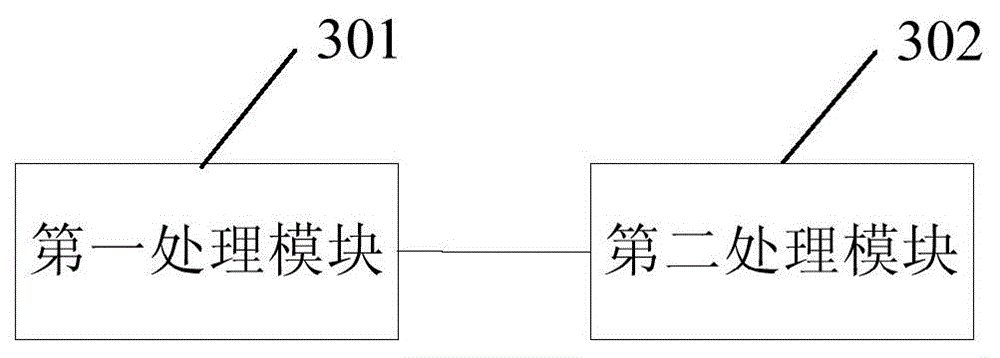
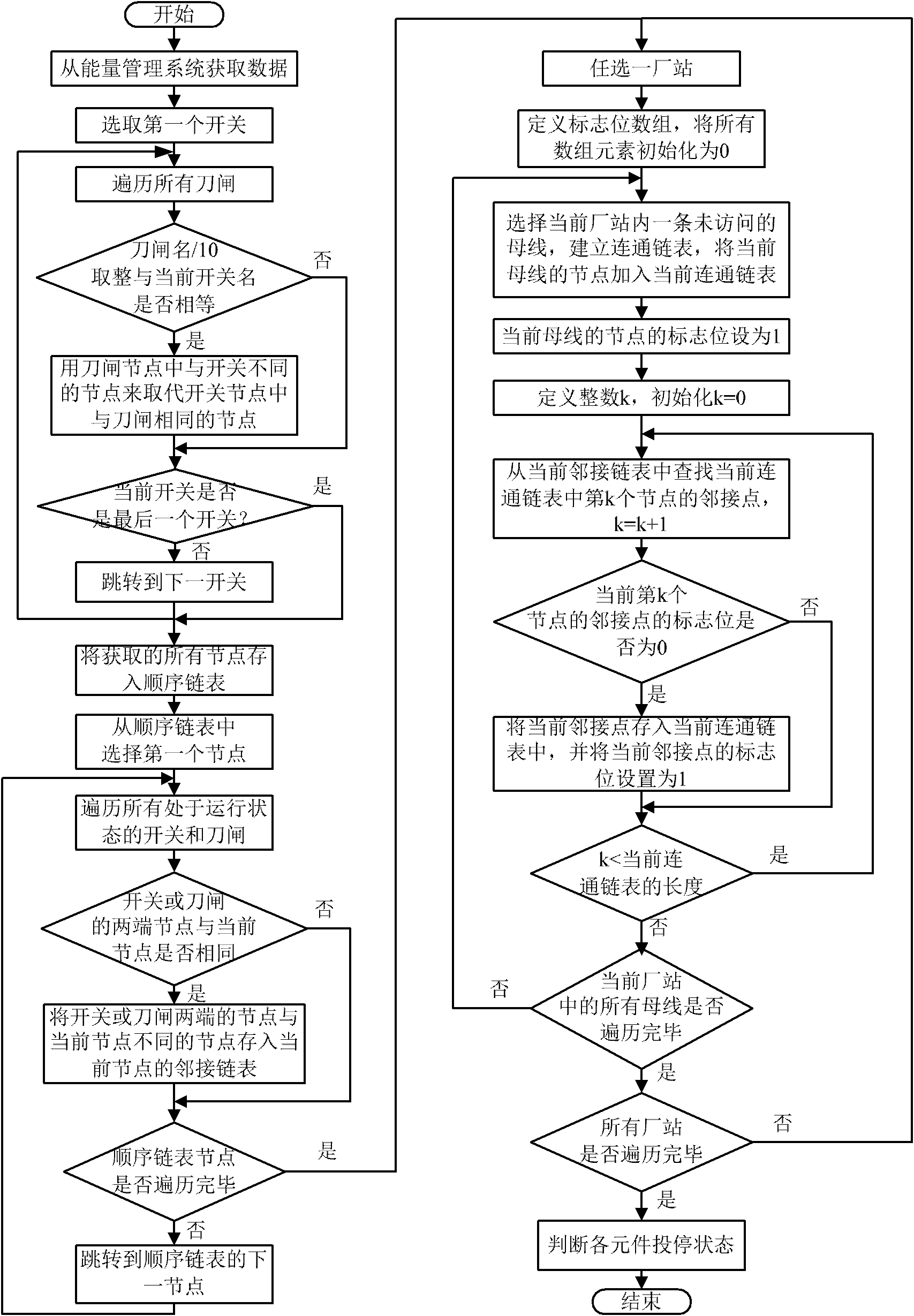
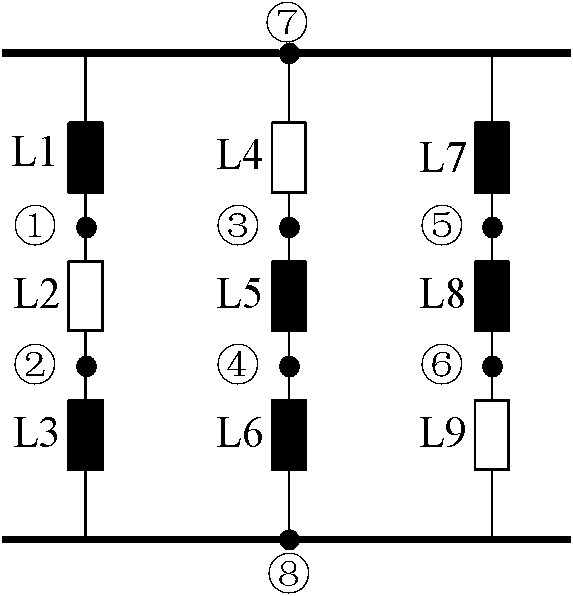
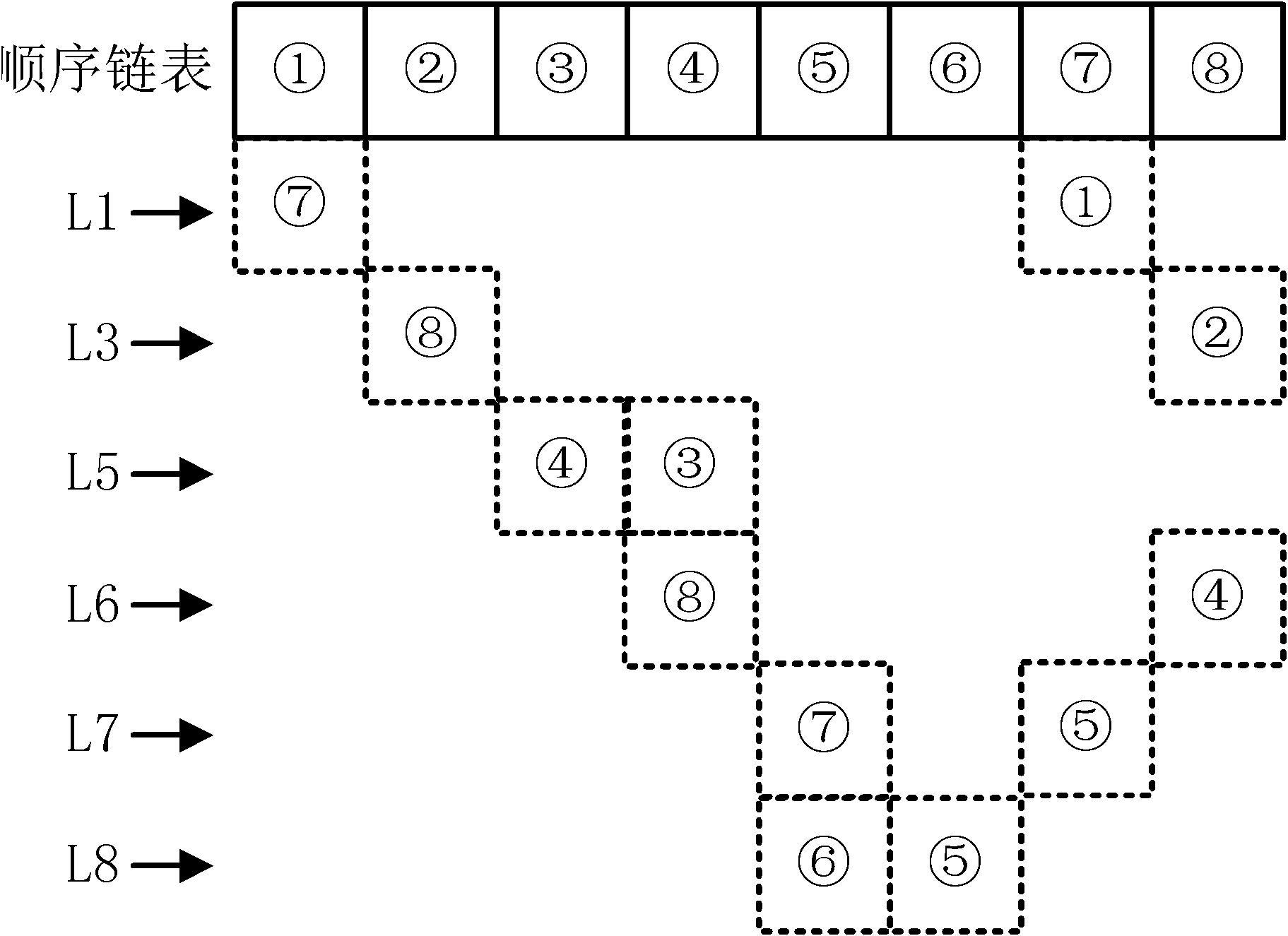
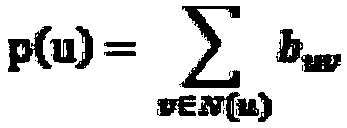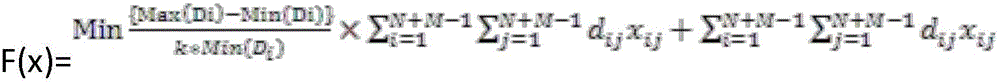Patents
Literature
114 results about "Adjacency list" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
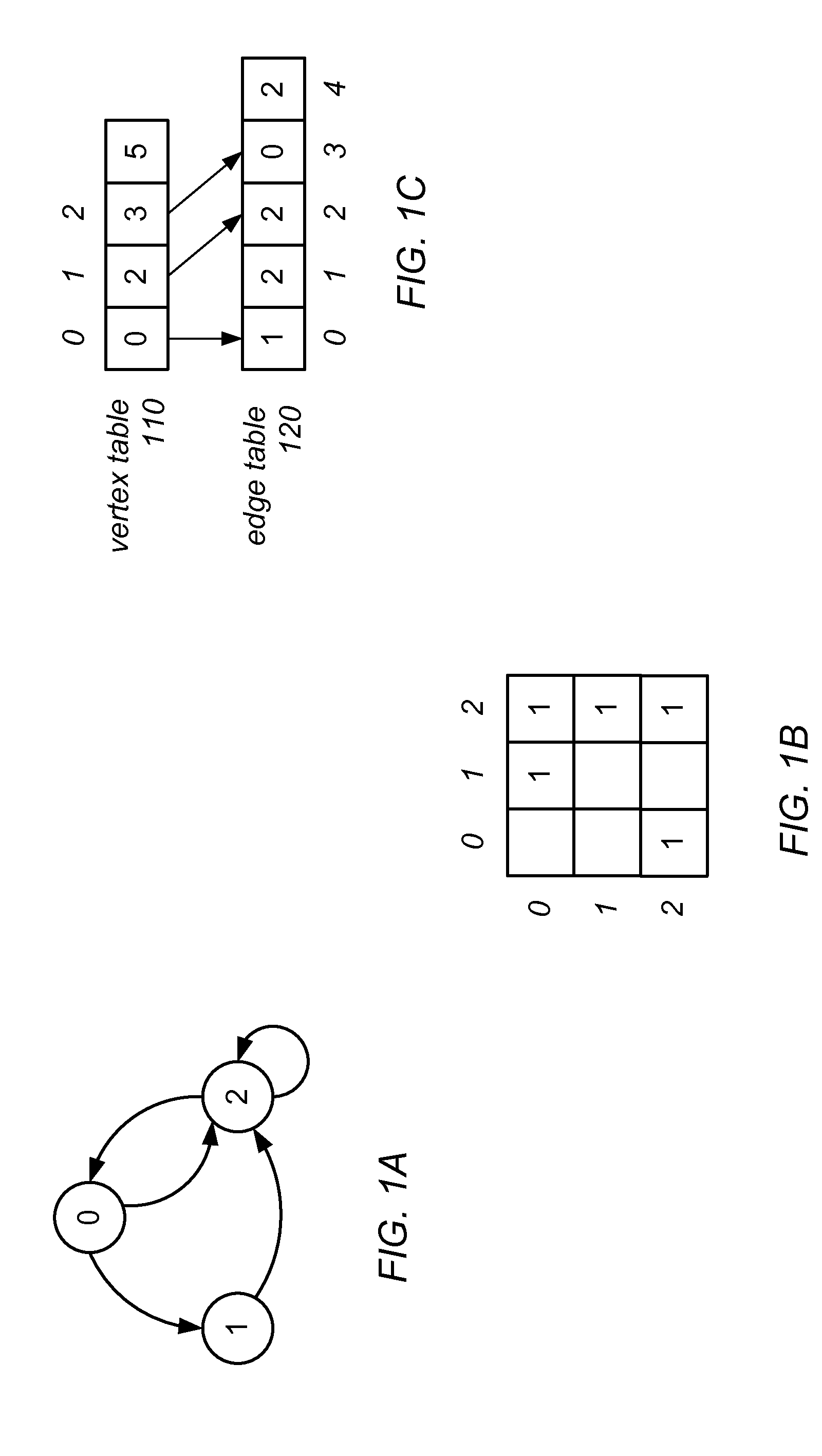
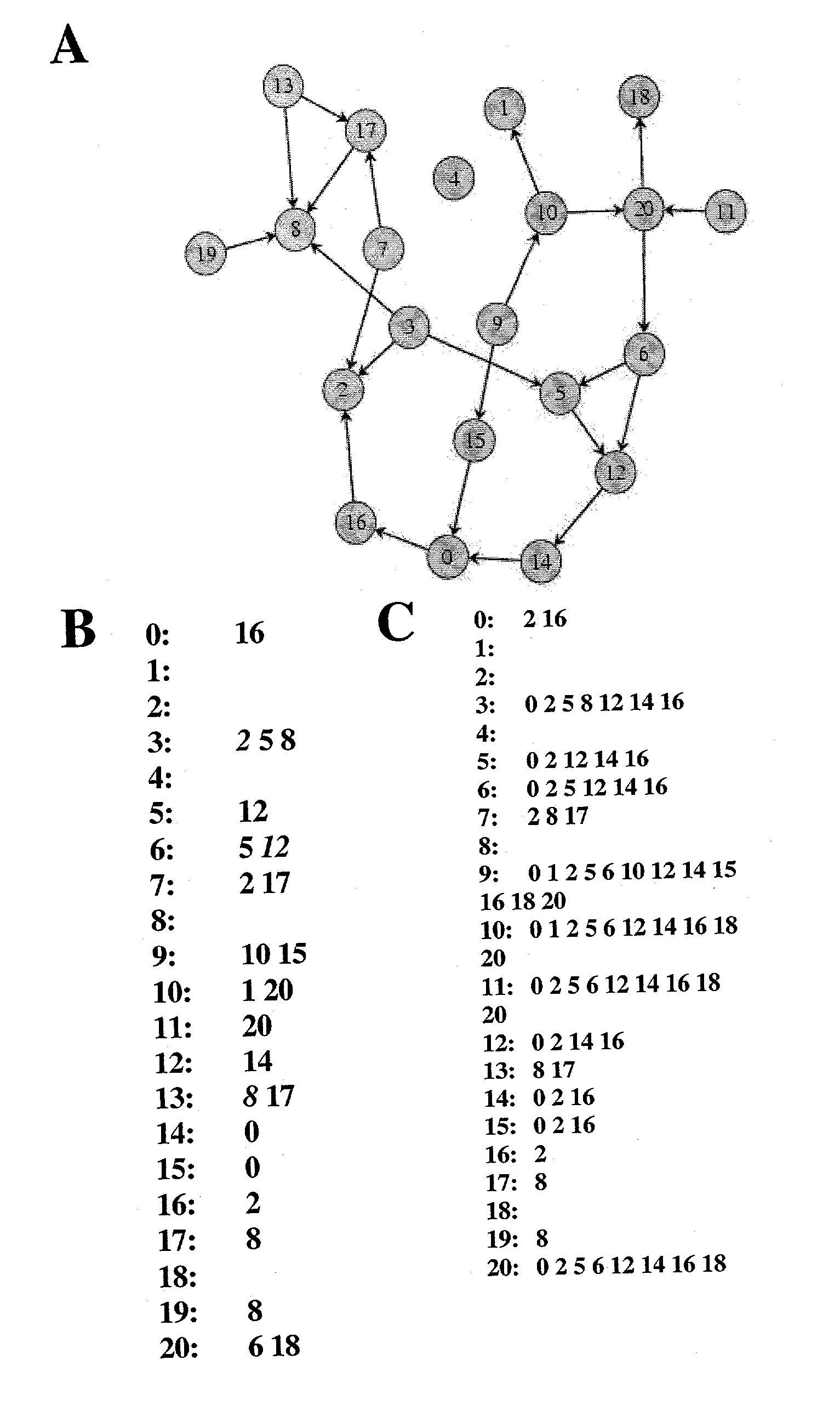
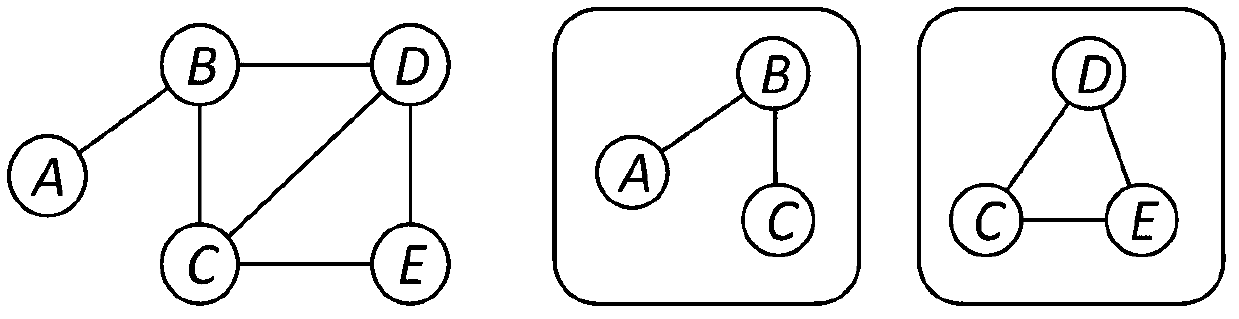
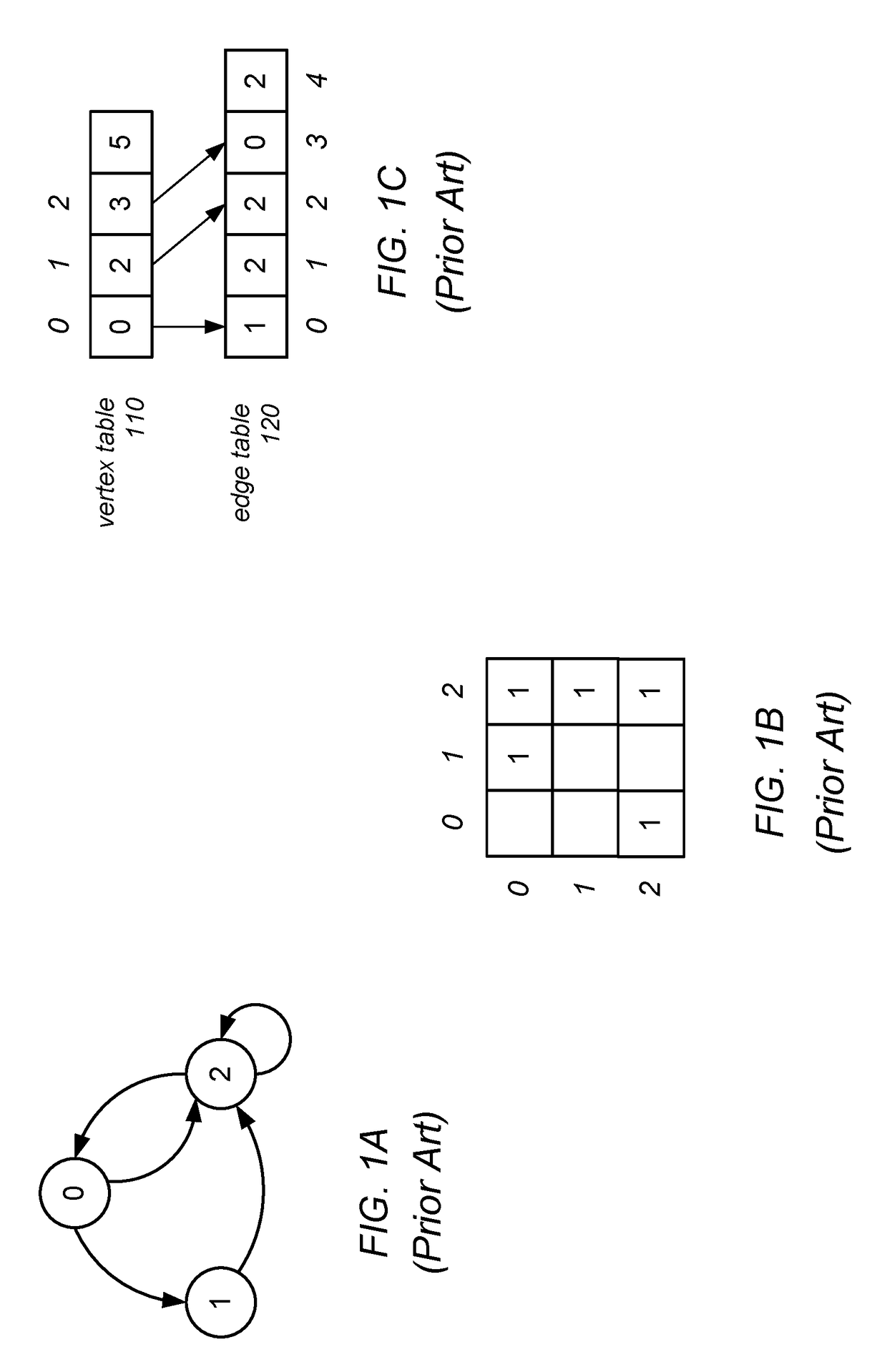
In graph theory and computer science, an adjacency list is a collection of unordered lists used to represent a finite graph. Each list describes the set of neighbors of a vertex in the graph. This is one of several commonly used representations of graphs for use in computer programs.
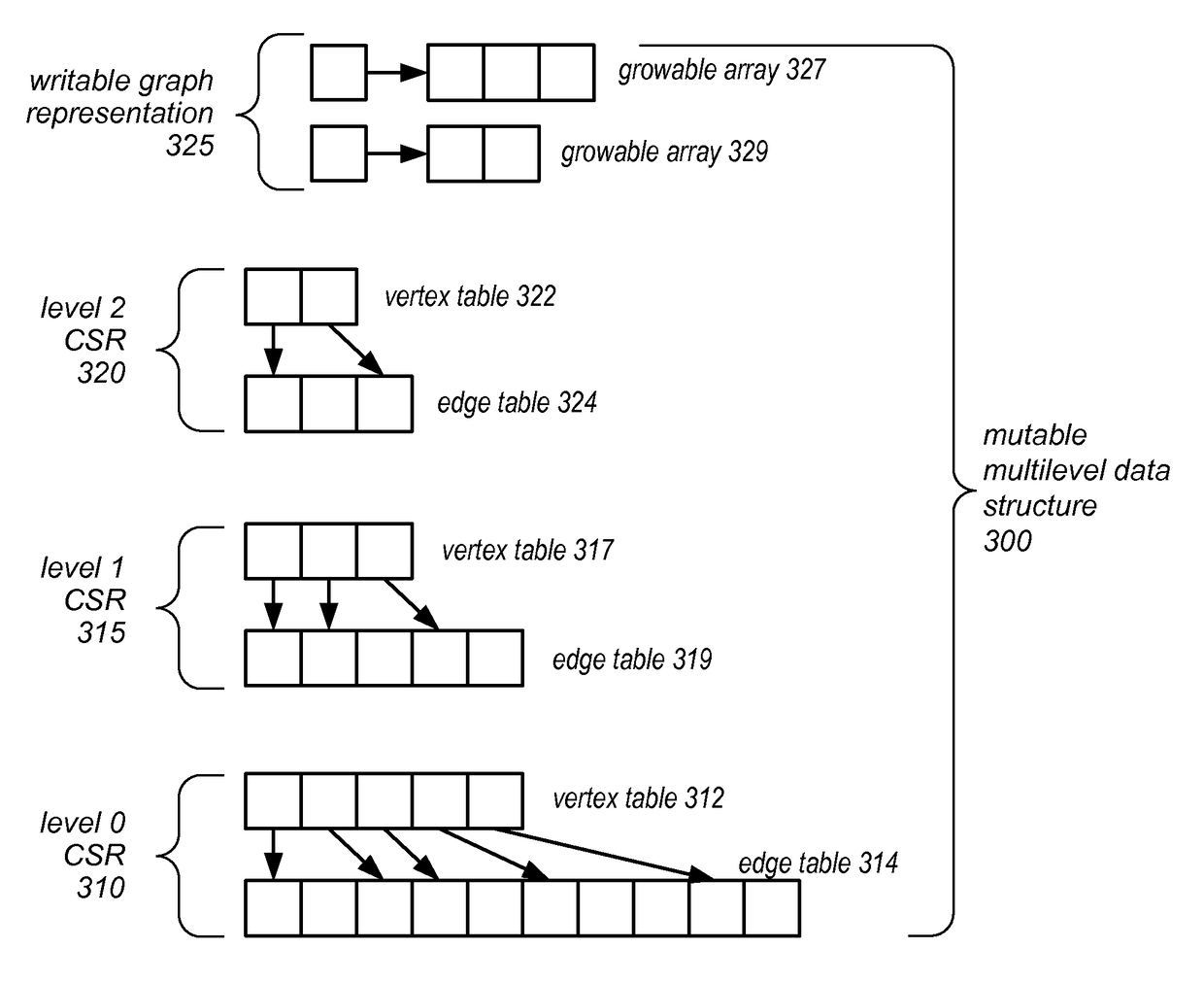
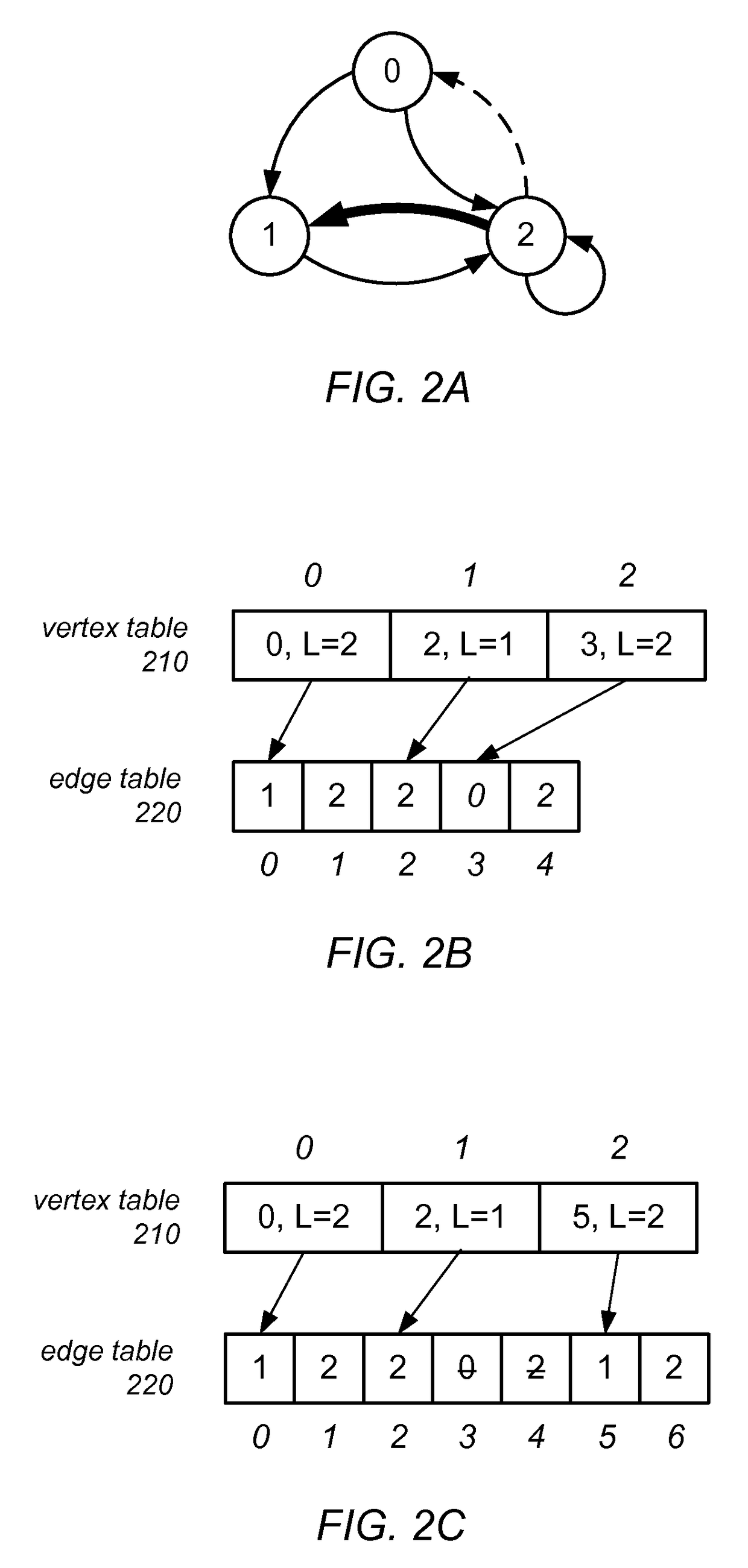
Graph Processing Using a Mutable Multilevel Graph Representation
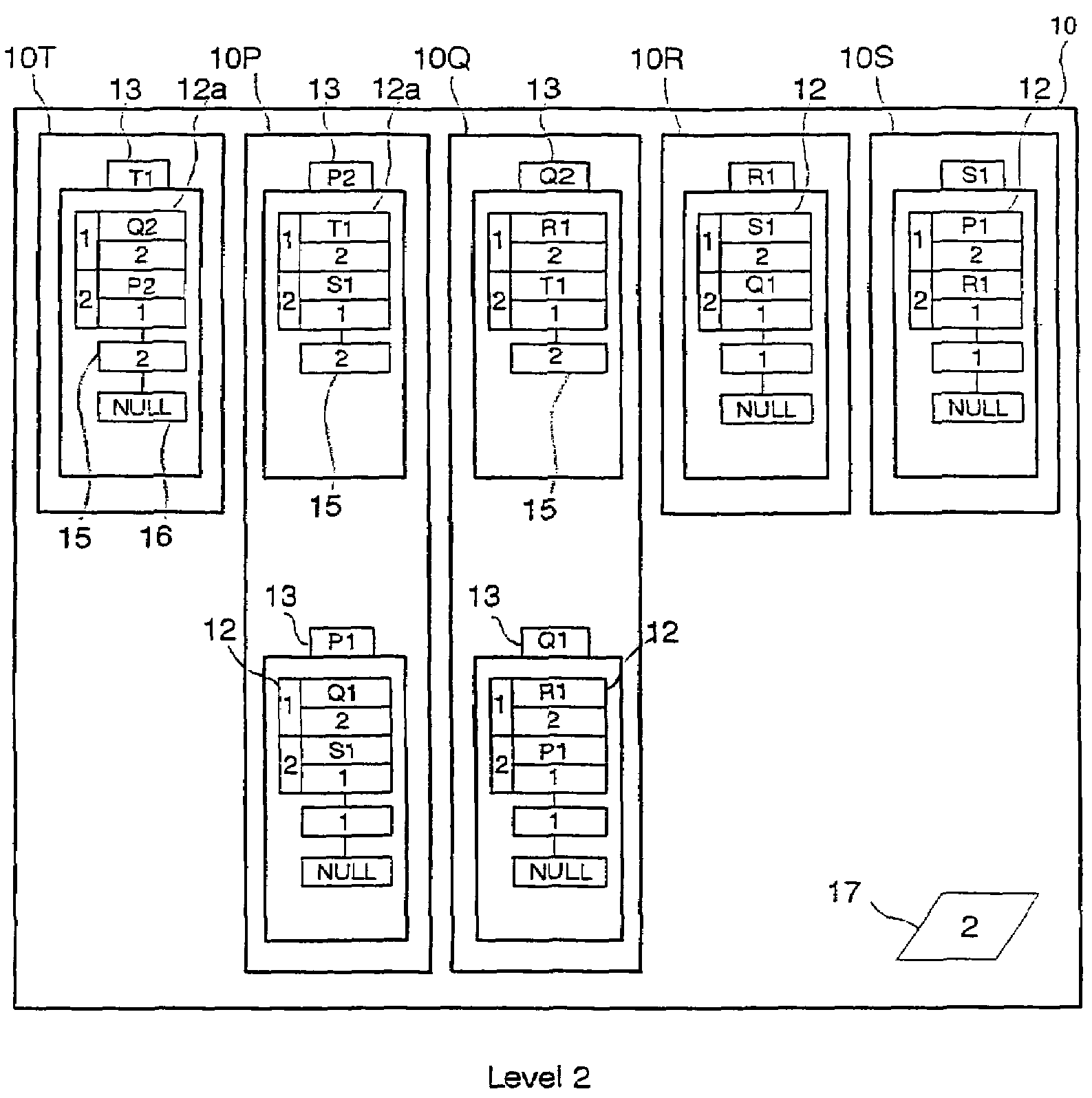
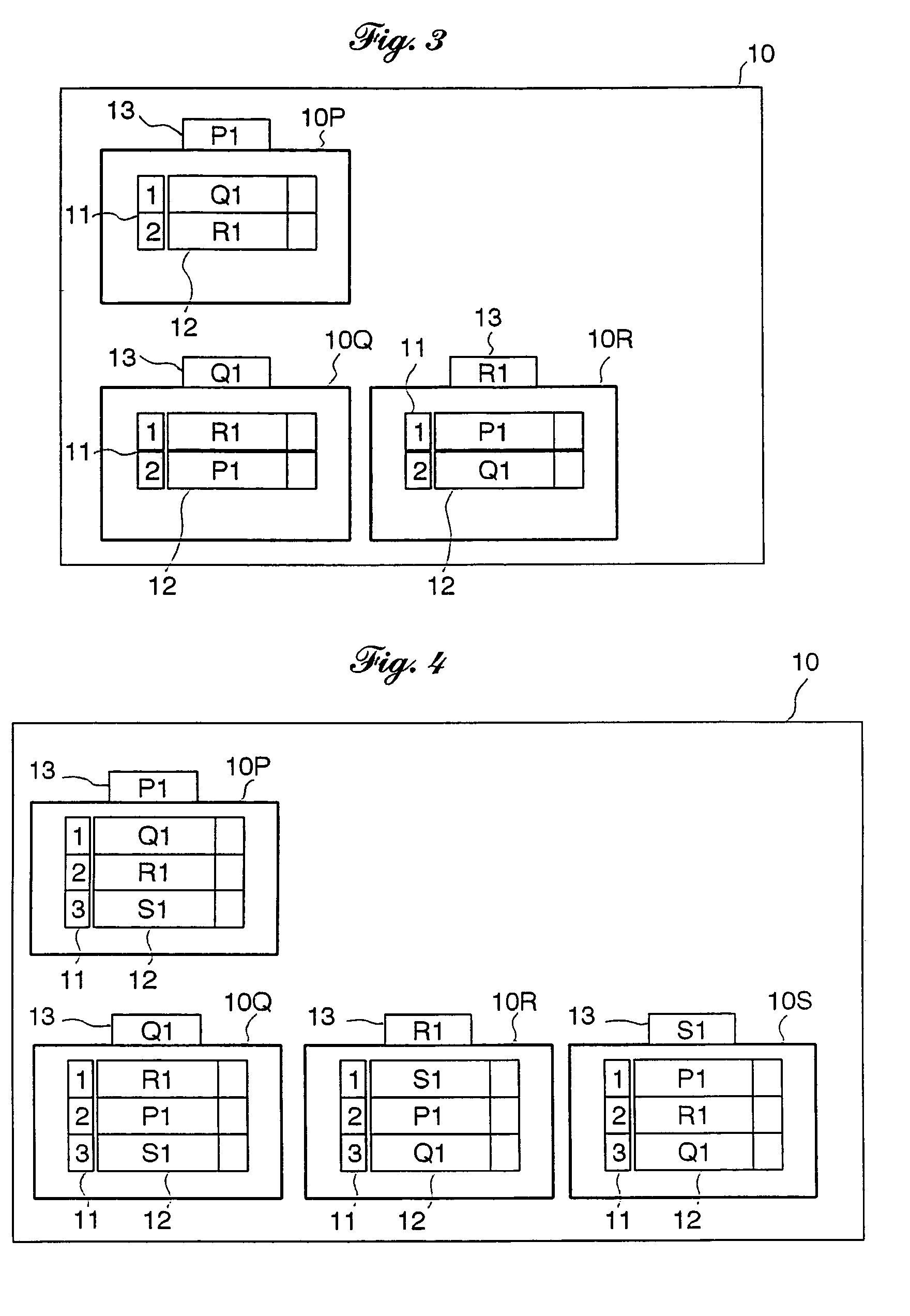
ActiveUS20160071233A1Improve performanceIncrease spacingDrawing from basic elementsImage memory managementTheoretical computer scienceAdjacency list
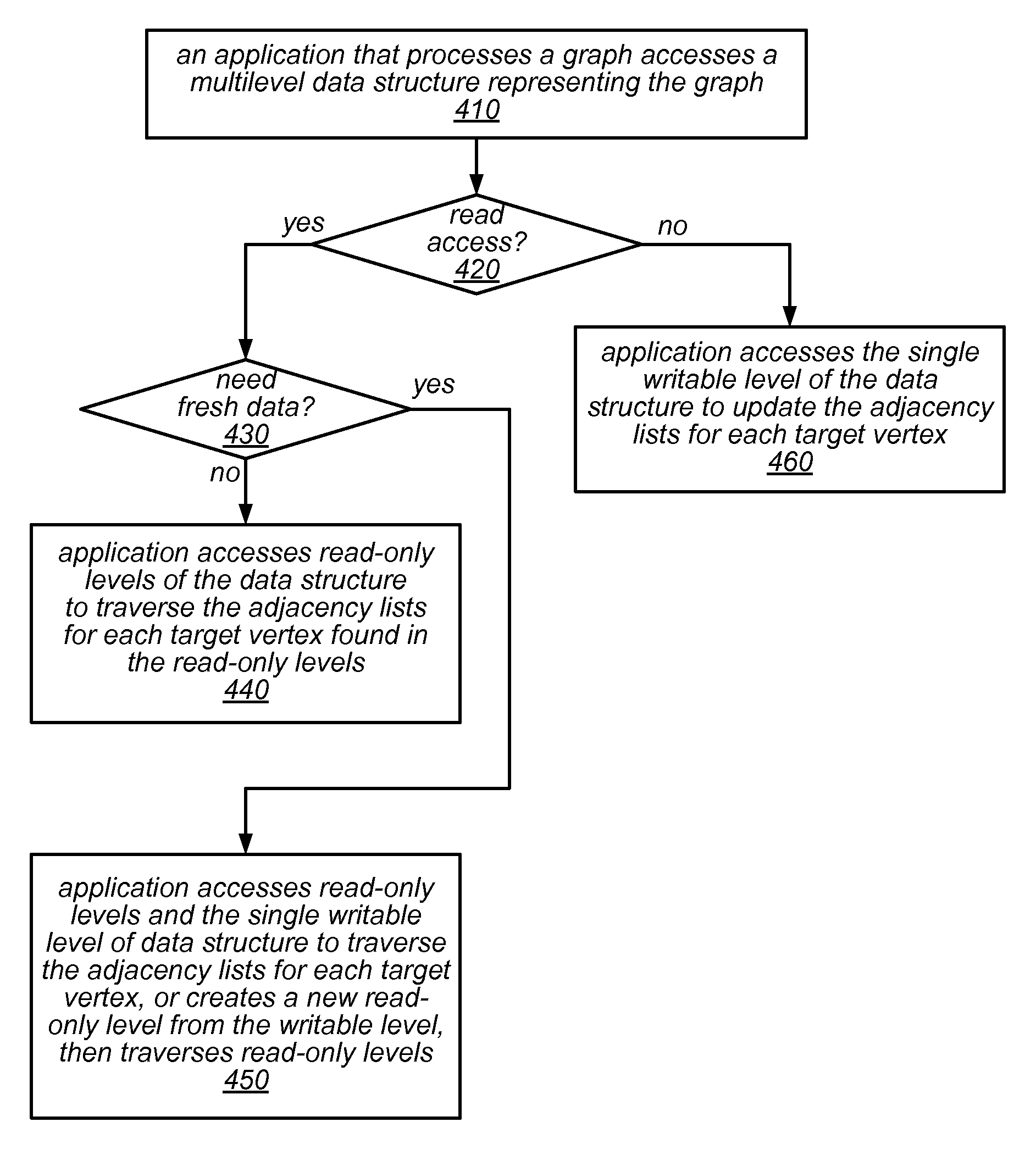
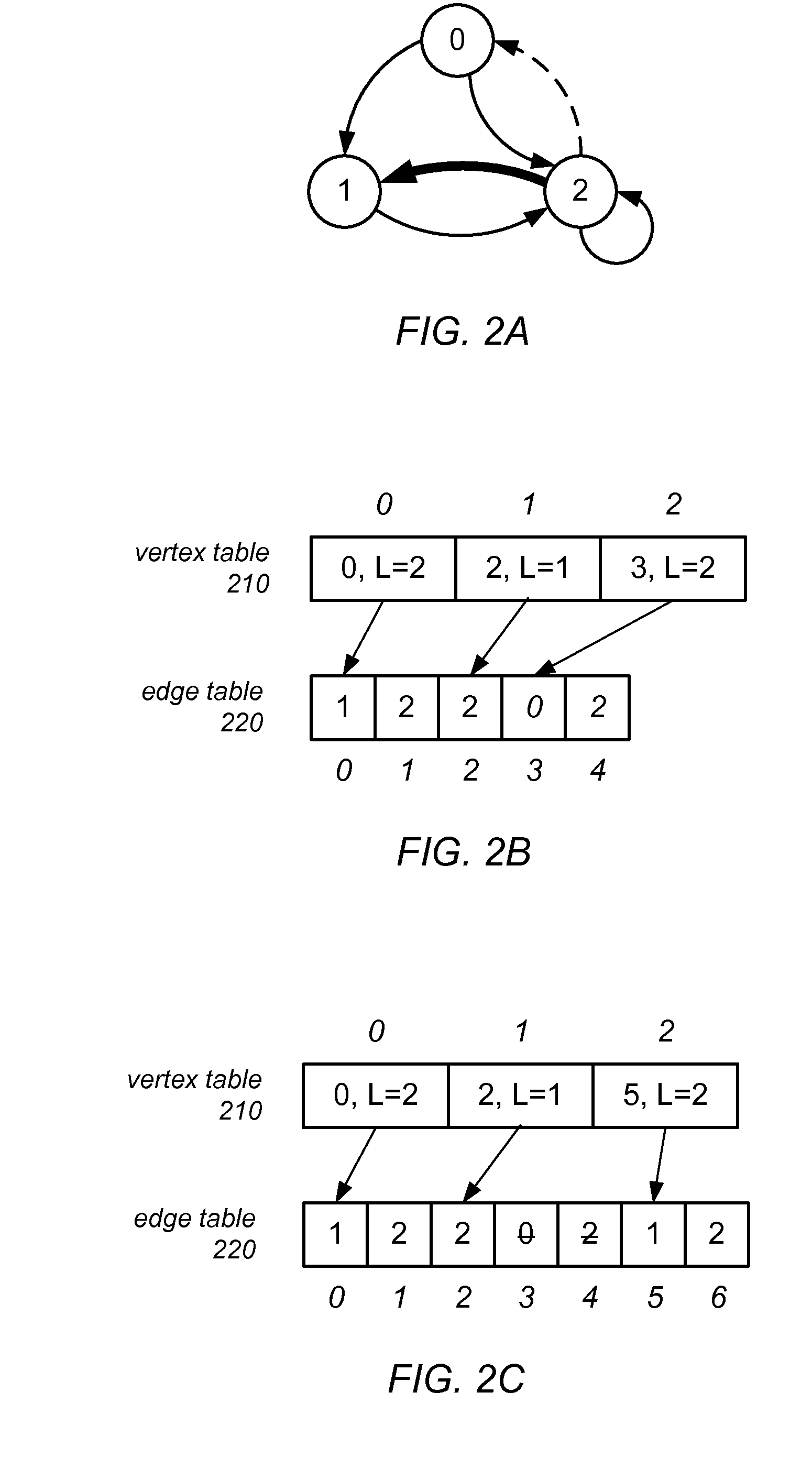
A mutable multilevel data structure representing a graph structure may include multiple read-only levels and a single writable level. Each read-only level may include a vertex table (which includes references to edge tables on the same level or a different level containing elements of adjacency lists for some vertices) and an edge table (which includes elements of adjacency lists that changed since the previous read-only level). A hybrid variant may switch between a performance-optimized variant (whose edge tables include complete adjacency lists for vertices whose edge sets were modified) and a space-optimized variant (whose edge tables include only newly added adjacency list elements). The vertex tables and / or the writable level may be implemented using copy-on-write arrays, each including an indirection table and multiple fixed-sized data pages. Computations may be run on the read-only levels or on the writable level and read-only levels.
Owner:ORACLE INT CORP
System and method for reconstructing pathways in large genetic networks from genetic perturbations
InactiveUS20030023388A1Reduce research costsPrecise positioningDigital data processing detailsDigital computer detailsGraphicsGenetic network
A system and method for reconstructing pathways in large genetic networks from genetic perturbations comprises an analysis method and system that applies a recursive algorithm for determining the path between every gene pair in an arbitrarily large genetic network from large-scale gene perturbation data and reconstructs all direct and indirect regulatory gene interactions in the network. Graph theory mathematics is applied to genetic network reconstruction in the following manner: Genetic perturbation data is used to identify all genes accessible from a perturbed gene to generate an accessibility list for the gene. Graph theory mathematics is applied to the accessibility list and its graph to determine a condensation of the graph as defined by the condensation's accessibility list. Graph theory mathematics is applied to the accessibility list, such as through a recursive algorithm performed on a desktop computer, to obtain an adjacency list for the gene that characterizes a genetic network.
Owner:STC UNM
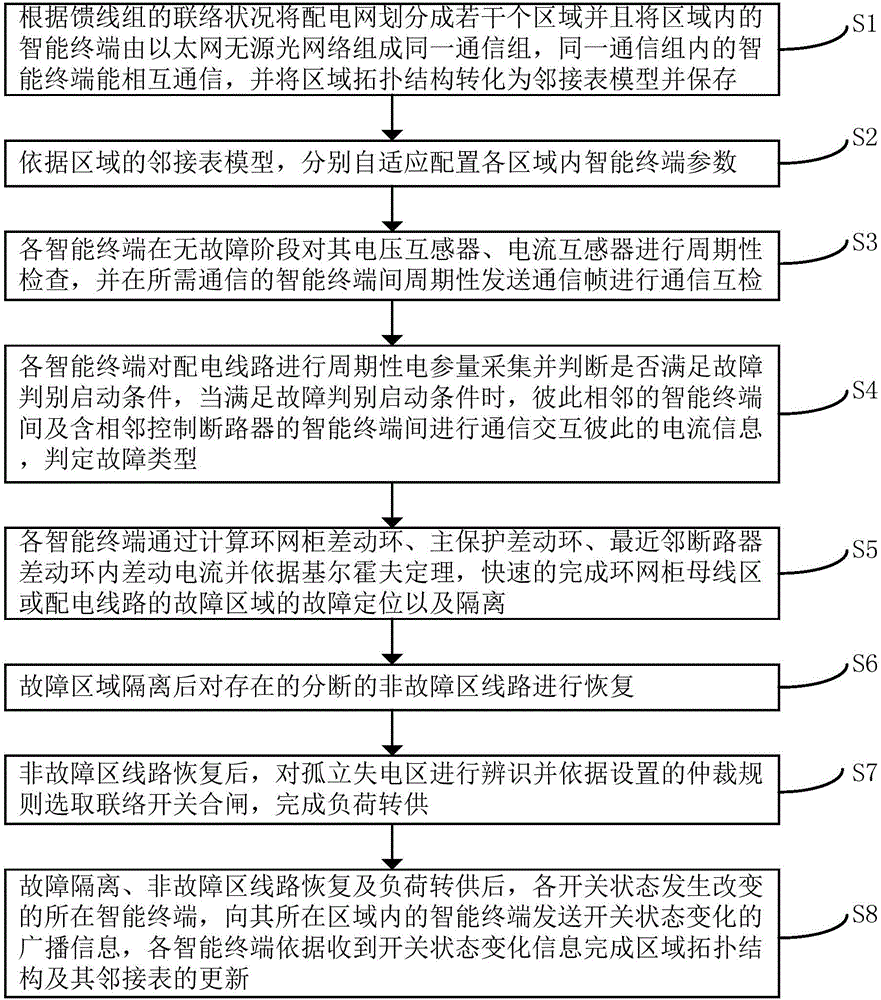
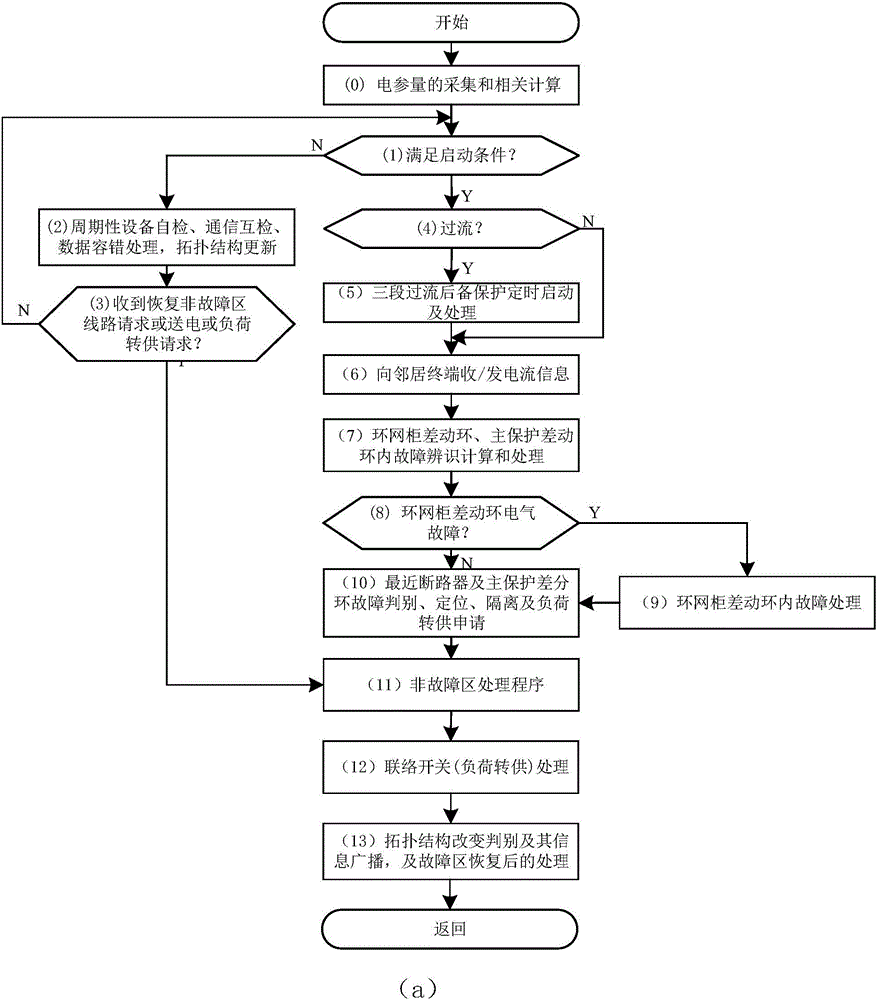
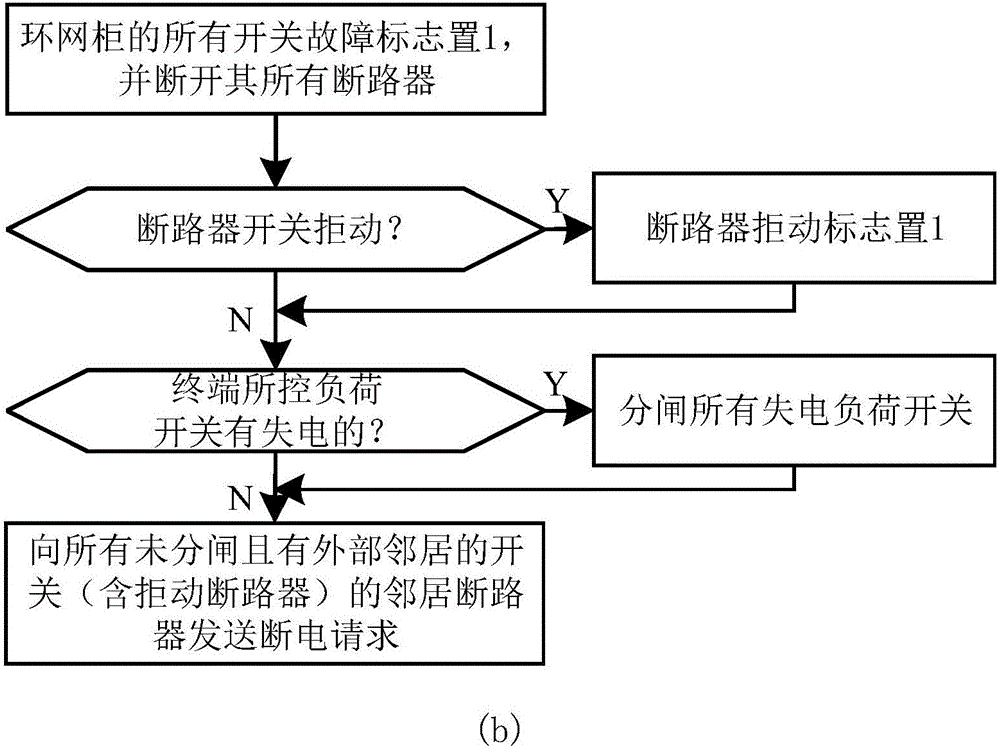
Adaptive self-healing protection method applied to distribution network containing hybrid switches
ActiveCN106230121AHigh fault location accuracyImprove accuracyEmergency protective circuit arrangementsInformation technology support systemSelf-healingInterconnection
The invention discloses an adaptive self-healing protection method applied to a distribution network containing hybrid switches. The method comprises the following steps: dividing a region, and converting a regional topology into an adjacency list model; adaptively configuring intelligent terminal parameters in each region respectively according to the regional adjacency list model; performing periodic equipment self-check and communication mutual check; performing fault detection and fault type recognition; positioning and isolating a fault; recovering a non-fault line; recognizing an isolated power loss region and selecting an interconnection switch; recognizing the isolated power loss region and selecting the interconnection switch to be turned on or off according to the set arbitration rule, thereby completing load transfer; and updating the regional topology and the adjacency list thereof. The method can adaptively realize fault type recognition, fault positioning, fault isolation, non-fault regional line recovery and load transfer of the distribution network containing hybrid switches by using peer-to-peer communication and mutual cooperation of intelligent terminals, and has the characteristics of high fault positioning accuracy, high adaptive self-healing response speed and strong practicability.
Owner:HUNAN UNIV
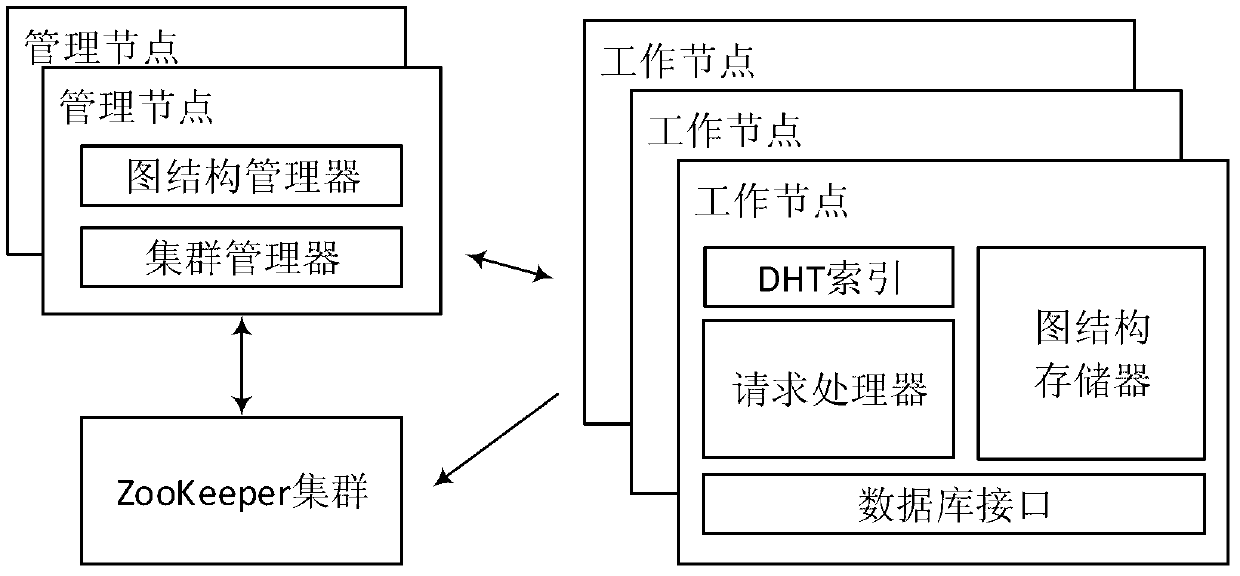
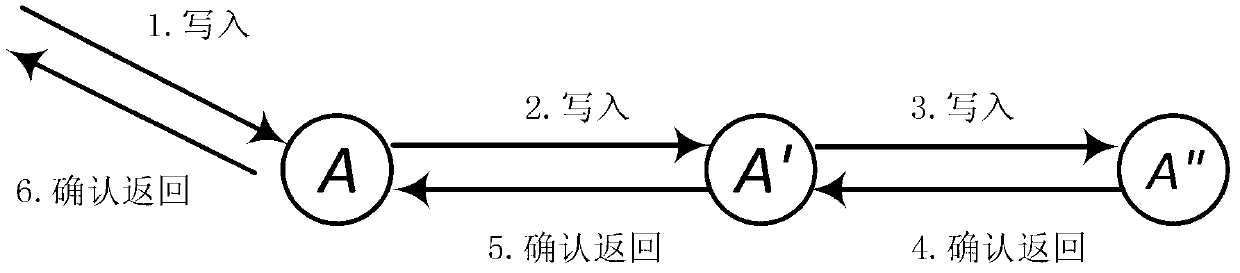
Data storage method and system suitable for social network graph
InactiveCN103345508AReduce RPC costReduce the number of cluster RPC requestsSpecial data processing applicationsDatabase interfaceSocial graph
The invention relates to a data storage method and system suitable for a social network graph. The method includes the steps that graph structure information of the social network graph is read in a side list or an adjacency list mode; a peak is separated into a plurality of sub peaks, and each sub peak has all the peak data and data on corresponding sides of the peak; with regard to sides, which are not distributed in partitions, in the graph, firstly the sides are distributed to one partition, and at the moment sides spanning the partitions are not generated; if the distribution is not succeed, one side spanning the partitions is generated. The system comprises a plurality of management nodes, a plurality of work nodes, and ZooKeeper clusters. Only one management node is in the working state at a same moment, and each work node comprises a PHT index, a graph structure storage, a request processor and a database interface. The data storage method and system suitable for the social network graph can be increased to reflect the change of a social network graph structure, reduces communication cost among servers, increases overall throughput of the servers, and improves user experience.
Owner:PEKING UNIV
Method, computer program product and data structure for representing two- or three-dimensional object modeling
InactiveUS7557803B2Lower requirementLight workloadRoad vehicles traffic controlImage data processing detailsAlgorithmTheoretical computer science
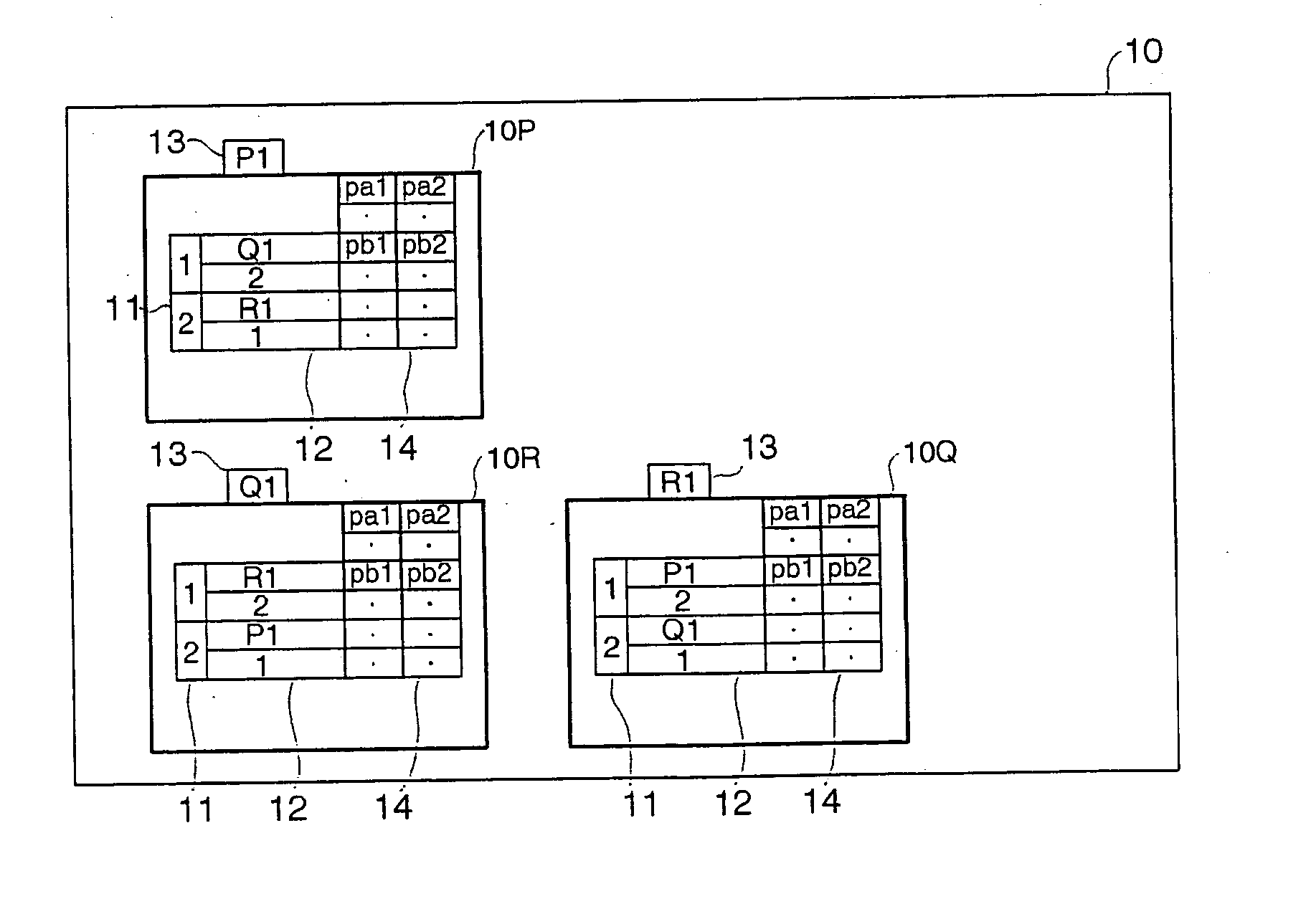
A data structure for a graph, which is composed by points and line segments connecting adjacent pairs of the points, respectively, of a two- or three-dimensional object comprises a set of point data of the individual points, each of the point data of the points consists of a clockwise or counter clockwise circular ordered adjacency list written in storage areas of a storage medium individually allocated to the point. The adjacency list describes a plurality of adjacent points associated with the point sequentially according to a circular adjacency order as viewed from outside of the graph with address pointers to the storage areas allocated to the adjacent points, respectively, and location pointers associated with the address pointers, respectively, to storage locations of adjacency lists of the adjacent points, respectively, where an address pointer of the point is written.
Owner:FURUKAWA SUSUMU +1
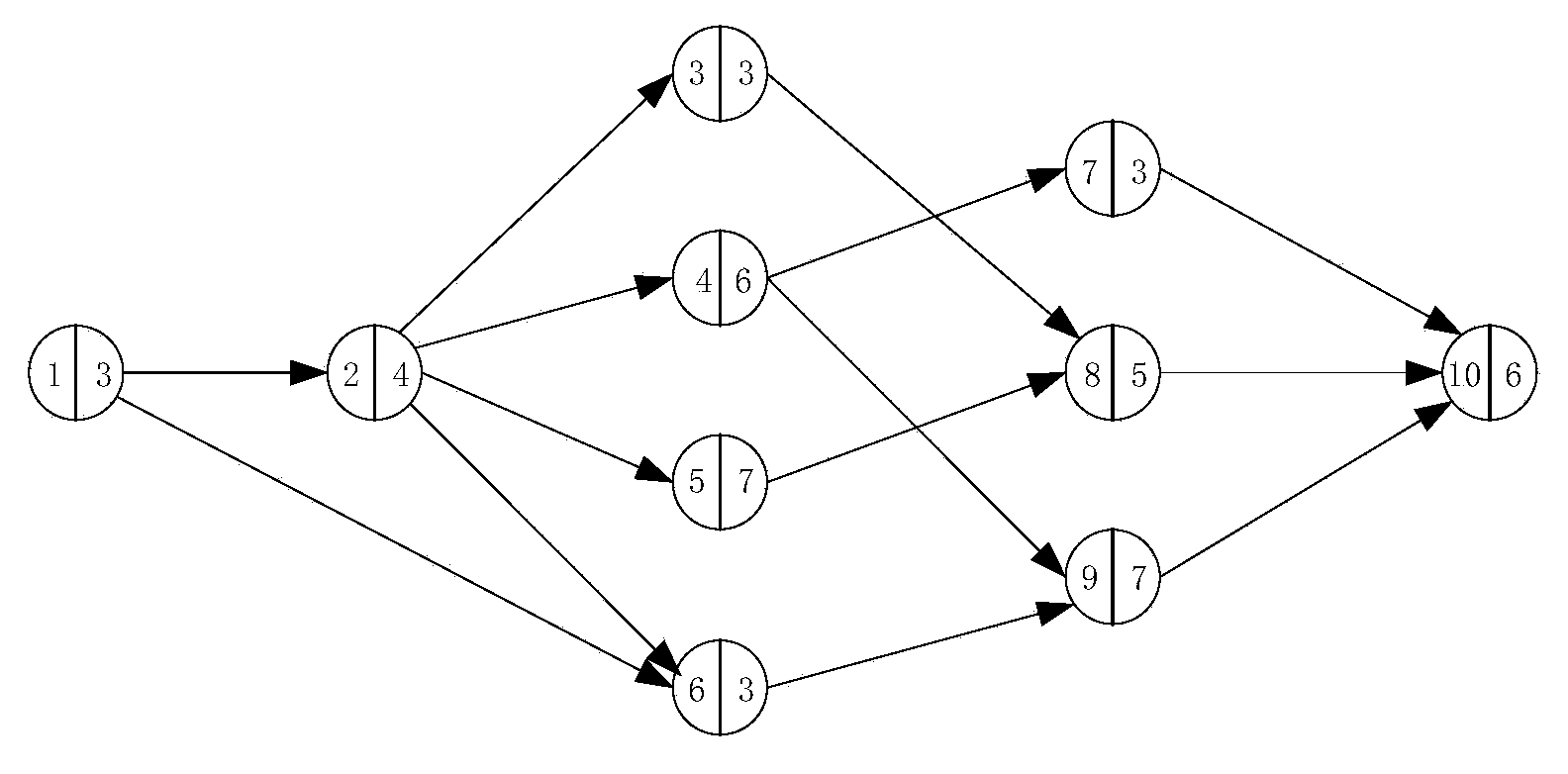
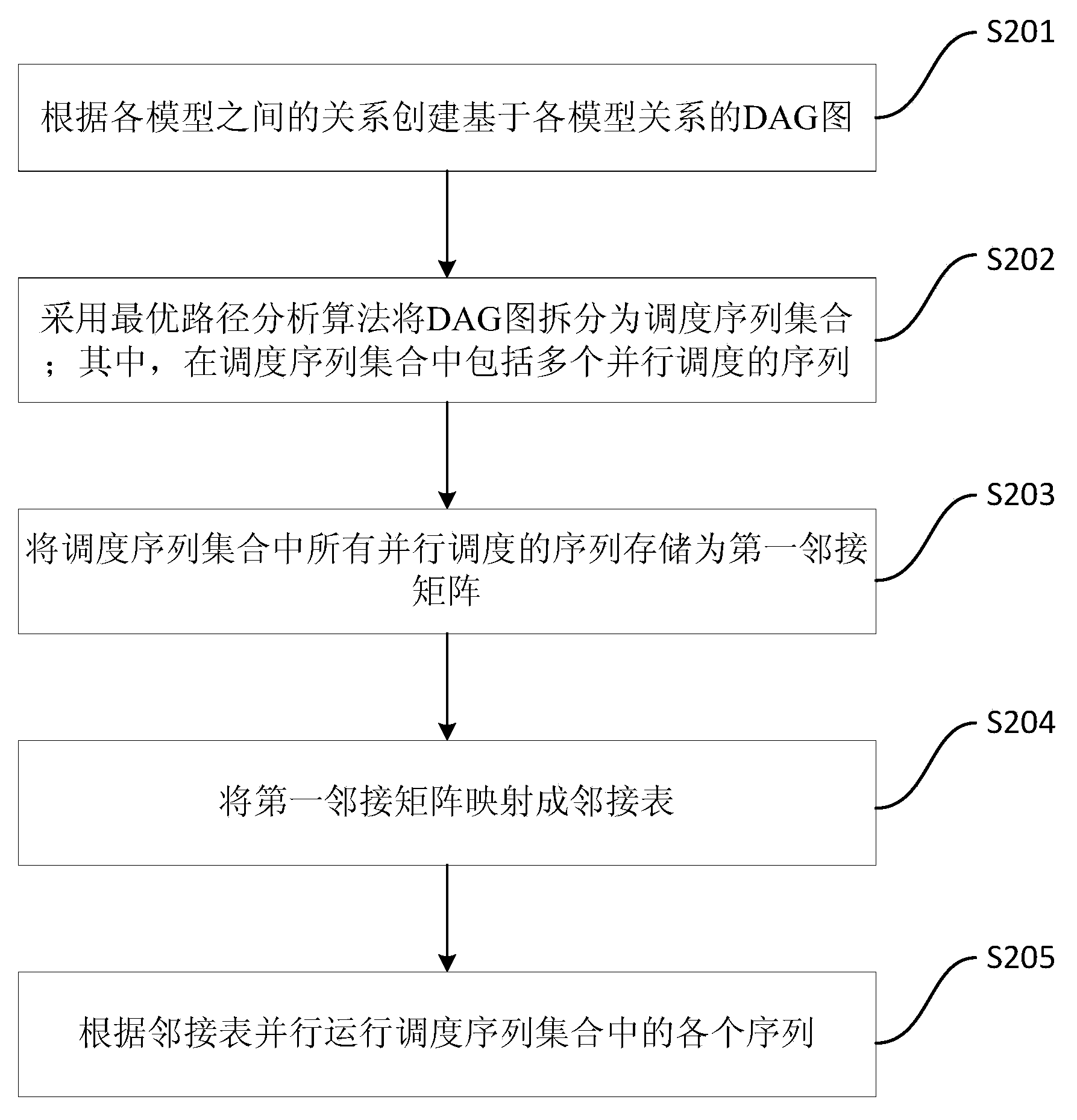
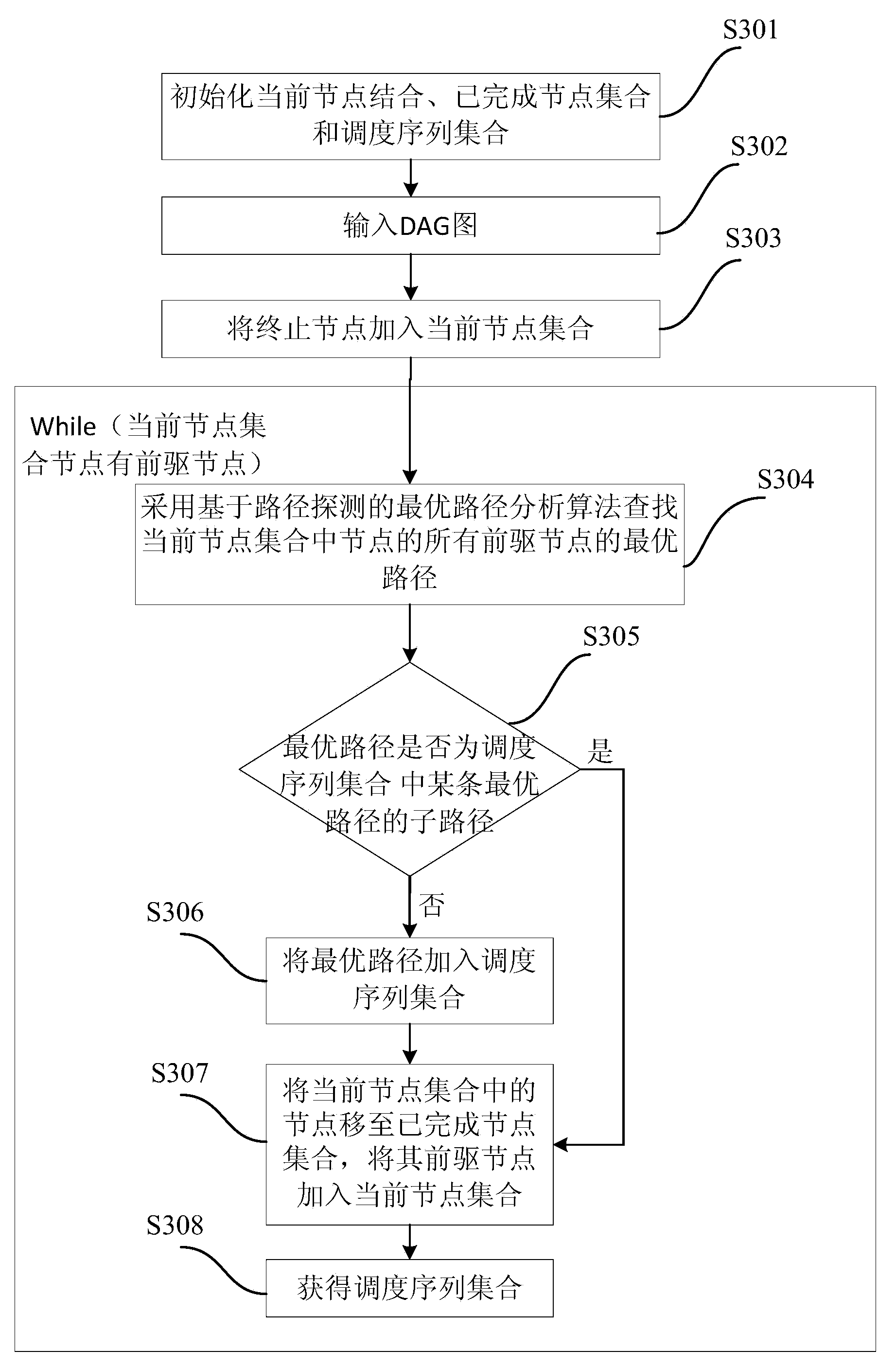
DAG (Directed Acyclic Graph) node optimal path-based multi-model parallel scheduling method and device
ActiveCN104239137ASolve complexityResolution timeProgram initiation/switchingResource allocationNODALRunning time
The invention provides a DAG (Directed Acyclic Graph) node optimal path-based multi-model parallel scheduling method and device. The method comprises the following steps of creating a DAG based on a relationship among models according to the relationship among the models; decomposing the DAG into a scheduling sequence set according to a path detection-based optimal path analysis algorithm, wherein the scheduling sequence set comprises a plurality of parallel scheduling sequences; saving all parallel scheduling sequences in the scheduling sequence set as a first adjacency matrix; mapping the first adjacency matrix into an adjacency list; running each sequence in the scheduling sequence set in parallel according to the adjacency list. According to the DAG node optimal path-based multi-model parallel scheduling method and device provided by the invention, the problems that the complexity is high and the running time is long in the existing decomposing method can be solved; the system resources can be fully utilized, and the multi-model scheduling running time is effectively shortened.
Owner:NEUSOFT CORP
Taxi passenger-carrying trajectory clustering algorithm Tr-OPTICS
InactiveCN107392245AImprove accuracyOptimize execution efficiencyData processing applicationsCharacter and pattern recognitionCluster algorithmComputation complexity
The invention discloses a taxi passenger-carrying trajectory clustering algorithm Tr-OPTICS. A research object of the algorithm is passenger-carrying trajectories; reachable distance of trajectories, concepts of core trajectories and search neighborhood scopes of the core trajectories are redefined. For passenger-carrying trajectories of large data volumes, an adjacency list is used for replacing a spatial index in the algorithm, and therefore calculation complexity of the algorithm can be lowered. Algorithm execution efficiency and accuracy of clustering results can be improved via the Tr-OPTICS algorithm put forward in the invention. Stability can be maintained despite different sample sizes, and a frequent pattern of passenger-carrying sub-trajectories can be effectively found based on clustering results via the algorithm disclosed in the invention.
Owner:NANJING UNIV OF INFORMATION SCI & TECH
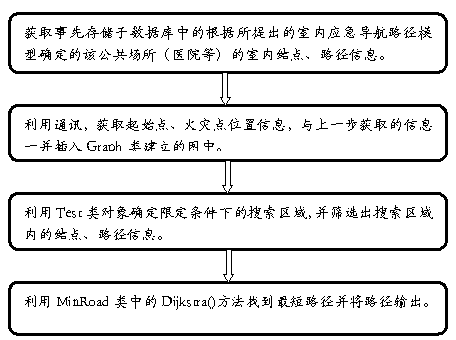
Indoor emergency path navigation method
InactiveCN103278171AWithout compromising accuracyImprove search efficiencyInstruments for road network navigationEllipsePath network
The invention discloses an indoor emergency path navigation method. The indoor emergency path navigation method comprises the steps of: deploying detecting nodes in an indoor scene corridor, deploying guide nodes at an intersection and an exit part; acquiring indoor scene nodes and path information through the detecting nodes and the guide nodes; acquiring position information of a starting point of a person and a dangerous point through the detecting nodes; building a path network diagram and storing by adopting a adjacency list data structure; determining a transferring target point of the person; limiting a search area within a rectangular area which takes the connecting line of the starting point and the target point as a diagonal to calculate the shortest path; expanding the search area to the minimum ellipse which comprises the rectangular area and takes the starting point and the target point as the two focal points and calculating the shortest path in the minimum ellipse; and according to the results of calculation, obtaining the shortest path. The indoor emergency path navigation method can be used for meeting the needs of emergency evacuation and navigation in emergency in public indoor spaces with large scales, complex spatial distribution and various types of people, such as hospitals, and is capable of reducing the time-space complexity, and improving the efficiency.
Owner:CHINA UNIV OF GEOSCIENCES (WUHAN)
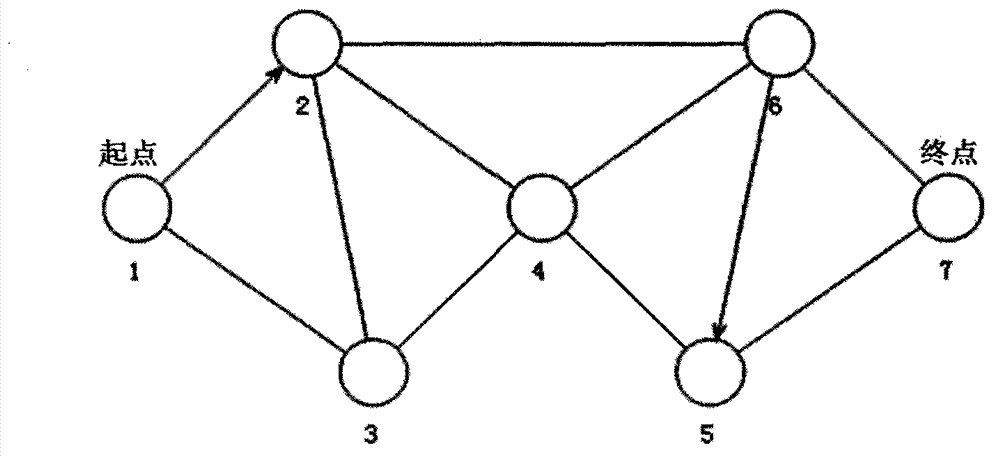
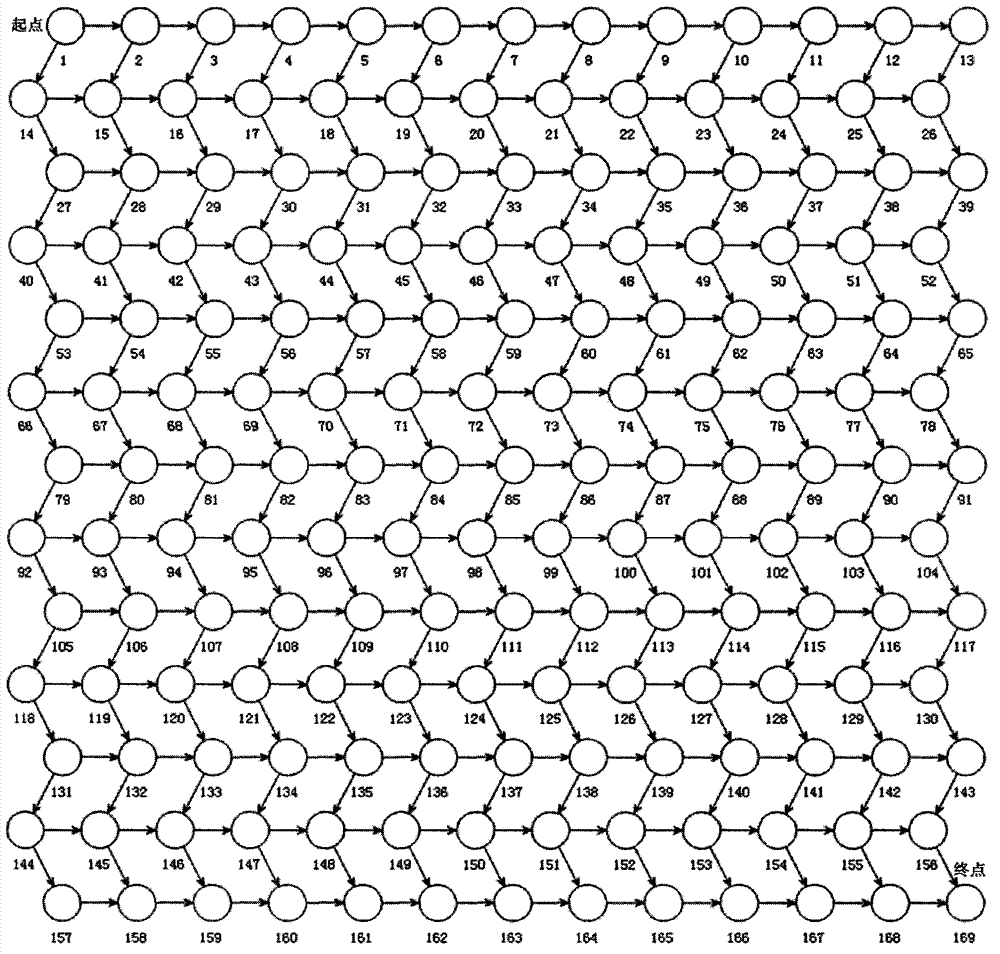
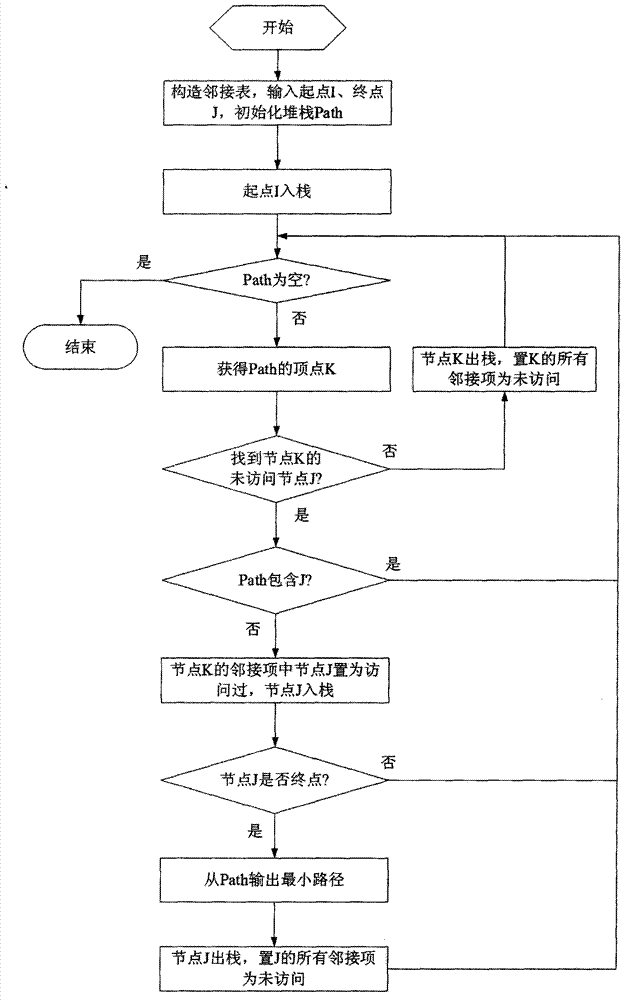
Network minimum path set determination method based on adjacency list
InactiveCN102880739ASimple methodImprove efficiencySpecial data processing applicationsDepth-first searchStructure of Management Information
The invention provides a network minimum path set determination method based on an adjacency list and aims to solve the problems about design simulation and performance evaluation of a large complex network system. The method mainly comprises the following two steps of: establishing a novel adjacency list according to a topological structure of a network; and traversing the adjacency list by using a depth-first search and backtracking combination method to determine all minimum paths. Nodes and links are not quantitatively restricted. The network minimum path set determination method based on the adjacency list is applicable to a directed network, an undirected network and a mixed network and has a wide application prospect in the large complex network systems such as power, communication, traffic, computers and municipal pipe networks.
Owner:中国兵器科学研究院
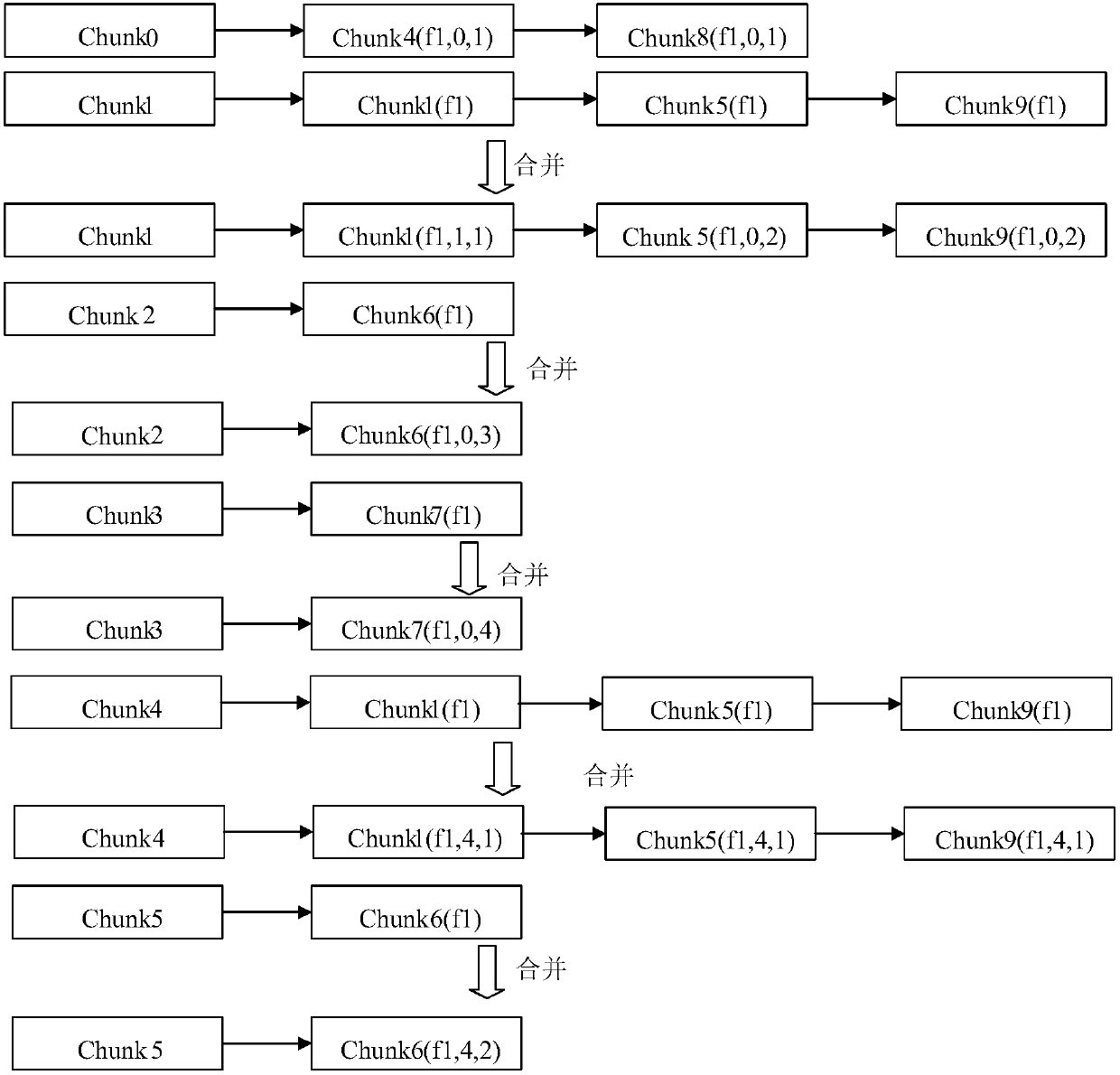
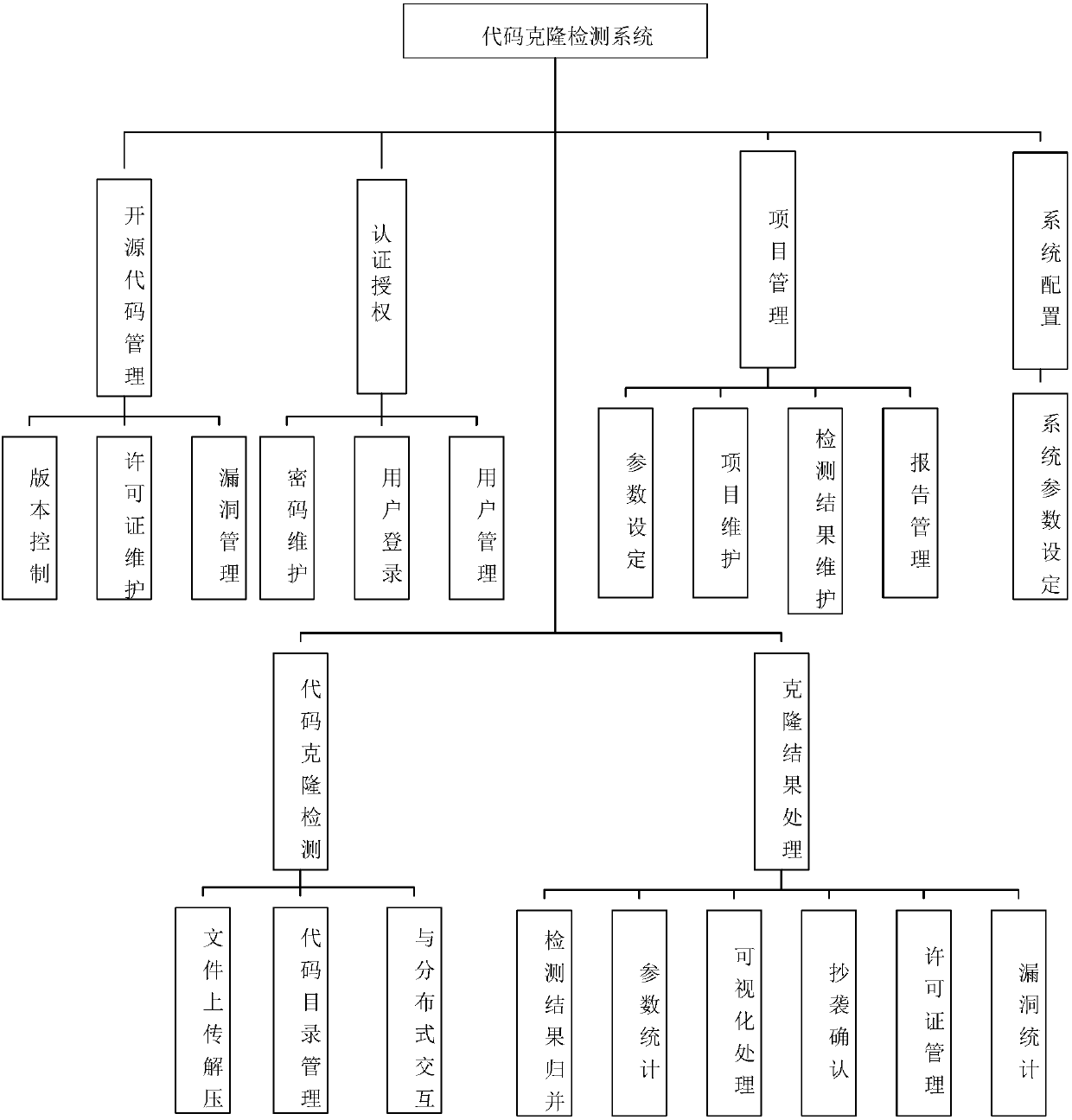
Method for carrying out combined detection on source code file cloning adjacency lists
InactiveCN107066262ARealize massive detectionSoftware engineeringSoftware testing/debuggingSource code fileDistributed index
The invention relates to a method for carrying out combined detection on source code file cloning adjacency lists. For an engineering project file, a fingerprint Chunk is constructed by using MD5 and a fingerprint library is established by taking the file as a unit and by taking scanning carried out on each line and fixed line number of codes as a granularity. The fingerprint library is stored in a MySQL database, and a detection algorithm is carried out by taking an ID of an open source project where a fingerprint is located and a Hash value of the Chunk as indexes so that detection of 0 to 3 clone classes can be performed. Namely, the invention discloses a scheme and algorithm for carrying out combined detection on source code file cloning adjacency lists on the basis of distributed indexes. According to the algorithm, cloned code files can be detected under the conditions that the time complexity is O (nm) and the space complexity is O (nm), so as to realize mass detection.
Owner:苏州棱镜七彩信息科技有限公司
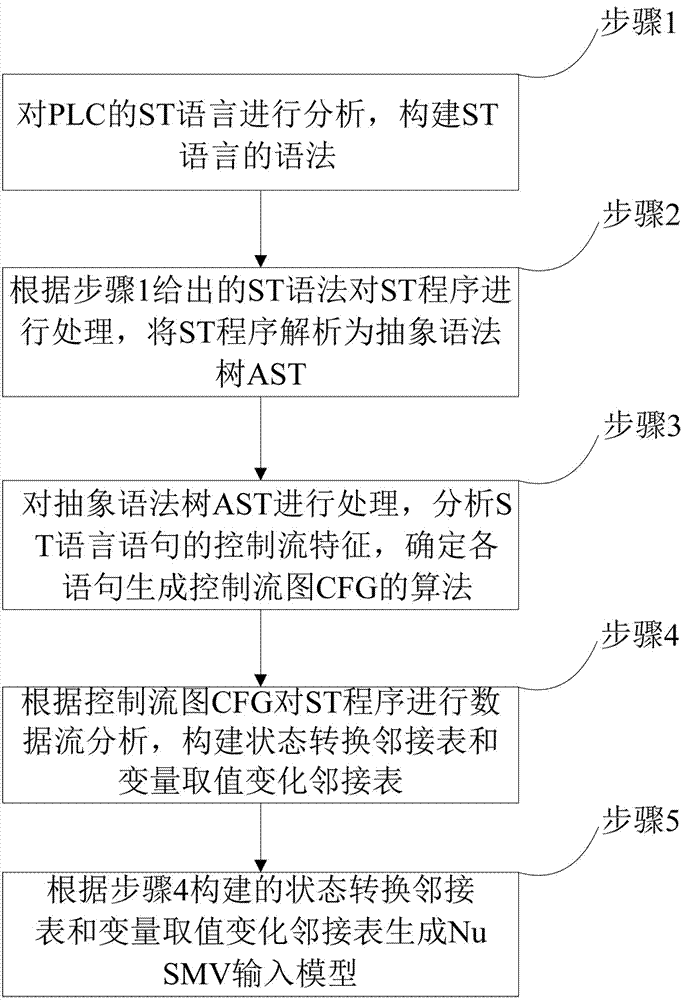
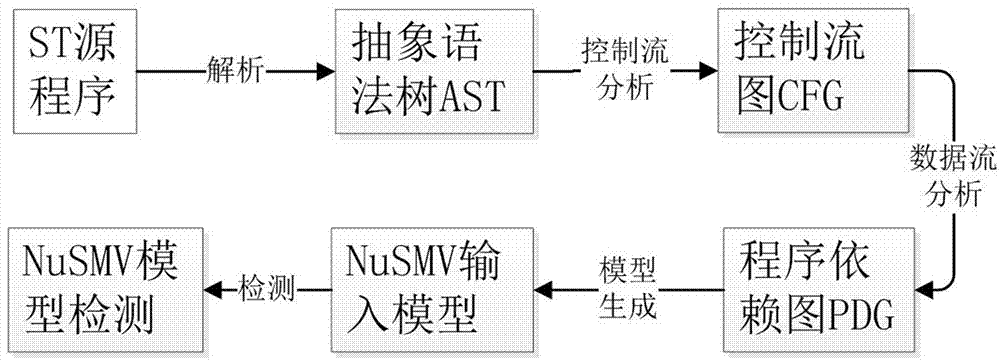
Automatic construction method for PLC (Programmable Logic Controller) program to NuSMV input model
ActiveCN107193745ASoftware testing/debuggingProgramme control in sequence/logic controllersConstruct stateState switching
The invention relates to the technical field of industrial automation control, in particular to an automatic construction method for a PLC (Programmable Logic Controller) program to a NuSMV input model. The method comprises the following steps that: analyzing the ST (Structured Text) language of the PLC, and constructing the grammar of the ST language; according to the given ST grammar, carrying out processing on a ST program, and analyzing the ST program into an AST (Abstract Syntax Tree); processing the AST, analyzing the control flow characteristics of a ST language statement, and determining the algorithm of each statement for generating a CFG (Control Flow Graph); according to the CFG, carrying out data flow analysis on the ST program, and constructing a state transition adjacency list and a variable value change adjacency list; and according to the constructed state transition adjacency list and variable value change adjacency list, generating the NuSMV input model. By use of the method, efficiency and accuracy for a NuSMV tool to carry out model detection on a PLM program are greatly improved, and the safety verification of an industrial control system PLC code is realized.
Owner:THE PLA INFORMATION ENG UNIV +1
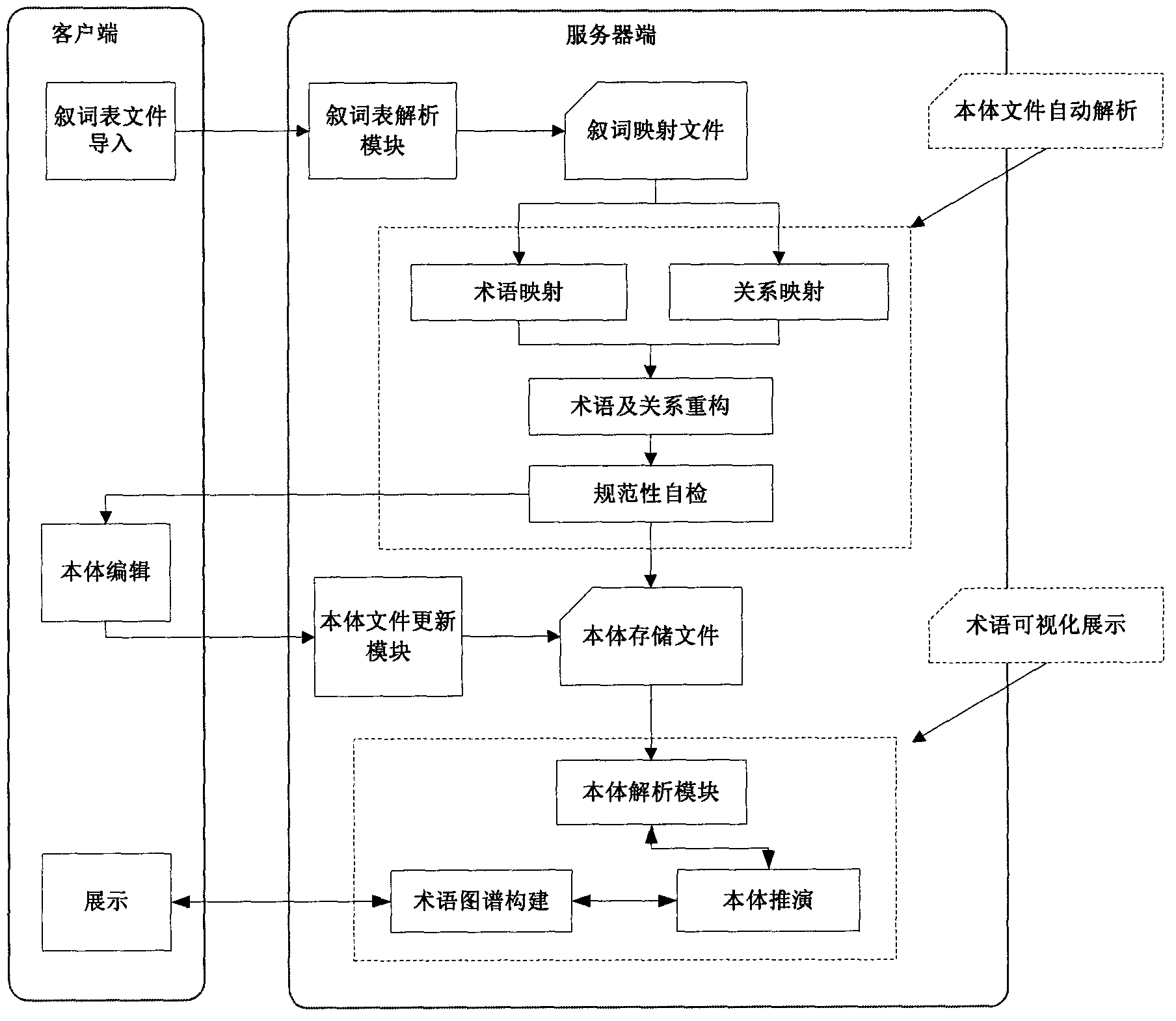
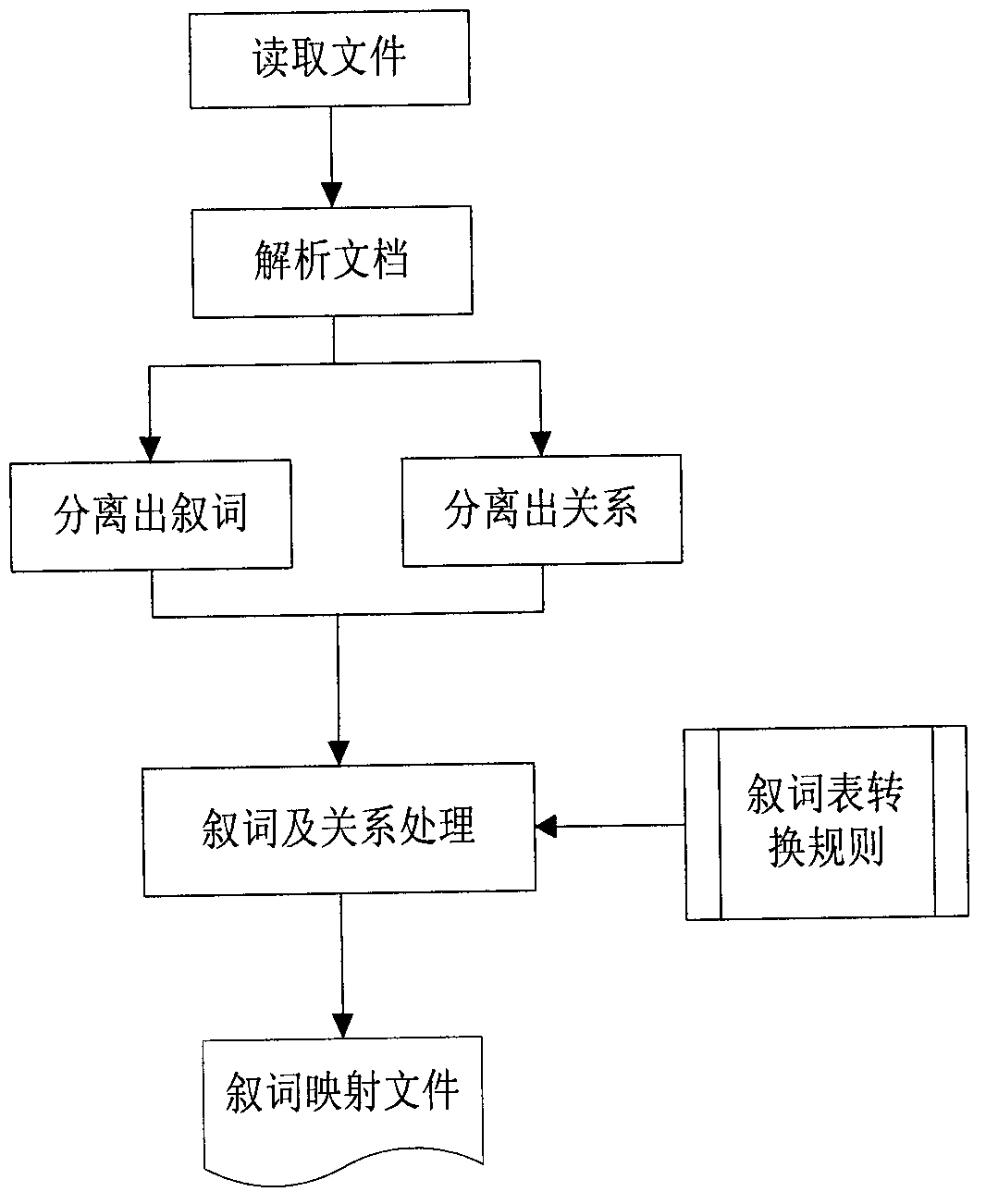
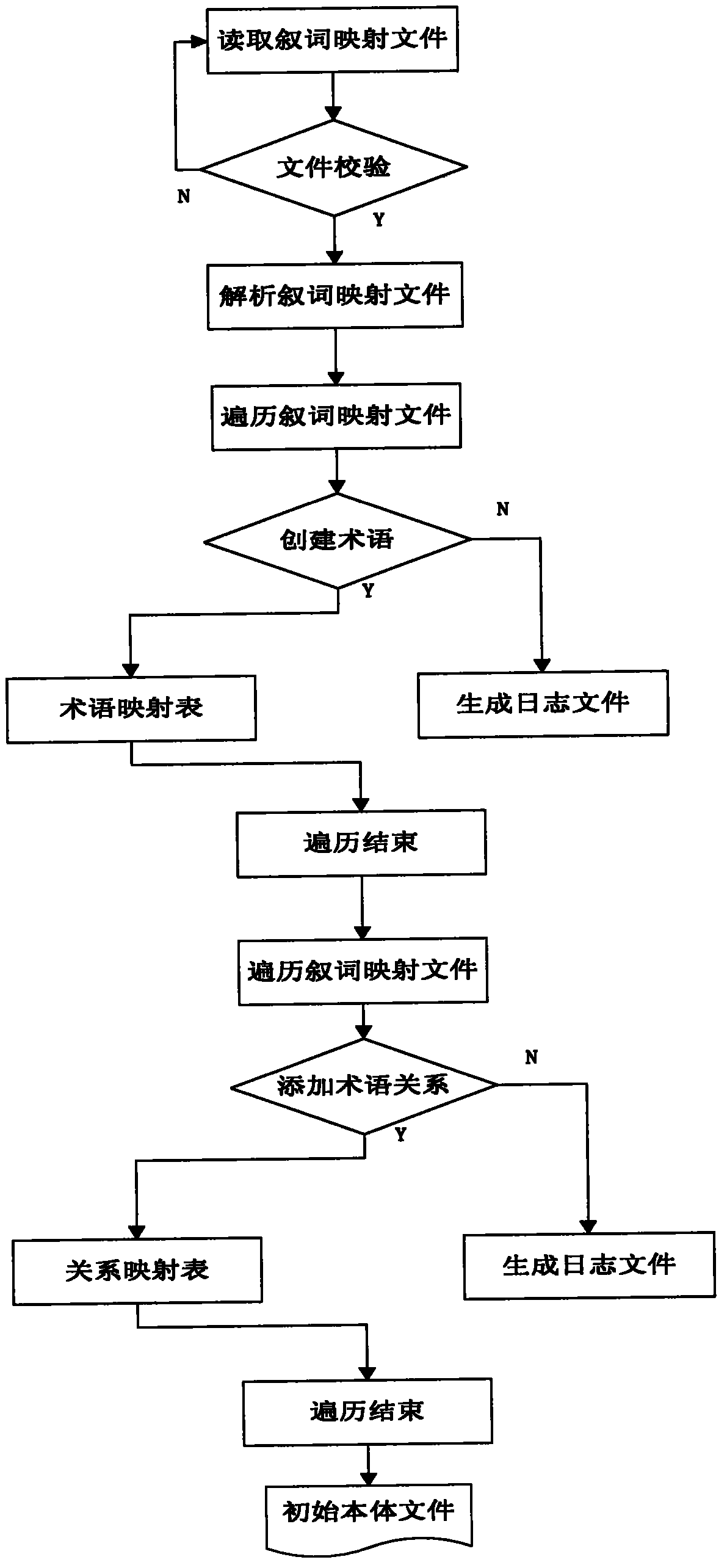
Noumenon automatic generating system and method thereof based on thesaurus
ActiveCN102982095AReduce typing errorsImprove efficiencySpecial data processing applicationsUser inputAdjacency list
The invention discloses a noumenon automatic generating system and a method of the noumenon automatic generating system based on a thesaurus. The noumenon automatic generating system and the method of the noumenon automatic generating system based on the thesaurus can automatically switch from the thesaurus to noumenon papers and comprises eight modules which include an analyzing module, a terminology and relation mapping module, a terminology and relation reconstitution module, a normative self-detection module, a noumenon papers upgrading module, a noumenon analyzing module,a noumenon deducing module and a terminology atlas constructing module. The noumenon automatic generating system provides an automatic ontology base generating system and a method of the.automatic ontology base generating system. A user does not need to manually edit terminology one by one and input faults of the user are reduced and efficiency is improved. Meanwhile, an adjacency list with a bidirectional structure is applied as a mapping list for terminology display for the first time, traditional forward atlas displaying and checking of relations among terms as well as backward atlas display and checking of relations among the terms are achieved on a terminology displaying layer. Checking relations among the terms are convenient for users. A single display manner is avoided and a search function is also supported so as to facilitate searching a term.
Owner:CHINA ACAD OF LAUNCH VEHICLE TECH
Fault indicator and distributed intelligent terminal matched overhead distribution network fault positioning method
ActiveCN105527540AReduce labor intensityLess investmentFault location by conductor typesInformation technology support systemFault indicatorDistributed intelligence
The invention relates to a fault indicator and distributed intelligent terminal matched overhead distribution network fault positioning method, and belongs to the technical field of relay protection of power systems. On the premise that overcurrent relay protection of a traditional distribution network is not changed, distributed intelligent terminals are installed on circuit breakers at all trunk section points and fault indicators are installed on all branch circuits, the installation positions of the distributed intelligent terminals are taken as nodes, a relation between the fault indicators and the nodes is defined according to the positions of the nodes and the fault indicators, and trunk units and branch units are divided and numbered to form a unit adjacency list. When faults occur, an automatic reclosing lock recloses transient faults, the distributed intelligent terminals isolate permanent faults, and meanwhile, the distributed intelligent terminals and the fault indicators detect current values and compare maximum branch current values in the relevant unit adjacency list to position trunk faults and branch faults.
Owner:DALI POWER SUPPLY BUREAU YUNNAN POWER GRID +1
Graph data storage and query method and device and computer readable storage medium
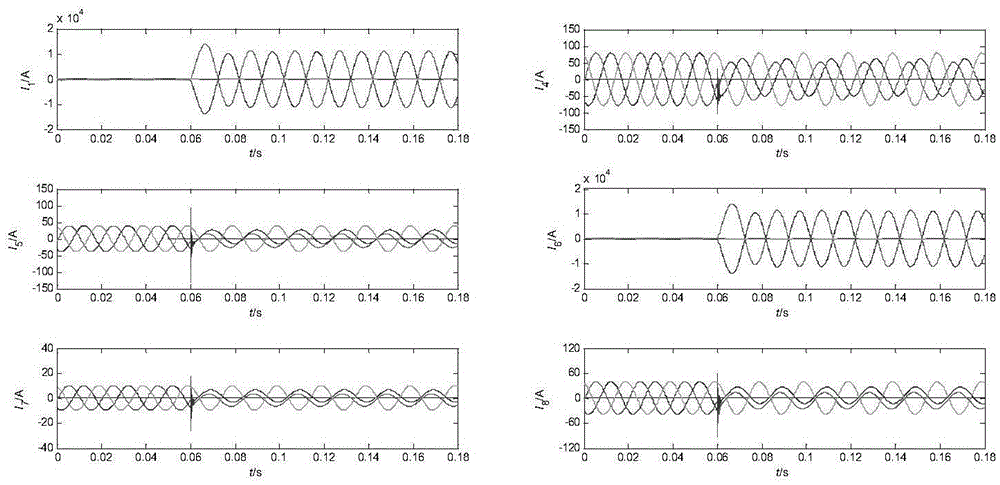
PendingCN110737659AEfficient storageEfficient query resultsRelational databasesDatabase distribution/replicationData setTheoretical computer science
The invention relates to a big data technology, and discloses a graph data storage and query method, which comprises the following steps of receiving a graph data set, creating a graph storage model through an adjacency list in a database, and taking the graph storage model as a storage mode of the graph data set; based on the storage mode, performing graph segmentation processing on the graph data set, and performing distributed storage on the graph data set after graph segmentation to obtain a target graph data set; and establishing a graph data index for the target graph data set, receivingquery content input by a user, querying the target graph data set by utilizing the graph data index according to the query content, and returning an obtained graph data query result to the user. Theinvention further provides a graph data storage and query device and a computer readable storage medium. According to the invention, efficient storage and query of graph data are realized.
Owner:PING AN TECH (SHENZHEN) CO LTD
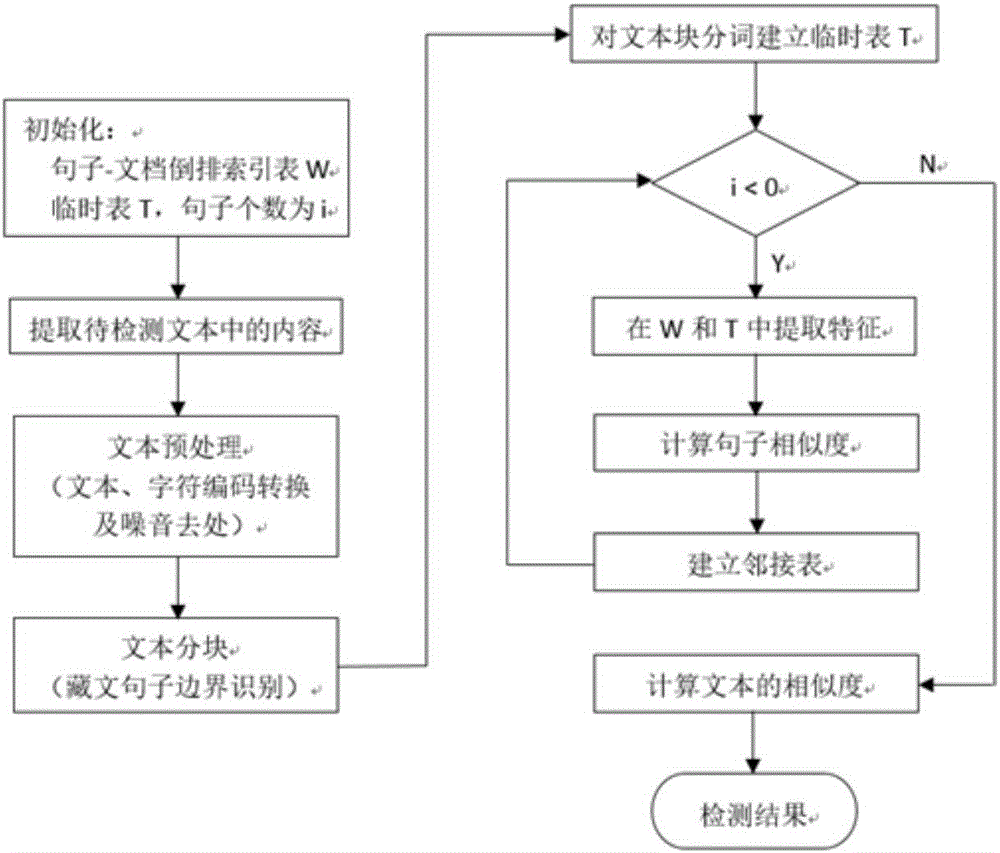
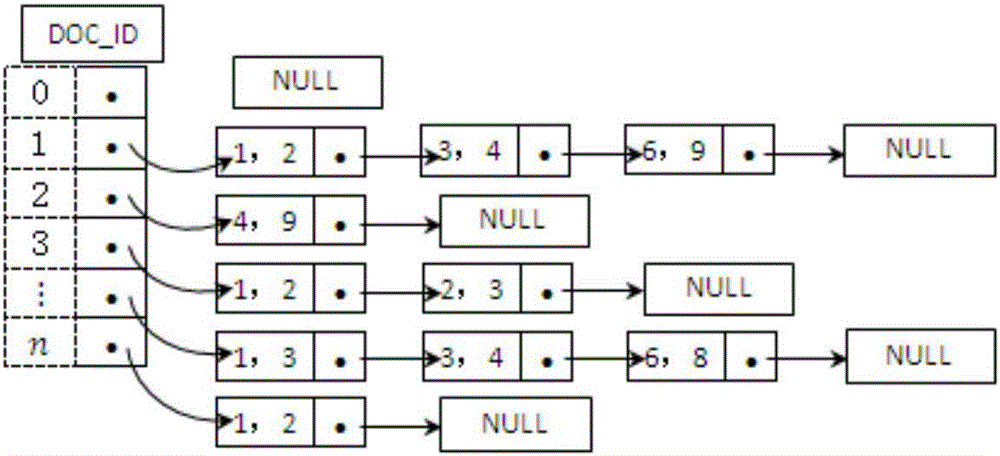
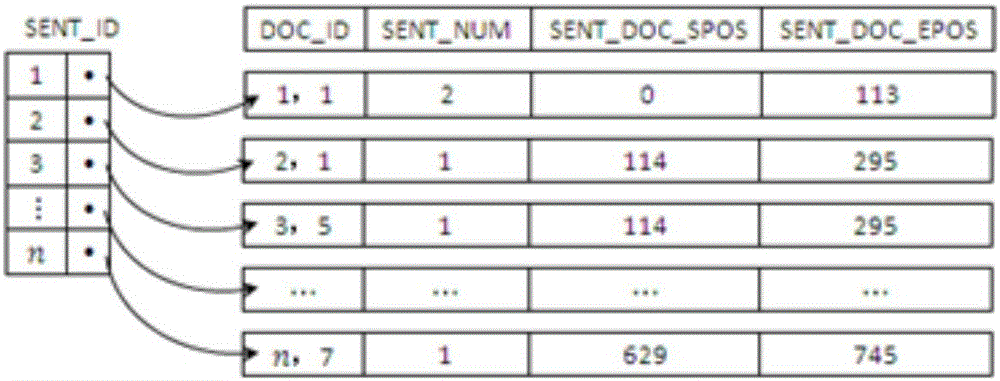
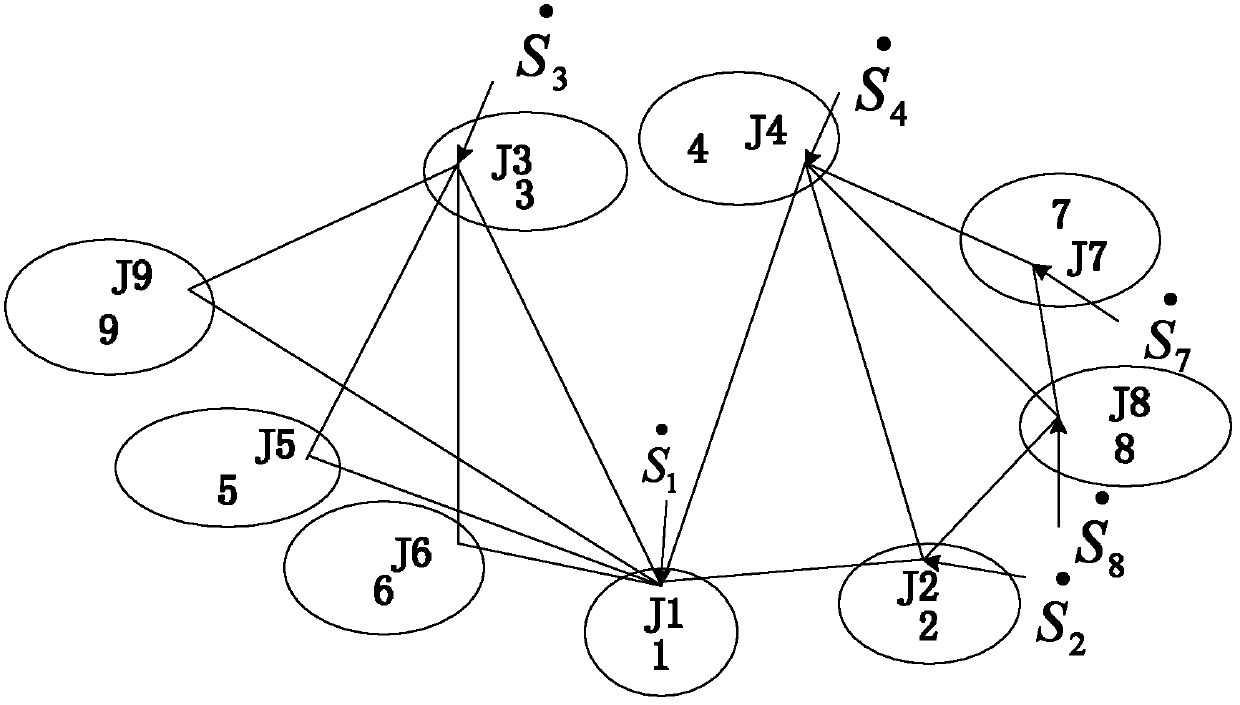
Tibetan language thesis copying detection method and Tibetan language thesis copying detection system based on Tibetan language sentence levels
PendingCN106227897AComputableSimplify complex relationshipsWeb data indexingNatural language data processingTerminal serverThe Internet
The invention discloses a Tibetan language thesis copying detection method and a Tibetan language thesis copying detection system based on Tibetan language sentence levels. The Tibetan language thesis copying detection method includes: subjecting Tibetan language text characters to code conversion and noise removal preprocessing; segmenting a text into text blocks according to sentences through boundary identification of Tibetan language sentences and establishing a temporary table of segmented text blocks; extracting and computing text features from a sentence-document inverted index table and the temporary table according to the number of the sentences to obtain sentence similarity; establishing an adjacency list in accordance with the sentence similarity, computing text block similarity and detecting copying of two Tibetan language theses according to a text block similarity value. The Tibetan language thesis copying detection system comprises a Tibetan language thesis copying detection device and a database, wherein the Tibetan language thesis copying detection device is connected to a client terminal server through the Internet, and the database is connected to the server and used for storing Tibetan language theses. The Tibetan language thesis copying detection device comprises a preprocessing module for code conversion and noise removal of the text characters, a temporary table module for constructing the segmented text blocks, an extracting module for constructing sentence text features and a copying detection module for detecting whether the theses have similar copied data or not.
Owner:QINGHAI UNIV FOR NATITIES
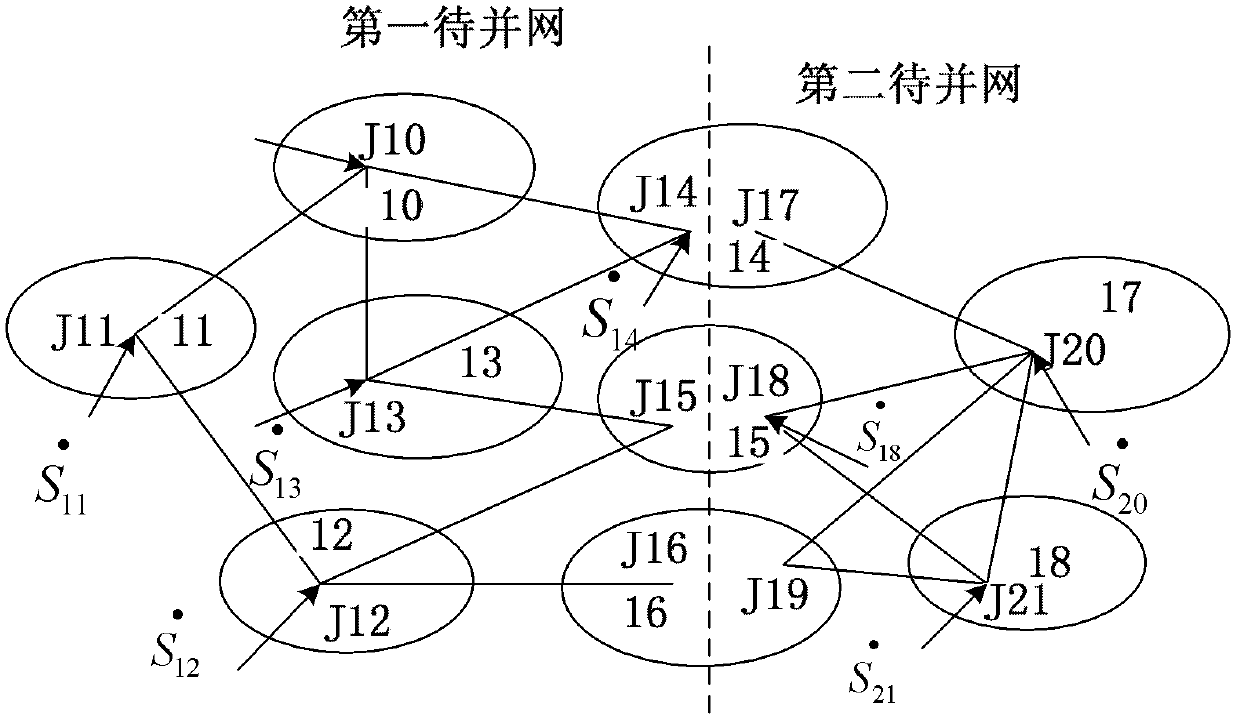
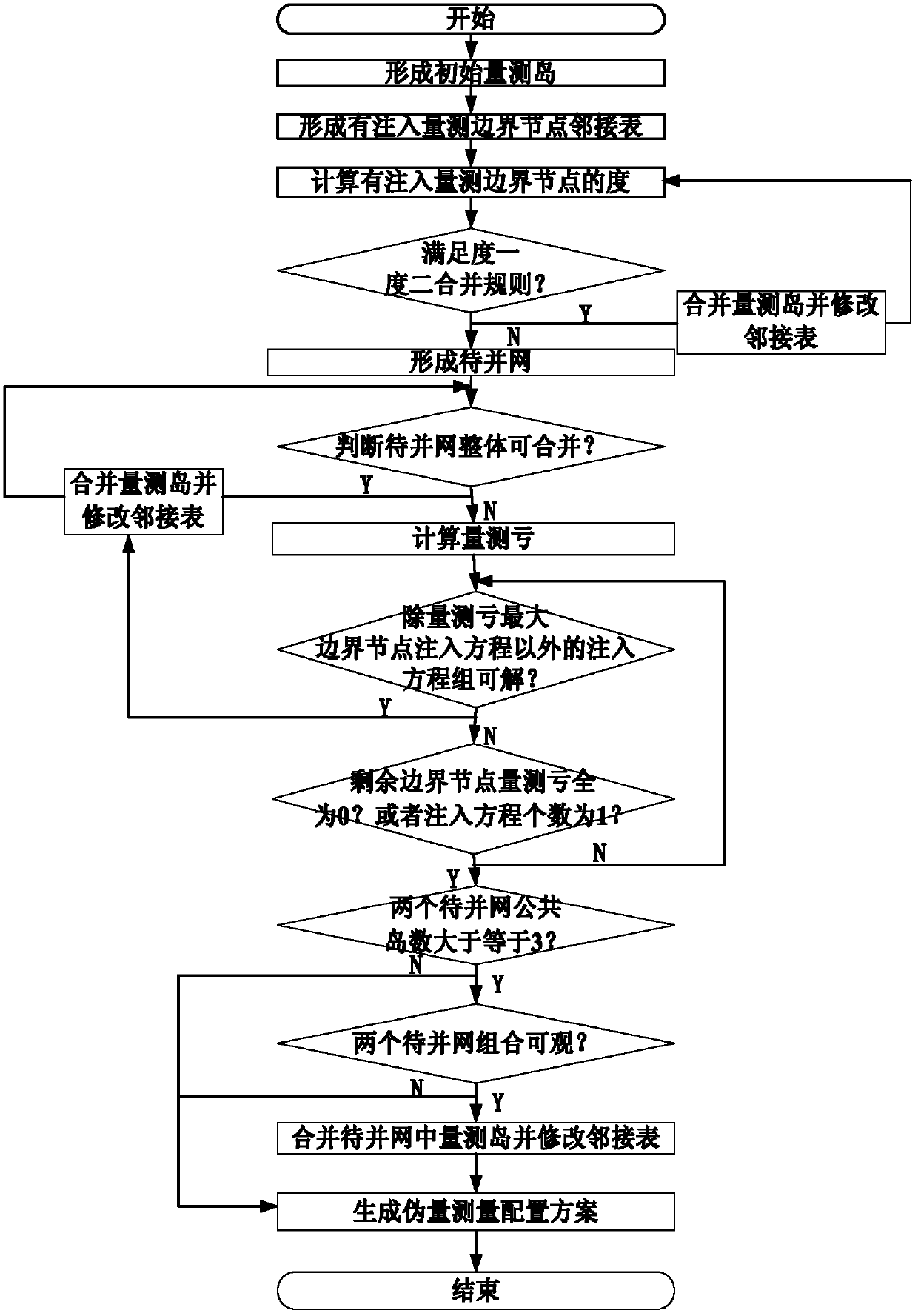
Topological observability analytical method based on adjacency list with injection measurement boundary nodes
The invention discloses a topological observability analytical method based on an adjacency list with injection measurement boundary nodes, which belongs to the technical field of operation and control of electric systems. The method includes the steps: firstly, forming initial measurement islands, namely using branch power flow measurement to form the initial measurement islands which form an integral electric network, wherein isolated nodes connected with no branch power flow measurement also need to be treated as independent initial measurement islands; secondly, forming the adjacency list with injection measurement boundary nodes, and combining the initial measurement islands through the adjacency list with injection measurement boundary nodes; thirdly, forming networks to be combined, and judging integral observability of the networks to be combined through the adjacency list with injection measurement boundary nodes; fourthly, combining the measurement islands which are integrally unobservable but locally observable in the networks to be combined; and fifthly, generating a pseudo measurement configuration scheme to prepare for state estimation. The topological observability analytical method has the advantages that pseudo measurement configuration is reduced, and precision of state estimation results is improved. Further, the pseudo measurement configuration is low in algorithm complexity and high in efficiency.
Owner:NORTH CHINA ELECTRIC POWER UNIV (BAODING)
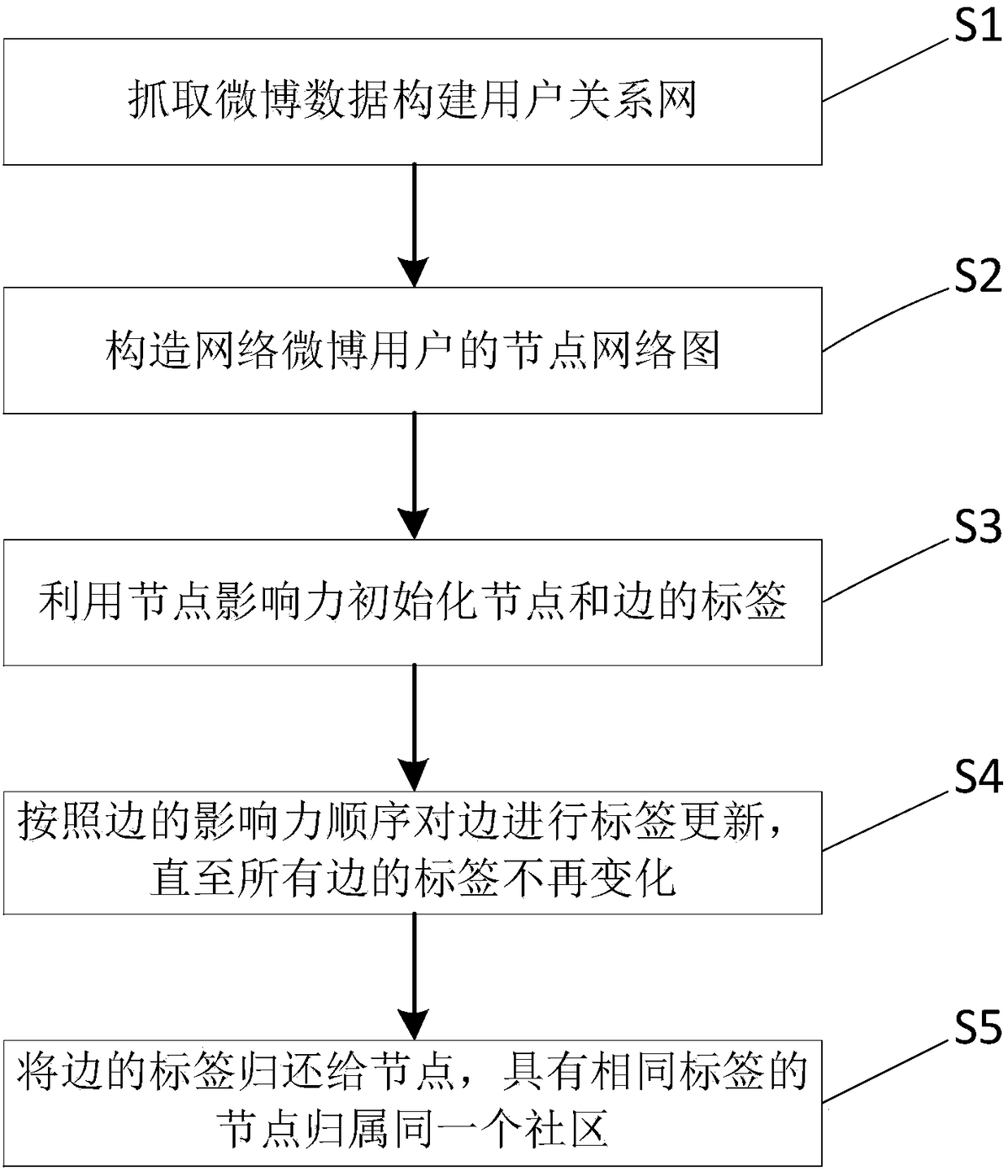
Microblog community discovery method based on node influence label propagation
InactiveCN108364234ASolve the division problemResolve discovery issuesData processing applicationsSpecial data processing applicationsMicrobloggingAlgorithm
The present invention provides a microblog community discovery method based on node influence label propagation. The method comprises the steps of: the step 1, performing extraction and cleaning of microblog network data, and constructing a user node adjacency list; the step 2, extracting data to construct a complex network diagram model, wherein the constructed model takes a microblog network node as a node and takes a relation between users as edges; the step 3, employing node influence to give one tag for each node in a graphic structure, and transmitting the tags to the edges of the nodes;the step 4, employing an edge tag propagation algorithm to update tags of the edges, and employing the edge influences to provide basis for the update sequence of the edges in the edge tag updating process; and the step 5, returning the tags of the edges to the nodes after the edge tags finish update, wherein the nodes generally have a plurality of edges, overlapped communities can be naturally generated.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
The method for supporting the mobile Zifeng radio sensor network system and node mobility
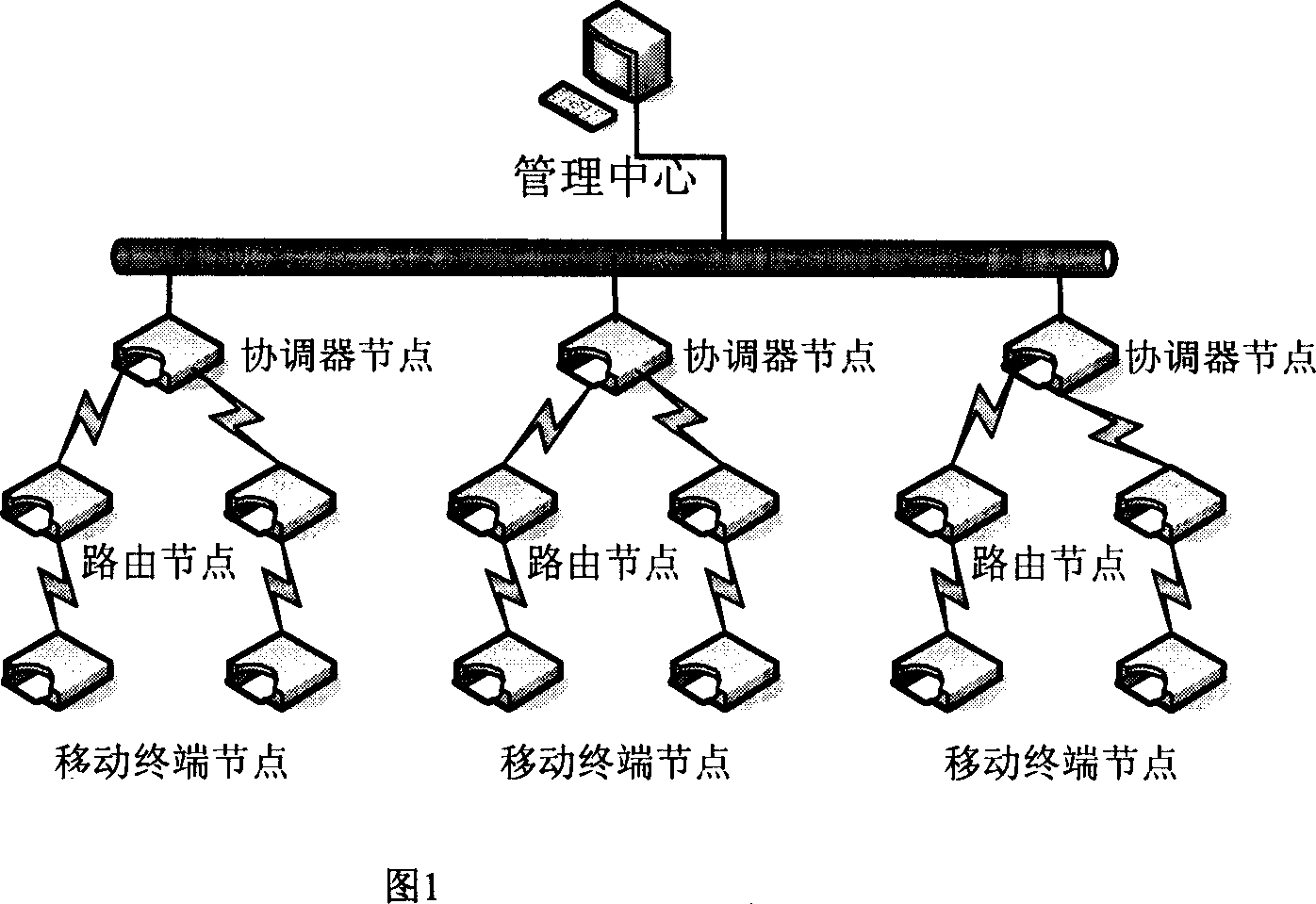
InactiveCN101018170AOvercome the disadvantage of not being able to join the network anymoreJoin in real timeData switching by path configurationWireless sensor networkingData acquisition
The mobile ZigBee wireless sensor network system comprises: a mobile terminal node, a known-position ZigBee route node, and a coordinator node of ZigBee network. Wherein, the coordinator node initiates to form a self-networking ZigBee network, the mobile node accesses into the network through near ZigBee route node or coordinator node, and every fullfunctional node adds connected device information into adjacency list. This invention adds dynamic management function for adjacency list, benefit to update excessive mobile nodes in limited memory, and improves capacity and flexibility for ZigBee network.
Owner:UNIV OF SCI & TECH BEIJING
Method and device of cross-card forwarding of message of distributed router
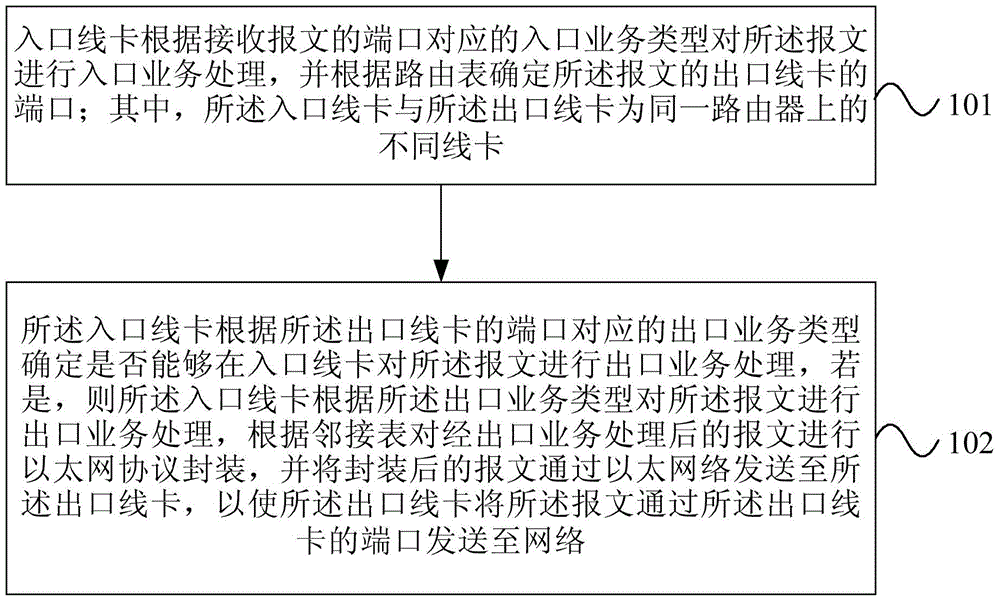
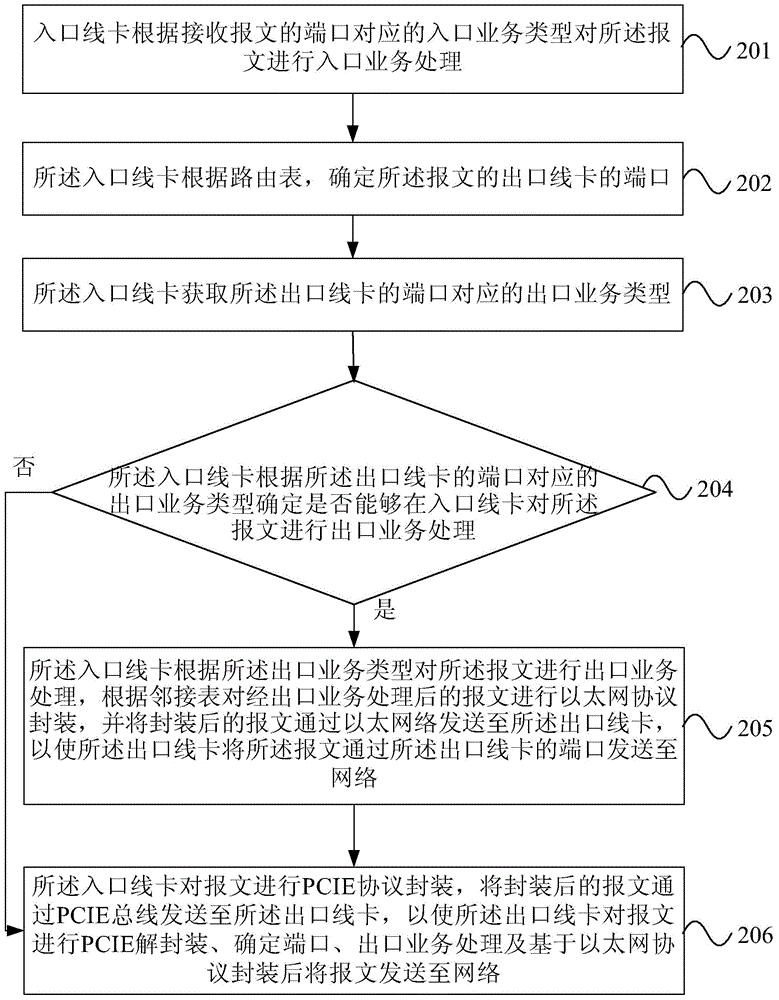
ActiveCN104158743ASolve the problem of low forwarding performanceImprove forwarding performanceData switching networksEthernet protocolLine card
The invention provides a method and a device of cross-card forwarding of a message of a distributed router. According to the method of cross-card forwarding of the message of the distributed router, when an inlet line card is determined to carry out export business processing on the message at the inlet line card according to an export business type corresponding to a port of an outlet line card, the inlet line card carries out export business processing on the message according to the export business type, Ethernet protocol packaging is carried out on the message subjected to the export business processing according to an adjacency list, and the packaged message is transmitted to the outlet line card through Ethernet, so that the message is transmitted to a network by the outlet line card through the port of the outlet line card, queuing in a processing process of the message on a CPU (Central Processing Unit) of the outlet line card is avoided, packaging or de-packaging processing based on a PCIE (Peripheral Component Interconnect Express) protocol, which is respectively carried out on the CPUs on the inlet line card and the outlet line card, is avoided, and the forwarding performance of the router is improved.
Owner:RUIJIE NETWORKS CO LTD
Method for acquiring real-time states of power grid element
InactiveCN102427274AHigh speedEmergency protective circuit arrangementsInformation technology support systemPower stationElectric power system
The invention provides a method for acquiring real-time states of a power grid element and belongs to the technical field of relay protection of power systems. The method comprises the following steps of: firstly, acquiring data from an energy management system; secondly, reducing the scale of a power grid by using an idea of fusing nodes; and finally, forming an adjacency list of all nodes of the power gird, analyzing the connectivity of power plants and power stations, and judging operating / non-operating states of the element. According to the method, the real-time states of the power grid can be fast acquired, the interface of a power grid online checking system and the energy management system is realized, and the speed of acquiring the real-time states is improved.
Owner:广西电网公司电力调度控制中心 +1
Gateway realization method for converting Ethernet data and digital video streaming
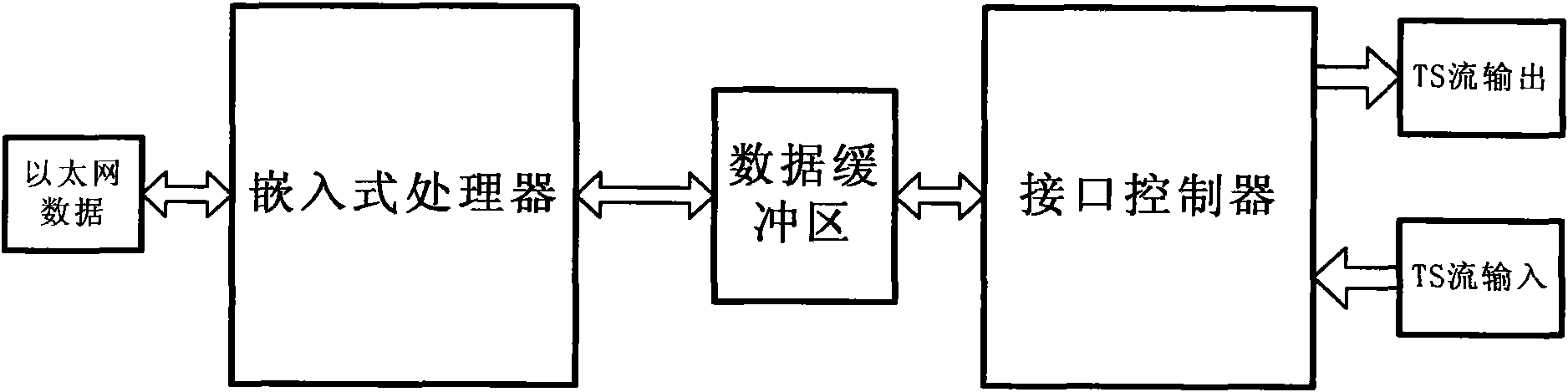
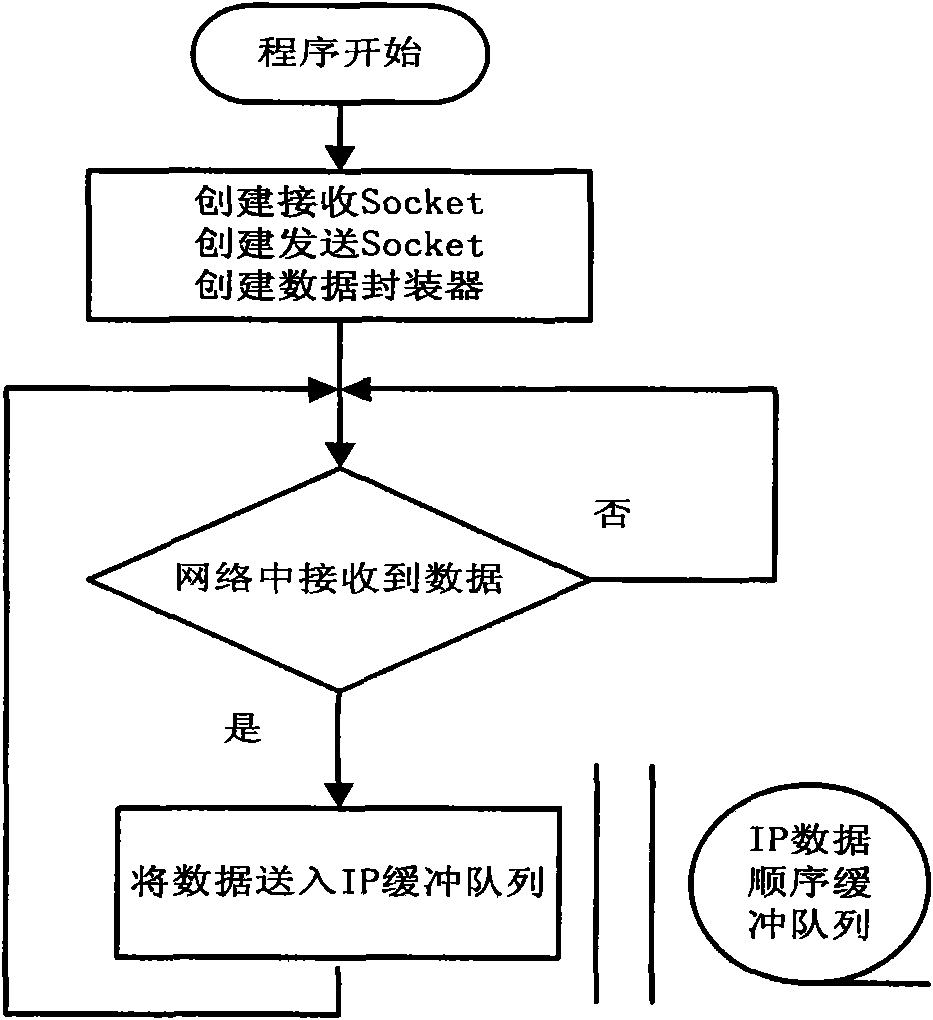
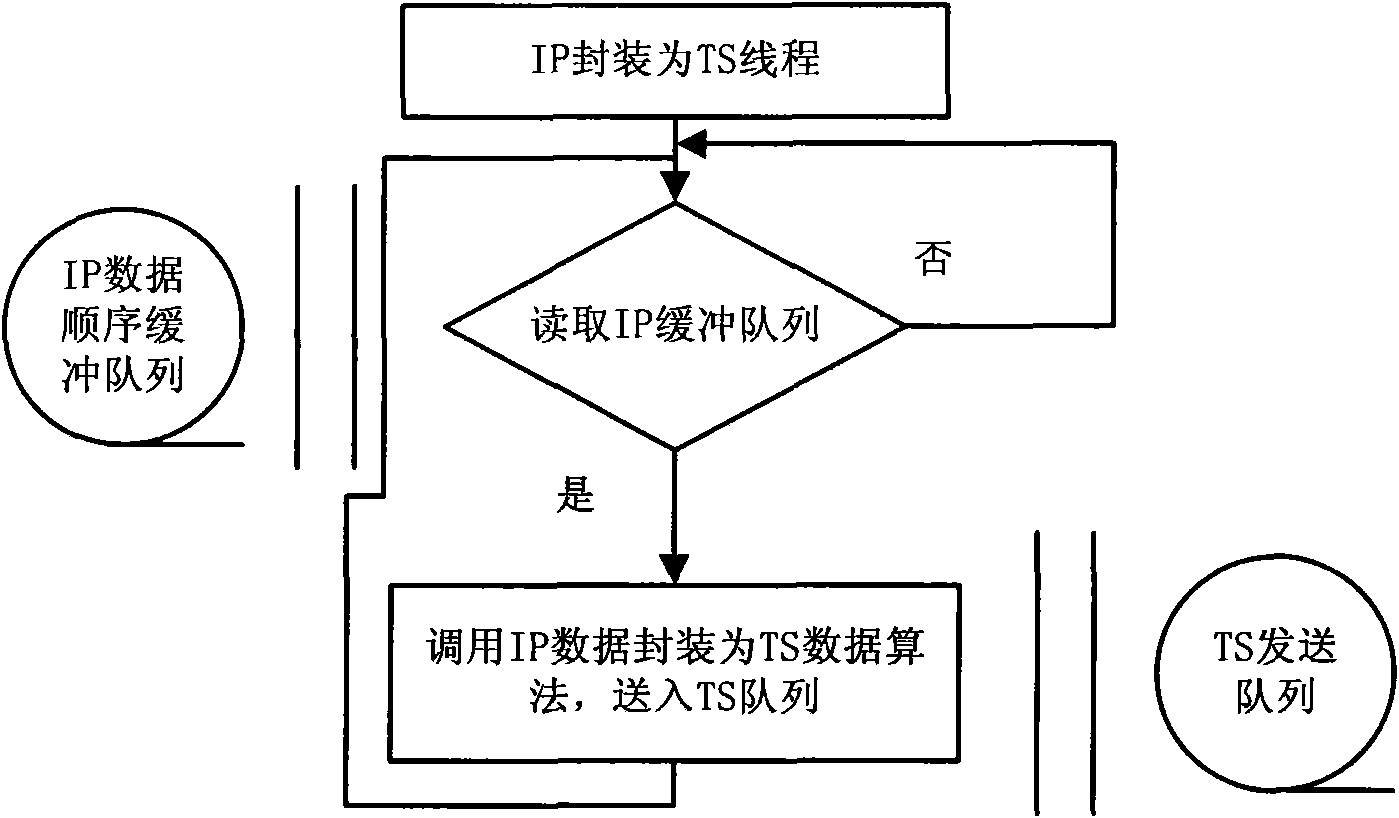
InactiveCN101610407AObvious advantageGood effectPulse modulation television signal transmissionNetwork connectionsDigital videoIp address
The invention provides a gateway realization method for converting Ethernet data and digital video streaming. The method comprises the following steps: format of network data and format of television video streaming data are mutually converted, namely, interconversion between IP packet and MPEG-2 TS streaming; an embedded processor adopts combination of double buffering configuration and single buffering configuration and configures a boot operation script so that the two configurations are converted from one to another; the double buffering configuration evens flow rate at an IP processing layer and processes each buffer area by a plurality of threads; the single buffering configuration adopts a mode of data buffering under a driving procedure state; an upper layer application program of an embedded system adopts a self-adaptive adjacency list method to automatically acquire the adjacency list in respective network segment and send the adjacency list to an opposite terminal to be converted; IP packet packaging thread and TS unlocking thread realize interconversion from IP format to TS format; and TS receiving thread and TS sending thread execute a complete reverse function in the embedded system. The two sides of wireless equipment can use IP address of the same net segment or the different network segments to work and realize long-distance bidirectional transmission or long-distance unidirectional transmission.
Owner:BEIJING UNIV OF CHEM TECH
Graph processing using a mutable multilevel graph representation
ActiveUS9734607B2Improve performanceIncrease spacingDigital data information retrievalDrawing from basic elementsTheoretical computer scienceAdjacency list
A mutable multilevel data structure representing a graph structure may include multiple read-only levels and a single writable level. Each read-only level may include a vertex table (with references to edge tables on the same level or a different level containing elements of adjacency lists for some vertices) and an edge table (with elements of adjacency lists that changed since the previous read-only level). A hybrid variant may switch between a performance-optimized variant (whose edge tables include complete adjacency lists for vertices whose edge sets were modified) and a space-optimized variant (whose edge tables include only newly added adjacency list elements). The vertex tables and / or the writable level may be implemented using copy-on-write arrays, each including an indirection table and multiple fixed-sized data pages. Computations may be run on the read-only levels or on the writable level and read-only levels.
Owner:ORACLE INT CORP
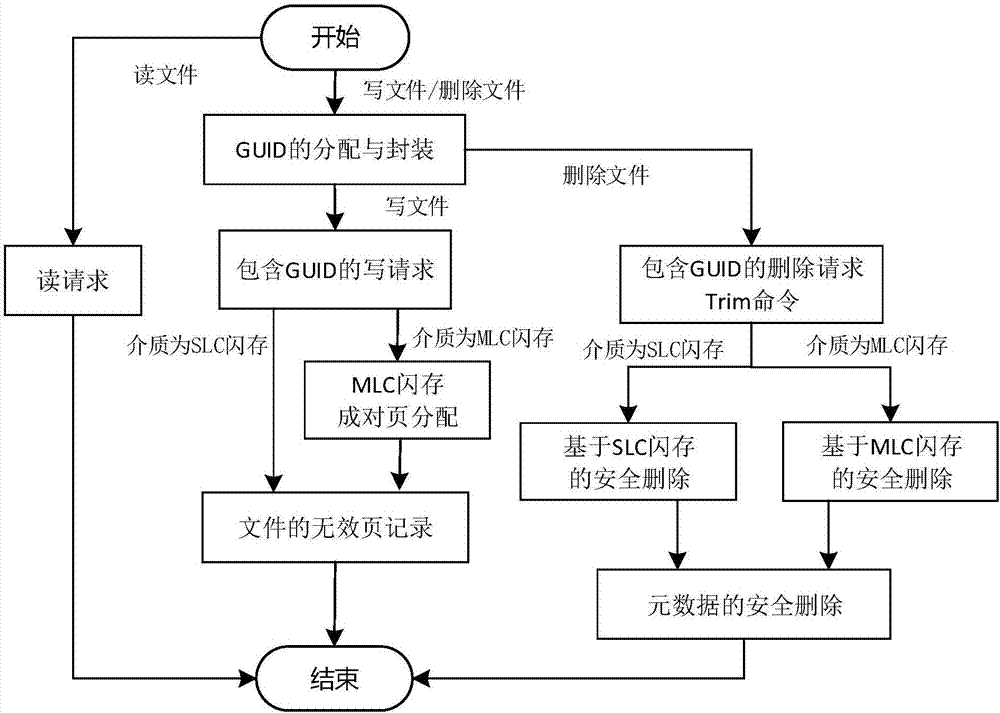
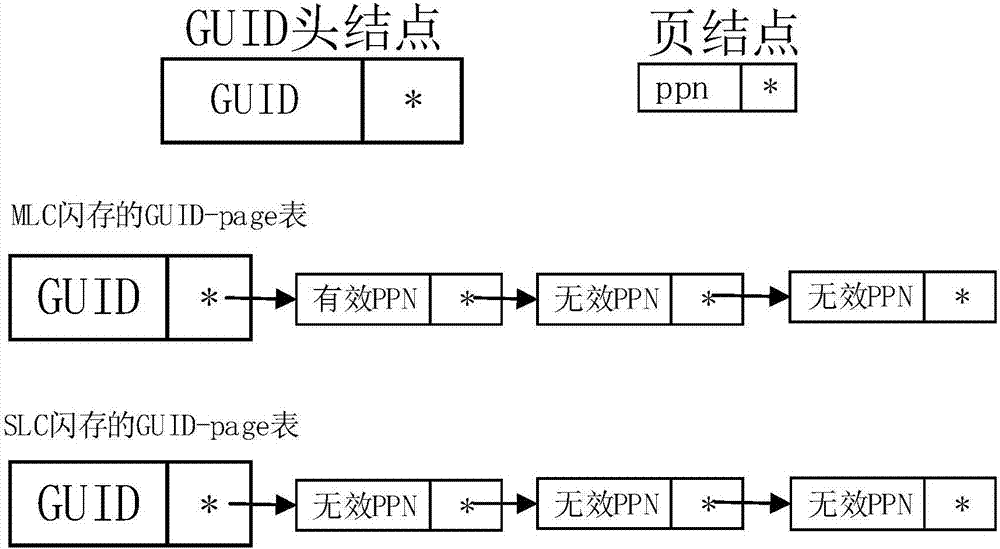
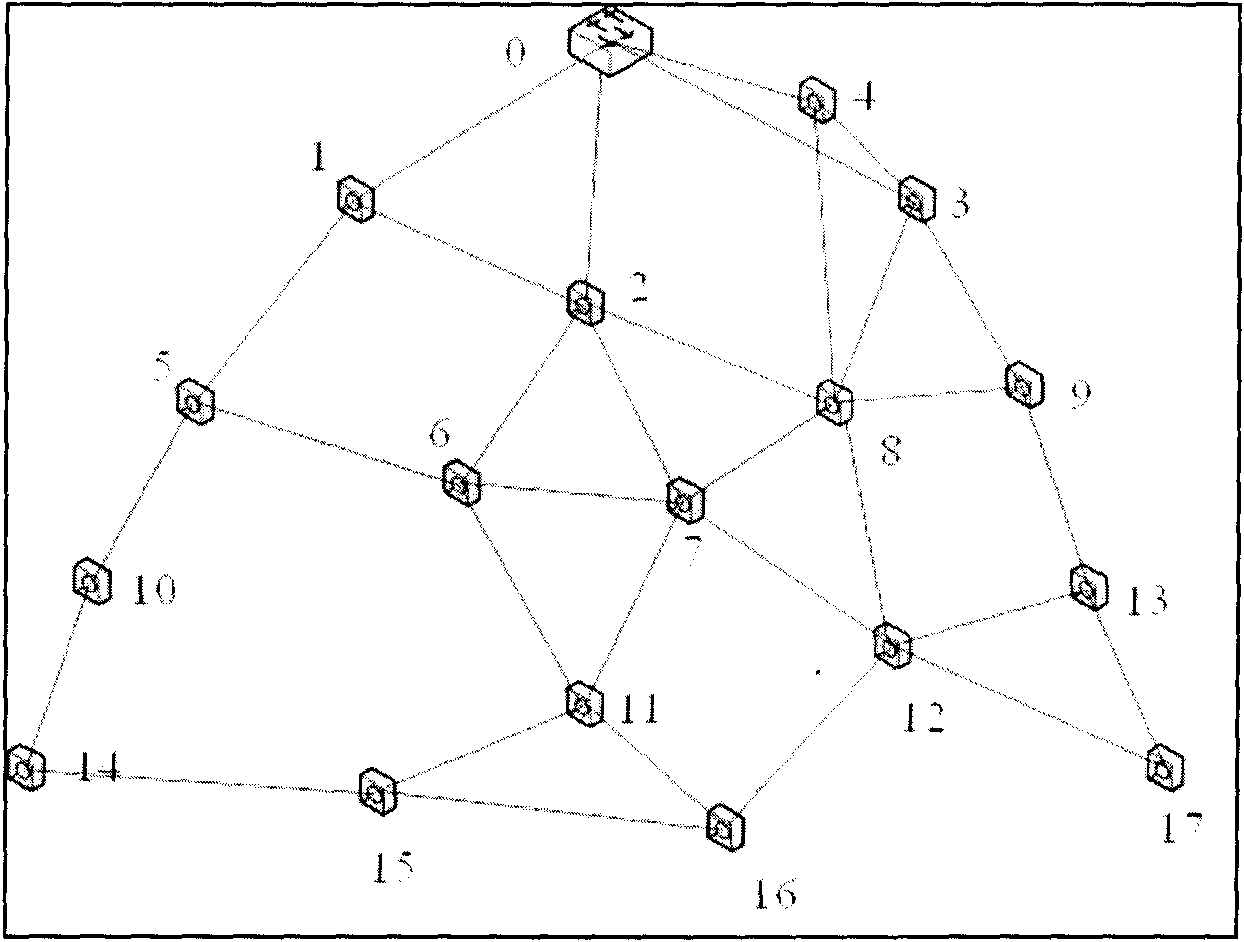
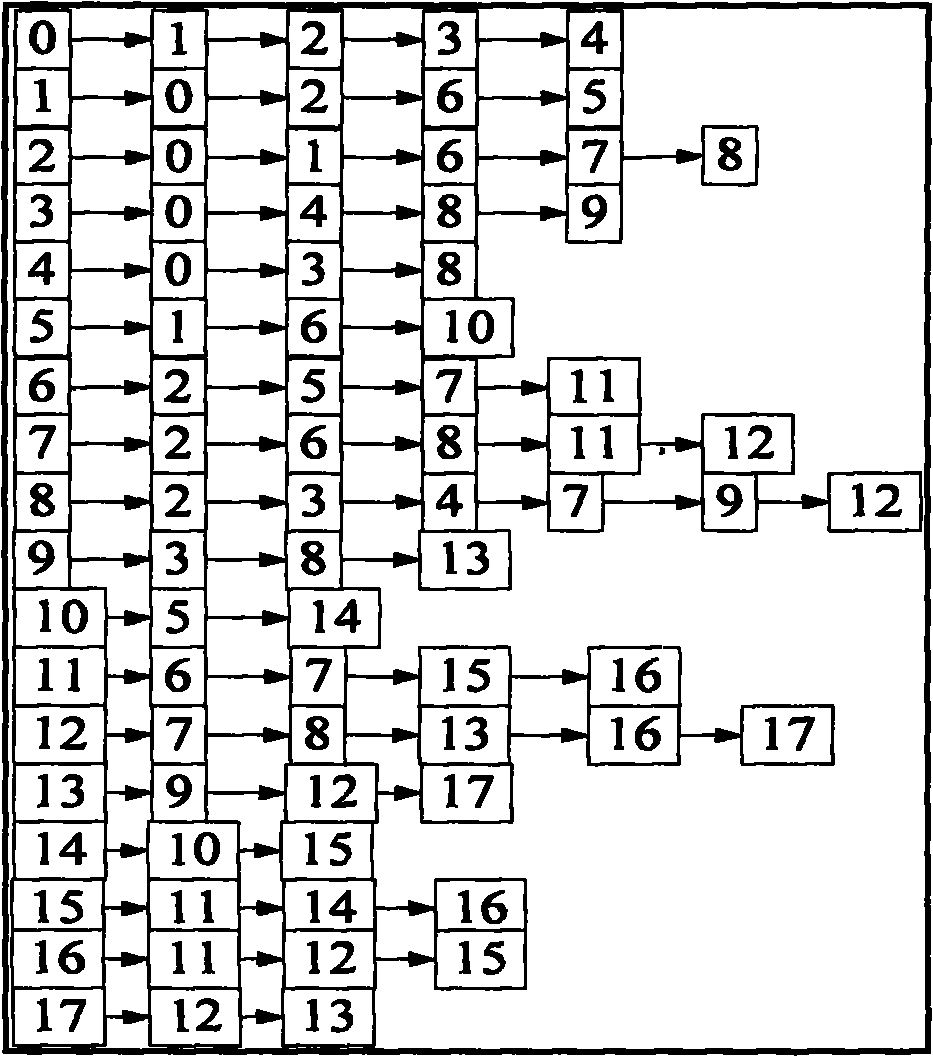
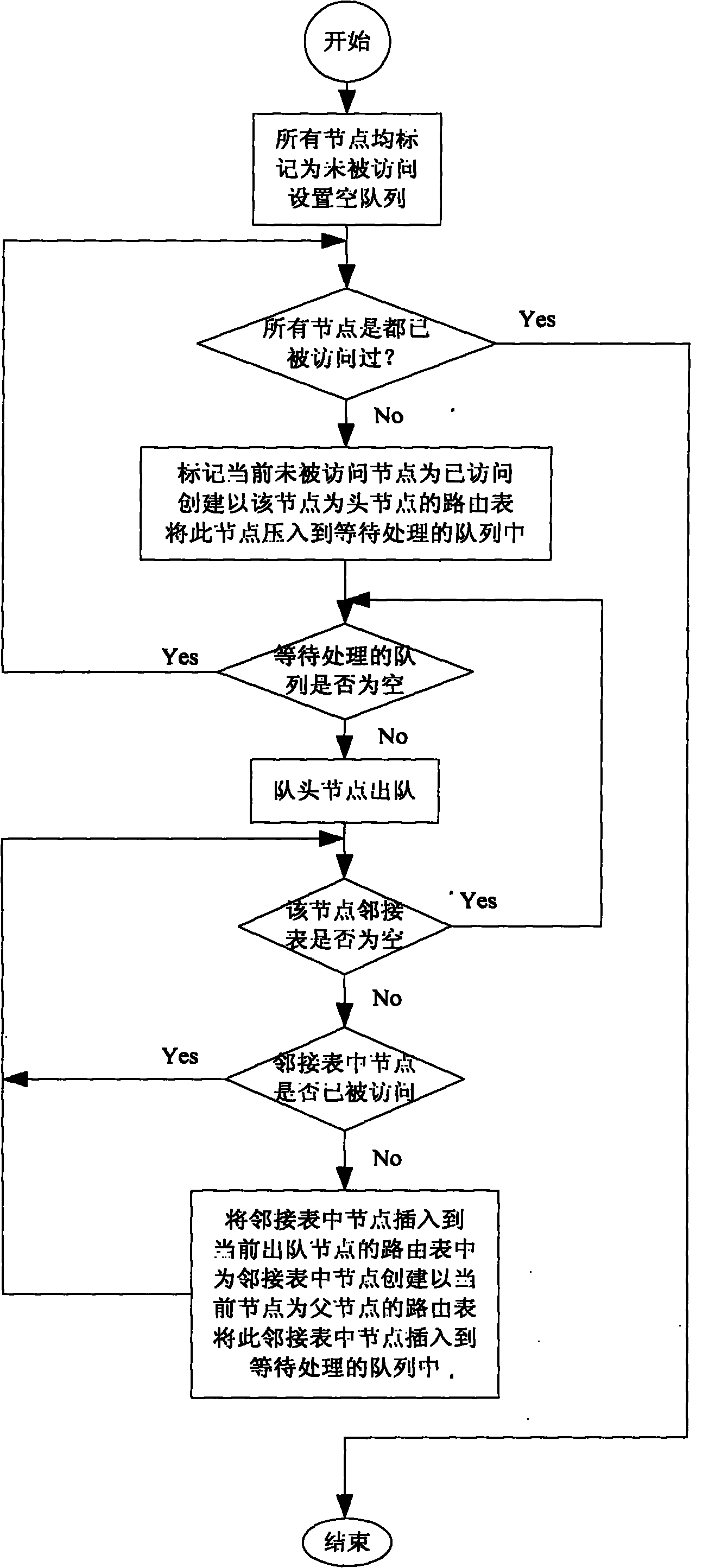
Flash memory secure deletion method and system based on file-level granularity
ActiveCN107037988AReduce the impact of read and write performanceSecure Delete EfficientInput/output to record carriersFile allocationGranularity
The invention discloses a flash memory secure deletion method based on file-level granularity and belongs to the field of computer storage. According to the method, a globally unique identifier (GUID) is distributed for each file, each GUID is encapsulated to each writing request and each deletion request of the corresponding file, and meanwhile a GUID-page adjacency list is constructed and used for recording invalid physical pages corresponding to each file in real time; and when a user deletes a certain file, equipment can find all the invalid physical pages and all valid physical pages corresponding to the file through a deletion command, and then a physical page overwriting technology is used for overwriting all the physical pages of the file to achieve the purpose of deleting the file securely. The invention furthermore discloses a flash memory secure deletion system based on file-level granularity. Through the technical scheme, the problem that a single file cannot be deleted efficiently and securely through an existing solid-state disk based on a flash memory medium is solved, and influences of secure deletion on read-write performance are reduced on the basis of securely deleting a single file through the solid-state disk.
Owner:HUAZHONG UNIV OF SCI & TECH
Improved globe entrepreneurship monitor (GEM) routing method
InactiveCN102131268AEasy to adjustLower energy billsHigh level techniquesWireless communicationImproved methodTraversal algorithms
The invention discloses an improved globe entrepreneurship monitor (GEM) routing method, which is characterized in that: virtual polar coordinates in a GEM routing method are converted into actual polar coordinates, and the method comprises the following steps of: A, drawing a network connectivity diagram, wherein a node data structure has a nested structure, a first 8-bit Id is a node identification code, a followed integer Number is a child node number, and by parity of reasoning, the second Id is an identification code of a first child node, and the followed Number is the number of the child node; and gathering nodes and processing the data of each node, and expressing the connecting relationship between nodes in an adjacency list form; and B, performing ring removal processing, namely performing ring removal processing on the adjacency list generated in the step A through a breadth-first traversal algorithm of the diagram. Compared with the prior art, the invention has the advantages that: the routing method has lower energy overhead, and the adjusting process is simple when a network topology is changed.
Owner:SHANGHAI ZUOANXINHUI ELECTRONICS TECH
Large-scale data parallel query method based on subgraph matching
InactiveCN109992593AImprove query efficiencyDigital data information retrievalSpecial data processing applicationsData setData graph
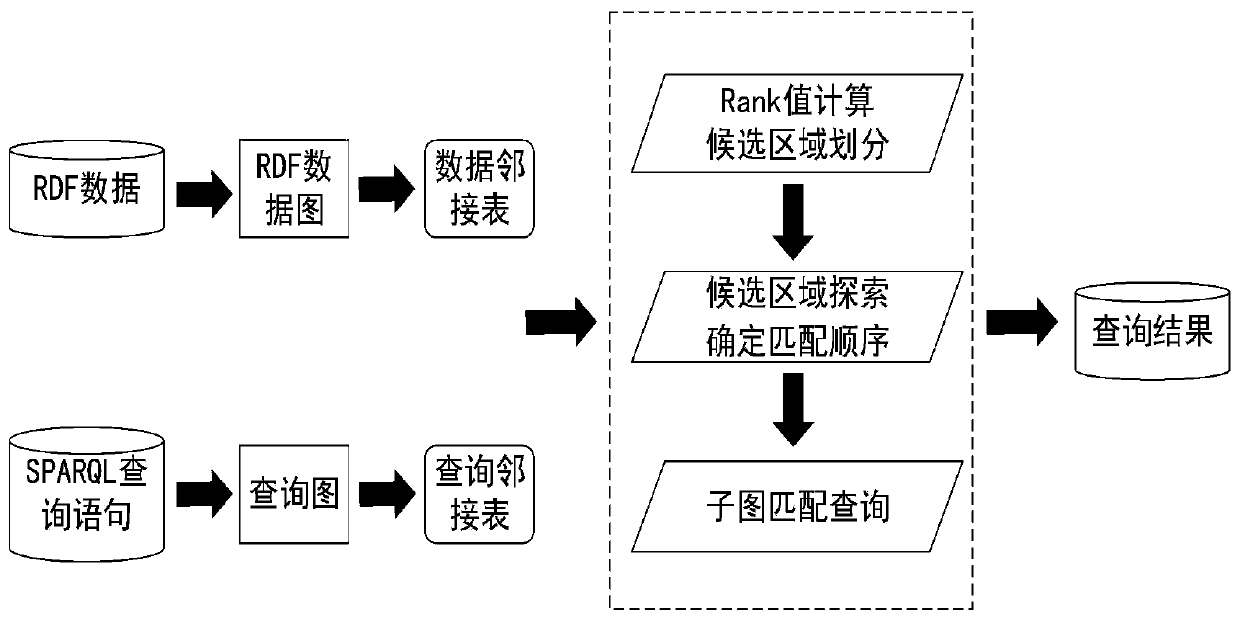
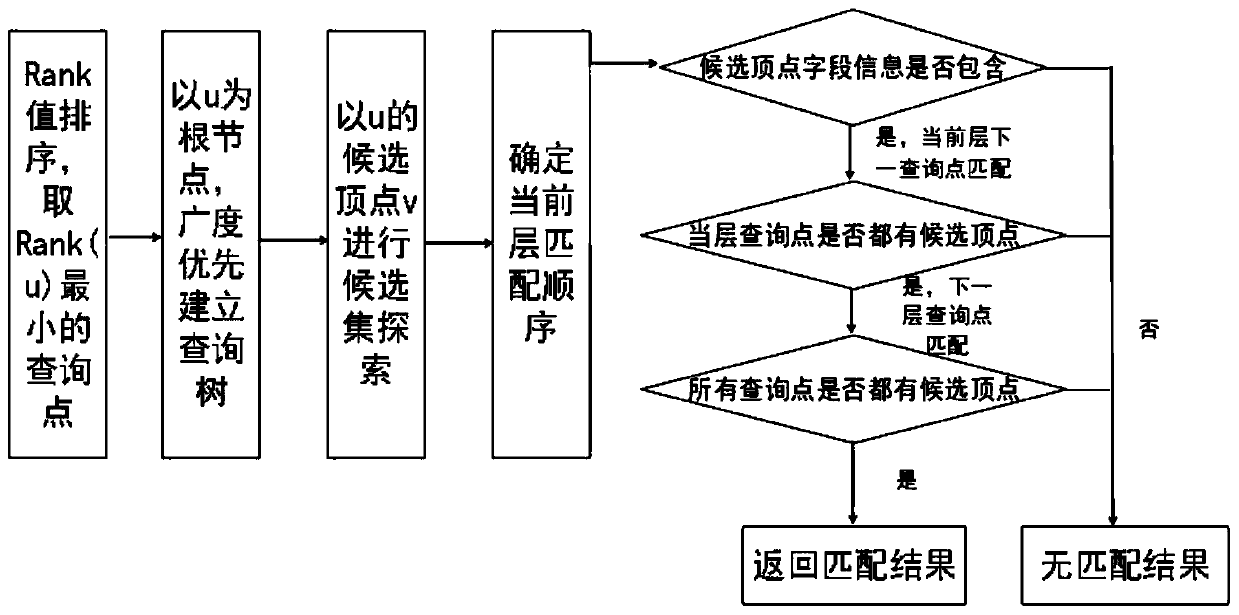
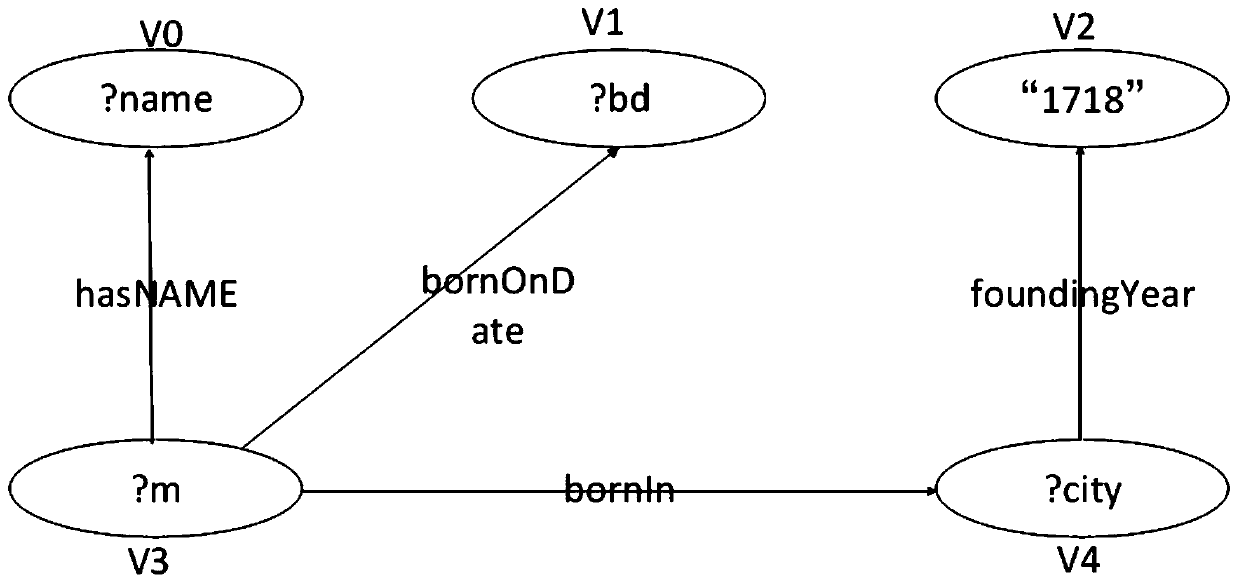
In recent years, with the rapid development of a computer network, the RDF data volume on the Web rapidly increases, especially a large number of large-scale RDF data sets appear, and the mass data often has a complex network relationship, so that a traditional centralized query scheme cannot rapidly and accurately obtain a query result. The invention discloses a large-scale data parallel query method based on subgraph matching. The method is combined with a distributed platform, and mainly aims to improve the data query efficiency in a large-scale data set. Firstly, an adjacency list storagescheme is adopted for a data graph and a query graph, topological information and attribute information of the graph are fully utilized, and a query process is converted into fields including a judgment process; and then, the problem of matching sequence selection is solved by accurately evaluating the candidate number of the query points of each candidate region, the generation of intermediate results is reduced, and the exploration process of multiple candidate regions can be solved in parallel. Through the mode, the query efficiency can be effectively improved, and an accurate query resultcan be obtained.
Owner:CENT SOUTH UNIV
Transformer substation intelligent tour inspection three-dimensional GIS (geographic information system) building method
InactiveCN106780739AGuaranteed uptimeImprove regulatory capacityForecastingResourcesGraphicsTransformer
The invention discloses a transformer substation intelligent tour inspection three-dimensional GIS (geographic information system) building method. The method includes: generating a route network; adopting Garmin equipment to collect longitude and latitude data of all points in all routes in a transformer substation; inputting the data of the points into a Map-source, selecting all key points to form an adjacency list, drawing specific routes according to information acquired by Garmin through AutoCAD software, and generating a file in a .shp format; step 2, building a three-dimensional scene. By the method, the main technical problems of a three-dimensional GIS system in the aspect of realization technology of power related industry in the prior art include low graphic rendering efficiency, incomplete display of geologic information, a lot of three-dimensional modeling work and difficulty in maintenance are solved.
Owner:ELECTRIC POWER SCI RES INST OF GUIZHOU POWER GRID CO LTD +1
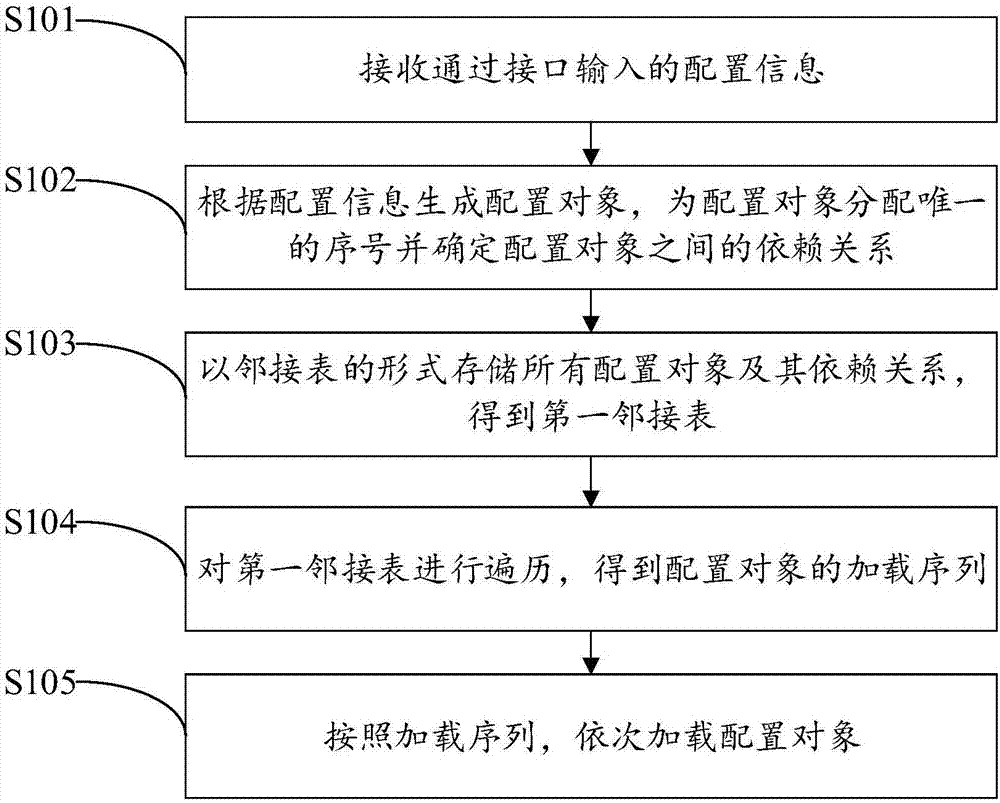
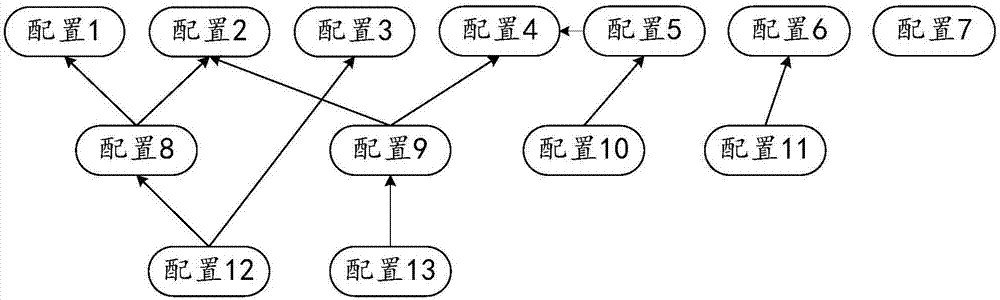
Configuration loading method and system
InactiveCN107092491AAchieve descriptiveRealize the structureSpecific program execution arrangementsExtensibilityMaintainability
The invention discloses a configuration loading method and system. The method comprises the steps of receiving configuration information input through an interface; generating configuration objects according to the configuration information, allocating unique sequence numbers to the configuration objects and determining a dependency relationship among the configuration objects; storing all the configuration objects and the dependency relationship among the configuration objects in an adjacency list form, and obtaining a first adjacency list; traversing the first adjacency list to obtain a loading sequence of the configuration objects; and loading the configuration objects in sequence according to the loading sequence. Through a universal loading framework, the configuration information is abstracted to the configuration objects, the configuration objects and the dependency relationships among the configuration objects are stored by using the adjacency list, automatic loading of the configuration objects is driven by traversing the adjacency list, and the loading sequence is ensured, so that configuration loading management and loading process structuring and automation are realized, the dependency relationship is describable, and the readability and maintainability are improved; and the framework is separated from a business, so that cross-component universality is realized and the expandability is enhanced.
Owner:CHINANETCENT TECH
Cable network branch diagram manufacturing method based on topological graph automatic layout
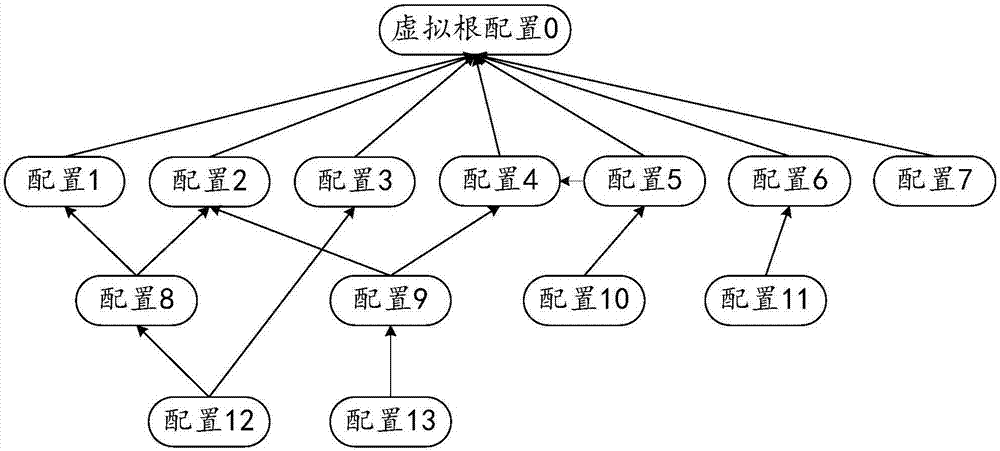
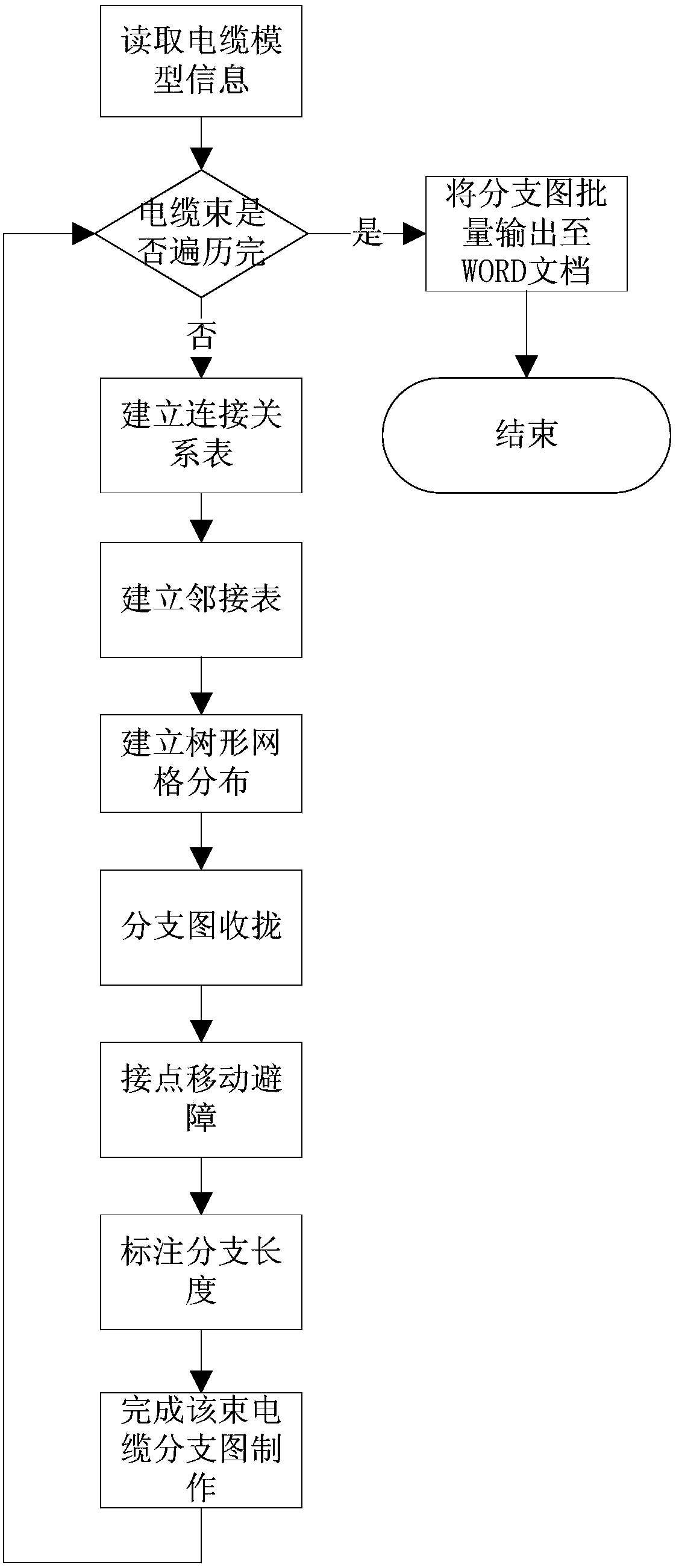
ActiveCN108182301AReduce process linksAvoid human errorGeometric CADDesign optimisation/simulationAlgorithmTopological graph
The invention provides a cable network branch diagram manufacturing method based on topological graph automatic layout. The method includes the following steps of browsing a cable network model structural tree and reading three-dimensional cable network model information to obtain all cable wire harness information (2) of a cable network model, and browsing all branches for a certain cable to obtain information of two ports of the cable and the length information; thirdly, browsing a connecting relation list, and establishing an adjacency list; fourthly, arranging all vortexes on grid points through the combination of tree-shaped layered layout and mesh layout, and calculating the actual positions of the nodes in the page according to the grid positions of nodes and the size of the page; fifthly, folding up branch diagrams; sixthly, browsing all the nodes on a trunk, doing different movements according to the types of the nodes so that no crossing or overlapping happens to drawing of the branch diagrams; seventhly, marking the length of connecting cords of the branch diagrams; eighthly, sequentially drawing other cable branch diagrams, and outputting the branch diagrams drawn in batches into a file for guiding production.
Owner:CHINA ACADEMY OF SPACE TECHNOLOGY
Method and system for mining risk propagation path based on knowledge graph
PendingCN112214614AEasy to analyzeComprehensive analysis and solutionRelational databasesSpecial data processing applicationsTheoretical computer scienceEngineering
The invention belongs to the technical field of financial data risk analysis, and relates to a method and system for mining a risk propagation path based on a knowledge graph. The method comprises thesteps: constructing the knowledge graph; extracting an adjacency matrix under each financial relationship according to the constructed knowledge graph; calculating a risk transfer probability by using a random walk algorithm to obtain a risk transfer probability matrix n, substituting the n financial relationships into a calculation formula of the risk transfer probability matrix n to obtain a risk transfer probability matrix n of the n financial relationships, and summing and averaging the obtained risk transfer probability matrix n to obtain a matrix I; establishing an adjacency list, and directly querying the risk propagation path in the adjacency list. The core concept of the knowledge graph is entities and relations, the relations between the entities are stored in a triple mode, andthe entities of different levels and the relations of different types can be integrated in one system. Through the relationship between entities such as companies and people, the problem is analyzedand solved more comprehensively from the global perspective.
Owner:民生科技有限责任公司
Method, computer program product and data structure for representing two- or three-dimensional object modeling
InactiveUS20060010141A1Reduce storage requirementsLight workloadRoad vehicles traffic controlSpecial data processing applicationsGraphicsComputer science
A data structure for a graph, which is composed by points and line segments connecting adjacent pairs of the points, respectively, of a two- or three-dimensional object comprises a set of point data of the individual points, each of the point data of the points consists of a clockwise or counter clockwise circular ordered adjacency list written in storage areas of a storage medium individually allocated to the point. The adjacency list describes a plurality of adjacent points associated with the point sequentially according to a circular adjacency order as viewed from outside of the graph with address pointers to the storage areas allocated to the adjacent points, respectively, and location pointers associated with the address pointers, respectively, to storage locations of adjacency lists of the adjacent points, respectively, where an address pointer of the point is written.
Owner:FURUKAWA SUSUMU +1
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com