Patents
Literature
11317 results about "Protection system" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
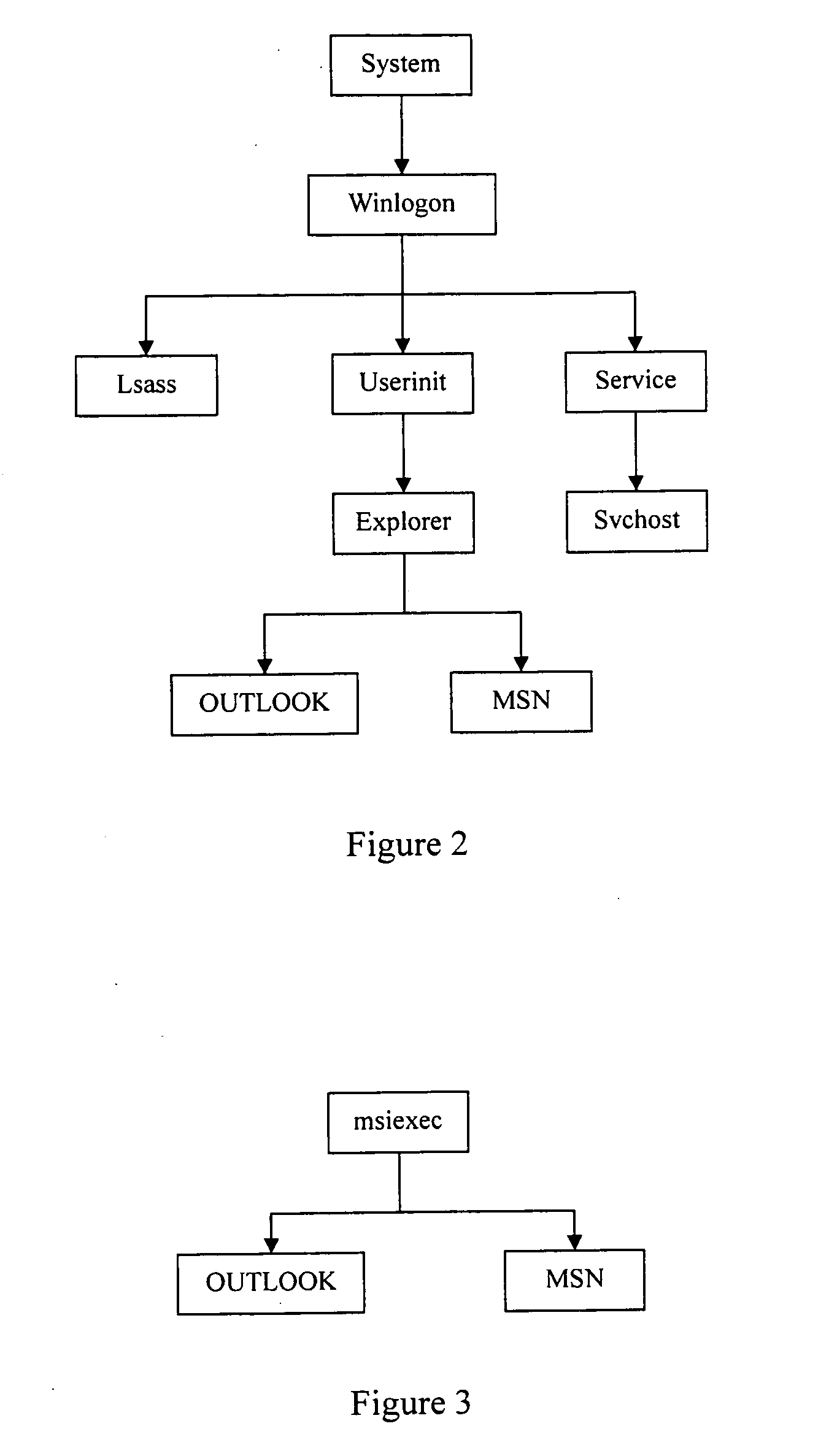
System protection is a Windows feature, called System Restore in the past versions of Windows, that creates and saves as restore points information about your PC's system files, software, drivers, and registry settings. It does this for all the drives that have system protection activated.
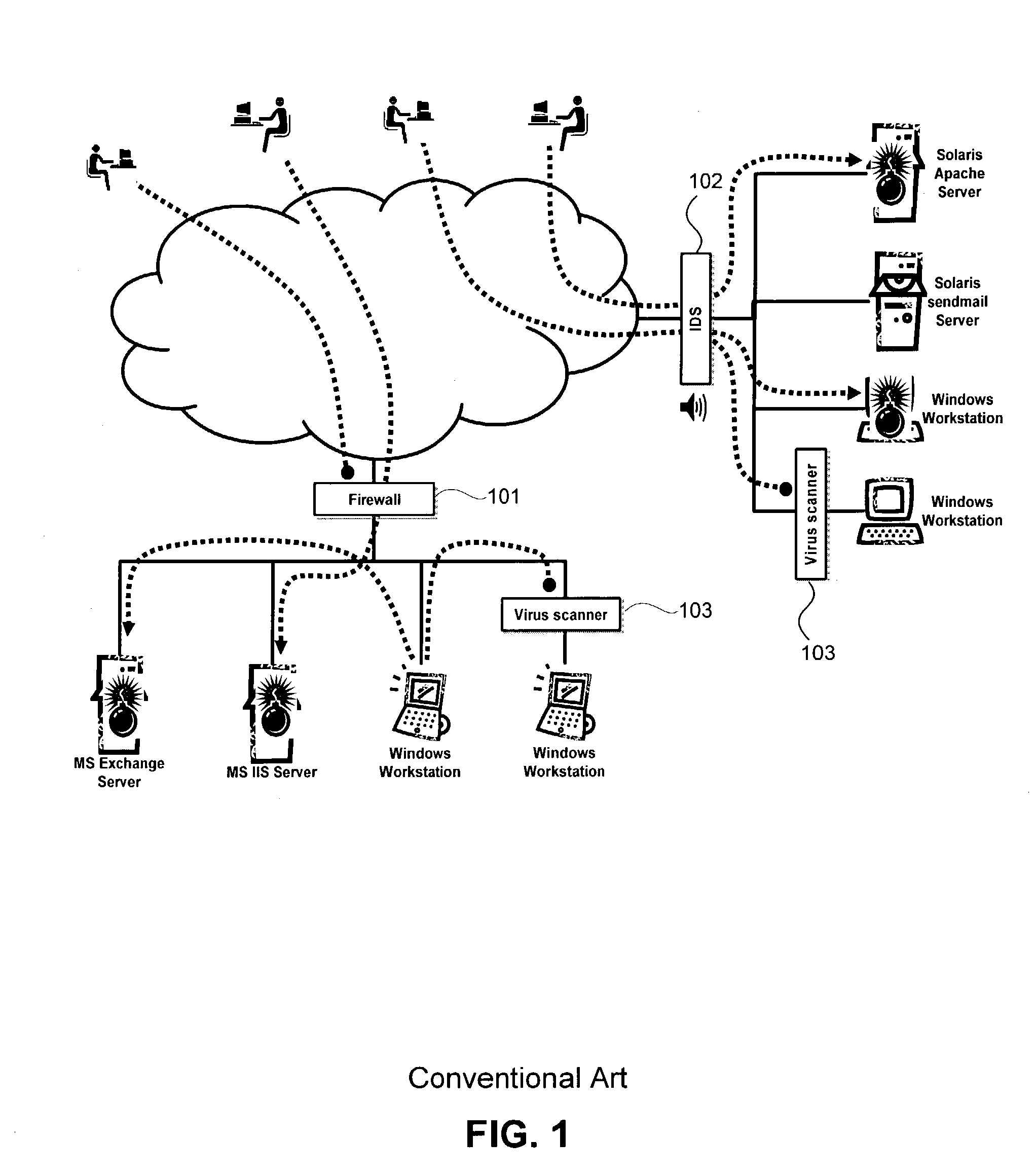
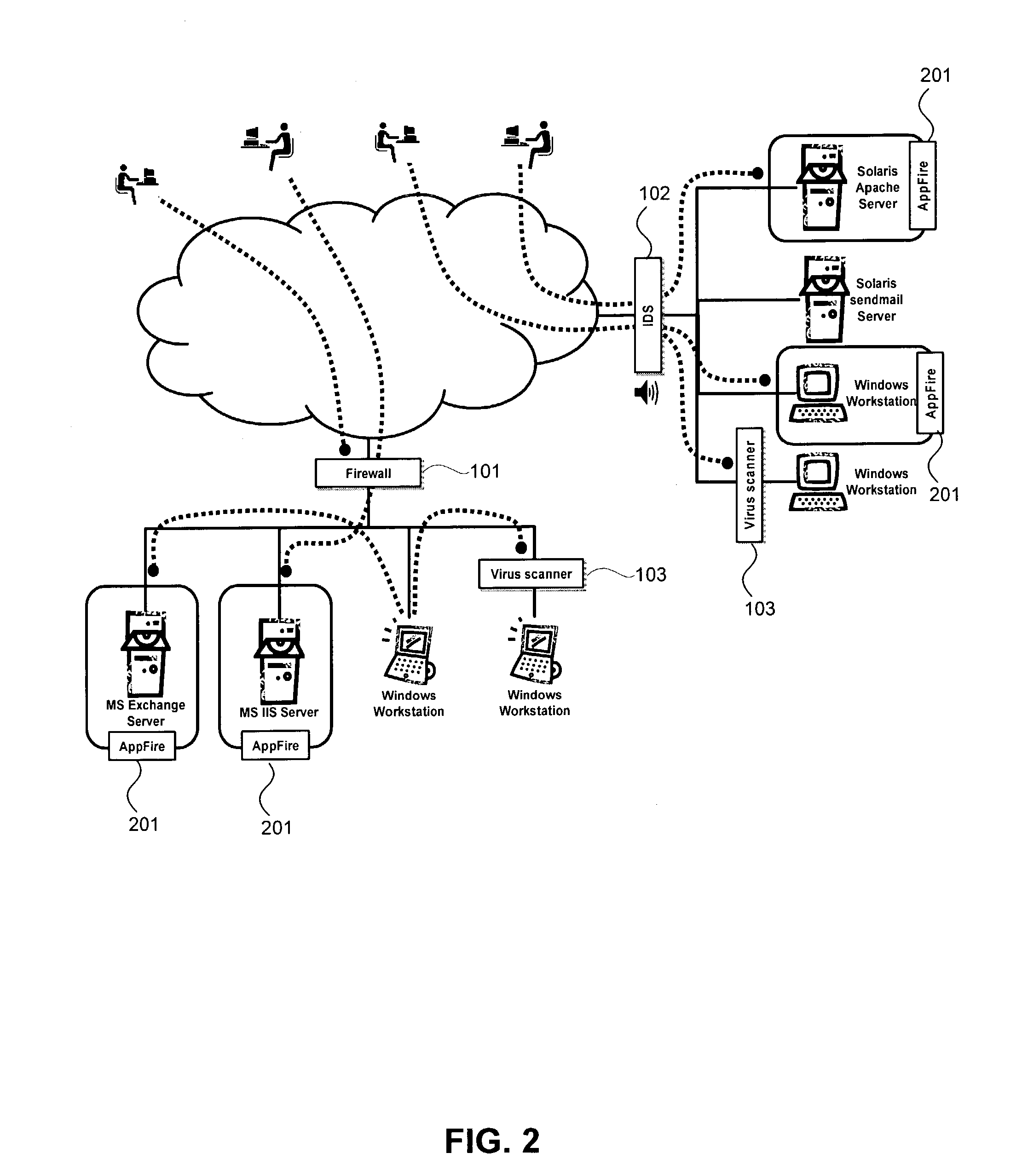
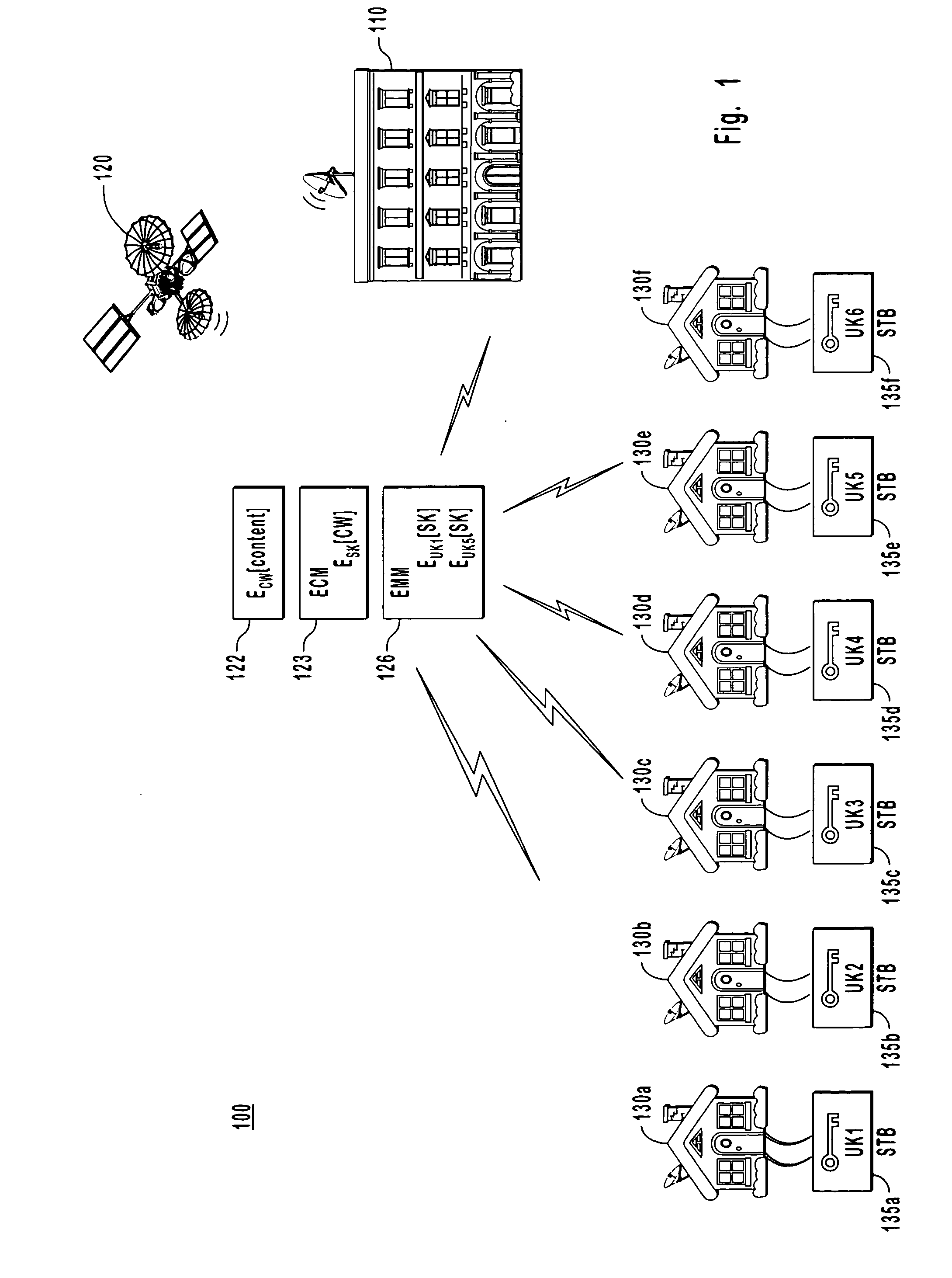
E-mail virus protection system and method
InactiveUS7506155B1Detection securityEnsuring Safe ExecutionHardware monitoringPlatform integrity maintainanceAdobeProtection system
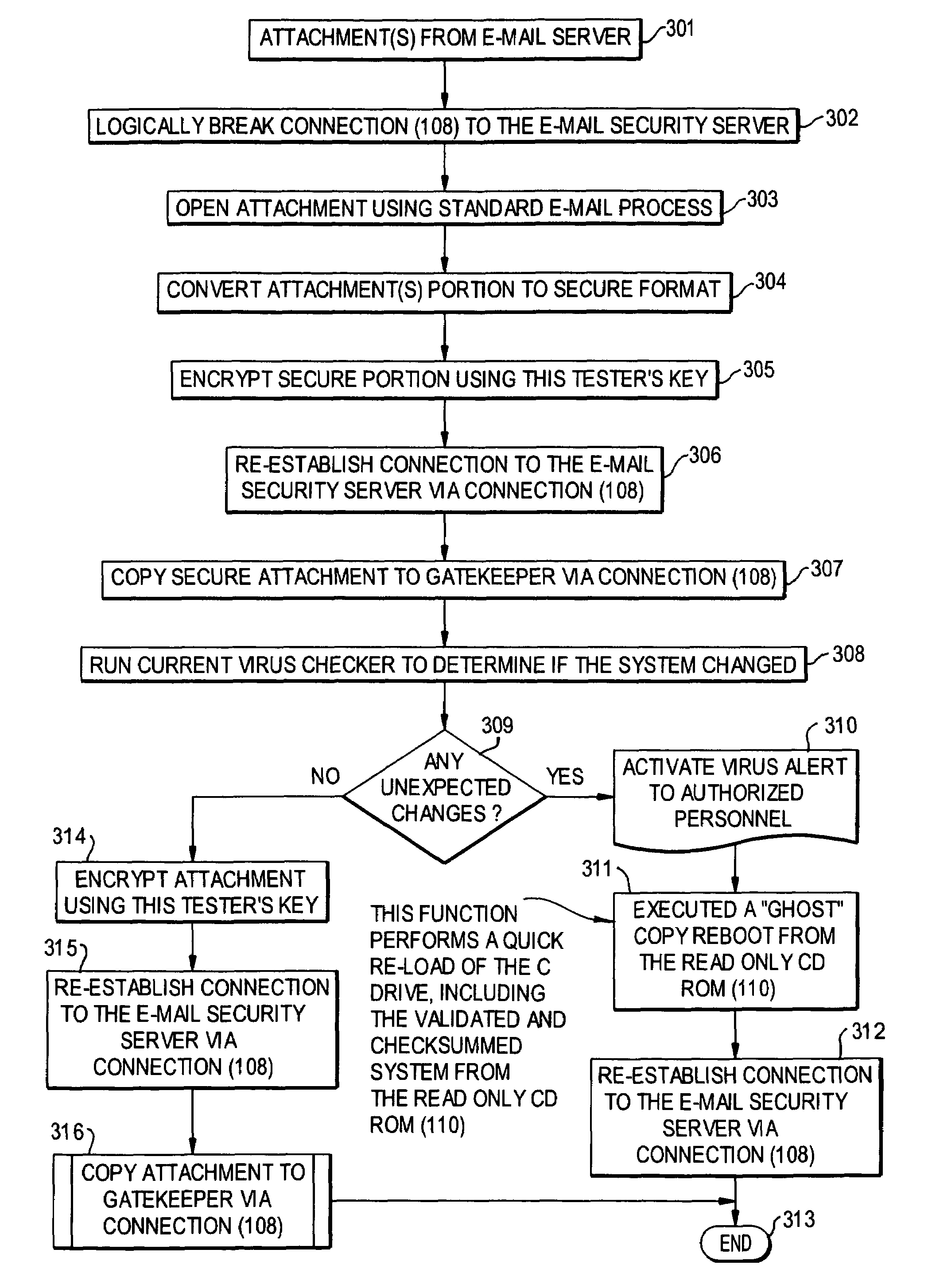
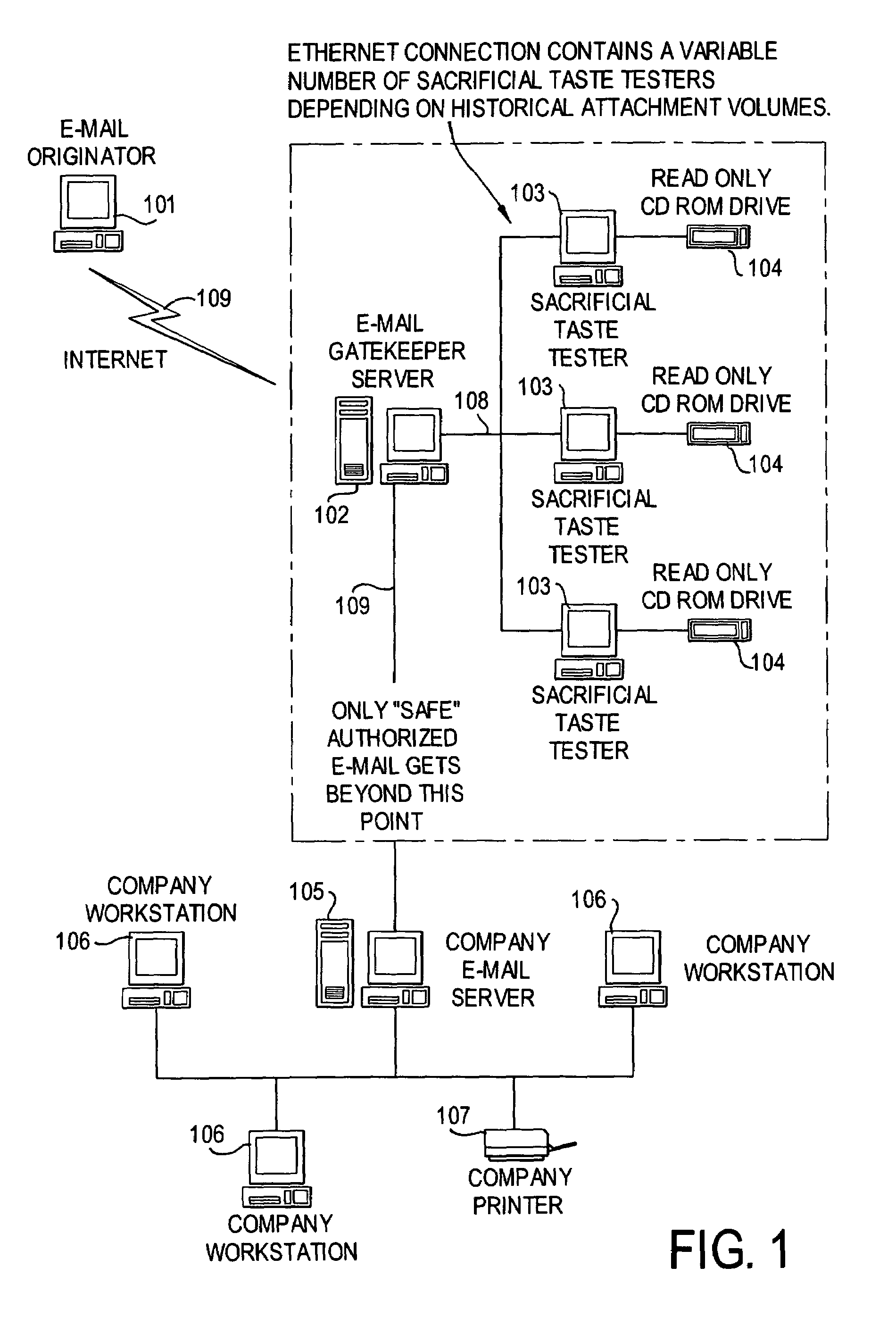
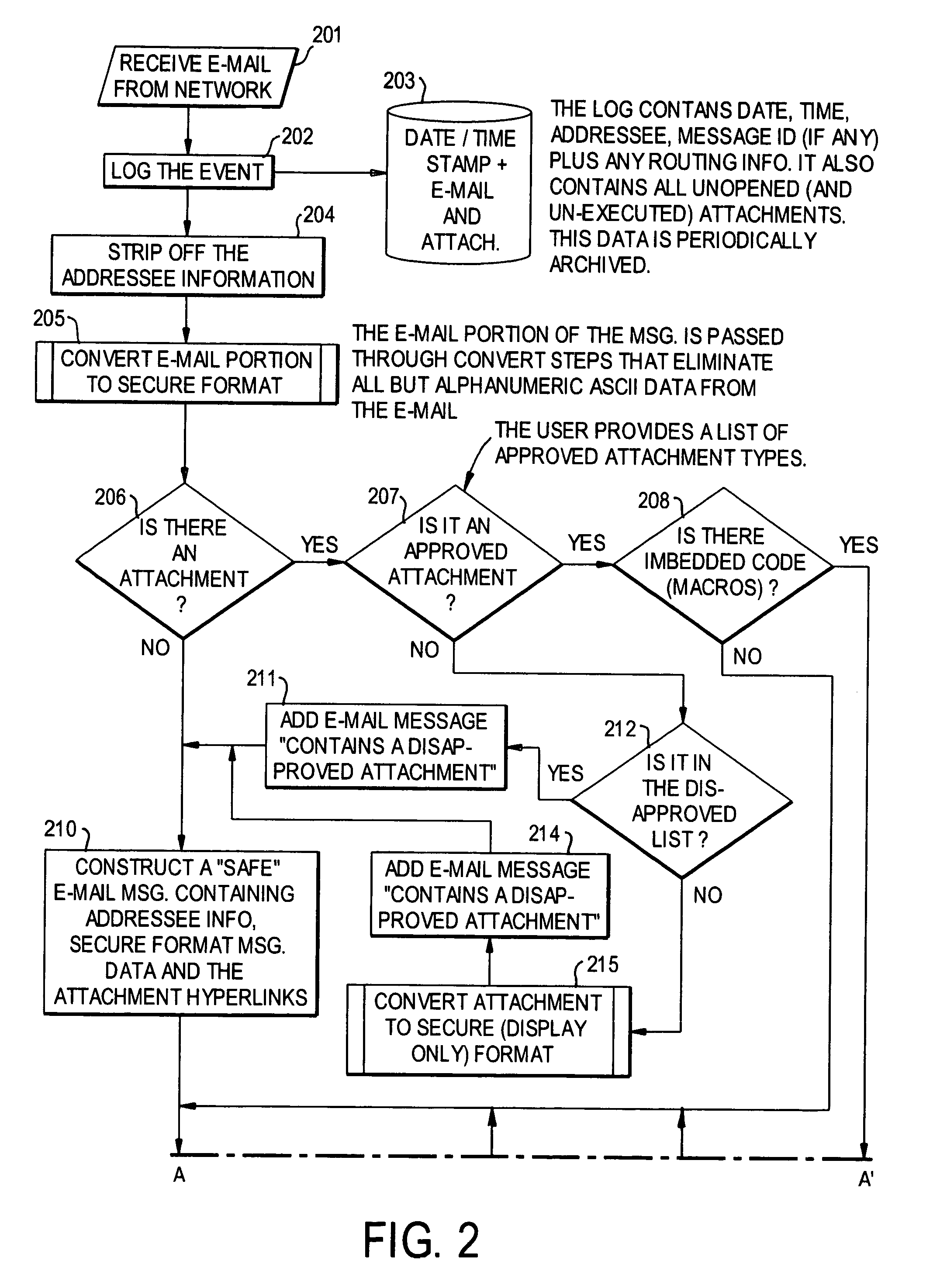
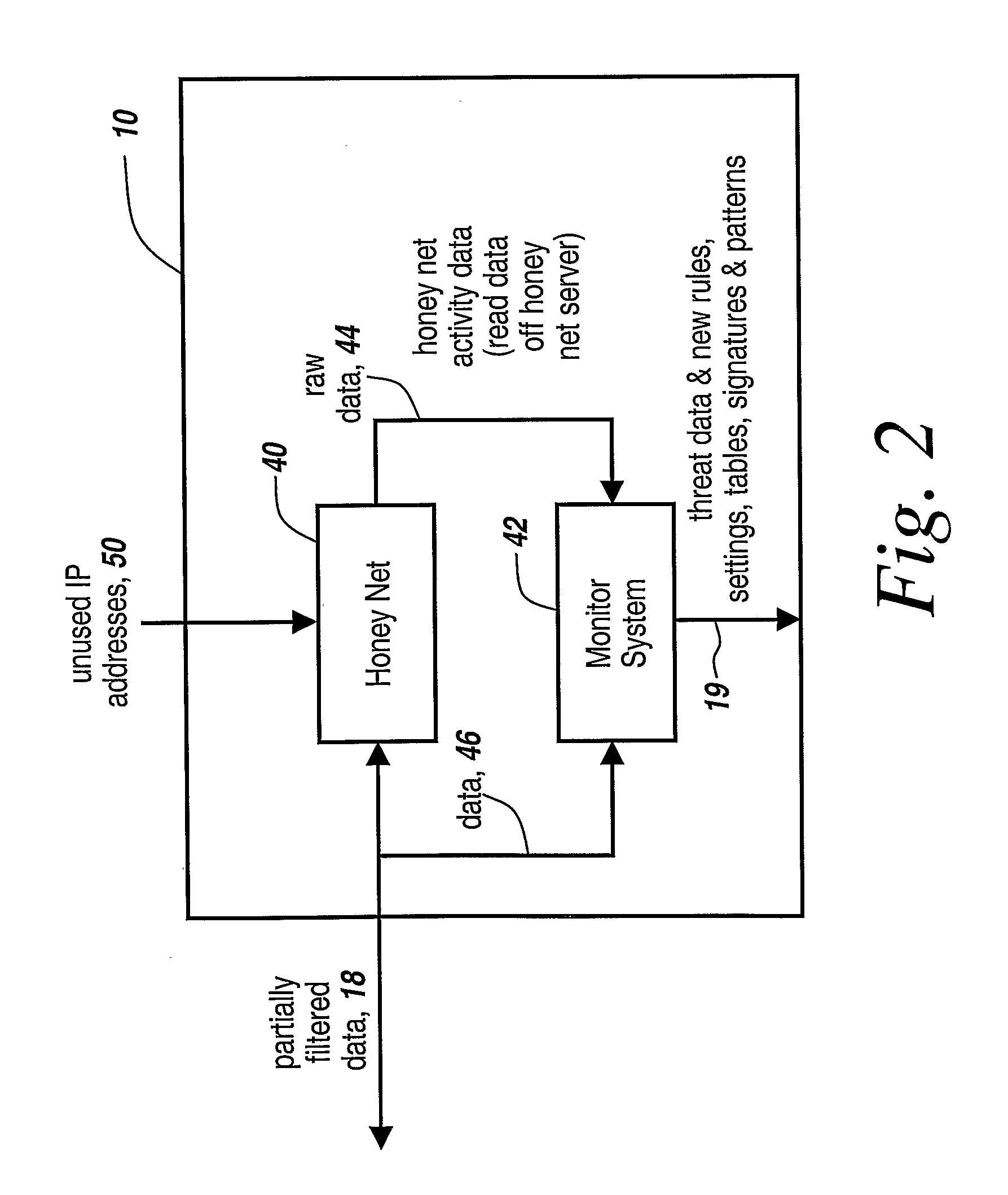
A network is protected from e-mail viruses through the use of a sacrificial server. Any executable programs or other suspicious parts of incoming e-mail messages are forwarded to a sacrificial server, where they are converted to non-executable format such as Adobe Acrobat PDF and sent to the recipient. The sacrificial server is then checked for virus activity. After the execution is completed, the sacrificial server is rebooted.
Owner:INTELLECTUAL VENTURES I LLC
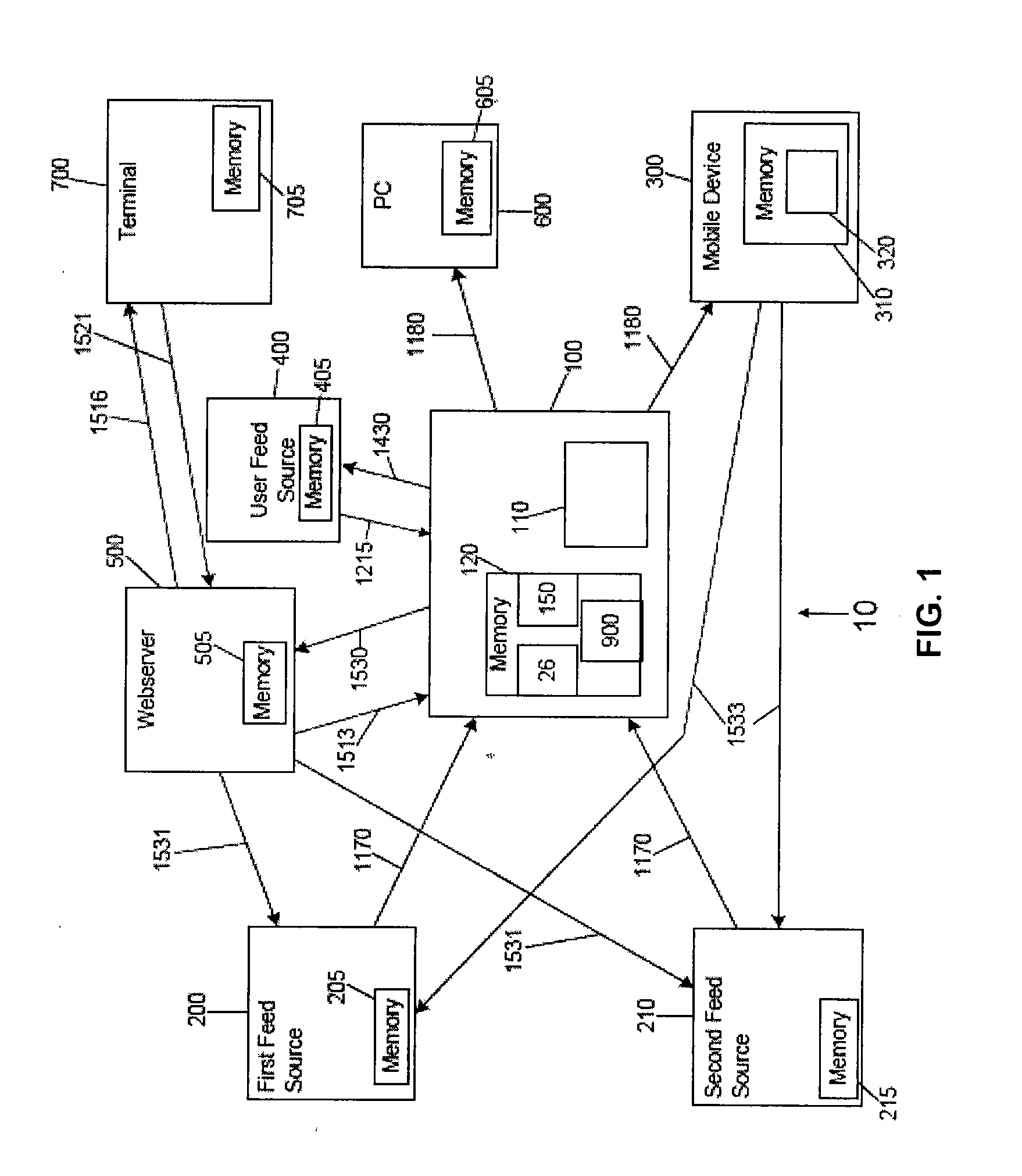
Information server and mobile delivery system and method
InactiveUS20090249076A1Digital data processing detailsUser identity/authority verificationThird partyPassword
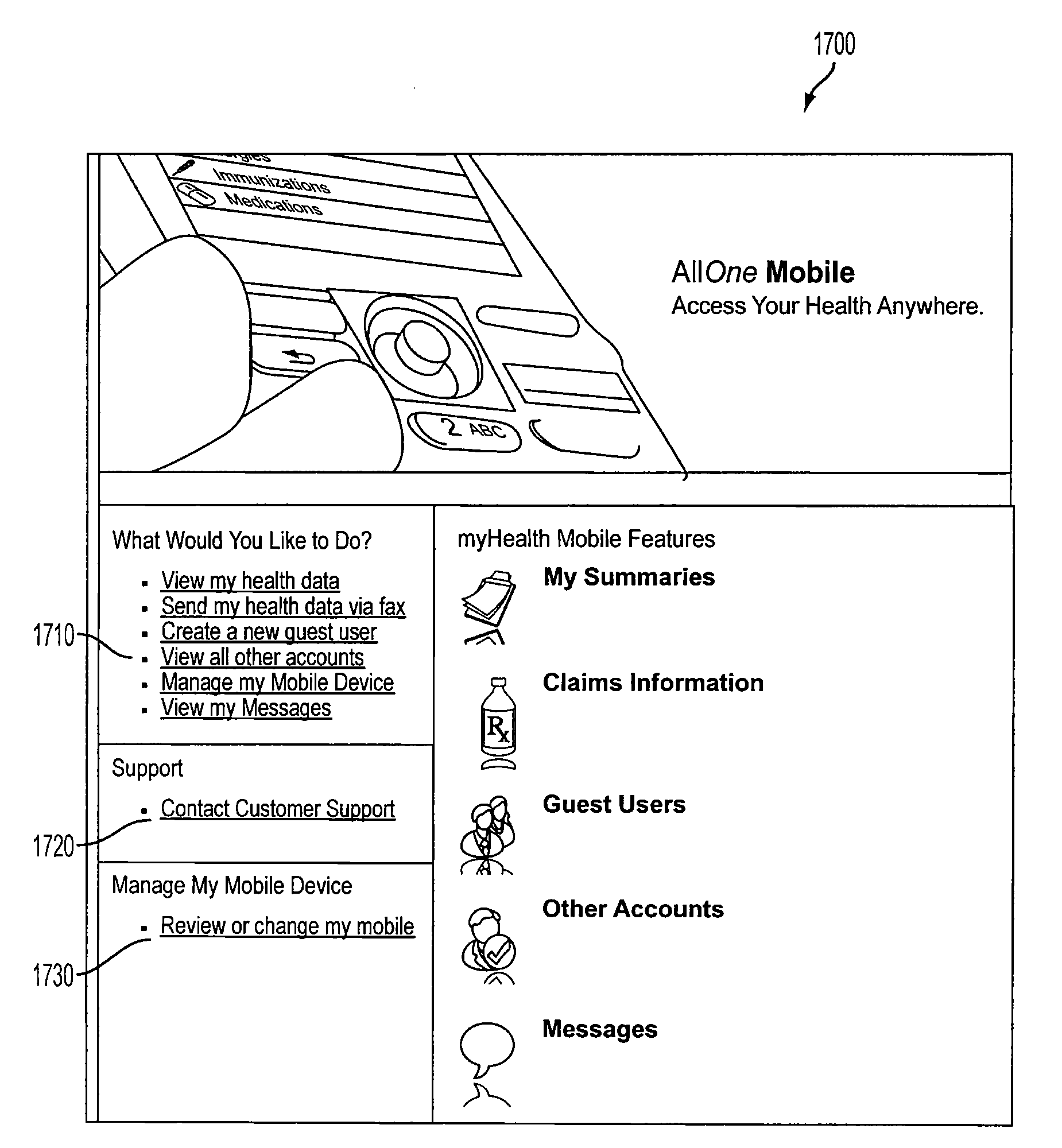
A user is provided with access to his or her account information using a client. The account information is stored on a server which receives the information from a feed source and transmits the information to the client. A method for downloading and installing specialized software for viewing the account information on the client is also provided. The information can be received from different feed sources in different formats and converted to a format that is compatible with the intended receiving client. Encryption can be used to protect the privacy of the users of the system and the account information therein. Additionally, a special access password and a privileged access routine can be used to provide access to an authorized third party user on a temporary basis.
Owner:ALLONE HEALTH GRP
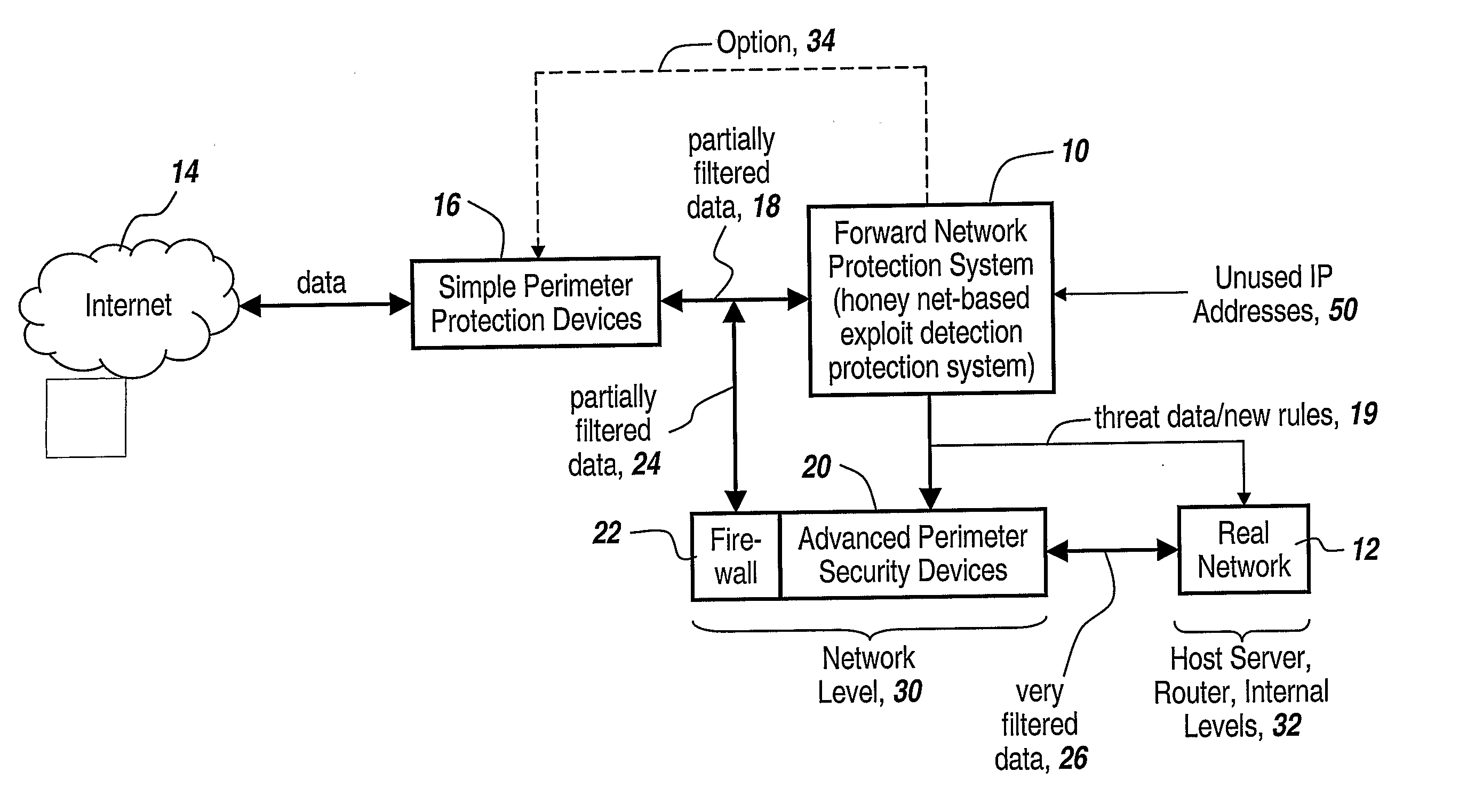
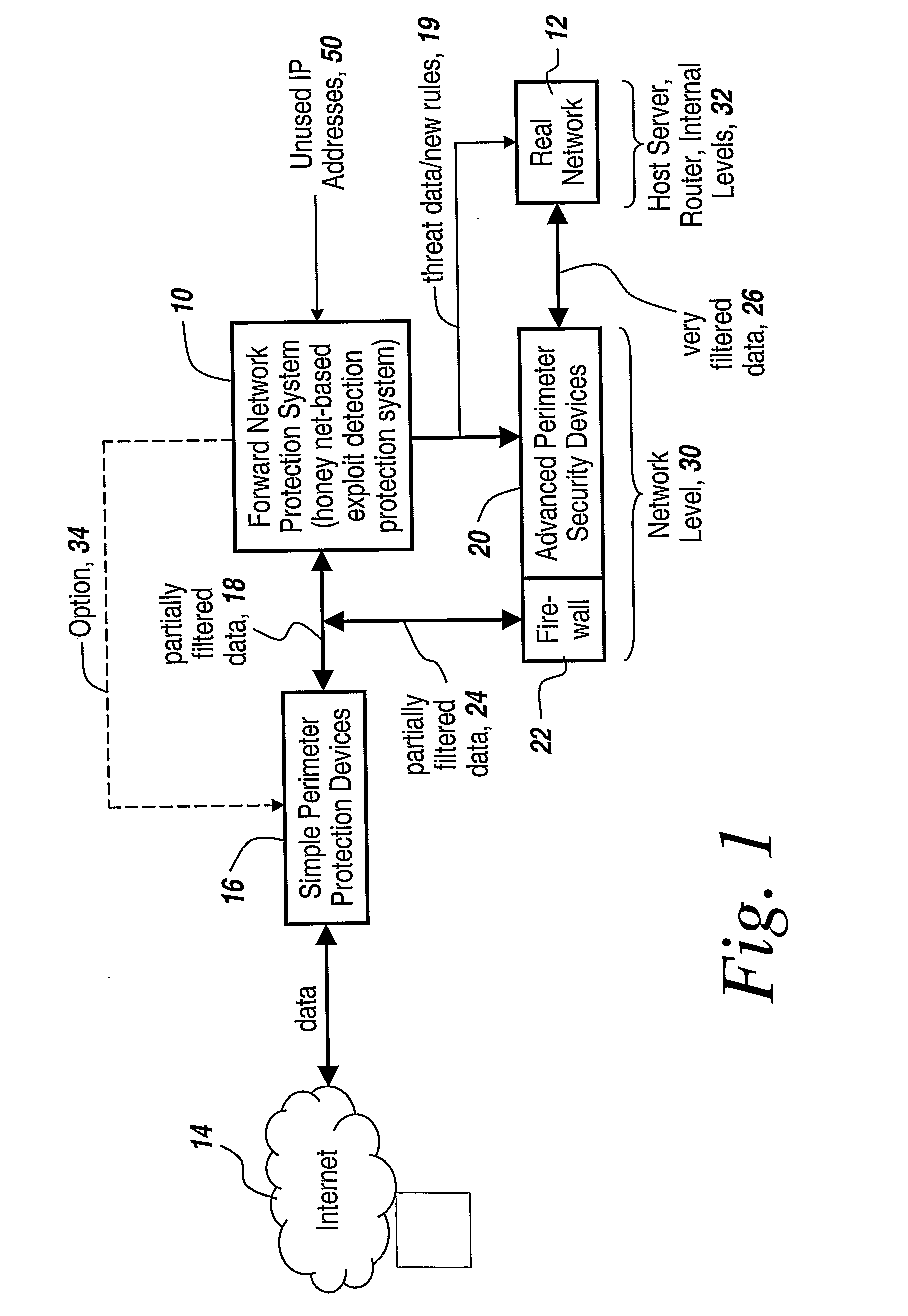
Method and Apparatus for Defending Against Zero-Day Worm-Based Attacks
InactiveUS20080098476A1Curb workloadEliminate usual spam and other simple attackMemory loss protectionError detection/correctionData packOperational system
Honey pots are used to attract computer attacks to a virtual operating system that is a virtual instantiation of a typical deployed operational system. Honey nets are a collection of these virtual systems assembled to create a virtual network. The subject system uses a forward deployed honey net combined with a parallel monitoring system collecting data into and from the honey net, leveraging the controlled environment to identify malicious behavior and new attacks. This honey net / monitoring pair is placed ahead of the real deployed operational network and the data it uncovers is used to reconfigure network protective devices in real time to prevent zero-day based attacks from entering the real network. The forward network protection system analyzes the data gathered by the honey pots and generates signatures and new rules for protection that are coupled to both advanced perimeter network security devices and to the real network itself so that these devices can be reconfigured with threat data and new rules to prevent infected packets from entering the real network and from propagating to other machines. Note the subject system applies to both zero-day exploit-based worms and also manual attacks conducted by an individual who is leveraging novel attack methods.
Owner:BAE SYST INFORMATION & ELECTRONICS SYST INTERGRATION INC
Malicious mobile code runtime monitoring system and methods
InactiveUS7058822B2Minimization requirementsEasy to updateMemory loss protectionDigital data processing detailsVisual BasicMonitoring system
Owner:FINJAN LLC
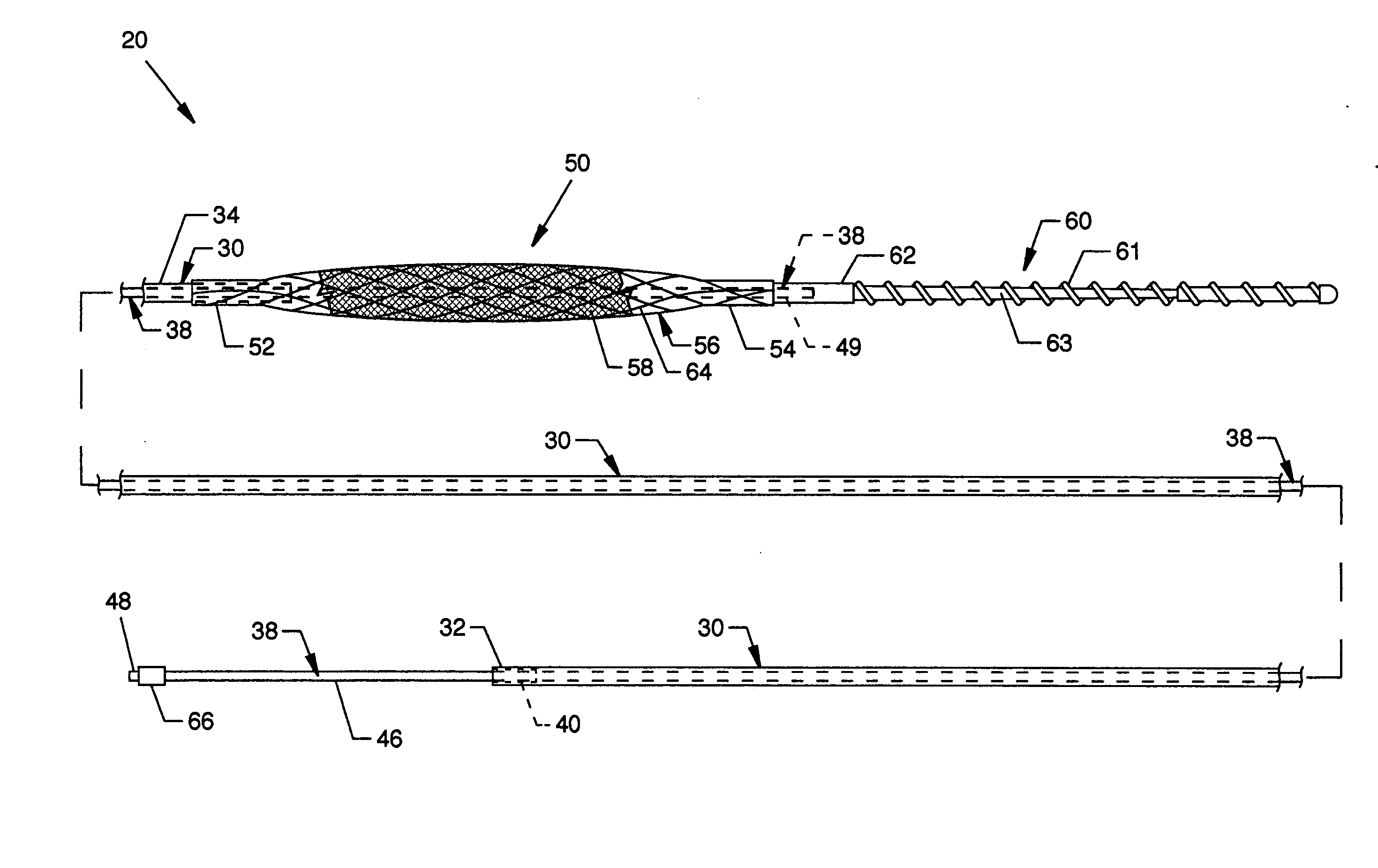
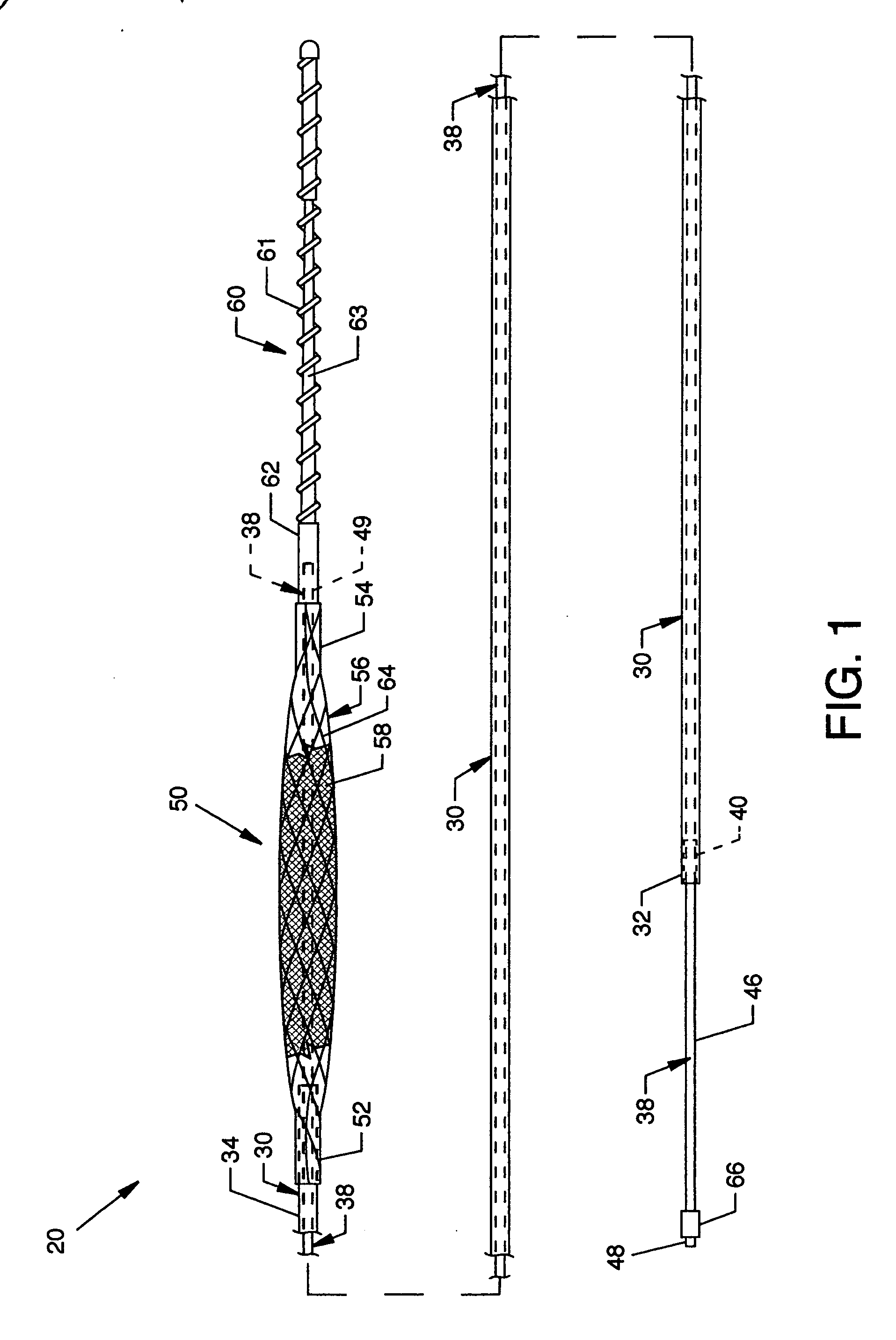
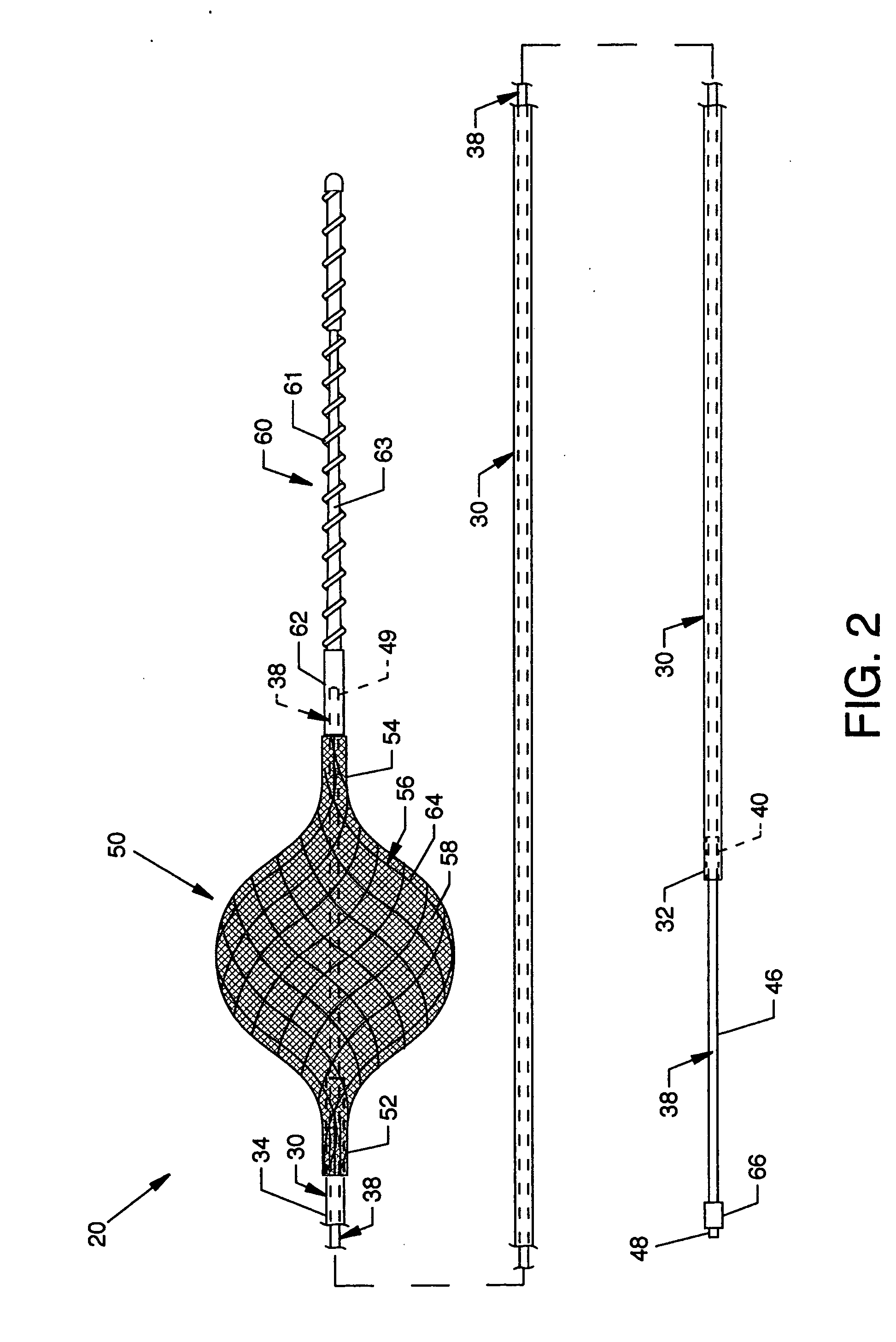
Guidewire having deployable sheathless protective filter
InactiveUS20050021075A1Reduce the potential for damageAvoid damageGuide wiresSurgeryFiberEngineering
A protective system or apparatus for use in vascular procedures includes a tubular guidewire, a control cable slidable within the tubular guidewire, and a sheathless filter. The control cable is attached to a distal end of the sheathless filter and the tubular guidewire is attached to a proximal end of the sheathless filter. Selective displacement of the control cable radially expands the sheathless filter to create a proximal exterior convex primary filter surface that is positionable downstream from a site of a vascular procedure. The sheathless filter also presents a distal interior concave secondary filter surface. Preferably, the sheathless filter is constructed of a braided wire framework in the form of a tube over which woven polymer fibers or strands are applied to create a filter mesh having a softer filter surface.
Owner:MEDRAD INC.
Behavior-based host-based intrusion prevention system
InactiveUS20040143749A1Memory loss protectionError detection/correctionMonitoring systemIntrusion prevention system
A method of protecting a system from attack that includes monitoring processes running on a system, identifying behavior of the processes and attributes of the processes, grouping the processes into process sets based on commonality of attributes, and generating behavior control descriptions for each process set.
Owner:SYMANTEC CORP
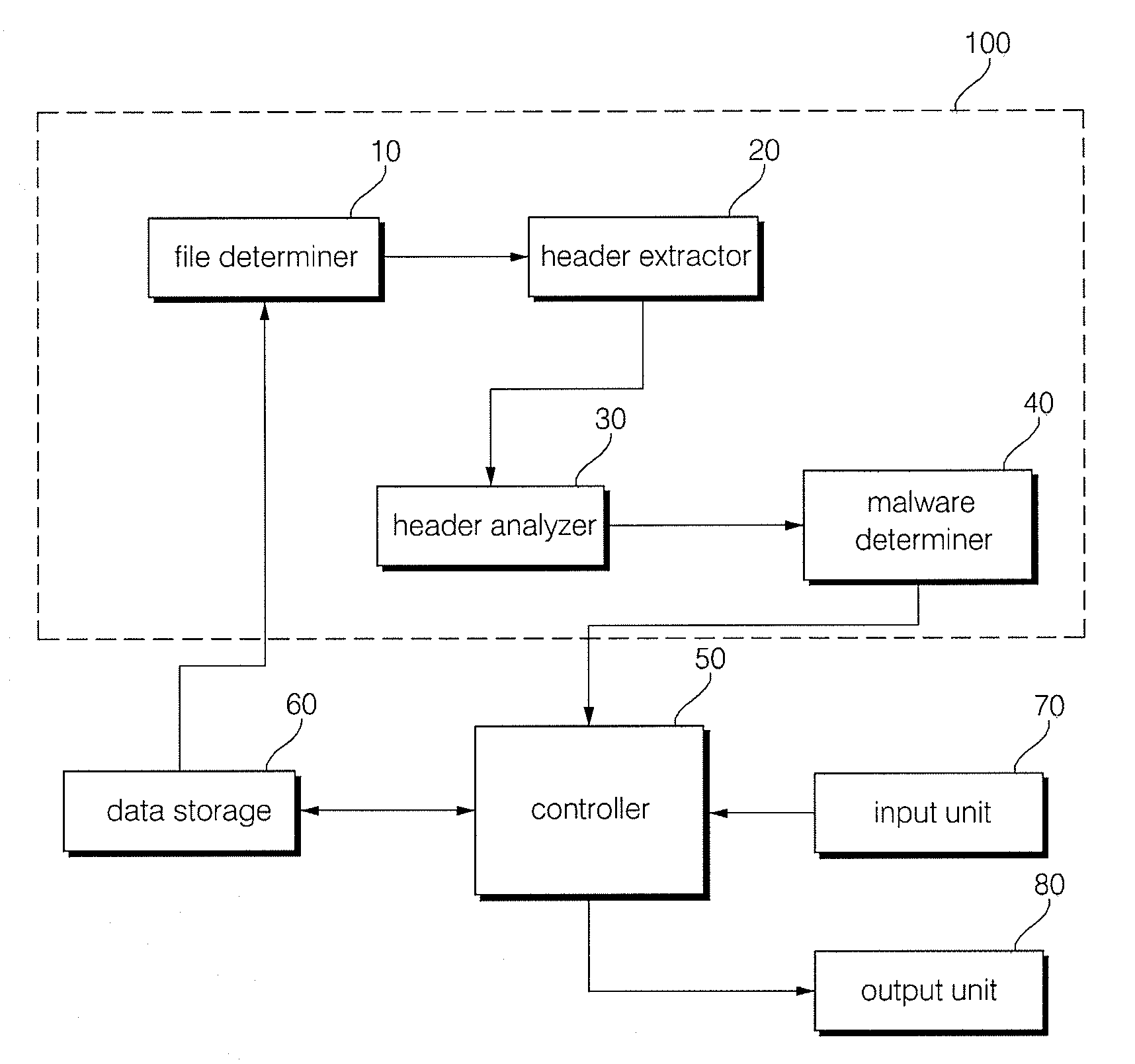
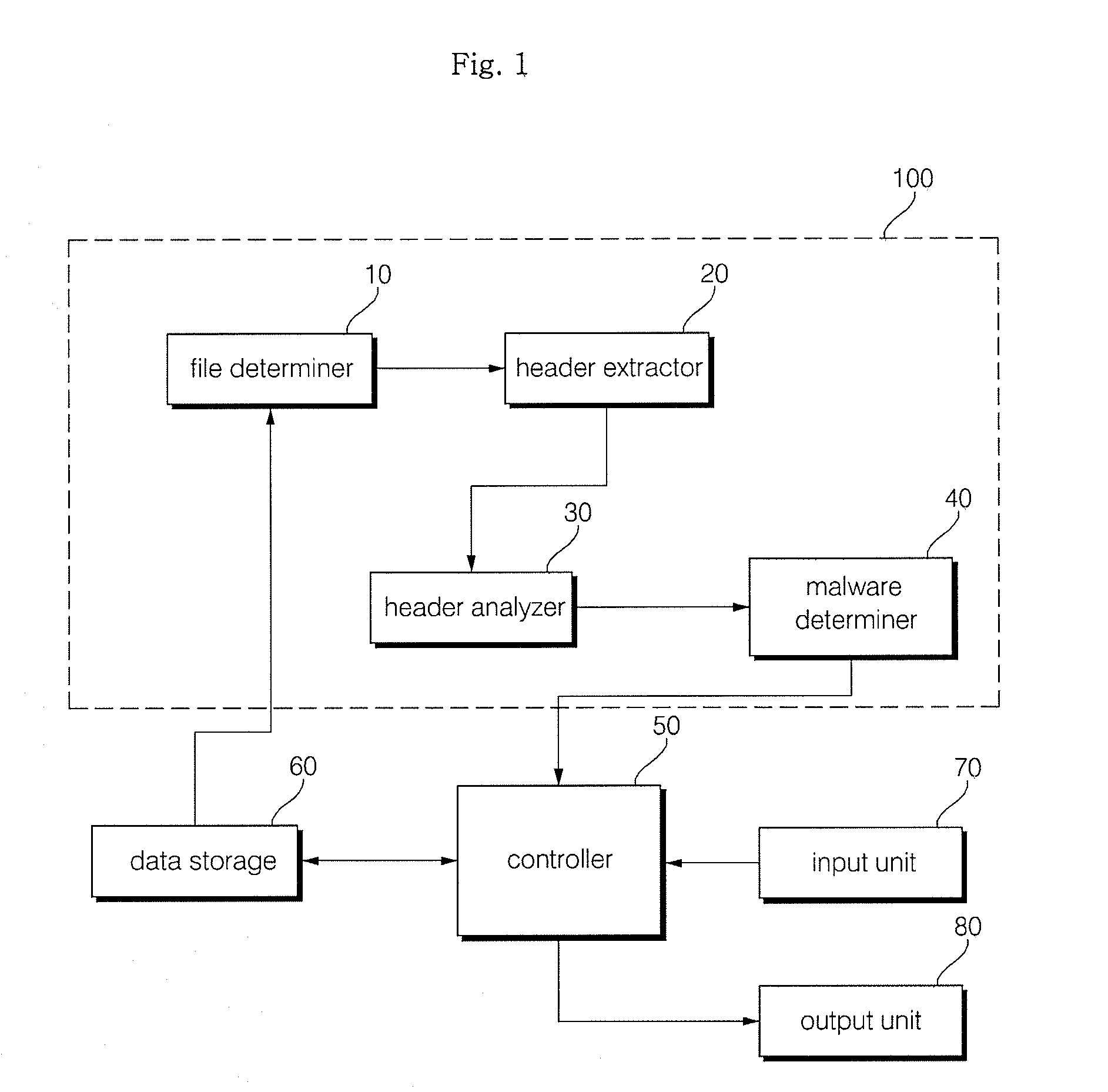
Method and apparatus for malware detection
InactiveUS20090133125A1Shorten detection timeImprove security levelMemory loss protectionUnauthorized memory use protectionMalwareProtection system
The present invention relates to an apparatus and method for detecting malware. The malware detection apparatus and method of the present invention determines whether a file is malware or not by analyzing the header of an executable file. Since the malware detection apparatus and method can quickly detect presence of malware, it can shorten detection time considerably. The malware detection apparatus and method can also detect even unknown malware as well as known malware to thereby estimate and determine presence of malware. Therefore, it is possible to cope with malware in advance, protect a system with a program, and increase security level remarkably.
Owner:ELECTRONICS & TELECOMM RES INST
Reconfigurable control architectures and algorithms for electric vehicle wireless energy transfer systems
InactiveUS20130062966A1Flexibility in design and implementationWithout riskCharging stationsTransformersElectric power transmissionEnergy transfer
A control architecture for electric vehicle wireless power transmission systems that may be segmented so that certain essential and / or standardized control circuits, programs, algorithms, and the like, are permanent to the system and so that other non-essential and / or augmentable control circuits, programs, algorithms, and the like, may be reconfigurable and / or customizable by a user of the system. The control architecture may be distributed to various components of the wireless power system so that a combination of local or low-level controls operating at relatively high-speed can protect critical functionality of the system while higher-level and relatively lower speed control loops can be used to control other local and system-wide functionality.
Owner:WITRICITY CORP
Entangled single-wall carbon nanotube solid material and methods for making same
InactiveUS6899945B2Material nanotechnologySynthetic resin layered productsCross-linkSolvent evaporation
Buckyrock is a three-dimensional, solid block material comprising an entangled network of single-wall carbon nanotubes (SWNT), wherein the block comprises greater than 75 wt % SWNT. SWNT buckyrock is mechanically strong, tough and impact resistant. The single-wall carbon nanotubes in buckyrock form are present in a random network of individual single-wall carbon nanotubes, SWNT “ropes” and combinations thereof. The random network of the SWNT or SWNT ropes can be held in place by non-covalent “cross-links” between the nanotubes at nanotube contact points. In one embodiment, SWNT buckyrock is made by forming a SWNT-water slurry, slowly removing water from the slurry which results in a SWNT-water paste, and allowing the paste to dry very slowly, such that the SWNT network of the SWNT-water paste is preserved during solvent evaporation. Buckyrock can be used in applications, such as ballistic protection systems, involving light-weight material with mechanical strength, toughness and impact resistance.
Owner:RICE UNIV
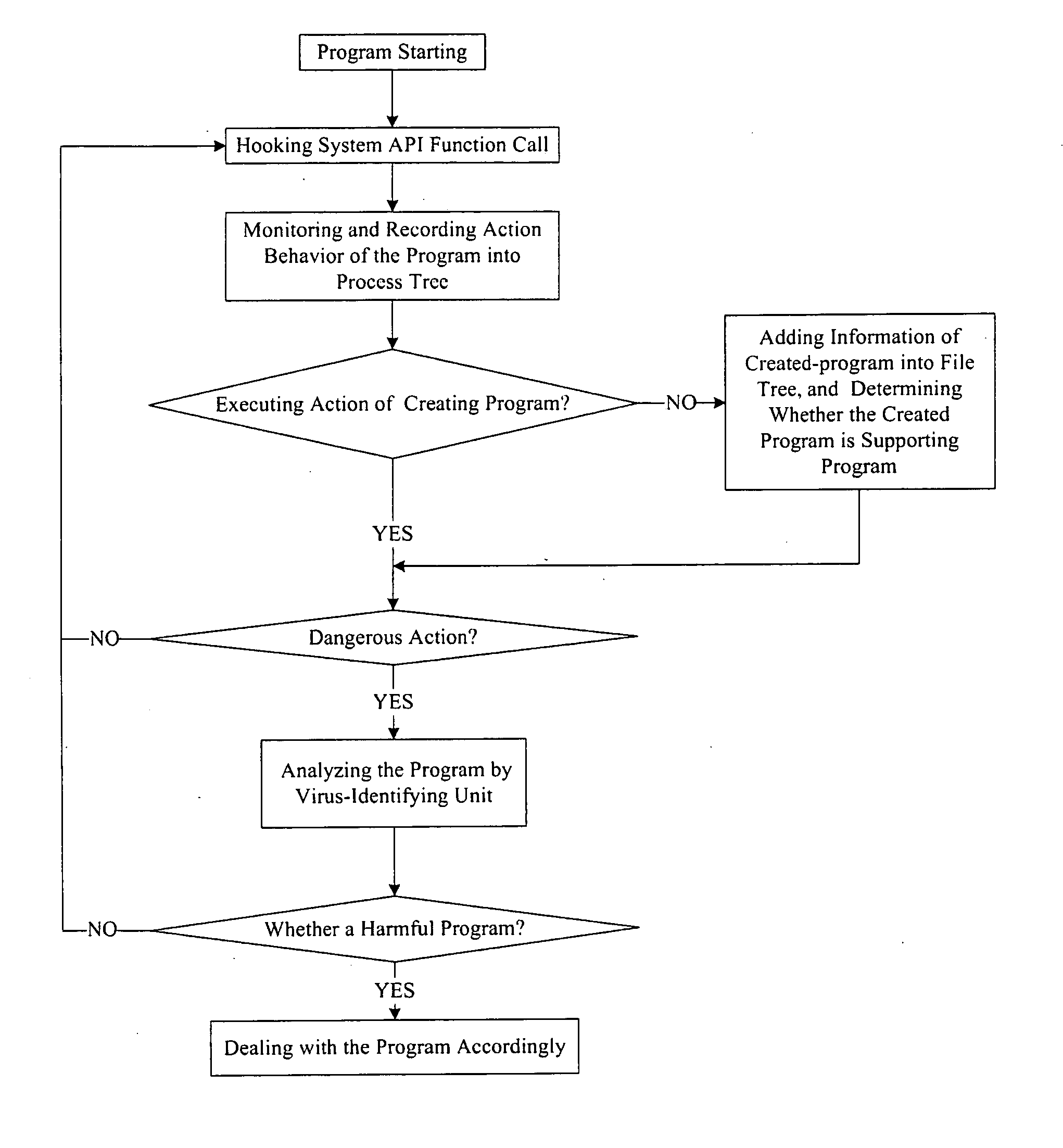
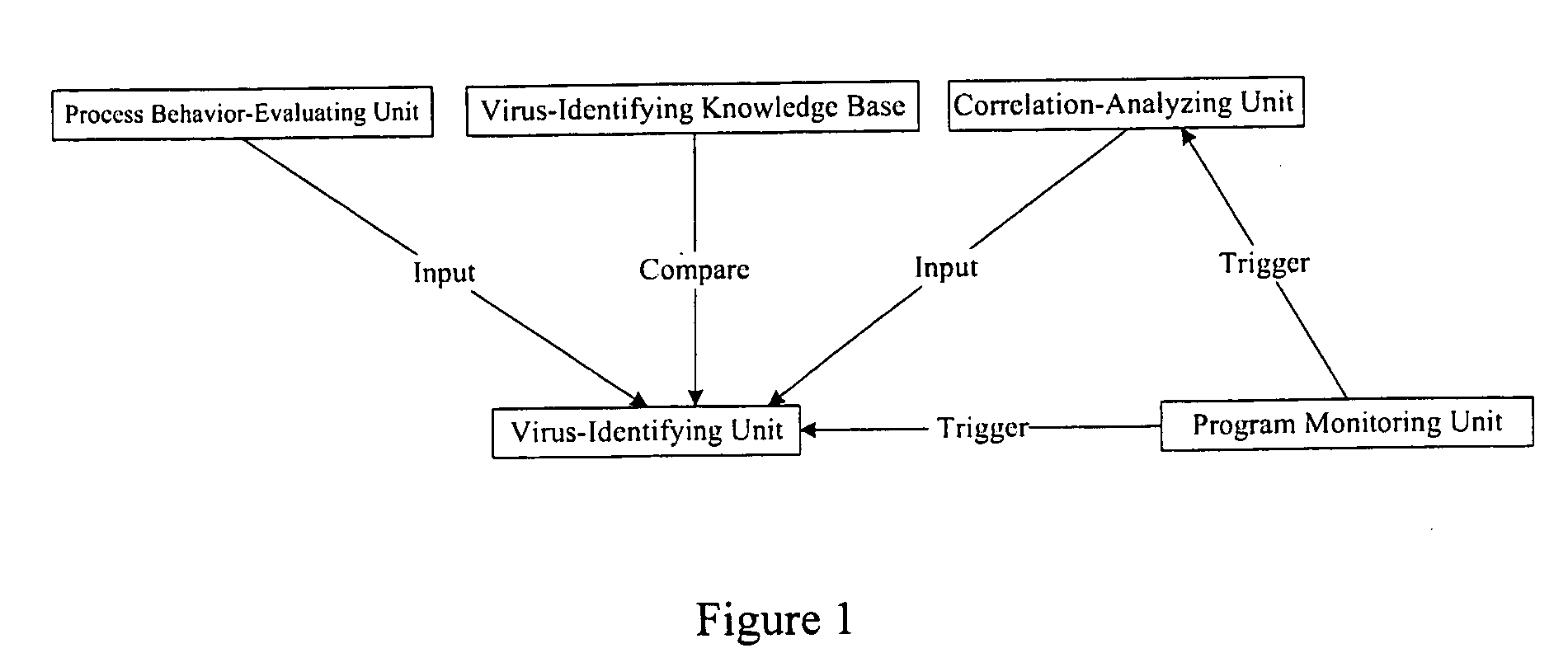
Antivirus protection system and method for computers
InactiveUS20080066179A1Reduce in quantitySimple methodMemory loss protectionUnauthorized memory use protectionProcess behaviorProgram behavior
The example embodiments herein relate to an antivirus protection system and method for computers based on program behavior analysis. The antivirus protection system may comprise: a Process Behavior-Evaluating Unit for identifying the programs existing in the user's computers and classifying them into normal programs and suspect programs; a Program-Monitoring Unit for monitoring and recording the actions and / or behaviors of programs; a Correlation-Analyzing Unit for creating correlative trees and analyzing the correlations of actions and / or behaviors of programs, the correlative trees comprising a process tree and a file tree; a Virus-Identifying Knowledge Base, comprising a Program-Behavior Knowledge Base and a Database of Attack-Identifying Rules; a Virus-Identifying Unit for comparing captured actions and / or behaviors to the information in the Virus-Identifying Knowledge Base to determine whether the program is a virus program. With the techniques of certain example embodiments, it may be possible to increase efficiency and reduce the need to upgrade virus codes after viruses become active, while also effectively blocking unknown viruses, Trojans, etc.
Owner:FUJIAN EASTERN MICROPOINT INFO TECH
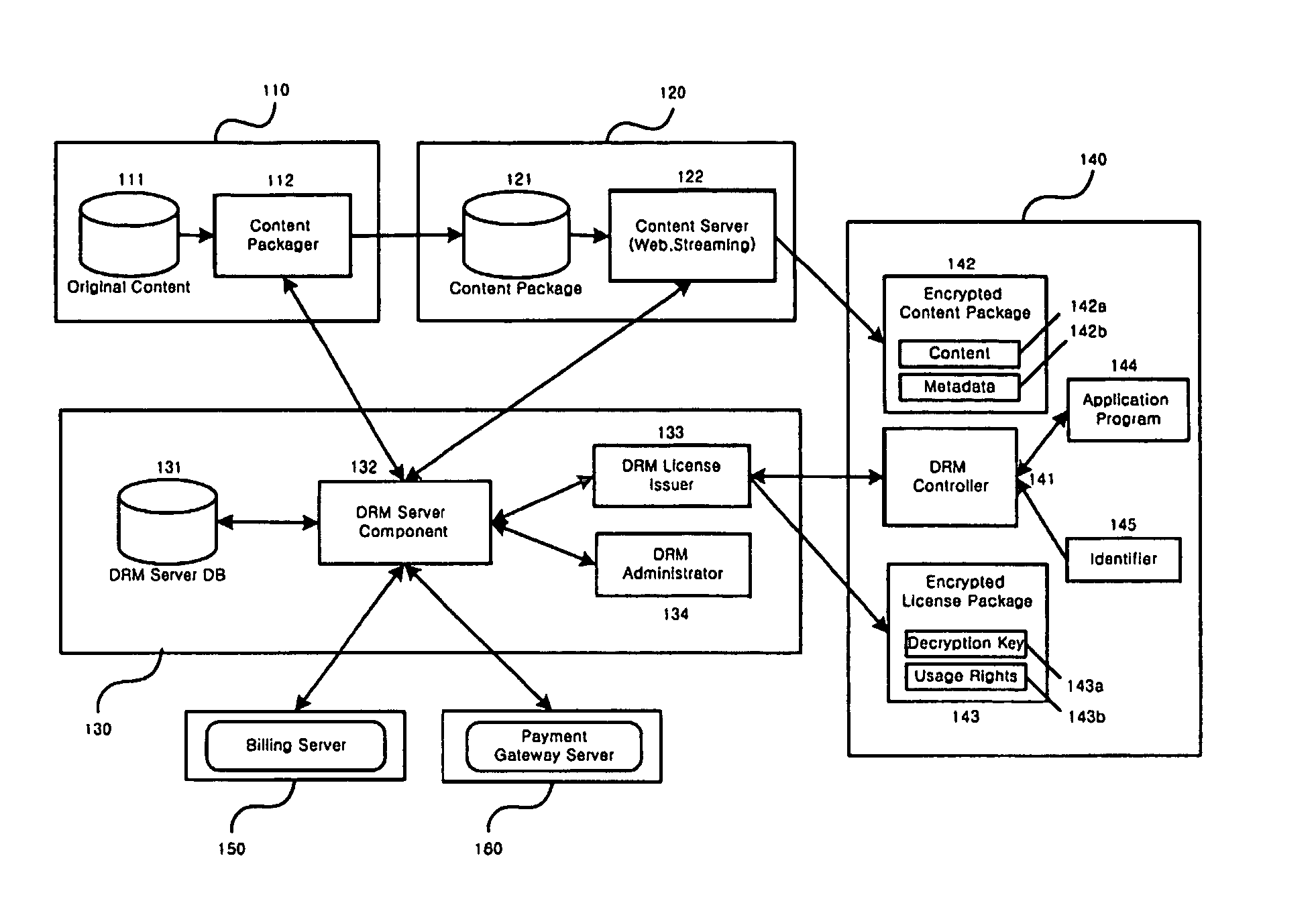
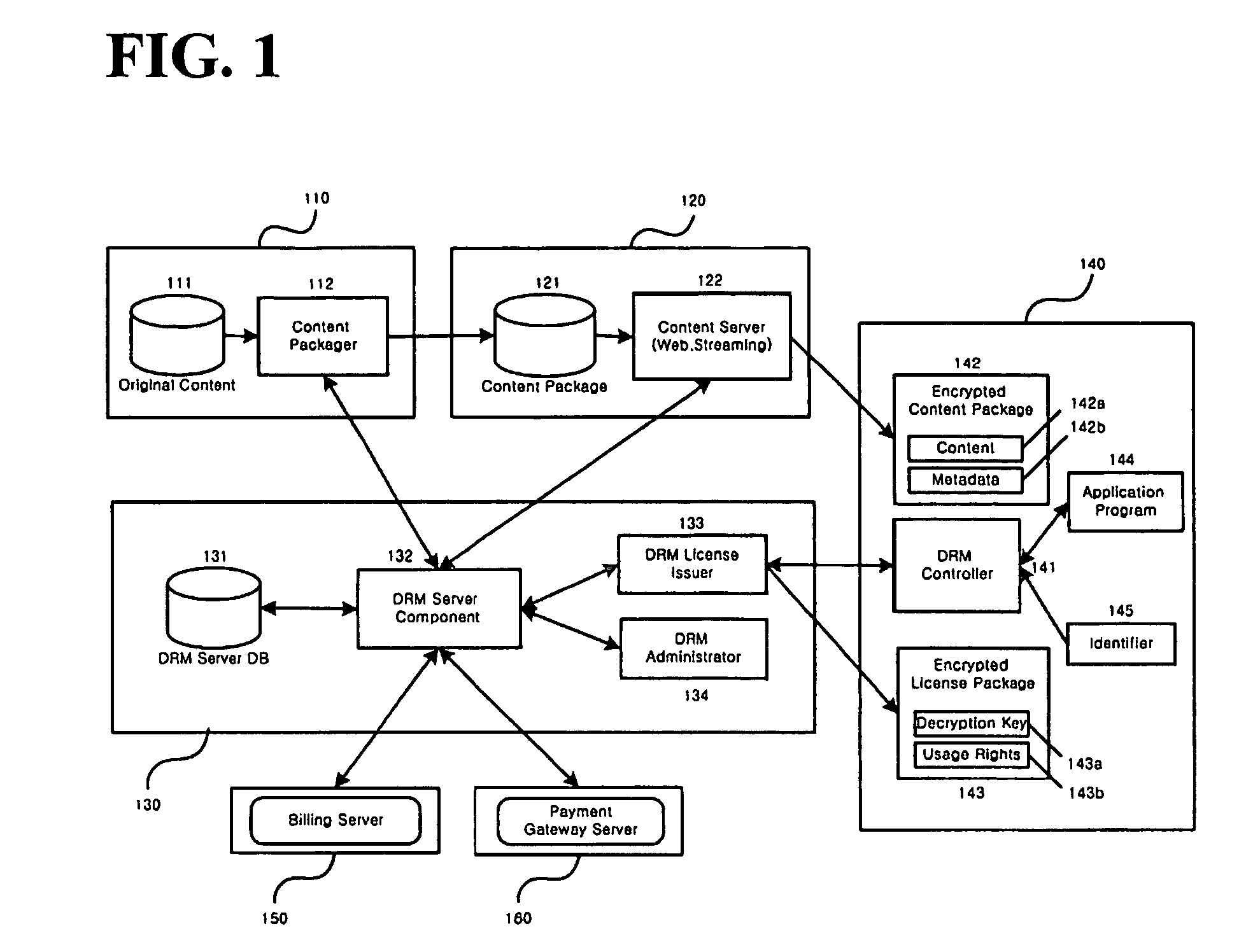
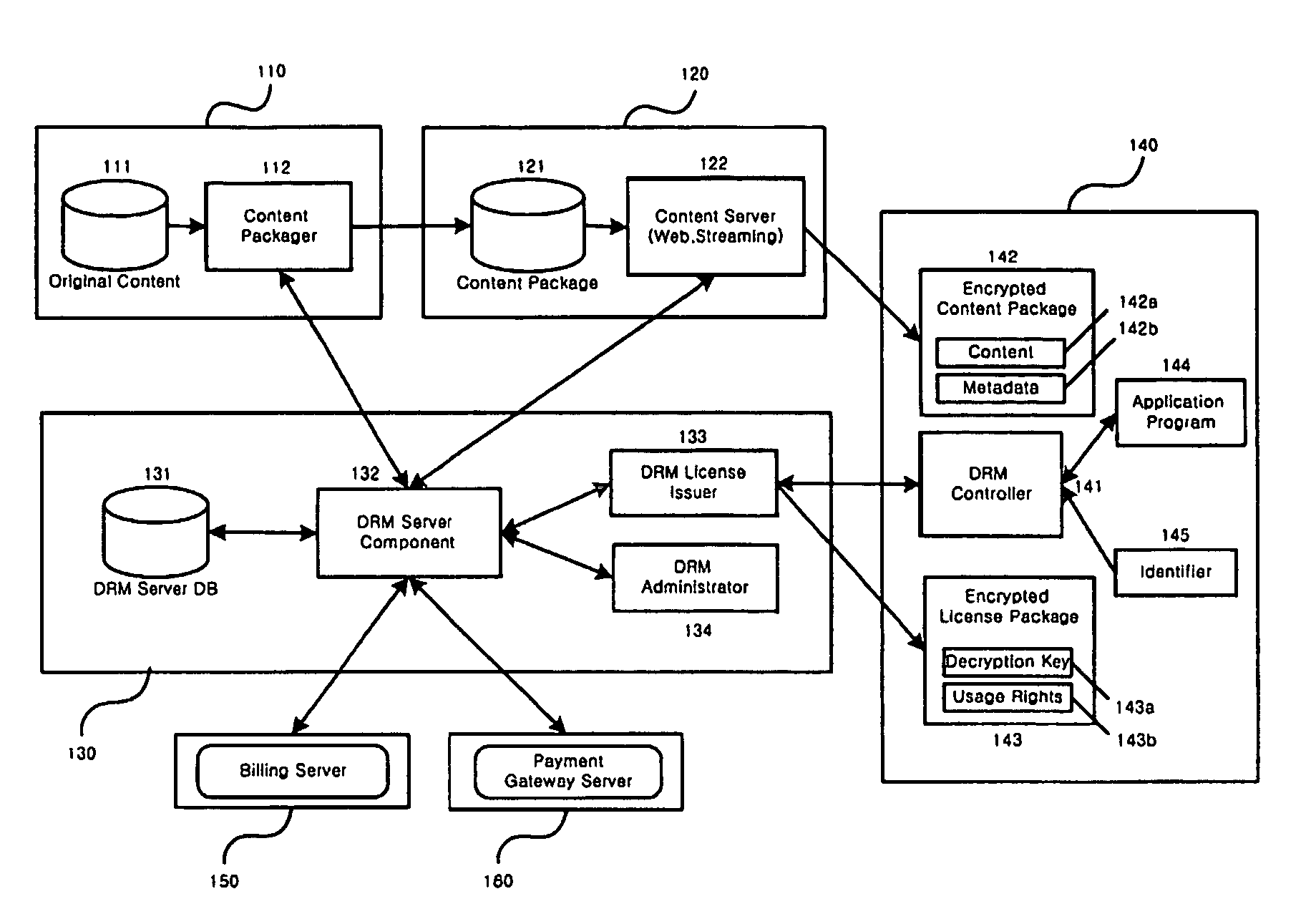
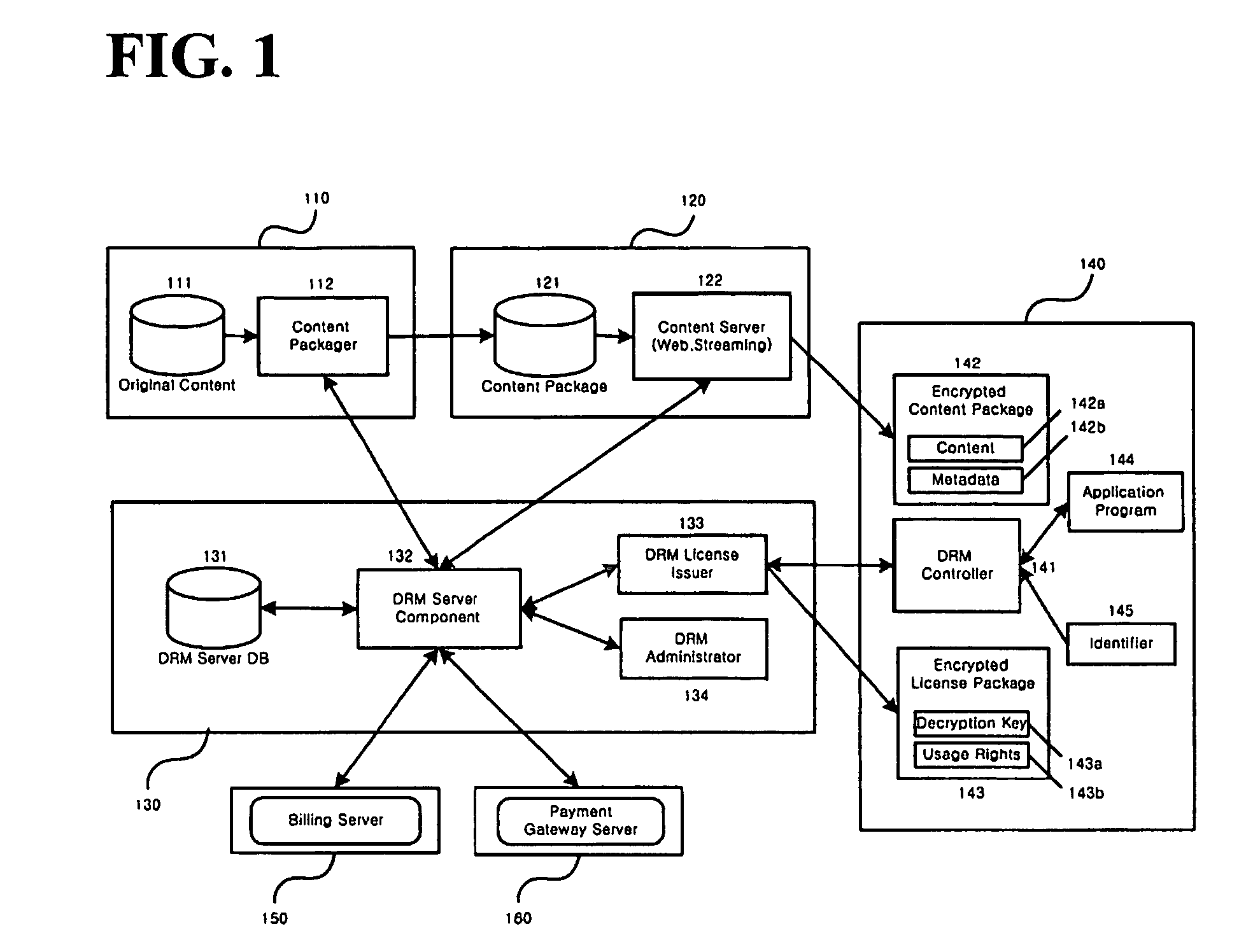
Method and system for the information protection of digital content
ActiveUS20050086501A1Add supportImprove securityDigital data processing detailsUser identity/authority verificationData packDigital content
The present invention relates to the information protection of digital content transferred by streaming and download service through wire or wireless Internet network. The information protection system in this invention suggests a drastic prevention method of copyrights infringement such as illegal copy and unauthorized distribution of digital content, by using of the encryption, decryption, distribution, and authentication technologies. This invention suggests the control technology of general viewer program, not the specific viewer program for information protection, using a network filter driver for streaming and file system filter driver for download service. The main function of network and file system filter driver is the filtering operation such as a hooking, changing, decrypting, and restoring of message and data packet, and transferring to the viewer program. The main idea and technology of this invention suggest higher secure and efficient digital information protection system for live / VOD / HTTP streaming and download service.
Owner:WOO JE HAK +6
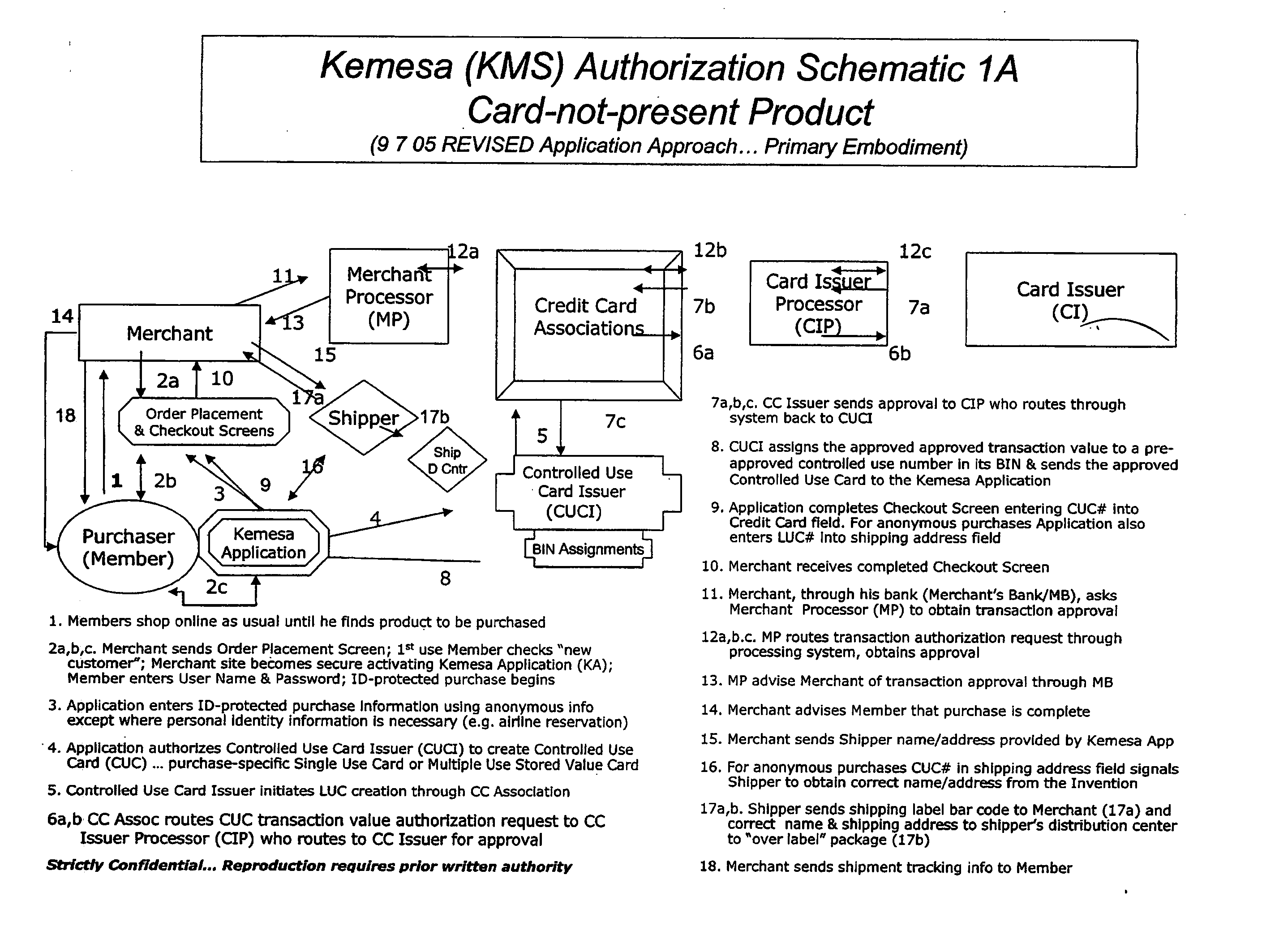
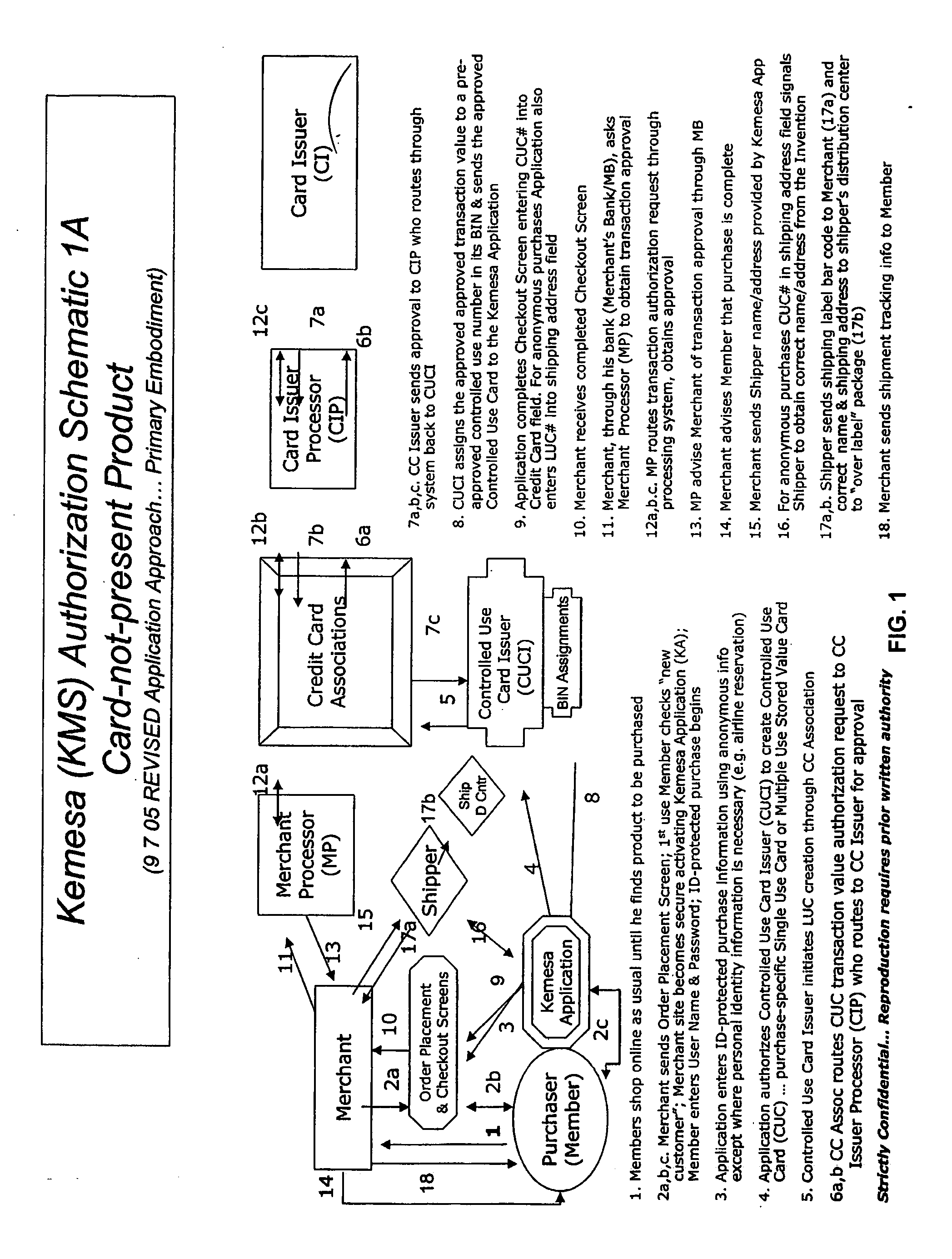
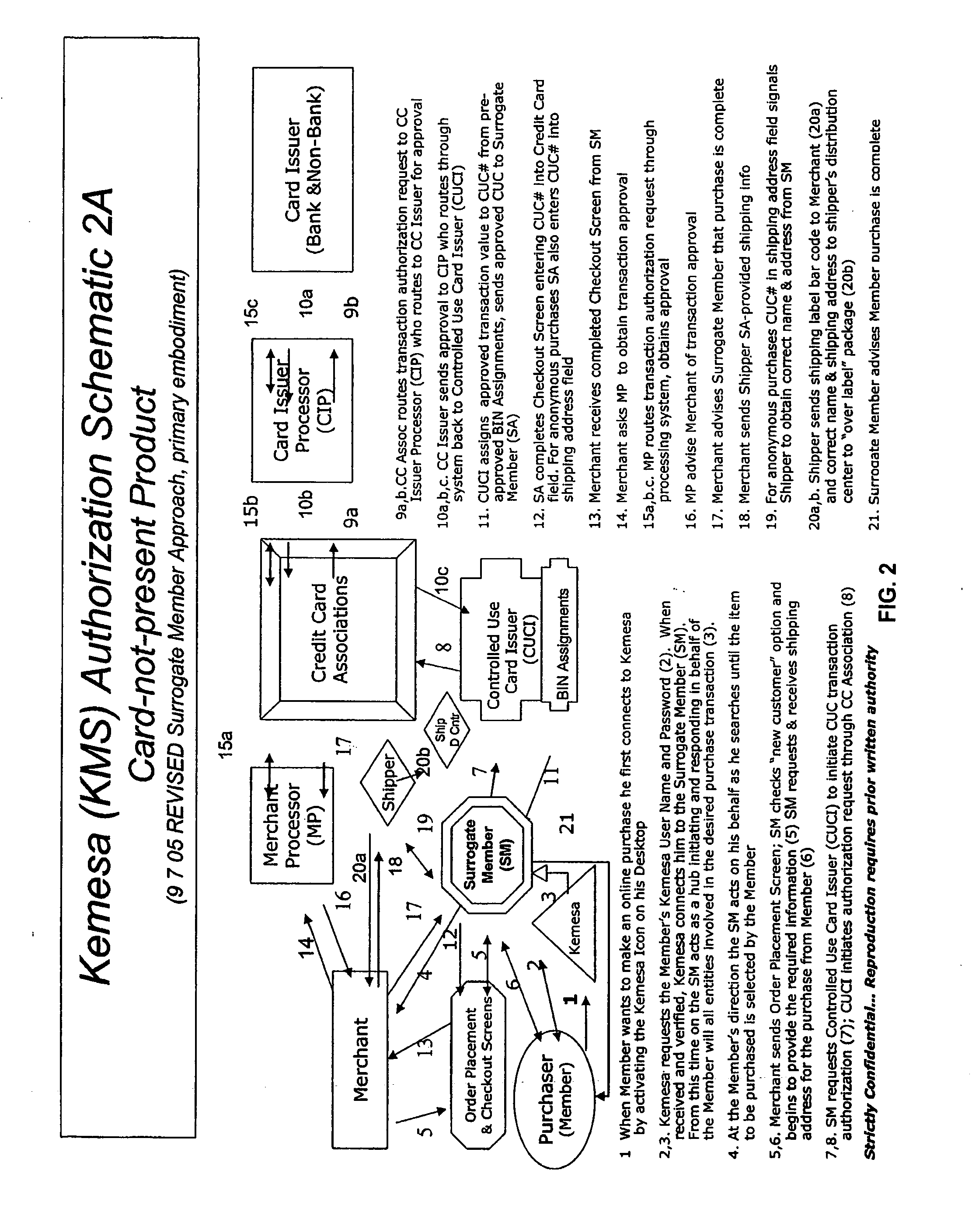
Identity theft and fraud protection system and method
ActiveUS20070083460A1Prevent theftMaximum anonymityFinanceDigital data protectionCredit cardEmail address
A system and method for preventing personal identity theft when making online and offline purchases requires a purchaser to first subscribe and become a member user by registering and providing relevant personal identity information. Once registered, the member is assigned a user name and a password. The subscribing member's personal identity information is then encrypted and stored at one or more highly secure locations. The ID protection system obtains a controlled use card (CUC) through a CUC issuer on behalf of the member for use to make each purchase transaction. The CUC is anonymous with respect to user (member) identity and may be a purchase-specific single-use card or a multiple-use stored value card with no traceable connection to any other financial account. When the member makes a secure online purchase, the system software enters anonymous information (i.e. not revealing the member's real name, email address, billing information, etc.) on the merchant's order placement screen, except in instances where the member's real identity information is required (e.g. airline tickets). The merchant receives the completed checkout screen, obtains credit approval through a credit card association, and sends the shipping information to a shipper which independently obtains the correct shipping name and address from the ID protection system prior to shipping the purchased product(s).
Owner:VIPR SYST +1
Method and system for the information protection of digital content
ActiveUS7484103B2Digital data processing detailsAnalogue secracy/subscription systemsDigital contentNetwork packet
The present invention relates to the information protection of digital content transferred by streaming and download service through wire or wireless Internet network. The information protection system in this invention suggests a drastic prevention method of copyrights infringement such as illegal copy and unauthorized distribution of digital content, by using of the encryption, decryption, distribution, and authentication technologies. This invention suggests the control technology of general viewer program, not the specific viewer program for information protection, using a network filter driver for streaming and file system filter driver for download service. The main function of network and file system filter driver is the filtering operation such as a hooking, changing, decrypting, and restoring of message and data packet, and transferring to the viewer program. The main idea and technology of this invention suggest higher secure and efficient digital information protection system for live / VOD / HTTP streaming and download service.
Owner:WOO JE HAK +6
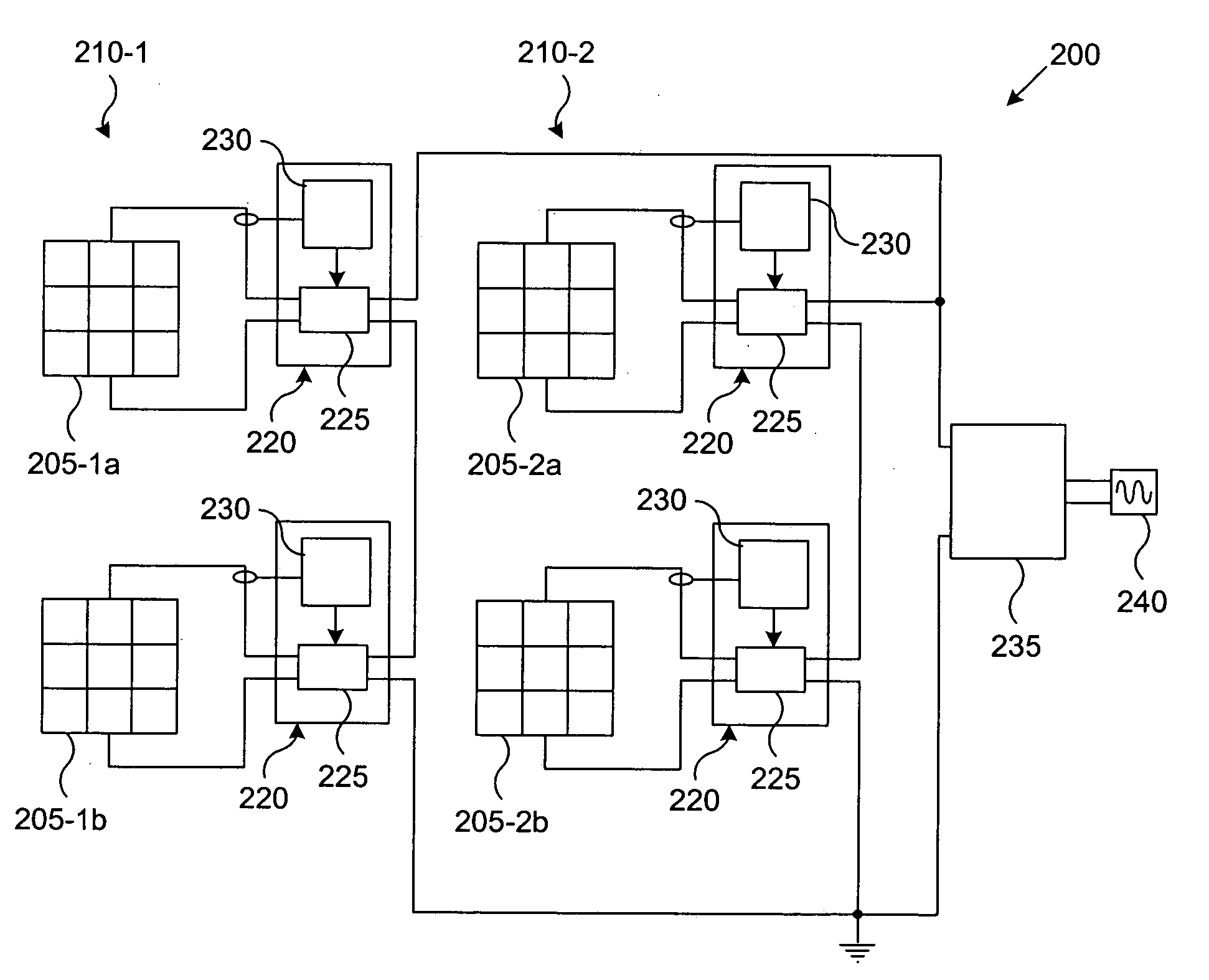
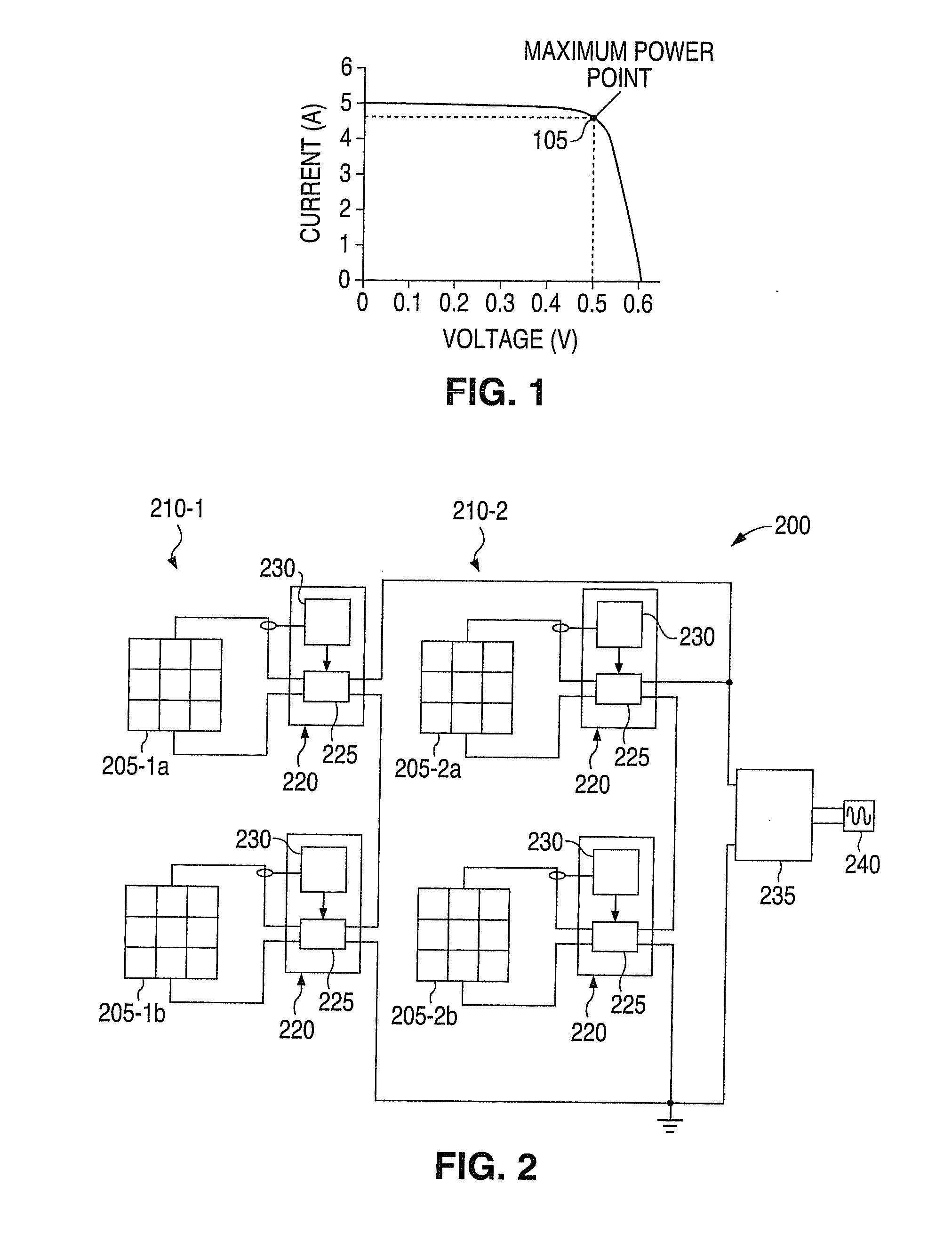
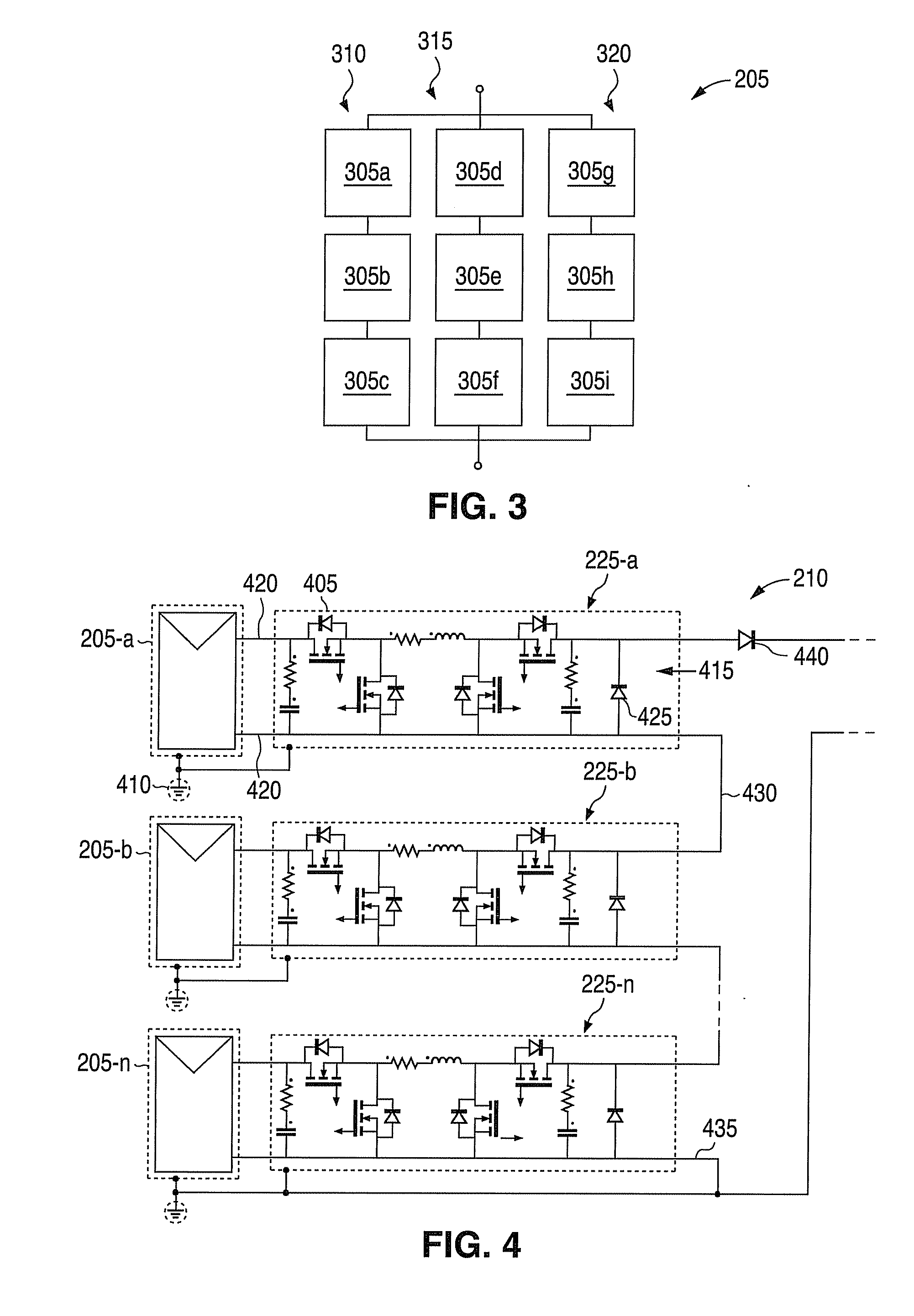
System and method for over-Voltage protection of a photovoltaic string with distributed maximum power point tracking
InactiveUS20100288327A1PV power plantsEmergency protective circuit arrangementsVoltage converterElectric power system
A string over-voltage protection system and method for arrays of photovoltaic panels. The system and method includes a device for use in a photovoltaic array power system. The device includes a voltage converter. The voltage converter is adapted to be coupled to a photovoltaic panel in a string of photovoltaic panels. The device also includes a string over-voltage protection circuit. The string over-voltage protection circuit is coupled to the voltage converter. The string over-voltage protection circuit senses a string voltage and determines if a string over-voltage condition exists. Additionally, the string over-voltage protection circuit is configured to disable the voltage converter in the event of a string over-voltage condition.
Owner:NAT SEMICON CORP
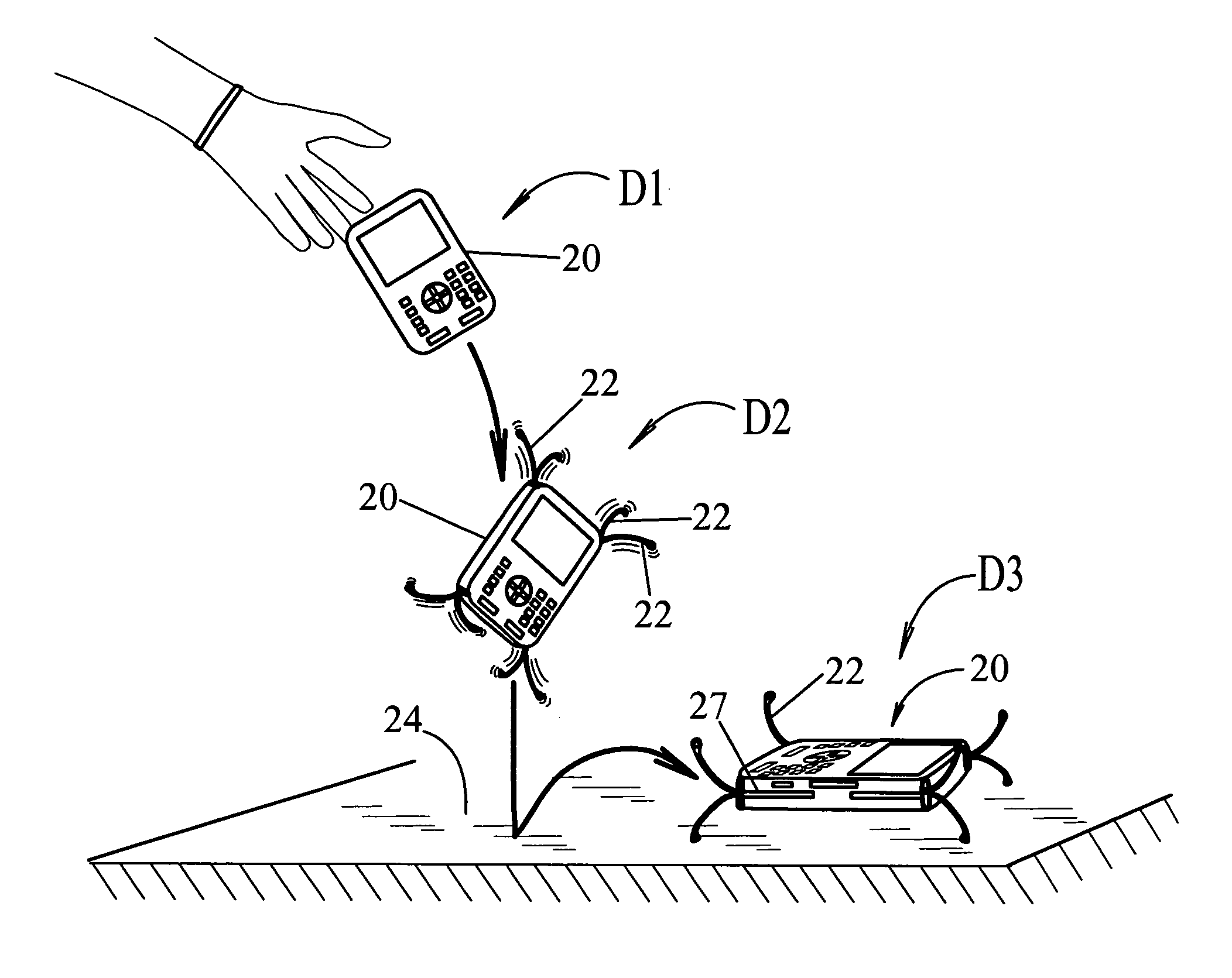
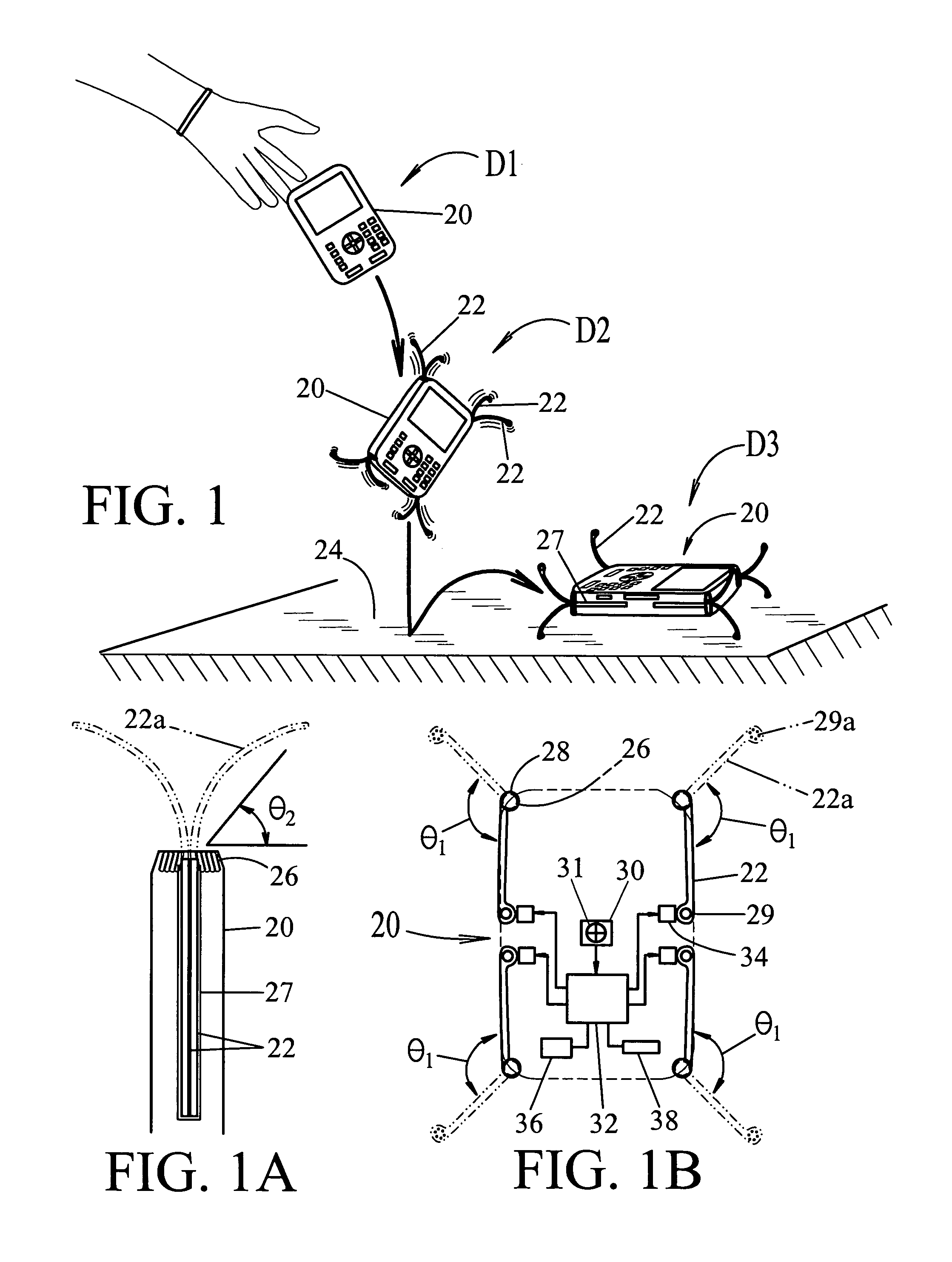
Active impact protection system
An impact protection system for a portable device, comprising a housing 20 with a plurality of impact absorbing arms 22 attached to housing 20 and having a retracted position and an extended position; an extension spring 26 connected to each arm provides forceful extension of the arms from their retracted position to their extended position; a free-fall detection sensor 30 defined within housing 20 for detecting dangerous free-fall conditions of the portable device and providing a signal to an activation controller 32 which is responsive to the free-fall detection sensor 30 and connected to the impact absorbing arms 22, whereby the arms are extended from their retracted position to their extended position upon detection of dangerous free-fall conditions to provide impact protection for the portable device.
Owner:RAGNER GARY DEAN
Tag multiplication
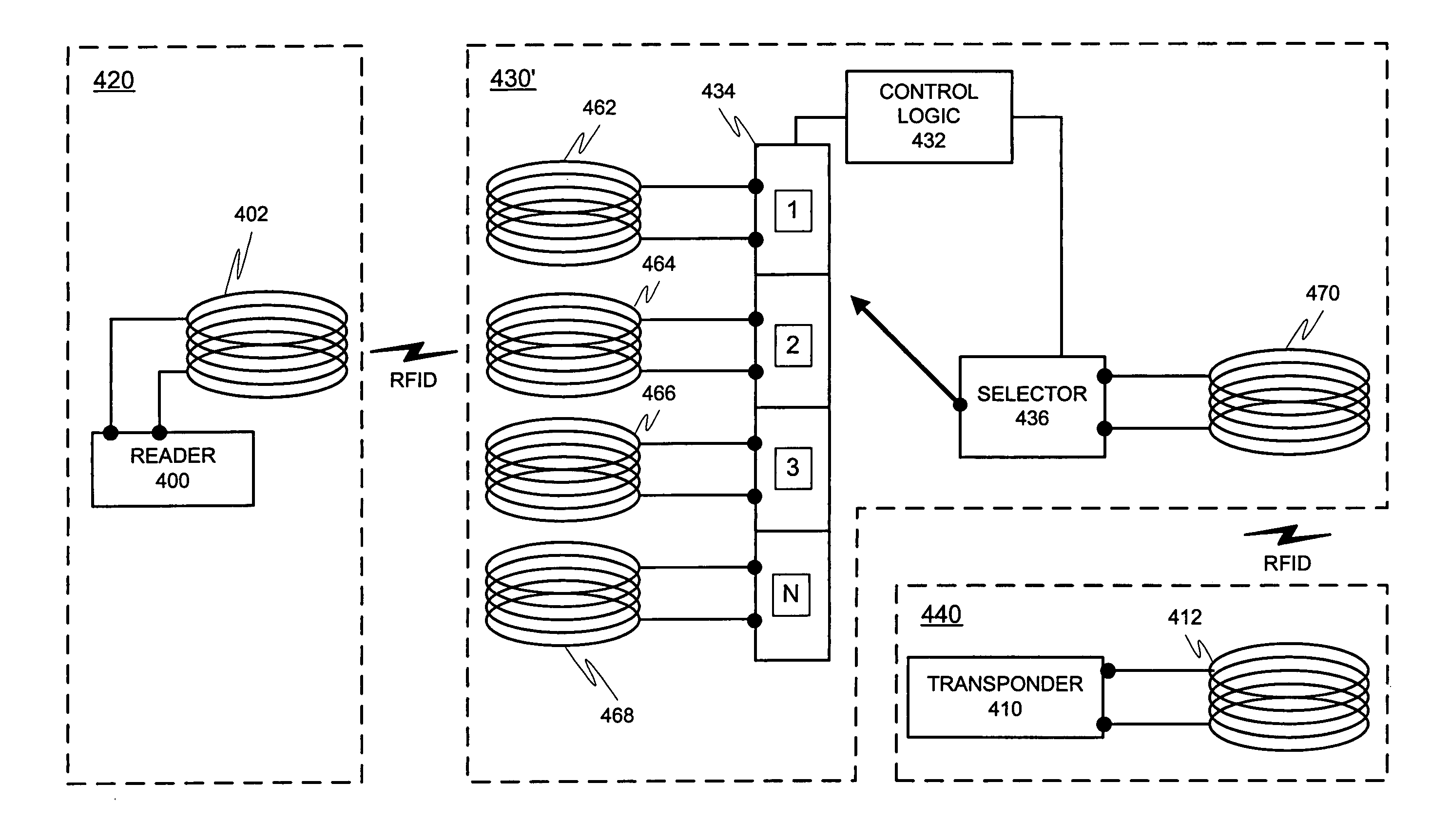
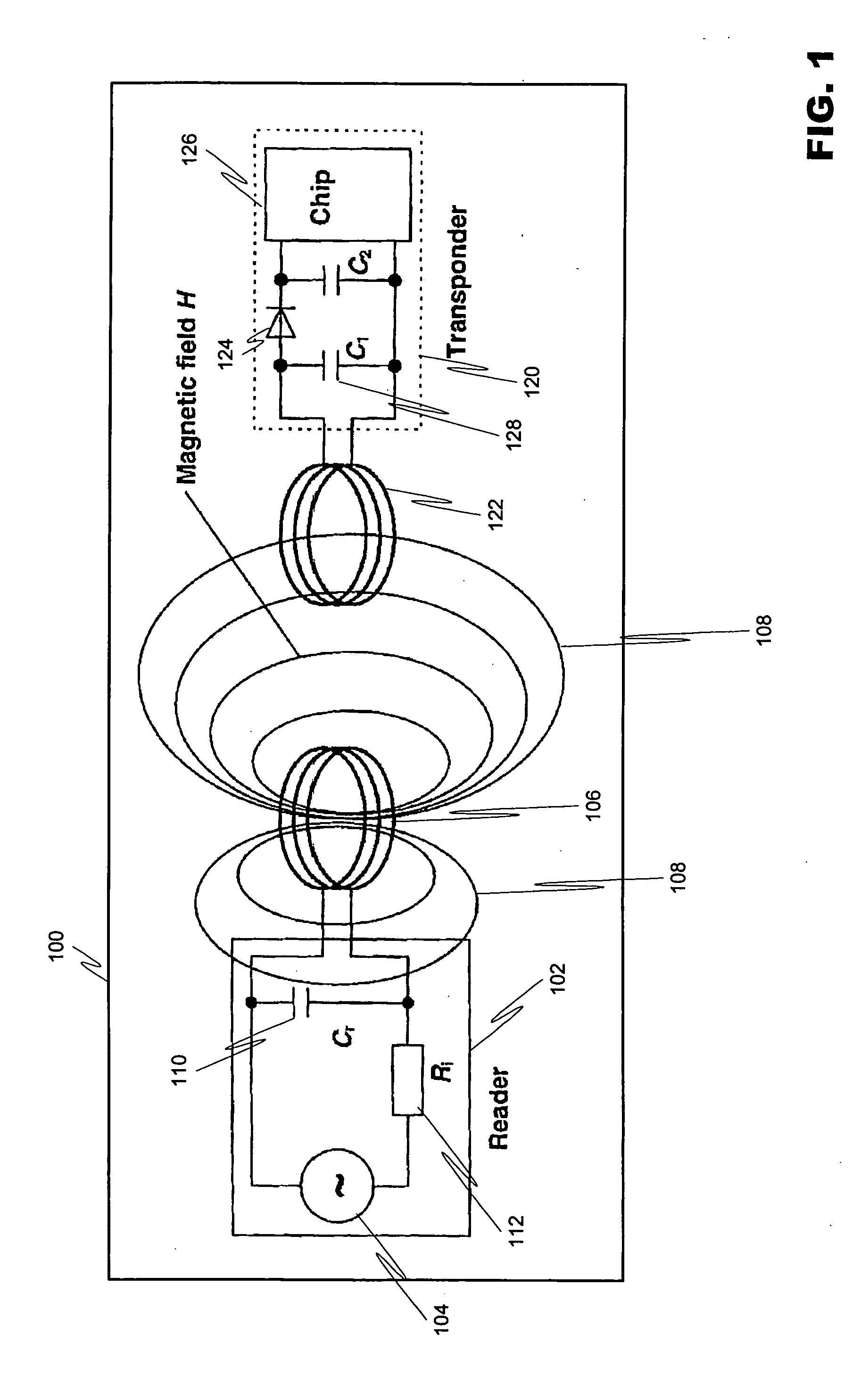
ActiveUS20070008140A1Effective communication rangeFacilitate communicationNear-field transmissionResonant long antennasSmart antennaDisplay device
An intelligent antenna system for extending the effective communication range of a machine-readable passive tag. The system includes intelligence that allows one of a plurality of extension antennas to be active at any given time in order to both facilitate communications and safeguard the system. The machine-readable tag and antenna system may be embedded in a structure. In a further embodiment, the system may include multiple passive tags that are active in correspondence to a display or advertisement currently being exhibited. The system includes means for operatively coupling a designated machine-readable tag to the embedded antenna network previously described. In a further embodiment of the invention, the machine-readable tag includes combined RFID and NFC functionality where both RFID listening functions and NFC read-write functions are to be available in the same NFC communications logic, where different RFID listening applications require different minimum separation distances between the reader and the NFC communications logic. The NFC communications logic chip is selectively connected to at least three antenna coils, the first antenna coil for operating with a first minimum separation distance between the reader and the NFC communications logic, the second antenna coil for operating with a second minimum separation distance between the reader and the NFC communications logic, and the third antenna coil for reading and writing. In a further embodiment of the invention, matching circuits are included with the respective antenna coils to tune the resonant frequency of the RLC oscillator circuit for each antenna coil in the NFC communications logic.
Owner:III HLDG 3
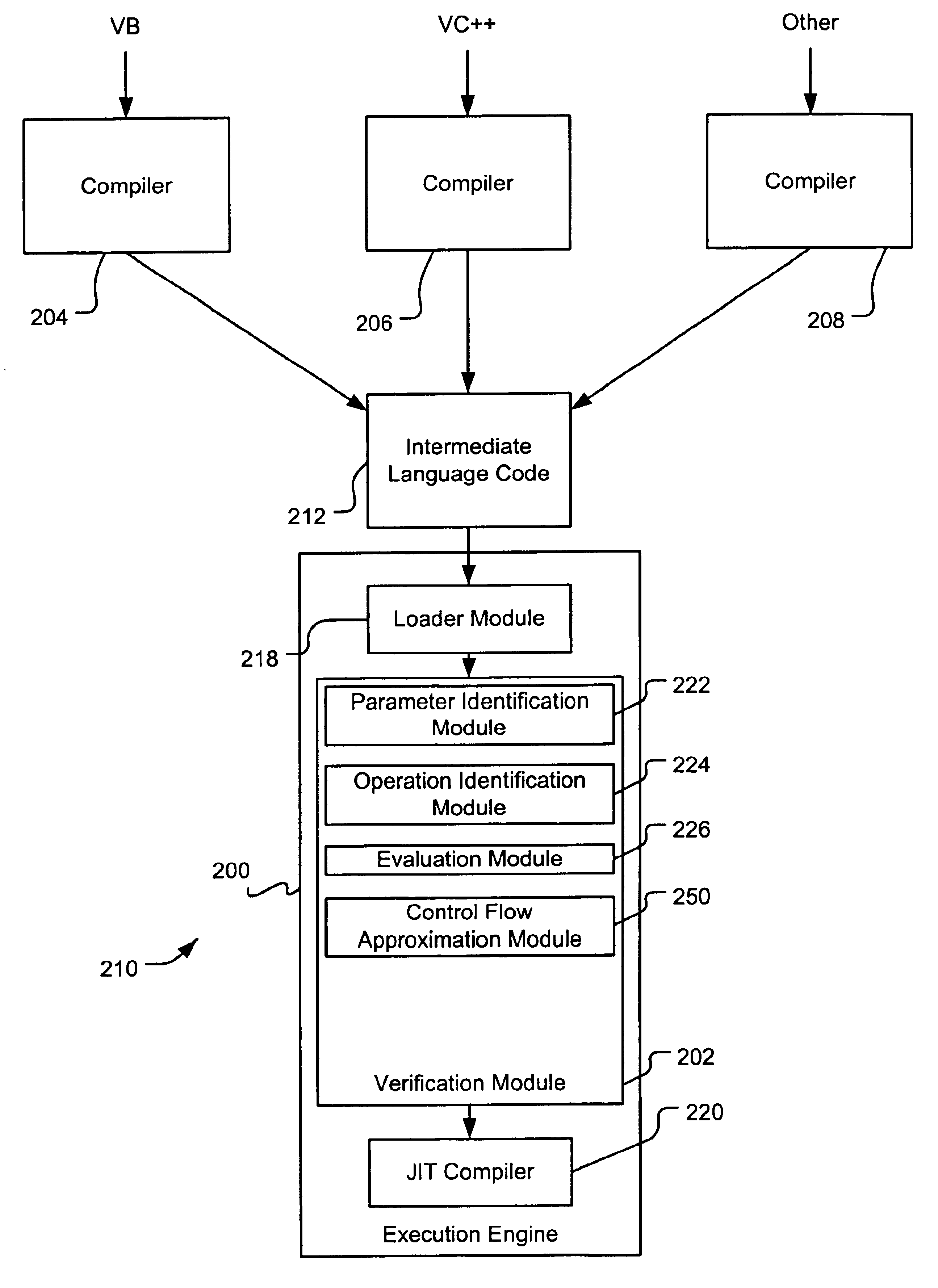
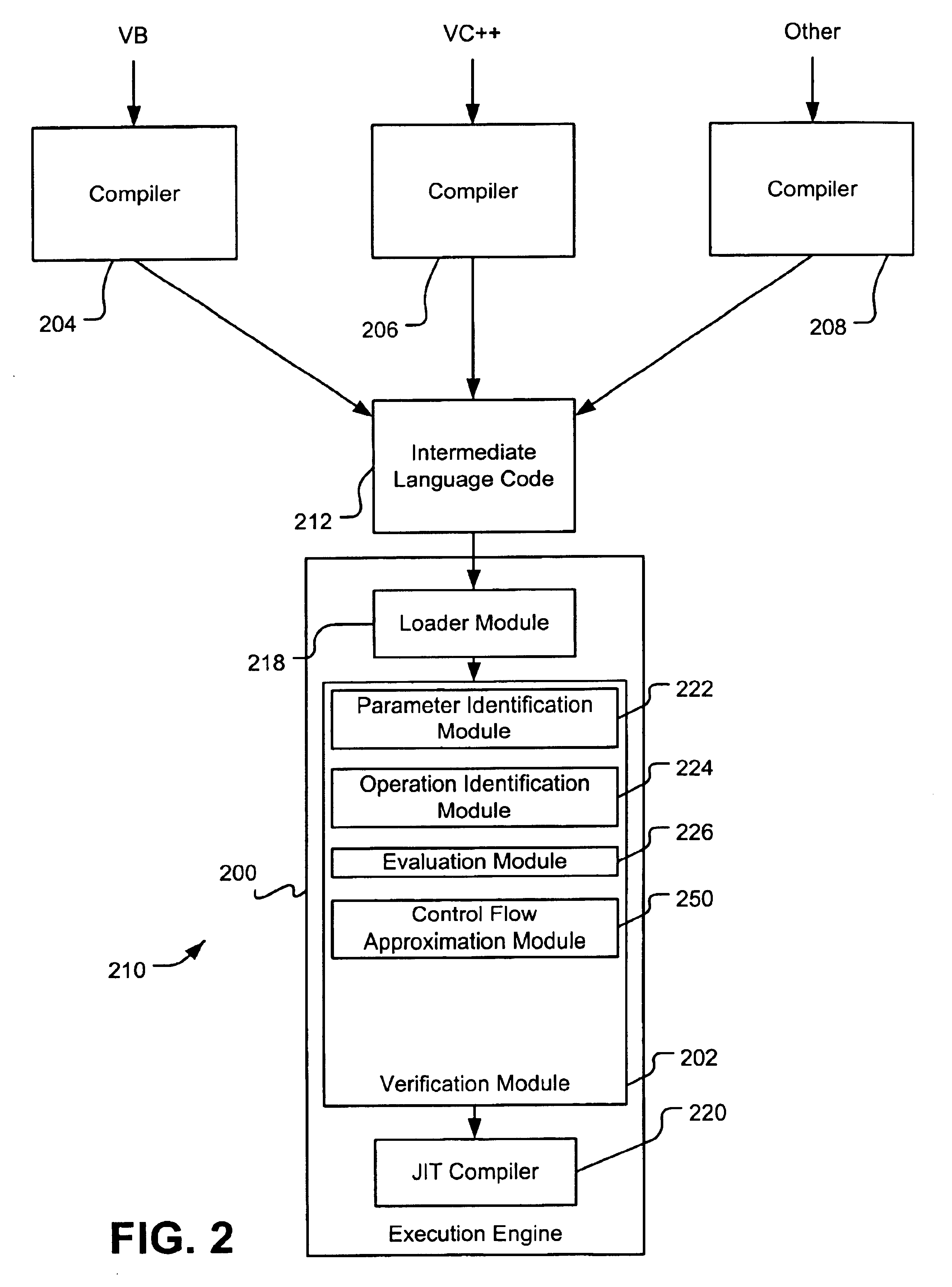
Verifying intermediate language code
InactiveUS6851108B1Existing techniqueRich varietyProgram loading/initiatingMemory systemsLanguage constructComputerized system
A verification module evaluates intermediate language code to verify that the code is type safe before passing the code for execution. Code that is not deemed type safe can cause execution errors, corrupt the runtime environment in which the code is executing, or cause unauthorized access to protected system resources. As such, the verification module protects a computer system from intentional or inadvertent breaches of the computer system's defenses. The verification module verifies the type safety of intermediate language code that supports significant high-level language constructs prohibited by verification modules in the prior art. One exemplary verification module verifies intermediate language code that includes one or more reference-based parameter, such as a pointer (or reference), a value class containing pointers, a RefAny parameter, or a nested pointer.
Owner:MICROSOFT TECH LICENSING LLC
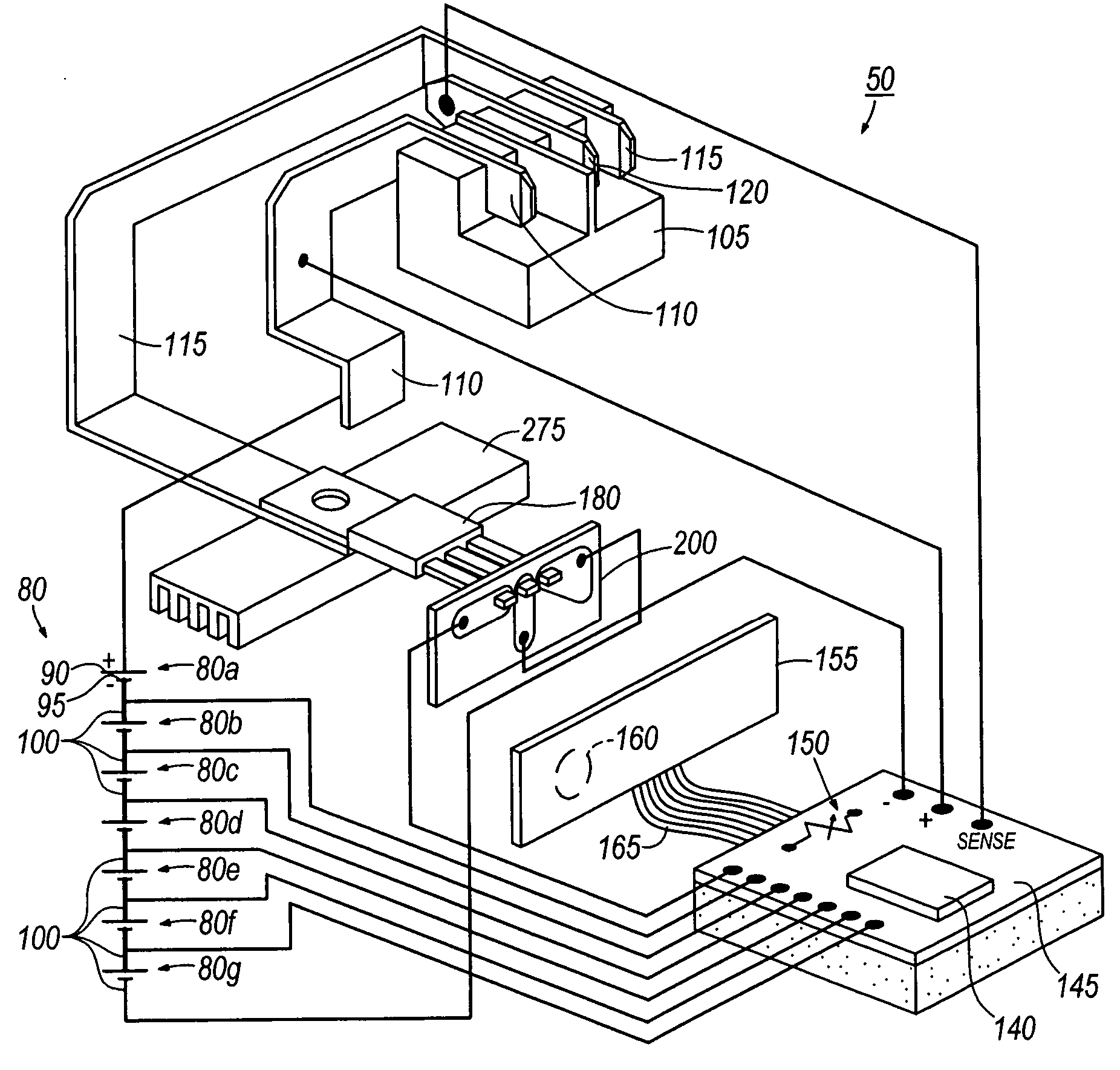
Method and system for battery protection
ActiveUS20050007068A1Solution to short lifeIrreversible damageCharge equalisation circuitEmergency protective circuit arrangementsElectrical devicesEngineering
A system and method for battery protection. In some aspects, a method of conducting an operation including a battery pack, includes the acts of monitoring a first battery pack condition at a first monitoring rate, determining when a second battery pack condition reaches a threshold, after the second battery pack condition reaches the threshold, monitoring the first battery pack condition at a second monitoring rate, the second monitoring rate being different than the first monitoring rate. In some aspects, a method of conducting an operation including a battery, the battery including a cell having a voltage, power being transferable between the cell and the electrical device, a controller operable to control a function of the battery pack, the controller being operable with a voltage at least one of equal to and greater than an operating voltage threshold, the cell being operable to selectively supply voltage to the controller, includes the act of enabling the controller to operate when the voltage supplied by the cell is below the operating voltage threshold.
Owner:MILWAUKEE ELECTRIC TOOL CORP
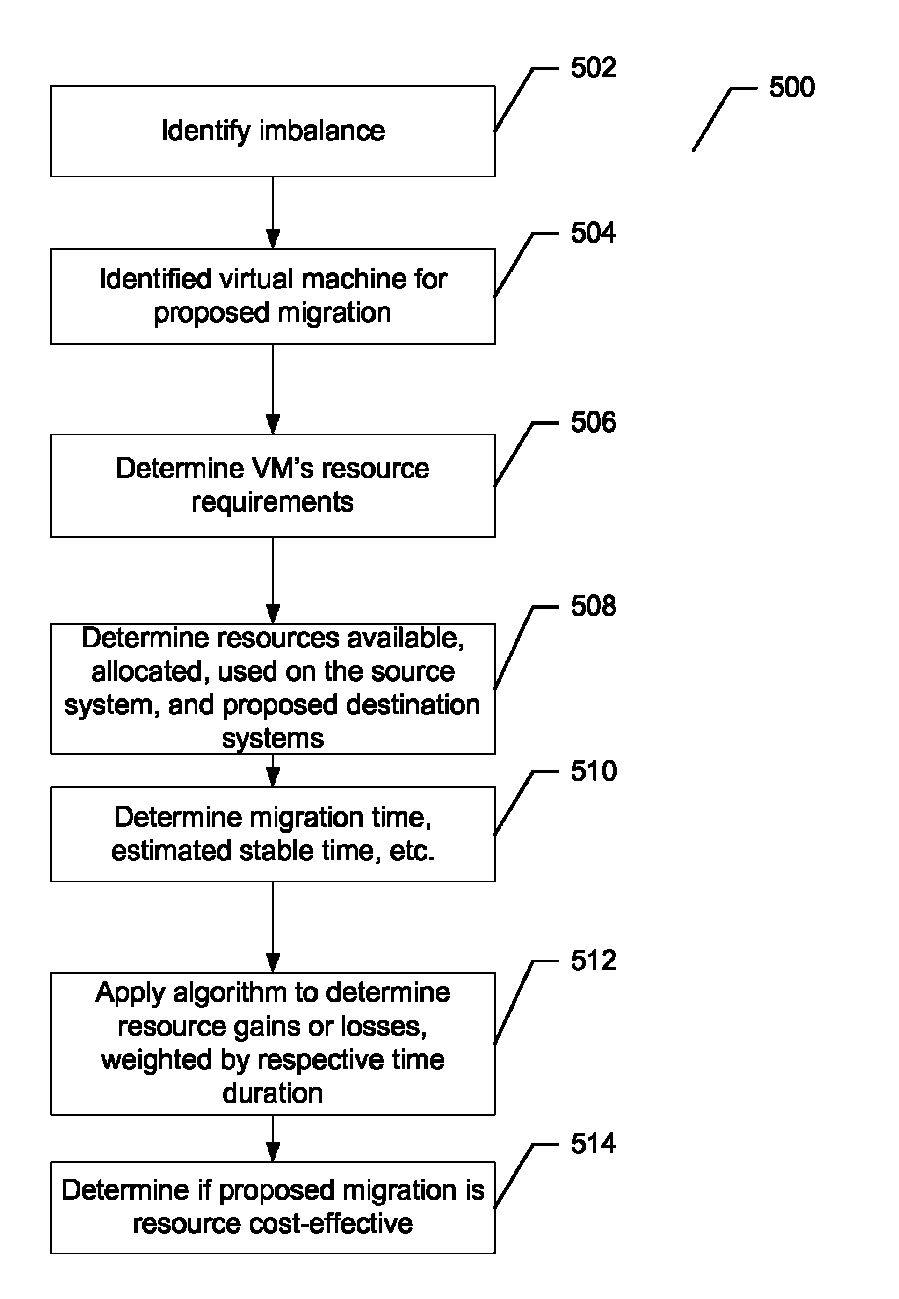
Method and system for determining a cost-benefit metric for potential virtual machine migrations
ActiveUS8095929B1Good for load balancingDigital computer detailsMultiprogramming arrangementsCost effectivenessProtection system
A cost-benefit metric for load balancing virtual machines is used to estimate a net gain in resource availability achieved by a proposed virtual machine migration. The cost-benefit metric can be used together with any other known metrics to evaluate candidate migrations. The metric takes into account stability of loads as well as migration cost, hence can protect a system from thrashing, i.e., frequently migrating virtual machines without gaining resource availability.
Owner:VMWARE INC
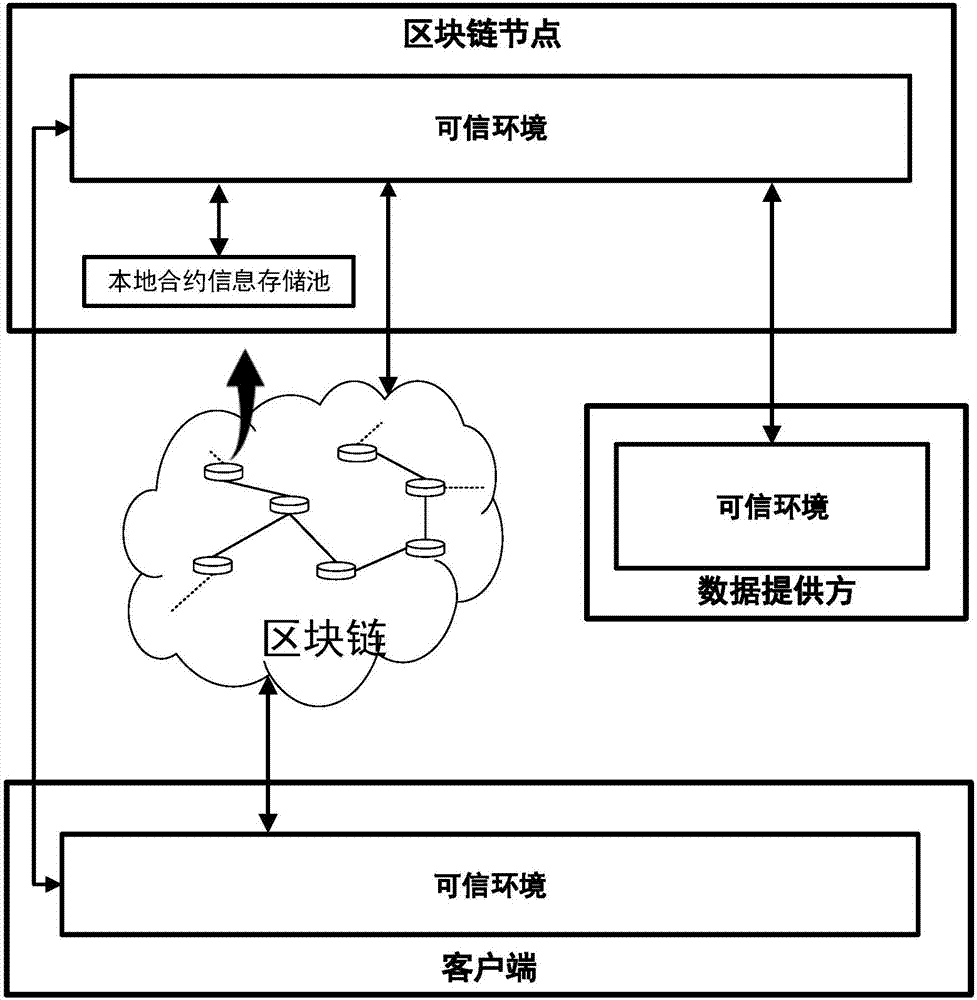
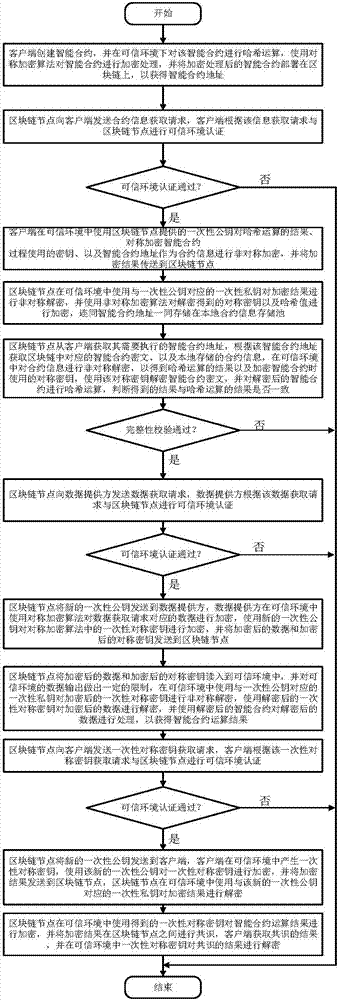
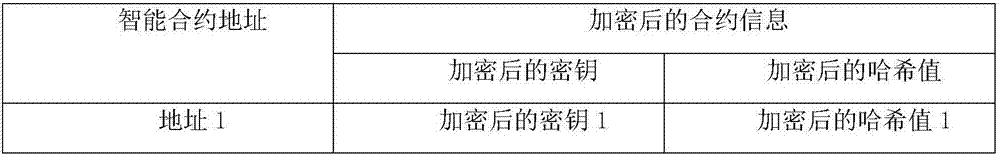
Smart contract protection method and system based on trusted environment
InactiveCN107342858ASolve the problem of smart contract versionSolve the problem of damage to rights and interestsKey distribution for secure communicationUser identity/authority verificationInformation processingInformation transmission
The invention discloses a smart contract protection system based on a trusted environment, including a client, block chain nodes, a data provider, a trusted environment, a non-trusted environment, a smart contract information processing module (A), a block chain node information transmission module (B) (such as a node interaction interface in the Ethereum), an input data transmission module (C), a smart contract execution module (D), a local contract information storage pool (E) and a block chain smart contract storage pool (F). The client is in communication connection with the block chain nodes. The data provider is in communication connection with the block chain nodes. The block chain nodes are in communication connection with one another. The technical problem that the copyright of smart contracts cannot be protected and the rights and interests of smart contract users are damaged due to the fact that the information of smart contracts may easily leak in the existing smart contract system and the technical problem that data may be stolen due to data leakage are solved.
Owner:武汉凤链科技有限公司
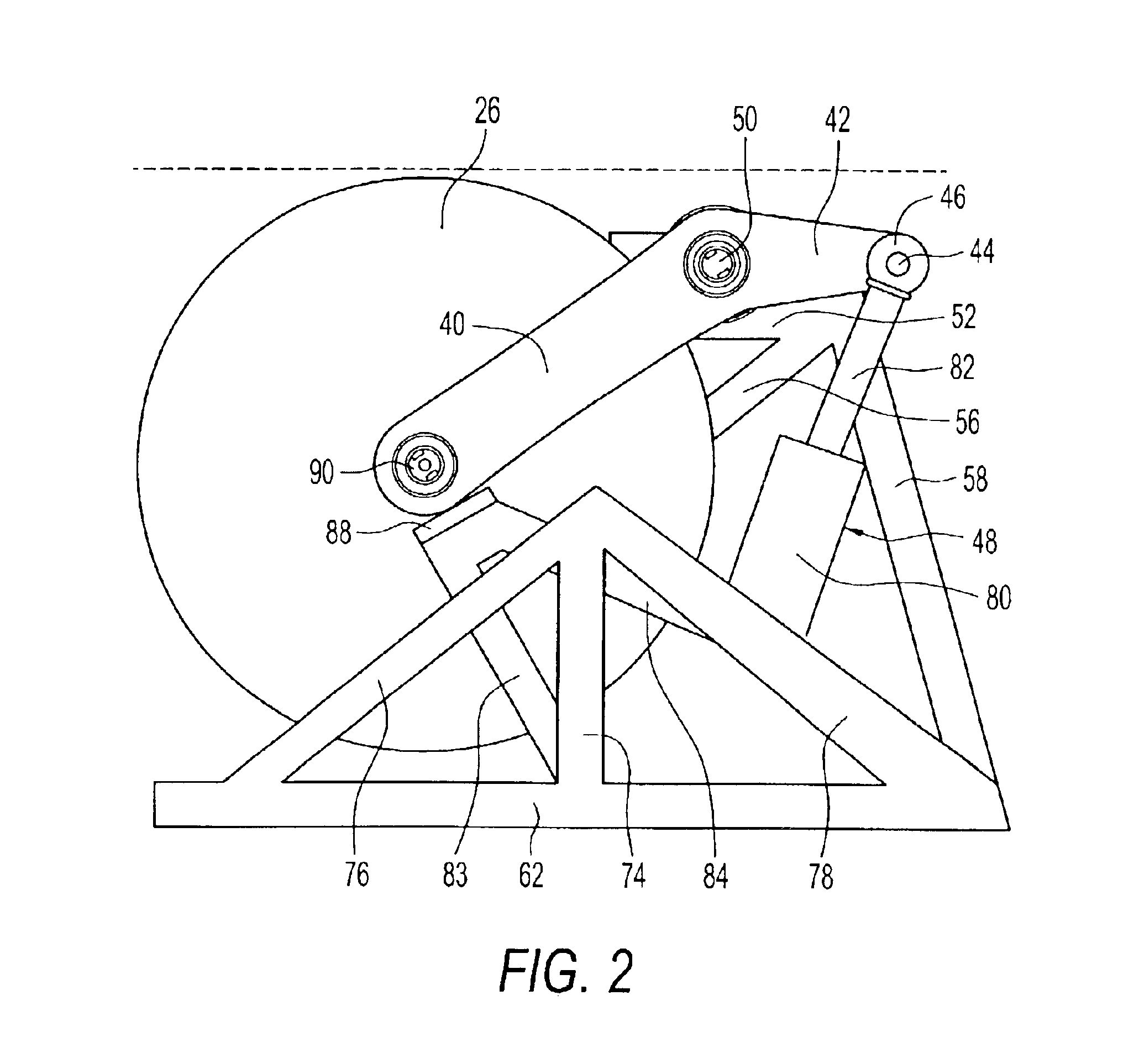
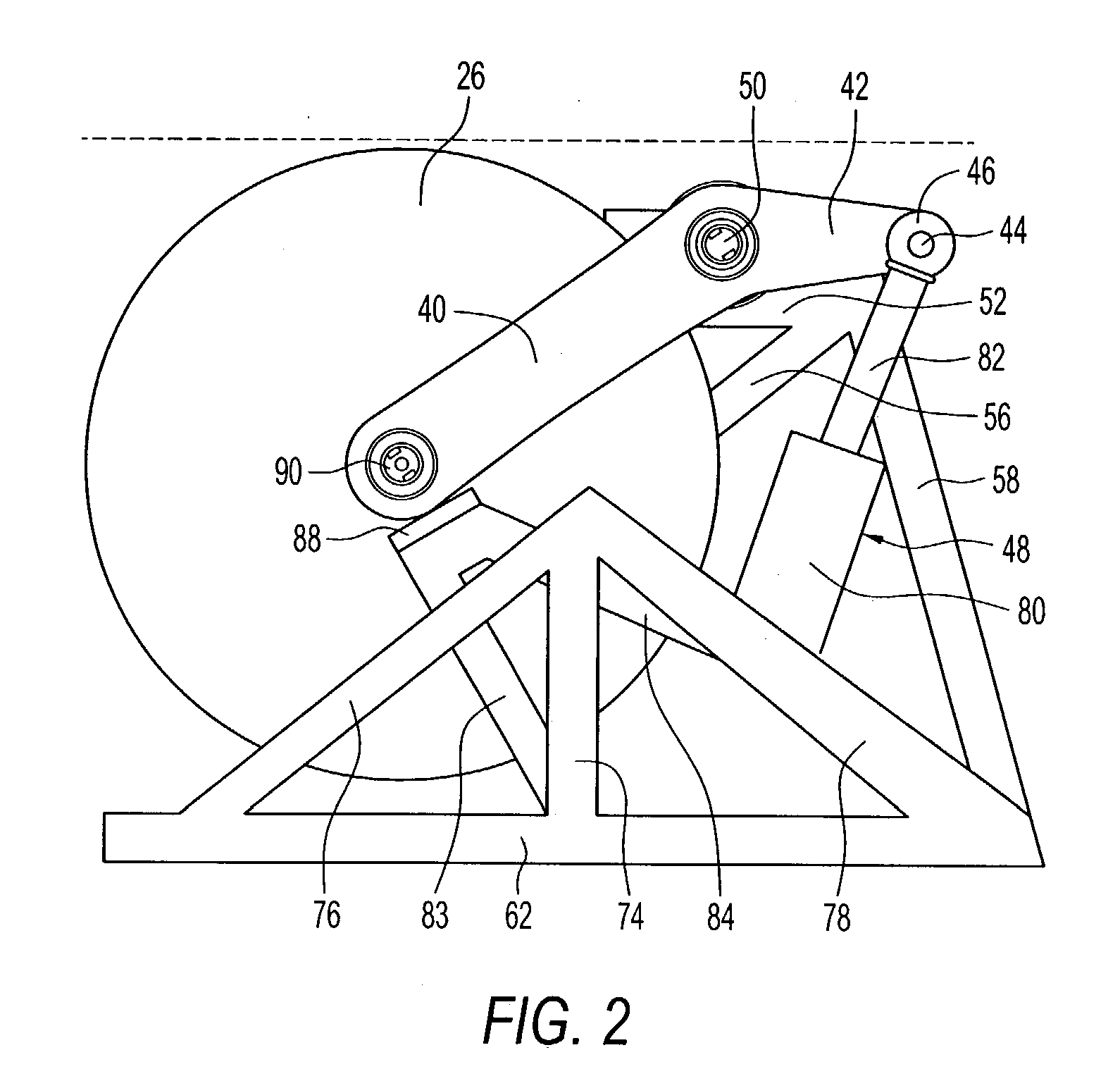
Safety detection and protection system for power tools
InactiveUS6922153B2Quick stopRule out the possibilityDC motor speed/torque controlEmergency protective circuit arrangementsPower toolProtection system
A detection system for detecting a dangerous condition for an operator using a power tool of the type which has an exposed blade relative to a work surface and a protection system for minimizing, if not eliminating the possibility of a user being injured by contacting the blade. In one preferred embodiment of the present invention, a proximity detection system is capable of detecting the presence of a user near the blade of a table saw and a protection system that can either retract the blade below the work surface of the table saw or terminate the drive torque to the blade which can result in rapid stopping of the saw blade by a work piece that is being cut.
Owner:CREDO TECH CORP +1
Safety detection and protection system for power tools
InactiveUS20040226800A1Quick stopQuick pullDC motor speed/torque controlEmergency protective circuit arrangementsPower toolProtection system
A detection system for detecting a dangerous condition for an operator using a power tool of the type which has an exposed blade relative to a work surface and a protection system for minimizing, if not eliminating the possibility of a user being injured by contacting the blade. In one preferred embodiment of the present invention, a proximity detection system is capable of detecting the presence of a user near the blade of a table saw and a protection system that can either retract the blade below the work surface of the table saw or terminate the drive torque to the blade which can result in rapid stopping of the saw blade by a work piece that is being cut.
Owner:CREDO TECH CORP +1
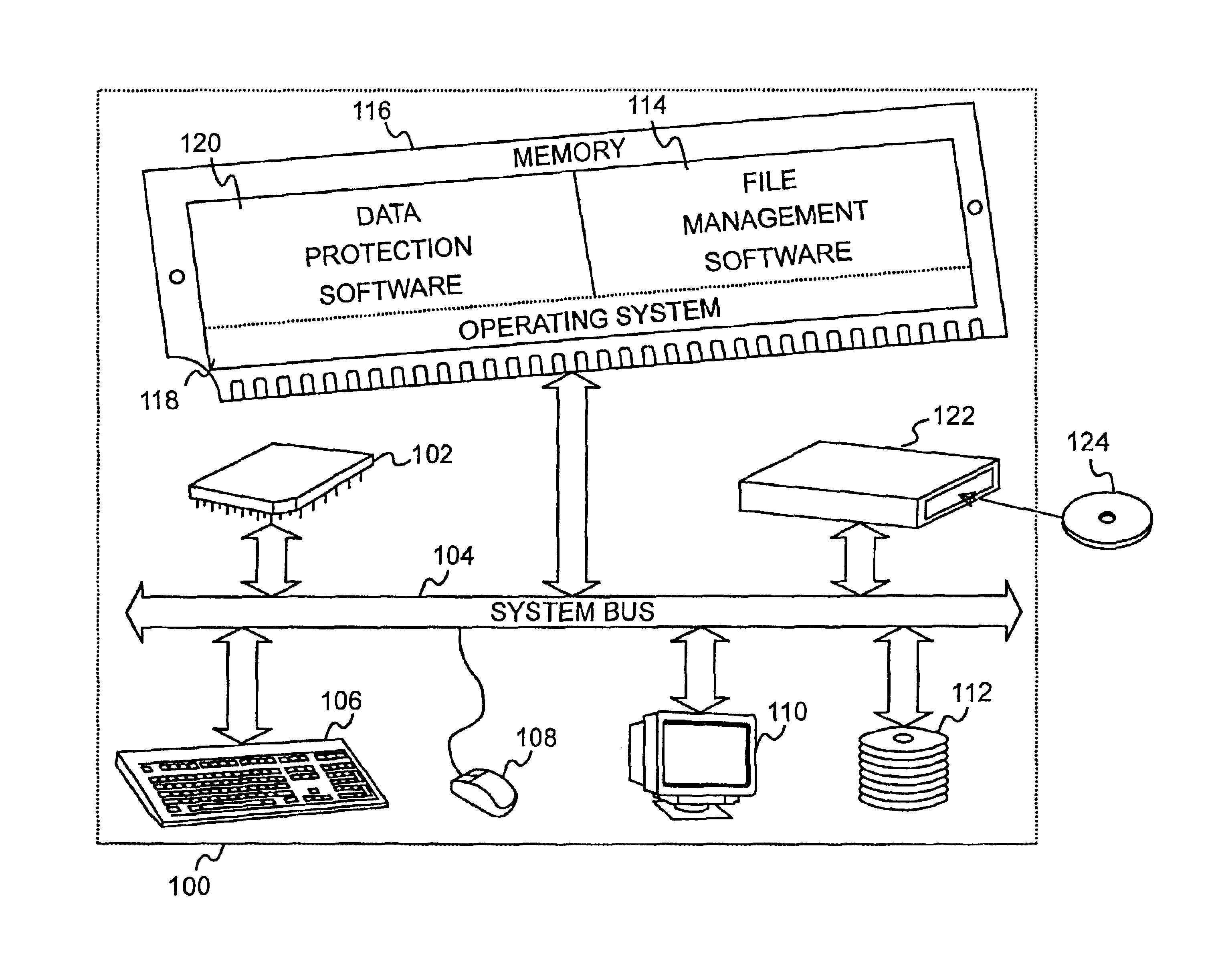
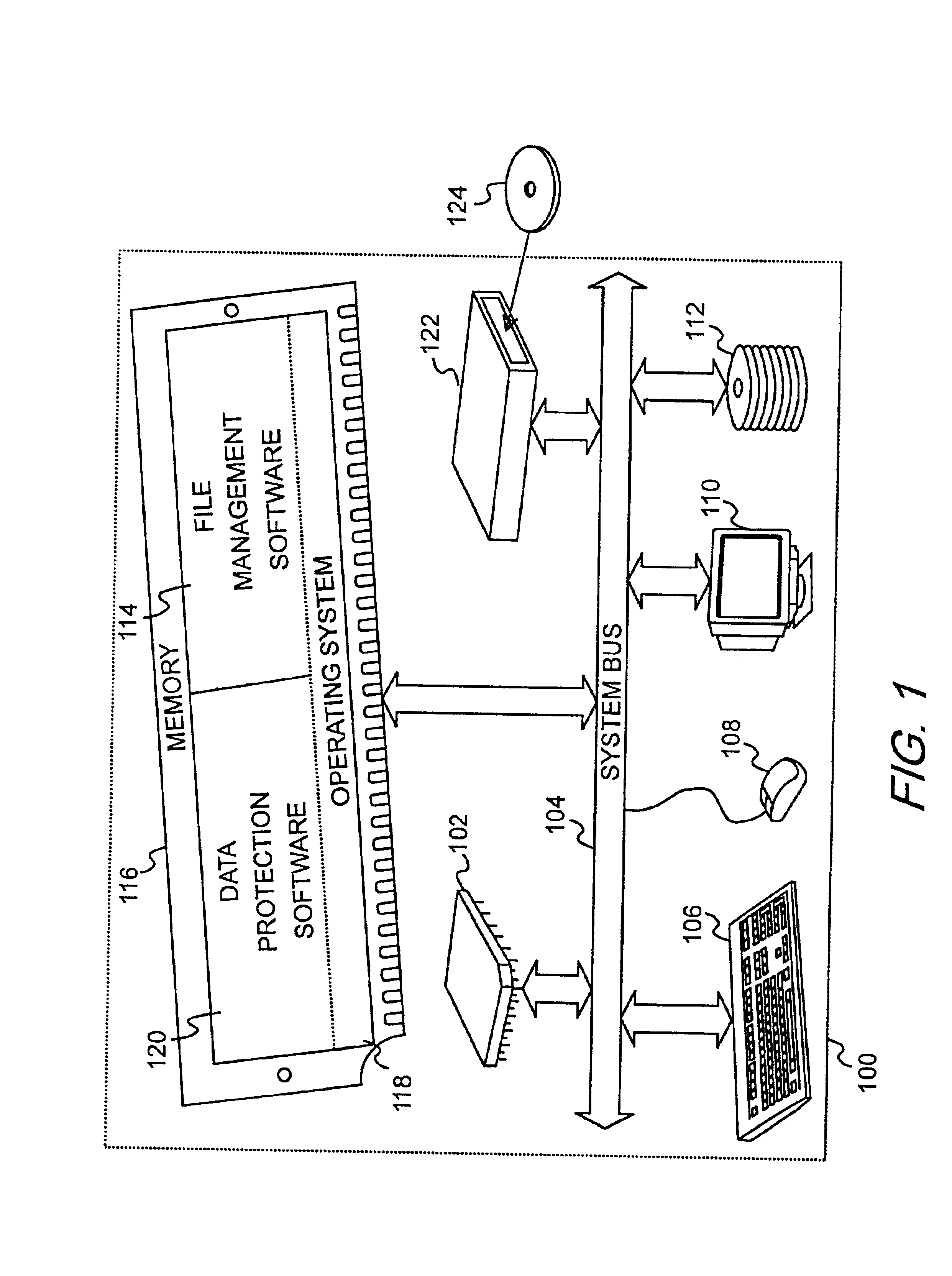
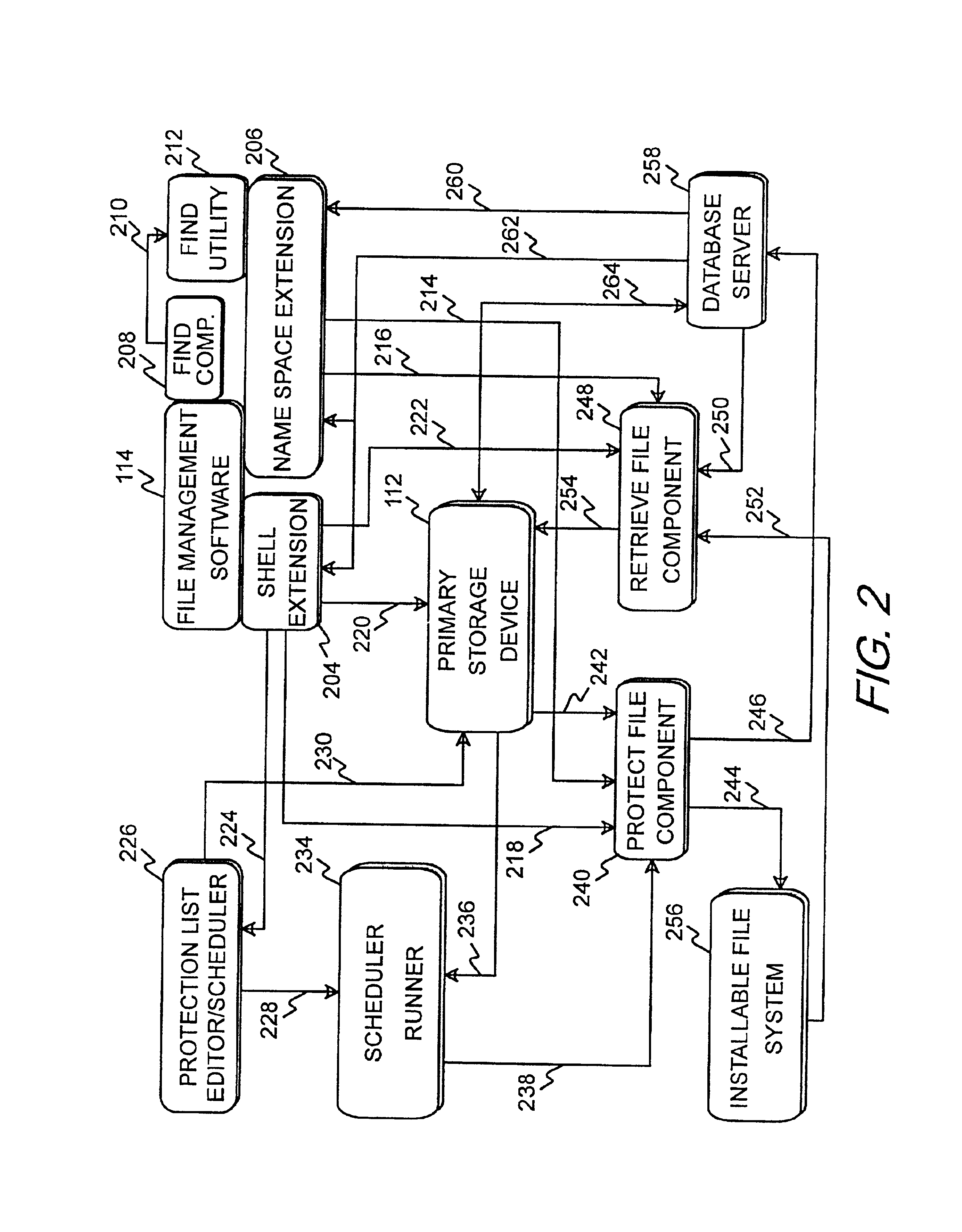
Integration of a database into file management software for protecting, tracking, and retrieving data
InactiveUS6839721B2Simple and efficientAccurate identificationData processing applicationsSpecial data processing applicationsProgram planningProtection system
A data protection system that integrates a database with Windows Explorer in the Microsoft Windows 9X and NT Environments that mimics the Windows Explorer user interface, enabling the user to apply already known use paradigms. The data protection system appears as an extension to Windows Explorer and visibly appears as a folder item called the data vault. The data vault is a virtual disk that represents the underlying database. The database creates records and stores information about files backed up to removable secondary storage medium. Files may be backed up manually or automatically. A schedule can be set up for automatic protection of selected files and file types. The database can be searched to find files for restoration purposes without having to load secondary storage medium. Once a file or files are selected, the data protection system indicates which labeled removable secondary storage medium must be loaded for retrieval.
Owner:HEWLETT PACKARD DEV CO LP
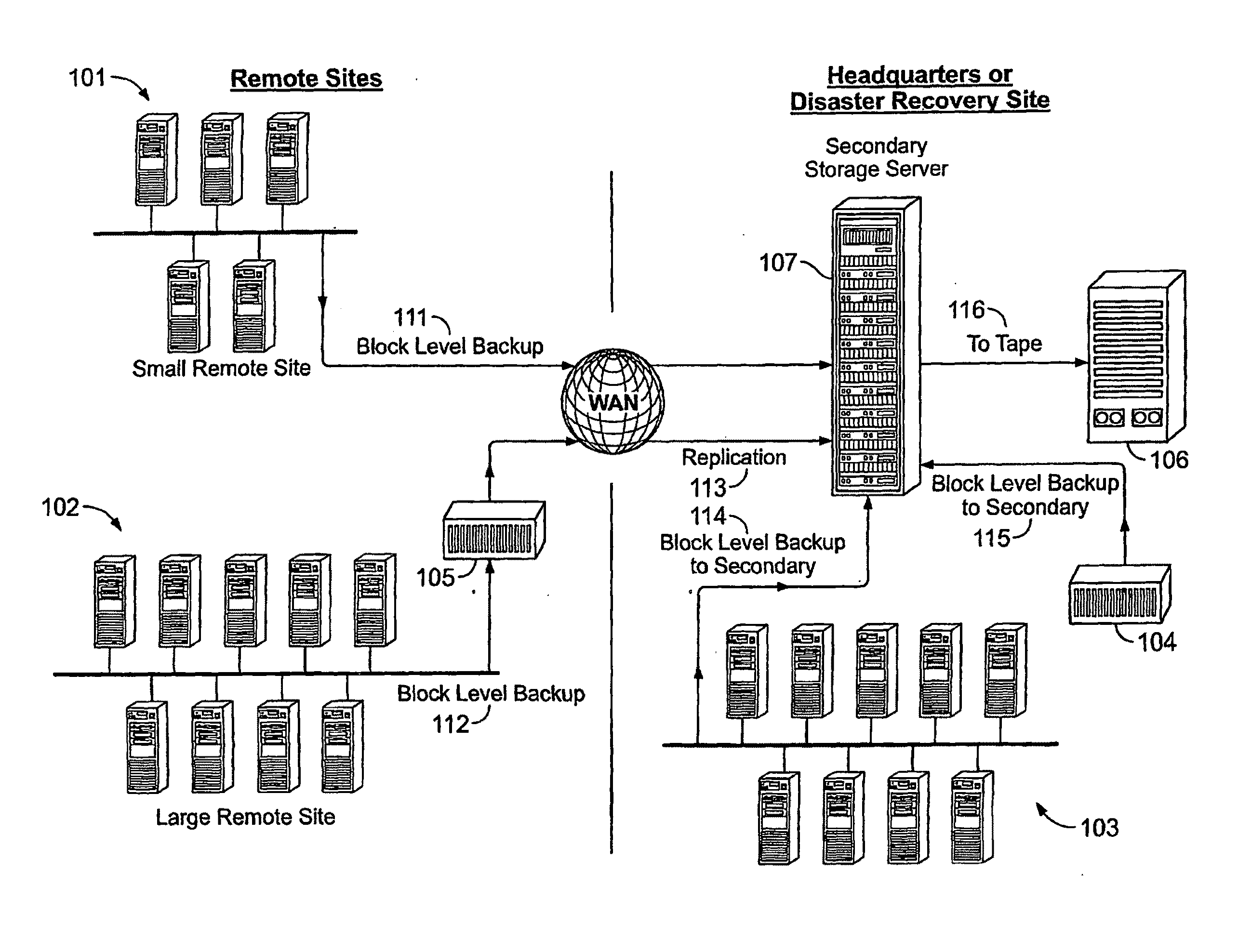
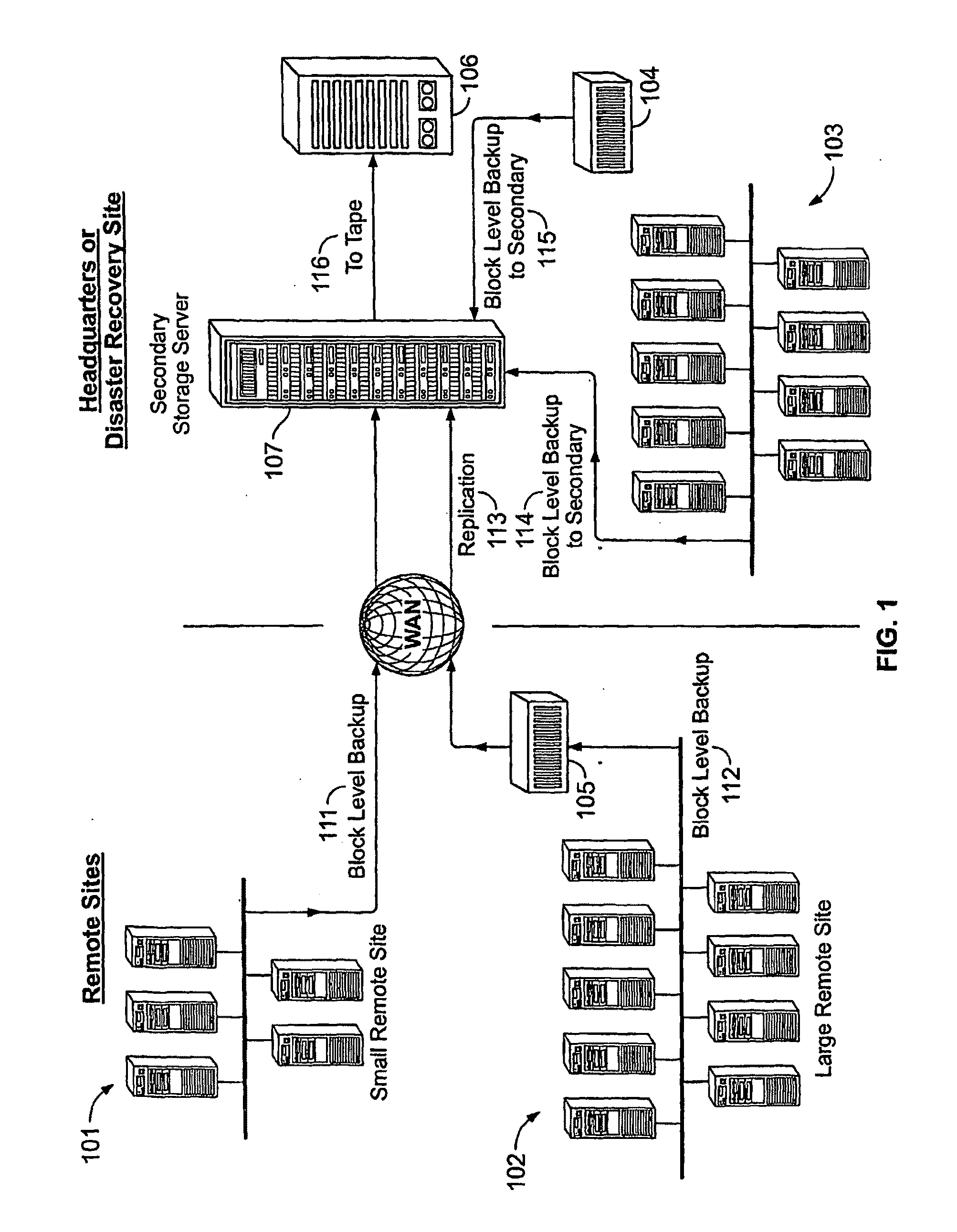
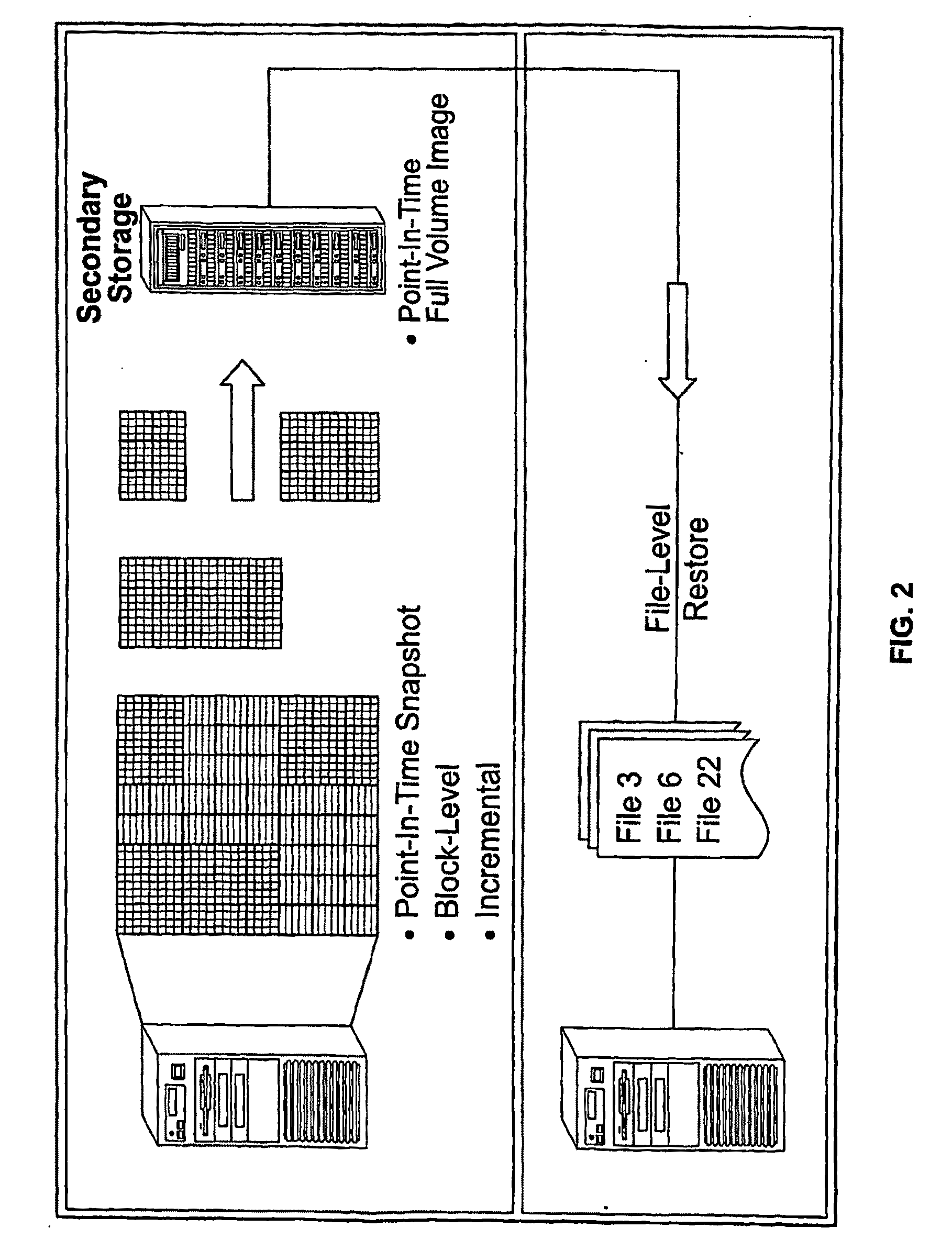
System And Method for High Performance Enterprise Data Protection
ActiveUS20100077160A1Improve performanceEliminate redundancyMemory loss protectionError detection/correctionOperational systemFile system
High performance, enterprise-level data protection system and method provides efficient block-level incremental snapshots of primary storage devices, and instant availability of such snapshots in immediately mountable form that can be directly used in place of the primary storage device. Related systems and applications are described, including an “Enterprise Image Destination” (EID) for backup images; a mirroring technique whereby a replacement physical primary facility may be created while working with a second storage unit as the primary source file system; and a technique for eliminating redundant data in backup images when multiple systems with partially common contents (e.g., operating system files, common databases, application executables, etc.) are being backed up. A number of examples showing “Fast Application Restore” (FAR) with the use of the invention are also provided.
Owner:CATALOGIC SOFTWARE
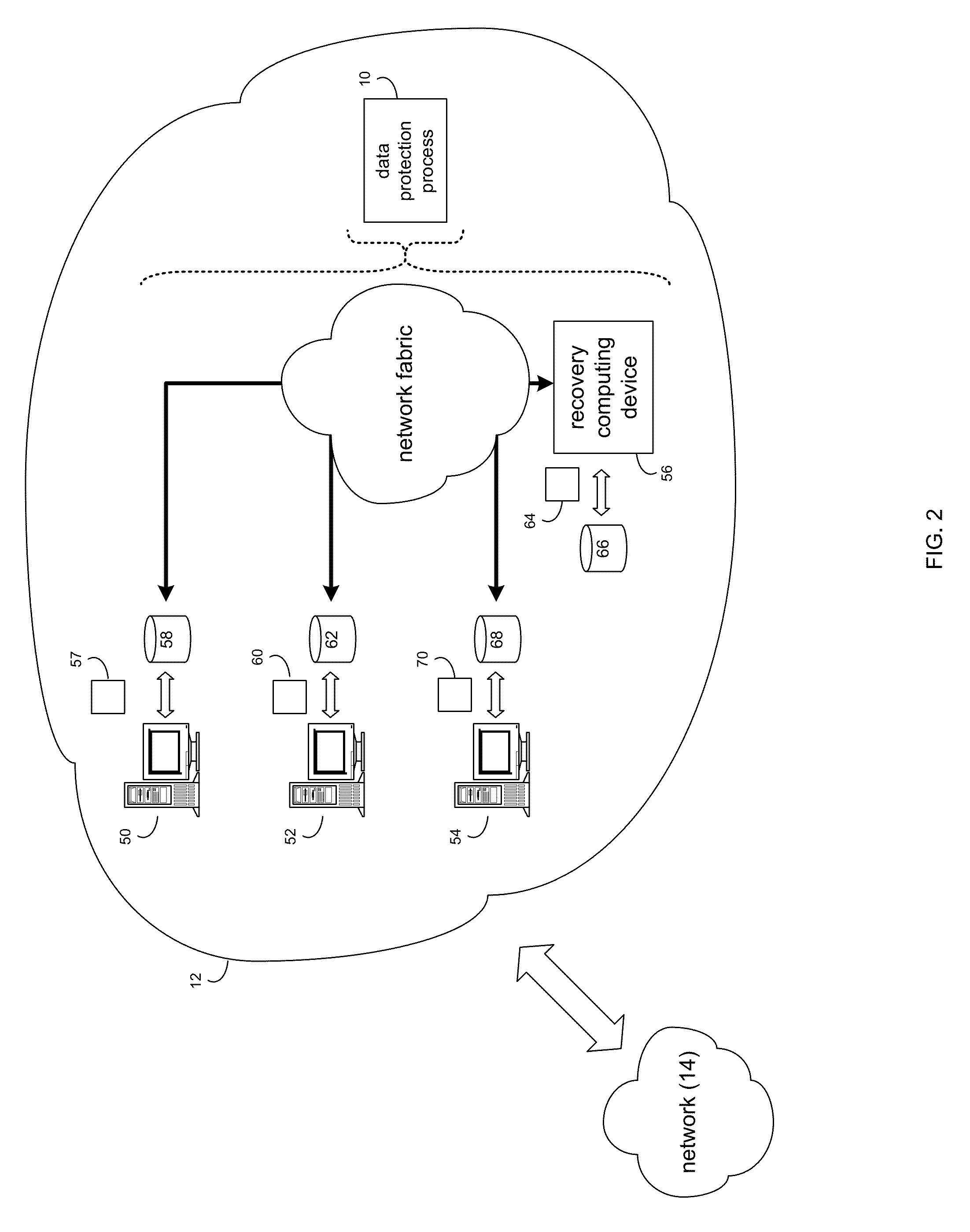
Data protection system and method
A system, computer-implemented method, and a computer program product for monitoring a first data portion written to a first storage device accessible by a first computing device. At least a second data portion written to at least a second storage device accessible by at least a second computing device is monitored. Recovery data is written to a recovery storage device external to and accessible by the first and the at least a second computing devices, wherein the recovery data is based, at least in part, upon the first and second data portions.
Owner:EMC IP HLDG CO LLC
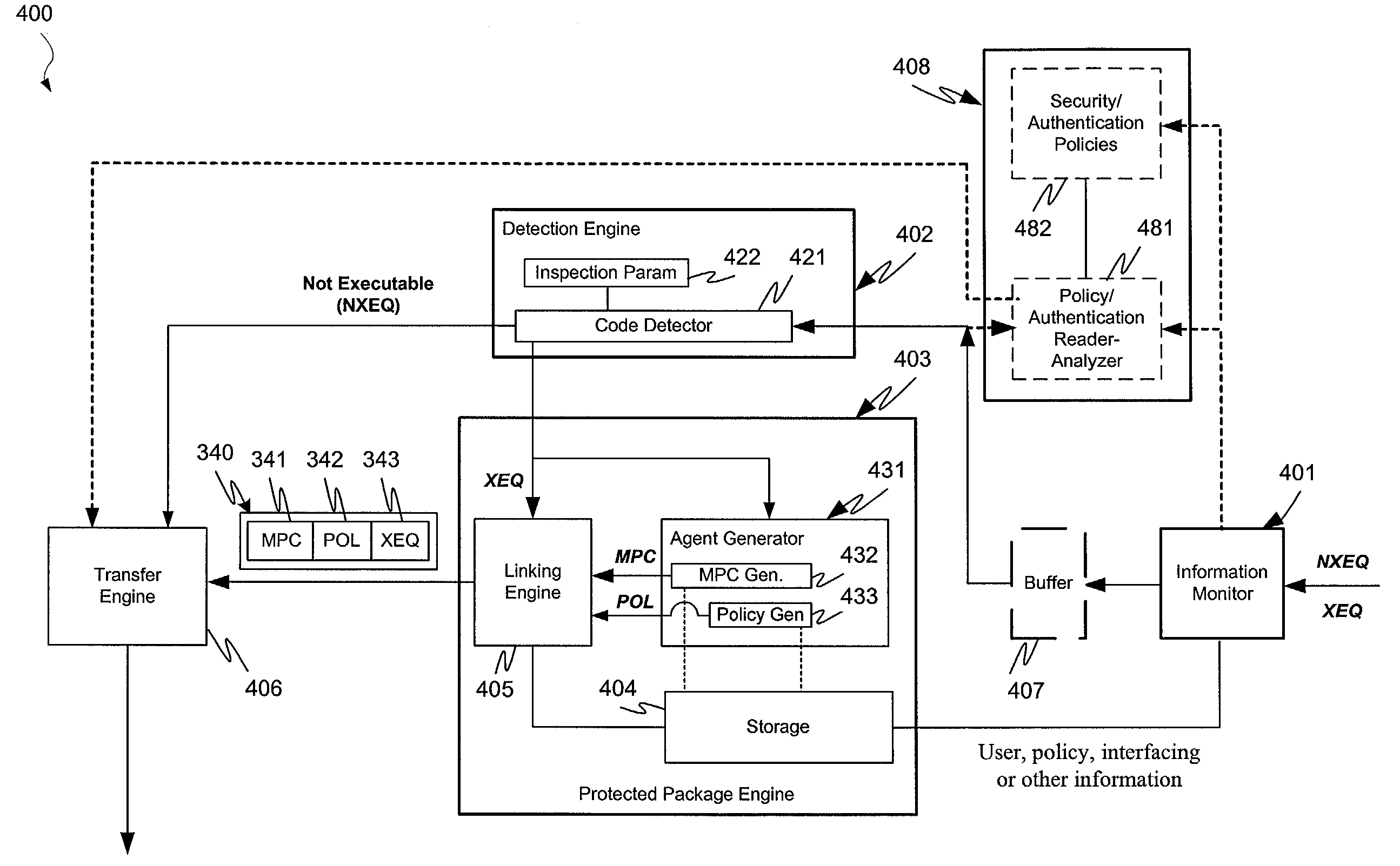
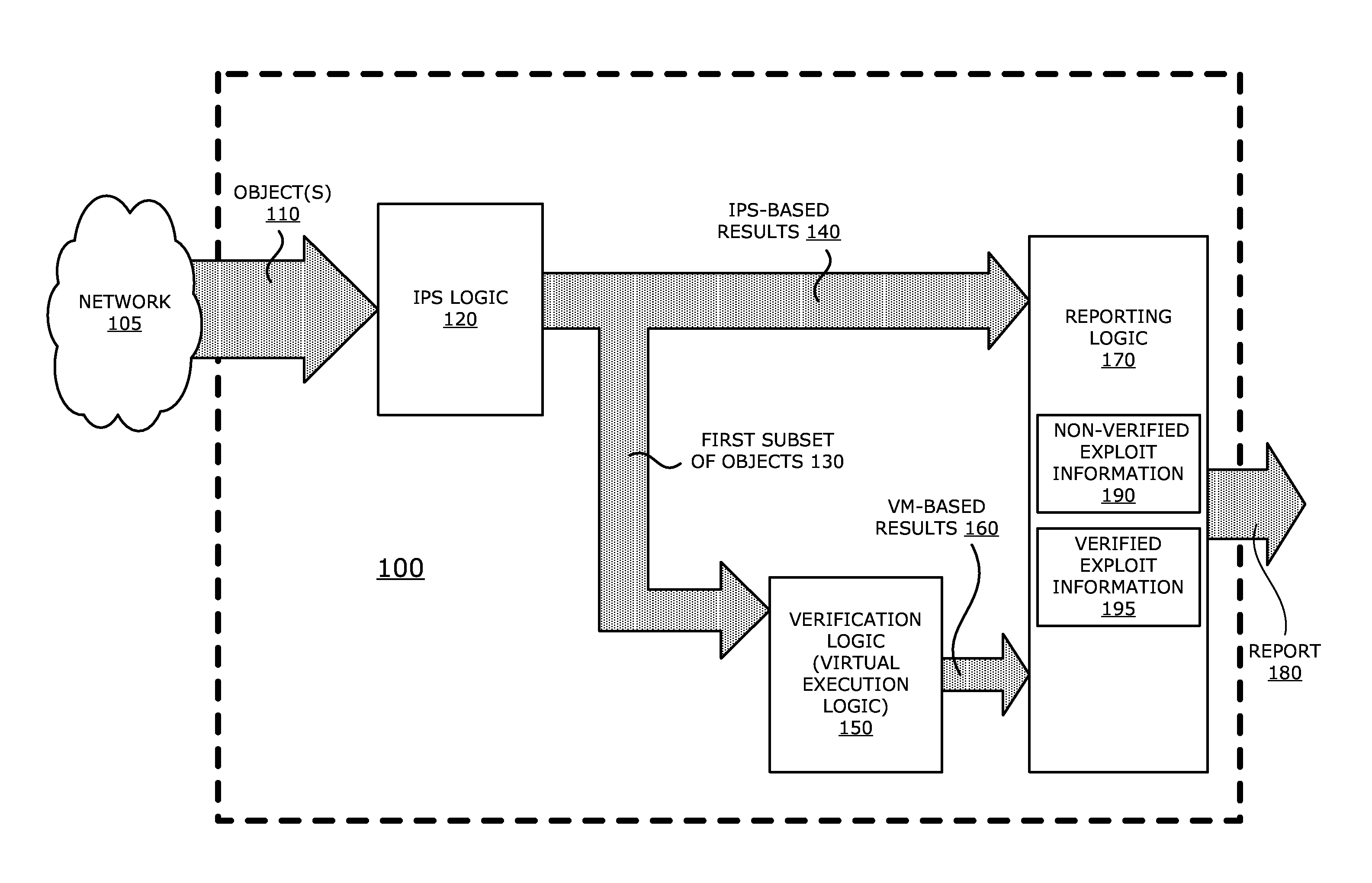
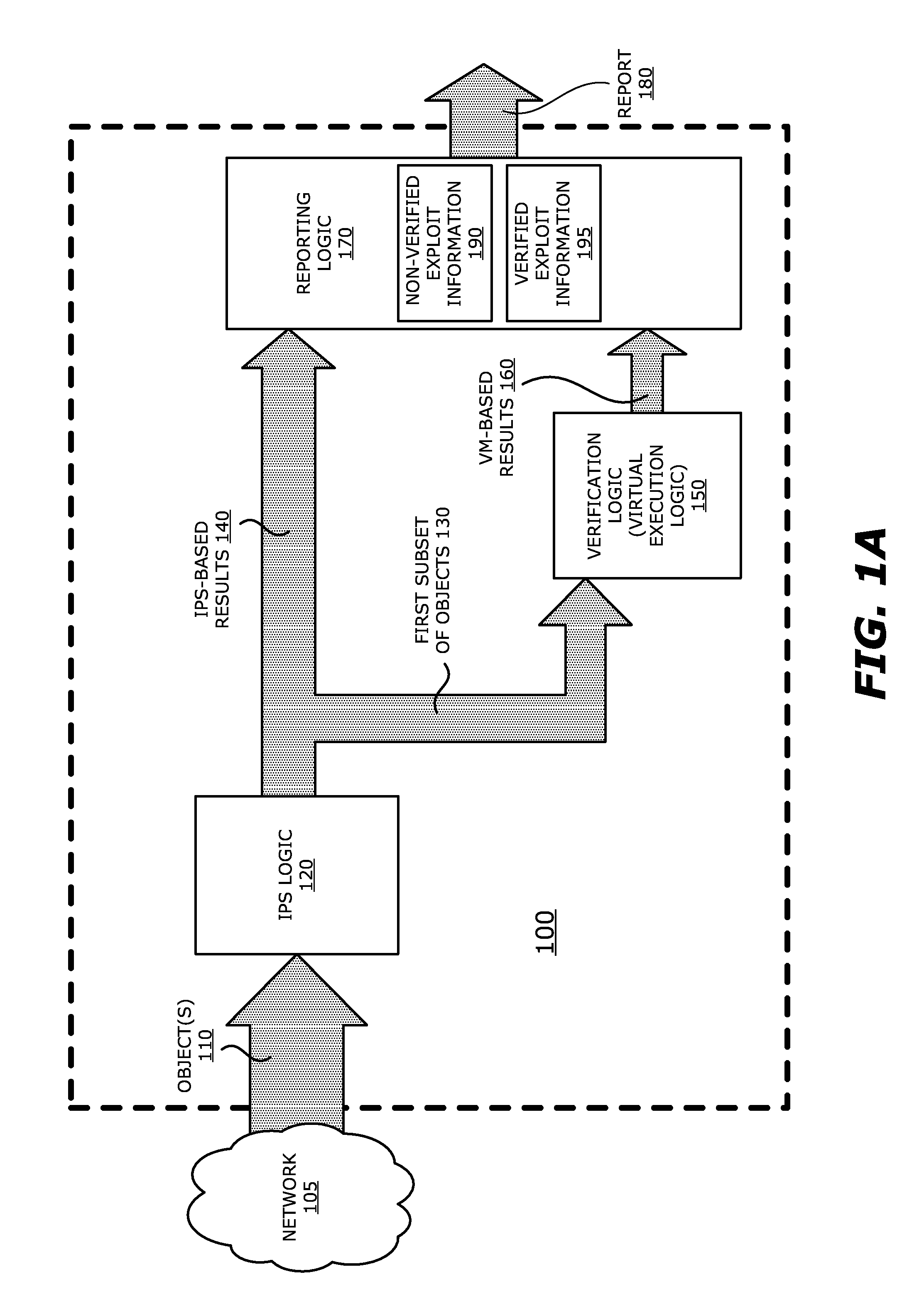
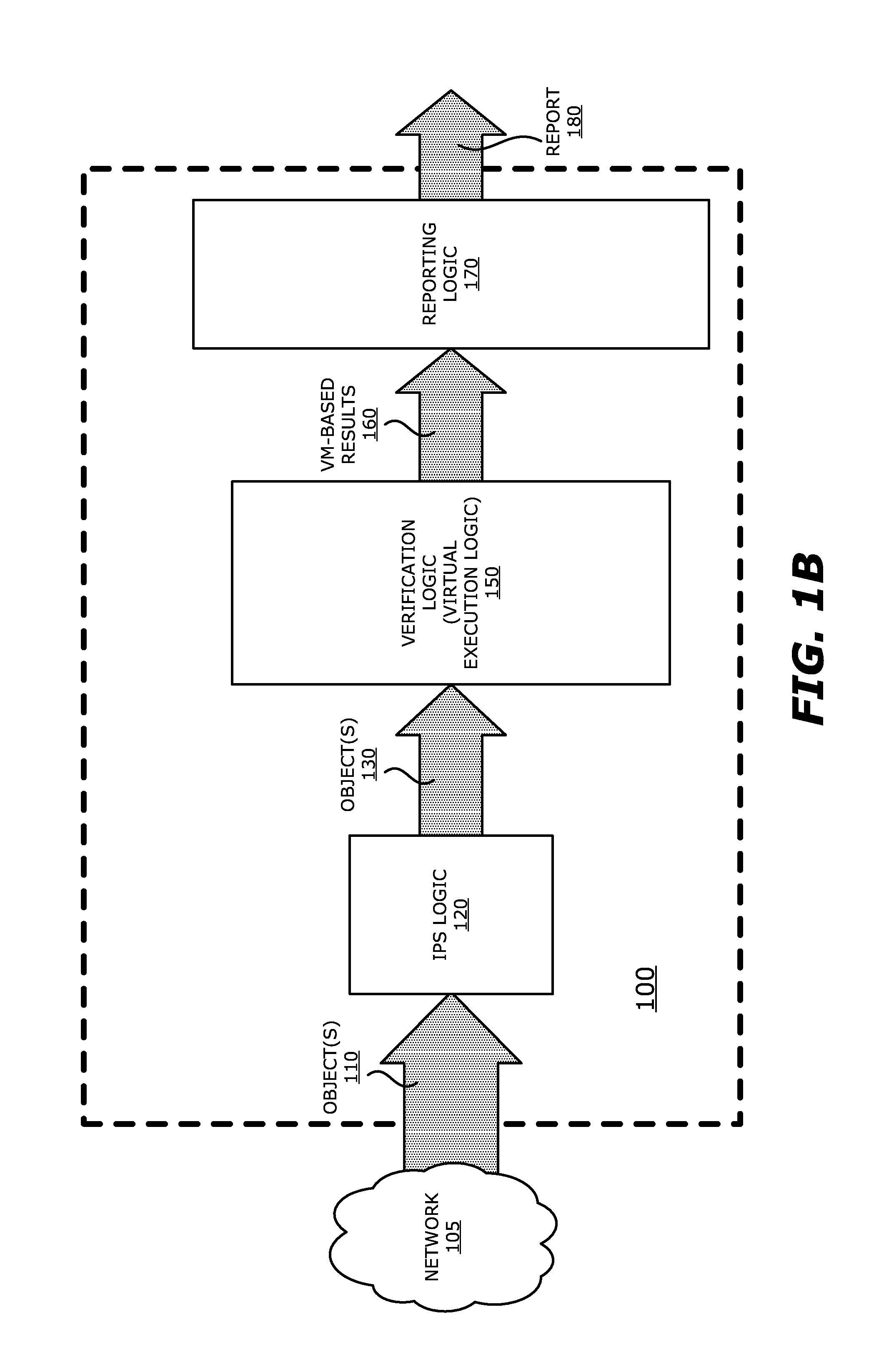
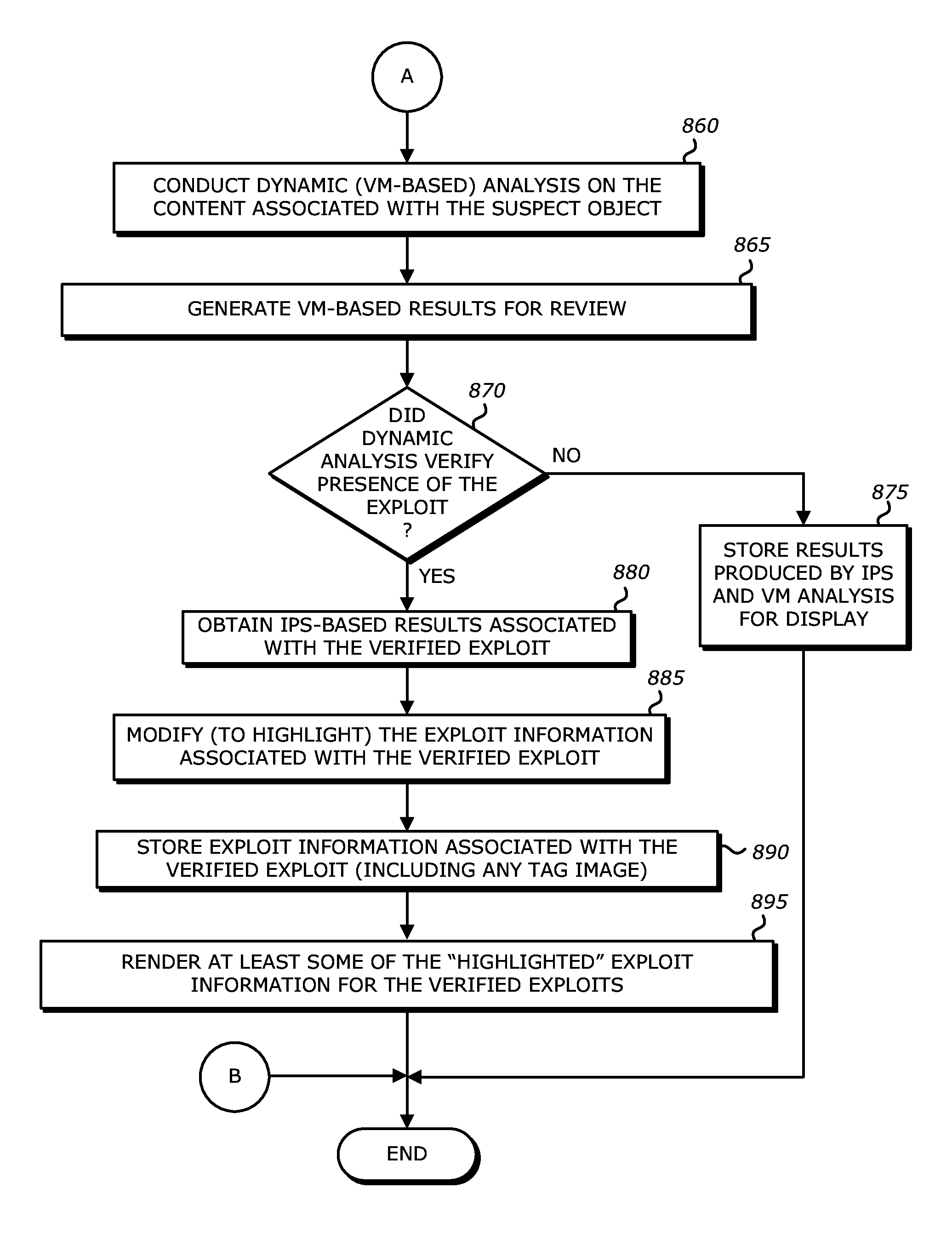
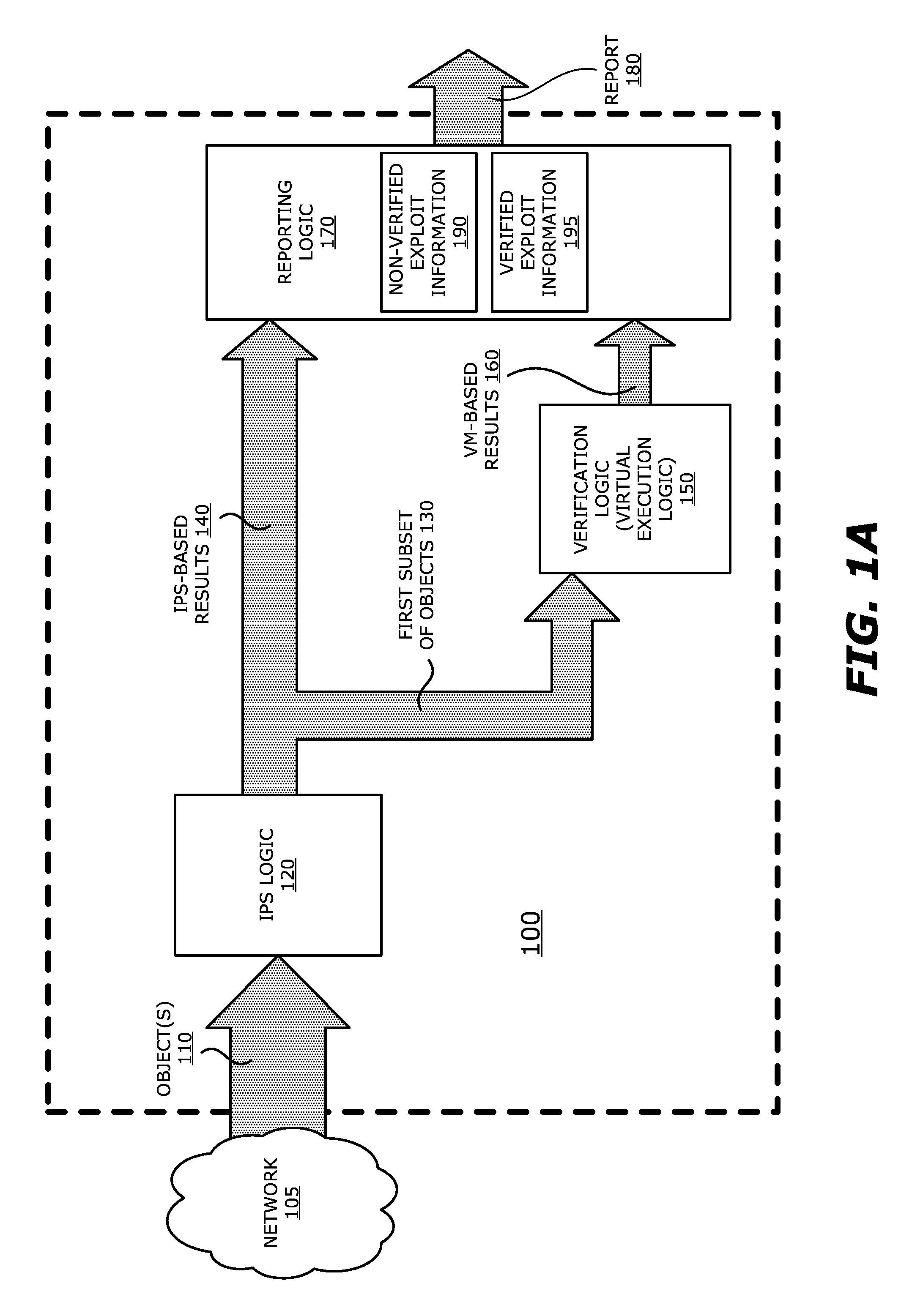
System, apparatus and method for automatically verifying exploits within suspect objects and highlighting the display information associated with the verified exploits
ActiveUS20150186645A1Quickly and easily determineReduce disadvantagesMemory loss protectionError detection/correctionAnomalous behaviorProtection system
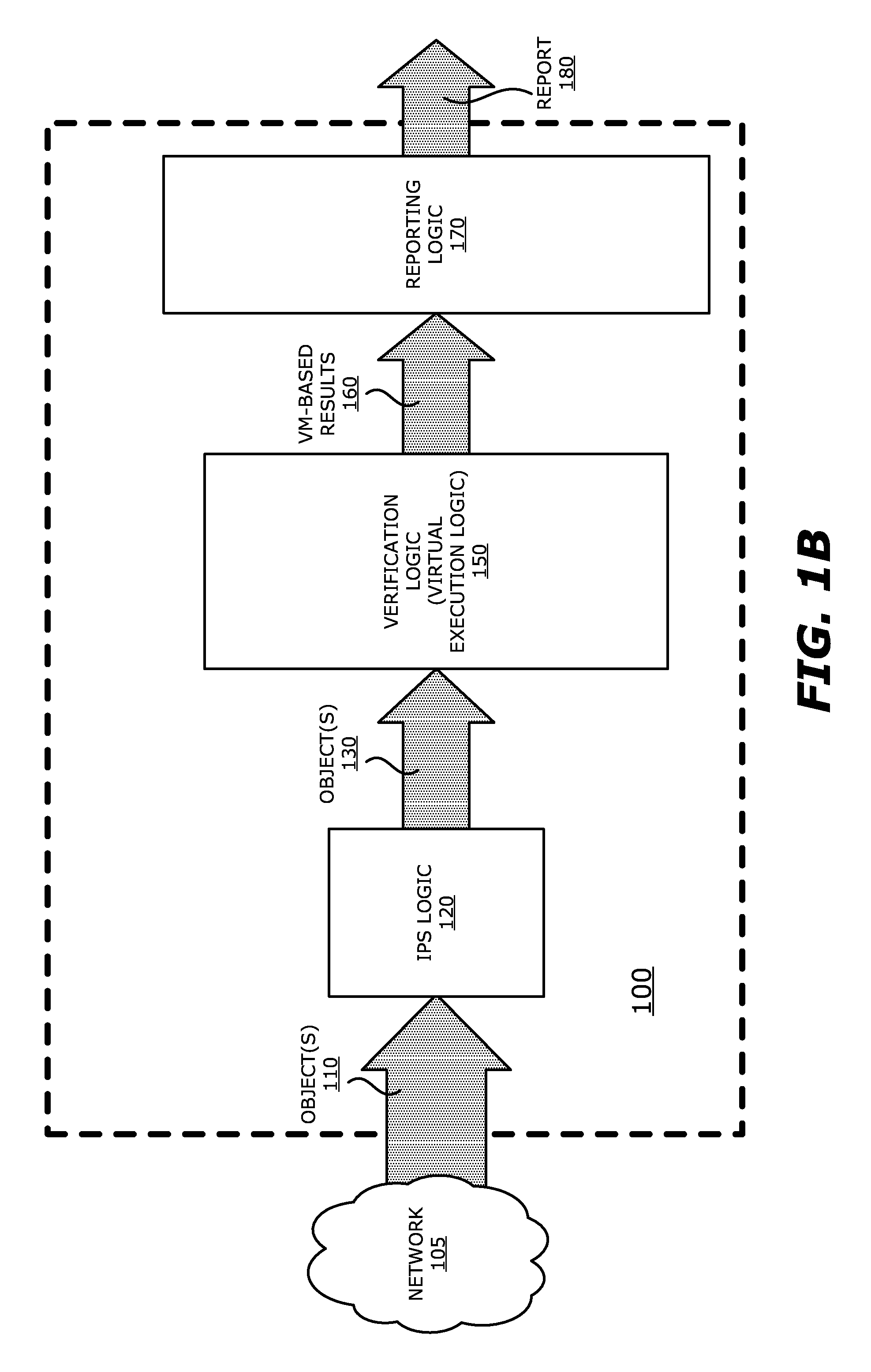
According to one embodiment, a threat detection system is integrated with intrusion protection system (IPS) logic and virtual execution logic. The IPS logic is configured to receive a first plurality of objects and filter the first plurality of objects by identifying a second plurality of objects as suspicious objects. The second plurality of objects is a subset of the first plurality of objects and is lesser or equal in number to the first plurality of objects. The virtual execution logic is configured to automatically verify whether any of the suspicious objects is an exploit. The virtual execution logic comprises at least one virtual machine configured to virtually process content within the suspicious objects and monitor for anomalous behaviors during the virtual processing that are indicative of exploits.
Owner:FIREEYE SECURITY HLDG US LLC
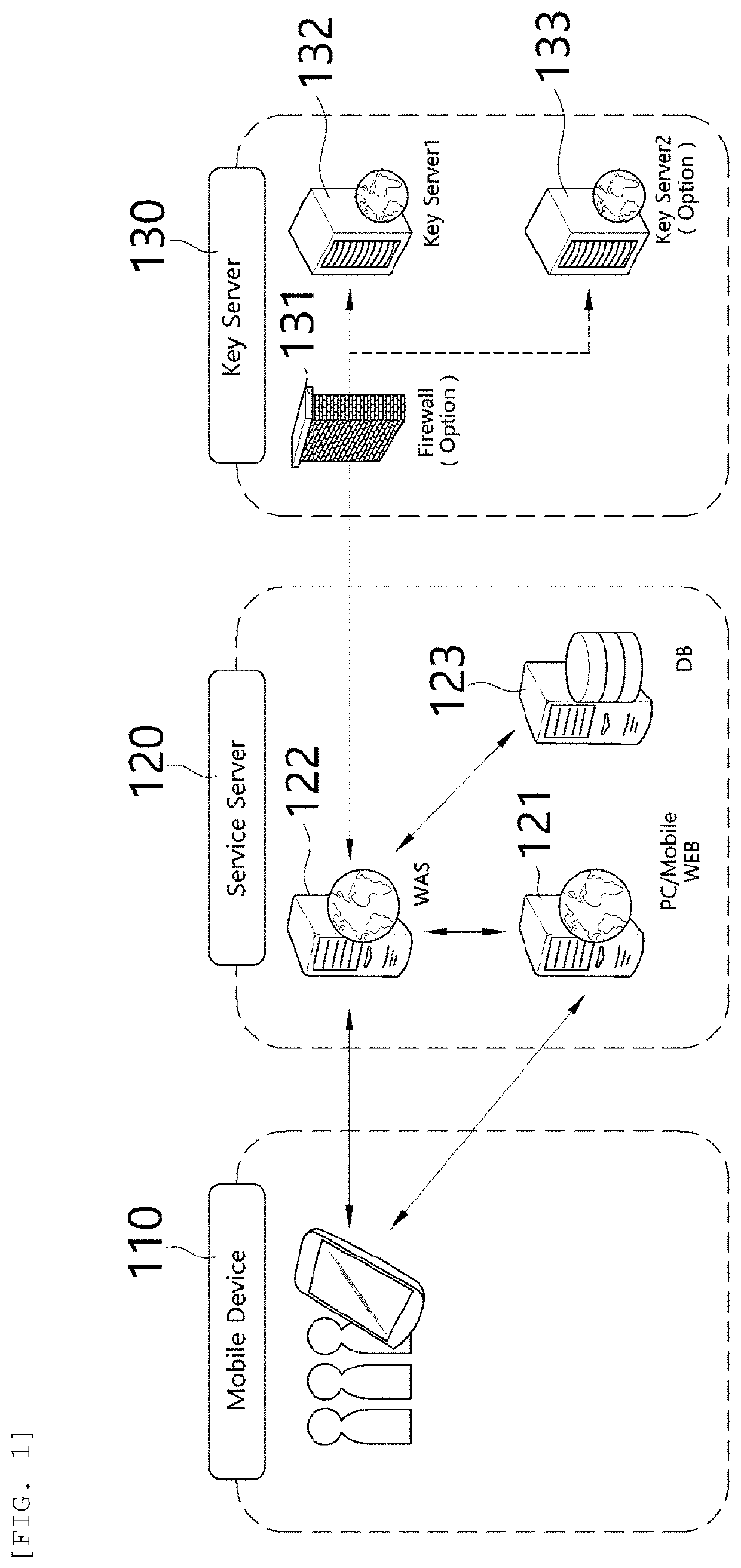
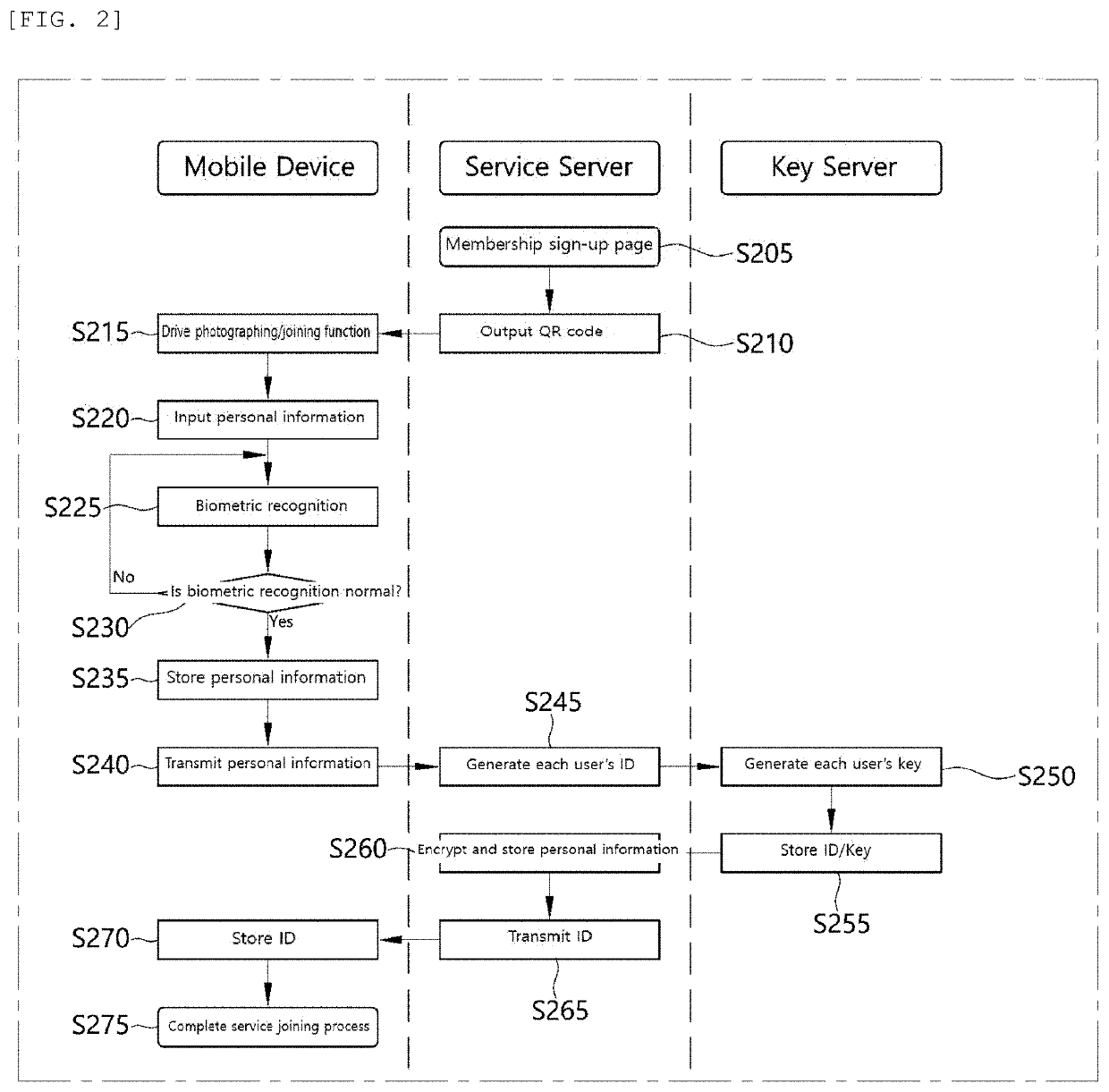
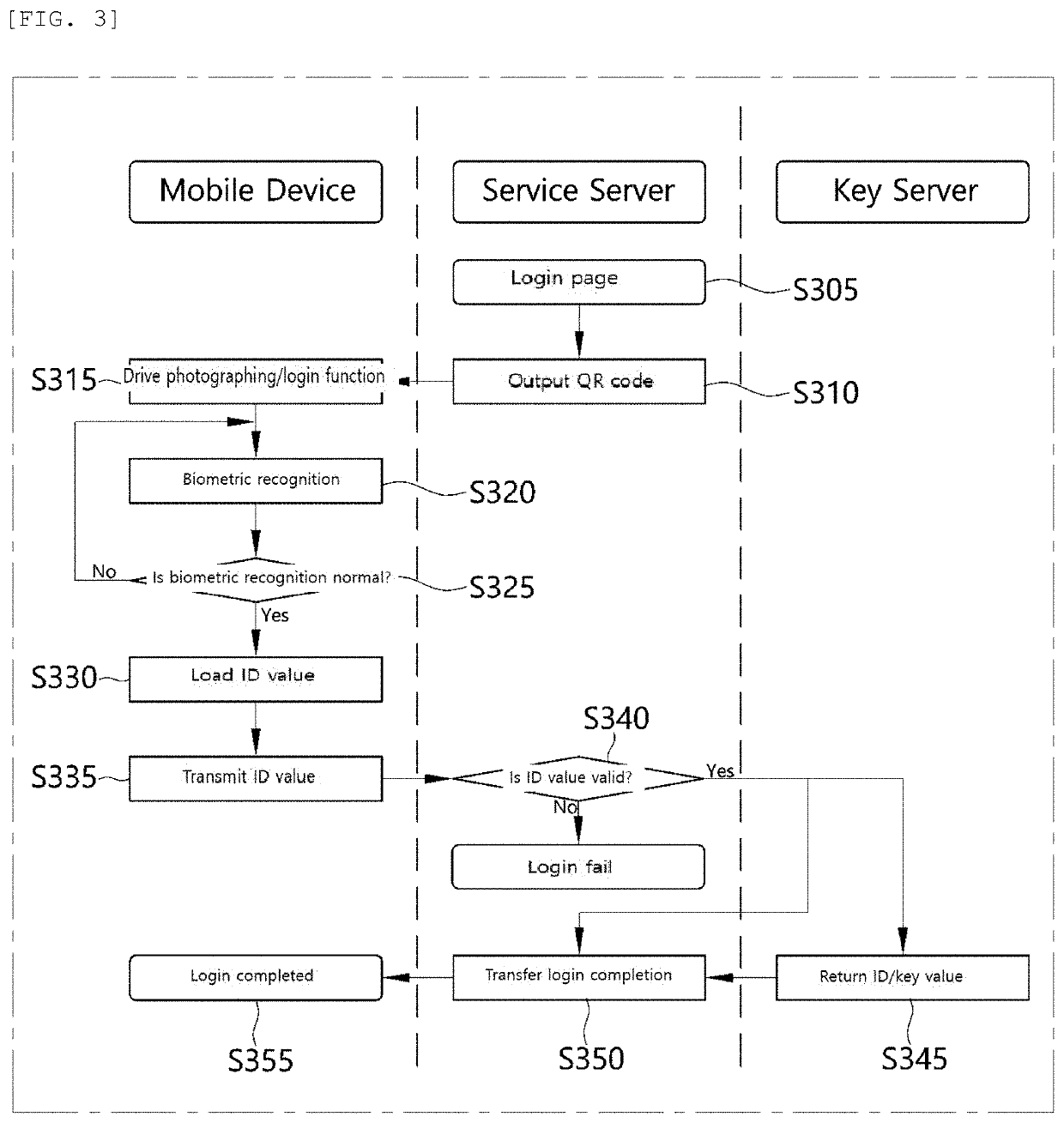
Method and system for protecting personal information infringement using division of authentication process and biometric authentication
InactiveUS20190384934A1Eliminate chancePreventing situationKey distribution for secure communicationUser identity/authority verificationComputer terminalBiometrics
A personal information infringement protection system, includes: a portable terminal having an application installed therein to photograph a QR code and recognize biometrics; a service server for storing the encrypted personal information, and generating an ID of a user and transmitting the ID to the portable terminal to be stored therein or informing the portable terminal of login completion when the ID received from the portable terminal is a valid ID; and a key server for generating a key value for encryption and decryption of the personal information, classifying and storing the key value by user, and providing the key value to the service server.
Owner:RENOMEDIA CO LTD
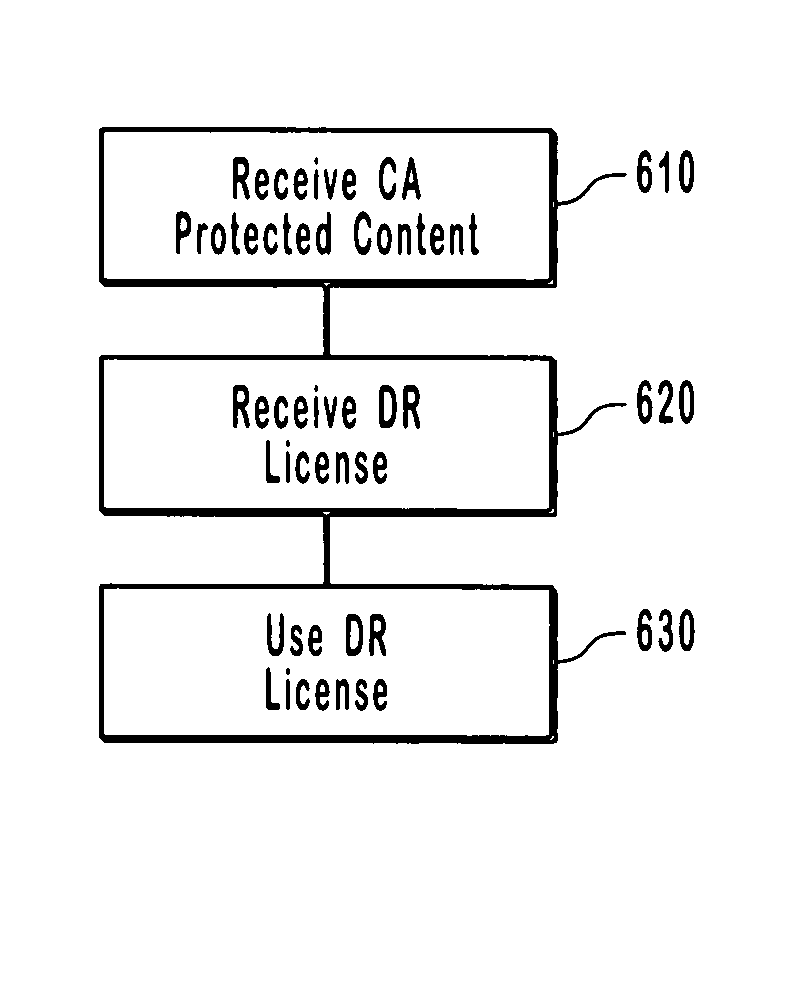
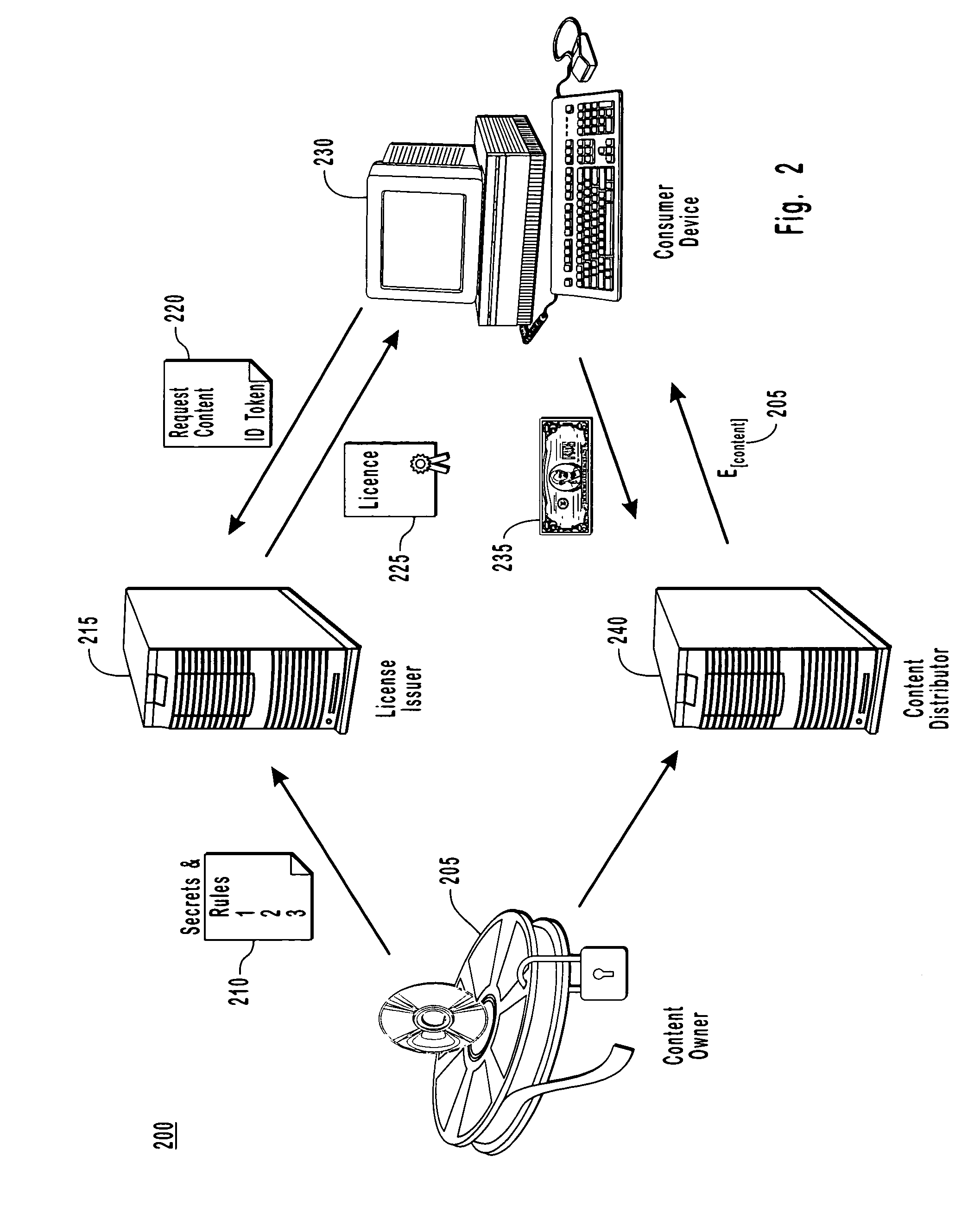
Conditional access to digital rights management conversion
ActiveUS20050182931A1Drying solid materials with heatUser identity/authority verificationSecurity kernelDigital rights management system
The present invention provides for an interface between two seemingly incompatible and different content protection systems. Accordingly, protected content may be transferred between the respective security kernels of a conditional access (CA) and digital rights management (DRM) systems, while maintaining security of the content and any associated protection information. The transfer and consumption of protected content and the associated content protection information may be achieved by temporarily or permanently binding the respective security kernels of the CA and DRM systems, transcribing content protection information, and potentially transcribing the content.
Owner:MICROSOFT TECH LICENSING LLC
System, apparatus and method for automatically verifying exploits within suspect objects and highlighting the display information associated with the verified exploits
ActiveUS9306974B1Quickly and easily determineReduce disadvantagesPlatform integrity maintainanceAlarmsAnomalous behaviorProtection system
Owner:FIREEYE SECURITY HLDG US LLC
Digital content protection system
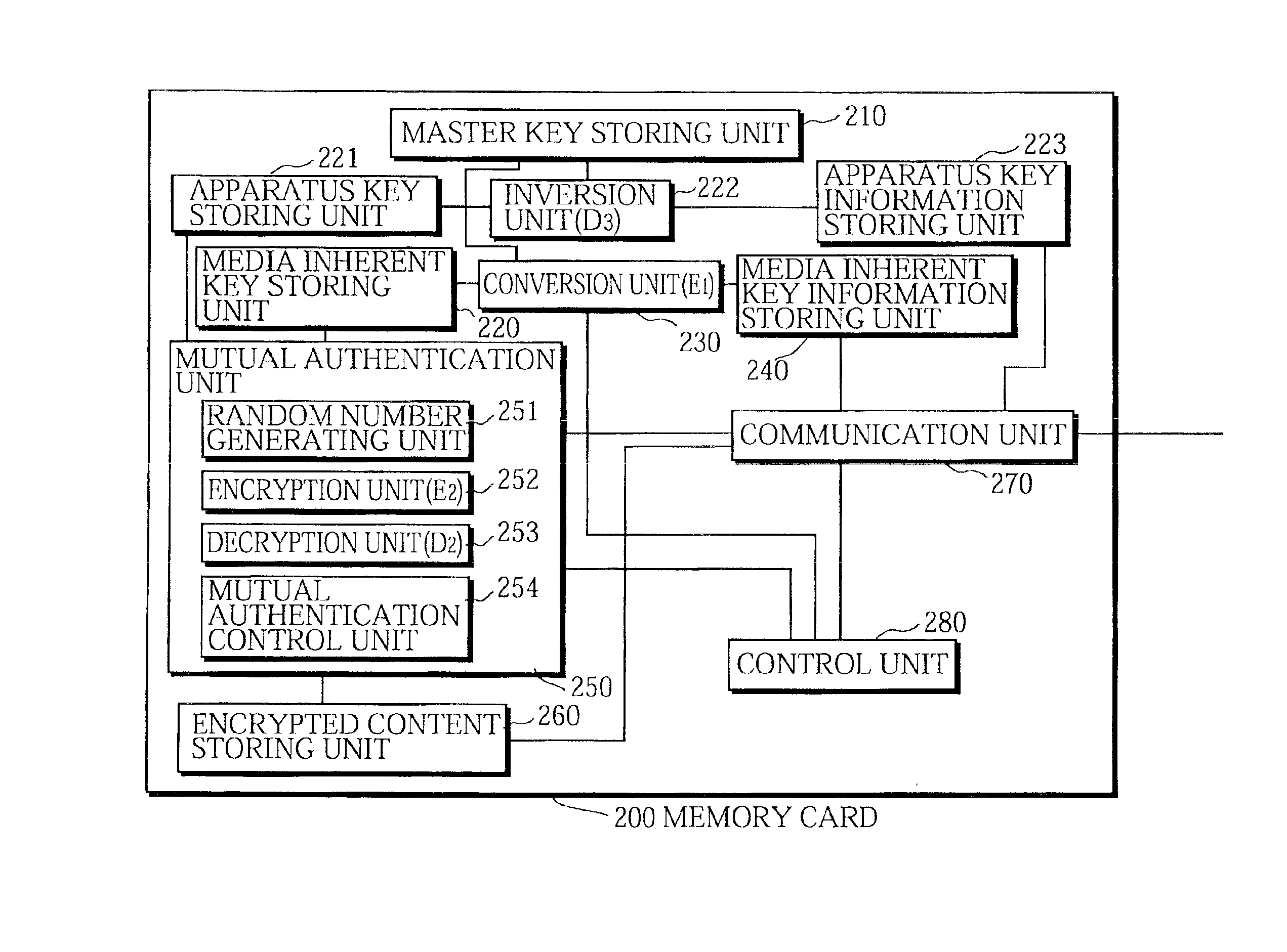
InactiveUS6859535B1Reduce scaleDigital data processing detailsUser identity/authority verificationDigital contentMediaFLO
The media inherent key storing unit 220 prestores an inherent key Ki, the conversion unit 230 generates an encrypted inherent key Ji from the inherent key read from the media inherent key storing unit 220, the random number generating unit 331 generates a random number R1, the encryption unit 252 generates an encrypted random number S1, the decryption unit 333 generates a random number R′1 from the encrypted random number R1, and the mutual authentication control unit 334 compares the random number R′1 with the random number R1 and, if the random number R′1 matches the random number R1, judges that the memory card 200 is an authorized device. If the memory card 200 and the memory card writer have successfully authenticated each other, the memory card writer encrypts a content using a decrypted inherent key. If the memory card 200 and the memory card reader have successfully authenticated each other, the memory card reader decrypts an encrypted content using the decrypted inherent key.
Owner:PANASONIC CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com