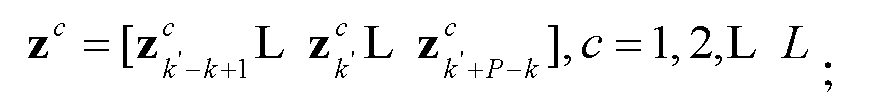Patents
Literature
133 results about "Copy detection" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
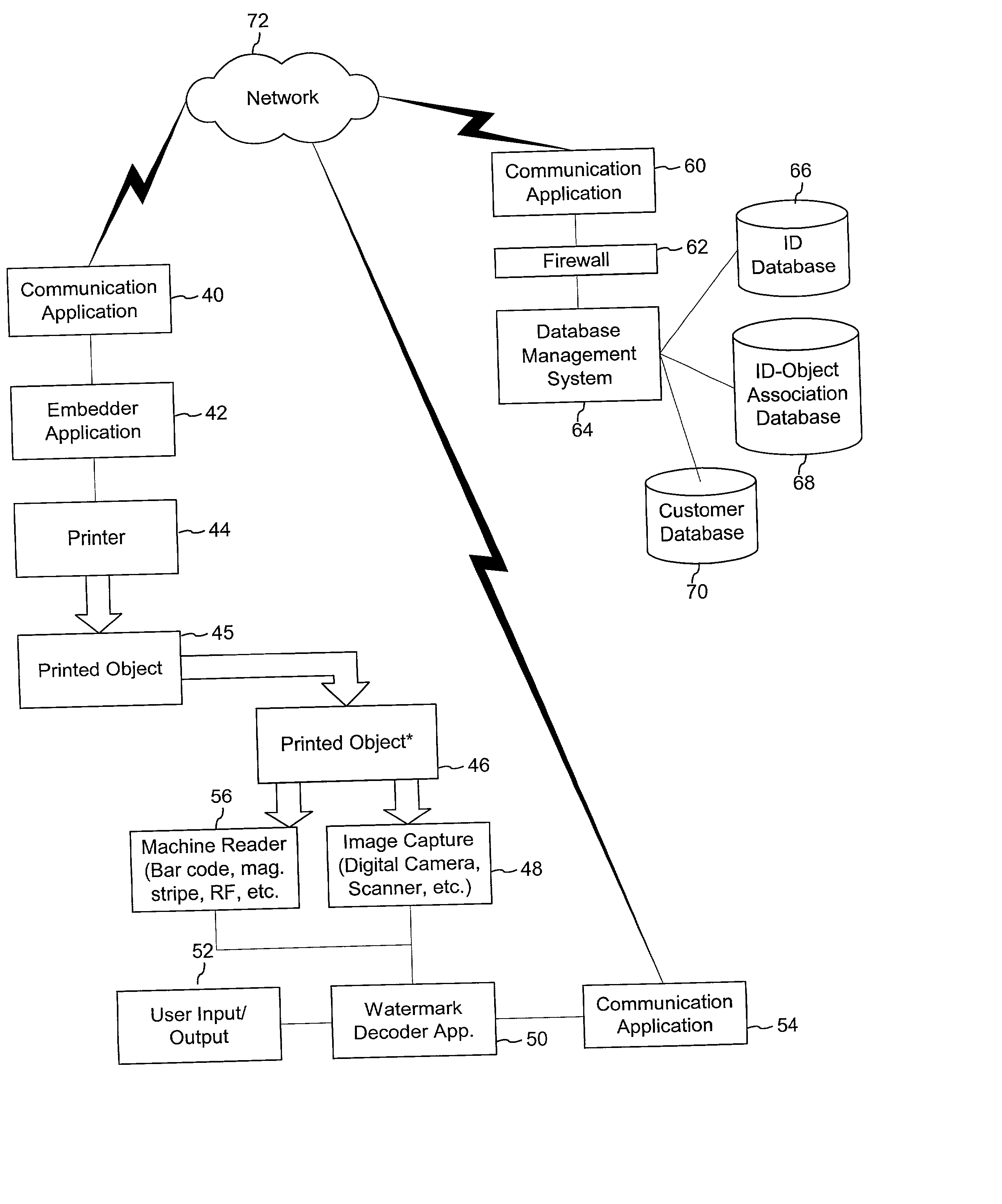
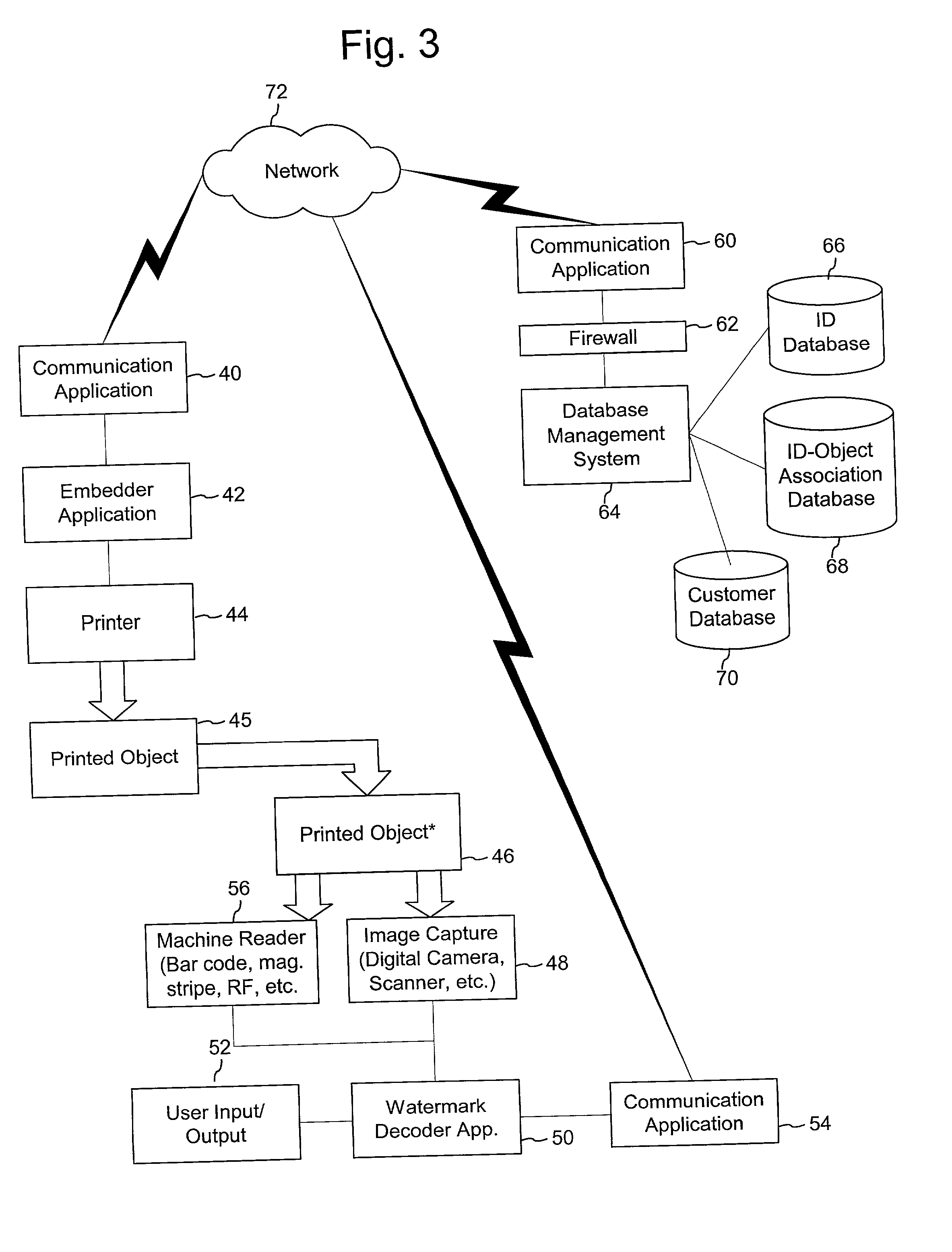
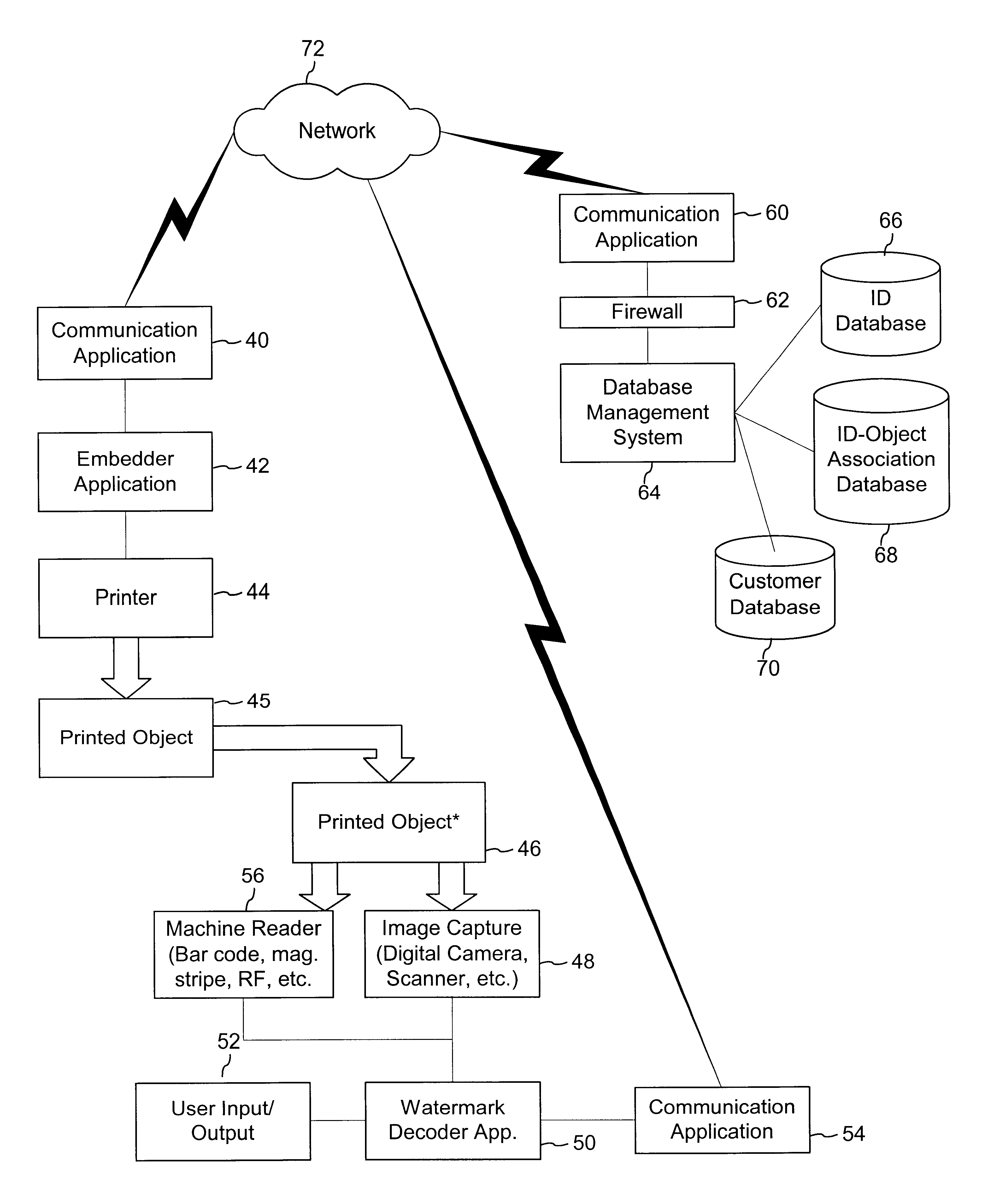
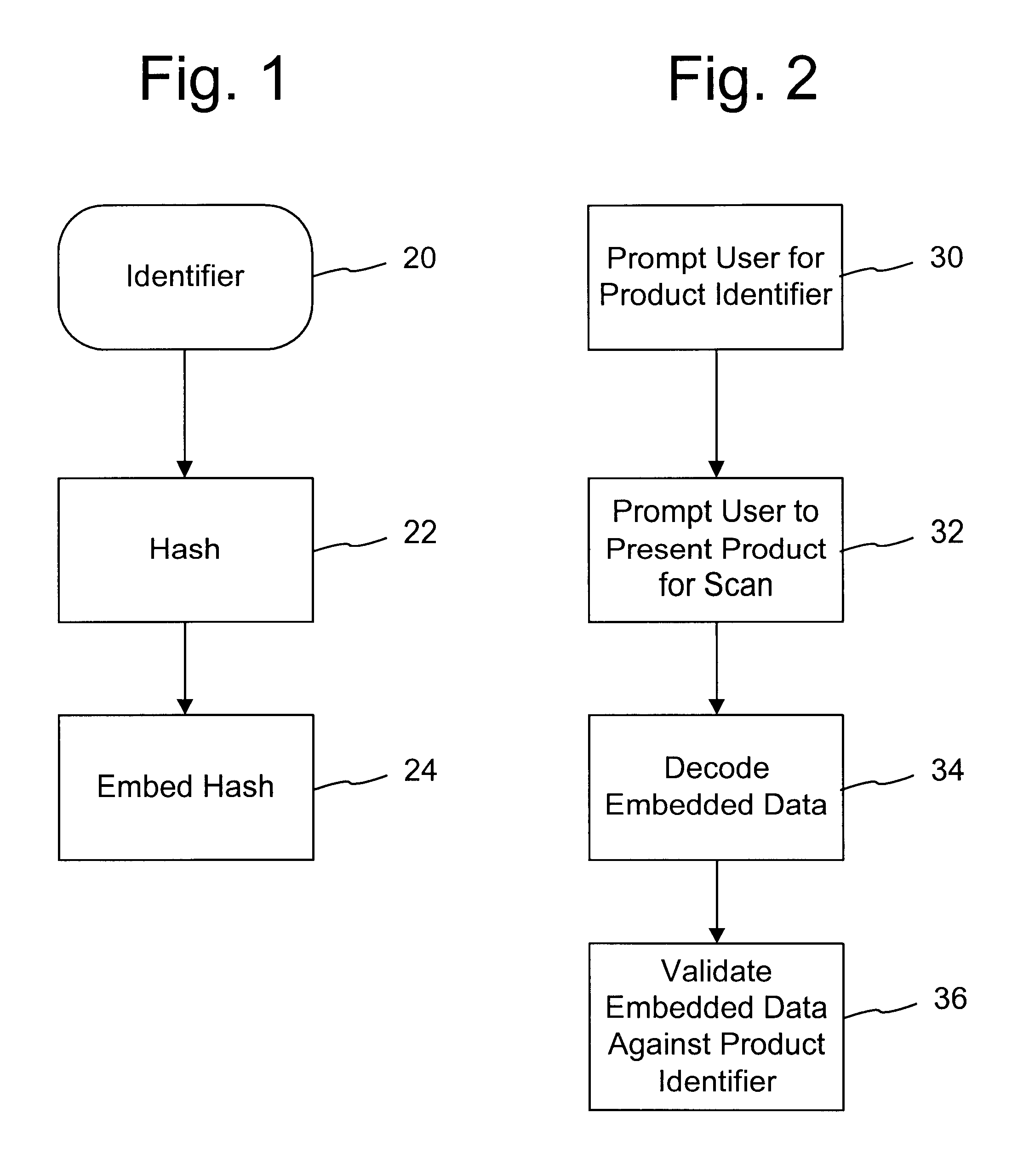
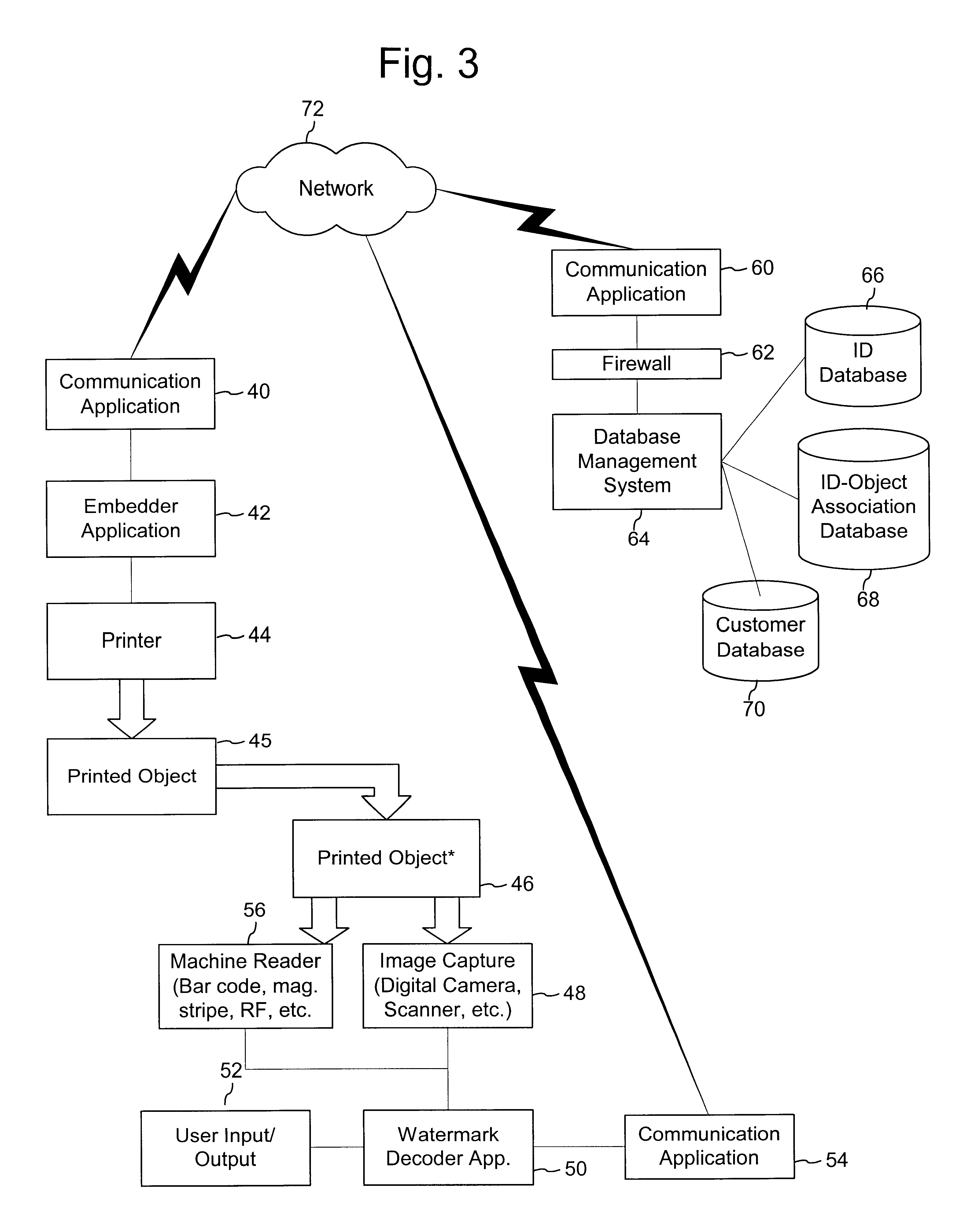
Authentication watermarks for printed objects and related applications
InactiveUS20020012445A1Correct Geometric DistortionMore dataOther printing matterPaper-money testing devicesRelevant informationCopy detection
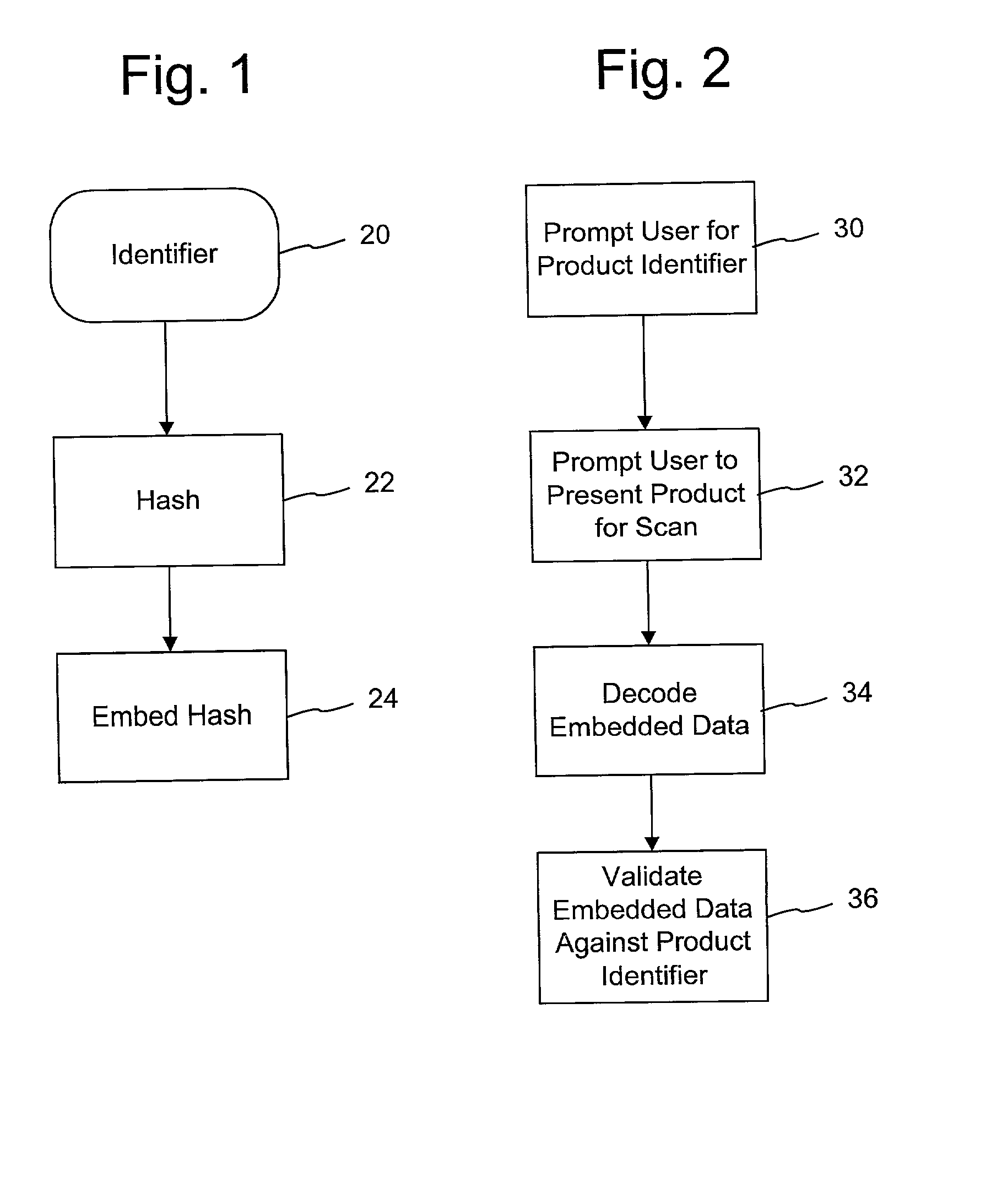
The disclosure describes systems for creating and authenticating printed objects using authentication and copy detection watermarks. For example, one verification system includes a watermark decoder and a verification module. The watermark decoder detects a copy detection watermark in a printed object to determine whether the printed object has been reproduced. The verification module processes a message decoded from an authentication watermark on the printed object to authenticate the printed object or bearer of the printed object. The authentication and copy detection watermarks may be implemented as the same or different watermarks. For example, the copy detection watermark may be a fragile watermark that carries the message and that degrades in response to a reproduction operation, such as photocopying or scanning and then reprinting the object. Alternatively, the authentication and copy detection watermarks may be separate watermarks embedded in an image that is printed on the object. The authentication watermark, in some applications, includes an identifier that links the object to a database entry with related information about the object. This related information can be used to check the bearer of the object by comparing it with attributes of the bearer (such as a user ID or photo) or the validity of the object by comparing it with attributes that are visible or machine readable on the object.
Owner:INTUIT INC
Authentication watermarks for printed objects and related applications
InactiveUS6823075B2More dataCompact formOther printing matterPaper-money testing devicesRelevant informationCopy detection
Owner:INTUIT INC
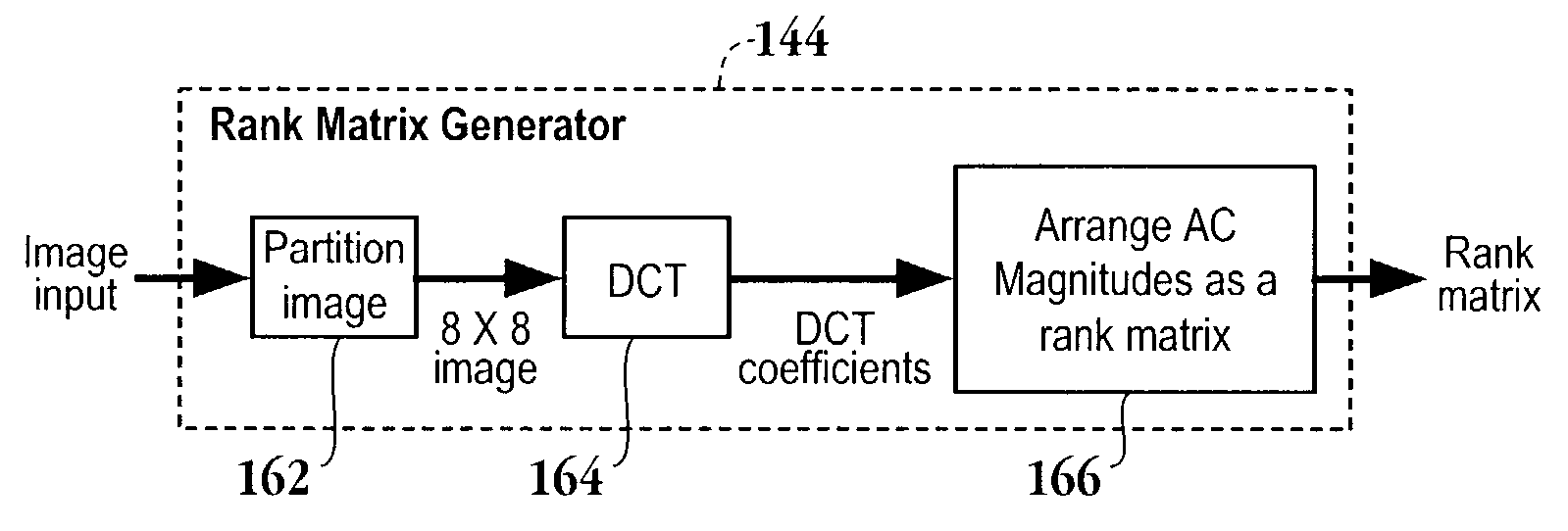
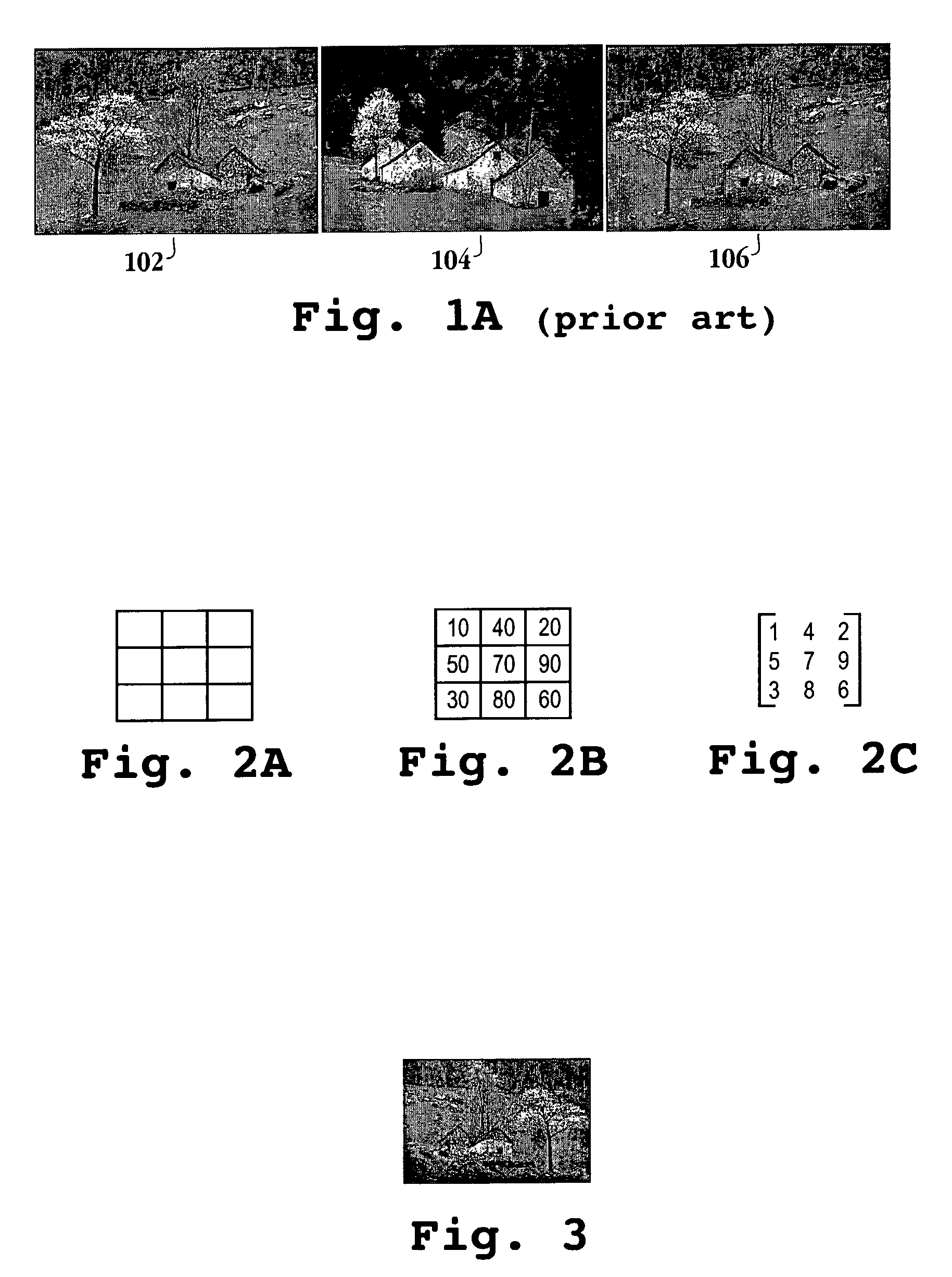
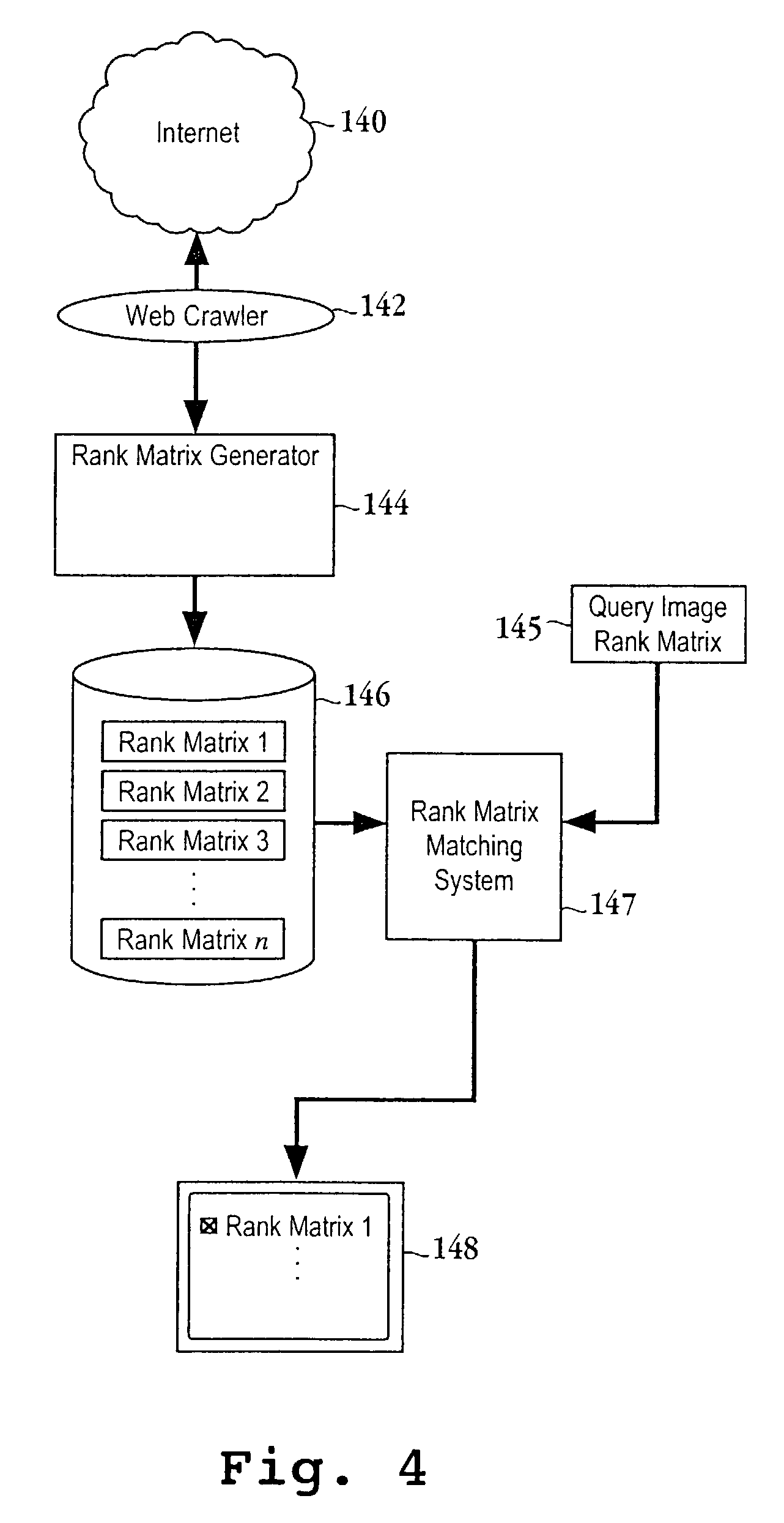
Method and apparatus for content-based image copy detection
InactiveUS7167574B2Digital data information retrievalCharacter and pattern recognitionComputerized systemCopy detection
A method for detecting a copy of a digital image initiates with dividing a suspected copy of a digital image into sub-images. Then, the average intensities associated with each of the sub-images is determined. Next, the average intensities are transformed into a series of coefficients. Then, a rank matrix from the series of coefficients is defined. Next, the rank matrix from the series of coefficients is compared to a rank matrix of a query image to determine if the suspected copy is an actual copy of the digital image. A computer readable media, a computer system and computer code configured to be executed on a computer system are also provided.
Owner:SEIKO EPSON CORP
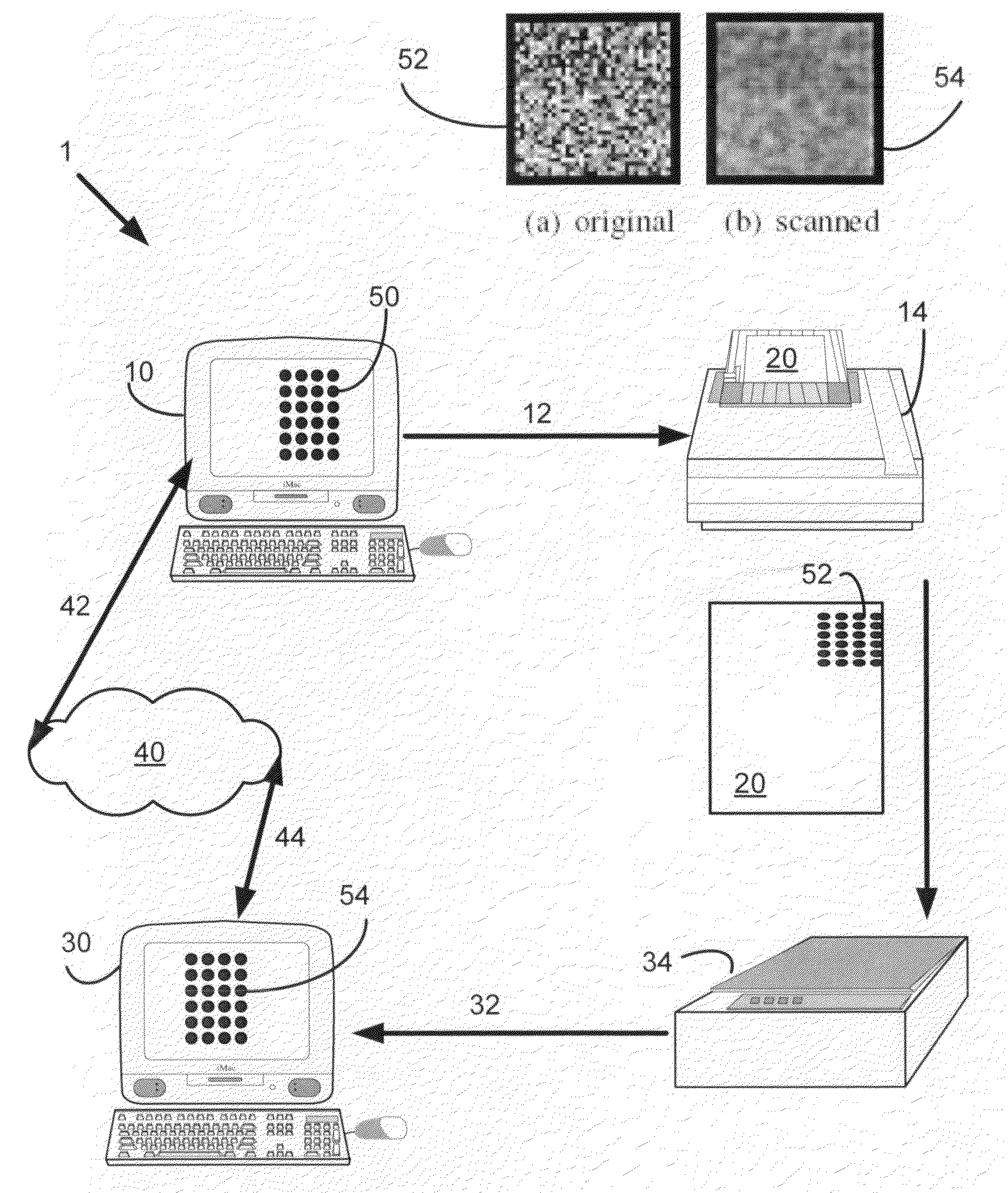
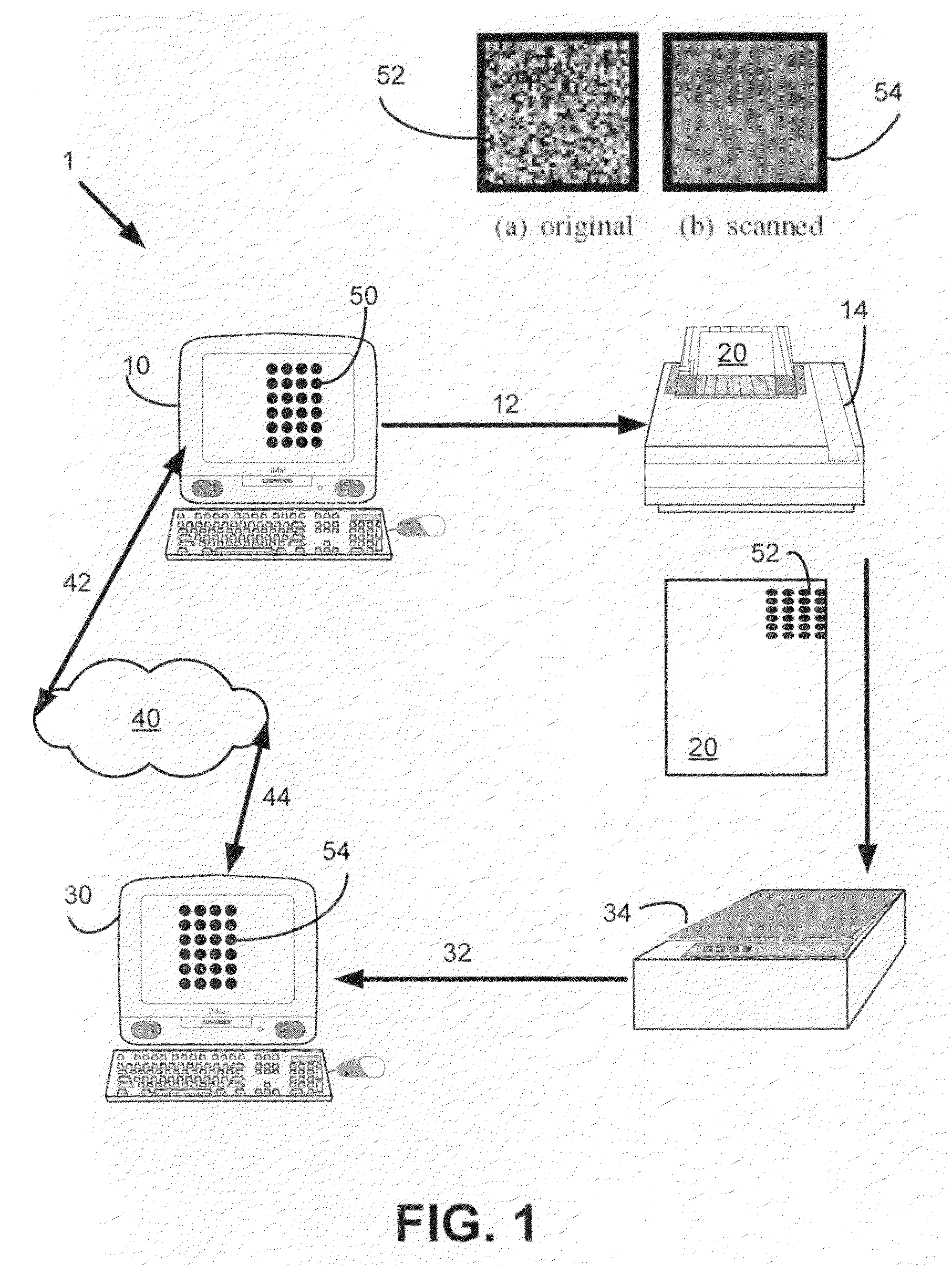
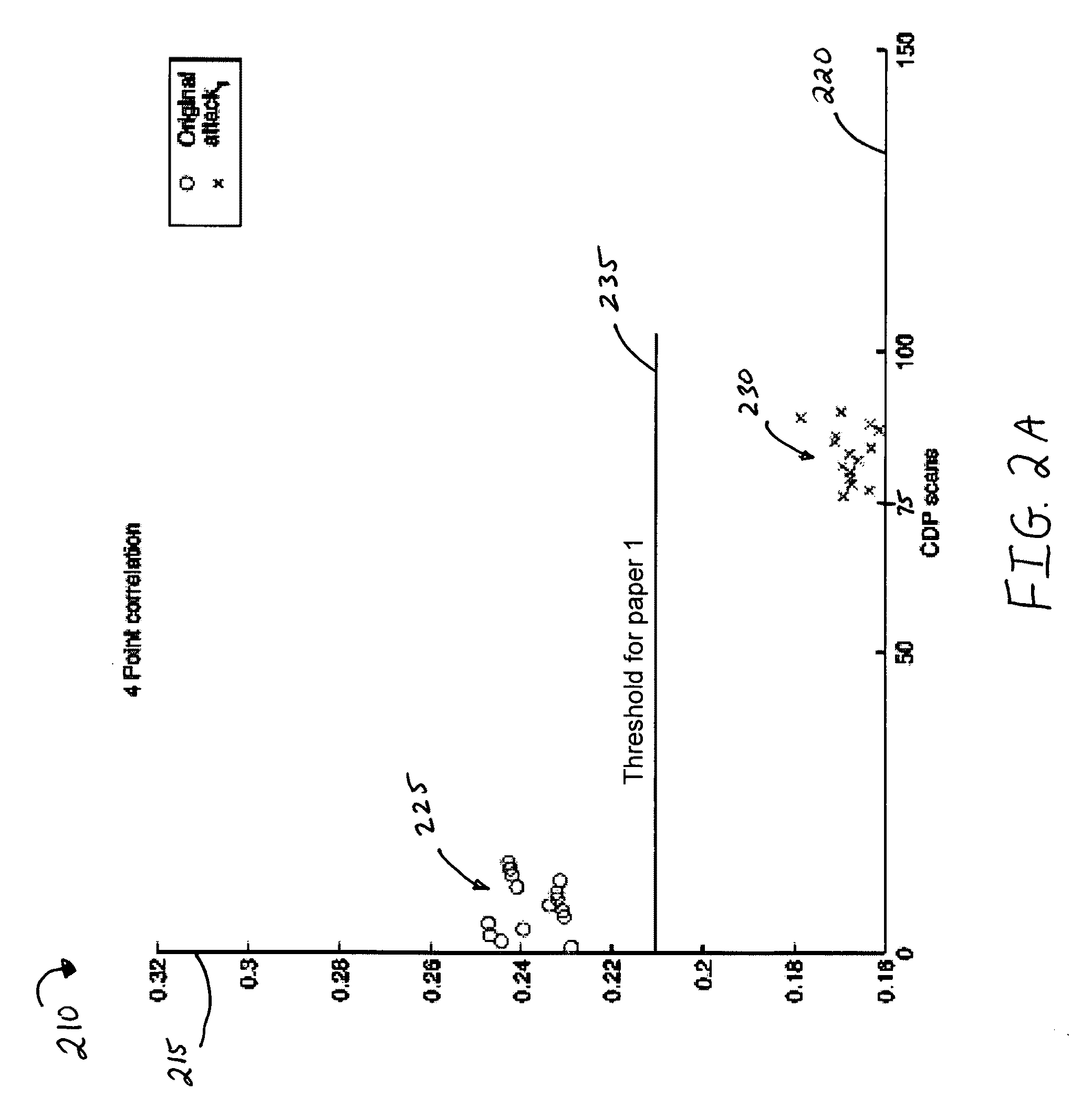
System and method for paper independent copy detection pattern
InactiveUS20100080471A1Efficient and robust verification thresholdDigital data processing detailsCharacter and pattern recognitionCopy detectionDocument preparation
Systems and methods for detecting copies of documents are described. In one example, a system and method for detecting copies of documents utilizes multiple authentication tests performed using original and scanned copy detection patterns. The system captures a CDP that may be skewed or improperly sized. The system also retrieves or reconstitutes the expected CDP. Then the system performs a first correlation to determine if the captured CDP indicates the correct document identification and then if necessary, one or more authentication tests are applied wherein the authentication test may be grouped into distinct orthogonal test groups. The authentication tests applied may be selected according to usefulness, system throughput or target document valuation parameters.
Owner:PITNEY BOWES INC
Network multimedia copyright active following and monitoring system
InactiveCN101794363AHigh-speed distributionHigh speed propagationTransmissionProgram/content distribution protectionComputer moduleMonitoring system
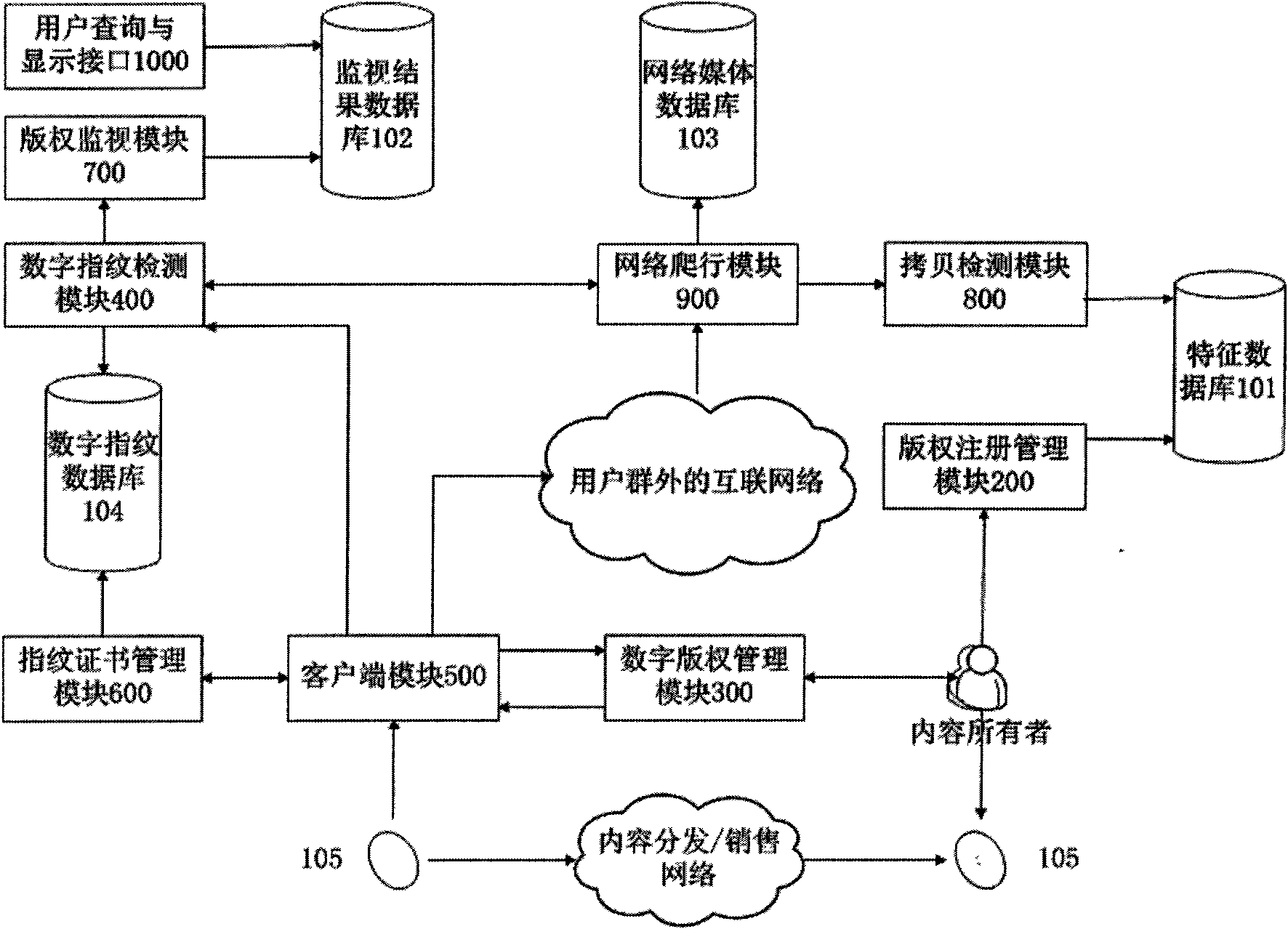
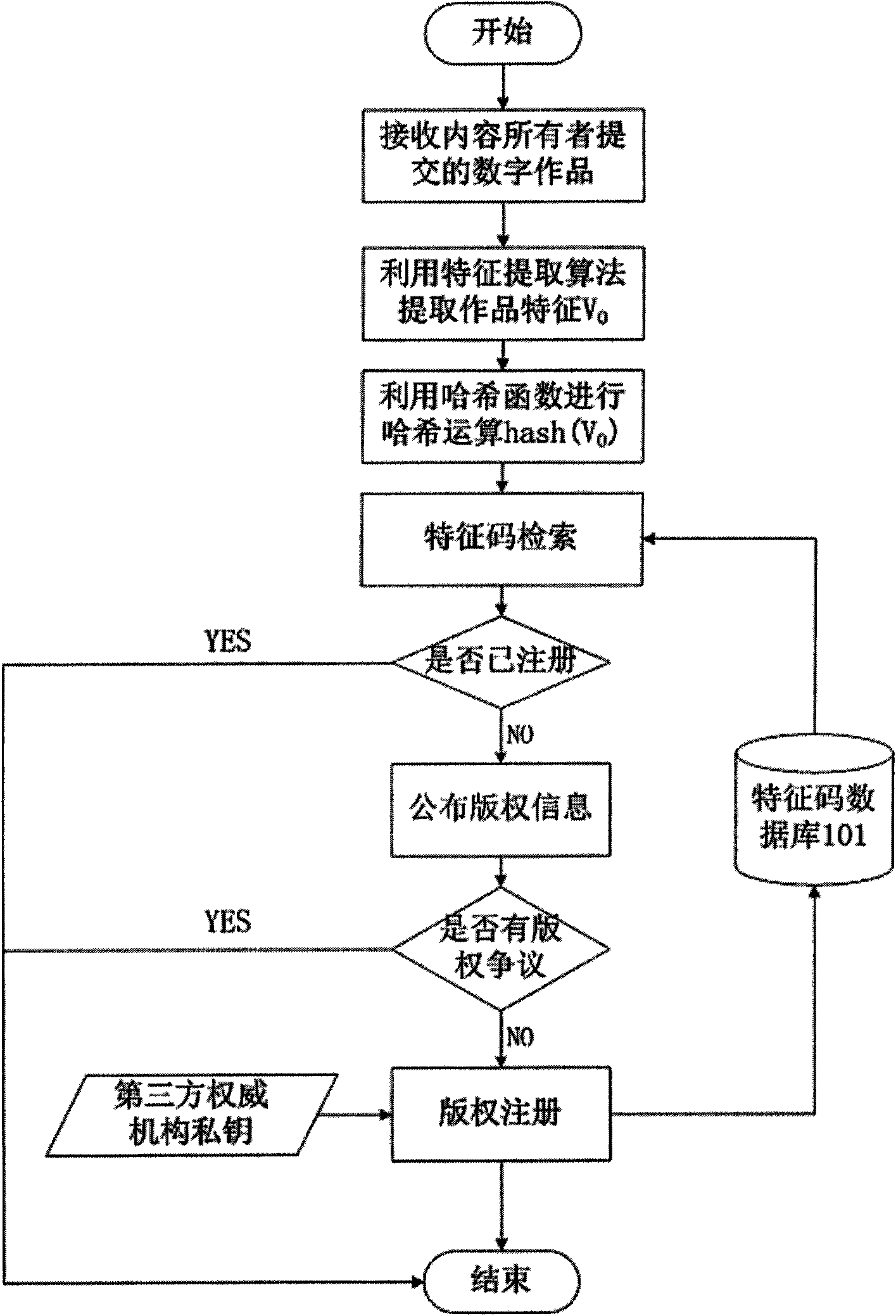
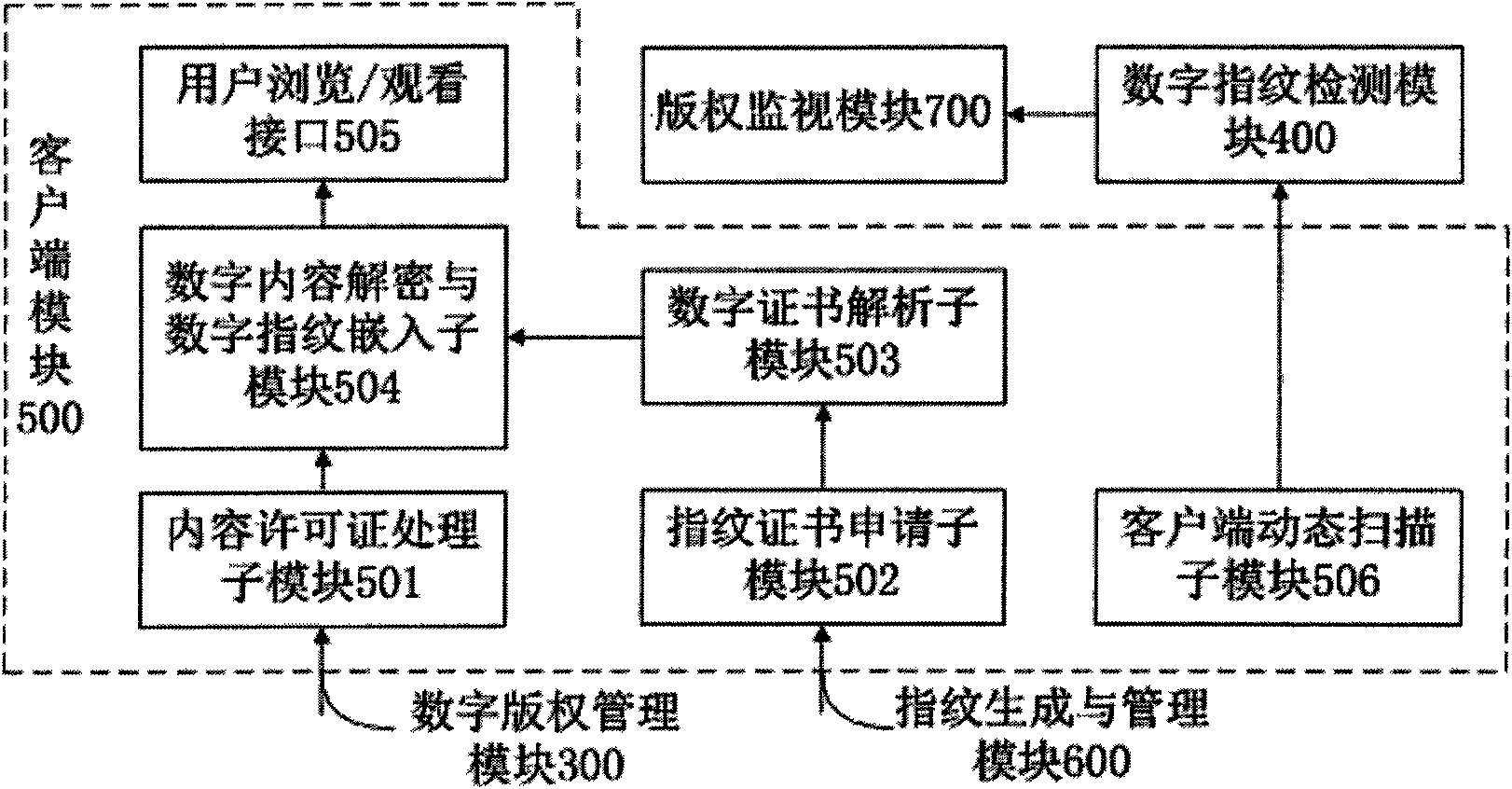
The invention discloses a network multimedia copyright active following and monitoring system. By taking digital fingerprinting and copy detection technology as a core and closely combining with a conventional DRM system, a frame for discovering, following, administrating and monitoring illegal multimedia copies under a network environment is constructed and an active following mechanism, digital fingerprint generation and embedding technology supporting bulk capacity users, copy detection technology and copyright registration and administration technology are realized. The system comprises a characteristic database, a monitoring result database, a network media database, a digital fingerprint database, a copyright registration and management module, a digital copyright management module, a digital fingerprint detection module, a client module, a fingerprint certificate management module, a copyright monitoring module, a copy detection module, a network crawling module and a user query and display interface. Aiming at problems existing in multimedia digital copyright, the invention provides the network multimedia copyright active following and monitoring system, which realizes the copyright active following mechanism and overcomes the shortcoming of the passiveness of a conventional digital fingerprint system.
Owner:HUAZHONG UNIV OF SCI & TECH
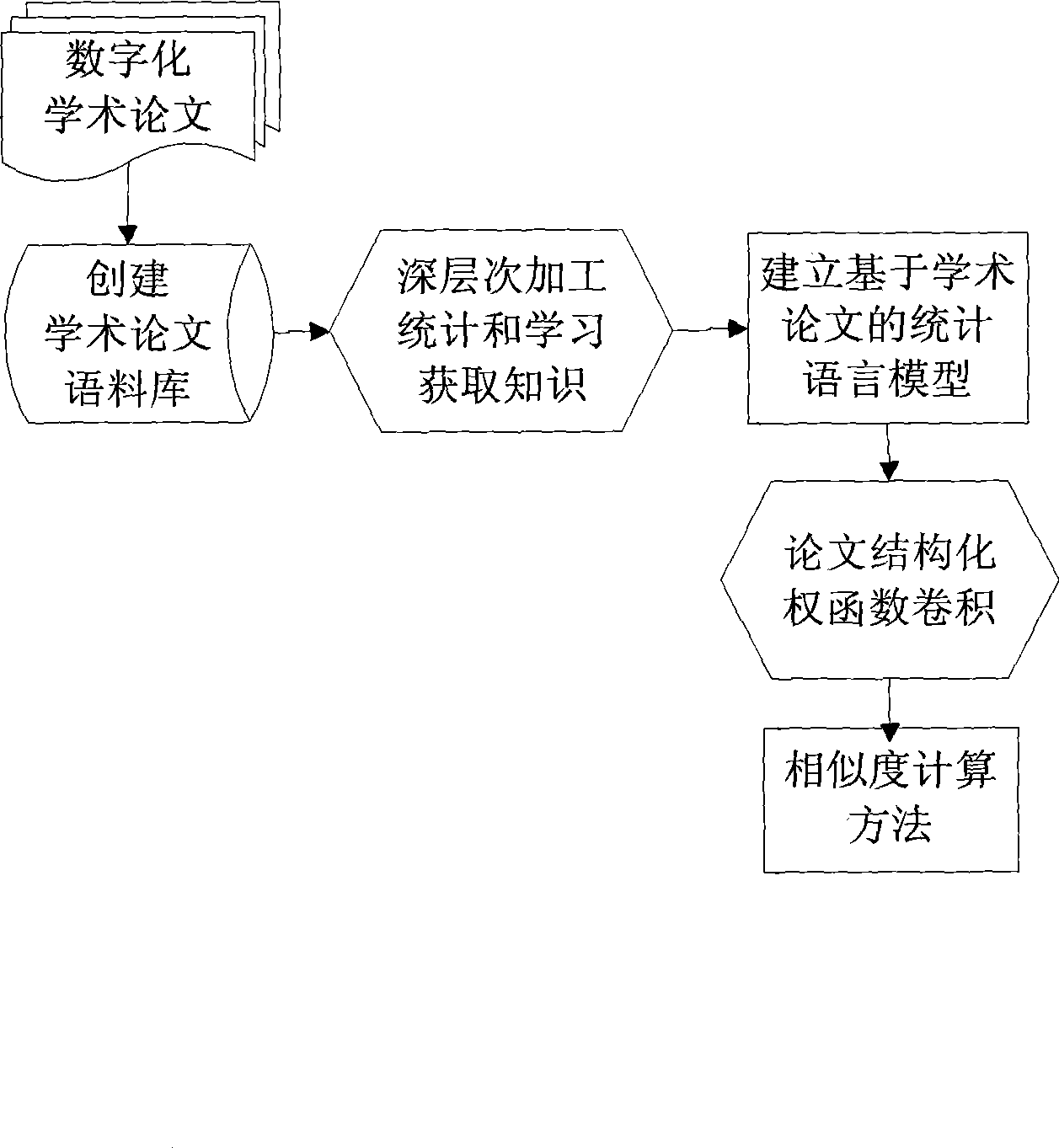
Detection method for academic dissertation similarity based on computer searching system
InactiveCN101369279AShorten the timeReduce excess spaceSpecial data processing applicationsUser inputCopy detection
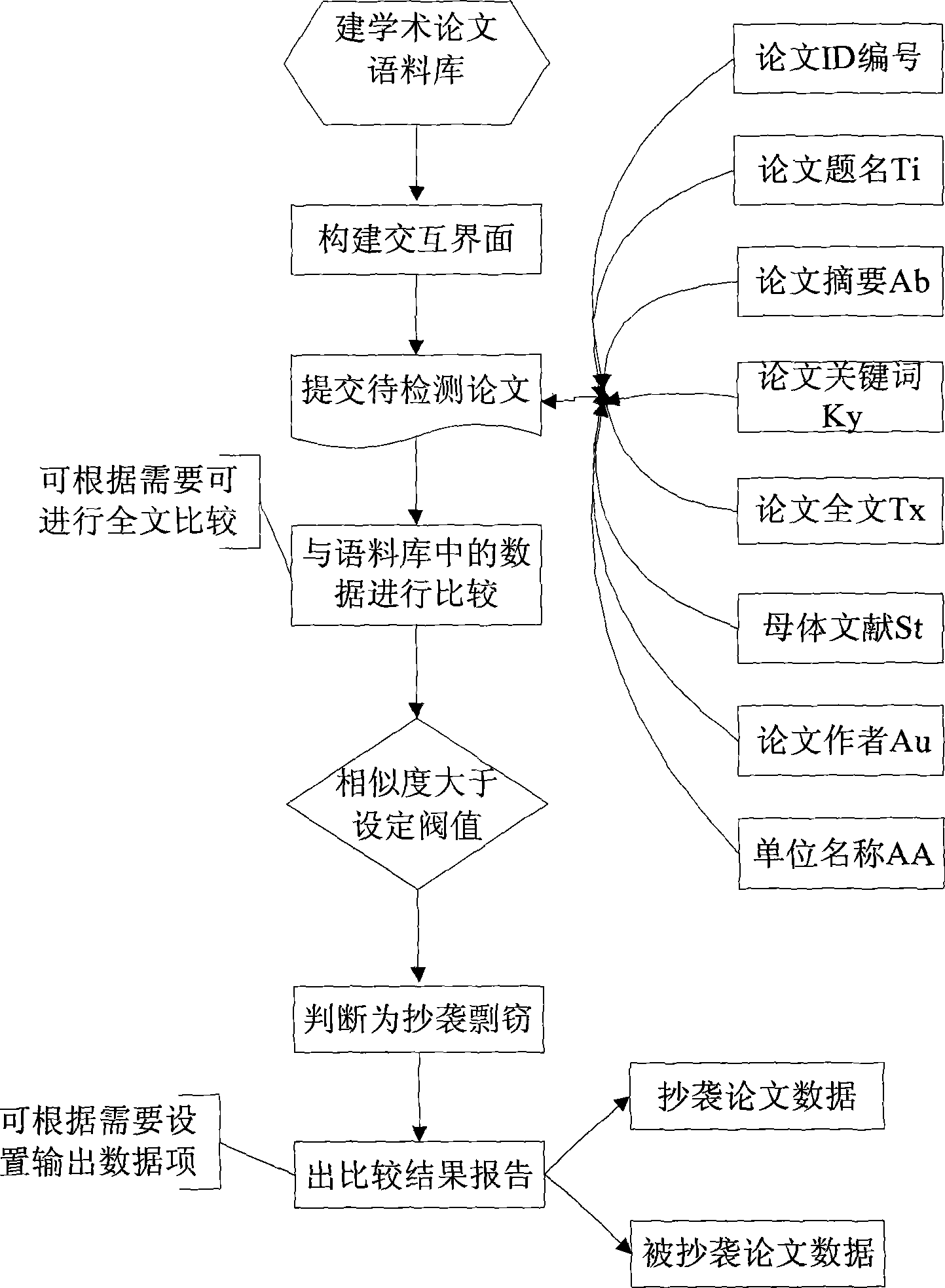
The invention relates to a detection method on similarity of academic thesis based on a computer searching system, to provide a searching model and a similarity algorithm with pertinence through using structures and language features of the academic thesis, thereby increasing speed and efficiency of copy edit of the expert when the thesis is submitted to a higher level for approval or revision. A technical scheme of the invention comprises: an academic thesis copy detecting method based on the computer searching system, comprising the steps of: the step of building an academic thesis database on a server; the step of building a storage space of the academic thesis data based on the computer searching system; the step of building an alternation window on the server for the user to input searching condition; the step of submitting the academic thesis to be detected; building the academic thesis data ans storing according to the set searching condition; the step of comparing the academic thesis data and the data in a source database; the step of submitting the compacting result to the user by the server.
Owner:JIANGSU UNIV
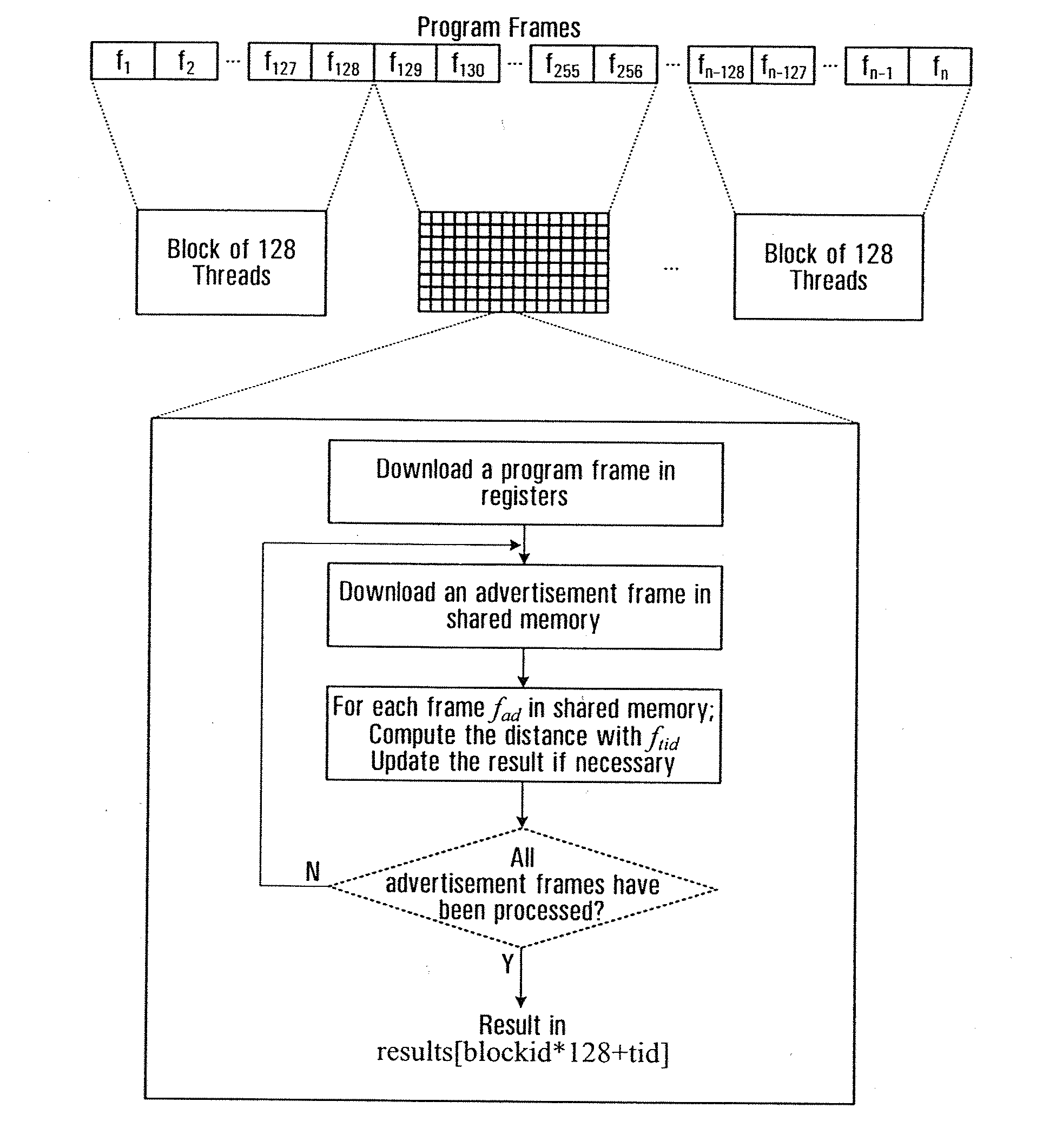
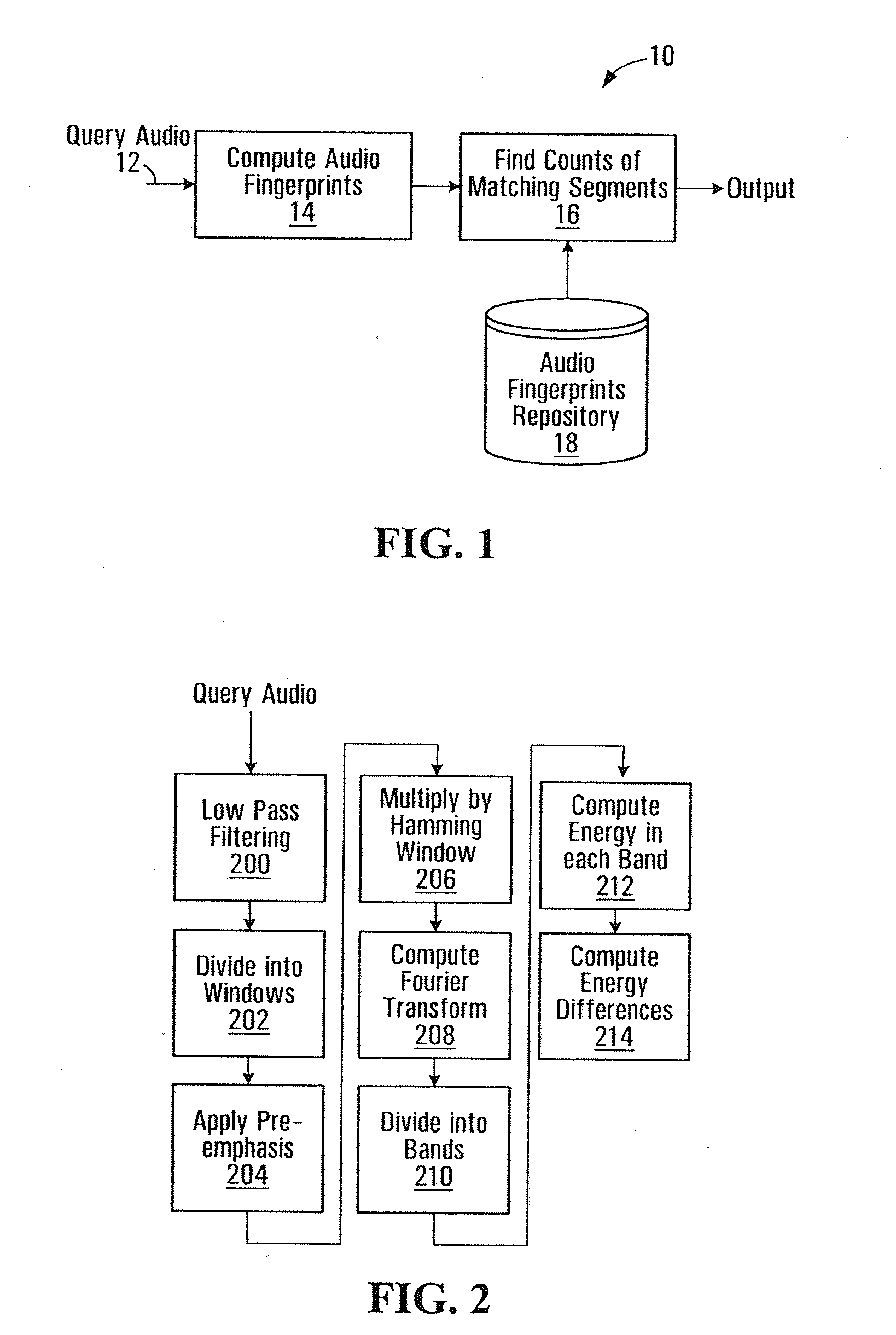
Content based audio copy detection
ActiveUS20110082877A1Electrophonic musical instrumentsDigital data processing detailsComputer hardwareCopy detection
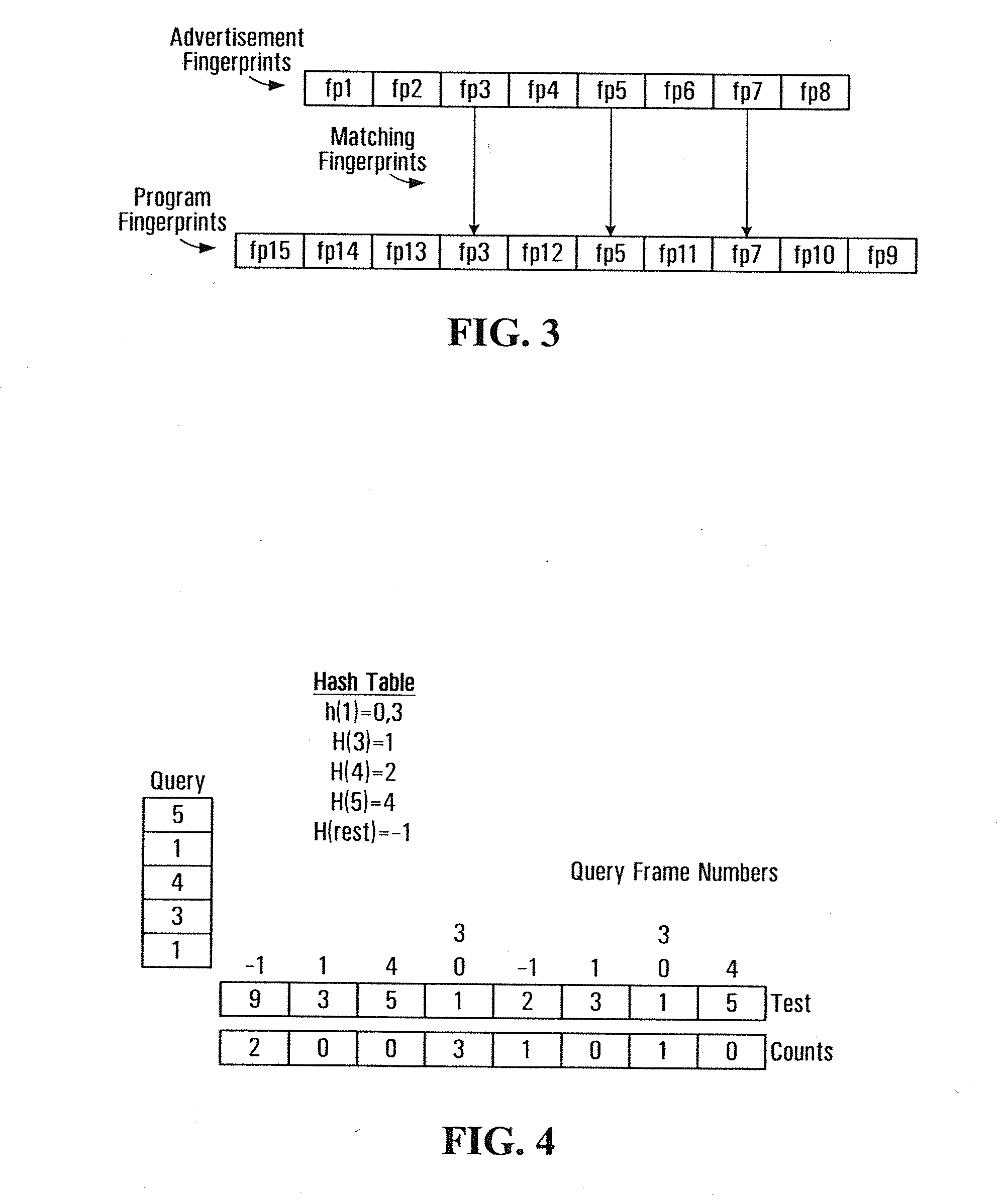
A method for performing audio copy detection, comprising, providing a query audio data, the query audio data having a succession of frames and also providing a plurality of test audio data units, each test audio data unit including a succession of frames. For each test audio data unit the method generates a test fingerprint set. The generation of the test fingerprint test including computing similarity measurements between at least one frame of the test audio data and a plurality of frames of the query audio data. A test audio data unit is then selected as a match for the query audio data at least in part on the basis of the fingerprint sets.
Owner:CENT DE RECH INFORMATIQUE DE MONTREAL
Image copying detection method based on local digital fingerprint
InactiveCN101853486AImprove robustnessStrong identification abilityImage data processing detailsSpecial data processing applicationsImage extractionFeature vector
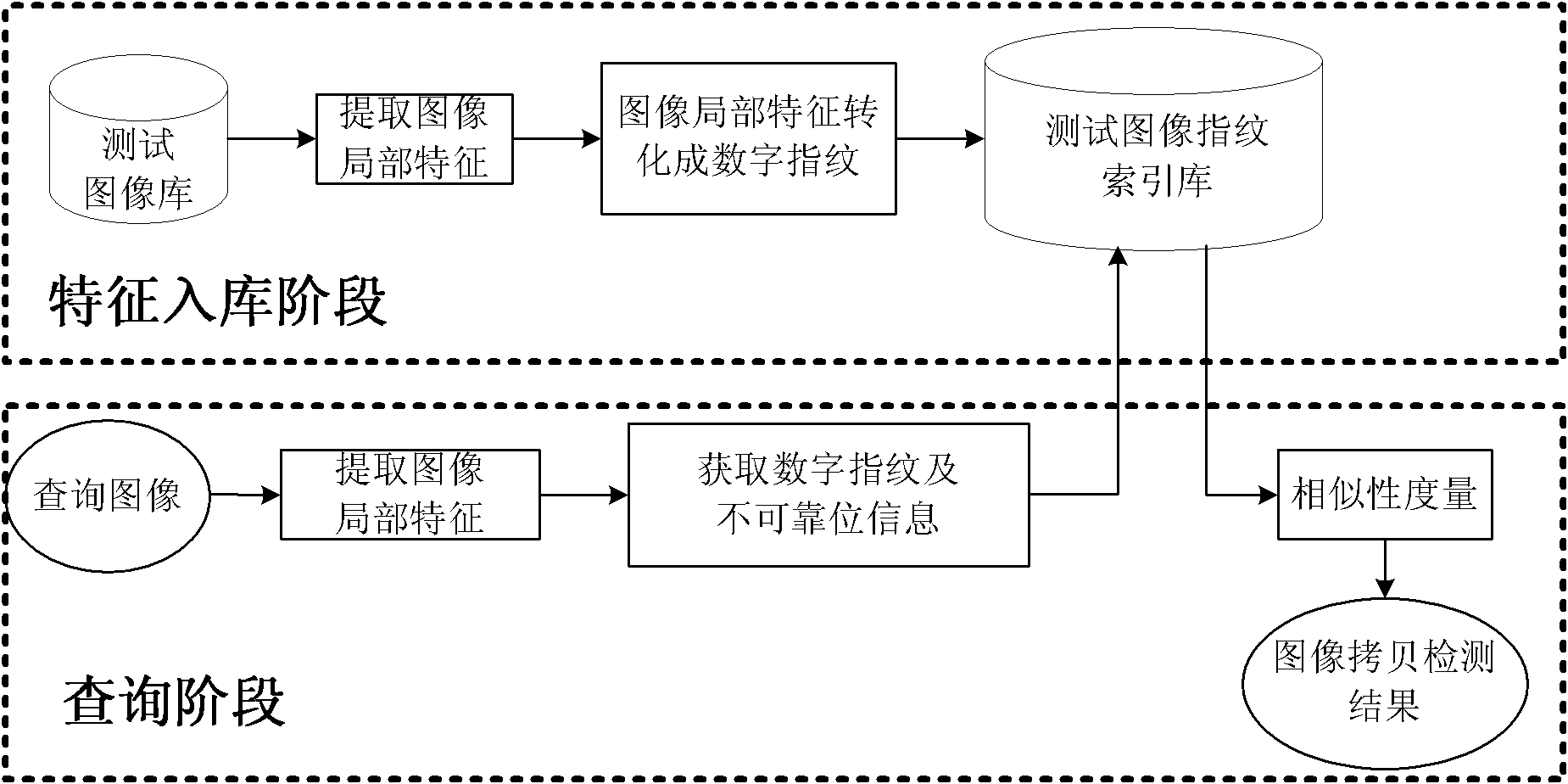
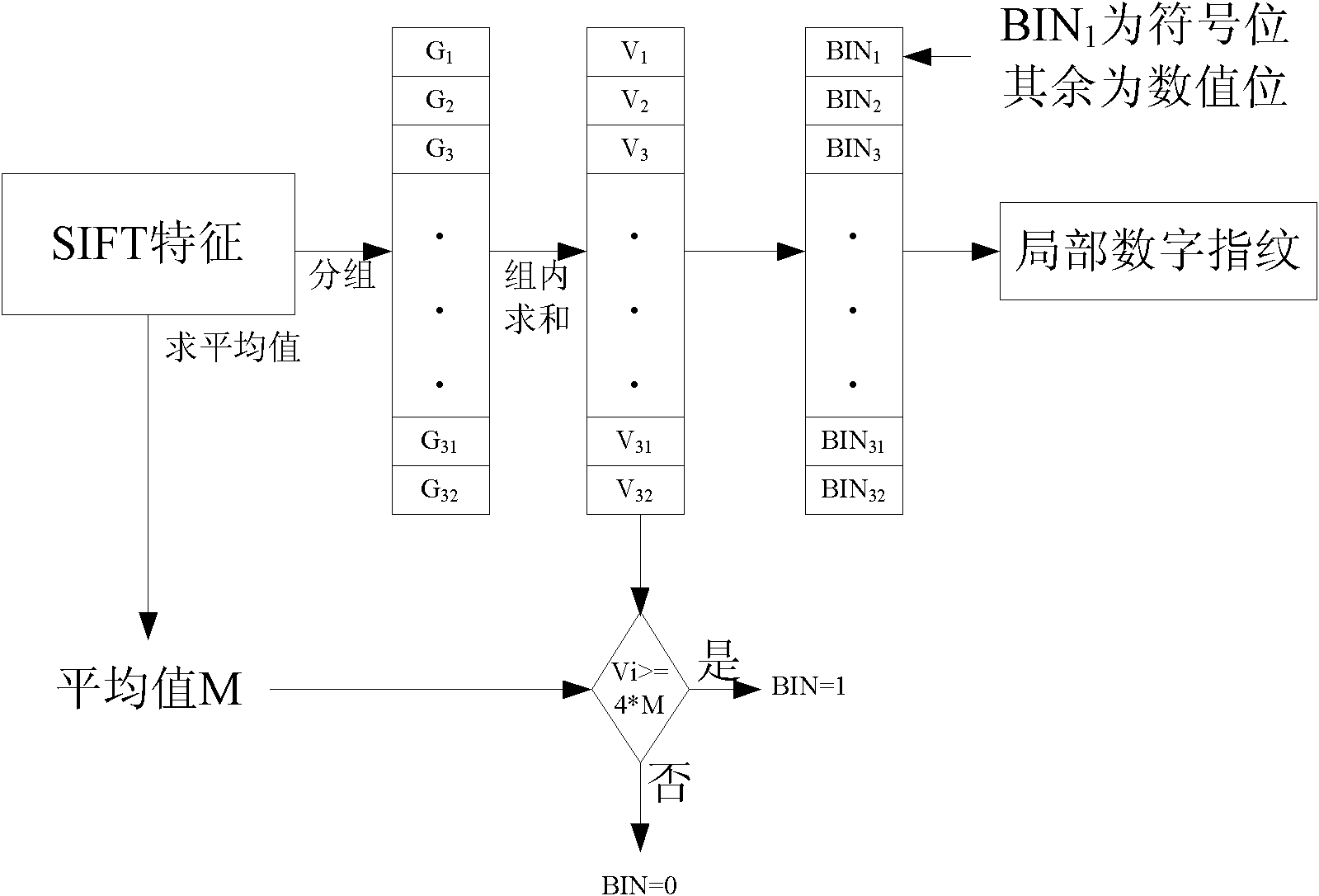
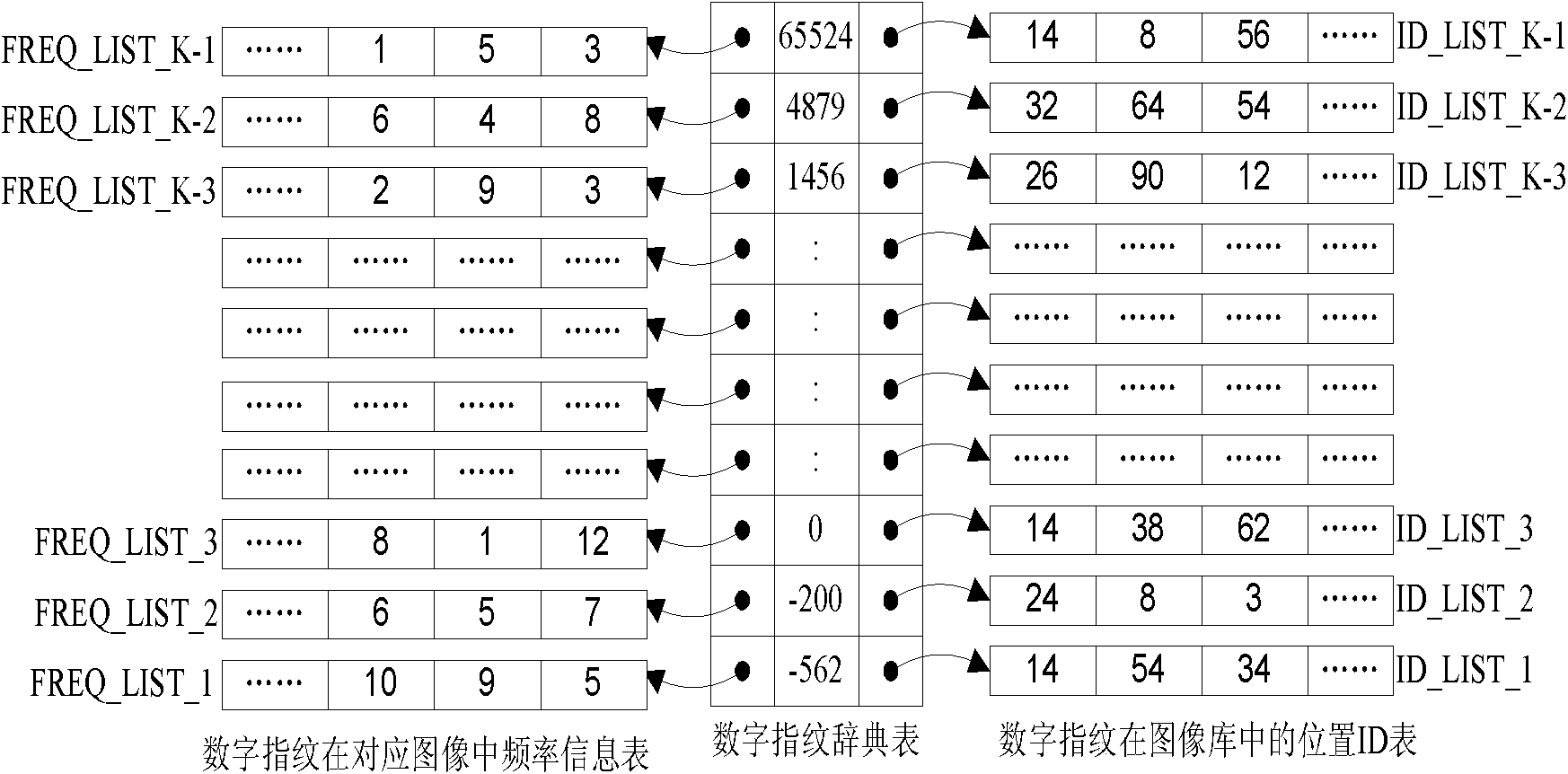
The invention discloses an image copying detection method based on local digital fingerprint, which comprises the following steps that: local SIFI features are extracted from each image in a tested image library, local digital fingerprint conversion is carried out to the high-dimensional SIFT feature vector and the frequency of the fingerprint in each image is calculated so as to establish a digital fingerprint database; and when the image is inquired, the SIFT features are first extracted from the inquired image and then converted into the digital fingerprint and the information of unreliable positions during the conversion process, then inquiry is carried out in an inverted index structure in a tested fingerprint library by integrating the unreliable information so as to quickly obtain and inquire a tested image set associated with the local digital fingerprint of the inquired image, measure the similarity of the inquired image and the associated tested image and judge whether is image is copied. In the detection of the copying performance, the method has very good recall rate and precision; and in detecting the copying efficiency, the method can also detect the copying of the inquired image.
Owner:HUAZHONG UNIV OF SCI & TECH
Image restoring apparatus and method thereof
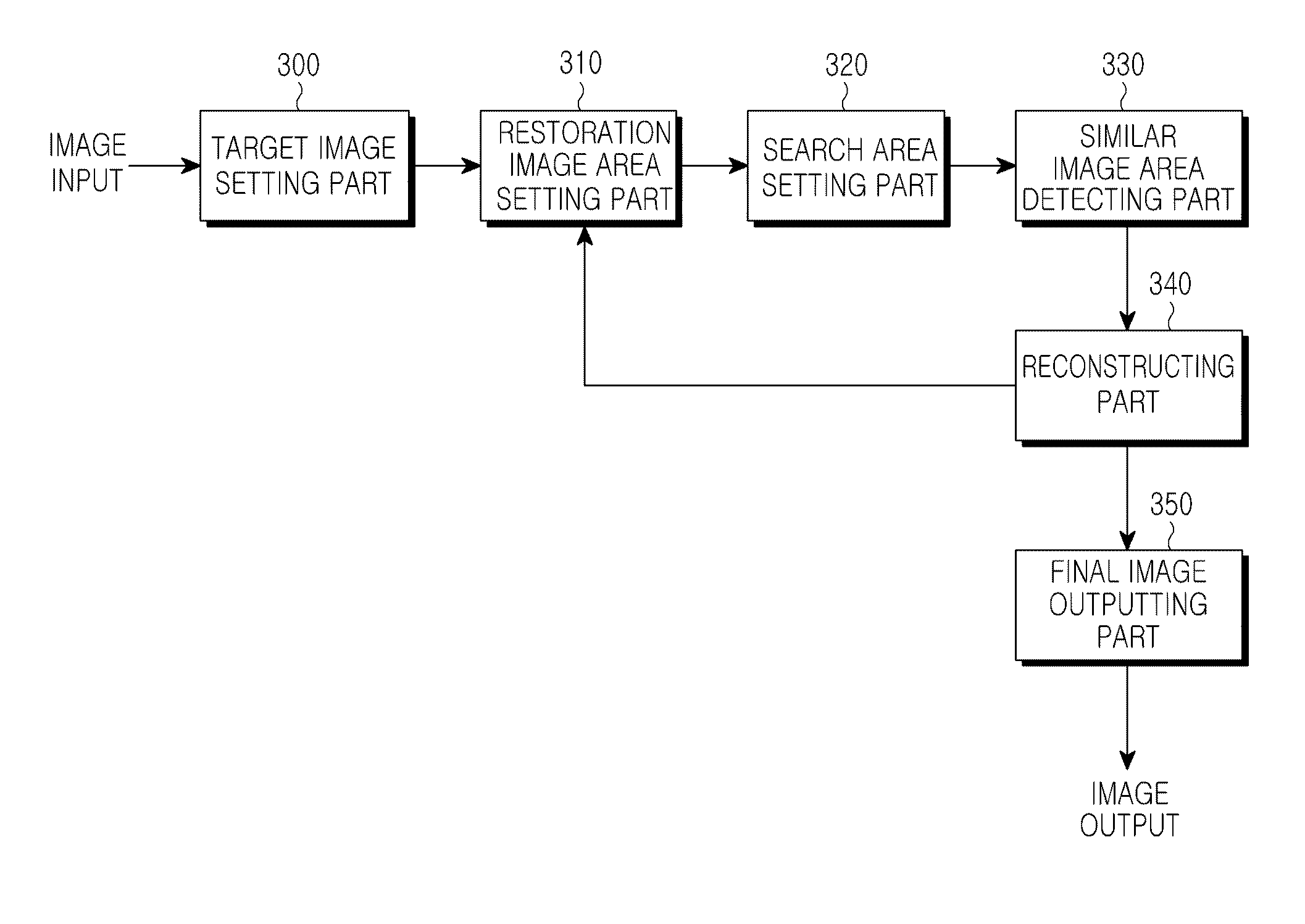
InactiveUS20100177978A1Reduce errorsRestore imageImage enhancementImage analysisCopy detectionImage restoration
Disclosed is an image restoring apparatus and a method thereof, which sets a restoration image area to establish a portion of a target image area to be restored as a restoration image area to be restored with priority according to a request for an image restoration; sets a search area to establish an area with a predetermined size including the restoration image area as a search area; detects a similar image area to search for the most similar image area to the restoration image area within the search area; and reconstructs the deteriorated image in a natural manner by copying the image of the detected similar image area and attaching the same to the restoration image area.
Owner:SAMSUNG ELECTRONICS CO LTD
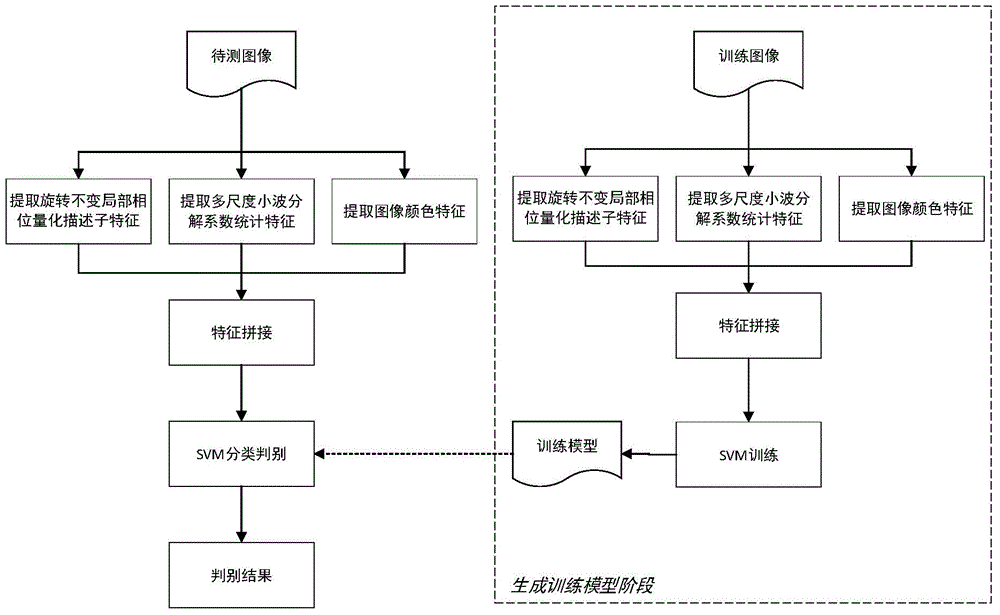
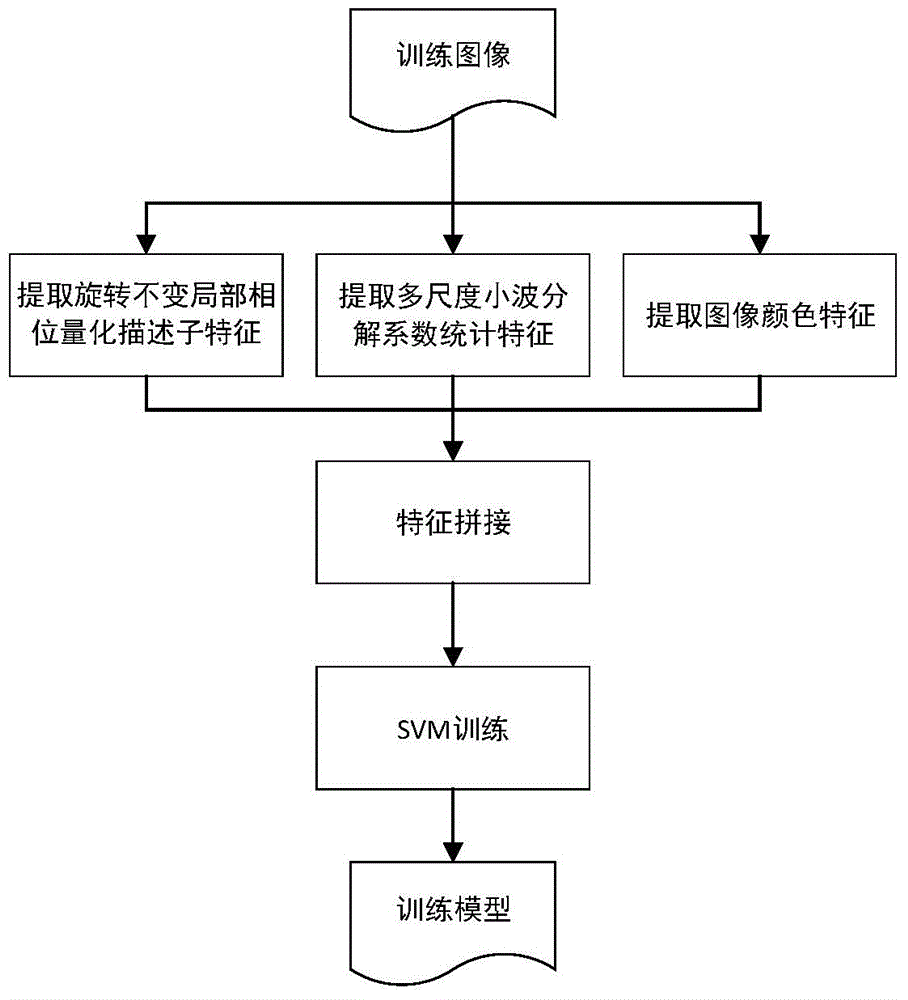
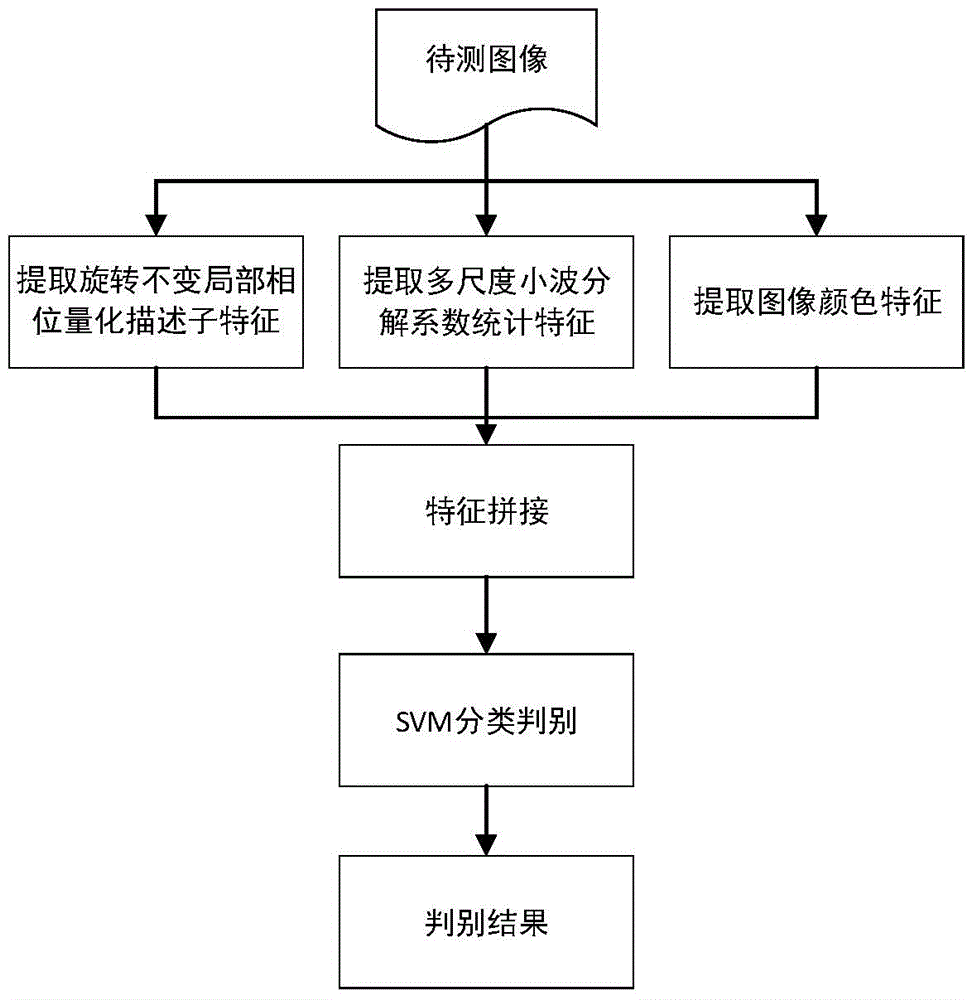
Multi-feature fusion based image copying detection method
The invention discloses a multi-feature fusion based image copying detection method. The multi-feature fusion based image copying detection method comprise the following steps of 1 extracting and stitching multiple groups of features of a training image, 2 utilizing a classifier to generate a training model, 3 extracting and stitching multiple groups of features of an image to be trained and 4 utilizing the generated training model and utilizing the classifier to judge the image to be trained. The multi-feature fusion based image copying detection method is different from any image copying detection method in the prior art and is a novel effective detection method.
Owner:SHANGHAI JIAO TONG UNIV
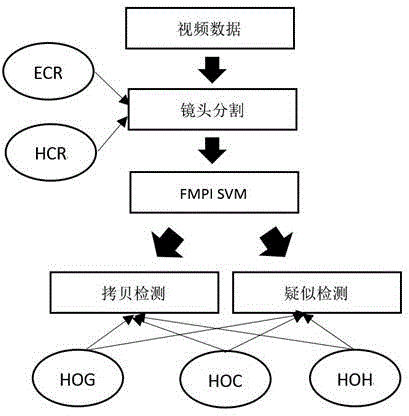
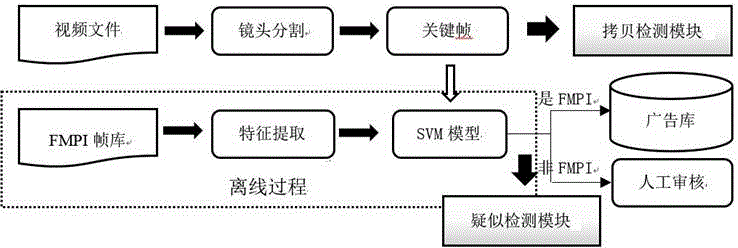
Automatic video advertisement detection method
InactiveCN103605991AAddress suboptimal situationsImprove efficiencyCharacter and pattern recognitionVideo processingEngineering
The invention belongs to the technical field of computer video processing and particularly relates to an automatic video advertisement detection method. The method comprises the following steps: a digital television signal or a local video format broadcast by a television station is input; then, shot segmentation, key frame extraction, FMPI frame classification, copy detection and suspected advertisement detection are carried out on a video by comprehensively adopting color, texture and edge features; and finally an advertisement component in the video is analyzed out. The automatic video advertisement detection method can be used for filtering advertisements in digital television rebroadcast and solving the problem of automatic video data annotation in projects. The method adopts the concept of FMPI key frame, greatly improves the advertisement copy detection accuracy and algorithm efficiency and provides a very reliable basis for making a classifier based on the characteristics of an FMPI key frame for suspected advertisement detection.
Owner:FUDAN UNIV
Robust image copy detection method base on content
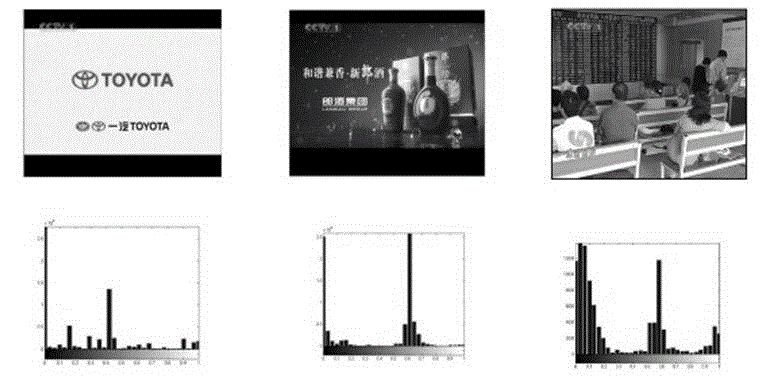
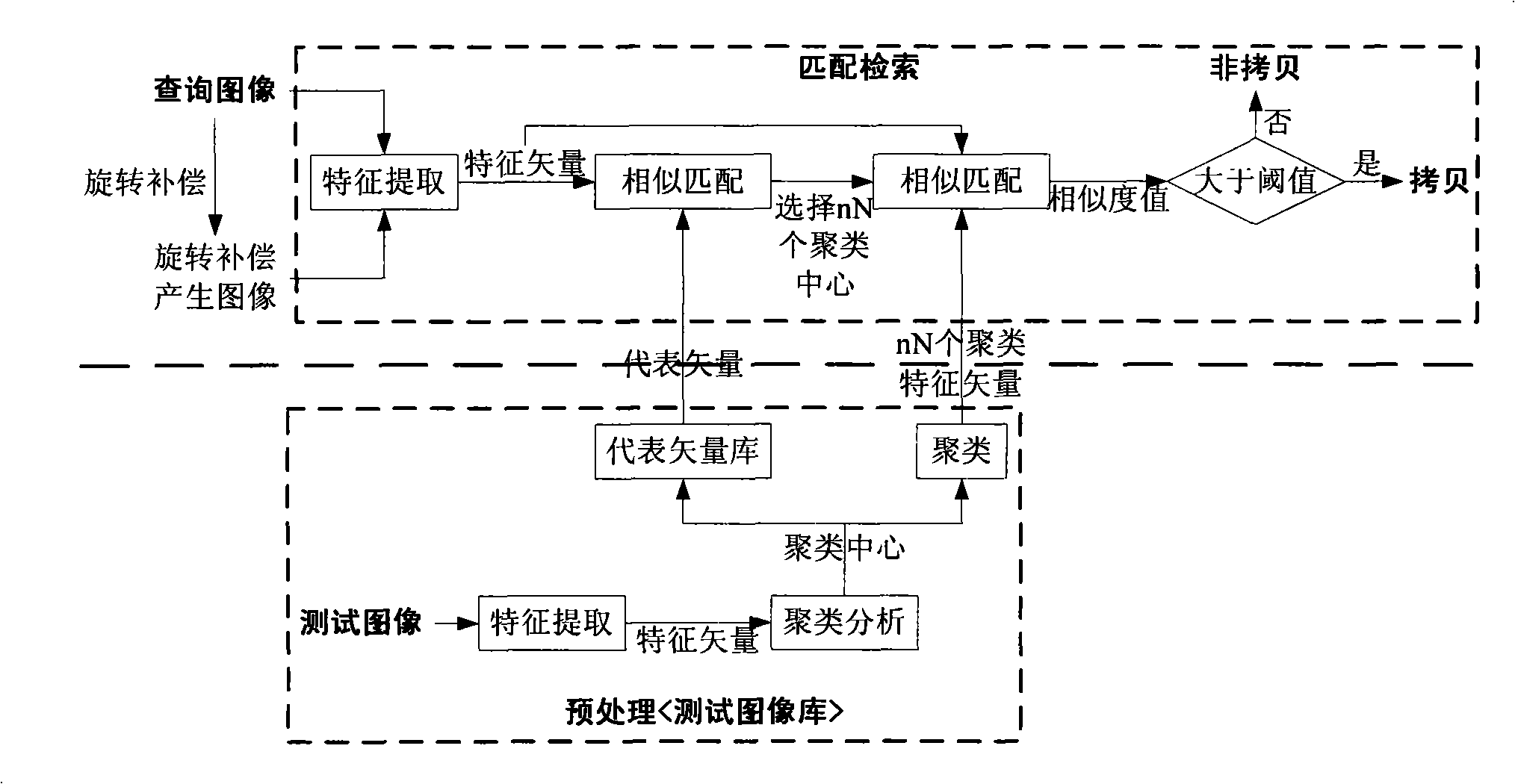
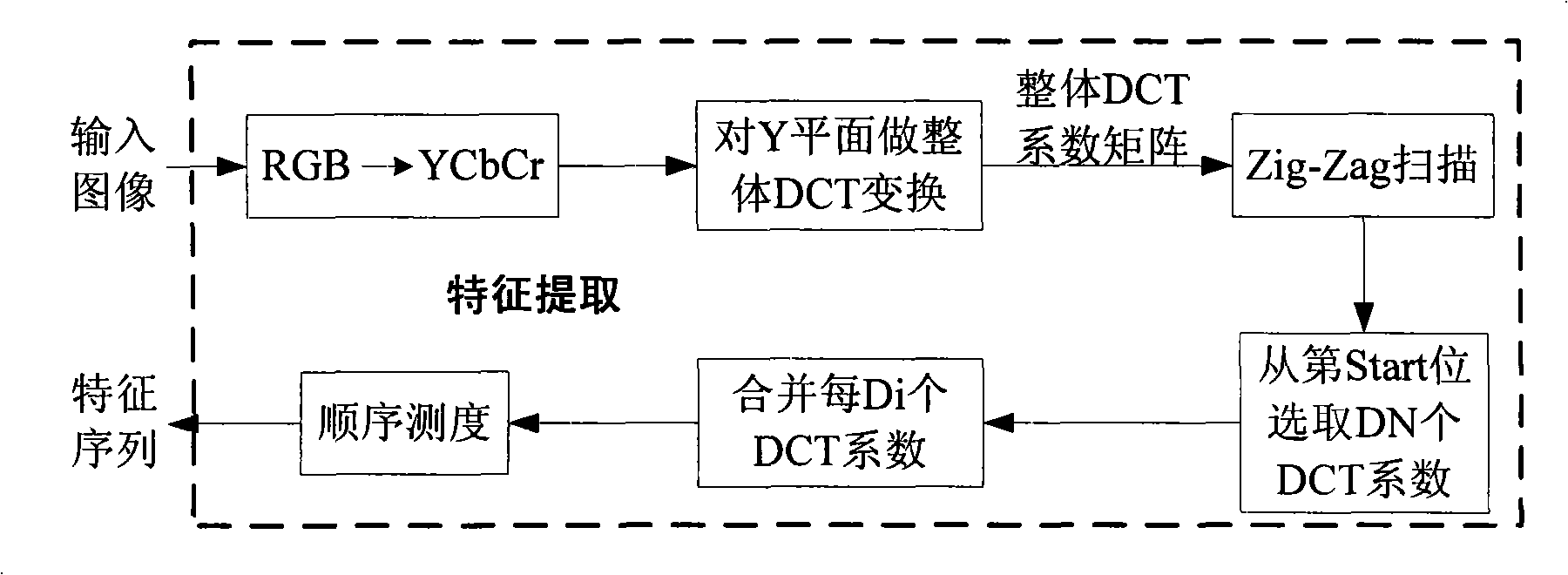
InactiveCN101308567AImprove robustnessImprove query efficiencyImage data processing detailsSpecial data processing applicationsFeature vectorDct transform
The invention discloses a content-based robust image copy detection method, which has the following steps: to extract the feature vector of the testing image; to select the integral DCT transform coefficients of a plane Y of the original image YCbCr color space, to calculate the order measurement of the coefficients to obtain a coefficient sequence which is used as the feature vector of the testing image; then to establish testing image representative vector libraries; to execute clustering analysis to the feature vector sets of the testing image representative vector libraries to select the feature vectors closest to the clustering center as the clustering representatives to constitute a clustering representative vector library; to respectively search the matched testing image representative vector libraries to inquire the image feature vectors and the image feature vectors after rotation compensation, and to determine the belonged class; then to execute sequential matching search to each image feature vector in the clustering, and to determine whether the copy of the inquired image exists. The invention shows a higher robustness to help improve the inquiring efficiency, and has practical value as well as wide application in digital image database arrangement, digital image copyright protection and piracy tracking.
Owner:HUAZHONG UNIV OF SCI & TECH
Method for carrying out harmful content recognition on network text and short message service
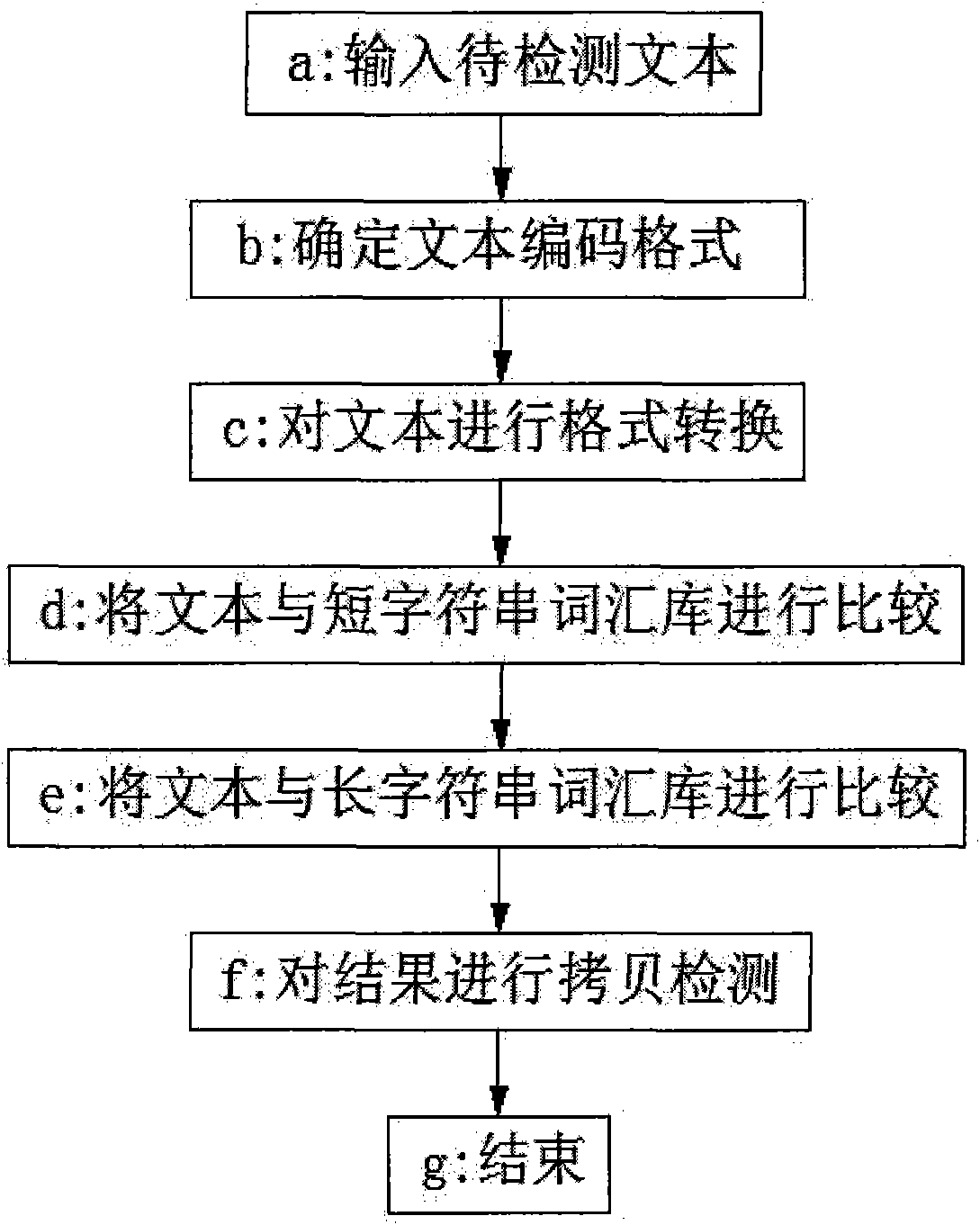
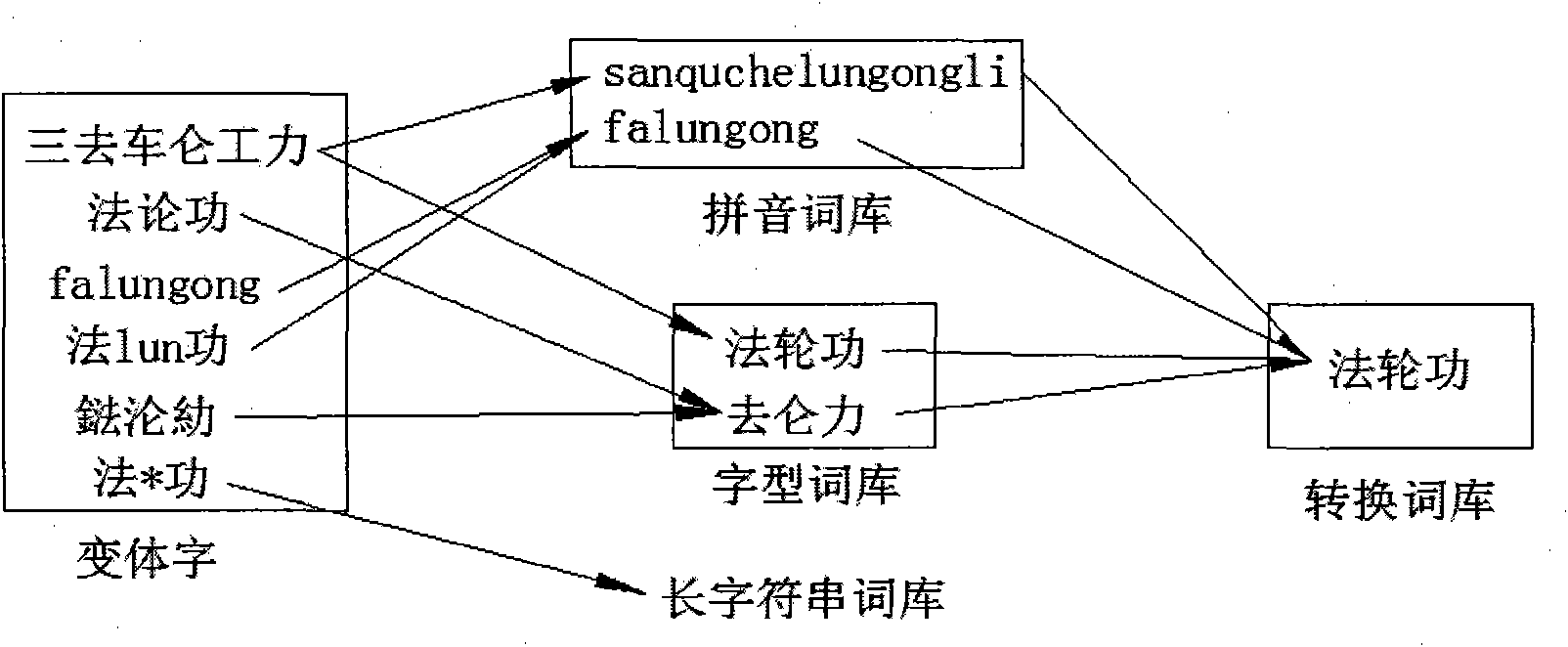
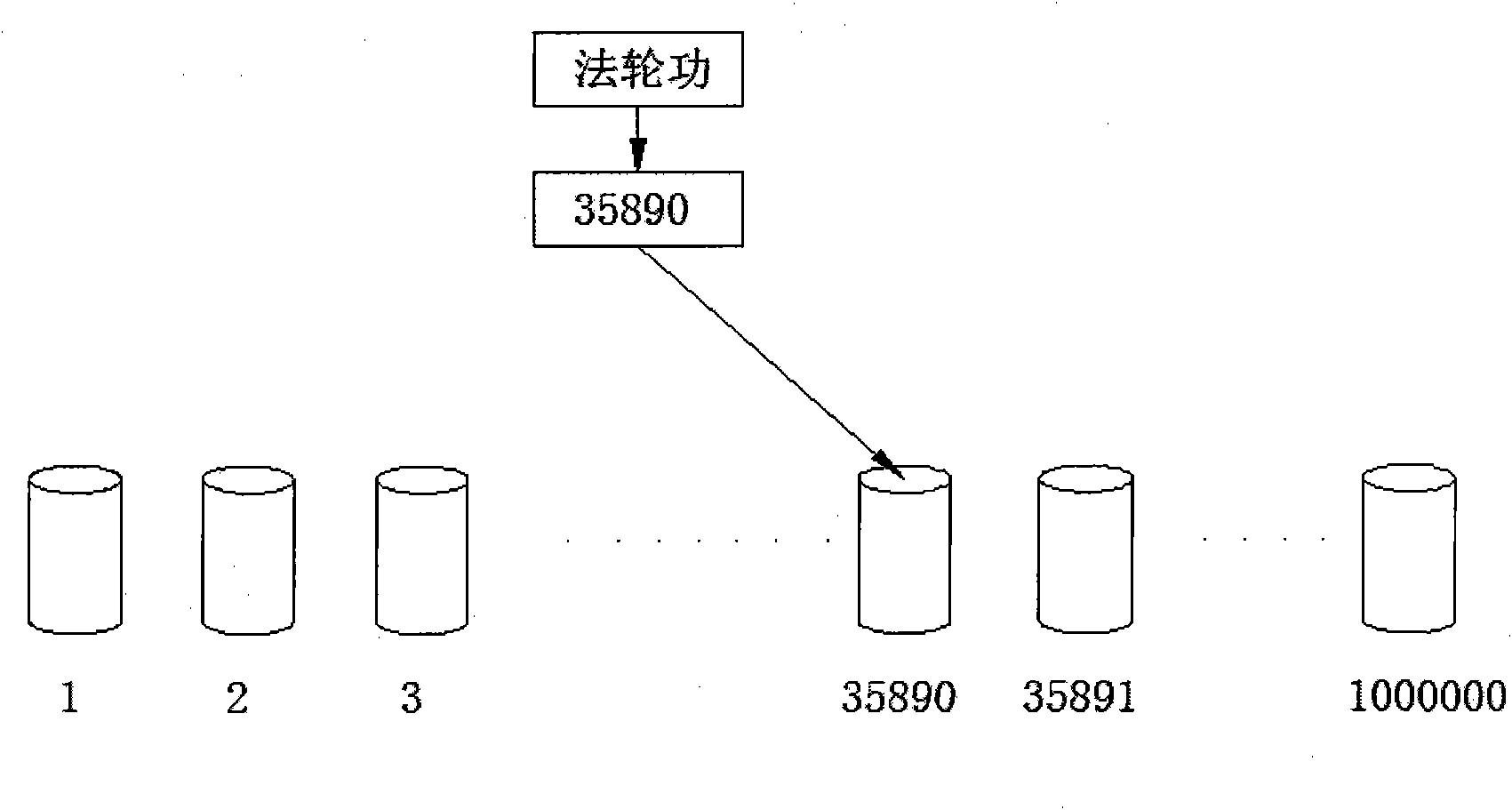
InactiveCN101876968AImprove efficiencyHigh speedSpecial data processing applicationsShort stringShort Message Service
The invention belongs to the technical field of text processing, in particular to a method for carrying out harmful content recognition on network text and short message service, which comprises the following steps of: inputting a text to be detected, determining a text coding format, carrying out format conversion on the text, comparing the text with a short string word bank, comparing the text with a long string word bank, carrying out copy detection on a result, and displaying a final result. The method can be used for the detection and the filtration on harmful, violent and reactionary texts in the internet, inhibits the spreading of the harmful content, and protects physical and psychological health of youngsters.
Owner:FUDAN UNIV
Audio frequency copy detection method based on similarity
The invention belongs to the technical field of audio frequency information processing and in particular relates to an audio frequency copy detection method based on similarity. The method comprises the following steps: firstly establishing a reference audio frequency signal database, segmenting the signals before entering the database so that the signals have equal length, wherein the reference audio frequency signals in the database are illegal or bad information; copying and detecting the audio frequency signal according to the established reference audio frequency database, namely, orderly extracting features, generating a histogram and computing the similarity; then judging whether the input audio signal has a copy containing the reference audio frequency in the database by a parallel algorithm so as to obtain the output result, namely the result of whether the audio frequency has illegal or bad information. The method provided by the invention can be used for detecting and filtering unhealthy, violent and retroactive audio on the internet and various audio frequency copy detection application systems to prevent various bad contents from spreading.
Owner:FUDAN UNIV
Method for identifying unsuitable content in colour digital image
The invention belongs to the digital image processing technical field, in particular to a method for identifying content in colour digital image. The invention includes an image copy detection algorithm and a pornography identification algorithm. The image copy detection algorithm adopts cascaded method, and firstly comparison of image second order entropy is used for reducing the range in image library. Then SSIM algorithm is used for obtaining similarity in the reduced range. The pornography identification algorithm includes four weak graders, a skin region proportion grader, a face quantity grader, an invariant moment grader and a skin region distribution grader concretely; the four graders output four confidence coefficients, so as to form a four-dimensional characteristic vector, and the vector is input into a strong grader, thus obtaining final result. The higher the result of the strong grader is, the bigger the probability that the content is pornographic is. The system and method has wide application value in the Internet management and control field.
Owner:FUDAN UNIV
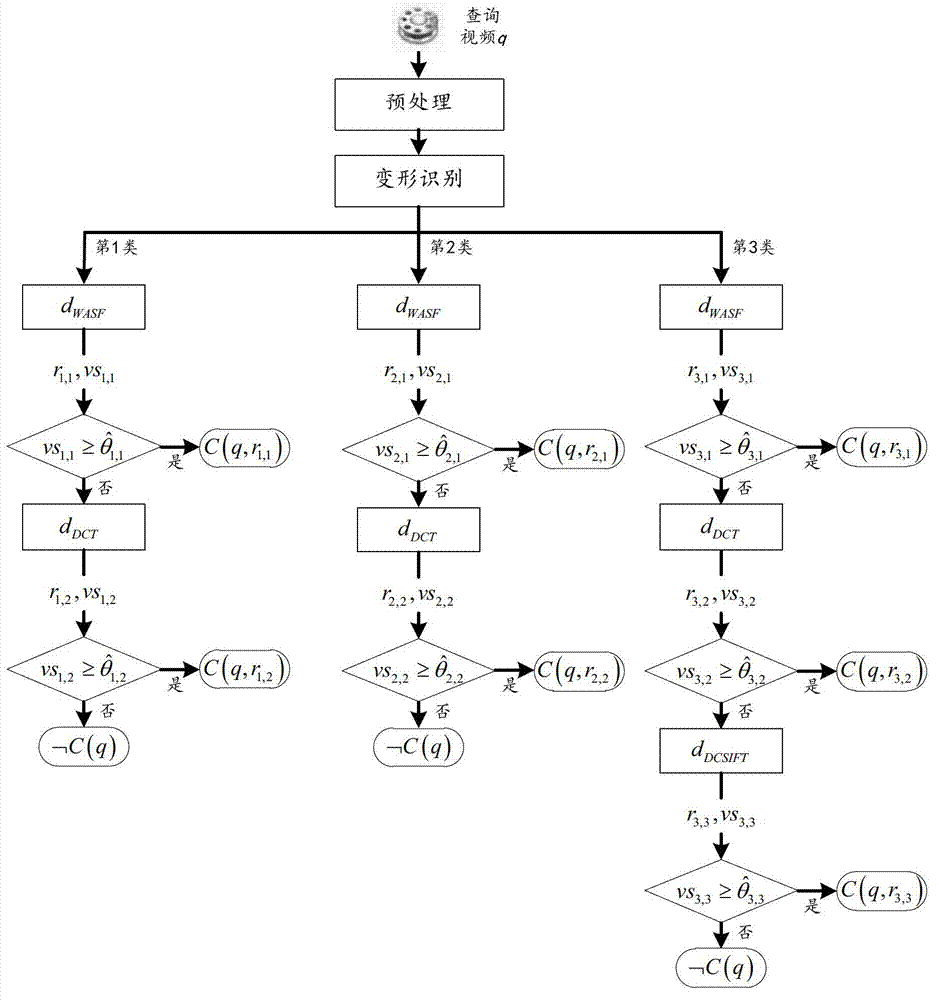
Video copy detection method and system based on soft cascade model sensitive to deformation
InactiveCN102737135AEasy to detectReduce the cost of time and spaceSpecial data processing applicationsTime domainFiltration
The invention provides a video copy detection method and a video copy detection system based on a soft cascade model sensitive to deformation. The method comprises the following steps of: preprocessing, namely extracting vision key frames and audio frames of which the formats are consistent from an inquiry video; identifying deformation, namely distinguishing the type of the deformation of the inquiry video, and transmitting the type information to a cascade detector chain corresponding to the type; and detecting, namely sequentially processing the inquiry video by detectors in the cascade detector chain until a certain detector determines that the inquiry video is a copy or all the detectors determine that the inquiry video is not a copy, wherein in a certain detector, the vision key frames or the audio frames of the inquiry video are searched according to a vision characteristic or an audio characteristic; and then a time domain pyramid trusted platform module (TPM) is used for integrating search results of the frame layers into a copy detection result of a video layer. According to the method and the system, whether the inquiry video is a copy of a given reference video base can be accurately and quickly distinguished; and the method and the system have great significance in application to the fields of digital copyright management, advertisement tracking, video content filtration and the like.
Owner:PEKING UNIV +1
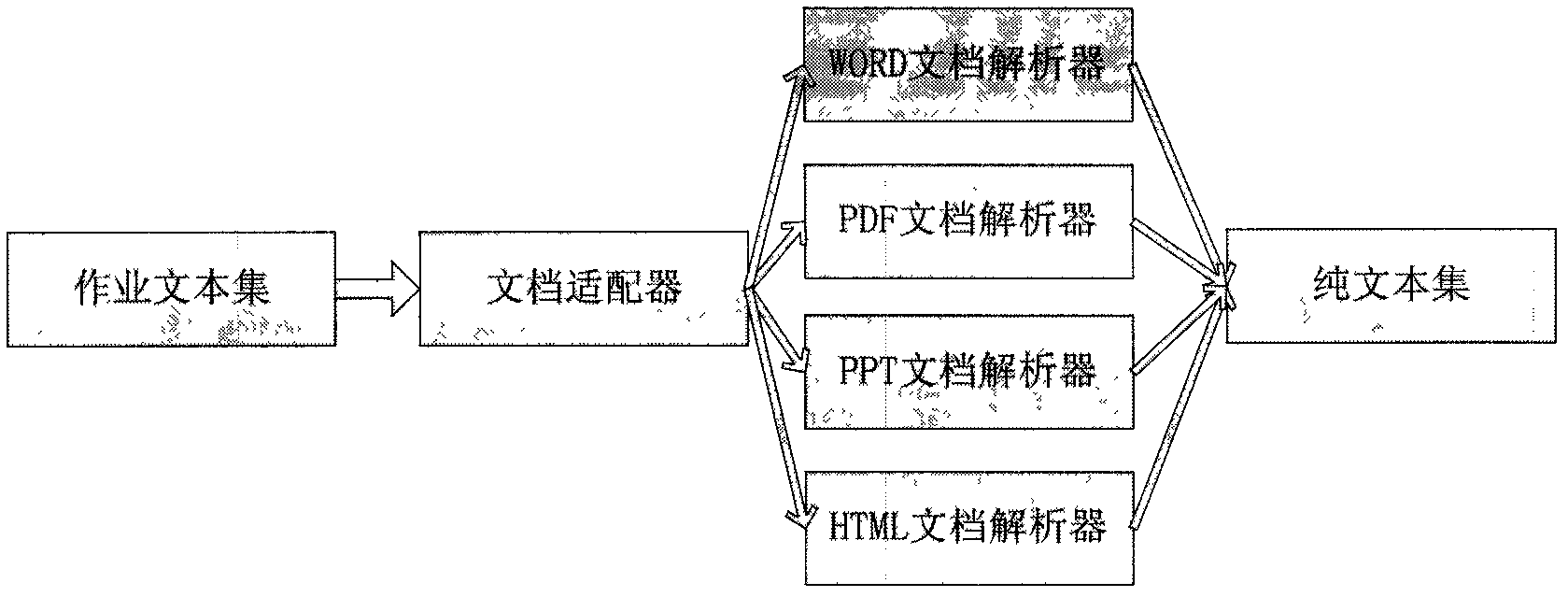
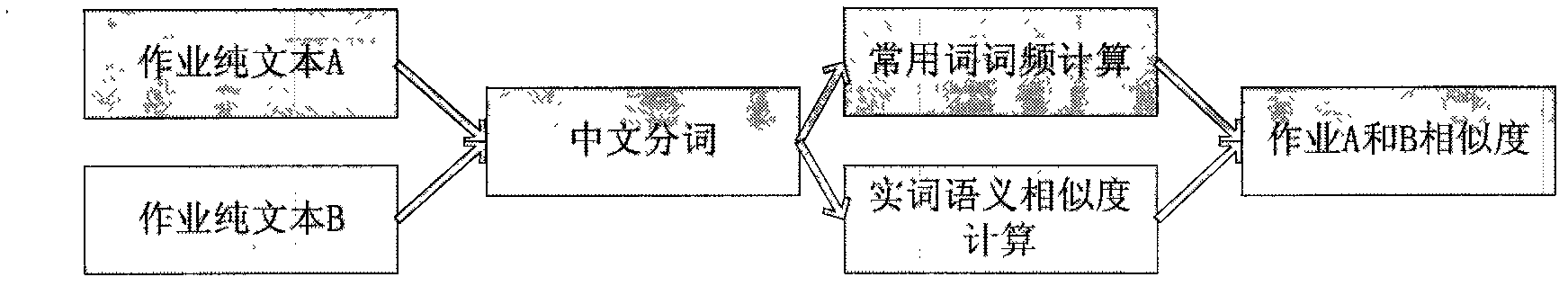
Electronic homework copying detection method
The invention relates to an electronic homework copying detection method, which comprises the following steps of: first performing document type adaptation and document content extraction on homework to be processed; then performing Chinese word segmentation and speech tagging on a processed plain text file, and calculating similarity between the homework according to the word frequency of high frequency words and the semantic similarity of content words; and finally fusing the similarity between the homework and the semantic similarity of the content words, and judging whether two documents are copied or not according to a threshold value. The method is characterized in that: copying detection on the electronic homework is realized by utilizing the word frequency of the high frequency words 'De', 'Yi', 'Shi', 'Le' and 'Wo' and the semantic similarity of the content words. By the method, the problems of the copying detection on batch homework in an E-learning system and detection on the homework copying ways of synonymous substitution, statement regulation and the like of students are solved; and the method can be used for performing the copying detection on the homework of various document types in a computer-aided teaching system.
Owner:NORTH CHINA UNIVERSITY OF TECHNOLOGY
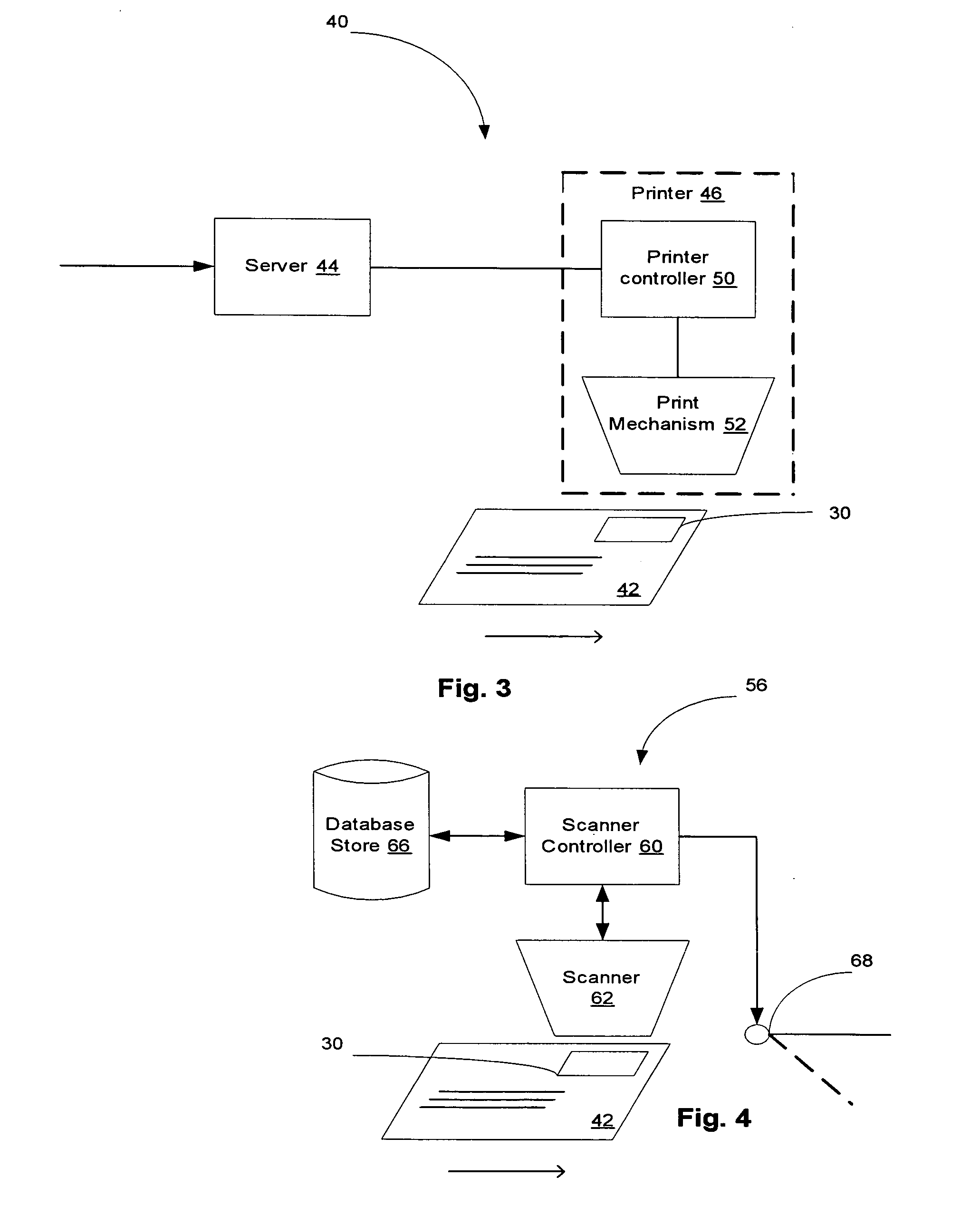
Method and system for printing an original image and for determining if a printed image is an original or has been altered
InactiveUS20060126094A1Paper-money testing devicesCharacter and pattern recognitionComputer printingCopy detection
A method and system for printing an original image which is protected against copying or alteration, such as a postal indicium, and for determining if that image has been altered. The image includes a copy detection feature and coded information linked to the copy detection feature. Altered images are detected by testing to determine if the link between the copy detection feature and the coded information if fact exists. The copy detection feature and the coded information can be linked by: 1) generating said copy detection feature as a pseudorandom function of said coded information; identifying a type of printer corresponding to said printer; and incorporating information identifying said type of printer into said image; or 2) creating a robust descriptor of said copy detection feature; and incorporating said descriptor into said coded information; or 3) creating a robust descriptor of said copy detection feature; and incorporating said descriptor into said coded information, and modifying said copy detection feature as a pseudorandom function of said coded information; or 4) generating said copy detection feature as a pseudorandom function of said coded information; creating a robust descriptor of said copy detection feature; and incorporating said descriptor into said coded information.
Owner:PITNEY BOWES INC
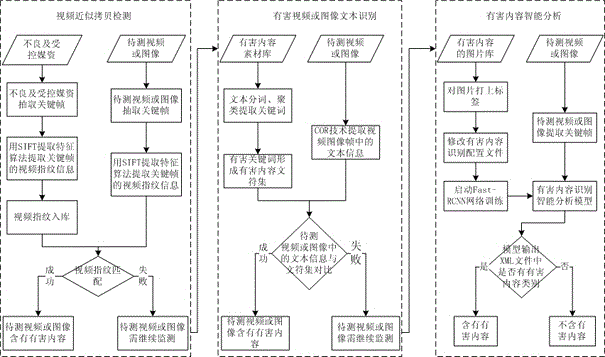
Identification method of harmful content of video
InactiveCN106708949AQuick identificationAchieve the purpose of multi-dimensional harmful content identificationSpecial data processing applicationsCopy detectionTwo step
The invention discloses an identification method of a harmful content of a video. The method includes steps of S1, performing video approximate copying detection on the video information; S2, identifying the harmful video text through a harmful video text identifying technology; S3, when the harmful information is not found from the video or image to be detected through above two steps, intelligently analyzing the harmful content of the video and re-identifying the content by the detecting algorithm of depth study goal. Through the method of combining the depth study, an SIFT feature pick-up algorithm and an OCR optical character identifying technology, the content to be detected in the video and the image can be rapidly identified, the purpose of identifying multi-dimensional harmful content of the video or image information can be achieved.
Owner:CHENGDU SANLING KAITIAN COMM IND
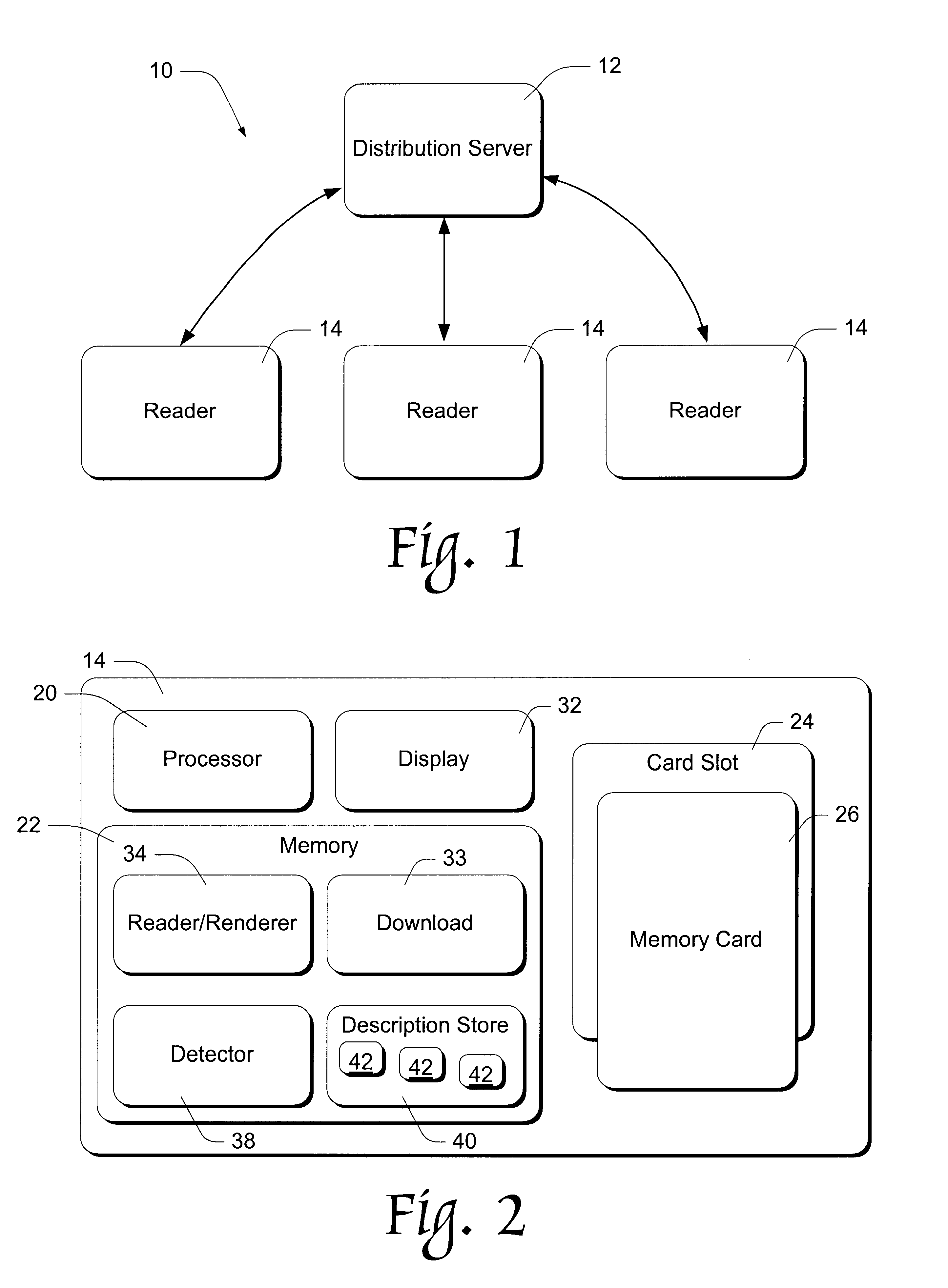
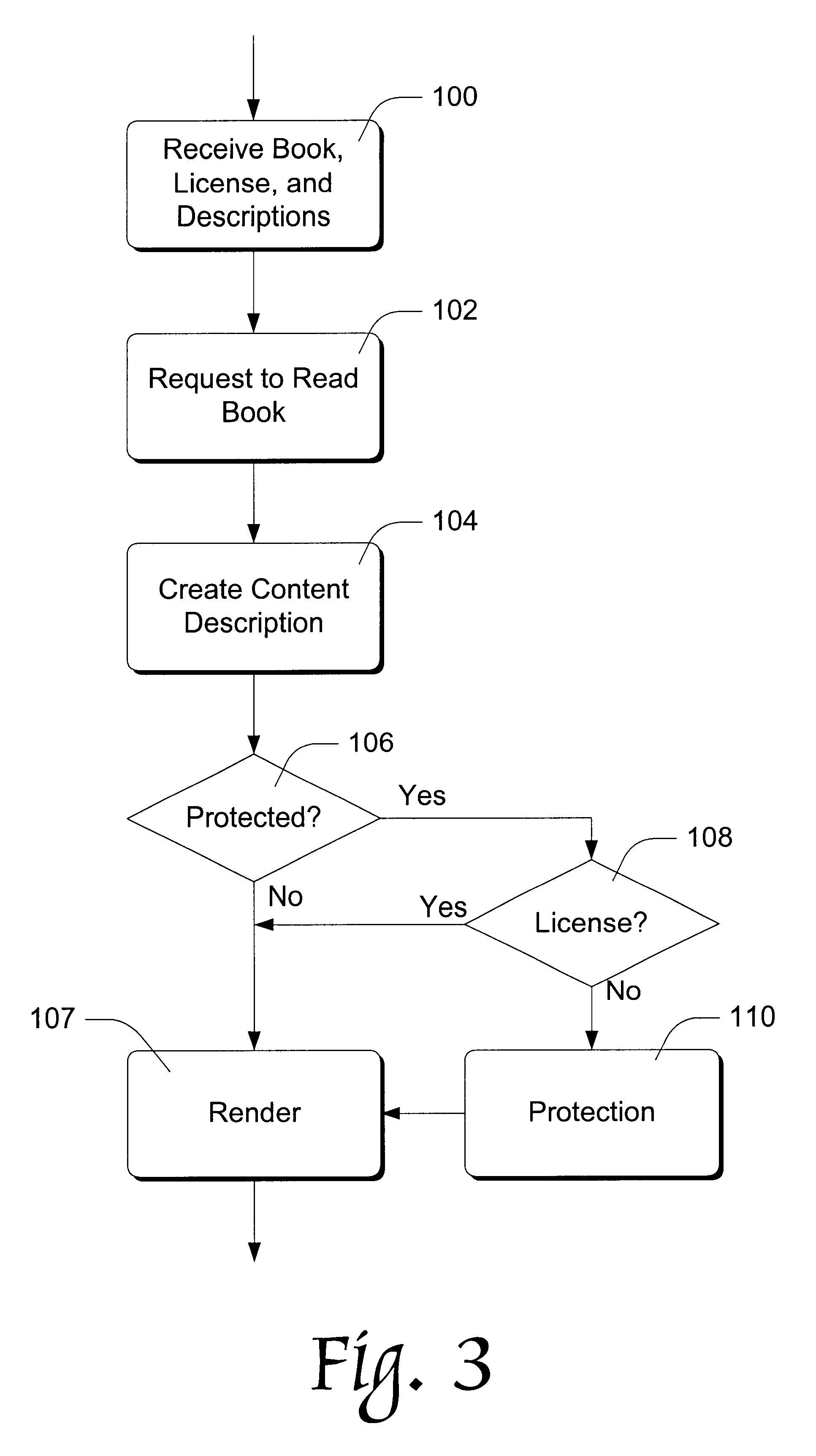
Copy detection for digitally-formatted works
An electronic book reader has a processor, a display surface, and access to a memory card upon which is stored a digitally-formatted creative work such as a book. In addition, the reader has access to a plurality of precompiled condensed content descriptions of respective books that are subject to copy restrictions. Before reading a given book, the reader creates a condensed content description of the book and compares it to the stored descriptions to determine whether the book is subject to copy restrictions. If it is, the reader checks for a valid license before allowing the user to read the book.
Owner:MICROSOFT TECH LICENSING LLC
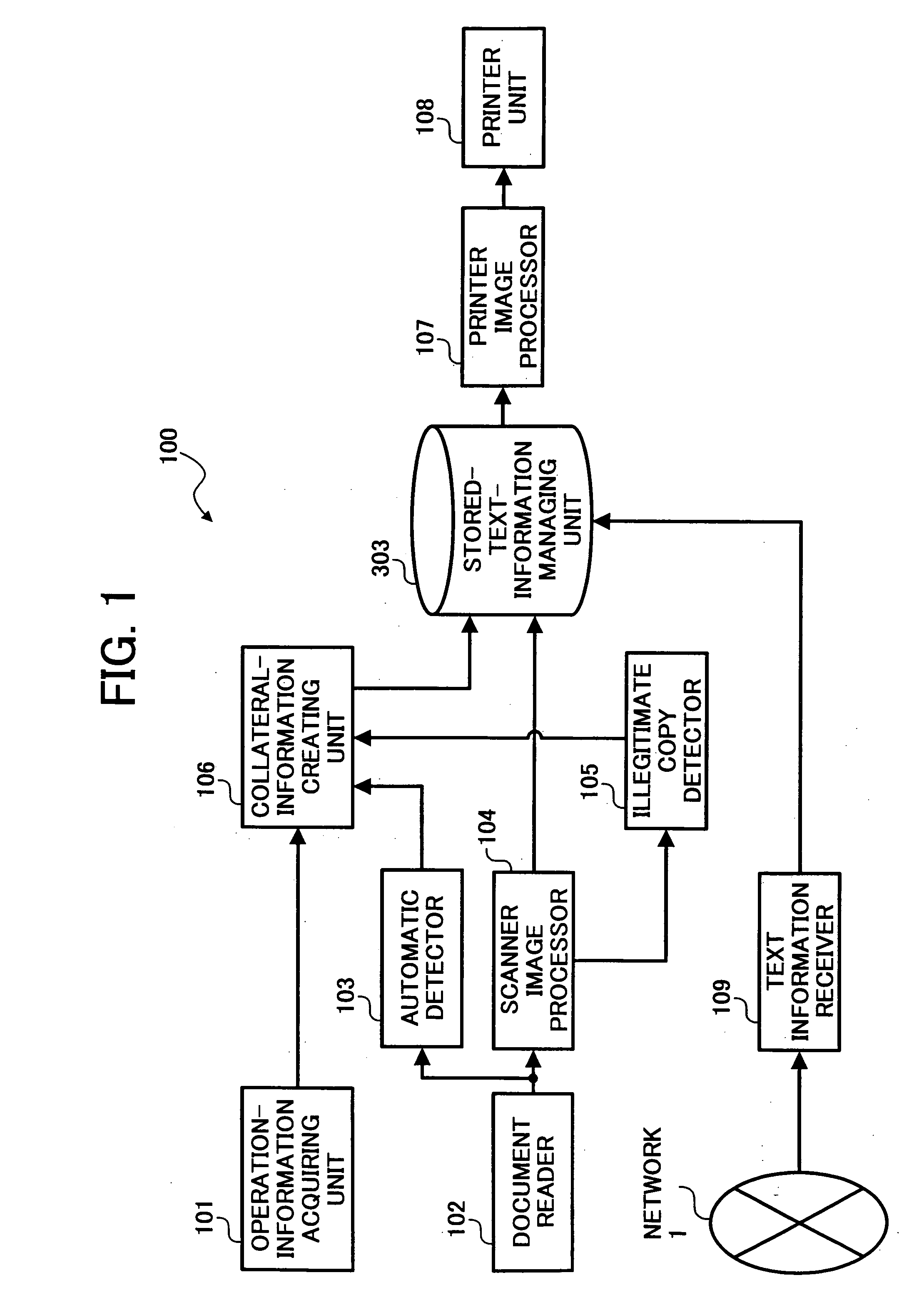
Image processing apparatus, image processing method, and computer product
InactiveUS20060061811A1Solve problemsComputer security arrangementsDigital output to print unitsImaging processingCopy detection
An image processing apparatus acquires image information and collateral information. The collateral information includes illegitimate-copy-detection information that indicates whether the image information is an illegitimate copy. When the illegitimate-copy-detection information indicates that the image information is an illegitimate copy, the image processing apparatus outputs the image information in an unreadable form.
Owner:RICOH KK
Fingerprint feature-based text copy detection system and method
ActiveCN105912514AImprove extraction efficiencyReduce text contentNatural language data processingSpecial data processing applicationsCode moduleHash function
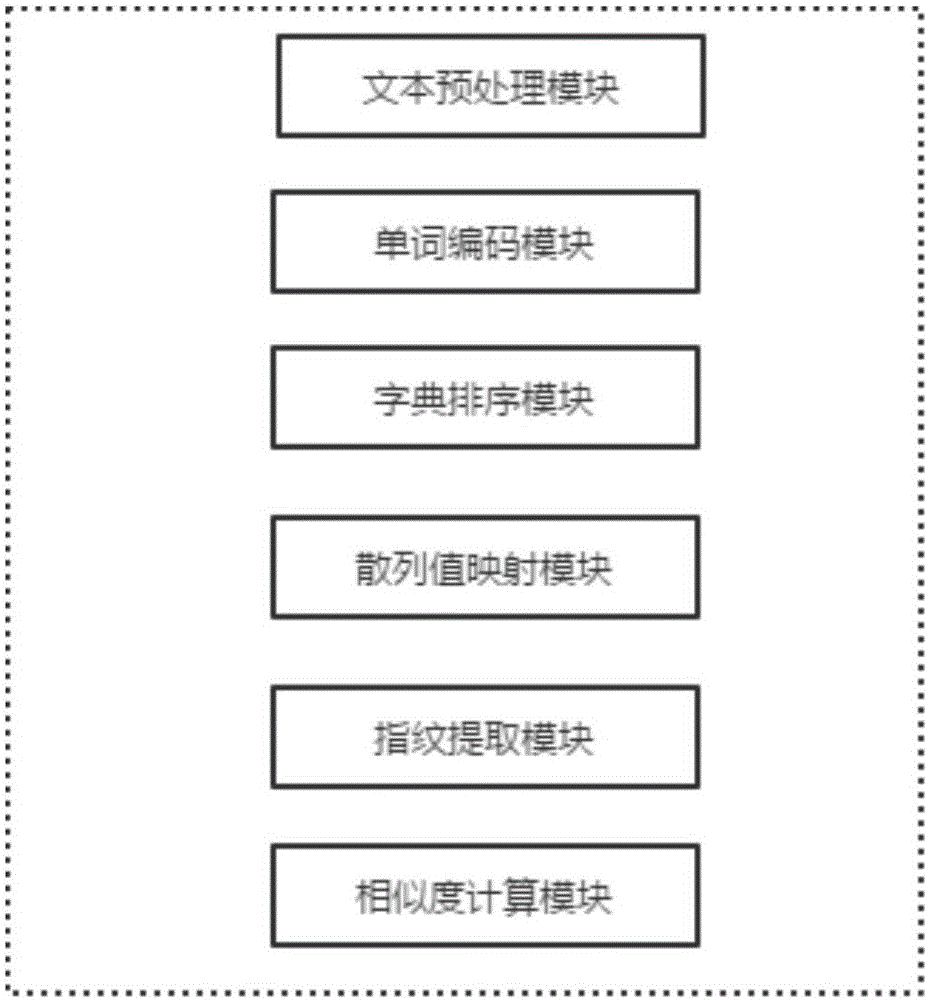
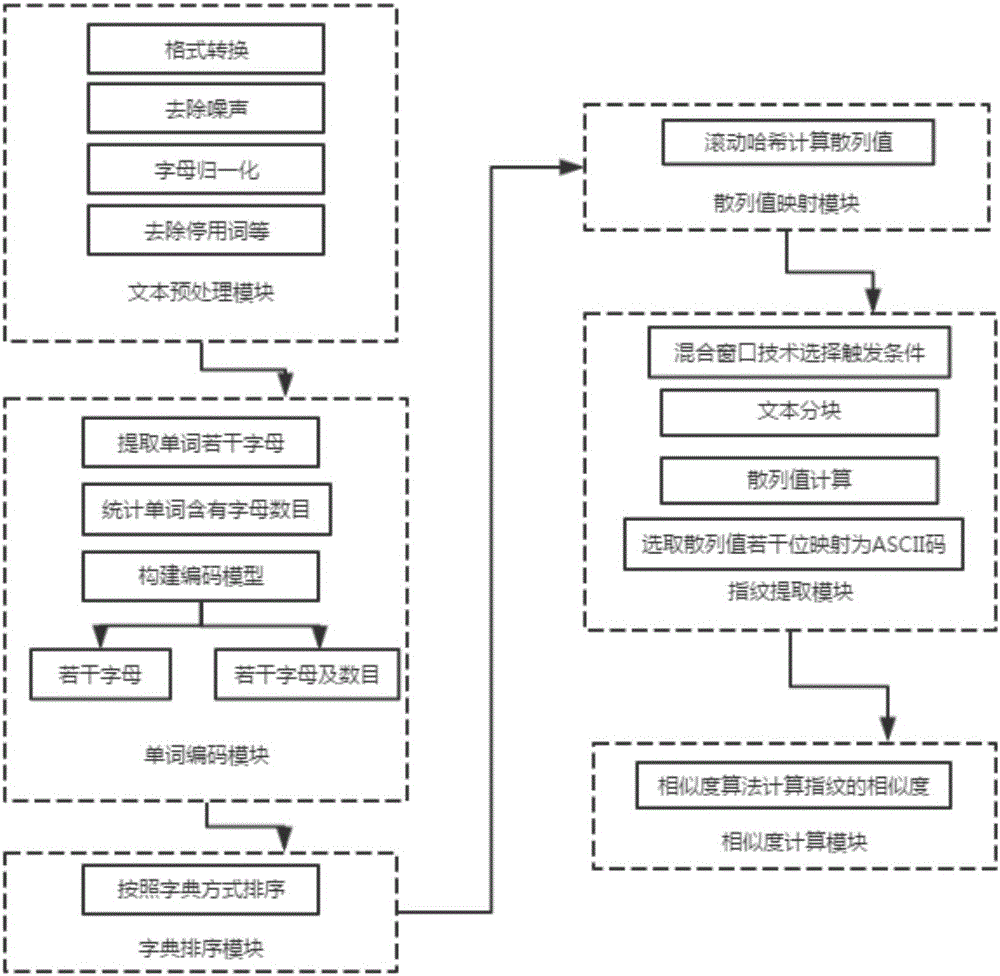
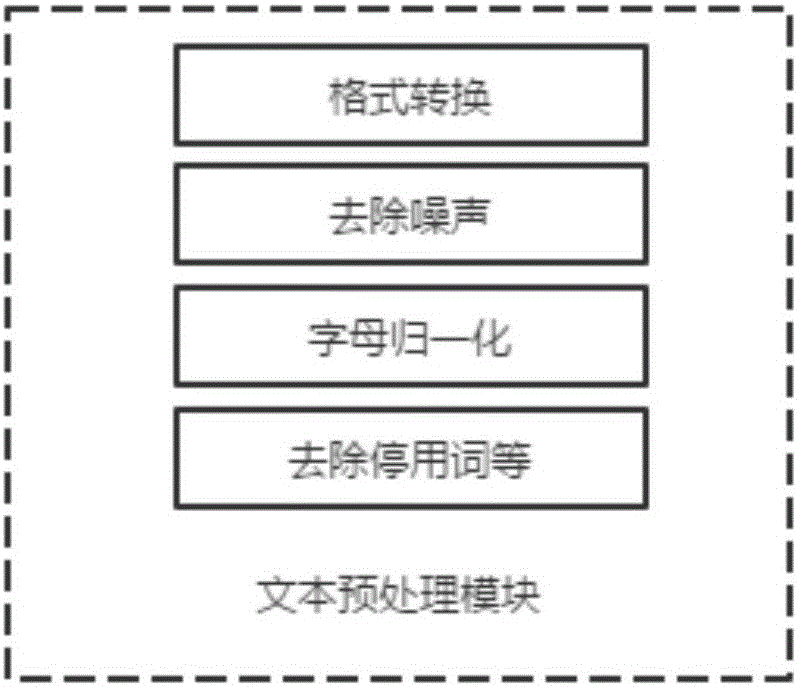
The invention discloses a fingerprint feature-based text copy detection system and method. The system comprises a text pretreatment module, a word coding module, a dictionary sorting module, hashed value mapping module, a fingerprint extraction module and a similarity calculation module, wherein the text pretreatment module is used for carrying out format conversion on a text, filtering noise in the text, normalizing words and removing the interferences of capital and small English letters; the word coding module is used for coding the words of the text after the pretreatment according to native characteristics of the words; the dictionary sorting module is used for carrying out sorting according to a dictionary manner by taking sentence as a unit, and removing punctuations in the text; the hashed value mapping module is used for carrying out hashed value calculation by utilizing a rolling hash function so as to obtain a hashed value sequence; the fingerprint extraction module is used for selecting a triggering condition on the basis of text content, carrying out blocking according to the triggering condition, calculating hash values of text blocks by utilizing a hash function, selecting a plurality of bits, at specific positions, of the hash values to be converted into ASCII codes and taking the ASCII codes as fingerprint features; the similarity calculation module is used for comparing the similarity of text fingerprints and calculating the similarity level of the text fingerprints by utilizing a similarity algorithm.
Owner:吴国华
Method, program, and apparatus for detecting a copy-prohibited document and prohibiting a reproduction of the detected copy prohibited document
InactiveUS8009305B2Hardware monitoringCharacter and pattern recognitionComputer hardwareReference map
Owner:RICOH KK
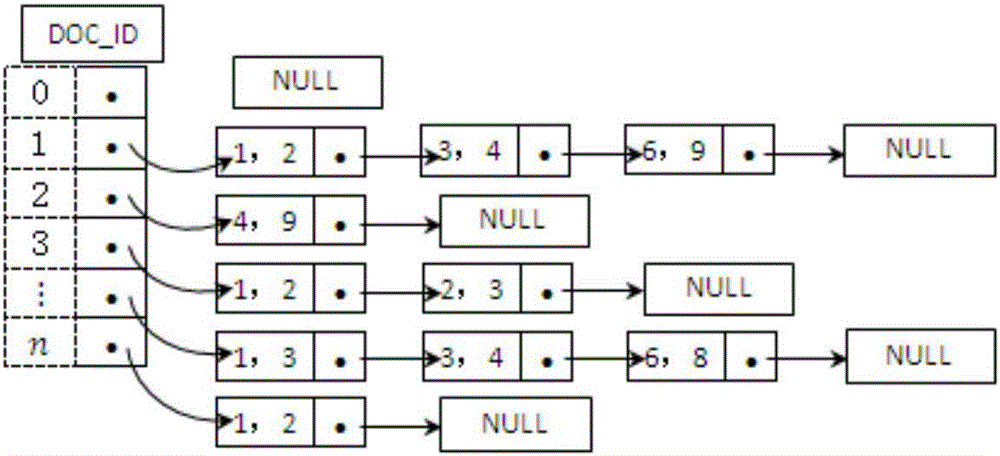
Tibetan language thesis copying detection method and Tibetan language thesis copying detection system based on Tibetan language sentence levels
PendingCN106227897AComputableSimplify complex relationshipsWeb data indexingNatural language data processingTerminal serverThe Internet
The invention discloses a Tibetan language thesis copying detection method and a Tibetan language thesis copying detection system based on Tibetan language sentence levels. The Tibetan language thesis copying detection method includes: subjecting Tibetan language text characters to code conversion and noise removal preprocessing; segmenting a text into text blocks according to sentences through boundary identification of Tibetan language sentences and establishing a temporary table of segmented text blocks; extracting and computing text features from a sentence-document inverted index table and the temporary table according to the number of the sentences to obtain sentence similarity; establishing an adjacency list in accordance with the sentence similarity, computing text block similarity and detecting copying of two Tibetan language theses according to a text block similarity value. The Tibetan language thesis copying detection system comprises a Tibetan language thesis copying detection device and a database, wherein the Tibetan language thesis copying detection device is connected to a client terminal server through the Internet, and the database is connected to the server and used for storing Tibetan language theses. The Tibetan language thesis copying detection device comprises a preprocessing module for code conversion and noise removal of the text characters, a temporary table module for constructing the segmented text blocks, an extracting module for constructing sentence text features and a copying detection module for detecting whether the theses have similar copied data or not.
Owner:QINGHAI UNIV FOR NATITIES
Computerized, Copy-Detection and Discrimination Apparatus and Method
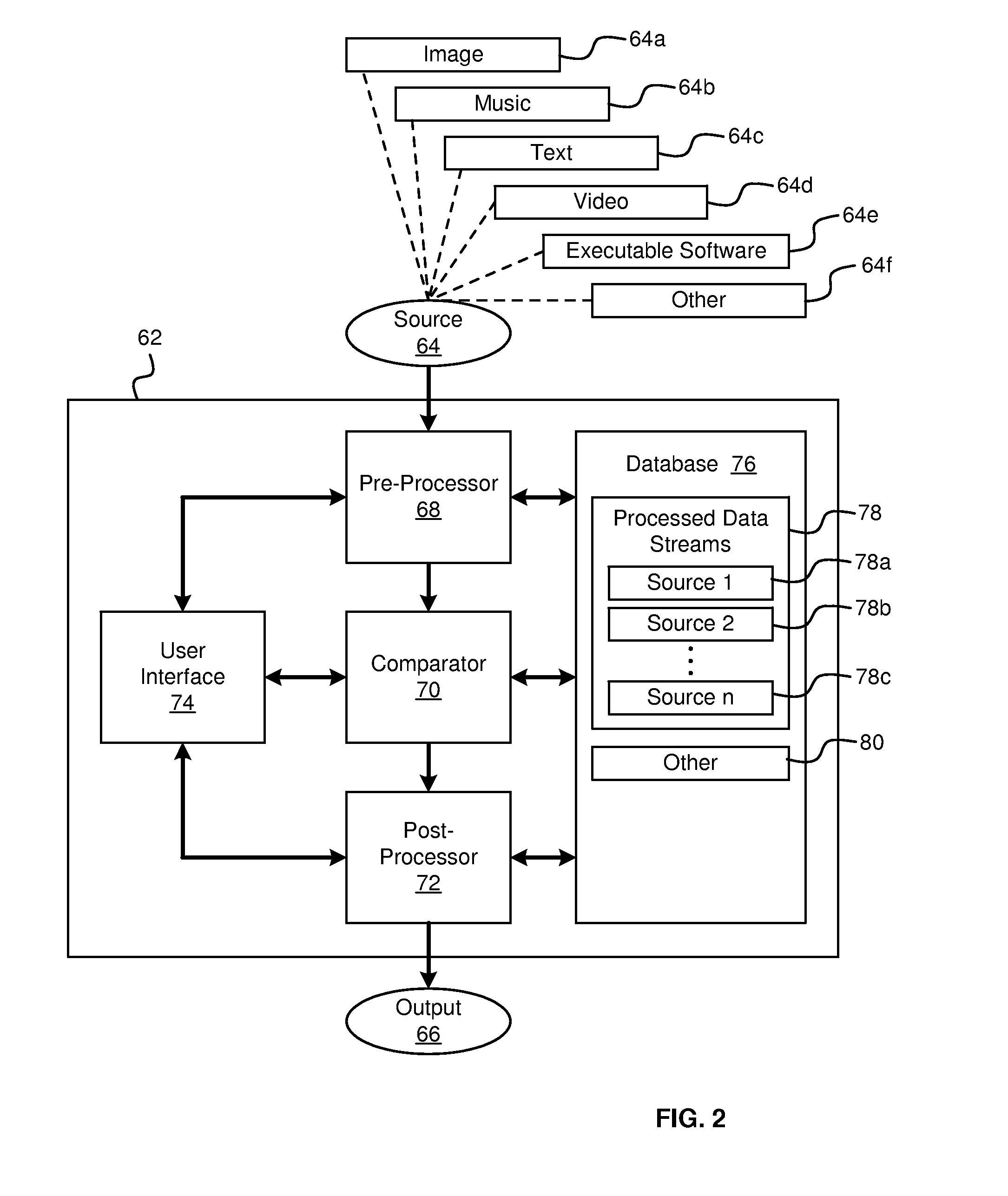
ActiveUS20080288653A1Input/output for user-computer interactionData processing applicationsSource materialData stream processing
An engine identifying segments or portions of one source material or source file common to or found in another source material or file. The engine may receive a first data stream in binary form as well as a second stream in binary form. The engine may include a data stream processor or pre-processor programed to translate the first and second data streams to generate respective first and second processed data streams. The commonality between the first and second processed data streams may be greater than the commonality between the first and second data streams themselves. Also, a comparator may be programmed to compare the first and second process data streams and identify binary segments found in both the first and second processed data streams.
Owner:ADAMS PHILLIP M
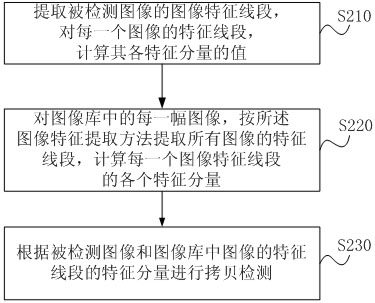
Image characteristic extraction method, device thereof, image copy detection method and system thereof
InactiveCN102629325AImprove detection accuracyImprove computing efficiencyCharacter and pattern recognitionColor imageFeature extraction
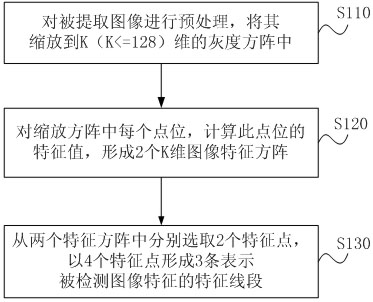
The invention discloses an image characteristic extraction method, a device thereof, an image copy detection method and a system thereof. The image characteristic extraction method includes the following steps of: zooming an extracted image to a K-dimensional gray matrix; for each point position in the matrix, combined with position and a gray value of other pixels, calculating a characteristic value, and forming two K-dimensional image characteristic matrices; and respectively selecting two points with maximum values in the two characteristic matrices as characteristic points, forming three line segments representing image characteristics with the above four characteristic points, and obtaining characteristics of the extracted image. Since when extracting the image characteristics, it is independent of color information of the image and is not related with an image size, and there is no extra overhead when carrying out characteristic extraction on a large size color image; the characteristic line segments are employed in an image characteristic extraction process, as long as image structure is not significantly changed, the image characteristic line segments are relatively stable, high detection precision is provided, and functions of detecting an attack type and analyzing attack intensity are provided.
Owner:SHENZHEN UNIV
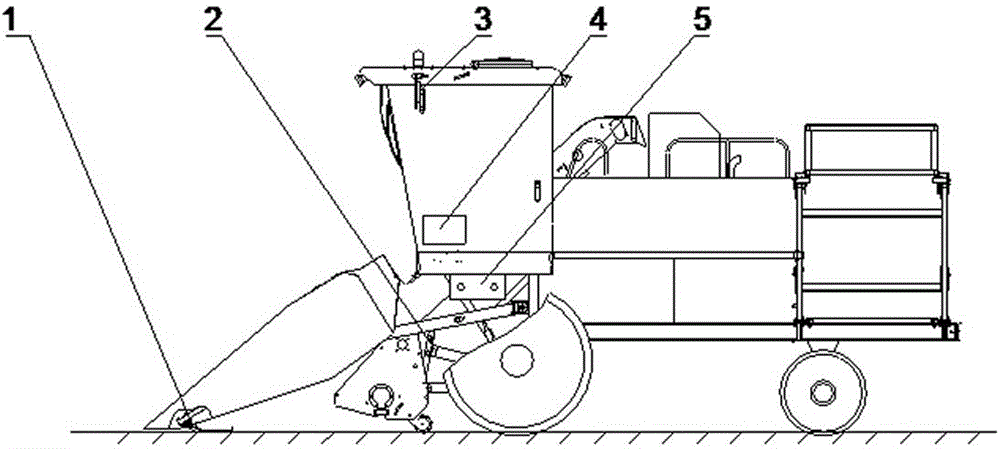
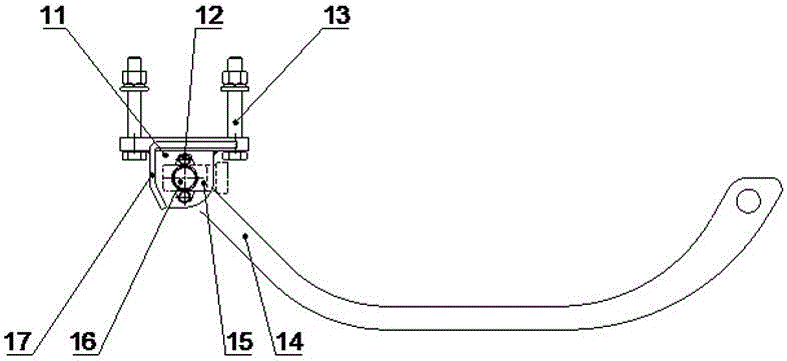
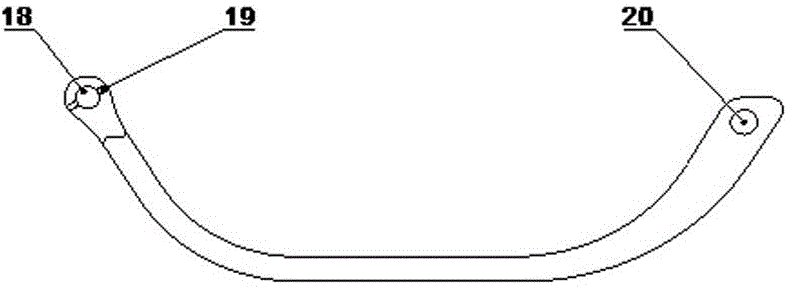
High copying system and method for harvesting table of maize harvesting machine
The invention discloses a high copying control system for a harvesting table of a maize harvesting machine. The system is composed of a copying detection device, a harvesting table lifting hydraulic cylinder, a touch screen, a controller, an electro-hydraulic proportional valve, a mechanical contact type guiding mechanism, a steering hydraulic cylinder, a steering detection sensor and the like. One end of the copying detection device is installed on a protecting tip at the front end of the harvesting table, the other end of the copying detection device is connected with the harvesting table through a chain, and during work, a copying rod makes contact with the ground through dead weight. The copying rod of the copying detection device and an angular displacement sensor rotary shaft rotate synchronously. When the high copying control system for the harvesting table of the maize harvesting machine carries out high copying work, the copying rod rotates around a base shaft hole along with surface relief, an angular displacement sensor feeds changed angle values back to the controller, the controller controls and adjusts actions of the electro-hydraulic proportional valve and the harvesting table lifting hydraulic cylinder, lifting of the harvesting table is achieved, and high copying actions are completed.
Owner:SHANDONG ACADEMY OF AGRI MACHINERY SCI
Video fingerprint method based on contourlet transformation model
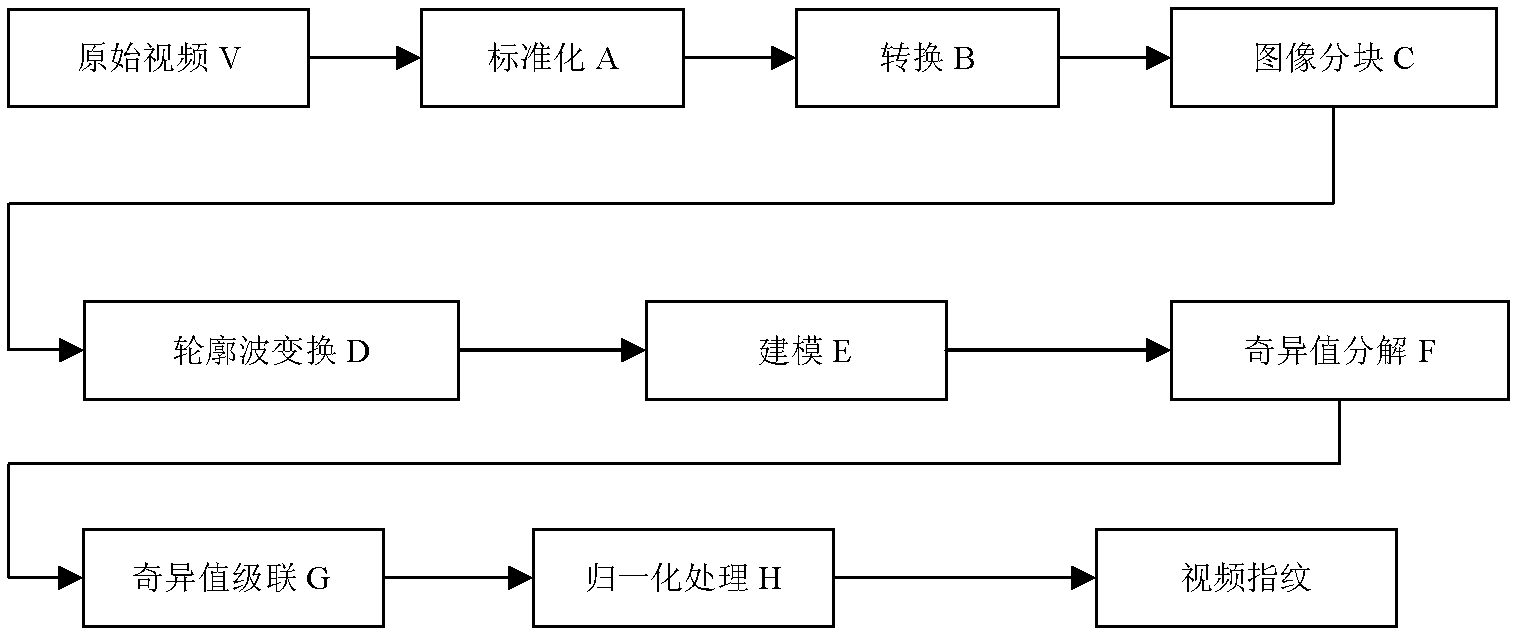
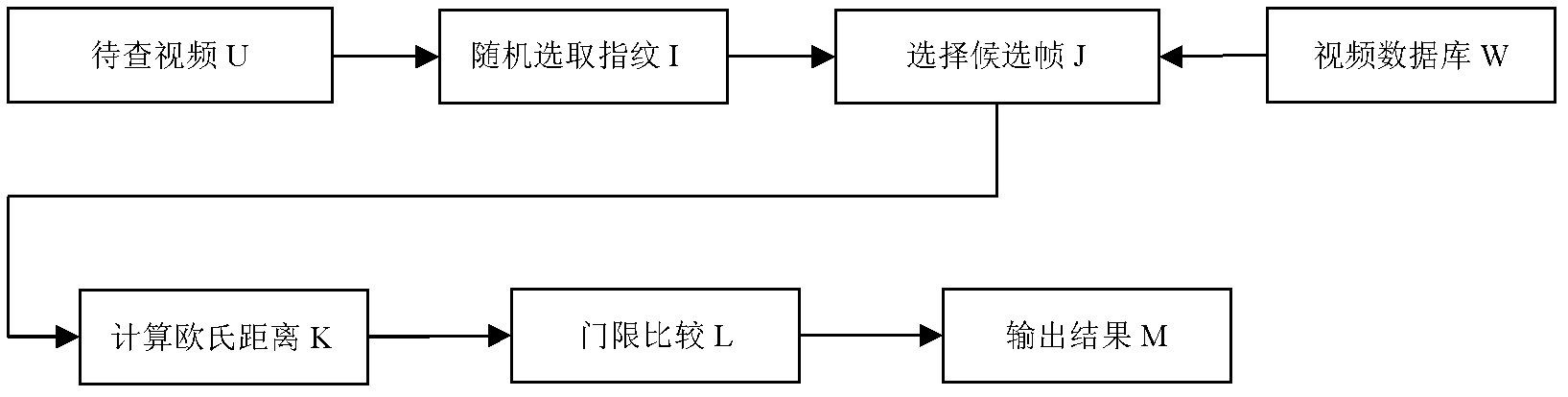
InactiveCN102547477AImprove robustnessEasy to identifyImage analysisSelective content distributionSingular value decompositionModel parameters
The invention discloses a video fingerprint method based on a contourlet transformation model, which is characterized by comprising the following steps of: standardizing a piece of video and segmenting each image; transforming each image block through a multi-scale and multi-directional contourlet, and using a hidden Markov tree technology to extract model parameters; decomposing singular values of a standard variance matrix of each block, extracting the maximum singular value, and cascading and normalizing the singular value to construct a video fingerprint vector; using a two-step search strategy in the fingerprint matching stage; and randomly selecting the fingerprint of each frame in the video to be checked, rapidly determining candidate video, and then measuring the similarity of the video to be tested and the candidate video according to the Euclidean distance. The stability, identification efficiency and search efficiency of video fingerprints can be improved, and the method can be widely applied in copy detection, retrieval, identification and copyright protection of video files.
Owner:HEFEI UNIV OF TECH
Text characteristic extracting method and document copy detection system based on sentence level
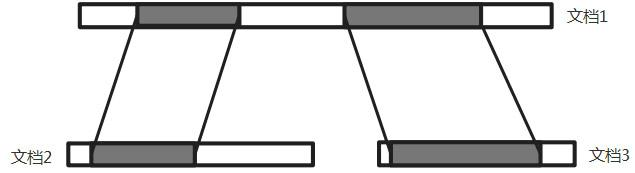
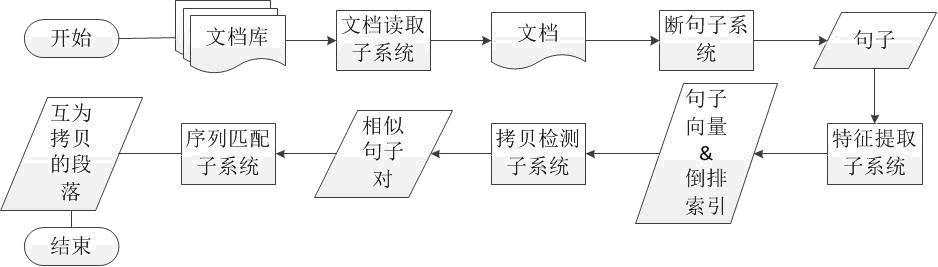
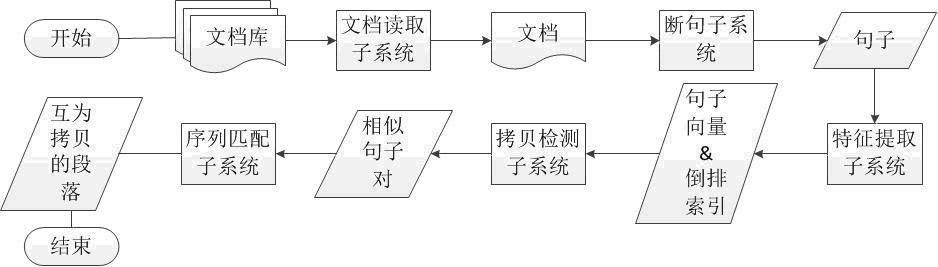
The invention belongs to the technical field of copy detection and particularly relates to a text characteristic extracting method and a document copy detection system based on sentence level. The invention provides the text characteristic extracting method based on the sentence level, and the method comprises the following steps: selecting a certain quantity of common vocabularies with the lowest reverse document frequency as antecedents, extracting improved Shingle characteristics to express the whole sentence. The invention also provides a document copy detection system based on the sentence level, and the system comprises a document reading subsystem, a segmenting subsystem, a characteristic extracting subsystem, a copy detection subsystem and a sequence matching subsystem, can accurately find out a document pair including part of copies in a document set at high speed, and positions the mutual copying range.
Owner:FUDAN UNIV
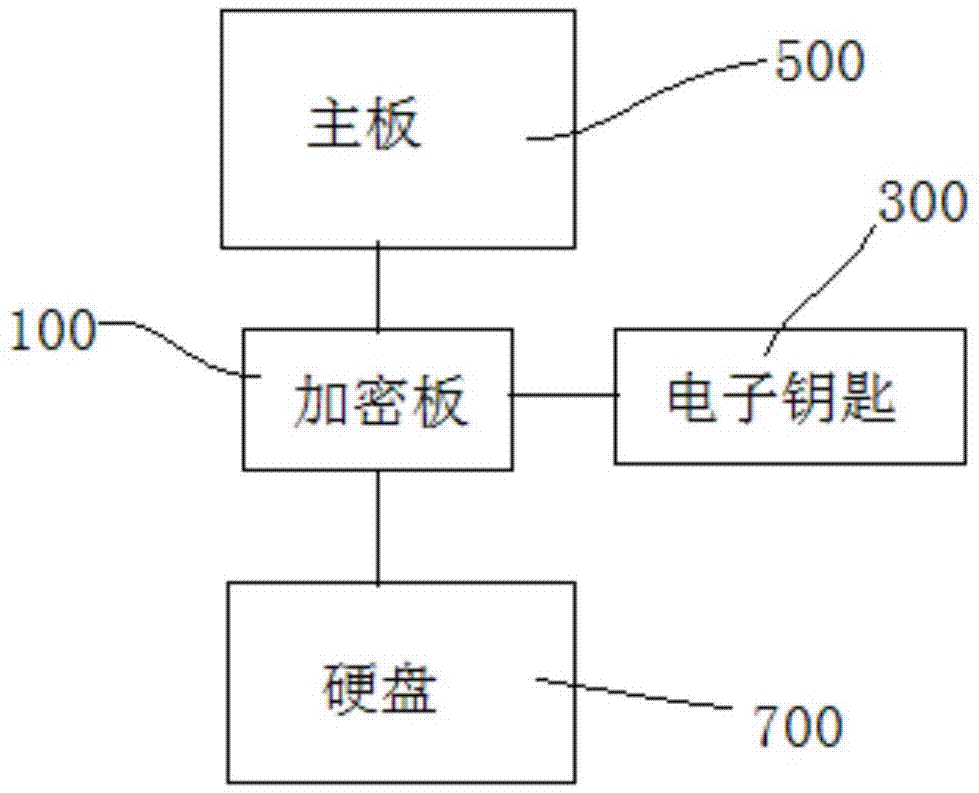
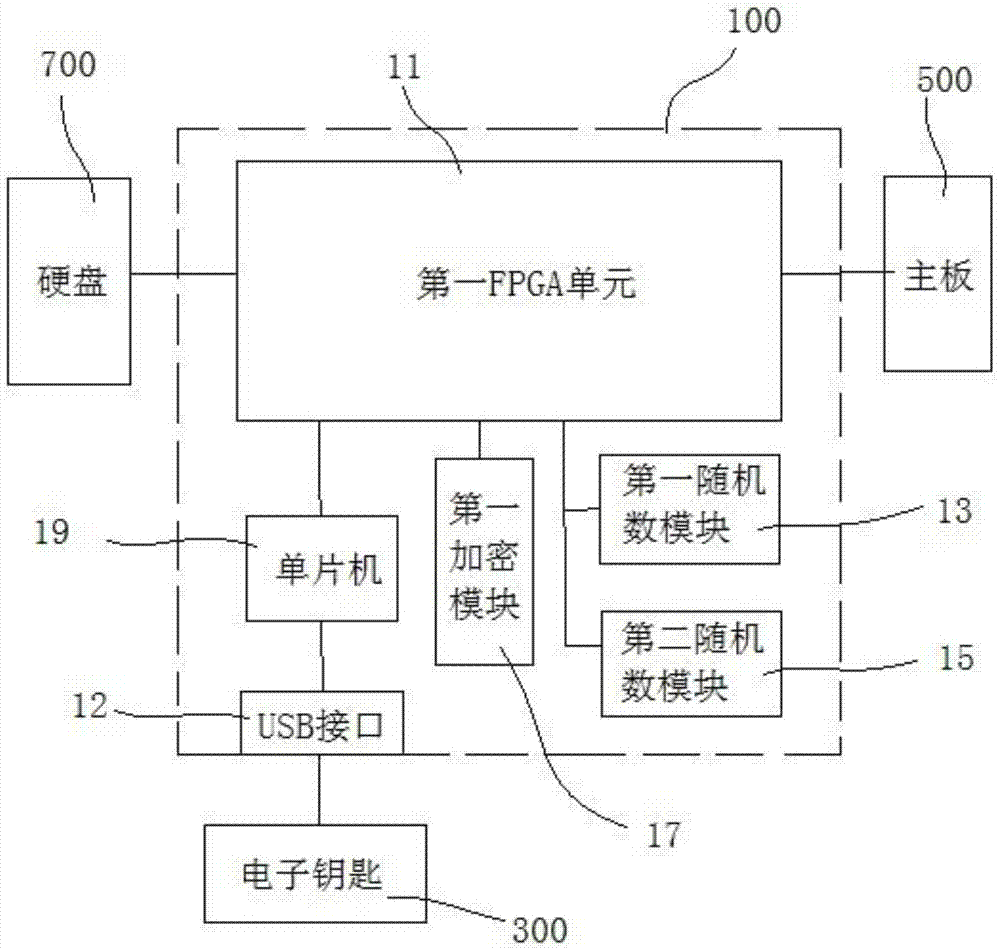
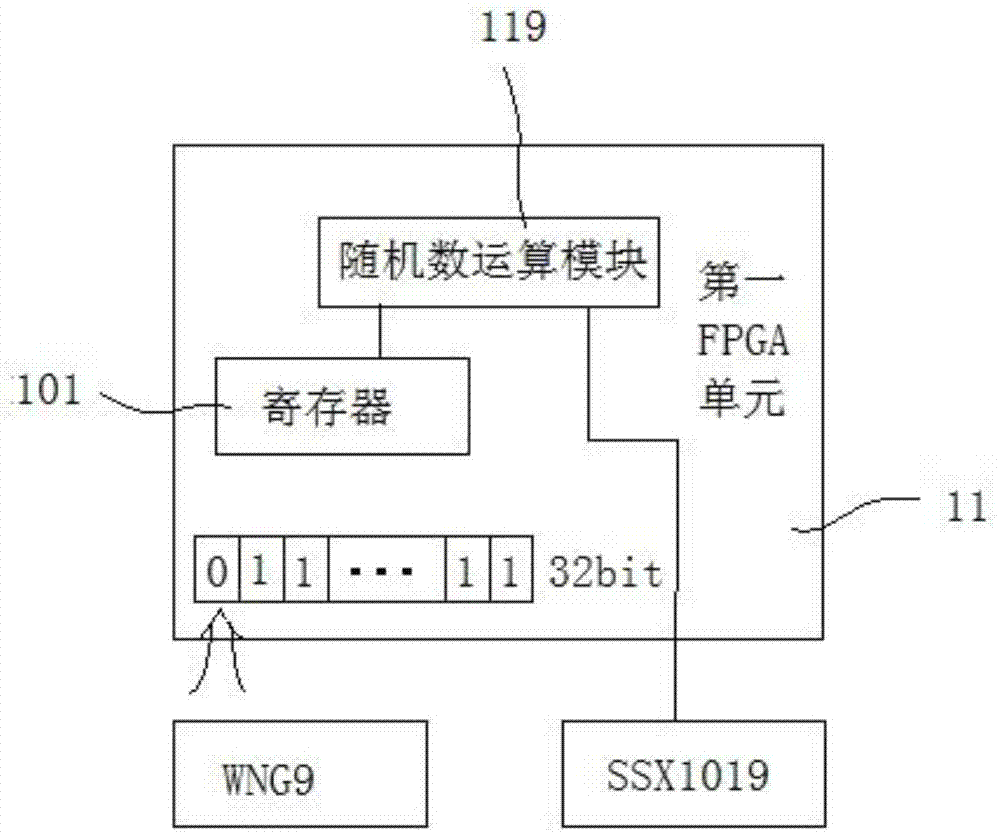
Management-use separated computer encryption lock
PendingCN106897640AImprove securityPrevent copyingInternal/peripheral component protectionDigital data authenticationConfidentialitySoftware engineering
A management-use separated computer encryption lock includes an encryption board inserted between a main board and a hard disk of a computer; an electronic key which is inserted in the encryption board and can perform real-time identity authentication with the encryption board; the electronic key and the encryption board perform real-time identity authentication and firmware anti-copy detection, and perform encryption on data accessing between the electronic key and the encryption board; after identity authentication and firmware anti-copy detection is completed, the electronic key combines a part of user key lists stored in an inner part and a part of user key lists of the encryption board, and a part of user keys are randomly selected from the key lists according to different storage partitions of the hard disk to perform encryption on data accessing the hard disk. The security of the computer encryption lock is high, the firmware will not be copied, encrypted data in the hard disk and electronic key and encryption board communication data are encrypted and will not be cracked, and the confidentiality is high.
Owner:SHENZHEN ZHENHUA MICROELECTRONICS +1
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com