Distributed key management method for ciphertext storage
A key management and distributed technology, applied in the field of distributed key management of ciphertext storage, can solve problems such as difficulty in key management
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
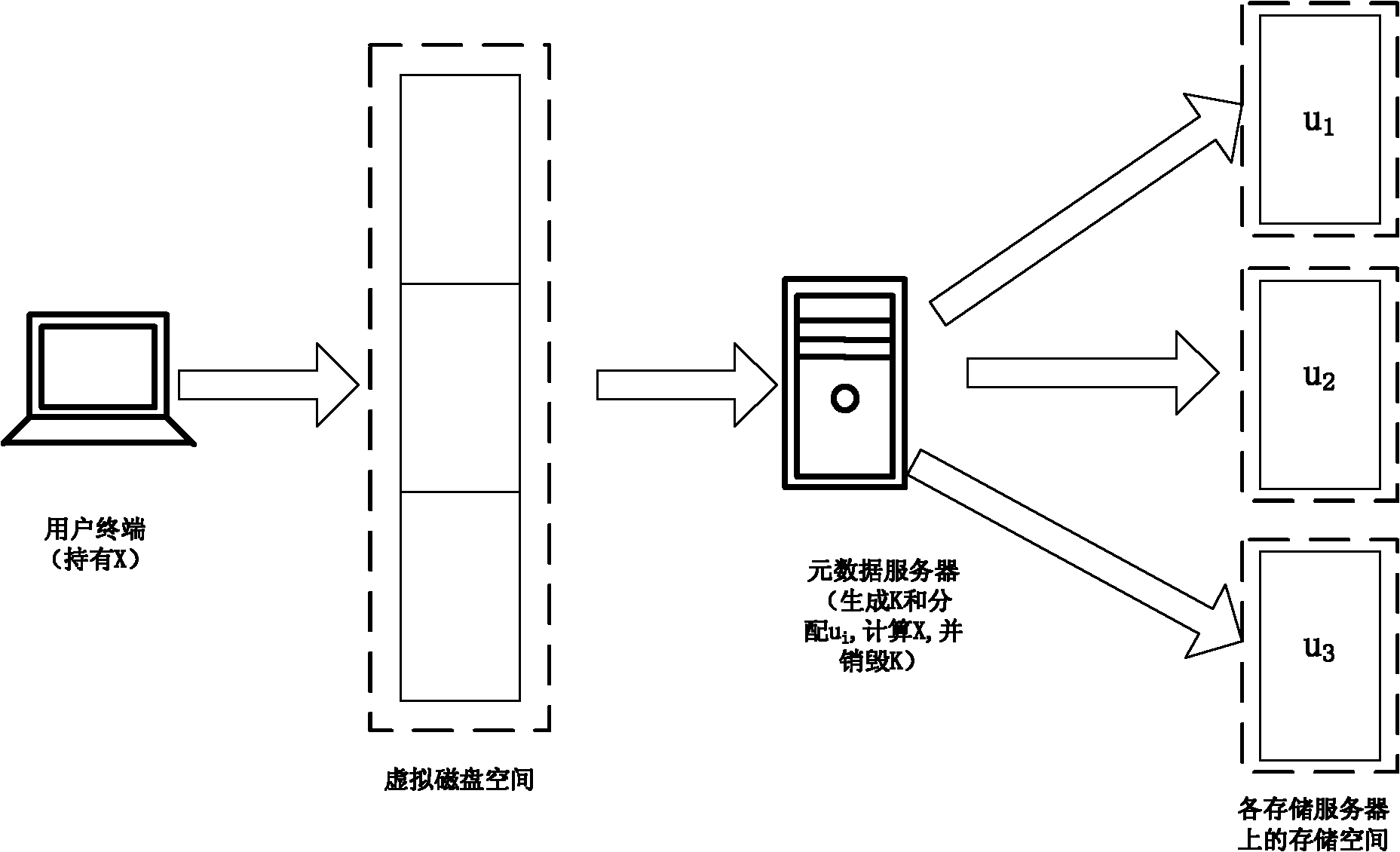
[0044] The inventive method is based on the following system configurations, figure 1 Shown:
[0045] 1. The data of registered users of the system are stored in different storage servers. These storage spaces together constitute the user's virtual disk space through network file sharing technology, and each piece of space is equivalent to a partition of the virtual disk;
[0046] 2. Each storage space is identified and distinguished by the IP information of the storage server where it is located and the summary value of the machine name. When the digest value of the content of the file uploaded by the user is the same as the identifier of the storage space, the file will be stored in the storage server with the identifier;
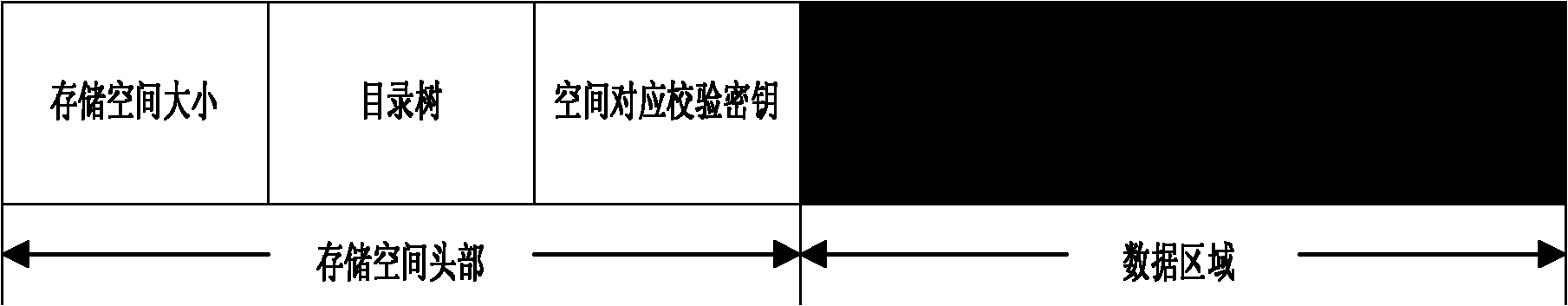
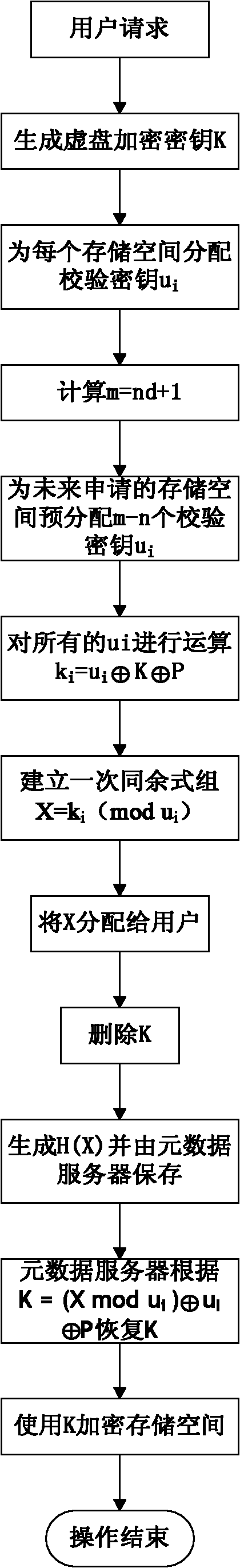
[0047] 3. Each storage space is divided into two parts: partition header and data area. The partition header stores the information of the storage space, such as the size of the data area, space directory tree information and key information. The data ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com