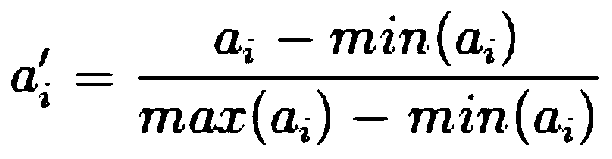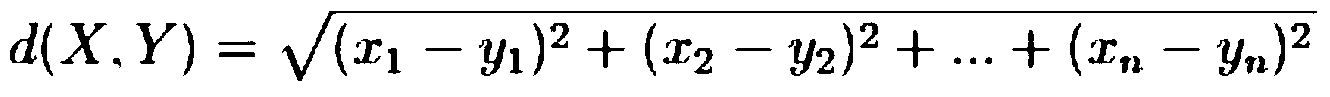Patents
Literature
373results about How to "Avoid analysis" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
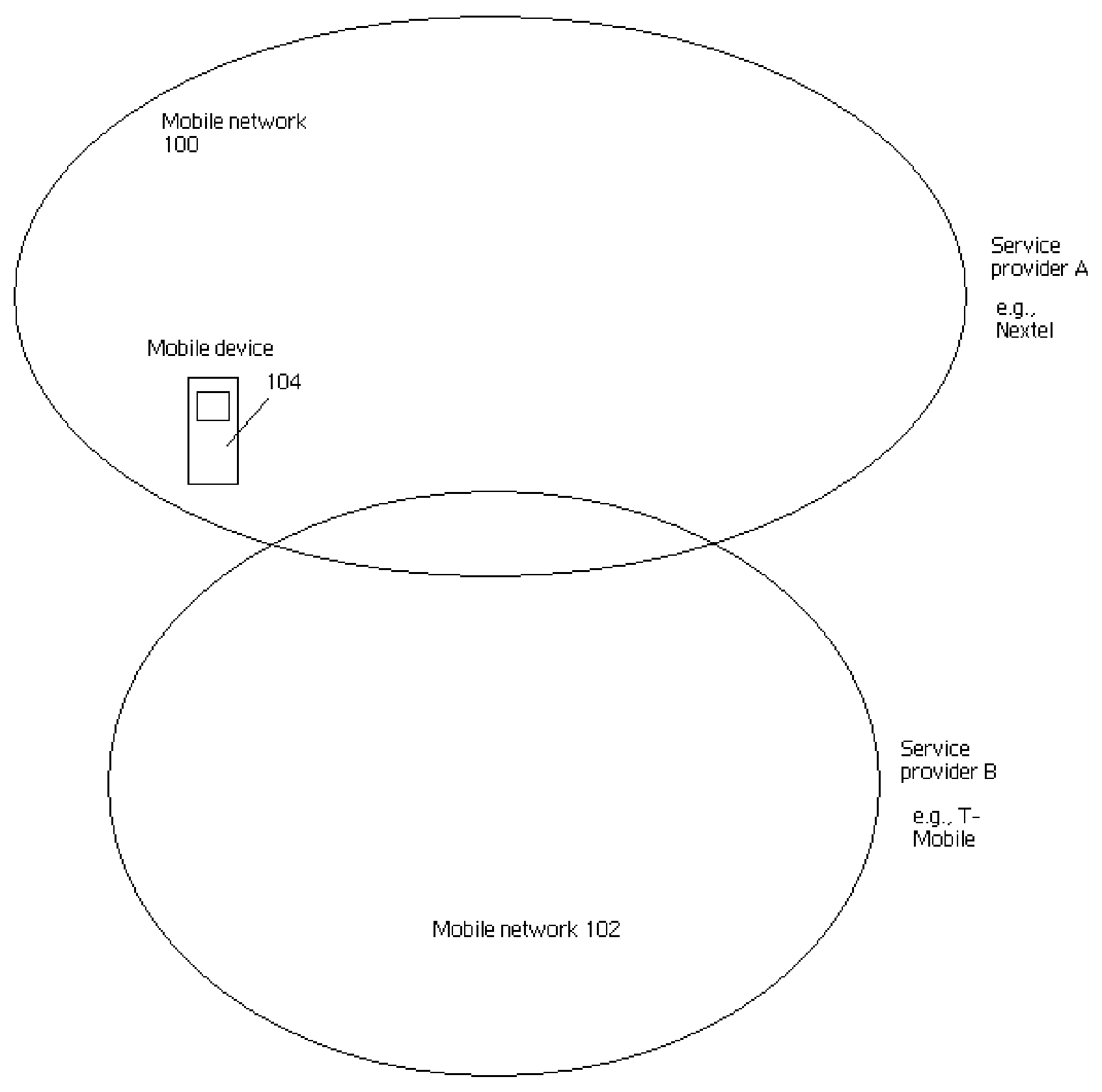
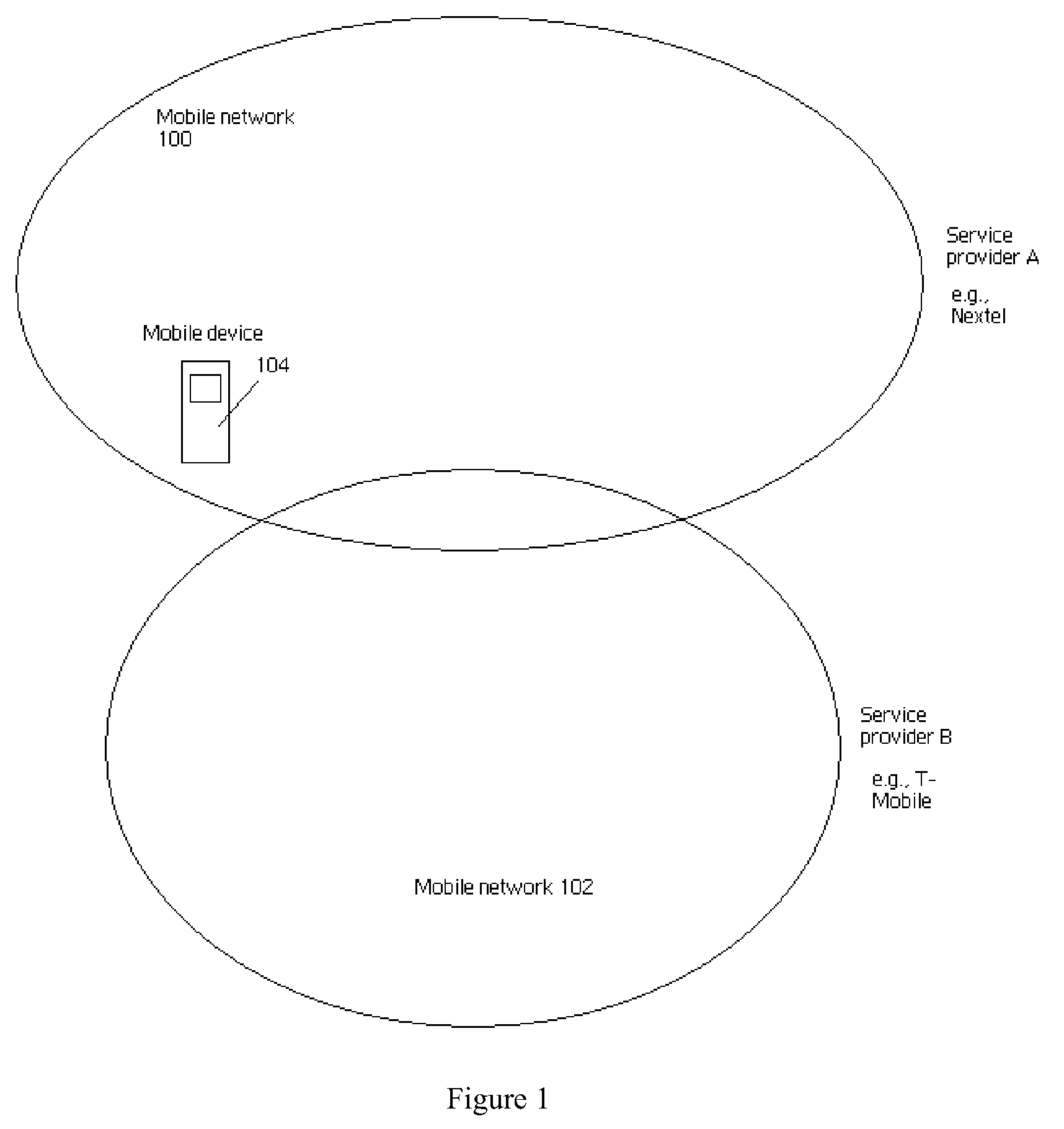
Differentiated management of wireless connectivity
ActiveUS8793304B2Avoid analysisMultiple digital computer combinationsTransmissionWireless mesh networkWireless connectivity
In some embodiments, a wireless management service provides the capability to manage connectivity between a device and one or more wireless networks on a differentiated basis. For example, network profiles may be managed in a way that is influenced by the identity of the user, such that profiles which are customized for a specific user may be established. Connectivity may also be managed in a way that is influenced by a session type ongoing on a device, such that when certain events occur (e.g., a request by one user to connect to or disconnect from a wireless network is processed), wireless connectivity employed by other users sharing the device is appropriately managed.
Owner:MICROSOFT TECH LICENSING LLC
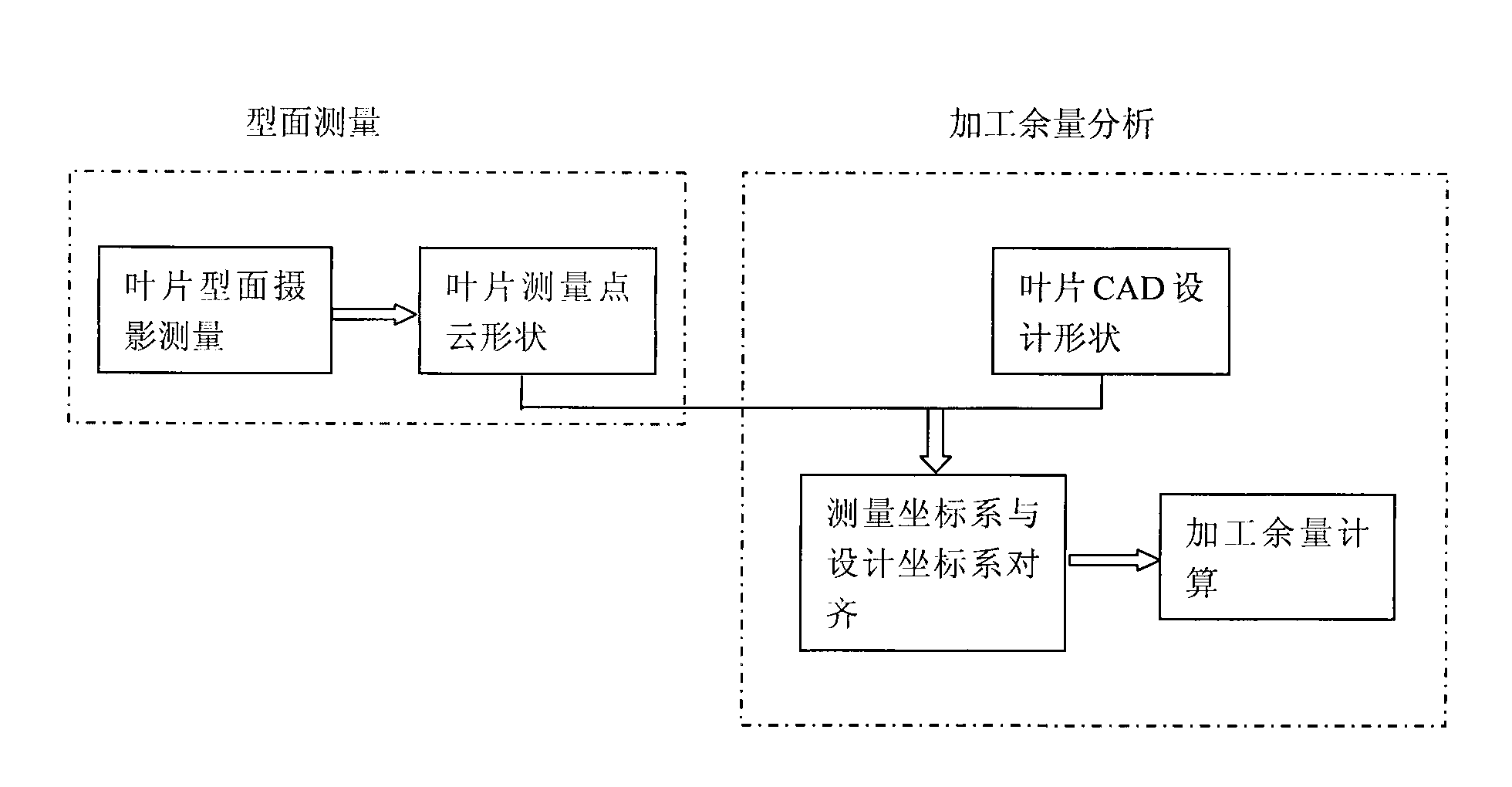
Water turbine blade blank profile measuring and machining allowance analyzing method
InactiveCN101634544AHigh speedImprove machining accuracyUsing optical meansCavitationMeasurement point
The invention relates to a water turbine blade blank profile measuring and machining allowance analyzing method capable of effectively solving the problem of water turbine blade blank profile measurement and machining allowance analysis to ensure the manufacturing quality and precision of the water turbine blades, comprising the following technical solutions: measuring the blade blanks by using a digital close range photogrammetry to obtain the measuring point cloud data shapes of the blank profiles consequently, aligning a measuring coordinate system where the measuring point clouds are located to a design coordinate system where a CAD design model is located, establishing a differential relation of free-form surface parameters with respect to rigid rotation parameters by using an analytic method derived by the multivariate of Newton iteration method to obtain a Jacobian matrix and Hessian matrix which are available for a target equation; then performing the numerical optimization calculation based on the LM method and Newton iteration method, and performing report or graphical output and print on the result. The inventive method is scientific, advanced, stable and reliable, and has high accuracy, thereby ensuring the hydraulic stability, production efficiency and cavitation property, and bringing enormous economic and social benefits.
Owner:郑州辰维科技股份有限公司
Five-axis linkage machine tool rotation shaft geometric error continuous measurement method
ActiveCN105136031AImprove measurement efficiencyRealize continuous acquisitionUsing optical meansContinuous measurementRotational axis
The invention discloses a five-axis linkage machine tool rotation shaft geometric error continuous measurement method. The method comprises the steps that a laser displacement sensor is arranged on a spindle of a five-axis linkage machine tool; three non-collinear calibration balls are arranged on the work bench, and the homogeneous coordinate expression of each calibration ball is set; a swing axis A and a rotary axis C are used as calibration axes; the laser displacement sensor is used to measure the position deviation of the center of each calibration ball in X , Y and Z directions when the swing axis A and the rotary axis C in different corners; and according to the position deviation of the center of each calibration ball and the homogeneous coordinate expression of each calibration ball, geometric errors of the swing axis A and the rotary axis C are calculated. According to the invention, an oblique surface is used to establish the mapping relationship among the position deviation of a rigid body to be measured in X, Y and Z directions; translation in X, Y and Z dimensions is mapped to distance change in a single dimension; one-time chucking and continuous sampling are realized at the same time; and the method has the advantages of high measurement efficiency and high precision.
Owner:HUAZHONG UNIV OF SCI & TECH
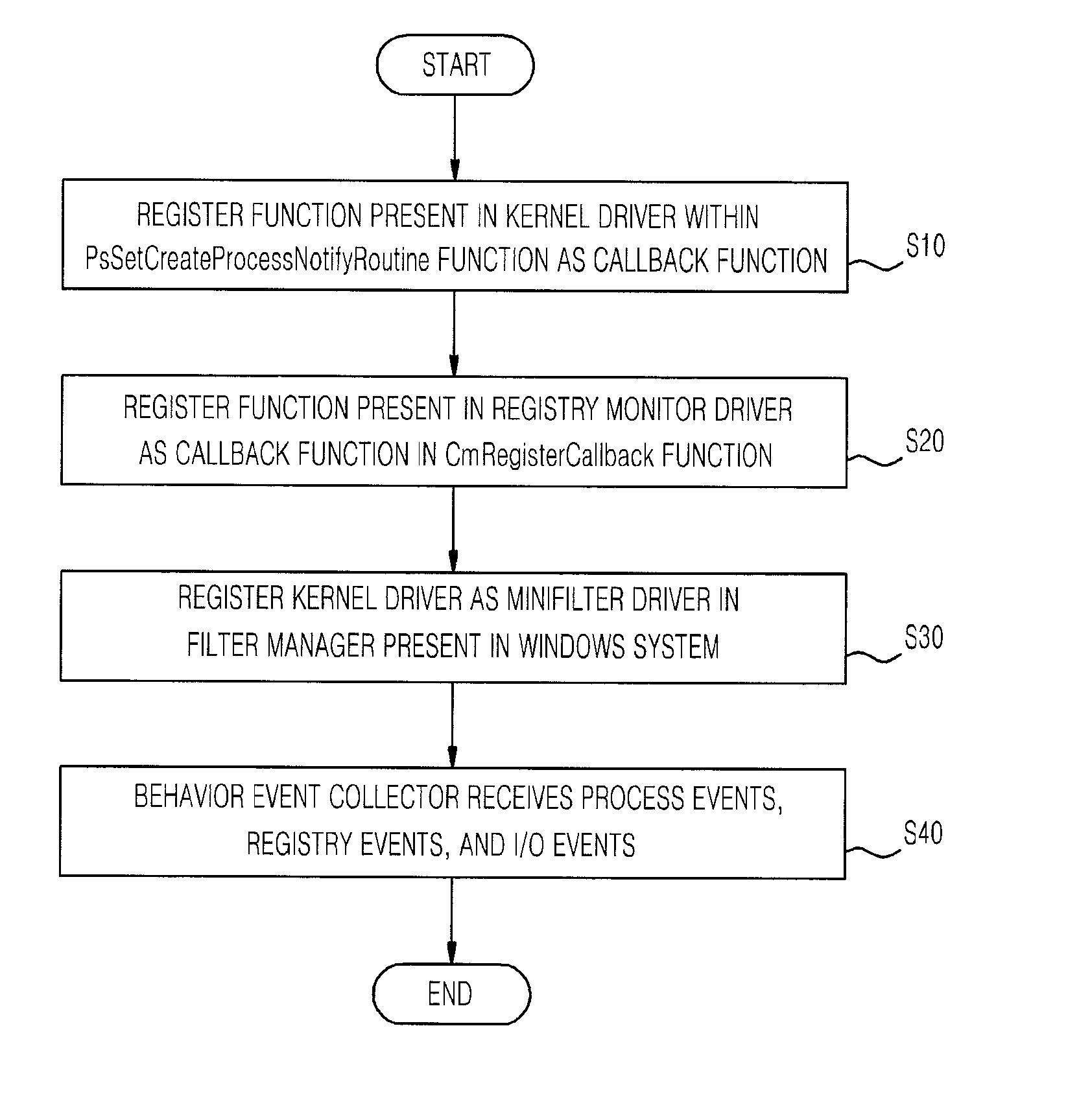
Malware auto-analysis system and method using kernel callback mechanism
InactiveUS20120079594A1Hamper efficiency of systemMalware may monitorMemory loss protectionError detection/correctionMalwareAnalysis method
In a malware auto-analysis method using a kernel callback mechanism, a function, present in a kernel driver within a PsSetCreateProcessNotifyRoutine function, is registered by a process monitor driver as a callback function when a computer boot. A function present in a registry monitor driver is registered by the registry monitor driver as a callback function in a CmRegisterCallback function when the driver is loaded. A kernel driver is registered by a file monitor driver as a mini-filter driver in a Filter Manager present in a Windows system. At least one of a process event, a registry event, or an Input / Output (I / O) event is received by a behavior event collector from the process monitor driver, the registry monitor driver, or the file monitor driver, respectively.
Owner:KOREA INTERNET & SECURITY AGENCY
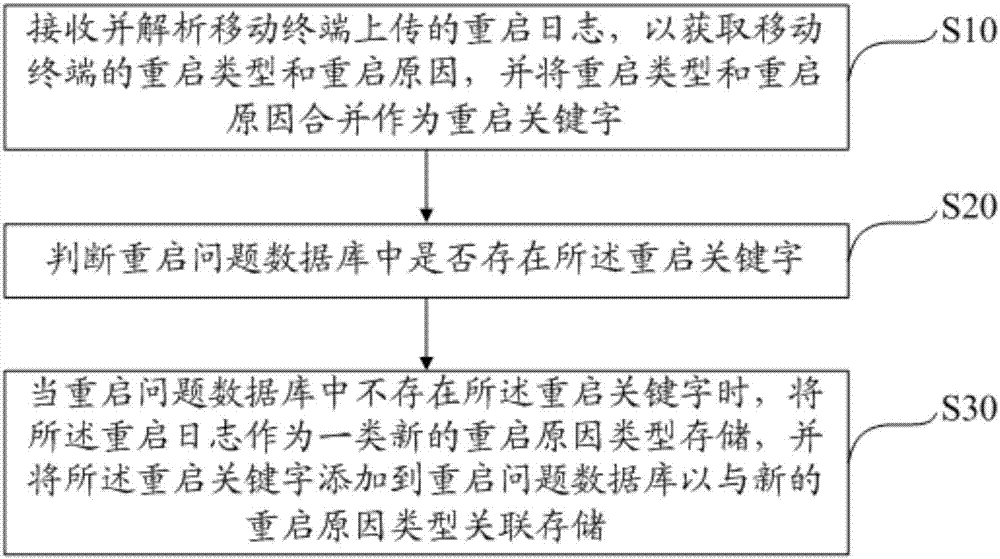
Method for merging reboot log, method and system for uploading reboot log and readable storage medium
The invention discloses a method for merging reboot log, a method and a system for uploading the reboot log and a readable storage medium. The method for merging the reboot log includes receiving and parsing the reboot log uploaded by mobile terminals to obtain reboot types and reboot reasons of the mobile terminals and merging the reboot types and the reboot reasons to obtain reboot keywords; judging whether the reboot keywords are available in reboot problem databases or not; storing the reboot log as a new reboot reason type when the reboot keywords are not available in the reboot problem databases and adding the reboot keywords into the reboot problem databases so as to associatively store the reboot keywords and the new reboot reason type. The methods, the system and the readable storage medium have the advantages that the reboot types and the reboot reasons are merged with one another to obtain the new reboot keywords, the reboot keywords are added into the reboot problem databases, accordingly, the reboot keywords and the new reboot reason type can be associatively stored, developers can know reasons for system reboot only by means of analyzing elements in the reboot problem databases, analysis on repeated types of reboot log can be omitted, and workload can be relieved.
Owner:NUBIA TECHNOLOGY CO LTD
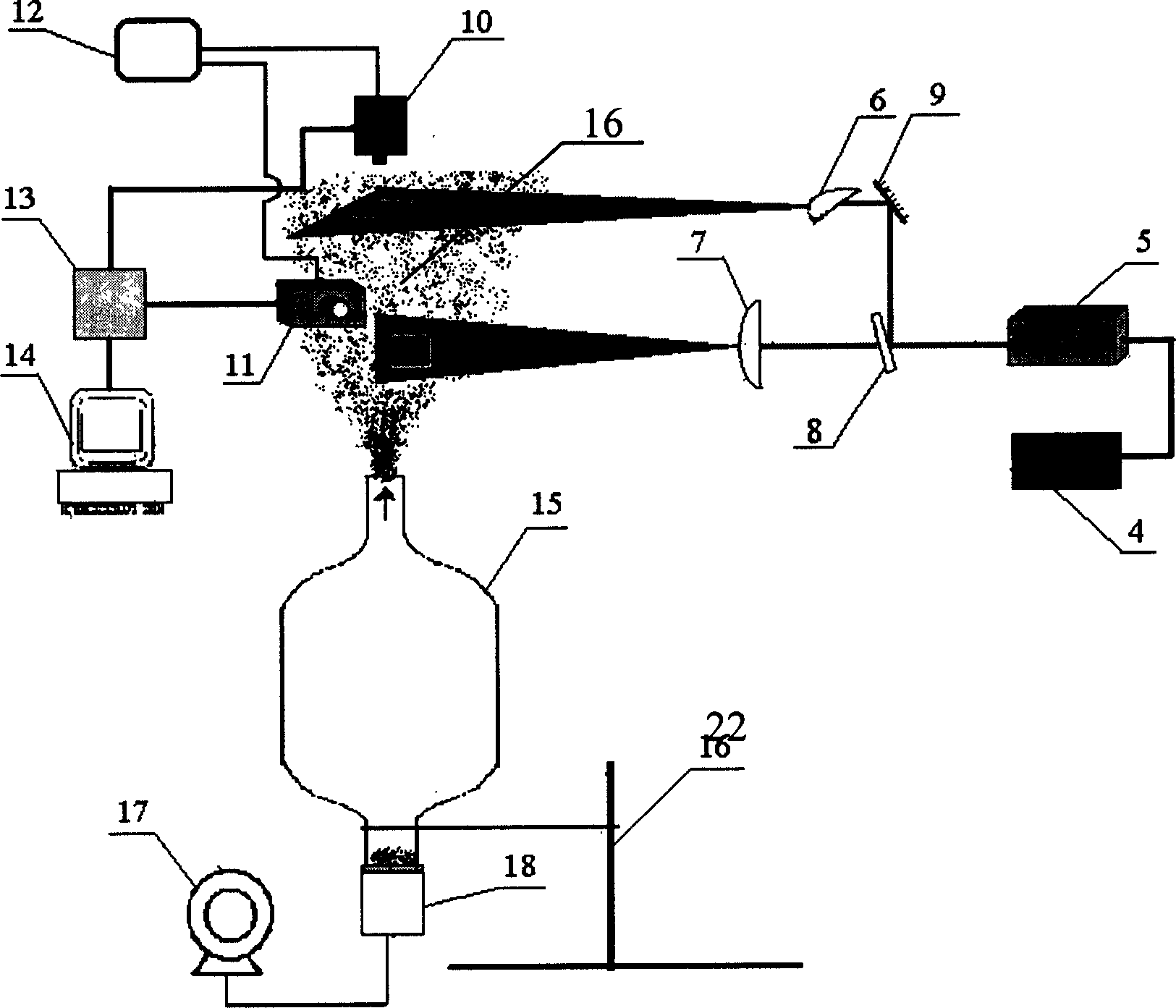
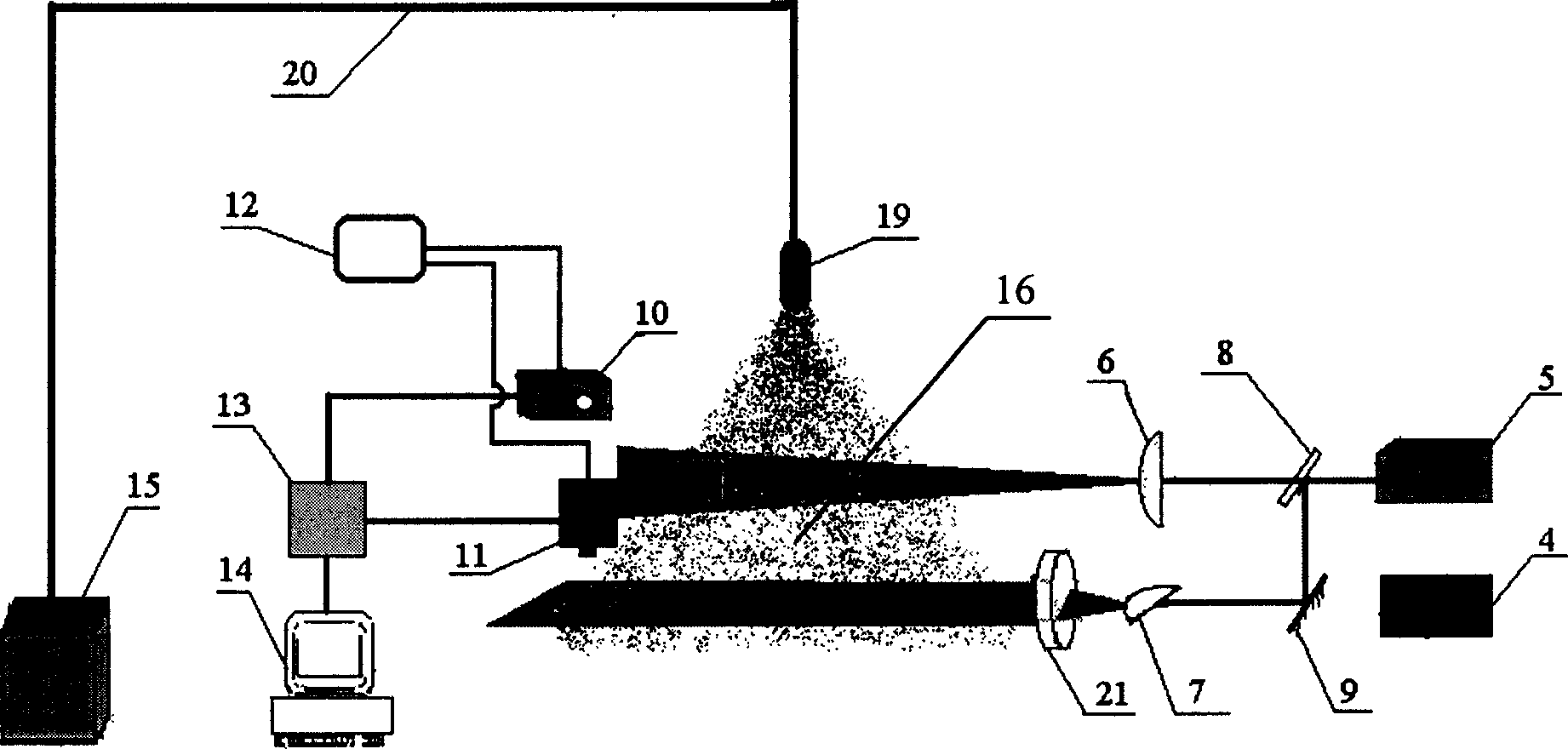
Particle field total-field measurement process and apparatus based on laser sheet optical image-forming
InactiveCN1464288ASolve the limitation that only the flow field velocity can be measuredSolve the shortcomings of single-point measurement methodsMeasurement devicesMeasurement deviceFull field
The present invention is whole particle field measuring method and equipment based on laminar laser imaging and features that particles in test flow field are illuminated with orthogonal laminar laser beams and two CCD cameras are used to take the particle motion locus images both in the direction perpendicular to the flow field and in the direction parallel to the flow field separately. The equivalent diameters of particles are determined via particle image distinction and statistical analysis of covered pixels, and the particle motion speeds, including magnitudes and directions, are determined via the distinction and analysis of particle motion locus image, so as to obtain the size spectrum and speed field distribution of particles in the imaging plane. The present invention needs no addition of tracing particle, and may be used widely in the two-phase and multi-phase flow field measurement in various fields.
Owner:UNIV OF SCI & TECH OF CHINA
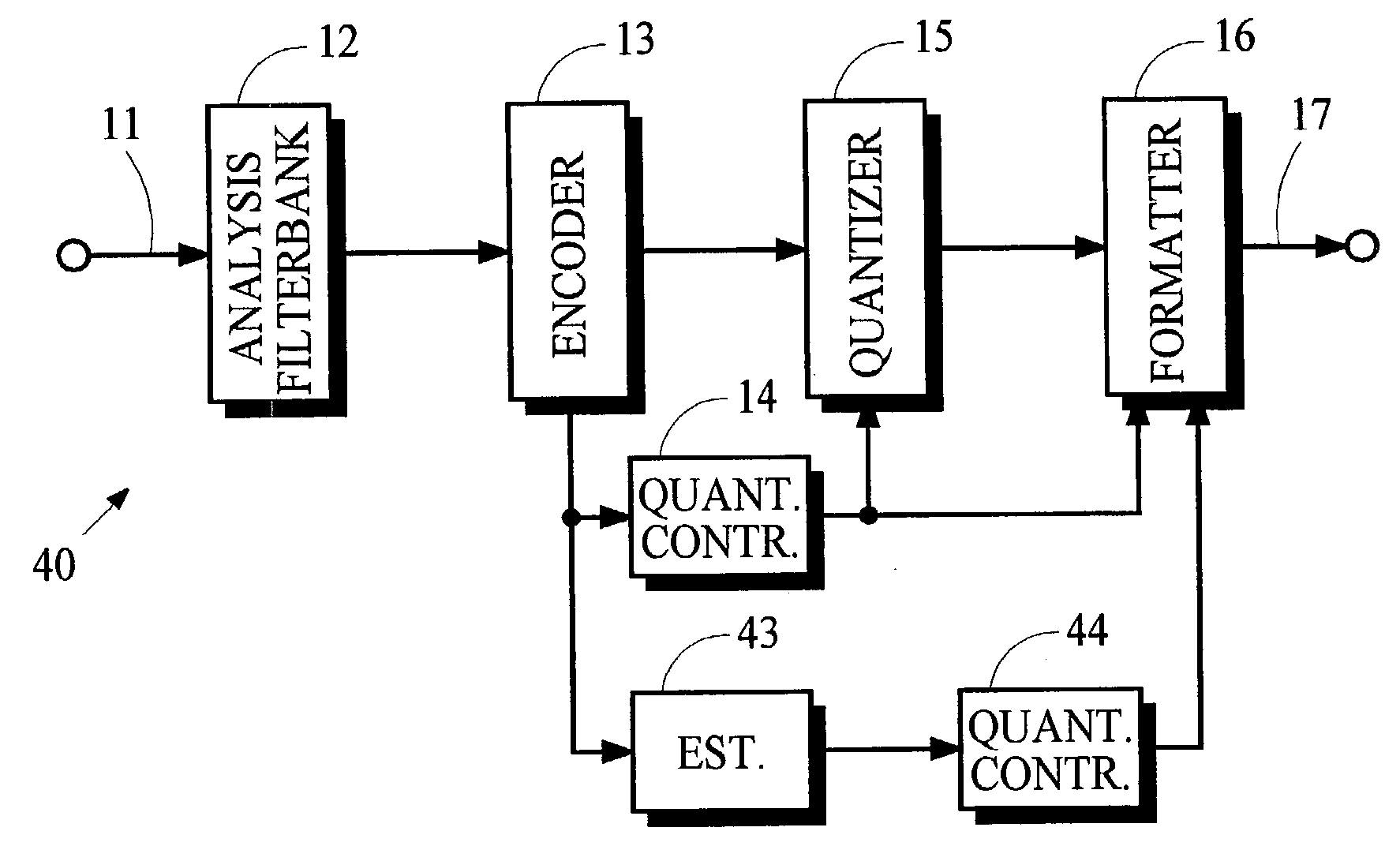
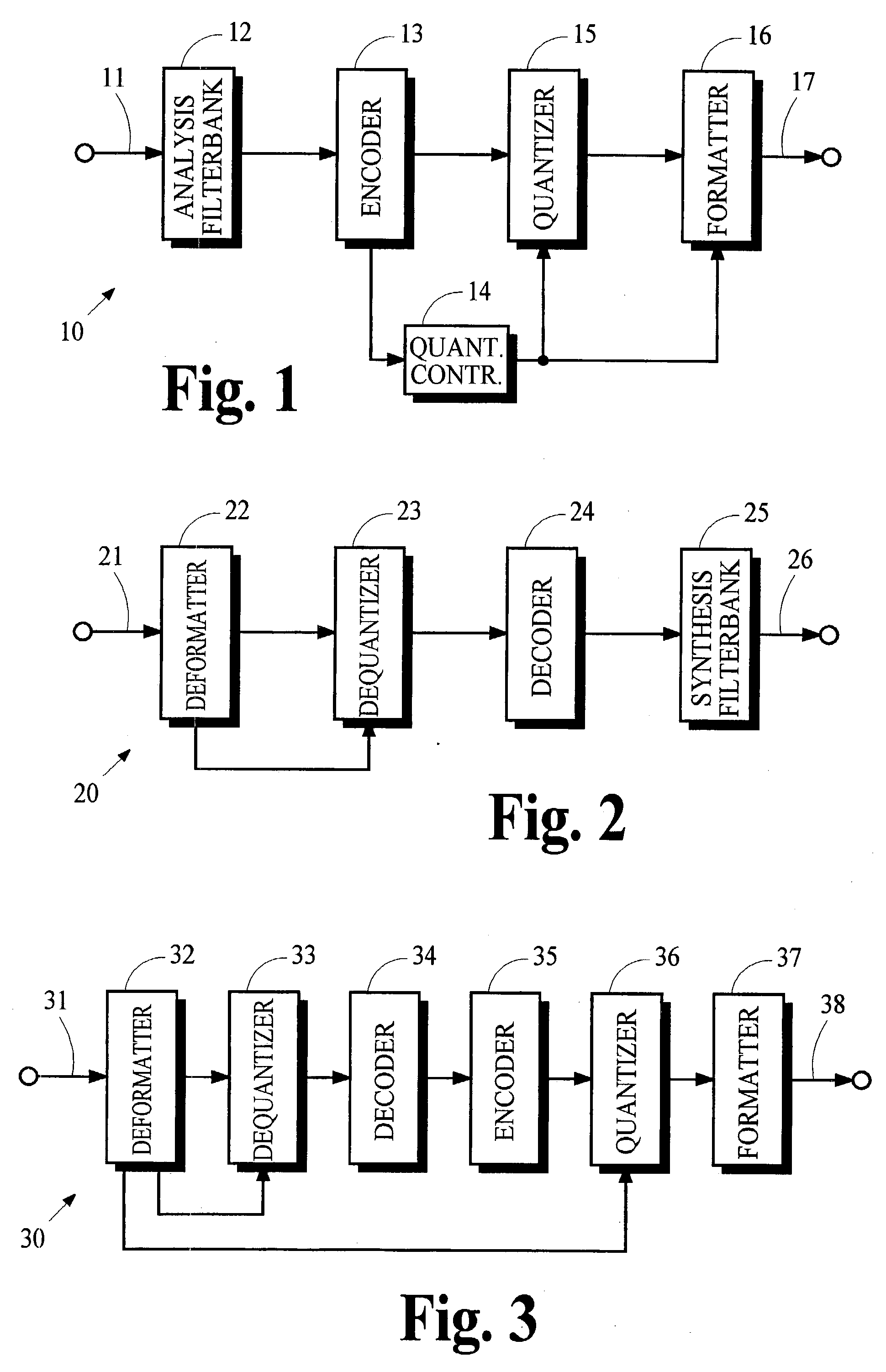
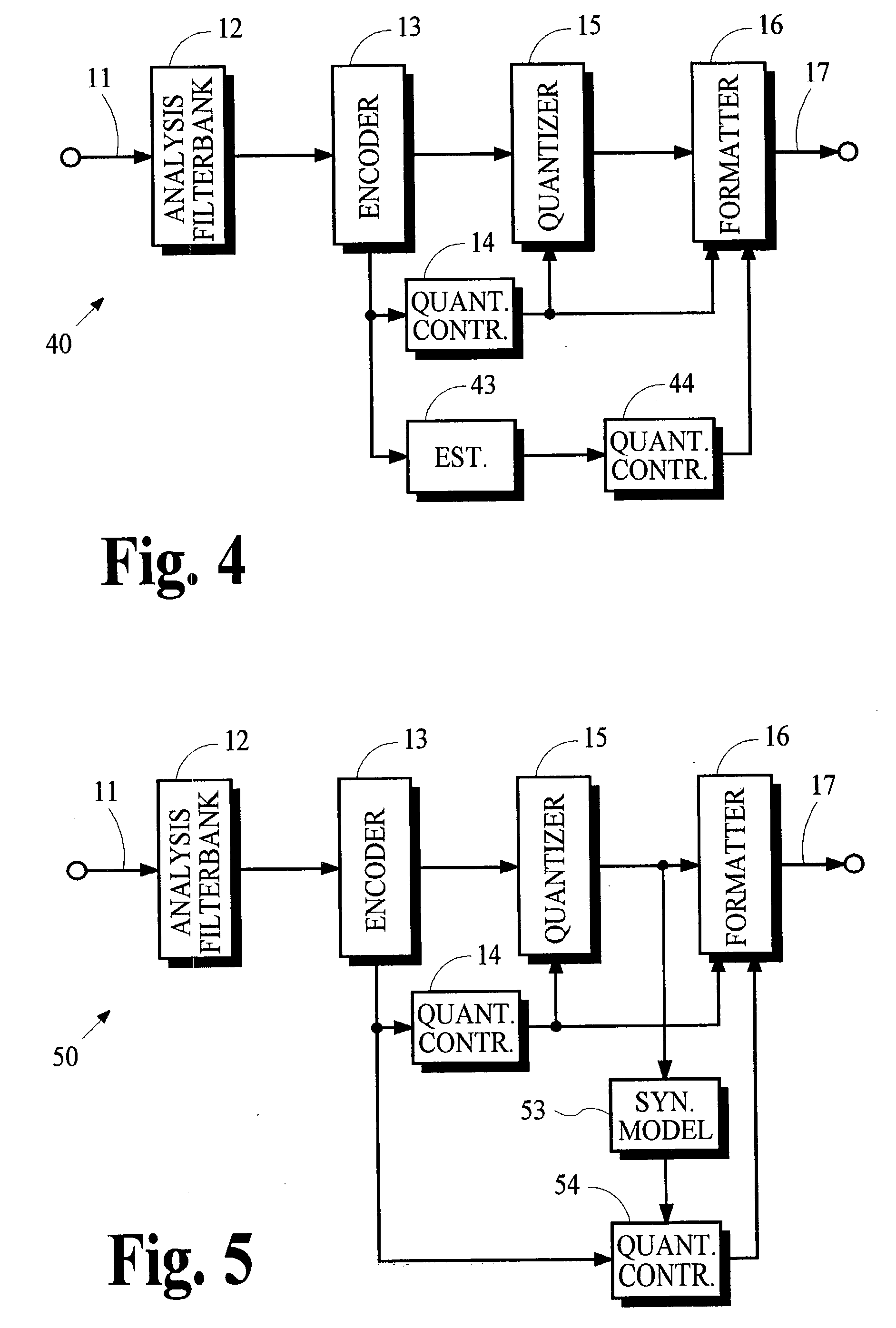
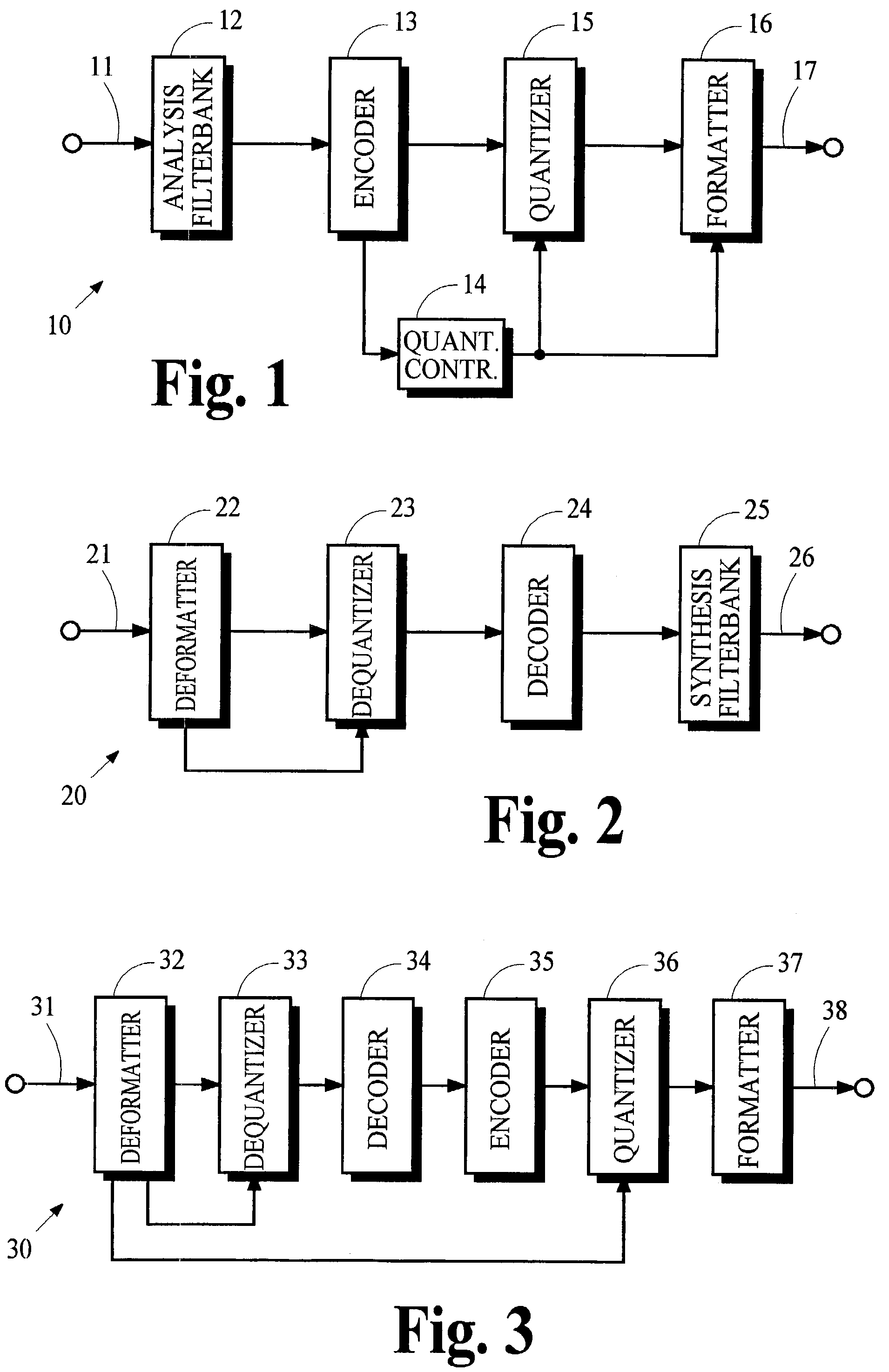
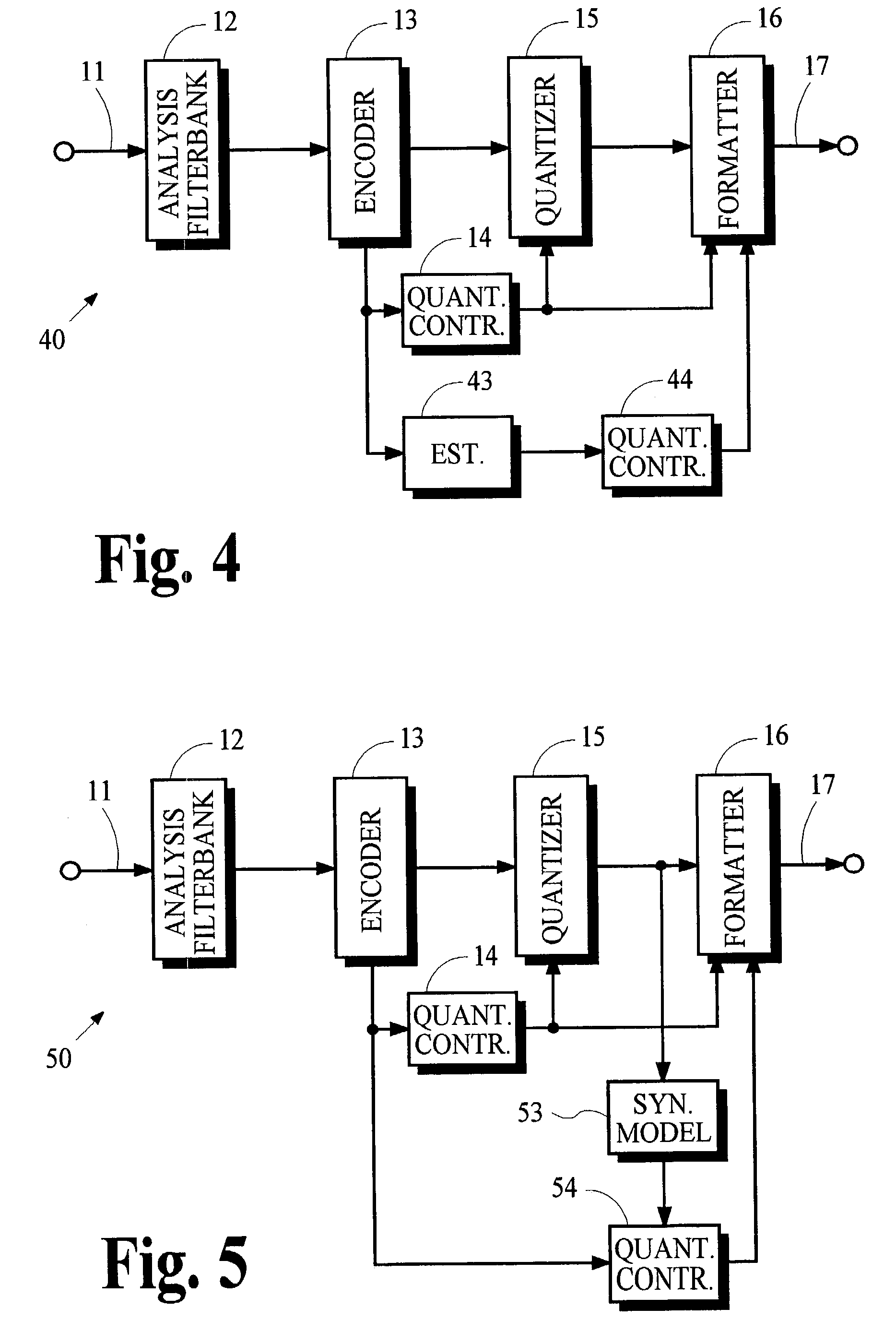
Conversion of synthesized spectral components for encoding and low-complexity transcoding
ActiveUS20040165667A1Quality improvementLow implementation costSpeech analysisTransmissionFrequency spectrumTranscoding
In an audio coding system, an encoding transmitter represents encoded spectral components as normalized floating-point numbers. The transmitter provides first and second control parameters that may be used to transcode the encoded spectral parameters. A transcoder uses first control parameters to partially decode the encoded components and uses second control parameters to re-encode the components. The transmitter determines the second control parameters by analyzing the effects of arithmetic operations in the partial-decoding process to identify situations where the floating-point representations lose normalization. Exponents associated with the numbers that lose normalization are modified and the modified exponents are used to calculate the second control parameters.
Owner:DOLBY LAB LICENSING CORP
Clustering algorithm-based exceptional event analysis method for evaluating whole state of electric meter
InactiveCN103630869AAvoid applicationAvoid analysisElectrical measurementsOvervoltageCluster algorithm
The invention discloses a clustering algorithm-based exceptional event analysis method for evaluating the whole state of an electric meter. The method comprises the steps of aiming at the abnormal users with overvoltage, overcurrent, wrong clock of the electric meter, undervoltage of the electric meter, overhigh temperature of the electric meter, opened cover of the electric meter, continuous exceeding on the upper limit of a load, voltage reverse phase sequence, current reverse phase sequence, inversed current, imbalanced voltage three phases, imbalanced current three phases and the like, the document information of the users are checked, and the users having documents with problems are filtered; for the users with the abnormity, the whole state of the electric meter is evaluated and analyzed by combining information such as marketing service metering fault, fault meter changing and information lack examining on site through the comprehensive analysis of the clustering algorithm according to multiple dimensions such as the manufacturer, the batch, the region, the type of the metering device, the voltage level, the user class and the line, a technical means and a reference basis are provided for whether an electric power company for on-site inspection needs to be performed and whether a shift plan needs to be made, and the method is accurate and has small errors.
Owner:STATE GRID CORP OF CHINA +1
Aryl- and heteroaryl-substituted tetrahydroisoquinolines and use thereof to block reuptake of norepinephrine, dopamine, and serotonin
ActiveUS20060052378A1Good curative effectQuick effectBiocideNervous disorderBenzoxazoleChemical structure
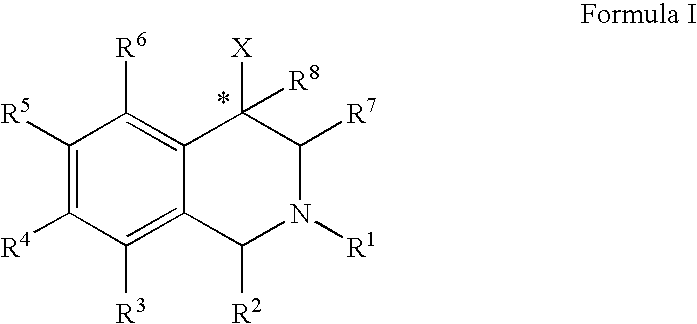
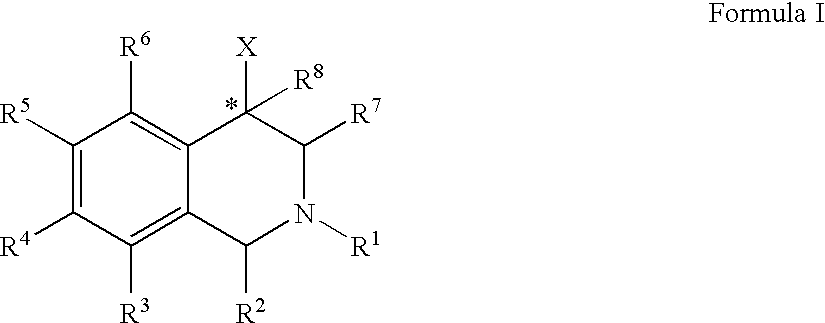
The compounds of the present invention are represented by the chemical structure found in Formula (I): wherein: the carbon atom designated * is in the R or S configuration; and X is a fused bicyclic carbocycle or heterocycle selected from the group consisting of benzofuranyl, benzo[b]thiophenyl, benzoisothiazolyl, benzoisoxazolyl, indazolyl, indolyl, isoindolyl, indolizinyl, benzoimidazolyl, benzooxazolyl, benzothiazolyl, benzotriazolyl, imidazo[1,2-a]pyridinyl, pyrazolo[1,5-a]pyridinyl, [1,2,4]triazolo[4,3-a]pyridinyl, thieno[2,3-b]pyridinyl, thieno[3,2-b]pyridinyl, 1H-pyrrolo[2,3-b]pyridinyl, indenyl, indanyl, dihydrobenzocycloheptenyl, tetrahydrobenzocycloheptenyl, dihydrobenzothiophenyl, dihydrobenzofuranyl, indolinyl, naphthyl, tetrahydronaphthyl, quinolinyl, isoquinolinyl, 4H-quinolizinyl, 9aH-quinolizinyl, quinazolinyl, cinnolinyl, phthalazinyl, quinoxalinyl, benzo[1,2,3]triazinyl, benzo[1,2,4]triazinyl, 2H-chromenyl, 4H-chromenyl, and a fused bicyclic carbocycle or fused bicyclic heterocycle optionally substituted with substituents (1 to 4 in number) as defined in R14; with R1, R2, R3, R4, R5, R6, R7, R8, and R14 defined herein.
Owner:ALBANY MOLECULAR RESEARCH INC
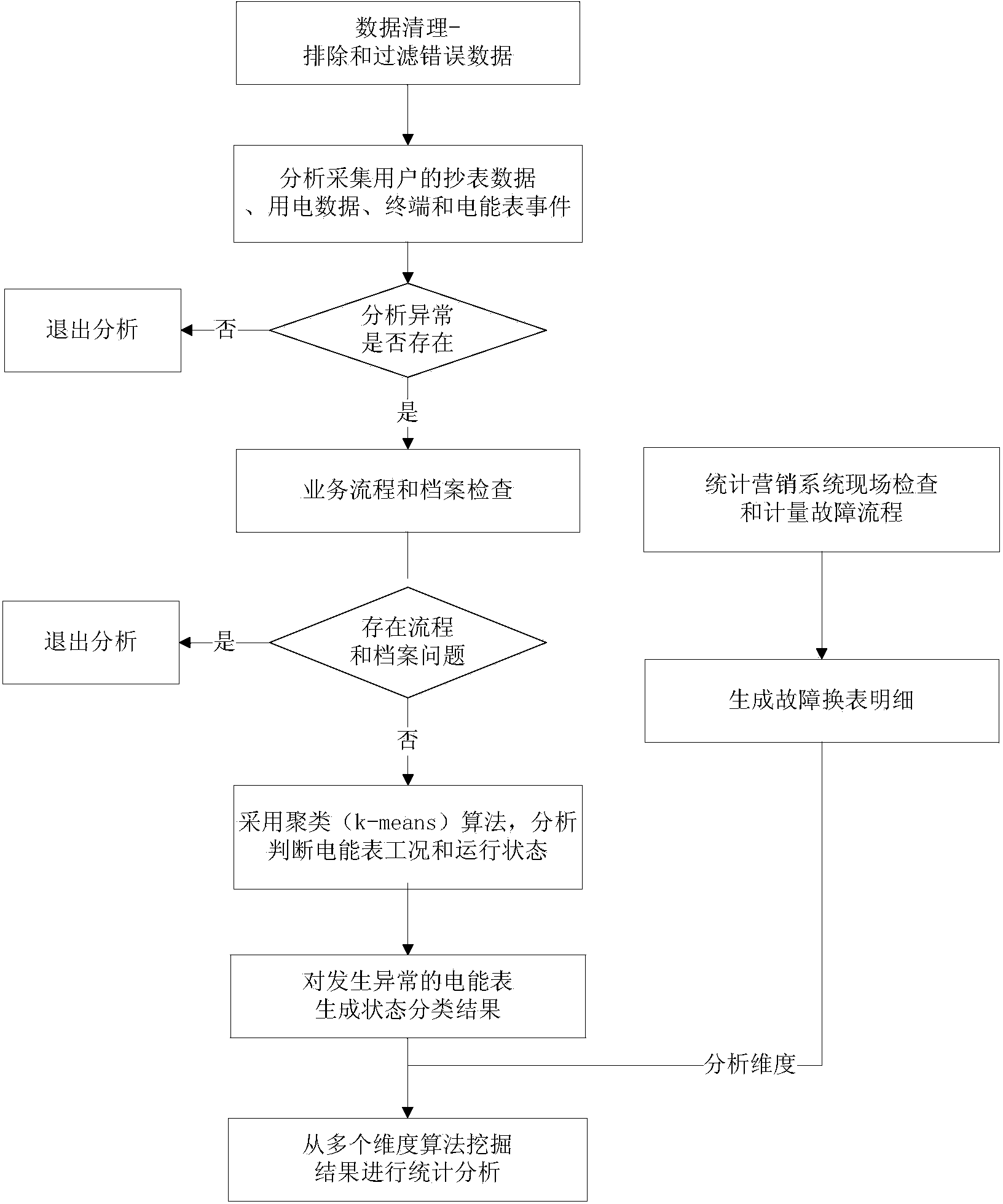
Conversion of synthesized spectral components for encoding and low-complexity transcoding
ActiveUS7318027B2Quality improvementLow implementation costSpeech analysisFrequency spectrumTranscoding
In an audio coding system, an encoding transmitter represents encoded spectral components as normalized floating-point numbers. The transmitter provides first and second control parameters that may be used to transcode the encoded spectral parameters. A transcoder uses first control parameters to partially decode the encoded components and uses second control parameters to re-encode the components. The transmitter determines the second control parameters by analyzing the effects of arithmetic operations in the partial-decoding process to identify situations where the floating-point representations lose normalization. Exponents associated with the numbers that lose normalization are modified and the modified exponents are used to calculate the second control parameters.
Owner:DOLBY LAB LICENSING CORP
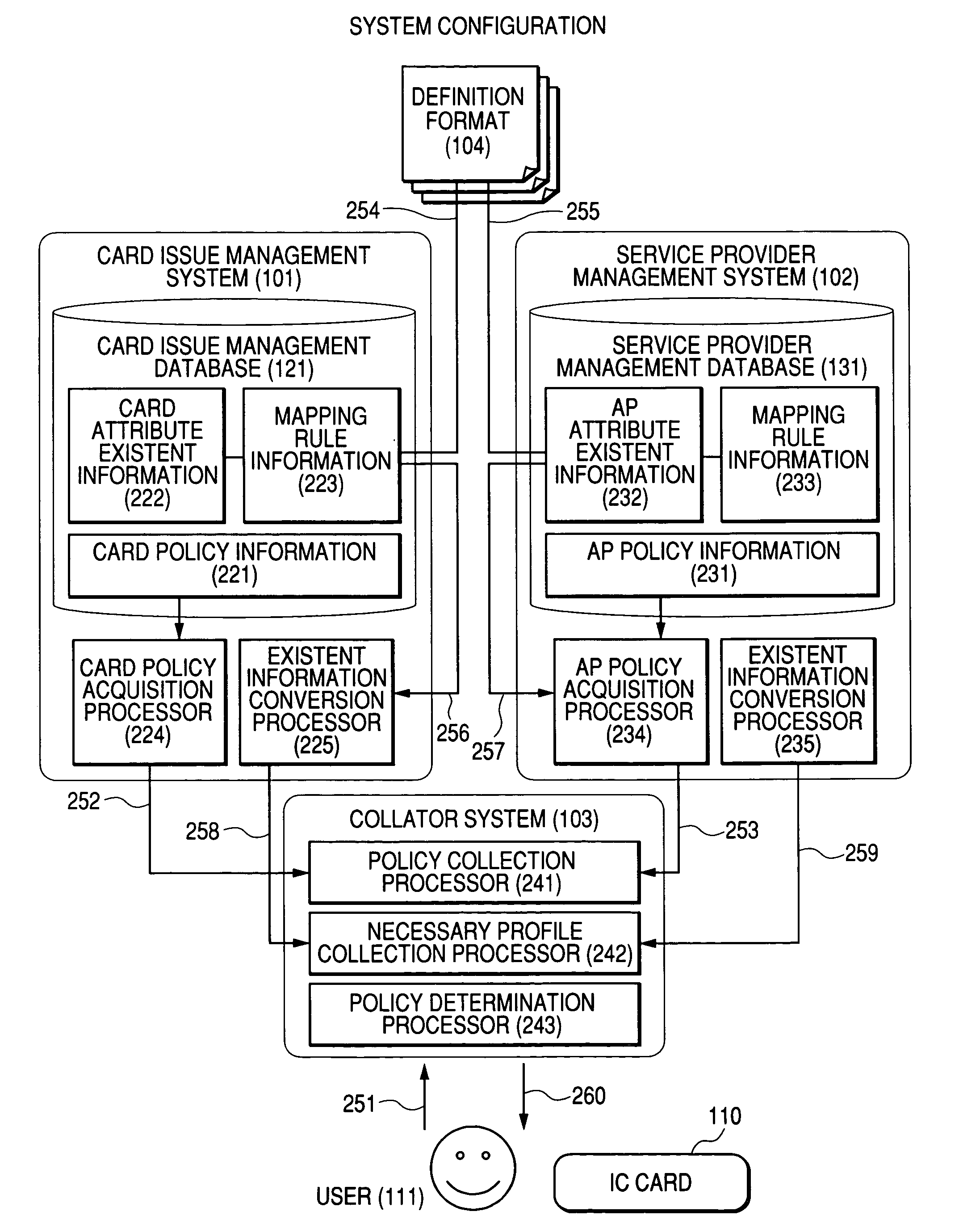
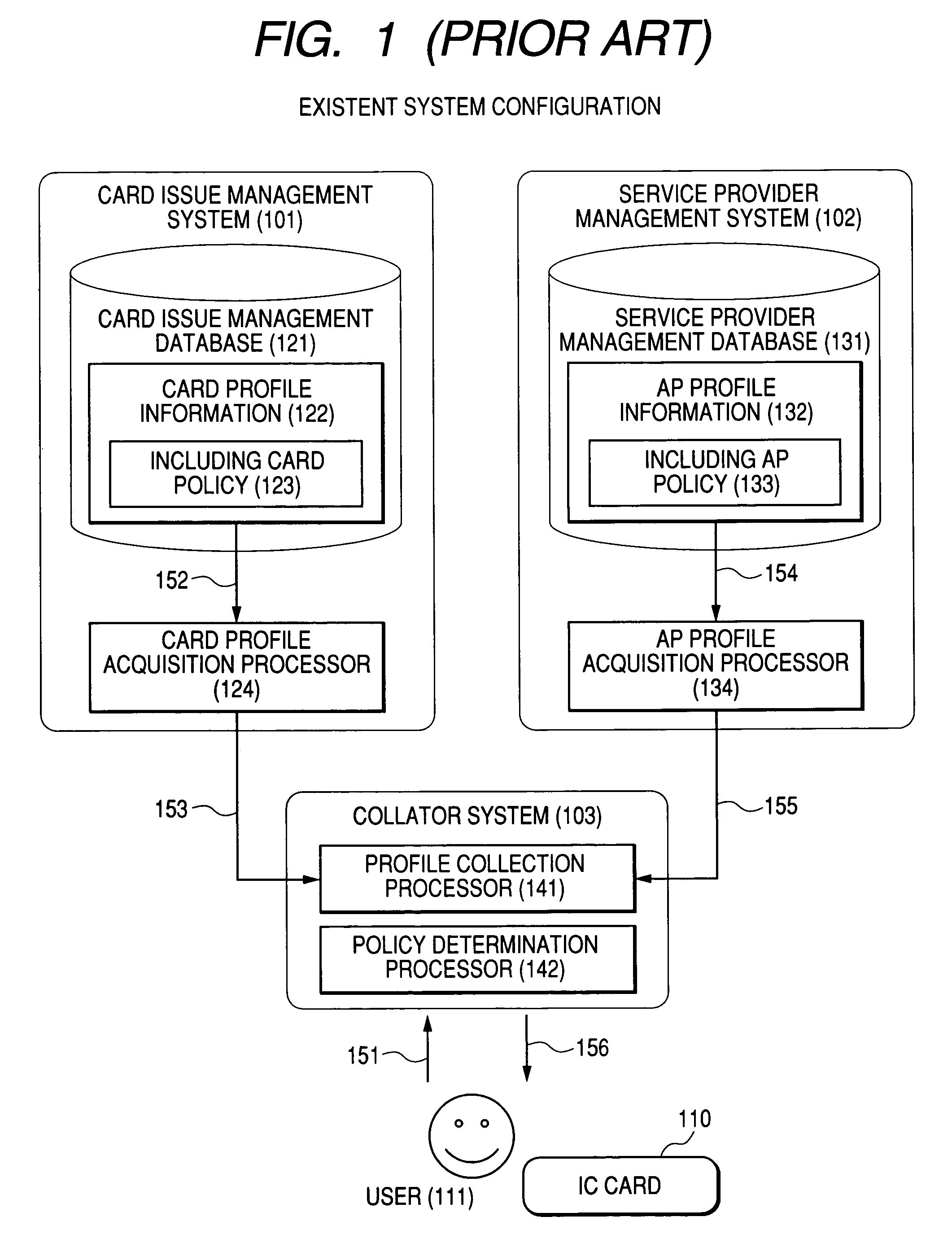
Integrated circuit card system and application loading method
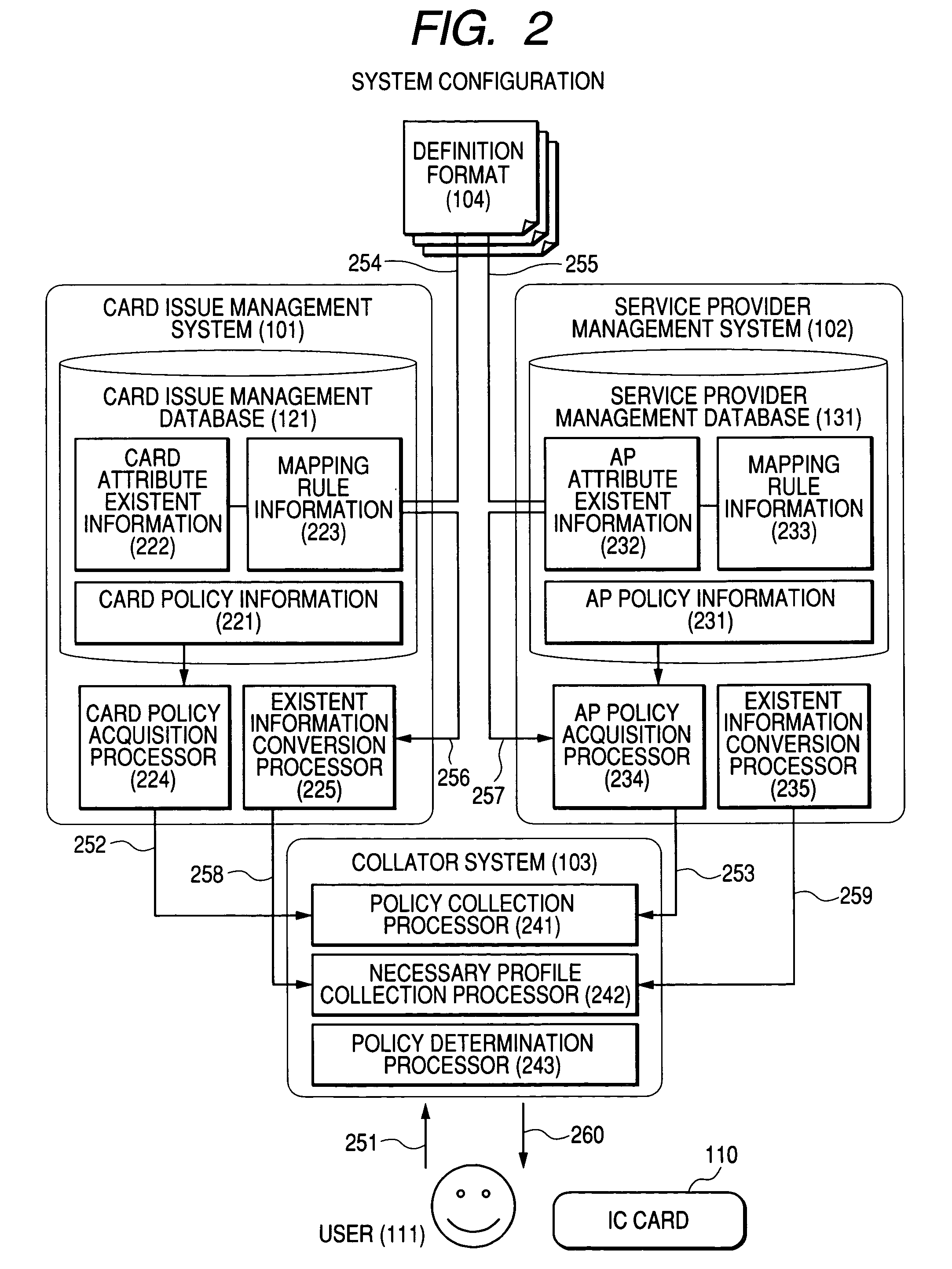
InactiveUS7487920B2Quantity minimizationAvoid analysisOther printing matterCo-operative working arrangementsService provisionService product management
An integrated circuit card operation management system and method are provided. In one example of the system, a collator system is provided for receiving a user request to determine whether the application program can be loaded, for acquiring a card policy from a card issue management system, and for acquiring an application program policy from a service provider management system. The collator system requests card related information of the card issue management system and requests application program related information of the service provider management system. The collator system specifies a definition format. The card issue management system and the service provider management system extract requested information from existent information, convert the requested information according to the specified definition format, and transmit the converted information to the collator system. Using the acquired policies and the acquired profiles, the collator system determines whether the application program can be loaded.
Owner:HITACHI LTD
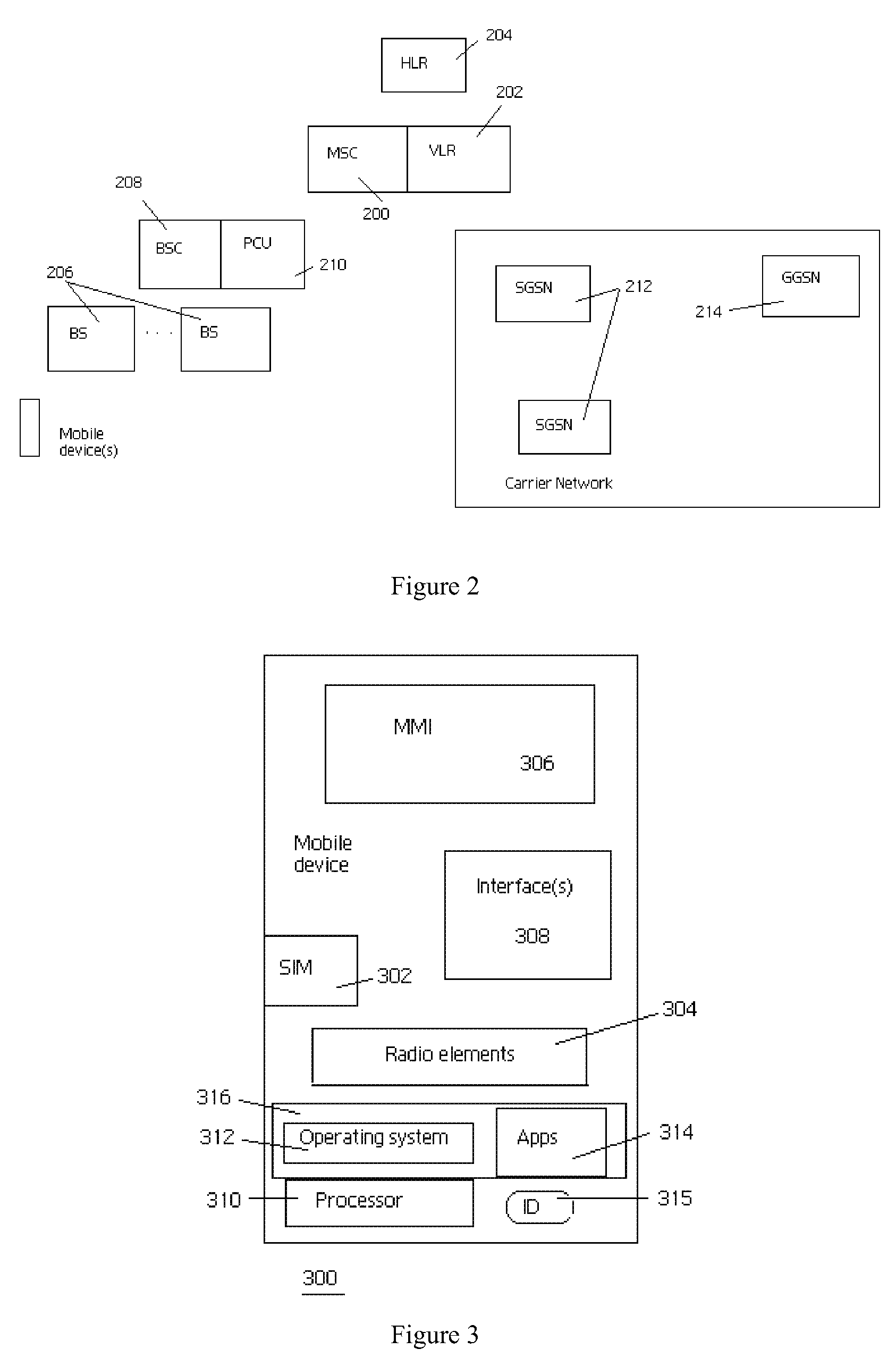
Method and apparatus for managing obfuscated mobile device user identities
InactiveUS20080293411A1Improve securityEnsuring privacyUnauthorised/fraudulent call preventionDigital data processing detailsUnique identifierMobile device
A mobile device identifier (such as an MSISDN) that typically accompanies a mobile device request is replaced with an “enriched” identifier that exposes the mobile device user's home operator but obfuscates the mobile device's (and, thus, the device user's) identity. In one embodiment, the identifier comprises a first part, and a second part. The first part comprises a data string that identifies (either directly or through a database lookup) the mobile device user's home operator. The second part, however, is an opaque data string, such as a one-time-use unique identifier (UID) or a value that is otherwise derived as a function of the MSISDN (or the like). The opaque data string encodes the mobile device's identity in a manner that preferably can be recovered only by the user's home operator. The present invention describes a method and apparatus for use in a home network to manage the generation, storage and use of the unique identifiers.
Owner:IBM CORP
Use of aryl- and heteroaryl-substituted tetrahydroisoquinolines to block reuptake of norepinephrine, dopamine, and serotonin
InactiveUS20060063766A1Little and no activityMinimal potential for substance abuseBiocideNervous disorderBenzoxazoleBenzene
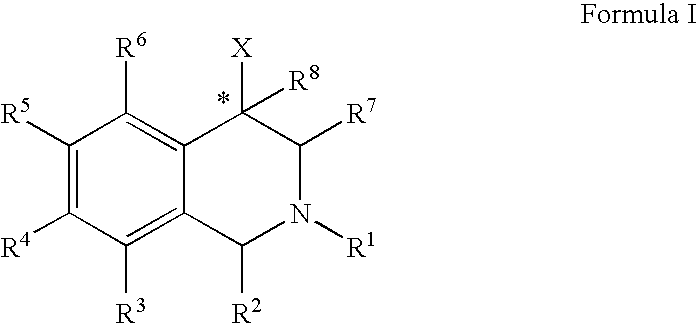
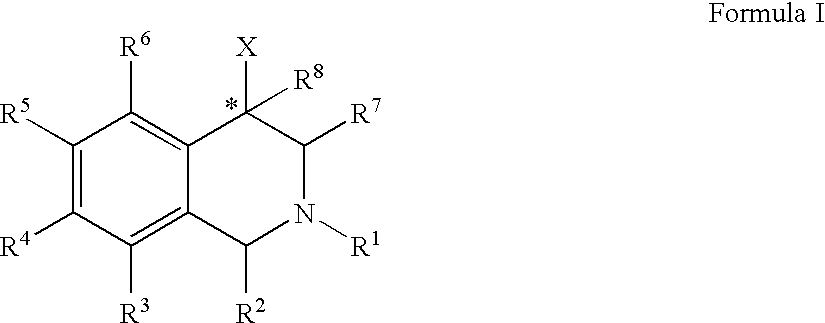
The compounds of the present invention are represented by the chemical structure found in Formula (I): wherein: the carbon atom designated * is in the R or S configuration; and X is a fused bicyclic carbocycle or heterocycle selected from the group consisting of benzofuranyl, benzo[b]thiophenyl, benzoisothiazolyl, benzoisoxazolyl, indazolyl, indolyl, isoindolyl, indolizinyl, benzoimidazolyl, benzooxazolyl, benzothiazolyl, benzotriazolyl, imidazo[1,2-a]pyridinyl, pyrazolo[1,5-a]pyridinyl, [1,2,4]triazolo[4,3-a]pyridinyl, thieno[2,3-b]pyridinyl, thieno[3,2-b]pyridinyl, 1H-pyrrolo[2,3-b]pyridinyl, indenyl, indanyl, dihydrobenzocycloheptenyl, tetrahydrobenzocycloheptenyl, dihydrobenzothiophenyl, dihydrobenzofuranyl, indolinyl, naphthyl, tetrahydronaphthyl, quinolinyl, isoquinolinyl, 4H-quinolizinyl, 9aH-quinolizinyl, quinazolinyl, cinnolinyl, phthalazinyl, quinoxalinyl, benzo[1,2,3]triazinyl, benzo[1,2,4]triazinyl, 2H-chromenyl, 4H-chromenyl, and a fused bicyclic carbocycle or fused bicyclic heterocycle optionally substituted with substituents (1 to 4 in number) as defined in R14; with R1, R2, R3, R4, R5, R6, R7, R8, and R14 defined herein.
Owner:ALBANY MOLECULAR RESEARCH INC
Systems and Methods for the Detection of Low-Level Harmful Substances in a Large Volume of Fluid
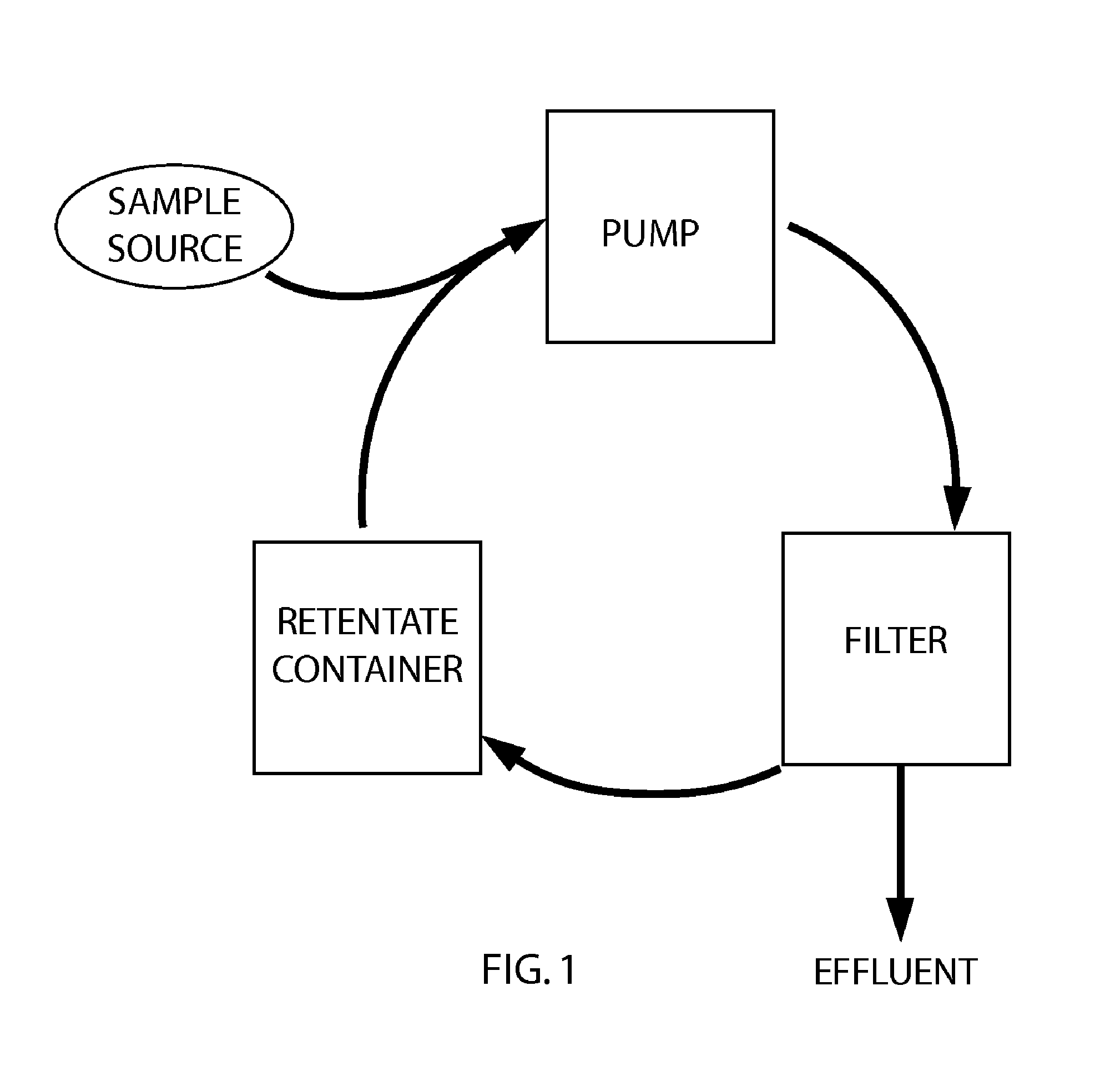
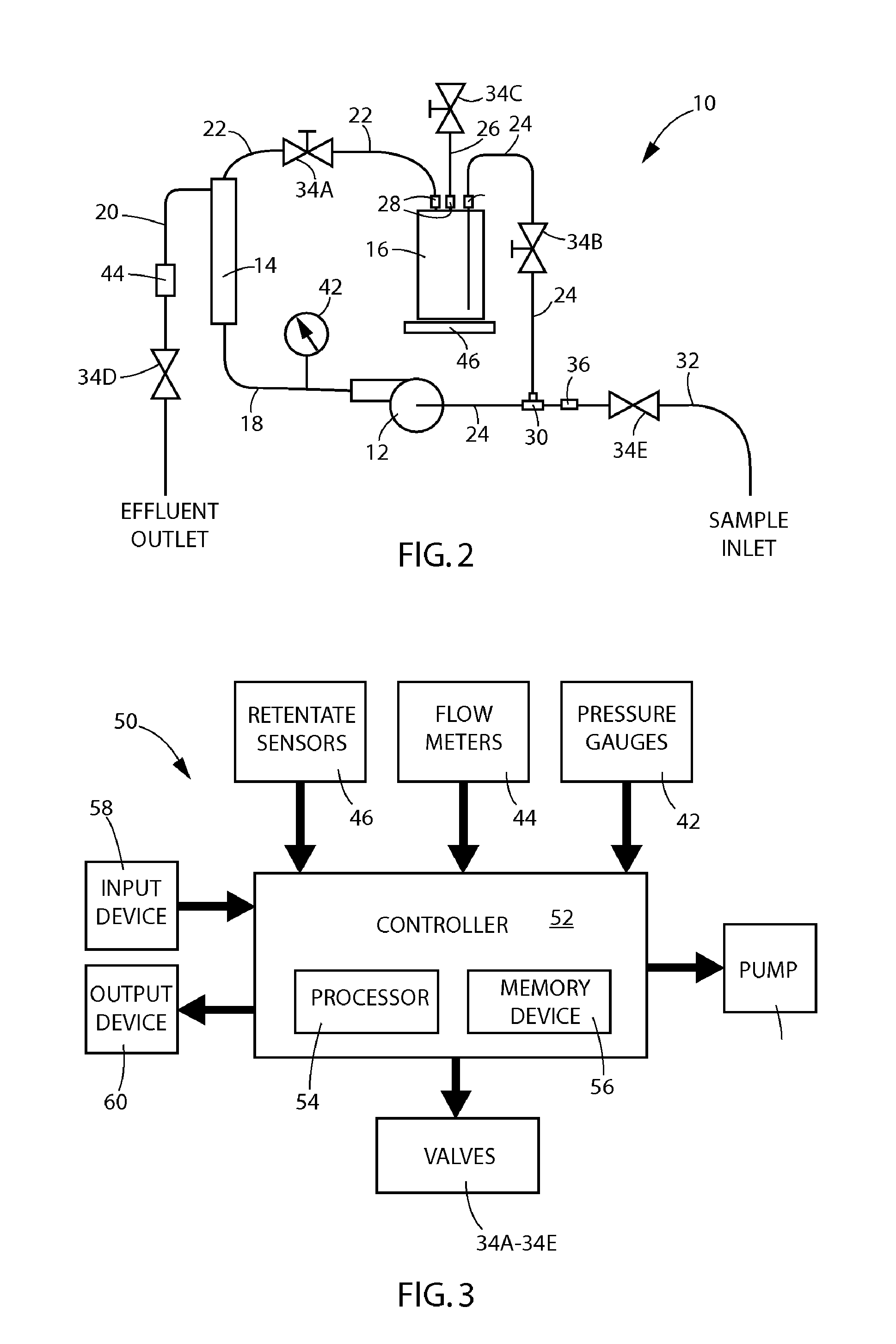
ActiveUS20130239666A1Lower the volumeObstruct passageSemi-permeable membranesComponent separationControl systemAmount of substance
A method and device for the detection of low-level harmful substances in a large volume of fluid comprising using a concentrator system to produce a retentate and analyzing the retantate for the presence of at one harmful substance. The concentrator system performs a method comprising pumping at least 10 liters of fluid from a sample source through a filter While pumping, the concentrator system diverts retentate from the filter into a container. The concentrator system also recirculates at least part of the retentate in the container again through the filter. The concentrator system controls the speed of the pump with a control system thereby maintaining a fluid pressure less than 25 psi during the pumping of the fluid; monitors the quantity of retentate within the container with a control system, and maintains a reduced volume level of retentate and a target volume of retentate.
Owner:ENVIRONMENTAL PROTECTION AGENCY US +1
Software protection method based on intermediate result compiling
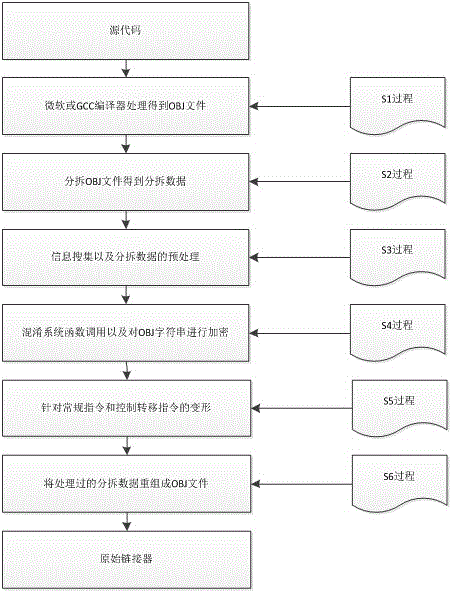
ActiveCN104091100APrevent illegal crackingAvoid analysisProgram/content distribution protectionSoftware engineeringConfusion
The invention discloses a software protection method based on intermediate result compiling. The software protection method includes the following steps (1), software source codes are compiled to obtain an original object file (OBJ); (2), the original OBJ is analyzed to obtain partitioned data aiming at the original OBJ; (3), the analysis result of the step (2) is preprocessed; (4), system function call is concealed, redundant functions are inserted, and global character strings used for a system are encrypted; (5), deformation is performed for a common instruction; (6), the scattered data obtained through processing in the processes are recombined to form the OBJ, and then an executable file is generated through link of a linker. Confusion and protection at the instruction level for the OBJ are achieved, errors can be avoided, the confusion effect and the confusion quality are improved, and software is prevented from being illegally cracked or analyzed.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
System and method for counting number of online users of live platform
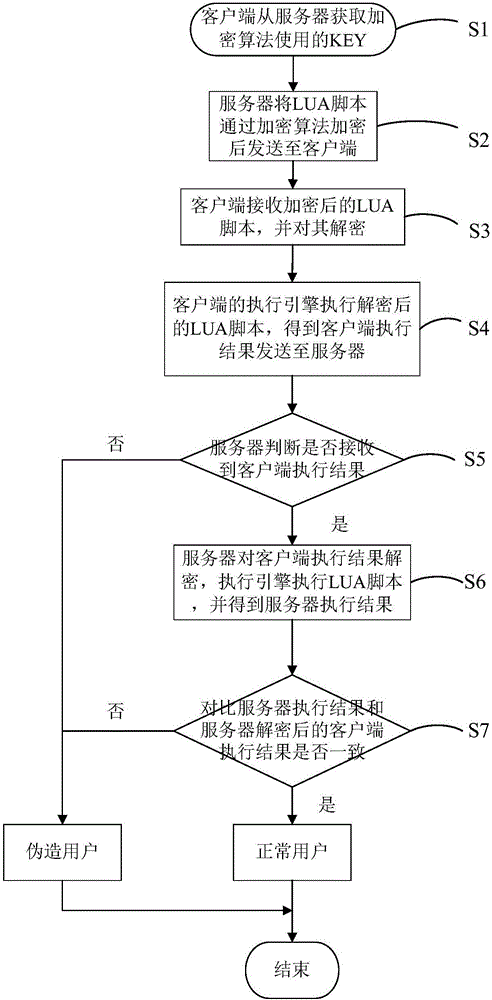
ActiveCN105959728APrevent malicious brushing of popularityPrevent reverse crackingSelective content distributionCiphertextCounting Number
The invention discloses a system and method for counting the number of online users of a live platform, and relates to the technical field of an internet live platform. The system comprises a server and a client. An LUA script is stored in the server; an execution engine for executing the LUA script is integrated in the server; after encrypting the LUA script by an encryption algorithm, the server sends the encrypted LUA script to the client; the client is used for receiving the encrypted LUA script sent by the server and a ciphertext KEY in the encryption algorithm and carrying out decryption on the encrypted LUA script; an execution engine for executing the LUA script is also integrated in the client; and the execution engine of the client executes the decrypted LUA script and sends a client execution result to the server after encrypting the client execution result by the encryption algorithm, and the server judges whether the client execution result is received and verifies the client execution result. According to the system and method disclosed by the invention, difficulty that a Hack counterfeits a login user can be increased, so that the counted number of the online users of the live platform tends to a real level.
Owner:WUHAN DOUYU NETWORK TECH CO LTD
Design internal stress analyzing method for hinged hollow plank girder bridge with reinforced transverse prestress
InactiveCN102953347AAvoid analysisSimulation is accurateBridge erection/assemblyBridge strengtheningPlankPre stress
The invention discloses a design internal stress analyzing method for a hinged hollow plank girder bridge with reinforced transverse prestress. Transverse prestress is applied to reinforce a hollow plank girder bridge with a hinged joint, and the reinforcing mode is one of effective measures for solving the single-plate force applying and the crack along the hinged joint of the hinged hollow plank girder bridge. The patent aims at the characteristics that the plank girder reinforced by the reinforcing method can bear bending bidirectional stress in the longitudinal and transverse directions, and simulates the reinforced hollow plank girder bridge to an orthotropic anisotropic plate and adopts a corresponding longitudinal-transverse rigidity hypothesis to propose an internal stress analyzing method for designing the bridges with the reinforced transverse prestress, so that the problem that no practical design calculation methods are available for the internal stress analysis of the hinged hollow plank girder bridge is solved, and meanwhile, the complexity and time consumption of the modeling calculation in the finite element software calculation are avoided.
Owner:HUA HUI ENGINEERING DESIGN GROUP CO LTD
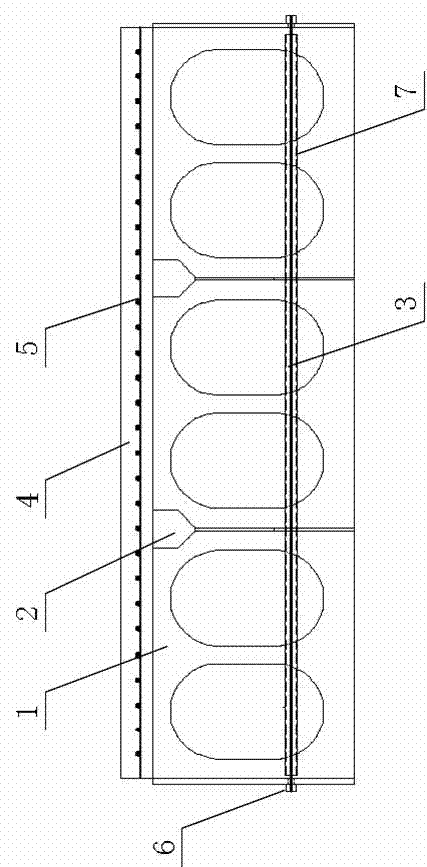
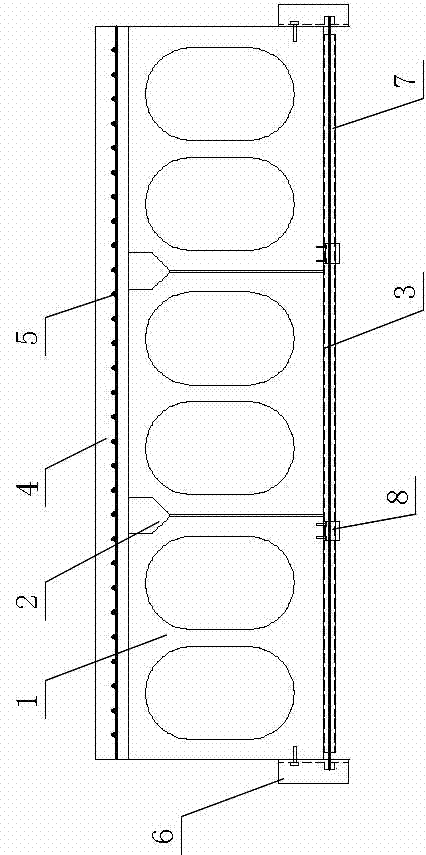
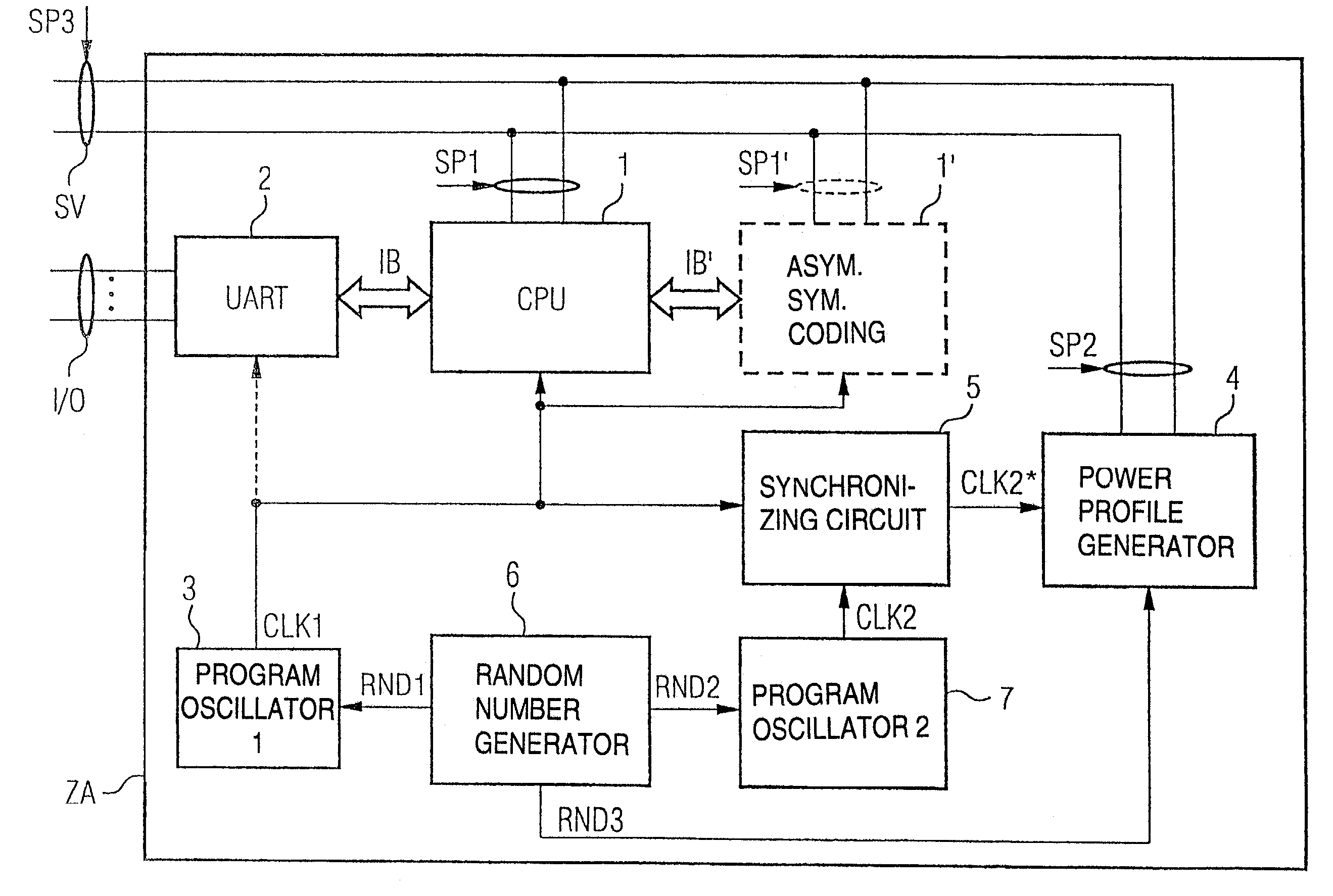
Power analysis resistant coding device
InactiveUS7127620B2Reliable preventionAvoid analysisEncryption apparatus with shift registers/memoriesPublic key for secure communicationPower analysisComputer hardware
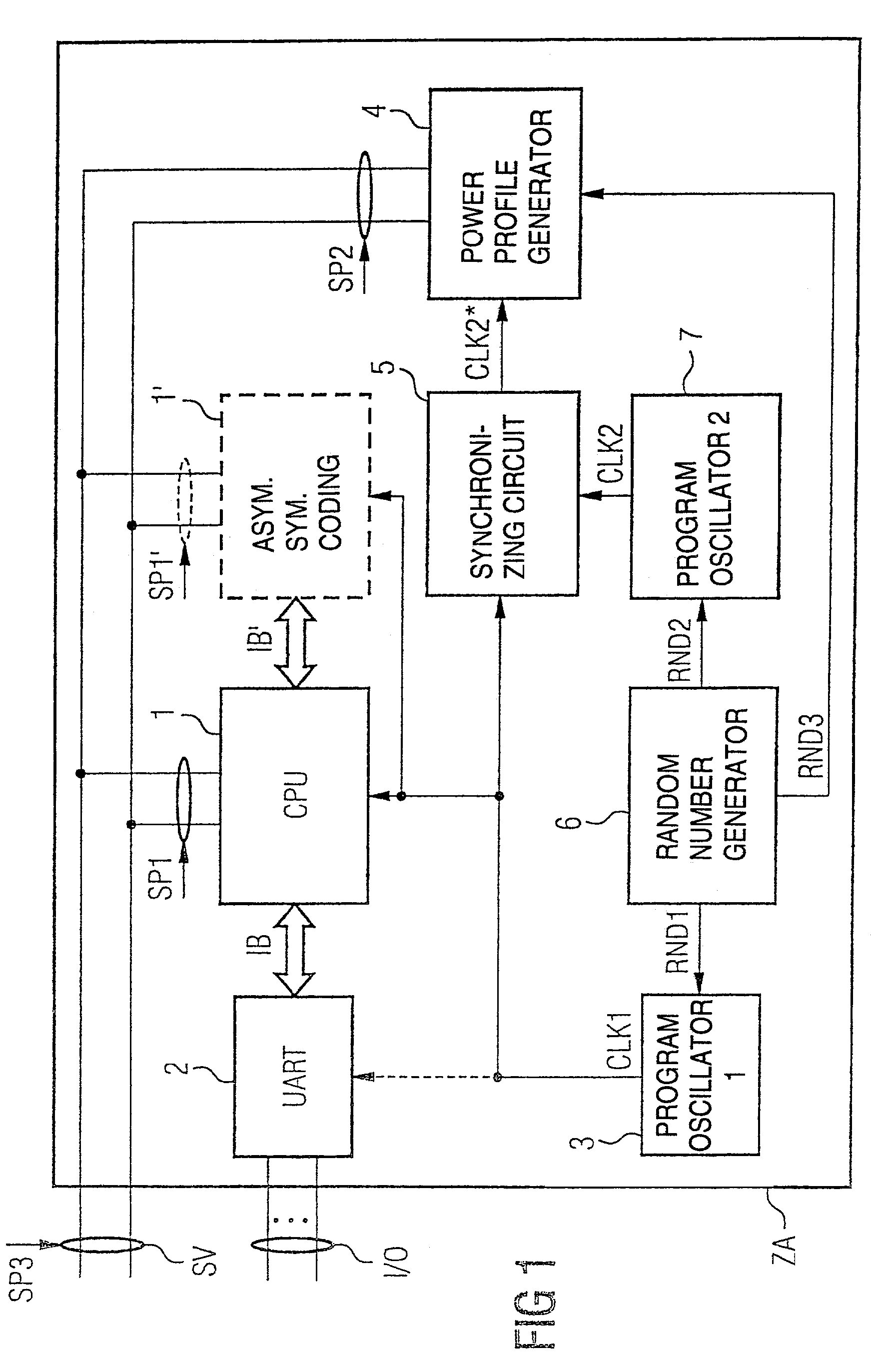
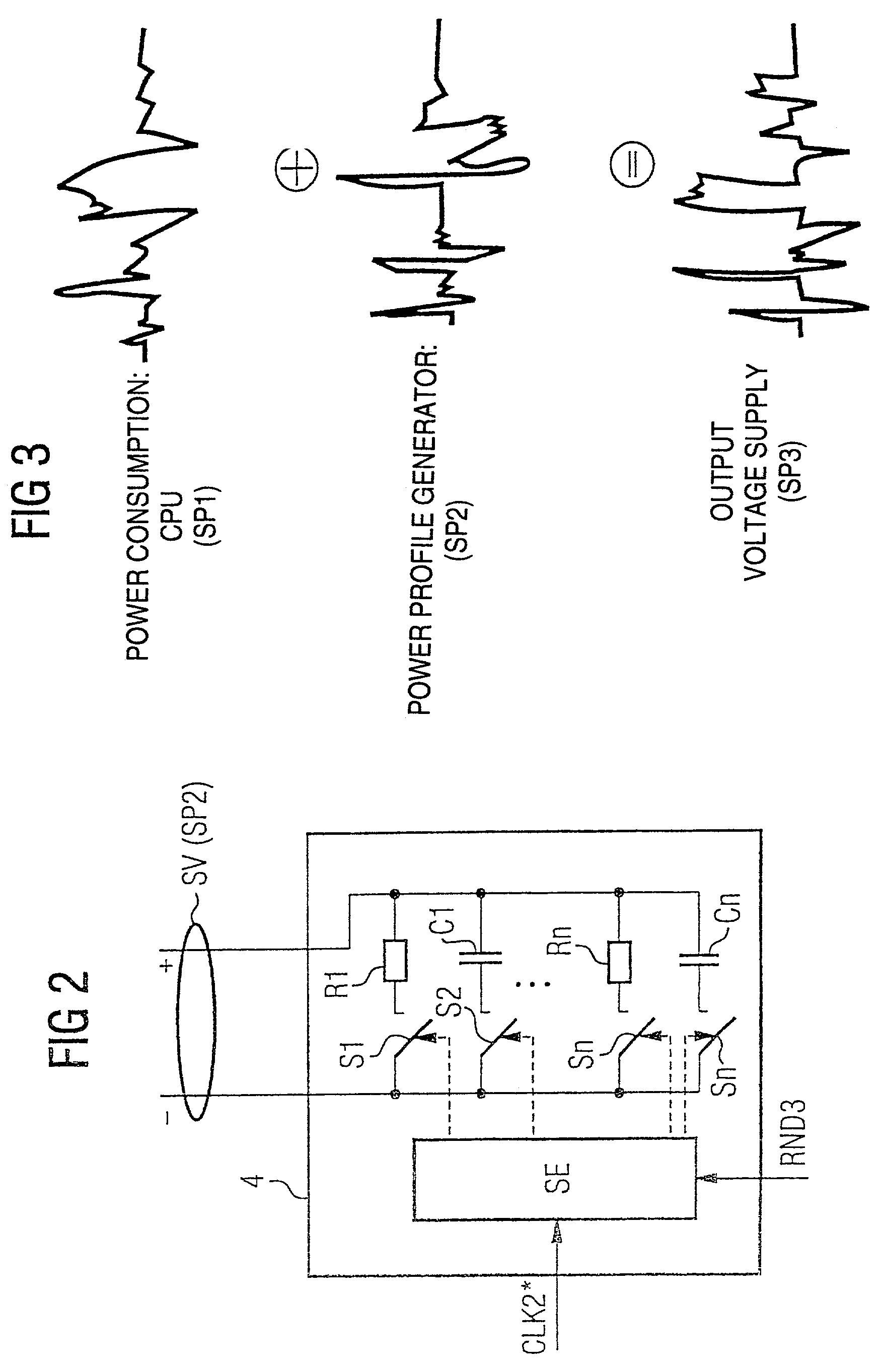
A coding device for implementing a cryptographic encryption and / or access authorization includes a data processing unit, a decoupling unit, a power supply interface, a main clock supply unit, and a power profile generator generating a power profile and superimposing it on a power profile of the data processing unit to prevent an attack by correlation analysis of the power profile.
Owner:INFINEON TECH AG
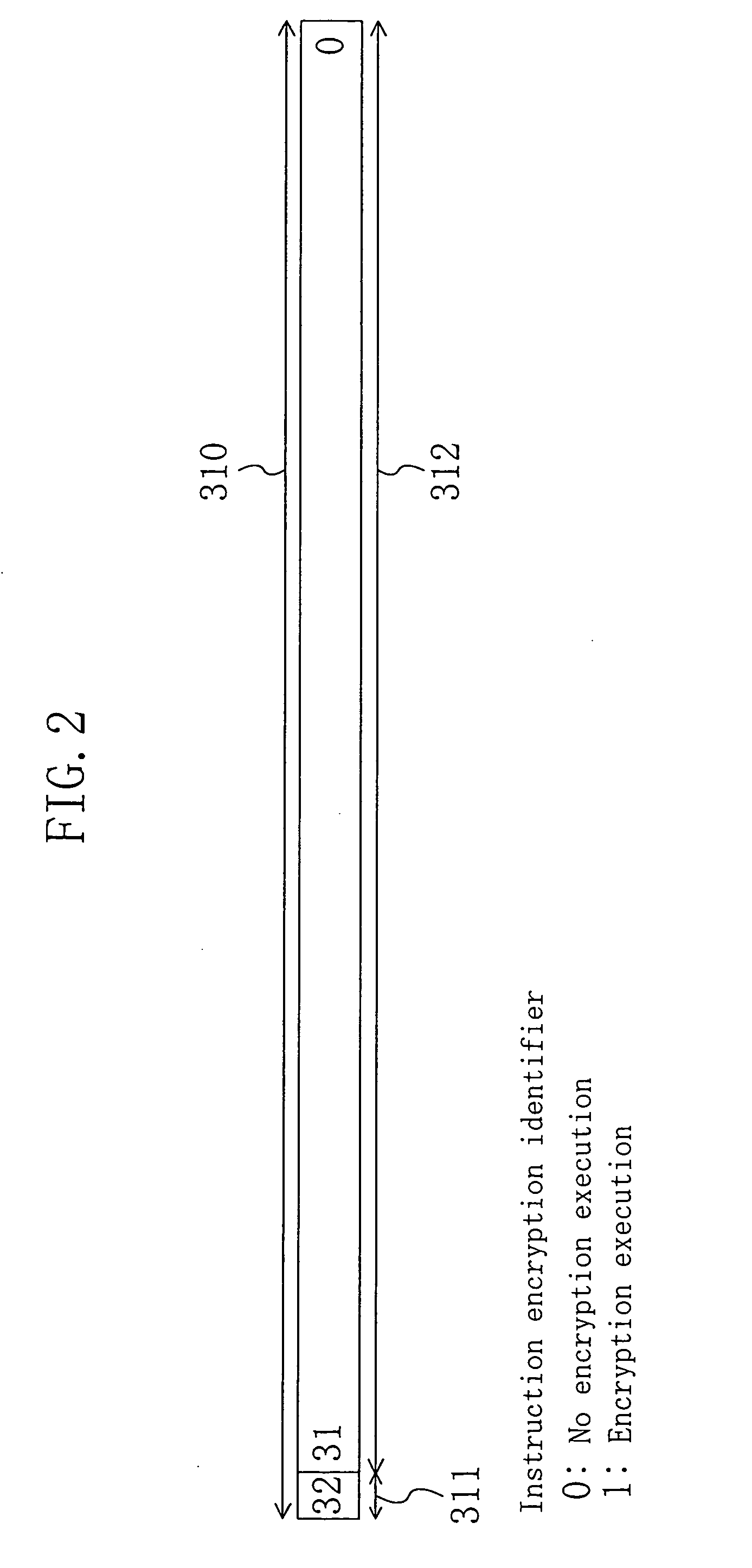
Encryption instruction processing apparatus
InactiveUS20060041747A1High degreeReduce processing timeMultiple keys/algorithms usageUser identity/authority verificationConfidentialityKey storage
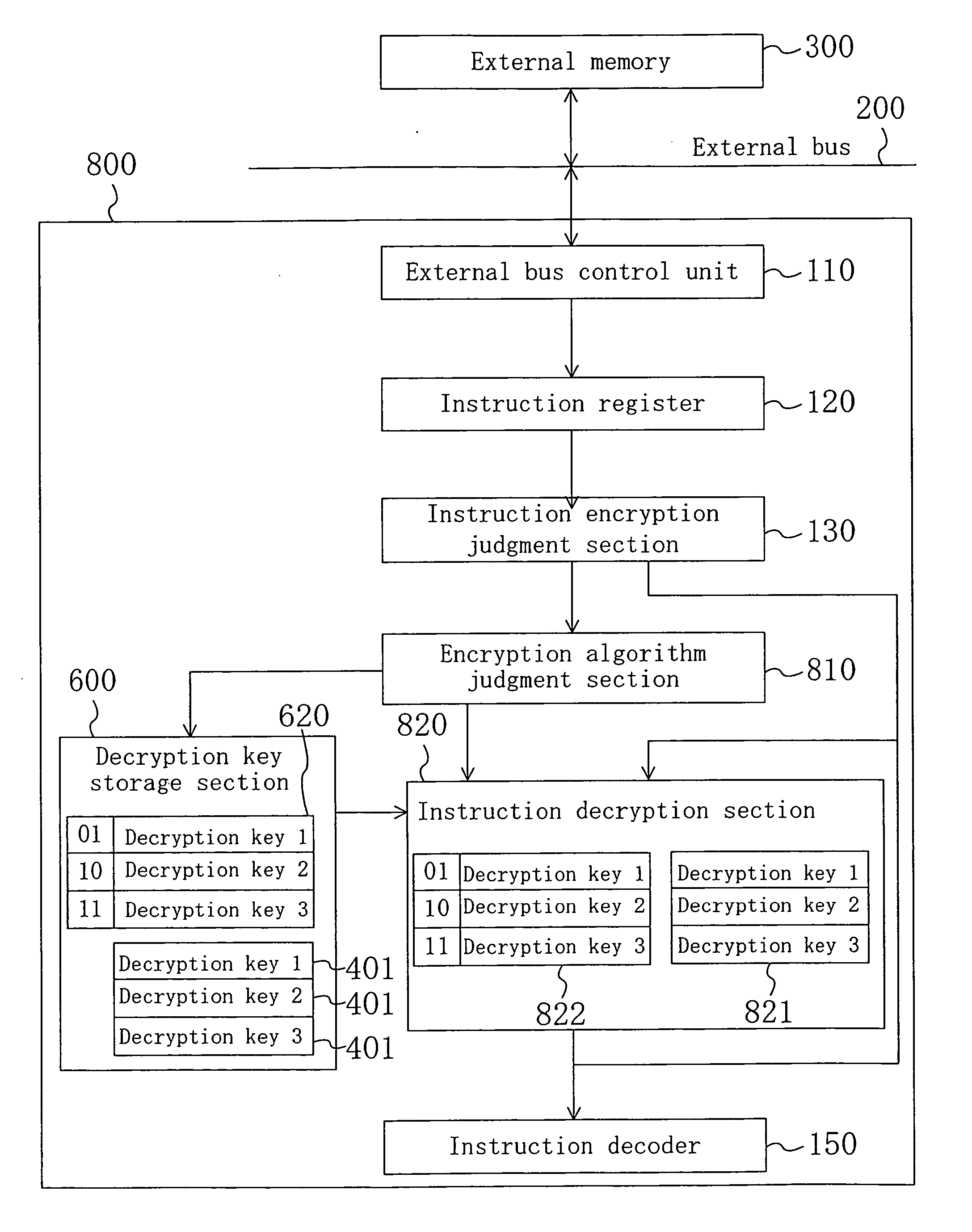
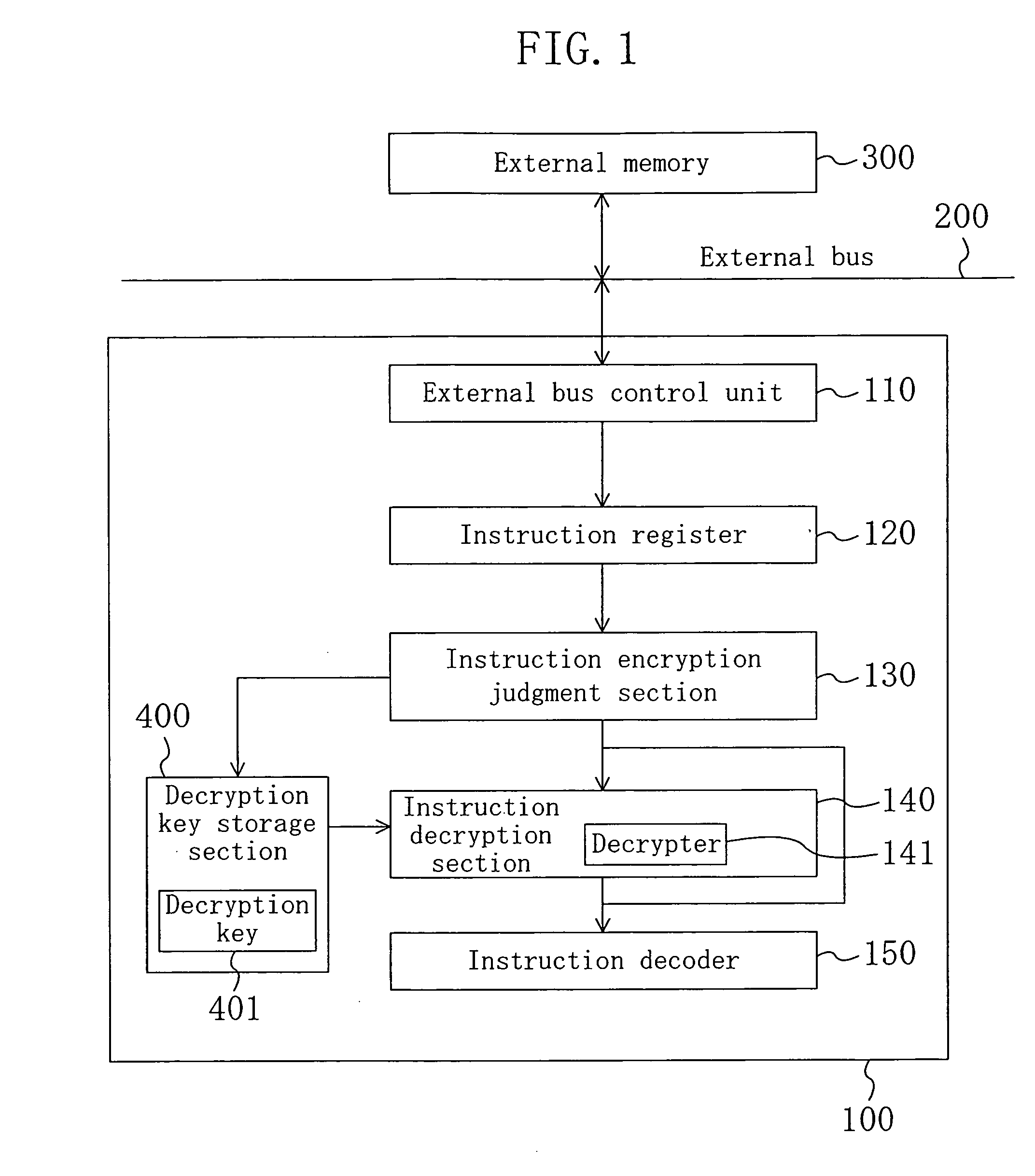
To provide an encryption instruction processing apparatus which makes it possible to reliably prevent fraud analysis of a program, encrypt only part of the program requiring protection so as to reduce a decryption time in a simple manner, and suppress increase in a hardware size, an encryption instruction processing apparatus is formed so that the apparatus includes an instruction decryption section and a decryption key storage section and decryption keys are stored in the encryption key storage section. Each of encryption extended instruction codes to be processed by the encryption instruction processing apparatus includes an instruction code and an instruction encryption identifier indicating whether or not the instruction code is encrypted. The instruction codes are encrypted according to the degree of confidentiality of each instruction code. In executing a program, according to a value for an instruction encryption identifier, the instruction decryption section decrypts an instruction code using the decryption key.
Owner:PANASONIC CORP
Devices and processes for data input
InactiveUS20130002571A1Reduce the possibilityAccurate data inputInput/output processes for data processingHuman–computer interactionUser interface
Devices are disclosed for inputting data to a touch sensitive user interface, which devices comprise a base operative to affix to the user interface, a button having an outer touch surface and an inner surface operative to engage the user interface to convey a data input signal thereto in response to presence of a user's finger at the outer touch surface of the button, and an arm connecting the button to the base; processes for data input are also disclosed.
Owner:TEN ONE DESIGN
Information processing system, information processing method, information processing program, computer readable medium and computer data signal
InactiveUS20080060072A1Avoid analysisMemory loss protectionUnauthorized memory use protectionInformation processingData signal
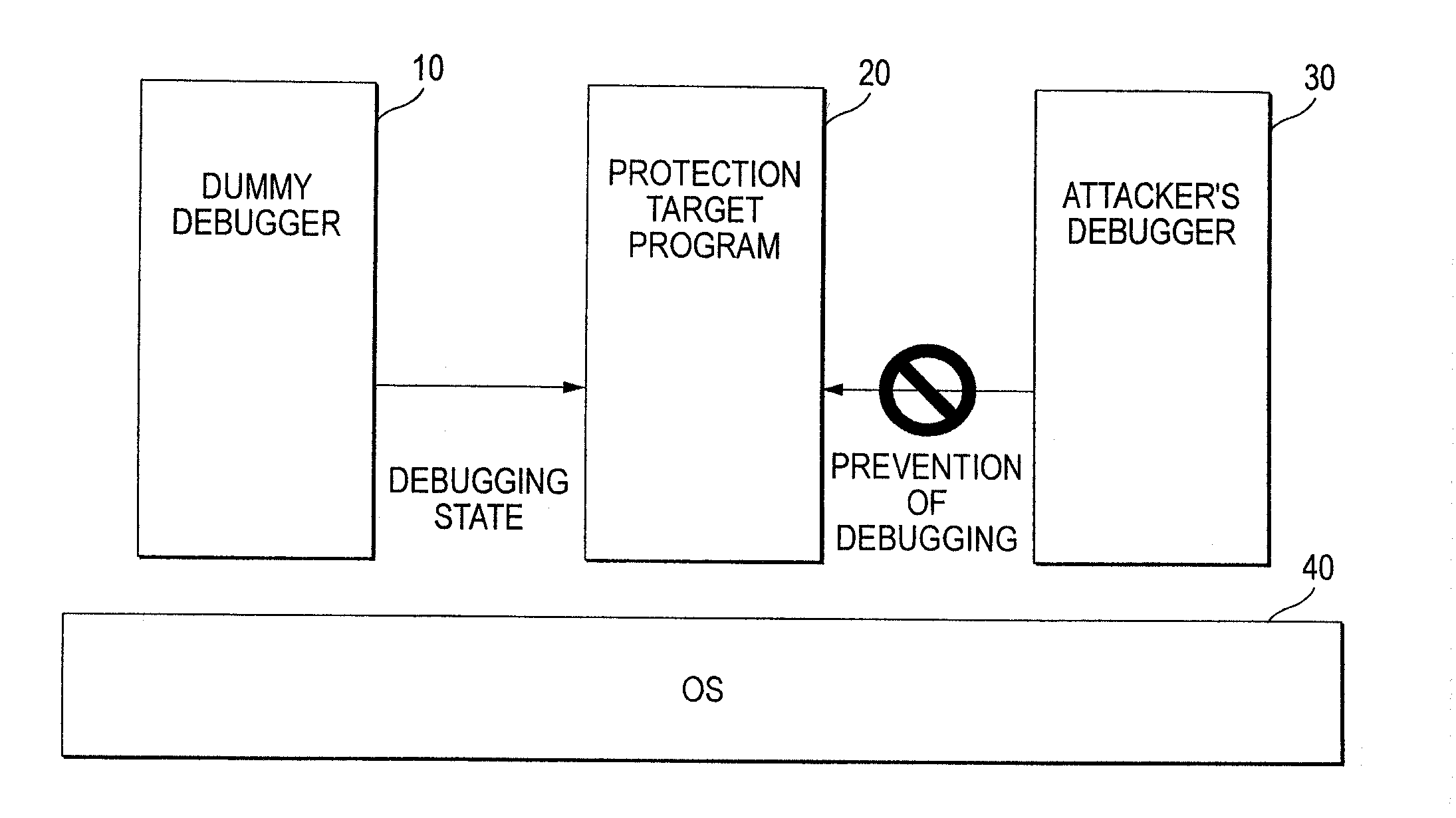
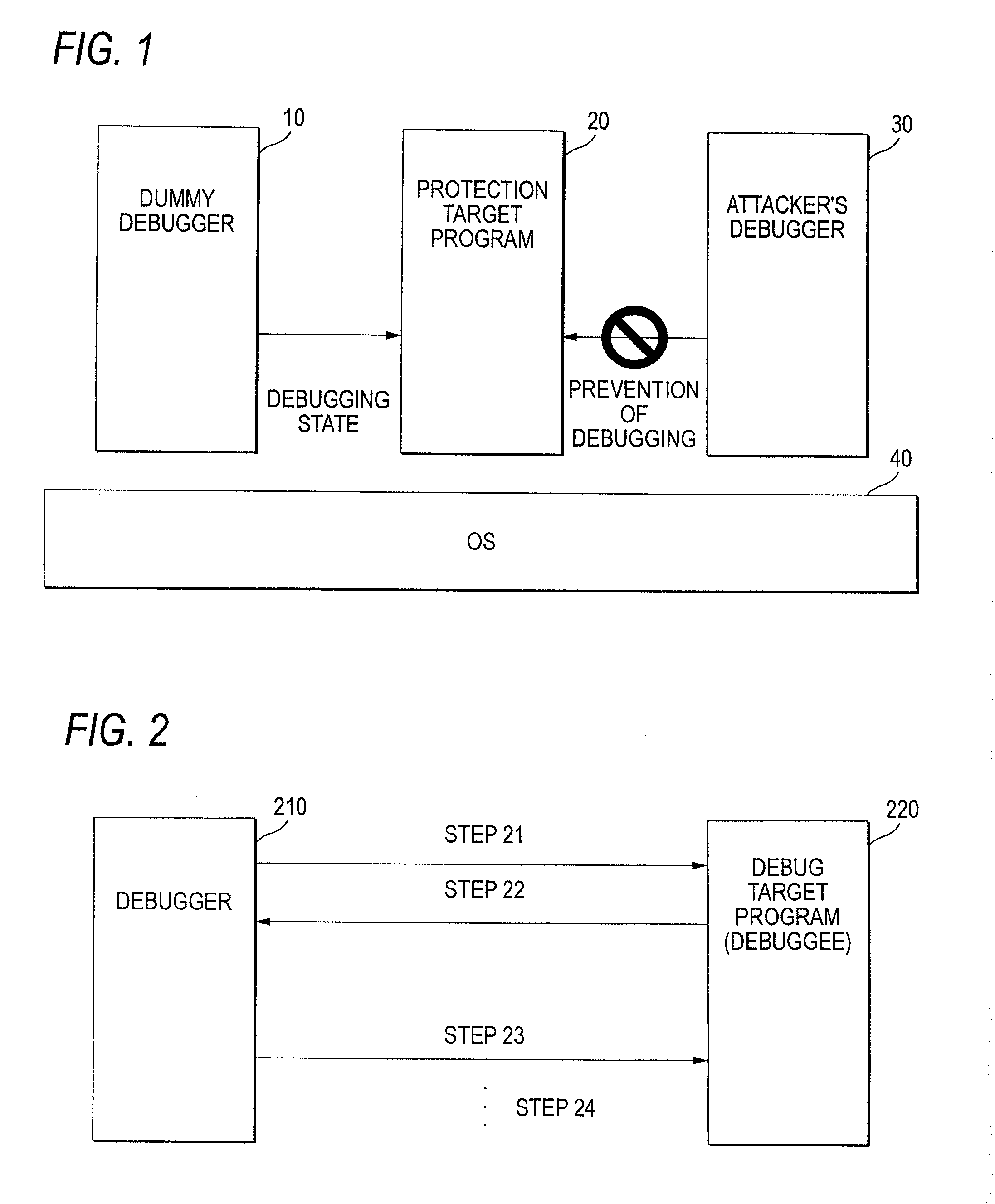
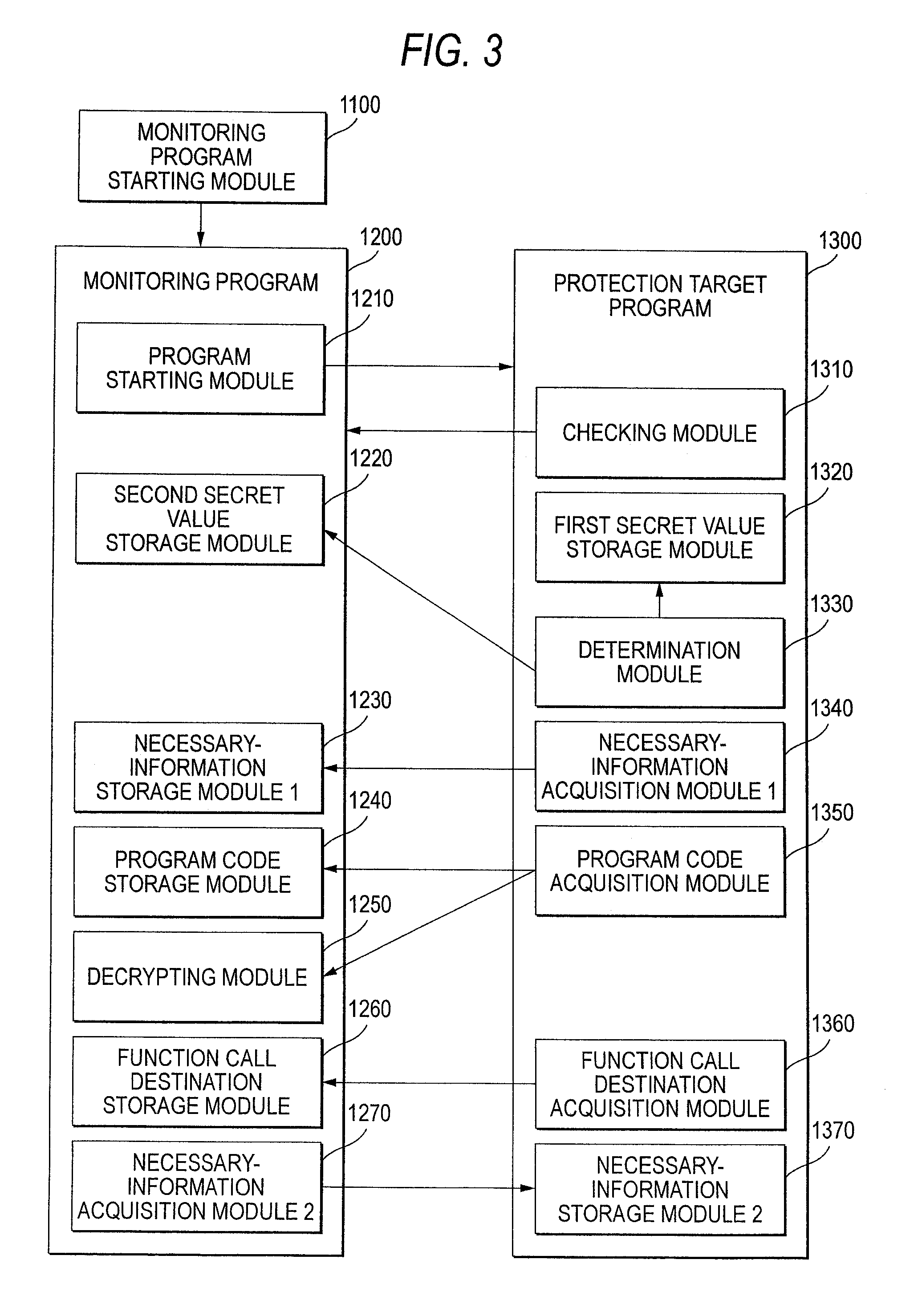
An information processing system includes a monitoring program starting unit and a protection target program monitoring unit. When a protection target program to be protected is started, the monitoring program starting unit starts a monitoring program that monitors the protection target program. The protection target program monitoring unit monitors the protection target program by the monitoring program.
Owner:FUJIFILM BUSINESS INNOVATION CORP
Mobile device with an obfuscated mobile device user identity
ActiveUS20080293378A1Improve securityEnsuring privacyUnauthorised/fraudulent call preventionEavesdropping prevention circuitsThird partyUnique identifier
A mobile device identifier (such as an MSISDN) that typically accompanies a mobile device request is replaced with an “enriched” identifier that exposes the mobile device user's home operator but obfuscates the mobile device's (and, thus, the device user's) identity. In one embodiment, the identifier comprises a first part, and a second part. The first part comprises a data string that identifies (either directly or through a database lookup) the mobile device user's home operator. The second part, however, is an opaque data string, such as a one-time-use unique identifier (UID) or a value that is otherwise derived as a function of the MSISDN (or the like). The opaque data string encodes the mobile device's identity in a manner that preferably can be recovered only by the user's home operator (or an entity authorized thereby). When the mobile device user roams into a foreign network, that network receives the enriched identifier in lieu of an MSISDN. The foreign network uses the first part to identify the mobile device user's home network, e.g., to determine whether to permit the requested access (or to provide some other value-added service). The foreign network, however, cannot decode the second part; thus, the mobile device's identity (as well as the identity of the mobile device user) remains obscured. This ensures that the user's privacy is maintained, while preventing third parties from building a profile of the device based on the requests that include the MSISDN or similar identifier.
Owner:IBM CORP
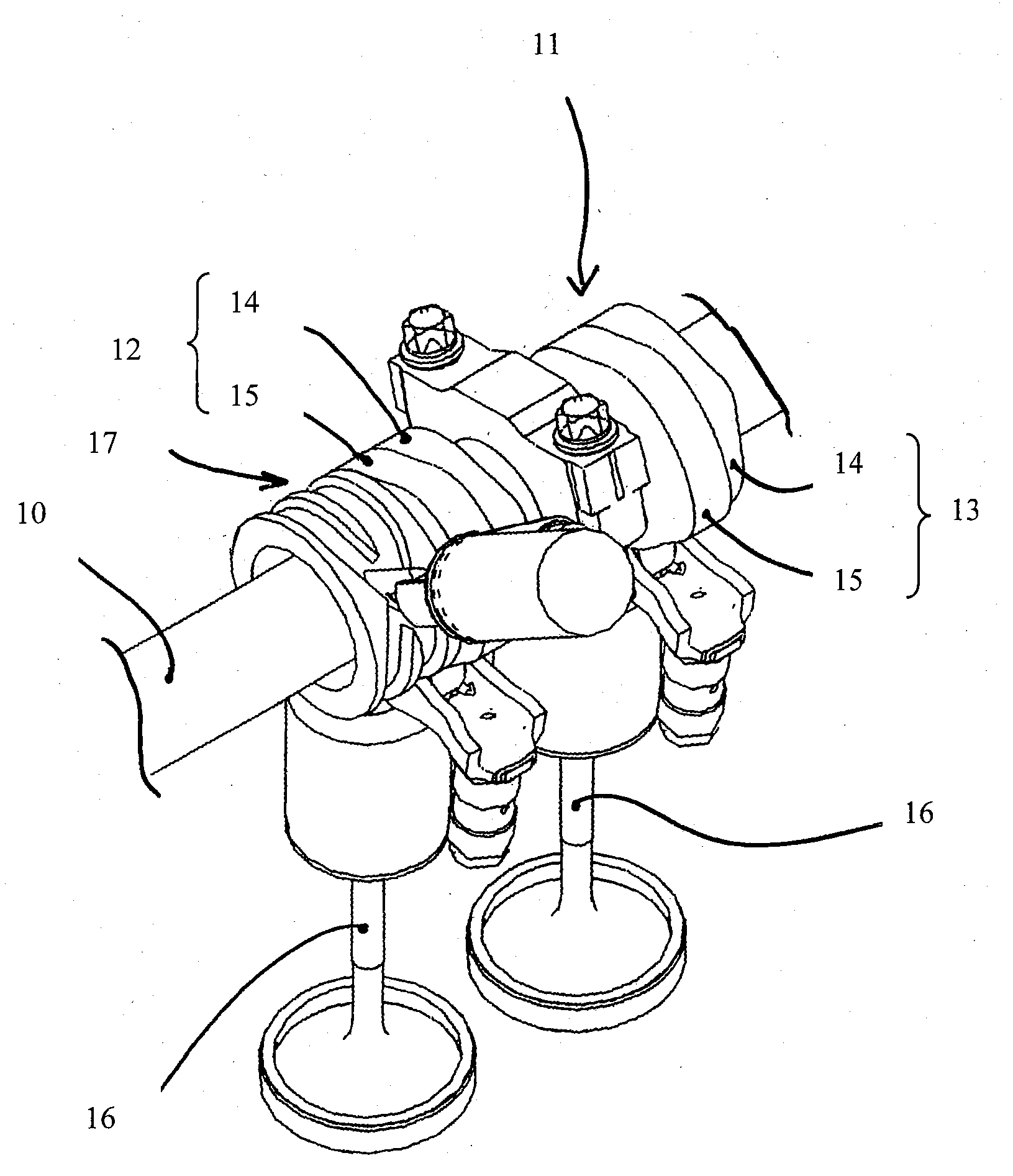
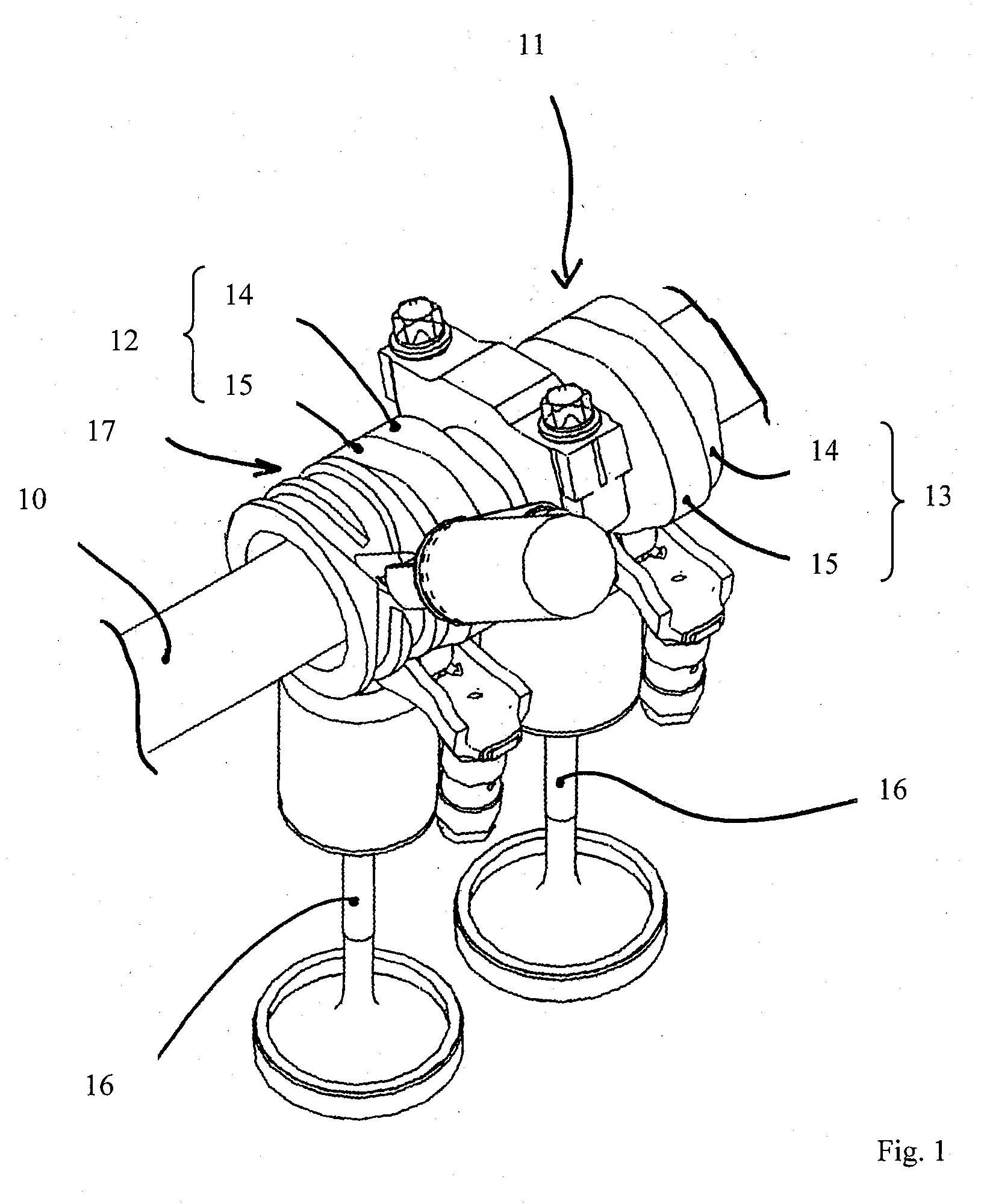
Valve drive of an internal combustion engine
ActiveUS20100126447A1Avoid interferenceAvoid analysisValve arrangementsMachines/enginesAxial displacementEngineering
A valve drive of an internal combustion engine, with a camshaft including cams for actuating gas-exchange valves, wherein at least one cam, which includes several cam faces, is guided nonrotatably but with freedom of axial movement on the camshaft; wherein a stroke profile, which cooperates with an actuating pin for the axial displacement of the cam or cam piece, is assigned to the associated axially displaceable cam or an axially displaceable cam piece comprising several cams; and wherein the stroke profile of the axially displaceable cam or cam piece in question includes intersecting stroke curves. A guide element is assigned to the end of the actuating pin which can be introduced into the stroke curve of the stroke profile of the associated axially displaceable cam or cam piece, this guide element being supported in such a way that it can rotate or pivot around the axis of the actuating pin.
Owner:DR ING H C F PORSCHE AG
Apparatus and method for measuring three-dimensional shape of wood block
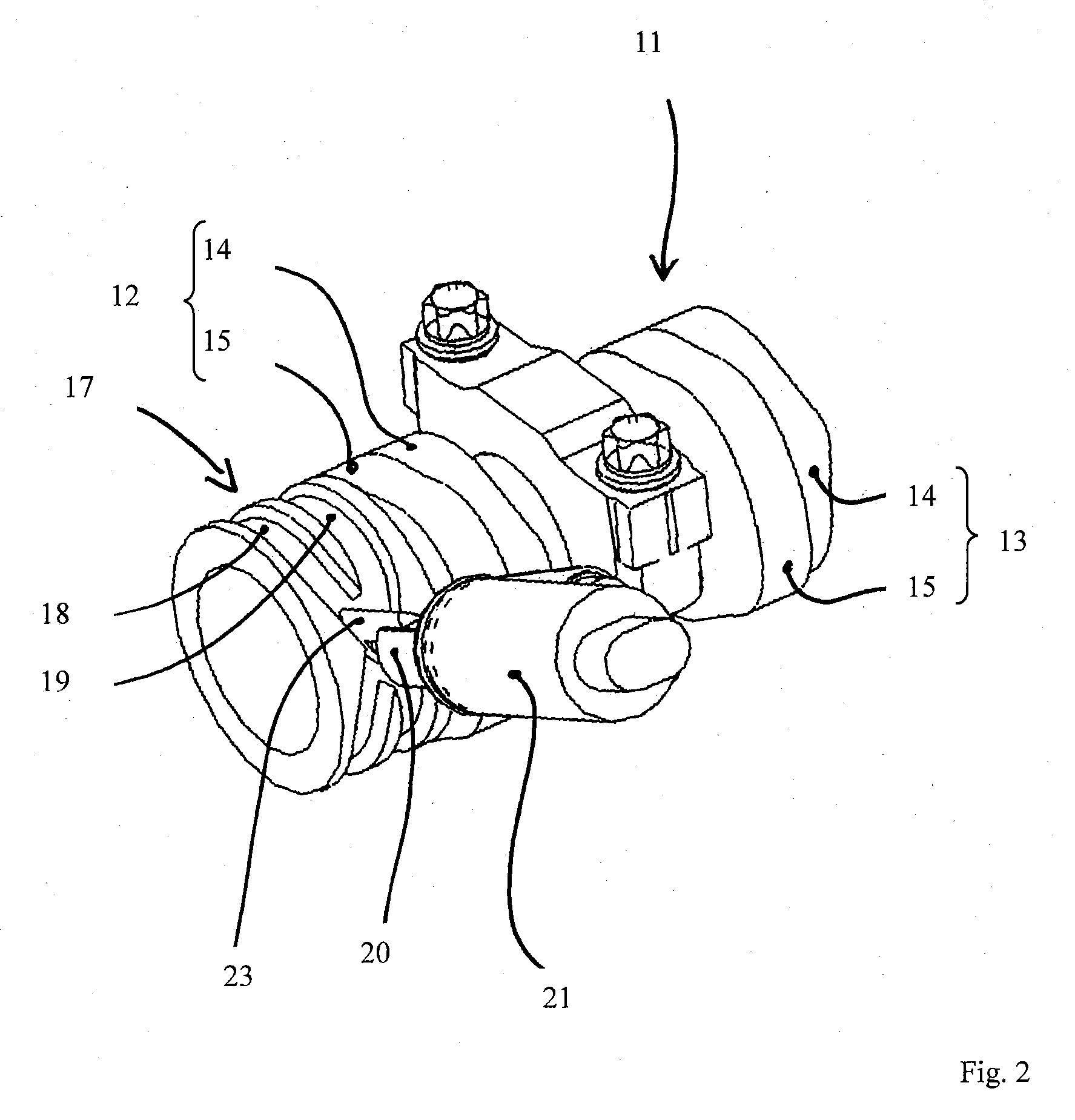
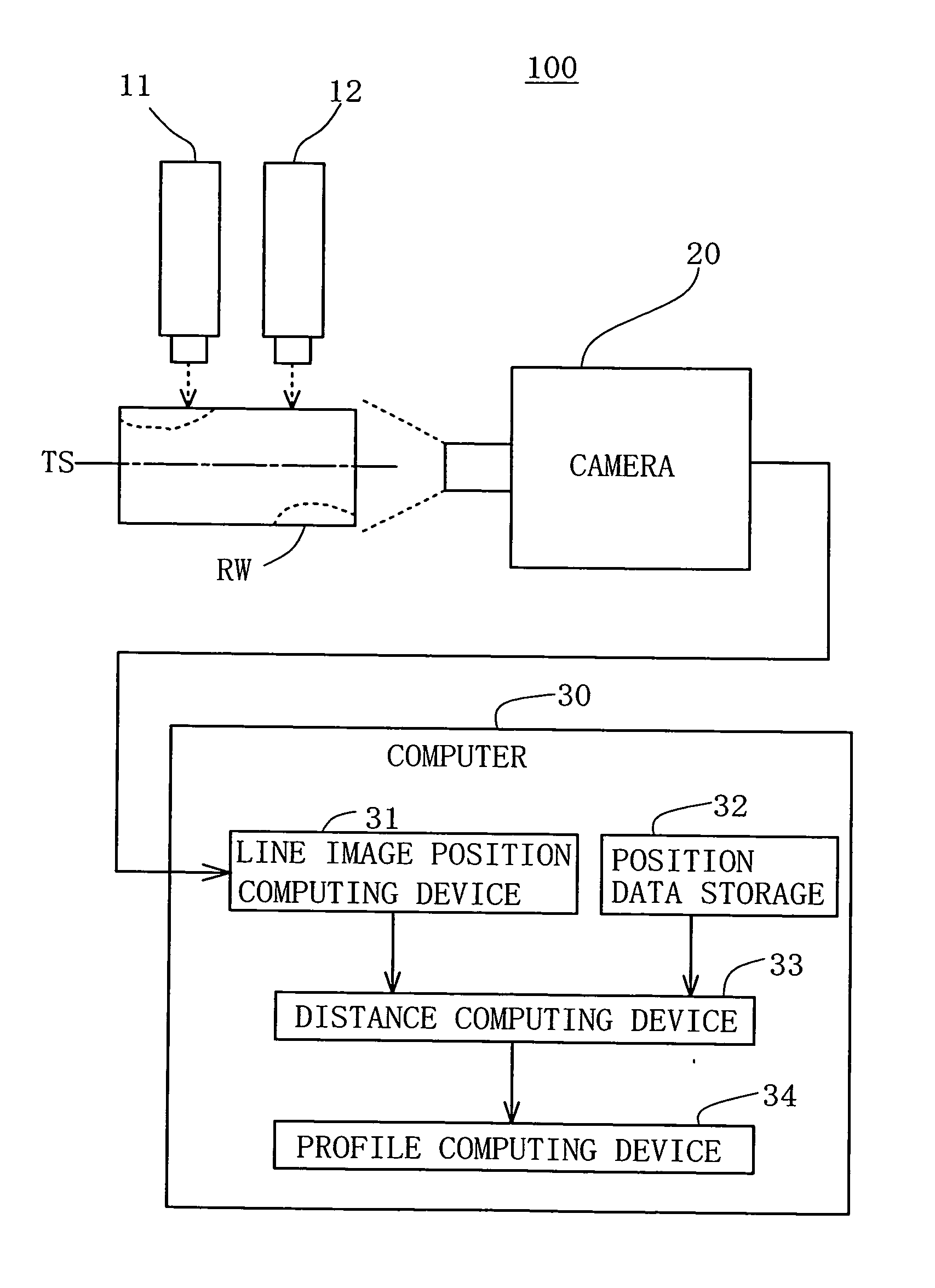
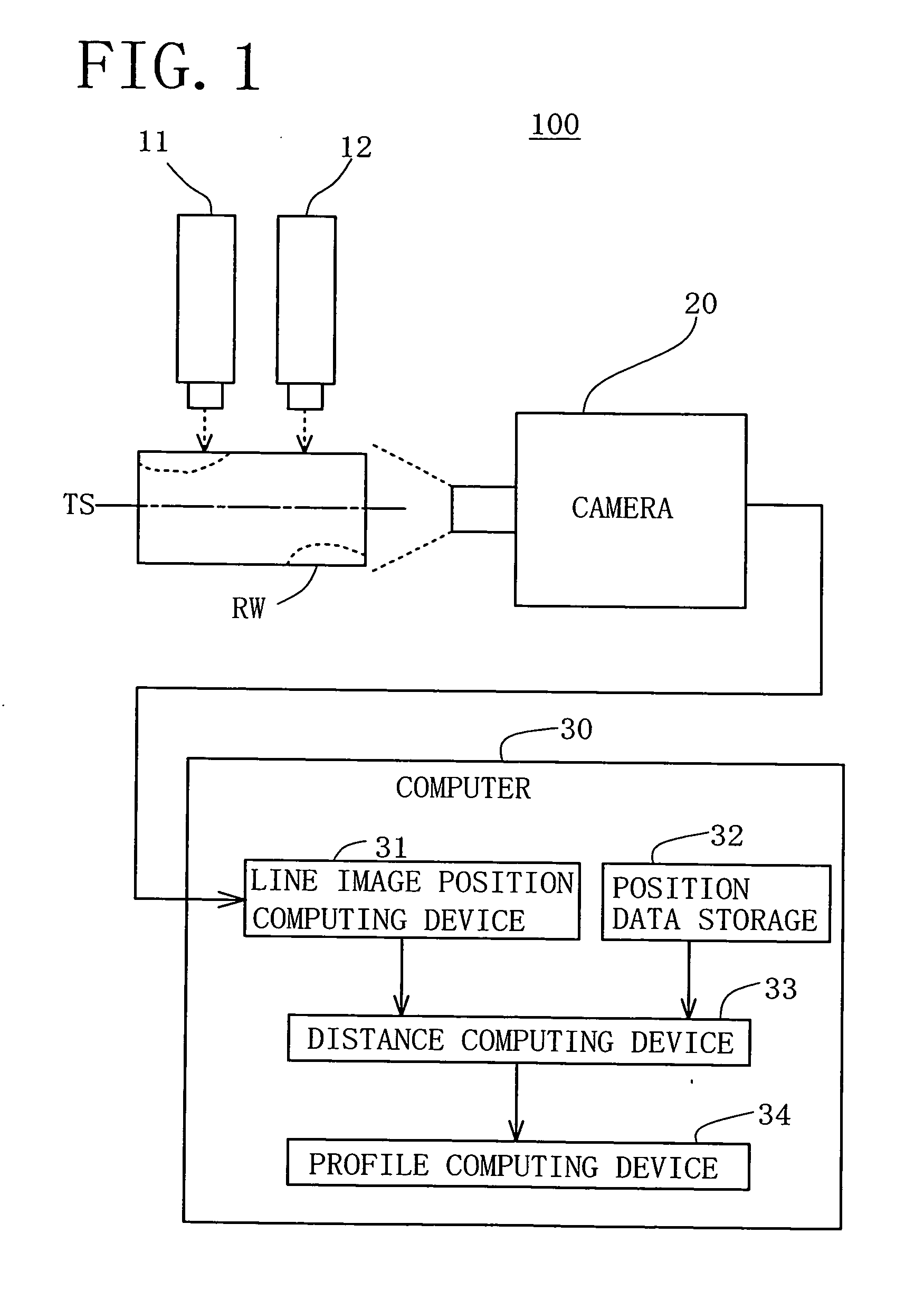
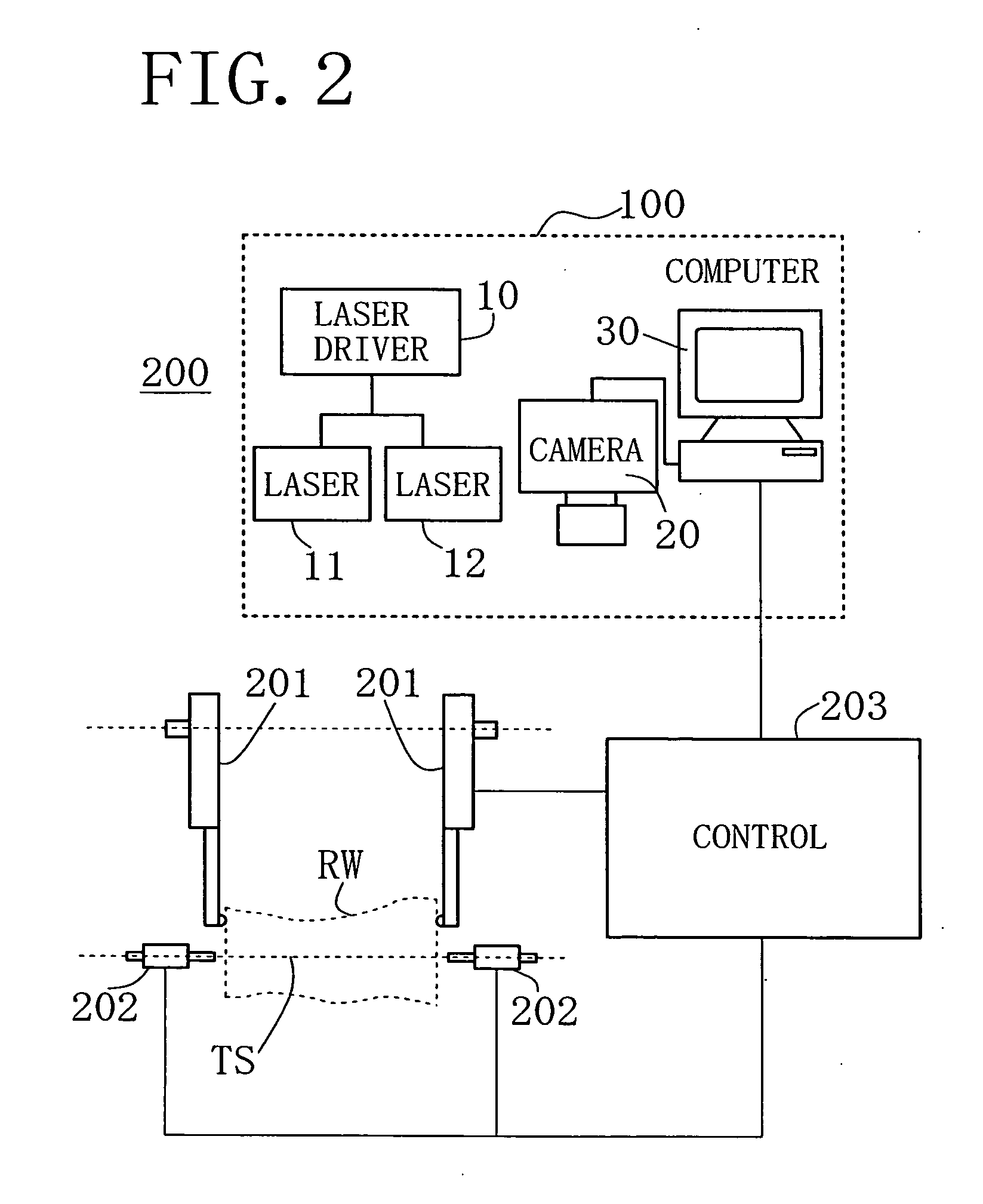
ActiveUS20100111367A1Improve accuracyResolution in measuring can be increasedCharacter and pattern recognitionUsing optical meansClassical mechanicsLight beam
An apparatus and a method for measuring three-dimensional shape of a wood block are disclosed. A planar light beam is projected by a light emitting device against a wood block rotatably supported on its tentative spin axis in such a way that two continuous lines extending parallel to the tentative spin axis for the entire block length are illuminated on the outer peripheral surface of the block. The block with the illuminated lines is photographed at a plurality of its angular positions by a imaging device. Based on data of the photographed line images, distances between the tentative spin axis and each of the illuminated lines on the outer peripheral surface of the block are computed at a plurality of cross-sections of the block along the tentative spin axis. Distances from the tentative spin axis to the outer peripheral surface of the block, including shapes of various irregularities on the surface of the block, are measured.
Owner:MEINAN MASCH WORKS INC
Method and apparatus for accessing a foreign network with an obfuscated mobile device user identity
ActiveUS20080293379A1Improve securityEnsuring privacyUnauthorised/fraudulent call preventionEavesdropping prevention circuitsThird partyUnique identifier
A mobile device identifier (such as an MSISDN) that typically accompanies a mobile device request is replaced with an “enriched” identifier that exposes the mobile device user's home operator but obfuscates the mobile device's (and, thus, the device user's) identity. In one embodiment, the identifier comprises a first part, and a second part. The first part comprises a data string that identifies (either directly or through a database lookup) the mobile device user's home operator. The second part, however, is an opaque data string, such as a one-time-use unique identifier (UID) or a value that is otherwise derived as a function of the MSISDN (or the like). The opaque data string encodes the mobile device's identity in a manner that preferably can be recovered only by the user's home operator (or an entity authorized thereby). When the mobile device user roams into a foreign network, that network receives the enriched identifier in lieu of an MSISDN. The foreign network uses the first part to identify the mobile device user's home network, e.g., to determine whether to permit the requested access (or to provide some other value-added service). The foreign network, however, cannot decode the second part; thus, the mobile device's identity (as well as the identity of the mobile device user) remains obscured. This ensures that the user's privacy is maintained, while preventing third parties from building a profile of the device based on the requests that include the MSISDN or similar identifier.
Owner:IBM CORP
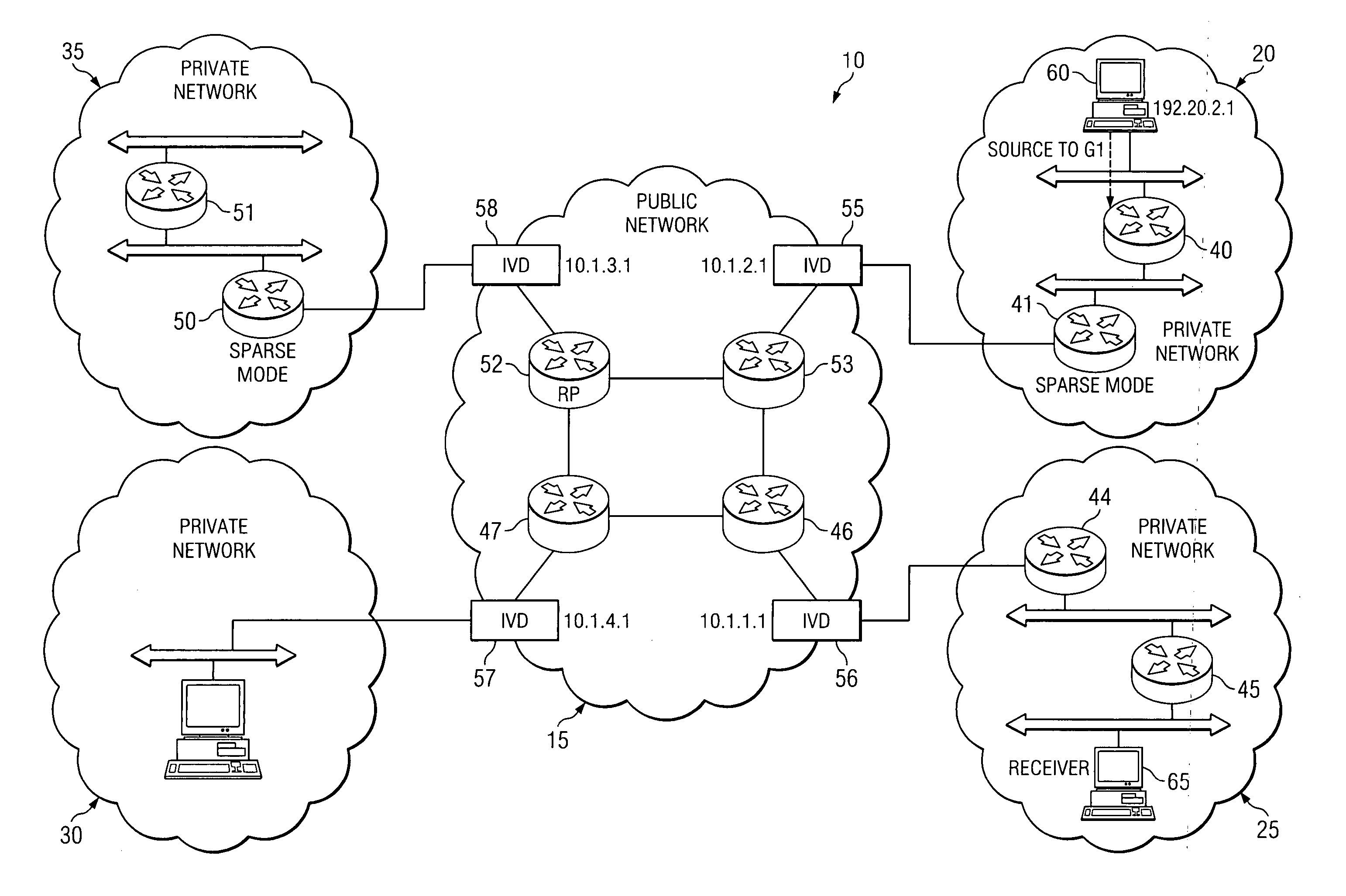
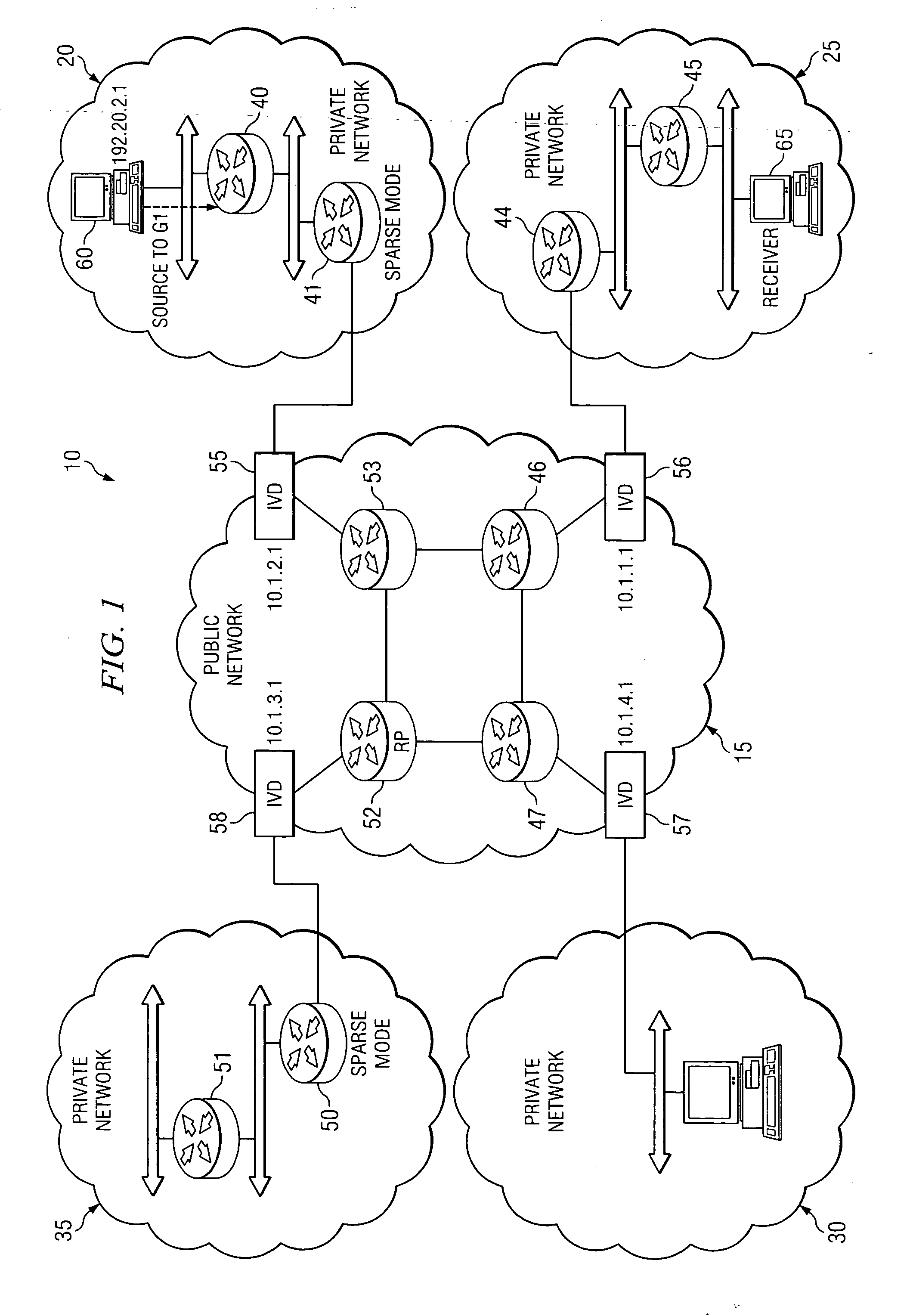
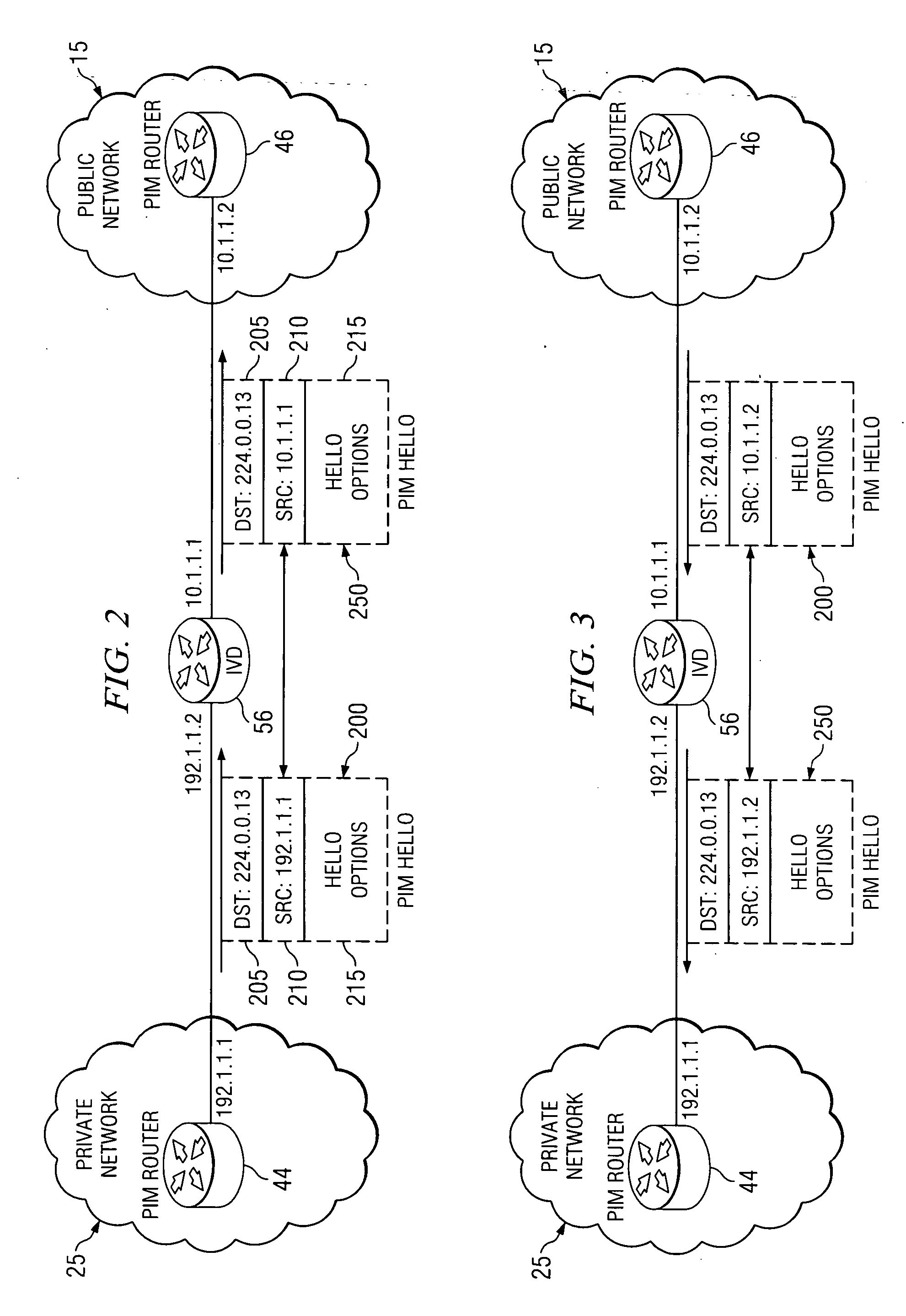
System and method for providing packet proxy services across virtual private networks
ActiveUS20070211735A1Prevent visibilityAvoid analysisData switching by path configurationWireless commuication servicesPrivate networkPublic network
A method is provided for proxy services between a public network and a private network. Such a method includes receiving a first packet having a destination address and a first source address; generating a second packet having the destination address and a second source address; and transmitting the second packet.
Owner:CISCO TECH INC
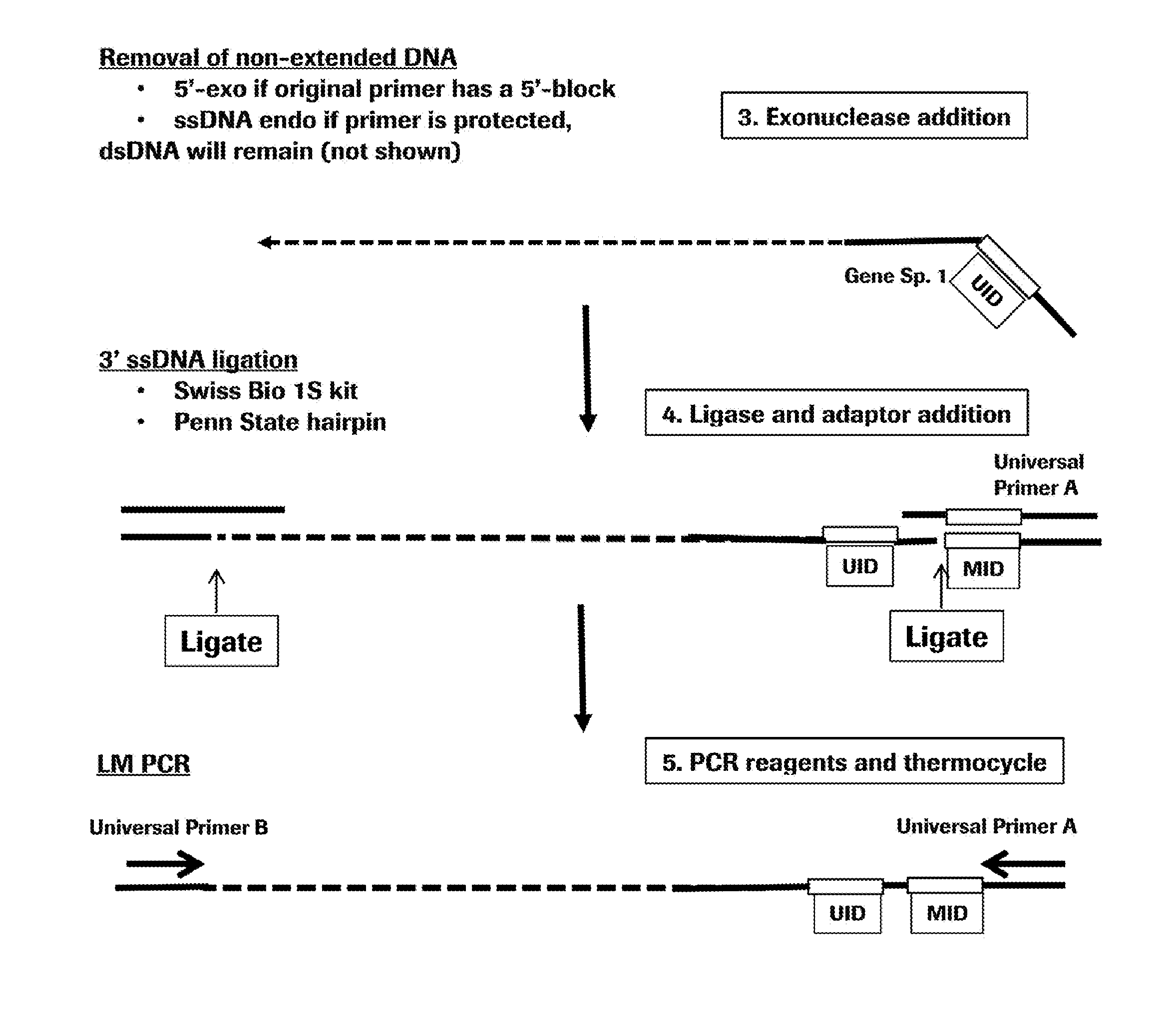
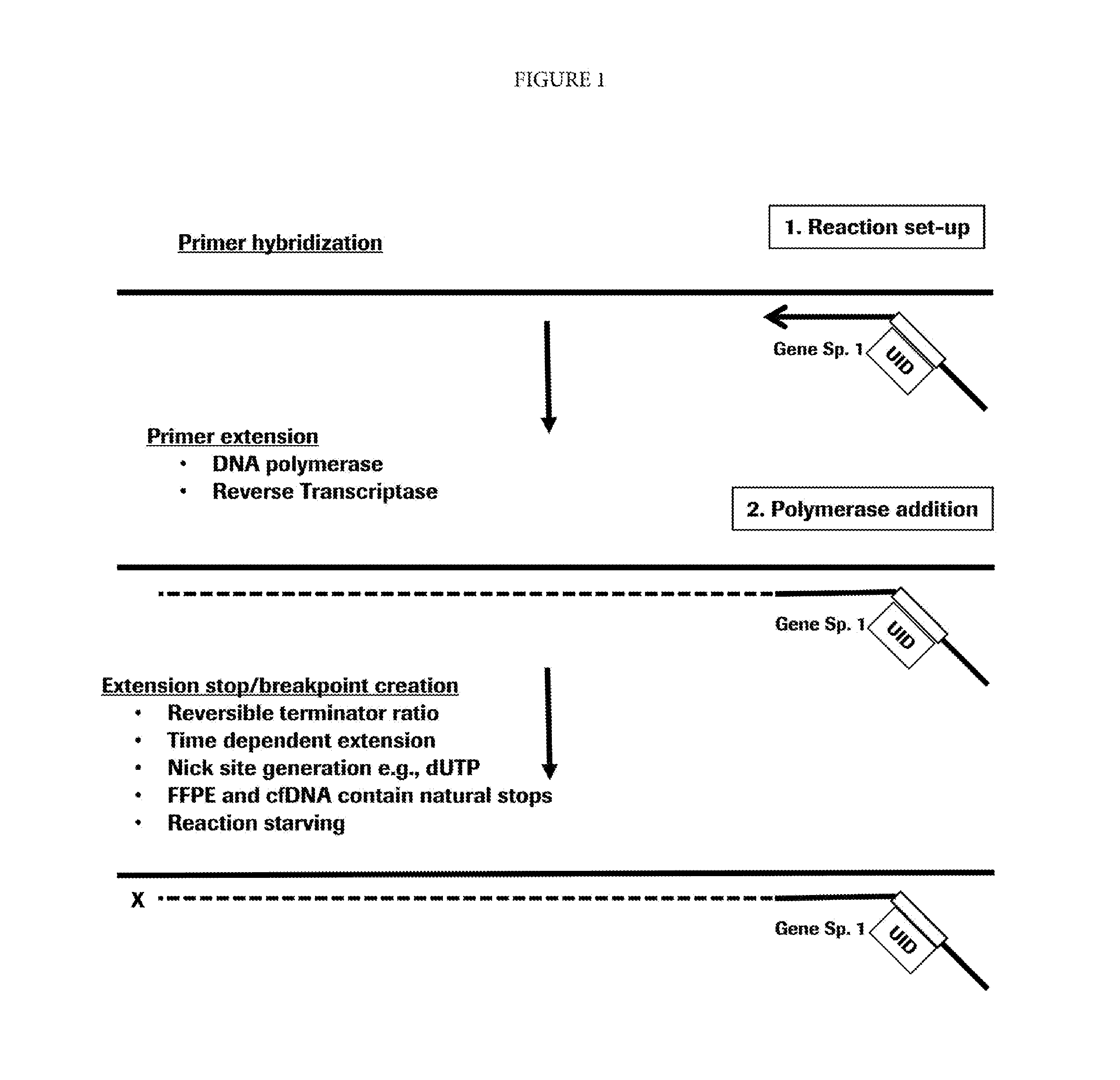
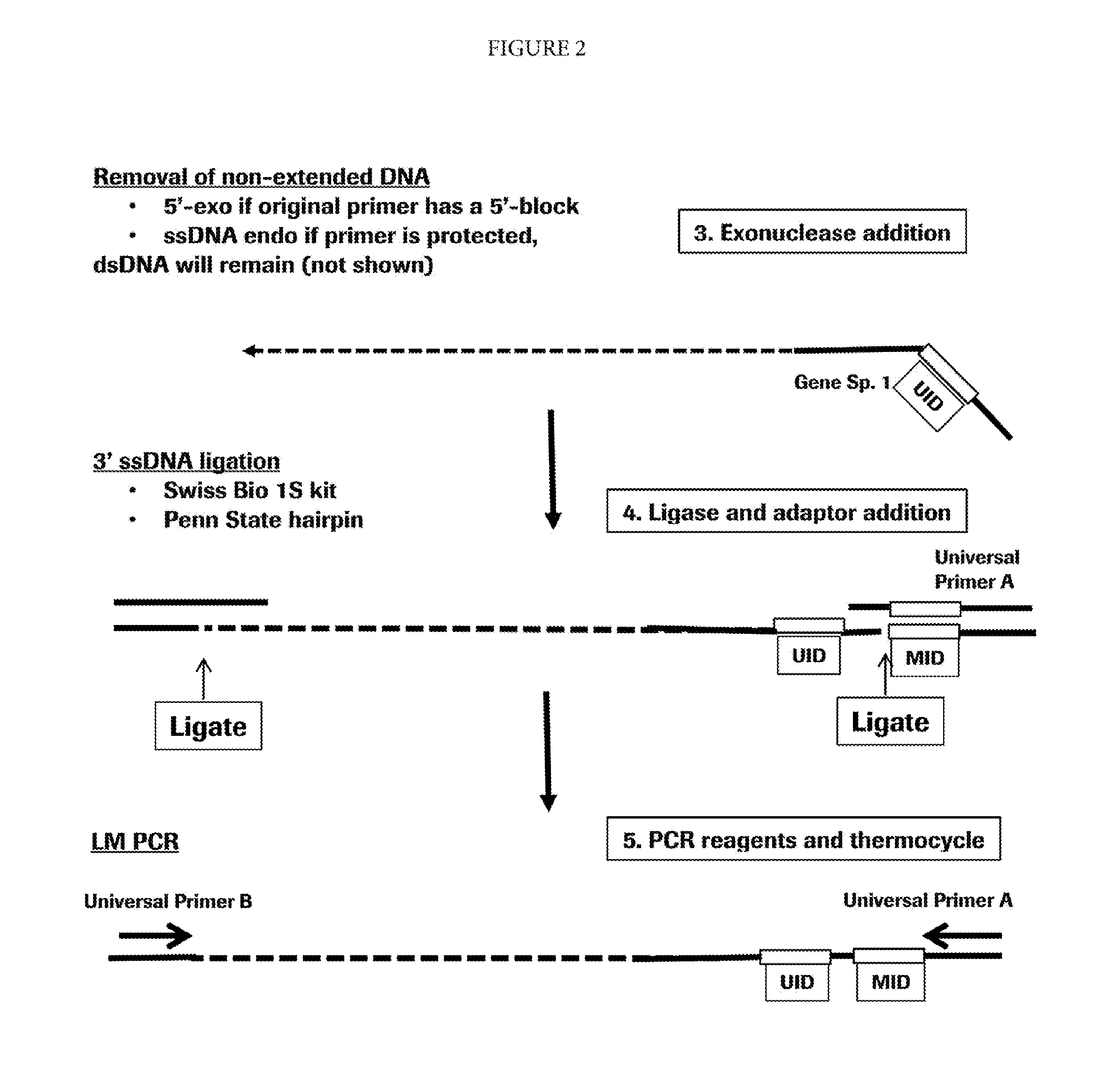
Target enrichment by single probe primer extension
The invention comprises methods and compositions for enriching for a target nucleic acid with a single primer extension and low-bias limited amplification.
Owner:ROCHE SEQUENCING SOLUTIONS INC
Apparatus for analyzing sample
ActiveUS20110176963A1Avoid stickingAvoid analysisLaboratory glasswaresColor/spectral properties measurementsAnalysis samplePhysics
Owner:PRECISIONBIOSENSOR INC
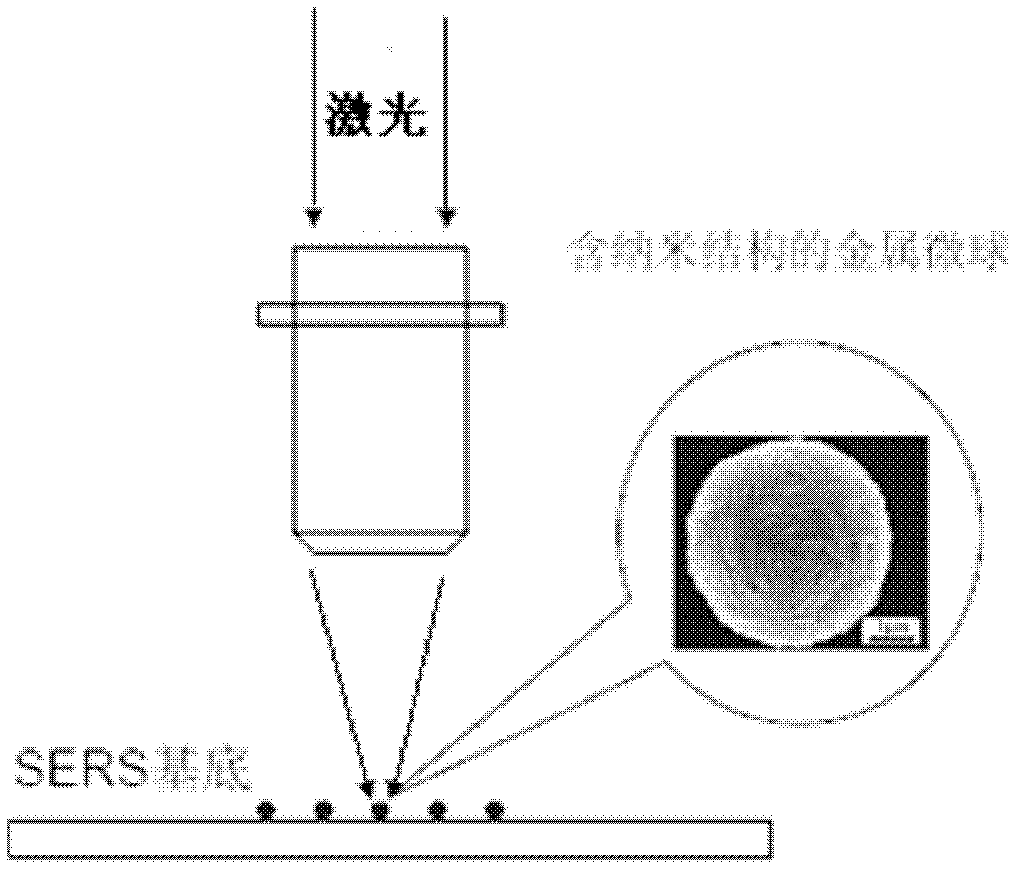
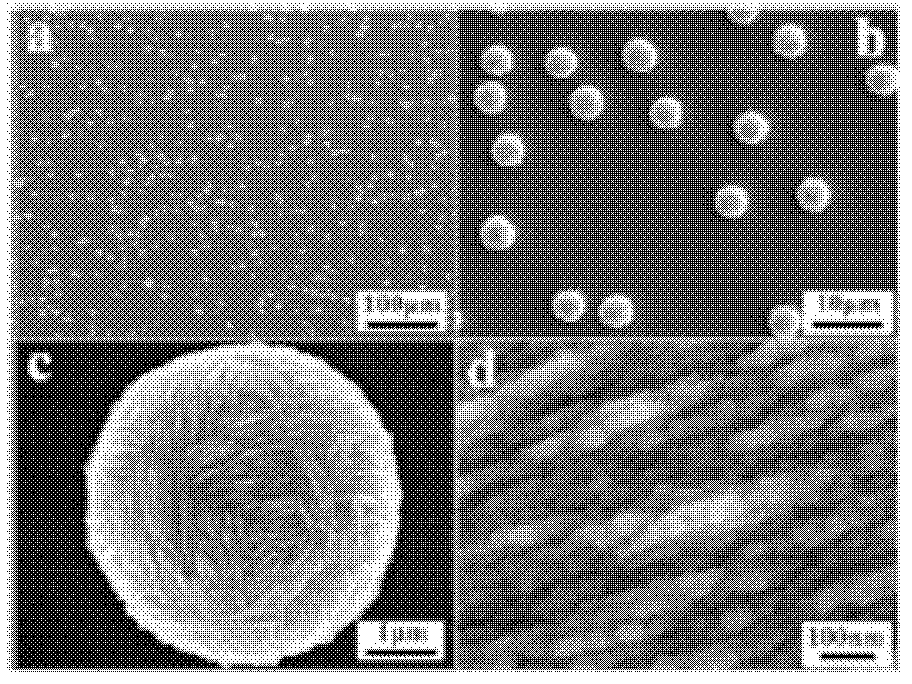
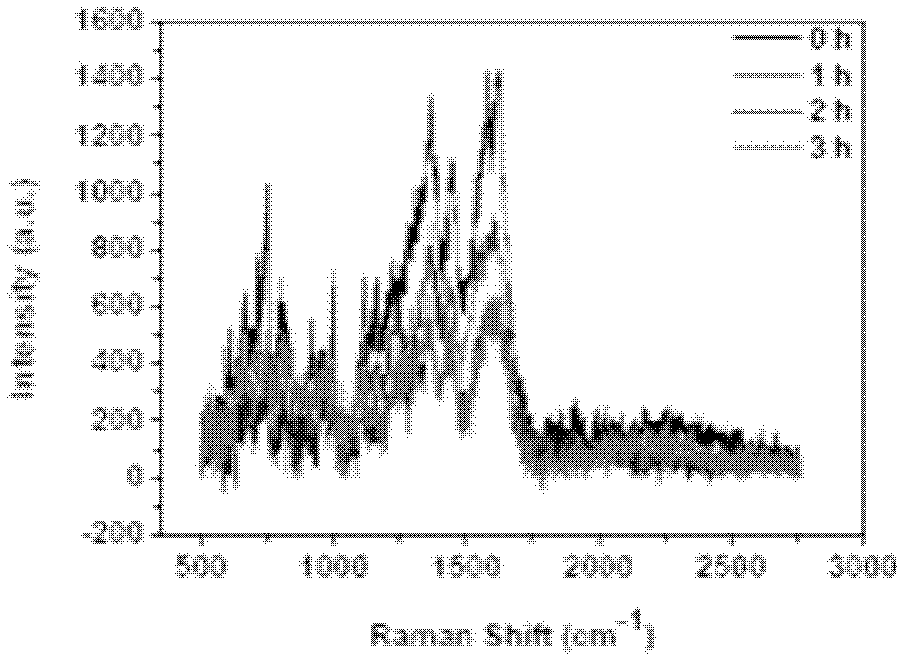
Method for detecting trace biomolecule ionizing radiation decomposition reaction based surface enhanced Raman spectrum
ActiveCN102628807AAvoid analysisEffective Radiation Biology ResearchRaman scatteringRadiation reactionIndirect action
The invention discloses a method for detecting trace biomolecule ionizing radiation decomposition reaction based surface enhanced Raman spectrum (SERS). The method comprises three SERS substrates suitable for the biomolecule radiation test and the corresponding test method. The method comprises the following steps: using a micron-sized semisphere consisting of a silver nano sheet as the SERS substrate and quantitatively measuring the radiation damage of a solid biological sample (such as protein) under the direction action of ionizing radiation; using a gold wrapped silicon dioxide submicron sphere as the SERS substrate, connecting DNA and quantitatively measuring the radiation damage of the DNA molecule of a solid biological sample under the direction action of ionizing radiation; and mixing silver colloid particles and a sample from a radiation reaction solution, measuring the product of the radiation decomposition reaction by utilizing SERS effect and researching the radiation damage of the biomolecule under the indirect action of radiation. Due to the method, the radiation decomposition reaction of the trace biomolecule caused by energetic ions can be subjected to on-line, non-destructive and trace detection conveniently.
Owner:HEFEI INSTITUTES OF PHYSICAL SCIENCE - CHINESE ACAD OF SCI
Automatic analyzer
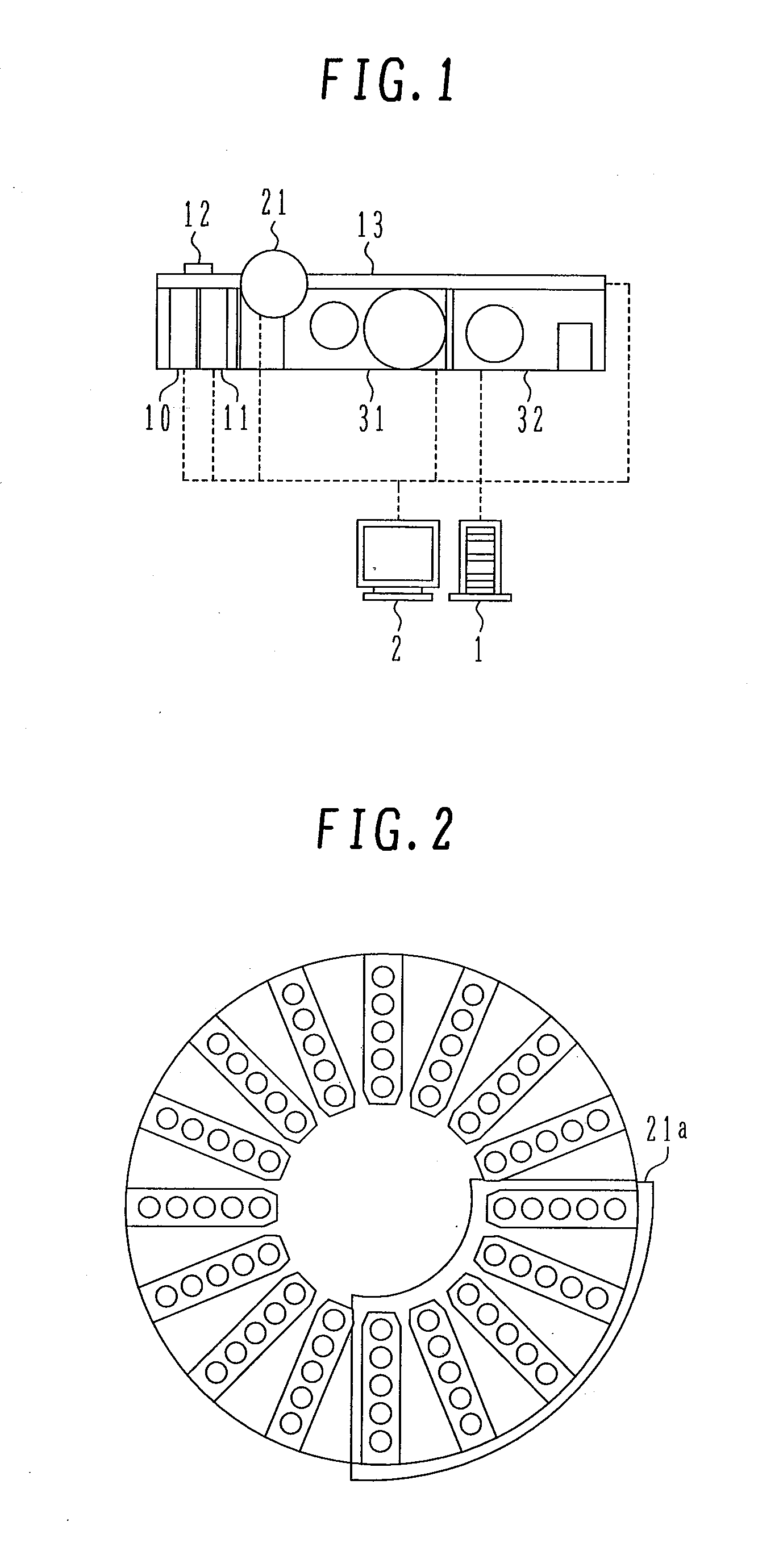
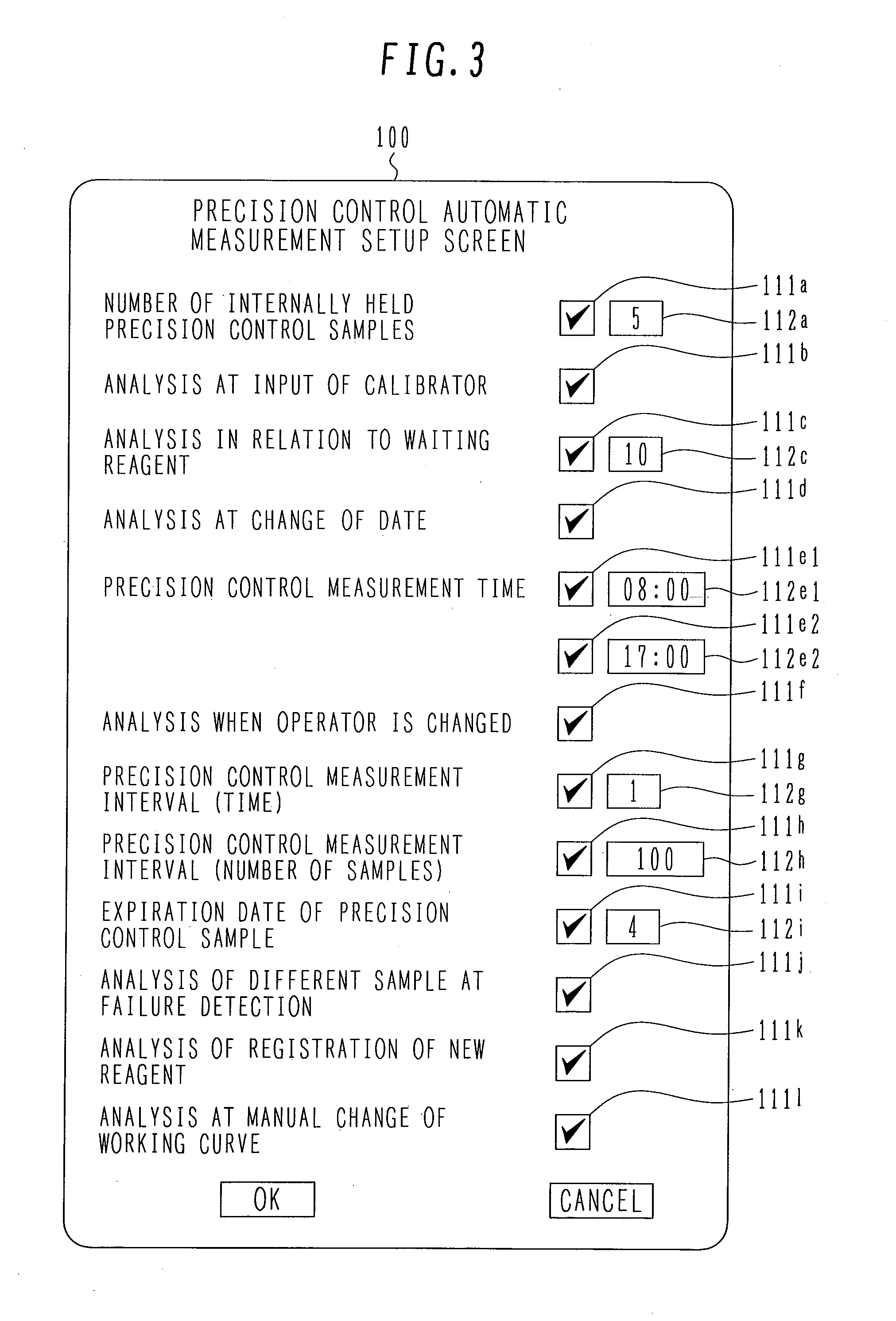
InactiveUS20080219887A1Avoid analysisEasy to controlSamplingMaterial analysis by optical meansAutomated analyzerMeasurement precision
An automatic analyzer is capable of performing analysis of a precision control sample in response to an external factor to alleviate the burden on the operator and surely performing precision control at appropriate timing at which precision control must be performed, thereby allowing automatic maintenance of the measurement precision. Analysis of a precision control sample is performed by creating an analysis request for the internally held precision control sample and then transferring the precision control sample in response to an external factor occurring, for example, when a calibrator is inputted in the analyzer, the number of remaining reagents under analysis satisfies a predetermined condition (becomes zero or falls below a specified value), the date changes, a specified time runs out, the operator is changed, the number of analyzed samples exceeds a specified value, a specified time period has elapsed, a new reagent is registered, a measurement failure is detected, etc.
Owner:HITACHI HIGH-TECH CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com