Patents
Literature
8254 results about "User identifier" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Unix-like operating systems identify a user by a value called a user identifier, often abbreviated to user ID or UID. The UID, along with the group identifier (GID) and other access control criteria, is used to determine which system resources a user can access. The password file maps textual user names to UIDs. UIDs are stored in the inodes of the Unix file system, running processes, tar archives, and the now-obsolete Network Information Service. In POSIX-compliant environments, the command-line command id gives the current user's UID, as well as more information such as the user name, primary user group and group identifier (GID).
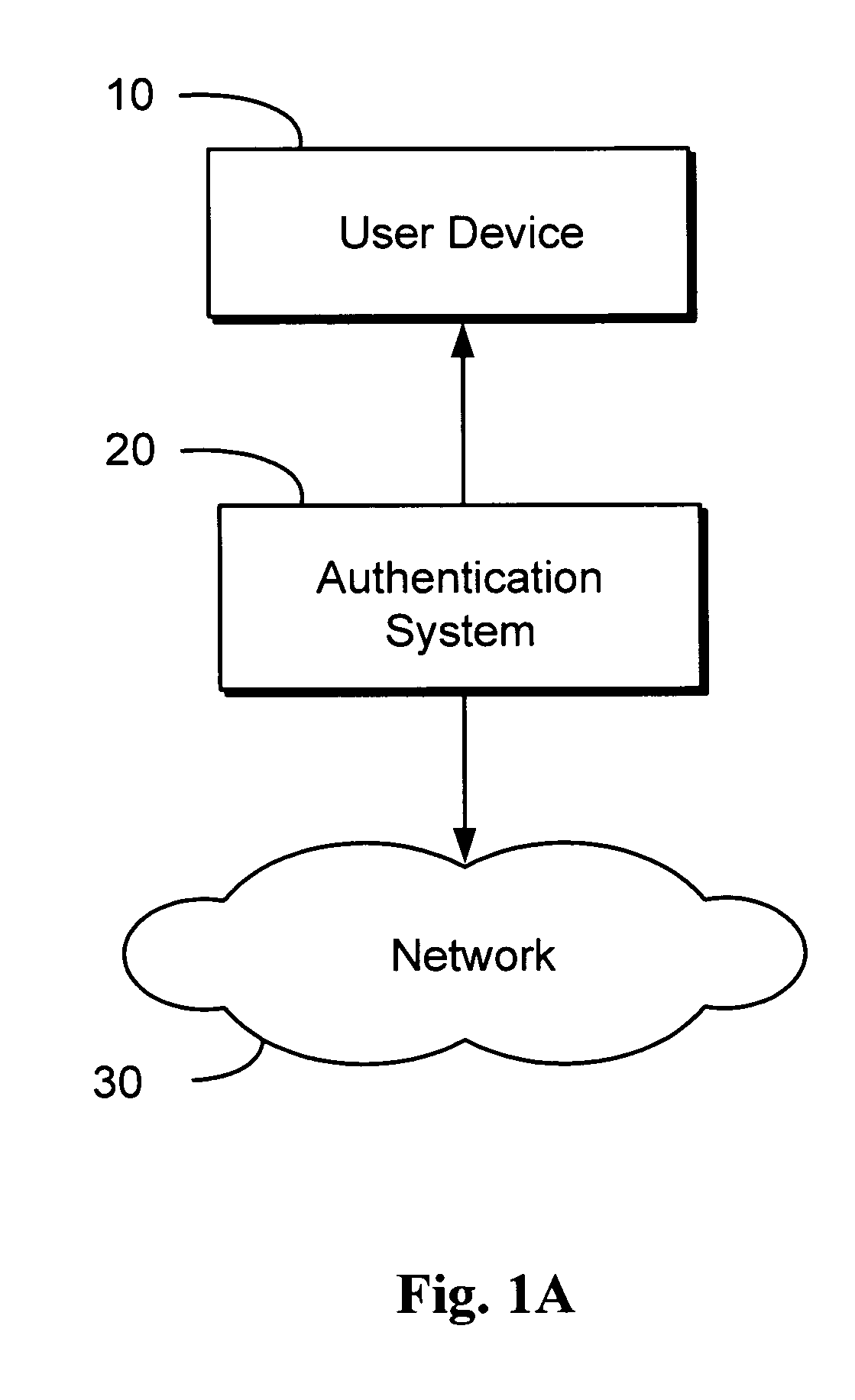
HTTP distributed remote user authentication system
InactiveUS6092196AExemption stepsAvoid necessityDigital data processing detailsUser identity/authority verificationUser authenticationUser identifier
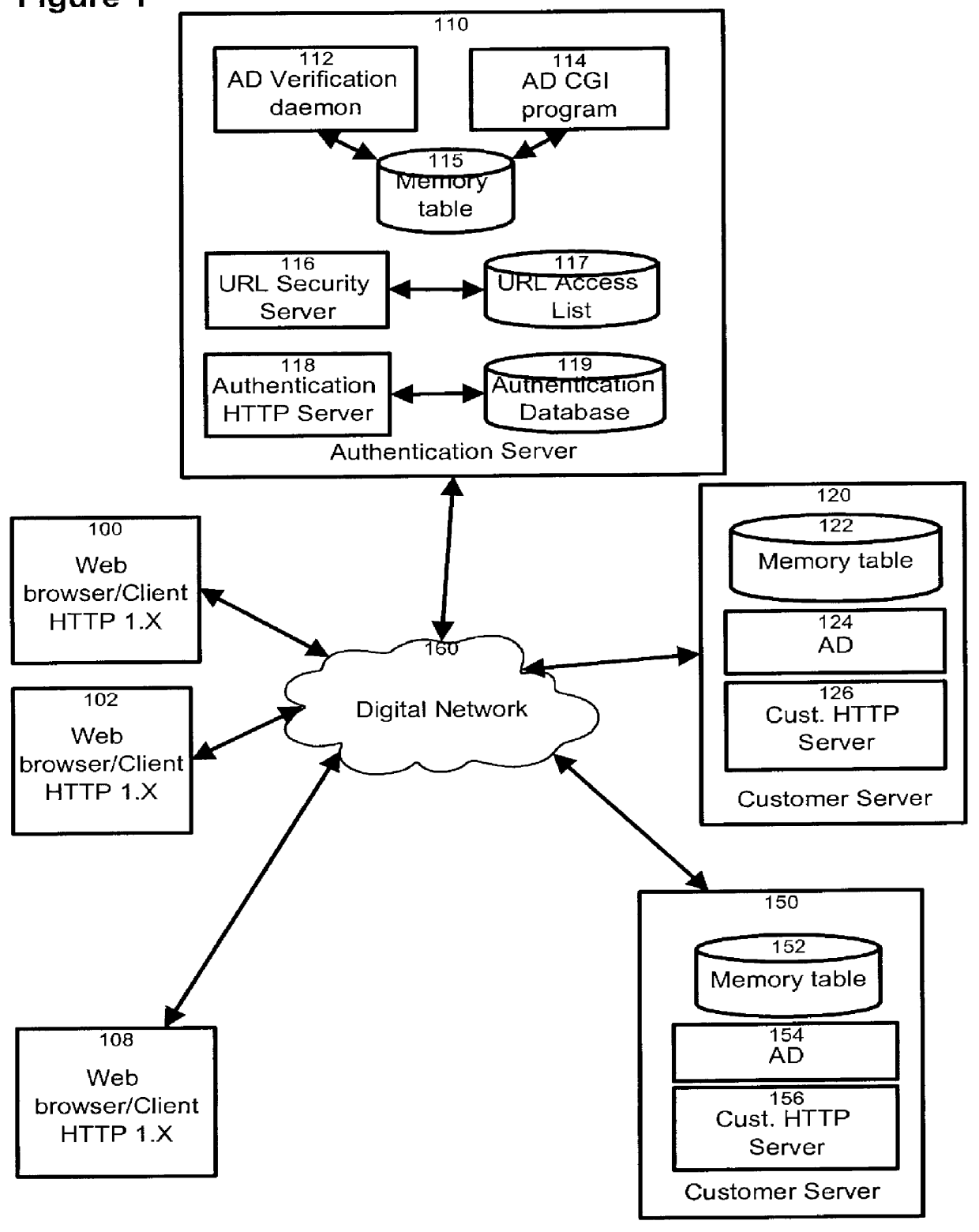
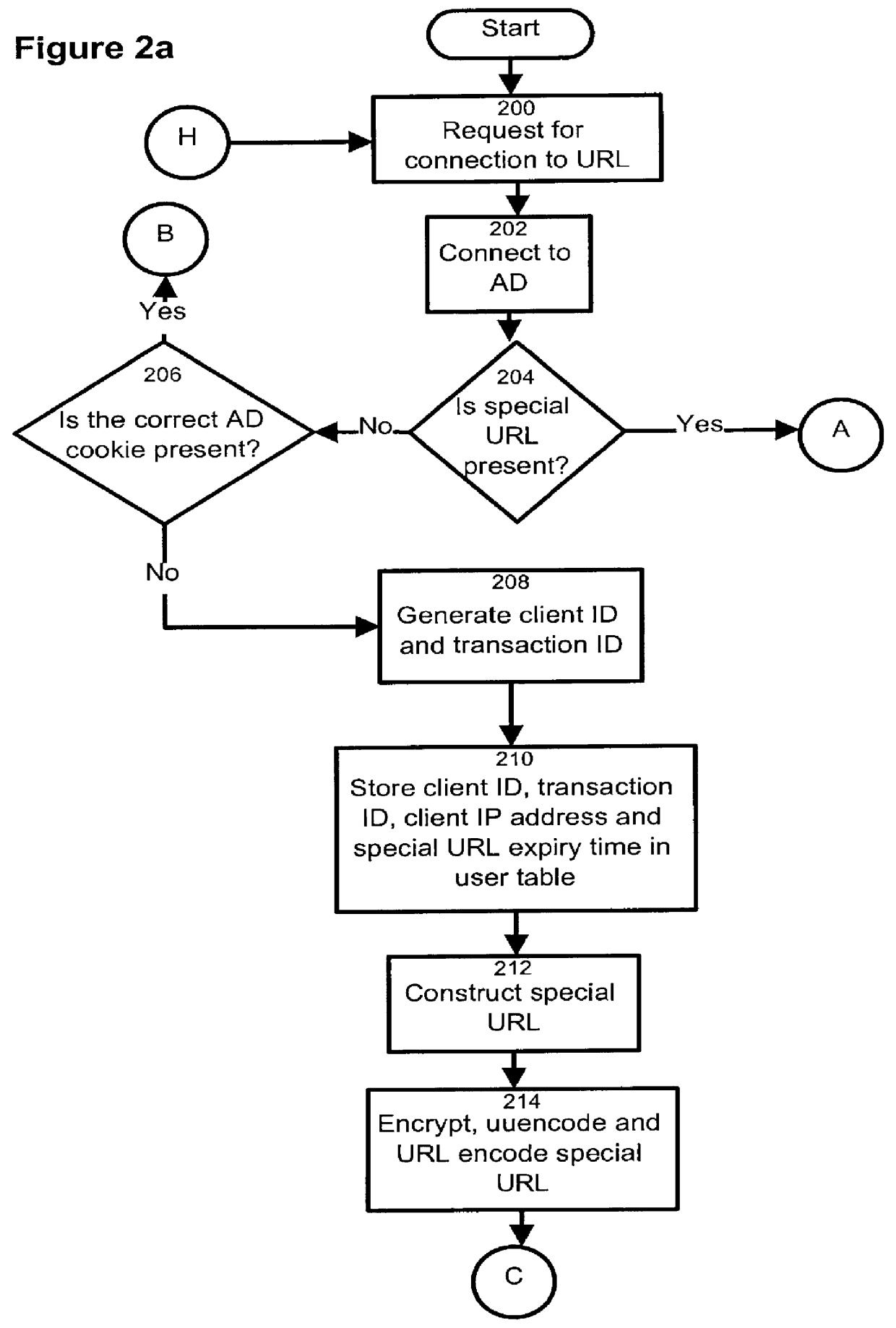
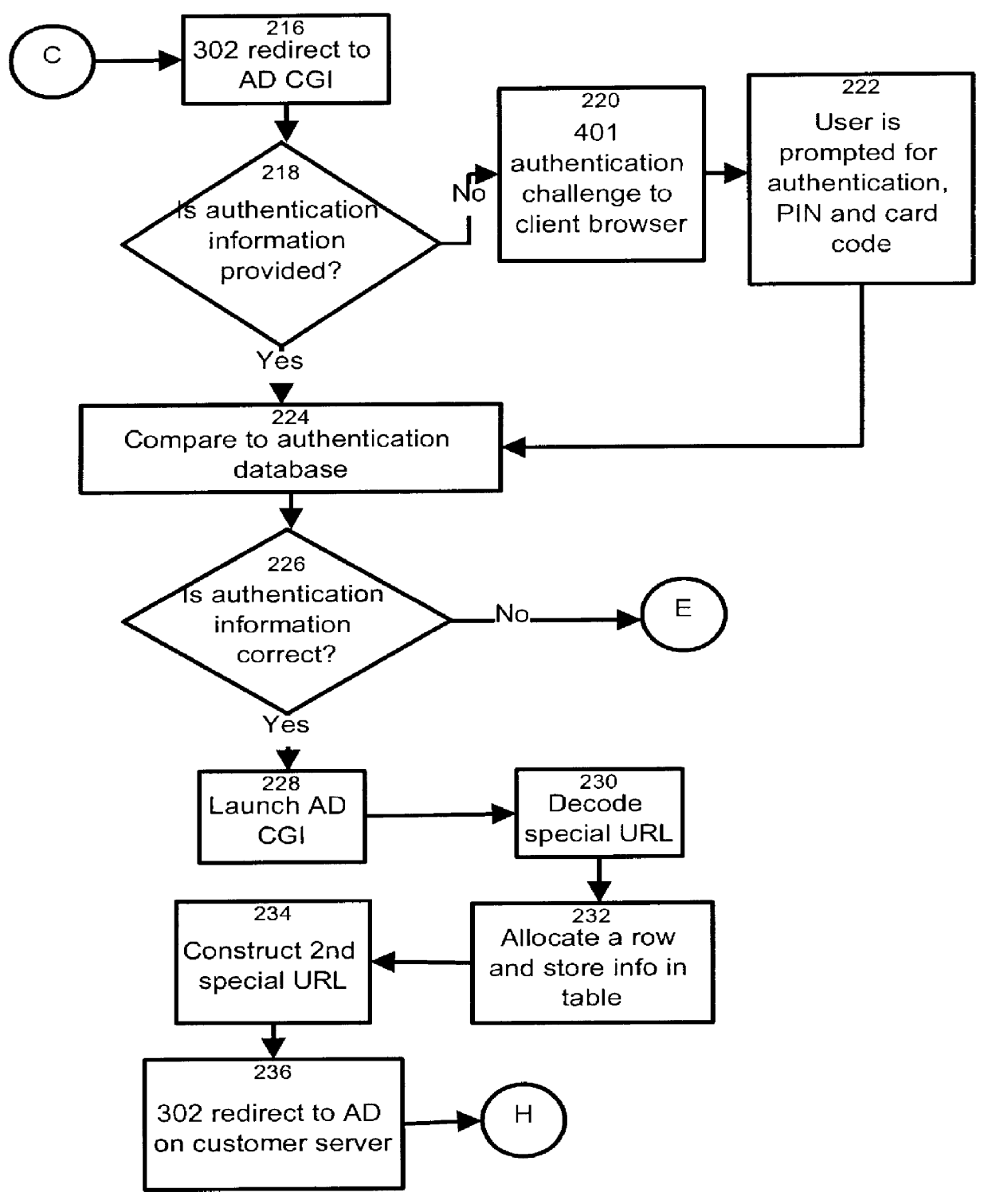
The present invention relates to the field of data and computer network security. Data and computer network security is of the utmost importance to most organizations that possess such networks. One of the difficulties that users and managers of these networks face is that the users have to provide a user ID and password every time they wish to access one of the organization's secured HTTP servers or URLs. This creates a problem for users and managers since lists of numerous user IDs and passwords need to be maintained and therefore can easily be lost or their confidentiality compromised. This invention addresses these problems by providing a transparent, scalable, single point of authentication for remote users across any number of HTTP servers anywhere on a data network, such as an Intranet, using any user ID and password scheme implemented by a main authentication HTTP server.
Owner:RPX CLEARINGHOUSE
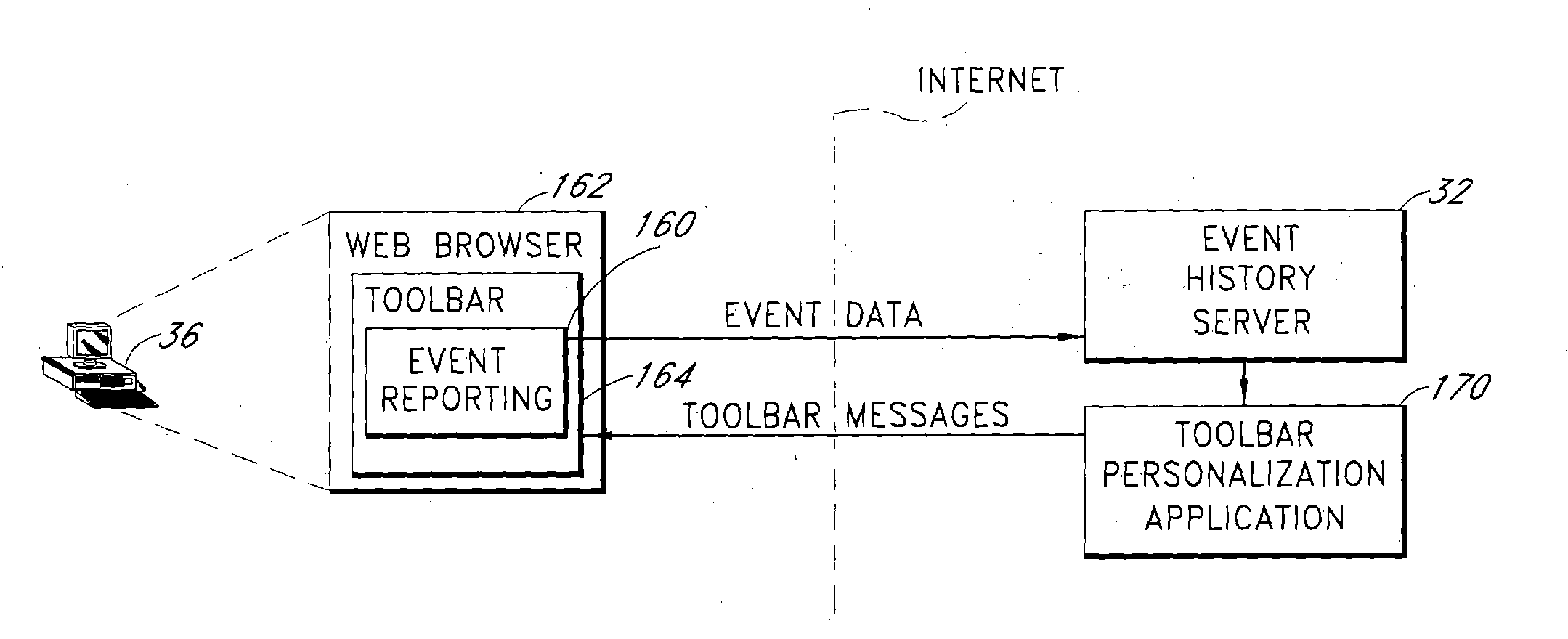
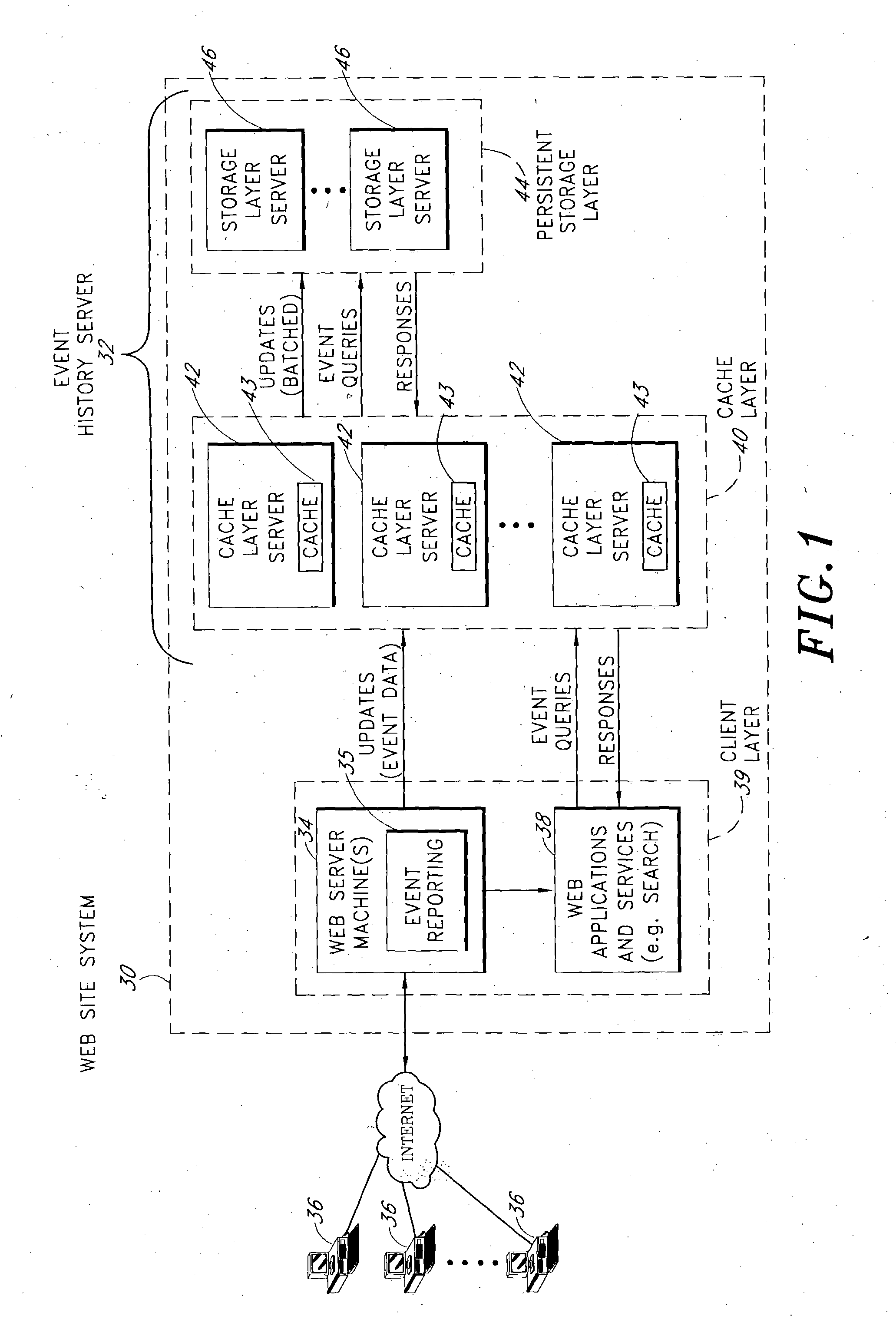
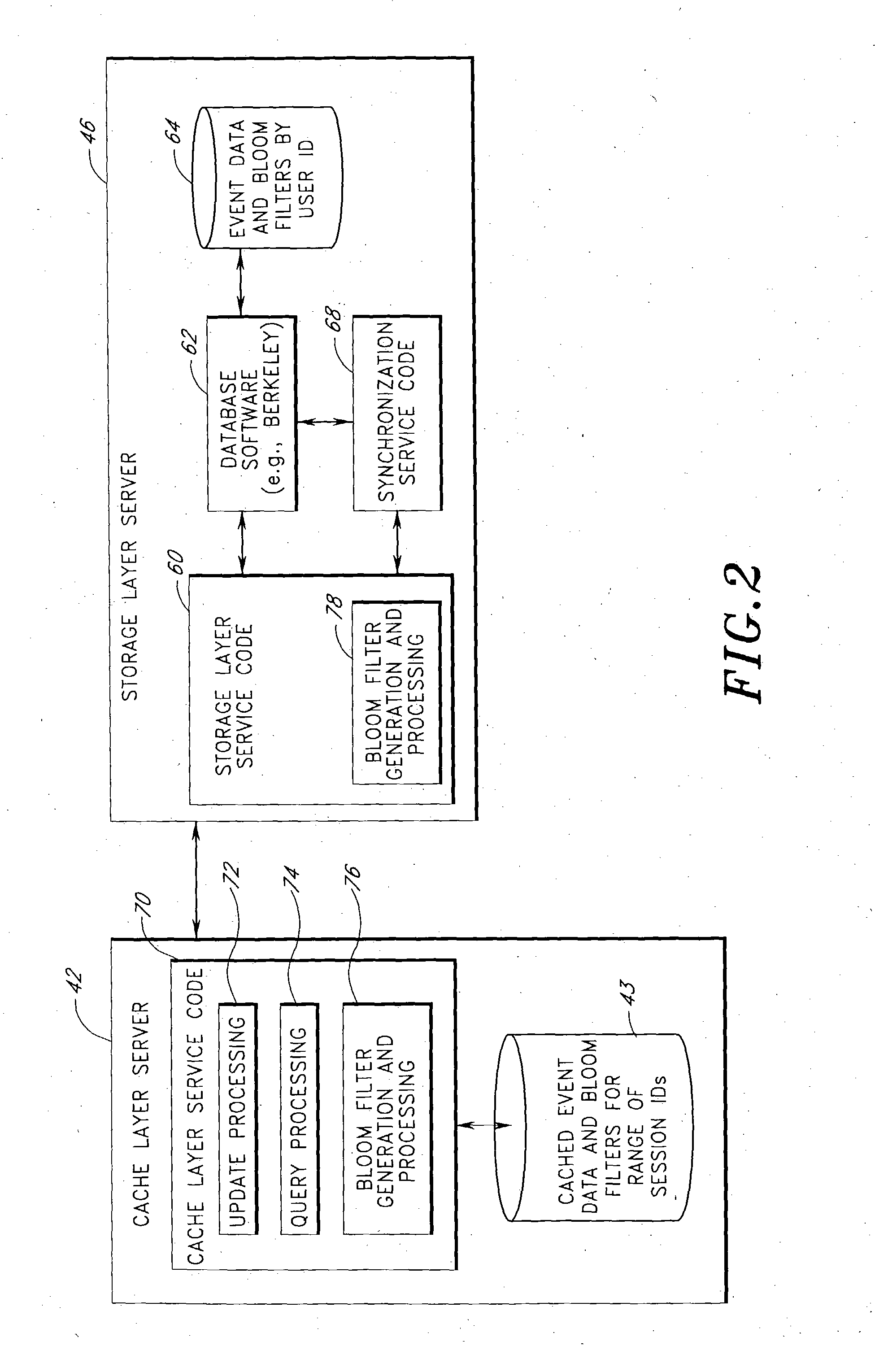
Server architecture and methods for persistently storing and serving event data
ActiveUS20050033803A1Effective evaluationMultiple digital computer combinationsWebsite content managementWeb siteEvent type
A web site system includes an event history server system that persistently stores event data reflective of events that occur during browsing sessions of web site users, and makes such data available to other applications and services in real time. The server system may, for example, be used to record information about every mouse click of every recognized user, and may also be used to record other types of events such as impressions and mouse-over events. The event data of a particular user may be retrieved from the server system based on event type, event time of occurrence, and various other criteria. In one embodiment, the server system includes a cache layer that caches event data by session ID, and includes a persistent storage layer the persistently stores the event data by user ID. Also disclosed are various application features that may be implemented using the stored event data.
Owner:AMAZON TECH INC
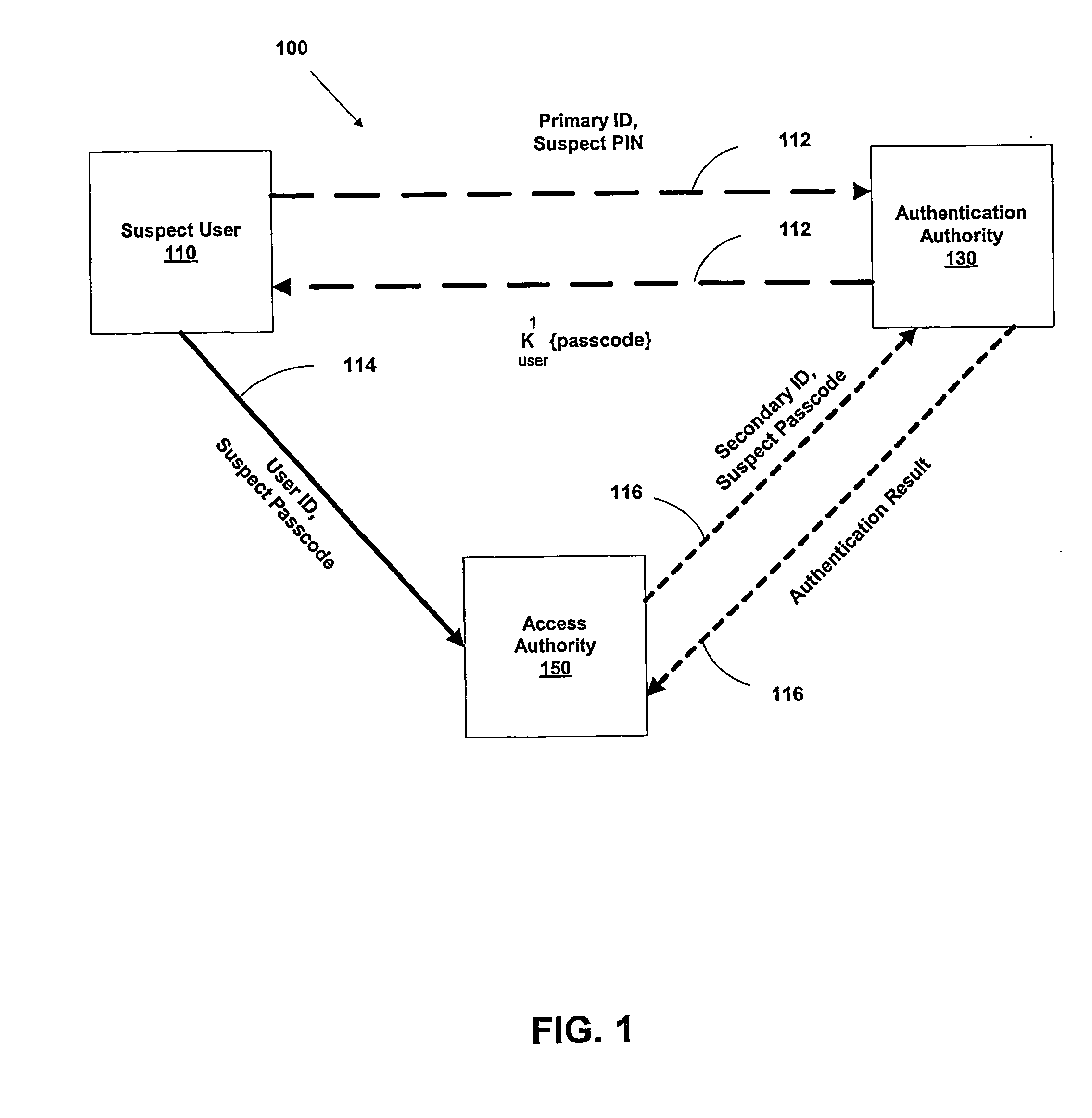
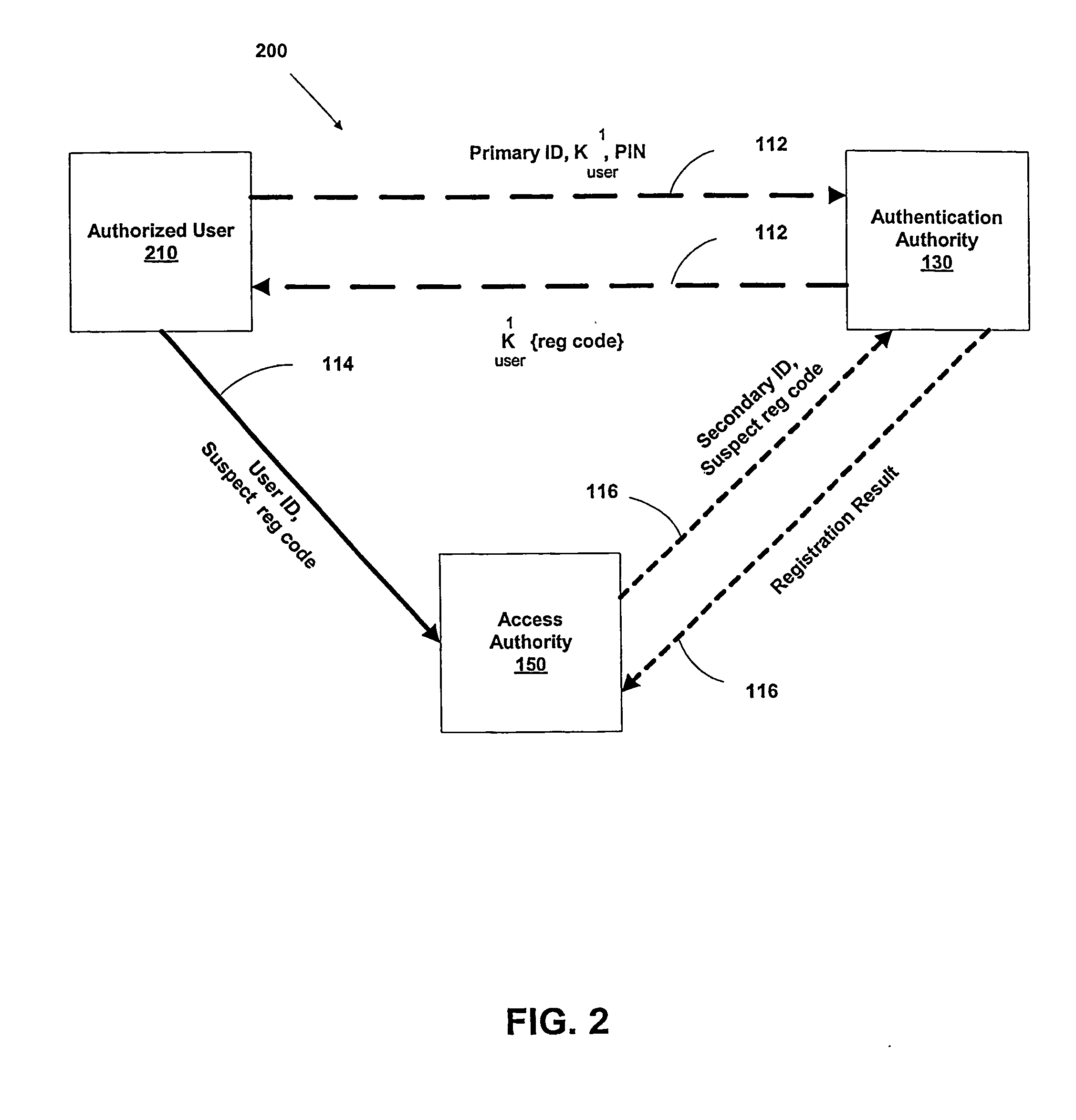
Multi-factor authentication system
InactiveUS20040187018A1Easy to understandUser identity/authority verificationUnauthorized memory use protectionPasswordUser identifier
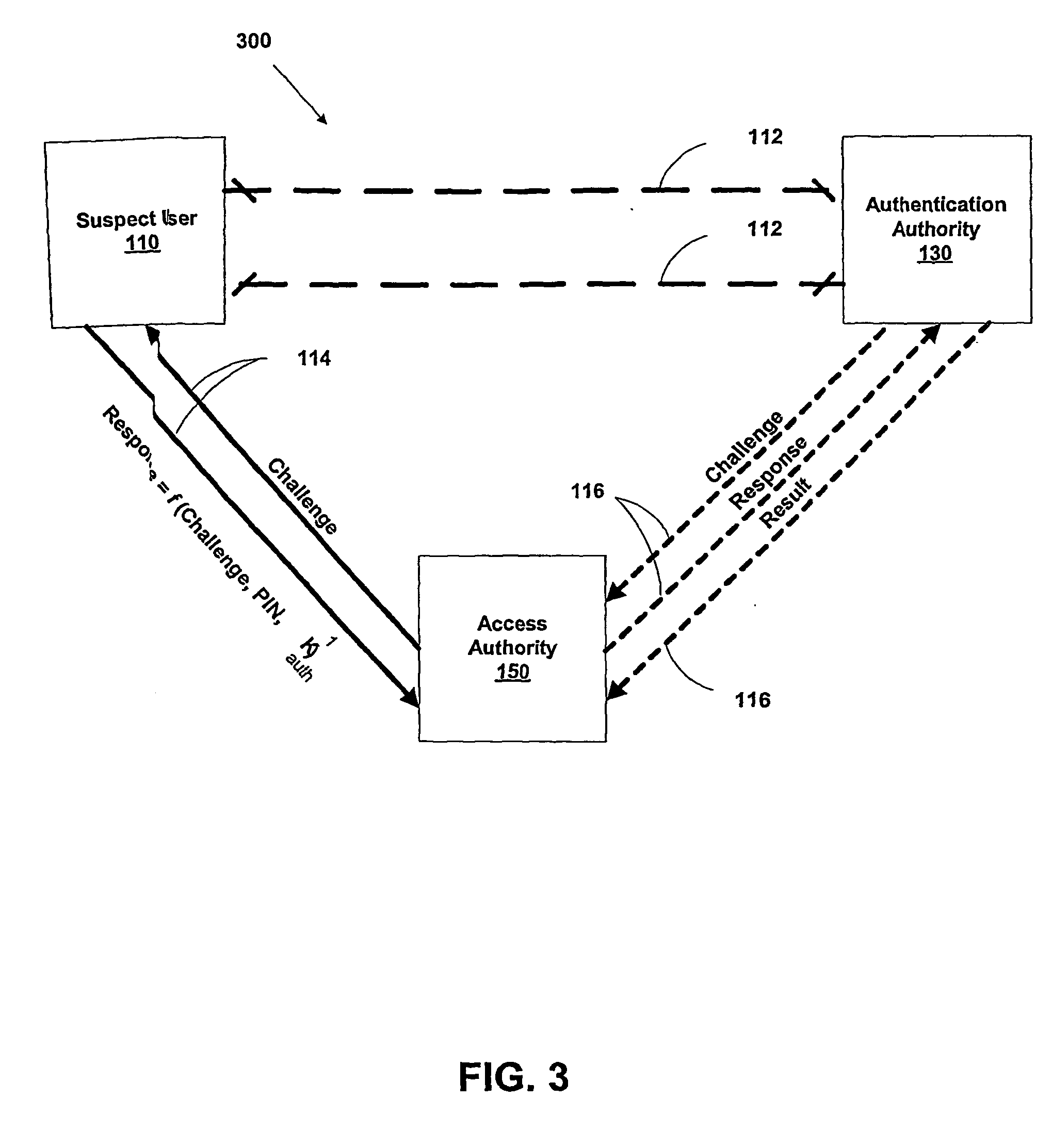
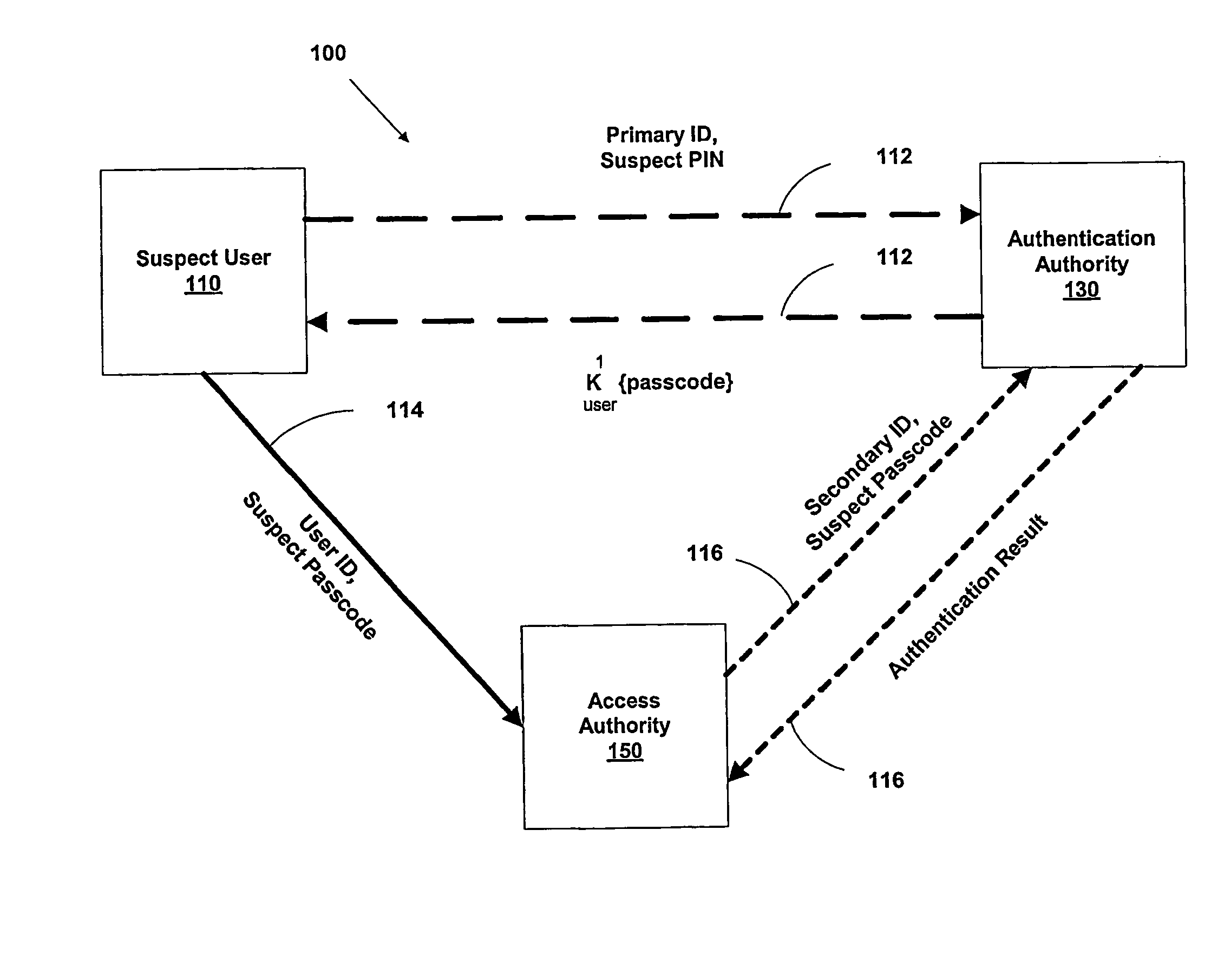
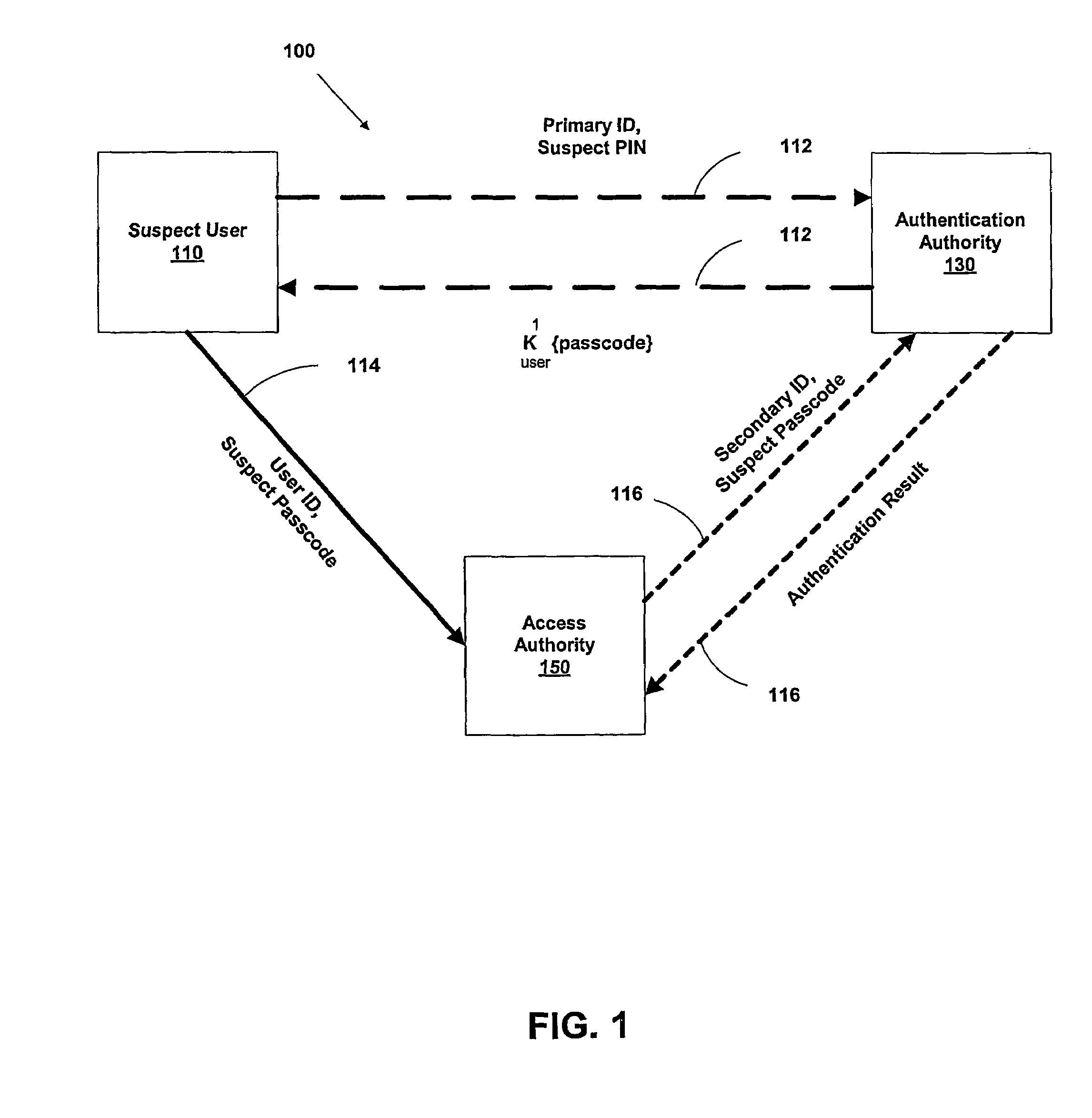
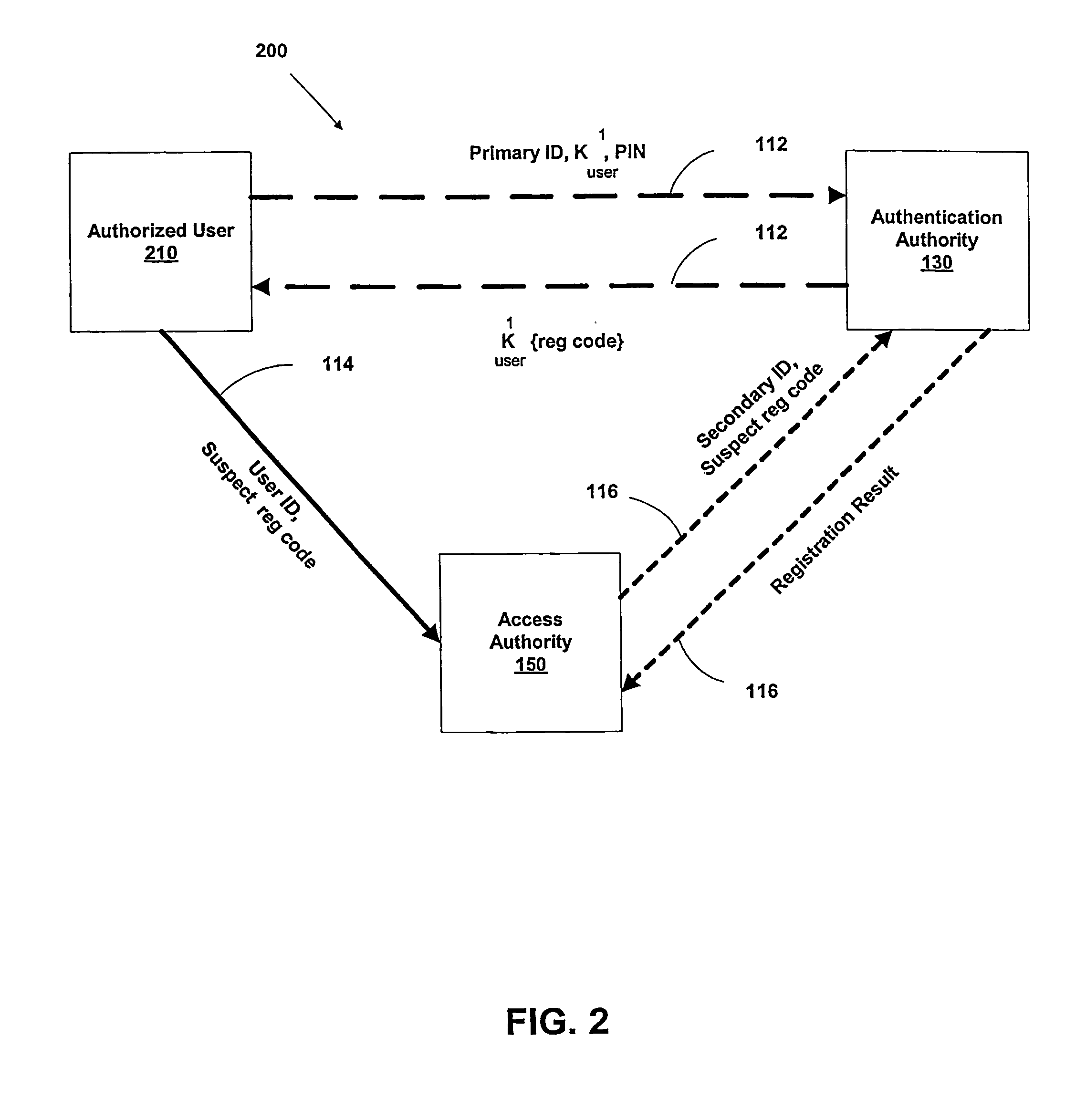
A suspect user (110) seeks access to a network resource from an access authority (150) utilizing a passcode received from an authentication authority (130). Initially, an ID of a device is bound with a PIN, the device ID is bound with a private key of the device, and the device ID is bound with a user ID that has been previously bound with a password of an authorized user. The device ID is bound with the user ID by authenticating the user ID using the password. Thereafter, the suspect user communicates the device ID and the PIN from the device over an ancillary communications network (112); the authentication authority responds back over the ancillary communications network with a passcode encrypted with the public key of the device; and the suspect user decrypts and communicates over a communications network (114) the passcode with the user ID to the access authority.
Owner:KARETEK HLDG LLC
Use of personal communication devices for user authentication
InactiveUS6993658B1Metering/charging/biilling arrangementsDigital data processing detailsPagerInternet privacy
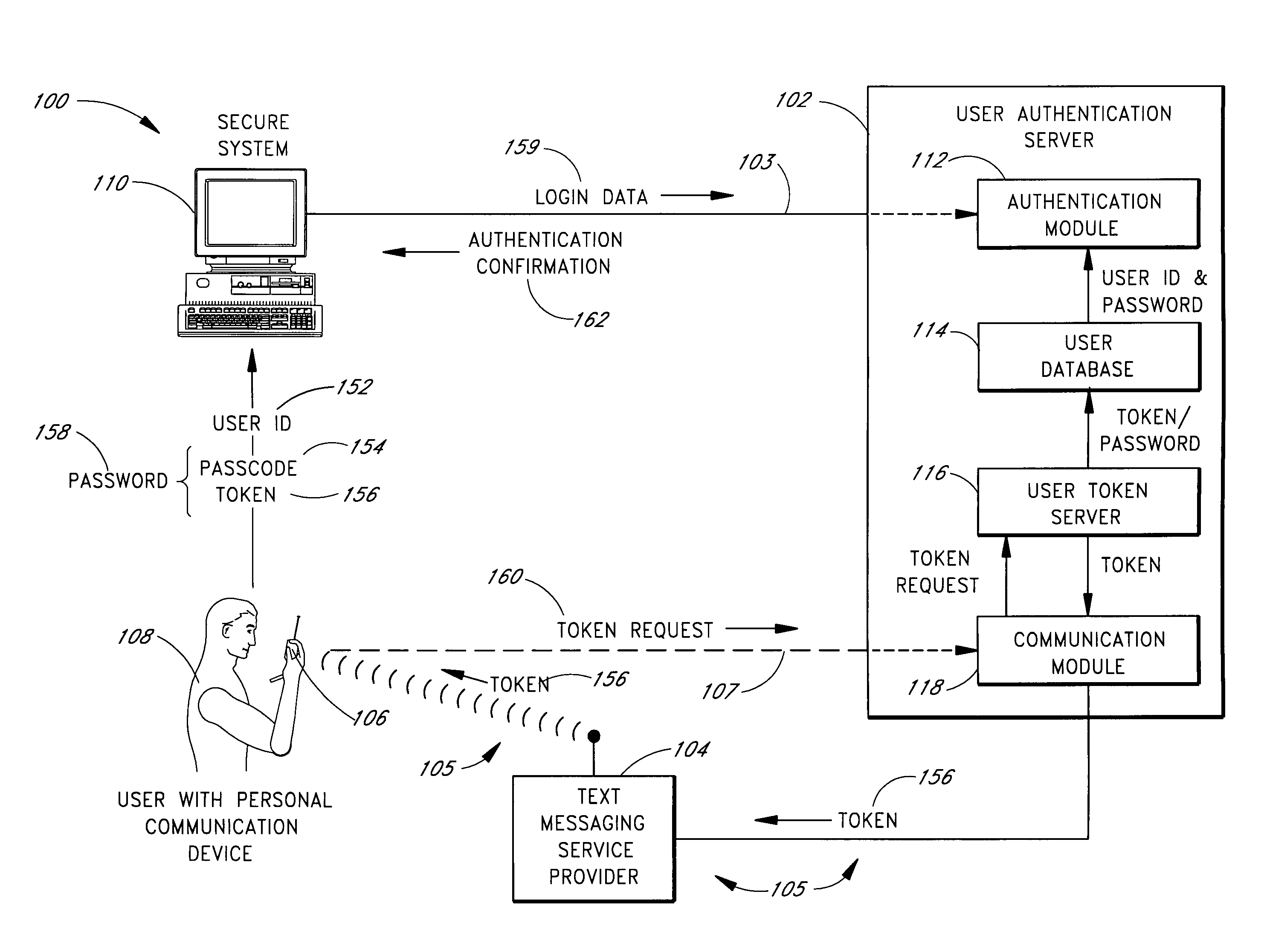
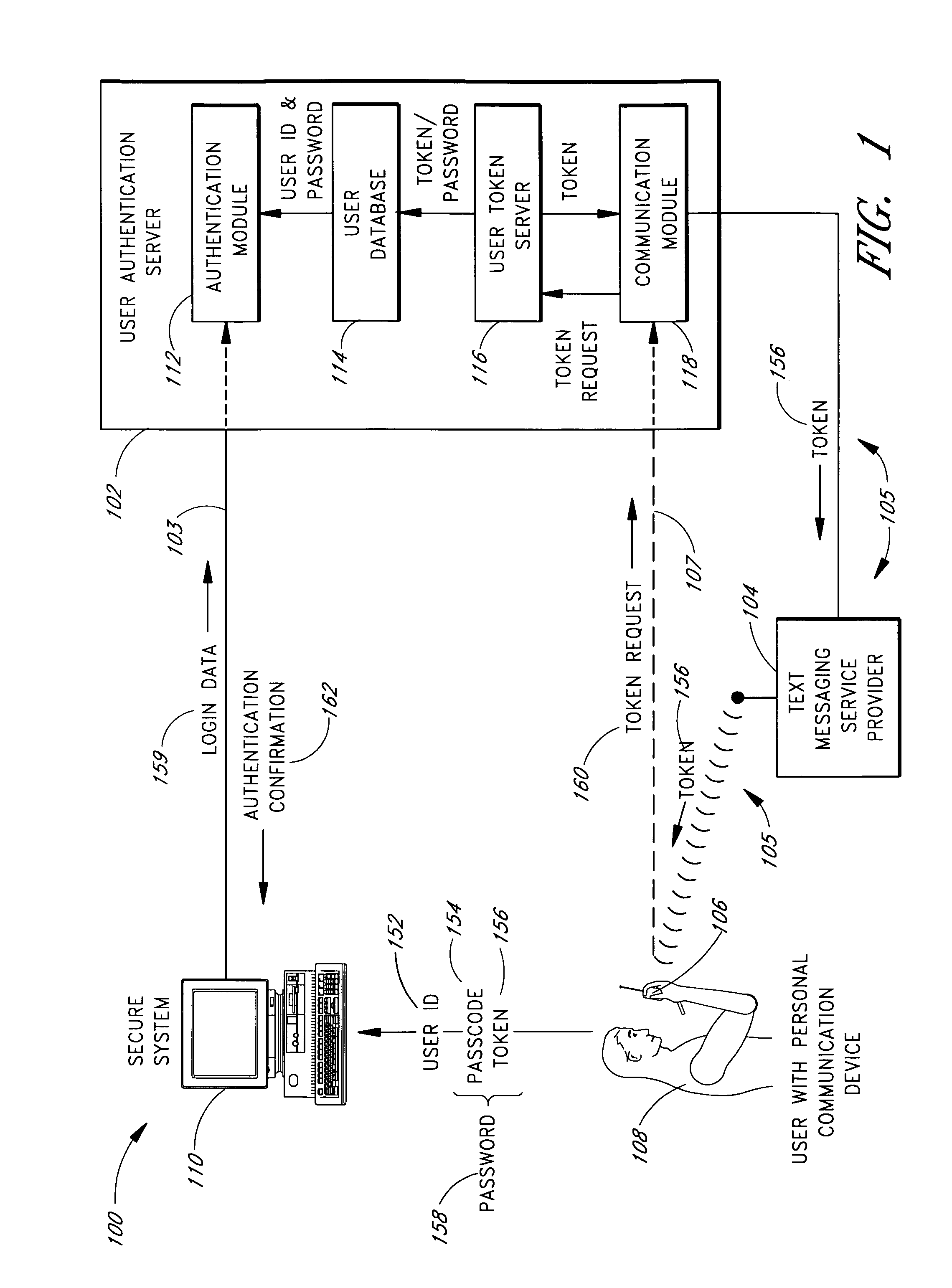
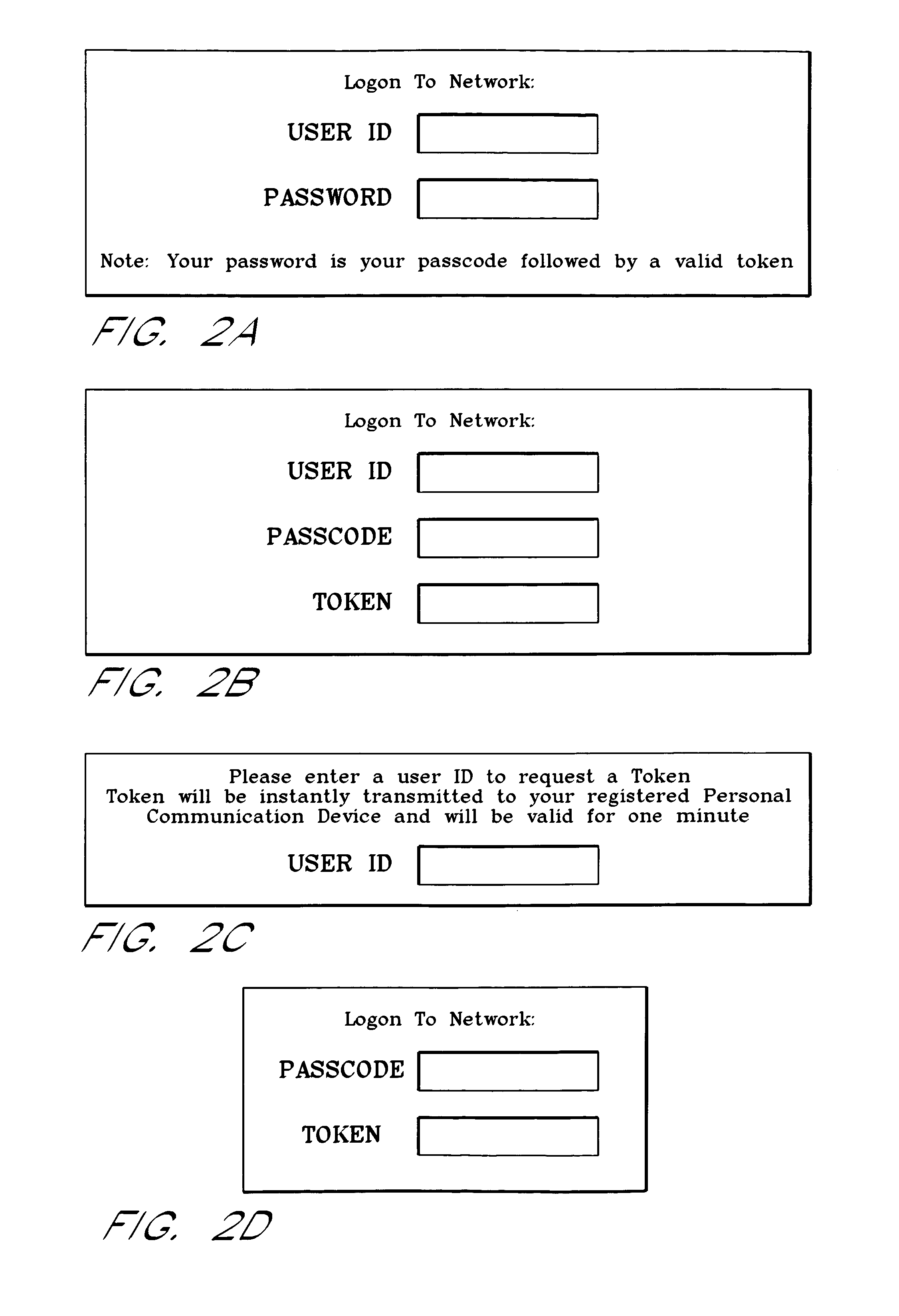
A password setting system for a secure system includes a user token server and a communication module. The user token server generates a random token in response to a request for a new password from a user. The server creates a new password by concatenating a secret passcode that is known to the user with the token. The server sets the password associated with the user's user ID to be the new password. The communication module transmits the token to a personal communication device, such as a mobile phone or a pager carried by the user. The user concatenates the secret passcode with the received token in order to form a valid password, which the user submits to gain access to the secure system. Accordingly, access to the system is based upon: nonsecret information known to the user, such as the user ID; secret information known to the user, such as the passcode; and information provided to the user through an object possessed by the user, such as the token.
Owner:DYNAPASS IP HLDG LLC
Multi-factor authentication system
InactiveUS7373515B2User identity/authority verificationUnauthorized memory use protectionPasswordUser identifier
Owner:KARETEK HLDG LLC
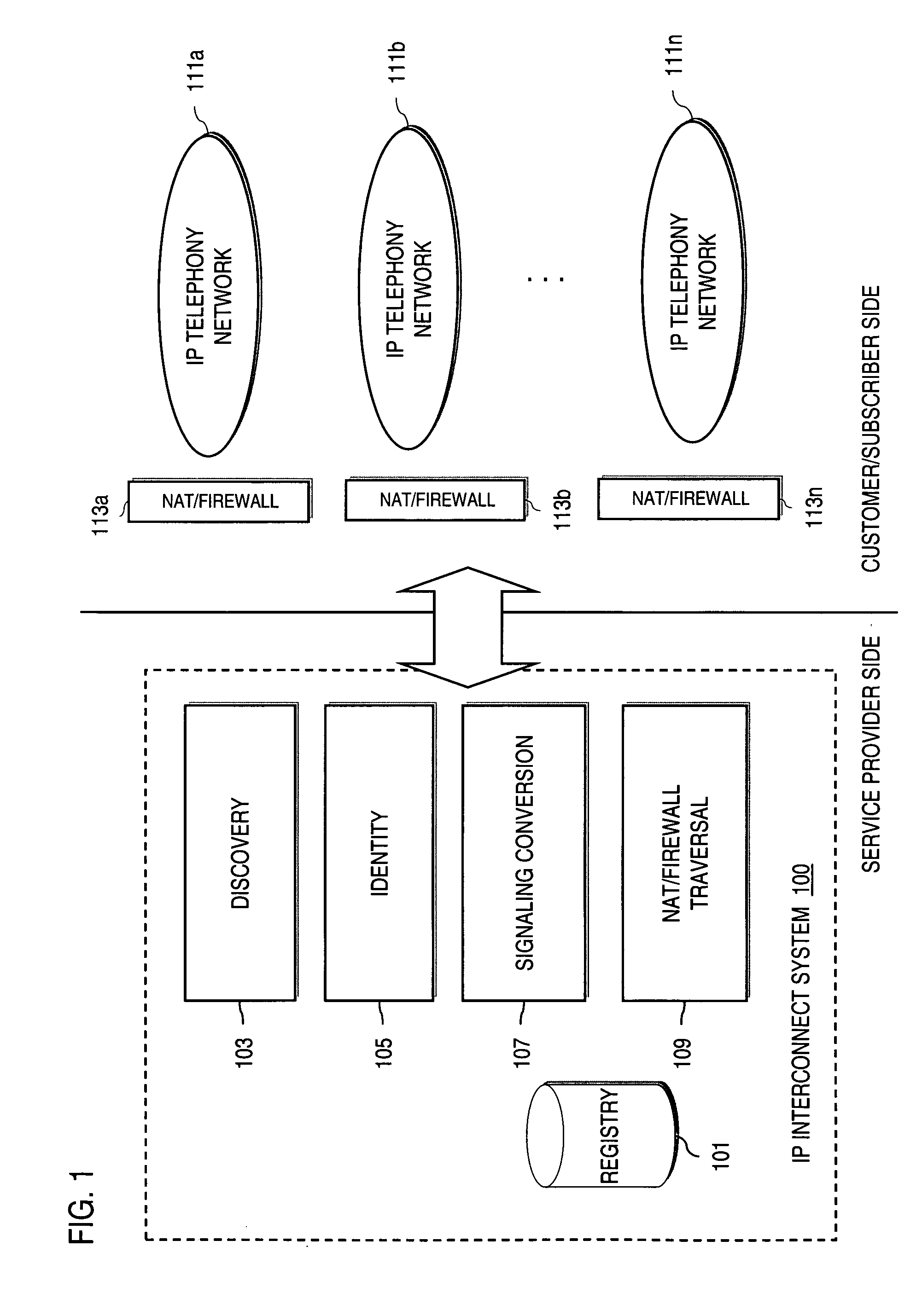
Method and system for providing voice over IP managed services utilizing a centralized data store
ActiveUS20070036143A1Interconnection arrangementsData switching by path configurationVoice over IPData memory
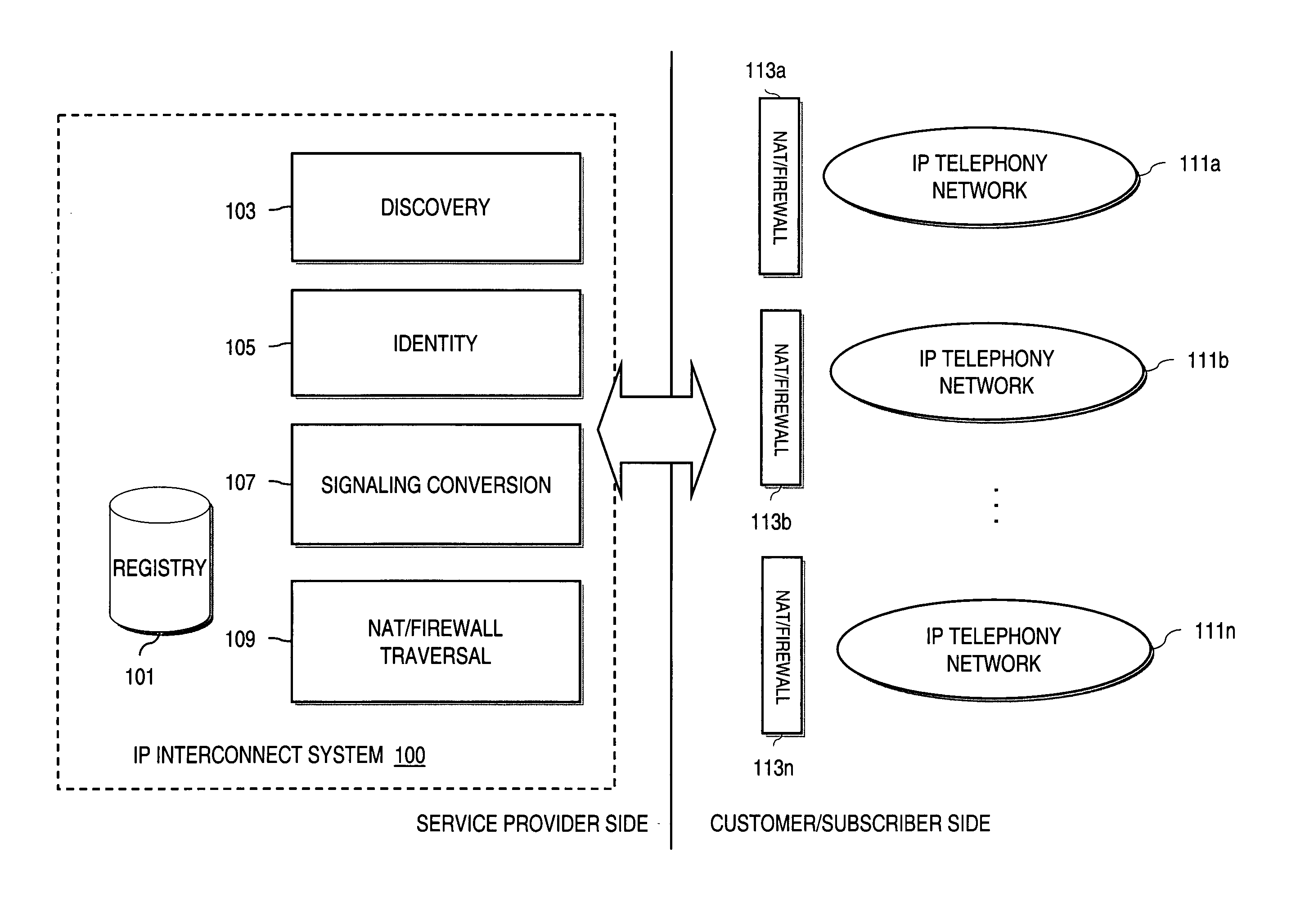
An approach provides interdomain traversal to support packetized voice transmissions. A centralized data store, maintained by a service provider, stores one or more user identifiers and an associated directory number. The centralized data store also stores routing information including one or more communication paths corresponding to the user identifier, wherein the routing information includes a data path or a circuit-switched path for establishing a call to the user. In response to a request for establishing the call to the directory number, the data store retrieves the routing information for use to establish the call.
Owner:VERIZON PATENT & LICENSING INC
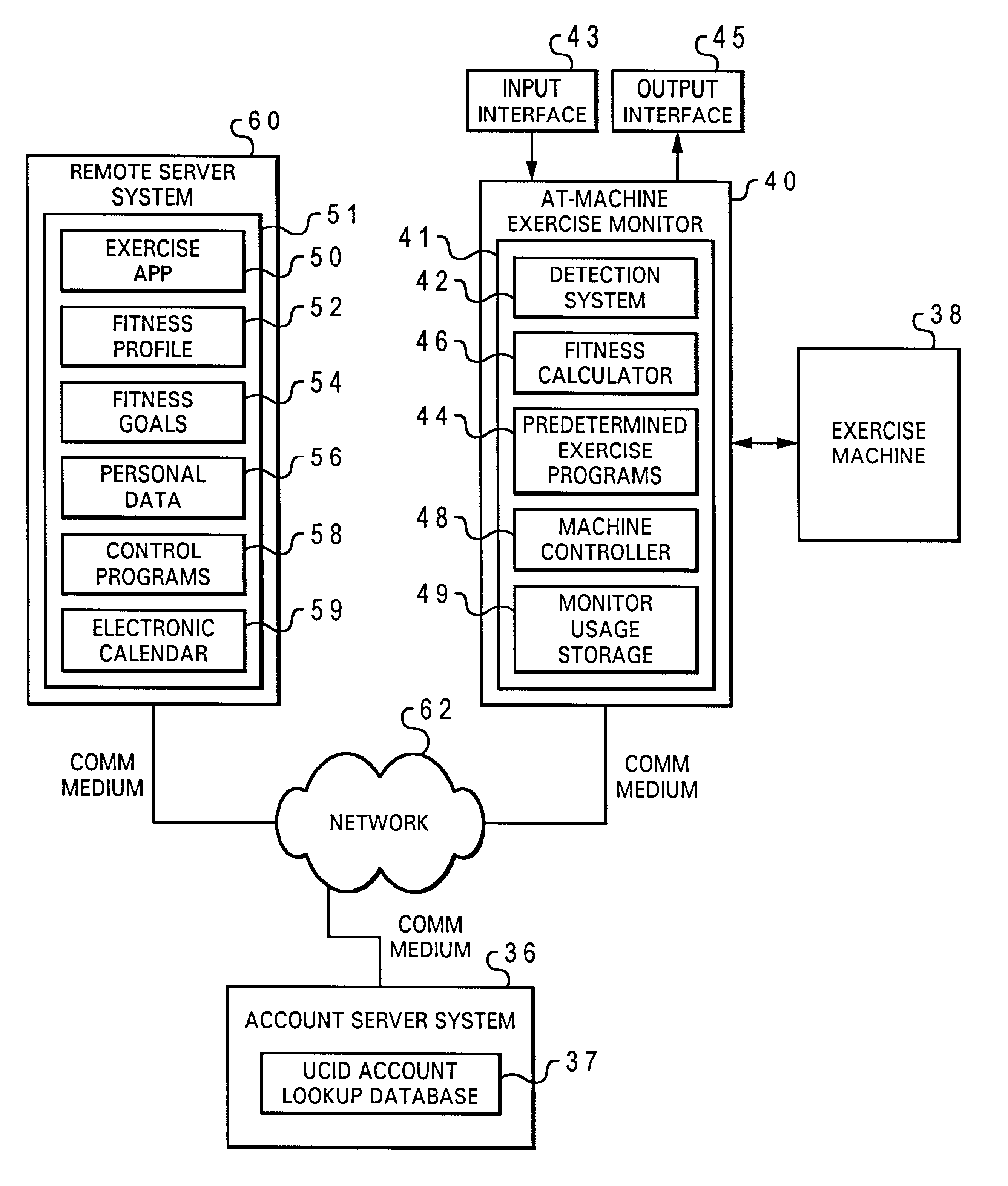
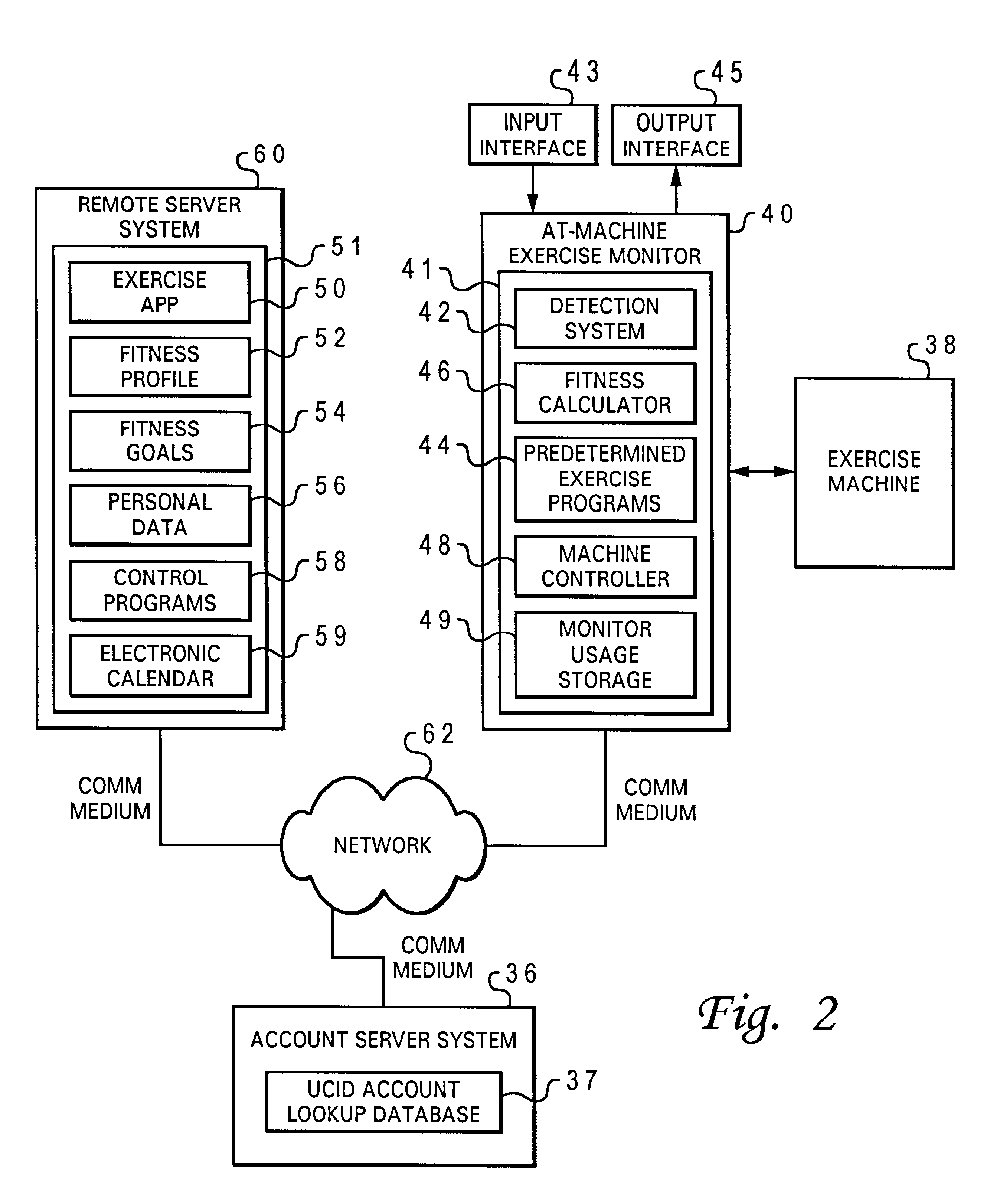
Monitoring fitness activity across diverse exercise machines utilizing a universally accessible server system
InactiveUS6601016B1Physical therapies and activitiesGymnastic exercisingUser identifierExercise machine
According to the present invention, current fitness indicators for a particular user are detected by a particular exercise machine monitoring device that monitors exercise performed by the particular user on a particular exercise machine. The current fitness indicators are transmitted in a particular transmittable data format to a universally accessible server system in accordance with a universal identifier associated with the particular user and stored at said universally accessible server system in accordance with the universal identifier as current fitness activity, such that real-time fitness activity for a user computed from fitness activity received from any of multiple diverse exercise machines over a period of time is monitored by a universally accessible server system according to a universal identifier for a particular user.
Owner:ICON HEALTH & FITNESS INC
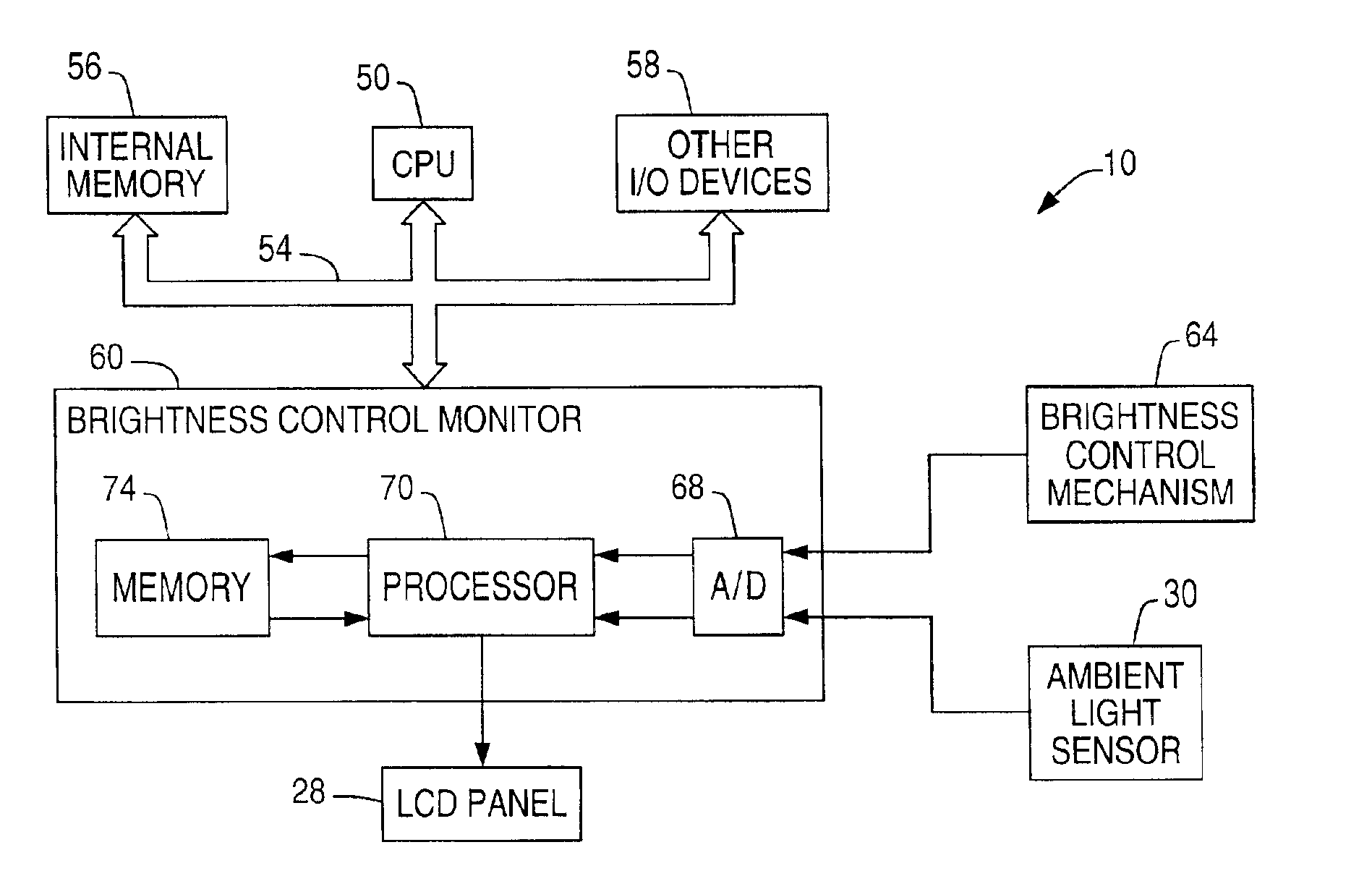
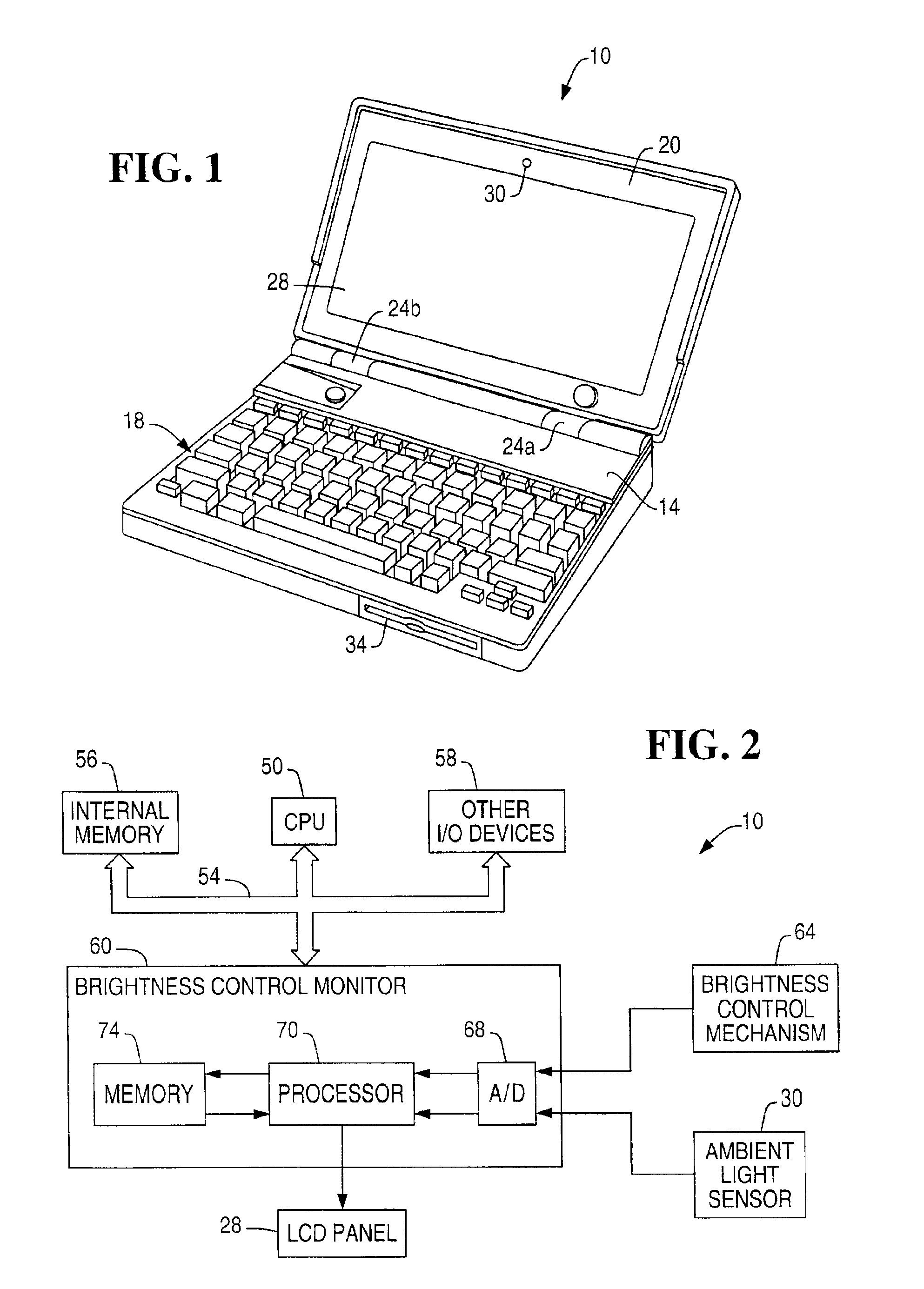
System and method for adjusting display brightness levels according to user preferences
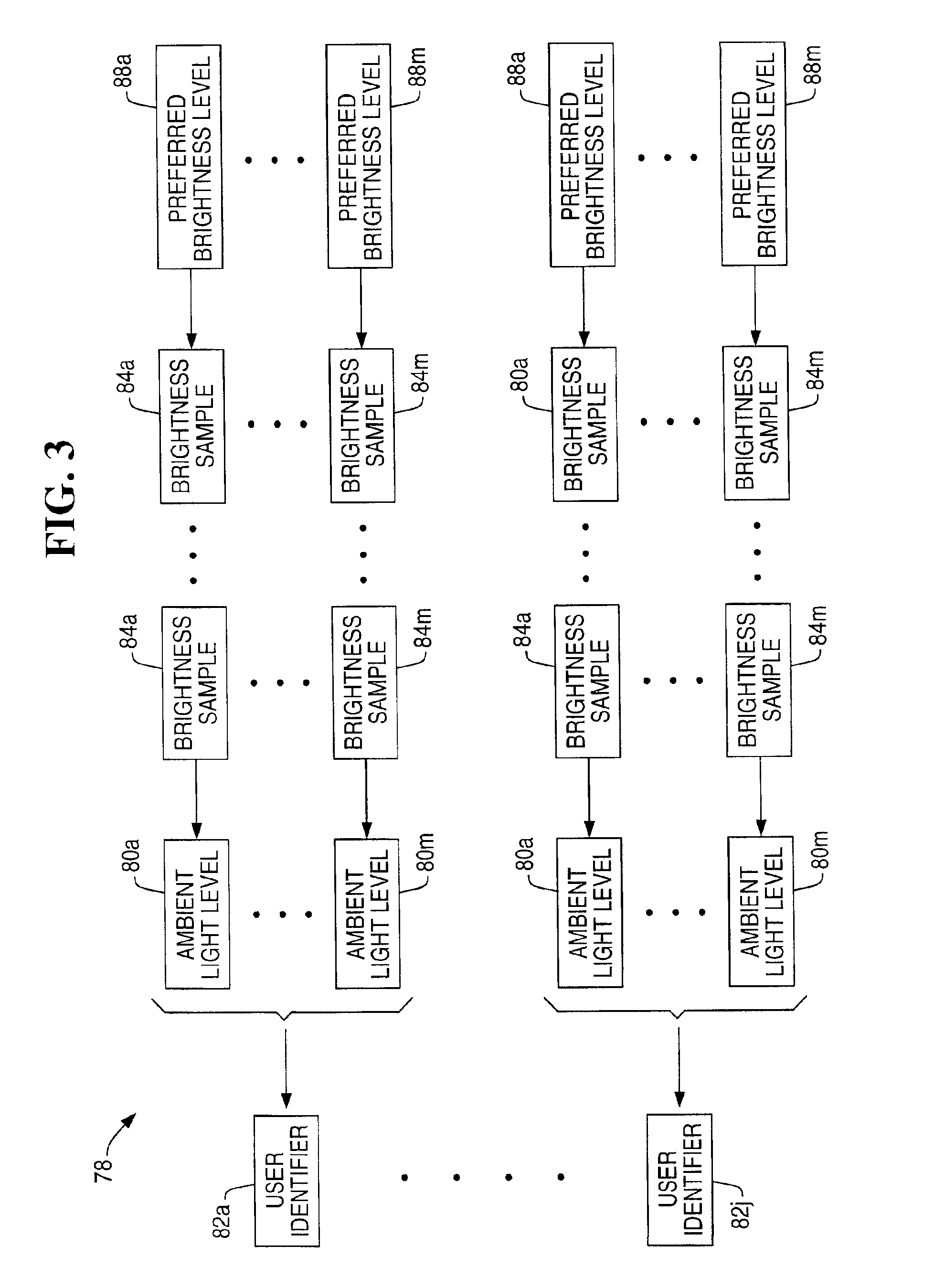
InactiveUS6870529B1Television system detailsColor television detailsComputer graphics (images)Monitoring system
A display brightness monitoring system associates a brightness level and an ambient light level with a user identifier. Ambient light signals are received from an ambient light sensor mounted in proximity of an electronic display. Brightness levels are received from a brightness control mechanism for user selection of a display brightness. The monitoring system collects brightness levels and associates them with one of the ambient light levels associated with a user identifier. Preferably, a plurality of brightness levels are collected for each ambient light level and are used to compute a preferred brightness level indicative of a user's preferred display brightness for a given ambient light level. The brightness levels may be statistically averaged for computation of the brightness level. A data structure for associating brightness levels with ambient light levels and associating ambient light levels with a user identifier may be used to segregate one user's brightness levels from those of another. In this manner, the display may be driven using the preferred brightness levels for the user authorized to use a computer without altering the brightness levels stored for other users.
Owner:NCR CORP
Wireless gaming network
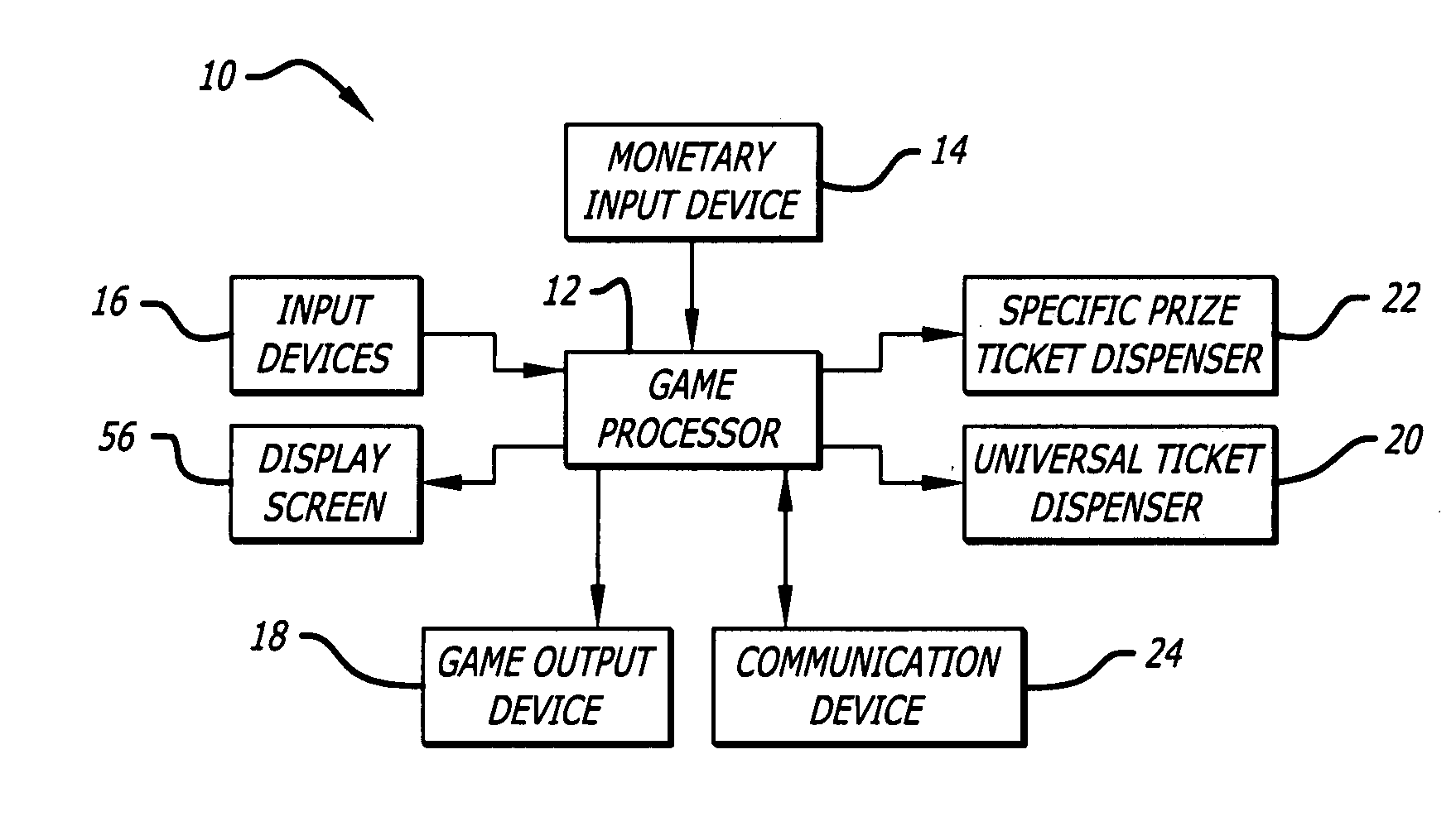
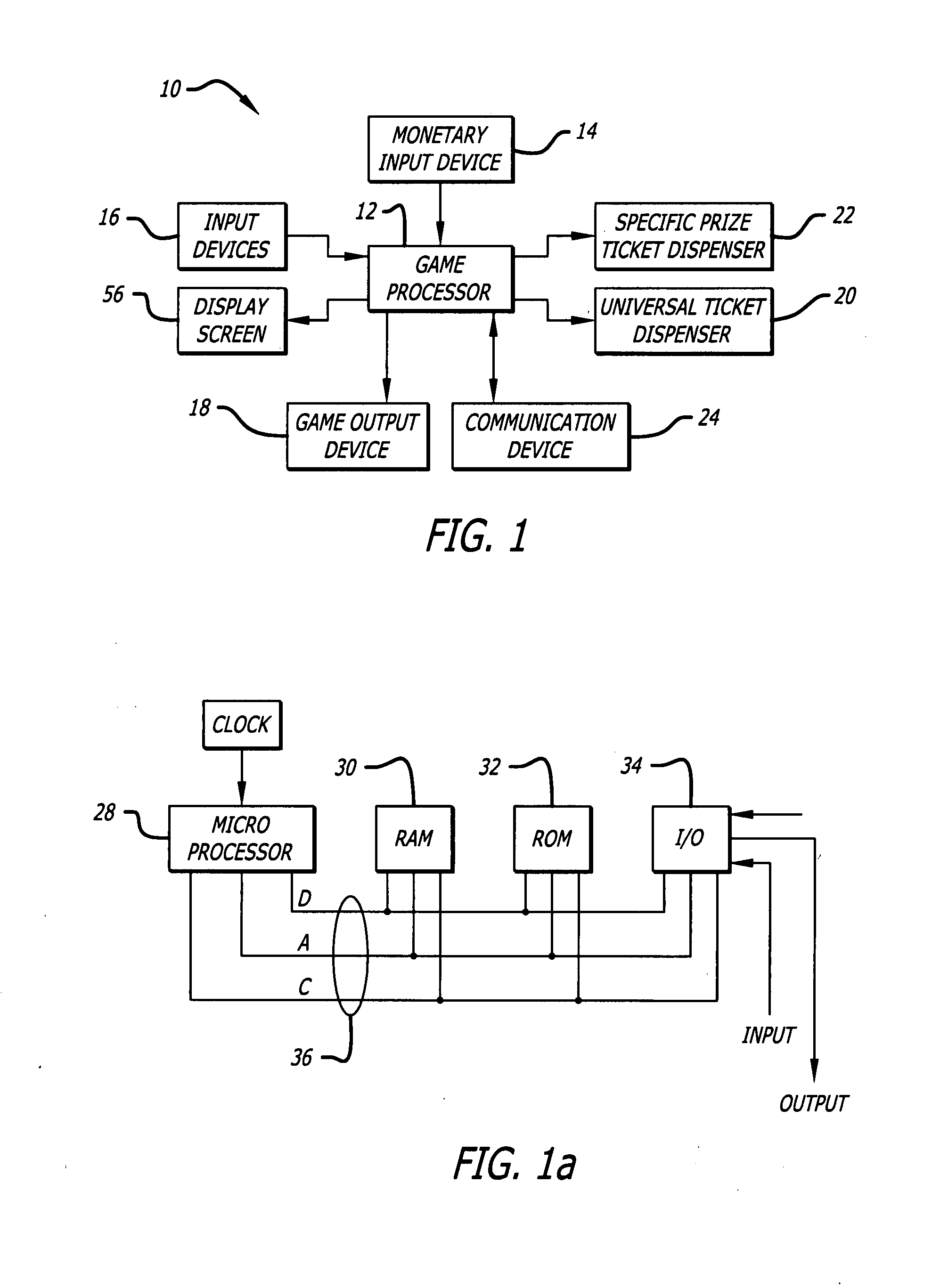
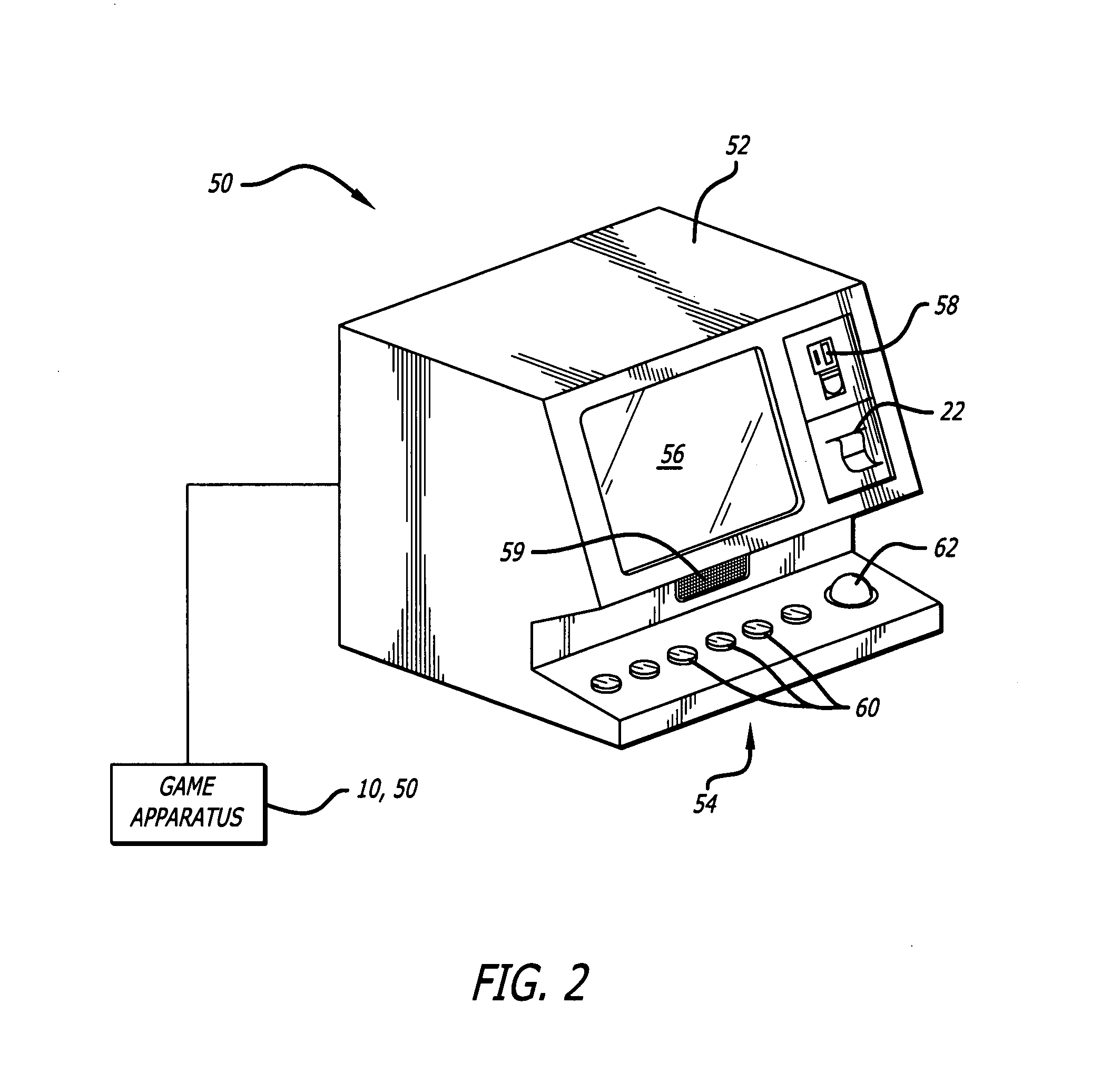
InactiveUS20080176619A1Facilitating playerBoard gamesApparatus for meter-controlled dispensingWeb siteWireless mesh network
The invention provides a prize redemption system for use with one or more game apparatuses. A game is provided on a game apparatus for a player to play in exchange for monetary input, and prize credits are credited to the player based on the game outcome. A prize selection menu is then displayed by the game apparatus, the menu including one or more prizes, where the player may select a prize that has a prize cost within the player's prize credit amount. The player is dispensed a specific prize ticket that is redeemable for the selected prize. The game apparatus can also provide specific prizes and tournament games played for a tournament prize contributed to by multiple players. An operator can adjust prizes and payout percentages of the system to achieve a desired profitability for game apparatuses. Prize input is entered into a prize table describing multiple available prizes and also describing payout information that indicates a desired amount of payout that the operator wishes to provide back to players of the game apparatus in terms of the value of the prizes. Prize information, such as prize costs and specific prize win ratios, is automatically determined by the system for each of the prizes in view of the desired profitability of the game apparatus.Additionally, the invention provides method and article of manufacture for implementing a user profile-driven gaming and prize redeeming system. The user profile-driven gaming and prize redemption system allows for the tailoring of a user's experience of playing a computer implemented game on a network gaming system by first receiving an identifier selected from a group of identifiers including a user identifier relating to the user (i.e., player) of the network gaming system, a game identifier relating to a particular game played by the user of the network gaming system, and a site identifier relating to the location (i.e. web site) from which the game is being played. The network gaming system then alters the computer-implemented game played by the user in a manner based upon the selected identifier. The foregoing technique may also be applied to a prize redemption system.
Owner:BALLY GAMING INC
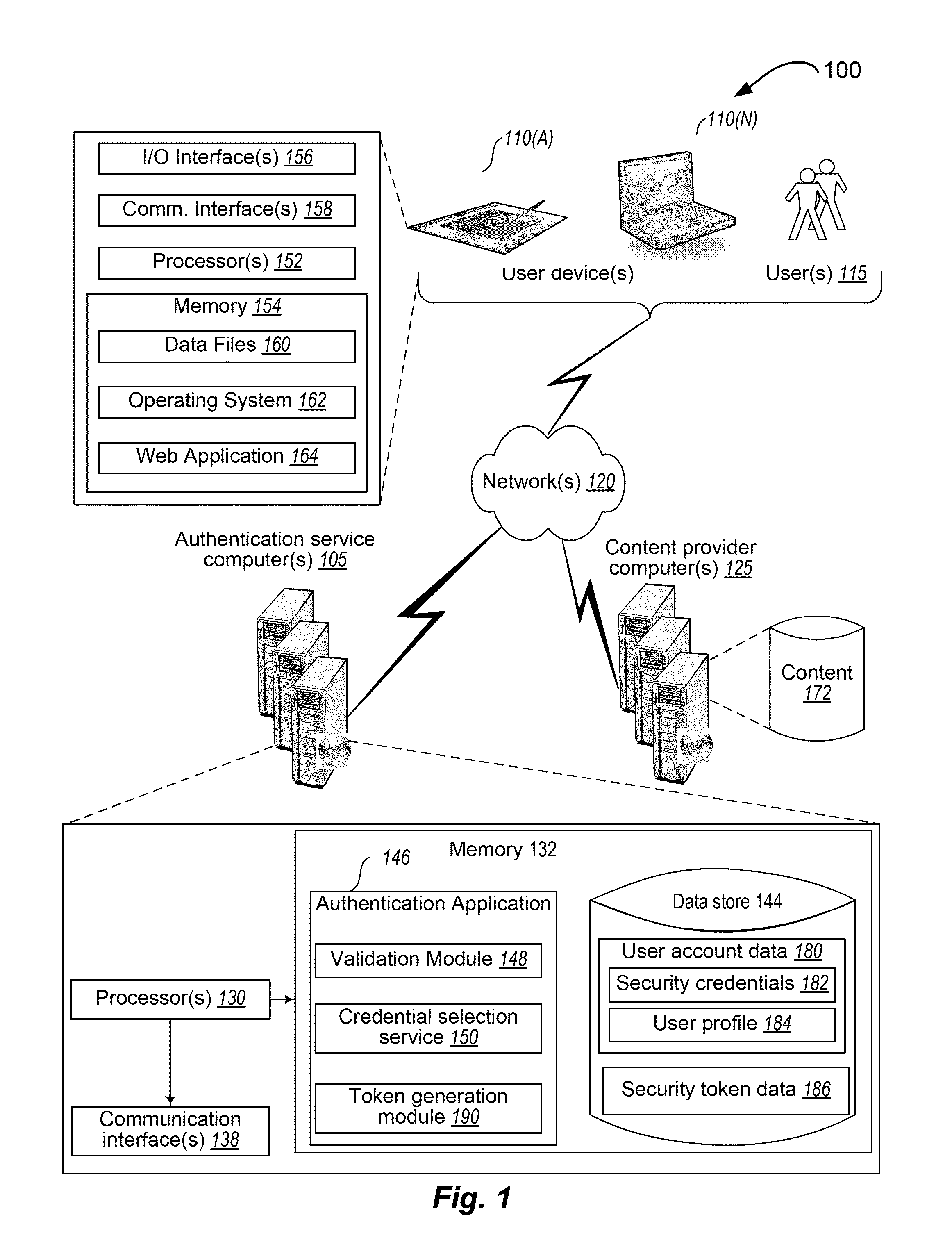
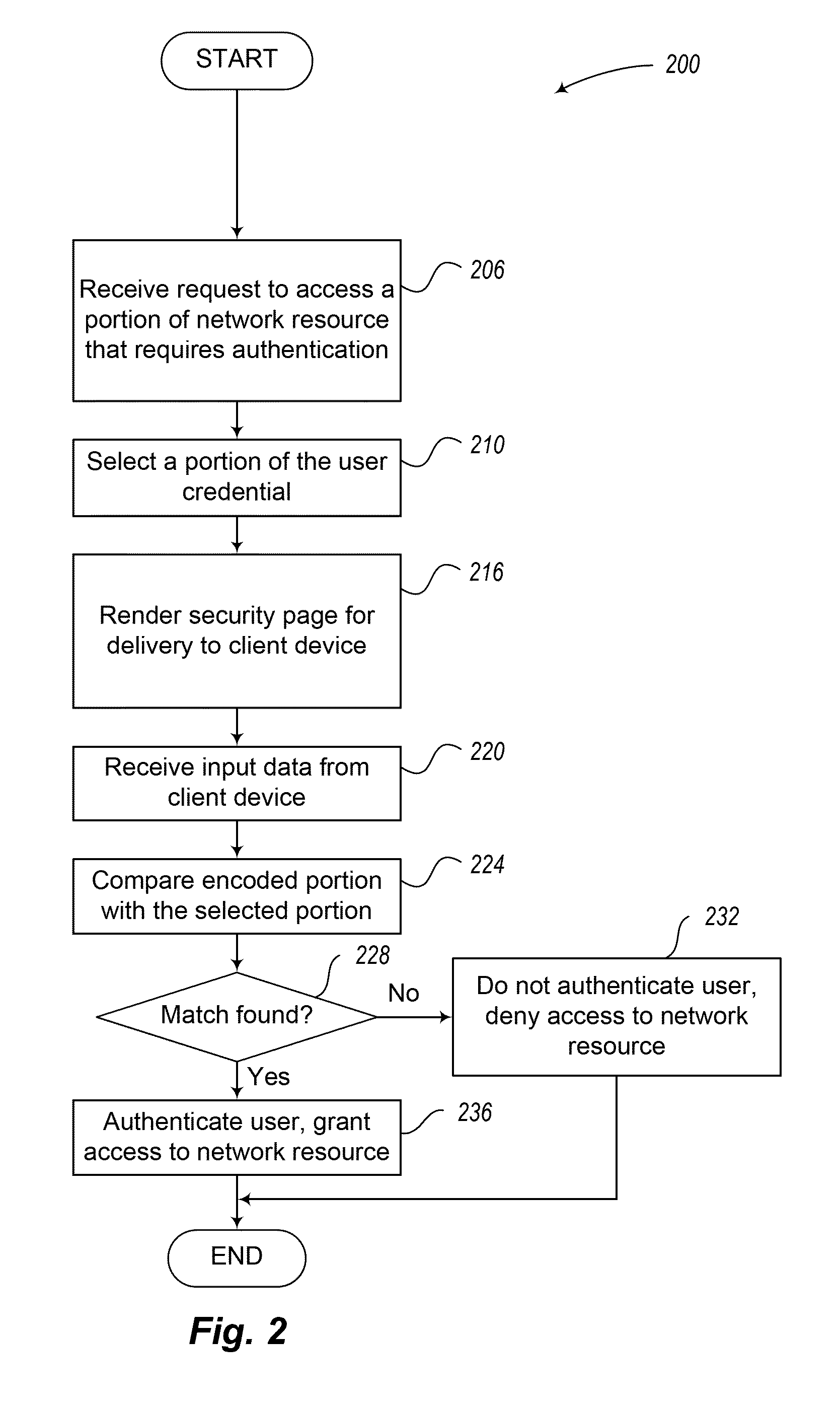
Techniques for user authentication
InactiveUS8613066B1Digital data processing detailsUser identity/authority verificationUser authenticationClient-side
Techniques for user authentication are disclosed. In some situations, the techniques include receiving, from a client device, an authentication request to access a network resource, the request including a user identifier, obtaining a security credential associated with the user identifier contained in the received request, generating an authorization code based on the obtained security credential, providing to the client device instructions to obtain first information corresponding to the generated authorization code, receiving, from the client device, the first information provided in response to the provided instructions, and, when the first information received from the client device corresponds to at least a portion of the generated authorization code, authorizing the client device to access the network resource.
Owner:AMAZON TECH INC
Method for customizing payment card transactions at the time of the transactions
InactiveUS20050086177A1Anonymous user systemsRecord carriers used with machinesThird partyTransaction data
A user can customize use of a payment card, which can be an electronic card, by selecting a customization variable for any given transaction. The customization variable involves at least one of the following steps: (1) customizing generation of a one-time card number; (2) customizing a user identifier; or (3) inclusion of a customization variable with information transmitted to a verification agency for validation of the given use. Multiple payment card transactions can be processed differently depending upon which customization variable is chosen for a given transaction. Different customization variables can be used for different accounts, different types of transactions, or to classify the transactions. A user can receive one bill, or multiple bills. Different levels of privacy can be accorded to transactions that use different customization variables. A user may pay the issuer for increased security, or the user may be paid by the issuer to allow transaction data to be distributed to third parties.
Owner:ANDERSON ROY L +2
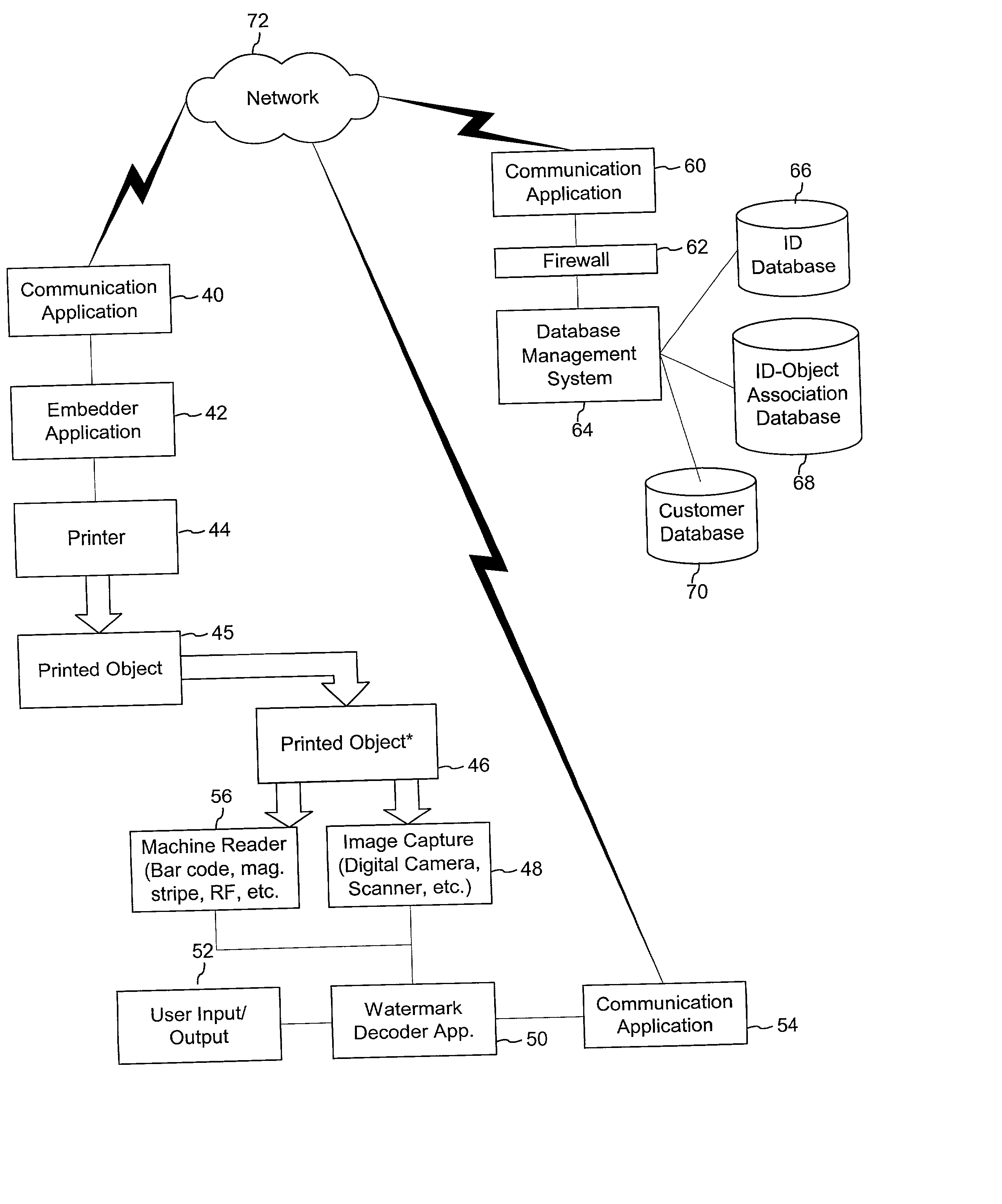
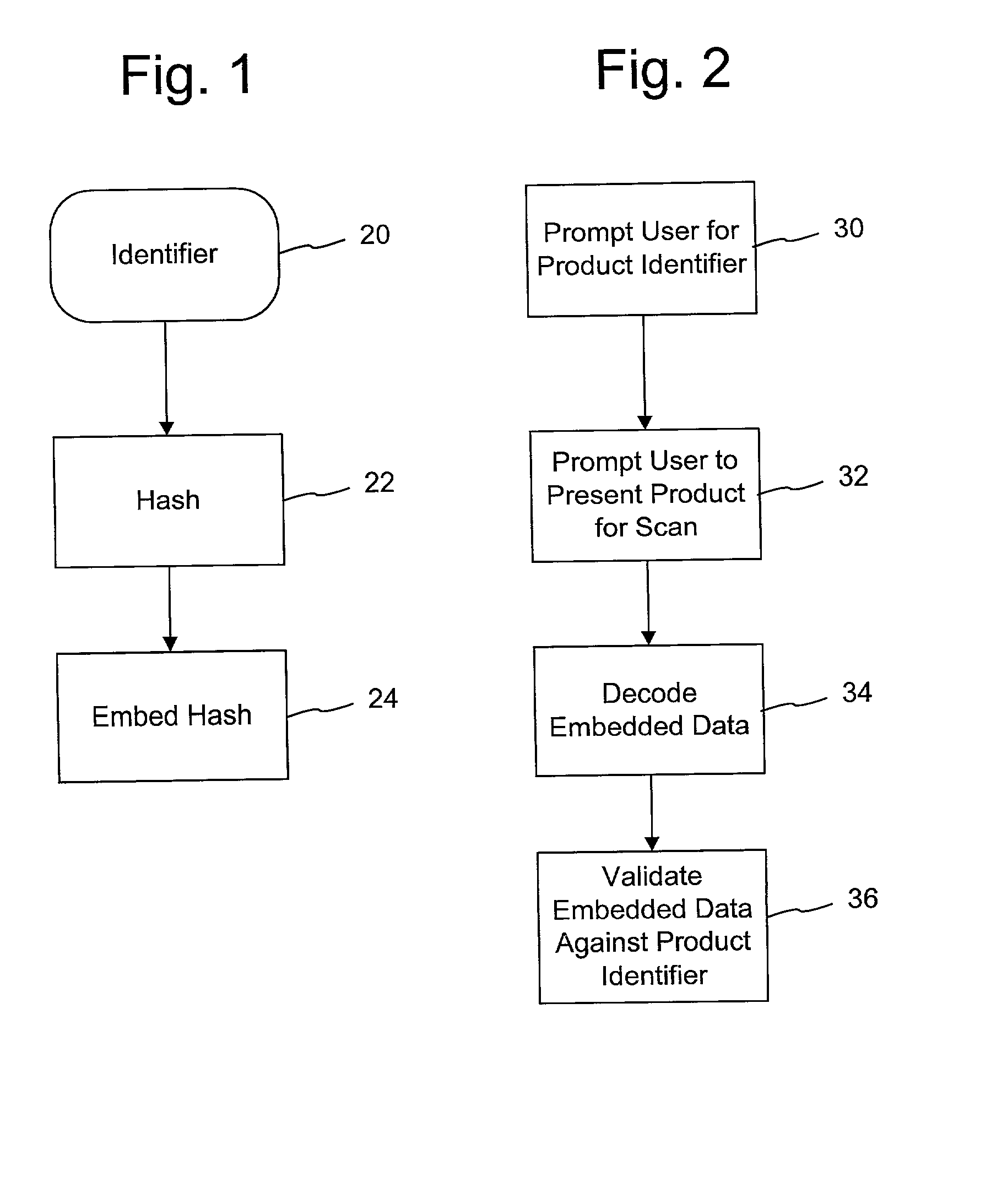
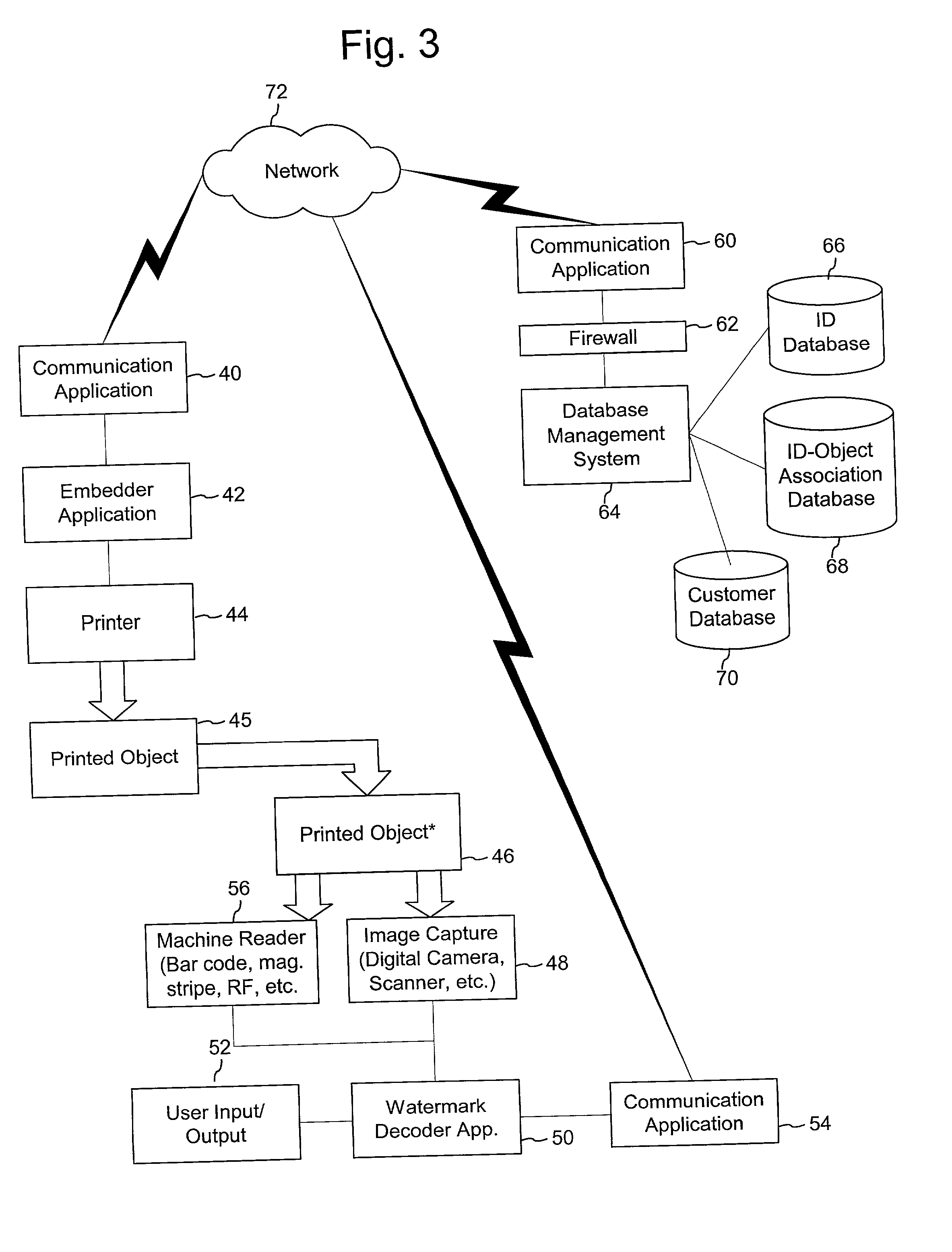
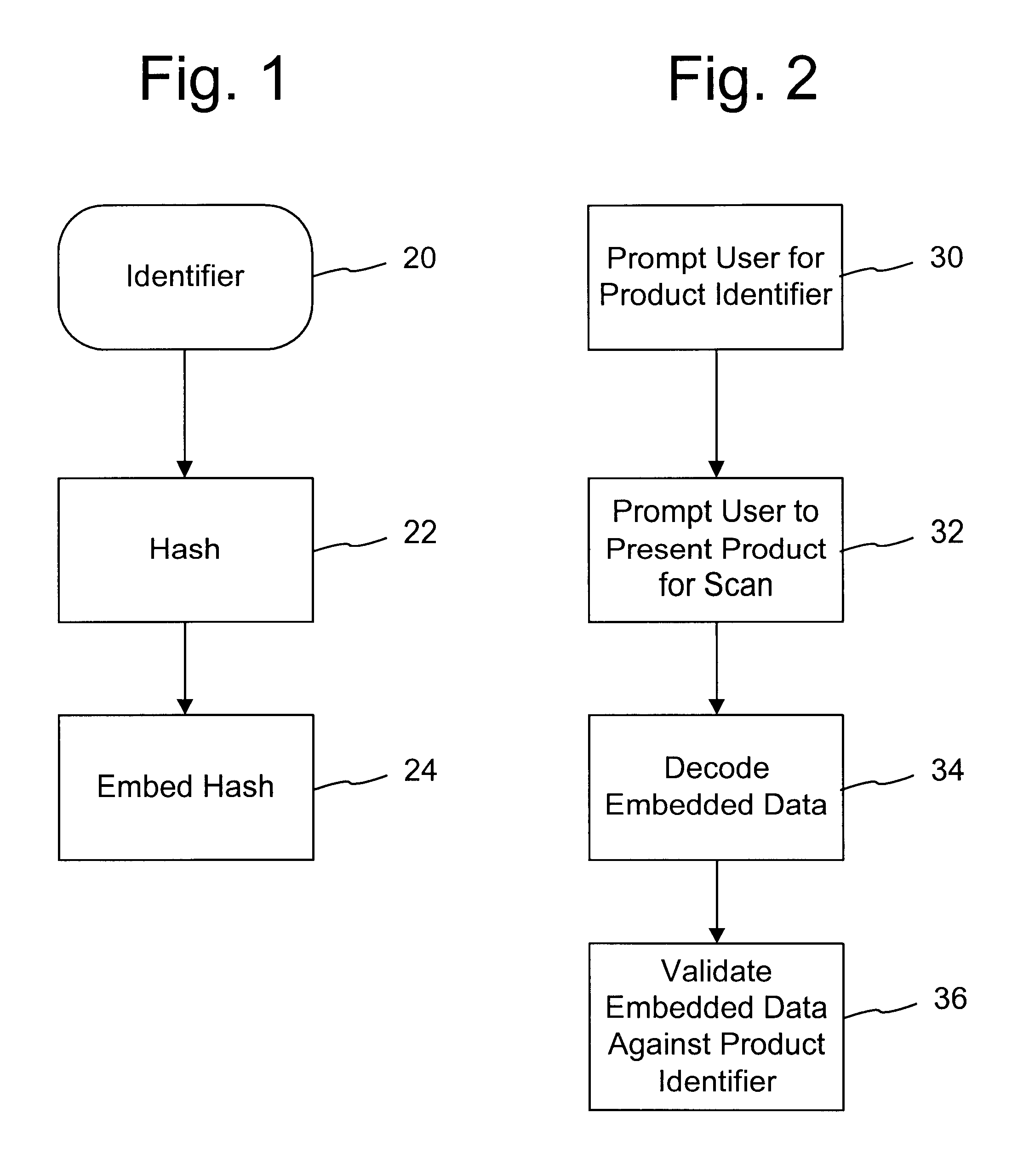
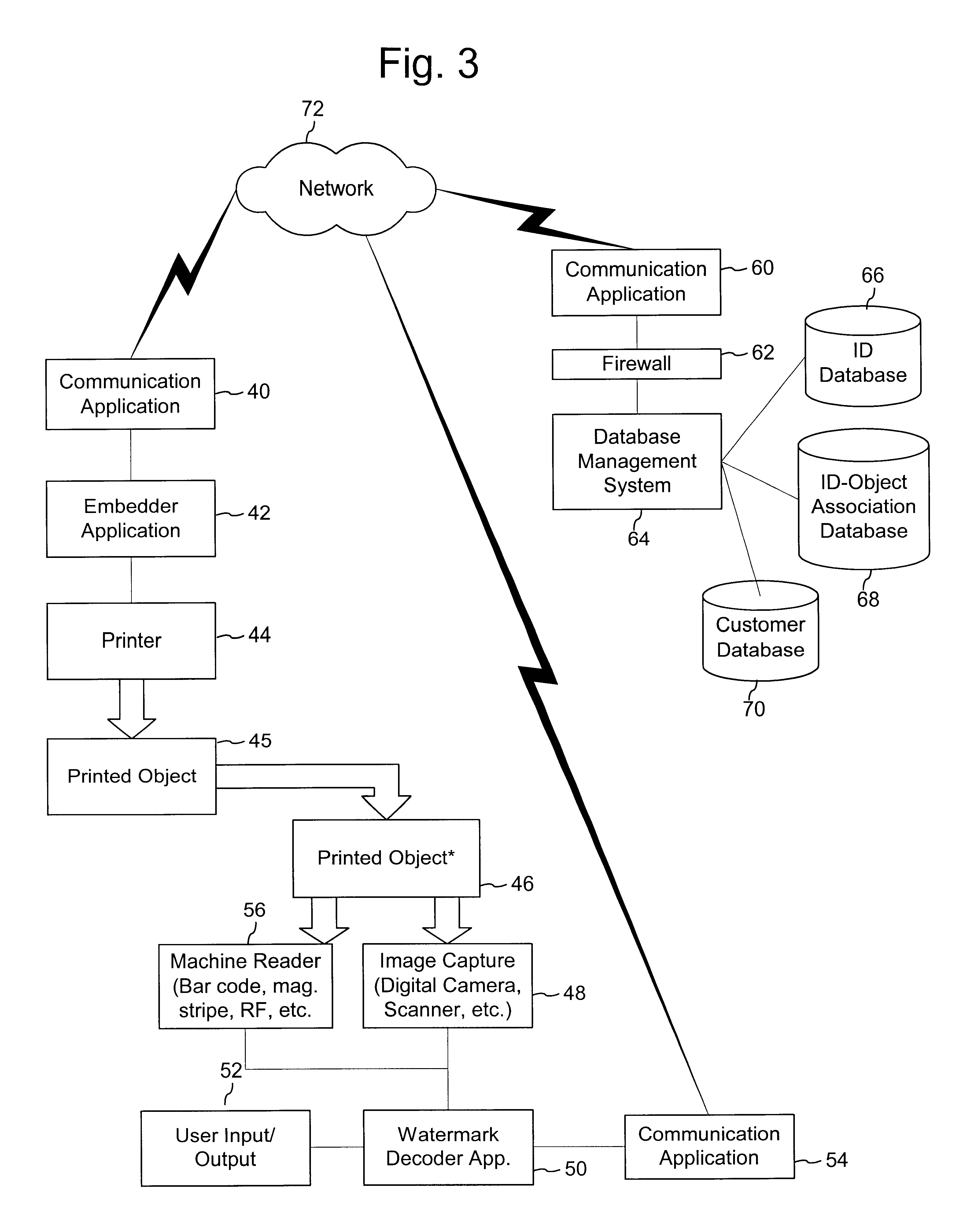
Authentication watermarks for printed objects and related applications
InactiveUS20020012445A1Correct Geometric DistortionMore dataOther printing matterPaper-money testing devicesRelevant informationCopy detection
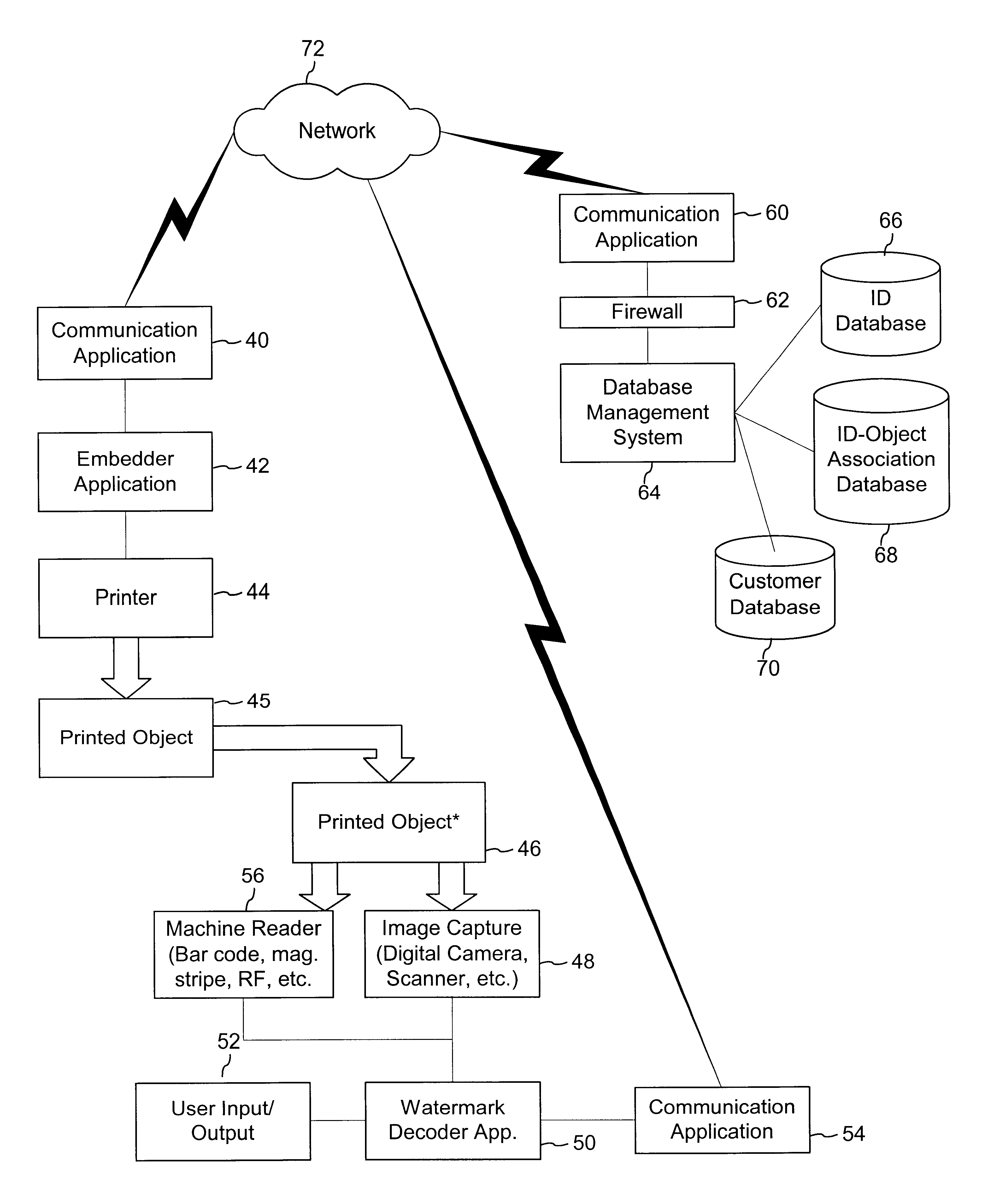
The disclosure describes systems for creating and authenticating printed objects using authentication and copy detection watermarks. For example, one verification system includes a watermark decoder and a verification module. The watermark decoder detects a copy detection watermark in a printed object to determine whether the printed object has been reproduced. The verification module processes a message decoded from an authentication watermark on the printed object to authenticate the printed object or bearer of the printed object. The authentication and copy detection watermarks may be implemented as the same or different watermarks. For example, the copy detection watermark may be a fragile watermark that carries the message and that degrades in response to a reproduction operation, such as photocopying or scanning and then reprinting the object. Alternatively, the authentication and copy detection watermarks may be separate watermarks embedded in an image that is printed on the object. The authentication watermark, in some applications, includes an identifier that links the object to a database entry with related information about the object. This related information can be used to check the bearer of the object by comparing it with attributes of the bearer (such as a user ID or photo) or the validity of the object by comparing it with attributes that are visible or machine readable on the object.
Owner:INTUIT INC
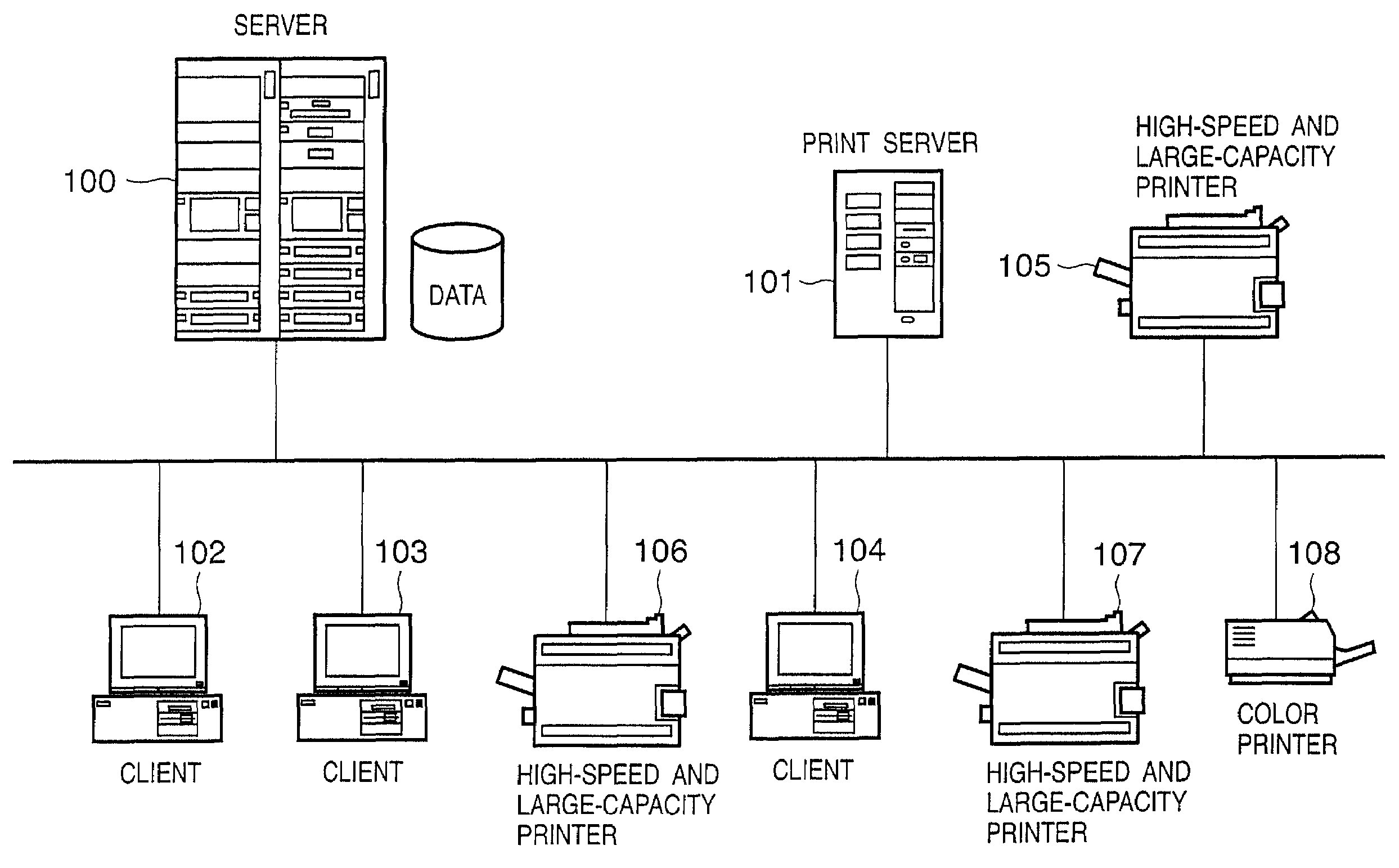
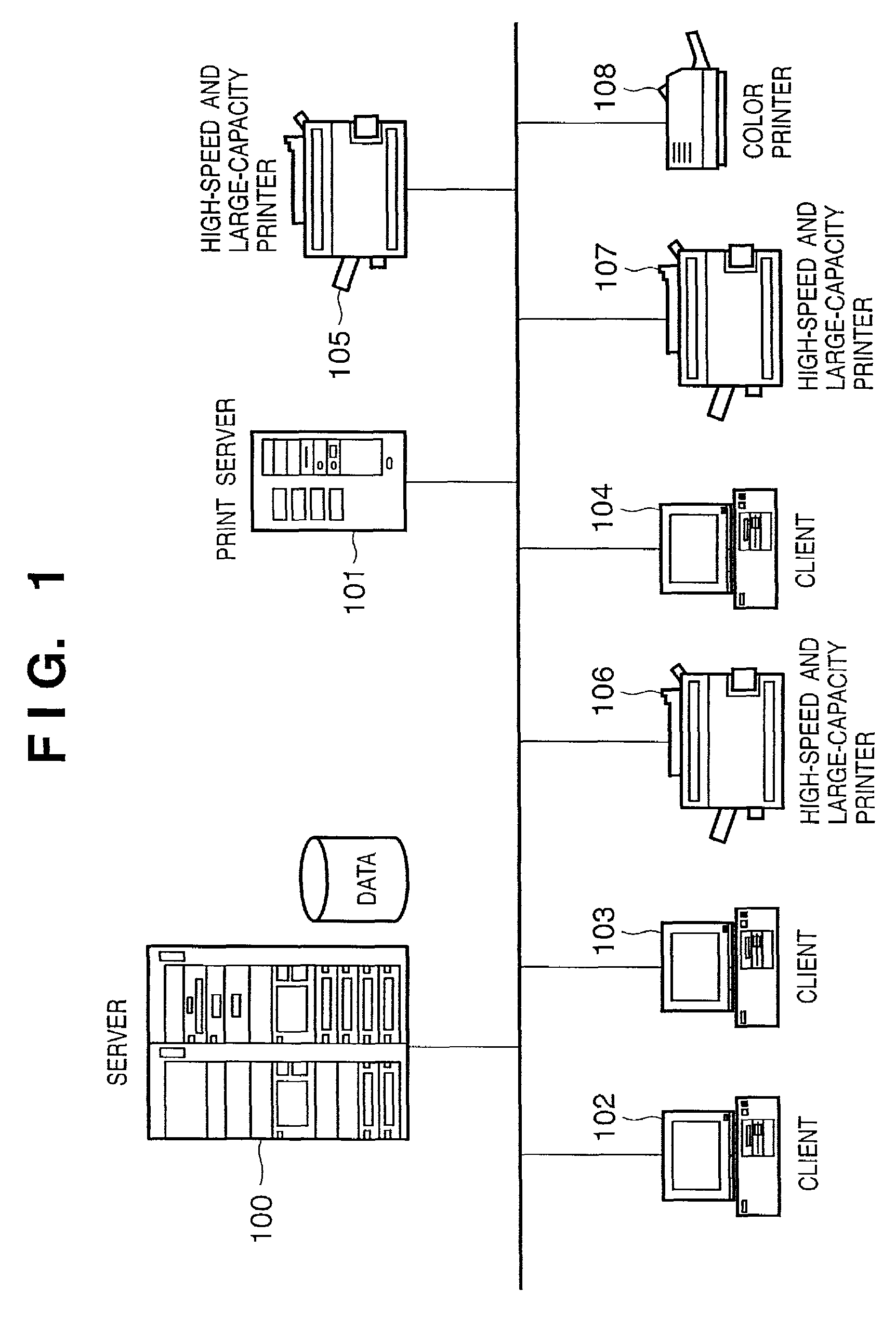
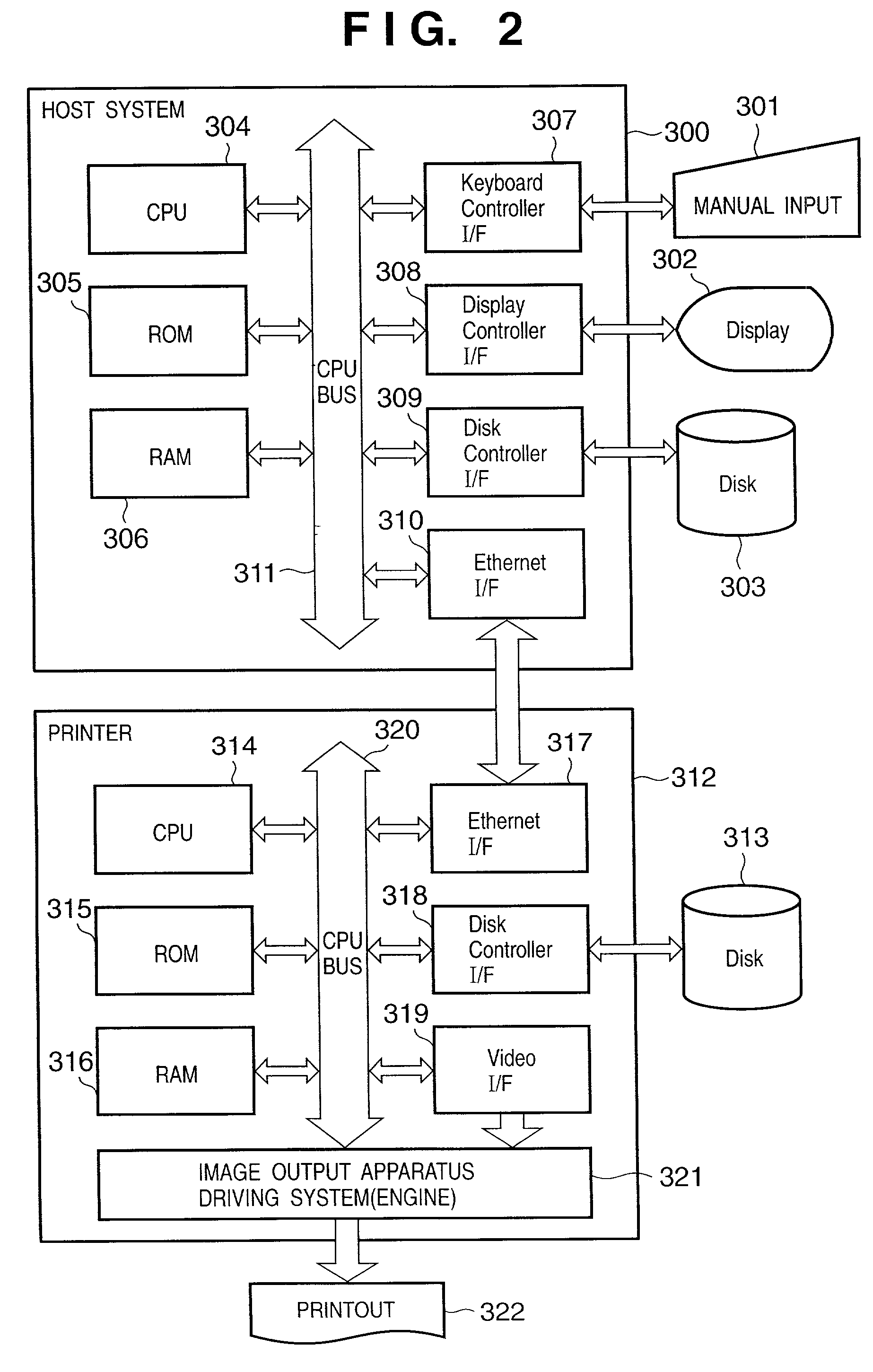
Automatic authentication method and system in print process
ActiveUS7313699B2Improve securityEliminate needDigital data processing detailsUser identity/authority verificationUser authenticationUser identifier
This invention provides an automatic authentication method and system in a print process, which can obviate the need for user's input operations of the user ID and password and can improve security since authentication is automatically done based on print information embedded in a file or information from an application program without any user's input.In a print process that requires user authentication, a printer driver extracts information related to an application and / or a document for the print process as attribute information, and user authentication is made by comparing the attribute information with information stored in a user registration information database of a server. If user authentication has succeeded, the printer driver controls a printer to print, and the server manages and stores accounting information and the like for respective departments in a department management information database.
Owner:CANON KK
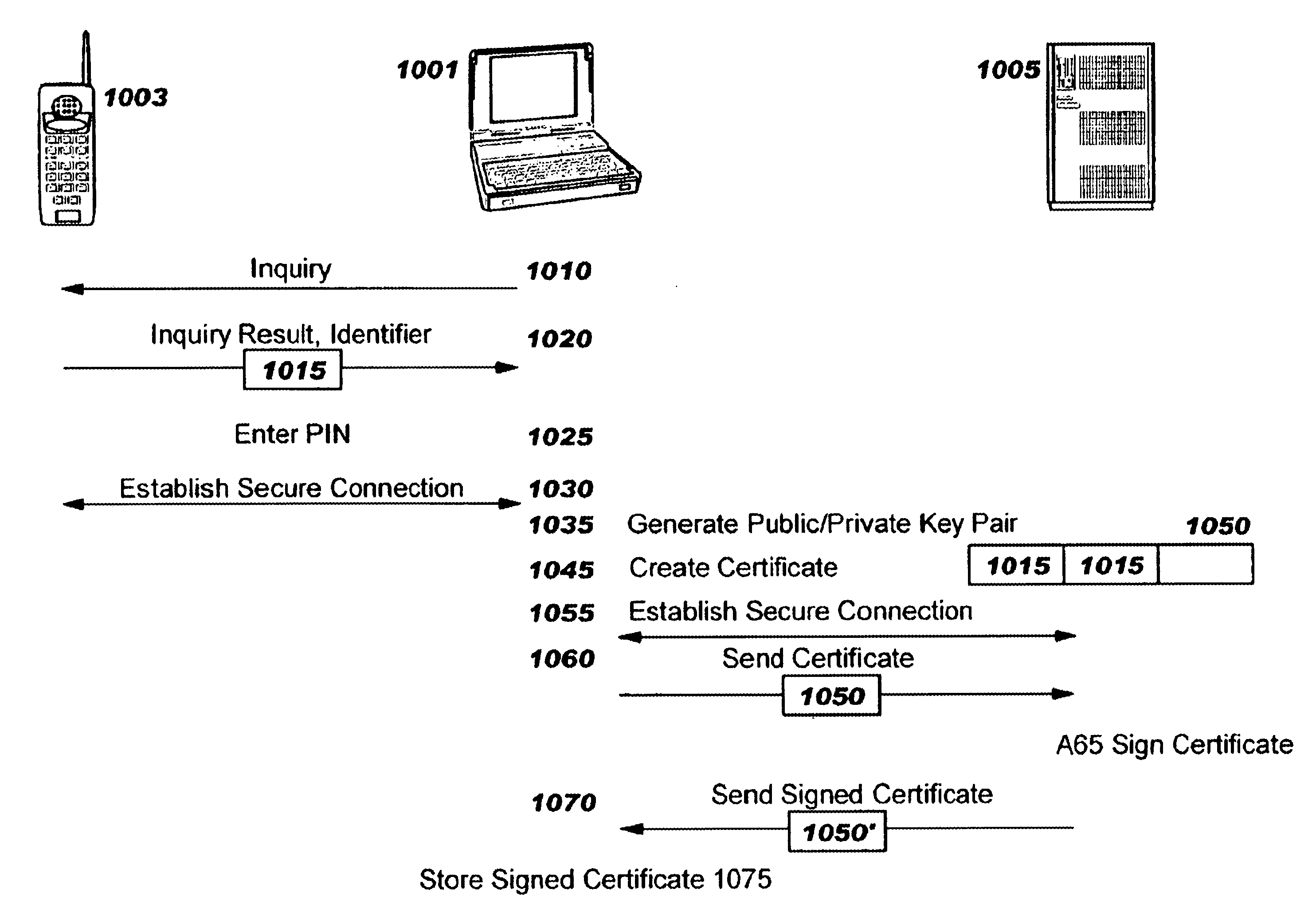
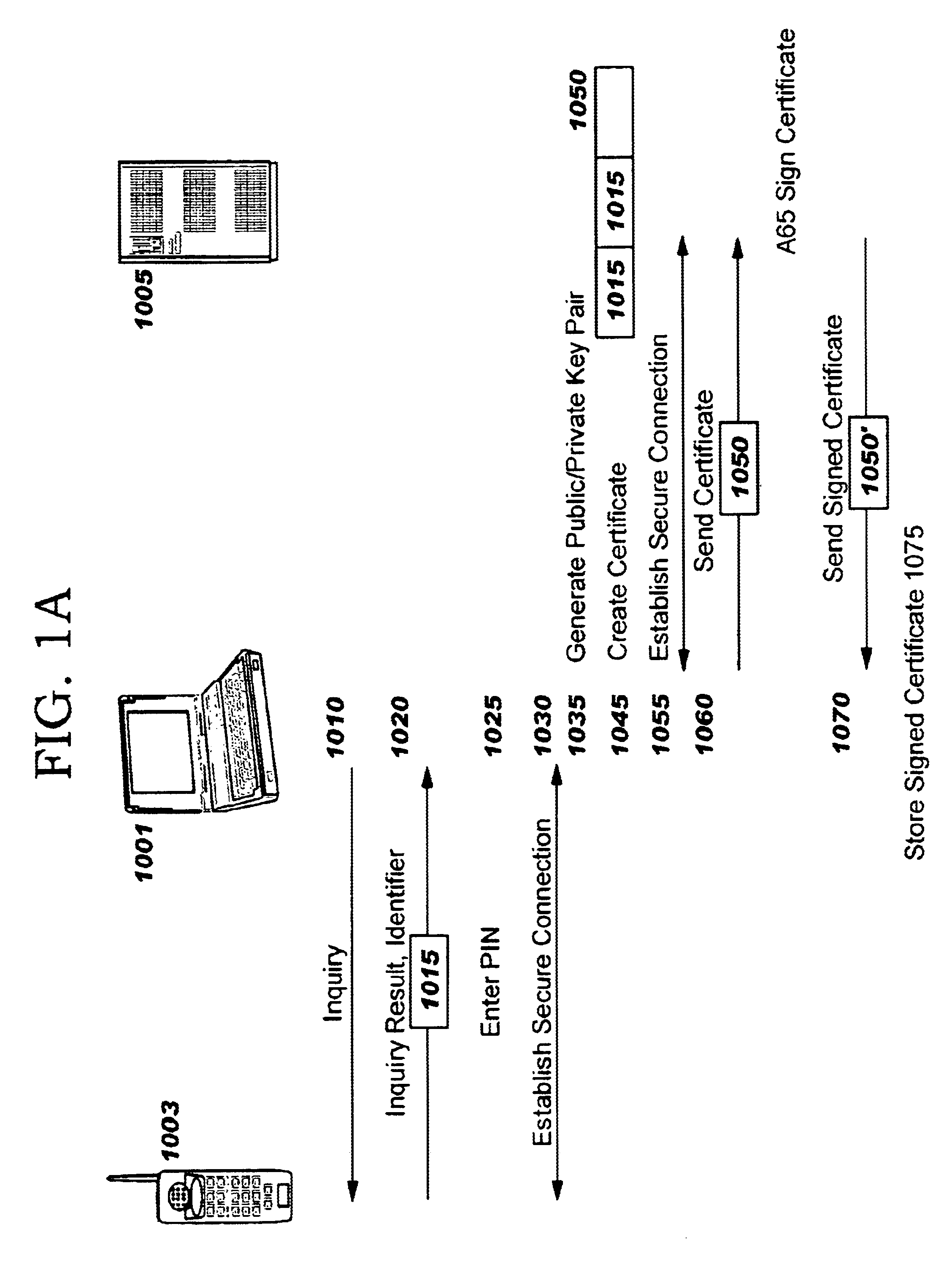
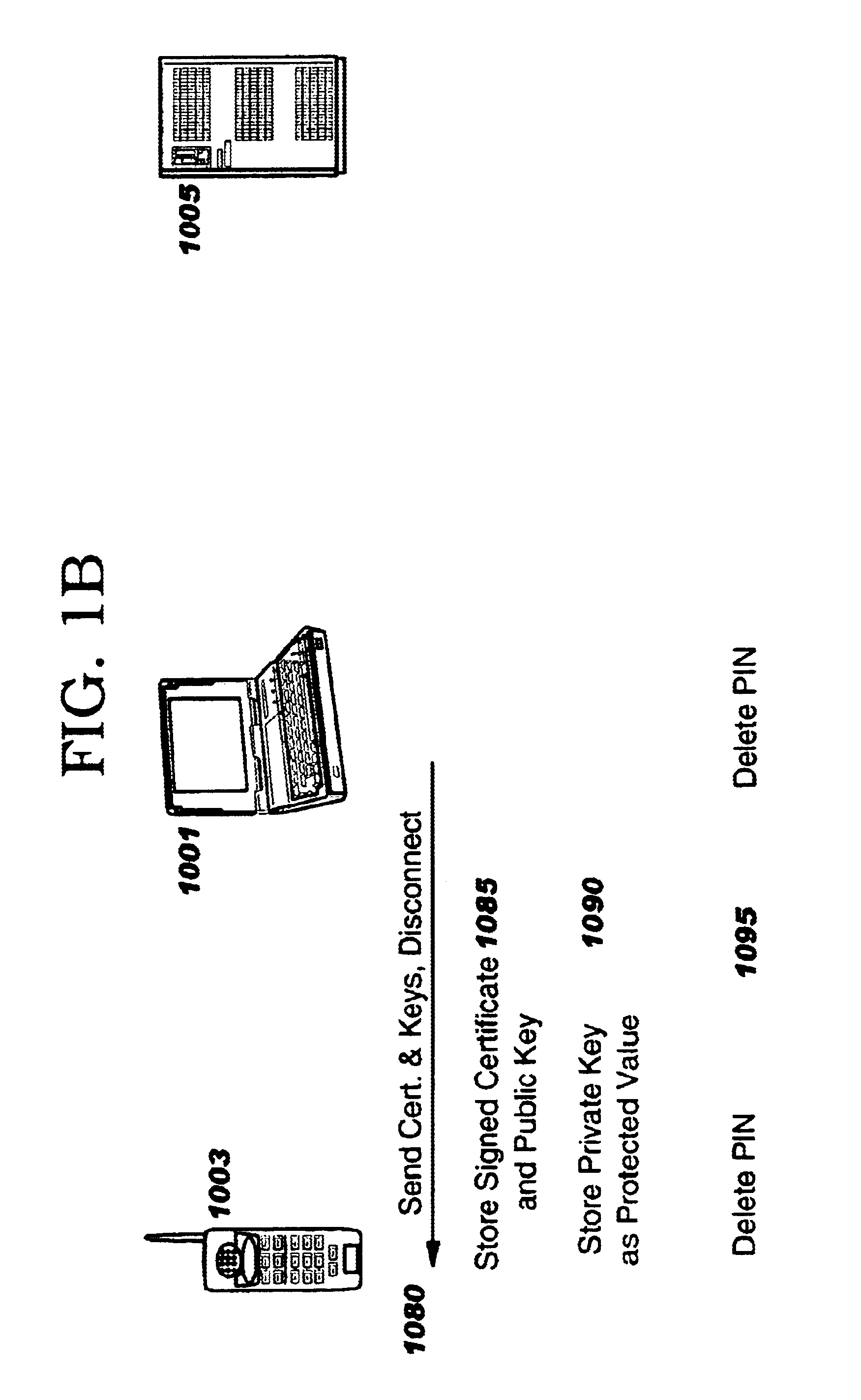
Method and apparatus for efficiently initializing secure communications among wireless devices
InactiveUS6886095B1Efficient administrationEliminating inflexibilityUser identity/authority verificationRadio/inductive link selection arrangementsSecure communicationRadio networks
A method and system for efficiently establishing secure communications between mobile devices in a radio network. The present invention utilizes public key cryptography and unique hardware identifiers to enable authorizations for access to wireless networks, such as picocells. The present invention prevents the mobile user from maintaining a plurality of secrets such as user identifier / password pairs, PINs, or encryption keys, for access to each device to which he might require access.
Owner:IBM CORP
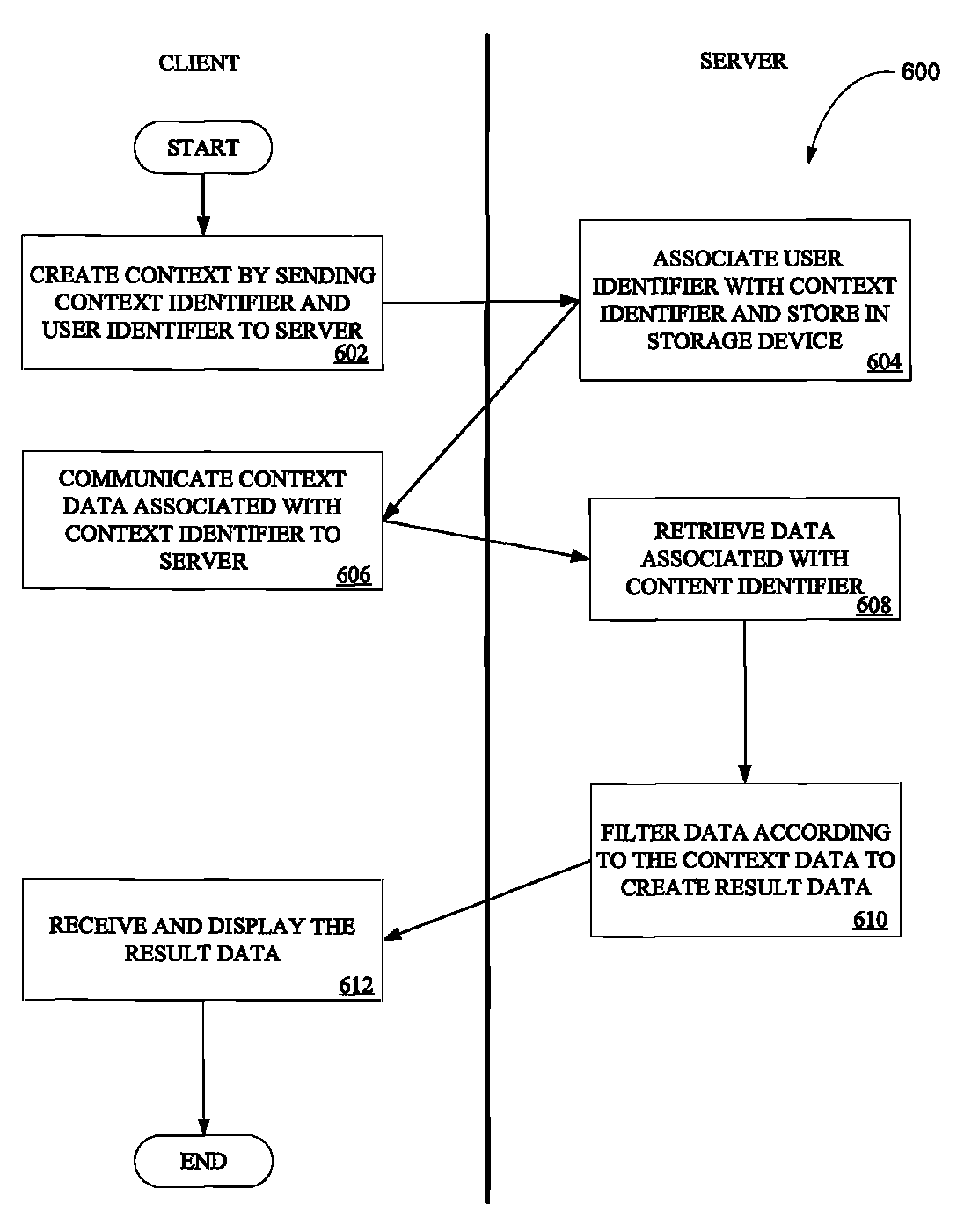
Shopping context engine
A system receives context data associated with a context and a user. The system then associates the context data to a user identifier and retrieves data associated with the context. The system then filters the data according to the context data to create result data. In another embodiment, the system also receives context data from a plurality of users, where the context data pertains to one or more attributes of a context. The system then using the context data ranks the one or more attributes of the context to create ranked data and generates a user interface based on the ranked data. In yet another embodiment, the system communicates context data associated with a context and a user to a server, and receives result data created by the server filtering data retrieved based on the context data. The system then generates a user interface based on the result data.
Owner:PAYPAL INC
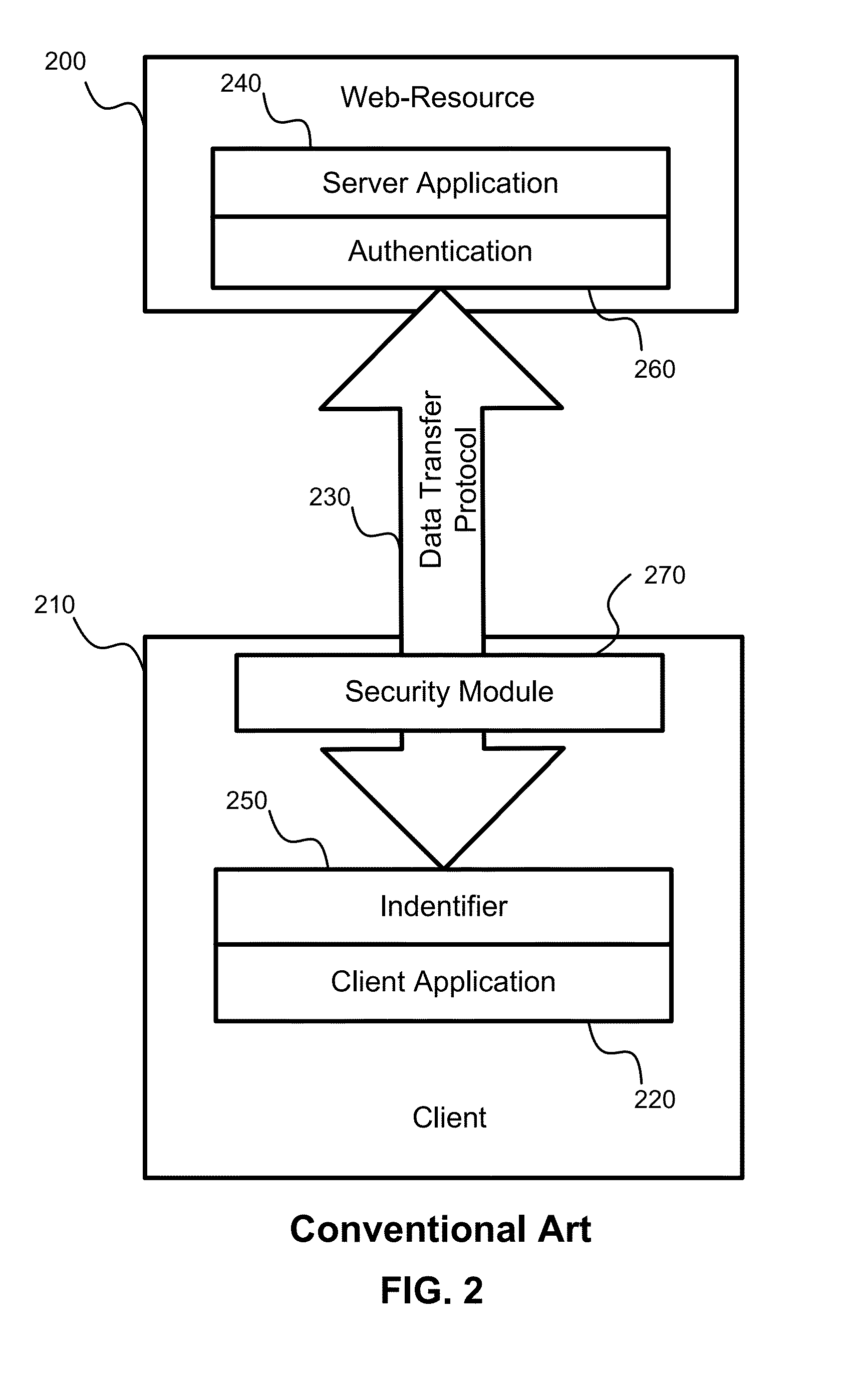
Protection against malware on web resources
ActiveUS8370939B2Memory loss protectionError detection/correctionUser identifierApplication software
Owner:AO KASPERSKY LAB
Method and system for monitoring online behavior at a remote site and creating online behavior profiles
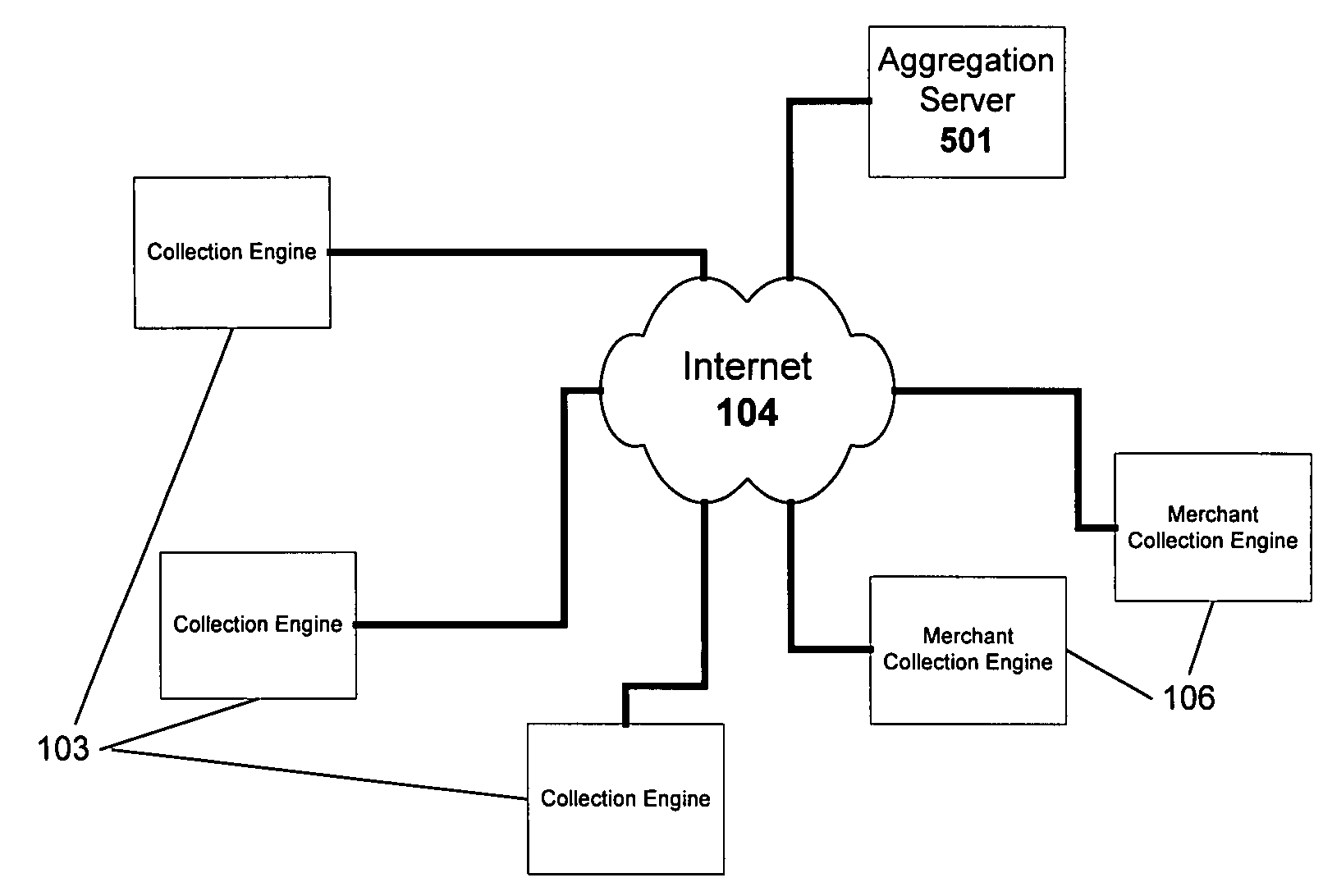
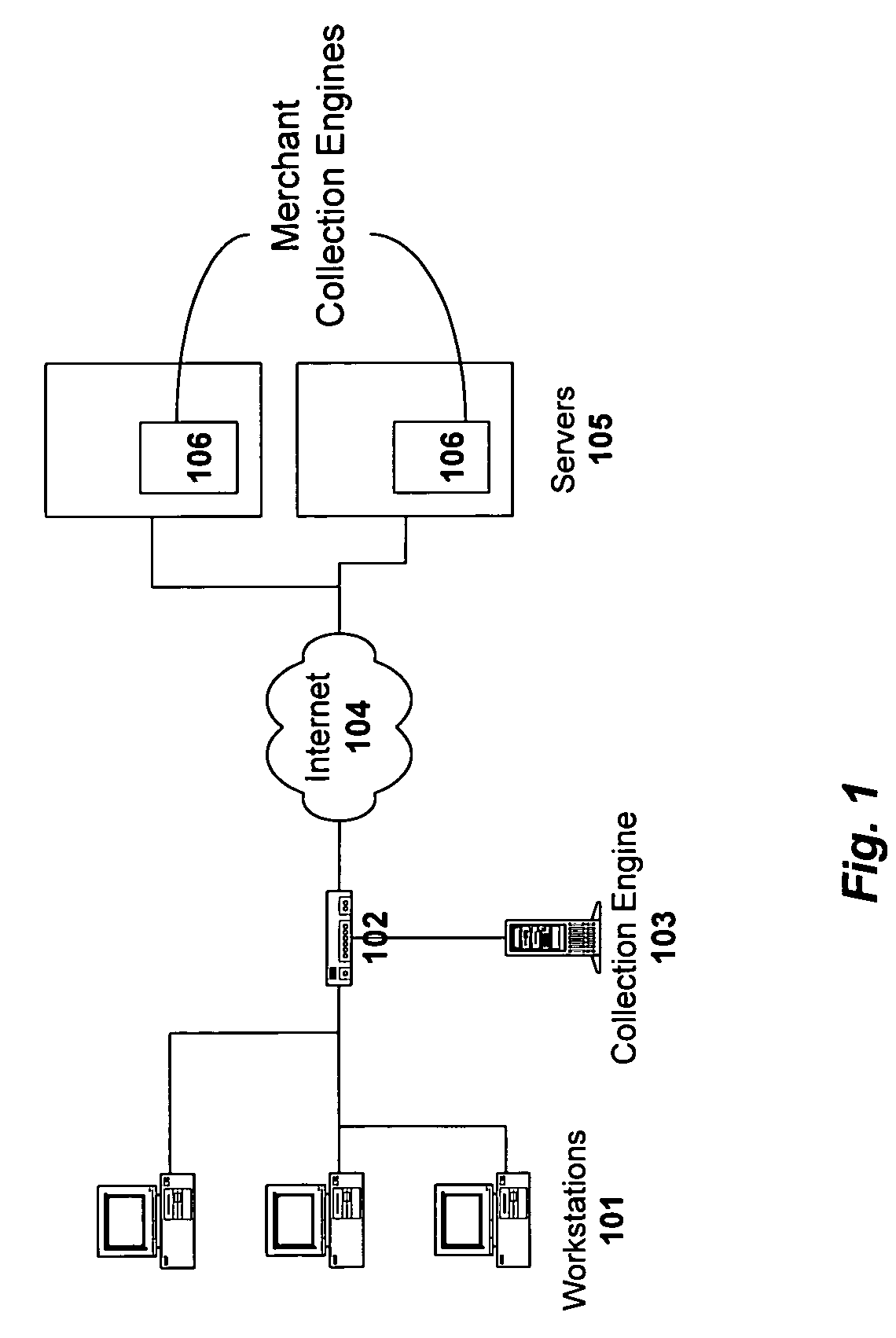
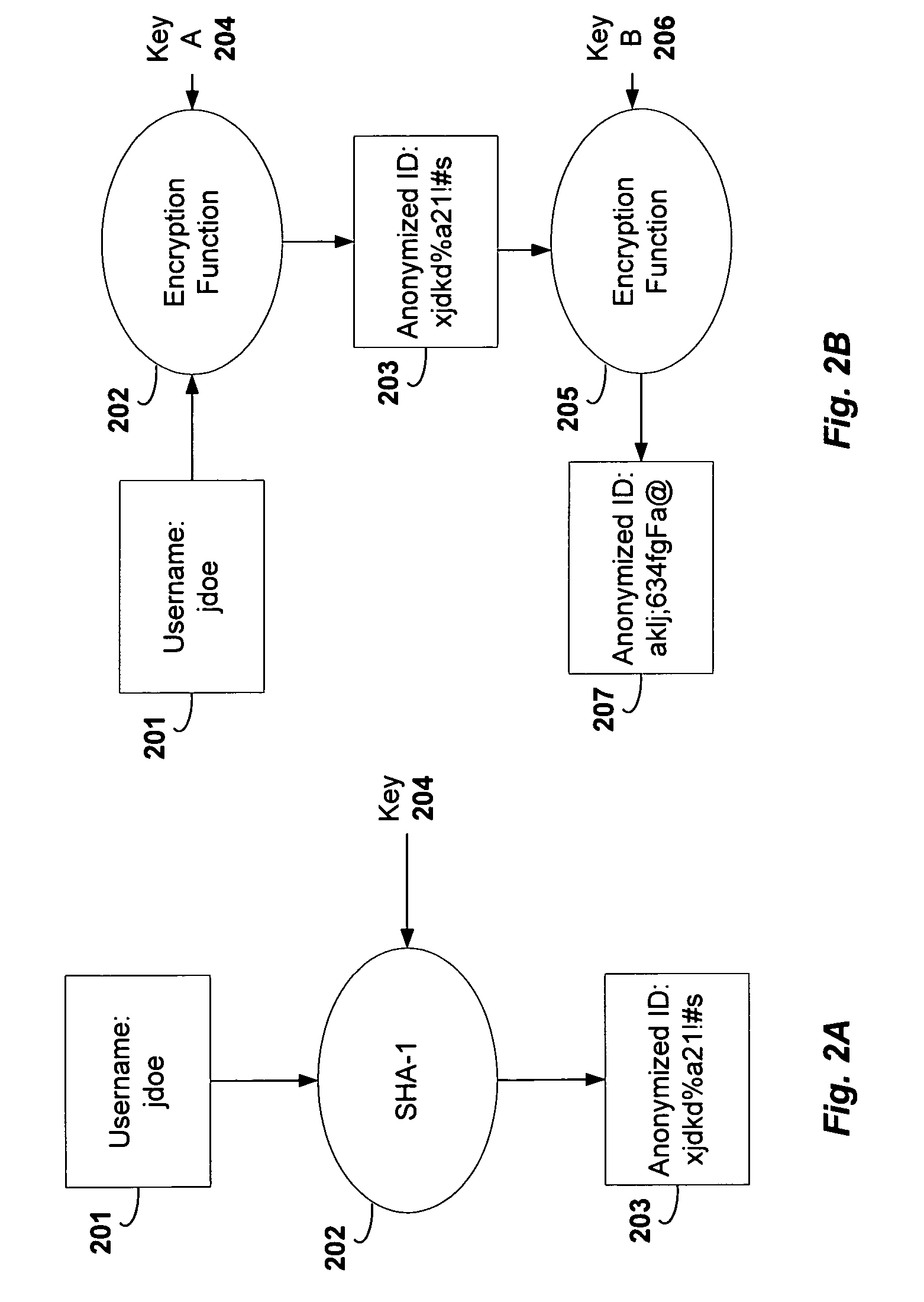
InactiveUS6983379B1Amount of timeHardware monitoringComputer security arrangementsInternet privacyTransaction data
A method and system for monitoring users on one or more computer networks, disassociating personally identifiable information from the collected data, and storing it in a database so that the privacy of the users is protected. The system includes monitoring transactions at both a client and at a server, collecting network transaction data, and aggregating the data collected at the client and at the server. The system receives a user identifier and uses it to create an anonymized identifier. The anonymized identifier is then associated with one or more users' computer network transactions. The data is stored by a collection engine and then aggregated to a central database server across a computer network.
Owner:PLURIMUS CORP +1
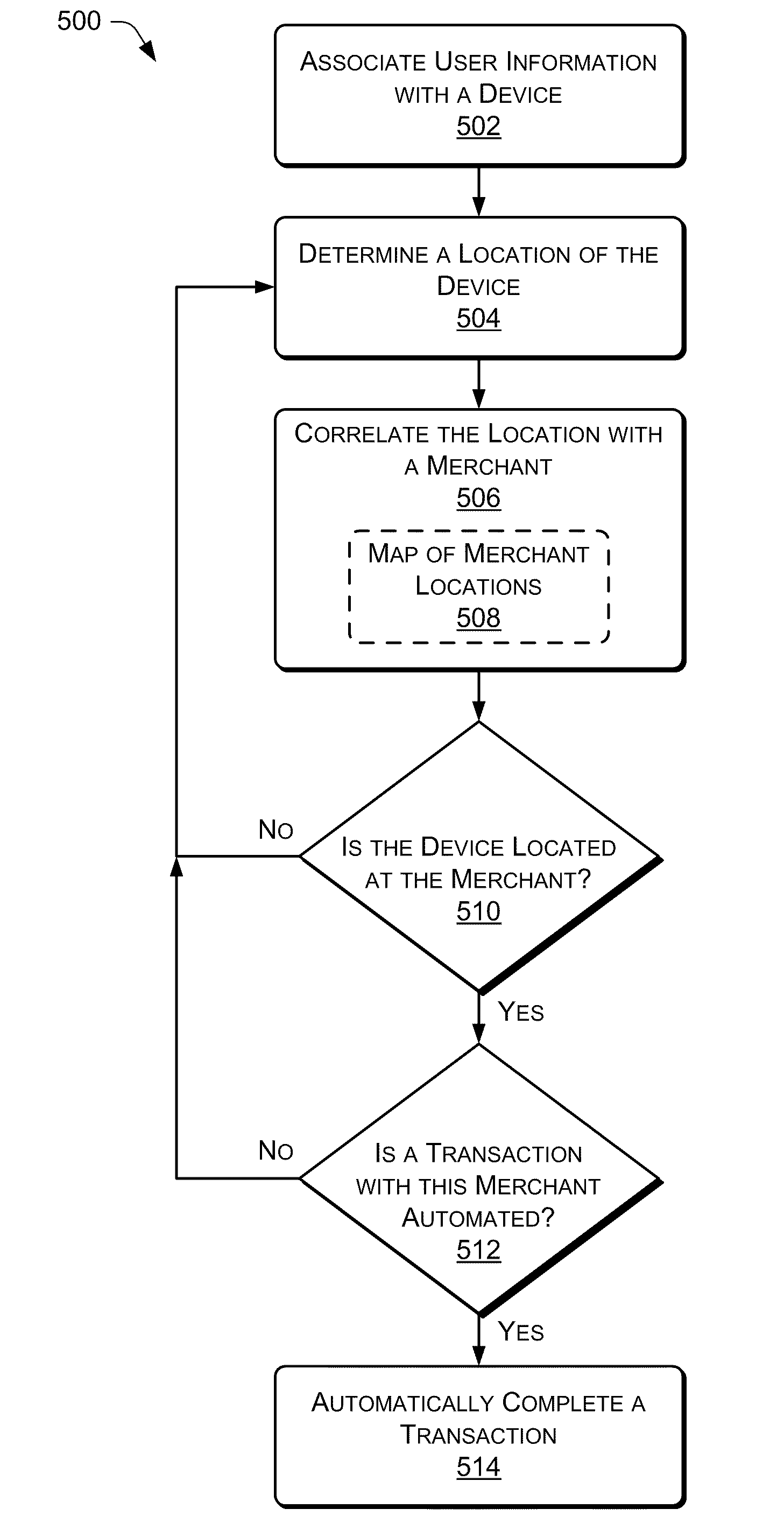
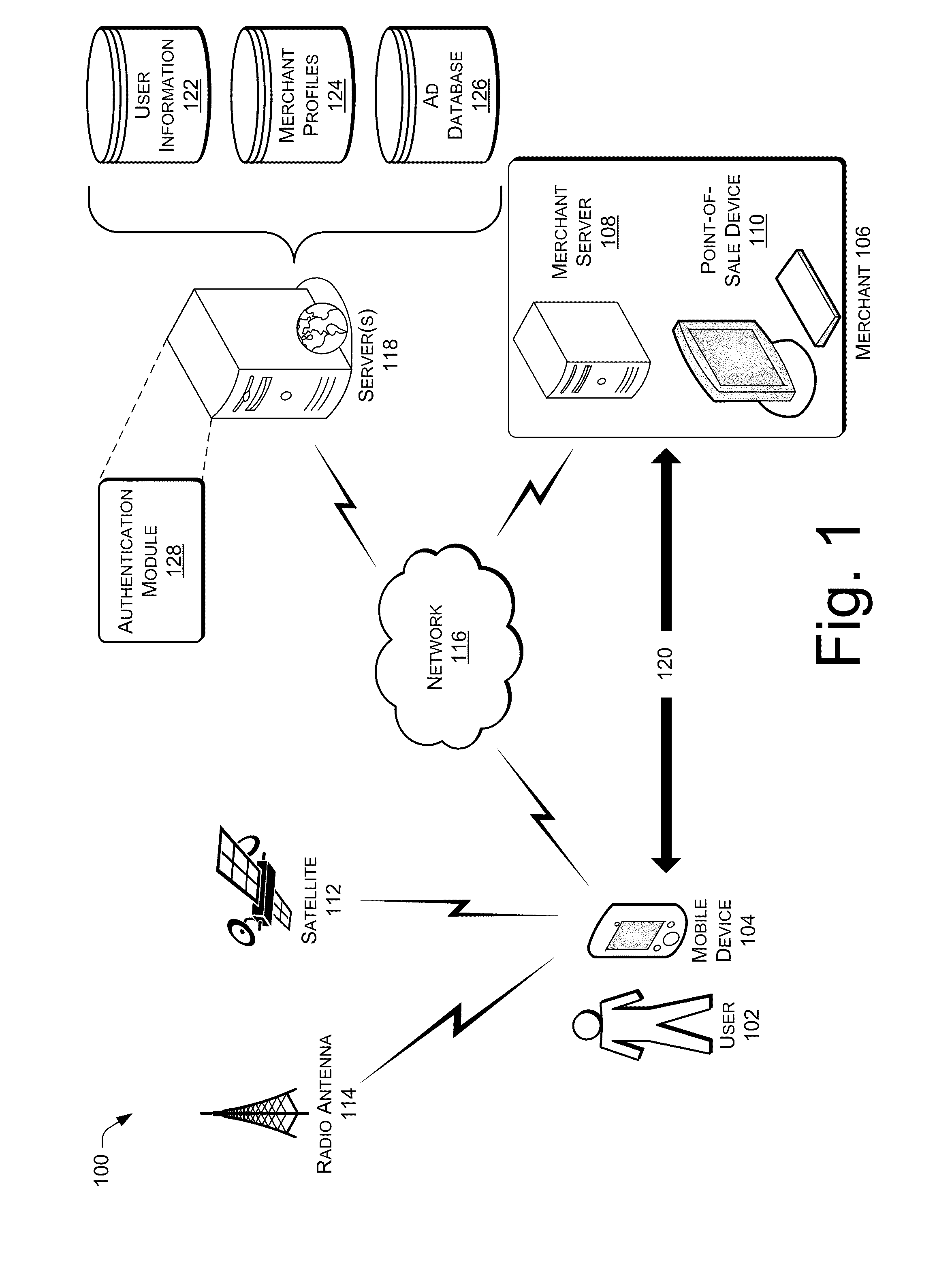
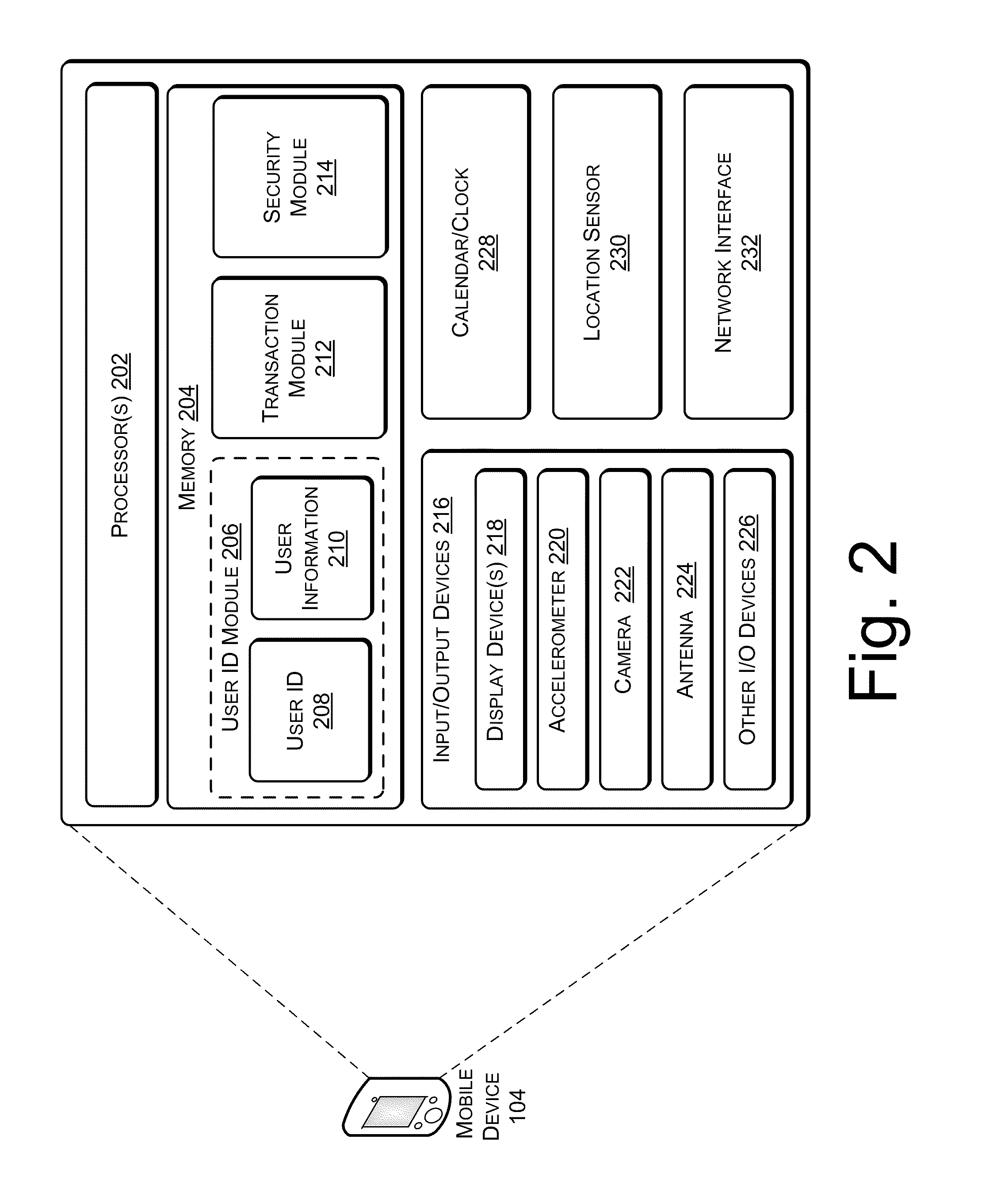
User Profile and Geolocation for Efficient Transactions
Techniques for providing friction-free transactions using geolocation and user identifiers are described herein. These techniques may ascertain a user's location based on a location of a mobile device. A transaction between the user and a merchant may be completed with zero or minimal input from the user based on the geolocation of the mobile device and the user identifiers. In some implementations, a transaction initiated earlier is completed when the mobile device arrives at the merchant. Additionally, a parent-child or similar relationship may be established between multiple devices. Security on the mobile device based may be provided by biometric identification and calculation of variance from regular movement patterns. Advertisements may be sent to the mobile device based on bids from merchants near to the mobile device. Promotions may be sent to the mobile device when more than a threshold number of mobile devices are located at the same merchant.
Owner:AMAZON TECH INC
Systems and methods for authenticating a device by a centralized data server
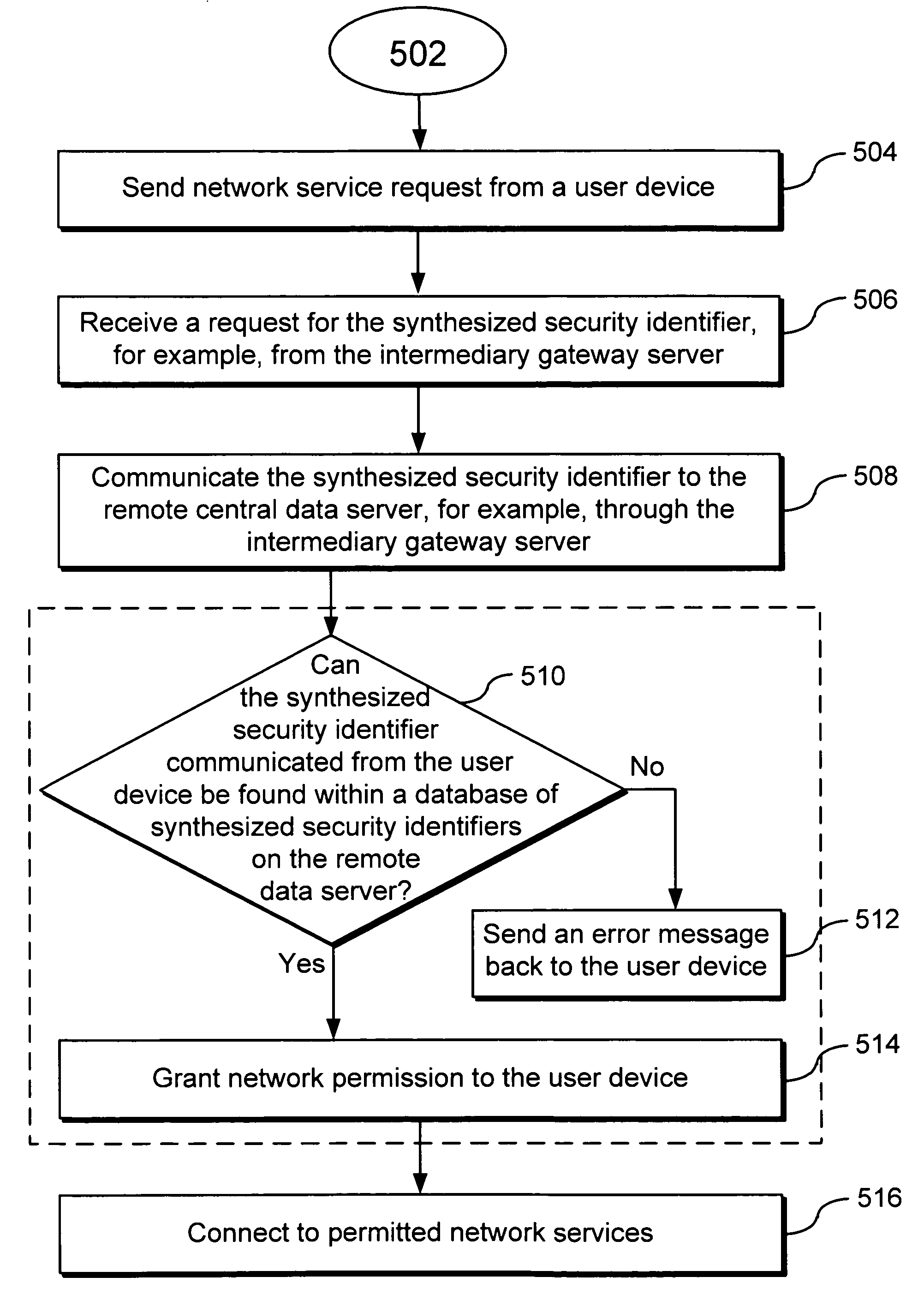
InactiveUS20080120707A1Digital data processing detailsUser identity/authority verificationUser deviceUser identifier
Systems, methods and apparatus for authenticating a query device using a centralized data server include associating and storing, on the server, for each respective device in a plurality of devices, a device identifier, a user identifier, and a synthesized security identifier that collectively authenticate the respective user device. An authentication request is received, at the centralized server, from an intermediary gateway server seeking verification of the query device. The request has a query device identifier or a query synthesized security identifier. Verification, at the centralized data server, of the query device is done by searching for a match between the query device identifier and a stored device identifier and a match between the query synthesized security identifier and a stored synthesized security identifier. The centralized data server communicates to the intermediary gateway server whether the identity of the query device is verified.
Owner:INNOFONE COM
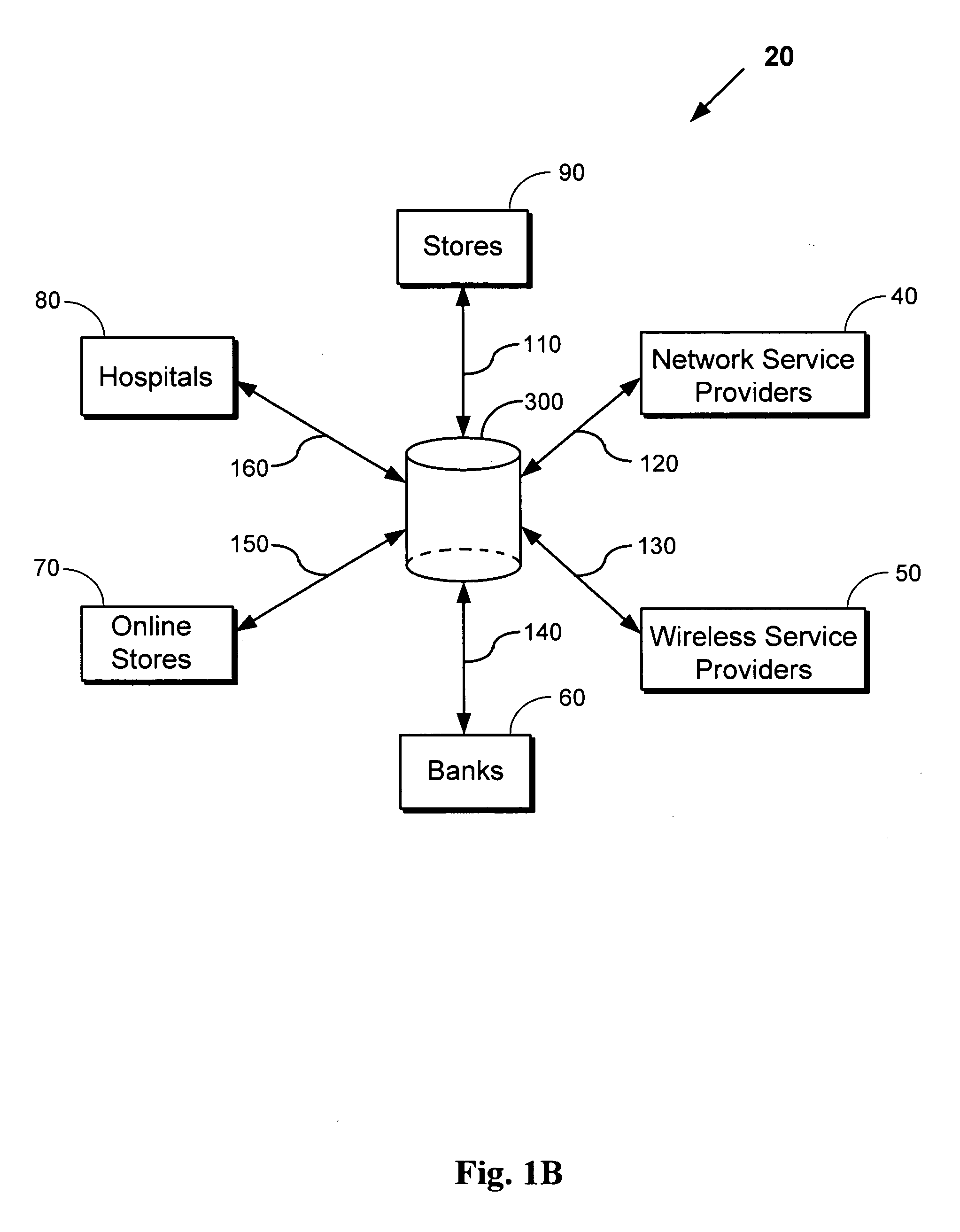
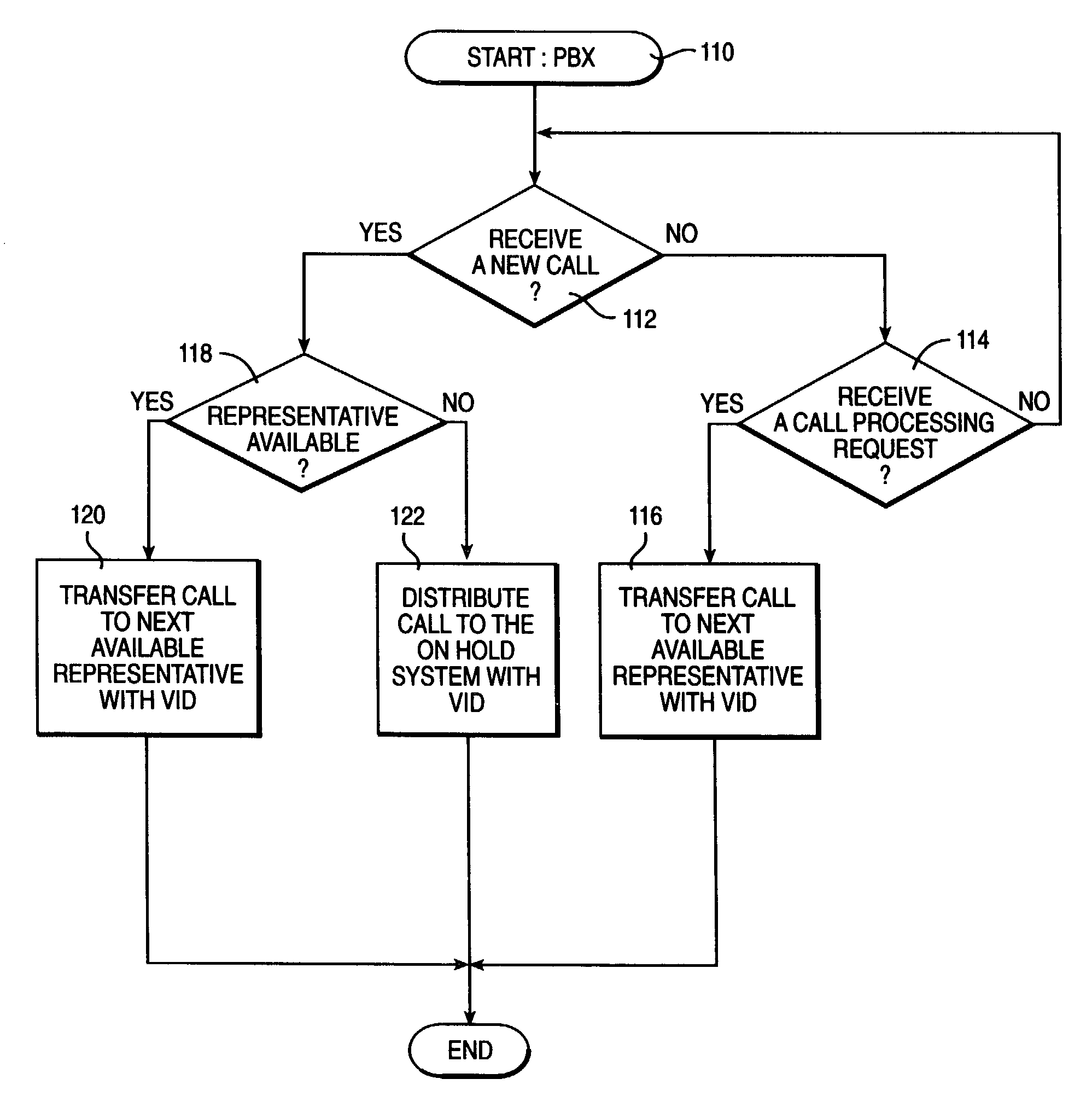
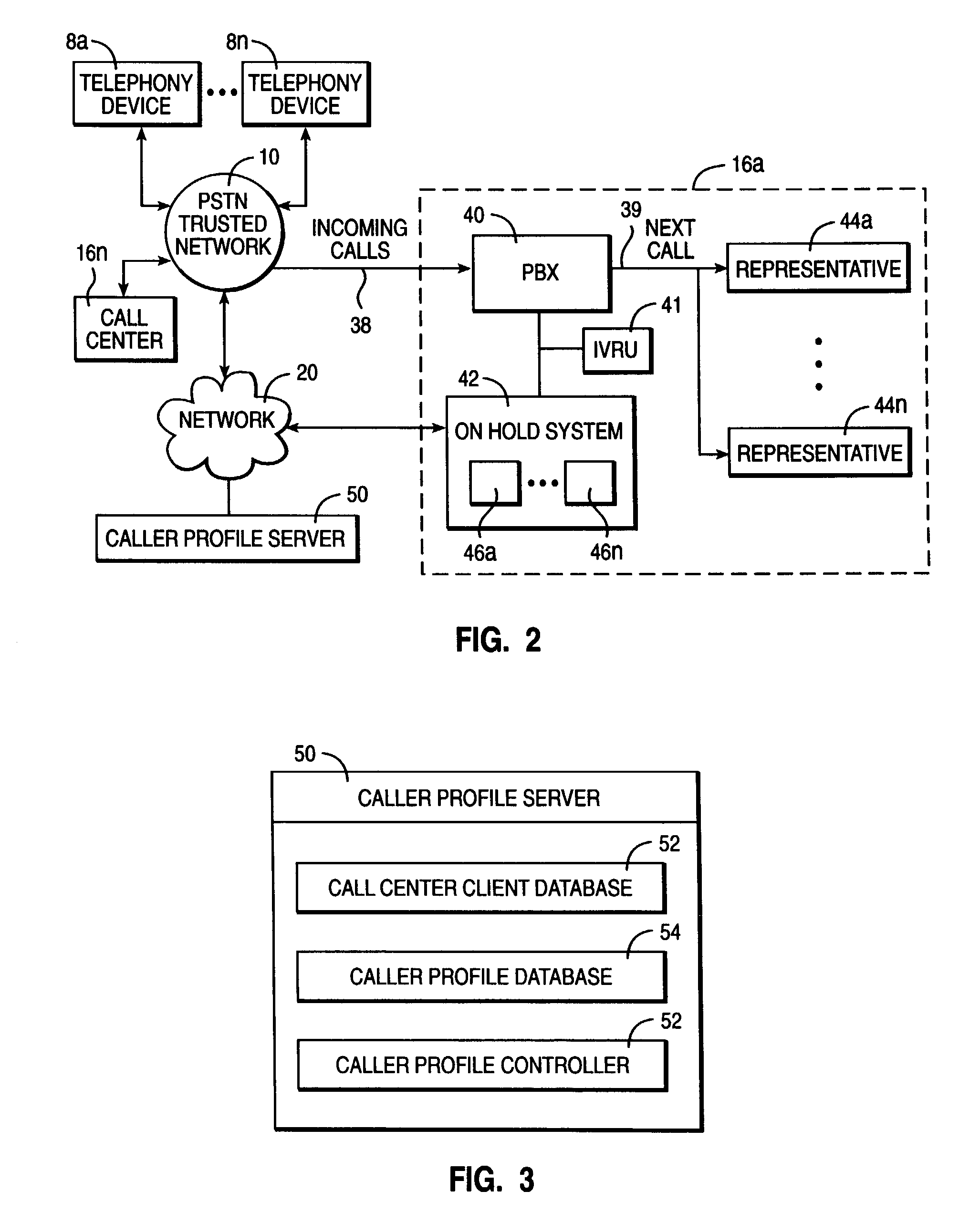
Managing caller profiles across multiple hold queues according to authenticated caller identifiers
InactiveUS7103172B2Television system scanning detailsAutomatic call-answering/message-recording/conversation-recordingUser identifierSpeech sound
A method, system, and program for managing caller profiles across multiple hold queues according to authenticated caller identifiers are provided. An identity of a caller of a call received at an on hold system is authenticated. The call is then placed in a hold queue. A caller profile associated with the identity of the caller is retrieved, such that services available to the caller while on hold are specified according to the caller profile. In particular, the caller profile is preferably retrieved from at least one caller profile server according to the caller identifier, where the at least one caller profile server is accessible to multiple on hold systems. Further, the identity of a caller may be authenticated by authenticating a voice sample received from the caller, such that a single identity for the caller may be authenticated at multiple call centers.
Owner:IBM CORP
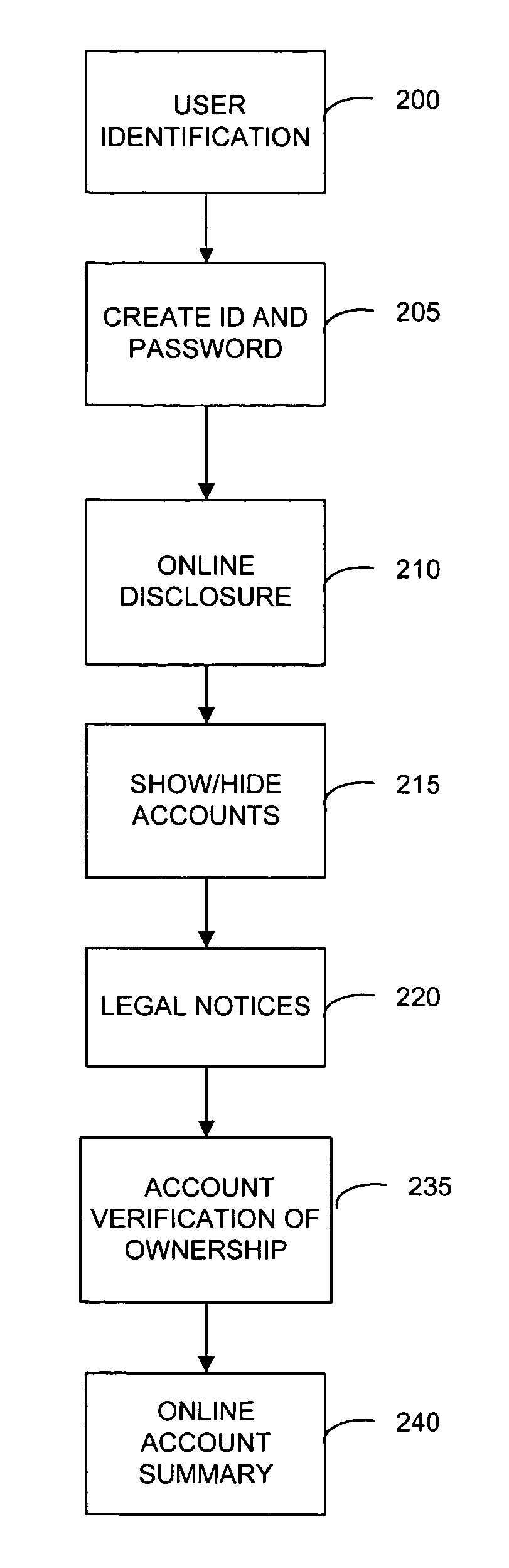
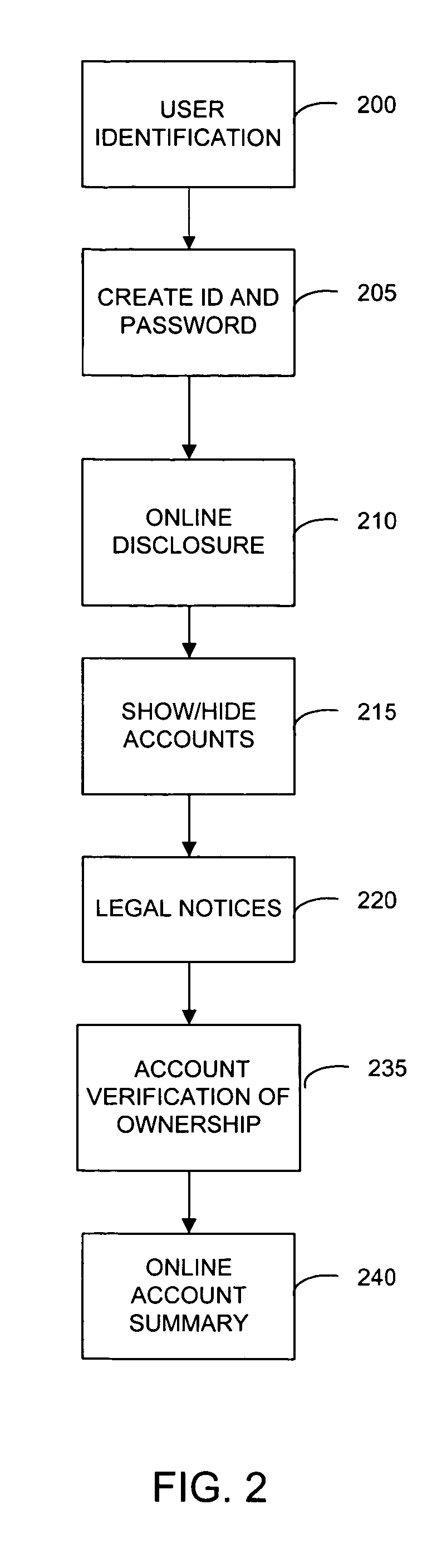
System and method for single sign on process for websites with multiple applications and services
InactiveUS7058817B1Reduce usageReduce supportFinanceUser identity/authority verificationPasswordThe Internet
A system and method for integrating the Internet front end sign on processes of the various systems of a financial institution which allows a customer to view and access its various financial accounts with the institution. During the initial sign up for the online access to its accounts, a customer creates it's User ID and password online during the same session. Once the customer has signed on (password) and verified ownership of at least one account, the system displays all of the customer's accounts that are available for access via the Internet website. The online ownership verification uses only a single account of the customer and the ownership verification criteria associated with the account. The account used for verifying a customer is first determined based on the accounts selected by the customer for accessing online. From the selected accounts, the system of the present invention creates a verification hierarchy with respect to the accounts. When determining the verification to use for the single ownership verification, the present invention selects the account from the hierarchy with the most stringent requirements.
Owner:JPMORGAN CHASE BANK NA
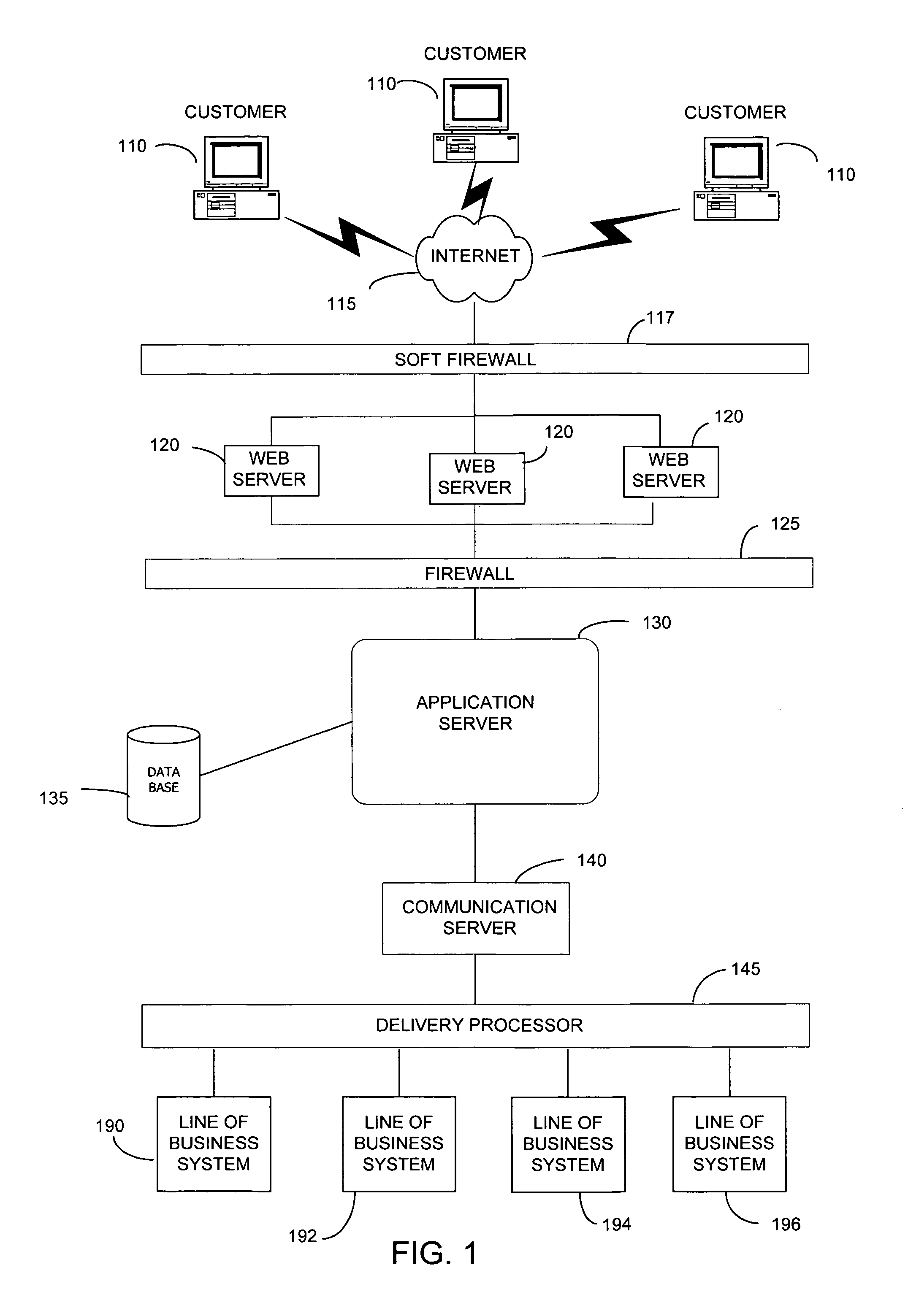
Dynamic content for online transactions
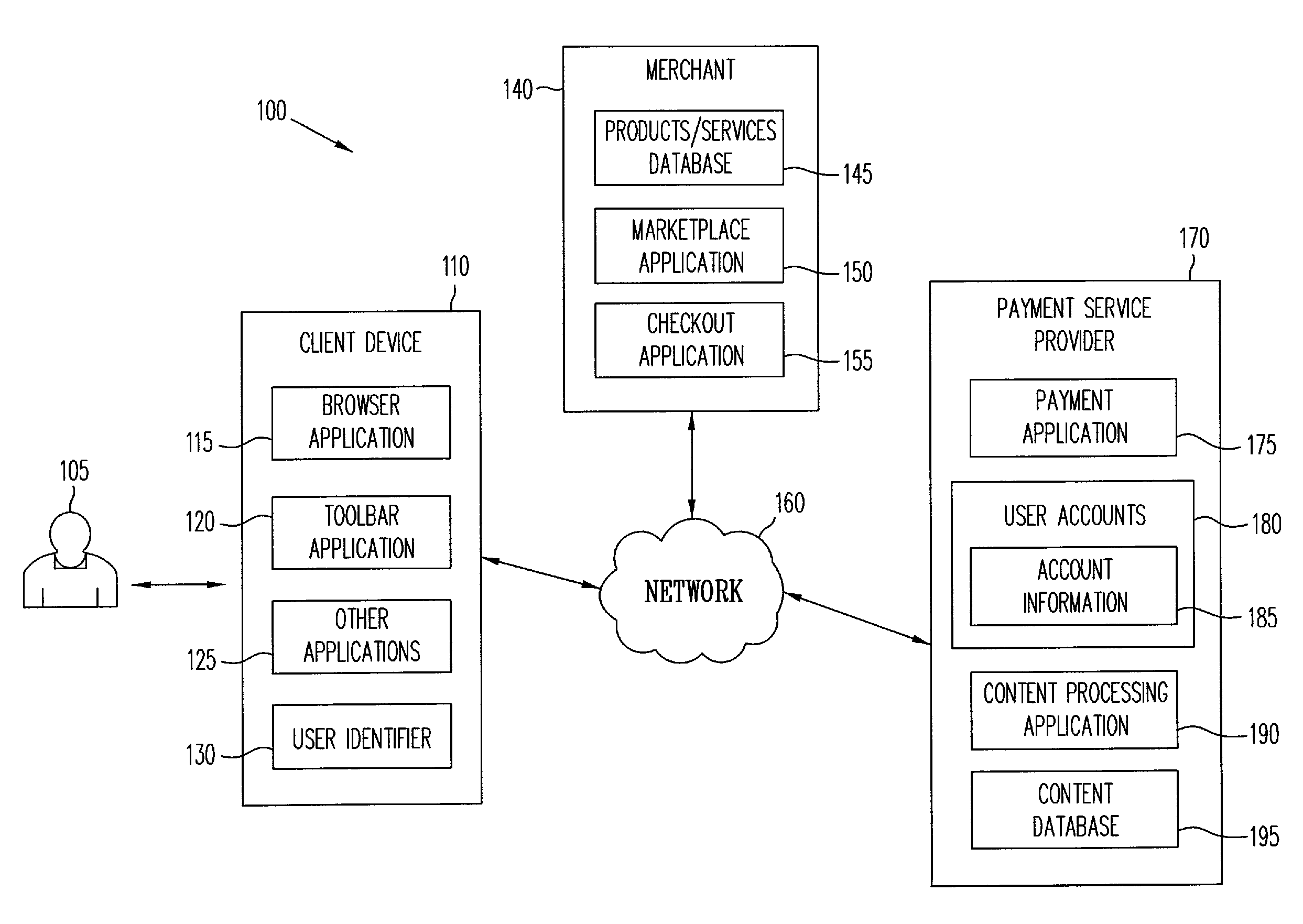
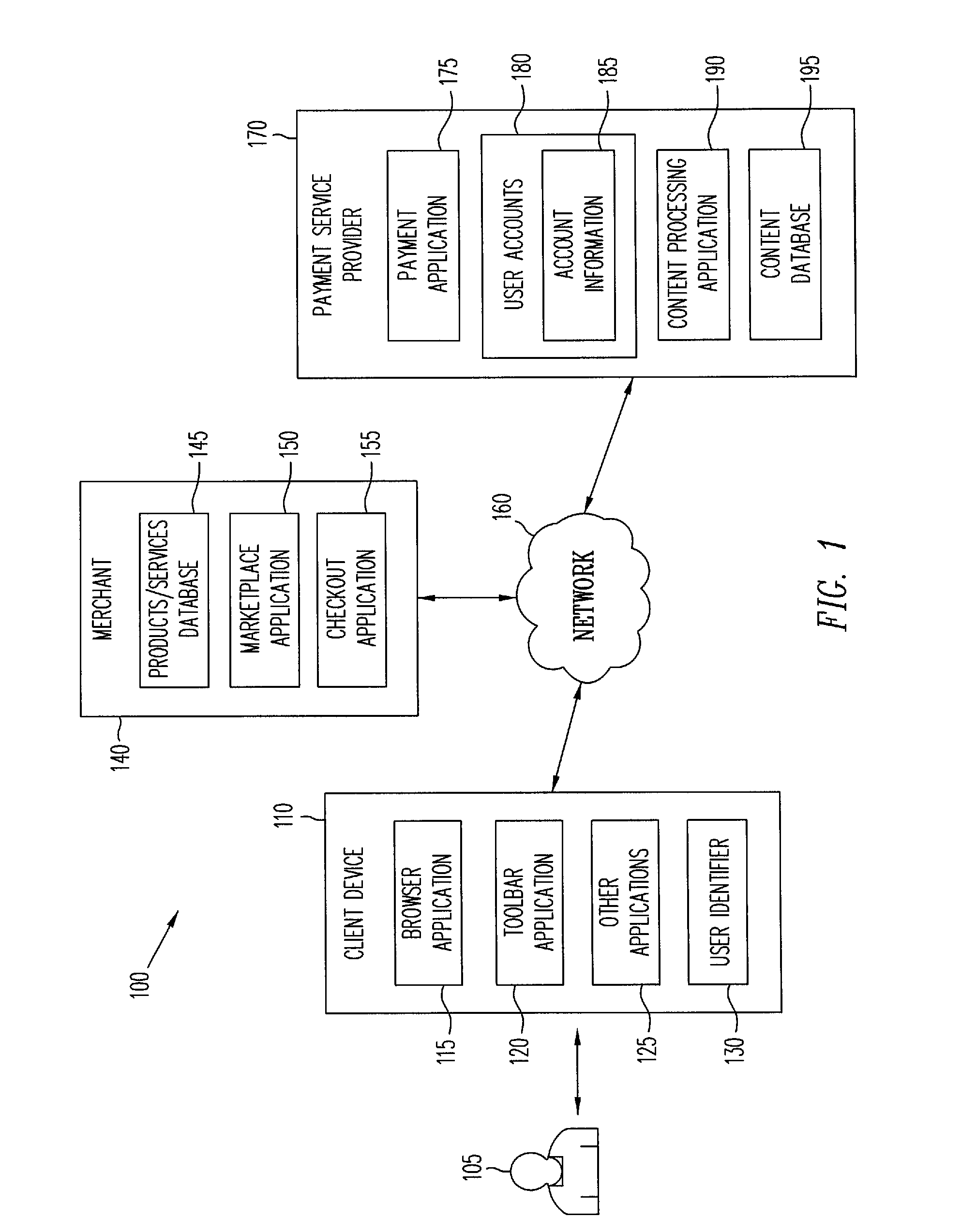
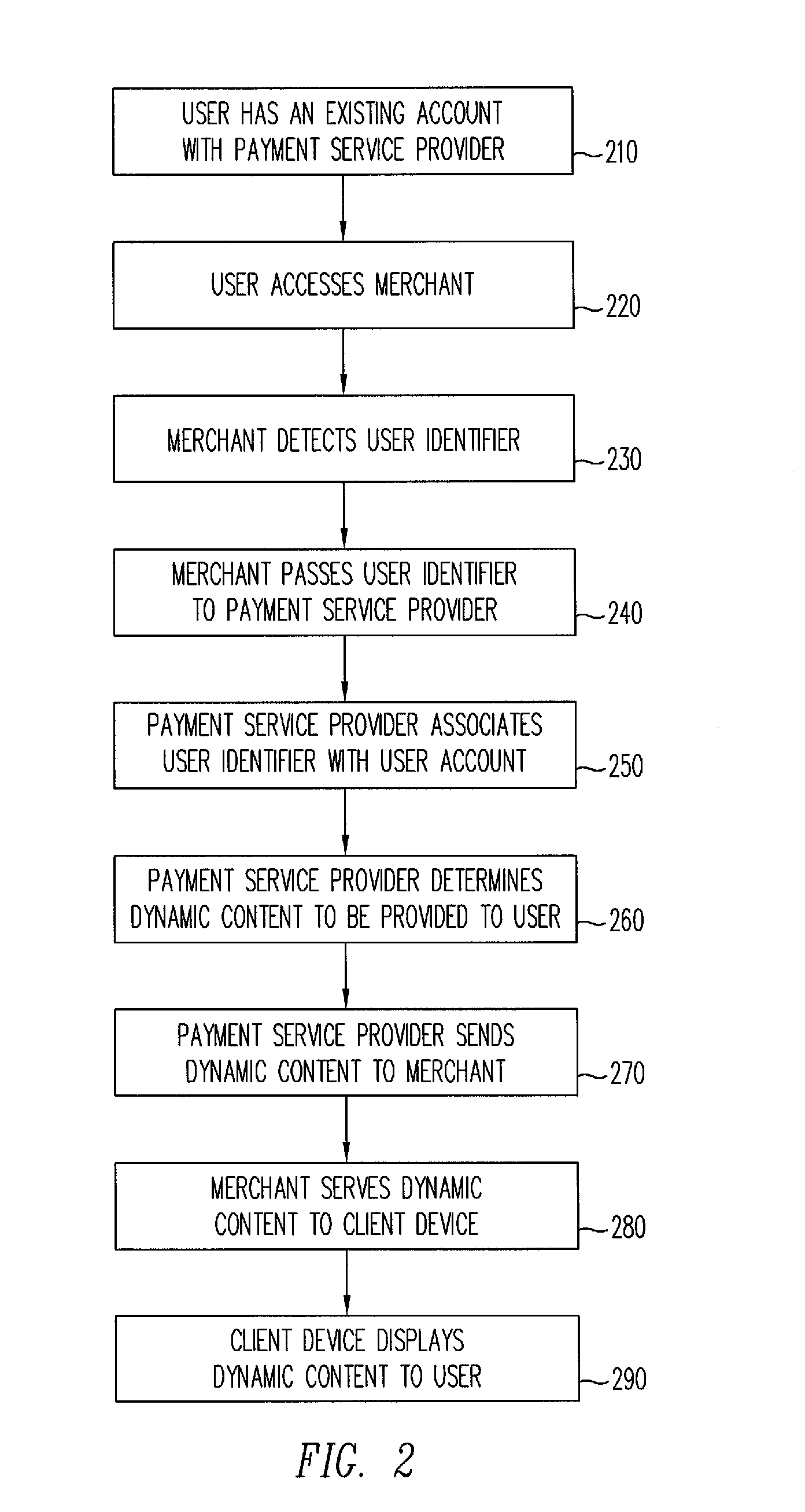
ActiveUS8028041B2Promote disseminationFinanceMultiple digital computer combinationsClient-sideUser identifier
Various methods and systems provide dynamic content to users of online payment service providers without requiring users to log in or otherwise actively engage the payment service providers. In one example, a method includes providing a client device with access to an online marketplace over a network. The method also includes facilitating transmission of a user identifier stored by the client device to a payment service provider. The method further includes receiving dynamic content from the payment service provider in response to the user identifier. In addition, the method includes serving the dynamic content to the client device over the network.
Owner:PAYPAL INC
Authentication watermarks for printed objects and related applications
InactiveUS6823075B2More dataCompact formOther printing matterPaper-money testing devicesRelevant informationCopy detection
Owner:INTUIT INC
Printing service method, system, and printer
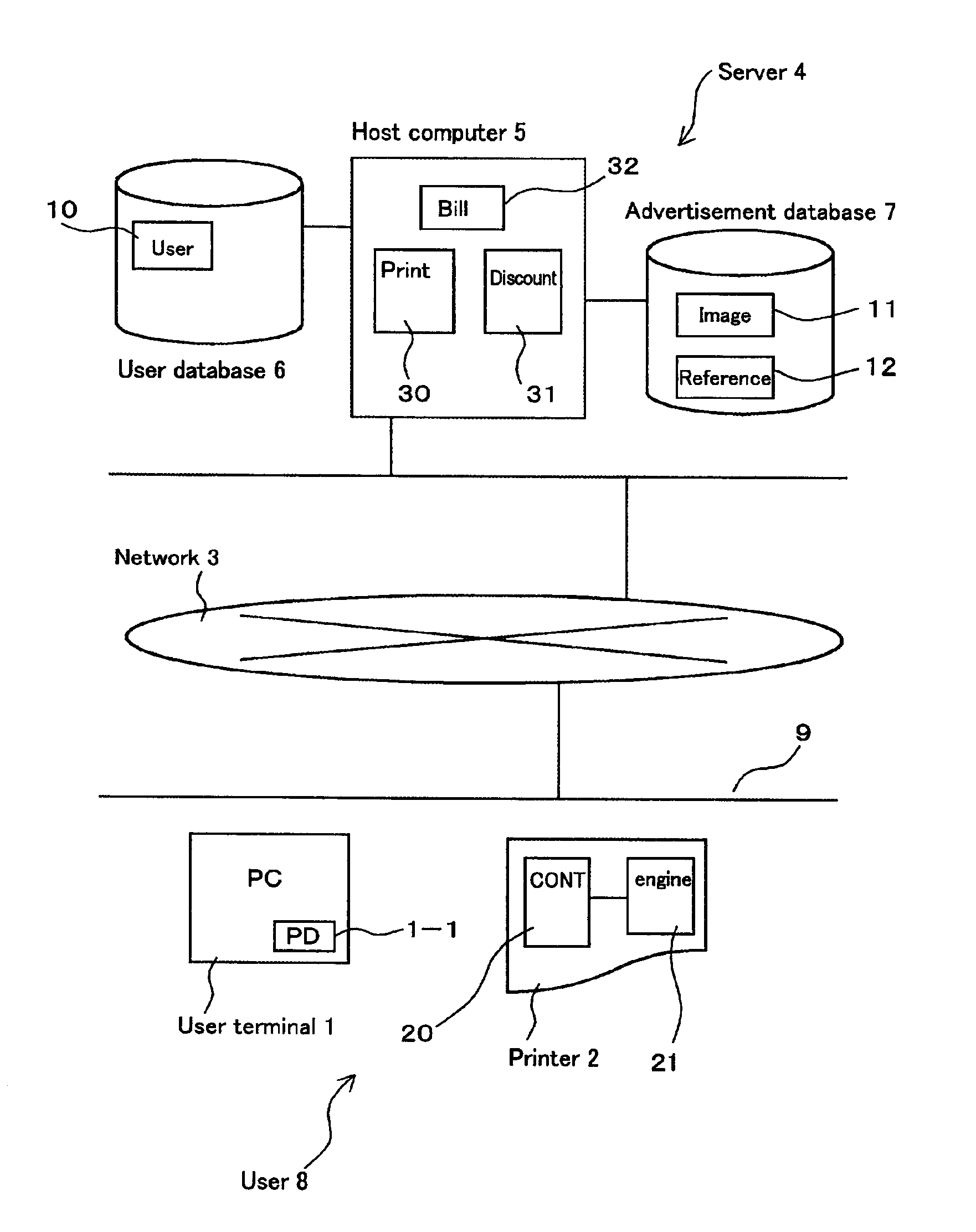
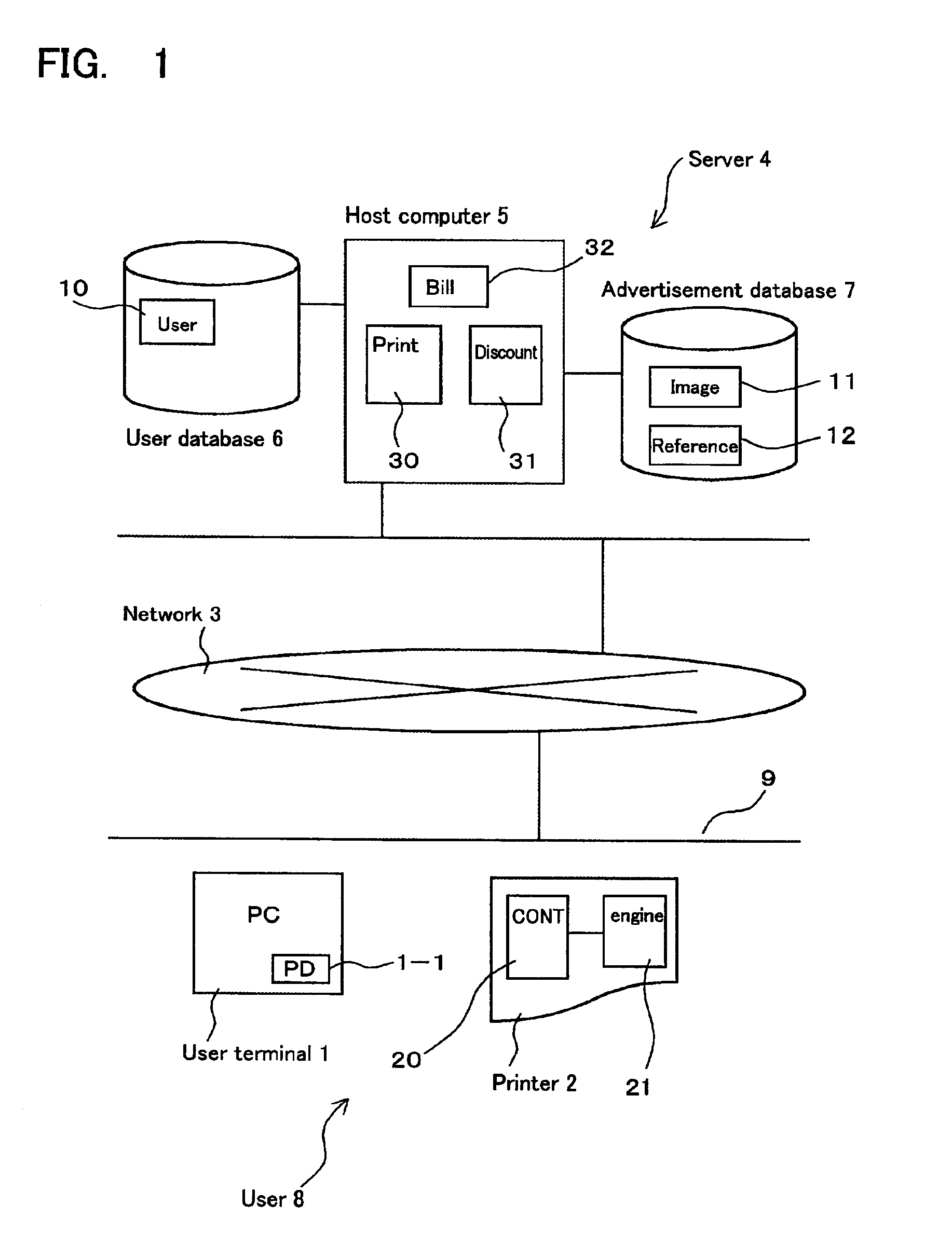
InactiveUS6882439B2Easy to introduceReduce waiting timeDigitally marking record carriersDigital computer detailsUser identifierWorld Wide Web
The Disclosure relates to a printing service method for discounting services by printing with advertisements and realizes various discount services. The present invention comprises: a printing step for sending printing management information along with the user ID to the server 4 through the network 3 when the user prints with advertisements with the user's printing device 2, and storing that information as an advertisement usage record for each user ID; a step for referencing the user's advertisement usage record, for least one service, selected by the user from among a plurality of services relating to the printing device that used the advertisement printing record, determining whether to authorize the discount for the selected service, and updating the advertisement usage record of the abovementioned user to perform the authorized discount service. A variety of discount services can be realized because the print operation with advertisements is managed by the server and the user can use the usage records.
Owner:FUJIFILM BUSINESS INNOVATION CORP
Content usage control system, content usage apparatus, computer readable recording medium with program recorded for computer to execute usage method
InactiveUS6873975B1Prevent illegal useImprove accuracyDigital data processing detailsAnalogue secracy/subscription systemsControl systemStructure of Management Information
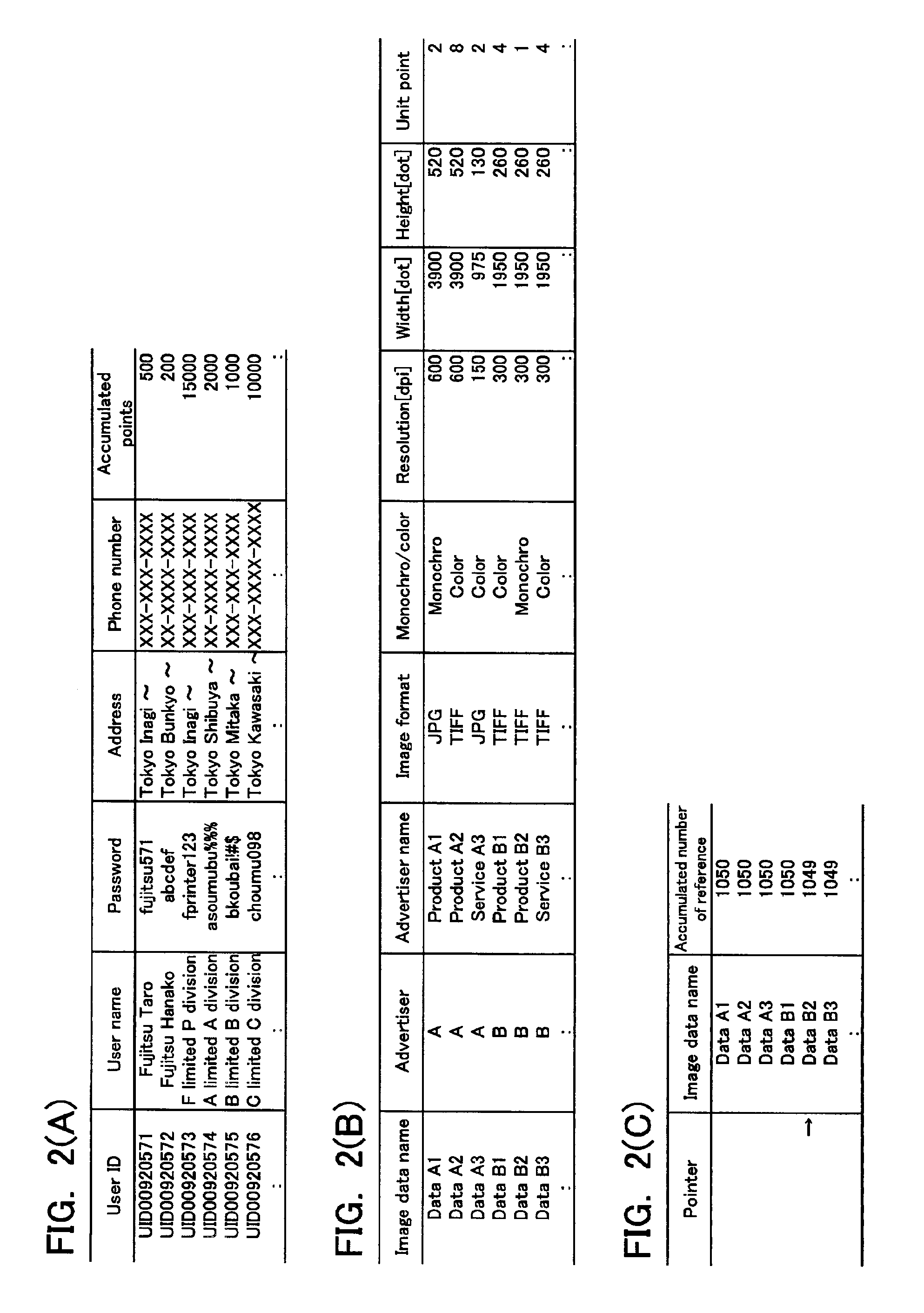
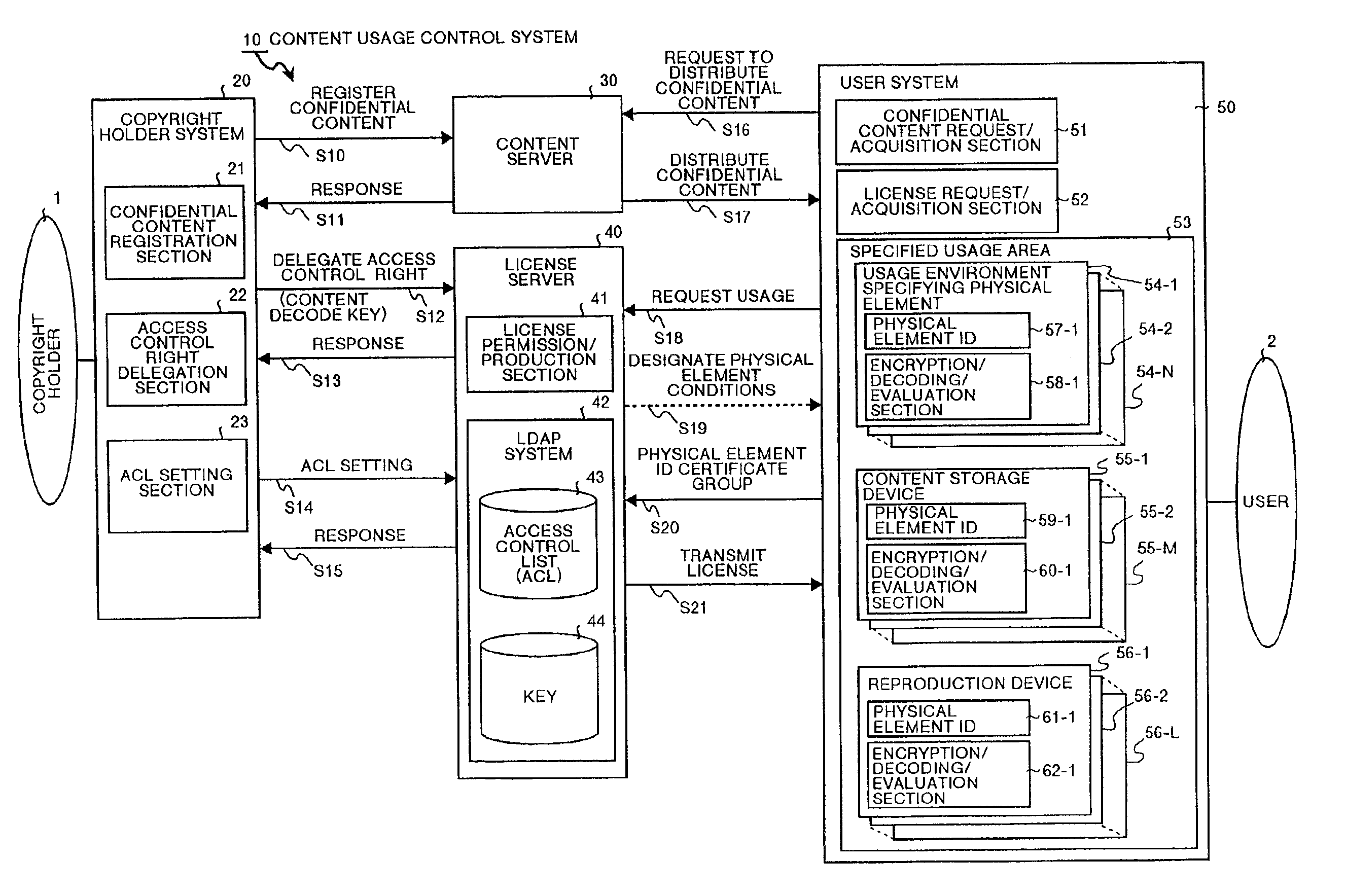
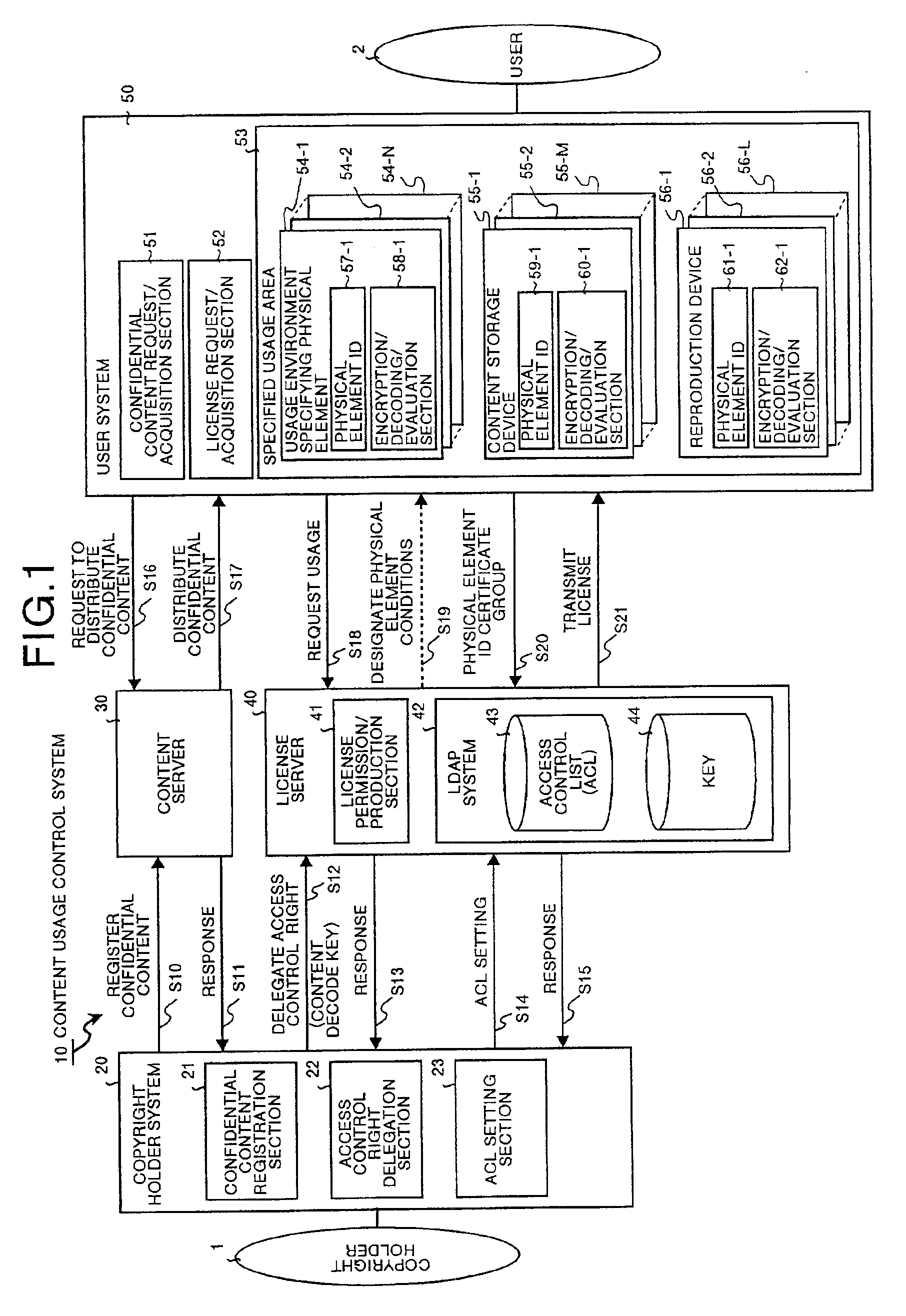
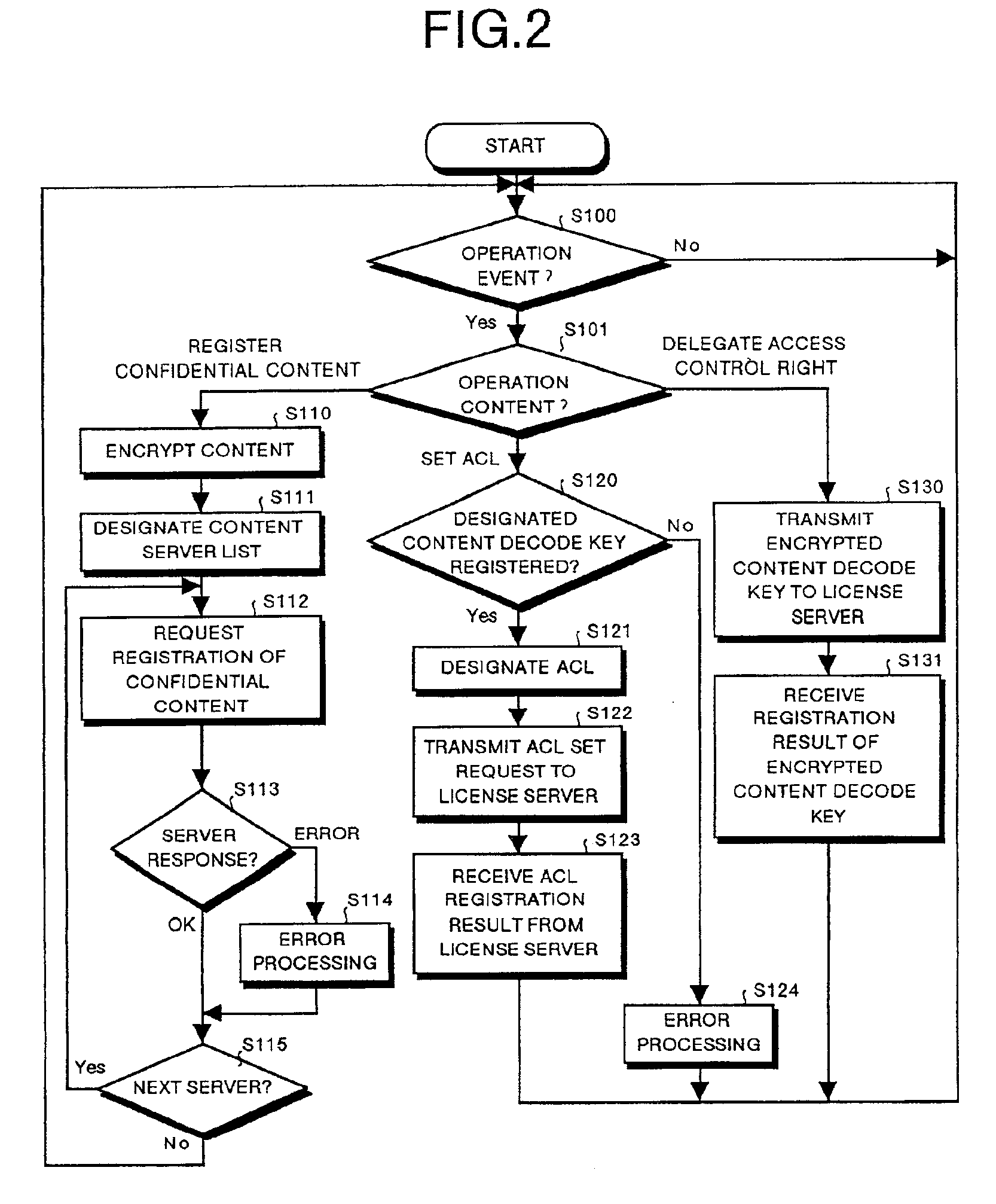
A content usage control system comprises a copyright holder system, content server, license server and user system. The ACL setting section of the copyright holder system sets a license ACL expressed as a structure by a combination of logic sums and logic products of a plurality of partial licenses for the content, based on the user ID and a plurality of physical element IDs including media used in the user system, and stores the license ACL in an access control list. The license server controls the usage of the content by the user utilizing the access control list.
Owner:FUJITSU LTD
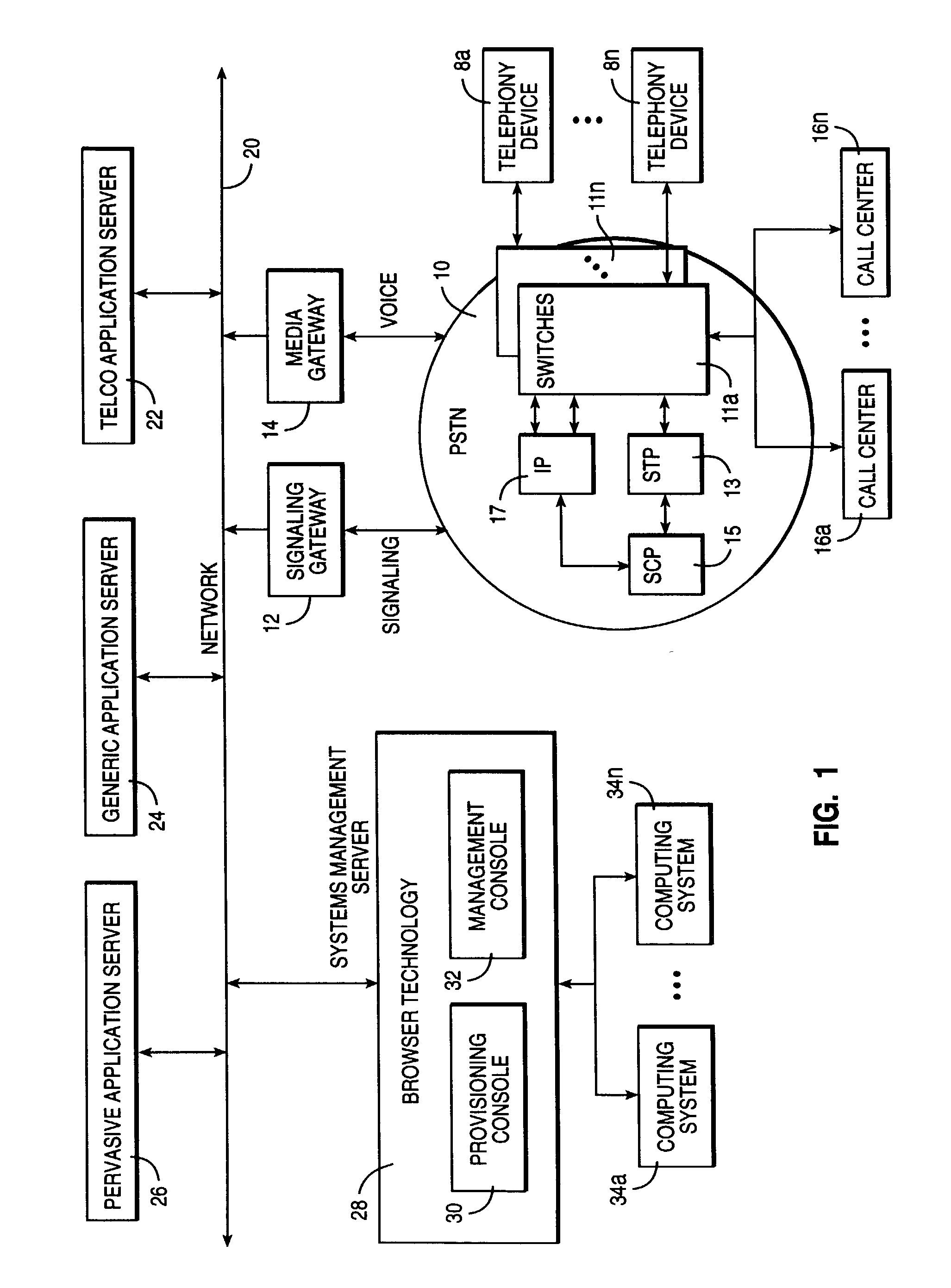
Mobile services
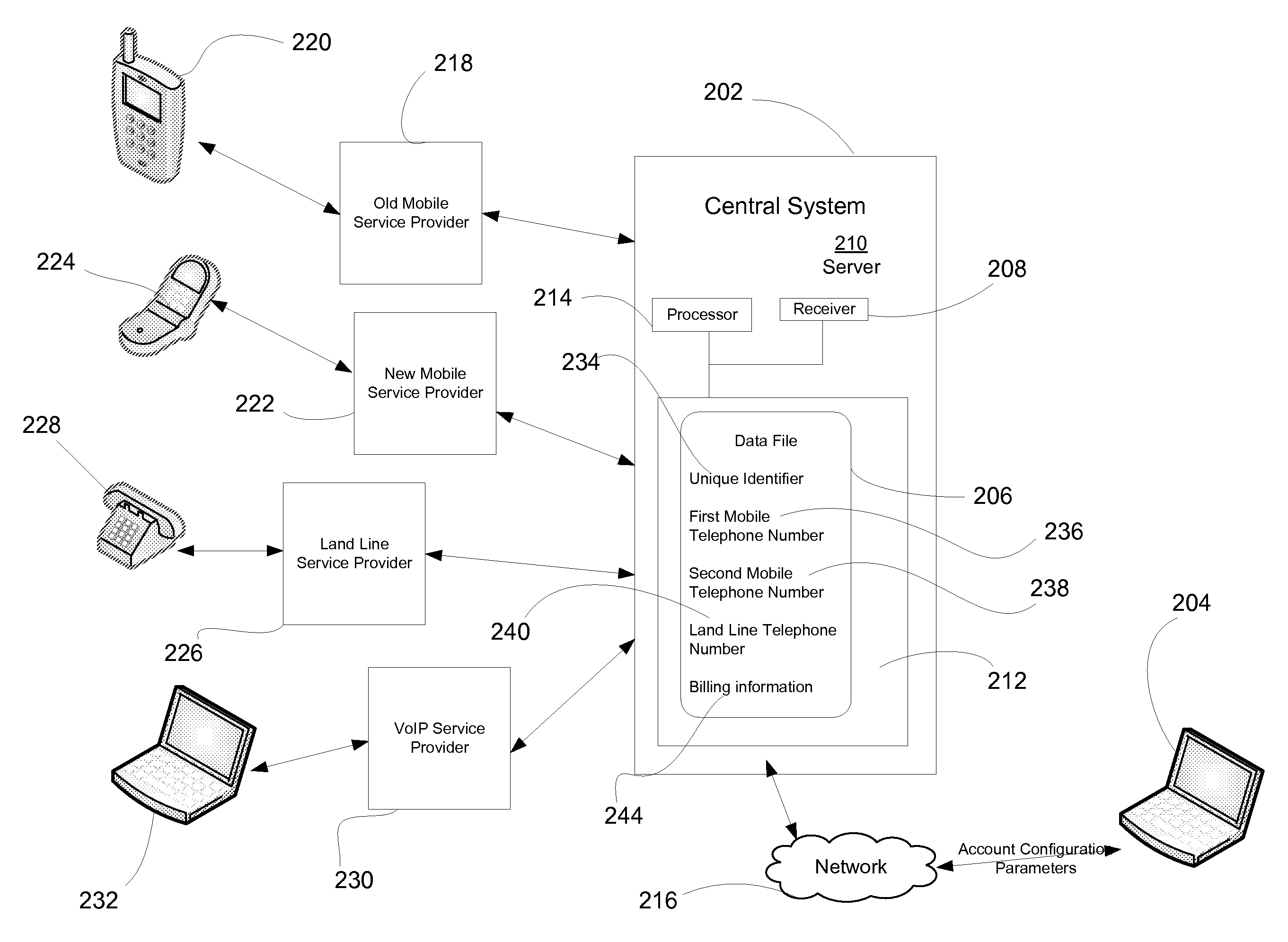
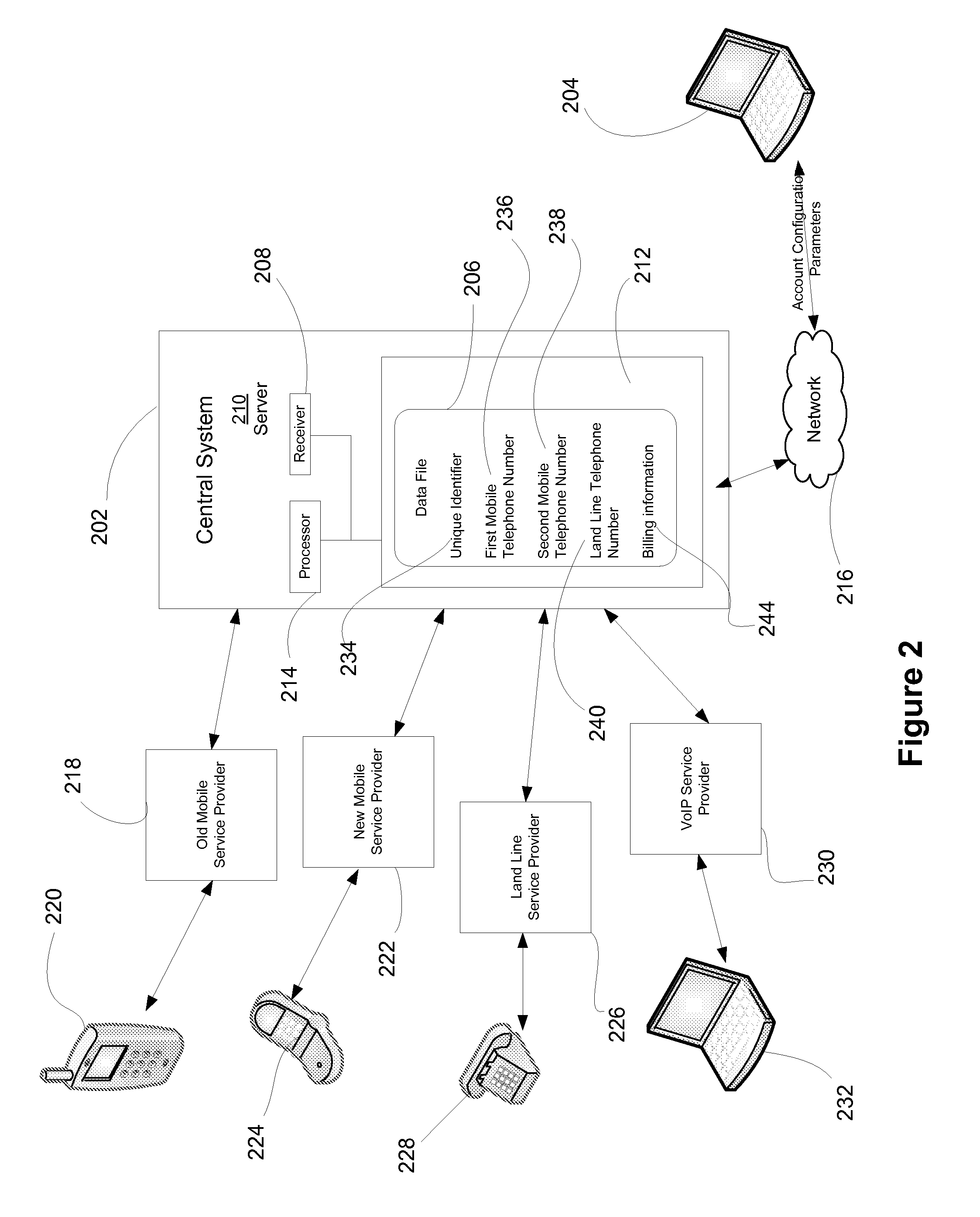
InactiveUS20090022301A1Interconnection arrangementsSpecial service for subscribersUser deviceUnique identifier
Systems and methods are disclosed for routing a telephone call to a central system. A plurality of telephone numbers may be associated with a unique identifier. The unique identifier is associated with a data file that is stored on the central system. The data file stores data such as a user's old telephone number and a user's new telephone number. When a request is received from a request initiator to the user's old telephone number, the central system may recognize the old telephone number because it is associated with the unique identifier and may route the request to the new telephone number. A user may register a user device with the unique identifier so that the user receives all requests by callers to the old telephone number and the new telephone number. A user may reject telephone calls and may be permitted to remotely access to the central system.
Owner:ACCENTURE GLOBAL SERVICES LTD
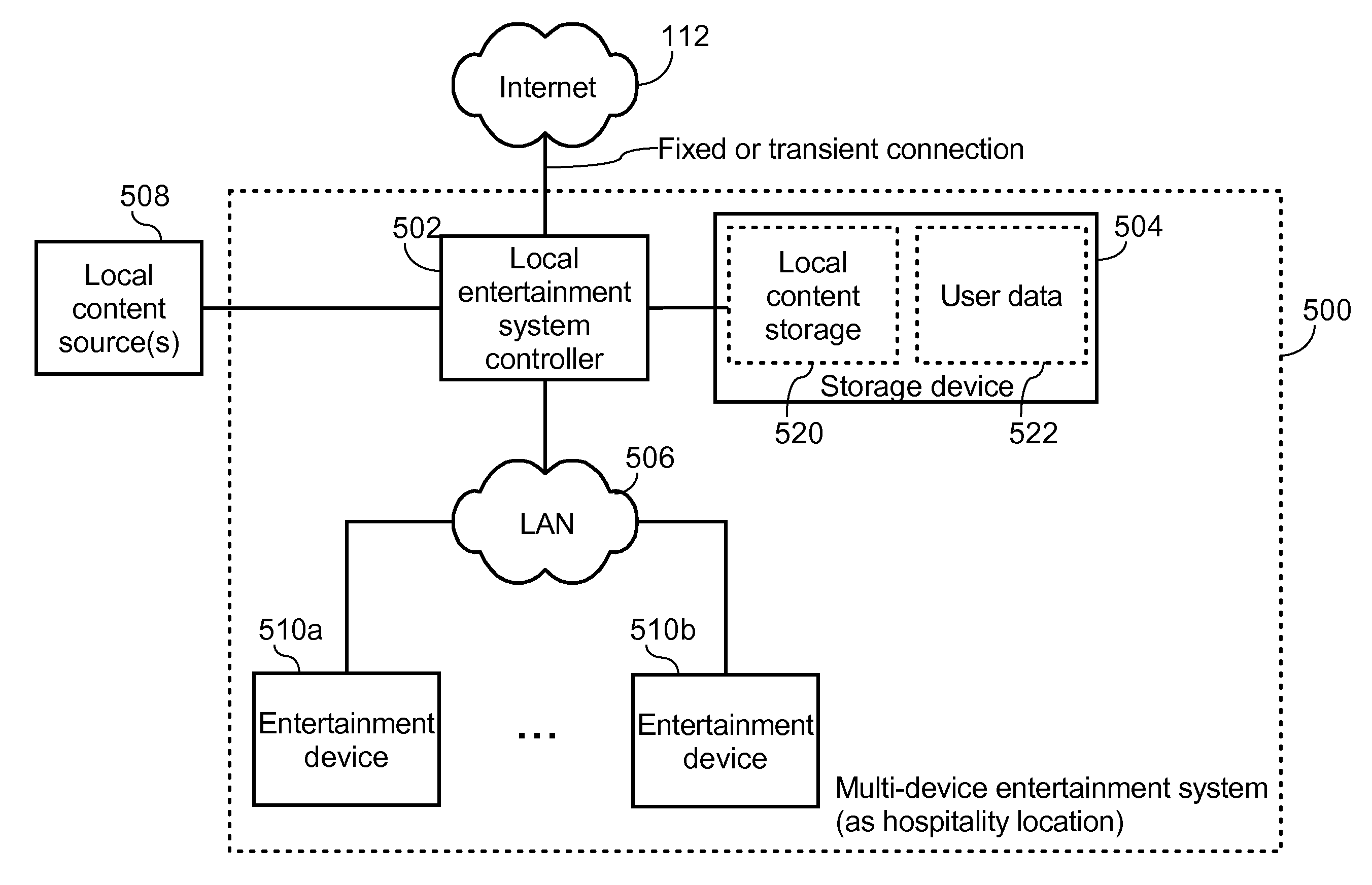
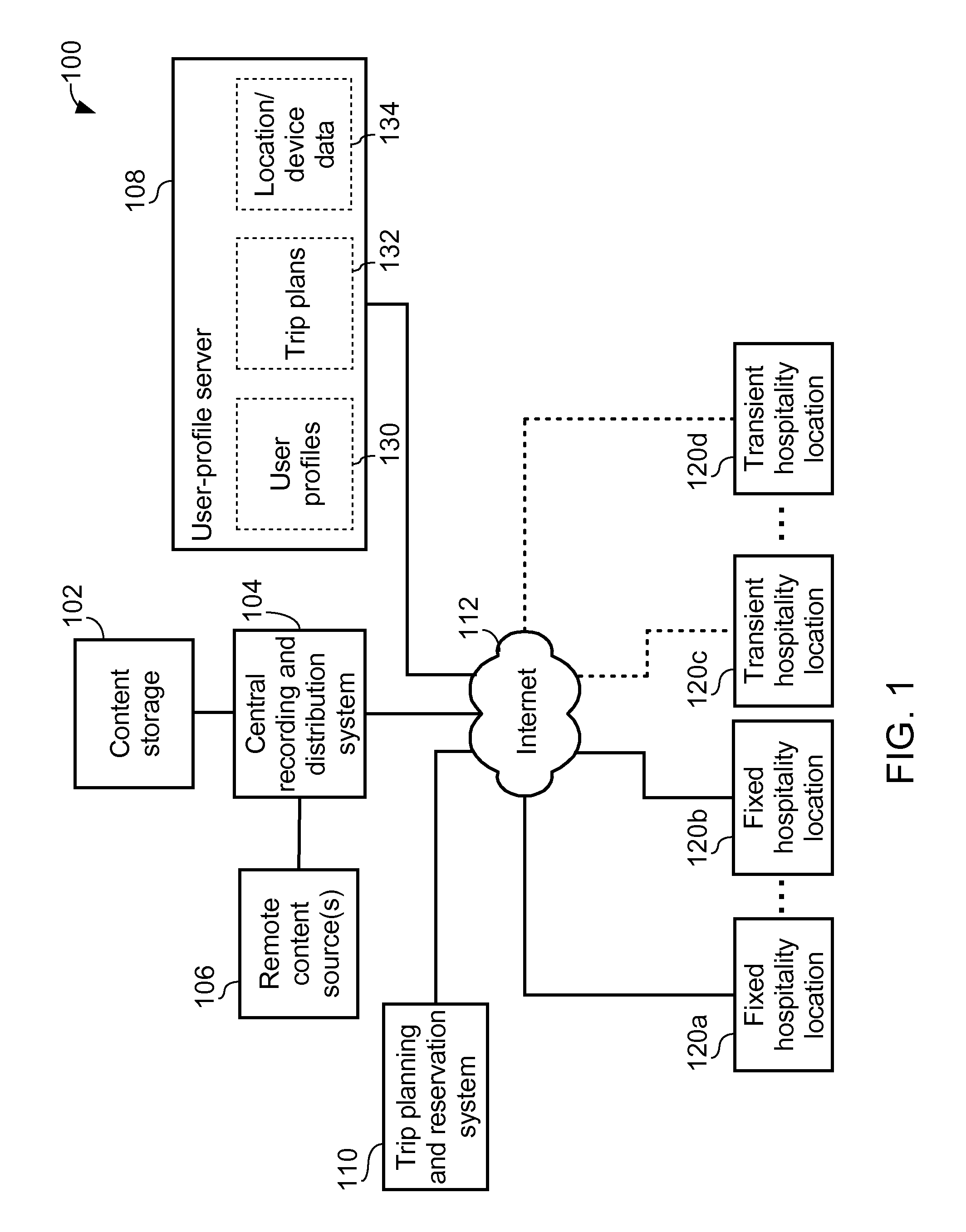
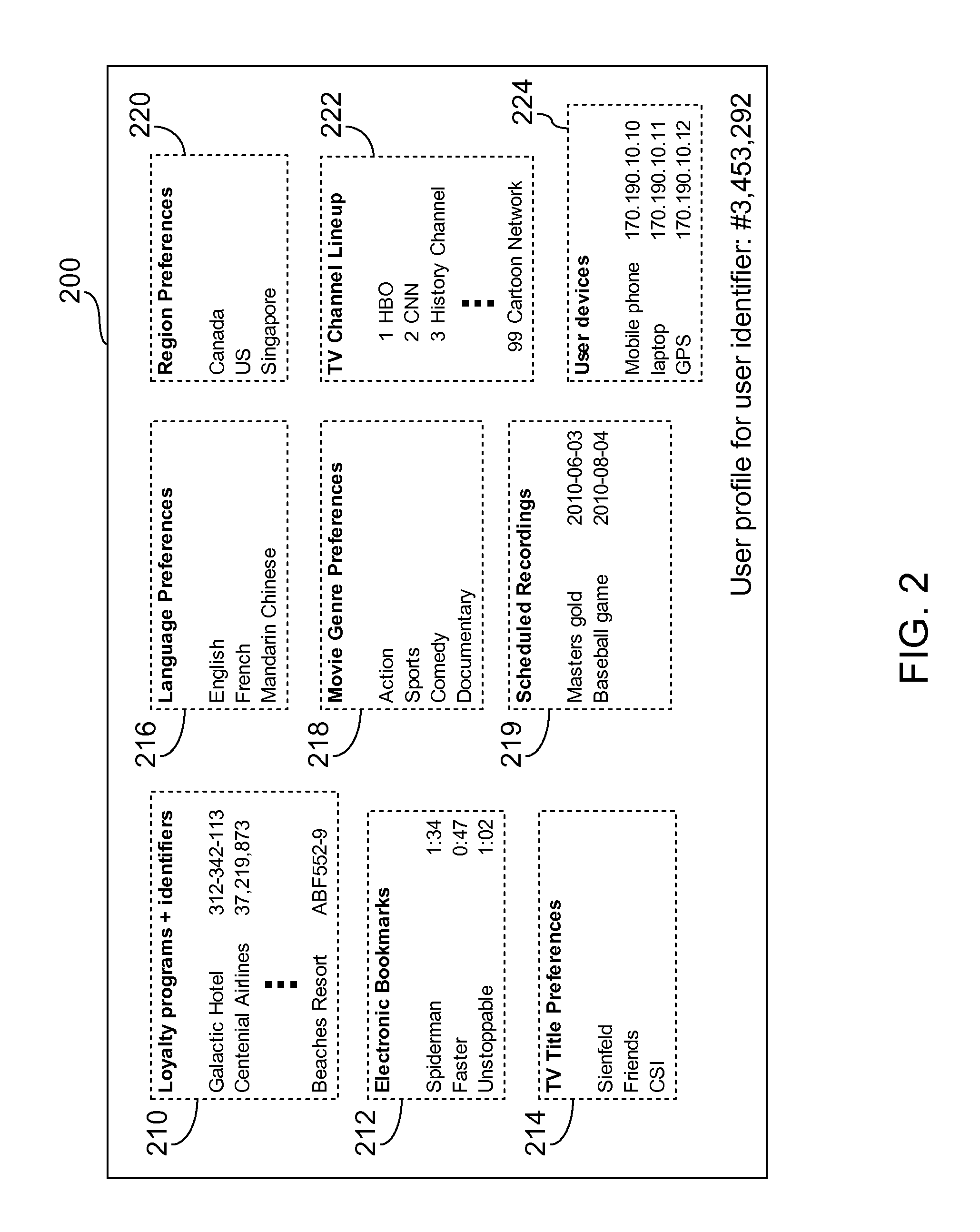
User-profile server for providing user-tailored entertainment experience across different entertainment devices and method thereof
ActiveUS20120011551A1Television system detailsDigital data processing detailsNetwork connectionUser identifier
A user-profile server for providing a user-tailored entertainment experience across different entertainment devices includes a network connection for coupling the user-profile server to a network. The user-profile server is configured for storing a user profile corresponding to a user identifier, and receiving via the network an electronic bookmark, the electronic bookmark being associated with the user identifier and pertaining to content that was not finished by a user at a first entertainment device. The user-profile server is further configured for updating the user profile to include the electronic bookmark, and communicating via the network at least the electronic bookmark to a controller of a second entertainment device to thereby allow the second entertainment device to play the content automatically starting from a position in the content corresponding to a position indicated by the electronic bookmark. The first entertainment device and the second entertainment device are different devices.
Owner:GUEST TEK INTERACTIVE ENTERTAINMENT
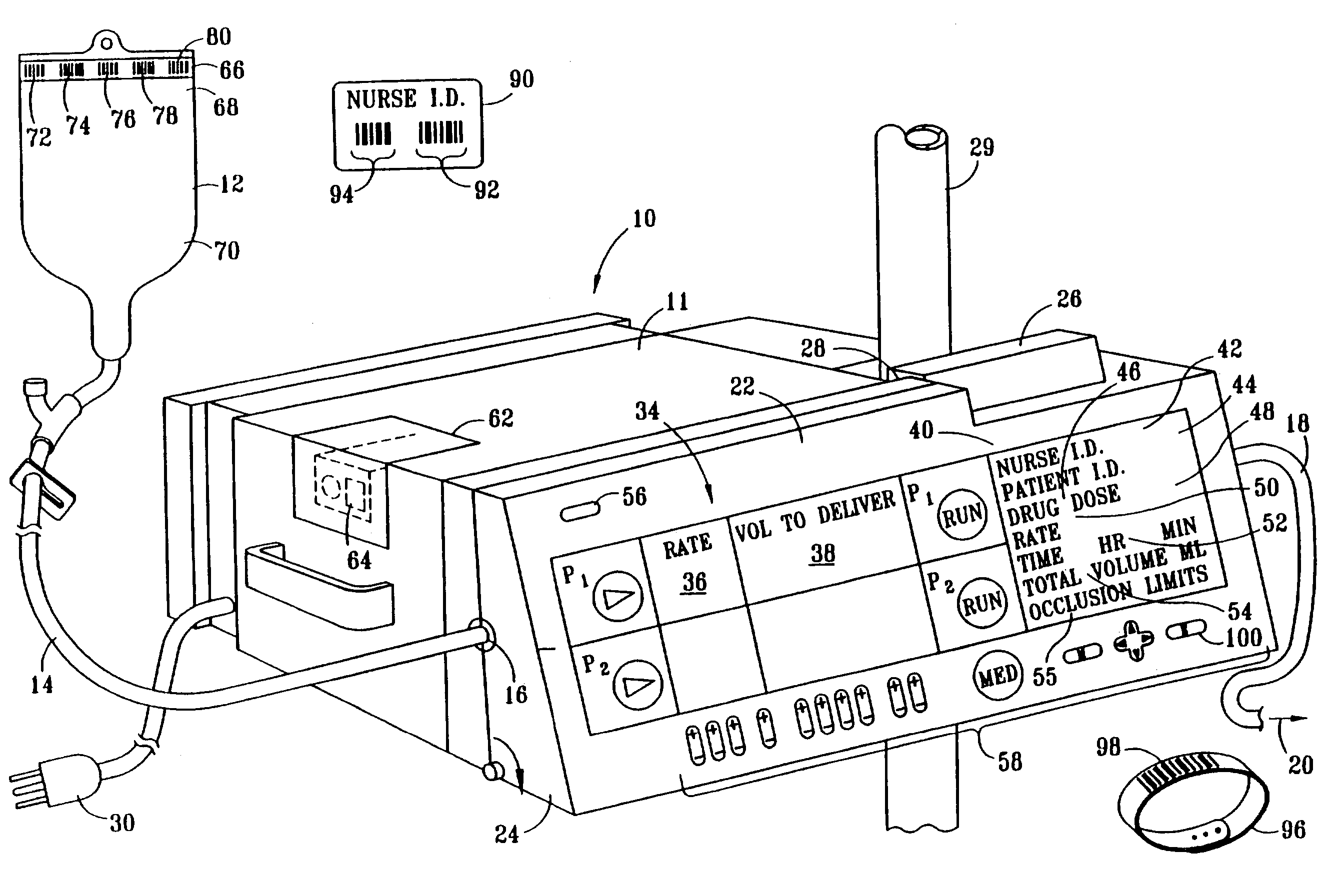
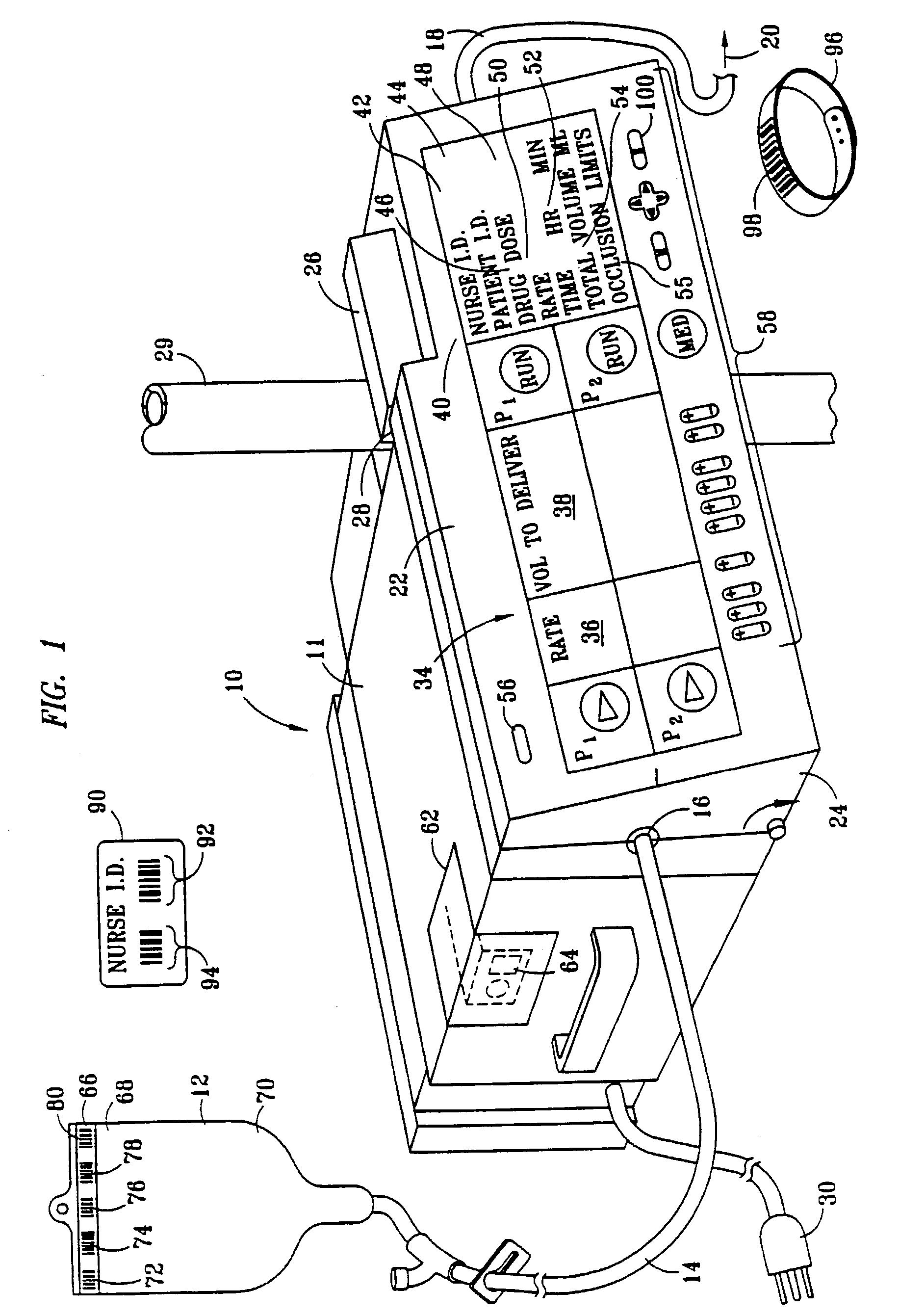
Security infusion pump with bar code reader
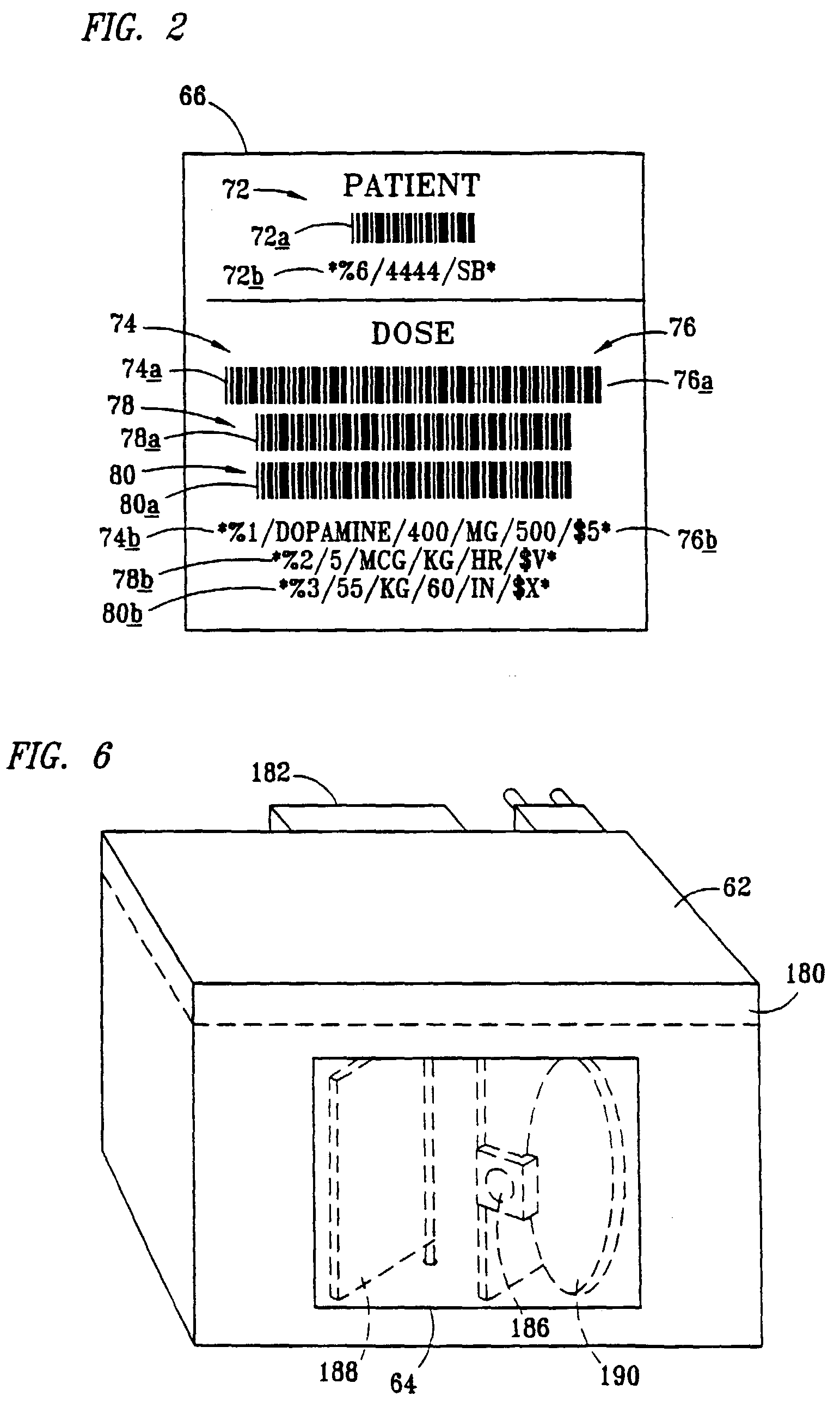
InactiveUS7236936B2Improve accuracyImprove securityDrug and medicationsMedical devicesData operationsBarcode
A medical infusion pump with a bar code reader having simplified and enhanced security features. The infusion pump with bar code reader is comprised of an infusion pump with a housing, a control display screen and control software for operating the infusion pump according to input infusion data. A bar code reader is contained in the infusion pump housing and operatively attached to communicate scanned bar code infusion data to the pump display screen and to the control software. At least one initialization button for starting execution of a bar code scanning program is operatively connected through circuitry in the pump, the program activating the bar code reader to scan for an authorized user code, for an authorized user ID code, for a patient ID code, and for infusion data compatible for operating the infusion pump. A confirmation program and confirmation buttons manually operable by the authorized user. Acceptable scanning of authorization code, authorized user ID code, patient ID code and infusion data must be manually confirmed by the authorized user prior to activating the pump to infuse fluids according to the infusion data.
Owner:B BRAUN MEDICAL
Data storage incorporating cryptographically enhanced data protection
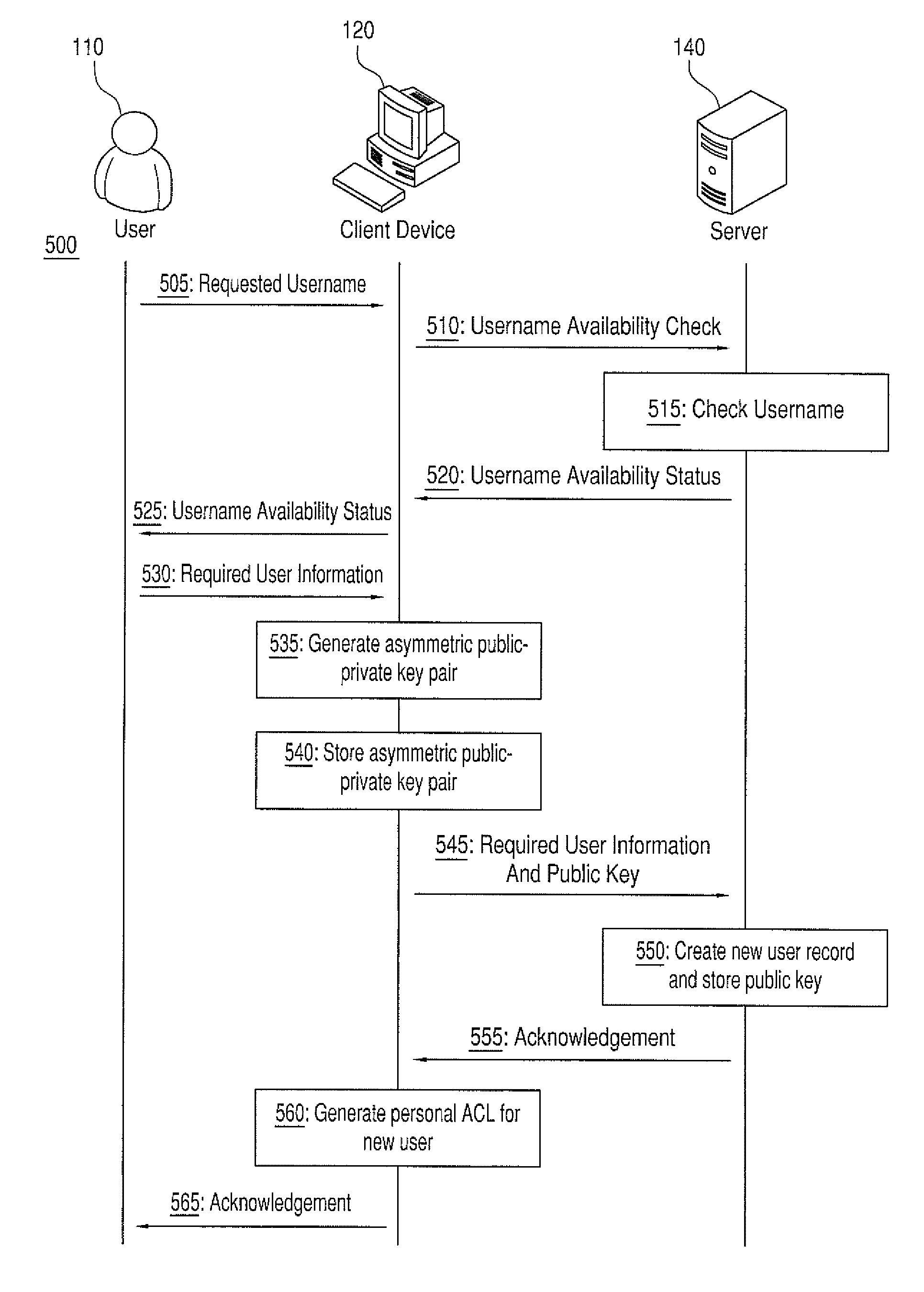
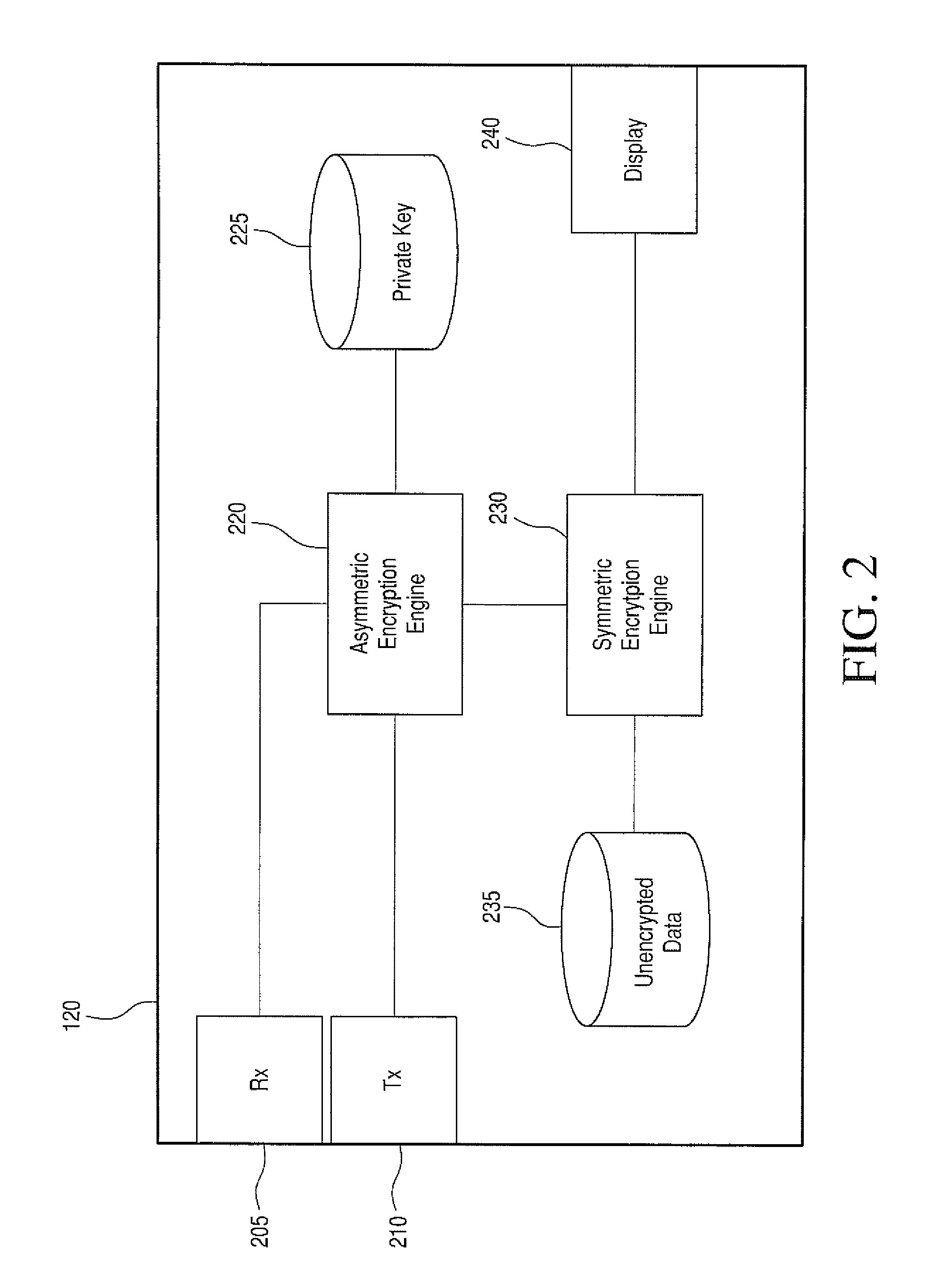
ActiveUS8856530B2Key distribution for secure communicationUser identity/authority verificationVLAN access control listUser identifier
Various exemplary embodiments relate to a system for storing encrypted data and providing access to a group of users. The system may include: a record of user accounts including: a user identifier and a public encryption key; an access control list (ACL) defining an access control policy including: permissions defining access to data objects associated with the ACL and an ACL key list including copies of a an ACL key encrypted with the public keys of the users; a user-data storage medium including: encrypted user data, stored as a plurality of data objects, each object associated with an ACL and encrypted with the ACL key, and meta-data; and an access controller configured to: receive a request for a data object, and send a copy of the data object and the ACL key encrypted with the public key of the user if the user has permission to access the data object.
Owner:ONYX PRIVACY
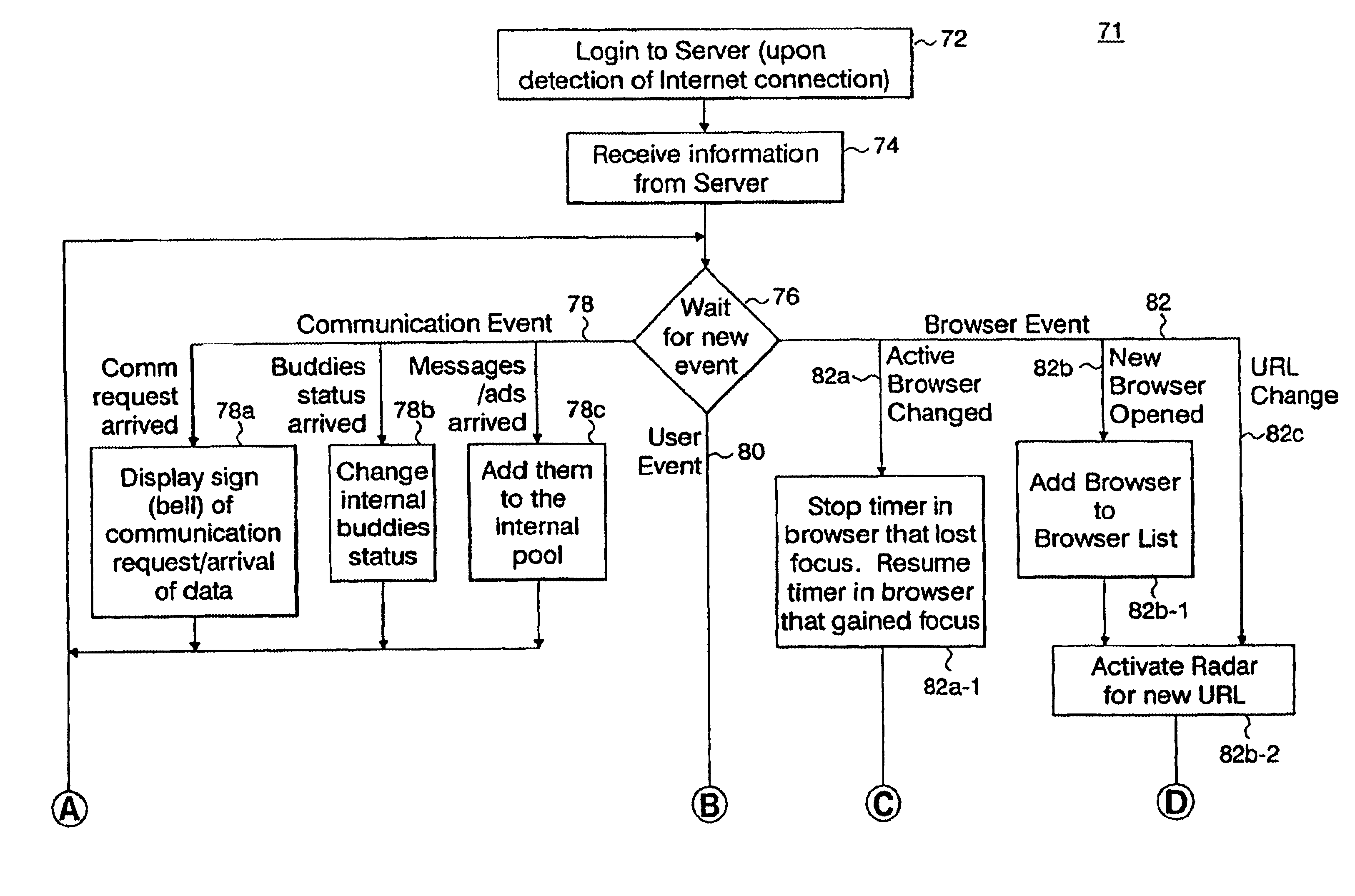
System and method for processing and presenting internet usage information to facilitate user communications
A method for facilitating a chat session between a first user and second users visiting a first web site comprising receiving, from the first user, a first user ID; receiving, from the second user, a second user ID; providing, to the first user, at least an indication of the second user ID; receiving, from the first user, a request to open one of a public chat session, a semi-public chat session and a private chat session with the second user; transmitting, to the second user, an indication that the first user has requested a chat session; and receiving, from the second user, an acceptance to enter the chat session designated by the first user. The method also comprises receiving from the first user a query regarding other users in a co-branded community visiting the first web site and searching a database to determine a response to the query.
Owner:COMVERSE
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com