Patents
Literature
152 results about "Handling Code" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
A coded value specifying a special handling requirement for the material or object. EXAMPLE(S): keep at room temperature, store upright.
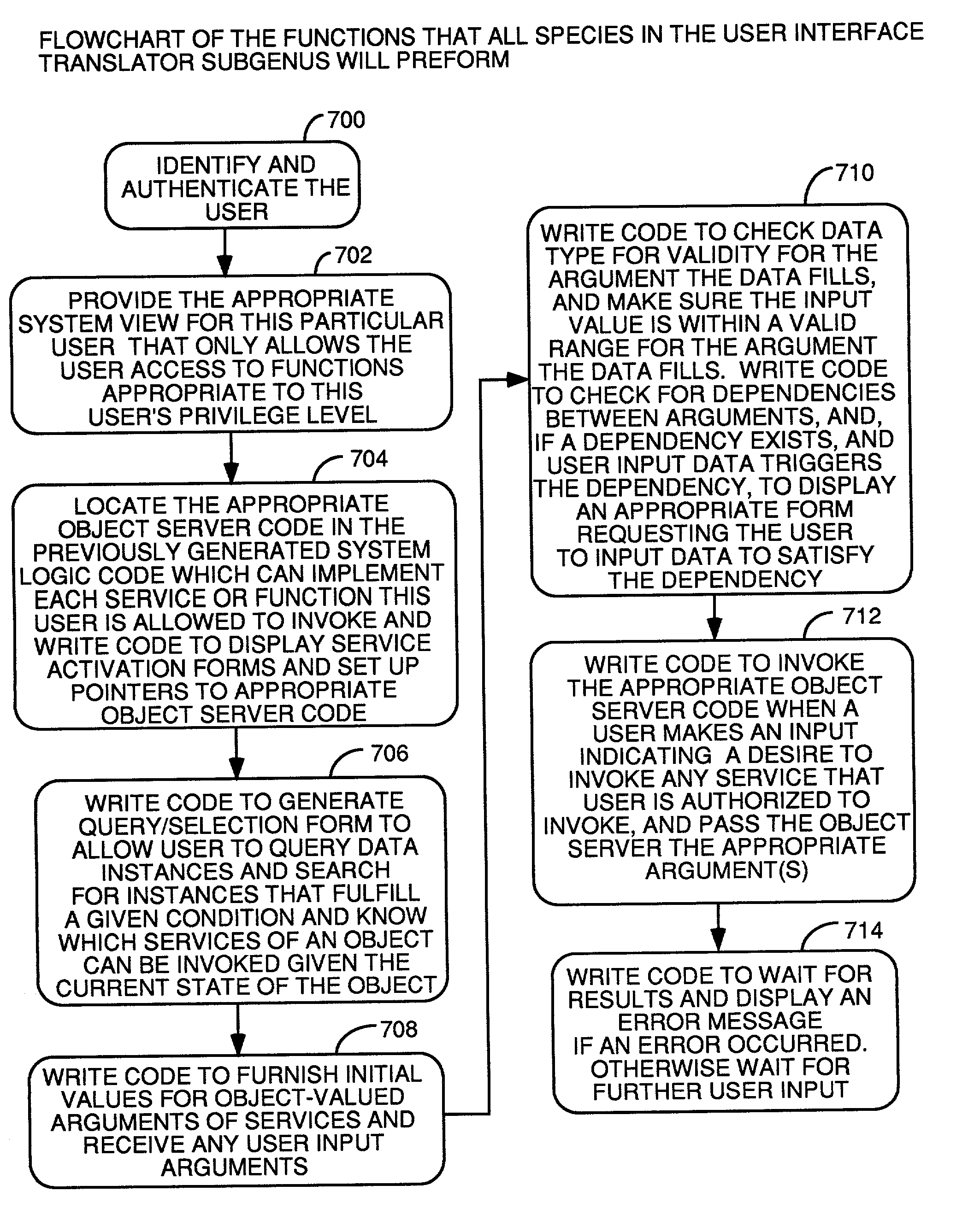
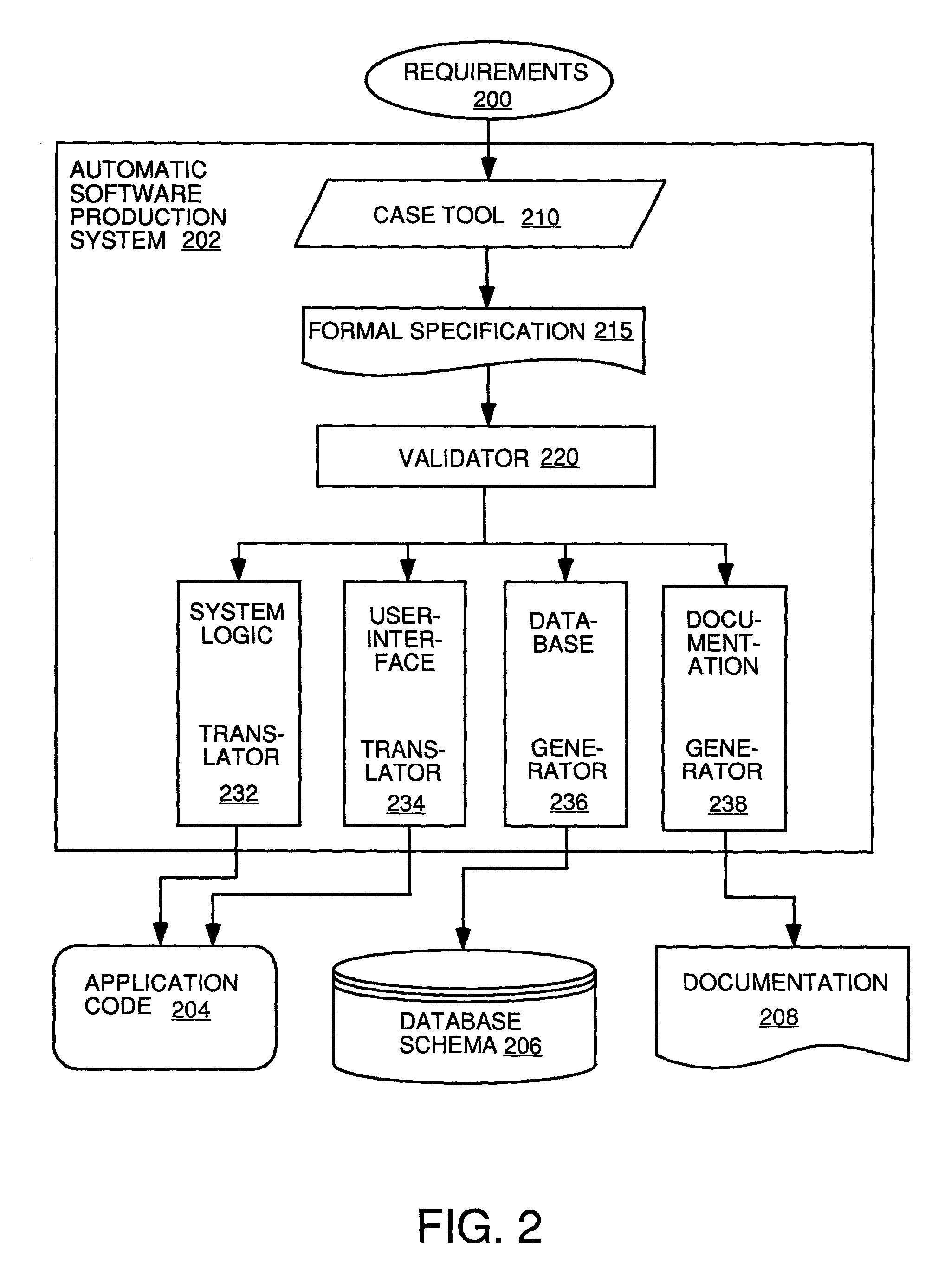
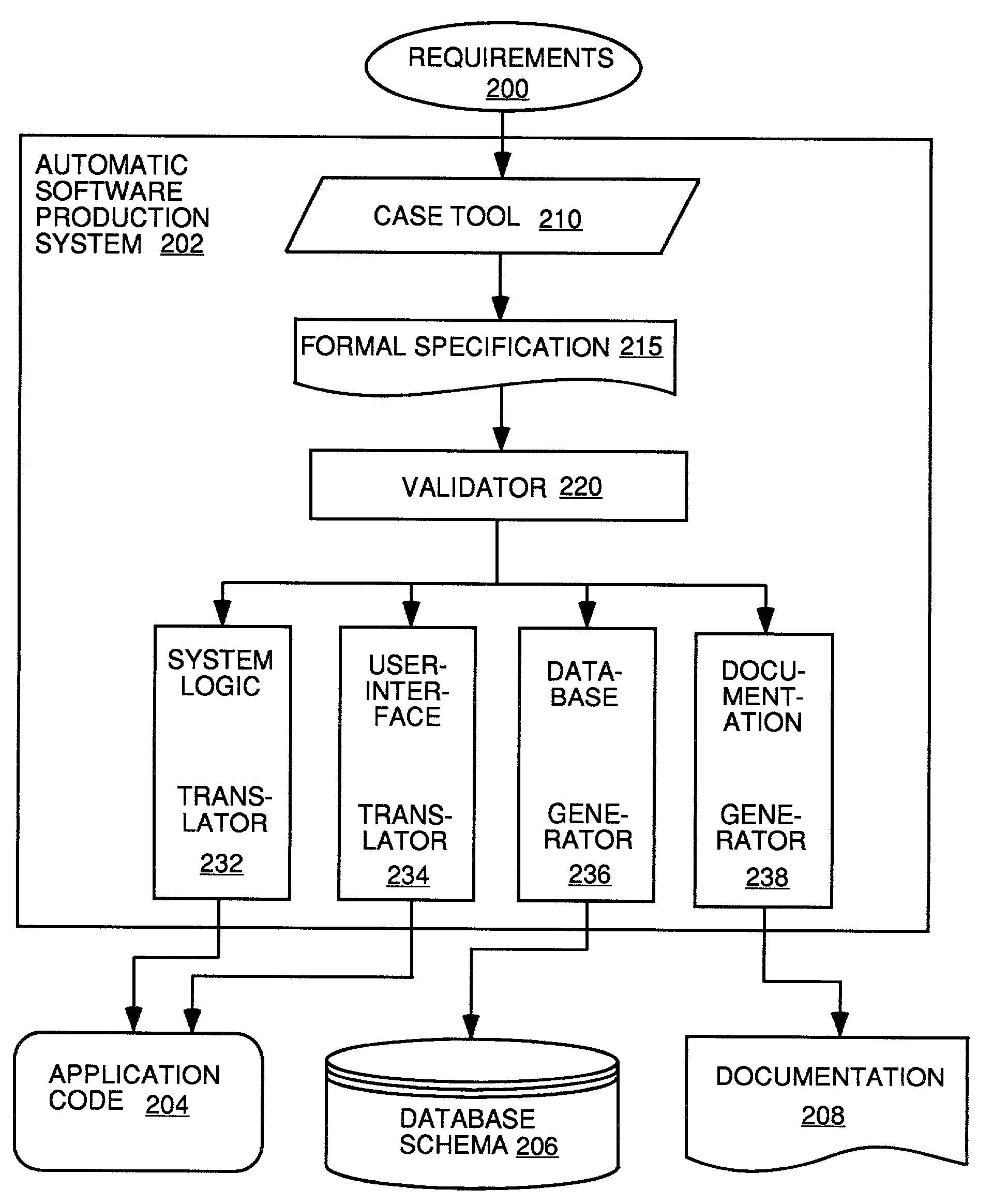
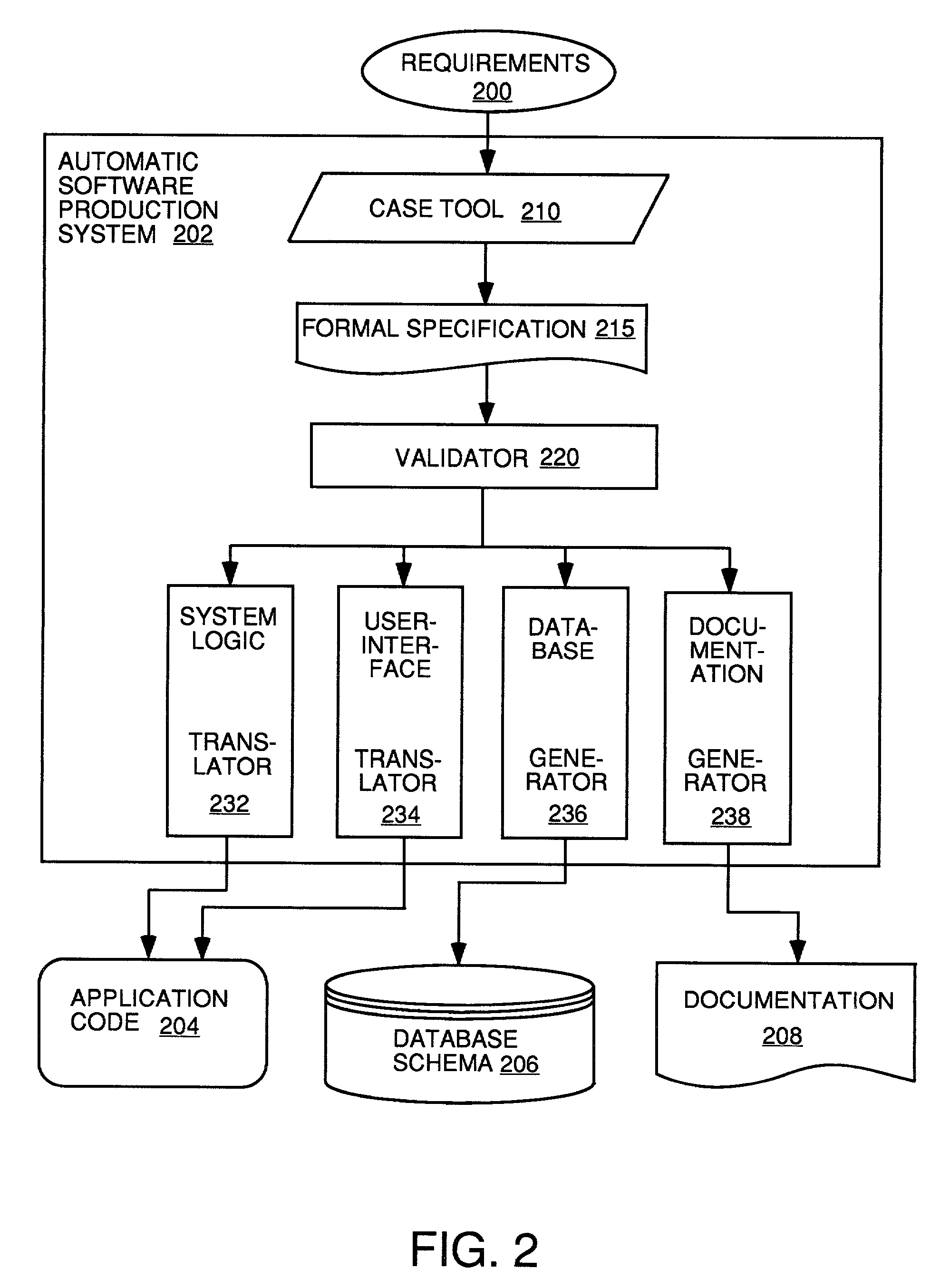
Automatic software production system
InactiveUS7137100B2Shorten the time to marketEasy to useDigital data information retrievalProgram documentationHandling CodeSystem requirements
Owner:SOSY
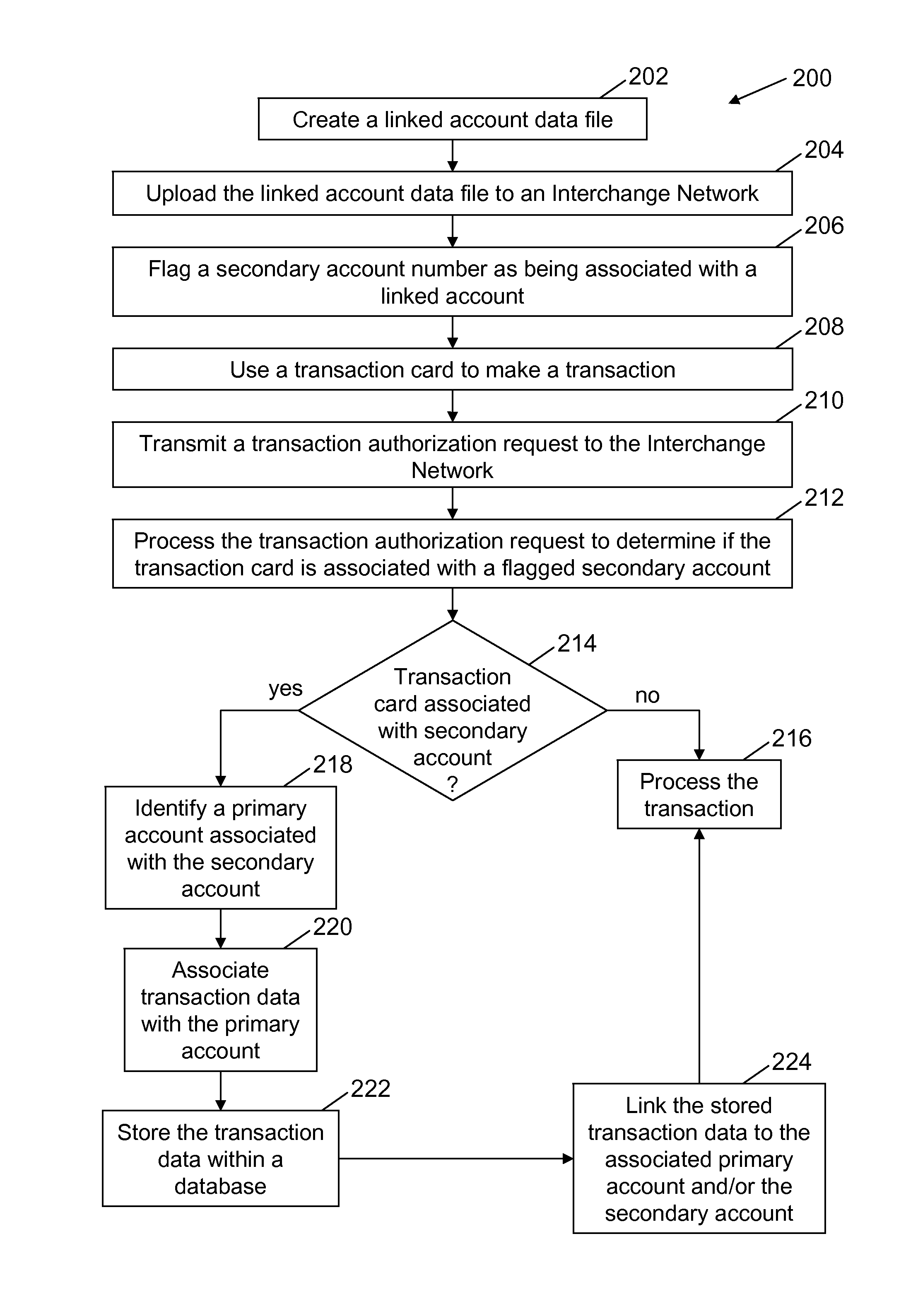
Methods and systems for linking multiple accounts
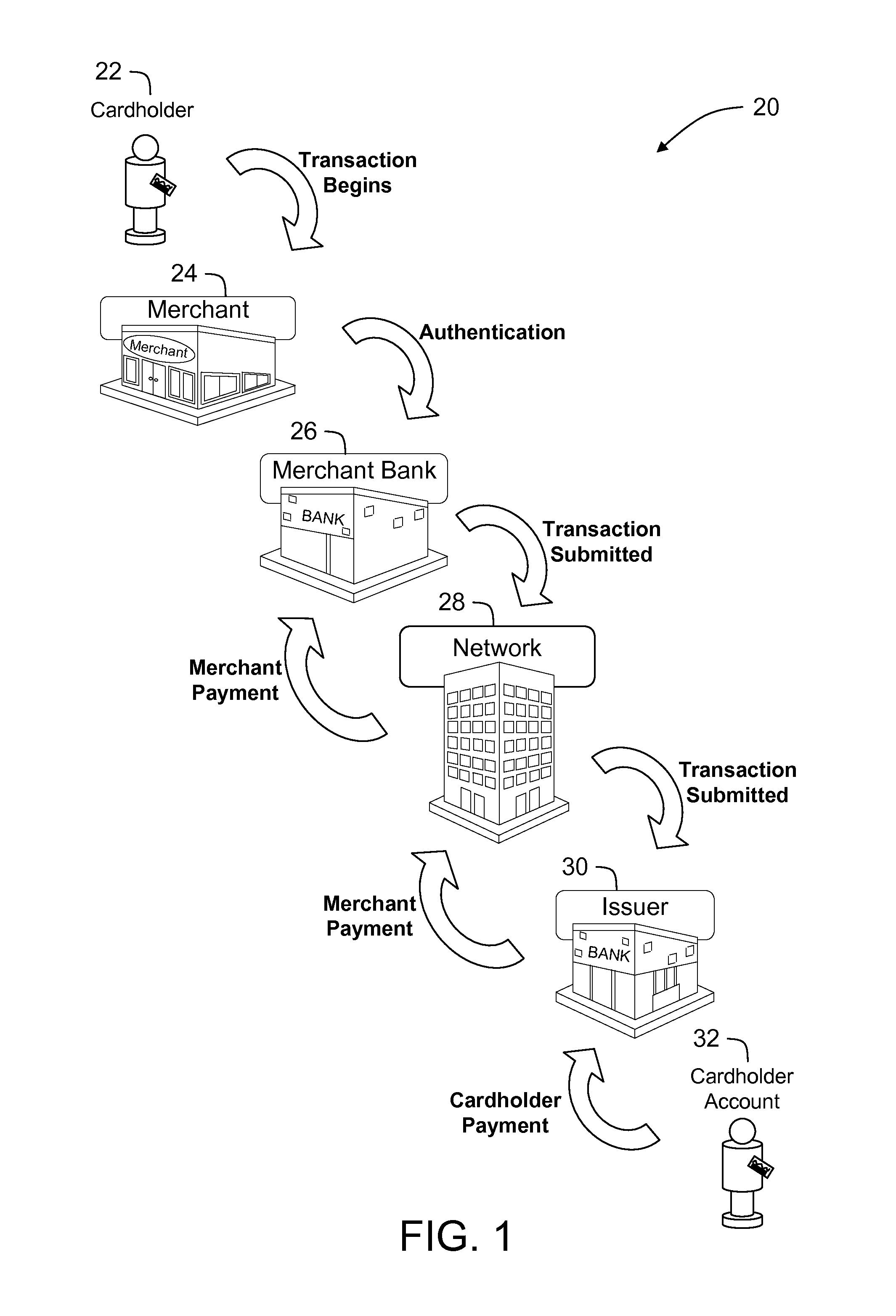
A method for processing a financial transaction using an interchange network computer coupled to a database is described. The transaction is initiated with a transaction card associated with a linked account. The method includes receiving, at the interchange network computer, a linked account data file for the first transaction card. The data file includes data associating the first card with a first secondary account and data linking the first secondary account to a first primary account. The method also includes storing the data file within the database and receiving a first authorization request message for the first transaction. The method also includes determining, based on data included within the first authorization request message, that the first card is associated with the first secondary account and processing the first authorization request message by applying at least one processing code associated with the first primary account to the first transaction.
Owner:MASTERCARD INT INC
Automatic software production system
InactiveUS20030167455A1Shorten the time to marketEasy to useDigital data information retrievalProgram documentationHandling CodeSystem requirements
An automated software production system is provided, in which system requirements are captured, converted into a formal specification, and validated for correctness and completeness. In addition, a translator is provided to automatically generate a complete, robust software application based on the validated formal specification, including user-interface code and error handling code.
Owner:IBORRA JOSE +1
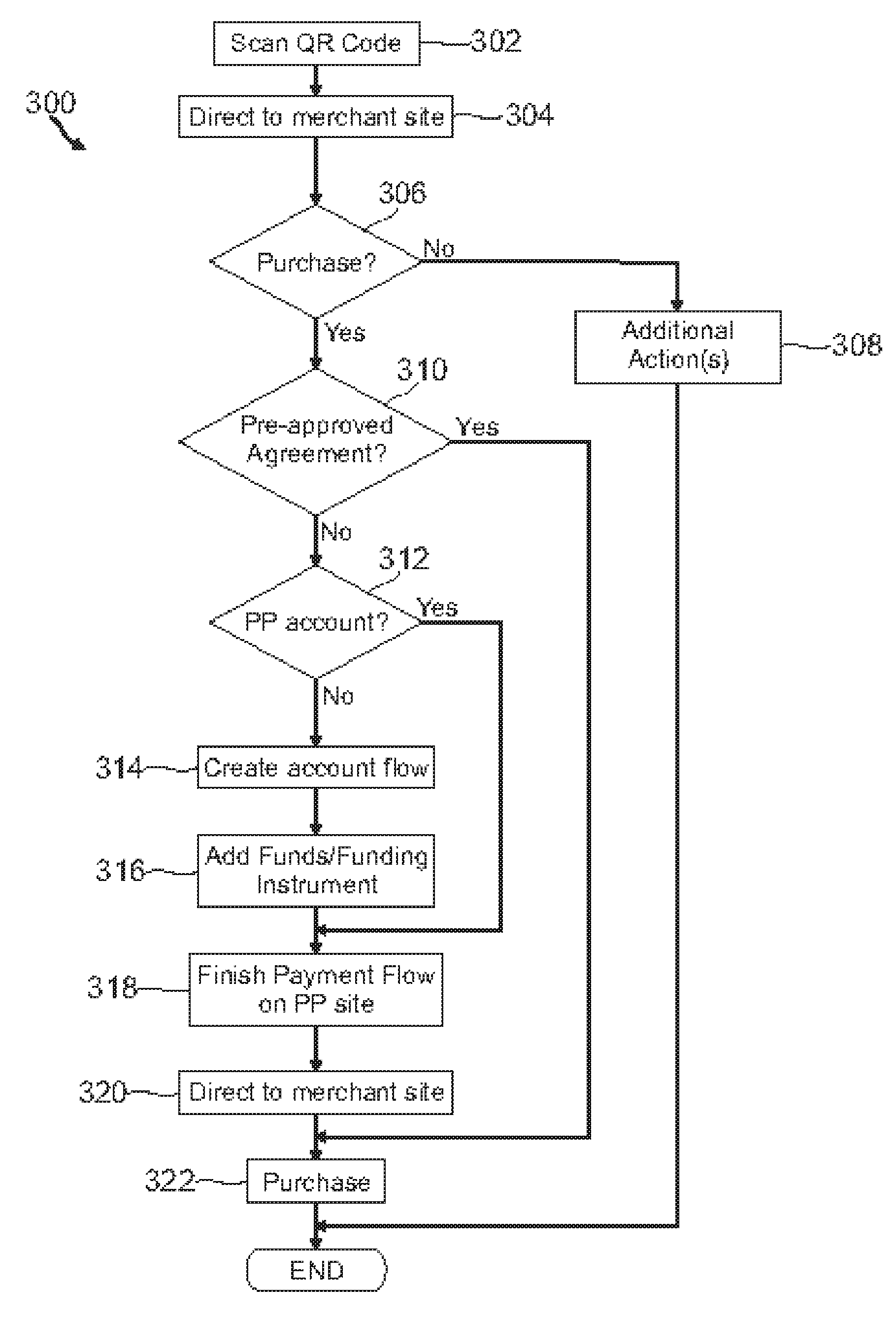
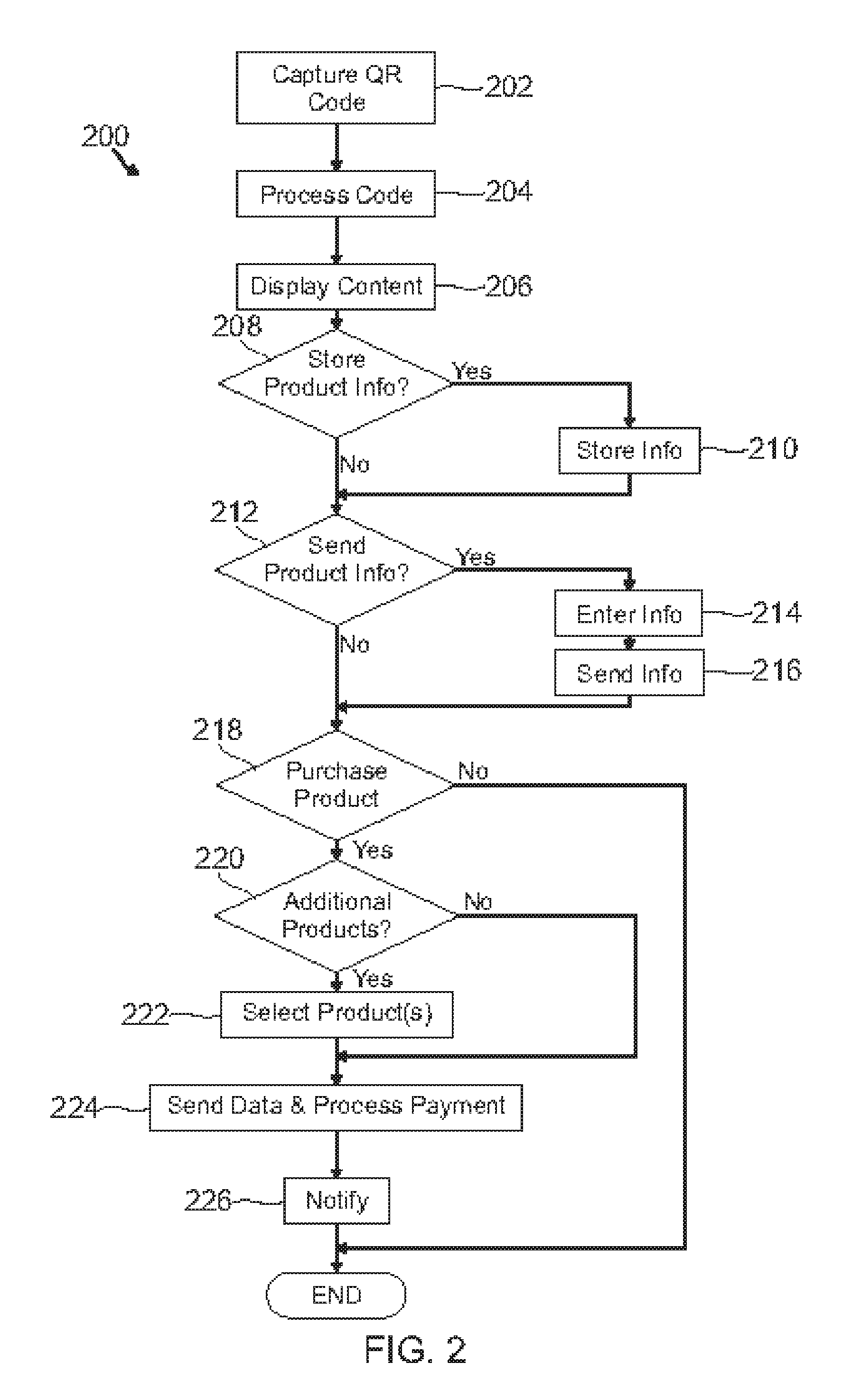
Payment using unique product identifier codes
InactiveUS20110137742A1Sufficient informationBuying/selling/leasing transactionsPayment circuitsPaymentHandling Code
Various methods and systems are provided to capture a unique product code, such as QR code, on a mobile device, process the information contained in the code, provide the user with options of making a purchase, including purchasing a plurality of selected products from different captured codes, and processing the payment via the user's mobile device.
Owner:PAYPAL INC
Code automatically generating device based on model component, system and method
InactiveCN101114226AClear structureEasy to implementSpecific program execution arrangementsHandling CodeComplete data
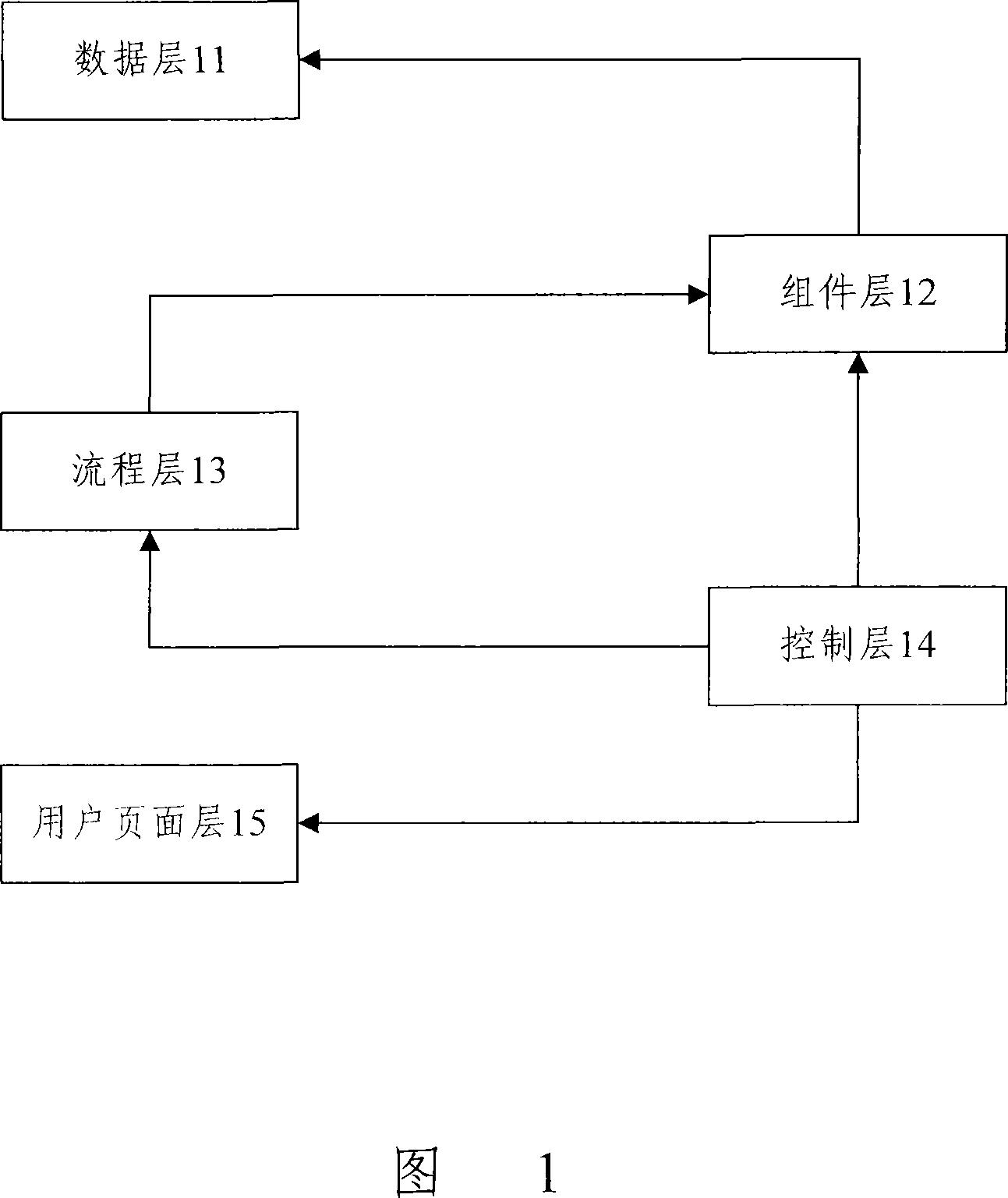
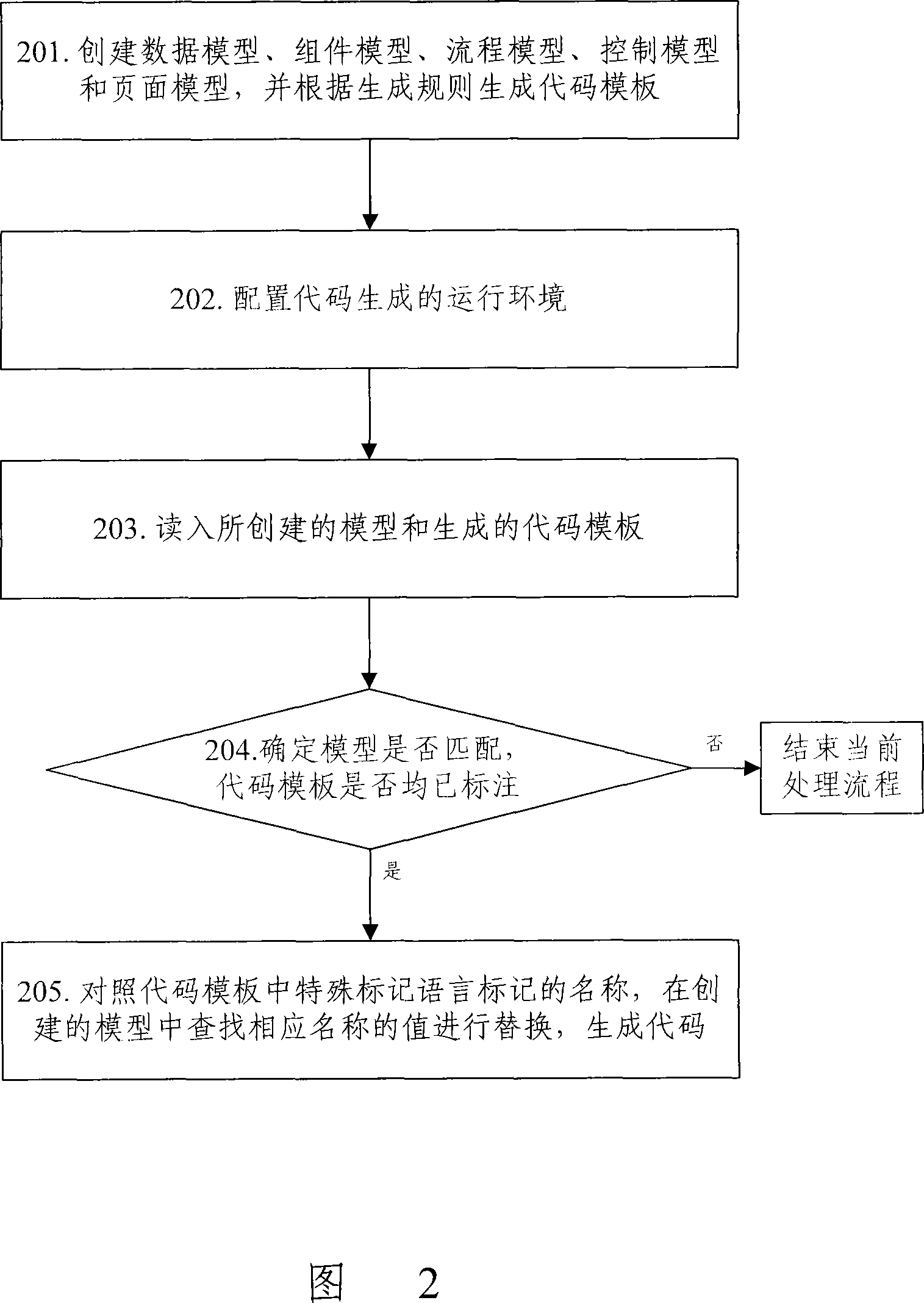
The invention discloses a code automatic generation method used for constructing a code automatic generation device, comprising a data layer, a component layer, a process layer, a control layer and a user interface layer, wherein, the five-layer structure is divided in accordance with functions, and every layer is independent and creates a corresponding processing model to complete data processing, component extraction, flow processing, function control and user interface processing. At the same time, a code template is created based on certain rules, and different processing codes are formed for different business objects. Based on the five-layer model and the code template, a code generating engine controls and calls the model of layers and the code template, which cooperate to complete the code automatic generation process. The invention also discloses a code automatic generation device and system; by adopting the invention, the development efficiency, the reusability and the standardization of software can be enhanced and code quality is improved.
Owner:北京中企开源信息技术有限公司
Method of and system for malicious software detection using critical address space protection
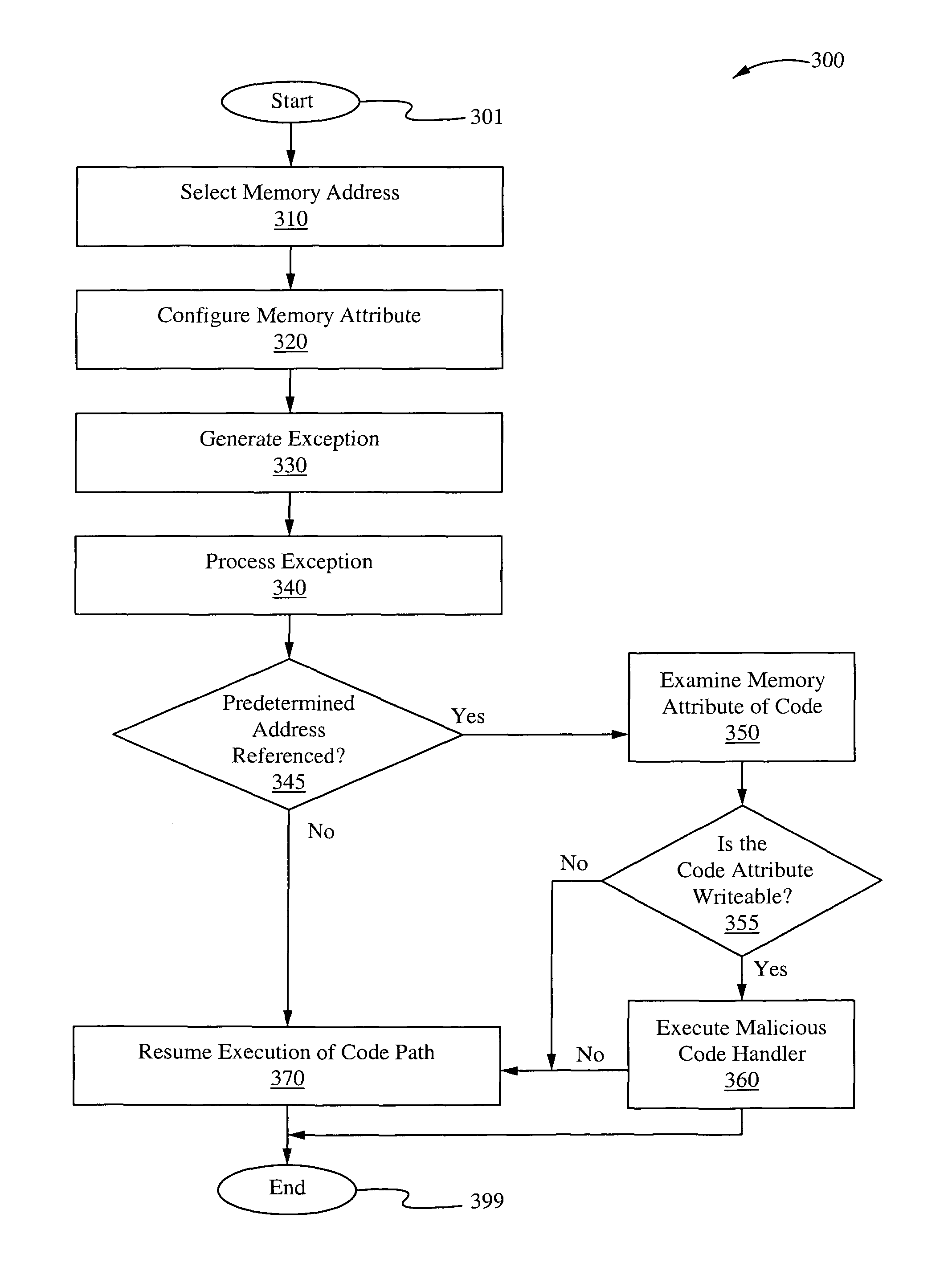
A method of identifying malicious code based on identifying software executing out of writable memory of the computer system. In one embodiment, the identification of the malicious code occurs when the code accesses a predetermined memory address. This address can reside in the address space of an application, a library, or an operating system component. In one embodiment, the access to the predetermined address generates an exception invoking exception handling code. The exception handling code checks the memory attributes of the code that caused the exception and determines whether the code was running in writeable memory.
Owner:MCAFEE LLC
Method and apparatus for analyzing machine control sequences
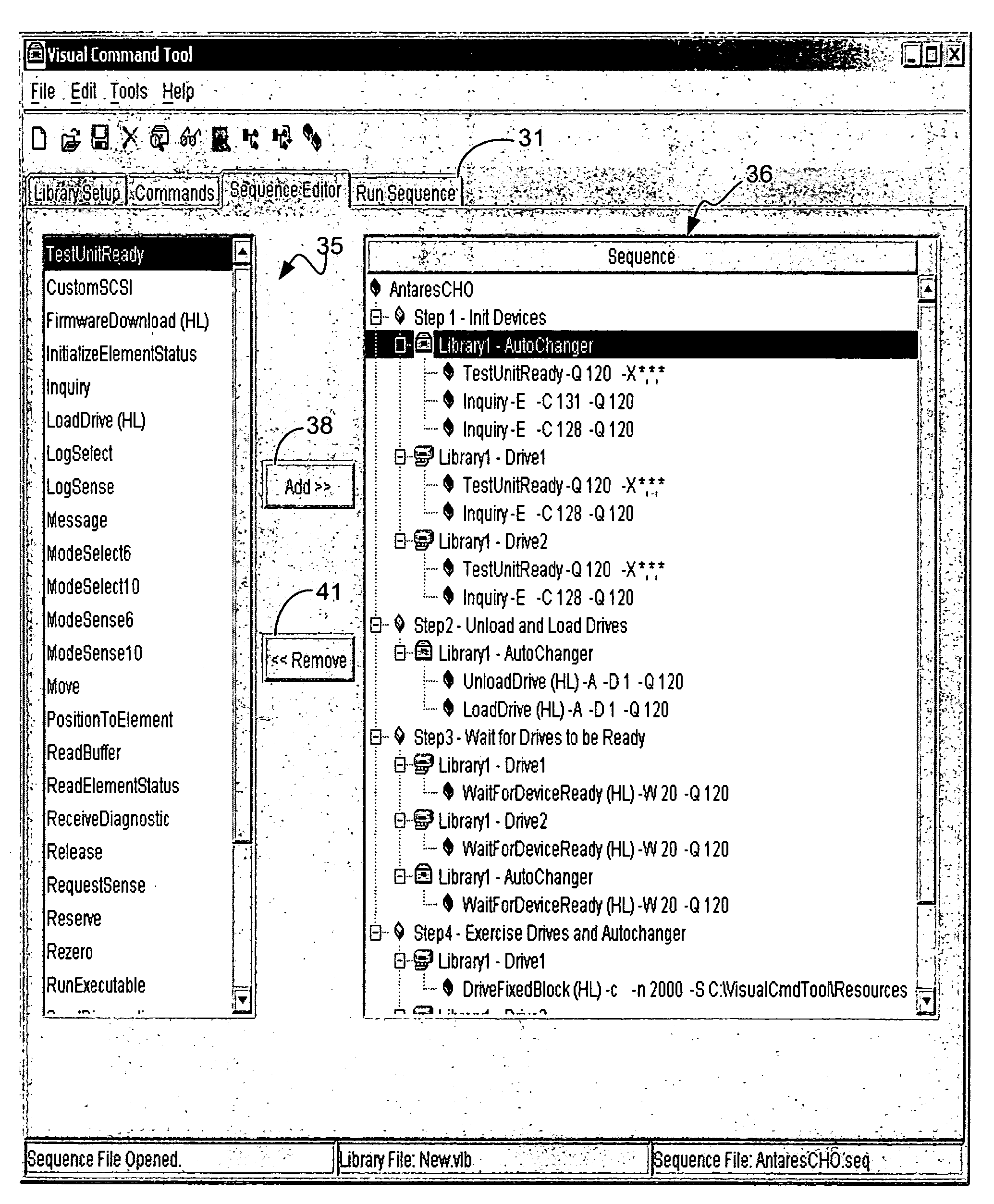
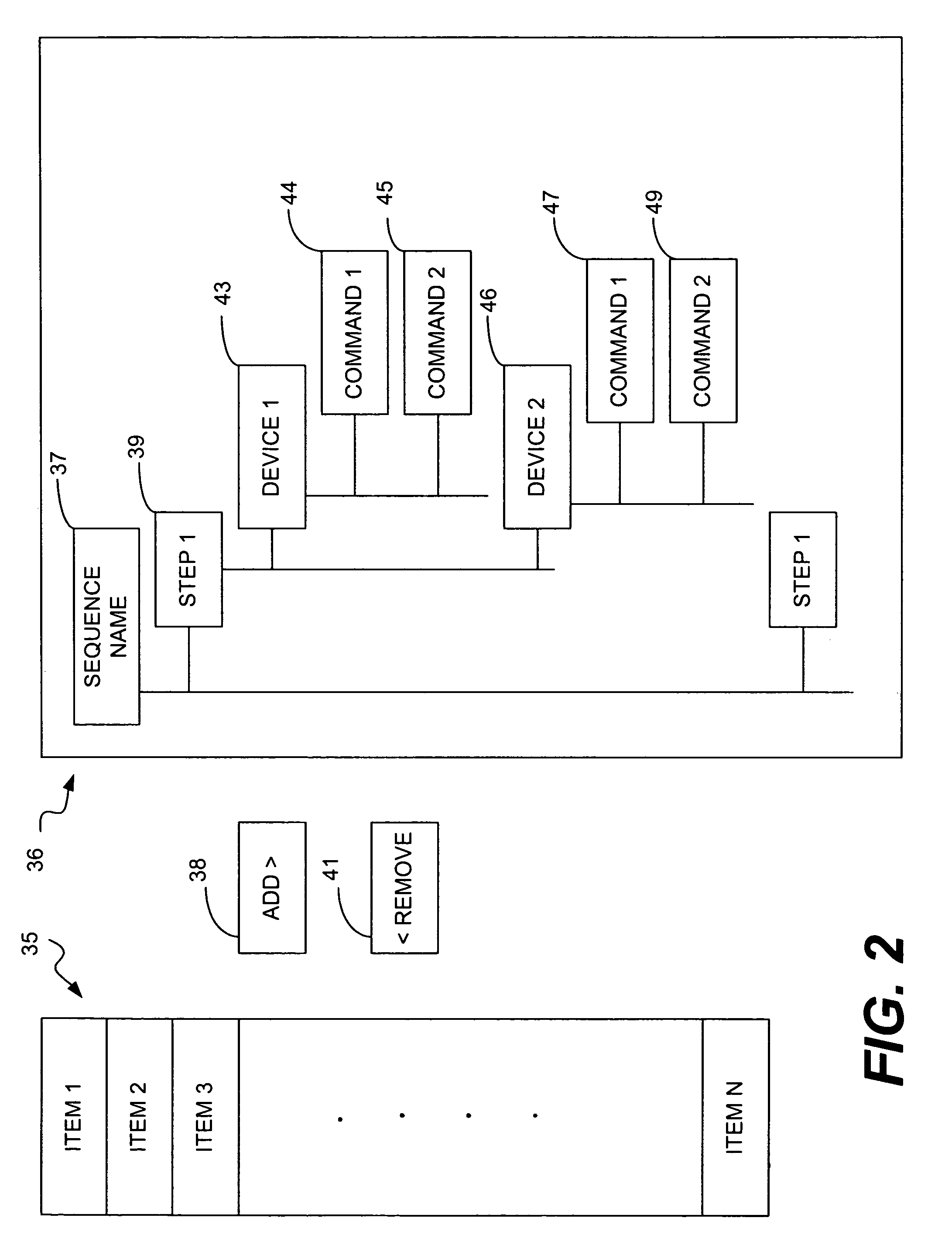
InactiveUS7367017B2Easy to analyzeEasy to understandCathode-ray tube indicatorsExecution for user interfacesGraphicsHandling Code
A graphical user interface (GUI) is provided that enables machine control sequences and the results of their execution to be easily and expediently analyzed. Logic is configured to execute GUI generation code and GUI user interaction handling code, and control a display device. When the logic executes the GUI generation code, a first window is displayed on the display device. The first window presents at least one option that enables a user to open a file comprising machine control sequence execution results resulting from execution of a machine control sequence. When the file is opened, a second window is displayed on the display device. The second window displays at least a summary of the execution results comprised in the file.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
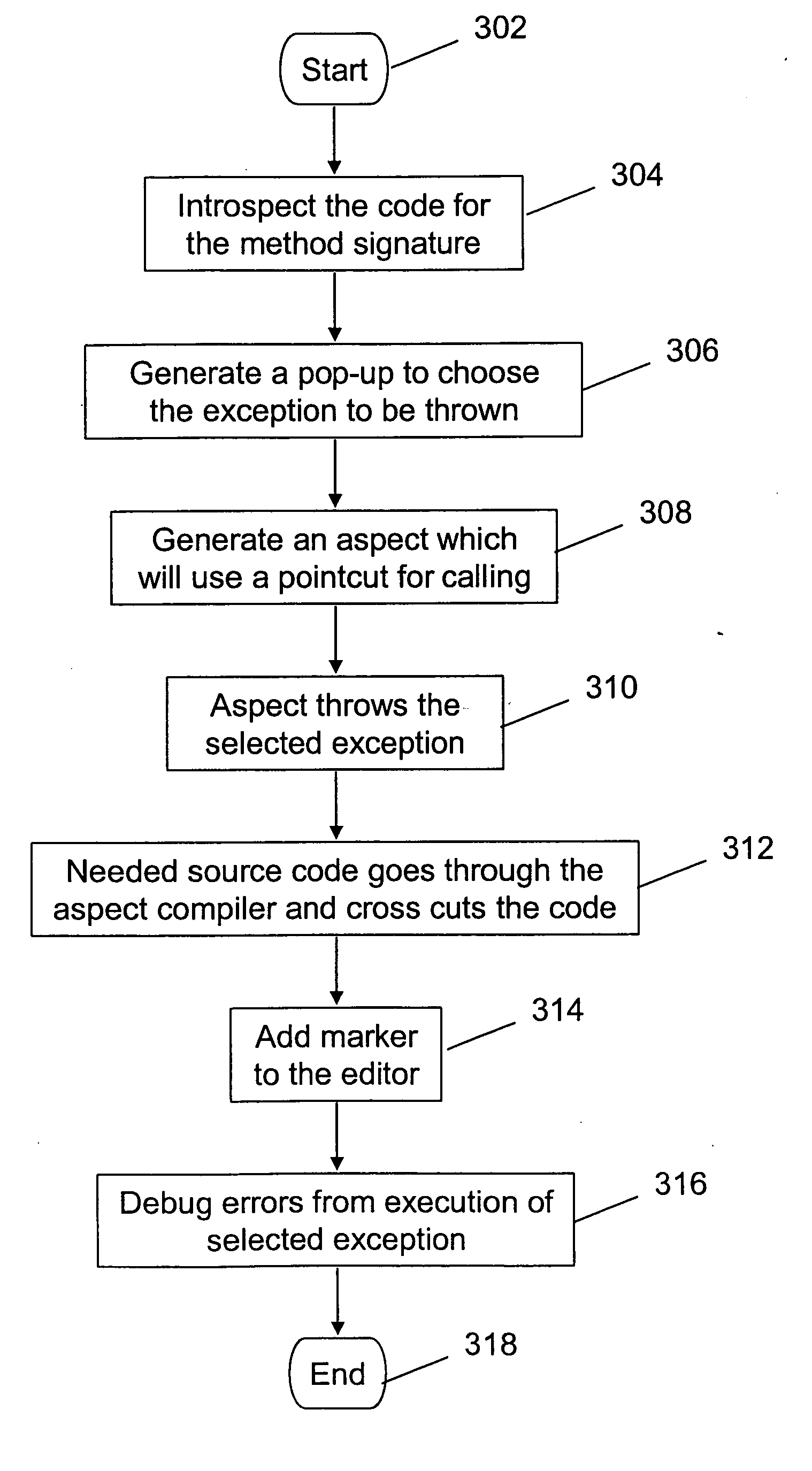
Exception thrower
InactiveUS20070162246A1Resistance/reactance/impedenceError detection/correctionComputer hardwareHandling Code
A method, apparatus and computer-usable medium for testing error handling code. The method includes selecting a method signature to be error tested; selecting an error associated with the method signature from a menu; generating an aspect to be used in a pointcut for an exception that is to be thrown for the selected error; invoking code that generates the selected error; and identifying resultant errors caused by a selected component of the selected error.
Owner:LINKEDIN
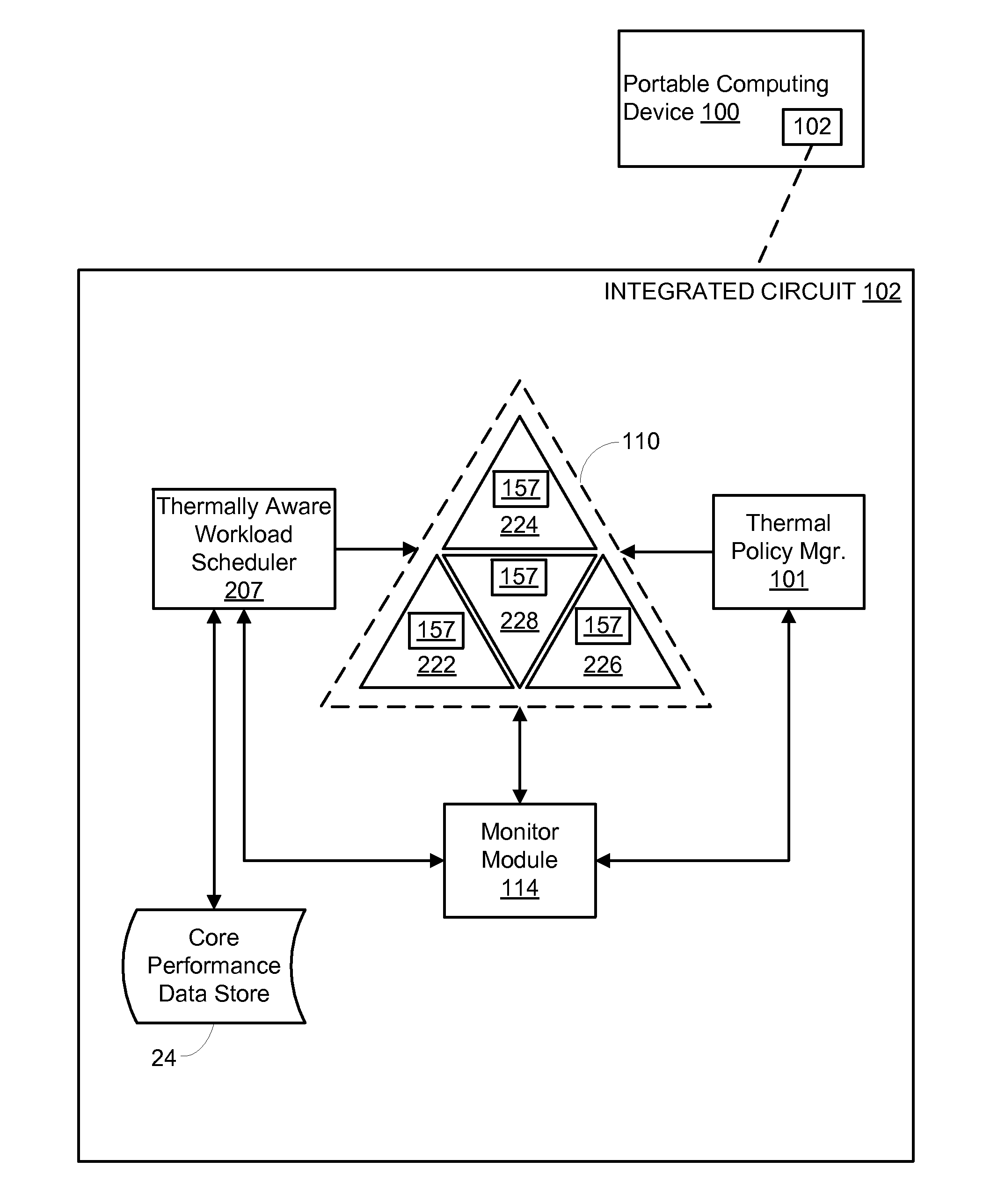
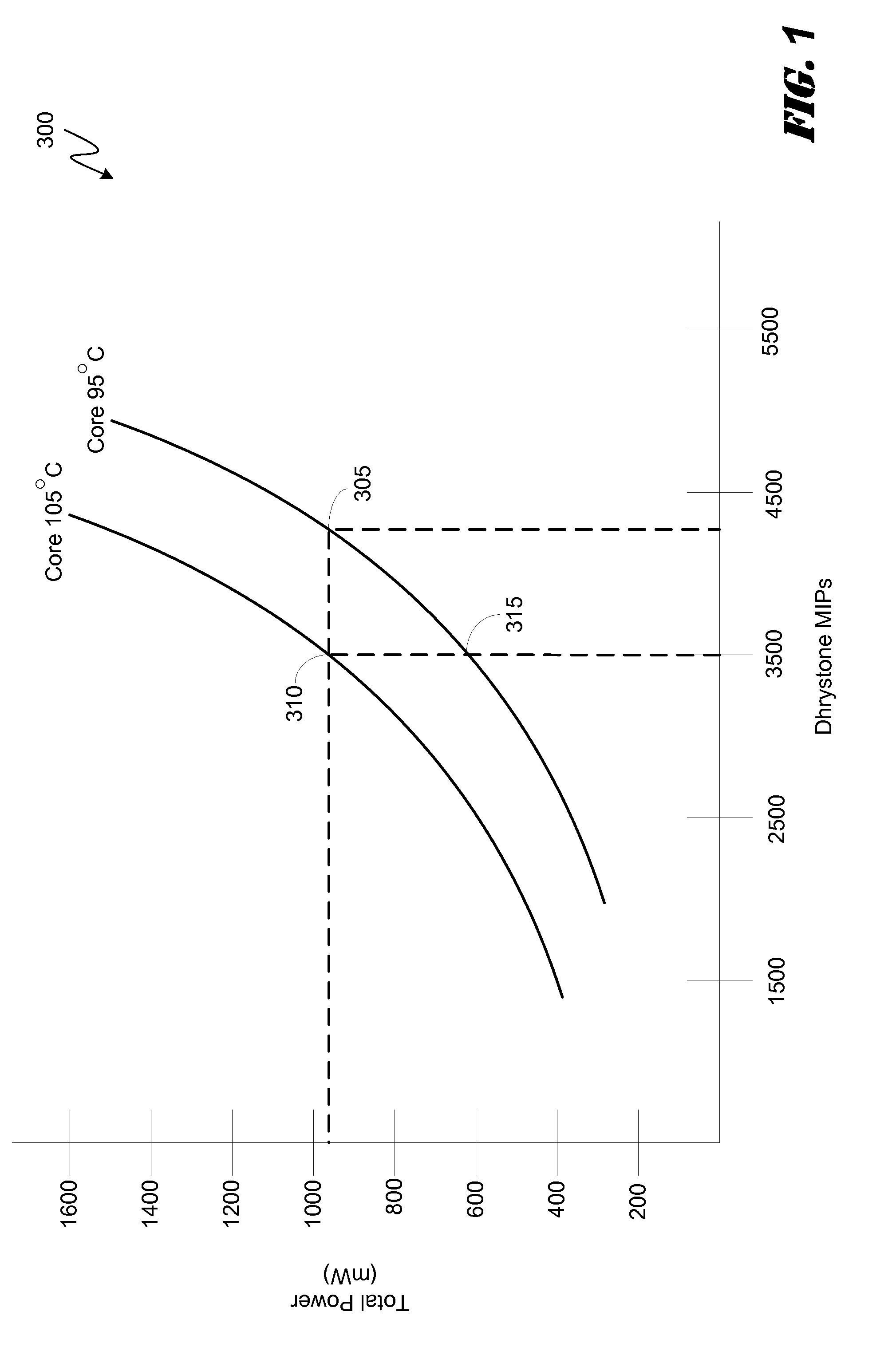
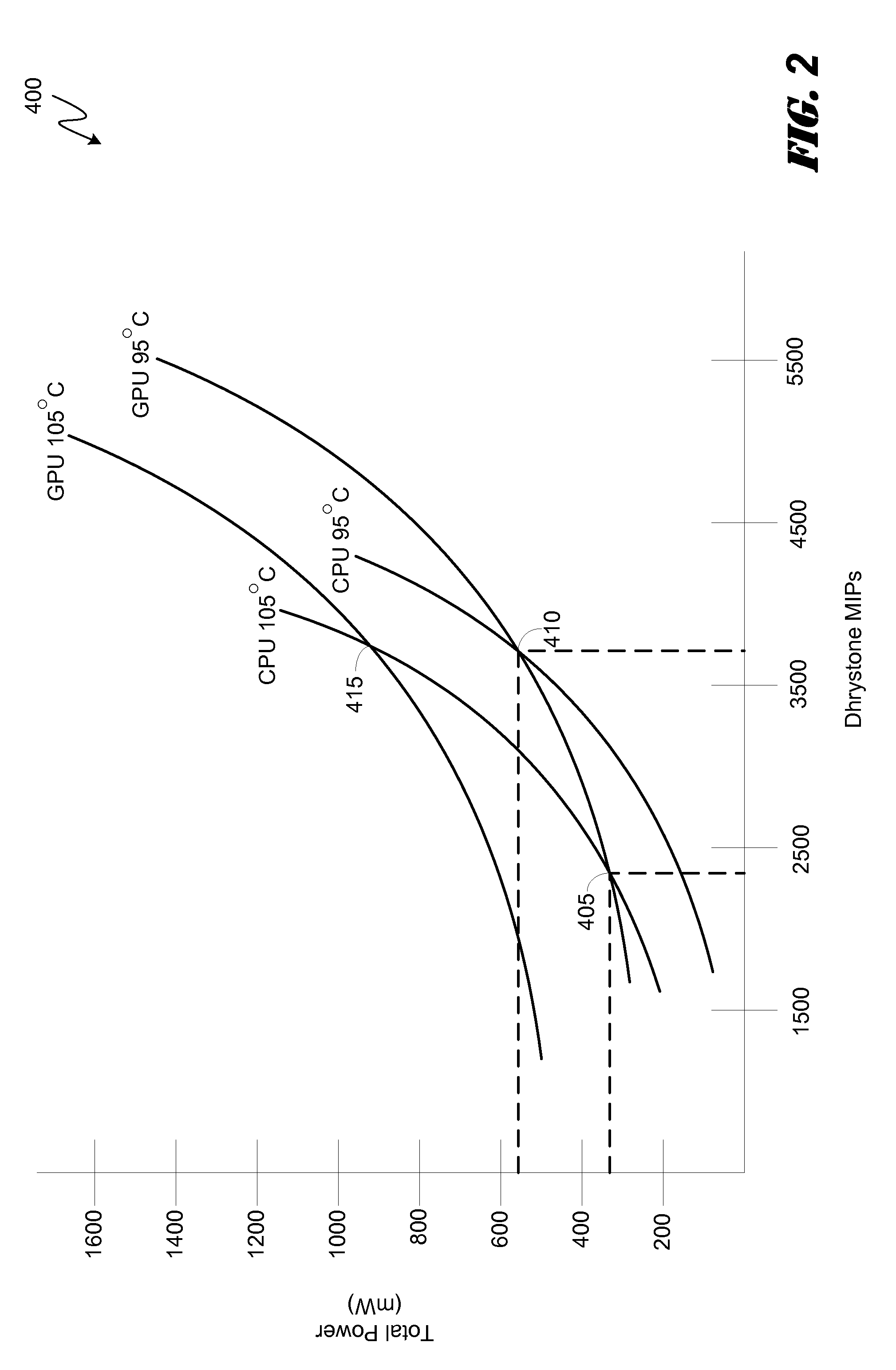
Thermally driven workload scheduling in a heterogeneous multi-processor system on a chip
ActiveUS20130132972A1Quality improvementHinder efficient processingEnergy efficient ICTError detection/correctionQuality of serviceHandling Code
Various embodiments of methods and systems for thermally aware scheduling of workloads in a portable computing device that contains a heterogeneous, multi-processor system on a chip (“SoC”) are disclosed. Because individual processing components in a heterogeneous, multi-processor SoC may exhibit different processing efficiencies at a given temperature, and because more than one of the processing components may be capable of processing a given block of code, thermally aware workload scheduling techniques that compare performance curves of the individual processing components at their measured operating temperatures can be leveraged to optimize quality of service (“QoS”) by allocating workloads in real time, or near real time, to the processing components best positioned to efficiently process the block of code.
Owner:QUALCOMM INC
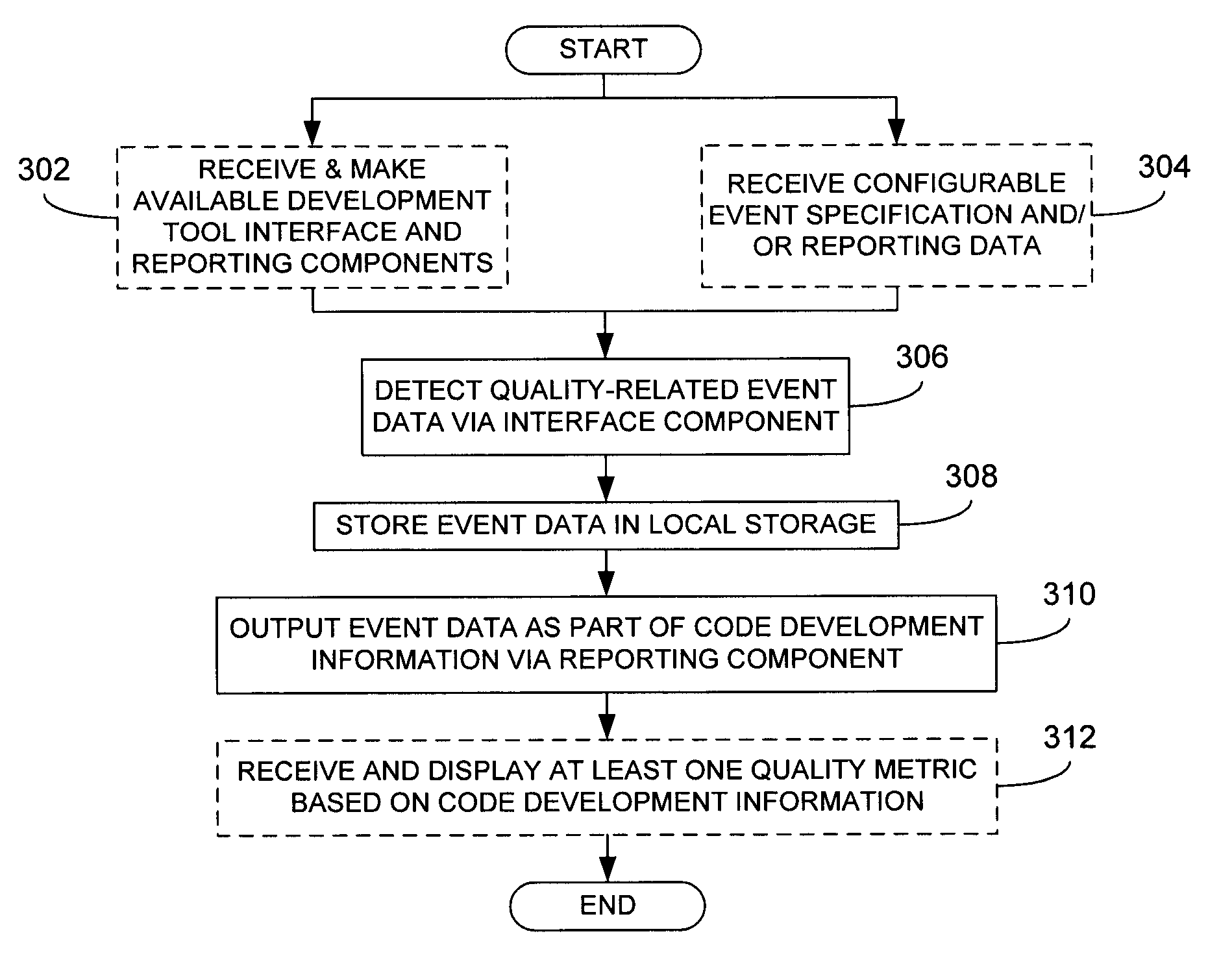
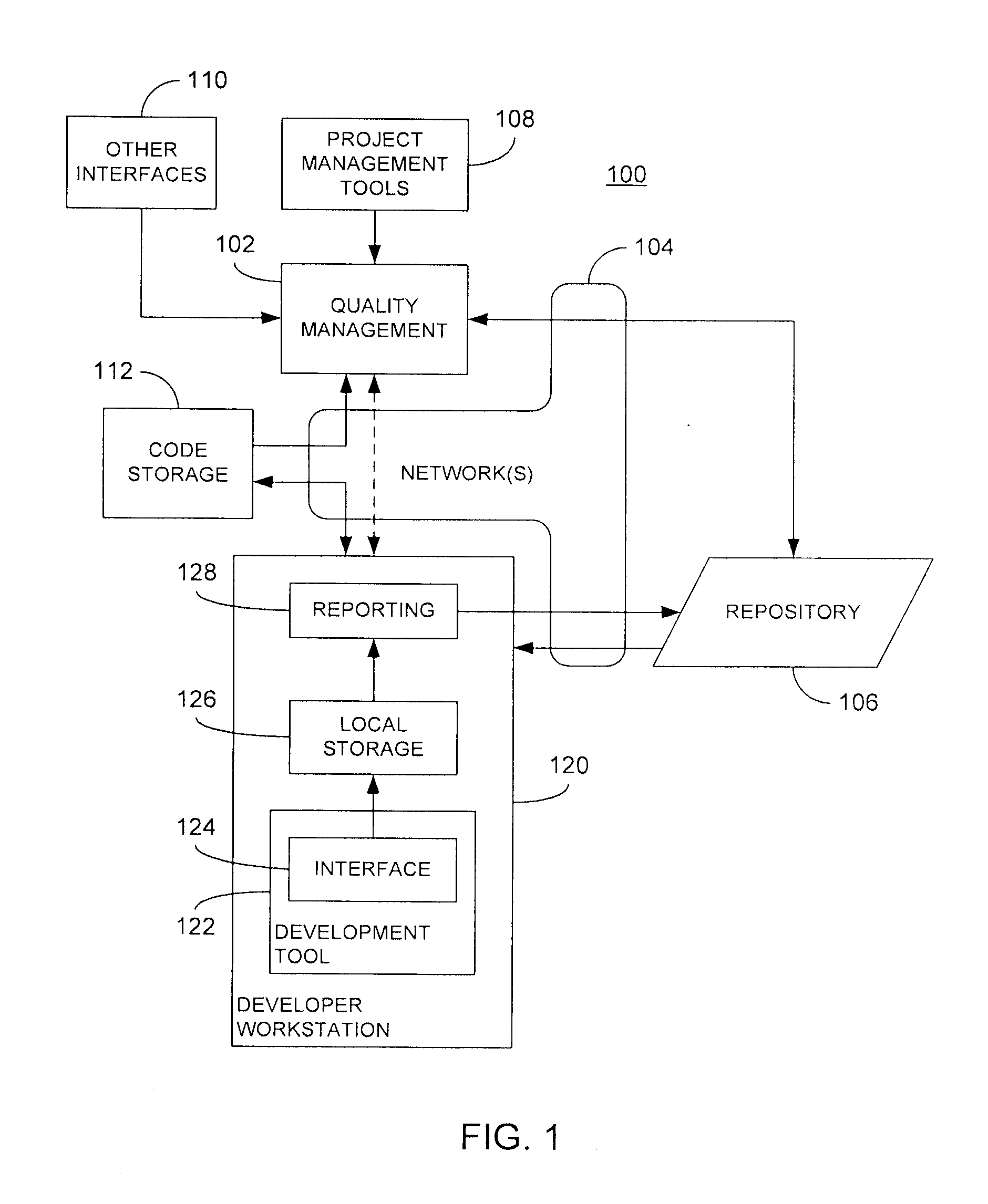
Collection and processing of code development information
ActiveUS20110055799A1Error detection/correctionSpecific program execution arrangementsHandling CodeDisplay device
Within each of a plurality of developer workstations contributing to a software development project, event data concerning at least one quality-related issue is collected via a development tool implemented by the developer workstation. The event data is stored locally and periodically output as at least part of code development information. The code development information is provided to a quality management component for subsequent processing, particularly the determination of one or more quality metrics. At least a portion of such quality metrics may be subsequently provided to the developer workstation for display on a suitable display device.
Owner:ACCENTURE GLOBAL SERVICES LTD
Stack memory selection upon exception in a data processing system
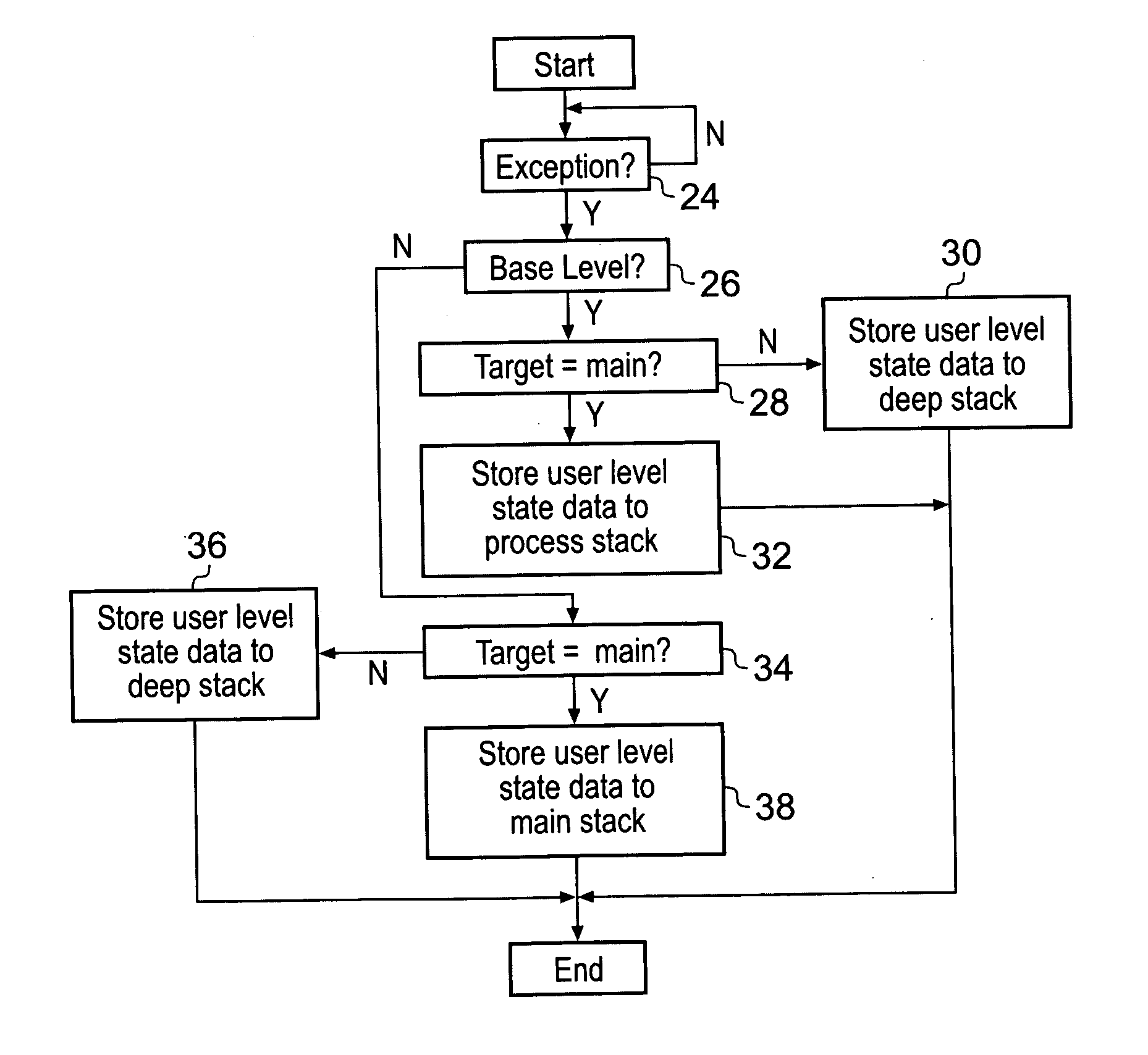
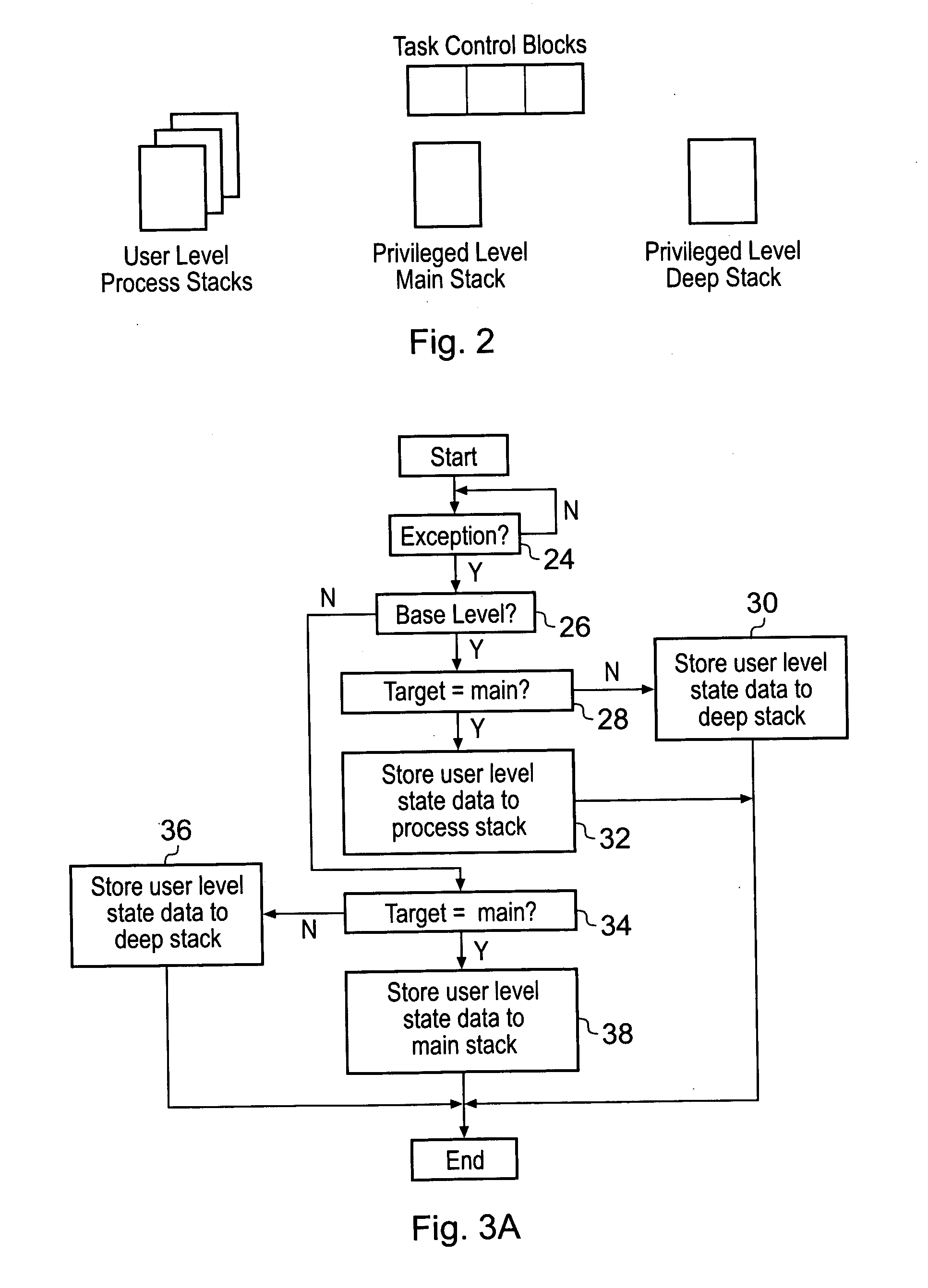
ActiveUS20070266374A1Reduce the possibilityReduce riskSpecific program execution arrangementsMemory systemsHandling CodeData processing system
A data processor 2 has privilege levels associated with it including a user level and a privileged level. The processor 2 also has multiple stack memories which can be used including one or more process stacks, a main stack and a deep stack. The stack memory to be used is de-coupled from the privilege level. An activation level state variable tracking the number of pending exceptions is held by the processor and used to modify which stack memory stores pending state values when an exception occurs. If the system is at a base level of activation, corresponding to currently no pending exceptions, then when an exception occurs the current state data is saved on the process stack with the main stack being available for the exception handling code. Particular exceptions can be flagged as requiring use of a deep stack rather than either the process stack or the main stack. If the system is not at the base level of activation, then the main stack is used to save state variables when an exception occurs rather than the process stack.
Owner:ARM LTD
System and method for memory management
InactiveUS20050188164A1Minimizing memory access latencyMaximizing and memory accessResource allocationMemory adressing/allocation/relocationHandling CodeParallel computing
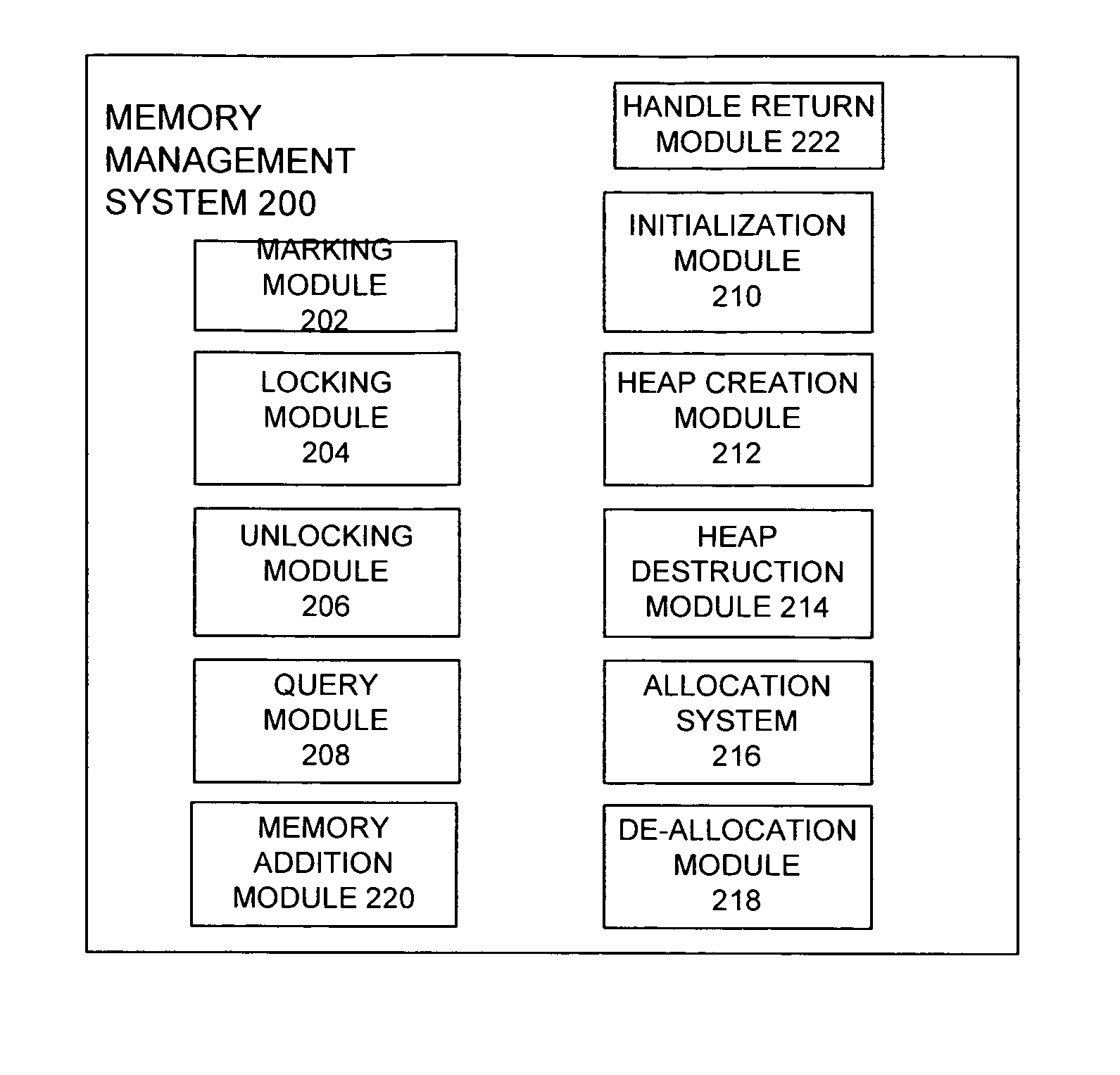
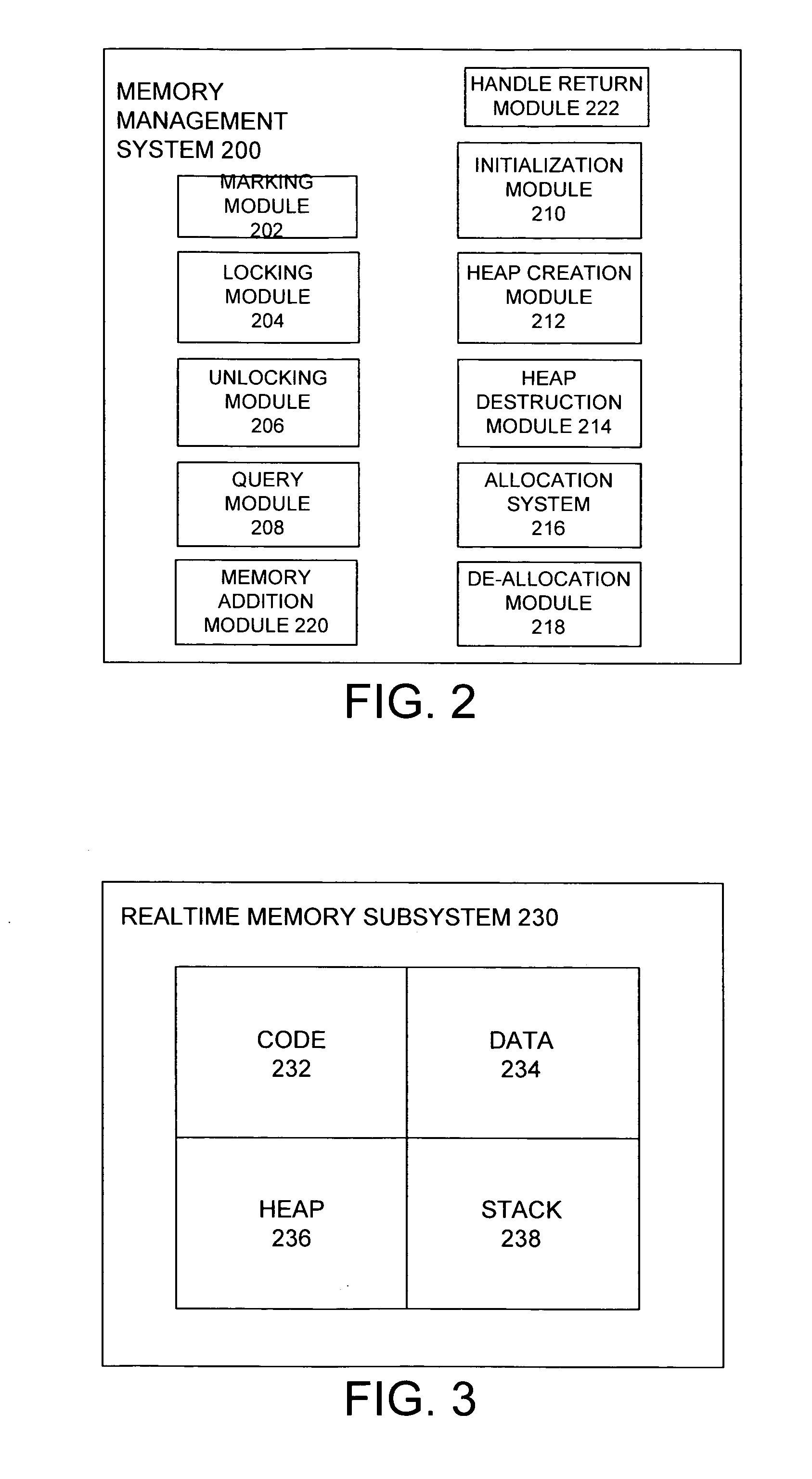
The present invention is directed to a method and system for minimizing memory access latency during realtime processing. The method includes a mechanism for marking information that will be accessed during realtime processing. The marked information may include code, data, heaps, stacks, as well as other information. The method includes support for locking down all of the marked information so that it is present in a computing machine's physical memory so that no page faults will be incurred during realtime processing. The method additionally enables realtime processing code to allocate and free memory in a non-blocking manner. It does so by enabling the creation of heaps for use during realtime processing, wherein each heap supports allocating and freeing memory in a non-blocking fashion. Each heap tracks freed memory blocks using individual non-blocking tracking lists for each memory block size supported by that heap. If a memory allocation request to a heap can be satisfied by using a memory block available on one of the lists of freed memory blocks, the method includes allocating the available memory block by popping the memory block from the tracking list. If no freed memory blocks of the desired size are available, then the method includes traversing a separate set of source memory blocks for that heap, and making the allocation in a non-blocking fashion from one of those blocks.
Owner:MICROSOFT TECH LICENSING LLC
Image coding and decoding apparatus, method of image coding and decoding, and recording medium for recording program for image coding and decoding
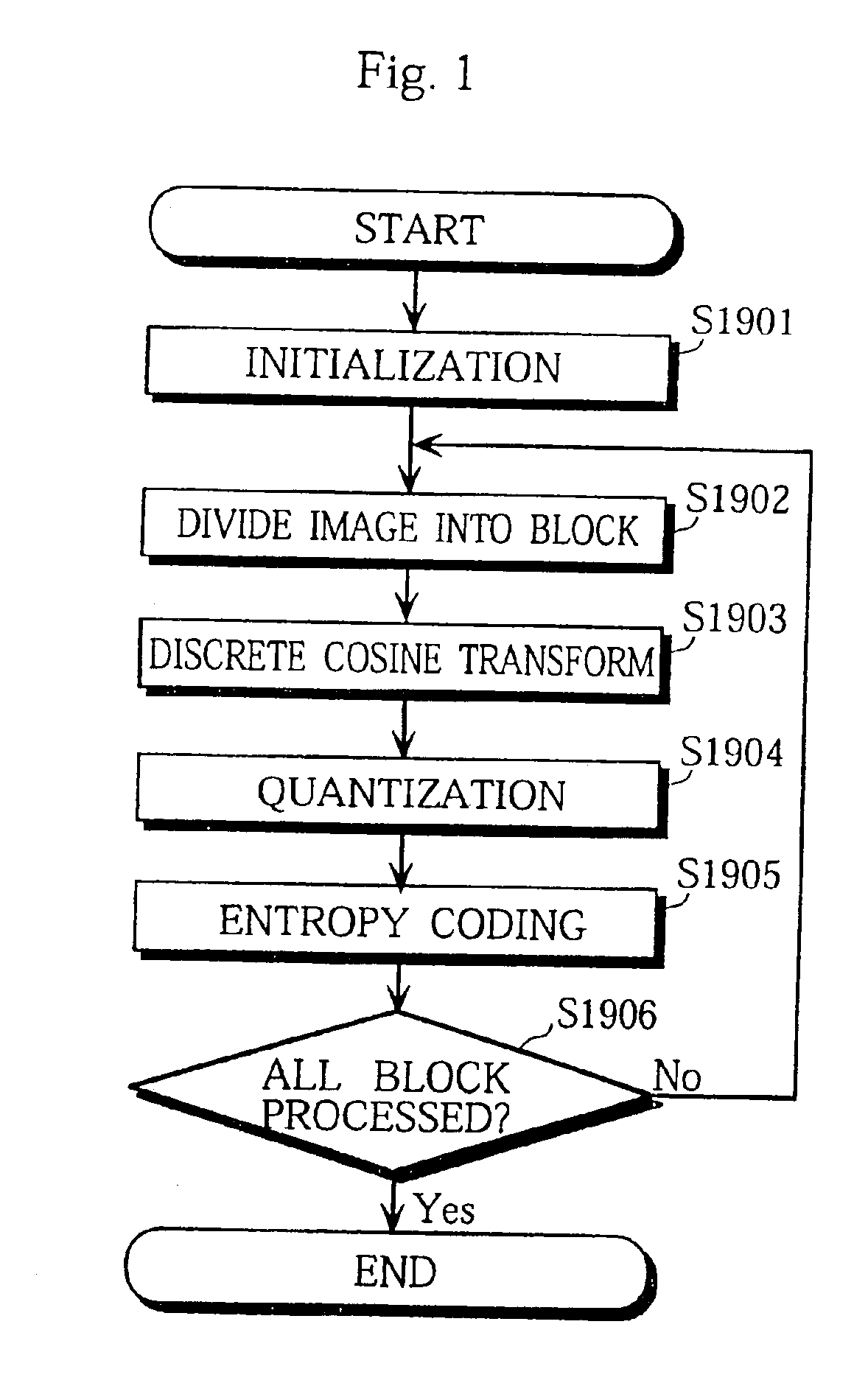
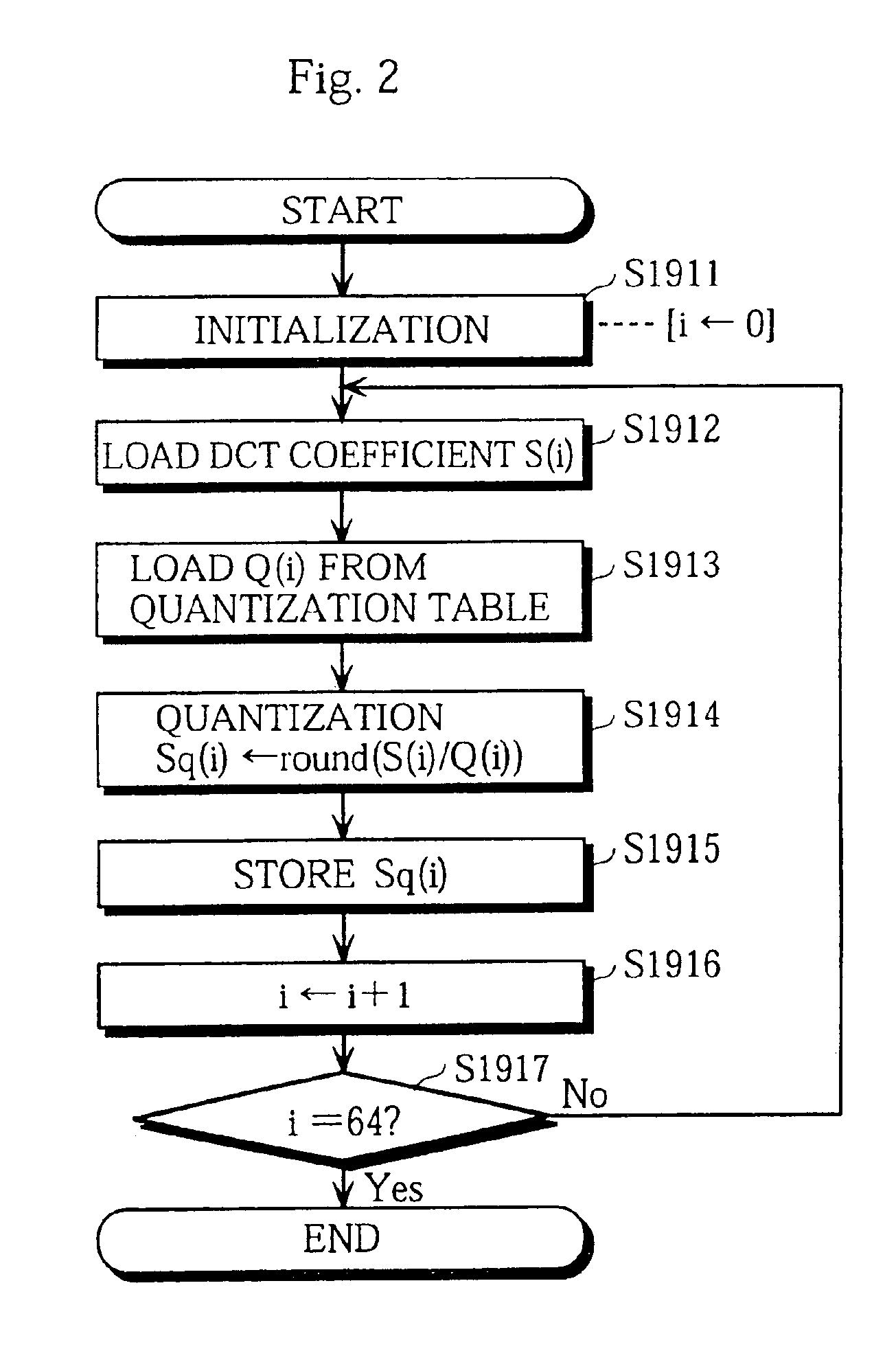
InactiveUS7079698B2Image degradationReduce processing timeCharacter and pattern recognitionImage codingHandling CodeComputer hardware
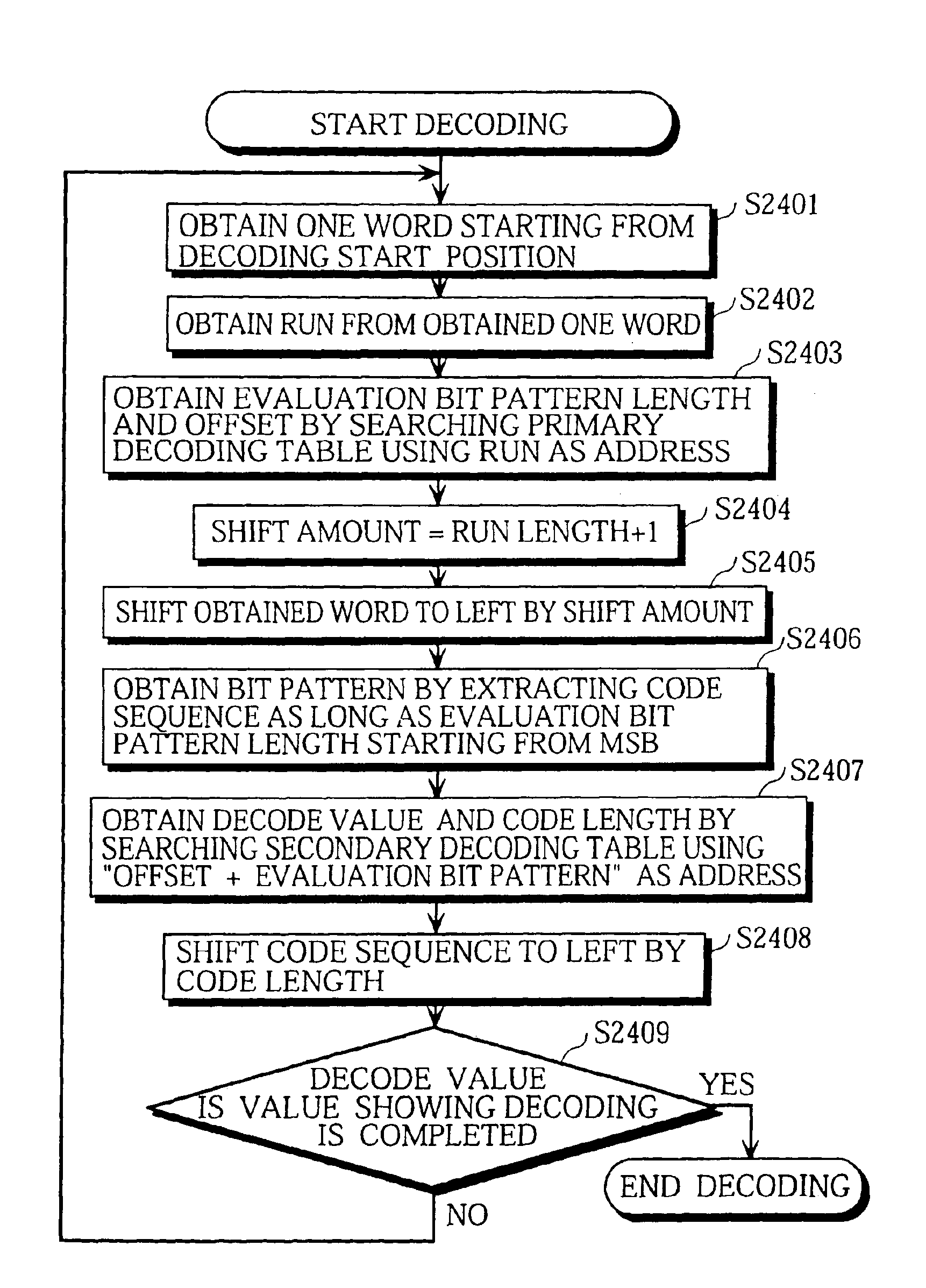
In an image decoding apparatus that generates a decoded image from a code sequence. The decoding apparatus has a bus, a computer and a memory, wherein the computer and the memory are connected to each other via the bus. The code sequence is generated by performing orthogonal transform, quantization and entropy coding on image data, which is stored in the memory. The decoding apparatus includes an entropy decoding unit, achieved by the computer, for reading one code out of the code sequence, which is stored in the memory, via the bus and performing entropy decoding on the read code in to generate a decode value. The apparatus also includes a coefficient generating unit, achieved by the computer, for generating at least one orthogonal transform coefficient according to the generated decode value. Also, a writing unit is achieved by the computer, for writing the generated at least one orthogonal transform coefficient into the memory via the bus. A decode controlling unit and the writing unit is provided for instructing the entropy decoding unit to process a next code out of the code sequence.
Owner:PANASONIC CORP
Image processing apparatus, control method therefor, and program
InactiveUS20110090534A1Reduce troublePromote recoveryDigitally marking record carriersDigital computer detailsProcessing InstructionHandling Code
An image processing apparatus includes a storage destination setting unit configured to set a storage destination for storing image data acquired by reading an image of a document by using a reading unit, an input unit configured to input first image data, which is acquired by reading an image of the document by using the reading unit, and second image data, which is acquired by reading an image of a document including a description of a processing instruction by using the reading unit, a determination unit configured to acquire processing instruction information by analyzing the second image data and to determine whether a description included in a processing target field of the first image data is appropriate according to processing target field information and a processing code included in the acquired processing instruction information, a transmission unit configured, if it is determined by the determination unit that the description in the processing target field is appropriate, to transmit the first image data to the storage destination set by the storage destination setting unit, a generation unit configured, if it is determined by the determination unit that the description in the processing target field is not appropriate, to generate processing instruction information to be used in re-storage processing including the storage destination, and an output unit configured to output data including the processing instruction information generated by the generation unit to a printing unit.
Owner:CANON KK
Authenticating a Remote Host to a Firewall
InactiveUS20110252462A1Easy maintenanceDigital data processing detailsUser identity/authority verificationHandling CodeTimer
A computer implemented method, system, and computer program product for authenticating a remote host to a firewall. The illustrative embodiments allow a requesting host separated from a target host by a firewall to determine, based on exception handling code, that an original request sent to the target host has been intercepted and blocked by the firewall. The illustrative embodiments also allow the requesting host to automatically provide credentials that authenticate the requesting host to the firewall. The illustrative embodiments are particularly applicable in situations when requests are invoked without any user interaction, such as when a timer expires. In such a case, there is no user to provide the needed credentials to authenticate the requesting host. The illustrative embodiments enable a requesting host to access a target host without requiring user intervention.
Owner:IBM CORP
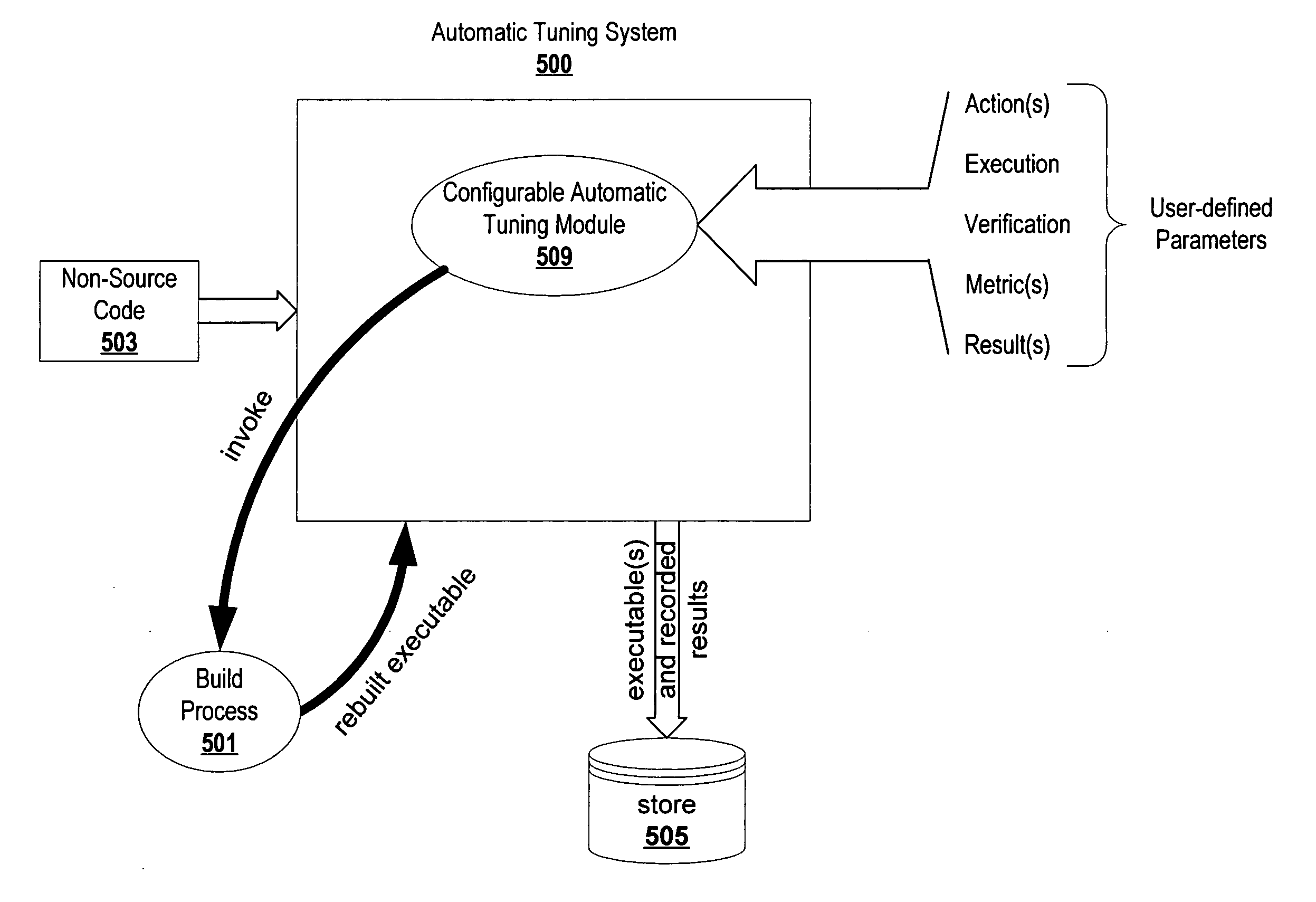
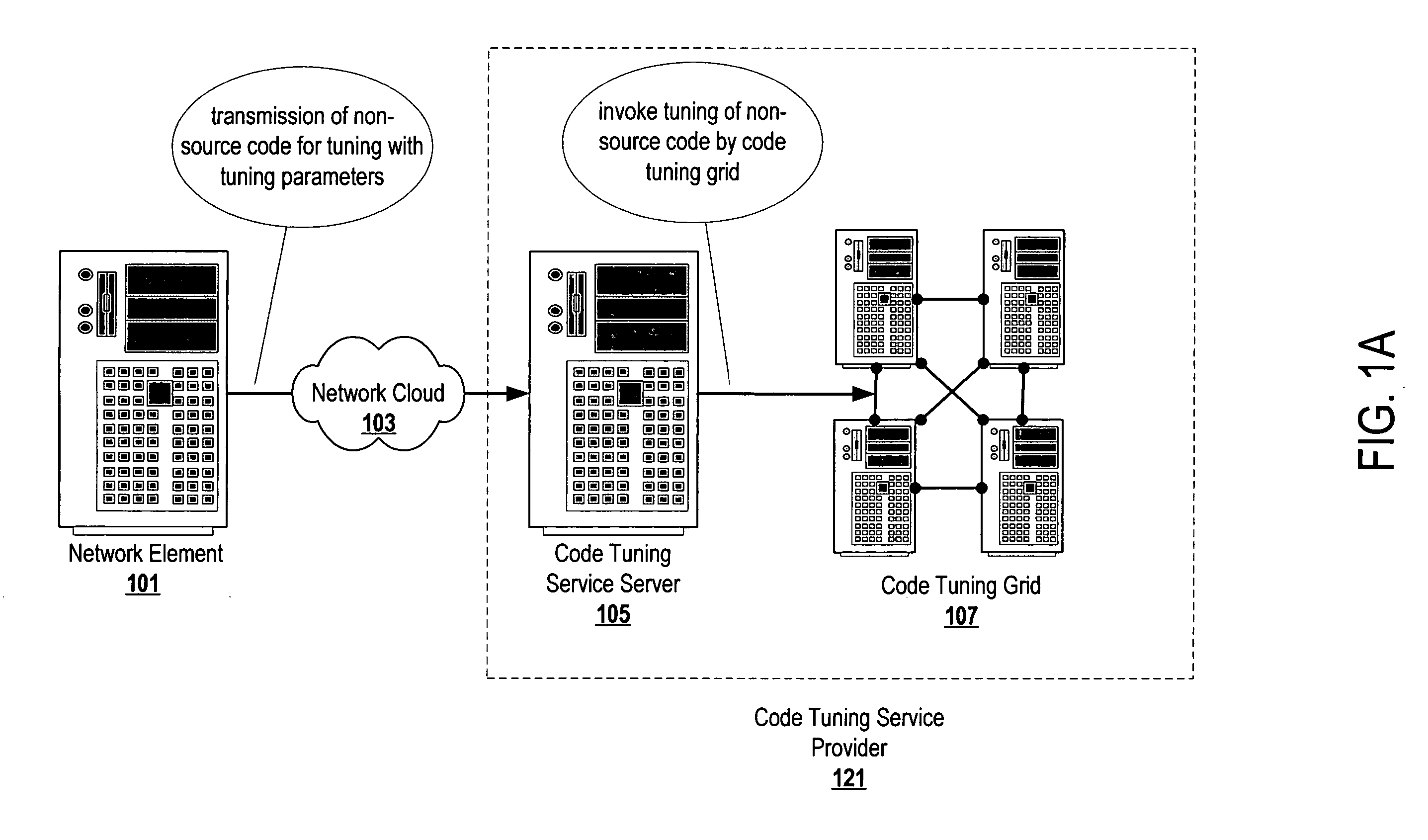
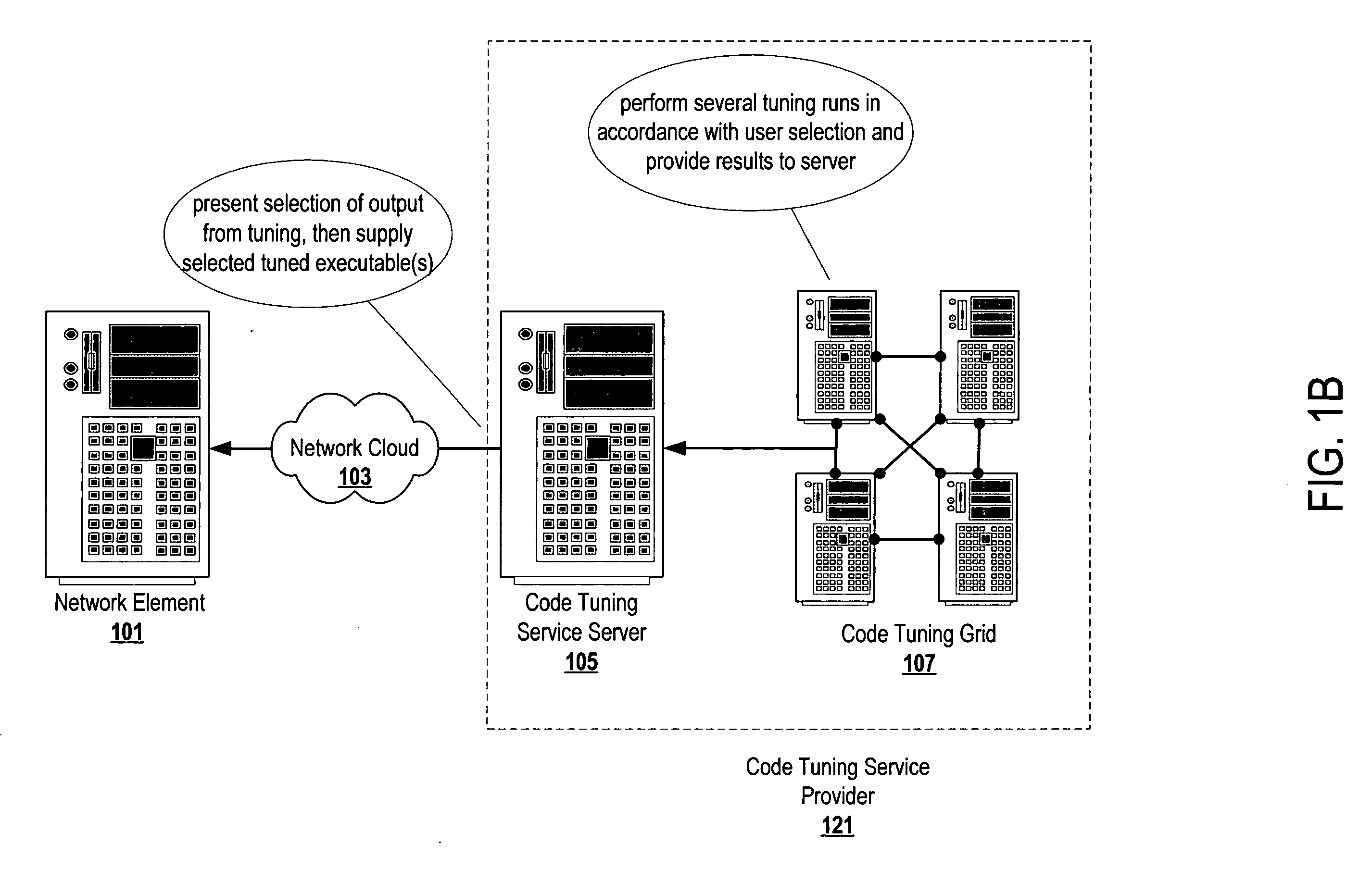
Automatic code tuning
ActiveUS20070061784A1Error detection/correctionSpecific program execution arrangementsHandling CodeParallel computing
Automatically executing commands to process code (e.g., compile commands, interpret commands, etc.) and recording code characteristic metric values (e.g., file size, execution time, etc.) allows automatic code tuning. The automatic turning system may execute predefined commands on codes, automatically intelligently build commands, both execute predefined commands and intelligently build upon those predefined commands, etc. With the automatic intelligent building of commands to build more effective commands, an automatic tuning system can efficiently and judiciously search through available code development tool options to find the more effective combinations of options to generate executable codes.
Owner:ORACLE INT CORP
Buffer management in a network device without SRAM
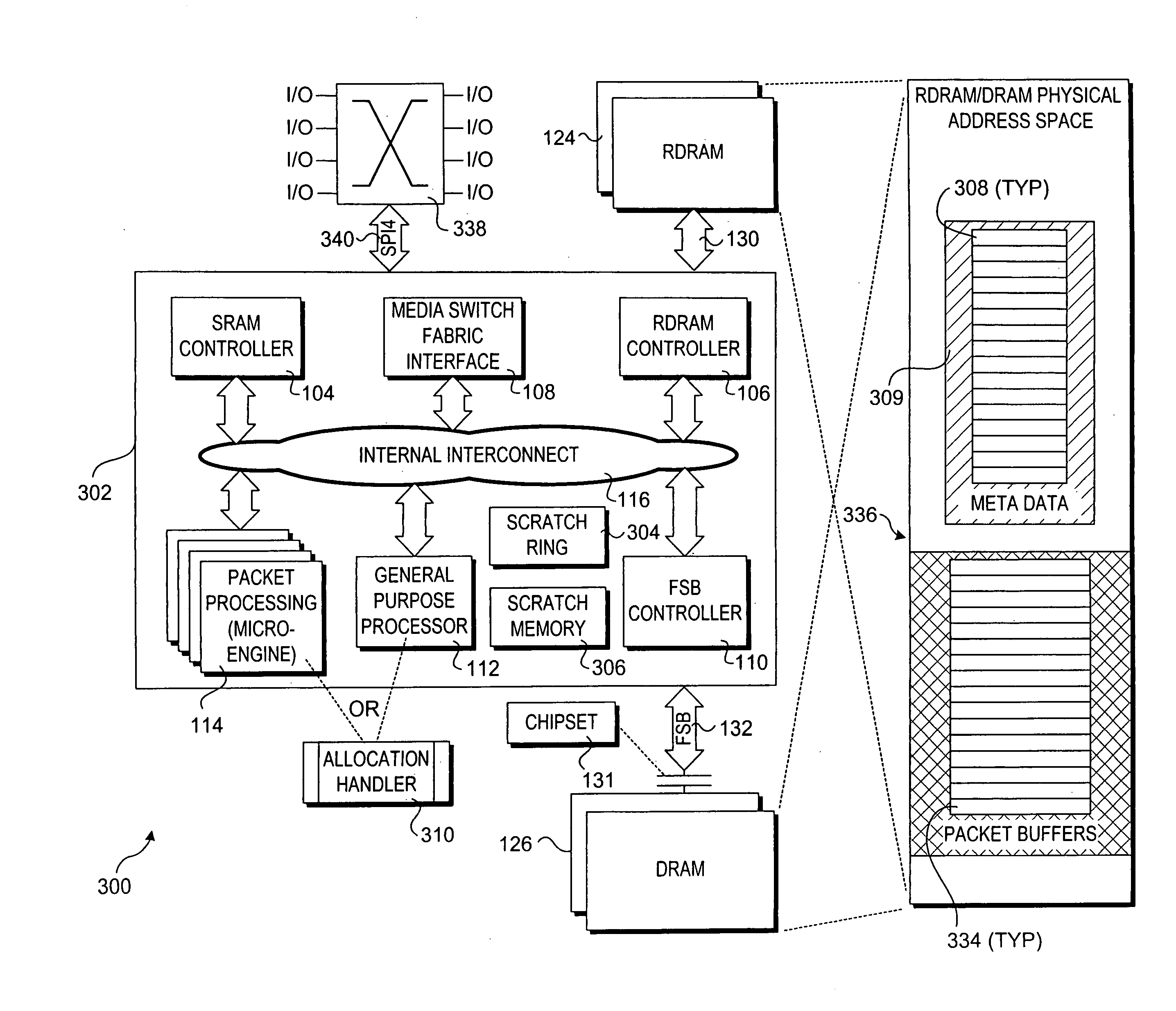
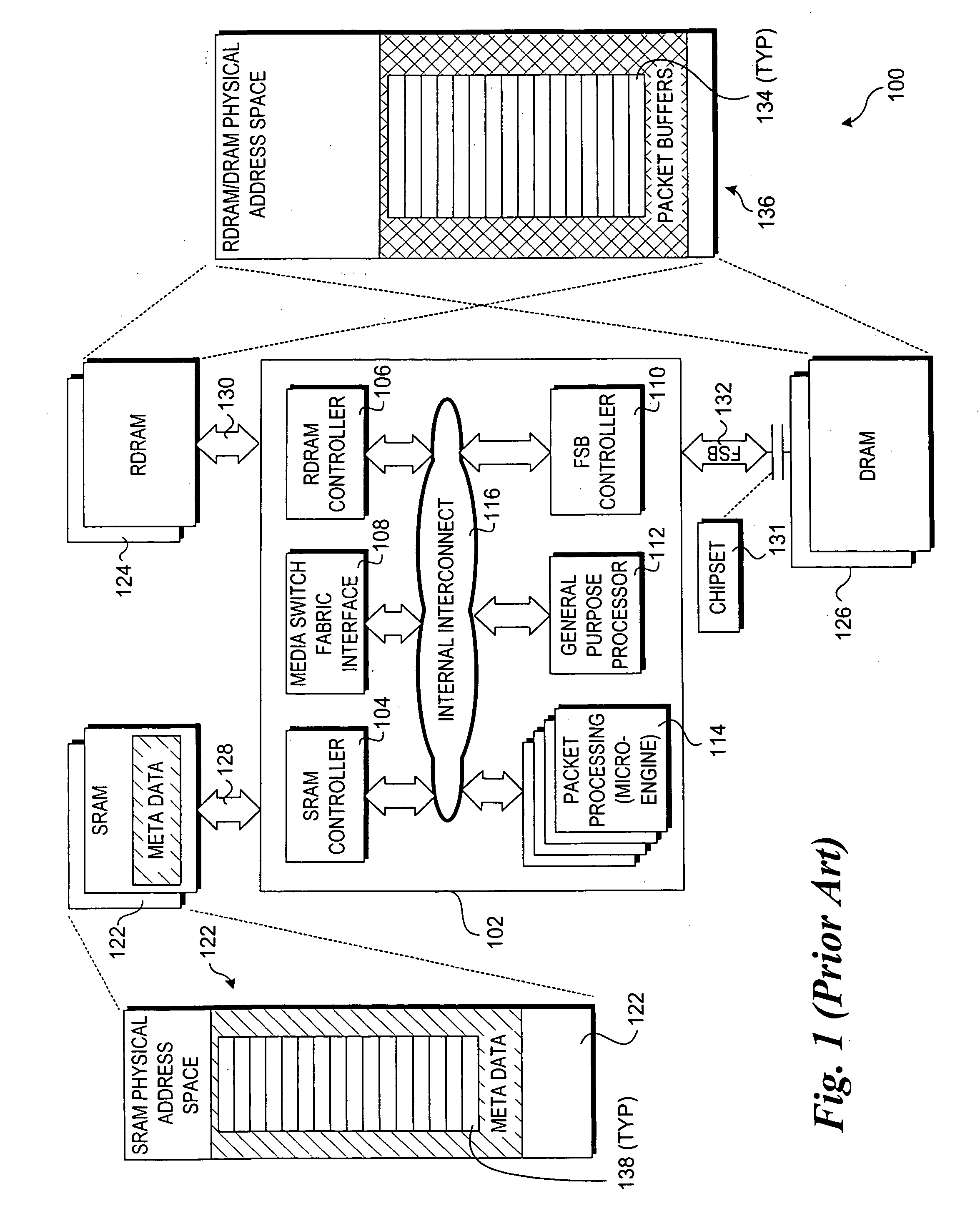
InactiveUS20060031628A1Memory loss protectionMultiple digital computer combinationsHandling CodeStatic random-access memory
A technique for performing buffer management on a network device without using static random access memory (SRAM). In one embodiment, a software-based buffer management scheme is used to allocate metadata buffers and packet buffers in one or more dynamic random access memory (DRAM) stores. As metadata buffers are allocated, pointers to those buffers are entered into a scratch ring. The metadata buffers are assigned for corresponding packet-processing operations. In one embodiment, metadata buffers are added in groups. A freed buffer count is maintained for each group, wherein a new group of buffers may be allocated if all buffers for the group have been freed. In one embodiment, the technique is facilitated by an application program interface (API) that contains buffer management functions that are callable by packet-processing code, wherein the are names and parameters of the API functions are identical to similar functions used for conventional buffer management operations employing SRAM.
Owner:INTEL CORP
Non-aligning access and storage processing method
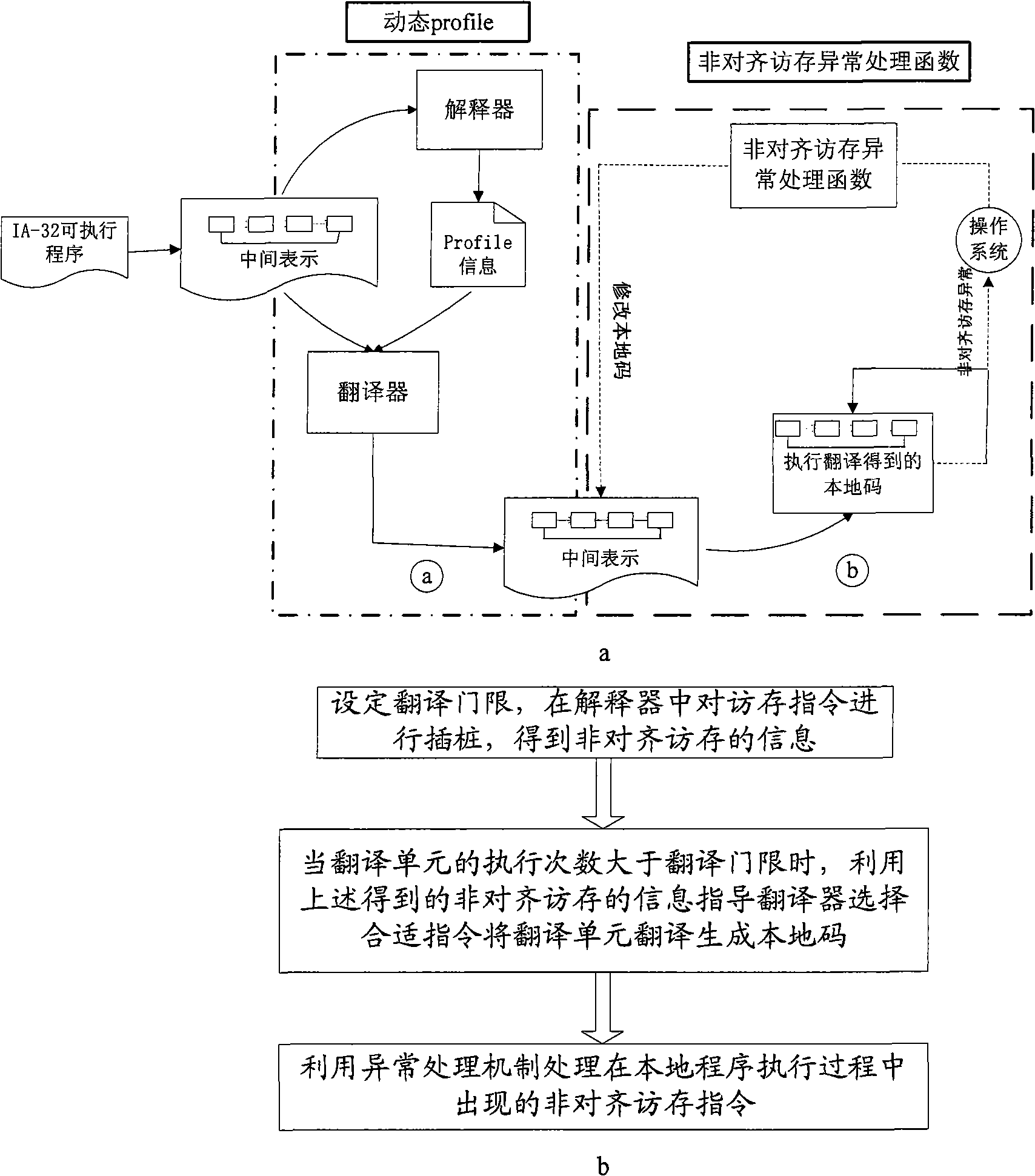
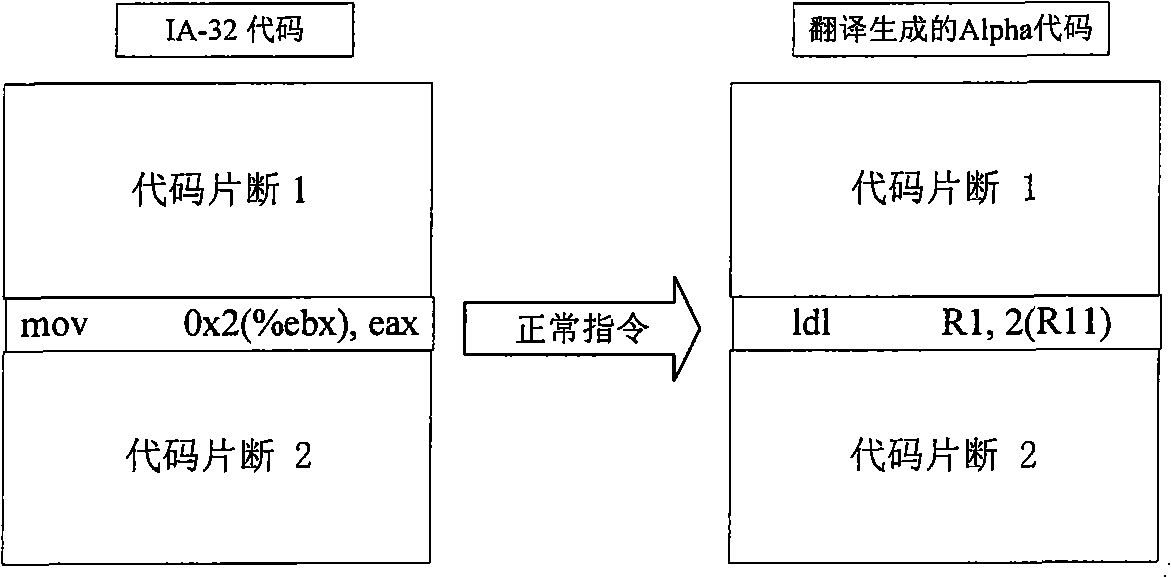
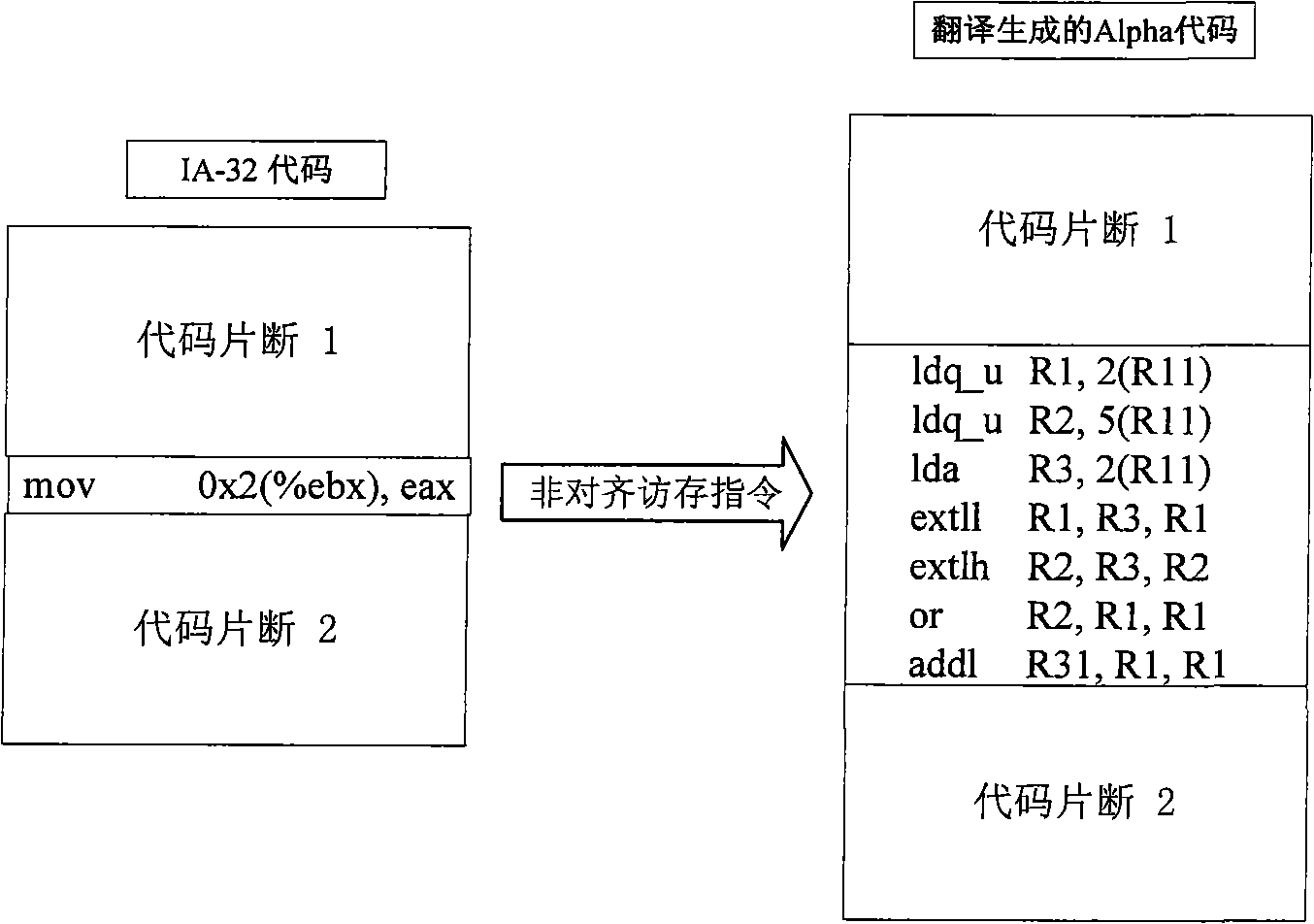
ActiveCN101299192AReduce the number of timesImprove efficiencyProgram controlMemory systemsHandling CodeMemory processing
A non-aligned access and memory processing method includes: setting translation threshold according to the objective set structure, executing pitching pile to the access and memory instructions in the translator, to obtain the non-aligned access and memory instruction information; when the implementation number of the translation unit is greater than the translation threshold, the non-aligned access and memory instruction information advises the translator to select a suitable instruction to translate the translation unit into the local code; the non-aligned access and memory instructions undiscovered by the translator pitching pile are generated into the corresponding non-aligned access and memory instruction sequence according to the exception handling mechanism, inserting in the exception handling address, and embedding in the executing code. Adoption of the method can largely reduce the number of exception times of the non-aligned access and memory produced in the binary translator, and improves the efficiency of the binary translator; can better handle the non-aligned access and memory exception appearing in the application program whose code implementation action varies with different input sets, and can effectively improve the operating efficiency of the binary translation system.
Owner:INST OF COMPUTING TECH CHINESE ACAD OF SCI
Multi-point touch panel
InactiveCN101271372ALower requirementLow costInput/output processes for data processingHandling CodeCamera lens
The invention provides a multi-point touch screen, which is a rectangular frame structure. The surrounding area of the frame is matched with the display screen area for installing the touch screen; an illuminating belt matched with the side length of the frame is arranged beside the frame to be as a reference; the illuminating belt reference surrounds an identification area, a sensor component is arranged on the corner of the frame; the sensor component includes an image sensor, an optical lens and a light filter. With 90-degree visual angle of the senor paralleling above the direction of the recognized area, the sensor covers the whole identification area; the visual angle vertical to the direction of the identification area ensures that the reference is in the visual angle of the sensor and the object entering the identification area to be captured by the sensor. The sensor is connected with a controller; the controller is provided with a communication port connected with an upper computer for data communication; the controller includes data for controlling a code reading sensor and the controller or the upper computer includes data processing code for handling the sensor data. The position and the size of the touch object are calculated according to the data. The touch screen achieves a large-size multi-point touch screen at low cost.
Owner:党韧
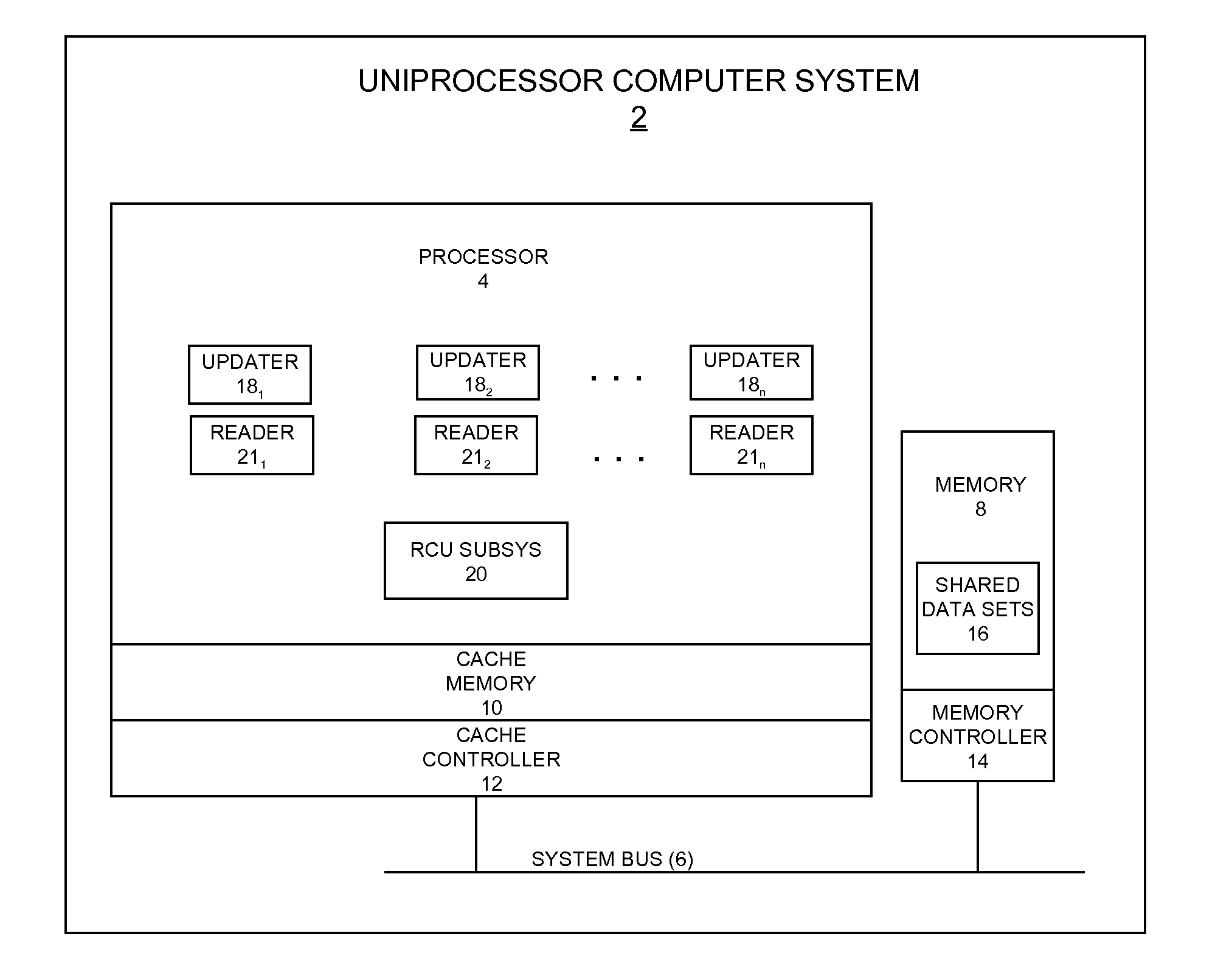
Expedited Module Unloading For Kernel Modules That Execute Read-Copy Update Callback Processing Code
InactiveUS20130152095A1Block completeMultiprogramming arrangementsMemory systemsHandling CodeQuiescent state
A technique for expediting the unloading of an operating system kernel module that executes read-copy update (RCU) callback processing code in a computing system having one or more processors. According to embodiments of the disclosed technique, an RCU callback is enqueued so that it can be processed by the kernel module's callback processing code following completion of a grace period in which each of the one or more processors has passed through a quiescent state. An expediting operation is performed to expedite processing of the RCU callback. The RCU callback is then processed and the kernel module is unloaded.
Owner:IBM CORP
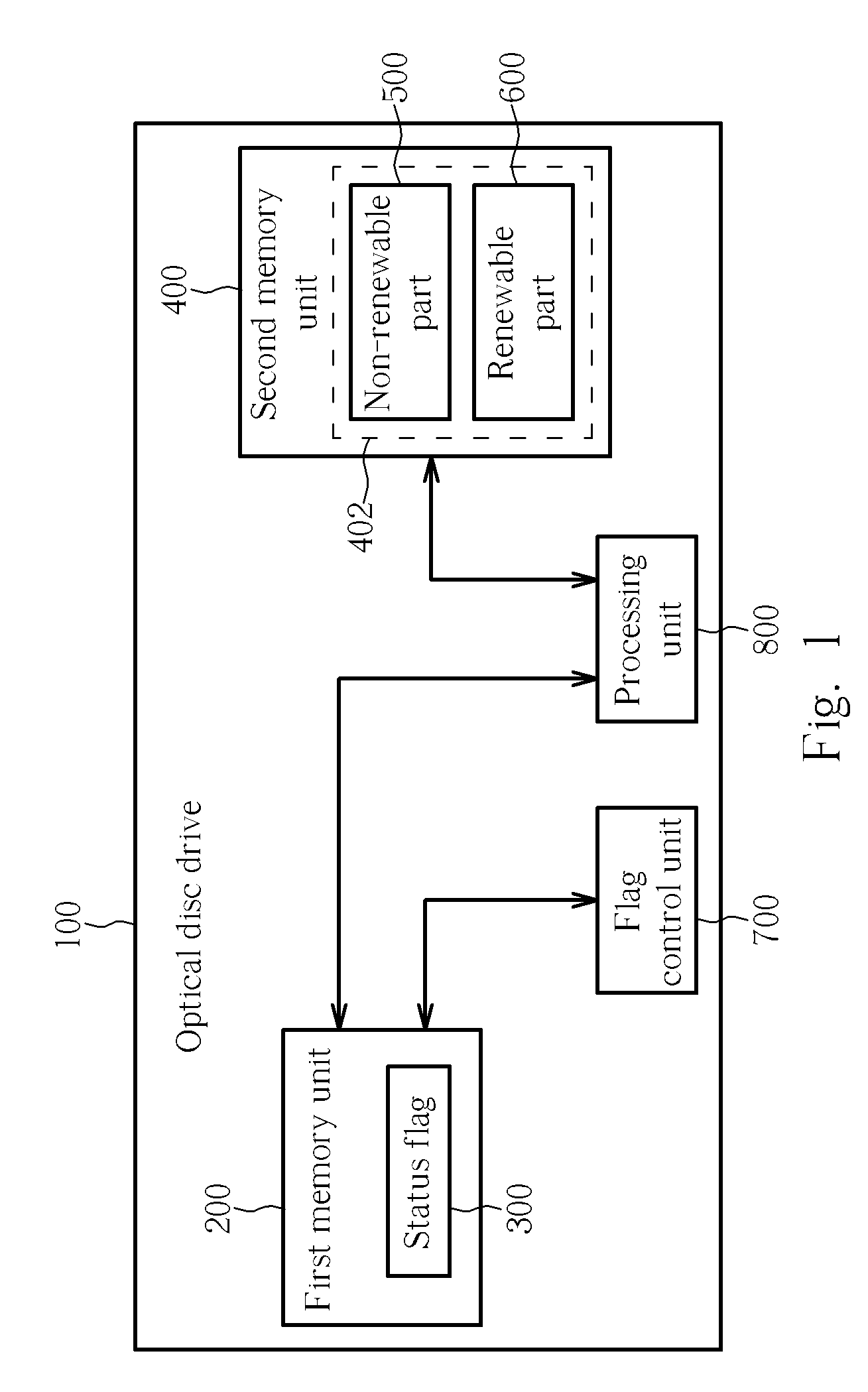
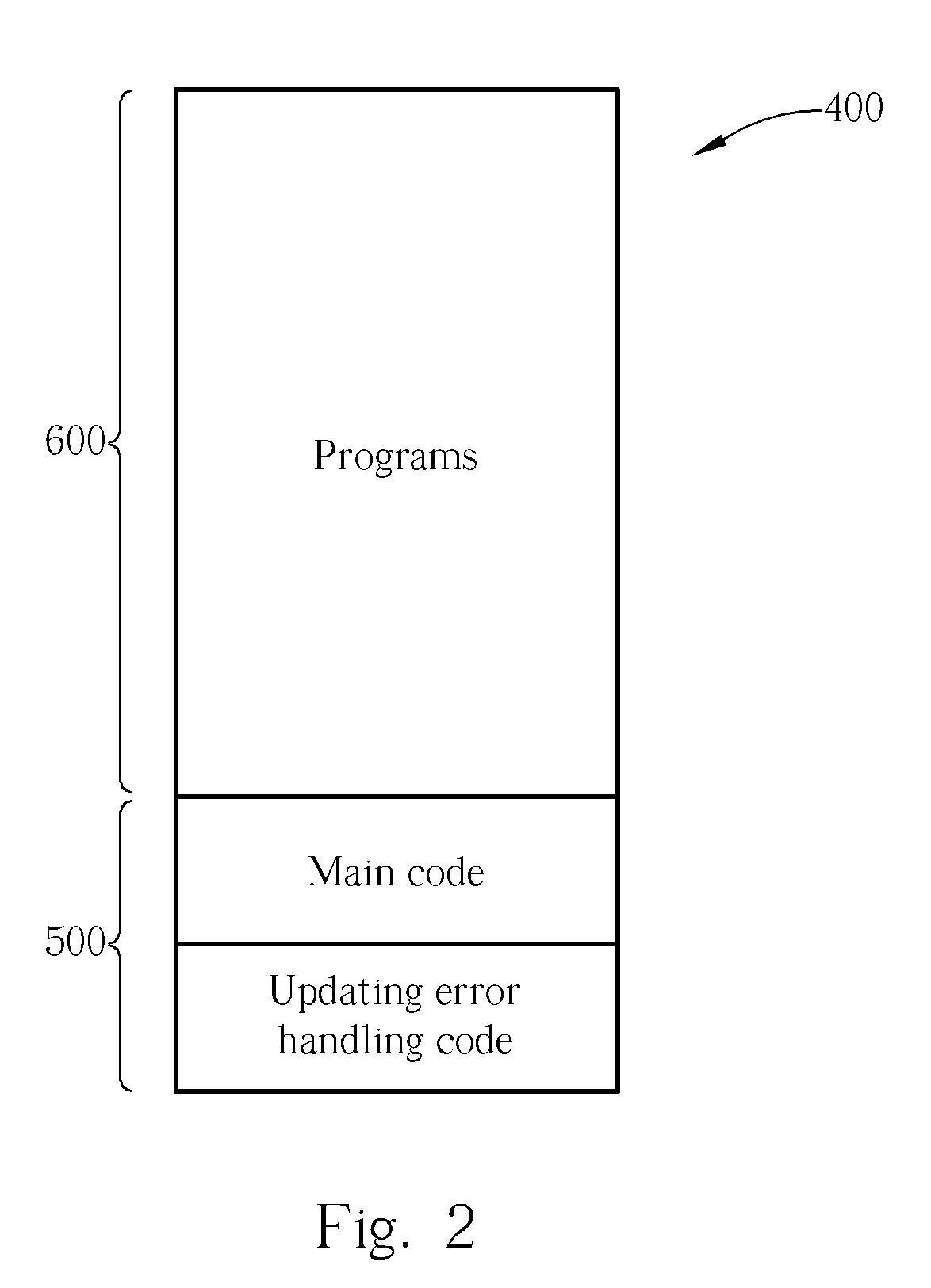
Microcode updating error handling apparatus and method thereof
Owner:REALTEK SEMICON CORP
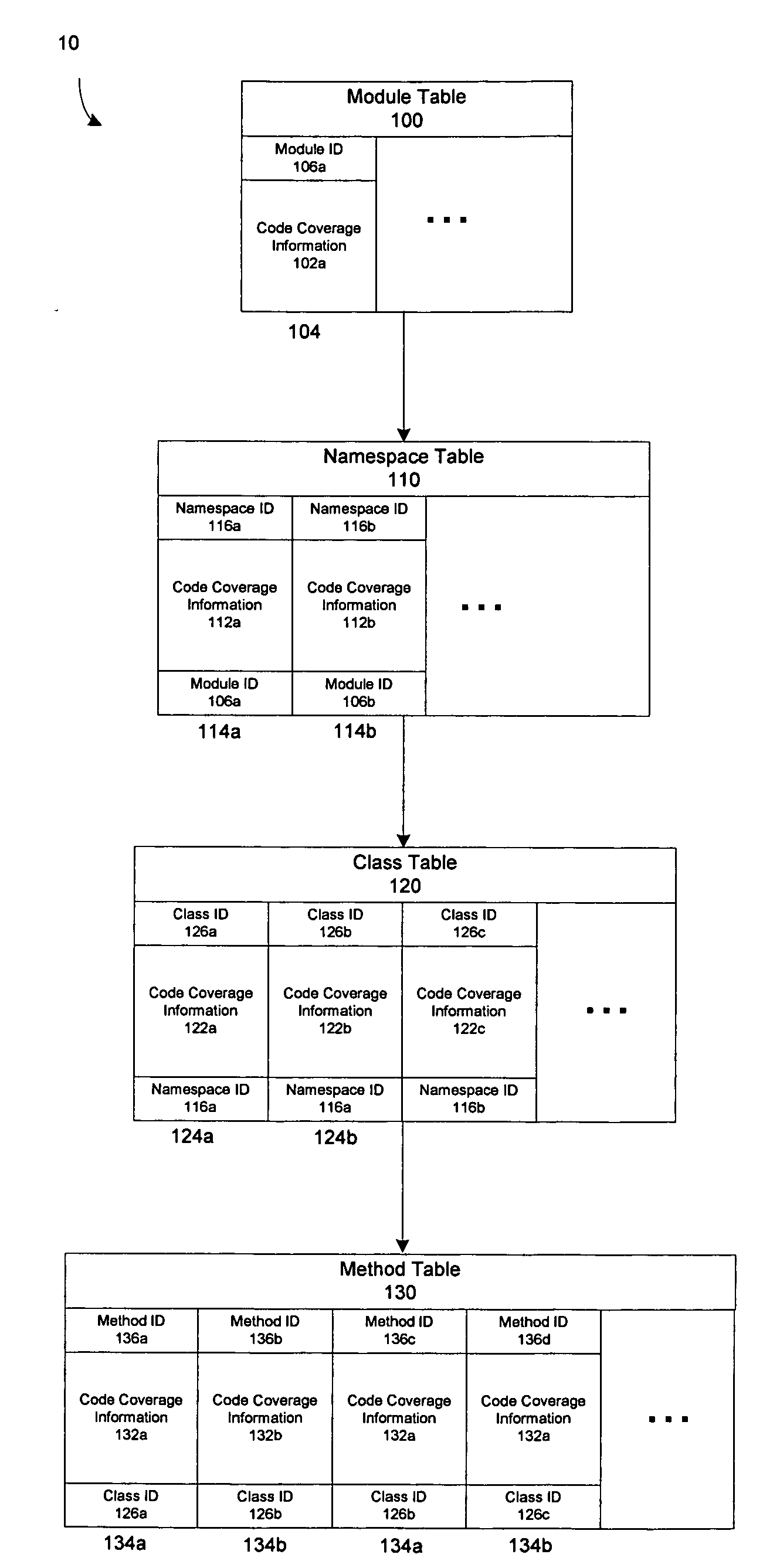
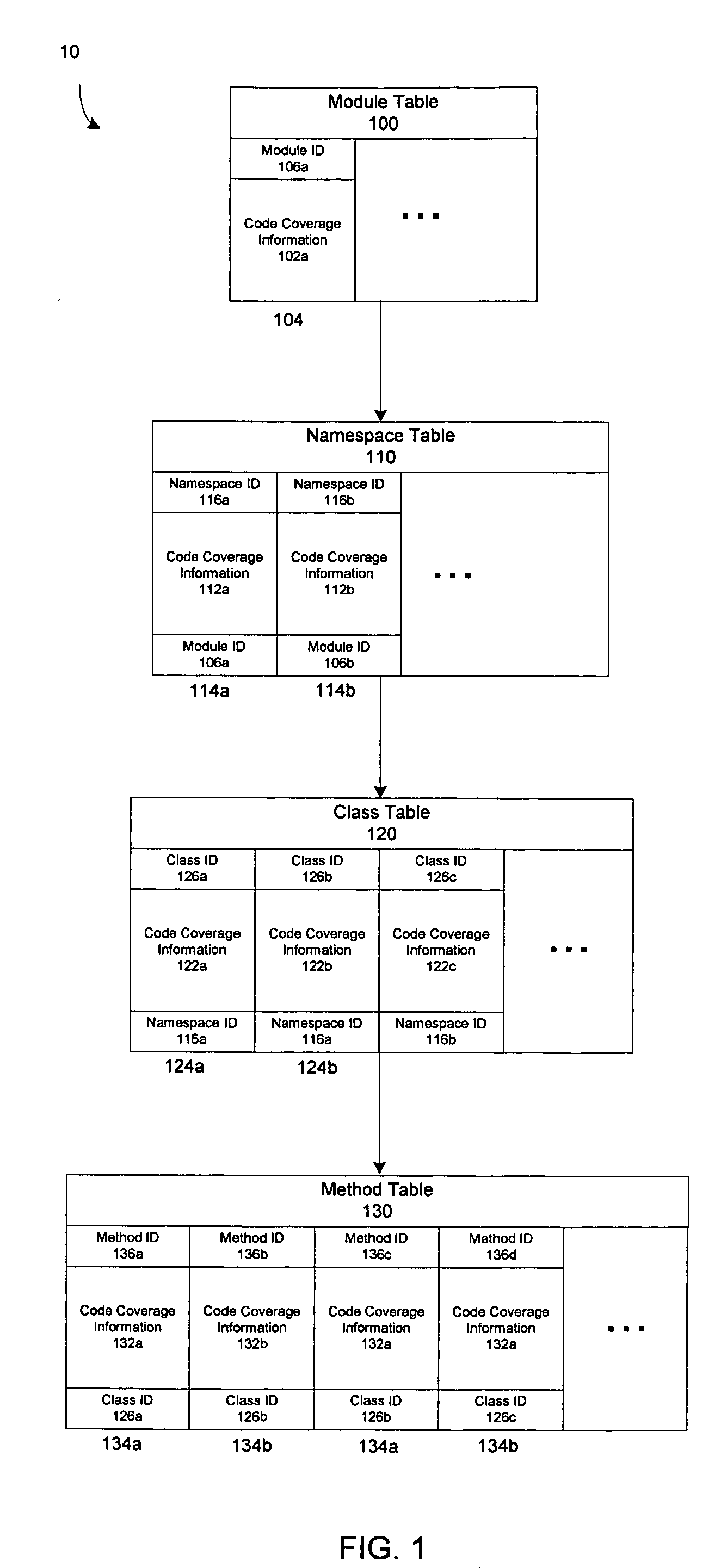
Methods and apparatus for handling code coverage data
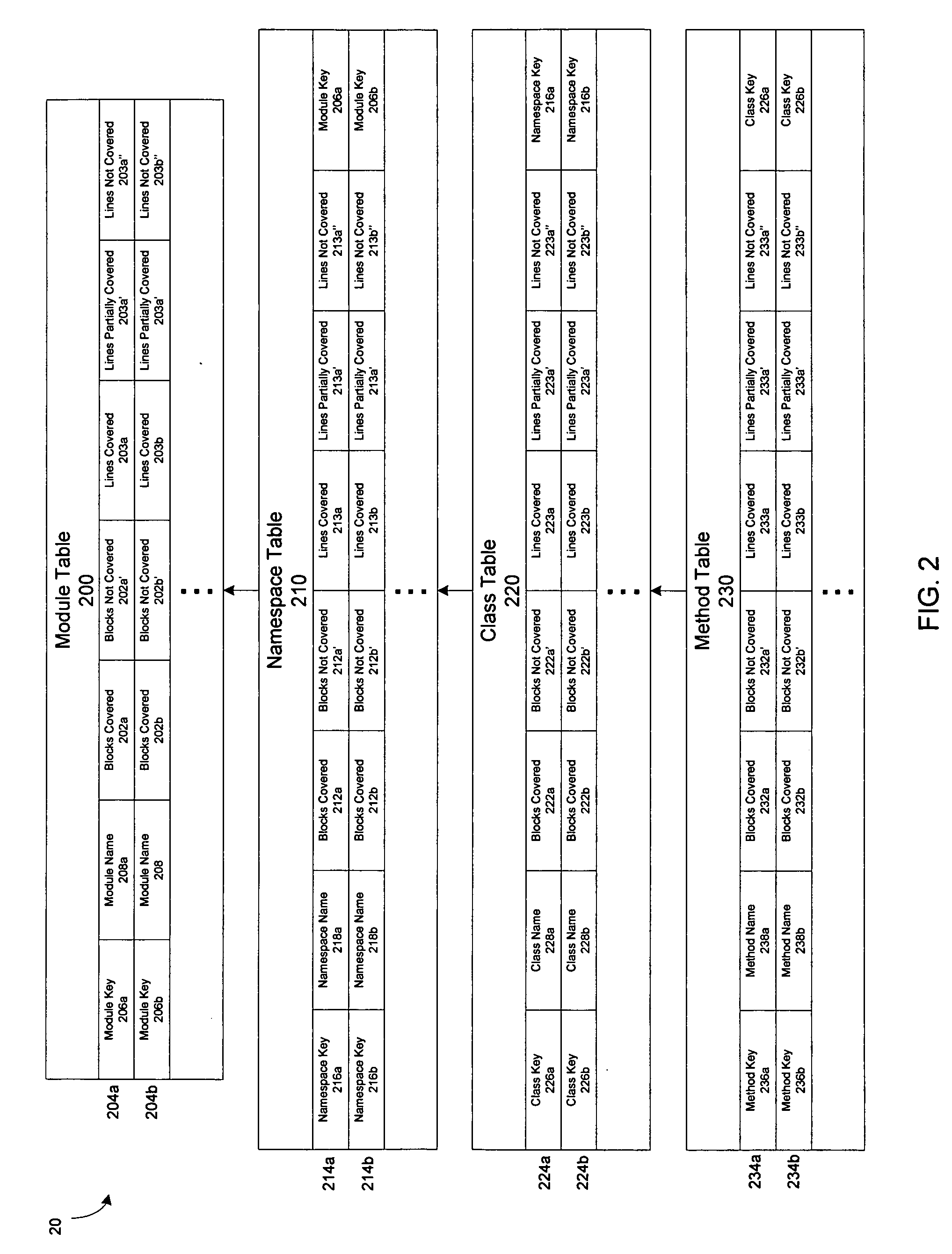
InactiveUS20060236156A1Easy to analyzeIntuitive interpretationError detection/correctionHandling CodeCode coverage
In one aspect, a method and apparatus for formatting code coverage data generated by performing one or more code coverage tests on a program module derived from computer code is provided, including organizing the code coverage data in a hierarchy having a plurality of tables, each of the plurality of tables configured to store information at one of successive levels of refinement, and storing, in each of the plurality of tables, code coverage information indicative of code coverage at a respective one of the successive levels of refinement. In another aspect, a data structure for storing code coverage data is provided, the data structure comprising a plurality of tables organized in a hierarchy having a plurality of levels, each of the plurality of levels corresponding to a respective construct in the programming paradigm used to structure the code, wherein each of the plurality of tables comprises a first location configured to store code coverage information at the level in the hierarchy at which the table is located.
Owner:MICROSOFT TECH LICENSING LLC
Apparatus, methods and articles of manufacture for intercepting, examining and controlling code, data and files and their transfer
InactiveUS7502829B2Efficient and effective mannerLittle and no operational effortMemory loss protectionError detection/correctionProgramming languageHandling Code
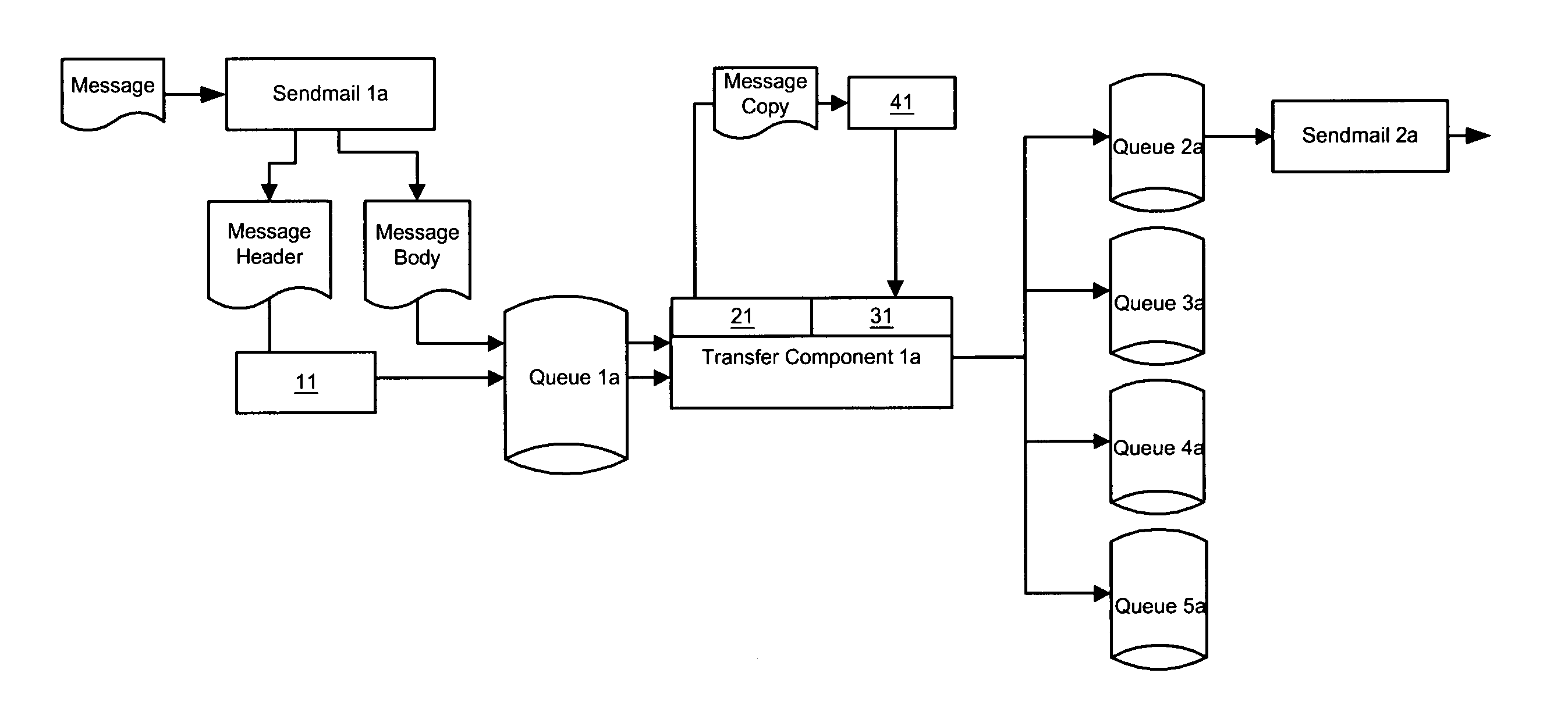
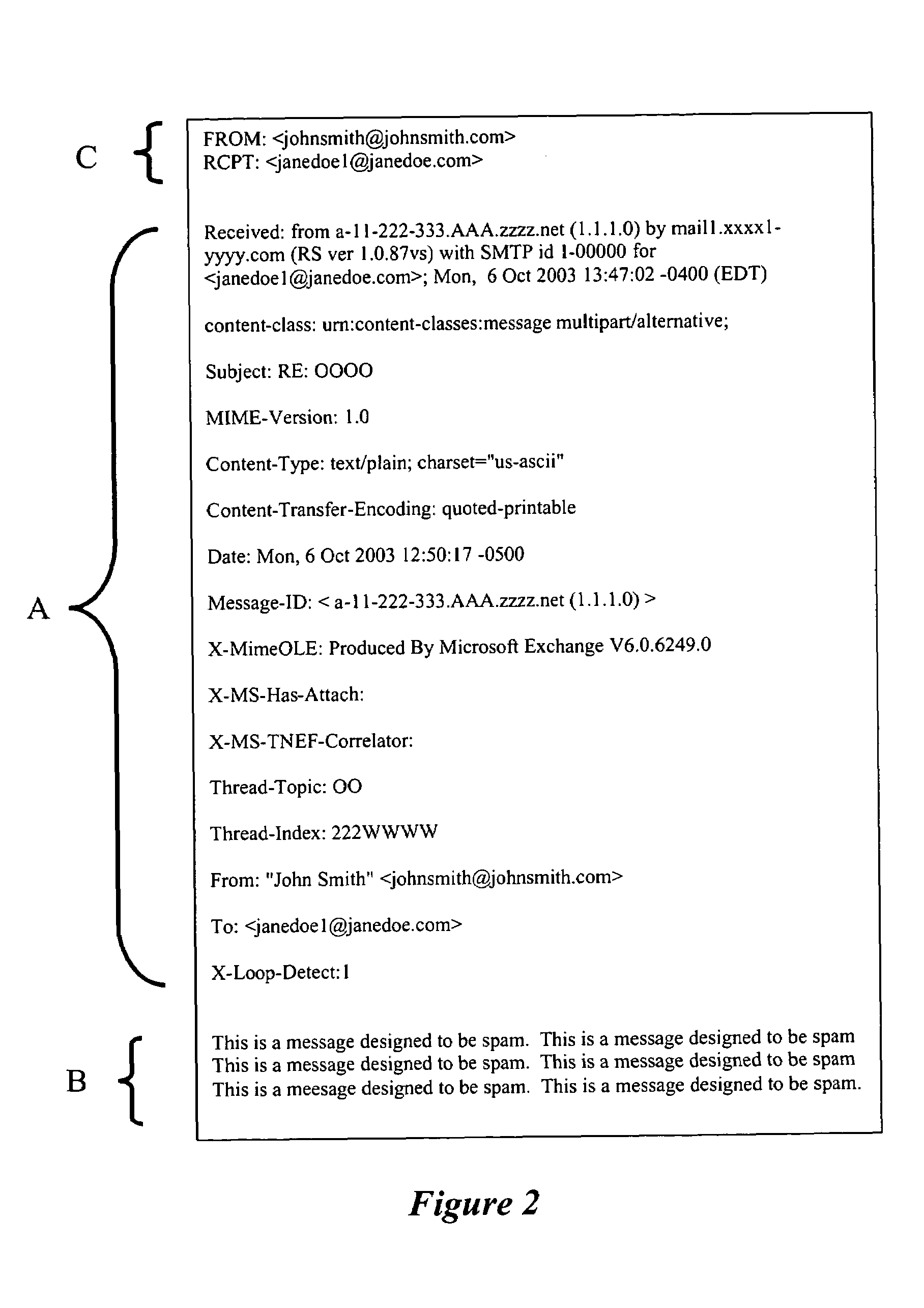
Apparatus, methods, and articles of manufacture are claimed for processing code comprising the preprocessing of code, transferring of the code from a storage area to a transfer component, decomposing the code, valuing the code, and comparing the code to a threshold value. The processing indicates the presence or absence of proscribed code, which may be spam, virii, confidential material, harassing material, etc. and so the code may be redirected. The especially preferred embodiments operate within a UNIX sendmail environment.
Owner:CYBERSOFT
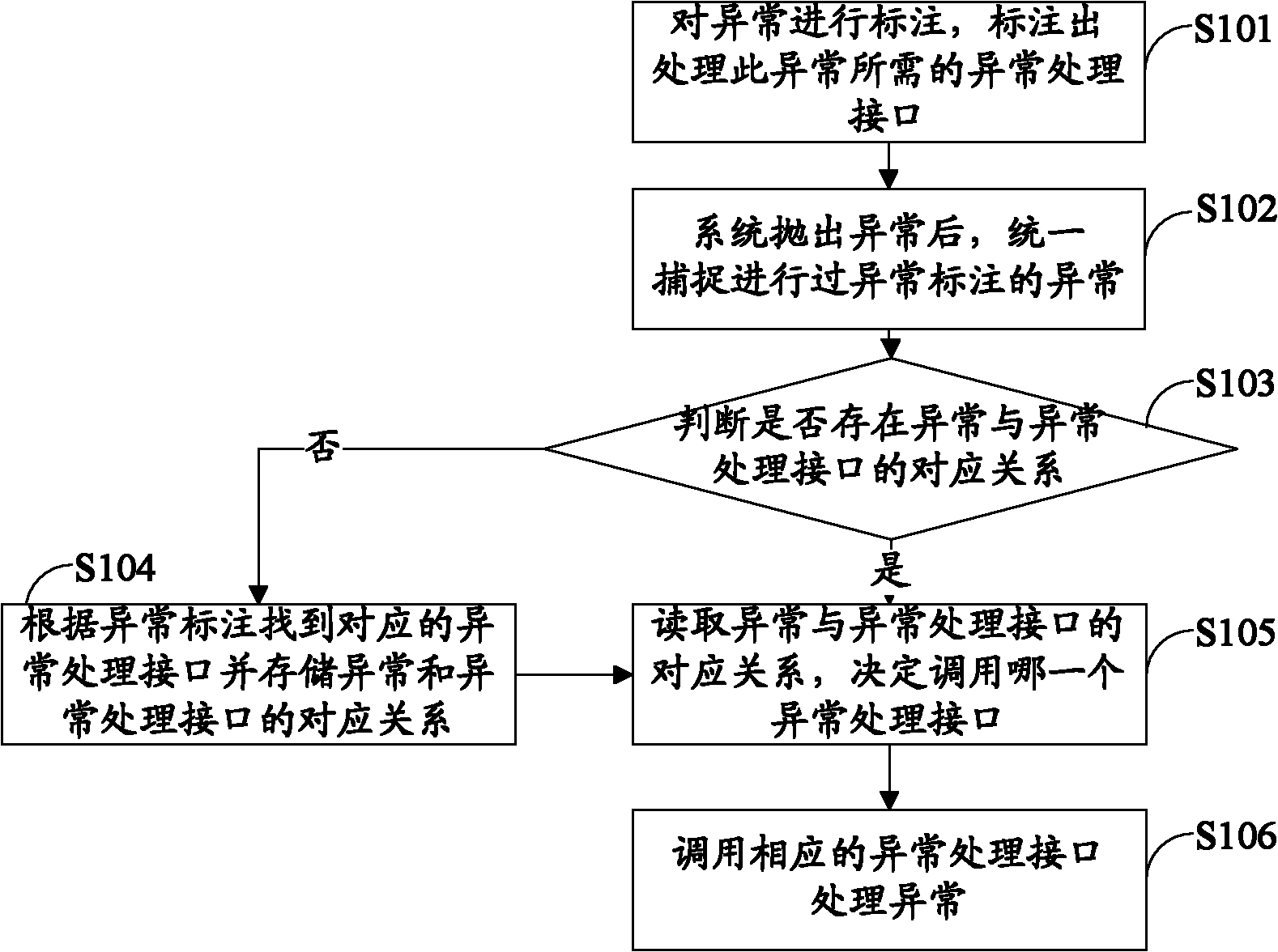
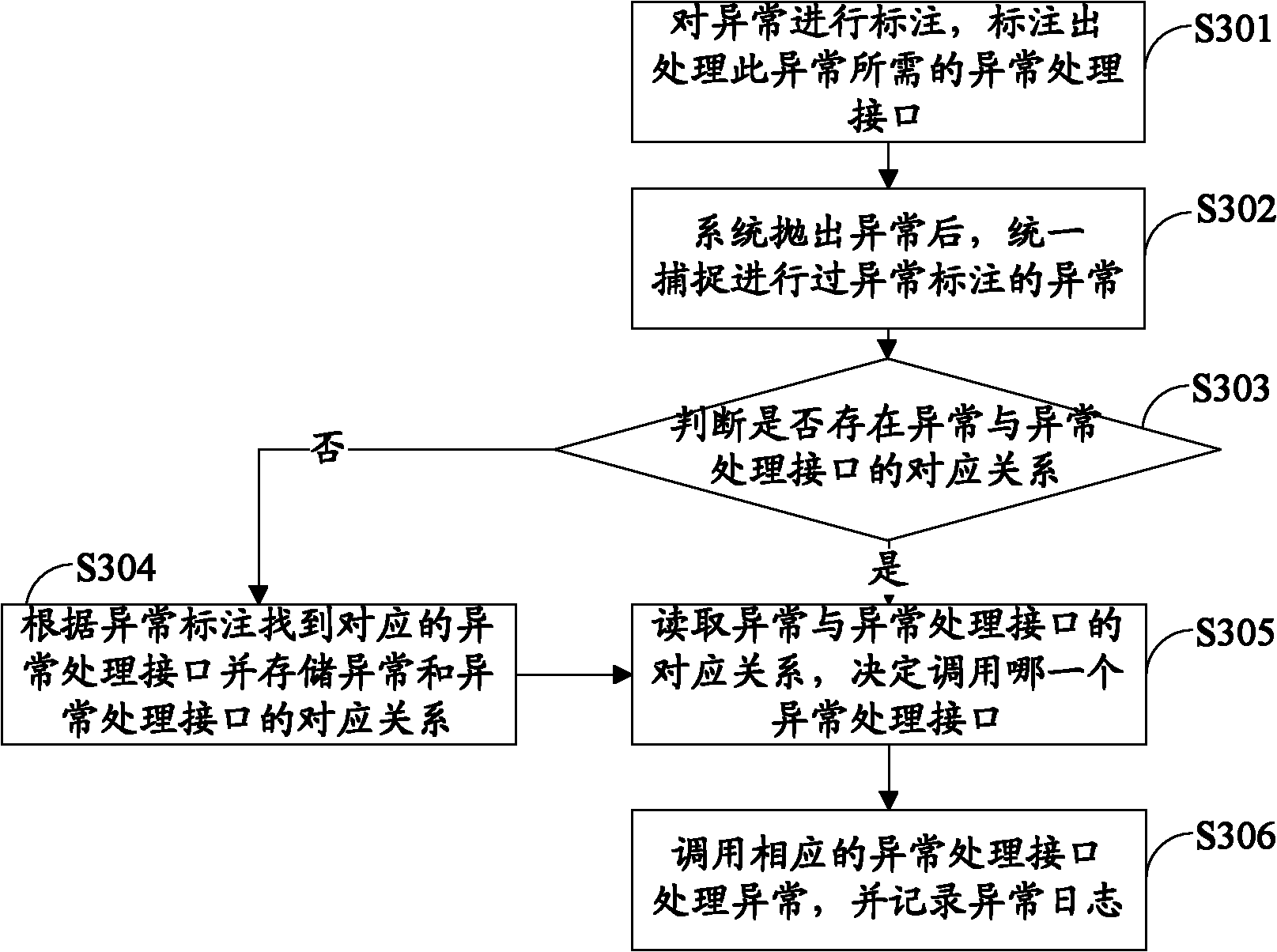
Exception handling method and device and software system
InactiveCN102385508ASolve the problem of writing a processing method separatelyReduce workloadSpecific program execution arrangementsHandling CodeSoftware system
The invention belongs to the field of computer software systems, and provides an exception handling method, an exception handling device and a software system. The method comprises the following steps of: marking an exception and marking an exception handling interface corresponding to the exception; uniformly acquiring exception subjected to exception marking after the exception is thrown out by the system; finding the corresponding exception handling interface according to the exception marking and storing a corresponding relation between the exception and the exception handling interface; and calling the exception handling interface to handle the exception. With the adoption of the method for uniformly and concentratedly handling the exception, the workload of a programmer and the chance of error are greatly reduced, a program code is simplified, the product quality is improved, the problem of independently writing a handling code when the exception occurs every time by the programmer is solved, and same handling on the exception of the same type is realized; moreover, the code is high in reusability, and the exception can be handled in different environments.
Owner:KINGDEE SOFTWARE(CHINA) CO LTD
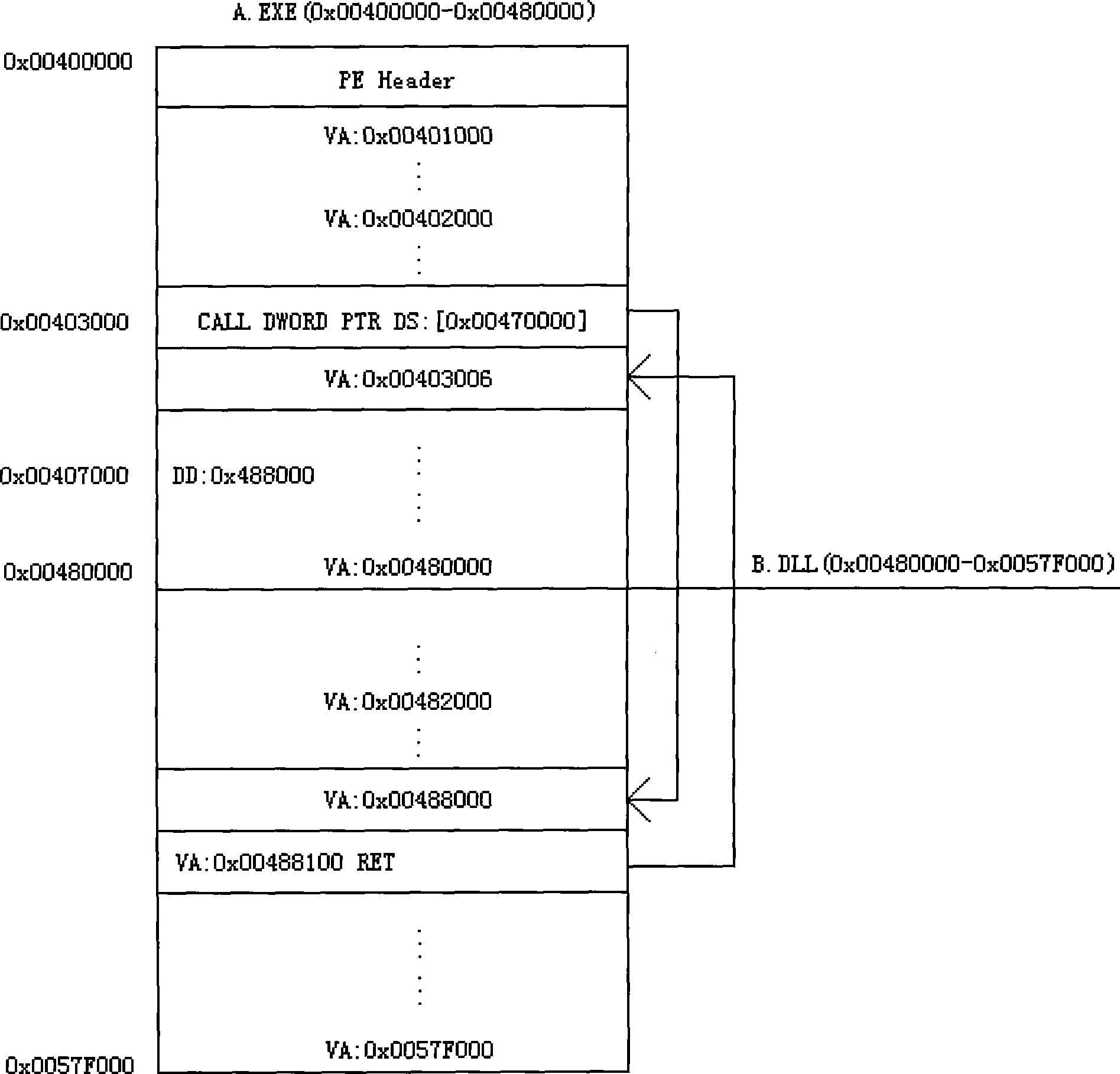
Combined execution method for PE document code
InactiveCN101504656APrevent illegal useAchieve protectionSpecial data processing applicationsHandling CodeDatabase
The invention discloses a merged execution method for PE file codes, which belongs to a file encryption technique and solves the problem that a single file code is easy to be illegally utilized in the prior art. The merged execution method for the PE file codes comprises: (1) establishing a PE file header; (2) establishing section information; (3) merging various PE file data to a corresponding section and forming a novel PE file; (4) processing mutual calling relations between various PE files; (5) attaching codes of initialized data of the various PE files to the novel PE file; and (6) adding an attached processing code for the merged PE file according to actual demands, and expanding corresponding functions. The method not only realizes the merging of various PE file codes but also can realize dynamic or static encryption of the merged PE file or addition of additional functional codes, effectively protect the various file codes, and prevent the single file code from being illegally utilized.
Owner:CHENGDU PANSHSOFT
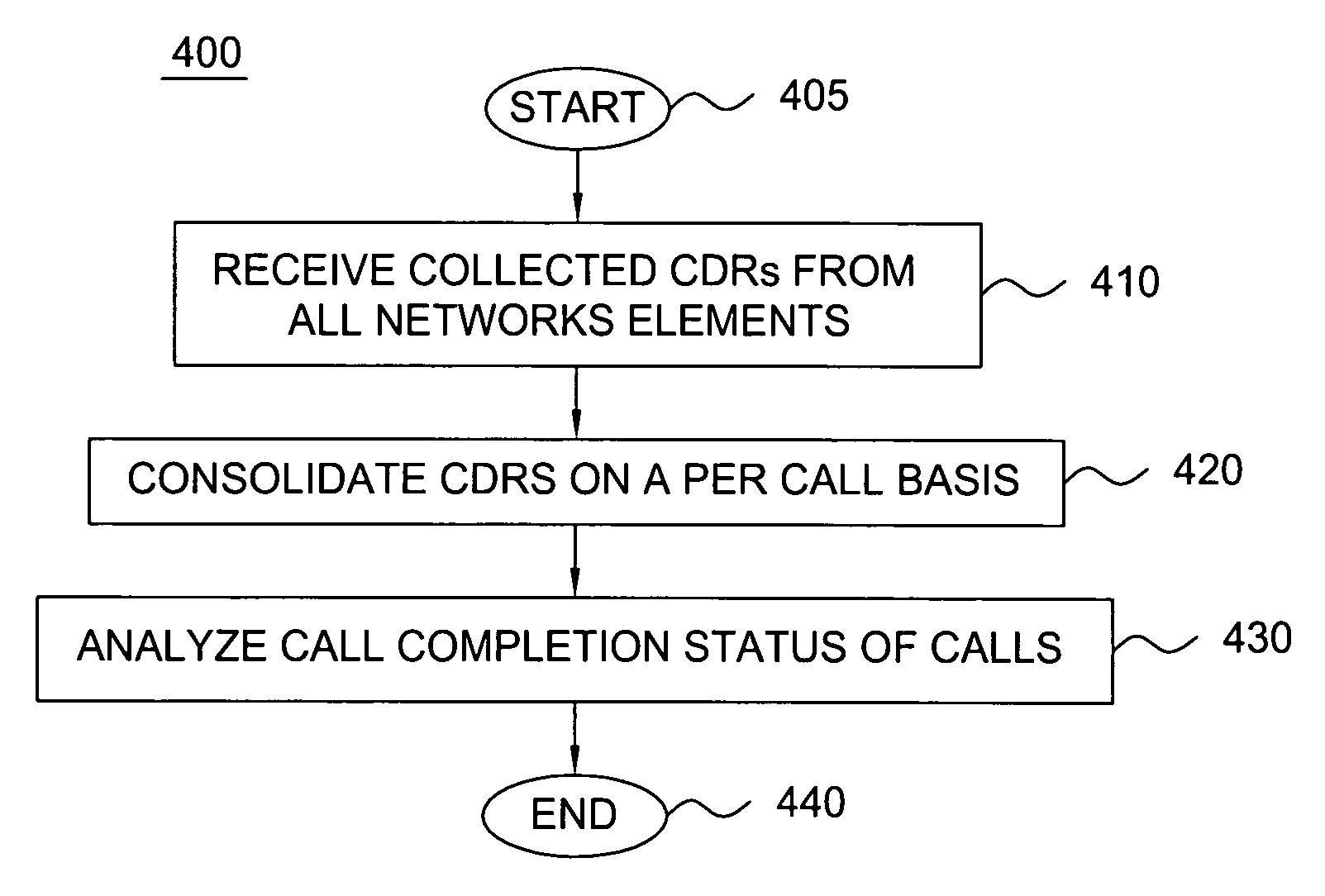
Method and apparatus for providing end-to-end call completion status
The present invention enables a method for following the state of a call and generating defects as function of call completion success as opposed to discrete events that happen at individual network elements during the call. In one embodiment, the invention uses Call Detail Records (CDR) to analyze the end-to-end completion status to measure per call basis defects instead of using defect codes generated by network elements on a per equipment basis. CDR is data associated with a telephone call, including the calling and the called numbers, the date and timestamp, the duration, the call setup delay, and the final handling code of the telephone call.
Owner:AMERICAN TELEPHONE & TELEGRAPH CO
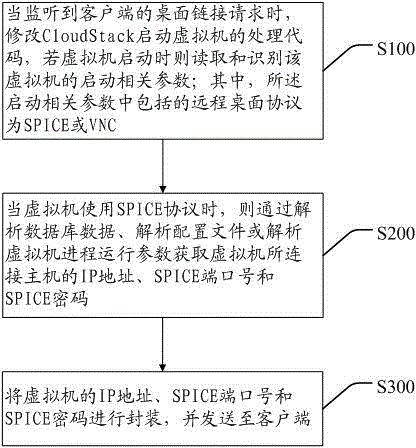
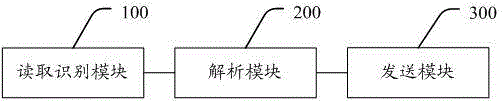
Method and system for logging virtual machine based on Cloud Stack platform
The invention discloses a method for logging a virtual machine based on a Cloud Stack platform and a system for logging the virtual machine. The method comprises the following steps: when desktop link demands of clients are monitored, processing codes for starting the virtual machine by Cloud Stack are amended, and relevant starting parameters of the virtual machine are read and identified when the virtual machine is started; the relevant starting parameters include remote desktop protocols such as SPICE (simulation program with integrated circuit emphasis) or VNC (virtual network computer); when SPICE protocols are used by the virtual machine, database data, configuration files or process operation parameters of the virtual machine are analyzed to acquire IP addresses, SPICE port numbers and SPICE passwords of the virtual machine connected with a host; IP addresses, SPICE port numbers and SPICE passwords of the virtual machine are packaged and transmitted to the clients. According to the method and the method, VNC and SPICE protocols are compatible in the Cloud Stack platform, thus the logging manner of an user is simplified and high in security.
Owner:SHENZHEN YANTANG TECH
System and method for dynamic runtime merging of real time streaming operator environments
InactiveUS20170235555A1Software engineeringProgram loading/initiatingHandling CodeComputerized system
A method, computer program product, and computer system for tracking tuples by ID as the tuples progress through an operator of a chain of operators within a processing element. Dynamic loading may be utilized to load a processing code for the operator in response to invoking fusion for the operator. Ownership of network I / O may be shifted from the operator to a final operator of the chain of operators within the processing element. A tuple ID may be rolled back to a last ID processed by the operator being added into the processing element.
Owner:IBM CORP
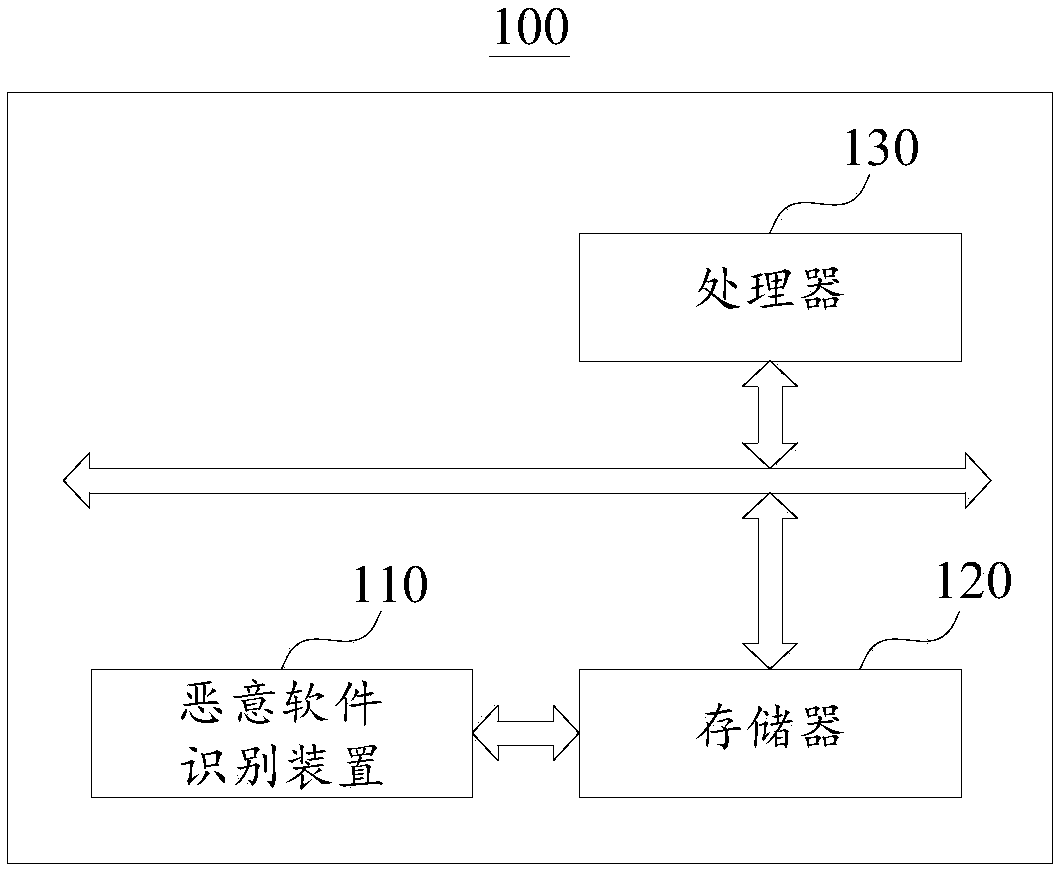
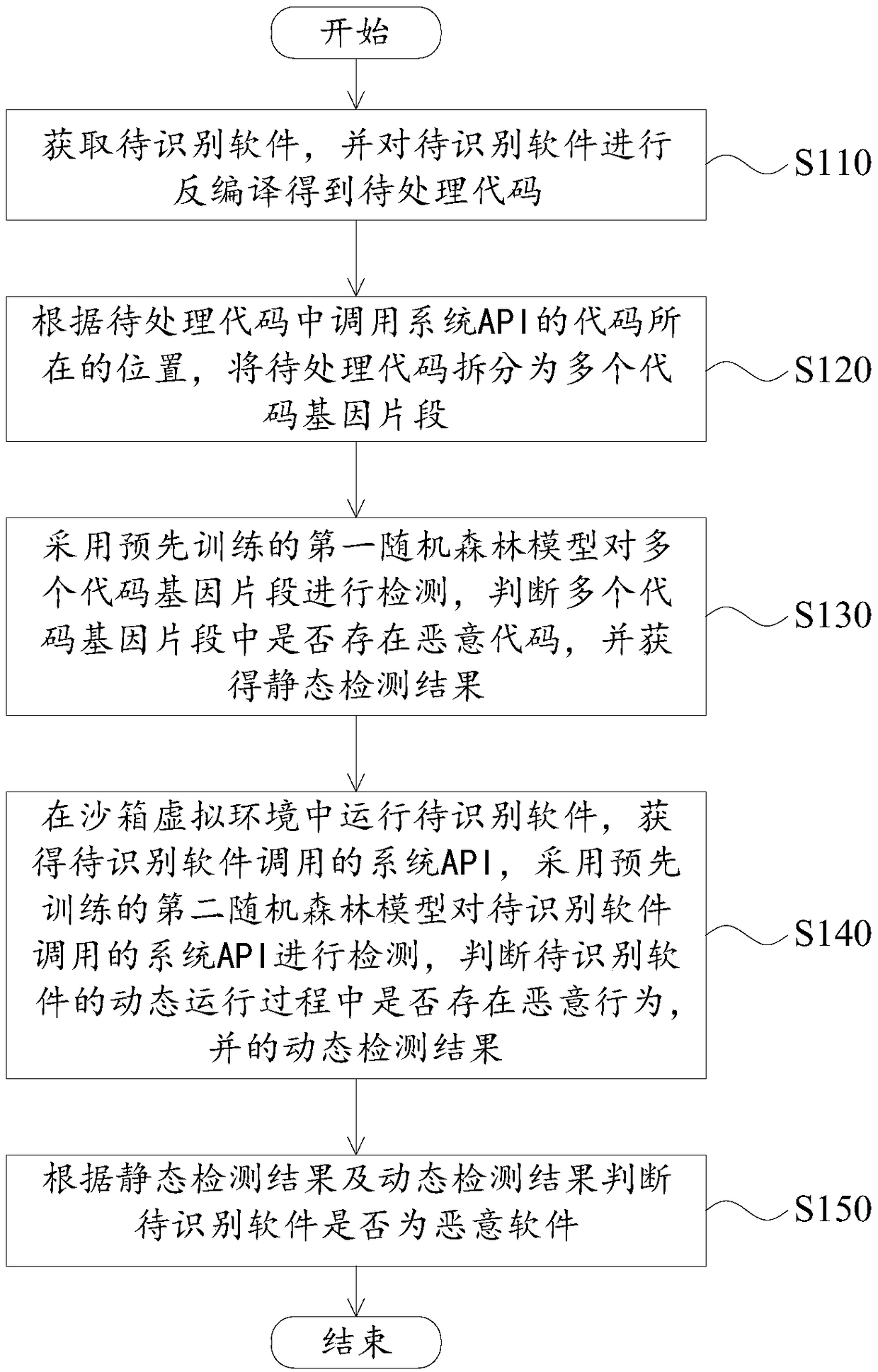
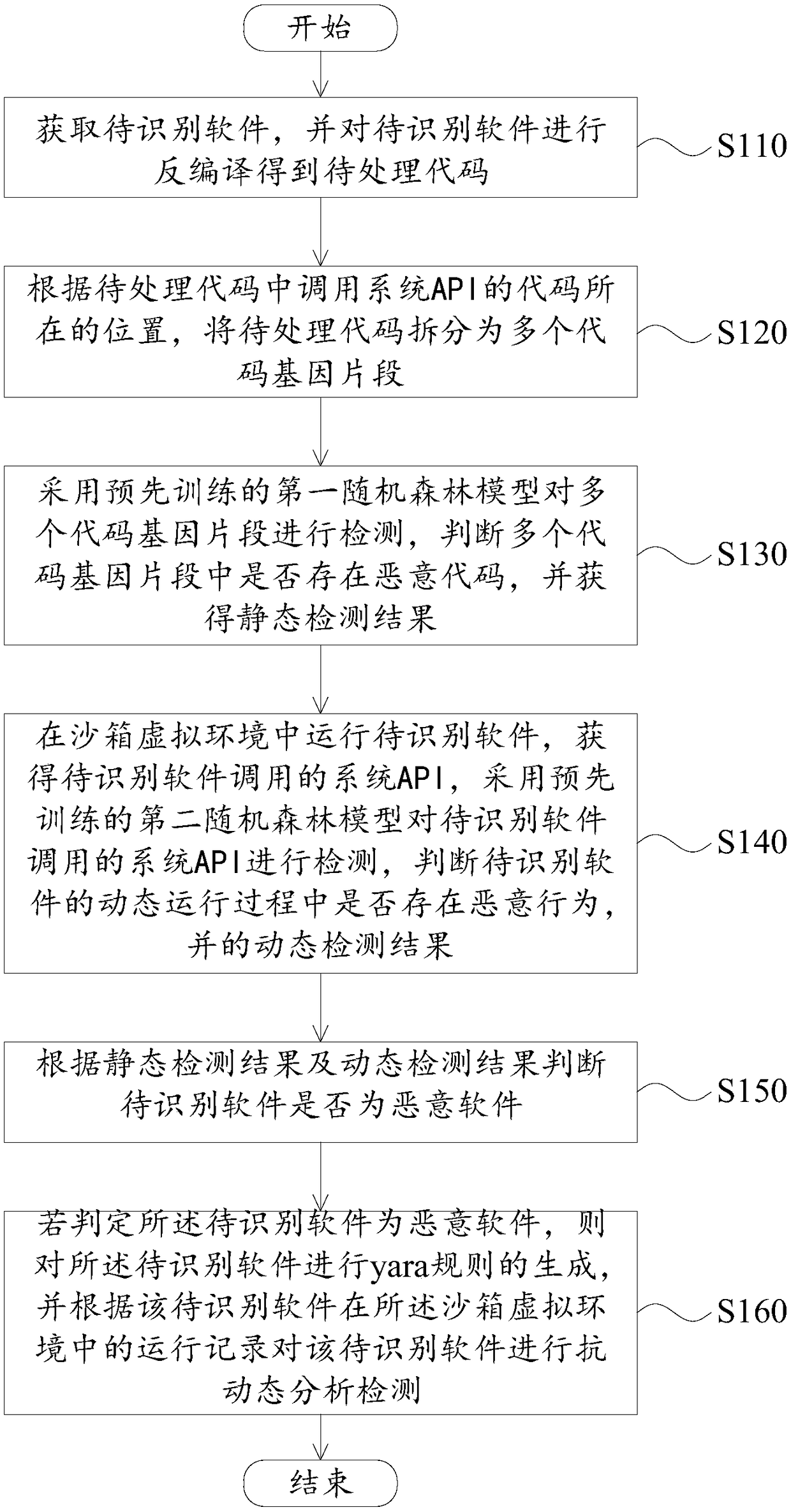
Malicious software identification method and apparatus, and electronic device
ActiveCN108734012AComprehensive recognitionHigh precisionPlatform integrity maintainanceHandling CodeSoftware engineering
The invention provides a malicious software identification method and apparatus, and an electronic device. The method comprises the following steps: obtaining to-be-identified software and performingdecompilation on the to-be-identified software to obtain a to-be-processed code; splitting the to-be-processed code into multiple code gene fragments according to a location where a code for calling asystem API is located in the to-be-processed code; detecting the multiple code gene fragments by using a first random forest model to obtain a static detection result; running the to-be-identified software in a sandbox virtual environment to obtain the system API called by the to-be-identified software, detecting the system API called by the to-be-identified software by using a second random forest model, judging whether a malicious behavior exists in a dynamic operation process of the to-be-identified software, and obtaining a dynamic detection result; and judging whether the to-be-identified software is malicious software according to the static detection result and the dynamic detection result. Therefore, the identification accuracy of malicious software can be effectively improved, and malicious software can be more comprehensively identified.
Owner:上海戎磐网络科技有限公司
Program creation method and program execution method
InactiveUS20010042209A1Keep for a long timeAvoid analysisDigital data processing detailsUnauthorized memory use protectionProgramming languageCode module
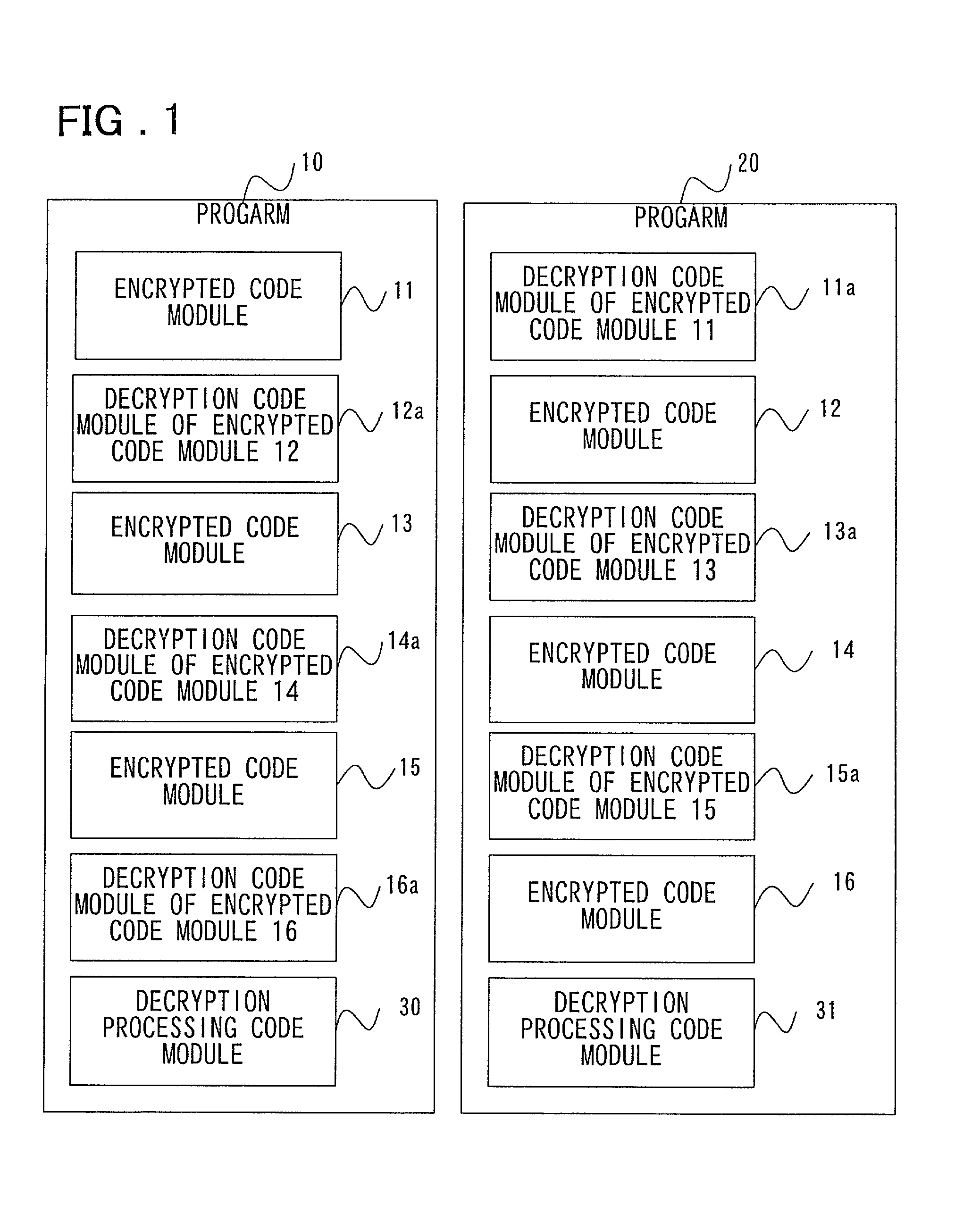
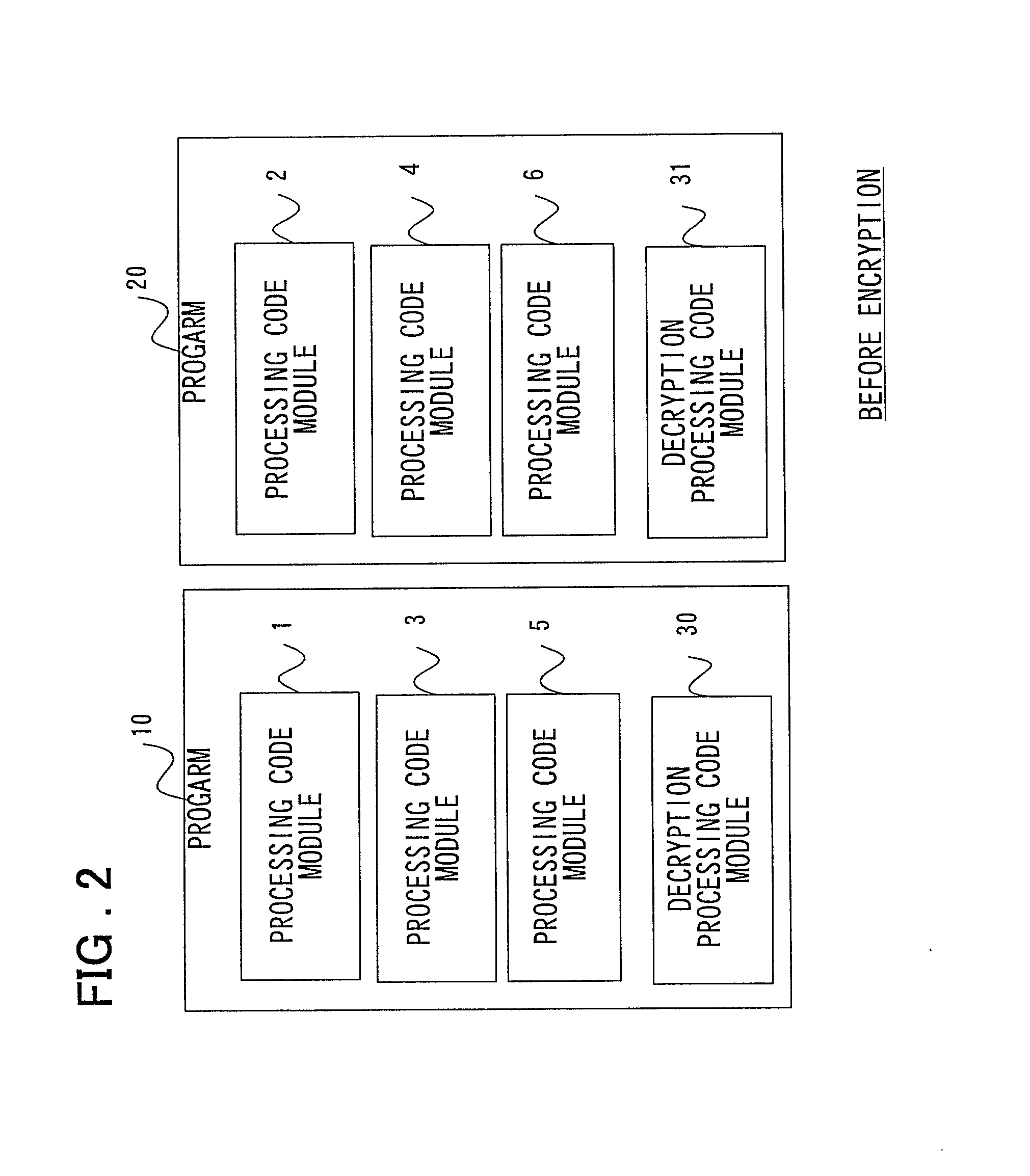
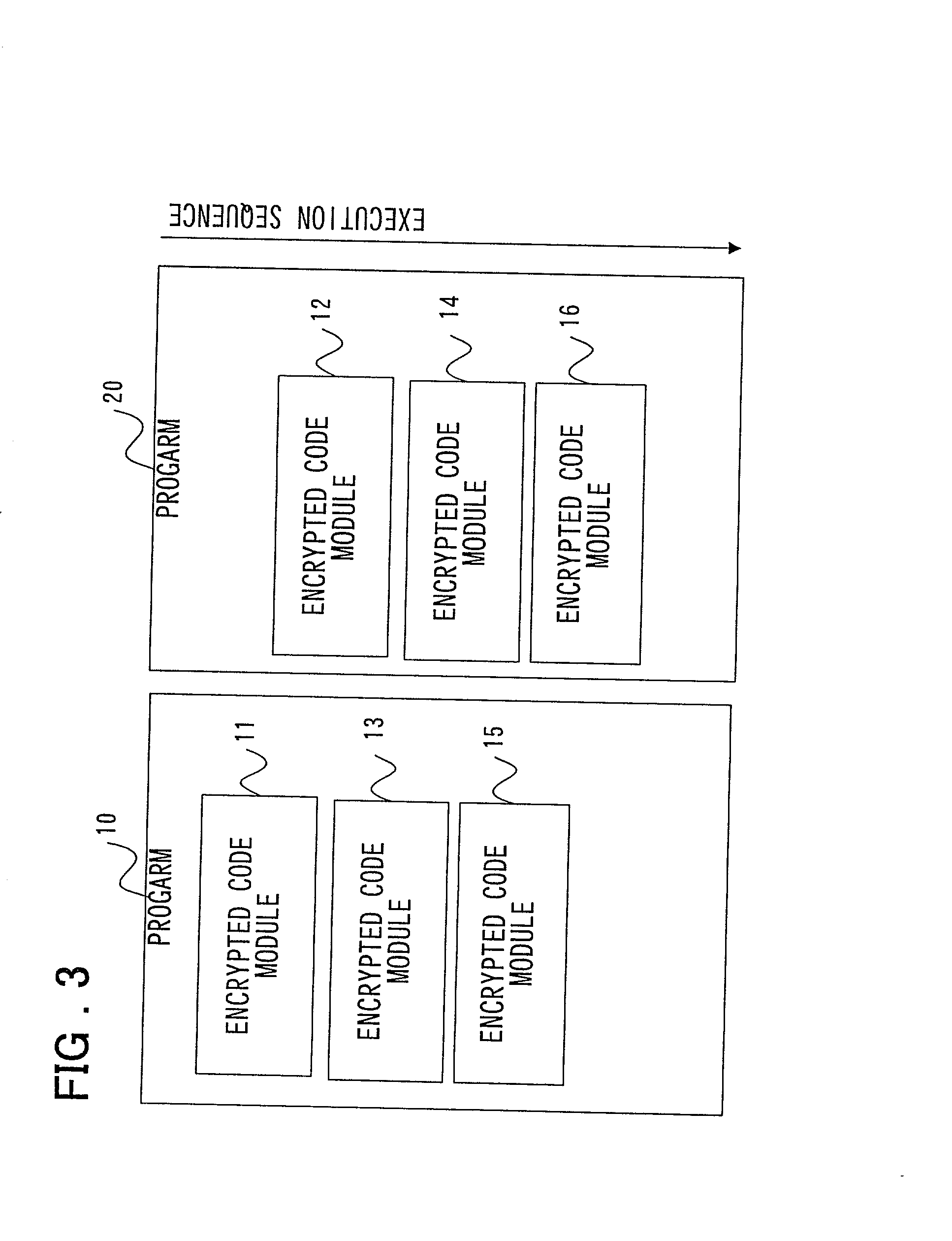
First program 10 comprises encrypted code modules 11, 13, and 15, decryption code modules 12a, 14a, and 16a of encrypted code modules 12, 14, and 16, and a first decryption processing code module 30. Also, second program 20 comprises encrypted code modules 12, 14, and 16, decryption code modules 11a, 13a, and 15a of the encrypted code modules 11, 13, and 15, and a second decryption processing code module 31. The encrypted code modules 11-16, which are created by encrypting processing code modules, are not converted back to the processing modules that perform original processing unless they are decrypted by the first and second decryption processing code modules 30 and 31, respectively.
Owner:RPX CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com