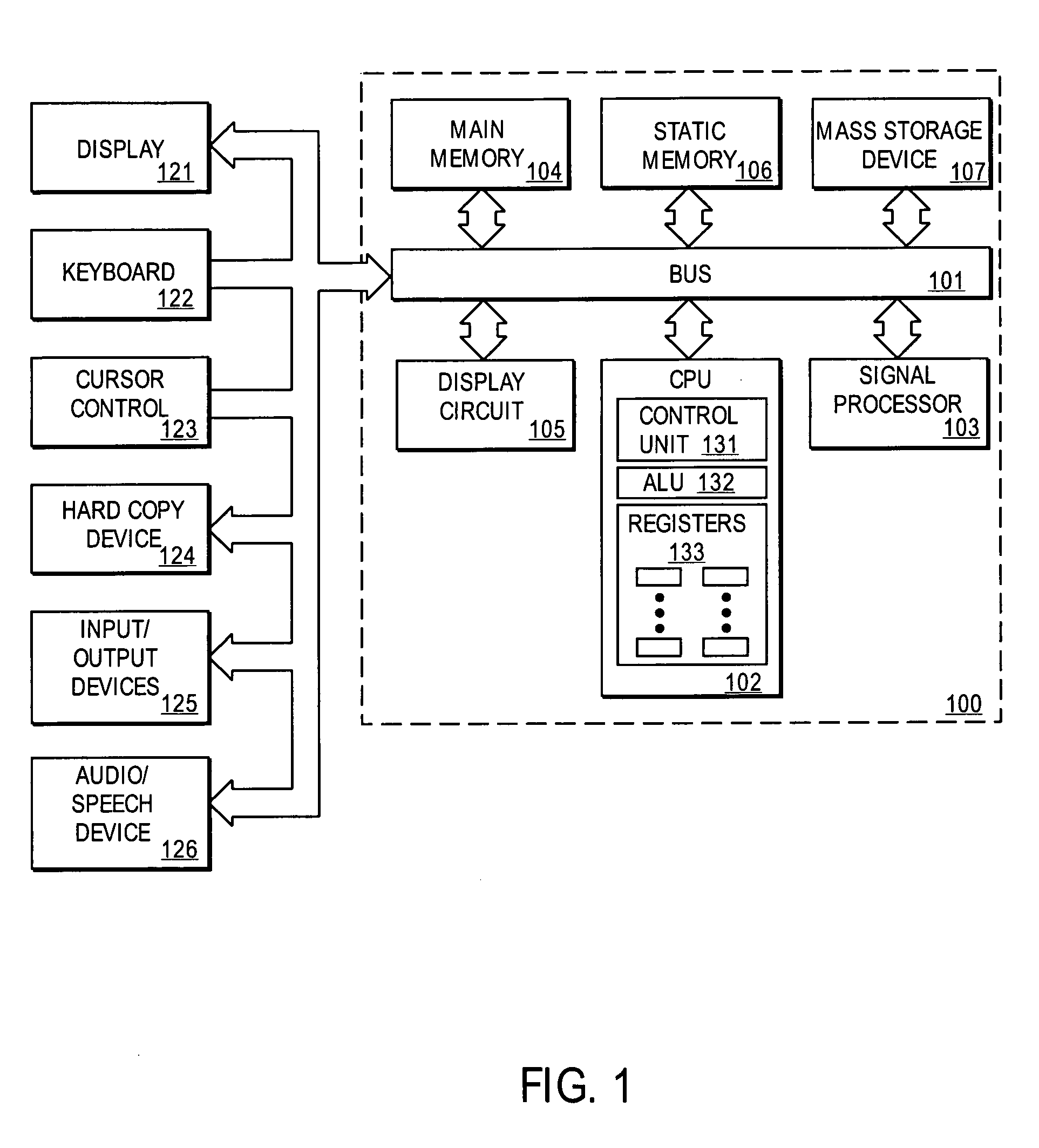
Patents
Literature
241 results about "System integrity" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
In telecommunications, the term system integrity has the following meanings: That condition of a system wherein its mandated operational and technical parameters are within the prescribed limits. The quality of an AIS when it performs its intended function in an unimpaired manner, free from deliberate or inadvertent unauthorized manipulation of the system. The state that exists when there is complete assurance that under all conditions an IT system is based on the logical correctness and reliability of the operating system, the logical completeness of the hardware and software that implement the protection mechanisms, and data integrity.
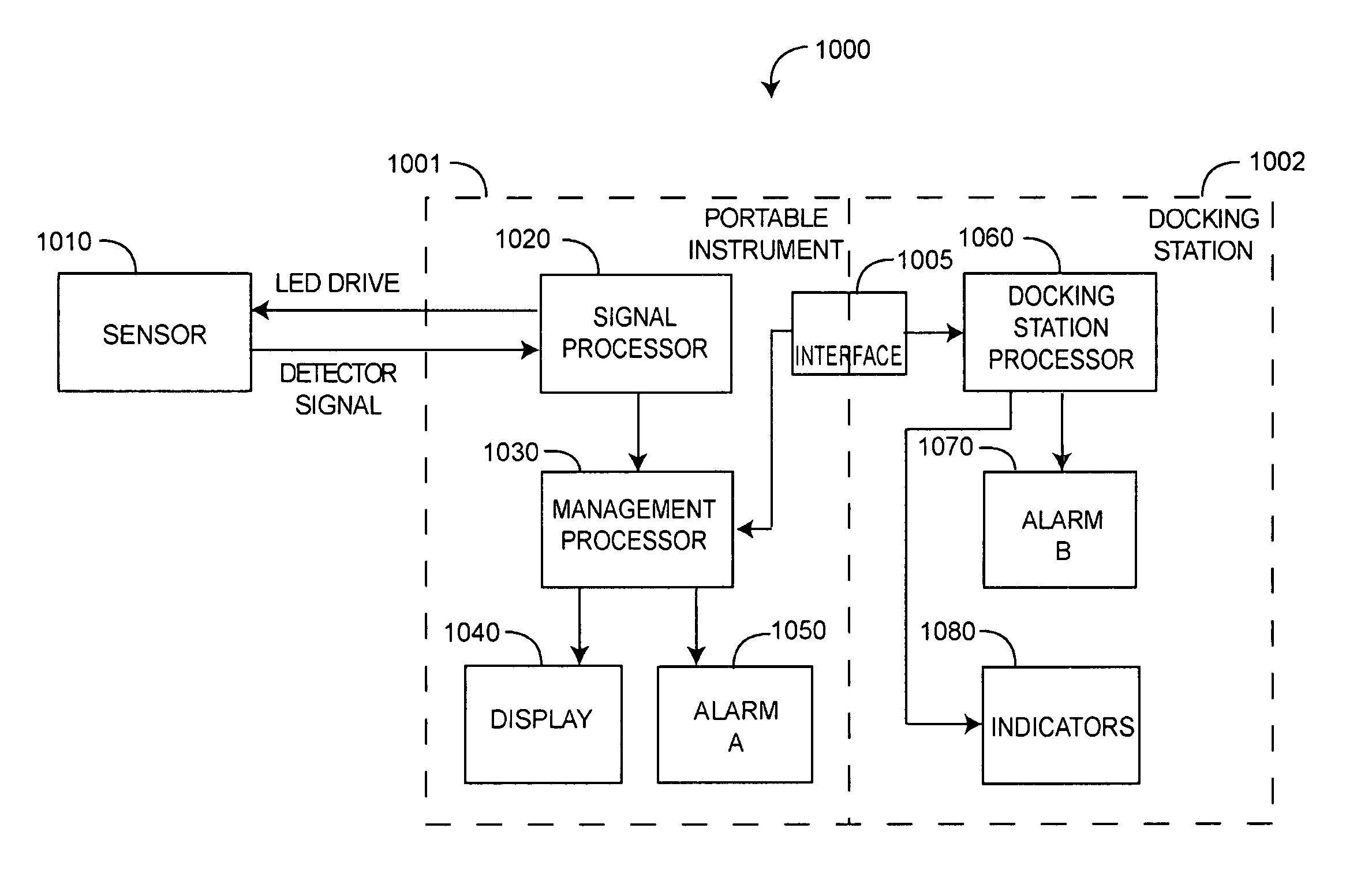
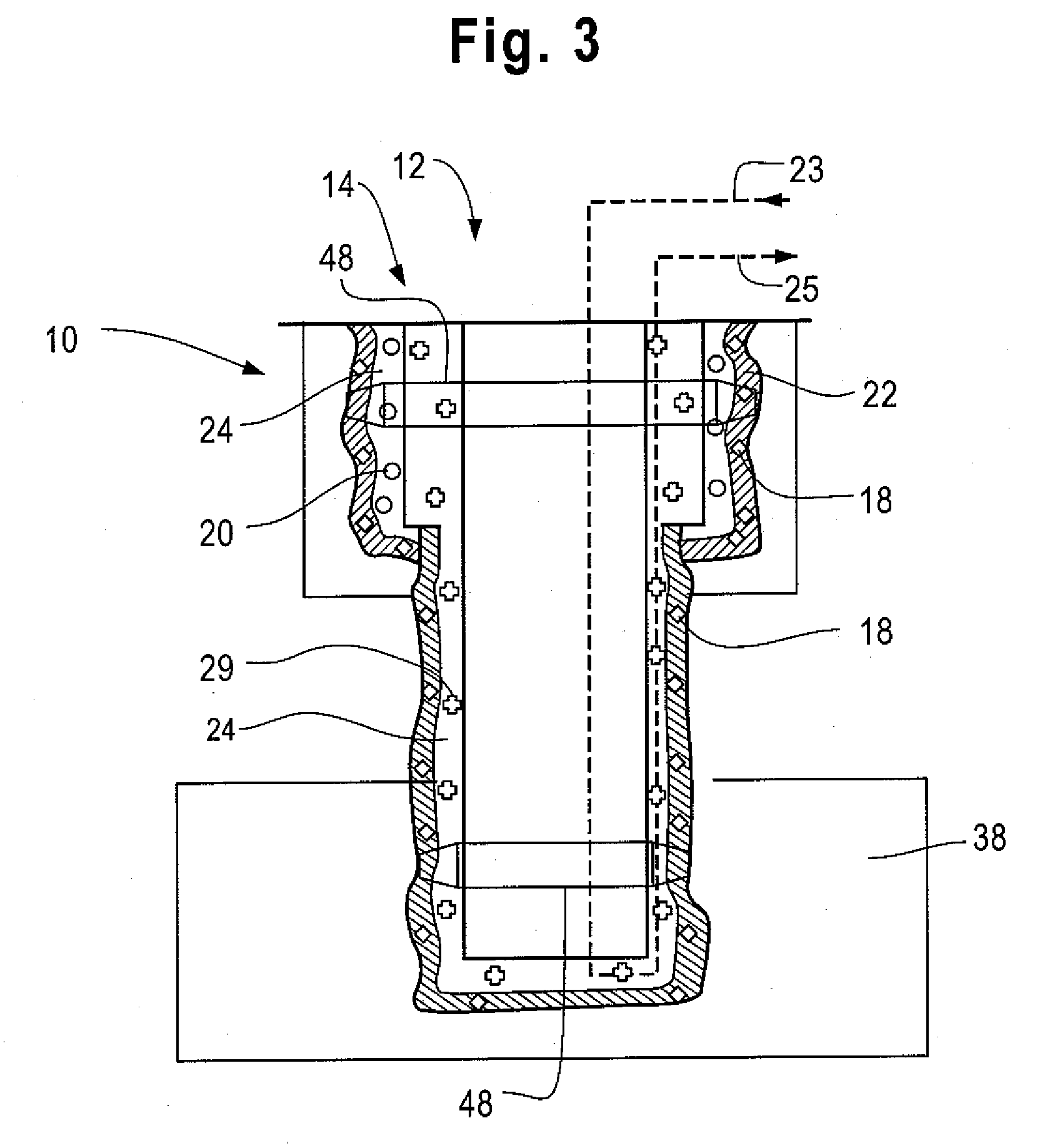
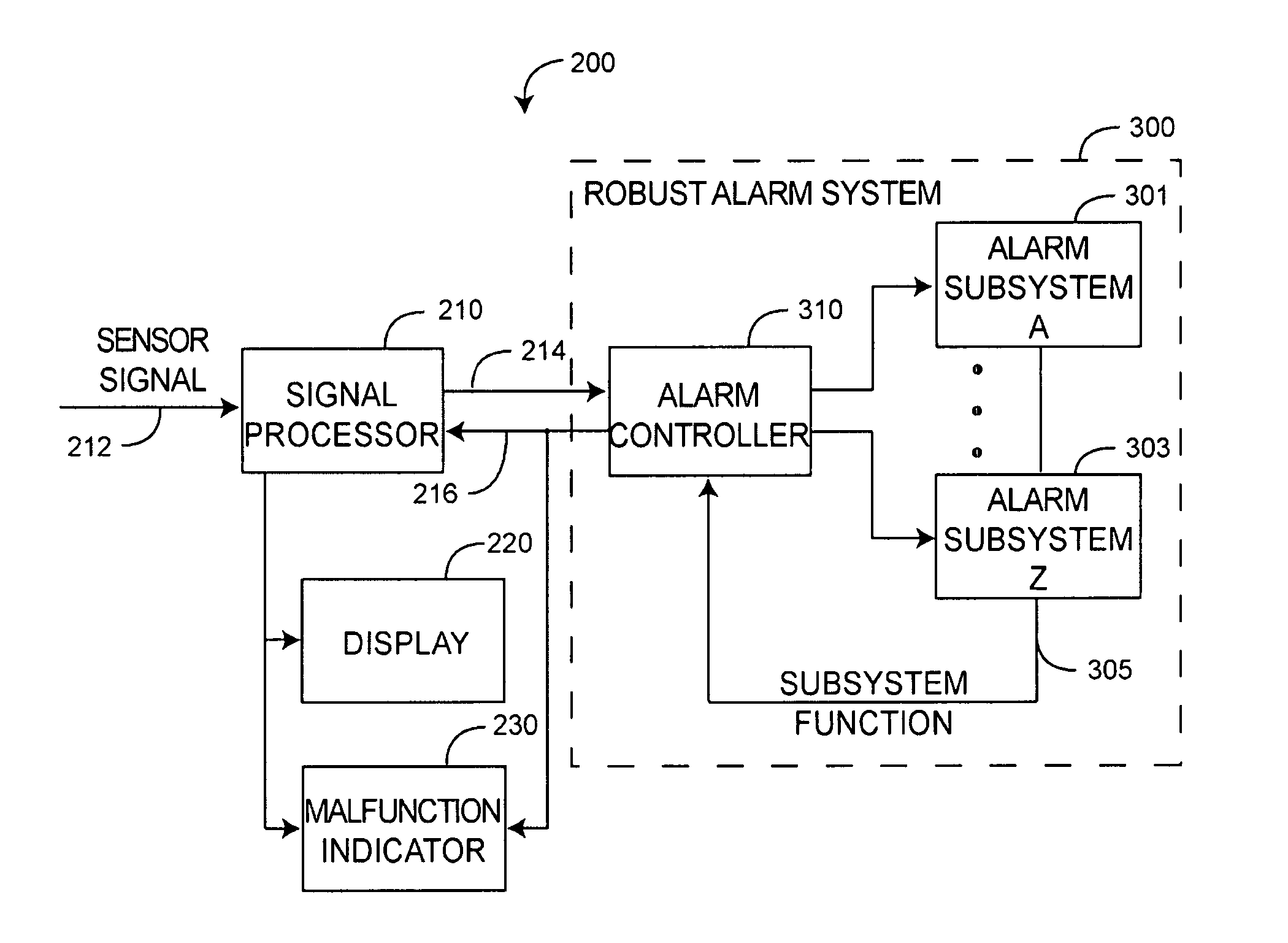
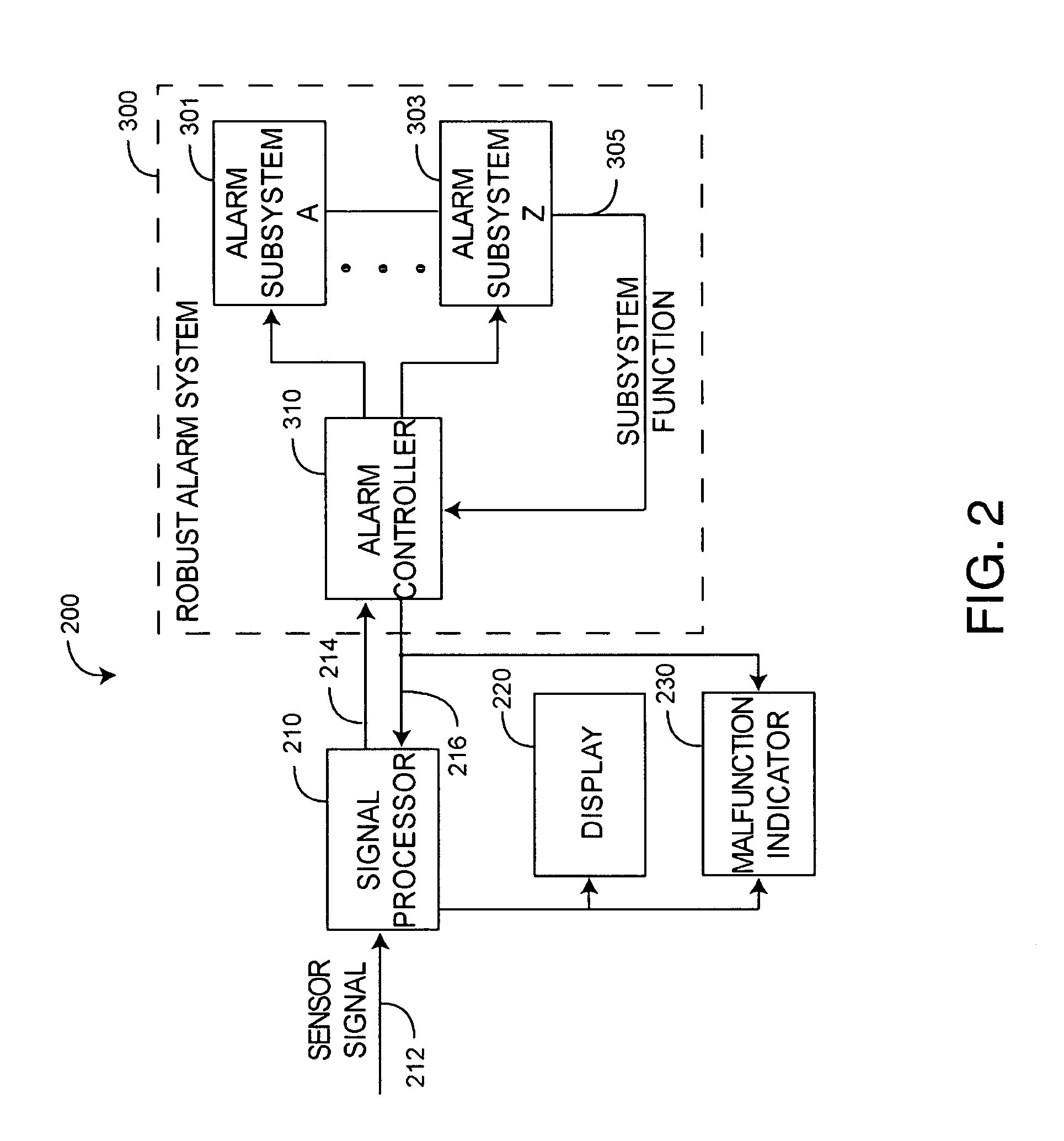
Robust alarm system
ActiveUS7962188B2Improve alarm reliabilityDiagnostic recording/measuringOptical sensorsFault indicatorControl theory
A robust alarm system has an alarm controller adapted to input an alarm trigger and to generate at least one alarm drive signal in response. Alarm subsystems input the alarm drive signal and activate one or more of multiple alarms accordingly. A subsystem function signal provides feedback to the alarm controller as to alarm subsystem integrity. A malfunction indicator is output from the alarm controller in response to a failure within the alarm subsystems.
Owner:JPMORGAN CHASE BANK NA
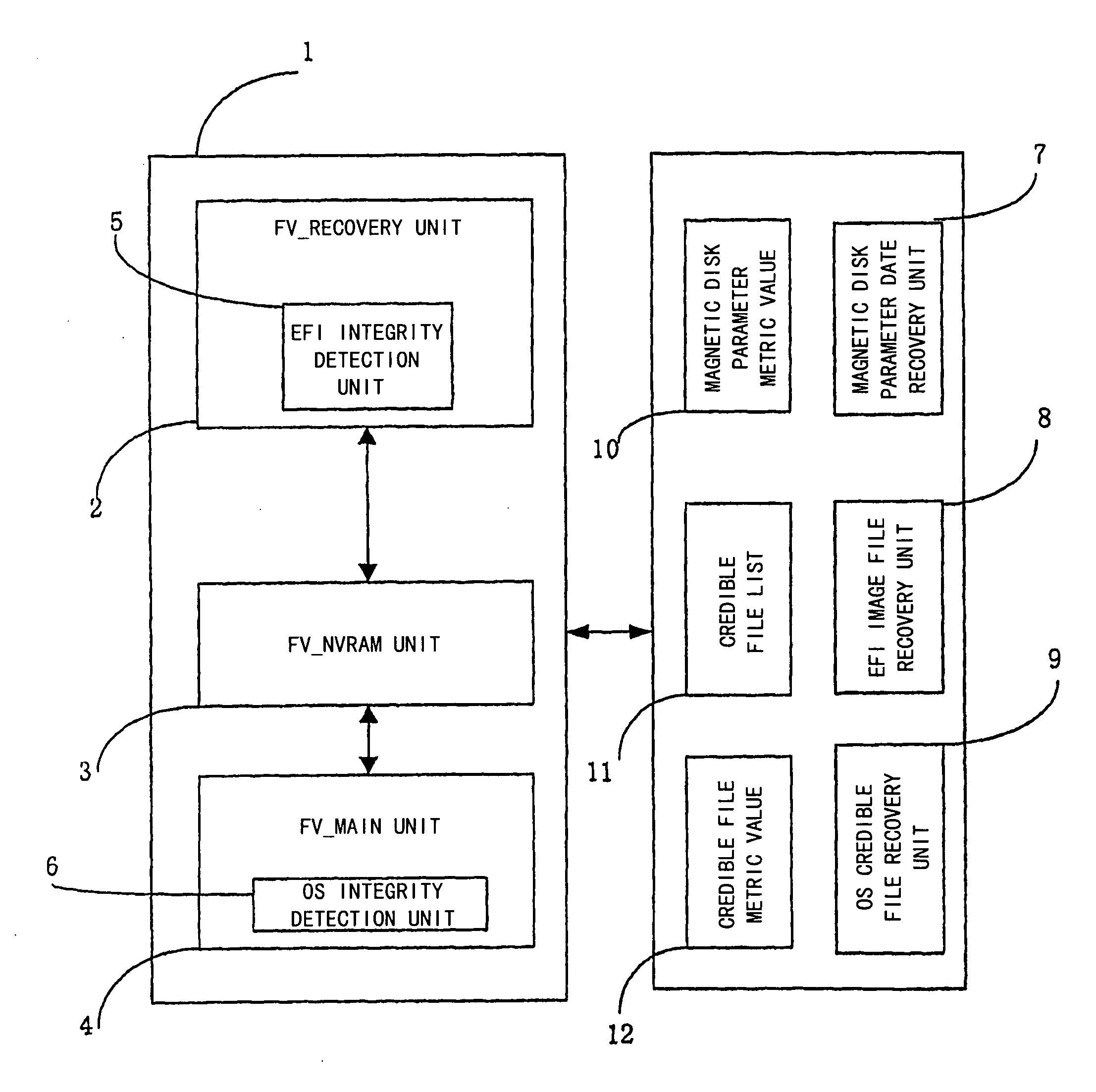
Computer System and Method for Performing Integrity Detection on the Same
InactiveUS20090300415A1Ensure consistencyEnsures strictnessFault responseDigital data processing detailsOperational systemComputerized system
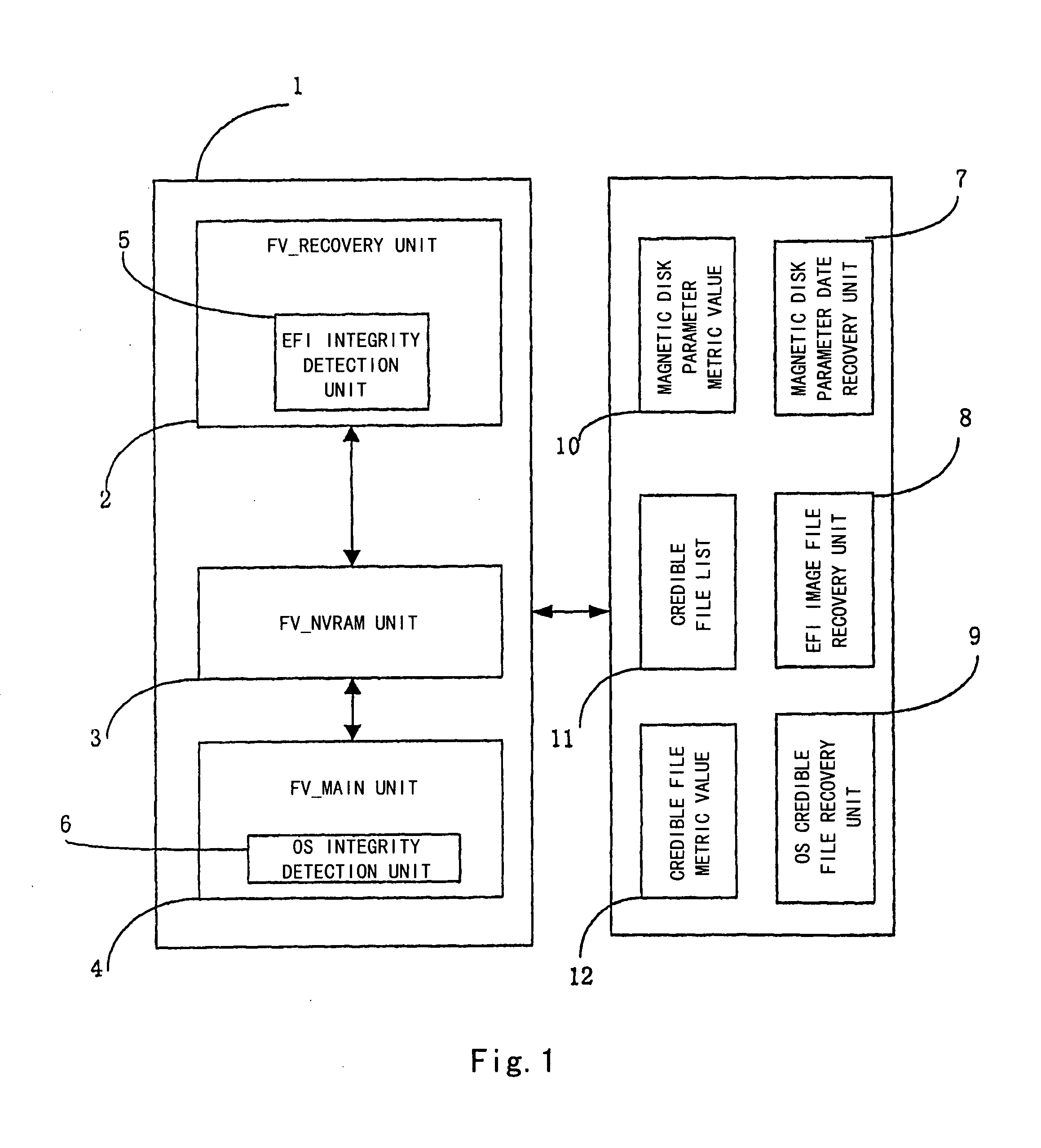
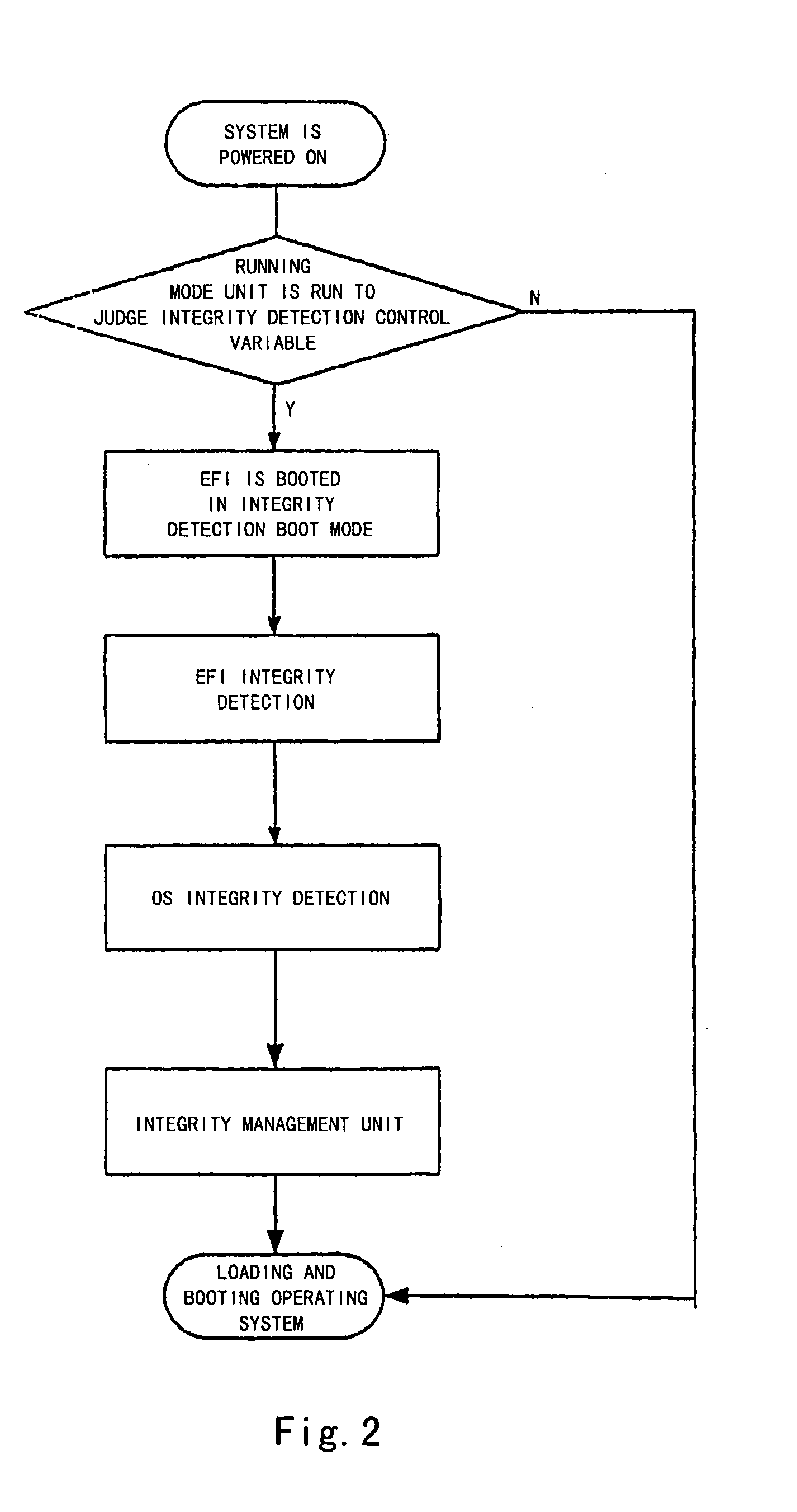
The present invention proposes a computer system and a method capable of performing integrity detection, comprising: a running mode unit which comprises an integrity detection boot variable to determine whether or not to initiate an integrity detection boot mode by judging said running mode unit; an EFI integrity detection unit (5), which is used for performing an integrity detection on EFI image codes in the integrity detection boot mode, and comprises an integrity metric value for being compared with an EFI integrity calculated value generated after the EFI integrity detection unit performs the integrity detection on the EFI image codes, to determine the integrity of the EFI image codes; an operating system integrity detection unit (6); and an integrity management unit. The present invention is based on the EFI BIOS to perform the integrity detection on the operating system during the pre-boot stage, having better reliability and security.
Owner:LENOVO (BEIJING) CO LTD
User configurable raid system with multiple data bus segments and removable electrical bridges
InactiveUS6076142ACarrier constructional parts dispositionError detection/correctionMass storageModem device
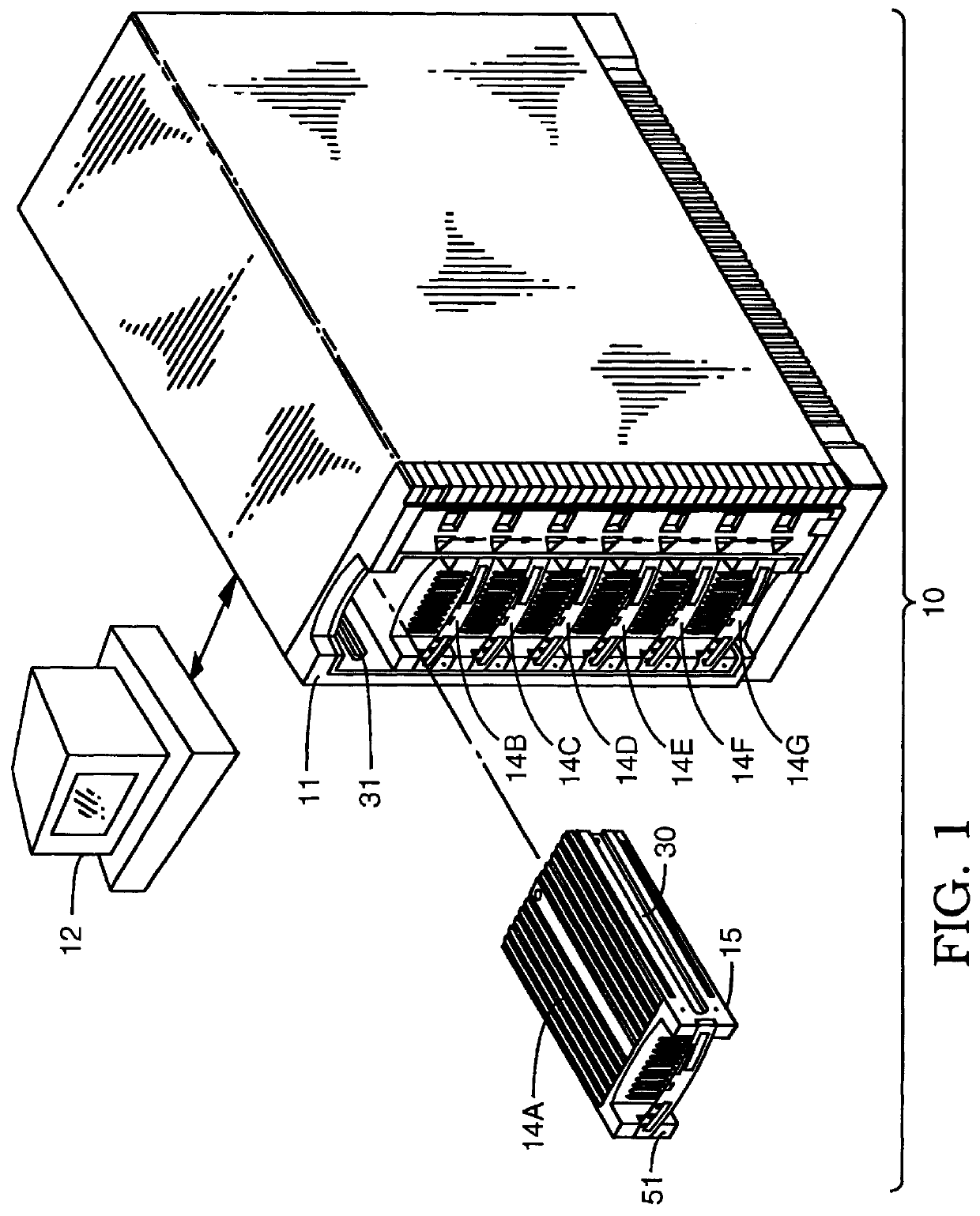
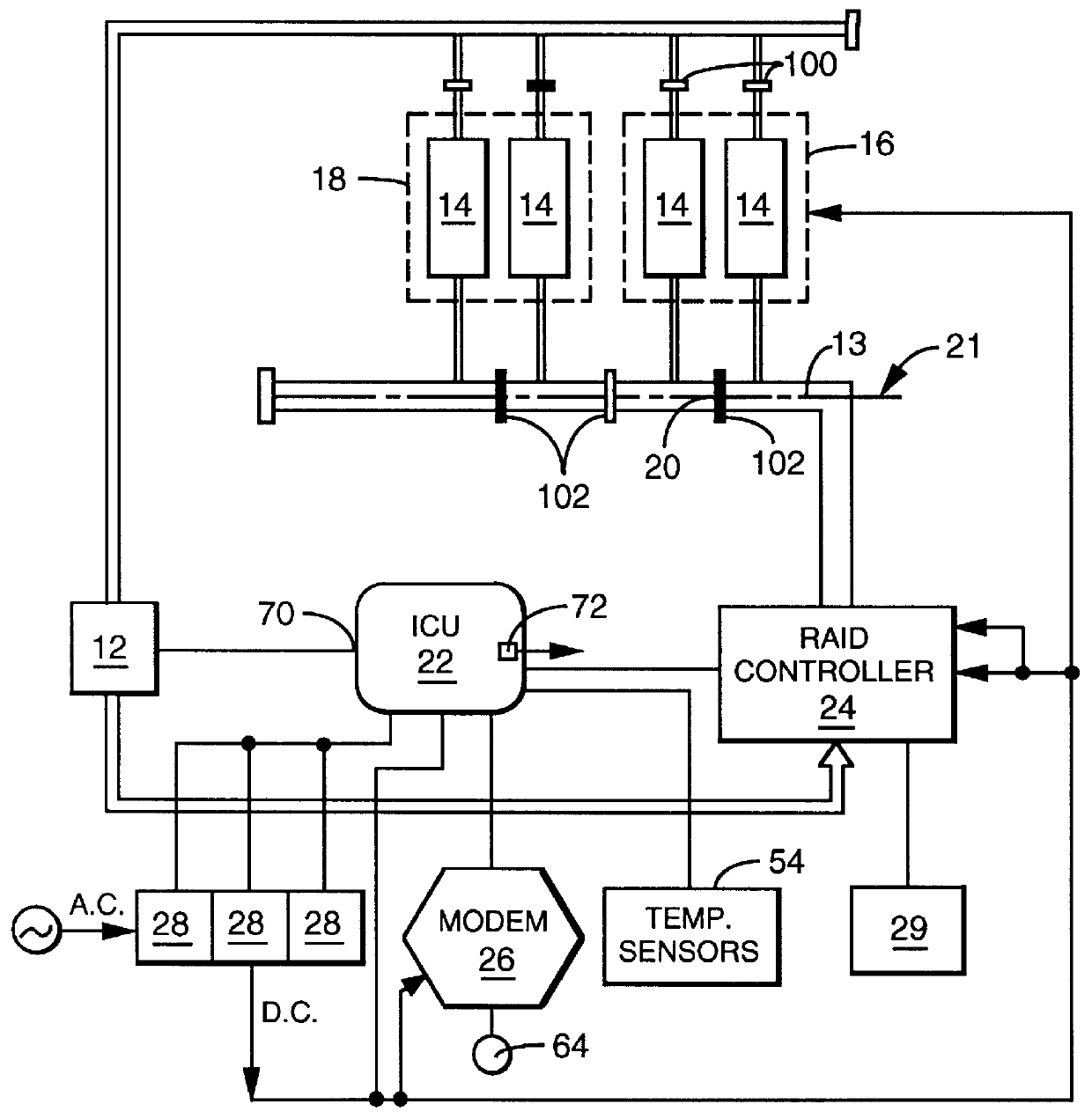
A user configurable RAID system designed to provide RAID functions as well as mass storage functions in a non-RAID mode. Flexibility is built into the system to allow the user to configure the SCSI bus to which removable drive modules are connected into one or more channels to define some of the drive modules in a RAID set and others as stand-alone drives which are independently operated or logically grouped and operated in a non-RAID mode. Removable internal SCSI bridges allow the SCSI bus to be configured into one or more channels. In the RAID mode, the system is configured to prevent a wrong drive from being removed from the system in the event of a drive failure. The system automatically unlatches only the failed drive. The RAID system includes an intelligent control unit ("ICU"), a RAID controller and a modem. The ICU allows the system administrator to access the RAID system Monitor Utility so that the status of the system may be monitored and its configuration changed. The ICU also monitors the failure status of the various components of the system. The ICU has a built-in pager feature that can be configured with the Monitor Utility to page the system administrator via the modem when a component or system failure is encountered. The RAID controller controls the functions of the RAID set as programmed and configured using the Monitor Utility. The Monitor Utility may be remotely accessed using a computer via the modem. Redundant removable power supply and fan units are provided to improve system integrity. The removable power supply and fan units are configured such when the unit is plugged into the system housing, the fan is first turned on and the power through the unit is allowed to stabilize before turning on the power supply to begin providing DC power to the components in the system. A set of manual release buttons are provided for manually unlatching the drive modules from the system housing. A locking mechanism is provided for simultaneously locking all the manual release buttons.
Owner:MICRONET TECH
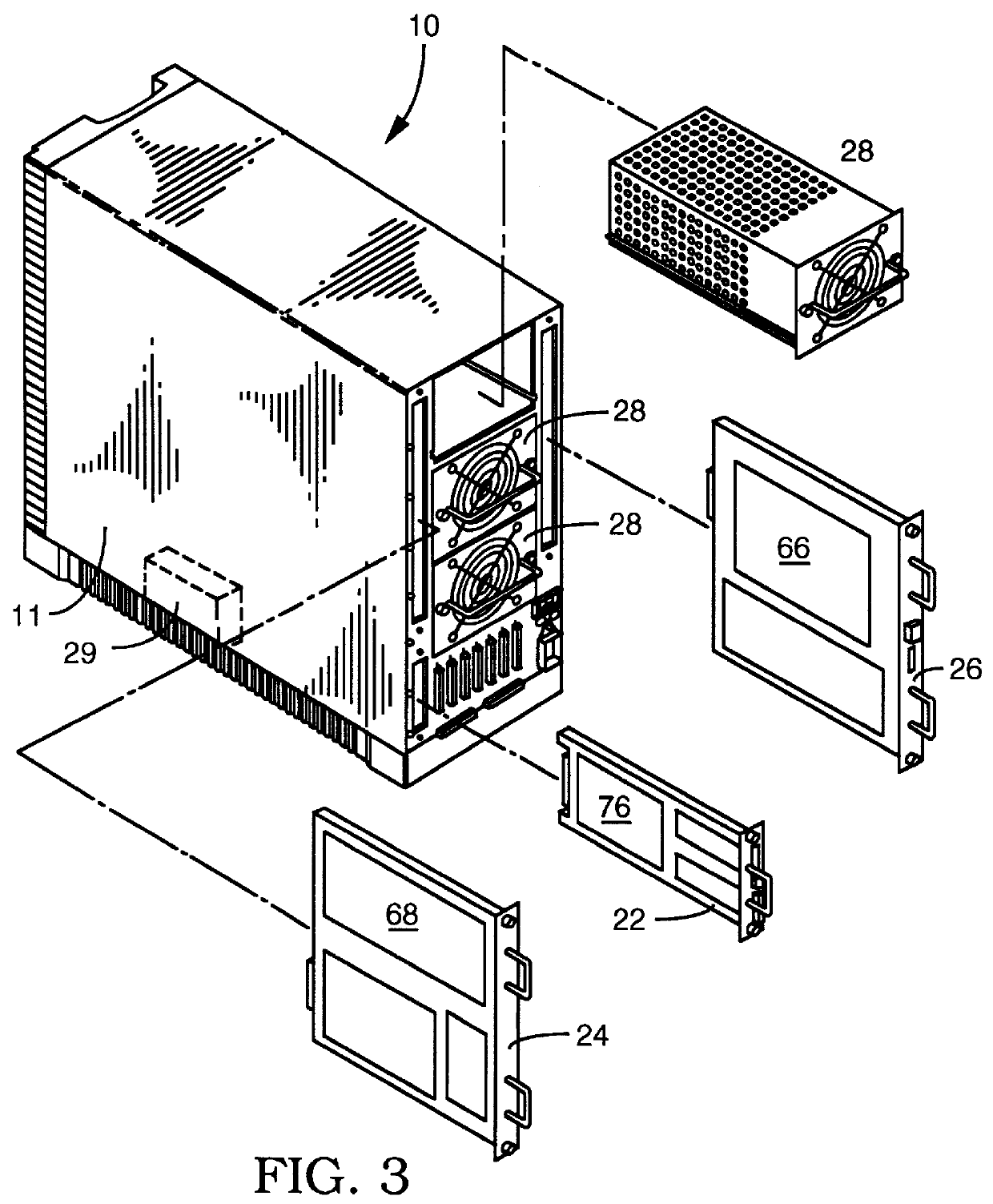
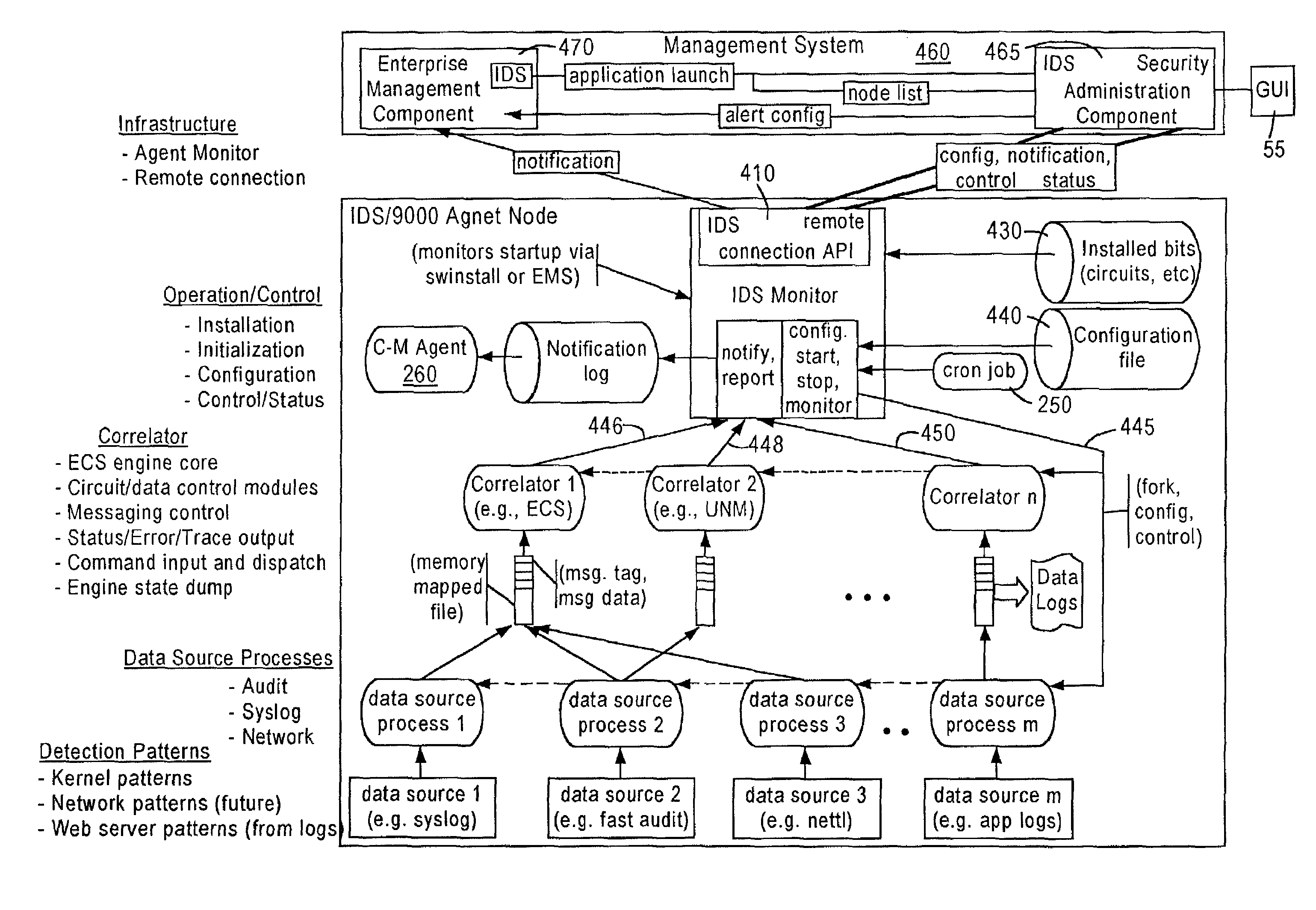
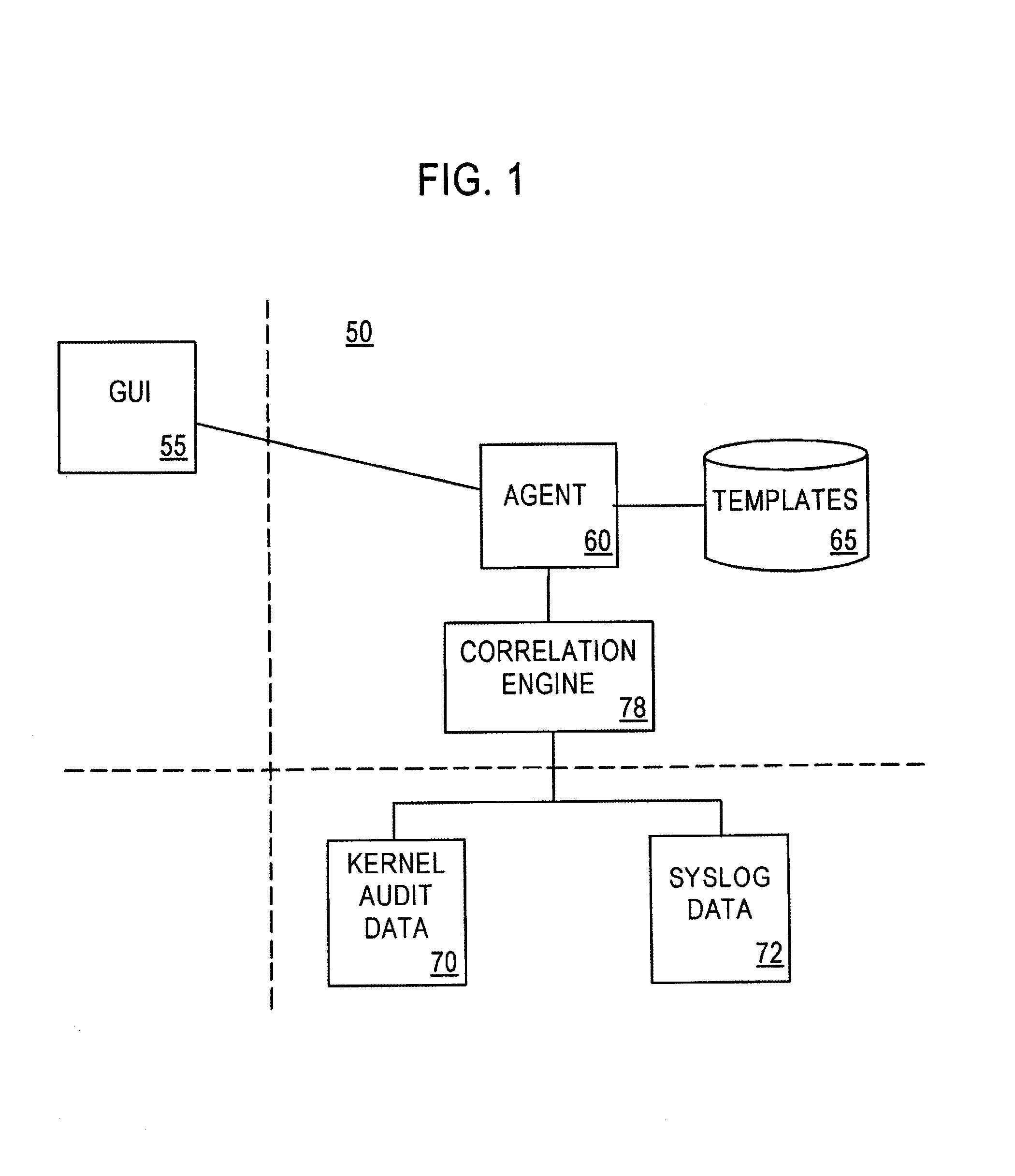
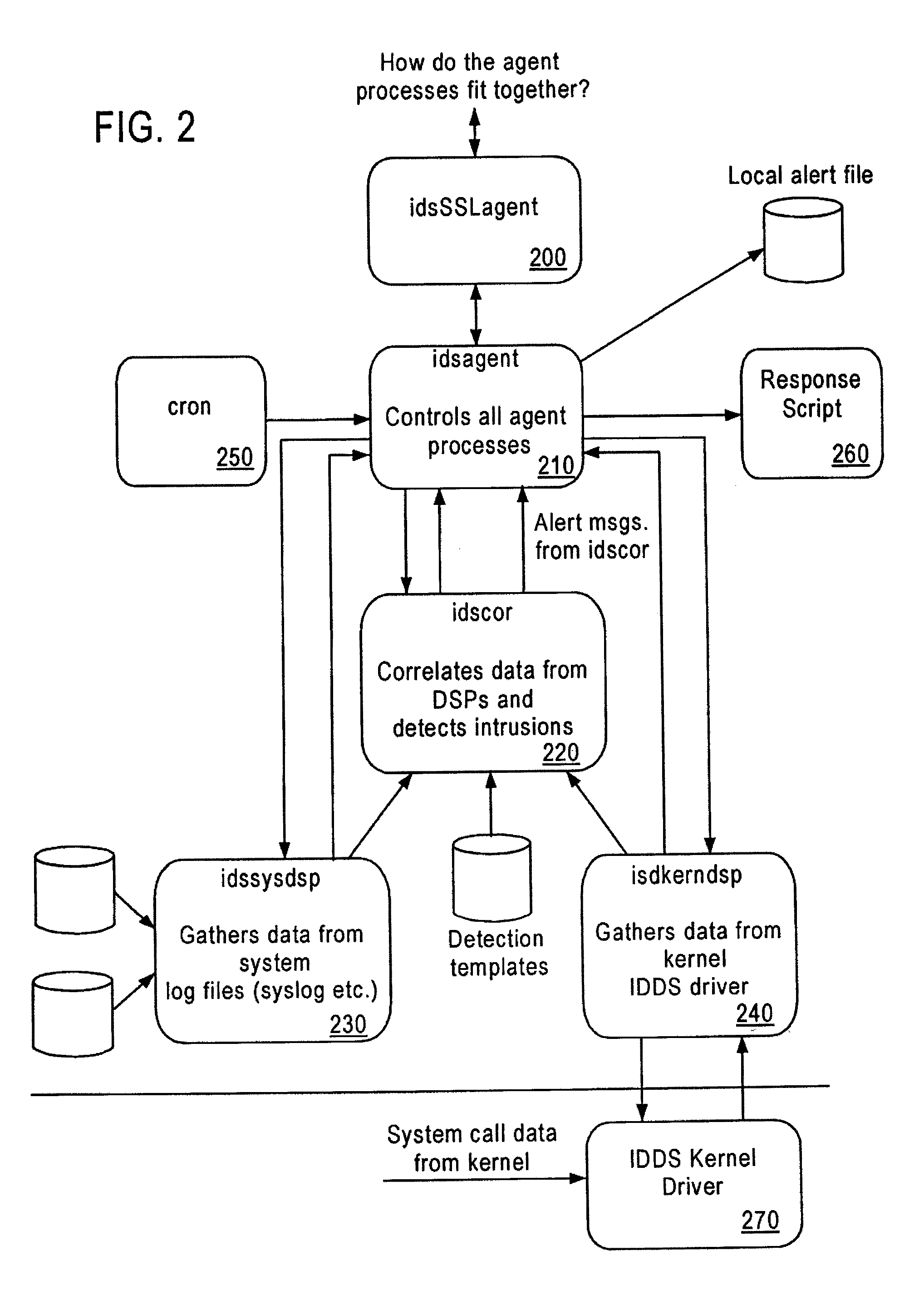
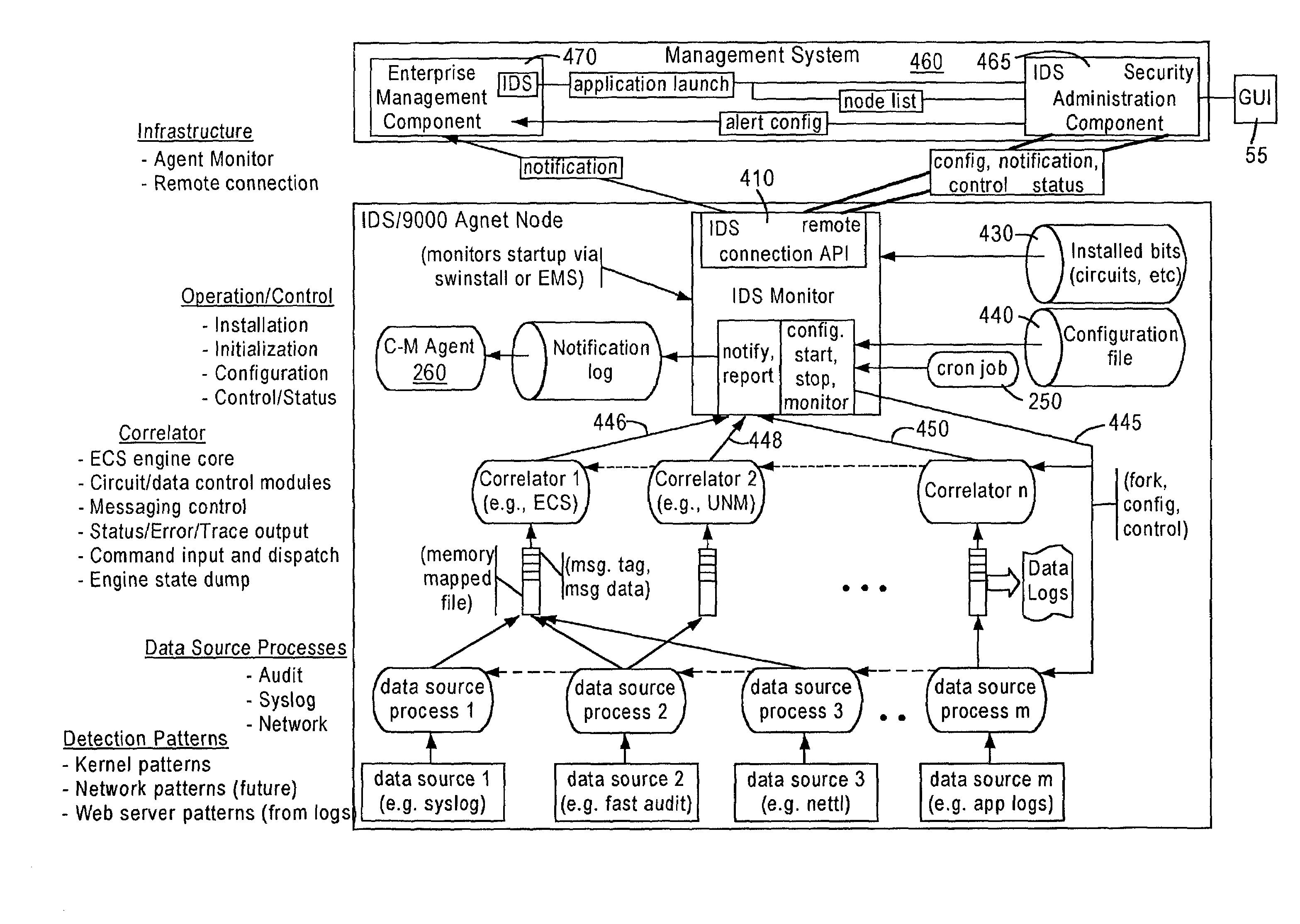
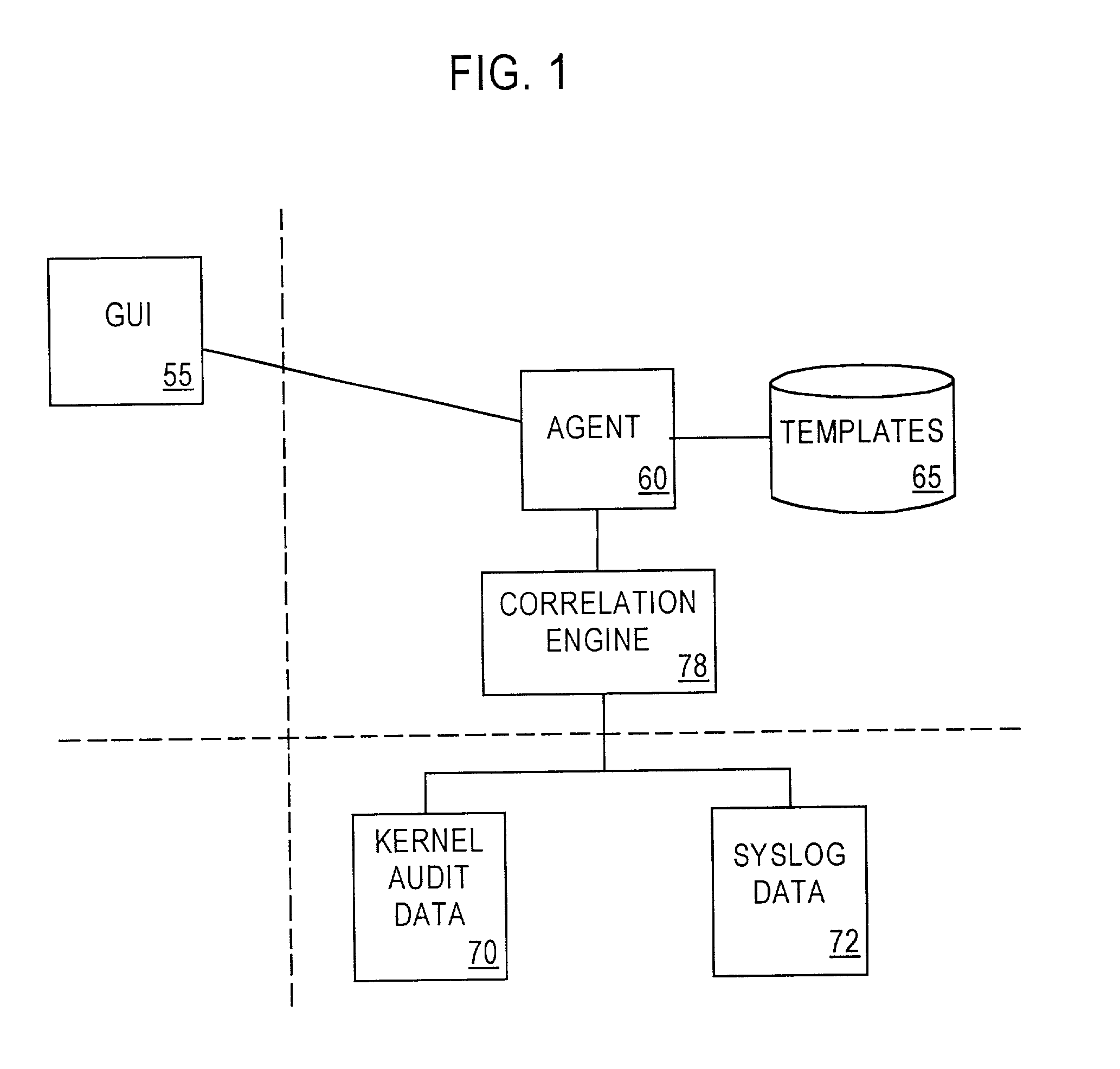
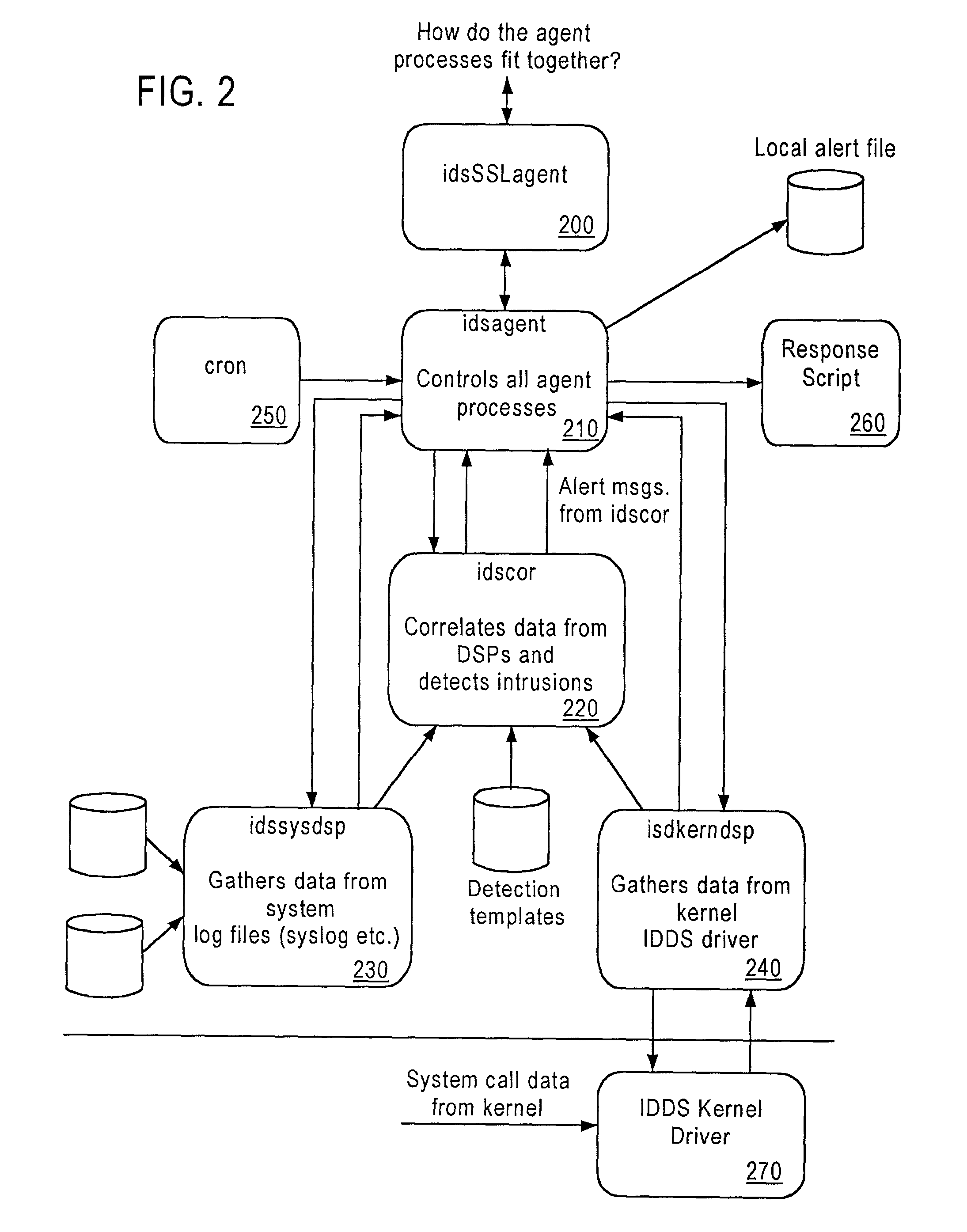
System and method for host and network based intrusion detection and response
InactiveUS7134141B2Accurate measurementFewer false positivesData processing applicationsMemory loss protectionOperational systemCritical system
The present application is directed to a host-based IDS on an HP-UX intrusion detection system that enhances local host-level security within the network. It should be understood that the present invention is also usable on, for example, Eglinux, solaris, aix windows 2000 operating systems. It does this by automatically monitoring each configured host system within the network for possible signs of unwanted and potentially damaging intrusions. If successful, such intrusions could lead to the loss of availability of key systems or could compromise system integrity.
Owner:HEWLETT PACKARD DEV CO LP
Computer architecture for an intrusion detection system
InactiveUS7007301B2Provide protectionAccurate measurementData processing applicationsMemory loss protectionOperational systemCritical system
The present application is directed to a host-based IDS on an HP-UX intrusion detection system that enhances local host-level security within the network. It should be understood that the present invention is also usable on, for example, Eglinux, solaris, aix windows 2000 operating systems. It does this by automatically monitoring each configured host system within the network for possible signs of unwanted and potentially damaging intrusions. If successful, such intrusions could lead to the loss of availability of key systems or could compromise system integrity.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
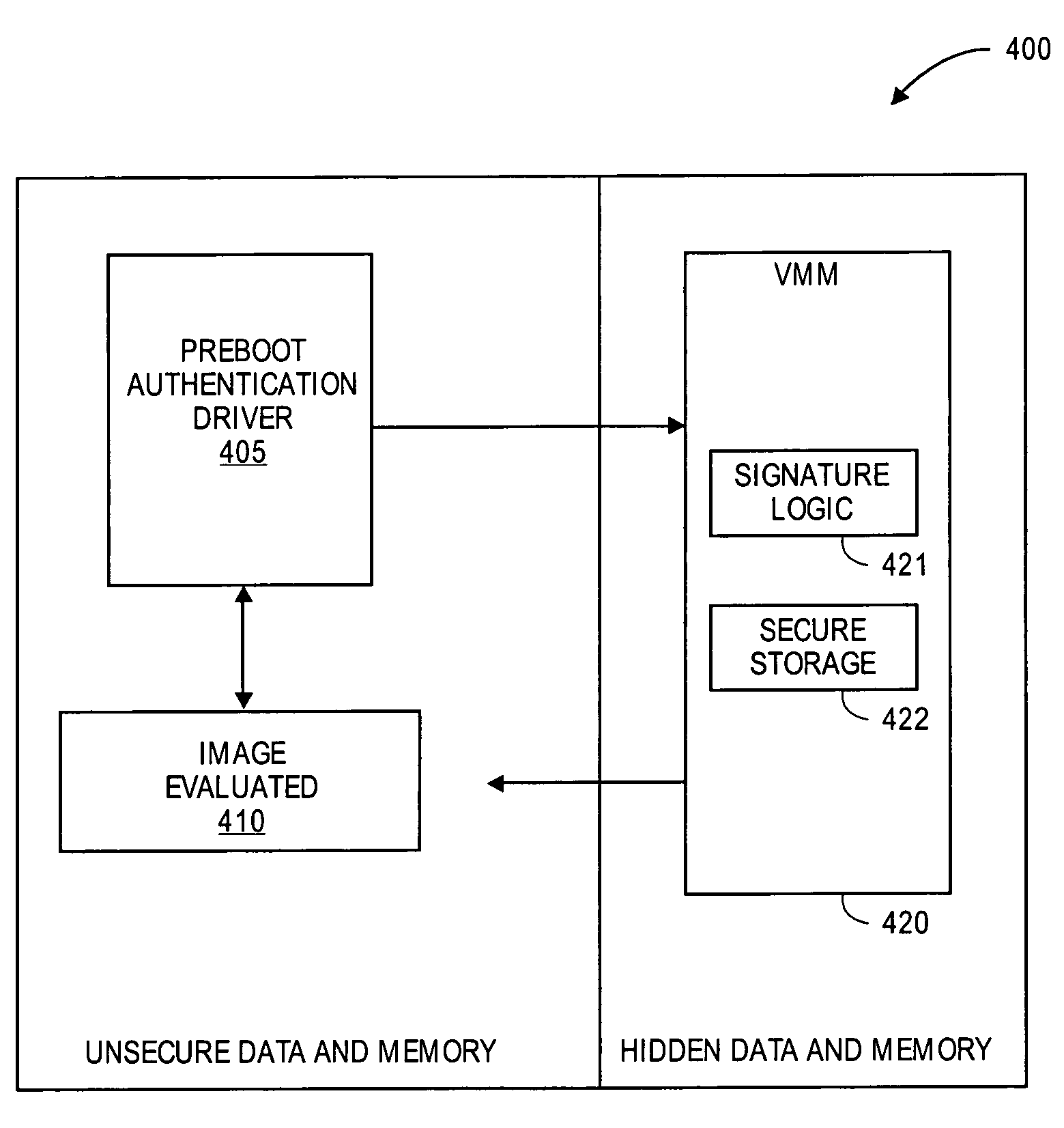
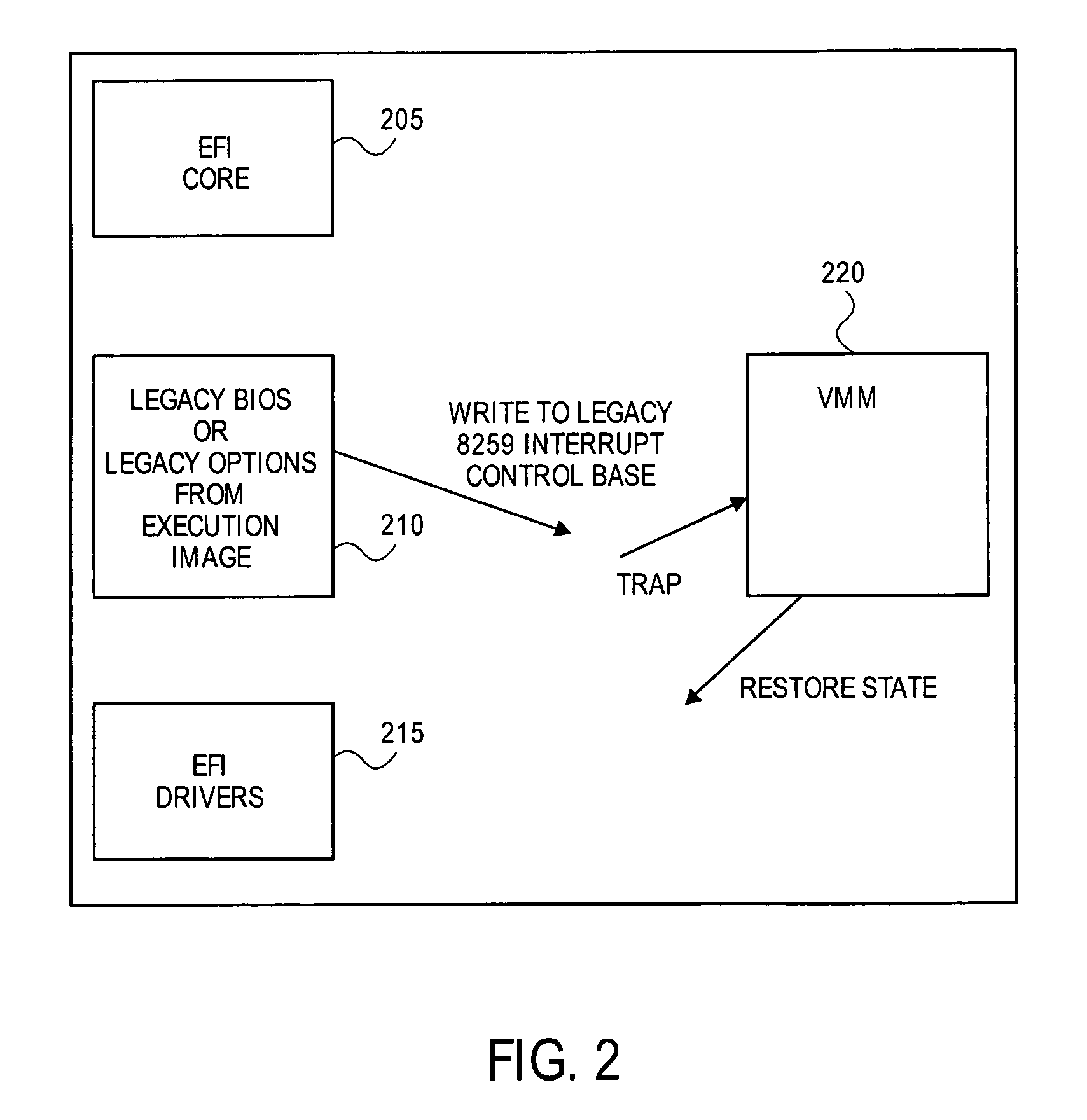
Method for providing system integrity and legacy environment emulation
InactiveUS7103529B2Protective structureProgram control using stored programsDigital computer detailsVirtualizationComputer compatibility
A method and apparatus to provide pre-boot security and legacy hardware and environment support for a computing system having an extensible firmware architecture is described. A virtual machine monitor is employed to provide the virtualization of system state for the purposes of running legacy compatibility code or protecting key data and code regions for safety and security. An application may be given access to a subset of the system resources, and access to portions of the memory map not designated for updates would trap (program interrupt) to the VMM. A VMM pre-boot policy agent may then protect state and unload any problematic software.
Owner:INTEL CORP
Medical infusion pumps
InactiveUS20090005729A1Reduce the amount requiredReliable conditionsProgramme controlMedical devicesInsulin infusionControl system
Disclosed is a medical infusion device including a dedicated processing unit for detecting abnormal operation of the operation of the device. Specifically, a watchdog controller is employed as an independent monitor of the functioning of microprocessors used in the medical infusion device for controlling things such as RF communication, insulin infusion, and system integrity. Through the use of an independently-powered watchdog control system, the accuracy and reliability of the device is enhanced, resulting in greater assurance to the patient receiving periodic or continuous infusion of a drug.
Owner:ANIMAS CORP
Method and system for monitoring system memory integrity
ActiveUS20090217377A1Efficient processingMemory loss protectionError detection/correctionOperational systemMonitoring system
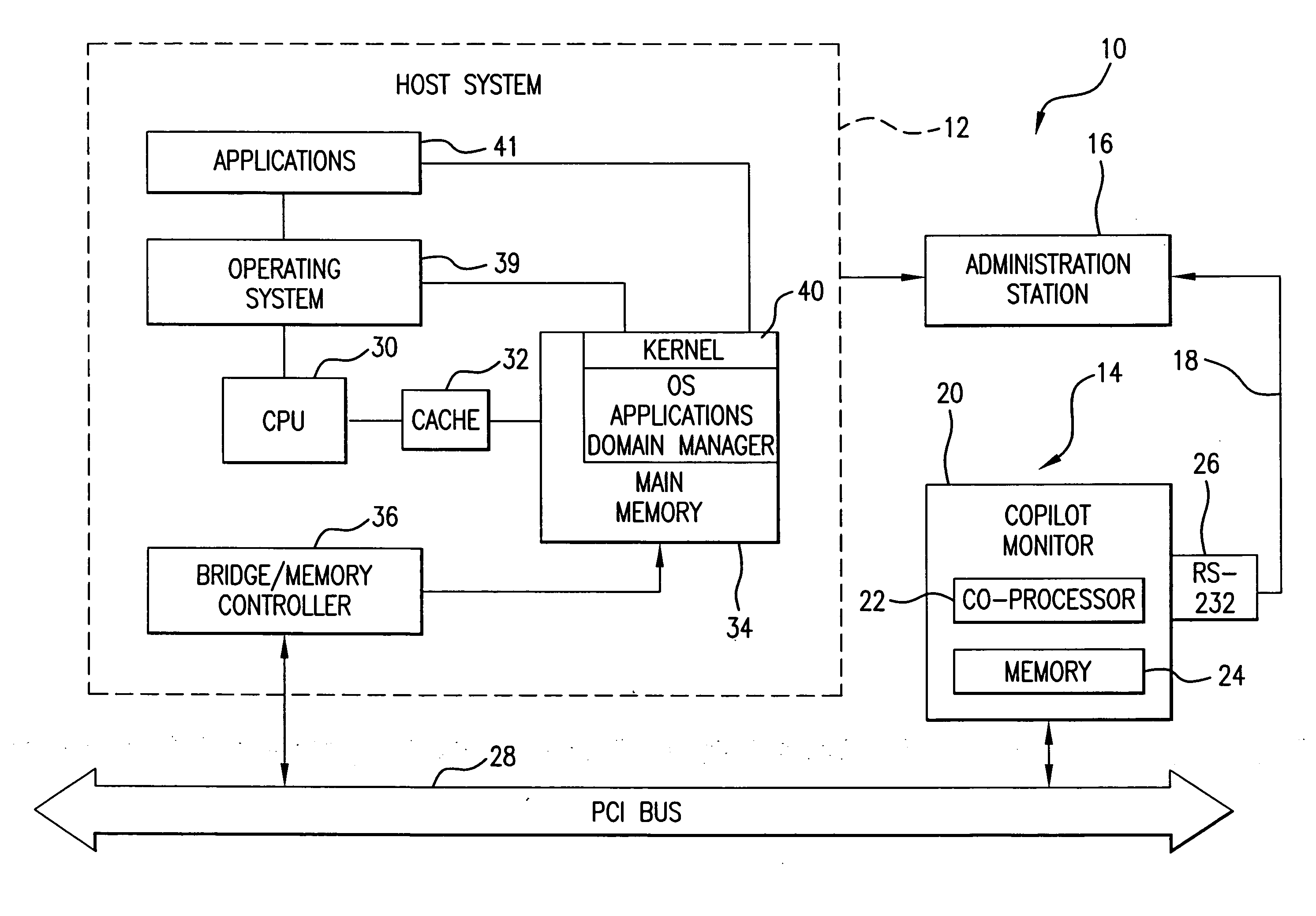
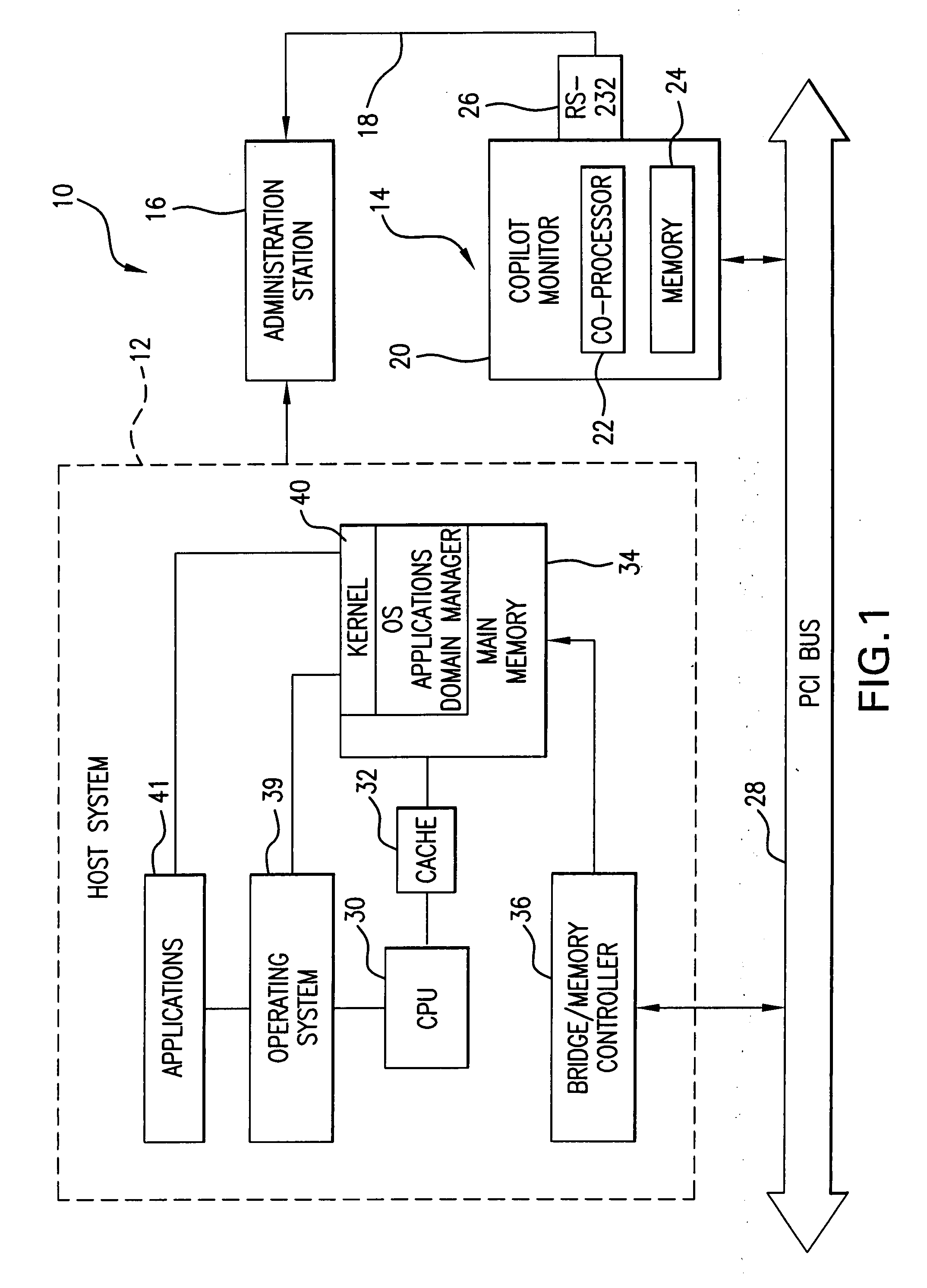
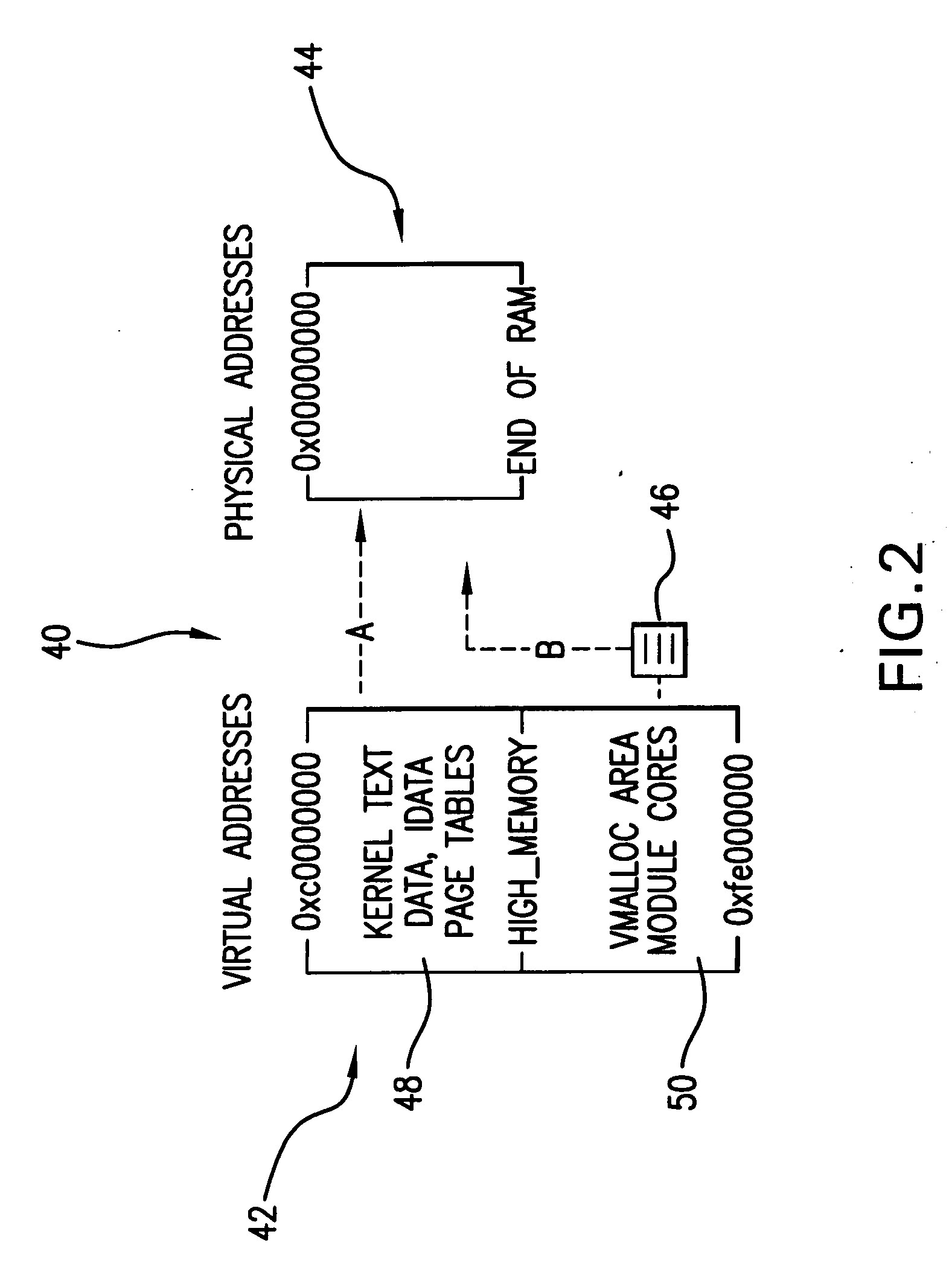
A host system integrity monitor for monitoring memory, operating systems, applications, domain manager, and other host system's structures of interest is isolated and independent of the CPU and operating system of commodity systems. The system requires no modifications to the protected (monitored) host's software, and operates correctly even when the host system is compromised. Either arranged as a stand-alone computer on the add-in card which communicates with the monitored host system through the PCI bus, or as the co-processor based monitor located on the motherboard of the host system, or residing on one of the virtual CPU while the monitored system resides on another virtual CPU, or residing within the domain manager of the host system, the monitor of the present invention monitors the integrity of the examined structure by calculating hash values of the structure, comparing them with expected hash values, and sending error reports once the discrepancy between these values is detected.
Owner:UNIV OF MARYLAND
Method and apparatus for managing redundant computer-based systems for fault tolerant computing
InactiveUS6178522B1Reduce Design ComplexityReliability increasing modificationsProgram synchronisationEffective solutionSystem integrity
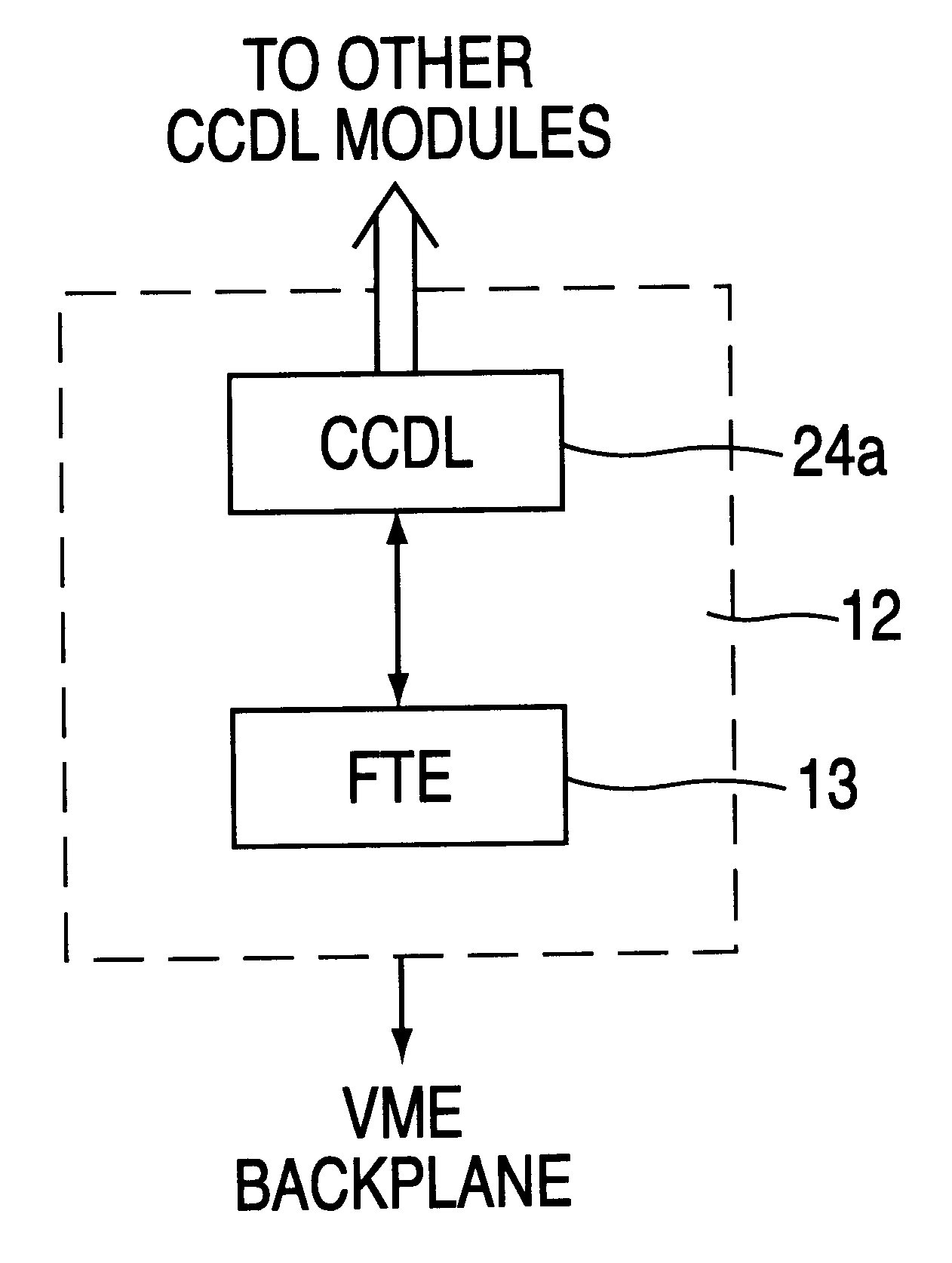
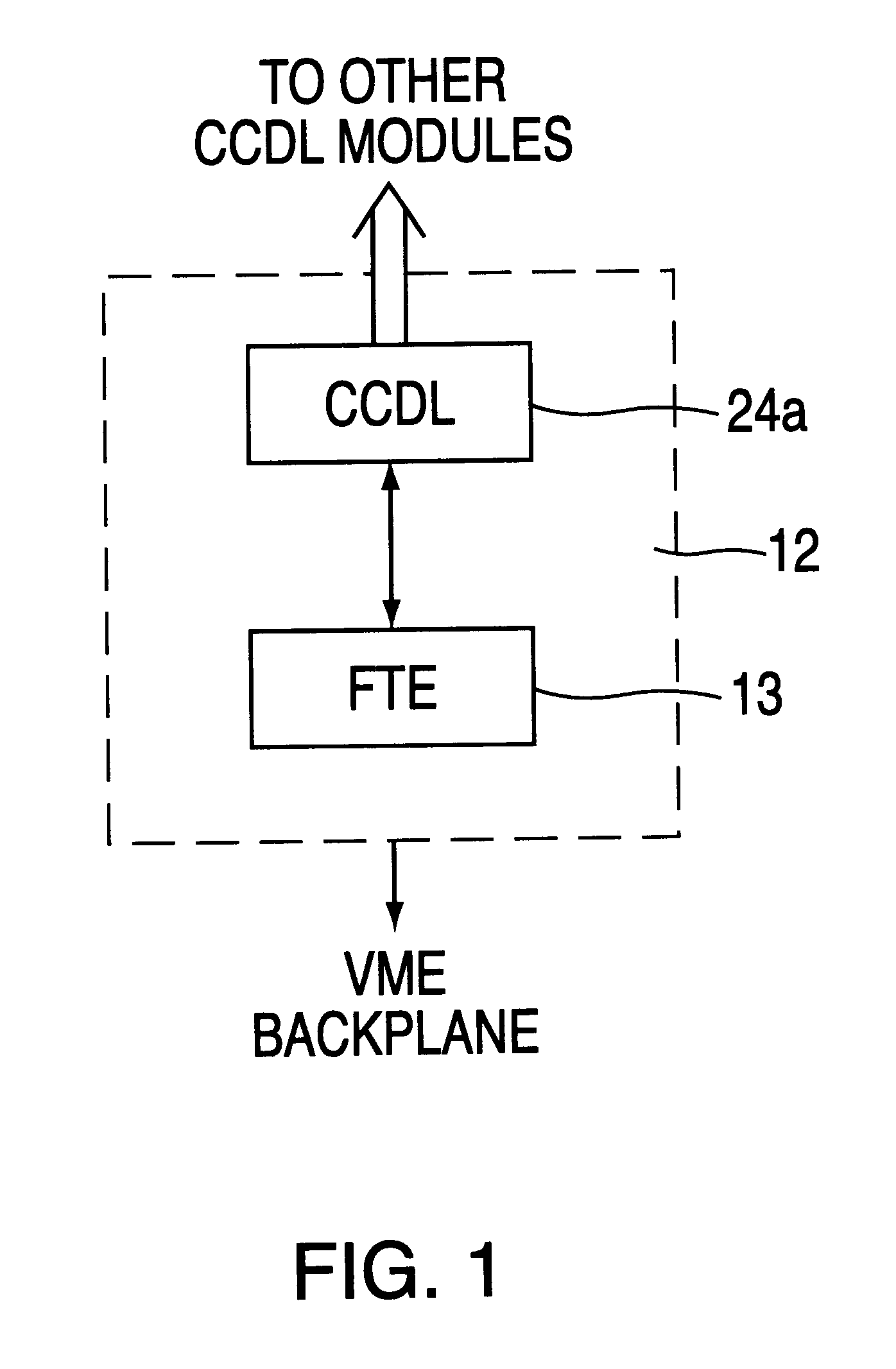
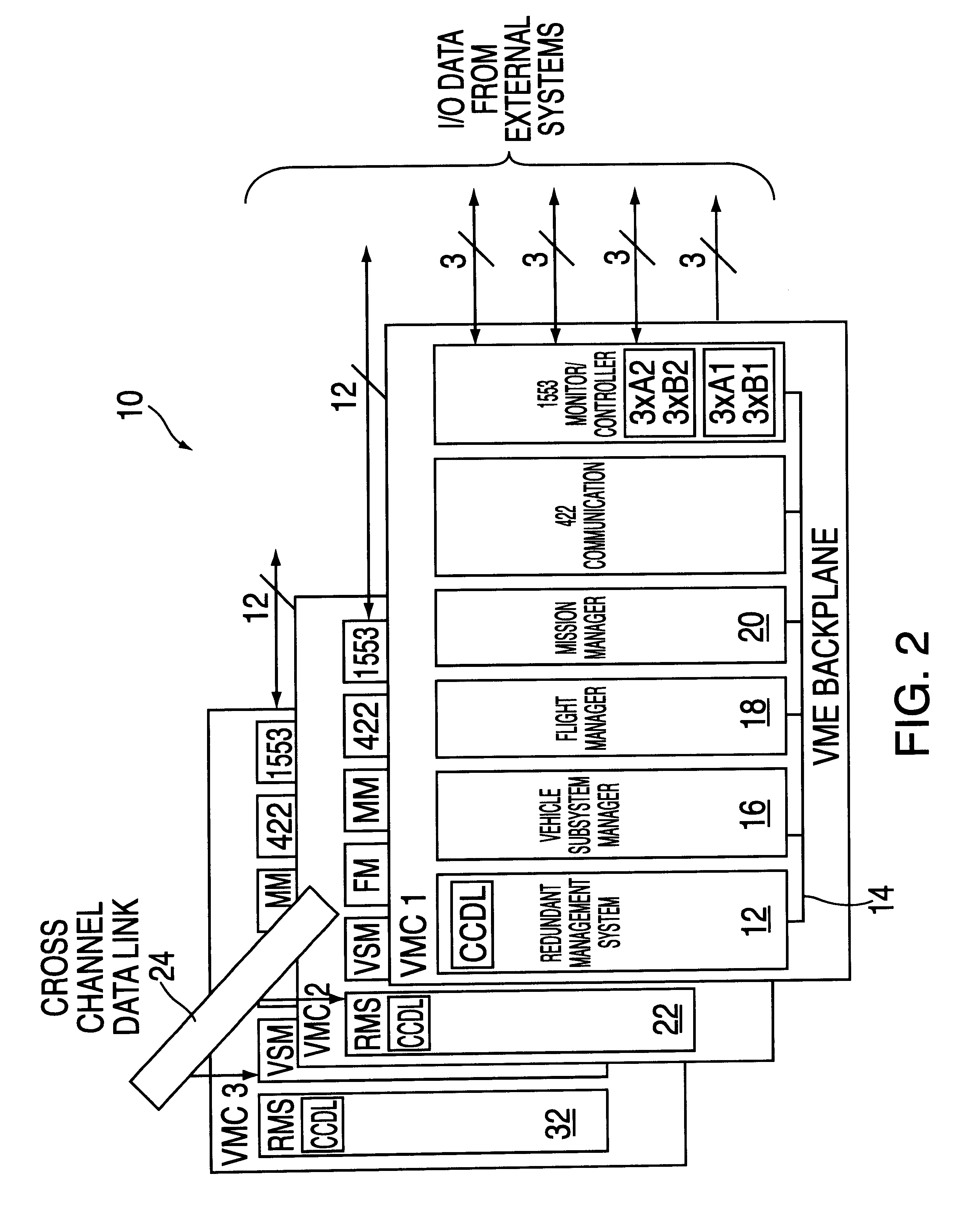
A stand alone Redundancy Management System (RMS) provides a cost-effective solution for managing redundant computer-based systems in order to achieve ultra-high system reliability, safety, fault tolerance, and mission success rate. The RMS includes a Cross Channel Data Link (CCDL) module and a Fault Tolerant Executive (FE) module. The CCDL module provides data communication for all channels, while the FTE module performs system functions such as synchronization, data voting, fault and error detection, isolation and recovery. System fault tolerance is achieved by detecting and masking erroneous data through data voting, and system integrity is ensured by a dynamically reconfigurable architecture that is capable of excluding faulty nodes from the system and re-admitting healthy nodes back into the system.
Owner:ALLIEDSIGNAL INC
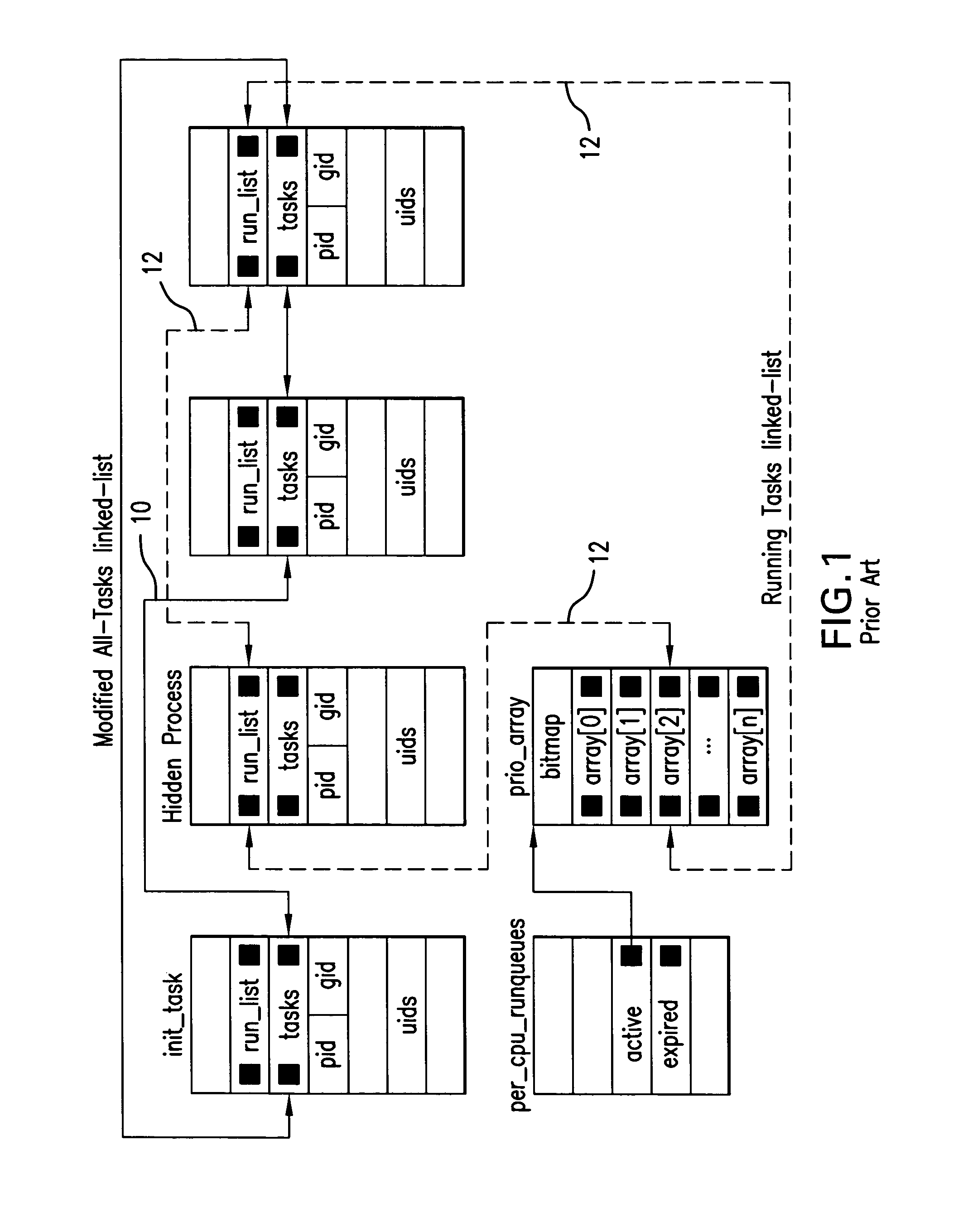
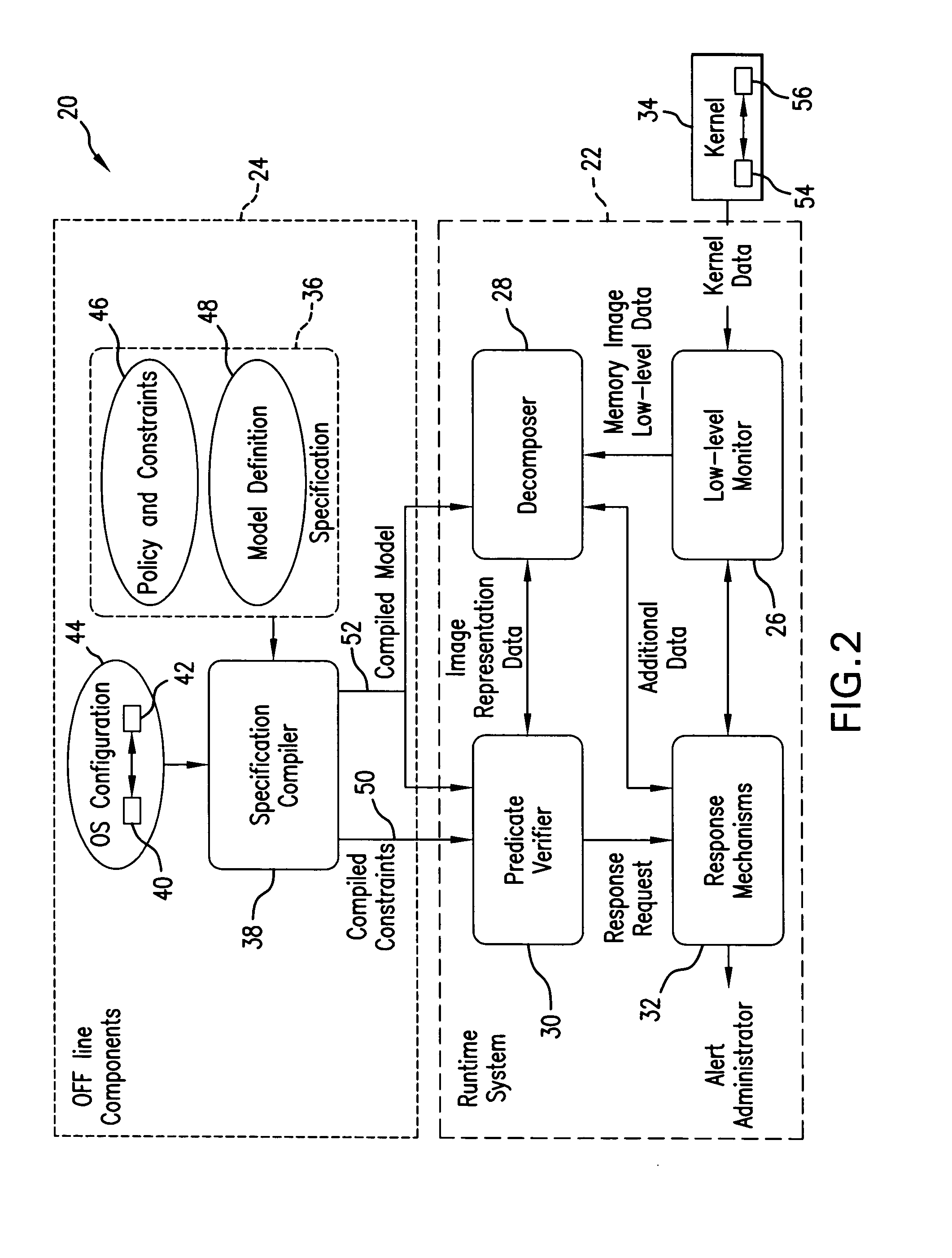
Method & system for monitoring integrity of running computer system
ActiveUS20070261120A1Digital data processing detailsAnalogue secracy/subscription systemsCourse of actionSystem monitor
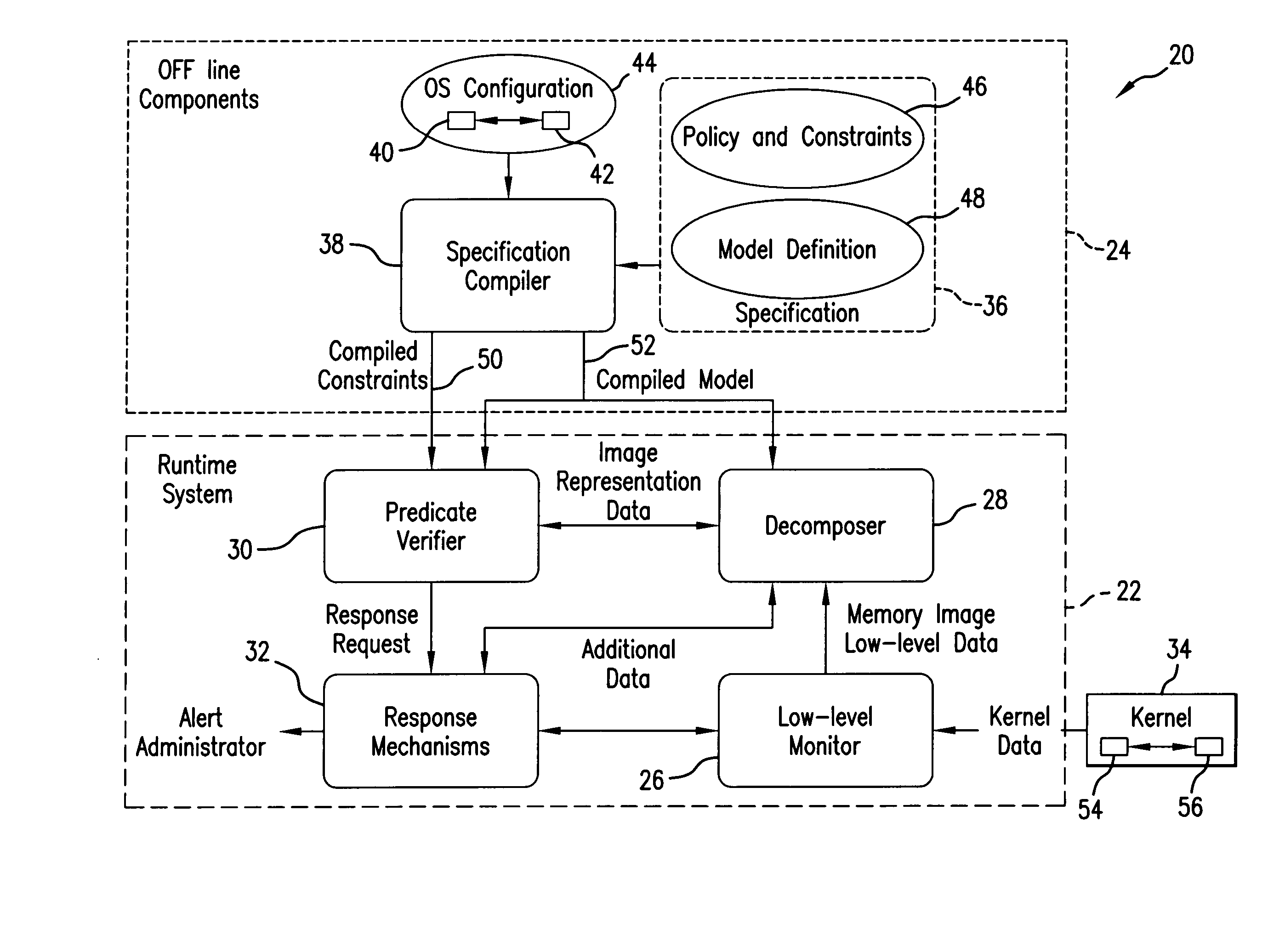
Monitoring integrity of a running computer system is based on creating a Test Model which includes predicates descriptive of invariant properties of security relevant objects and their attributes in the monitored structure known-to-be “healthy”, acquiring memory image of a portion of the running monitored structure, decomposing the acquired memory image to retrieve representation of the security relevant objects of interest, by implementing the attributes of the Test Model, and verifying, by implementing the predicates, whether the invariant properties defined in the Test Model remain unchanged for the running host system. If a discrepancy is detected, a signal indicative of a detected discrepancy is transmitted to a management entity for analysis and formulating a course of action.
Owner:MICROSOFT TECH LICENSING LLC
Apparatus And Method For A Wireless Sensor To Monitor Barrier System Integrity
This invention relates to an apparatus and a method for a wireless sensor to monitor barrier system integrity, such as used or employed during sequestration of greenhouse gases. This invention includes an apparatus for integrity monitoring of a borehole suitable for sequestration of greenhouse gases. The apparatus includes one or more sensors for placement outside of a casing to monitor a borehole, and a tool for movement within the casing to power and interrogate the one or more sensors. This invention also includes a method for monitoring integrity of a borehole suitable for sequestration of greenhouse gases or other types of well. The method includes the step of disposing one or more sensors outside a casing and the step of powering the one or more sensors with a tool inside the casing. The method also includes the step of interrogating the one or more sensors with the tool to monitor an engineered borehole and / or a natural caprock seal.
Owner:BP CORP NORTH AMERICA INC
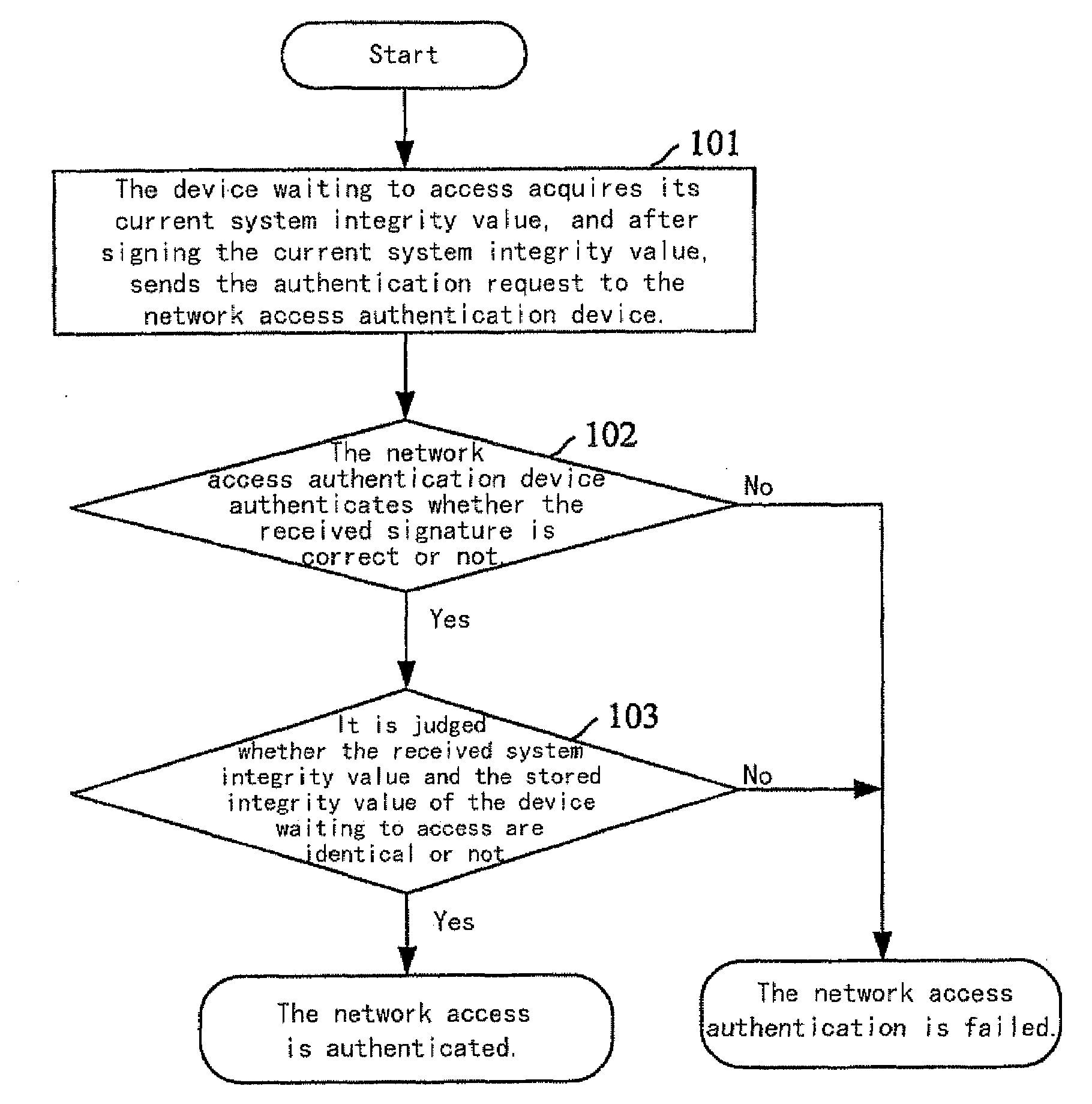
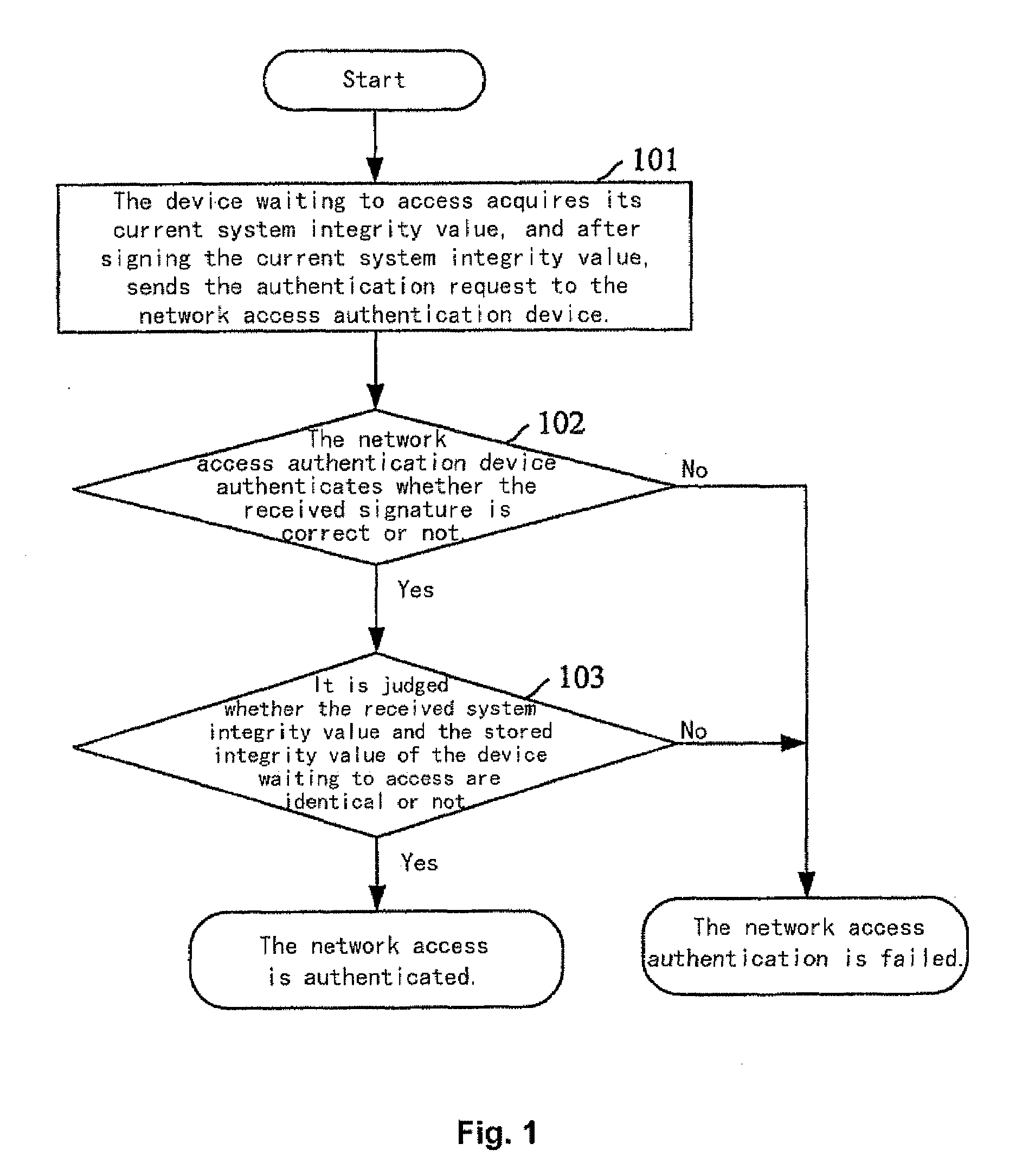
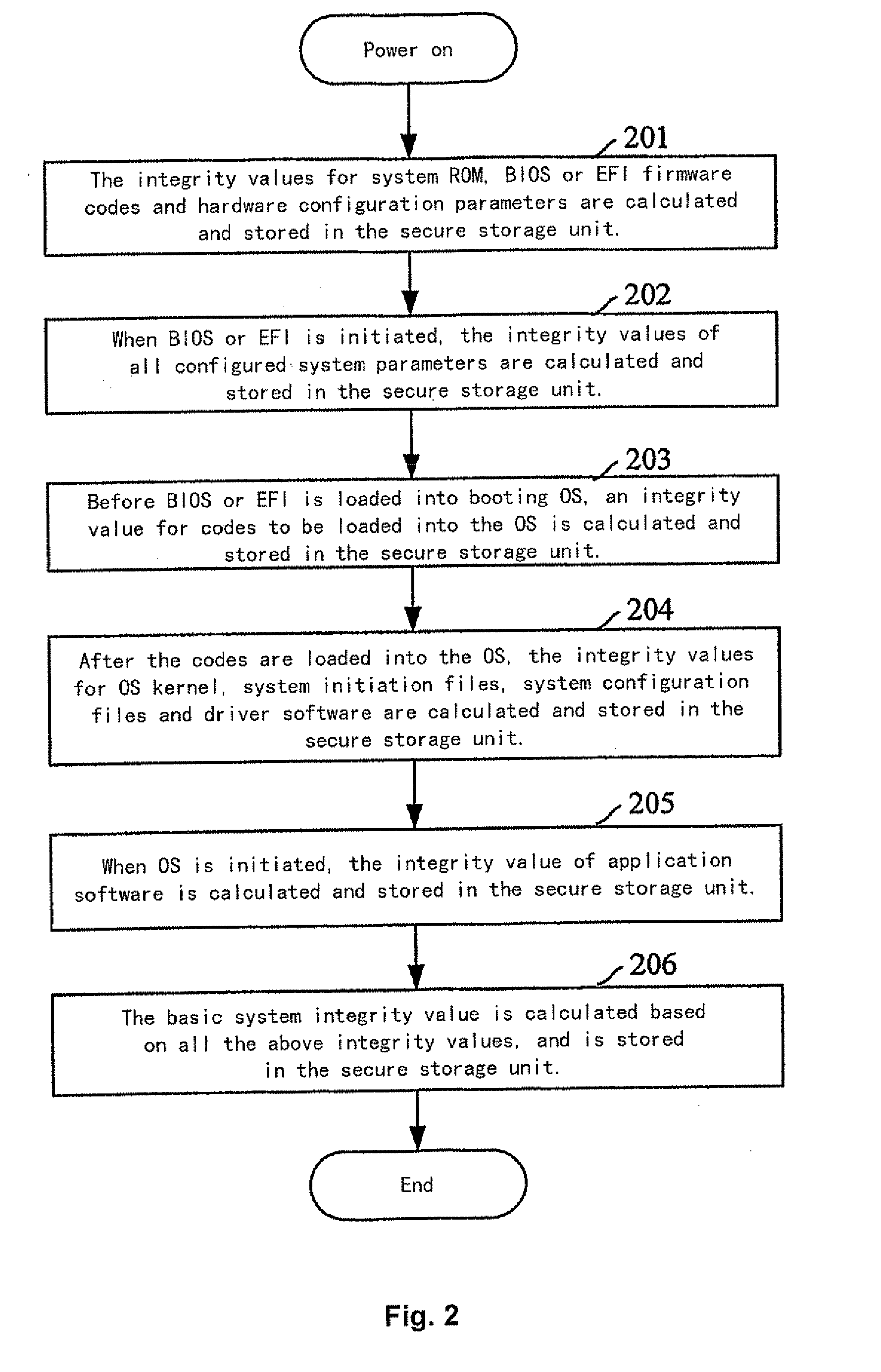
Method for realizing network access authentication
ActiveUS20090019528A1Ensure safetyDigital data processing detailsUser identity/authority verificationSystem integrityAuthentication
A method for realizing network access authentication, wherein a network access authentication device pre-storing a system integrity value of a device waiting to access and a correspondence between each device waiting to access and its system integrity value. When the device waiting to access needs to access the network, it acquires its current system integrity value, and sends the current system integrity value to the network access authentication device; the network access authentication device judges whether the received current system integrity value of the device waiting to access and its stored integrity value of the device waiting to access are identical or not, and in a case where the received current system integrity value of the device waiting to access and its stored integrity value of the device waiting to access are identical, it determines that the network access is authenticated. As such, the network access device could determine the real status of the device waiting to access, and ensure the device accessing to the network is really secure, thereby ensuring the security of the network.
Owner:LENOVO SOFTWARE +1
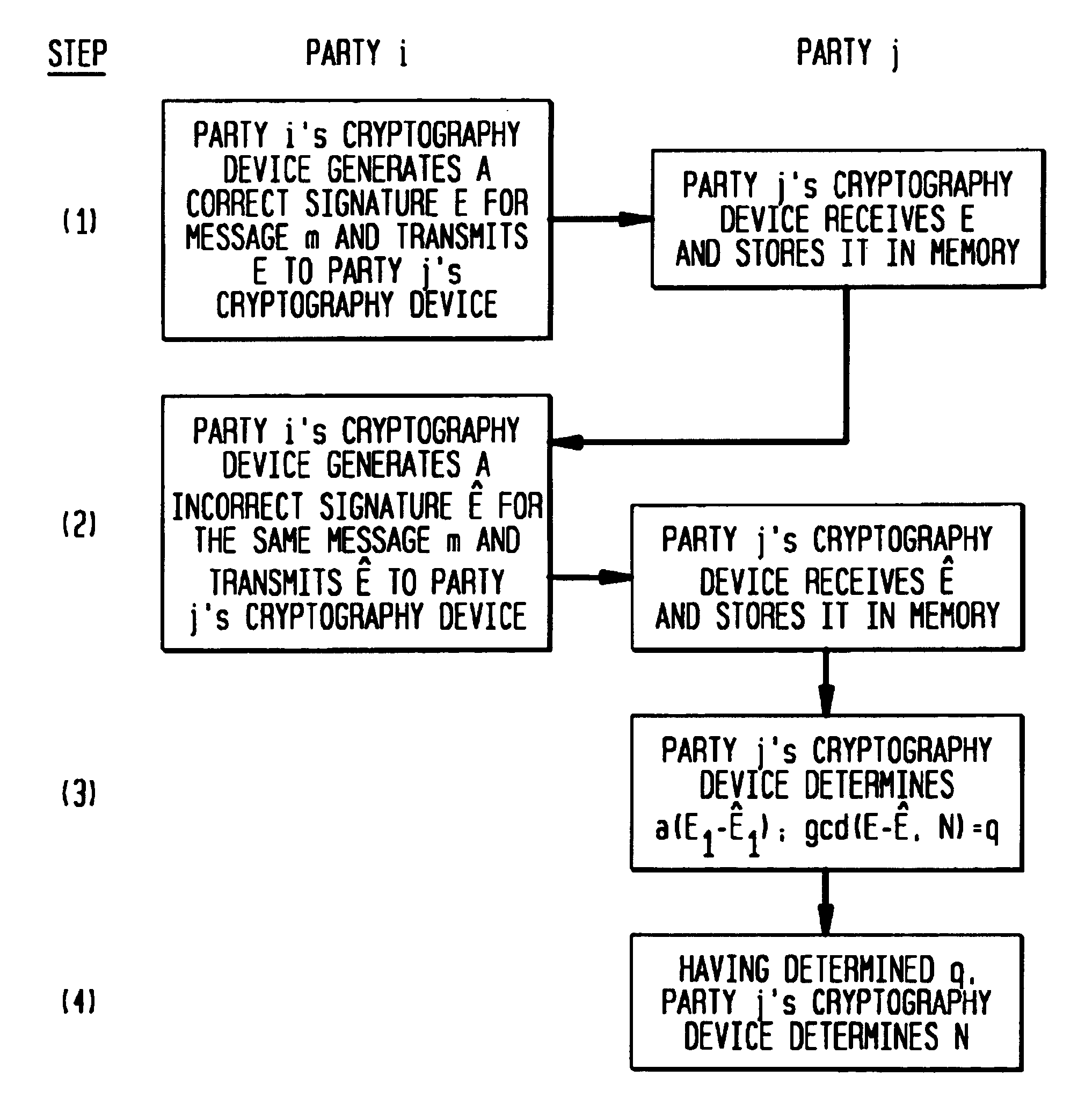
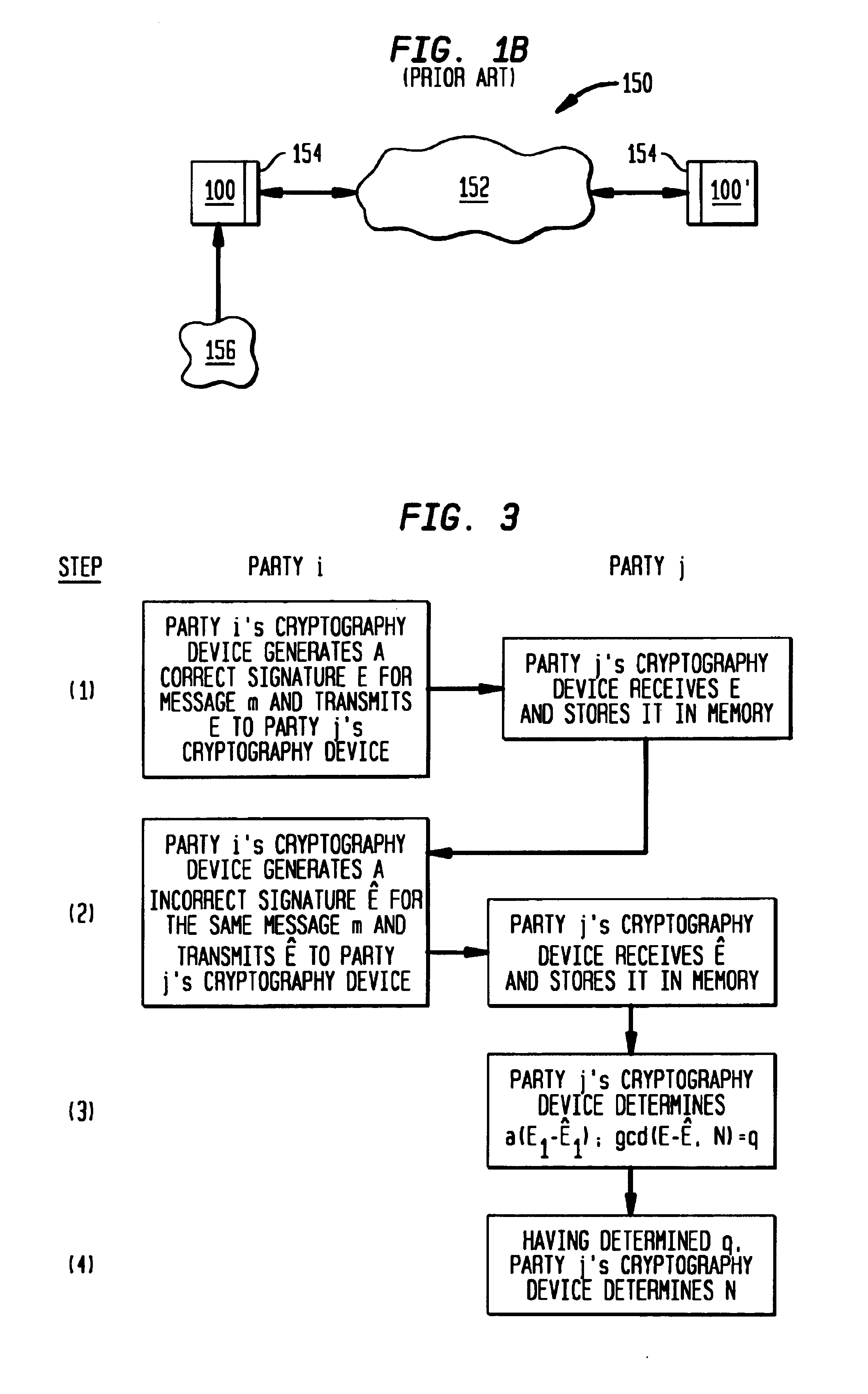
Method of using transient faults to verify the security of a cryptosystem
InactiveUS6965673B1Avoid calculationKey distribution for secure communicationPublic key for secure communicationPhysical stressUser Error
A useful method of verifying the integrity of a cryptosystem involves using erroneous outputs to obtain secret information. In certain signature schemes which use the Chinese Remainder Theorem, a correct signature of a message and an erroneous signature of the same message permit the modulus to be easily obtained. If the content of the message is known, such cryptosystems may be cracked with only an erroneous signature of the message. Certain other authorization schemes may be cracked by analyzing a number of erroneous outputs caused by a particular type of error called a “register fault.” A security expert or cryptosystem designer may intentionally induce a tamper proof device generate a faulty computation by subjecting the device, such as a smart card, to physical stress, such as certain types of radiation, atypical voltage levels, or a higher clock rate than the device was designed to accommodate. Cryptosystems should be impervious to the attacks described herein. If not, the system should be modified or discarded.
Owner:HANGER SOLUTIONS LLC
Web-based Information Management System
ActiveUS20140012922A1Shorten the timeImprove data consistencyMultiple digital computer combinationsWebsite content managementData validationData display
A web-based information management system allows a group of users to collect, validate, and share data of unknown types and volume in real time over the Internet. The project work environment for a group can be created, modified, and reset instantly during any project life and between project life cycles by a plurality of methods without effecting system integrity and core functions such as data validation, searches and sorting, data preservation, data display feature, and productive data entry methods.
Owner:WU JIANQING
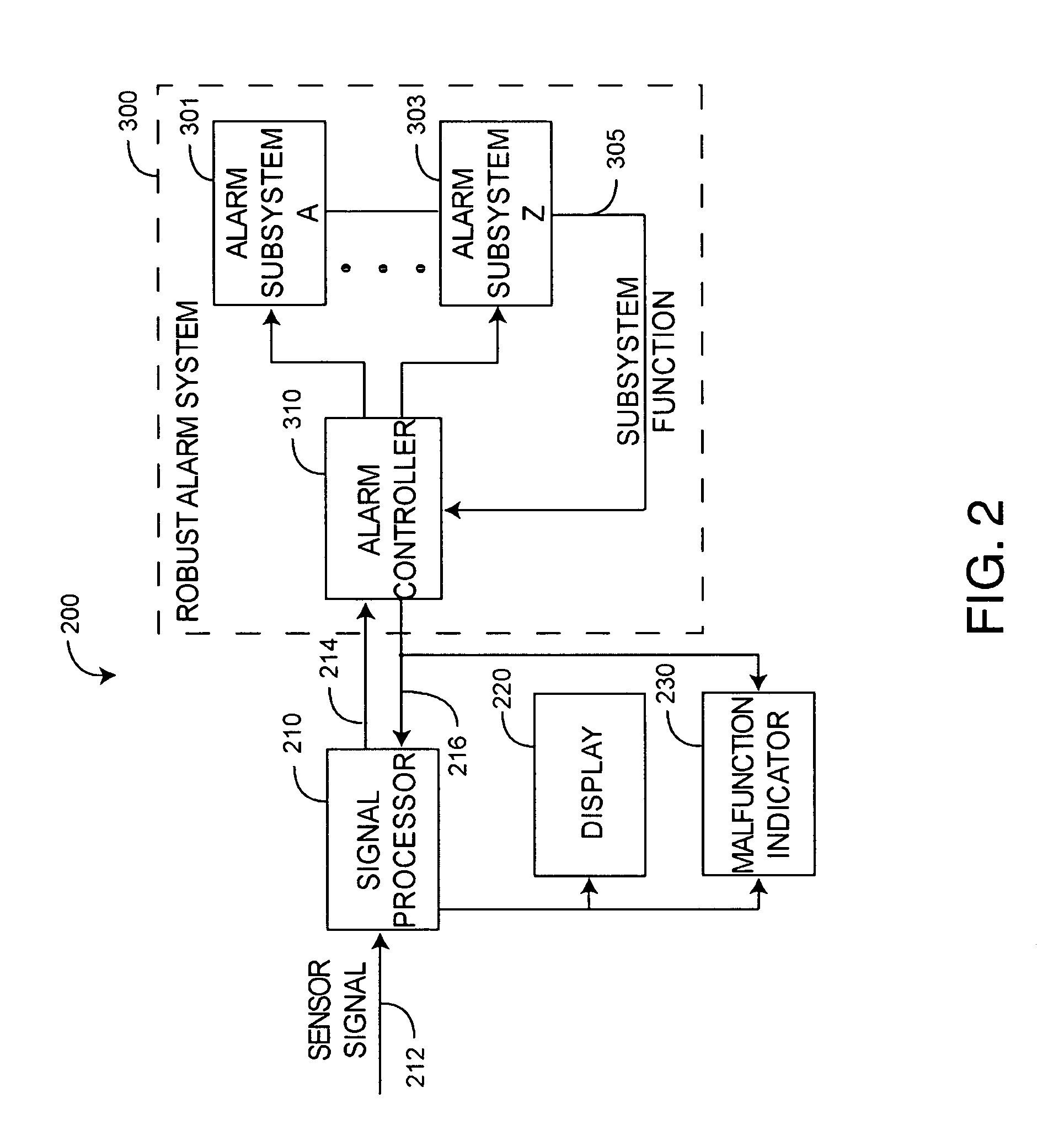
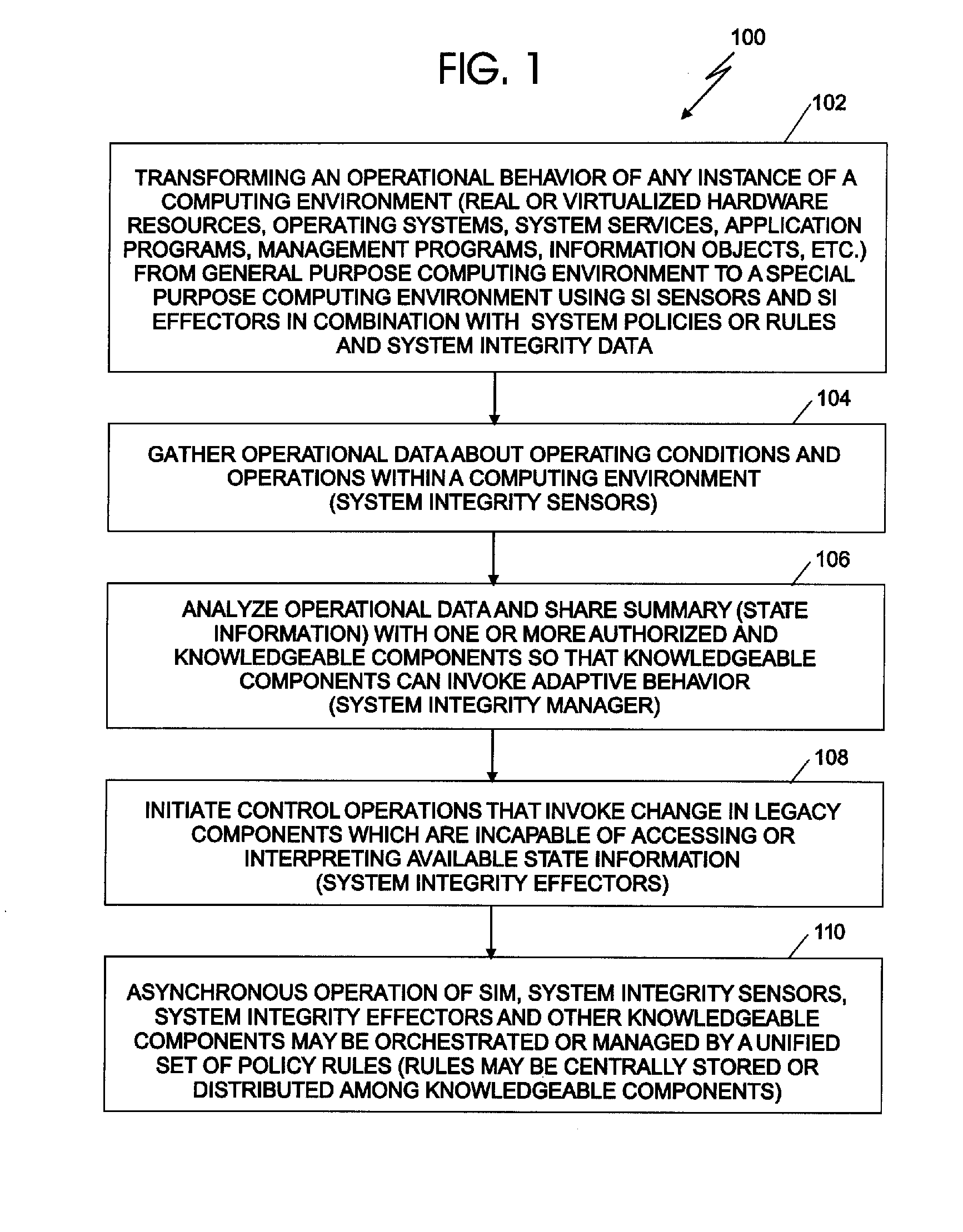
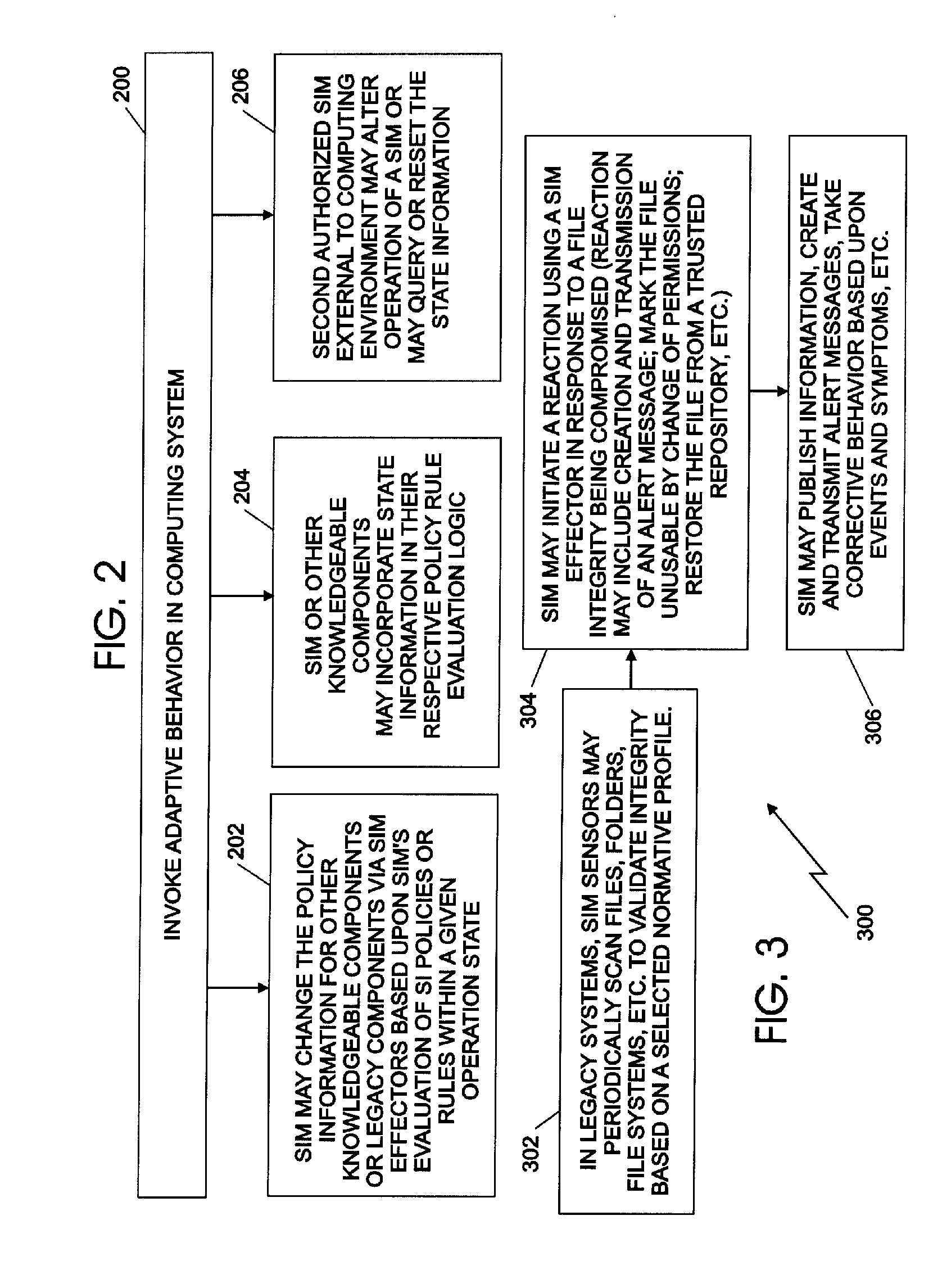
System integrity manager
InactiveUS20070044151A1Provide securityMemory loss protectionError detection/correctionComputer hardwareGeneral purpose
A system integrity manager, system, computer program product and method for providing security may include transforming an operational behavior of an instance of a computing system from a general purpose computing system to a special purpose computing system. The operational behavior may be transformed by using at least one of a system integrity sensor and a system integrity effector and a set of system integrity policies and system integrity data.
Owner:IBM CORP
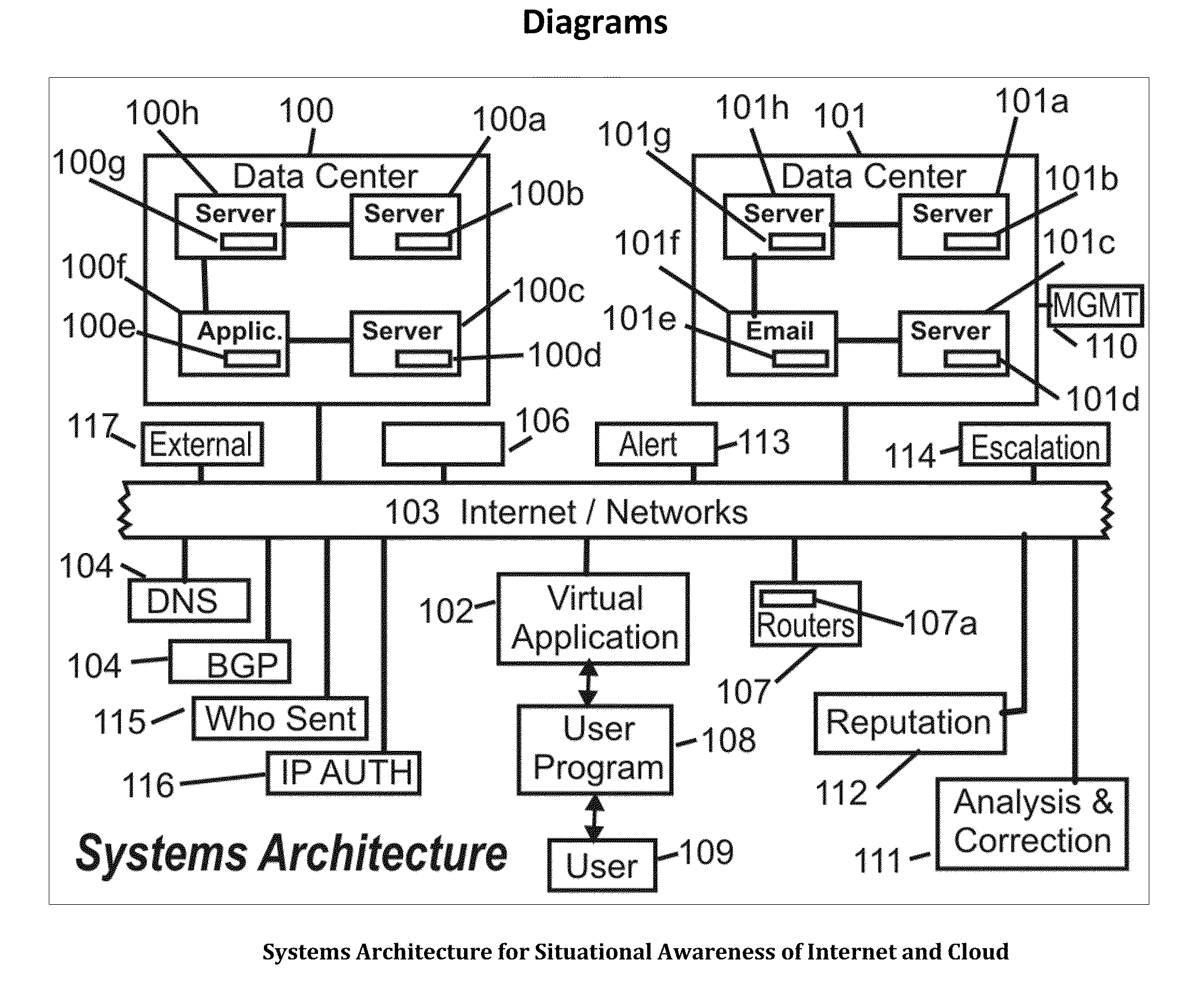
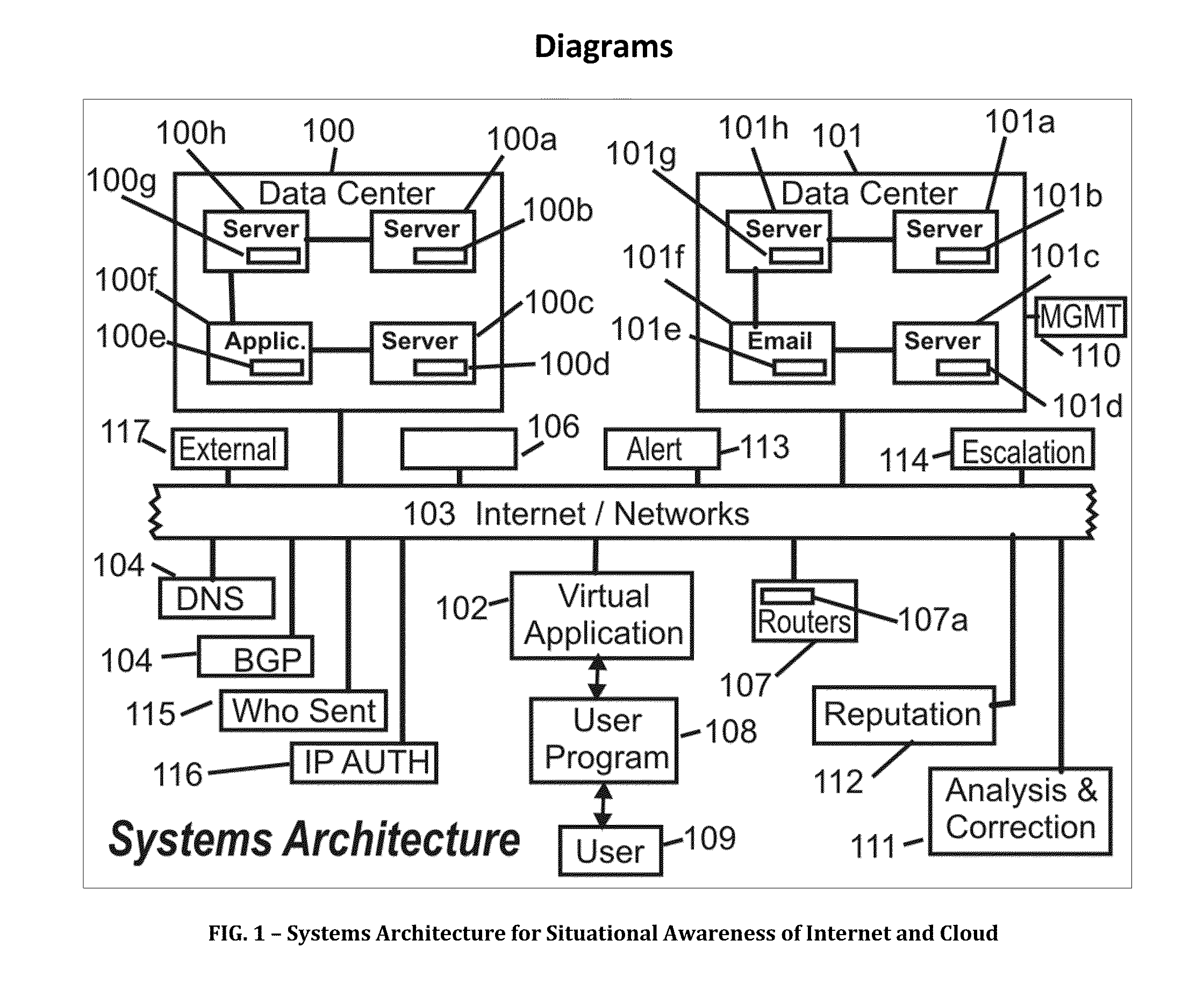
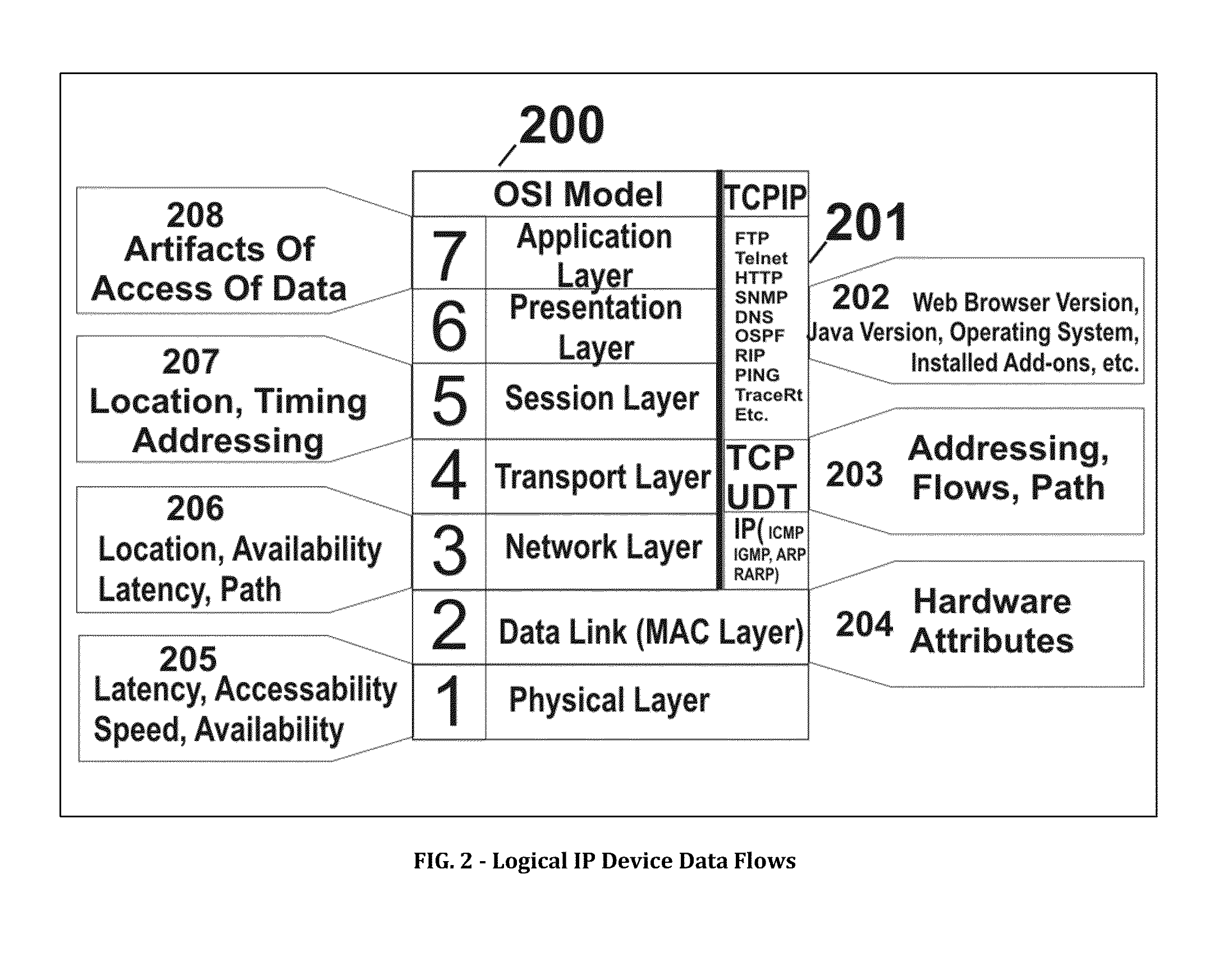
Systems, methods and devices for providing situational awareness, mitigation, risk analysis of assets, applications and infrastructure in the internet and cloud
InactiveUS20120011590A1Memory loss protectionError detection/correctionAnalysis dataApplication software
The present invention determines a situational awareness for alerting, mitigating error, distortion or failures, and managing the Internet (or equally component intranets), connected networks and cloud infrastructure. Specifically, this invention focuses on determining who originates messages, from what system, and the path taken, thereby analyzing the reputation of all the nodes and links through which data passes.It can provide a mechanism determine the ongoing veracity of the “purported” device, and maintain a reputation database of devices, data, applications and networks for analysis of how the Internet is being used or potentially subverted—effectively creating a score indicating component and total system integrity. It can calculate a correlation of risk analysis of all adjacent data describing the universe of the Internet. This invention will be particularly useful for helping detect and mitigate compromises to data, networks, systems and other assets within the Internet and Cloud.
Owner:DONOVAN JOHN JOSEPH
Robust alarm system
ActiveUS20070109115A1Improve alarm reliabilityDiagnostic recording/measuringOptical sensorsFault indicatorControl theory
A robust alarm system has an alarm controller adapted to input an alarm trigger and to generate at least one alarm drive signal in response. Alarm subsystems input the alarm drive signal and activate one or more of multiple alarms accordingly. A subsystem function signal provides feedback to the alarm controller as to alarm subsystem integrity. A malfunction indicator is output from the alarm controller in response to a failure within the alarm subsystems.
Owner:JPMORGAN CHASE BANK NA
Apparatus and method for a wireless sensor to monitor barrier system integrity
Owner:BP CORP NORTH AMERICA INC
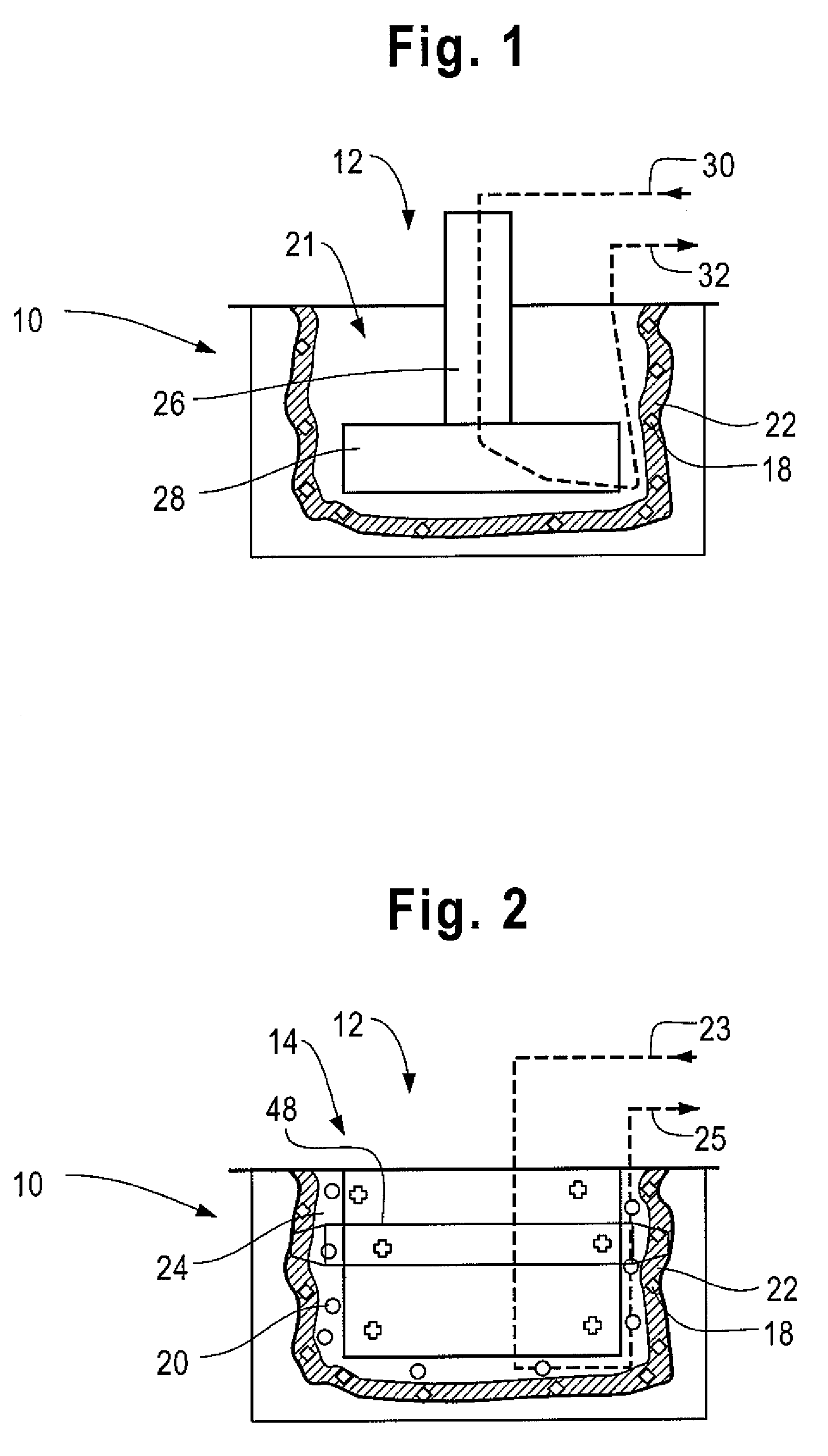
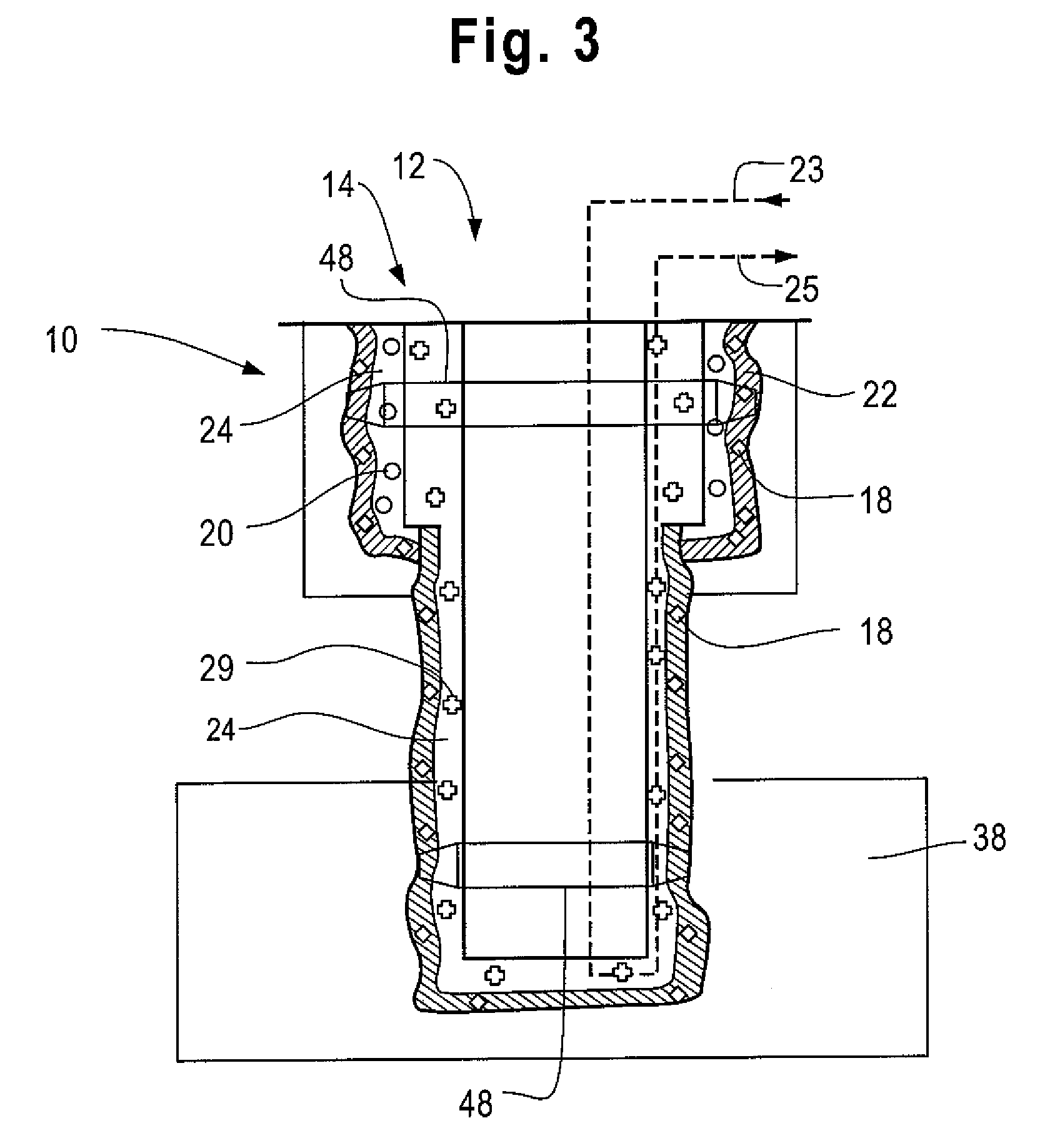
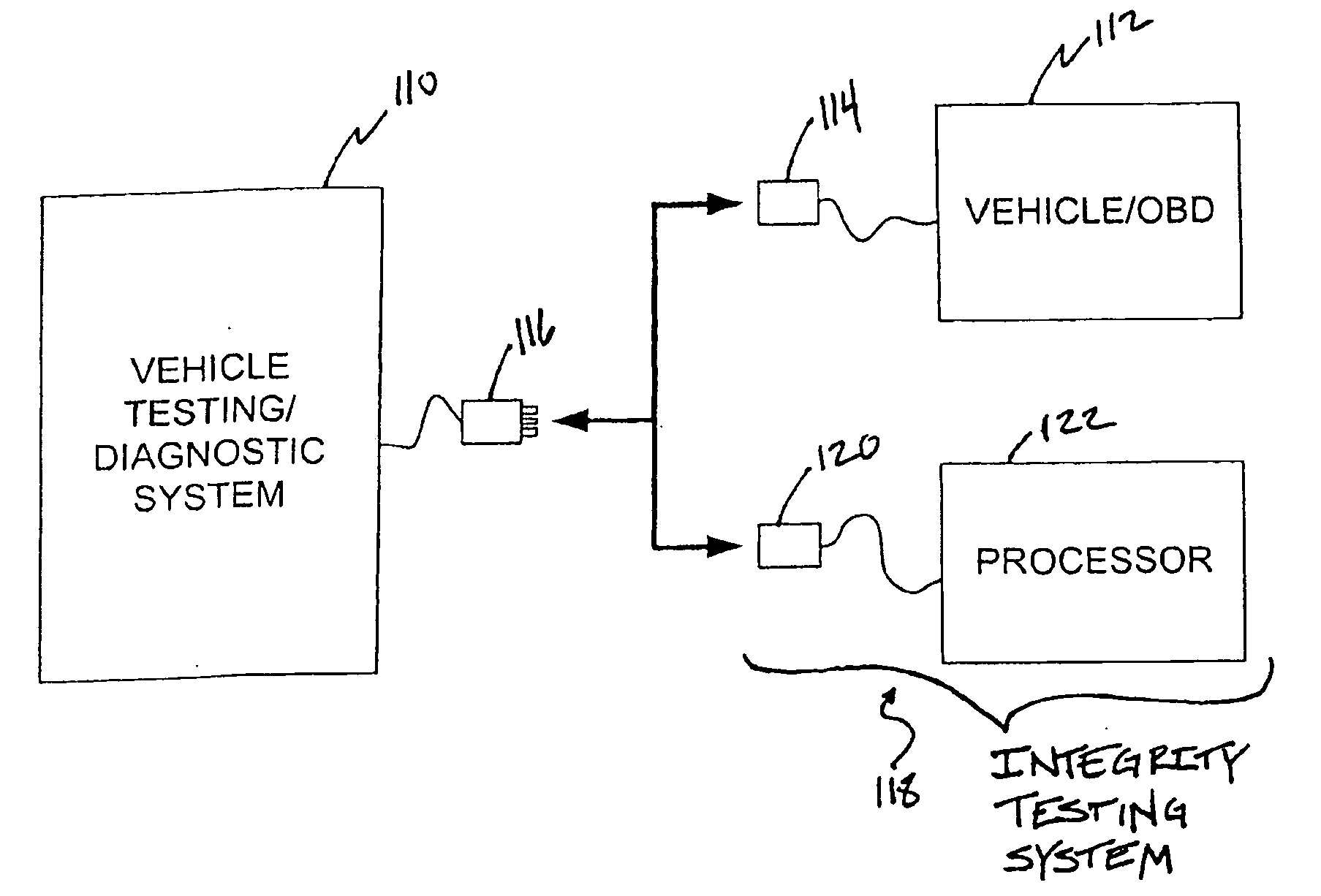
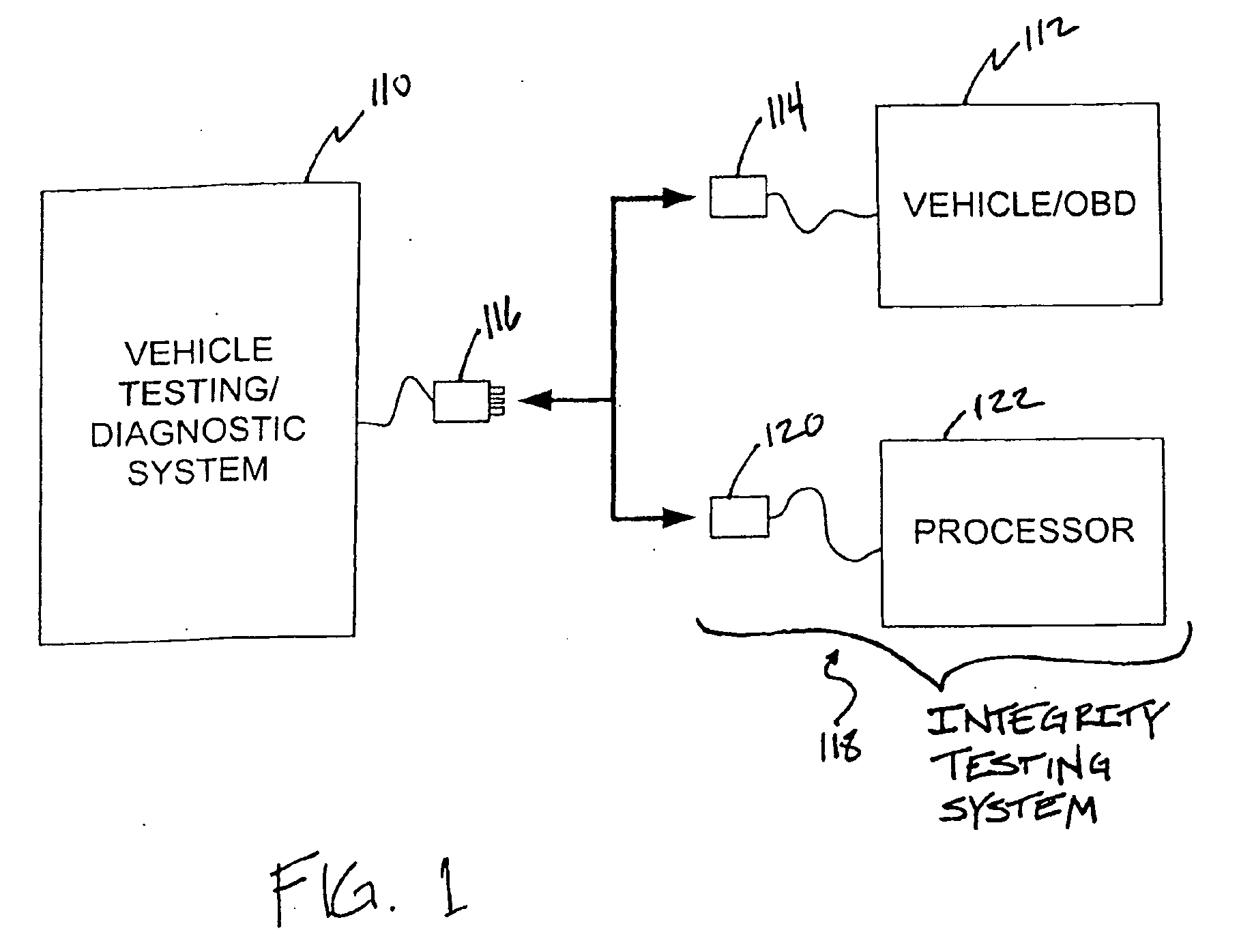
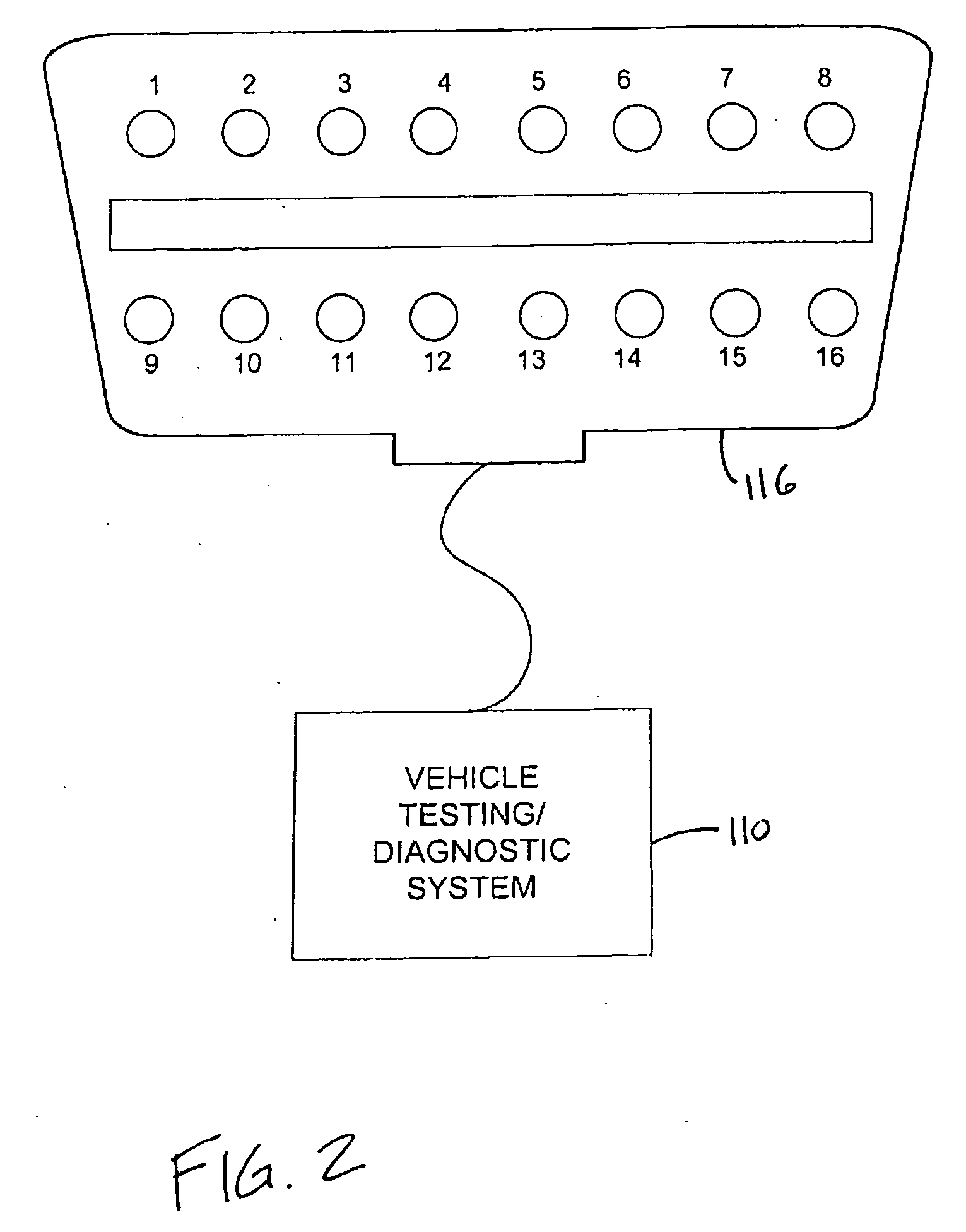
System and method for testing the integrity of a vehicle testing/diagnostic system
InactiveUS20070043488A1Not capableVehicle testingRegistering/indicating working of vehiclesEngineeringIntegrity testing
A system and method for testing the integrity of a vehicle testing / diagnostic system is provided. Examples of vehicle testing / diagnostic systems may include any equipment (portable or stationary) found in an automotive maintenance and / or testing environment (or other environment) that is capable of communicating with vehicle on-board diagnostic (OBD) systems. Prior to conducting an OBD test on one or more vehicles, an integrity testing system interfaces with a vehicle testing / diagnostic system to determine whether the vehicle testing / diagnostic system is capable of communicating via one or more predetermined communications protocols.
Owner:ENVIROTEST SYST HLDG CORP
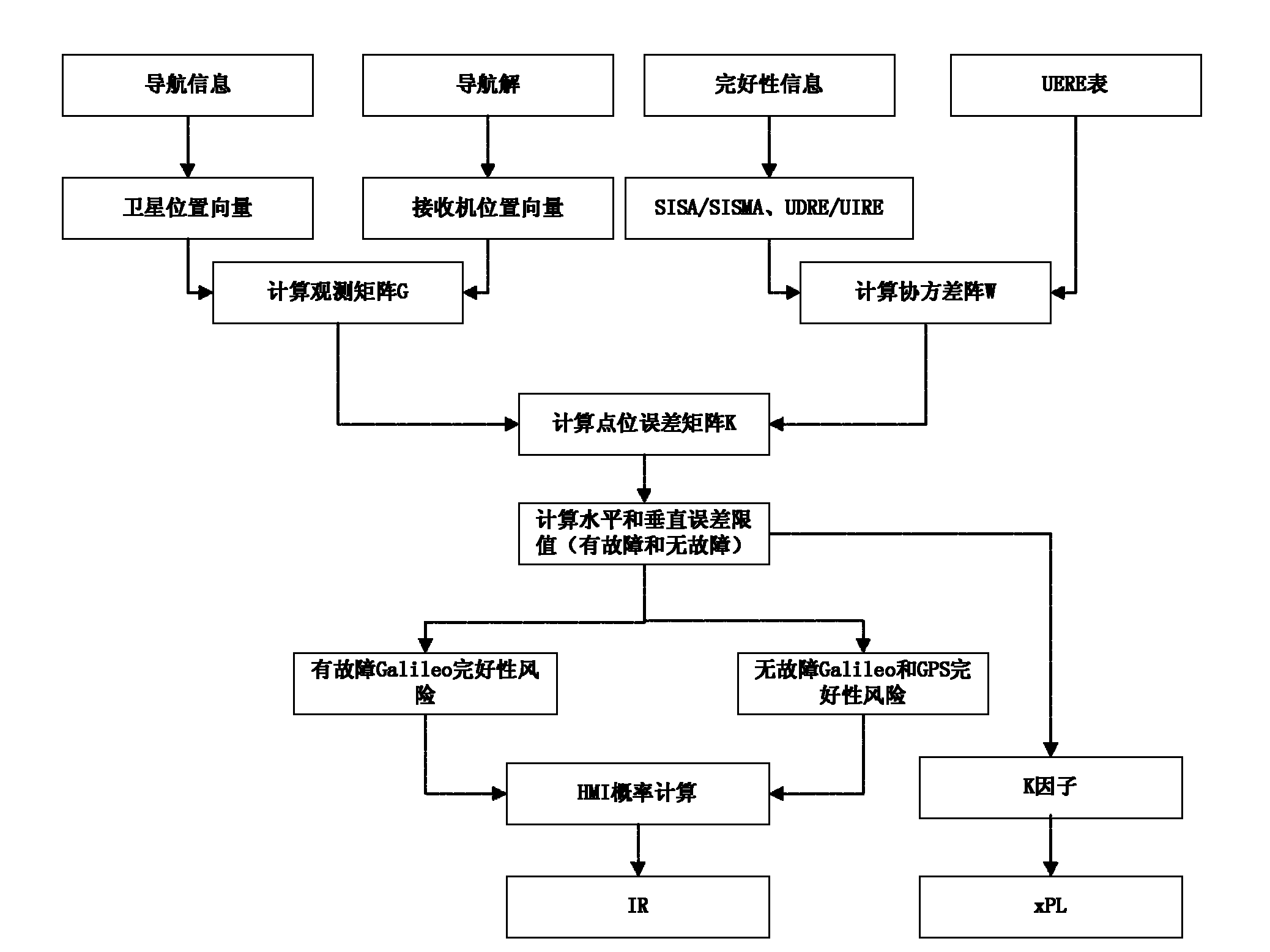
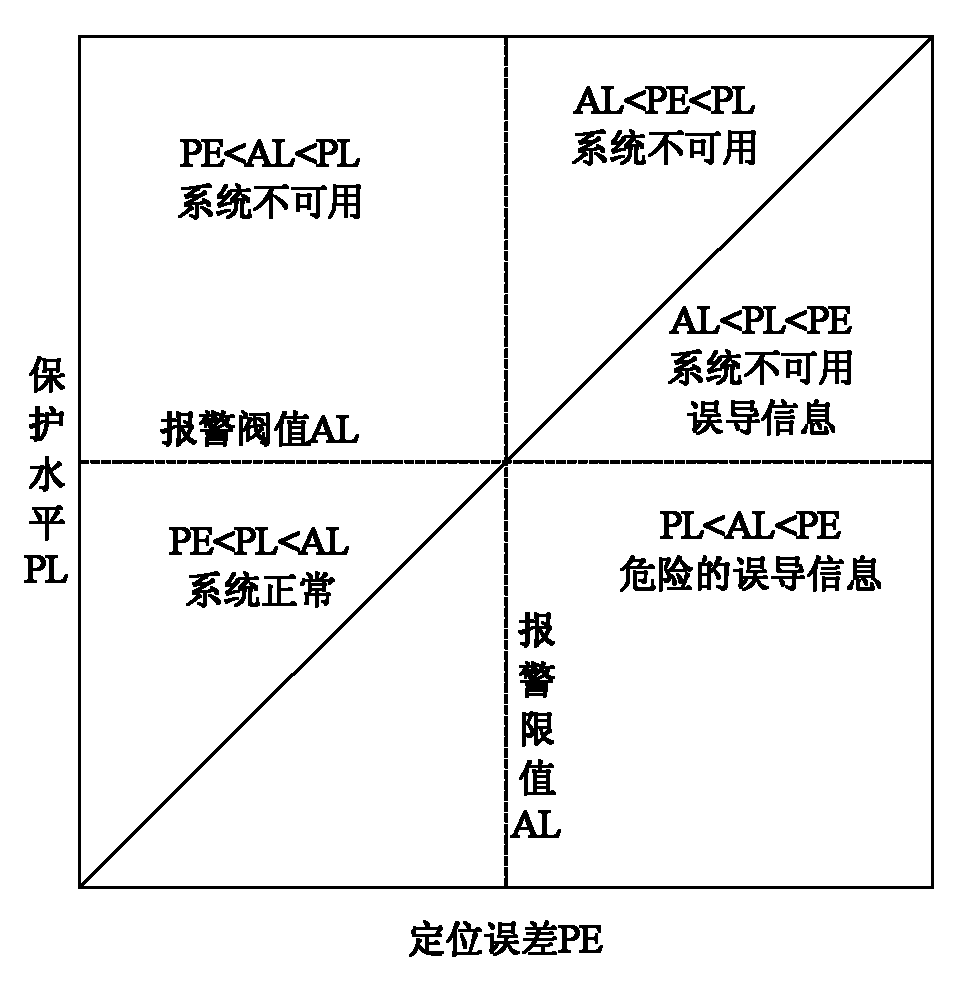
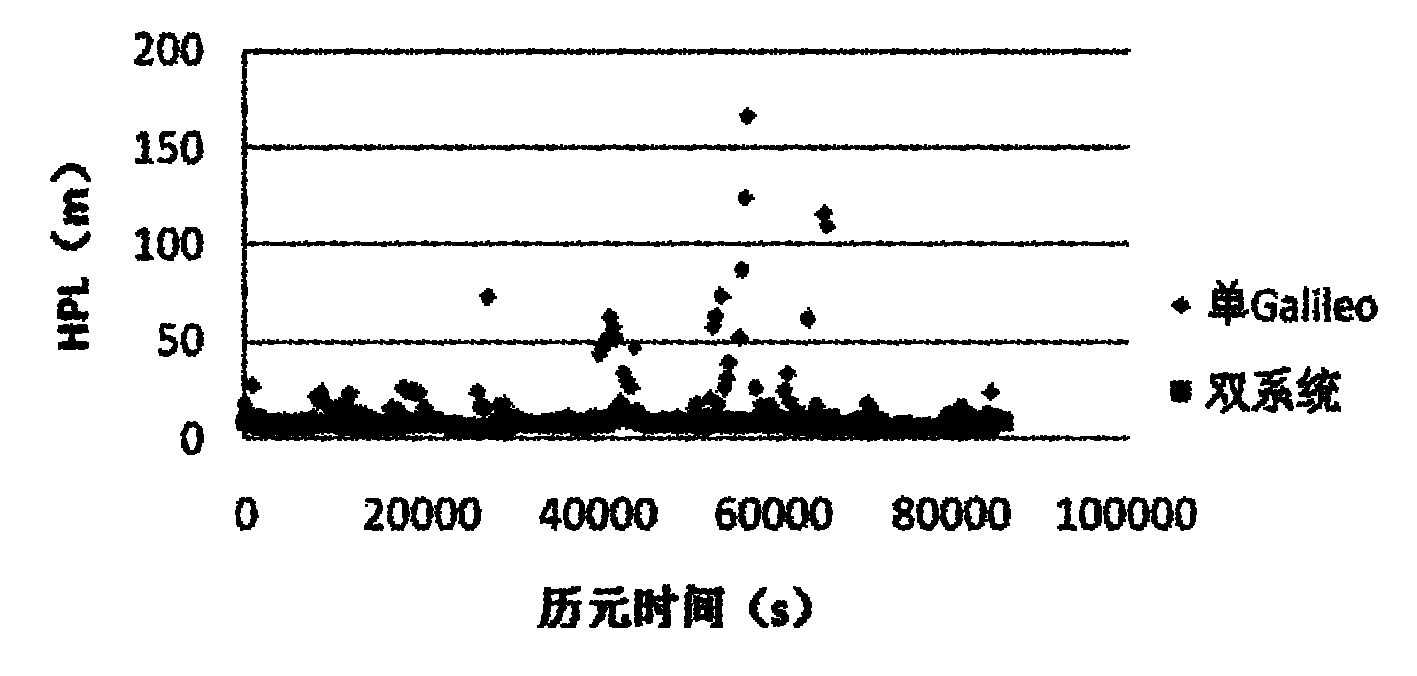
Galileo system integrity concept-based multimode user integrity assessing method
ActiveCN102096075AImprove integrityImprove usabilitySatellite radio beaconingSpecial data processing applicationsEarth observationEuropean Geostationary Navigation Overlay Service
The invention belongs to the field of the integrity study of a satellite navigation system in the technical field of earth observation and navigation, and provides a Galileo system integrity concept-based multimode user integrity assessing method. In the method, the conventional Galileo user integrity concept is used in two systems directly, for a non-Galileo system (such as European geostationary navigation overlay service (EGNOS)), input parameters are needed to be pretreated appropriately, so that the input parameters are converted into information available in a Galileo user integrity algorithm, and the change in values of an integrity risk (IR) and / or a protection level (xPL) is monitored during integrity analysis. In the method, the assessment of multisystem user integrity is realized by using a more advanced Galileo system integrity concept; and by comparing and analyzing integrity calculation results of a single system and a multisystem, the availability of positioning resultsof users is improved substantially under the condition of the multisystem, and the user integrity is improved to a large extent.
Owner:CHINA AEROSPACE KEGONG INFORMATION TECH RES INST
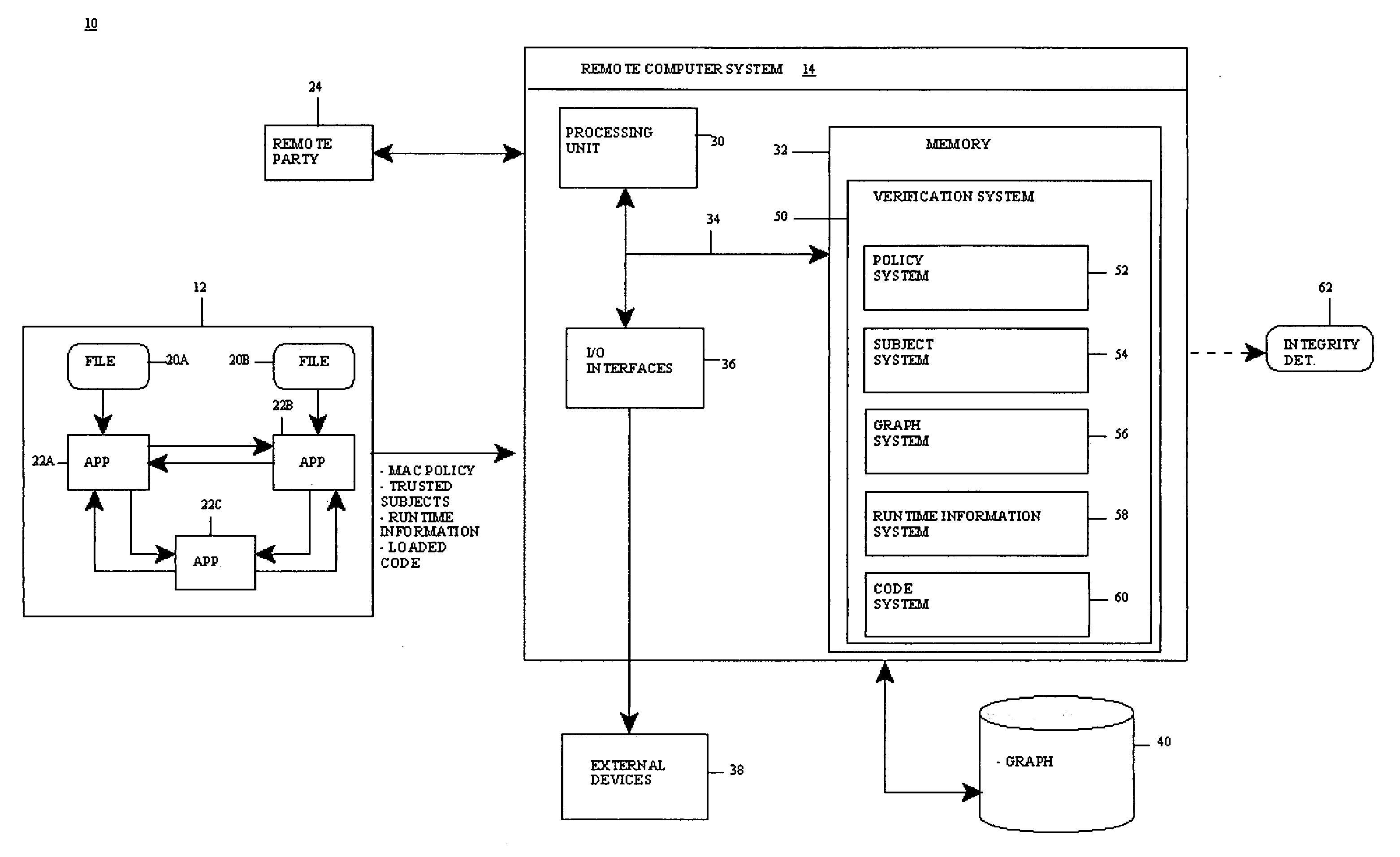
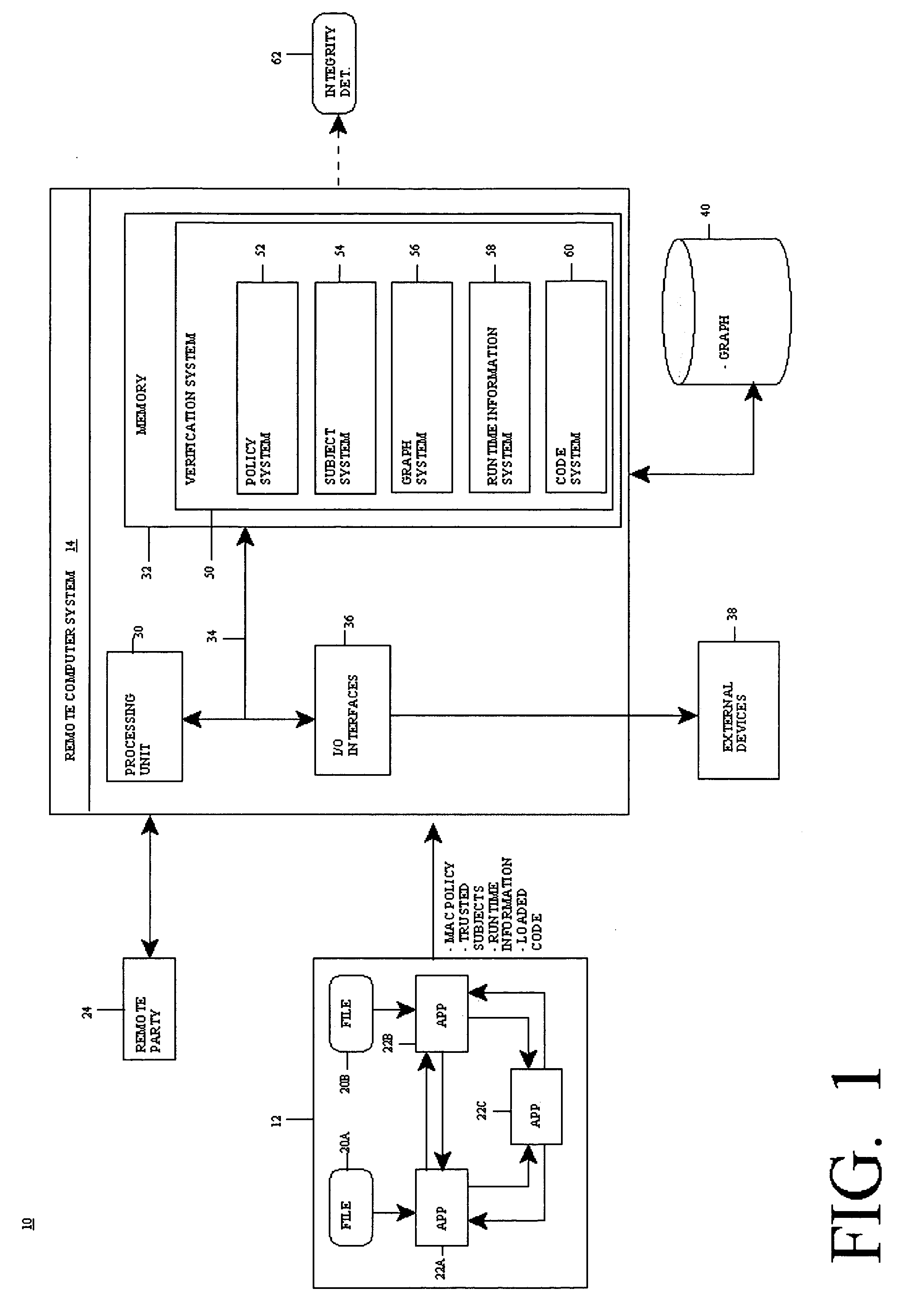
Method, system and program product for remotely verifying integrity of a system
InactiveUS20070107046A1Memory loss protectionDigital data processing detailsComputer hardwareSystem integrity
The present invention provides a computer-implemented method system and program product for remotely verifying (e.g., analytic) integrity of a system. Specifically, at startup of the system an access control policy that sets forth information flows within the system is read and a set of trusted subjects that interact with a target application in the system is determined. Based on the access information flows and the set of trusted subjects, an information flow graph of the system is constructed. At runtime of the target application, runtime information and program code loaded into the set of trusted subjects are measured. Measuring the program code that is loaded allows the remote party to verify that the program code is “expected” program code for the set of trusted subjects.
Owner:IBM CORP
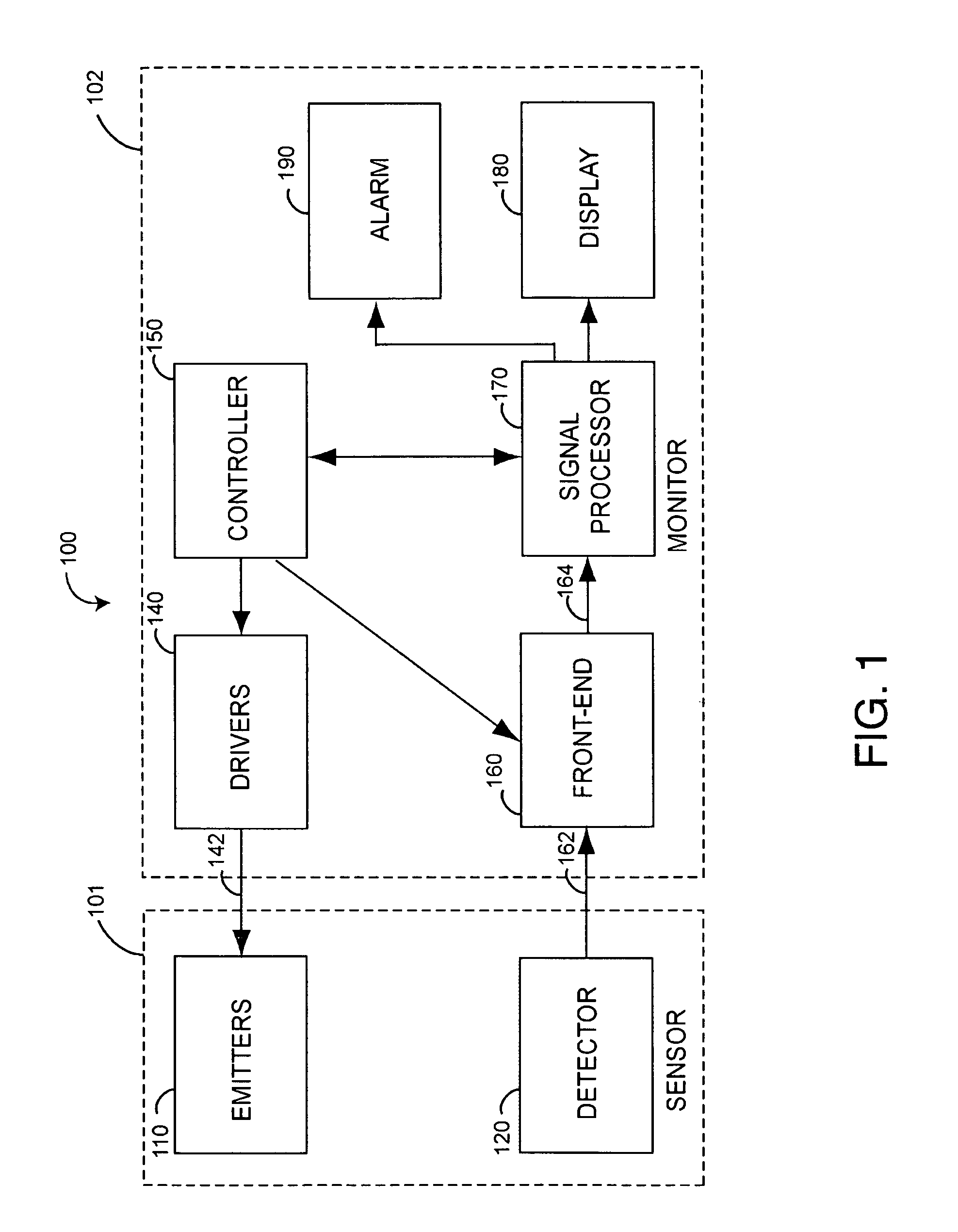
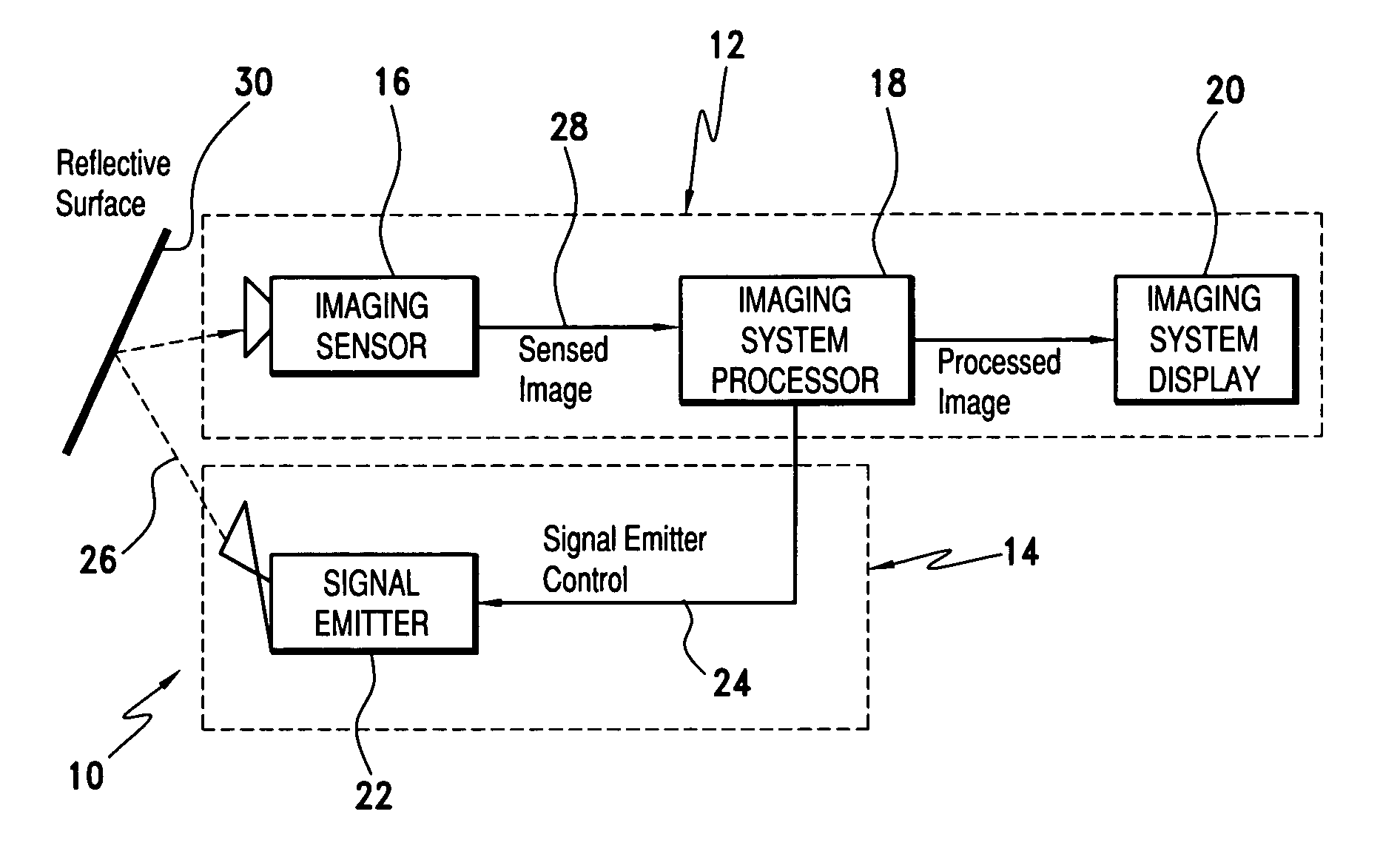
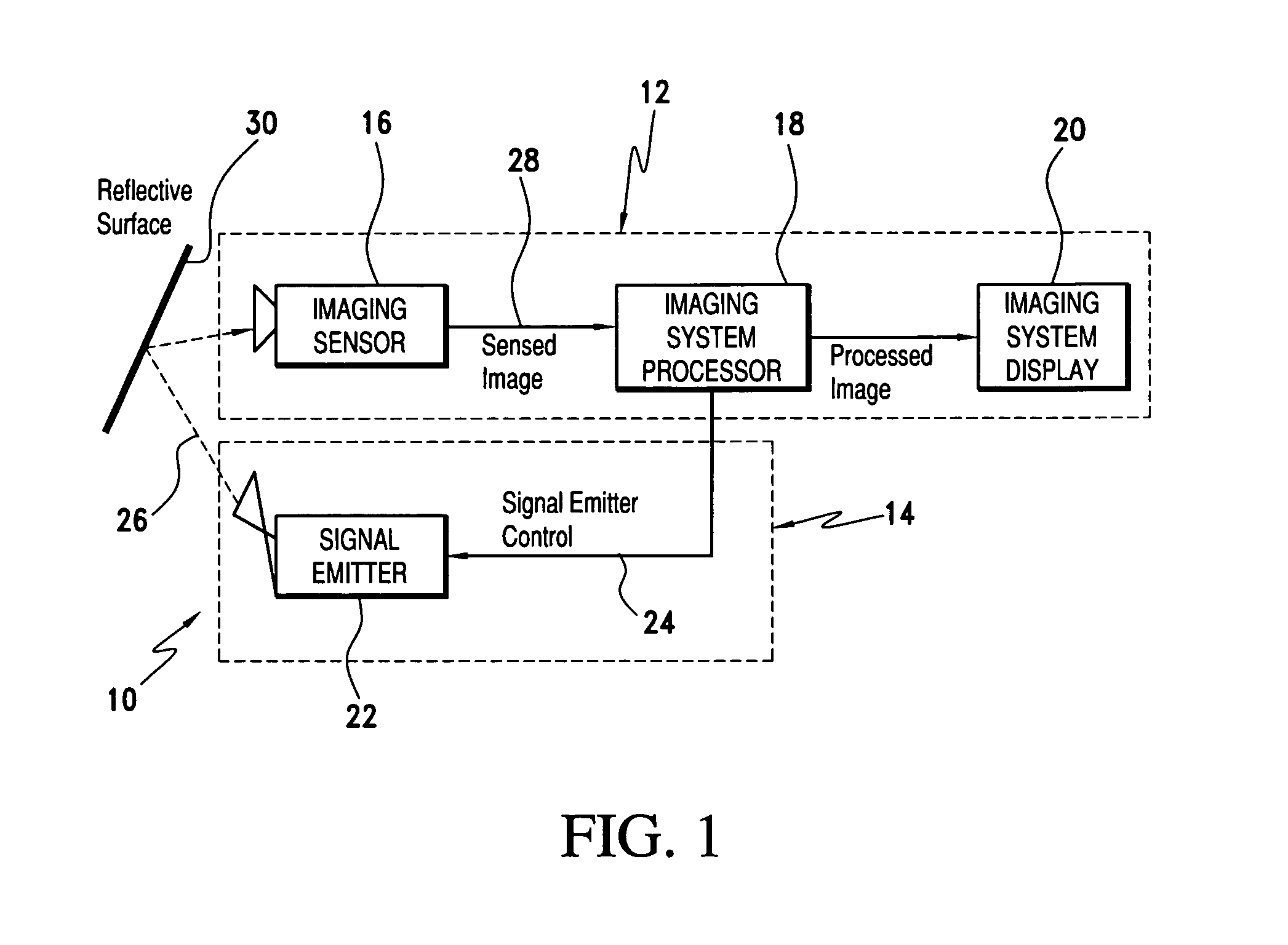
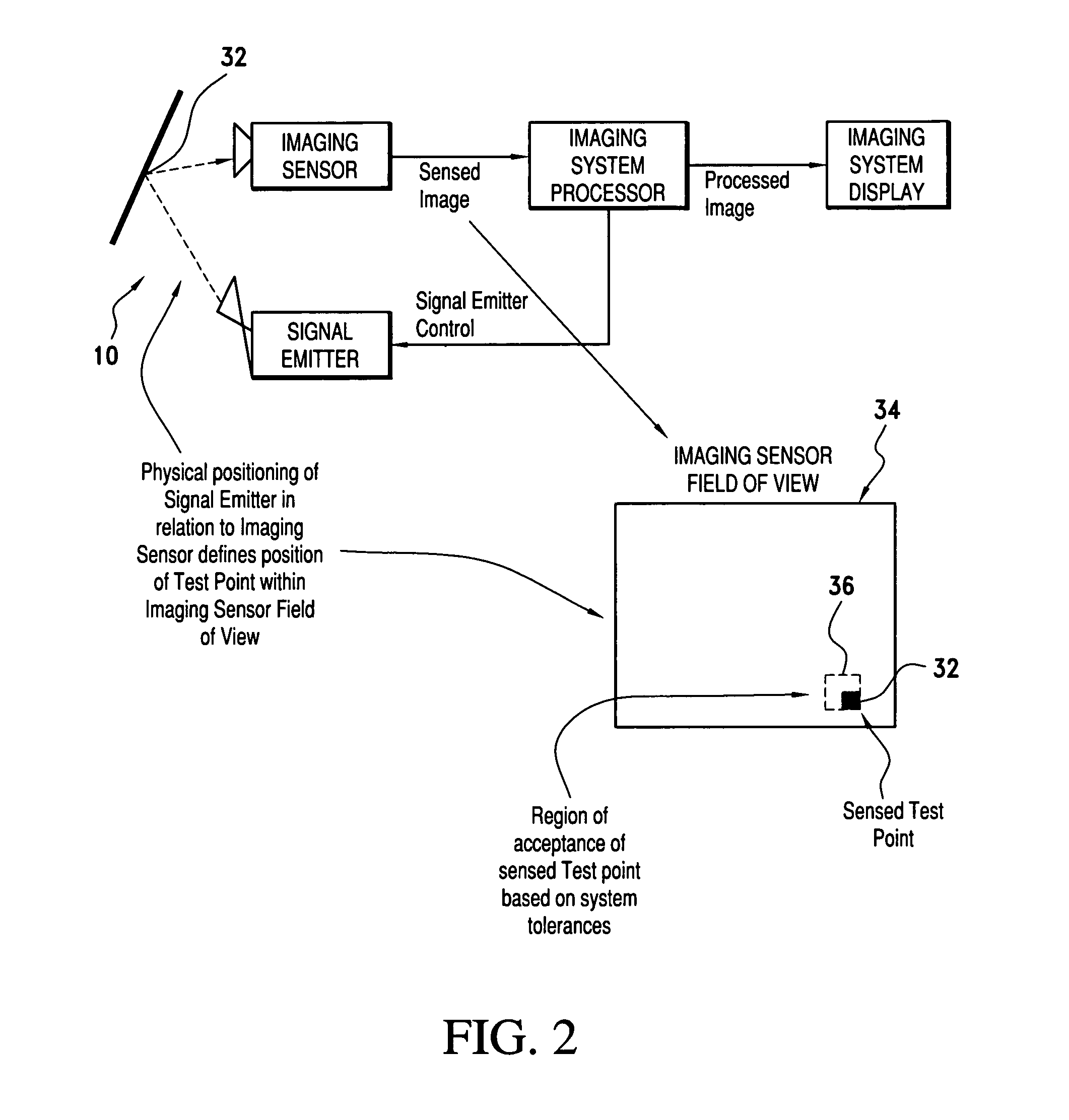
Scene imaging system integrity monitor and method thereof
A scene imaging system (SIS) integrity monitor for monitoring the required operation of an imaging sensor of an SIS. The SIS is of a type including: i) an imaging sensor, ii) an imaging system processor, and iii) an imaging system display. The SIS integrity monitor includes a signal emitter assembly for receiving emitter drive signals from an imaging system processor and directing a monitoring image into the active field of view of an imaging sensor for sensed image generation. The generated image is provided to the imaging system processor for analysis. The imaging system processor evaluates the location and modulation state of the generated image to determine if faults exist in the image generation or image display paths.
Owner:ROCKWELL COLLINS INC
Long period chiral fiber grating apparatus
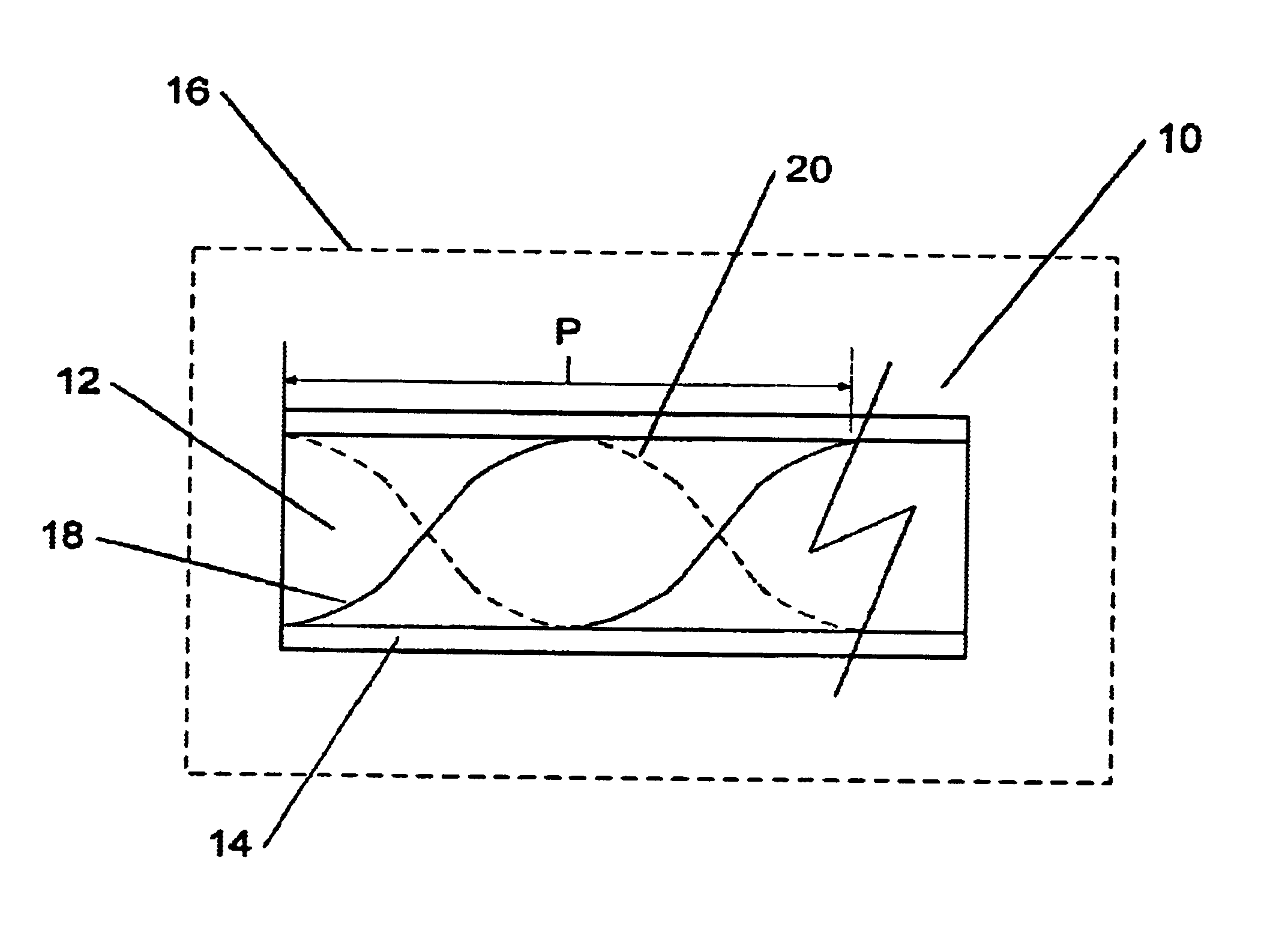
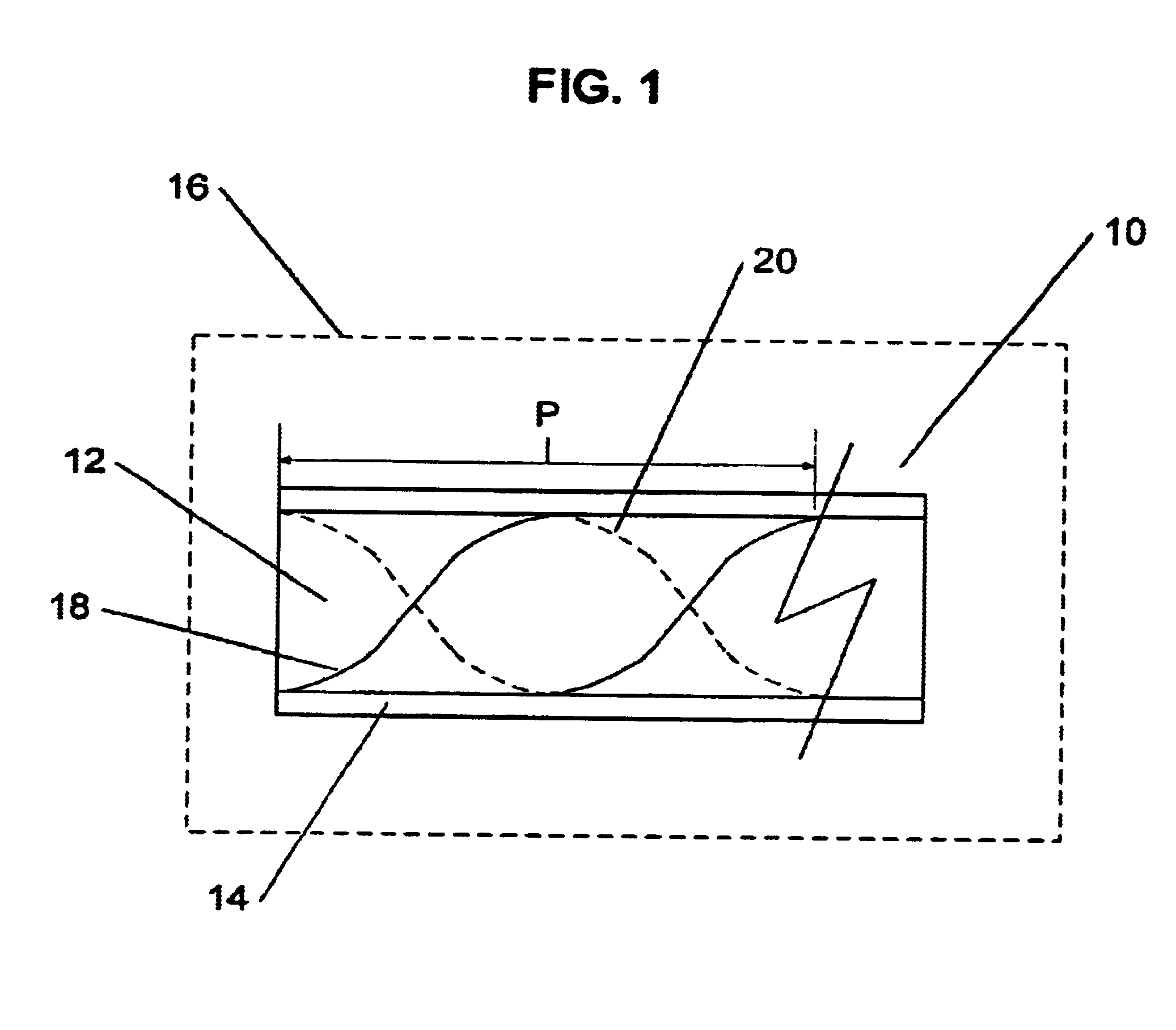
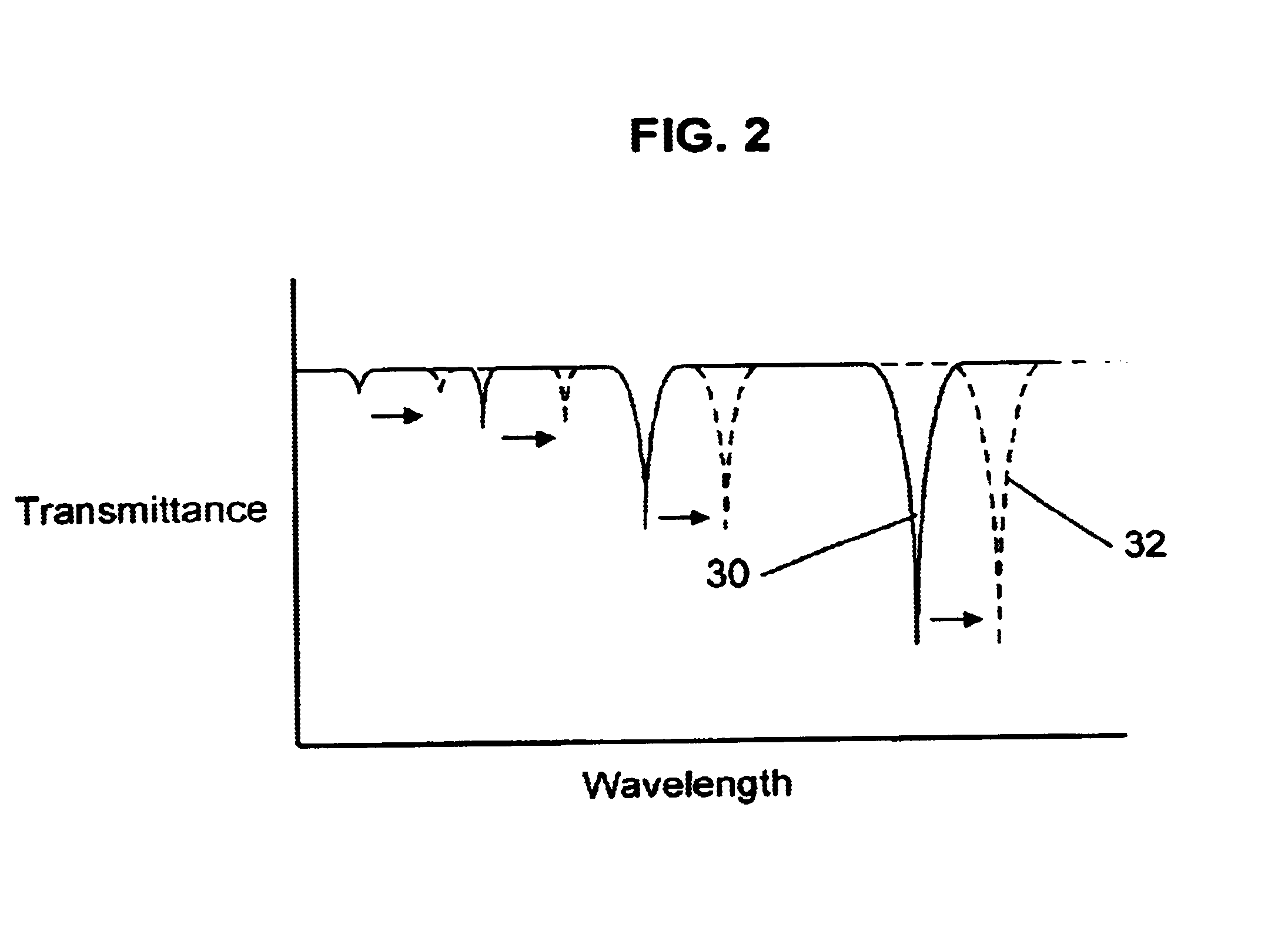
InactiveUS6925230B2Easy to useForce measurement by measuring optical property variationThermometers using physical/chemical changesGratingFrequency spectrum
A long period chiral fiber grating (“LPCFG”) that has a number of advantageous properties that can be readily utilized in a number of different applications is provided. The inventive LPCFG is a fiber grating having a pitch that exceeds the wavelength of light propagating therethrough. The LPCFG includes a number of dips in its transmission spectrum, but does not reflect any portion of the signal passing therethrough. The LPCFG is sensitive to changes in the refractive index of its external environment (or in the refractive index of a coating covering the LPCFG cladding). In response to changes in the external refractive index, the transmission dips shift proportionally to changes in the index, thus enabling the use of LPCFG as a fiber sensor element. In addition, the LPCFG is polarization sensitive—one circular polarized wave of one handedness is coupled to the cladding mode stronger than the wave of the other polarization handedness. This enables the LPCFG to be readily utilized in polarizers and for shaping the polarization spectra of signals passing therethrough (in one embodiment configured as multiple LPCFG elements having different pitches). The polarization sensitivity of the inventive LPCFG can also be used for verifying system integrity in chiral fiber sensor systems. In other embodiments of the present invention, the novel LPCFG can be used for modulating amplitude of the light signal propagating therethrough, or as a resonant active structure for add / drop filters.
Owner:CHIRAL PHOTONICS
Secure computer system integrity check
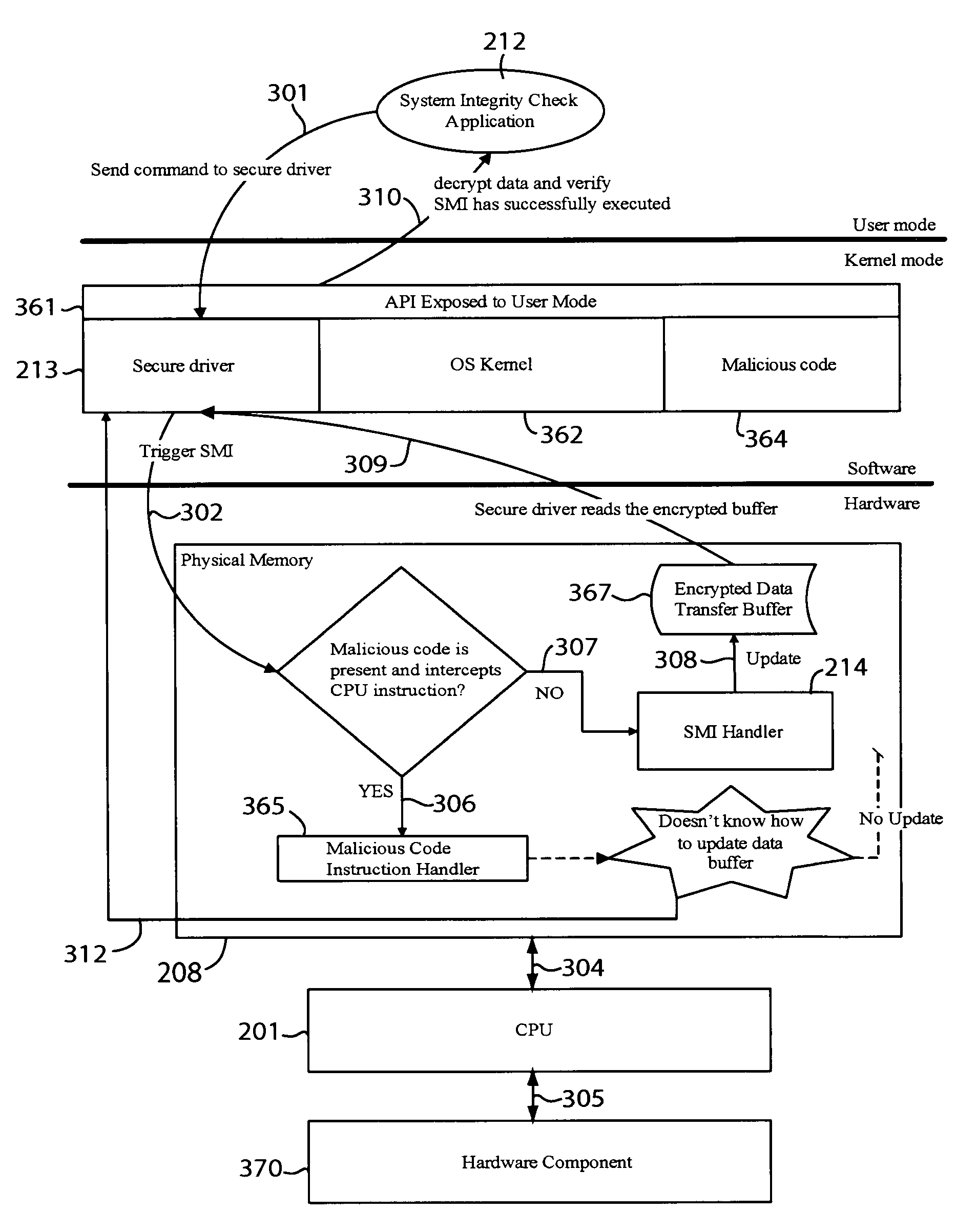
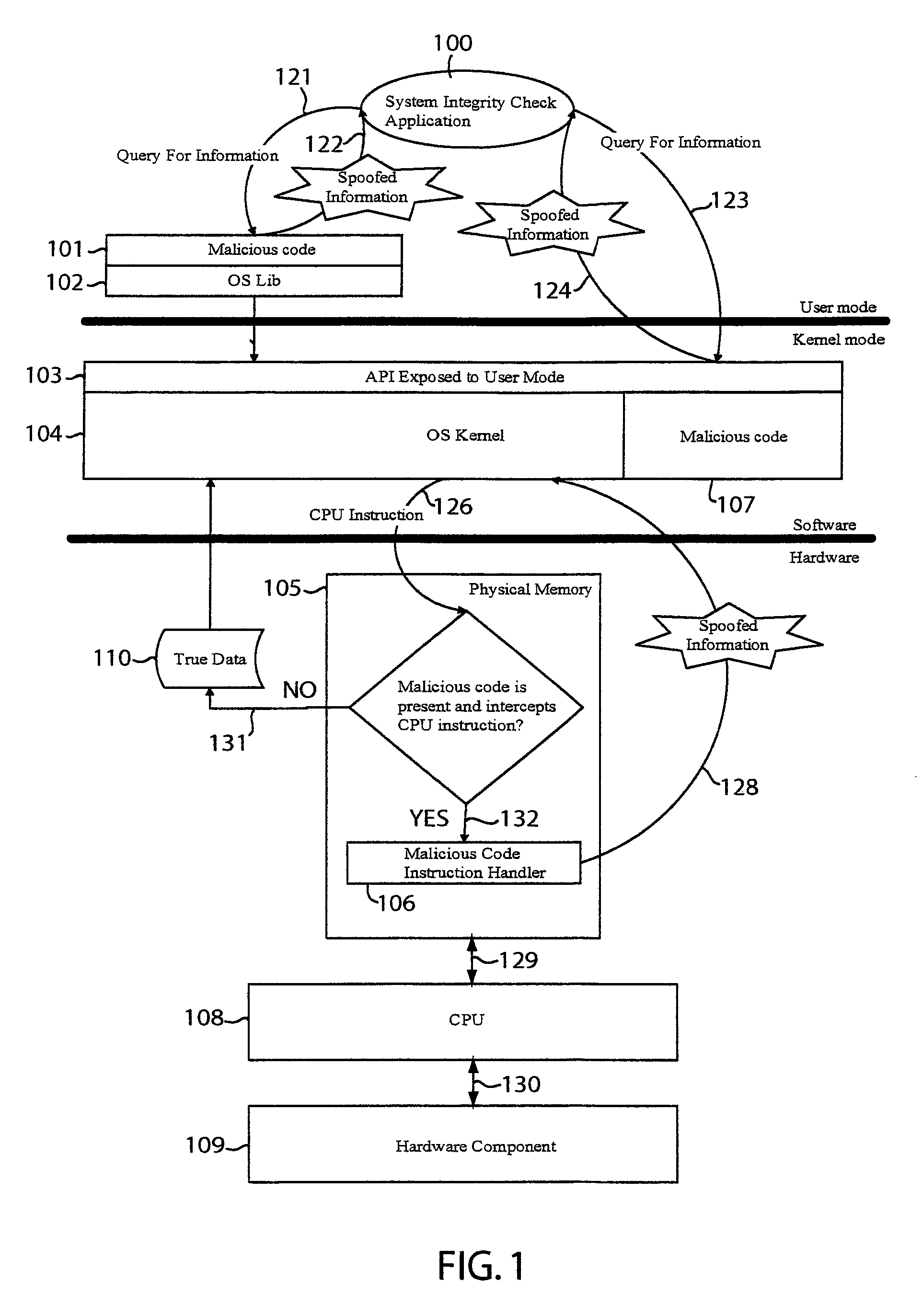
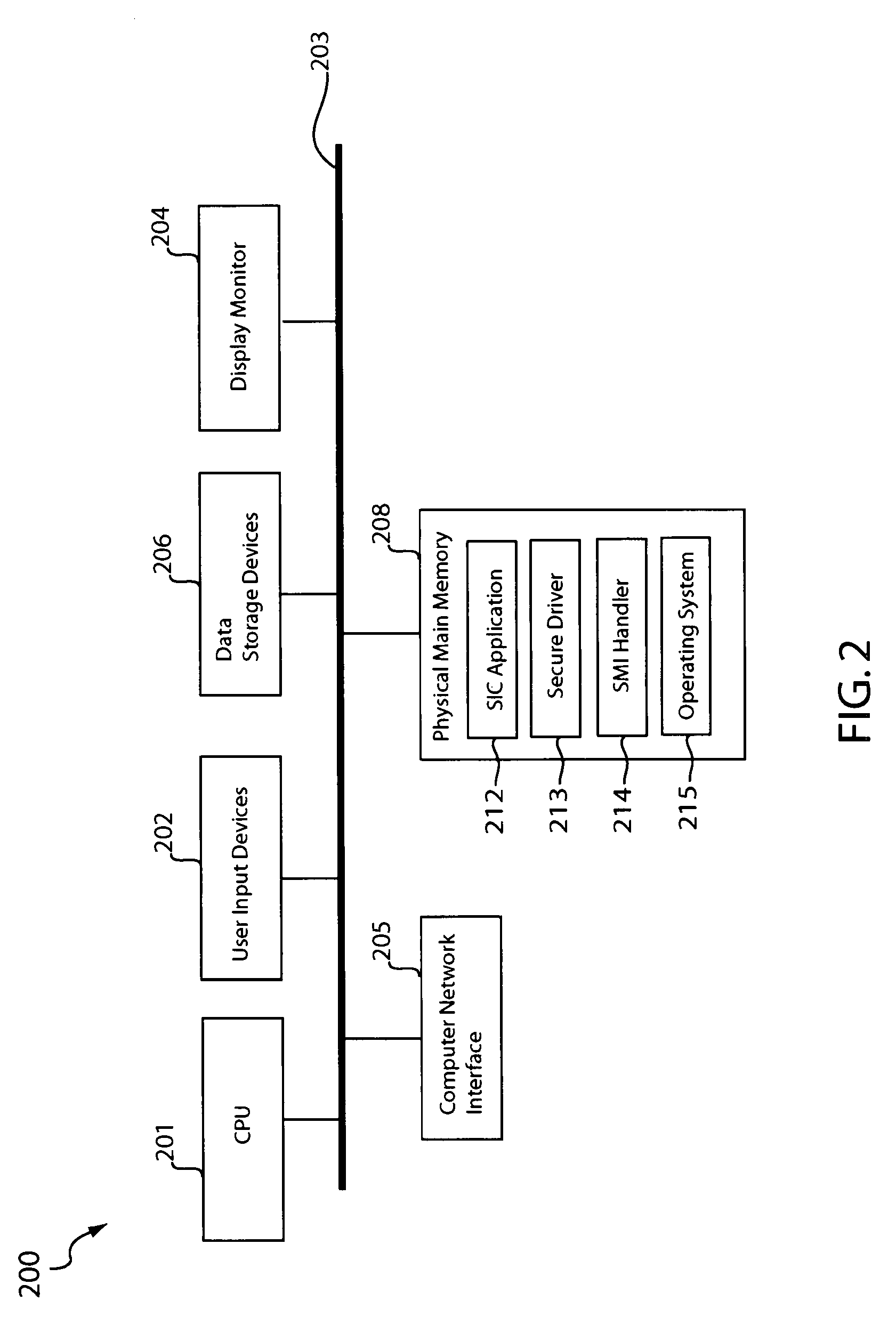
ActiveUS8578477B1Memory loss protectionDigital data processing detailsApplication softwareData transmission
The integrity of a computer may be checked by issuing a command to read data from a hardware component of the computer and retrieving the data from a data transfer buffer. The command may be sent to a secure driver that places the central processing unit (CPU) of the computer in system management mode to trigger execution of a system management interrupt (SMI) handler. The SMI handler may read the data from the hardware component, encrypt the data, and place the encrypted data in the data transfer buffer. A system integrity check application program may read the encrypted data to determine presence of malicious code based on the data. For example, the application program may infer presence of malicious code when the encrypted data does not conform to a particular encryption algorithm or when the data does not appear in the data transfer buffer.
Owner:TREND MICRO INC
Full-digital power controller for satellite
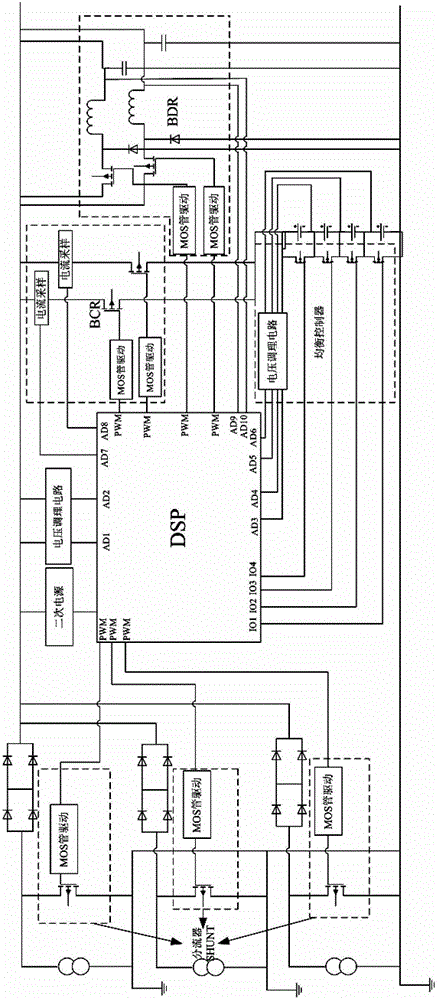
InactiveCN102723756ASimple designReduce erectionBatteries circuit arrangementsElectric powerControl mannerElectrode array
The invention discloses a full-digital power controller for a satellite. The full-digital power controller comprises a shunt, a charging controller, a discharging regulator, a balance controller and a central processor based on a DSP (digital signal processor). The power controller adopts a three-region control mode including a shunt region, a charging region and a discharging region, and the three regions are distinguished by using the DSP for sampling bus voltage. The balance controller samples the voltage of each lithium battery through the DSP to realize a balance control algorithm in DSP software so as to realize balance control among the lithium batteries. By the full-digital power controller for the satellite, full-digital control of a satellite power system is realized, a great quantity of hardware circuits, such as MEA (multi-electrode array) circuits and PWM (pulse width modulation) generation circuits are saved, the system integrity is improved, and system reliability is fundamentally and greatly improved.
Owner:SHANGHAI SATELLITE ENG INST
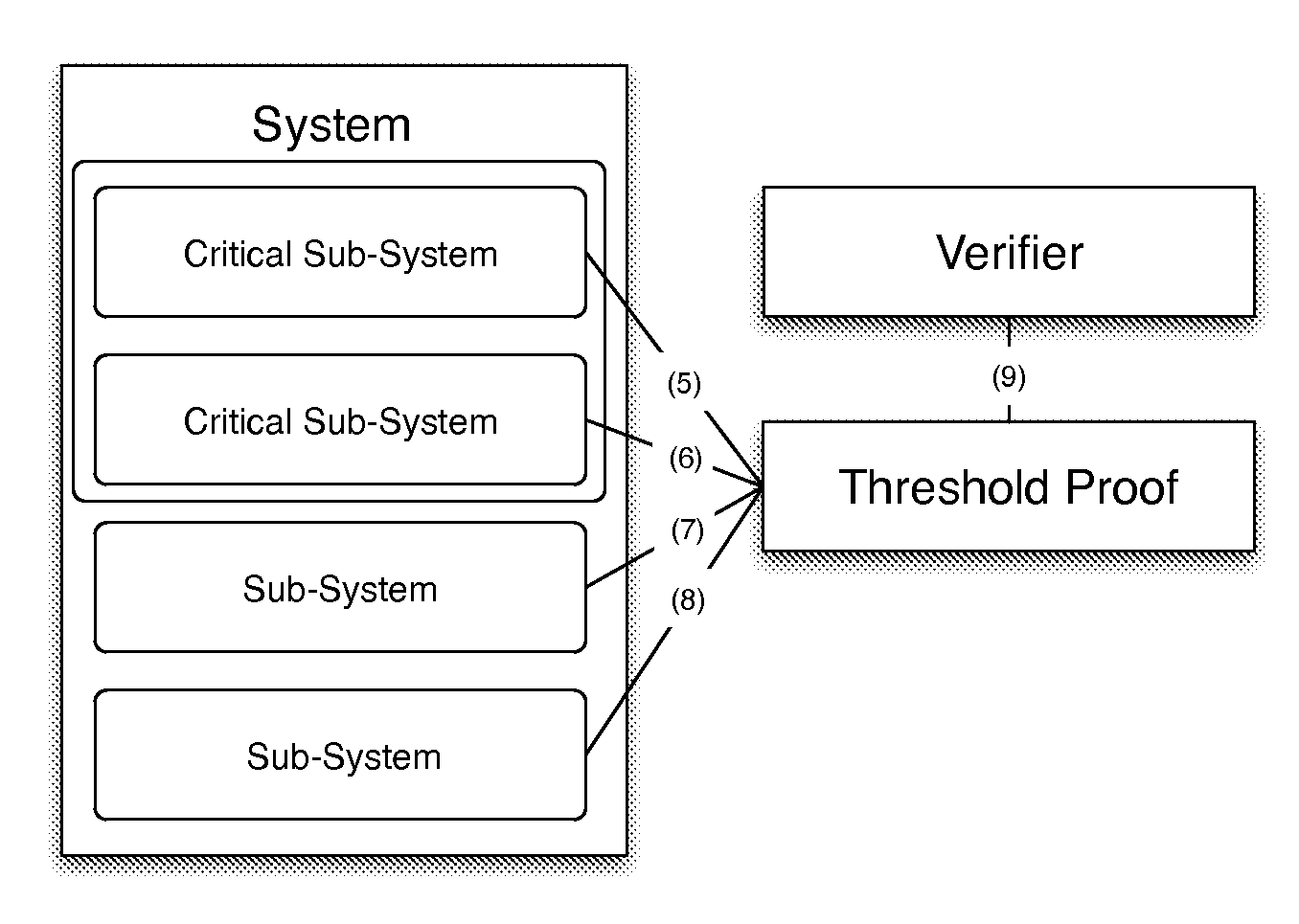
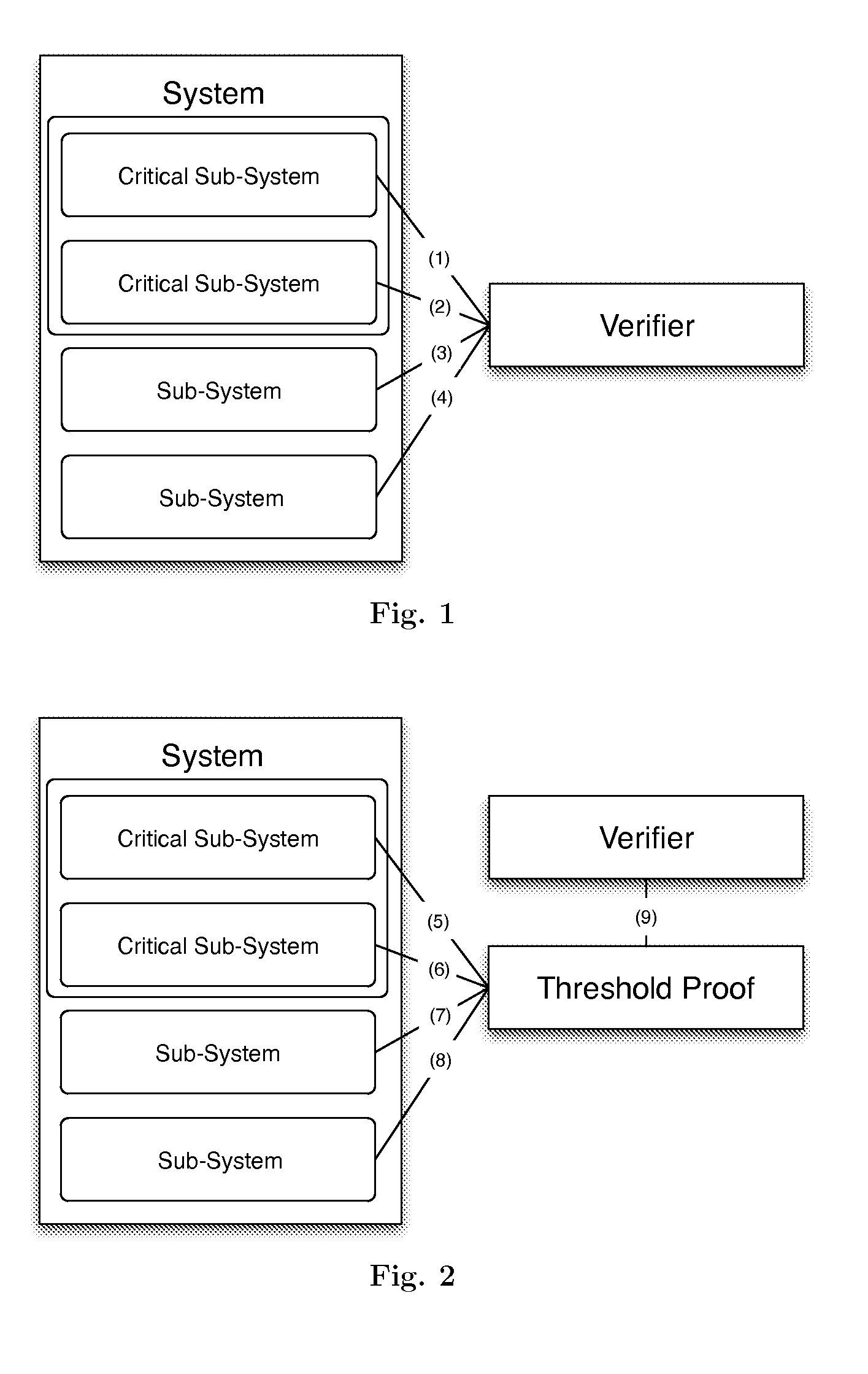
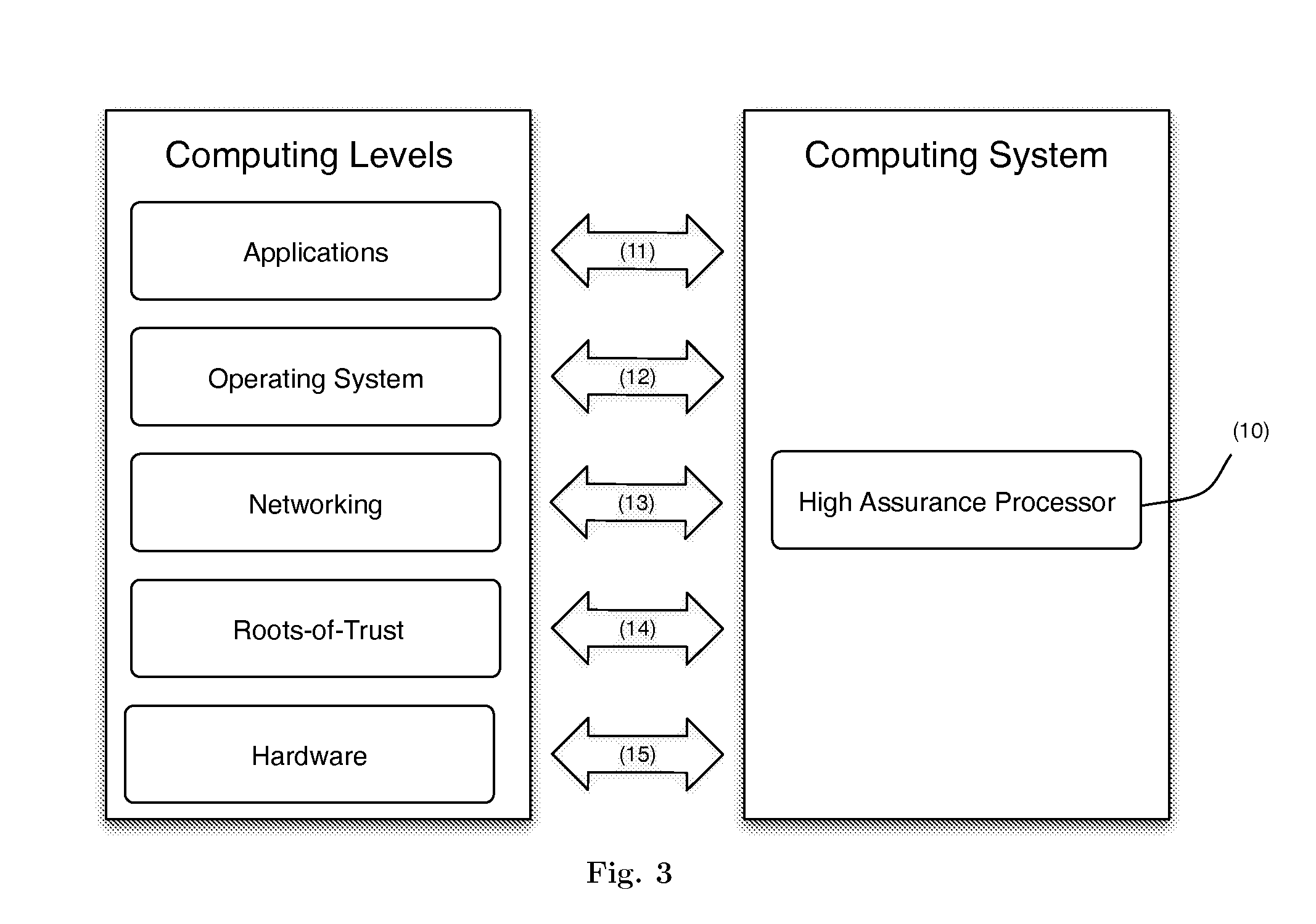
System and device for verifying the integrity of a system from its subcomponents
ActiveUS20150317480A1Digital data processing detailsUser identity/authority verificationVerification systemComputer security
A system and device for verifying the integrity of a system from its subcomponents, the system comprising a plurality of subcomponents each having a physical state, the system and the device comprising a processor that is connected to each of the subcomponents, the processor configured to verify systemic integrity by performing verification on some or all specified subcomponents. The verification may be individual (1,1) or threshold (n,1), and may be interactive or non-interactive.
Owner:ANALOG DEVICES INC
Leakage detection method for a pressurised medical appliance
InactiveUS7076993B2Prevent air leakageBlood stagnation preventionDetection of fluid at leakage pointAxial compressorEngineering
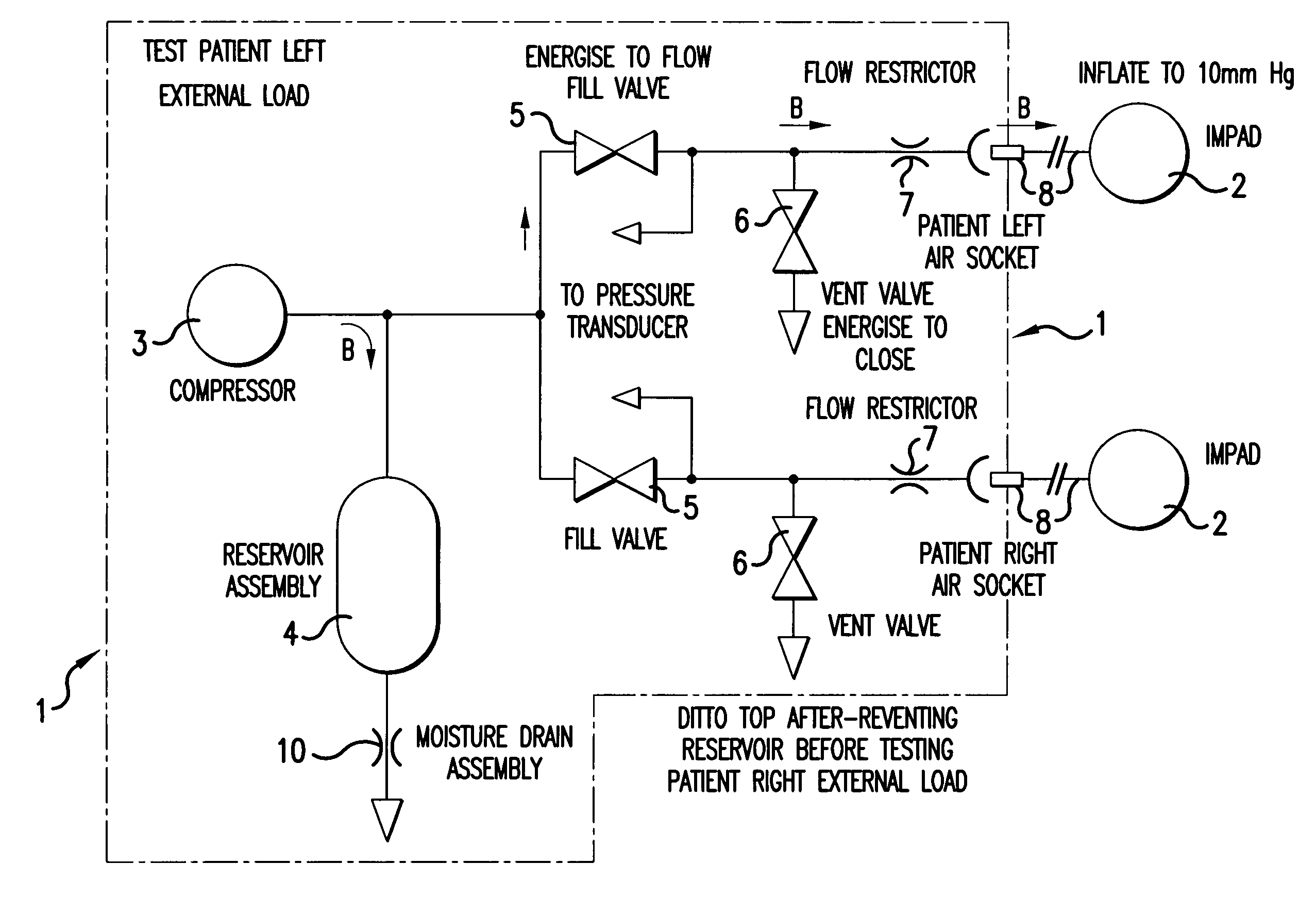
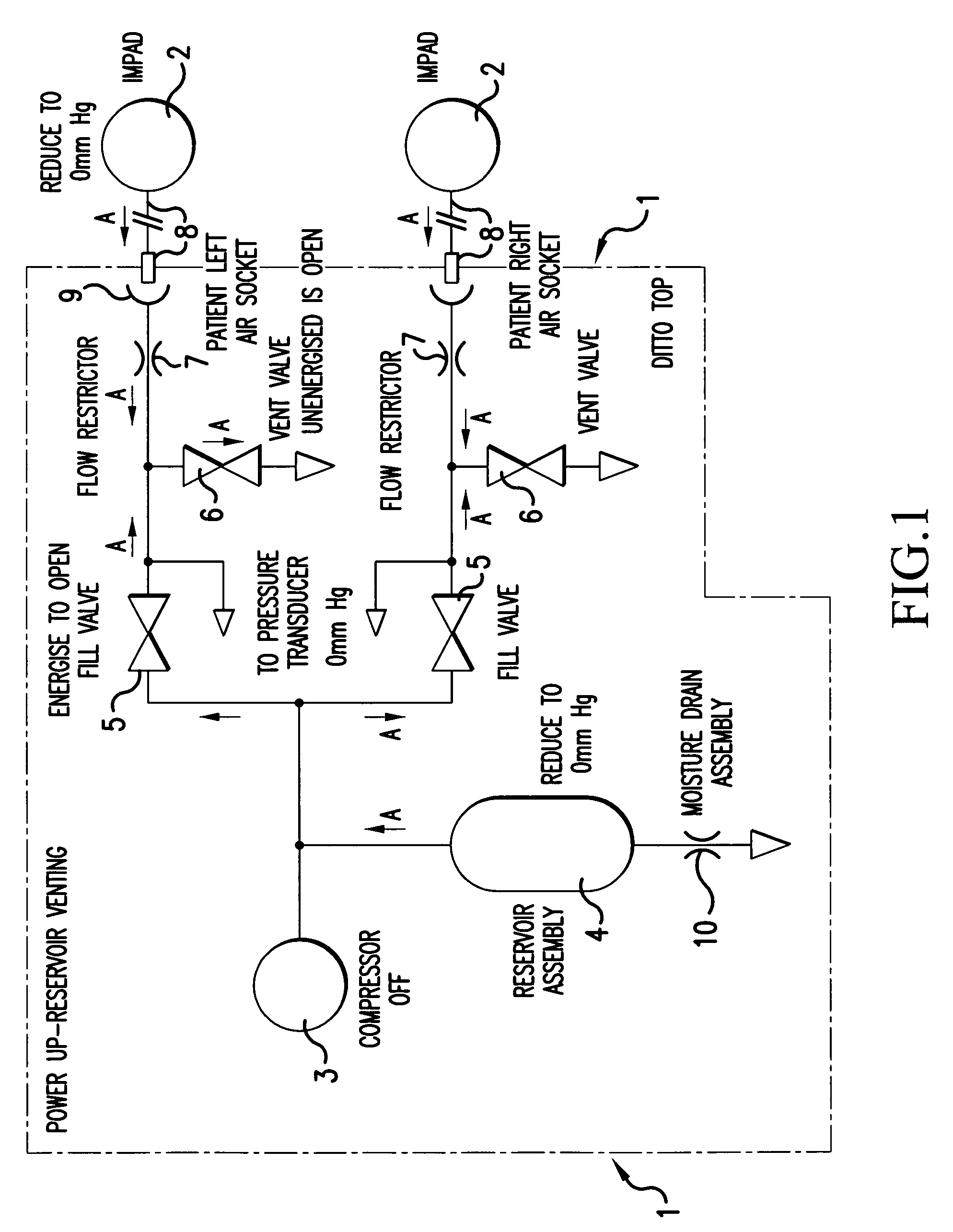
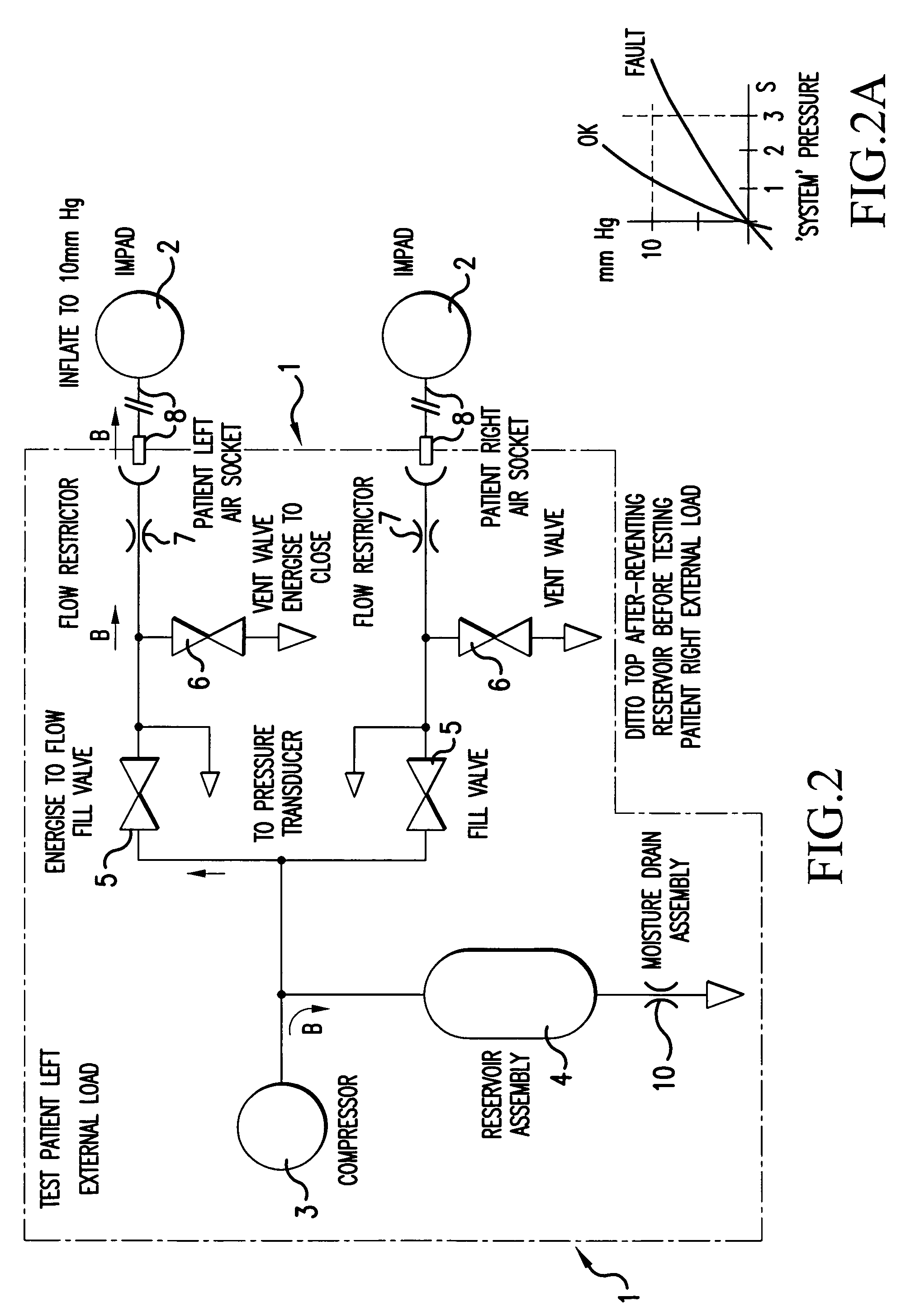
A method for detecting leakage in a pressurised medical appliance prior to normal operation, the system including an air compressor and an inflatable bag or bladder coupled to the air compressor through the intermediary of a fill valve allowing air to pass to the bladder and a vent valve for venting the system, the fill valve and the vent valve being selectively operable during said normal operation to deliver cyclical pulses of air to inflate and deflate the bladder, the detection method comprising a) opening the fill valve to vent the system to atmospheric pressure, b) closing the vent valve, c) pressurising the system by means of the air compressor to a pre-determined threshold value, d) monitoring the pressure gradient or rise over a period of time to said threshold value and e) comparing the pressure gradient over said period of time or at intervals of time within said period of time with a pre-specified pressure gradient indicative of system integrity whereby to determine the presence or otherwise of air leakage in the system.
Owner:CARDINAL HEALTH IRELAND UNLTD
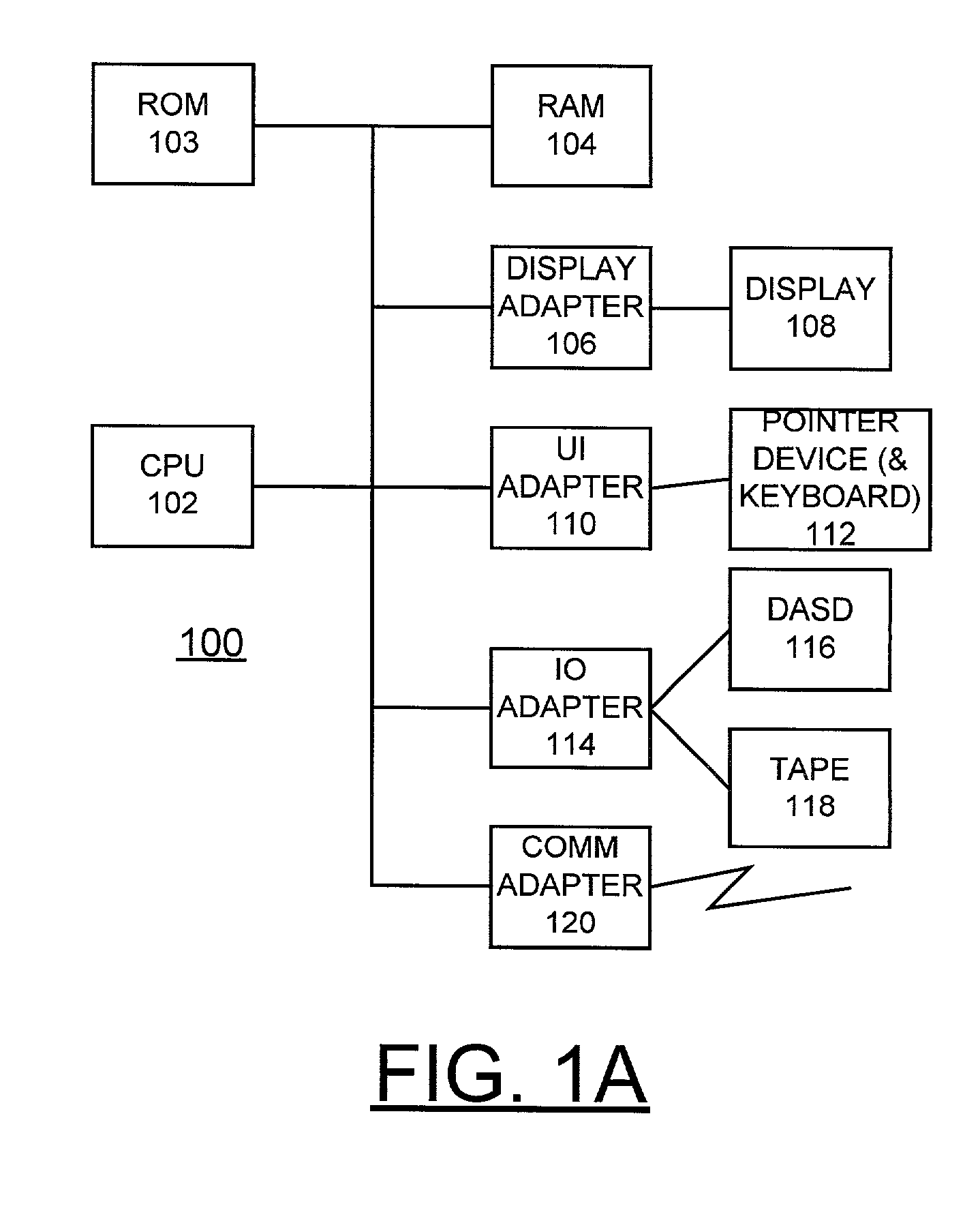
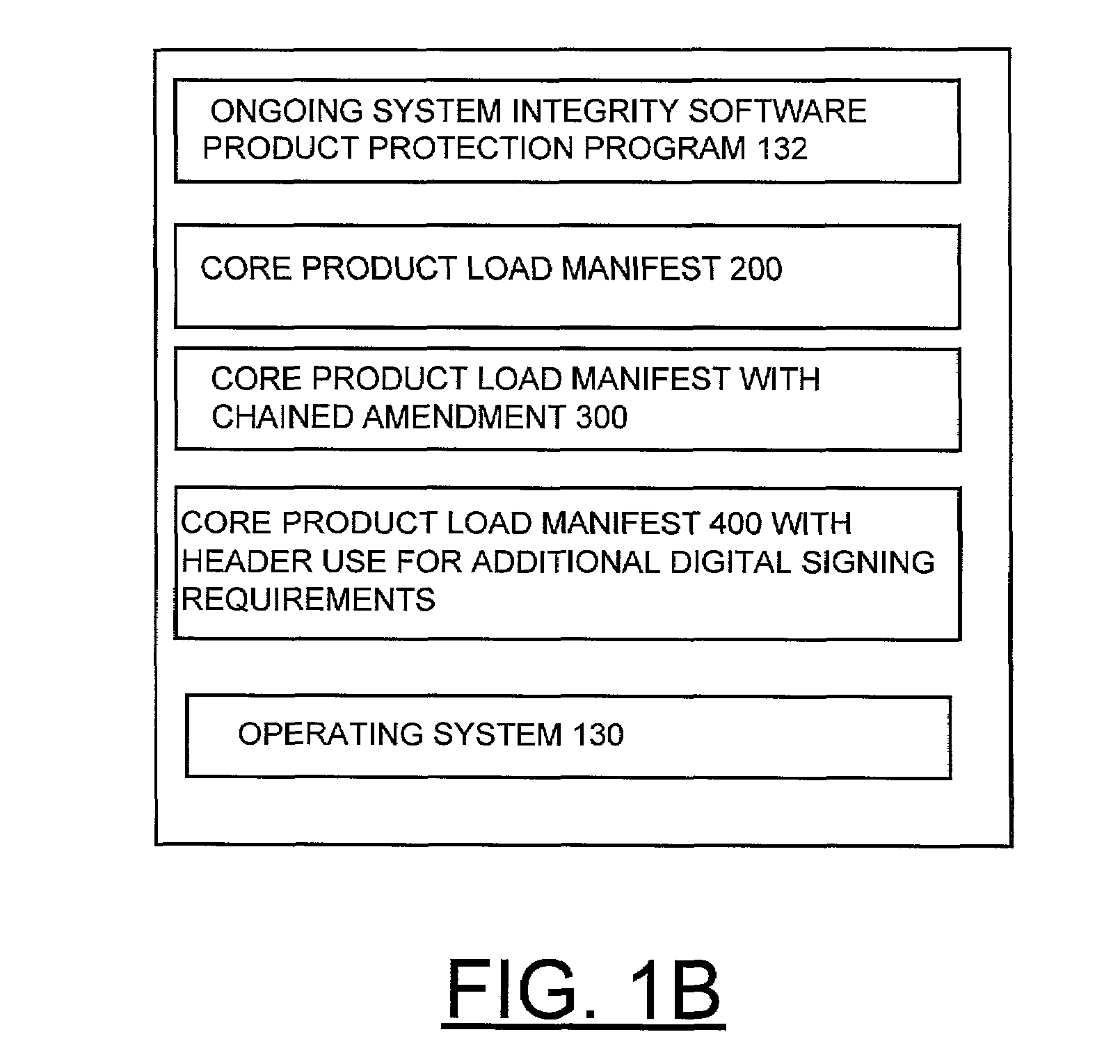
Method and apparatus for protecting ongoing system integrity of a software product using digital signatures
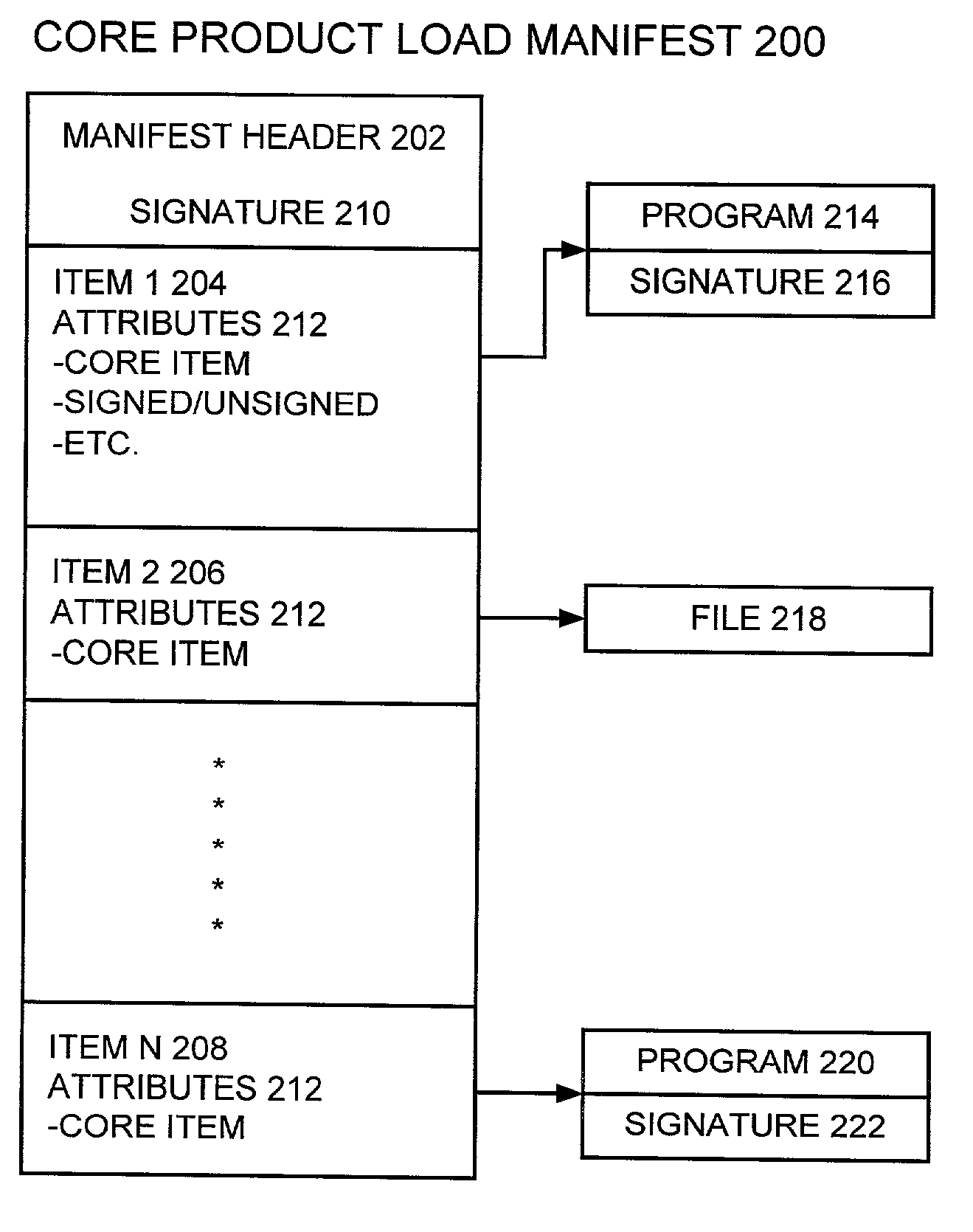
InactiveUS7093132B2Digital data processing detailsUser identity/authority verificationCore productDigital signature
A method, apparatus and computer program product are provided for protecting ongoing system integrity of a software product using digital signatures. A core product load manifest for protecting ongoing system integrity of a software product having a plurality of pieces includes a manifest header including header attributes of the software product. A list of a plurality of manifest items is stored with the manifest header. Each manifest item identifies a corresponding piece of the software product. Each manifest item includes at least one attribute. A manifest digital signature is stored with the manifest header. The manifest header, the header attributes, each of the plurality of items, and each item attribute are included in the manifest digital signature. A digital signature is computed for each signable piece of the software product and is stored with the piece of the software product. The digital signature of each signed software product piece is excluded from the core product load manifest. An amended manifest is created for identifying added and deleted pieces of the software product and is chained to the core product load manifest. Each signable, added item in the amended manifest has a digital signature that is excluded from the amended manifest.
Owner:IBM CORP
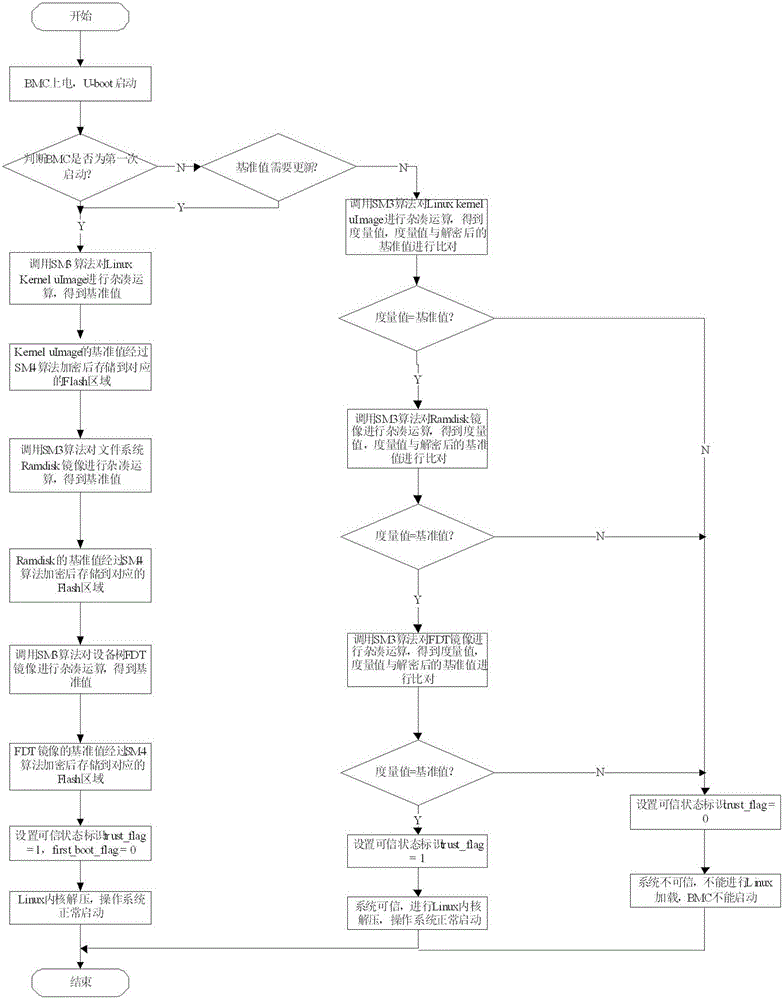
BMC U-boot trusted starting control method
InactiveCN106384052AEnsure credibleIntegrity guaranteedPlatform integrity maintainanceFile systemLinux kernel
The invention discloses a BMC U-boot trusted starting control method; the method comprises the following steps: using SM3 and SM4 cipher algorithms (SM3 refers to a cipher hash algorithm, SM4 refers to a symmetry cipher algorithm) to determine measure and trusted states of a Linux core mirror image, a file system mirror image and an equipment tree mirror image in a U-boot starting guide system process, i.e., comparing a measure value with a reference value; starting an operating system if the measure value-reference value contrast passes, thus allowing the BMC to enter a trusted environment; stop guiding the operating system if the measure value-reference value is not consistent, allowing a BMC administrator to process, thus finally building up a BMC system platform trusted execution environment. Compared with the prior art, the BMC U-boot trusted starting control method can ensure the system integrity and no malicious code is implanted, thus ensuring the trusted BMC system platform execution environment, and helping domestic BMC chip core competitiveness; the BMC U-boot trusted starting control method is strong in practical value, wide in application scope, and easy to promote.
Owner:LANGCHAO ELECTRONIC INFORMATION IND CO LTD
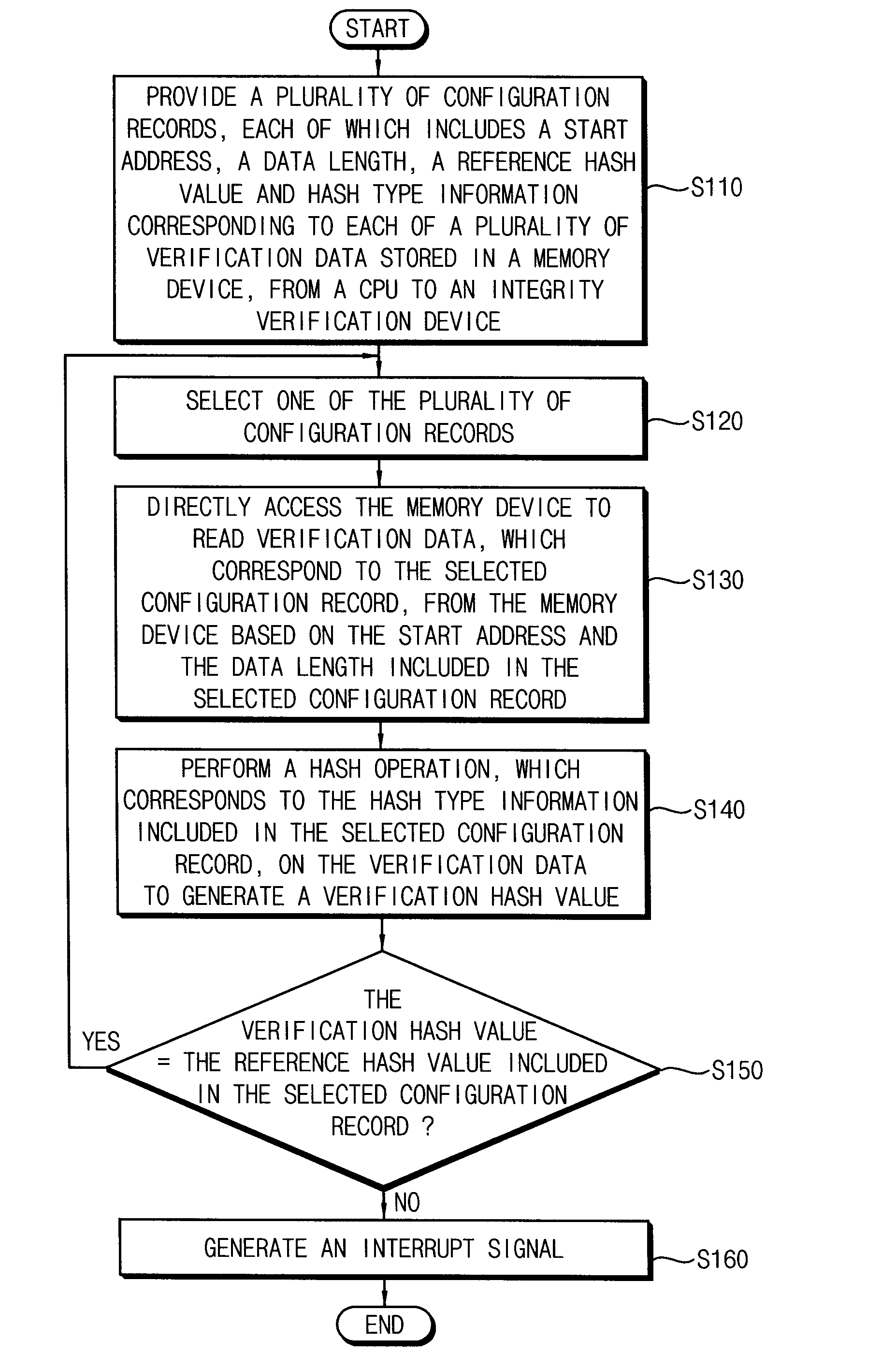
Electronic system having integrity verification device
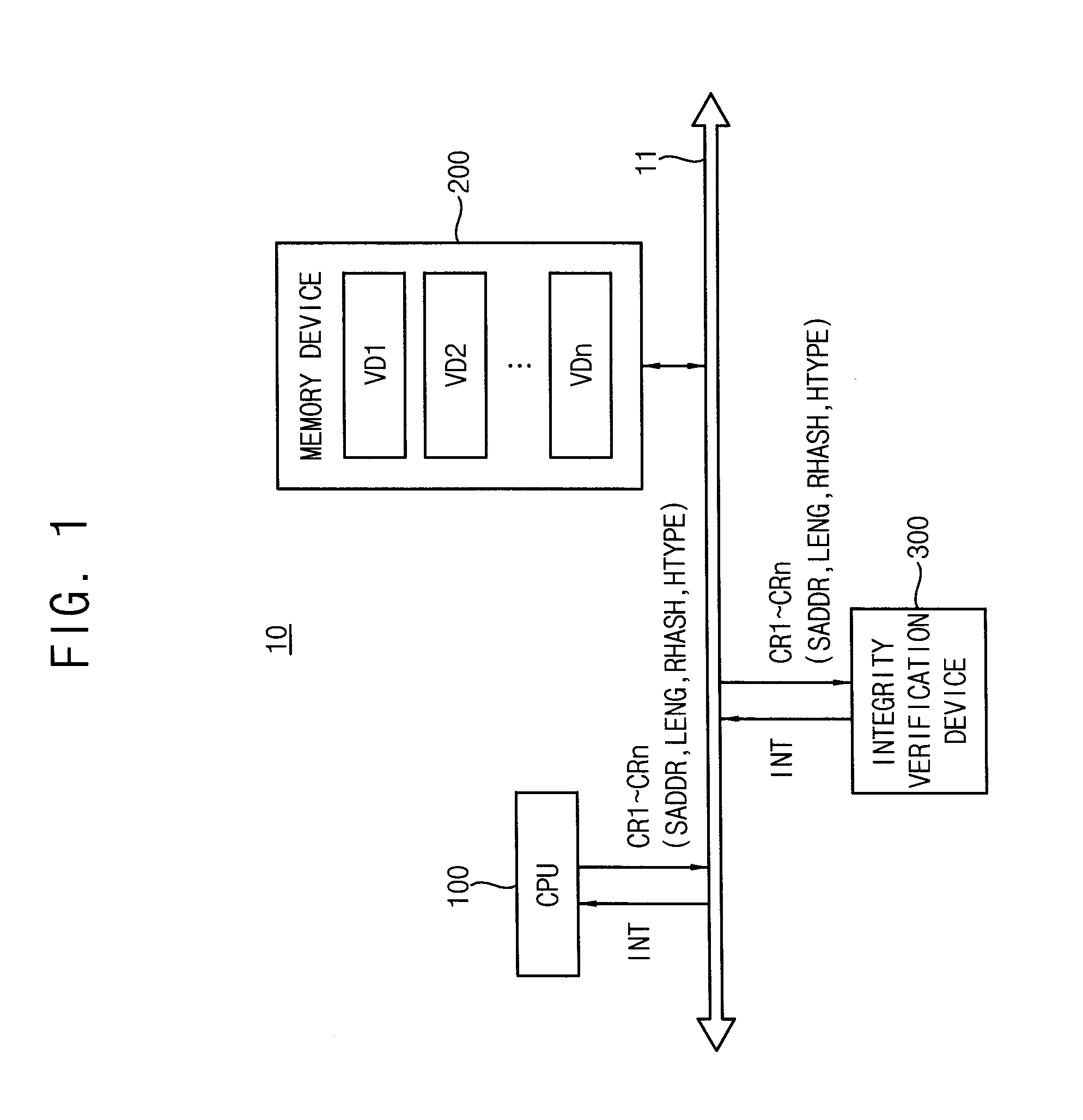
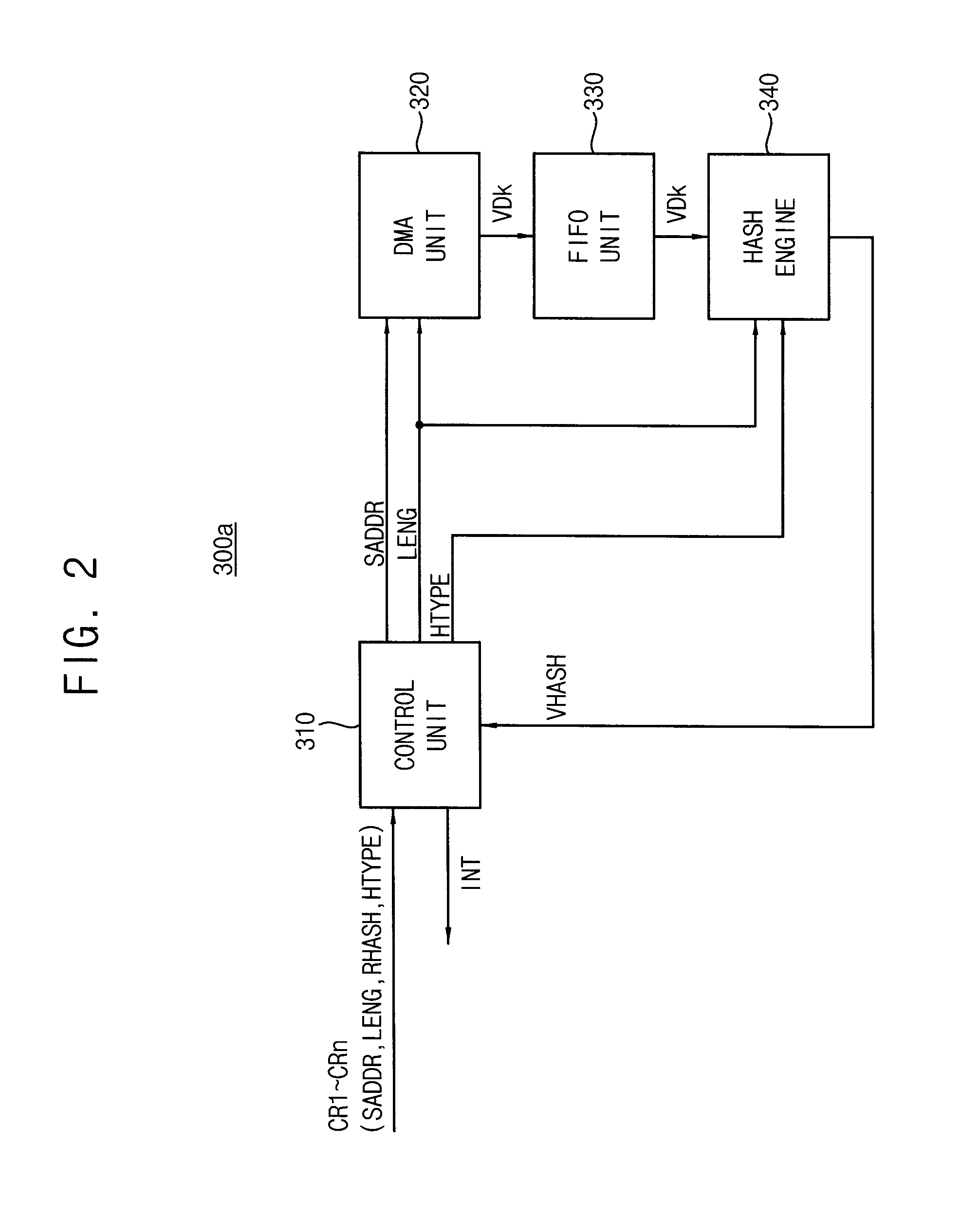
ActiveUS20150254458A1Efficient detectionMemory loss protectionError detection/correctionElectronic systemsData storing
Provided are an electronic system, an integrity verification device, and a method of performing an integrity verification operation. The electronic system includes: a memory device; a processor configured to provide a plurality of configuration records corresponding to a plurality of verification data stored in the memory device, each of the configuration records including a start address, a data length, and a reference hash value for a corresponding verification data; and an integrity verification device configured to: store the configuration records, select a configuration record, directly access the memory device to read verification data, corresponding to the selected configuration record, based on the start address and the data length included in the selected configuration record, perform a hash operation on the verification data to obtain a verification hash value, and output an interrupt signal based on the verification hash value and the reference hash value comprised in the selected configuration record.
Owner:SAMSUNG ELECTRONICS CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com