Authority-identifying method of internet protocol multi-media sub-system
A multimedia subsystem and authentication technology, applied in the field of IP multimedia subsystem authentication, can solve the problems of authentication failure, no solution provided, and reduced service quality in the authentication mode
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 6 example
[0249] refer to Figure 9a and Figure 9b , the sixth embodiment of the present invention comprises the following steps:
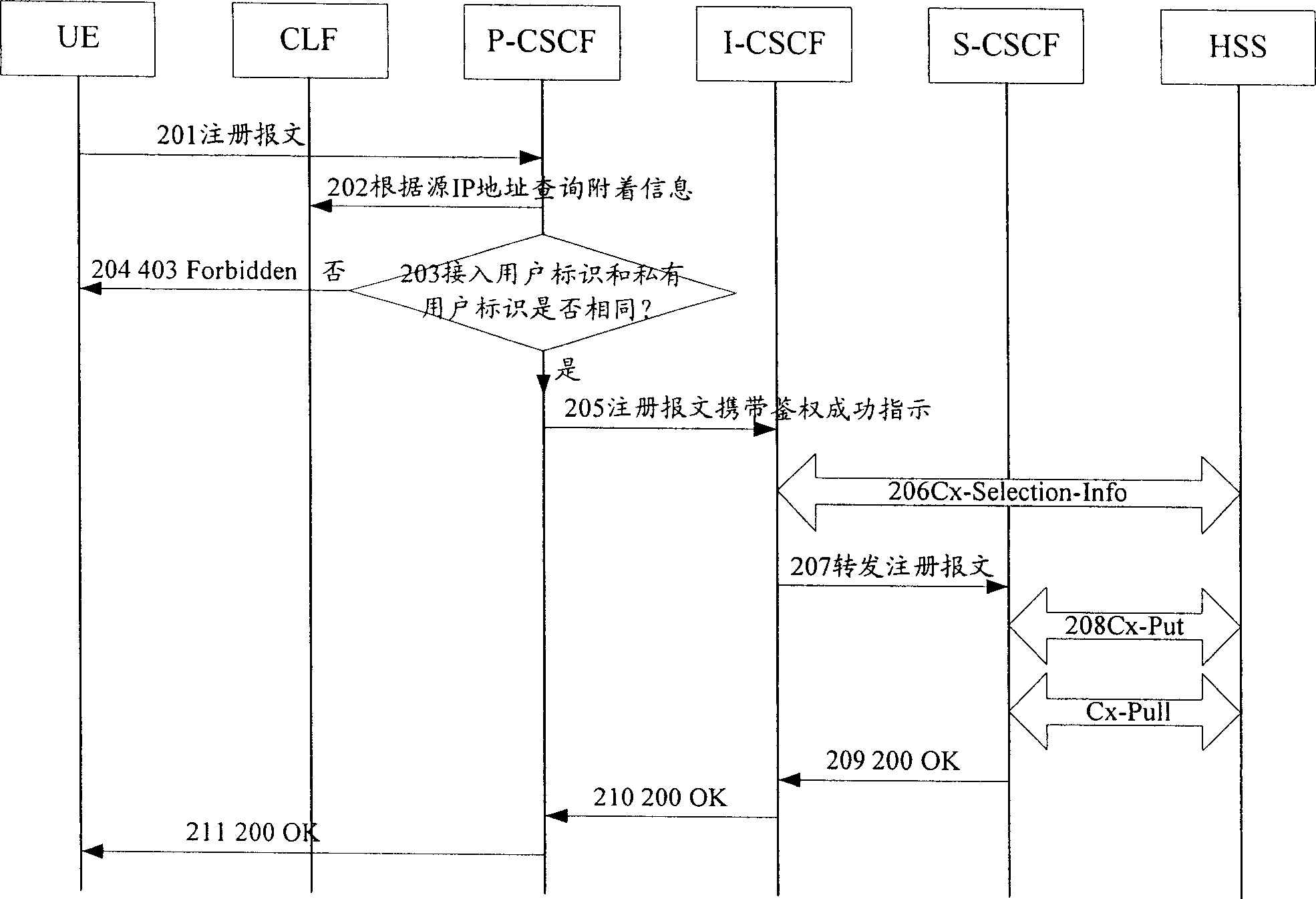
[0250] In step 901, the UE sends a registration message Register to the P-CSCF, and the message carries an access operator identifier and an access user identifier.
[0251] In step 902, the P-CSCF determines the CLF according to the access operator ID in the registration message and the preset correspondence between the access operator ID and the CLF.
[0252] In step 903, the P-CSCF queries the above determined CLF for the attachment information of the user at the access layer according to the access user identifier in the registration message. The data record of attachment information corresponding to the private user ID is pre-stored in the CLF, and the attachment information includes IP address information, location information, etc., but does not include the binding ID in the prior art. If there is no data record of the access user ID in the CLF, ...
no. 7 example
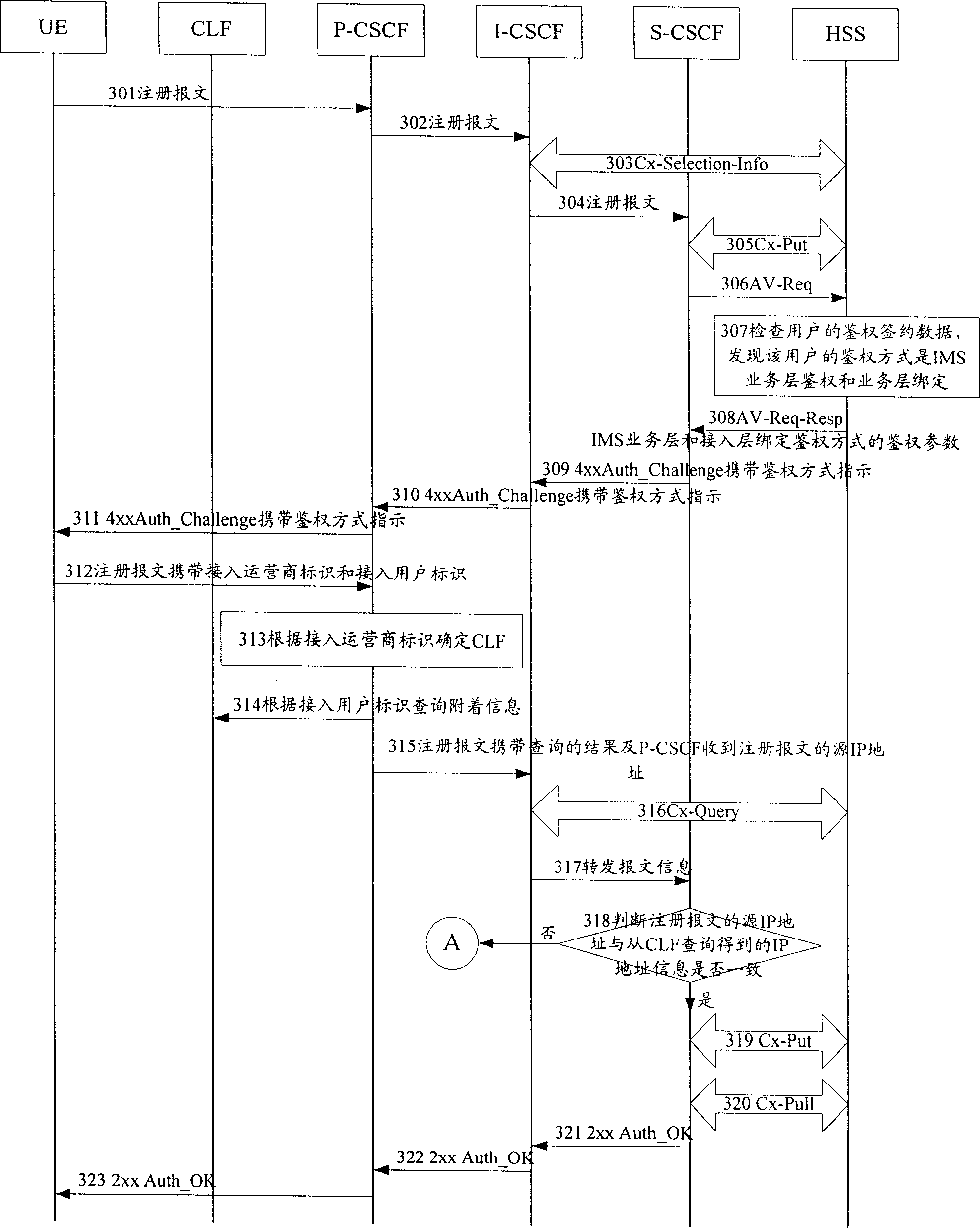
[0283] refer to Figure 10a and Figure 10b , the seventh embodiment of the present invention includes the following steps:
[0284] In step 1001, the UE sends a registration message Register to the P-CSCF, and the message carries an access operator identifier and an access user identifier.
[0285] In step 1002, the P-CSCF determines the CLF according to the access operator ID in the registration message and the preset correspondence between the access operator ID and the CLF.
[0286] In step 1003, the P-CSCF searches the CLF determined above for the attachment information of the user at the access layer according to the access user identifier in the registration message. The data record of attachment information corresponding to the private user ID is pre-stored in the CLF, and the attachment information includes IP address information, location information, etc., but does not include the binding ID in the prior art. If there is no data record of the access user ID in th...
no. 8 example
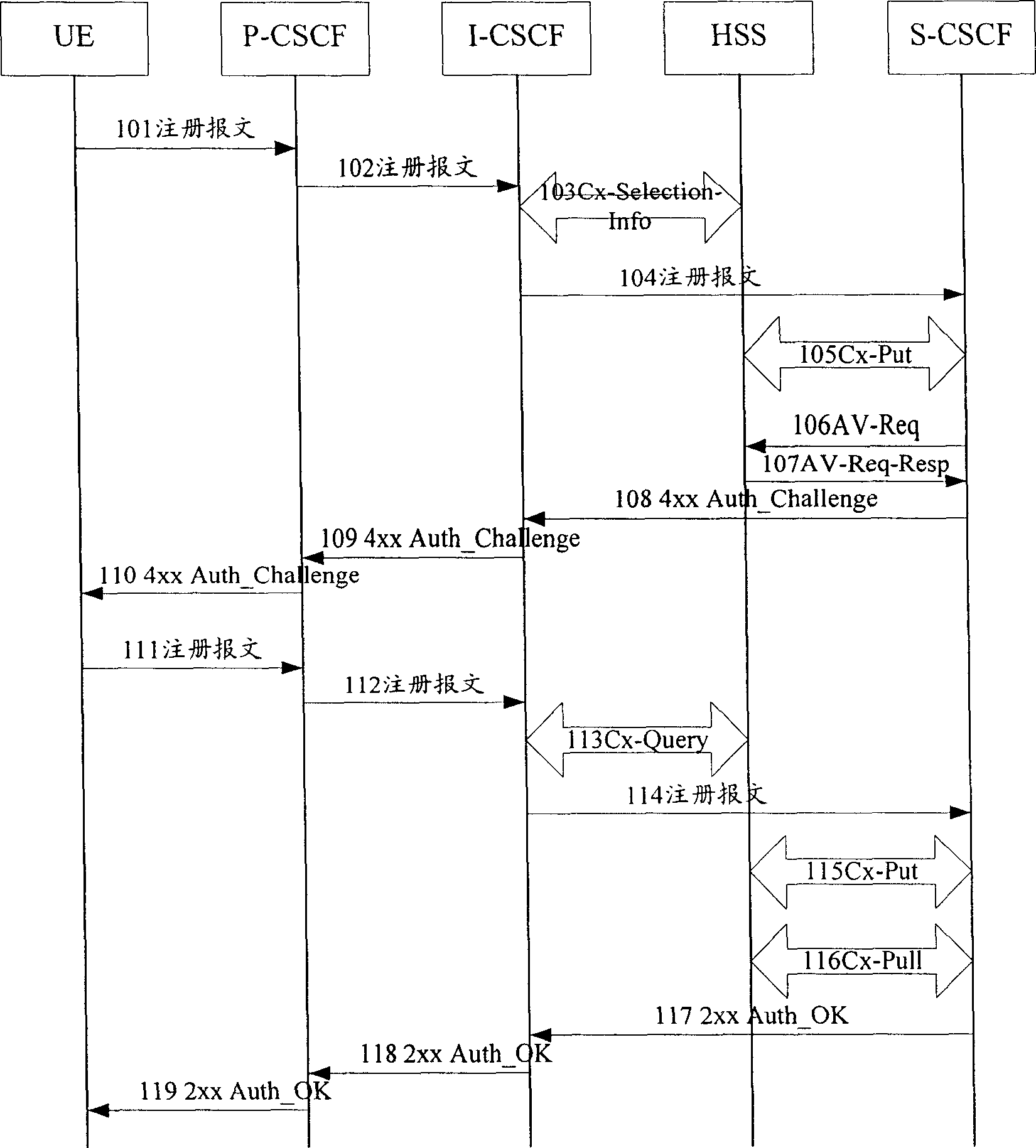
[0317] refer to Figure 11a and Figure 11b , the eighth embodiment of the present invention comprises the following steps:
[0318] Step 1101, the UE sends a registration message Register to the P-CSCF.
[0319] In step 1102, the P-CSCF forwards the UE's Register message to the I-CSCF.
[0320] Step 1103, the I-CSCF and the HSS select the corresponding S-CSCF through the Cx-Selection-Info message, that is, the I-CSCF sends a request to the HSS to search the user attributes in the HSS to determine which S-CSCF will process the registration report arts.
[0321] In step 1104, the I-CSCF forwards the UE's registration message Register to the S-CSCF determined in step 1103.
[0322] In step 1105, the S-CSCF and the HSS update the S-CSCF indication information on the HSS through a Cx-Put message, and inform the HSS that the subsequent processing of the user will be performed in this S-CSCF.
[0323]In step 1106, the S-CSCF sends an AV-Req message to the HSS to request the use...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com