Patents
Literature
281 results about "Program monitoring" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Antivirus protection system and method for computers
InactiveUS20080066179A1Reduce in quantitySimple methodMemory loss protectionUnauthorized memory use protectionProcess behaviorProgram behavior
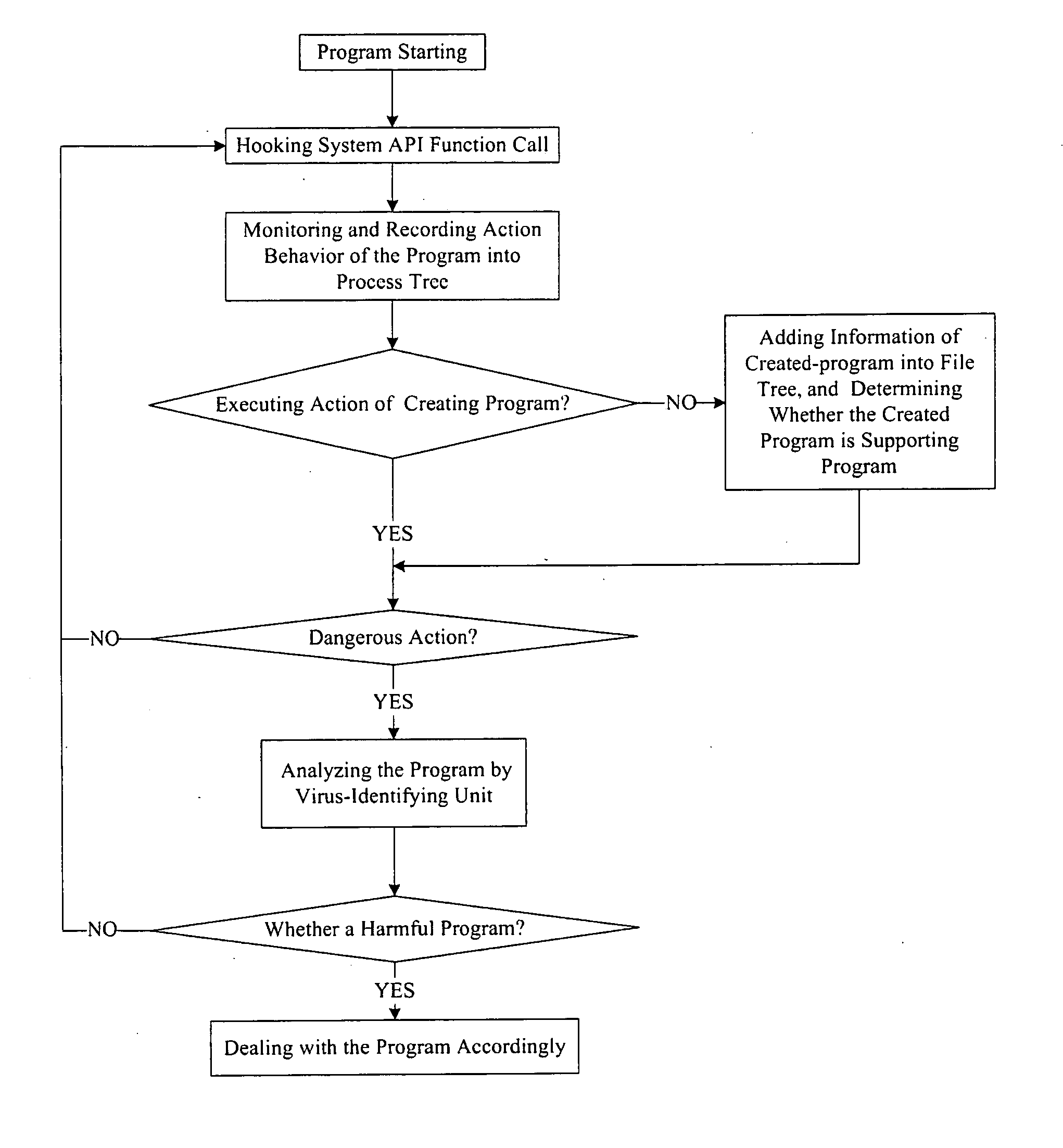
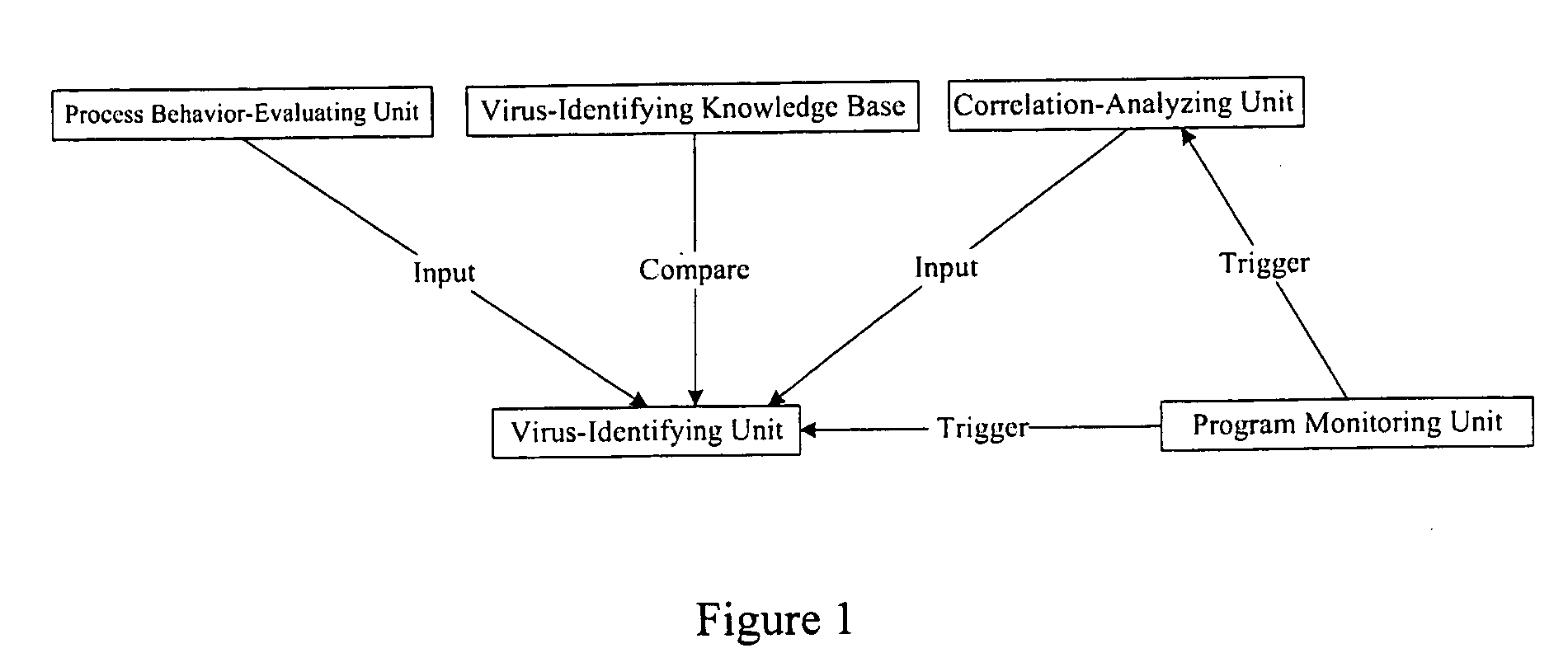
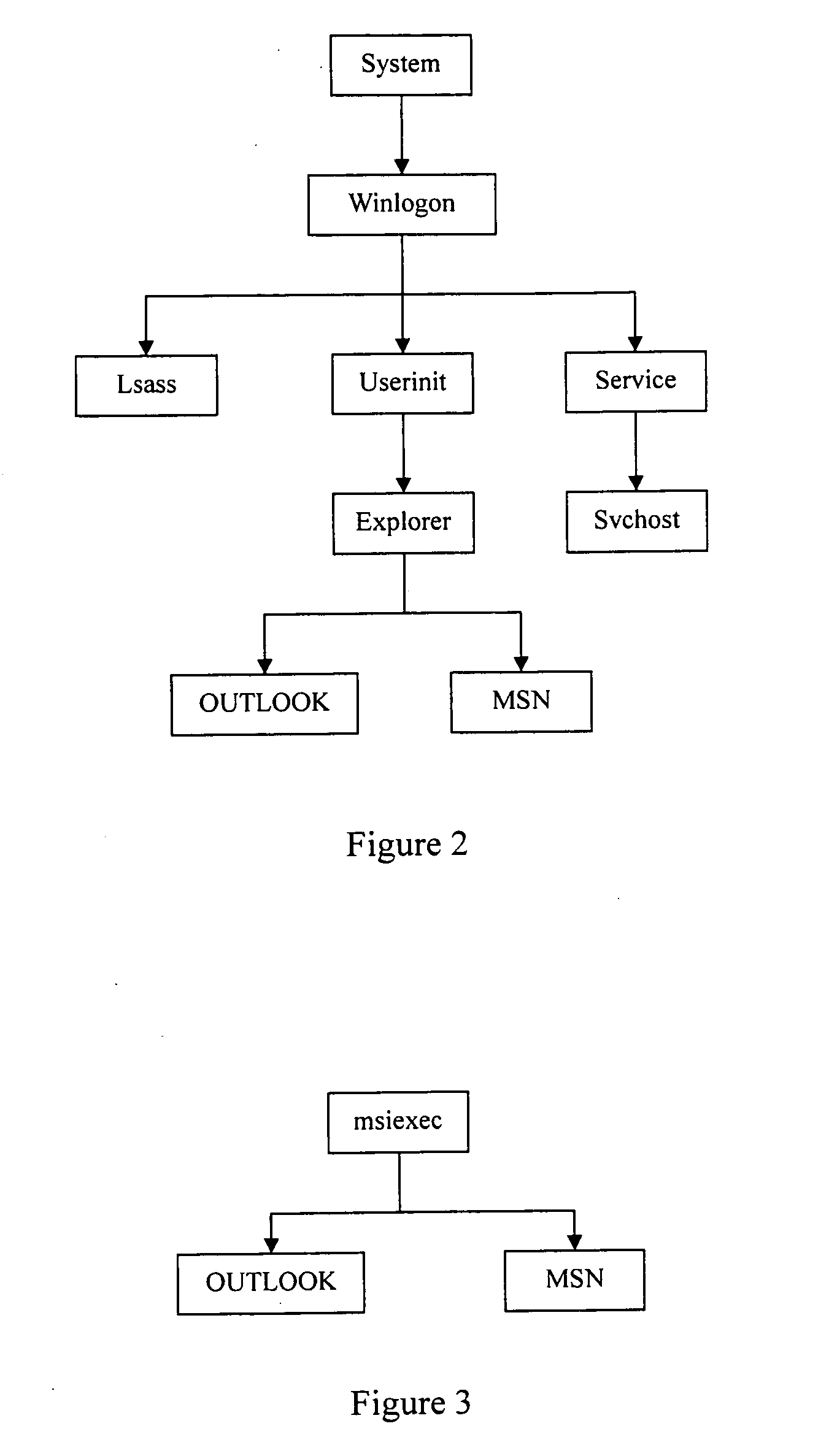
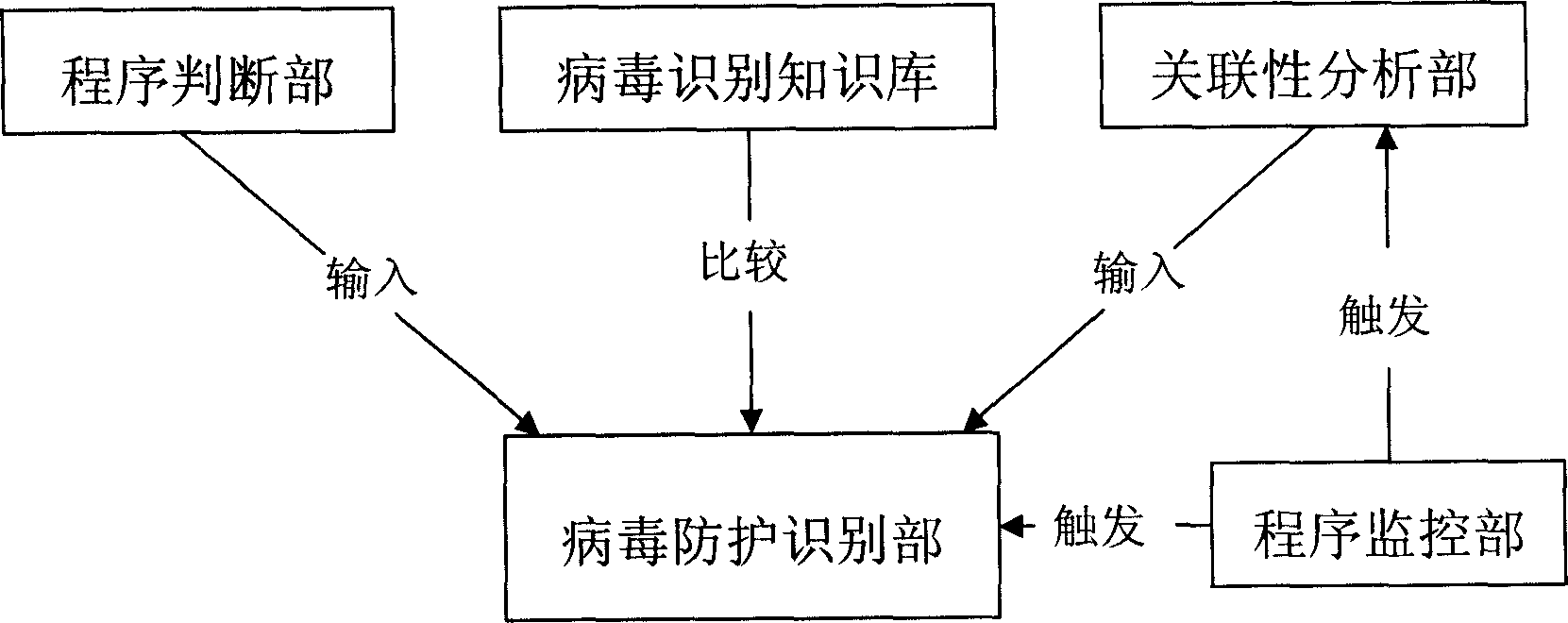
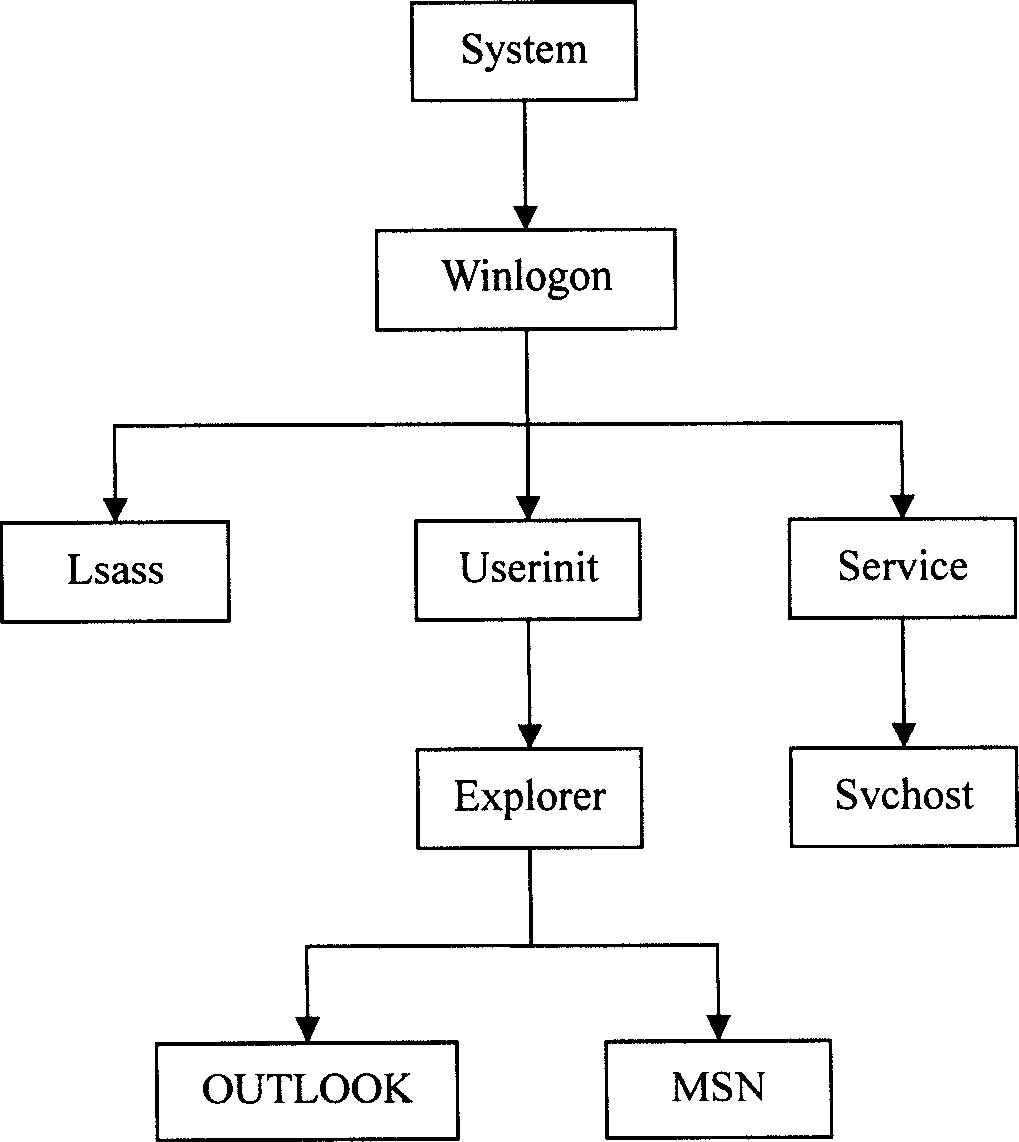
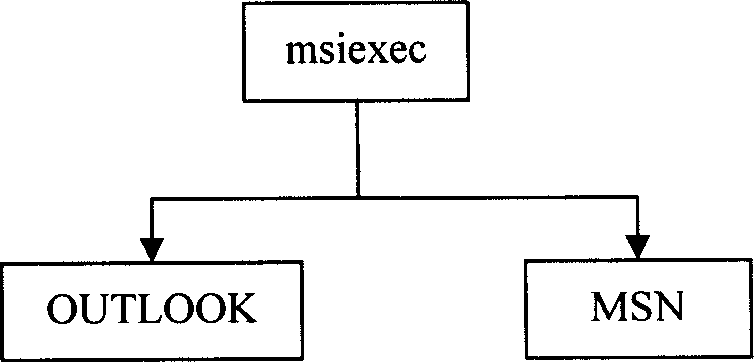
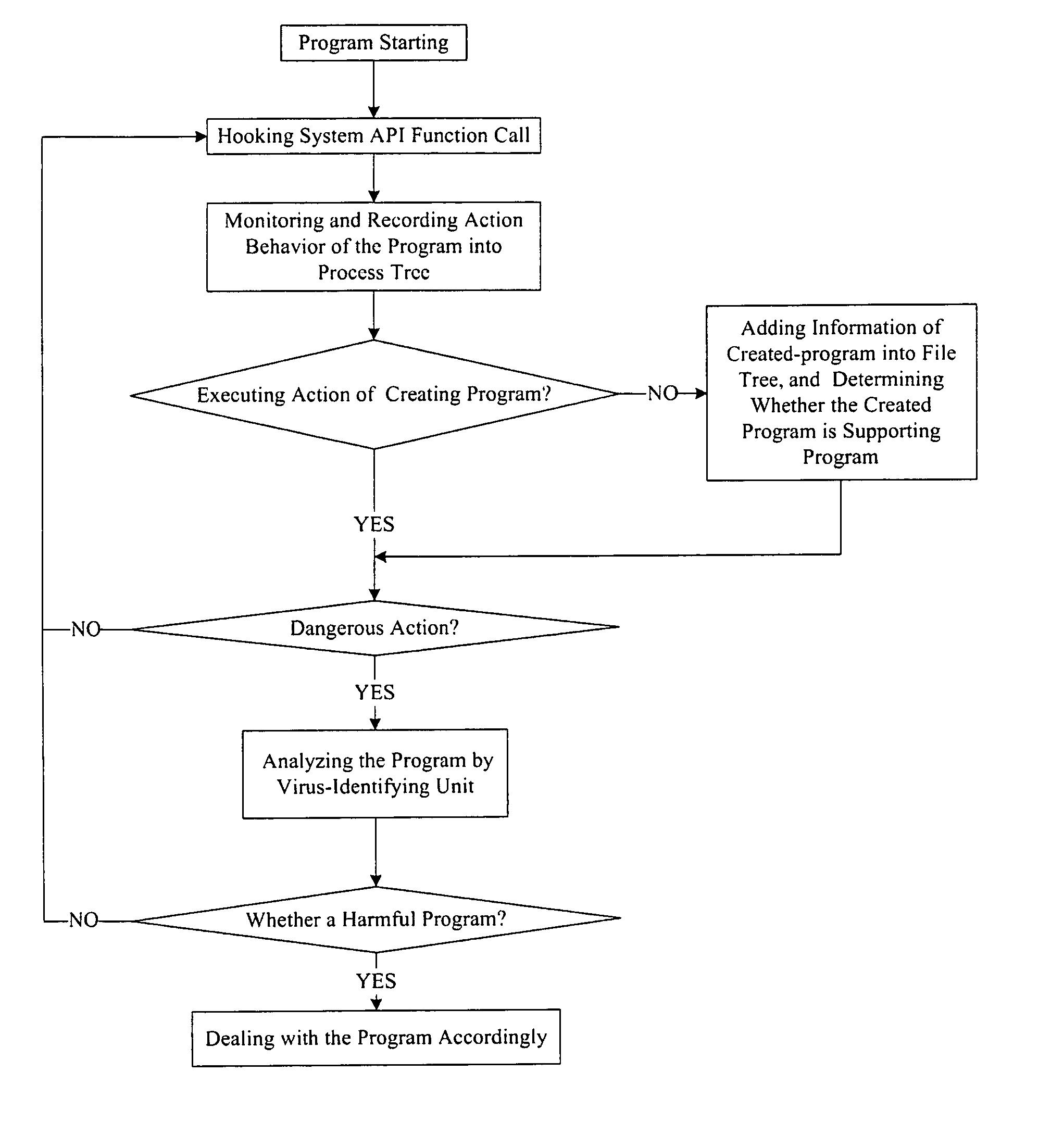
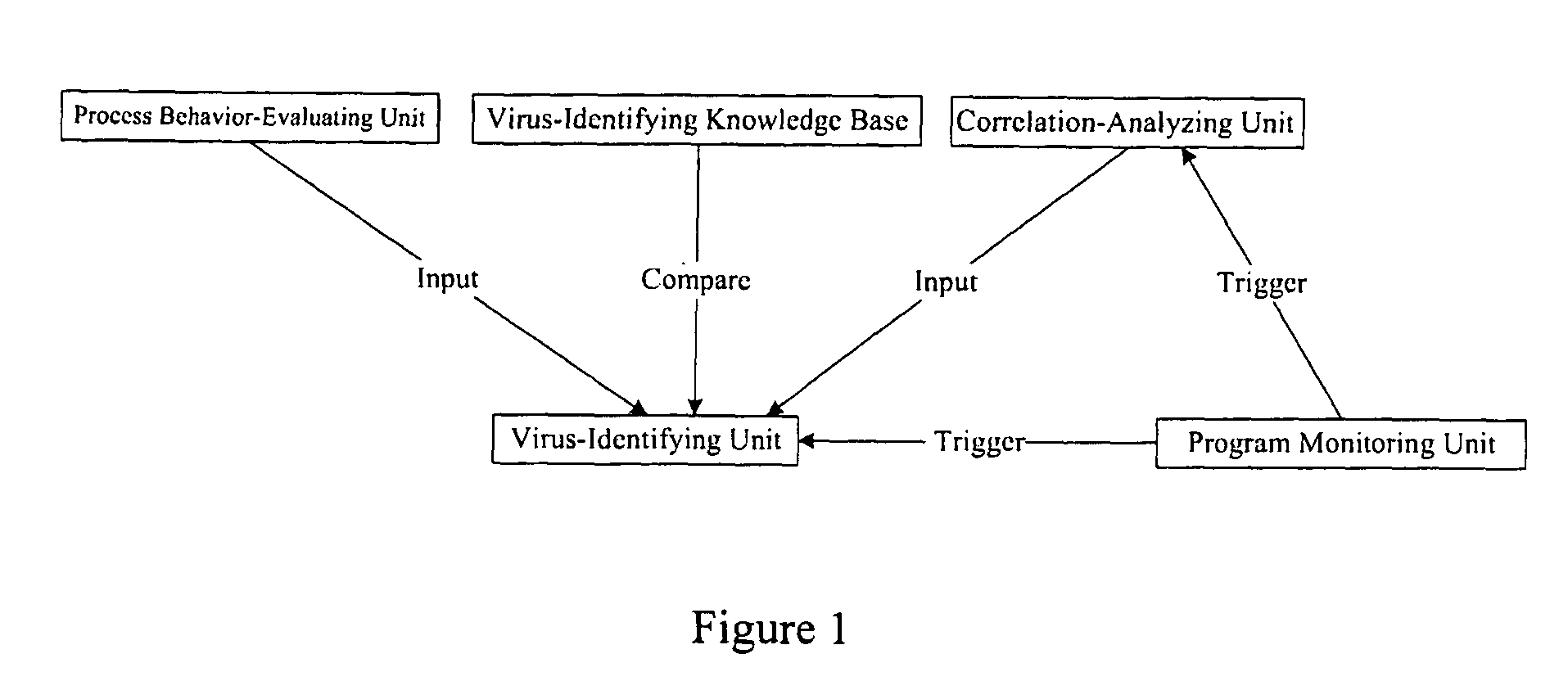
The example embodiments herein relate to an antivirus protection system and method for computers based on program behavior analysis. The antivirus protection system may comprise: a Process Behavior-Evaluating Unit for identifying the programs existing in the user's computers and classifying them into normal programs and suspect programs; a Program-Monitoring Unit for monitoring and recording the actions and / or behaviors of programs; a Correlation-Analyzing Unit for creating correlative trees and analyzing the correlations of actions and / or behaviors of programs, the correlative trees comprising a process tree and a file tree; a Virus-Identifying Knowledge Base, comprising a Program-Behavior Knowledge Base and a Database of Attack-Identifying Rules; a Virus-Identifying Unit for comparing captured actions and / or behaviors to the information in the Virus-Identifying Knowledge Base to determine whether the program is a virus program. With the techniques of certain example embodiments, it may be possible to increase efficiency and reduce the need to upgrade virus codes after viruses become active, while also effectively blocking unknown viruses, Trojans, etc.
Owner:FUJIAN EASTERN MICROPOINT INFO TECH
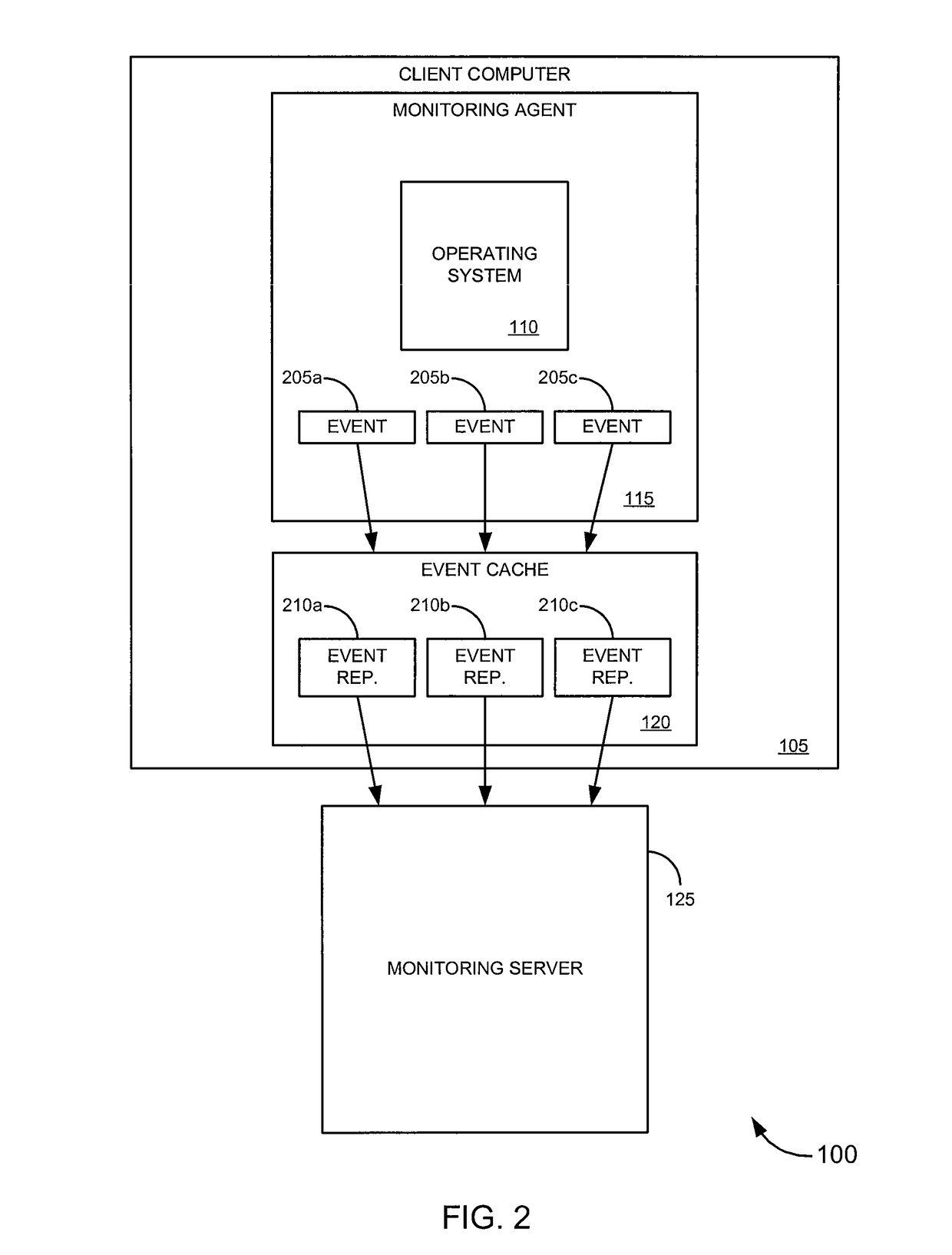
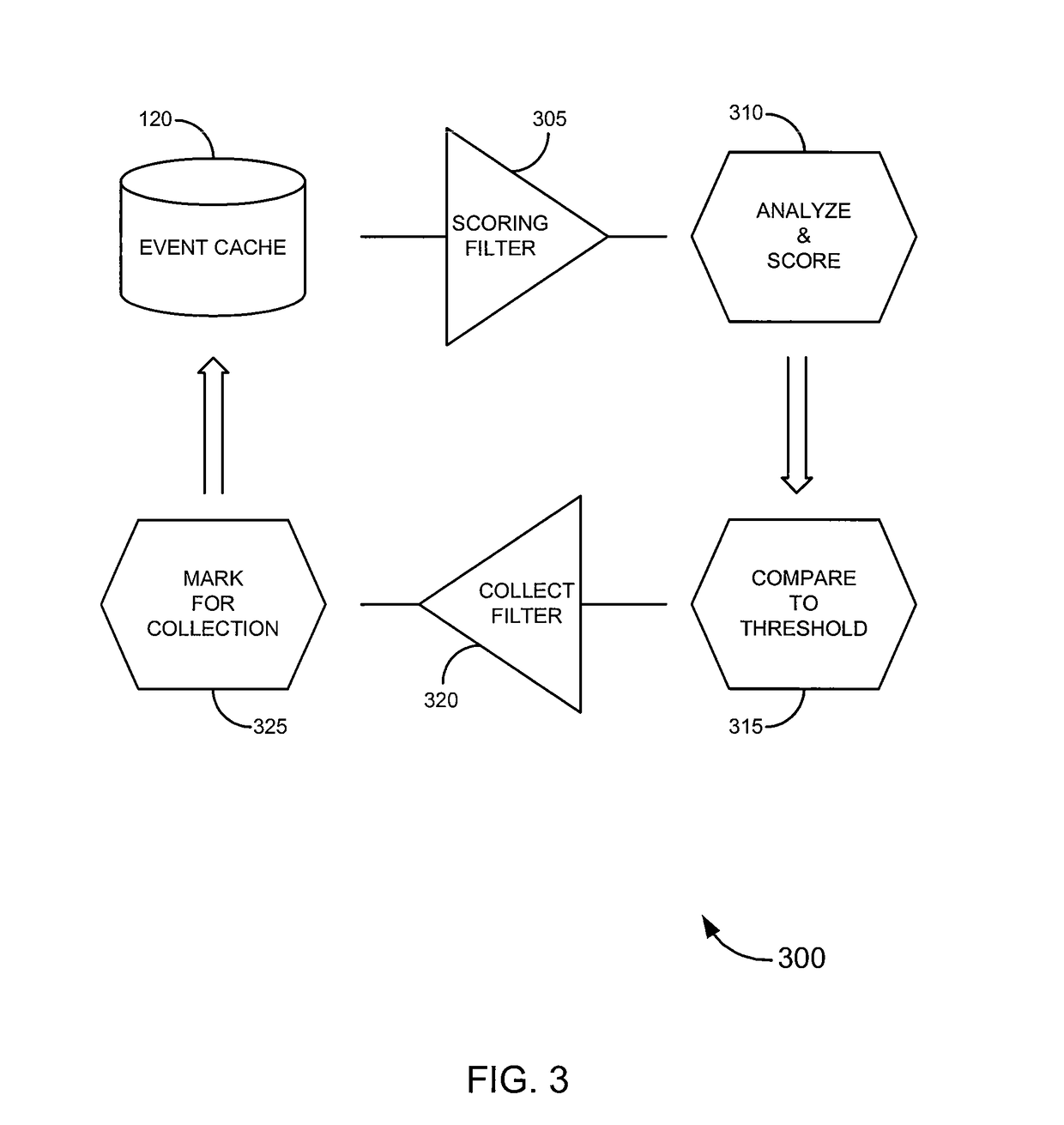
Event monitoring and collection
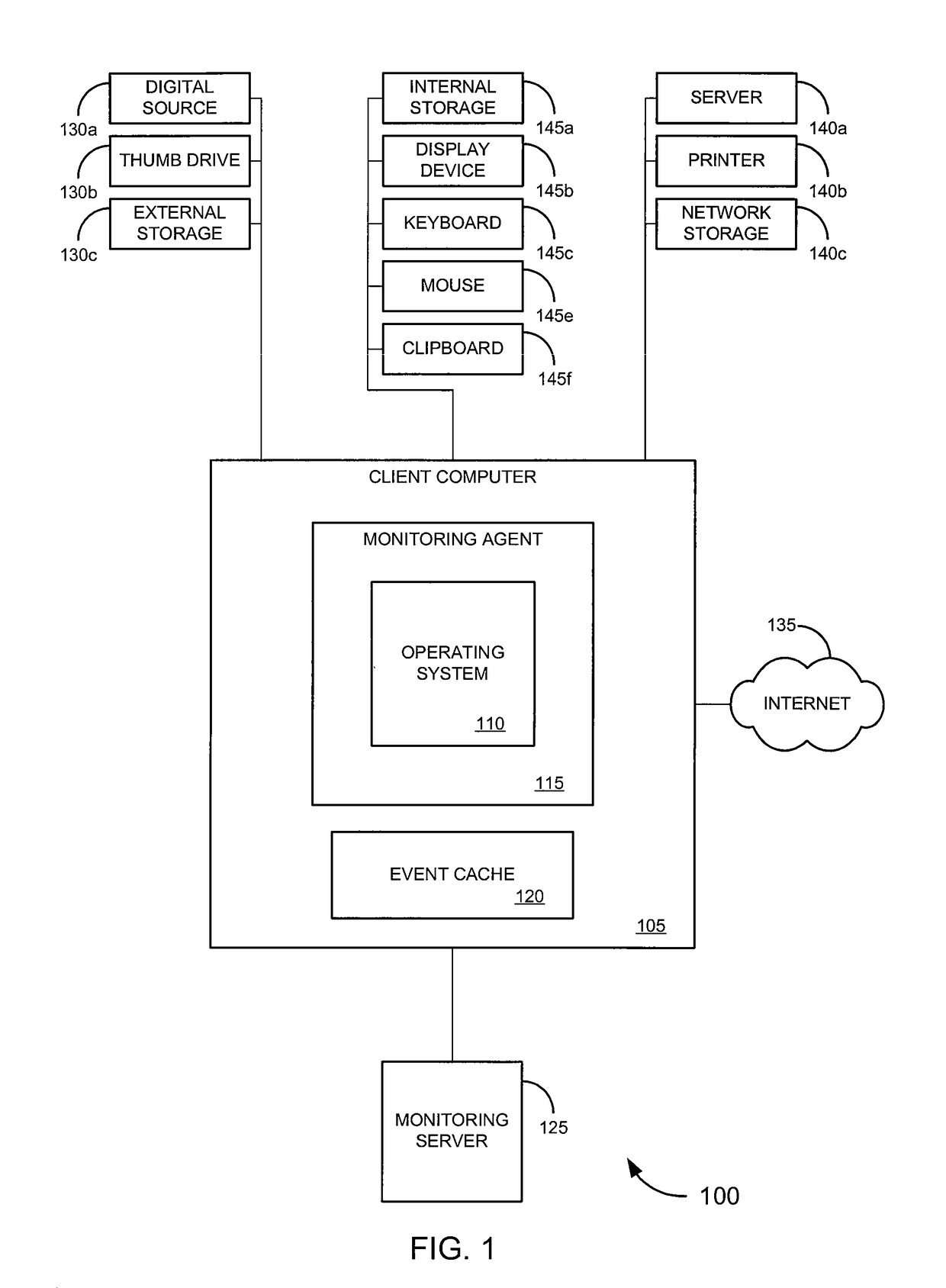
ActiveUS8122122B1PowerfulAvoid detectionDigital computer detailsComputer security arrangementsApplication softwareEvent monitoring
Embodiments of the invention provide systems, software and methods for monitoring events on a computer. In a set of embodiments, a monitoring application monitors events on a monitored computer. Each of the monitored events may be analyzed, and based on the analysis, some or all of the monitored events may be collected. A variety of rules may be used in analyzing events. In some cases, collected events can be queued, for example, by storing a representation of each collected event in an event cache. When connectivity with a monitoring computer is available, a connection with the monitoring computer may be established, and / or the queued events may be transmitted to the monitoring computer. In a particular set of embodiments, the monitoring application is designed to avoid detection by a user of the monitored computer.
Owner:SILICON VALLEY BANK
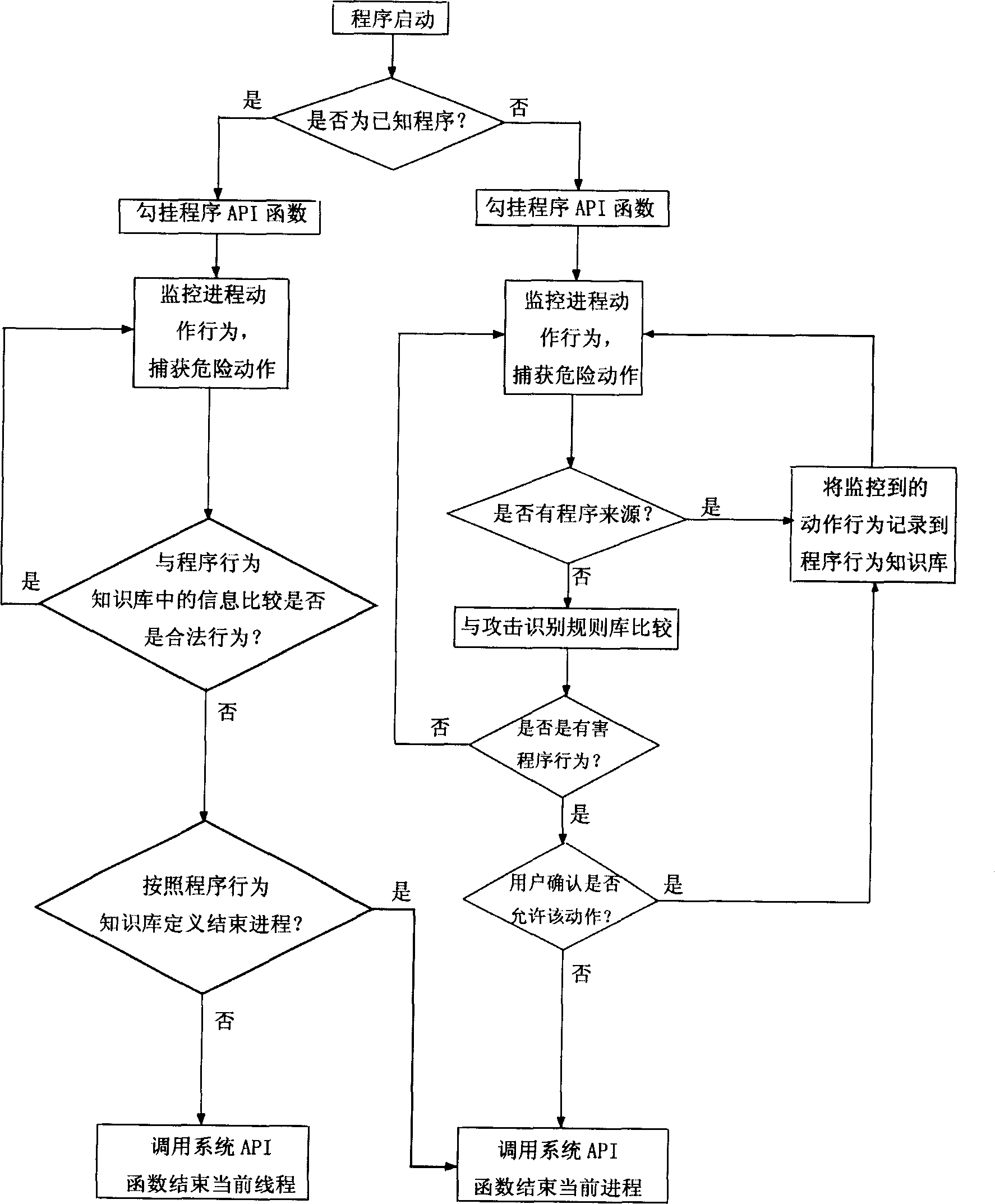
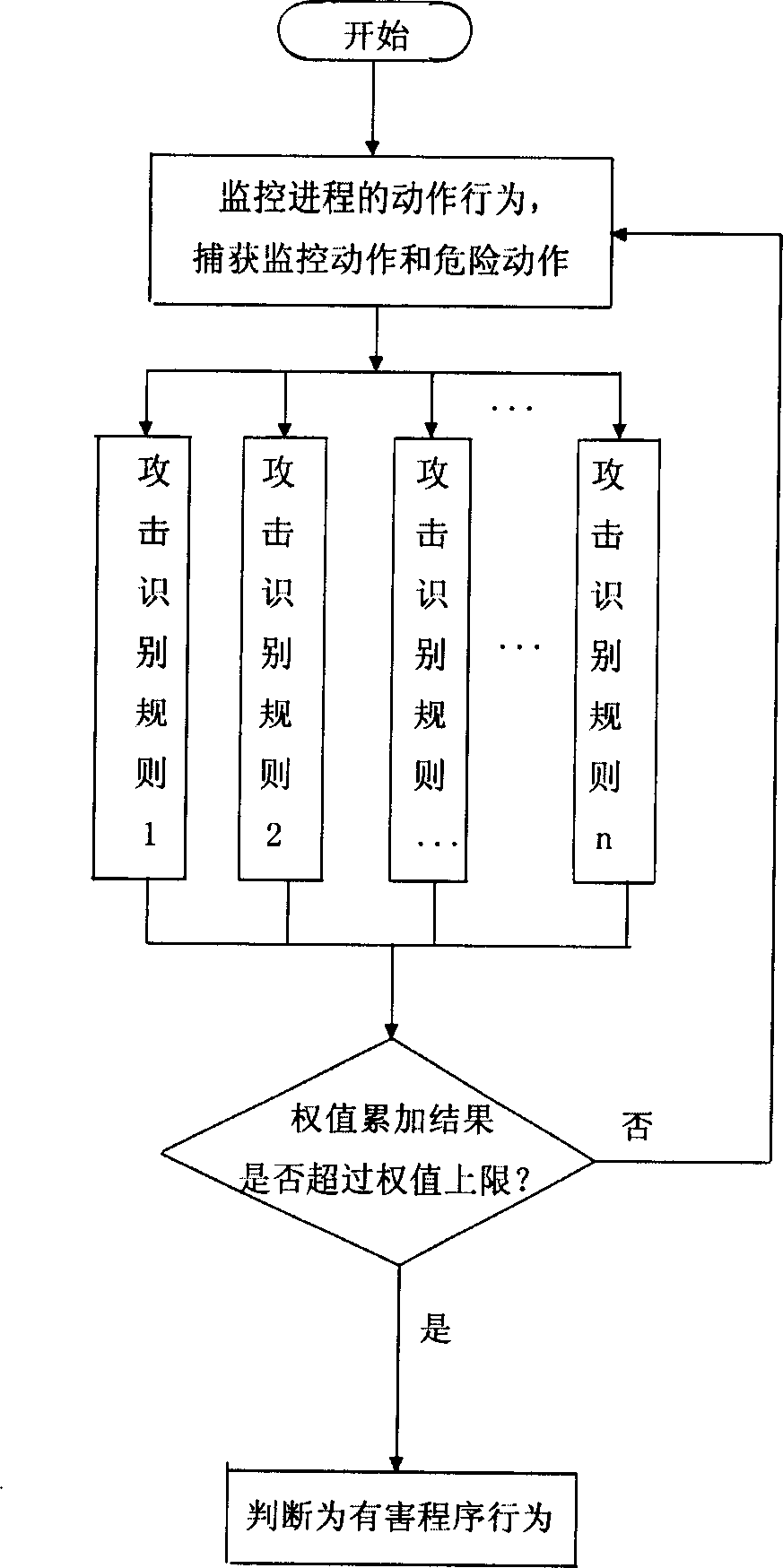
Computer protecting method based on programm behaviour analysis
ActiveCN1818823AEasy to useDigital data processing detailsTransmissionUnknown procedureProgram behavior
A computer protection method based on program behavior analysis includes monitoring its actuation behavior and comparing it with its legal actuation behavior stored in program behavior knowledge bank then judging whether known program is attacked illegally or not for known program; monitoring its actuation behavior and comparing it with attack identification rule stored in attack identification rule bank then judging whether it is harmful program or not for unknown program.
Owner:北京东方微点信息技术有限责任公司
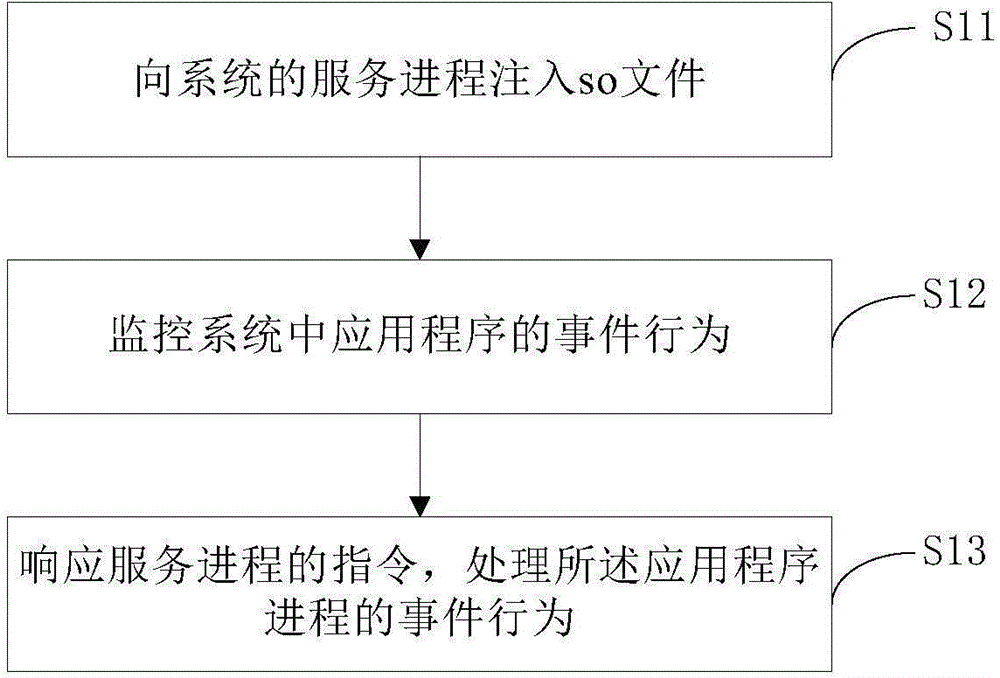
Application program monitoring method and device
ActiveCN102110220ALose controlAvoid spendingPlatform integrity maintainanceStatistical analysisApplication software
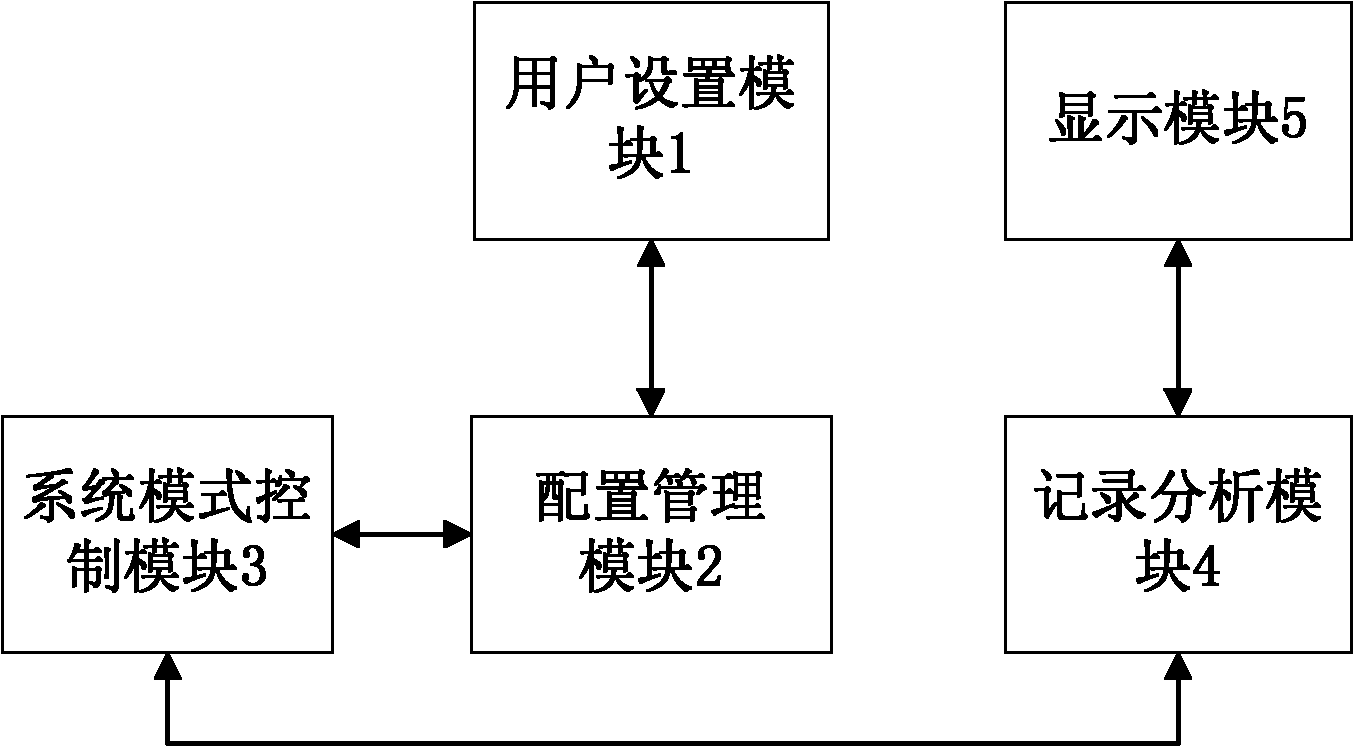
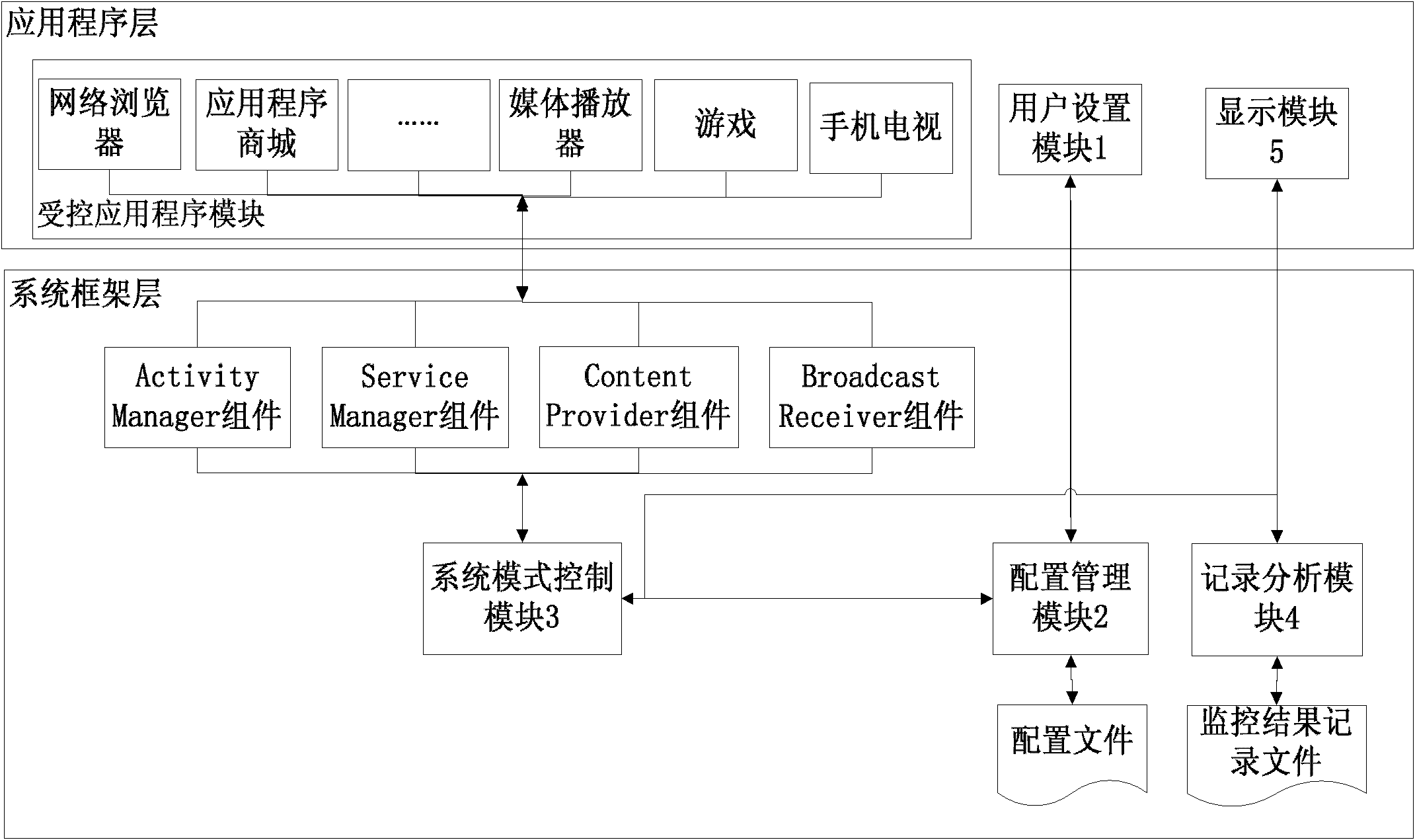
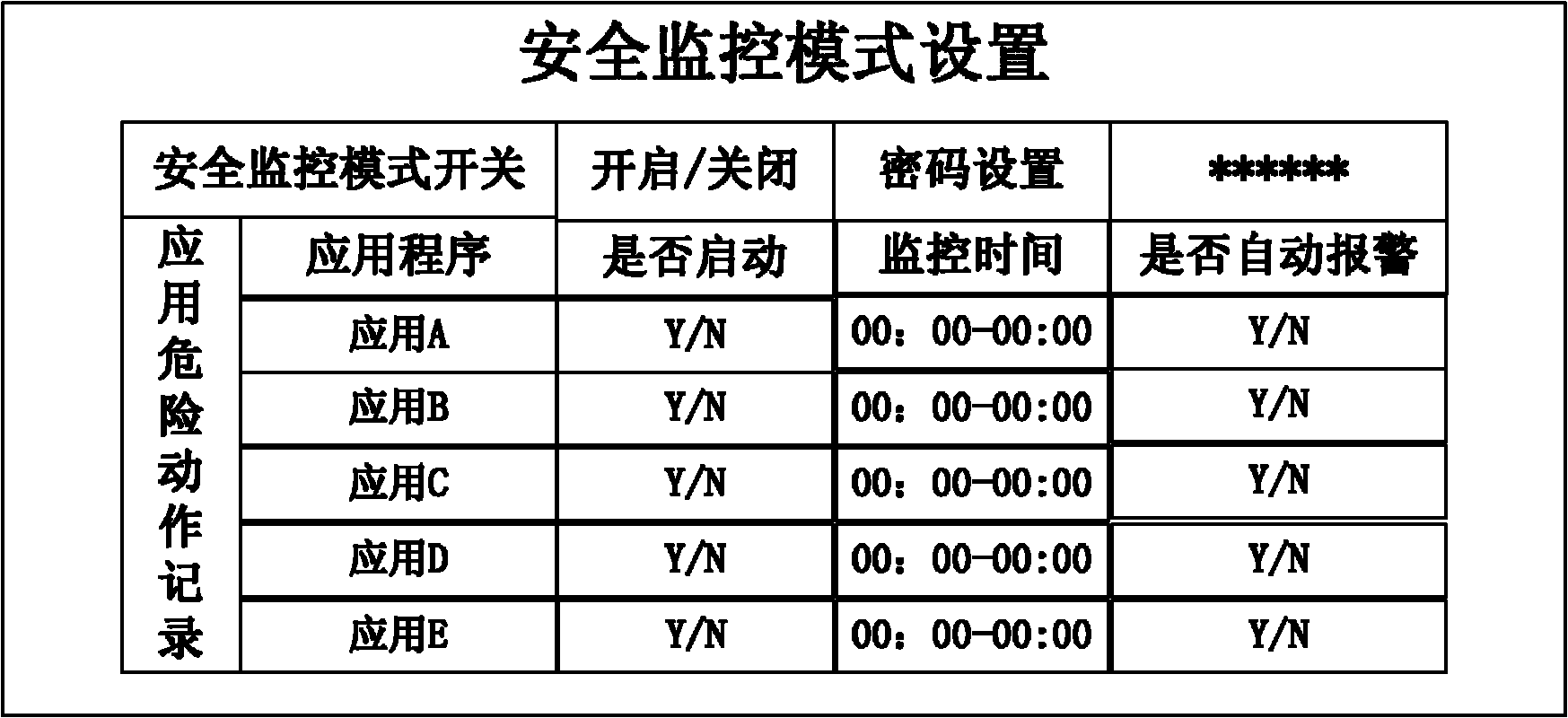
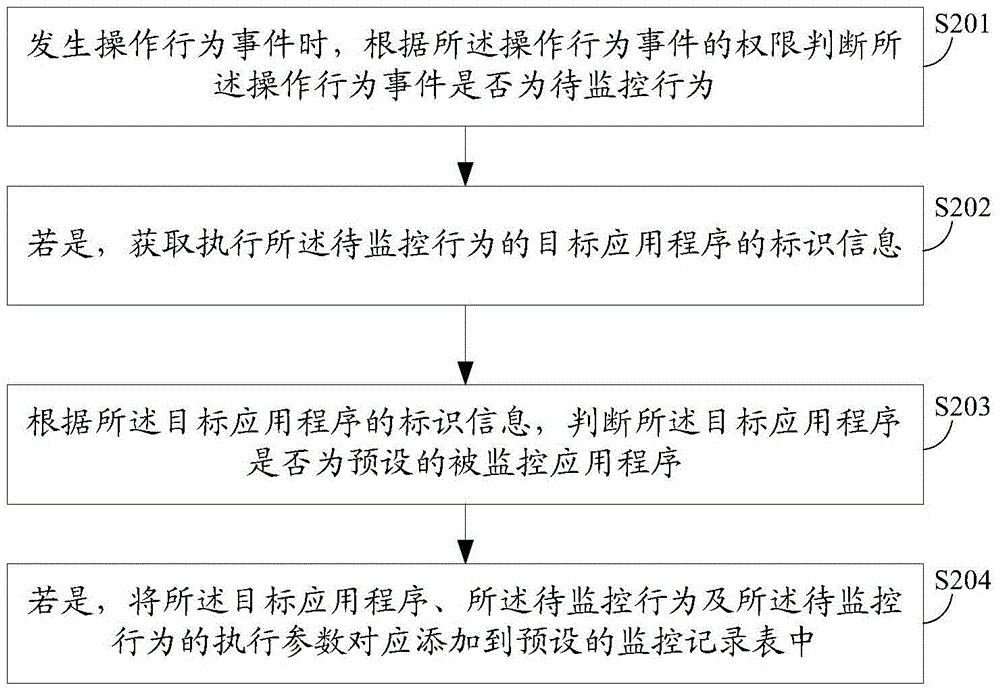
The invention discloses an application program monitoring method and an application program monitoring device. The method comprises the following steps of: when an operation authority is acquired in an application program and the corresponding operation is executed, recording the operation to be monitored and the attribute parameter thereof; and analyzing the security level of the application program according to the recorded operation of the application program and the attribute parameter, and prompting a user of the security level. The monitoring parameter of the application program is defined and maintained in a system framework, so that the application program is uniformly managed; and the security level assessment of the application program is obtained by weight statistical analysis.
Owner:SHENZHEN TRANSSION HLDG CO LTD
System and method for continuous monitoring and measurement of performance of computers on network
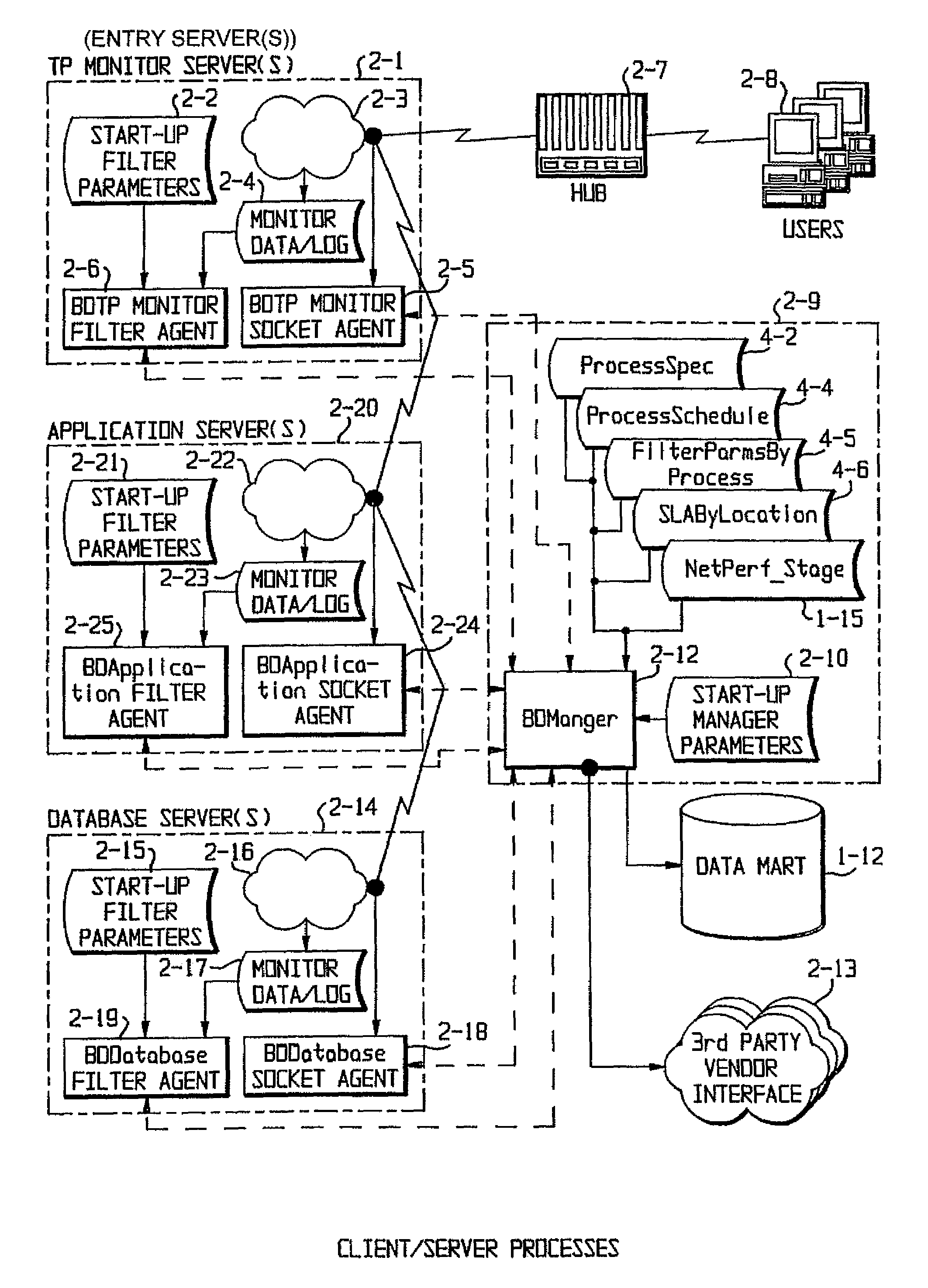
InactiveUS7577701B1Valuable informationAccurately reflectMultiple digital computer combinationsData switching networksThe InternetNetworked system
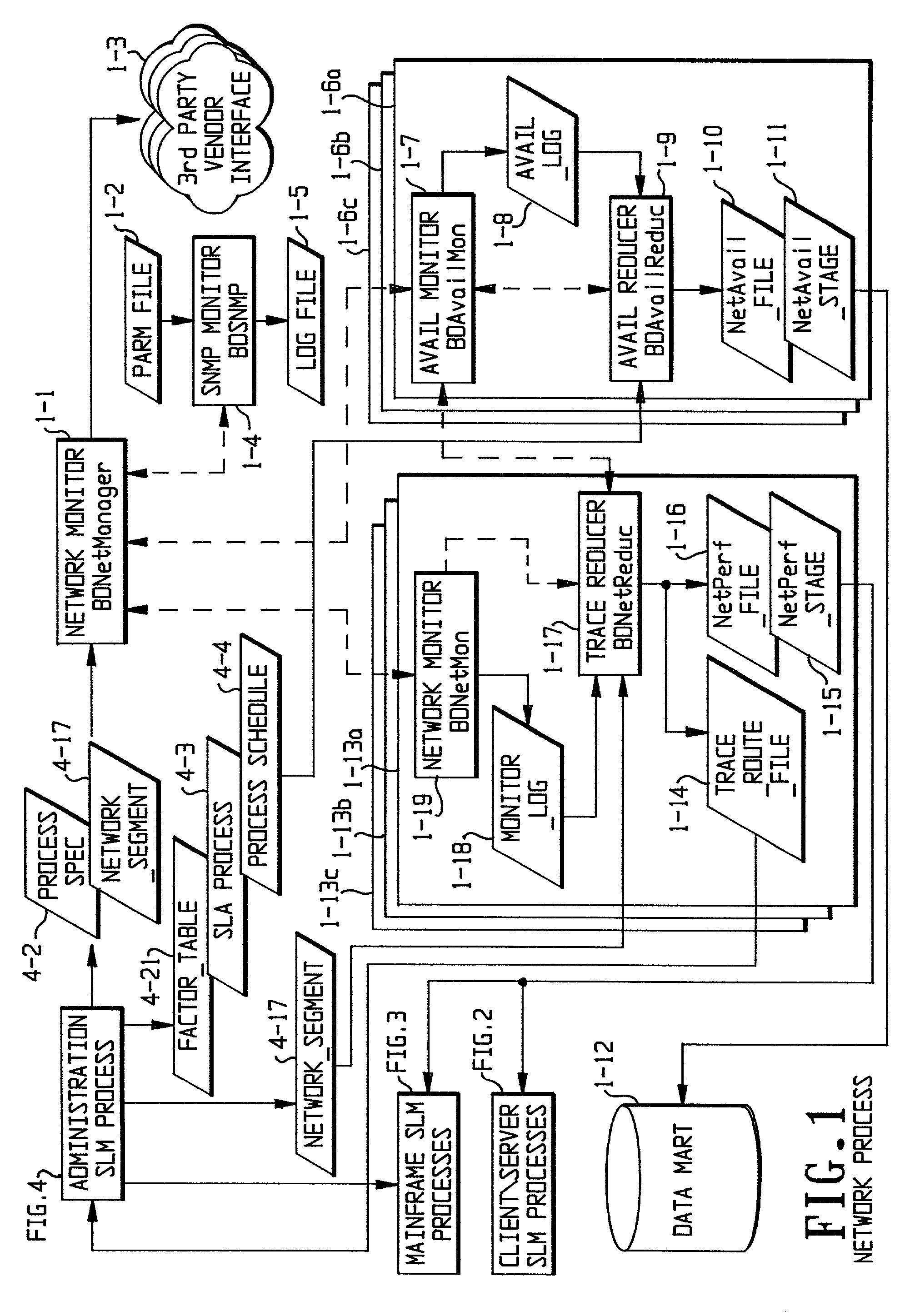
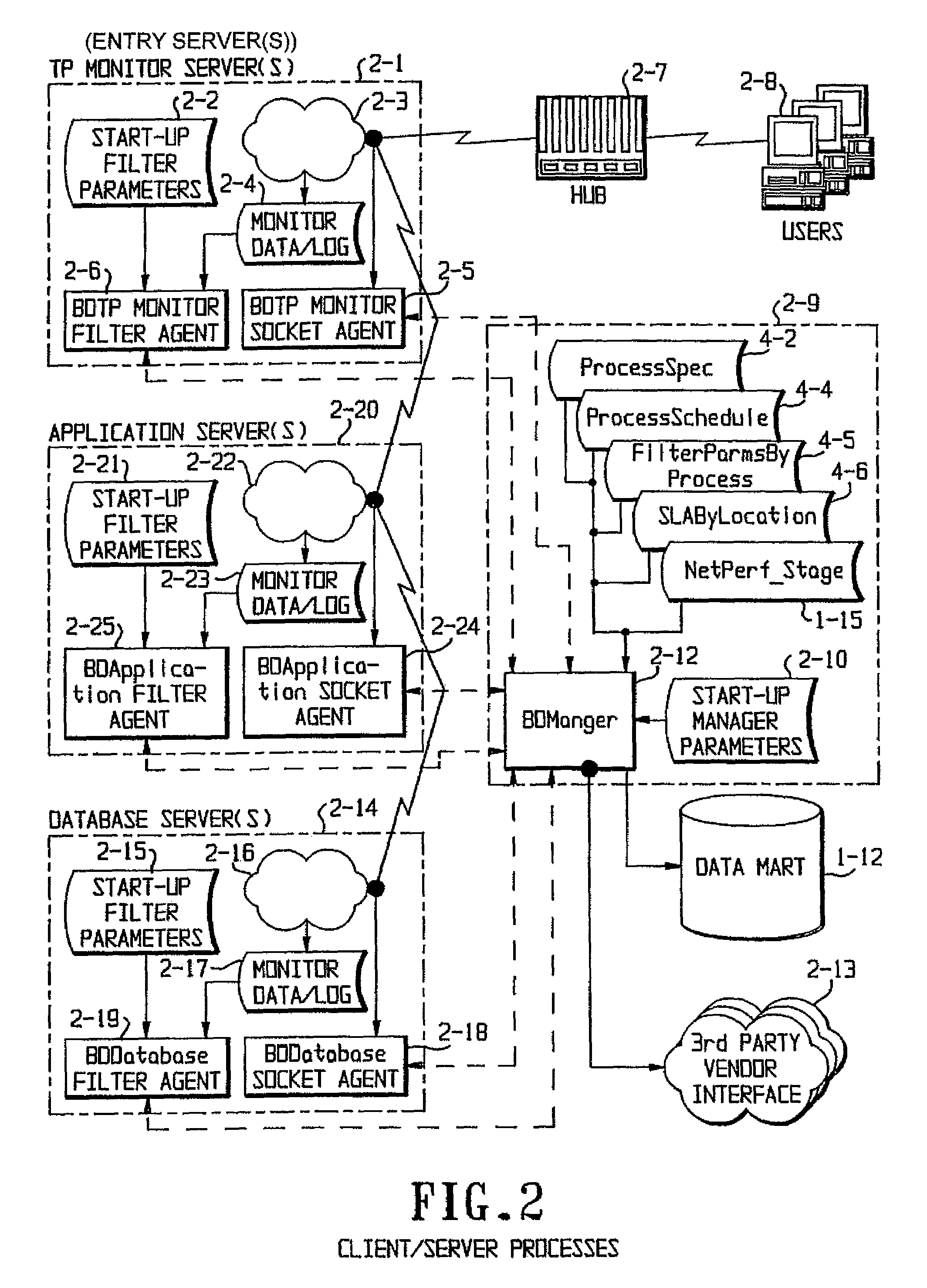
Performance on a networked system is monitored through five interlocking monitoring techniques. A network monitoring process causes pseudo messages to be sent from various points in the network and monitors the progress of the pseudo messages. A client-server monitoring process monitors server availability and receives logs from various client-server processes and determines the performance of both server and server processes, which can be grouped by end-user location. A mainframe monitoring process monitors the performance of the various hardware and software components on a mainframe. A reporting and administration process compiles reports and makes them remotely available over the Internet. An e-business monitoring process monitors servers accessible to customers over the Internet by use of a Java applet which sends time stamps indicating access. The five processes are tied together through a central data repository, called a data mart.
Owner:MAGNAFOX LLC
Program monitoring method and defending method thereof, as well as relevant device
ActiveCN104598809AHook implementationAvoid markingPlatform integrity maintainanceTemporary variableProgram monitoring
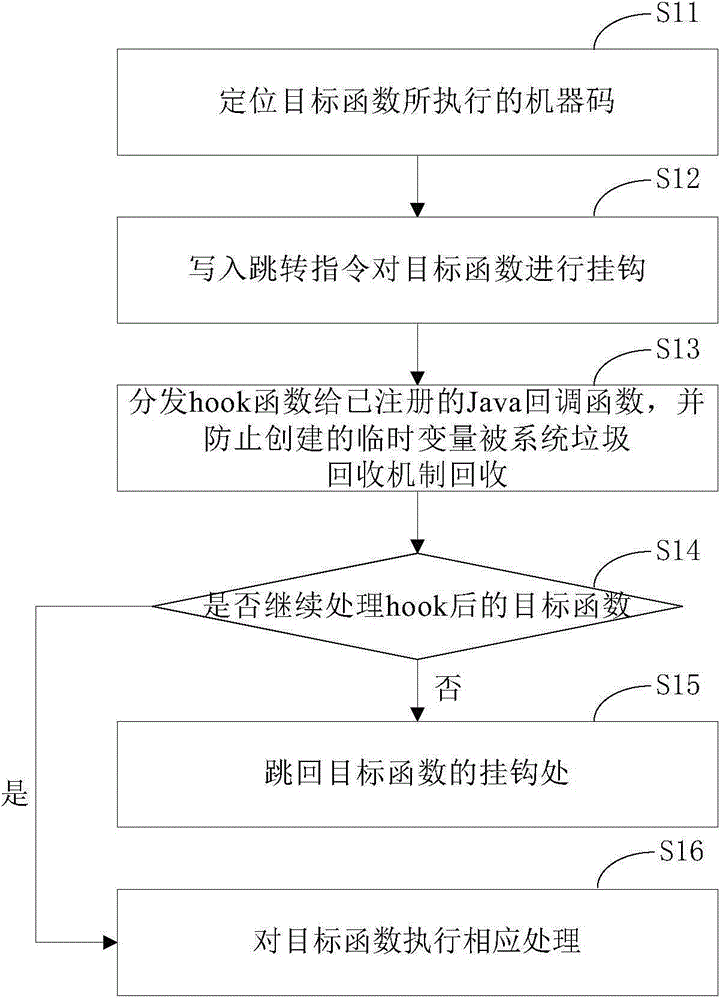
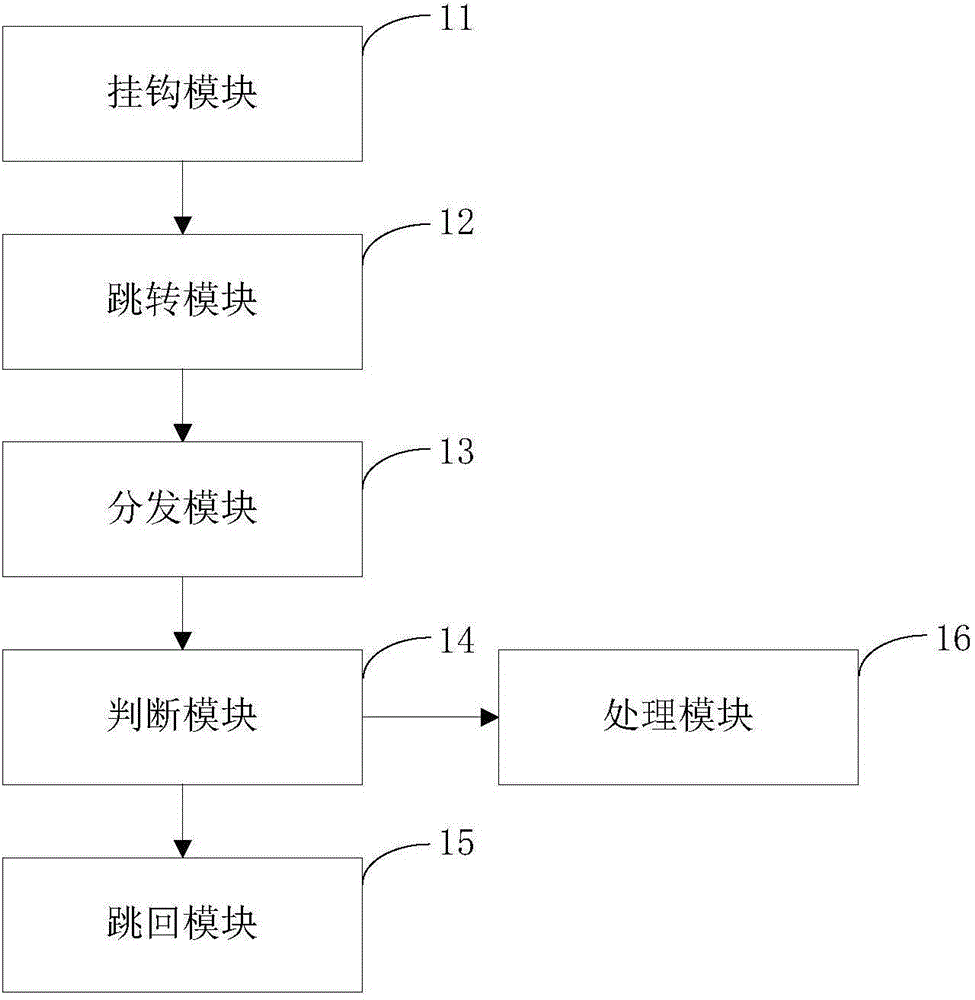
The invention provides a program monitoring method and device. The program monitoring method comprises the following steps: writing in a skip instruction for positioned objective functions so as to perform a hook operation; distributing hook functions to registered Java callback functions, and preventing created temporary variables from being collected by a garbage collection mechanism of a system; enabling the objective functions which are not processed to skip back to hook positions, or else, continuing to process the objective functions. Through the adoption of the program monitoring method disclosed by the invention, any Java function of an Android system under an ART mode can be monitored without destroying the stack of the objective functions, so that the garbage collection mechanism of the ART can perform normal memory collection. The invention further provides a program defending method and device, which realize a defending mechanism of the Android system under the ART mode by adopting the program monitoring method disclosed by the invention.
Owner:BEIJING QIHOO TECH CO LTD
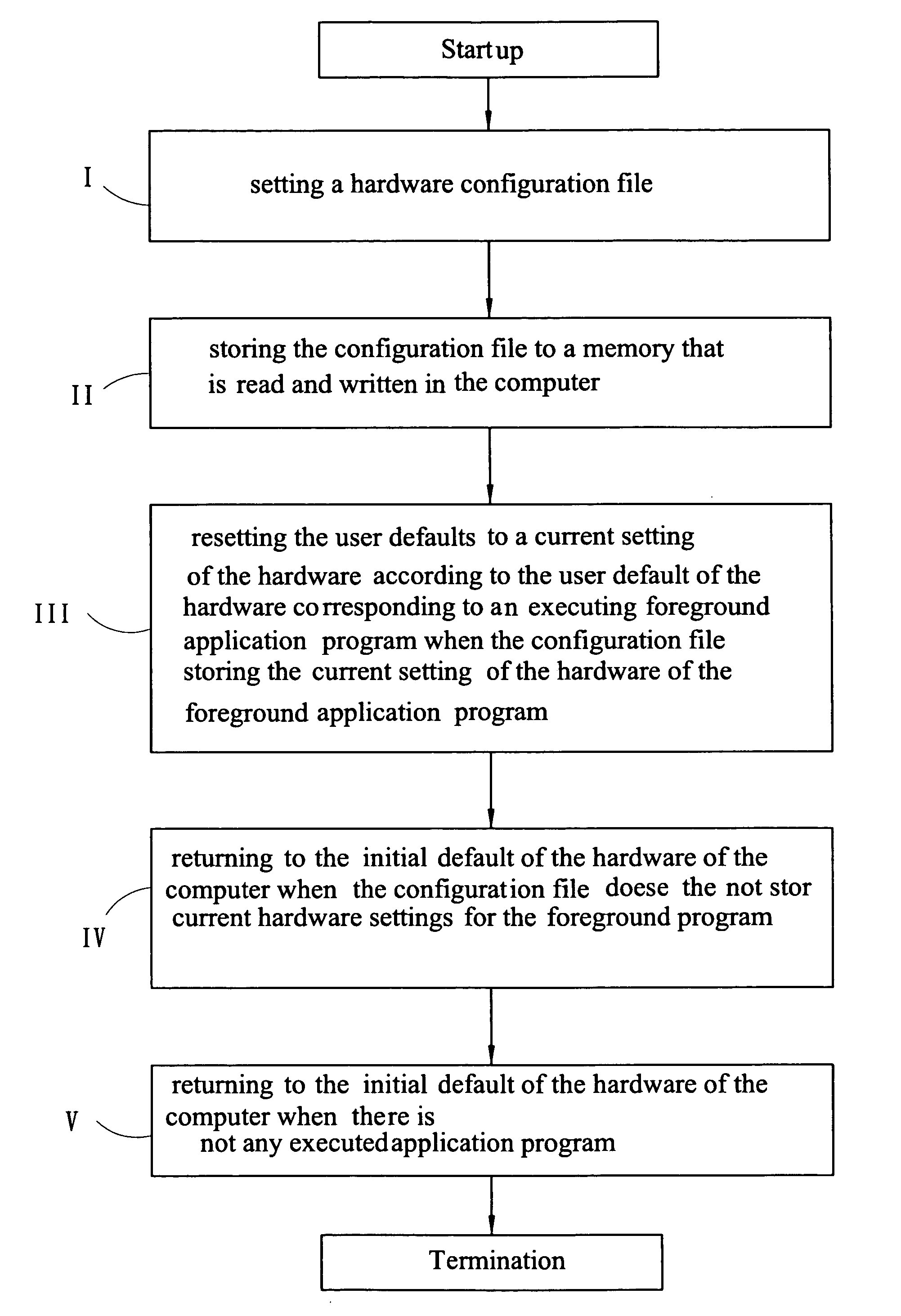
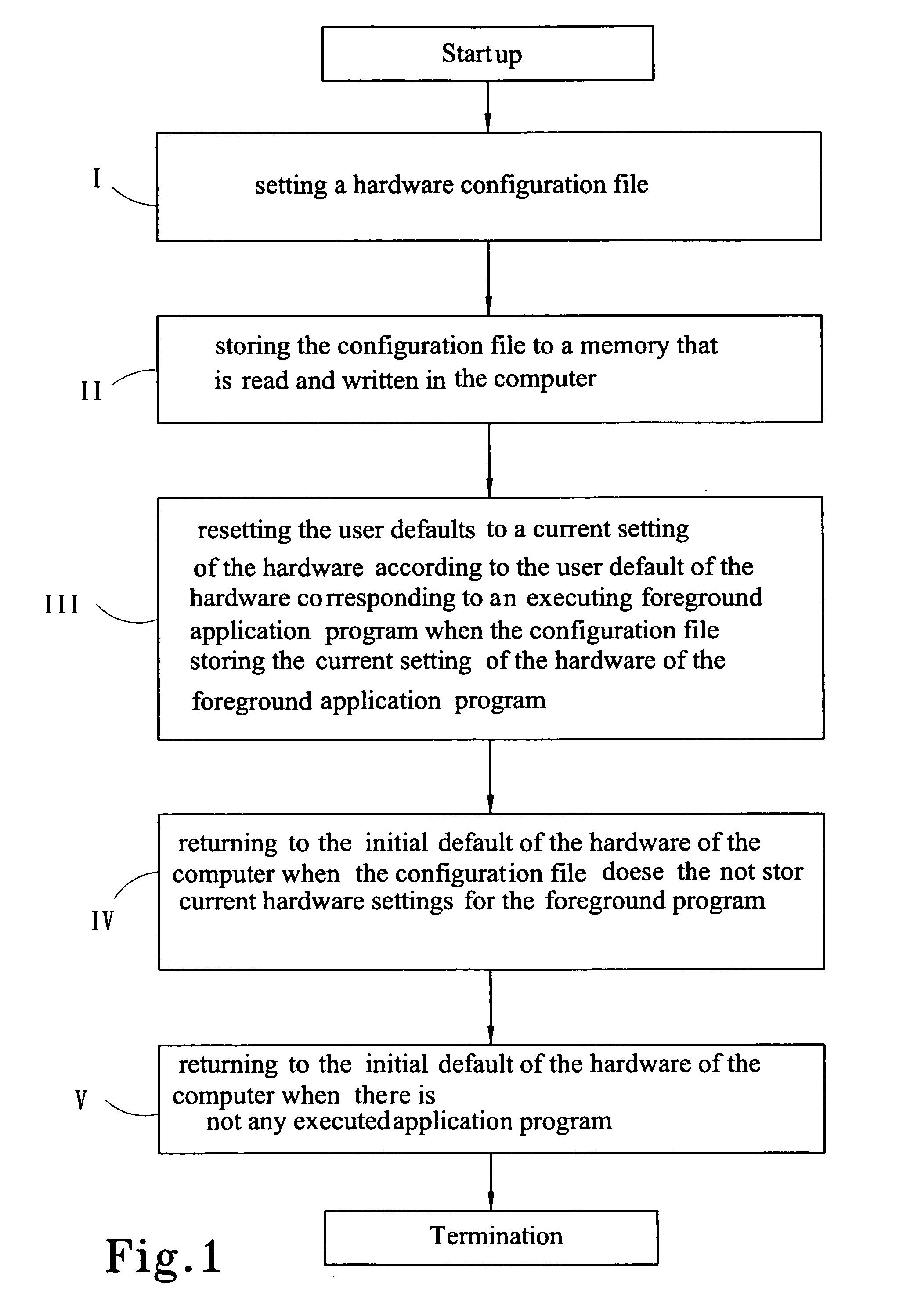
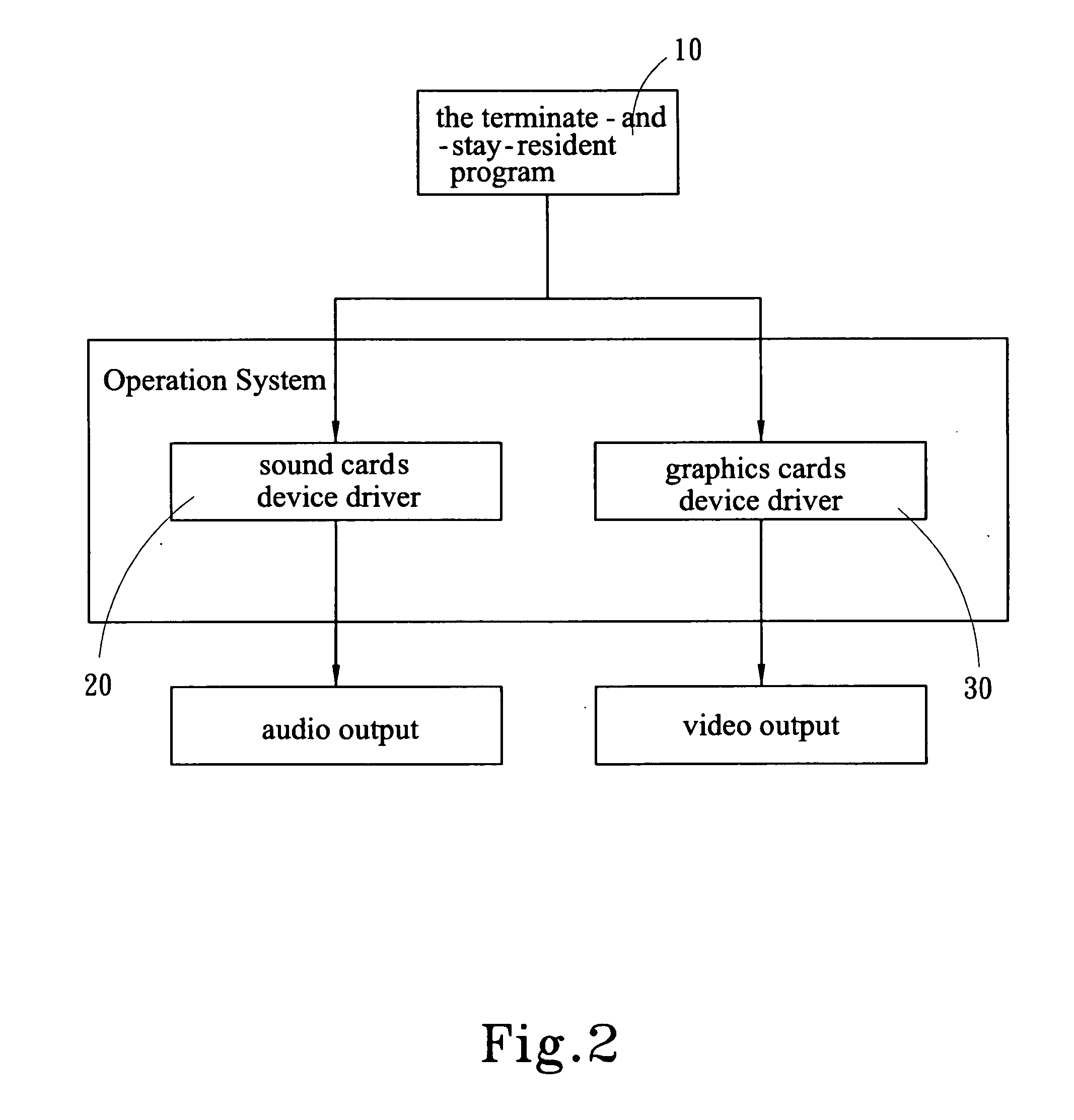
Method for automatically changing the hardware settings of a computer in accordance with an executing application program
InactiveUS20050204125A1Data resettingProgram loading/initiatingInitTerminate and stay resident program
The present invention provides a method for changing the hardware settings on a computer automatically in accordance with an executed application program. The method dynamically changes the setting, e.g. voltage, frequency, rotational speed of a fan, sound volume, sound effect, etc. of the hardware of the computer in accordance with the current executed application program of the computer automatically to meet the hardware requirements of the of the user in accordance with a specific application program. According to the method, the setting of the hardware corresponding to the application program is stored in a configuration file of the hardware, and the initialization and termination of all application programs are monitored by utilizing a terminate-and-stay-resident program of the computer. A user the terminate-and-stay-resident program can automatically revise the current settings of the hardware of the computer to a user default of the hardware, which is defined by the user if the application program which is defined in advance is executed, and return to the initial default of the computer if the program is finished.
Owner:UNIVERSAL ABIT HONDLING COMPANY
Computer anti-virus protection system and method
The invention relates to a computer anti-virus protecting system and relative method, based on program behavior analysis, wherein said invention is characterized in that: it comprises a program judge part for recognizing the program of user computer and dividing the program into normal and abnormal ones; a program detecting part for detecting and recording the program behavior; a relevance analyzing part for building relevance tree to process relevance analysis, while said relevance tree comprises loading relevance tree and building relevance tree; a virus recognize information base comprising a program behavior information base and a impact recognize rule base; and a virus protective recognize part for comparing the picked behavior and the information of virus recognize information base, to judge if said program is virus. The invention can improve efficiency and avoid refresh delay of virus code.
Owner:北京东方微点信息技术有限责任公司
Antivirus protection system and method for computers
InactiveUS7870612B2Reduce in quantitySimple methodMemory loss protectionUnauthorized memory use protectionProcess behaviorCorrelation analysis
Owner:FUJIAN EASTERN MICROPOINT INFO TECH
Program monitoring management system based on digital water-print and two-way top-set box
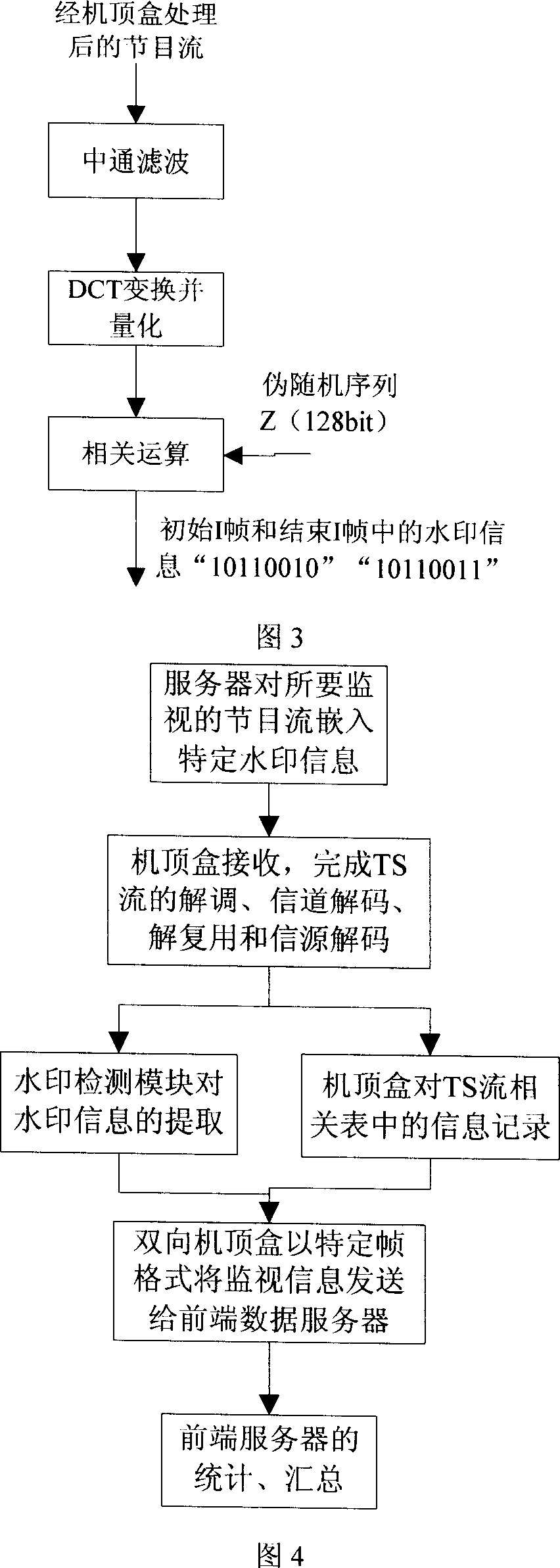
InactiveCN101047833AAccurate playbackTelevision system detailsAnalogue secracy/subscription systemsProgram monitoringBroadcast time
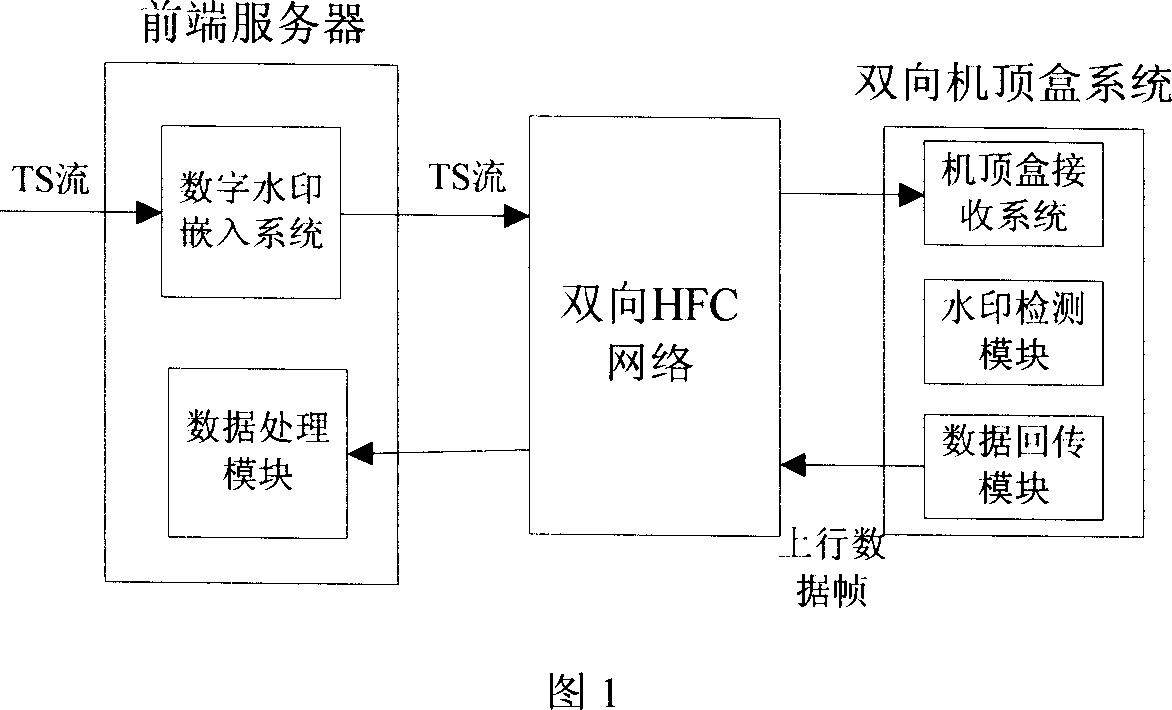
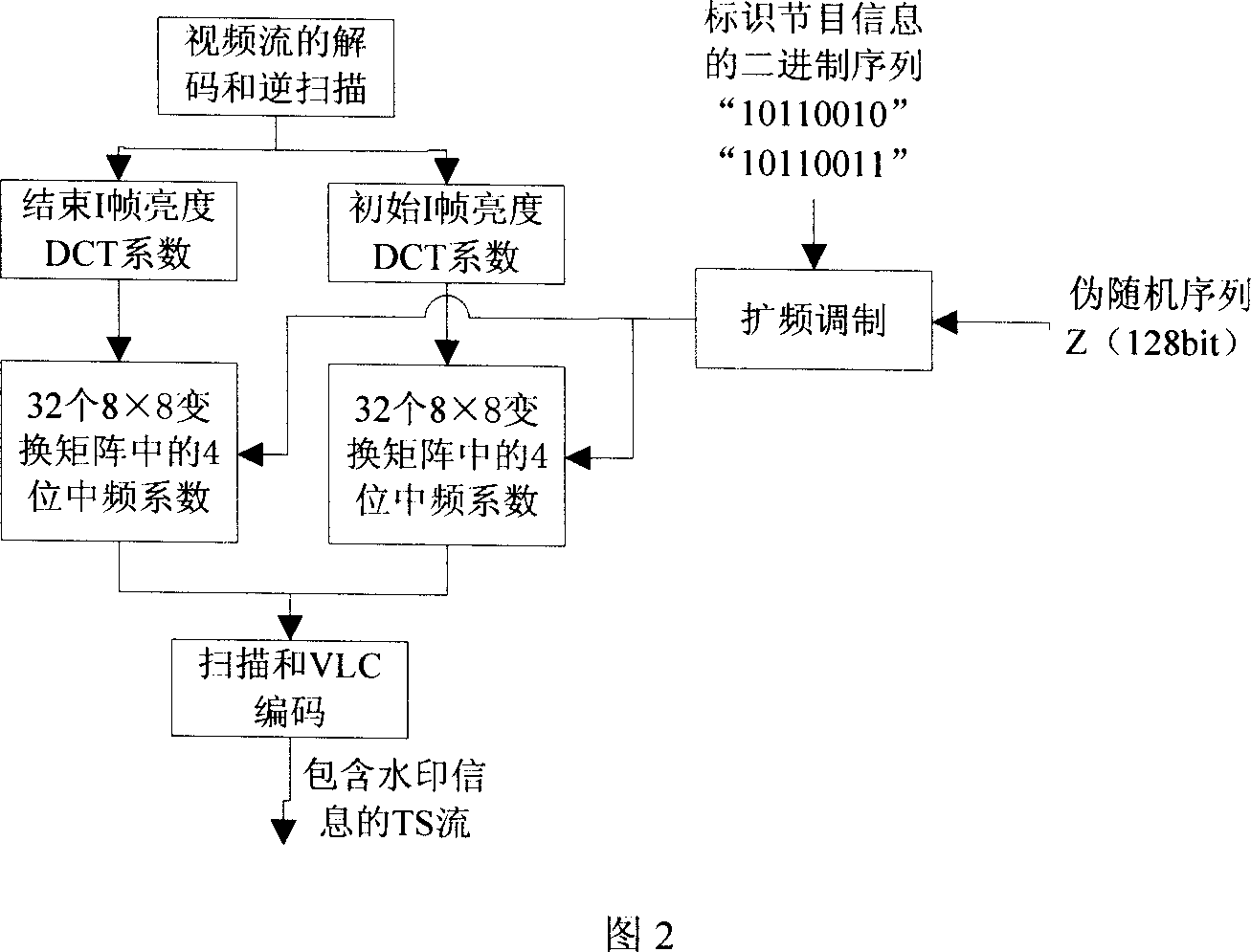
This invention utilizes digital watermark technology to identify program content and test and process the digital watermark information inserted into a specific program of a 2-way set-top box to finish collection of owners of copyright, the play time and length, then a back-transfer module finishes the transfer of information from the box to the front system to finish further data process, which can also finish the control to the box and the watermark test module by a dual channel.
Owner:LANGCHAO ELECTRONIC INFORMATION IND CO LTD
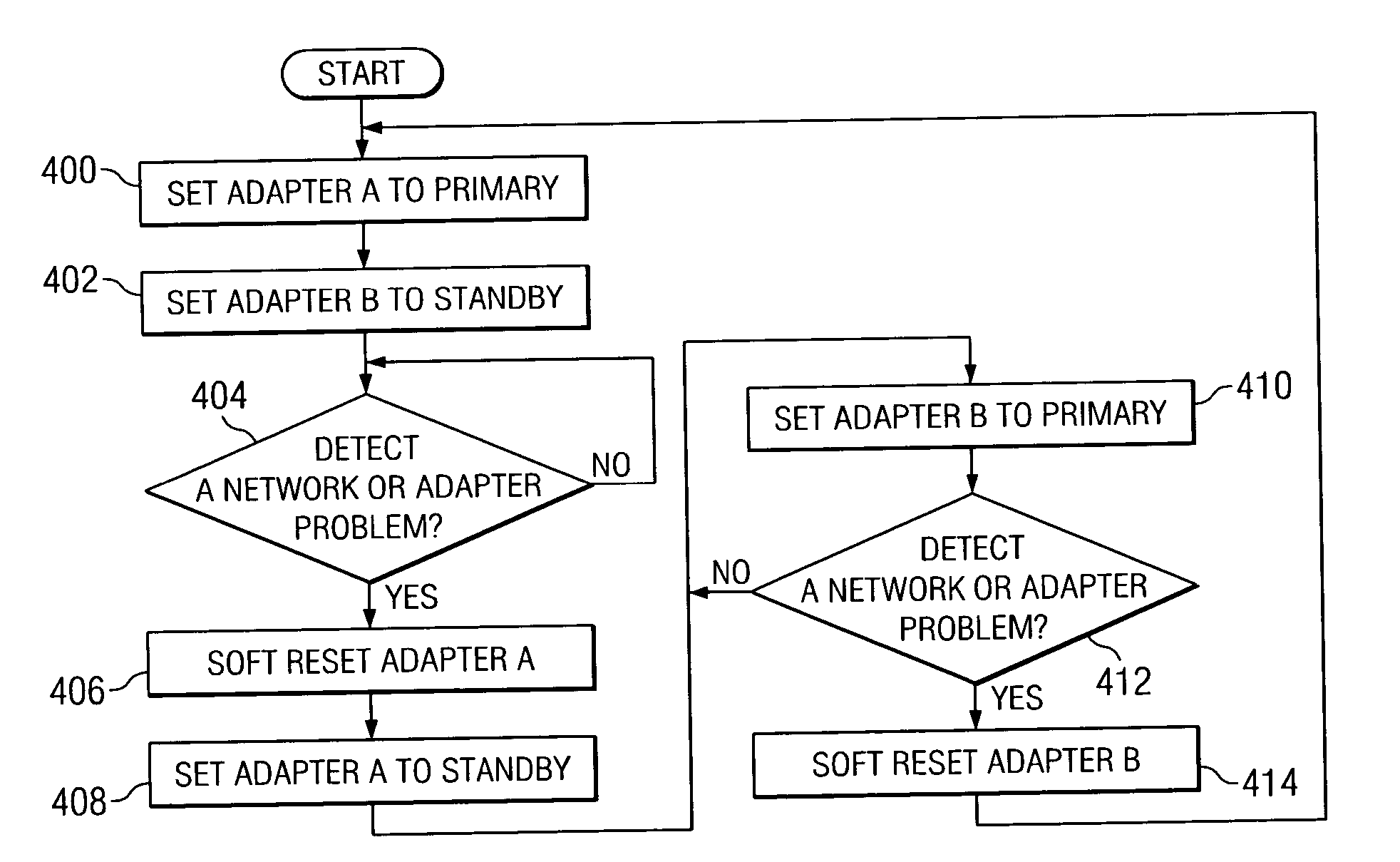
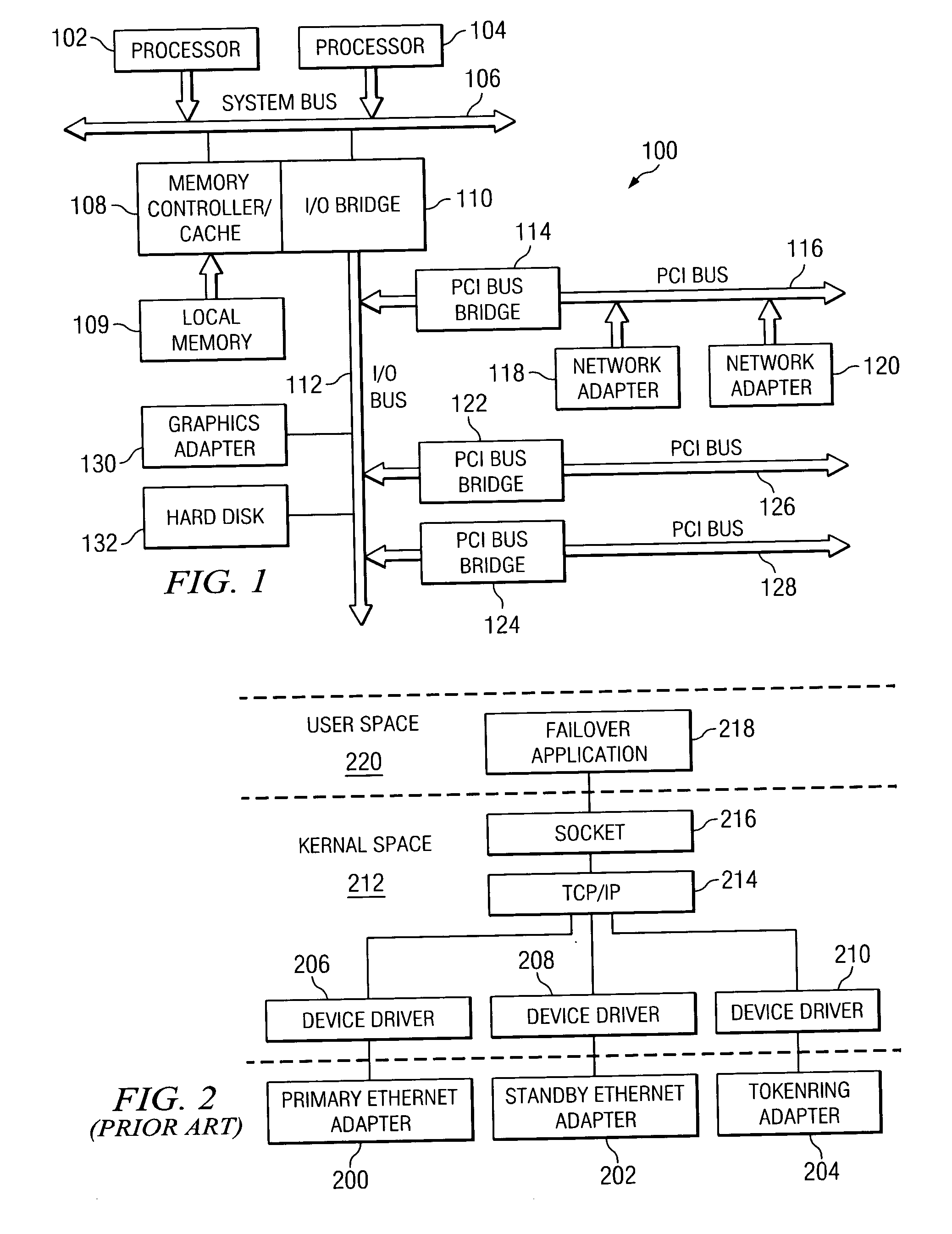
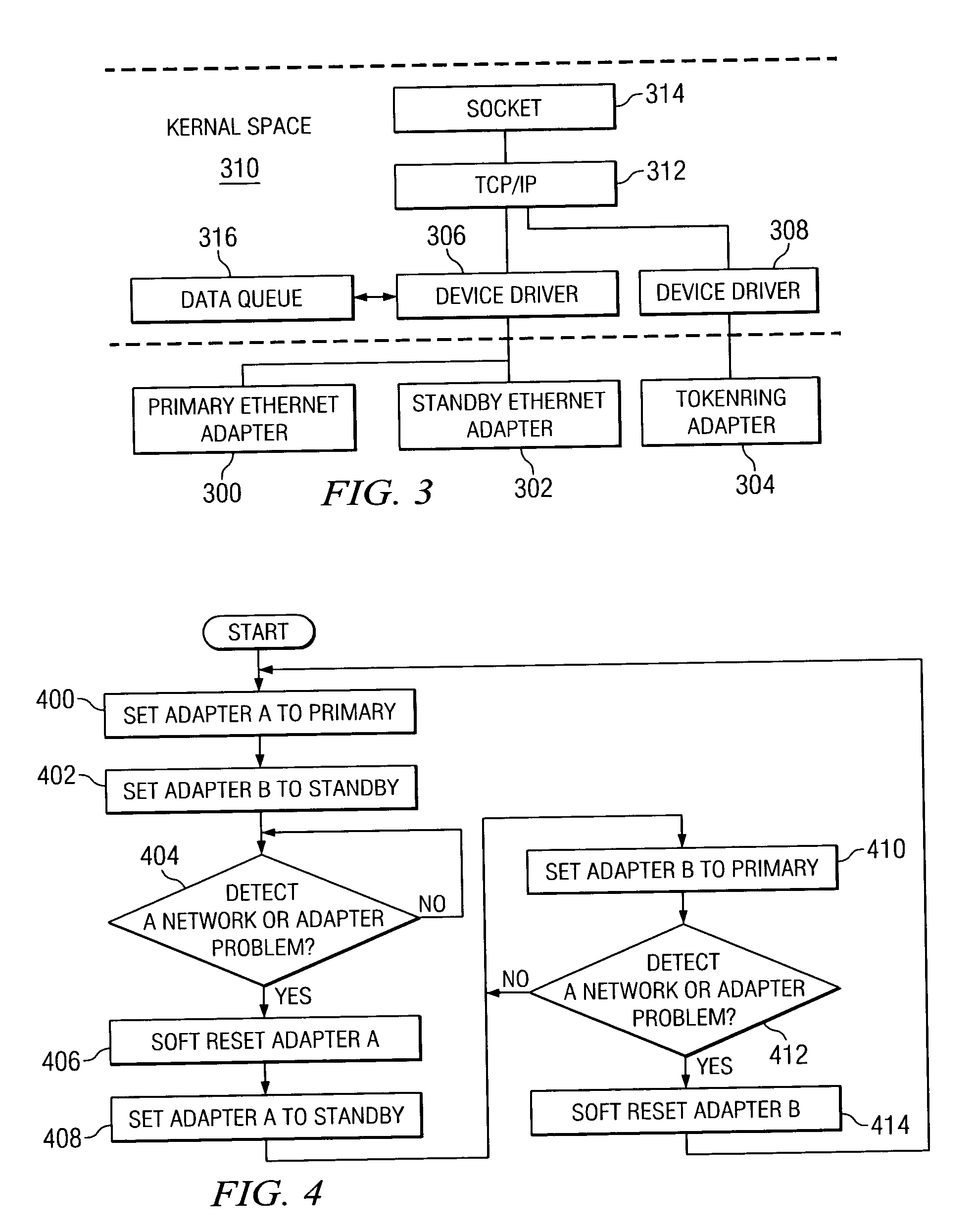
Method and apparatus for managing adapters in a data processing system
A method, apparatus and computer instructions for handling a failure of a primary adapter in a data processing system. The primary adapter is monitored for the failure by the device driver. A standby adapter handled by the device driver is switched in place of the primary adapter in response to detecting the failure.
Owner:IBM CORP
Programmed monitoring device and programmed monitoring method
Owner:YONYOU NETWORK TECH
Client program monitoring method, device and client
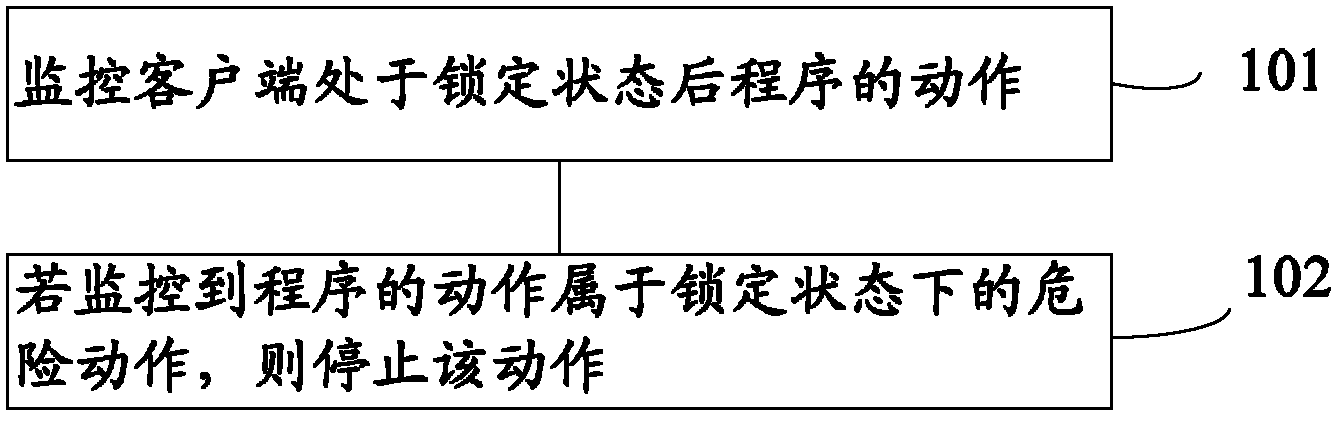
InactiveCN102279912AProtection securityProtect interestsHardware monitoringComputer security arrangementsProgram monitoringOperating system
The invention provides a method for monitoring a client program, comprising the following steps: monitoring the program action after the client is in a locked state; and stopping the action if the monitored action of the program is a dangerous action in the locked state. The present invention also provides a client program monitoring device for realizing the aforementioned method and a client with the monitoring device. The client program monitoring method, device and client of the present invention can monitor the programs in the client in idle state such as standby, and avoid malicious programs from performing dangerous actions.
Owner:QIZHI SOFTWARE (BEIJING) CO LTD
Method for monitoring application program based on window platform
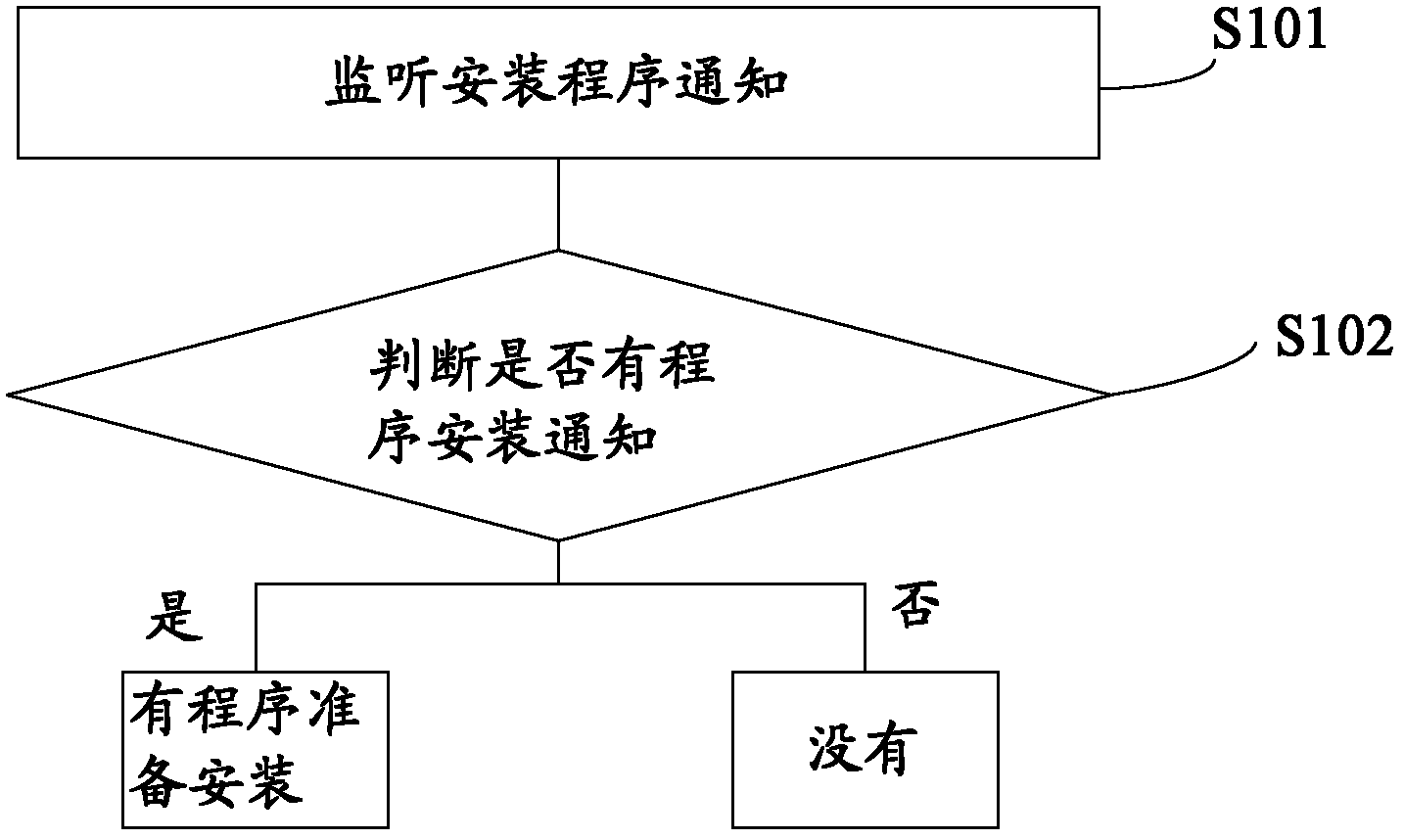
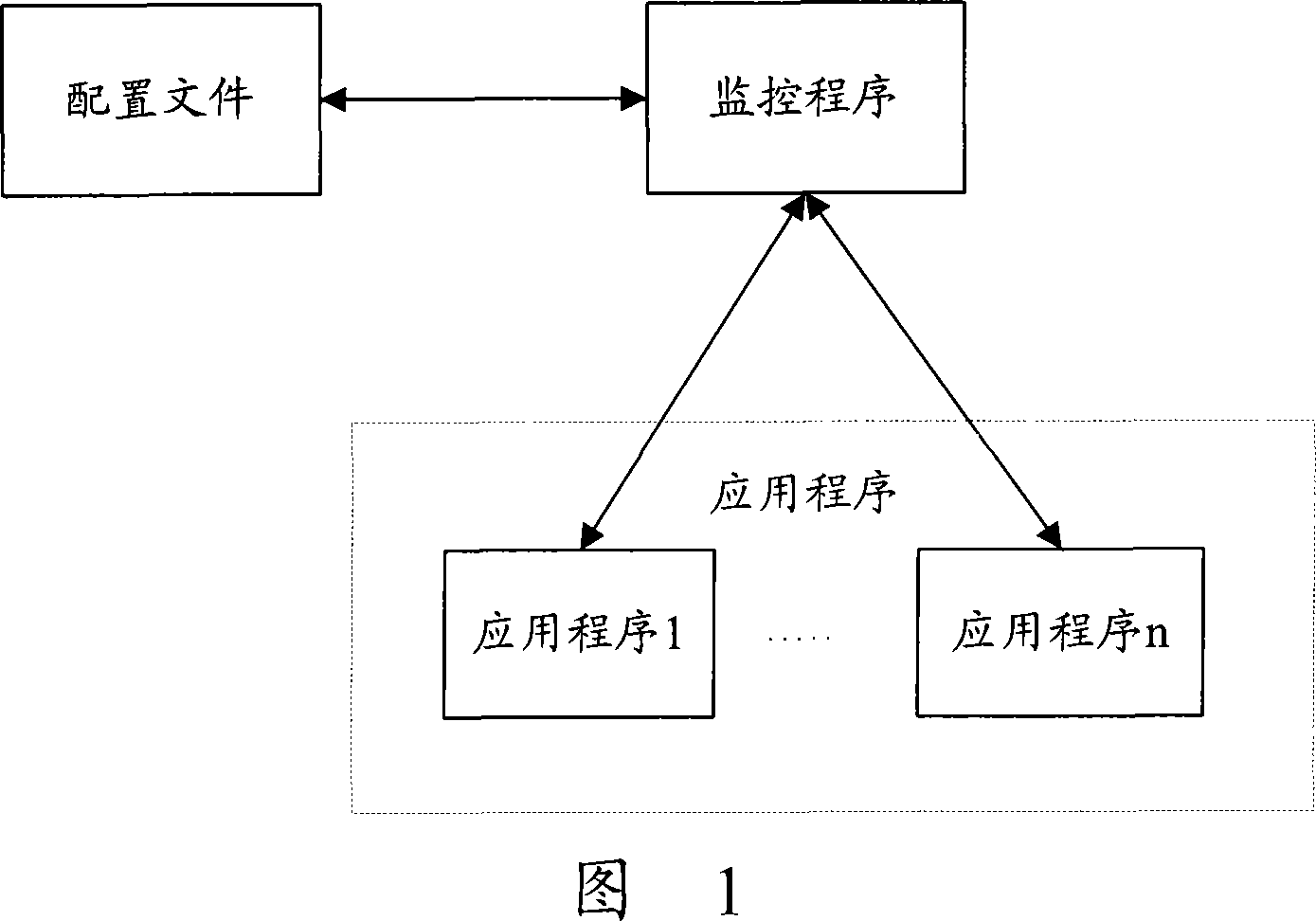
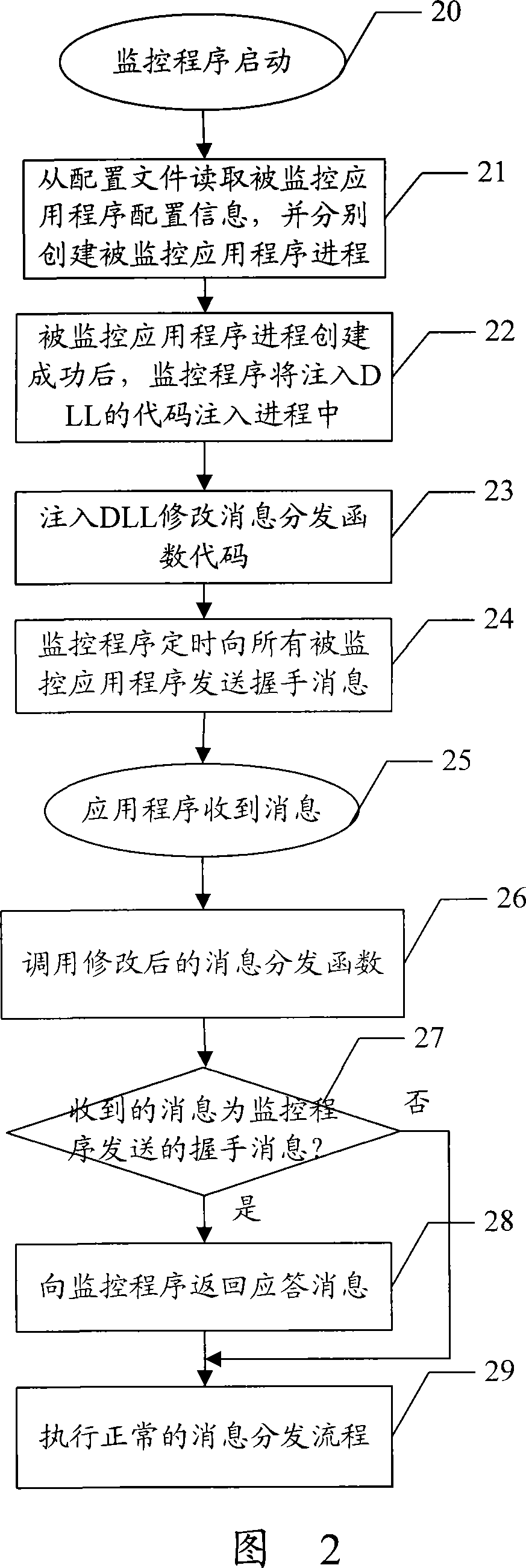
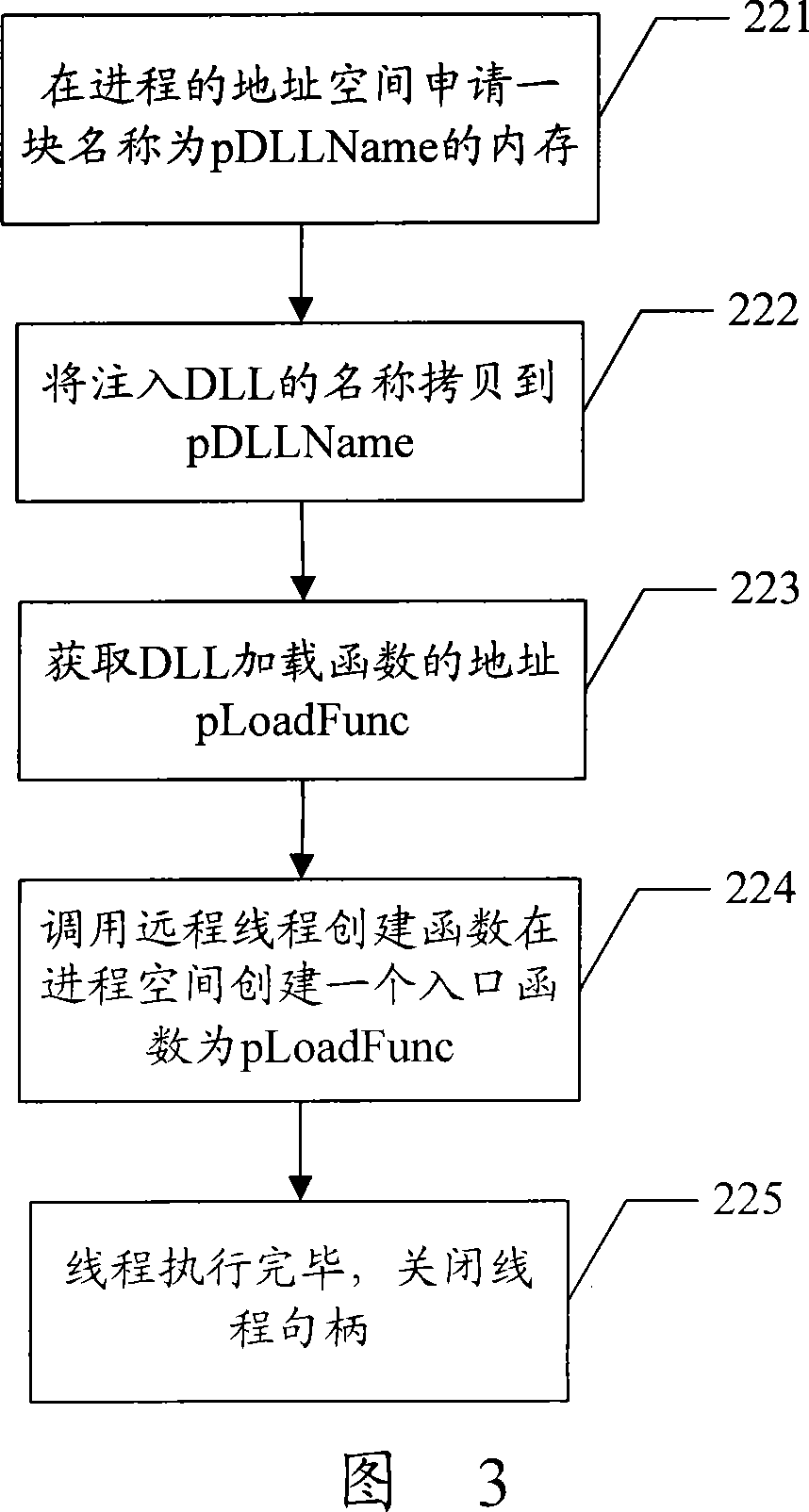
InactiveCN101227630AImprove scalabilityAccurate real-time monitoringSupervisory/monitoring/testing arrangementsData switching networksCode injectionApplication software
The invention discloses an application program monitoring process based on a window platform, which comprises the following steps respectively establishing a process of the application program which is monitored after the starting of the monitor program, wherein the monitor program inputs the code which belongs to a dynamic link library (DLL), inputting a message distribution function code in a modification process of DLL, sending handshaking messages to all the monitored programs by the monitor program on a scheduled time, transferring modified message distribution function by the monitored programs the after receiving the message, sanding a return answer message to the monitor program after the message distribution function ascertains the massage is the handshaking message which is sent by the monitor program. The monitoring method of the invention adopts the DLL inputting mode to modify the code of the system information distribution function, which enables the system information distribution function to capture and answer the handshaking message from the monitor program without adding code combined monitoring in application programs, and has the advantages of good scalability and can realize a accurate real-time monitor.
Owner:ZTE CORP
Information processing system, information processing method, information processing program, computer readable medium and computer data signal
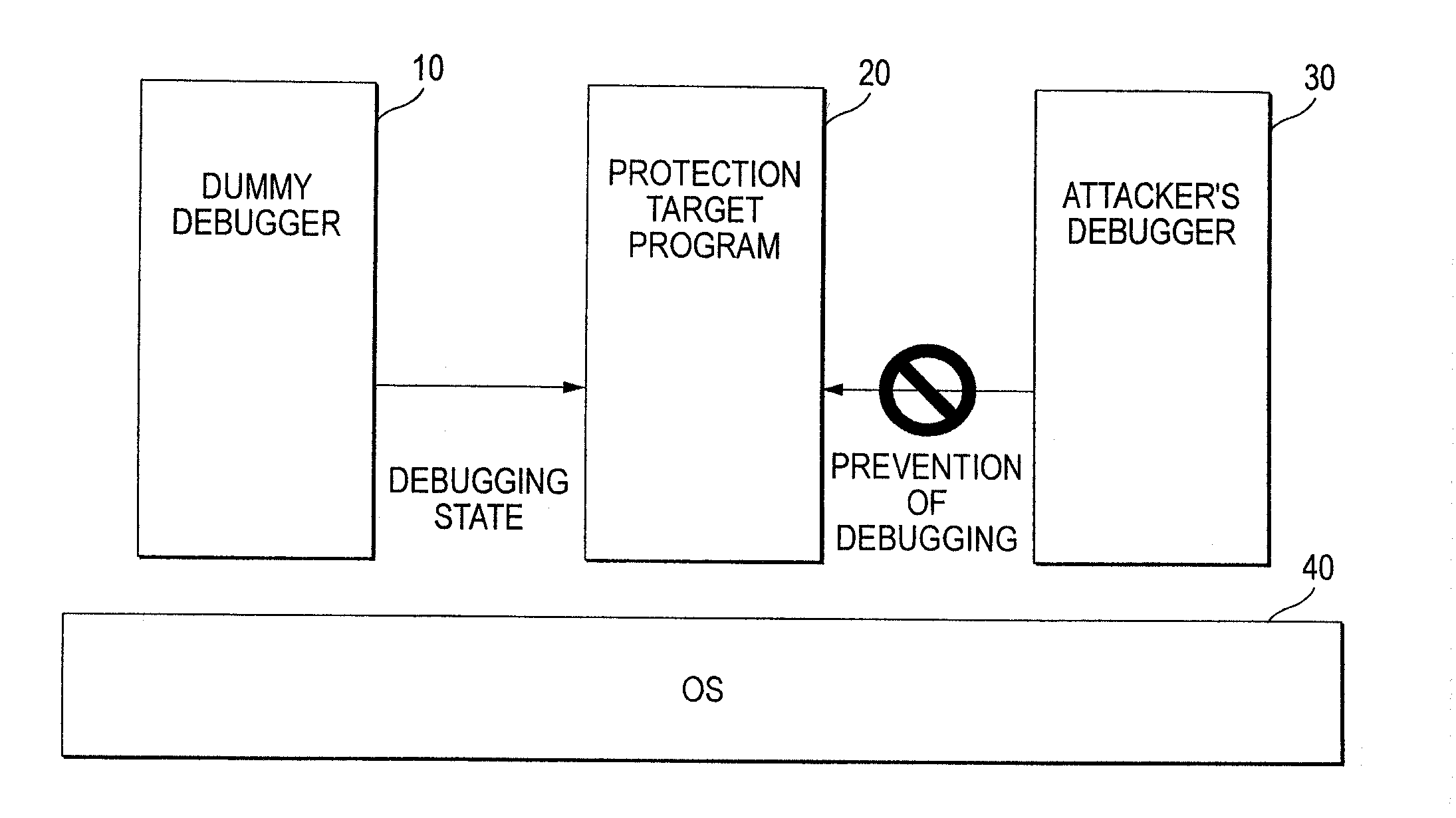
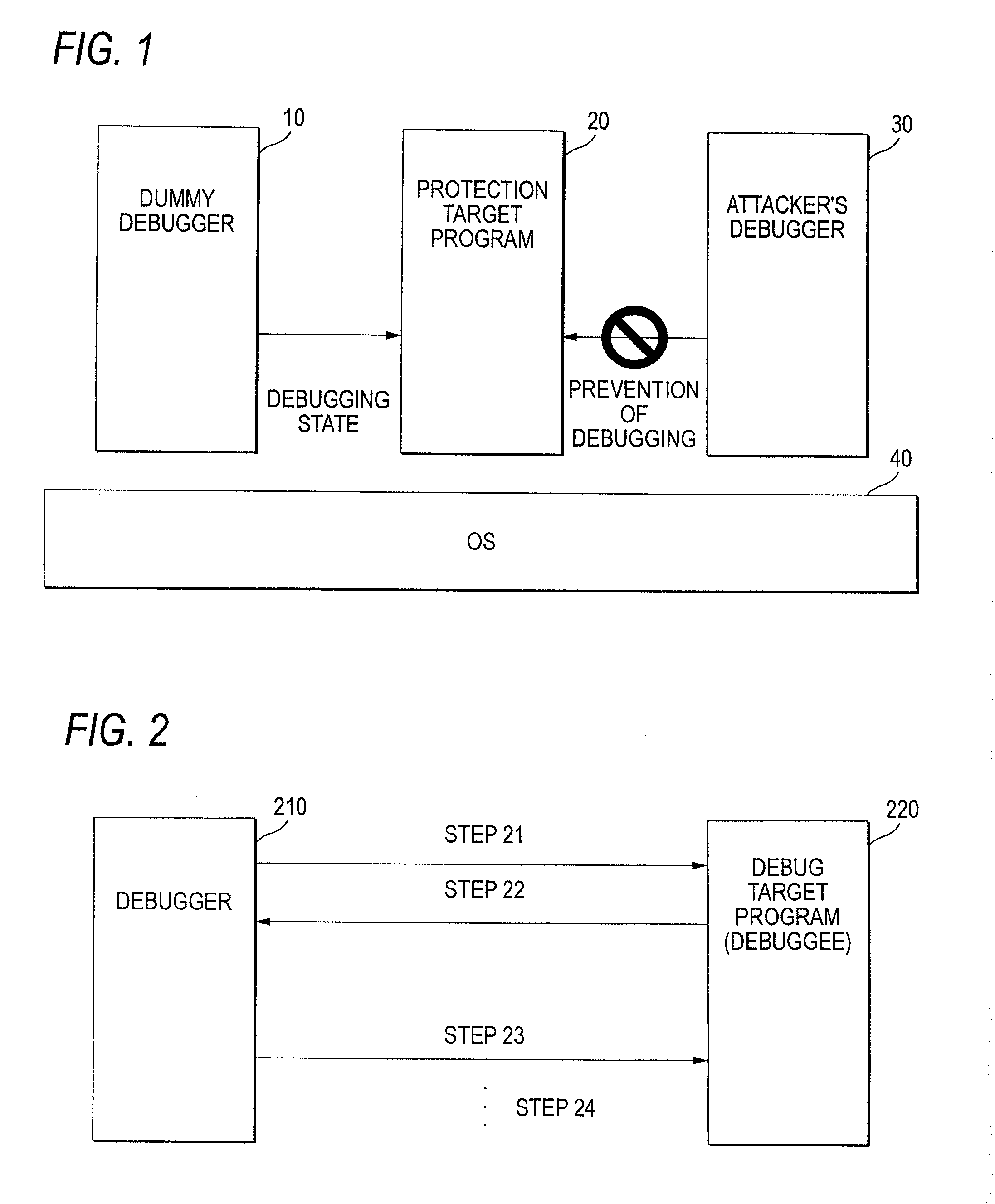
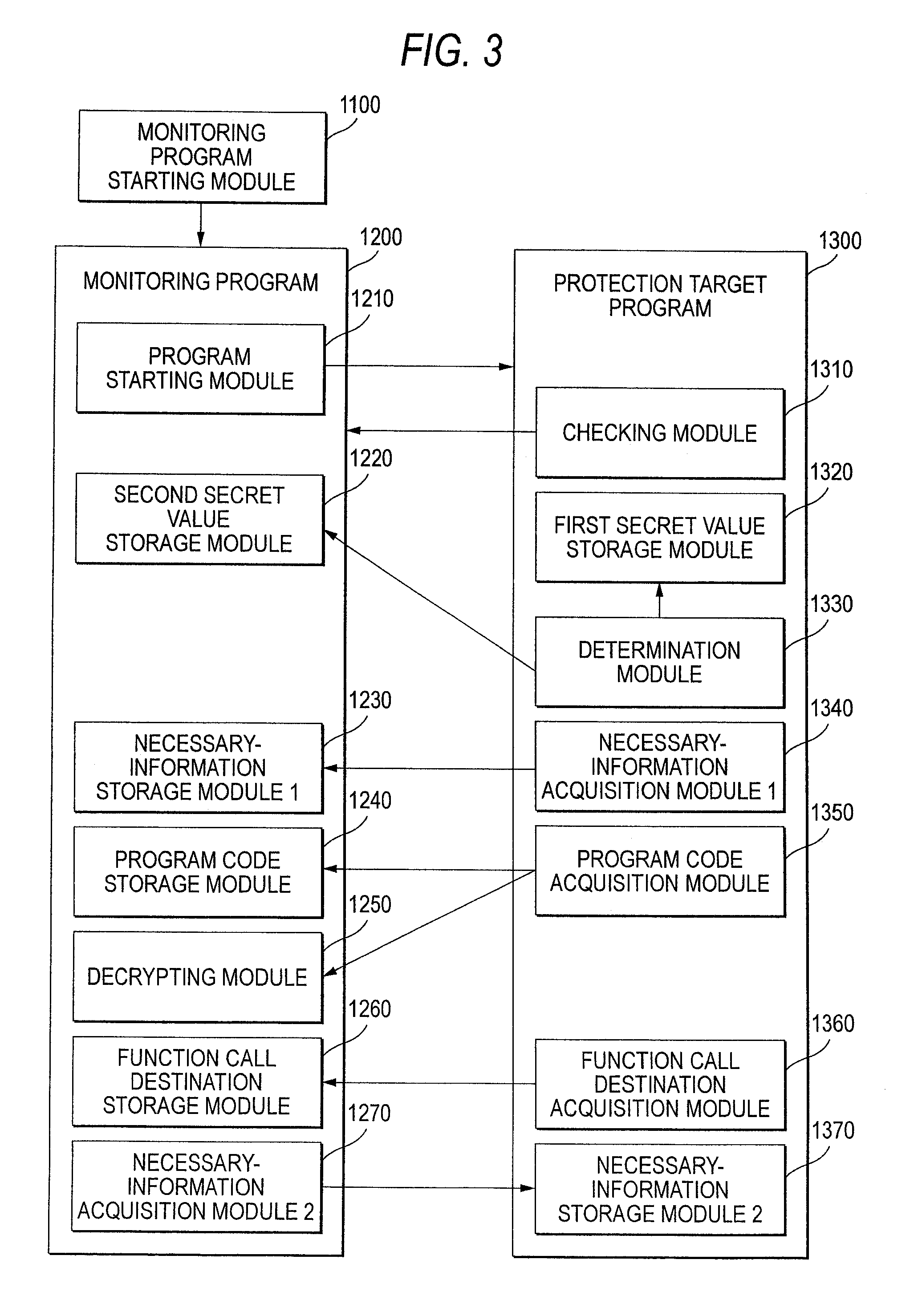
InactiveUS20080060072A1Avoid analysisMemory loss protectionUnauthorized memory use protectionInformation processingData signal
An information processing system includes a monitoring program starting unit and a protection target program monitoring unit. When a protection target program to be protected is started, the monitoring program starting unit starts a monitoring program that monitors the protection target program. The protection target program monitoring unit monitors the protection target program by the monitoring program.
Owner:FUJIFILM BUSINESS INNOVATION CORP
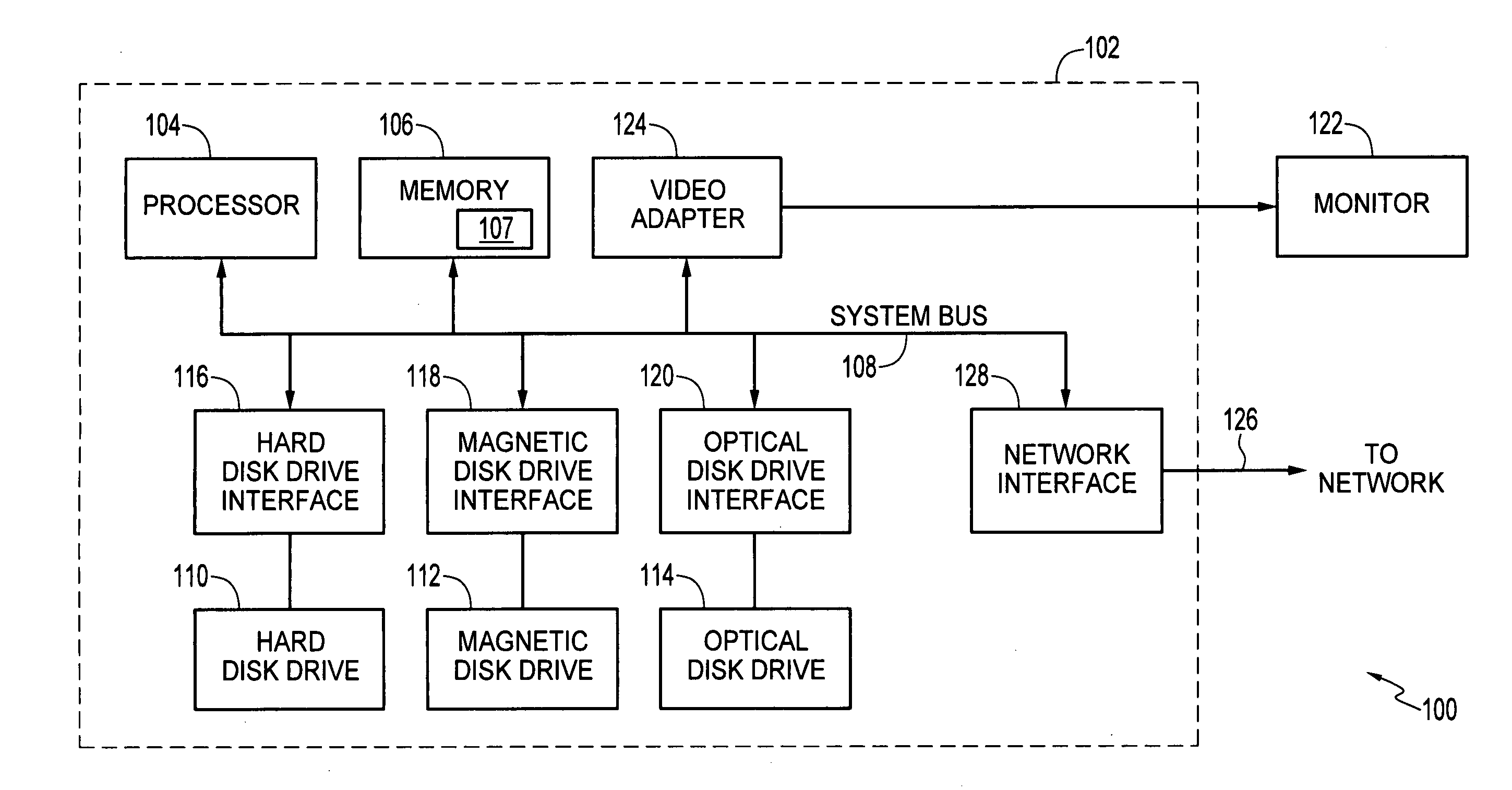
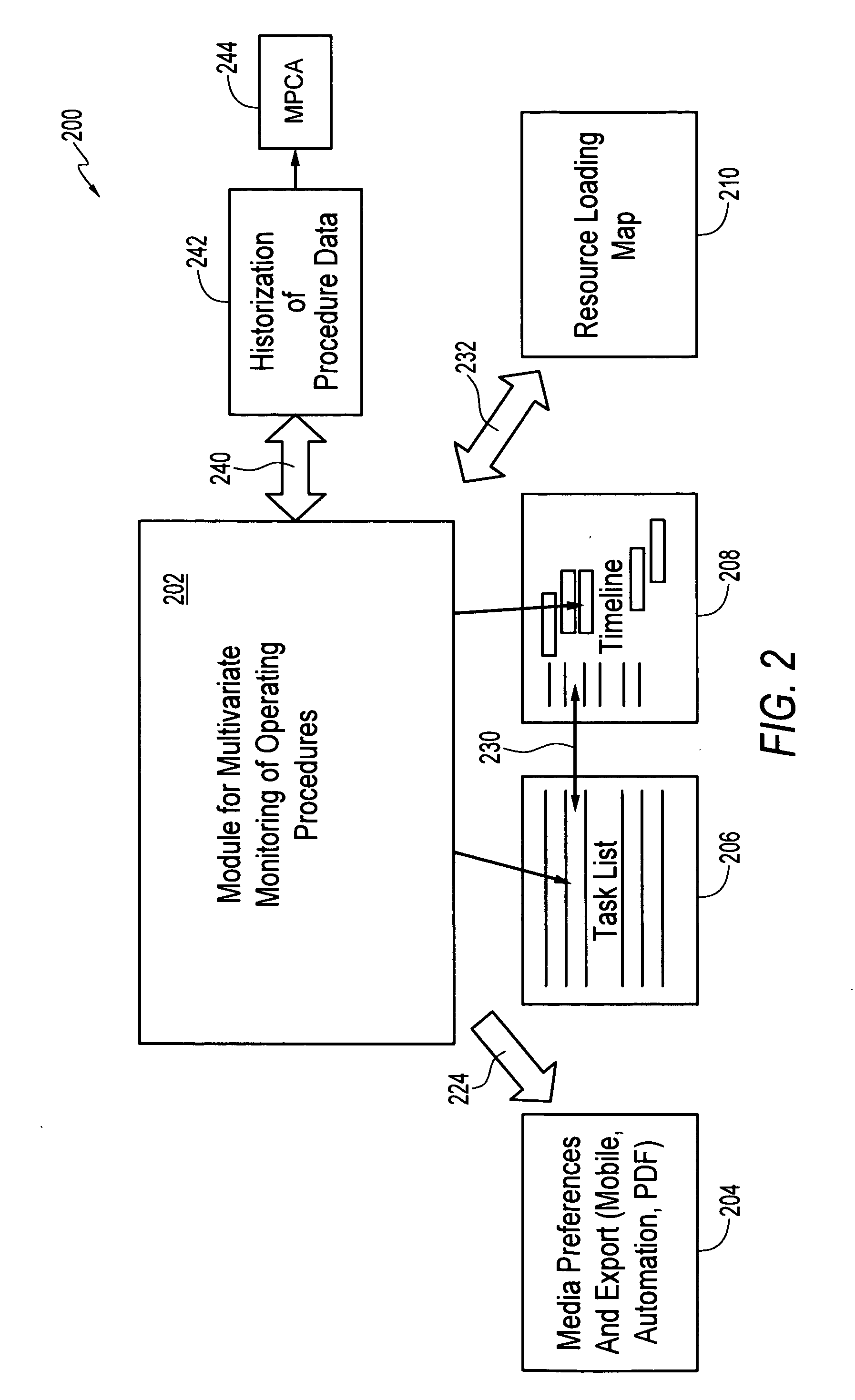
Multivariate monitoring of operating procedures
InactiveUS20070265801A1Detected as abnormalityTesting/monitoring control systemsNuclear monitoringPrincipal component analysisProgram monitoring
A computer implemented method, system and program product for monitoring operating procedures in a production environment. Data can be compiled indicative of an operating procedure. A plurality of executions of the operating procedure can then be analyzed. A Multiway Principal Component Analysis (MPCA) model can be utilized to detect one or more abnormalities associated with the operating procedure, in response to analyzing the plurality of executions of the operating procedure, in order to compare, monitor and diagnose an impact of variations in one or more executions of the operating procedure.
Owner:HONEYWELL INT INC
Application program monitoring method and device
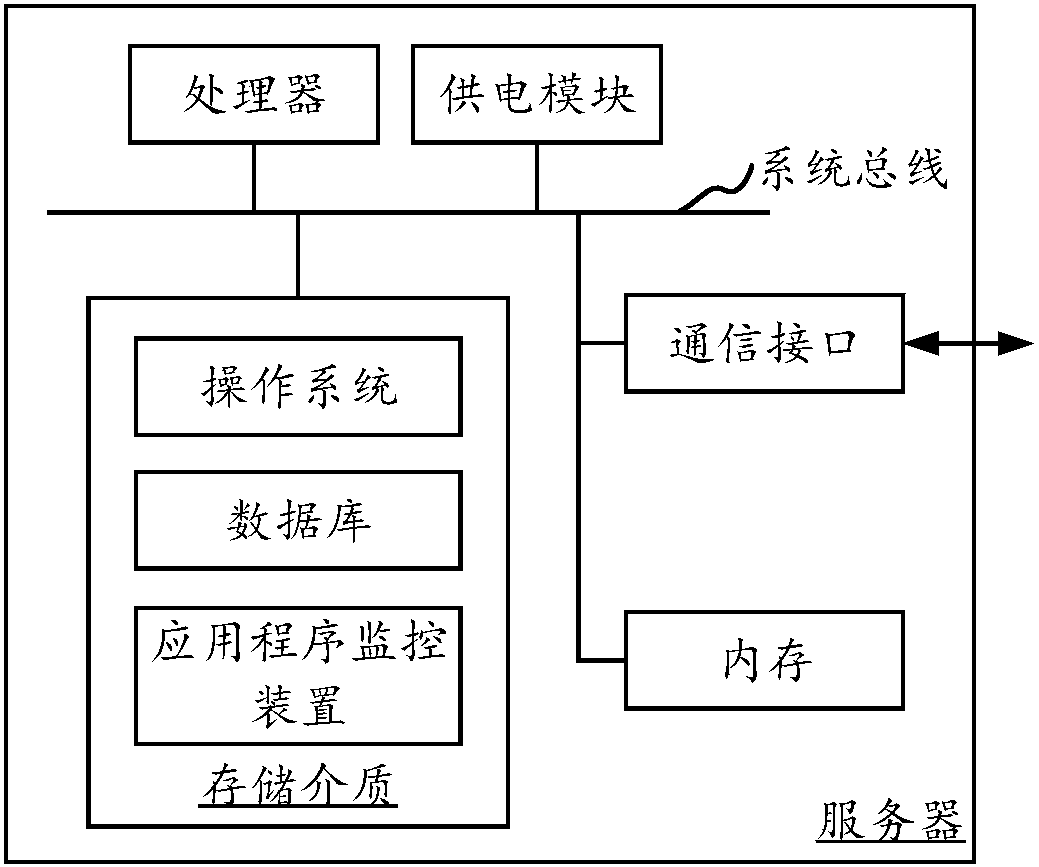
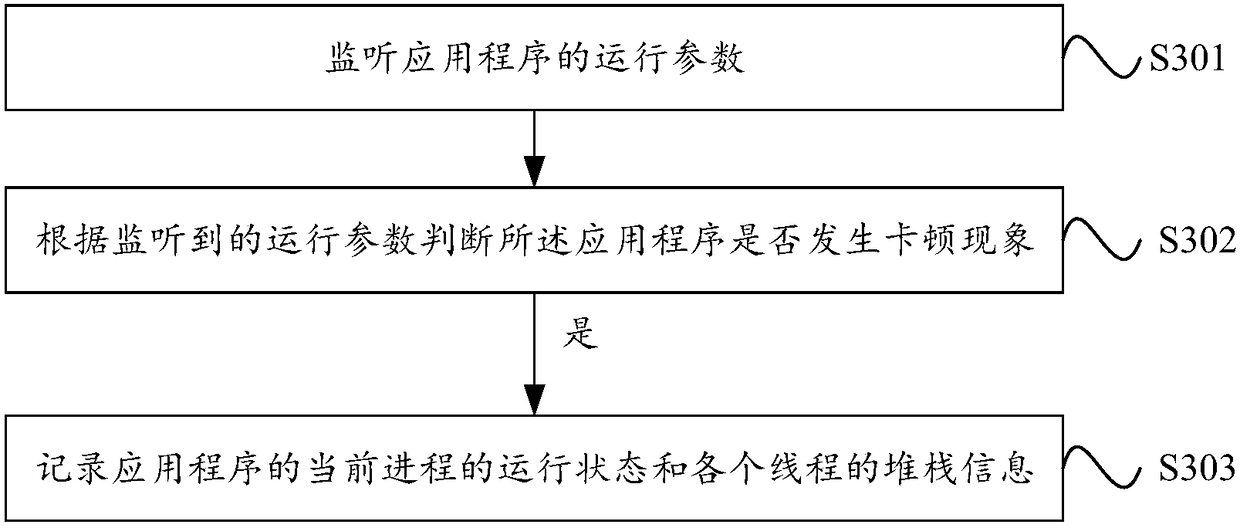
ActiveCN108345524ACaton phenomenon monitoringImprove accuracyHardware monitoringProgram monitoringOperating system
The invention discloses an application program monitoring method and device. The method of one embodiment comprises the following steps that: monitoring the operation parameter of an application program; according to the monitored operation parameter, judging whether the application program is subjected to a phenomenon of being stuck; and when a judgment result shows that the application program is subjected to the phenomenon of being stuck, recording the operation state of the current process of the application program and the stack information of each thread. By use of the scheme of the embodiment, the stuck phenomenon of the application program can be monitored under a situation of a stuck site is kept, and therefore, the monitoring and analysis accuracy of the stuck phenomenon of the application program is improved.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Failure management method and computer
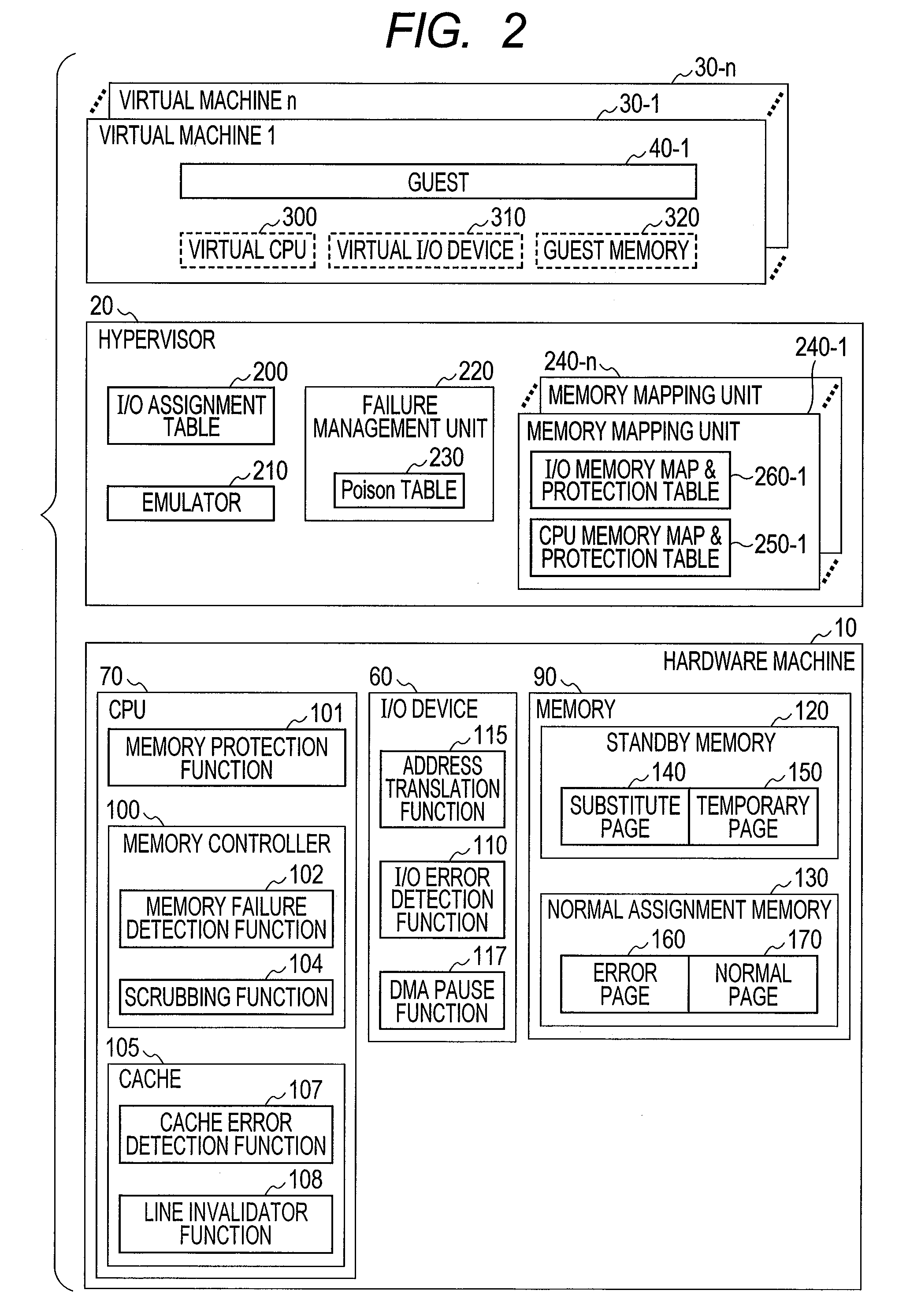
InactiveUS20110271152A1Limited effectLimited rangeNon-redundant fault processingRelevant informationProgram monitoring
A failure management method for a computer including a processor, and a memory connected to the processor, and in which the processor containing a memory protection function, executes a first software program and a second software program monitoring the operation of the first software program, and the second software program retains error information including address information and access-related information; and the method implemented by the by the second software program includes a step for detecting the occurrence of errors in the memory; and a step for prohibiting access to the address of the memory where the error occurred, and monitoring the access state; and a step for executing the failure processing when accessing by the first software program of the address of the memory where the error occurred was detected.
Owner:HITACHI LTD
Application program monitoring system and monitoring method
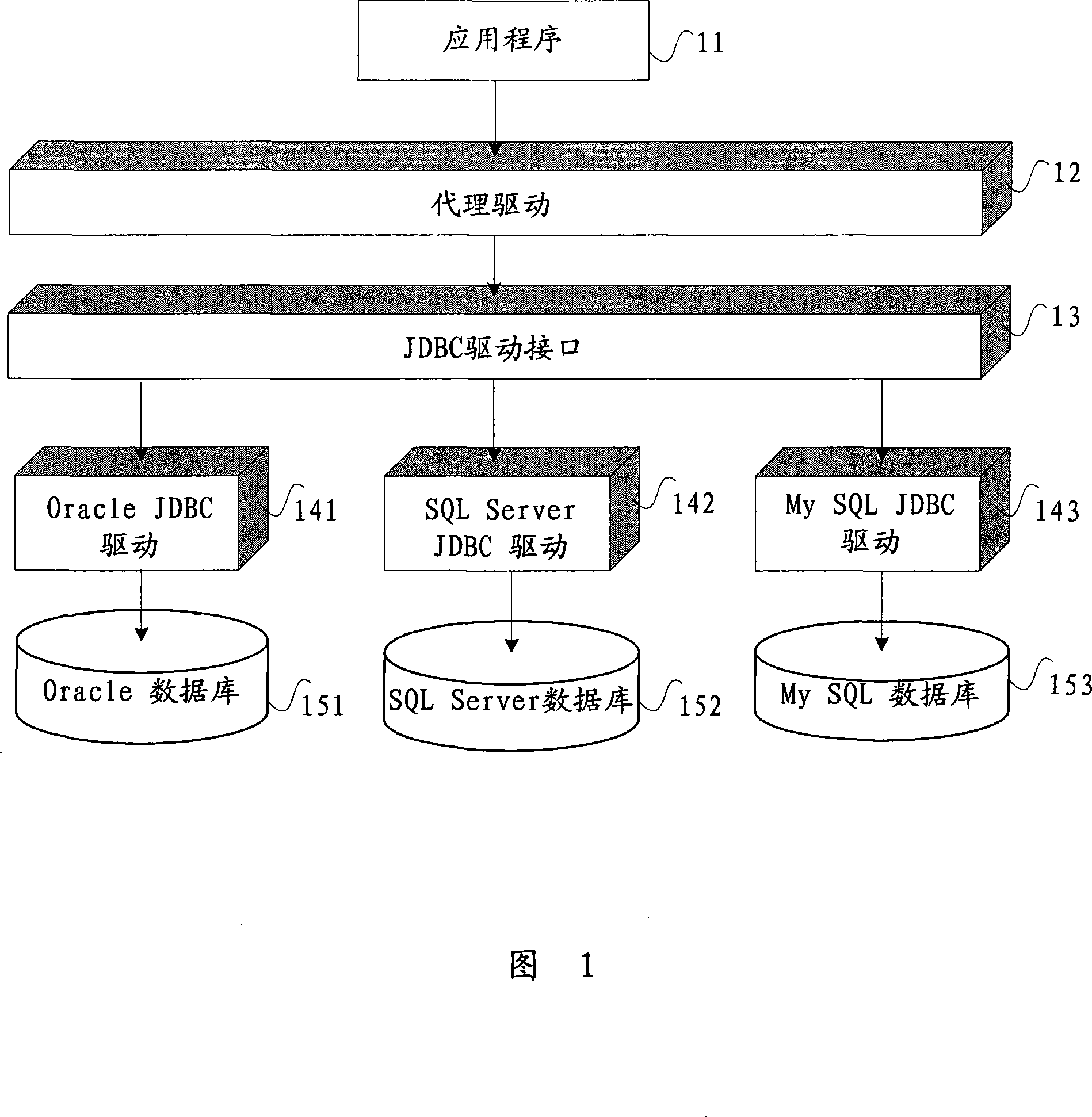
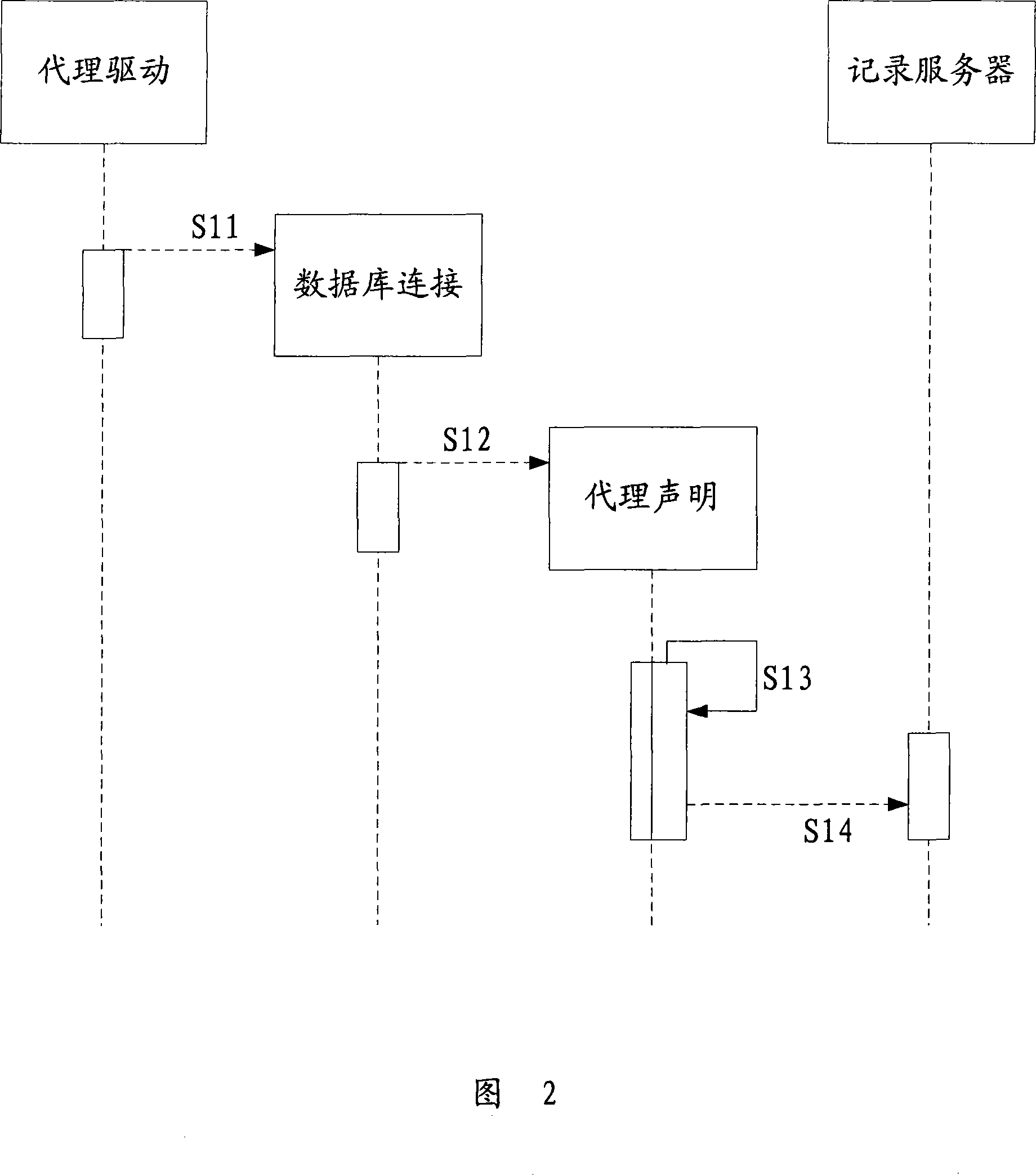
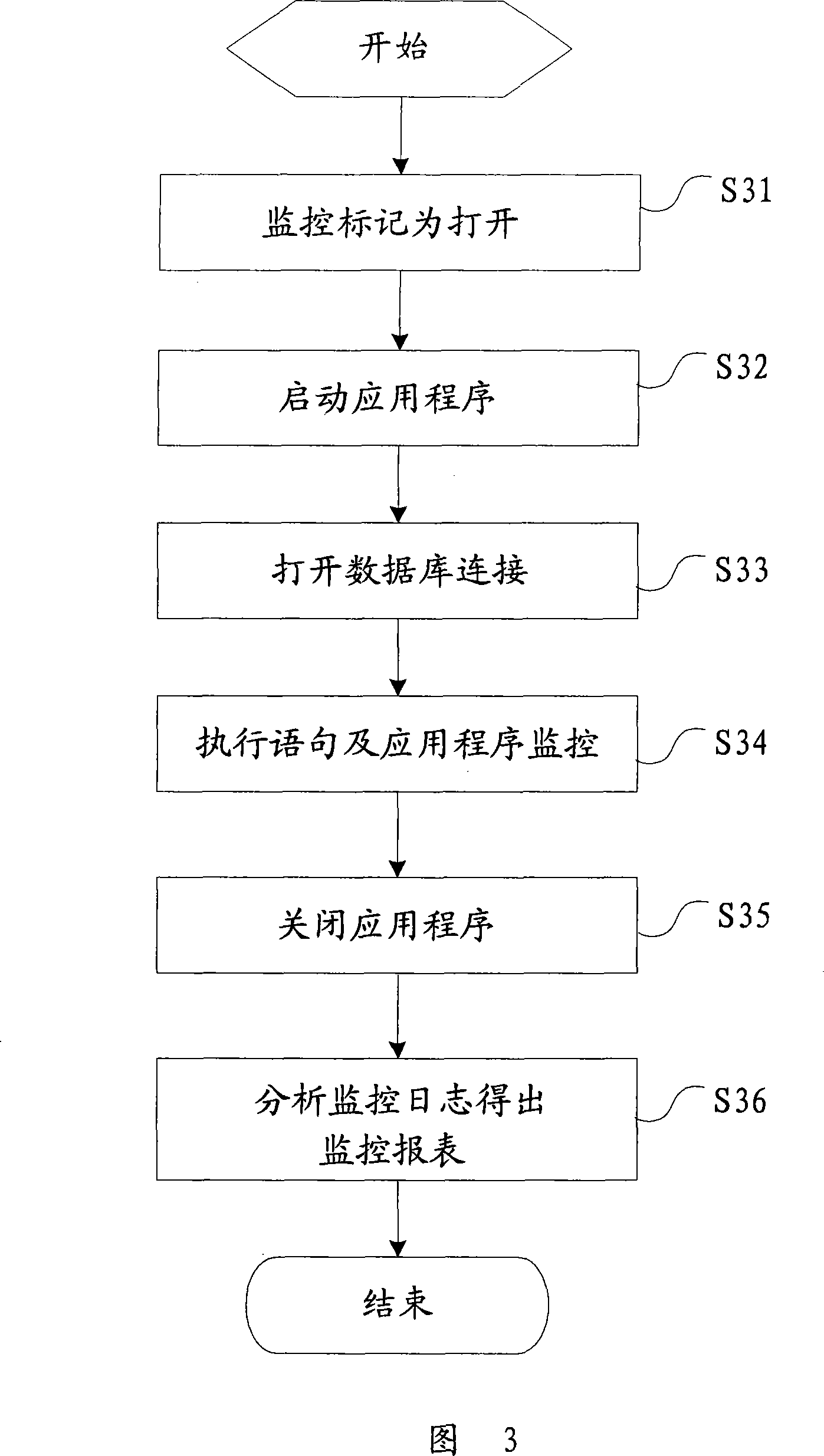
ActiveCN101226497ARealize monitoringRealize managementHardware monitoringSpecial data processing applicationsThird partyApplication software
The invention provides an application program detecting system, which comprises a JDBC drive interface, at least one database drive and at least one data, wherein the database via a relative database drive is connected with the JDBC drive interface, to receive and execute the statement of one application program via the JDBC drive interface. The invention further comprises a proxy drive respectively connected with relative databases via the JDBC drive interface and at least one database drive to receive the statement of one application program and record the detection information generated by execute statement. The invention provides a relative application program detecting method. The inventive system and method can detect and manage the execution condition of SQL statement via proxy drive, which can easily realize detection and management on databases and realize the detection and management on SQL statement on database drive layer, without third party detecting tools. The invention has the advantages of database spanning, easy detection and simple management.
Owner:KINGDEE SOFTWARE(CHINA) CO LTD
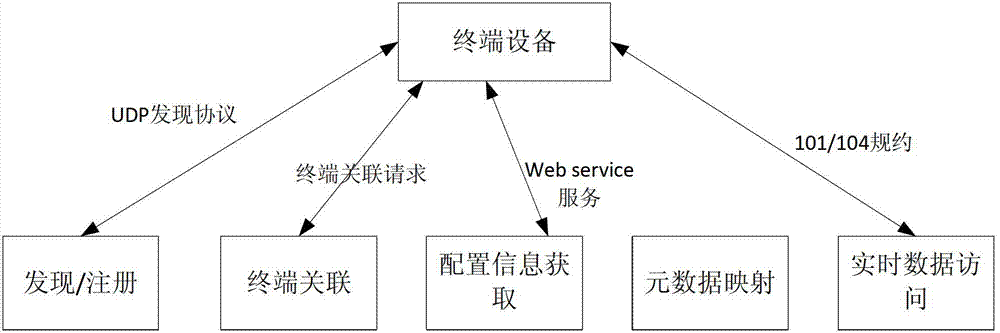
Power distribution network terminal access method based on IEC61850 standard
ActiveCN103326465AImprove work efficiencyImprove accuracyCircuit arrangementsInformation technology support systemWeb serviceElectric power system
The invention relates to the field of power system and automation, in particular to a power distribution network terminal access method based on the IEC61850 standard. The method includes the following steps that (1) a power distribution terminal gets access to a port of a program monitoring UDP networking protocol, and data packages are broadcast, found and registered at regular intervals; (2) whether the correlation function of the power distribution terminal passes audits or not is judged; (3) access to the web service port of the power distribution terminal is carried out, and configuration information of the power distribution terminal is obtained; (4) a point table of measure points is generated from the configuration information; (5) the generated point table of the measure points is applied to a distribution automation system. The whole process of the power distribution network terminal access is automatic without manual intervention, namely the power distribution network terminal is of a plug-and-play type, workload of distribution automation and possibility of error occurrence are greatly reduced, implementation difficulty and implementation cost of the distribution automation are reduced, the construction of the distribution automation is promoted, and working efficiency and working correctness of the distribution automation are improved, so that the level of distribution network automation operation is improved, and outage cost is reduced.
Owner:STATE GRID CORP OF CHINA +3
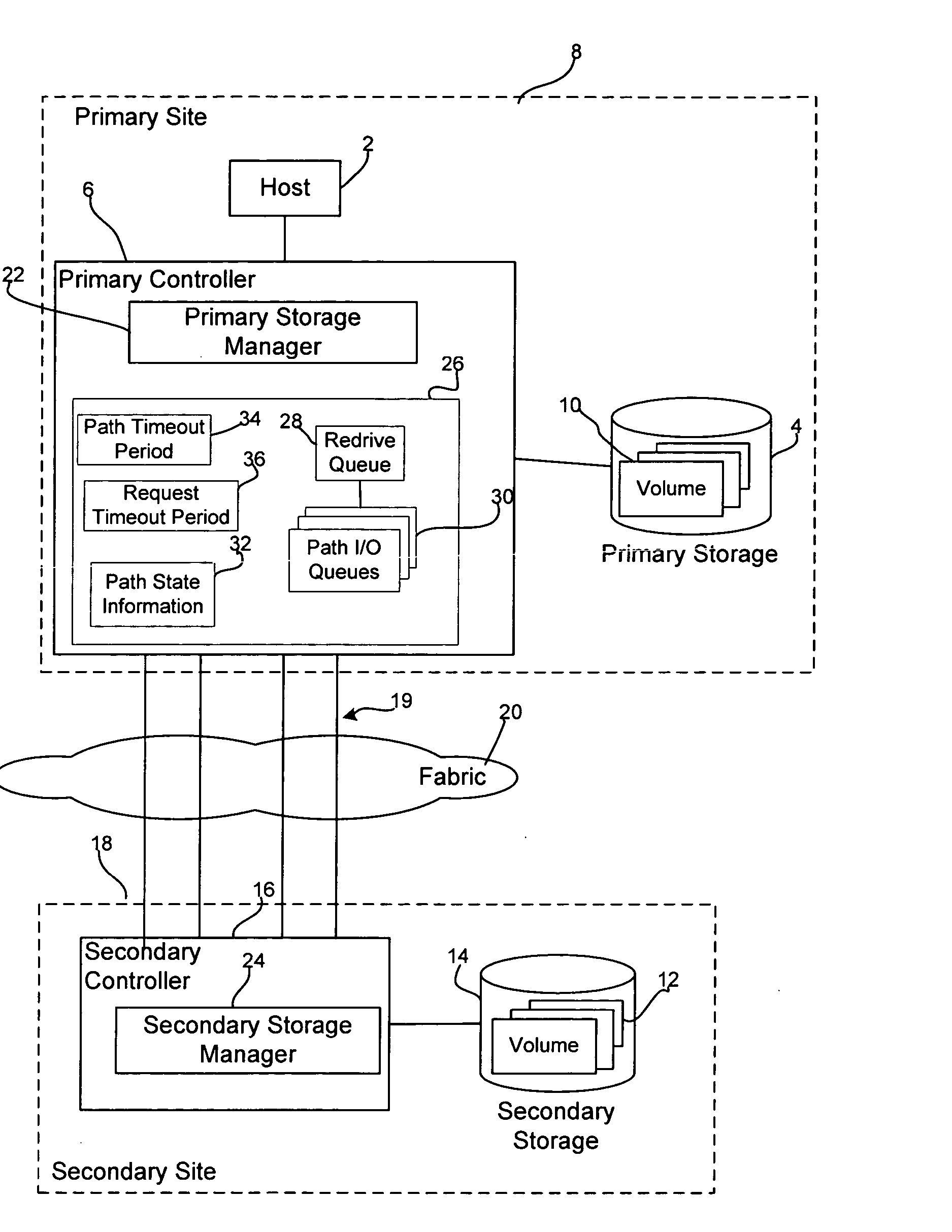
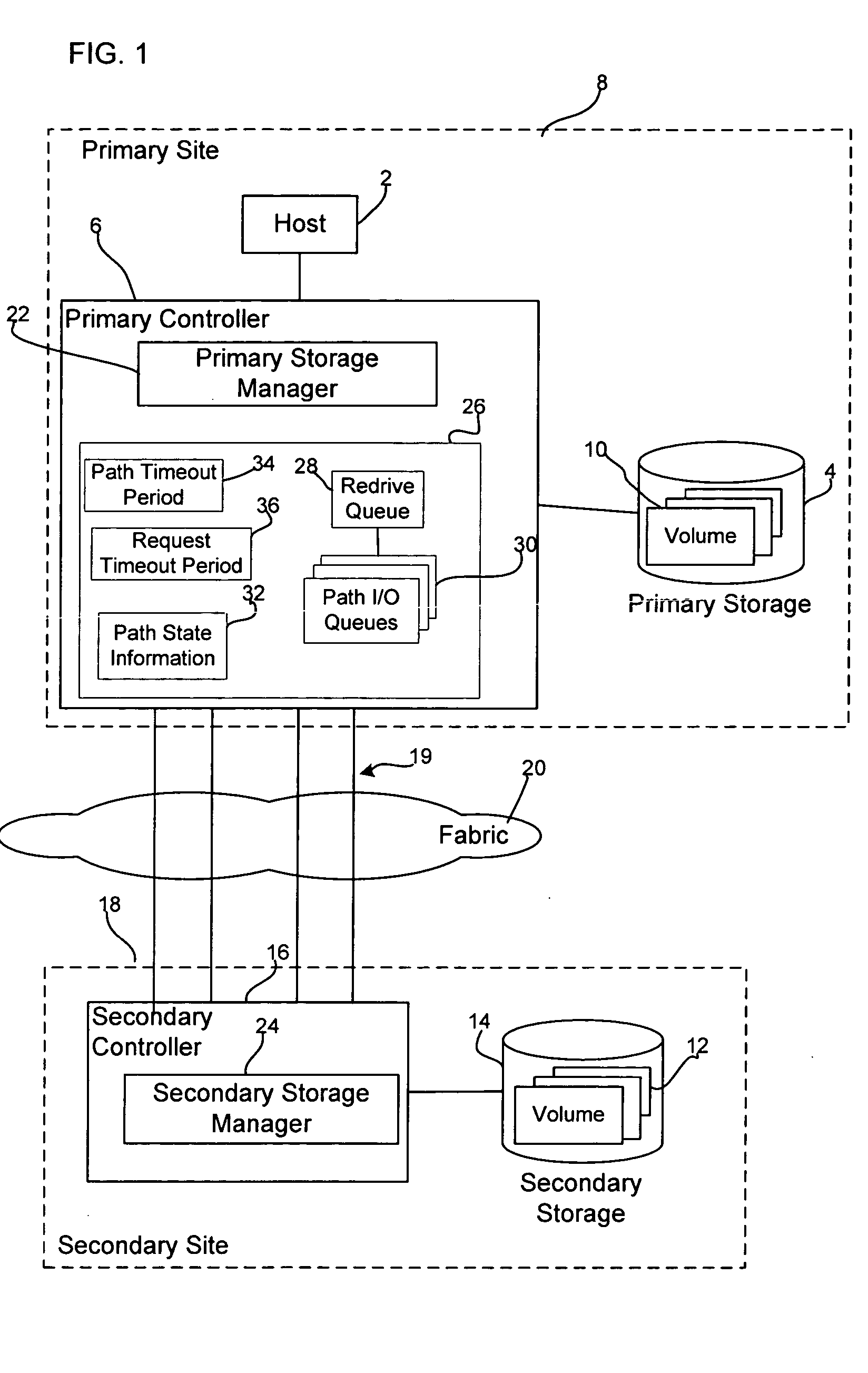
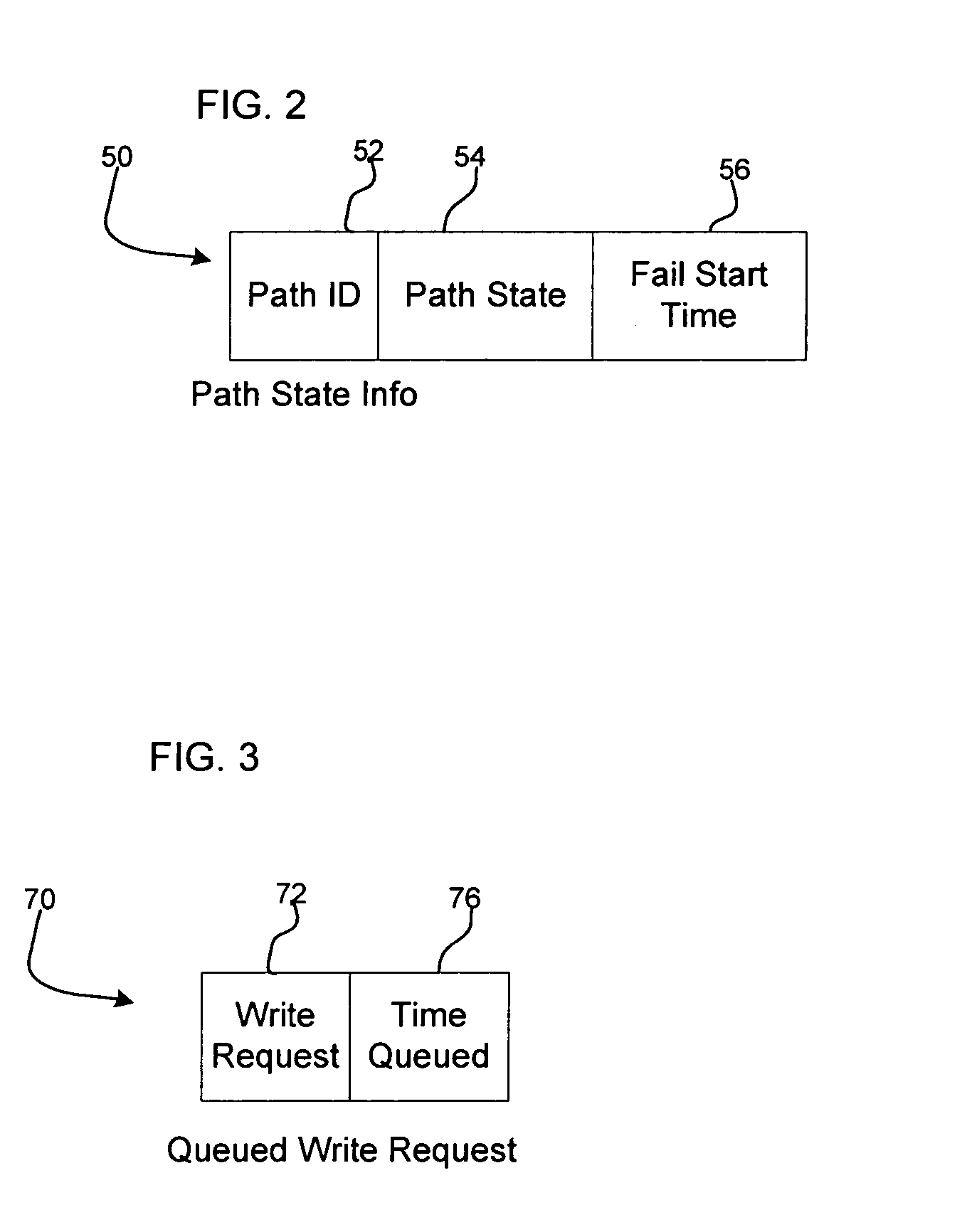
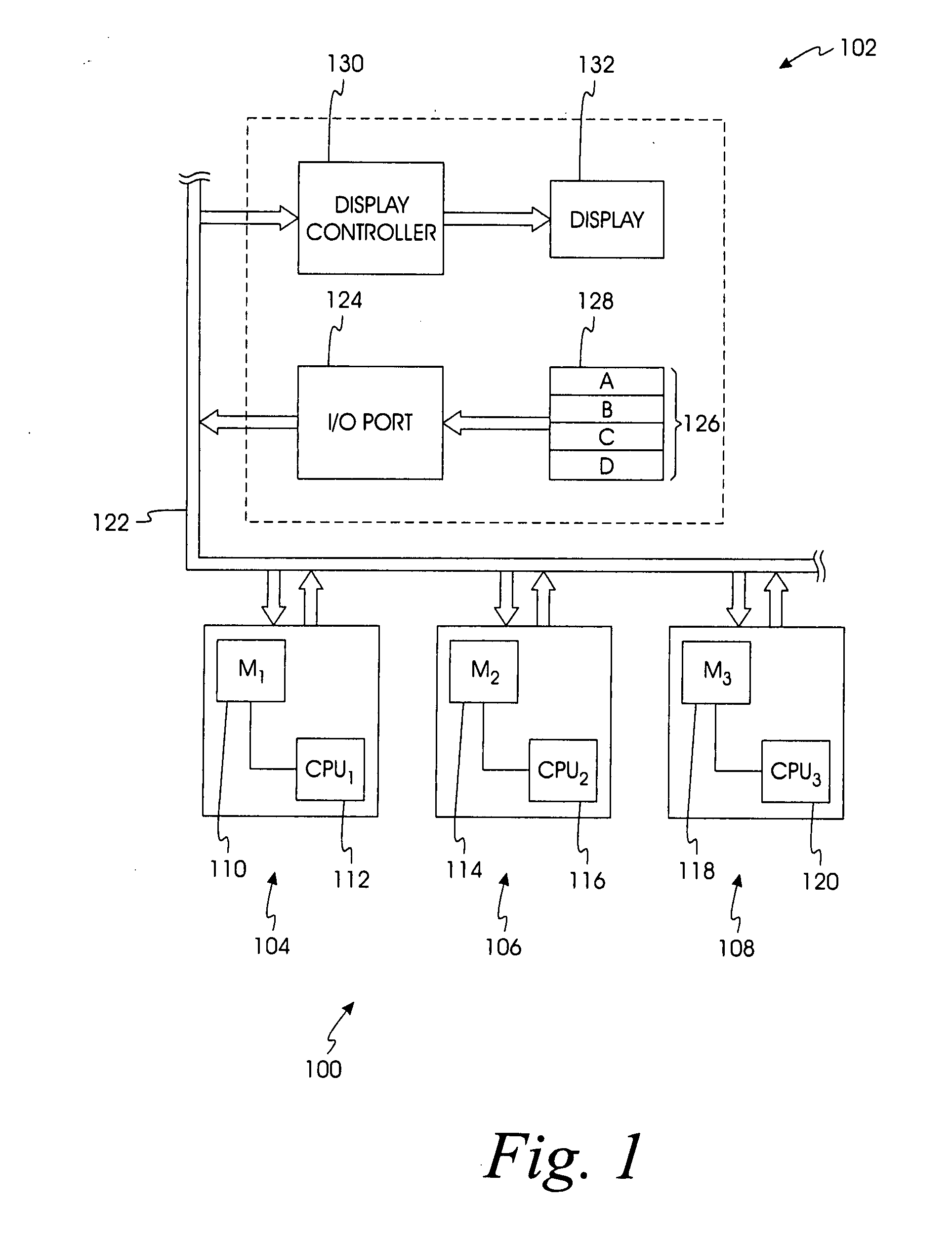
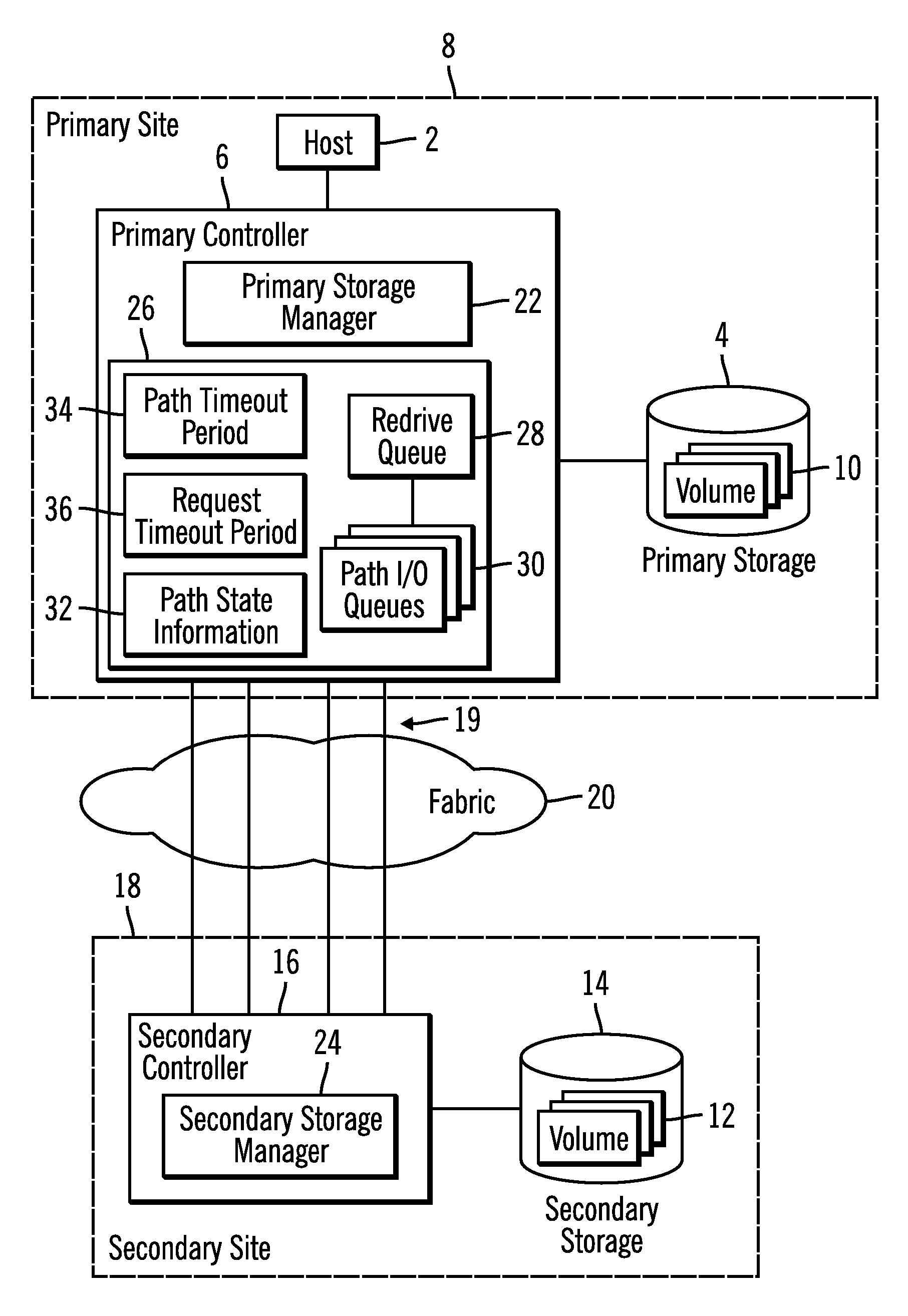
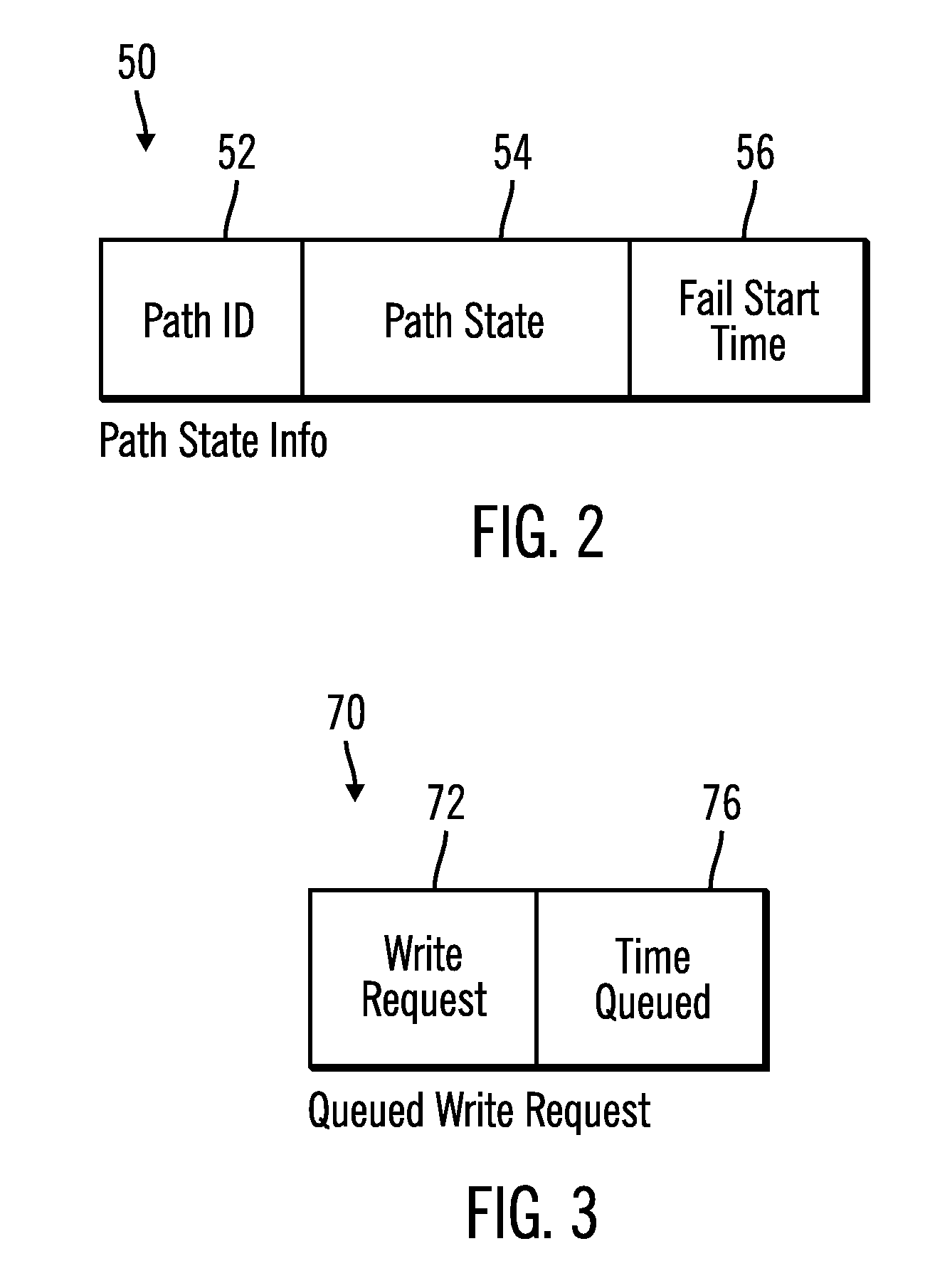
Method, system, and program for transmitting input/output requests from a primary controller to a secondary controller
InactiveUS20050114741A1Redundant operation error correctionRedundant hardware error correctionEngineeringProgram monitoring
Provided are a method, system, and program monitoring paths between a first controller and second controller. A determination is made as to whether one path has been unavailable for a predetermined time period in response to detecting that the path is unavailable. Indication is made that the path is in a first failed state if the path has been unavailable for more than the predetermined time period and indication is made that the path is in a second failed state if the path has not been unavailable for the predetermined time period.
Owner:GLOBALFOUNDRIES INC
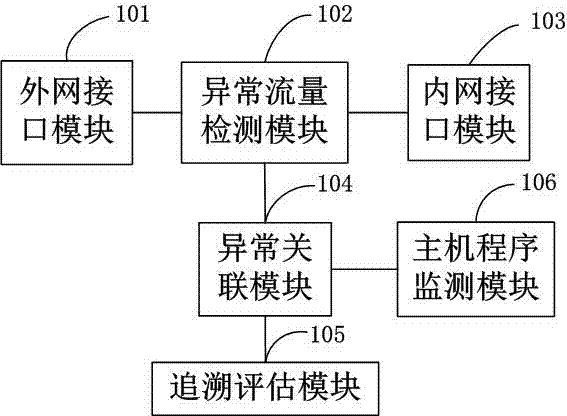
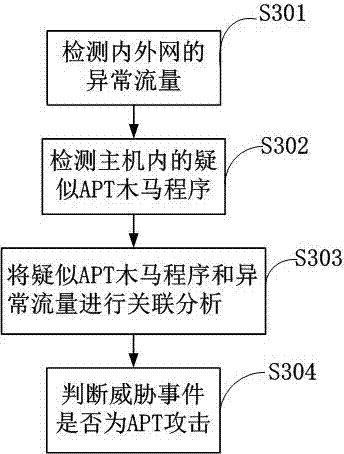
APT firewall
The invention relates to the field of information security, and specifically, the invention relates to an APT firewall system. An extranet interface module 101, an abnormal flow detection module 102, an intranet interface module 103, an abnormal association module 104, a retrospective evaluation module 105 and a host program monitoring module 106 are integrated in the system for detecting the flow of an extranet and an intranet in real time, monitoring the program process in real time and further decomposing and identifying abnormal flow and abnormal behaviors containing APT threats so as to locate the APT threat level, intercept the APT communication, clear the APT Trojan program and eliminate the threat attacks and the potential safety hazards.
Owner:深圳耀东安全科技有限公司
Program setting method, program monitoring method, and devices and systems for program setting and monitoring
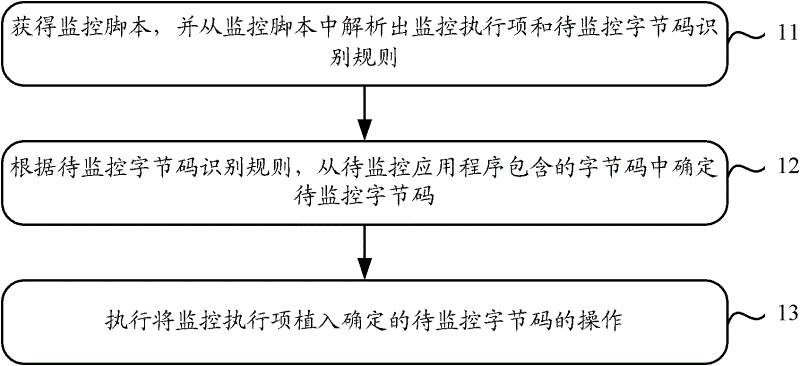
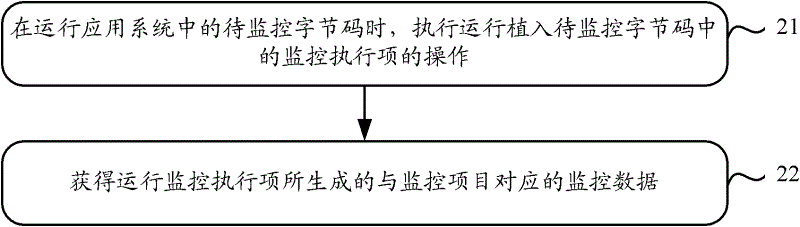
The invention discloses a program setting method, a program setting device and a program setting system which are used for solving the problem of low processing efficiency of a Java application system monitoring scheme adopted in the prior art on the condition that a monitoring point changes. The program setting method comprises acquiring a monitoring script, analyzing a monitoring implementation item and a recognition rule of byte-codes to be monitored from the monitoring script, and enabling the monitoring implementation item to comprise information of a monitoring program of an indicating pin on the byte-codes to be monitored; determining the byte-codes to be monitored from byte-codes contained in an application program to be monitored according to the recognition rule of the byte-codes to be monitored; and executing operation of implanting the monitoring implementation item in the determined byte-codes to be monitored. An embodiment further provides a program monitoring method, a program monitoring device and a program monitoring system.
Owner:ALIBABA GRP HLDG LTD
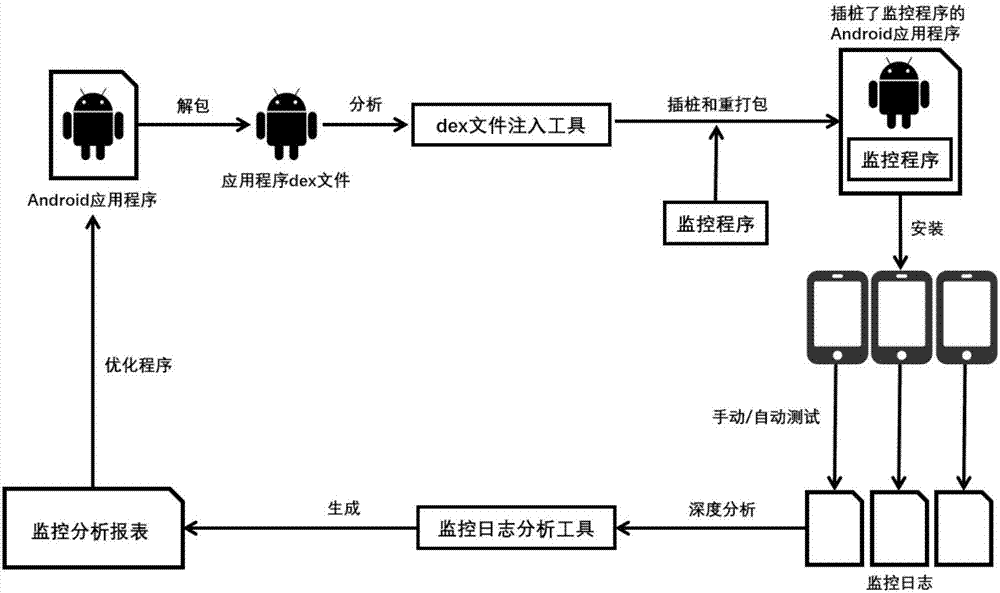
Android program monitoring system and method based on bytecode instrumentation
The present invention provides an Android program monitoring system based on the bytecode instrumentation. The system comprises: an Android program dex file injection module based on the bytecode analysis, for injecting the Android program monitoring dex file into the Android program; an Android program monitoring module, for storing the Android program monitoring dex file; and a monitoring log analysis module, for extracting and analyzing the Android device monitoring log. The present invention also provides an Android program monitoring method based on the bytecode instrumentation. By virtue of the method, the Android program monitoring dex file is injected into the Android program, the monitoring log is generated through the Android program monitoring dex file, and the monitoring analysis report with multiple dimensions is obtained by analyzing the monitoring log; and according to the system and method disclosed by the present invention, the monitoring information is collected without modifying the program source code.
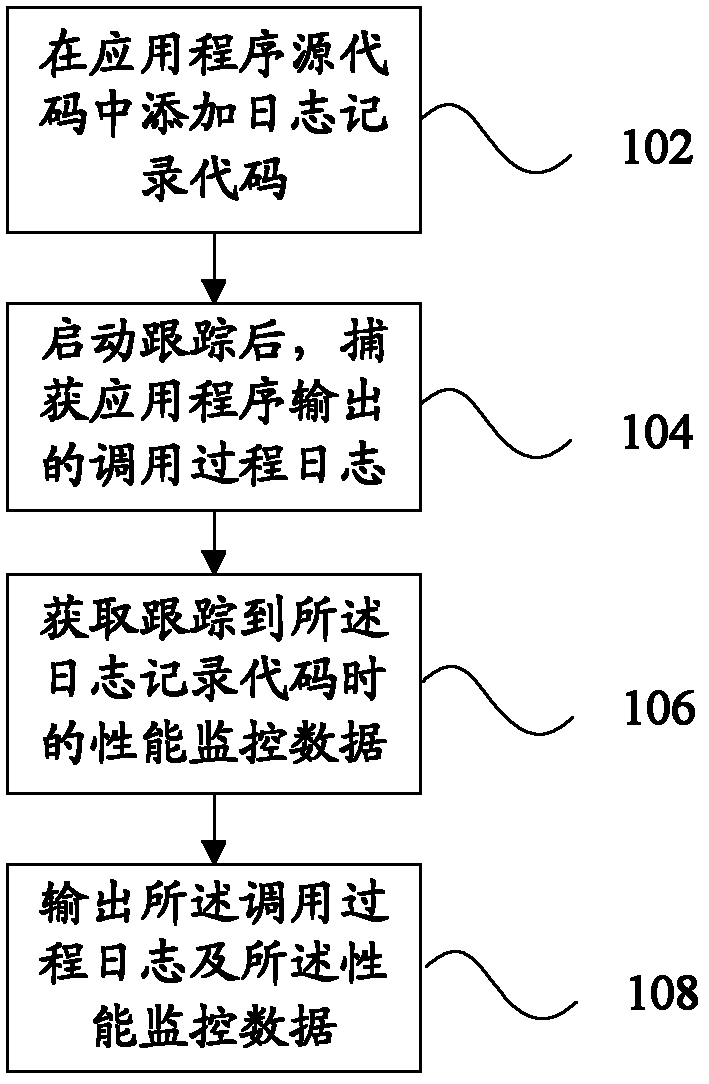
Owner:SHANGHAI JIAO TONG UNIV
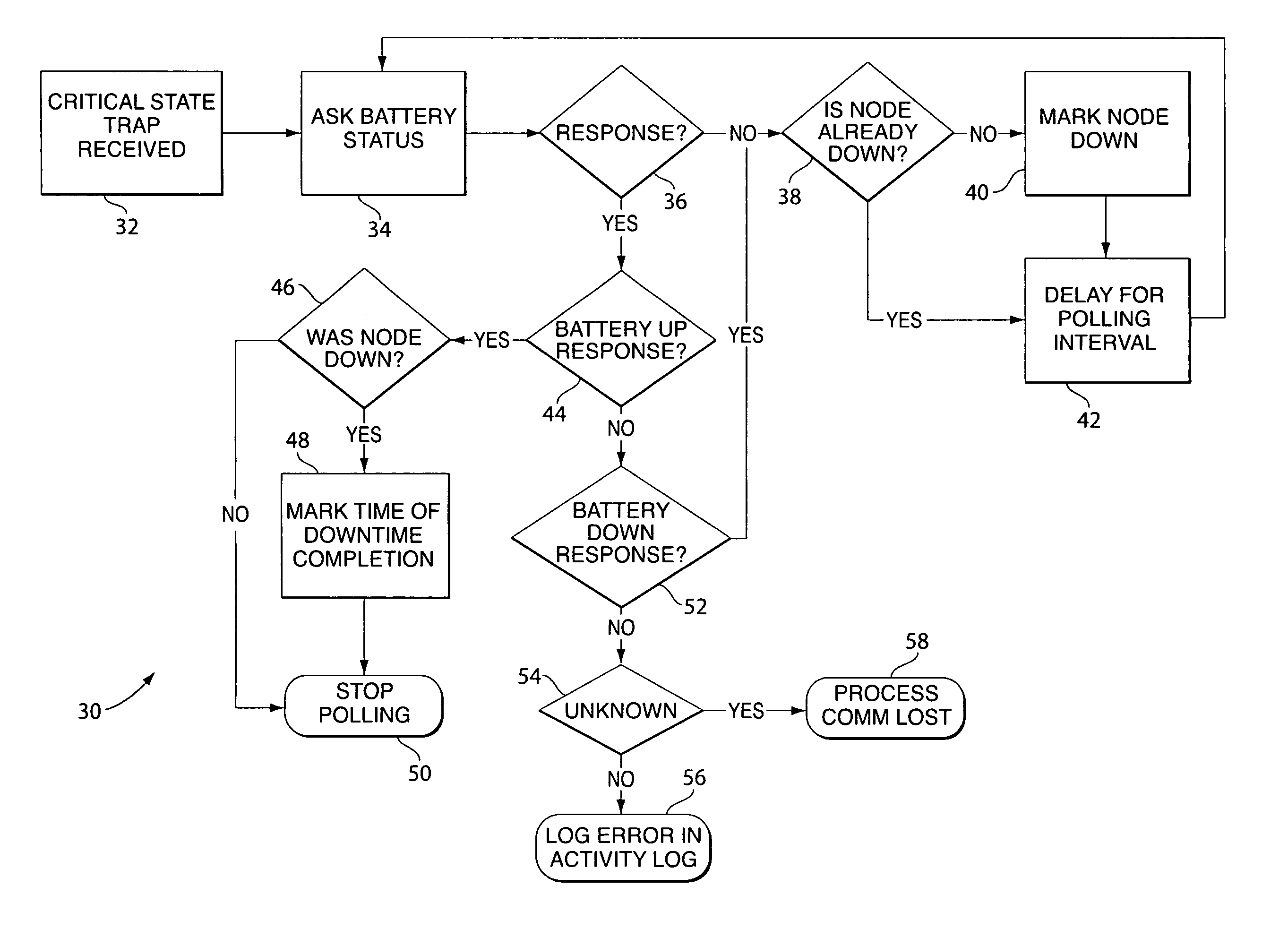
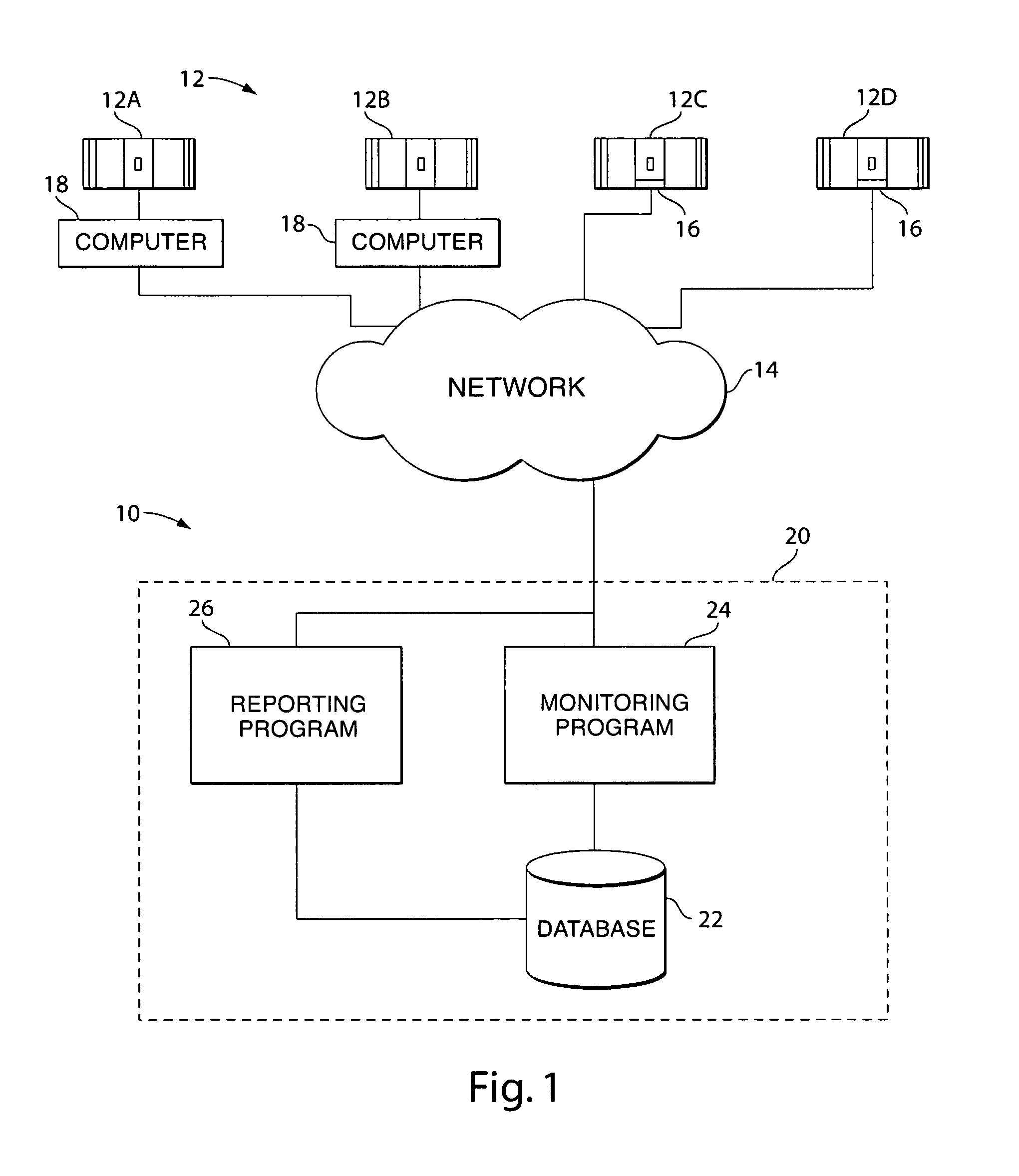
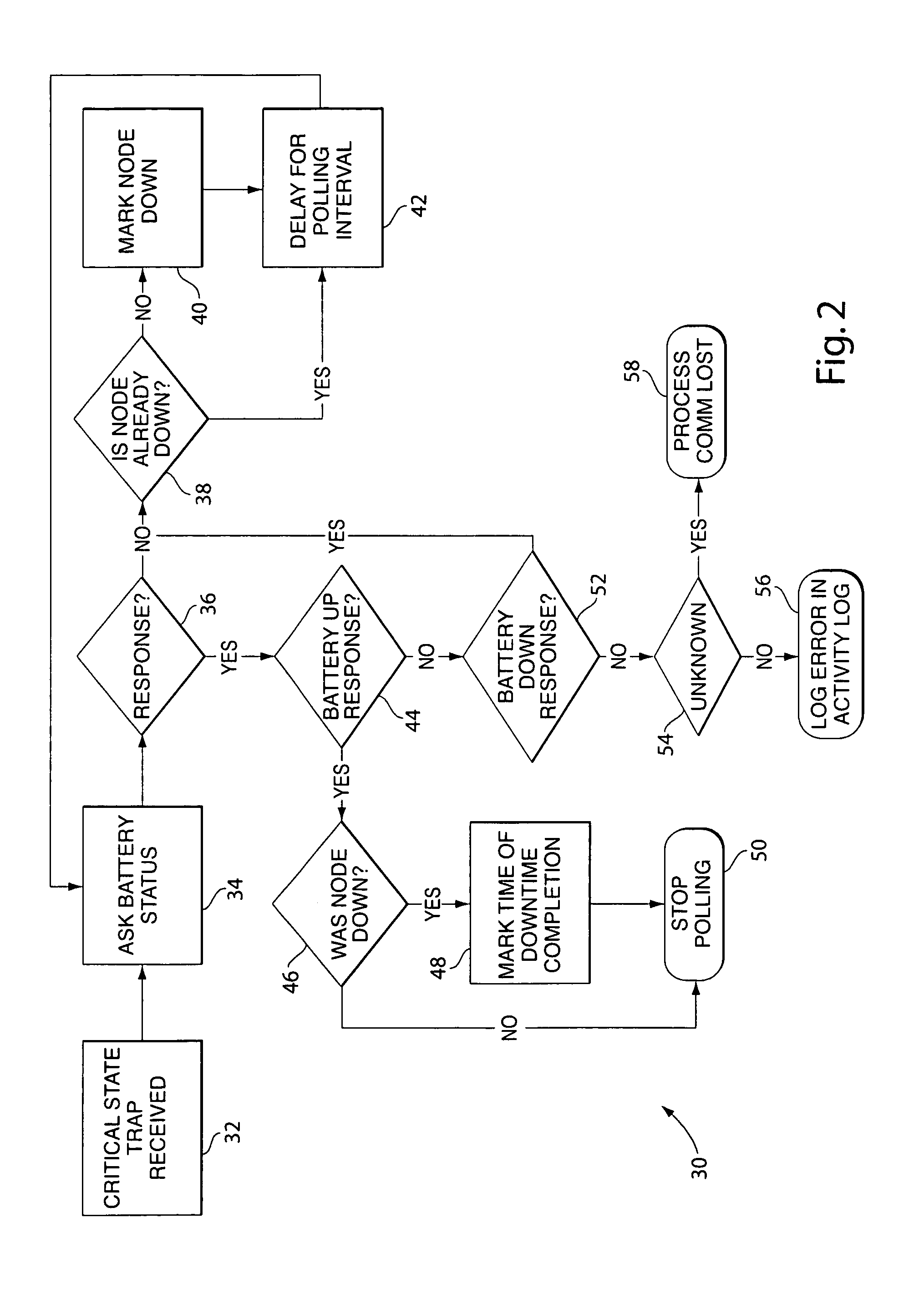
Power supply critical state monitoring system
InactiveUS7114098B2Obtain status informationEasy to getError detection/correctionInformation technology support systemMonitoring systemEngineering
A system and method for providing critical state monitoring for a power supply, such as an uninterruptible power supply (UPS), is provided. In one embodiment, the invention includes a notification system for at least one power supply coupled to a computer network and adapted to transmit information such as a trap over the computer network when one of the power supplies undergoes the entry of a critical state, wherein the notification system includes a computer system connected to the computer network and has running on it a monitoring program, a reporting program and a database. The monitoring program monitors the network and detects the information being associated with the entry of the critical state. The database stores the information relating to the information transmitted over the network being associated with the entry of the critical state. The reporting program reports over the computer network the information relating to the duration of the critical state. In another embodiment, the invention includes a method of providing over a computer network a notification of a power supply in a critical state.
Owner:AMERICA POWER CONVERSION CORP
Remote display chain for mutiple user interface applications
InactiveUS20080238712A1Electric signal transmission systemsSpecial tariff metersKey pressingUser input
A multi-master serial bus that connects multiple utility monitoring devices with multiple remote electronic display units. The display units include an I2C microprocessor with an integrated LCD controller for controlling an LCD display and a set of buttons for changing what is displayed on the LCD display. They also include an I / O to I2C driver for sending button key presses to the remote monitoring device, which communicates the requested data to be displayed back to the display unit via the multi-master serial bus. Each remote electronic display unit has a unique address assigned to it, and when a user input is detected on the I2C bus by the utility monitoring device, the controller in the utility monitoring device sends monitored data to the detected address for display on the remote electronic display unit.
Owner:SQUARE D CO
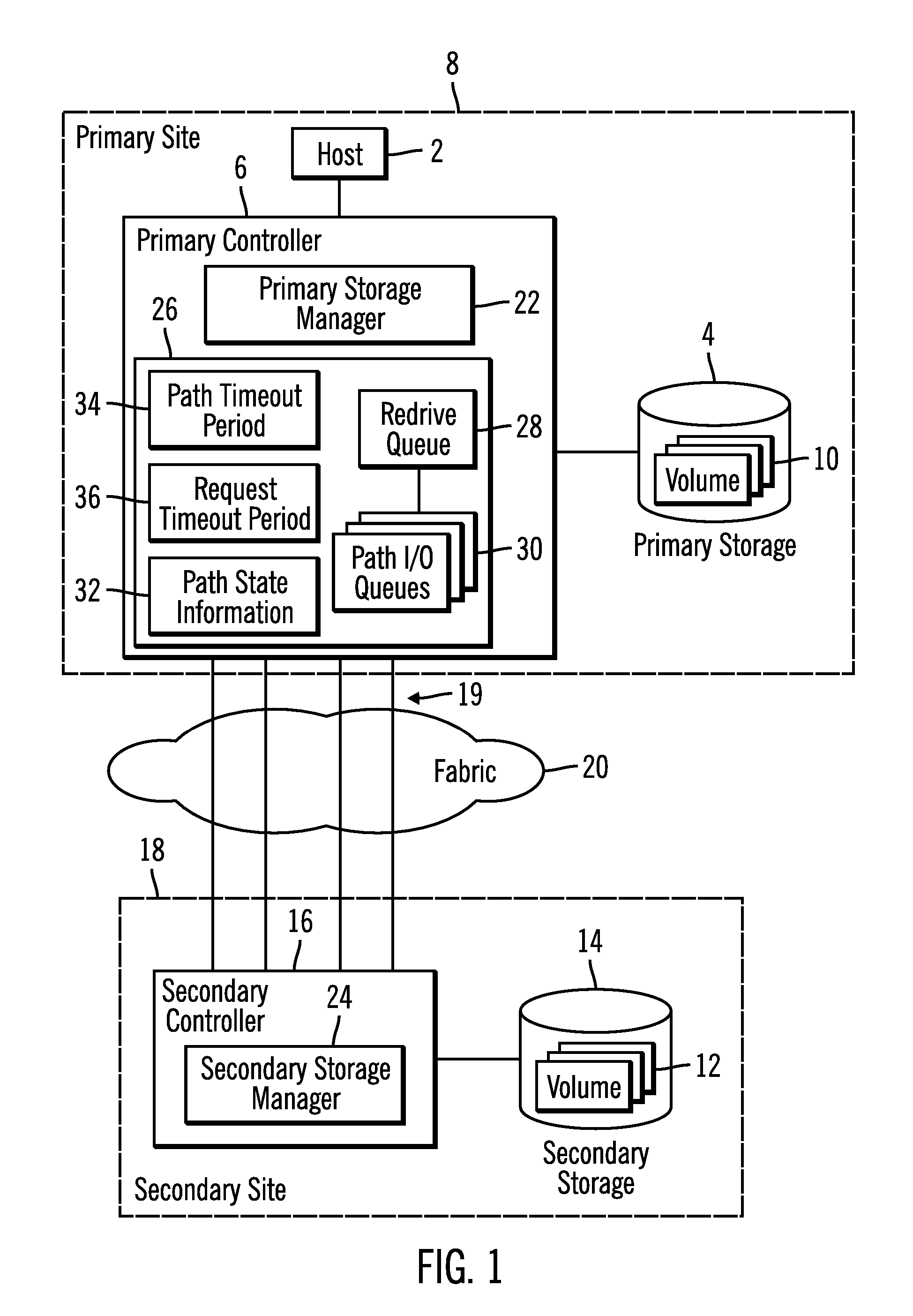
Method, system, and program for transmitting input/output requests from a first controller to a second controller
InactiveUS20070022317A1Redundant operation error correctionRedundant hardware error correctionTime segmentEngineering
Provided are a method, system, and program monitoring paths between a first controller and second controller. A determination is made as to whether one path has been unavailable for a predetermined time period in response to detecting that the path is unavailable. Indication is made that the path is in a first failed state if the path has been unavailable for more than the predetermined time period and indication is made that the path is in a second failed state if the path has not been unavailable for the predetermined time period.
Owner:GLOBALFOUNDRIES INC
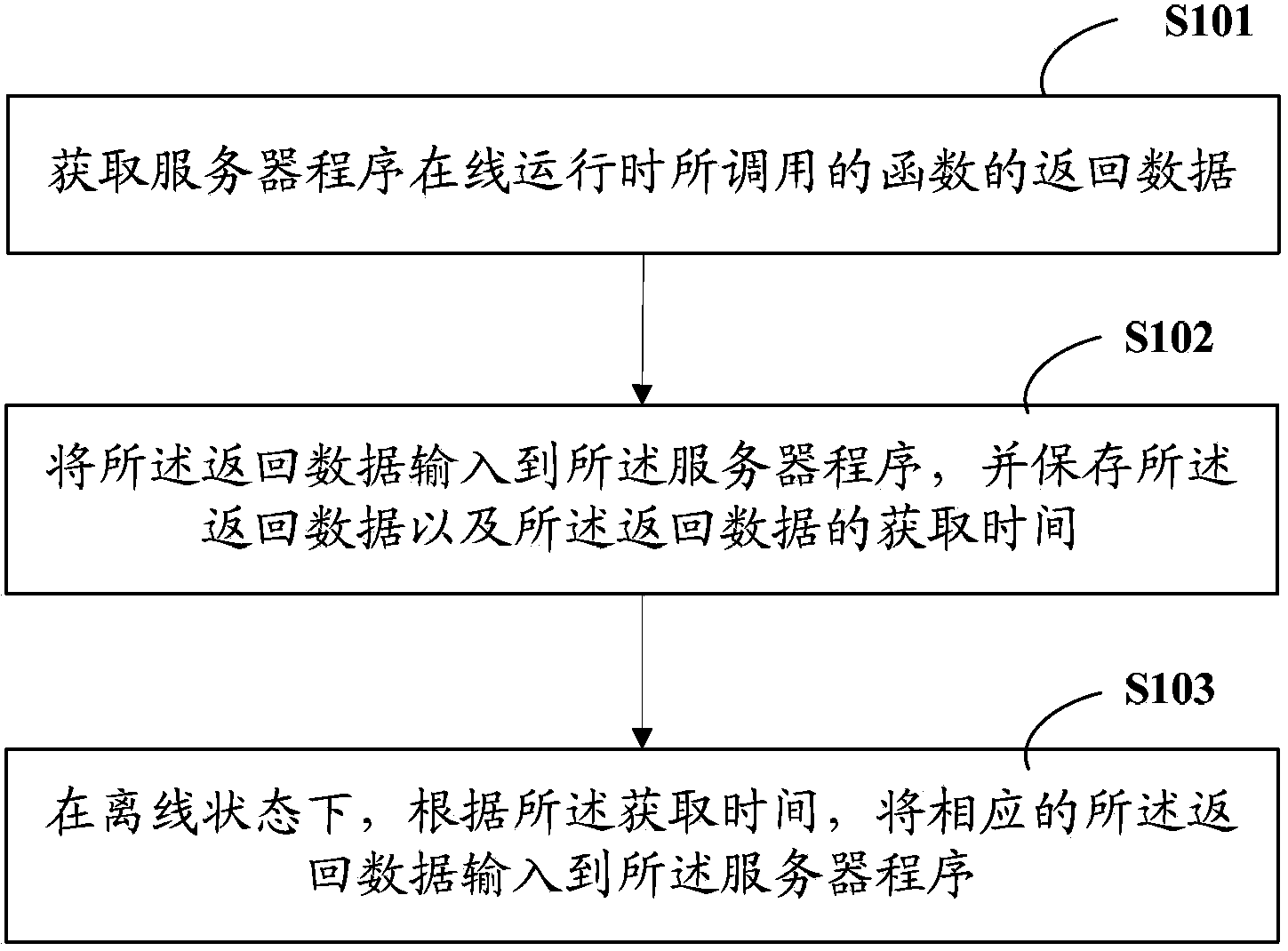
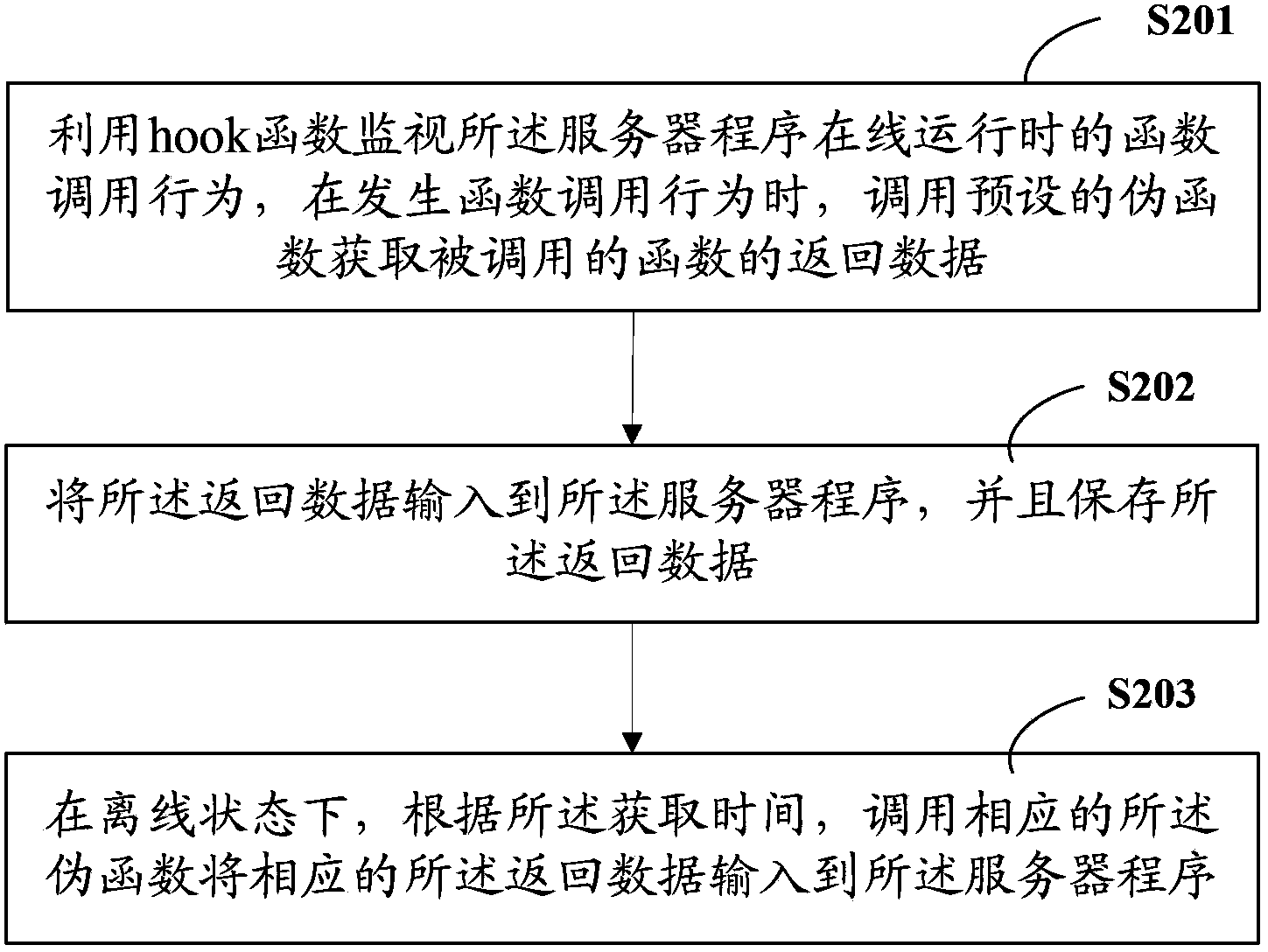
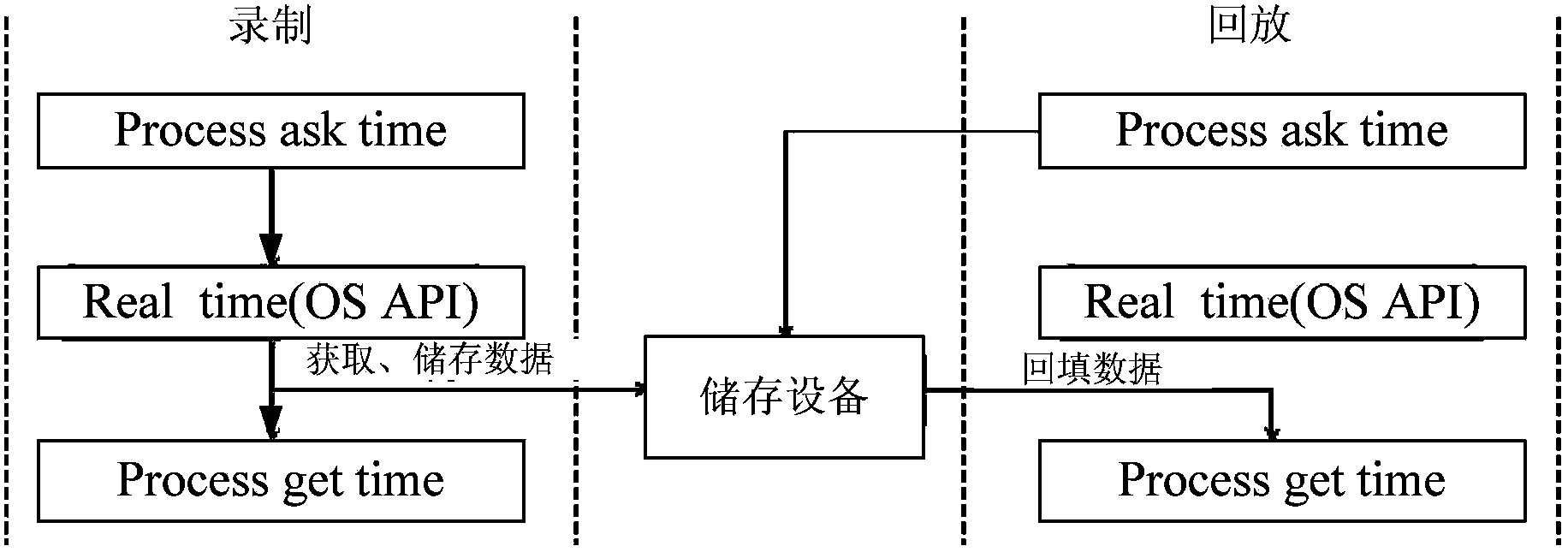
Server program monitoring method and system of server program
ActiveCN103544095AGuaranteed uptimeLess impact on efficiency of online operationHardware monitoringTest analysisProgram monitoring
The invention provides a server program monitoring method and a system of a server program. The method comprises the steps of obtaining the return data of functions called when the server program is in on-line operation, inputting the return data to the server program, and storing the return data and the obtaining time of the return data; in an off-line state, inputting the corresponding return data to the server program according to the obtaining time. The server program monitoring method and the system of the server program record all the input of the server program. According to the recorded data, complete restoration of the on-line operation state of the server program can be achieved in the off-line state, a server at restoration time can be used as a base to conduct testing analysis of the performance of the server program and reoccurrence of BUG which occasionally appears in the development process of the server program, or analyze access user behavior of the server and the similar application.
Owner:SHENZHEN TENCENT COMP SYST CO LTD
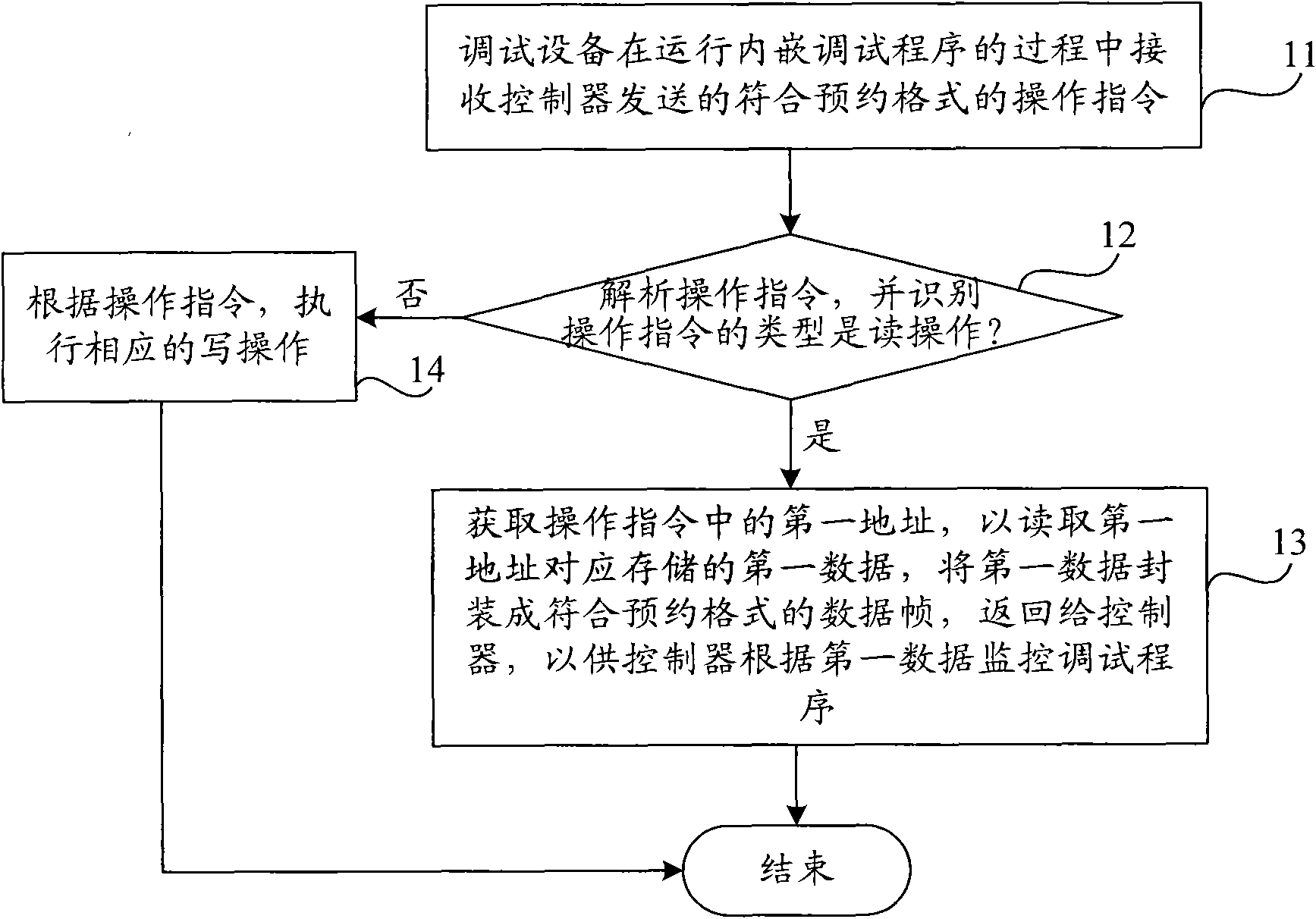
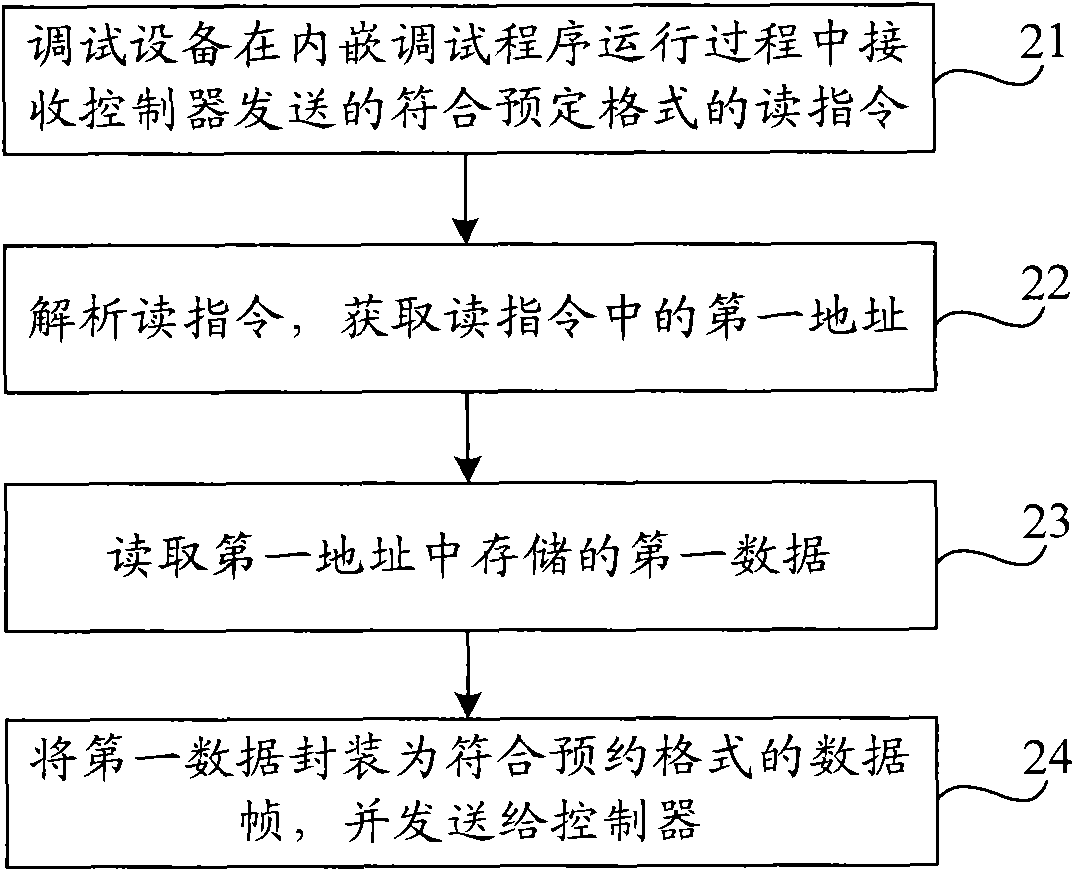
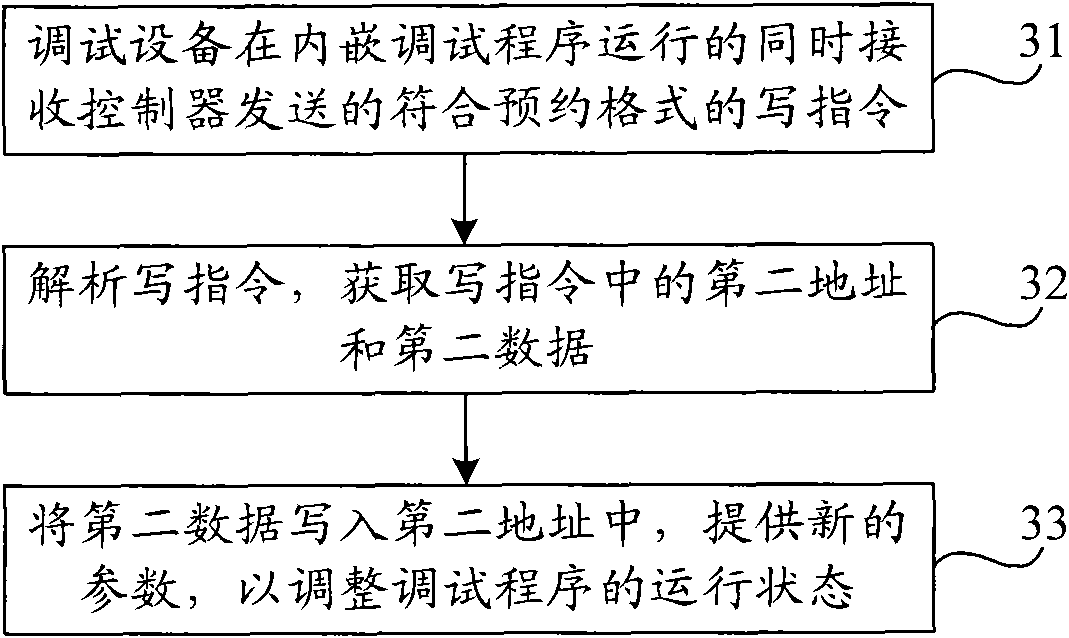
Debugging program monitoring method and device
InactiveCN101876935ARun without interruptionEnsure safetyHardware monitoringSoftware testing/debuggingComputer hardwareElectrical devices
The invention provides debugging program monitoring method and device. The method comprises the steps of: receiving an operating command sent by a controller and according with an appointed format by debugging equipment in a process of operating an embedded debugging program; analyzing the operating command by the debugging equipment, and recognizing the type of the operating command; and if the debugging equipment recognizes the type of the operating command to be a read operating type, obtaining a first address in the operating command to read stored first data corresponding to the first address, packaging the first data into a data frame with the appointed format, and returning to the controller so that the controller monitors the debugging program according to the first data. The device comprises an interface module, an operating command receiving module, an analyzing and recognizing module, a first acquiring module, a reading module, a packaging module and a sending module. The debugging program monitoring method and device can realize the monitoring on the operating state of the debugging program in a process of operating the debugging program of high-power electrical equipment.
Owner:CHINA CNR CORPORATION
Application program monitoring method and terminal
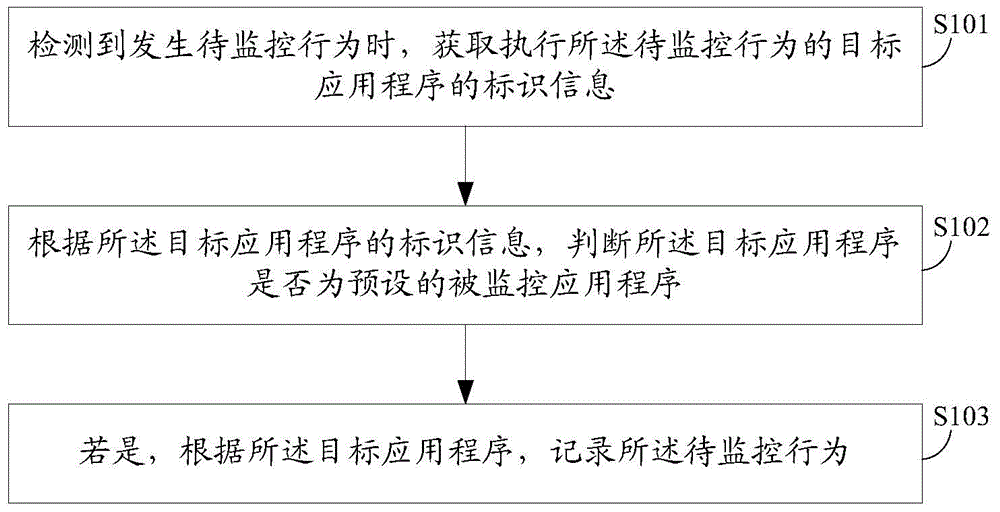
InactiveCN104915599APrevent theftImprove securityPlatform integrity maintainanceApplication softwareData storing
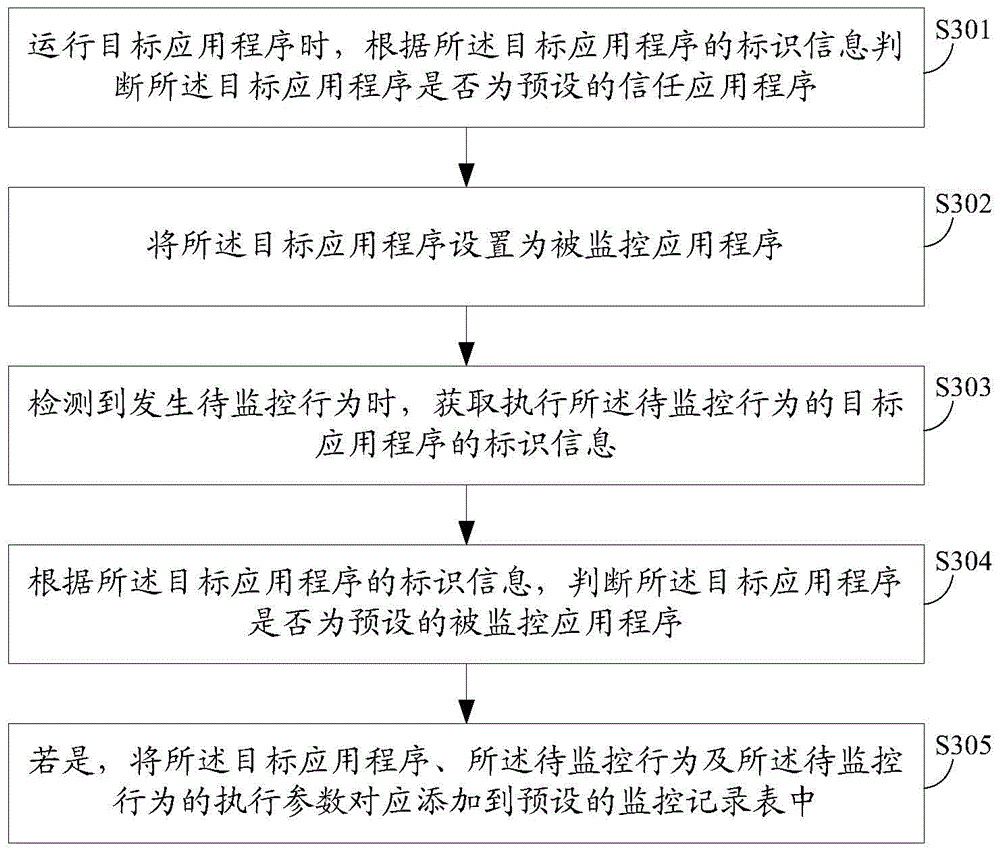
The embodiment of the invention discloses an application program monitoring method and a terminal. The application program monitoring method comprises the following steps: when the condition that a to-be-monitored behavior occurs is detected, acquiring the identification information of a target application program for executing the to-be-monitored behavior; according to the identification information of the target application program, judging the target application program is a preset a monitored application program or not; if yes, according to the target application program, recording the to-be-monitored behavior. By adopting the application program monitoring method and the terminal disclosed by the embodiment of the invention, a behavior, which threatens the security of user data, executed by the application program can be monitored and recorded, therefore data stored in the terminal is prevented from being stolen, and the security of the terminal is enhanced.
Owner:GUANGDONG OPPO MOBILE TELECOMM CORP LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com