Patents
Literature
603 results about "Network Computer" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
The Network Computer (or NC) was a diskless desktop computer device made by Oracle Corporation from about 1996 to 2000. The devices were designed and manufactured by an alliance, which included Sun Microsystems, IBM, and others. The devices were designed with minimum specifications, based on the Network Computer Reference Profile. The brand was also employed as a marketing term to try to popularize this design of computer within enterprise and among consumers.
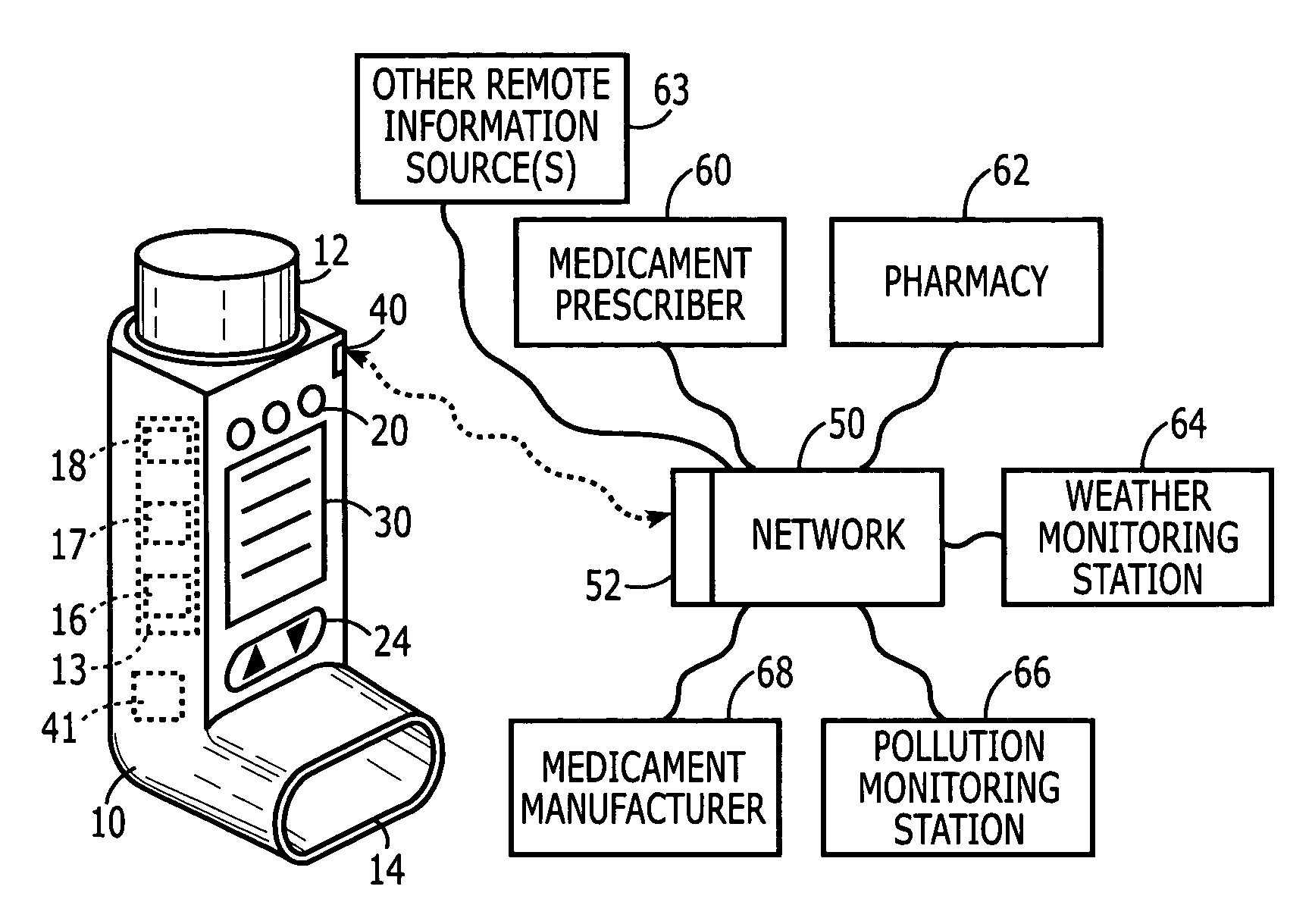
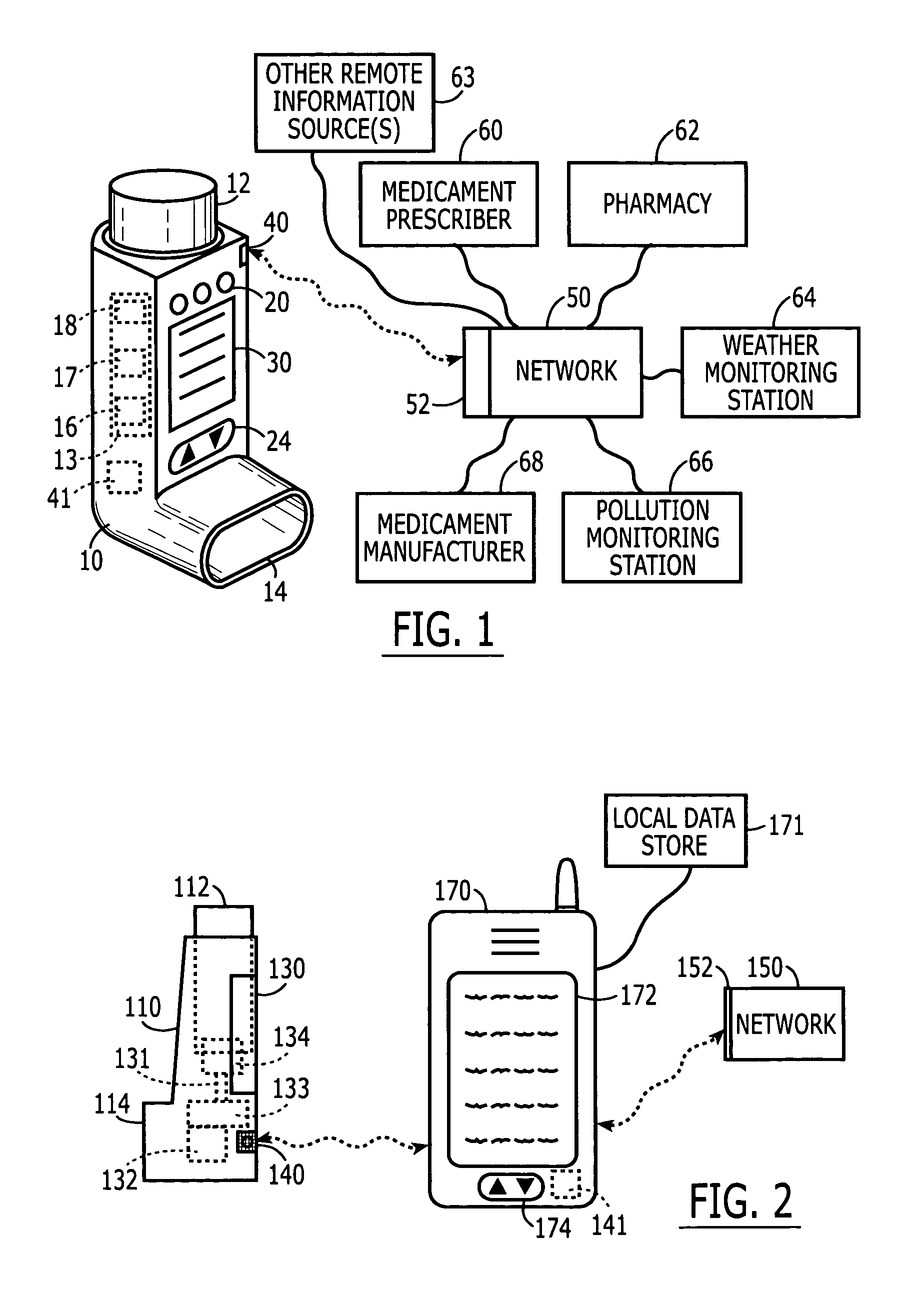
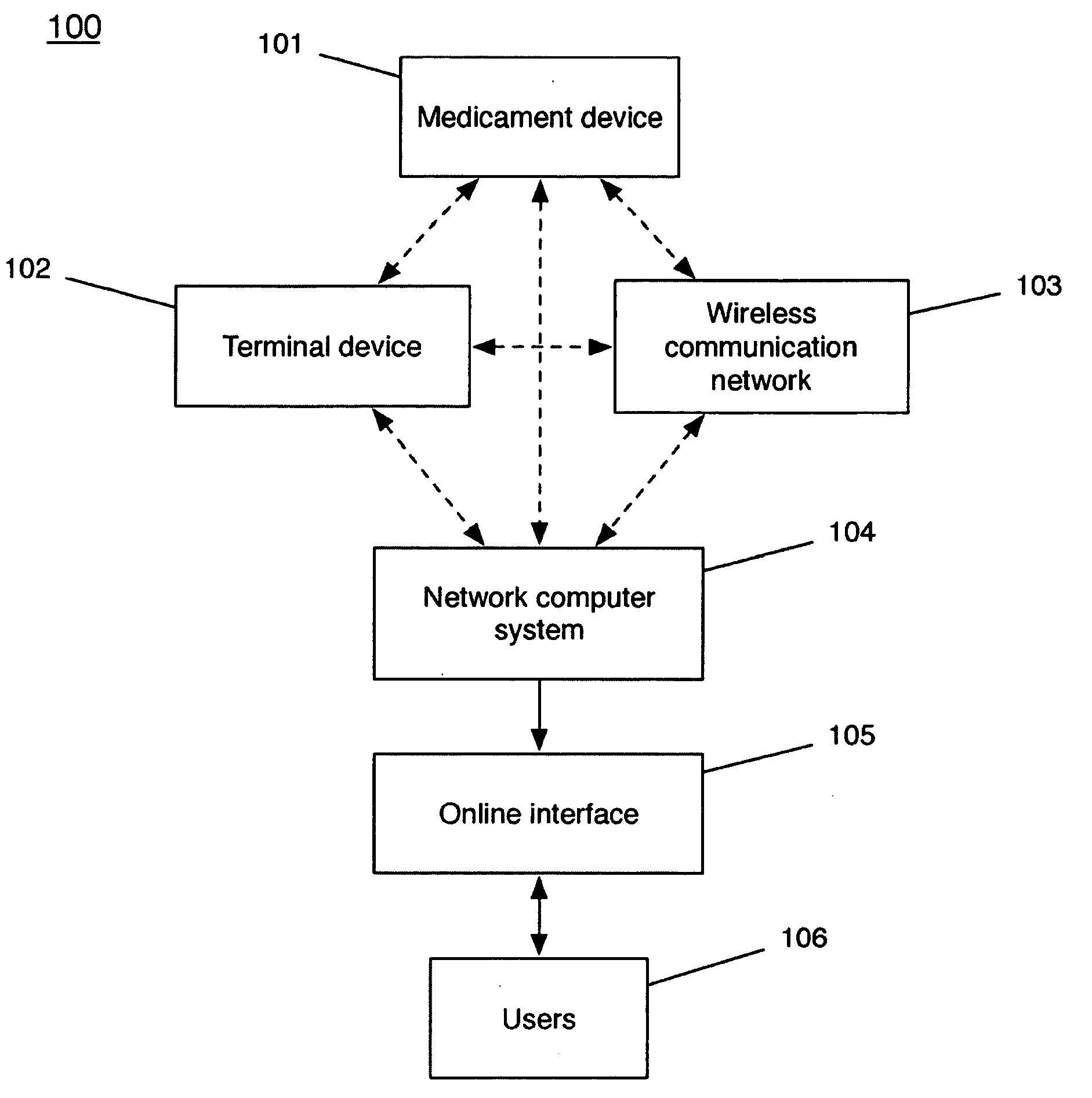
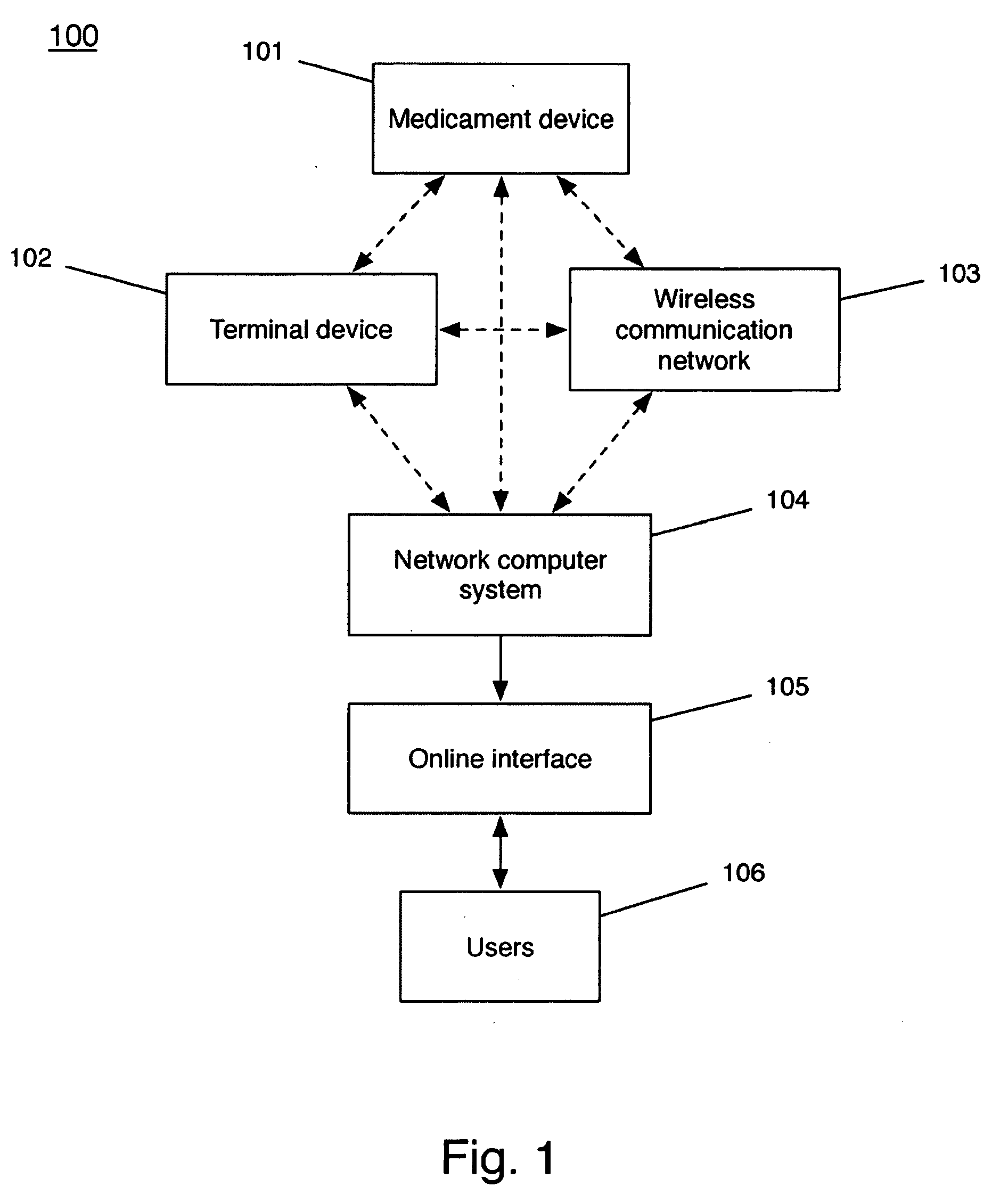
Medicament delivery system
InactiveUS6958691B1Simple systemEasy accessDigital data processing detailsDrug and medicationsComputer scienceDelivery system
There is provided a system for the delivery of medicament comprising a medicament container; a dispensing mechanism for dispensing medicament from the medicament container; an electronic data management system; and a communicator for wireless communication with a network computer system to enable communication of data between the network computer system and the electronic data management system. The electronic data management system comprises a memory for storage of data; a microprocessor for performing operations on the data; and a transmitter for transmitting a signal relating to the data or the outcome of an operation on the data.
Owner:GLAXO WELLCOME INC
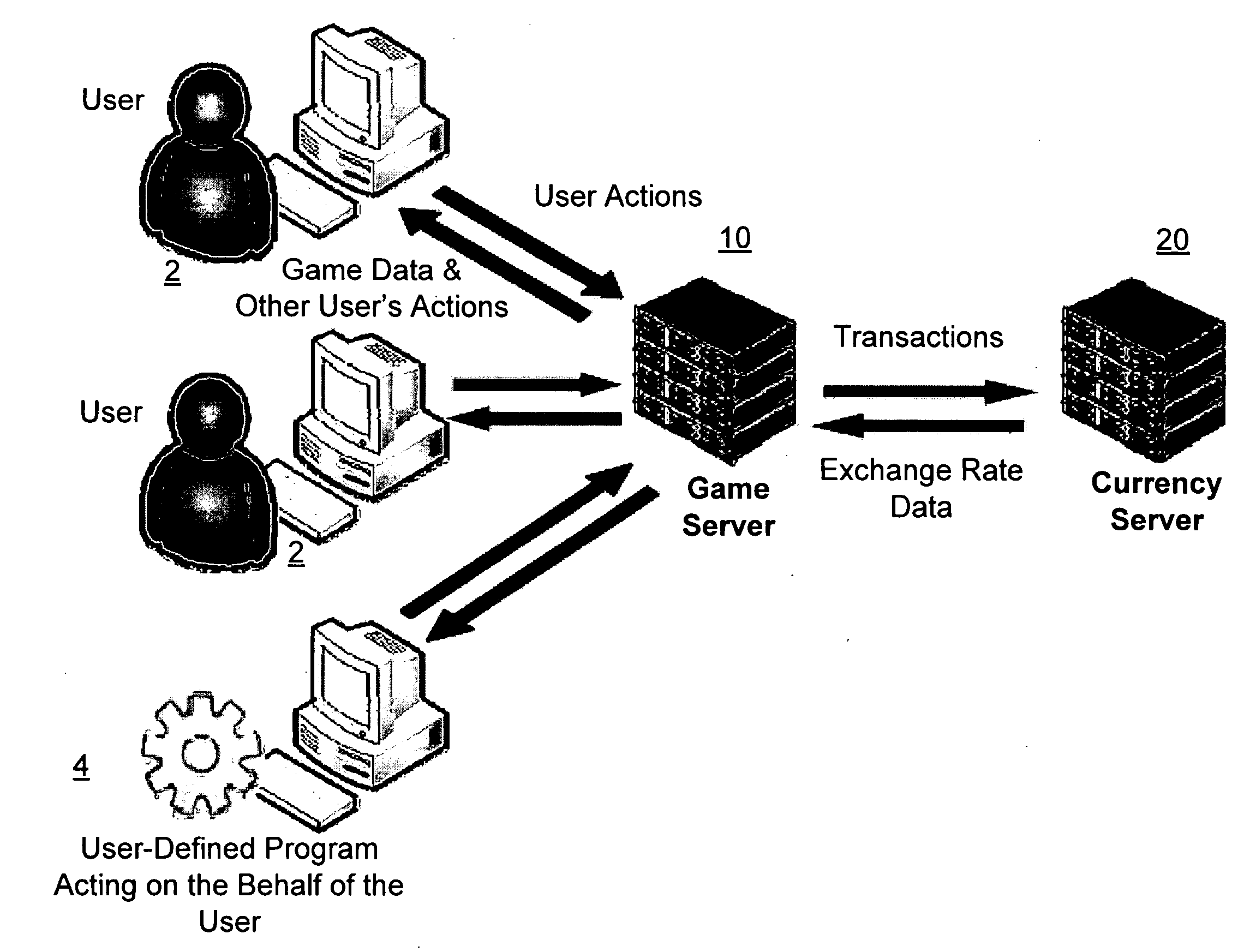
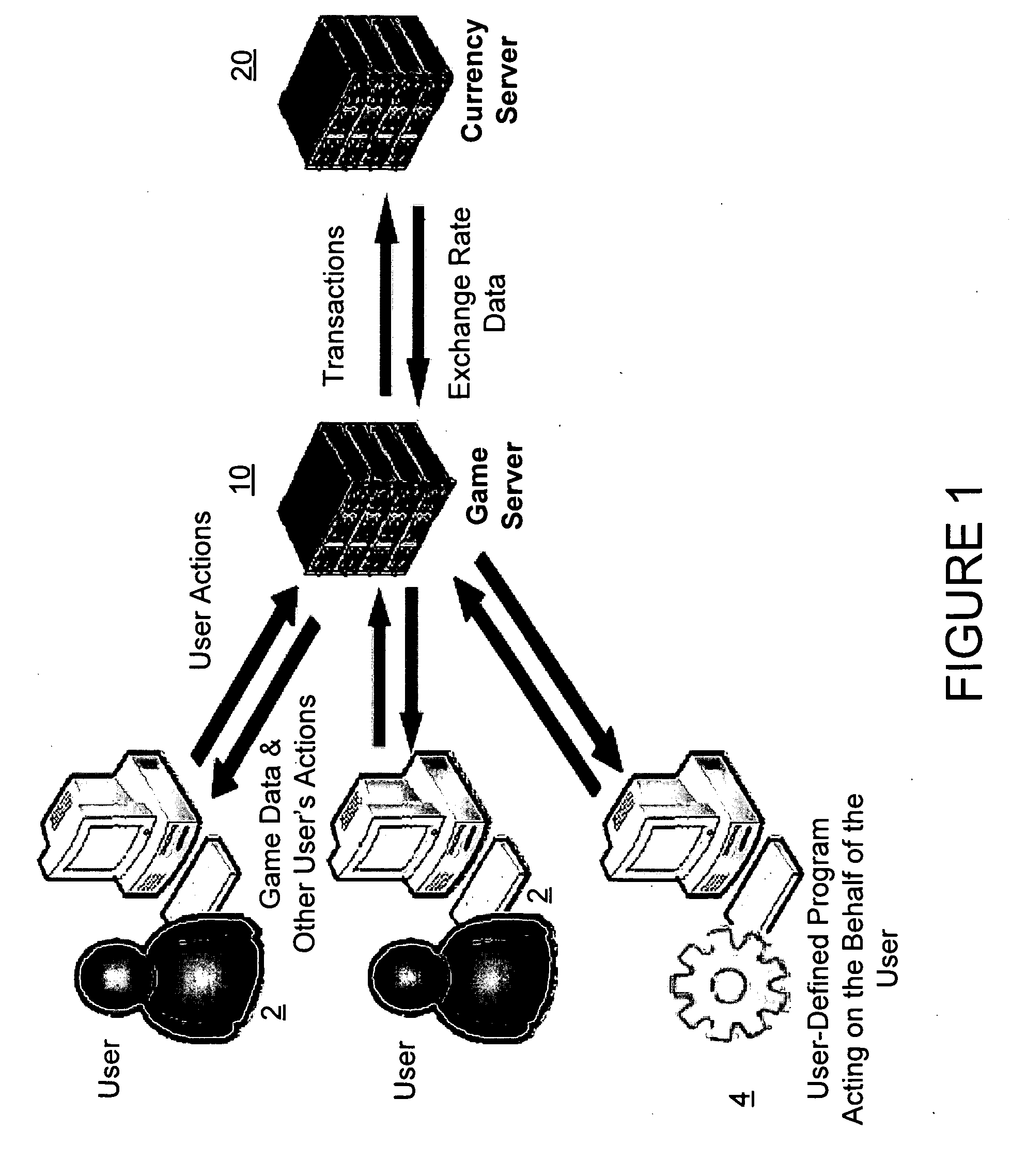
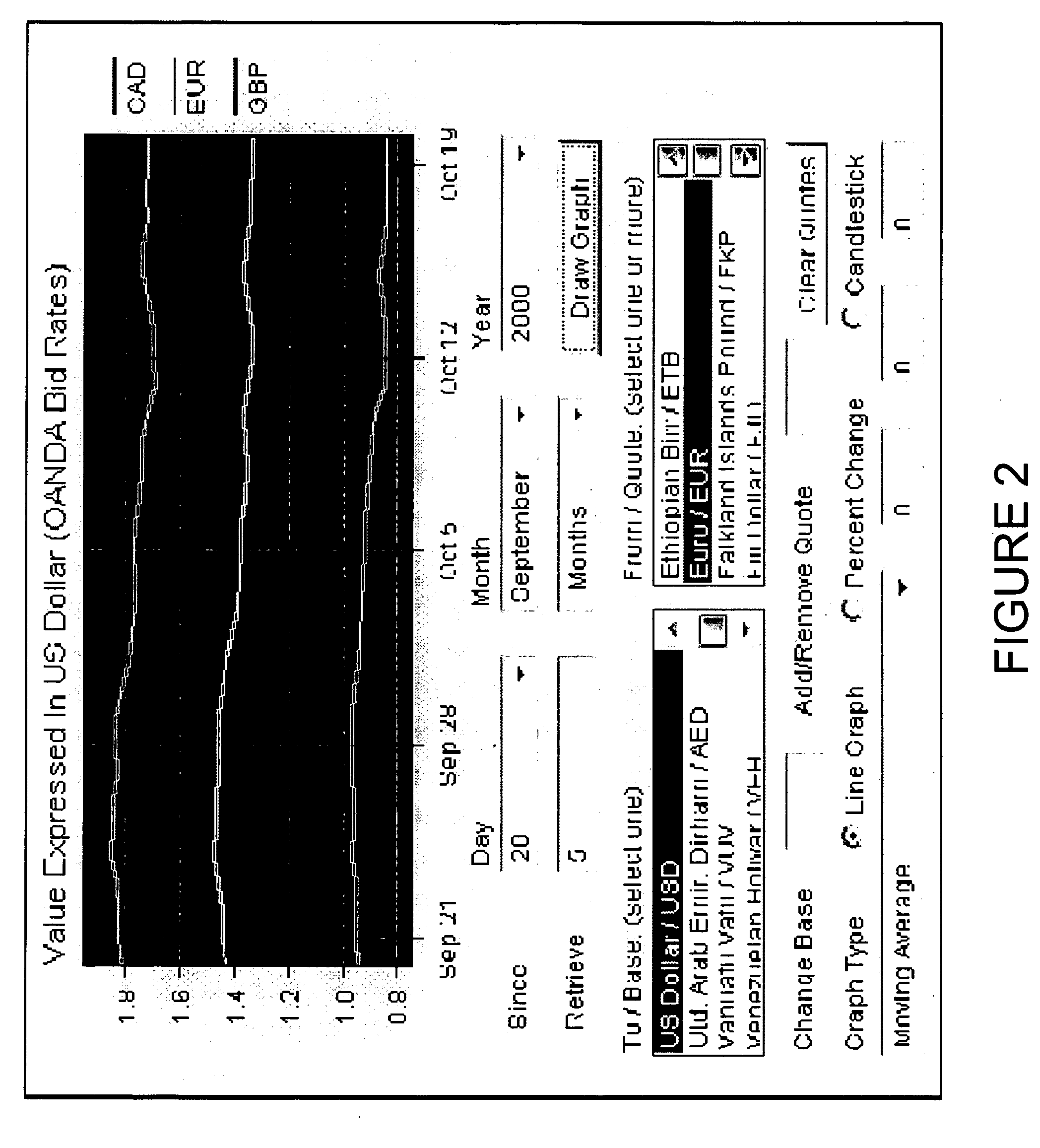
Network computer game linked to real-time financial data
InactiveUS20090181777A1Apparatus for meter-controlled dispensingVideo gamesFinancial transactionMarket based
A network-based computer game that both uses real-time financial data to affect game state and uses participants' actions to determine and engage in financial transactions. A game server receives financial data on market conditions (such as currency markets) from a financial server and regularly synchronizes user's game environments to match the financial data. The game server propagates financial data to the game or games, coordinates communication (if any) between the games, and can initiate the opening and closing of positions in the financial market based on players' game behavior. The financial market can be a currency market, where one nation's currency can be exchanged for another currency at a certain exchange rate.
Owner:FINANCIAL DATA GAMES
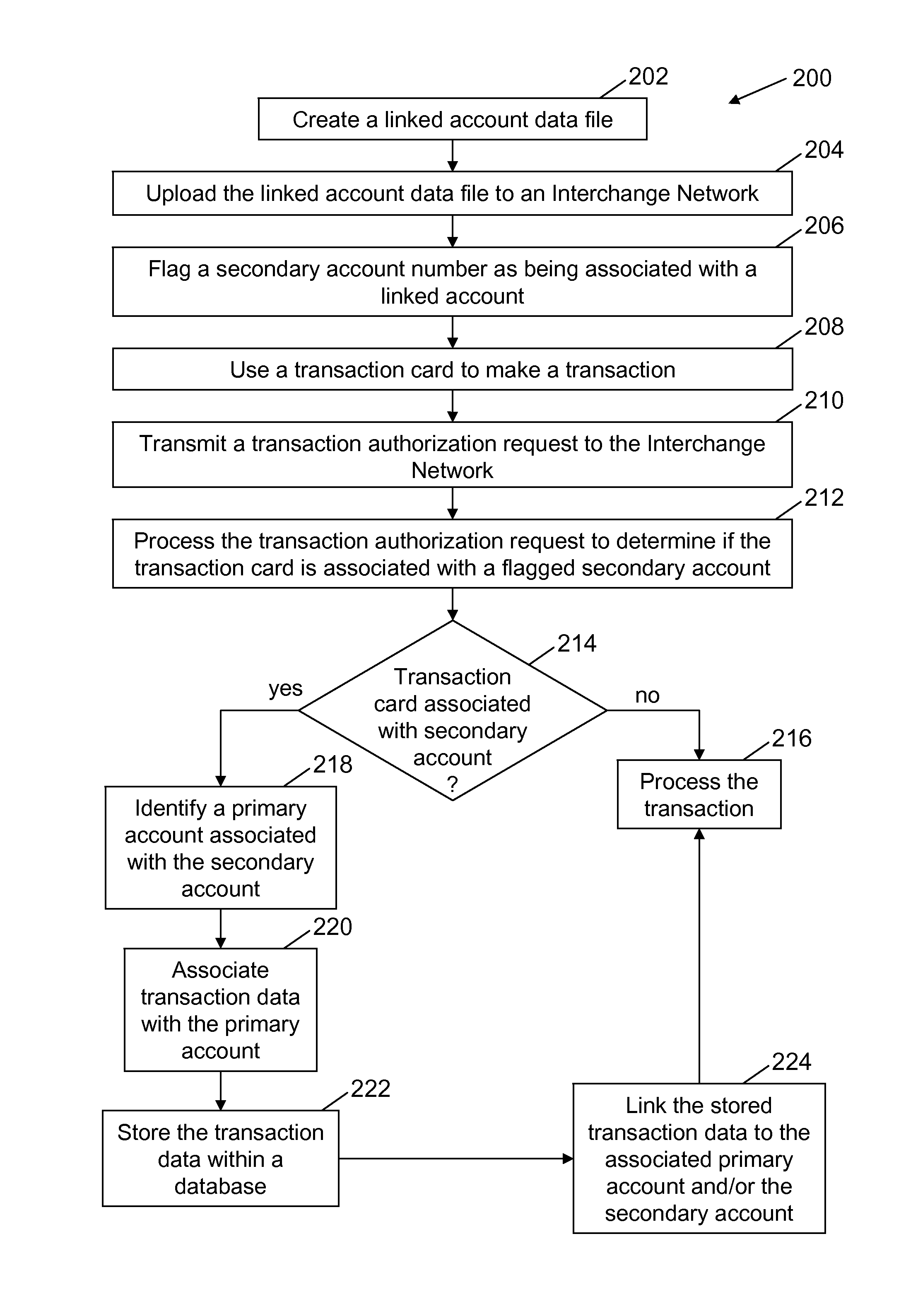
Methods and systems for linking multiple accounts
A method for processing a financial transaction using an interchange network computer coupled to a database is described. The transaction is initiated with a transaction card associated with a linked account. The method includes receiving, at the interchange network computer, a linked account data file for the first transaction card. The data file includes data associating the first card with a first secondary account and data linking the first secondary account to a first primary account. The method also includes storing the data file within the database and receiving a first authorization request message for the first transaction. The method also includes determining, based on data included within the first authorization request message, that the first card is associated with the first secondary account and processing the first authorization request message by applying at least one processing code associated with the first primary account to the first transaction.
Owner:MASTERCARD INT INC
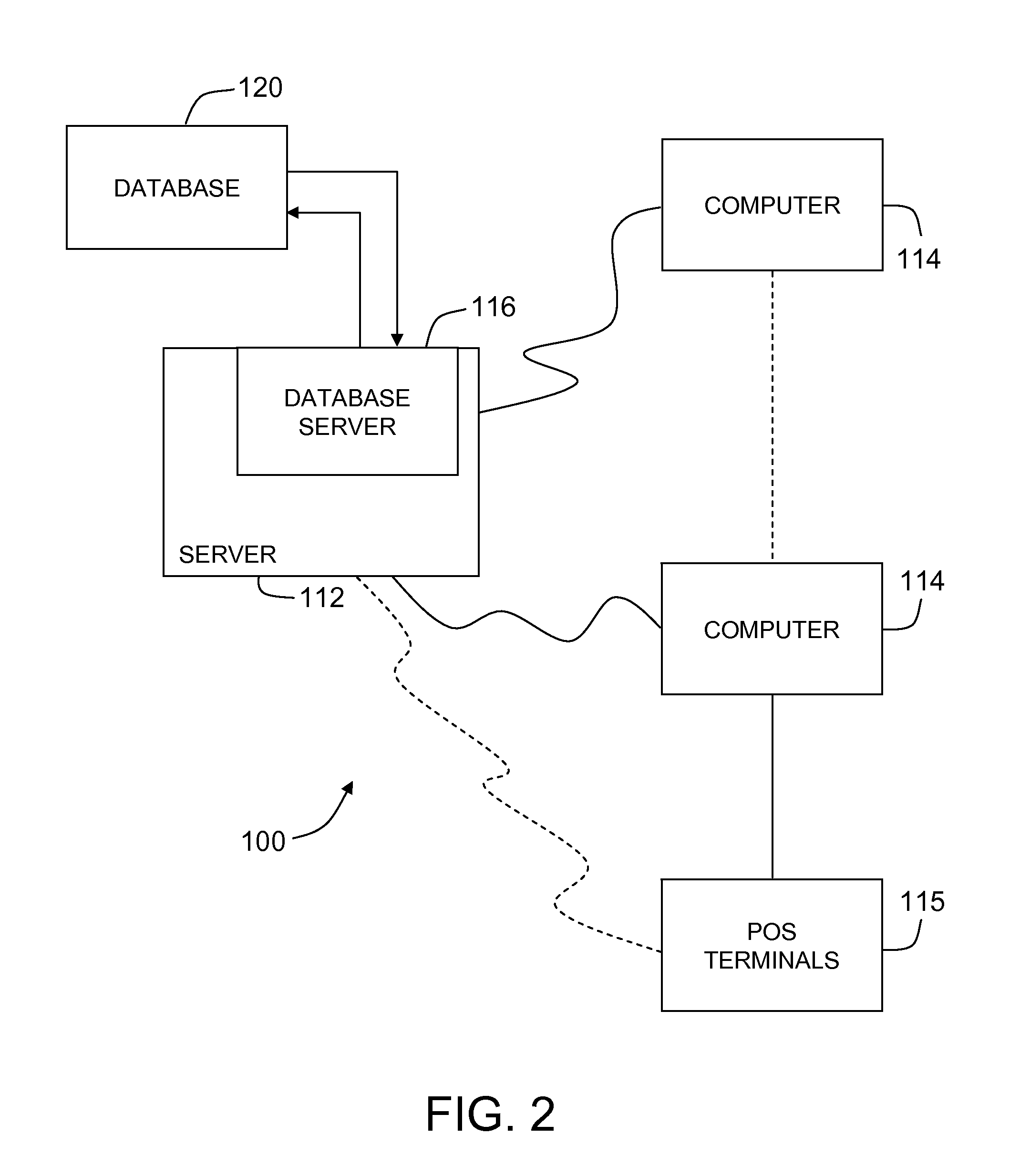
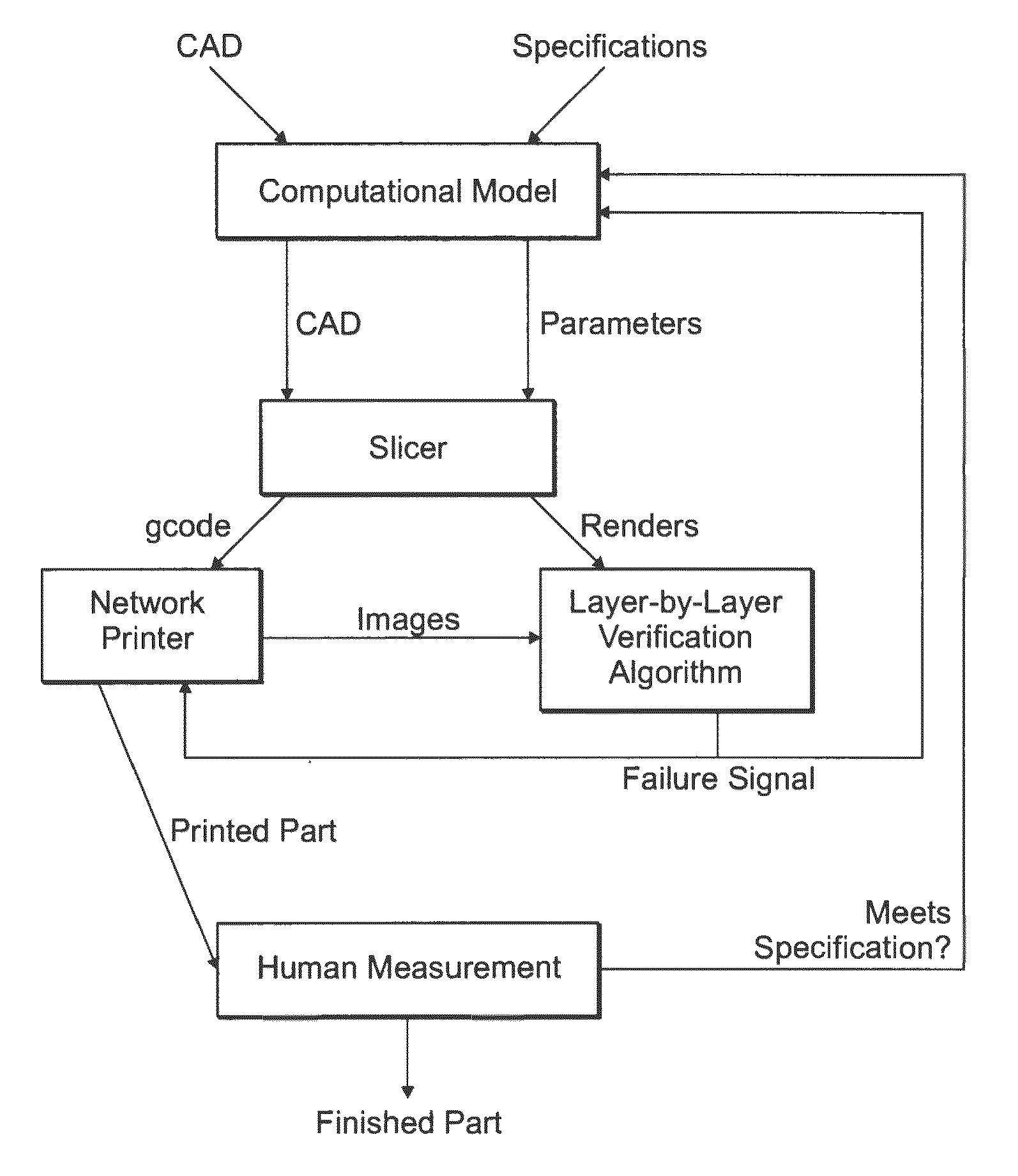
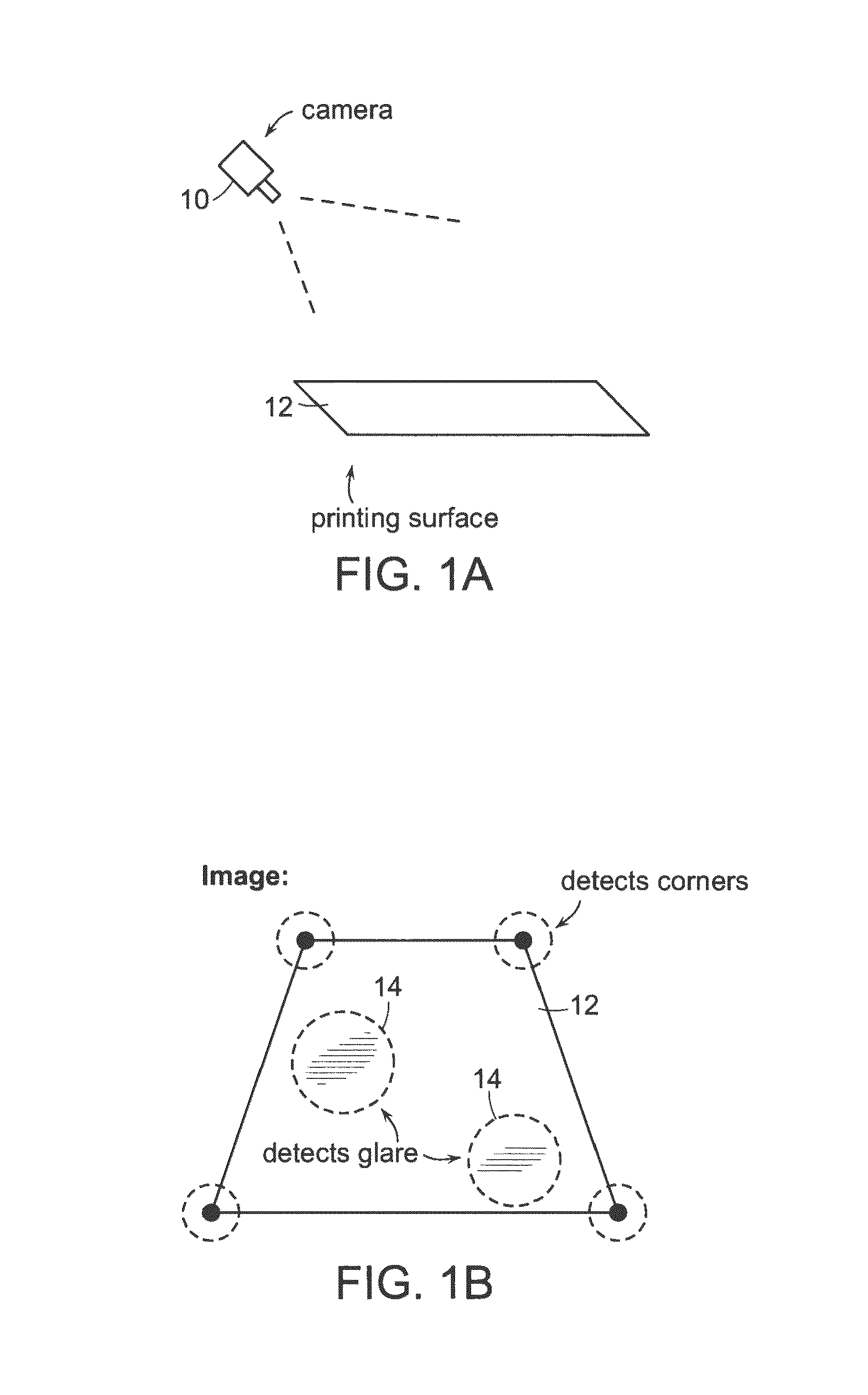
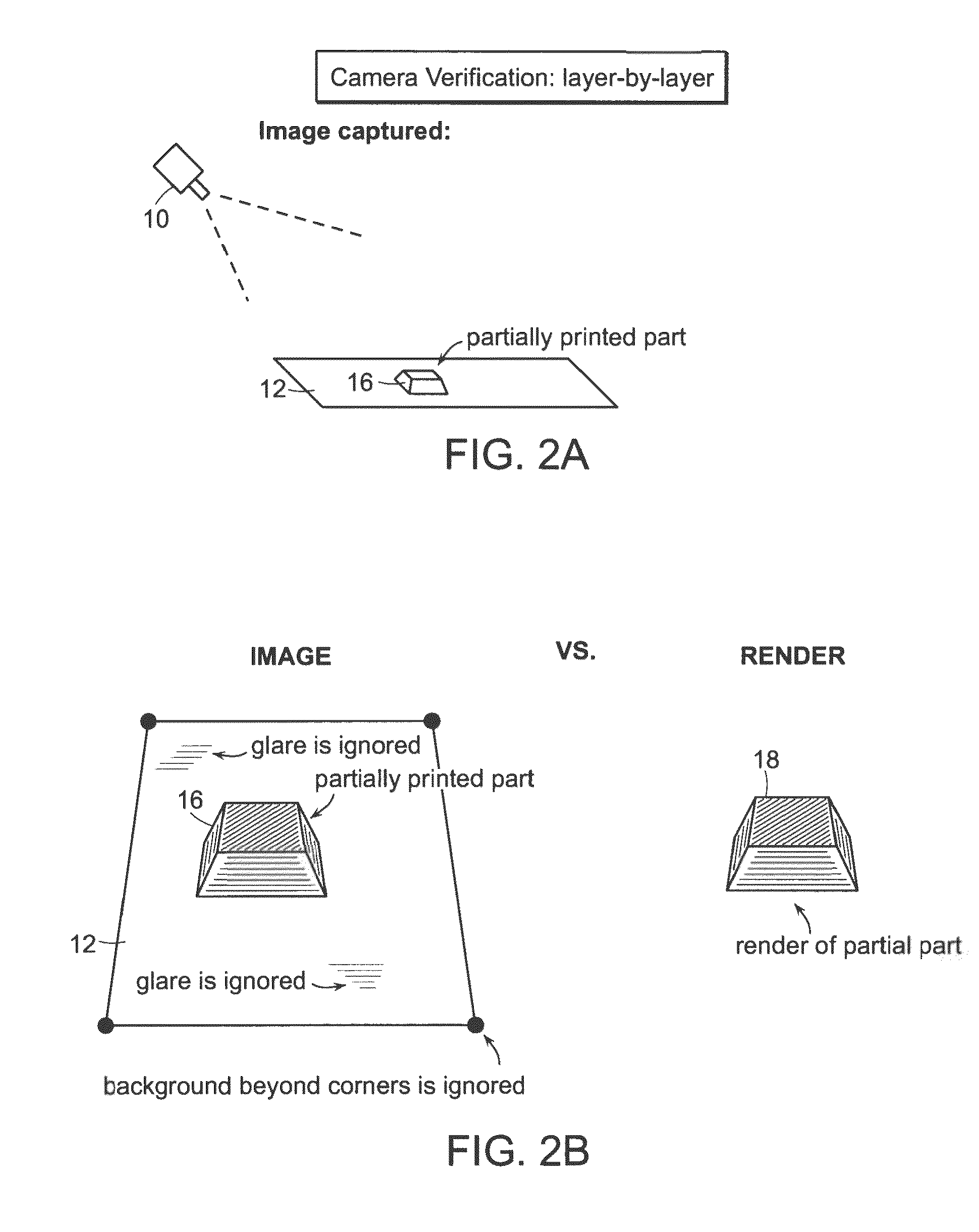
Automatic Process Control of Additive Manufacturing Device
ActiveUS20150045928A1Minimize the numberImprove efficiencyAdditive manufacturing apparatusComputing modelsAutomatic process controlAccessible image
Automatic process control of additive manufacturing. The system includes an additive manufacturing device for making an object and a local network computer controlling the device. At least one camera is provided with a view of a manufacturing volume of the device to generate network accessible images of the object. The computer is programmed to stop the manufacturing process when the object is defective based en the images of the object.
Owner:MASSACHUSETTS INST OF TECH
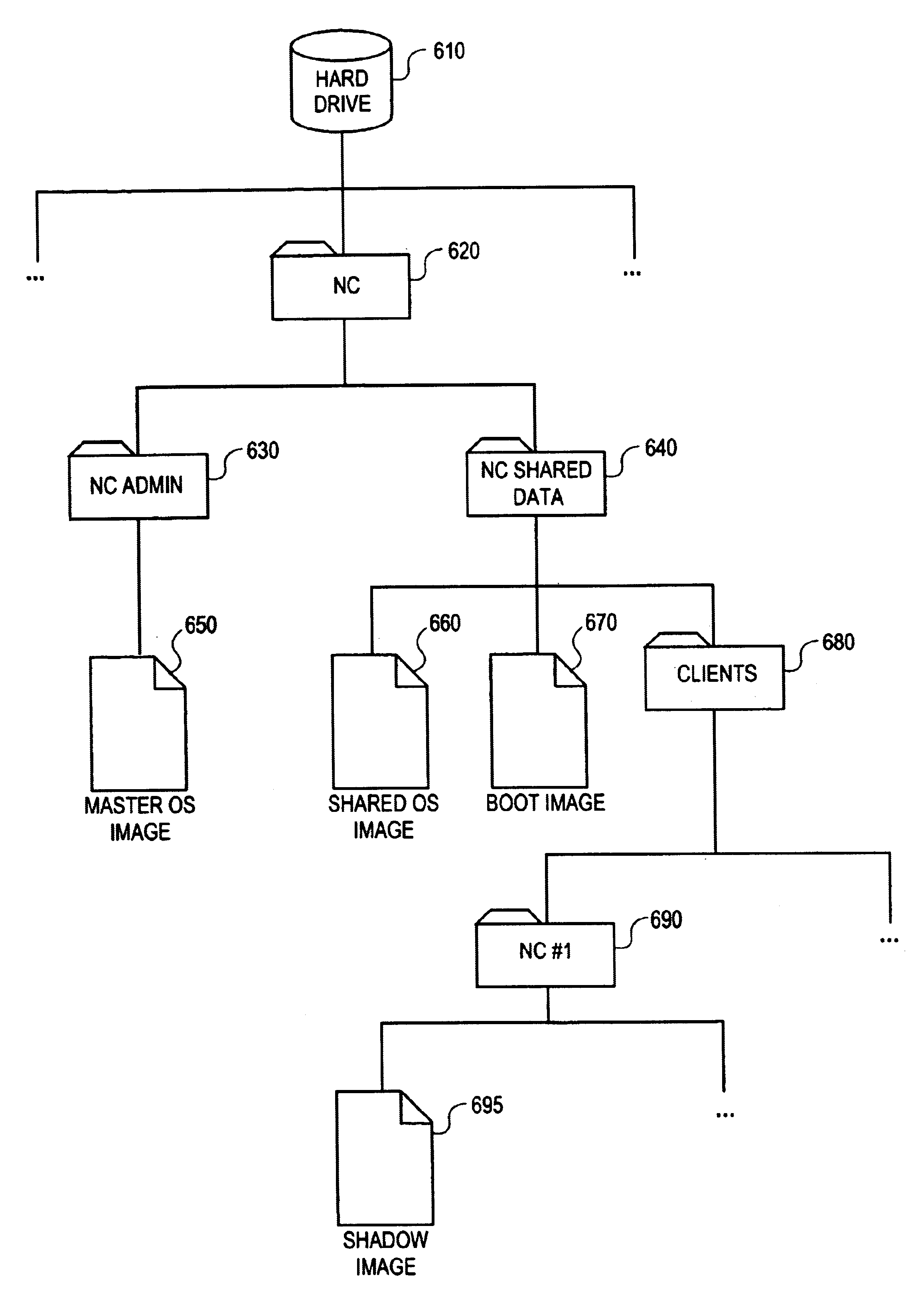
Providing a reliable operating system for clients of a net-booted environment
InactiveUS6751658B1Multiple digital computer combinationsProgram loading/initiatingOperational systemNetwork booting
A method and apparatus are provided for supplying a reliable and maintainable operating system in a net-booted environment. According to one embodiment, a network computer (NC) client boots from a boot image provided by an NC server. The boot image includes information identifying the location of one or more system volumes on the NC server that contain operating system software. In response to an attempt to modify the contents of the one or more system volumes, the NC client causes information identifying the modification to be recorded on the NC server separate from the one or more system volumes in a storage area associated with the NC client.
Owner:APPLE INC
Device and method to monitor, track, map, and analyze usage of metered-dose inhalers in real-time
ActiveUS20090194104A1Easy to manageEasy to identifyRespiratorsDrug and medicationsClinical careComputer science
A system and method for accurately and reliably determining and recording the time, date and location where a medication is used, and a system and method for transmitting, collecting, and using that data to improve clinical care, disease management, and public health surveillance. The device allows information concerning drug usage, including the time, date and location of use, to be transmitted to a remote network computer system so that the data can be evaluated to determine current impairment and future risk, and to identify changes in the frequency, timing, or location of medication usage indicative of change in disease control or management, and to examine spatial, temporal or demographic patterns of medication use or absence of use among individuals and groups. In addition, the device may further be configured to transmit signals indicative of its status, condition or other results to the remote network computer system.
Owner:RECIPROCAL LABS CORP D B A PROPELLER HEALTH
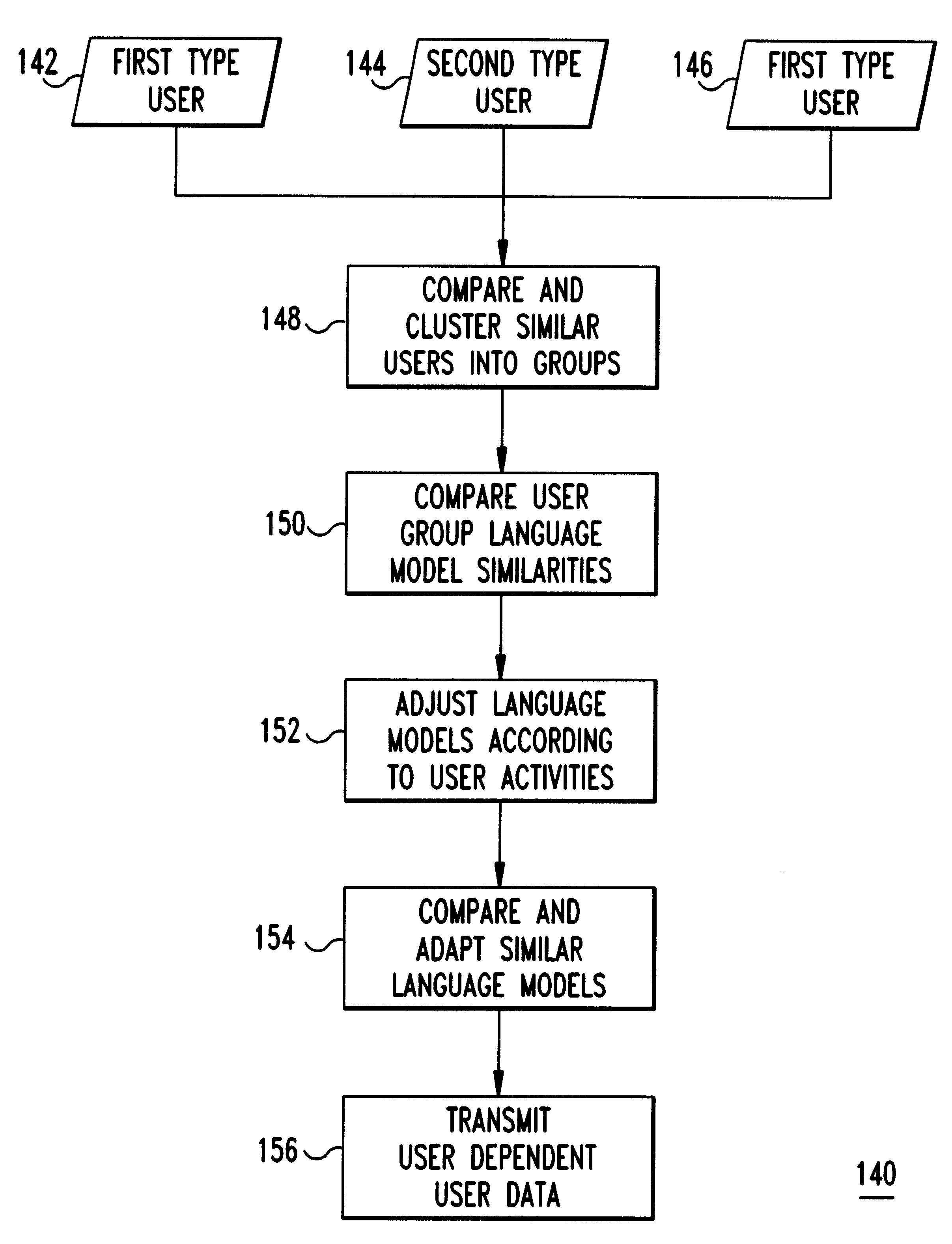
Language model adaptation via network of similar users
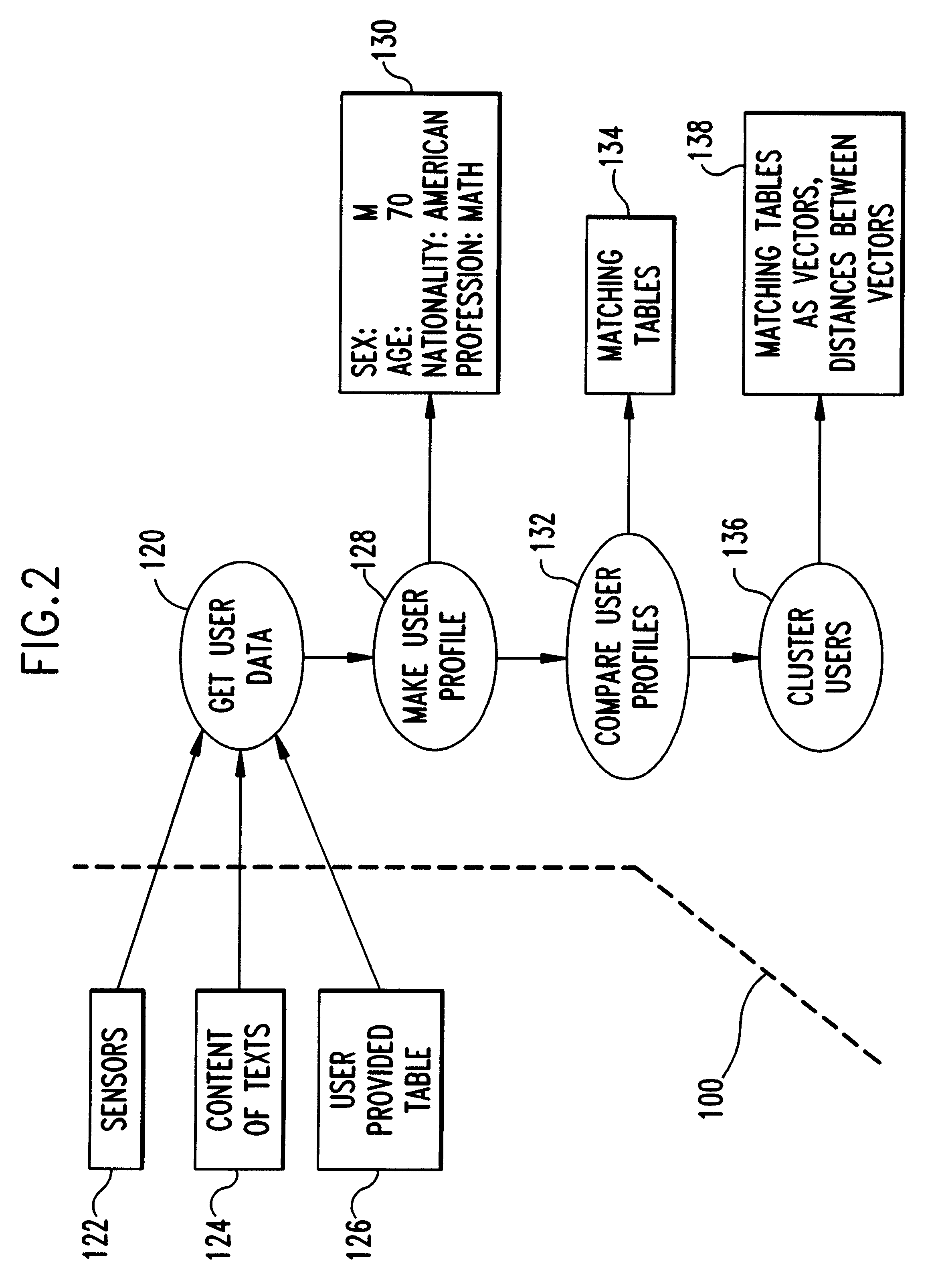
A language recognition system, method and program product for recognizing language based input from computer users on a network of connected computers. Each computer includes at least one user based language model trained for a corresponding user for automatic speech recognition, handwriting recognition, machine translation, gesture recognition or other similar actions that require interpretation of user activities. Network computer users are clustered into classes of similar users according to user similarities such as, nationality, profession, sex, age, etc. User characteristics are collected by sensors and from databases and, then, distributed over the network during user activities. Language models with similarities among similar users on the network are identified. The language models include a language model domain, with similar language models being clustered according to their domains. Language models identified as similar are modified in response to user production activities. After modification of one language model, other identified similar language models are compared and adapted. Also, user data, including information about user activities and language model data, is transmitted over the network to other similar users. Language models are adapted only in response to similar user activities, when these activities are recorded and transmitted over the network. Language models are given a global context based on similar users that are connected together over the network.
Owner:NUANCE COMM INC
Licensed application installer
InactiveUS6948168B1Data processing applicationsSoftware engineeringComputer terminalApplication software
A method and system of installing licensed software on an end user's computer comprising having a program storage device and a unique computer identifier distinguishing the end user computer from other computers, e.g., a BIOS serial number or a network adapter address. The network computer contains a plurality of different software for license to end users and a database listing computer identifiers licensed to run the software. The end user computer sends to the network computer a command to run a program identifying to the end user computer the software listed as licensed by the computer identifier of the end user computer. The network computer contacts the end user computer and determine its end user computer identifier, verifies listing of the end user computer identifier in the network computer database, and identifies to the end user computer all of the software on the network computer program storage device listed as licensed by the computer identifier of the end user computer using an executable program on the network computer. The end user computer sends to the network computer a selection of the software to be downloaded. The network computer downloads the selected software and installs it on the end user computer program storage device.
Owner:ACTIVISION PUBLISHING
System and method for resolving vulnerabilities in a computer network
InactiveUS20110138469A1Memory loss protectionError detection/correctionSecurity levelComputer science
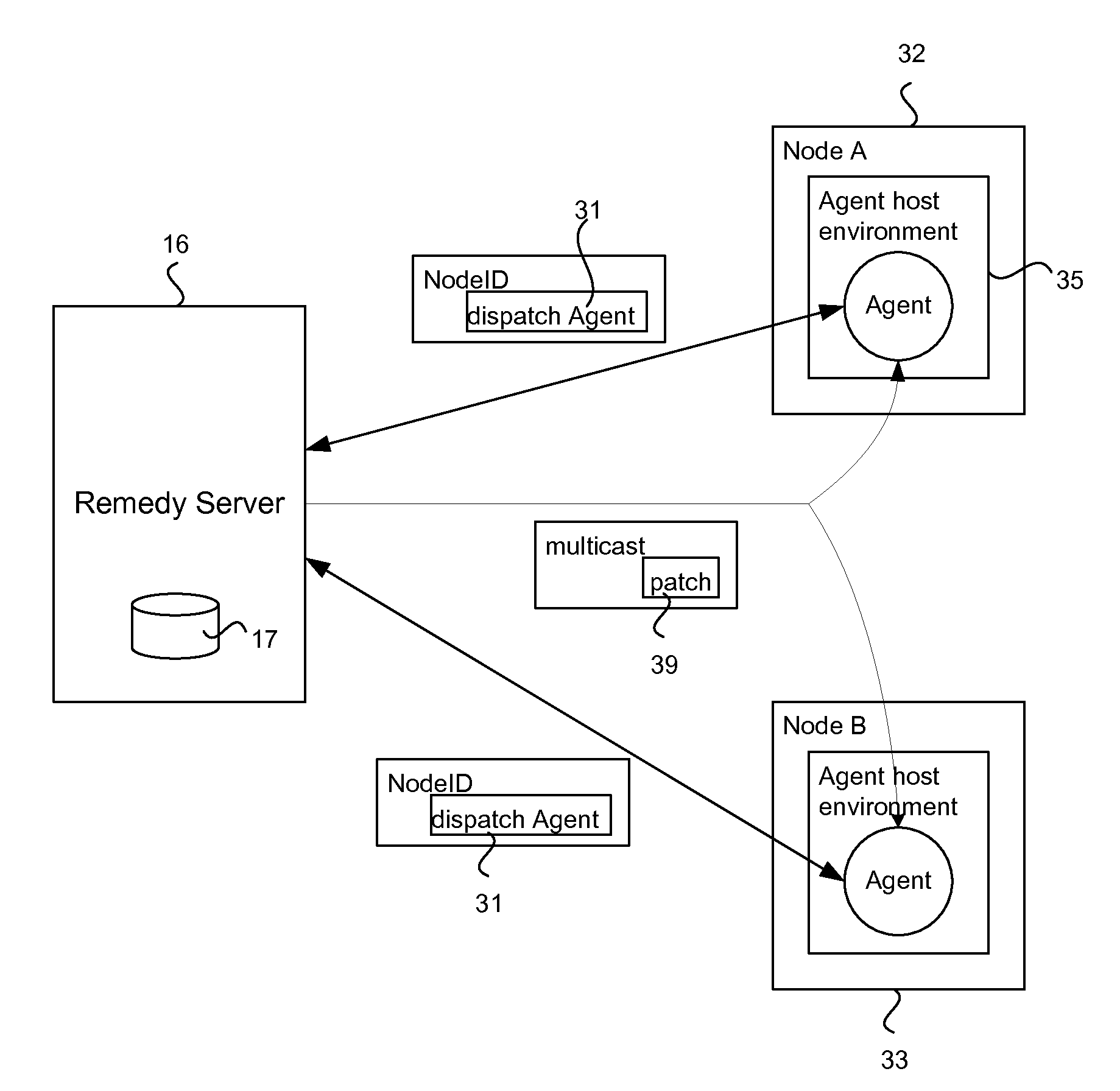
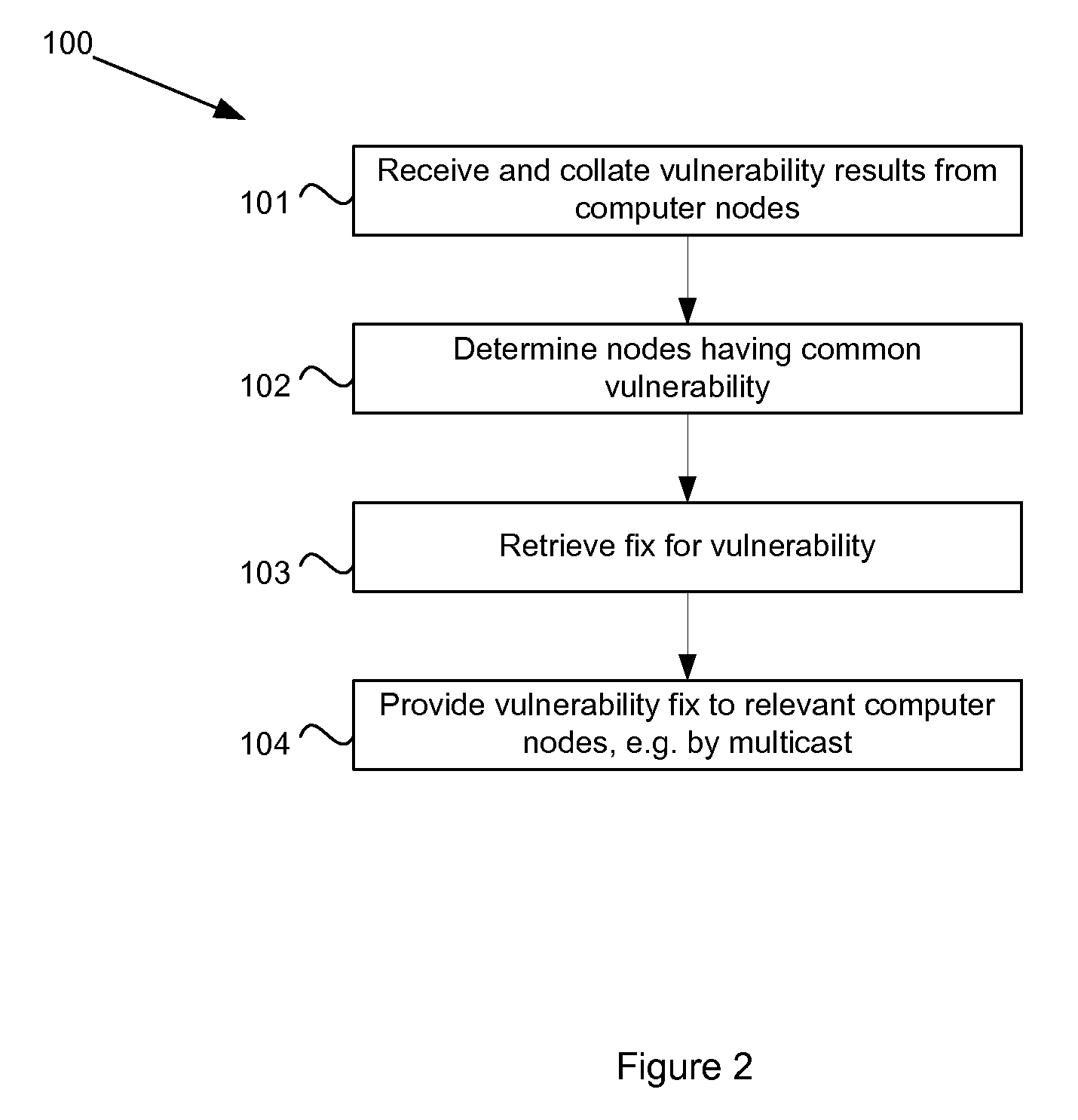
In a computer network, a remedy server may be provided that controls vulnerability scans of the computer nodes. The remedy server determines a security level of a computer node and dispatches an agent to the node with a scan matching the security level. The agent executes the scan and reports the scan results to the remedy server. The remedy server collates scan results from a plurality of the network computers and determines which computers have a common vulnerability. A fix for the vulnerability, such as an executable patch file, is retrieved and multicast to those relevant computers.
Owner:OSOCAD REMOTE LIABILITY
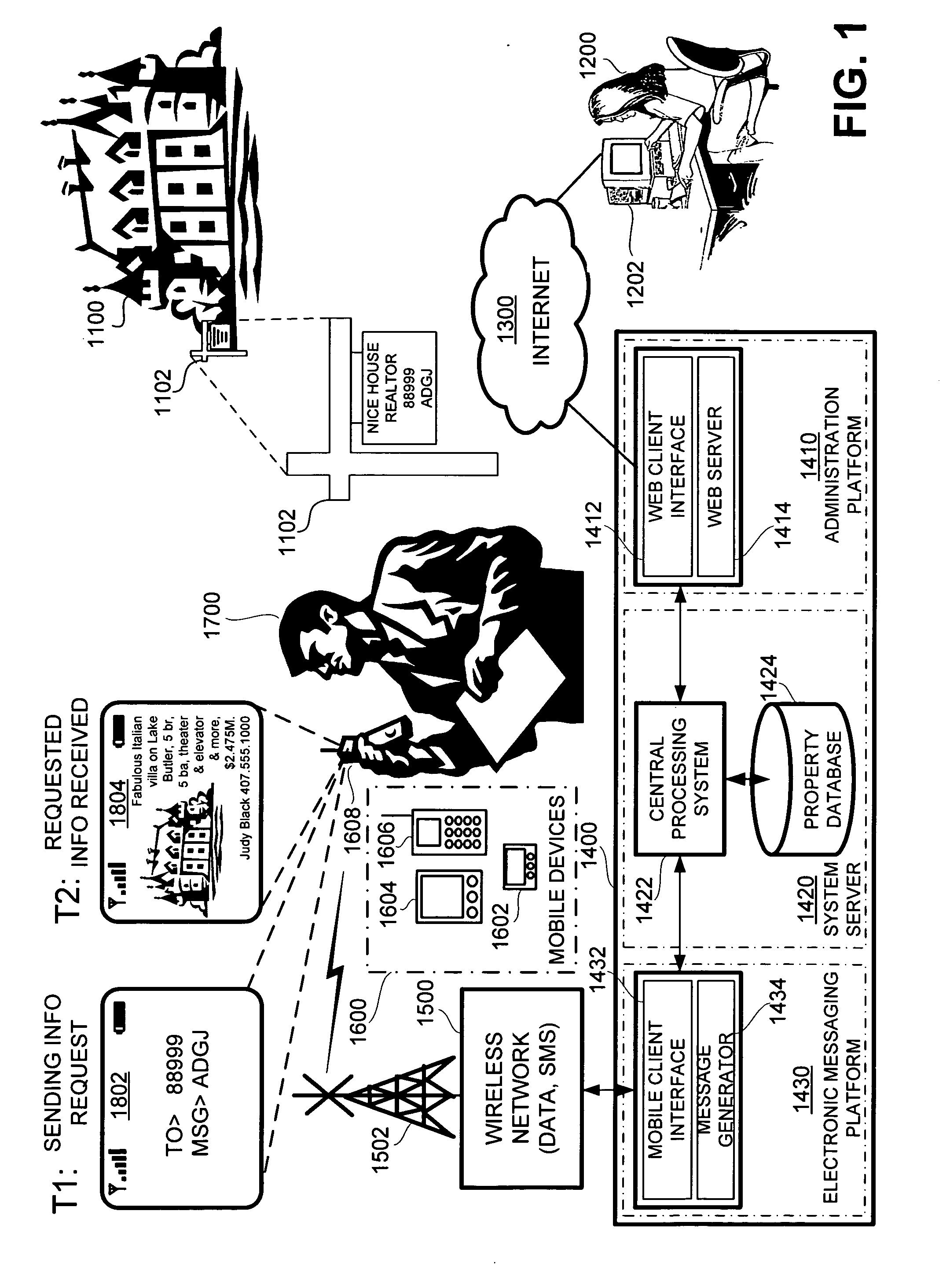
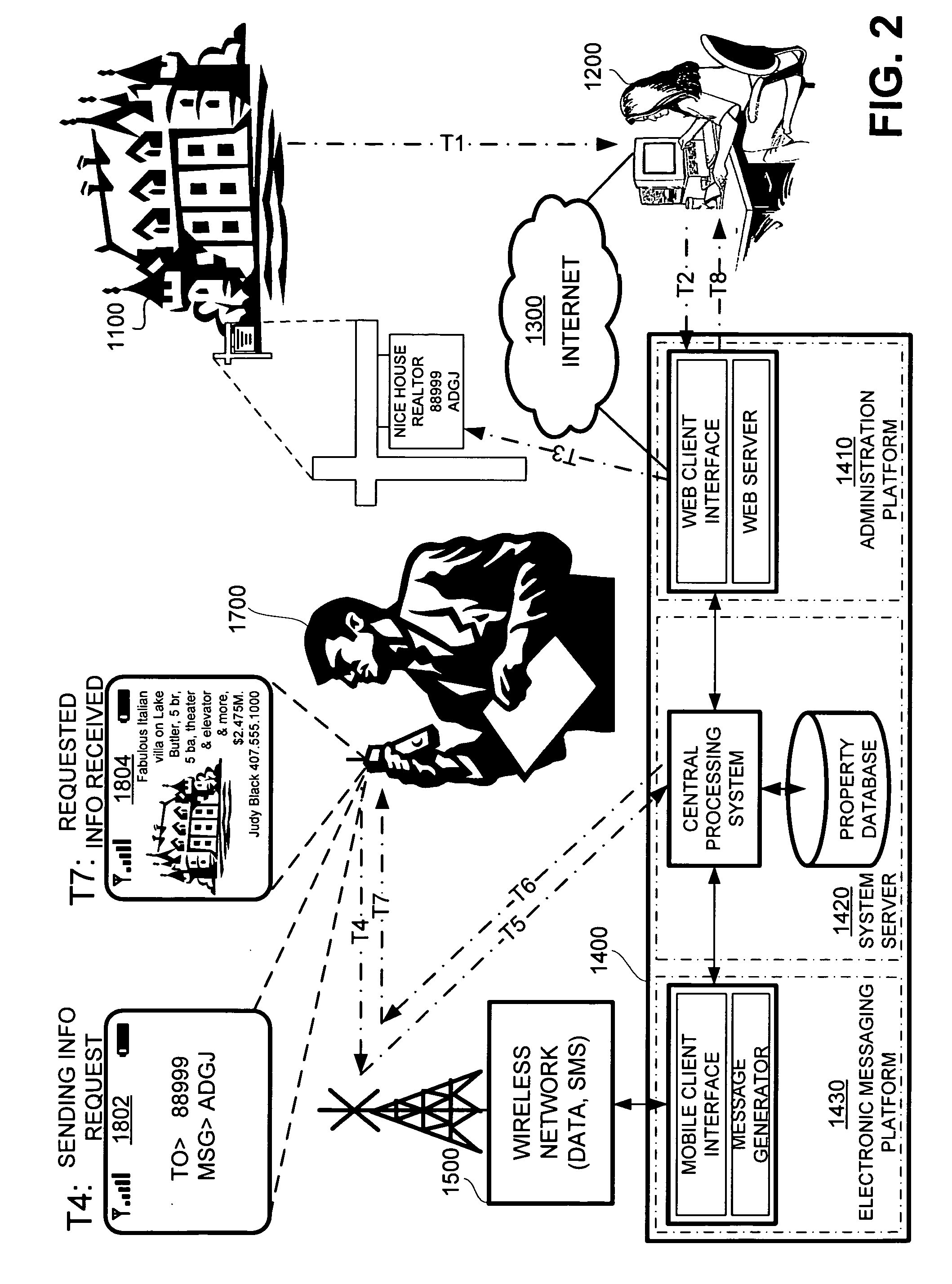
Wireless interactive property advertising system and methods
InactiveUS20060194572A1Special service for subscribersRadio/inductive link selection arrangementsMobile deviceData bank
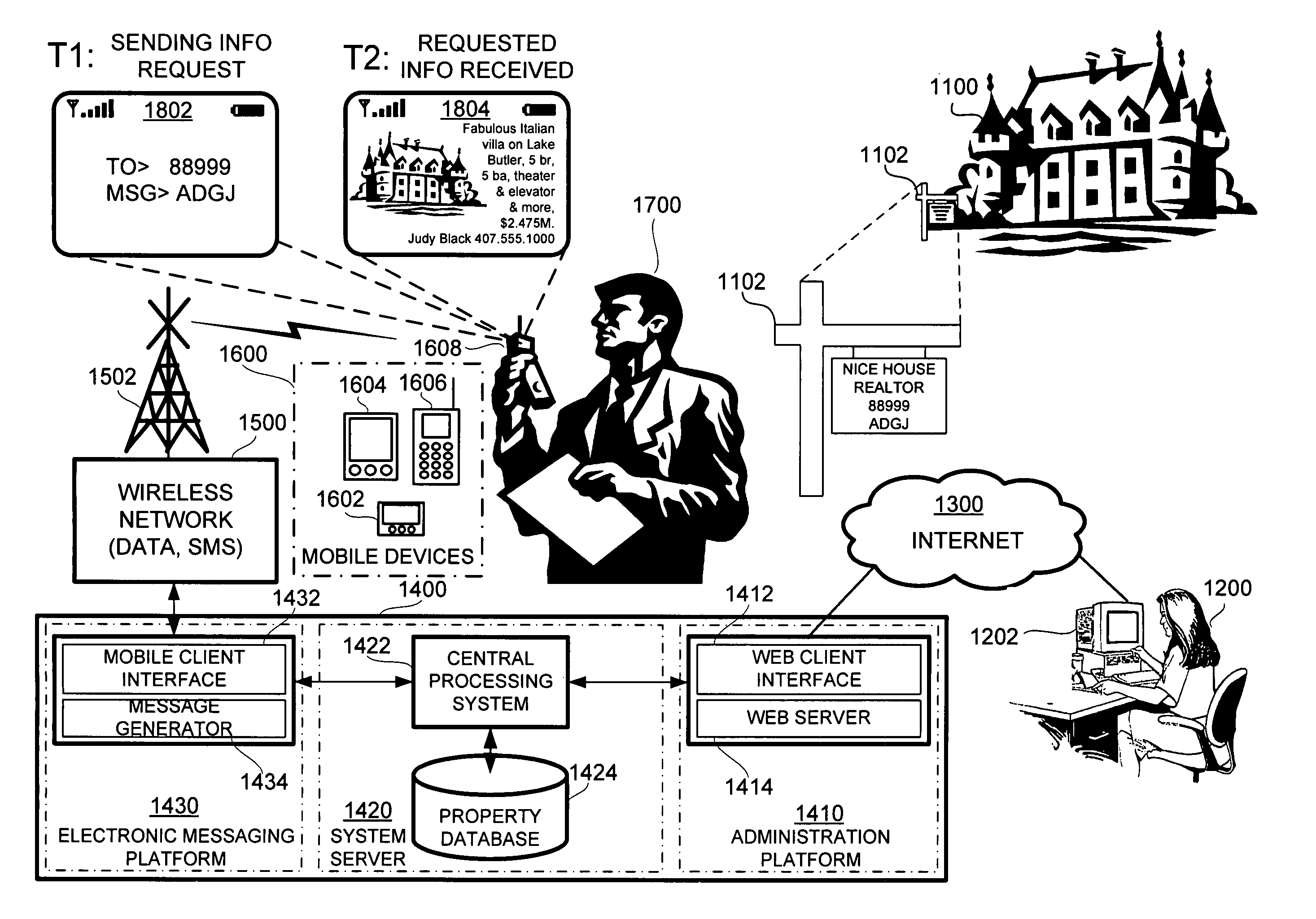
A system for providing property information about a property over a wireless network to an interested party having a mobile device, comprising: (a) an advertisement associated with the property, the advertisement having a shortcode and a keyword, and (b) a networked computer system having a property database containing property information for the property; the property information being retrievable from the property database based on the shortcode and the keyword. In operation, the interested party requests the property information about the property by sending a message with the shortcode and the keyword over the wireless network using the mobile device and, in response, the networked computer system retrieves the property information about the property associated with the shortcode and the keyword from the property database and transmits the property information to the mobile device of the interested party.
Owner:CLEARSKY MOBILE MEDIA
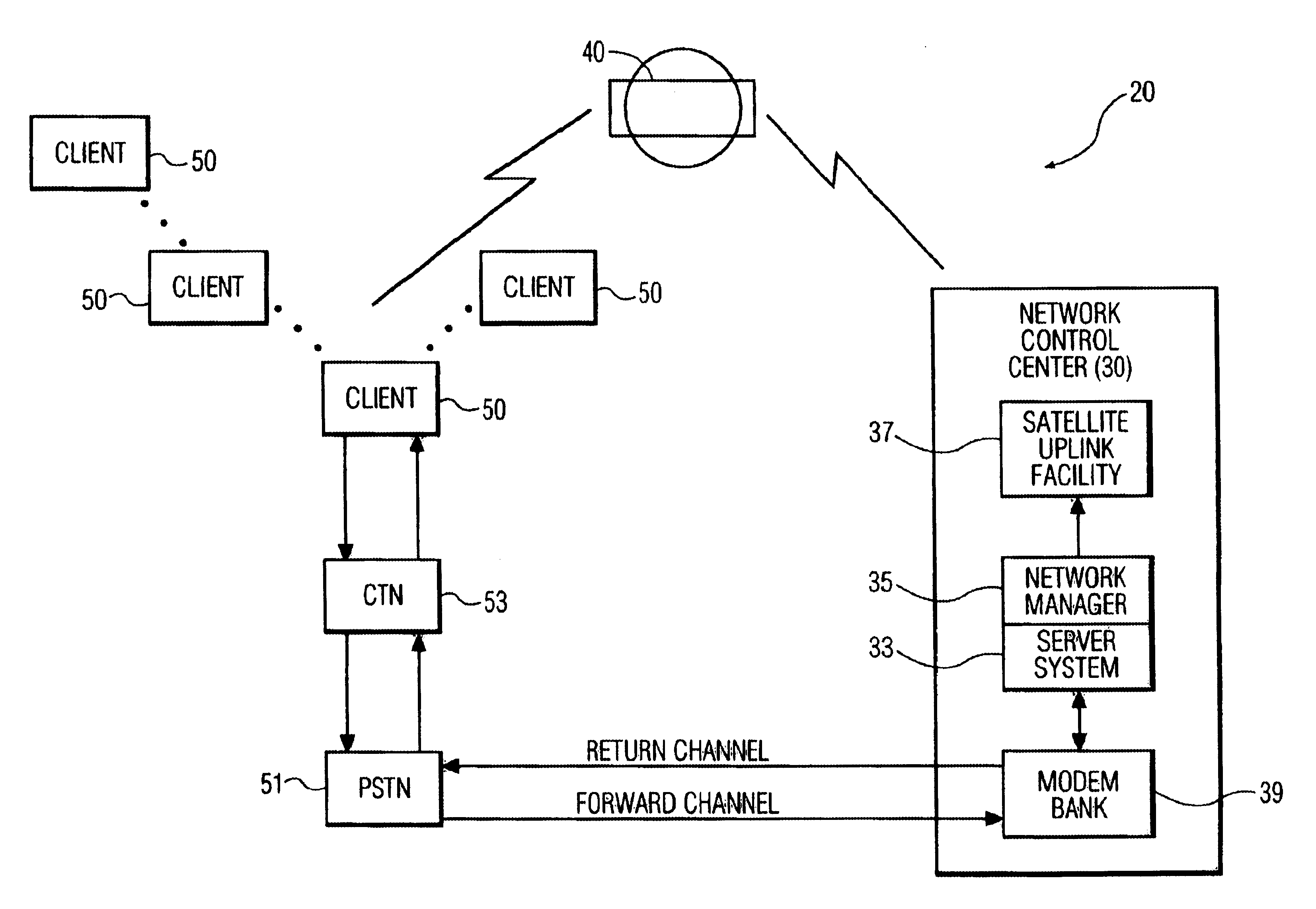
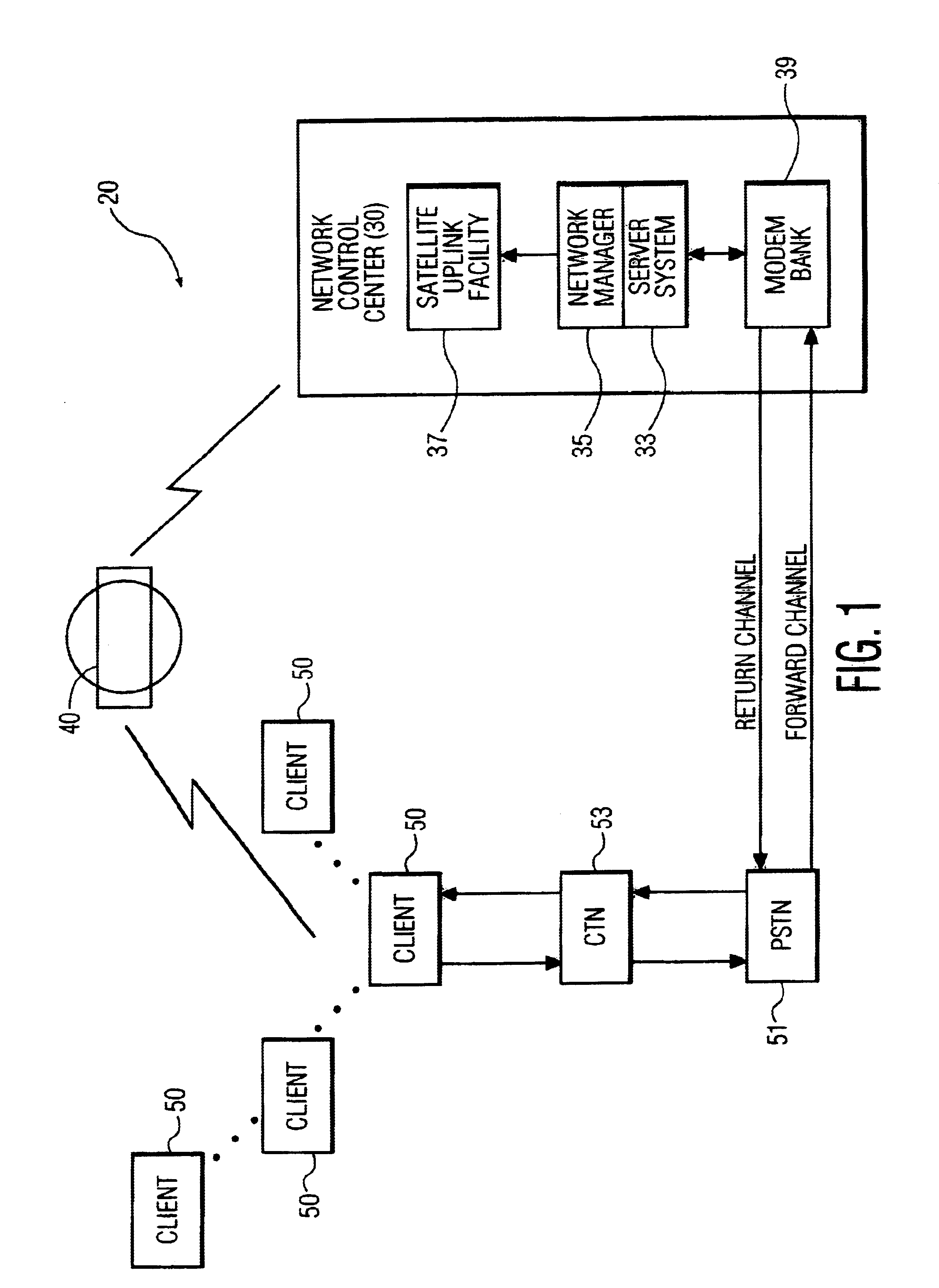
System for broadcasting software applications and portable data communications device for use in such a system
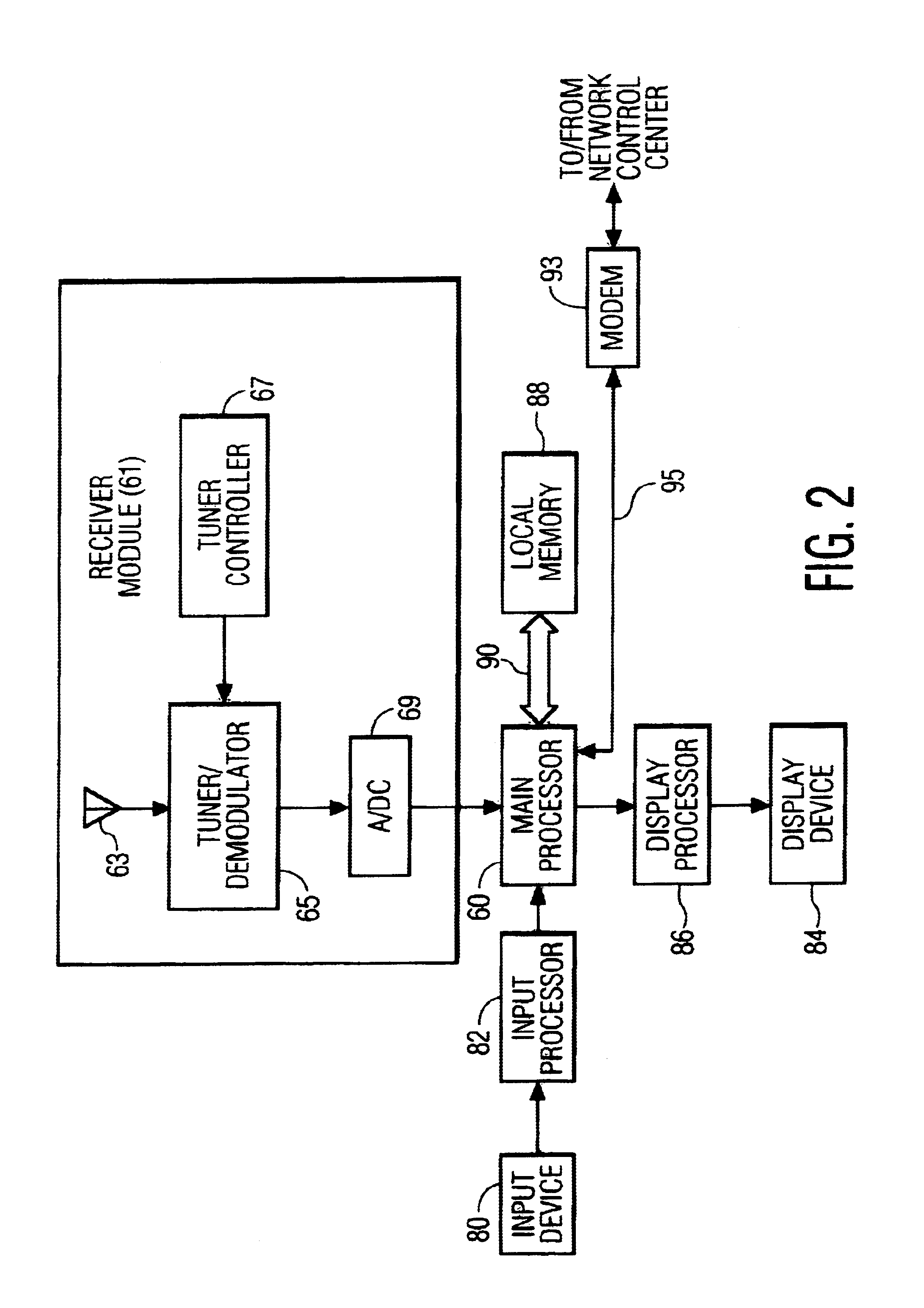
InactiveUS6928468B2Error prevention/detection by using return channelFrequency-division multiplex detailsModem deviceApplication software
A communications system consisting of a server system that stores software applications, a broadcast system that broadcasts the software applications, and a multiplicity of portable clients that each include a receiver having a tuner that is selectively tunable to receive a selected one of the software applications broadcasted by the broadcast system. The portable clients can be any type of portable data communications device, such as a hand-held, palm-top, or notebook computing device, a PDA, an intelligent cellular phone, or any other personal multimedia appliance or Network Computer (NC). The broadcast system can be any suitable satellite or terrestrial air or cable broadcast system. The software applications can consist of a broad spectrum of different software applications, such as word processing, video games, spreadsheets, address books, calendars, and the like. Each of the portable data communications devices includes a receiver that has a tuner that is selectively tunable to receive a selected one of a plurality of software applications broadcasted by a broadcast system, a user-interface that enables a user to select one of the broadcasted software applications for downloading, a processor for executing the downloaded software applications, and a modem for establishing a two-way communications link with a network control system. The two-way communications link includes a forward channel over which the portable data communication device can transmit client data to the network control system, and a return channel over which the network control system can transmit system data to the portable data communication device. The client data can include requests for unrecoverable software application data and client software download request data.
Owner:KONINK PHILIPS ELECTRONICS NV
Networked computer system
A networked computer system has a plurality of servers and a plurality of distributed clients, which may be devices or computers. Each client has a boot operating system (OS). Upon startup, the boot OS in each client automatically initiates a connection to one of the servers via the Internet. The boot OS can detect the type of medium (e.g., cable modem, DSL) to which the client is connected. The server automatically downloads a base OS and dynamically configures a suite of applications on the client without running the standard installation programs. One included application is an Internet telephony application, allowing a user to plug a standard telephone into the client appliance or computer, pick up the telephone, and automatically dial out using long distance Internet telephony. Optionally, the server may download a plurality of operating systems that are automatically initiated to run concurrently on the client. The clients use a random access memory (RAM) caching technique. A first portion of each OS or application is downloaded at startup and maintained in the client RAM, containing the files needed to launch the OS or application. If the client processes a request for an OS or application program file not in the client's RAM, the requested file is automatically downloaded from the server.
Owner:HUGHES TREVOR
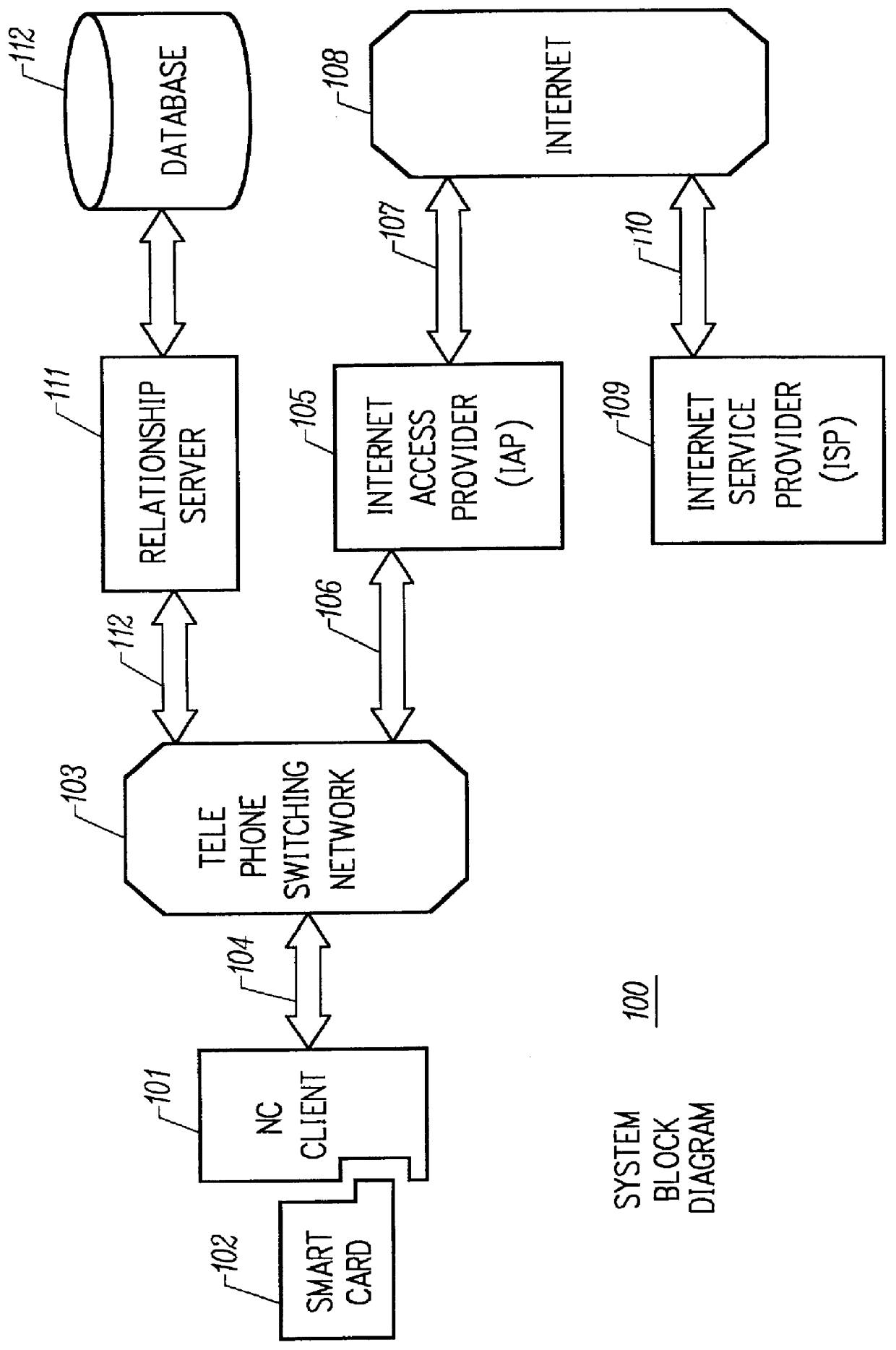
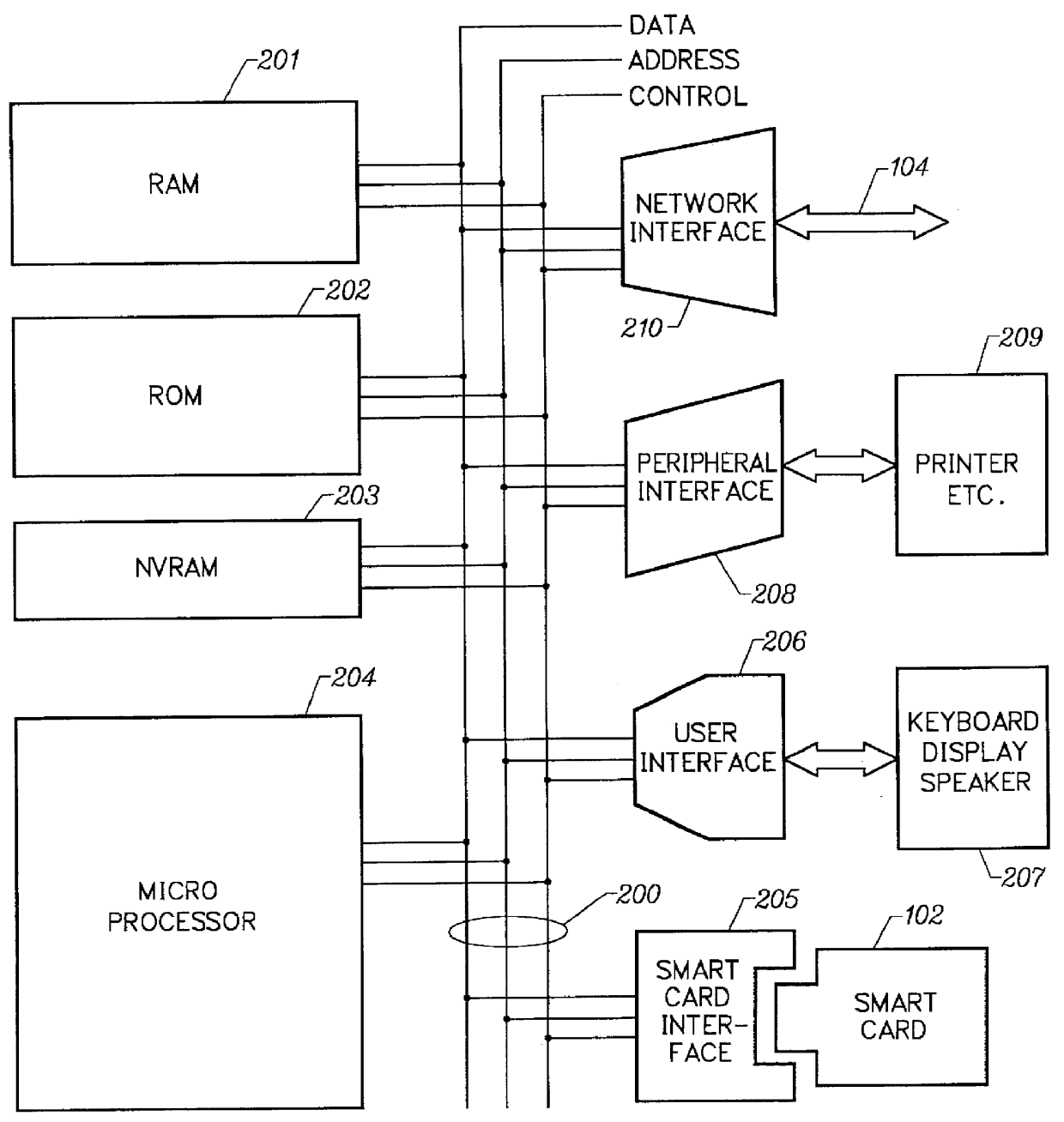
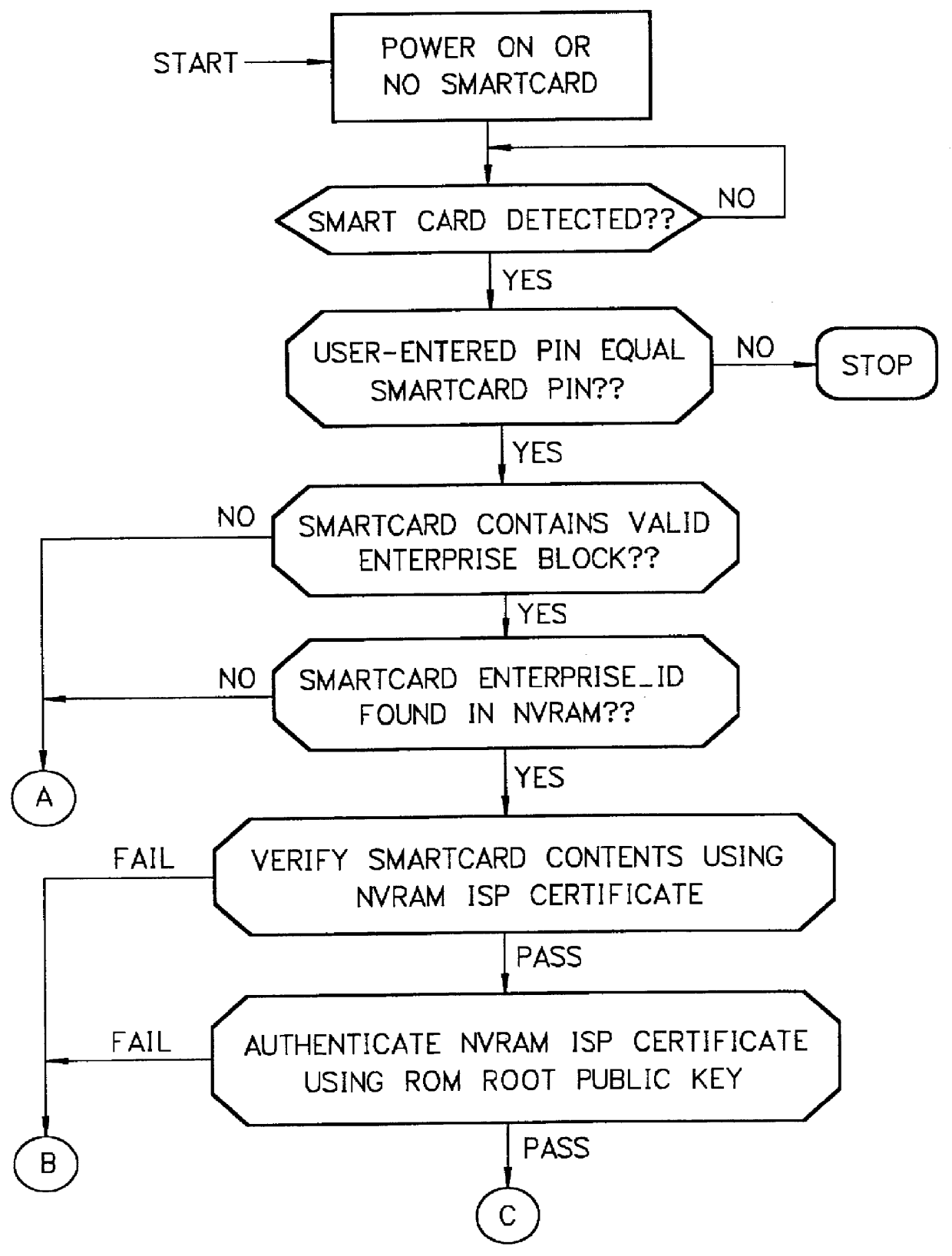
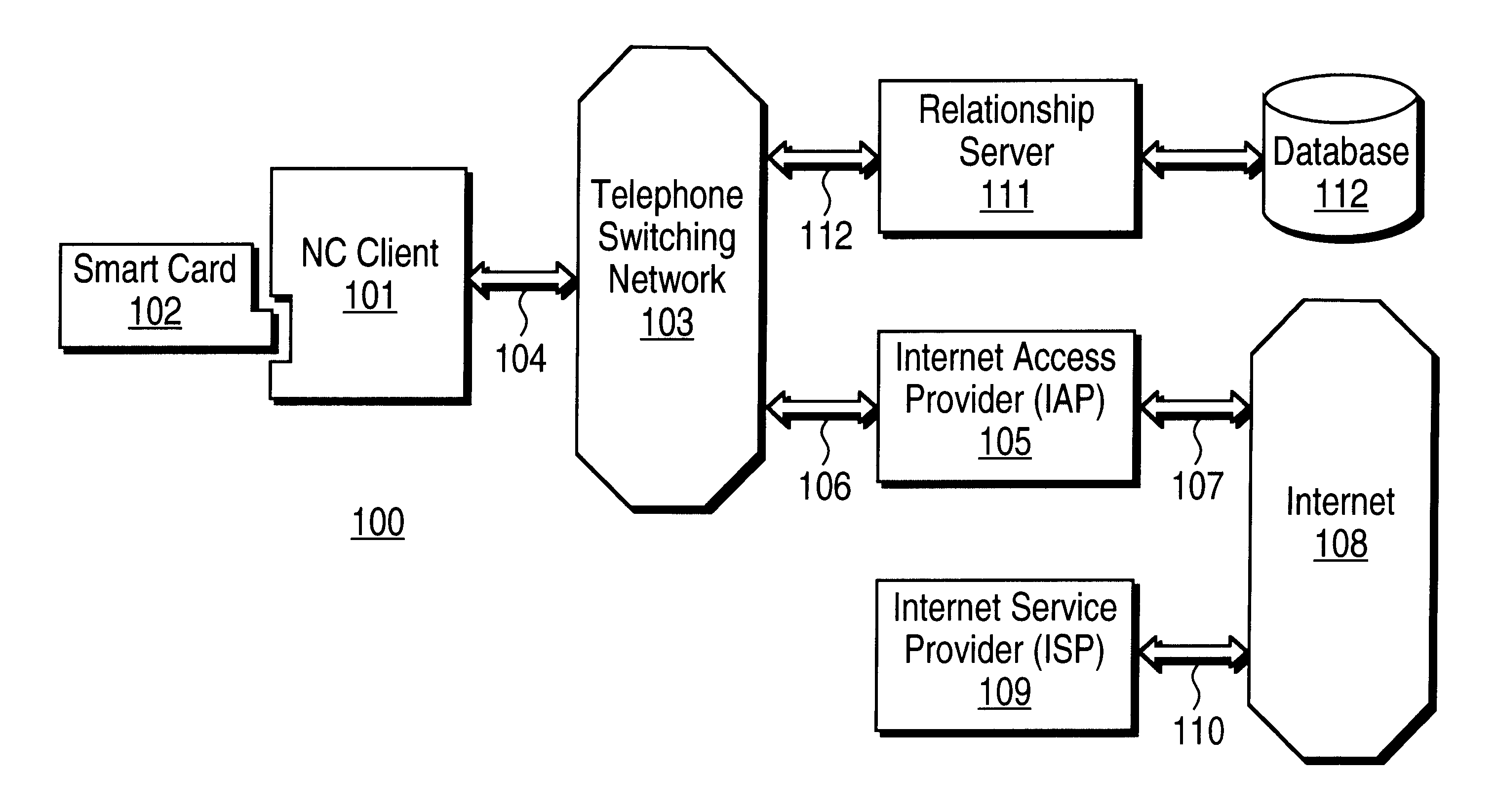
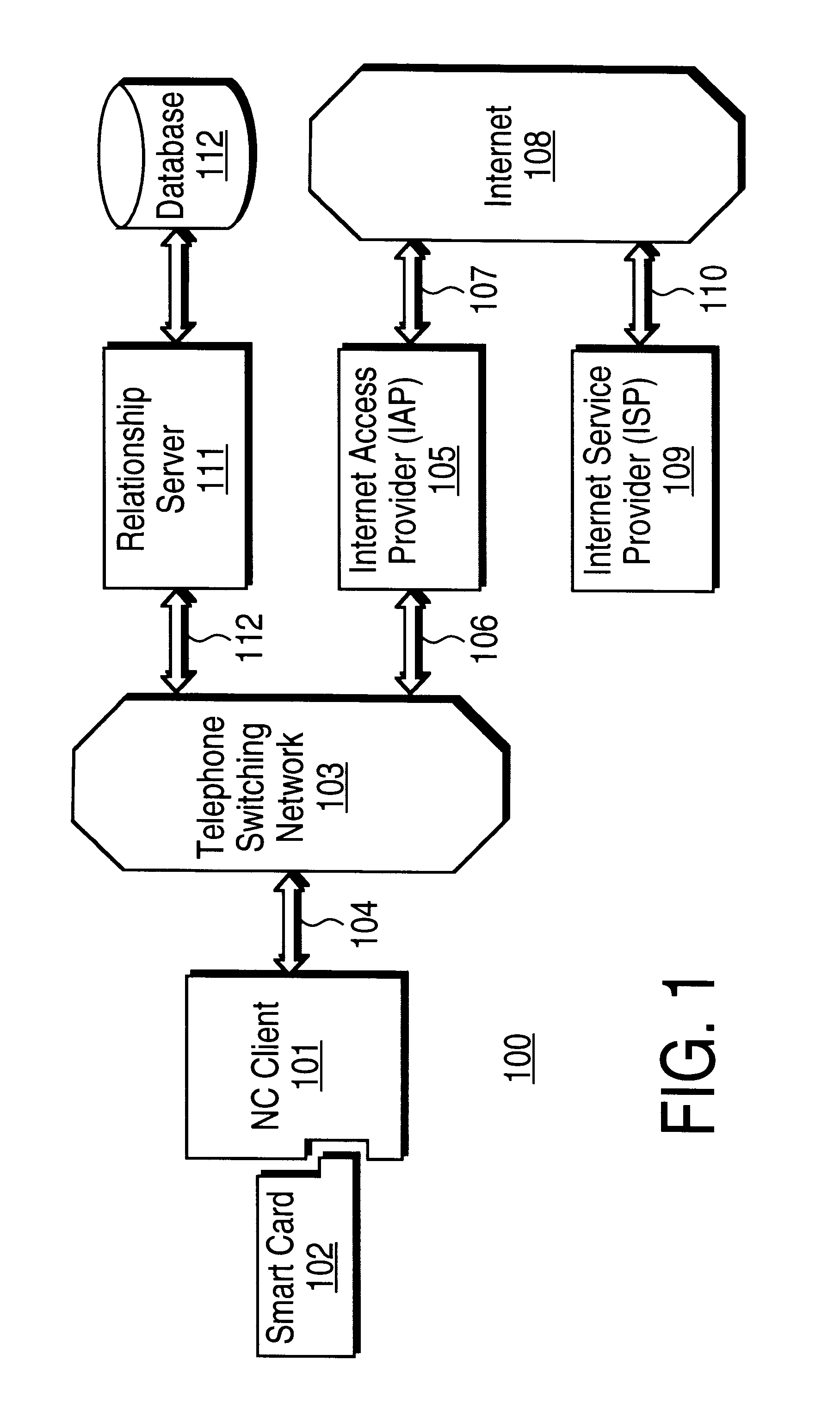
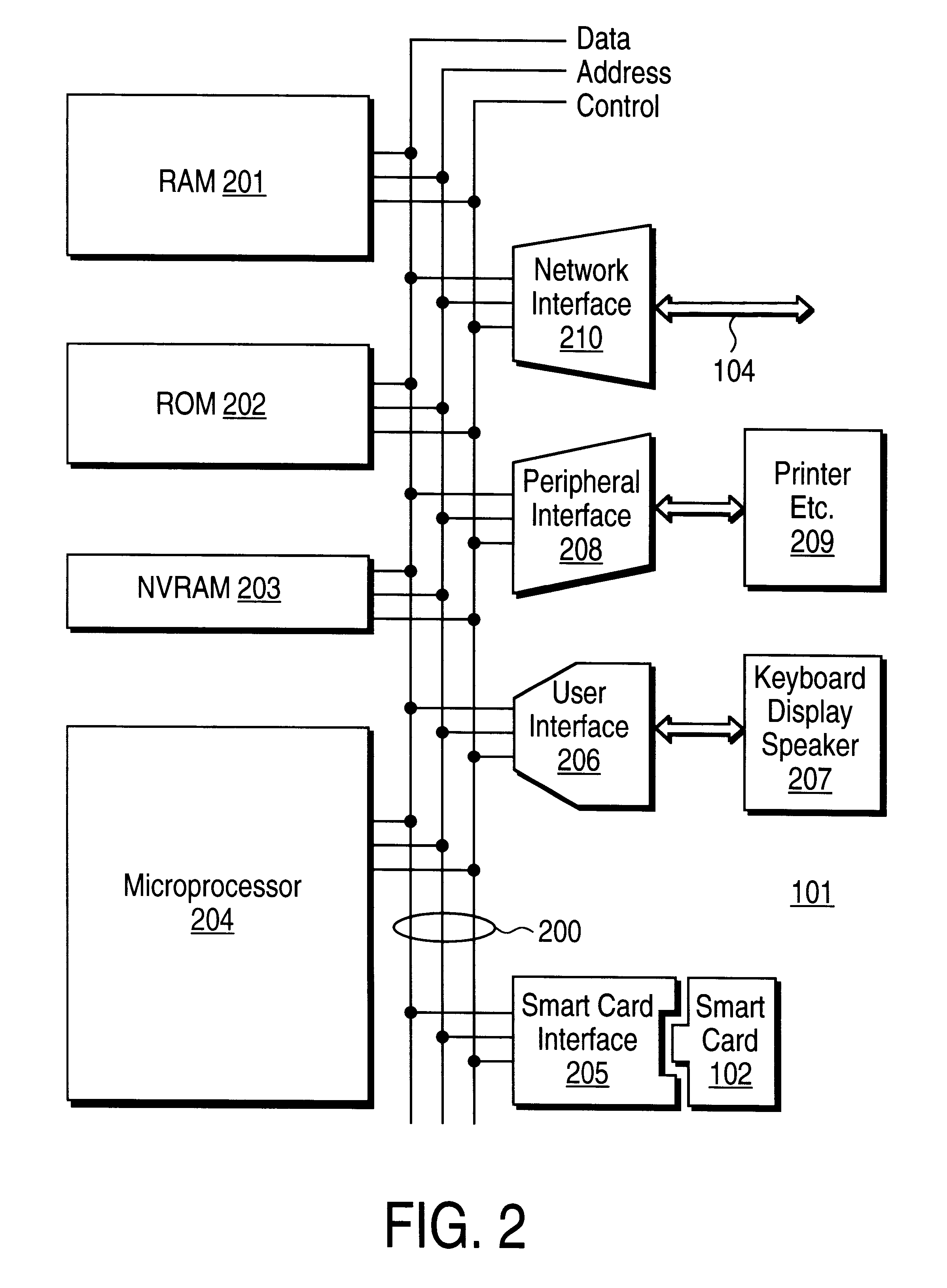
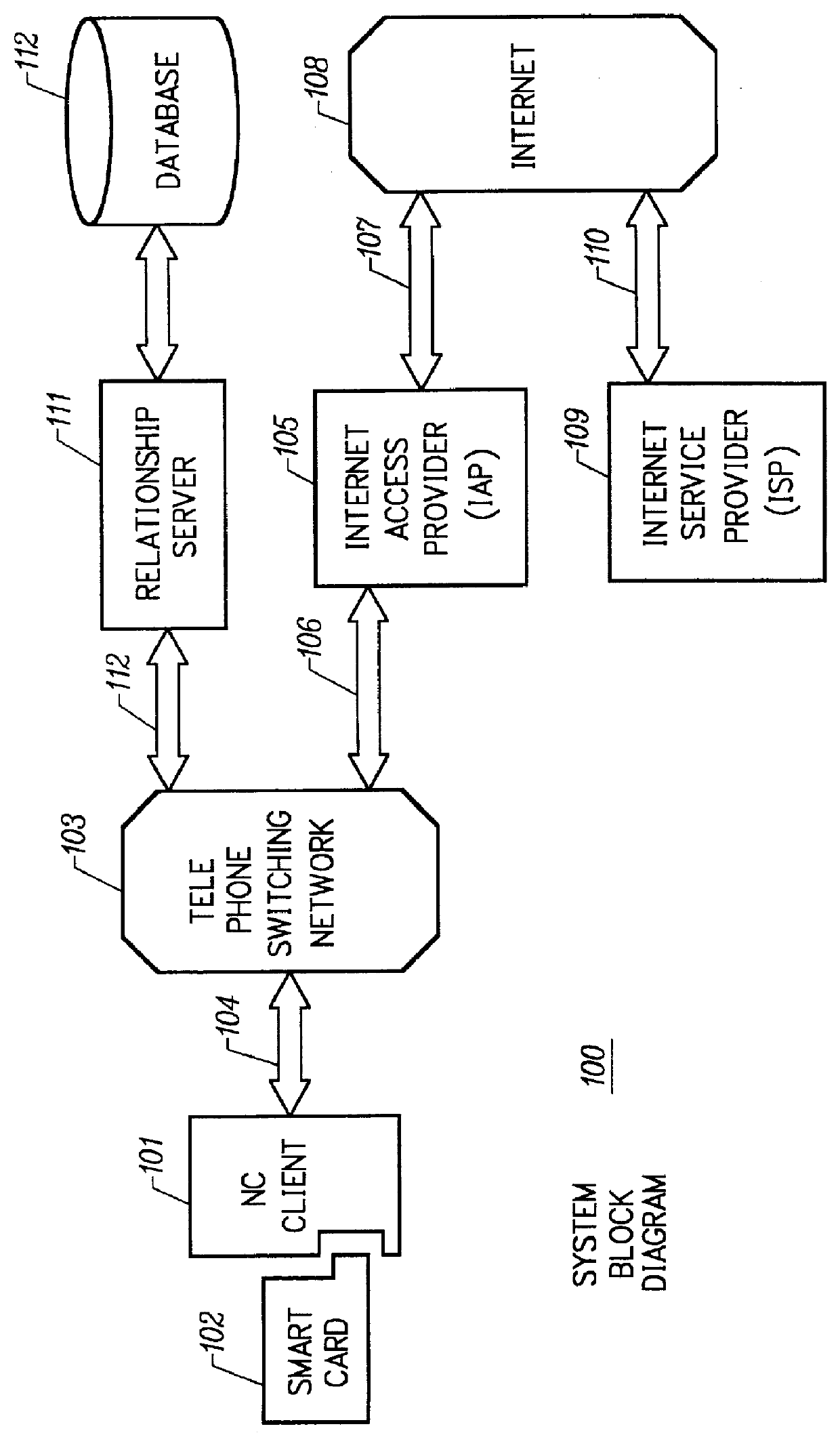
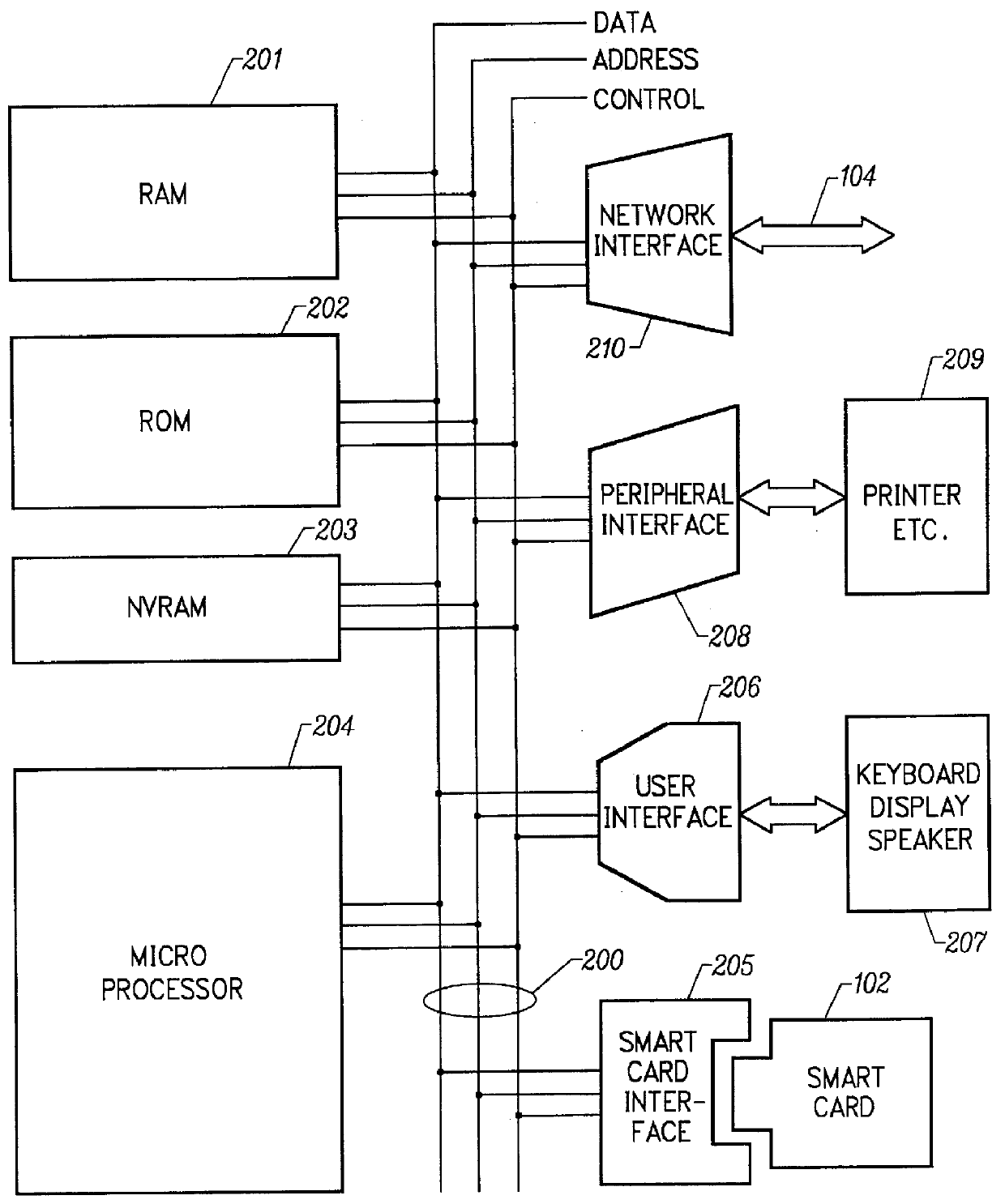
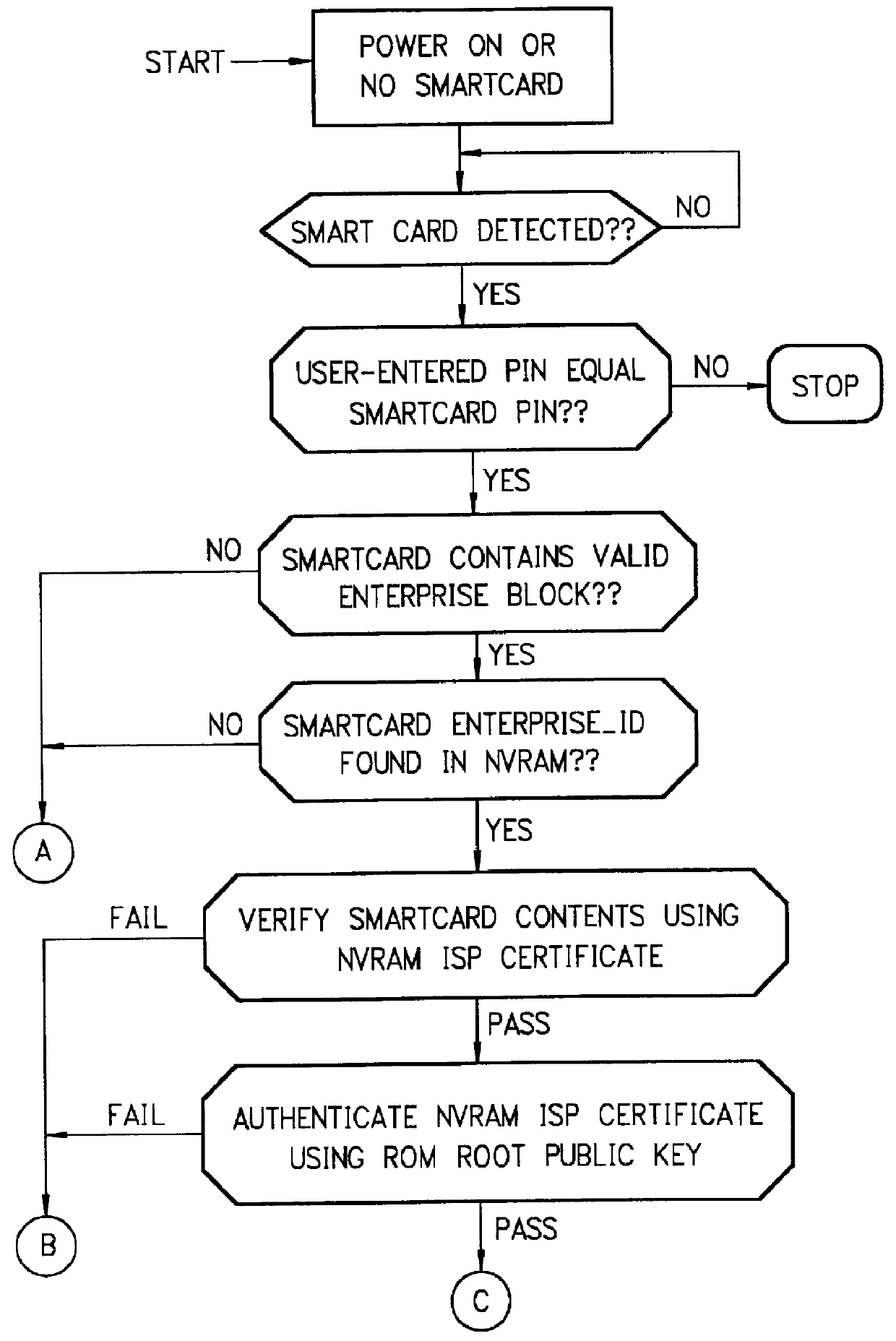
Mechanism for users with internet service provider smart cards to roam among geographically disparate authorized network computer client devices without mediation of a central authority
InactiveUS6108789ADigital data processing detailsUser identity/authority verificationDigital signatureServer allocation
User specific internet service provider (ISP) account information is stored on the user's smart card, but the ISP specific connection information is stored within a network computer client device (NC). When the NC is first powered on and used, it calls the relationship server to receive connection information corresponding to the ISP that is either specified on the first user's smart card or is otherwise chosen by the first user. This connection information is preferably stored in non-volatile memory within the NC, so that even if the NC is powered down, it maintains the ability to connect to the ISP designated by its previous user. Each ISP is designated by a unique enterprise identification number assigned by the relationship server. When a subsequent user inserts his smart card into an NC, the NC compares the enterprise identification number on the smart card to the enterprise identification number within the NC. If the enterprise identification numbers match, the NC connects to the IAP already stored in the NC without dialing the relationship server. Only if the enterprise identification numbers do not match must the NC then dial the relationship server to download connection information for the ISP designated by the smart card enterprise identification number. In the preferred embodiment, the ISP contents of the smart card are digitally signed by the ISP. If the enterprise identification numbers match, then the ISP contents of the smart card are cryptographically authenticated using the public key within the authorized usage certificate for the ISP. If the cryptographic authentication fails, then the NC reprograms the smart card.
Owner:COMCAST CABLE COMM MANAGEMENT LLC
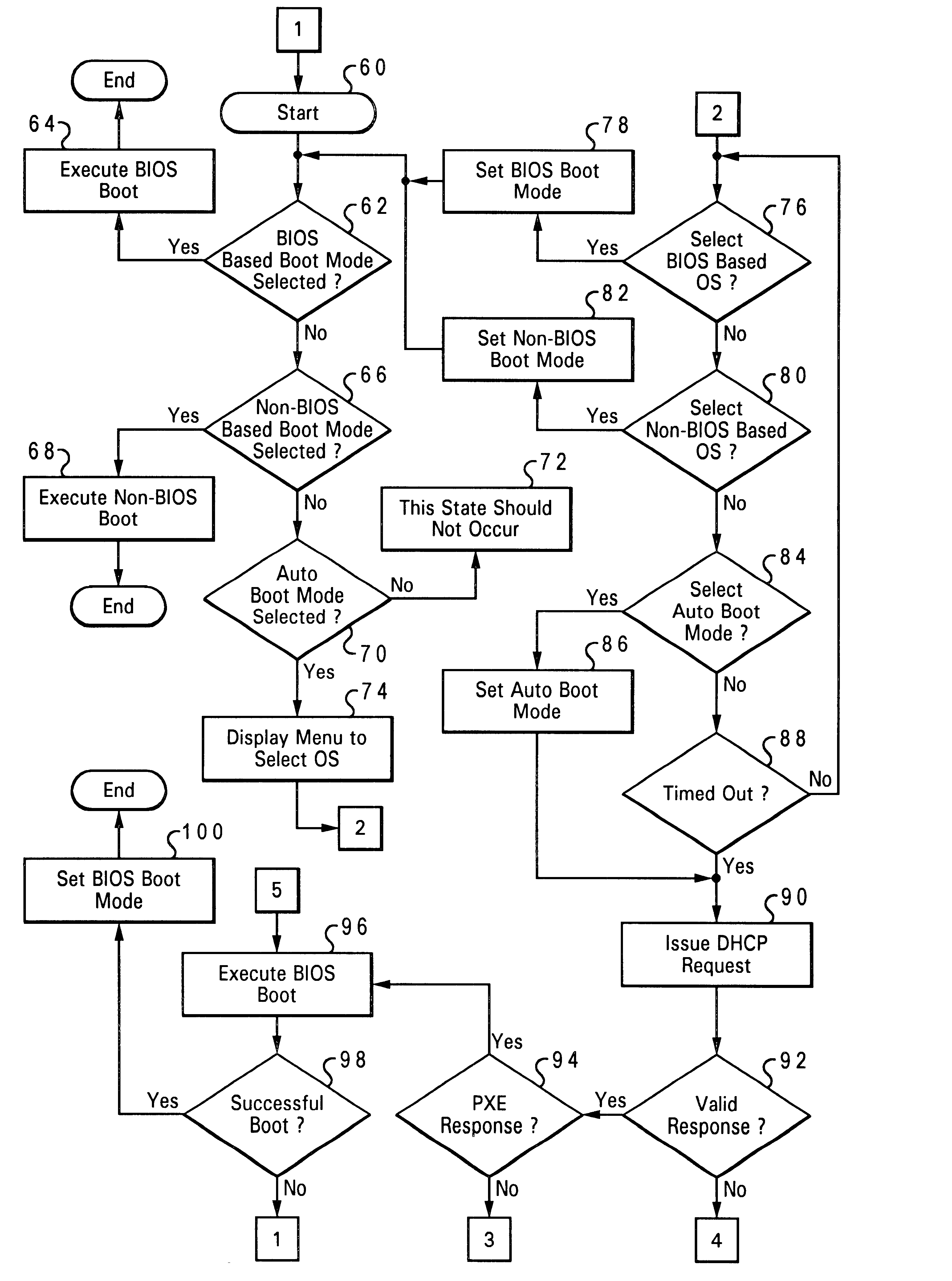
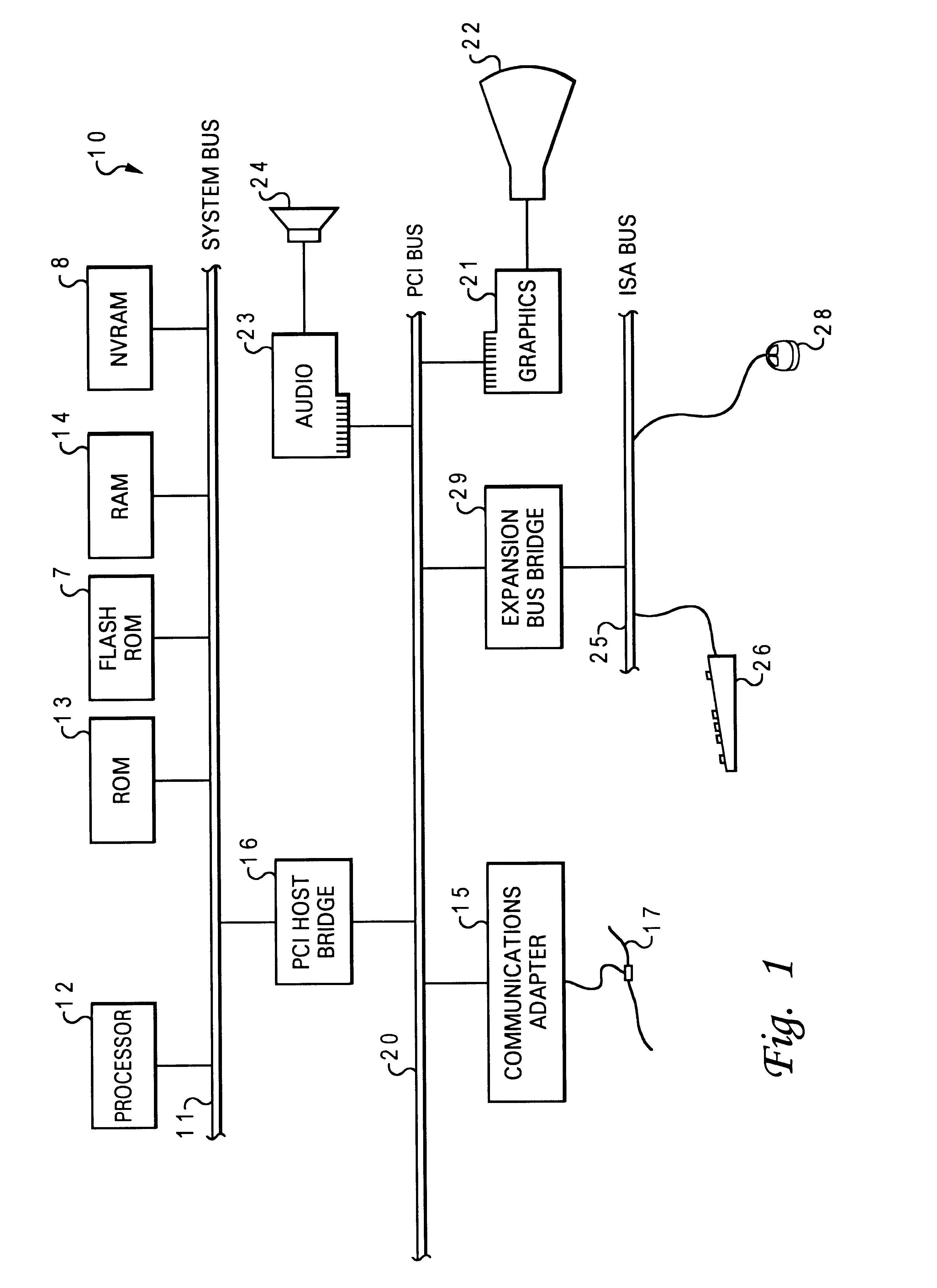
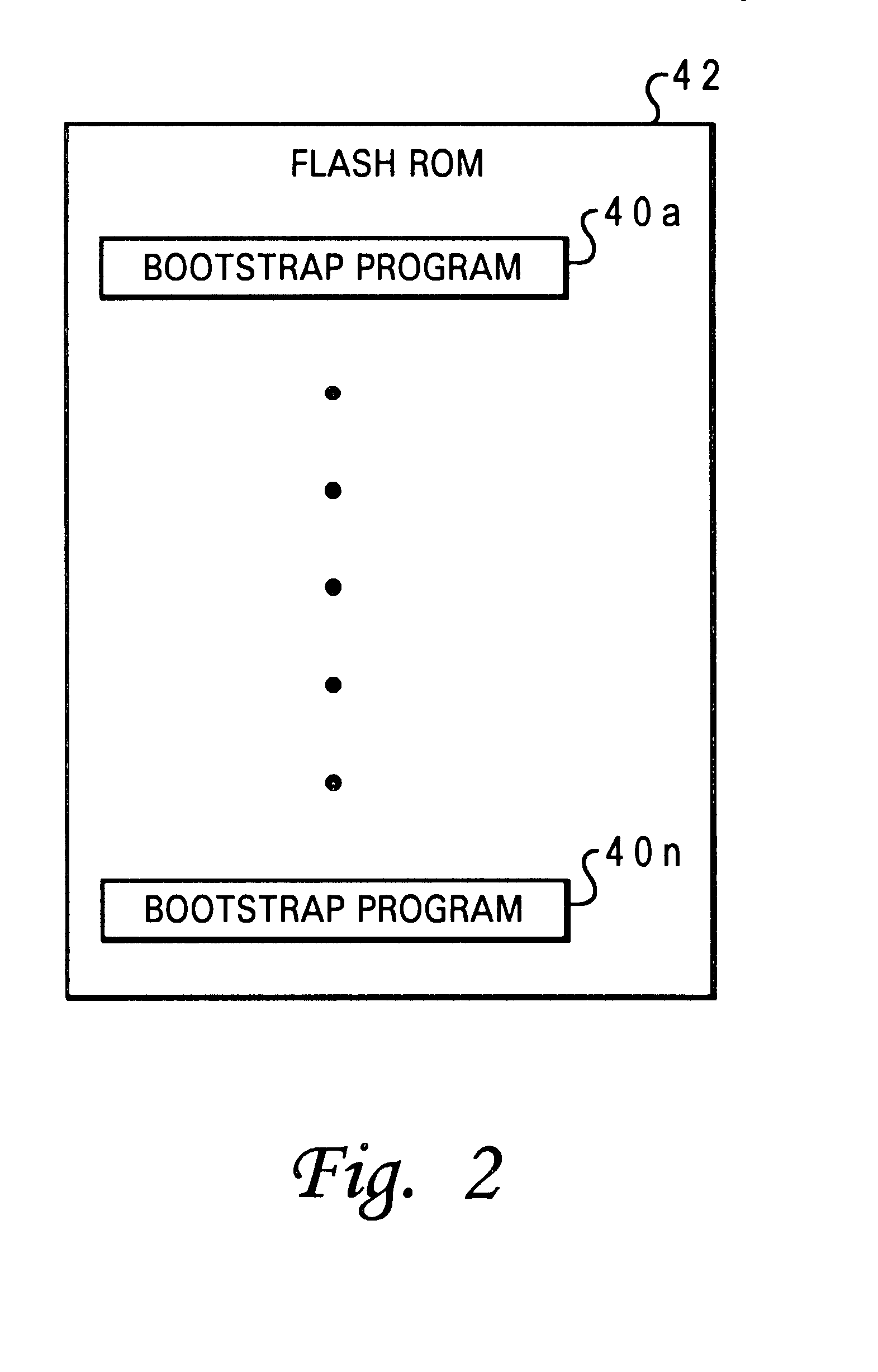
Method and system for automatically configuring the boot process of a computer having multiple bootstrap programs within a network computer system
InactiveUS6490677B1Automatically configuring the boot process of a network computerDigital computer detailsProgram loading/initiatingAuto-configurationProcess configuration
A method and system for automatically configuring a boot process of a network computer initially connected within a network comprising at least one server. A request is broadcast from a network computer to a network for an available server, upon a first initiation of the network computer within the network. Responses from the broadcast are gathered which indicate whether a server is available. A selected boot program is then executed from among multiple boot programs available in the network computer. The selected boot program and the identity of an available server are stored as boot process configuration settings in a nonvolatile storage of the network computer, in response to successful execution of the boot program, such that a subsequent boot process of a network computer is automatically configured.
Owner:LENOVO PC INT
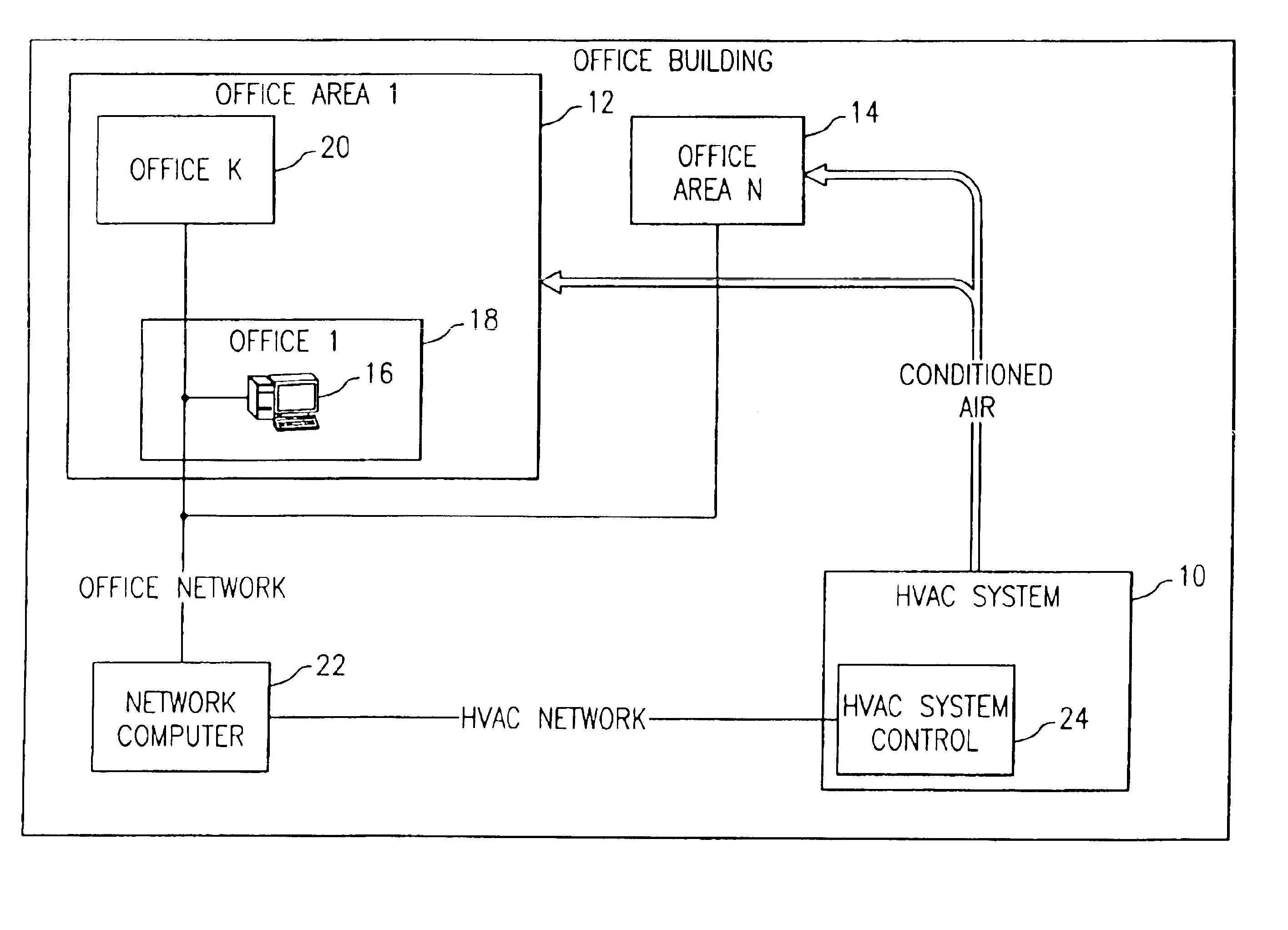
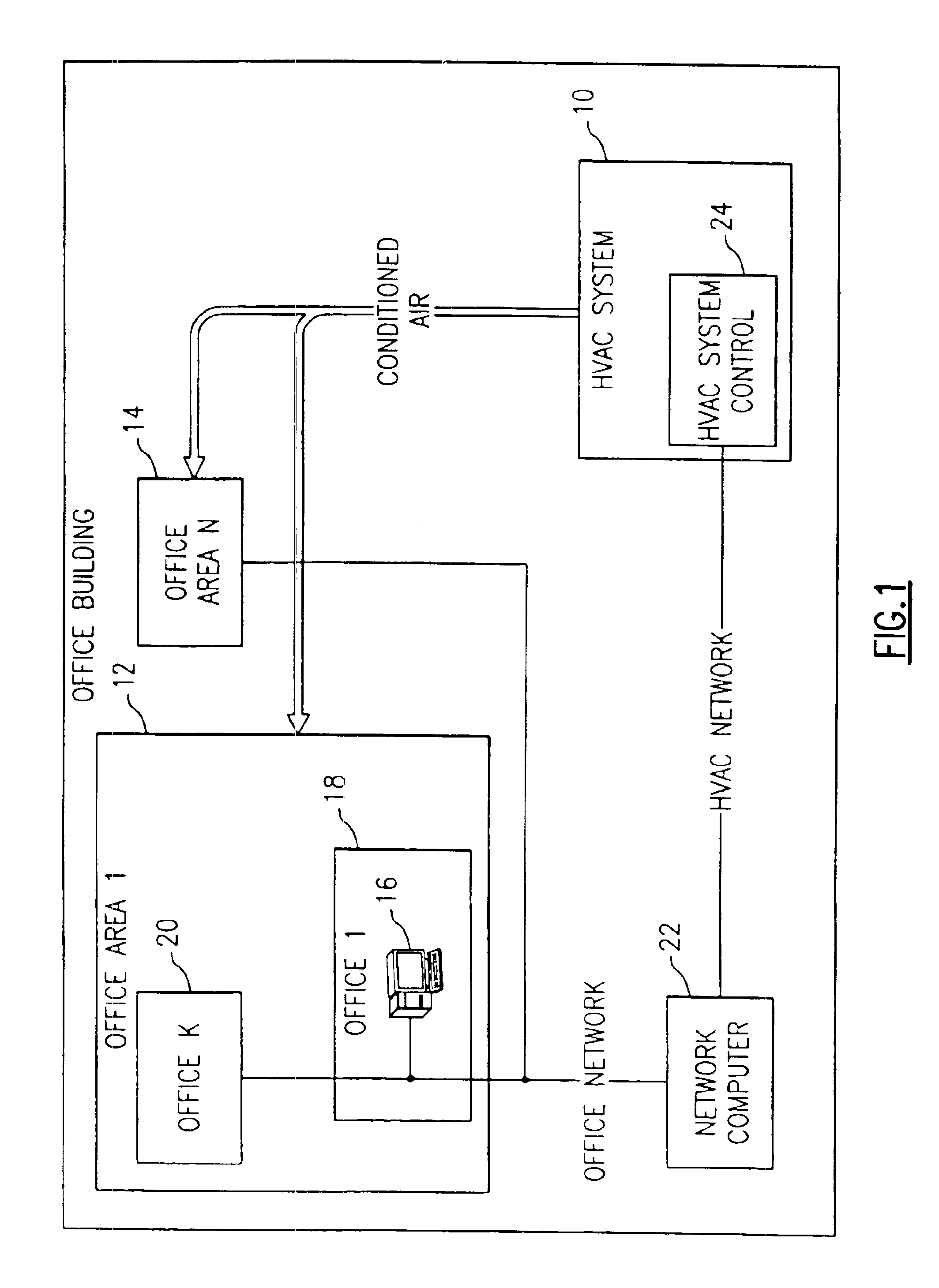
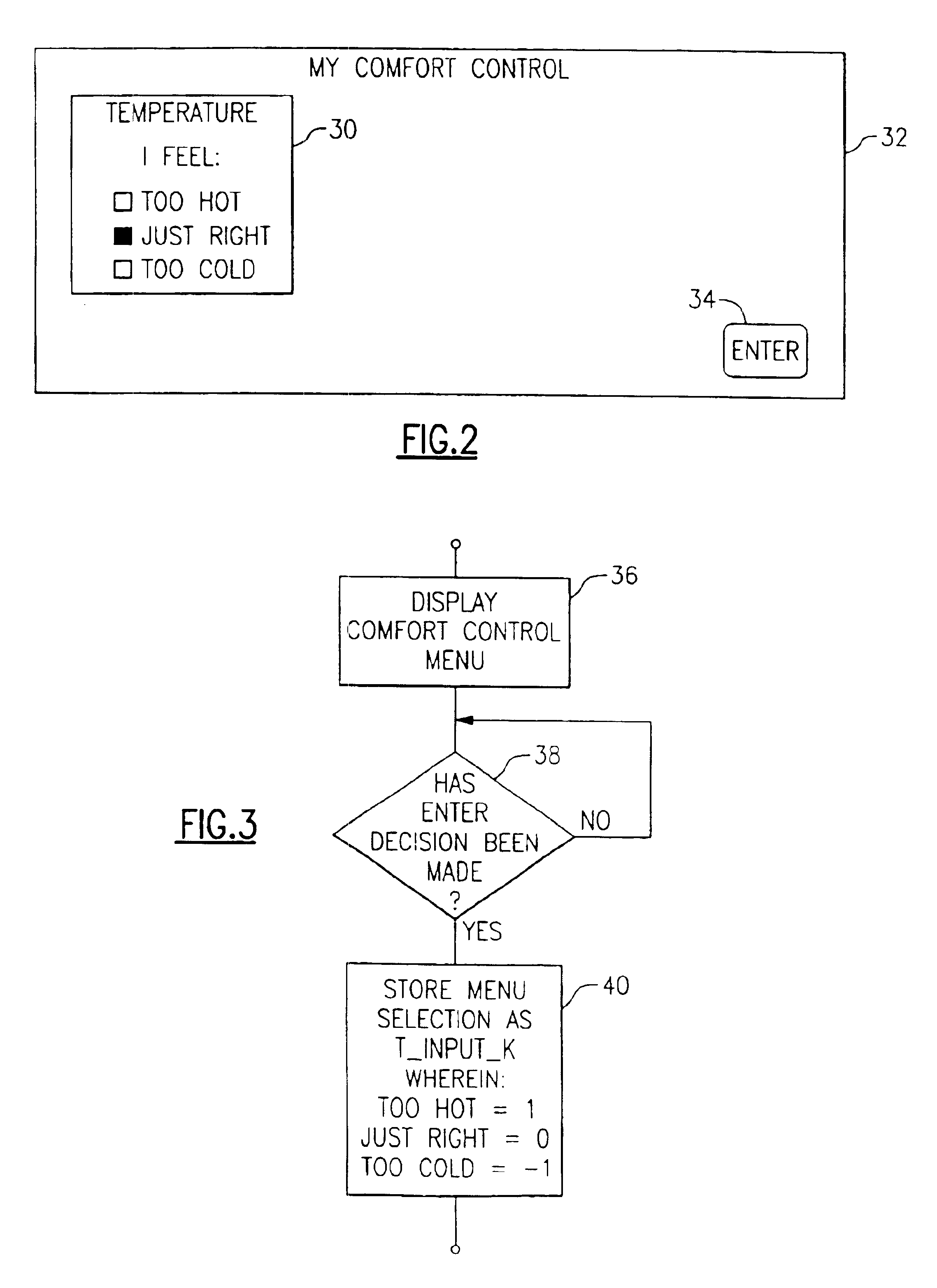
Location adjusted HVAC control
A system and method allows occupants in various locations to provide indications as to their respective levels of comfort. The indications as to comfort level are provided to a network computer. The network computer is operative to compute overall levels of comfort for each location by using a weighting factor for that location in combination with the indications as to levels of comfort These overall levels of comfort are sent to an HVAC control for further analysis prior to controlling the HVAC system that is to provide conditioned air to the locations. The resulting control of the HVAC system is influenced by the over weighting or under weighting factors used in computing the comfort levels for the locations.
Owner:CARRIER CORP
Internet service provider preliminary user registration mechanism provided by centralized authority
InactiveUS6385651B2Digital data processing detailsMultiple digital computer combinationsRelational databaseDigital signature
User and network computer client device (NC) registration with an internet service provider (ISP) occurs in two phases: the first phase with the relationship server and the second phase with the ISP. In the first phase, the NC sends the relationship server a unique identifier of the NC manufacturer, such as the manufacturer identification number. In the preferred embodiment, the NC also transmits an enterprise identification number from a smart card uniquely specifying the ISP to which the user wishes to connect. The relationship server queries a relationship database using the manufacturer and enterprise identification numbers. In the preferred embodiment, the relationship server determines whether the specified manufacturer has authorized connection to the specified ISP; if no authorization exists in the relationship server database, then the relationship server disconnects from the NC. Otherwise, the relationship server transmits NC connection information and initial registration contents for the ISP to the NC. The NC preferably writes the initial registration contents to the user's smart card. In the preferred embodiment, the initial registration contents is identical for all users of the same ISP and is digitally signed by the ISP. The second phase of the user registration is entirely governed by the ISP. Upon authentication of the ISP using the authorized usage certificate for the ISP within the NC, the ISP is free to overwrite the user's initial registration contents user specific ISP account information that the ISP digitally signs. In the preferred embodiment, although the initial registration contents for the ISP on the user's smart card is overwritten during the second phase of user registration, the NC connection information remains the same after registration with the ISP. Although the ISP is allowed to overwrite this data (either the smart card contents or the NVRAM contents) at anytime.
Owner:TVWORKS
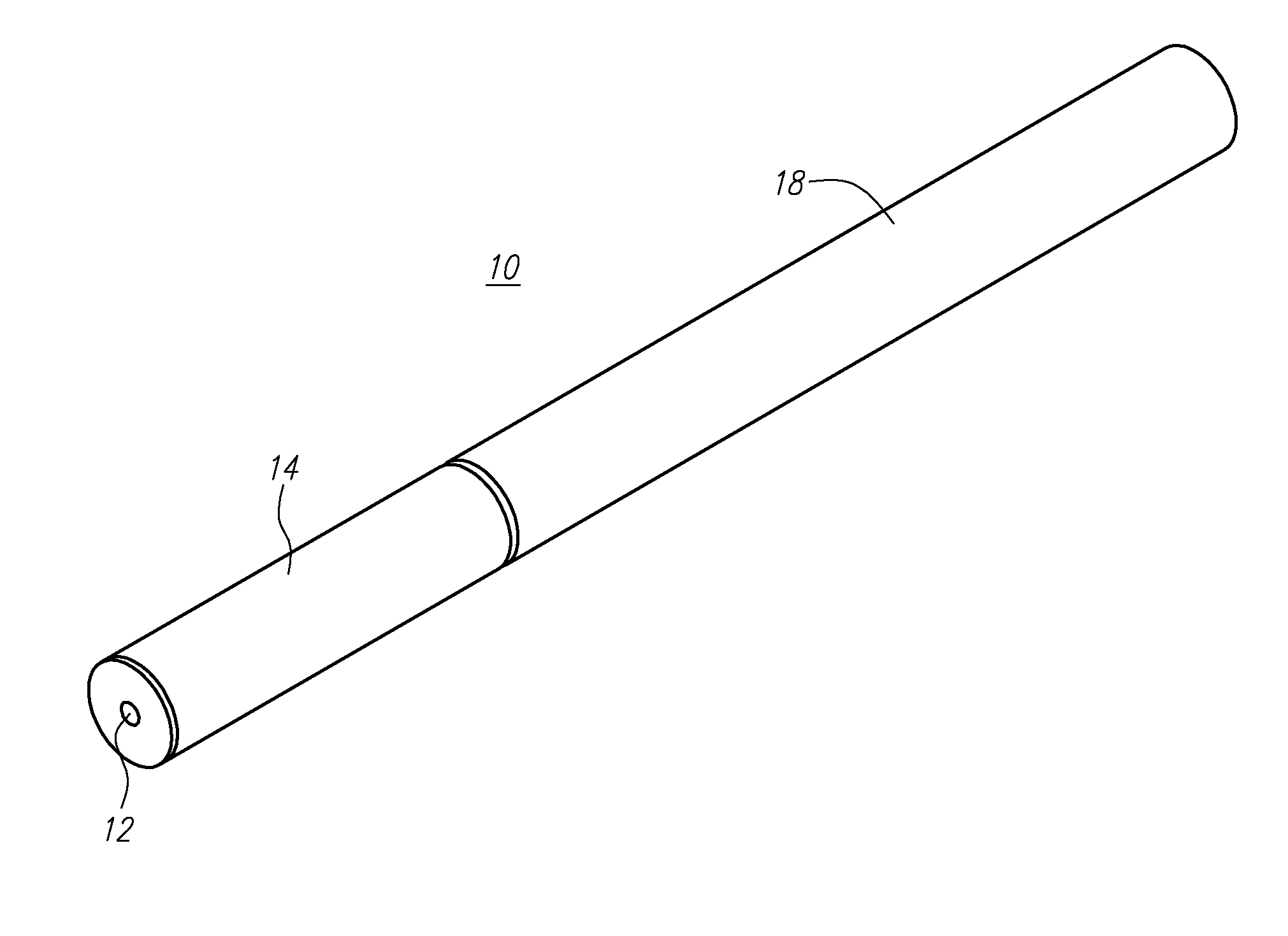
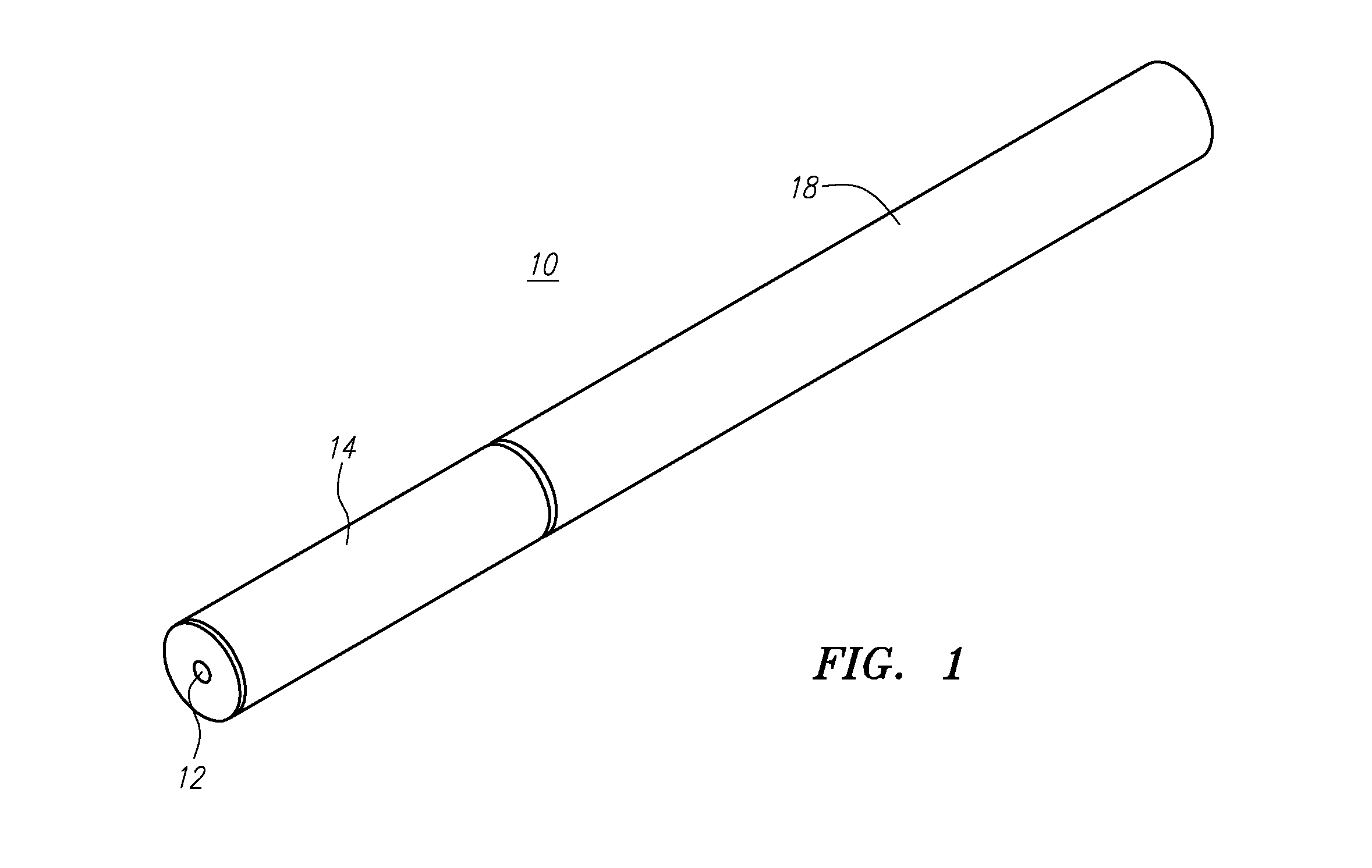
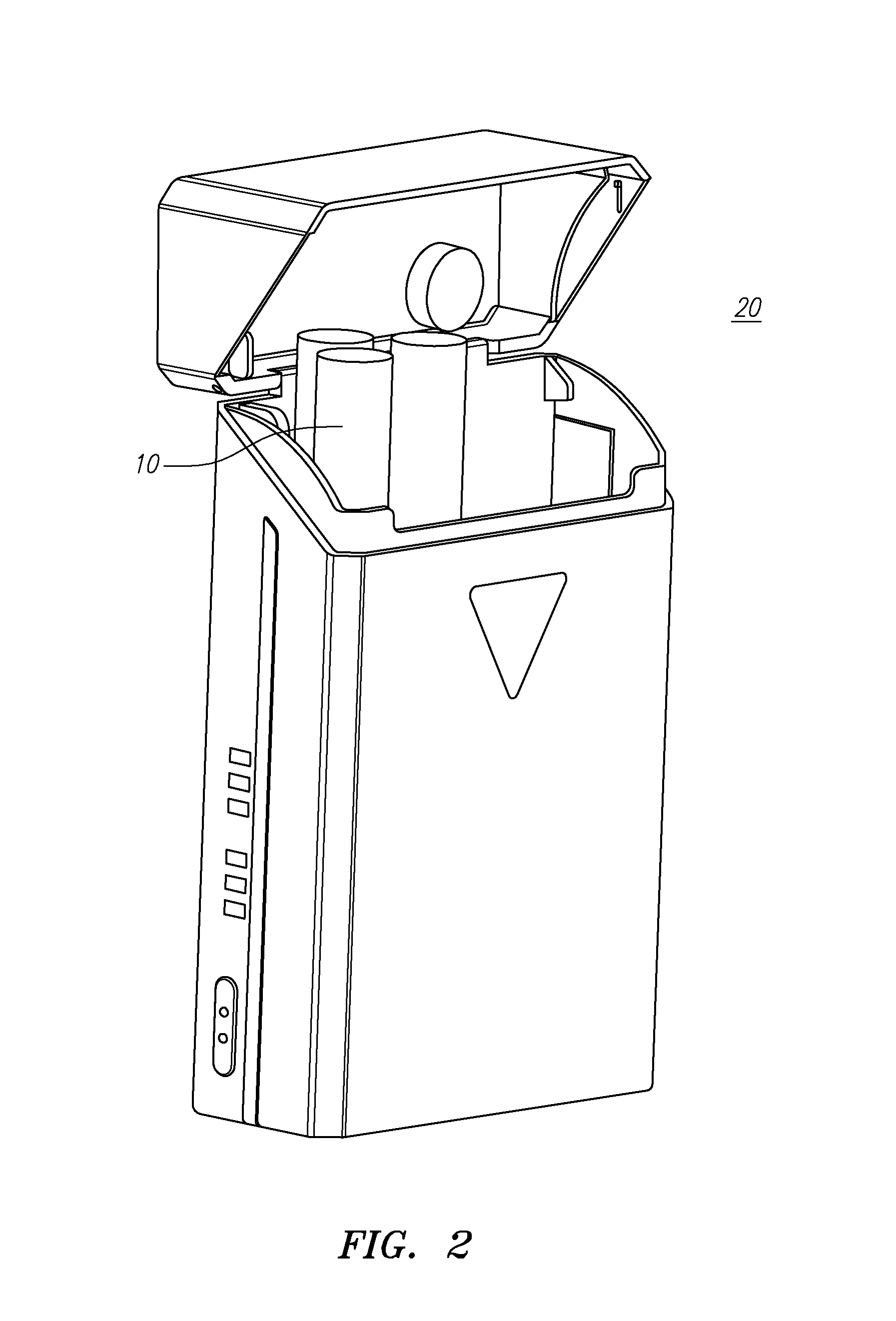
Subscription service for electronic cigarettes
A model for a subscription service for electronic cigarettes includes an e-Cig retailer with a network computer that is configured to communicate with an e-Cig, an e-Cig charging pack, a mobile phone of an e-Cig user, a subscription database, and / or a manufacturer of e-Cigs.
Owner:FONTEM HLDG 1
Global network computers
InactiveUS20060177226A1High potential economic savingOptimize networkMultiple digital computer combinationsProgram controlBroadband transmissionThe Internet
This invention generally relates to one or more computer networks having computers like personal computers or network servers with microprocessors linked by broadband transmission means and having hardware, software, firmware, and other means such that at least one parallel processing operation occurs that involve at least two computers in the network. More particularly, this invention relates to one or more large networks composed of smaller networks and large numbers of computers connected, like the Internet, wherein more than one separate parallel processing operation involving more than one different set of computers occurs simultaneously and wherein ongoing processing linkages can be established between virtually any microprocessors of separate computers connected to the network. Still more particularly, this invention relates to business arrangements enabling the shared used of network microprocessors for parallel and other processing, wherein personal computer owners provide microprocessor processing power to a network, preferably for parallel processing, in exchange for network linkage to other personal and other computers supplied by network providers, including linkage to other microprocessors for parallel or other processing; the basis of the exchange between owners and providers being whatever terms to which the parties agree, subject to governing laws, regulations, or rules, including payment from either party to the other based on periodic measurement of net use or provision of processing power.
Owner:ELLIS III FRAMPTON E
Method and device for installing alowed application program
InactiveCN1141641CData processing applicationsDigital data processing detailsApplication softwareComputer science
A method for installing licensed software on an end user's computer comprising having a program storage device and a unique computer identifier. The network computer contains a plurality of different software for license to end users and a database listing computer identifiers licensed to run the software. The end user computer sends to the network computer a command to run a program identifying to the end user computer the software listed as licensed by the computer identifier of the end user computer. The network computer downloads the selected software and installs it on the end user computer program storage device.
Owner:ACTIVISION PUBLISHING
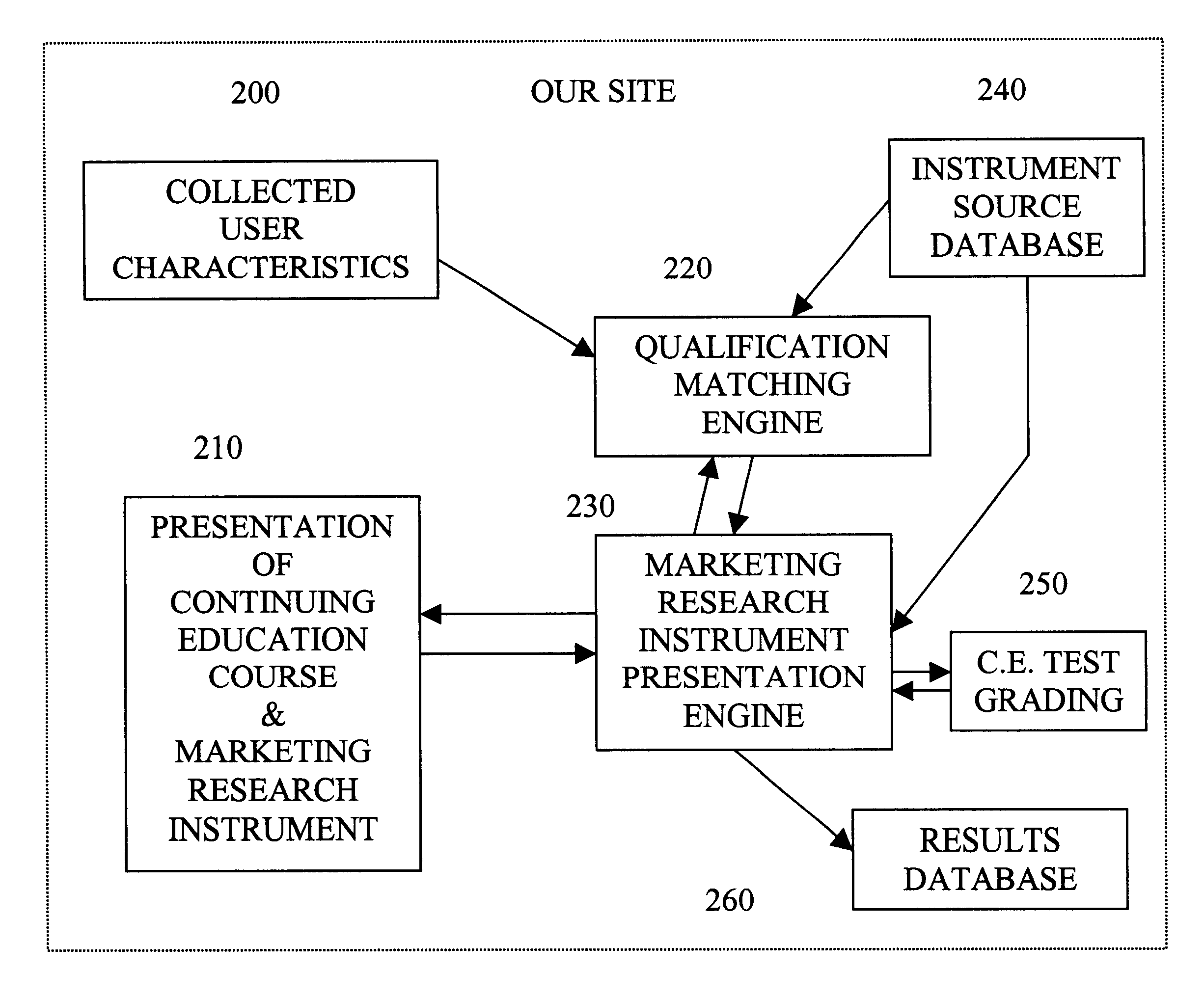
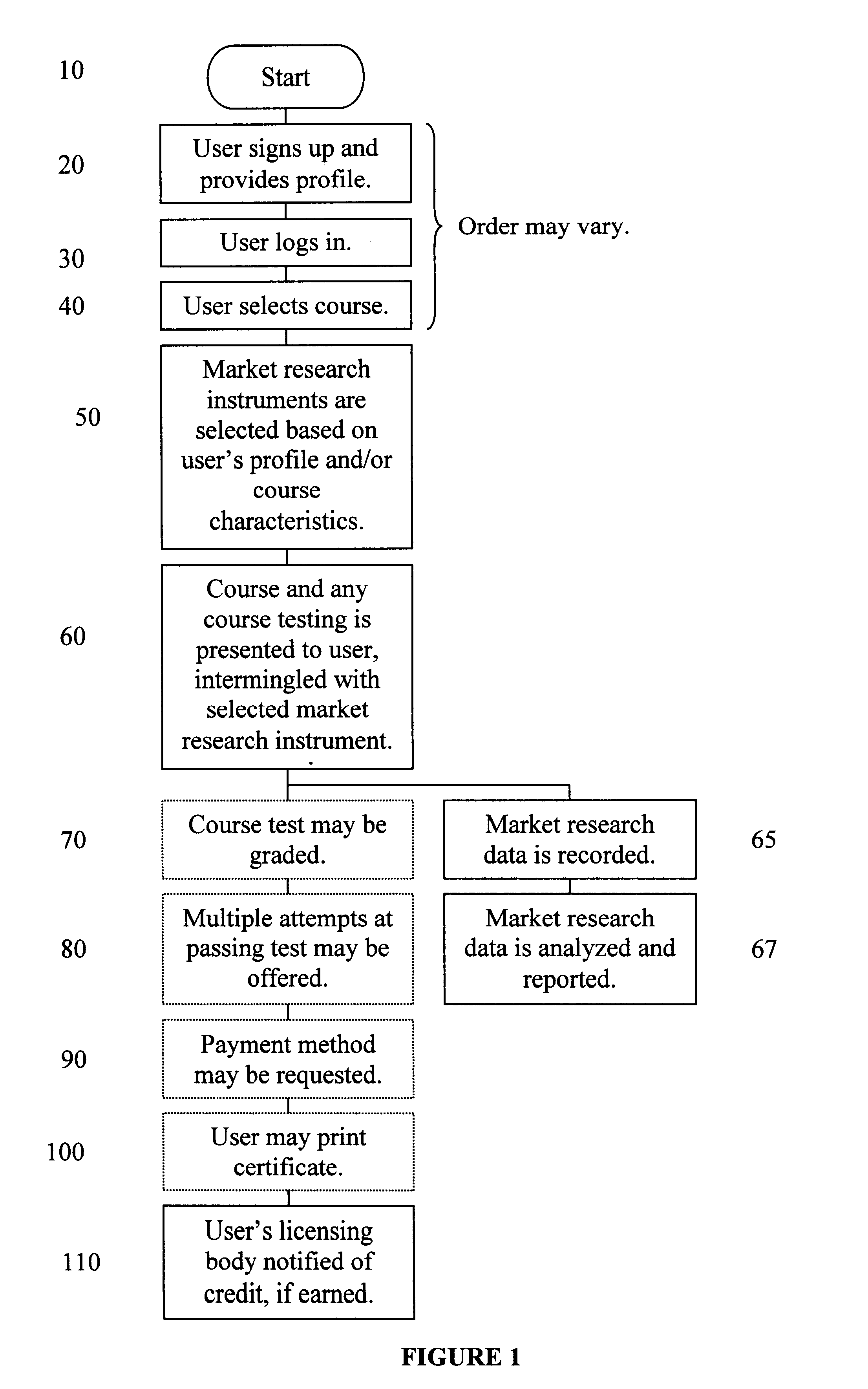
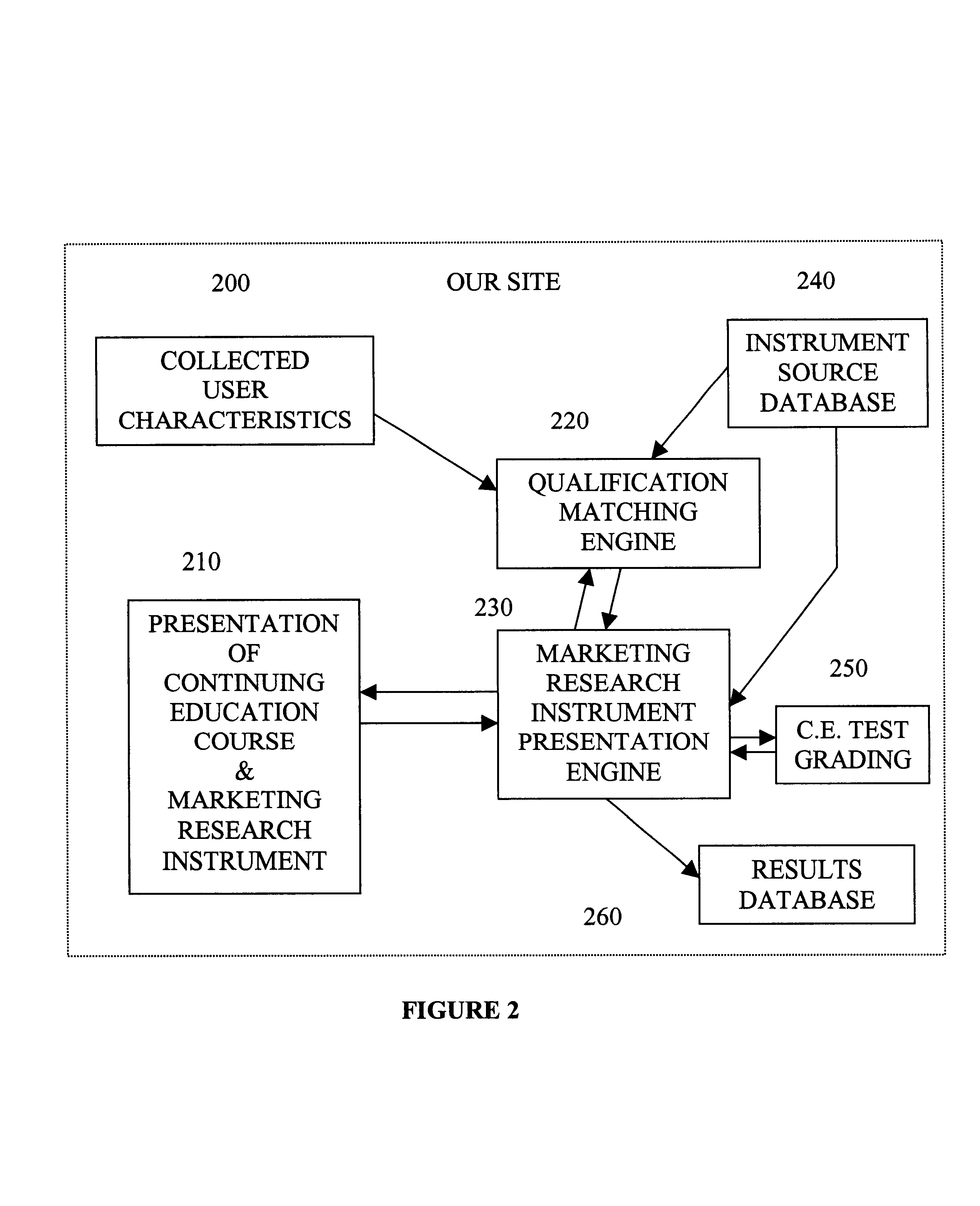
Method and apparatus for market research using education courses and related information
InactiveUS6778807B1Improving identification and selection and incentive and responsivenessMinimize biasCosmonautic condition simulationsTwo-way working systemsTelevision systemCommunications system
Methods and apparatus for assessing and linking market research questions to participant's (user's) credentials, where the market research questions are integrated into selected continuing education courses or product training. The users may not earn credit for such continuing education unless they answer the market research questions. This method allows a mechanism to perform market research on any group of professionals that require continuing education or training. The method and apparatus of the various embodiments of the present invention have applications on the Internet, stand-alone and networked computer systems, integrated computer-television systems, and conventional communication systems, such as voice telephony.
Owner:DOCUMUS
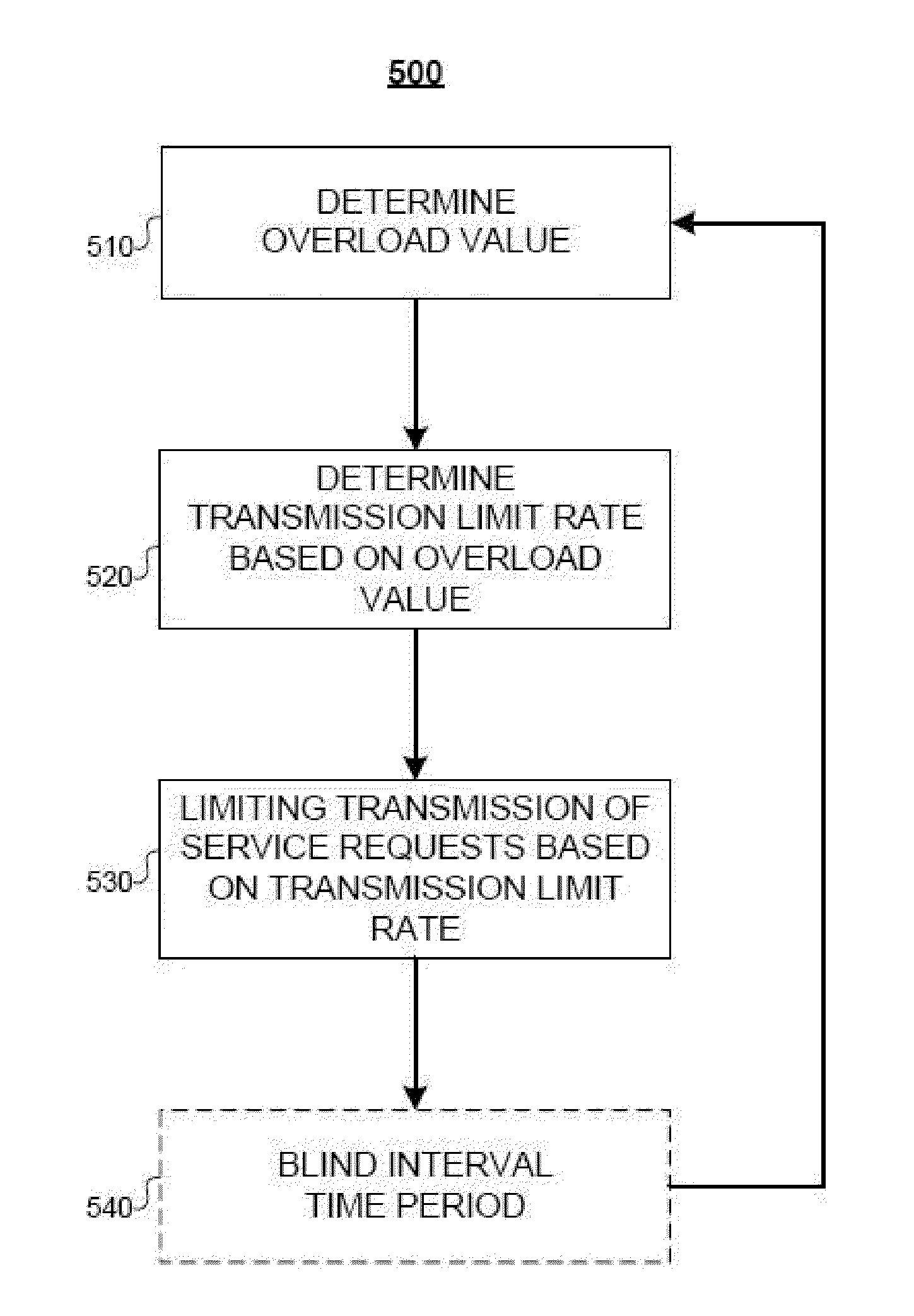
Methods and apparatus for detecting and limiting focused server overload in a network
InactiveUS20100274893A1Low transfer rateReduce in quantityEnergy efficient ICTDigital computer detailsHash functionComputer program
Computer-based methods and apparatuses, including computer program products, are described for detecting and limiting focused server overload in a network. A feedback message is received from a downstream server, wherein the feedback message includes a communication protocol statistic. The methods and apparatuses determine which of one or more counters that store a number of feedback messages received that include the statistic, from an array of counters, are associated with the downstream server using one or more hash functions based on information included in the feedback message. The one or more counters are incremented in response to the feedback message including the statistic. Using the one or more hash functions, a value of the number stored in the one or more counters is determined. The value is determined to be indicative of an overload episode in the network for the downstream server based on whether the value satisfies a predetermined criteria.
Owner:SONUS NETWORKS
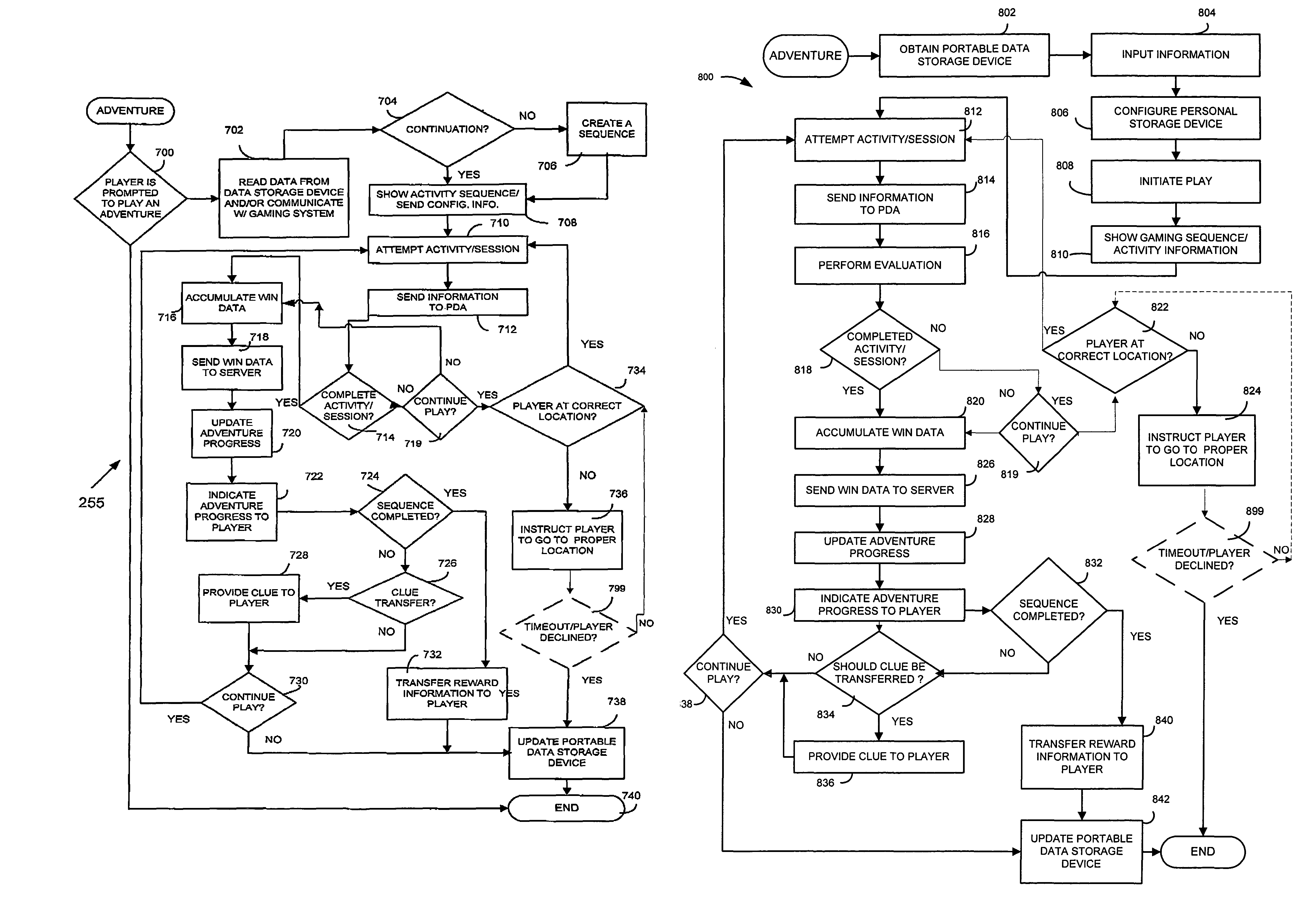
Adventure sequence activities
ActiveUS7892097B2Apparatus for meter-controlled dispensingVideo gamesComputer hardwareSwitched communication network
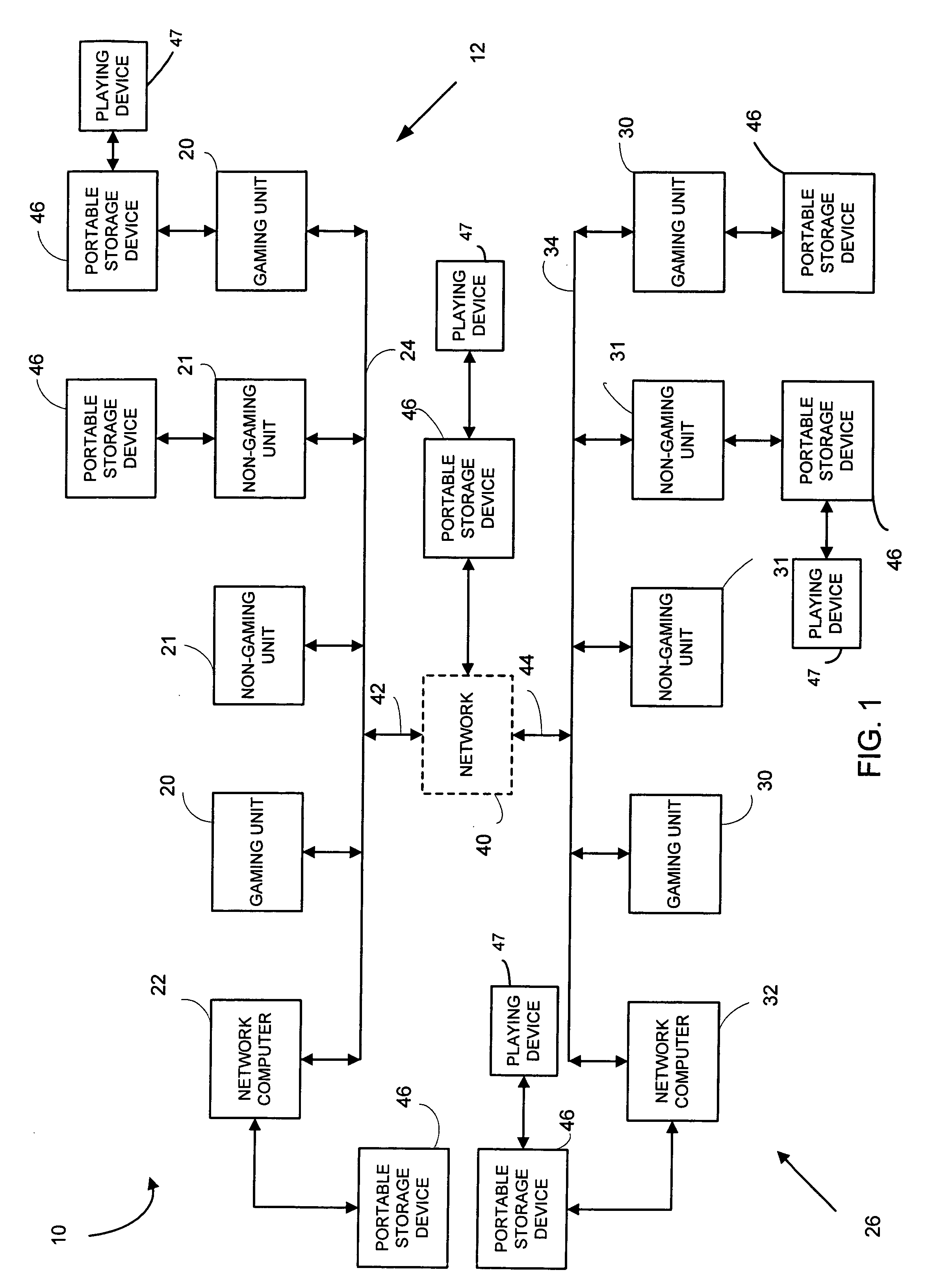
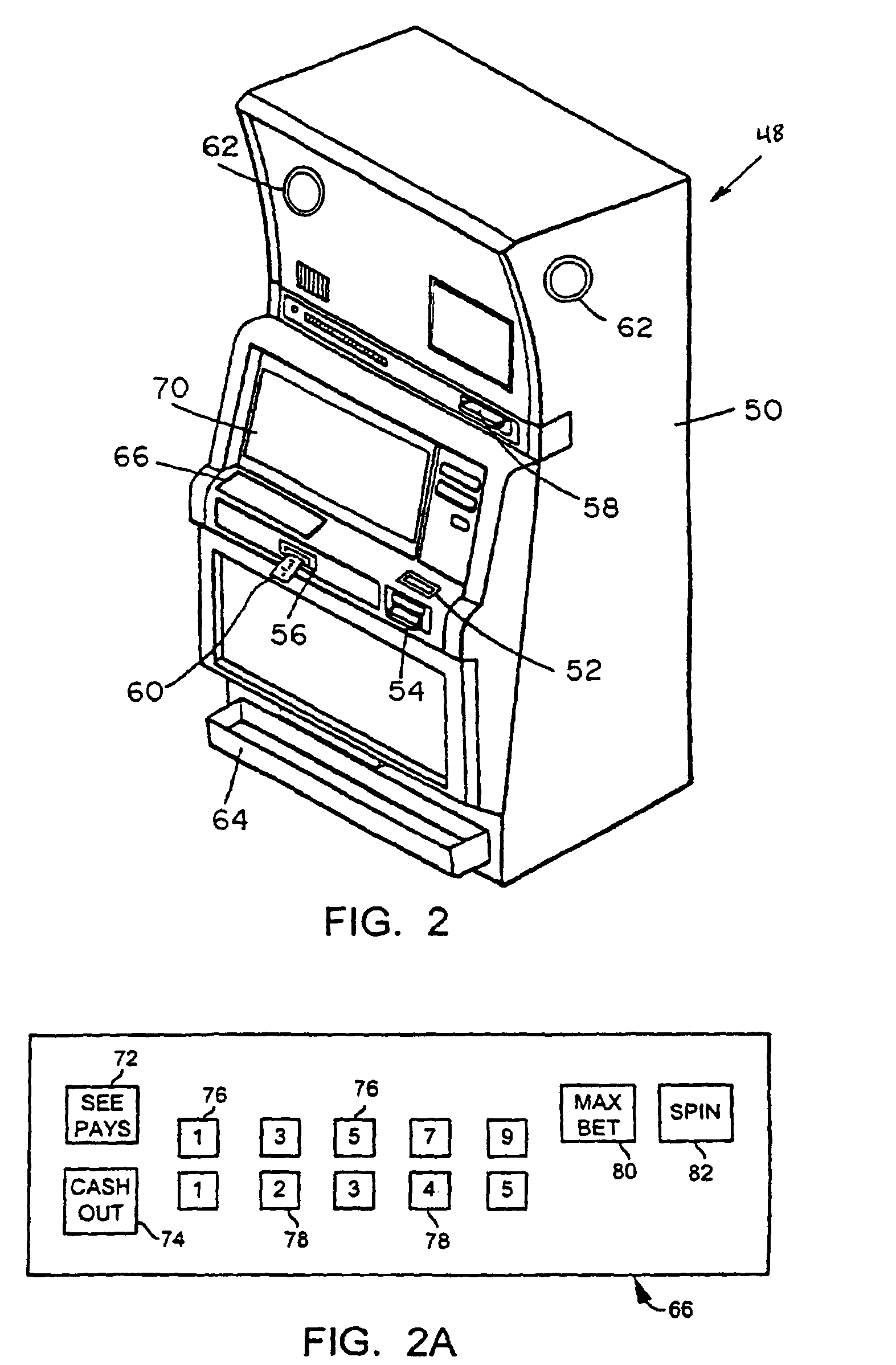
A gaming system includes a communication network, a portable data storage device having information associated with a player stored therein and a plurality of gaming units communicatively coupled to the communication network. Each of the gaming units includes an interface for reading and for storing information within the portable data storage device. The gaming system also includes a network computer communicatively coupled to the communication network and the plurality of gaming units. The network computer is programmed to enable the player to play a group of the plurality of gaming units in a particular sequence based on the information associated with the player stored within the portable data storage device.
Owner:IGT
Networked computer system for communicating and operating in a virtual reality environment
ActiveUS20070288598A1Facilitate communication and operationMultiple digital computer combinationsTransmissionVirtual realityFacilitated communication
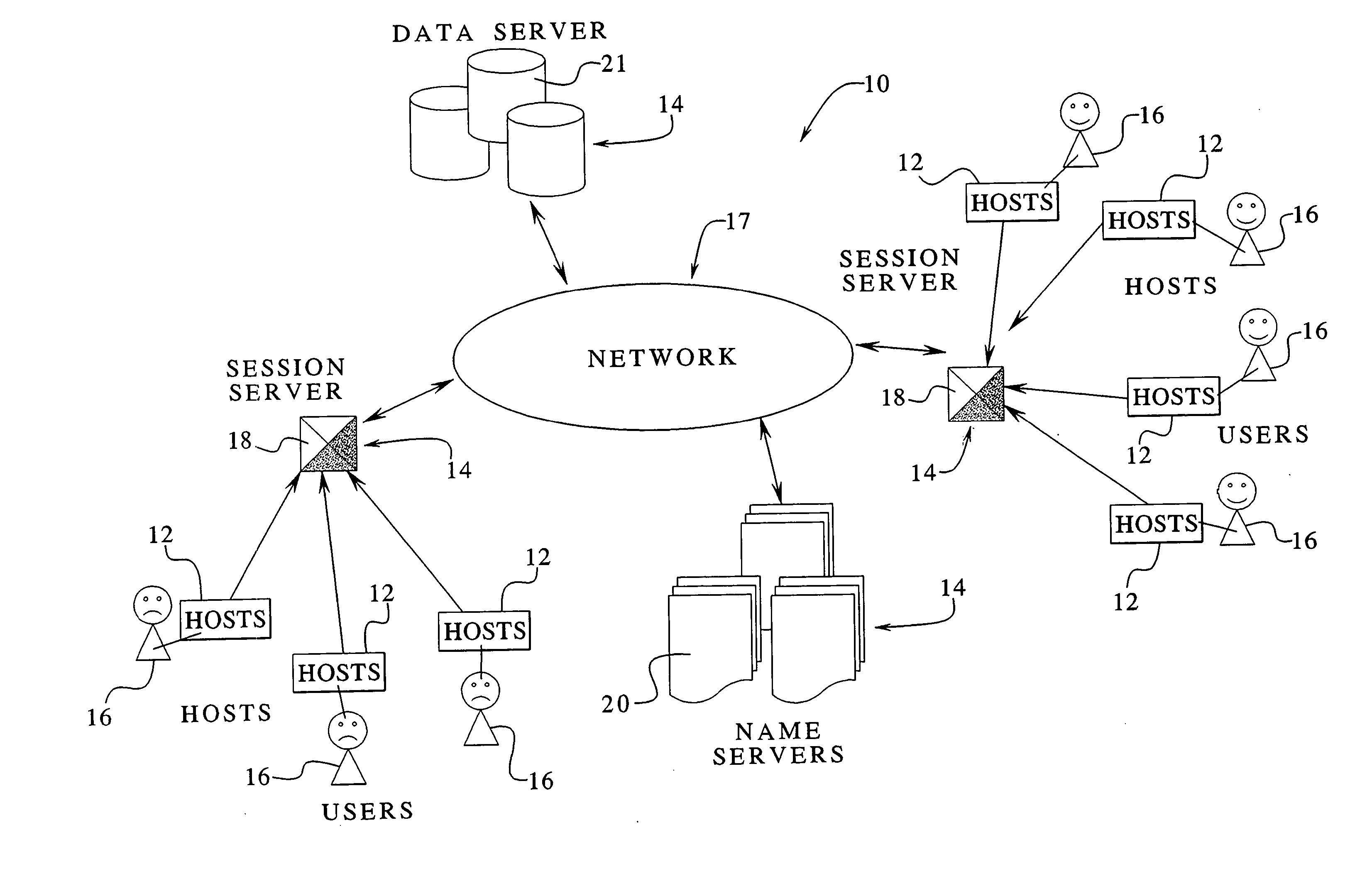
The present invention relates to interactive virtual reality networked computer systems and methods that facilitate communication and operation in a virtual reality environment. The virtual reality networked computer system has an infrastructure that includes a number of users, hosts and servers. The interconnected hosts and servers allow users to effectively locate, activate, access and interact within virtual reality environments in a variety of different ways. For example, users can establish user groups such that interaction within the virtual reality environment occurs between hosts (accessed by users) without the need of a central or dedicated server.
Owner:XDYNE
Interactive computer network and method of operation
InactiveUS6182123B1Shorten the timeImpression capsDental impression compositionsDistributed objectData memory
A distributed processing, interactive computer network and method of operation is described. The network is designed to provide very large numbers of simultaneous users access to large numbers of applications which feature interactive text / graphic sessions. The network includes one or more host computers having application data stores; a plurality of concentrator computers, also including application data stores, the concentrator computers being connected in groups of one of more to each of the host computers; and a plurality of reception system computers connected in groups of one or more to each of the concentrator computers, the reception system computers being arranged so that respective users can request interactive applications at the reception system computers. In accordance with the design, the reception system computers also include application data stores. The method for operating the network includes steps for generating the interactive text / graphic sessions from objects that include data and / or program instructions. Additionally, the method features steps for distributing objects among the data stores of the network computers, and, thereafter, permitting the reception system computer at which an application is requested to selectively collect objects required for the application from the network and the respective reception system so that the requested application may be presented at the reception system based on the objects collected. This operation decreases processing demand on the higher-level network elements, permitting them to function primarily as data supply and maintenance resources, thereby reducing network complexity, cost and response time.
Owner:IBM CORP
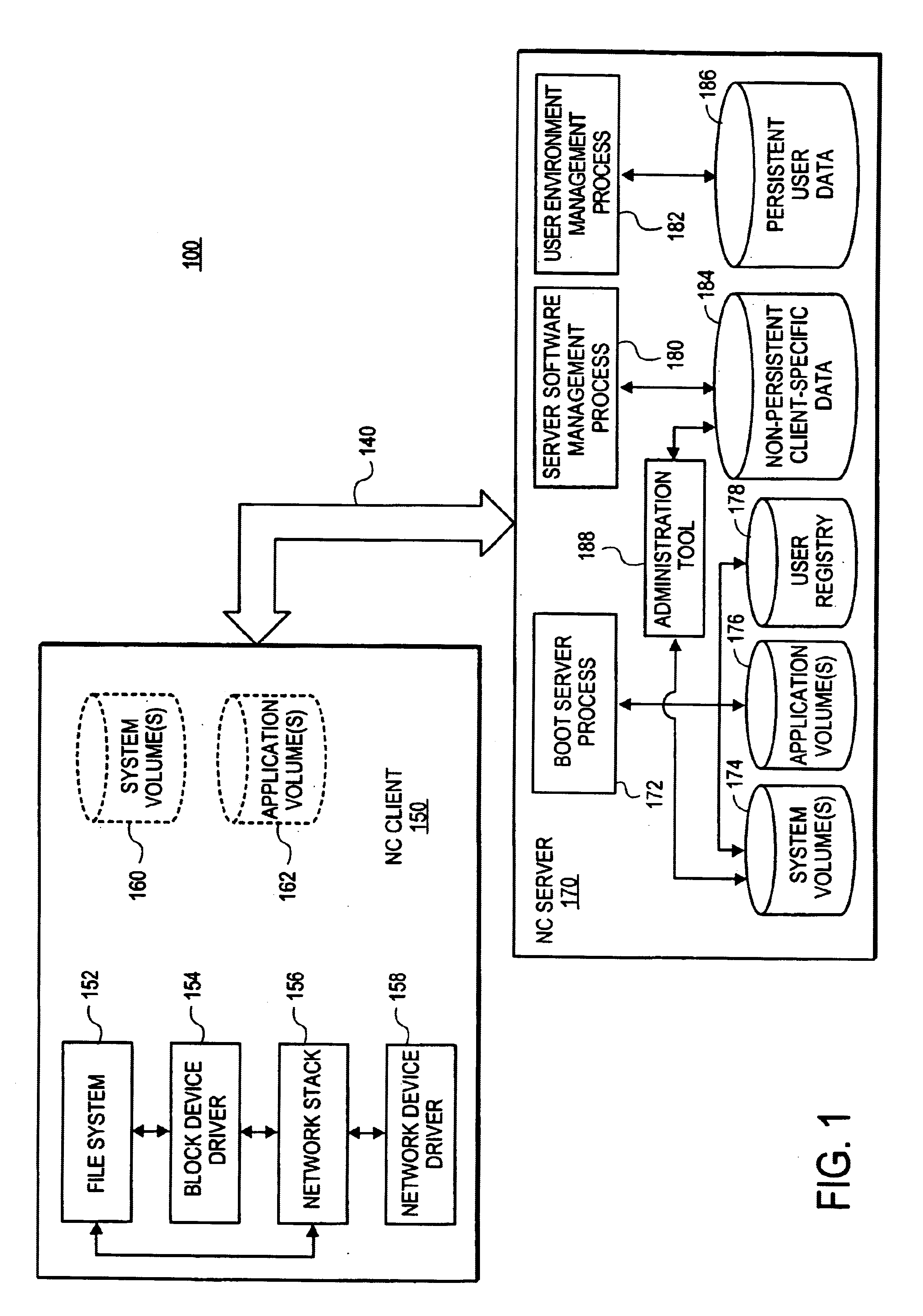
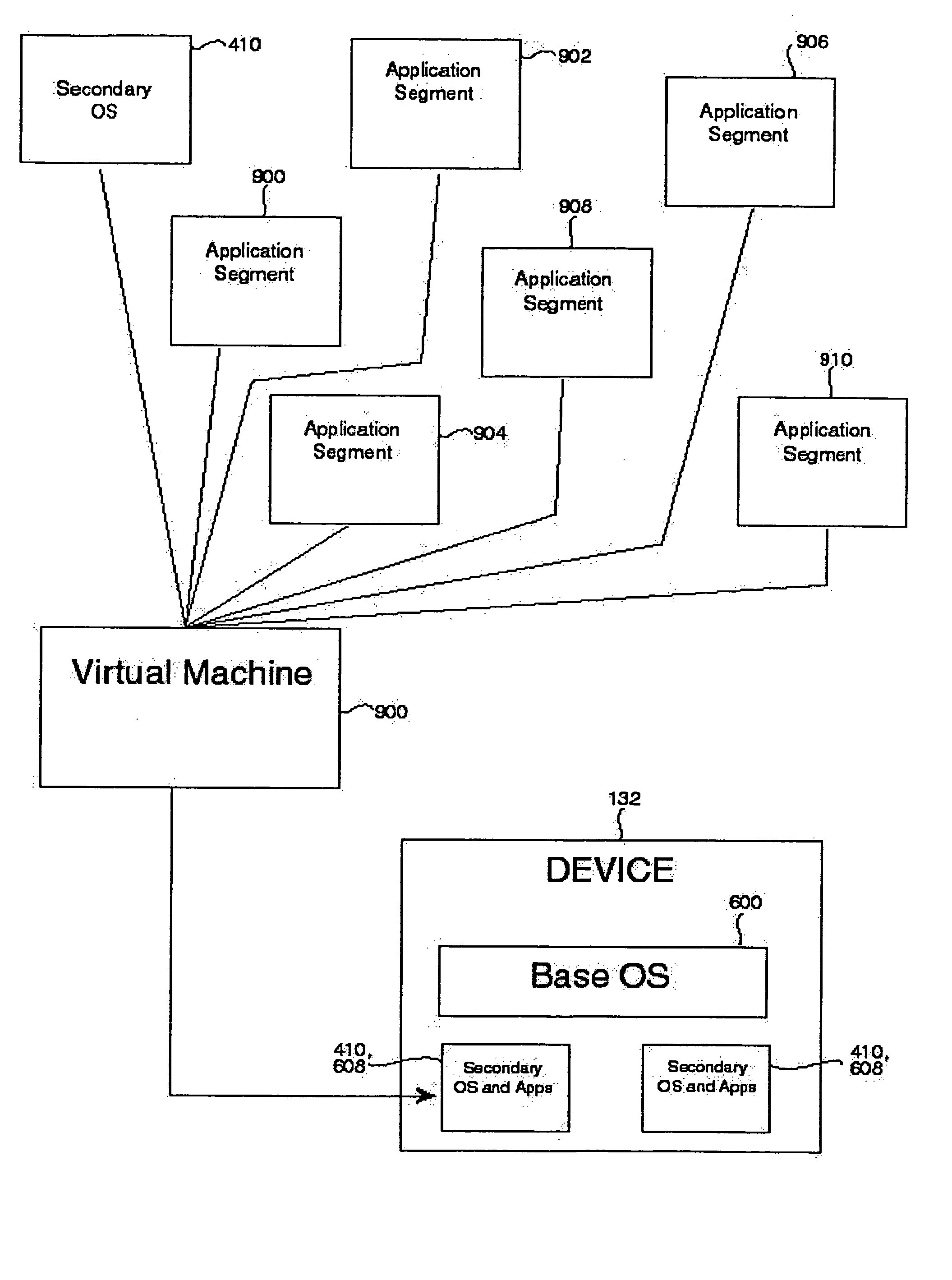
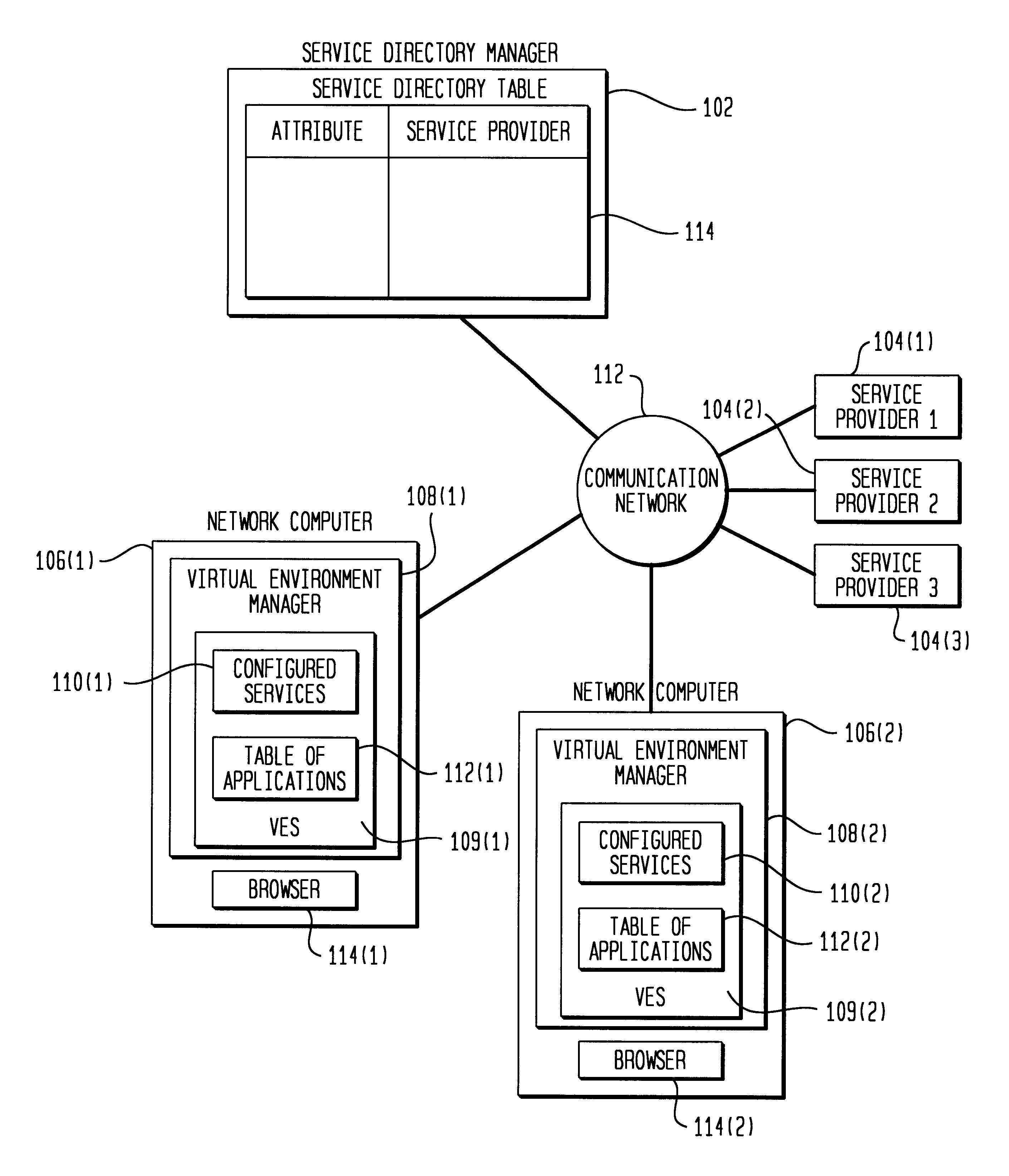
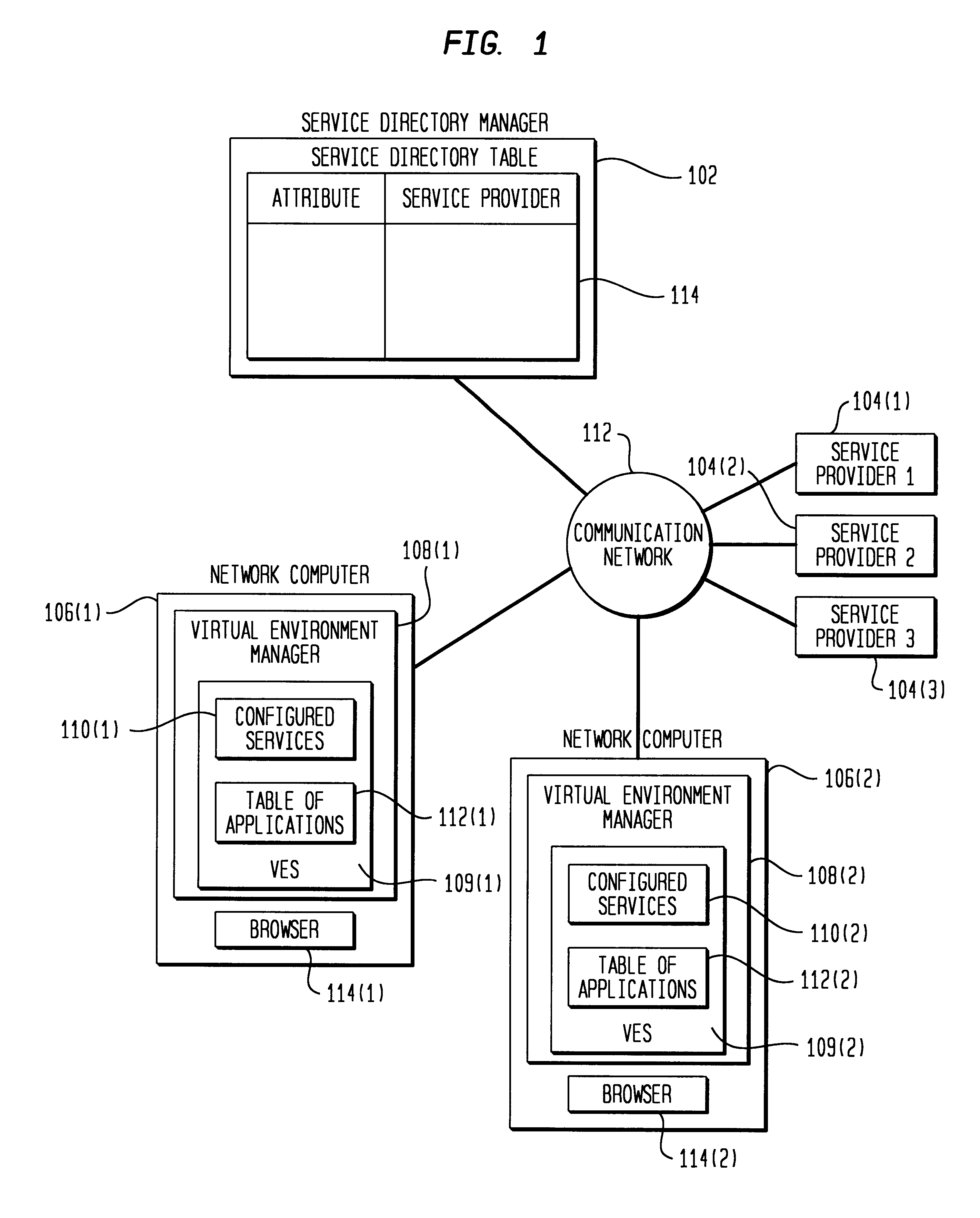
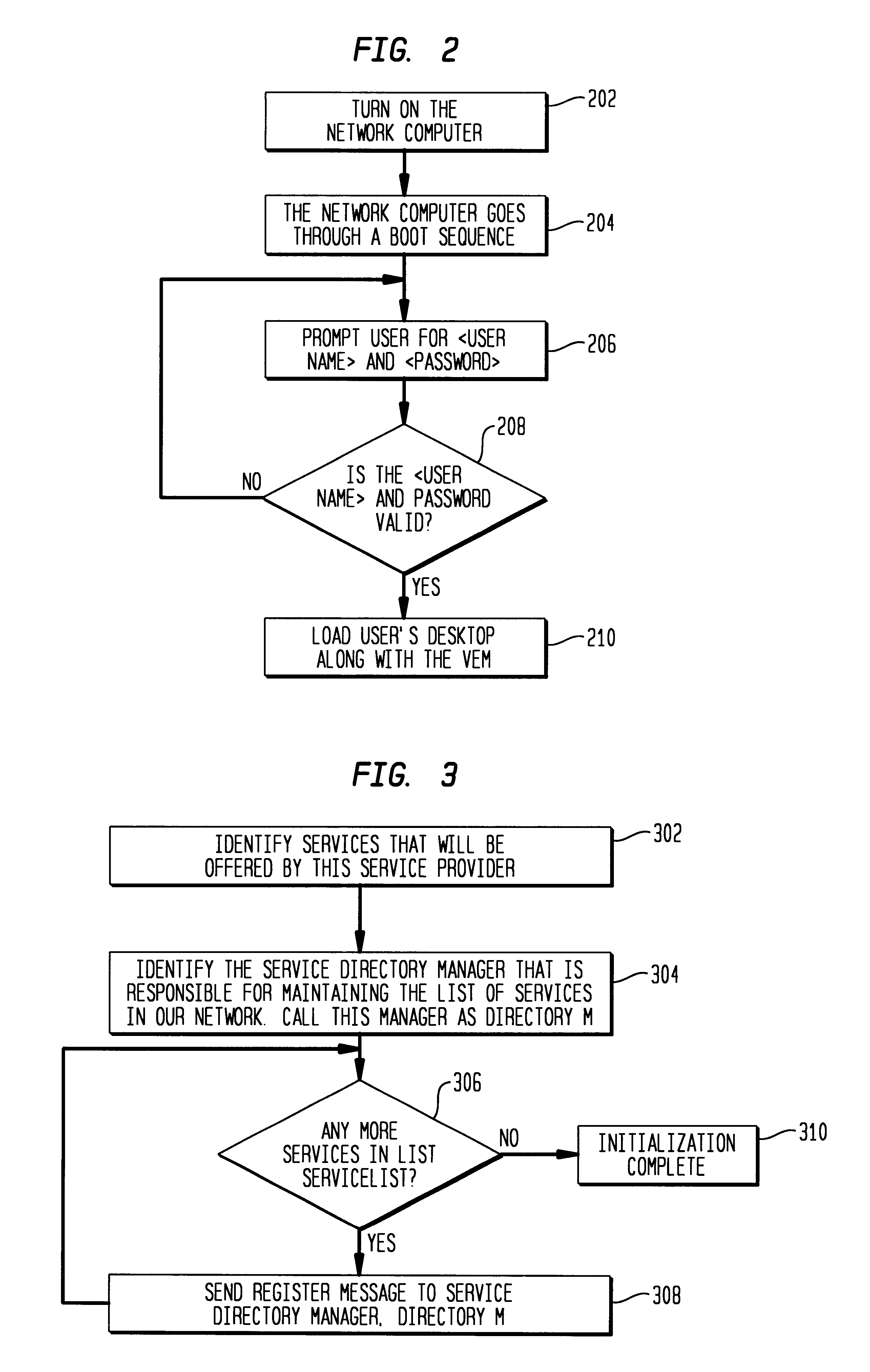
Virtual environment manager for network computers
InactiveUS6757729B1Interprogram communicationMultiple digital computer combinationsApplication softwareClient-side
A system and method for a downloadable just-in-time middleware called VEM that provides access to network services, including system services such as printing and local storage, to applications that run on Network Computers. The VEM configures the default client services and stores information about these services. When an application executing on the Network Computer wishes to use one of the services, it communicates with its local VEM. The VEM returns a handle to the appropriate service to complete the service request.
Owner:IBM CORP
On line monitor for a control device
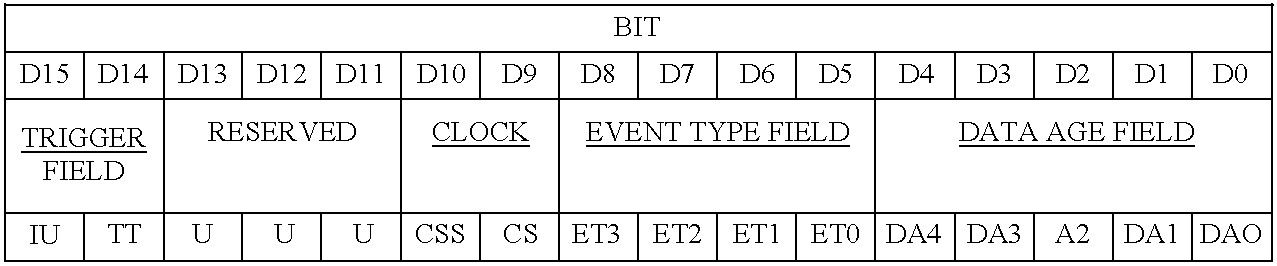
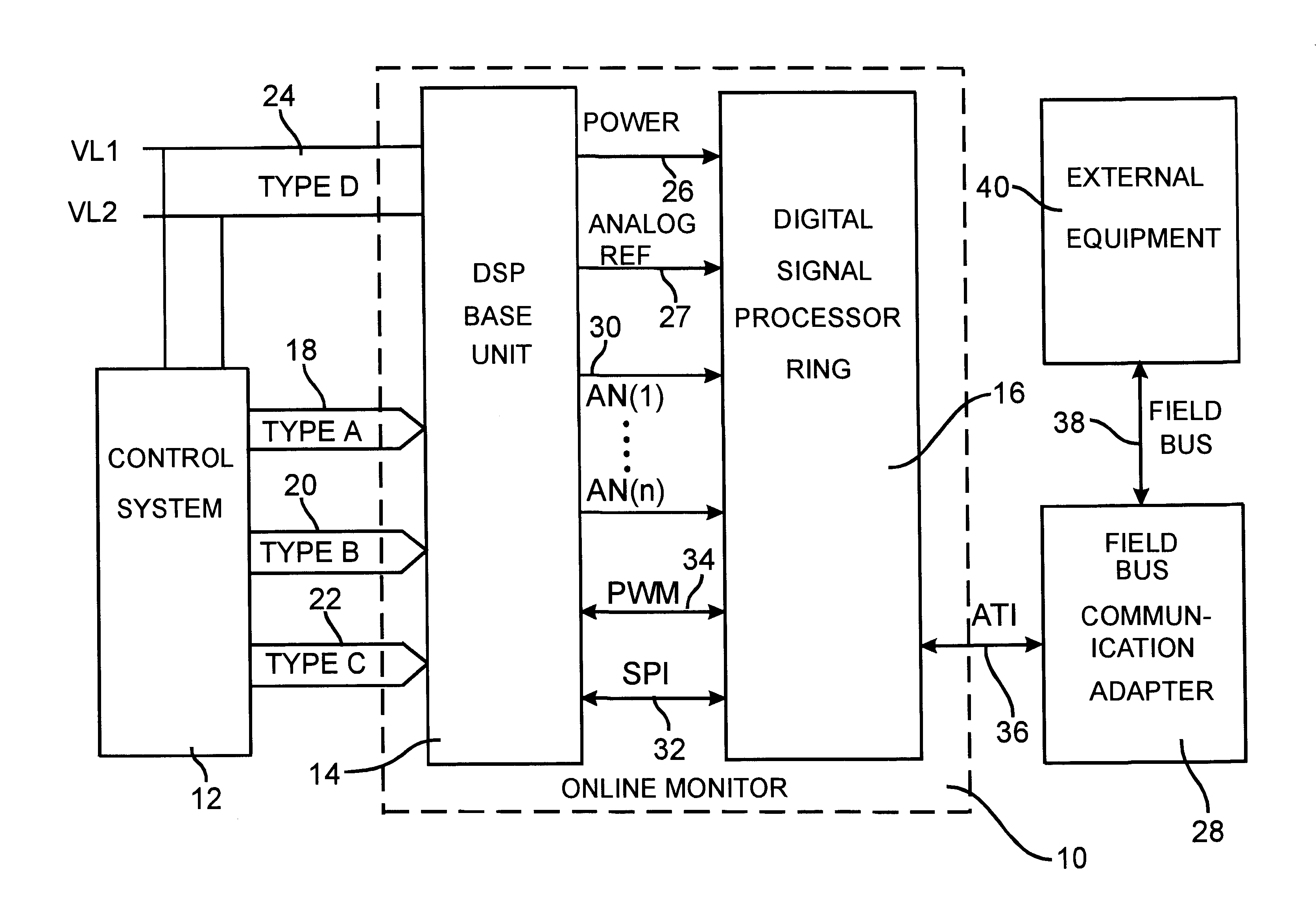
InactiveUS6611724B1Computer controlSimulator controlDigital signal processingCommunication interface
An online monitor that can be permanently attached to a device to be monitored continuously monitors a set of analog signals and initiates data capture over a window of time when a user programmable set of conditions is satisfied. The online monitor includes a digital signal processing unit, a modular, interchangeable, analog signal conditioning base unit that can be tailored to the specific requirements of the process to be monitored and a modular, interchangeable, communication interface unit. The interface unit permits the digital signal processing unit to exchange data with external equipment such as network computers via a number of industry standard communication fieldbus protocols. The online monitor provides the capability to define the trigger condition under which data capture is initiated by comparing a user defined signal to a function of the instantaneous value of another signal or constant. Data captured is stored indefinitely in internally battery backed memory and the instant at which data capture is initiated is determined accurately via a time tagging function, so the data can be retrieved at a later time.
Owner:SQUARE D CO
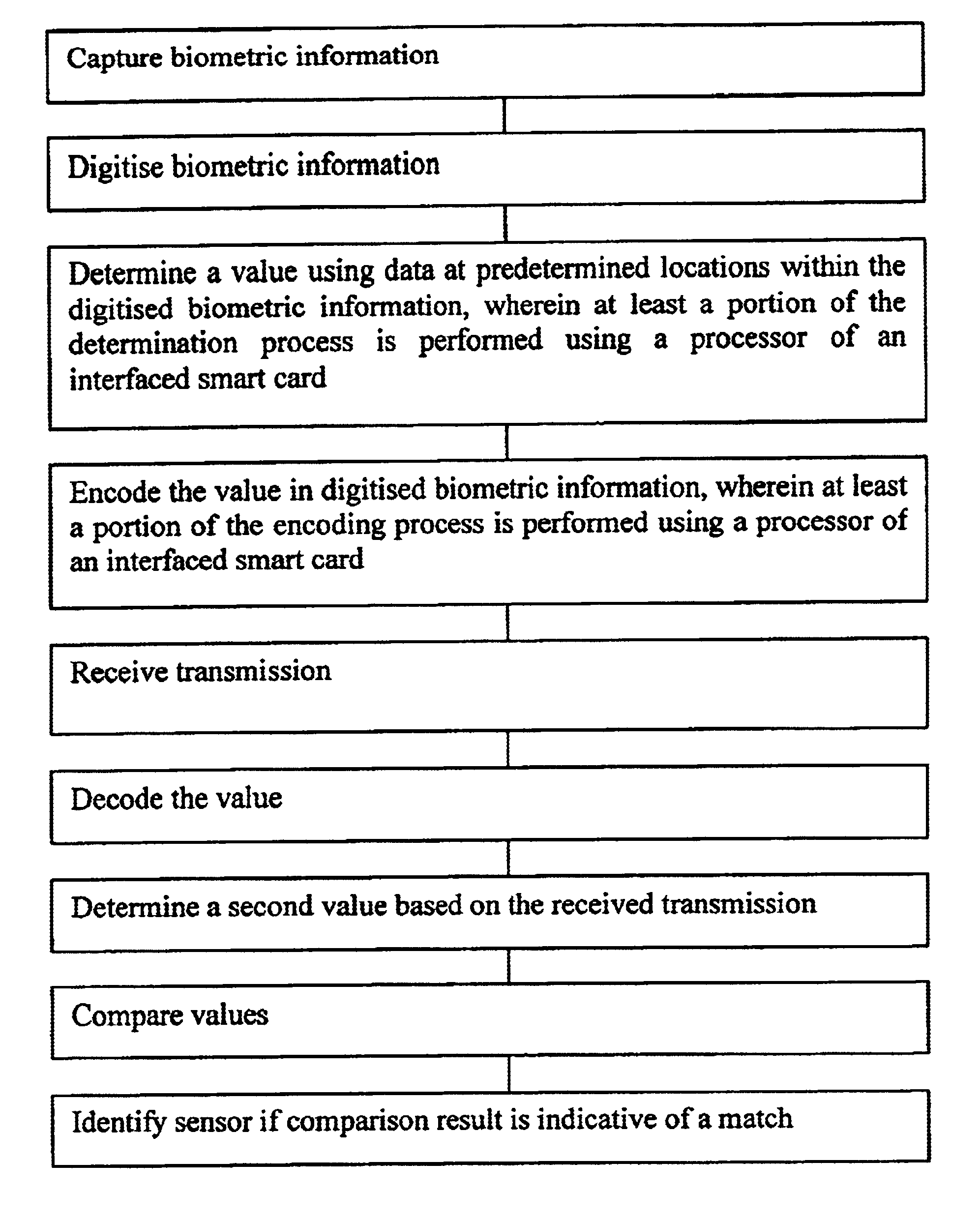
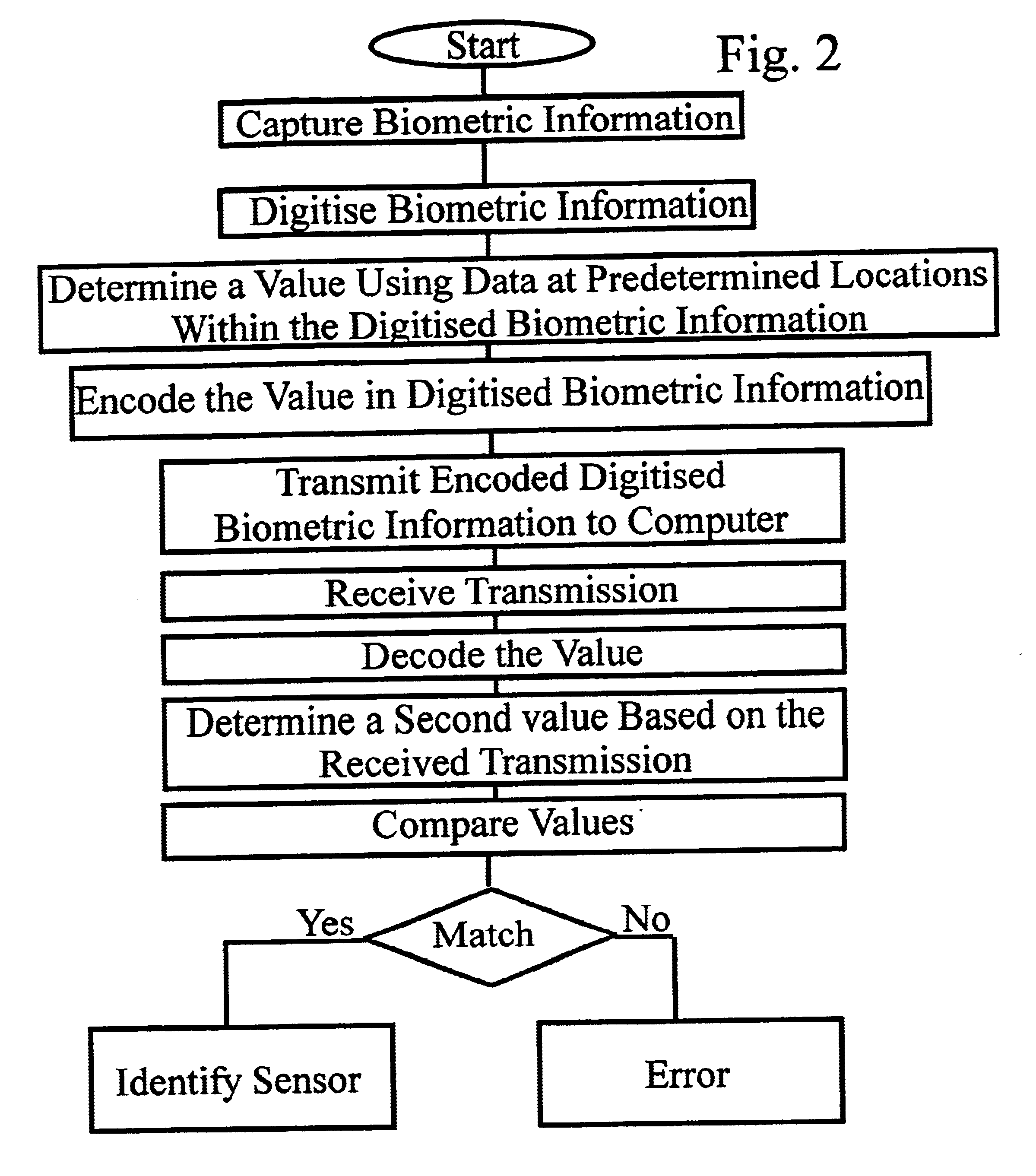
Method of detecting authorised biometric information sensor
InactiveUS6901154B2Electric signal transmission systemsDigital data processing detailsComputer hardwareCommunications system
In the past, a contact imaging device was physically secured to prevent tampering. When used with network computer systems or communications systems, securing a contact imager is difficult. According to the invention, a method is proposed for securing a contact imaging device from tampering and for ensuring a contact imaging device is an authorised contact imaging device for use with a personal computer, a network application, or a communications application.
Owner:ACTIVIDENTITY
Communication system including a client controlled gateway for concurrent voice/data messaging with a data server
InactiveUS6163536ASpecial service for subscribersData switching by path configurationModem deviceNetworked Transport of RTCM via Internet Protocol
A communication system includes a client controlled gateway enabling concurrent voice / data transmission in a distributed information network and a communication network between the client and a service representative of a host system provider. A computer and a modem couple the client to the gateway in the communication network over a single communication path. The computer includes a browser for searching the distributed network. The browser includes "plug-in" programs which interact with the data server in supporting voice calls between the client and the host system. The gateway functions as a shared voice data (SVD) server to couple the client to the data server after authentication of the client's identification (ID) and password. The gateway transfers data between the client and the data server over the distributed network in accordance with screens presented to the client by the host system. Concurrently, voice service is provided between a representative of the host system and the client over the communication network using "action buttons" appearing in selected screens presented to the client by the host system provider over the distributed network. One "action button" enables the client to initiate voice transmissions over the communication network concurrently while data is being transmitted over the distributed network. Another "action button" enables the host provider to initiate voice transmission over the communication network concurrently while data is being transmitted over the distributed network.
Owner:IBM CORP
Mechanism for dynamically binding a network computer client device to an approved internet service provider
InactiveUS6112305AUser identity/authority verificationSecret communicationDigital signatureSmart card
All network computer client device (NC) manufacturers' authorizations to connect to specific internet service providers (ISPs) are maintained in a central database associated with a relationship server. The relationship server issues digital certificates which associate various ISPs to their respective public keys. Each ISP is assigned a unique enterprise identification number by the relationship server. To authorize a specific ISP, the manufacturer begins with the relationship server's ISP certificate. The manufacturer computes and appends its own digital signature for the relationship server's ISP certificate, thereby creating an ISP usage certificate valid for its NCs which it sends back to the relationship server. Upon first powering on, each NC dials the relationship server and transmits its manufacturer identification number. The relationship server uses the manufacturer identification number to find the ISP usage certificates corresponding to the NC manufacturer. The relationship server then sends to the NC the ISP usage certificate corresponding to the enterprise identification number, or corresponding to the user's selection if no enterprise identification number on the smart card is established. The NC performs a cryptographic verification of the ISP usage certificate using the manufacturer's public key which is permanently stored in the NC in read only memory. Only if the verification of the ISP usage certificate is successful, thus indicating that the ISP usage certificate is signed by the manufacturer does the NC then attempts to connect to the ISP. When an ISP and manufacturer terminate an agreement, the relationship server disables the ISP's managed access software; when the NC's attempt to connect to the ISP fails, the NC then dials the relationship server to receive a new ISP usage certificate.
Owner:COMCAST CABLE COMM MANAGEMENT LLC
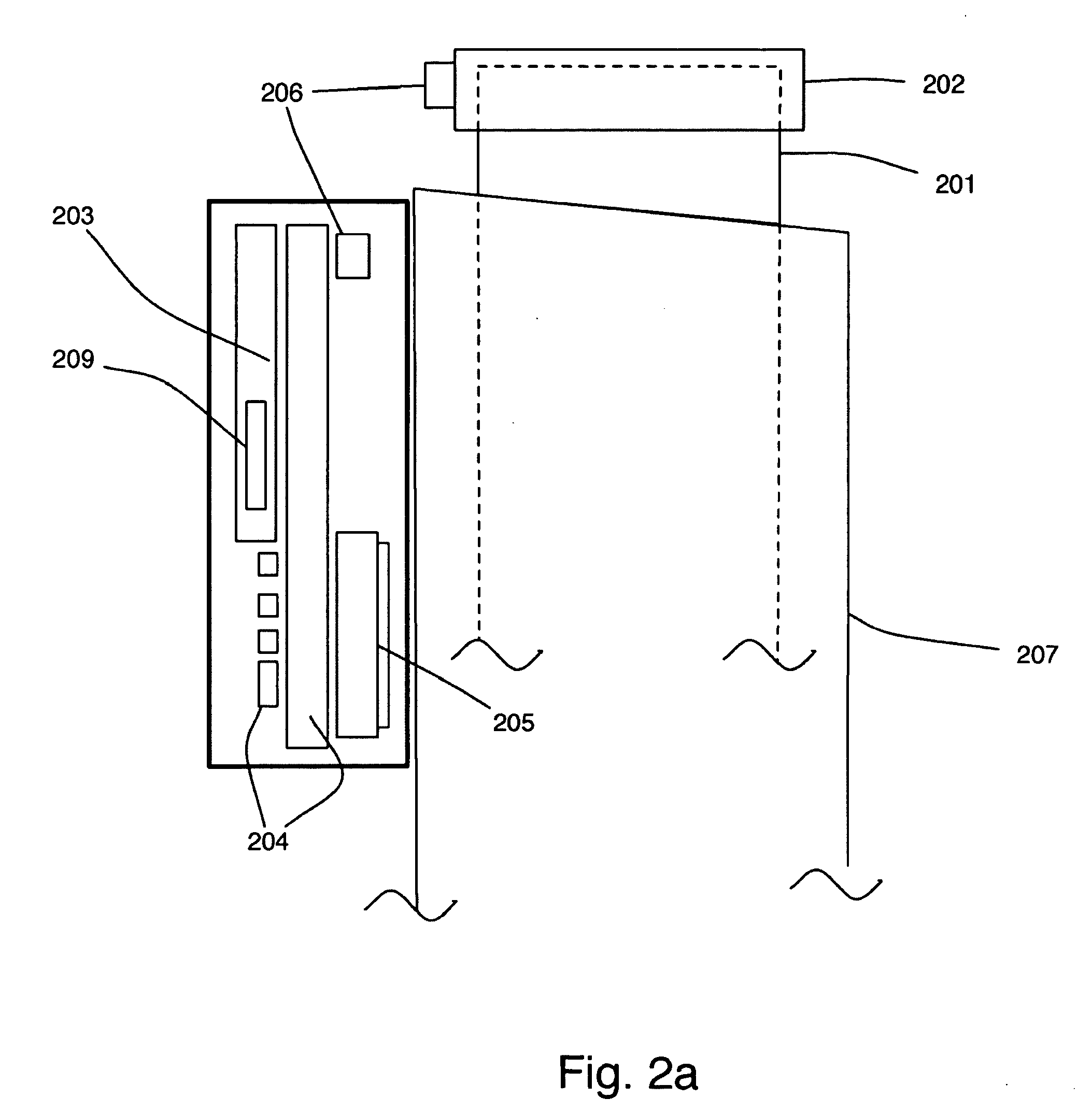
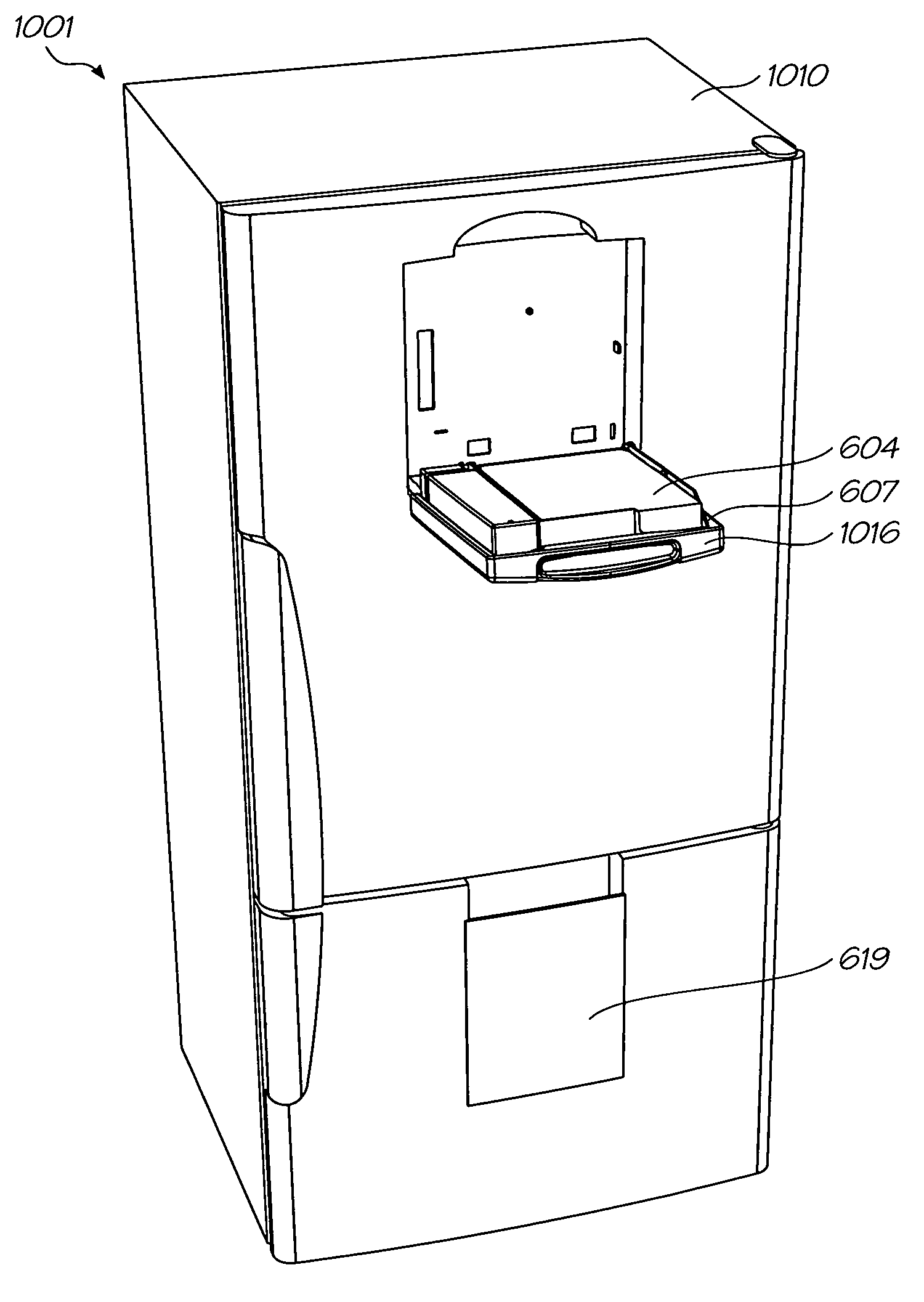
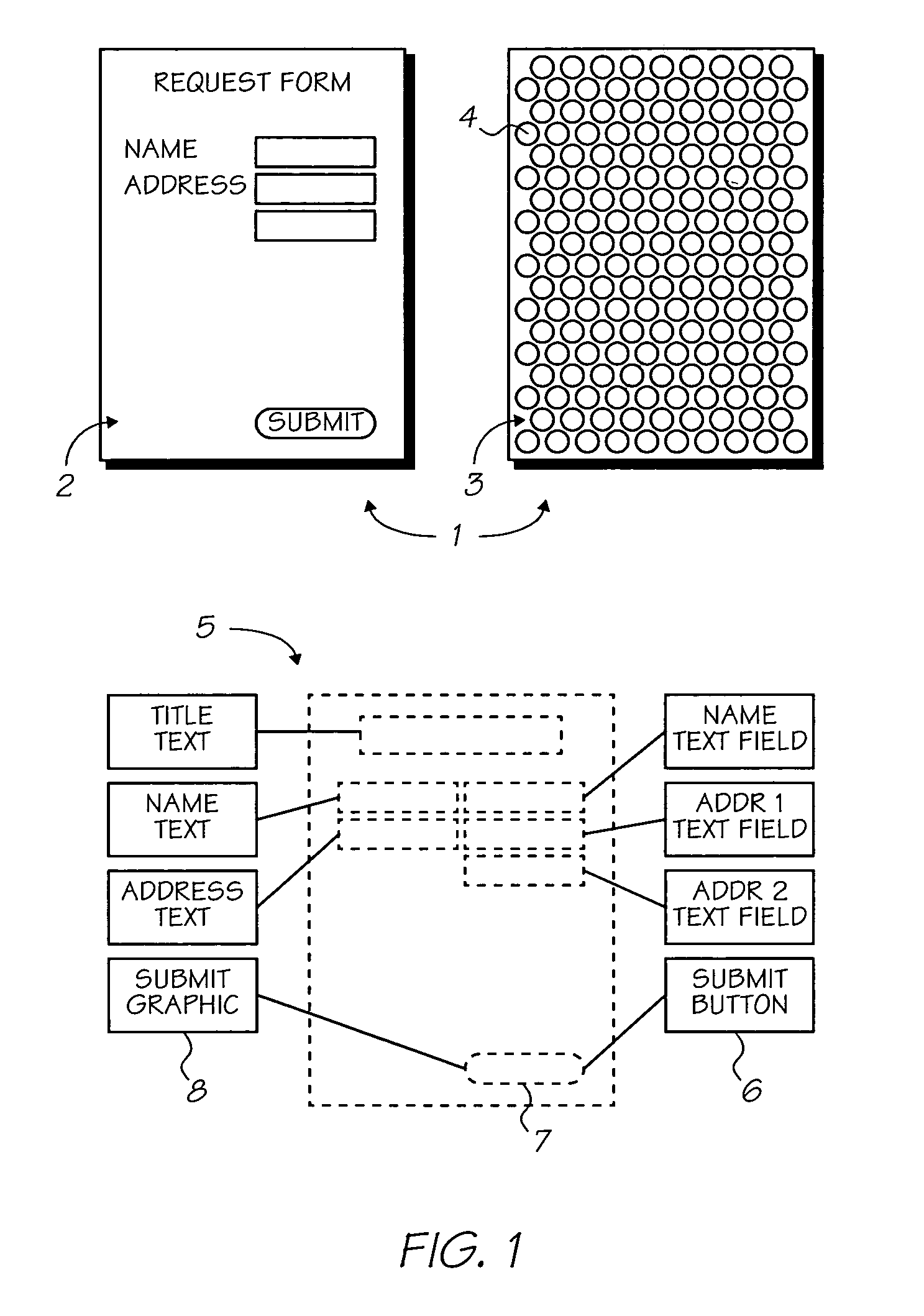
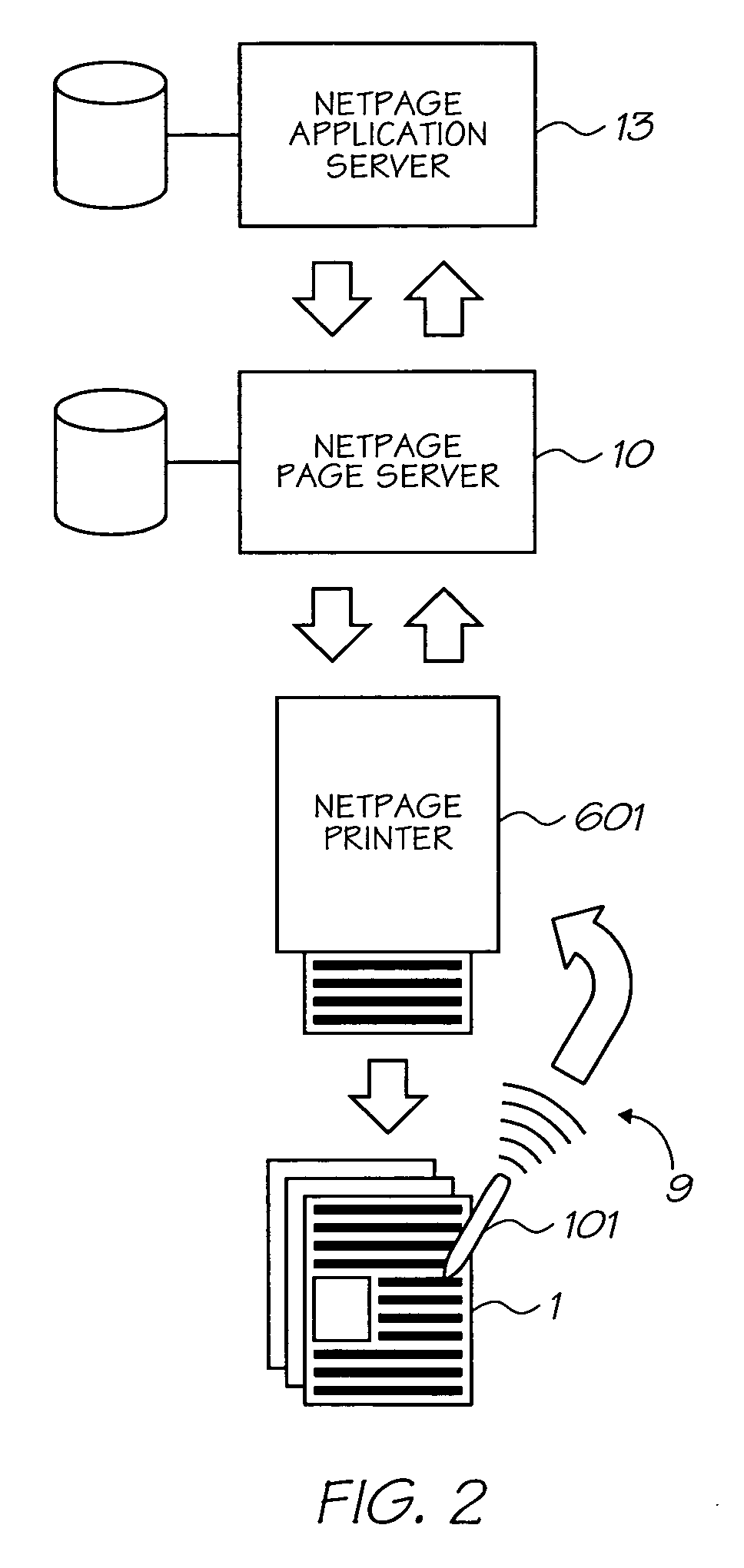
Apparatus for interaction with a network computer system
InactiveUS6927871B1Easy to readRobustly coffee spillDigitally marking record carriersOther printing matterNetwork terminationComputer module
The present invention relates to an apparatus enabling interaction with a network computer system. It has particular application to a system employing a printer for printing an interface onto a surface to produce an interface surface.According to one aspect of the invention, there is provided an apparatus enabling interaction with a network computer system, the apparatus including:an appliance for storing and cooling produce for use by an appliance user; anda printer device integrated into said appliance, the printer device being operatively interconnectable with said network computer system, the printer device including a printer module operable to print at least one form delivered from said network computer system, and the printer device being configured to receive indicating data from a sensing device operated by an appliance user, the sensing device when placed in an operative position relative to said at least one form sensing the indicating data.By means of the invention, a network terminal comprising an interactive printer device can be incorporated into, say, the door of a domestic refrigerator. Such an appliance is readily accessible, and is regularly visited by those who may be making use of the network terminal.
Owner:SILVERBROOK RES PTY LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com