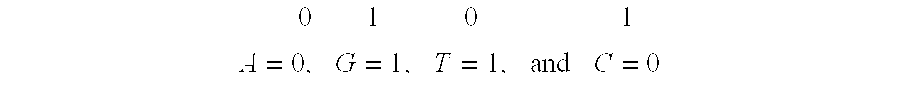Patents
Literature
1142results about "Comparison of digital values" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
System and method for determination of a horizontal minimum of digital values
ActiveUS8650232B2Logic circuits characterised by logic functionComputation using non-contact making devicesComputer science
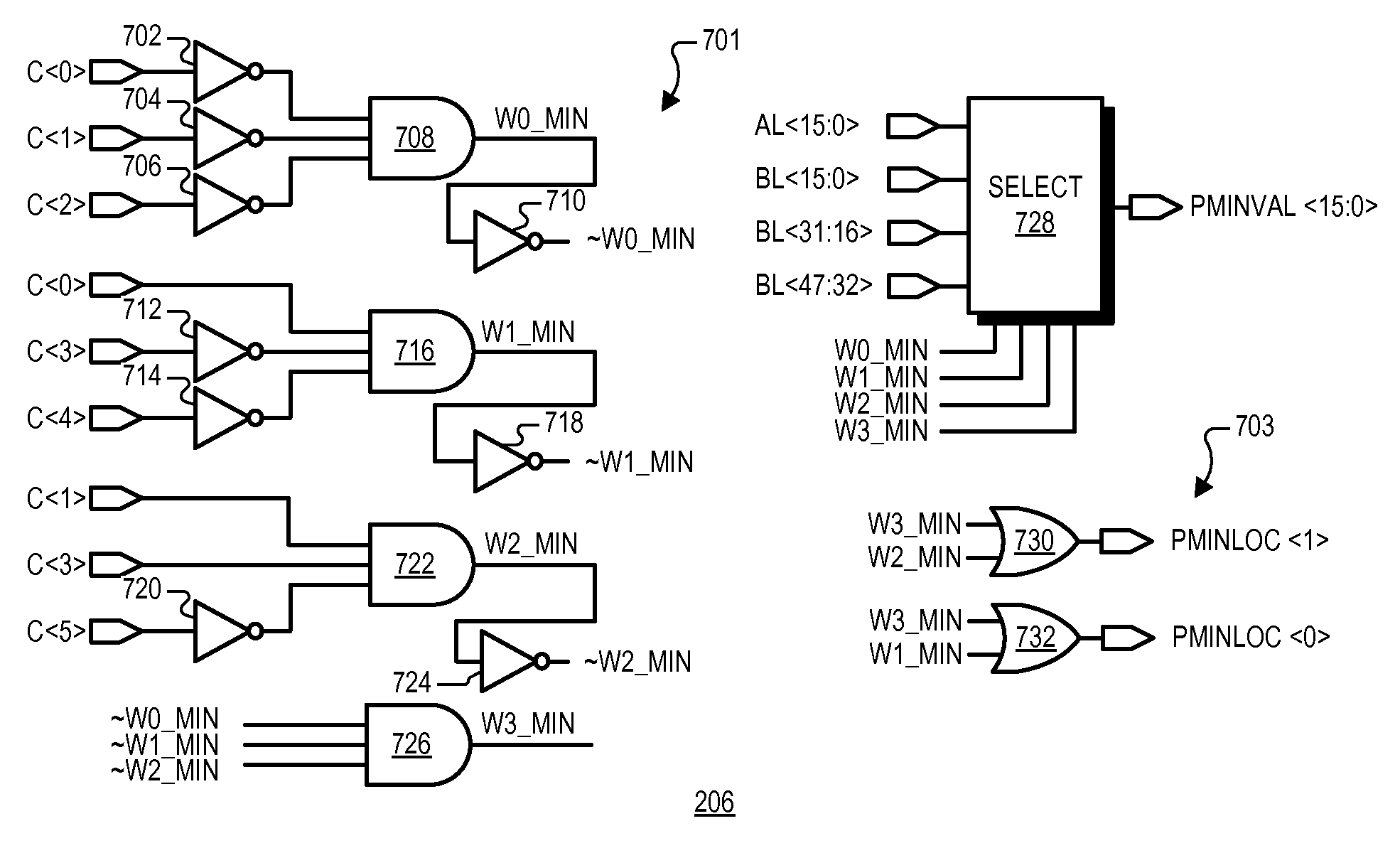
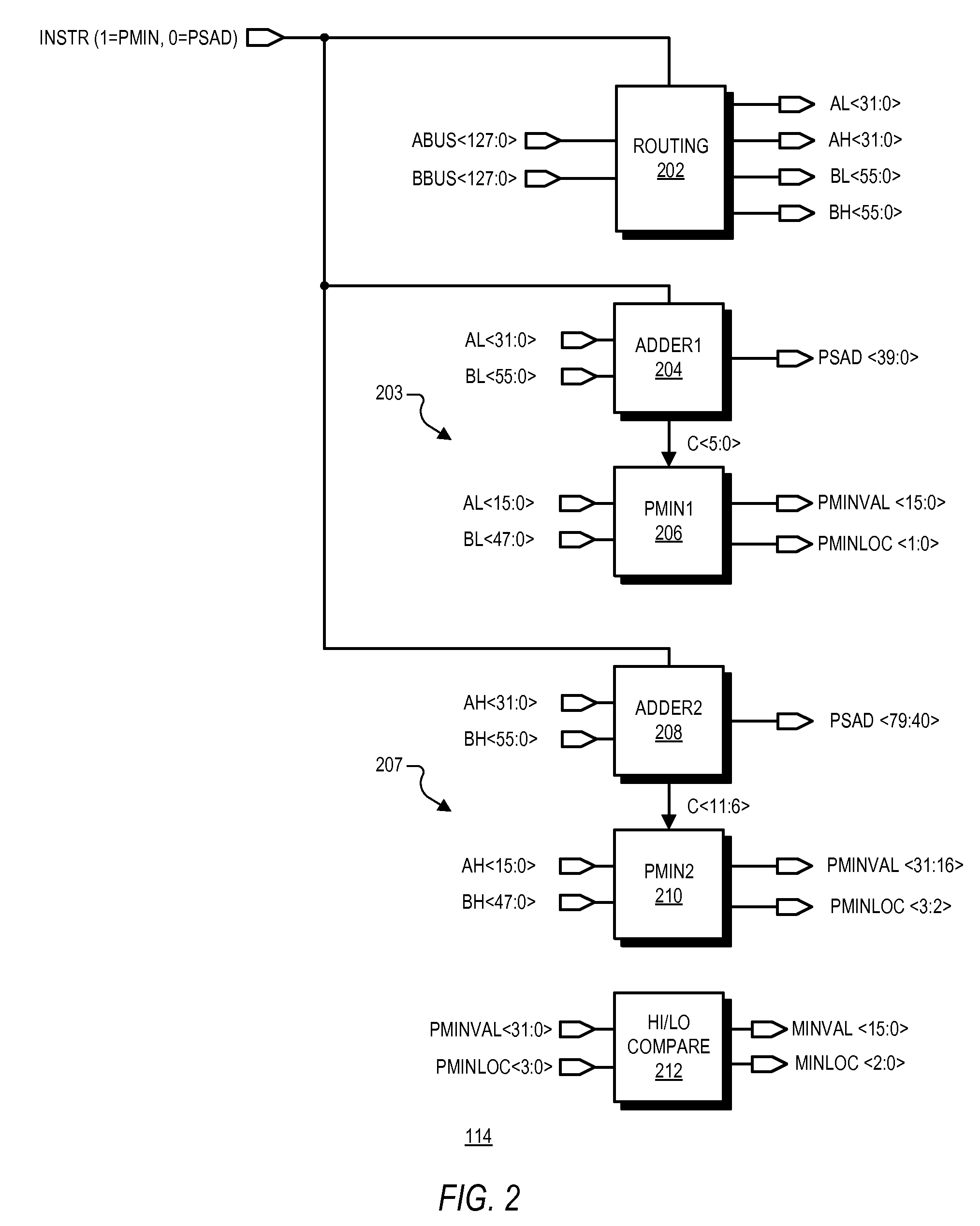
A system for fast determination of a horizontal minimum of multiple digital values including a difference circuit and a compare circuit. The difference circuit may include first and second adders in which the first adder compares upper bits of a first digital value with upper bits of a second digital value and provides a first carry output and a propagate output. The second adder compares lower bits of the first digital value with lower bits of the second digital value and provides a second carry output. The compare circuit determines whether the first digital value is greater than the second digital value based on the carry and propagate outputs. Multiple difference circuits may be used to compare each of multiple digital values with every other digital value to provide corresponding compare bits, which are then used to determine a minimum one of the digital values and its corresponding location.
Owner:VIA TECH INC
Processing architecture having a compare capability
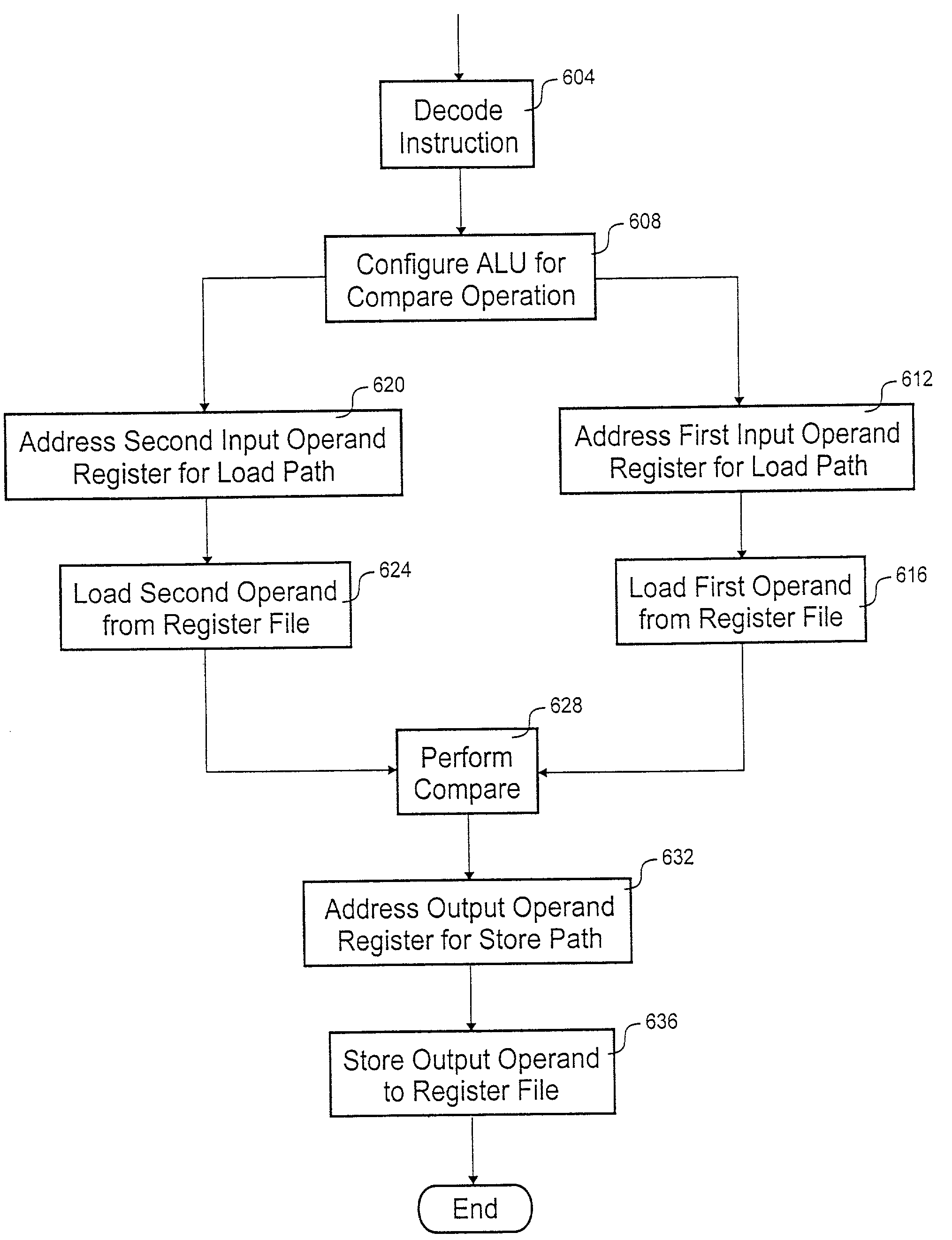
According to the invention, a processing core that executes a compare instruction is disclosed. The processing core includes a register file, comparison logic, decode logic, and a store path. Included in the register file are a number of general-purpose registers. The general-purpose registers include a first input operand register, a second input operand register and an output operand register. Comparison logic is coupled to the register file. The comparison logic tests for at least two of the following relationships: less than, equal to, greater than and no valid relationship. The decode logic selects the output operand register from the plurality of general-purpose registers. The store path extends between the comparison logic and the selected output operand register.
Owner:ORACLE INT CORP
Error detection and rejection for a diagnostic testing system
ActiveUS20080254544A1Minimize impactError preventionTransmission systemsMeasurement deviceComputer science
A system for measuring a property of a sample is provided. The system comprises a diagnostic measuring device having a memory and a diagnostic test strip for collecting the sample. The strip has embedded thereon a pattern representative of at least first data and second data, the first data being data representing at least one of parameters related to measuring the property, codes usable for calibration of the diagnostic measuring device, or parameters indicating proper connection between the measuring device and the test strip and the second data usable for detecting and rejecting potential errors affecting the proper measurement of the property.
Owner:TRIVIDIA HEALTH
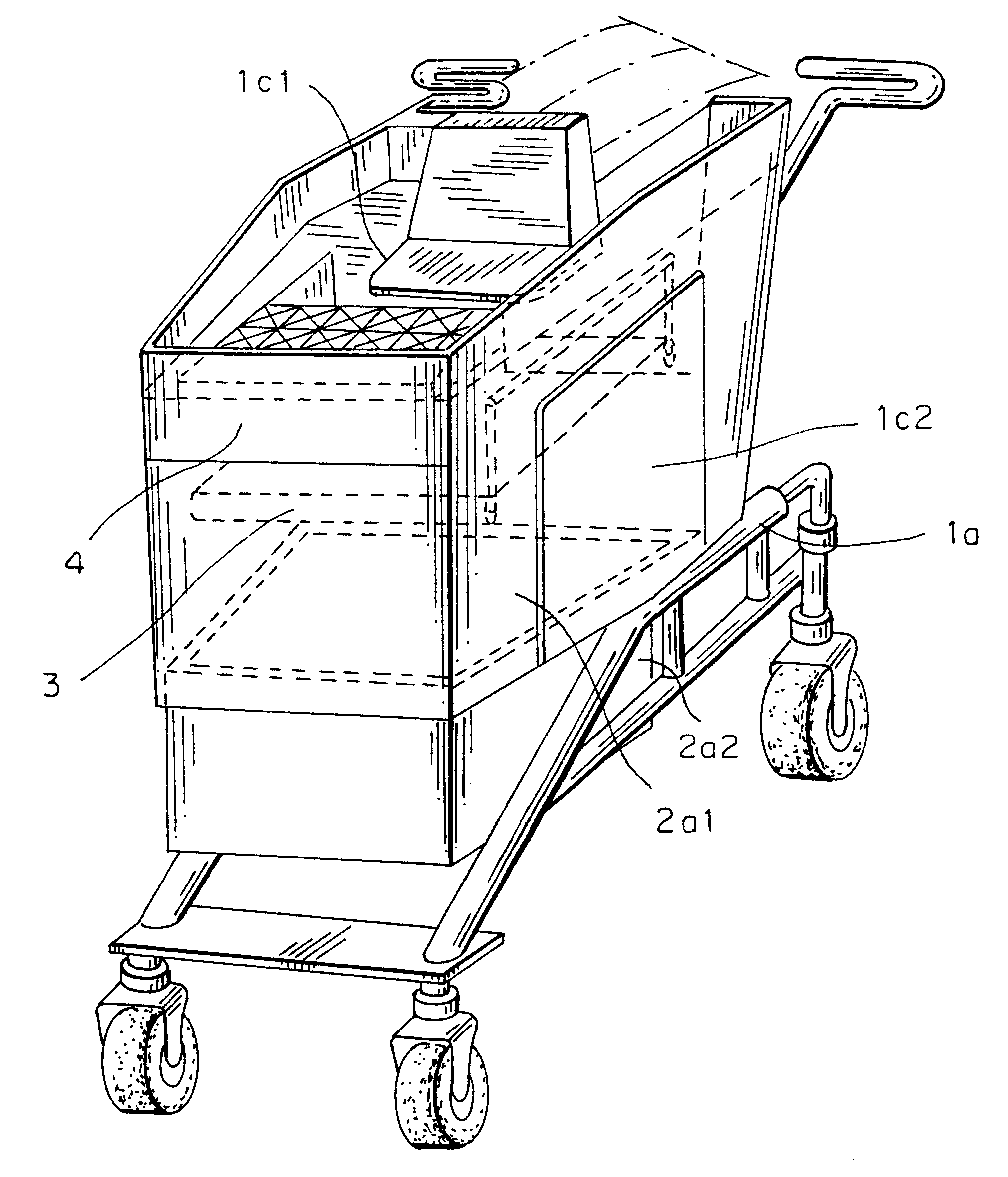
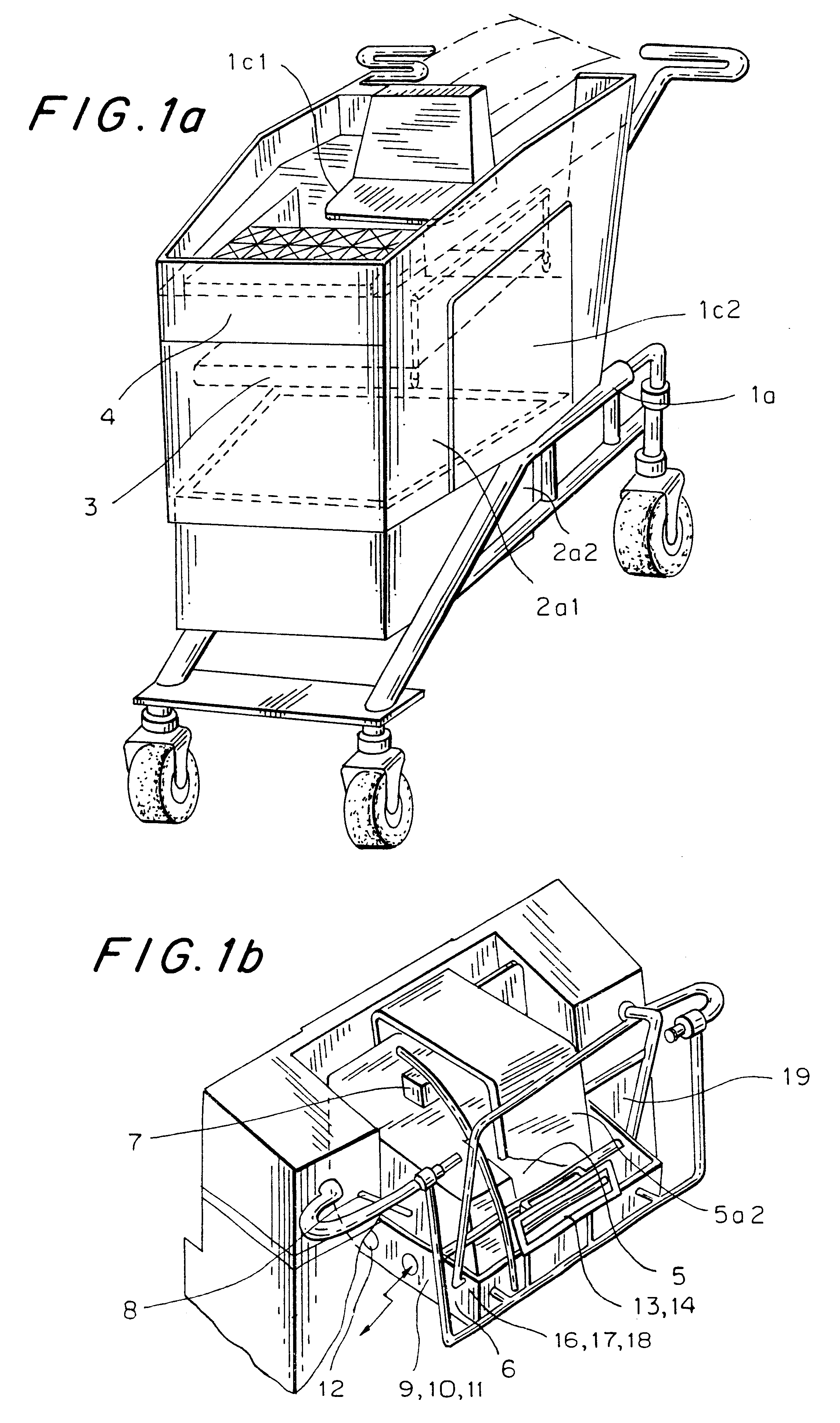
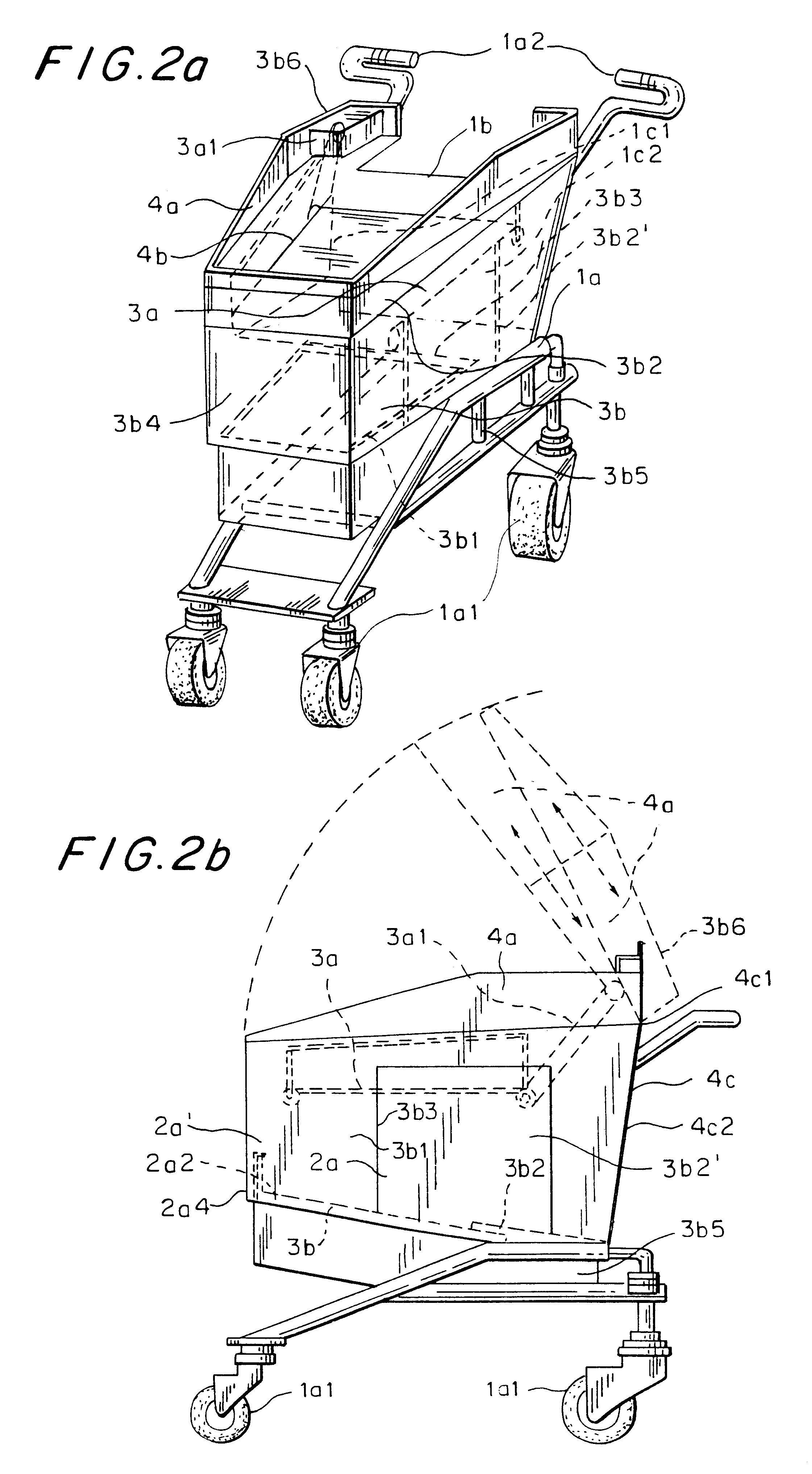
Computerized shopping cart with storage and distribution system, for supermarket use
InactiveUS6435407B1Soften aerial detachmentEase fitCredit registering devices actuationCo-operative working arrangementsDistribution systemBarcode
A system including a computerized shopping cart that includes a closed mechanical cart (1) which interconnects / disconnects to units for the insertion / storage of products upon manual command managed by a shopping computer aimed at managing shopping problems and controlling all electronic functions, i.e. automatic system for optically scanning (7) bar codes (UPC / EAN standard), one for checking (8) the correctness of the customer's operations, one emitting the intelligent multimedia commercial message, one for the wireless exchange of data with the outside, for use in supermarkets. The system provides shopping info (8) (list of products on sale, location, price, other), or of the product being purchased (price, whether it is on sale, partial groceries bill), or already purchased (list of purchased items) or to be purchased (remaining shopping list), guided by appropriate interactive messages (acoustic, visual.
Owner:FIORDELISI LUIGI
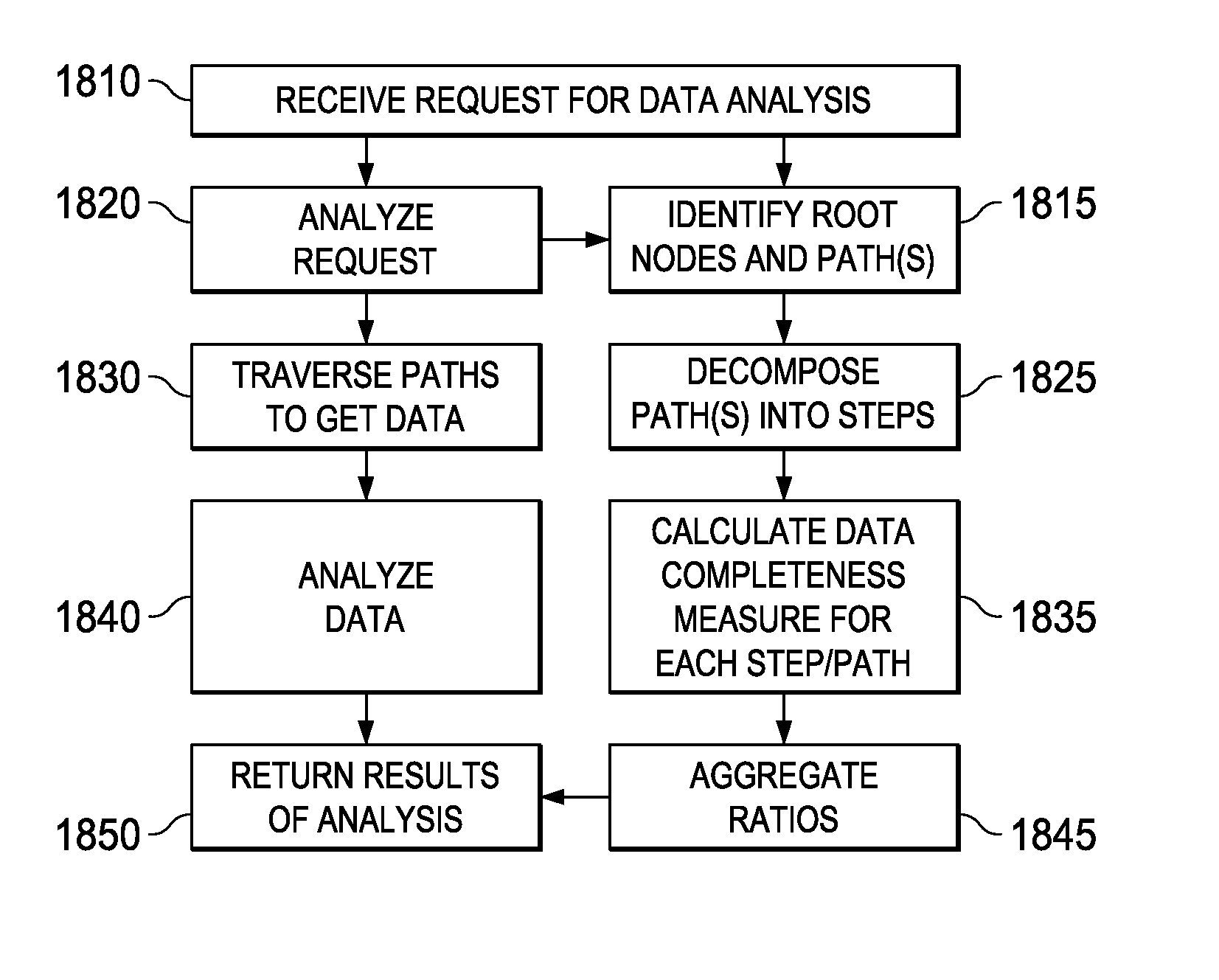
Method and system for determination of data completeness for analytic data calculations
ActiveUS9280581B1Digital data information retrievalComparison of digital valuesData integrityAnalysis data
A system, method and computer program product capable of determining data completeness associated with an analysis based on a data model at the same time that the data in the data model is being analyzed. A root node may be determined, and all paths from the root node discovered. Each path is decomposed into steps, and a ratio is calculated for each step. The ratios may be multiplied for each path, and the aggregate of the paths may determine a measure of the data completeness corresponding to the analysis and return the results of the analysis and the measure of data completeness at the same time.
Owner:TROUX TECHNOLOGIES
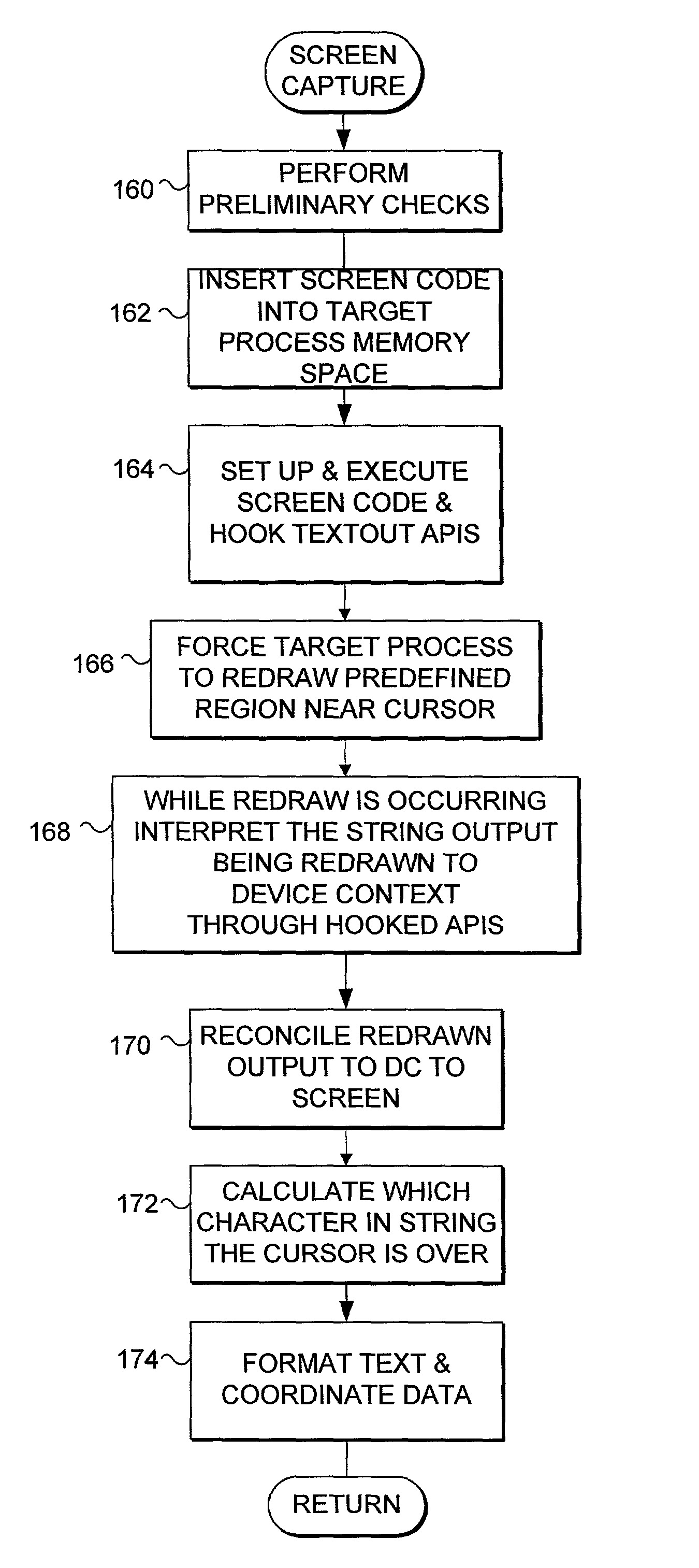
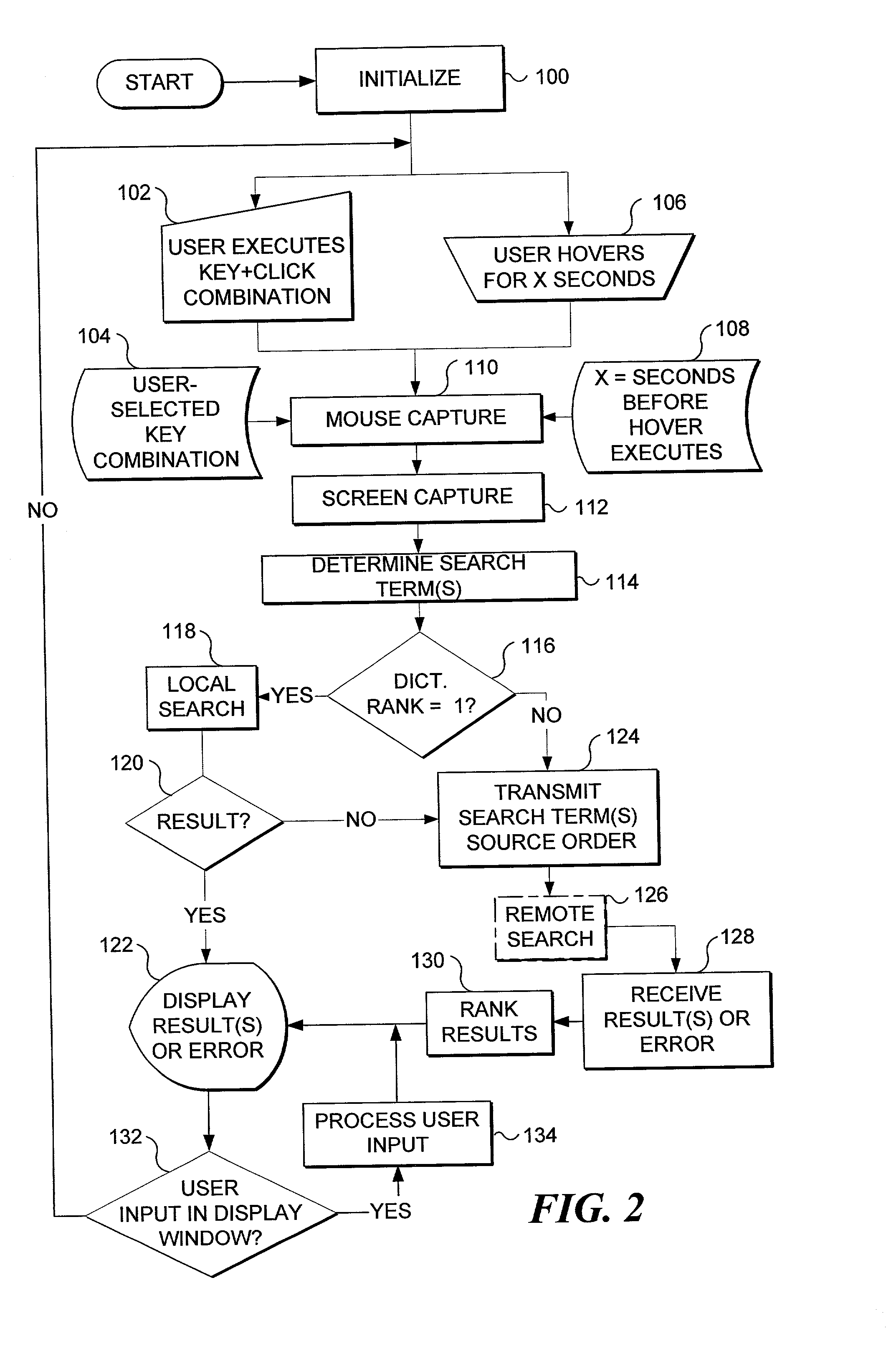
Electronic content search and delivery based on cursor location
InactiveUS7100123B1Faster and reliable word recognitionFaster and reliable recognitionUnstructured textual data retrievalComparison of digital valuesOperational systemData storing
An electronic search is automatically initiated when a cursor hovers in one location for a predetermined time. A target process associated with a target window is forced to re-render data to the target window in an update region that includes the detected cursor location. From the re-rendered data, a primary word and context words near the cursor location are determined. One or more local or remote electronic data stores are searched for substantive content related to the words. The content is prioritized according to user preference and displayed in a semitransparent window that is persistently visible to a user, yet does not obscure other content in an underlying window and does not shift the focus from an active window. Re-rendering is accomplished by invalidating an update region of the target window, and forcing the operating system to issue a paint message, causing the target process to redraw the update region.
Owner:MICROSOFT TECH LICENSING LLC
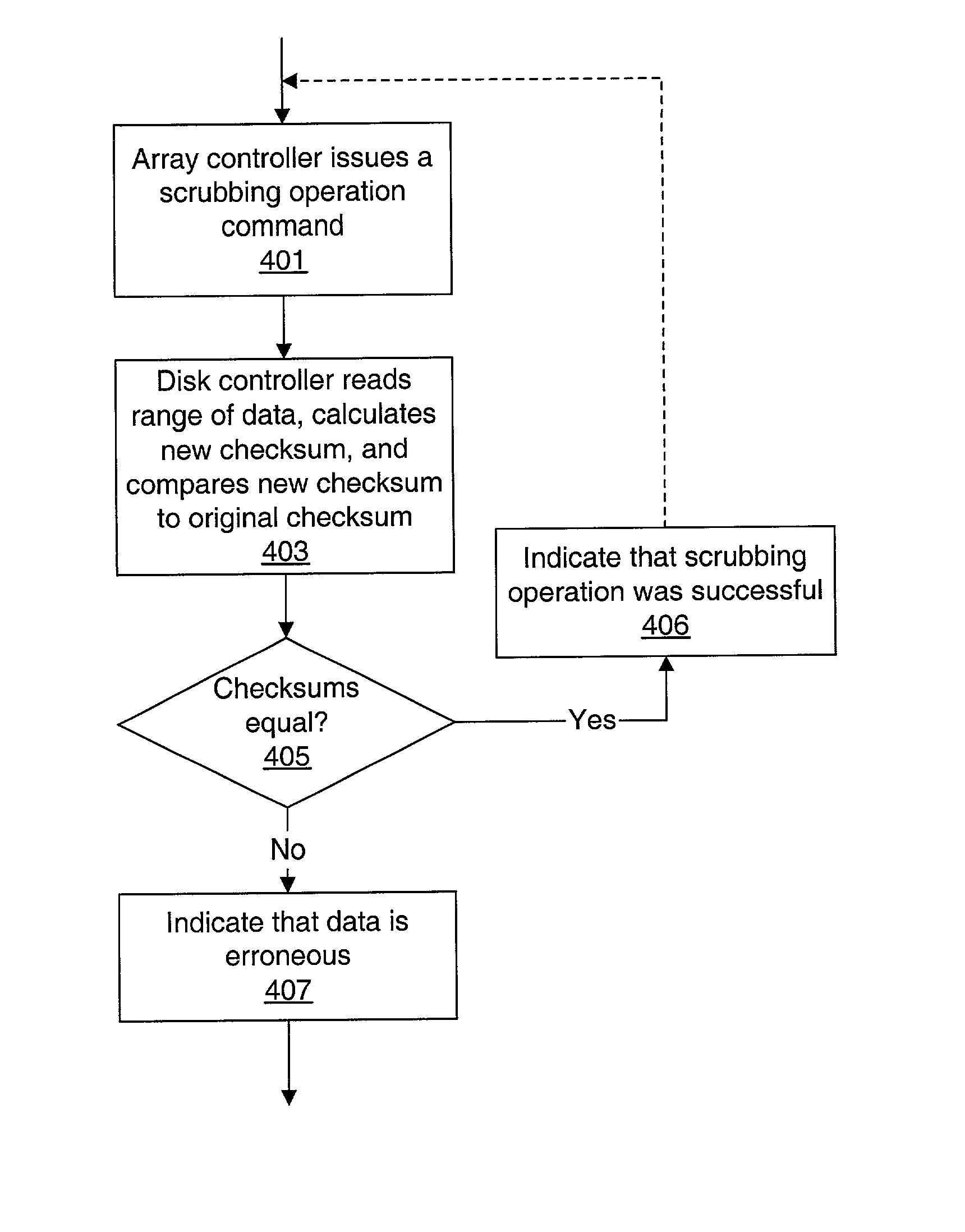
Storage array employing scrubbing operations at the disk-controller level
A storage system comprises a storage array controller and a storage array, which includes multiple disk drives and disk drive controllers. The storage array controller issues scrubbing operation commands to one or more of the disk drive controllers. In response, each disk drive controller that receives a scrubbing operation command reads data from within a data range from at least one of the disk drives, calculates a new checksum for the data, and compares the new checksum to a preexisting checksum for the data. If the new checksum doesn't equal the preexisting checksum, the data within the data range is determined to be erroneous.
Owner:ORACLE INT CORP
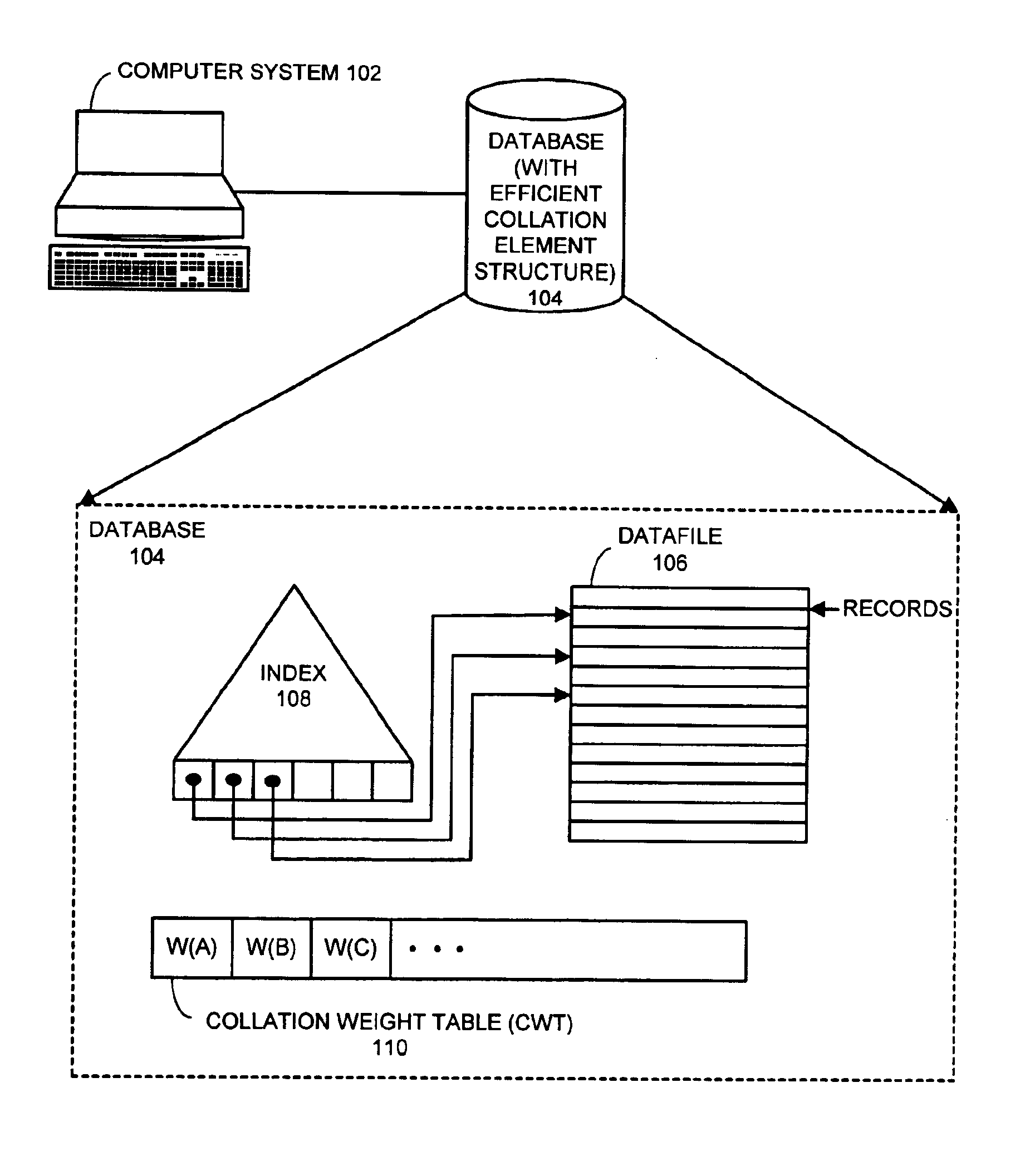
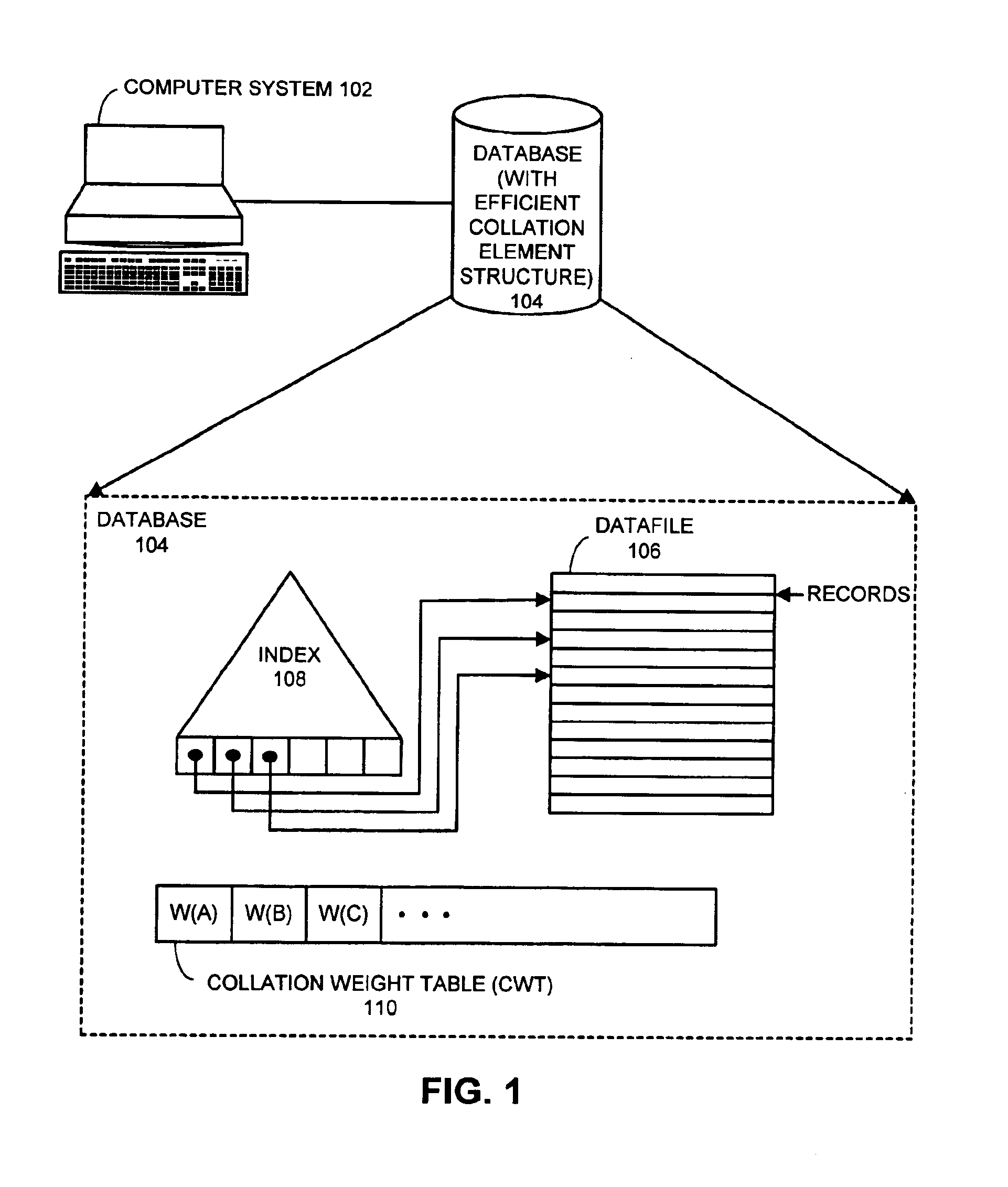
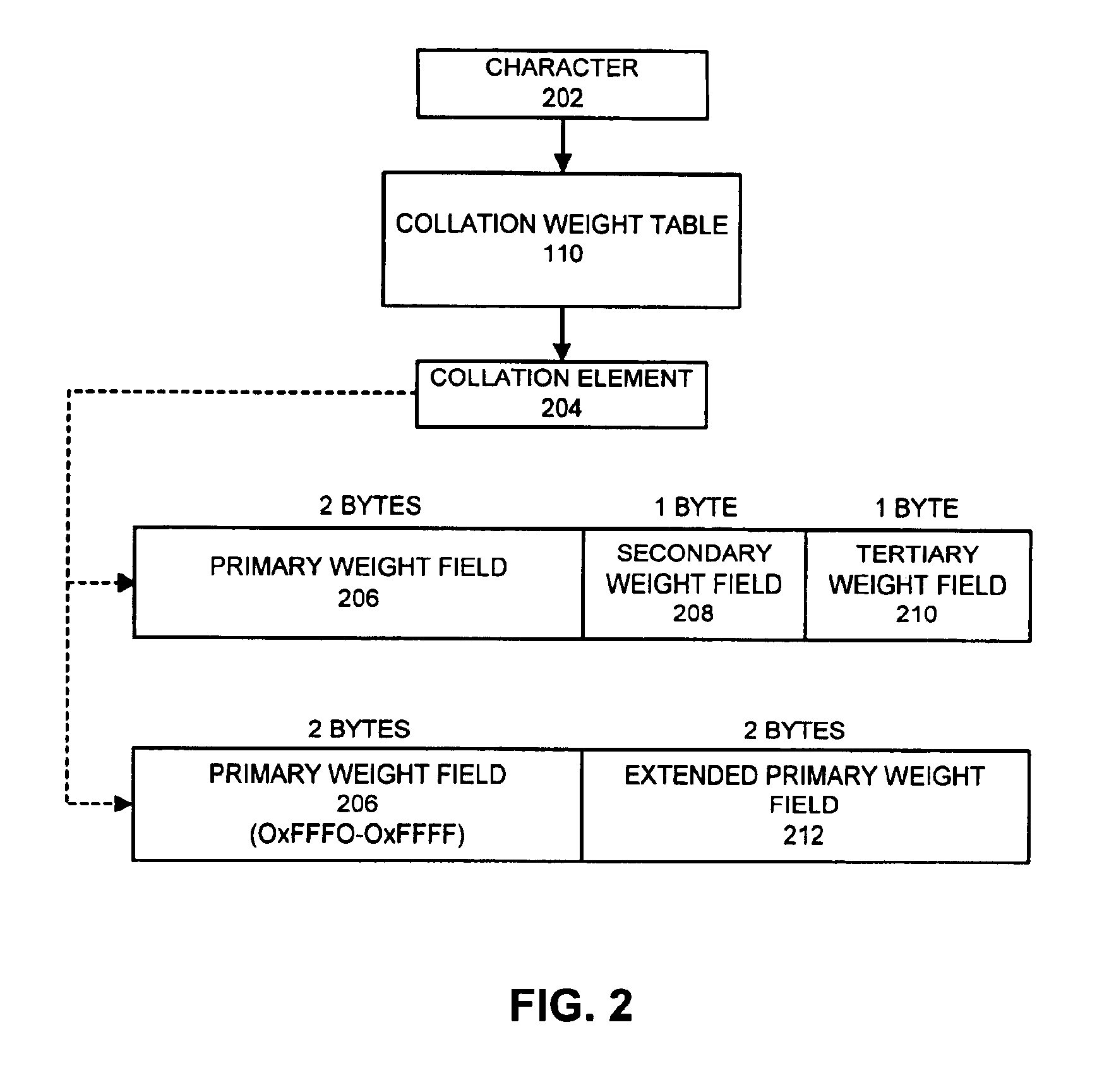
Efficient collation element structure for handling large numbers of characters
InactiveUS6877003B2Easy to useData processing applicationsComparison of digital valuesComputer scienceWeight value
One embodiment of the present invention provides a system for facilitating use of a collation element that supports a large number of characters. The system operates by receiving the collation element and reading a primary weight value from a primary weight field within the collation element. If the primary weight value falls within a reserved set of values, the system reads an additional portion of the primary weight value from both a secondary weight field and a tertiary weight field within the collation element. On the other hand, if the primary weight value is not within the reserved set of values, the system reads a secondary weight value from the secondary weight field, and also reads a tertiary weight value from the tertiary weight field.
Owner:ORACLE INT CORP
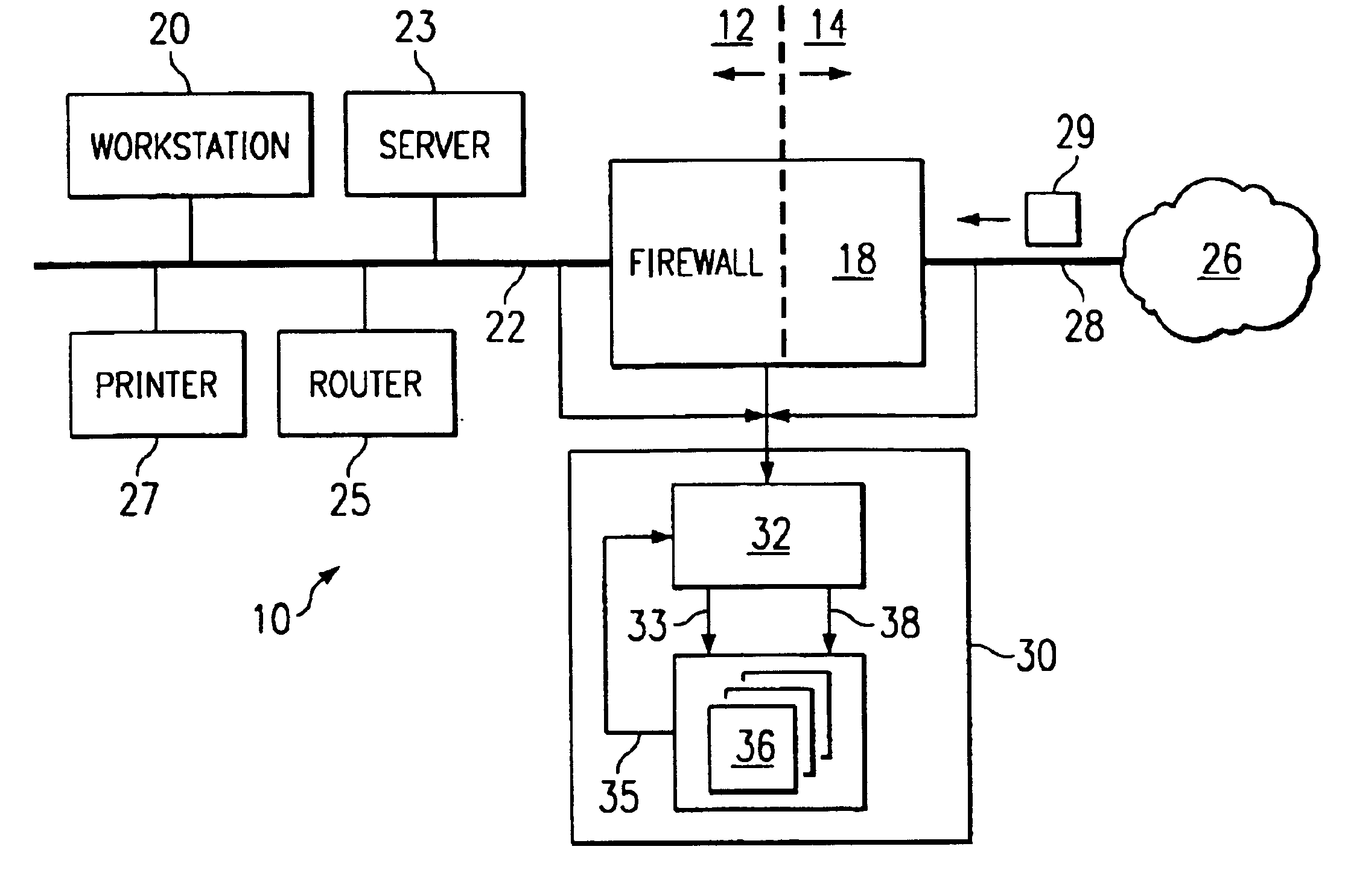
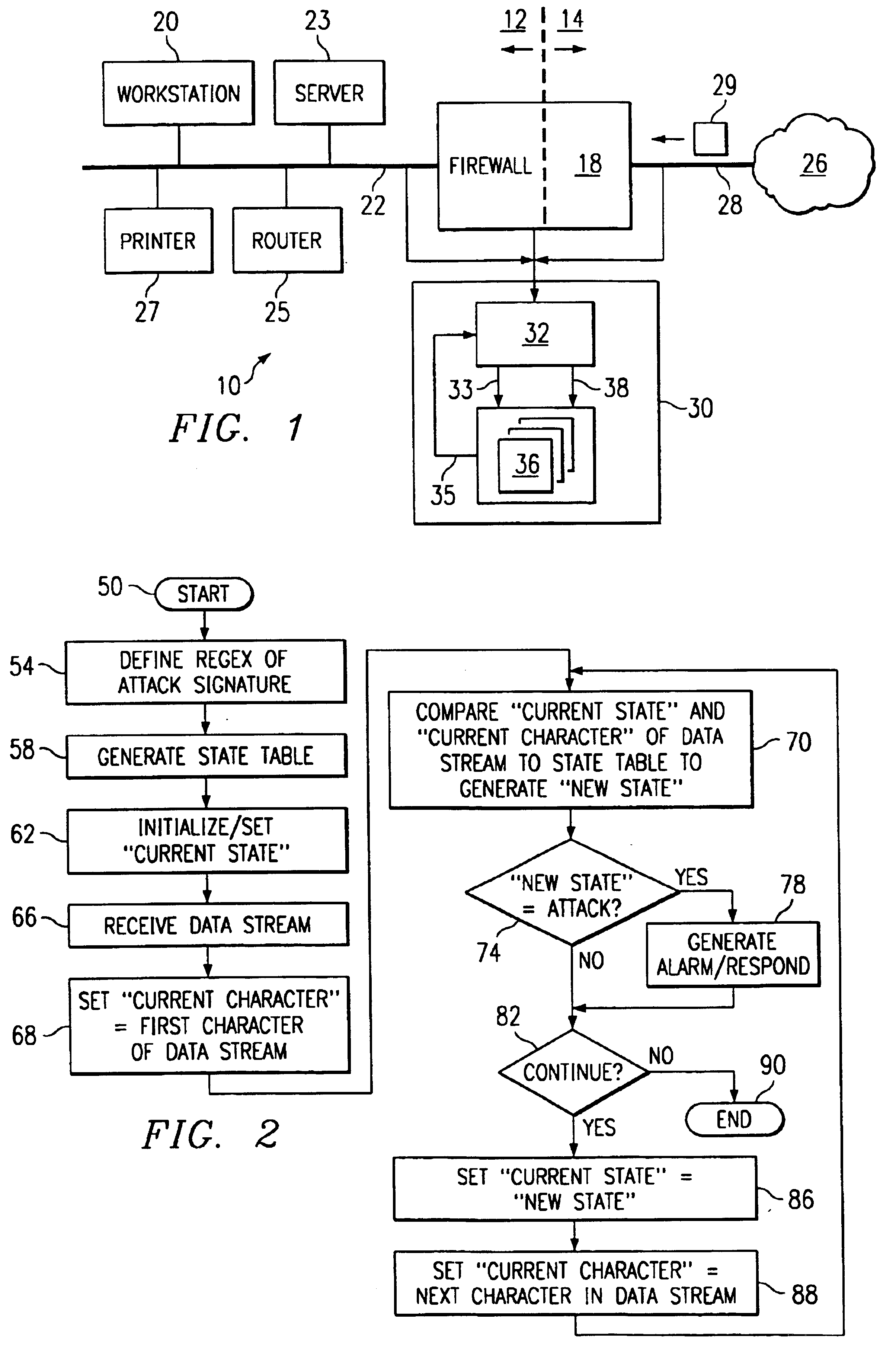
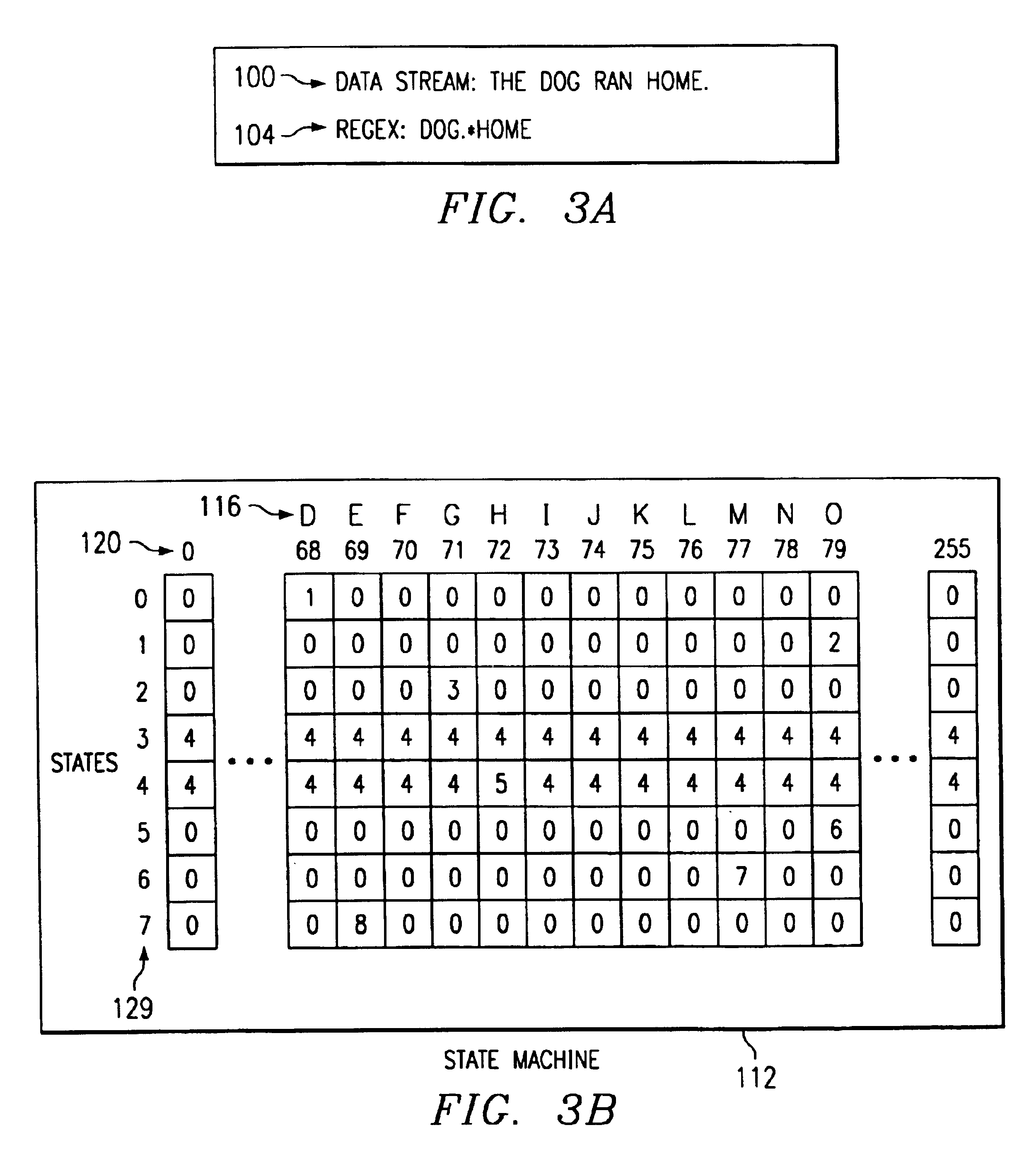
Binary state machine system and method for REGEX processing of a data stream in an intrusion detection system
InactiveUS6880087B1Reduce needPreserve memory resourceMemory loss protectionCode conversionData streamTheoretical computer science
A binary state machine system and method for REGEX processing of a data stream in an intrusion detection system are disclosed. The method comprises maintaining a state table. The state table is indexed such that inputs comprising a current state and a current character yield an output of a new state. The new state is related to an indication of an attack on a computer network. The method further includes maintaining the current state. An input stream comprising a plurality of characters is received. A first character of the input stream is selected as the current character. The current character and the current state are compared to the state table to generate a new state.
Owner:CISCO TECH INC
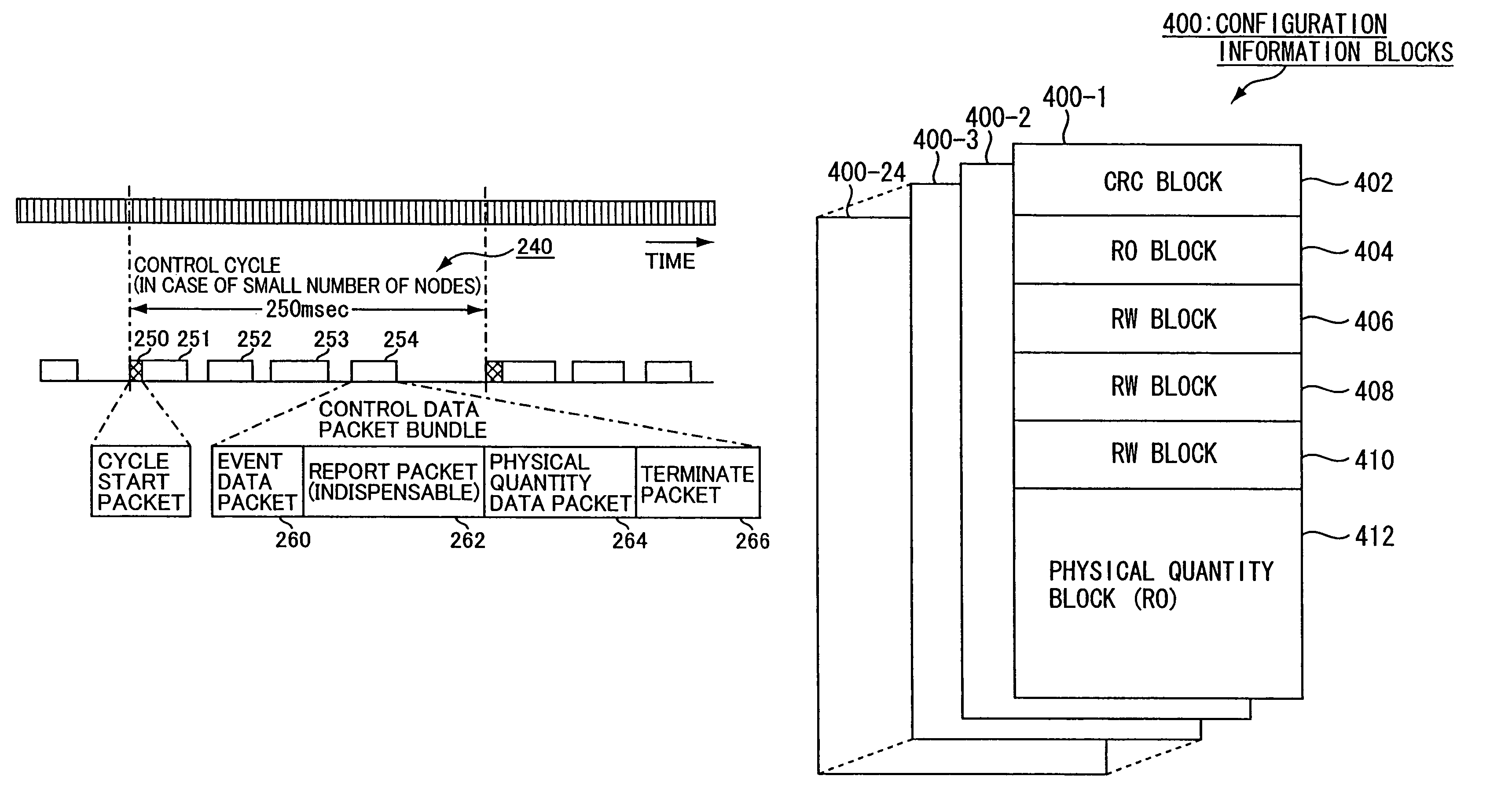
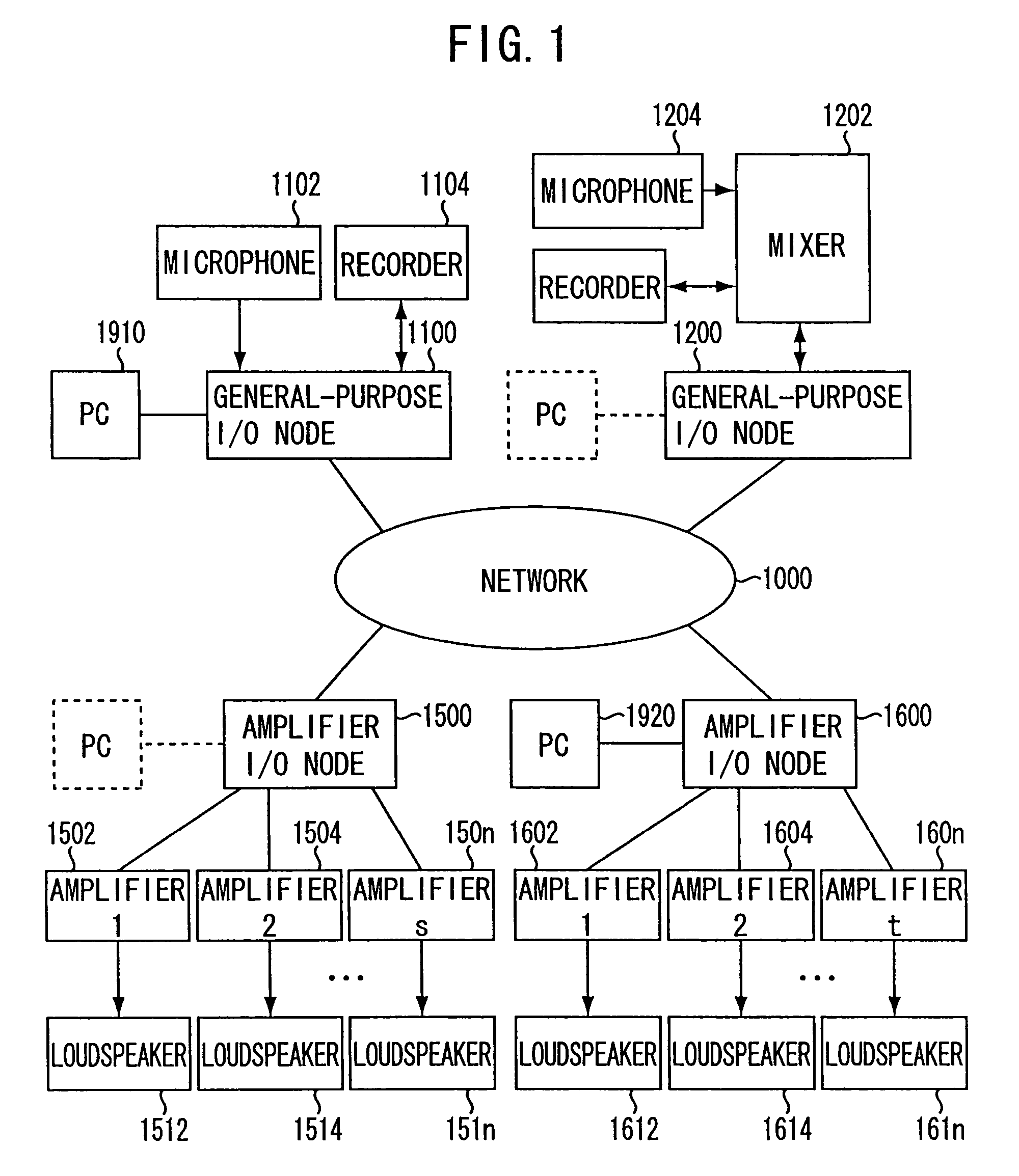
Signal transmission apparatus
A signal transmission apparatus is connected to a network as one node among a plurality of nodes involved in the network which is provided with an audio signal transmission period for transmitting a plurality of channels of audio signals each transmission cycle and a control data transmission period for transmitting control data of the plurality of the nodes each control cycle by using an idle time period other than the audio signal transmission period. In the signal transmission apparatus, a storage section stores configuration information of the one node. A transmitting section transmits the control data including an error checking code of the configuration information. A receiving section receives request data from another node, the request data requesting the one node for transmission of an information block of the configuration information. A control section controls the transmitting section to transmit the information block in response to the request data.
Owner:YAMAHA CORP
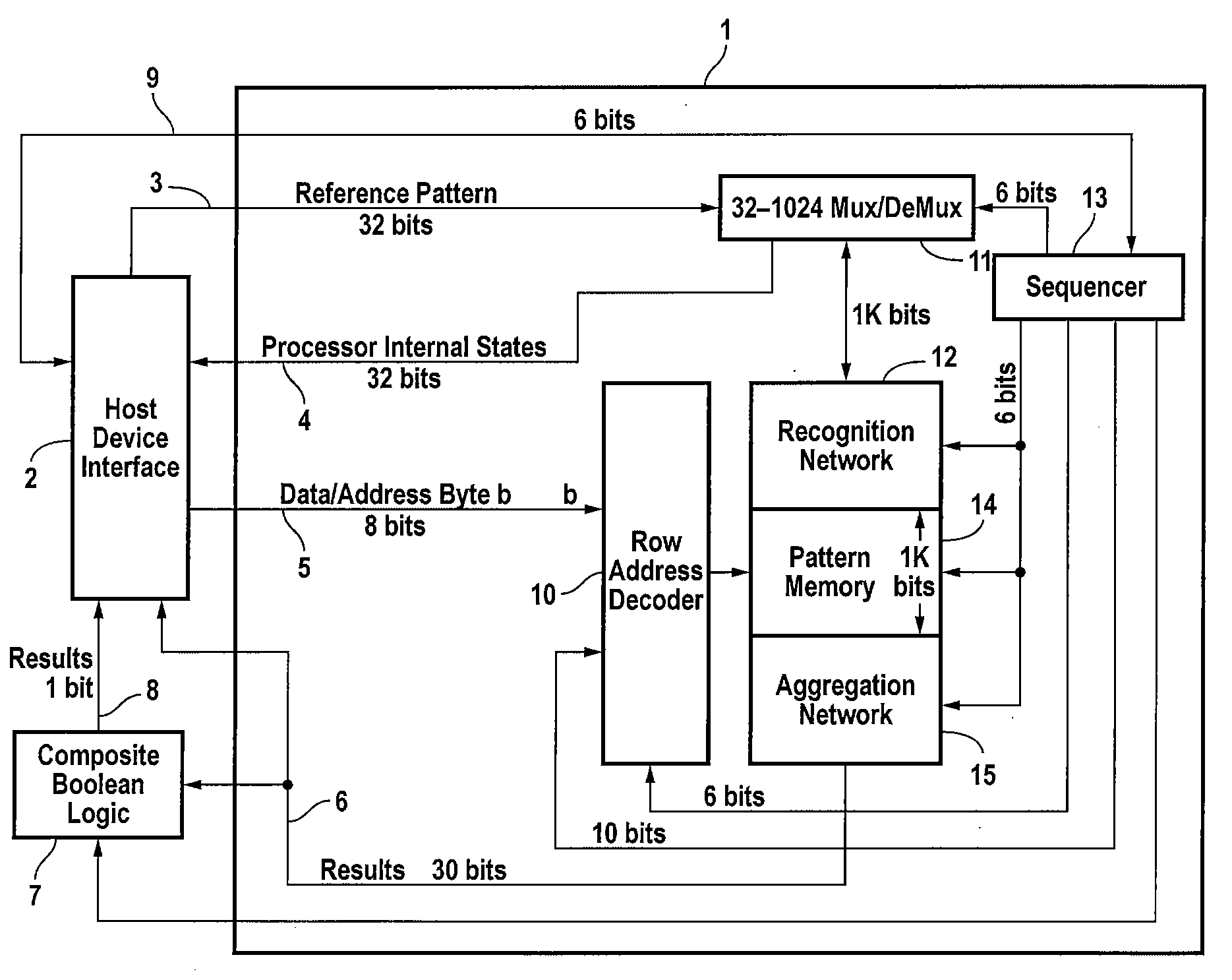
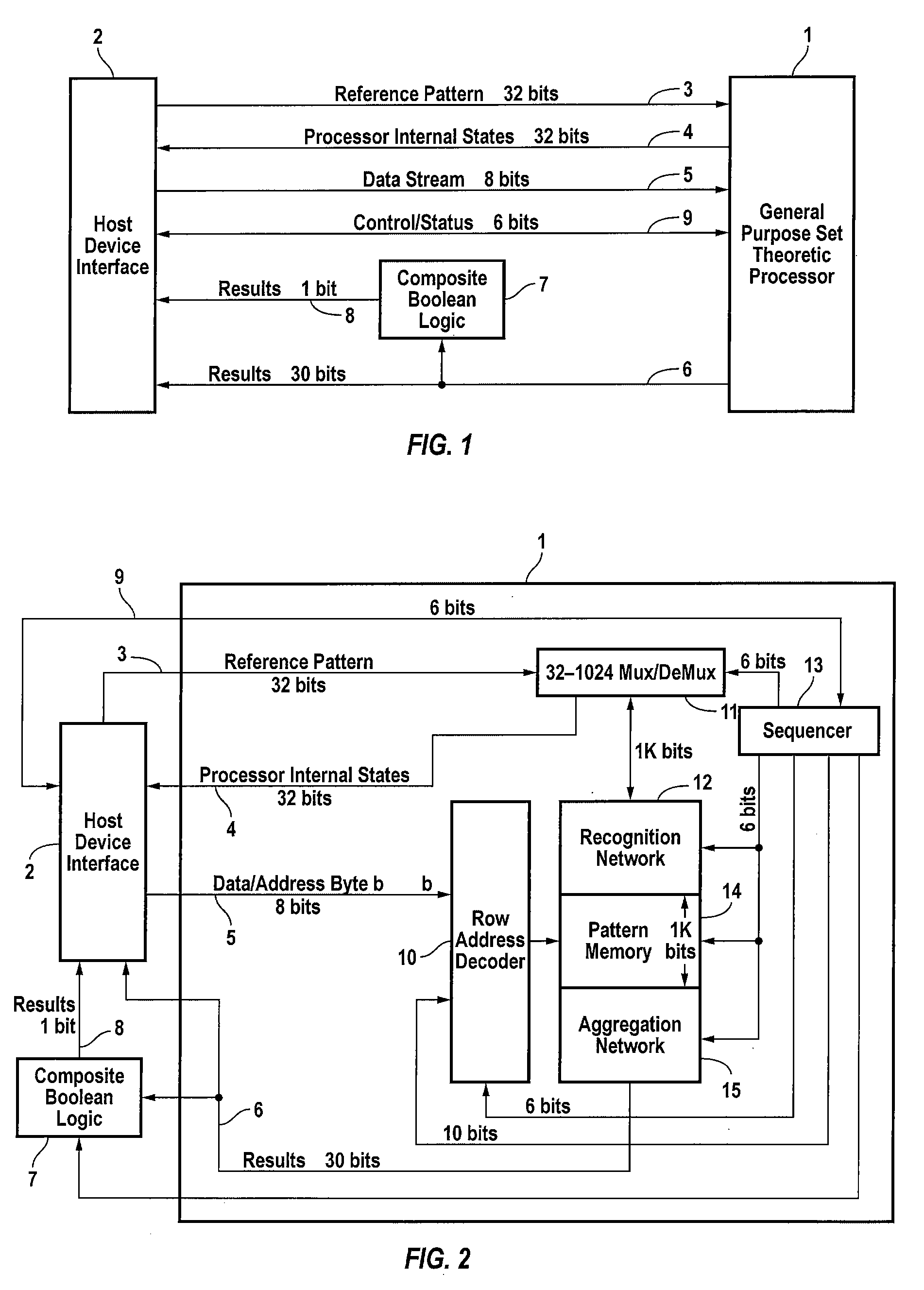
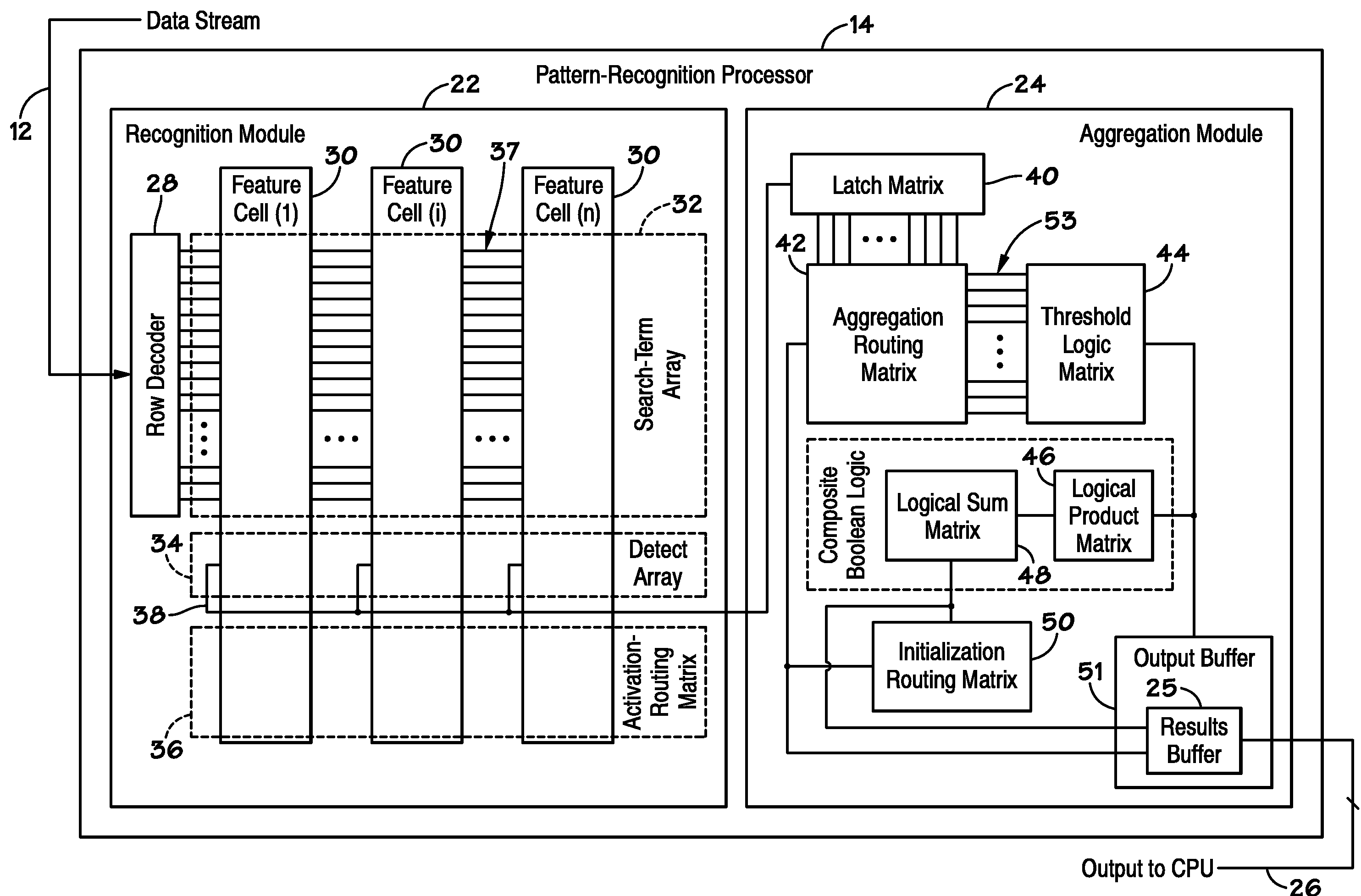
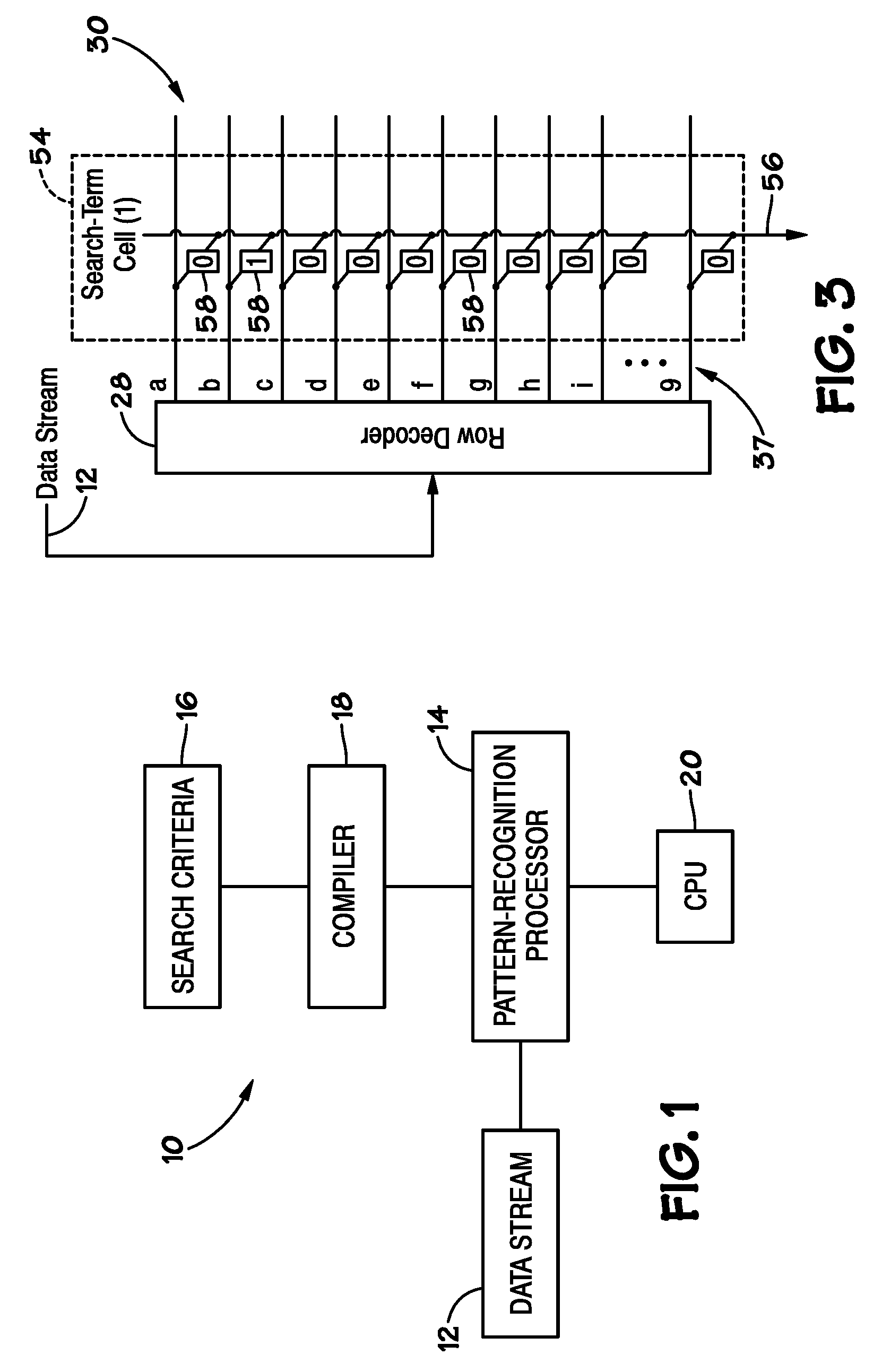
General Purpose Set Theoretic Processor
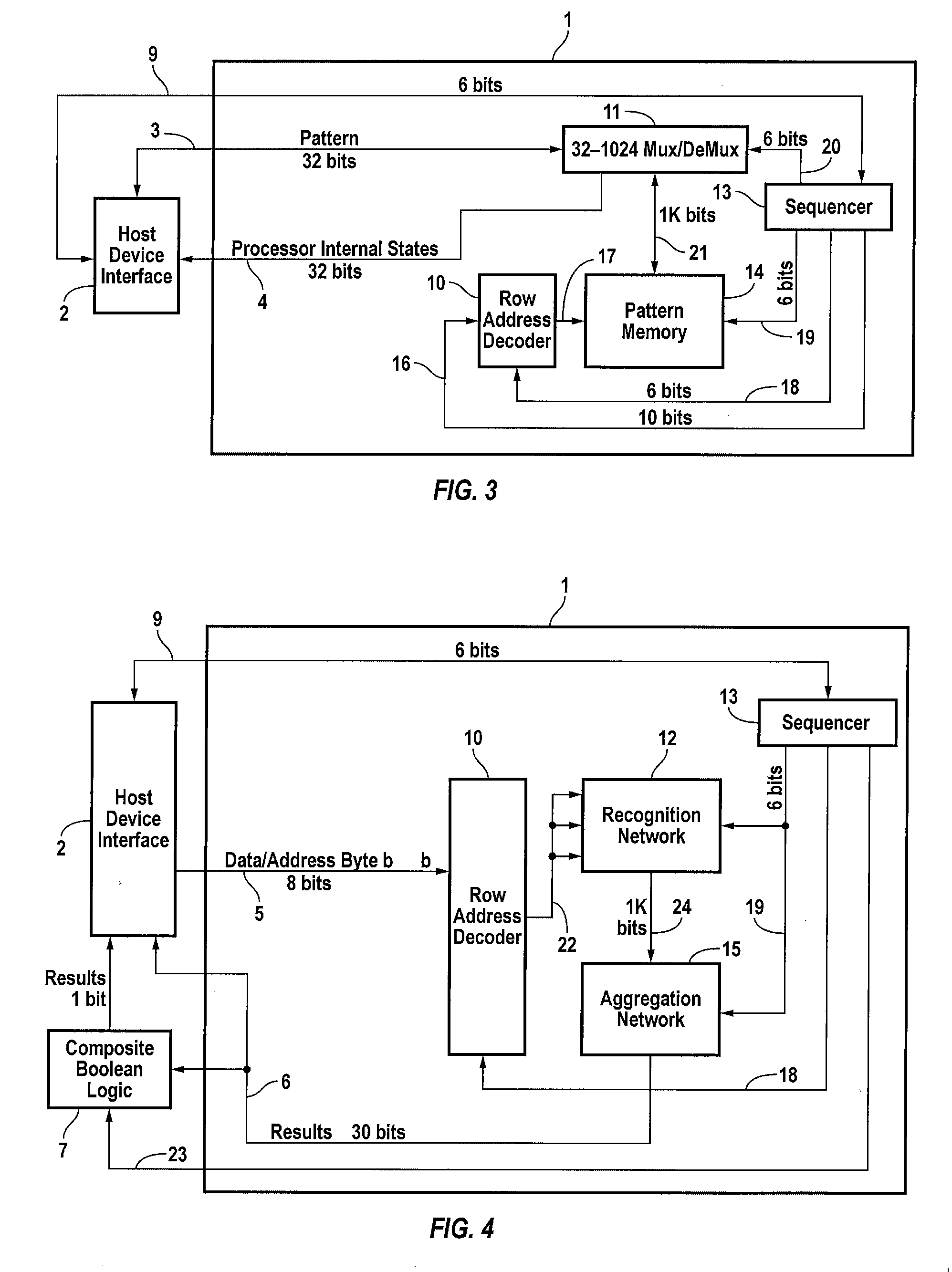
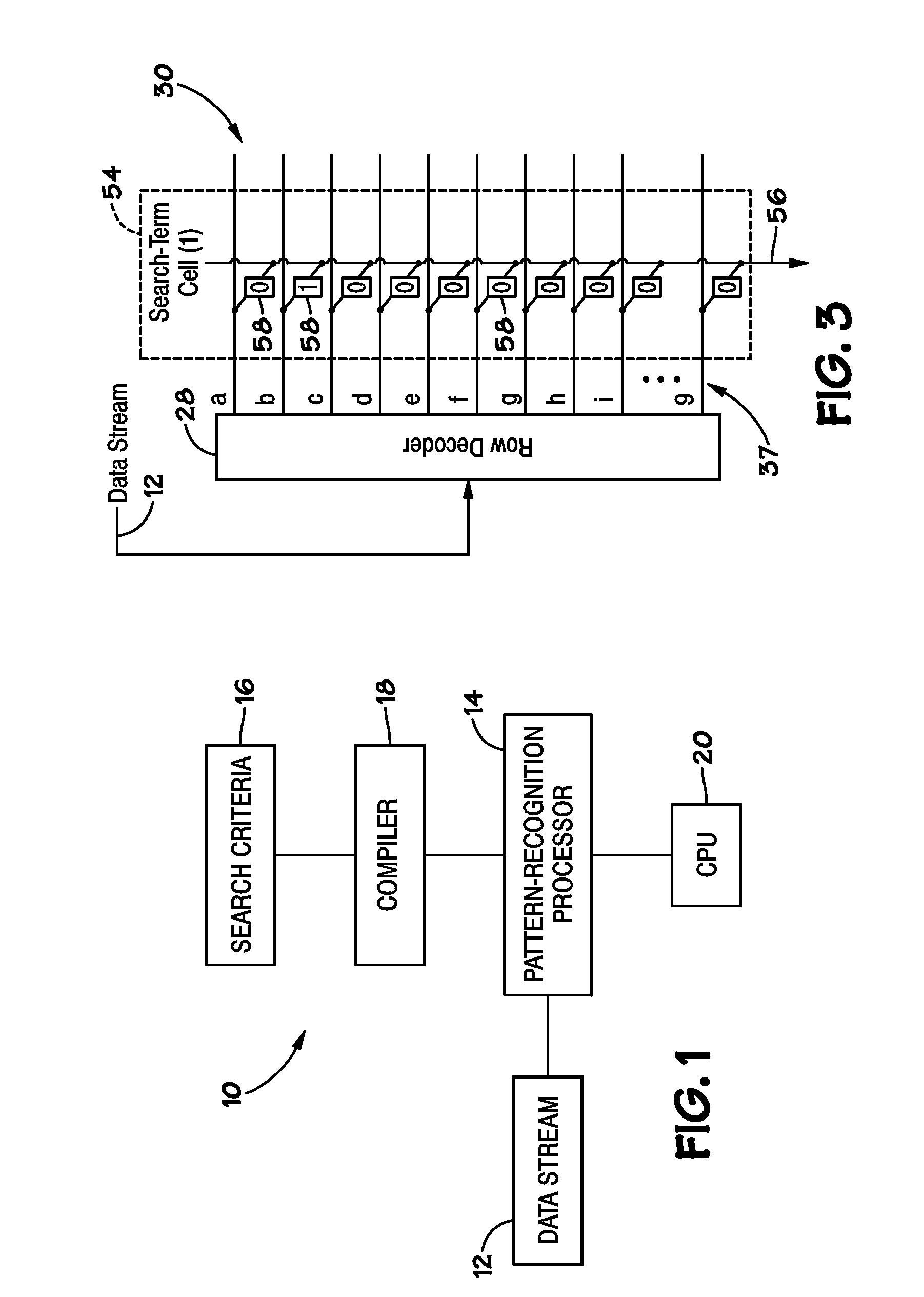
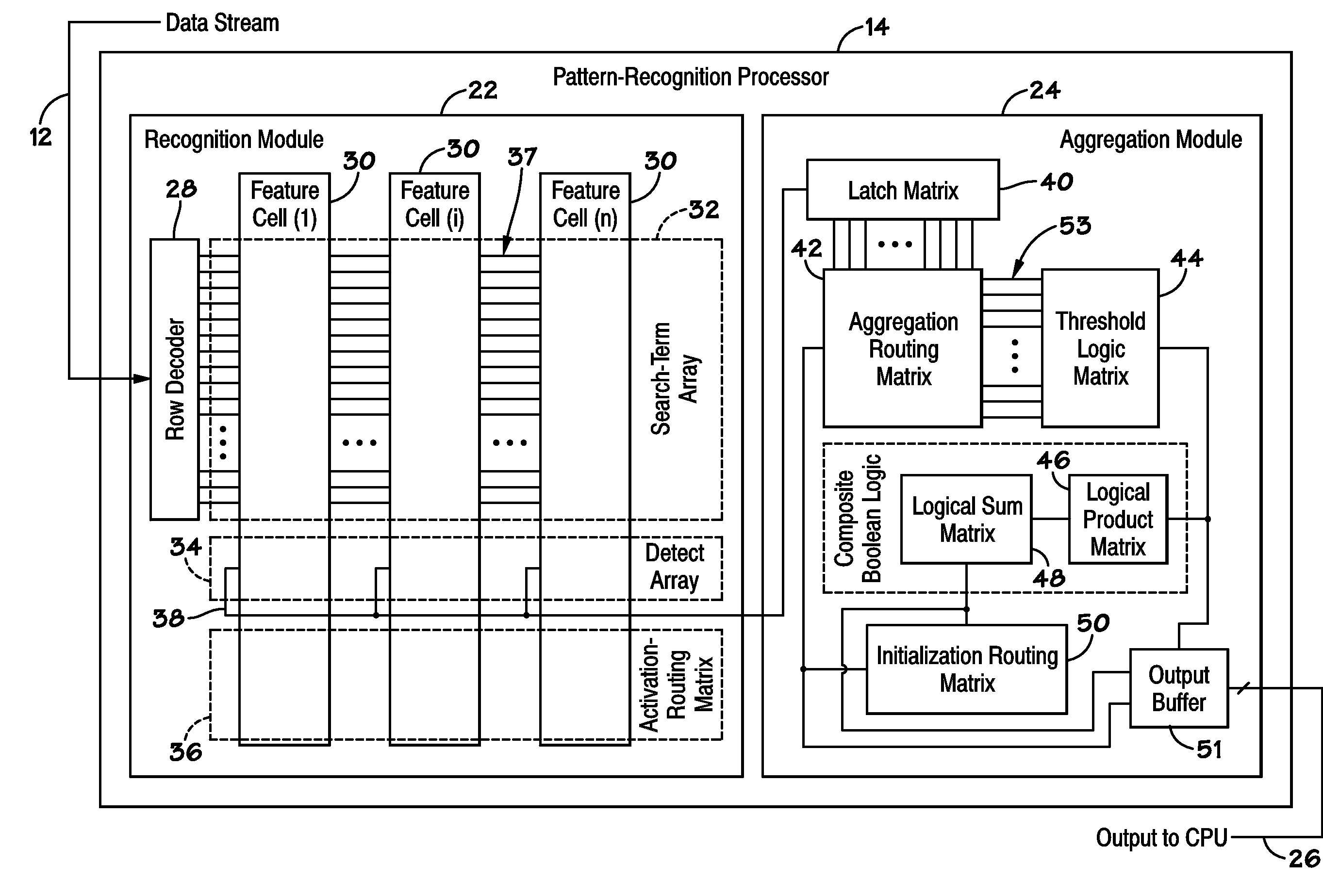
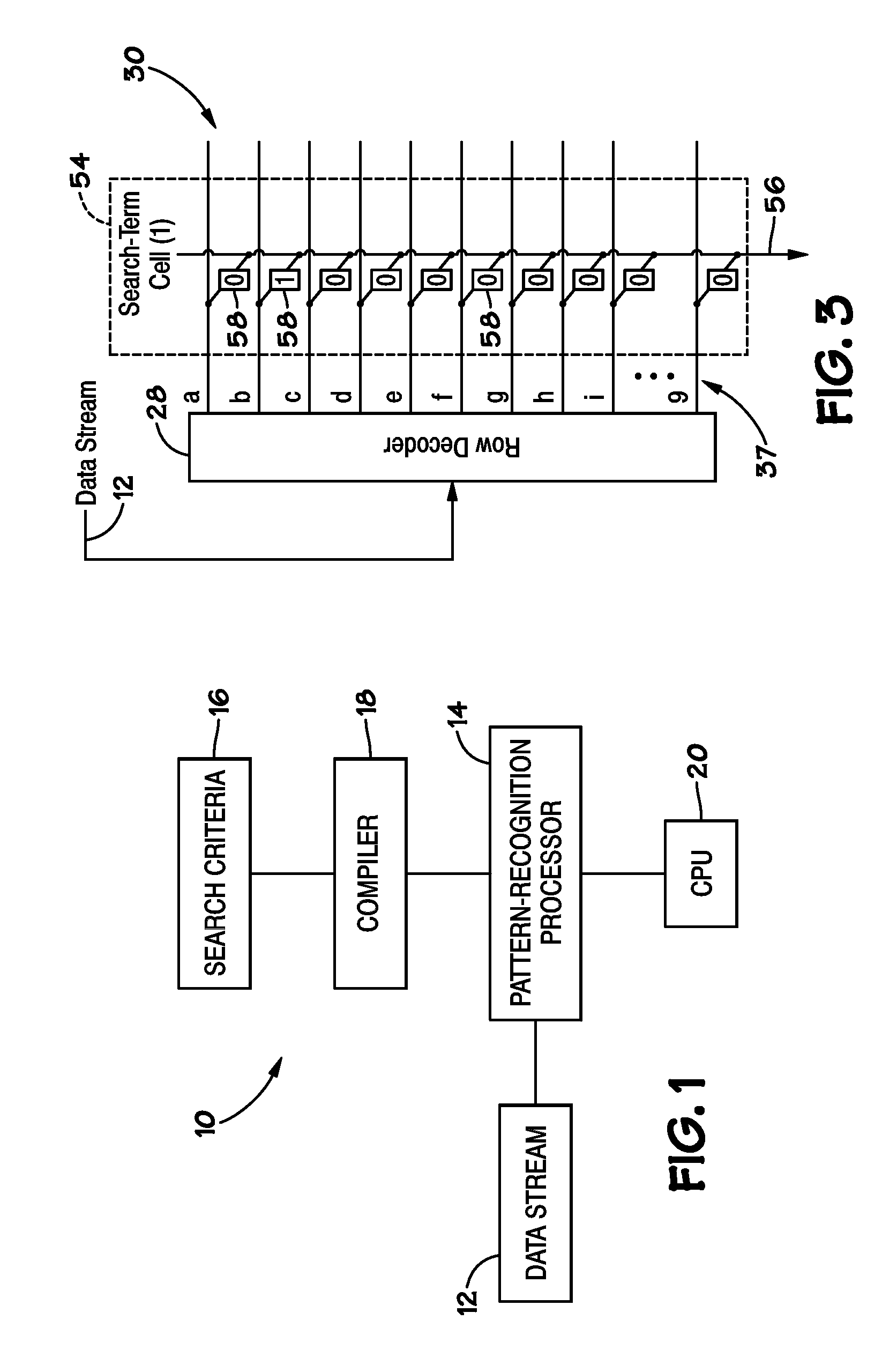
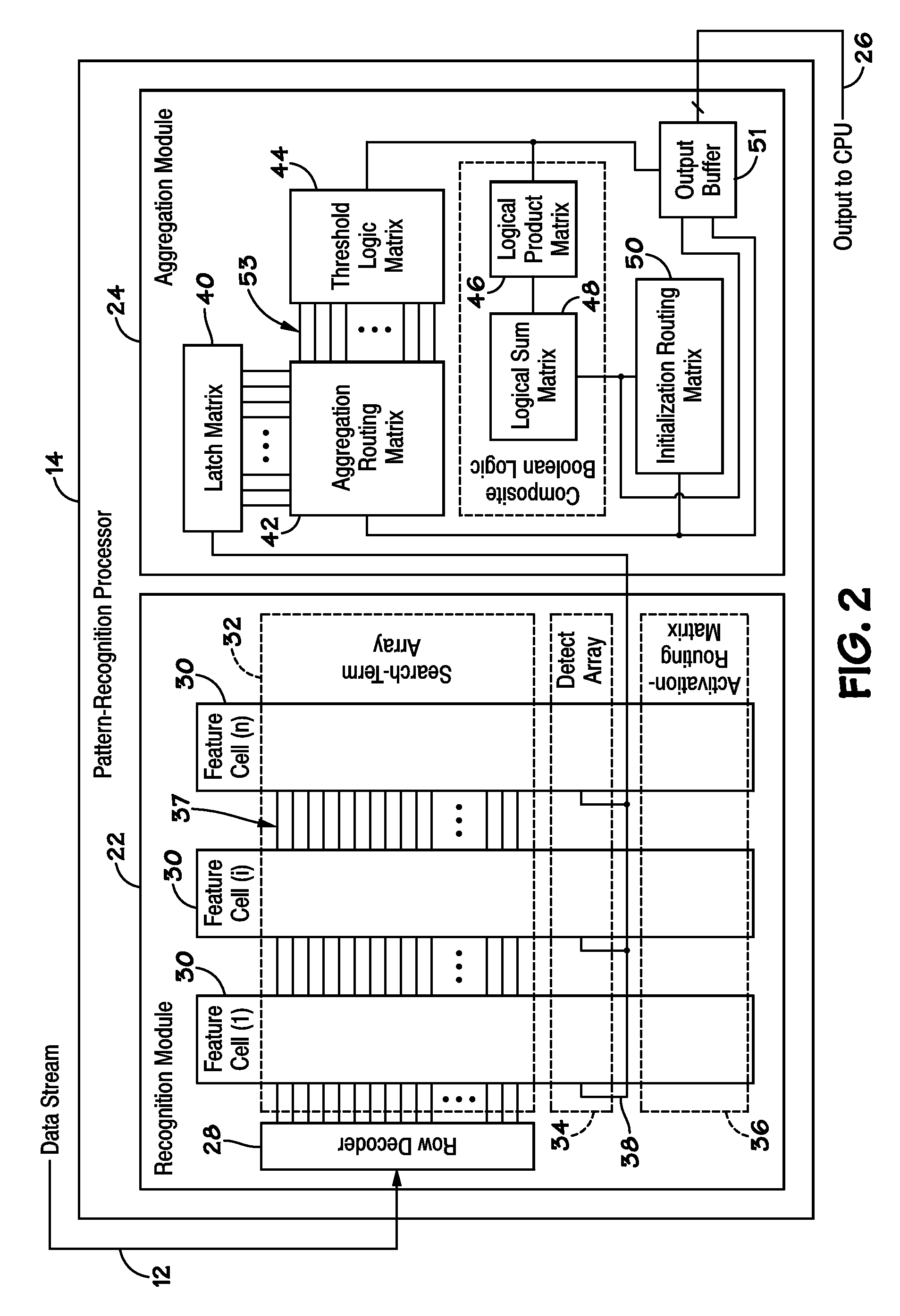
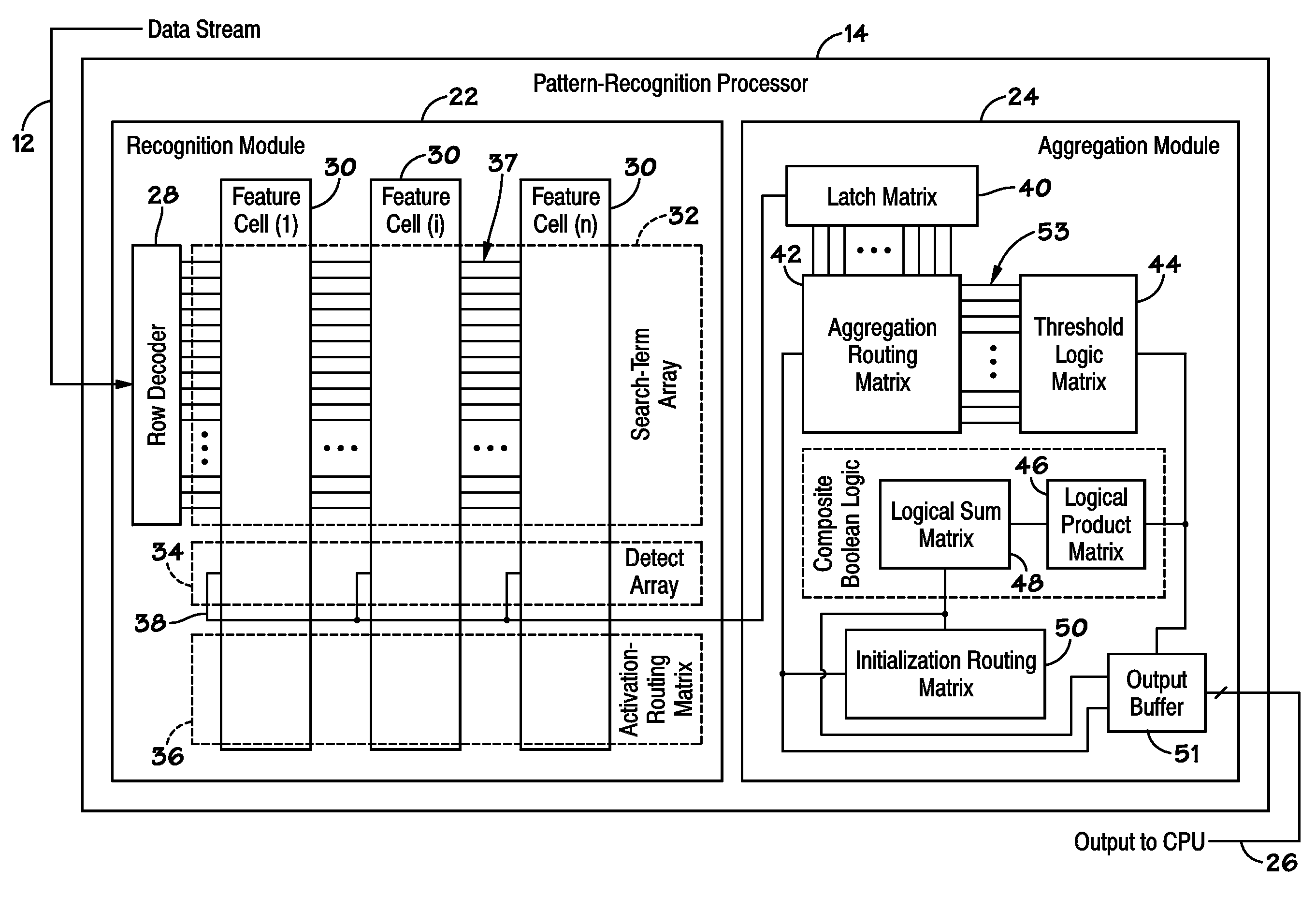
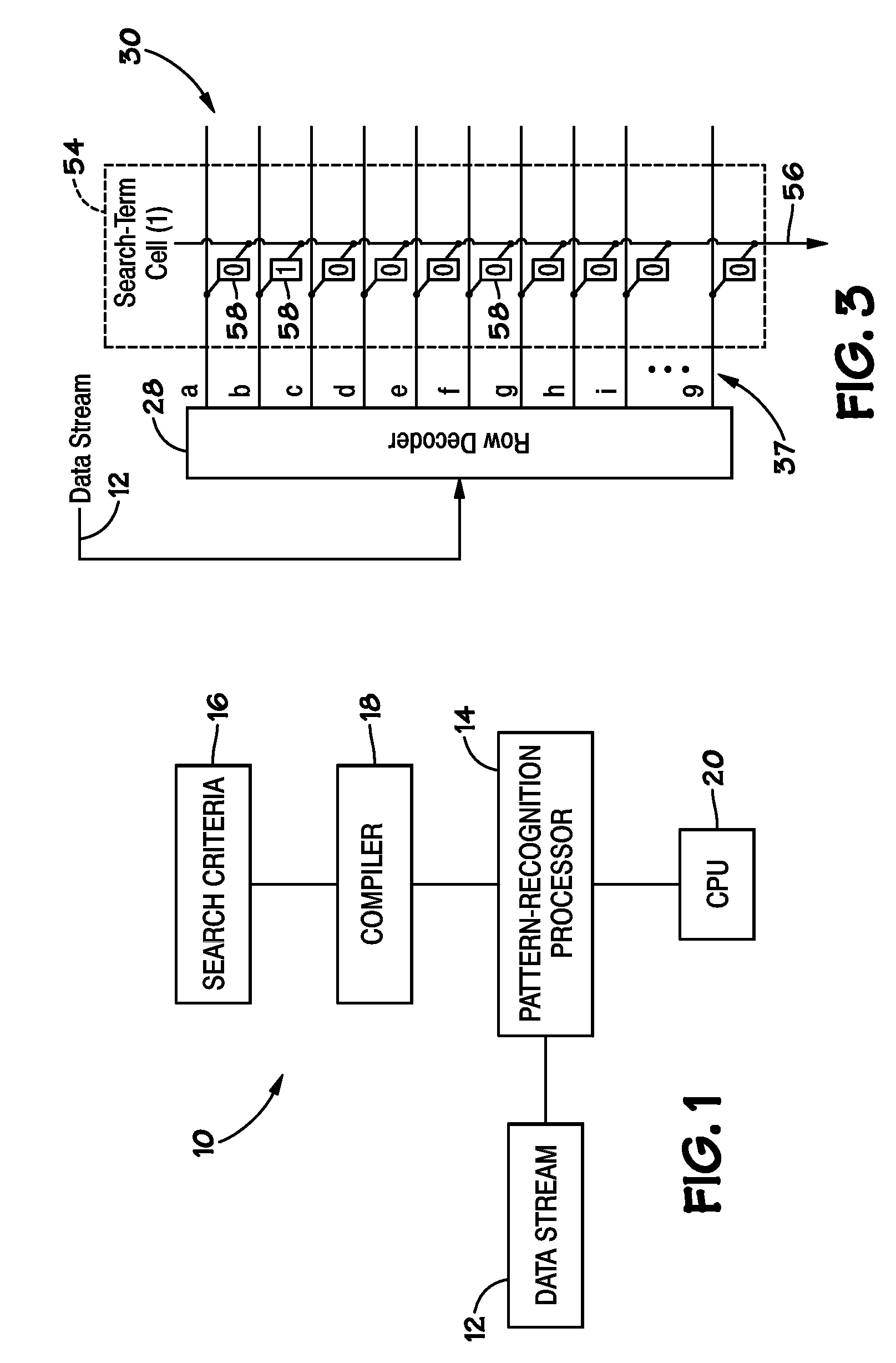
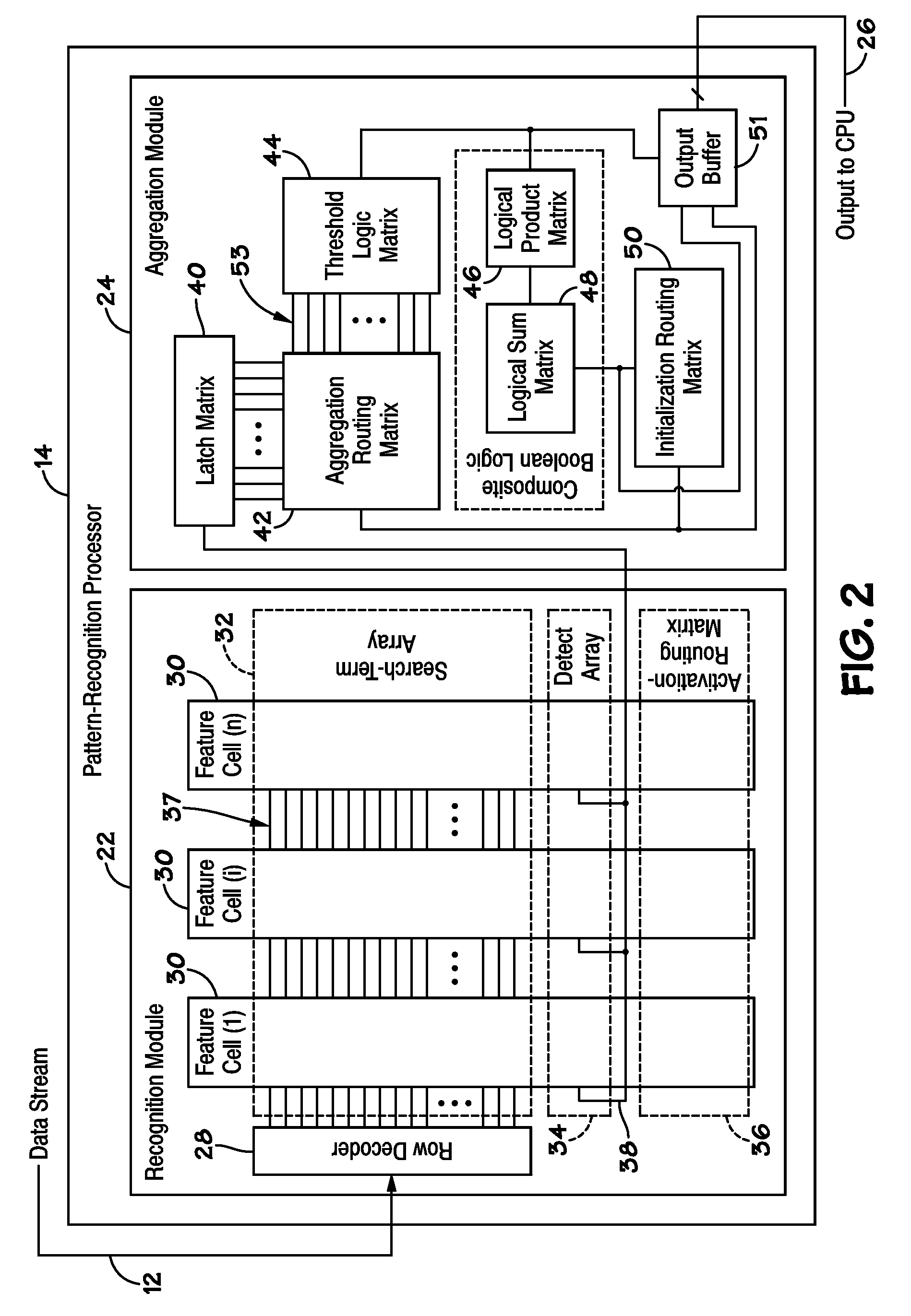
ActiveUS20070127482A1Low costLow of configurabilityDigital computer detailsCharacter and pattern recognitionGeneral purposeData stream
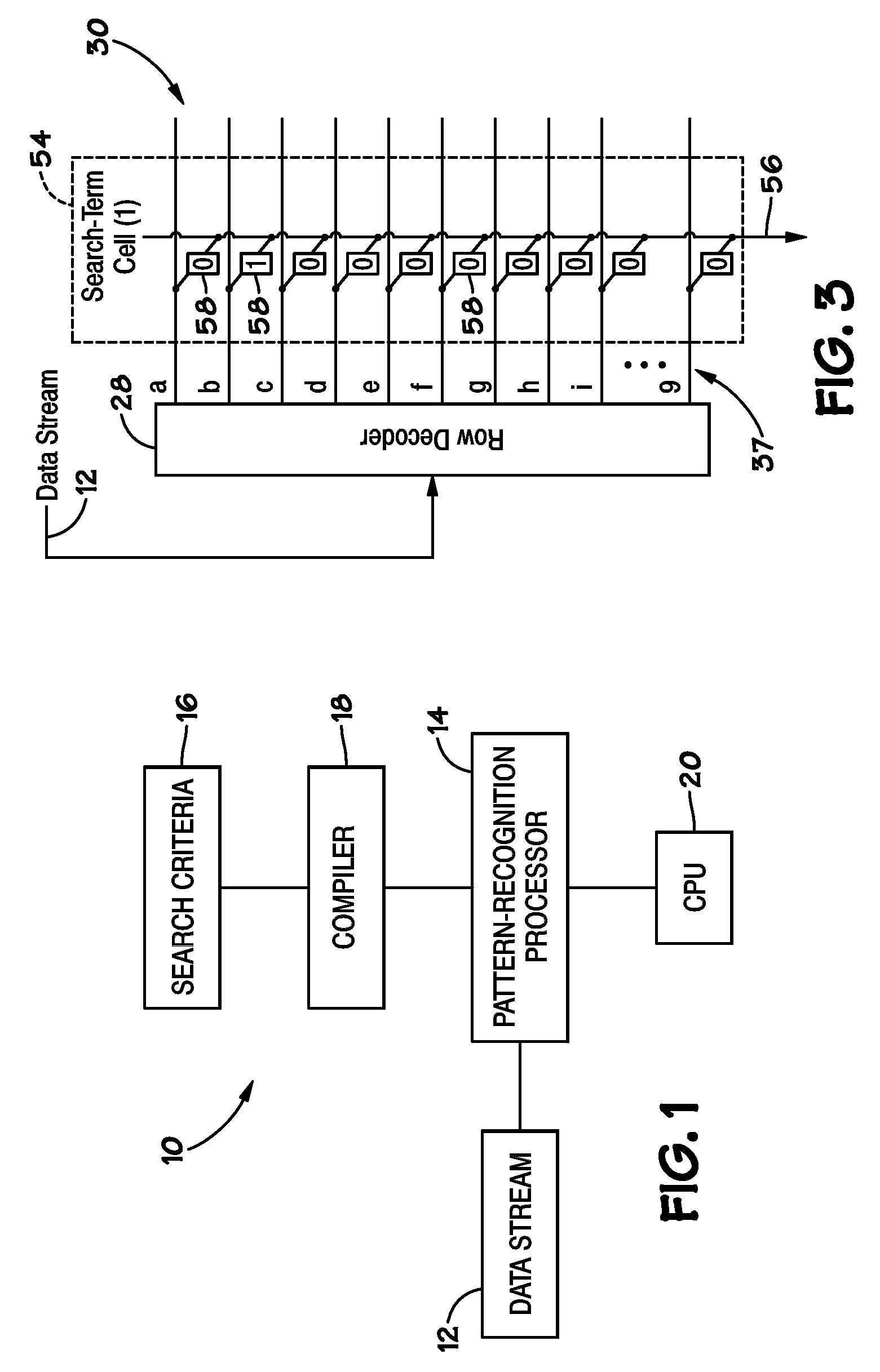
A general purpose processor architecture (methods and apparatuses) that can discern all subsets of a serial data stream which fulfill an arbitrarily complex reference pattern. The invention comprises an ordered set of Detection Cells conditionally interconnected according to the reference pattern and operationally controlling one another's states through the network. The invention preferably includes a Host Interface to enable reporting of Results from a search session as well as the input and control of reference patterns and source data.
Owner:HARRIS CURTIS L
Incremental search of keyword strings
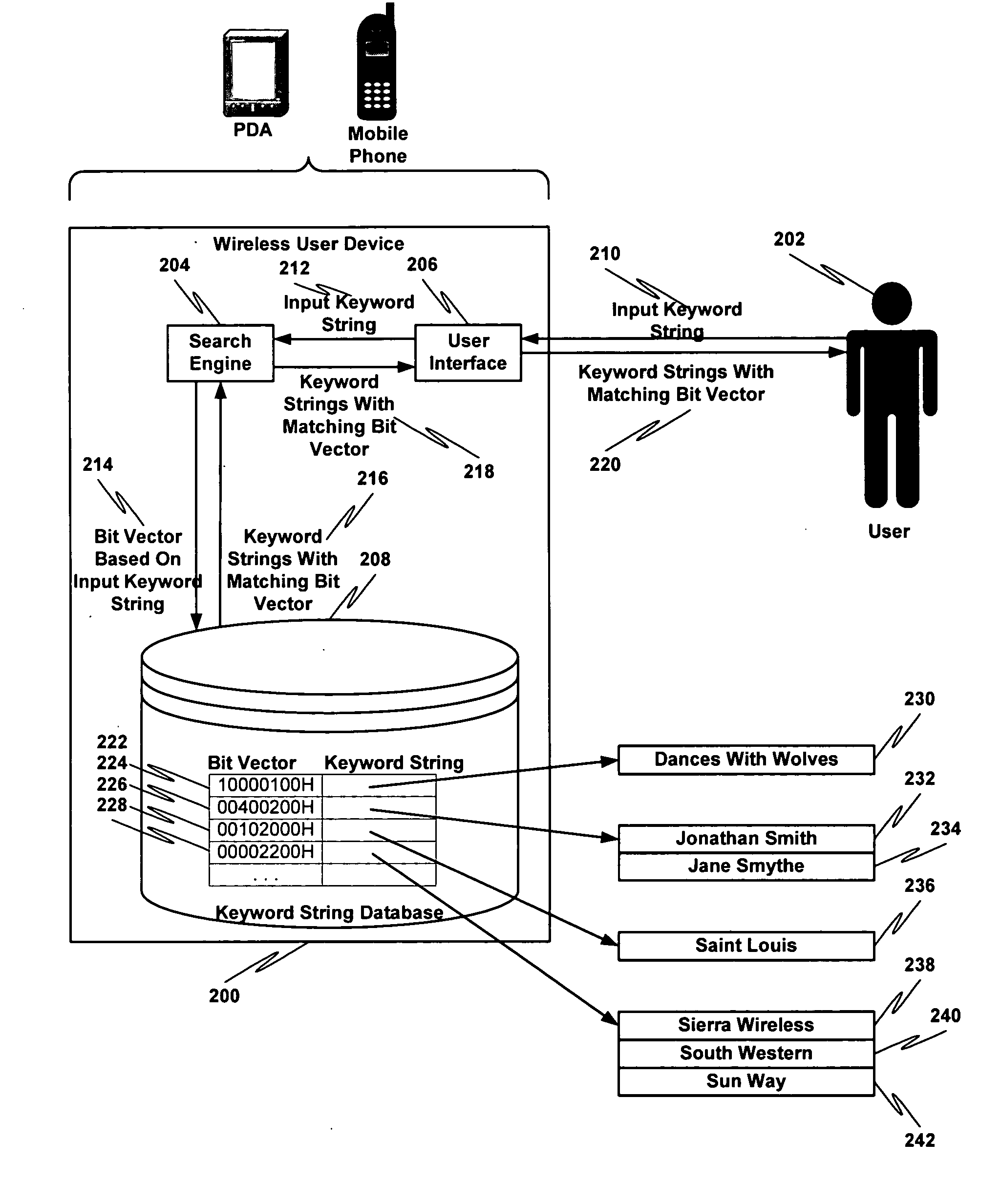
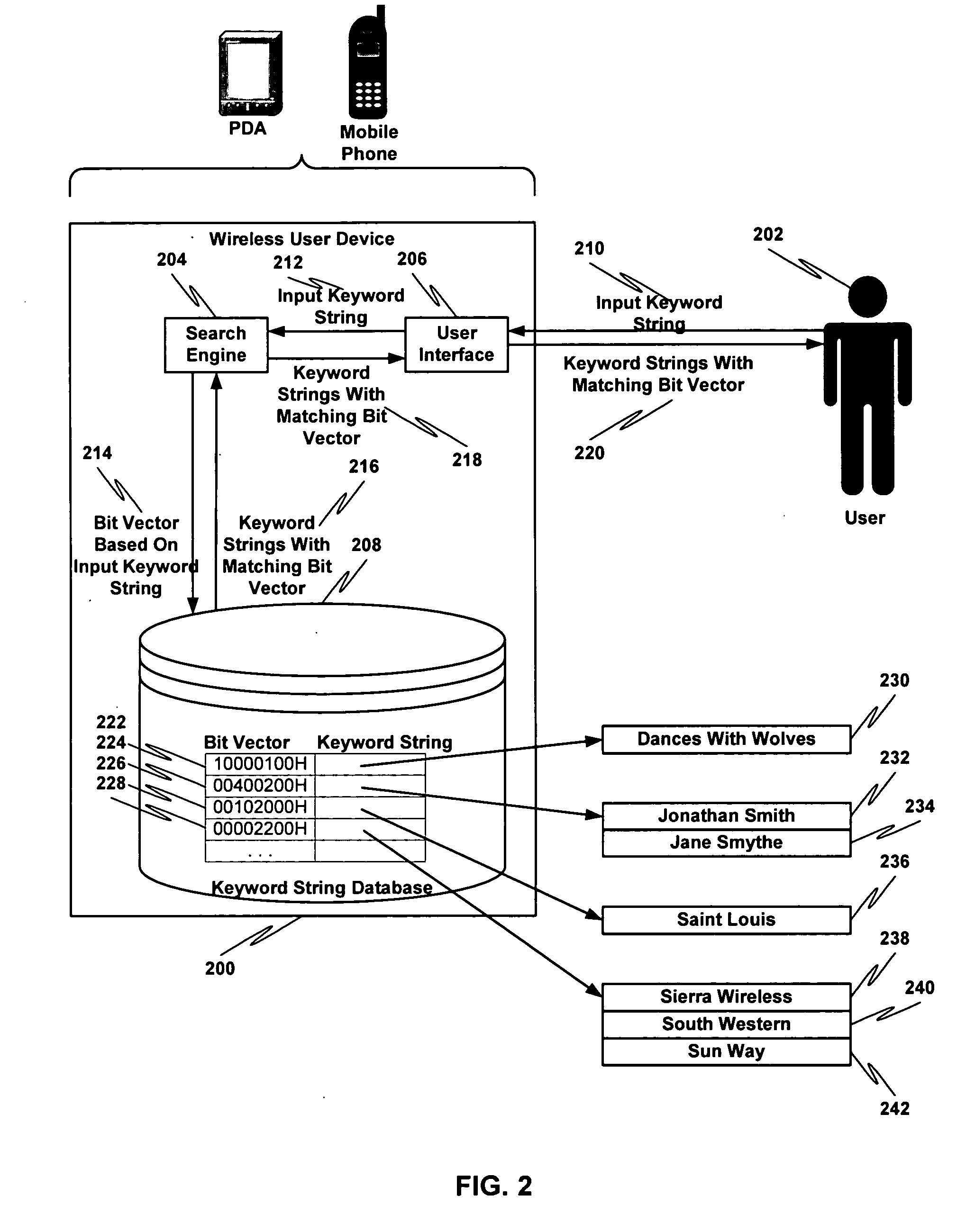
InactiveUS20050086234A1Digital data information retrievalComparison of digital valuesTheoretical computer scienceKeyword search
An incremental keyword search may be performed by receiving an input keyword string comprising one or more words having one or more symbols, creating a bit vector based at least in part on the input keyword string, comparing the bit vector with one or more other bit vectors representing at least one candidate keyword string to create a set of matching bit vectors and applying a conventional keyword matching algorithm to the at least one candidate keyword string represented by the matching bit vectors. Any matching candidate keyword strings are presented.
Owner:SIERRA WIRELESS
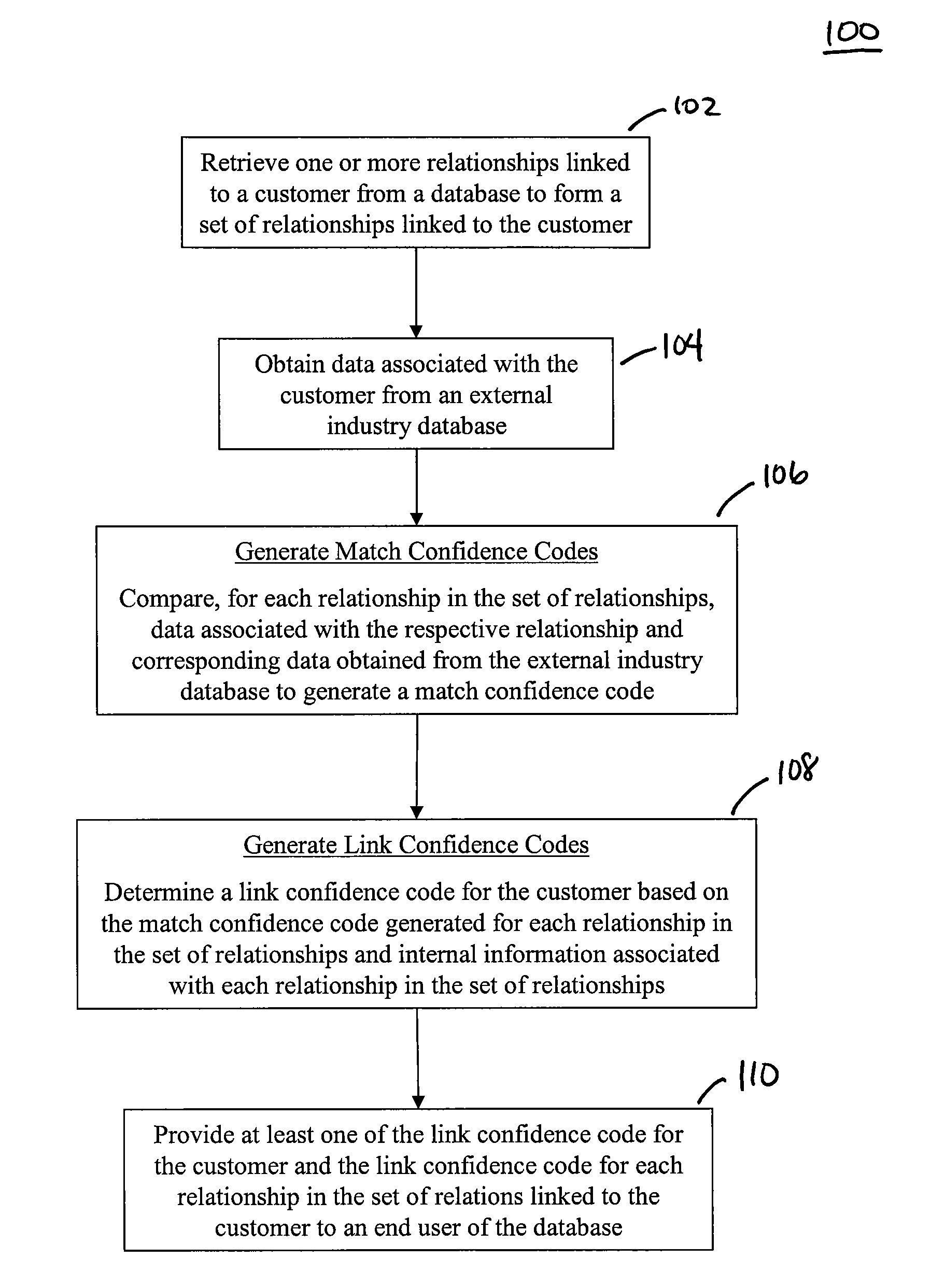
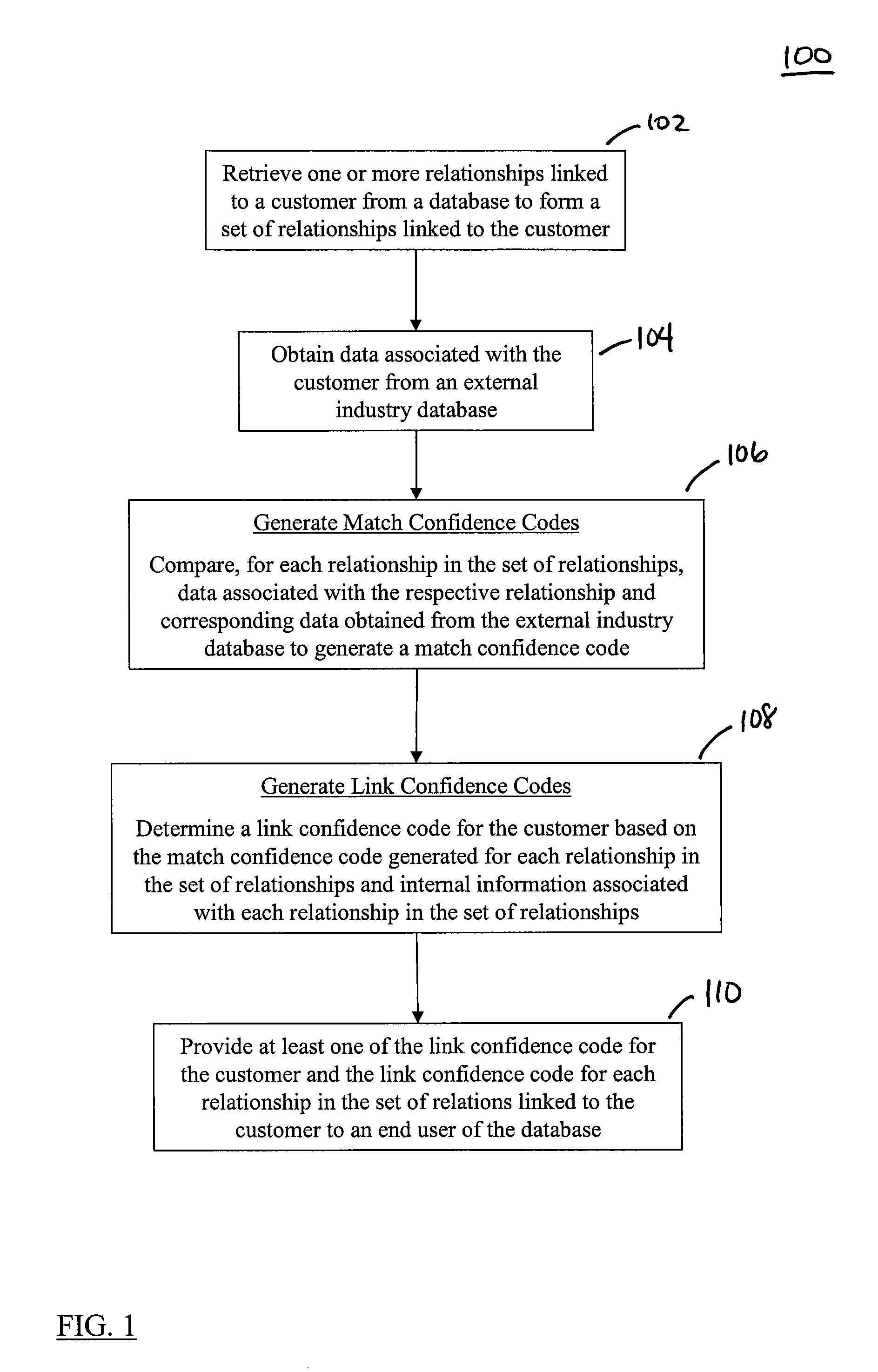
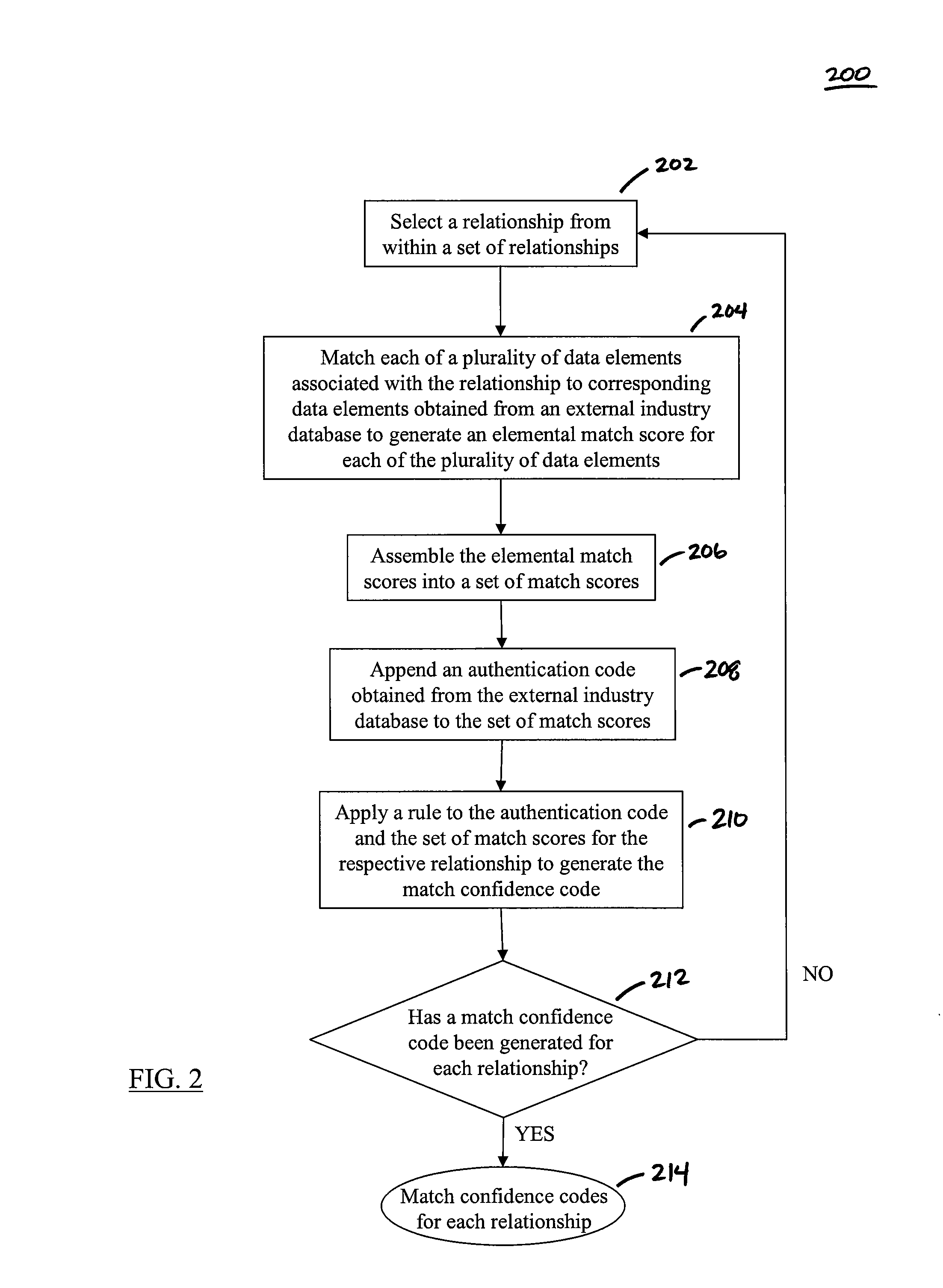
Methods, Systems, and Computer Program Products for Generating Data Quality Indicators for Relationships in a Database
The disclosed methods, systems, and computer-program products allow a business to generate data quality indicators for relationships in a database. In an embodiment, one or more relationships linked to a customer are retrieved from a database to form a set of relationships. A match confidence code is generated for each relationship based on a score generated by the comparison of customer data associated with the respective relationship and corresponding customer data obtained from an external industry database. A link confidence code is subsequently determined for the customer based on a score generated by the scores used to define the match confidence code for each relationship in the set of relationships and on internal data associated with each relationship in the set of relationships. The link confidence code for the customer and the match confidence codes and the respective scores for the set of relationships may be provided to an end user of the database in order to improve decisions made by the end user at the customer level.
Owner:LIBERTY PEAK VENTURES LLC
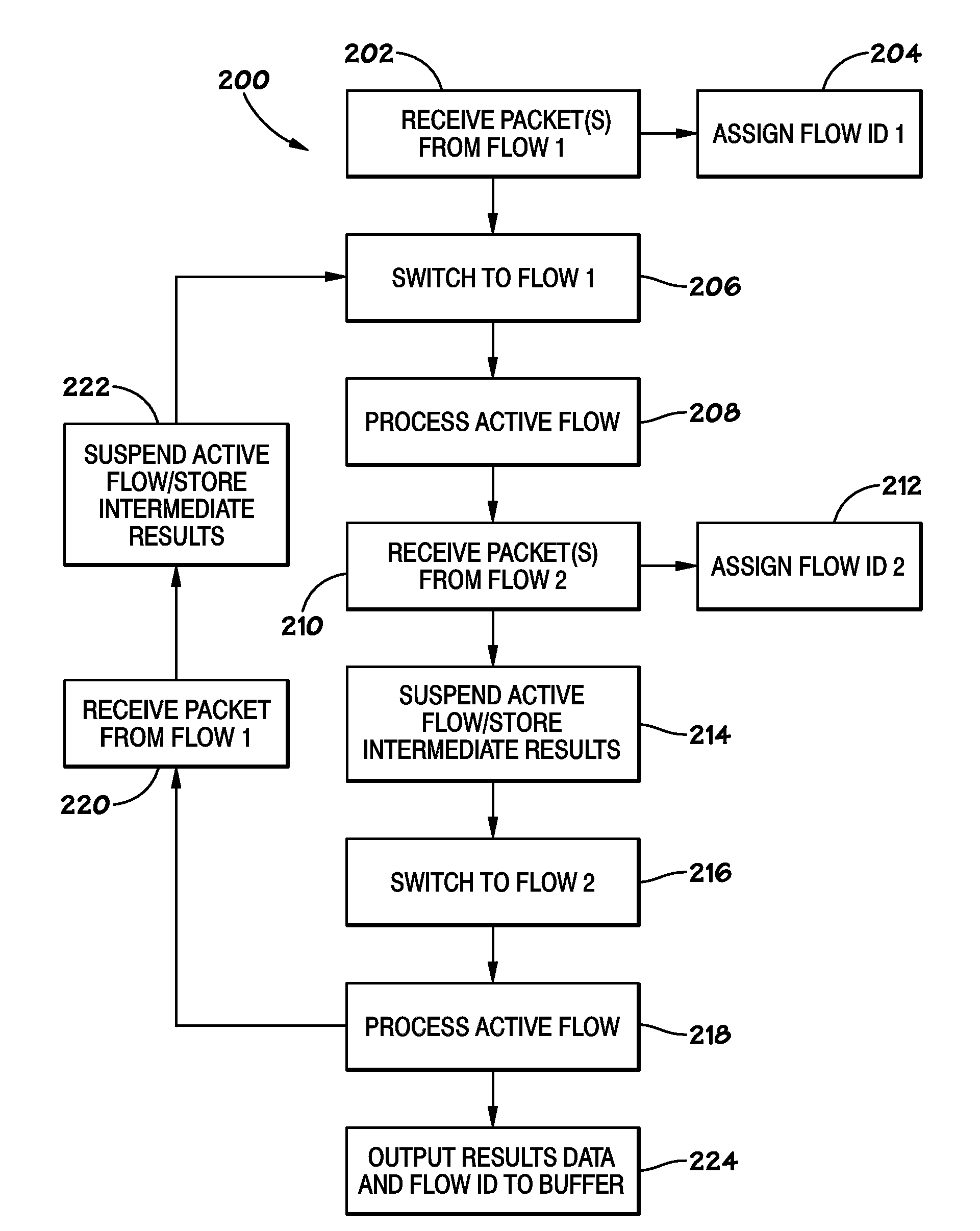
Systems and Methods to Enable Identification of Different Data Sets
ActiveUS20100138432A1Multiple digital computer combinationsComparison of digital valuesData setData stream
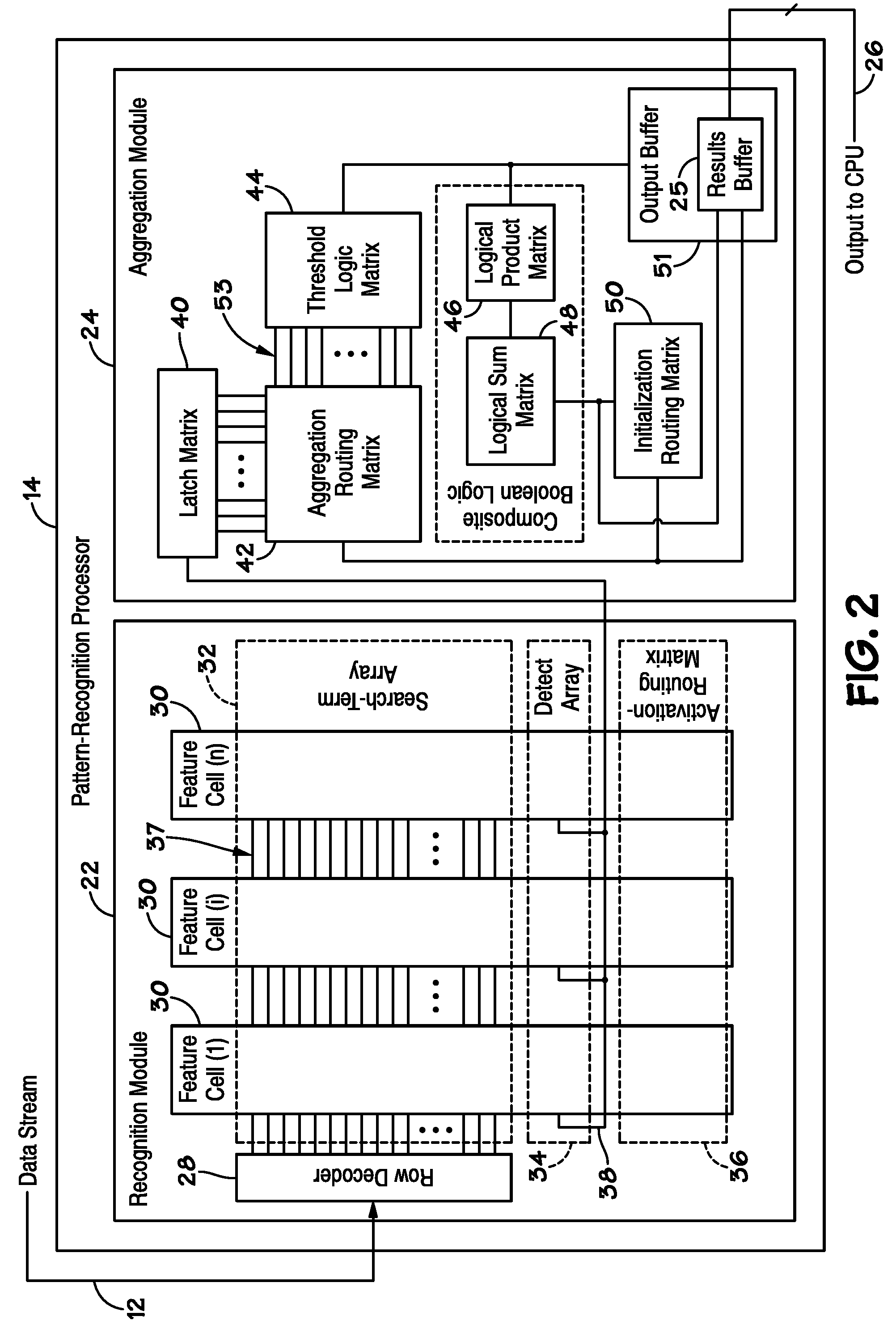
Systems and methods are provided, such as those that enable identification of data flows and corresponding results in a pattern-recognition processor. In one embodiment, a system may include the pattern-recognition processor and a flow identification register, wherein a unique flow identifier for each data flow is stored in the register. The system may include a results buffer that stores the results data and the flow identifier for each data flow, so that the results data may be related to a specific data flow.
Owner:MICRON TECH INC
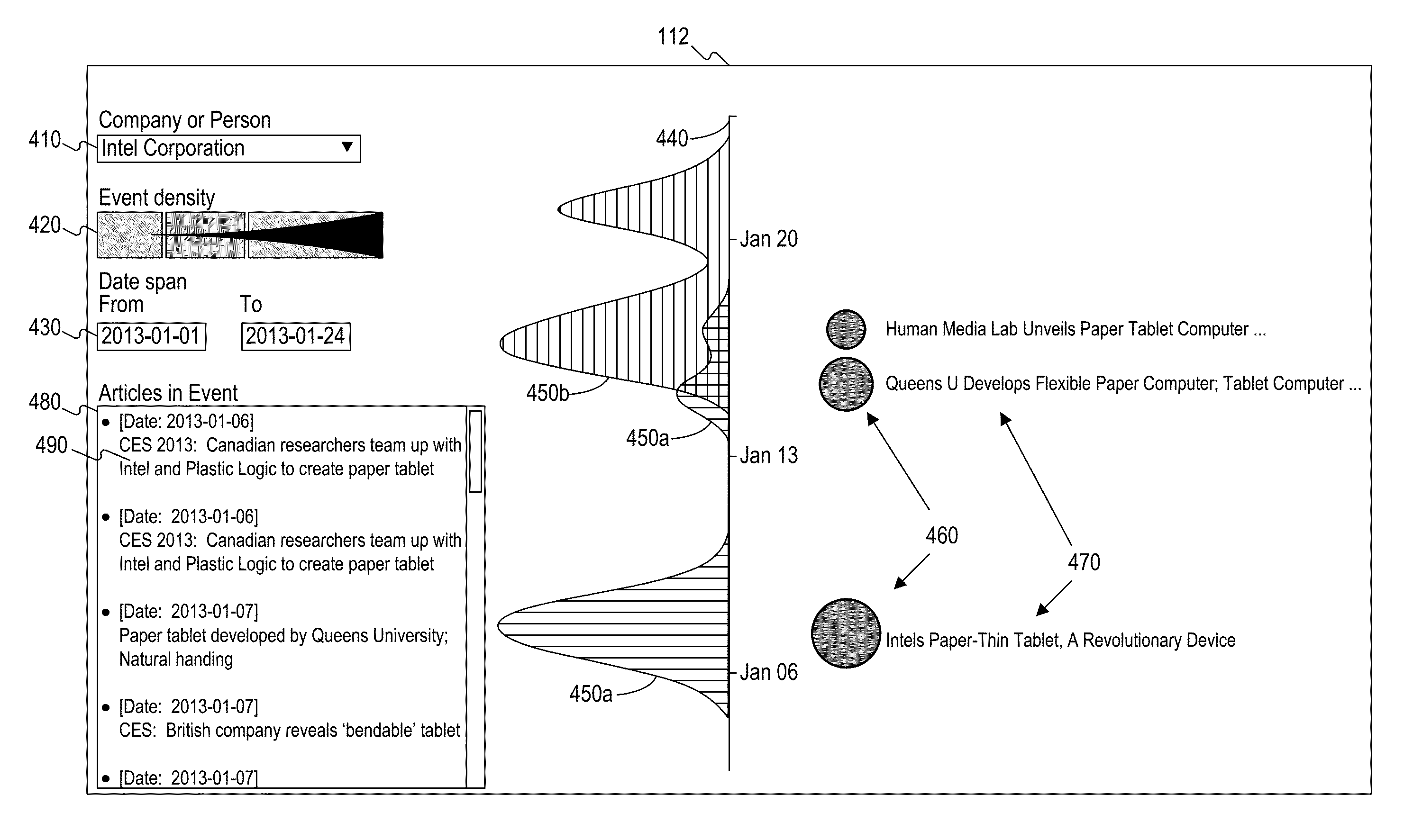
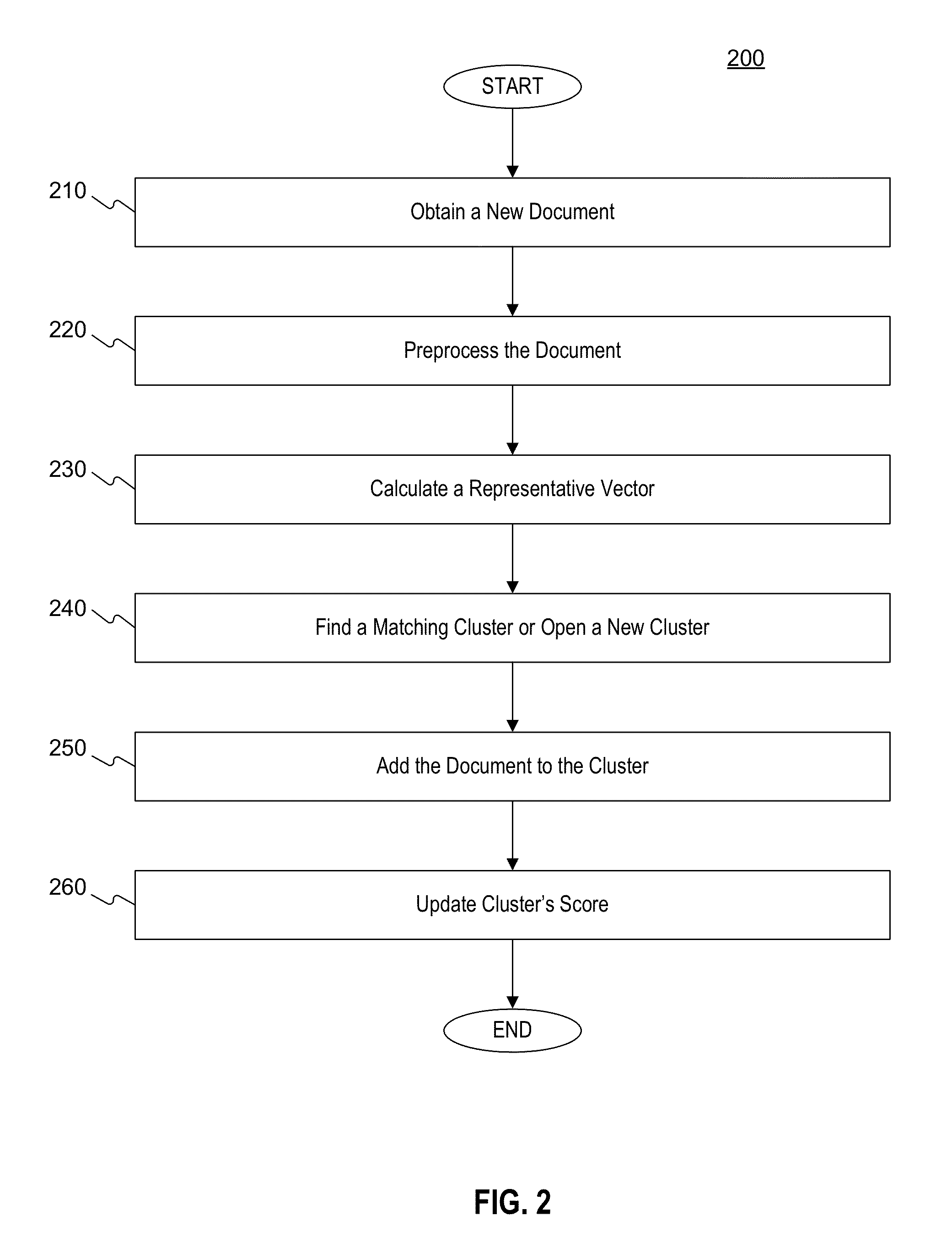
System and method for news events detection and visualization
Systems and methods are disclosed for news events detection and visualization. In accordance with one implementation, a method is provided for news events detection and visualization. The method includes, for example, obtaining a document, obtaining from the document a plurality of tokens, obtaining a document vector based on a plurality of frequencies associated with the plurality of tokens, obtaining one or more clusters of documents, each cluster associated with a plurality of documents and a cluster vector, determining a matching cluster from the one or more clusters based at least on the similarity between the document vector and the cluster vector of the matching cluster, and updating a database to associate the document with the matching cluster.
Owner:PALANTIR TECHNOLOGIES
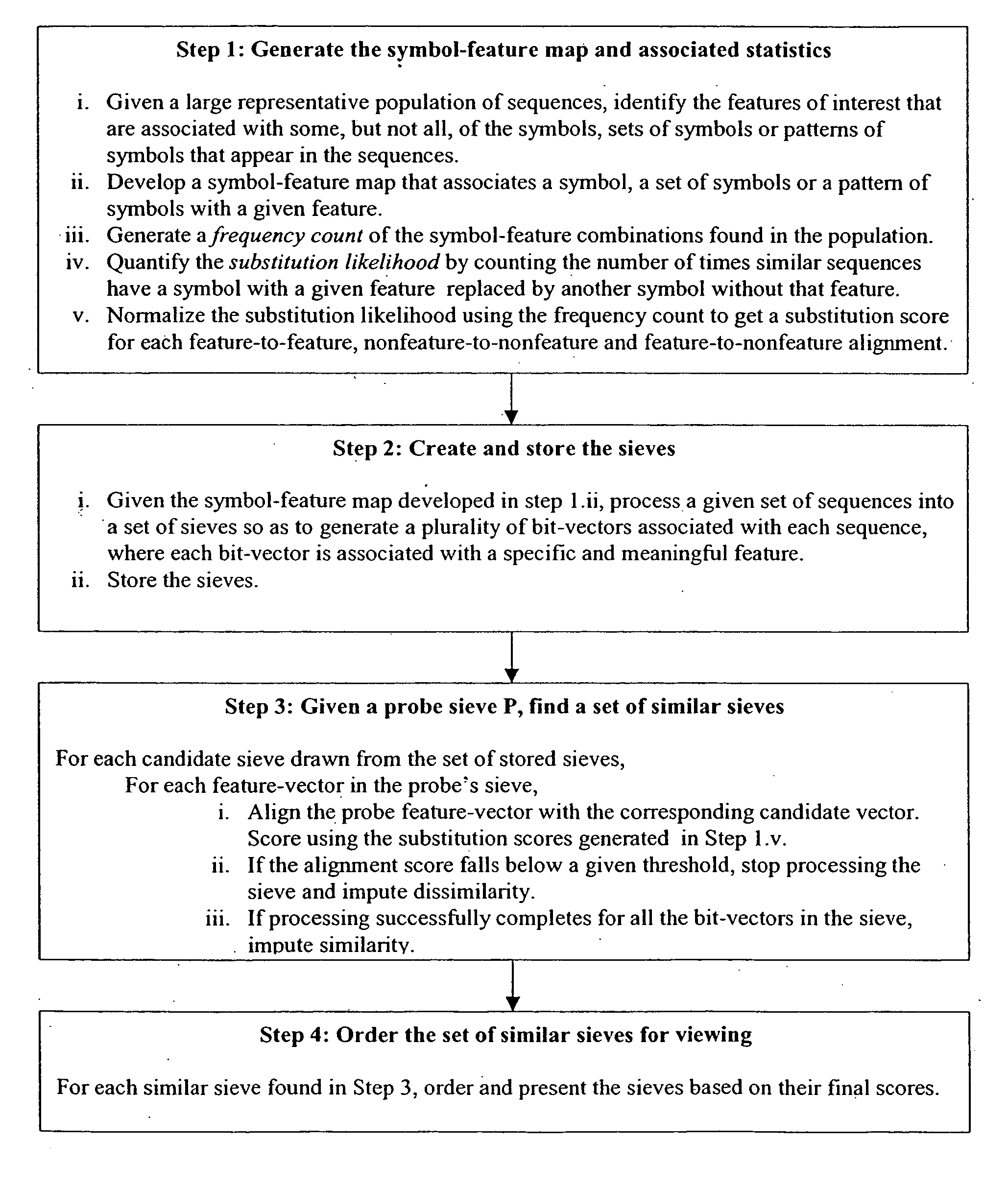
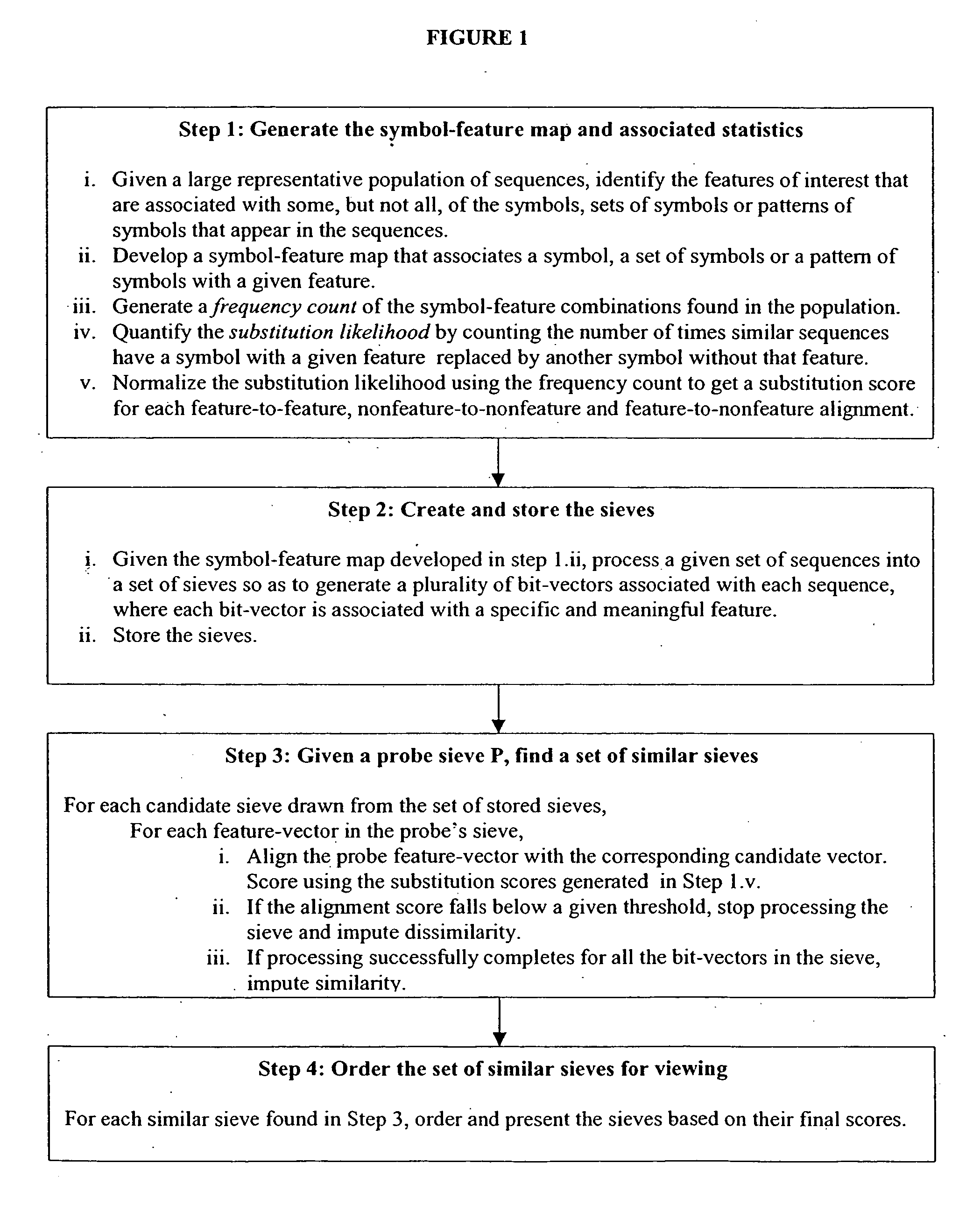
System and method for pattern recognition in sequential data
InactiveUS20050187916A1Easy to useIncrease speedSequence analysisComparison of digital valuesMedical diagnosisSequential data
The present invention is based on the encoding of sequential data or sequences in a novel manner that permits efficient storage and processing of sequential data, as well as methods for searching sequences or databases of sequences. The methods and systems of the current invention may be adapted broadly to various fields of application and to a variety of sequences types. For example, the current invention has broad application including to the fields of bioinformatics, molecular biology, pharmacogenomics, phonetic sequences, lexicographic sequences, signal analysis, game playing, law enforcement, biometrics, medical diagnosis, equipment maintenance and micro-array data analysis.
Owner:ELORET CORP
Buses for Pattern-Recognition Processors
InactiveUS20100174887A1General purpose stored program computerCharacter and pattern recognitionMemory busParallel computing
Disclosed are methods and systems, among which is a system that includes a pattern-recognition processor, a central processing unit (CPU) coupled to the pattern-recognition processor via a pattern-recognition bus, and memory coupled to the CPU via a memory bus. In some embodiments, the pattern-recognition bus and the memory bus form about the same number of connections to the pattern-recognition processor and the memory, respectively.
Owner:MICRON TECH INC
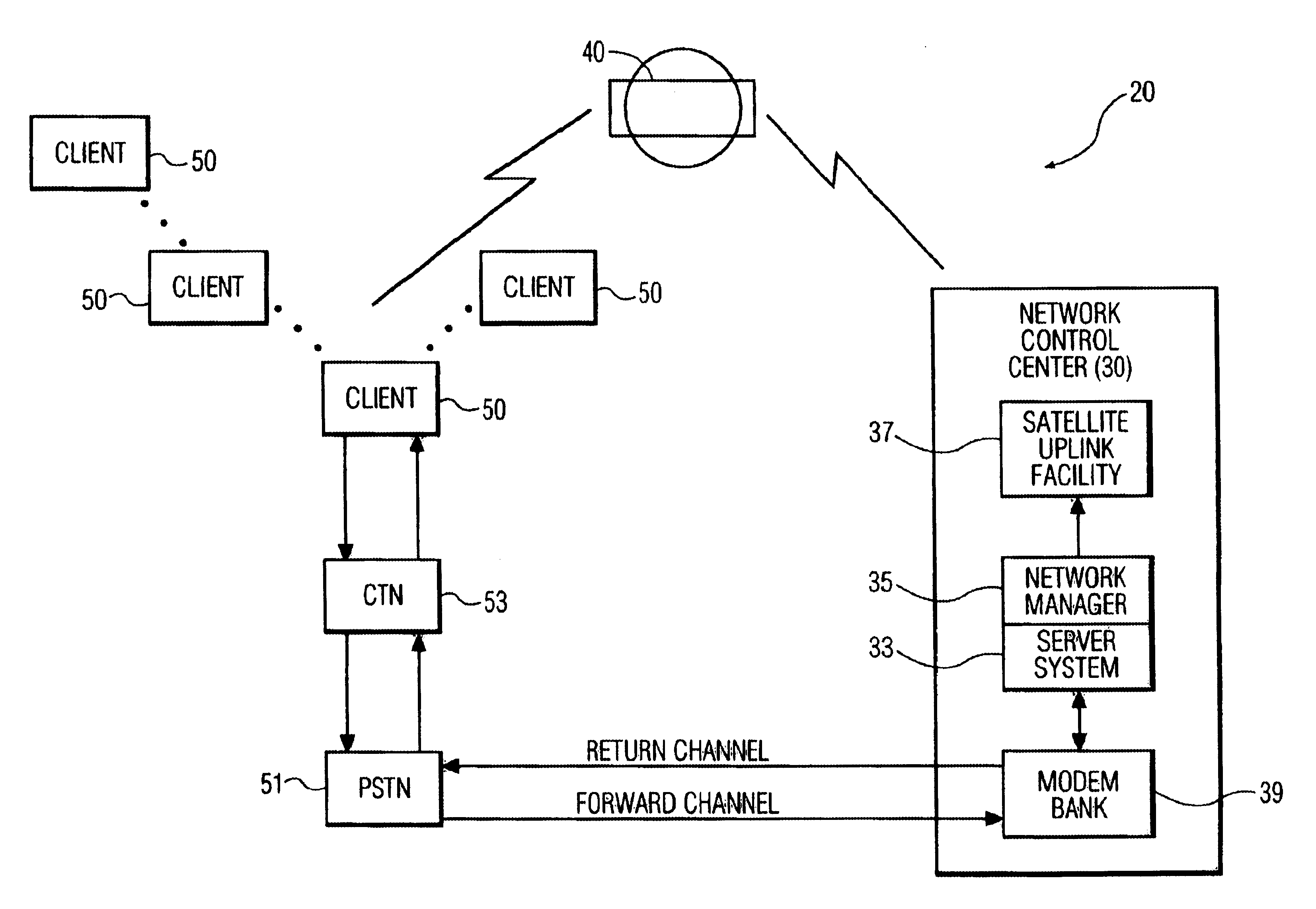
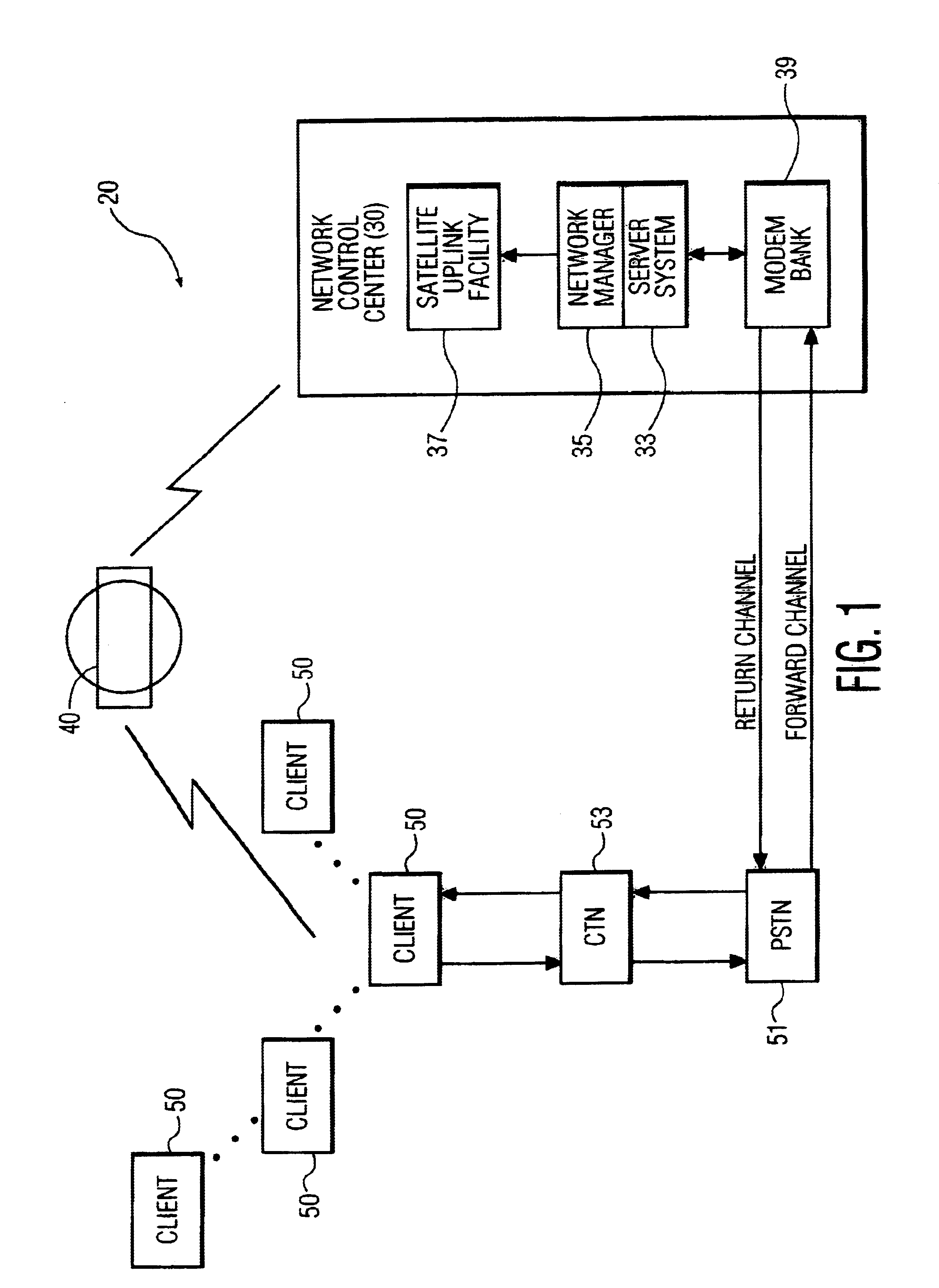
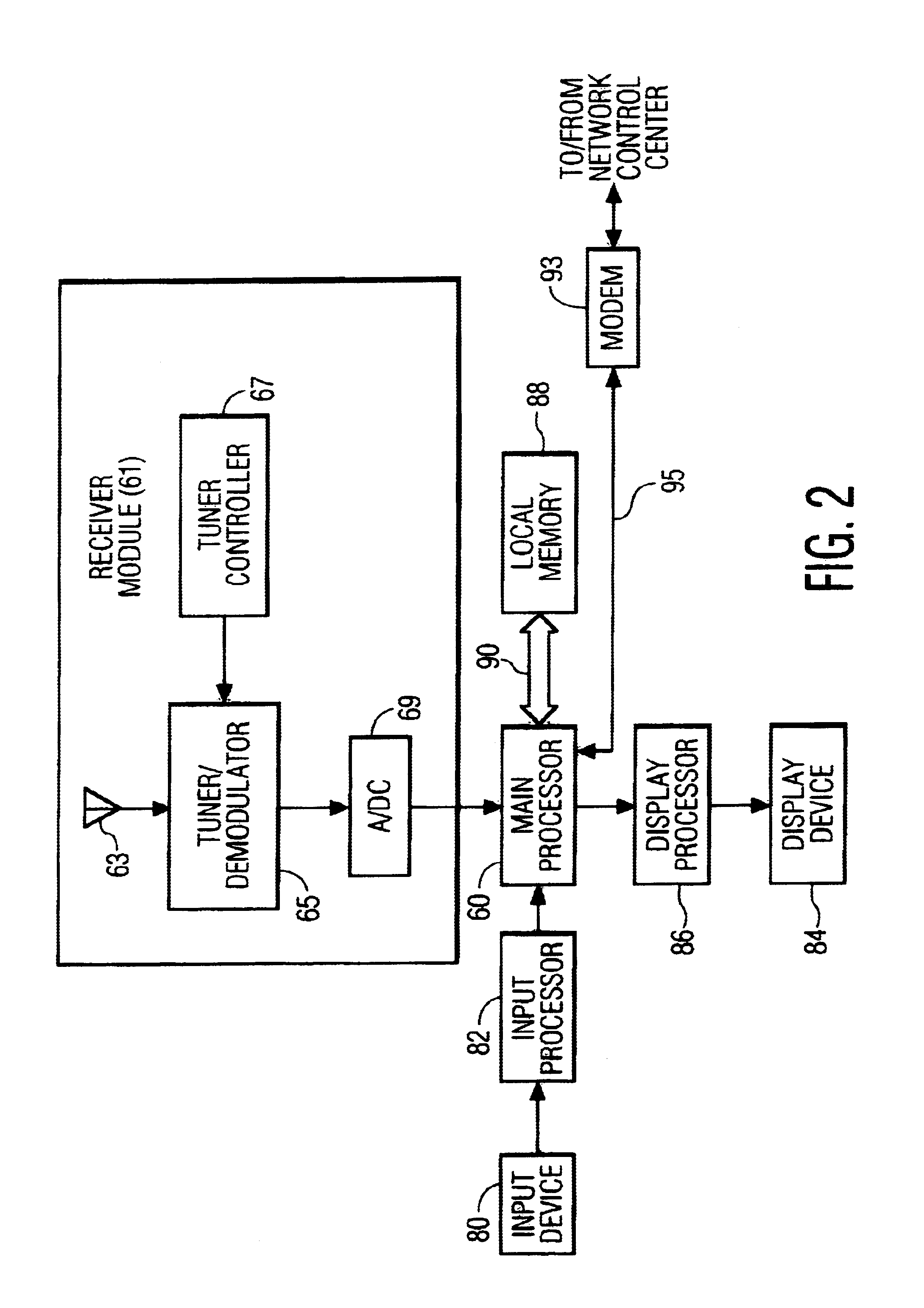
System for broadcasting software applications and portable data communications device for use in such a system
InactiveUS6928468B2Error prevention/detection by using return channelFrequency-division multiplex detailsModem deviceApplication software
A communications system consisting of a server system that stores software applications, a broadcast system that broadcasts the software applications, and a multiplicity of portable clients that each include a receiver having a tuner that is selectively tunable to receive a selected one of the software applications broadcasted by the broadcast system. The portable clients can be any type of portable data communications device, such as a hand-held, palm-top, or notebook computing device, a PDA, an intelligent cellular phone, or any other personal multimedia appliance or Network Computer (NC). The broadcast system can be any suitable satellite or terrestrial air or cable broadcast system. The software applications can consist of a broad spectrum of different software applications, such as word processing, video games, spreadsheets, address books, calendars, and the like. Each of the portable data communications devices includes a receiver that has a tuner that is selectively tunable to receive a selected one of a plurality of software applications broadcasted by a broadcast system, a user-interface that enables a user to select one of the broadcasted software applications for downloading, a processor for executing the downloaded software applications, and a modem for establishing a two-way communications link with a network control system. The two-way communications link includes a forward channel over which the portable data communication device can transmit client data to the network control system, and a return channel over which the network control system can transmit system data to the portable data communication device. The client data can include requests for unrecoverable software application data and client software download request data.
Owner:KONINK PHILIPS ELECTRONICS NV
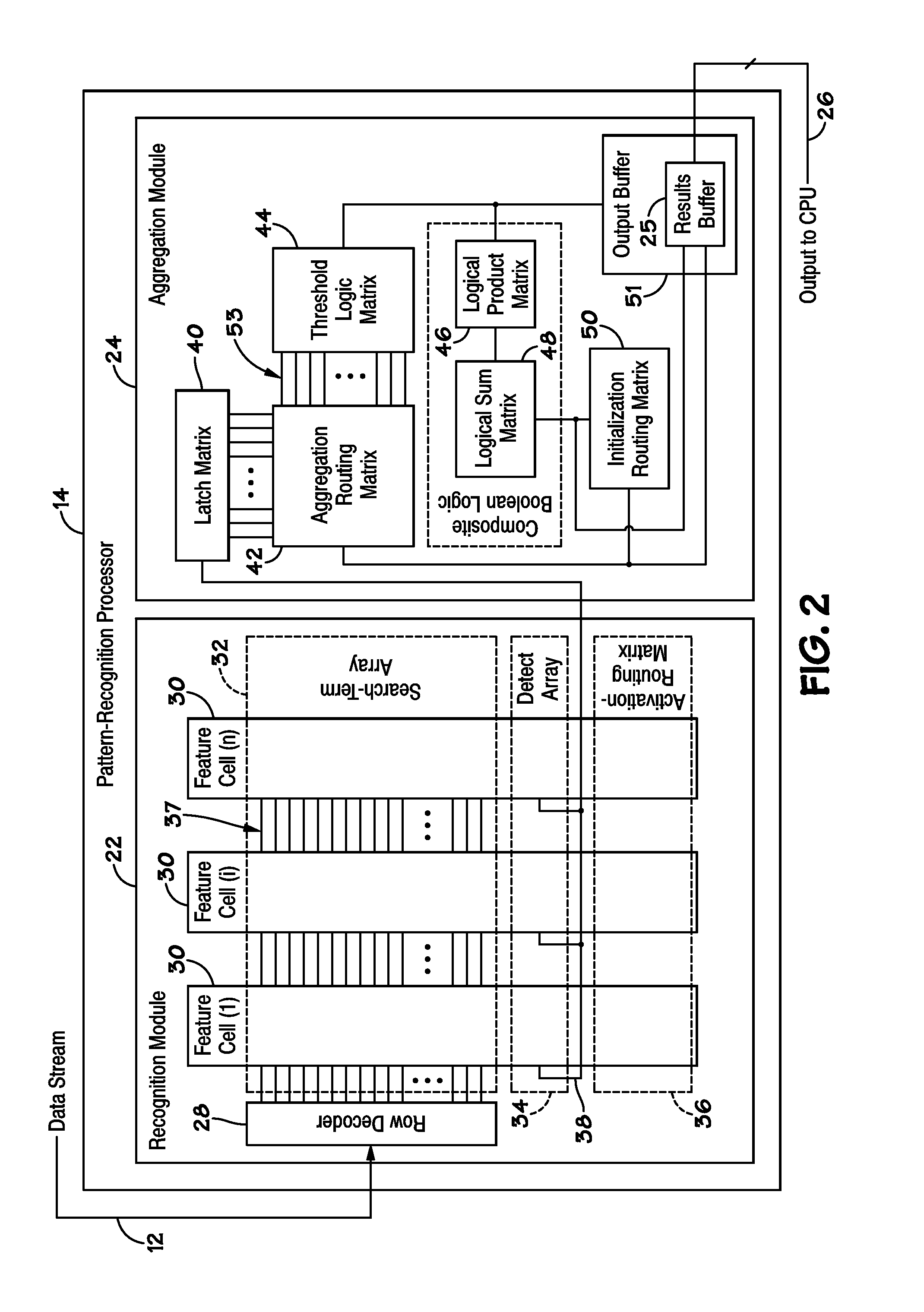
Devices, systems, and methods for communicating pattern matching results of a parallel pattern search engine
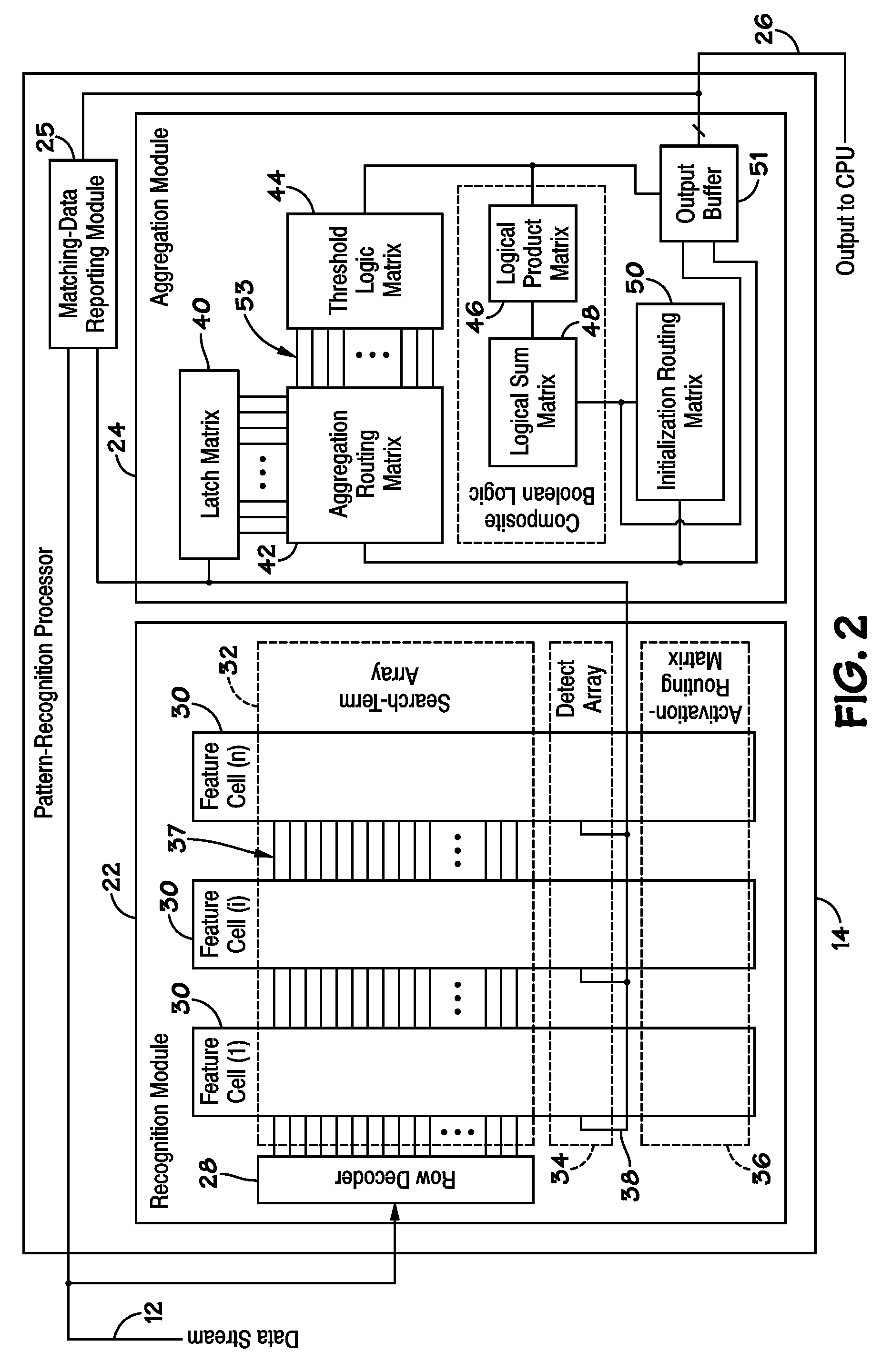
ActiveUS20100185647A1Error detection/correctionComparison of digital valuesSearch functionPattern recognition
Disclosed are methods and devices, among which is a system that includes a device that includes one or more pattern-recognition processors for searching a data stream. The pattern-recognition cluster may include various search pattern matching matrices and mask modules which may be utilized to perform various searching functions. Additionally, a buffer may be utilized to individually store the various results from pattern matching matrices and mask modules for subsequent retrieval.
Owner:MICRON TECH INC
Apparatus and method for automatically authenticating a network client
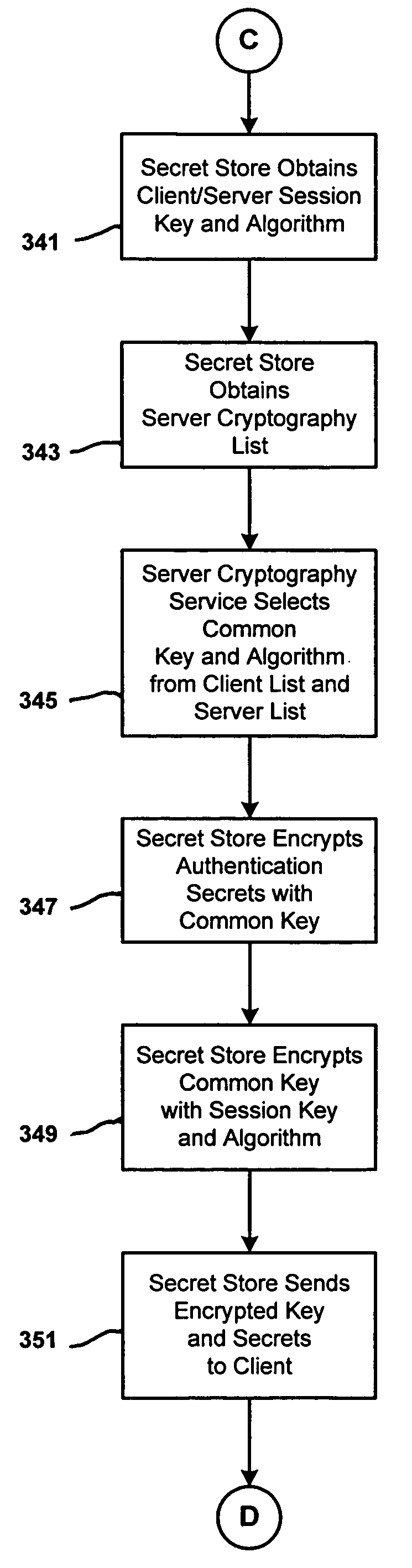
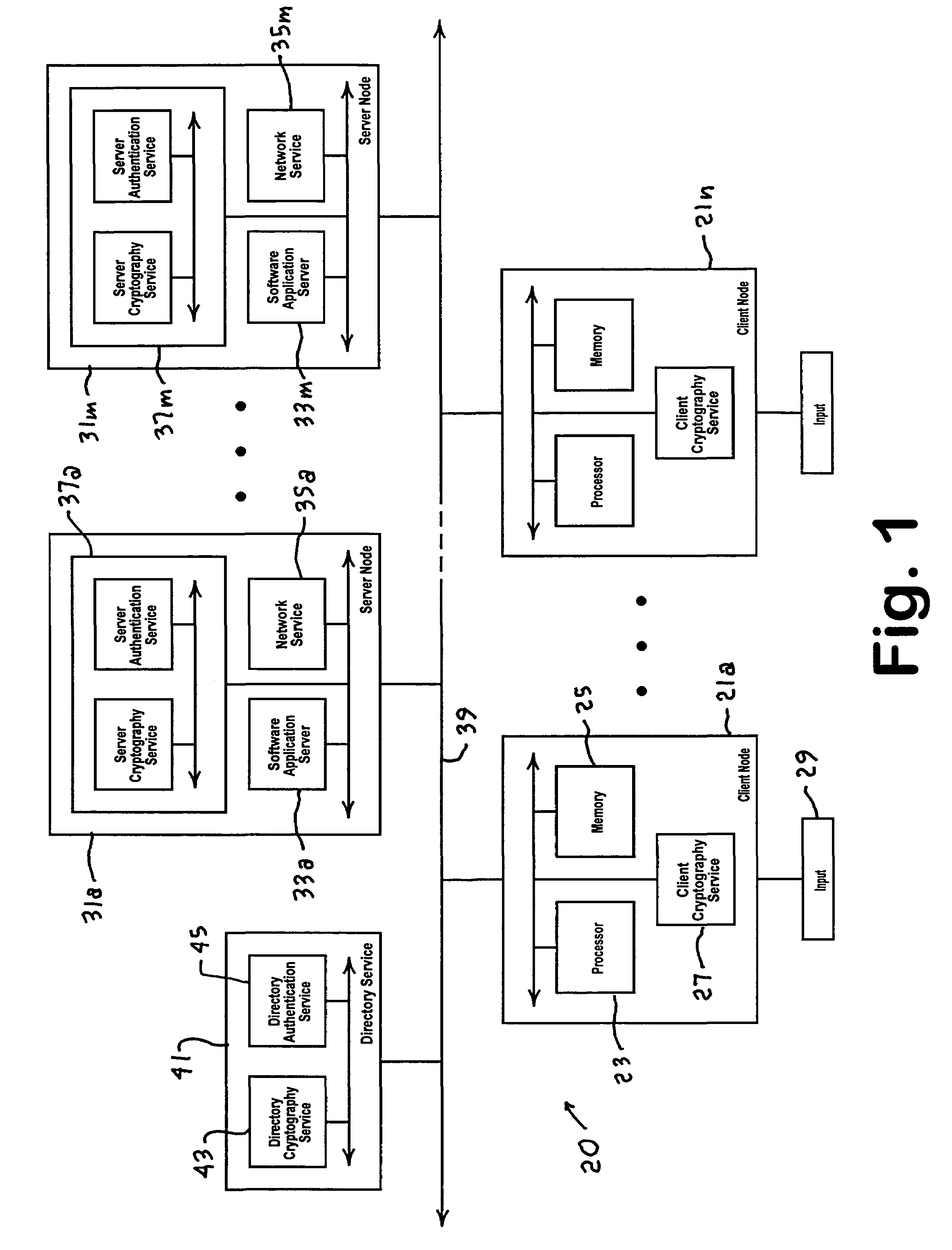
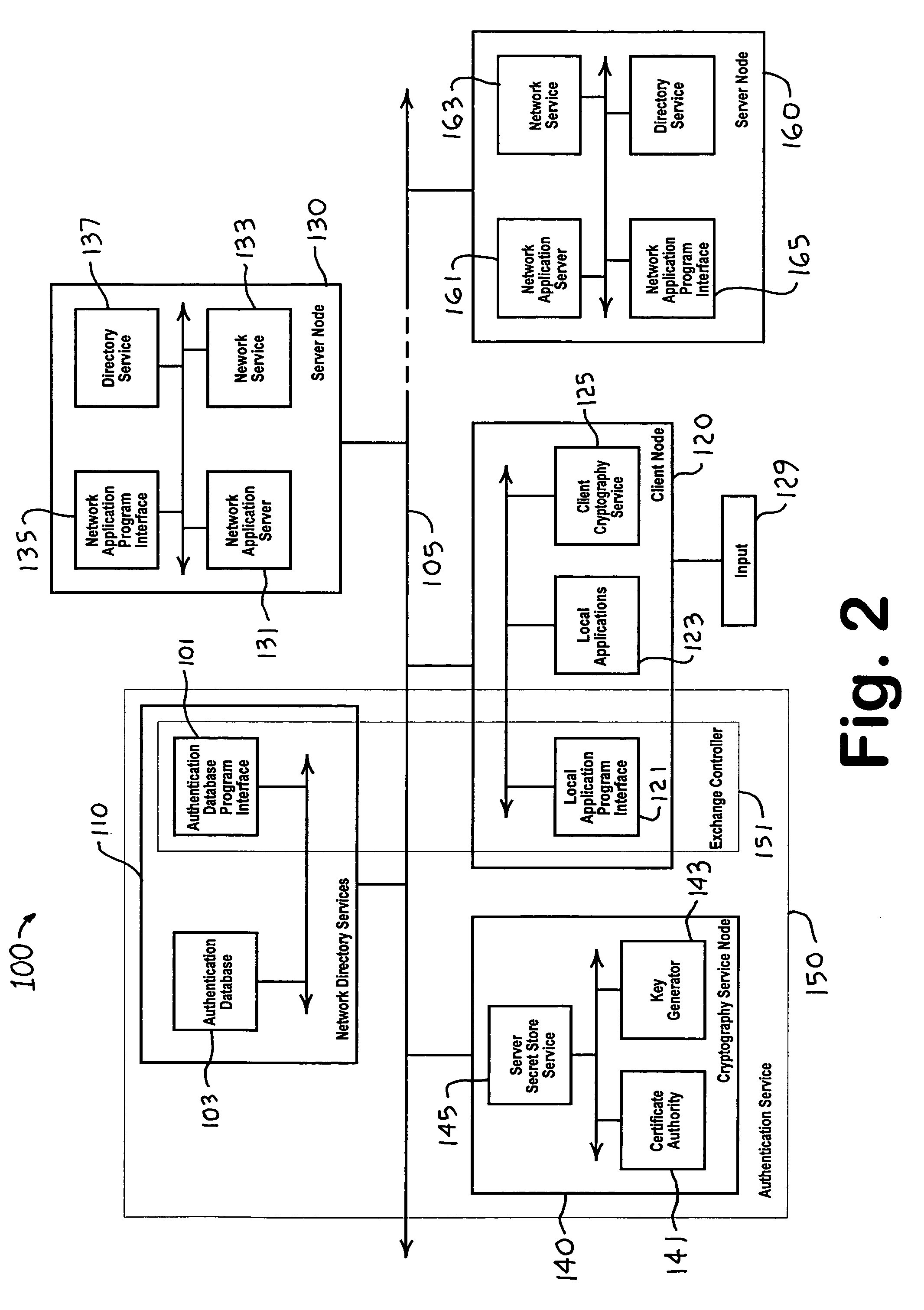
InactiveUS7231517B1Key distribution for secure communicationMultiple digital computer combinationsAccess networkWeb authentication
A distributed authentication system includes a cryptography service node, and a client node interface coupled to a network authentication database, for providing automatic authentication to enable the client node to access network resources, such as applications or services, resident in one or more network server nodes. Authentication secrets corresponding to the network resources are each encrypted with a respective strong key and stored in the authentication database. Authentication of the client node is accomplished with the retrieval of an authentication secret corresponding to a requested network resource. The retrieval process includes: i) decrypting the authentication secret using the strong key and encrypting the secret using a second key, and ii) sending a copy of the second key encrypted with a third key along with the encrypted secret to the requesting client node via a communication medium.
Owner:APPLE INC
Method and Systems for Power Consumption Management of a Pattern-Recognition Processor
ActiveUS20100174929A1Volume/mass flow measurementPower supply for data processingElectrical conductorParallel computing
Owner:MICRON TECH INC
Pattern-Recognition Processor with Matching-Data Reporting Module
Disclosed are methods and devices, among which is a device that includes a pattern-recognition processor. The pattern-recognition processor may include a matching-data reporting module, which may have a buffer and a match event table. The buffer may be coupled to a data stream and configured to store at least part of the data stream, and the match event table may be configured to store data indicative of a buffer location corresponding with a start of a search criterion being satisfied.
Owner:MICRON TECH INC
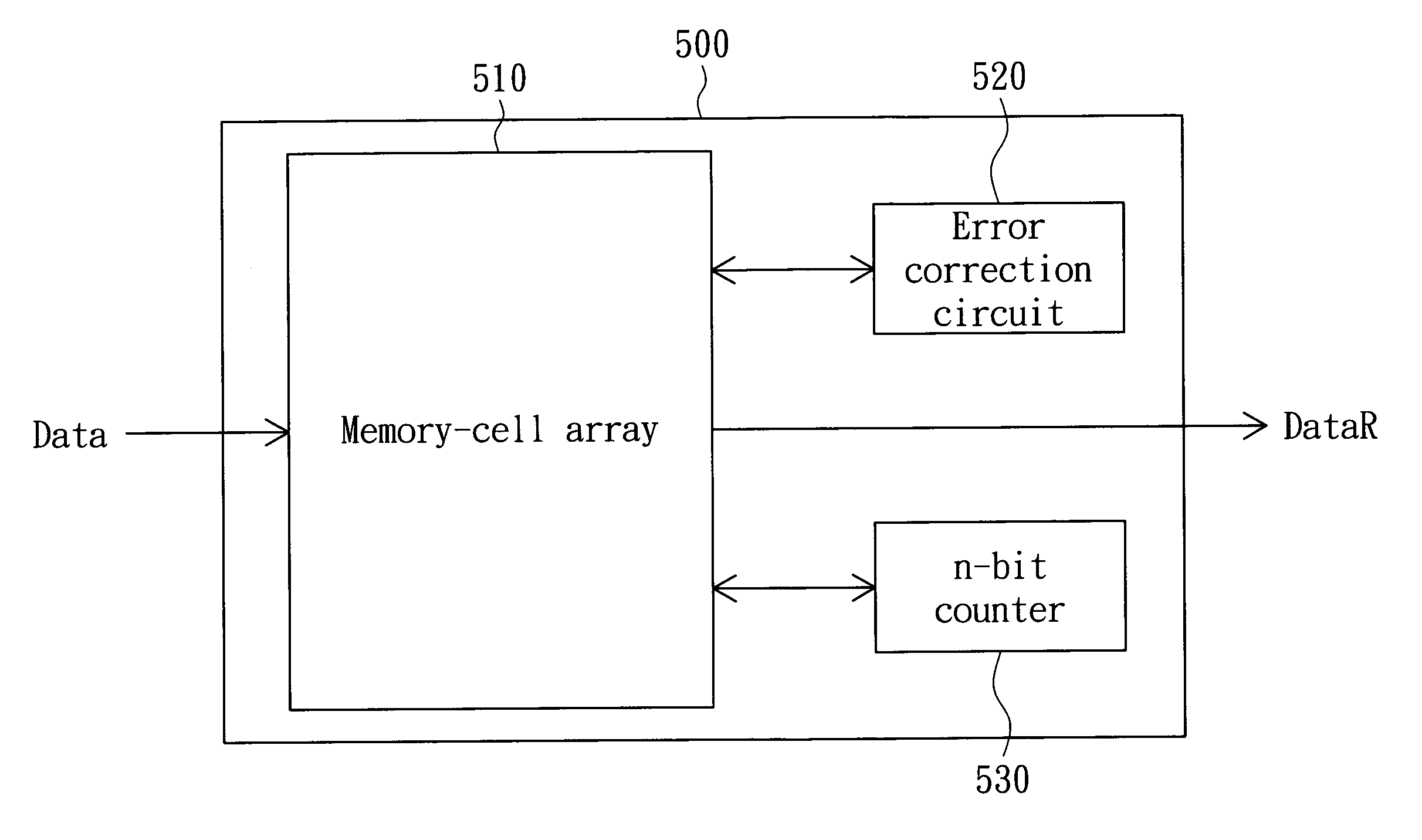
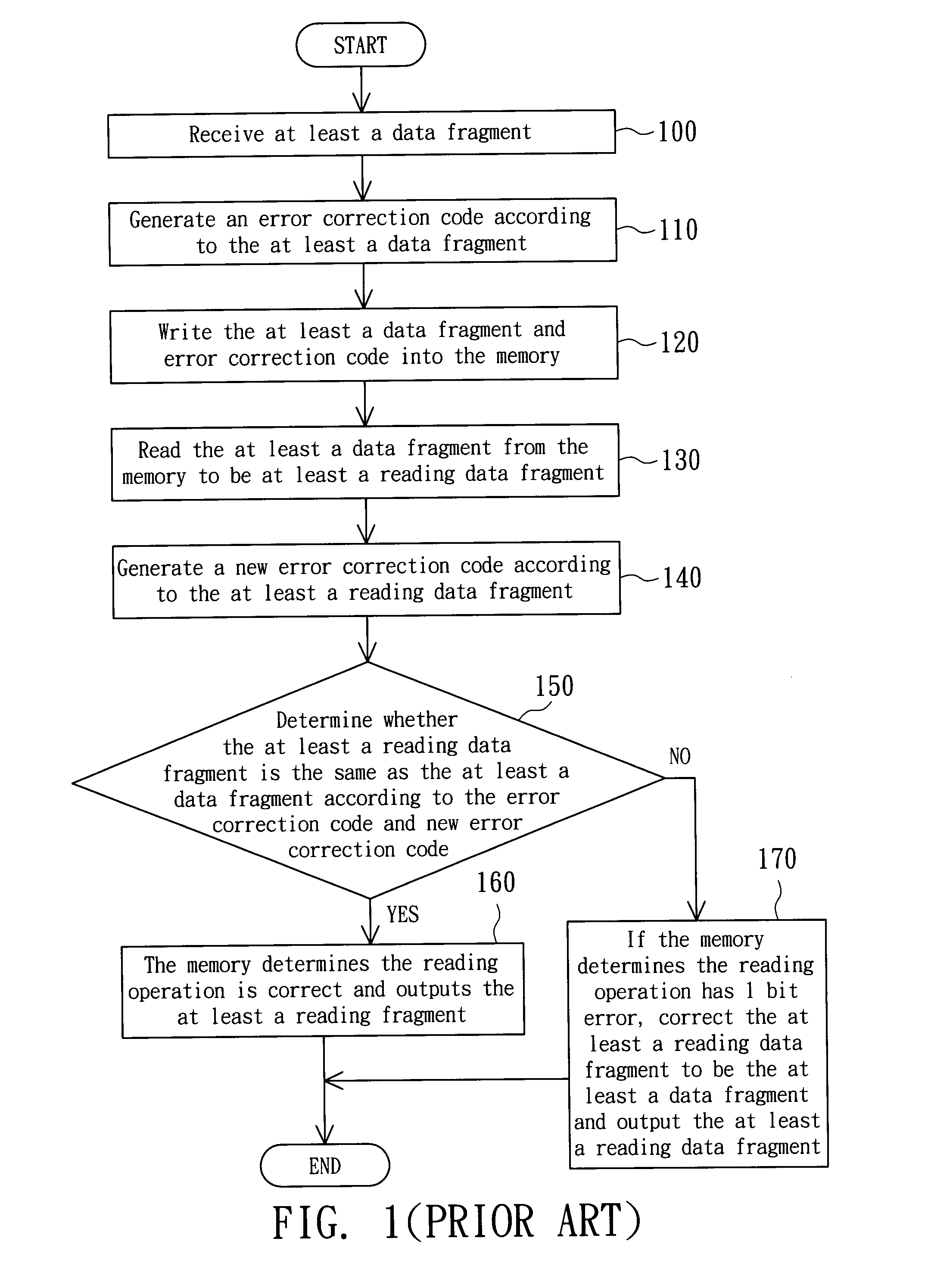
Memory and method for checking reading errors thereof
ActiveUS7925960B2Improve accuracySave memory spaceError detection/correctionCode conversionComputer scienceData fragment
Owner:MACRONIX INT CO LTD
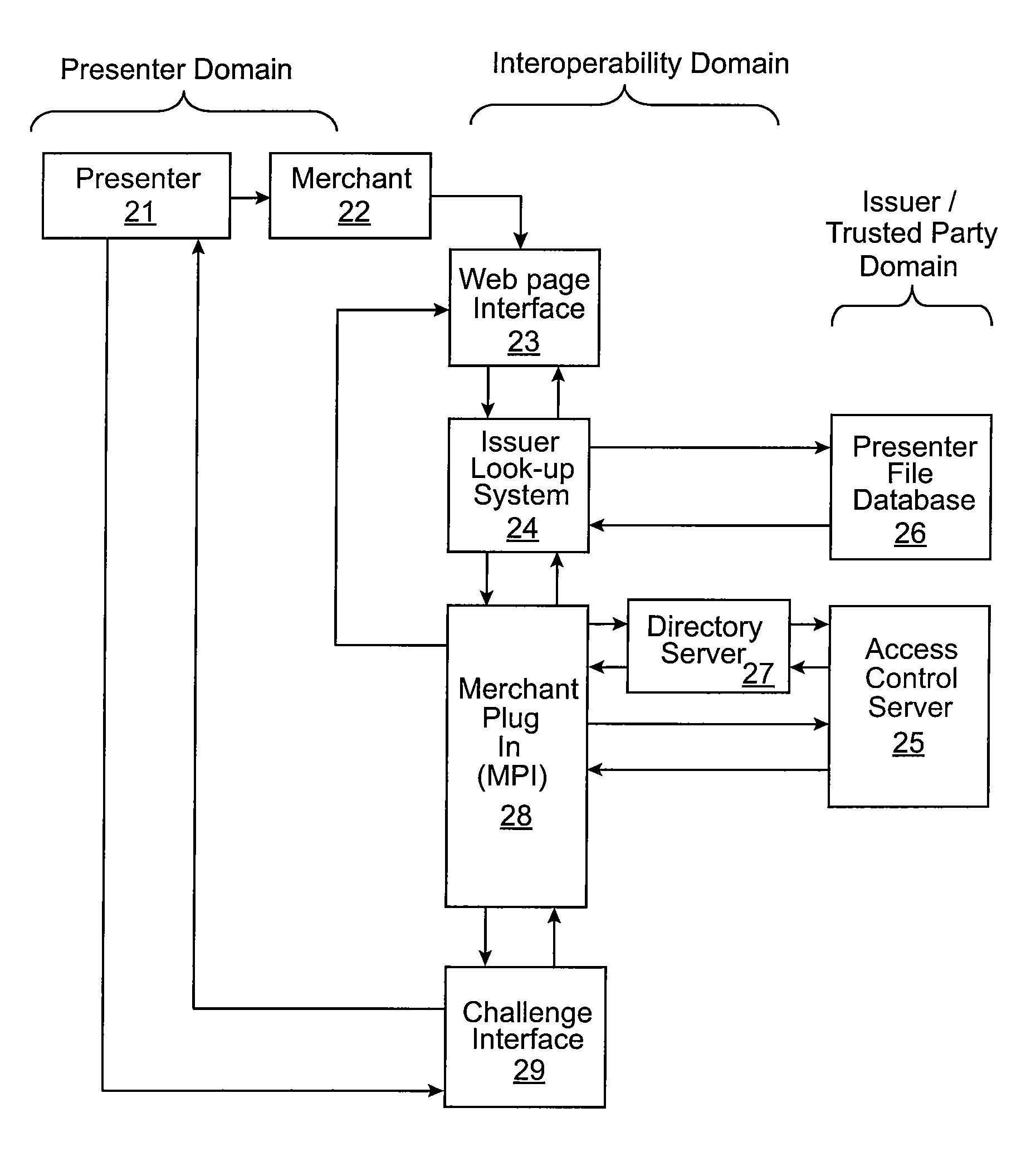
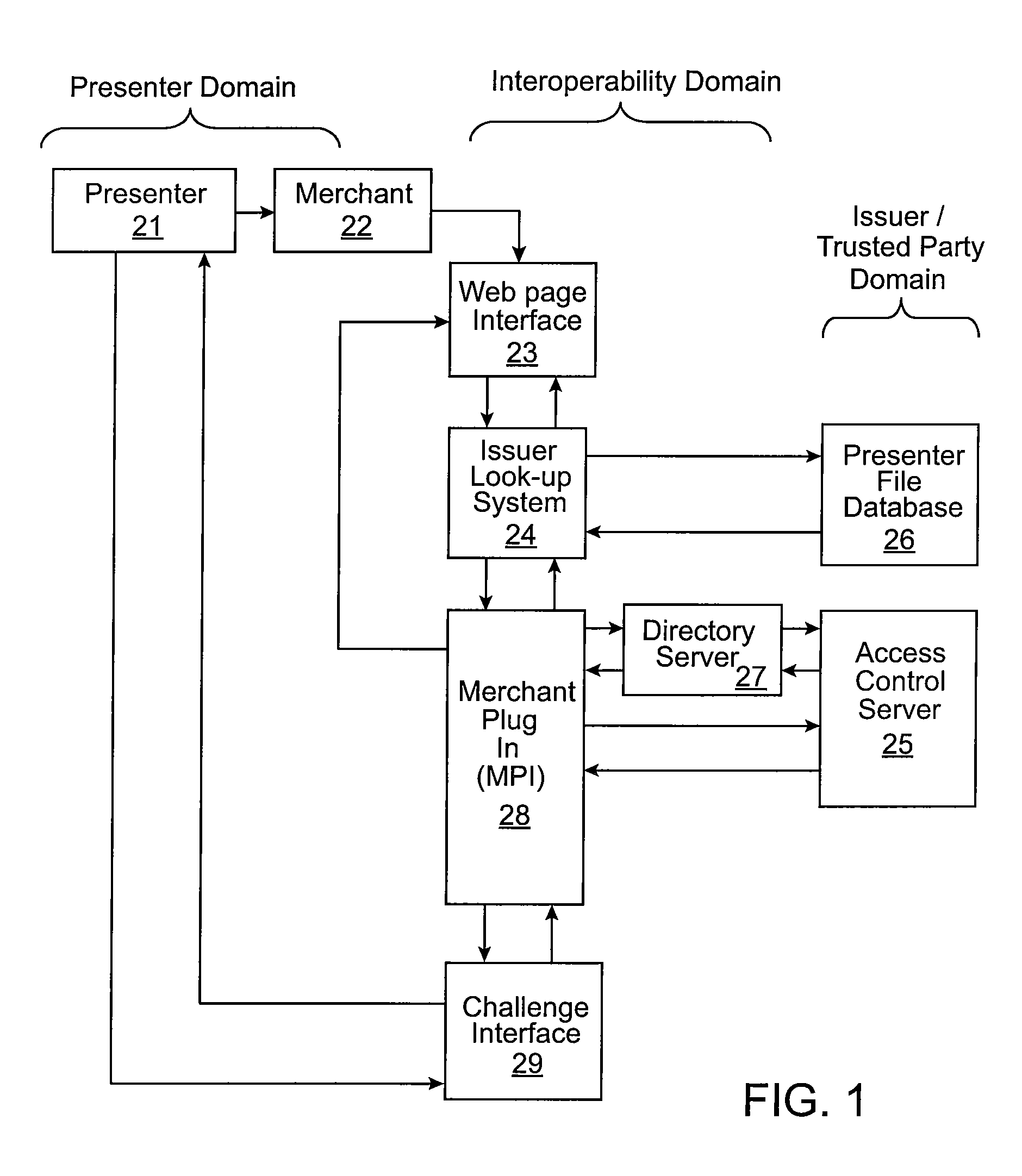
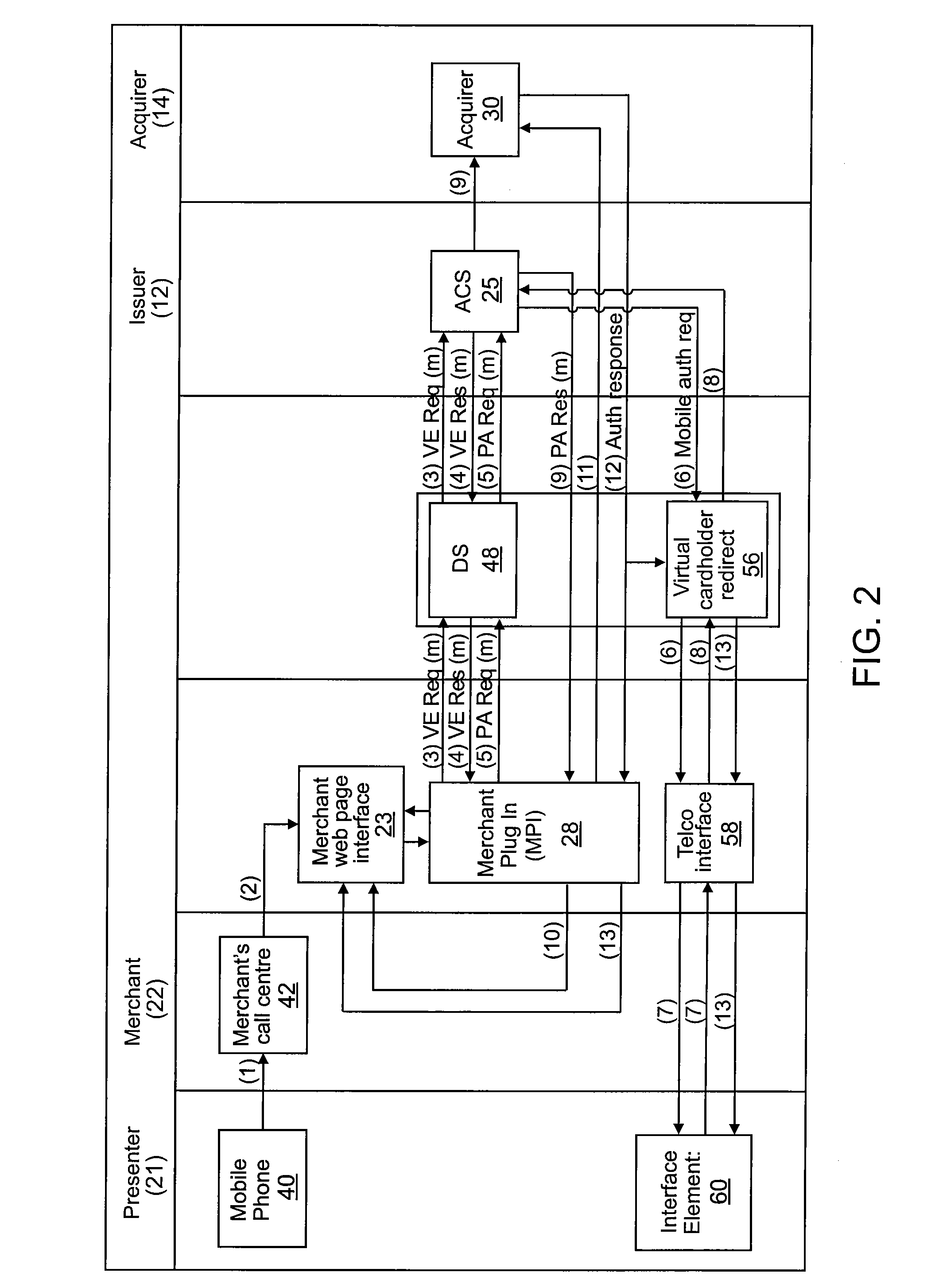
Method and system for authenticating a party to a transaction
ActiveUS20090037982A1User identity/authority verificationMultiple digital computer combinationsComputer security
One embodiment of the invention is directed to a method including receiving an alias identifier associated with an account associated with a presenter, determining an associated trusted party using the alias identifier, sending a verification request message to the trusted party after determining the associated trusted party, and receiving a verification response message
Owner:VISA USA INC (US)
Text joins for data cleansing and integration in a relational database management system
InactiveUS20050027717A1Relational databasesComparison of digital valuesCosine similarityRelational database management system
Owner:AMERICAN TELEPHONE & TELEGRAPH CO +1
Error recovery within processing stages of an integrated circuit
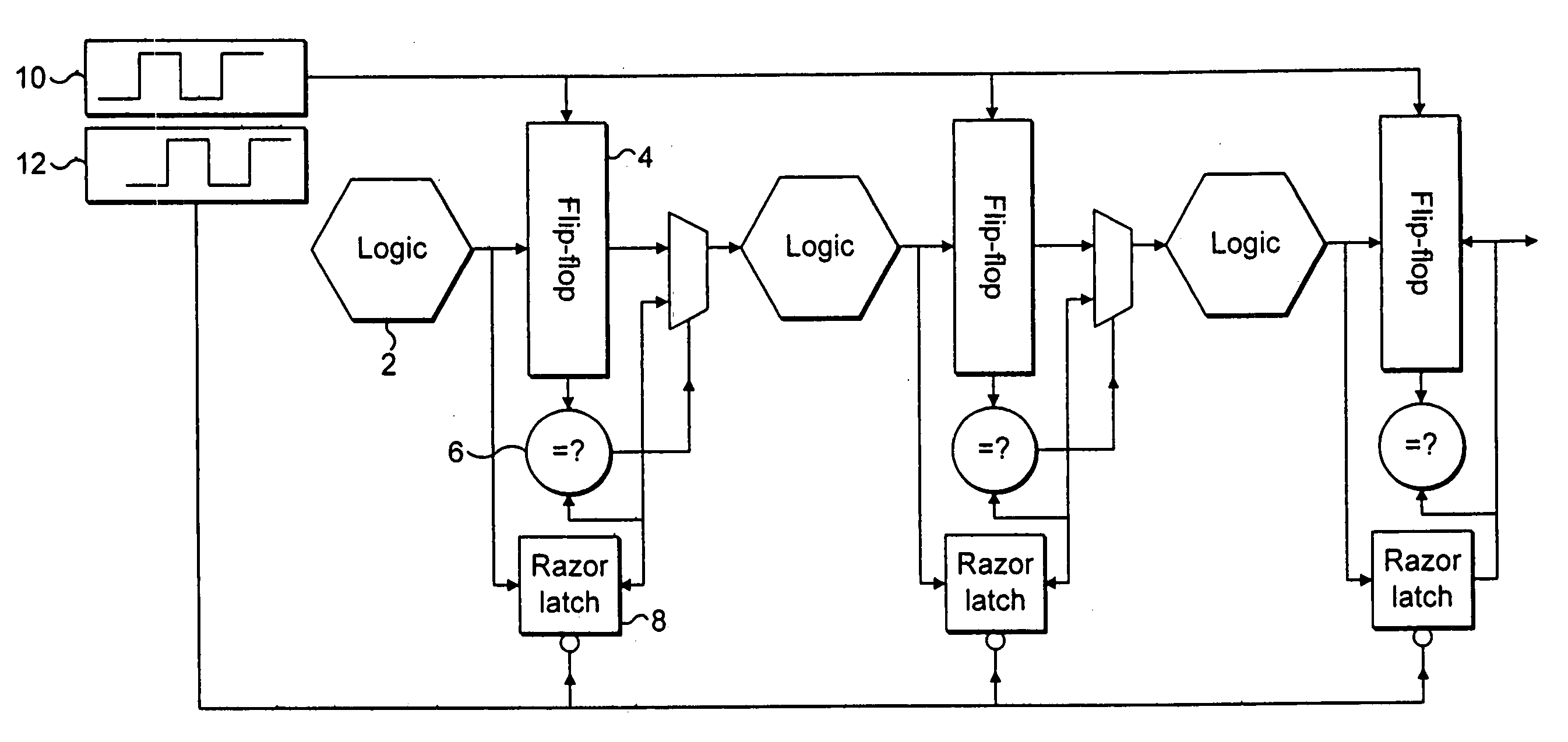
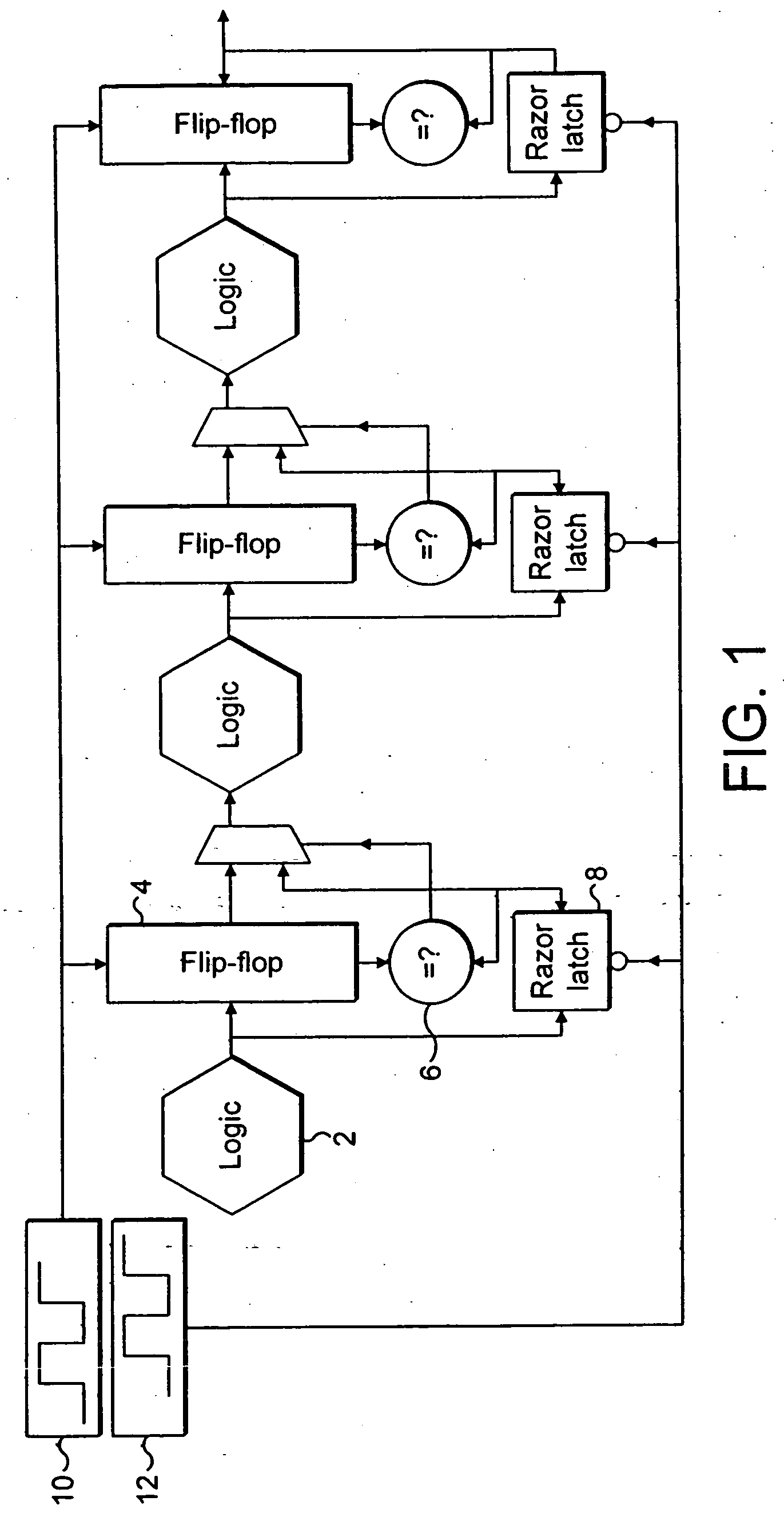
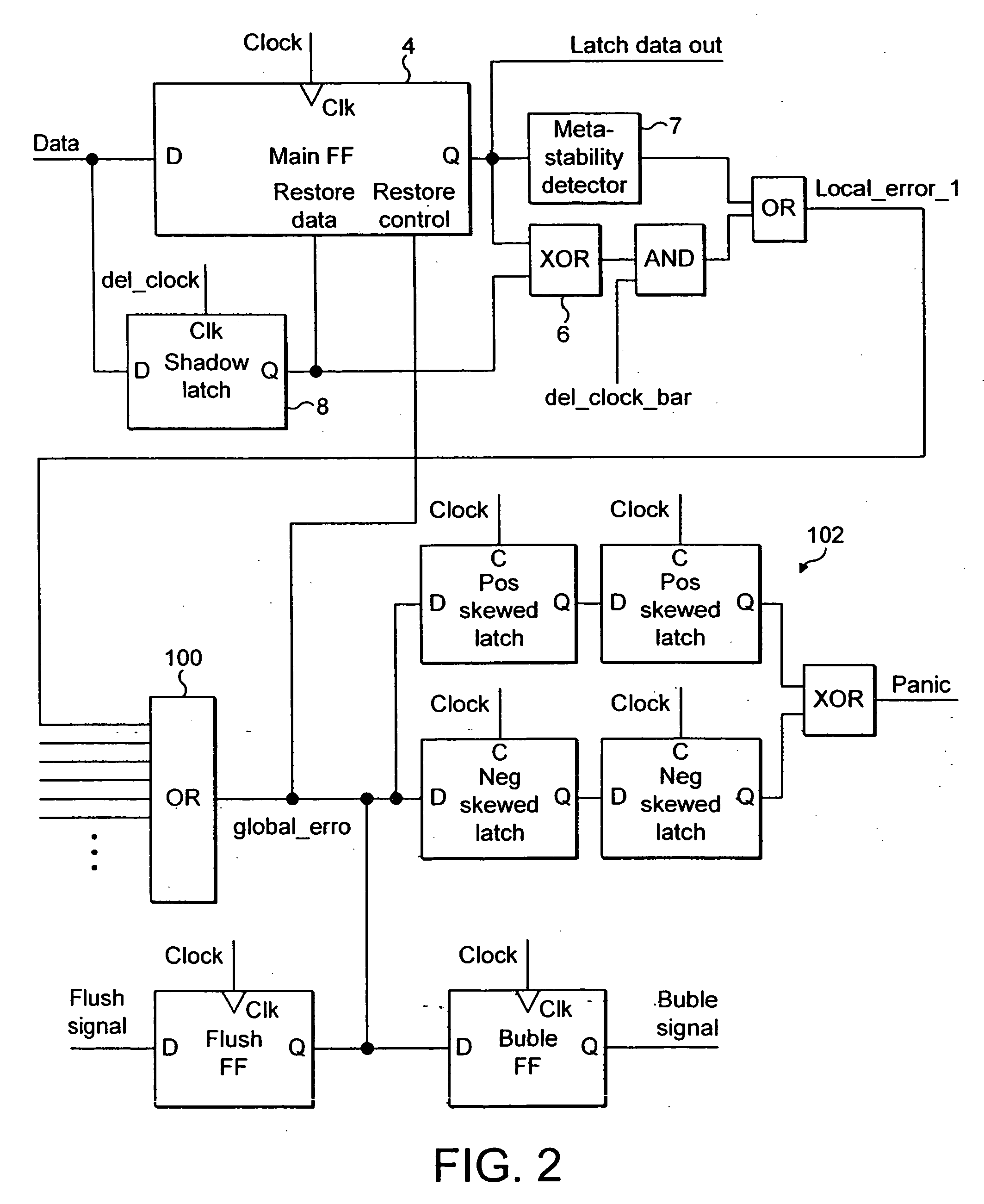
ActiveUS20050246613A1Easy to modifyReduce the possibilityCode conversionFrequency/rate-modulated pulse demodulationError checkClock rate
An integrated circuit includes a plurality of processing stages each including processing logic 1014, a non-delayed signal-capture element 1016, a delayed signal-capture element 1018 and a comparator 1024. The non-delayed signal-capture element 1016 captures an output from the processing logic 1014 at a non-delayed capture time. At a later delayed capture time, the delayed signal-capture element 1018 also captures a value from the processing logic 1014. An error detection circuit 1026 and error correction circuit 1028 detect and correct random errors in the delayed value and supplies an error-checked delayed value to the comparator 1024. The comparator 1024 compares the error-checked delayed value and the non-delayed value and if they are not equal this indicates that the non-delayed value was captured too soon and should be replaced by the error-checked delayed value. The non-delayed value is passed to the subsequent processing stage immediately following its capture and accordingly error recovery mechanisms are used to suppress the erroneous processing which has occurred by the subsequent processing stages, such as gating the clock and allowing the correct signal values to propagate through the subsequent processing logic before restarting the clock. The operating parameters of the integrated circuit, such as the clock frequency, the operating voltage, the body biased voltage, temperature and the like are adjusted so as to maintain a finite non-zero error rate in a manner that increases overall performance.
Owner:ARM LTD +1
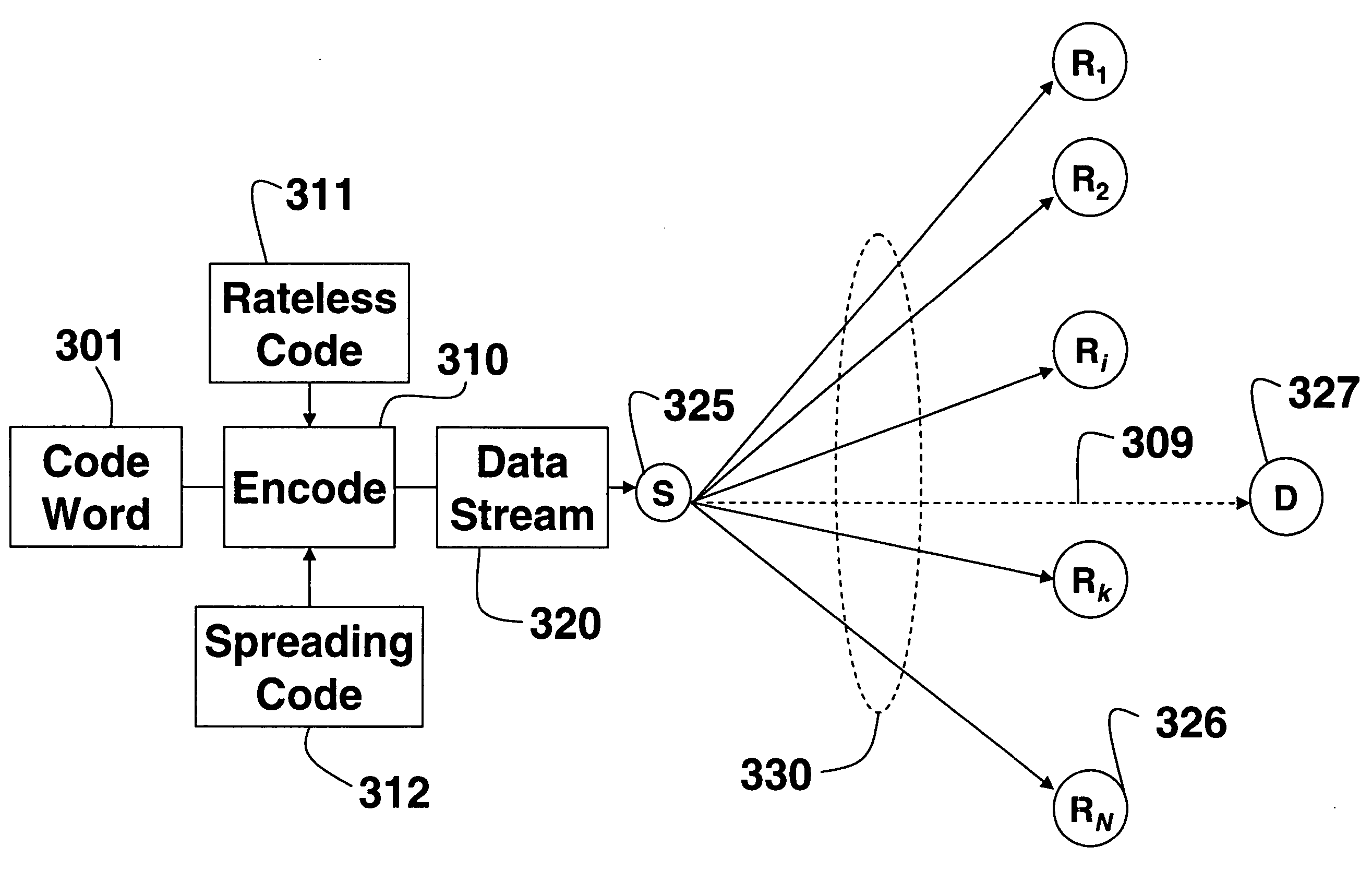
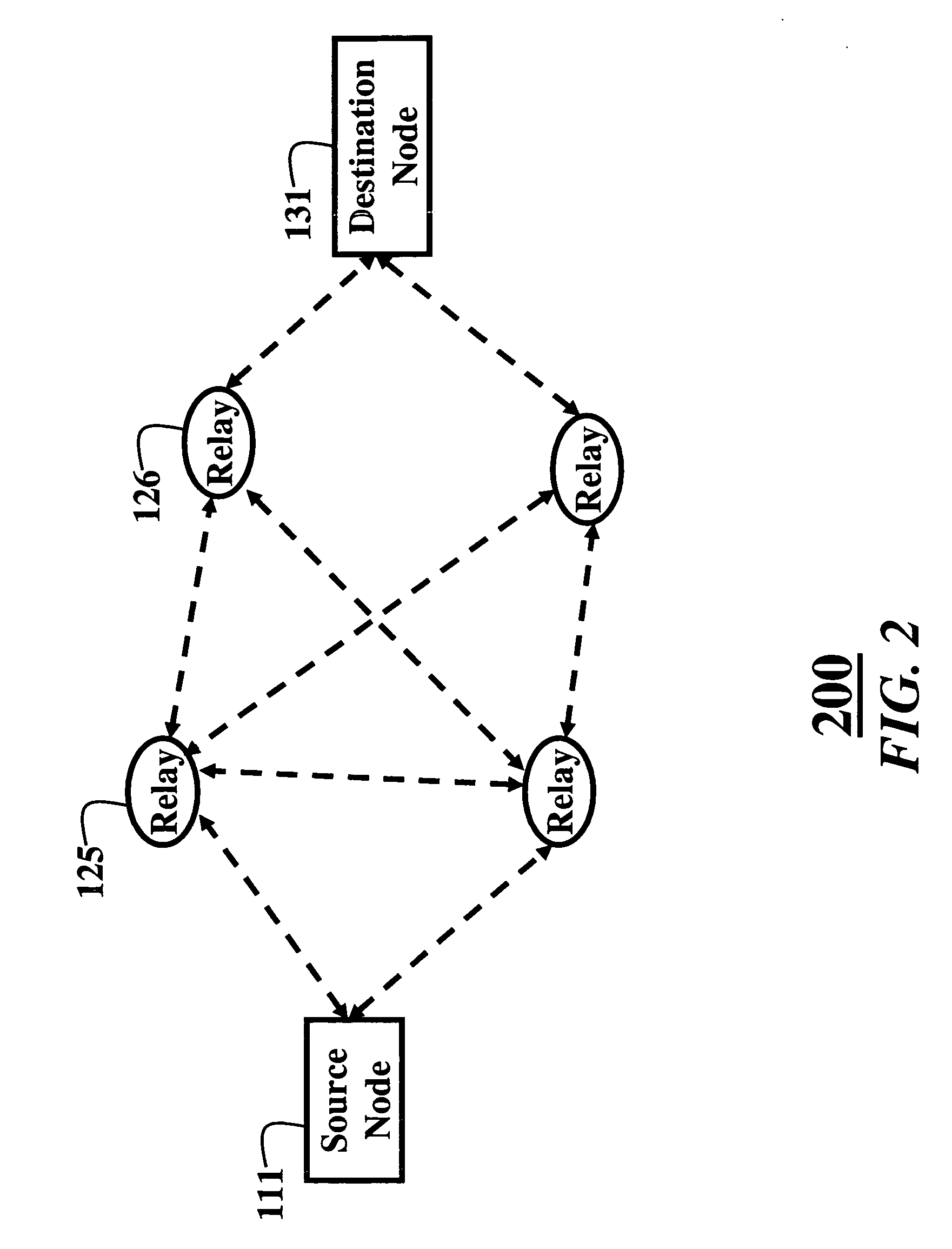
Cooperative relay networks using rateless codes
InactiveUS20070217432A1Solve the large power consumptionTransmission time smallPower managementSite diversityData streamBroadcasting
A system and method for communicating information in a wireless cooperative relay network of nodes, the nodes including a source, a set of relays, and a destination. The source broadcasts a code word encoded as a data stream using a rateless code. The relays receive the data stream, decode the data stream to recover the code word, and reencode and transmit the recovered code word as the data stream with the rateless code. The destination receives and decodes the reencoded data streams to recover the code word.
Owner:MITSUBISHI ELECTRIC RES LAB INC
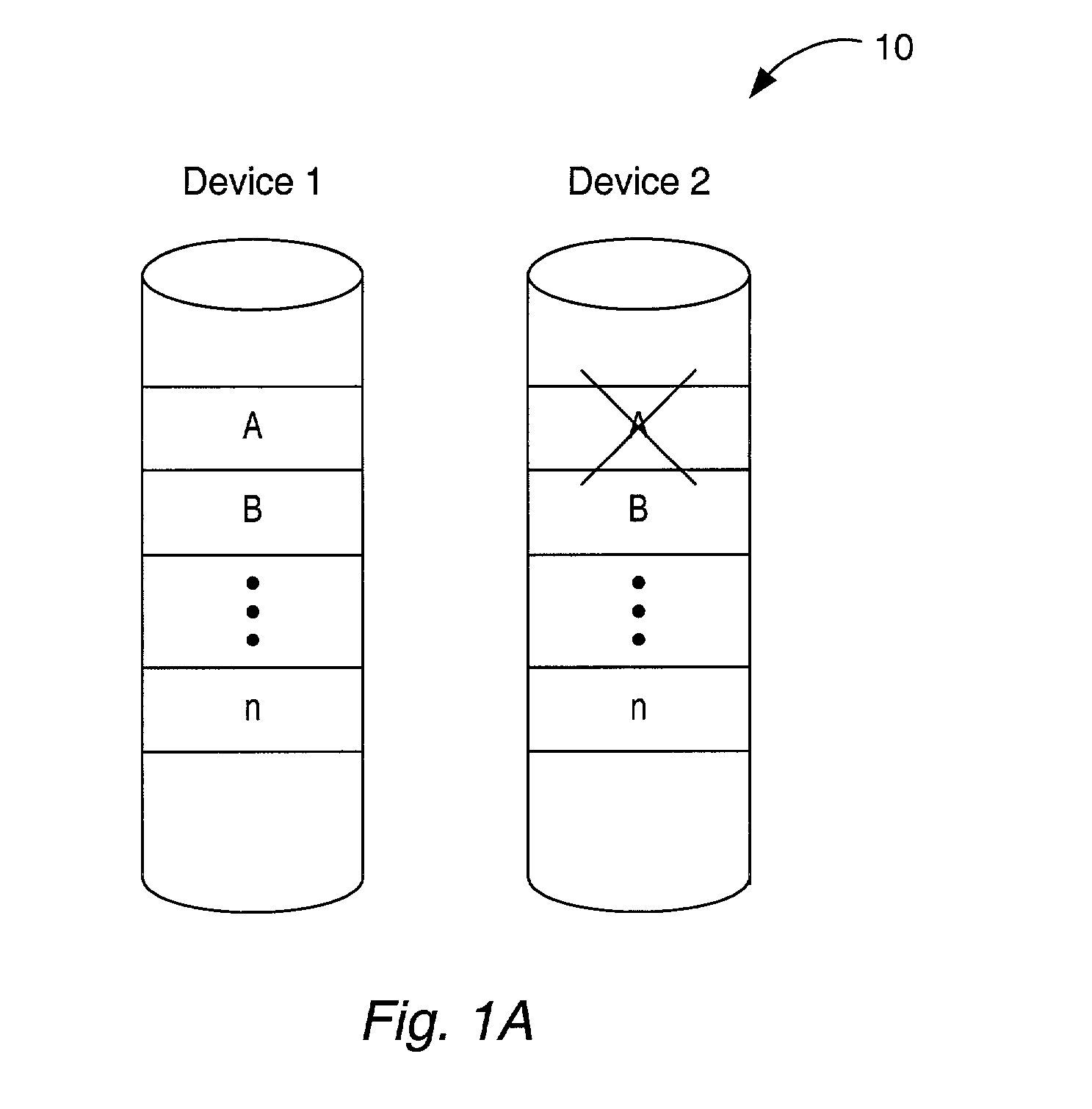
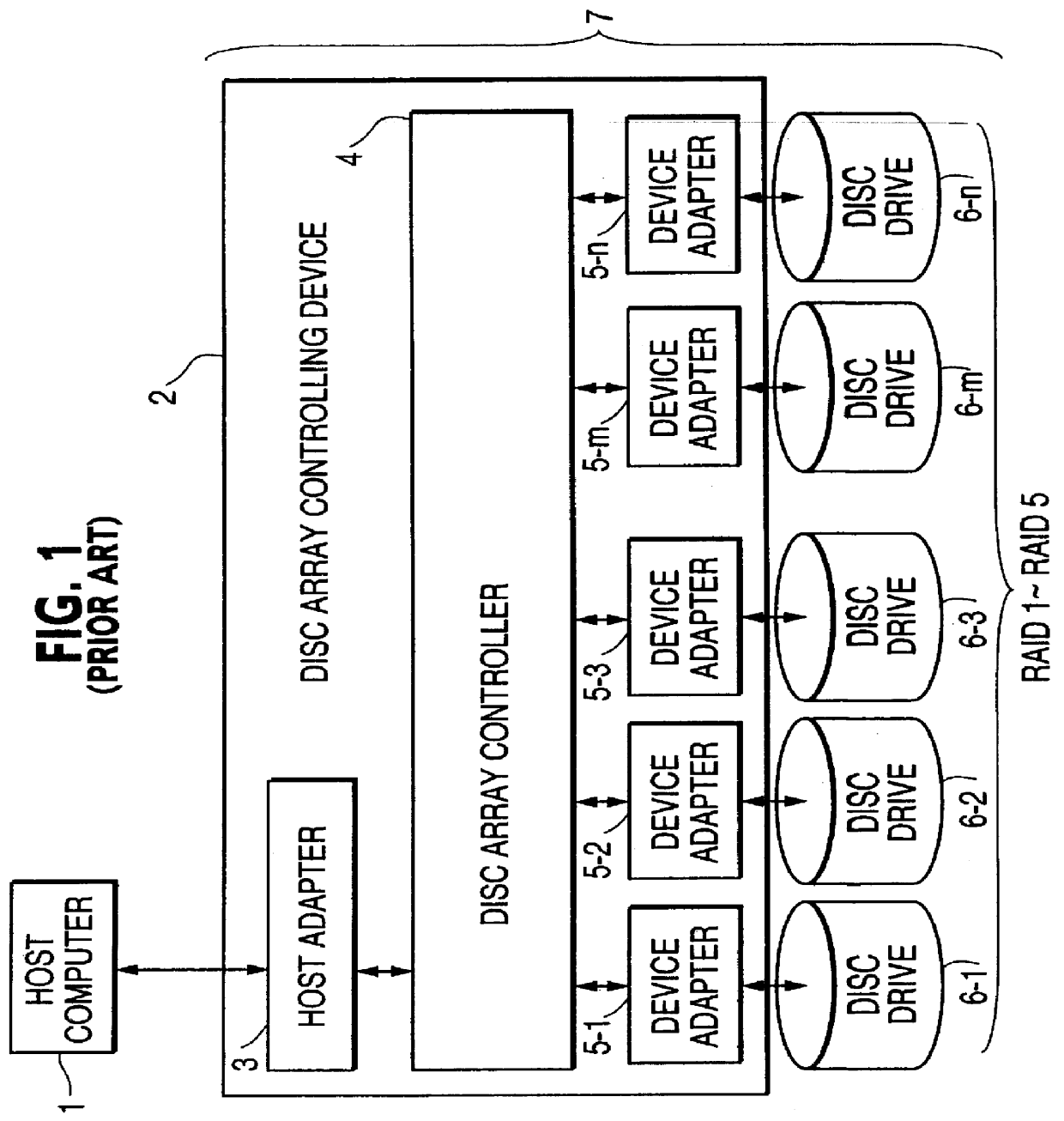
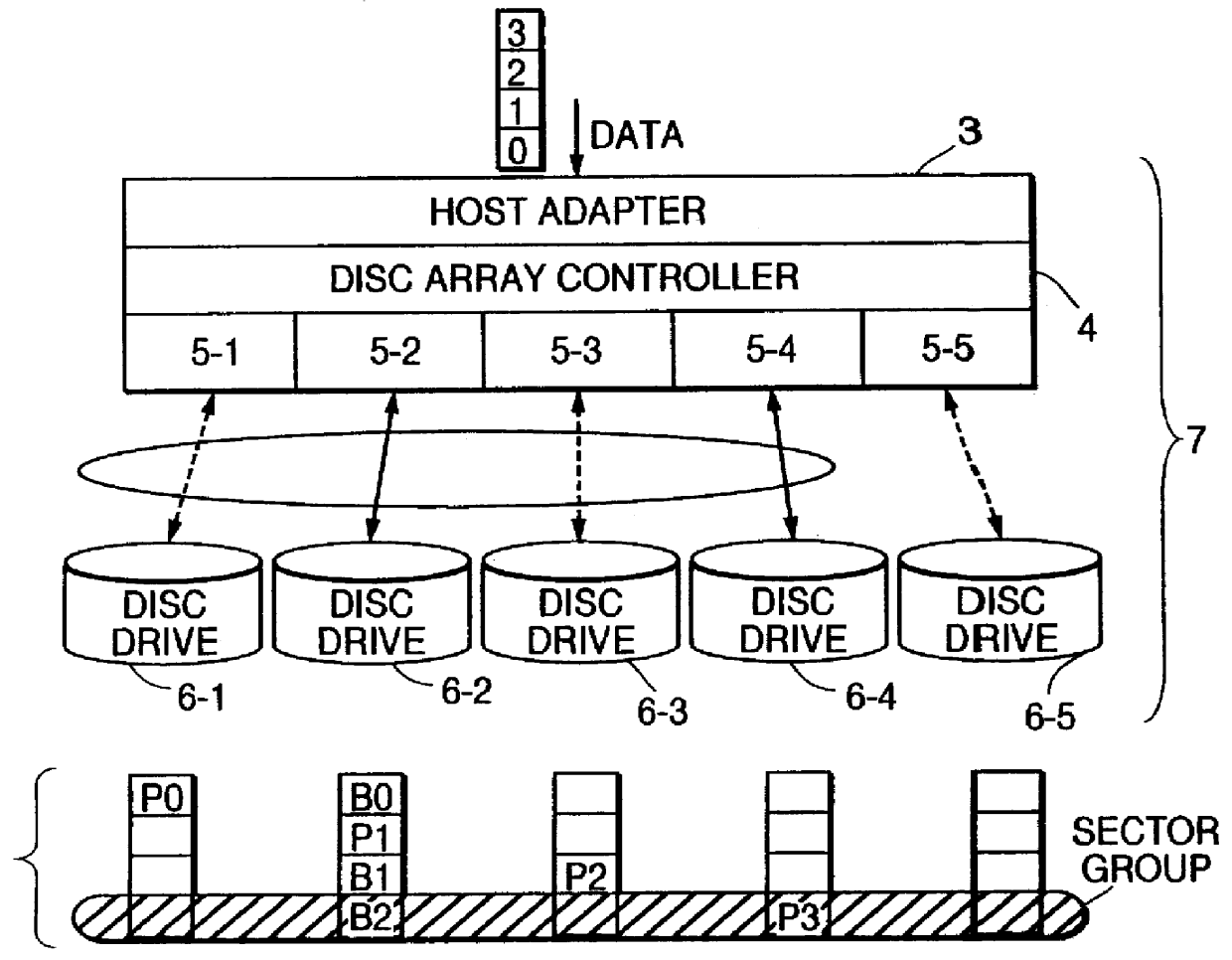
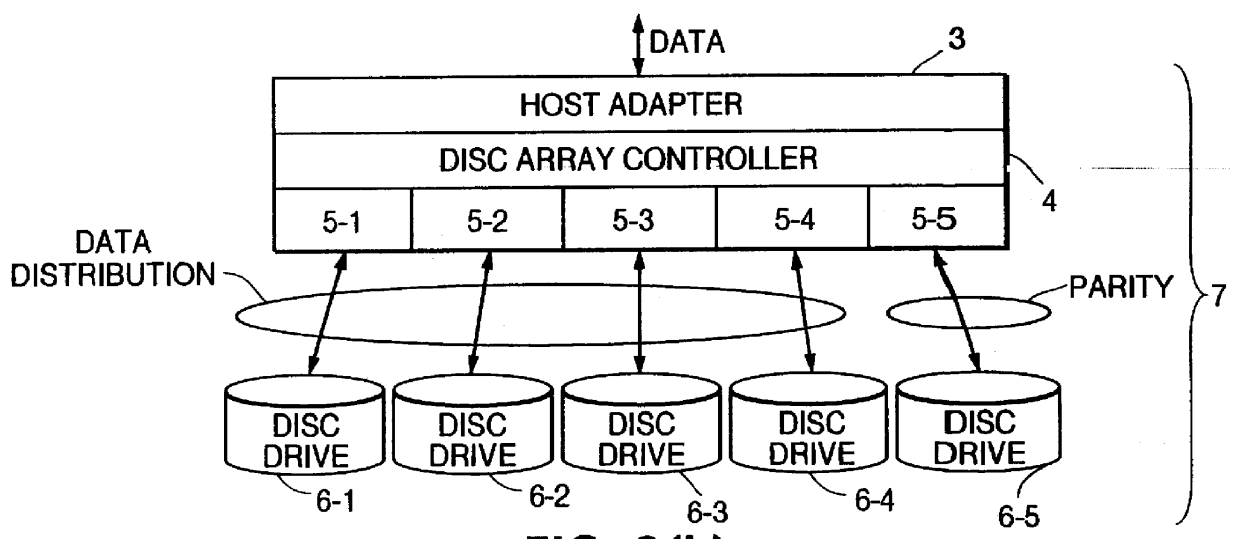
Disc array apparatus checking and restructuring data read from attached disc drives
The present invention relates to a disc array apparatus assuring that even if contradiction is detected in matching of parity data during a read parity check, correct host data is Restructured and can always be transferred to the host. The disc array apparatus of the present invention is particularly applicable to disc drives in the RAID configuration. For example, in a disc array apparatus of the present invention implementing RAID level 3, the disc array apparatus adds CRC data to data transferred from a host computer, divides the data, generates parity from the divided data, and stores the data and the parity data into the disc drives. During a read operation, the disc array apparatus of the present invention executes a read parity check. If contradiction is detected between the parity data stored in the disc drives and the parity data generated during the read parity check, the disc array controller sequentially assumes, one disc drive at a time, that one of the disc drives is storing erroneous data, restructures the host data from the divided data and parity data of the disc drives other than the disc drive storing erroneous data for each assumption, and executes a CRC check on the restructured host data for each assumption. Restructured host data is determined to be correct host data when the CRC check detects no error. The principle of the present invention is also implemented in other RAID levels, and using data such as time or counter value, to determine and restructure erroneous data.
Owner:FUJITSU LTD
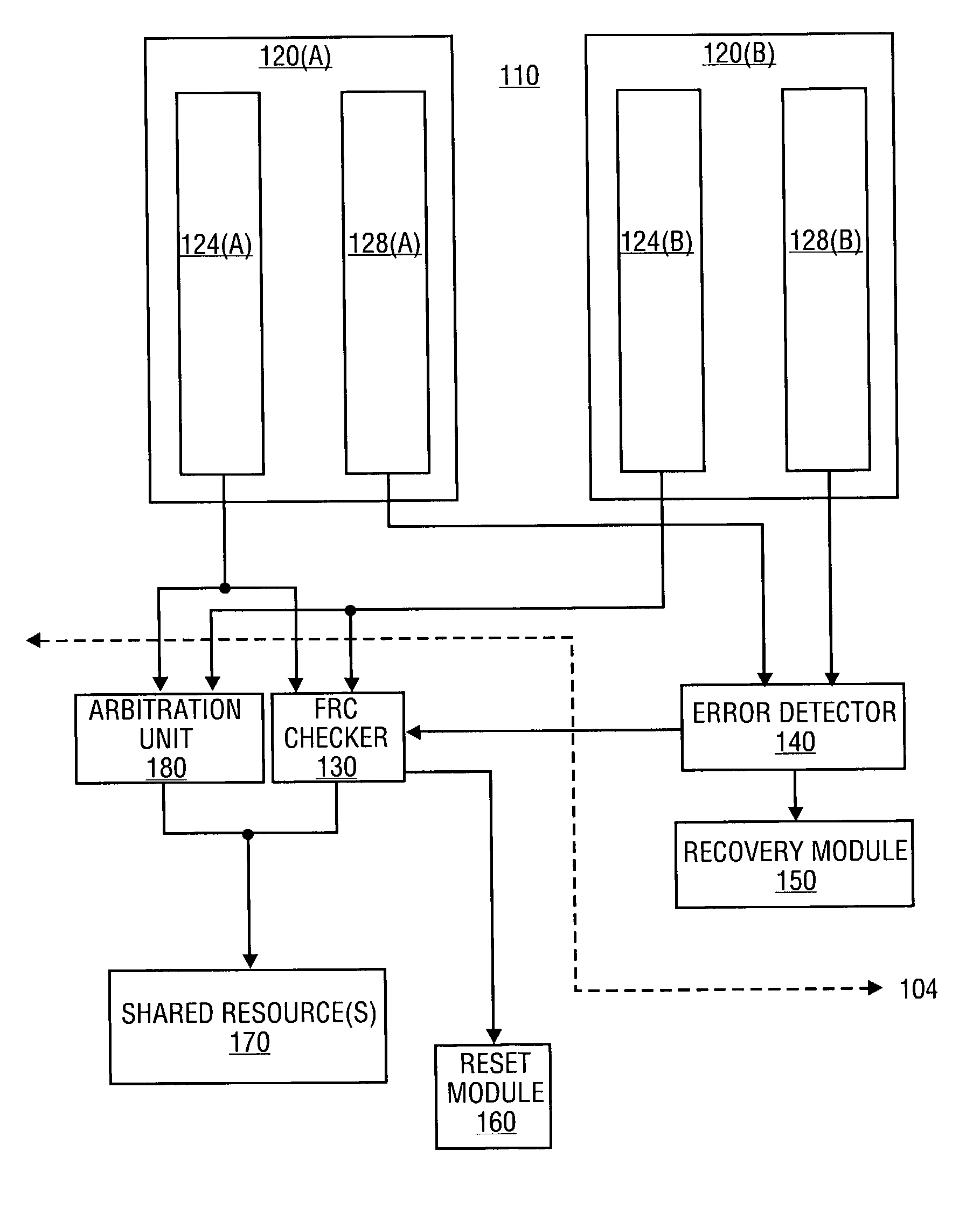
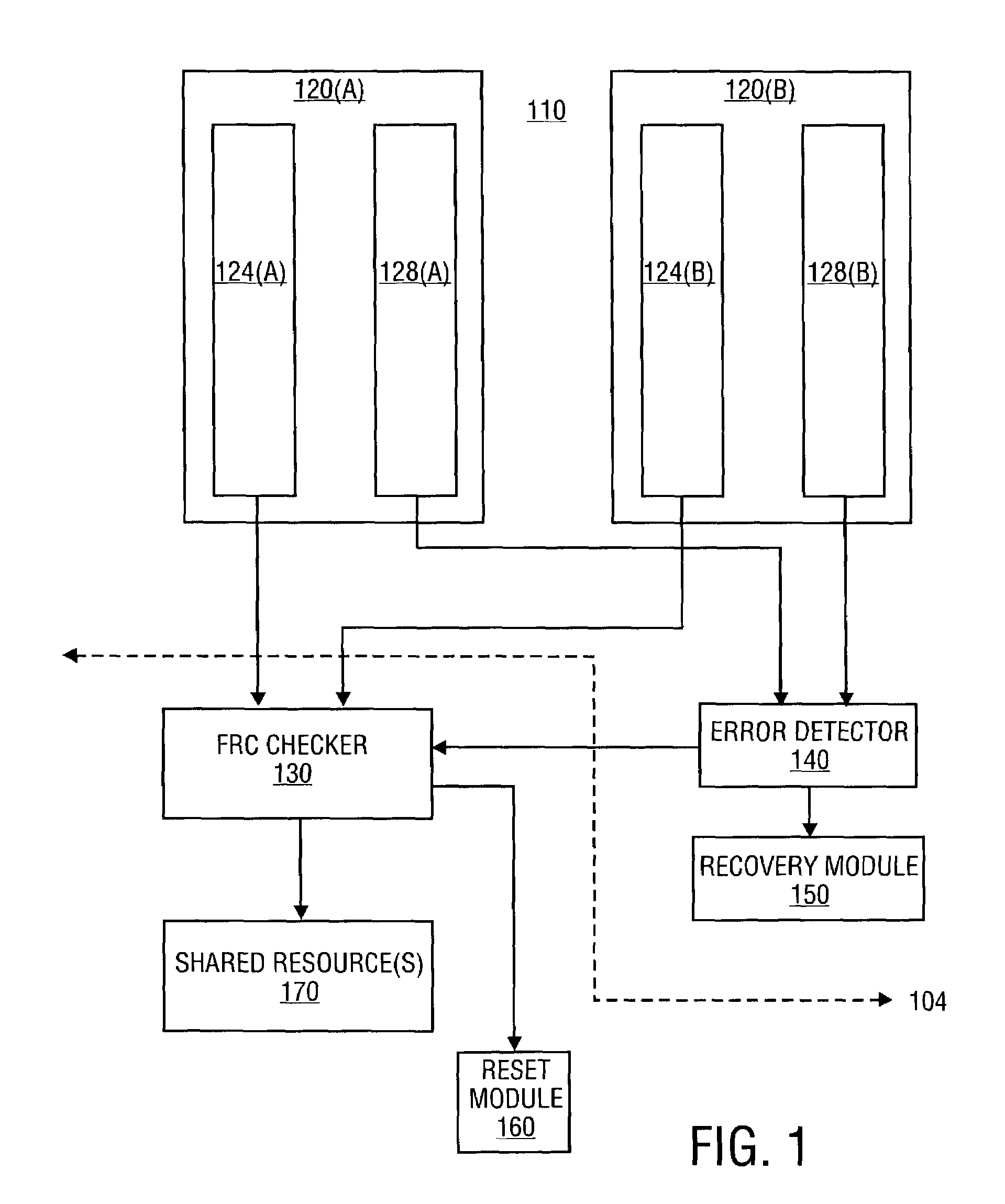
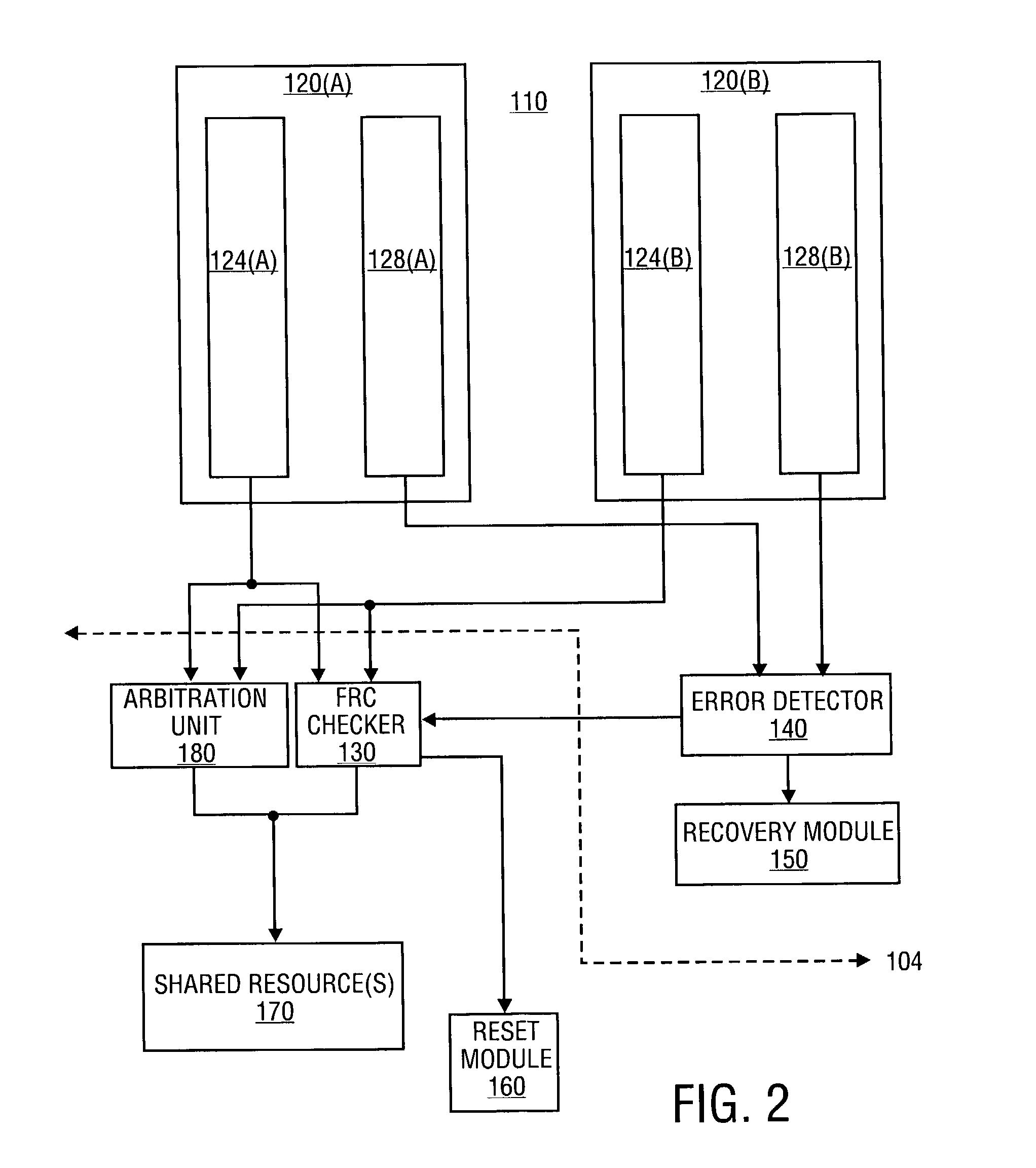
On-die mechanism for high-reliability processor
A processor includes first and second execution cores that operate in a redundant (FRC) mode, an FRC check unit to compare results from the first and second execution cores, and an error check unit to detect recoverable errors in the first and second cores. The error detector disables the FRC checker, responsive to detection of a recoverable error. A multi-mode embodiment of the processor implements a multi-core mode in addition to the FRC mode. An arbitration unit regulates access to resources shared by the first and second execution cores in multi-core mode. The FRC checker is located proximate to the arbitration unit in the multi-mode embodiment.
Owner:INTEL CORP
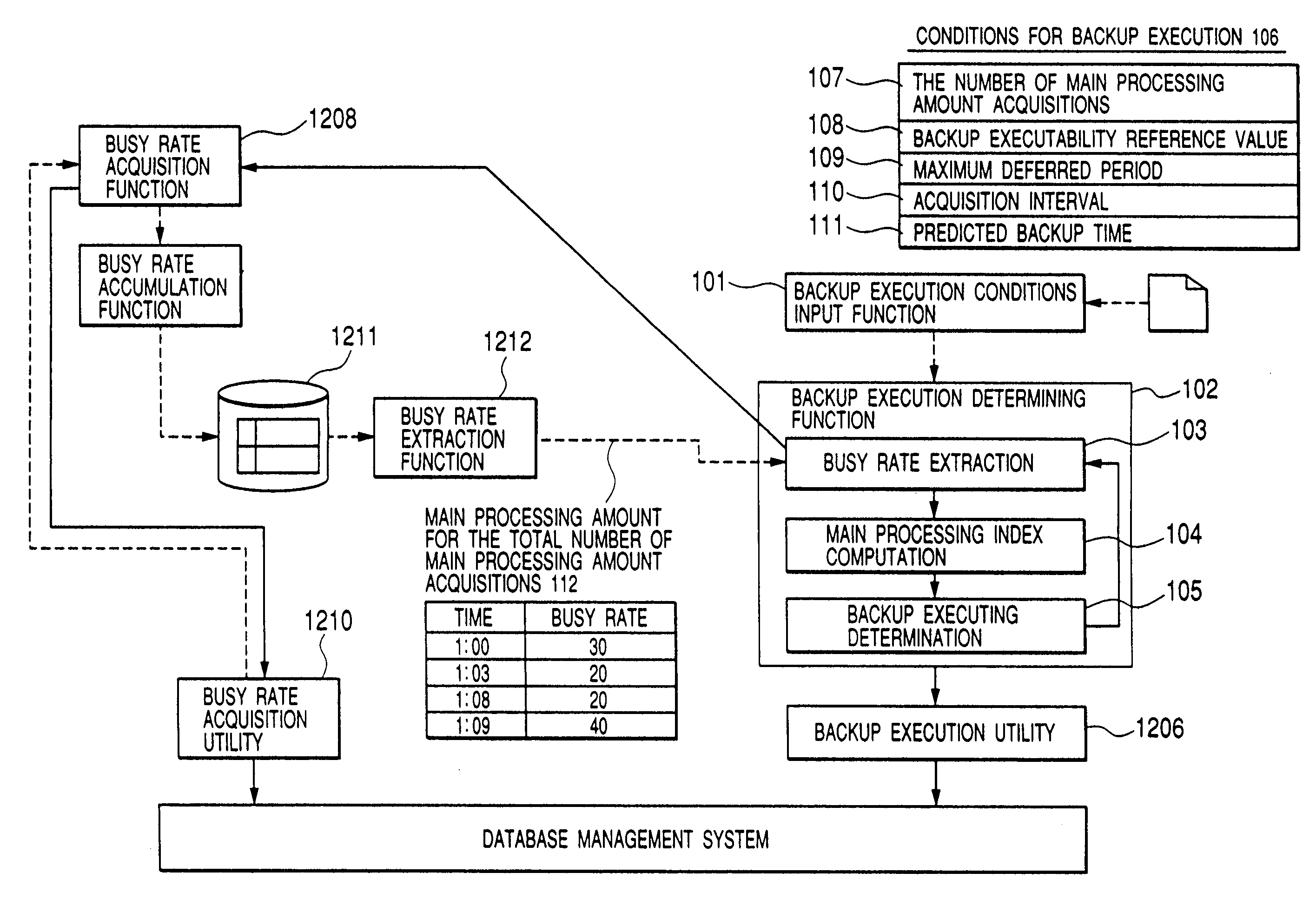
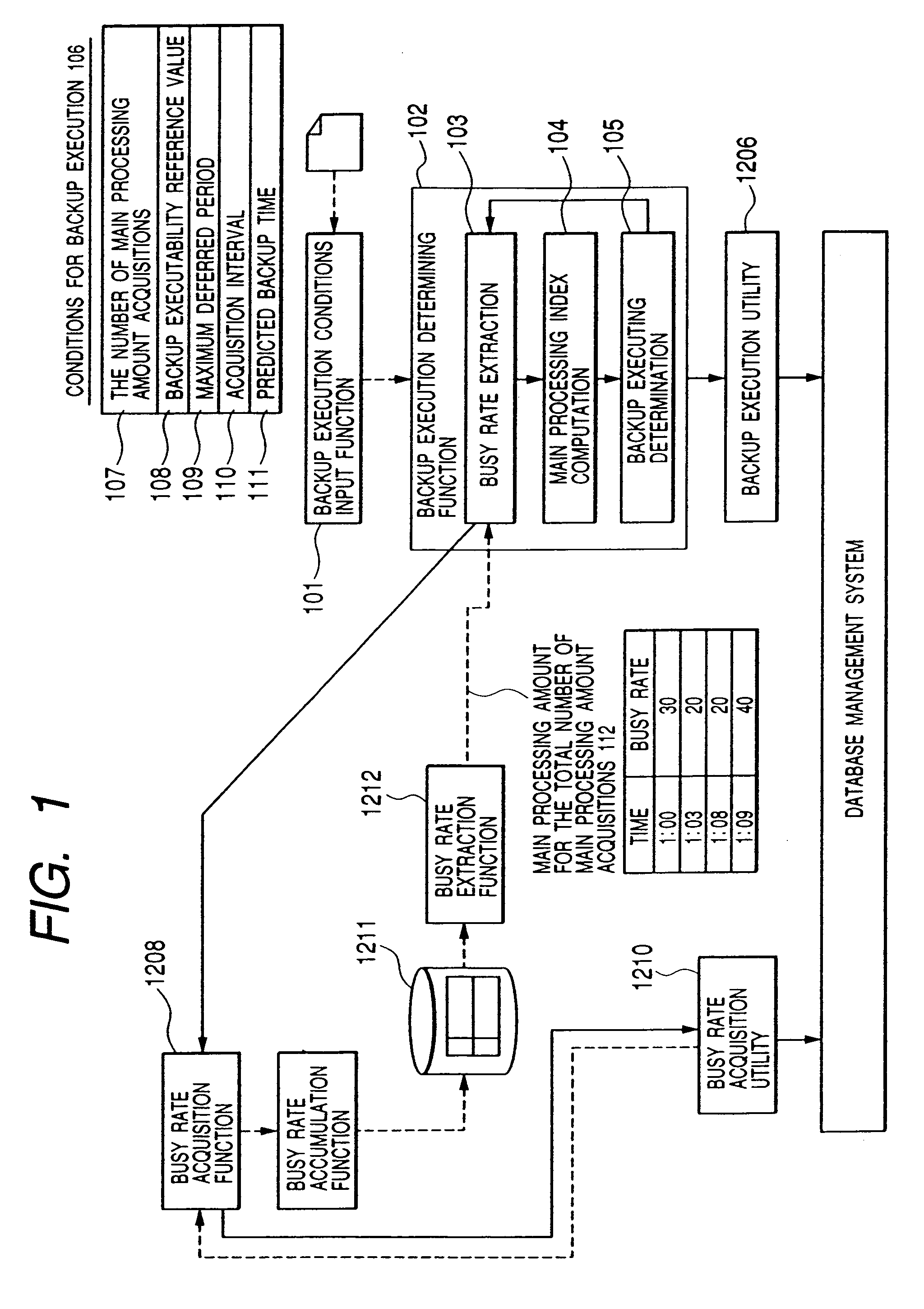
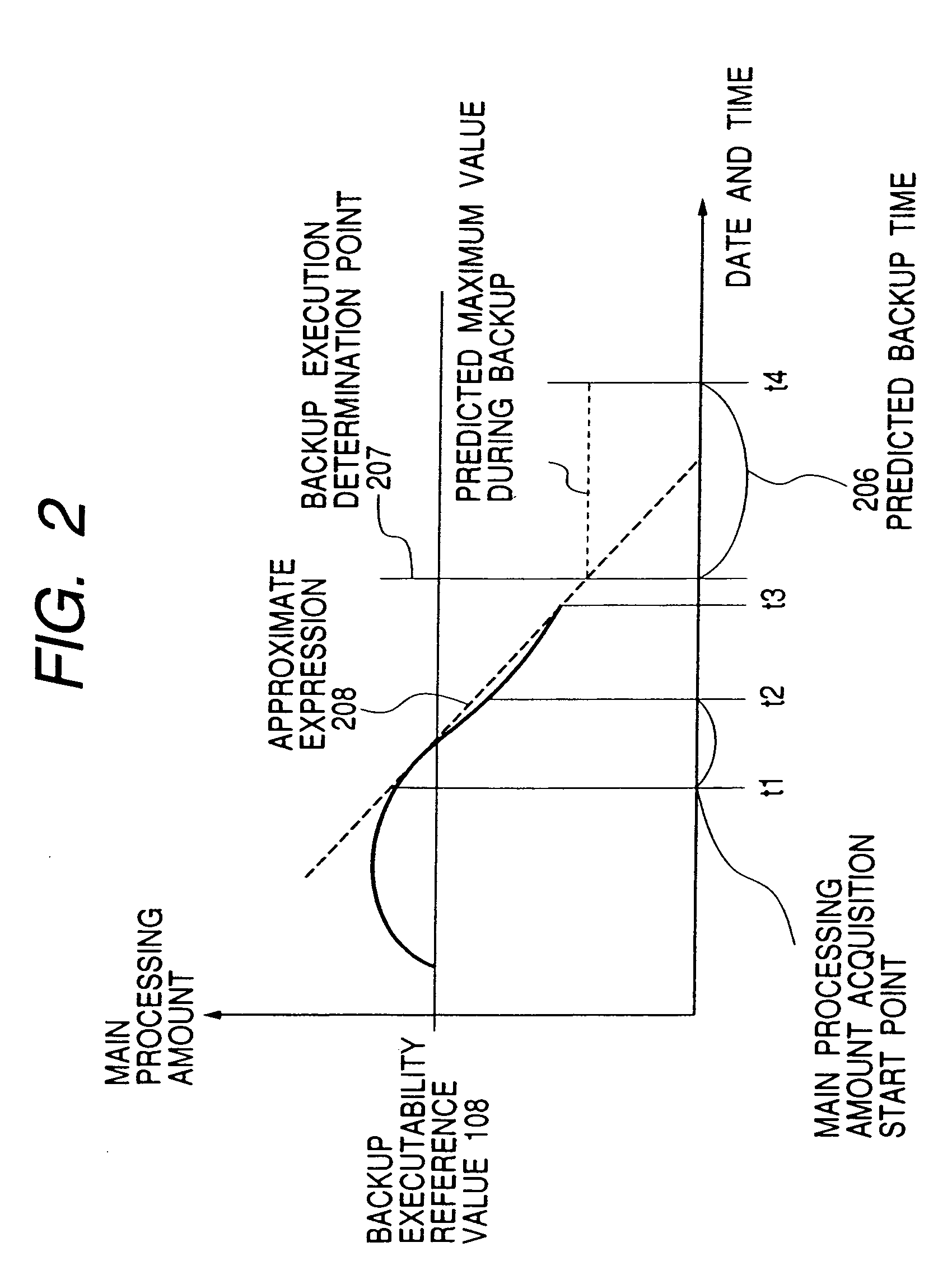
Method for determining execution of backup on a database
InactiveUS7421460B2Reduce adverse effectsAffect processComparison of digital valuesRedundant operation error correctionParallel computingTime frame
The amount of work processing (main processing amount) of a database is acquired and accumulated. A value (main processing index) indicating the transition of the amount of main processing amount available in a time frame that is presumed to be required for backup is calculated by using the amounts of main processing accumulated during the latest period of time. The main processing index is compared with the backup executability reference value which is a threshold value determining the backup executability. If the main processing index is smaller than the threshold value, backup is executed. If the main processing index is larger than the threshold value, backup is not executed but the amount of main processing is again acquired to calculate the main processing index, and the main processing index is compared with the backup executability reference value.
Owner:HITACHI LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com