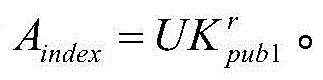Patents
Literature
1125 results about "Search function" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
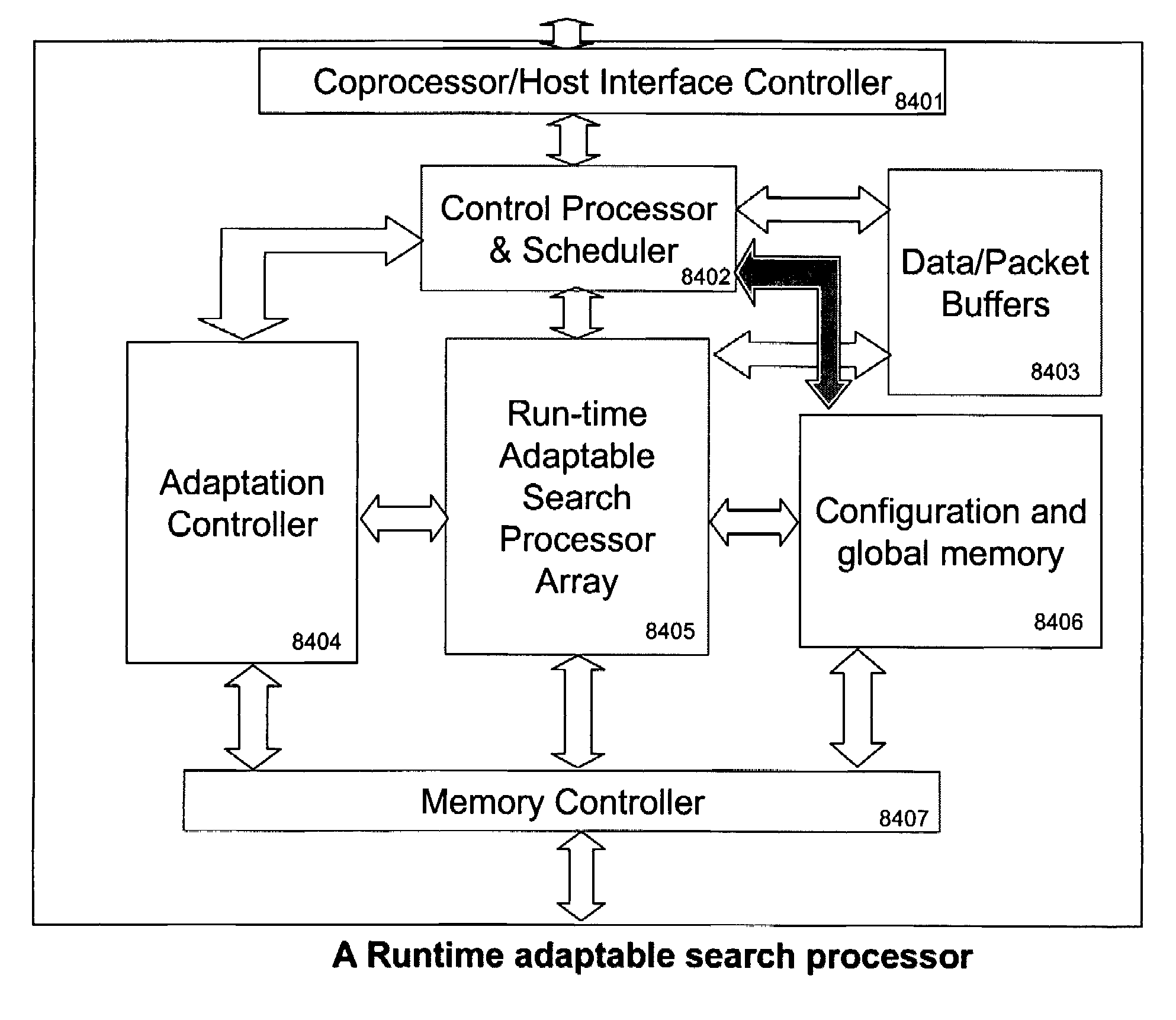
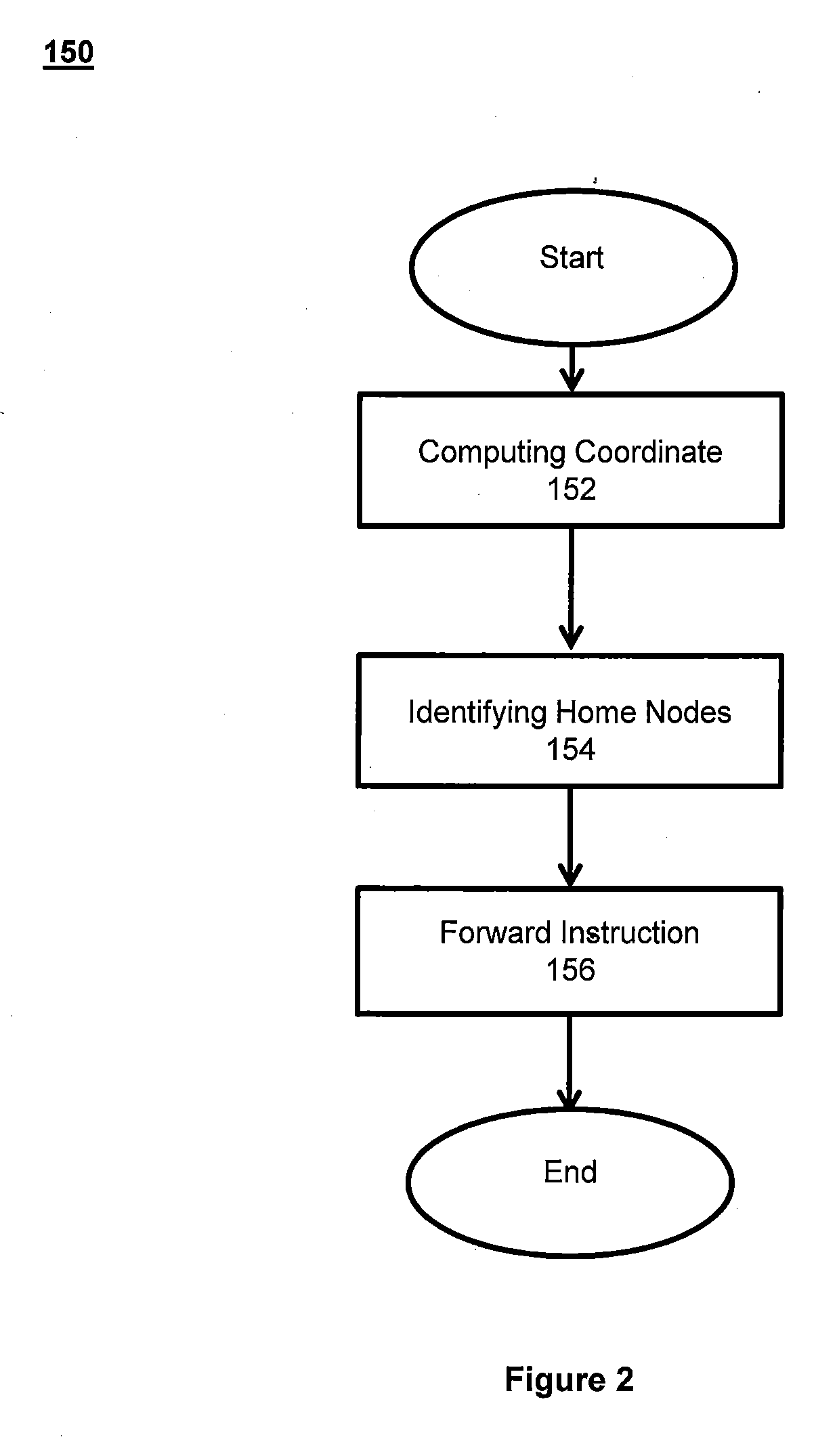
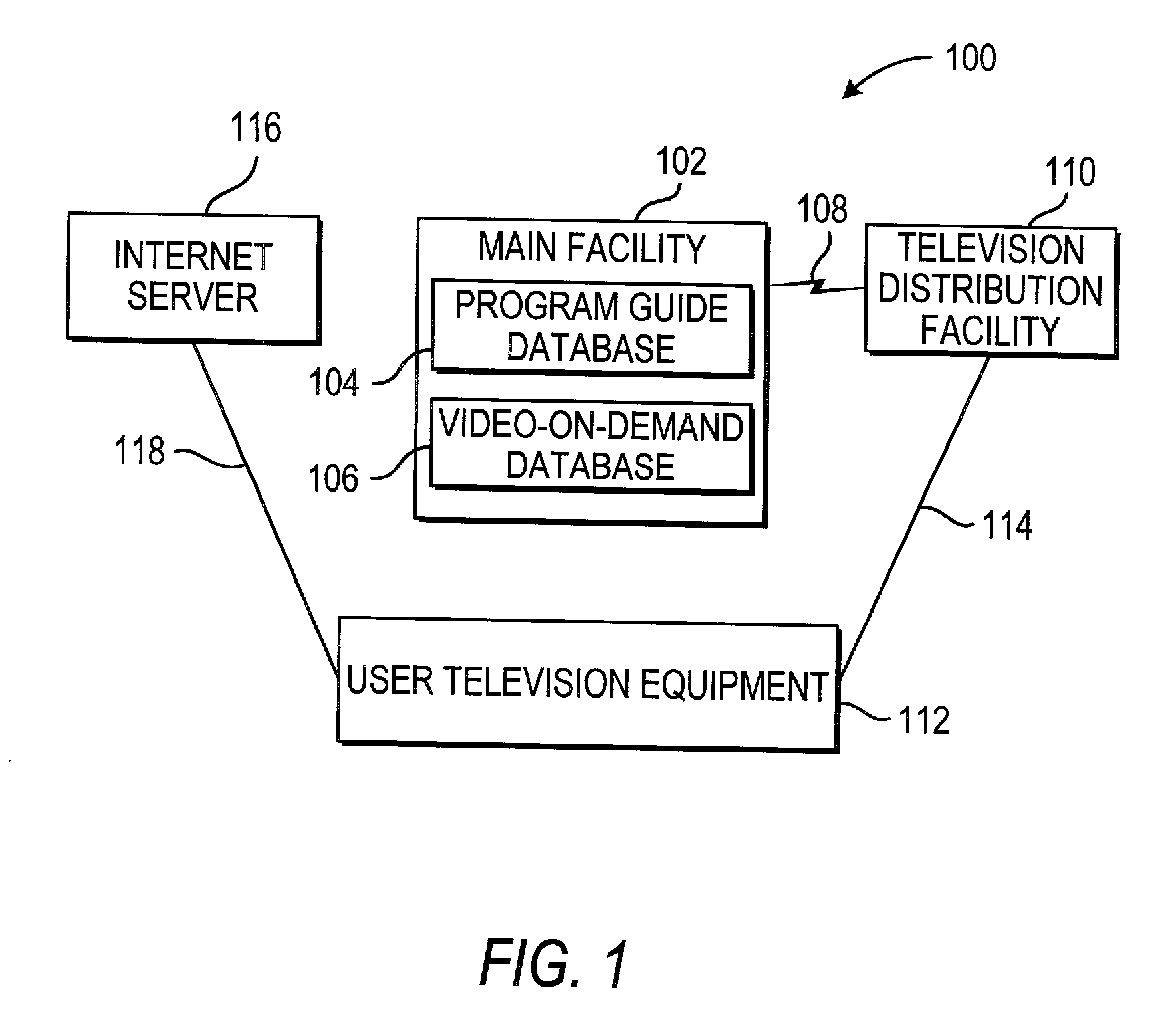
Runtime adaptable search processor
ActiveUS20060136570A1Reduce stacking processImproving host CPU performanceWeb data indexingMultiple digital computer combinationsData packInternal memory
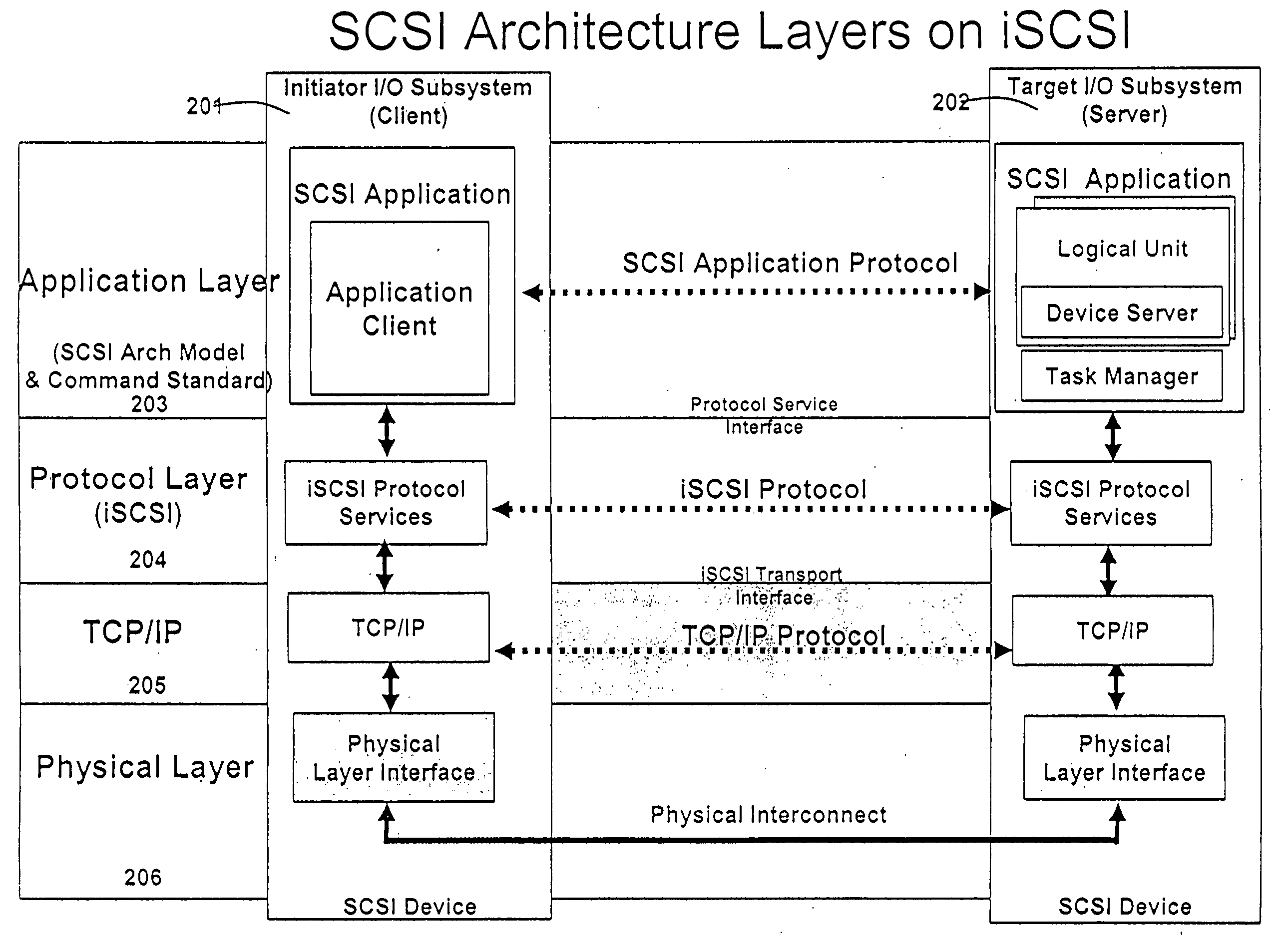
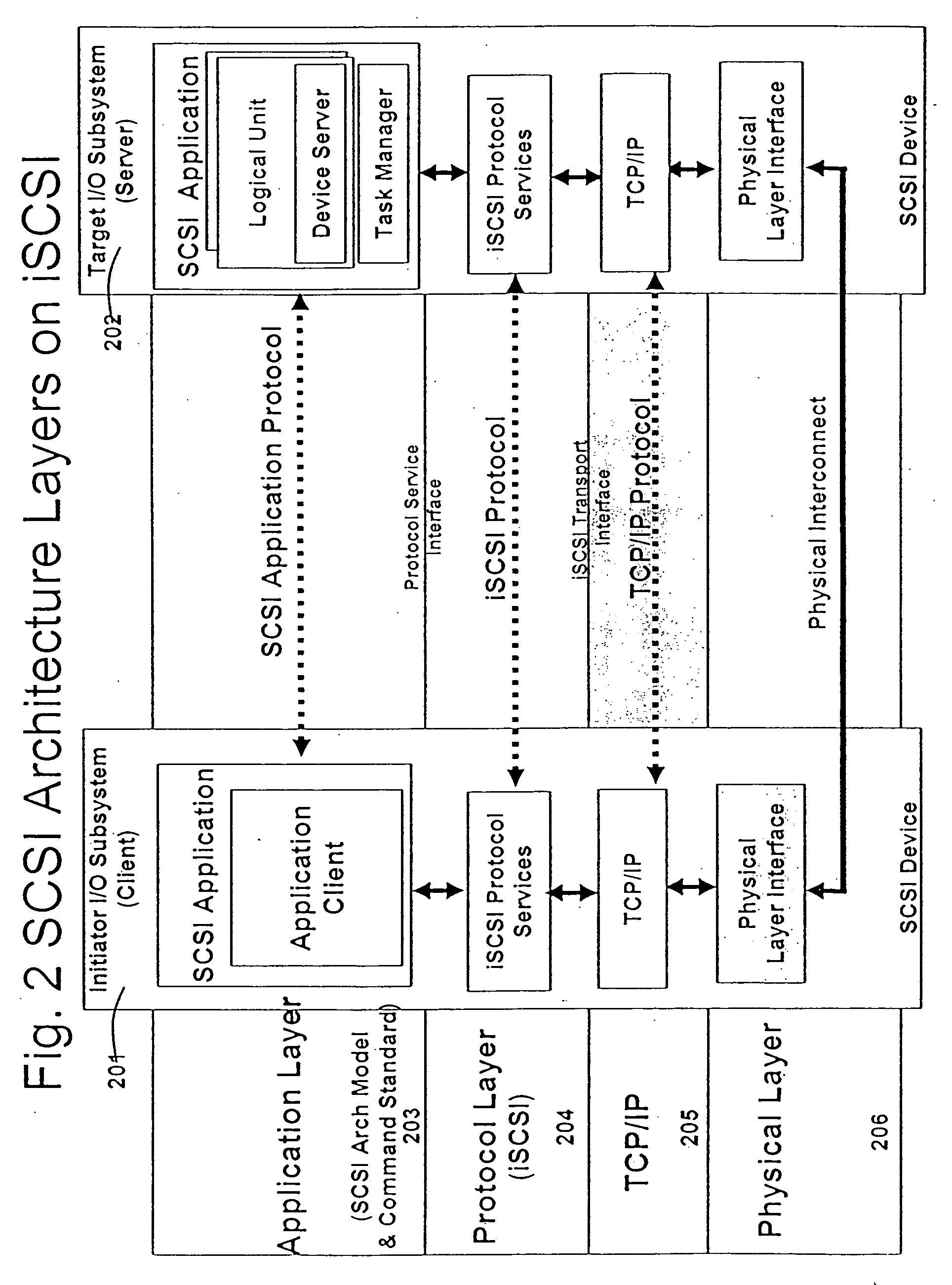
A runtime adaptable search processor is disclosed. The search processor provides high speed content search capability to meet the performance need of network line rates growing to 1 Gbps, 10 Gbps and higher. he search processor provides a unique combination of NFA and DFA based search engines that can process incoming data in parallel to perform the search against the specific rules programmed in the search engines. The processor architecture also provides capabilities to transport and process Internet Protocol (IP) packets from Layer 2 through transport protocol layer and may also provide packet inspection through Layer 7. Further, a runtime adaptable processor is coupled to the protocol processing hardware and may be dynamically adapted to perform hardware tasks as per the needs of the network traffic being sent or received and / or the policies programmed or services or applications being supported. A set of engines may perform pass-through packet classification, policy processing and / or security processing enabling packet streaming through the architecture at nearly the full line rate. A high performance content search and rules processing security processor is disclosed which may be used for application layer and network layer security. scheduler schedules packets to packet processors for processing. An internal memory or local session database cache stores a session information database for a certain number of active sessions. The session information that is not in the internal memory is stored and retrieved to / from an additional memory. An application running on an initiator or target can in certain instantiations register a region of memory, which is made available to its peer(s) for access directly without substantial host intervention through RDMA data transfer. A security system is also disclosed that enables a new way of implementing security capabilities inside enterprise networks in a distributed manner using a protocol processing hardware with appropriate security features.
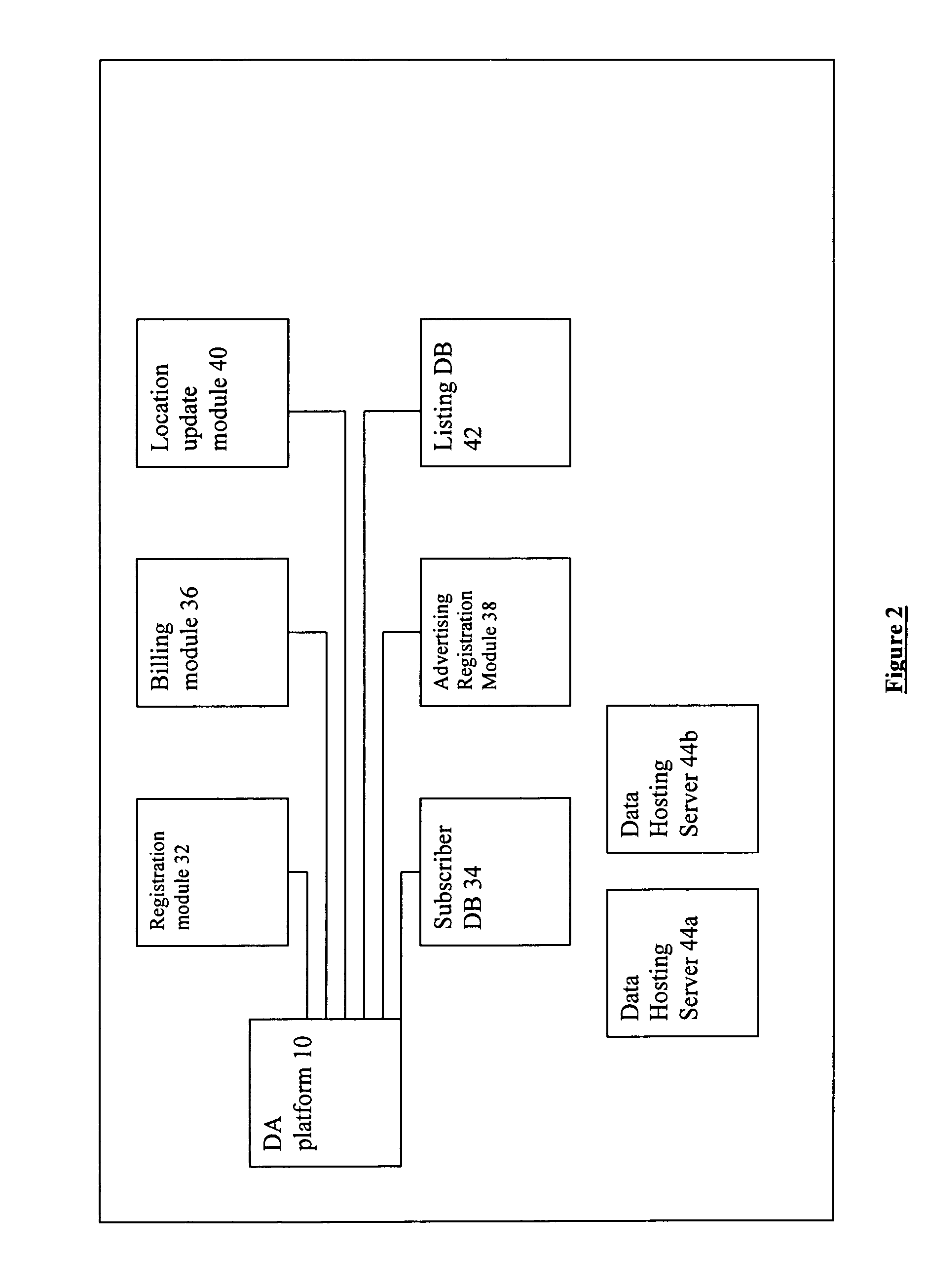
Owner:MEMORY ACCESS TECH LLC
Runtime adaptable search processor
ActiveUS7685254B2Improve application performanceLarge capacityWeb data indexingMemory adressing/allocation/relocationPacket schedulingSchema for Object-Oriented XML
A runtime adaptable search processor is disclosed. The search processor provides high speed content search capability to meet the performance need of network line rates growing to 1 Gbps, 10 Gbps and higher. The search processor provides a unique combination of NFA and DFA based search engines that can process incoming data in parallel to perform the search against the specific rules programmed in the search engines. The processor architecture also provides capabilities to transport and process Internet Protocol (IP) packets from Layer 2 through transport protocol layer and may also provide packet inspection through Layer 7. Further, a runtime adaptable processor is coupled to the protocol processing hardware and may be dynamically adapted to perform hardware tasks as per the needs of the network traffic being sent or received and / or the policies programmed or services or applications being supported. A set of engines may perform pass-through packet classification, policy processing and / or security processing enabling packet streaming through the architecture at nearly the full line rate. A high performance content search and rules processing security processor is disclosed which may be used for application layer and network layer security. Scheduler schedules packets to packet processors for processing. An internal memory or local session database cache stores a session information database for a certain number of active sessions. The session information that is not in the internal memory is stored and retrieved to / from an additional memory. An application running on an initiator or target can in certain instantiations register a region of memory, which is made available to its peer(s) for access directly without substantial host intervention through RDMA data transfer. A security system is also disclosed that enables a new way of implementing security capabilities inside enterprise networks in a distributed manner using a protocol processing hardware with appropriate security features.
Owner:MEMORY ACCESS TECH LLC
System and methods for mapping and searching objects in multidimensional space
ActiveUS20130138646A1Reduce in quantitySpeed up searchWeb data indexingDigital data processing detailsData miningMultidimensional space
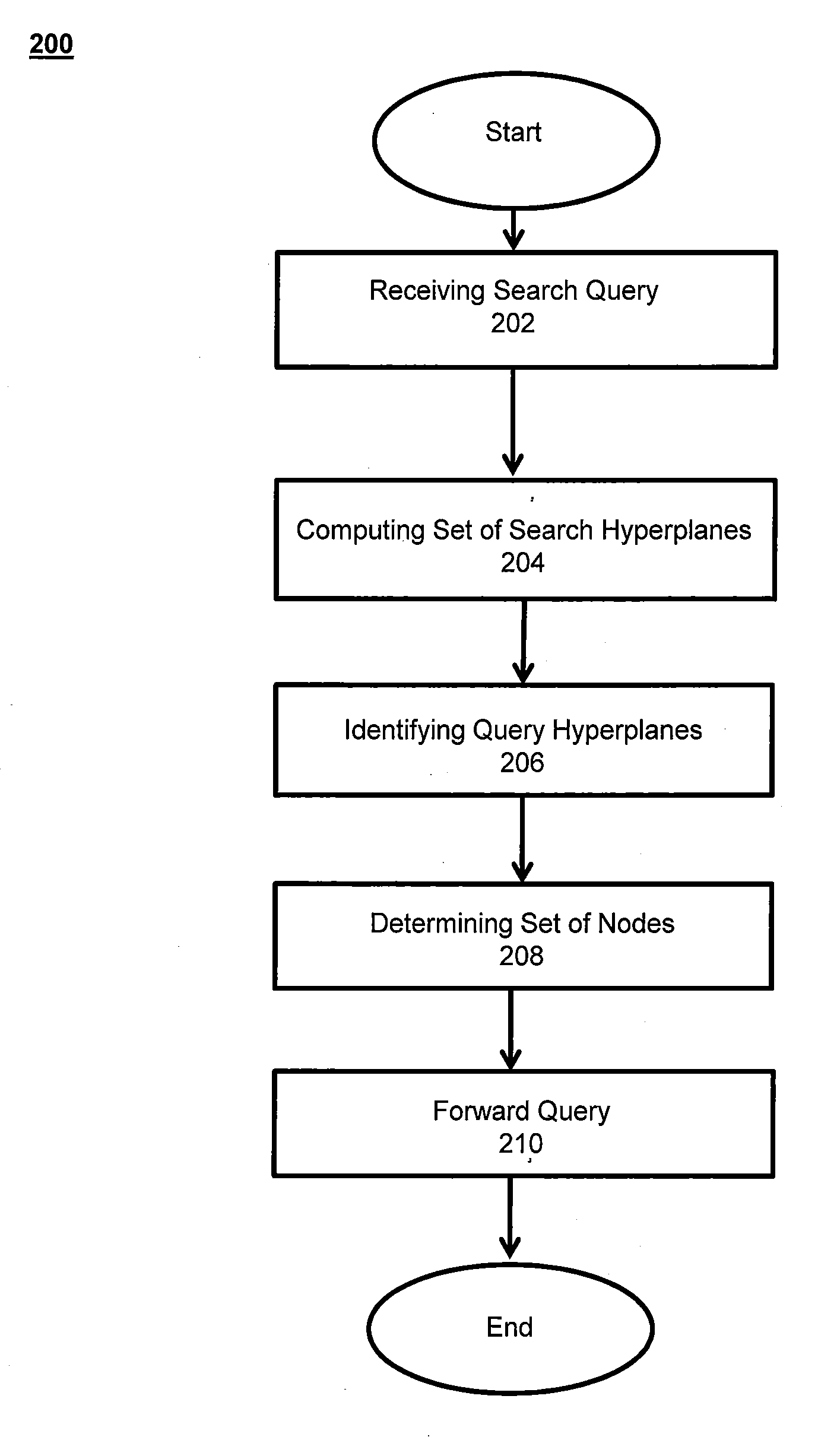
This invention relates to a system and methods for determining the placement of an object in a distributed key-value store by mapping the object to nodes in multidimensional hyperspace. A search function supports efficient object retrieval, even when the search query requests multiple objects and specifies them through non-primary keys. In response to a search query, the search is translated into hyperregions in the hyperspace to determine the set of nodes that hold the queried data object. The number of contacted nodes and the number of scanned objects are significantly reduced in comparison to prior art techniques.
Owner:CORNELL UNIVERSITY
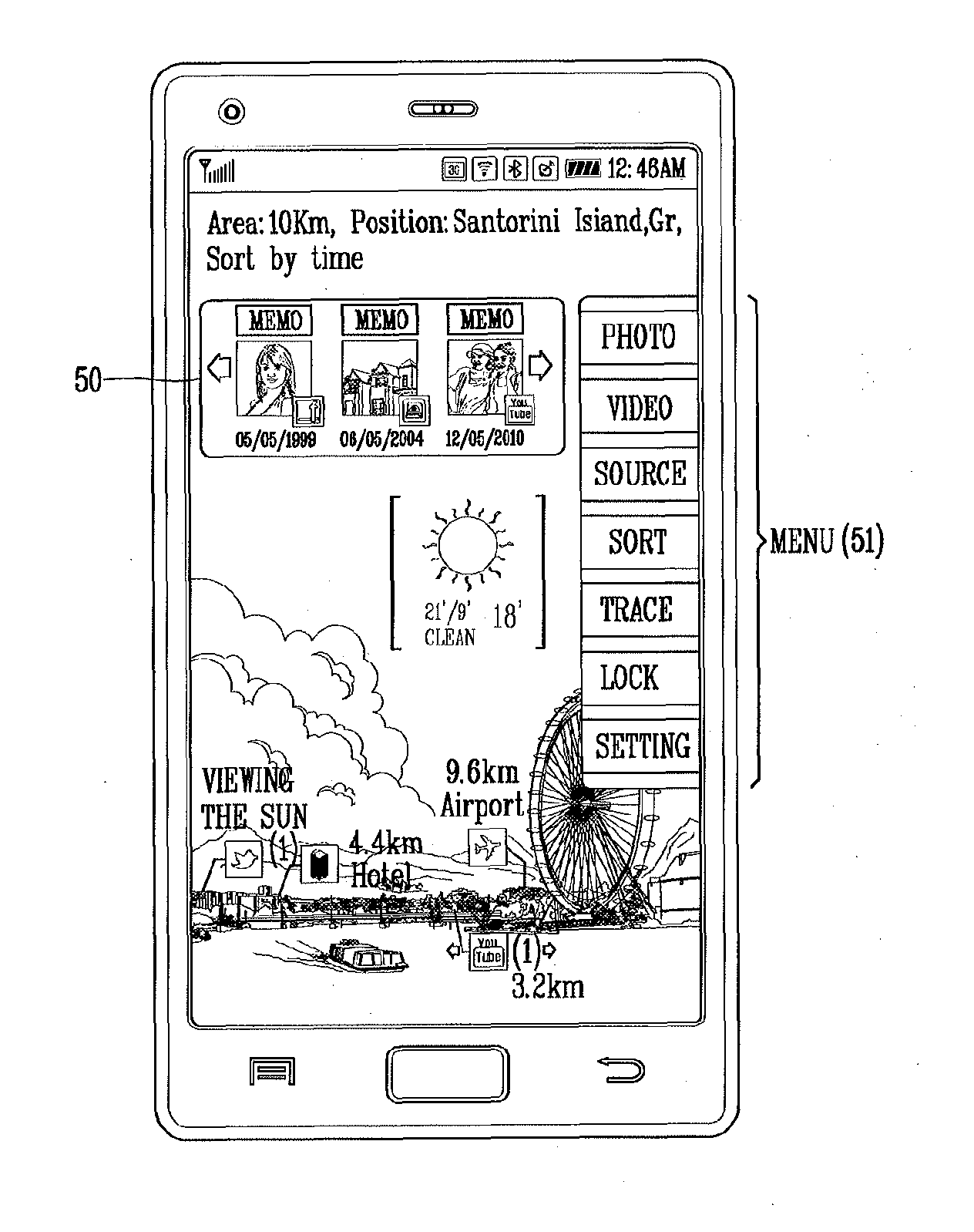
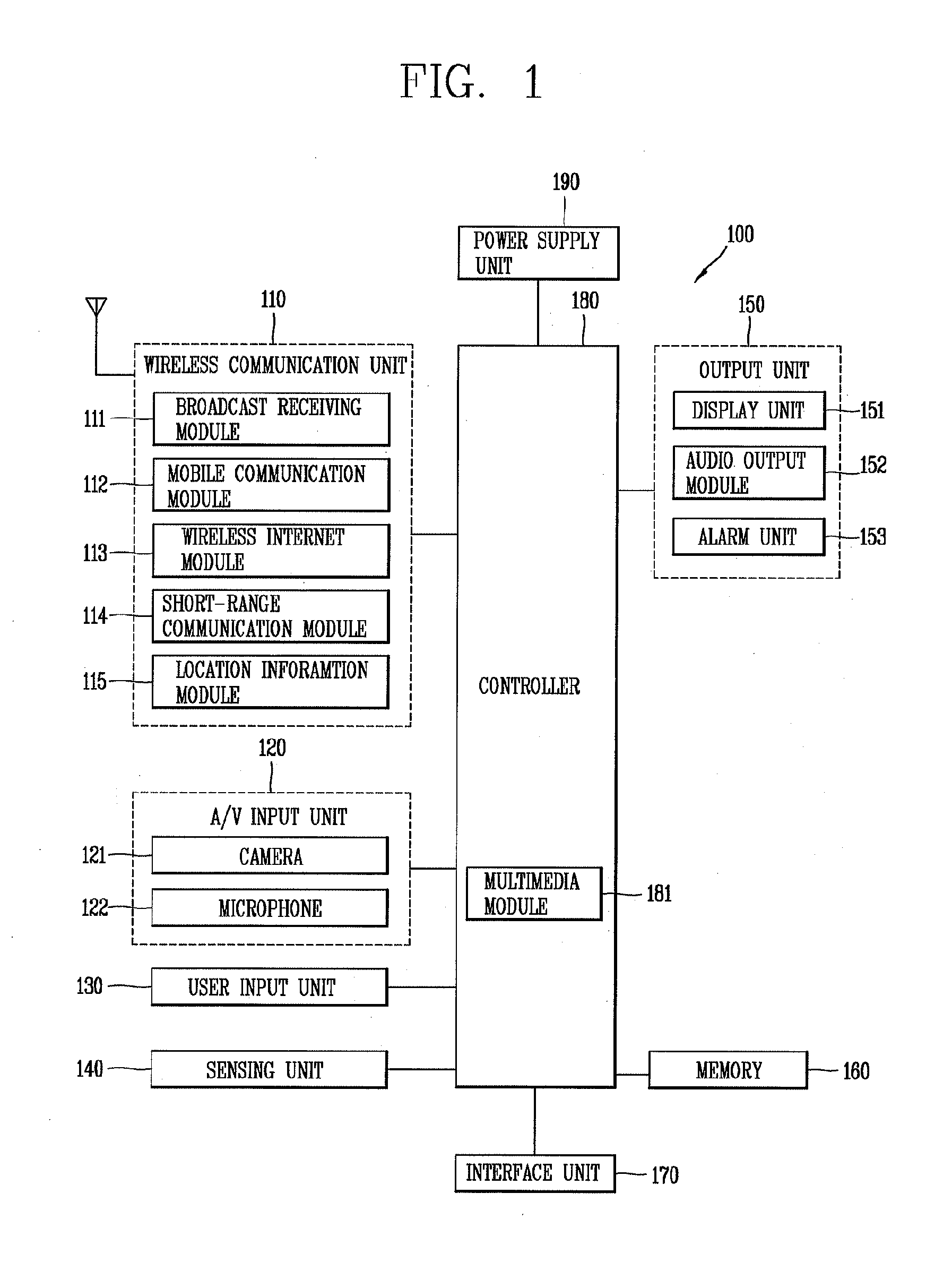
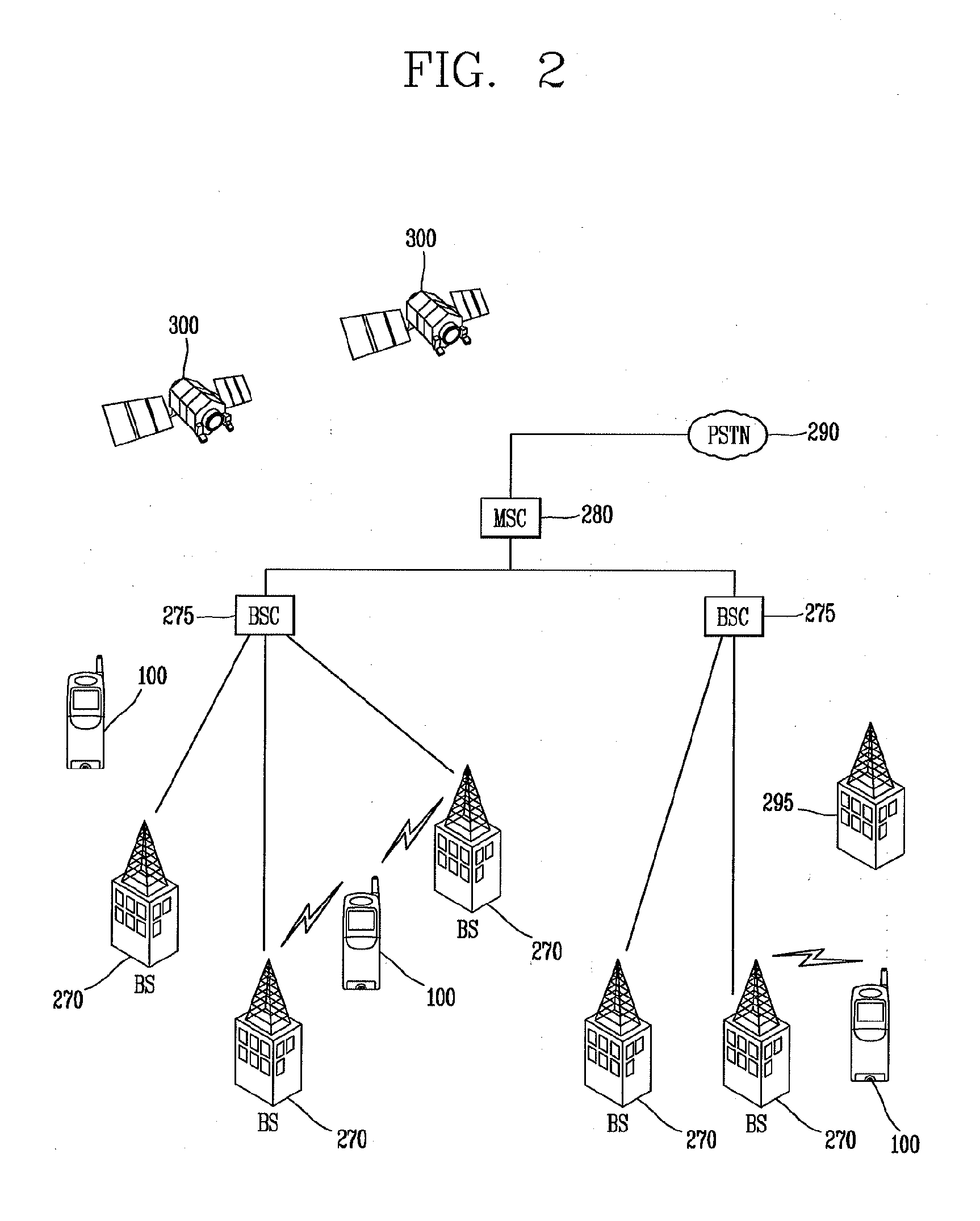
Mobile terminal and photo searching method thereof
InactiveUS20130198176A1Digital data processing detailsMetadata still image retrievalPosition dependentAugmented reality
The present disclosure relates to a mobile terminal and a photo search method thereof capable of searching and displaying photos shared by the cloud and SNS systems in connection with a specific location on a camera view using augmented reality. To this end, according to the present disclosure, when a photo search function is selected on an augmented reality based camera view, photo information associated with at least one location on which the focus of the camera view is placed is searched from a network system to sort and display the searched photo information on the camera view, thereby allowing the user to conveniently search photos associated with old memories.
Owner:LG ELECTRONICS INC
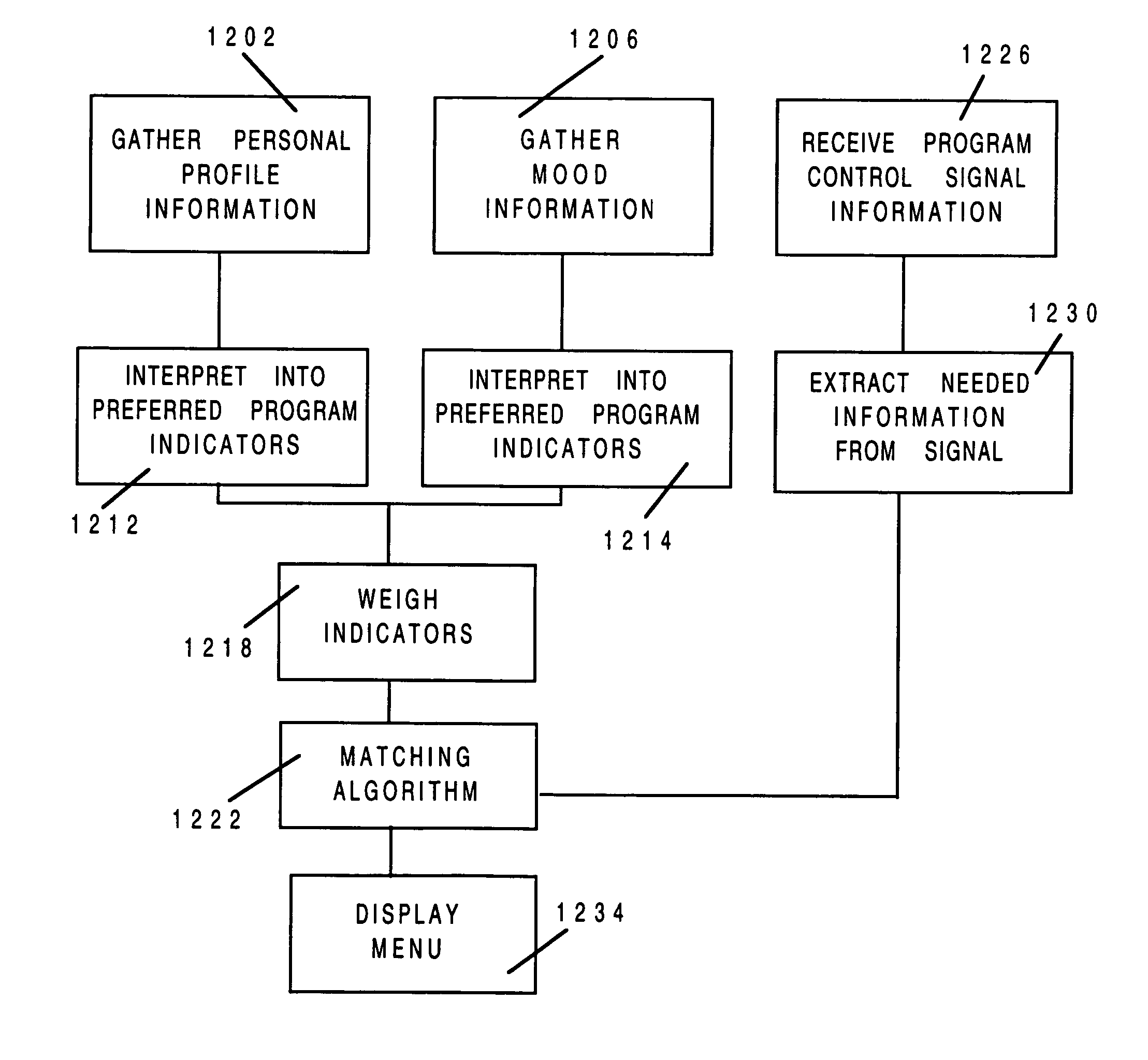
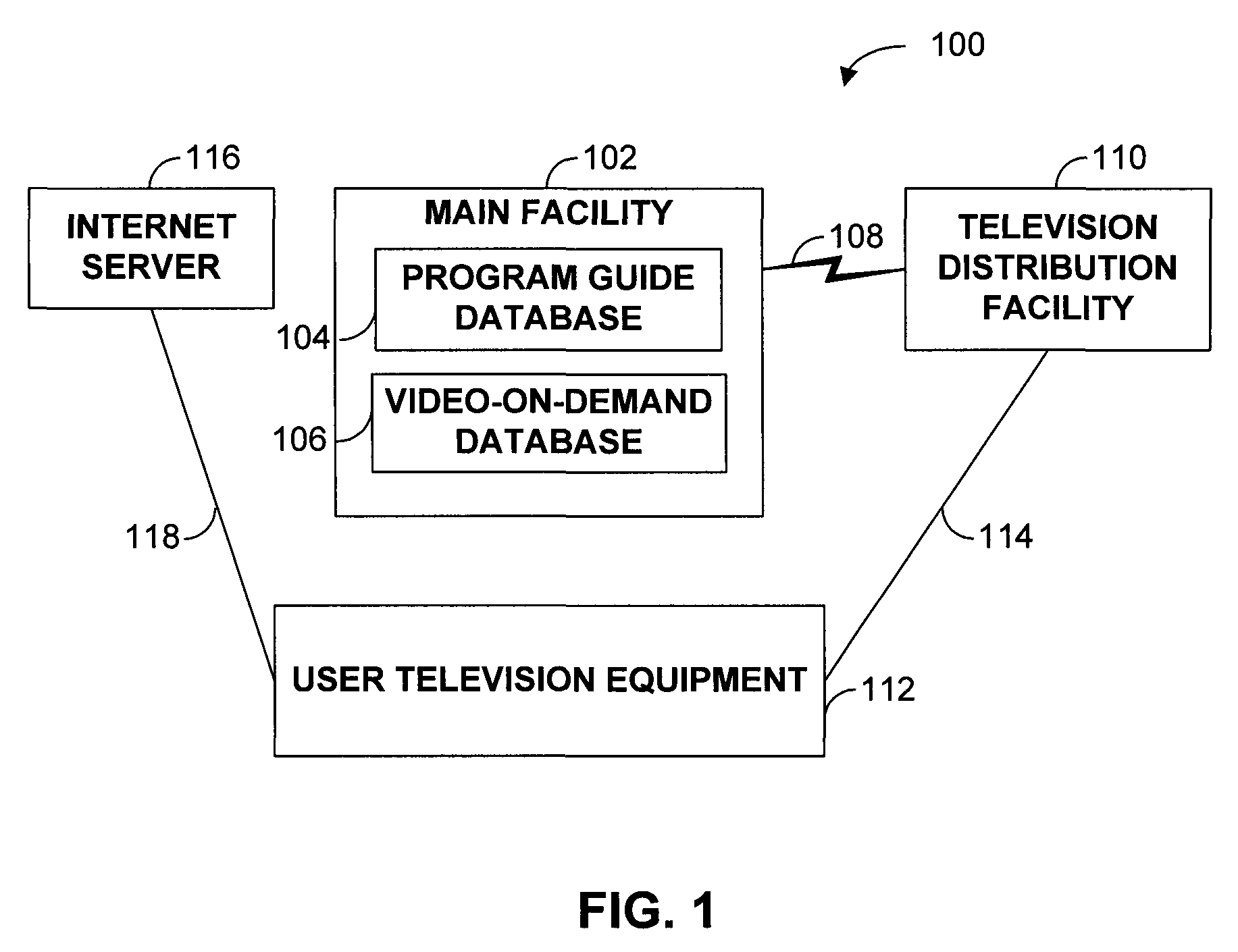
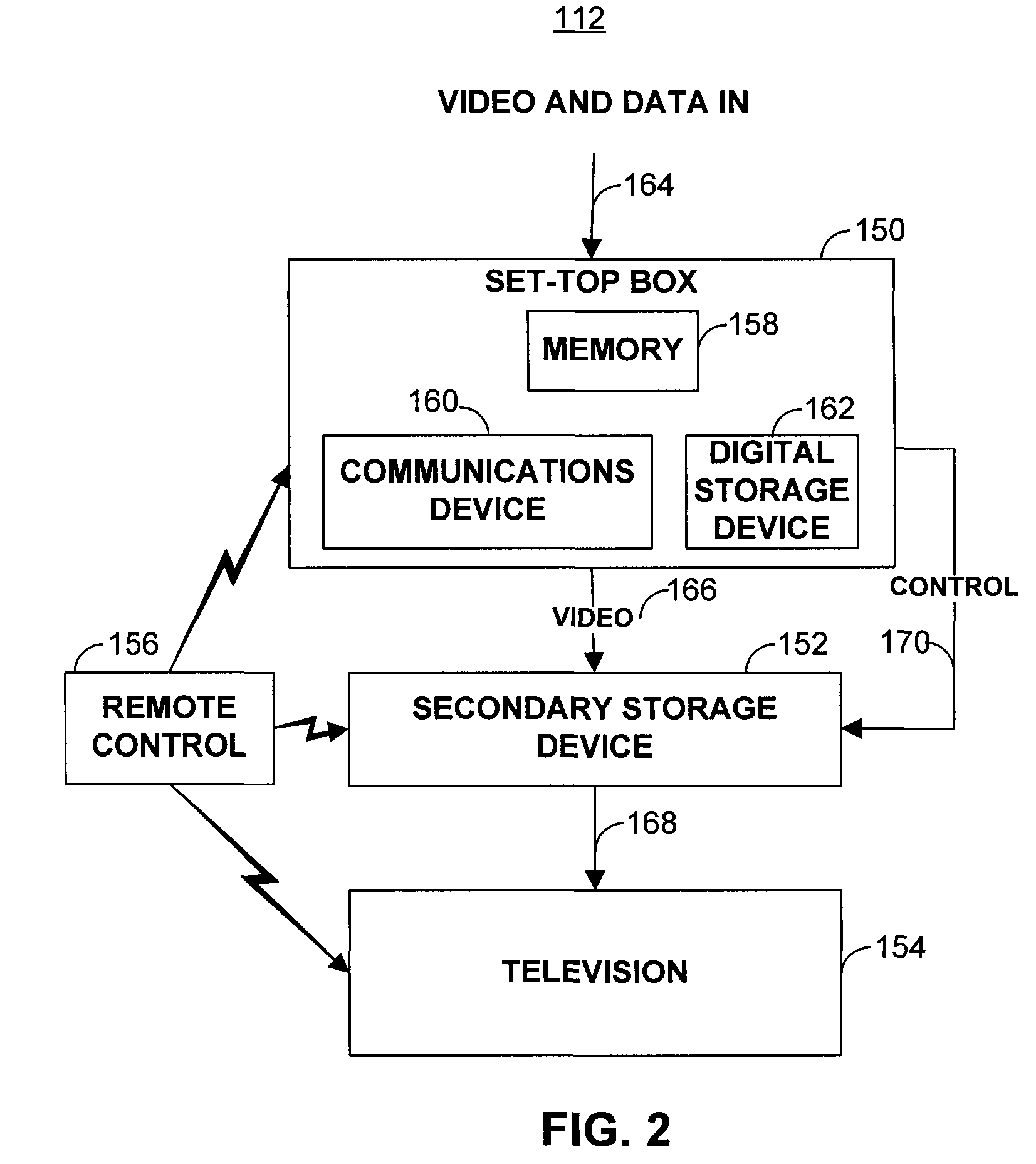
Method and apparatus for interactive program suggestion
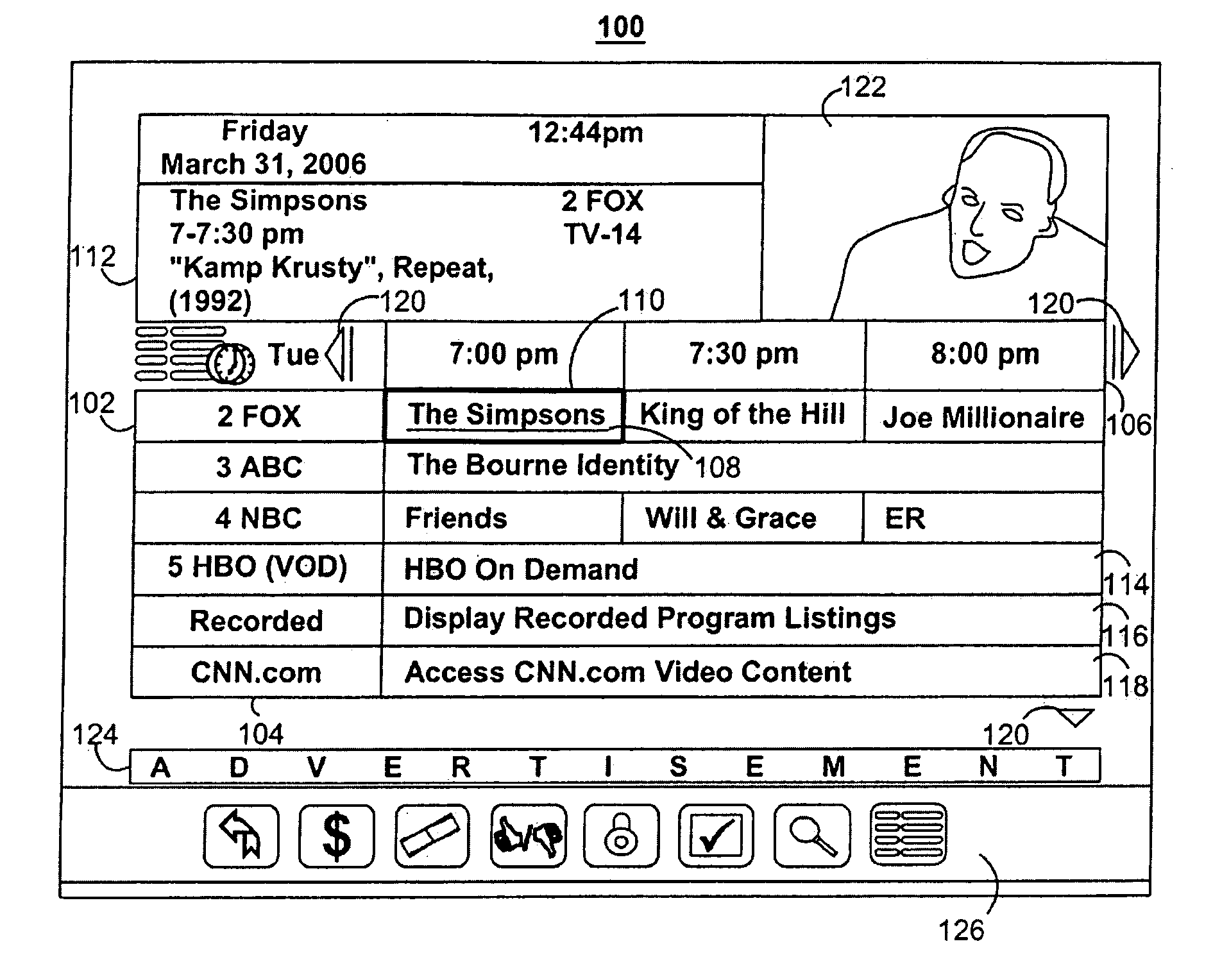
InactiveUS7013478B1Television system detailsBroadcast information characterisationComputer terminalElectronic book
A method and an apparatus suggests programs for viewing by a subscriber. Terminals installed at a subscriber's home and at central locations, such as bookstores, video rental stores and libraries, provide responsive or intelligent search functions to suggest programs for viewing according to a subscriber's viewing preferences. Responsive searching includes posing questions to and receiving answers from the subscribers. Intelligent searching includes gathering historical data, such as the subscriber's history of programs watched. The programs include videotapes, videodiscs, television programs and electronic books. Subscribers indicate their selection and order the programs using a menu system. An automated billing system tracks the programs ordered.
Owner:COX COMMUNICATIONS
Features for use with advanced set-top applications on interactive television systems
InactiveUS20050235319A1Television system detailsAnalogue secracy/subscription systemsTelevision systemInteractive television
Advanced features for interactive television applications are described, including a back feature, a forward feature, a history feature, a go to feature, an extras feature, a reminder feature, a favorites feature, a parental control feature, and a search feature. Features may be inter-resource. Support for multiple data paths, Internet access, interactive services, and user profiles are also described.
Owner:UNITED VIDEO PROPERTIES
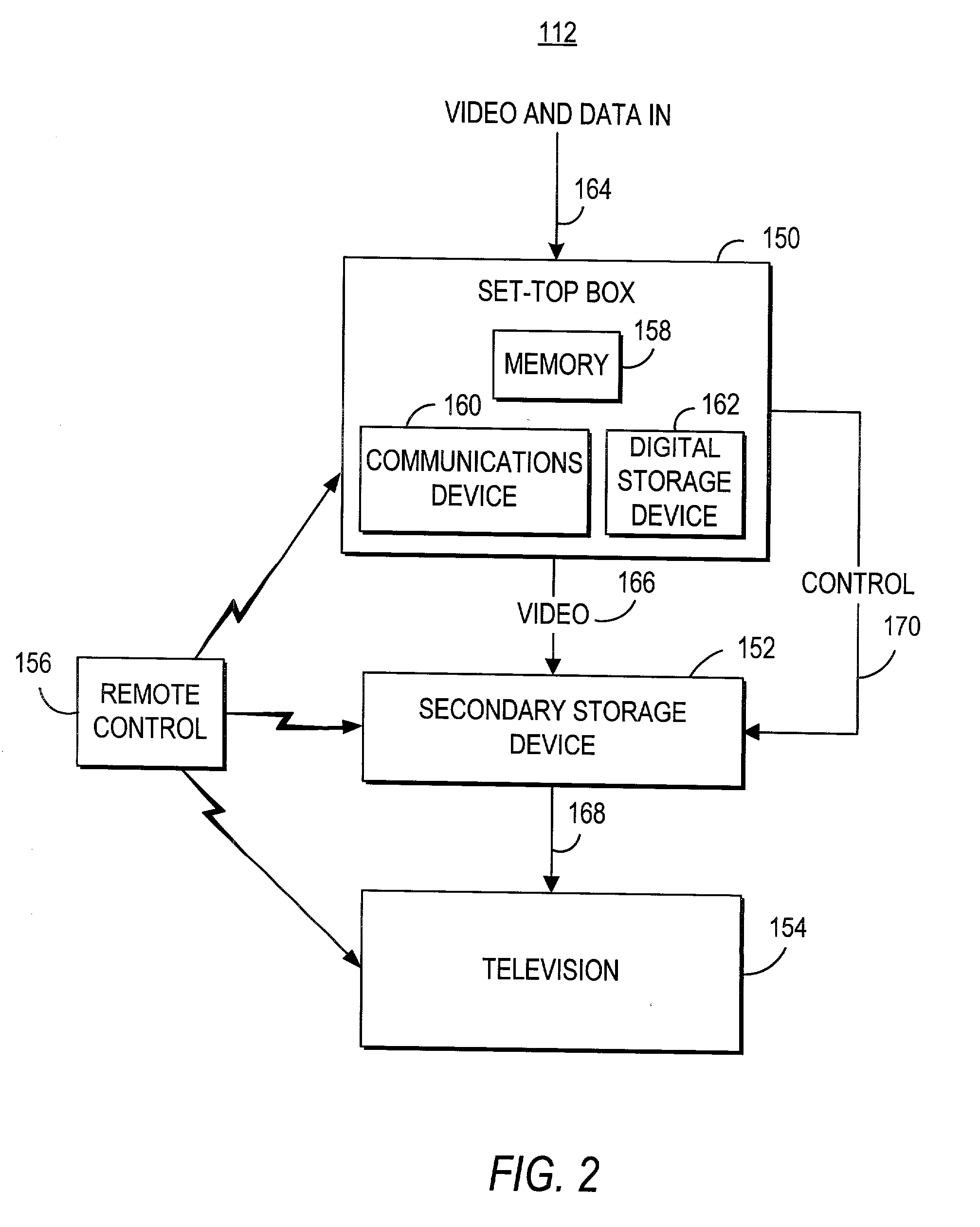
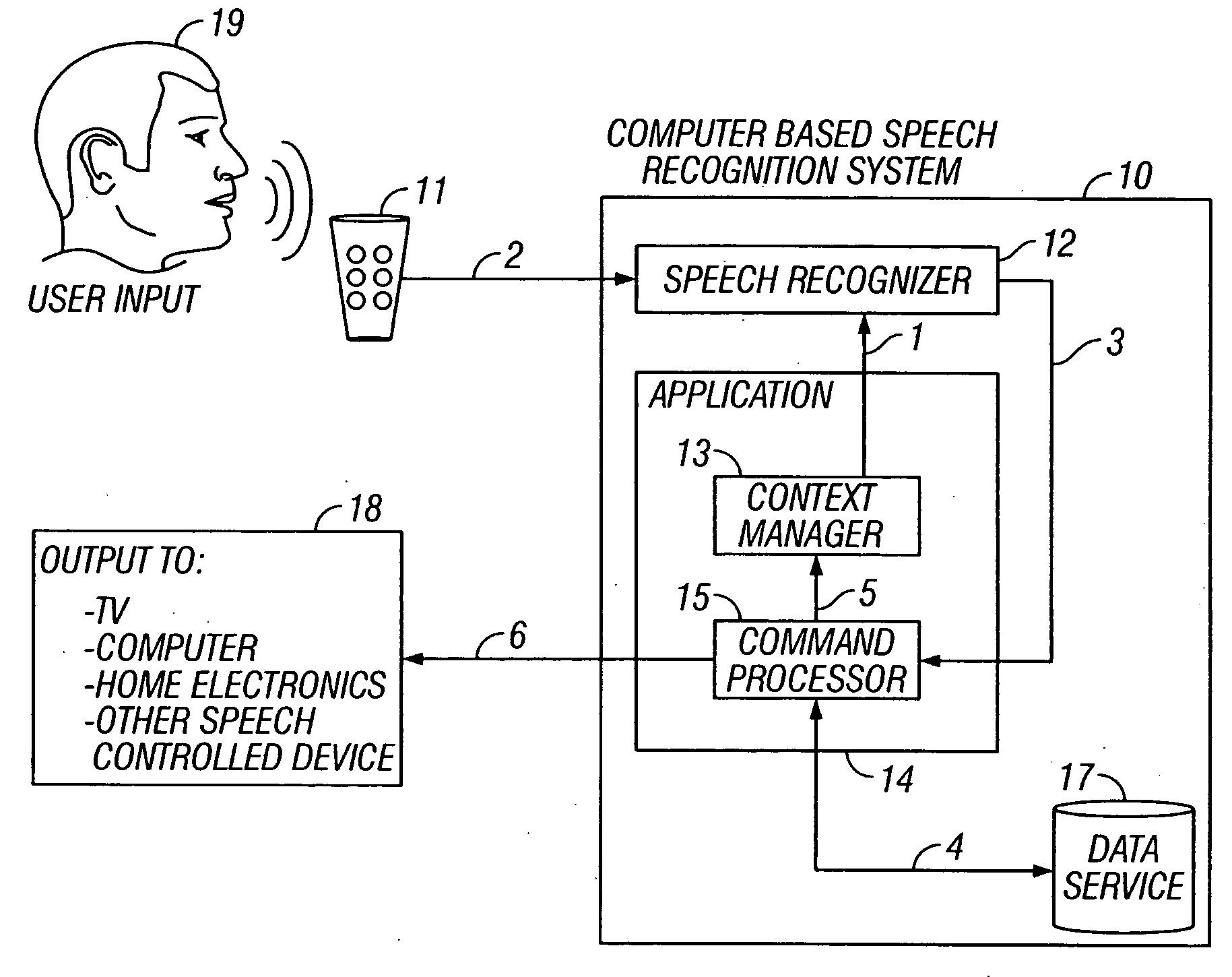
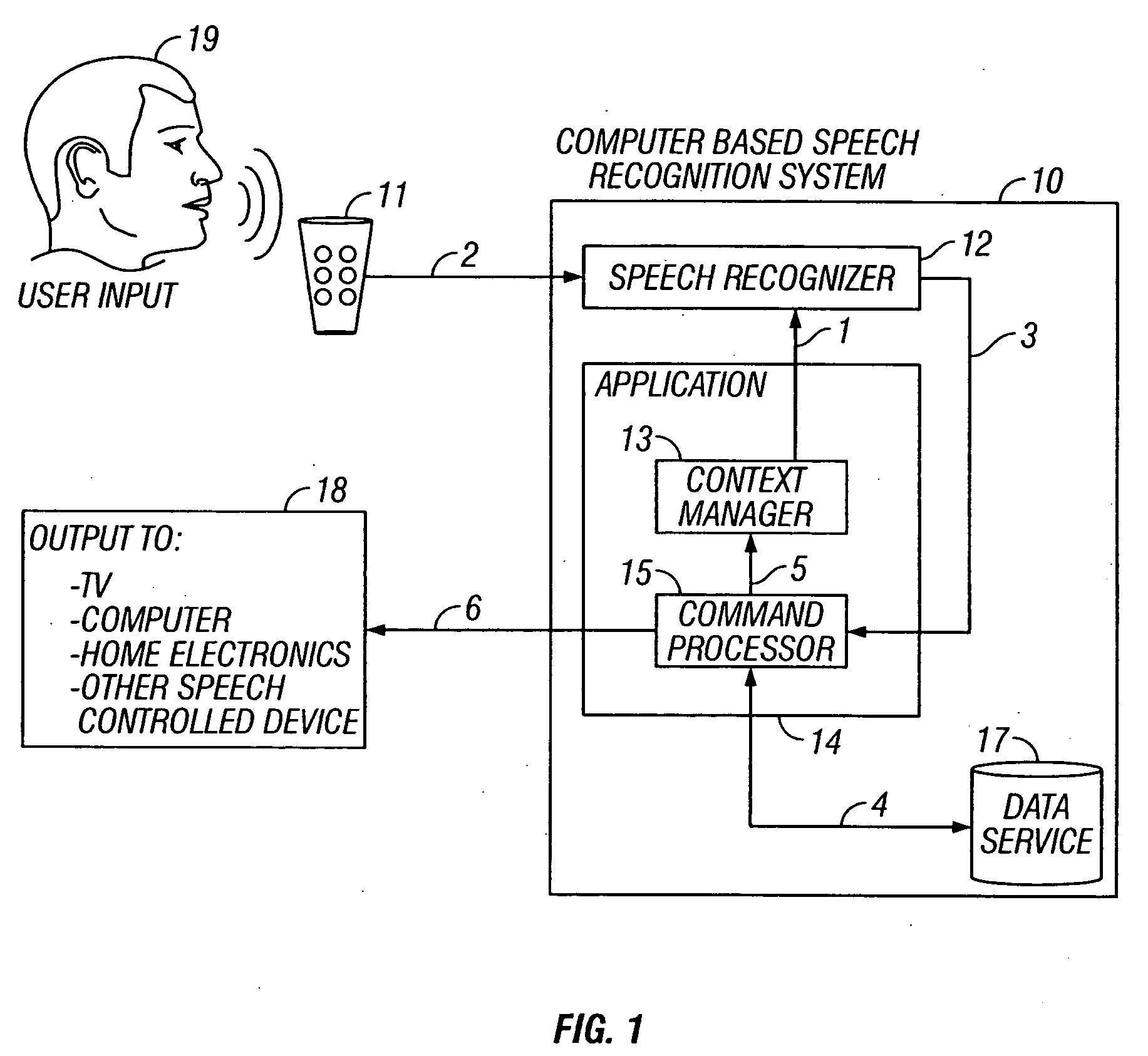
Speech controlled access to content on a presentation medium
One embodiment of the invention provides television viewers with an intuitive and easy-to-use way to find the programs they want and to control their television viewing experience. In a further embodiment, a speech control interface, in combination with a variety of search functions, is provided such that television viewers have an intuitive and easy-to-use way to find the programs and information they want. The invention also provides the use of personalization as a way to filter and deliver relevant content and services to users based upon individual preferences. Another aspect of the invention provides a hierarchical user interface for speech-controlled, interactive applications, that gives television viewers an intuitive and easy-to-use way to find the programs they want and to control their television viewing experience. The invention also provides a method and apparatus where the channel lineup in a television service is dynamic and changeable, i.e. the list of available channels can be modified, in real time, to suit the preferences and usage of a particular subscriber. Further, the invention provides a method and apparatus that addresses the use of speaker, group, language, or emotional state identification systems to target advertising, to users who are or are not enrolled in a speaker ID system.
Owner:PROMPTU SYST CORP
Internet-based search system and method of use
An Internet-based search system and method of use. The system in its various embodiments includes an electronic database. The database includes one or more topical categories of information and wherein the categories are further divided into datasets of one or more pre-selected web locations. The invention also includes an Internet remote in communication with the database. The Internet remote includes in its various embodiments, a title bar, one or more advertising windows, a channel selector, a navigation palette, a navigation panel, and an optional set of additional links. In operation, a user selects a channel from the channel selector, which then causes the display of one or more categories in the navigation palette. Upon selection of the desired category, one or more subcategory bars appear in the navigation panel, the selection of which causes the display of one or more links to either a website, or a particular page within a website. Alternatively, the user may enter a search term and, upon selection of a web site, that search term is passed to the selected site employing its own search function. In either circumstance, when the user selects a link, that link displays in a separate companion web browser such that both the remote and companion browser are simultaneously viewable.
Owner:HOPKINS KEVIN +1
Access to Trusted User-Generated Content Using Social Networks
A method to access trusted user generated content (UGC) is provided. User registration information containing one or more identities is obtained. Each identity corresponds to an internet social network that is facilitated by one of a plurality of social network sites. The social relationships are collected using the provided user identities at the different social network sites and user extended social networks are created for each user by joining the social relationships collected. Then, UGC is collected from the plurality of social network sites and the collected UGC is correlated with the extended social networks. The correlated UGC is filtered according to the user configuration of a user making a request, and then the results are presented to the requesting user. A search function is provided to obtain information on demand, or alternatively, a user receives feeds of information according to configured information regarding the user's extended social network.
Owner:R2 SOLUTIONS
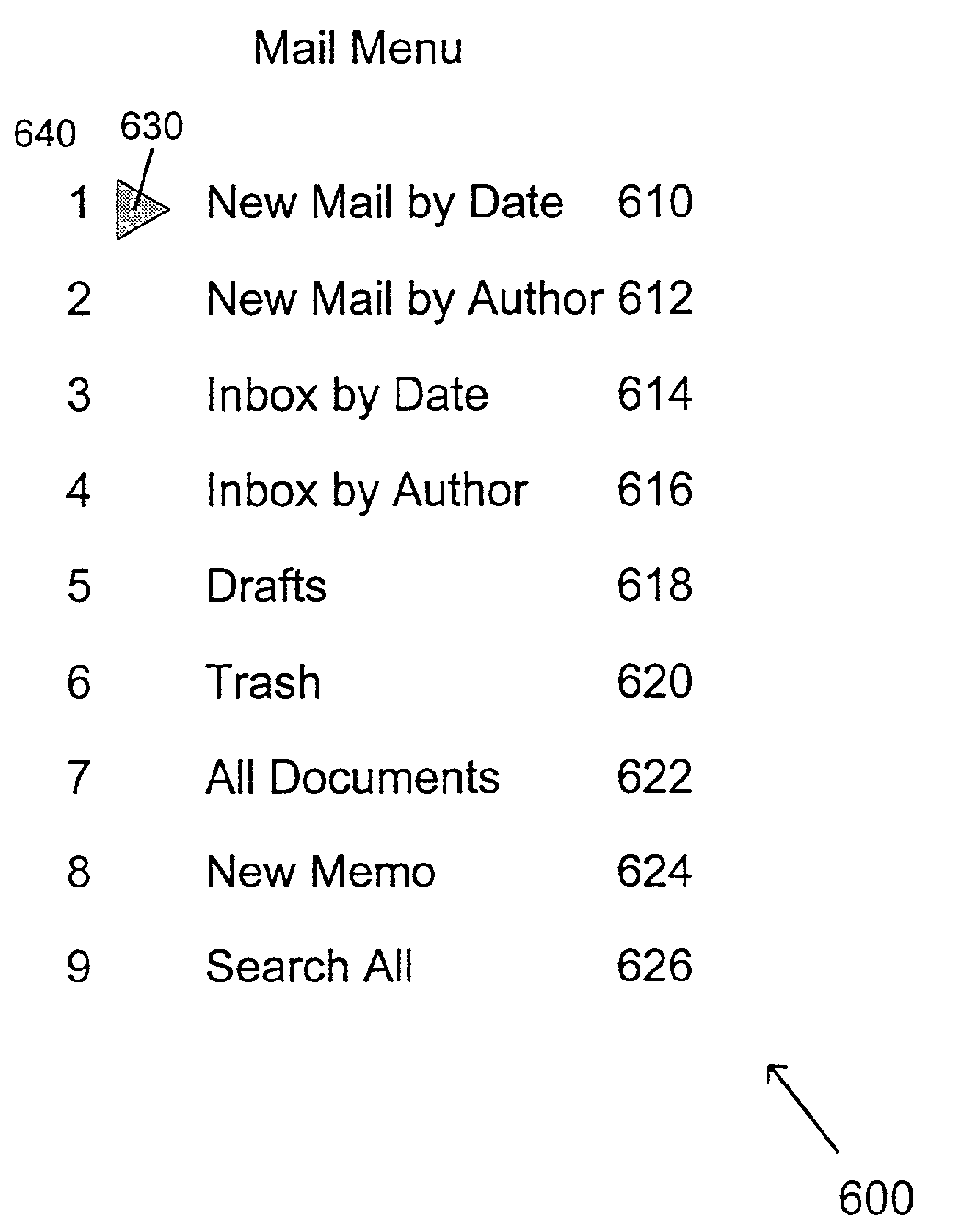
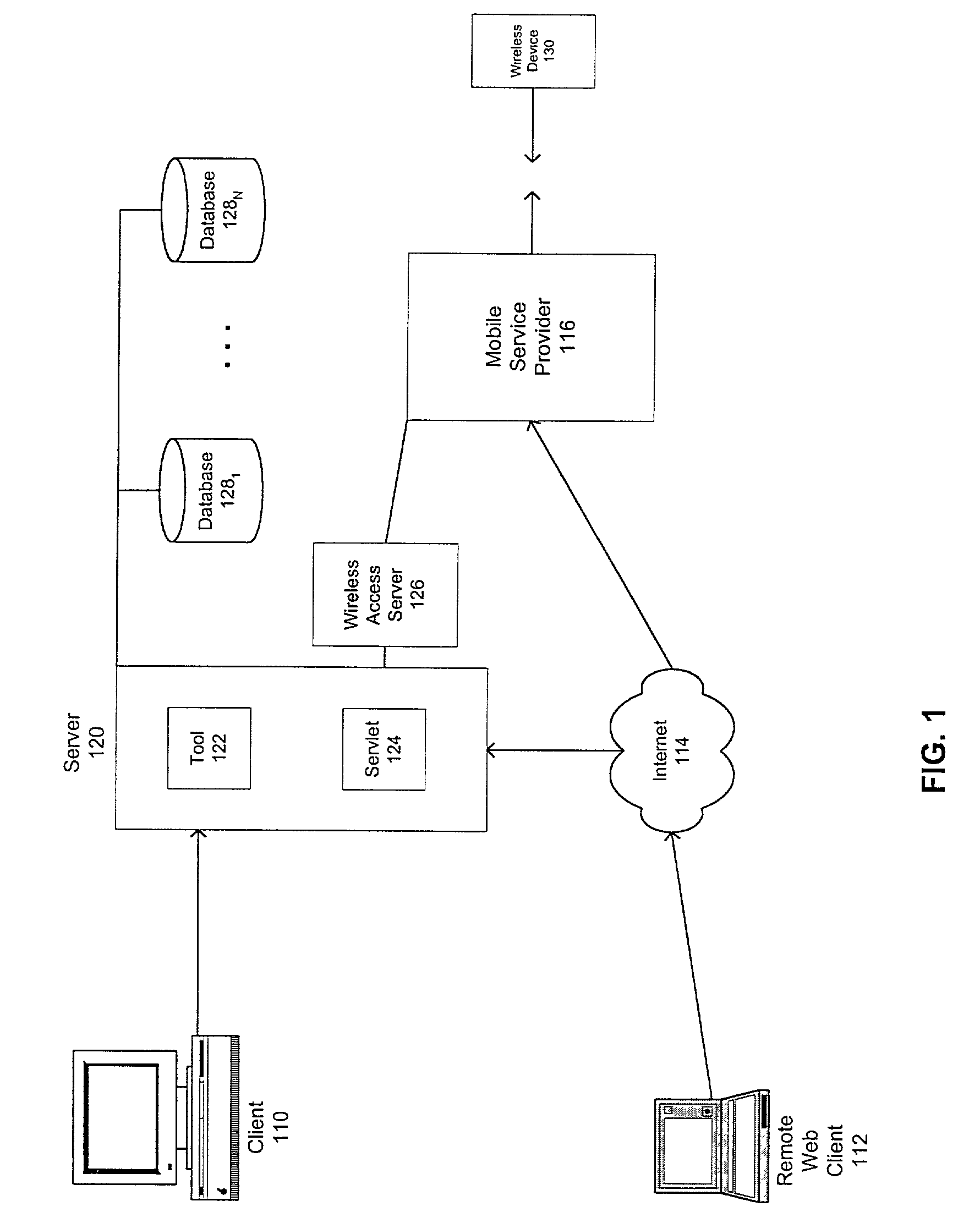
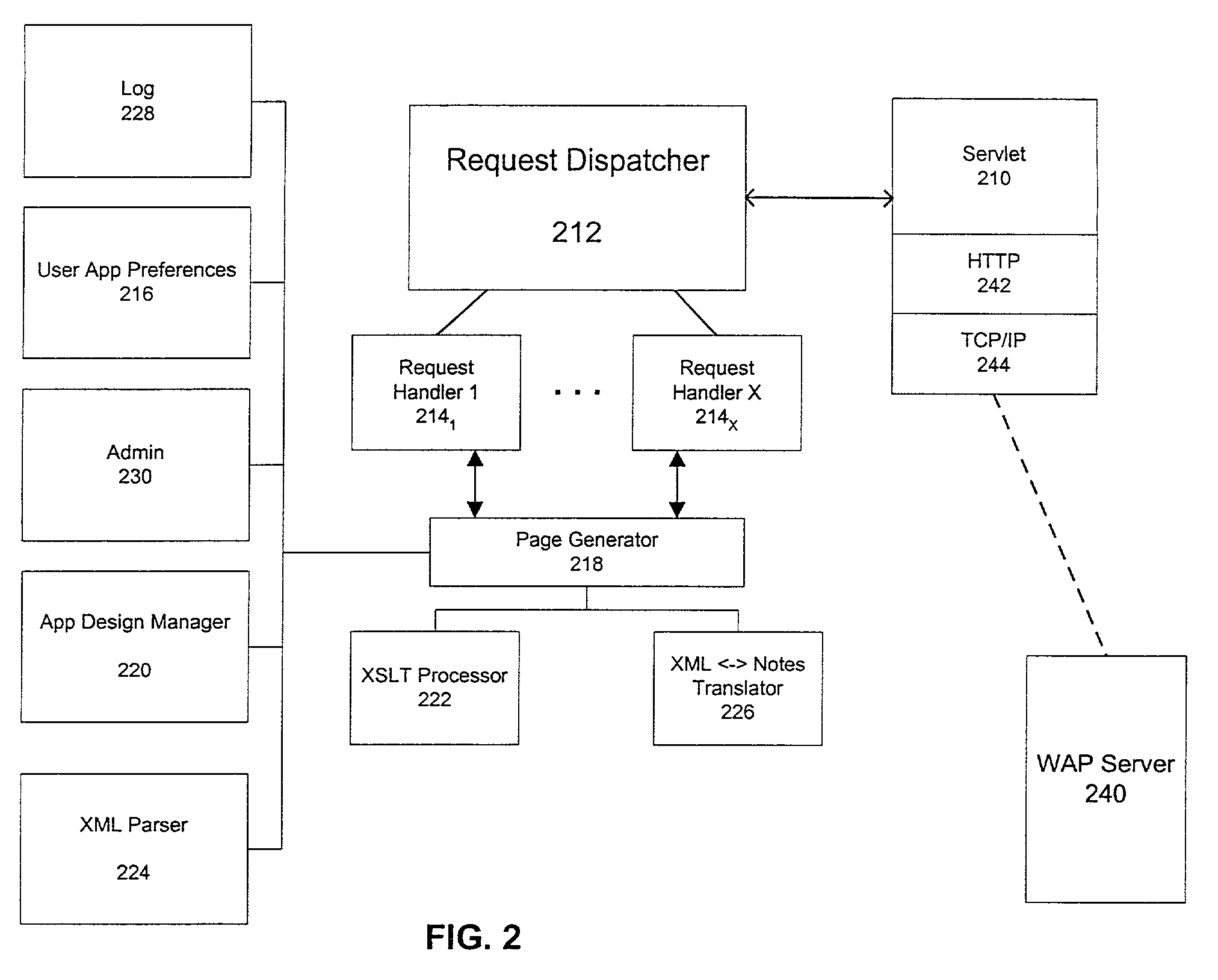
System and method for providing search capabilties on a wireless device
InactiveUS6983310B2Increase reachData processing applicationsSpecial service for subscribersDocumentation procedureWireless data
A system and method for enabling users to send and receive messages and other information from mobile devices and enabling users to access server-based information using mobile devices over wireless data networks are disclosed. The present invention further provides search capabilities on a wireless device. Search criteria may include searching messages (e.g., emails, memos, and / or other correspondences and documents) based on various fields, such as sender, date, subject and other parts of a message. Other search criteria may also be used. The present invention may also provide an application search form to perform various search functions. A search form may contain a formula field where the field may contain a select formula that may be evaluated on the server for the search operation. This formula typically may reference other fields on the search form.
Owner:DAEDALUS GRP LLC
Systems and methods for a search-based email client
InactiveUS20050144241A1Eliminating cogitationExpand the scope ofDigital data processing detailsMultiple digital computer combinationsUser needsRelevant information
A search-based email client may incorporate a number of useful features. A search function can default to a search of all email contexts, thereby eliminating user cogitation over which context an email message may be stored in. Furthermore, the search function can automatically search for related personal content and / or related information on the internet or other computer network, and present this useful information to the user in addition to the returned emails. The search function can be integrated into a user interface to allow for one-click searches on any likely search field. The search function can search the body of email messages by default, thereby widening the scope of default searches and eliminating potentially missed information and user need to proactively widen their search. A search function can search attachments, which also provides a wider search scope.
Owner:OATH INC
Enhanced directory assistance system and method including location search functions
InactiveUS20070072591A1Special service for subscribersRadio/inductive link selection arrangementsTargeted advertisingMobile service
A method for sending a targeted advertising campaign to a plurality of mobile phone devices, comprises the step of receiving geographic information relating to geographic location of mobile phone devices, wherein the information is collected from a plurality of corresponding mobile service providers. The method includes the step of maintaining a subscriber database that contains contact information relating to a plurality of subscribers. The system interacts with an advertiser so as to receive advertising content intended for targeted mobile phone devices. Furthermore, the system communicates the advertising content to the targeted mobile phone devices that are located within a specified distance from a location specified by the advertiser.
Owner:MCGARY FAITH +1
Content navigator graphical user interface system and method
InactiveUS7313805B1Conveniently and efficiently navigateEffectively linkedTelevision system detailsColor television detailsGraphicsRelevant information
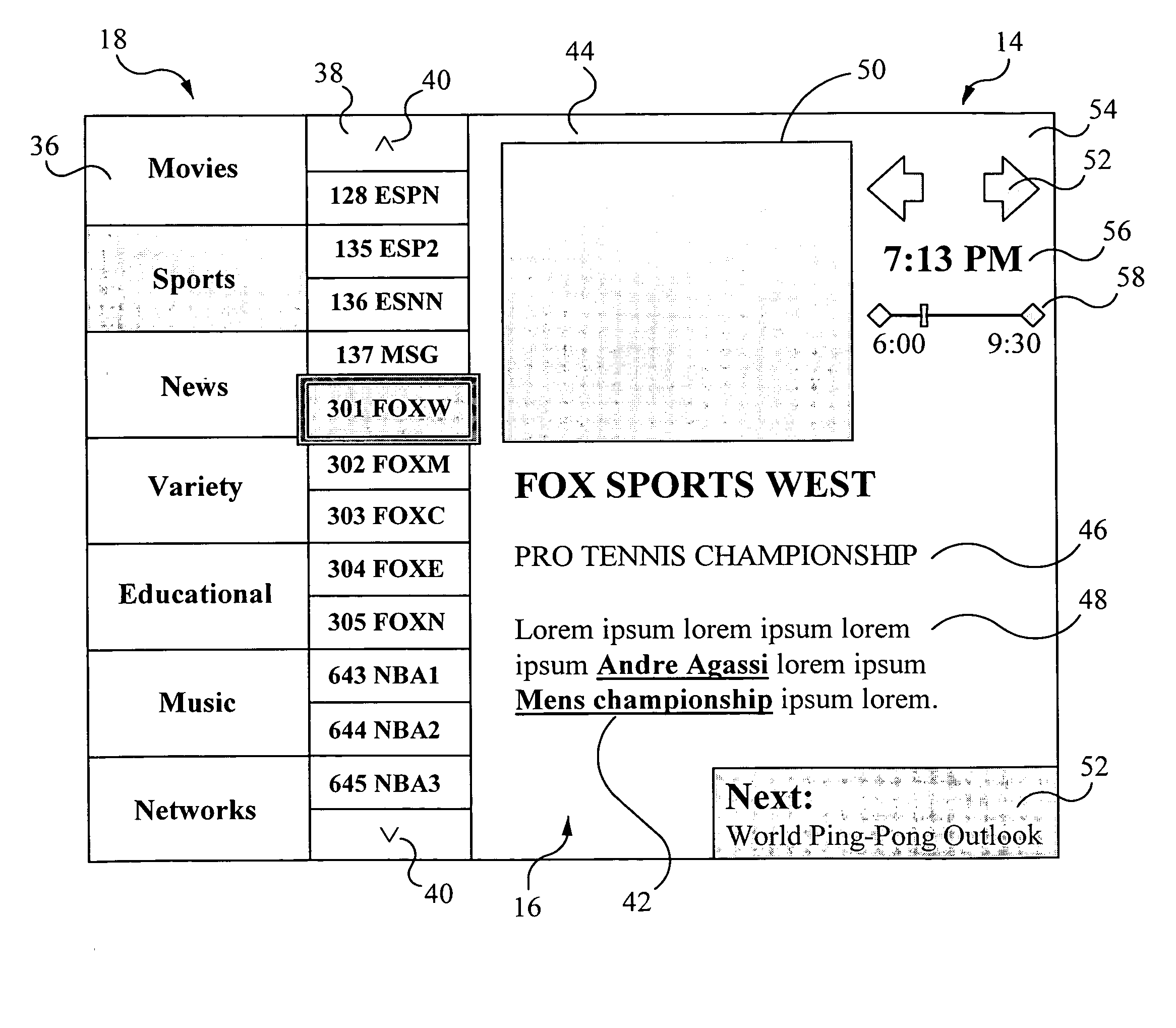
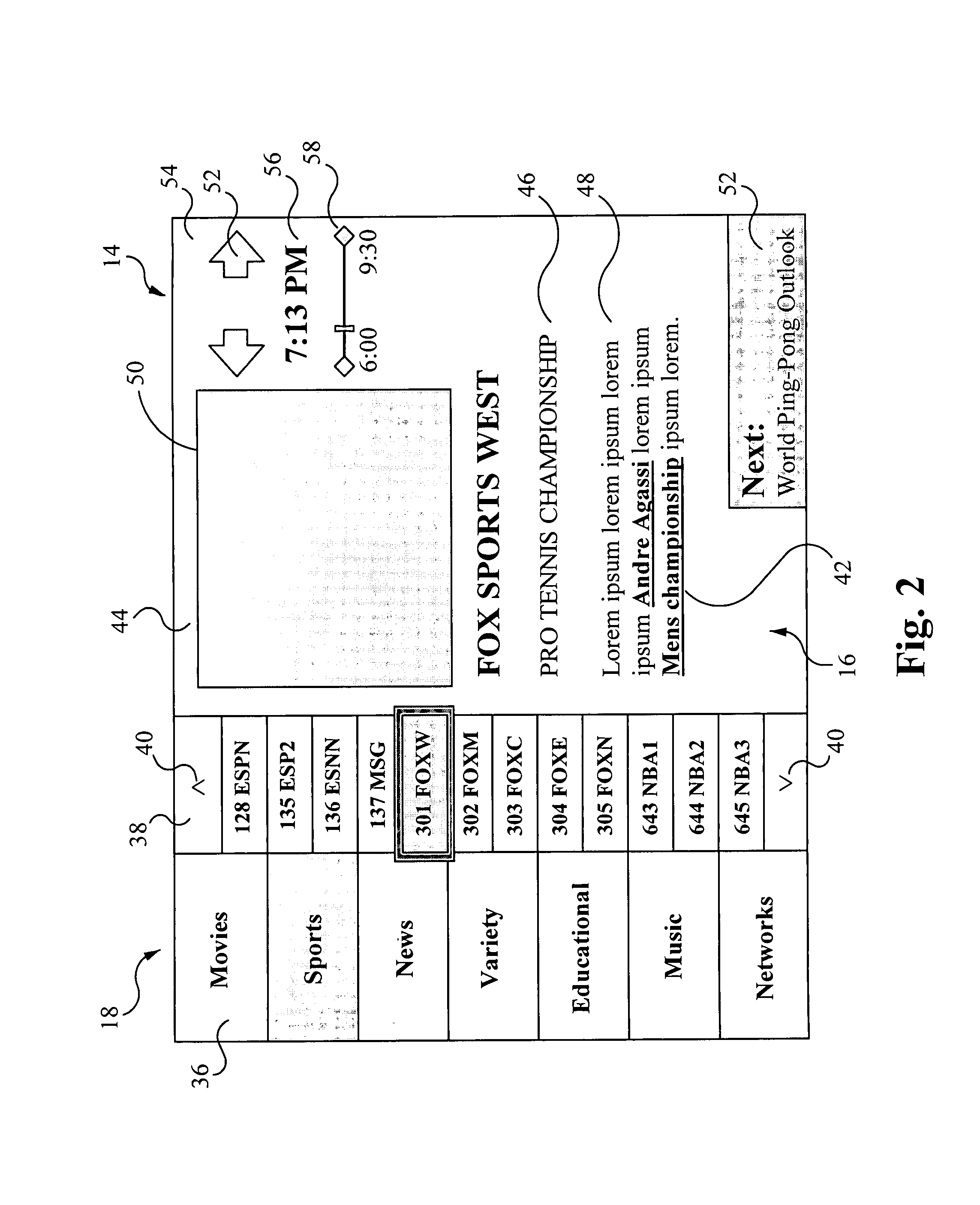
In a system and method for enabling a user to simultaneously display a set of selectable categories, a set of channels related to a selected category, and individual content associated with a selected channel, of potential interest to the user. The system includes a graphical user interface which includes a set of selectable categories, sets of channels, each set of which includes channels which are relevant to each selectable category, and individual content, each of which is associated with a selectable channel and a selectable category. The graphical user interface uses hypertext markup language as the content description language, for enabling generation of guide information with links to related information and search functionality. The graphical user interface is further adapted to enable the selection of a category, a related channel, and associated individual content by the user. The internet websites and the internet content may be displayed in the same context as the video content.
Owner:SONY CORP +1
Case-Centric Medical Records System with Social Networking
A case-centric medical records system with social networking capabilities is disclosed. Using the system, users can build charts that are centered around a single procedure or treatment and include physician notes as well as imagery and video relating to the procedure. Users can also build social networks around their records by identifying colleagues with whom chart data can be shared. Search functions allow the charts to be searched by diagnosis and procedure codes or by other keywords or information. Users can search their networks of colleagues for relevant experience and expertise and can search and review their colleagues' charts to gain insights.
Owner:SURGICHART
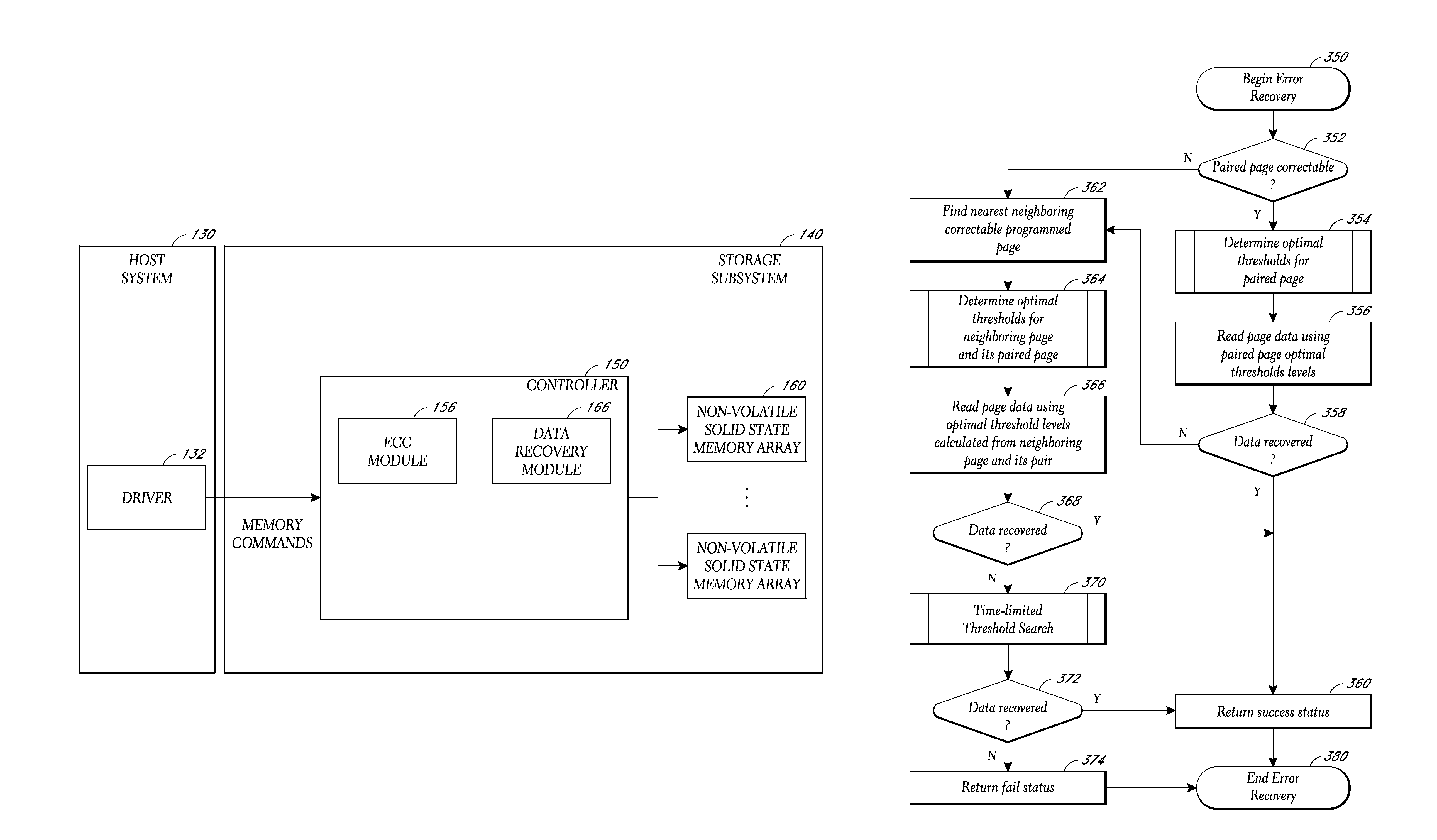
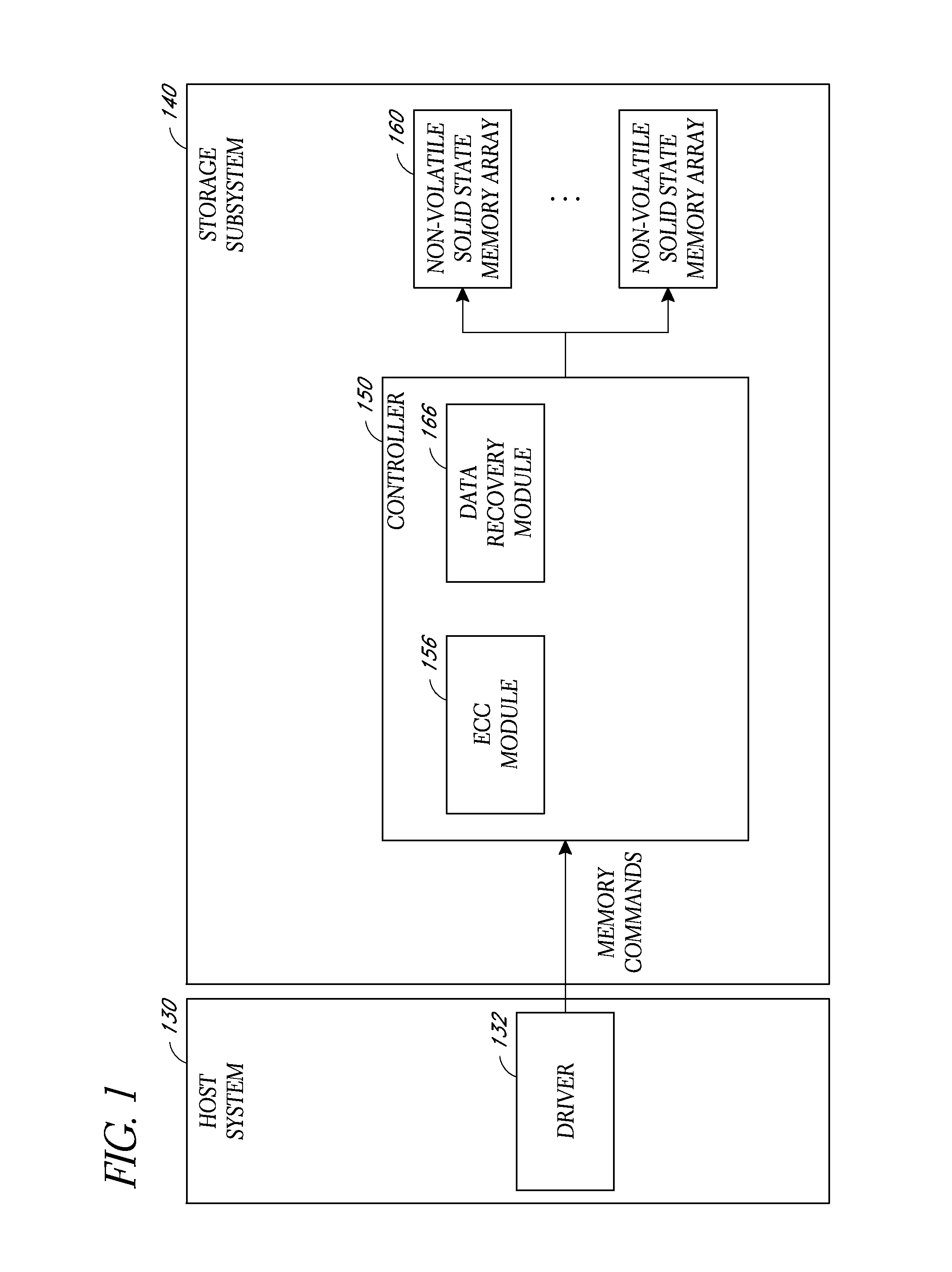
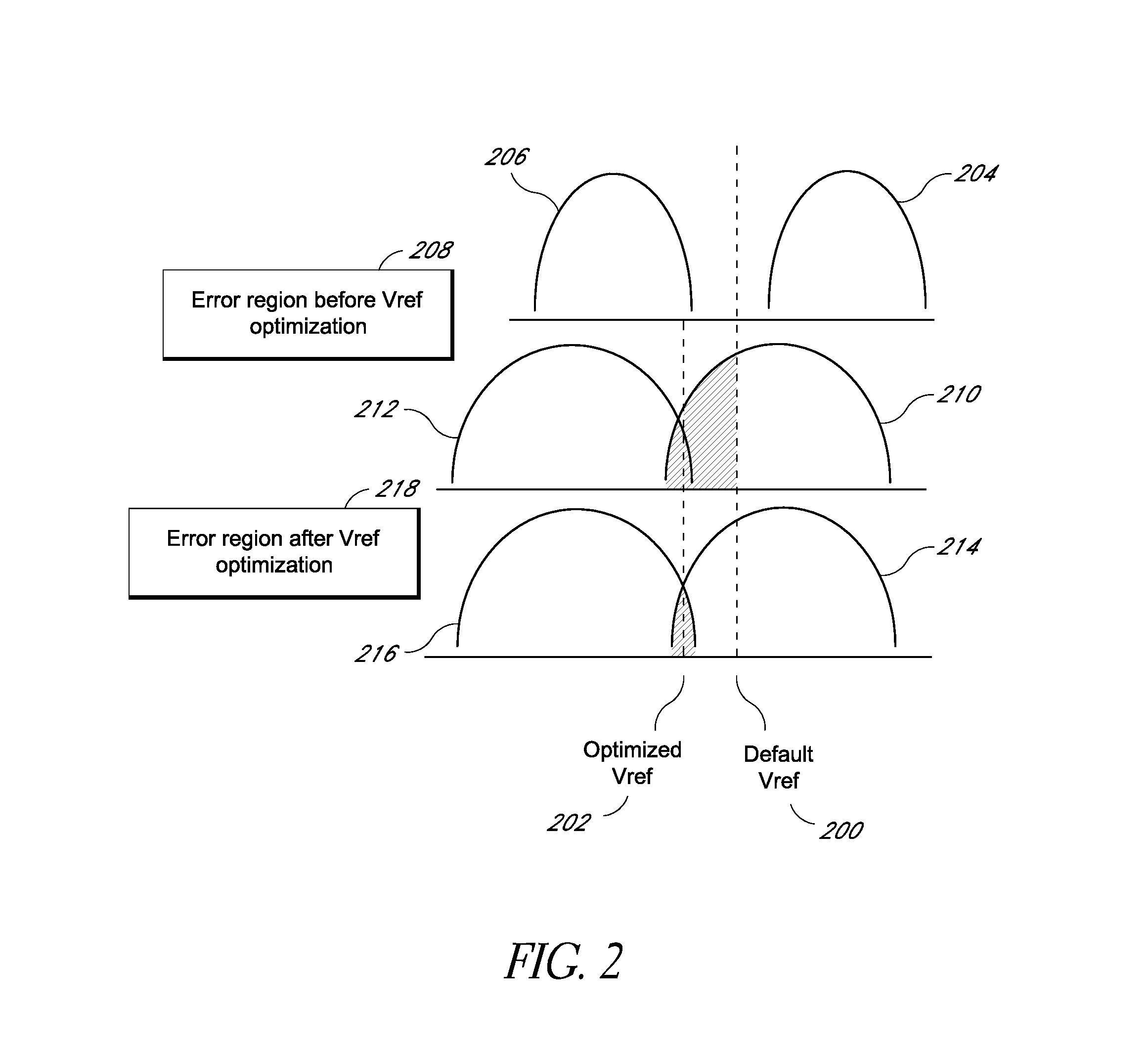
System and method for data recovery in a solid state storage device
Embodiments of solid-state storage system are provided herein include data recovery mechanism to recover data upon detection of a read error (e.g., an uncorrectable ECC error) in a storage element such as a page. In various embodiments, the system is configured to determine optimal reference voltage value(s) by evaluating the reference voltage value(s) of page(s) that are related to the page where the failure occurred. The related page(a) may include a page that is paired with the initial page where the failure occurred (e.g., the paired pages reside in a common memory cell), or a neighboring page that is physically near the page where the initial page, and / or a paired page of the neighboring page. In another embodiment, the system is configured to perform a time-limited search function to attempt to determine optimal reference voltage values through an iterative process that adjusts voltage values in a progression to determine a set of values that can retrieve the data.
Owner:WESTERN DIGITAL TECH INC
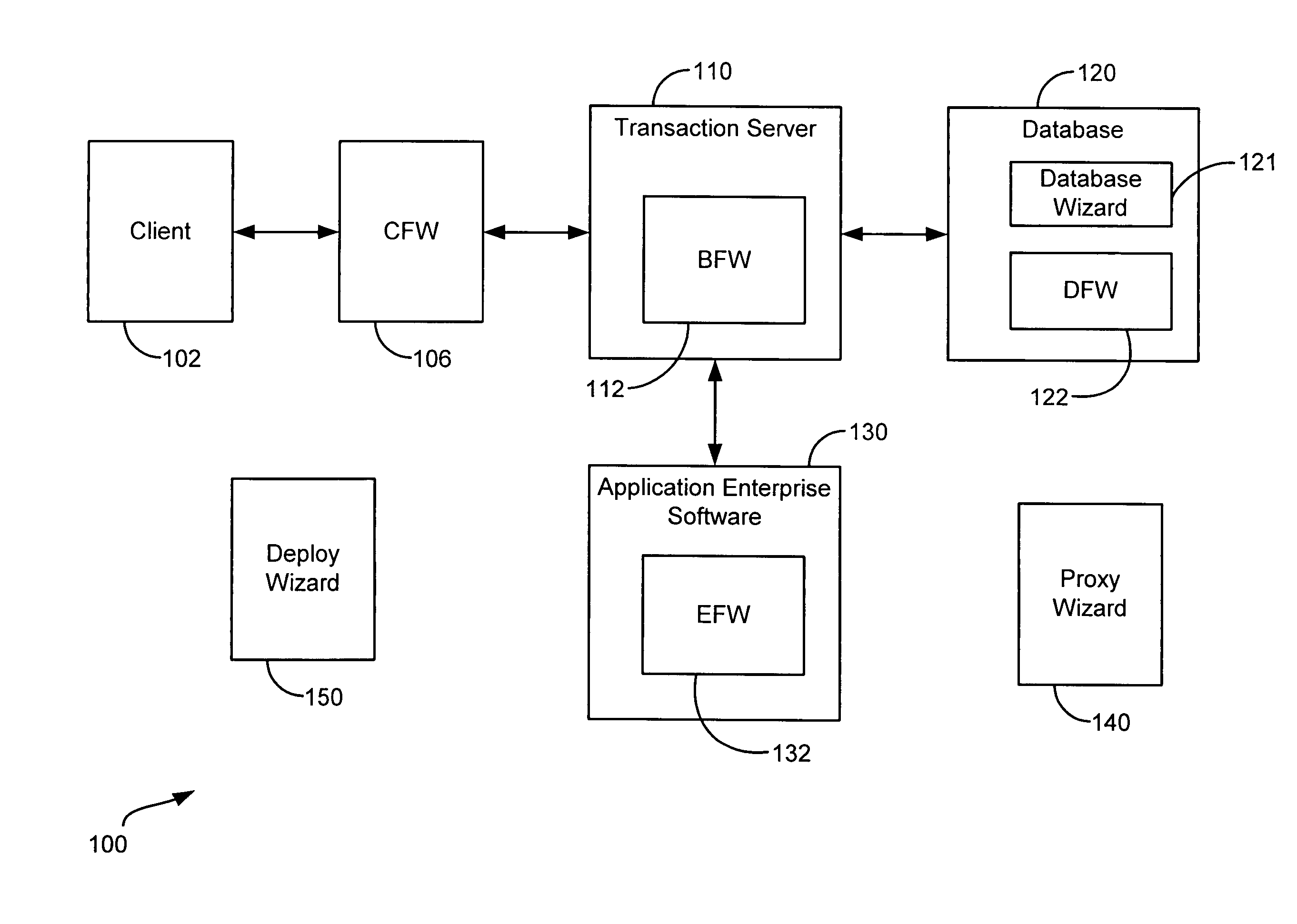
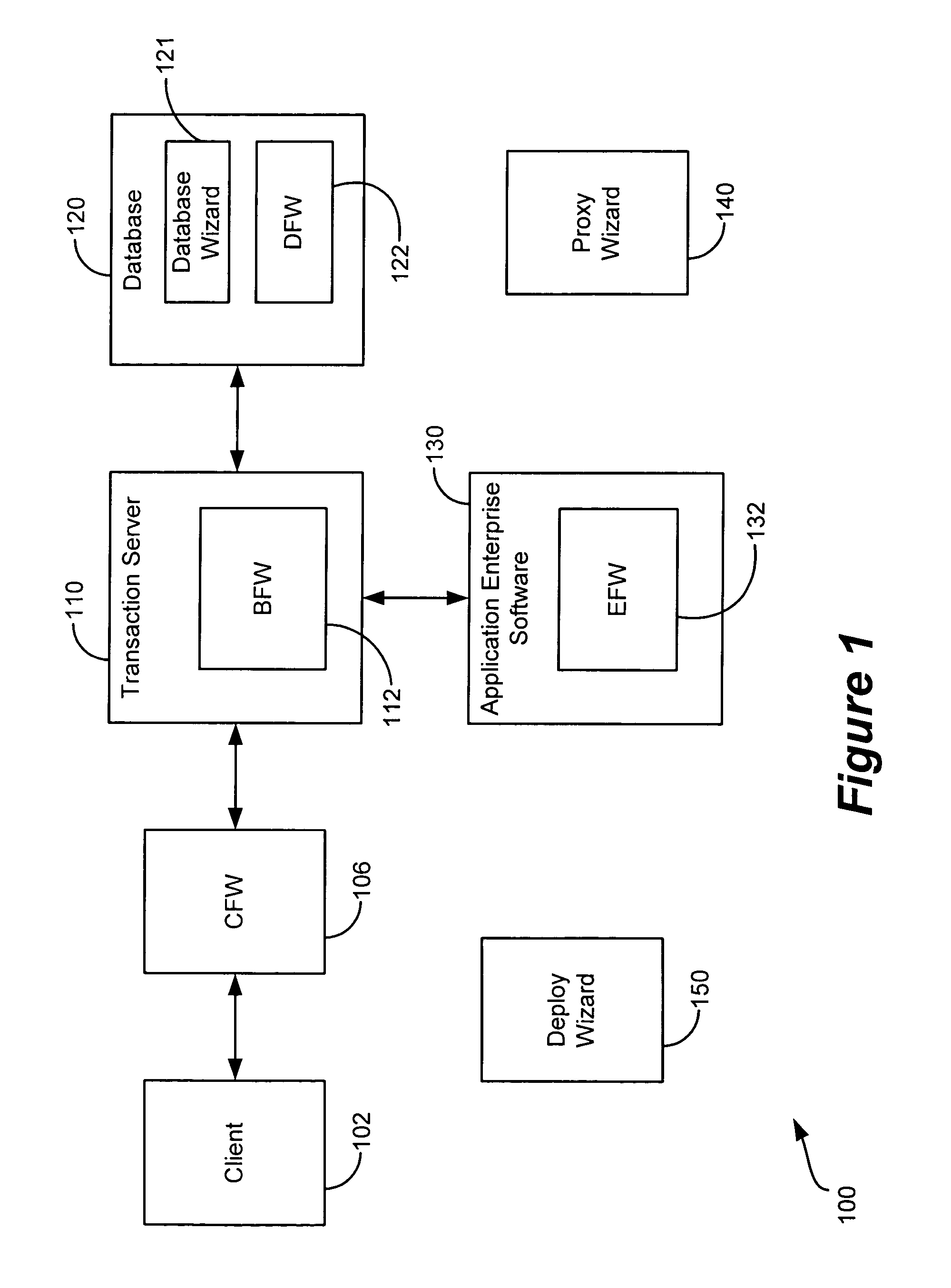
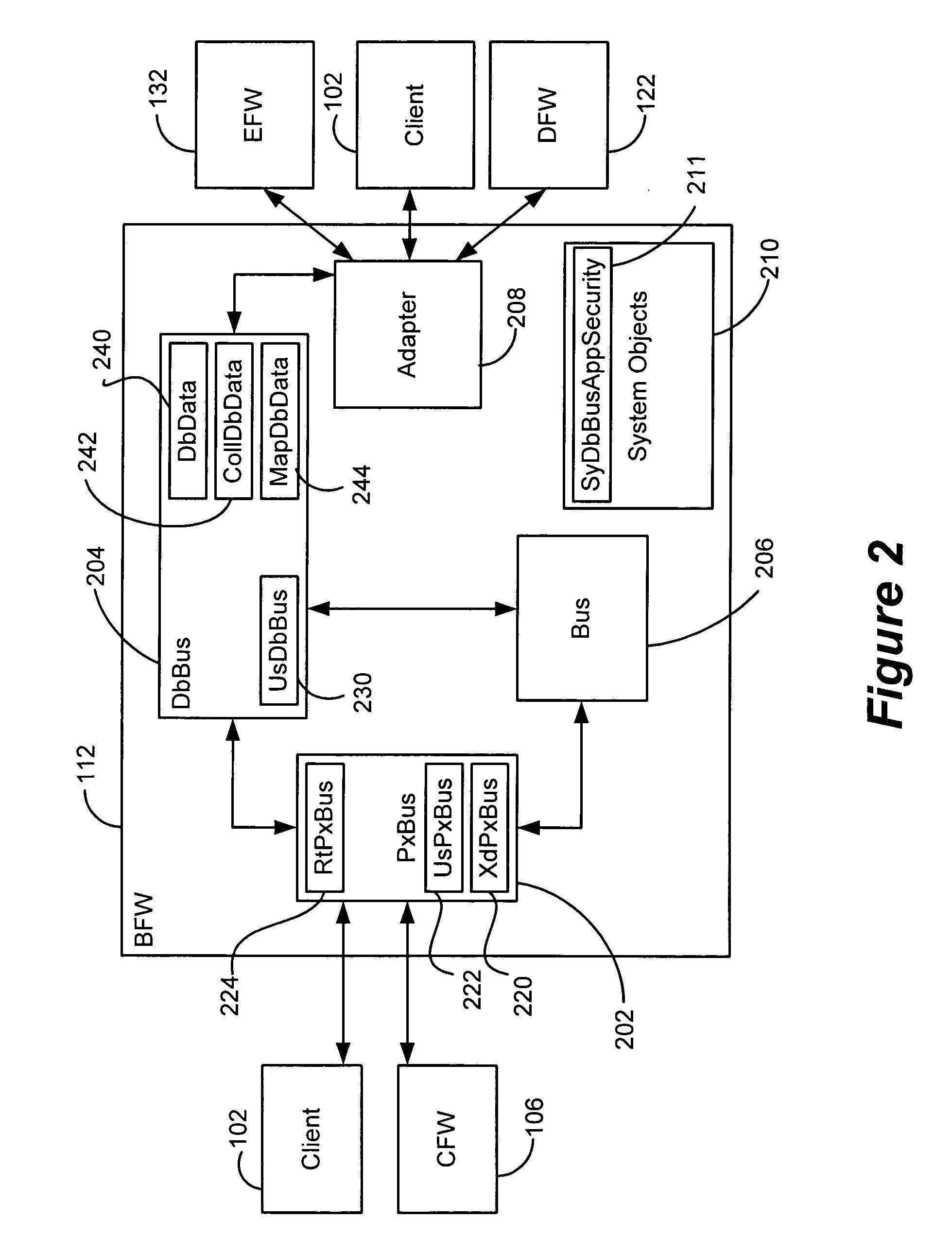
Generic framework for applying object-oriented models to multi-tiered enterprise applications
A system and method are provided for the structured, rapid development and deployment of software components that together, would constitute a robust multi-tiered enterprise software application. Four sub-components are provided for handling various aspects of the business objects. A client framework is used to interact with client users and client software processes. A database framework is used to handle data retention and search functions. An external framework is used to interact with software processes that are outside the gambit of the present system. Finally, a business framework is used to operate the business objects themselves. The business framework can be configured under the services of a transaction server.
Owner:MARATHON PETROLEUM
Systems and methods for integrating search capability in interactive video
InactiveUS20090113475A1Eliminate needTelevision system detailsDigital data processing detailsInteractive videoAmbiguity
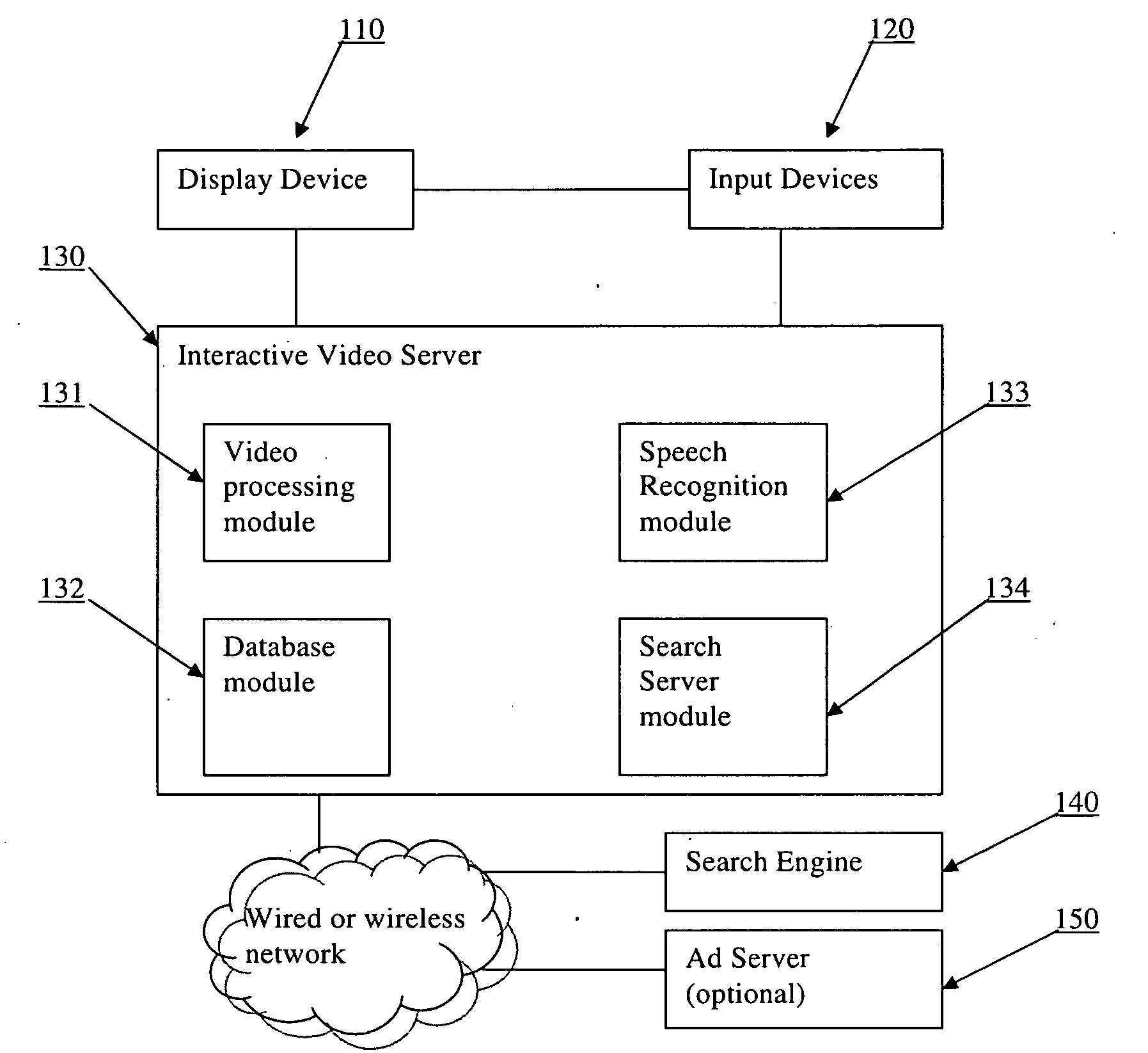
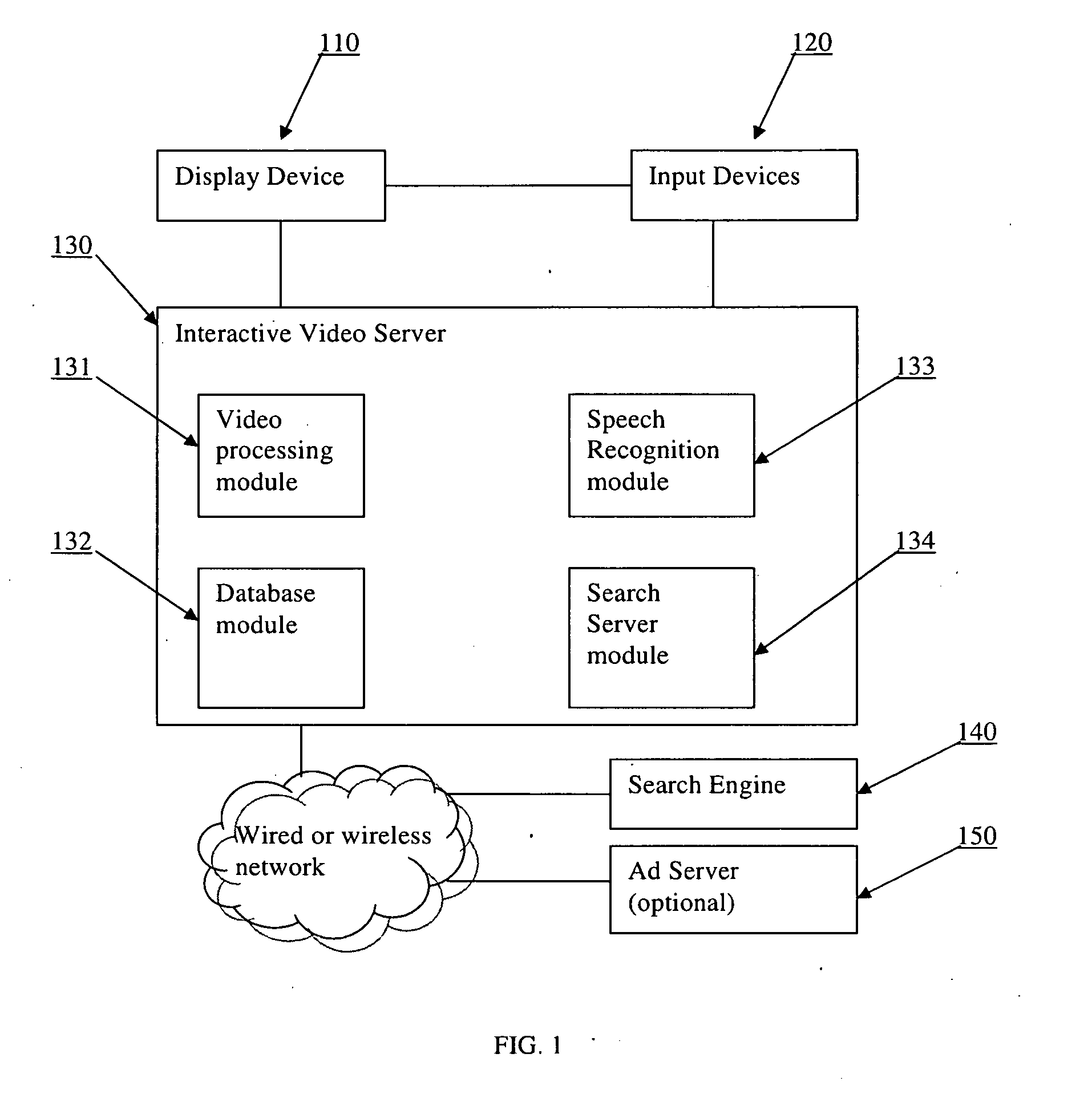
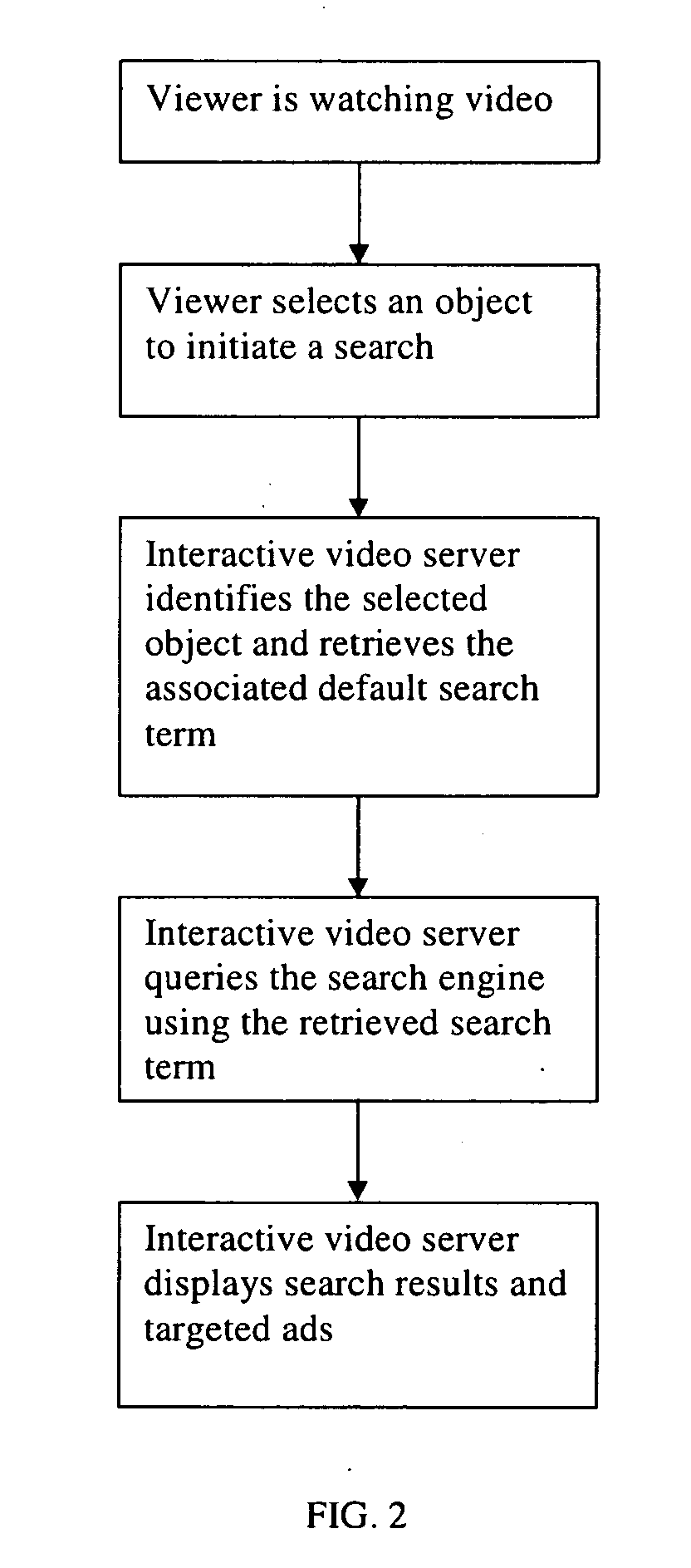
This invention is a system and method that enables video viewers to search for information about objects or events shown or mentioned in a video through a search engine. The system integrates search capability into interactive videos seamlessly. When viewers of such a video want to search for information about something they see on the screen, they can click on it to trigger a search request. Upon receiving a search request, the system will automatically use an appropriate search term to query a search engine. The search results will be displayed as an overlay on the screen or in a separate window. Targeted ads that are relevant to the search term are delivered and displayed alongside search results. The system also allows viewers to initiate a search using voice commands. Further, the system resolves ambiguity by allowing viewers to select one of multiple searchable items when necessary.
Owner:LI YI
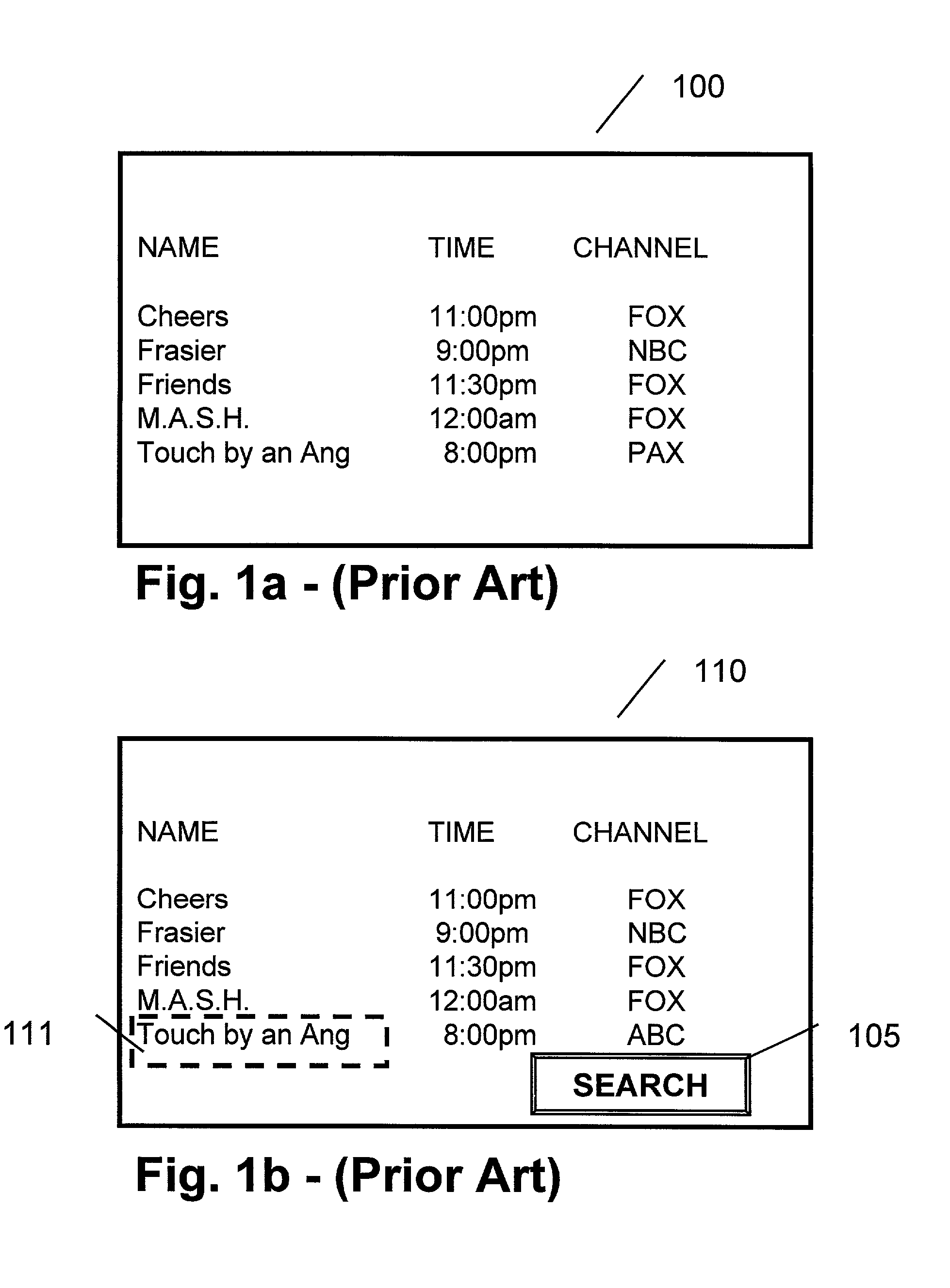
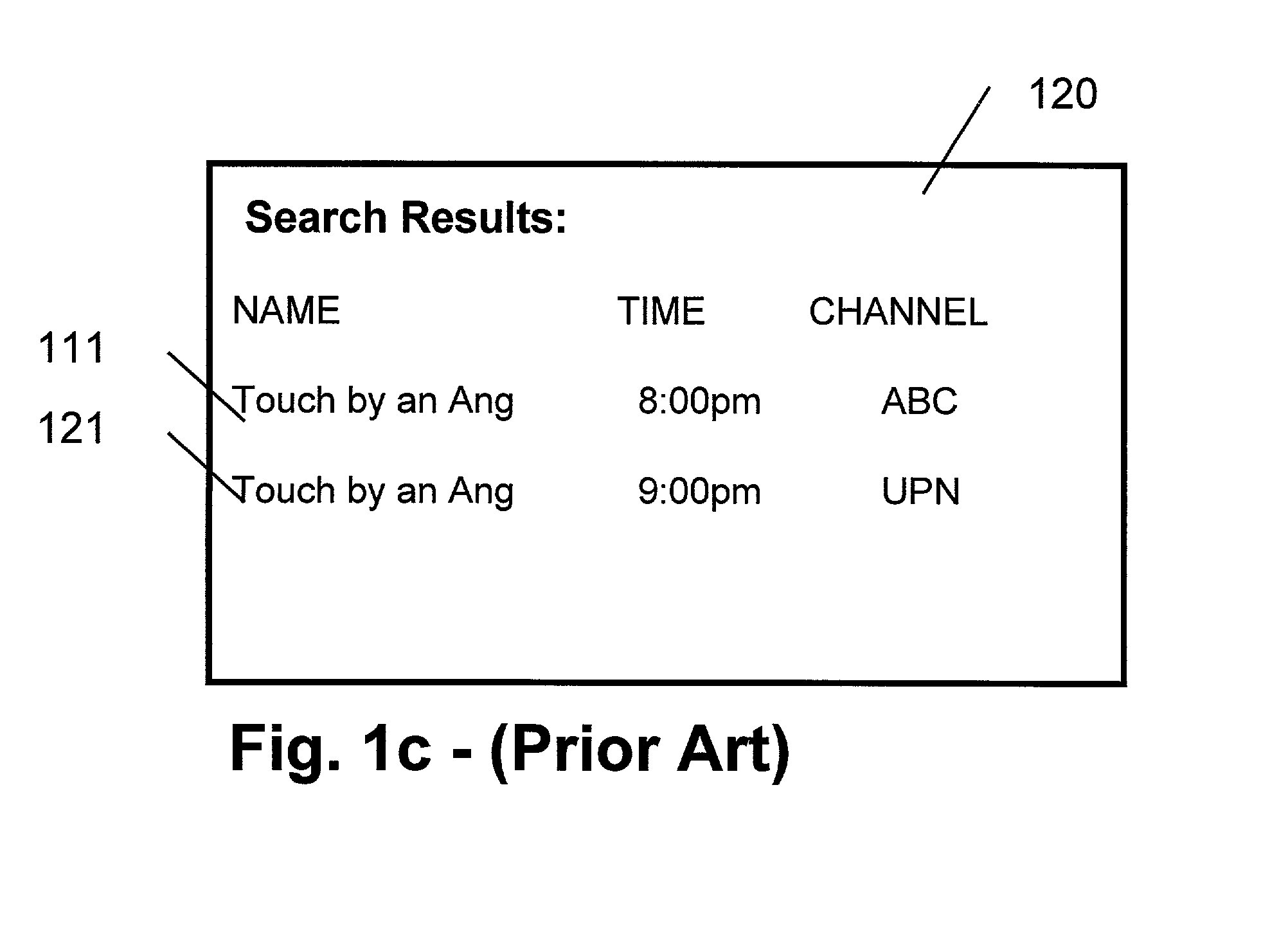
Method and apparatus for finding the same of similar shows
InactiveUS7213256B1Television system detailsColor television detailsExact matchElectronic program guide
A method and apparatus providing for expanded search functionality in an electronic program guide (EPG) for television is described. The expanded search function finds show titles that are the same or similar to the show title of the program data currently displayed by the EPG. The expanded search function also finds shows similar to the one currently displayed by the EPG by using additional search elements based on the descriptive part of the EPG program data, such as actors, director, genre, etc., as well as search parameters based on the show time, channel, etc. Rather than only finding exact matches, the expanded search function uses fuzzy logic to find near matches and prioritizes the results according to the search elements and parameters as specified by the viewer.
Owner:JLB VENTURES LLC
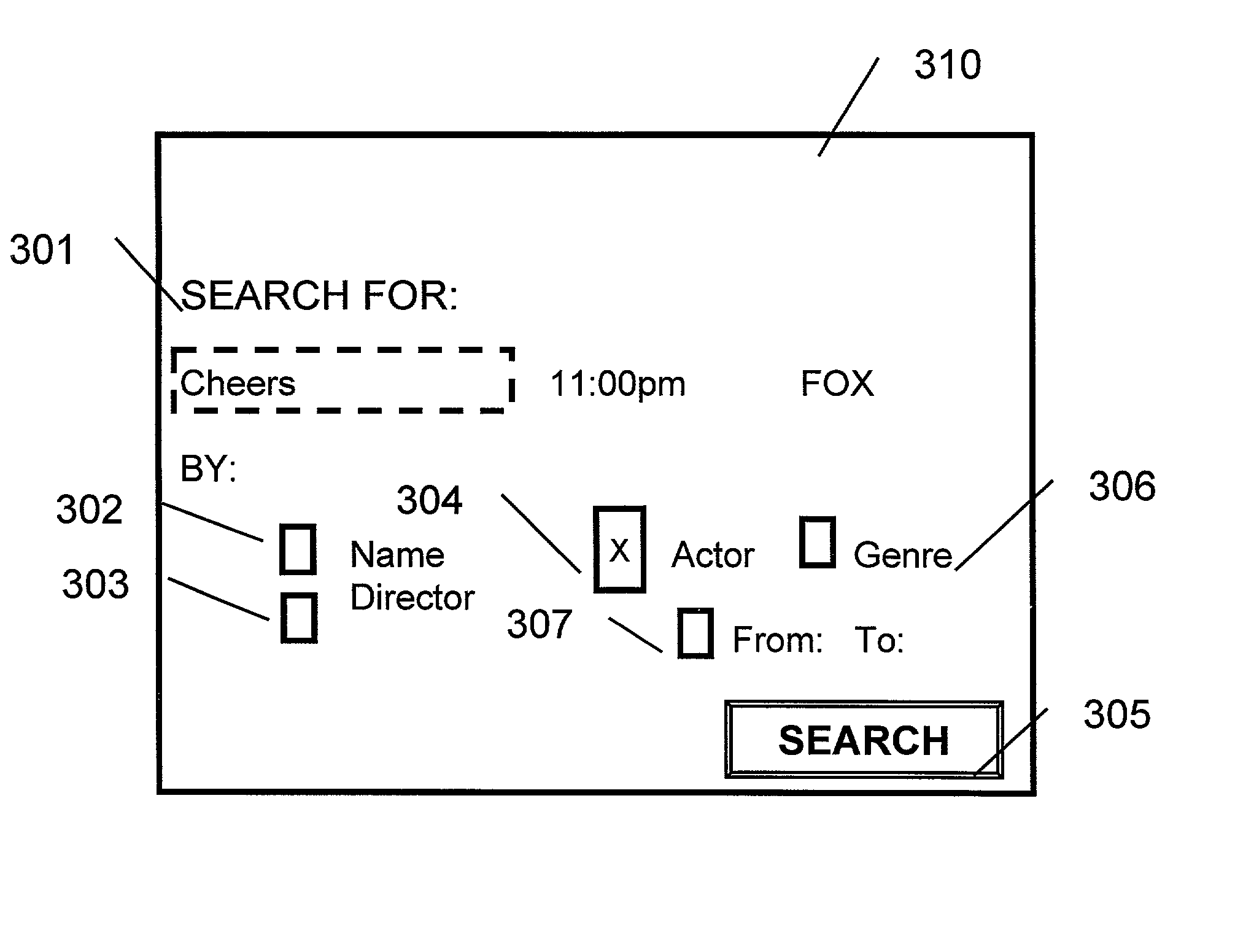
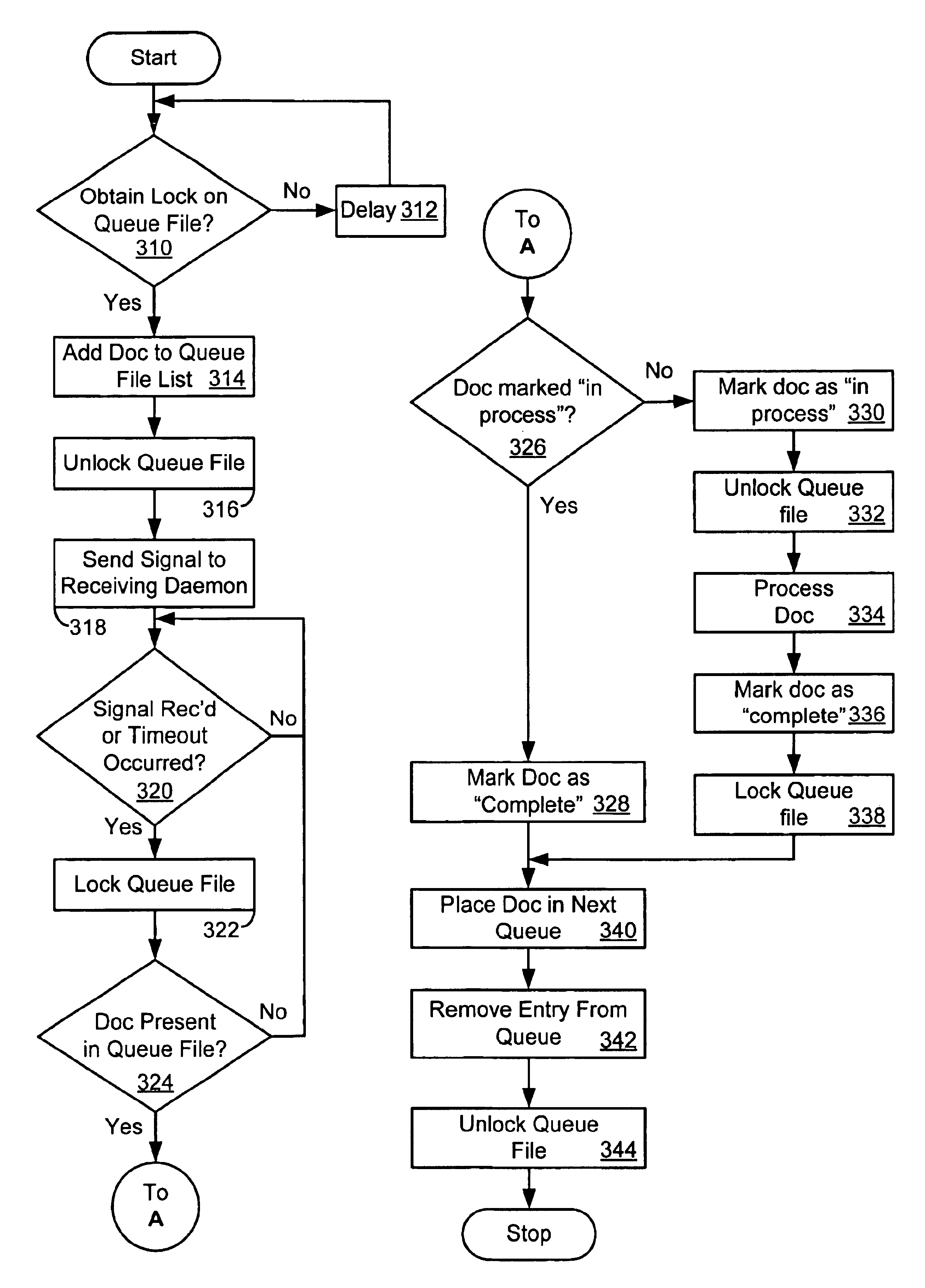
System and method of managing queues by maintaining metadata files having attributes corresponding to capture of electronic document and using the metadata files to selectively lock the electronic document
InactiveUS6978297B1Multiple digital computer combinationsOffice automationElectronic documentGraphics
A method and apparatus for managing electronic documents within a network. A series of processes perform electronic document capture, indexing, and searching functions within a networked environment. A graphical web-based user interface is provided to facilitate user interaction with the apparatus.
Owner:RICOH KK
Server-centric search function in an interactive program guide
InactiveUS7373652B1Quickly and efficiently searchTelevision system detailsColor television detailsDistribution systemData library
Techniques for searching a program guide database. In accordance with a method, one or more search criteria (e.g., keywords) are received and a request for a search is then sent, along with the search criteria, to a head end of an information distribution system. In response, one or more search results are received from the head end. In this server-centric system, the program guide database is searched at the head end. The search results can be displayed on one search result IPG page (or more, if necessary) or displayed one at a time on the respective IPG page that includes the search result. Upon receiving an indication that a particular search result has been selected, one or more streams associated with the selected search result can be retrieved and decoded to recover the selected program, which can then be displayed.
Owner:TIVO CORP
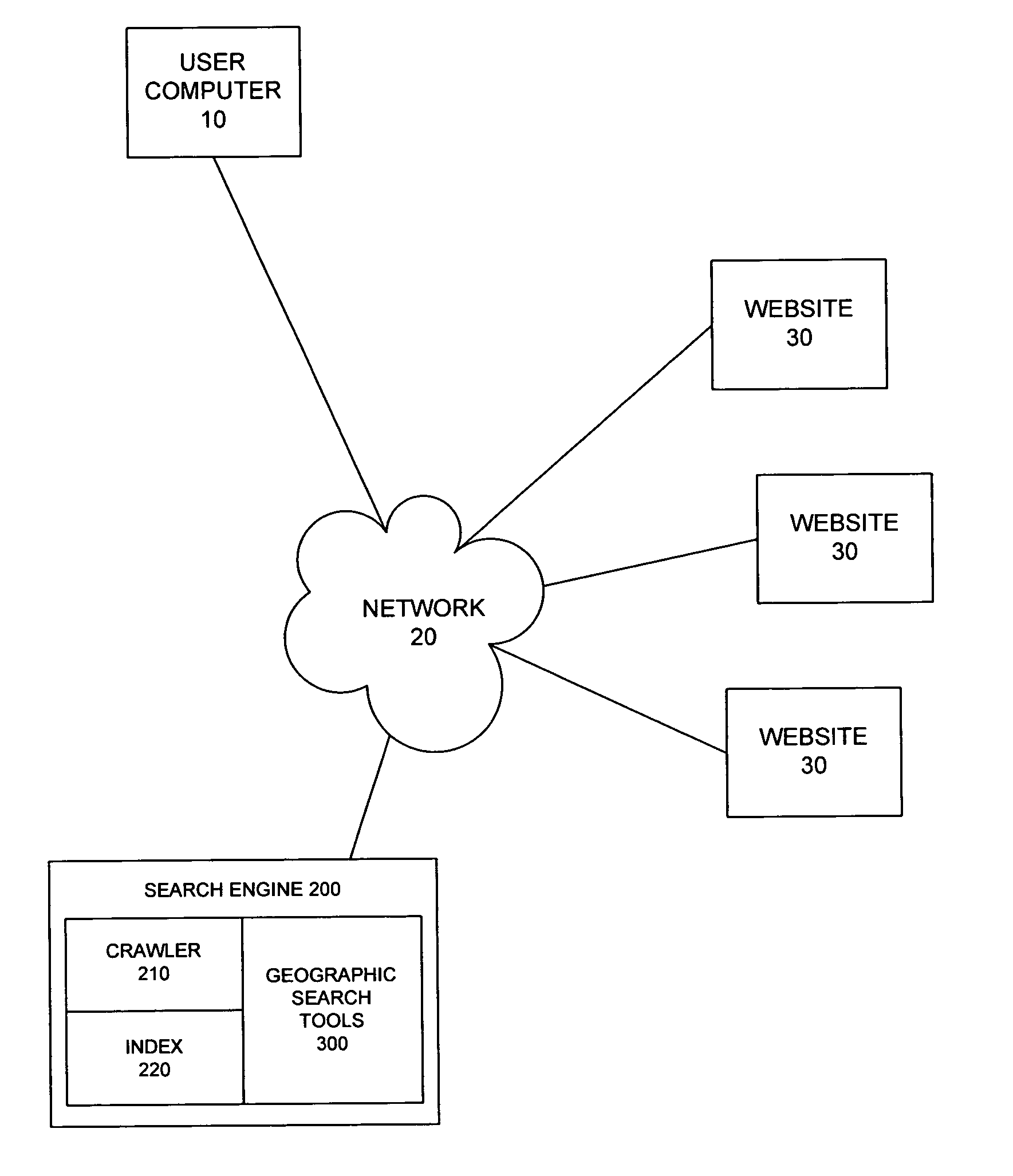
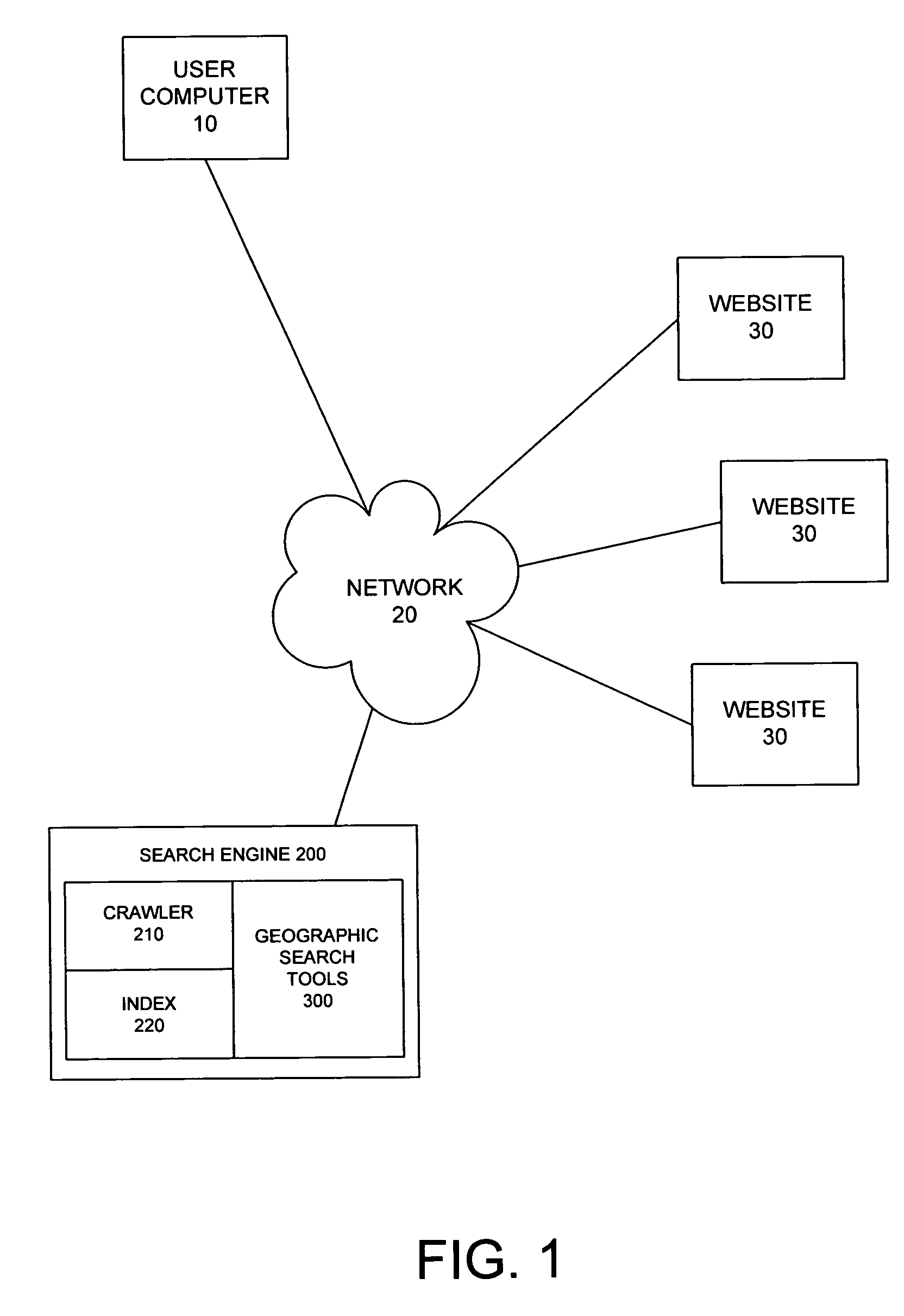
System and method for providing a geographic search function
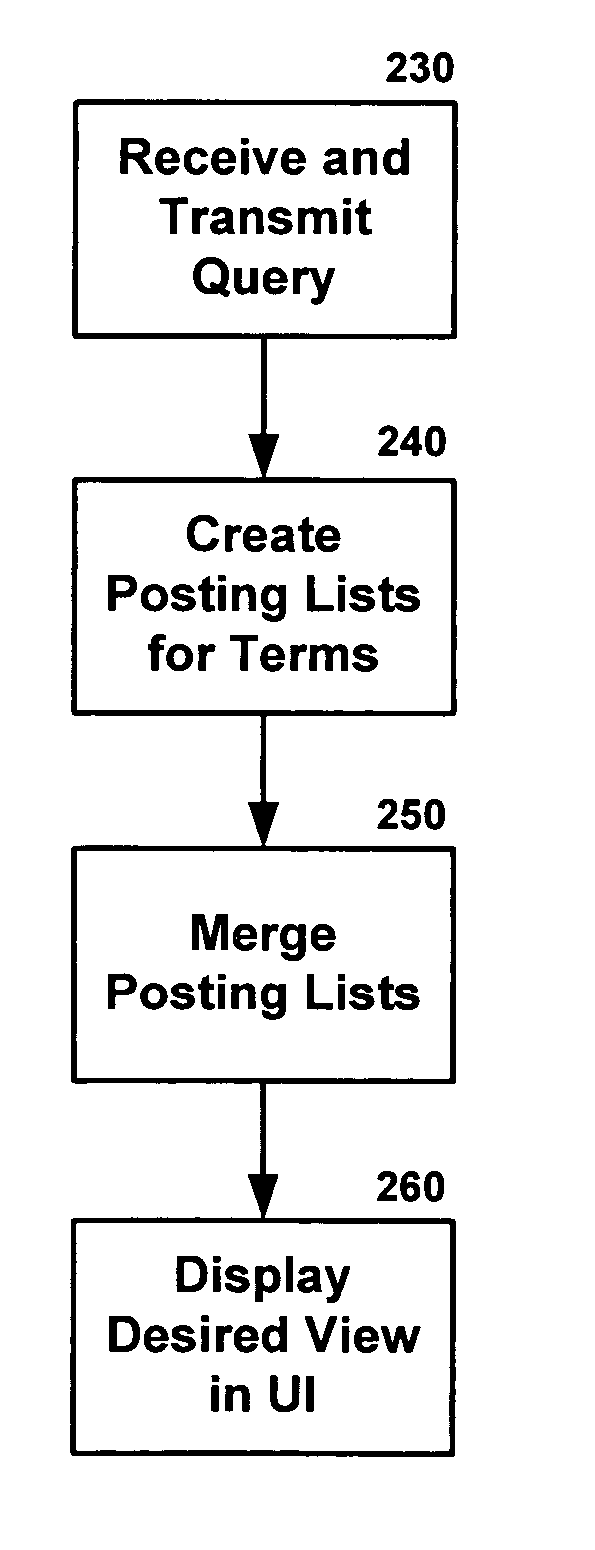
InactiveUS20060106778A1Digital data information retrievalDigital data processing detailsSearch engine indexingSearch function
A system and method are provided for implementing a geographic search mode in connection with a search engine. The method may include indexing geographic locations for resources available to the search engine in a search engine index. The method may additionally include determining a target location for a particular user upon receiving a user query from the particular user and searching the search engine index for geographic location matches matching the target location.
Owner:MICROSOFT TECH LICENSING LLC
Devices, systems, and methods for communicating pattern matching results of a parallel pattern search engine
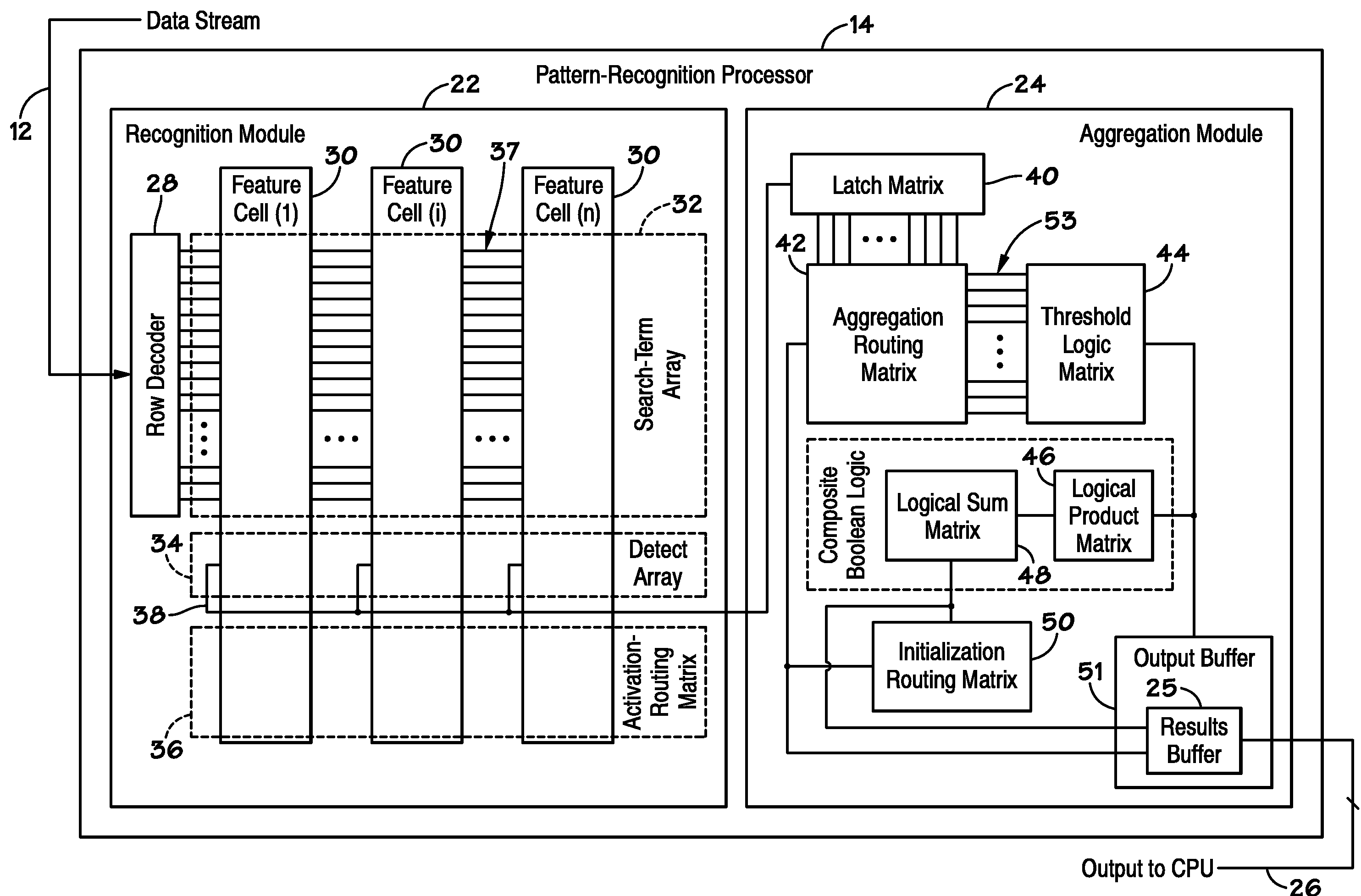
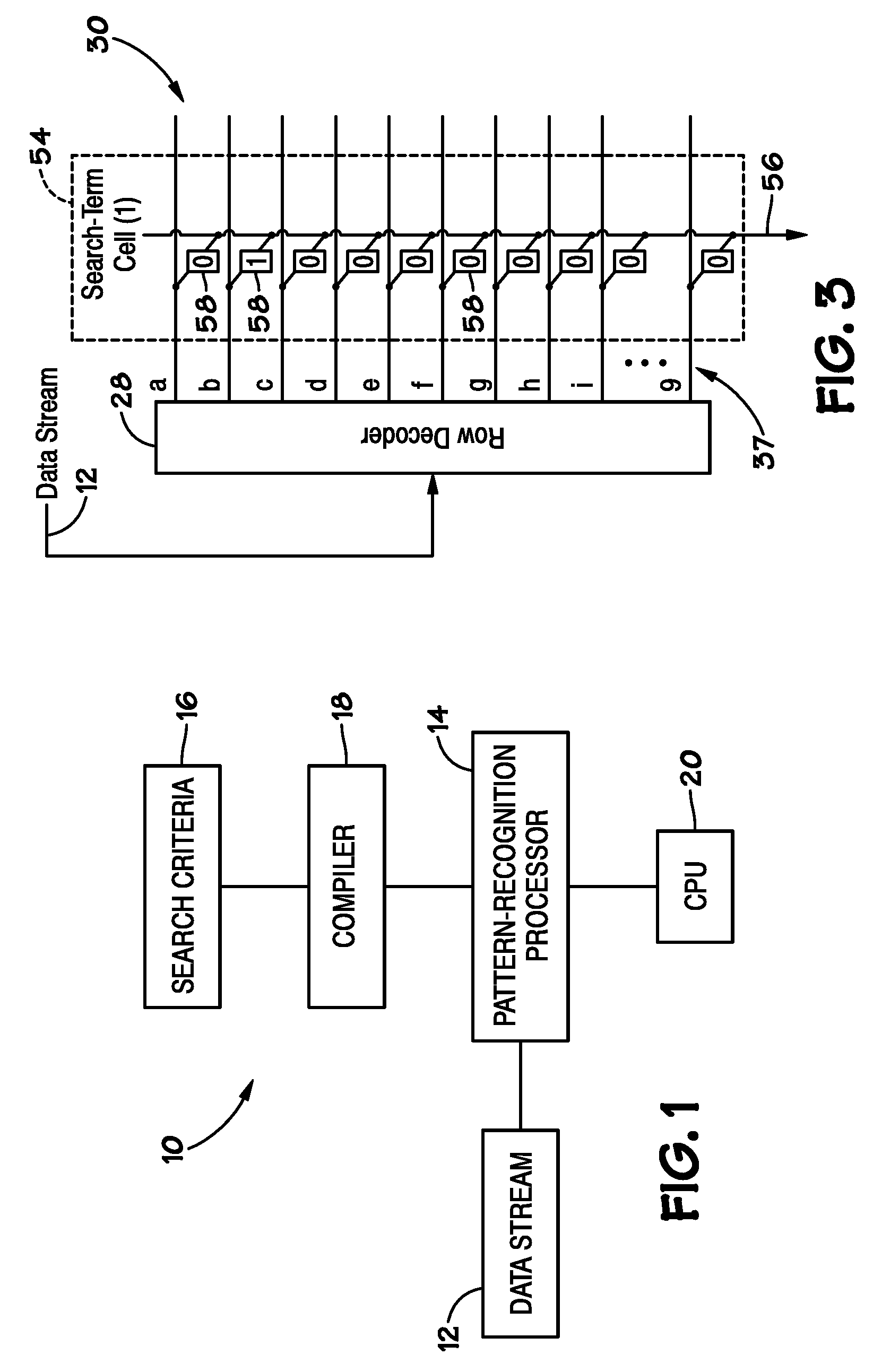
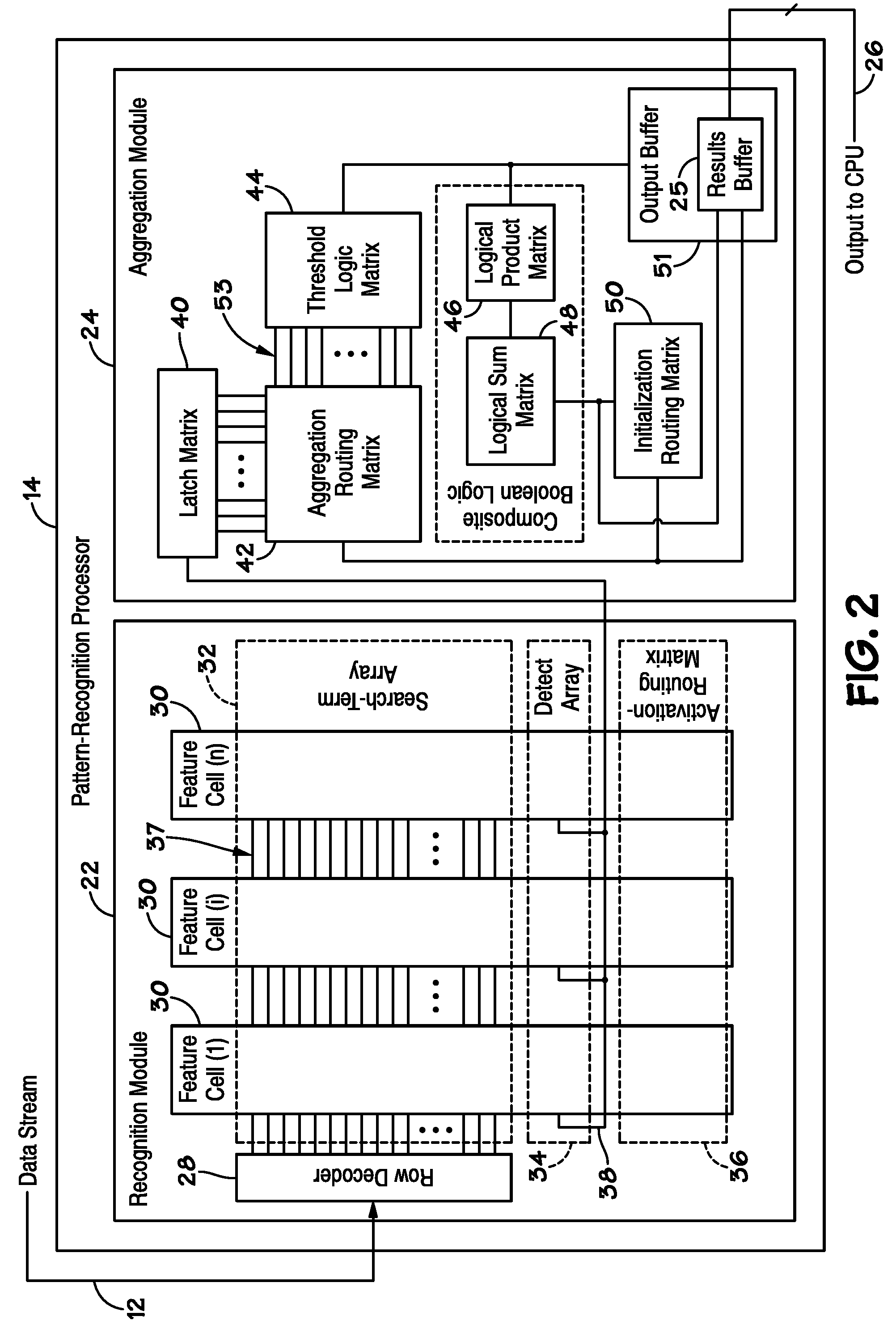
ActiveUS20100185647A1Error detection/correctionComparison of digital valuesSearch functionPattern recognition
Disclosed are methods and devices, among which is a system that includes a device that includes one or more pattern-recognition processors for searching a data stream. The pattern-recognition cluster may include various search pattern matching matrices and mask modules which may be utilized to perform various searching functions. Additionally, a buffer may be utilized to individually store the various results from pattern matching matrices and mask modules for subsequent retrieval.
Owner:MICRON TECH INC
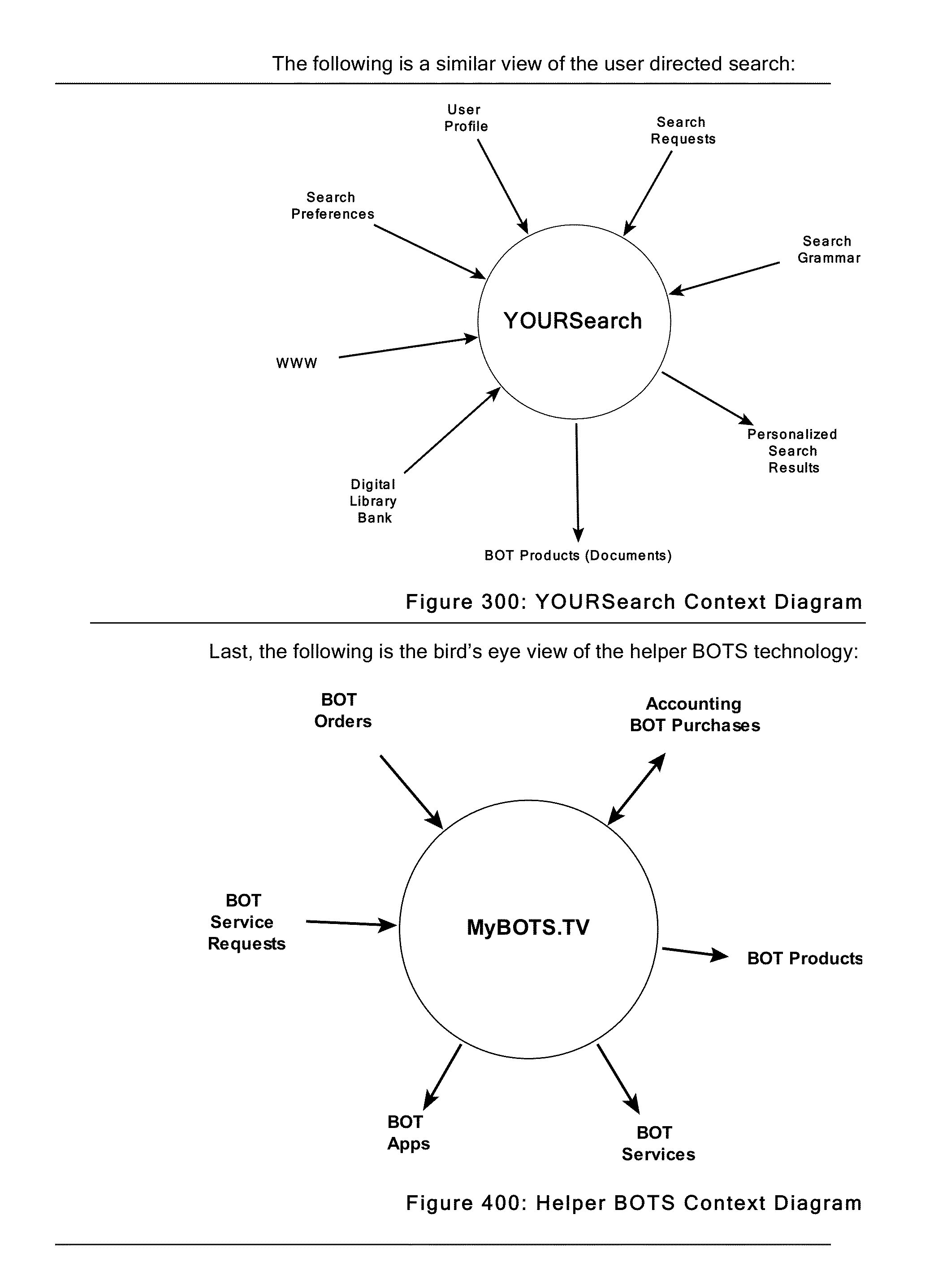
Personal helper bot system
InactiveUS20160044380A1Eliminate needFocused and complexTelevision system detailsColor television detailsCredit cardDocumentation procedure
MyBOTS.Tv—the personal helper BOT system utilizes a customizable personal assistant in the form of an avatar to engage its owner in a conversational manner with natural language commands to coordinate activity of a team of autonomous helper BOTs. Among a variety of other tasks, BOTs, which are software applications that run automated tasks over the Internet, collaborate to create the owner's schedule, maintain his / her to-do list, obtain personally interesting information, provide personalized services and searches, perform web site transactions, use all types of web apps, complete tasks and / or synthesize useful products for their owners.In some embodiments, the helper BOTs system leverages Digital Library (DL) Architectures to house elements that they intelligently serve. The underlying Digital Library Architecture features an induction process that elicits facts about incoming elements that can be judged by a panel of agents. Agents judge elements according to areas of discretion which are of interest to the consumer population. The judgments are then stored as part of each element's metadata. Helper BOTs then deliver the elements intelligently by probabilistically ranking, sorting, classifying, and / or presenting and serving them to users in accordance with value preferences indicated in their profiles. One such embodiment, (which has been previously published as a Virtual Knowledge Architecture for Interactive Television) ranks and serves TV programs to people based on the value preferences set in their profile(s).In other embodiments, helper BOTs leverage user-directed search paradigms to refine and customize the search function according to the searcher's preferences, style and demographic information. In these embodiments, helper BOTs are directed by way of a search construction wizard to return search results in accordance with searcher profiles and demands such as language, context of content, age of document, and age appropriateness. In this regard, searcher preferences refer not only to the search itself, but to the style, presentation, and appropriateness of the search results which can not only be a list of links but delivered as synthesized living document products incorporating new media elements.Some helper BOT embodiments will help people to perform financial transactions requiring highly sensitive and personal information such as credit card numbers, bank account information and the like. These embodiments require the use of BOT security. BOT security will utilize x.509 digital certificate technology assigned to the avatar by its human owner. The cryptographic key will be utilized to perform all related transactions and protect any information deemed sensitive on behalf of its owner in a secure manner through secure network tunnels.Further embodiments enable an extensible set of commercially available BOTs to be obtained on the MyBOTs.Tv web site in the BOTS Store. This has begun with the 12 “EmBOTiments” presented here. These BOTs perform individual tasks autonomously but may also work in collaboration with each other. Each BOT processes inputs and can be parameterized. Hence, a BOT API enables the creation of stored programs that capture the teamwork interaction and makes their function re-usable. An extensible grammar makes it possible for the evolving baseline of useful stored programs to be called by name so that BOT teams can be dispatched by the user's avatar on demand.
Owner:BARRETT BERTRAND
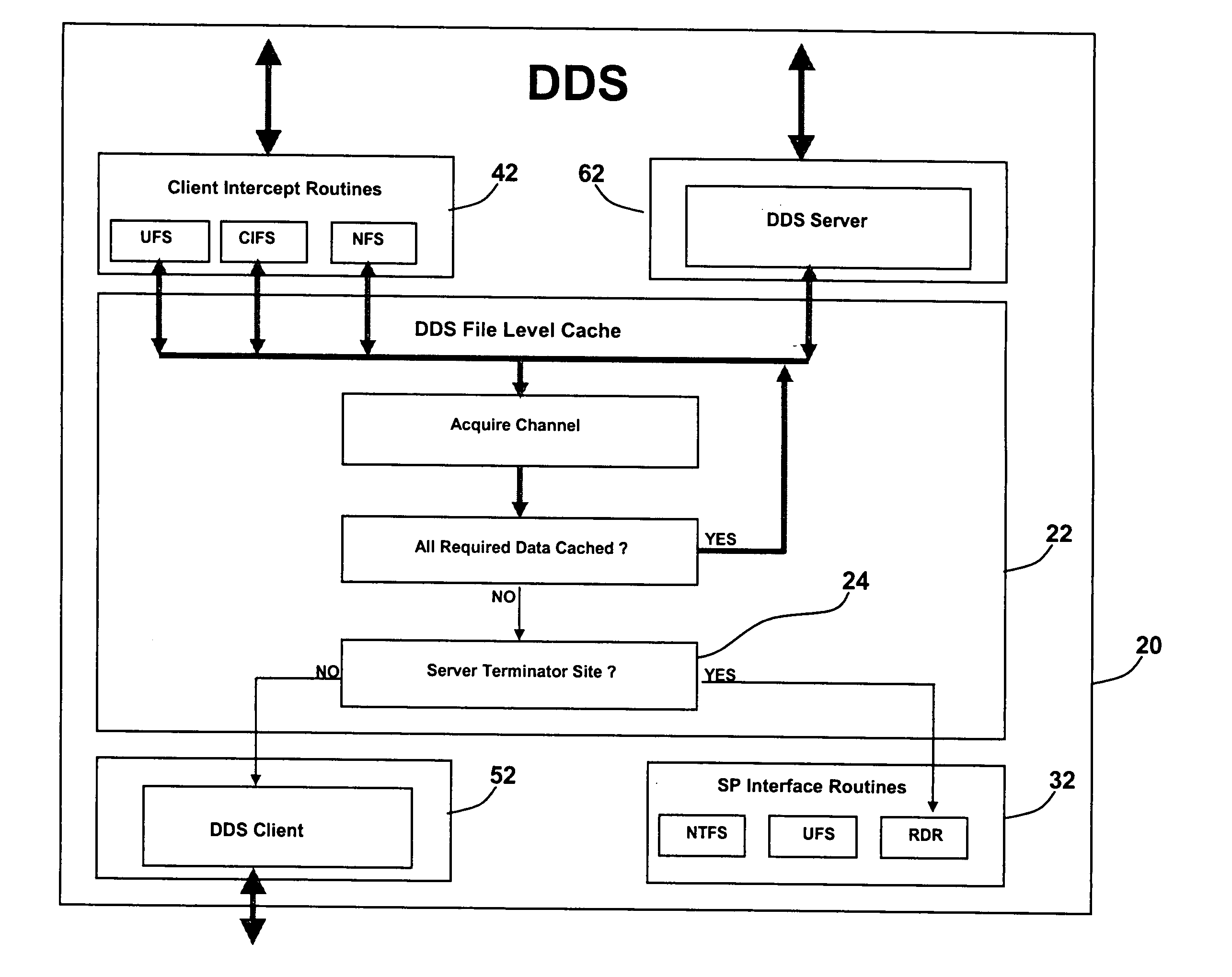
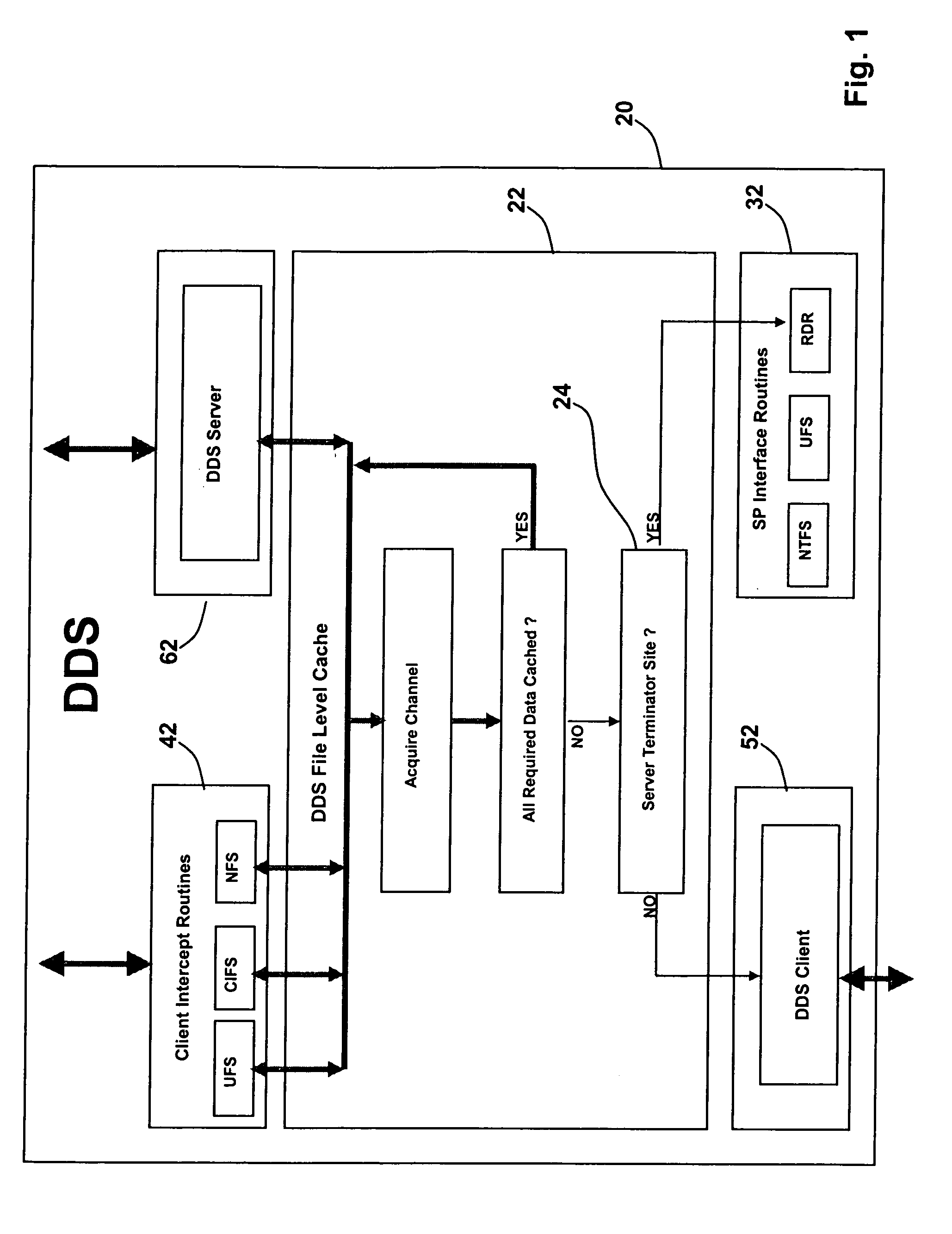
Full text search capabilities integrated into distributed file systems
ActiveUS20060053157A1Efficiently streamedMaintain consistencyDigital data information retrievalDigital data processing detailsFull text searchAppleTalk
A hierarchical distributed search mechanism is integrated into a distributed file system. Traditional file system APIs (create, open, close, read, write, link, rename, delete, . . . ) and the over-the-wire protocols employed to project these APIs into remote client sites (CIFS, NFS, DDS, Appletalk) are extended to enable the dynamic creation of temporary directories containing links to objects identified by search engines (executing at sites “close” to “their” data) as meeting the search criteria specified by the first parameter of a search function call. The search function, derived from the standard file system API function create, is added to the file system API.
Owner:PITTS WILLIAM M
Systems and methods for synchronizing time-shifted media content and related communications
InactiveUS20090235298A1Strengthen the systemImprove methodTelevision system detailsTwo-way working systemsTime segmentDisplay device
A method for assigning attributes to media content. A media content is first displayed on a television, computer, or other display. A communication created by a user while viewing the media content is then received. The communication is then analyzed, and at least a portion of the communication is linked to a portion of the media content. The communication is also analyzed to identify relevant keywords which are then saved as attributes of the media content. The assigned word or phrase can be used to recommend the media content to other viewers or to find the media content in response to a search function. A method for synchronizing communications with time-shifted media content is also disclosed. A media content such as a television program is displayed during a time period other than its original broadcast time. Communications created by users while watching the media content are then received. The received communications are time-stamped so they can be synchronized with the run-time of the media content. The communications may be analyzed to select and display targeted advertising.
Owner:UNITED VIDEO PROPERTIES
Intelligent agent and interface to provide enhanced search
ActiveUS20170242899A1Digital data information retrievalSpecial data processing applicationsIntelligent agentInformation retrieval
Owner:META PLATFORMS INC
Motion estimation architecture for area and power reduction
InactiveUS6020934AReduce power consumptionReduce circuitTelevision system detailsPicture reproducers using cathode ray tubesMotion vectorChipset
A method for compensating for reduced picture quality when combining a multi-chip encoding chipset into a single integrated semiconductor IC. The method includes additional functions provided on the single IC to compensate for the negative effects on picture quality produced as a result of rounding 8 bit luminance pixel data to 5 bits, where the luminance data values are supplied as input to the search function. The additional functions are collectively referred to as motion biasing and are applied to influence the choice of a "best match" motion type, which is well known in the art. The biasing is performed by the addition of a weight factor to a total difference result that is calculated by the search function. The biasing is applied only for the purpose of influencing the choice of a reference frame that is not necessarily the frame which produces an optimal motion vector, but rather will result in using fewer bits to encode macroblocks.
Owner:IBM CORP
Features for use with advanced set-top applications on interactive television systems
InactiveUS20080282294A1Television system detailsAnalogue secracy/subscription systemsTelevision systemInteractive television
Advanced features for interactive television applications are described, including a back feature, a forward feature, a history feature, a go to feature, an extras feature, a reminder feature, a favorites feature, a parental control feature, and a search feature. Features may be inter-resource. Support for multiple data paths, Internet access, interactive services, and user profiles are also described.
Owner:ALL MEDIA GUIDE +10
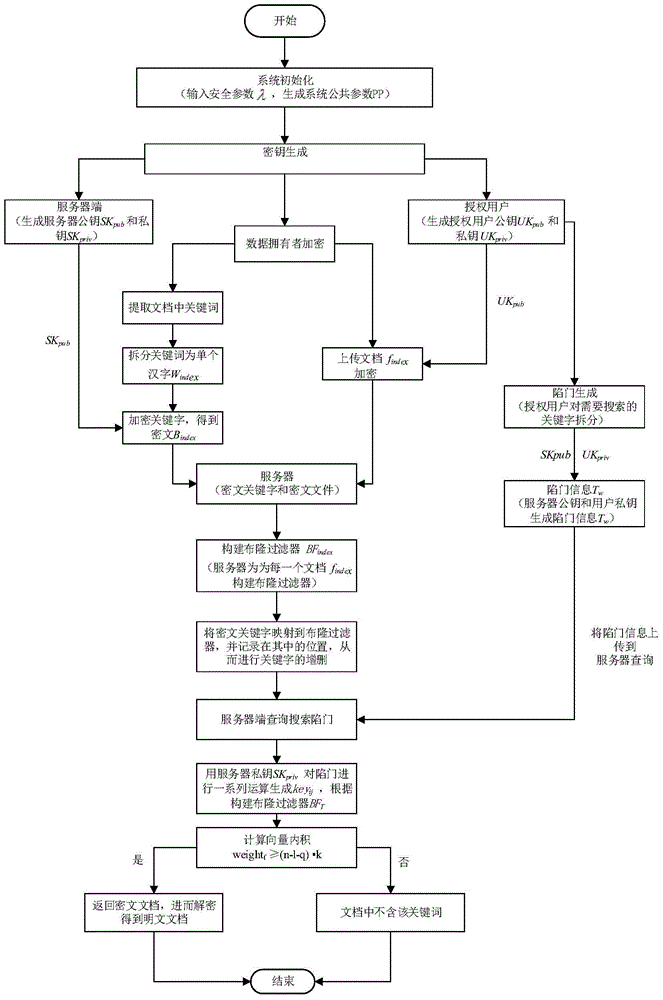
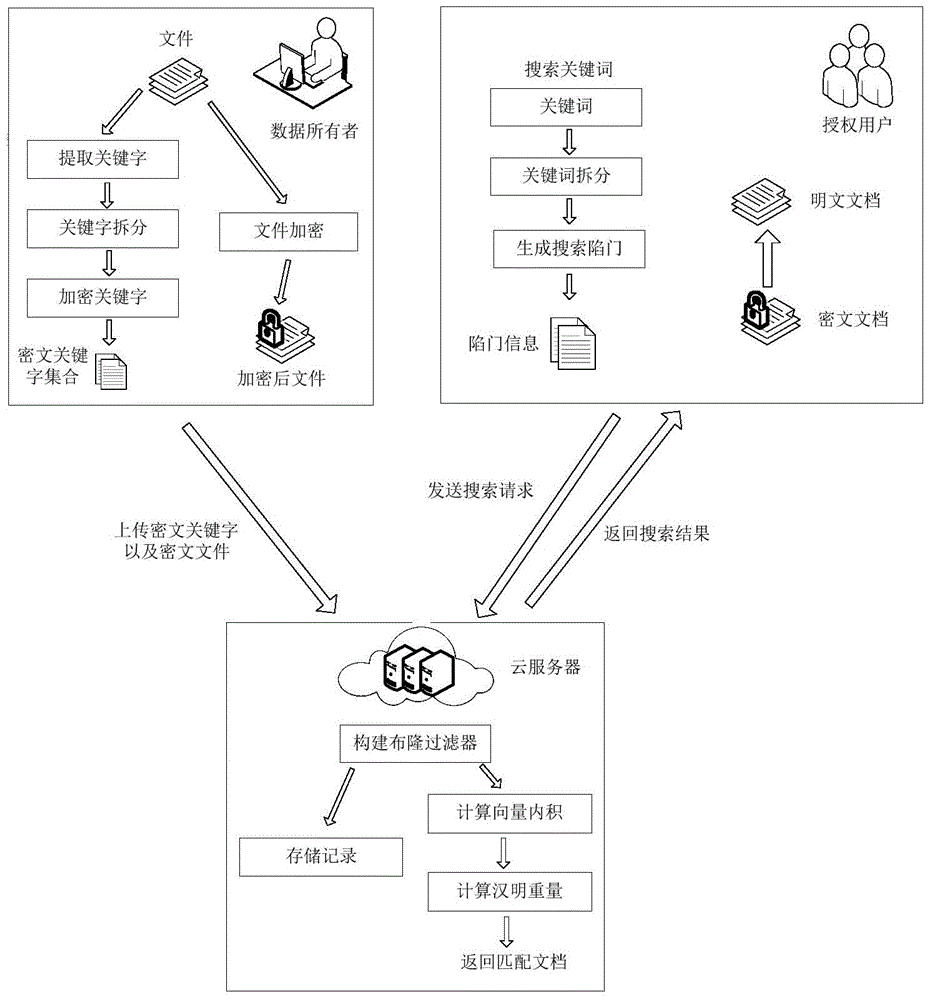
Searchable encryption method based on Chinese in cloud environment
ActiveCN105681280ASearchable implementationSearchable encryption implementationTransmissionSpecial data processing applicationsDocument preparationSearch function
The invention discloses a searchable encryption method based on Chinese in a cloud environment. A dynamic searchable encryption scheme is finished based on the features of a PEKS scheme and a Bloom filter; a ciphertext search function is finished in an insecure channel; fuzzy keyword search based on a public key searchable encryption scheme is supported; multi-keyword search of the Chinese is supported; the keywords in a document are dynamically added or deleted; according to the method provided by the invention, an inner product operation is carried out through constructing a search vector and a file vector so as to finish a fuzzy search matching function; the similarity weight of the keywords in the document and the keywords of a search trap door is calculated through importing the vectors; the ciphertext search function and the fuzzy keyword search function are realized; the ciphertext keywords can be securely transmitted on a public channel in adoption of a server and user double-key pair mode; in application of a hash function and a pseudo-random function, through the scheme, the keyword selection attack can be resisted effectively; and the ciphertext is searched under a condition that the cloud server is semi-trusted.
Owner:XIDIAN UNIV
Mobile communication terminal with multi-input device and method of using the same
InactiveUS20050140657A1Input/output for user-computer interactionEmergency actuatorsMulti inputKey pressing
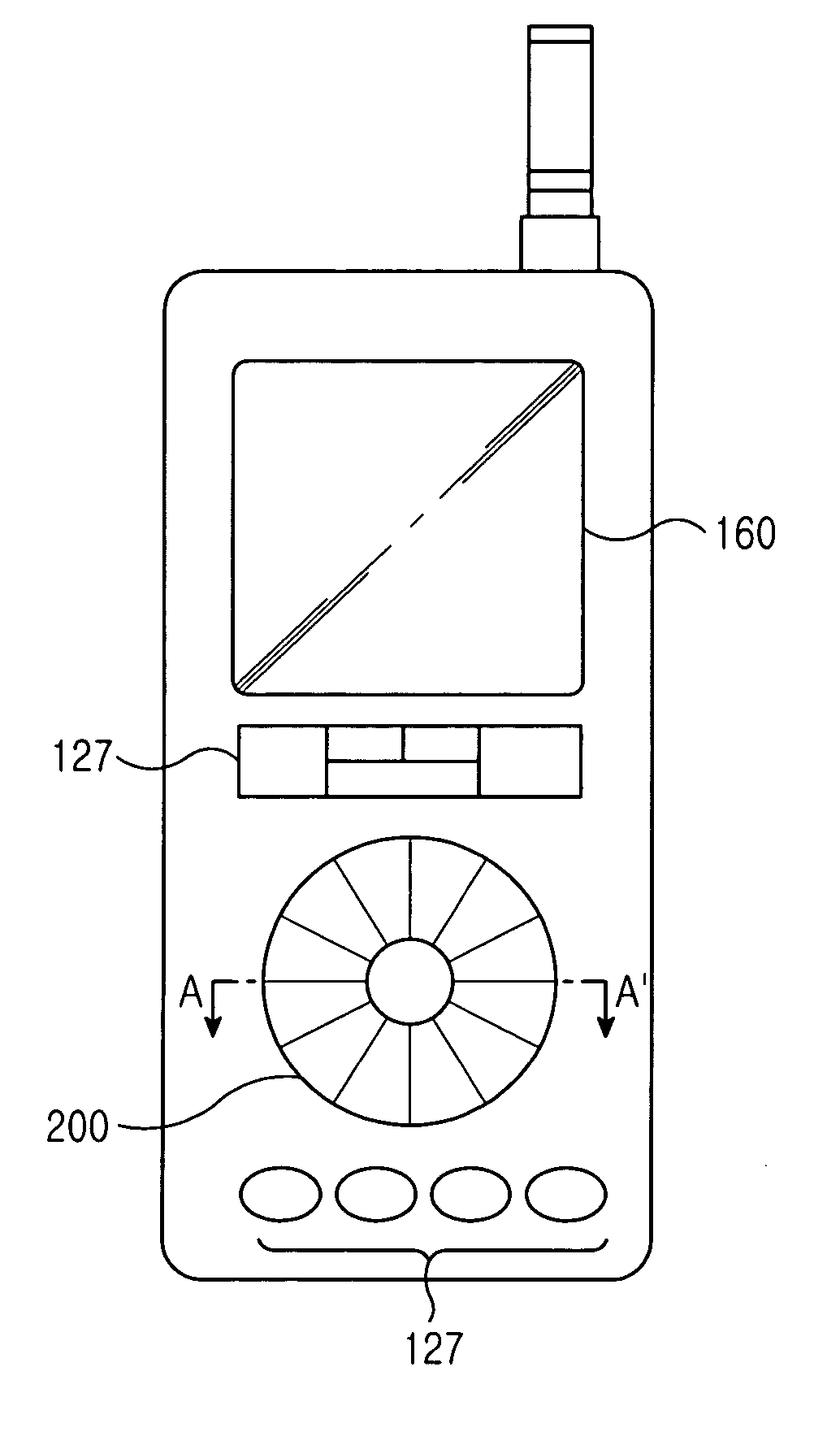
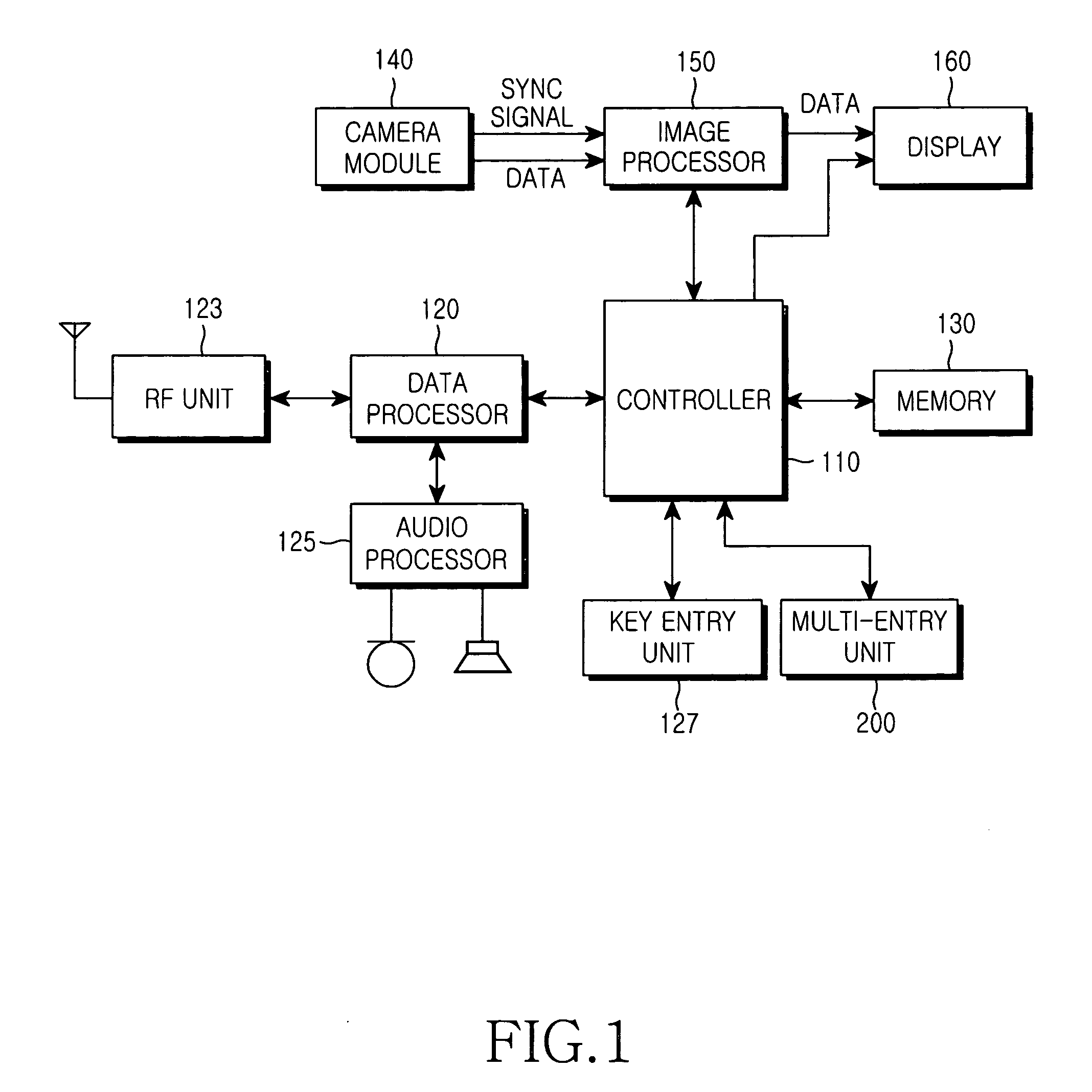
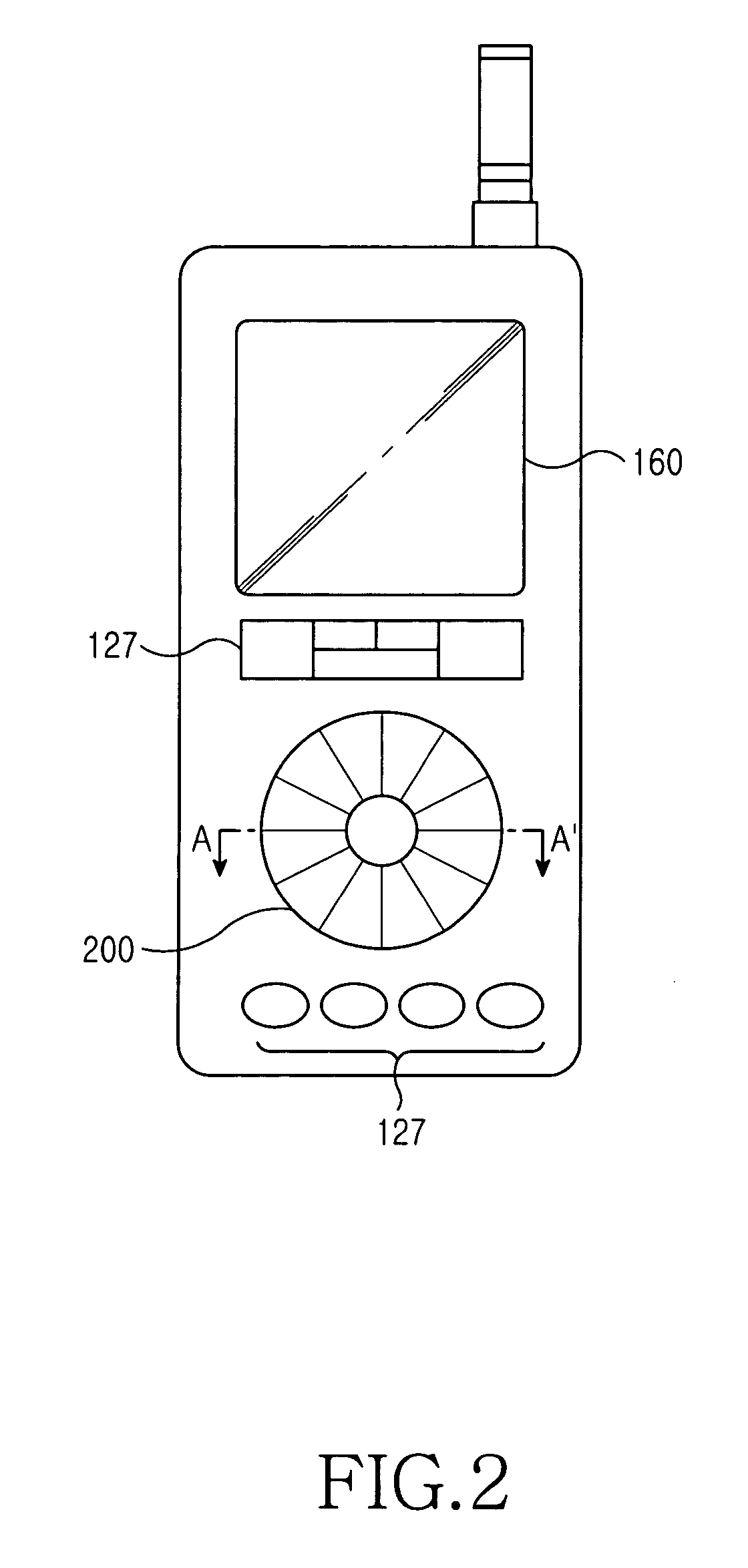
A mobile communication terminal with a multi-input device and a method of using the same is provided. The mobile terminal performs an entry function and a search function using a multi-entry unit. The multi-entry unit includes a light-emitting sheet having a variety of colors, and being illuminated with designated colors according to character categories during a touch-entry mode for a key entry function; a sense pad for detecting a key entry signal during the touch-entry mode, and detecting a selection signal generated by rotation during the wheel mode; a transparent ground sheet for separating the sense pad from the light-emitting sheet; and an injection material in which characters displayed during the touch-entry mode are differently formed according to their categories, and the characters are illuminated with their unique colors through the light-emitting sheet so that desired characters are displayed.
Owner:SAMSUNG ELECTRONICS CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com