Patents
Literature
156 results about "Visual Basic" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Visual Basic is a third-generation event-driven programming language from Microsoft for its Component Object Model (COM) programming model first released in 1991 and declared legacy during 2008. Microsoft intended Visual Basic to be relatively easy to learn and use. Visual Basic was derived from BASIC and enables the rapid application development (RAD) of graphical user interface (GUI) applications, access to databases using Data Access Objects, Remote Data Objects, or ActiveX Data Objects, and creation of ActiveX controls and objects.
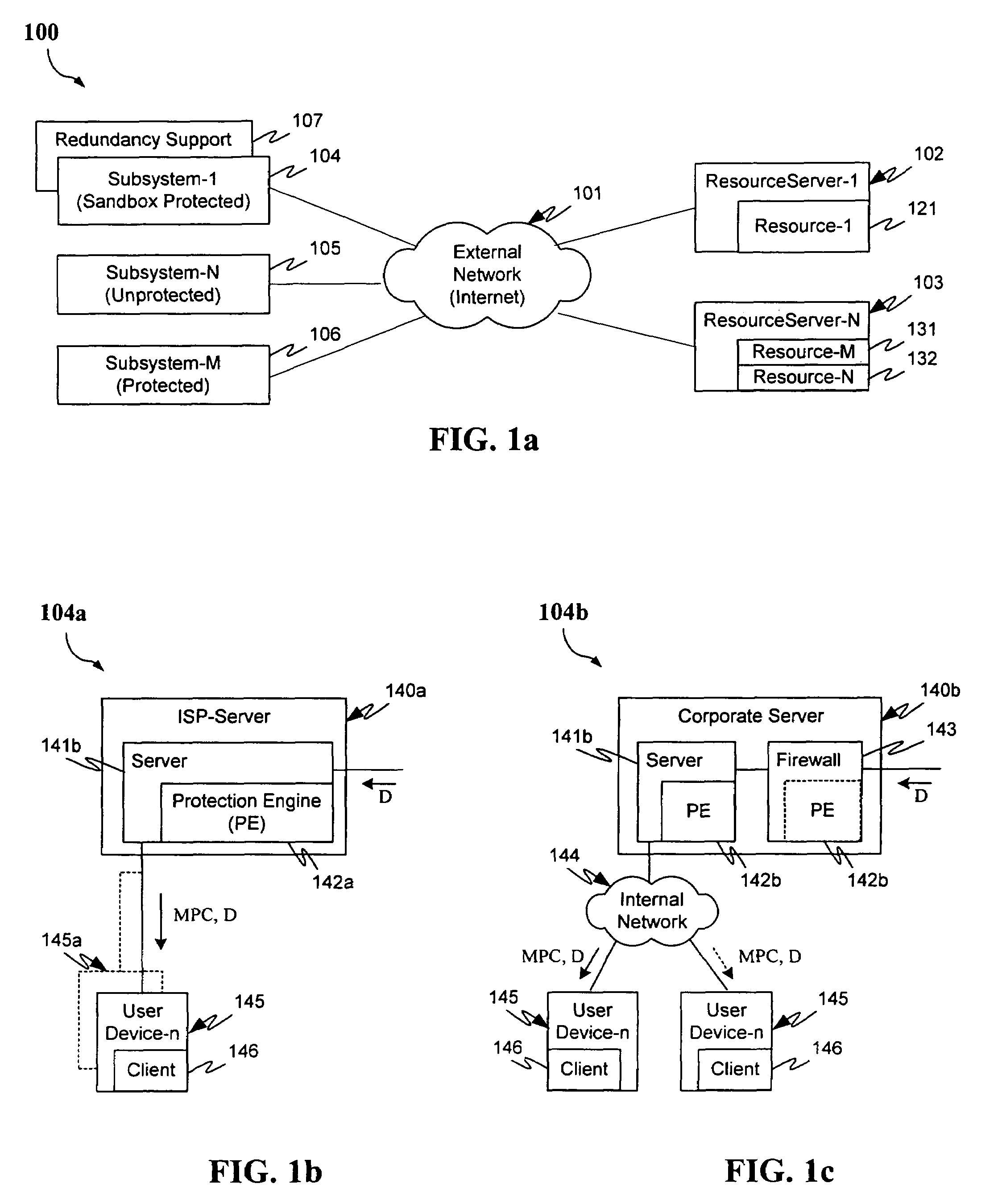
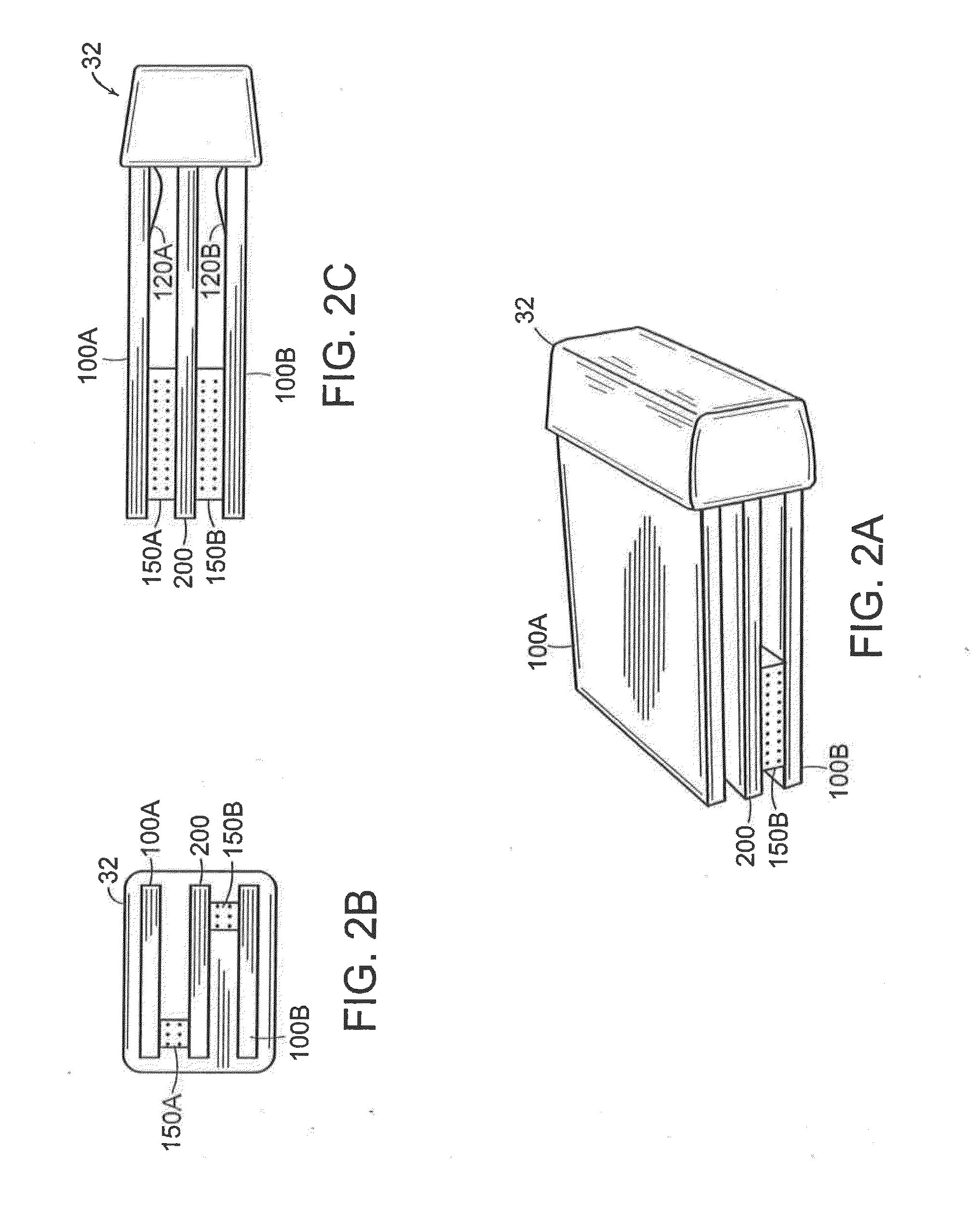
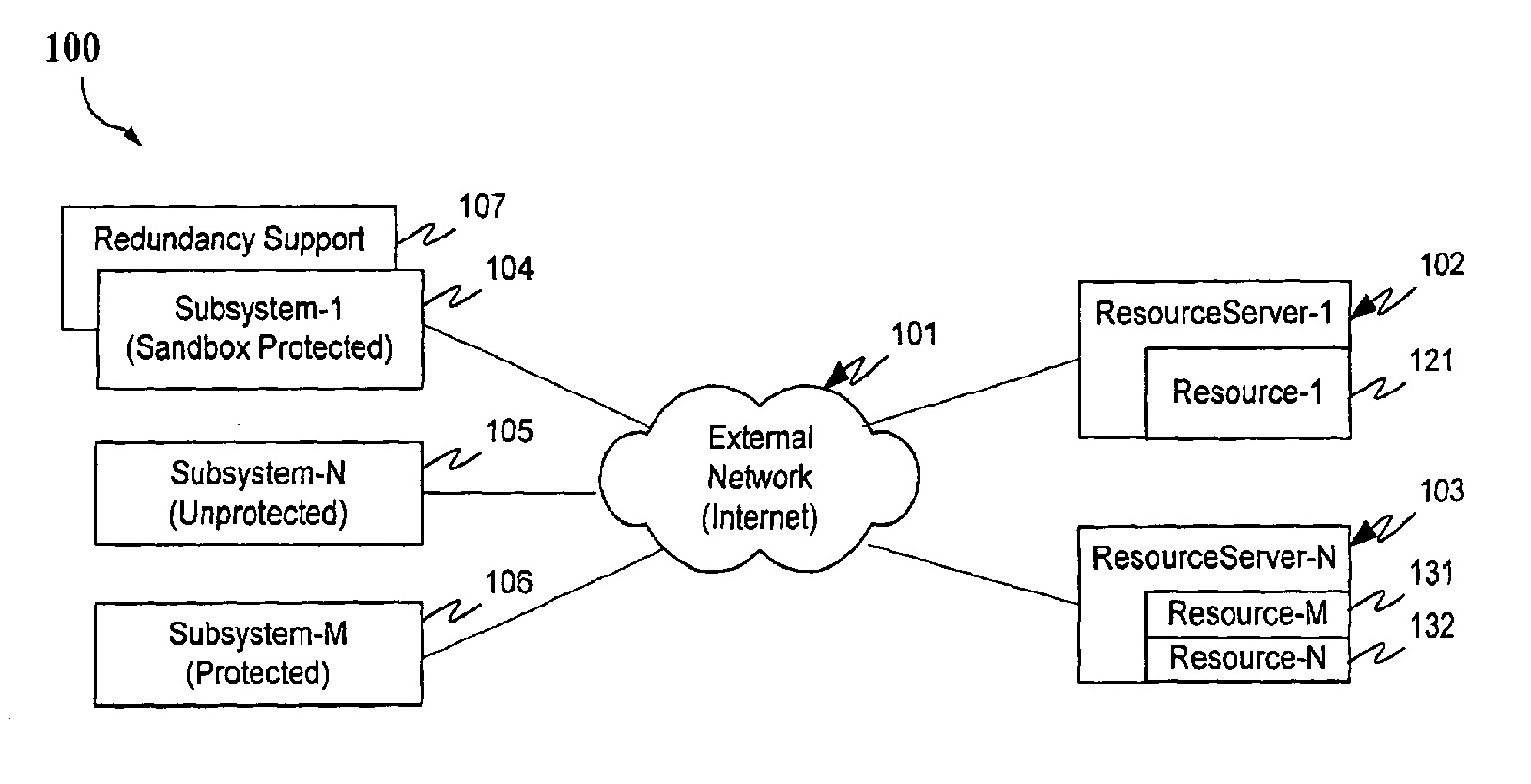
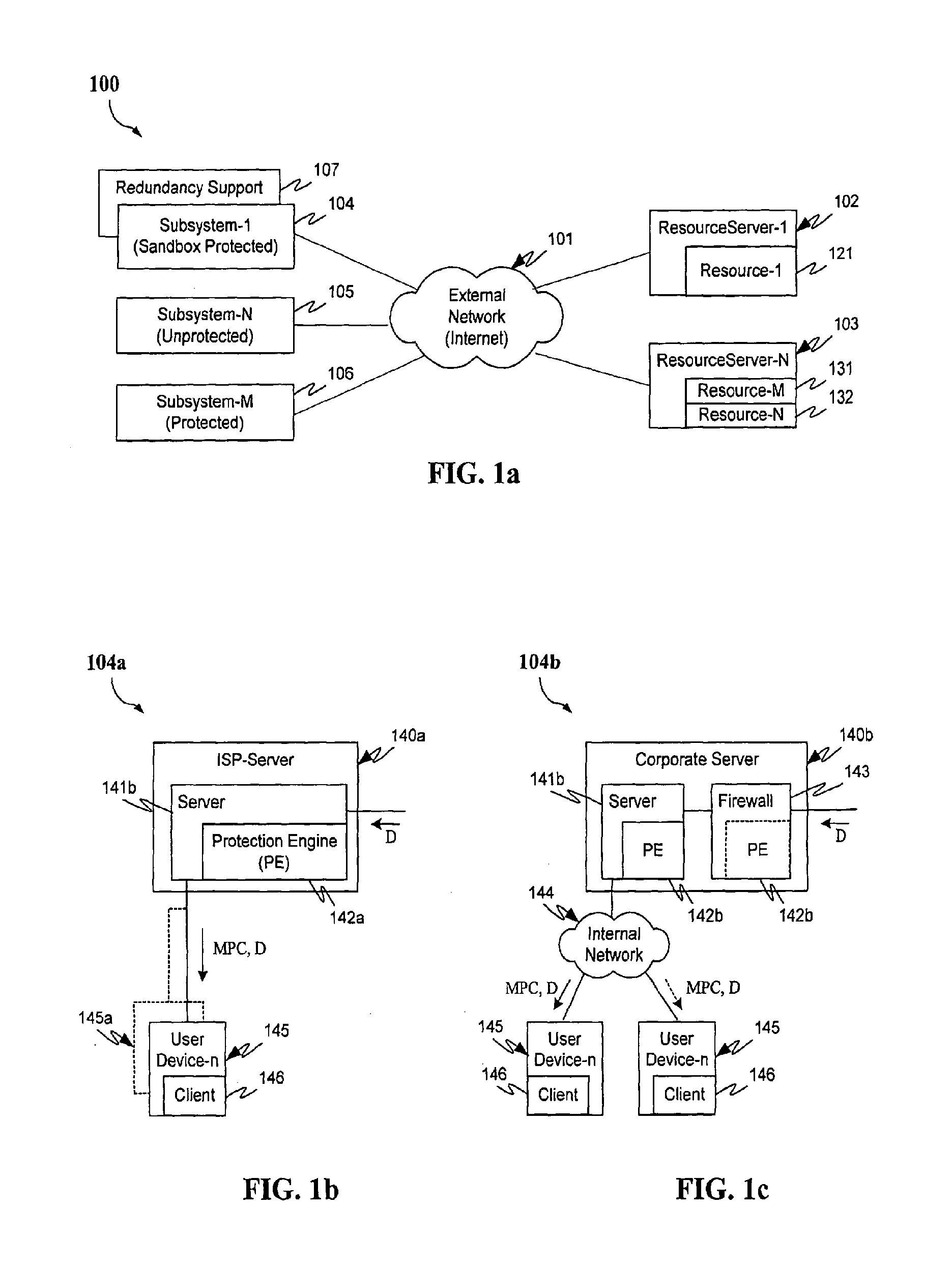
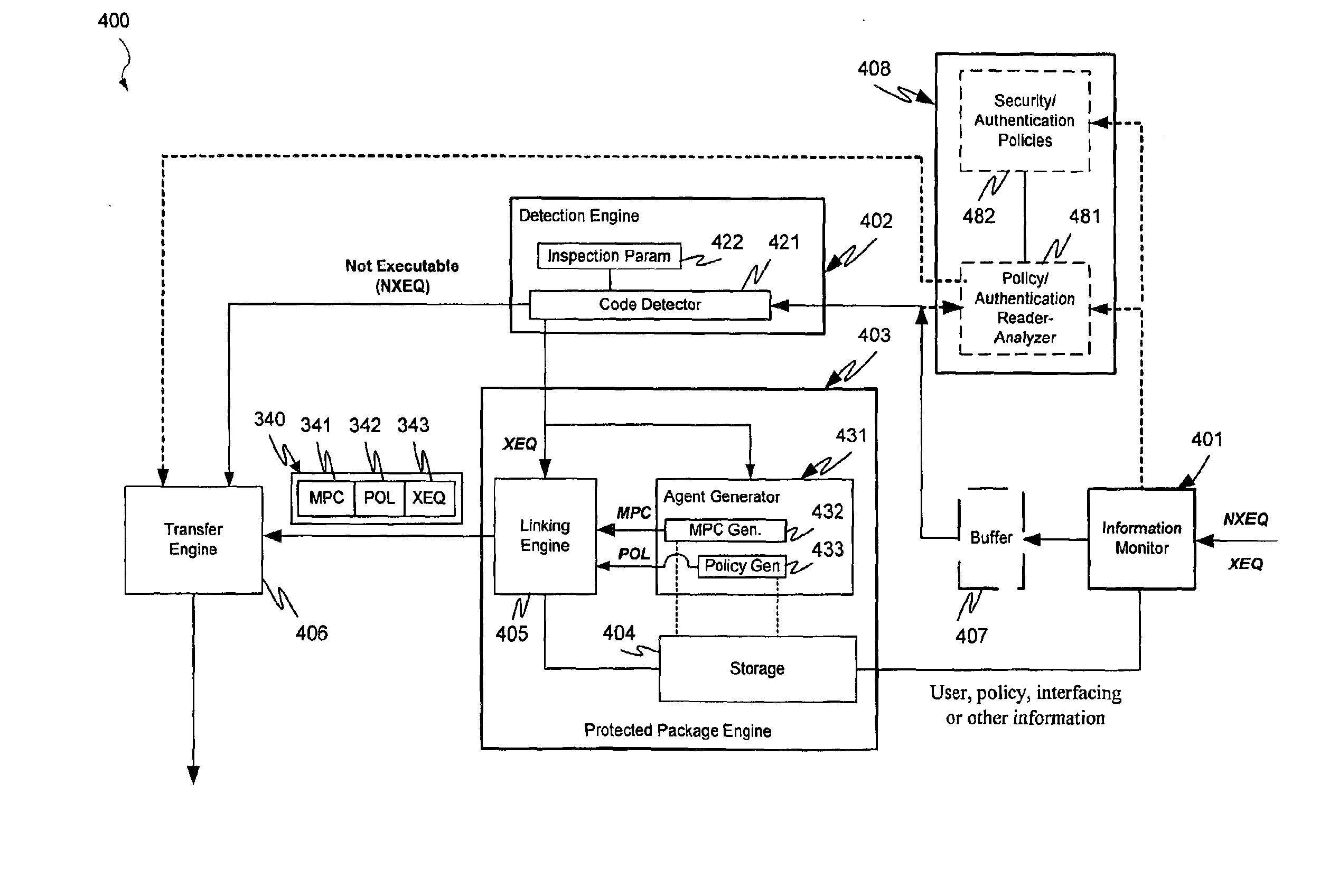
Malicious mobile code runtime monitoring system and methods
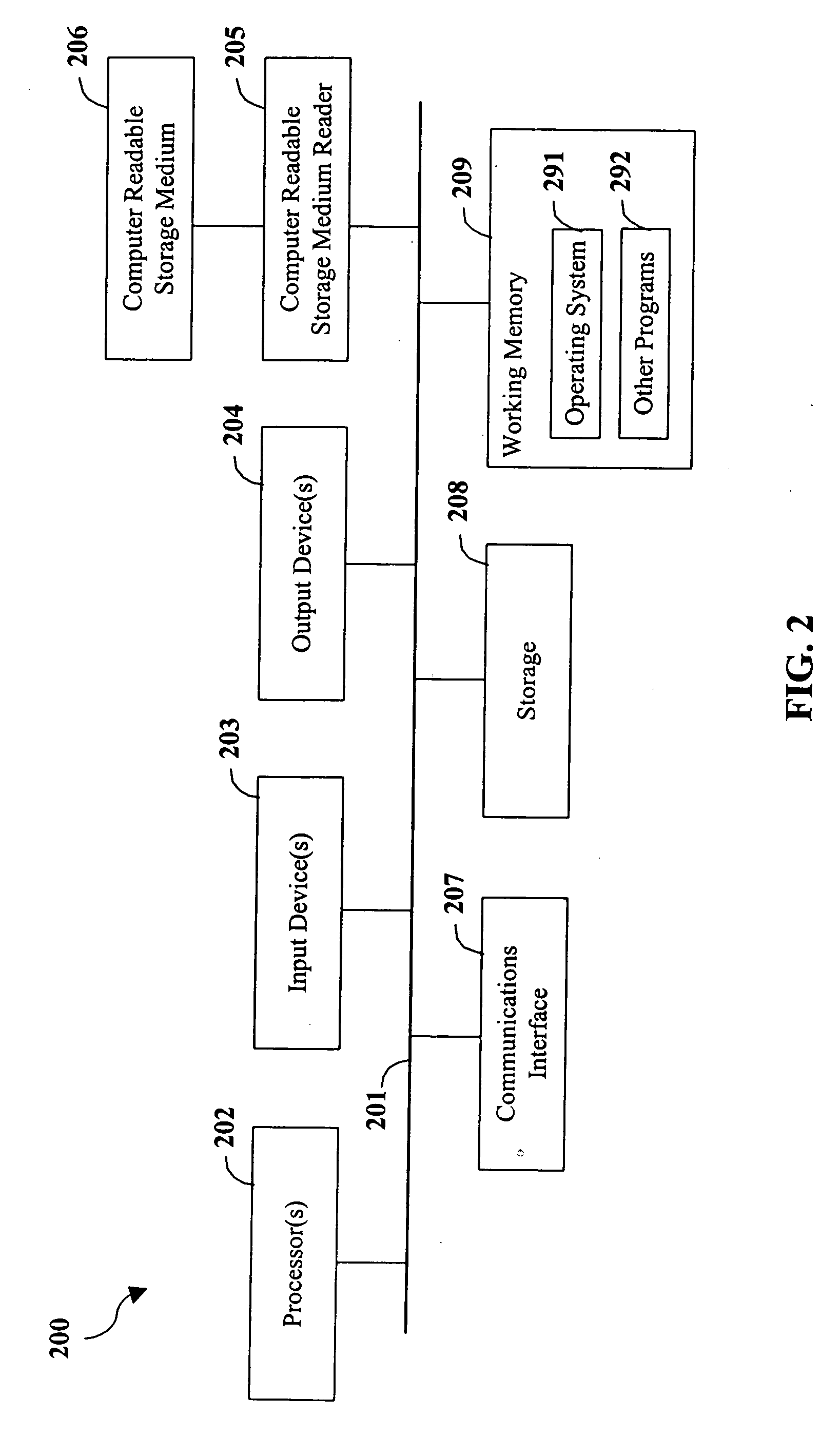
InactiveUS7058822B2Minimization requirementsEasy to updateMemory loss protectionDigital data processing detailsVisual BasicMonitoring system
Owner:FINJAN LLC
System and method for developing and deploying computer applications over a network
InactiveUS20050155027A1Reduce bandwidth costsReduce maintenance costsNatural language data processingProgram loading/initiatingVisual BasicOperational system
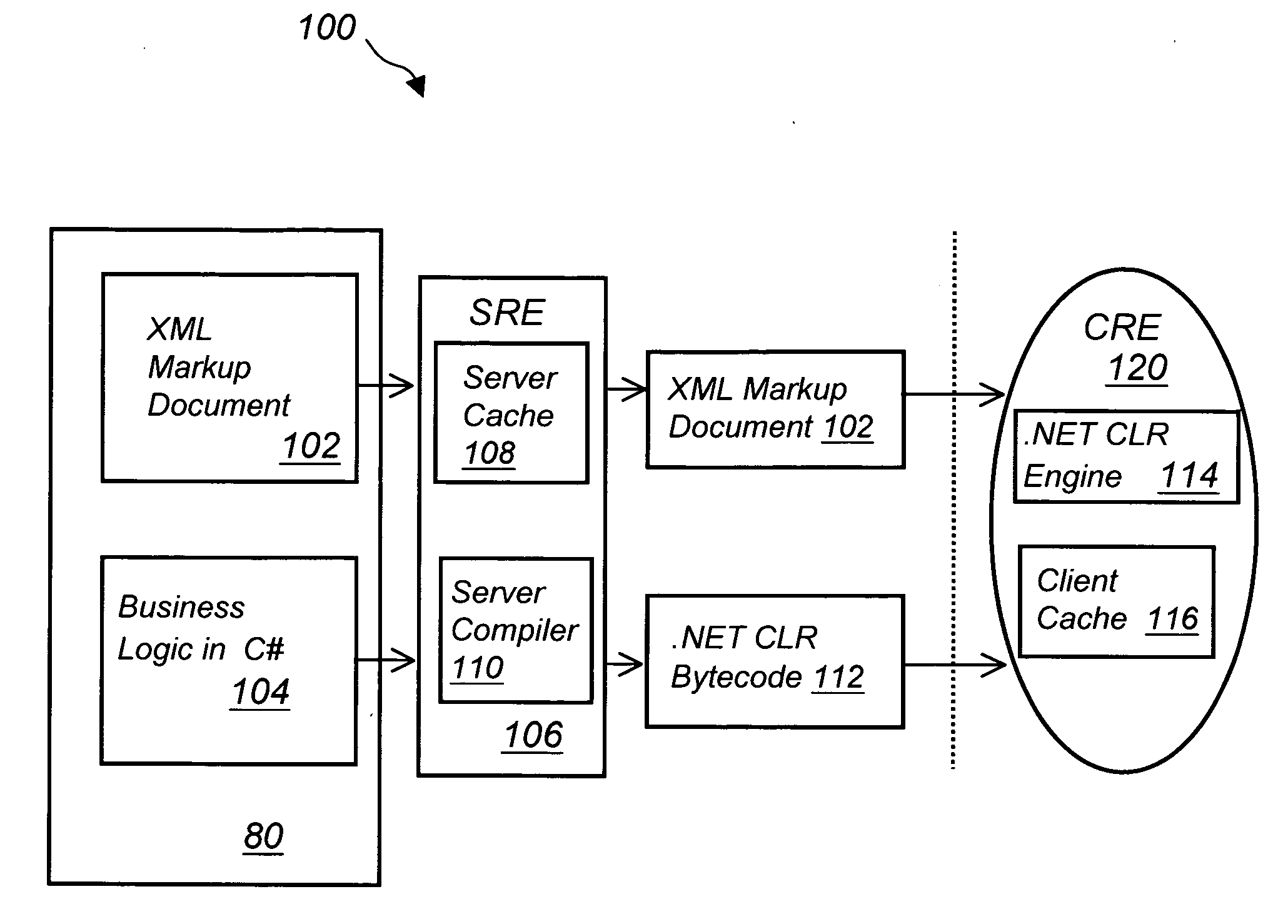
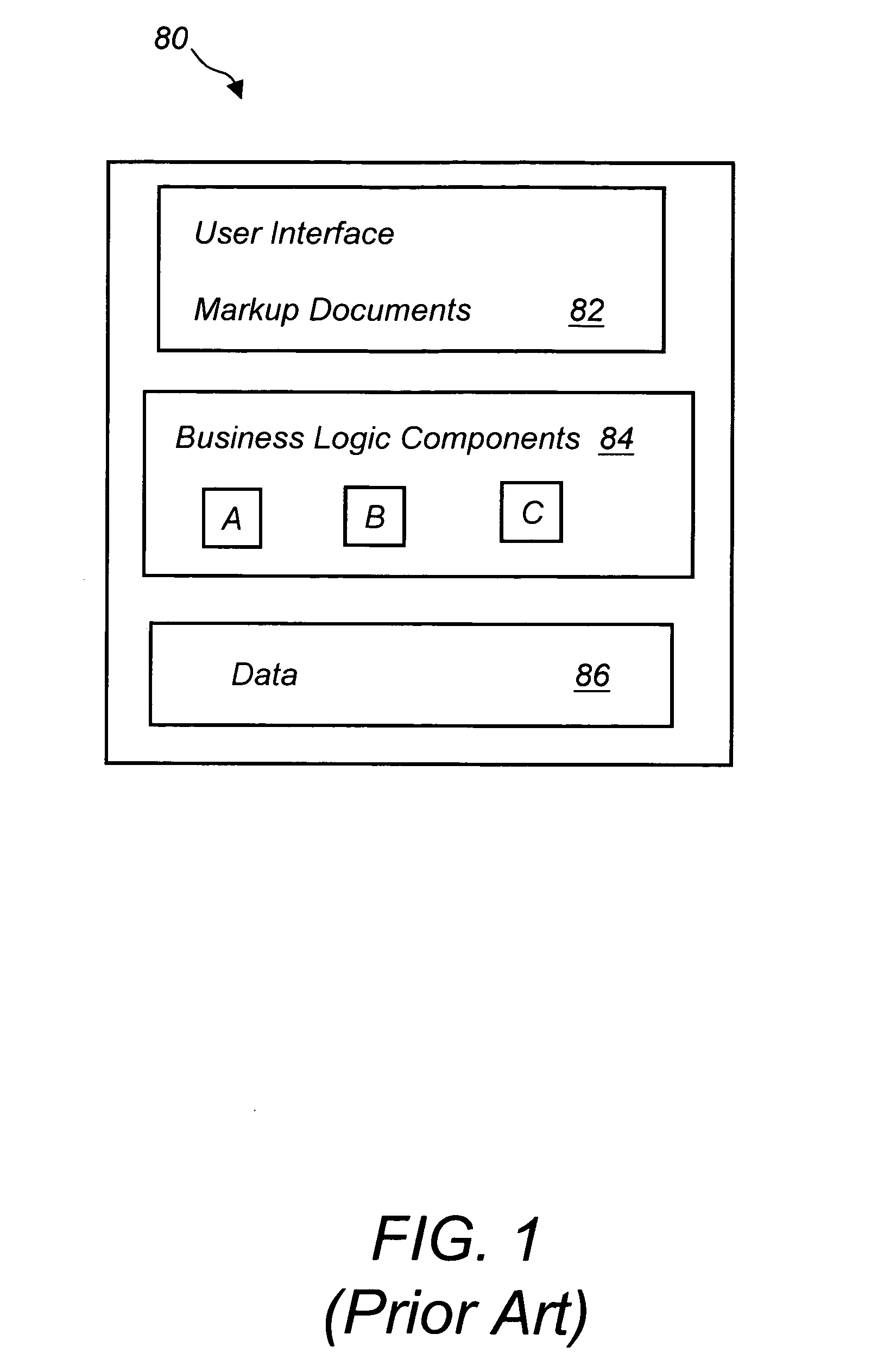
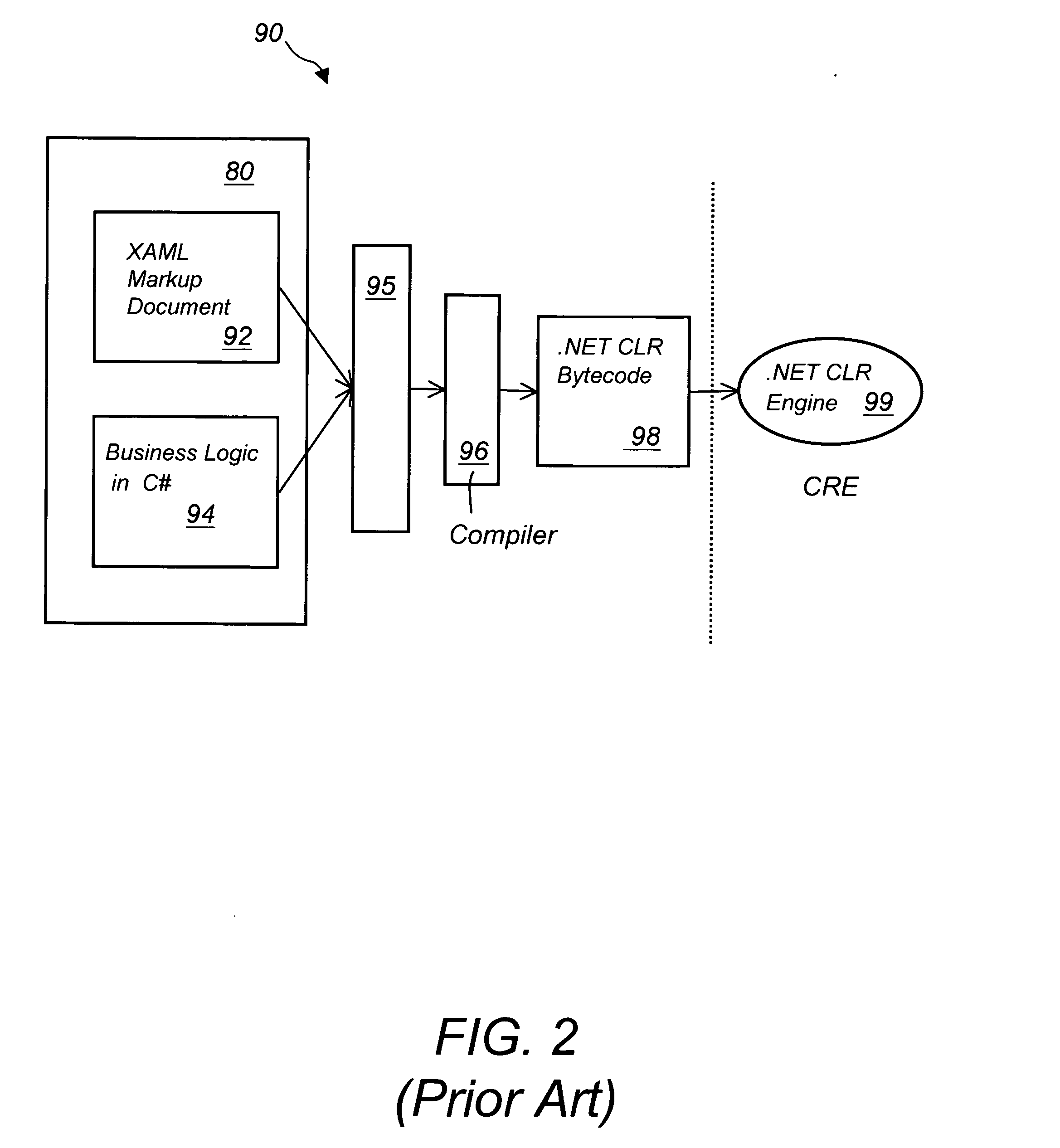
A method of developing a computer application by coding a markup document in an XML markup language, coding a business logic component using any programming language, compiling the business logic component into a specific executable code, converting the XML document into a specific markup language document and deploying the converted markup document and the executable code to a client machine running a specific operating system via a network connection. The XML markup document can be converted in any markup language including XUL, SVG, Xforms, XML related languages, HTML, HTML related languages, text, and combinations thereof. The business logic component can be written using any programming language including Java, JavaScript, J#, C#, C, C++, Visual Basic, ActionScript, XSL, XQuery, and XPath, among others. The computer application can run in any operating system including next generation Windows Longhorn, Windows 2000, Linux, Unix, Apple or Palm operating systems, among others.
Owner:NEXAWEB
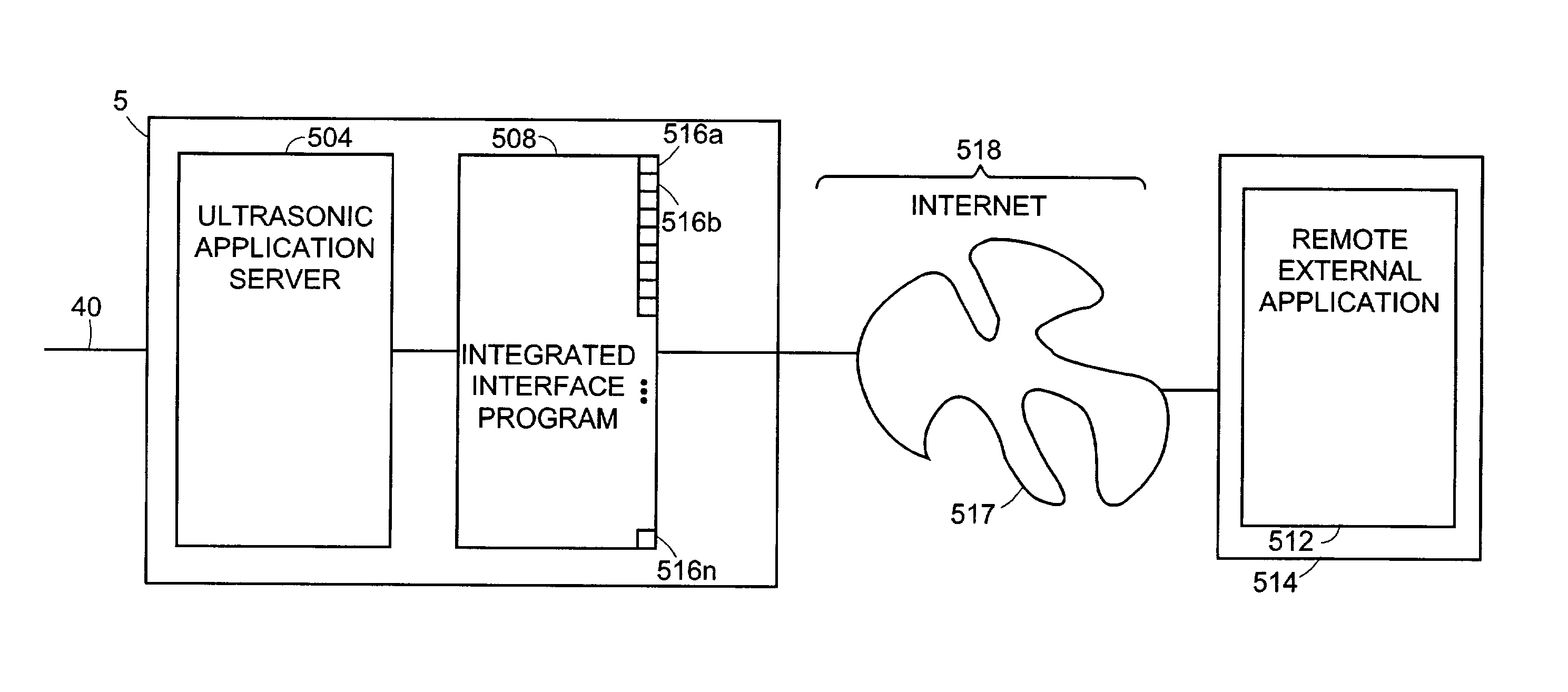
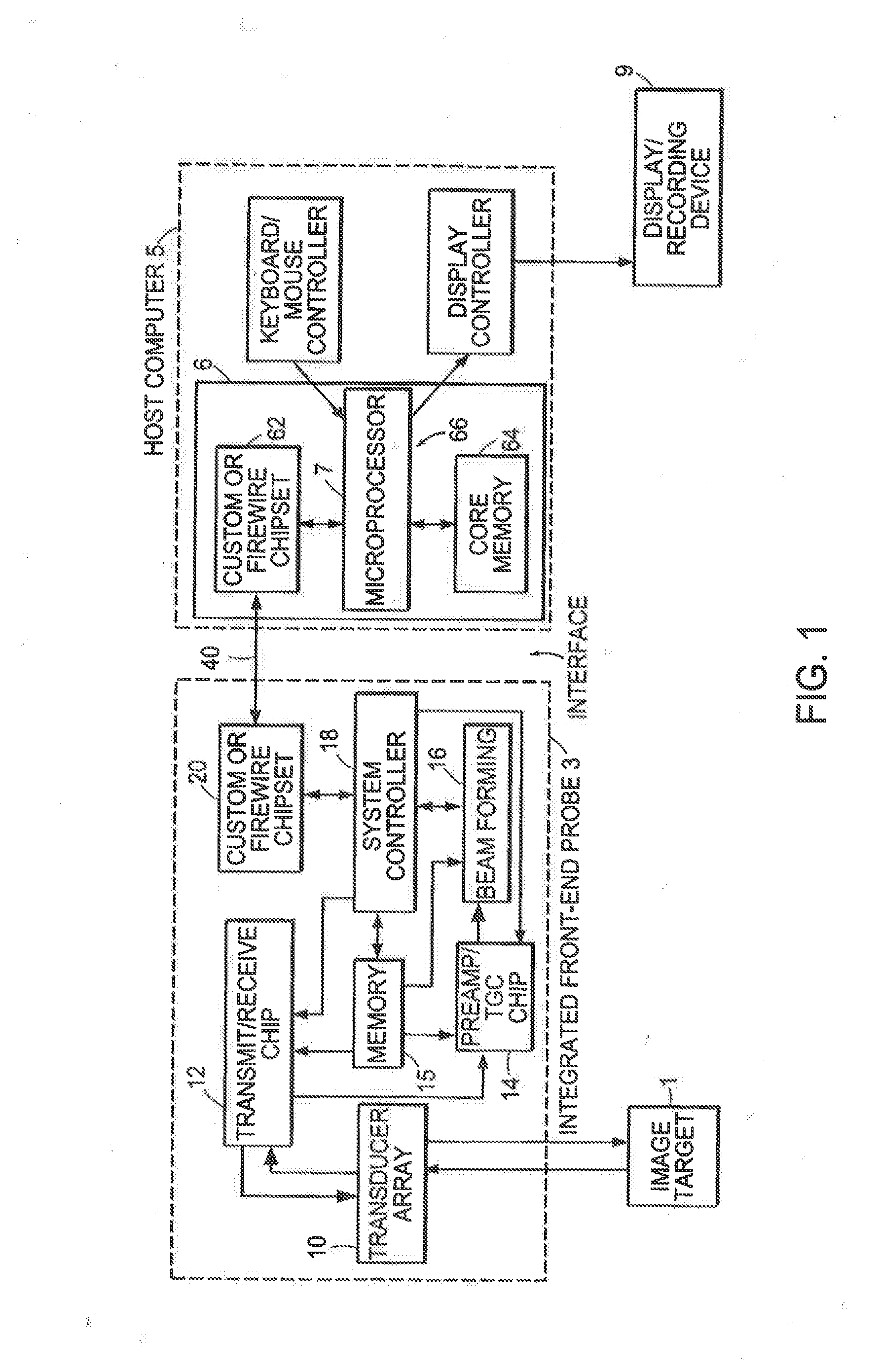
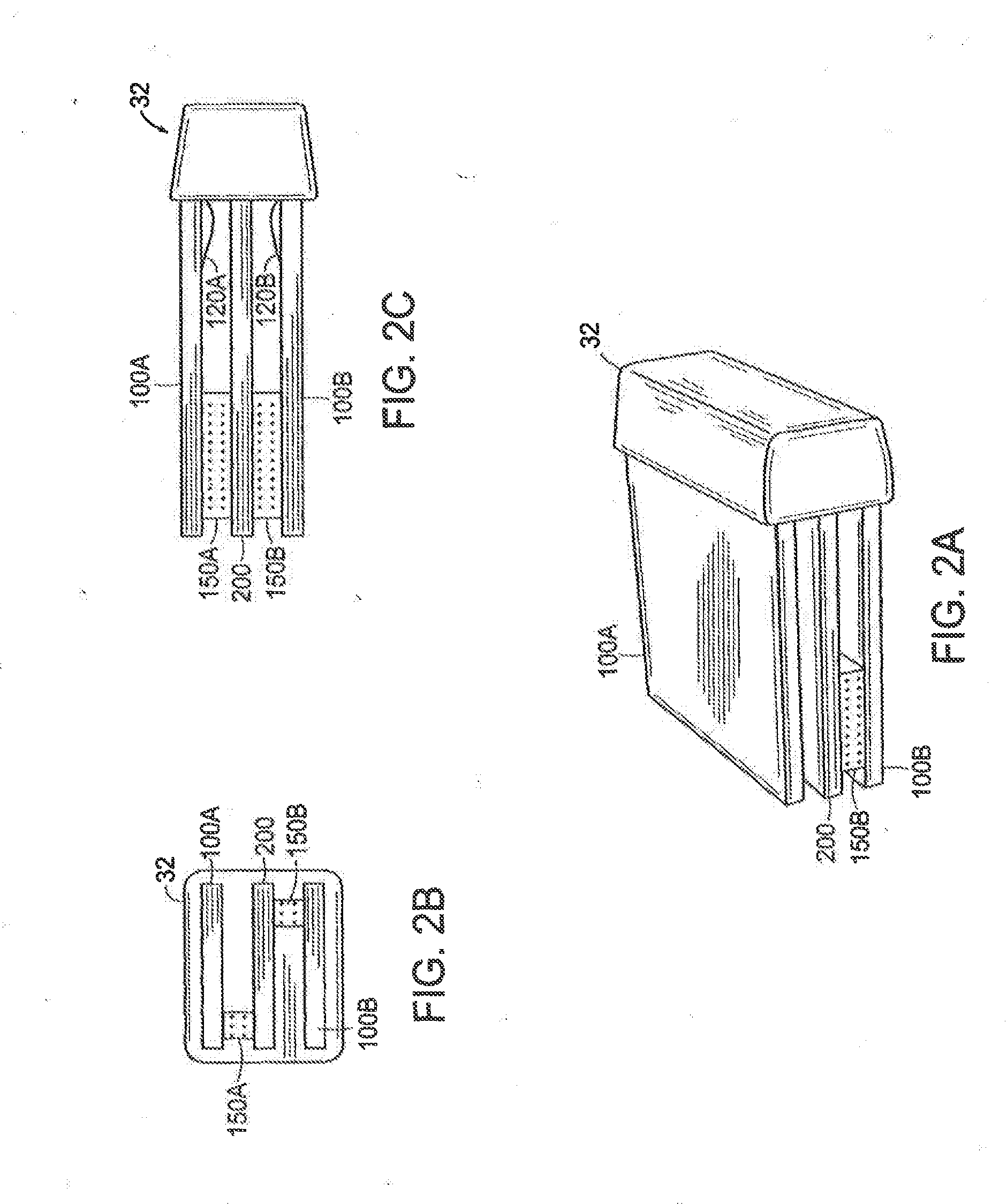
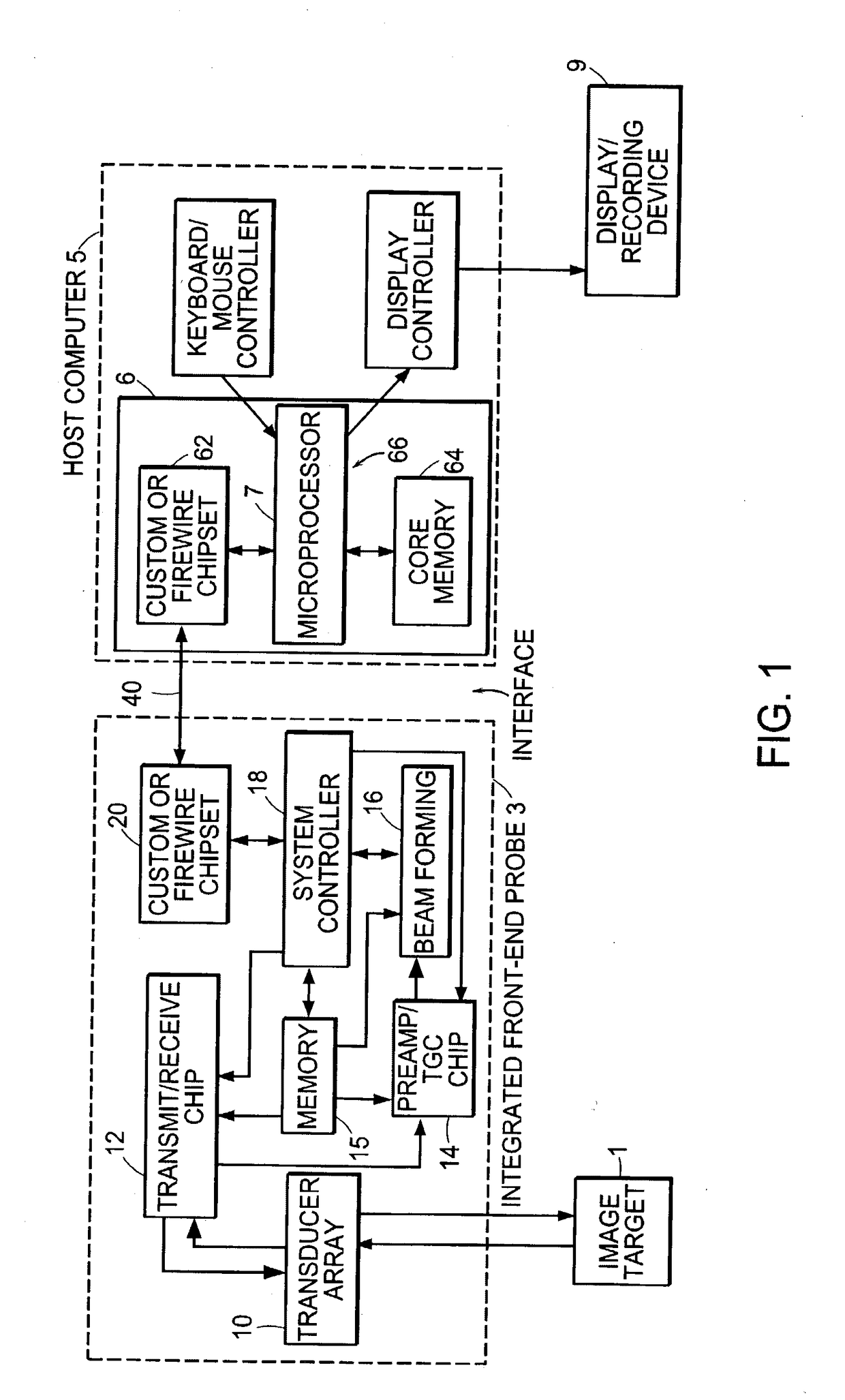
Methods for controlling an ultrasound imaging procedure and providing ultrasound images to an external non-ultrasound application via a network
InactiveUS9402601B1Simplifies cable requirementDifficult to upgradePhysical therapies and activitiesMechanical/radiation/invasive therapiesVisual BasicSonification
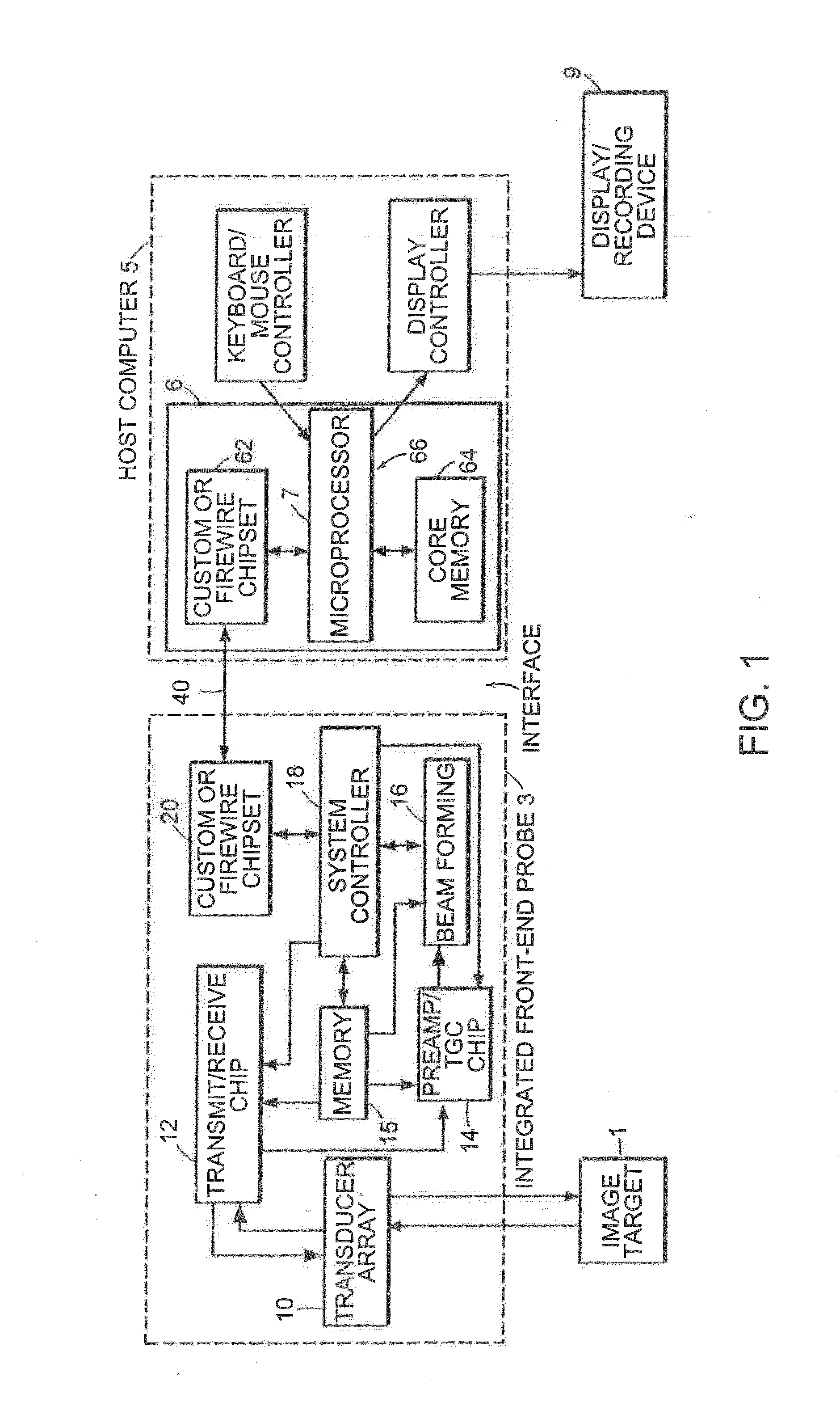
A hand-held ultrasound system includes integrated electronics within an ergonomic housing. The electronics includes control circuitry, beamforming and circuitry transducer drive circuitry. The electronics communicate with a host computer using an industry standard high speed serial bus. The ultrasonic imaging system is operable on a standard, commercially available, user computing device without specific hardware modifications, and is adapted to interface with an external application without modification to the ultrasonic imaging system to allow a user to gather ultrasonic data on a standard user computing device such as a PC, and employ the data so gathered via an independent external application without requiring a custom system, expensive hardware modifications, or system rebuilds. An integrated interface program allows such ultrasonic data to be invoked by a variety of such external applications having access to the integrated interface program via a standard, predetermined platform such as visual basic or c++.
Owner:TERATECH CORP
User Interface Image Element Display and Adaptation System
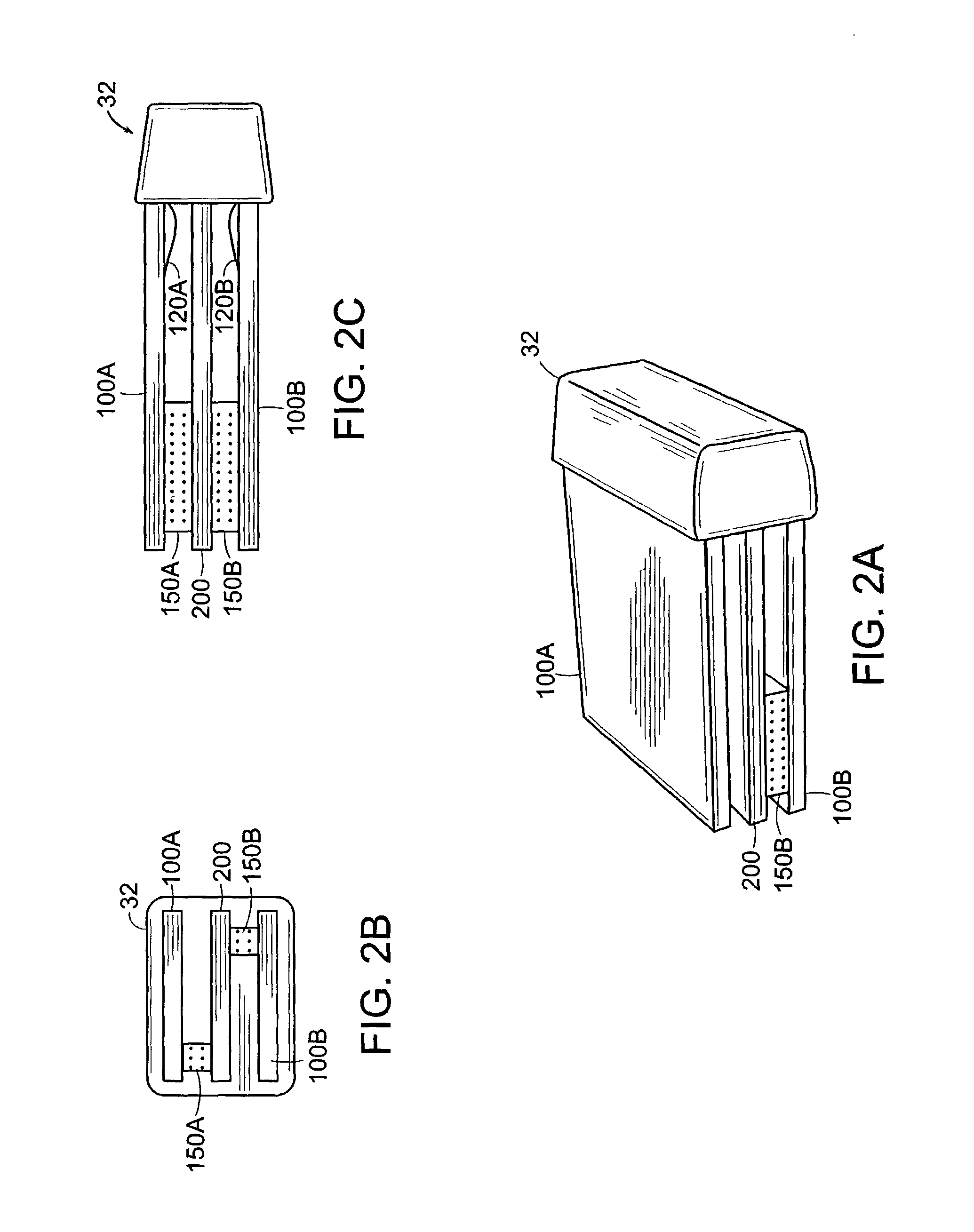
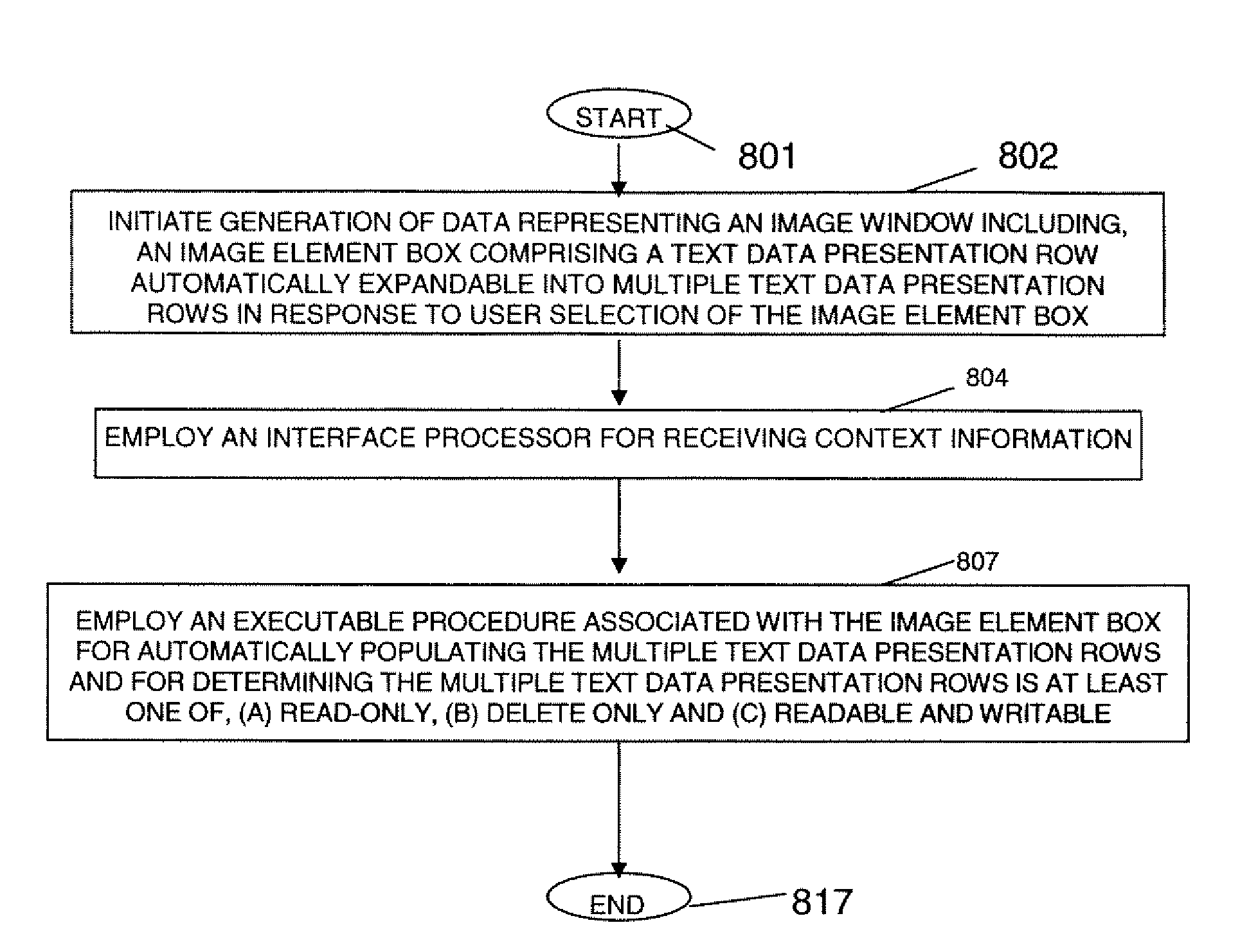
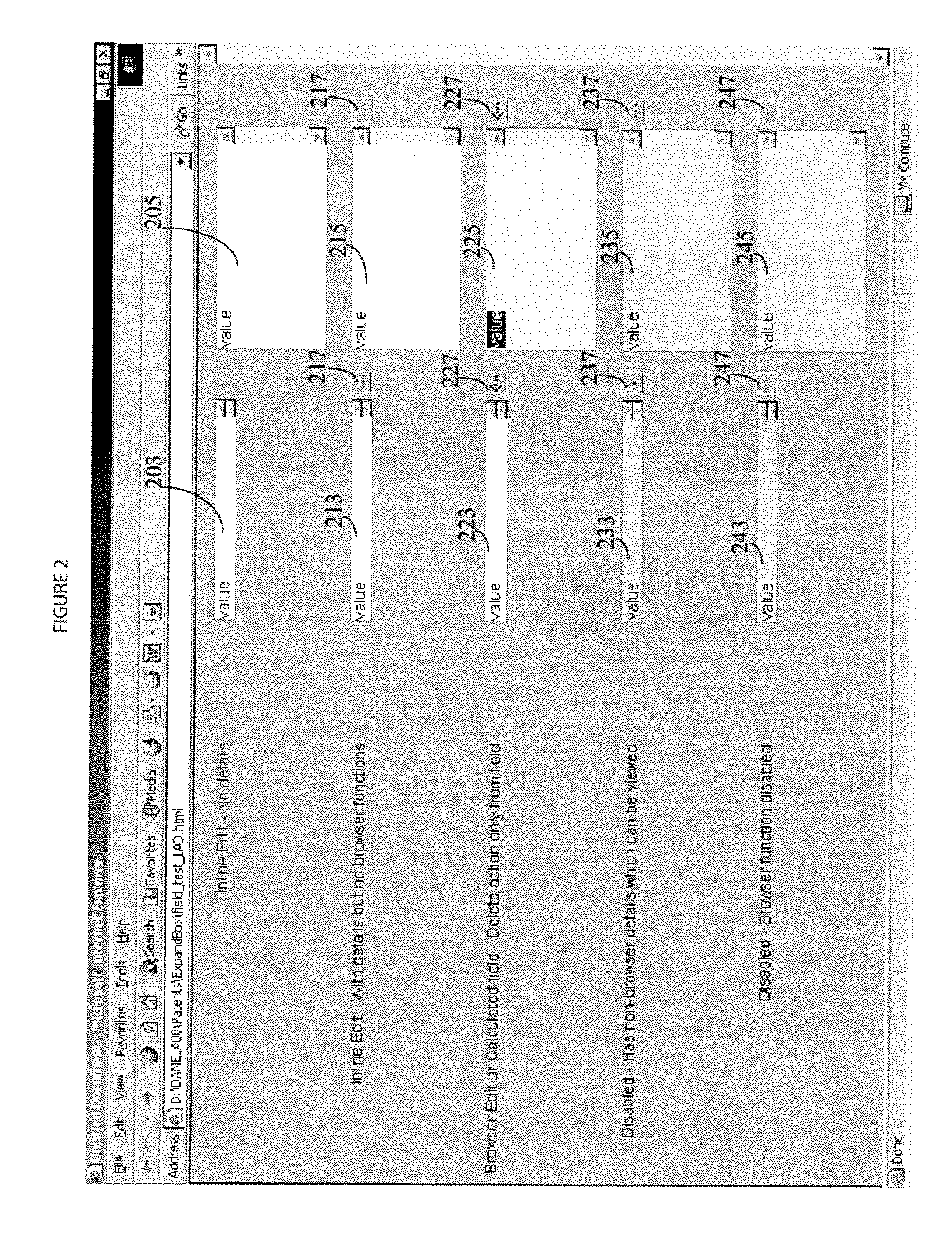
A system provides a single-click expandable data control implemented in a user interface development language as a data entry and viewing element including options enabling or restricting data entry and specifying a related dialog for entry or selection of data for a primary display field. A system provides a single-click expandable data element in HTML, for example, as a data entry and viewing element that is used within a user interface interactive page to allow a single line-height data display using a single mouse click to expand or collapse data, thereby providing a simple means for a user to view or enter larger amounts of data than typically fit within the limited screen space. A user interface system adaptively presents information to a user. The system includes a display processor for initiating generation of data representing an image. The image includes, an image element box comprising a text data presentation row automatically expandable into multiple text data presentation rows in response to user selection of the image element box. An executable procedure associated with the image element box determines whether text in the multiple text data presentation rows is at least one of, (a) delete only, (b) read-only and (c) readable and writable. The executable procedure is in a user interface compatible code language (e.g., HTML, SGML, XML, Visual Basic) and execution of the executable procedure is initiated in response to user selection of the image element box.
Owner:SIEMENS MEDICAL SOLUTIONS USA INC
Hybrid CNC control system
InactiveUS20020091460A1Accurate recordReliable processingSpecial data processing applicationsNumerical controlVisual BasicNumerical control
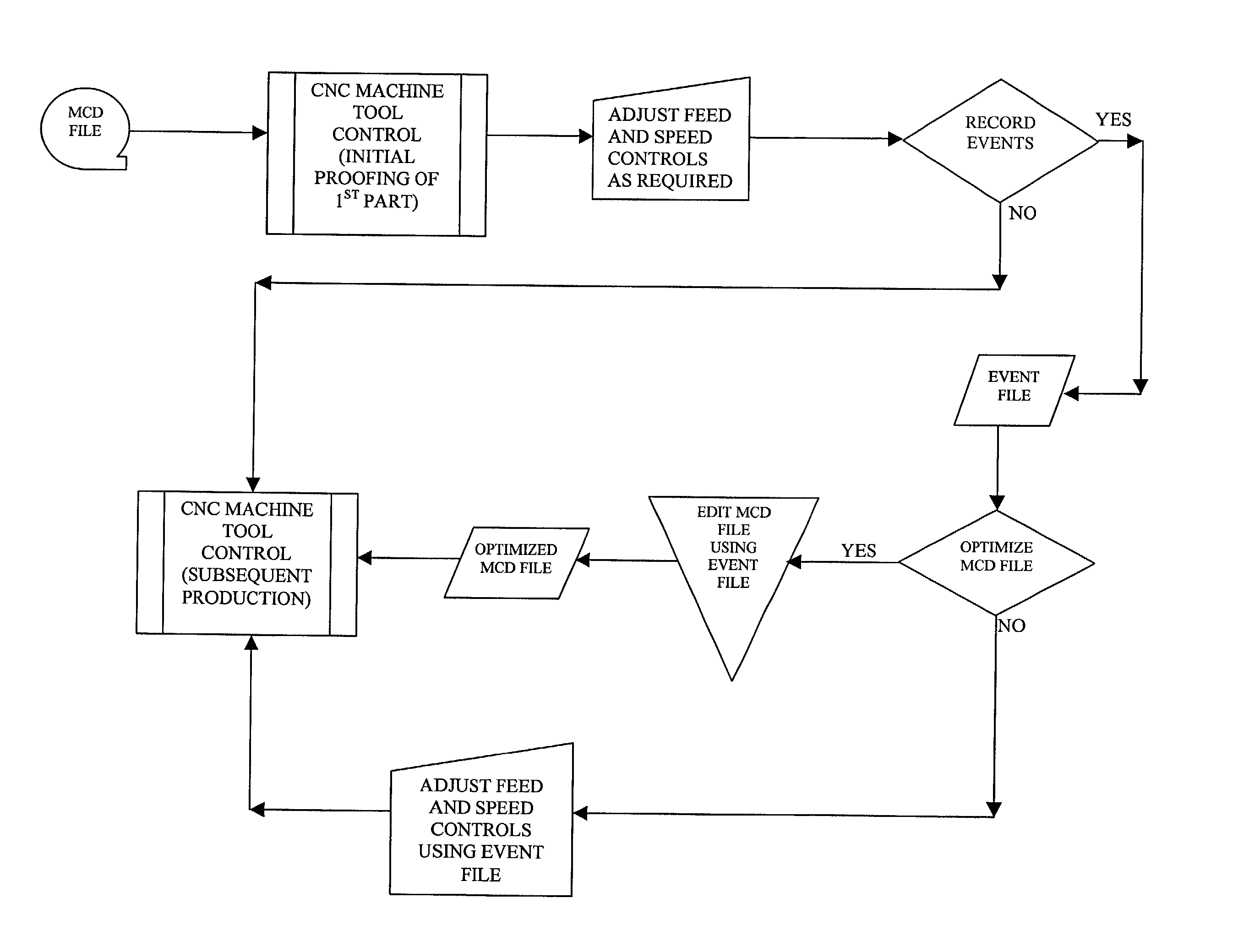
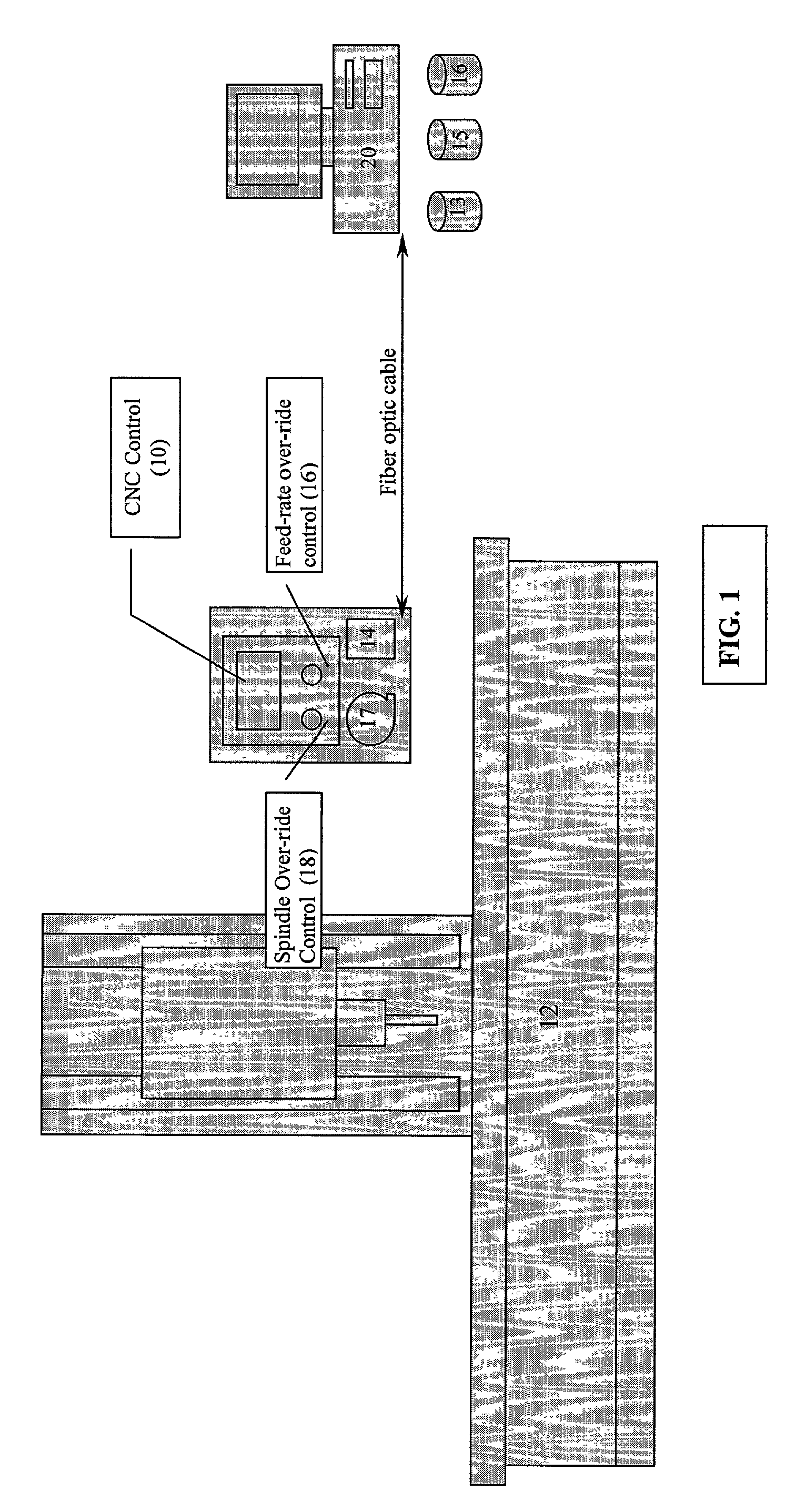
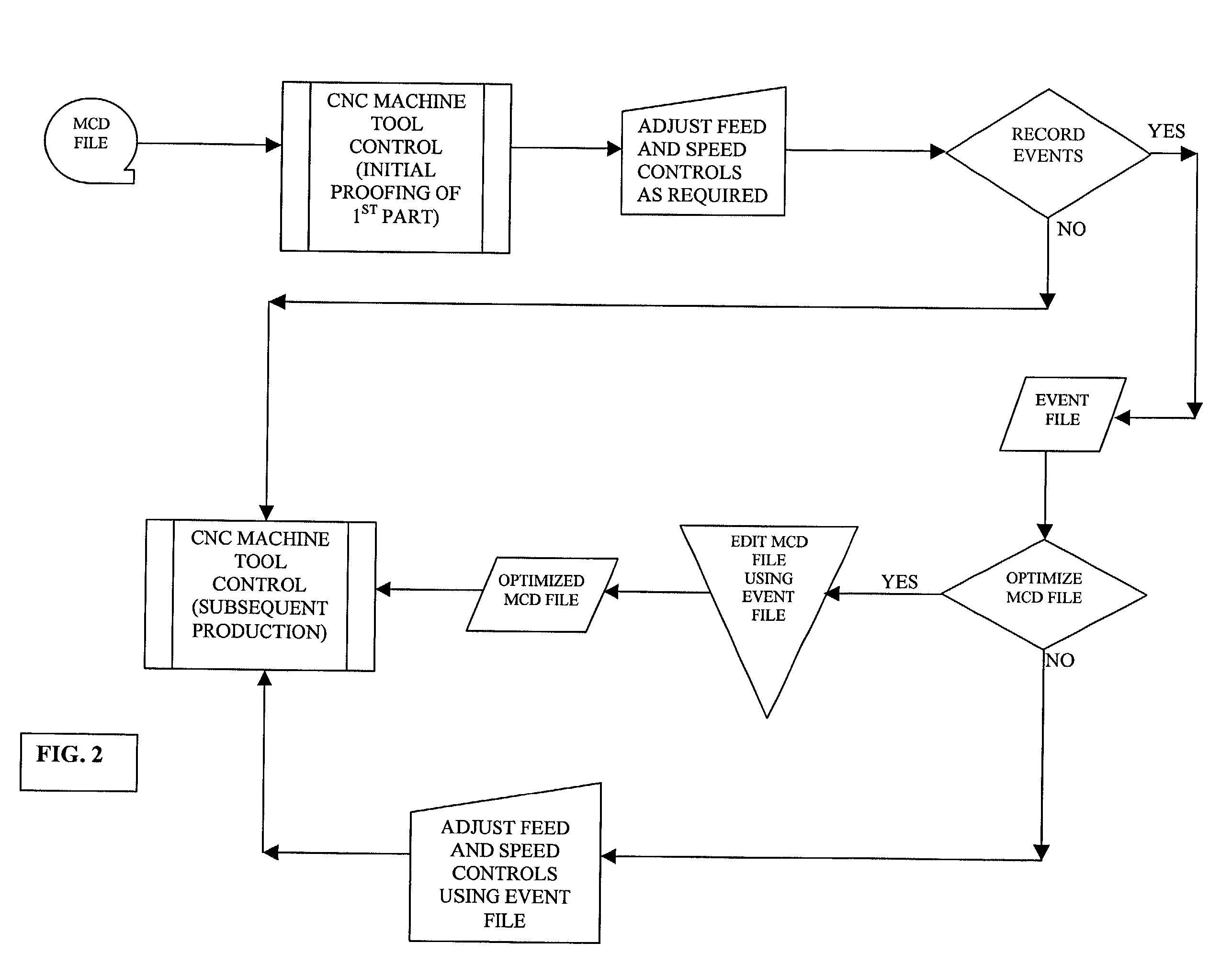
The present invention demonstrates an improved CNC Control system, which integrates operator-induced changes into the pre-programmed CNC machining process. The improved CNC Control system develops a Human Activity Storage Program (HASP), which is used for subsequent production in conjunction with and simultaneously with the Numerical Control Program thereby enhancing the production process by integrating the skilled machinist's input into the production process. The numerical control program of a CNC machine is interfaced with an IBM compatible personal computer (PC) to make information relative to the block number, feed-rate and / or spindle speed over-ride values available at the personal computer. If the CNC Control has been re-configured properly (with regard to the ladder interface and operating system) a PC computer is not required. During the machining of a part the machine operator will manually over-ride the feed-rate and / or the spindle speed to optimize machining performance. Through the use of VISUAL BASIC OR C++programming modules and routines, the spindle speed and feed-rate controls (located at the CNC Control) are polled at frequent or 5OO ms intervals. The status or over-ridden values of these controls are correlated to the active block number in use during each polled sequence and this information is written to an "event file". After the subject part has been completed, one of two options can be used. An "edit phase" is initiated which utilizes the information in the "event file" to reconstruct the MCD file. After the edit phase is complete, the resultant output "Optimized MCD" can be used to produce like parts with confidence that all motion is running at peak performance and all programmed trajectories are maintained. The cycle can be repeated again (if desired) to ensure even greater efficiency while cutting. In the alternative, the event file can be employed to "command" the CNC Control with respect to feed-rate and / or spindle speed over-ride settings.
Owner:ALLEN WILLIAM D
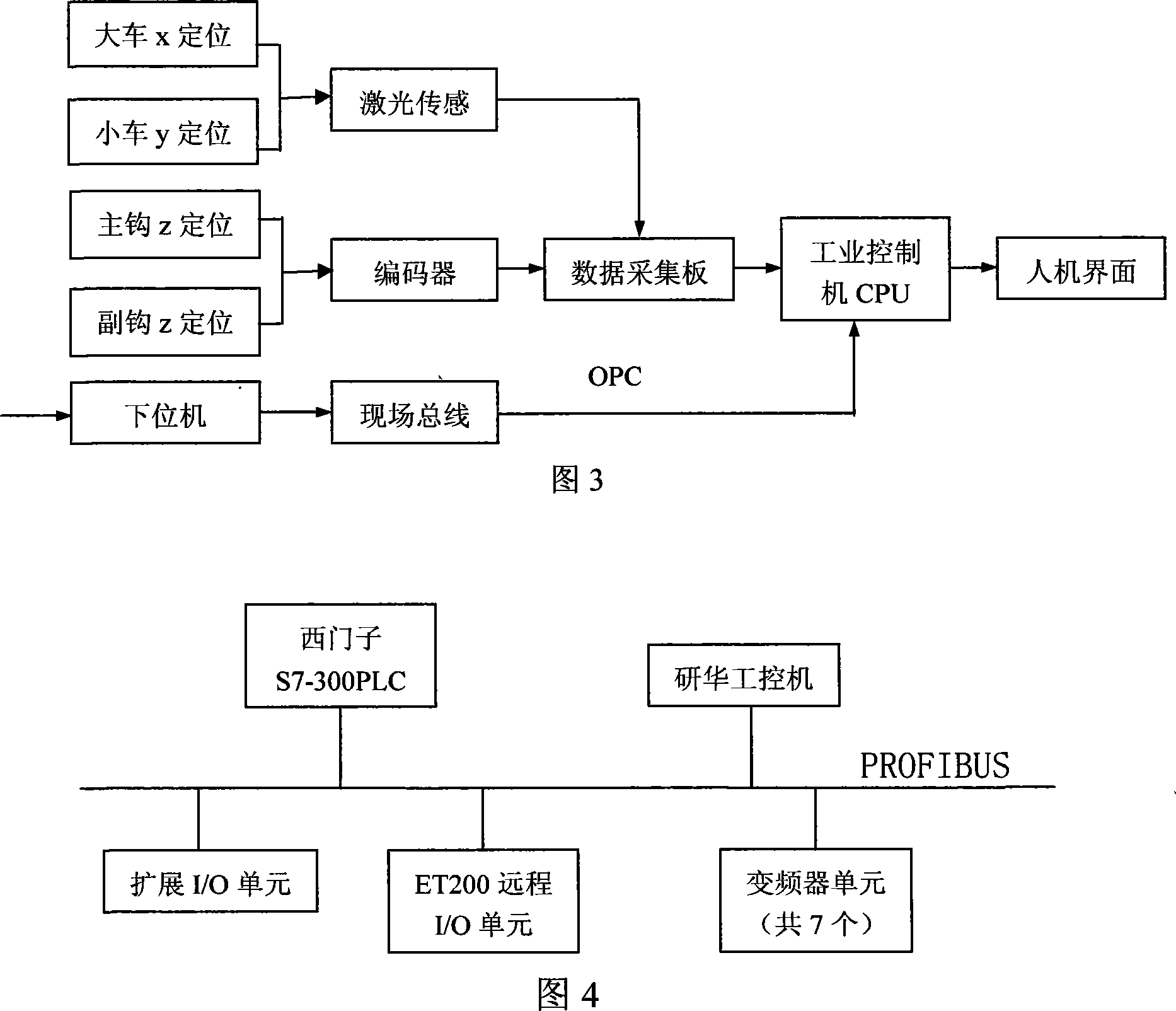
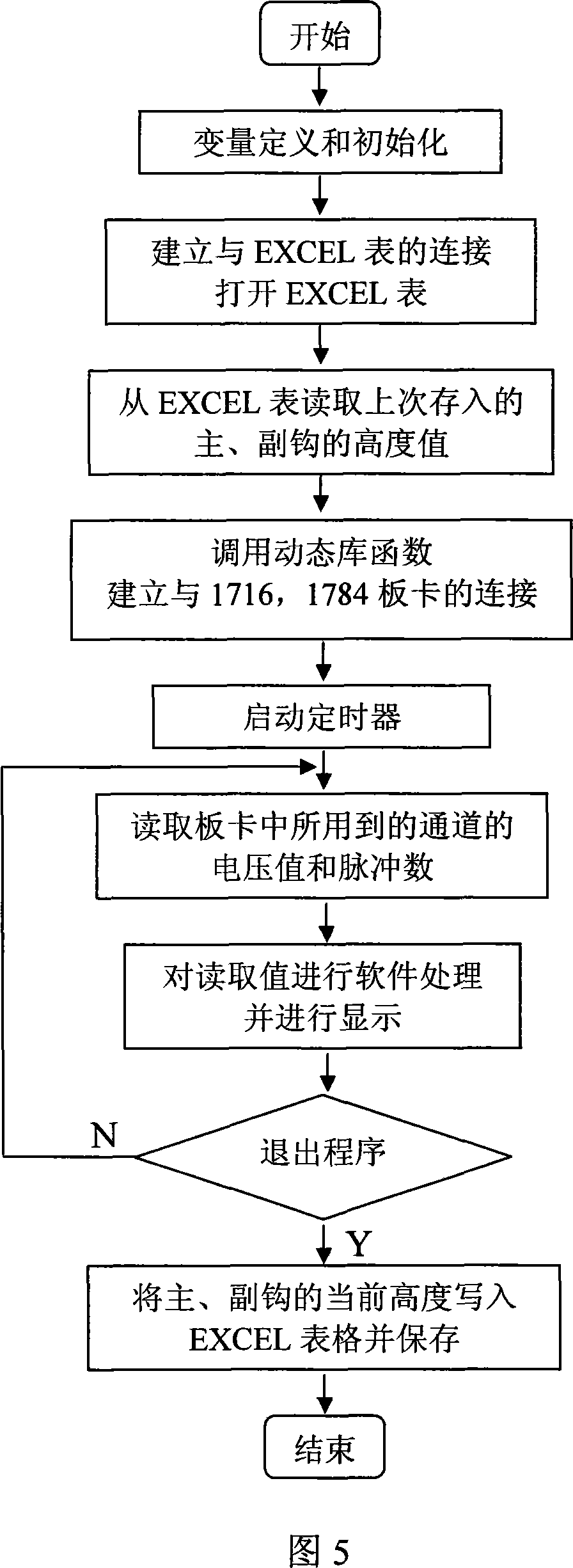
Traveling crane positioning system and positioning method
InactiveCN101143686AAccurately run reference dataIntuitive surface informationLoad-engaging elementsVisual BasicData acquisition
The invention relates to an overhead traveling crane positioning system and a positioning method, which adopts an industrial control computer as the core, organically integrates the industrial control computer, data collection cards, a lower computer PLC and a sensor and fully displays the advantages of all the parts. Without changing the design and the control scheme of the original overhead traveling crane, the invention adopts a high-precision laser sensor and an encoder to measure and obtain the distances in the x, y and z directions of the overhead traveling crane, sends the distances into the CPU of the industrial control computer by different types of data collection cards, meanwhile, adopts the OPC technology to read the running status of the overhead traveling crane from the lower computer PLC to an upper computer: the industrial control computer through a CAN-bus, and then composes the data processing and interface display programs in Visual Basic and other high-level languages in the industrial control computer, to real time display the running position and status of the overhead traveling crane, so as to provide precise running data of the overhead traveling crane for the operator and lay a solid research foundation for the overhead traveling crane to be driven without a driver with high precision.
Owner:TIANJIN UNIVERSITY OF TECHNOLOGY
Malicious mobile code runtime monitoring system and methods
InactiveUS20060026677A1Minimizing serverMinimizing client resource requirementMemory loss protectionError detection/correctionVisual BasicMonitoring system
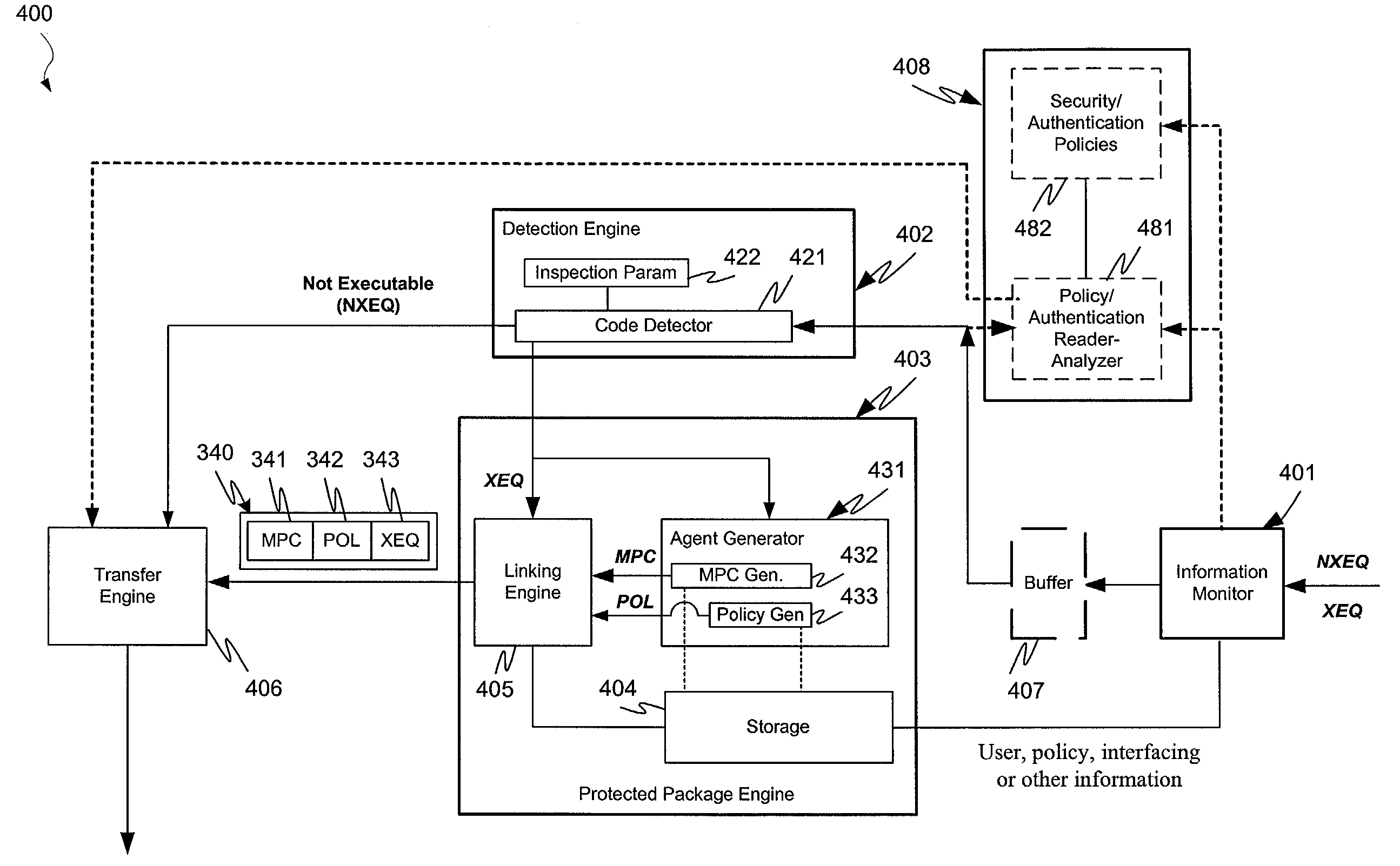
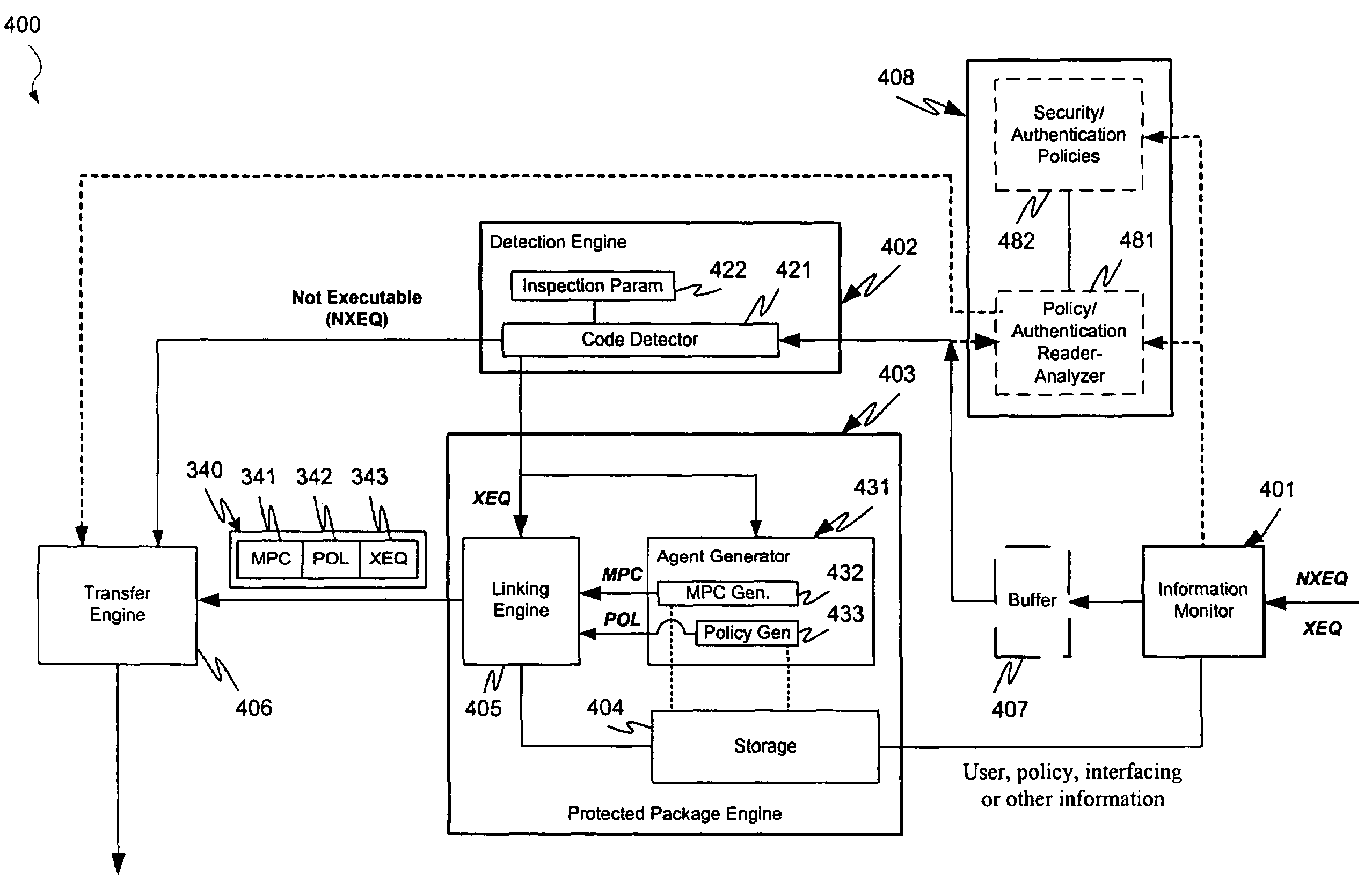
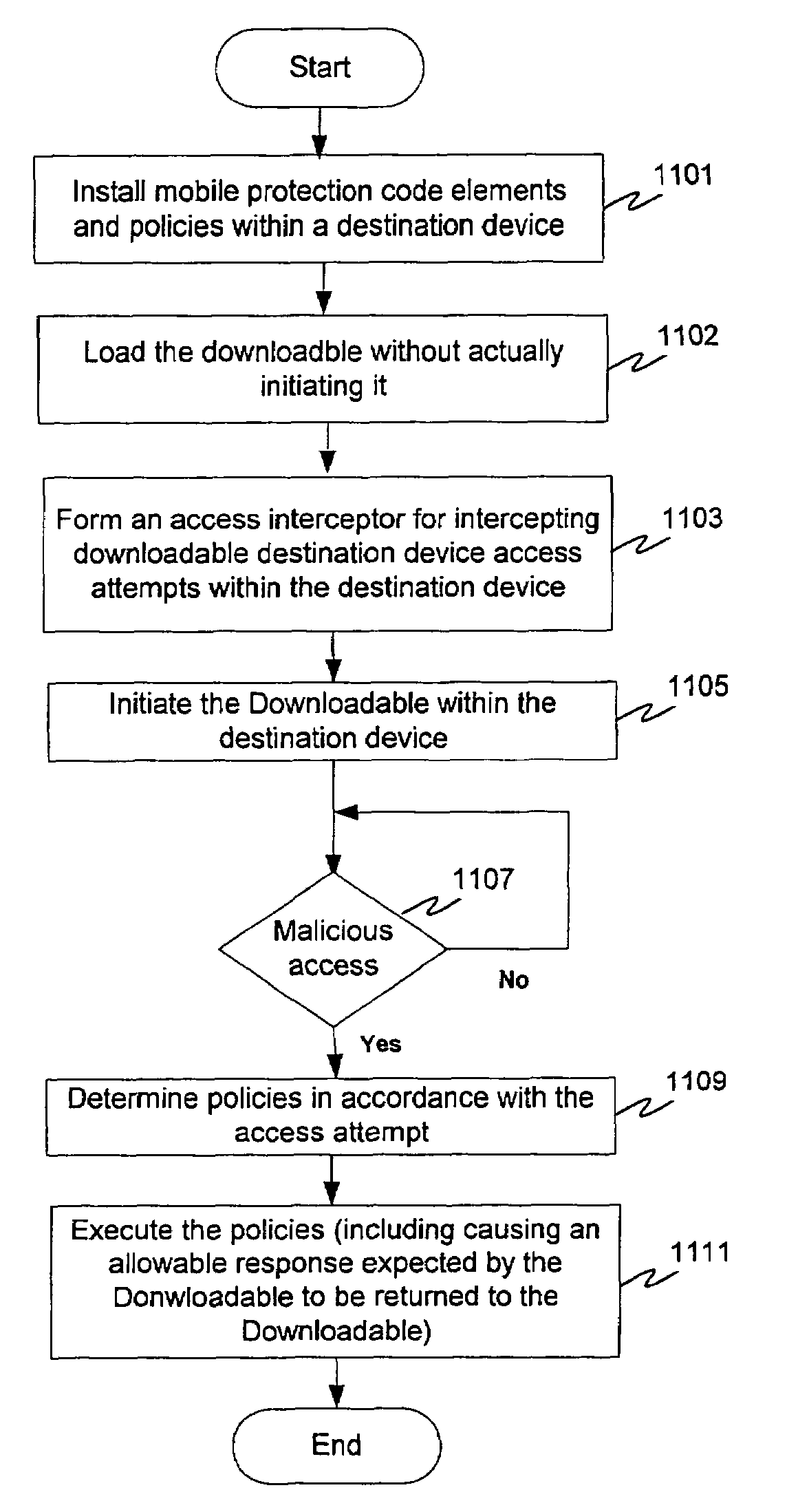
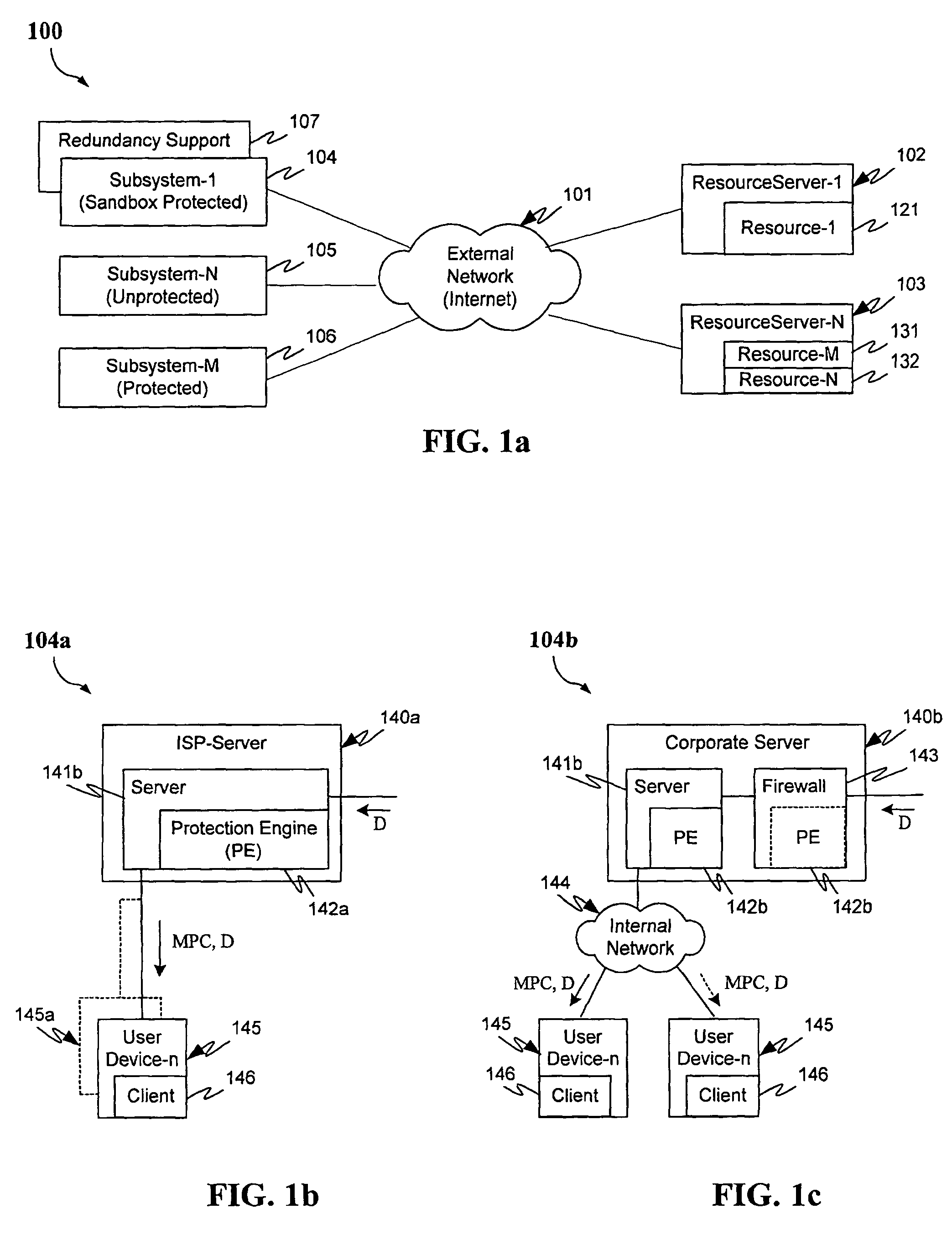
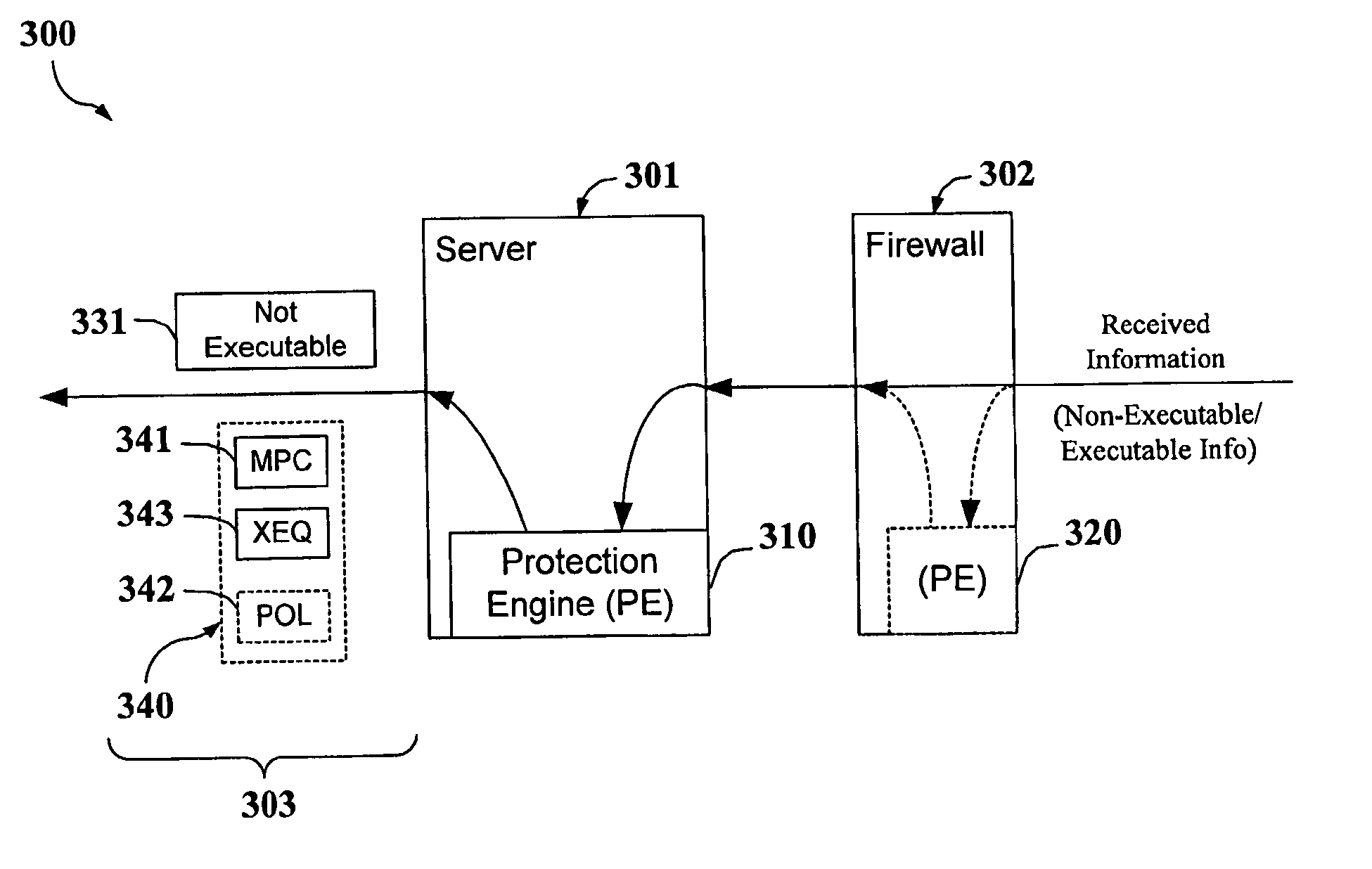
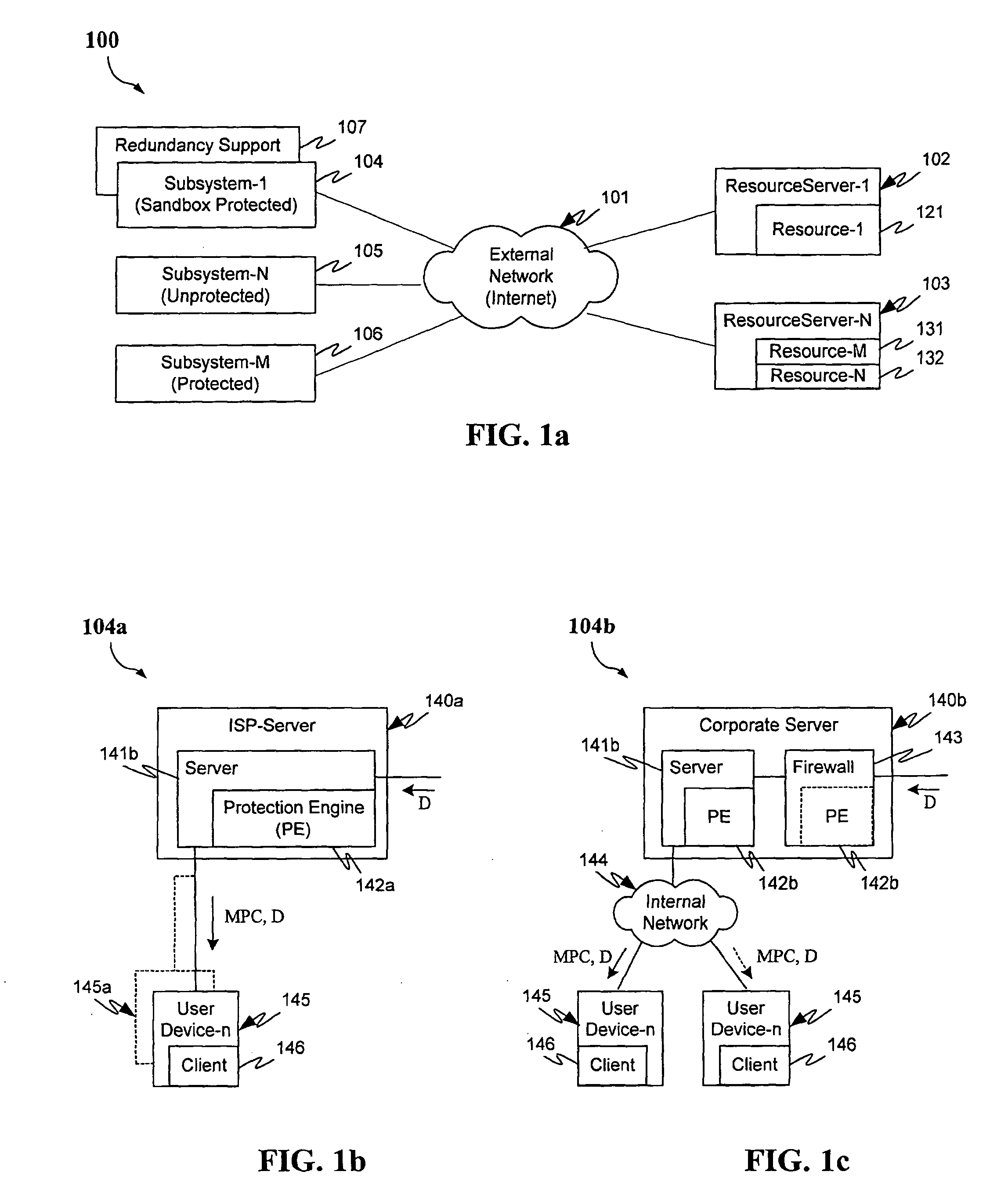
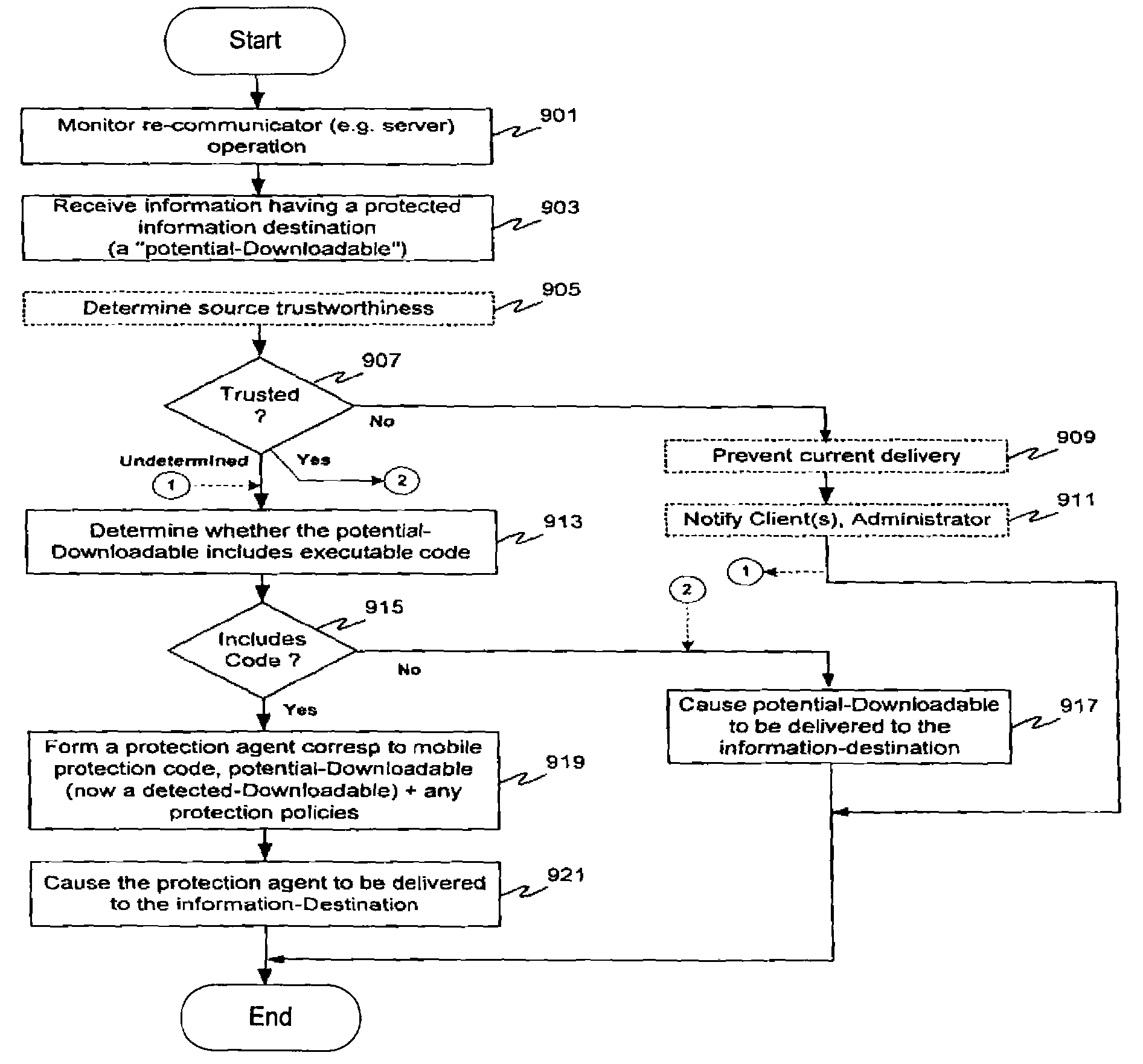
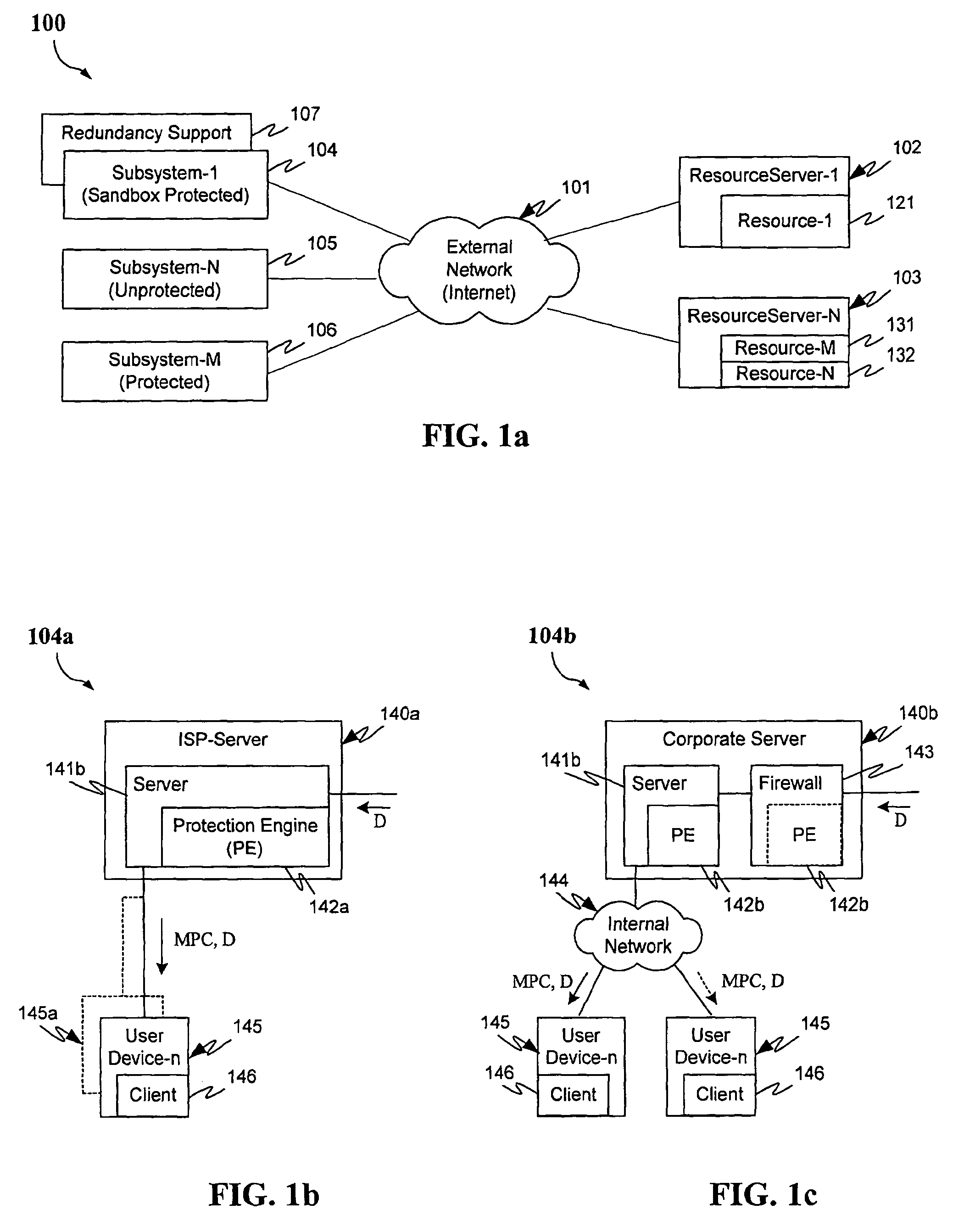
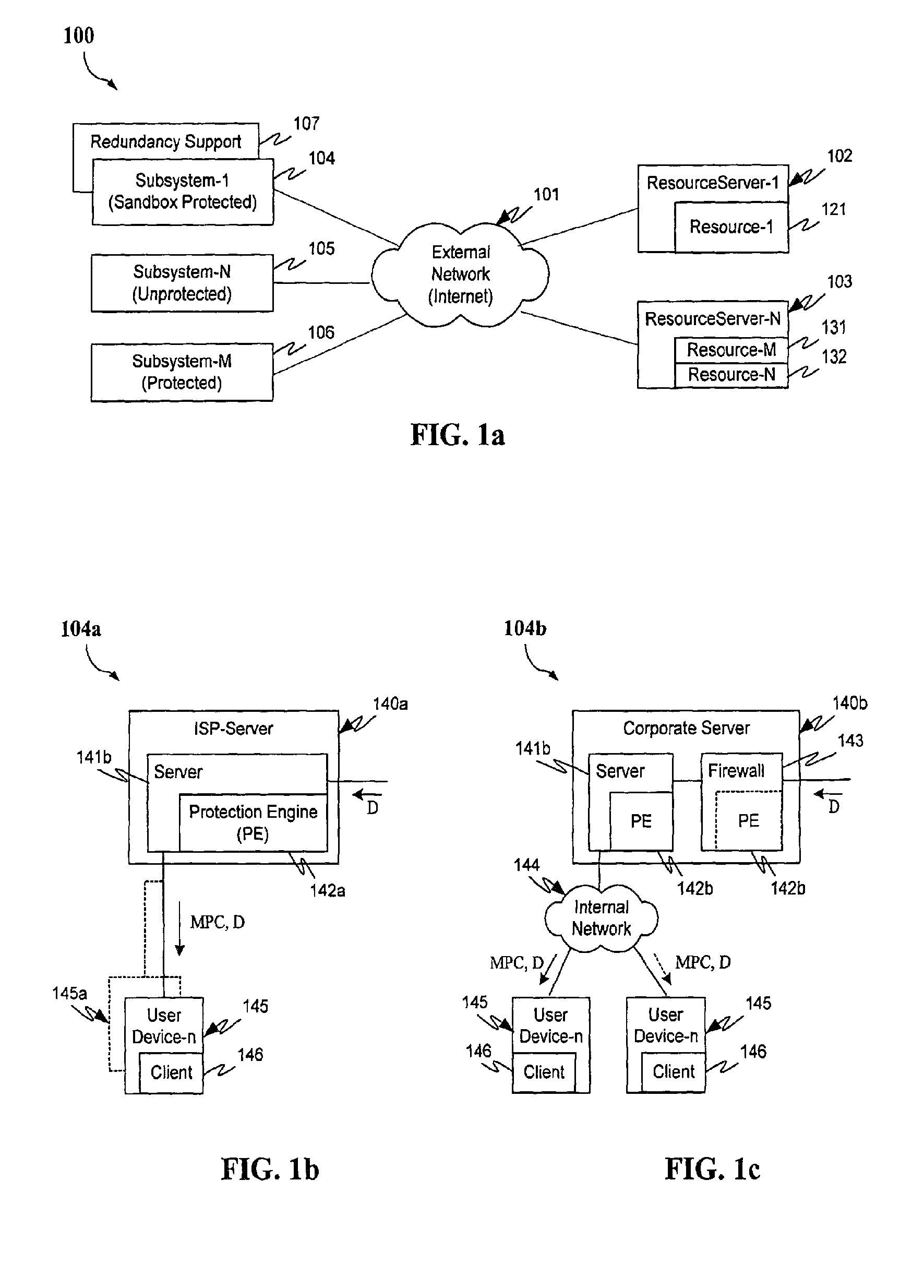
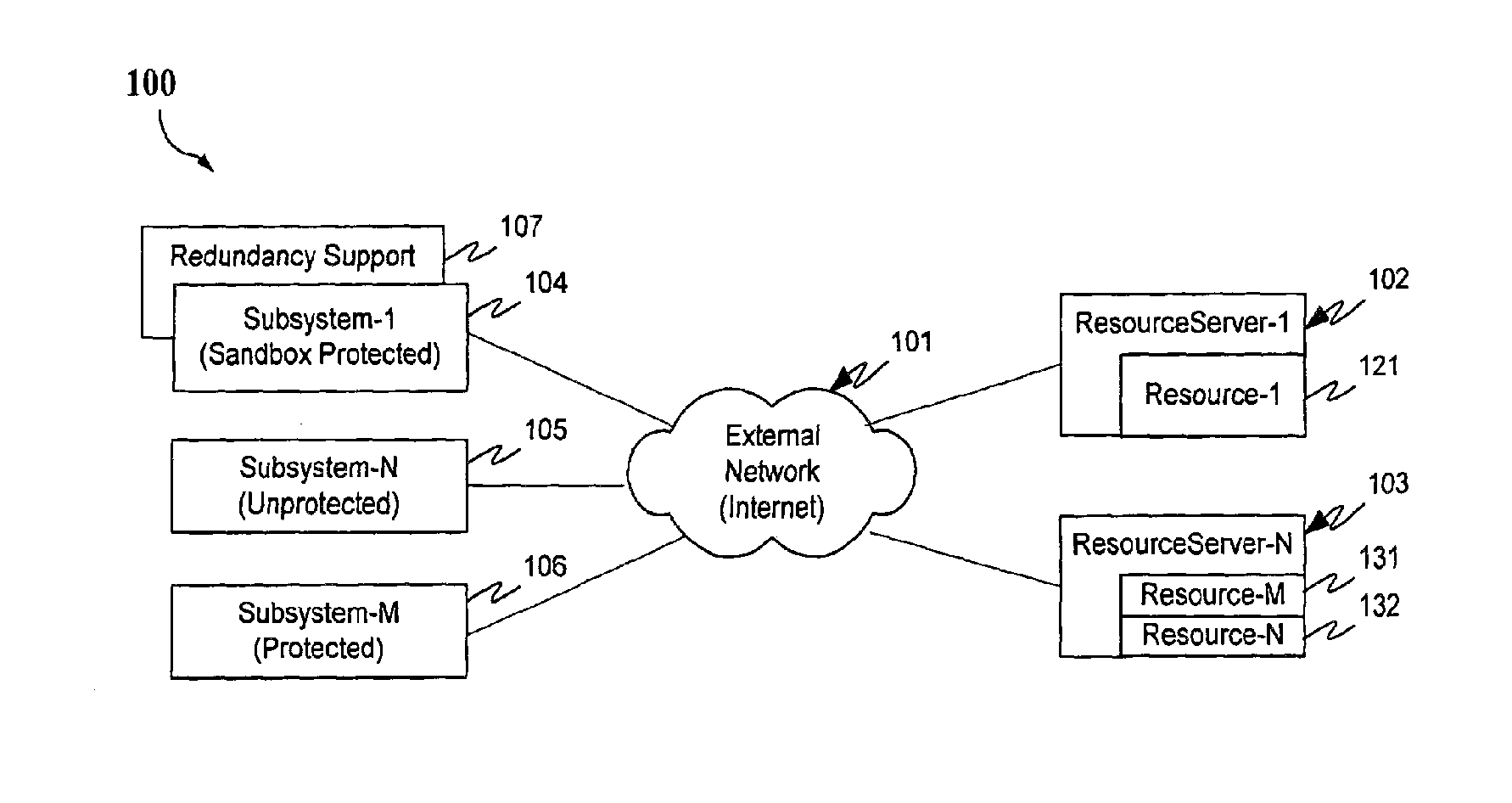
Protection systems and methods provide for protecting one or more personal computers (“PCs”) and / or other intermittently or persistently network accessible devices or processes from undesirable or otherwise malicious operations of Java™ applets, ActiveX™ controls, JavaScript™ scripts, Visual Basic scripts, add-ins, downloaded / uploaded programs or other “Downloadables” or “mobile code” in whole or part. A protection engine embodiment provides, within a server, firewall or other suitable “re-communicator,” for monitoring information received by the communicator, determining whether received information does or is likely to include executable code, and if so, causes mobile protection code (MPC) to be transferred to and rendered operable within a destination device of the received information, more suitably by forming a protection agent including the MPC, protection policies and a detected-Downloadable. An MPC embodiment further provides, within a Downloadable-destination, for initiating the Downloadable, enabling malicious Downloadable operation attempts to be received by the MPC, and causing (predetermined) corresponding operations to be executed in response to the attempts, more suitably in conjunction with protection policies.
Owner:FINJAN LLC
Malicious mobile code runtime monitoring system and methods
InactiveUS7647633B2Minimization requirementsEasy to updateMemory loss protectionDigital data processing detailsVisual BasicMonitoring system
Protection systems and methods provide for protecting one or more personal computers (“PCs”) and / or other intermittently or persistently network accessible devices or processes from undesirable or otherwise malicious operations of Java™ applets, ActiveX™ controls, JavaScript™ scripts, Visual Basic scripts, add-ins, downloaded / uploaded programs or other “Downloadables” or “mobile code” in whole or part. A protection engine embodiment provides, within a server, firewall or other suitable “re-communicator,” for monitoring information received by the communicator, determining whether received information does or is likely to include executable code, and if so, causes mobile protection code (MPC) to be transferred to and rendered operable within a destination device of the received information, more suitably by forming a protection agent including the MPC, protection policies and a detected-Downloadable. An MPC embodiment further provides, within a Downloadable-destination, for initiating the Downloadable, enabling malicious Downloadable operation attempts to be received by the MPC, and causing (predetermined) corresponding operations to be executed in response to the attempts, more suitably in conjunction with protection policies.
Owner:FINJAN LLC
Method and system for protecting a computer and a network from hostile downloadables
InactiveUS7613926B2Minimization requirementsEasy to updateMemory loss protectionUser identity/authority verificationVisual BasicPersonal computer
Protection systems and methods provide for protecting one or more personal computers (“PCs”) and / or other intermittently or persistently network accessible devices or processes from undesirable or otherwise malicious operations of Java™ applets, ActiveX™ controls, JavaScript™ scripts, Visual Basic scripts, add-ins, downloaded / uploaded programs or other “Downloadables” or “mobile code” in whole or part. A protection engine embodiment provides, within a server, firewall or other suitable “re-communicator,” for monitoring information received by the communicator, determining whether received information does or is likely to include executable code, and if so, causes mobile protection code (MPC) to be transferred to and rendered operable within a destination device of the received information, more suitably by forming a protection agent including the MPC, protection policies and a detected-Downloadable. An MPC embodiment further provides, within a Downloadable-destination, for initiating the Downloadable, enabling malicious Downloadable operation attempts to be received by the MPC, and causing (predetermined) corresponding operations to be executed in response to the attempts, more suitably in conjunction with protection policies.
Owner:FINJAN LLC
Work state virtual simulation system for electric haulage shearer based on different geological conditions
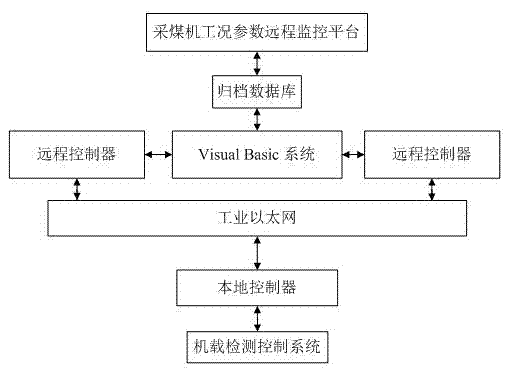
InactiveCN102759909AReal-time display of working statusIncrease authenticityTotal factory controlProgramme total factory controlVisual BasicAutomatic control
A work state virtual simulation system for an electric haulage shearer based on different geological conditions belongs to automatic control and system simulation of shearers. The work state virtual simulation system comprises devices and a method, wherein the devices consist of a shearer work condition remote monitoring platform, a database, a remote controller, a visual basic system, an industrial Ethernet, a local controller and a machine-mounted detection control system. The method comprises the following steps of: acquiring shearer work condition parameters for the machine-mounted detection control system; carrying out data analysis on the shearer work condition parameters; finally, transmitting the shearer work condition parameters to the shearer monitoring platform for detecting and achieving through the local controller and the industrial Ethernet; on the basis of accessing an achieving database in real time, drawing fully mechanized coal faces under different geological conditions by applying a virtual real technology; and driving a shearer virtual sample machine to realize real reappearance of the work state of the shearer. A shearer virtual sample machine model is driven by using real-time work condition parameters provided by the machine-mounted detection control system, so that a shearer virtual simulation system has the field feeling entering the fully mechanized coal faces and favorable interaction.
Owner:CHINA UNIV OF MINING & TECH
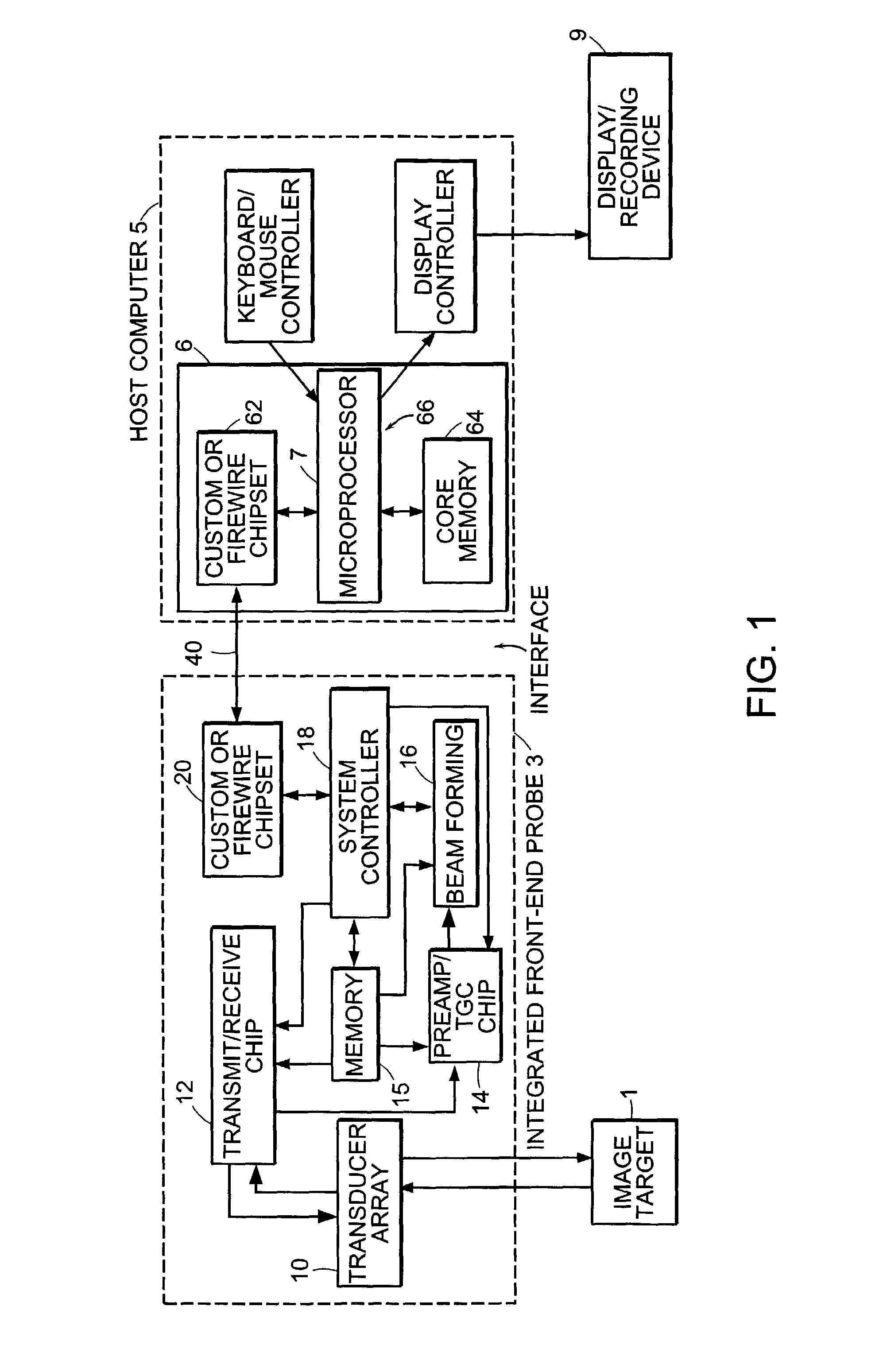
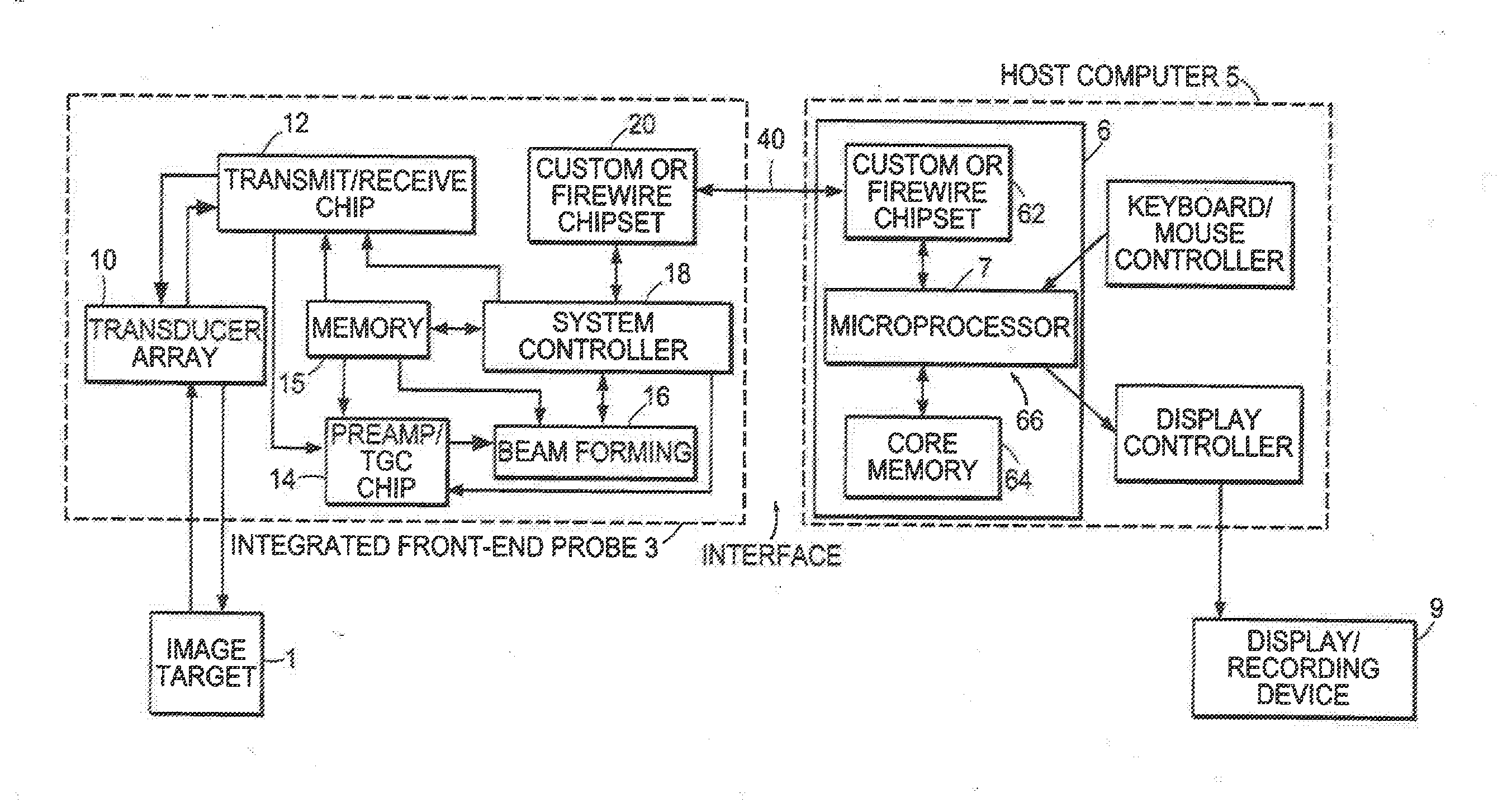
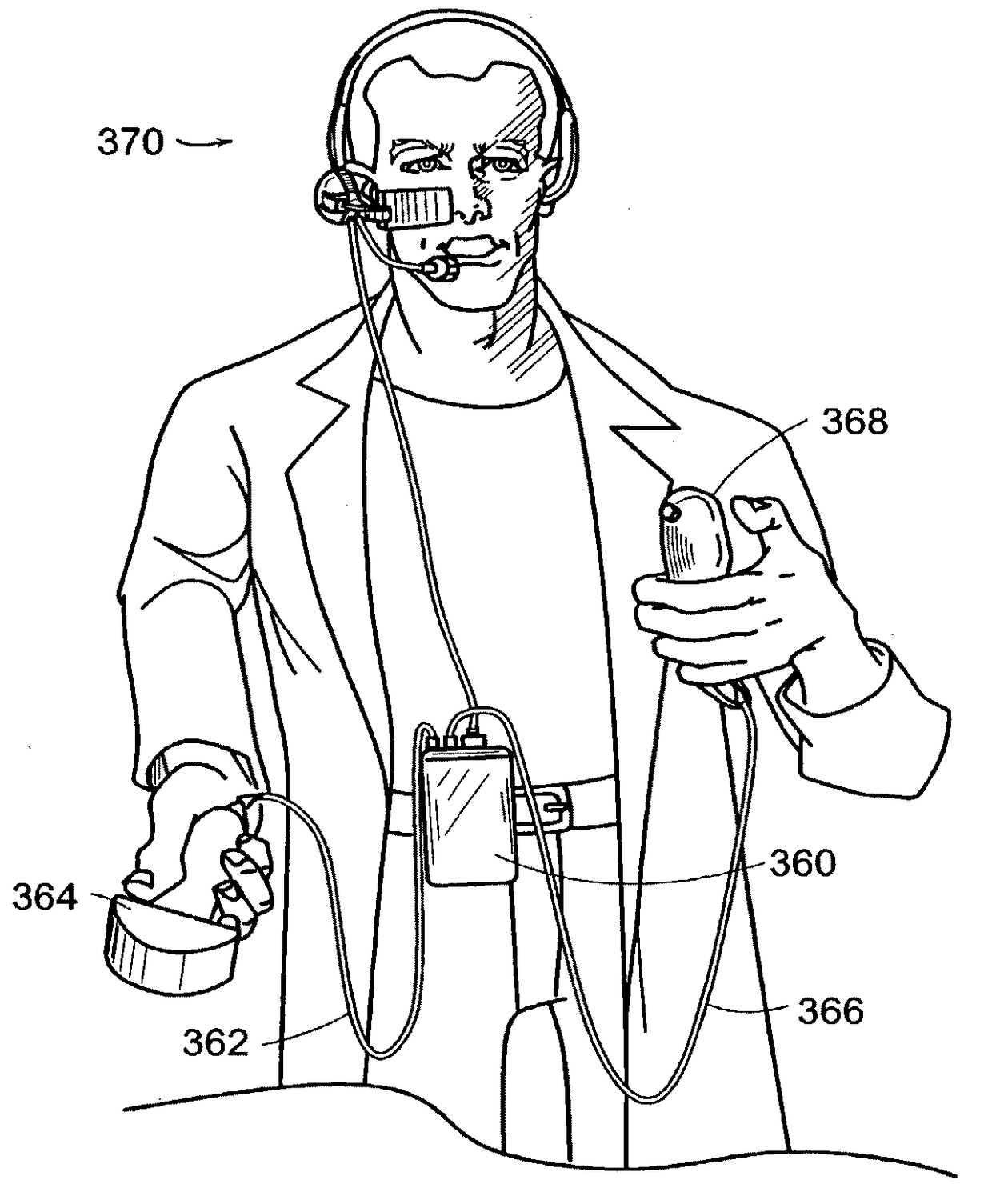
Ultrasound probe with integrated electronics
InactiveUS20140051984A1Simplifies cable requirementDifficult to upgradeVaccination/ovulation diagnosticsCatheterVisual BasicSonification
A hand-held ultrasound system includes integrated electronics within an ergonomic housing. The electronics includes control circuitry, beamforming and circuitry transducer drive circuitry. The electronics communicate with a host computer using an industry standard high speed serial bus. The ultrasonic imaging system is operable on a standard, commercially available, user computing device without specific hardware modifications, and is adapted to interface with an external application without modification to the ultrasonic imaging system to allow a user to gather ultrasonic data on a standard user computing device such as a PC, and employ the data so gathered via an independent external application without requiring a custom system, expensive hardware modifications, or system rebuilds. An integrated interface program allows such ultrasonic data to be invoked by a variety of such external applications having access to the integrated interface program via a standard, predetermined platform such as visual basic or c++.
Owner:TERATECH CORP
Method and system for protecting a computer and a network from hostile downloadables
InactiveUS20060149968A1Minimizing serverMinimizing client resource requirementMemory loss protectionError detection/correctionVisual BasicPersonal computer
Protection systems and methods provide for protecting one or more personal computers (“PCs”) and / or other intermittently or persistently network accessible devices or processes from undesirable or otherwise malicious operations of Java™ applets, ActiveX™ controls, JavaScript™ scripts, Visual Basic scripts, add-ins, downloaded / uploaded programs or other “Downloadables” or “mobile code” in whole or part. A protection engine embodiment provides, within a server, firewall or other suitable “re-communicator,” for monitoring information received by the communicator, determining whether received information does or is likely to include executable code, and if so, causes mobile protection code (MPC) to be transferred to and rendered operable within a destination device of the received information, more suitably by forming a protection agent including the MPC, protection policies and a detected-Downloadable. An MPC embodiment further provides, within a Downloadable-destination, for initiating the Downloadable, enabling malicious Downloadable operation attempts to be received by the MPC, and causing (predetermined) corresponding operations to be executed in response to the attempts, more suitably in conjunction with protection policies.
Owner:FINJAN LLC
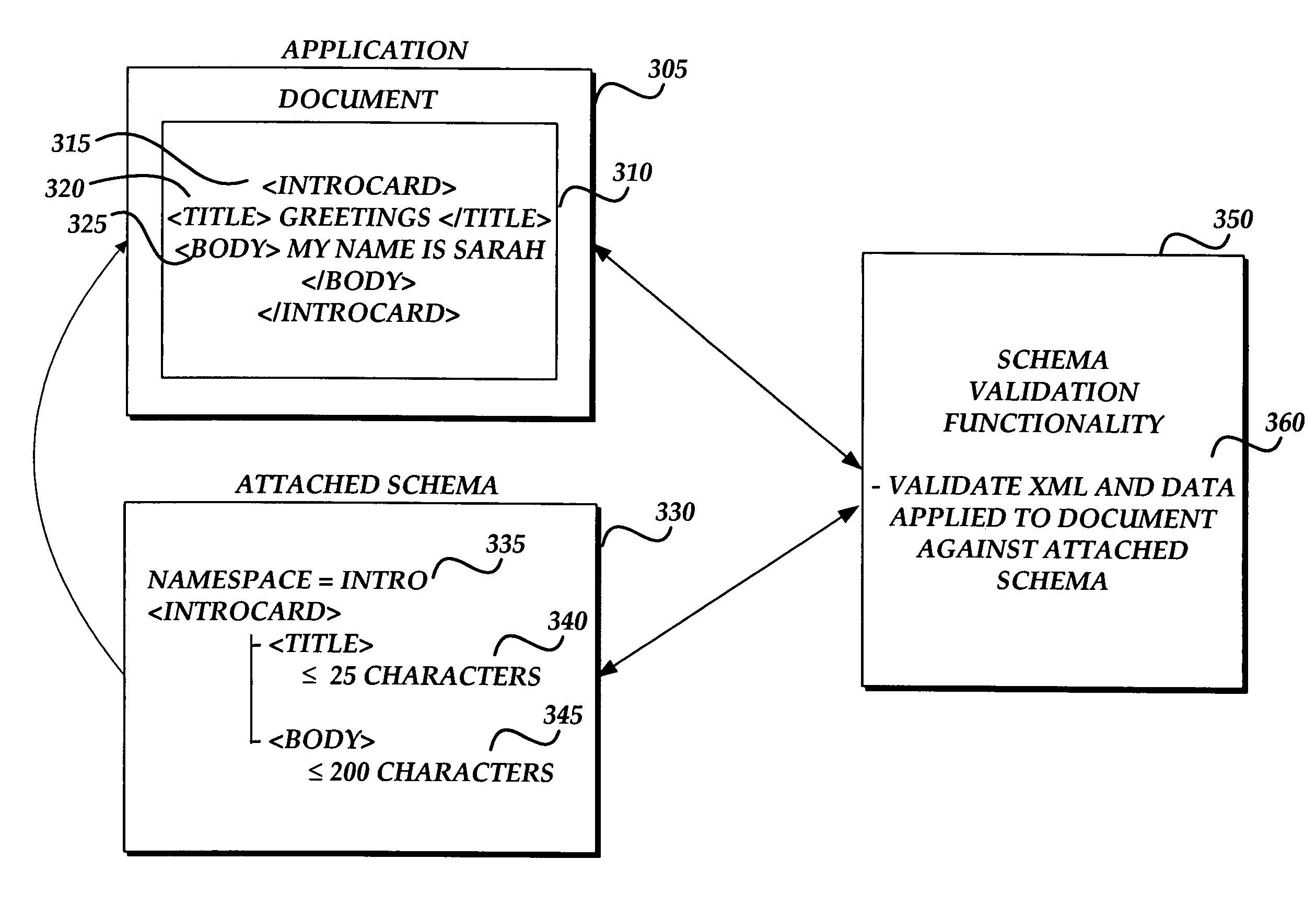
Programmable object model for extensible markup language schema validation
InactiveUS7487515B1Natural language data processingSpecial data processing applicationsVisual BasicXML schema
A programmable object model includes a plurality of object-oriented message calls for application programming interfaces allowing a user to programmatically access the schema validation model of an application by sending message calls and required parameters to the schema validation model to customize or otherwise modify the operation of the schema validation model as desired by the user. Once the user has access to the schema validation model of an application, the user may attach Extensible Markup Language (XML) schema files to a document and control definitions, grammatical rules, and other settings dictated by the attached XML schema file. The user also is allowed to customize the application's native schema validation functionality with user-defined rules and error text. The XML schema validation model of an application may be accessed from a user-created program written according to a variety of different languages such as C, C++, C#, and Visual Basic.
Owner:MICROSOFT TECH LICENSING LLC
Ultrasound probe with integrated electronics
InactiveUS20160338676A1Simplifies cable requirementDifficult to upgradePhysical therapies and activitiesMechanical/radiation/invasive therapiesVisual BasicSonification
A hand-held ultrasound system includes integrated electronics within an ergonomic housing. The electronics includes control circuitry, beamforming and circuitry transducer drive circuitry. The electronics communicate with a host computer using an industry standard high speed serial bus. The ultrasonic imaging system is operable on a standard, commercially available, user computing device without specific hardware modifications, and is adapted to interface with an external application without modification to the ultrasonic imaging system to allow a user to gather ultrasonic data on a standard user computing device such as a PC, and employ the data so gathered via an independent external application without requiring a custom system, expensive hardware modifications, or system rebuilds. An integrated interface program allows such ultrasonic data to be invoked by a variety of such external applications having access to the integrated interface program via a standard, predetermined platform such as visual basic or c++.
Owner:TERATECH CORP
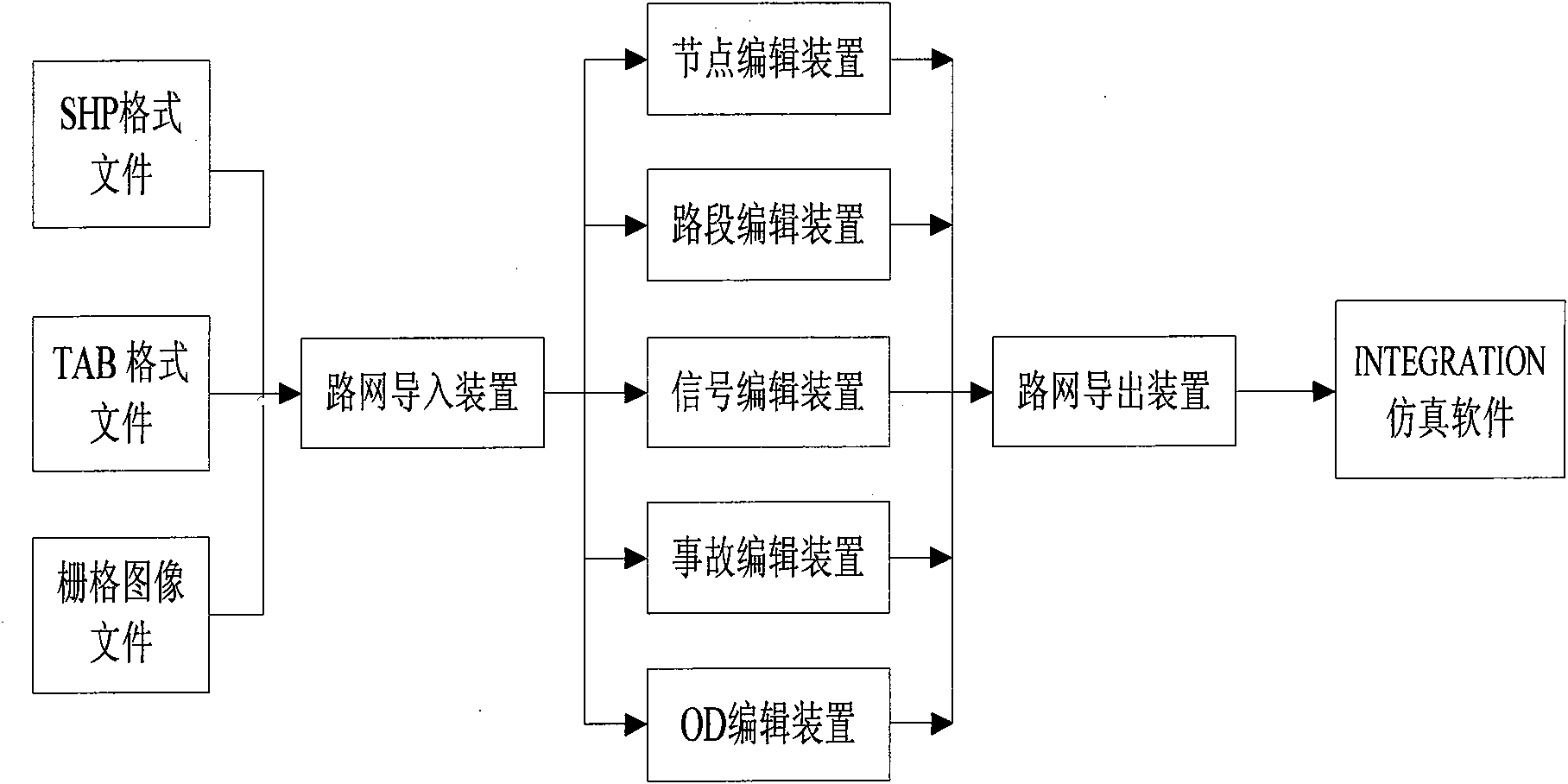
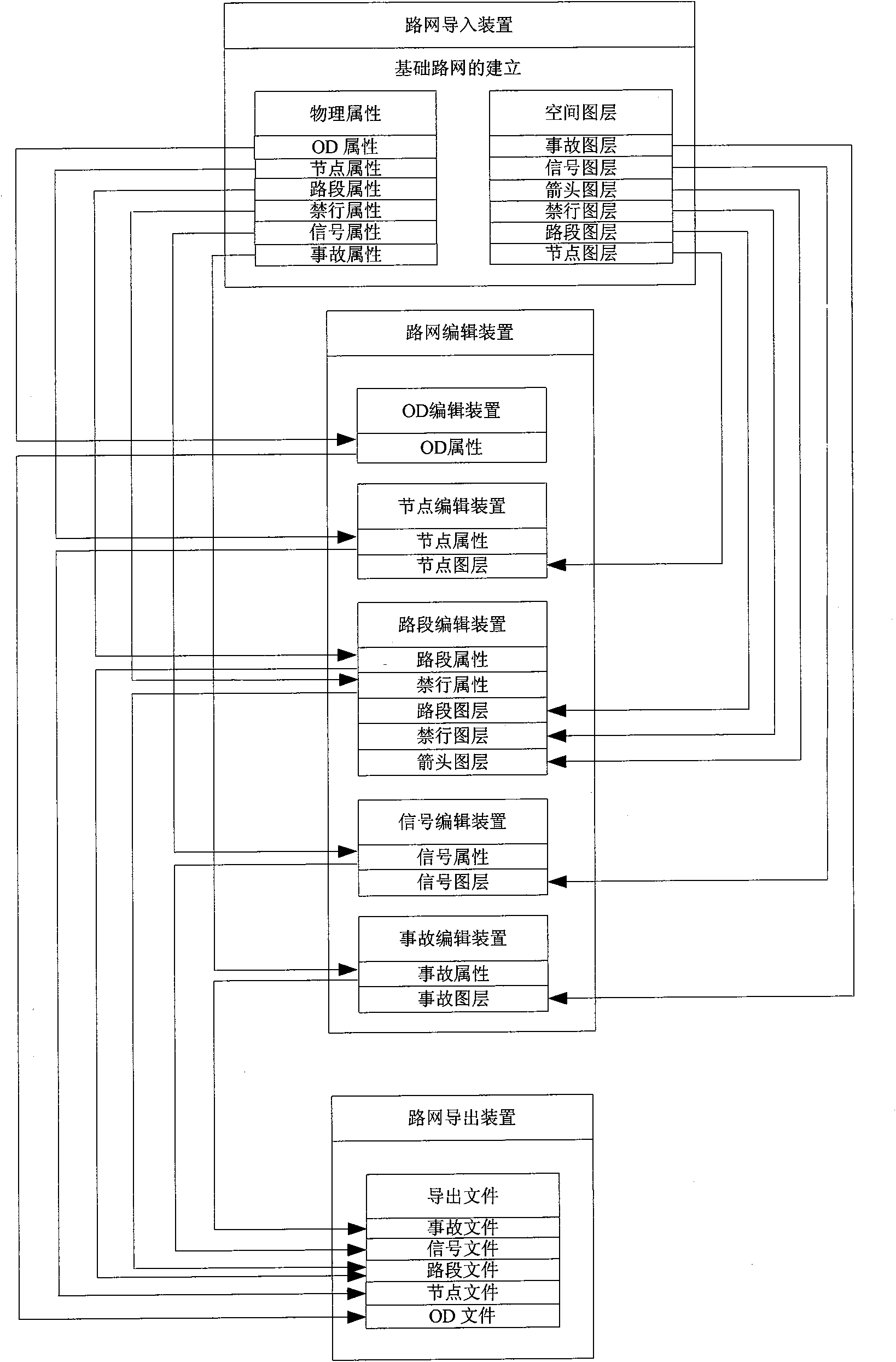
Simulation-system-oriented road network drawing device and method therefor
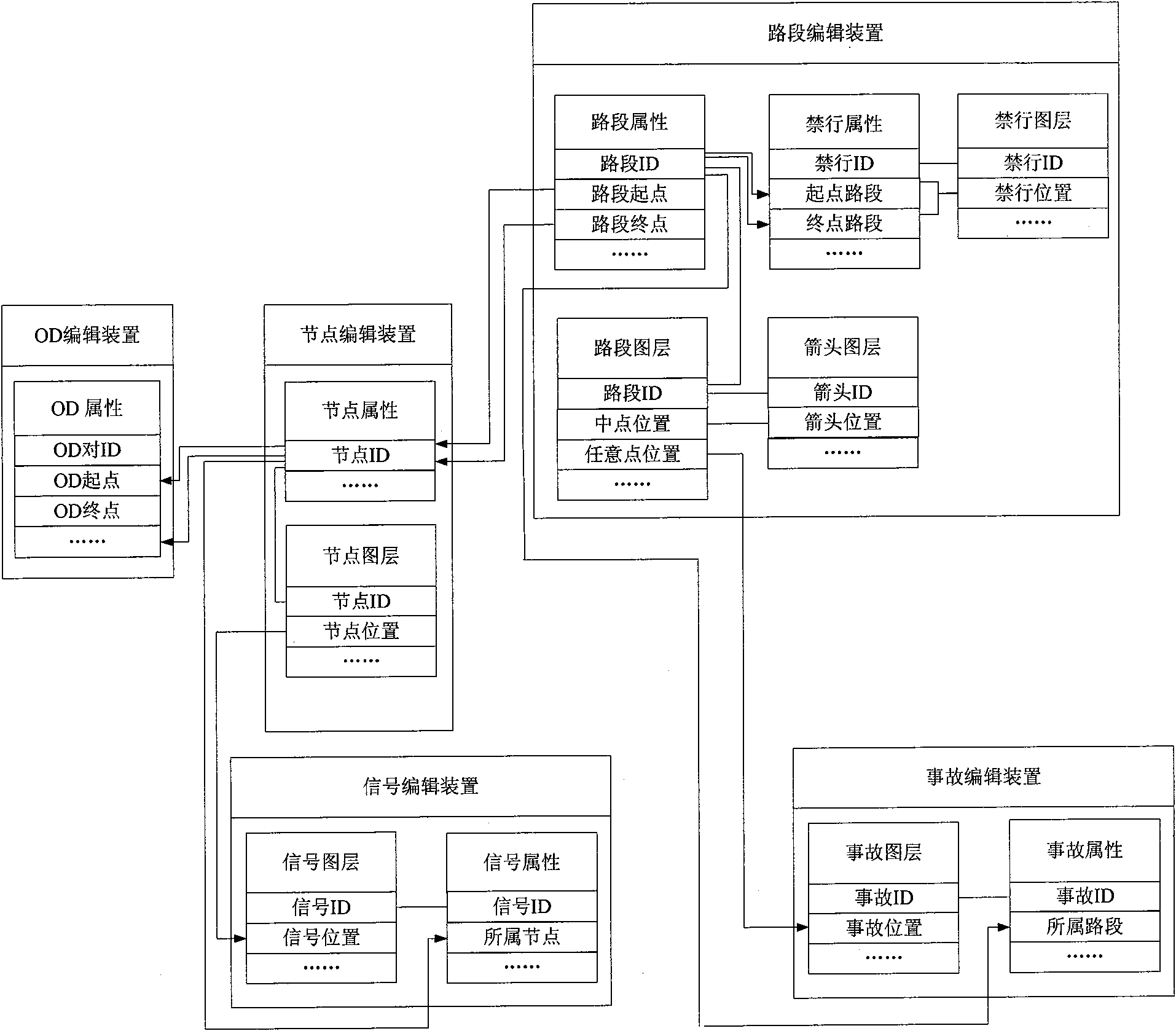
InactiveCN101640001ARealize visual editingEasy to operateRoad vehicles traffic controlMaps/plans/chartsVisual BasicRoad networks
The invention relates to a simulation-system-oriented road network drawing device and a method therefor; the method comprises: a map transformation method, a node segmentation method, a node moving method, a road section direction changing method, a road section translation method and a node combination method. The device mainly comprises a road network introduction device, a node editing device,a road section editing device, a signal editing device, an accident editing device, a trip starting and finishing point editing device and a road network guiding device. The device not only can realize visualization edit of the road network and improves the maneuverability of a simulation system, but also is developed based on visual basic and MAPX, so that an executable file can be generated, andthe device can be operated and executed independent of any other software, thus improving the convenience of the software can be improved. All the functions of the device can be realized by various relations and methods inside all devices and among different devices.
Owner:BEIJING JIAOTONG UNIV
Malicious mobile code runtime monitoring system and methods
InactiveUS8079086B1Minimization requirementsEasy to updateMemory loss protectionUser identity/authority verificationVisual BasicMonitoring system
Protection systems and methods provide for protecting one or more personal computers (“PCs”) and / or other intermittently or persistently network accessible devices or processes from undesirable or otherwise malicious operations of Java TN applets, ActiveX™ controls, JavaScript™ scripts, Visual Basic scripts, add-ins, downloaded / uploaded programs or other “Downloadables” or “mobile code” in whole or part. A protection engine embodiment provides, within a server, firewall or other suitable “recommunicator,” for monitoring information received by the communicator, determining whether received information does or is likely to include executable code, and if so, causes mobile protection code (MPC) to be transferred to and rendered operable within a destination device of the received information, more suitably by forming a protection agent including the MPC, protection policies and a detected-Downloadable. An MPC embodiment further provides, within a Downloadable-destination, for initiating the Downloadable, enabling malicious Downloadable operation attempts to be received by the MPC, and causing (predetermined) corresponding operations to be executed in response to the attempts, more suitably in conjunction with protection policies.
Owner:FINJAN LLC
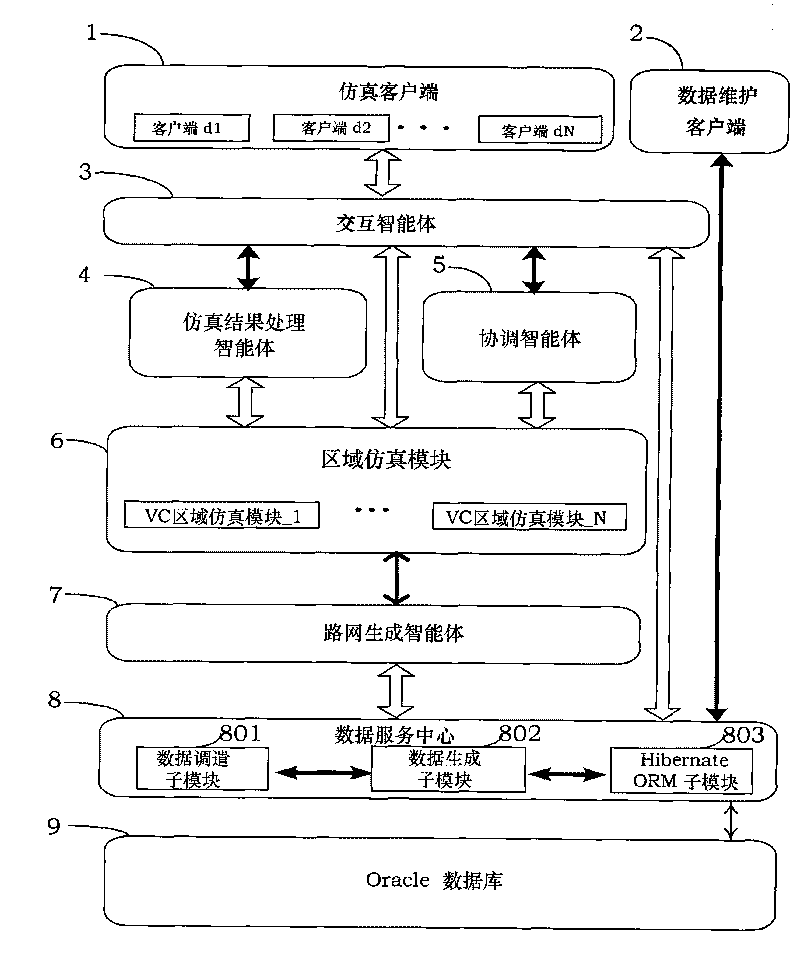
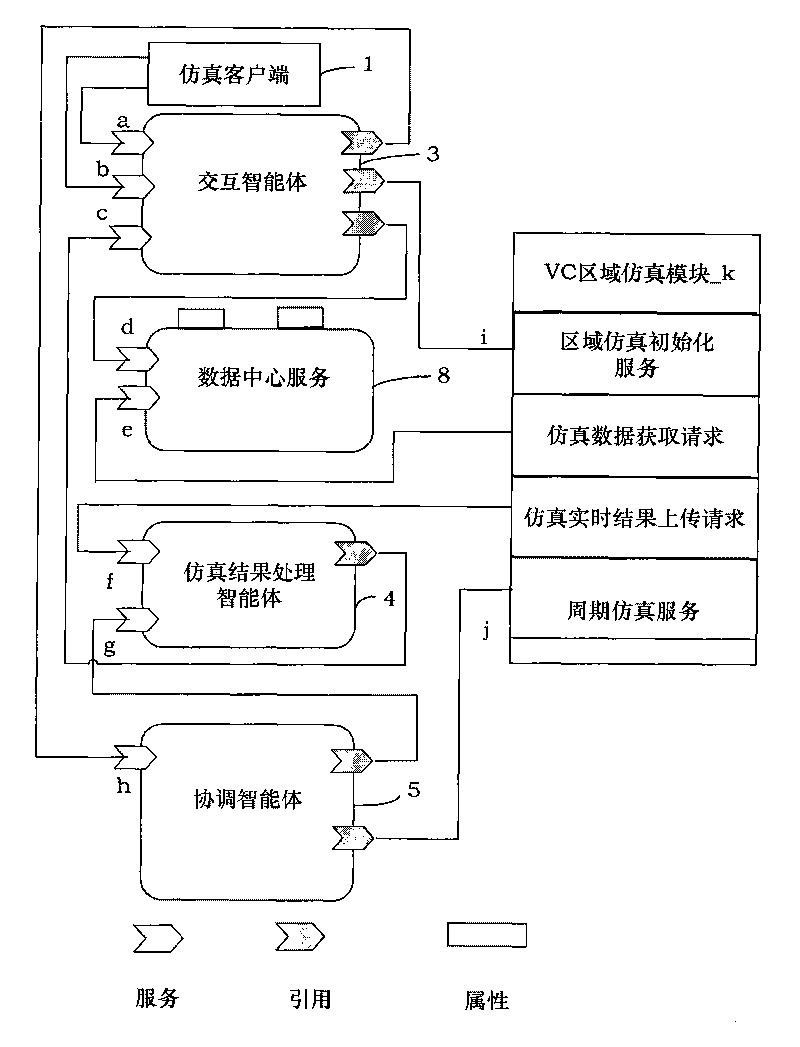
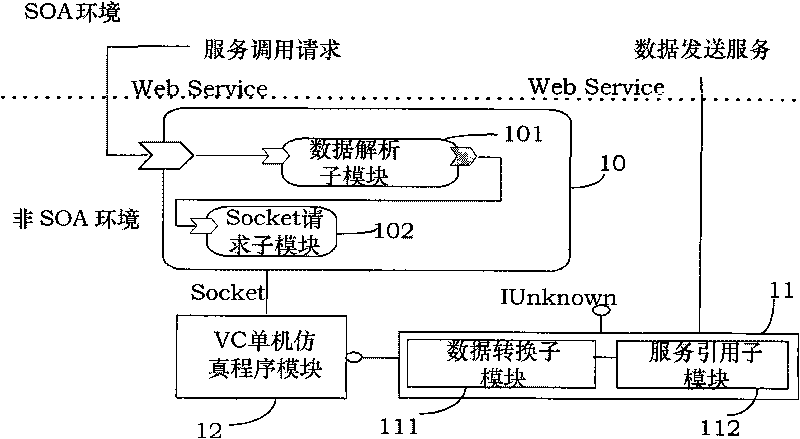
Distributed traffic simulating platform based on Service-Oriented Architecture (SOA) and simulating method thereof
InactiveCN101710361AIncrease flexibilityEase of decentralized developmentRoad vehicles traffic controlSpecial data processing applicationsVisual BasicService Component Architecture
The invention discloses a distributed traffic simulating platform based on a Service-Oriented Architecture (SOA) and a simulating method thereof. The distributed traffic simulating platform mainly comprises modules, such as an interactive intelligent agent, a simulating result processing intelligent agent, a coordinating intelligent agent, a road network generating intelligent agent, an area simulating module, a data service center, and the like. The simulation based on a large-scale real road network is finished by the mutual coordination of different intelligent agents. The modules are finished by a service component architecture (SCA), Visual C++ and Visual Basic. In addition, the invention is provided with an SOA access module based on the SCA, which is used for integrating the traditional single-machine simulating program. The invention meets the requirement of the distributed simulating platform on isomerism, improves the flexibility of a system, the reusability of a business model and the interoperability of service and leads the system to be easy for integration.
Owner:BEIHANG UNIV
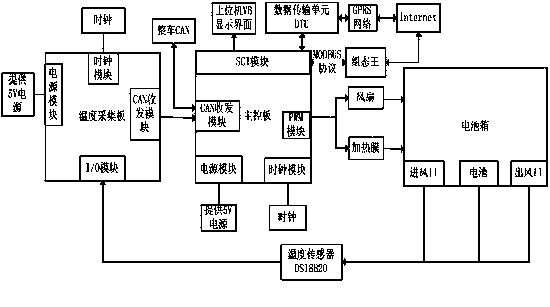
Constant-temperature battery box of electric automobile and heat management control method of constant-temperature battery box
InactiveCN103730707AIncrease usable capacityExtended service lifeSmall-sized cells cases/jacketsLarge-sized cells cases/jacketsVisual BasicModel selection
Owner:长春北车电动汽车有限公司
Malicious Mobile Code Runtime Monitoring System and Methods
InactiveUS20120117651A1Minimization requirementsEasy to updateMemory loss protectionError detection/correctionVisual BasicMonitoring system
Owner:FINJAN LLC
Malicious mobile code runtime monitoring system and methods
InactiveUS9219755B2Minimization requirementsEasy to updatePlatform integrity maintainanceTransmissionVisual BasicMonitoring system
Protection systems and methods provide for protecting one or more personal computers (“PCs”) and / or other intermittently or persistently network accessible devices or processes from undesirable or otherwise malicious operations of Java TN applets, ActiveX™ controls, JavaScript™ scripts, Visual Basic scripts, add-ins, downloaded / uploaded programs or other “Downloadables” or “mobile code” in whole or part. A protection engine embodiment provides for monitoring information received, determining whether received information does or is likely to include executable code, and if so, causes mobile protection code (MPC) to be transferred to and rendered operable within a destination device of the received information. An MPC embodiment further provides, within a Downloadable-destination, for initiating the Downloadable, enabling malicious Downloadable operation attempts to be received by the MPC, and causing (predetermined) corresponding operations to be executed in response to the attempts.
Owner:FINJAN LLC
Malicious Mobile Code Runtime Monitoring System and Methods
InactiveUS20150288720A1Minimizing serverMinimizing client resource requirementPlatform integrity maintainanceTransmissionVisual BasicMonitoring system
Protection systems and methods provide for protecting one or more personal computers (“PCs”) and / or other intermittently or persistently network accessible devices or processes from undesirable or otherwise malicious operations of Java TN applets, ActiveX™ controls, JavaScript™ scripts, Visual Basic scripts, add-ins, downloaded / uploaded programs or other “Downloadables” or “mobile code” in whole or part. A protection engine embodiment provides for monitoring information received, determining whether received information does or is likely to include executable code, and if so, causes mobile protection code (MPC) to be transferred to and rendered operable within a destination device of the received information. An MPC embodiment further provides, within a Downloadable-destination, for initiating the Downloadable, enabling malicious Downloadable operation attempts to be received by the MPC, and causing (predetermined) corresponding operations to be executed in response to the attempts.
Owner:FINJAN LLC
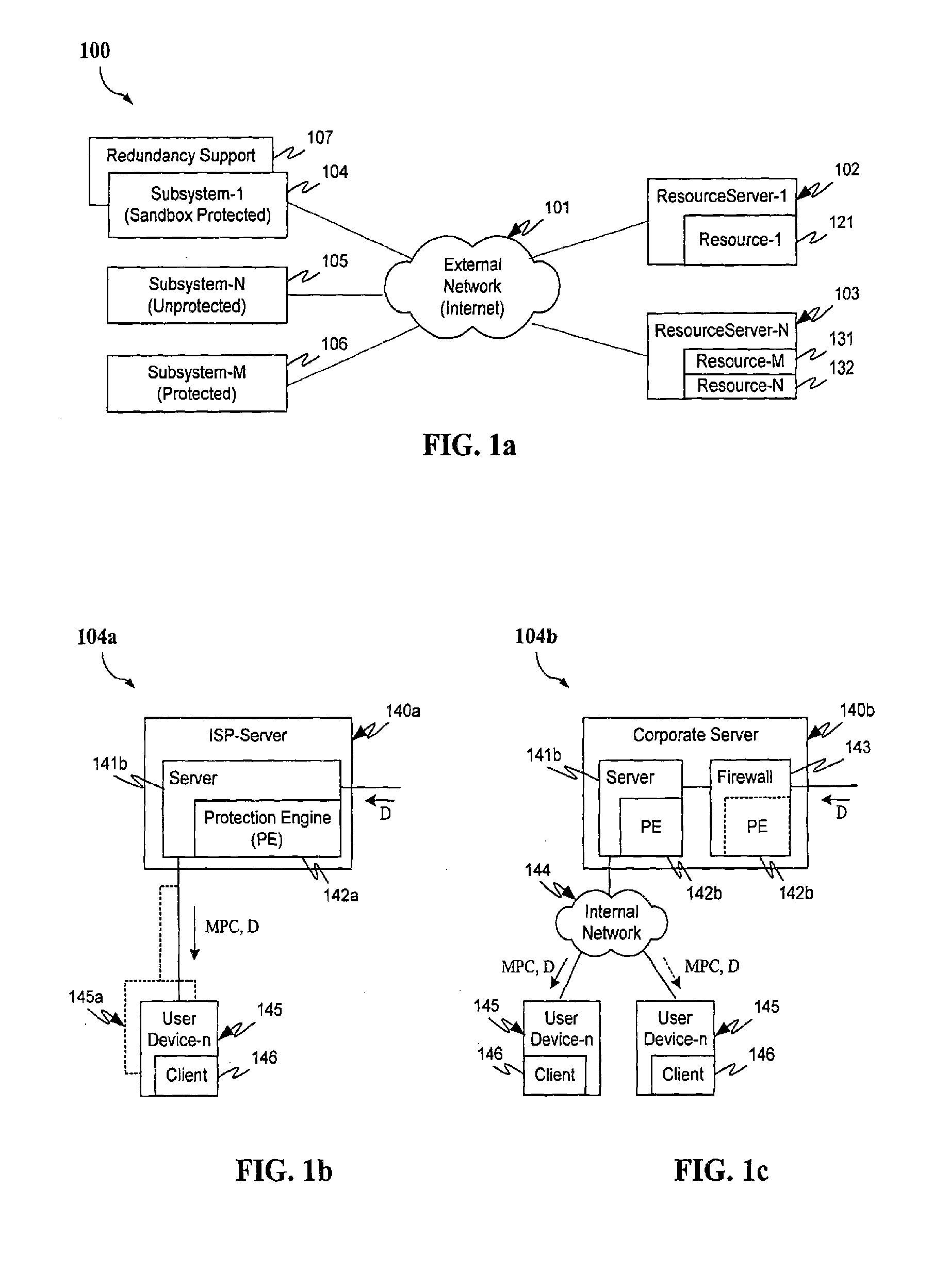
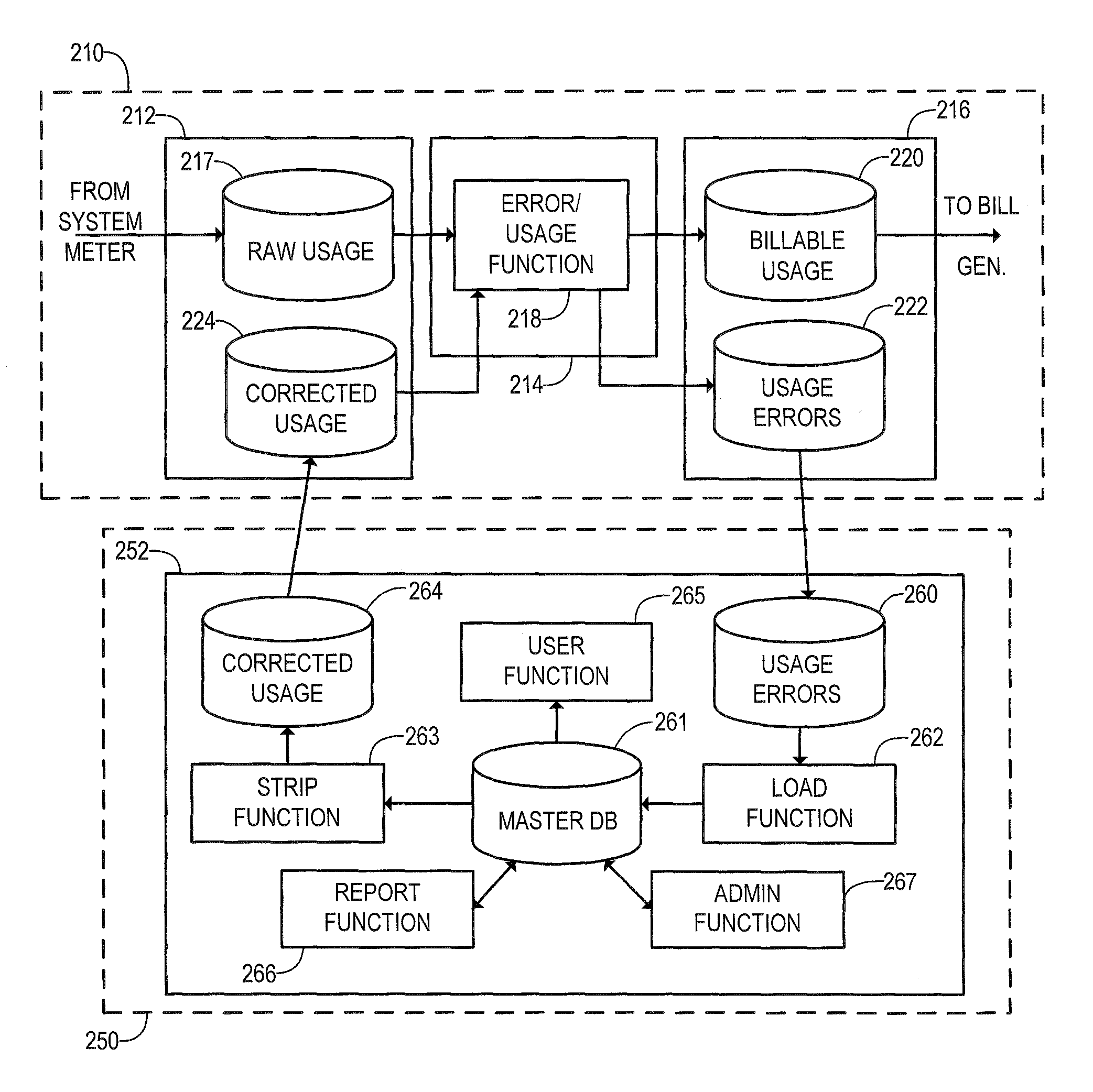
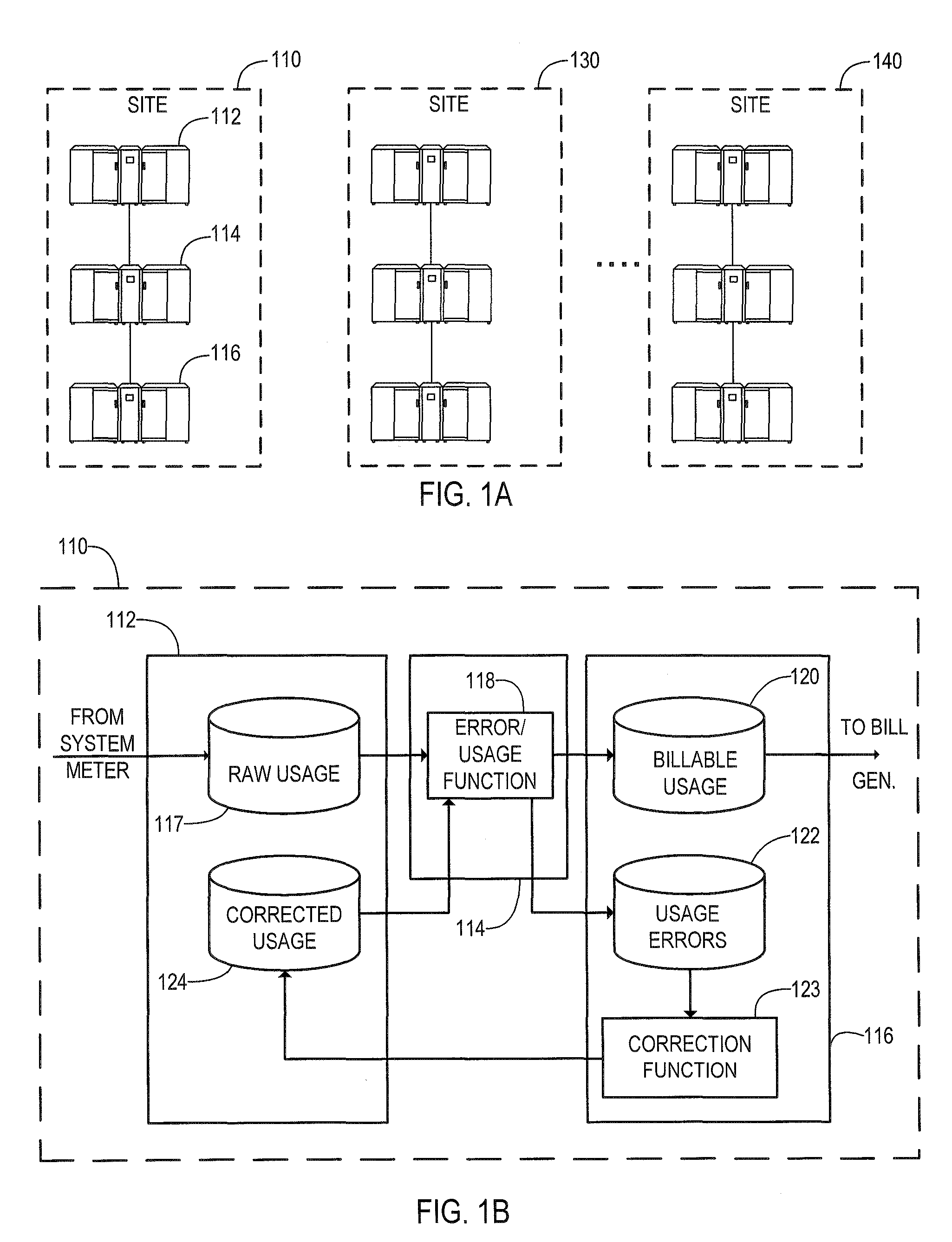
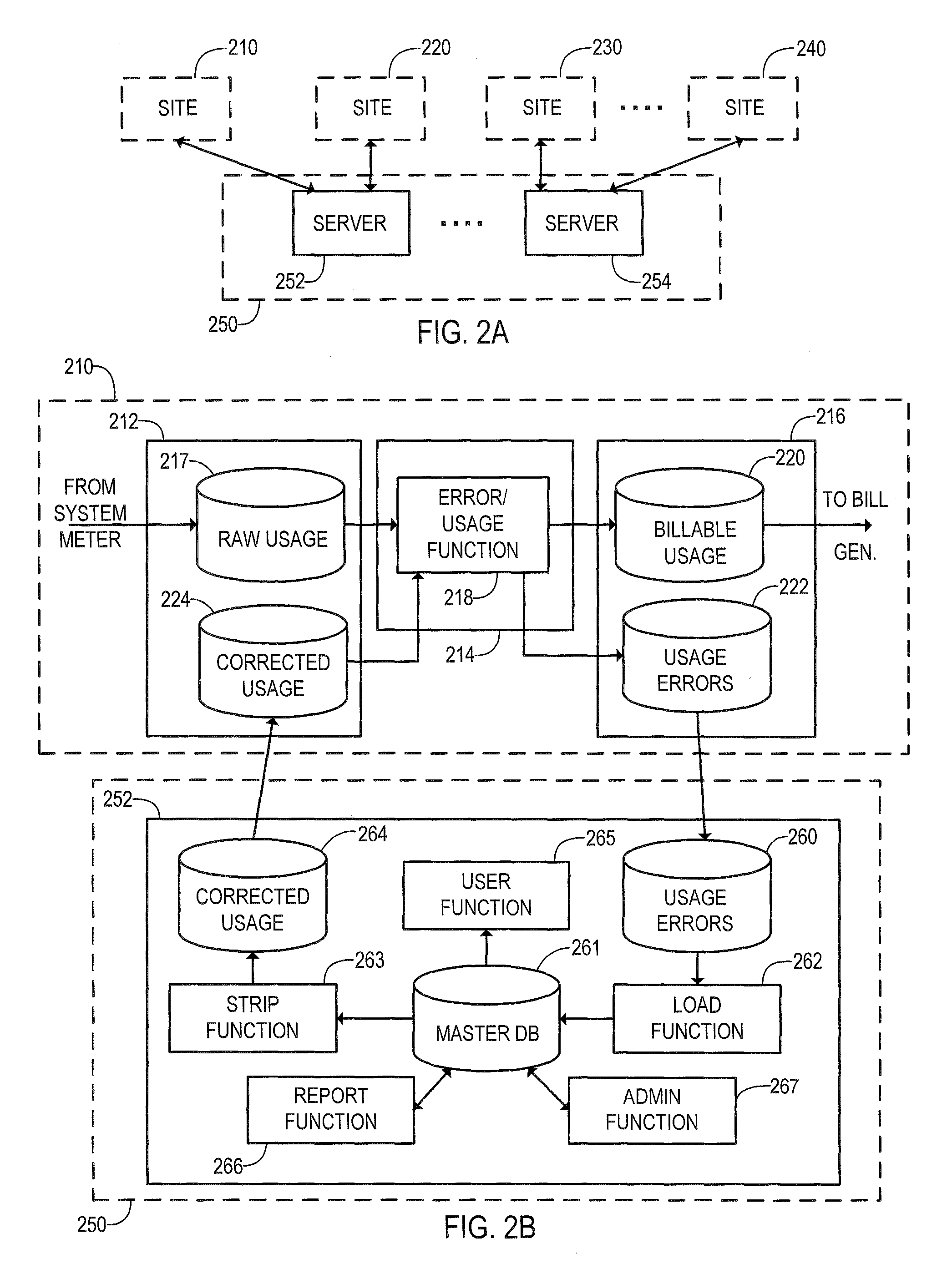
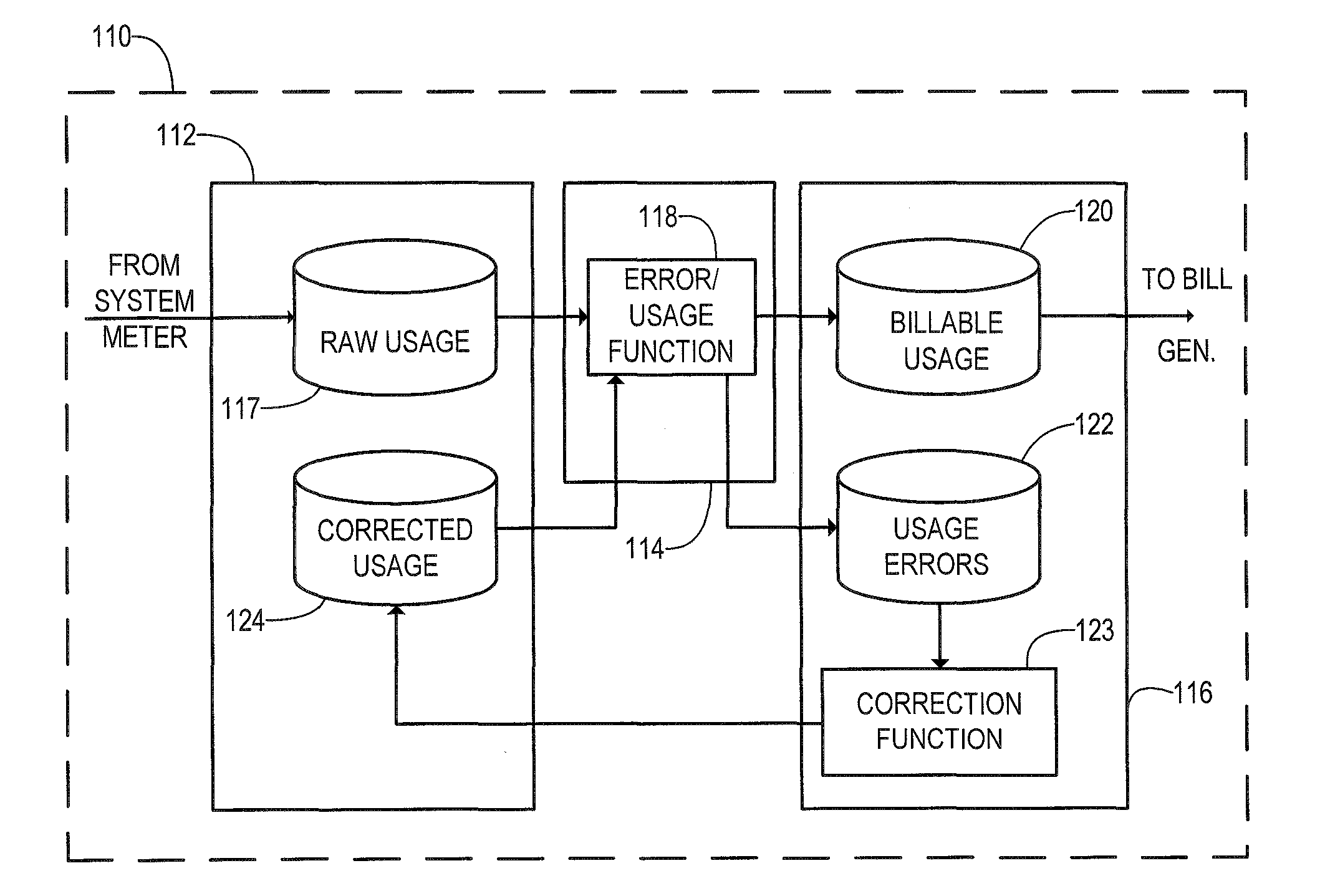
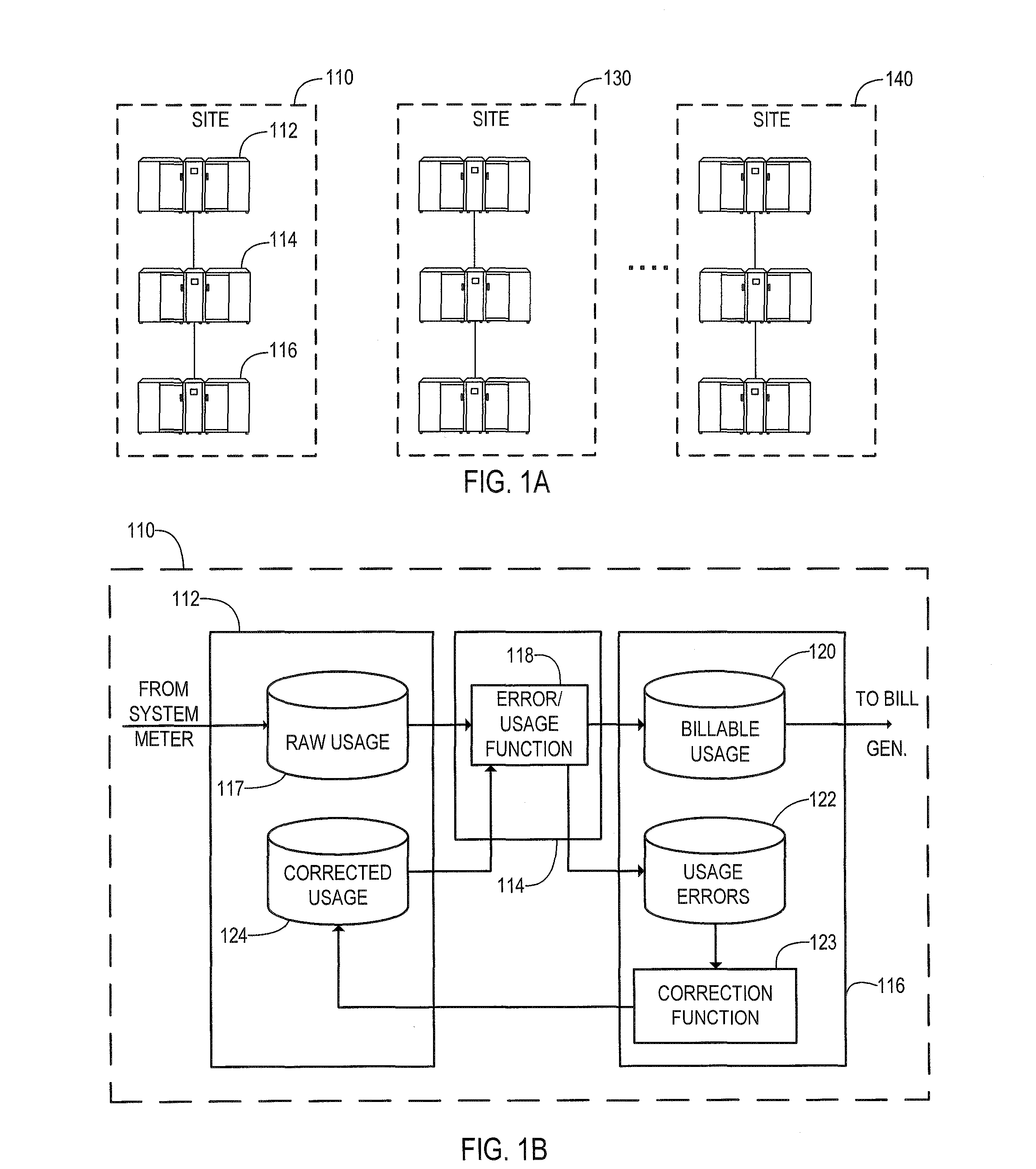
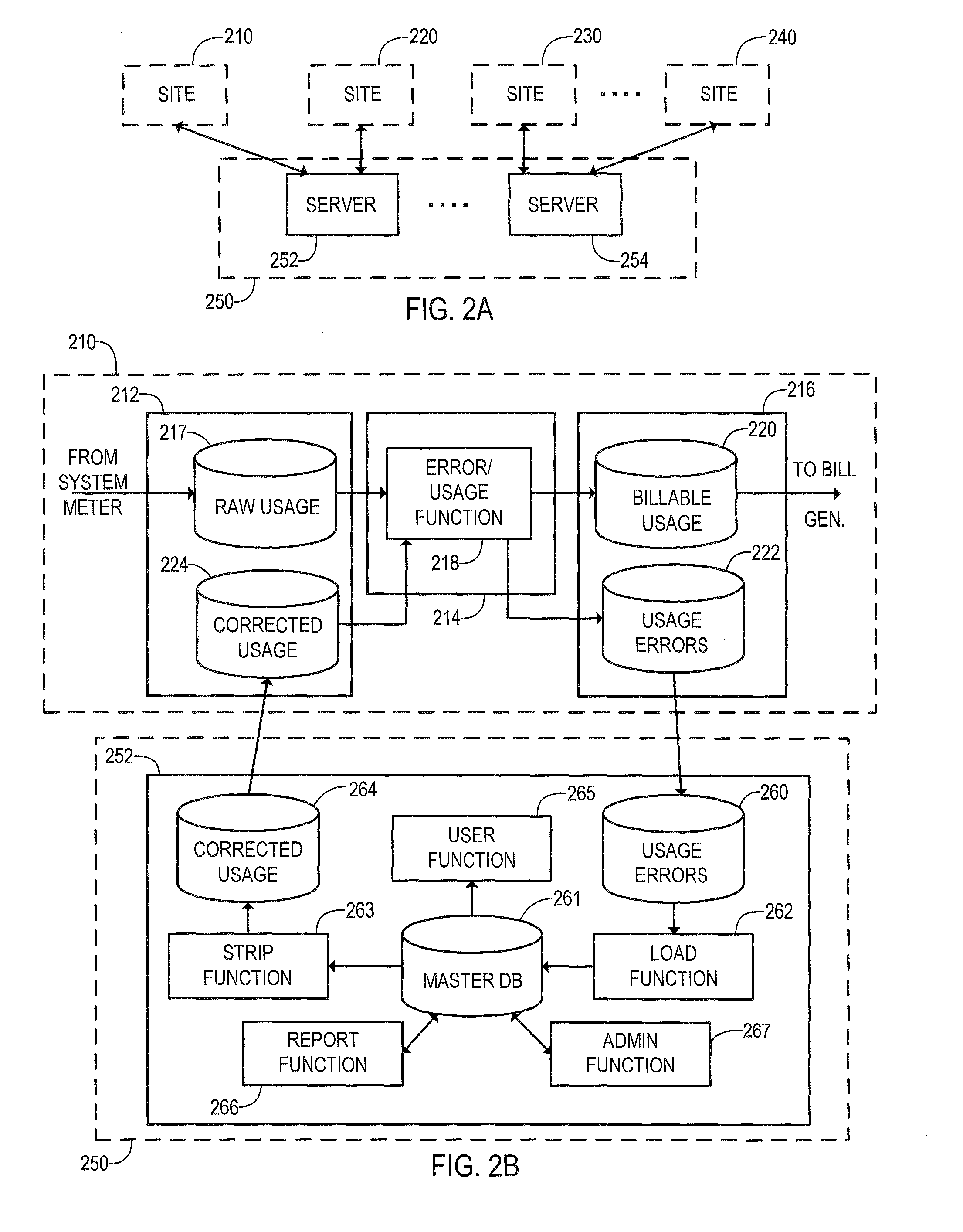
Method and system for server-based error processing in support of legacy-based usage and billing systems
An error processing system comprising a client / server based PC application supported by SQL Server databases for use with legacy usage metering and billing services. The error processing system provides increased functionality, flexibility and reliability of error processing at a much lower cost than was possible using error processing and correction systems built into legacy usage metering systems. Error processing is simplified for users by implementation of a PC based GUI screens developed in Visual Basic.
Owner:BELLSOUTH INTPROP COR
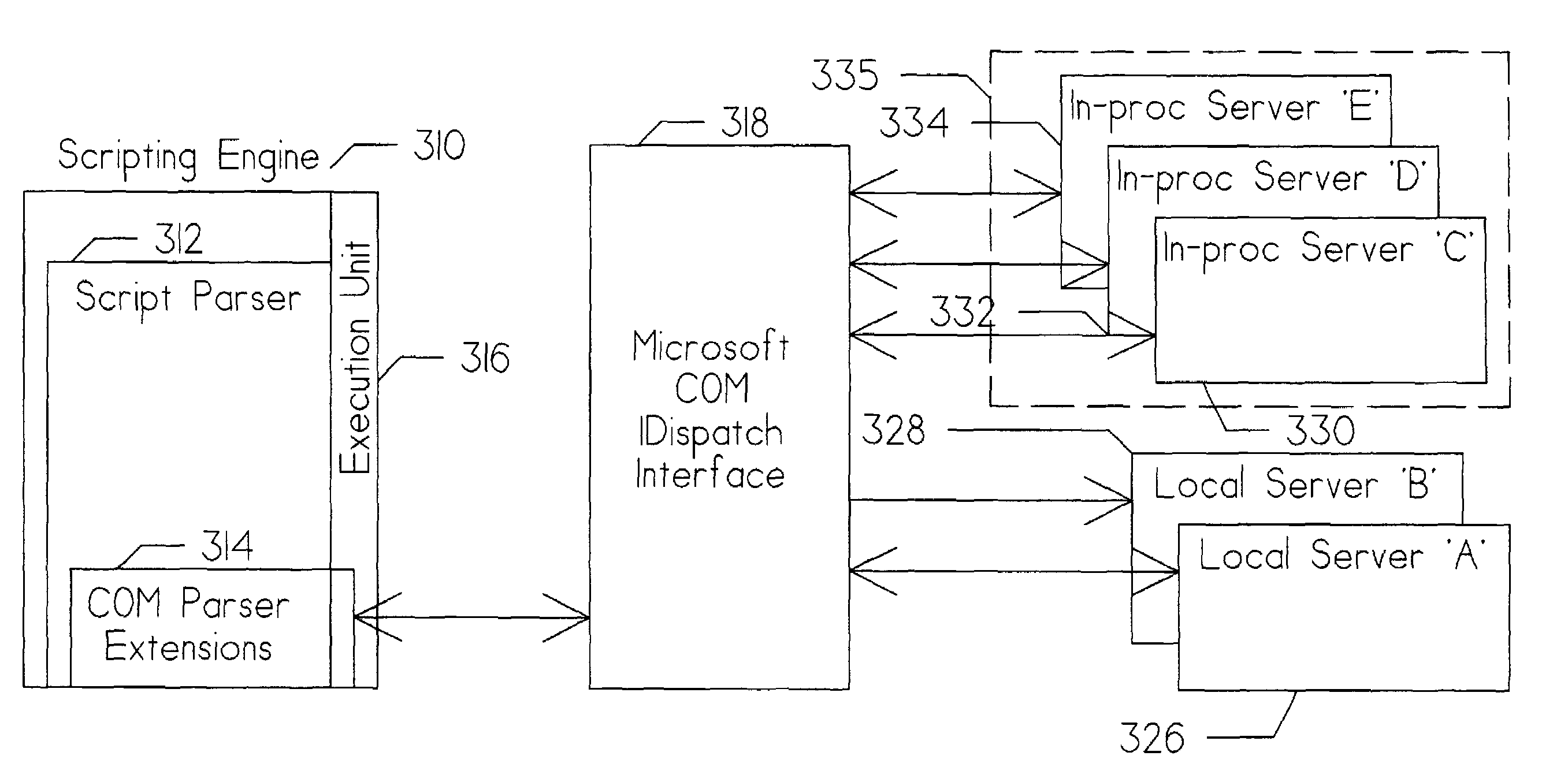
Method for protecting the program environment of a microsoft component object model (COM) client
ActiveUS7363377B1Effective isolationMinimize the numberSpecific access rightsComputer security arrangementsComponent Object ModelVisual Basic
An apparatus for and method of creating a standardized interface between Microsoft Component Object Model environment and a non-compatible legacy environment. The technique is equally effective for both object oriented and non-object oriented scripting protocols. The interface is scripted in the native legacy command language thereby freeing the interface developer from the need to create script in both the legacy command language and a Microsoft COM compatible language, such as Visual Basic. A determination is made upon an attempt to instantiate a COM server whether the server is local or in-process. If in-process and registered, the server is instantiated within a surrogate server to isolate the calling client from potential corruption of its memory space or copying of its sensitive data by the registered in-process server. This apparatus and method operates transparently to users and administrators, such that the client memory space and sensitive data is protected without requiring special COM server registration.
Owner:JOHNSON CHARLES A
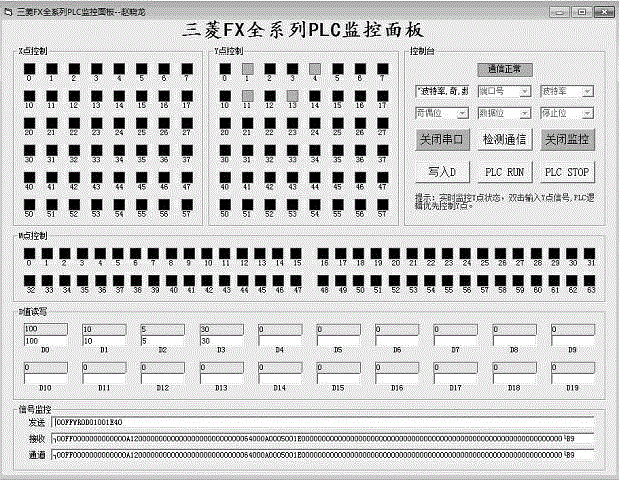
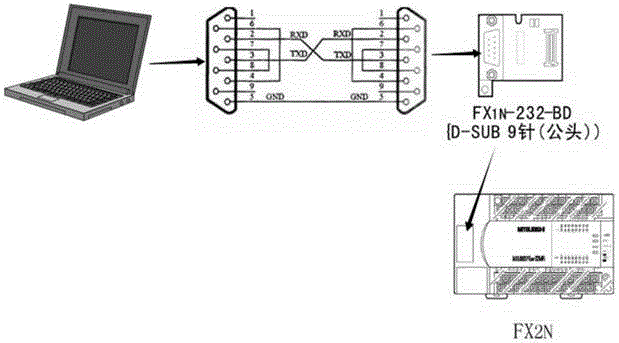
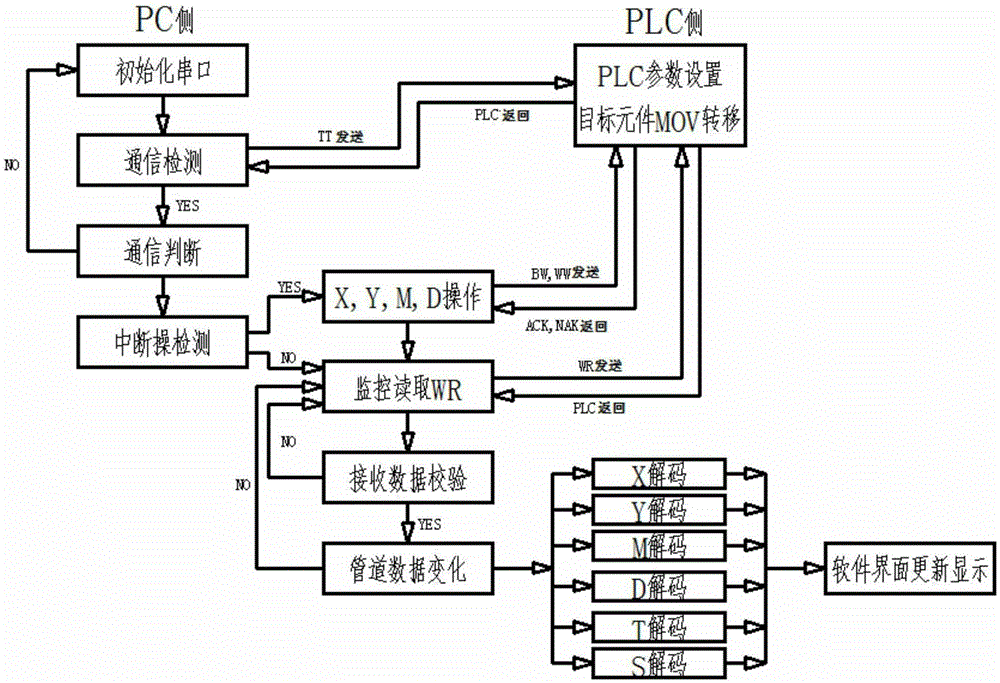
Realization method of logic control of VB/VC (Microsoft Visual Basic 6.0/Microsoft Visual C++) and PLC (Programmable Logic Controller) on the basis of serial communication
InactiveCN105353715AReduce computing loadShort response timeProgramme control in sequence/logic controllersVisual BasicProgrammable logic controller
The present invention provides a realization method of logic control of VB / VC (Microsoft Visual Basic 6.0 / Microsoft Visual C++) and PLC (Programmable Logic Controller) on the basis of serial communication. The realization method provided by the invention is free of writing a logic T-shaped program in the PLC of a lower computer, all the logic controls may be realized at an upper computer, and industrial control may be realized. According to the new method provided by the invention, the upper computer is only needed to send instruments to realize monitoring of an input port and an output port with no need for writing any logic program in the PLC, and only one instrument is sent to perform all the stable and reliable monitoring of objects to be monitored (X, Y M, D and other elements); through adoption of a 'pipeline' mode in the aspect of signal decoding, operation coincidence of a CPU is reduced, and the response time of a program is short; and programs may be managed by category, the PLC of any point may be controlled without point limitation, and wiring, free of circuit interlocking, is greatly simplified in the aspect of circuit connection with safety and convenience.
Owner:SHANGHAI UNIV
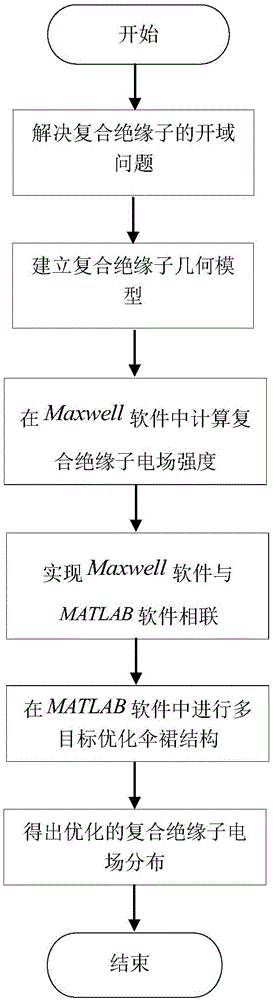
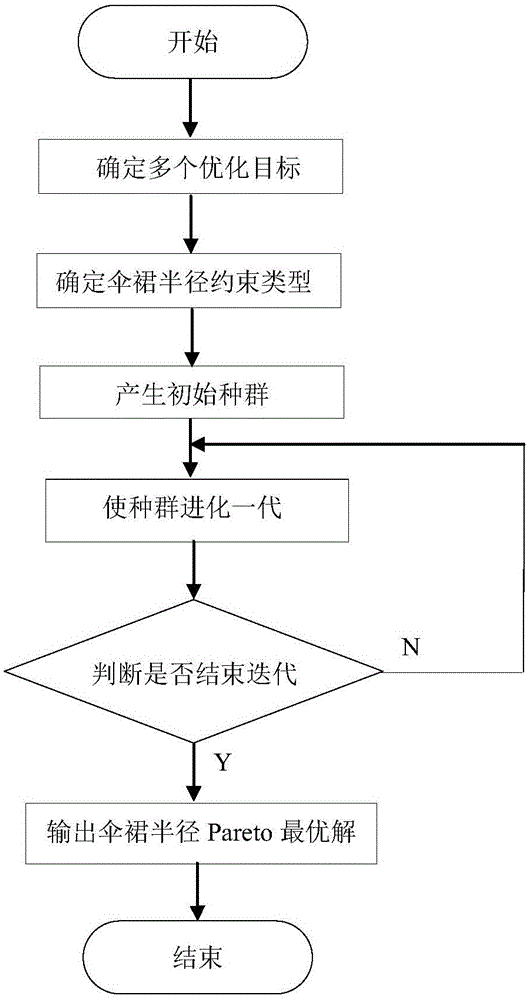
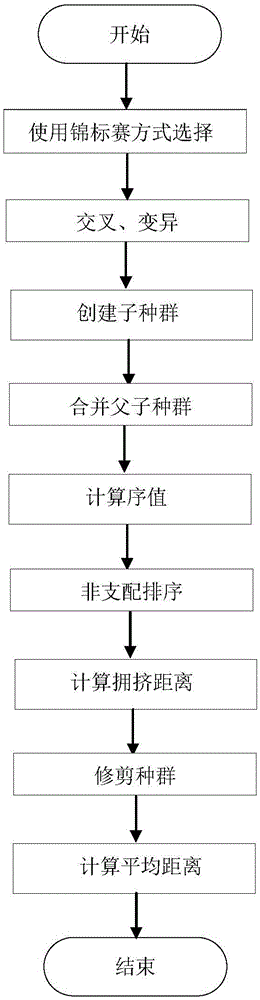
Composite insulator electric field optimization method based on multi-target genetic algorithm
ActiveCN105005675AGuaranteed correctnessDominant Field Strength DistributionGenetic modelsSpecial data processing applicationsData connectionVisual Basic
The invention discloses a composite insulator electric field optimization method based on a multi-target genetic algorithm. The method comprises steps as follows: 1) solving an electrostatic field open domain problem; 2) establishing a composite insulator geometric model; 3) performing numerical computation on the composite insulator electric field intensity in Maxwell software; 4) in order to break through the limitation of a Maxwell software optimization module, adopting the VB (visual basic) script of the Maxwell software to realize data connection of the Maxwell software and MATLAB software; 5) in the MATLAB software, optimizing shed radiuses with the multi-target genetic algorithm; 6) obtaining optimized composite insulator electric field distribution. According to the method, the field intensity Range_E minimization and the field intensity gradient Max_GradE minimization are taken as multiple optimization targets, and large, medium and small shed radiuses of a composite insulator are optimized, so that the composite insulator electric field distribution is more uniform.
Owner:HOHAI UNIV CHANGZHOU
Ultrasound probe with integrated electronics
InactiveUS20170105706A1Simplifies cable requirementDifficult to upgradePhysical therapies and activitiesMechanical/radiation/invasive therapiesVisual BasicSonification
A hand-held ultrasound system includes integrated electronics within an ergonomic housing. The electronics includes control circuitry, beamforming and circuitry transducer drive circuitry. The electronics communicate with a host computer using an industry standard high speed serial bus. The ultrasonic imaging system is operable on a standard, commercially available, user computing device without specific hardware modifications, and is adapted to interface with an external application without modification to the ultrasonic imaging system to allow a user to gather ultrasonic data on a standard user computing device such as a PC, and employ the data so gathered via an independent external application without requiring a custom system, expensive hardware modifications, or system rebuilds. An integrated interface program allows such ultrasonic data to be invoked by a variety of such external applications having access to the integrated interface program via a standard, predetermined platform such as visual basic or c++.
Owner:TERATECH CORP
Method for constructing CAM (computer-aided manufacturing) system for punching for automobile girders
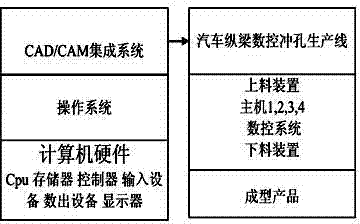
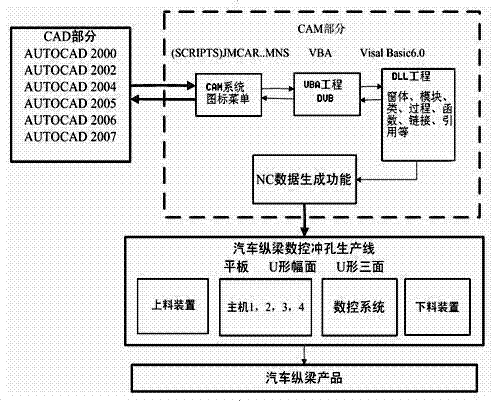
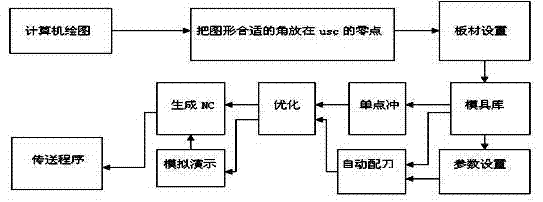
ActiveCN102707669ARealize integrationAvoid reducing service lifeProgramme controlComputer controlNumerical controlVisual Basic
A method for constructing a CAM (computer-aided manufacturing) system for punching for automobile girders is characterized by including selecting the types of used numerical-control punching production lines for the automobile girders; creating projects corresponding to the types of the numerical-control punching production lines for the automobile girders, building mathematical models of algorithms, and building generic modules; determining the types of the projects as Activex DII and compiling the types of the projects into types of dynamic linking libraries; writing and compiling interface programs connected with the dynamic linking libraries by VBA (visual basic for application); writing scripts for the various types of numerical-control punching production lines, and creating a CAM icon menu file and icons corresponding to various items; packaging various documents such as the CAM icon menu file, the interface programs written by the VBA, each class-generation DLL (dynamic linking library) compiled by VB (visual basic), development interfaces provided in the form of VB types, windows, the modules, the projects, an encryption method and instructions in a SETUP to form installation programs of the various types of numerical-control punching production lines for the automobile girders; and adding a CAM menu into a menu self-defining term in a CAD (computer-aided design).
Owner:广州市力鼎汽车零部件有限公司
Method and system for server-based error processing in support of legacy-based usage and billing systems
An error processing system comprising a client / server based PC application supported by SQL Server databases for use with legacy usage metering and billing services. The error processing system provides increased functionality, flexibility and reliability of error processing at a much lower cost than was possible using error processing and correction systems built into legacy usage metering systems. Error processing is simplified for users by implementation of a PC based GUI screens developed in Visual Basic.
Owner:AT&T INTPROP I LP
Tri-component magnetic survey system in borehole
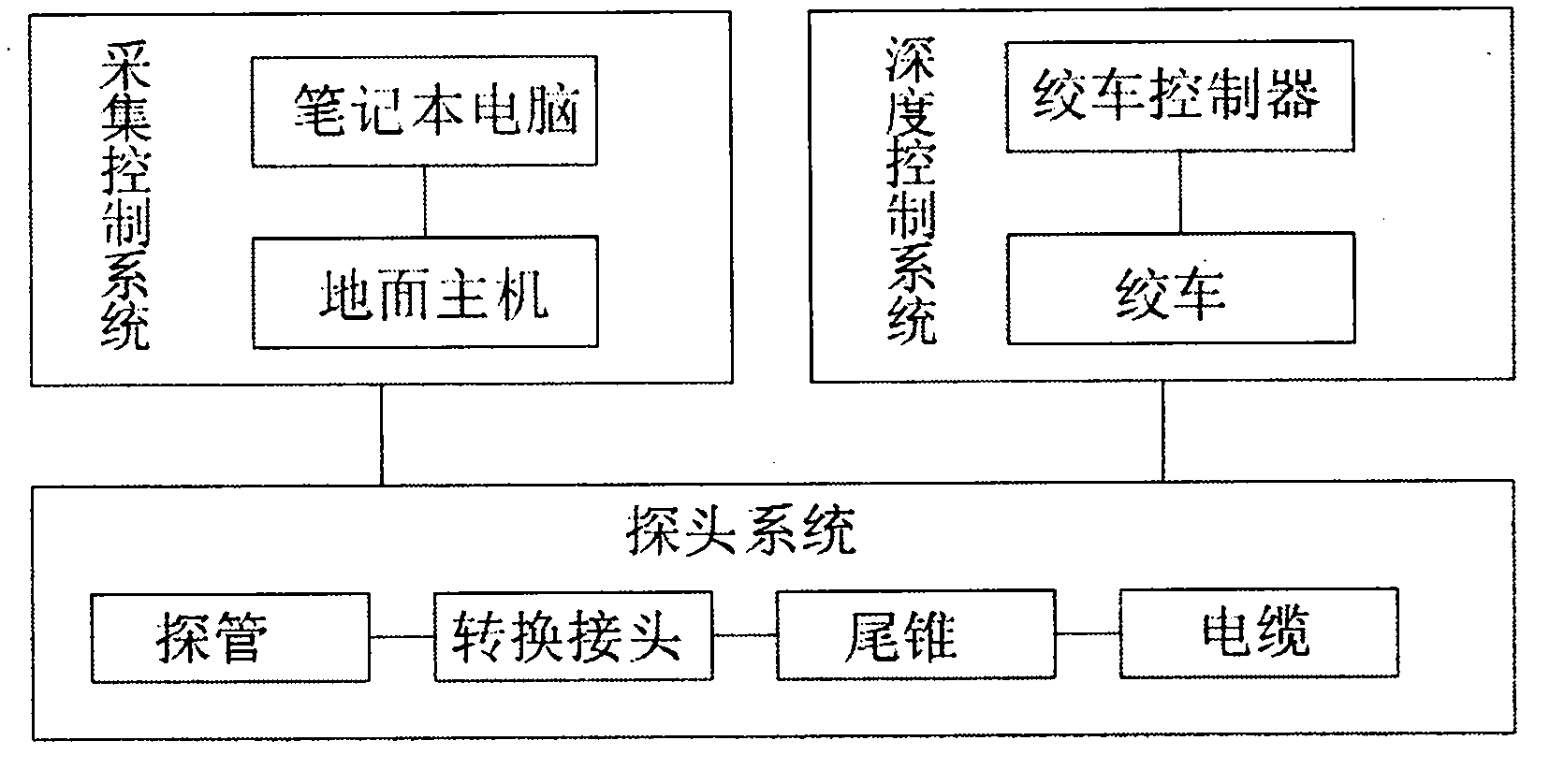
InactiveCN102183794AImprove detection accuracyRealize magnetic measurementElectric/magnetic detection for well-loggingAcoustic wave reradiationVisual BasicReal-time data
The invention relates to a tri-component magnetic survey system in borehole, belonging to a technical product in the field of tri-component magnetic survey in borehole. The hardware system of the invention comprising the purchased devices is subjected to system debugging and is therefore improved in performance. The software consists of a data reading module, a data calculation module, a data graphing module, a result deducing module and an image module compiled by a development platform Visual Basic 6.0. By processing, graphing, analyzing and explaining the data collected during the drilling process, the system can find ores and solve various geological problems, thereby increasing the ore finding ratio of drilling and reducing the engineering cost of drilling. The system has the advantages of high stability, deep investigation depth, high investigation precision and high-speed efficient real-time data processing, and is not only fit for finding strongly magnetic minerals but also for finding more weakly magnetic minerals or other minerals symbiotic to weakly magnetic minerals.
Owner:KUNMING PROSPECTING DESIGN INST OF CHINA NONFERROUS METALS IND
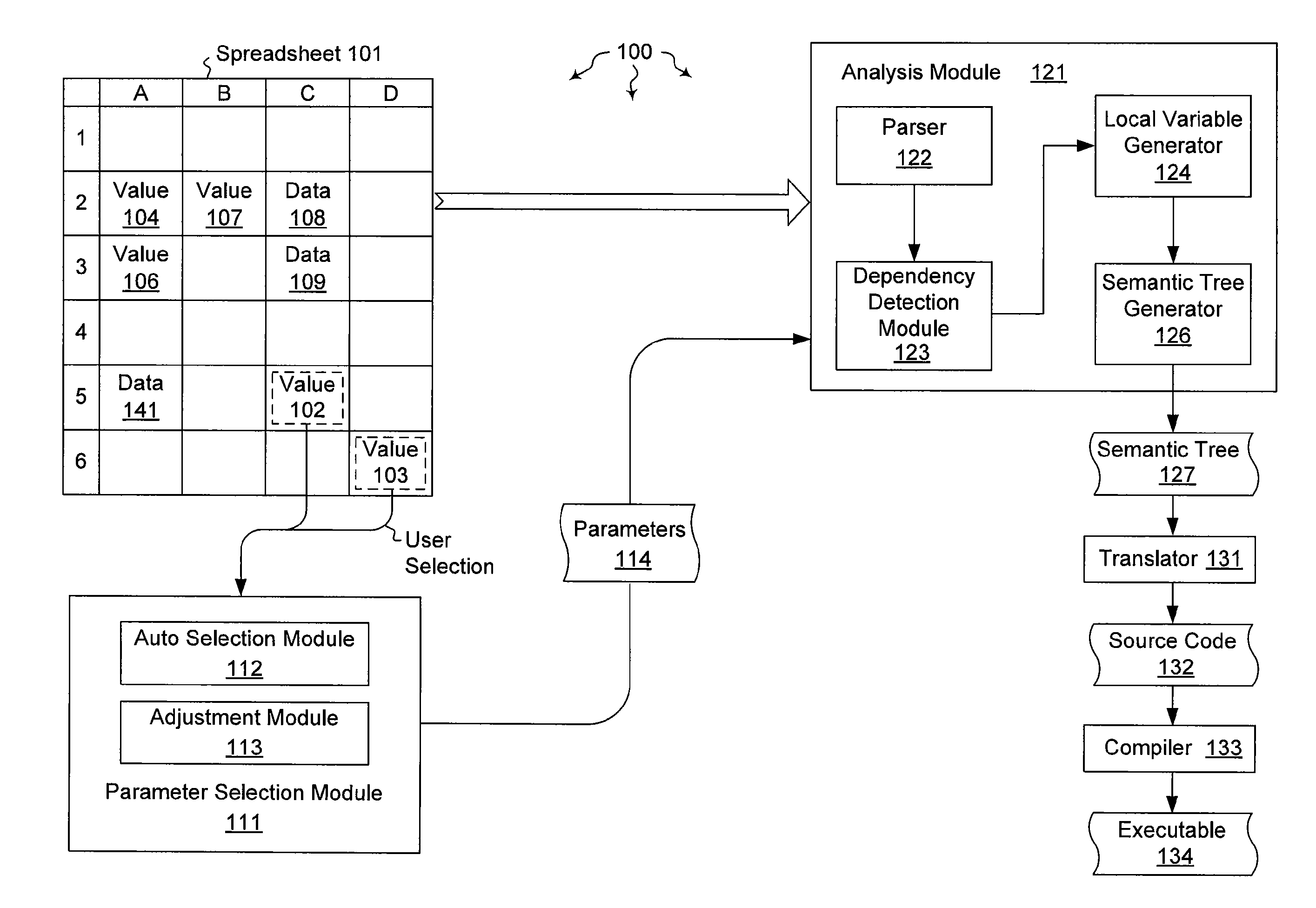
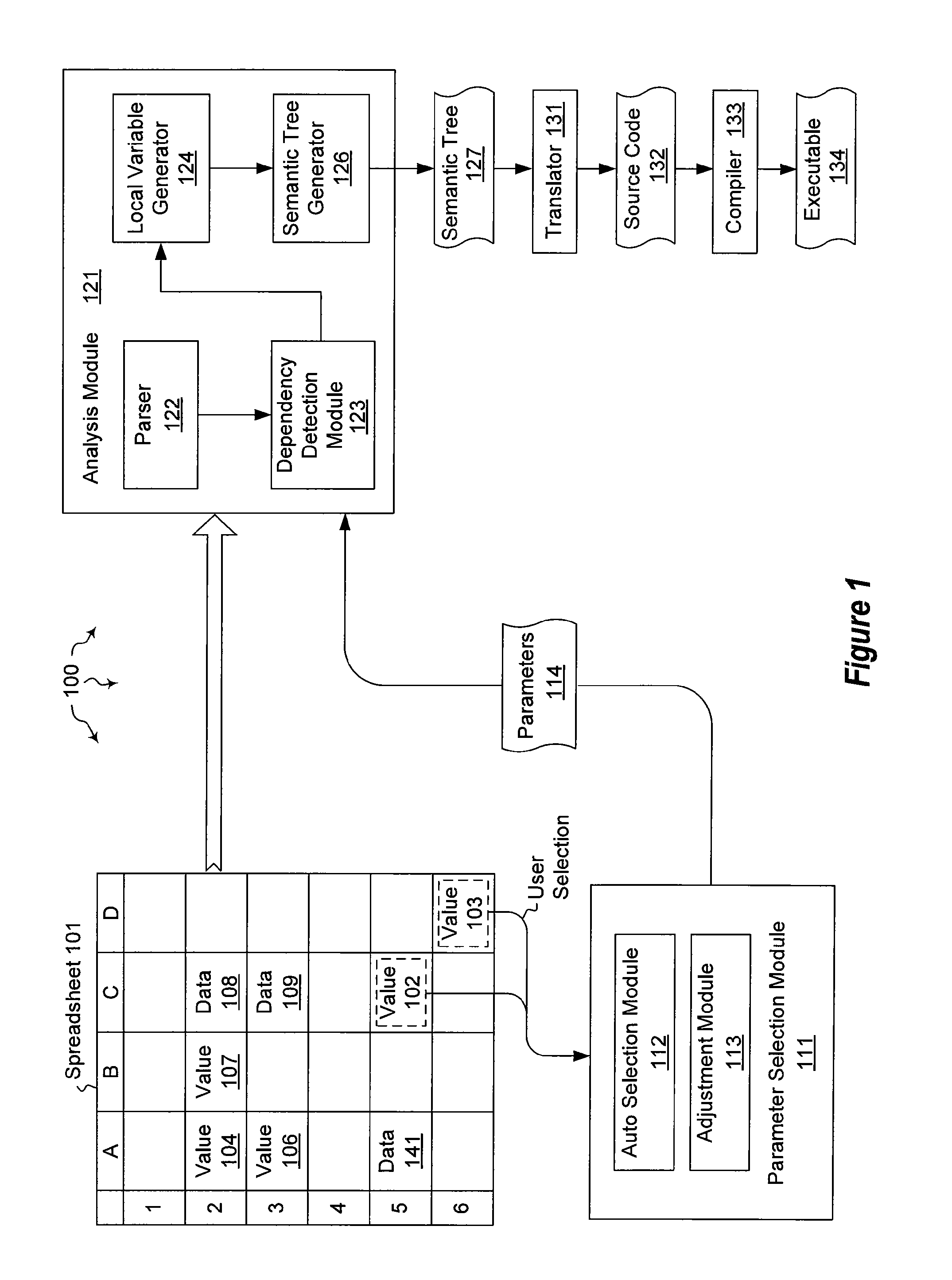
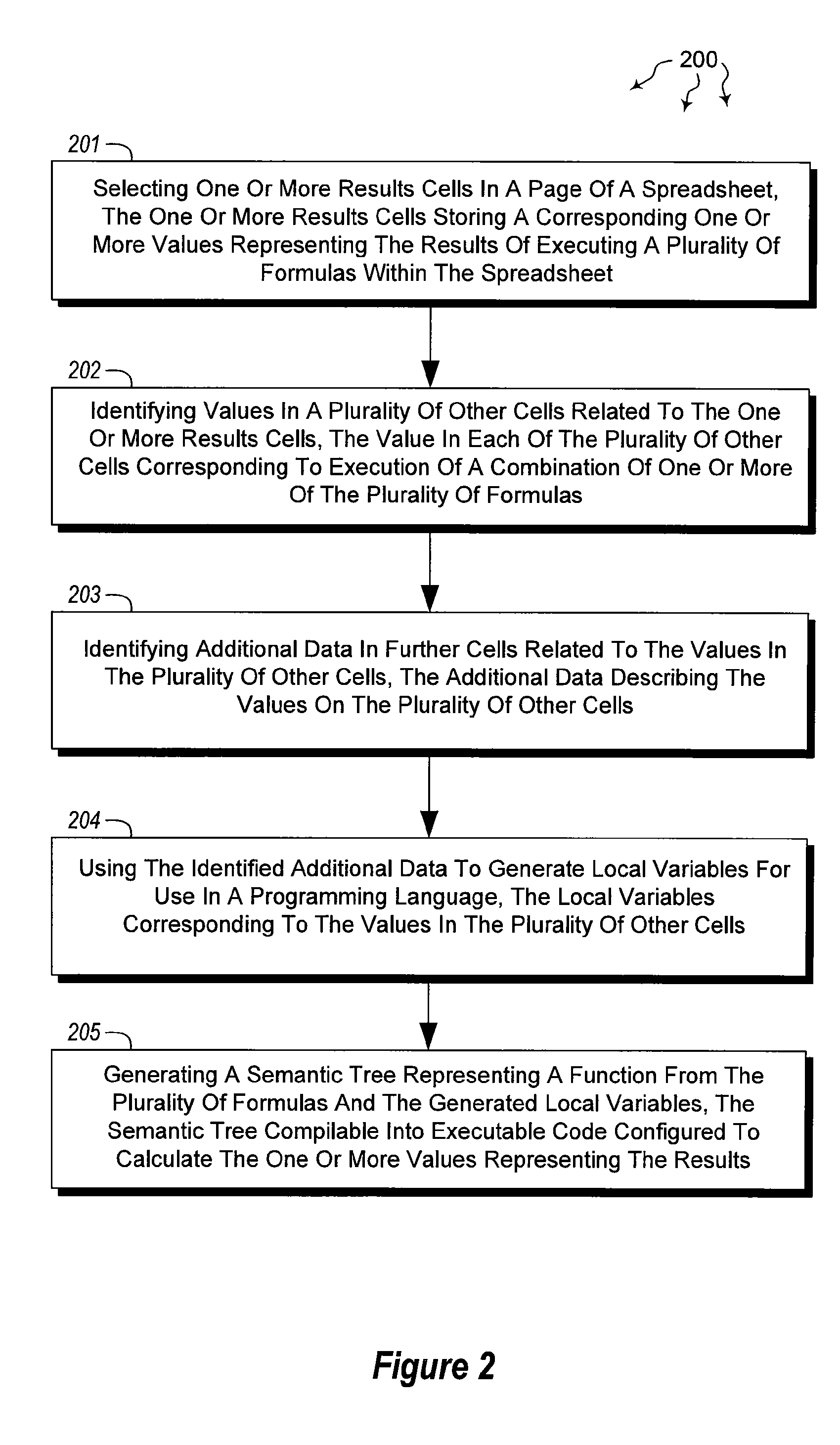
Creating text functions from a spreadsheet
The present invention extends to methods, systems, and computer program products for creating text functions form a spreadsheet. Embodiments of the invention extract functions from spreadsheets and represent the functions in textual form. Representation in textual form promotes code reuse, clarify, expressive power, and better performance. Text can be rendered in virtually any programming language, such as, for example, C#, C++, Visual Basic (“VB”), etc. In some embodiments, programming language extensibility to support spreadsheet compatible data types and functions is utilized.
Owner:MICROSOFT TECH LICENSING LLC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com