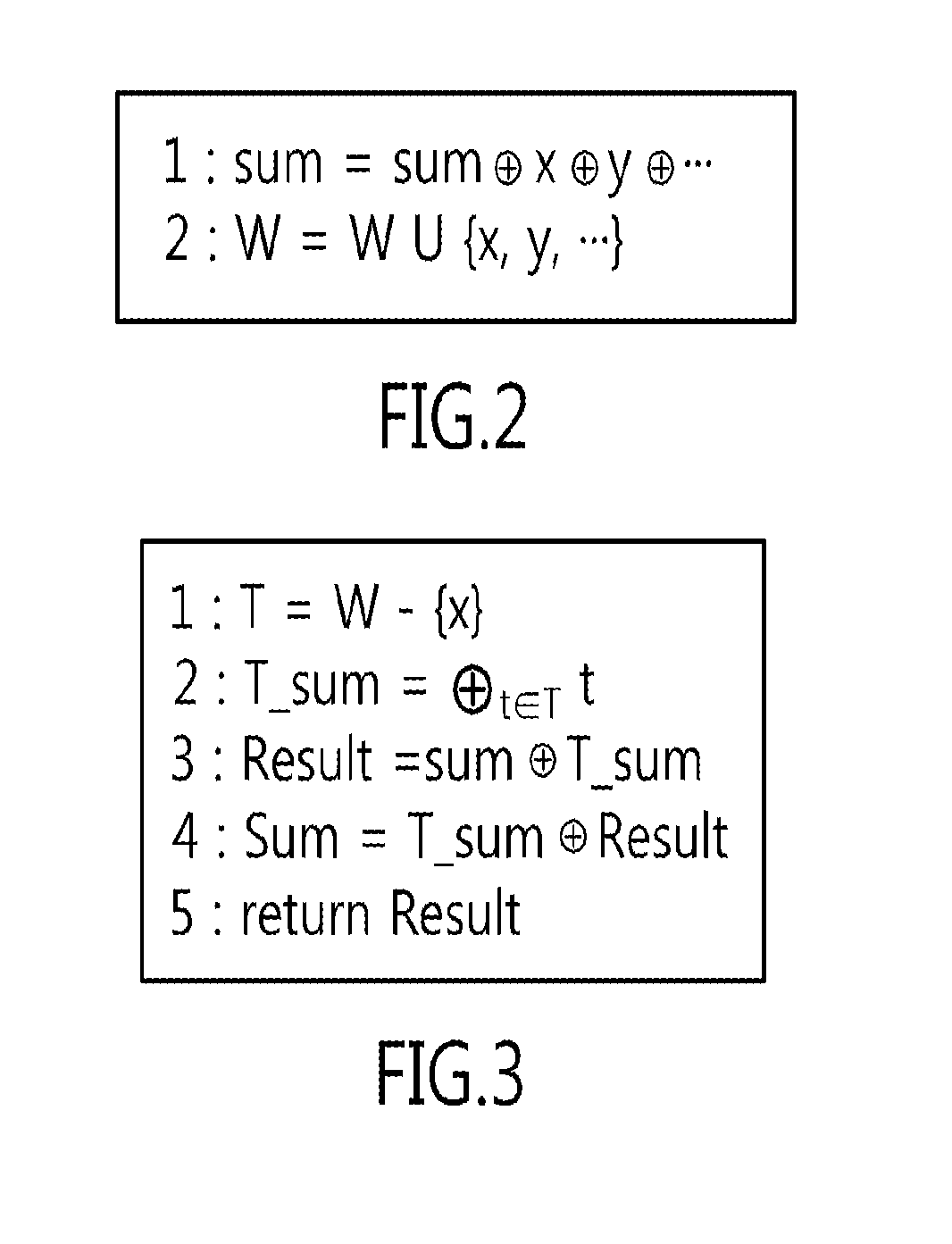
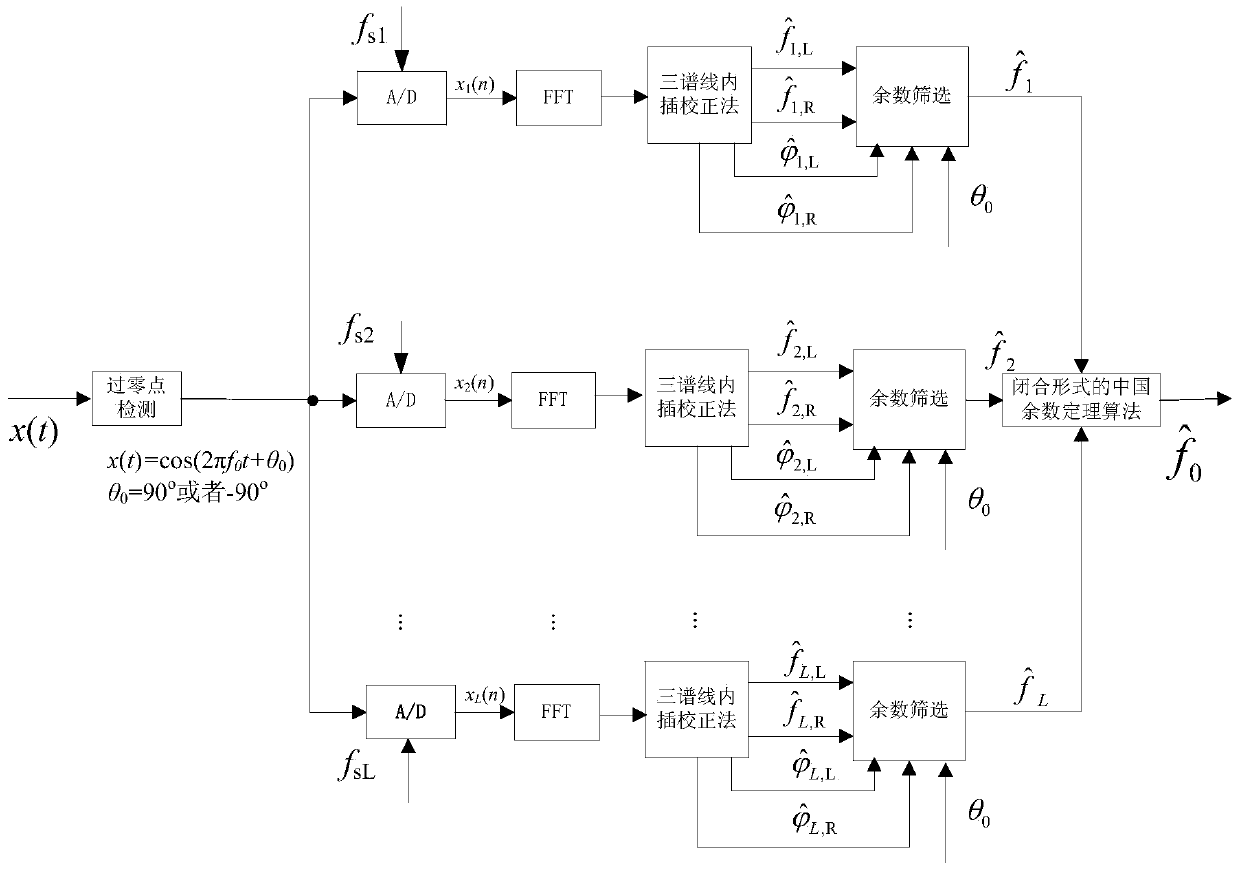
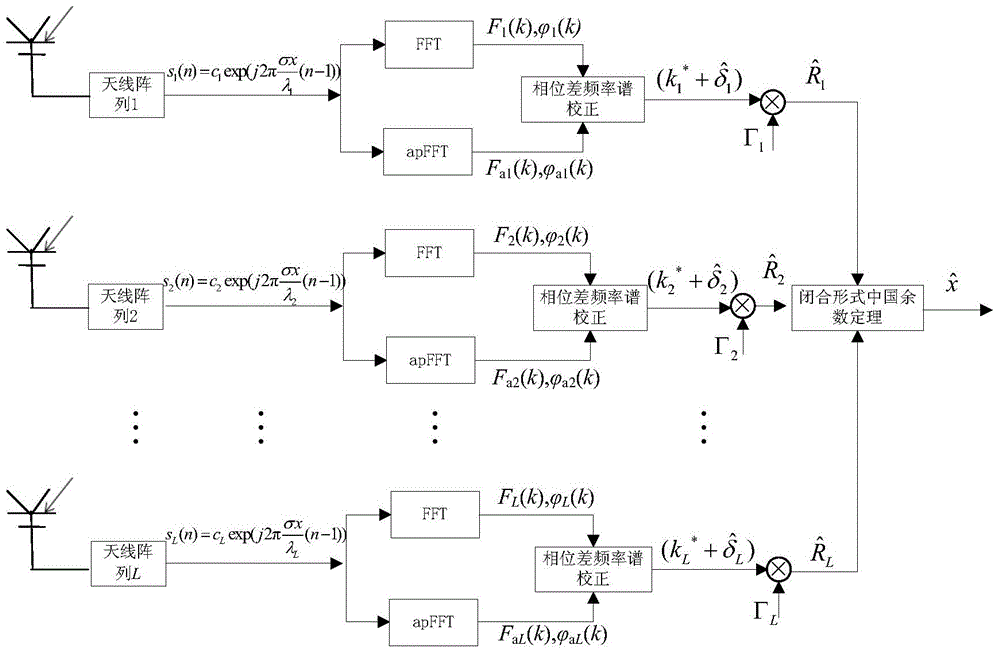
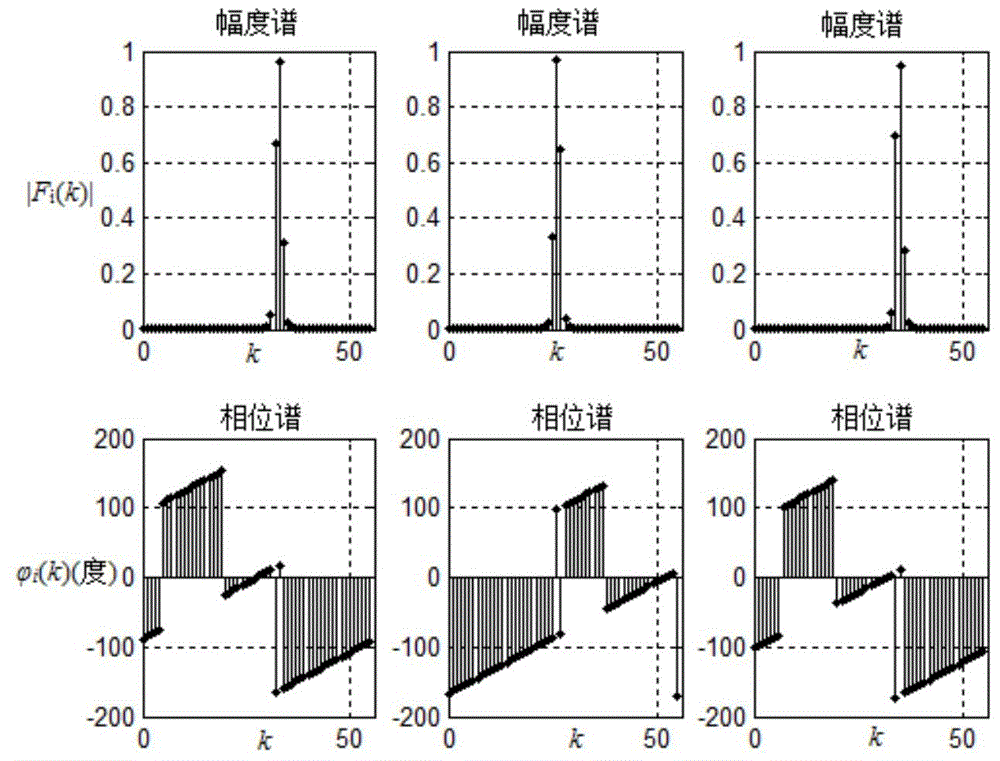
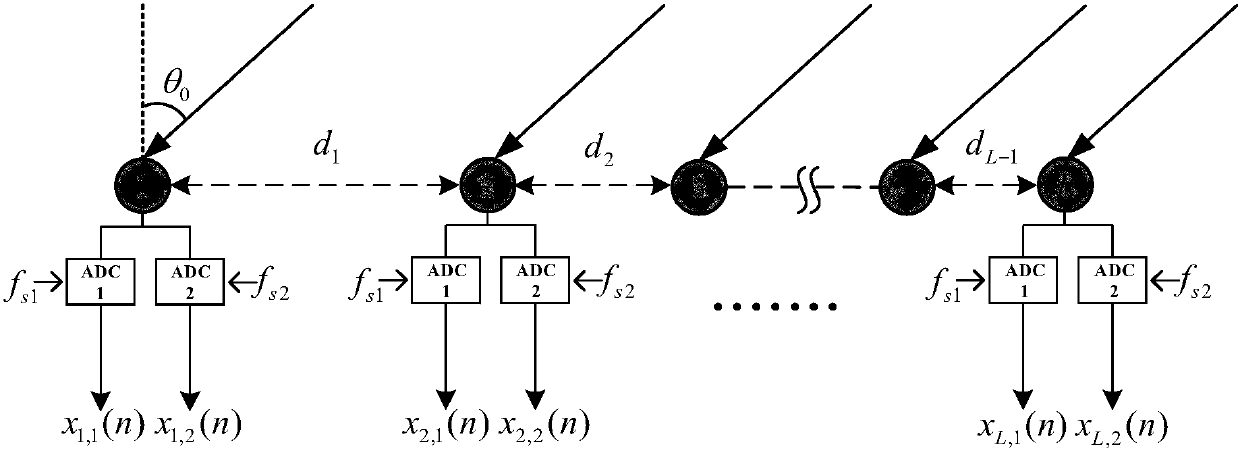
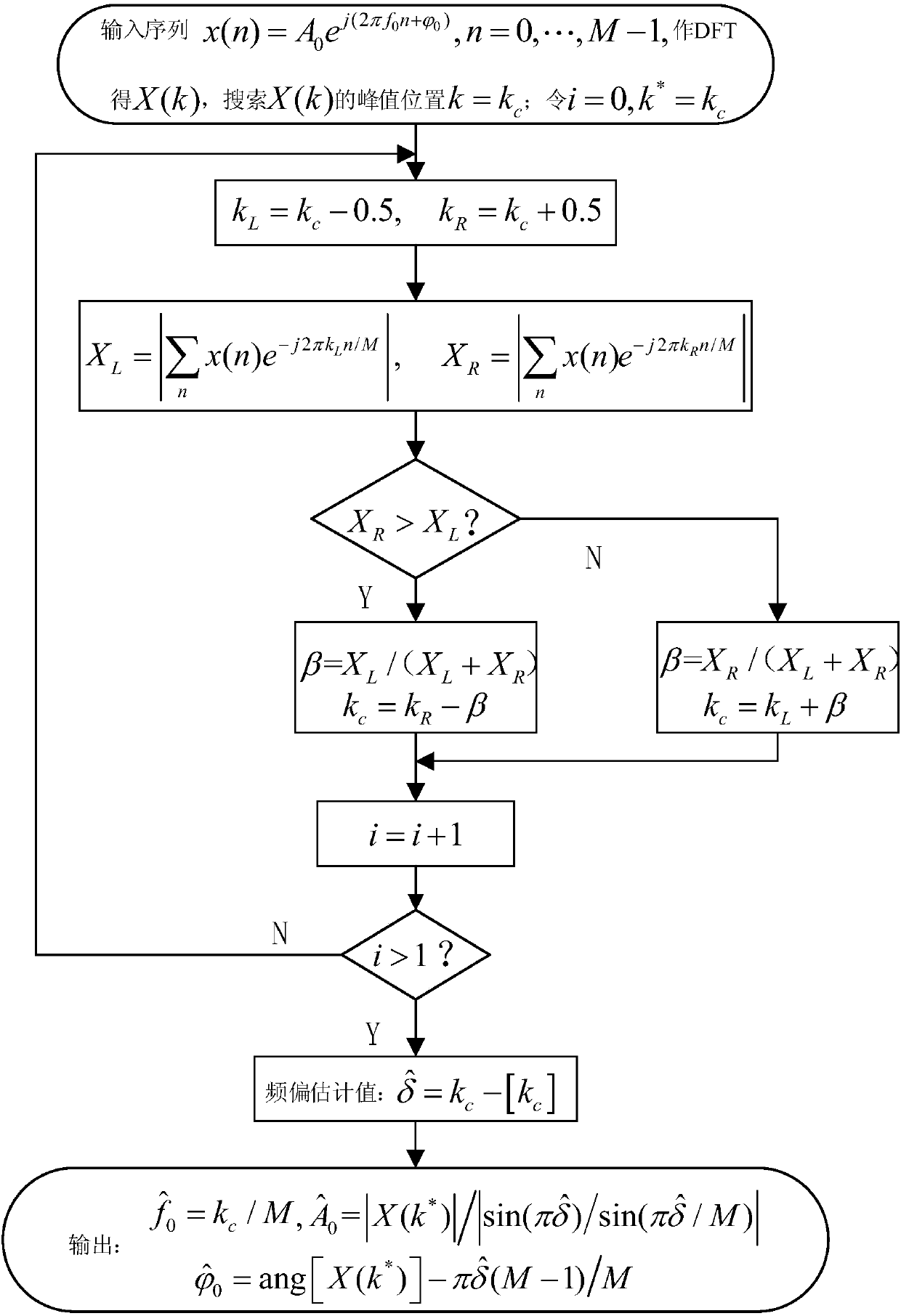
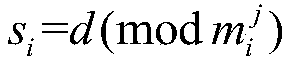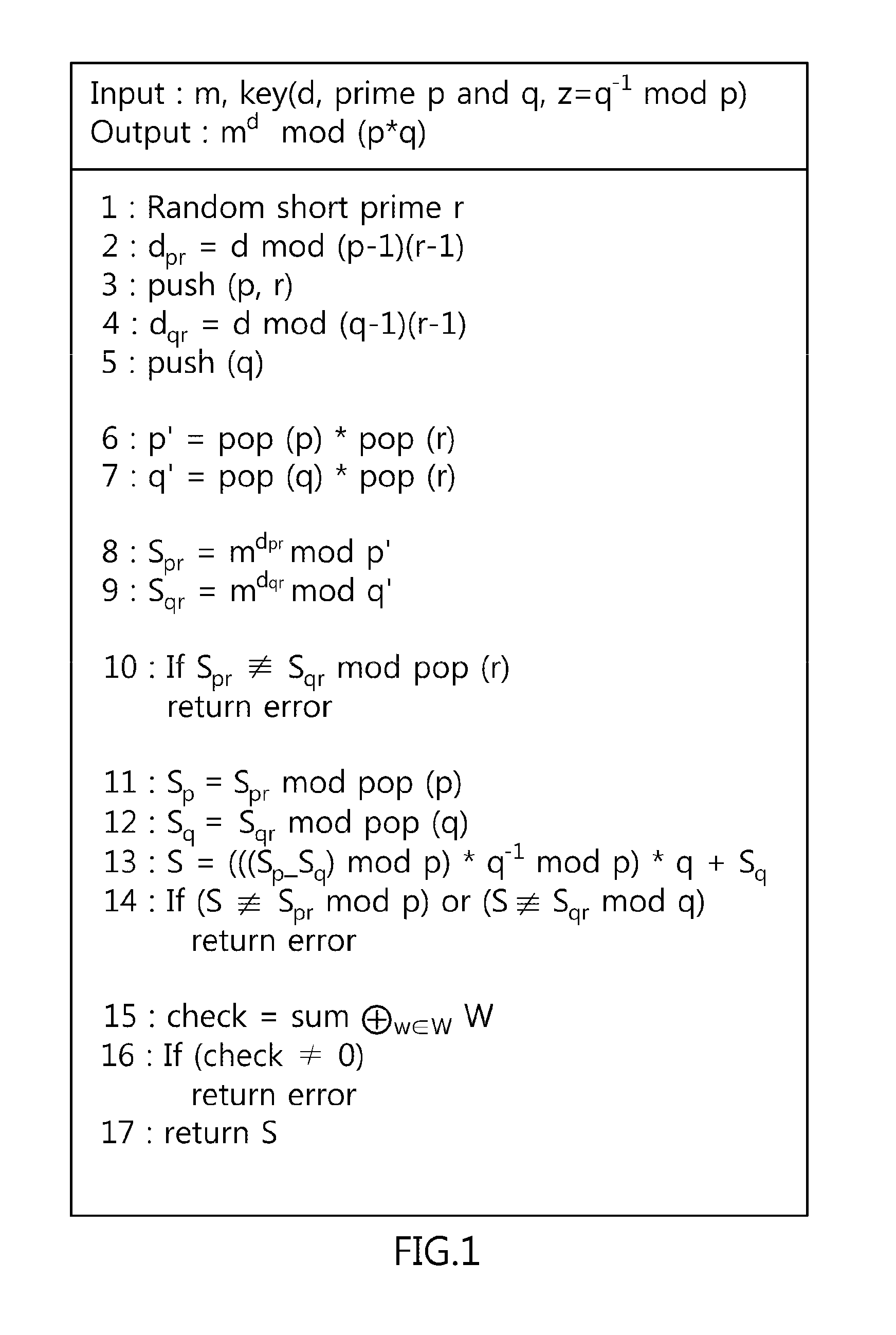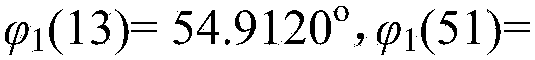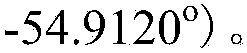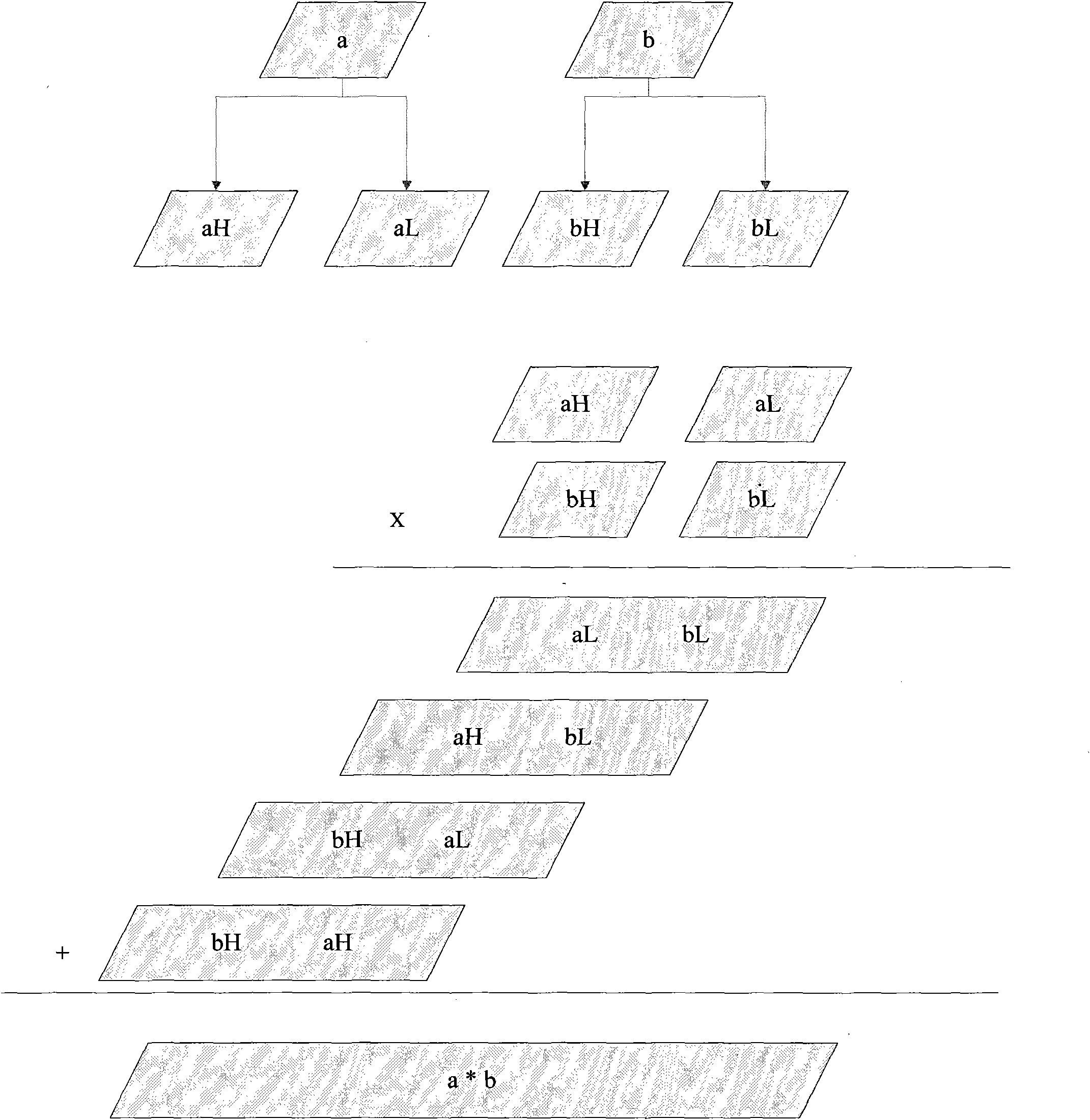Patents
Literature
167 results about "Chinese remainder theorem" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
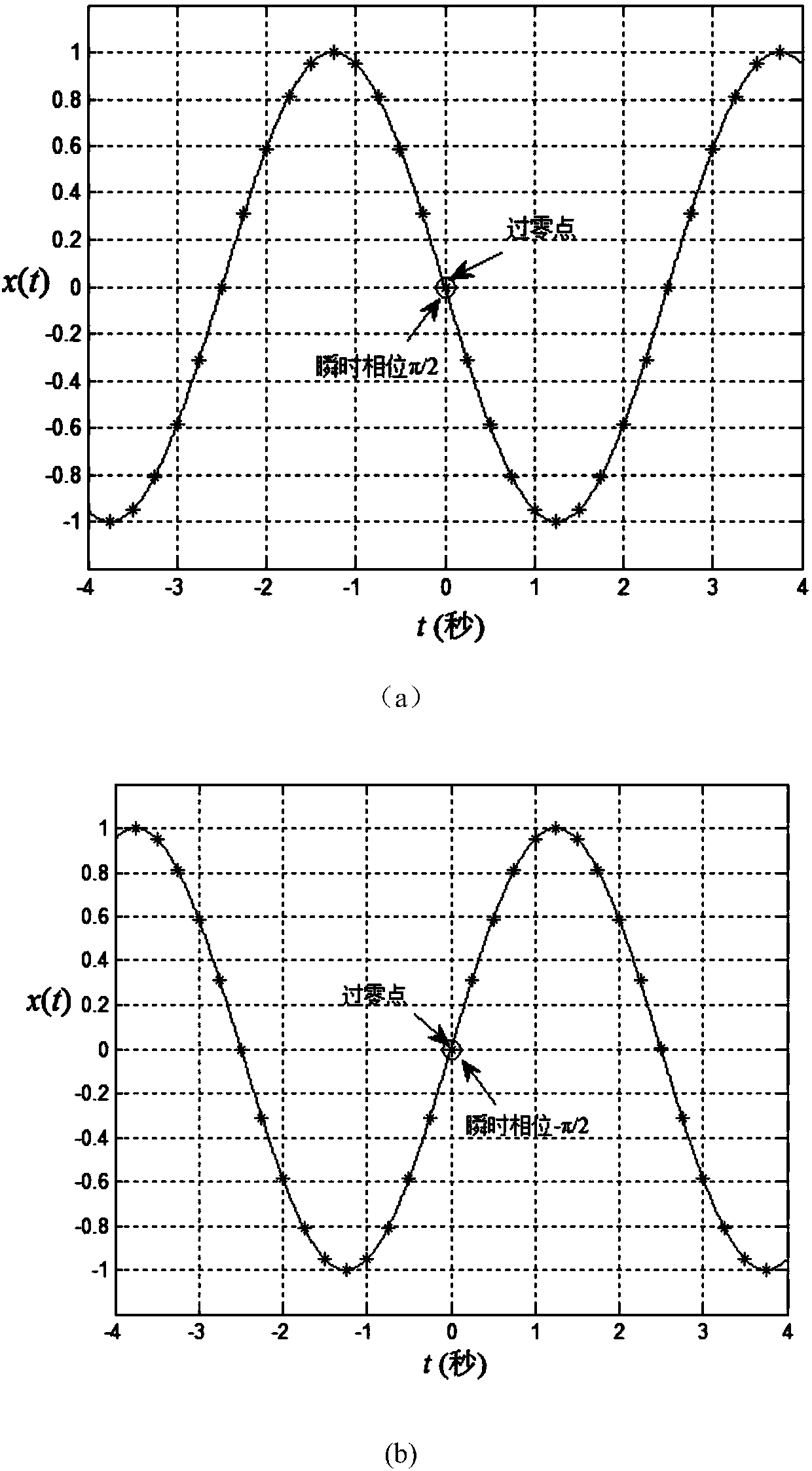
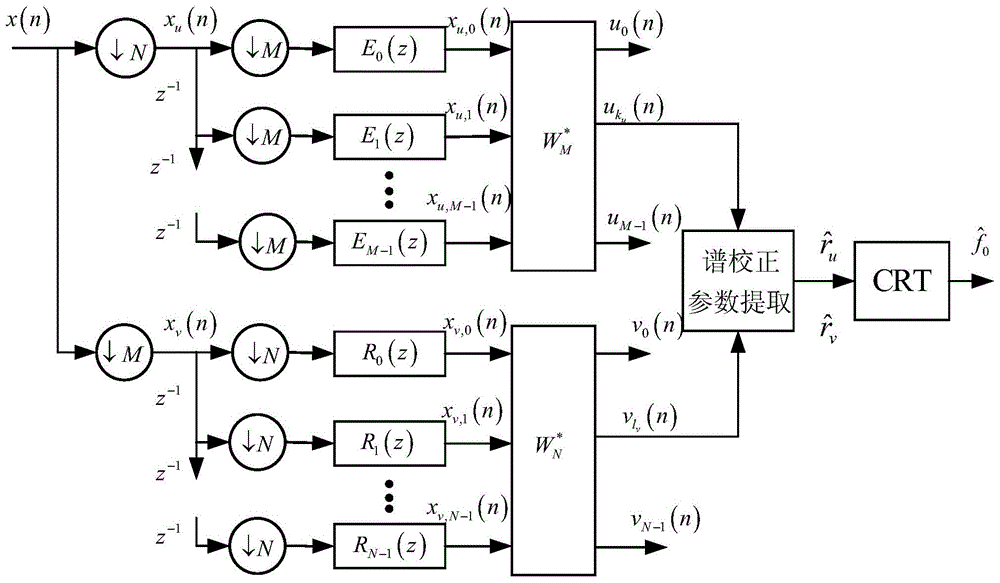
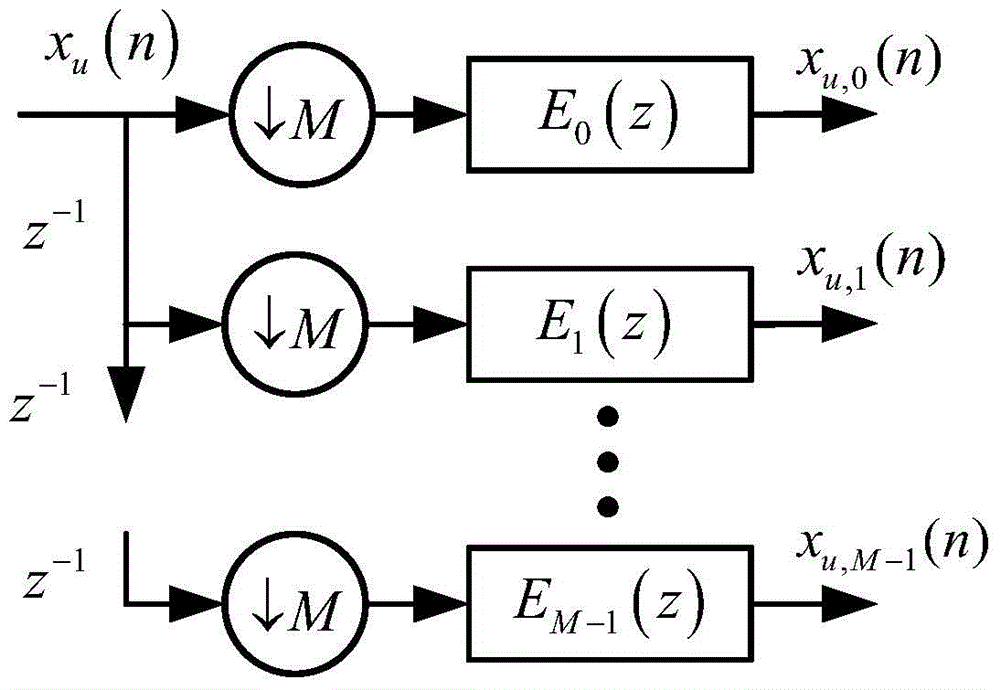
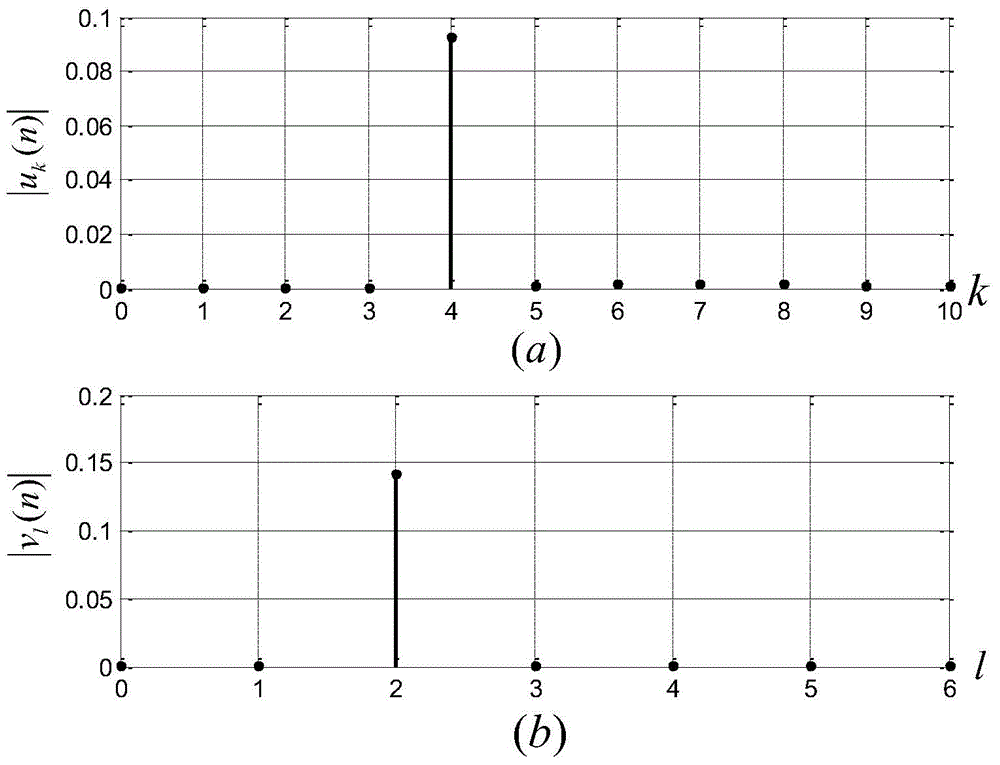
The Chinese remainder theorem is a theorem of number theory, which states that if one knows the remainders of the Euclidean division of an integer n by several integers, then one can determine uniquely the remainder of the division of n by the product of these integers, under the condition that the divisors are pairwise coprime.
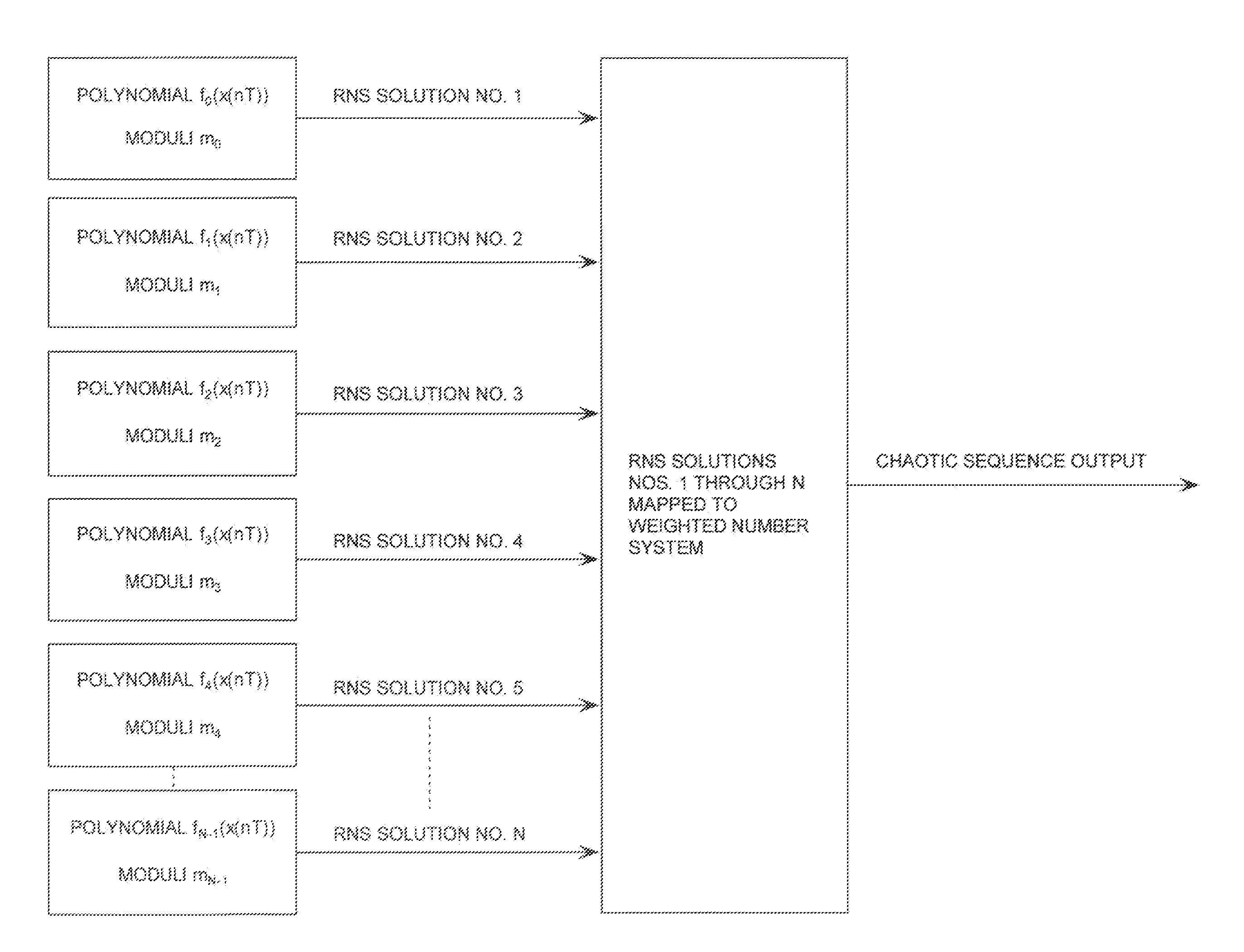
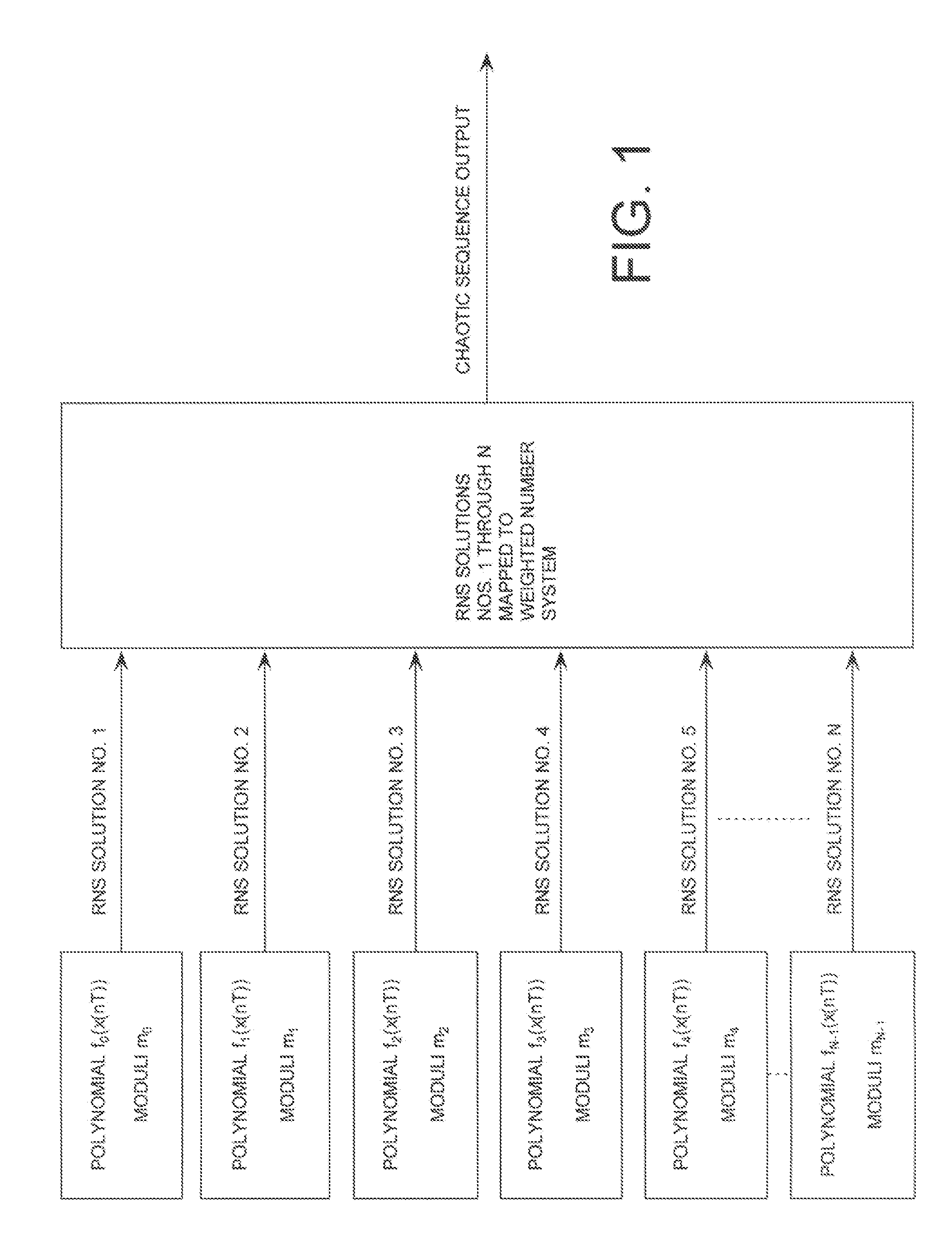
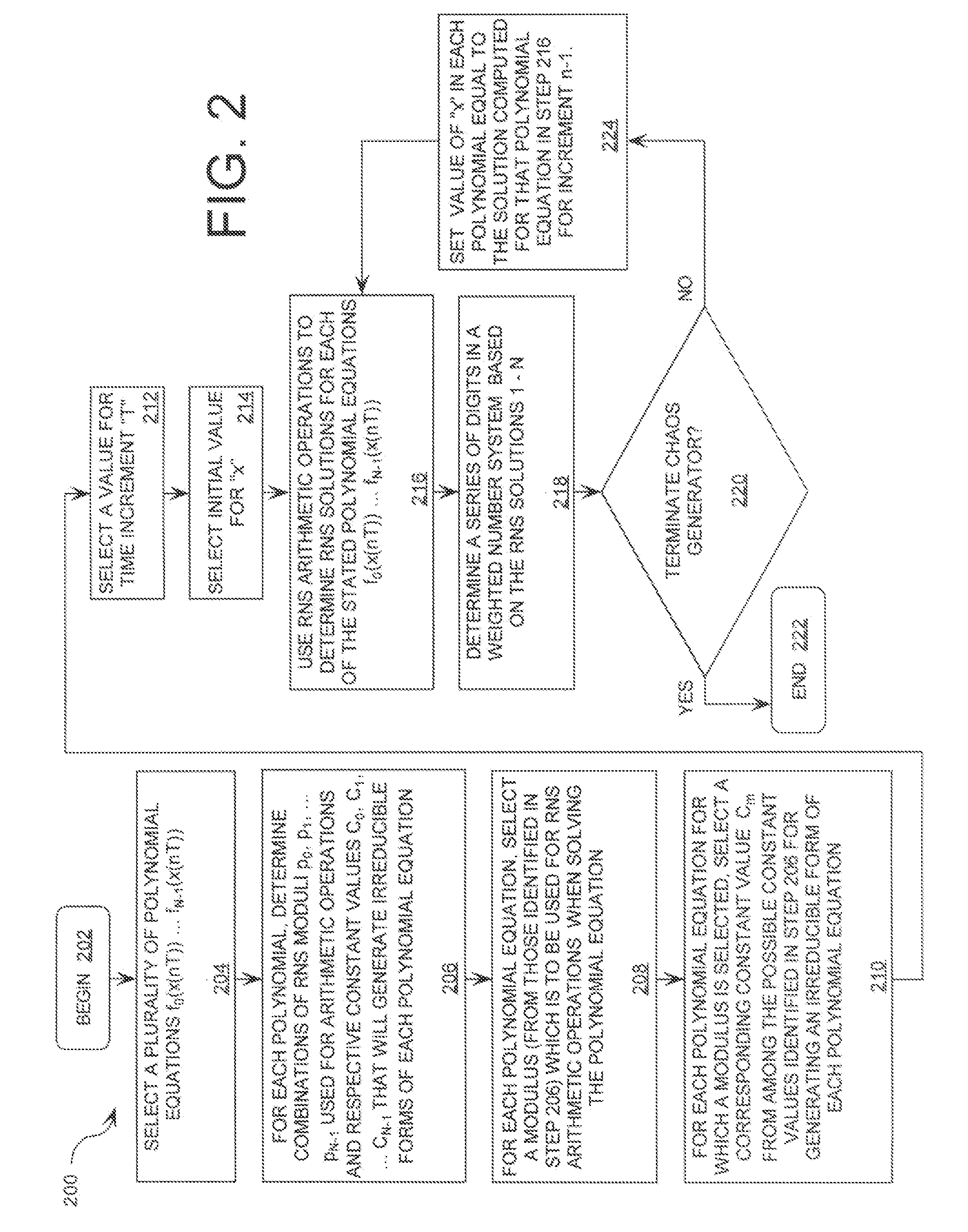
Digital Generation of a Chaotic Numerical Sequence
ActiveUS20080263119A1Random number generatorsComputations using residue arithmeticNumbering systemChinese remainder theorem
A method is provided for generating a chaotic sequence. The method includes selecting a plurality of polynomial equations. The method also includes using residue number system (RNS) arithmetic operations to respectively determine solutions for the polynomial equations. The solutions are iteratively computed and expressed as RNS residue values. The method further includes determining a series of digits in a weighted number system (e.g., a binary number system) based on the RNS residue values. According to an aspect of the invention, the method includes using a Chinese Remainder Theorem process to determine a series of digits in the weighted number system based on the RNS residue values. According to another aspect of the invention, the determining step comprises identifying a number in the weighted number system that is defined by the RNS residue values.
Owner:HARRIS CORP
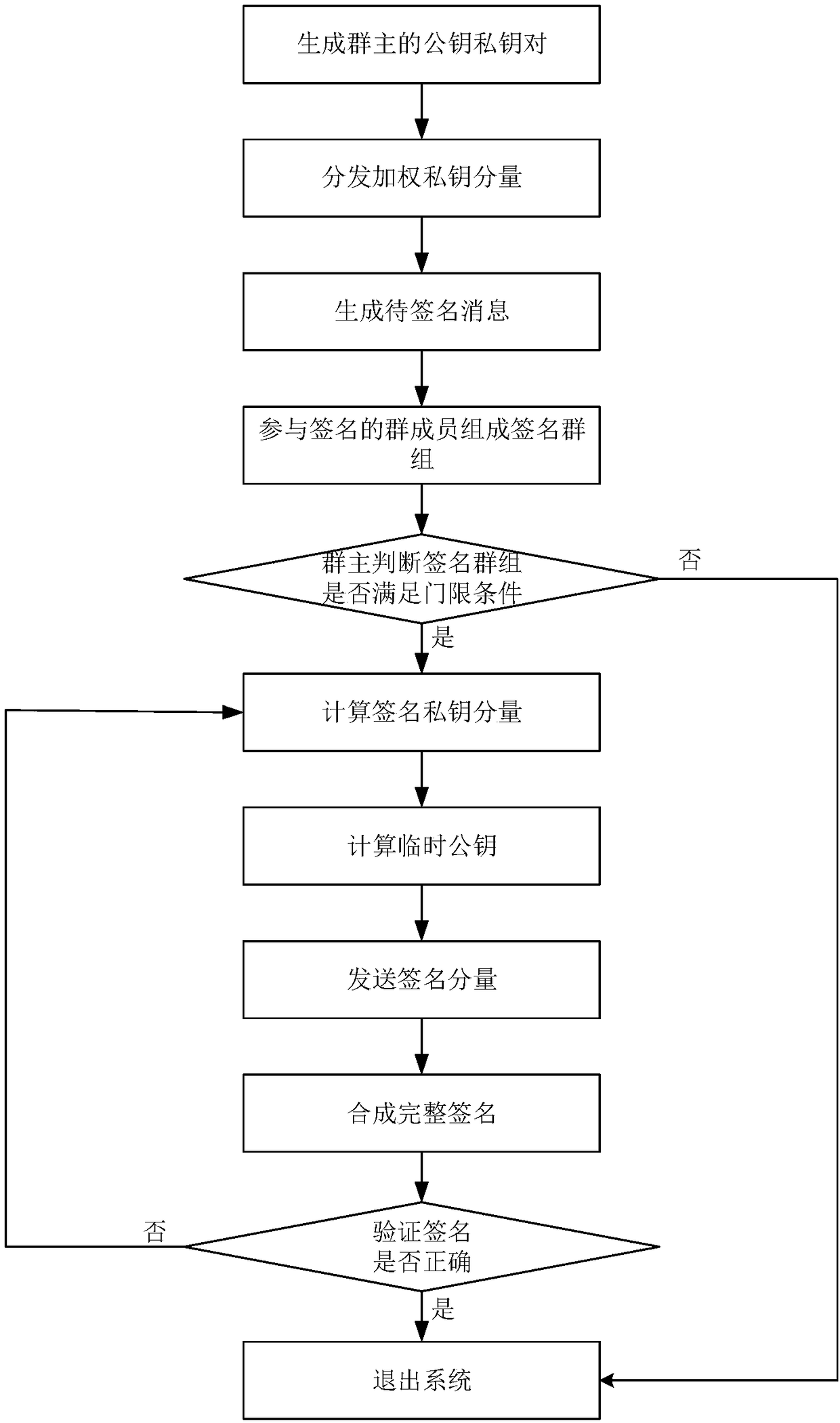
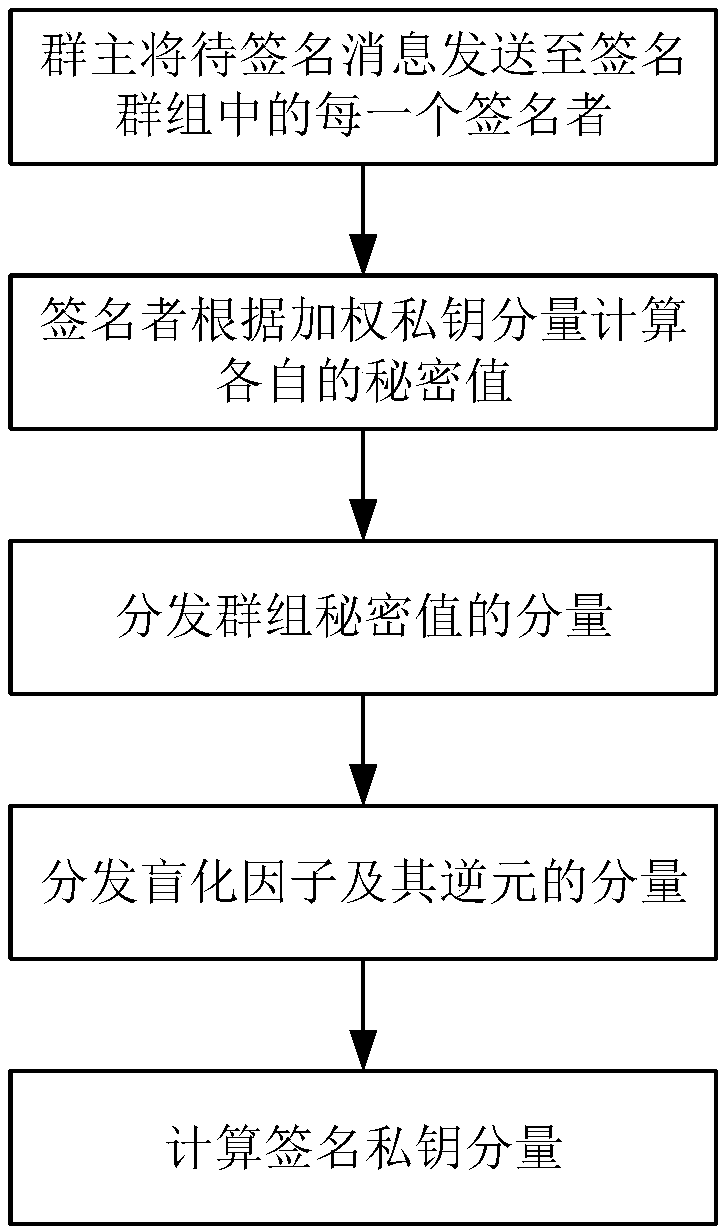
Block chain asset transaction transfer method based on weighted threshold signature algorithm
ActiveCN109377360AOvercoming the Disadvantages of LeakageImprove securityKey distribution for secure communicationFinanceChinese remainder theoremBlockchain
The invention discloses a block chain asset transaction transfer method based on a weighted threshold signature algorithm. The specific implementation steps include: 1, generating a public-key privatekey pair of a group master; 2, distributING a weighted private key component; 3, generatING a message to be signed; 4, a plurality of group memberS form a signature group; 5, that group mast judges whet the signature group satisfies the threshold condition; 6, calculatING a signature private key component; 7, calculatING a temporary public key; 8, sending a signature component; 9, synthesizing acomplete signature; 10, verifying that signature; 11. Exiting the system. The invention adopts threshold signature algorithm, reduces the risk of private key disclosure, and guarantees the security ofblock chain asset transaction transfer. A weighted secret sharing technique based on Chinese Residue Theorem (CRT) is used to improve the efficiency of signature generation algorithm.
Owner:XIDIAN UNIV
Method and system for measuring passive intermodulation generation point of microwave device by using electromagnetic wave phase
InactiveCN102156139AAccurate measurementMaterial analysis using wave/particle radiationMicrowavePhase difference
The invention discloses a method and system for measuring a passive intermodulation generation point of a microwave device by using an electromagnetic wave phase. Two paths of signals with different frequencies are combined into one path by a combiner and then enter a detected device via an end TX of a duplexer to be passively intermodulated in the detected device; one part of intermodulation product returns to the duplexer and enters a receiving loop via an end RX. After two paths of signals with different frequencies in a transmission loop are mixed, a signal component having the same frequency with the intermodulation product can be extracted; a phase of the signal component is compared with that of the obtained intermodulation product; and a phase difference generated by roundtrip of the signal in a measuring device is obtained after a phase difference caused by the measuring system is removed. A passive intermodulation generation position is obtained according to phase difference analysis. The method for measuring the passive intermodulation generation point, disclosed by the invention, which is realized by using a relation between the electromagnetic wave phase and a transmission distance and combining with the Chinese remainder theorem, can be used for accurately detecting the passive intermodulation generation position of the microwave device, thereby providing support for fast solving the passive intermodulation problem.
Owner:ZHEJIANG UNIV
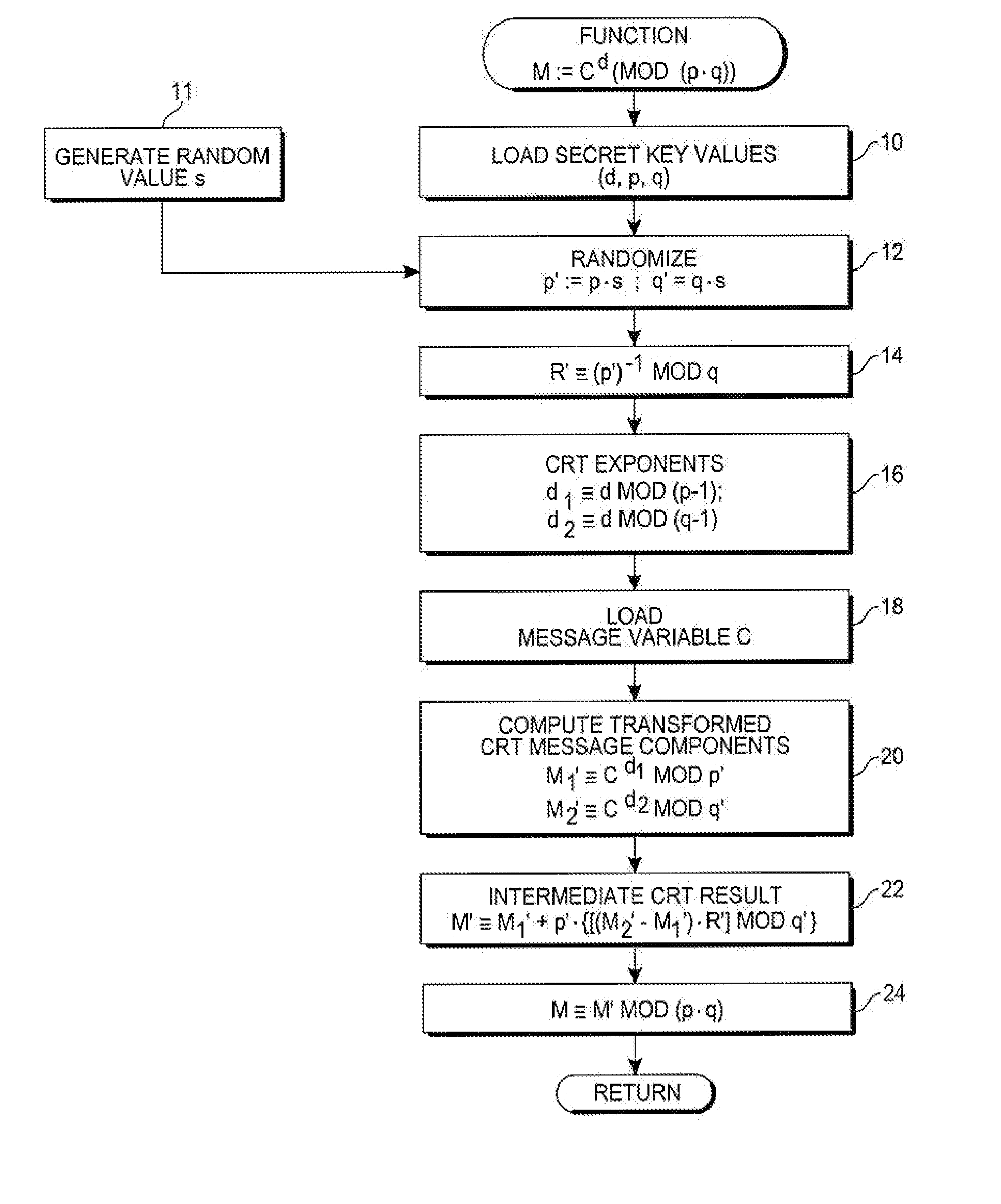
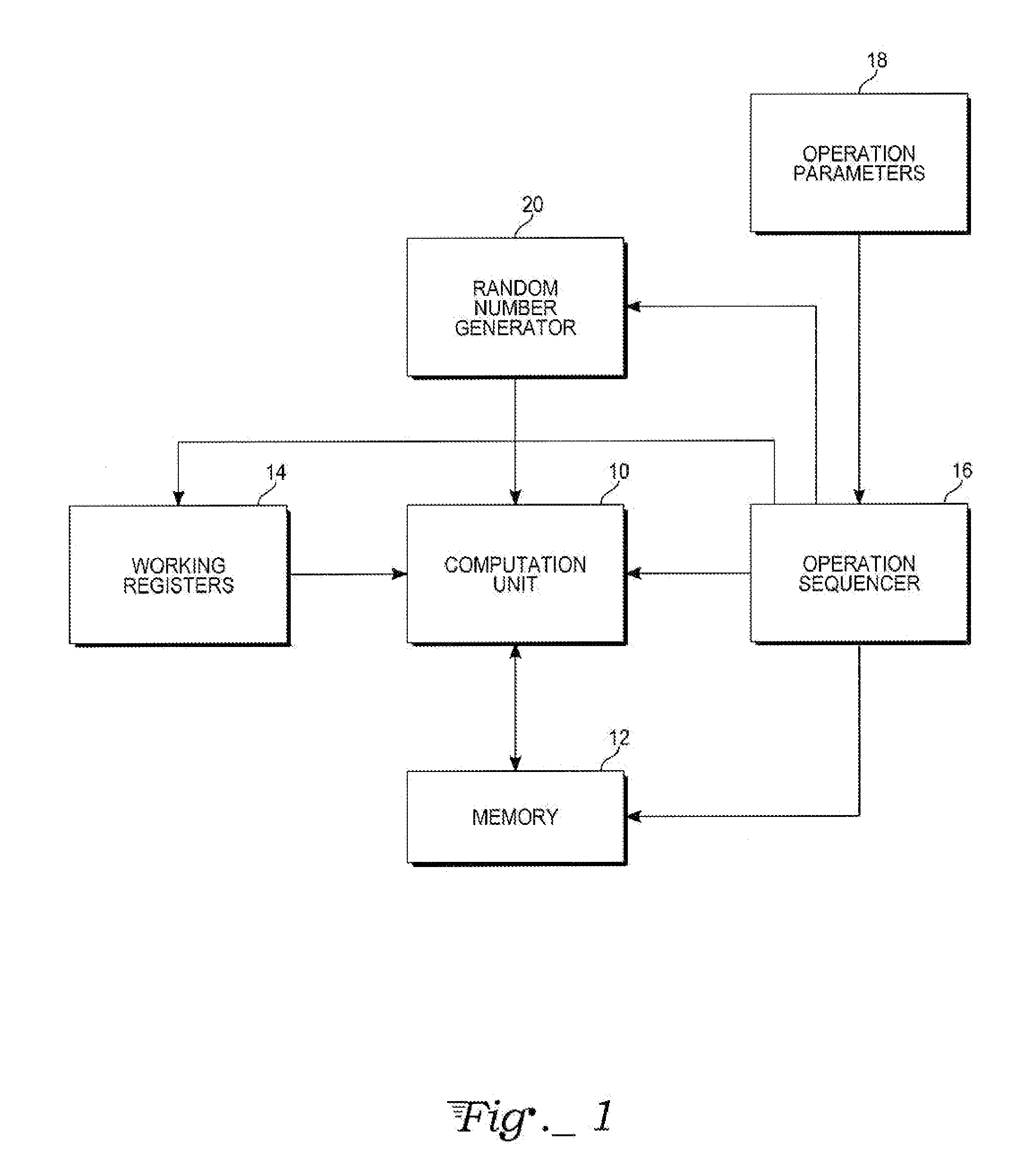
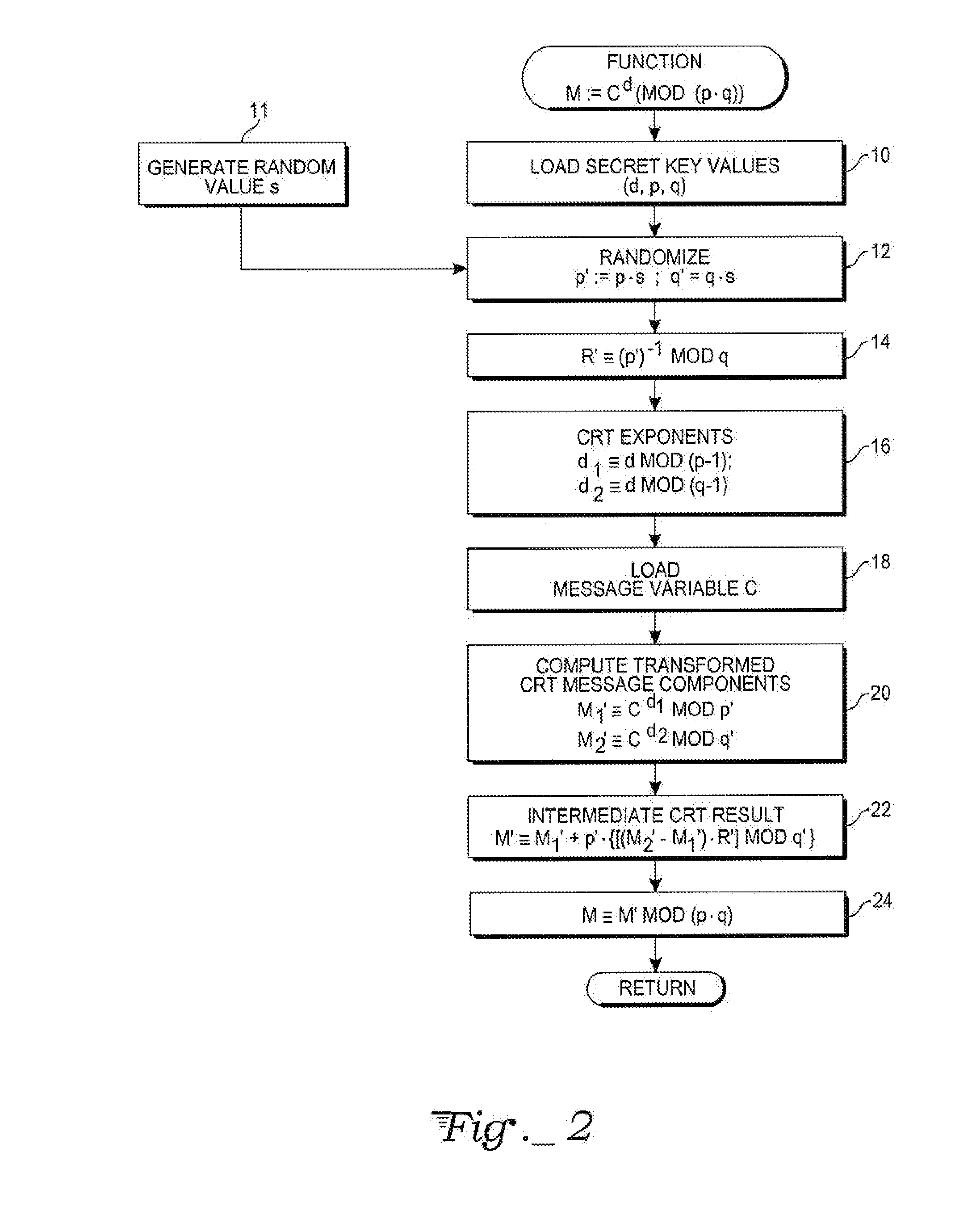
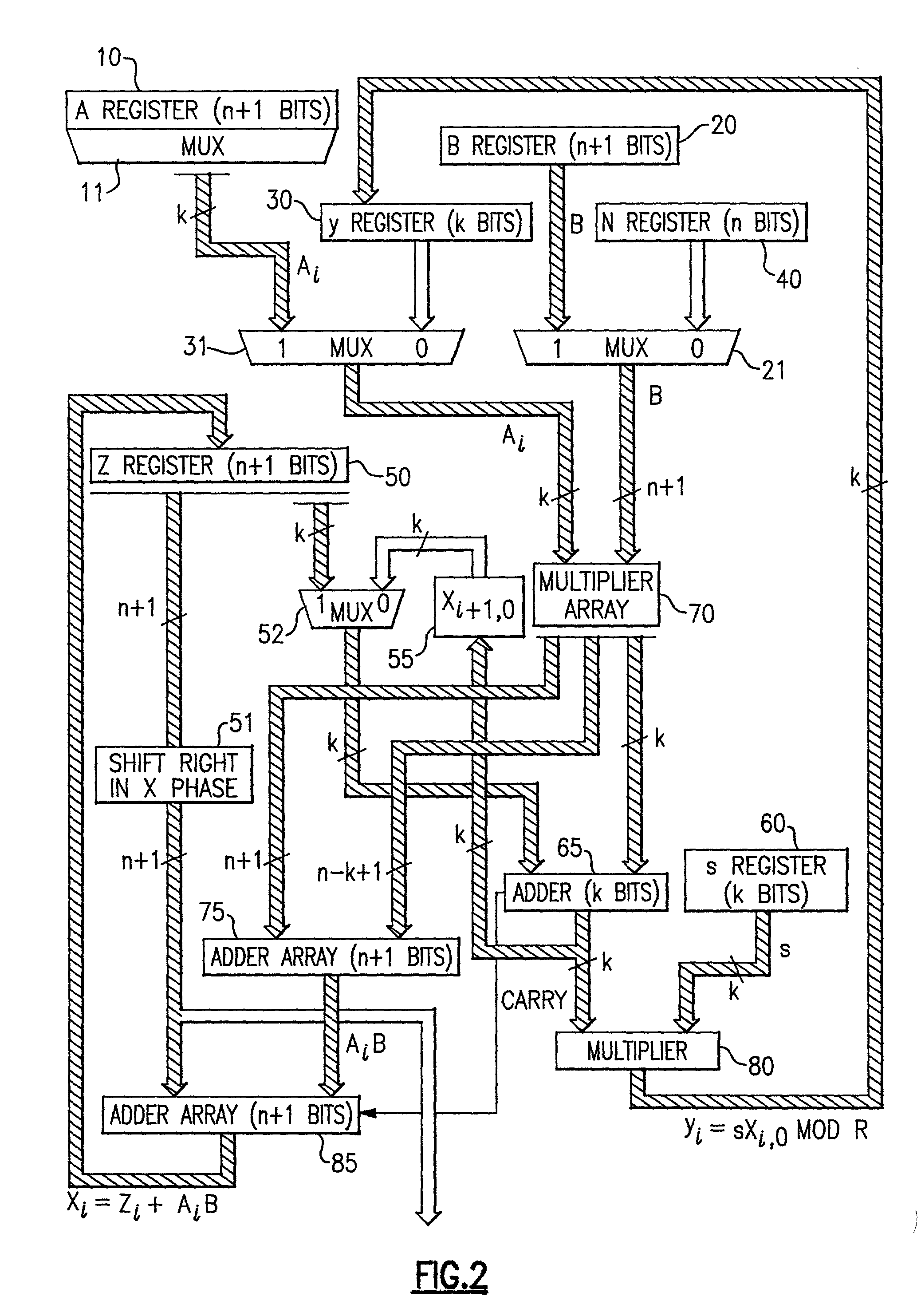
Chinese remainder theorem - based computation method for cryptosystems
ActiveUS20080226064A1Less computational intenseSecure against cryptanalysisRandom number generatorsPublic key for secure communicationChinese remainder theoremCryptosystem
A computer hardware implemented cryptography method computes a modular exponentiation, M:=Cd (mod p·q) upon a message data value C using a Chinese Remainder Theorem (CRT) based technique. To secure against cryptanalysis,, the private key moduli p and q are transformed by multiplication with a generated random value s, so that p′:=p·s and q′:=q·s. The CRT steps of the modular exponentiation are applied using the transformed moduli p′ and q′ to obtain a random intermediate message data value M′. A final reduction of M′ modulo p·q yields the final message data value M. Values needed for the computation are loaded into data storage and accessed as needed by electronic processing hardware.
Owner:CRYPTOGRAPHY RESEARCH
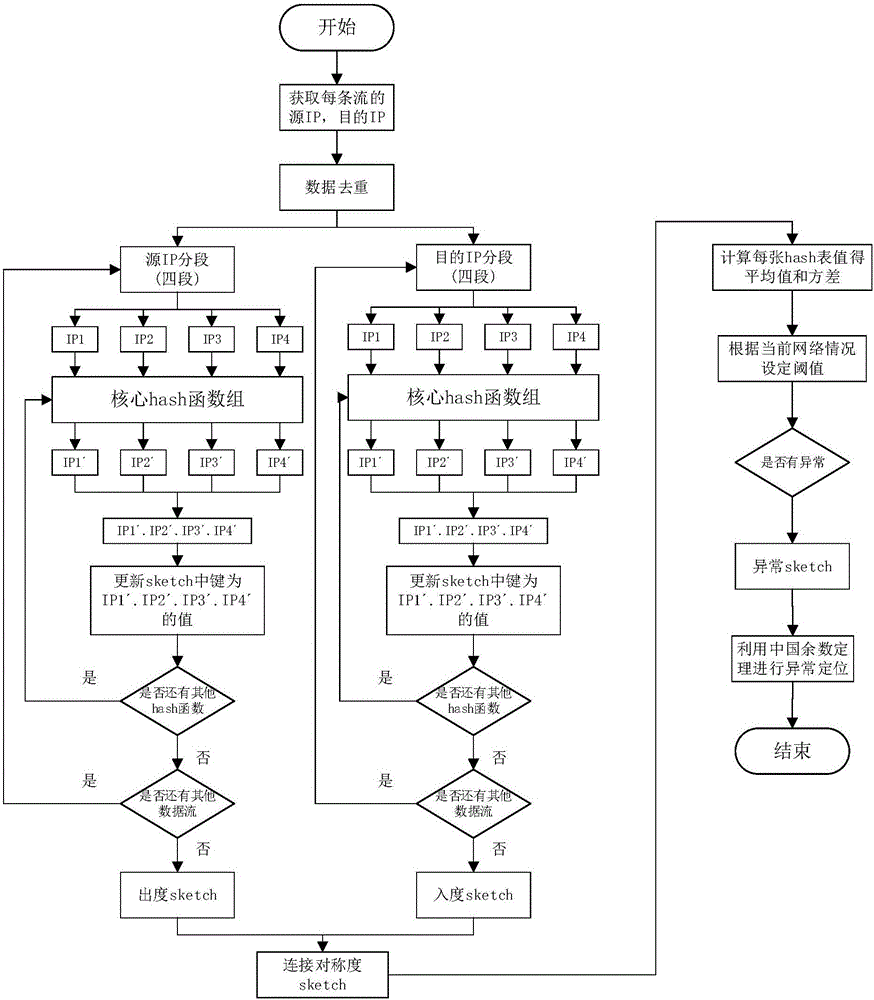
Network traffic abnormality detection and positioning method based on symmetry degree sketch
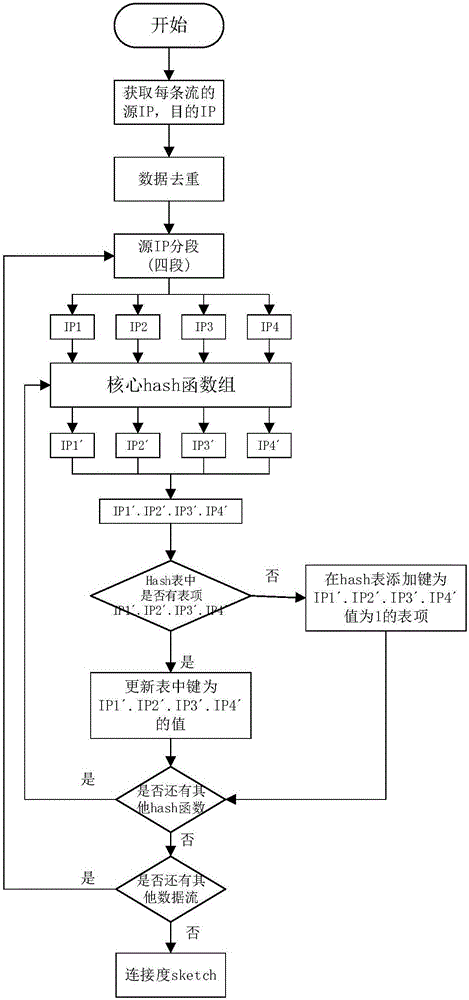
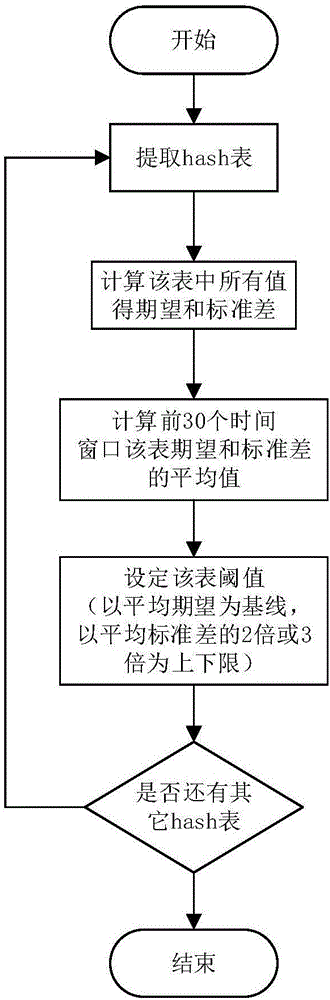
The invention discloses a network traffic abnormality detection and positioning method based on a symmetry degree sketch. An abnormal behavior is detected through adoption of connection symmetry degree. The detection granularity and precision are higher than those of a traditional method based on traffic feature statistics. The invention provides a calculation method-connection degree sketch of the connection symmetry degree, an IP address is divided into four segments according to structure features of the IP address, and each segment is mapped through adoption of a corresponding hash function group, so the length of a hash table is effectively reduced, a conflict generation probability is effectively reduced, and the relatively precise host connection symmetry degree is obtained. A method for obtaining a threshold value according to distribution condition of self features of the traffic is provided, and the obtained threshold value is changed in real time according to the network traffic features, so the features of the abnormal behavior can be captured relatively accurately, and a relatively good effect is obtained. Through design of a core hash function group of the sketch and utilization of the Chinese remainder theorem, an abnormal source is analyzed and solved, and a solution process is simple and efficient, and a result is accurate.
Owner:XI AN JIAOTONG UNIV
Method and device for measuring frequencies of high-frequency cosine signals under undersampling rate
InactiveCN103941087ARealize measurementExpand the measurement rangeFrequency measurement arrangementDigital signal processingFrequency spectrum
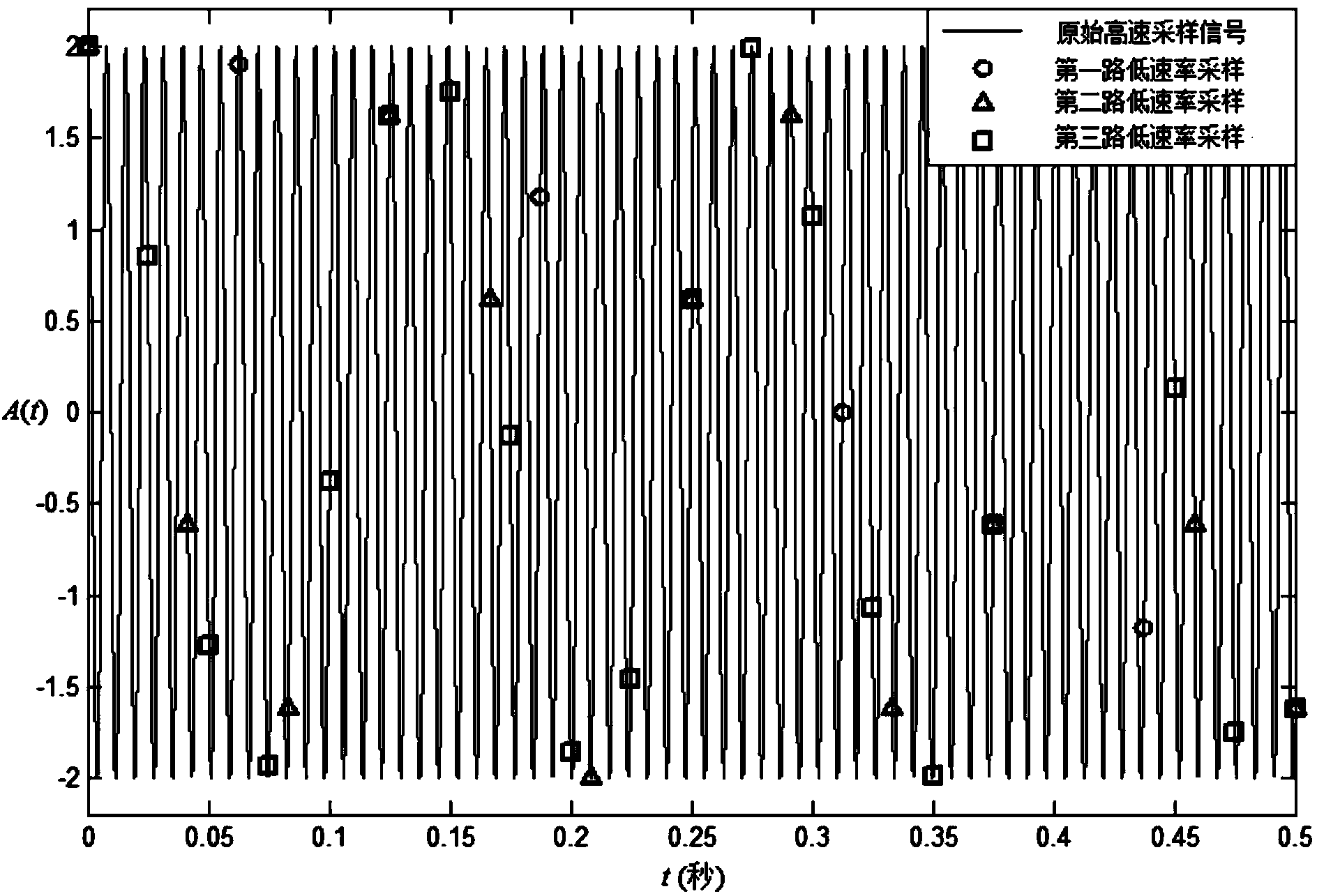
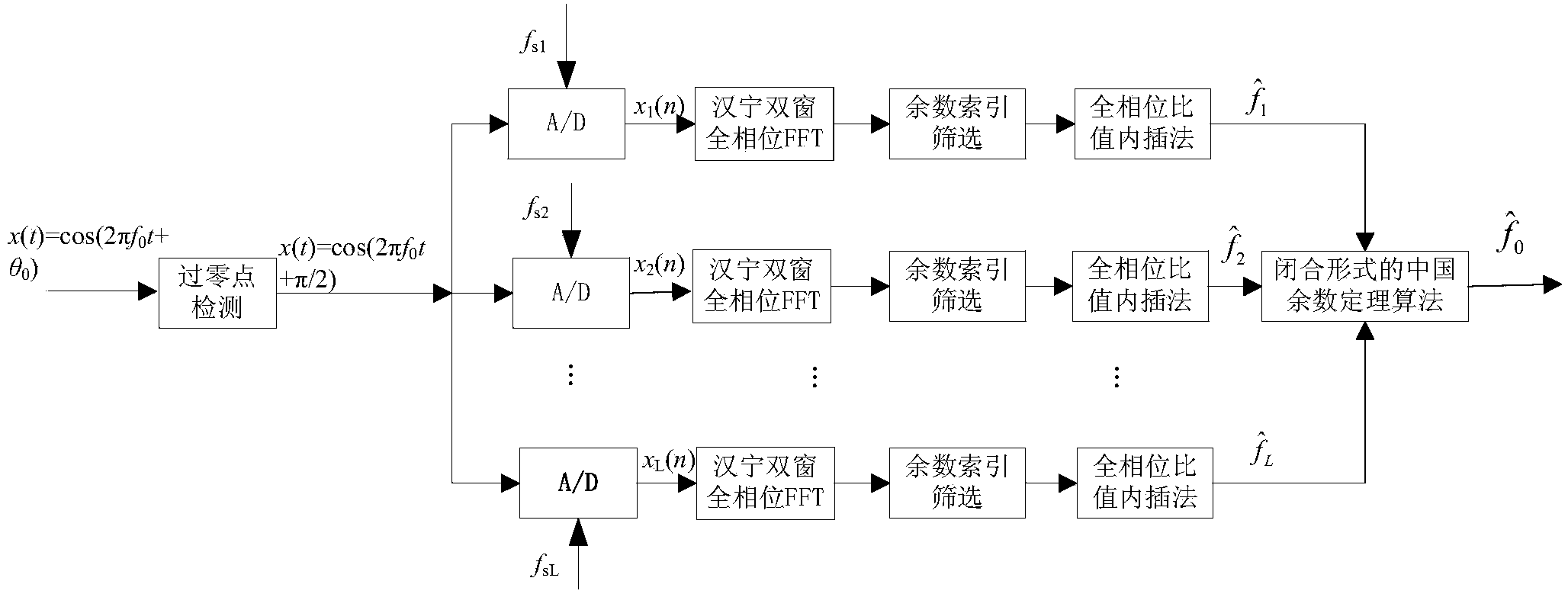
The invention discloses a method and device for measuring the frequencies of high-frequency cosine signals under the undersampling rate, and relates to the field of digital signal processing. By combining the type of the zero crossing point with the distribution characteristic of apFFT phase spectrums, L spectrum position index values are selected from 2L peak value magnitude spectrum positions; according to the remainder selecting result, each apFFT phase spectrum is corrected through the all-phase ratio interpolation method so that the frequency of the apFFT phase spectrum can be estimated; the frequency estimation value obtained after each apFFT phase spectrum is corrected is used as a remainder, the remainders are processed according to the Chinese remainder theorem of the closed analysis form, and the frequencies of the original high-frequency signals are reconstituted through the frequency estimation values. According to the method and the device, the frequencies of the multiple paths of high-frequency cosine signals under the undersampling rate are measured, and the measuring range of the frequencies of the high-frequency signals is greatly widened; the novel spectrum correction method is adopted, and therefore the measuring accuracy of the frequencies of the high-frequency cosine signals is improved, and novel anti-noise performance of the high-frequency cosine signals under the low undersampling rate is ensured.
Owner:TIANJIN UNIV
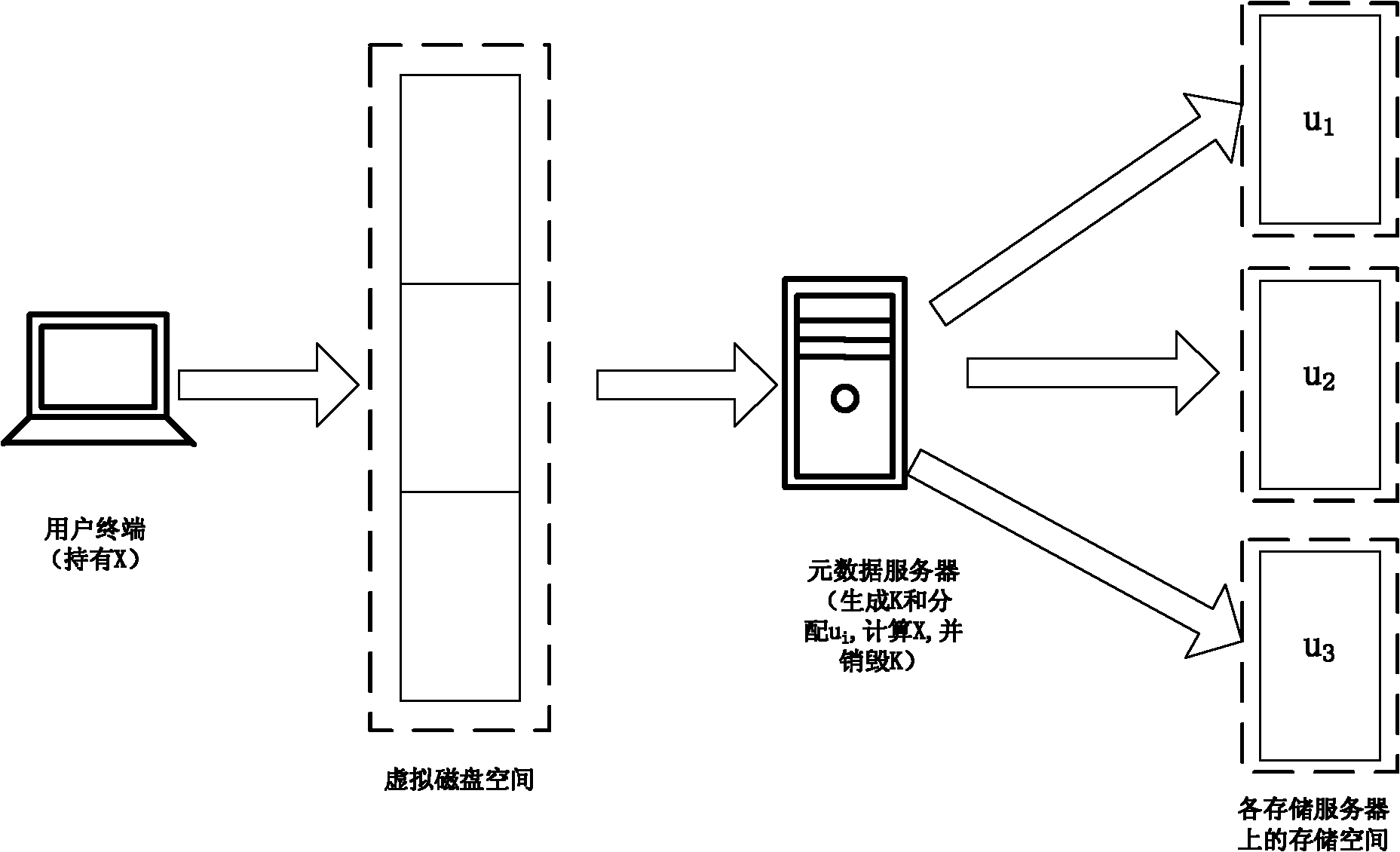
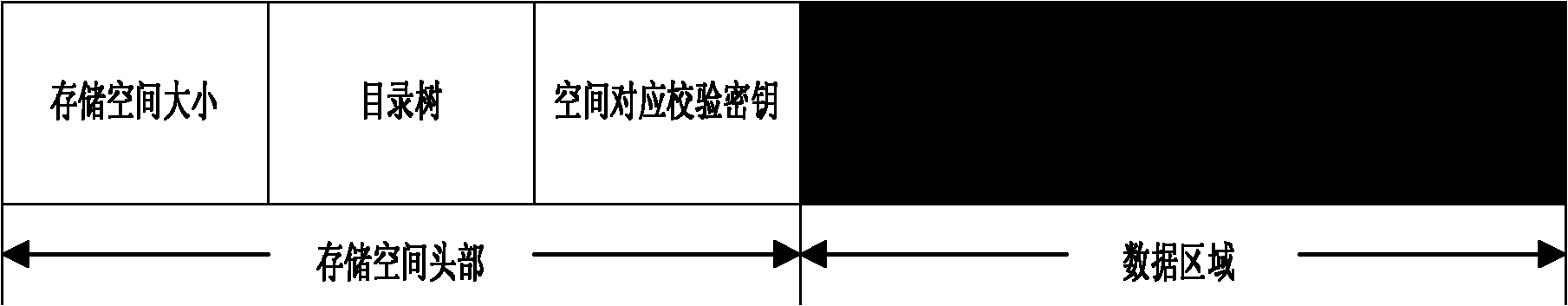
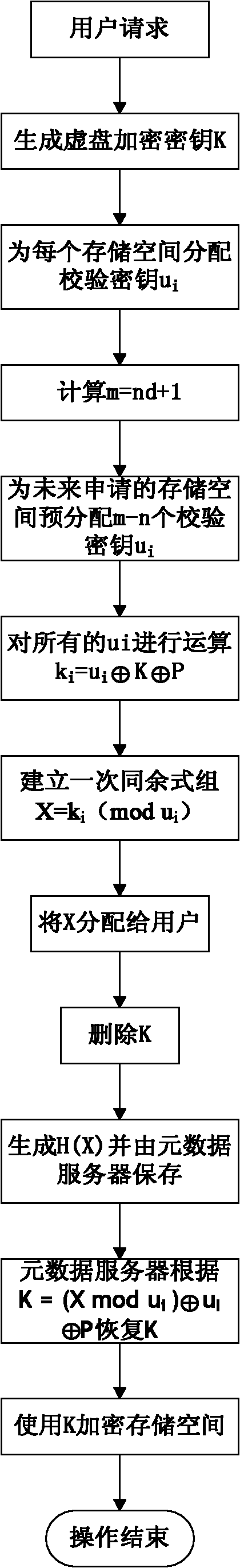
Distributed key management method for ciphertext storage
ActiveCN101917403AFusion simpleImprove securityKey distribution for secure communicationMultiple keys/algorithms usageCiphertextChinese remainder theorem
The invention discloses a distributed key management method for ciphertext storage. The method utilizes the uniqueness of the solution under the modulus to the congruence expression of first degree in the Chinese Remainder Theorem and the operational convenience of XOR. Due to the uniqueness of the solution of congruence expression of first degree, the encrypting information of a plurality of storage spaces of a user is finally depended on a single datum and saved by the user and corresponds to the user one by one. Such key management and user management are much easier, and a foundation is provided for the realization of distributed key management. The real keys to encrypted data are destroyed in a system after the key distribution to guarantee a high security, and the data encryption keys have to be recovered from other information. By the method, the management of secure metadata can be easily integrated with that of original normal metadata in a file system without extra system configurations; the expenses for guaranteeing the security of the system are saved, and the security of the secure metadata of the system is improved.
Owner:江西浅蓝信息科技有限公司
Multi-baseline and multi-band InSAR phase unwrapping method based on Chinese remainder theorem
InactiveCN101866002AImprove solvabilityImprove accuracyRadio wave reradiation/reflectionTerrainMulti band
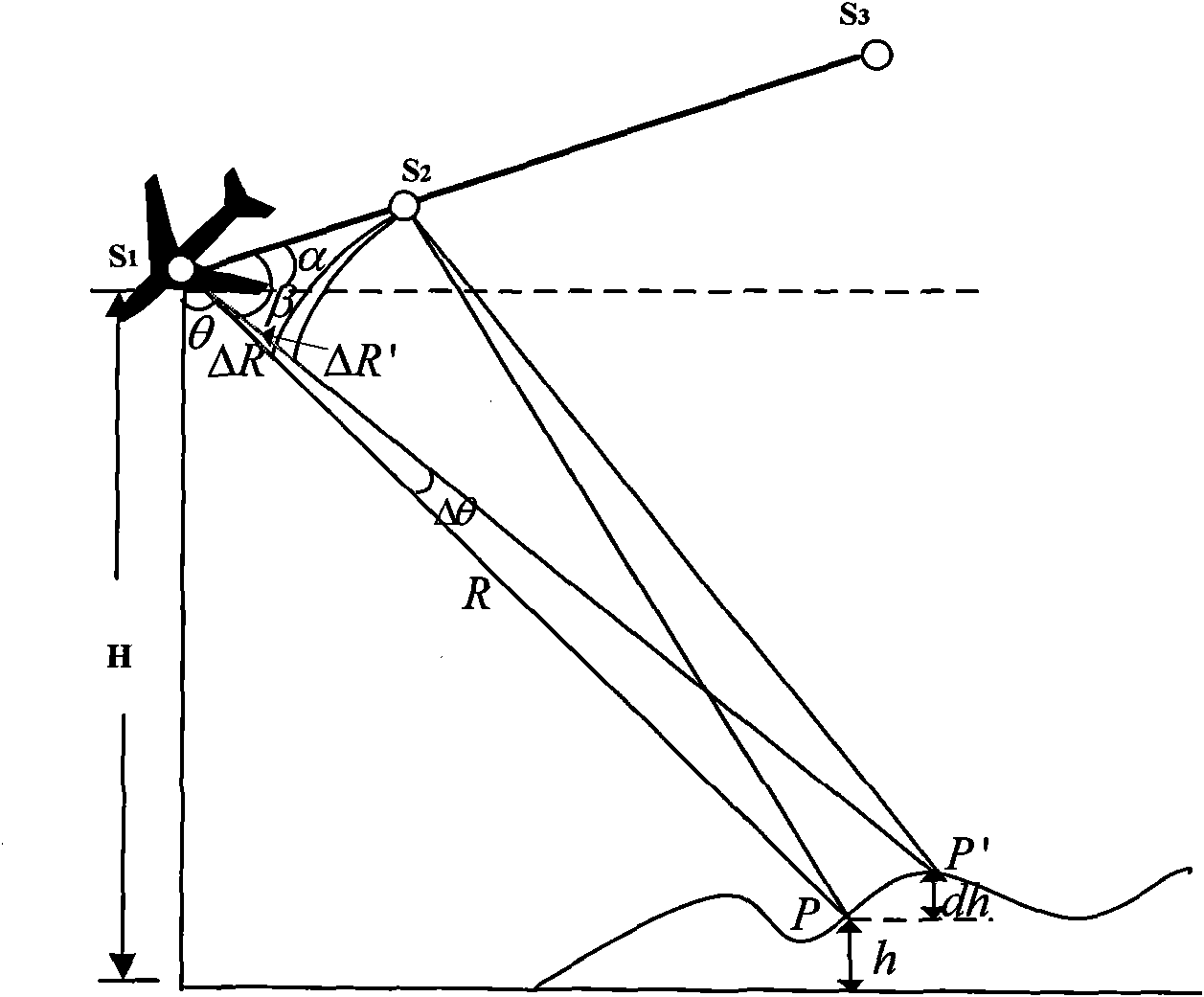
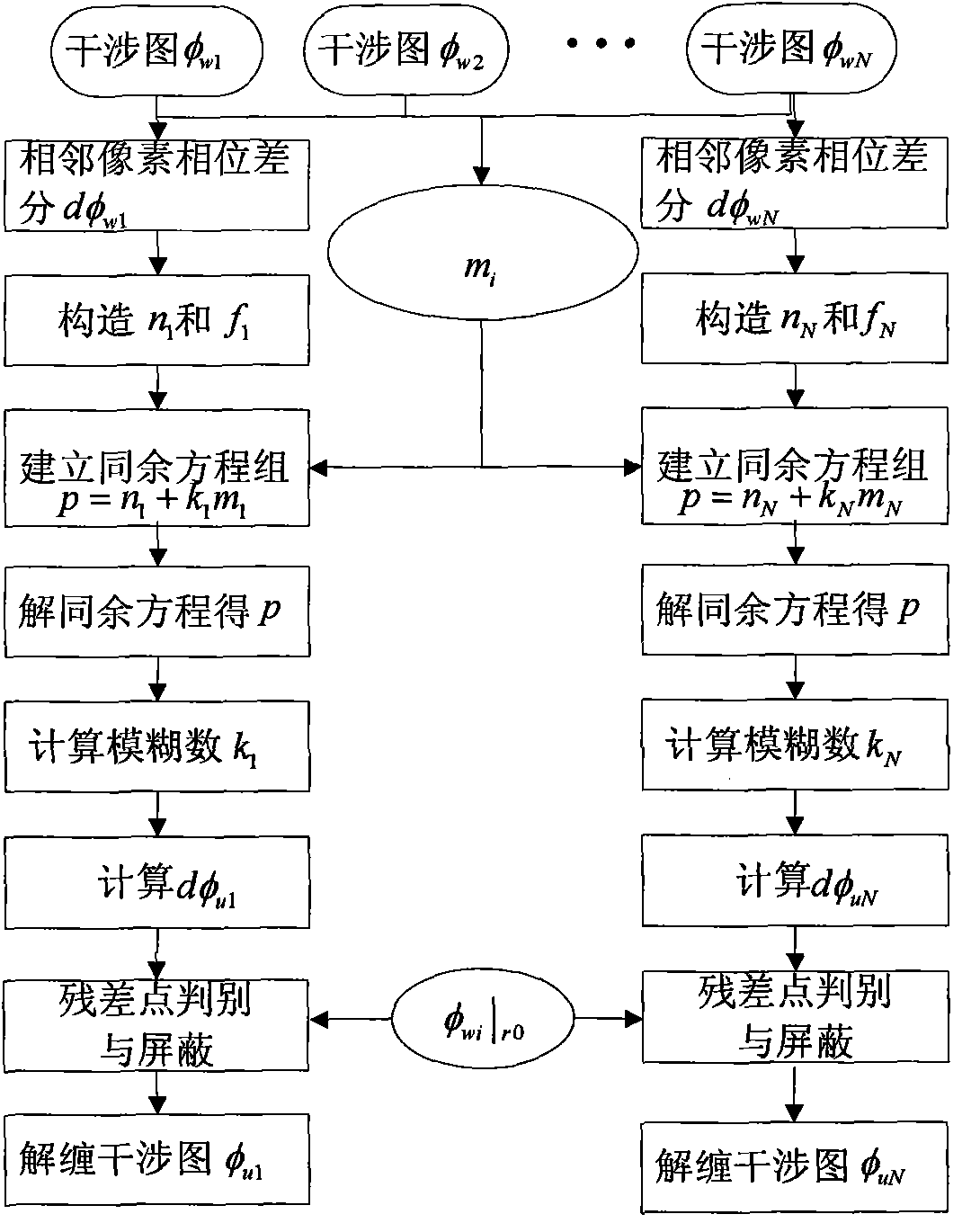
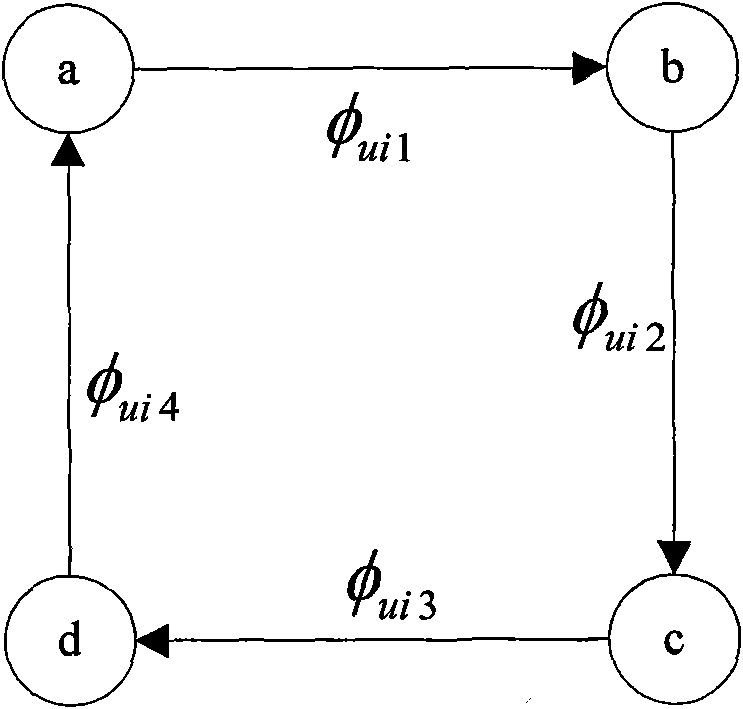
The invention discloses a multi-baseline and multi-band InSAR phase unwrapping method based on Chinese remainder theorem, which comprises the following steps: 1. respectively obtaining N multi-baseline InSAR interferograms, the ratio of any two baselines after registration of which is a rational number, and N multi-band InSAR interferograms; 2. calculating phase difference of adjacent pixels; 3. constructing a modulus ratio according to a wavelength ratio, thus constructing an integral cycle number ni and a residue number fi; 4. establishing congruence equations about a fuzzy number of fuzzy phase differential; 5. calculating p; 6. calculating the fuzzy number ki; 7. calculating interferometric phase differential after unwrapping, and 8. calculating the unwrapping phase Phiui of any pixel element in the interferograms. The method makes full use of the existing InSAR data, gives full play to the advantages of low processing difficulty and high processing accuracy of the technology of obtaining DEM through the multi-baseline and multi-band InSAR, effectively solves the problem of phase unwrapping of aliasing interference fringes in under-sampled situations in undulating terrain areas and improves the solvability and accuracy of the phase unwrapping.
Owner:THE PLA INFORMATION ENG UNIV
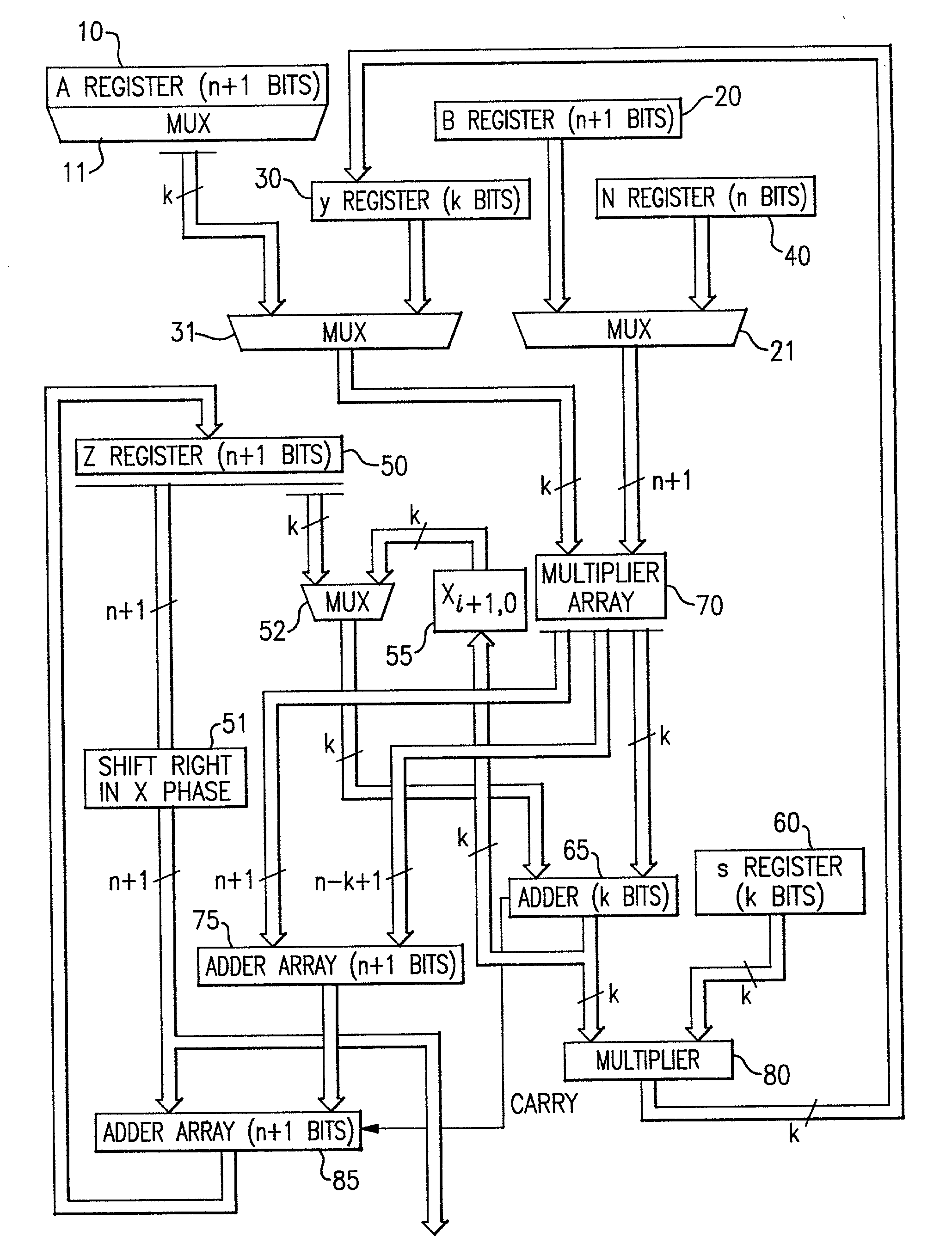
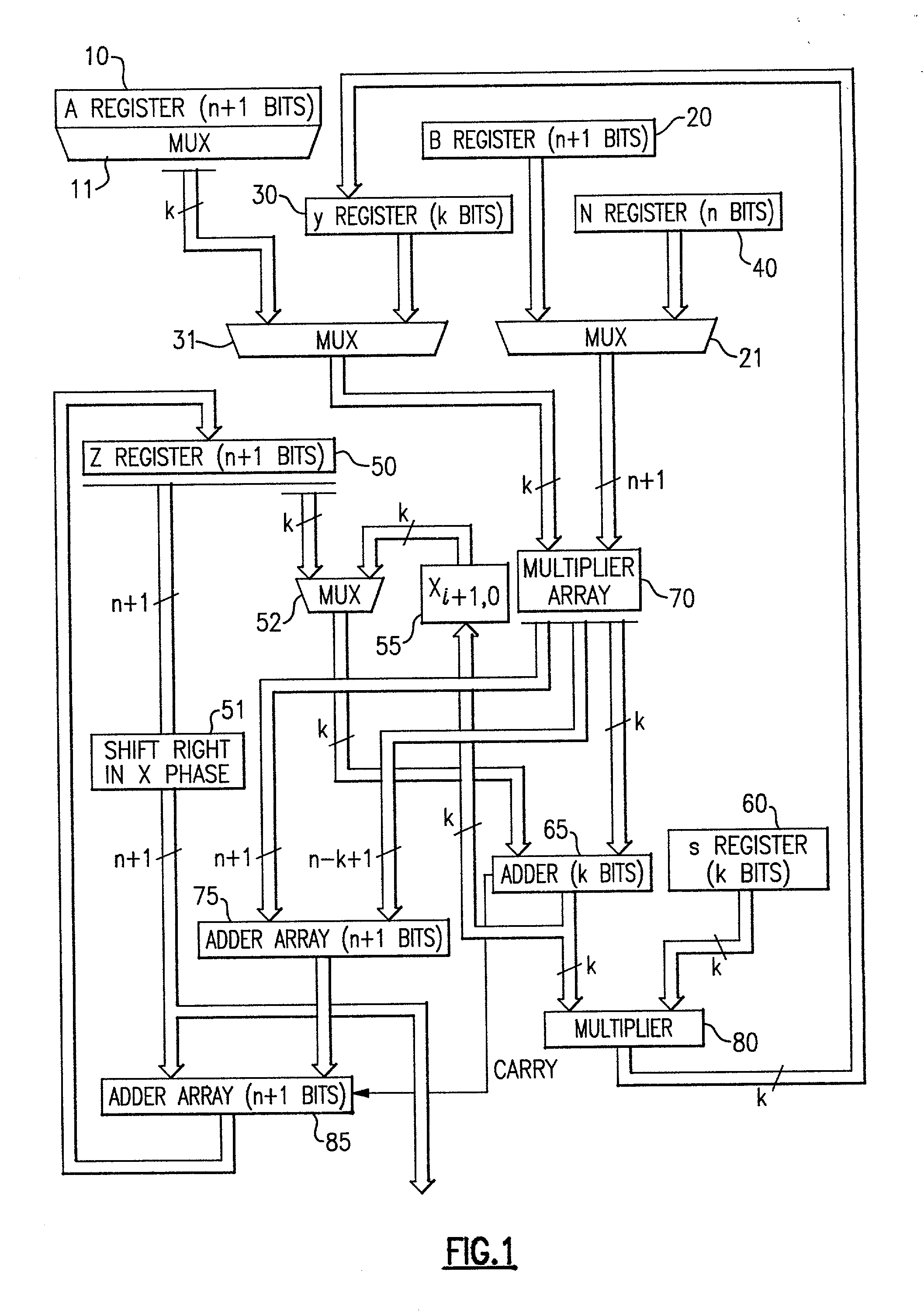
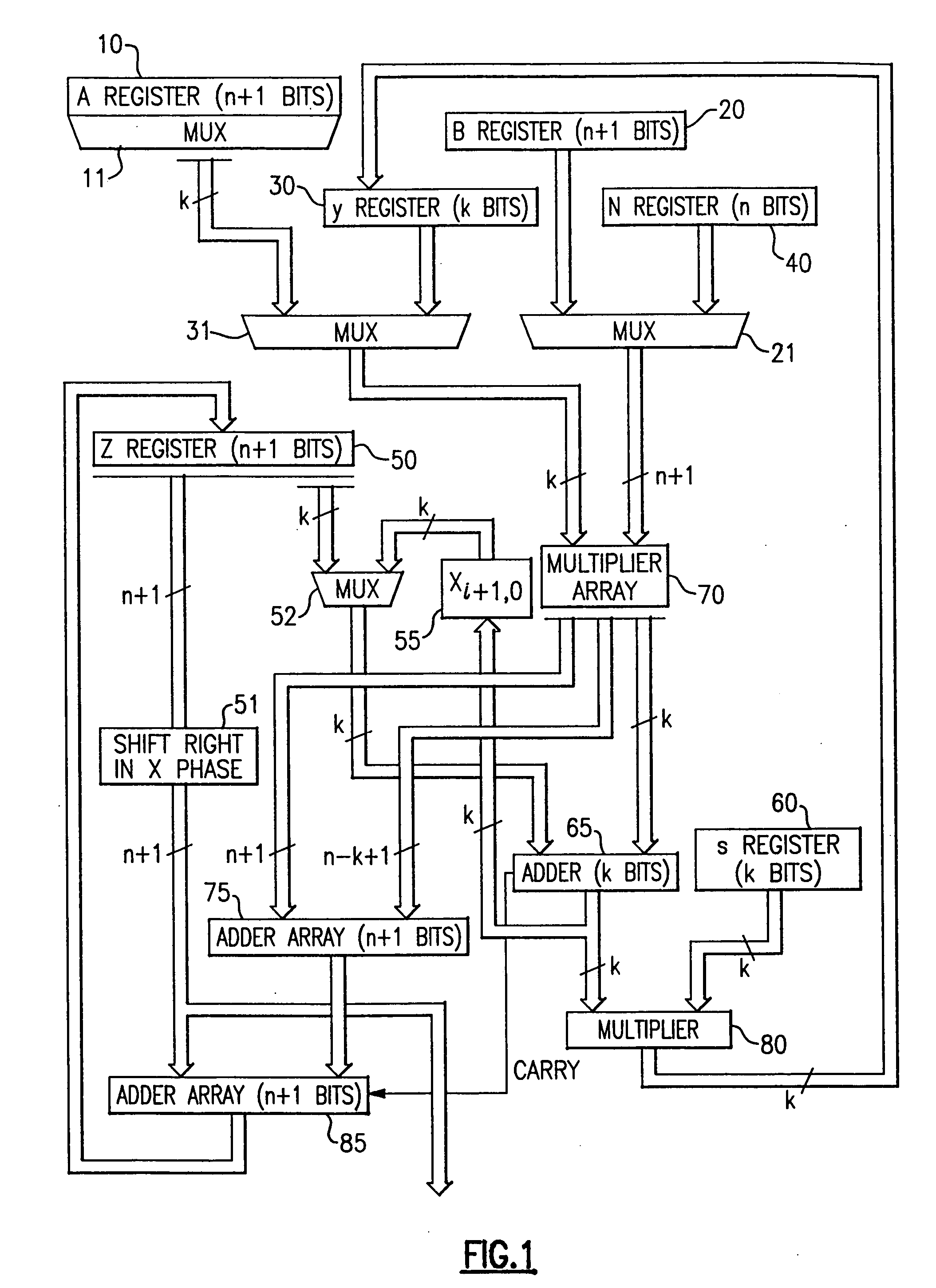
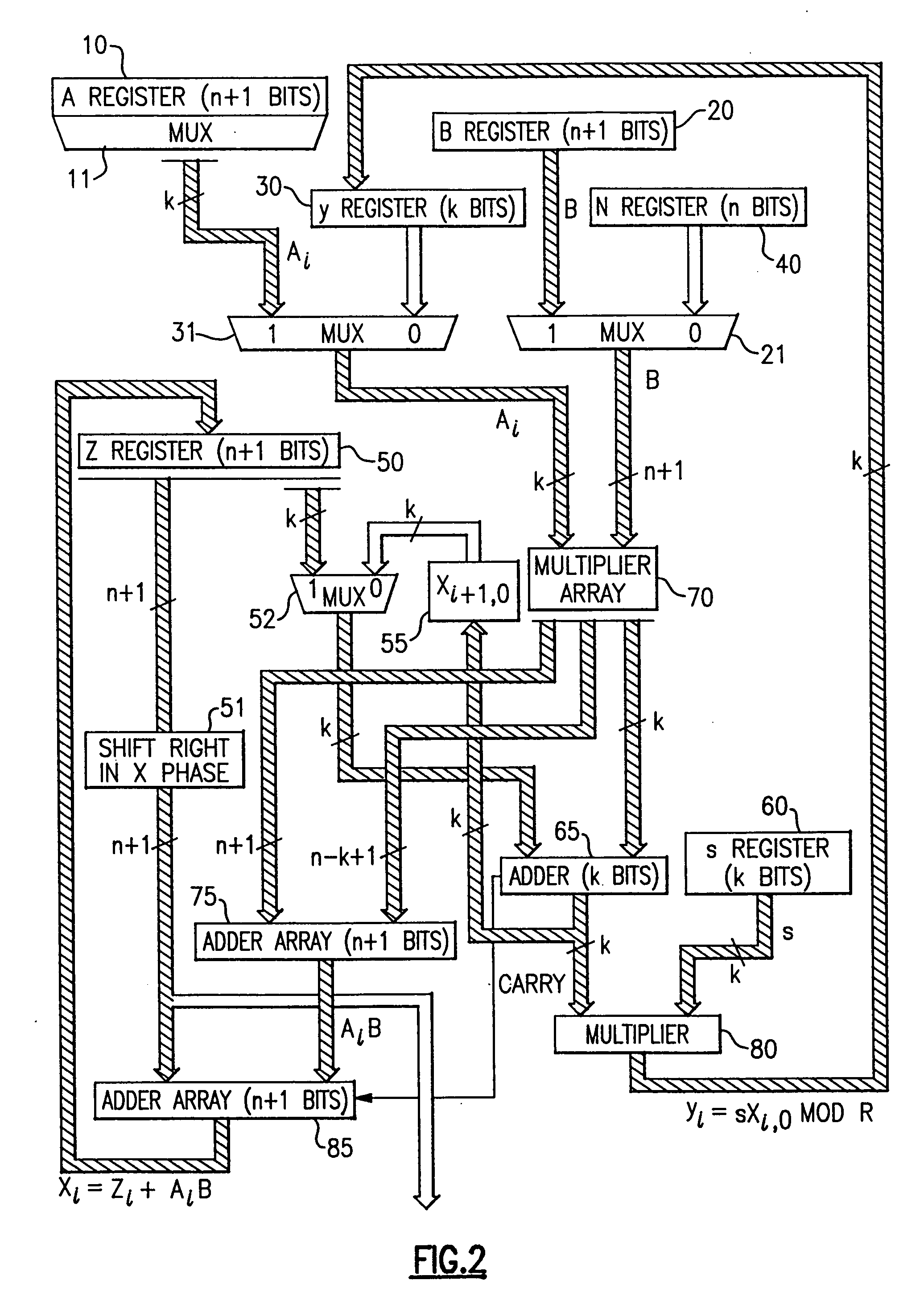
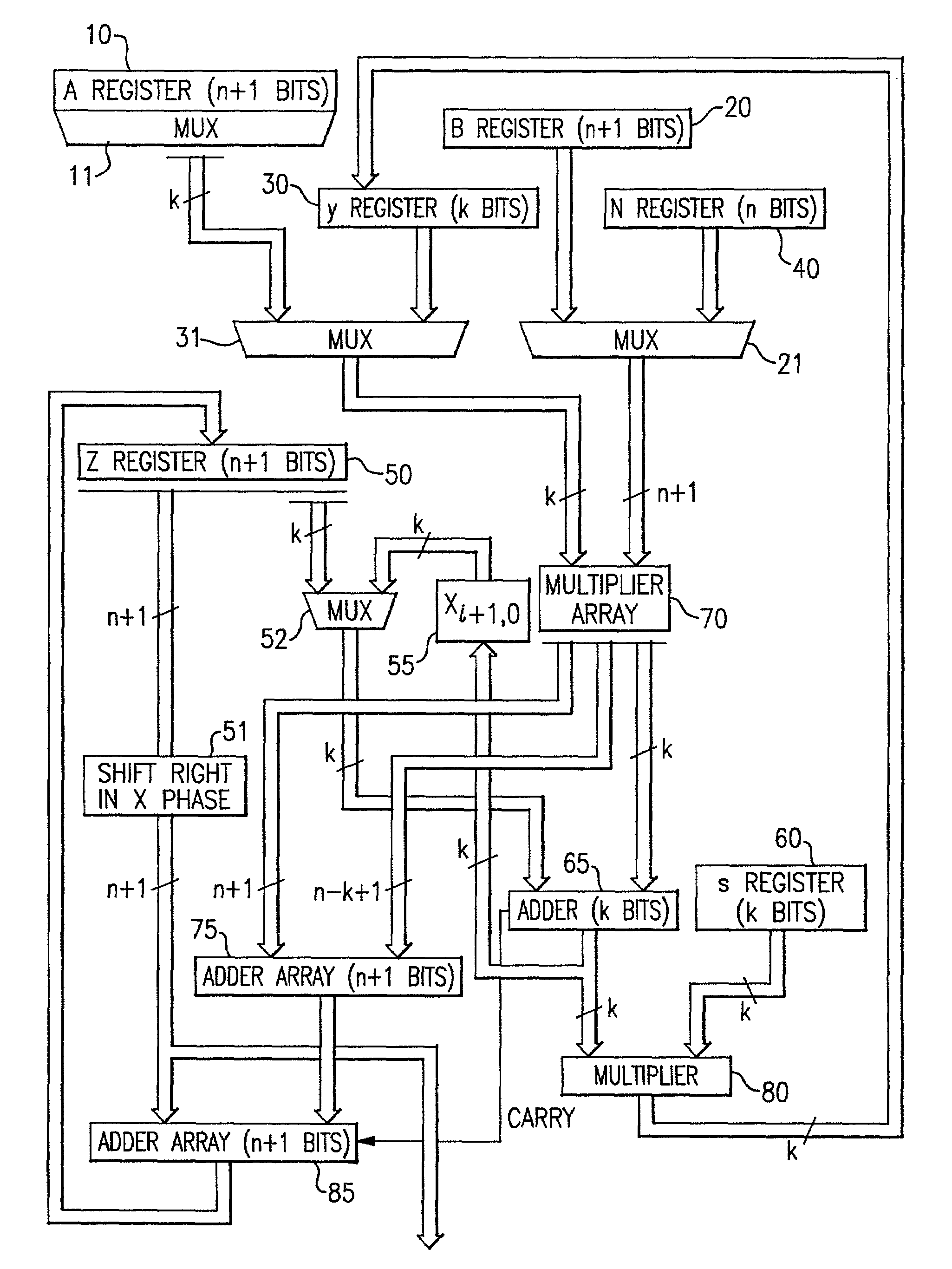
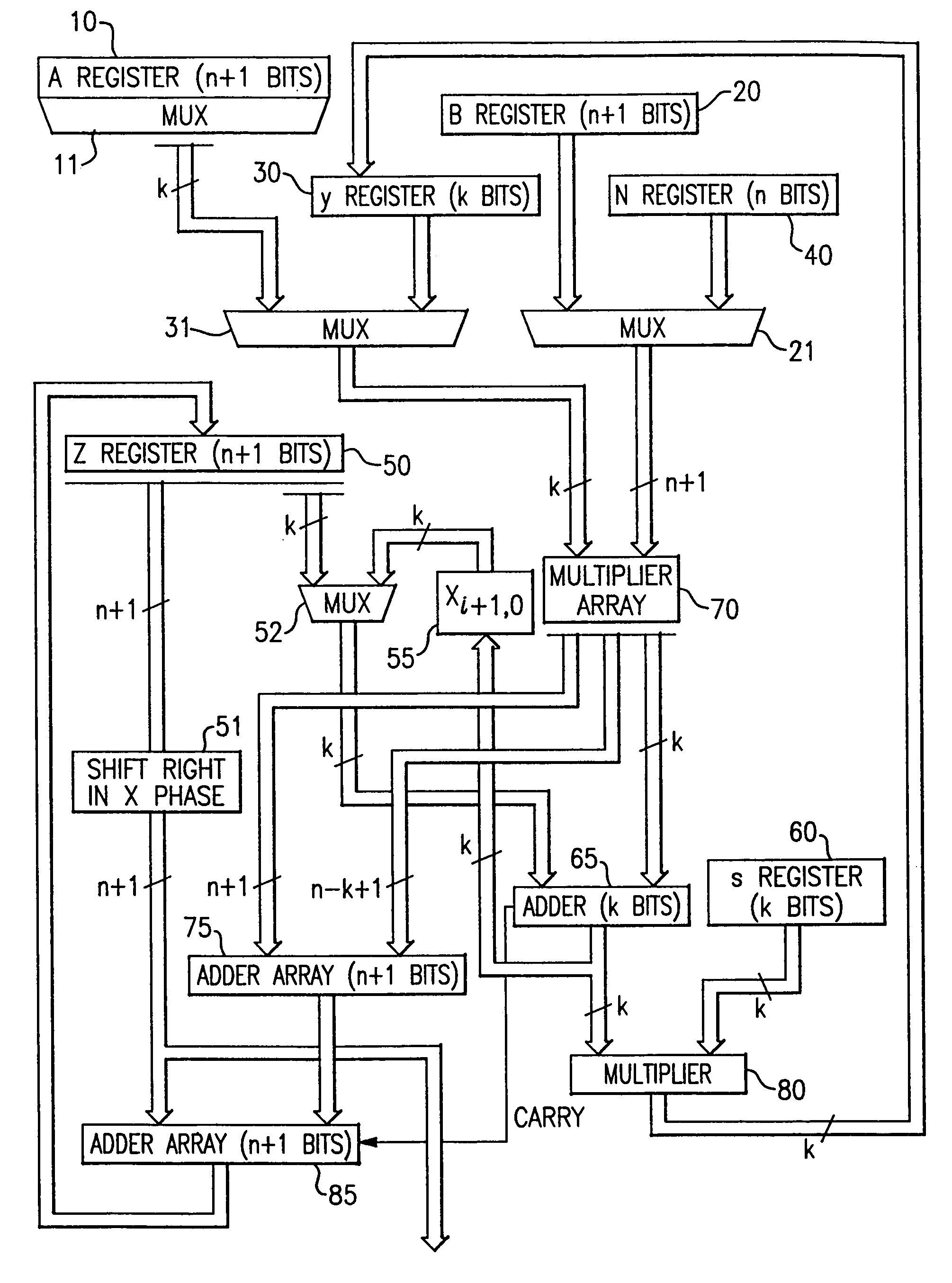
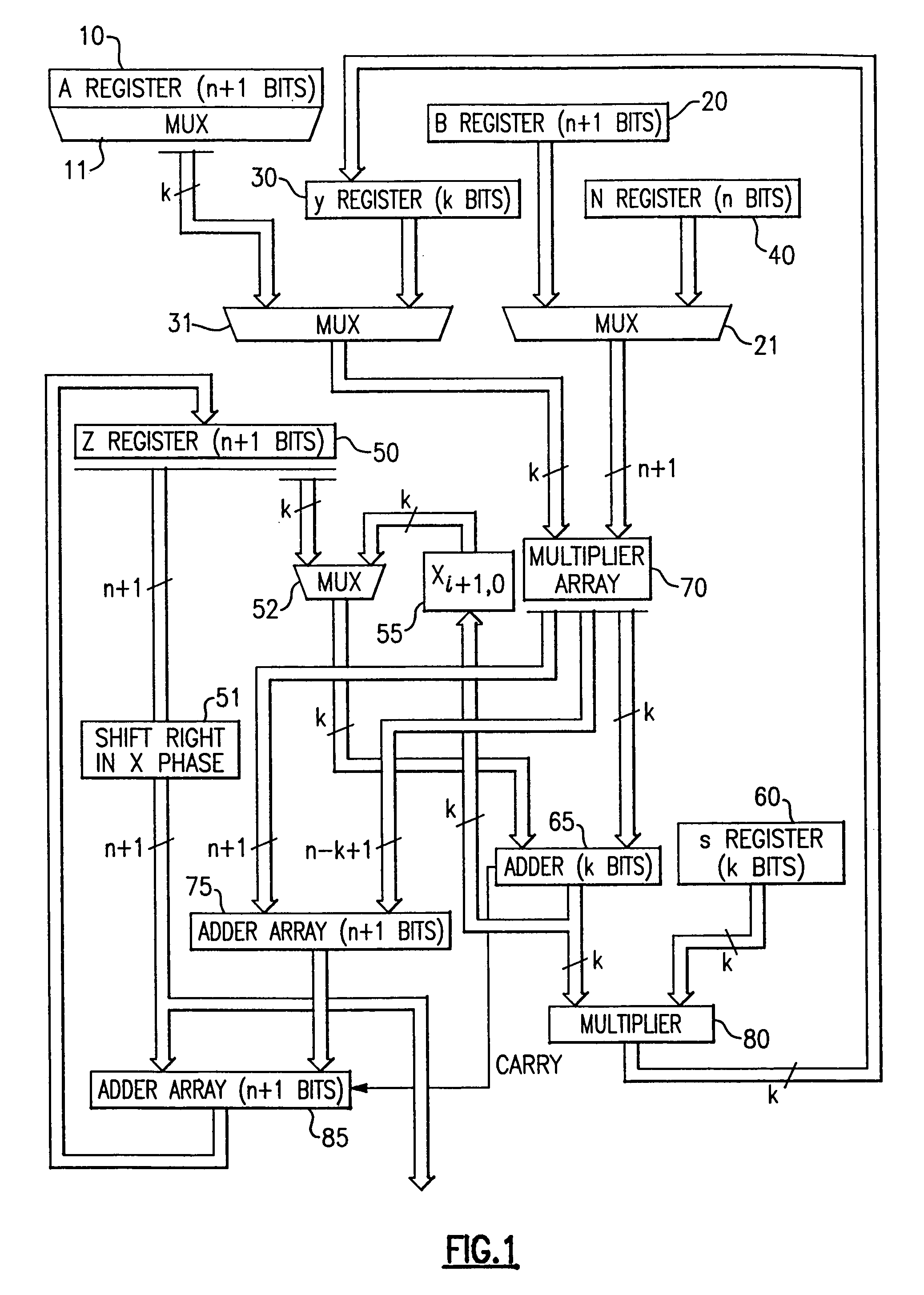
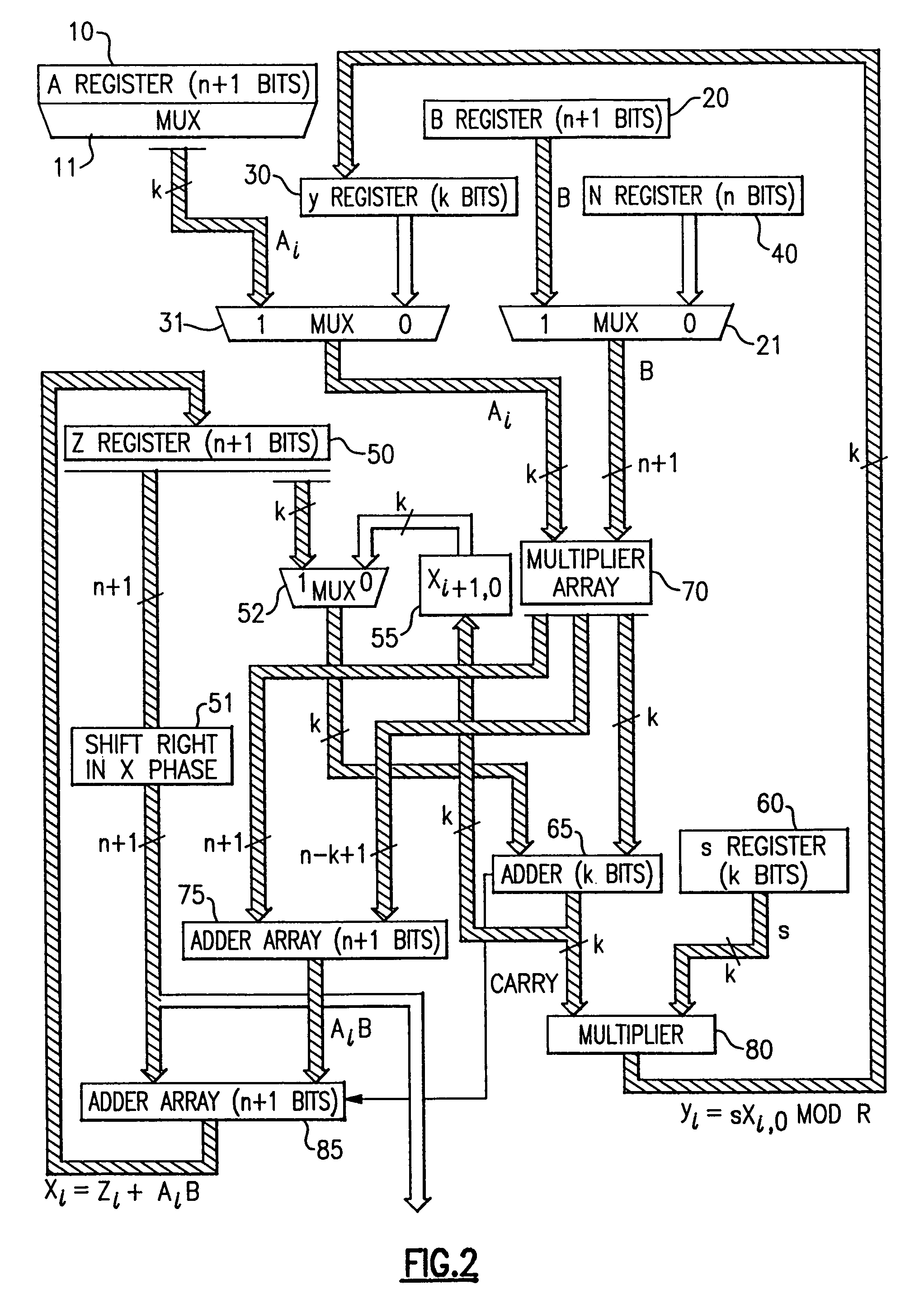
Circuits for calculating modular multiplicative inverse
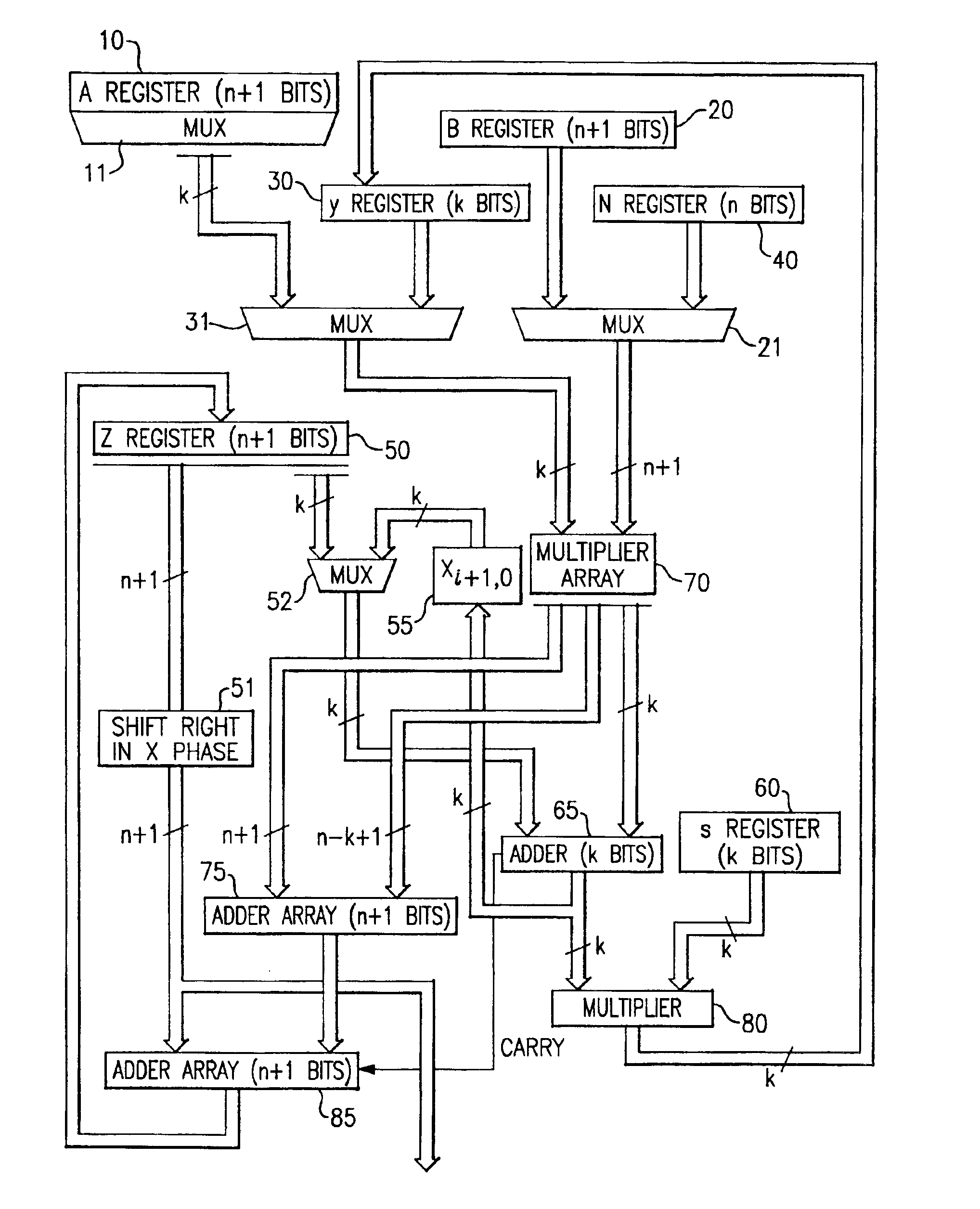
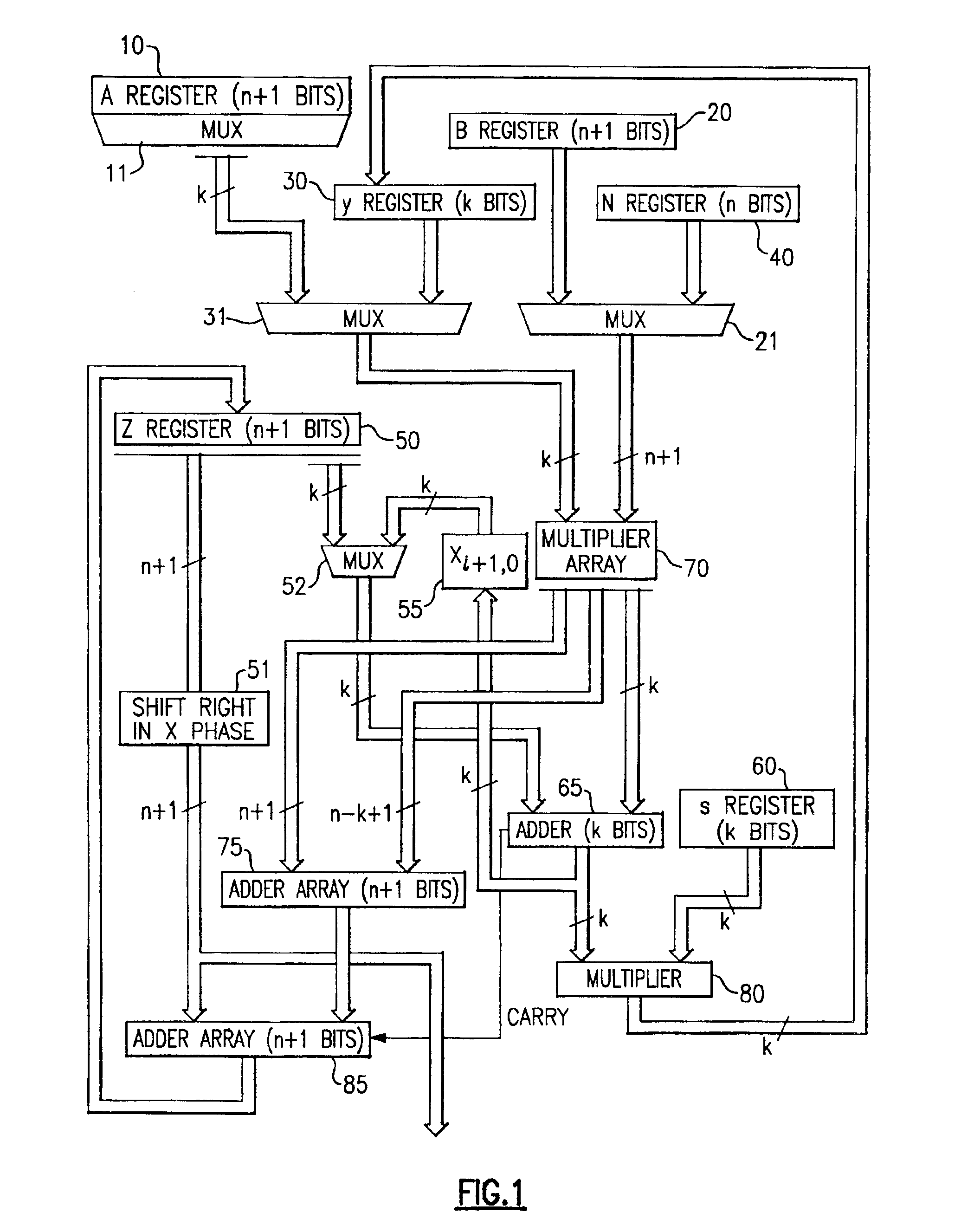
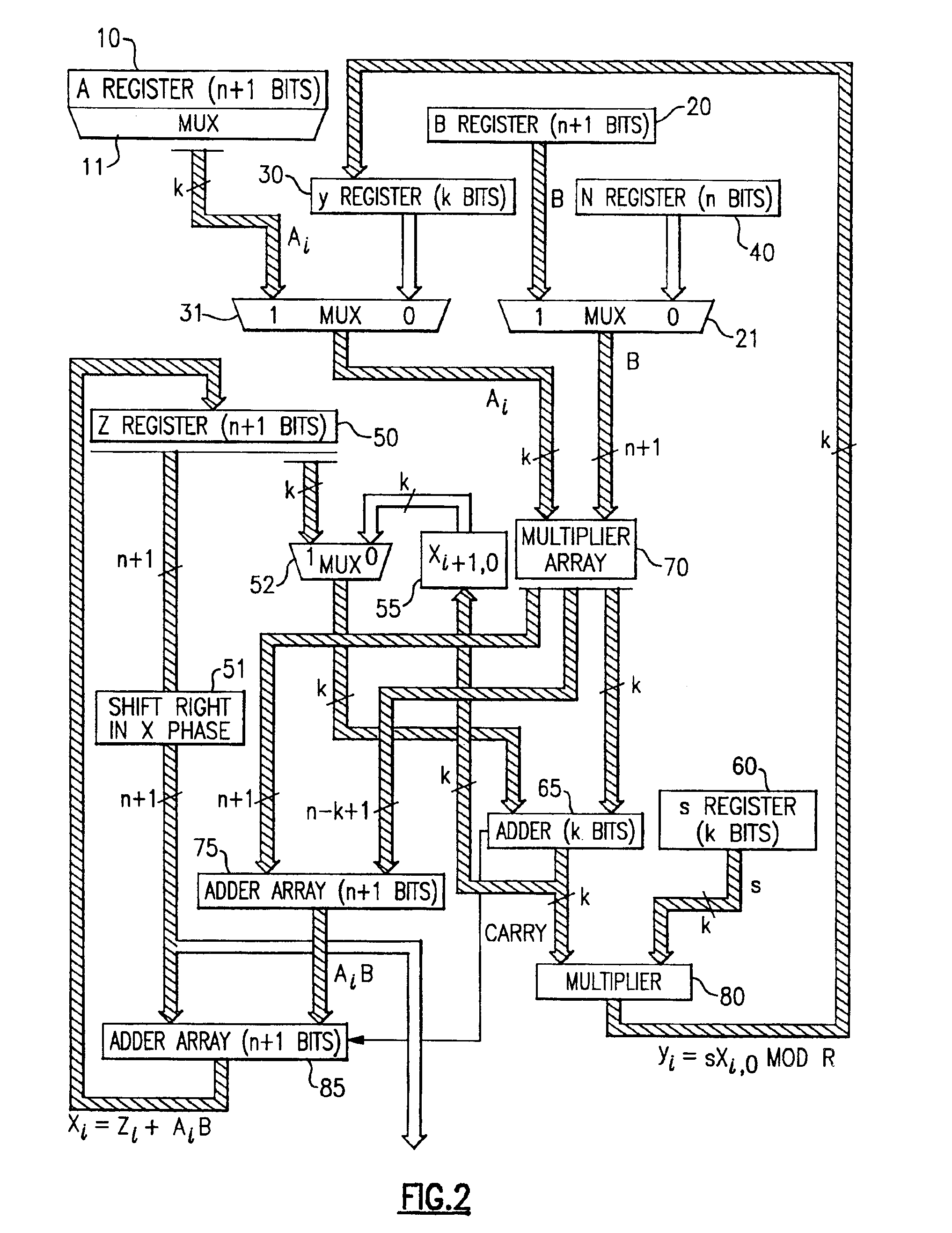
InactiveUS20050185791A1Small sizeObvious advantagesPublic key for secure communicationComputation using non-contact making devicesHardware structureChinese remainder theorem
The modular exponentiation function used in public key encryption and decryption systems is implemented in a standalone engine having at its core modular multiplication circuits which operate in two phases which share overlapping hardware structures. The partitioning of large arrays in the hardware structure, for multiplication and addition, into smaller structures results in a multiplier design comprising a series of nearly identical processing elements linked together in a chained fashion. As a result of the two-phase operation and the chaining together of partitioned processing elements, the overall structure is operable in a pipelined fashion to improve throughput and speed. The chained processing elements are constructed so as to provide a partitionable chain with separate parts for processing factors of the modulus. In this mode, the system is particularly useful for exploiting characteristics of the Chinese Remainder Theorem to perform rapid exponentiation operations. A checksum mechanism is also provided to insure accurate operation without impacting speed and without significantly increasing complexity. While the present disclosure is directed to a complex system which includes a number of features, the present application is particularly directed to the incorporation and integration of circuits used for calculating a modular multiplicative inverse used as an input parameter to the process.
Owner:INTELLECTUAL DISCOVERY INC
Harnessing high throughput sequencing for multiplexed specimen analysis
InactiveUS20120185177A1ConfidenceMicrobiological testing/measurementLibrary member identificationChinese remainder theoremUnique identifier
A method of associating a DNA sequence with a specimen pooled among a plurality of specimens, where the specimens may be pooled according to any number of pooling schemes, including the Chinese Remainder Theorem, random pool selection, shifted transversal design, and Chinese Remainder Sieve. A unique identifier is associated with each specimen according to the pooling scheme such that a decoder may associate a DNA sequence with each specimen after next-generation sequencing according to the unique identifier and the chosen pooling scheme.
Owner:COLD SPRING HARBOR LAB INC
Method for testing the security of an electronic device against an attack, and electronic device implementing countermeasures
ActiveUS20140075203A1Digital data processing detailsUnauthorized memory use protectionComputer networkChinese remainder theorem
A method of testing security of an electronic device against a combination of a side-channel attack and a fault-injection attack implemented during a method of cryptographic processing that includes: delivering a message signature based on a secret parameter and implementing a recombination of at least two intermediate values according to the Chinese remainder theorem; and verifying the signature on the basis of at least one public exponent. The method of testing includes: transmitting a plurality of messages to be signed by said electronic device; disturbing each message, including modifying the message by inserting an identical error for each message, before executing a step of determining one of the intermediate values; and analyzing physical measurements, obtained during the step of verifying the signature as a function of the message to be signed, the identical error for each message, and an assumption of a value of part of the secret parameter.
Owner:IDEMIA FRANCE
Single-frequency signal short sample high precision frequency measurement method and device based on relatively prime perception
ActiveCN104897962ASmall sample sizeReduce time delayFrequency analysisFrequency spectrumFrequency measurements
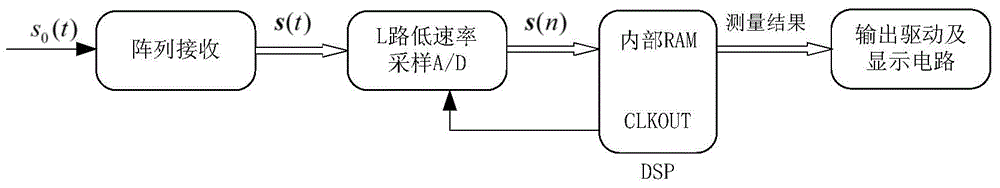
The invention discloses a single-frequency signal short sample high precision frequency measurement method and device based on relatively prime perception; the method comprises the following steps: carrying out discrete fourier transformation (DFT) for a multichannel output sequence formed by multichannel sparse signals, thus obtaining a DET converted output sequence; carrying out spectrum peak scanning for the DET converted output sequence so as to obtain a spectrum peak position index, using the index to obtain a peak DET spectral line, using a phase difference method to carry out spectrum correction, thus obtaining corrected frequency; using the corrected frequency as a remainder, using a Chinese remainder theorem in a closed parse form to process, thus reconstructing an original signal frequency. The device comprises a digital signal processor, an output drive, and a display circuit thereof; the digital signal processor is used for calculating so as to reconstruct the original signal frequency; the output drive and the display circuit thereof can display the original signal frequency. The single-frequency signal short sample high precision frequency measurement method and device can reduce spectrum estimation time delay, and improve sample utilization rate.
Owner:TIANJIN UNIV
Method of preventing fault-injection attacks on chinese remainder theorem-rivest shamir adleman cryptographic operations and recording medium for storing program implementing the same
InactiveUS20130208886A1Computationally efficientAvoid attackDigital data processing detailsPublic key for secure communicationComputer hardwareChinese remainder theorem
Disclosed herein are a method of preventing fault-injection attacks on Chinese Remainder Theorem (CRT)-Rivest Shamir Adleman (RSA) cryptographic operations, and a recording medium for storing a program implementing the same. First, the method receives first and second primes, that is, different primes, and a randomly selected prime, that is, a random prime, which are used for CRT-RSA cryptographic operations. Thereafter, a cumulative value is calculated by performing an XOR (Exclusive OR) operation on the first prime, the second prime, and the random prime using a push function. Thereafter, the first prime, the second prime, and the random prime are loaded by performing an XOR operation on the cumulative value using a pop function corresponding to the push function. Finally, CRT-RSA operations are executed by computing modulo operations based on the first prime and the second prime.
Owner:ELECTRONICS & TELECOMM RES INST
High precision frequency measurement method and instrument at under-sampling rate
InactiveCN104007316ARealize measurementExpand the measurement rangeSpectral/fourier analysisFrequency measurement arrangementFrequency measurementsChinese remainder theorem
The invention discloses a high precision frequency measurement method and instrument at the under-sampling rate. The method includes the steps that spectrum correction is conducted through a triple-spectrum-line interpolation method, L pairs of frequency estimated values obtained after spectrum correction is obtained, and L pairs of phase information obtained after peak position correction is obtained; with the combination of the zero crossing point type and the L pairs of phase information obtained after correction, L frequency estimation values are picked out from the L pairs of frequency estimation values; all spectrum correction values and the L frequency estimation values are adopted as the remainder, and the frequency of an original high-frequency signal is reconstituted according to the Chinese remainder theorem in the closed analytical form. According to the measurement instrument, a single to be tested is subjected to the zero crossing point measurement processing firstly, and the original phase of the signal to be tested is determined; then sample sequences are obtained after analog / digital converter sampling with multi-path sampling frequency is conducted, the sample sequences enter a DSP device in the form of parallel digital input respectively, and frequency estimation of a high-frequency signal is obtained after internal processing is conducted through the DSP device; finally the frequency value is displayed with the help of an output driver and a display circuit of the output driver.
Owner:TIANJIN UNIV
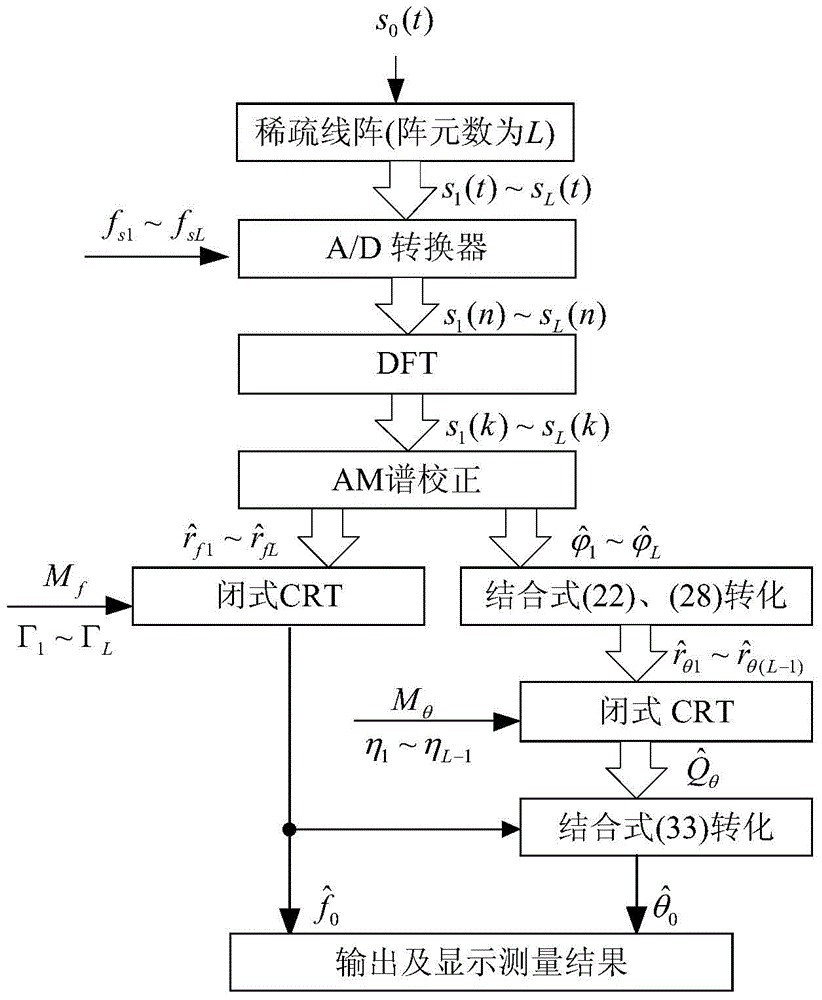
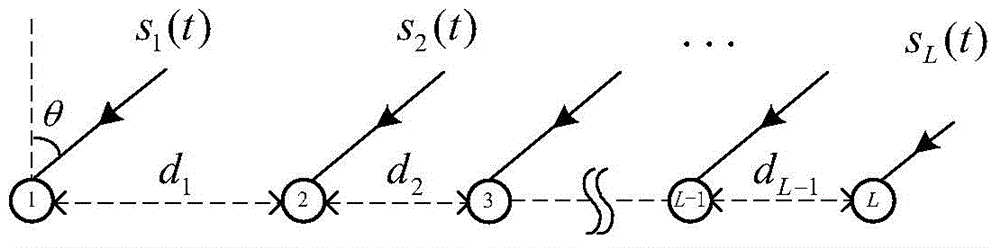
Frequency and DOA joint measurement method and device based on Chinese remainder theorem
InactiveCN104914408AAchieve estimatesFlexible layoutRadio wave direction/deviation determination systemsSample sequenceSparse array
The invention discloses a frequency and DOA joint measurement method and device based on the Chinese remainder theorem. The method comprises the following steps: arranging a non-uniform linear array comprising L antenna array elements, A / D converters on the antenna array elements each carrying out parallel undersampling to obtain L-path sample sequences; carrying out N-point DFT on the L-path sample sequences and carrying frequency and phase correction on the DFT results through an estimator to obtain L pairs of frequency estimation values and phase estimation values after correction; and carrying out frequency and phase reconstruction through the L pairs of frequency estimation values and phase estimation values and the closed-type Chinese remainder theorem to obtain signal frequency and direction of arrival (DOA) estimation values. The multi-path low-rate undersampling scheme is adopted to realize measurement of high-frequency signals; in the method, the limitation is broken through, and a flexible sparse array layout plan is designed; array parameters are reasonably set with practical engineering requirements being combined; and with the method, DOA parameters can be reconstructed accurately.
Owner:TIANJIN UNIV
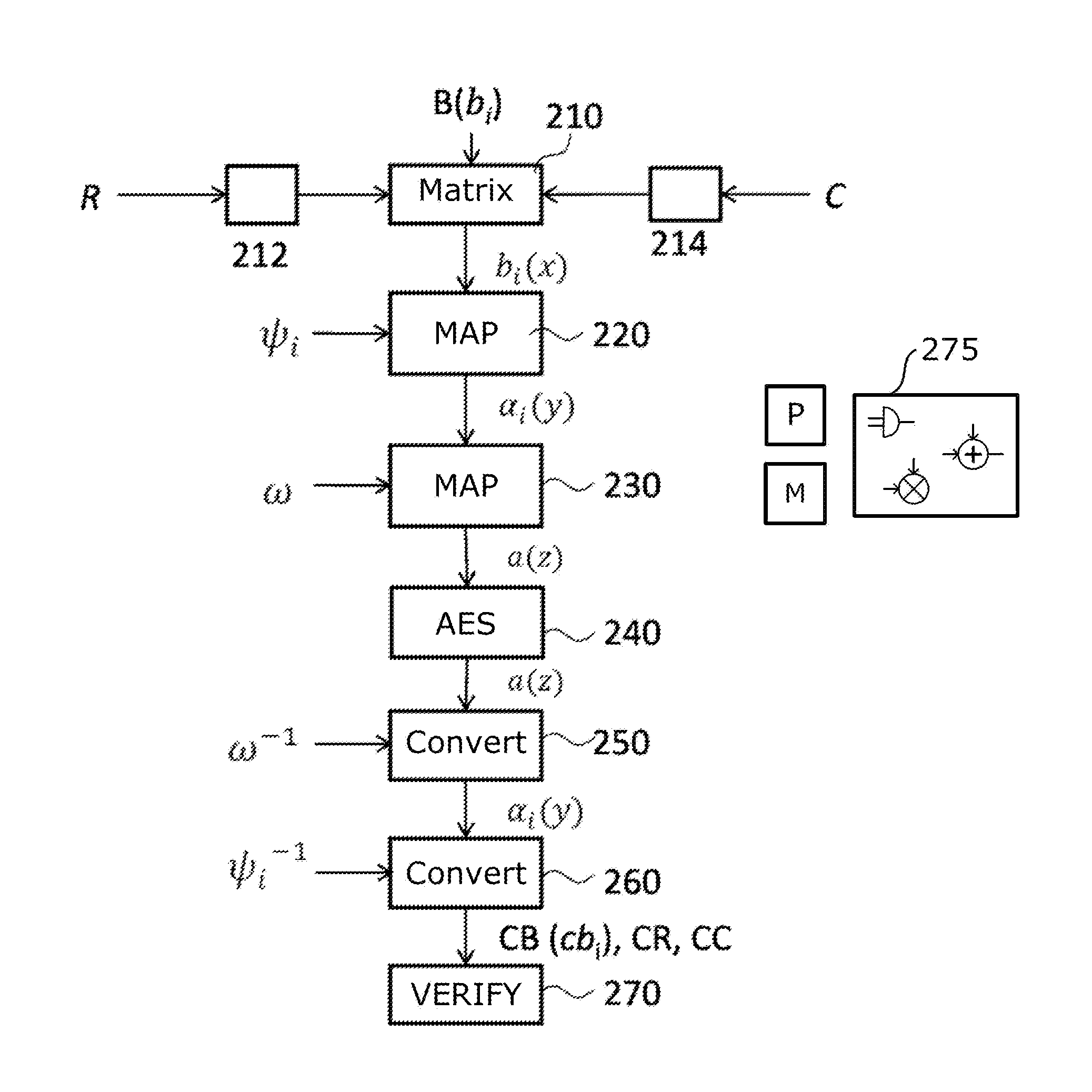
Method for performing an encryption of an aes type, and corresponding system and computer program product
ActiveUS20150270967A1Improve securityMultiple keys/algorithms usagePublic key for secure communicationChinese remainder theoremTheoretical computer science
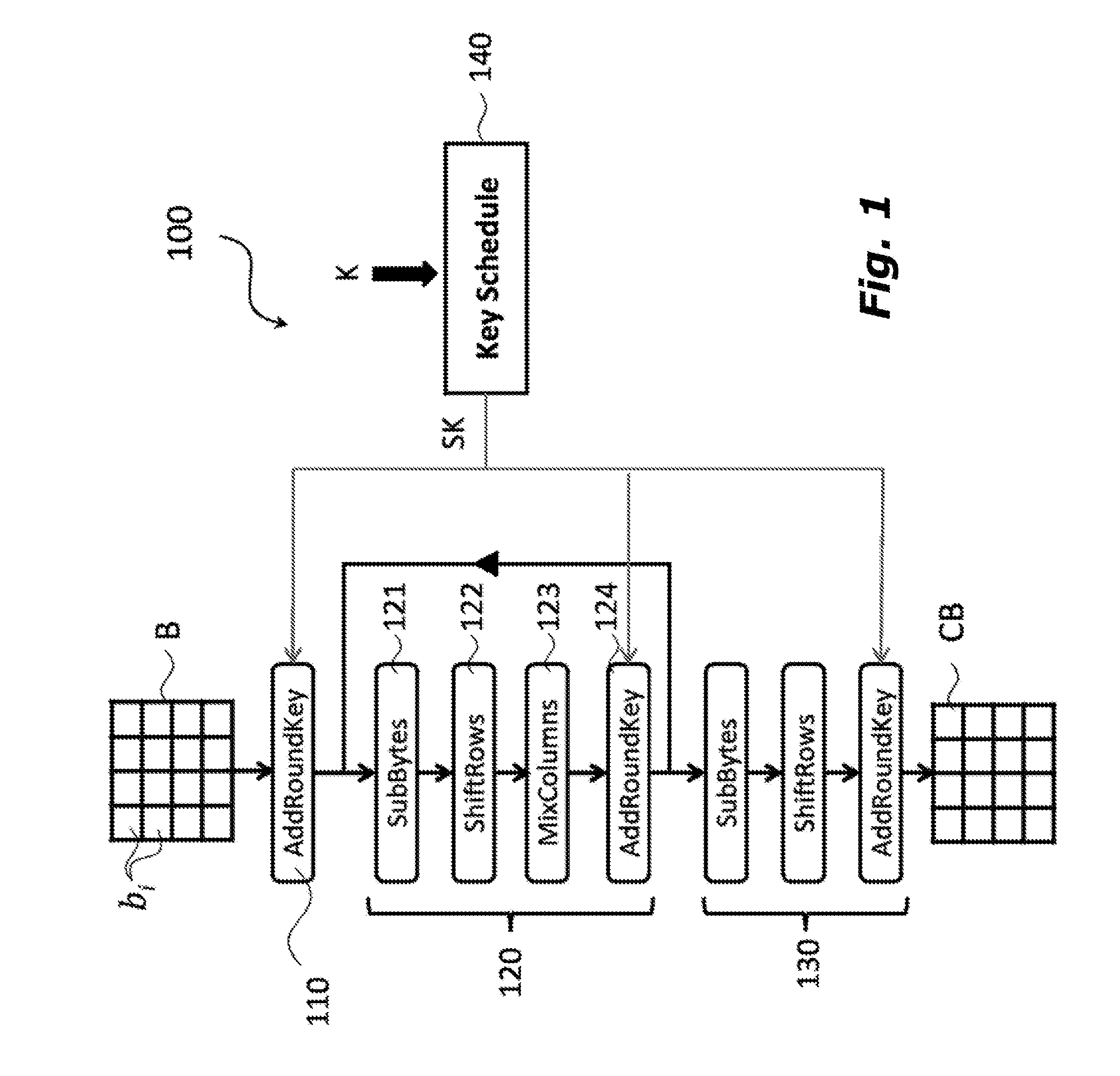
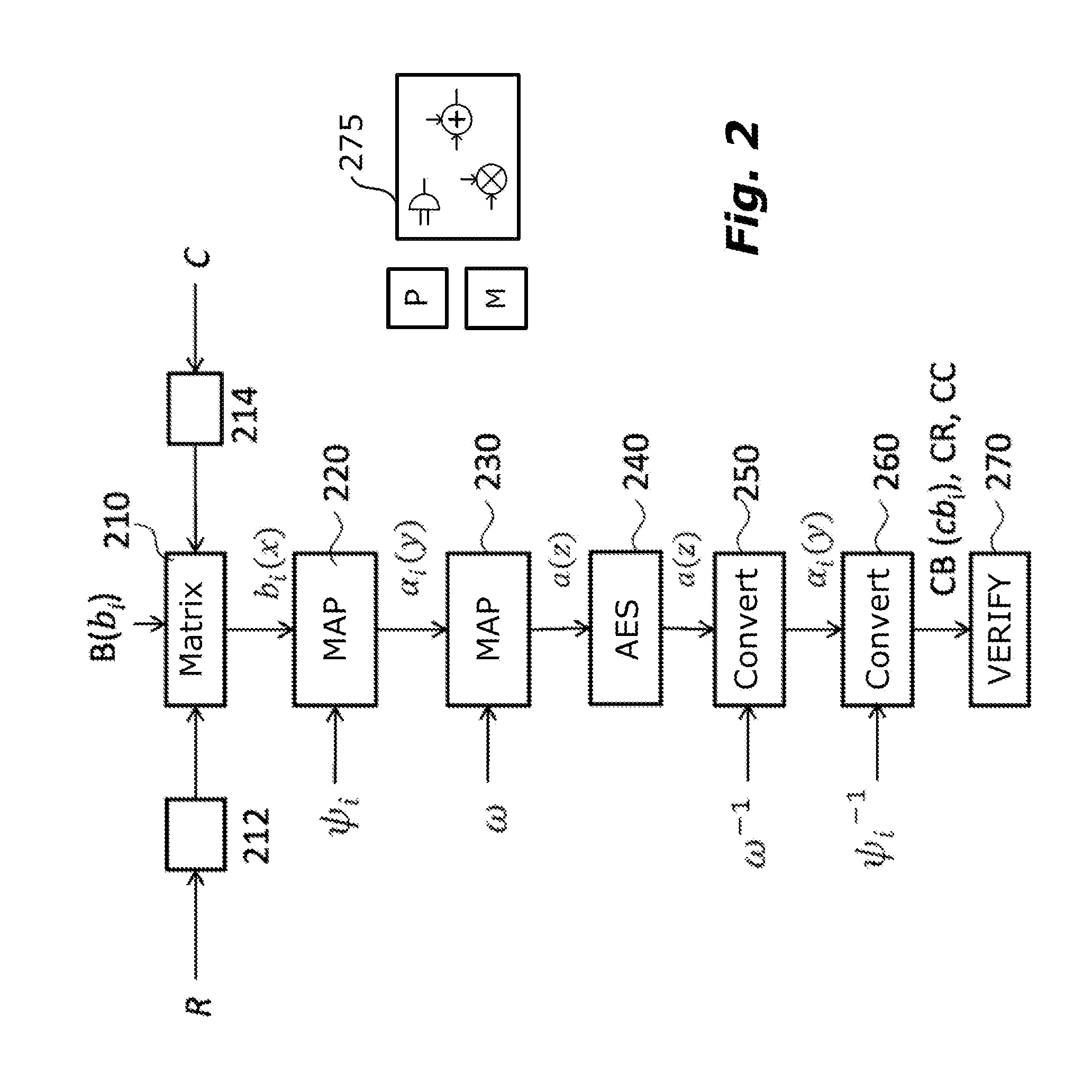
A polynomial representation (bi(x)) in an AES finite field(Z2[x](r(x)))of input bytes (bi) of a state matrix (B) is obtained. A plurality (1) of irreducible polynomials (fi(y)) and a moving map (ψi) are used to map each polynomial (bi(x)) of the polynomial representation into a respective field of polynomials(Z2[y](fi(y)))computed with respect to one of the irreducible polynomials (fi(y)), to obtain respective moved polynomials (αi(y)). The moved polynomials (αi(y)) are mapped into a polynomial (a(z)) of a polynomial ring(Z2[z](p(z))),obtained by applying an isomorphism (ω) between the fields of polynomials(Z2[y](fi(y)))and the polynomial ring(Z2[z](p(z)))based upon the Chinese remainder theorem (CRT). AES encryption is applied to the polynomial (a(z)). The polynomial (a(z)) is reconverted into the AES finite field(Z2[x](r(x)))to obtain an encrypted state matrix (CB).
Owner:STMICROELECTRONICS SRL
Encryption operating apparatus and method having side-channel attack resistance
ActiveUS7065788B2Increase speedSafe to attackMemory loss protectionError detection/correctionComputer hardwareChinese remainder theorem
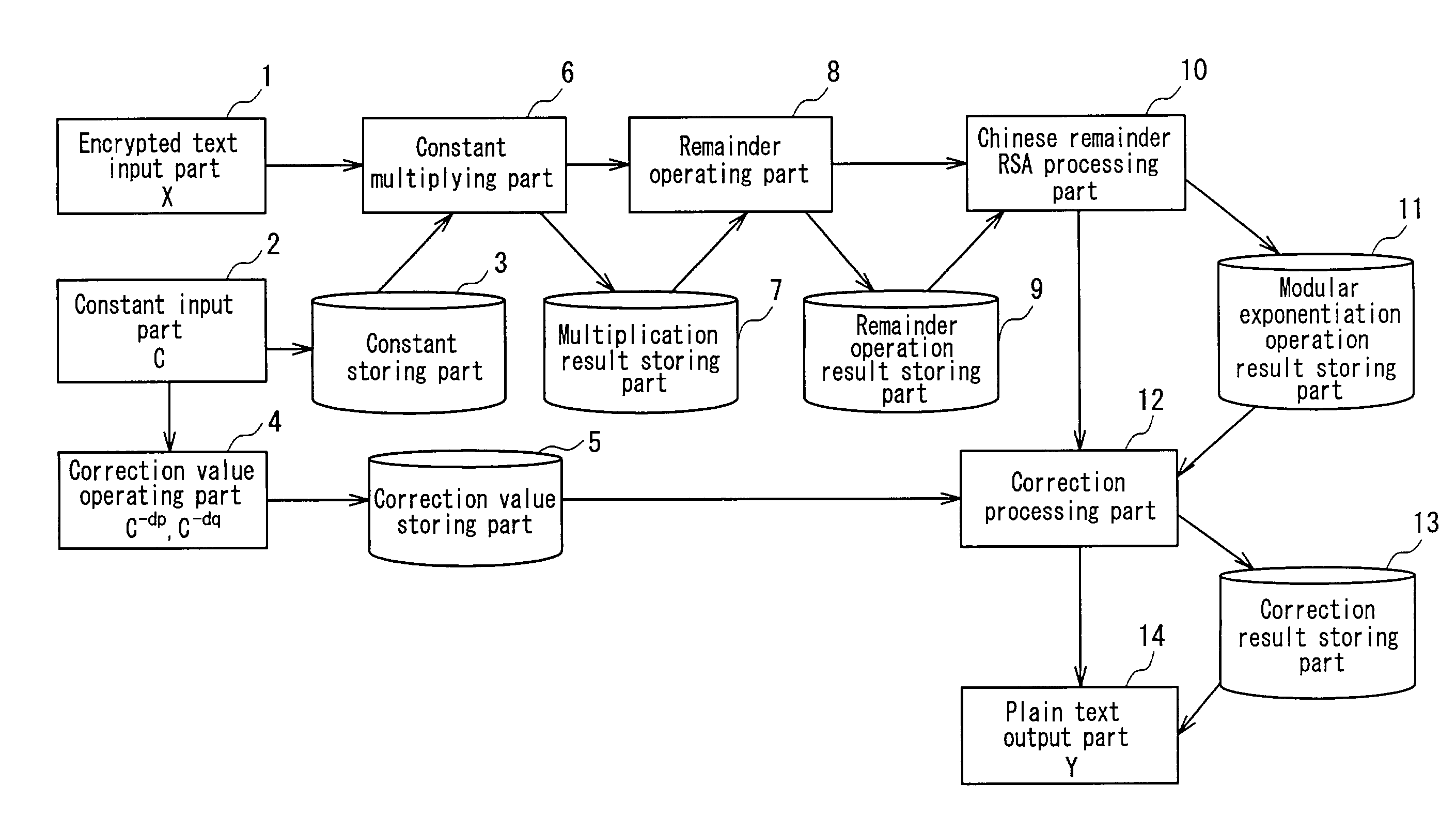
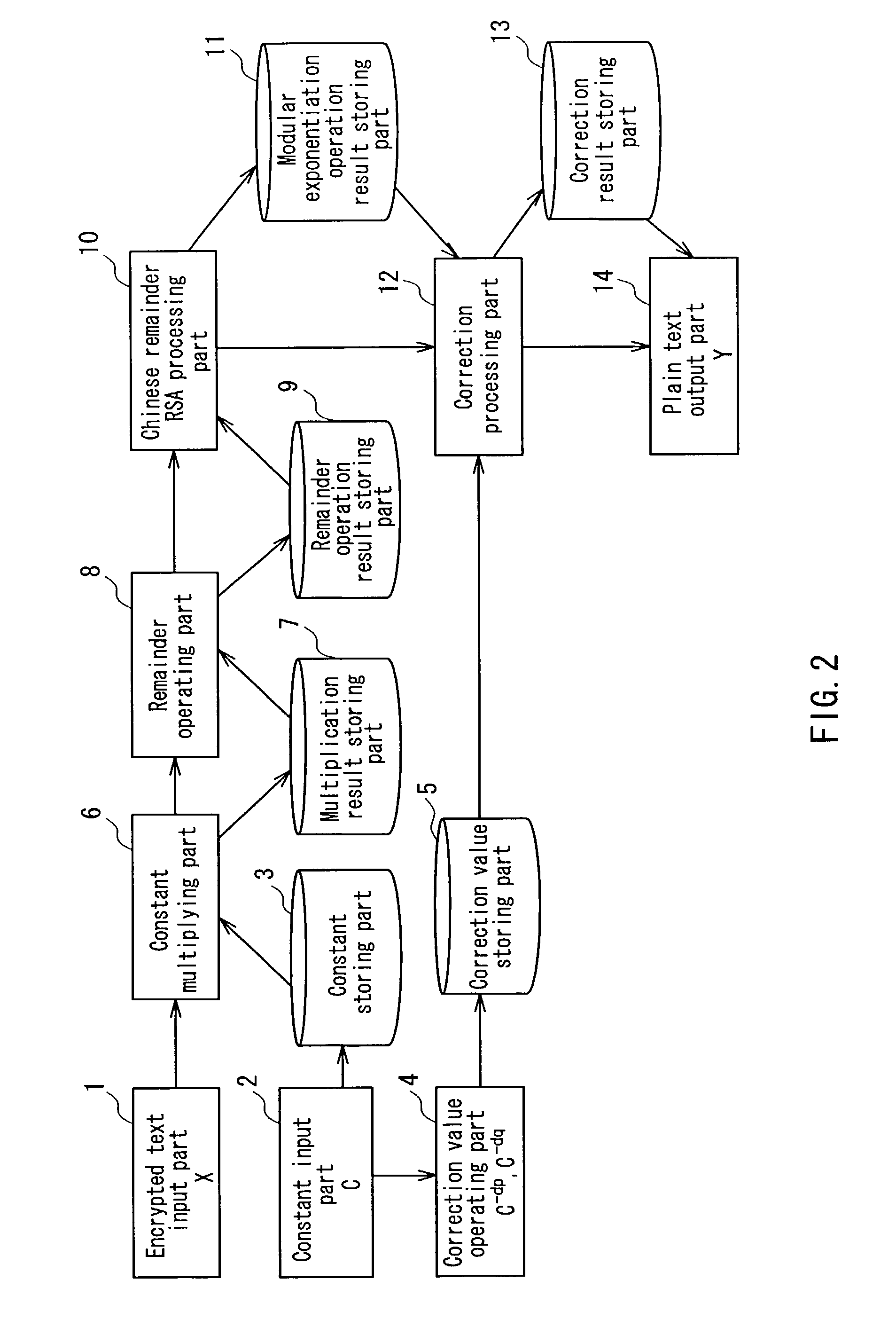
Ciphertext X and a constant C having relationships C>p and C>q with respect to secret keys p and q are input, and correction values C−dp and C−dq (dp=d mod (p−1), dq=d mod (q−1)) are obtained. Then, the ciphertext X is multiplied by the constant C. A remainder operation using the secret key p or q as a remainder value is conducted with respect to the multiplication result. A modular exponentiation operation based on a Chinese remainder theorem is conducted with respect to the remainder operation result, and a correction operation using a correction value C−dp or C−dq is conducted. Thereafter, plaintext Y before being encrypted is calculated.
Owner:FUJITSU LTD
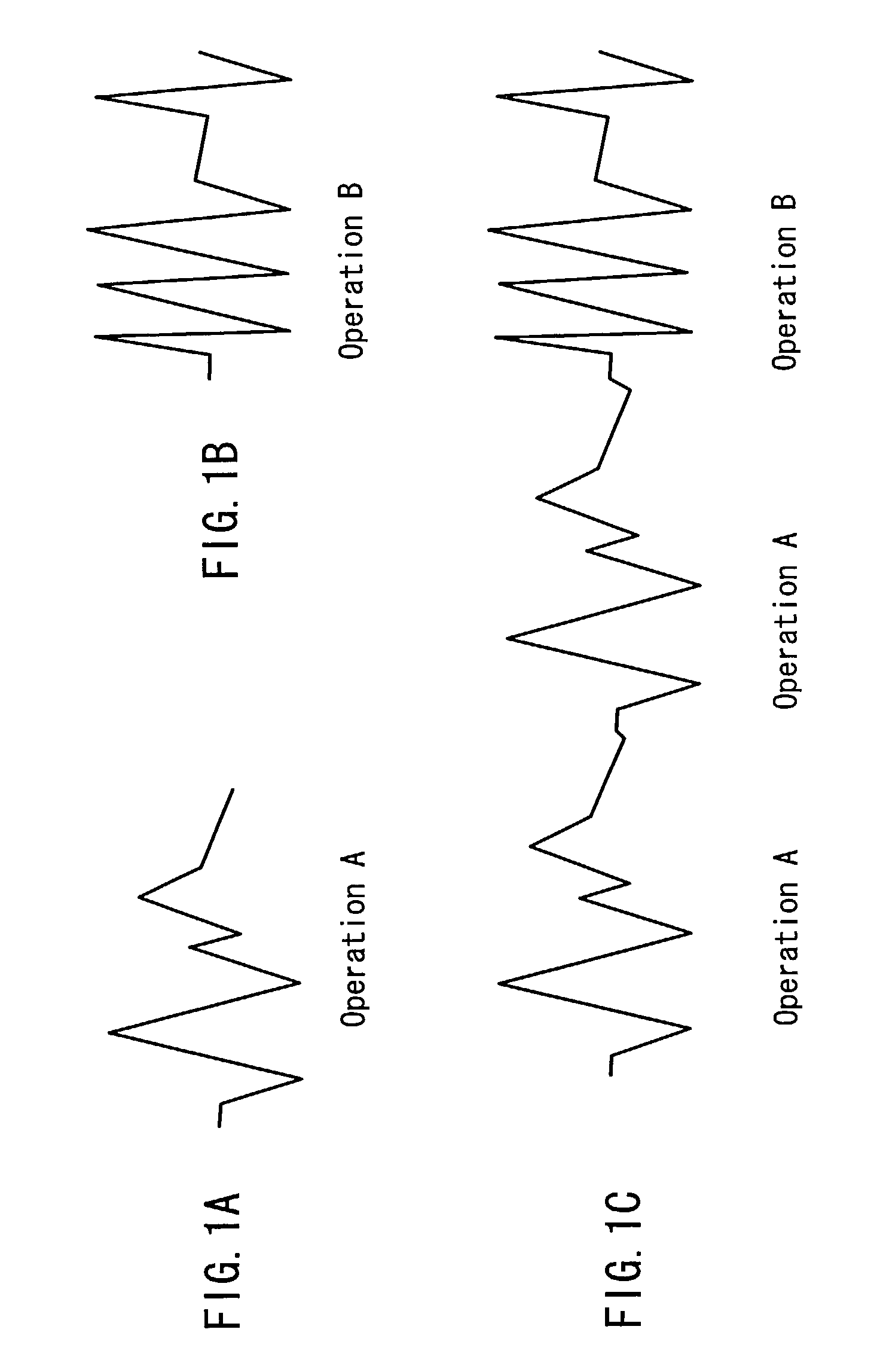
Method for checking modular multiplication
InactiveUS6914983B2Improve performanceSmall sizeError detection/correctionSecret communicationHardware structureChinese remainder theorem
The modular exponentiation function used in public key encryption and decryption systems is implemented in a standalone engine having at its core modular multiplication circuits which operate in two phases which share overlapping hardware structures. The partitioning of large arrays in the hardware structure, for multiplication and addition, into smaller structures results in a multiplier design comprising a series of nearly identical processing elements linked together in a chained fashion. As a result of the two-phase operation and the chaining together of partitioned processing elements, the overall structure is operable in a pipelined fashion to improve throughput and speed. The chained processing elements are constructed so as to provide a partitionable chain with separate parts for processing factors of the modulus. In this mode, the system is particularly useful for exploiting characteristics of the Chinese Remainder Theorem to perform rapid exponentiation operations. A checksum mechanism is also provided to insure accurate operation without impacting speed and without significantly increasing complexity. While the present disclosure is directed to a complex system which includes a number of features, the present application is particularly directed a system and method for performing modular checksum operations.
Owner:IBM CORP
Method and apparatus for protecting an rsa calculation on an output by means of the chinese remainder theorem
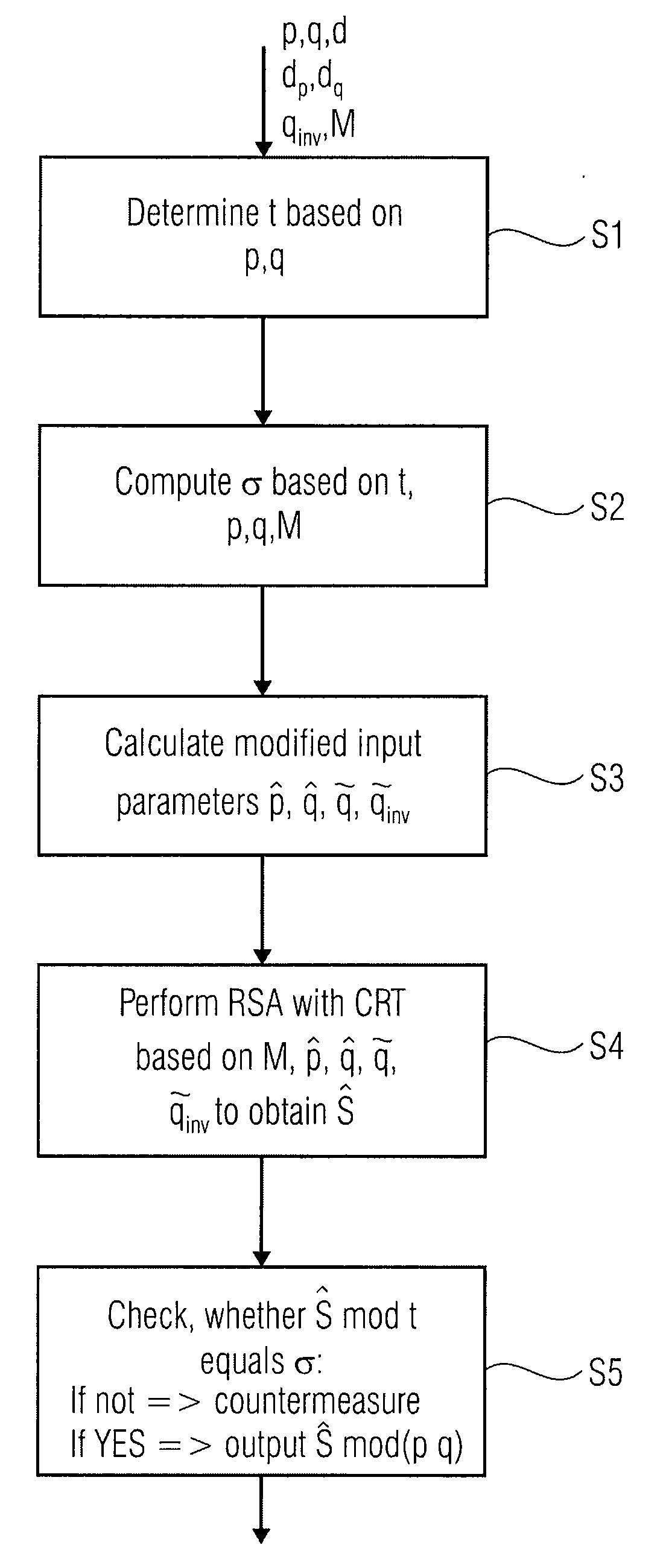
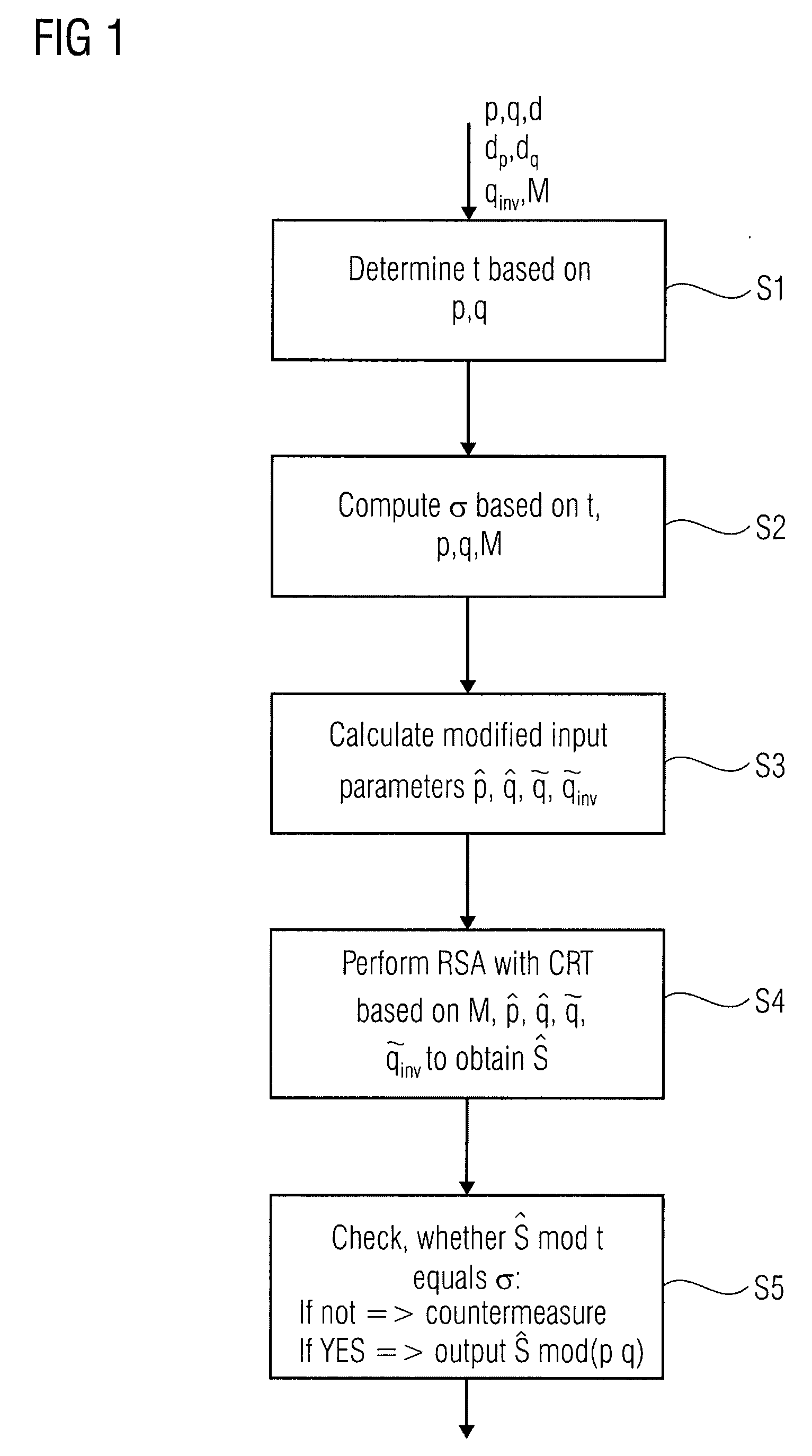
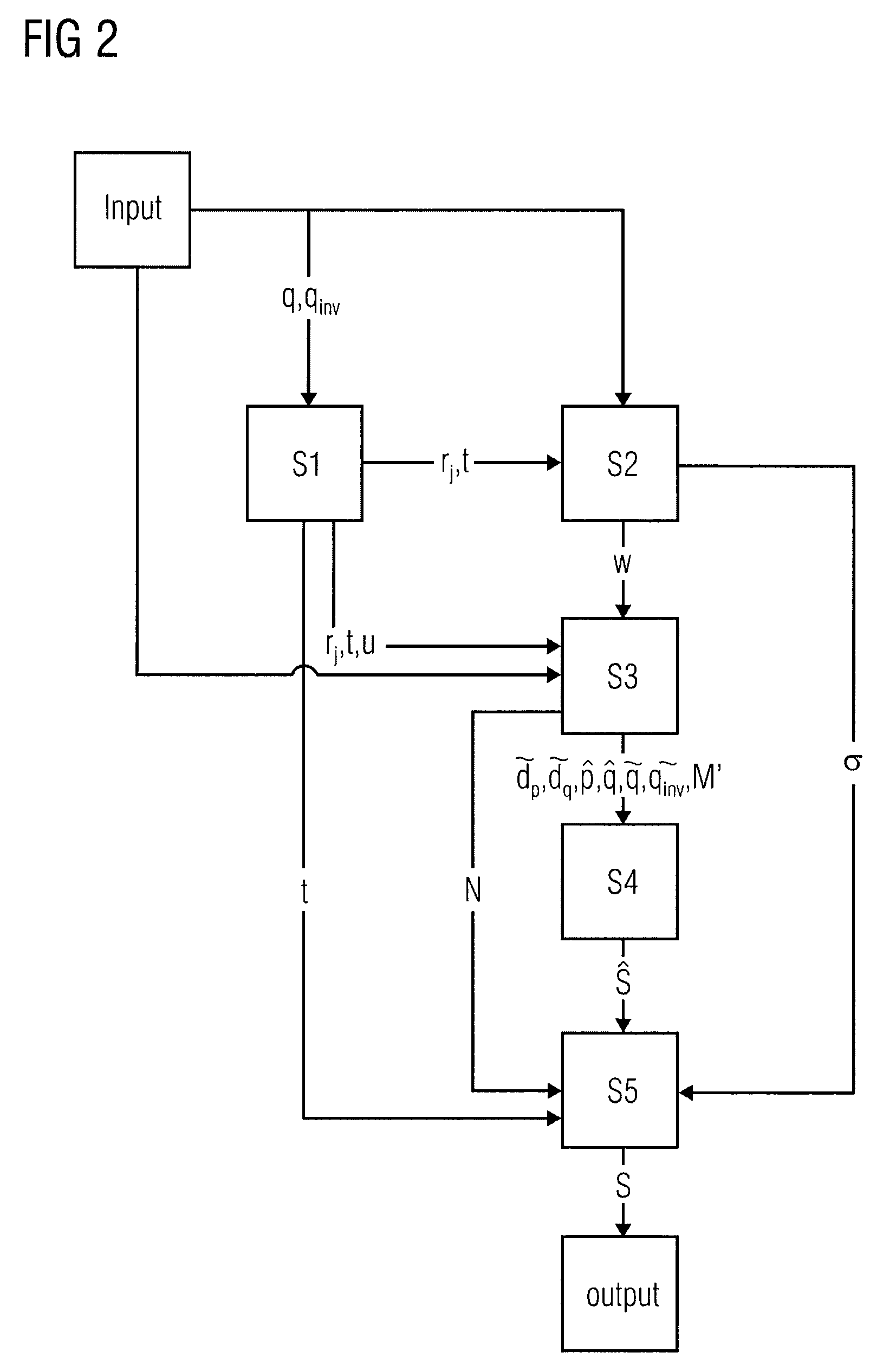
ActiveUS20090110187A1Encryption apparatus with shift registers/memoriesPublic key for secure communicationCountermeasureChinese remainder theorem
An apparatus for protecting an RSA calculation of an output based on input values by means of the Chinese remainder theorem, the apparatus comprising for a first determining device adapted to determine a first security parameter based on the input values, a computing device adapted to compute a control value based on the first security parameter and the input values, a calculating device adapted to calculate a modified input parameters based on the input values and the first security parameter, for a performing device adapted to perform the RSA calculation based on the modified input values to obtain a single modified output, and for a second determining device adapted to determine whether the single modified output is in a predetermined relation to the control value and applying a countermeasure in case the predetermined relation is not fulfilled.
Owner:INFINEON TECH AG
Anti-attack method for electronic components using RSA public key encryption algorithm
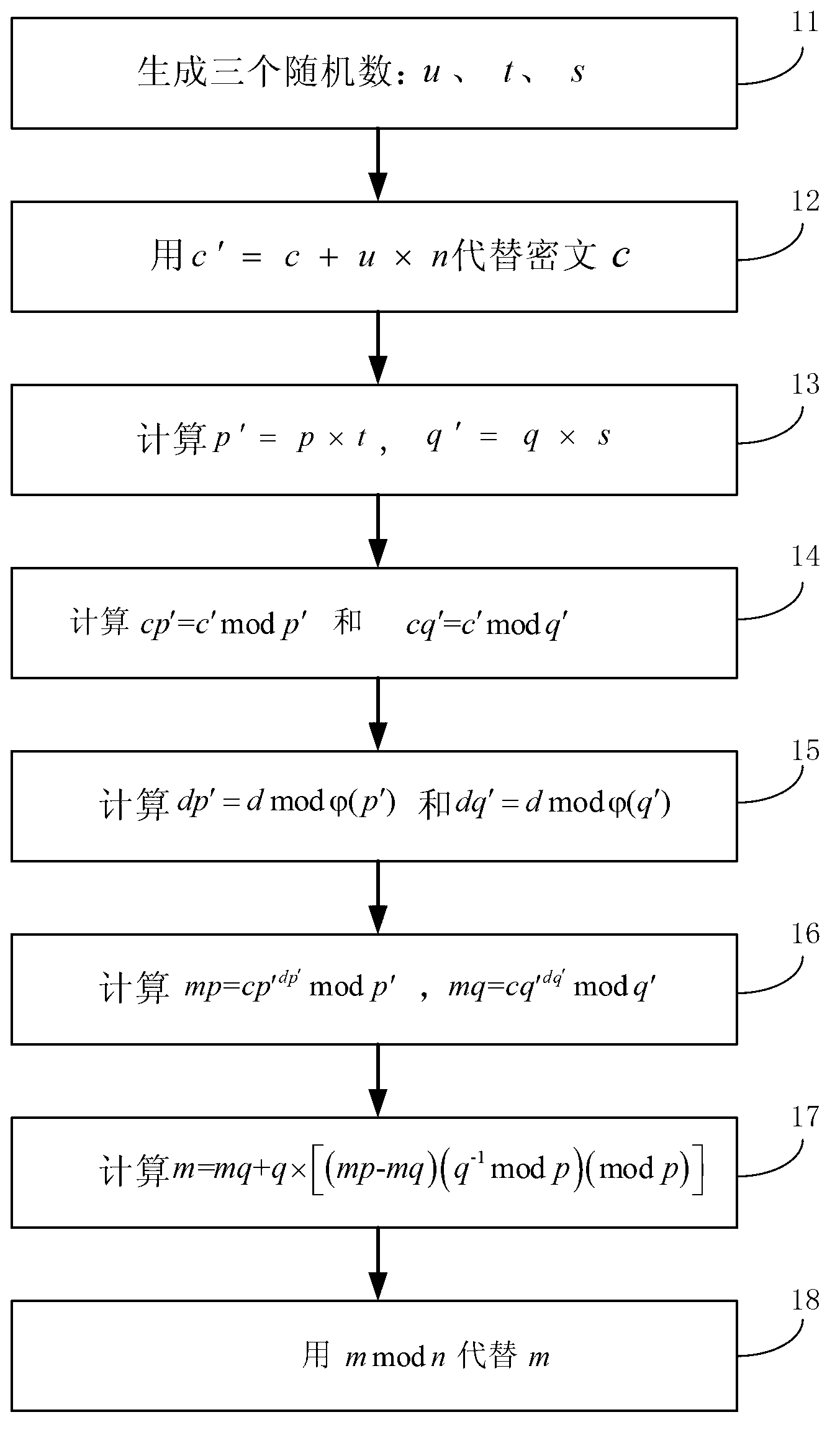
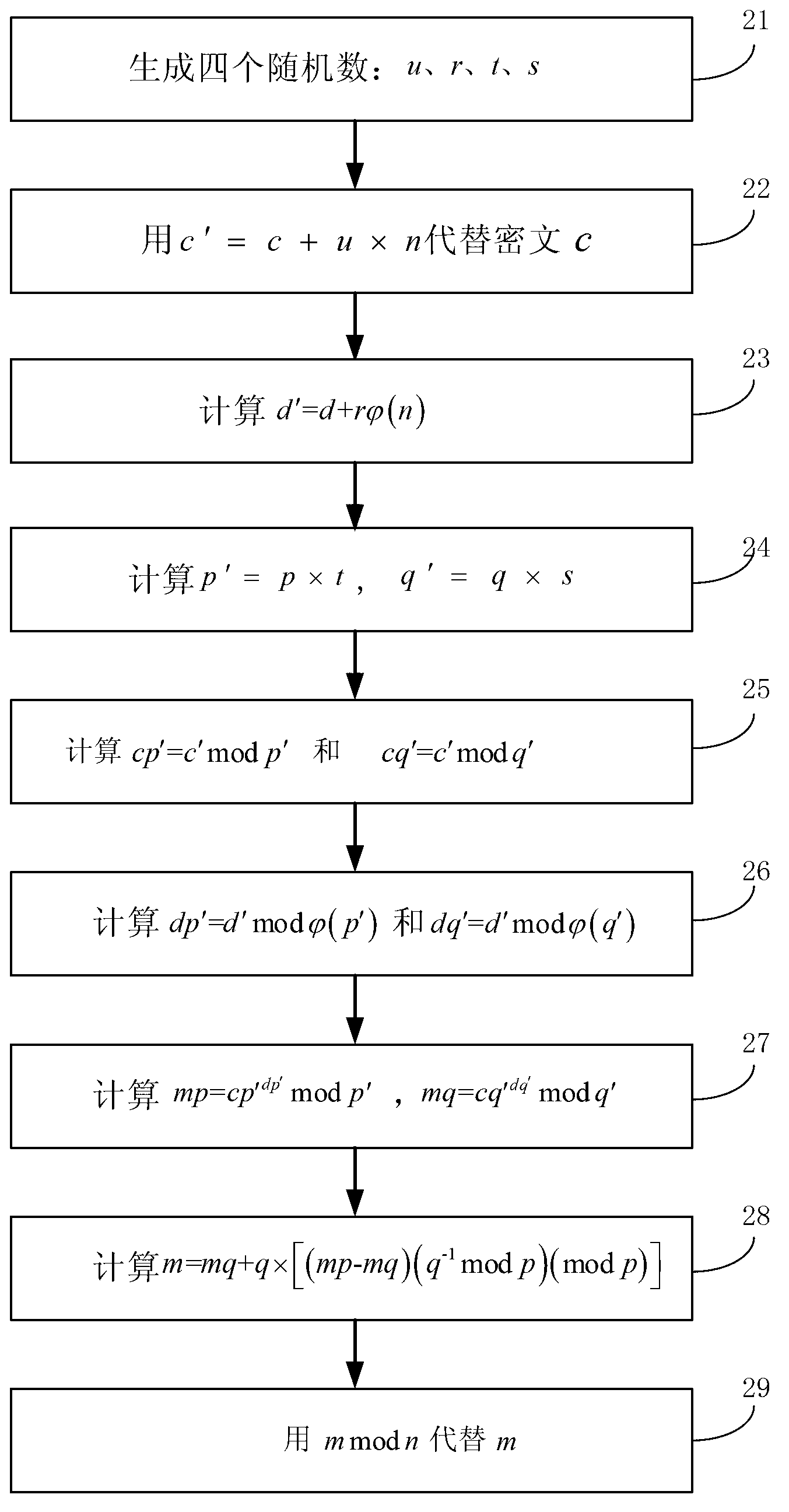
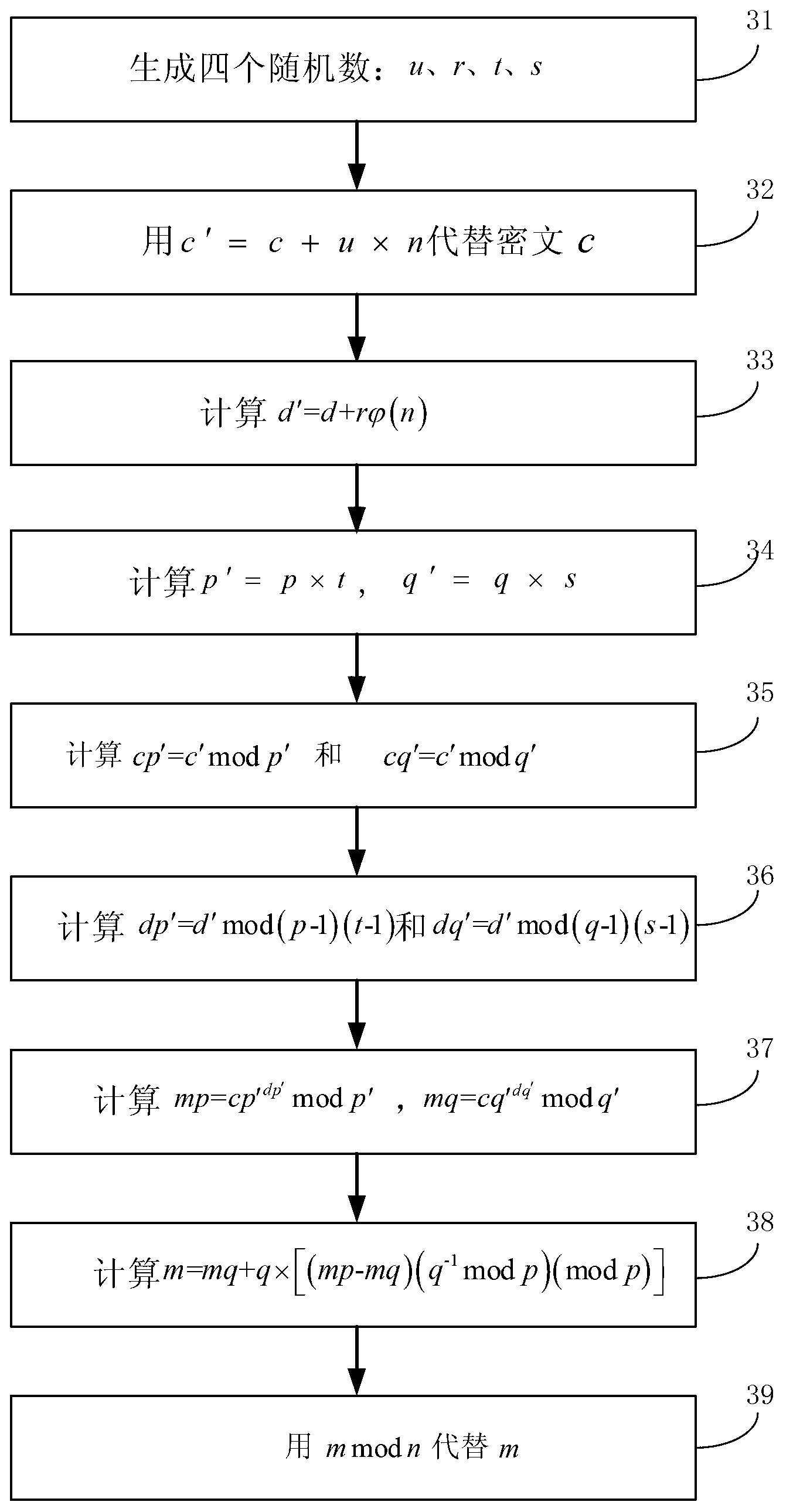
InactiveCN103067164AAchieve the effect of defending against DPA attacksPublic key for secure communicationChinese remainder theoremCiphertext
The invention relates to an anti-attack method for electronic components using a RSA public key encryption algorithm. The anti-attack method for the electronic components using the RSA public key encryption algorithm comprises: the method is adopted when a RSA decipherment algorithm using a Chinese remainder theorem is executed every time, and a ciphertext c, a secret key d, a secret key n, a secret key p and a secret key q are as input. The method comprises: three random numbers which are u, t and s are generated; c'=c+u*n replaces the ciphertext c; p'=p*t and q'=q*s; cp'=c' mod p' and cq'=c' mod; mp=cp'<dp'> mod p and mq=cq'<dq'> mod q'; m=mq+q*((mp-mq)(q-1 mod p)(mod p)); m mod n substitutes for m; and p and d are two different prime numbers with same bit length and respectively are euler functions of n, p' and q'. The anti-attack method for the electronic components using the RSA public key encryption algorithm may enable a DPA attacker not to get secret parameters of the decipherment algorithm effectively through extraneous information of intermediate data deposed by a microprocessor, so that the effect of defending DPA attack is achieved.
Owner:KTMICRO ELECTRONICS
Interferometer Direction Finding Method Based on Chinese Remainder Theorem
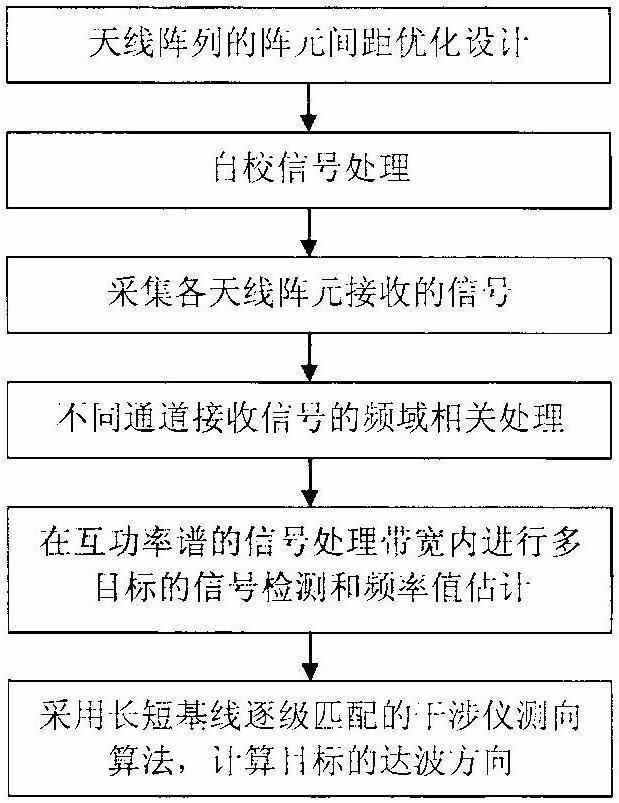
ActiveCN111903218BSolving Difficult-to-Optimize Design ProblemsIncrease the lengthDirection findersChinese remainder theoremAmbiguity
The invention discloses an interferometer direction finding method based on the Chinese remainder theorem, which relates to an interferometer direction finding technology in the field of radio direction finding. In the case that the antenna shape and array size are fixed, the present invention uses the Chinese remainder theorem to design an antenna array form with the best performance, which solves the phase ambiguity problem; and adopts long and short baseline matching step by step and virtual array processing technology to effectively expand the The equivalent baseline length improves the accuracy of direction finding. The equipment manufactured by the invention has the advantages of simple operation, reliable performance, convenient algorithm, high precision of direction finding and the like. It is especially suitable for accurate direction finding and positioning for radiation sources such as communication, radar, and measurement and control in the detection equipment in the field of military electronic countermeasures.
Owner:NO 54 INST OF CHINA ELECTRONICS SCI & TECH GRP
High-capacity digital watermarking method combining multi-scale characteristics and Chinese remainder theorem
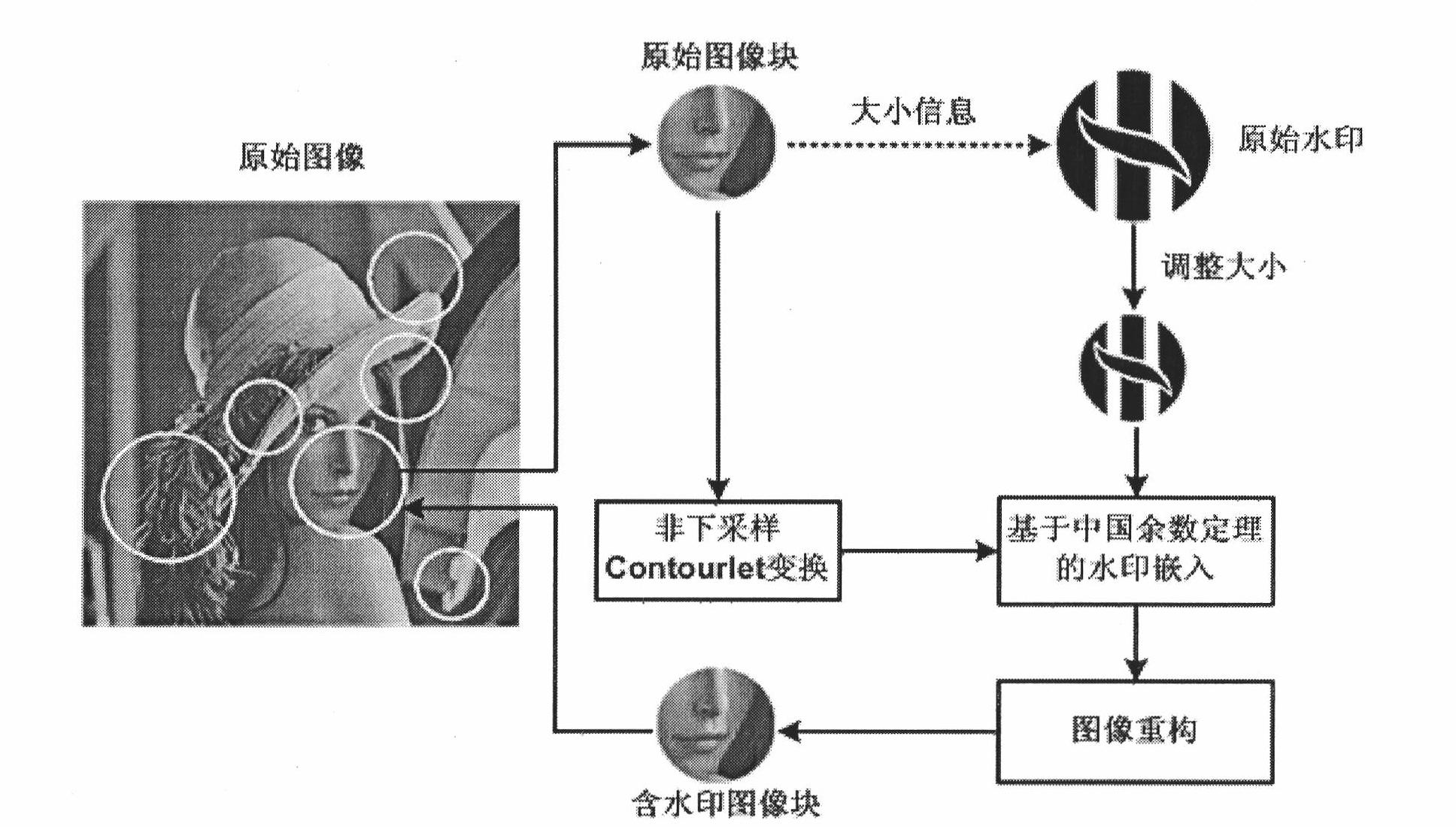
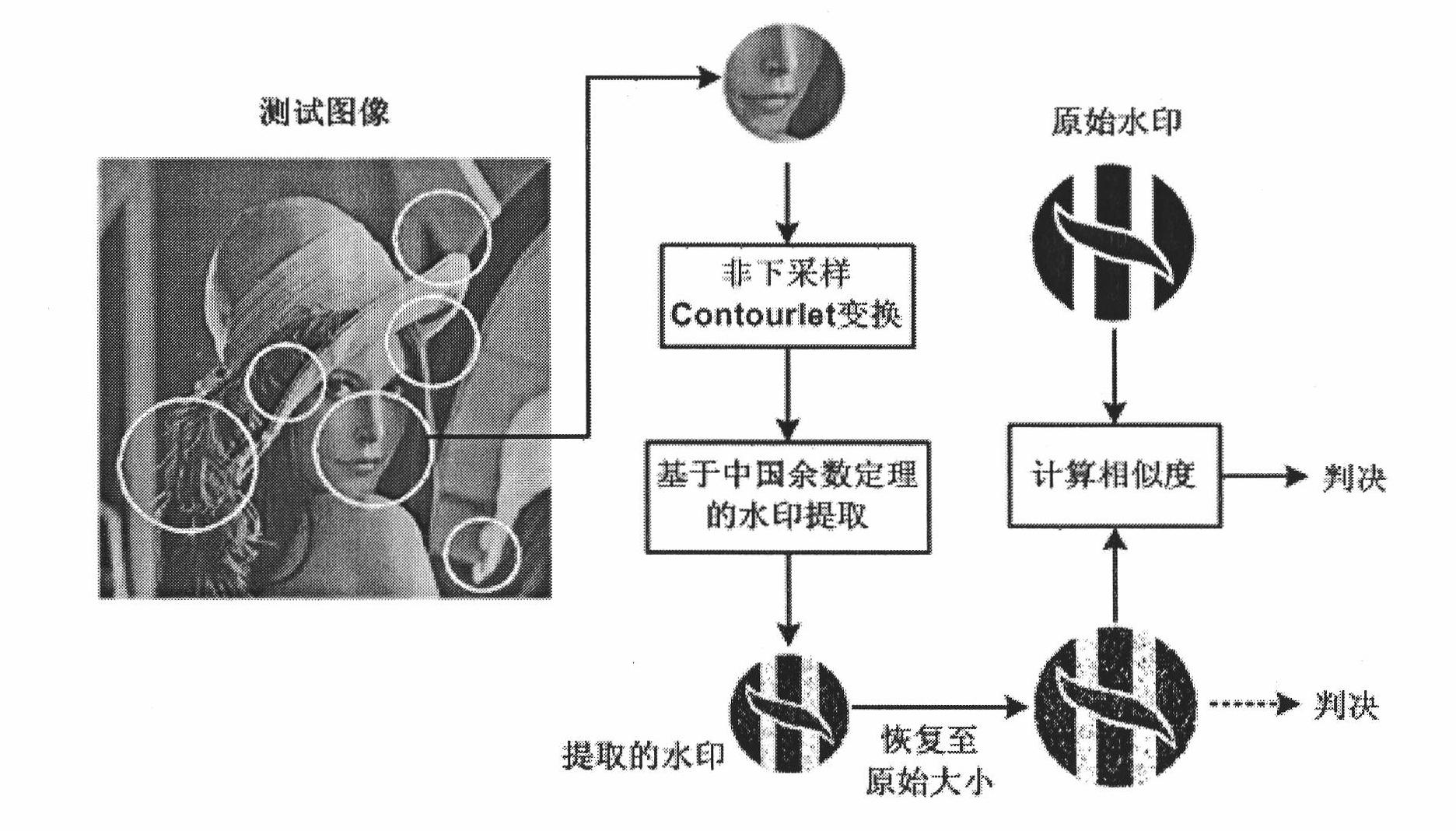
InactiveCN102044055AImmutableEffective Watermark ExtractionImage data processing detailsPattern recognitionImaging processing
The invention discloses a high-capacity digital watermarking method combining multi-scale characteristics and a Chinese remainder theorem, which is a high-capacity digital watermarking method used for covert communication and digital images. The method is used for determining positions for embedding and extracting watermarks by using multi-scale characteristic points with multiple-invariance, and embedding binary watermark images in a non-subsampled profile wave domain by using the Chinese remainder theorem. Before embedding, the watermark images are adjusted correspondingly according to an embedding region to ensure that watermark signals are adaptive to the embedding region. During extracting, a region containing watermarks is positioned by using a same method first, and the watermarks are extracted in the non-subsampled profile wave domain according to the Chinese remainder theorem. In the method, while high-capacity watermark signals are embedded, images containing the watermarks can obtain very high quality; and the extracted watermarks can resist conventional image processing operations and geometric transformations such as rotation, zooming, translation and the like, and the geometric transformations of the extracted watermarks and images are kept consistent for protecting the copyrights of the convert communication and the digital images.
Owner:CHINA UNIV OF MINING & TECH
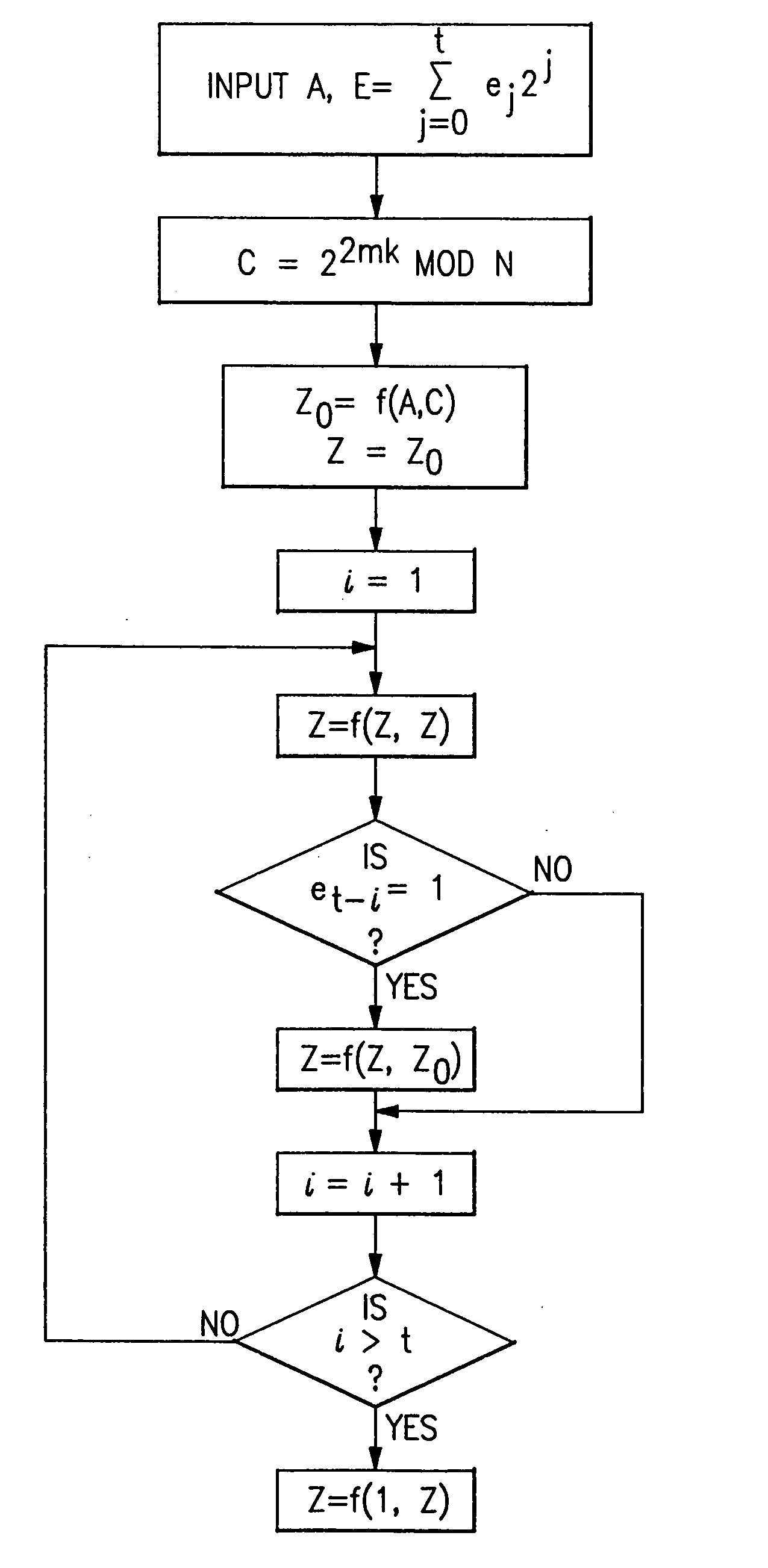
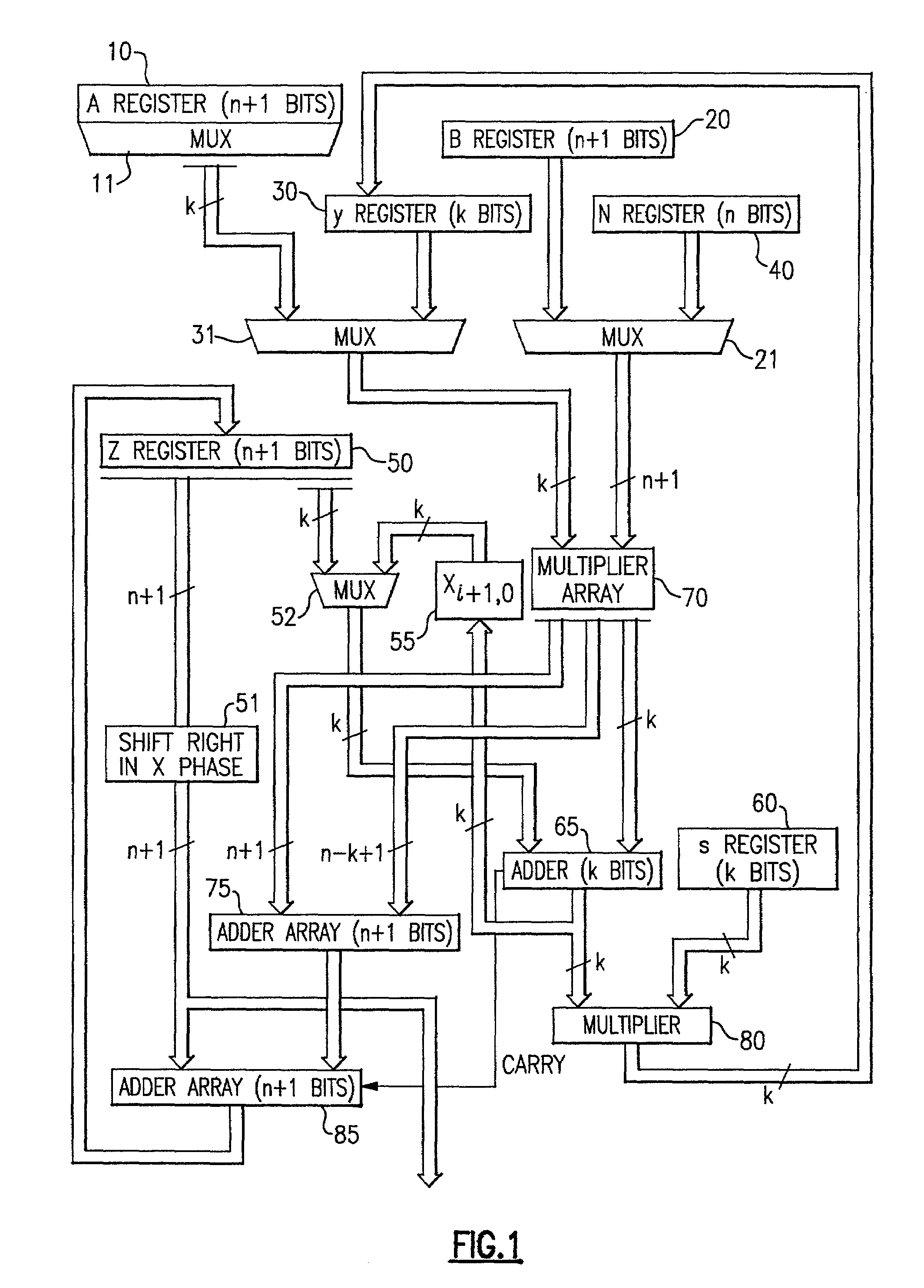
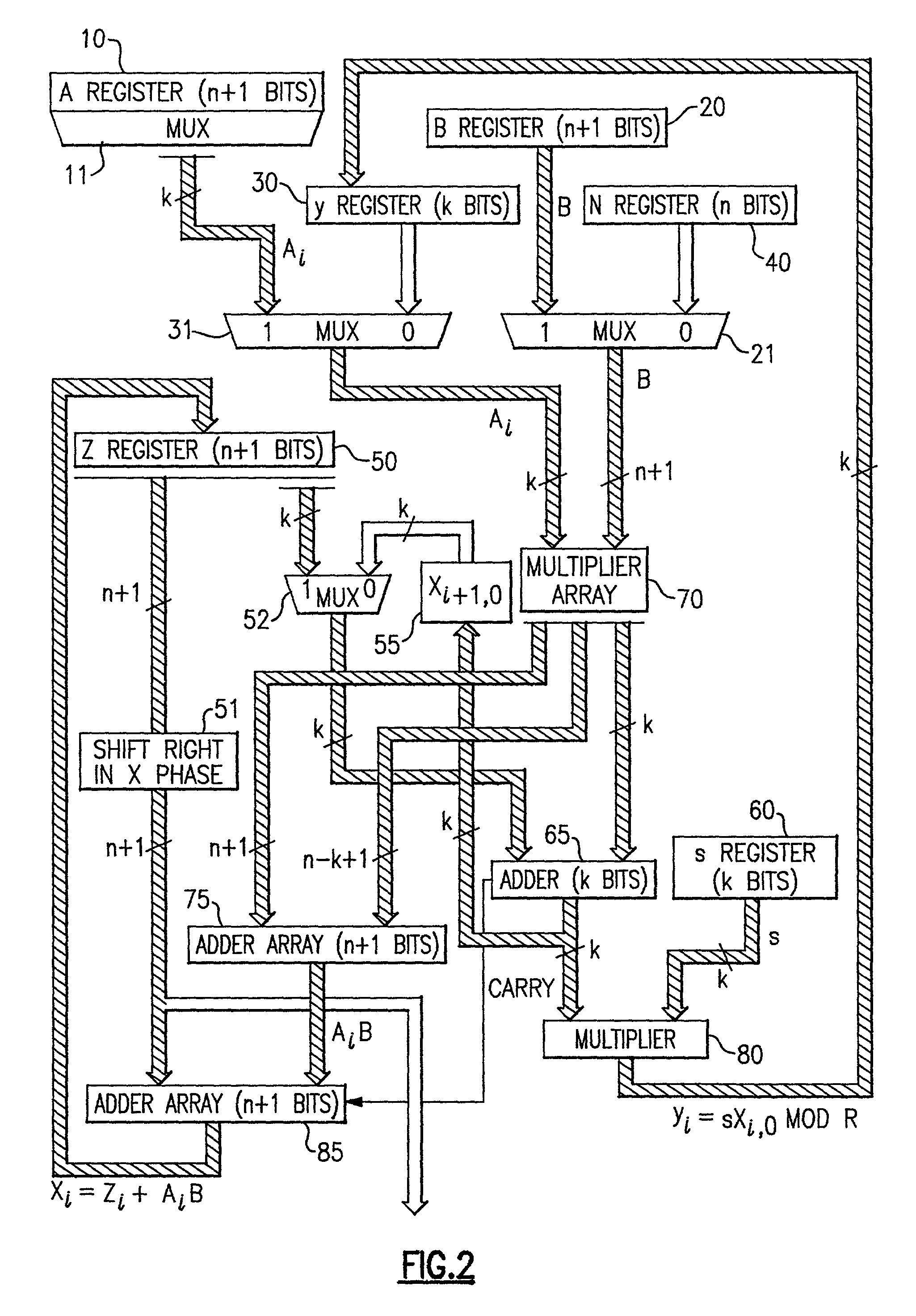
Circuits and methods for modular exponentiation
InactiveUS20050188209A1Improve performanceSmall sizeComputer security arrangementsSecret communicationHardware structureChinese remainder theorem
The modular exponentiation function used in public key encryption and decryption systems is implemented in a standalone engine having at its core modular multiplication circuits which operate in two phases which share overlapping hardware structures. The partitioning of large arrays in the hardware structure, for multiplication and addition, into smaller structures results in a multiplier design comprising a series of nearly identical processing elements linked together in a chained fashion. As a result of the two-phase operation and the chaining together of partitioned processing elements, the overall structure is operable in a pipelined fashion to improve throughput and speed. The chained processing elements are constructed so as to provide a partitionable chain with separate parts for processing factors of the modulus. In this mode, the system is particularly useful for exploiting characteristics of the Chinese Remainder Theorem to perform rapid exponentiation operations. A checksum mechanism is also provided to insure accurate operation without impacting speed and without significantly increasing complexity. While the present disclosure is directed to a complex system which includes a number of features, the present application is particularly directed to circuits and methods for carrying out modular exponentiation.
Owner:IBM CORP
Circuits for calculating modular multiplicative inverse
InactiveUS6978016B2Small sizeObvious advantagesPublic key for secure communicationComputation using non-contact making devicesHardware structureChinese remainder theorem
The modular exponentiation function used in public key encryption and decryption systems is implemented in a standalone engine having at its core modular multiplication circuits which operate in two phases which share overlapping hardware structures. The partitioning of large arrays in the hardware structure, for multiplication and addition, into smaller structures results in a multiplier design which includes a series of nearly identical processing elements linked together in a chained fashion. As a result of the two-phase operation and the chaining together of partitioned processing elements, the overall structure is operable in a pipelined fashion to improve throughput and speed. The chained processing elements are constructed so as to provide a partitionable chain with separate parts for processing factors of the modulus. In this mode, the system is particularly useful for exploiting characteristics of the Chinese Remainder Theorem to perform rapid exponentiation operations. A checksum mechanism is also provided to insure accurate operation without impacting speed and without significantly increasing complexity. While the present disclosure is directed to a complex system which includes a number of features, the present application is particularly directed to the incorporation and integration of circuits used for calculating a modular multiplicative inverse used as an input parameter to the process.
Owner:INTELLECTUAL DISCOVERY INC
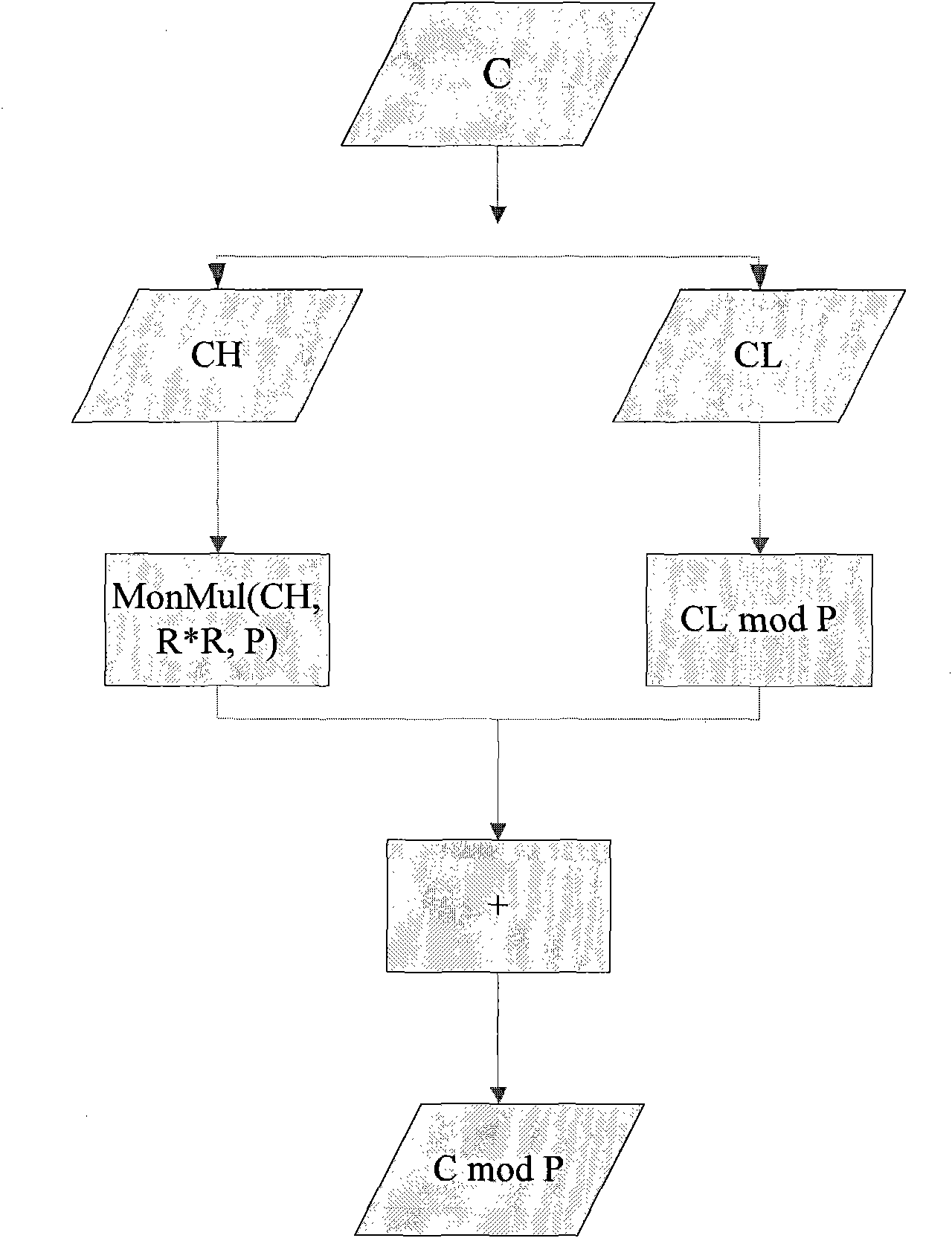
RSA (Ron Rivest, Adi Shamir and Leonard Adleman) algorithm digital signature method
ActiveCN102571342ALow costFast to marketKey distribution for secure communicationUser identity/authority verificationCoprocessorDigital signature
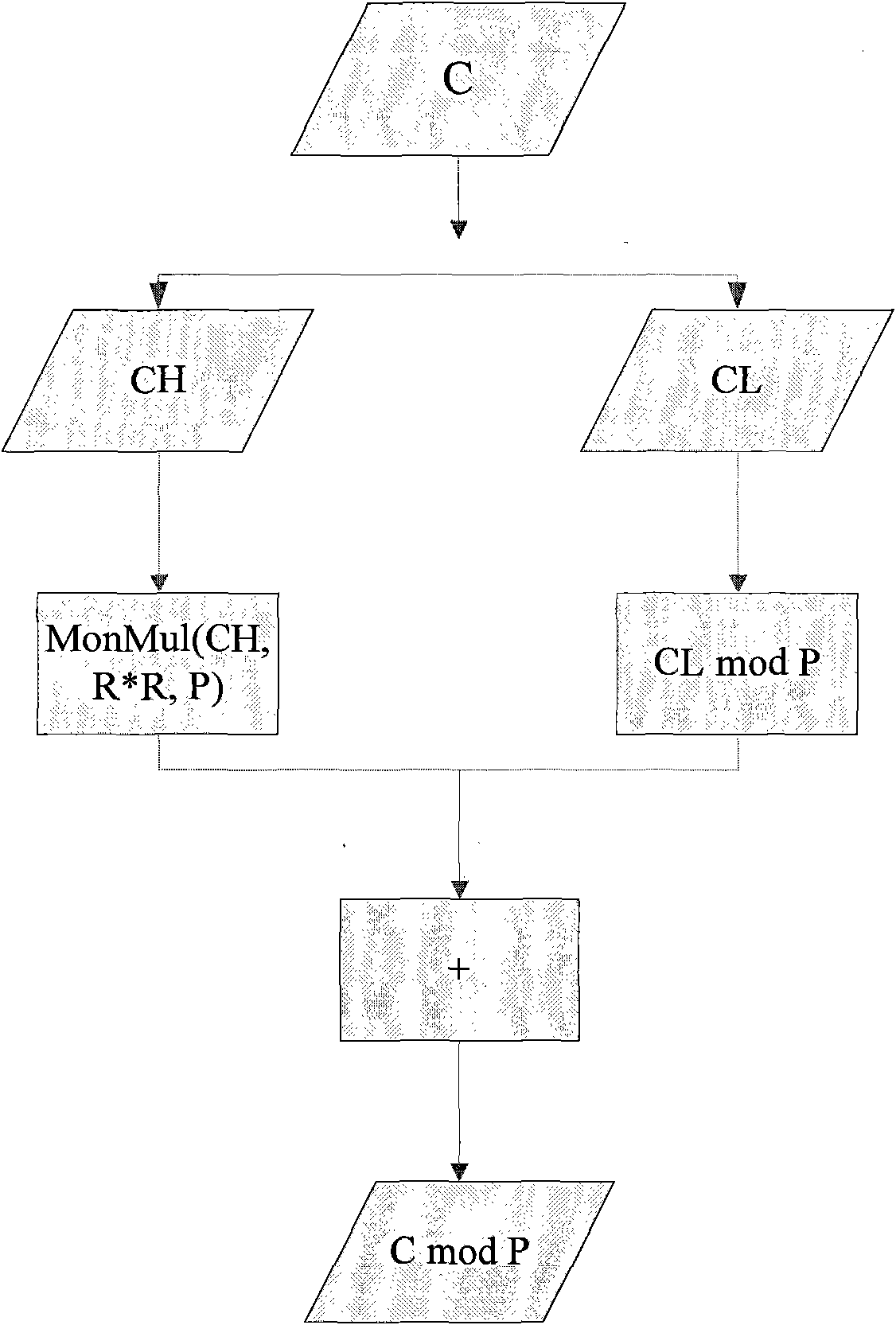
The invention designs an RSA (Ron Rivest, Adi Shamir and Leonard Adleman) algorithm digital signature method which realizes a 1408-bit RSA private key operation technology based on a 1024-bit hardware coprocessor and is mainly applied to the field of safety calculation of smart cards. A parameter in a large-bit-length RSA private key operation is calculated by utilizing a modular multiplier with small bit length, for example, a parameter in 1408-bit or 2048-bit RSA private key operation is calculated by utilizing a modular multiplier of 1024 bits. The RSA private key operation utilizes a Chinese remainder theorem and can be used for reducing the operation length of a main operation-modular exponentiation, but an operation of a key parameter, such as C mod P, C mod Q and a multiply operation, wherein the C represents a plain text, the length of the C is double the lengths of the P and the Q; and the multiply operation is accelerated by utilizing the modular multiplier, and a final result is also over the calculation capability of the modular multiplier. In the technology of the invention, the C is split into two numbers with the small bit lengths to calculate the C mod P by mainly utilizing the algorithm deformation of modular arithmetic; and the multiply operation larger than the length of the modular multiplier is calculated through a quarter multiply operation.
Owner:BEIJING CEC HUADA ELECTRONIC DESIGN CO LTD
Privacy protection and integrity detection method for multi-application data fusion of wireless sensor network
ActiveCN109121134AAchieve protectionEasy to detectNetwork topologiesSecurity arrangementWireless mesh networkCiphertext
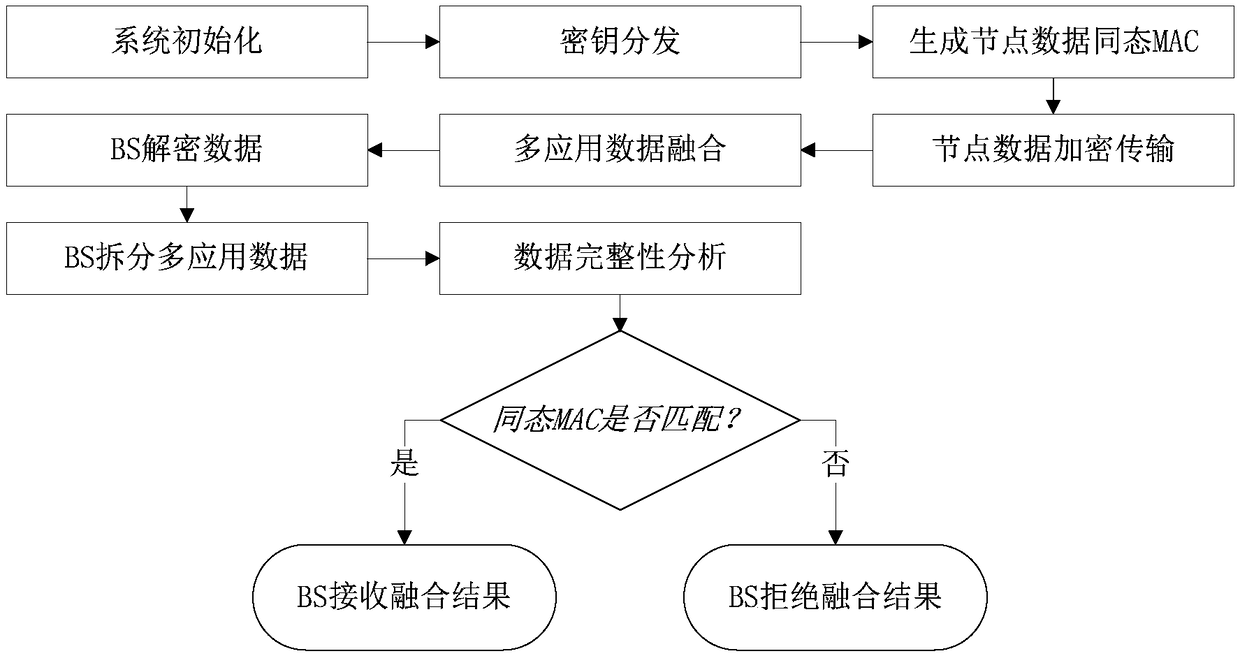
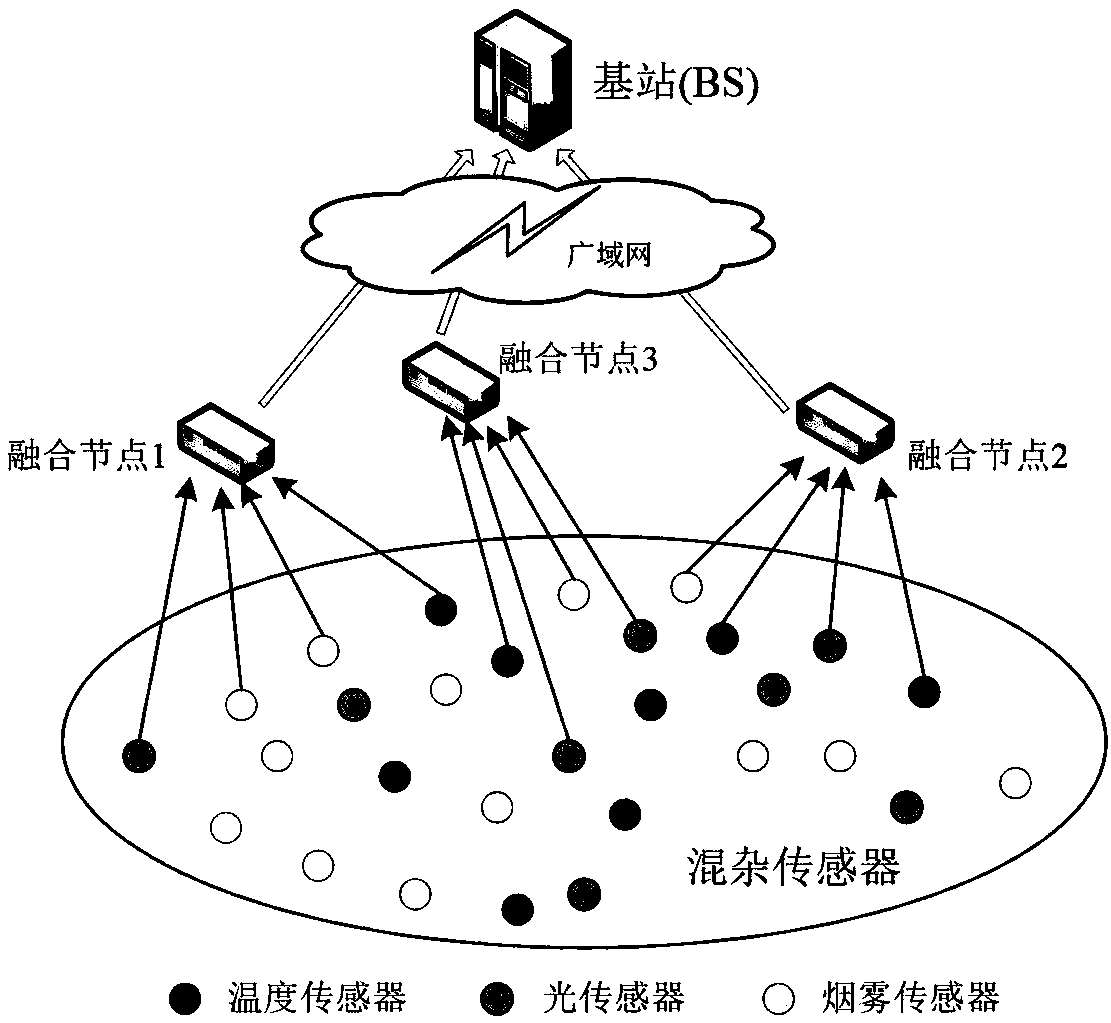
The invention, which belongs to the technical field of information security and internet-of-things application, discloses a privacy protection and integrity detection method for multi-application datafusion of a wireless sensor network. Privacy protection and integrity detection are carried out on collected and integrated multi-application data in a multi-application environment of a sensor network, so that a problem that the privacy data are stolen and tampered during the fusion and transmission processes is solved. According to the invention, privacy protection of the integrated data is realized by using a homomorphic Paillier encryption method; with a homomorphic MAC method, the integrity of the integrated data is detected at a base station; and then the base station separates different application data from an integration ciphertext based on the Chinese remainder theorem (CRT). The analysis shows that the privacy protection and integrity detection method not only has high error tolerance for node failures or data losses but also has high security and low energy consumption. The method is implemented simply with low cost and is easy to popularize.
Owner:CHUZHOU UNIV
Doppler shift measuring method and device thereof
InactiveCN103983957AReduce transmission frequencyLow costRadio wave reradiation/reflectionTarget signalPhase difference
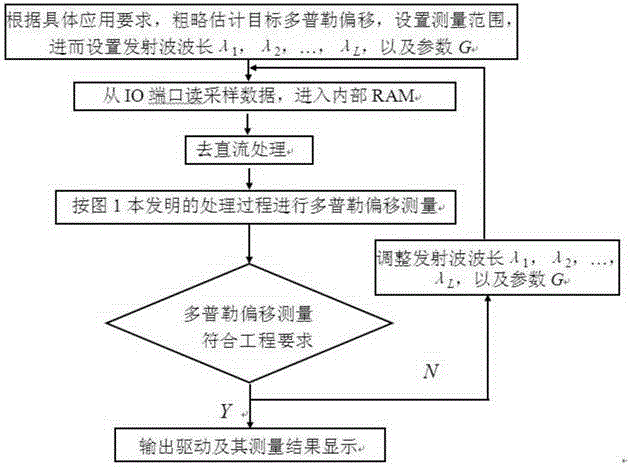
The invention discloses a Doppler shift measuring method and a device thereof. The Doppler shift measuring method comprises the steps of detecting the same moving target through L branches of local receiving antenna arrays of different low frequency bands, receiving and obtaining L branches of SAR signals, and storing the L branches of SAR signals; carrying out fast Fourier transformation and Hanning double-window all-phase fast Fourier transformation on the L branches of SAR signals to obtain a magnitude spectrum and a phase spectrum respectively; carrying out spectrum correction on the peak value position through the phase difference frequency correction method to obtain corrected peak value position estimation and then obtain remainder information; according to the remainder information obtained through spectrum correction of each branch, processing remainders according to the Chinese remainder theorem of the closed analytical form to reconstruct Doppler shift estimation of target signals. According to the device, a radar detects a target to be detected to obtain L branches of SAR values, the SAR values enter a DSP in a parallel digital input mode and are processed by the DSP to obtain Doppler shift estimation of the moving target to be detected, and finally, Doppler shift values are displayed by means of a drive and a display module of the drive.
Owner:TIANJIN UNIV
Multi-signal-source frequency and DOA joint detection method and device
ActiveCN107656237ALow costImplement samplingSpectral/fourier analysisRadio wave finder monitoring/testingChinese remainder theoremComputer science
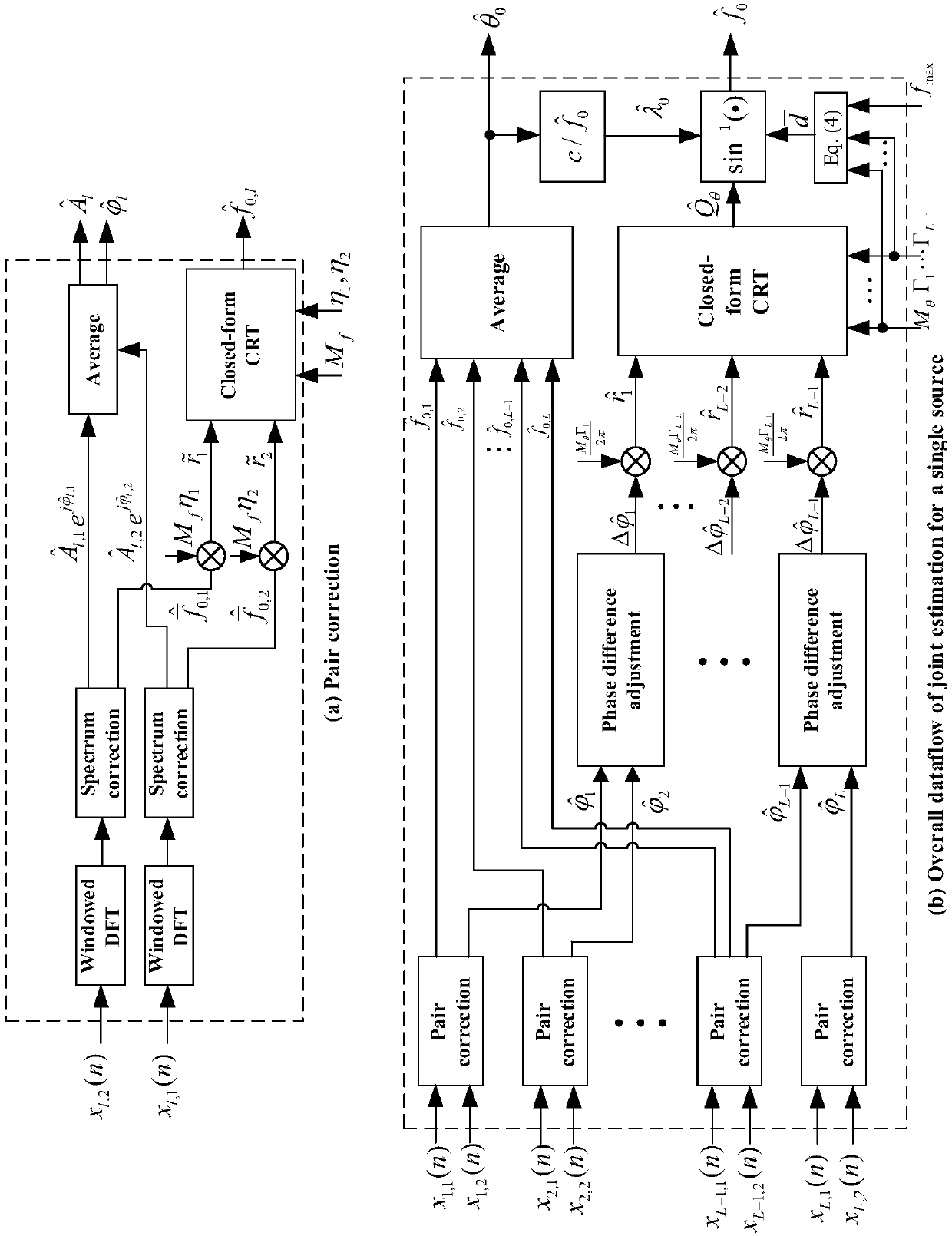
The invention discloses a multi-signal-source frequency and DOA joint detection method and a multi-signal-source frequency and DOA joint detection device. The multi-signal-source frequency and DOA joint detection method comprises the steps of: conducting Mf-point DFT on L paths of signal samples, correcting frequencies and phases of DFT results by using a Tsui spectrum corrector to obtain a parameter group of corrected D groups of frequencies, phases and amplitude values, and constructing D direction vectors by using the parameter group; grouping and matching the D direction vectors accordingto the minimum distance to obtain D pieces of signal source parameter matching information; constructing a frequency remainder group according to the D pieces of signal source parameter matching information, and substituting the frequency remainder group into a closed type robust Chinese remainder theorem (CRT) model for reconstruction, so as to obtain a frequency estimated value; and acquiring L-1 phase differences according to the D pieces of signal source parameter matching information, constructing a phase reminder group, substituting the phase remainder group and a reconstructed module value group into the closed type robust CRT model for reconstruction to obtain an intermediate parameter, and calculating to obtain a DOA estimated value. The multi-signal-source frequency and DOA jointdetection method and the multi-signal-source frequency and DOA joint detection device realize the high-precision frequency and DOA joint estimation of multiple pairs of targets.
Owner:TIANJIN UNIV
Interferometric inverse synthetic aperture radar (InISAR) hyperactivity target-oriented imaging and motion trail reconstruction method based on time frequency analysis
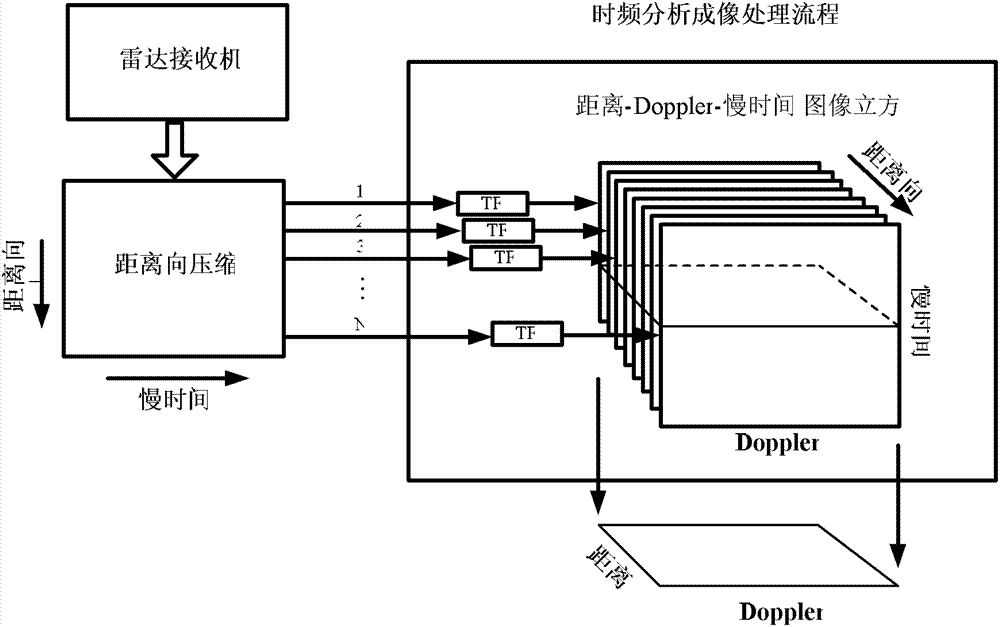
ActiveCN103091682ABreak through the defect of uncertain imaging azimuth and positionHigh azimuth positioning accuracyElectromagnetic wave reradiationTime–frequency analysisReconstruction method
The invention discloses an interferometric inverse synthetic aperture radar (InISAR) hyperactivity target-oriented imaging and motion trail reconstruction method based on a time frequency analysis, and relates to radar imaging. Due to the fact that radar is motionless, an inverse synthetic aperture radar (ISAR) eliminates and stills noise jamming to a high-pass filter through directions after pulse pressure. Signals STF1(t~, tm, f), STF2(t~, tm, f) and STF3(t~ , tm, f) of three channels after eliminating the noise jamming convert to time domain, conduct time frequency analyses along each distance door respectively, get signals and conduct rectification and interference between one slow time and moment t and three groups of signals STF1(t~, t, f), STF2(t~, t, f), and STF3(t~, t, f) which are extracted from time frequency analysis results. A threshold is used for processing interferometric phases which acquire target scattering points, a comparison with reference scattering points which are located in the middle of beams and the target scattering pints are made, and fuzzy values of drift angles of the target scattering points are achieved. Multi-baseline being combined with Chinese remainder theorem enables fuzzy ranges of drift angle measuring to expand to whole beam width, target direction locations are achieved, and instantaneous time domain imaging is achieved. The reconstruction method has effects on all slow times and moments, all imaging results are observed along tm order, and hyperactivity target motion trail reconstruction is achieved.
Owner:INST OF ELECTRONICS CHINESE ACAD OF SCI
Circuits and methods for modular exponentiation
InactiveUS6963977B2Small sizeObvious advantagesComputer security arrangementsSecret communicationHardware structureModular exponentiation
Owner:INT BUSINESS MASCH CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com