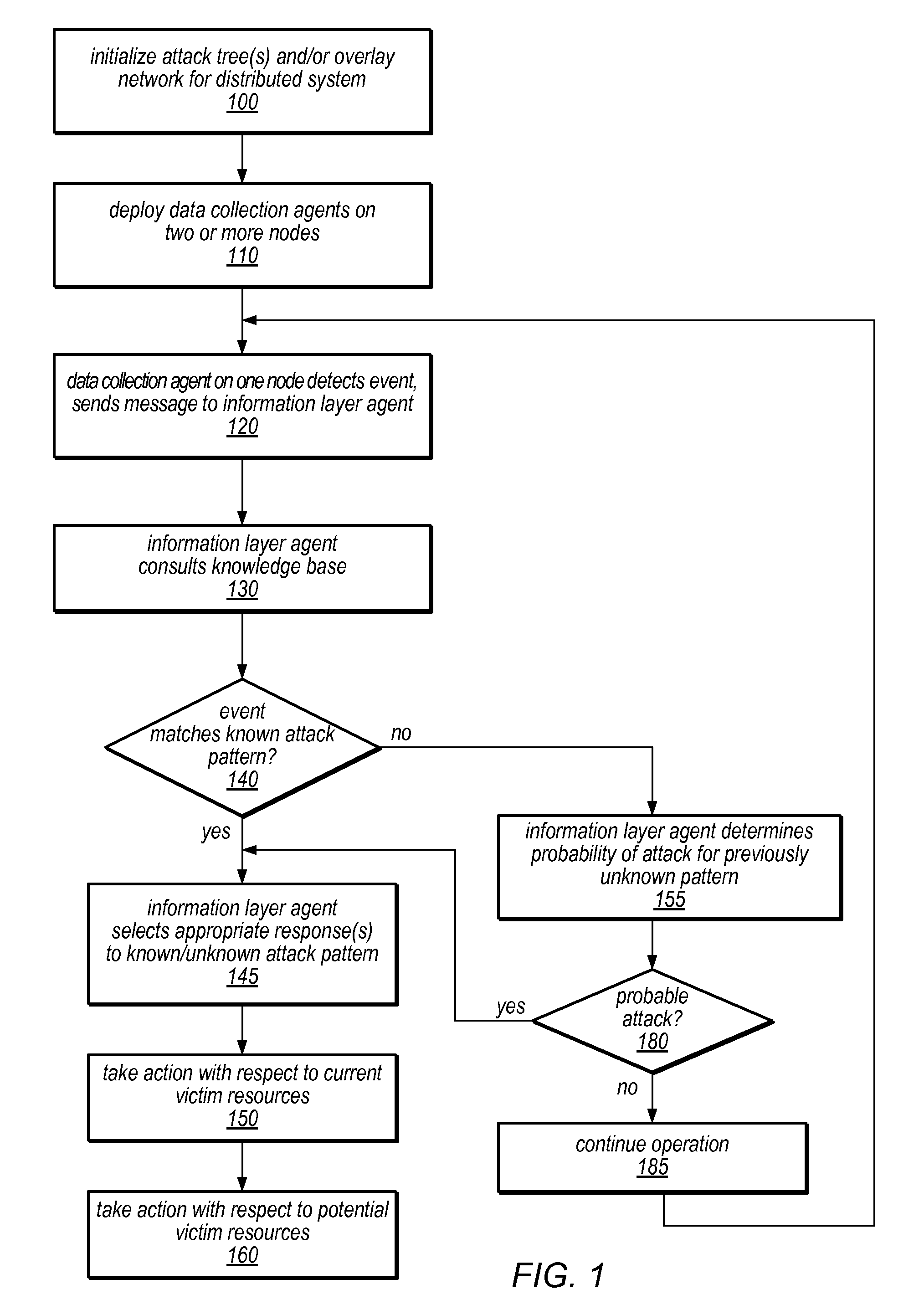
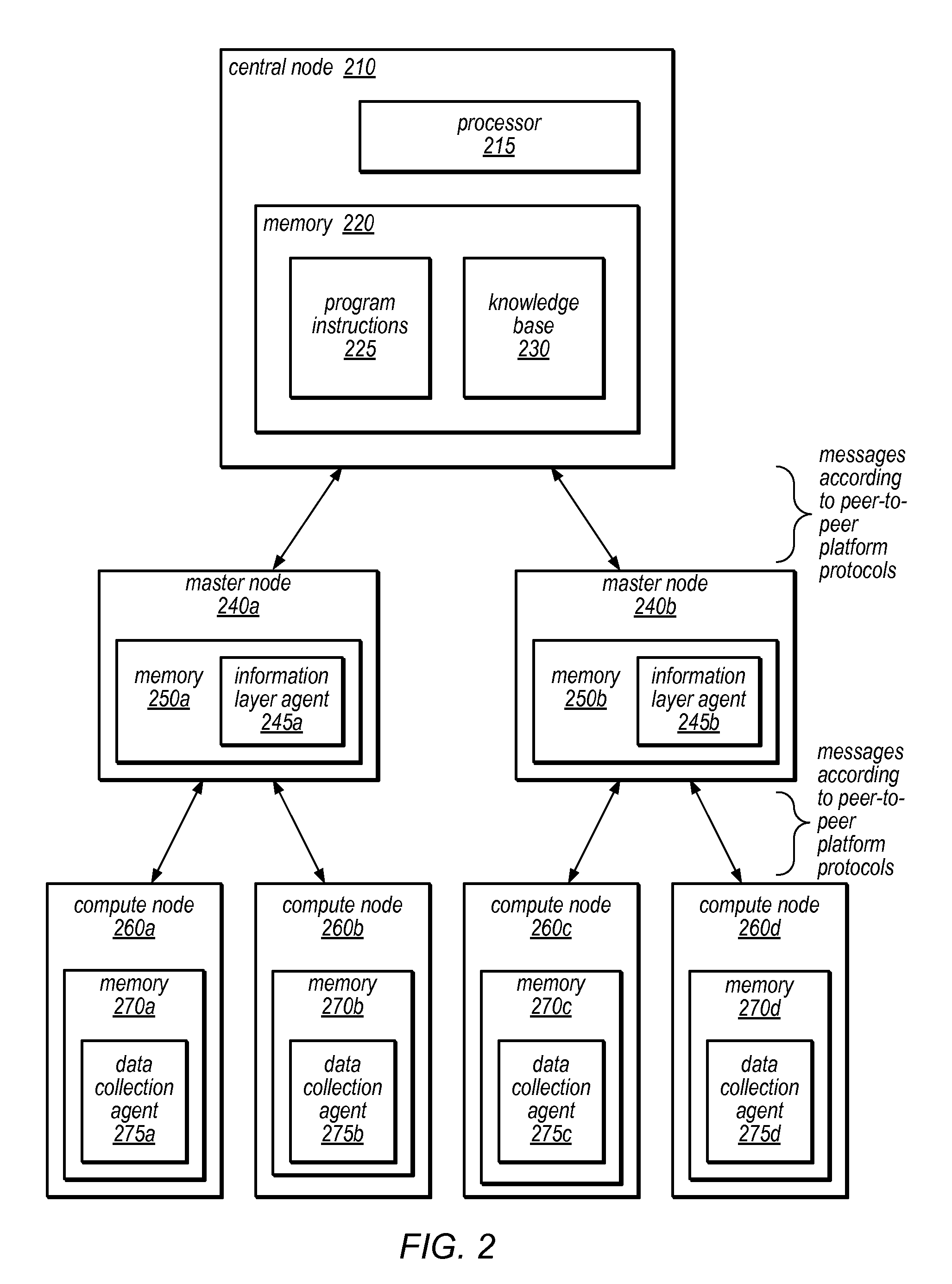
Systems and methods for discovery and classification of denial of service attacks in a distributed computing system may employ local agents on nodes thereof to detect resource-related events. An information later agent may determine if events indicate attacks, perform clustering analysis to determine if they represent known or unknown attack patterns, classify the attacks, and initiate appropriate responses to prevent and / or mitigate the attack, including sending warnings and / or modifying resource pool(s). The information layer agent may consult a knowledge base comprising information associated with known attack patterns, including state-action mappings. An attack tree model and an overlay network (over which detection and / or response messages may be sent) may be constructed for the distributed system. They may be dynamically modified in response to changes in system configuration, state, and / or workload. Reinforcement learning may be applied to the tuning of attack detection and classification techniques and to the identification of appropriate responses.
Owner:ORACLE INT CORP
Immersible thermal mass flow meter
ActiveUS6971274B2Quality improvementImprove measurement qualityVolume/mass flow by thermal effectsThin film sensorEngineering
Owner:SIERRA INSTR
Internet database system
InactiveUS6523036B1Data processing applicationsDigital data processing detailsApplication serverHash function
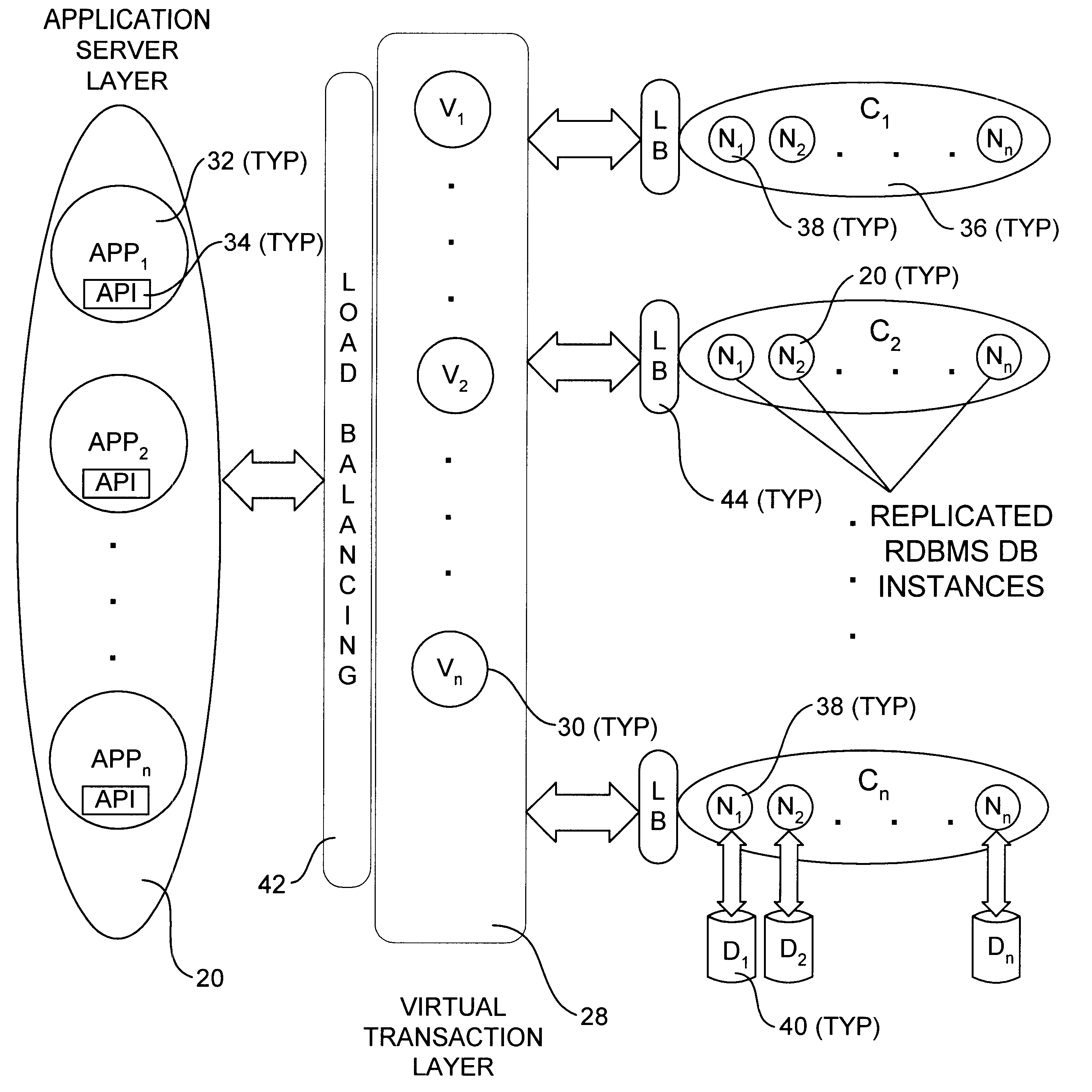
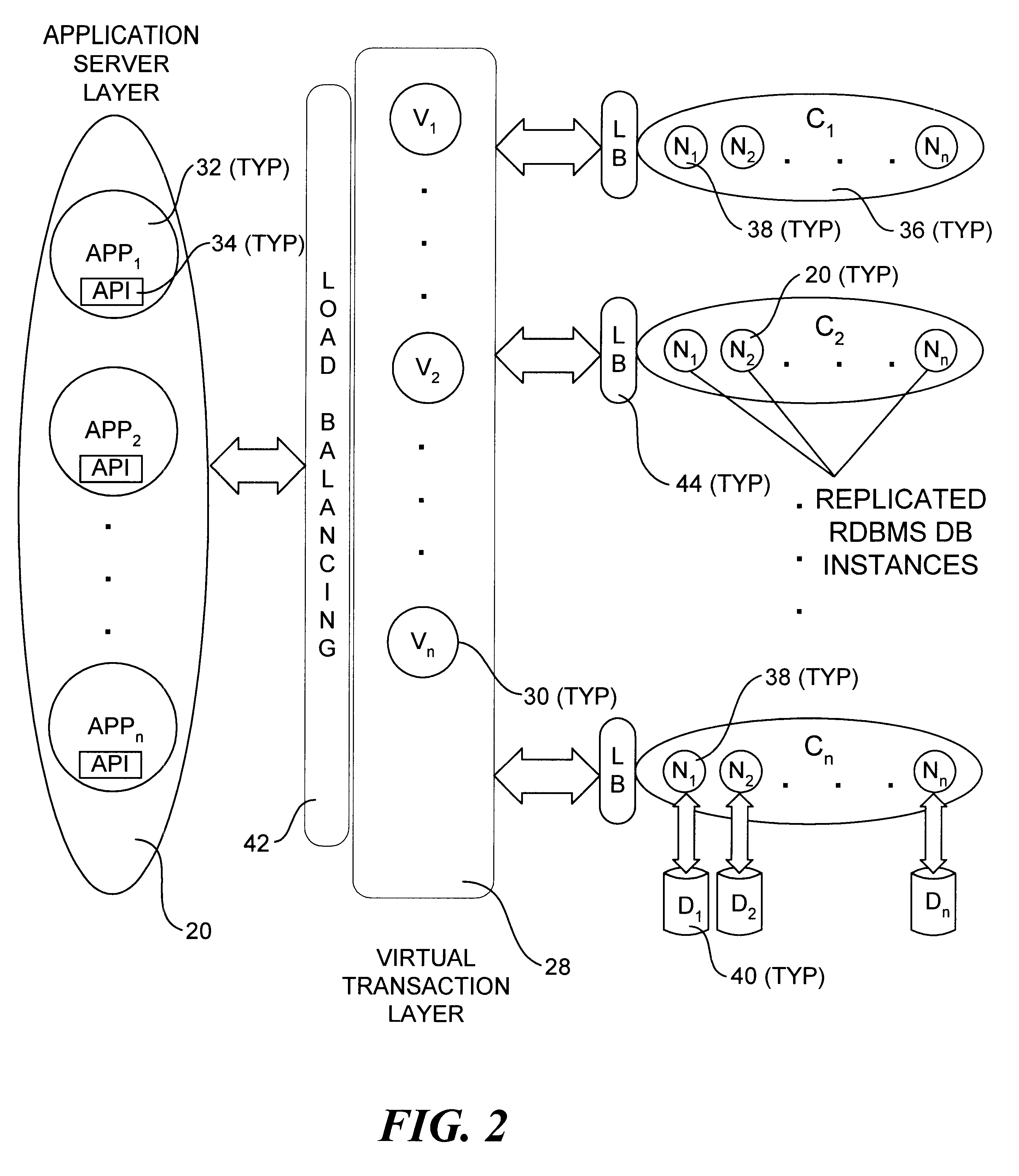
An incrementally-scalable database system and method. The system architecture enables database servers to be scaled by adding resources, such as additional servers, without requiring that the system be taken offline. Such scaling includes both adding one or more computer servers to a given server cluster, which enables an increase in database read transaction throughput, and adding one or more server clusters to the system configuration, which provides for increased read and write transaction throughput. The system also provides for load balancing read transactions across each server cluster, and load balancing write transactions across a plurality of server clusters. The system architecture includes an application server layer including one or more computers on which an application program(s) is running, a database server layer comprising two or more server clusters that each include two or more computer servers with replicated data, and an intermediate "virtual transaction" layer that includes at least two computers that facilitate database transactions with one or more databases operating in the database server layer. Data in the database(s) are evenly distributed across the server clusters in fragmented mutually exclusive subsets of data based on a hashing function. An application program interface is provided so as to enable application programs to perform a full range of database transactions without regard for where data is stored, or what database(s) is operating in the database server layer.
Owner:EMC IP HLDG CO LLC
Method and system for delivering media services and application over networks
InactiveUS6769127B1Flexible designTelevision system detailsPulse modulation television signal transmissionSystem configurationDelivery system
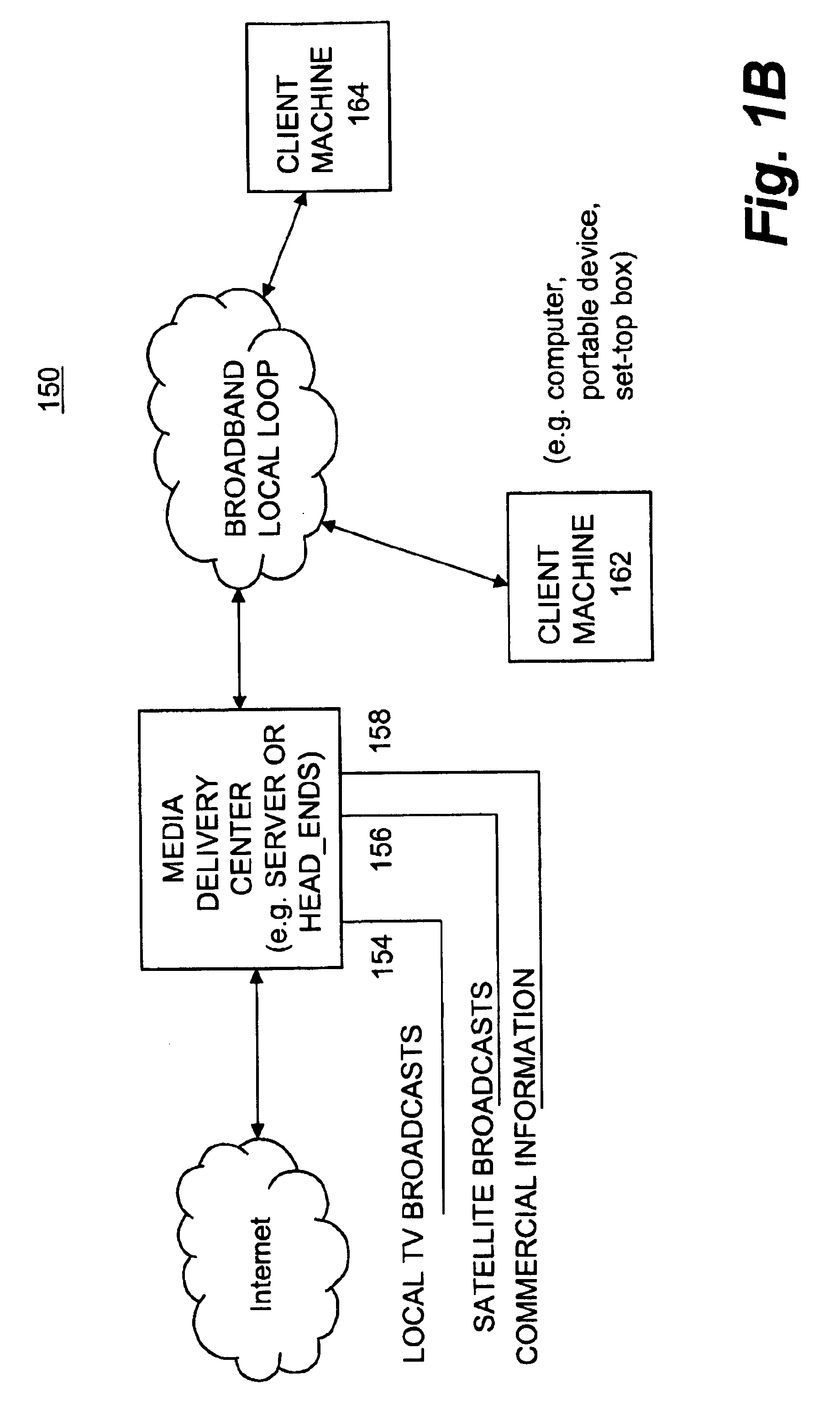
A media system that centrally manages and stores media contents and also controls the delivery of media content to subscribers is disclosed. According to one aspect, an administrator can control program scheduling, rates, service packages and system configuration for a media delivery system. Additionally, the administrator may also control billing, transaction monitoring, and customer relations. According to another aspect, the media delivery system provides subscribers with centrally managed storage for paused or recorded media. Still another aspect is that the media delivery system can restrict various administrators to different modules of the media delivery system.
Owner:MINERVA NETWORKS
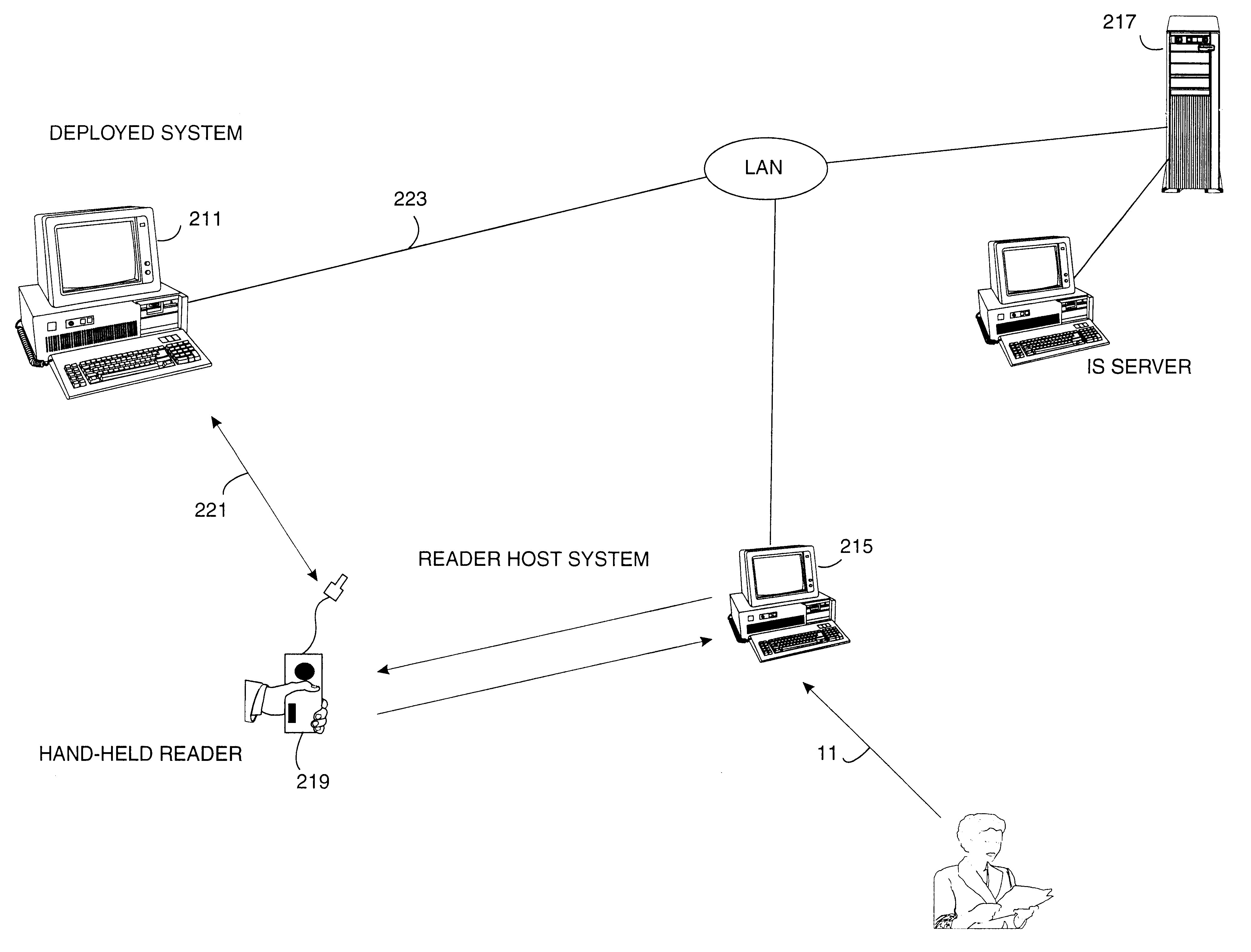
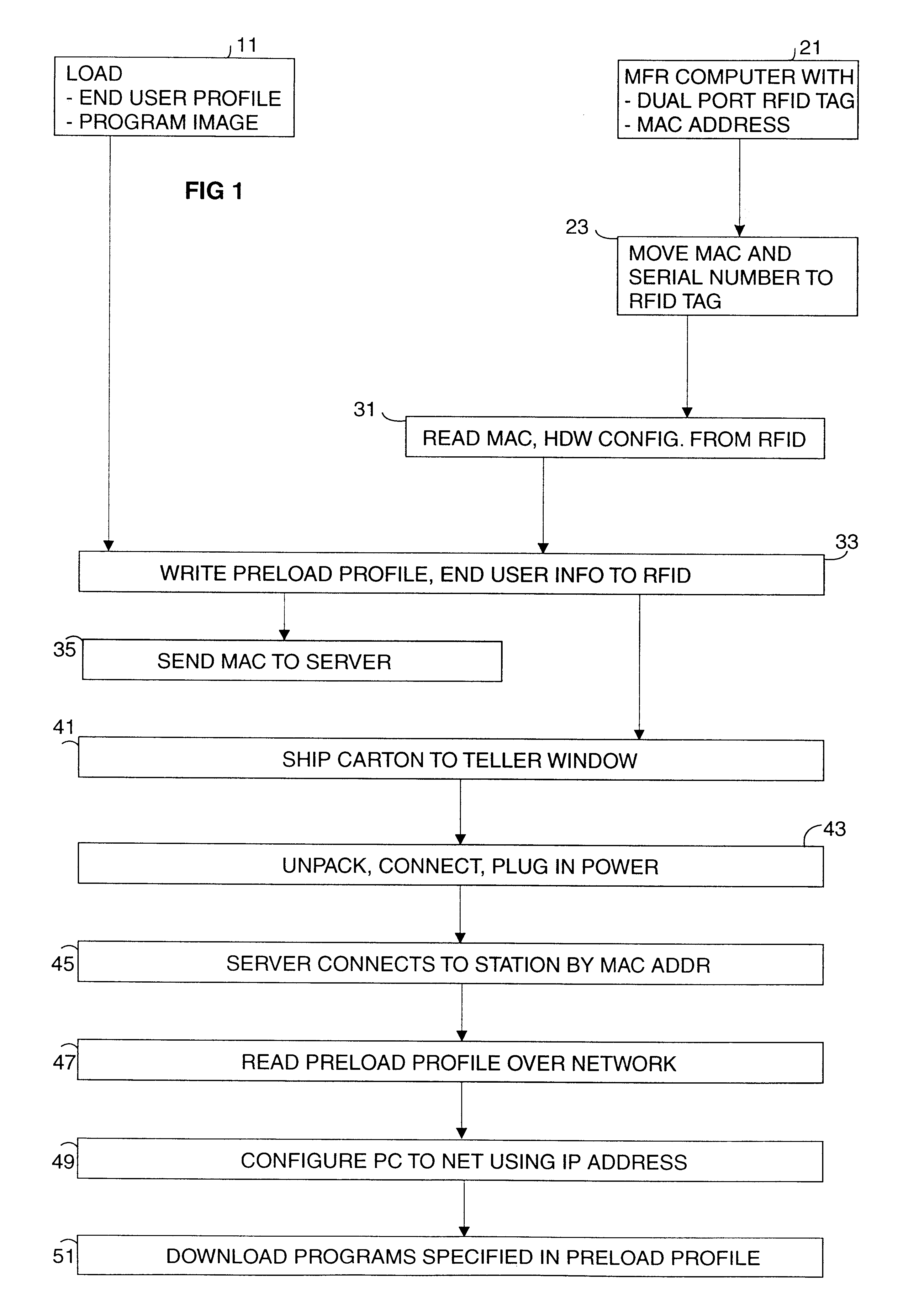
Method and economical direct connected apparatus for deploying and tracking computers
A method of asset control and workstation computer deployment that utilizes a dual port electronic memory identification RFID tag to hold serial number and hardware and software configuration profiles as well as user information. The RFID tag is mapped into the workstation computer memory space and can also be read and written by radio frequency signalling through a wired plug and access flap in a shipping carton. Serial numbers and MAC address is stored on the tag by the manufacturer. User information, workstation profile and software image information is stored onto the tag while the computer is being received for forwarding to the final workstation destination without the need to unpack and power up the computer. The information stored on the tag is used to allow automated system configuration and software downloading to the computer.
Owner:IBM CORP
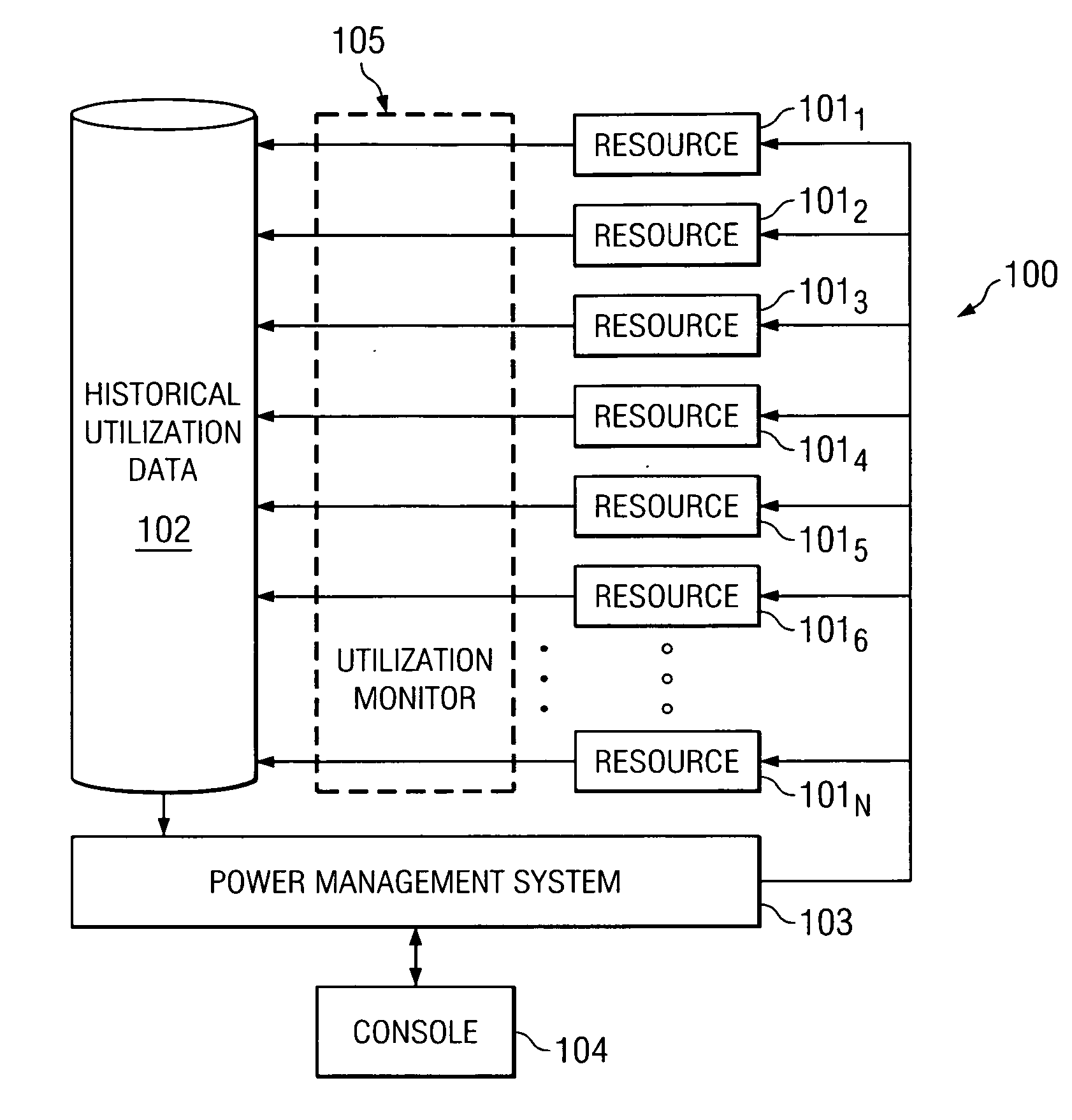
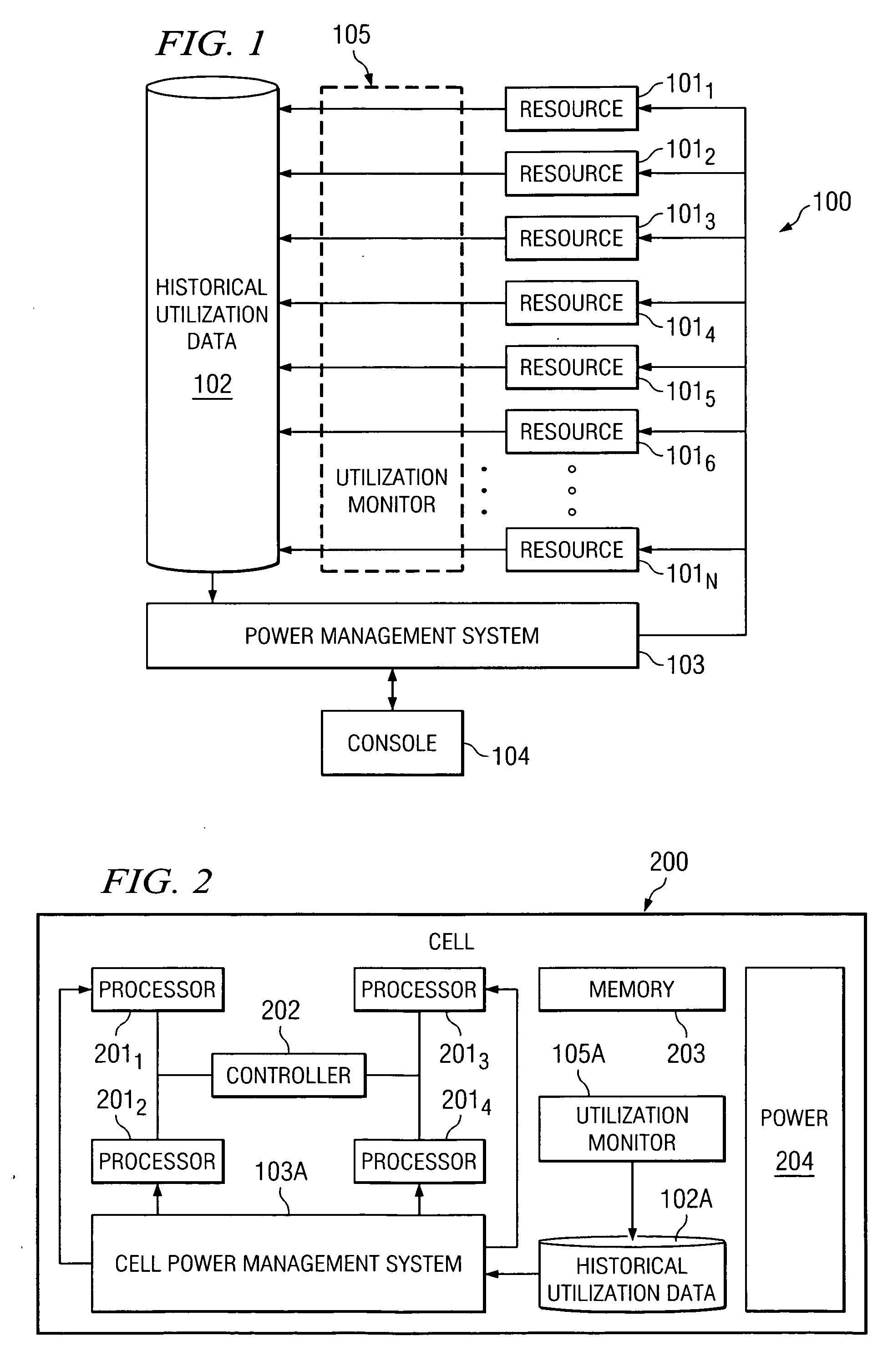
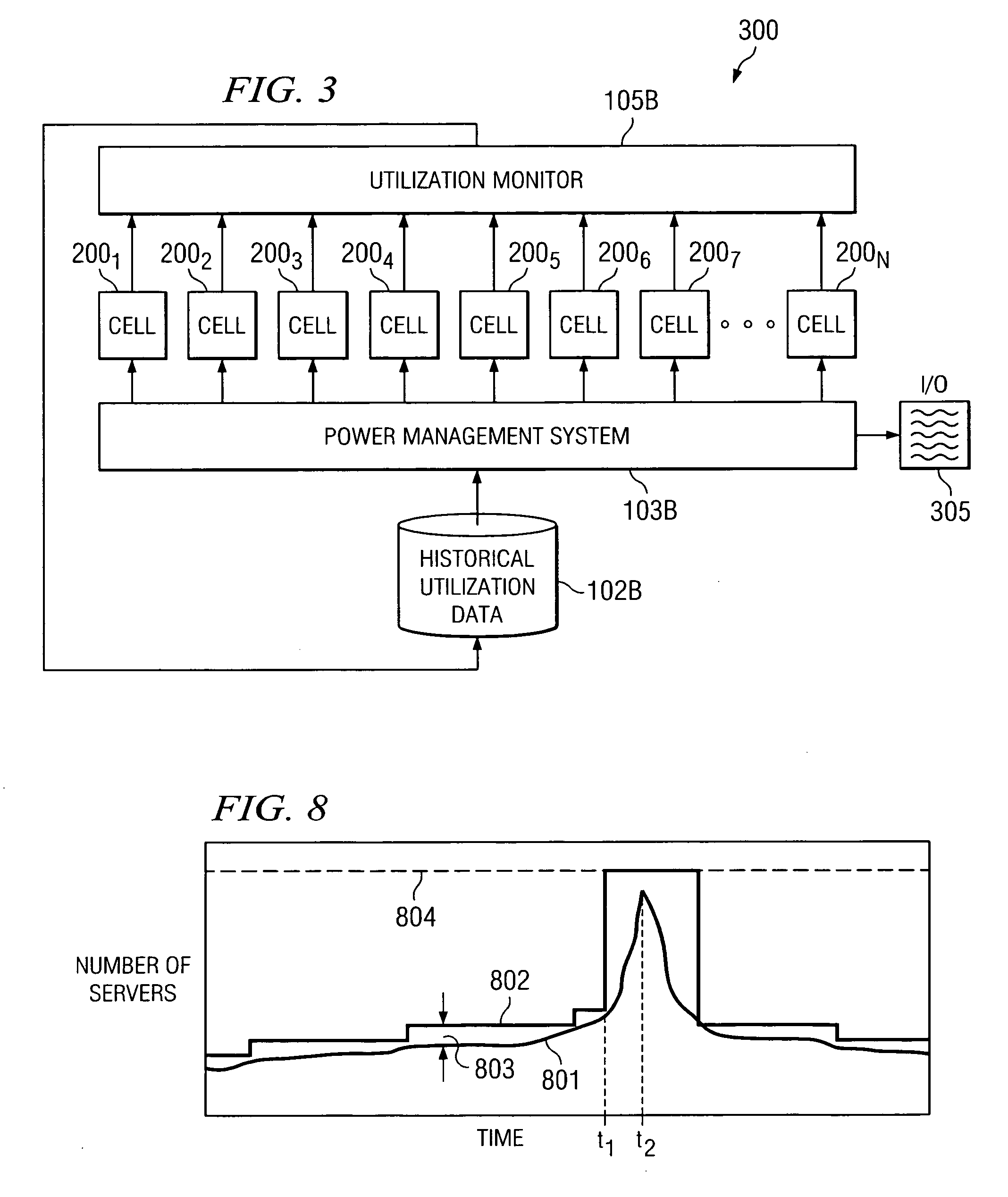
System and method for controlling power to resources based on historical utilization data
ActiveUS20060184287A1Energy efficient ICTMechanical power/torque controlResource basedSystem configuration
A method comprises collecting utilization data for a resource, and predicting by a power management system, based on the collected utilization data, future utilization of the resource. The method further comprises controlling, by the power management system, power to the resource, based at least in part on the predicted future utilization of the resource. In one embodiment, the utilization data is collected for a plurality of resources that are operable to perform tasks, and the method further comprises determining, by the power management system, how many of the resources are needed to provide a desired capacity for servicing the predicted future utilization of the resources for performing the tasks. The method further comprises configuring, by the power management system, ones of the resources exceeding the determined number of resources needed to provide the desired capacity in a reduced power-consumption mode.
Owner:MOSAID TECH
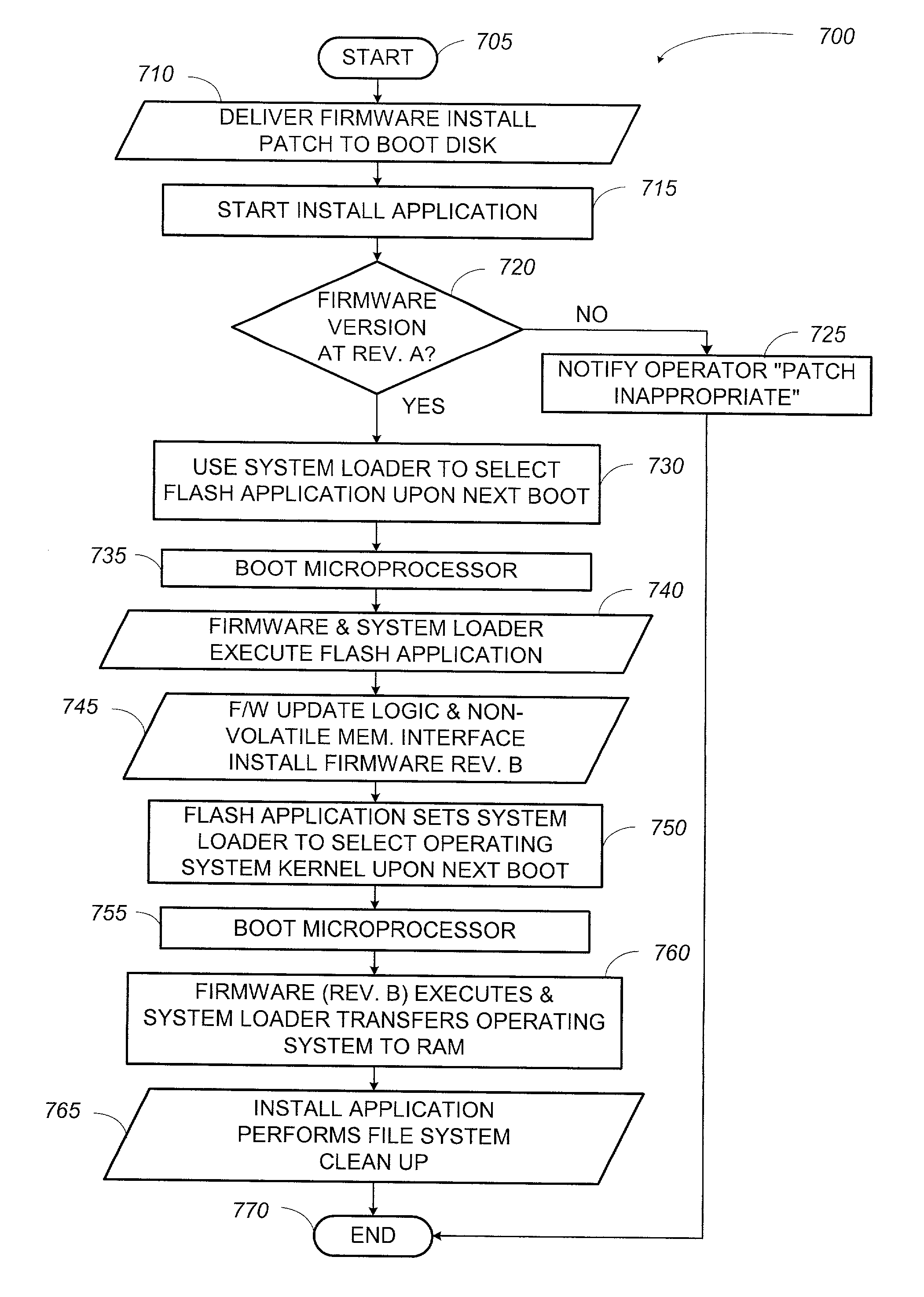
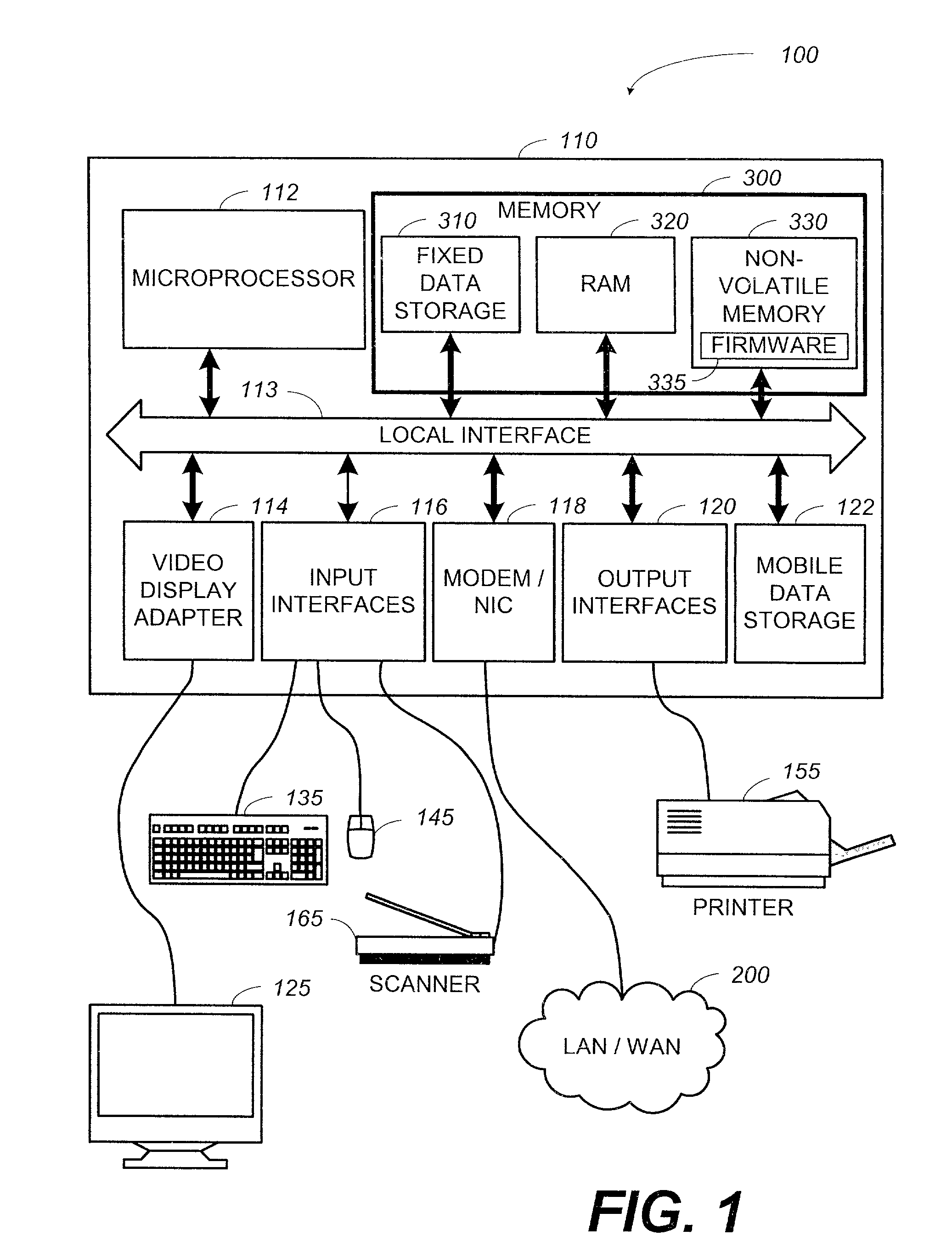
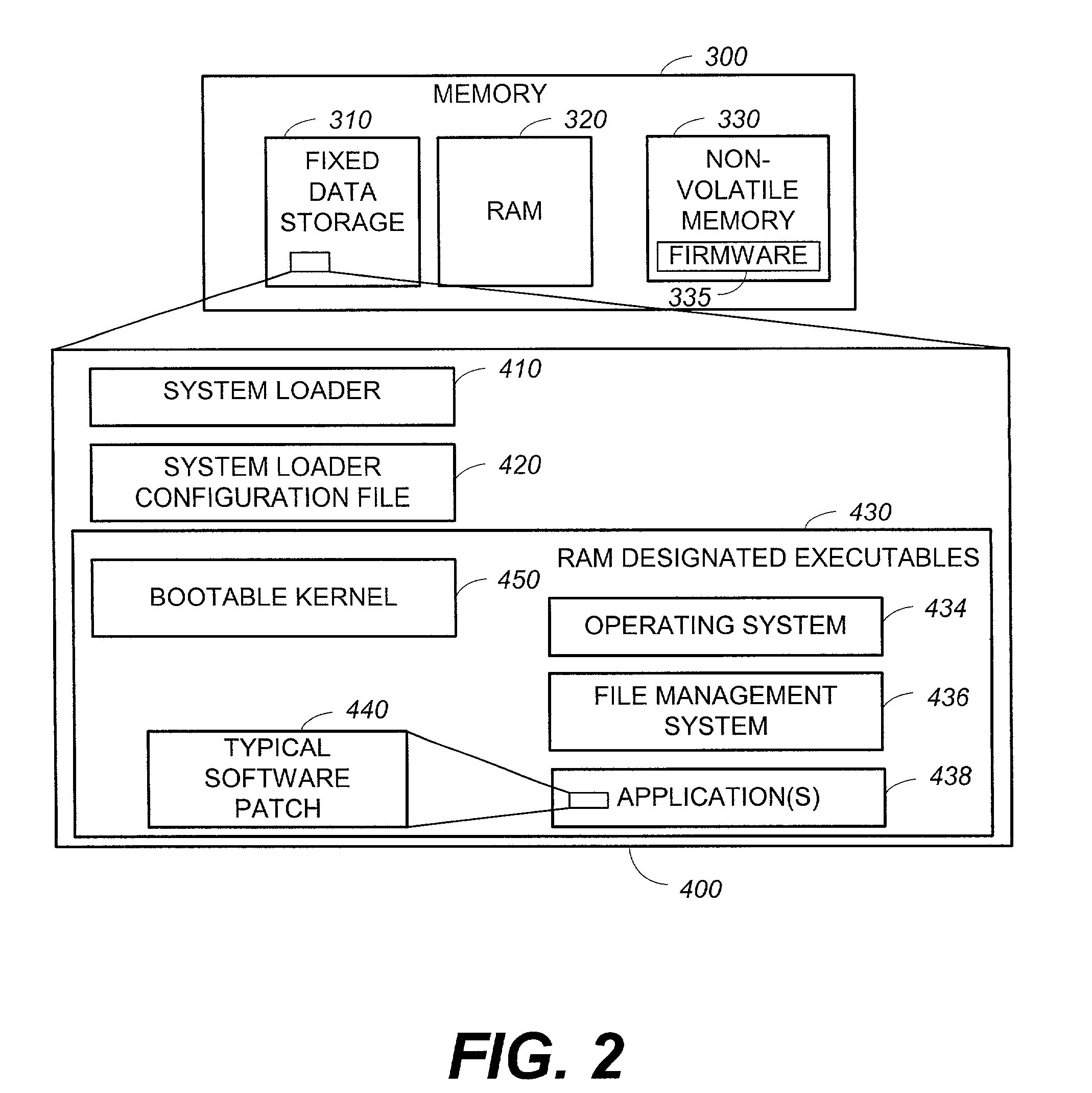
System and method for updating firmware
InactiveUS7055148B2Avoid manual interventionDigital computer detailsProgram loading/initiatingOperational systemFirmware version
A system and a method that uses a software application operable under a current firmware / operating system configuration to install a new firmware version without “compromising” the operating system are presented. The software application may configure a computer system to install a plurality of software fixes configured to enhance functionality under a new firmware / operating system environment after the firmware has been successfully upgraded. Such functionality enhancements may be associated with external peripherals, as well as, input / output circuit cards, processors, and the like. In addition, the software application may configure the computing device to “boot” under the new firmware / operating system environment upon subsequent system initializations. Furthermore, the software application permits the distribution of firmware upgrades via a network. The capability to install firmware remotely permits a system administrator to “push” the new firmware to a plurality of network coupled computing devices, thus avoiding manual intervention at each device.
Owner:HEWLETT PACKARD DEV CO LP
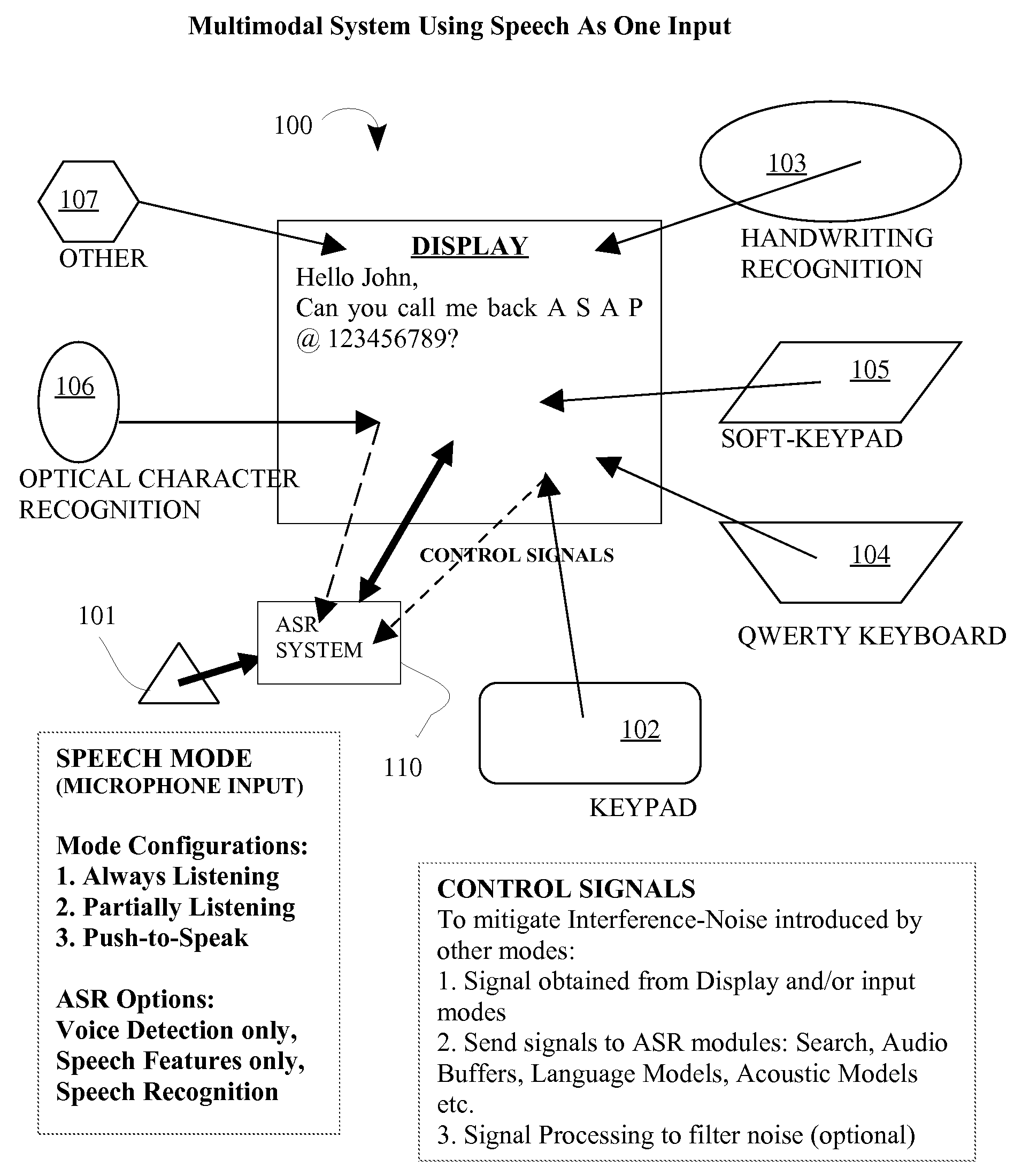
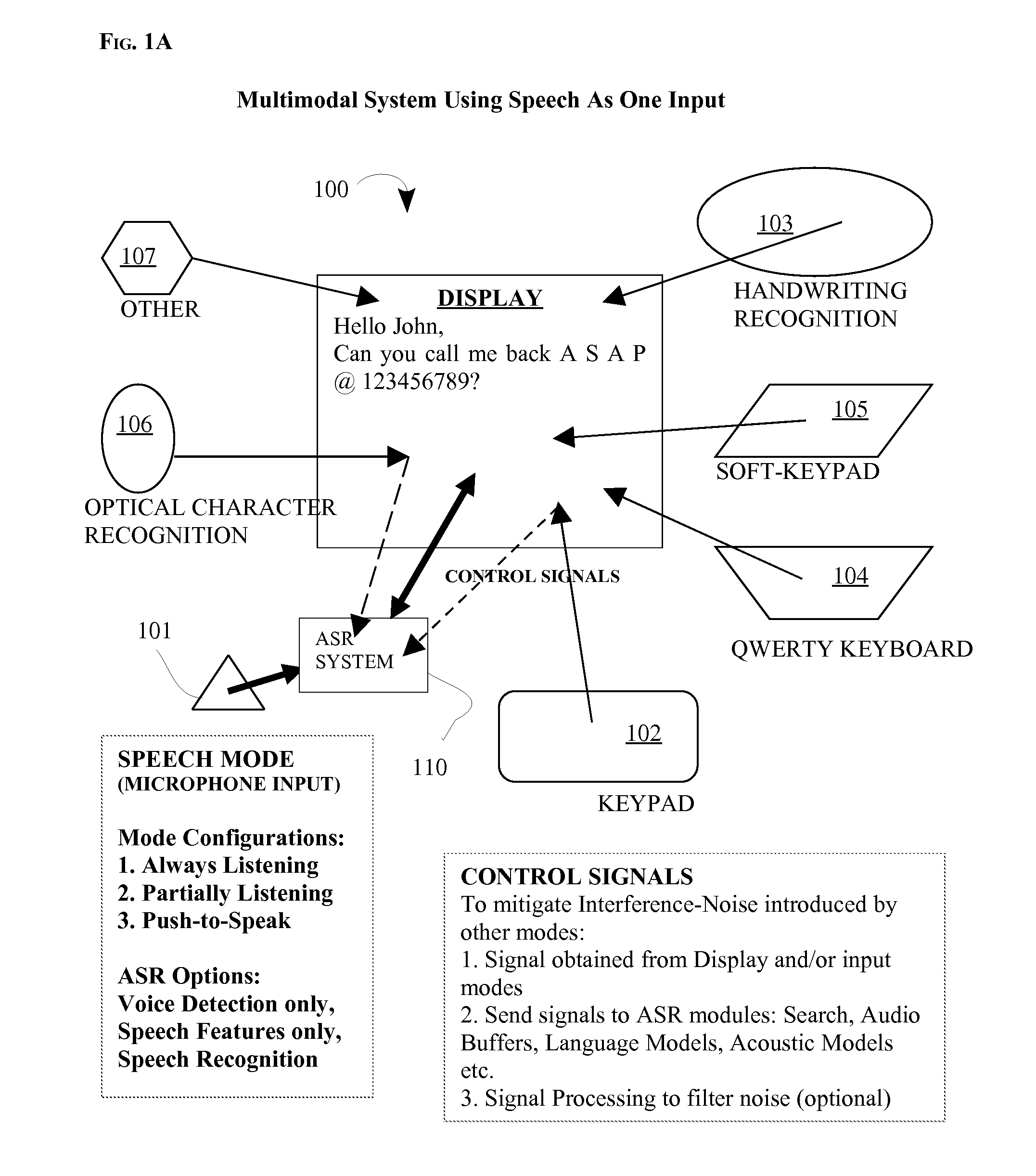
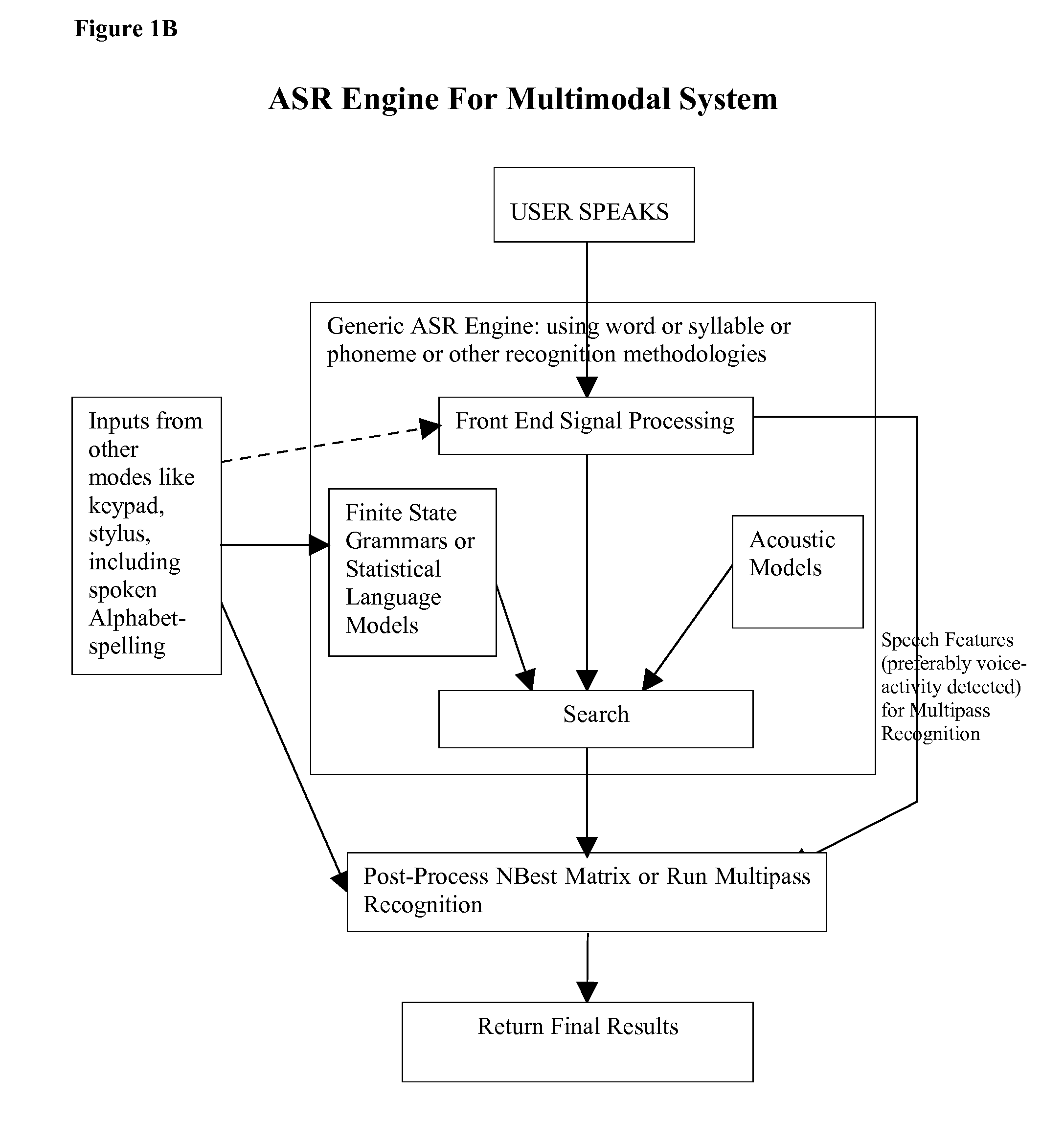
Multimodal speech recognition system
ActiveUS20080133228A1Increase speedImprove easeSpeech recognitionSpeech identificationSystem configuration
The disclosure describes an overall system / method for text-input using a multimodal interface with speech recognition. Specifically, pluralities of modes interact with the main speech mode to provide the speech-recognition system with partial knowledge of the text corresponding to the spoken utterance forming the input to the speech recognition system. The knowledge from other modes is used to dynamically change the ASR system's active vocabulary thereby significantly increasing recognition accuracy and significantly reducing processing requirements. Additionally, the speech recognition system is configured using three different system configurations (always listening, partially listening, and push-to-speak) and for each one of those three different user-interfaces are proposed (speak-and-type, type-and-speak, and speak-while-typing). Finally, the overall user-interface of the proposed system is designed such that it enhances existing standard text-input methods; thereby minimizing the behavior change for mobile users.
Owner:RAO ASHWIN P
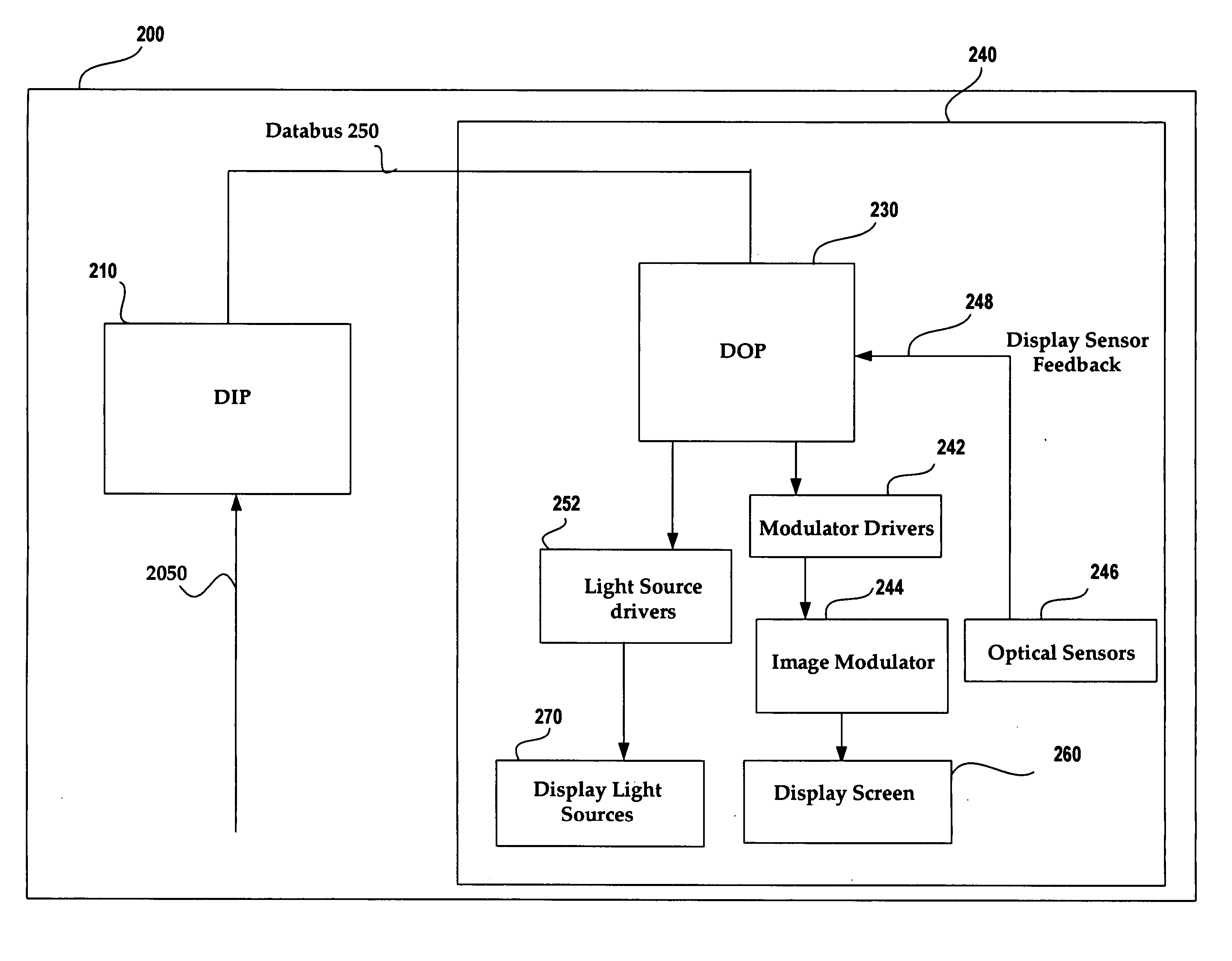
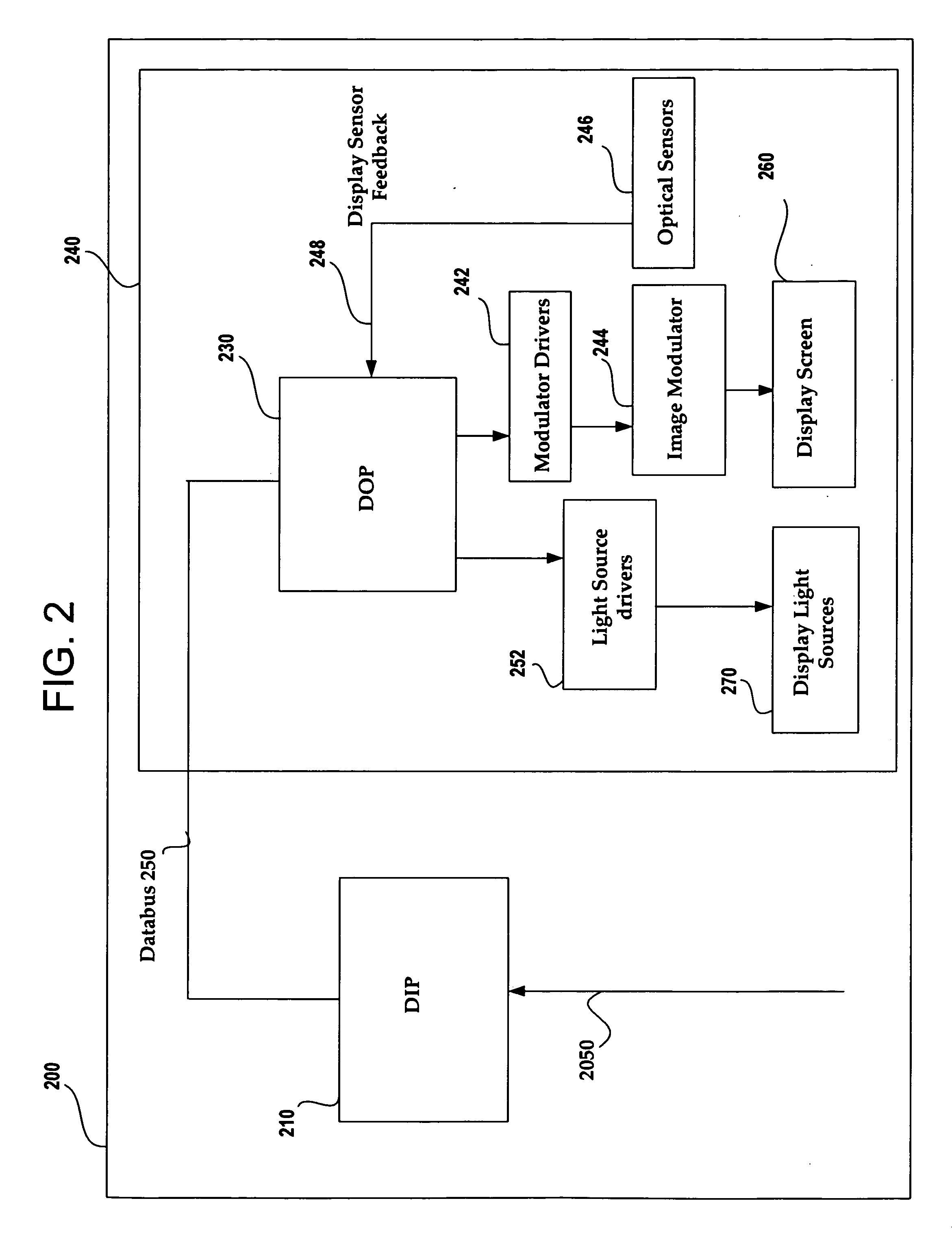
Image and light source modulation for a digital display system
ActiveUS20070035706A1Improve display qualityImprove consistencyTelevision system detailsProjectorsDisplay deviceSystem configuration
Image processing enhances display quality by controlling both the image modulator and the light sources to produce the best possible visual images. The image processing system utilizes a combination of user inputs, system configuration, design information, sensor feedback, pixel modulation information, and lighting control information to characterize the display environment on a per pixel basis. This per pixel characterization information is combined with one or more frames of the incoming real time display data. The image processing system processes each incoming pixel and produces a modified corresponding output pixel. Each pixel of each frame is processed accordingly. In addition to producing modified output pixels, the image processing system produces control information for the light sources. The light source control information can control individual lamps, tubes or LEDs, or can control a block or subset of the light sources. The resulting display has improved image consistency, enhanced color gamut, higher dynamic range and is better able to portray high motion content.
Owner:SAMSUNG ELECTRONICS CO LTD
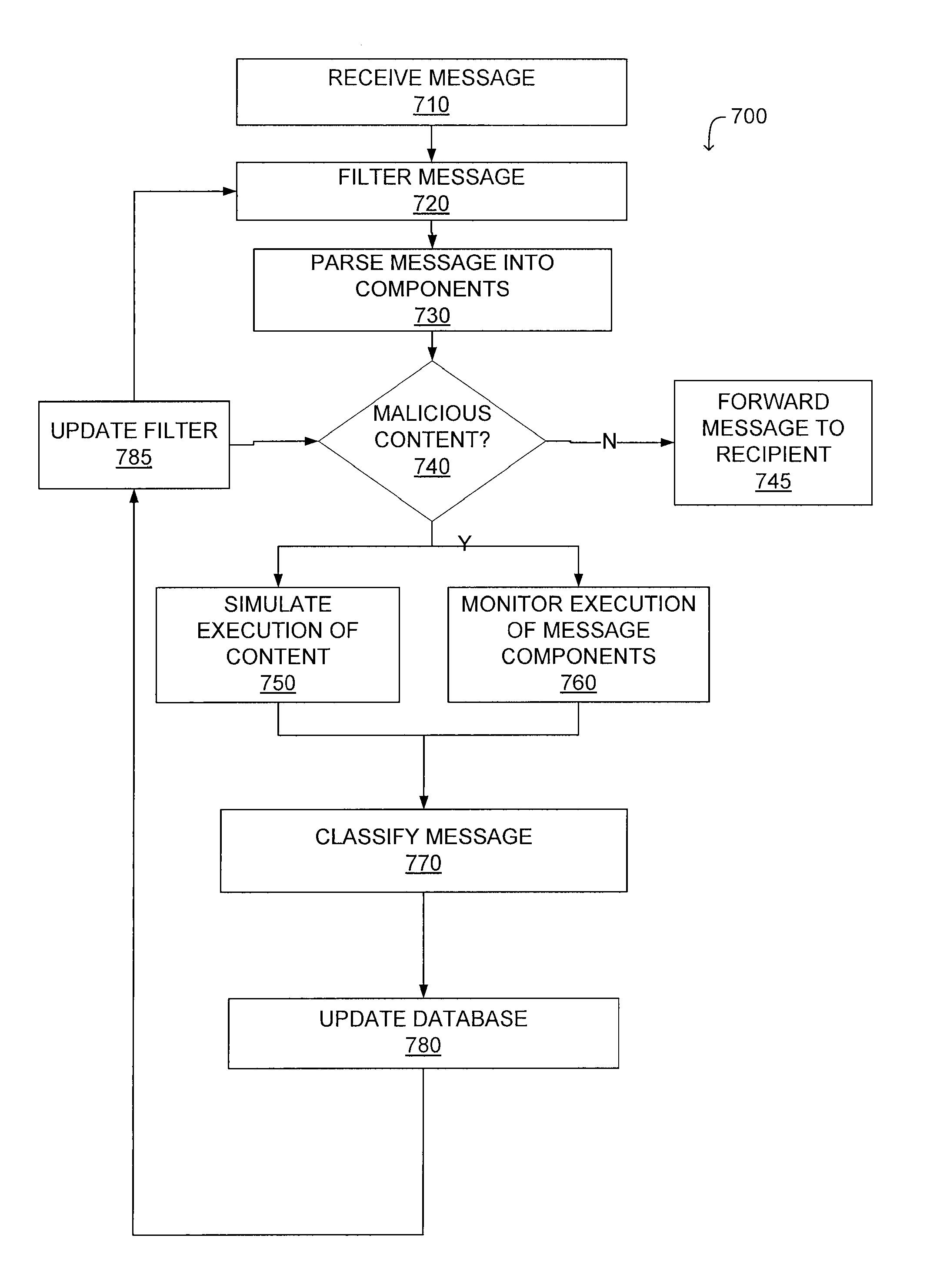
System and method for malicious software detection in multiple protocols
ActiveUS8321936B1Overcome limitationsEasy to detectMemory loss protectionError detection/correctionTransport systemSystem configuration
A system and a method for detecting malicious content associated with an electronic message are described. An electronic message, such as an e-mail, a chat request, a torrent file or a text message is initially received. The electronic message can then be compared to known viruses using pattern or signature matching techniques. The electronic message is then transmitted to a virtual machine which executes the electronic message in an environment simulating the destination computing system of the electronic message. The virtual machine monitors execution of the electronic message to identify one or more malicious actions and classifies the electronic message accordingly. For example, message component execution is monitored for attempts to access system files, attempts to access user information, attempts to transmit system configuration data or attempts to transmit user information.
Owner:AVINTI CORP
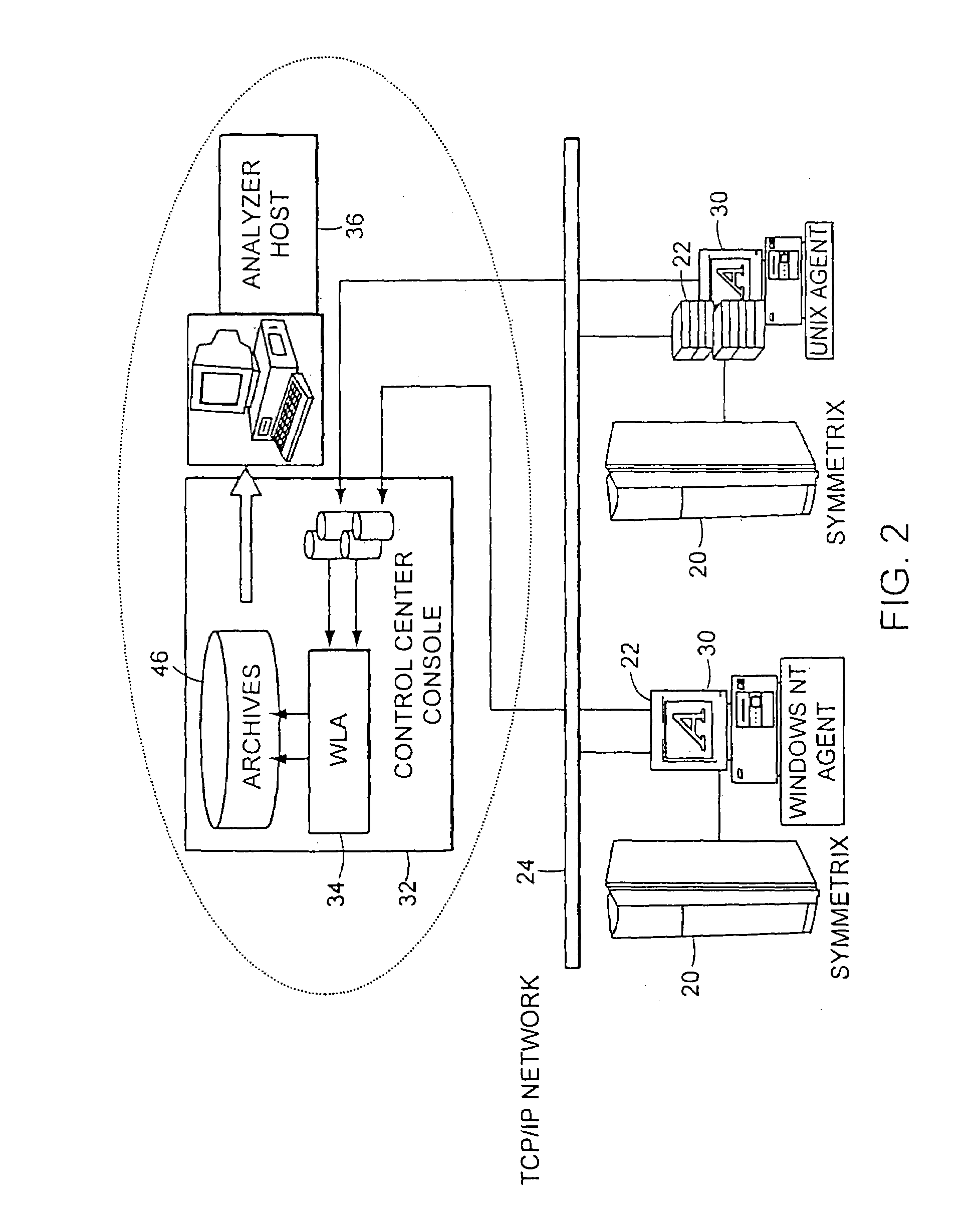
Method and storage and manipulation of storage system metrics
InactiveUS7082441B1Promote generationEasy accessData processing applicationsError detection/correctionData operationsData description
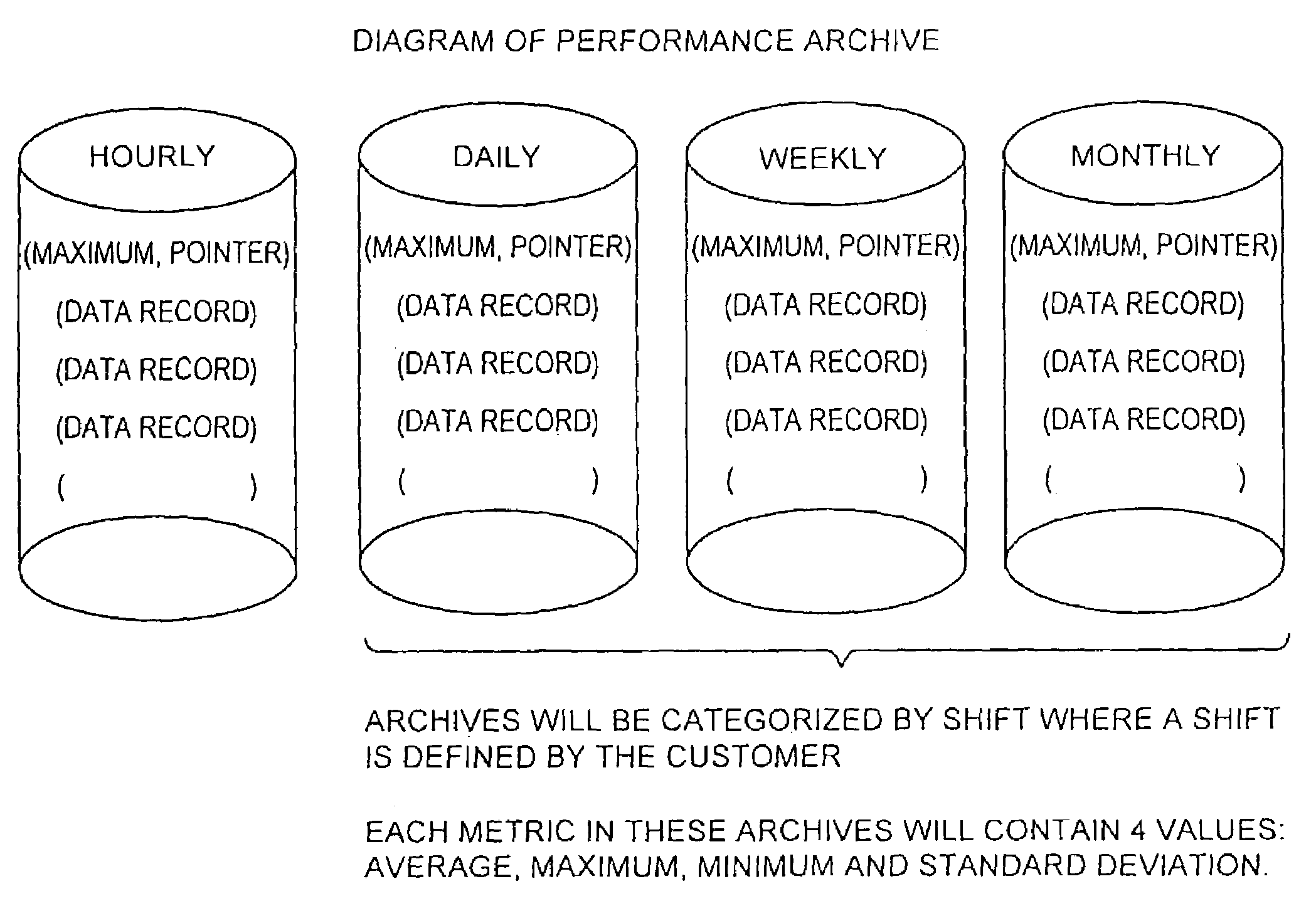
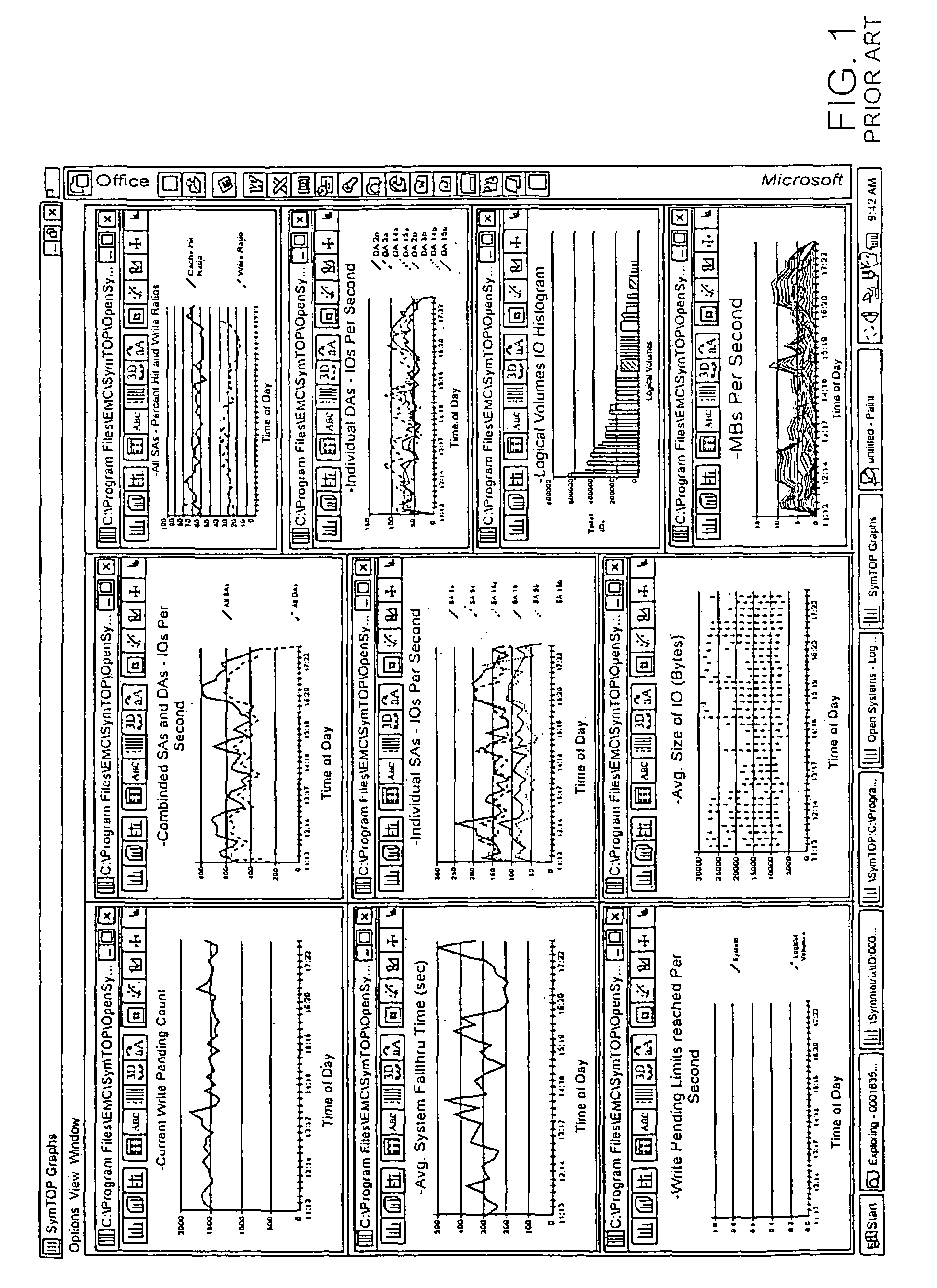
A method for storage and manipulation of storage system metrics incorporates a self-describing format wherein each data file includes a header block that contains the description and order of the periodic data. The header block is followed by a data block in which the data items are presented in the order that they appear in the data description block for that category. Two types of data are managed, including Base Metrics and Derived Metrics. Base Metrics are metrics that appear in the data file sent by an agent. Derived Metrics are computed based on a set of functions that derive new metrics from the base metrics as well as from previously defined derived metrics. A subset of the data block or file describes the configuration of the storage system at the time that the data file was created. Thus the data file contains a header section that in addition to describing the metrics also describes the configuration. A performance view component a user interface that facilitates access to the archives, and data manipulation effecting enhanced performance analysis, workload characterization and capacity planning. The performance view component facilitates generation of factory and user defined views of monitored metrics / parameters. Metrics from a storage system can be correlated using the performance view features, and parameters across machines can be correlated as well. System configuration(s) can be viewed and changed via the performance view user interface.
Owner:EMC IP HLDG CO LLC
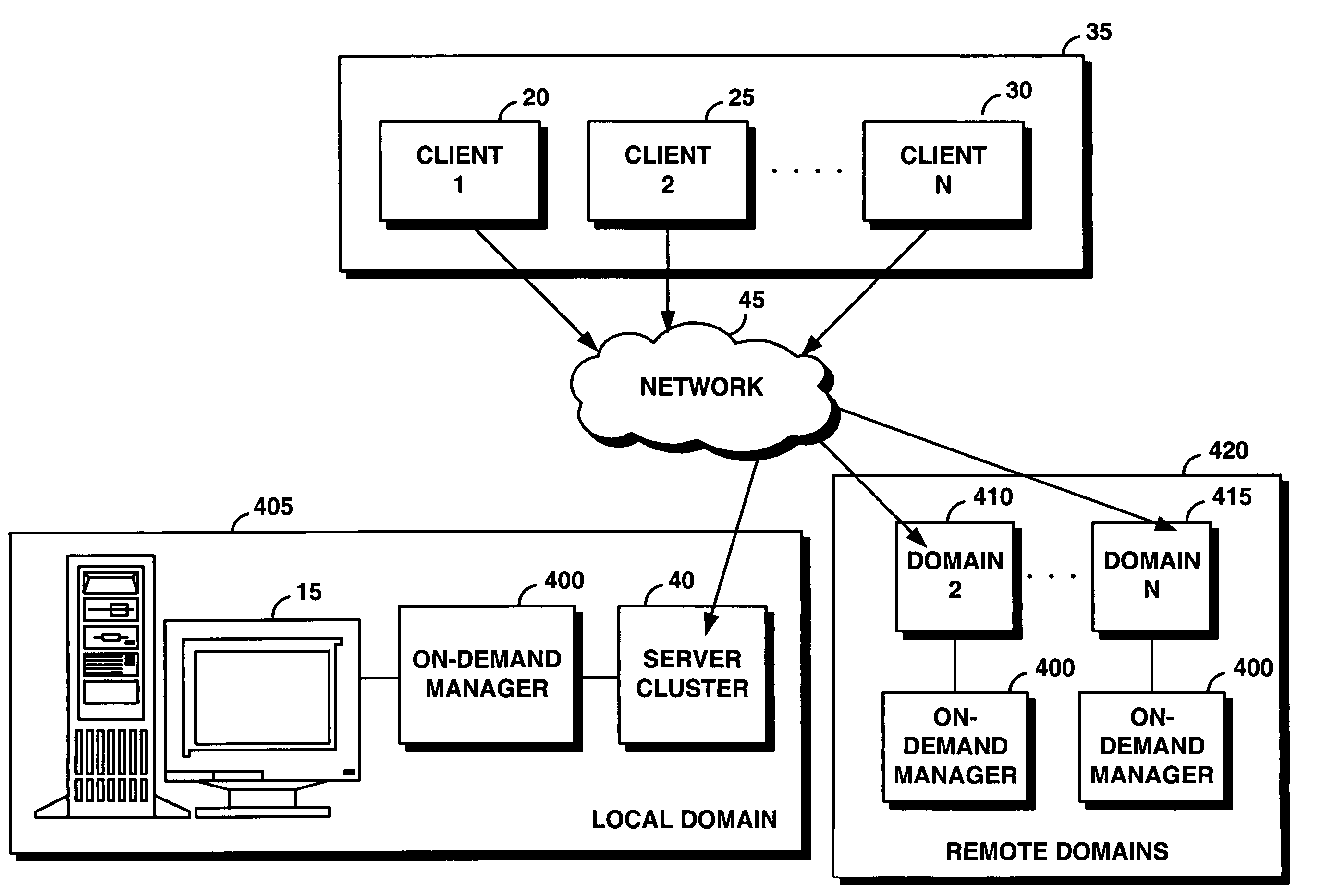
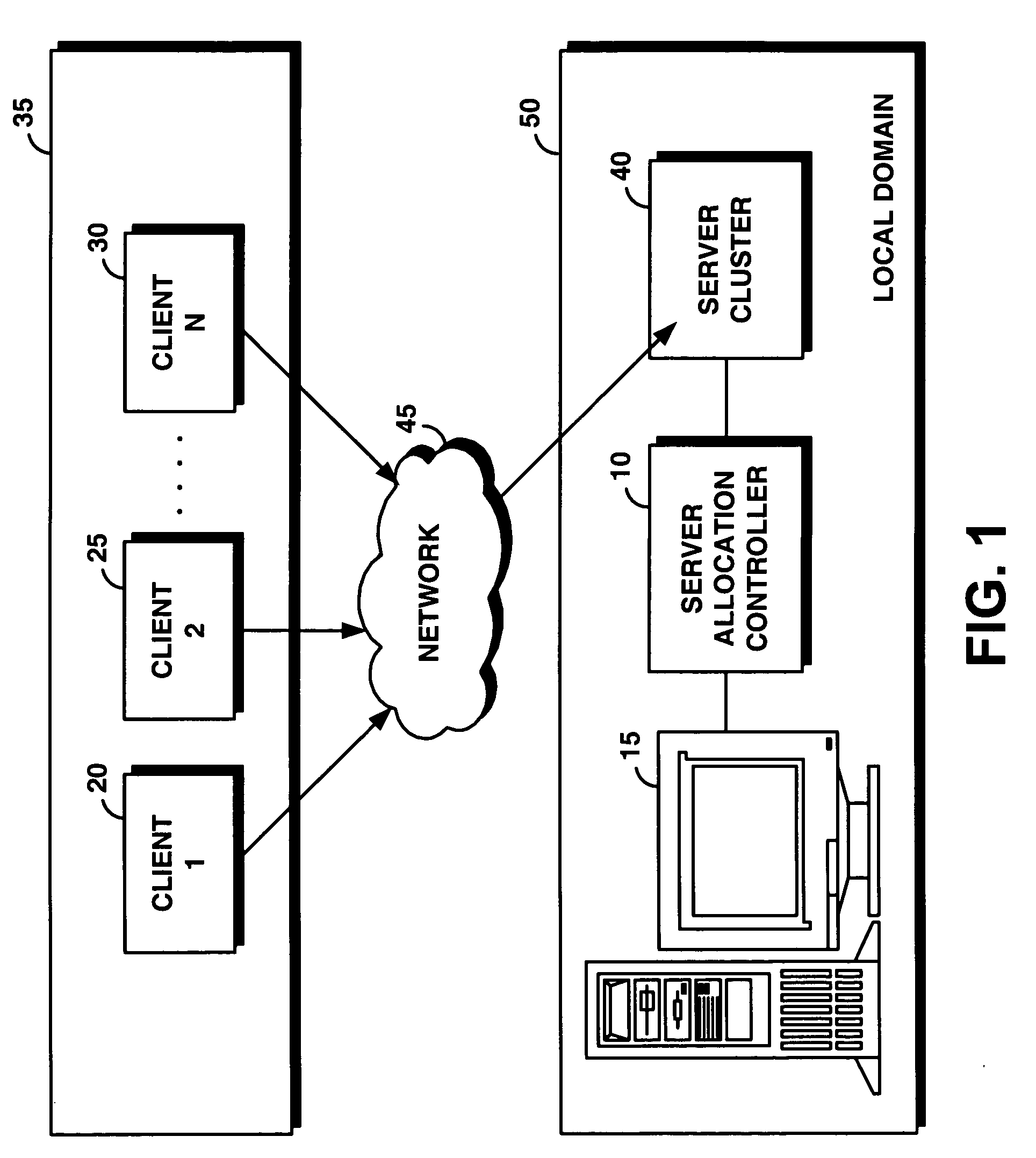
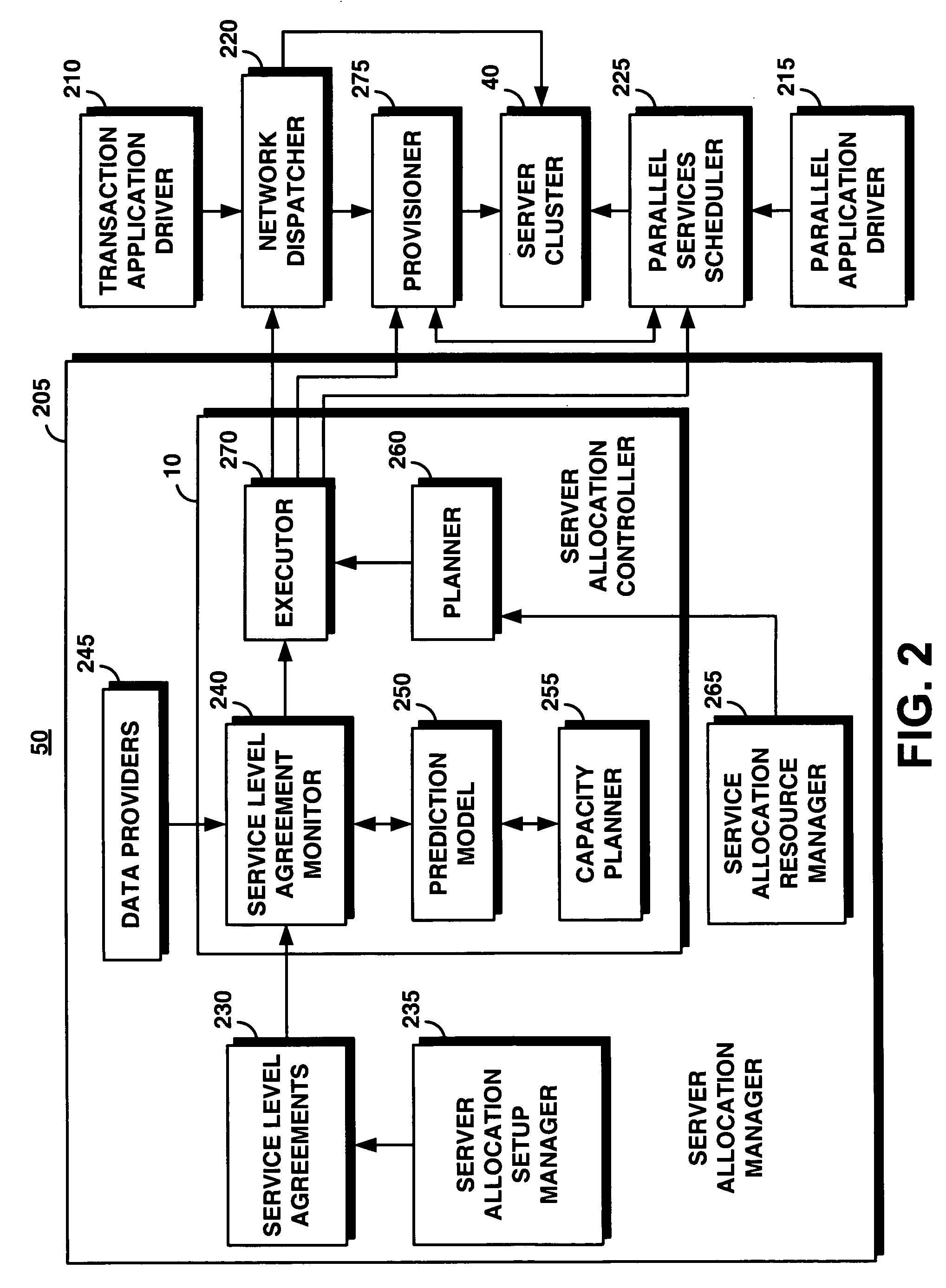
System and method for supporting transaction and parallel services across multiple domains based on service level agreenments
InactiveUS20050165925A1Facilitates dynamic allocationResource allocationDigital computer detailsService-level agreementData processing system
An on-demand manager provides an improved distributed data processing system for facilitating dynamic allocation of computing resources among multiple domains based on a current workload and service level agreements. Based on a service level agreement, the on-demand manager monitors and predicts the load on the system. If the current or predicted load cannot be handled with the current system configuration, the on-demand manager determines additional resources needed to handle the workload. If the service level agreement violations cannot be handled by reconfiguring resources at a domain, the on-demand manager sends a resource request to other domains. These other domains analyze their own commitments and may accept the resource request, reject the request, or counter-propose with an offer of resources and a corresponding service level agreement. Once the requesting domain has acquired resources, workload load balancers are reconfigured to allocate some of the workload from the requesting site to the acquired remote resources.
Owner:IBM CORP
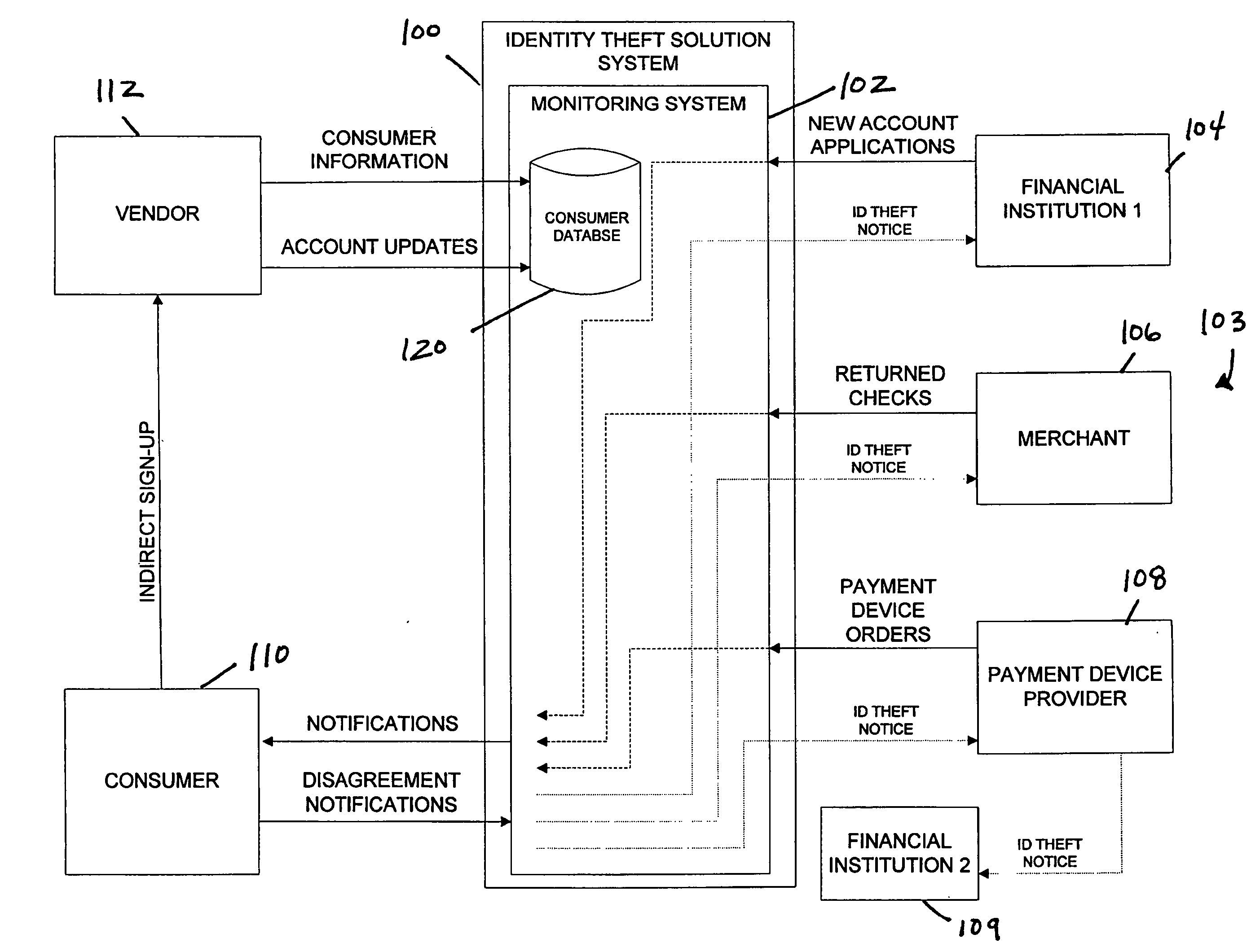
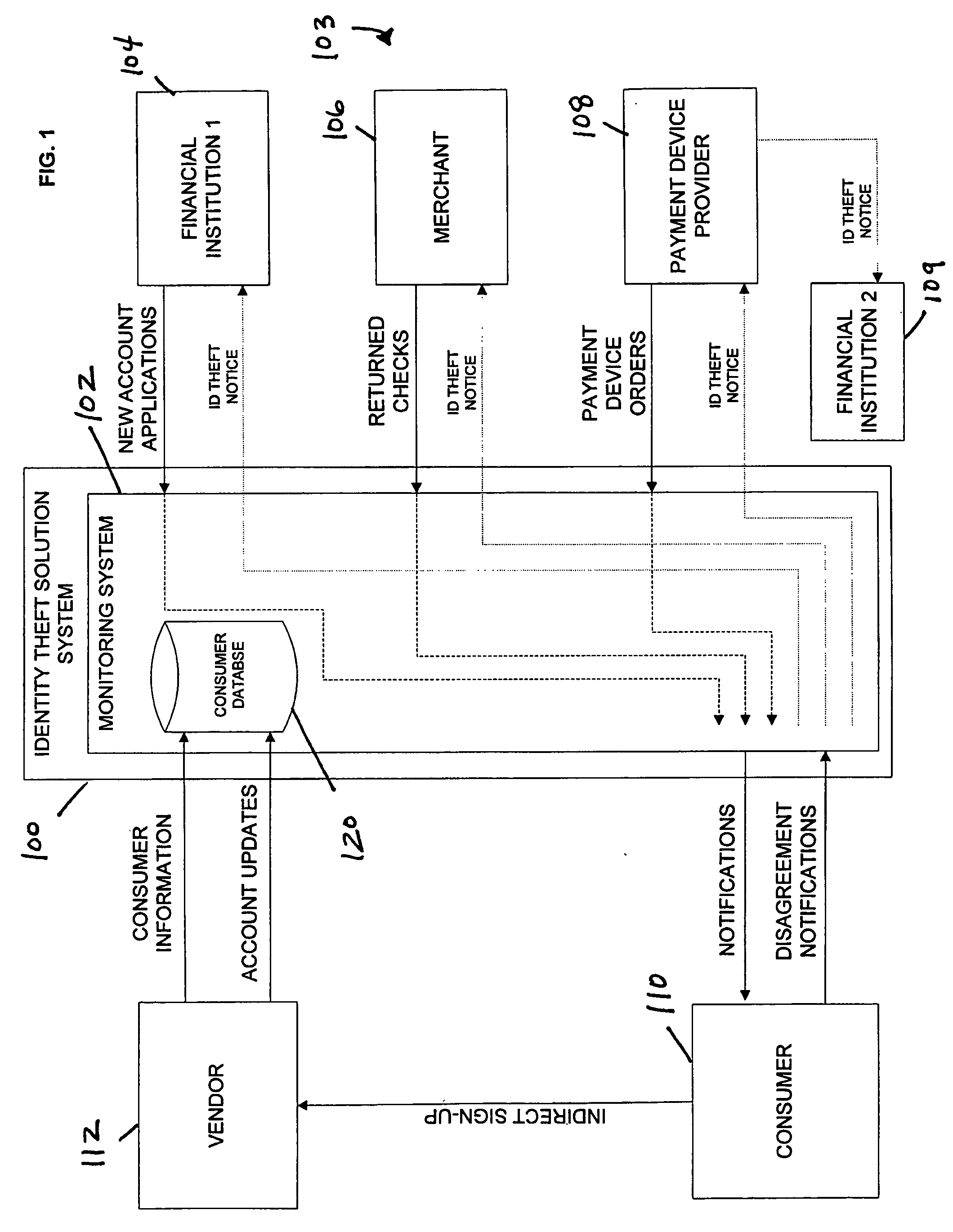
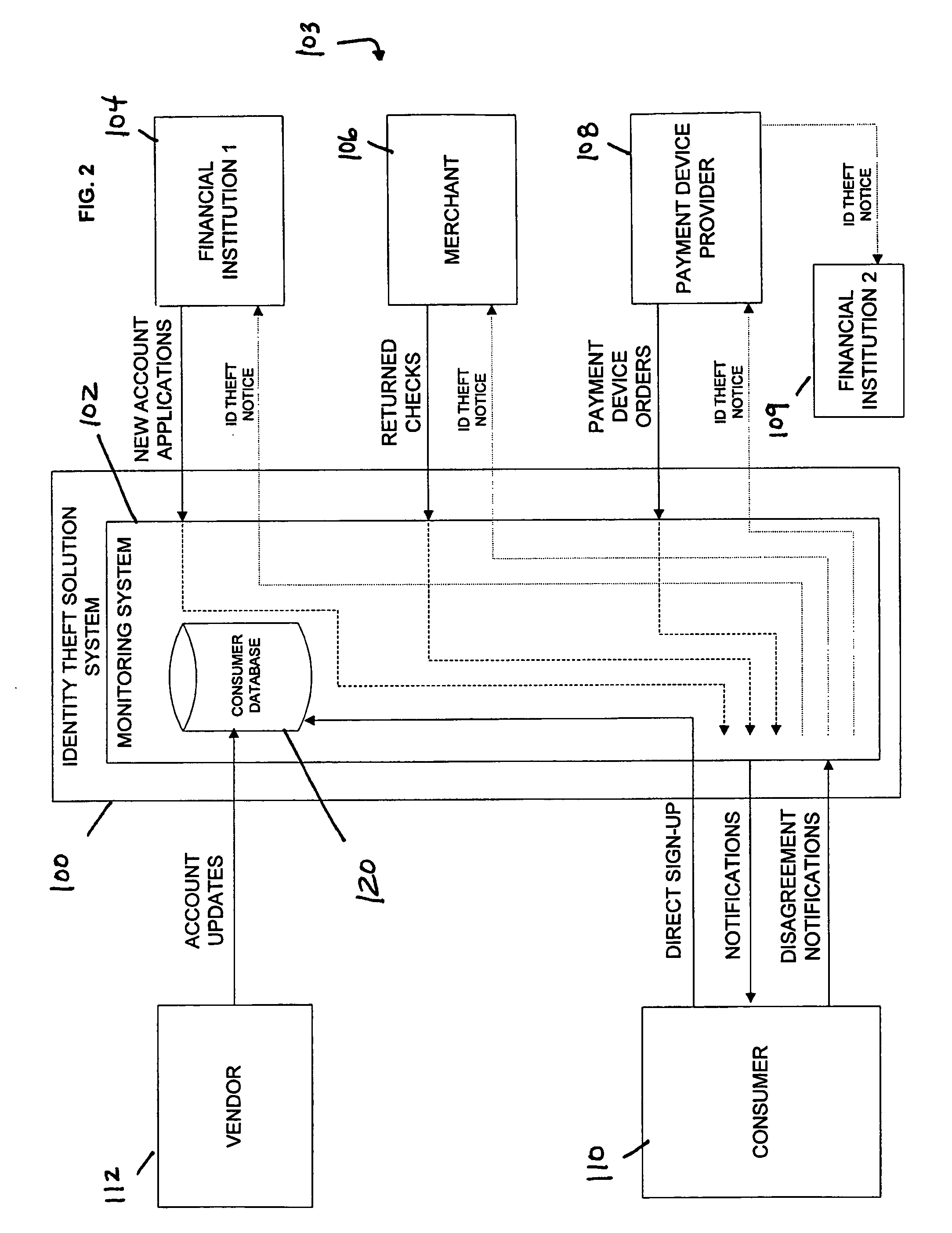
Identity theft monitoring and prevention
InactiveUS20060271457A1Prevent and limit potential financialPrevent and limit and reputation lossFinanceSecret communicationIdentity theftSystem configuration
Systems and methods of monitoring financial information of a consumer for fraudulent activity. One system can include an identity verification system configured to verify an identity of a consumer. The system can include a new account identity theft detection system configured to determine a first score for a new account application submitted by the consumer, the first score indicating likelihood that the new account application is fraudulent, and an address analyzer configured to determine a second score for an address modification submitted by the consumer, the second score indicating likelihood that the address modification is fraudulent.
Owner:EFUNDS CORP
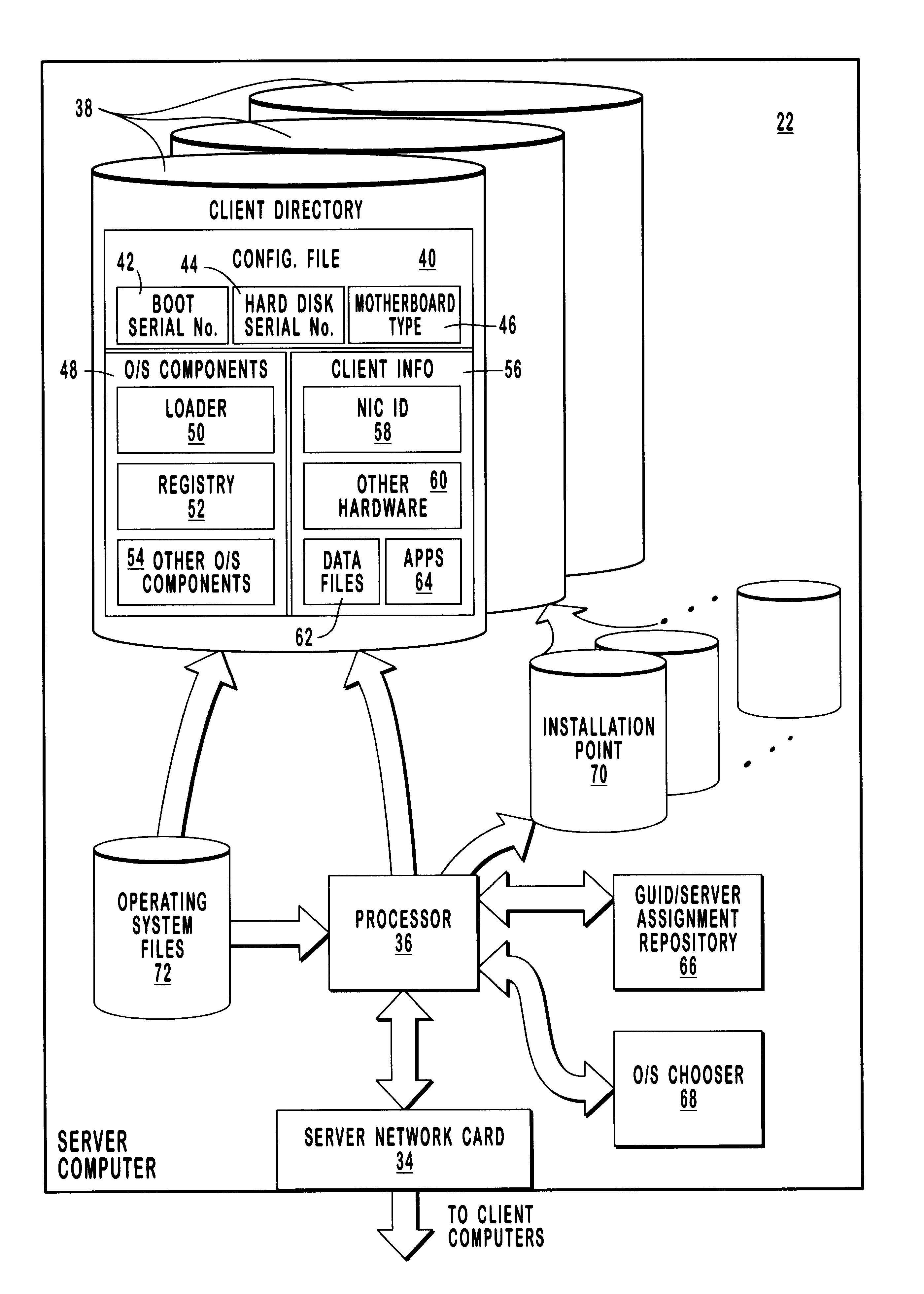
Correcting for changed client machine hardware when using a server-based operating system
InactiveUS6209089B1Reduces administrative effortReduce attentionDigital computer detailsEmergency protective arrangements for automatic disconnectionComputer hardwareOperational system
Methods and systems for adjusting an operating system configuration according to changes in hardware components of a client computer. The adjusted operating system can boot on the client computer regardless of changes in the hardware configuration of the client computer since it was last connected to a network server. Before the operating system boots, a preliminary connection is established between the client computer and the server. During the preliminary connection, the system identifies hardware components that are new and that must be supported by the operating system for bootup to occur. In particular, the server sends information relating to the previous client hardware configuration to the client computer. The client computer compares its current hardware configuration to the previous hardware configuration information, thereby identifying its new hardware components. Information identifying the new hardware components is sent to the server. The server locates operating system components or device drivers that support the new hardware components and stores them in a specified repository at the server. The operating system, which is now reconfigured to support the current client hardware components, is downloaded to the client computer and boots thereon.
Owner:MICROSOFT TECH LICENSING LLC
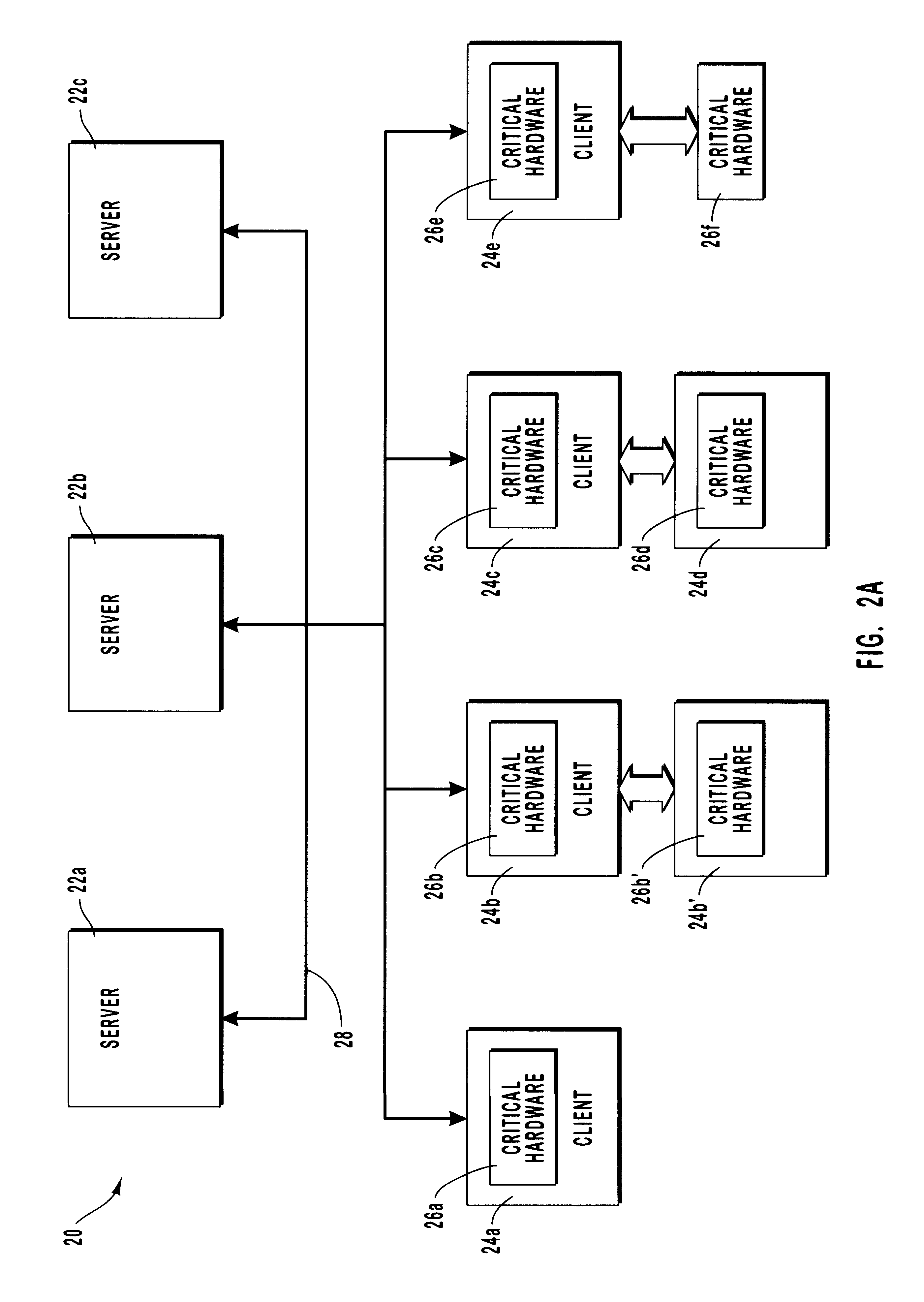
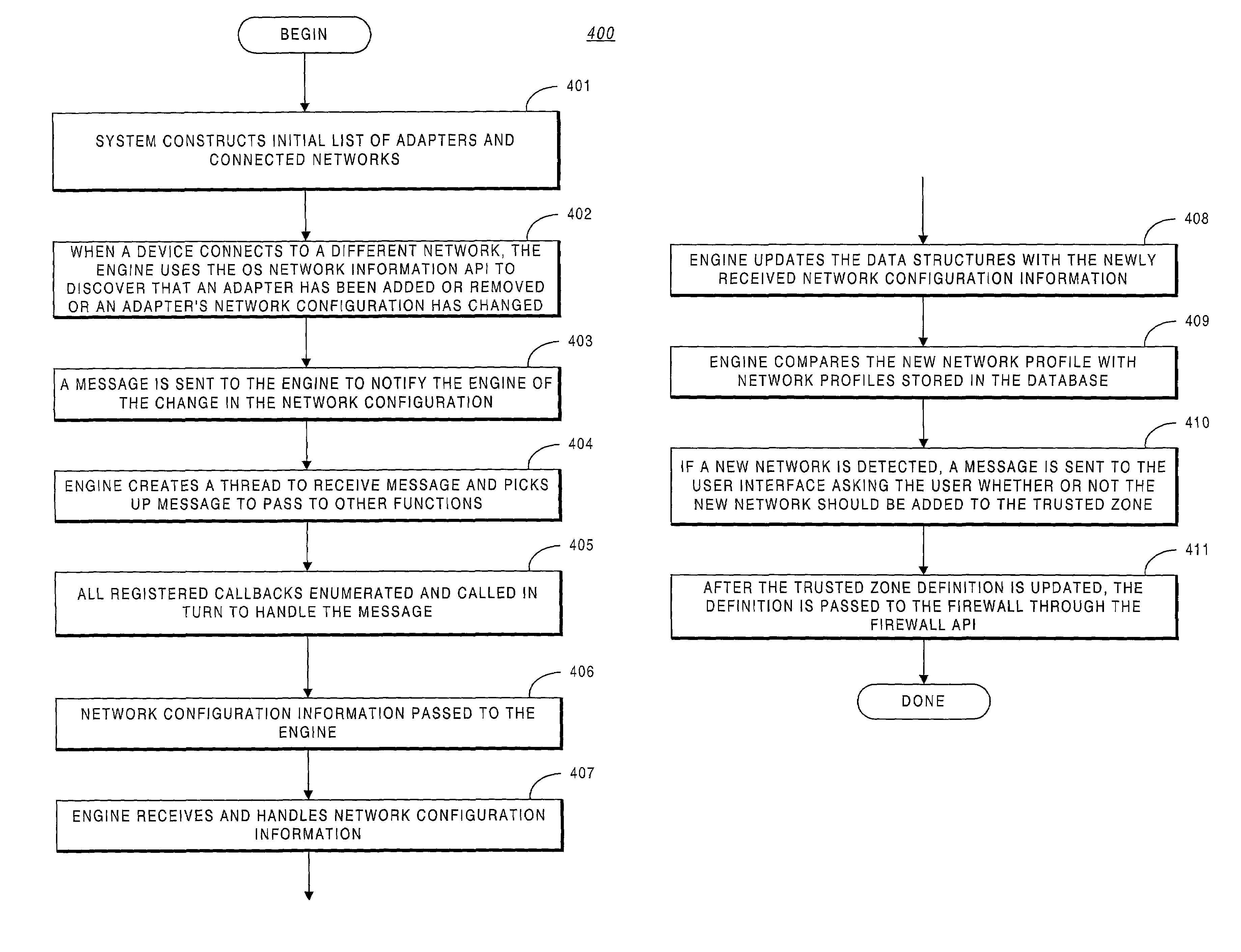
System methodology for automatic local network discovery and firewall reconfiguration for mobile computing devices
ActiveUS7222359B2Easy to detectDigital data processing detailsMultiple digital computer combinationsNetwork generationUnique identifier
A system providing methodologies for automatically detecting when a computing device is plugged into a new network is described. The system includes methods for detecting a connection to a new network by receiving notice of, and evaluating, changes to an existing network configuration. The system profiles and generates an identity for the new network. This includes collecting information about the network to uniquely identify it and generating a unique identifier for the network. Once a network has been profiled, a user may decide whether or not to include it as part of a trusted zone. Alternatively, this decision may be guided by policy established by a system administrator or user. The system automatically reconfigures a firewall to include or exclude the network from the trusted zone based upon this decision. The profile of each network is stored so that the next time the device is connected to the same network it remembers the network and applies the same security settings previously adopted. The stored profile also facilitates the detection of changes to the network configuration or the connection to a new network.
Owner:CHECK POINT SOFTWARE TECH INC
Method and tool for network vulnerability analysis
InactiveUS7013395B1Avoid low successLow “ effort ” costMemory loss protectionUnauthorized memory use protectionLimited resourcesCountermeasure
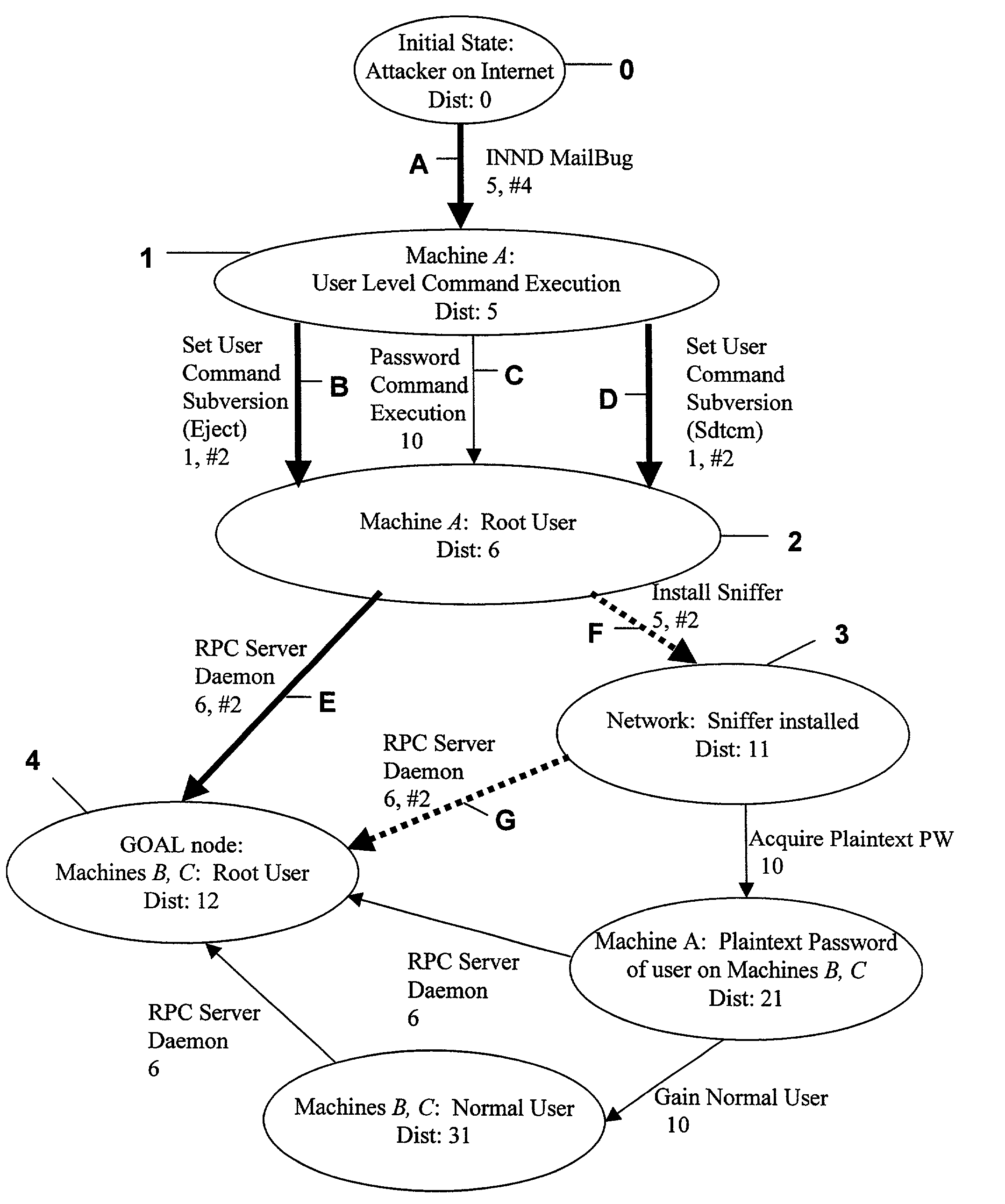
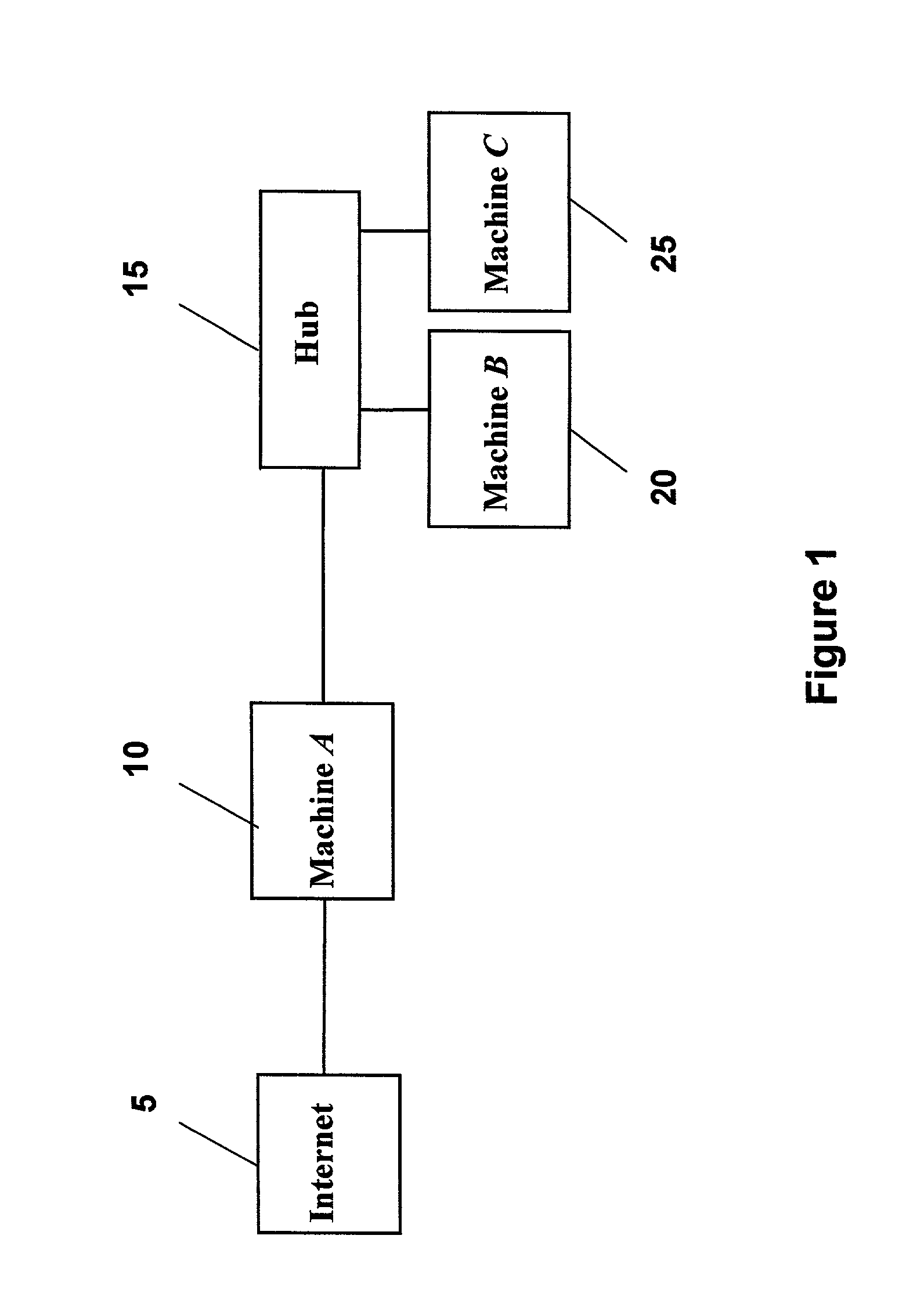
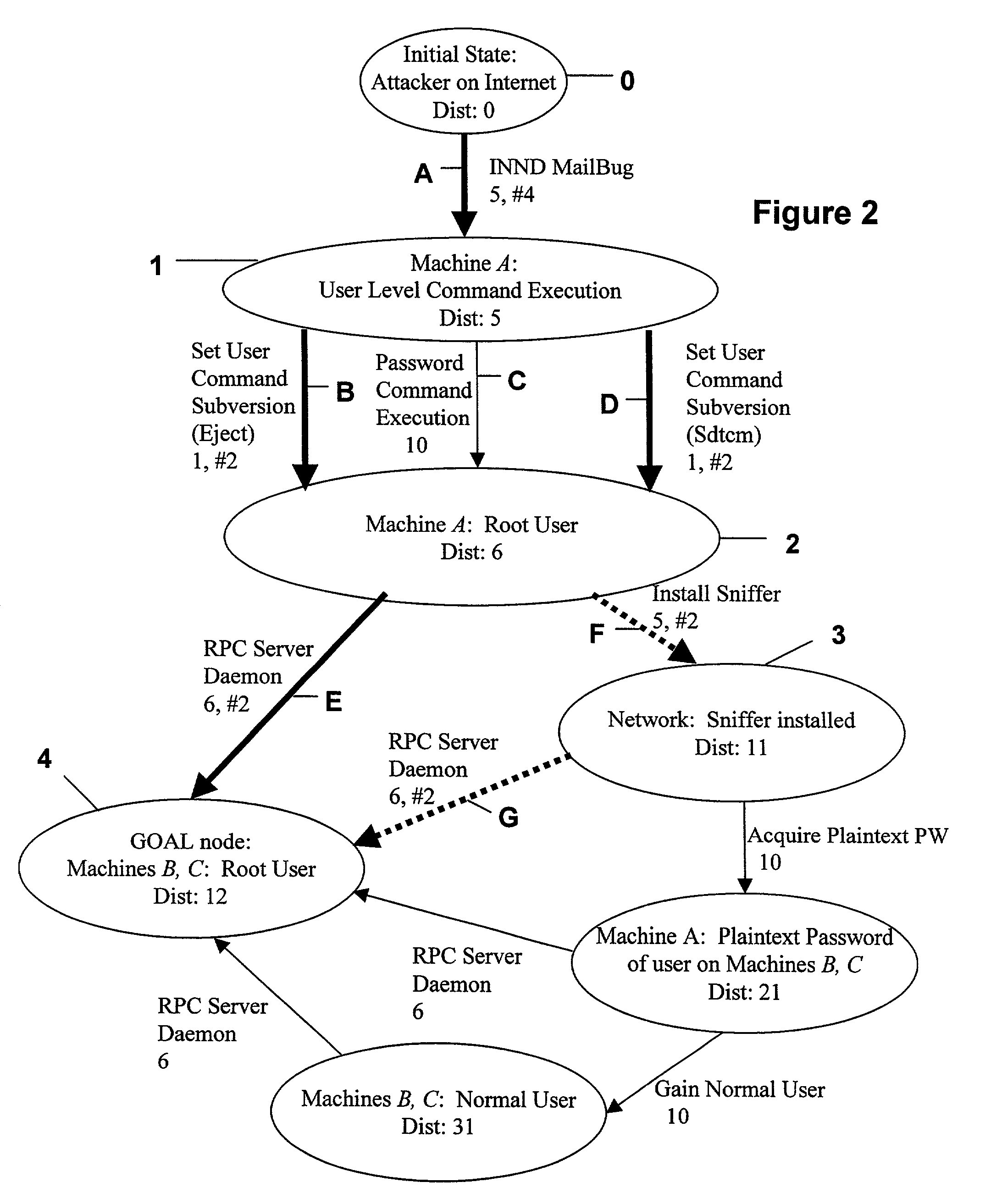
A computer system analysis tool and method that will allow for qualitative and quantitative assessment of security attributes and vulnerabilities in systems including computer networks. The invention is based on generation of attack graphs wherein each node represents a possible attack state and each edge represents a change in state caused by a single action taken by an attacker or unwitting assistant. Edges are weighted using metrics such as attacker effort, likelihood of attack success, or time to succeed. Generation of an attack graph is accomplished by matching information about attack requirements (specified in “attack templates”) to information about computer system configuration (contained in a configuration file that can be updated to reflect system changes occurring during the course of an attack) and assumed attacker capabilities (reflected in “attacker profiles”). High risk attack paths, which correspond to those considered suited to application of attack countermeasures given limited resources for applying countermeasures, are identified by finding “epsilon optimal paths.”
Owner:SANDIA NAT LAB
System and Method to Control a Wireless Power Transmission System by Configuration of Wireless Power Transmission Control Parameters
ActiveUS20160056966A1Preventing contradictory configurationNetwork topologiesHybrid transportElectric forceWeb browser
A system and method to control a wireless power transmission system by configuration of wireless power transmission control parameters is disclosed. The configuration of the system may be performed by an operator using a standard web browser on a computing device where the system configuration GUI presented to the operator may be functionally identical regardless of the computing device running the browser. The system configuration GUI may be connected to system through a system configuration API. According to some aspects of this embodiment, a method to control wireless power transmission system by configuration of wireless power transmission control parameters may include accessing the system configuration GUI, displaying operational or other parameter to configure the system, selecting an operational parameter, configuring the selected operational parameter, and then continuing to configure others operational parameter if needed, storing configuration parameters in the computer memory, and communicating configuration parameters to others system computers.
Owner:ENERGOUS CORPORATION
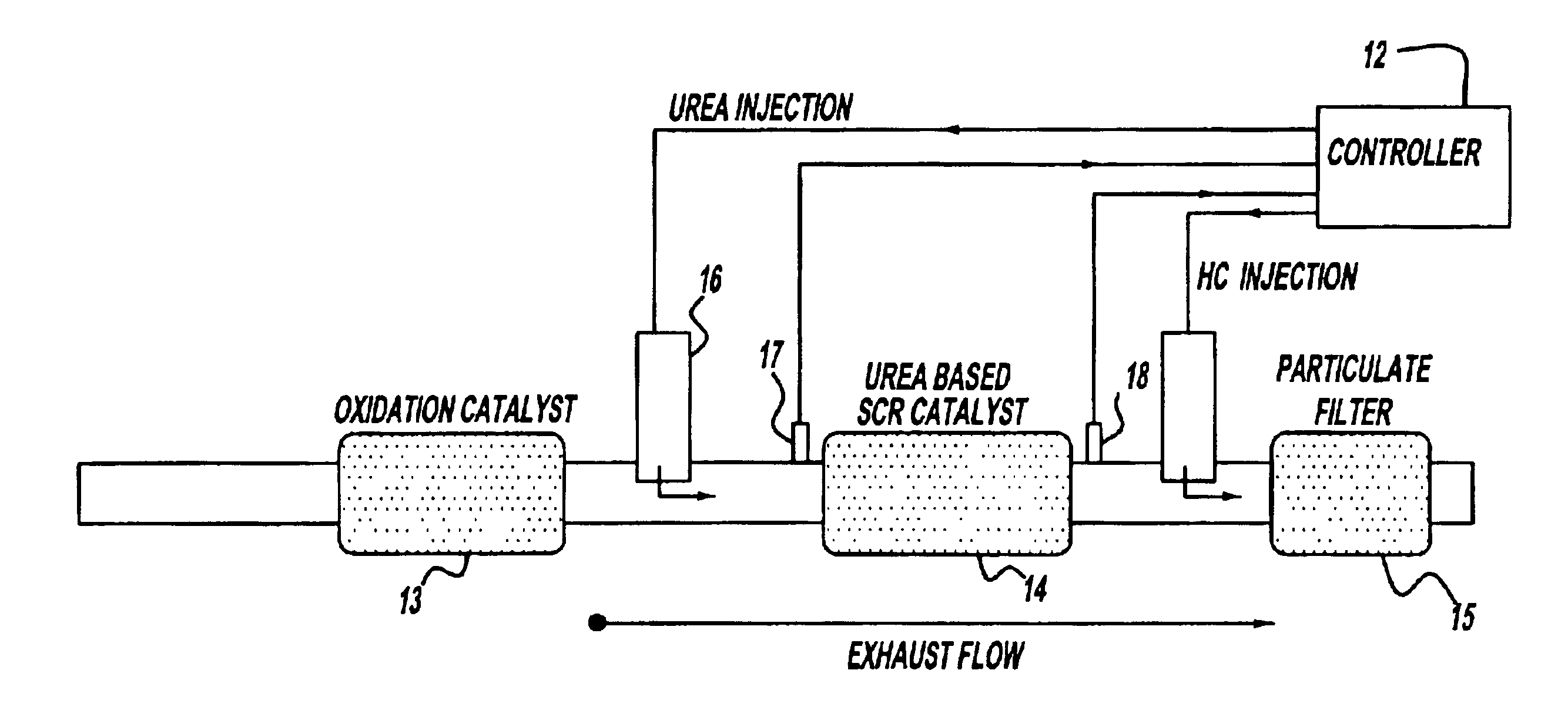
Exhaust gas aftertreatment systems
InactiveUS6928806B2Improve NOx conversion efficiencyHigh operating temperatureElectrical controlInternal combustion piston enginesExhaust fumesSystem configuration
A system for effective NOx and particulate matter control in a diesel or other lean burn internal combustion engine is presented. The system includes a urea-based SCR catalyst having an oxidation catalyst coupled upstream of it and a particulate filter coupled downstream of the SCR catalyst. This system configuration results in improved NOx conversion due to fast SCR catalyst warm-up and higher operating temperatures. Additionally, placing the particulate filter last in this system configuration reduces tailpipe ammonia emissions as well as prevents any thermal damage to the SCR catalyst due to the particulate filter regeneration.
Owner:FORD GLOBAL TECH LLC
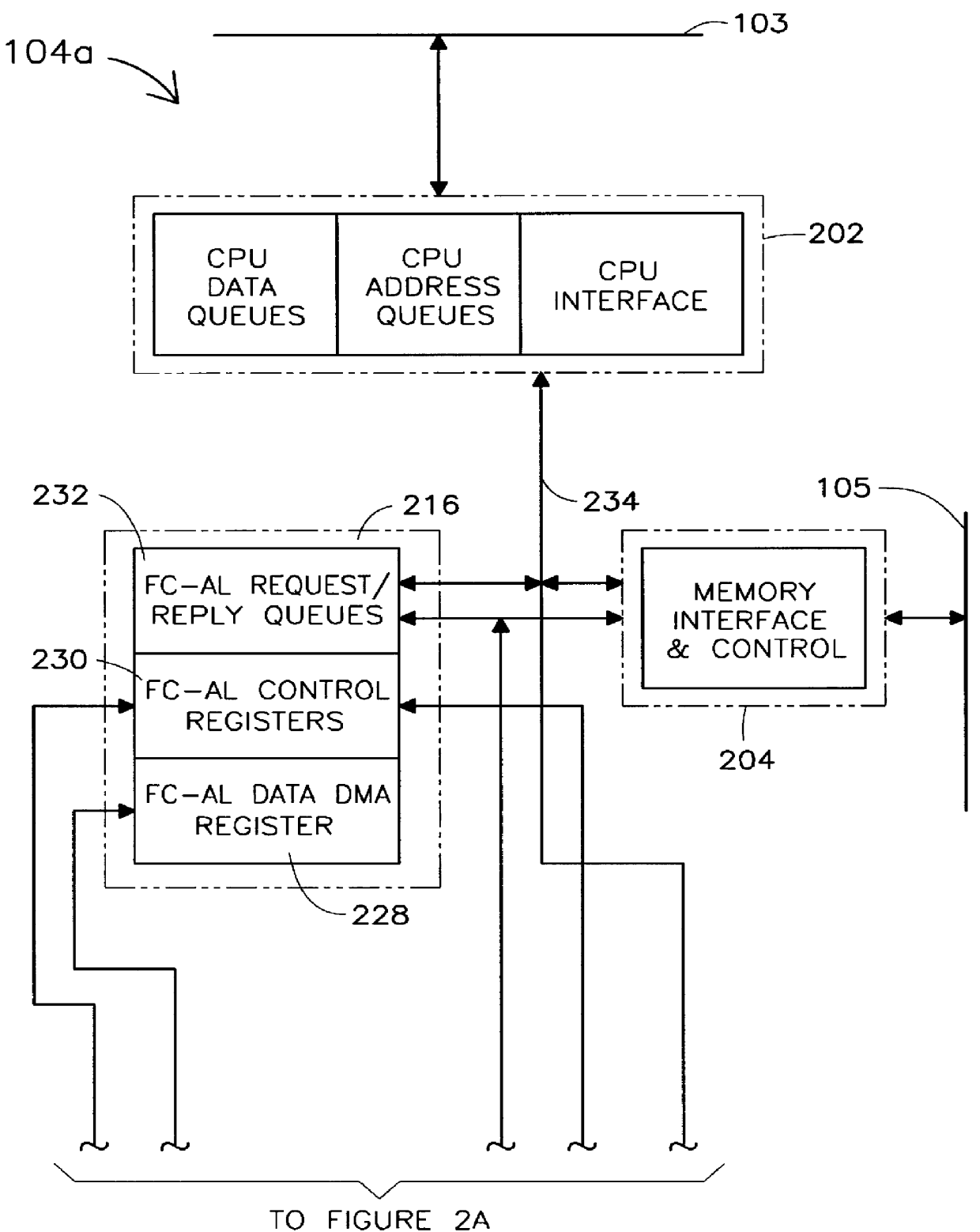
Dual purpose apparatus, method and system for accelerated graphics port and fibre channel arbitrated loop interfaces
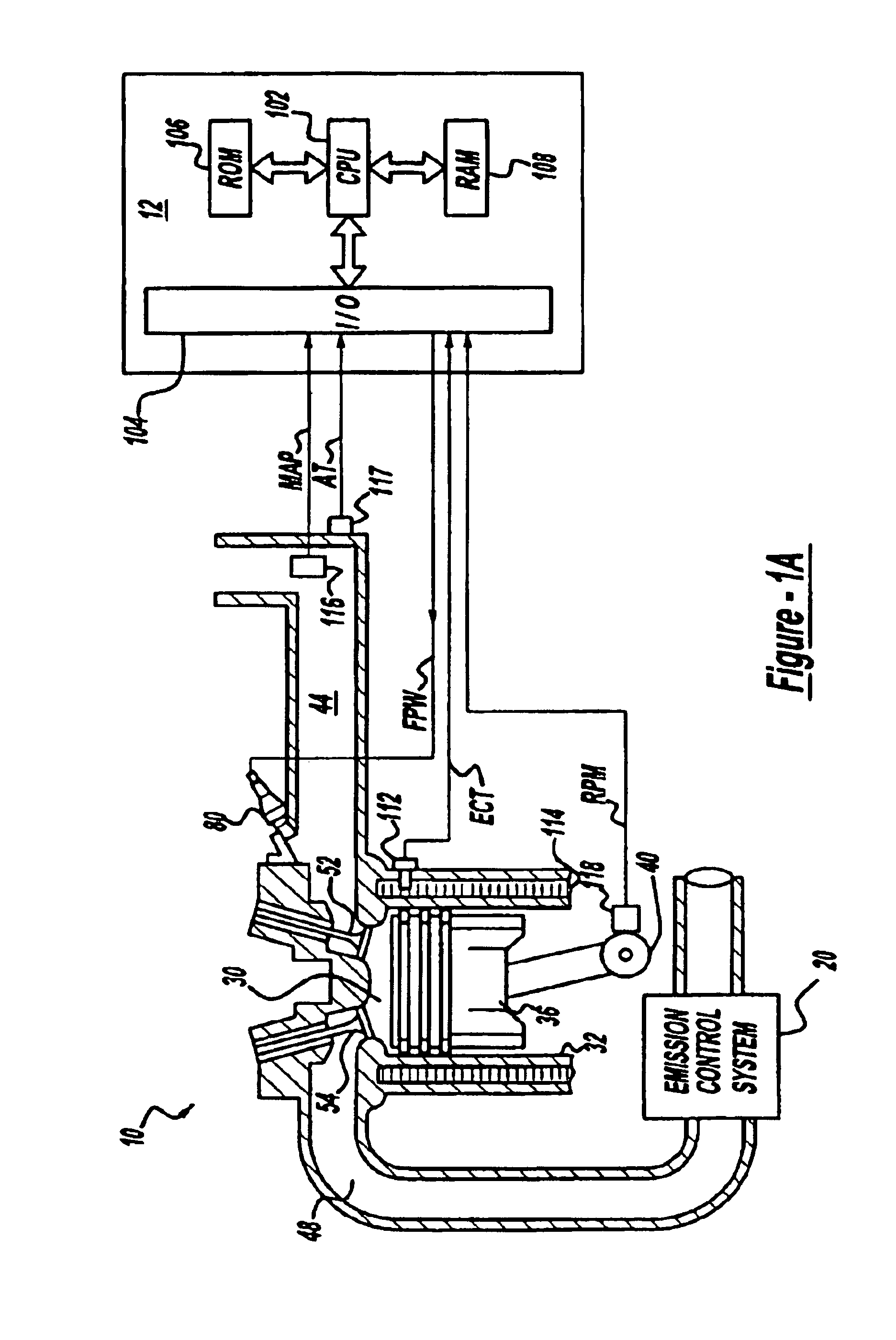
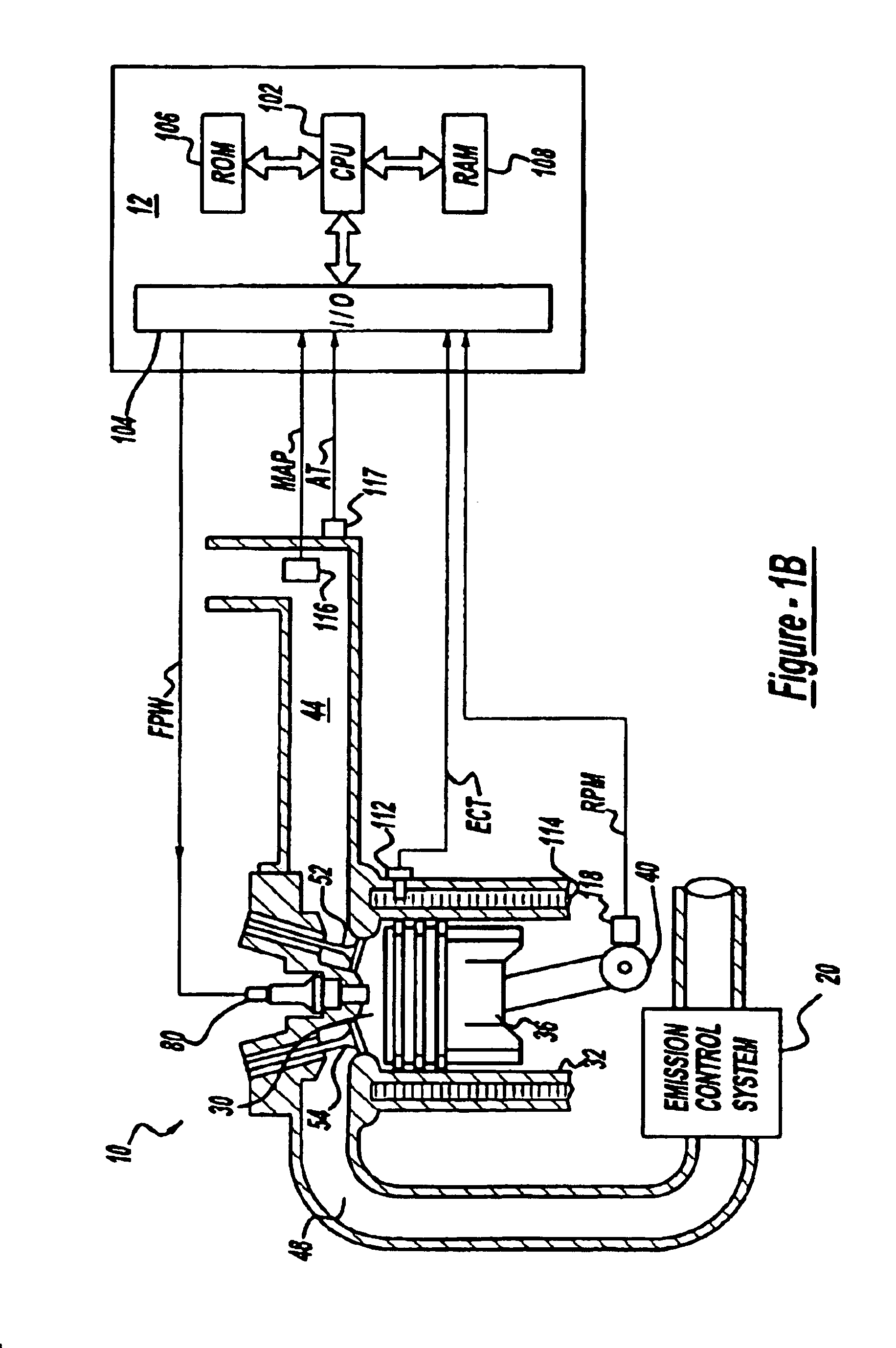
InactiveUS6057863ALow costIncrease the number ofDigital computer detailsImage data processing detailsFiberComputer hardware
A multiple use core logic chipset is provided in a computer system that may be configured either as a bridge between an accelerated graphics port ("AGP") bus and host and memory buses, or as an interface bridge between a Fibre Channel Arbitrated Loop ("FC-AL") interface and the host and memory buses. The function of the multiple use chipset is determined at the time of manufacture of the computer system or in the field whether an AGP bus bridge or an FC-AL bridge interface is to be implemented. Selection of the type of bus bridge (AGP or FC-AL bridge interface) in the multiple use core logic chipset may be made by a hardware signal input, or by software during computer system configuration or power on self test ("POST"). Software configuration may also be determined upon detection of either an AGP or a FC-AL bridge interface device connected to the common AGP / FC-AL bus. FC-AL information may be stored in the computer system main memory using the high speed FC-AL bridge interface.
Owner:HEWLETT PACKARD DEV CO LP +1
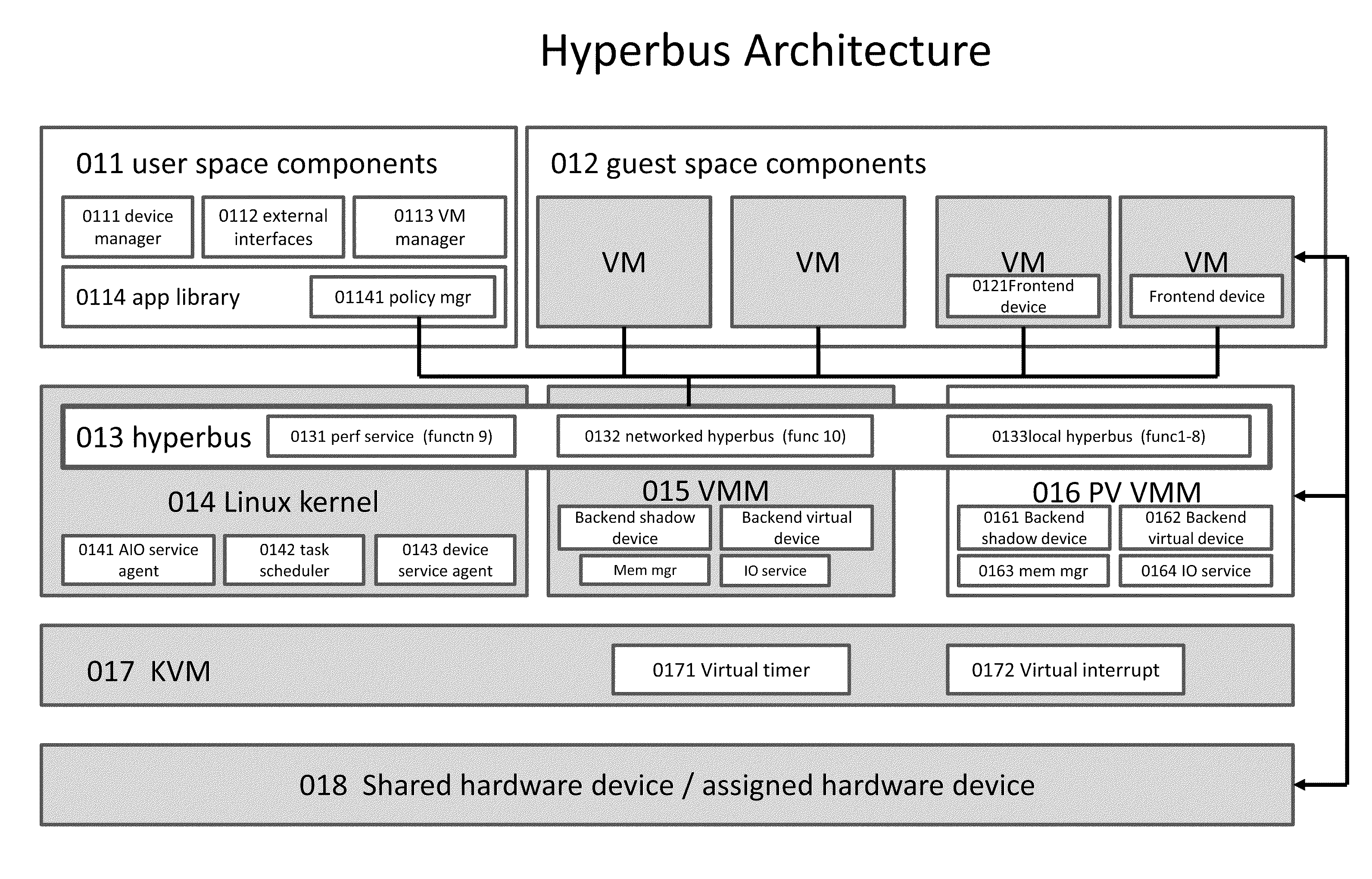
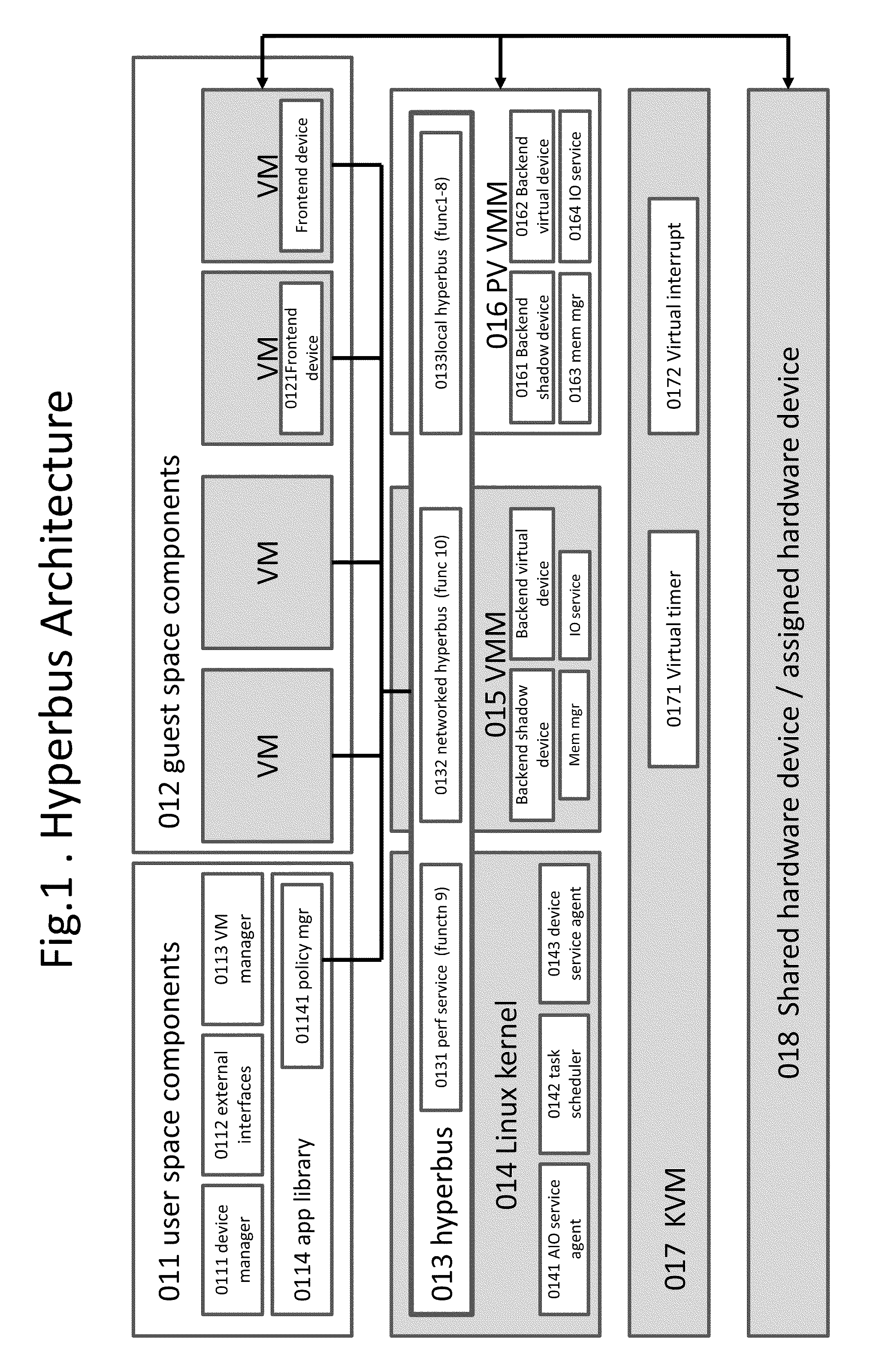
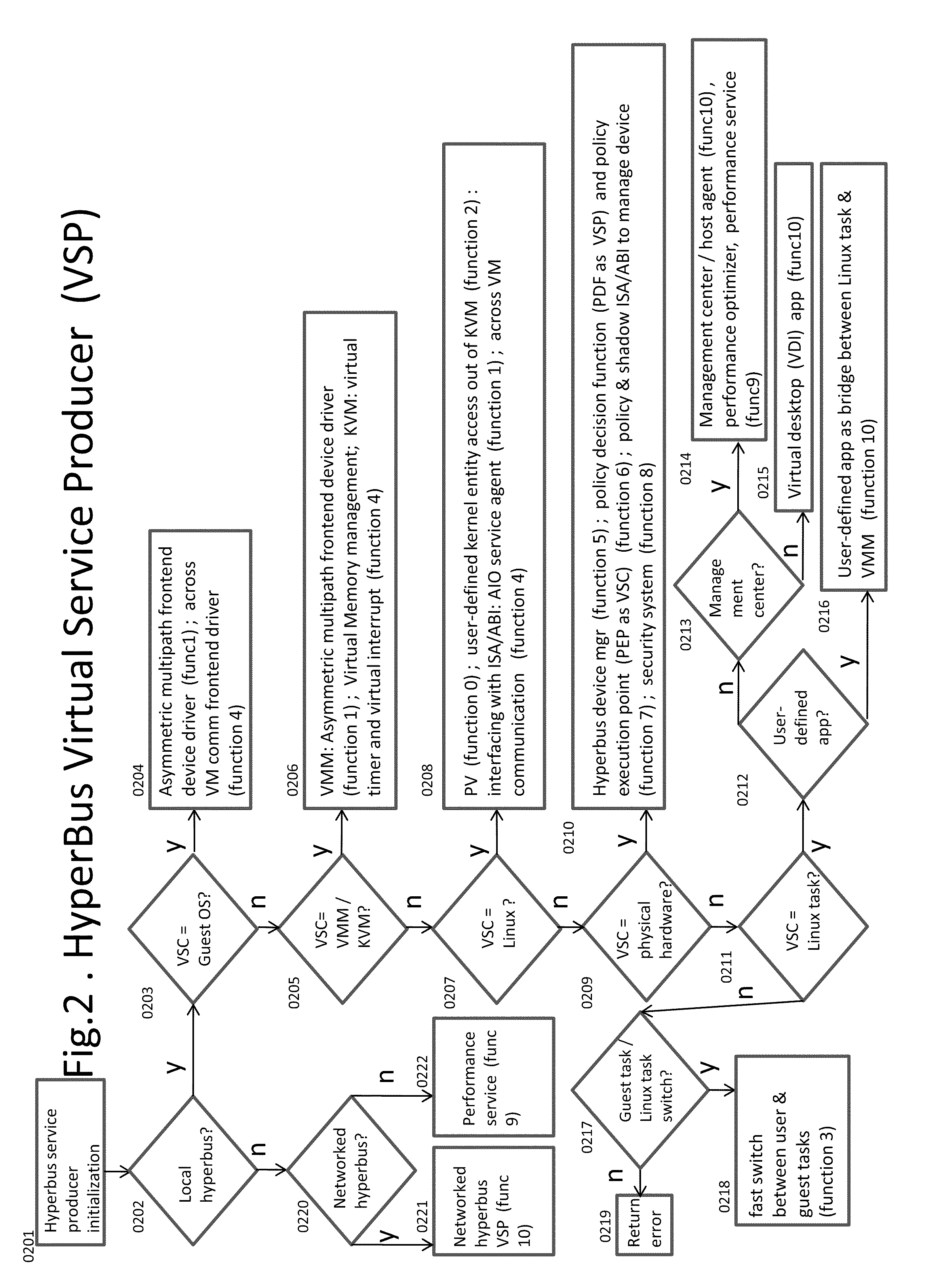
Kernel Bus System to Build Virtual Machine Monitor and the Performance Service Framework and Method Therefor
InactiveUS20110296411A1Fast deliveryImprove performanceSoftware simulation/interpretation/emulationMemory systemsVirtualizationSystem configuration
Some embodiments concern a kernel bus system for building at least one virtual machine monitor. The kernel bus system is based on kernel-based virtual machine. The kernel bus system is configured to run on a host computer. The host computer comprising one or more processors, one or more hardware devices, and memory. The kernel bus system can include: (a) a hyperbus; (b) one or more user space components; (c) one or more guest space components configured to interact with the one or more user space components via the hyperbus; (d) one or more VMM components having one or more frontend devices configure to perform I / O operations with the one or more hardware devices of the host computer using a zero-copy method or non-pass-thru method; (e) one or more para-virtualization components having (1) a virtual interrupt configured to use one or more processor instructions to swap the one or more processors of the host computer between a kernel space and a guest space; and (2) a virtual I / O driver configured to enable synchronous I / O signaling, asynchronous I / O signaling and payload delivery, and pass-through delivery independent an QEMU emulation; and (f) one or more KVM components. The hyperbus, the one or more user space components, the one or more guest space components, the one or more VMM components, the one or more para-virtualization components, and the one or more KVM components are configured to run on the one or more processors of the host computer. Other embodiments are disclosed.
Owner:TRANSOFT
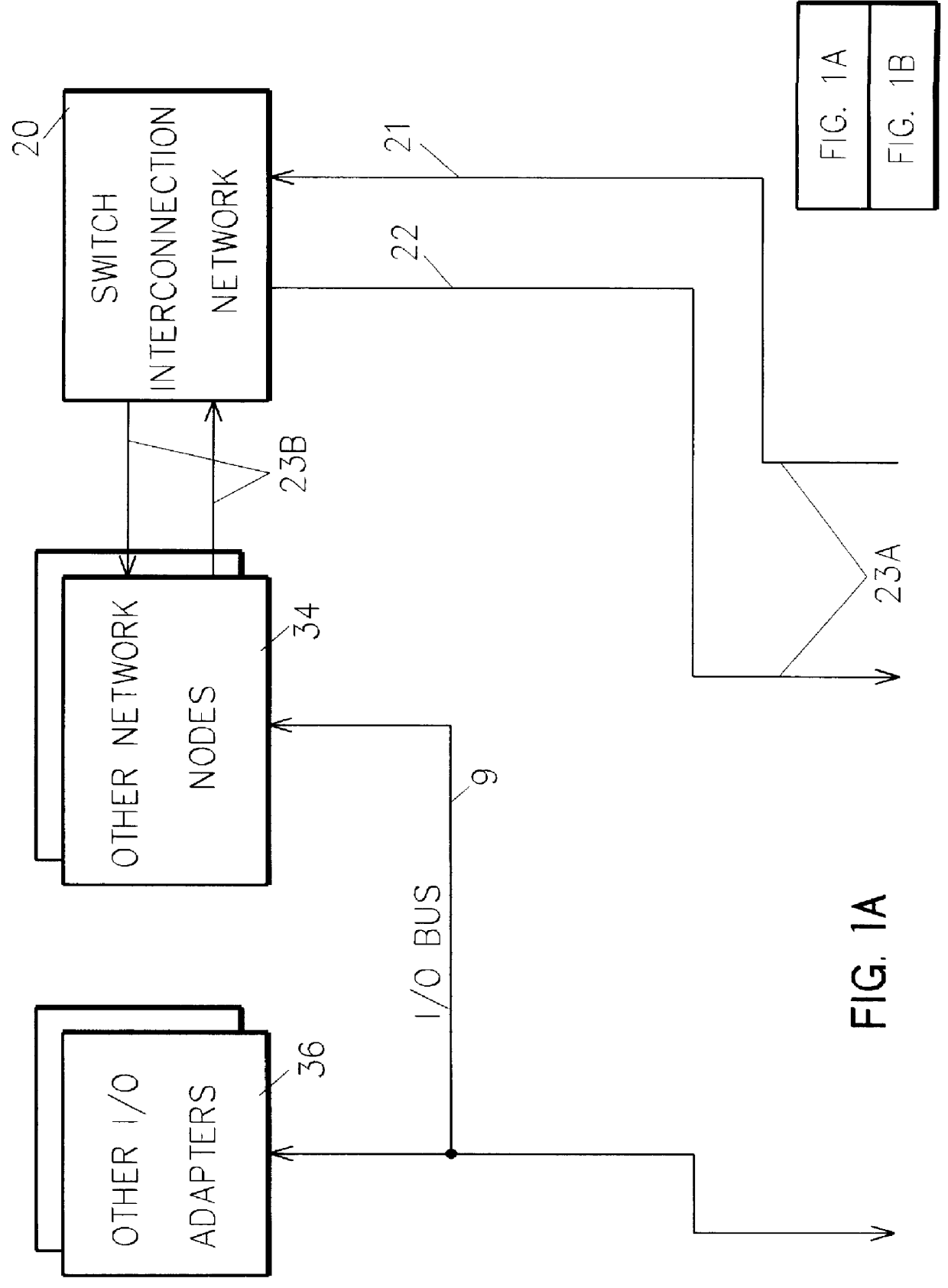
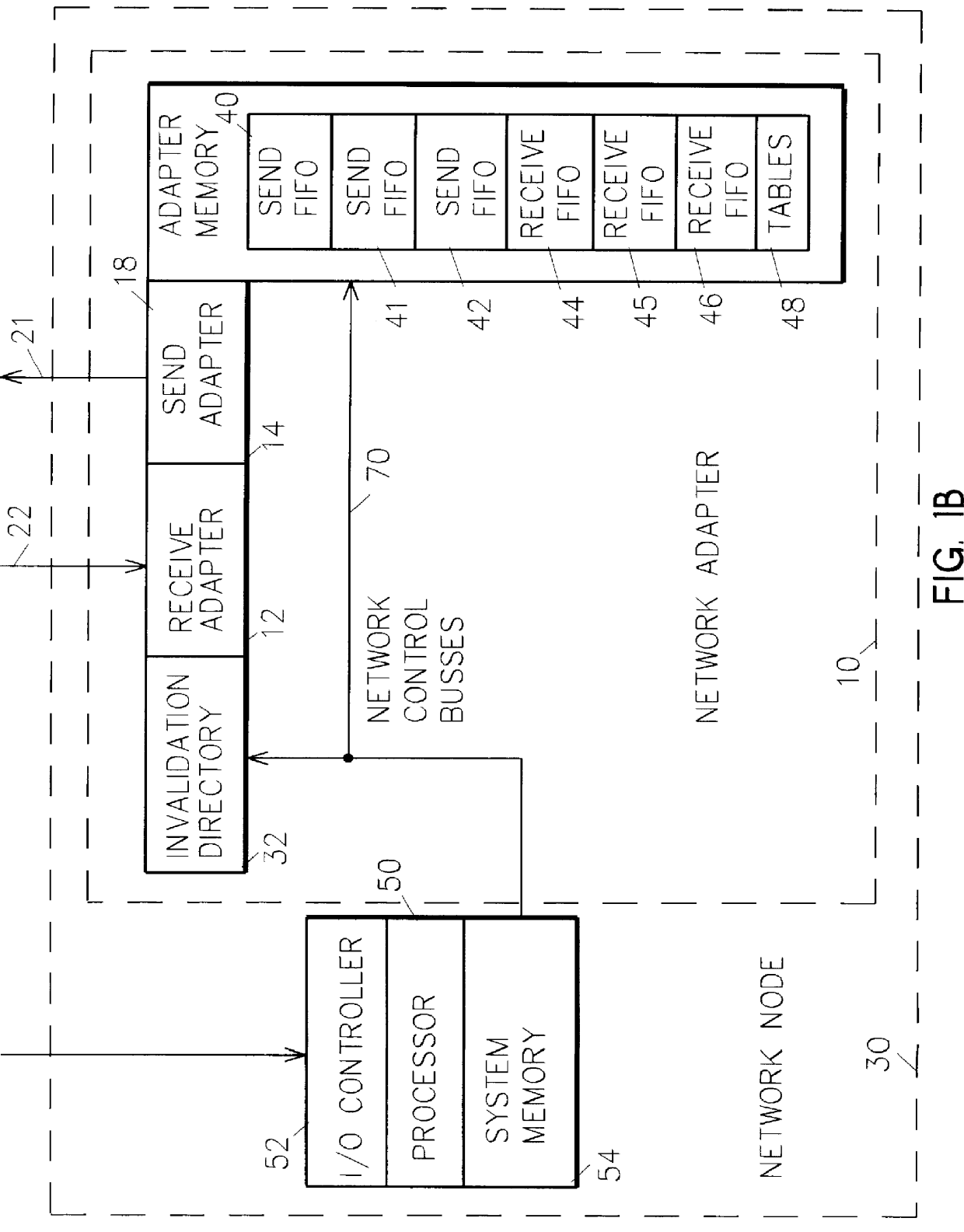
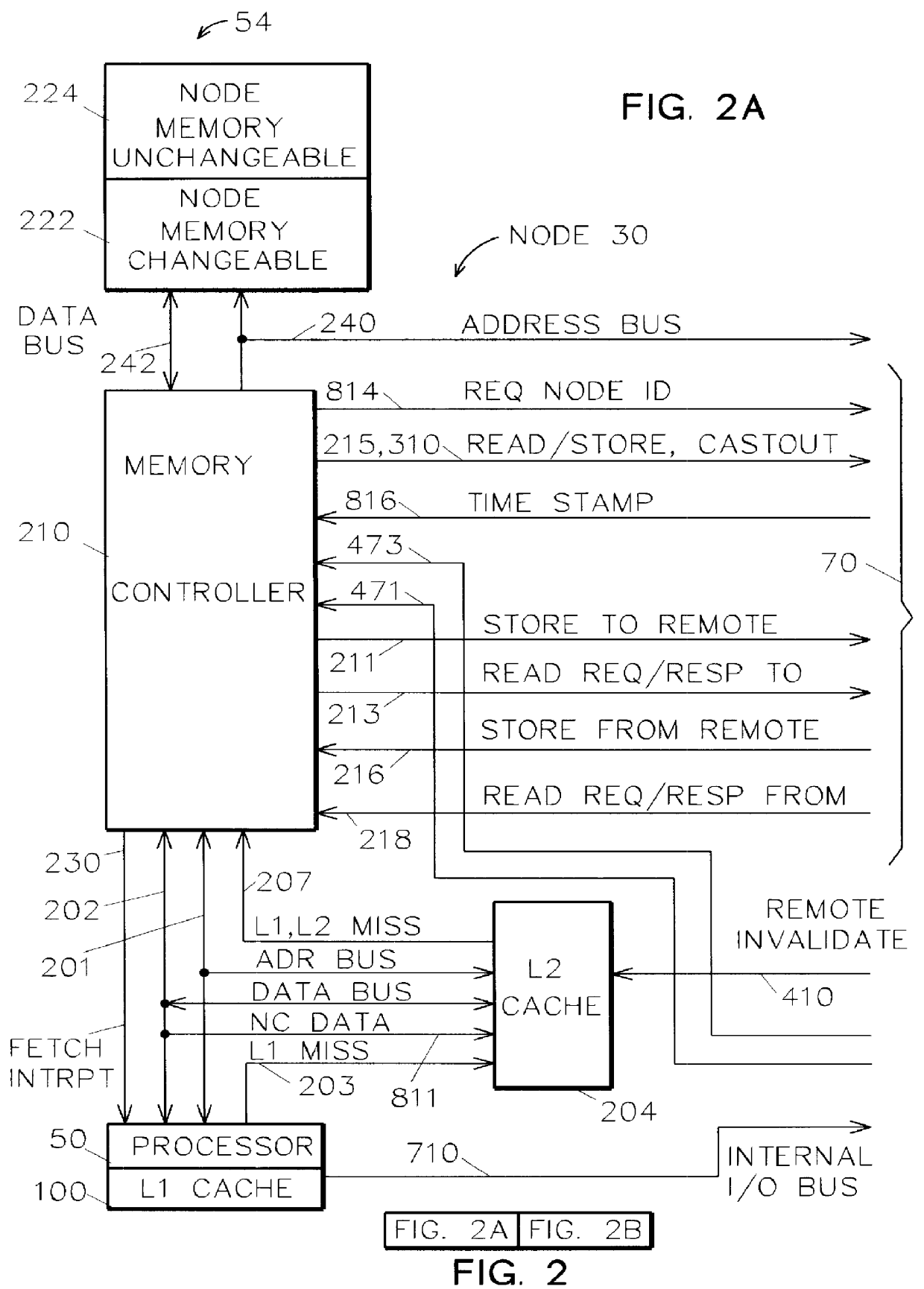
Memory controller for controlling memory accesses across networks in distributed shared memory processing systems
InactiveUS6044438AMore efficient cache coherent systemData processing applicationsMemory adressing/allocation/relocationRemote memory accessRemote direct memory access
A shared memory parallel processing system interconnected by a multi-stage network combines new system configuration techniques with special-purpose hardware to provide remote memory accesses across the network, while controlling cache coherency efficiently across the network. The system configuration techniques include a systematic method for partitioning and controlling the memory in relation to local verses remote accesses and changeable verses unchangeable data. Most of the special-purpose hardware is implemented in the memory controller and network adapter, which implements three send FIFOs and three receive FIFOs at each node to segregate and handle efficiently invalidate functions, remote stores, and remote accesses requiring cache coherency. The segregation of these three functions into different send and receive FIFOs greatly facilitates the cache coherency function over the network. In addition, the network itself is tailored to provide the best efficiency for remote accesses.
Owner:IBM CORP
Systems and methods for sealing in site-isolated reactors
InactiveUS20070199510A1Semiconductor/solid-state device manufacturingChemical vapor deposition coatingComputer moduleEngineering
Substrate processing systems and methods are described for site-isolated processing of substrates. The processing systems include numerous site-isolated reactors (SIRs). The processing systems include a reactor block having a cell array that includes numerous SIRs. A sleeve is coupled to an interior of each of the SIRs. The sleeve includes a compliance device configured to dynamically control a vertical position of the sleeve in the SIR. A sealing system is configured to provide a seal between a region of a substrate and the interior of each of the SIRs. The processing system can include numerous modules that comprise one or more site-isolated reactors (SIRs) configured for one or more of molecular self-assembly and combinatorial processing of substrates.
Owner:INTERMOLECULAR
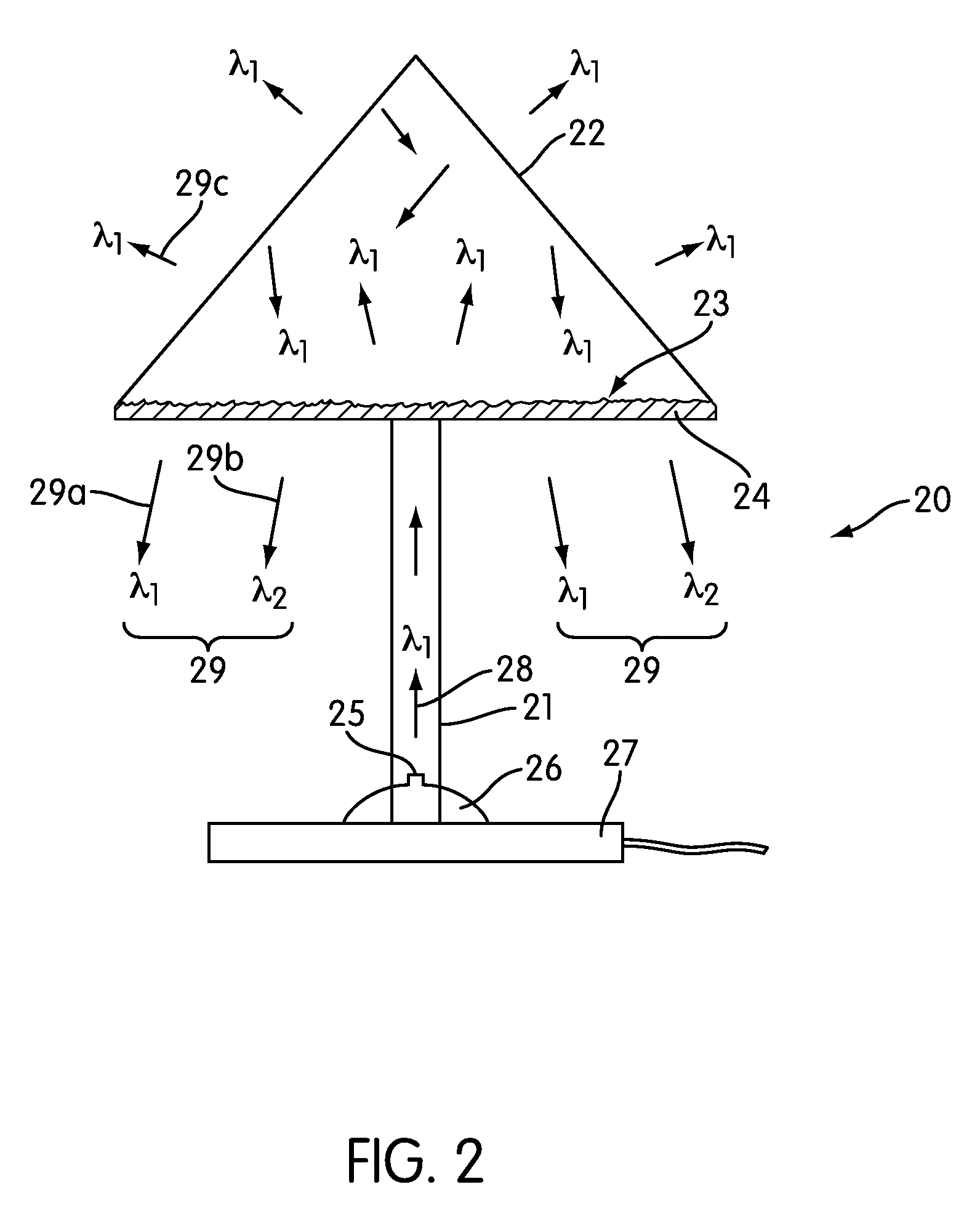
Light emitting diode lighting system
InactiveUS20080192458A1Accelerate emissionsPlanar light sourcesPoint-like light sourcePhotoluminescenceEffect light
A lighting system for generating an illumination product comprises an excitation source, blue / UV LED, operable to generate excitation radiation and a remotely located phosphor, photo luminescent material. Excitation radiation is guided from the excitation source to the phosphor by a waveguiding medium, the waveguiding medium being configured such that the distance the radiation travels from the excitation source to the phosphor layer is at least one centimeter in length. The UV / blue excitation source provides excitation radiation to the phosphor(s), causing the phosphor(s) to photo luminesce, and it may also provide a component of the final illumination product. The configuration of the waveguide allows a greater flexibility in lighting system configurations, such as hanging lighting fixtures, desk lighting fixtures, floor standing lighting fixtures, desk lamps, track lighting, spot lighting, accent lighting, lighting panels, inspection lamps and endoscopes.
Owner:INTEMATIX
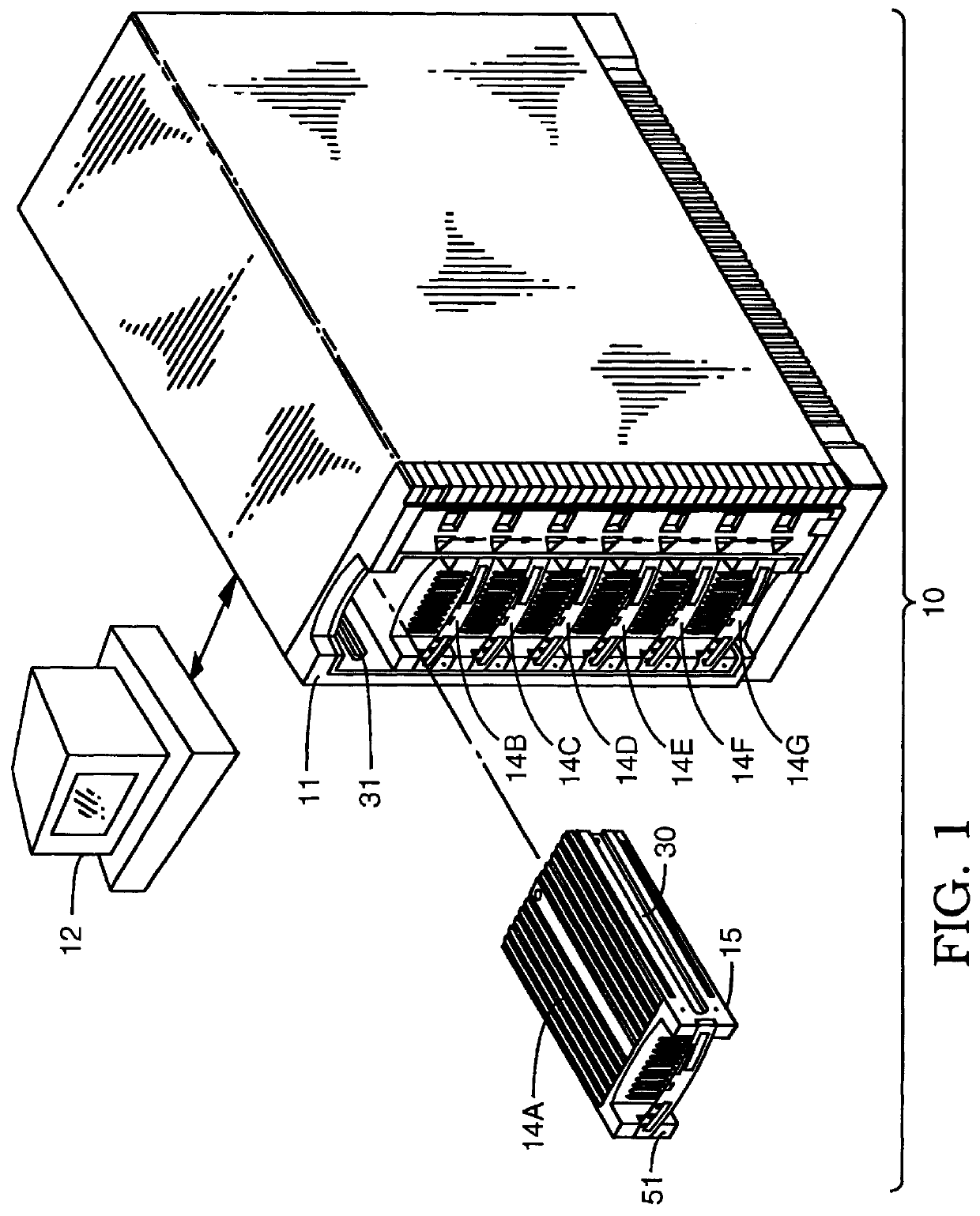
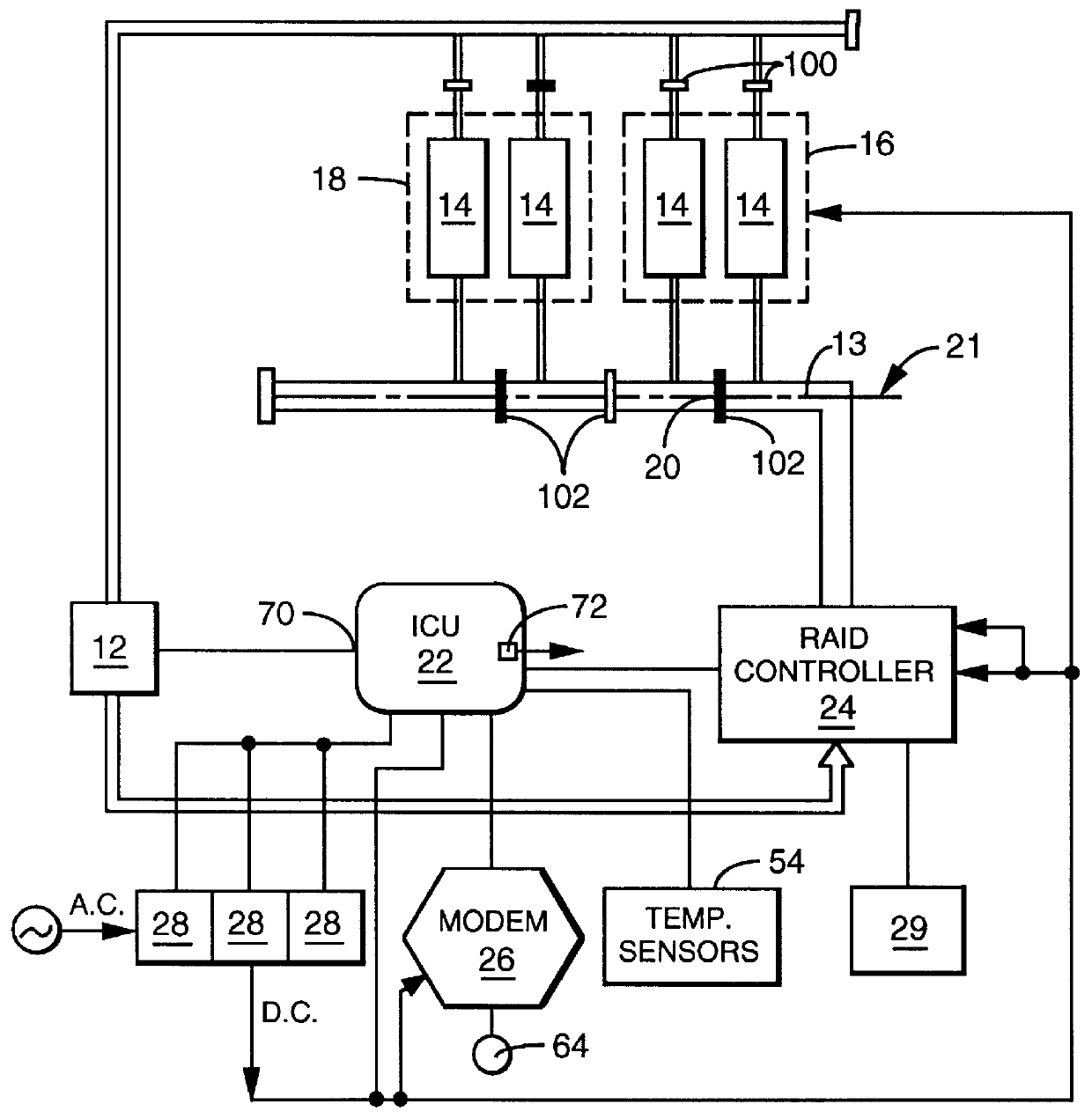
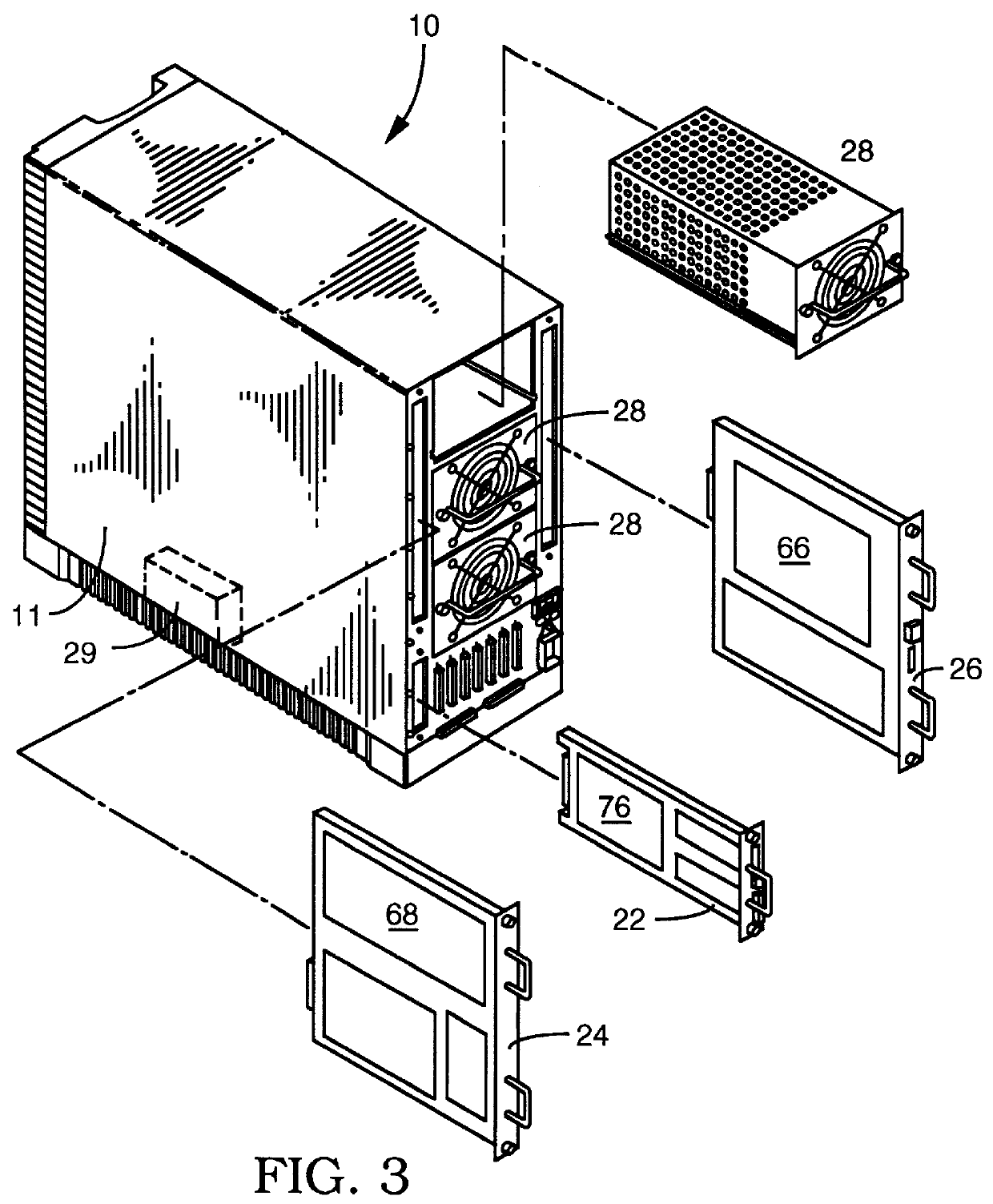
User configurable raid system with multiple data bus segments and removable electrical bridges
InactiveUS6076142ACarrier constructional parts dispositionError detection/correctionMass storageModem device
A user configurable RAID system designed to provide RAID functions as well as mass storage functions in a non-RAID mode. Flexibility is built into the system to allow the user to configure the SCSI bus to which removable drive modules are connected into one or more channels to define some of the drive modules in a RAID set and others as stand-alone drives which are independently operated or logically grouped and operated in a non-RAID mode. Removable internal SCSI bridges allow the SCSI bus to be configured into one or more channels. In the RAID mode, the system is configured to prevent a wrong drive from being removed from the system in the event of a drive failure. The system automatically unlatches only the failed drive. The RAID system includes an intelligent control unit ("ICU"), a RAID controller and a modem. The ICU allows the system administrator to access the RAID system Monitor Utility so that the status of the system may be monitored and its configuration changed. The ICU also monitors the failure status of the various components of the system. The ICU has a built-in pager feature that can be configured with the Monitor Utility to page the system administrator via the modem when a component or system failure is encountered. The RAID controller controls the functions of the RAID set as programmed and configured using the Monitor Utility. The Monitor Utility may be remotely accessed using a computer via the modem. Redundant removable power supply and fan units are provided to improve system integrity. The removable power supply and fan units are configured such when the unit is plugged into the system housing, the fan is first turned on and the power through the unit is allowed to stabilize before turning on the power supply to begin providing DC power to the components in the system. A set of manual release buttons are provided for manually unlatching the drive modules from the system housing. A locking mechanism is provided for simultaneously locking all the manual release buttons.
Owner:MICRONET TECH
System methodology for automatic local network discovery and firewall reconfiguration for mobile computing devices
ActiveUS20030167405A1Easy to detectDigital data processing detailsHardware monitoringNetwork generationUnique identifier
A system providing methodologies for automatically detecting when a computing device is plugged into a new network is described. The system includes methods for detecting a connection to a new network by receiving notice of, and evaluating, changes to an existing network configuration. The system profiles and generates an identity for the new network. This includes collecting information about the network to uniquely identify it and generating a unique identifier for the network. Once a network has been profiled, a user may decide whether or not to include it as part of a trusted zone. Alternatively, this decision may be guided by policy established by a system administrator or user. The system automatically reconfigures a firewall to include or exclude the network from the trusted zone based upon this decision. The profile of each network is stored so that the next time the device is connected to the same network it remembers the network and applies the same security settings previously adopted. The stored profile also facilitates the detection of changes to the network configuration or the connection to a new network.
Owner:CHECK POINT SOFTWARE TECH INC
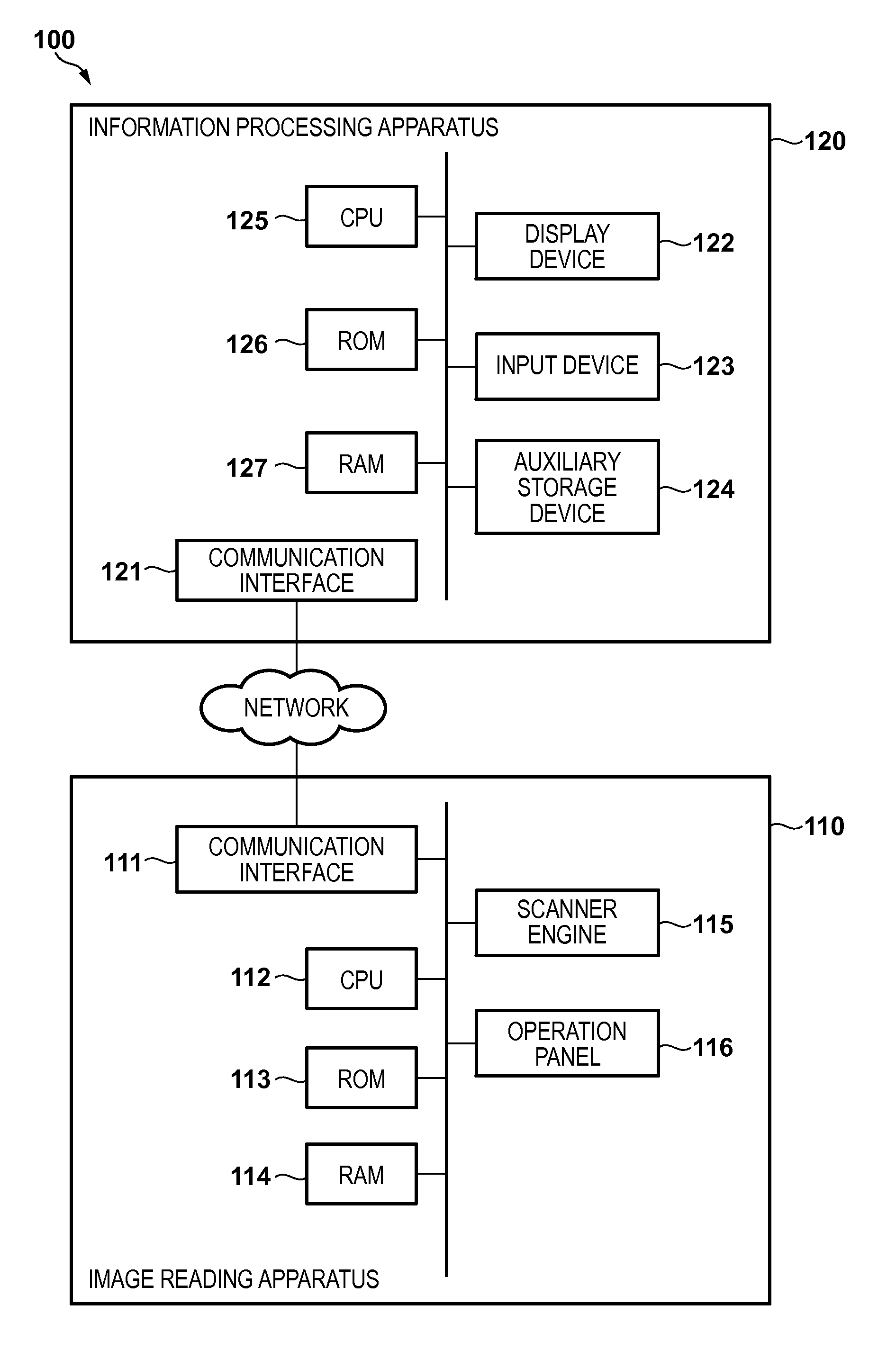
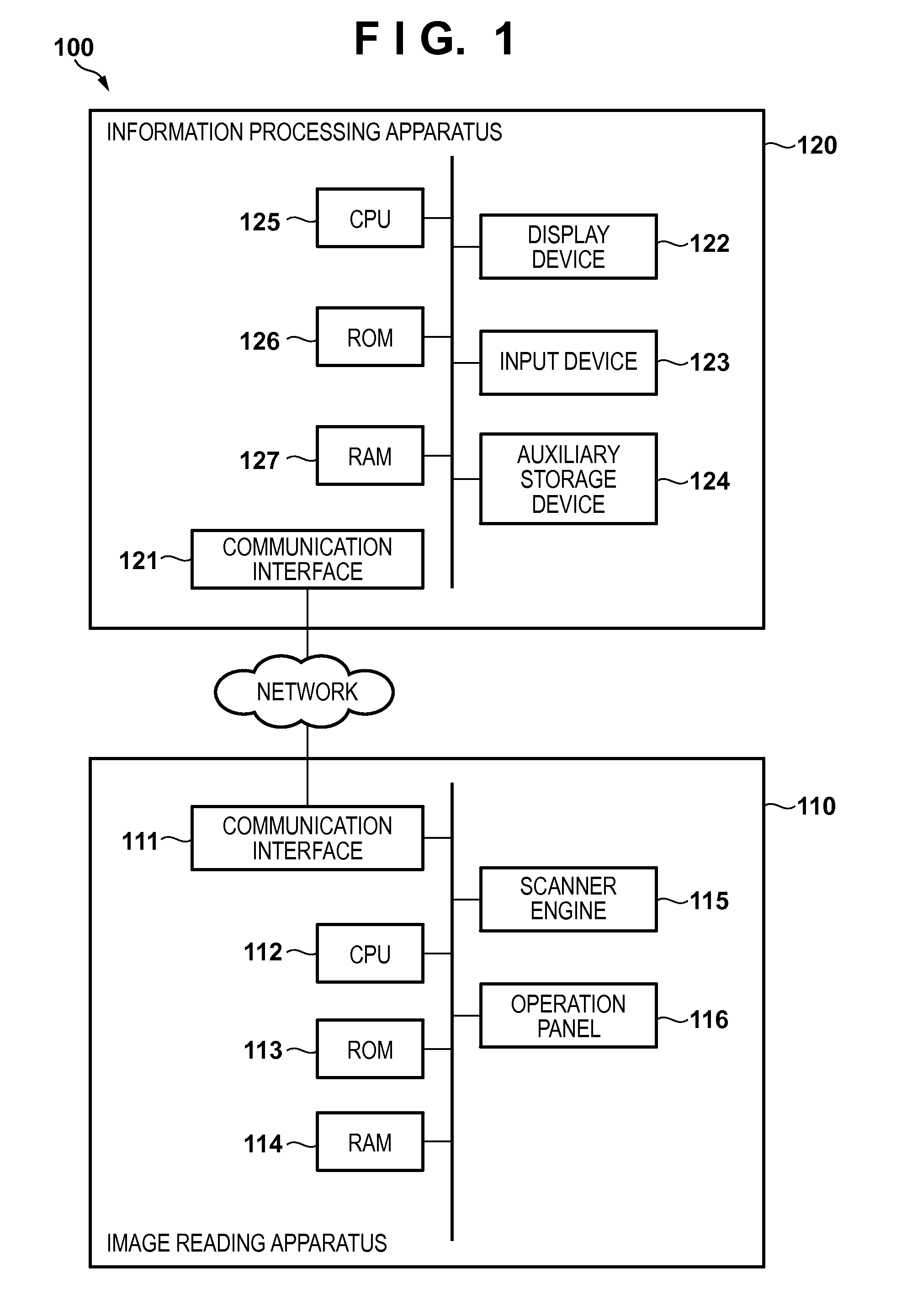
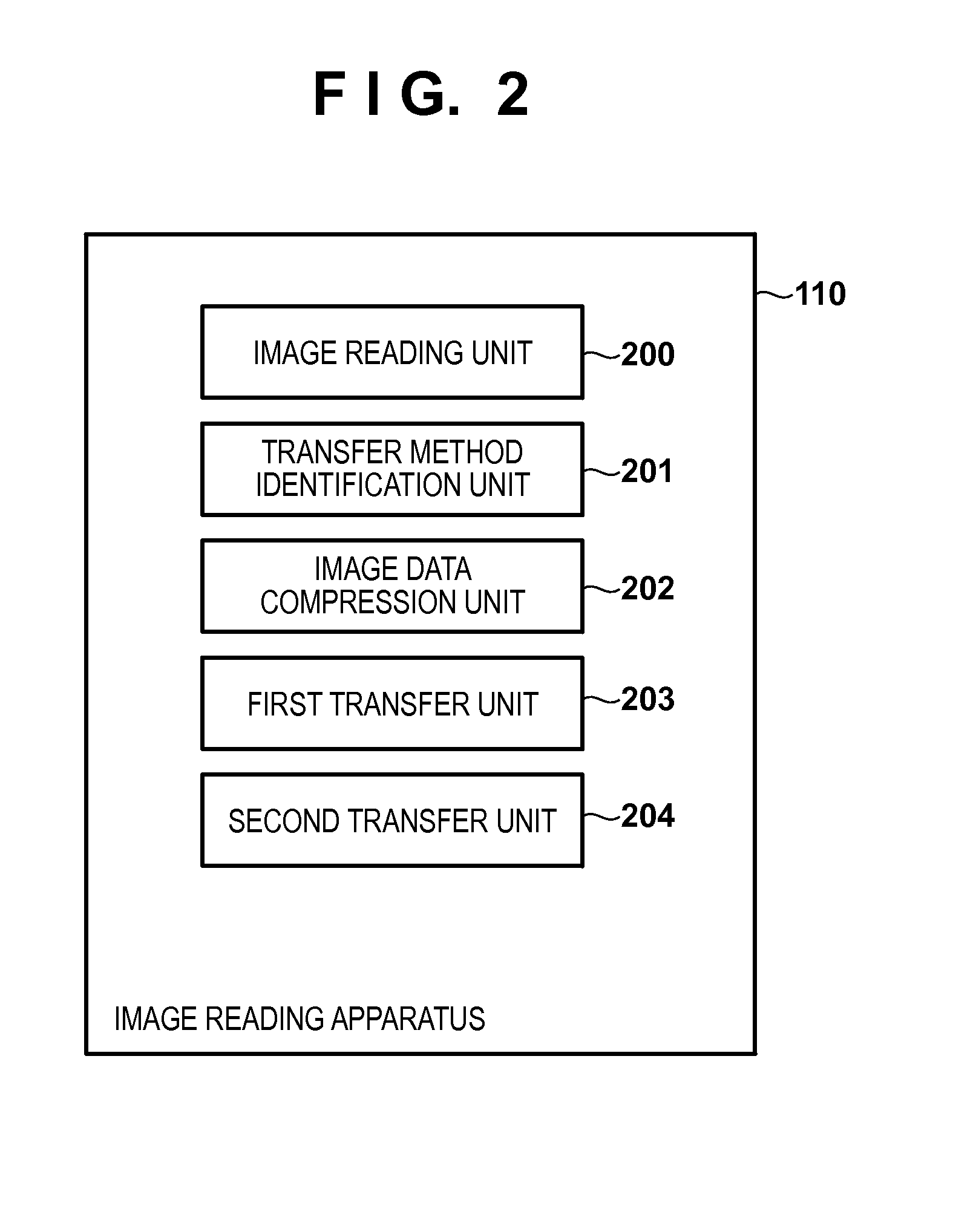
Transfer controlling method, transfer controlling apparatus, and storage medium storing program
The data format of image data when an image reading apparatus transfers, to an external apparatus, the image data obtained by reading an original by the image reading apparatus is decided based on system configuration information of the image reading apparatus and setting information corresponding to processing to be executed on the image data in the external apparatus. Control for transferring, from the image reading apparatus to the external apparatus, the image data of the decided data format is performed.
Owner:CANON KK
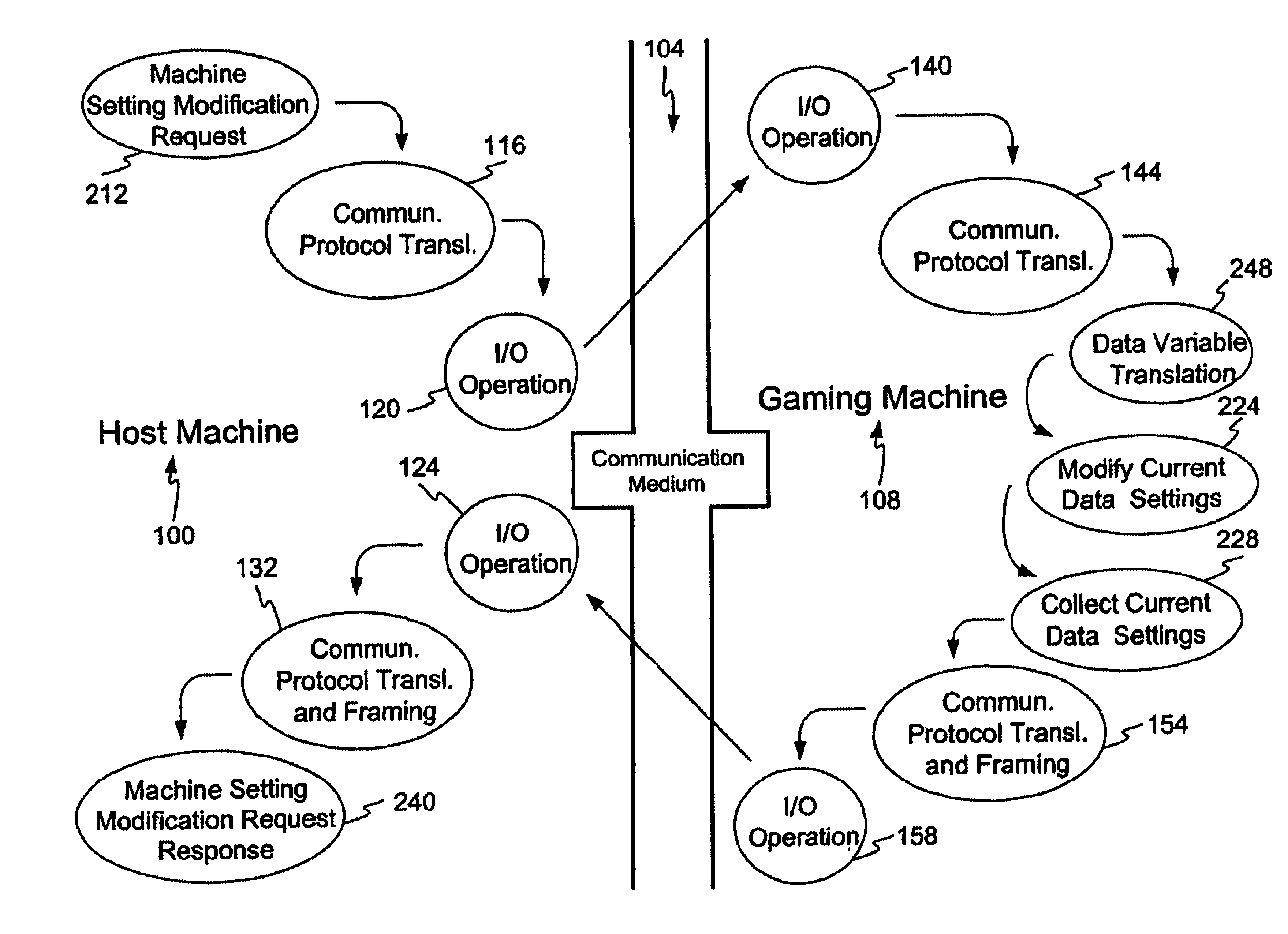
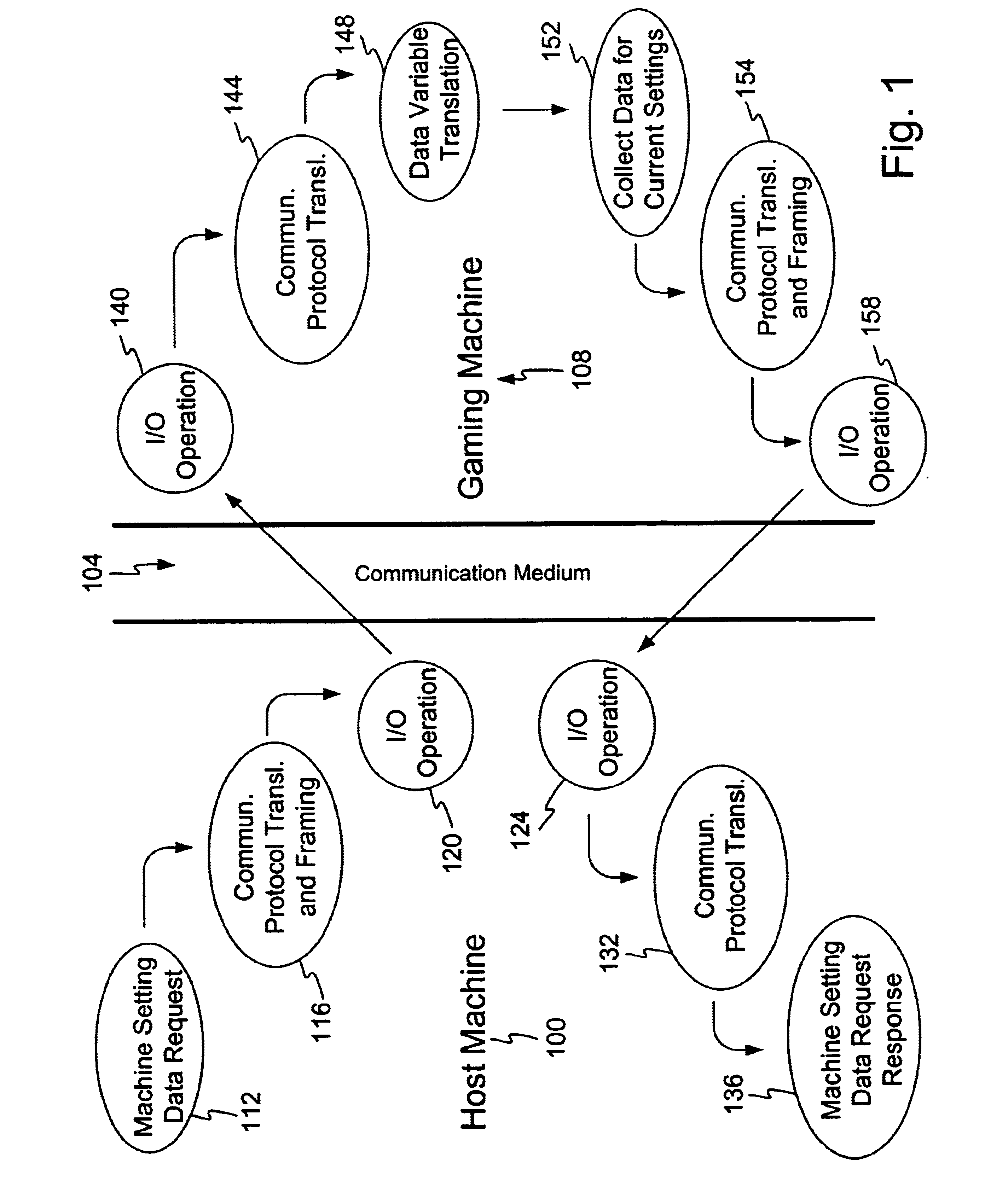
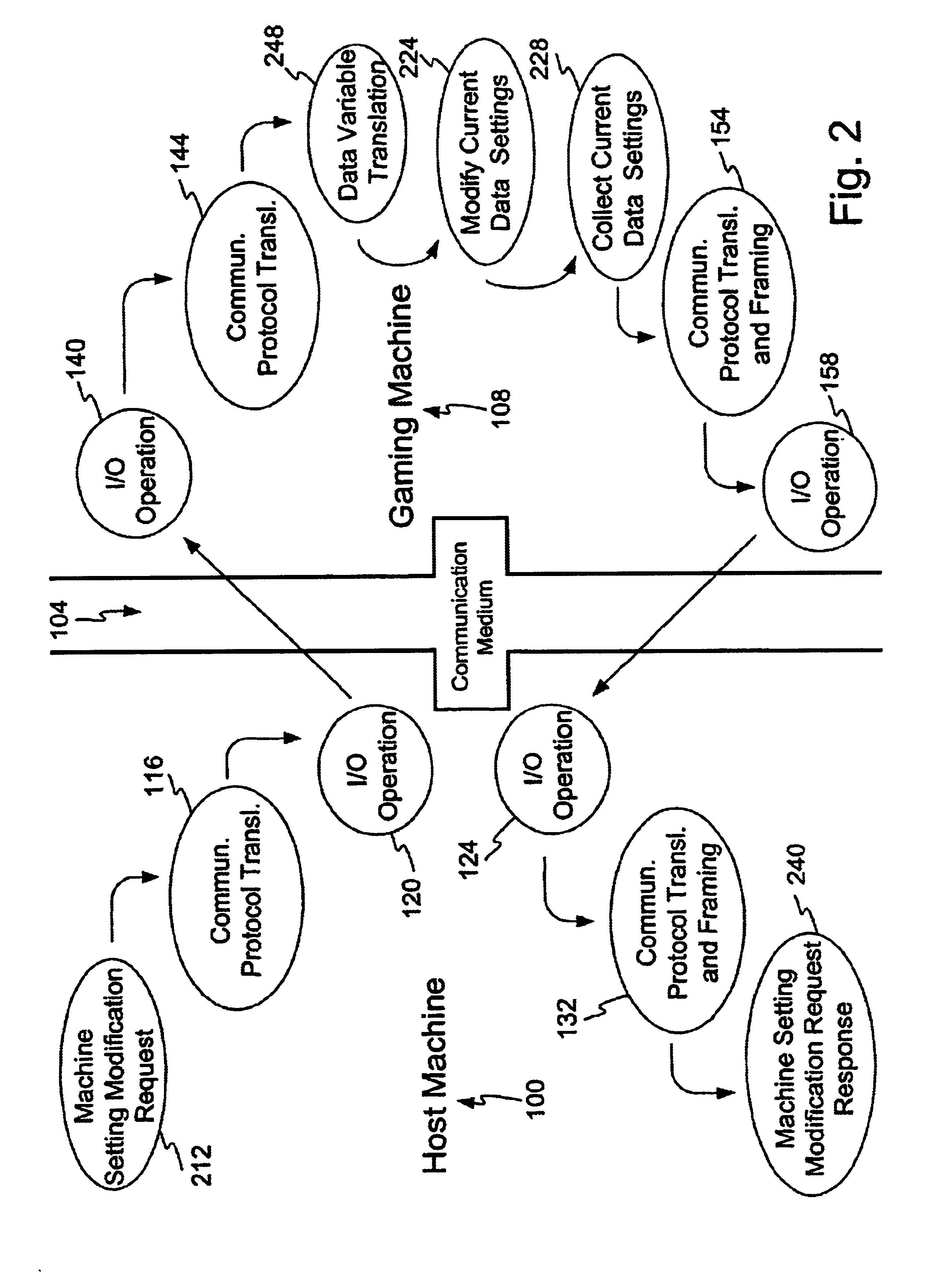
Communication protocol for gaming system configuration
InactiveUS6884174B2Overcomes drawbackApparatus for meter-controlled dispensingVideo gamesComputer hardwareNetwork Communication Protocols
A method and apparatus for communicating gaming machine settings is disclosed. In one embodiment a universal configuration communication protocol is provided for retrieving or modifying, over a network, current gaming machine setting of a remotely located gaming machine. A translation table may be implemented with the communication protocol to achieve variable translation between different gaming machine platforms. In one embodiment the gaming machine status is requested prior to activating the communication protocol to prevent interruption of game play. In one embodiment activation of the communication protocol may result in the gaming machine momentarily entering an inactive status.
Owner:IGT
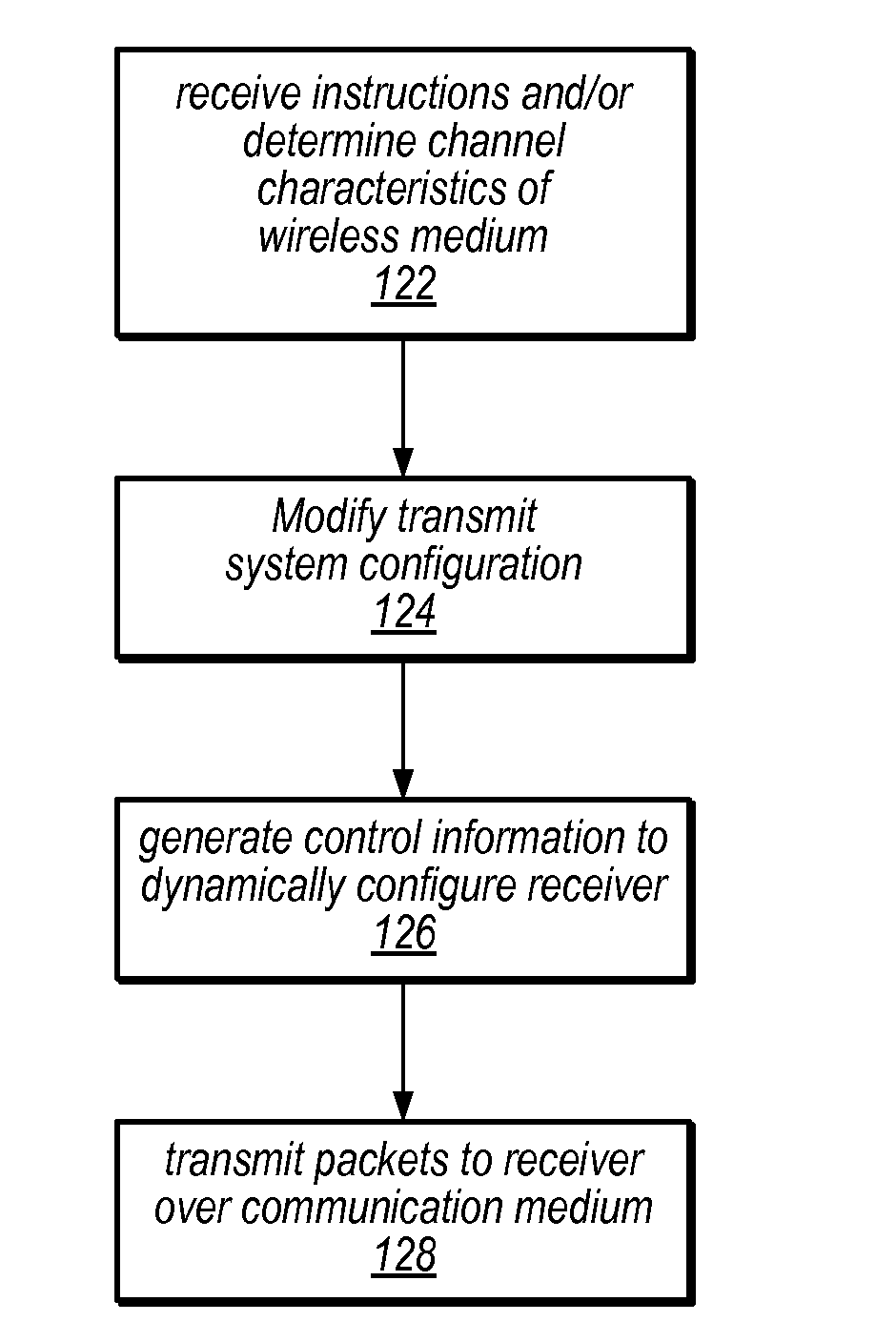
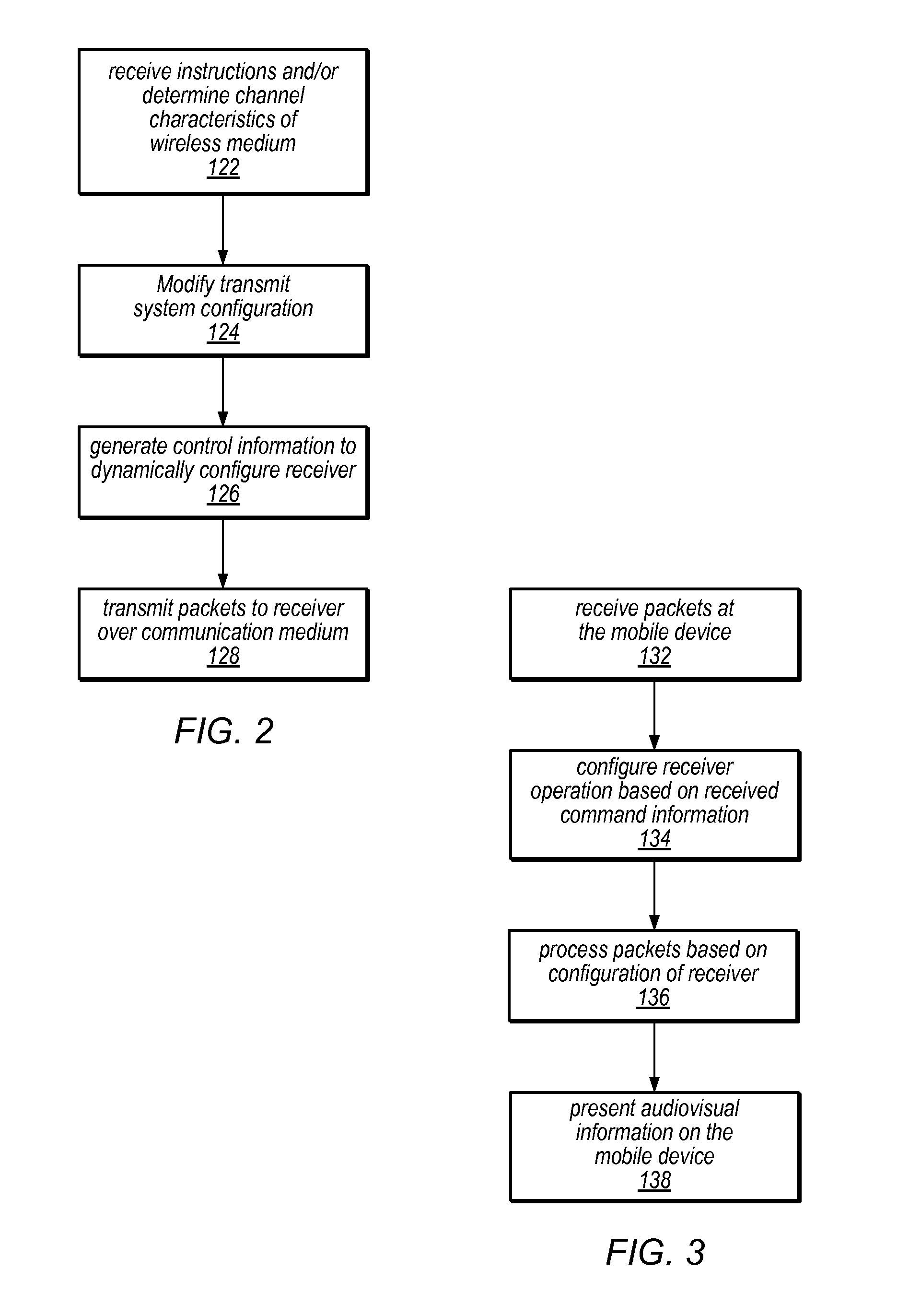
Mobile television broadcast system
ActiveUS20090013356A1Efficiently specifiedFunction increaseCode conversionError correction/detection by combining multiple code structuresCurrent channelSystem configuration
A digital television broadcast system with transmission and / or reception of digital television signals for improved mobile reception. The communication layers in the transmit and receive portions of the transmission system can be dynamically modified, e.g., based on usage patterns or current channel characteristics. The transmission system also provides for cross layer control, whereby parameters in various of the communication layers are analyzed to determine appropriate updates to the system configuration.
Owner:COHERENT LOGIX
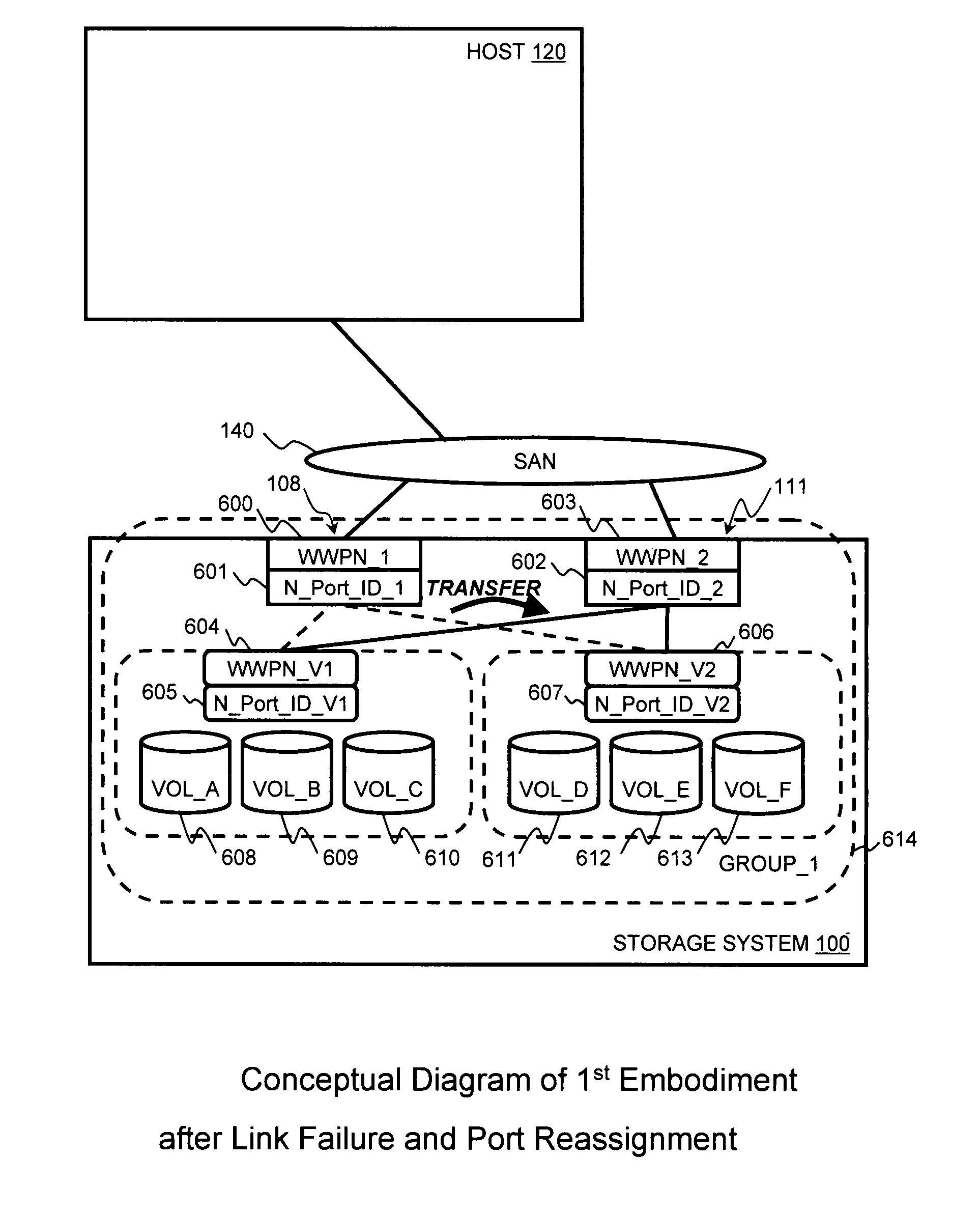
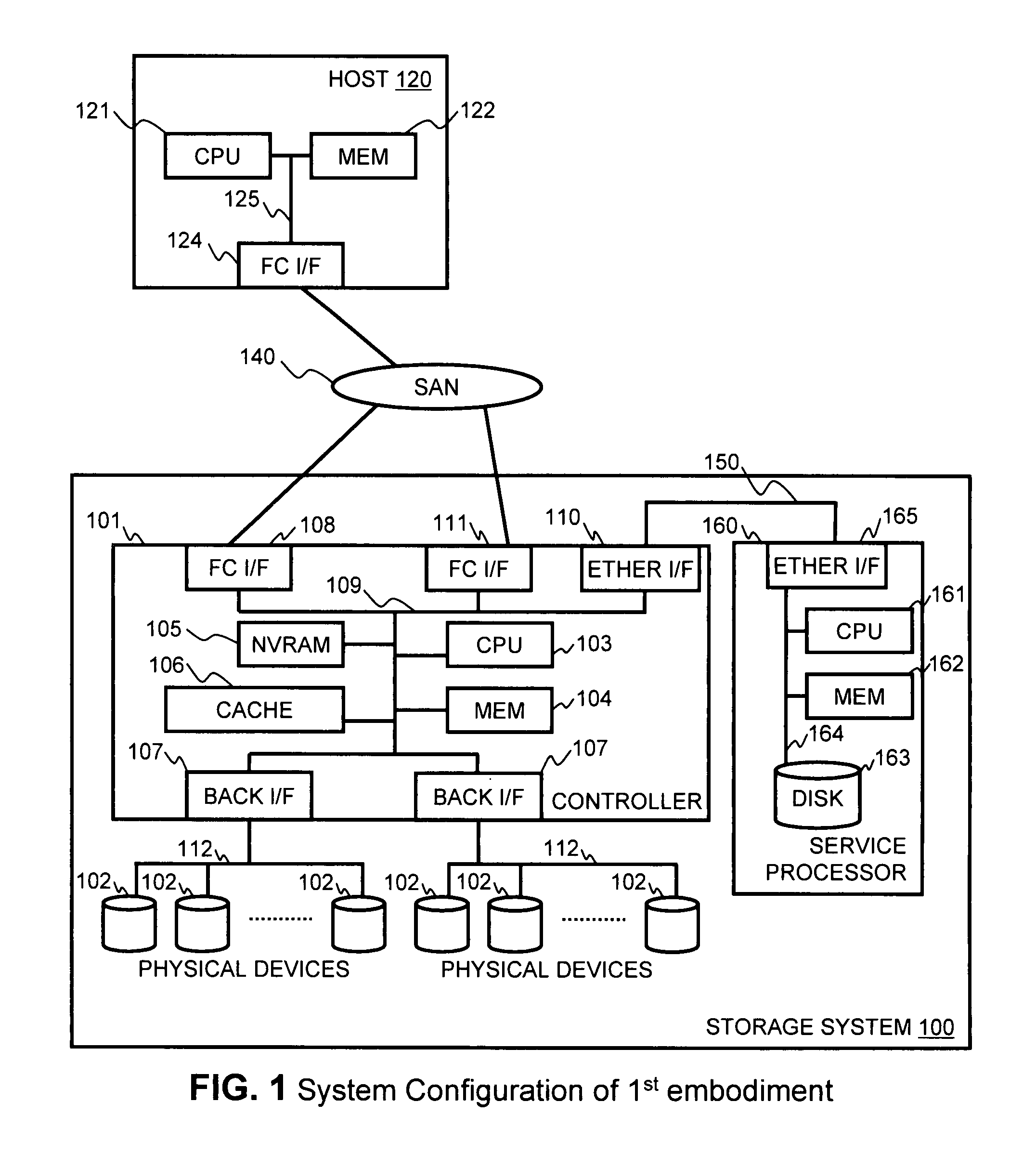
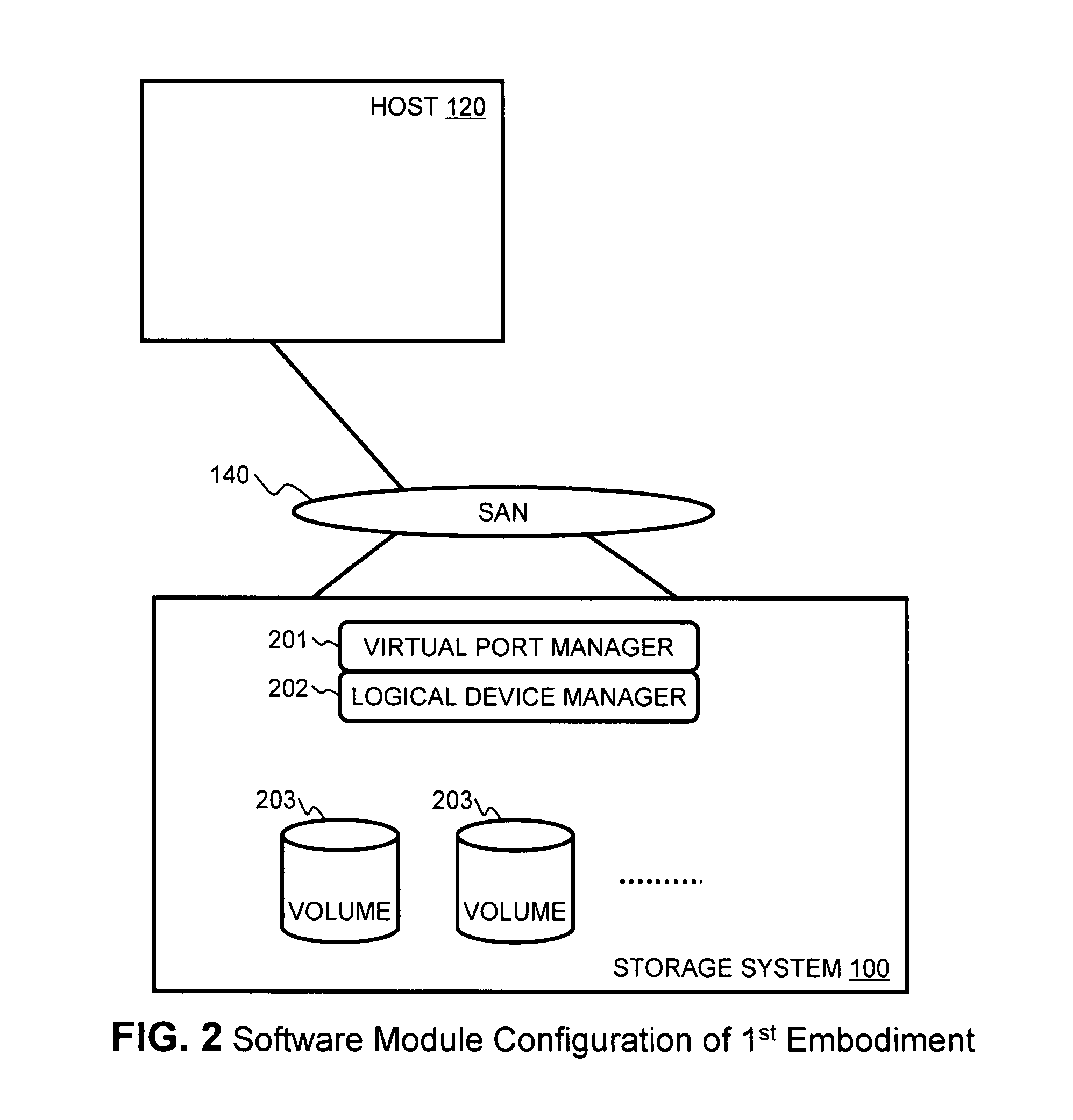
Method and apparatus for managing virtual ports on storage systems
InactiveUS7836332B2Error detection/correctionMultiprogramming arrangementsSystem configurationEngineering
Owner:HITACHI LTD
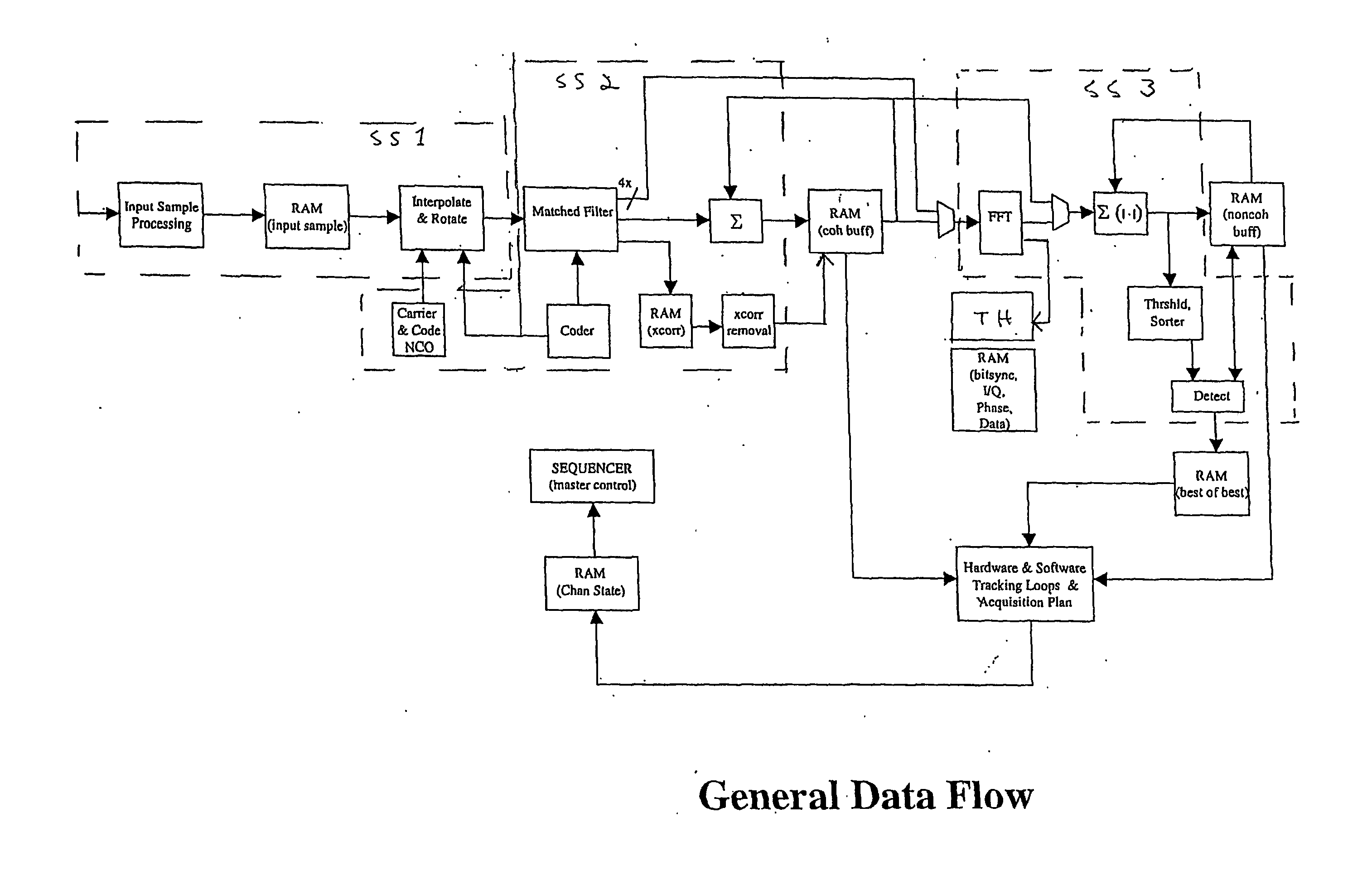
Signal Processing System for Satellite Positioning Signals
InactiveUS20110102258A1Beacon systemsSatellite radio beaconingControl signalFourier transform on finite groups
A signal processing system for processing satellite positioning signals is described. The system comprises at least one processor and a signal processor operating under a number of operational modes. The signal processor includes at last one of a signal processing subsystem, a fast Fourier transform (FFT) subsystem, and a memory subsystem that are each dynamically and independently configurable in response to the operational modes. Further, the system includes a controller that couples to control transfer of data among the signal processing subsystem and the FFT subsystem via the memory subsystem. Configurability of the memory subsystem includes configuring the memory subsystem into regions according to the operational modes where each region is accessible in one of a number of manners according to the operational modes.
Owner:CSR TECH INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com