Patents
Literature
93 results about "Command language" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
A command language is a language for job control in computing. It is a domain-specific and interpreted language; common examples of a command language are shell or batch programming languages. These languages can be used directly at the command line, but can also automate tasks that would normally be performed manually at the command line. They share this domain—lightweight automation—with scripting languages, though a command language usually has stronger coupling to the underlying operating system. Command languages often have either very simple grammars or syntaxes very close to natural language, to shallow the learning curve, as with many other domain-specific languages.
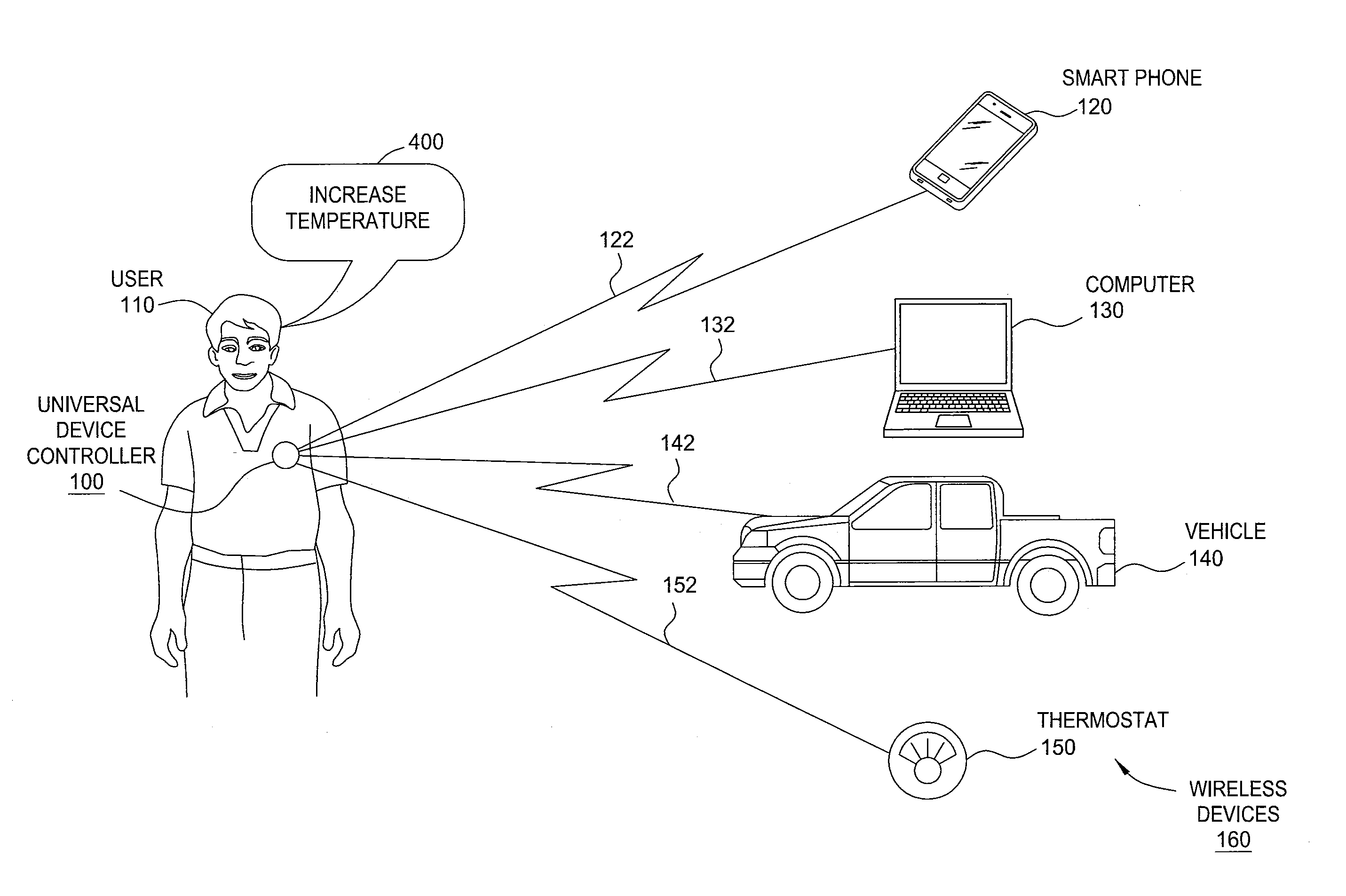
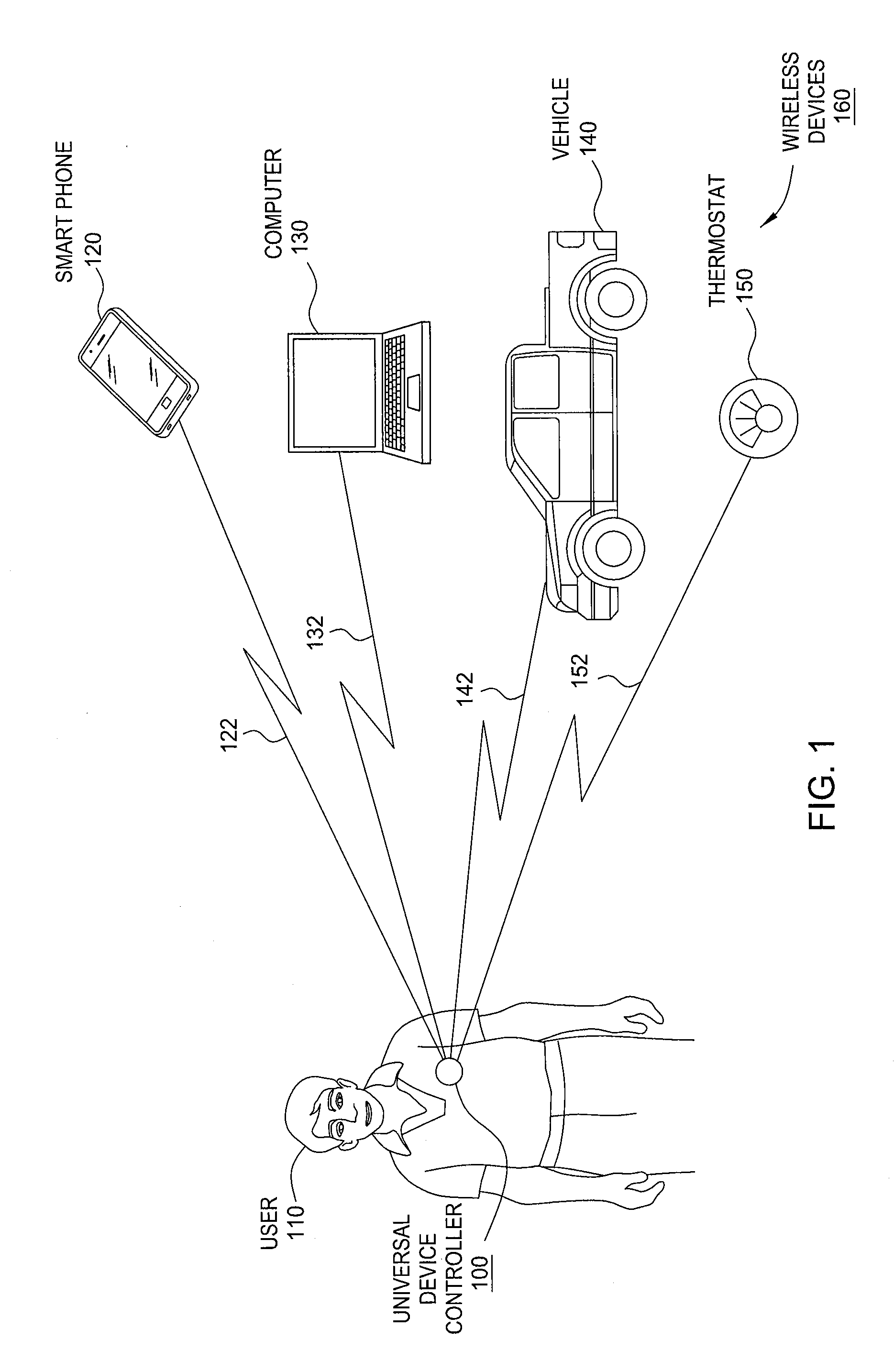
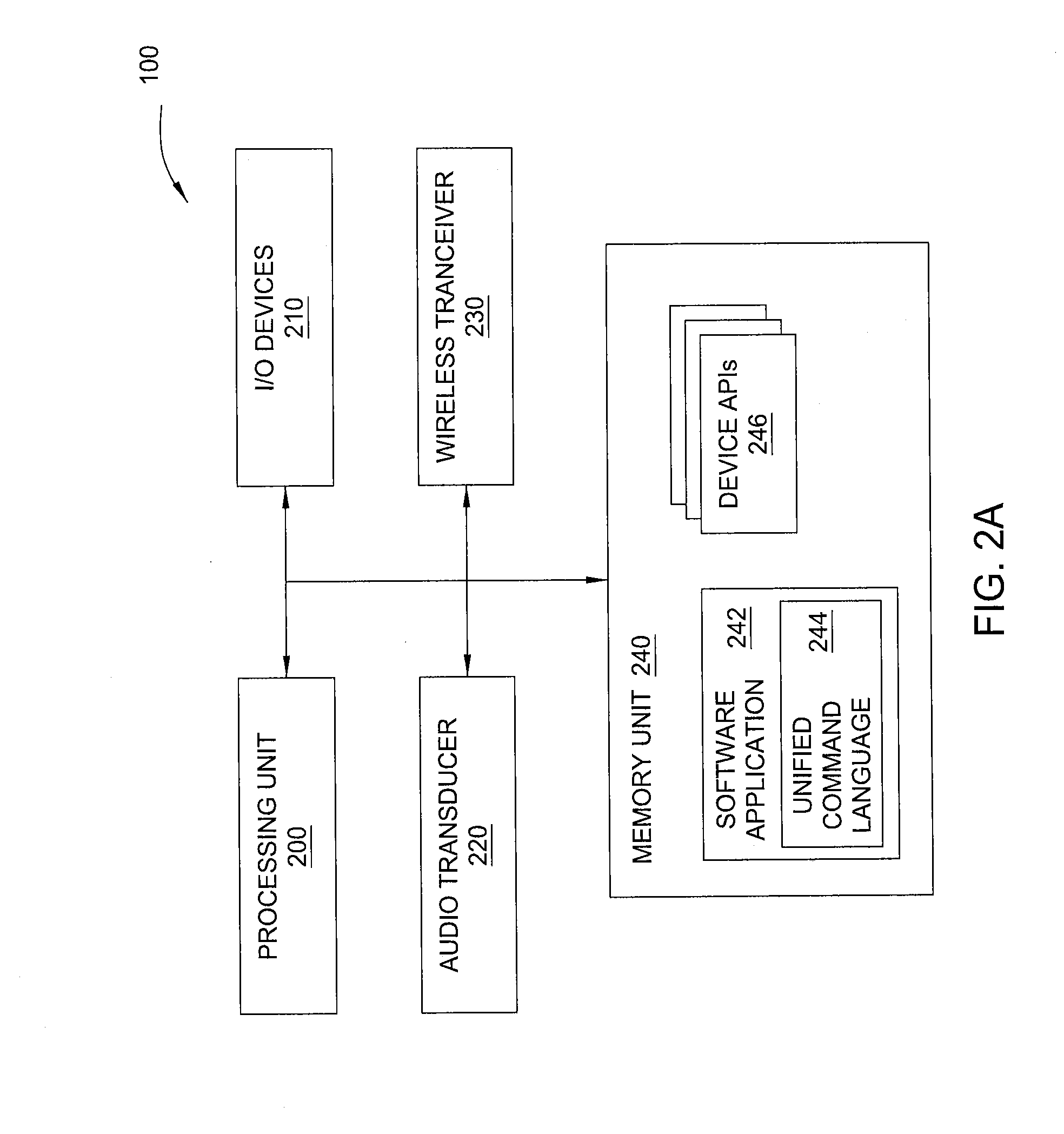
Wireless control of linked devices
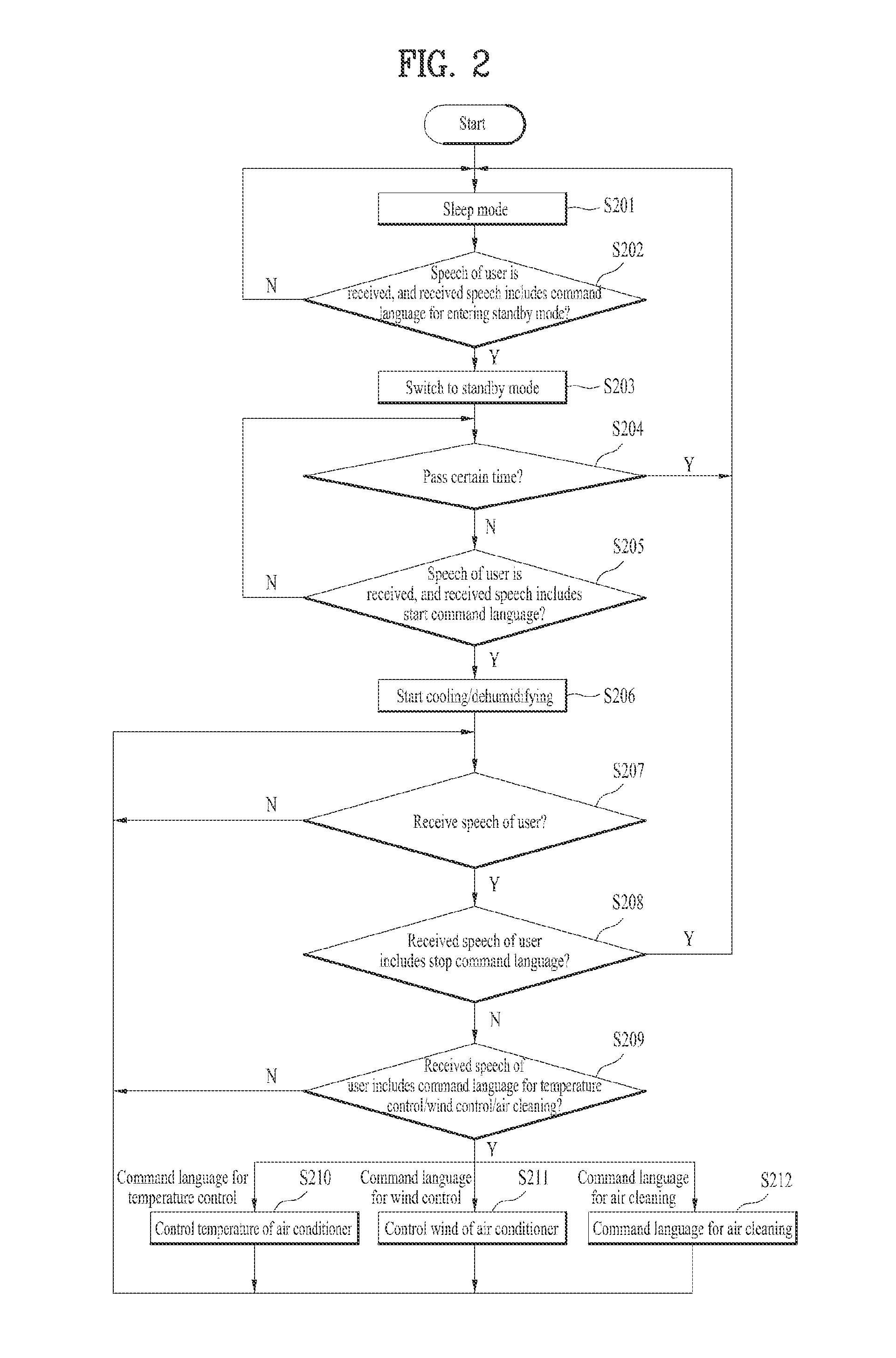
A universal device controller is configured to operate as a proxy mechanism for interacting with a plurality of different devices wirelessly coupled to the universal device controller. When a user of the universal device controller verbally expresses a command from a universal command language understood by the device, the universal device controller analyzes the verbal expression of the user and identifies a wireless device capable of executing the associated command. The universal device controller then identifies an API for interacting with the identified device and translates the verbal expression into a device command that the identified device is capable of executing. The universal device controller then issues the device command to the identified device.
Owner:HARMAN INT IND INC
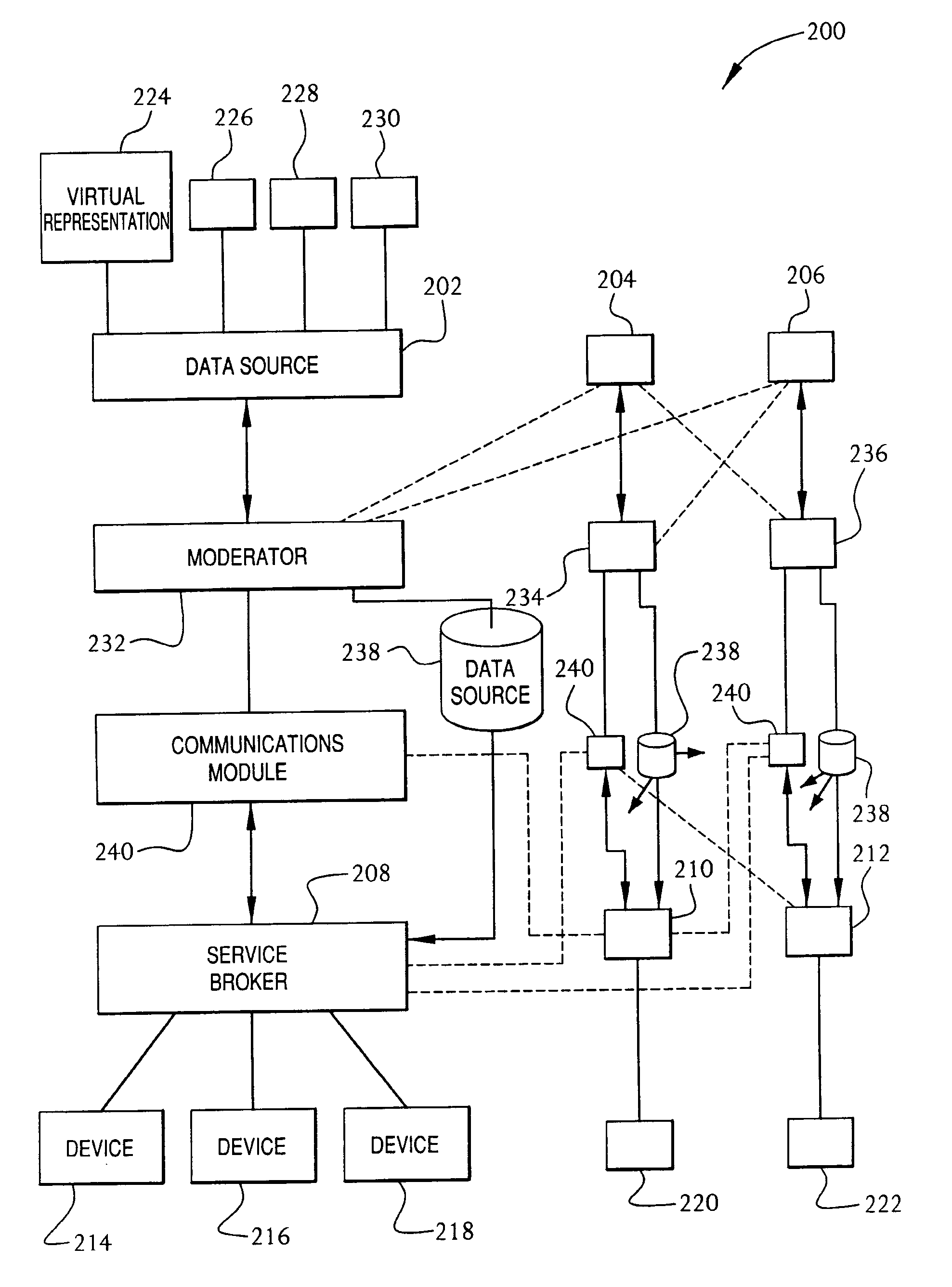
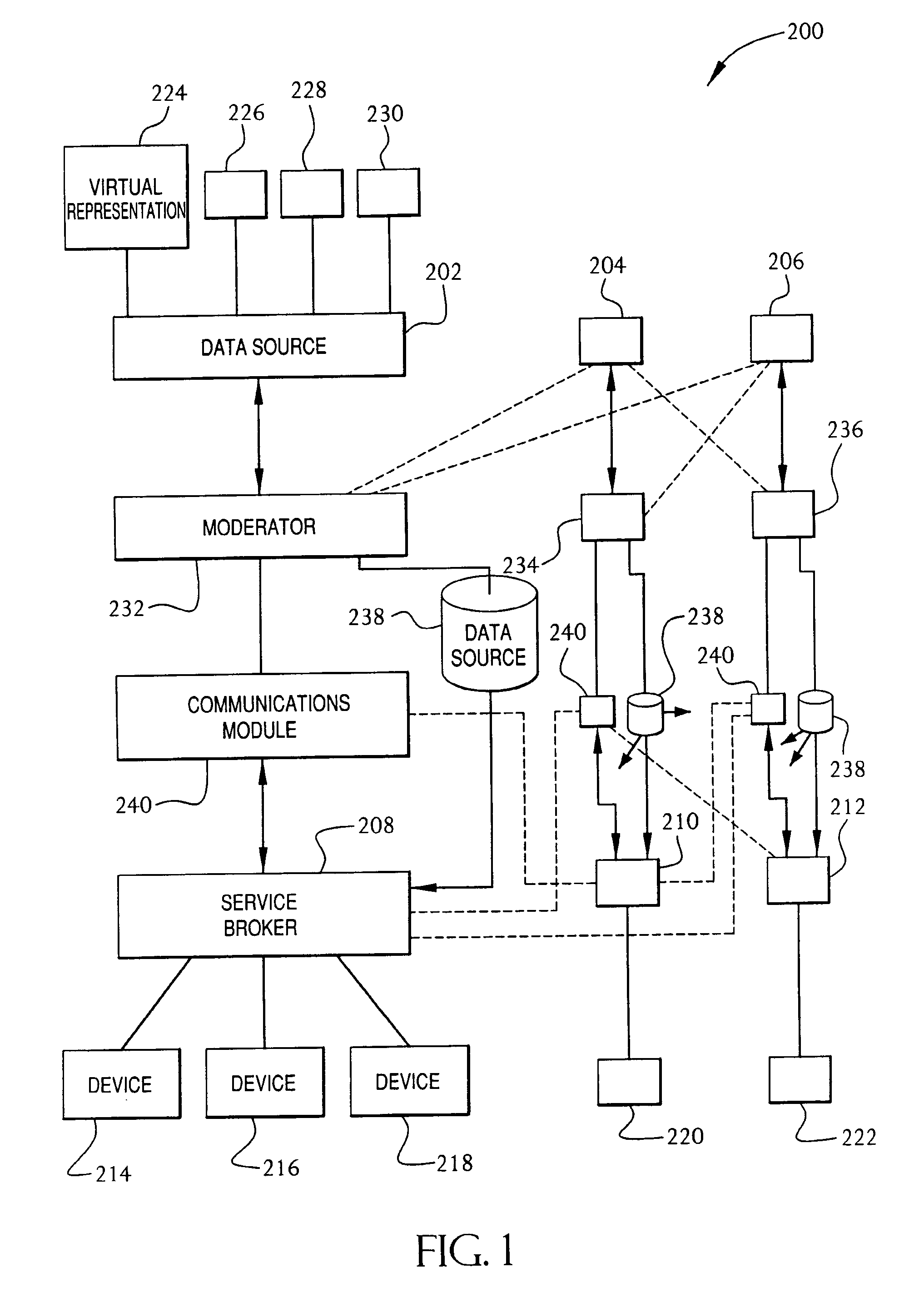
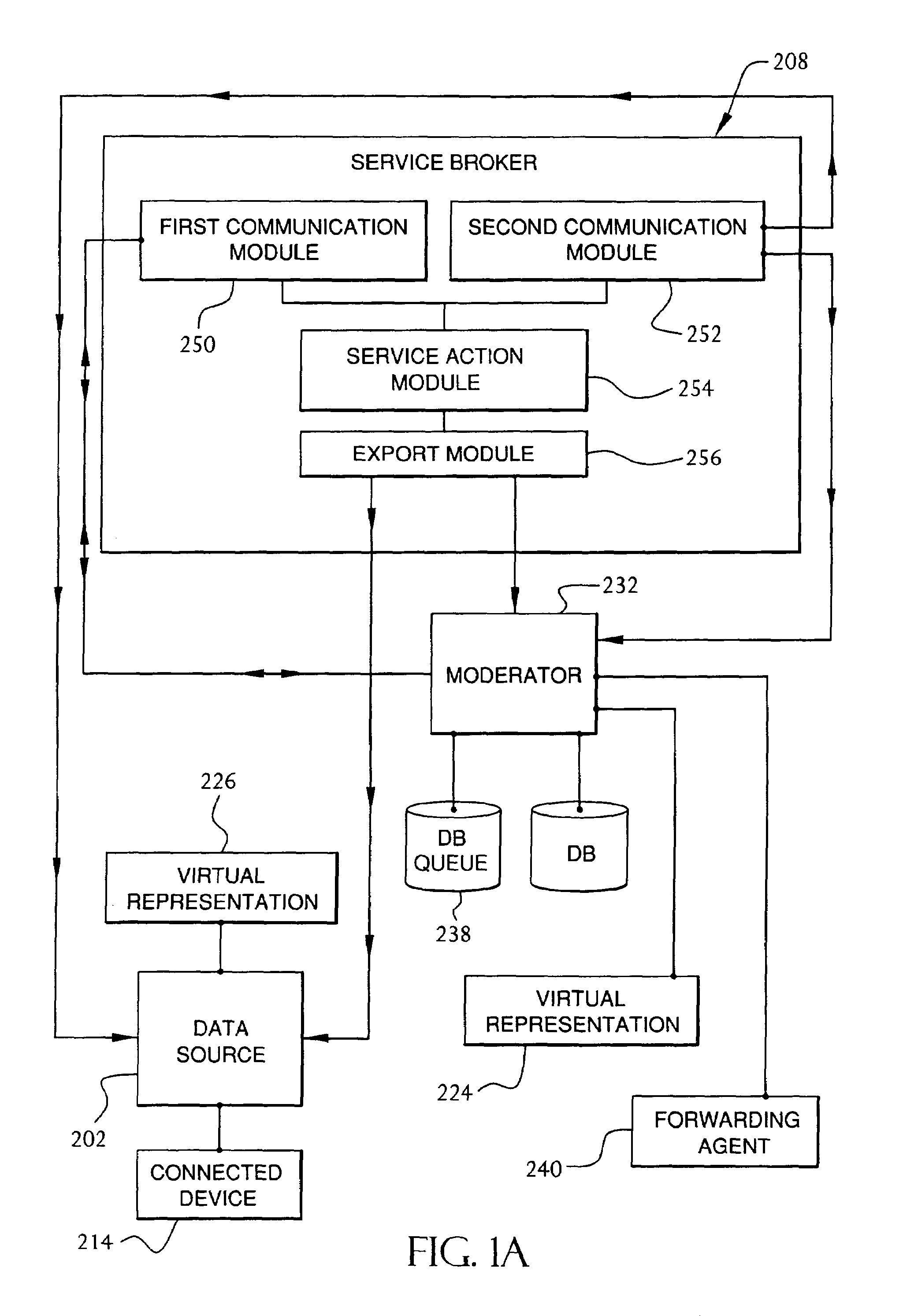
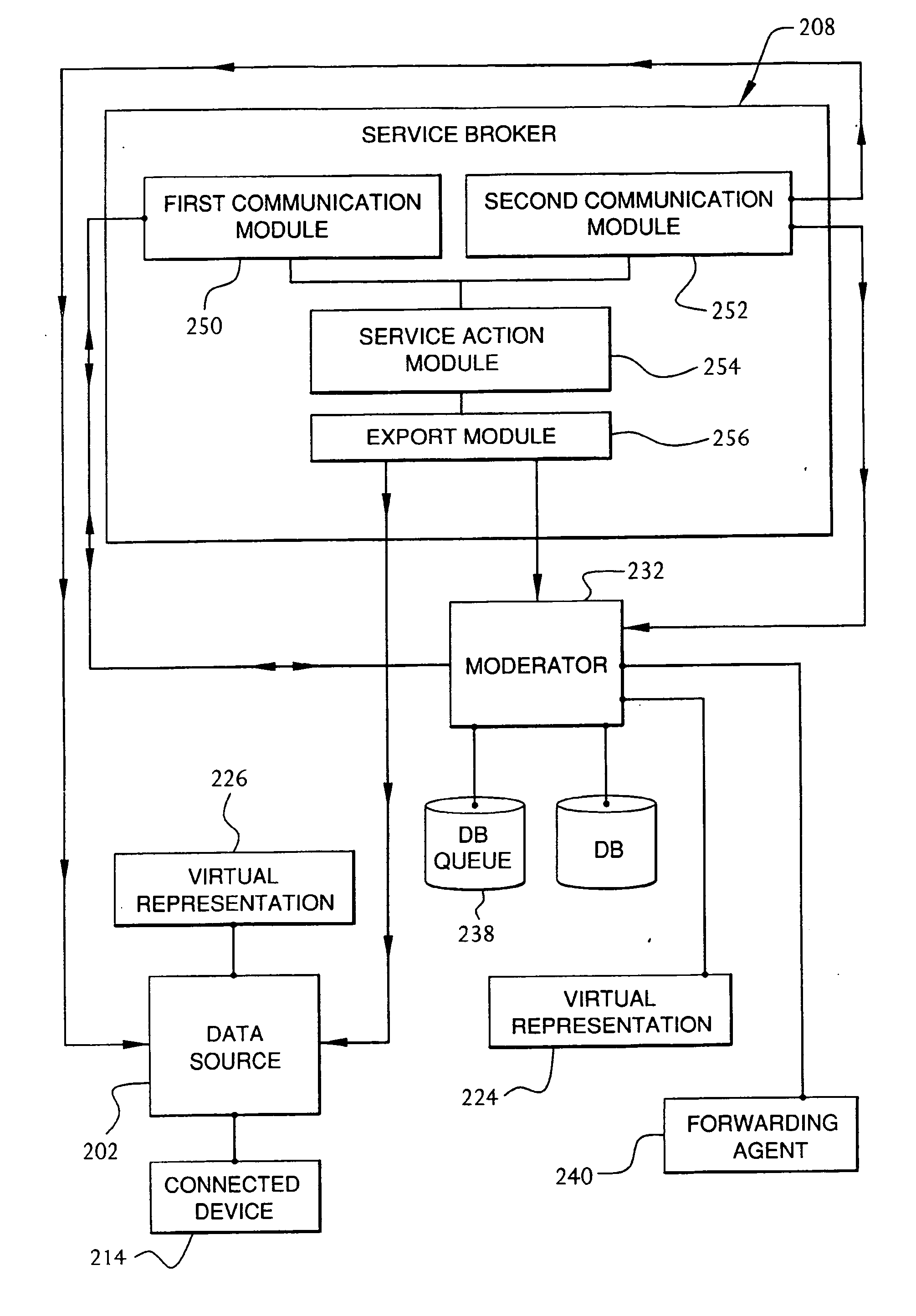
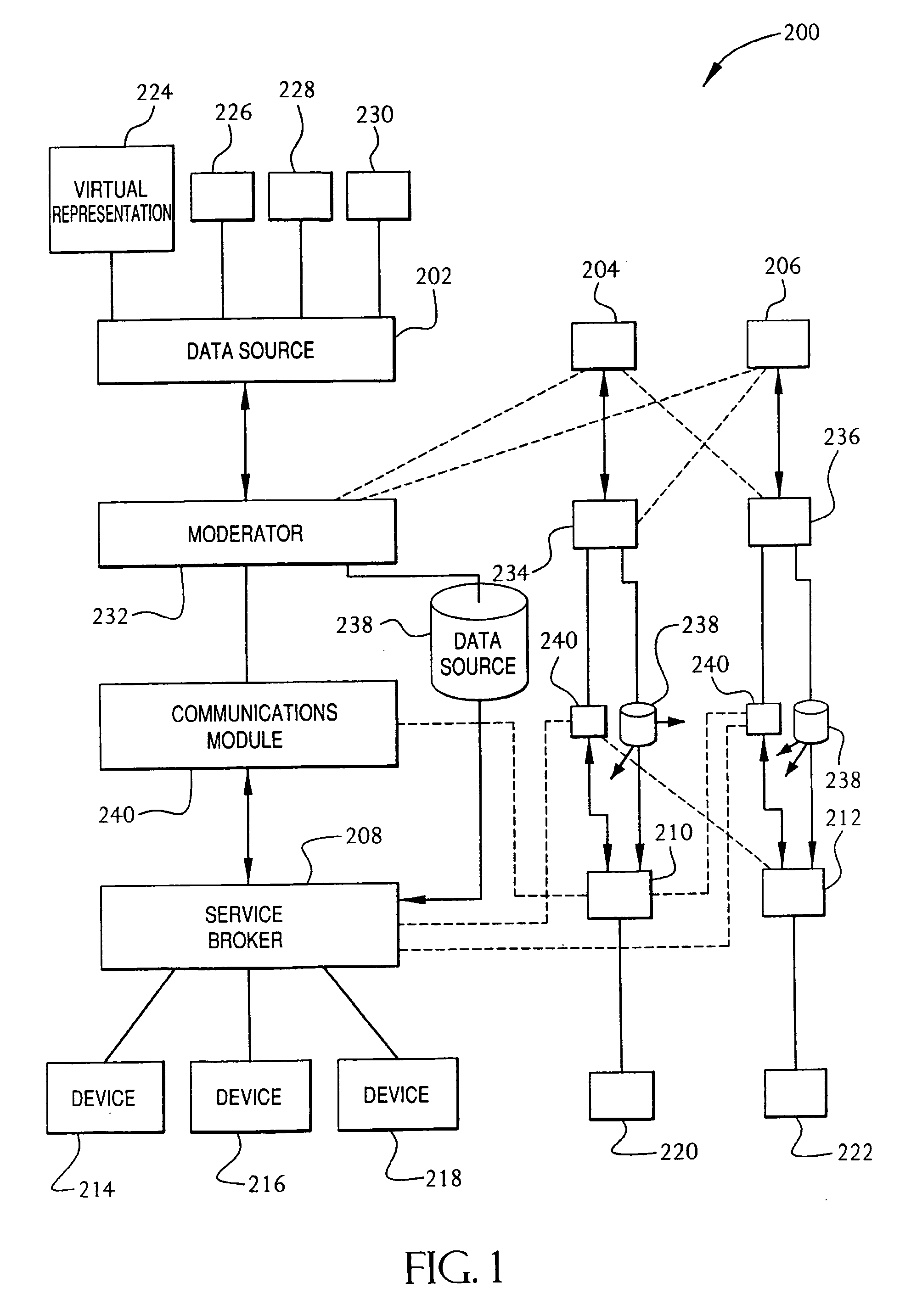
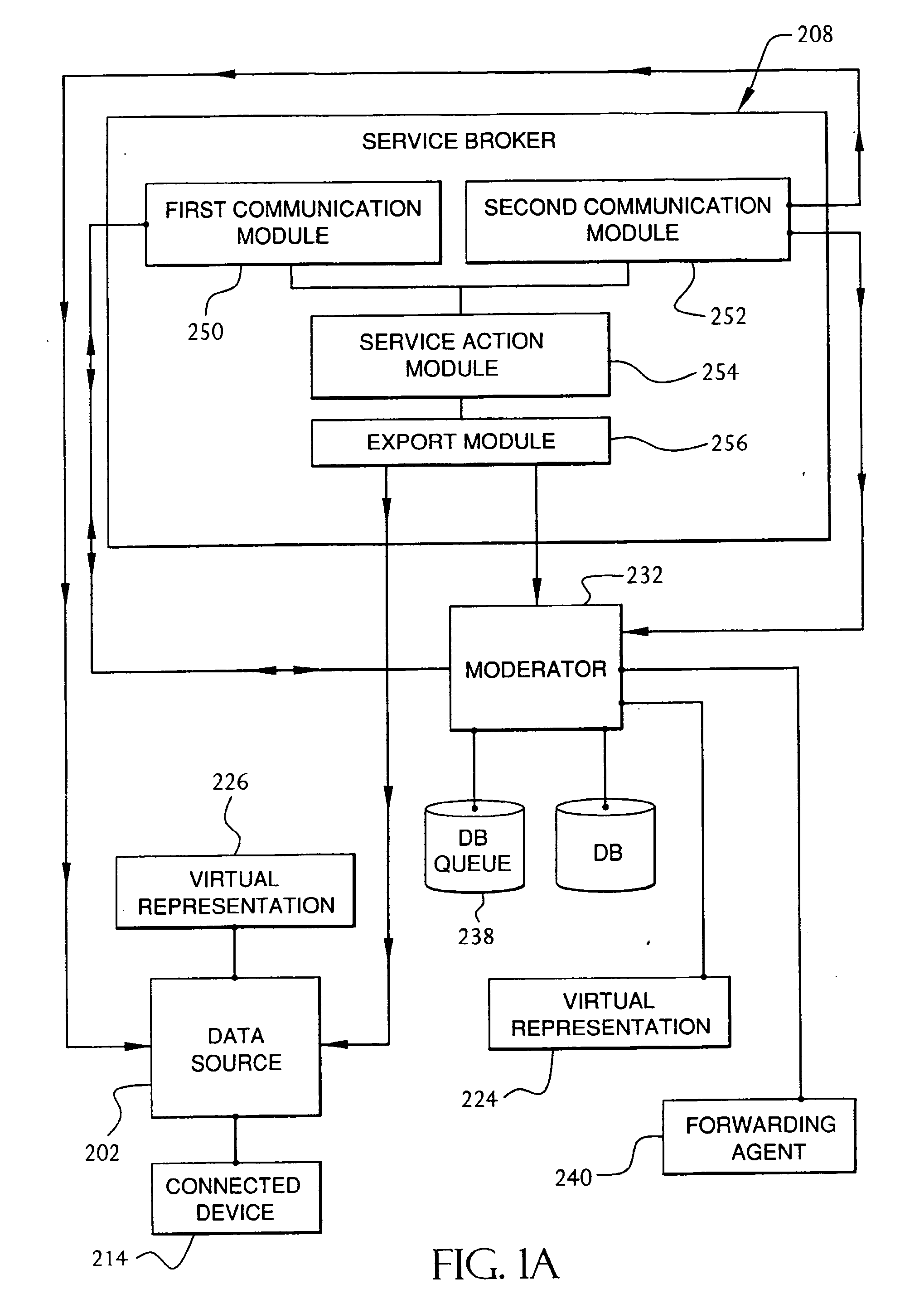
Service broker for processing data from a data network
InactiveUS7032002B1Multiple digital computer combinationsStore-and-forward switching systemsCommand languageServer appliance
A method and system for communication between server-less computing devices or clients in computers communicating over networks, such as the World Wide Web (WWW) using stateless protocols, e.g., HTTP. In this scheme, there are two classes of clients which can operate independently or can be combined in computers communicating over the network: a) clients that issue commands and request status or data, and b) clients that function as service brokers for providing services and processing commands, updating status and providing specific data—resembleing a server device but without accessible TCP / IP ports. Each service providing device is authenticated, retains a unique identity and establishes a soft state with the globally accessible server or servers. All devices and clients can compile and process a globally common command language established between all communicating network clients. The central server includes a CGI processing program and a database to retain client specific information. The server database represents a collection of queues, each having a client unique identifiable status, pending commands and / or data components. In this scheme, commands and signaling transmitted between the servers and clients utilize standard HTTP protocol semantics and HTML or standard markup language syntax. Clients encapsulate or embed information as parameters passed to HTTP CGI as a set of standard HTTP conversations. A CGI processing program converts, parses or processes each conversation and passes arguments with or without data to queues.
Owner:AT&T DIGITAL LIFE
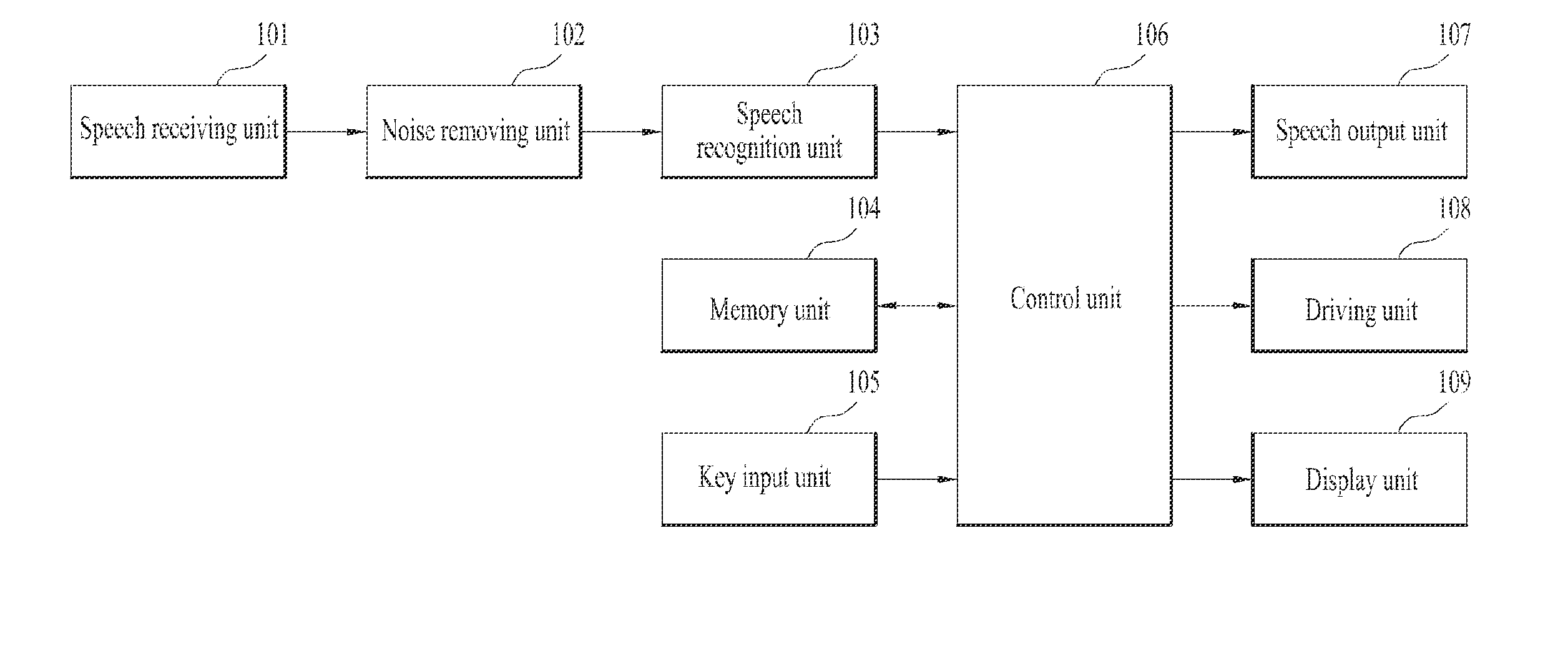
Apparatus and method for driving electric device using speech recognition
InactiveUS20140149118A1Solve the inconvenienceImproper operationSpeech recognitionCommand languageSpeech identification
An apparatus and method for driving an electric device using speech recognition are disclosed. The method for driving an electric device using speech recognition includes switching an operation stop state to a pre-operation speech recognition standby mode if a first keyword is recognized at the operation stop state; starting basic operation of the device if a second keyword is recognized at the pre-operation speech recognition standby mode; and performing a corresponding command if at least one of a plurality of command languages that may be recognized by a user command is recognized within a predefined time during the basic operation, wherein the first keyword, the second keyword and the plurality of command languages are different from one another.
Owner:LG ELECTRONICS INC
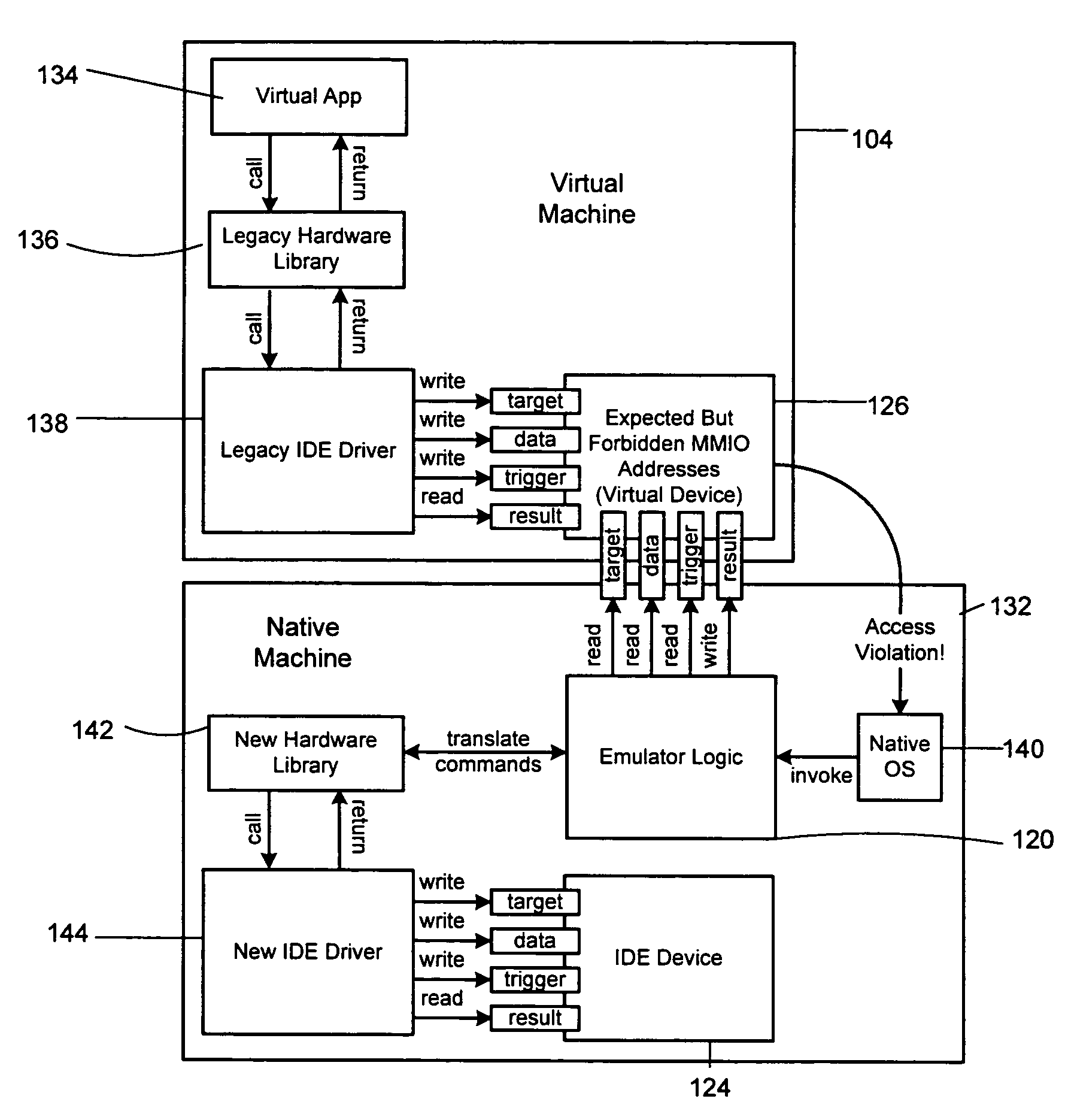
Virtual operating system device communication relying on memory access violations
InactiveUS20060259292A1Reducing permissionInternal/peripheral component protectionSoftware simulation/interpretation/emulationVirtualizationOperational system
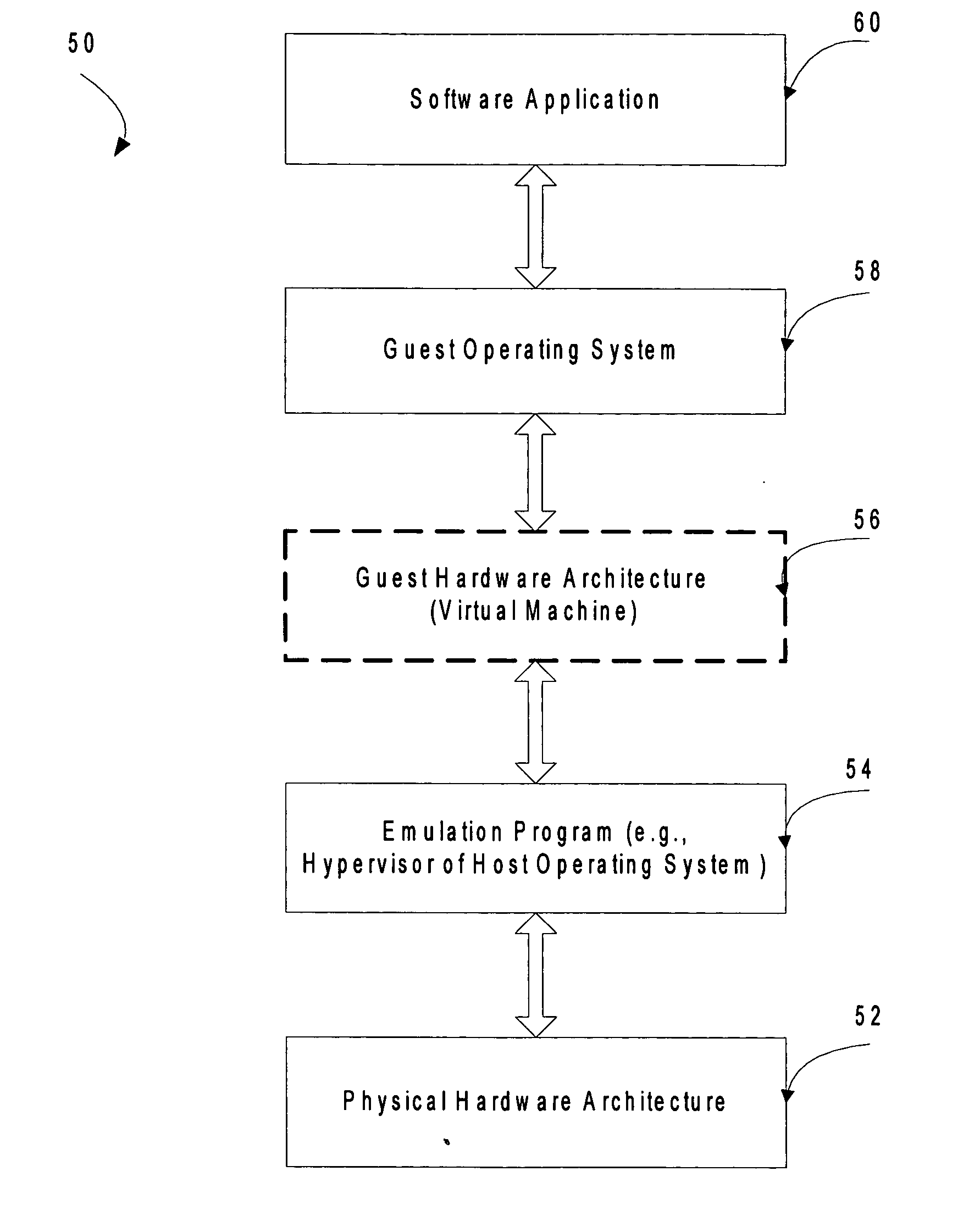
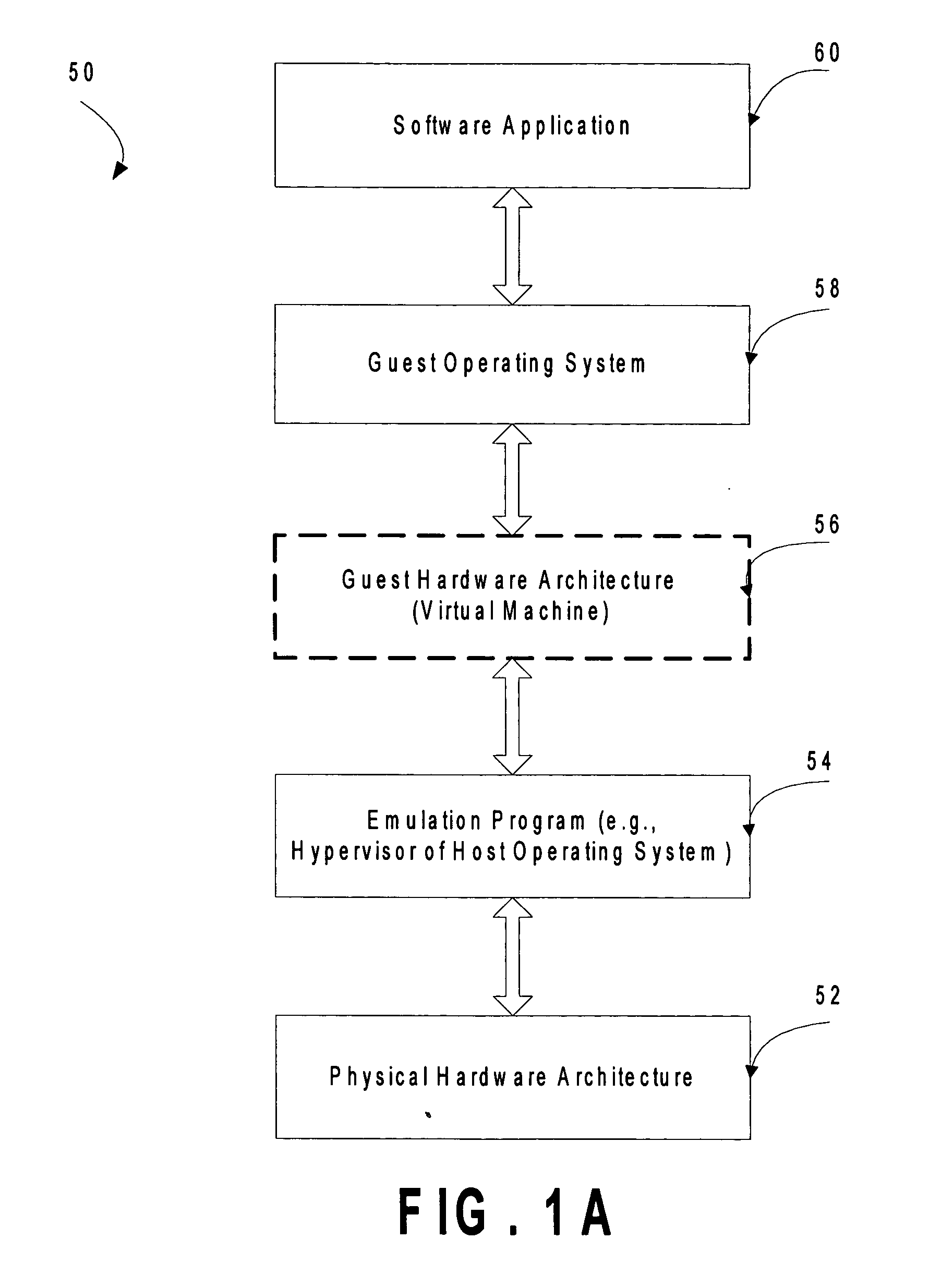
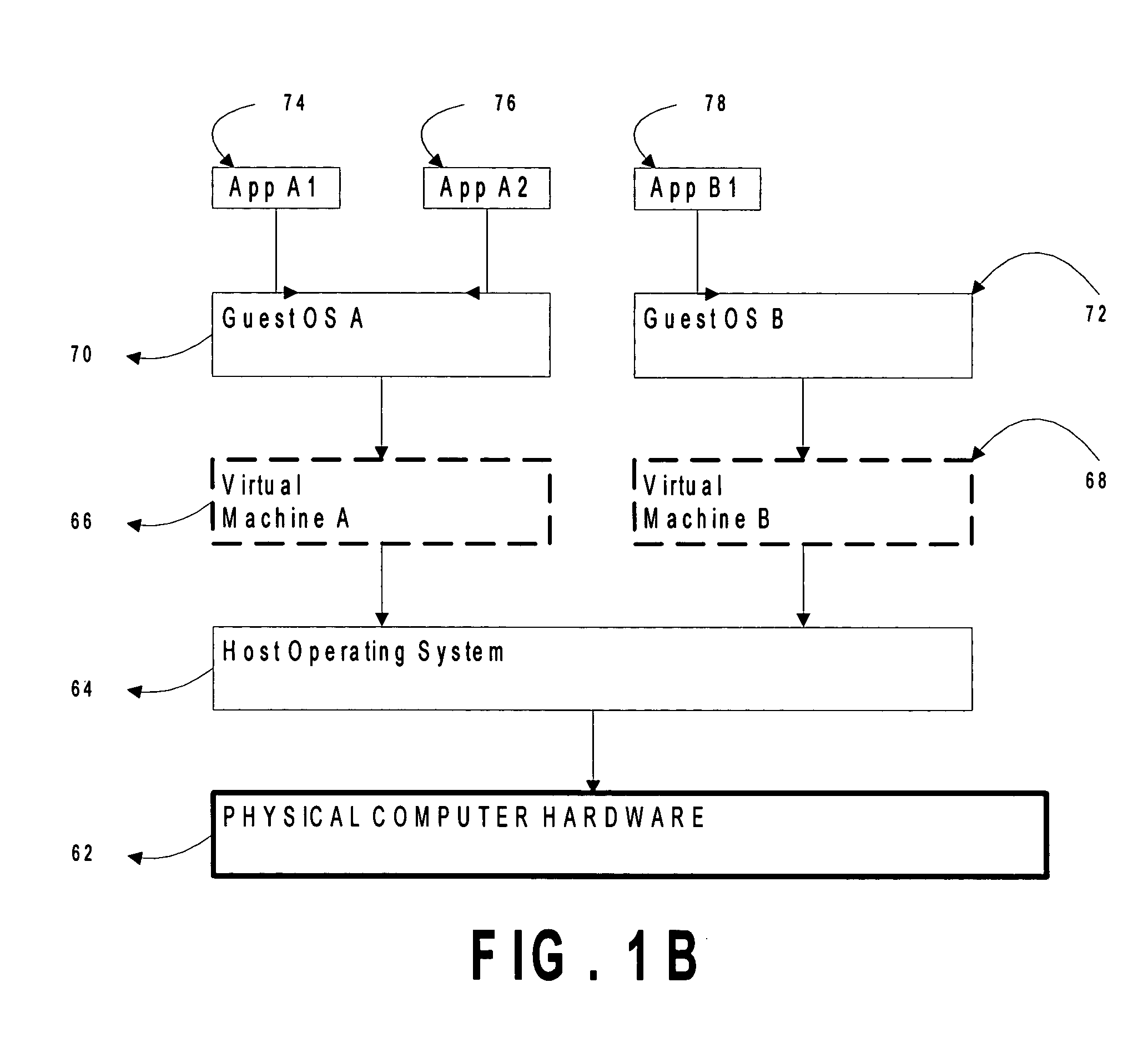
Attempts by drivers of a virtualized legacy computer game to communicate with nonexistent legacy game system hardware are converted into calls to actual hardware of the host computer game system. An access control list (ACL) restricting and / or reducing page permissions is used to explicitly forbid the drivers of the legacy computer game operating on the virtualized legacy computer game platform from writing to the MMIO addresses of the legacy computer game system. When the operating system of the virtualized legacy computer game platform attempts to touch its driver memory by writing to the MMIO addresses, the operating system of the host computer game system perceives a memory access violation, suspends the virtual machine implementing the virtualized computer game platform, and passes the intended write to an exception handler of the host operating system. The exception handler of the host operating system translates the attempted hardware access command into the command language of the host operating system and then returns control to the operating system of the virtualized legacy computer game platform. The legacy game is completely unaware of this address translation in that it sees only a successful hardware result and proceeds.
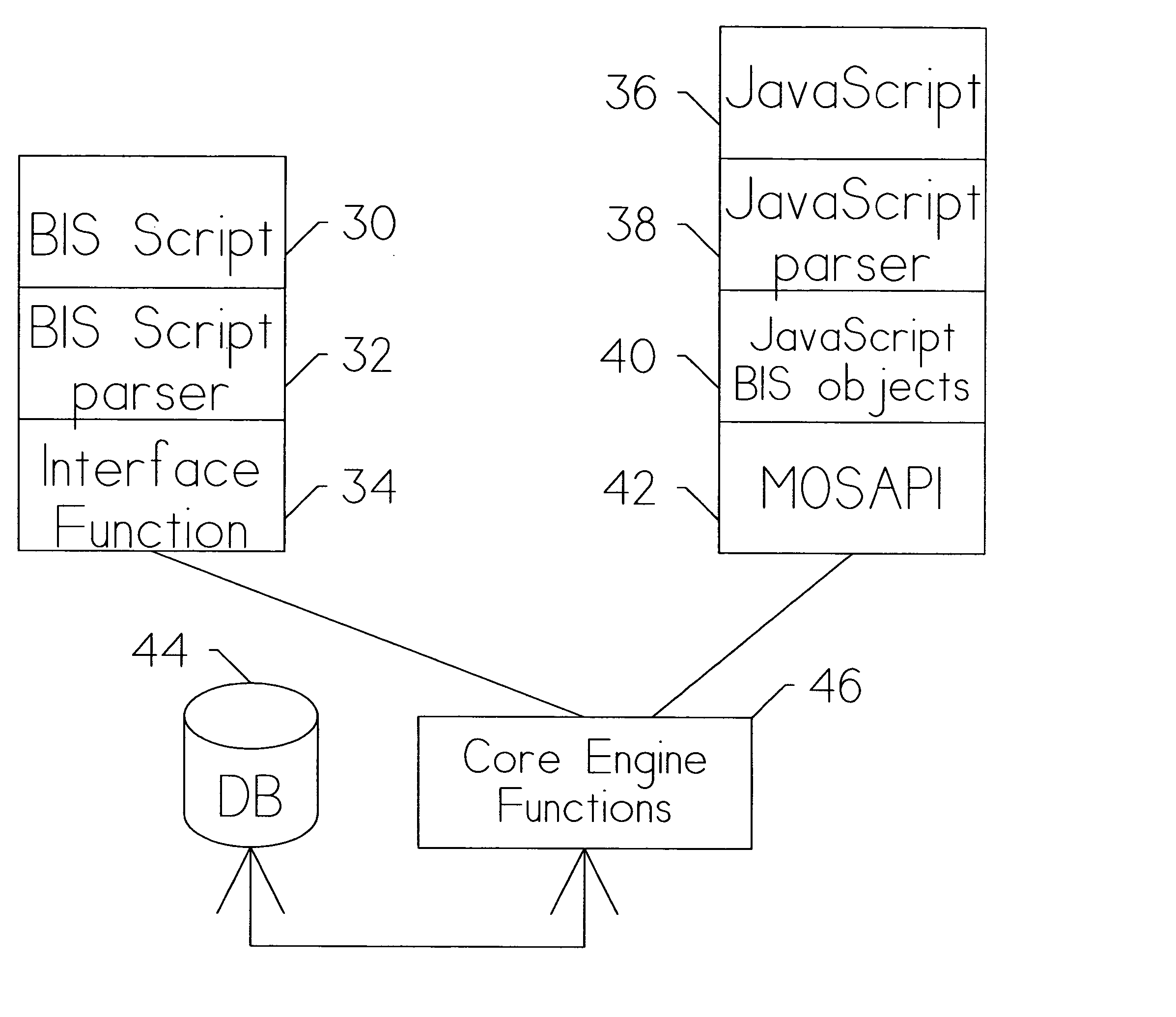
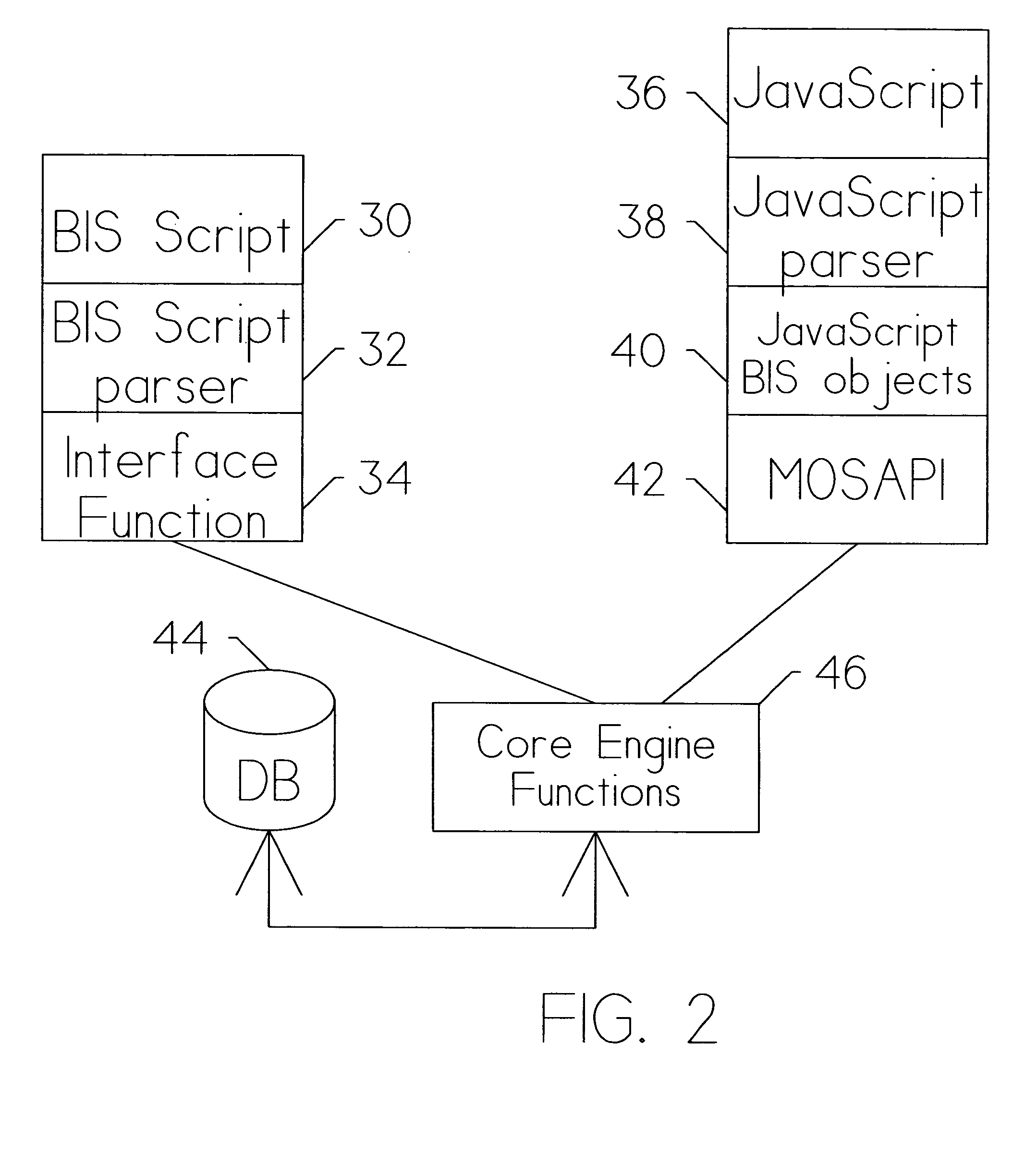
Owner:MICROSOFT TECH LICENSING LLC
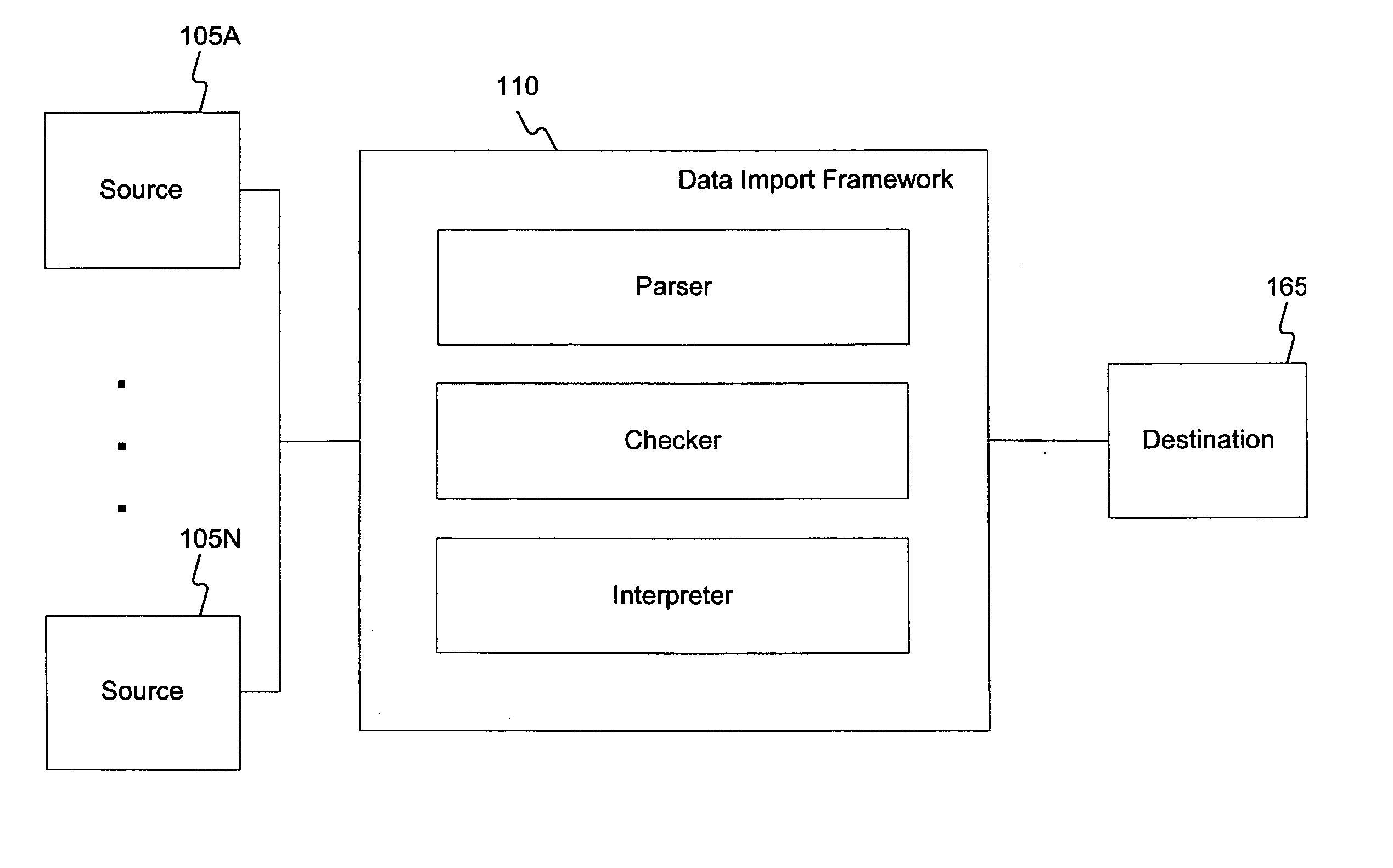
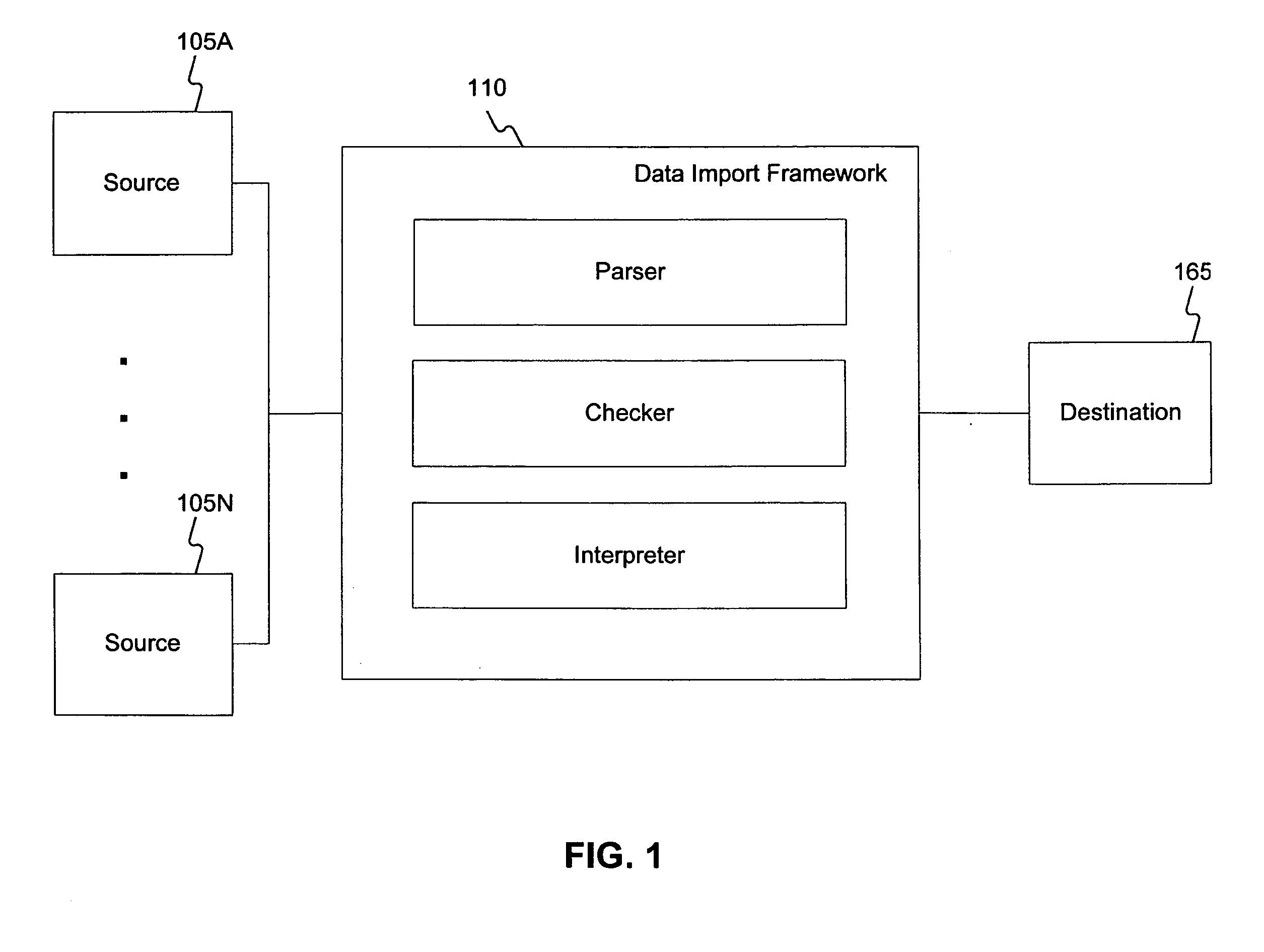
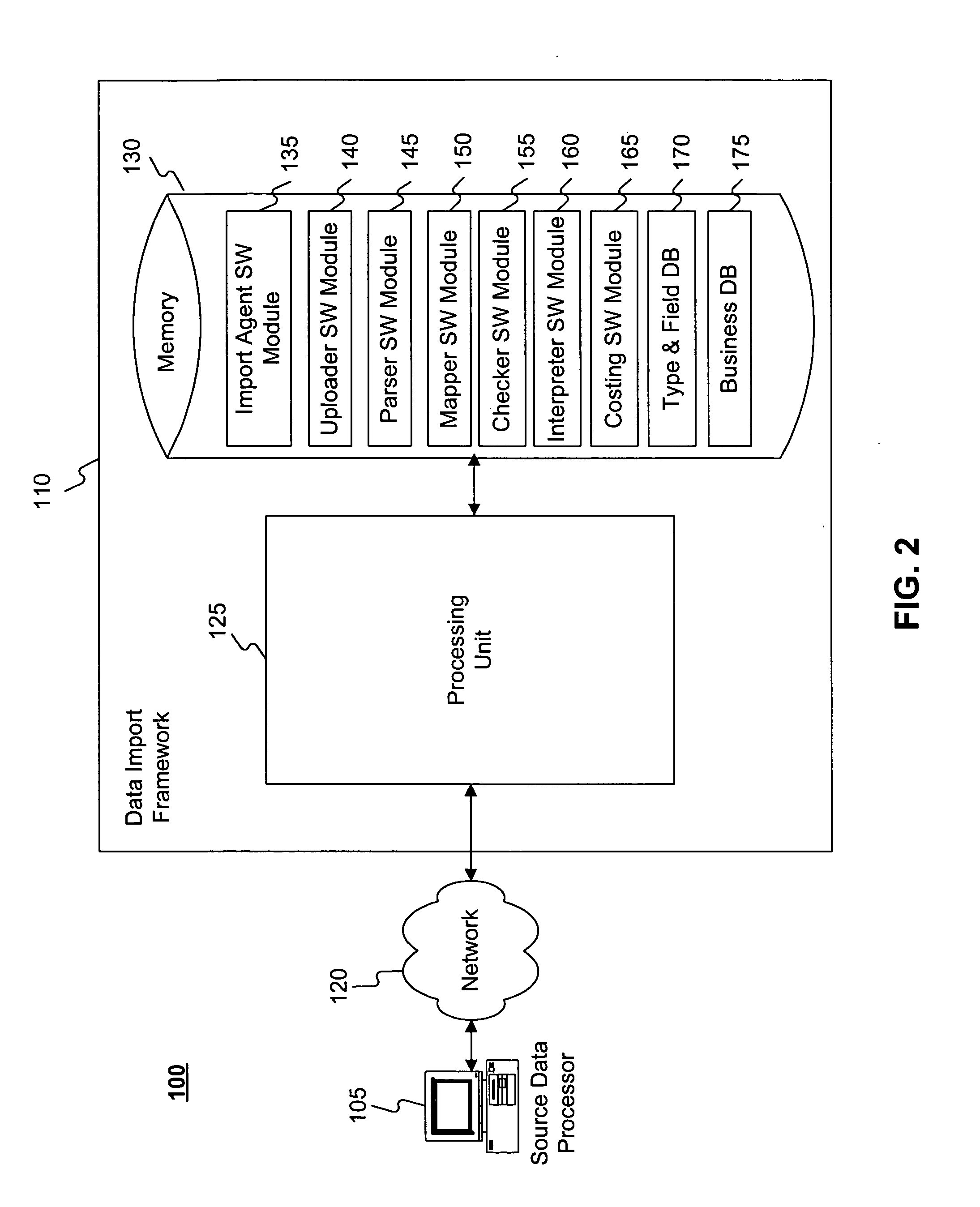
Methods and systems for importing source data
ActiveUS20050257125A1Transformation of program codeDigital data processing detailsCommand languageData system
Systems and methods are disclosed for importing source data. The disclosed systems and methods may include uploading the source data from at least one source system and translating the source data into command language commands. Furthermore, the disclosed systems and methods may include checking the command language commands for completeness or consistency and executing the command language commands to generate import data for at least one destination.
Owner:SAP AG
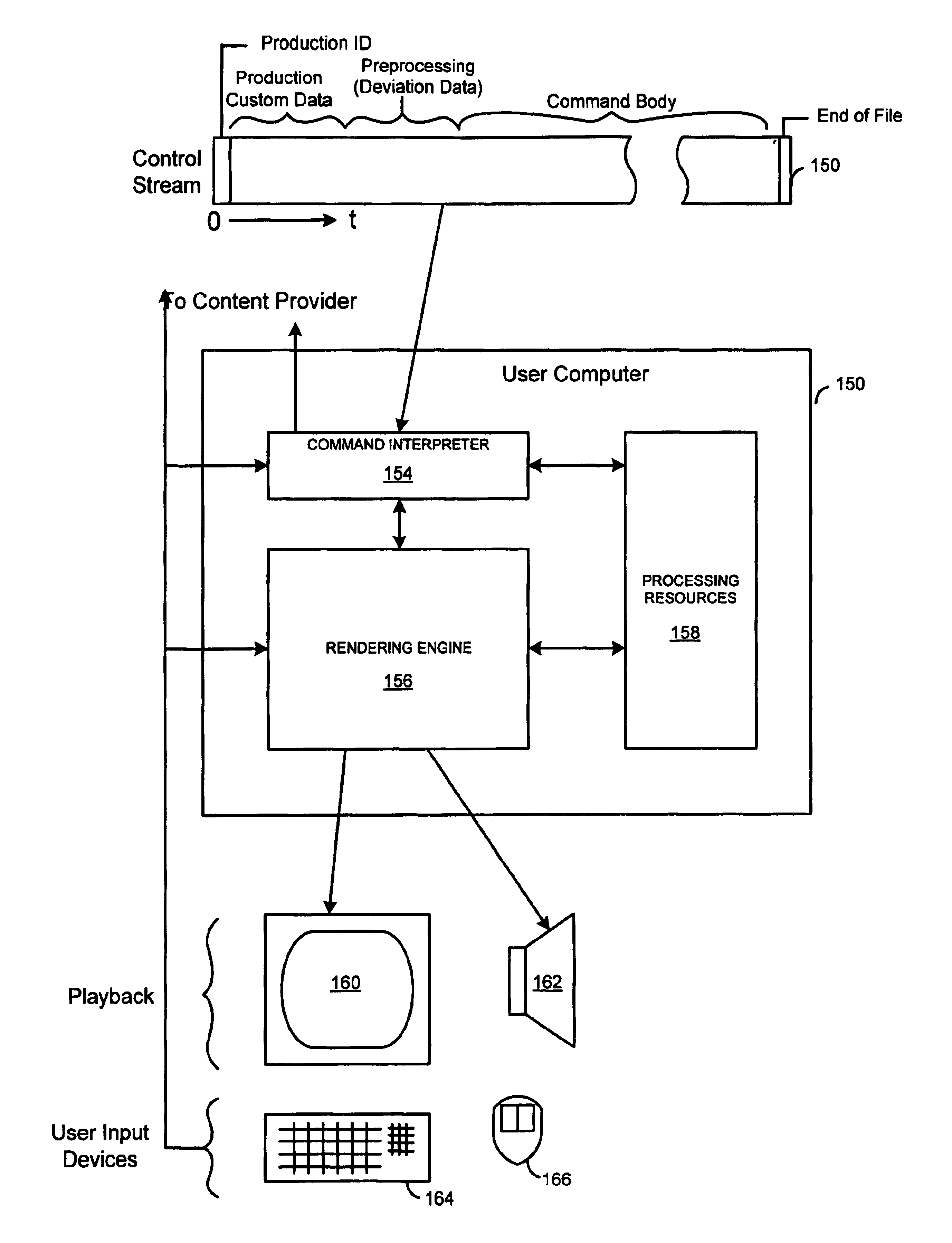
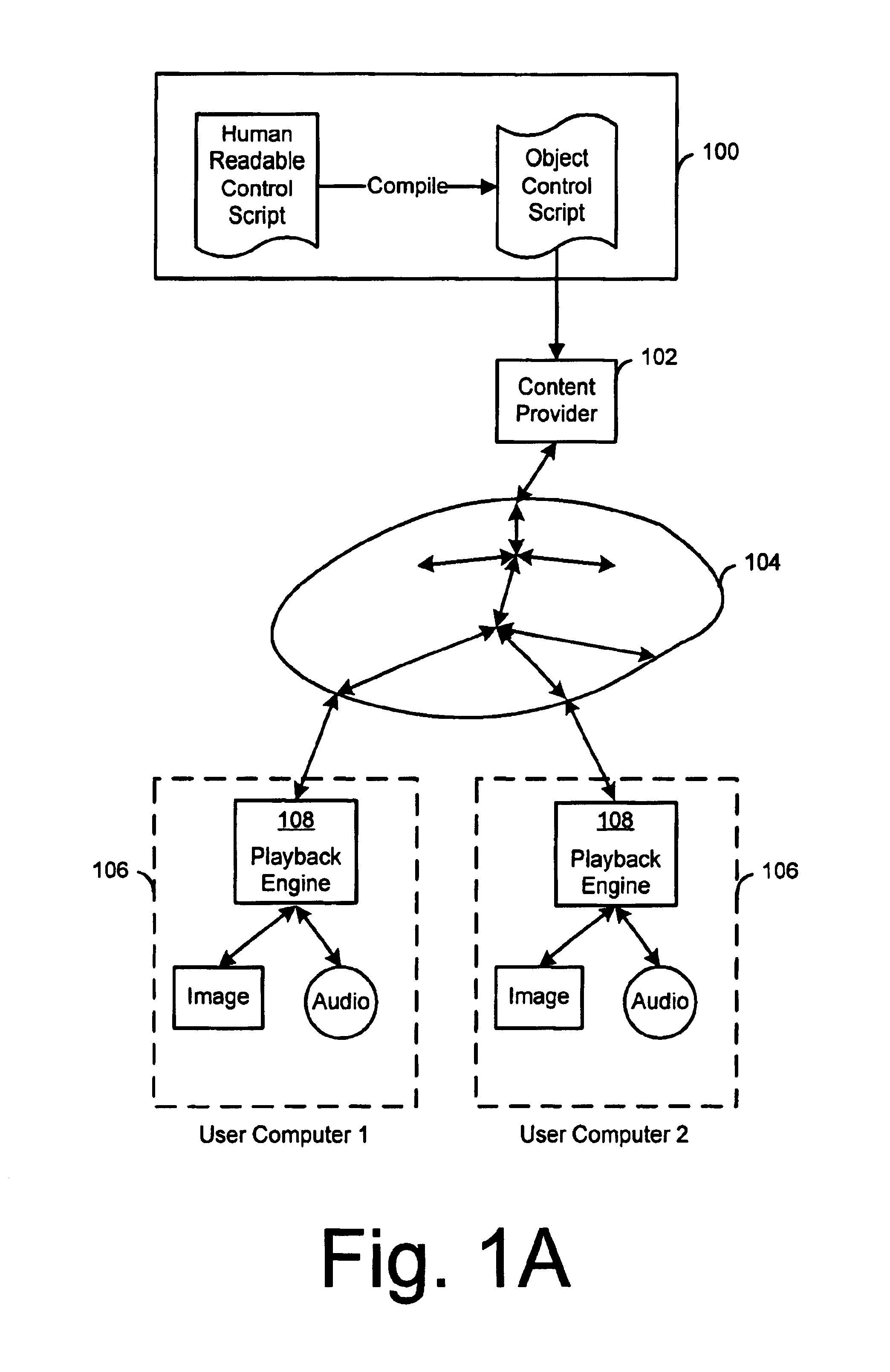
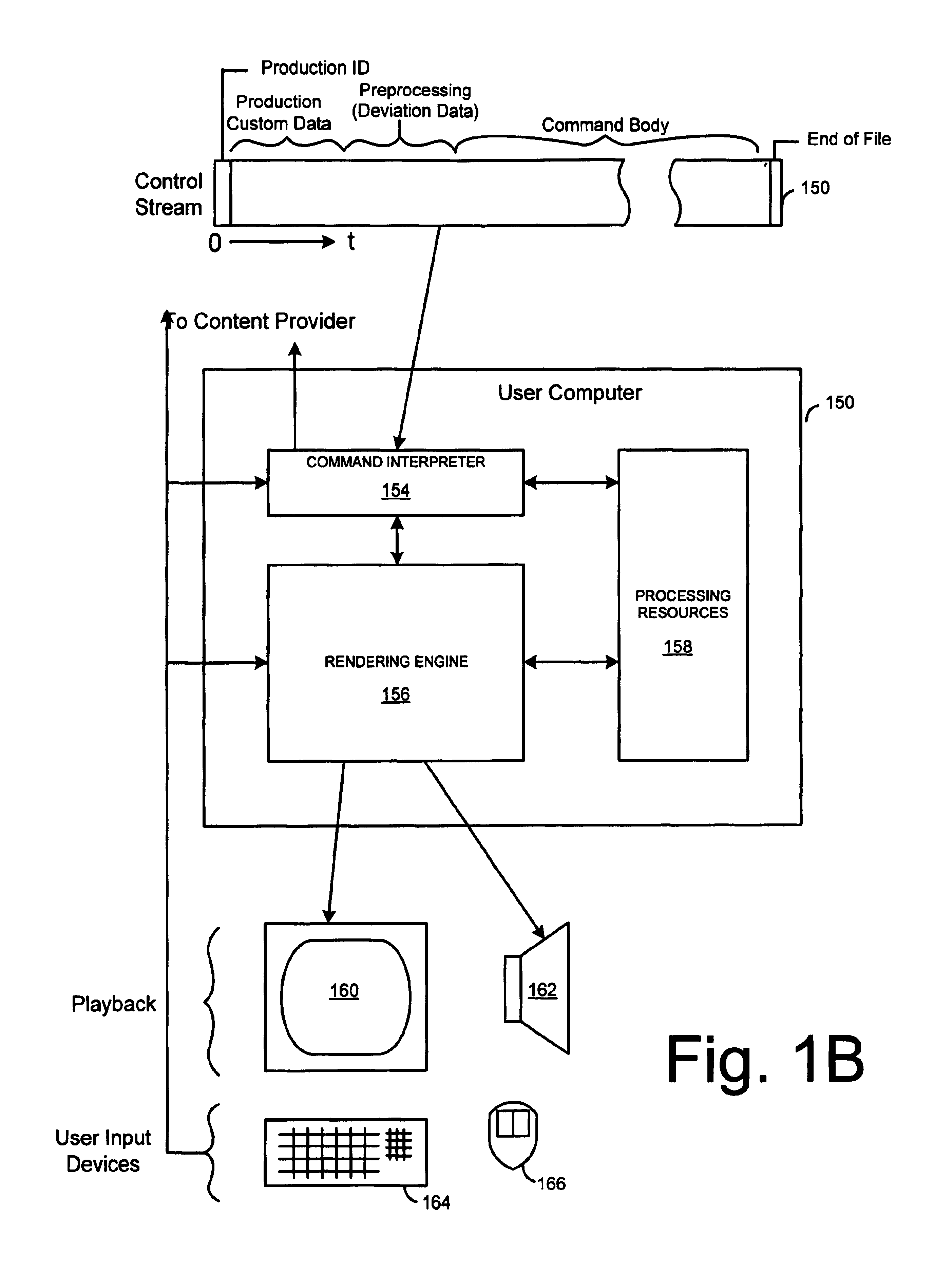
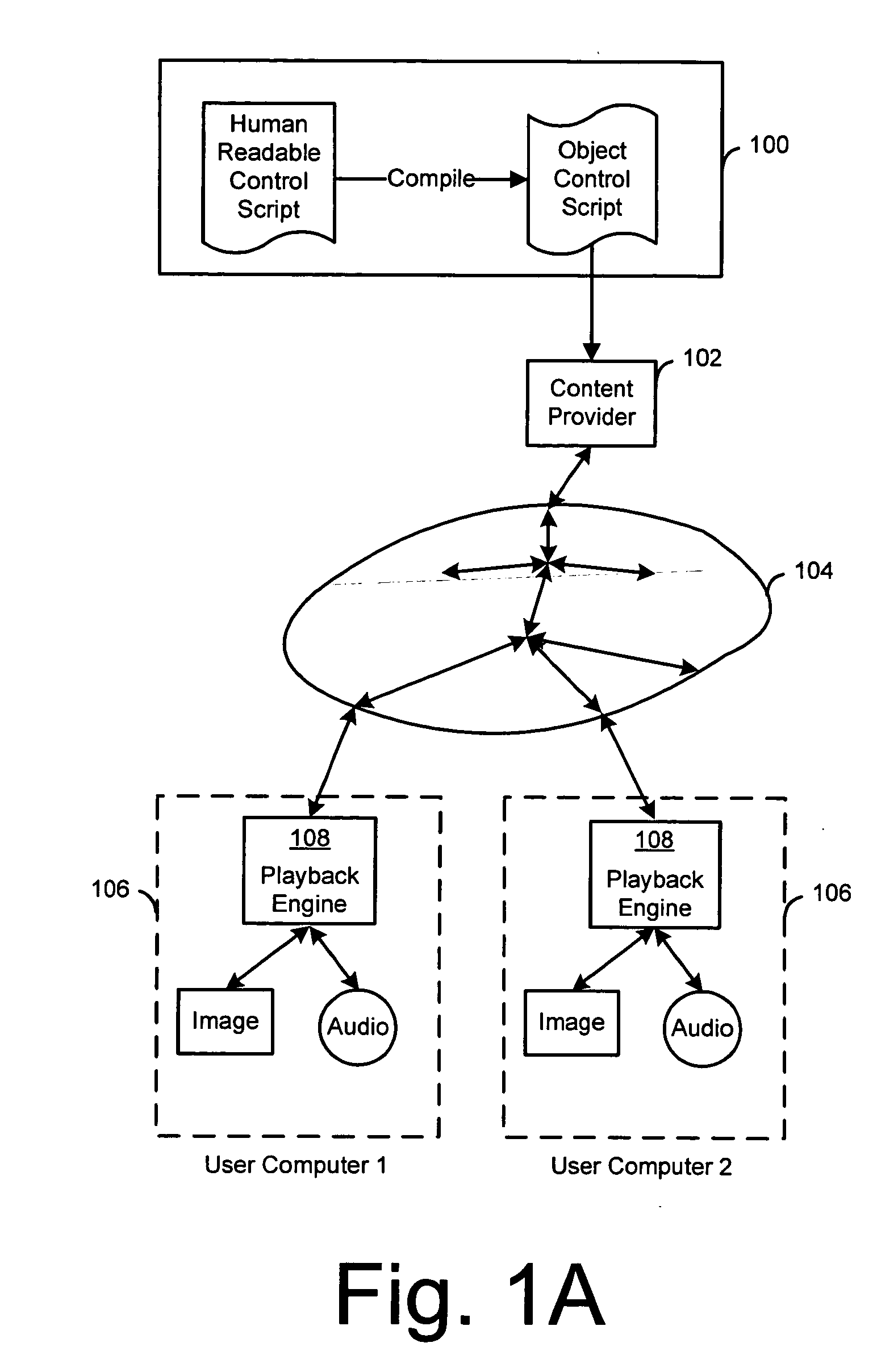
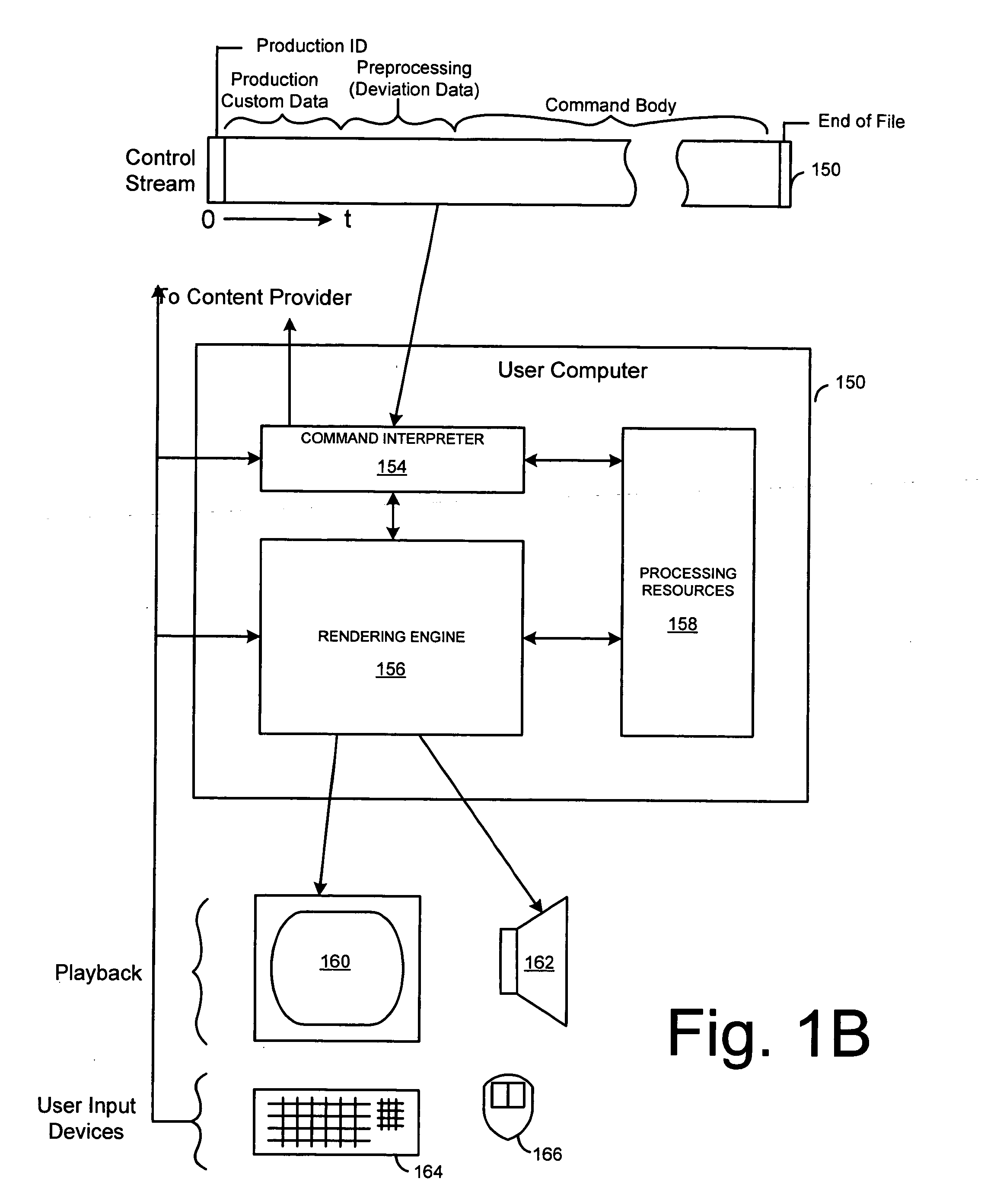
Creation and playback of computer-generated productions using script-controlled rendering engines
InactiveUS6947044B1Simple to useUnderstand intuitiveDigital data processing detailsPicture reproducers using cathode ray tubesViewpointsCommand language
A system for controlling a rendering engine by using specialized commands. The commands are used to generate a production, such as a television show, at an end-user's computer that executes the rendering engine. In one embodiment, the commands are sent over a network, such as the Internet, to achieve broadcasts of video programs at very high compression and efficiency. Commands for setting and moving camera viewpoints, animating characters, and defining or controlling scenes and sounds are described. At a fine level of control math models and coordinate systems can be used make specifications. At a coarse level of control the command language approaches the text format traditionally used in television or movie scripts. Simple names for objects within a scene are used to identify items, directions and paths. Commands are further simplified by having the rendering engine use defaults when specifications are left out. For example, when a camera direction is not specified, the system assumes that the viewpoint is to be the current action area. The system provides a hierarchy of detail levels. Movement commands can be defaulted or specified. Synchronized speech can be specified as digital audio or as text which is used to synthesize the speech.
Owner:DIGIMEDIA TECH LLC
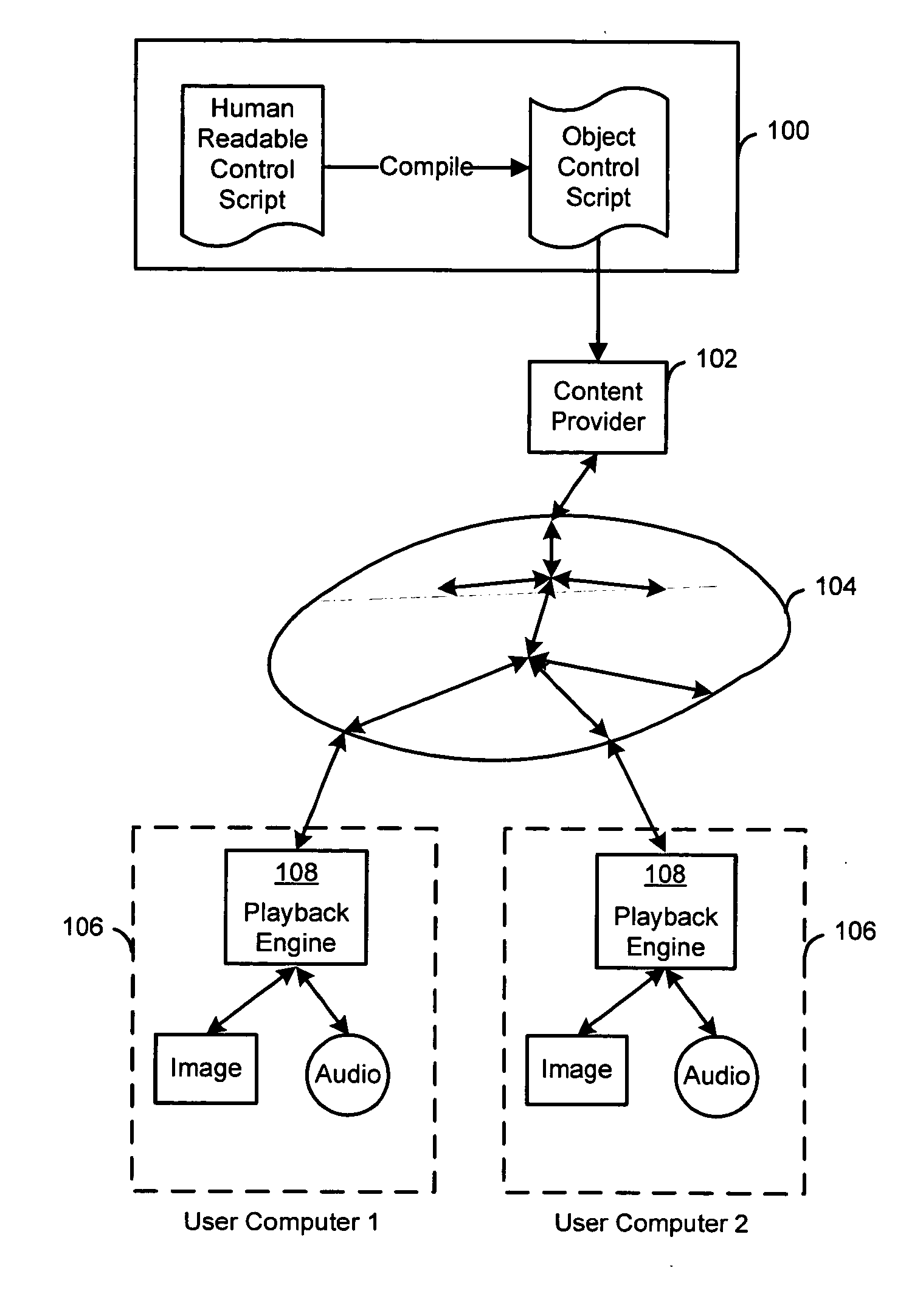
Creation and playback of computer-generated productions using script-controlled rendering engines
InactiveUS20050171964A1Simple to useUnderstand intuitiveIndoor gamesComputing modelsViewpointsCommand language
A system for controlling a rendering engine by using specialized commands. The commands are used to generate a production, such as a television show, at an end-user's computer that executes the rendering engine. In one embodiment, the commands are sent over a network, such as the Internet, to achieve broadcasts of video programs at very high compression and efficiency. Commands for setting and moving camera viewpoints, animating characters, and defining or controlling scenes and sounds are described. At a fine level of control math models and coordinate systems can be used make specifications. At a coarse level of control the command language approaches the text format traditionally used in television or movie scripts. Simple names for objects within a scene are used to identify items, directions and paths. Commands are further simplified by having the rendering engine use defaults when specifications are left out. For example, when a camera direction is not specified, the system assumes that the viewpoint is to be the current action area. The system provides a hierarchy of detail levels. Movement commands can be defaulted or specified. Synchronized speech can be specified as digital audio or as text which is used to synthesize the speech.
Owner:DIGIMEDIA TECH LLC
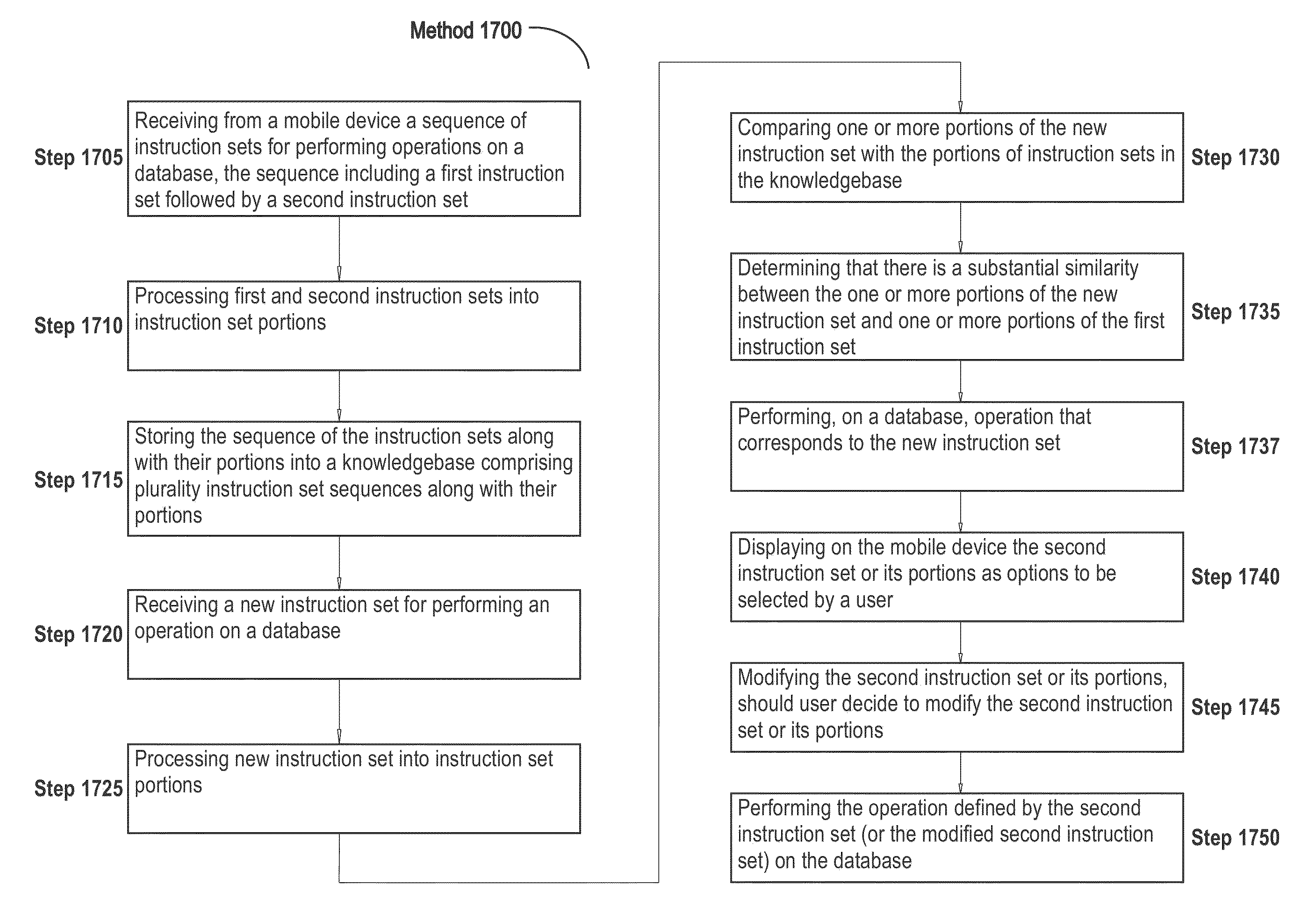
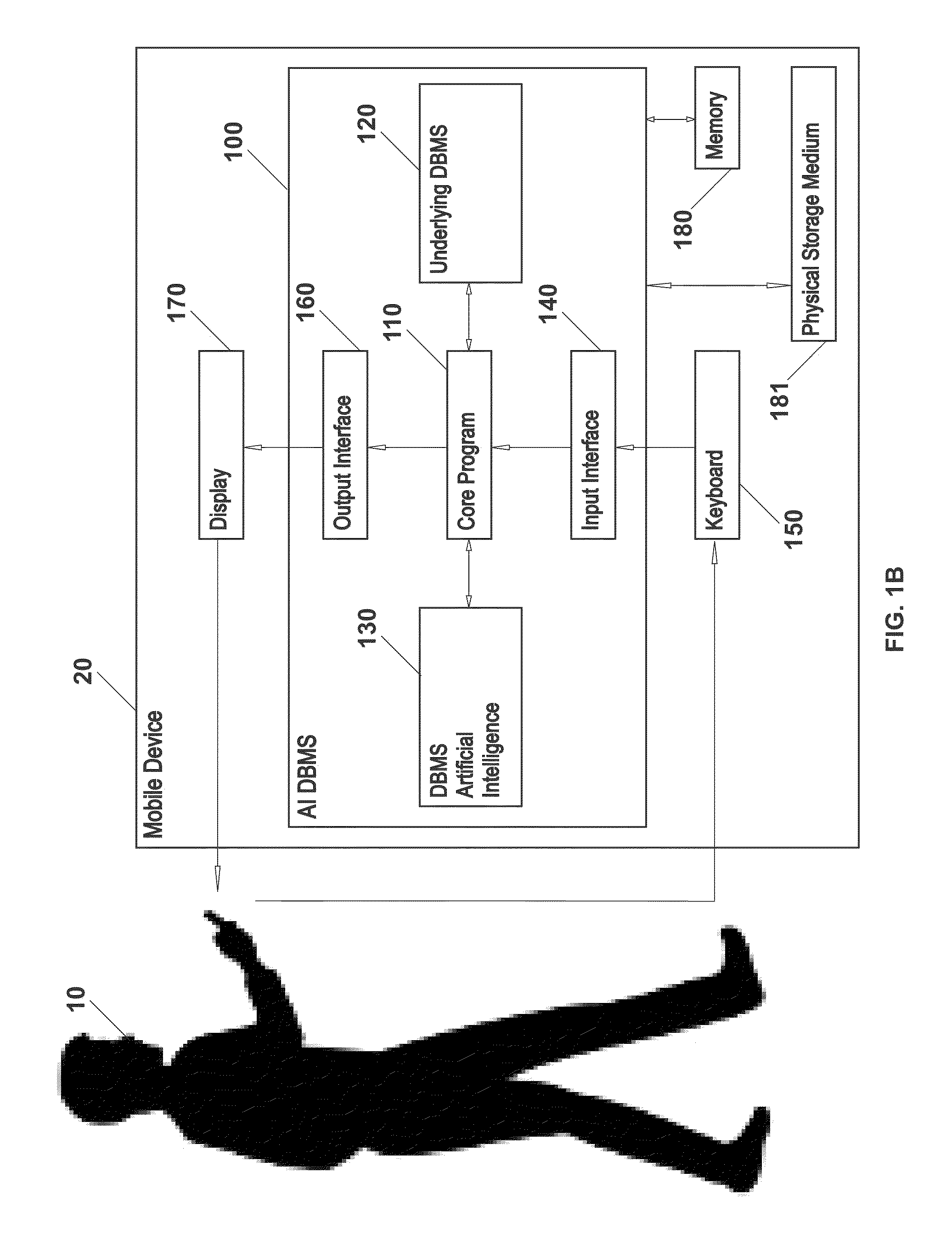
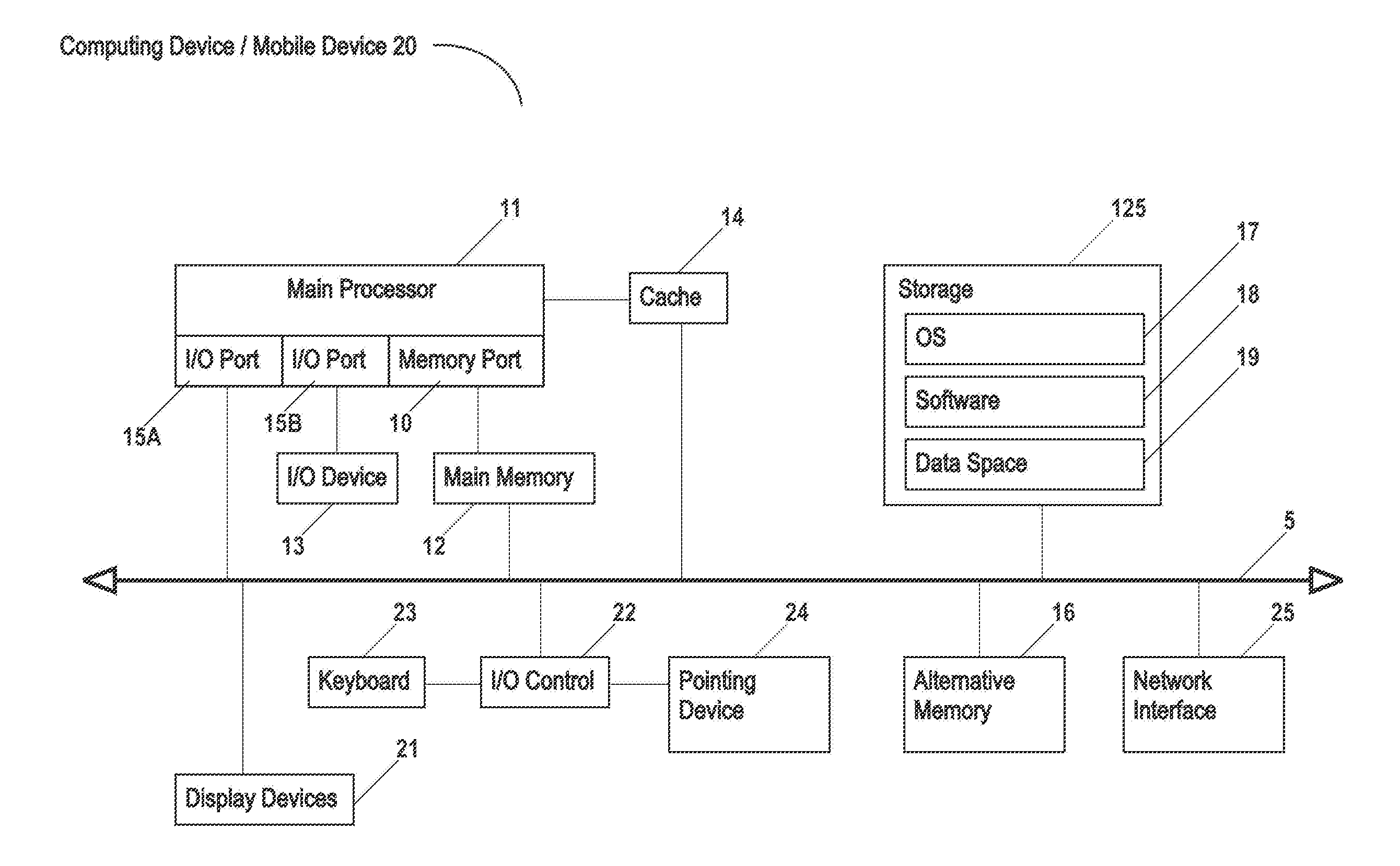
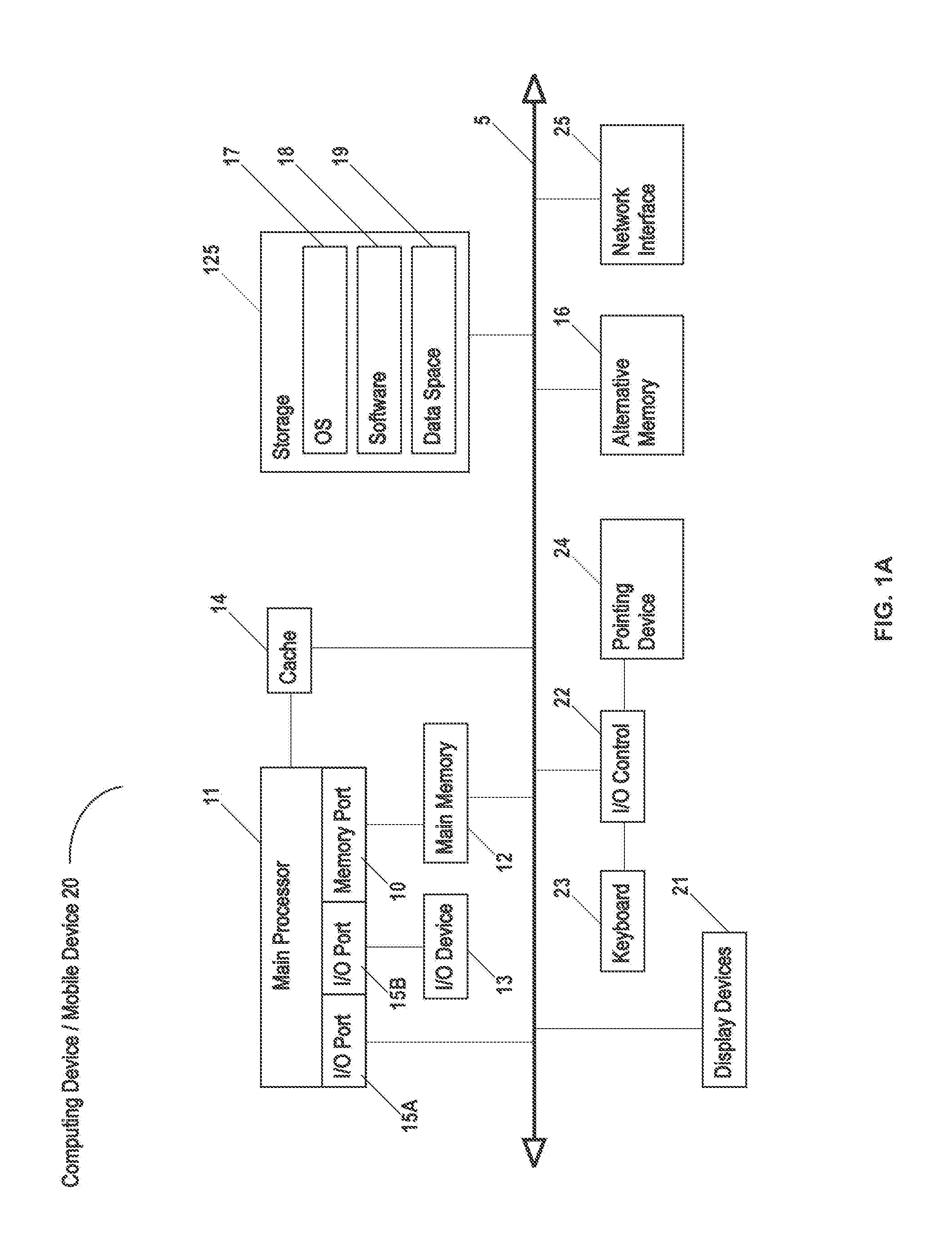
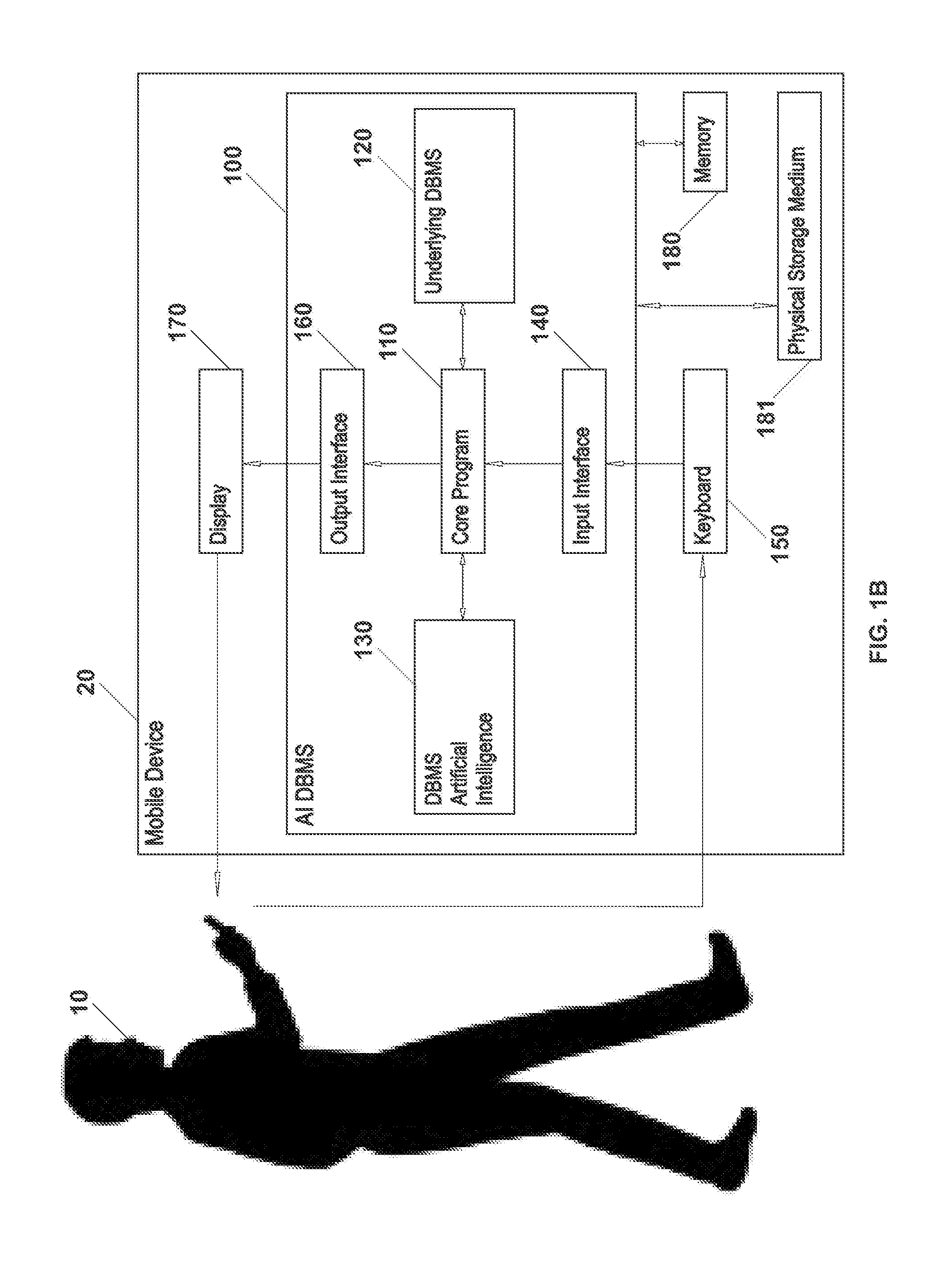
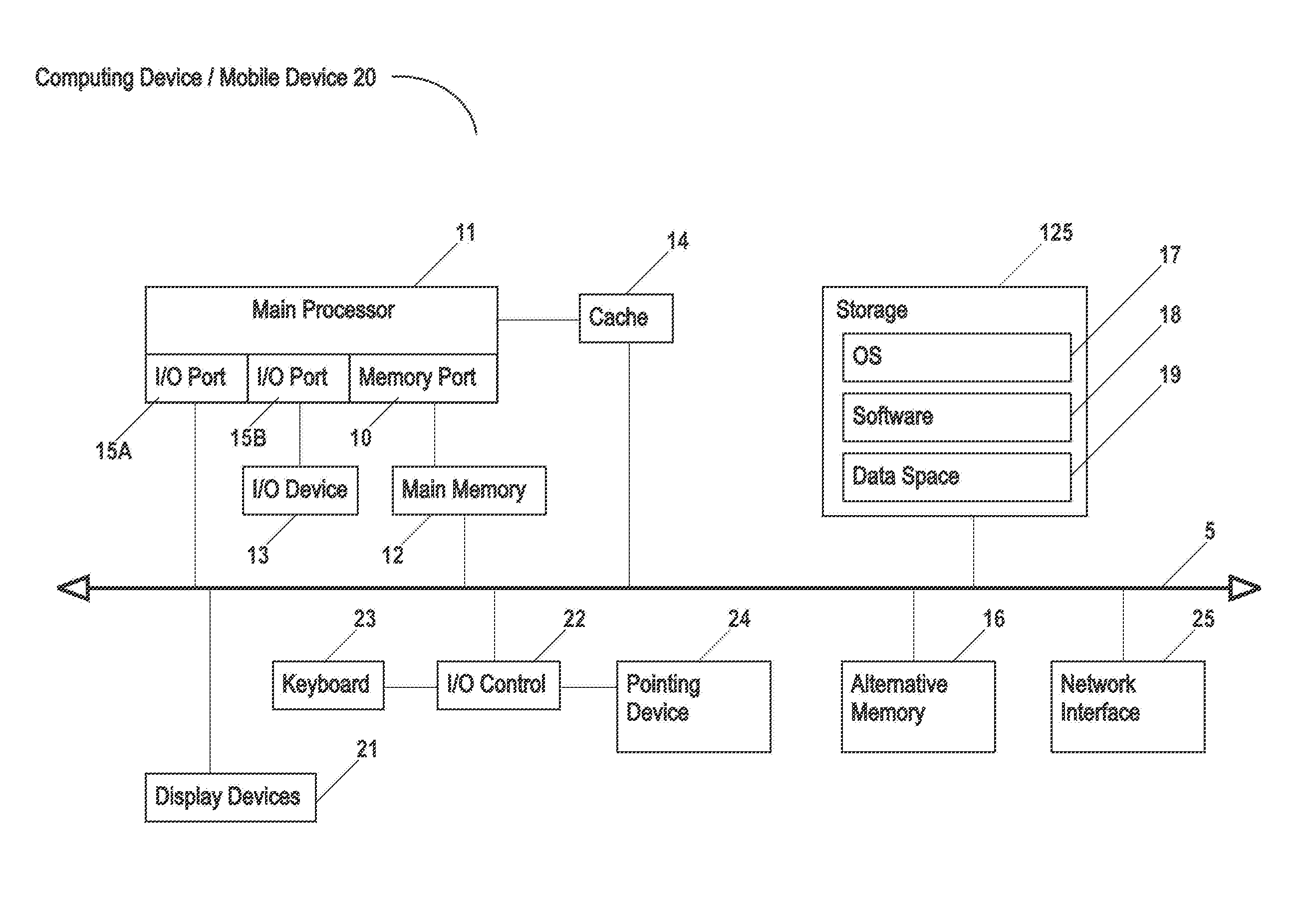
Systems and methods of using an artificially intelligent database management system and interfaces for mobile, embedded, and other computing devices
ActiveUS9367806B1Relational databasesSpeech recognitionCommand languageRelational database management system
The current disclosure generally relates to database management systems (DBMSs) and may be generally directed to methods and systems of using artificial intelligence (i.e. machine learning and / or anticipation functionalities, etc.) to learn a user's use of a DBMS, store this “knowledge” in a knowledgebase, and anticipate the user's future operating intentions. The current disclosure may also be generally directed to associative methods and systems of constructing DBMS commands. The current disclosure may also be generally directed to methods and systems of using a simplified DBMS command language (SDCL) for associative DBMS command construction. The current disclosure may also be generally directed to artificially intelligent methods and systems for associative DBMS command construction. The current disclosure may also be generally directed to methods and systems for associative DBMS command construction through voice input. Other methods, systems, features, elements and / or their embodiments are also disclosed.
Owner:COSIC JASMIN
Screen scraping interface
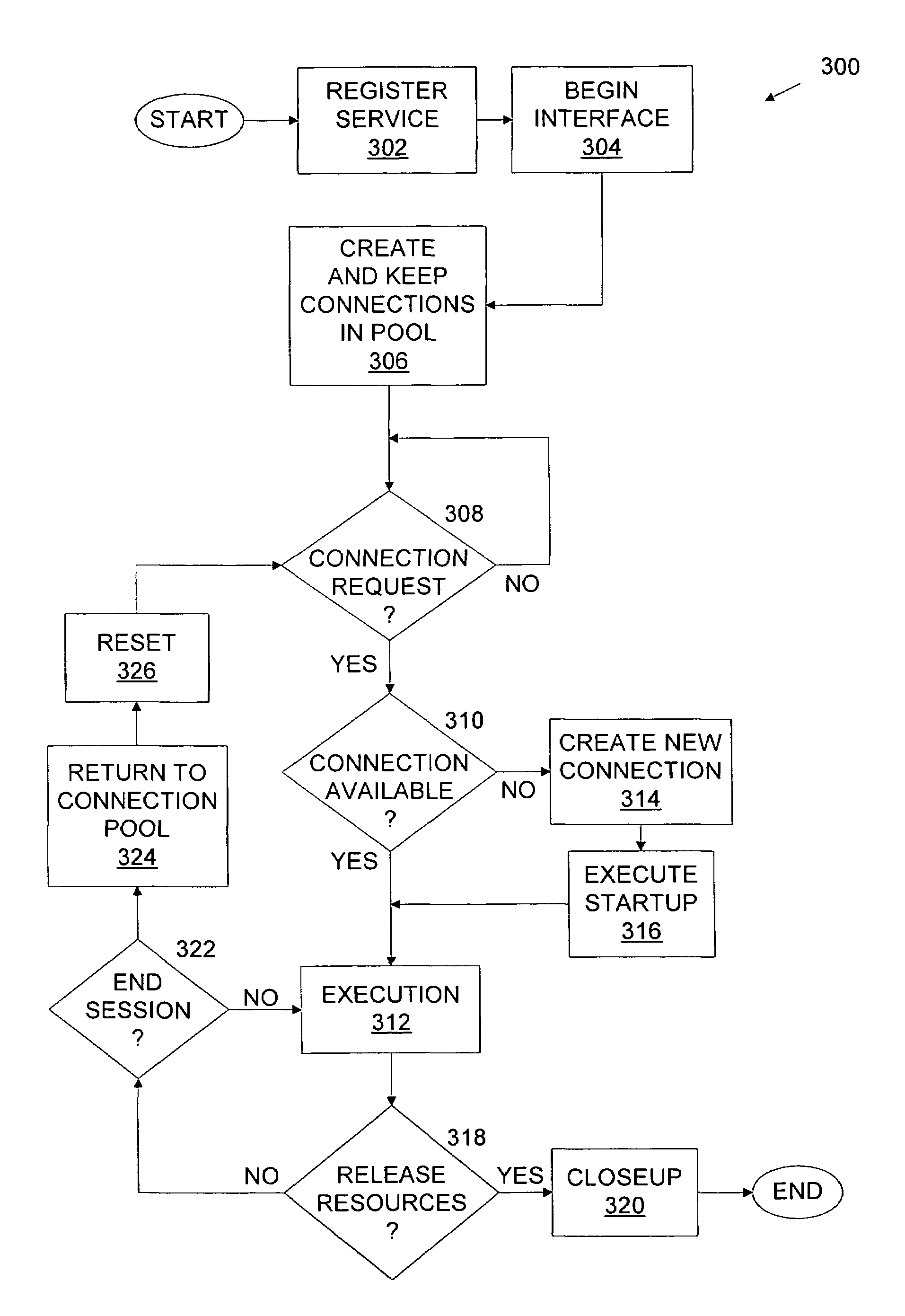
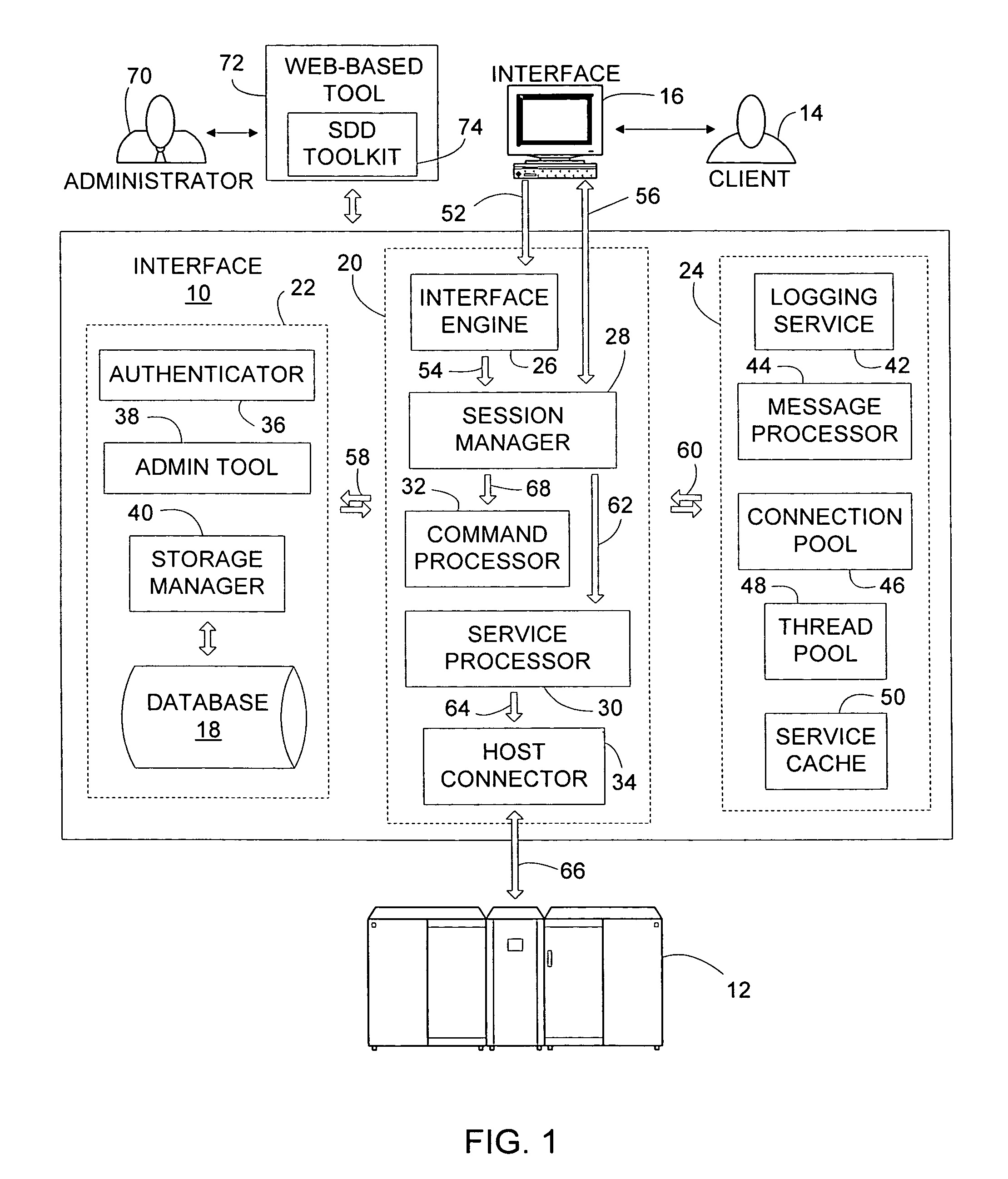
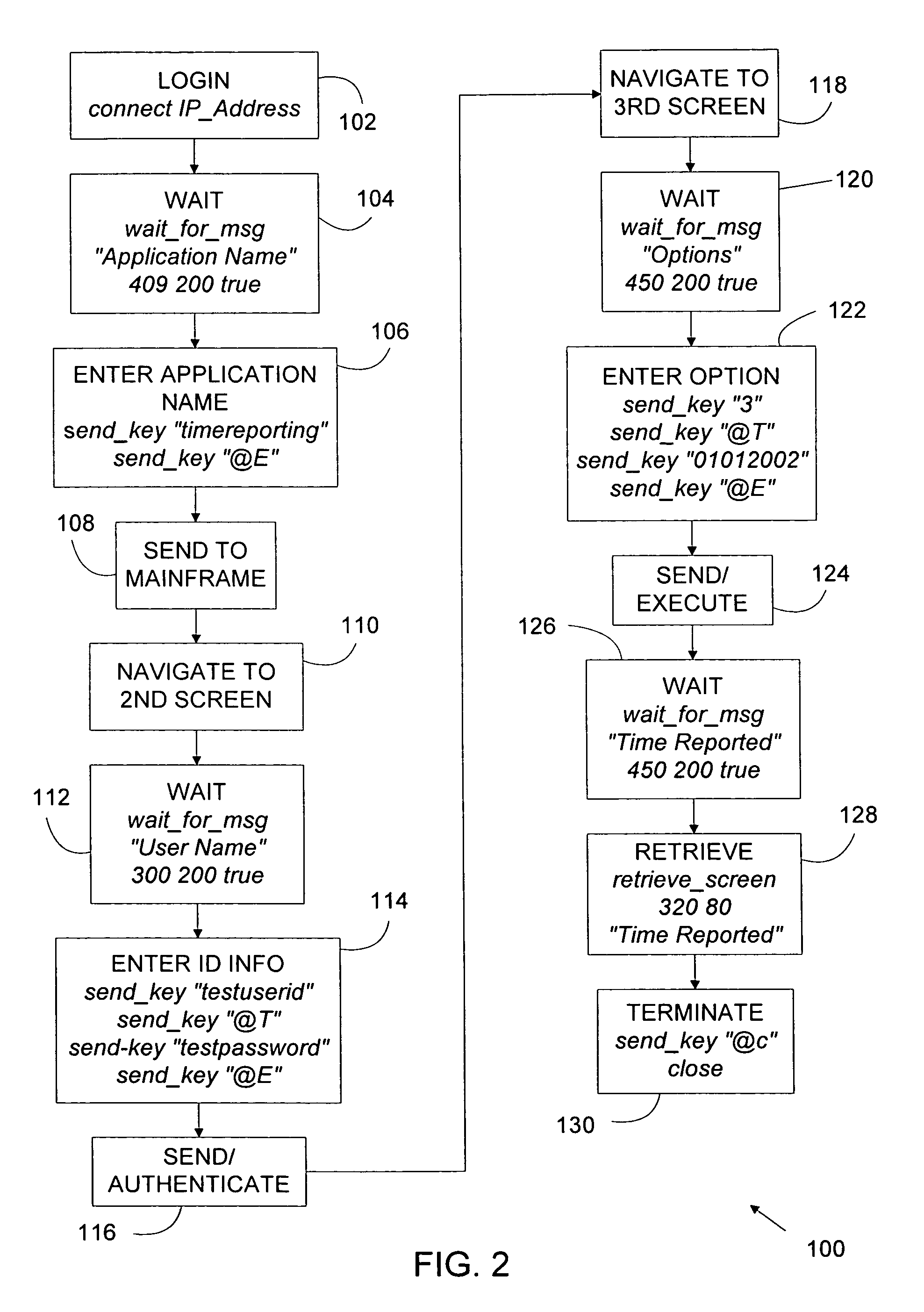
InactiveUS7647370B1Improve performanceMultiple digital computer combinationsTransmissionCycle controlCommand language
An interface can serve as a client-mainframe interface, enabling clients to develop applications without a need to understand mainframe processes and screen flows. Extended Tool Command Language (Tcl) can define services that can include a series of interactions with a mainframe system and service definitions can be added or updated on the interface during operation of the interface without disrupting processing. The service definitions can enable the interface to receive XML requests from a client, parse the XML requests, execute the service scripts to interact with the mainframe systems, generate the result in a XML format and send the XML file back to the client. Fundamental Mainframe Interactions (FMI) commands can interact with the mainframe systems and enable the specification of the XML structure of the request and response. The interface can provide efficient connection pooling management and connection life cycle control to improve the performance of the mainframe system interactions.
Owner:VERIZON PATENT & LICENSING INC
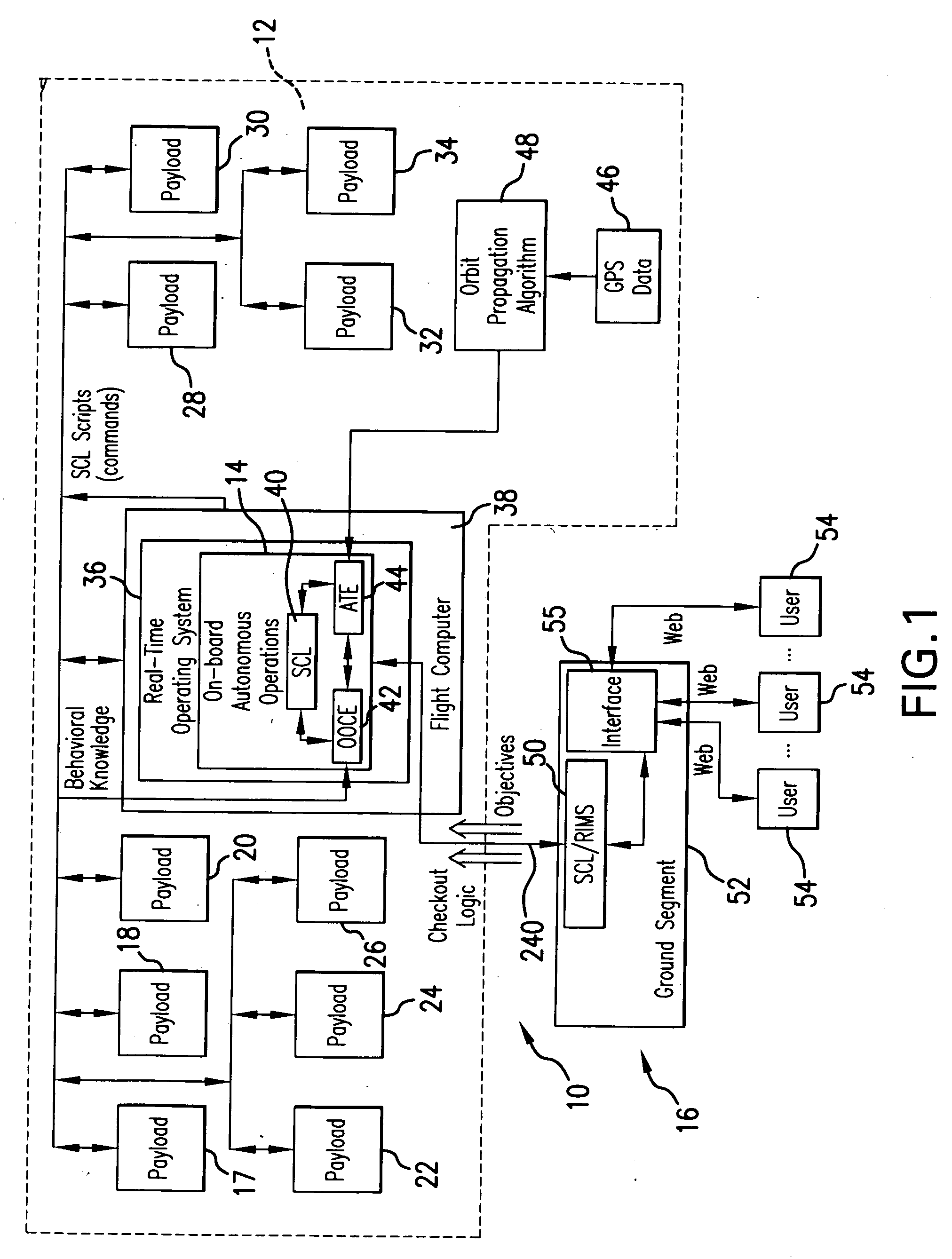
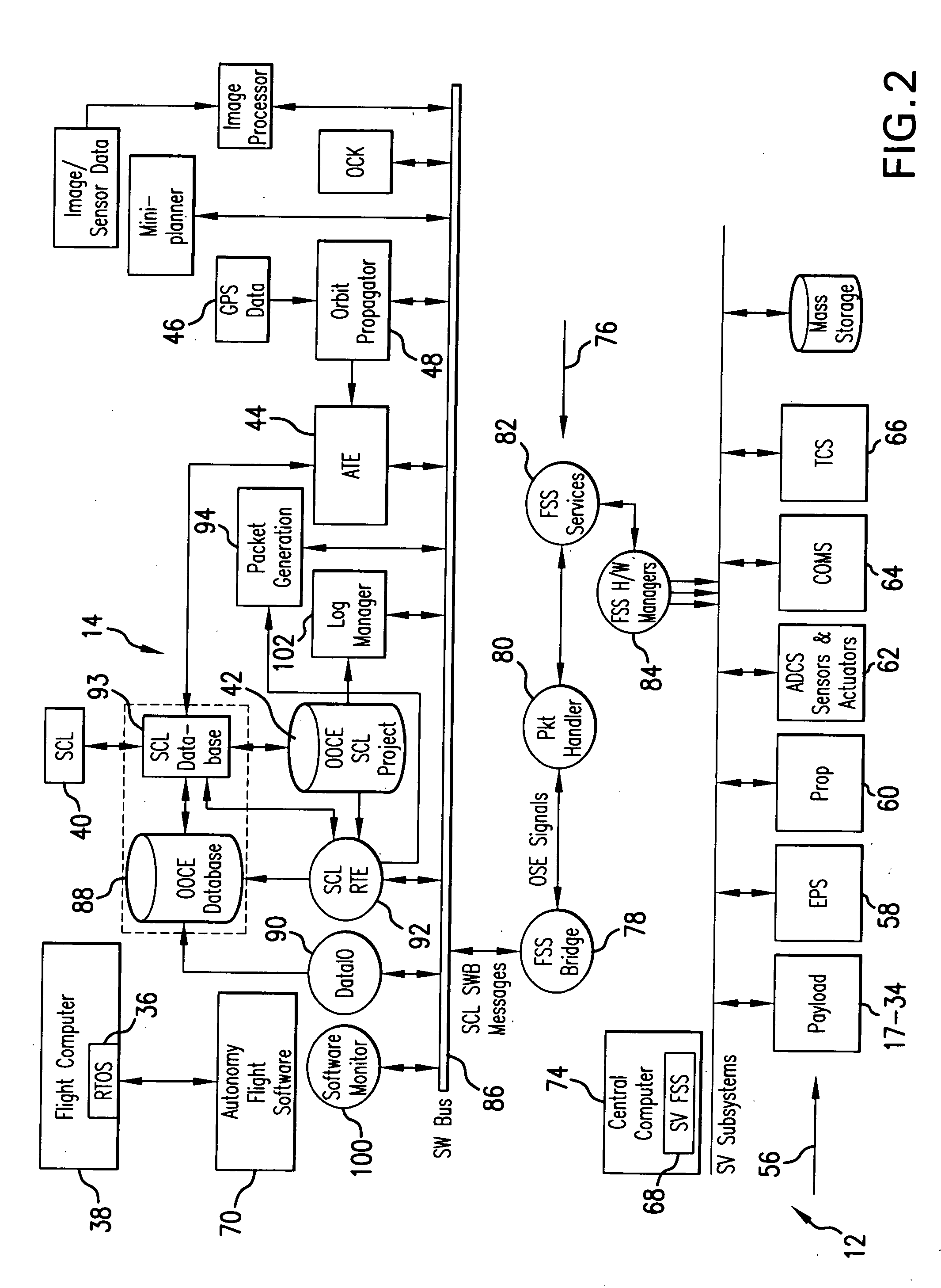
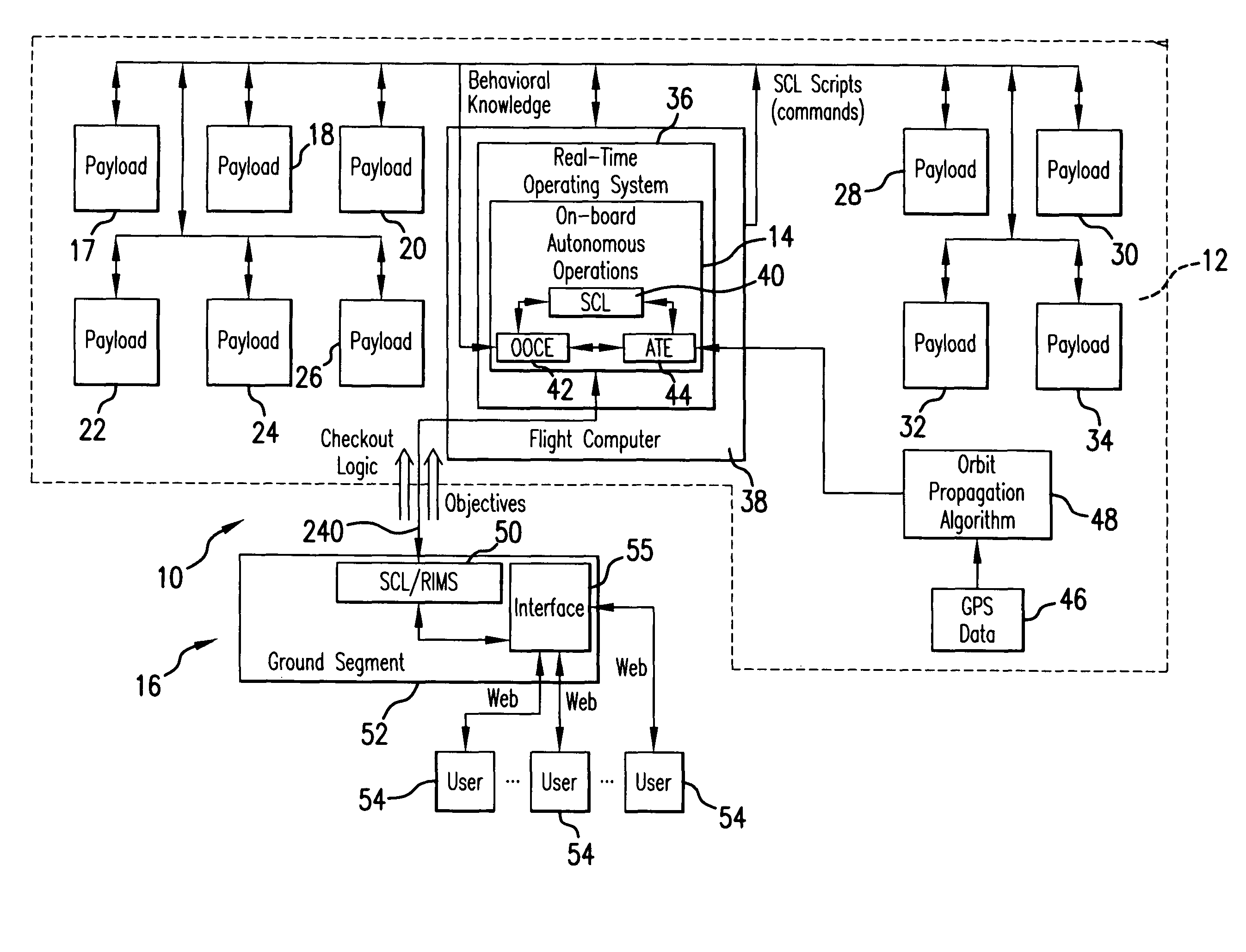
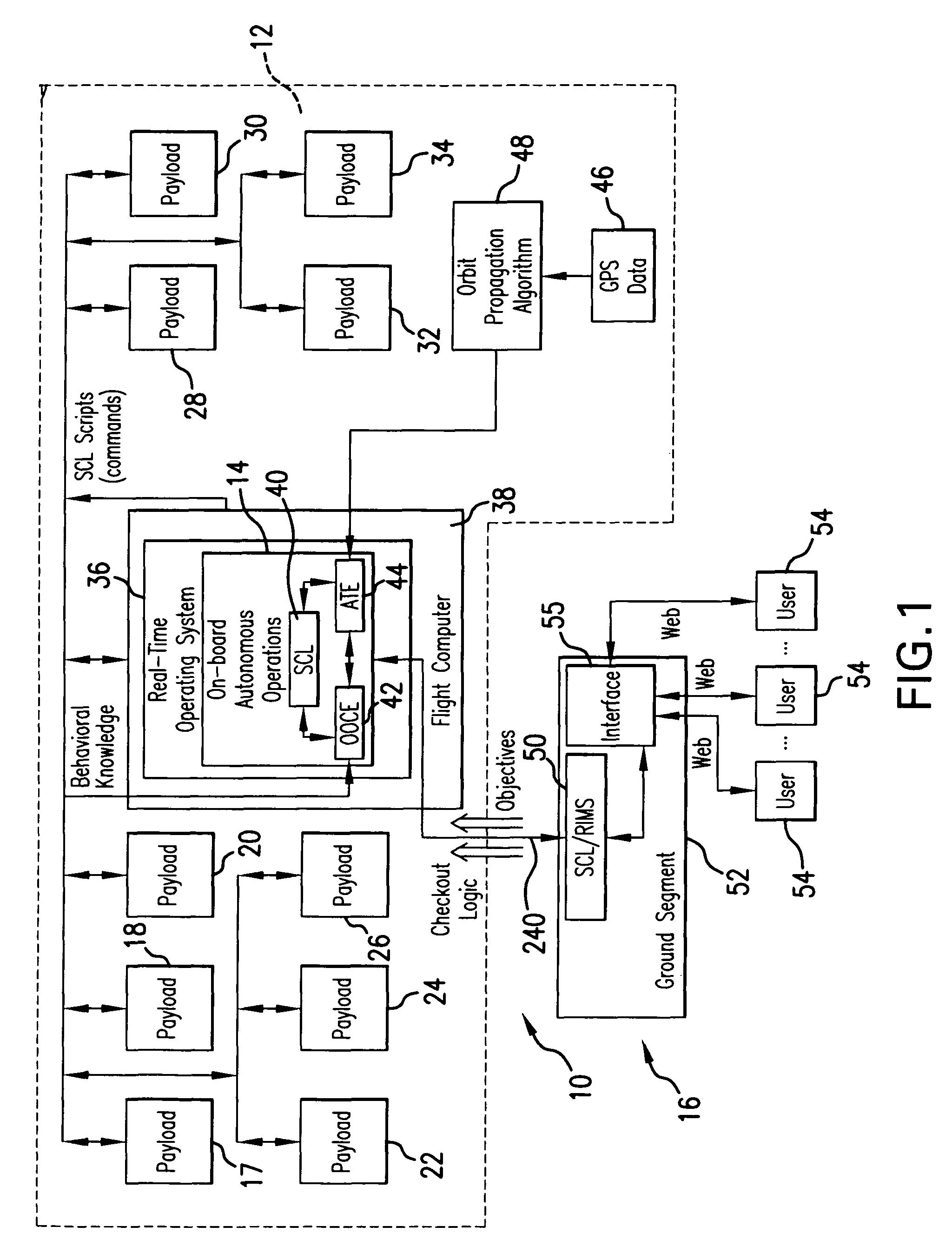
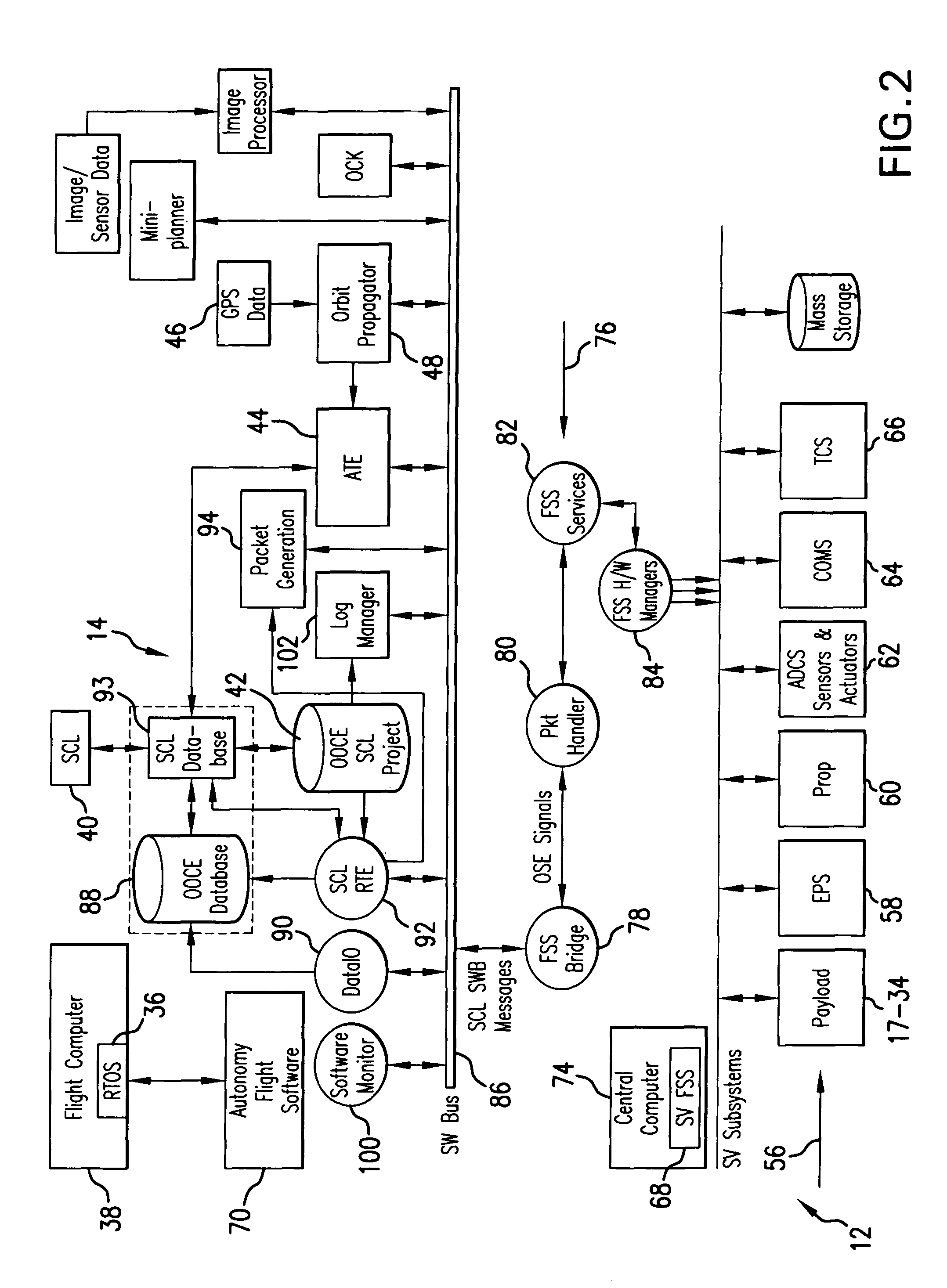
Intelligent system and method for spacecraft autonomous operations
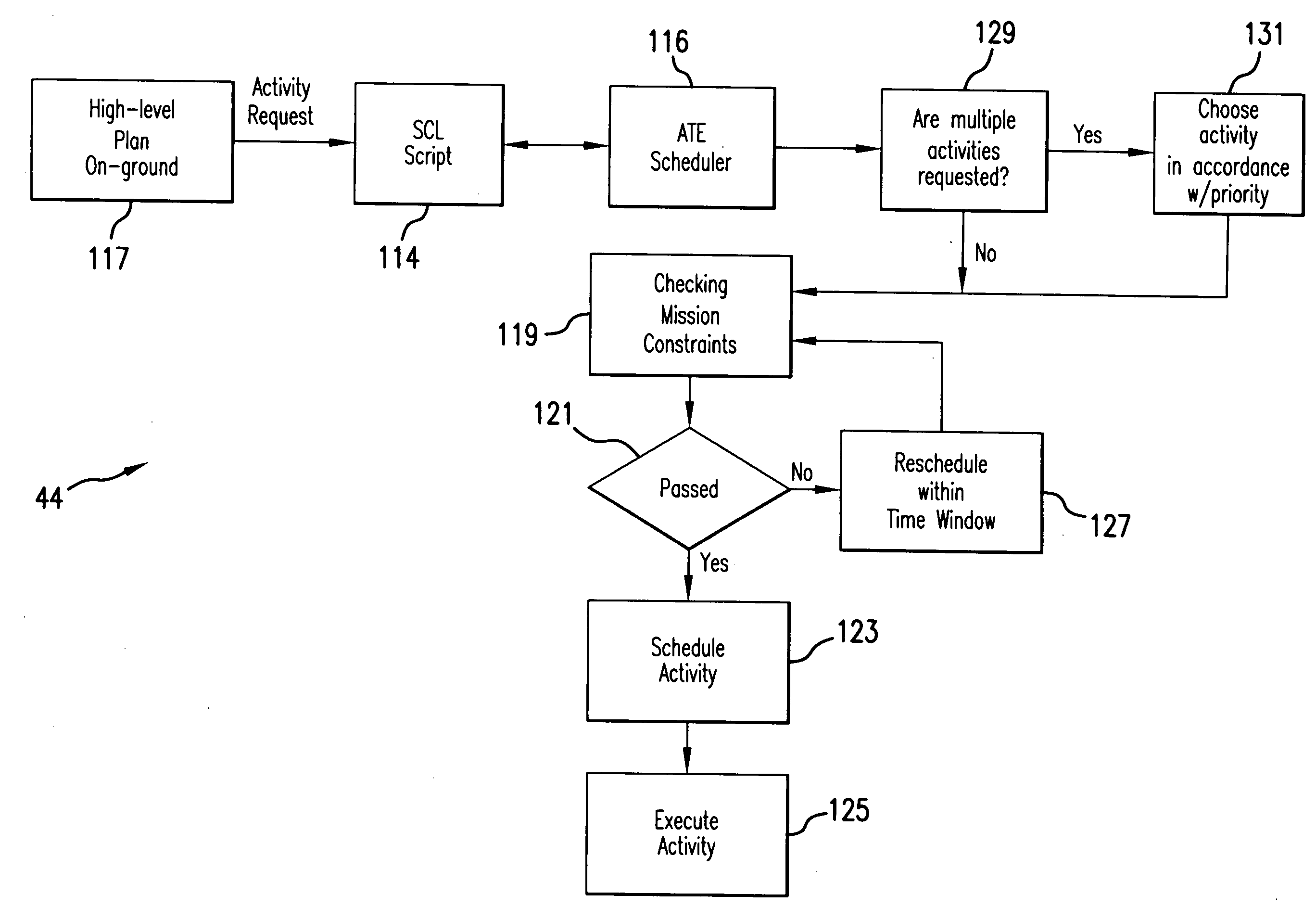
InactiveUS20090157236A1Improve responsivenessReduce time delayVehicle testingComputer controlOn boardCommand language
The intelligent system for autonomous spacecraft operations includes an on-board Autonomous Operations subsystem integrated with an on-ground Web-based Remote Intelligent Monitor System (RIMS) providing interface between on-ground users and the autonomous operations intelligent system. The on-board Autonomous Operation subsystem includes an On-Orbit Checkout Engine (OOCE) unit and an Autonomous Tasking Engine (ATE) unit. Spacecraft Command Language (SCL) engine underlies the operations of the OOCE, ATE and RIMS, and serves as an executer of commands sequences. The OOCE uses the SCL engine to execute a series of SCL command scripts to perform a rapid on-orbit checkout of subsystems / components of the spacecraft in 1-3 days. The ATE is a planning and scheduling tool which receives requests for “activities” and uses the SCL scripts to verify the validity of the “activity” prior to execution, and scheduling the “activity” for execution or re-scheduling the same depending on verification results. Automated Mission Planning System (AMPS) supports the ATE operations. The ATE uses a priority schedule if multiple “activities” are to be executed.
Owner:SRA INTERNATIONAL
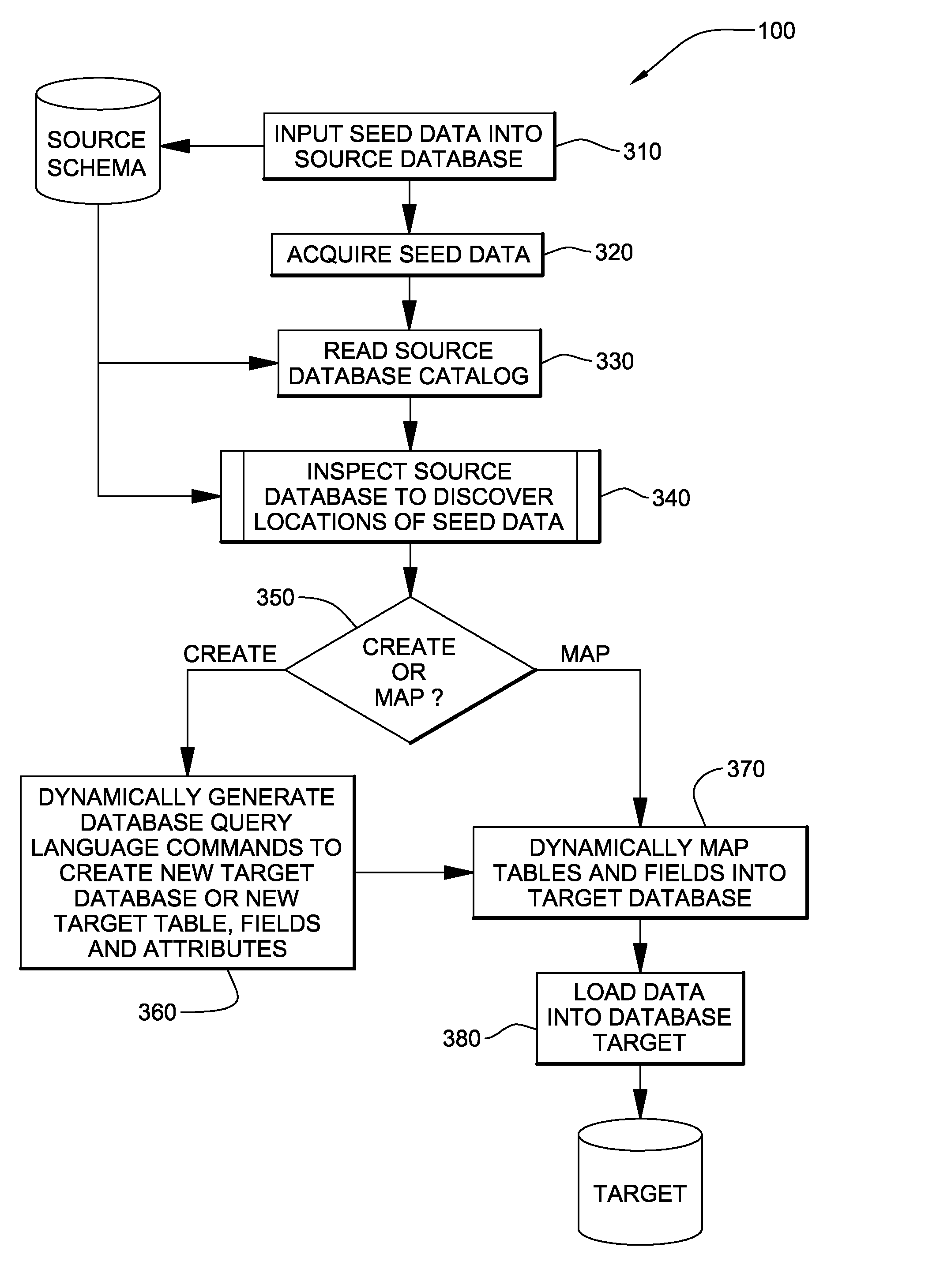
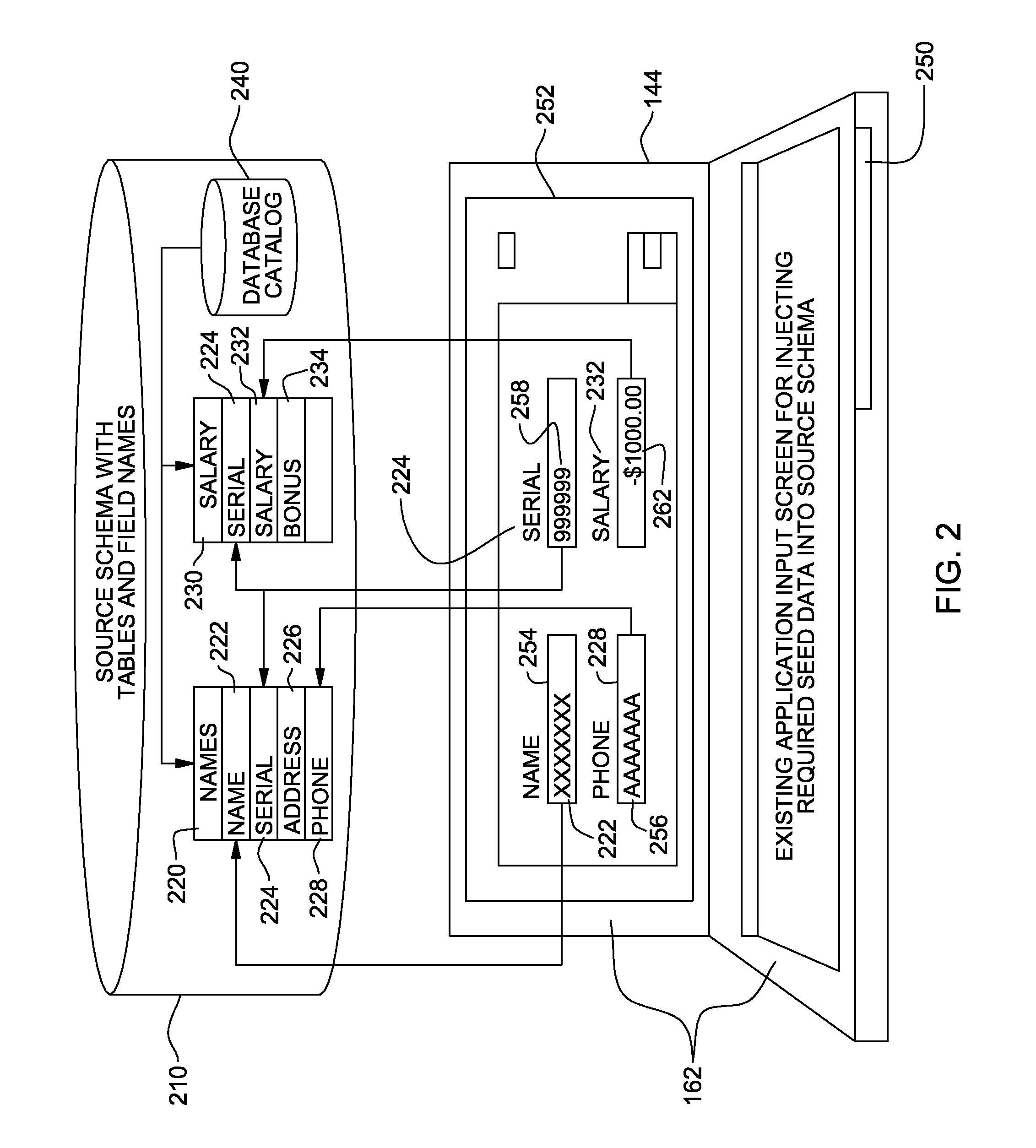
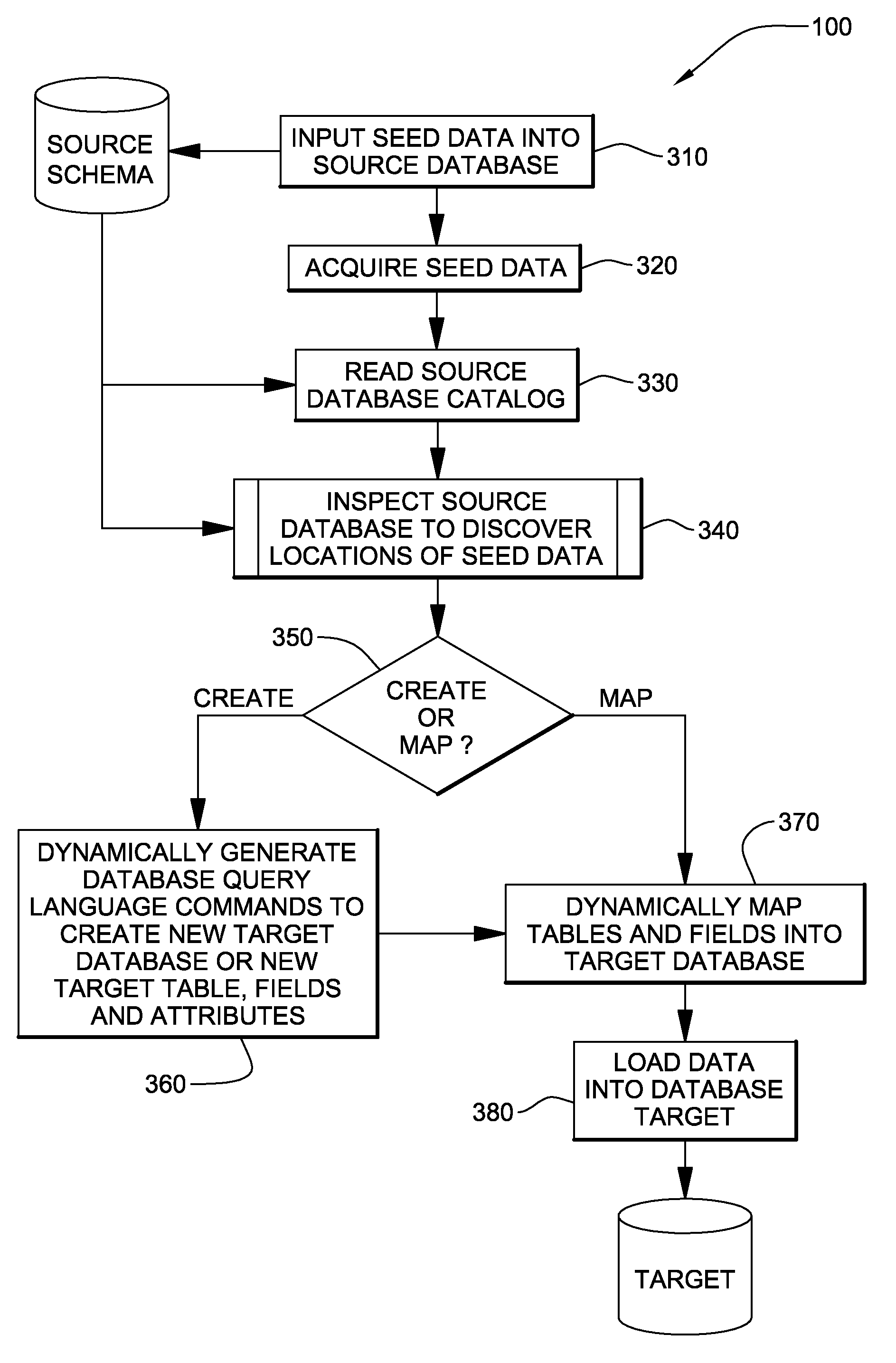
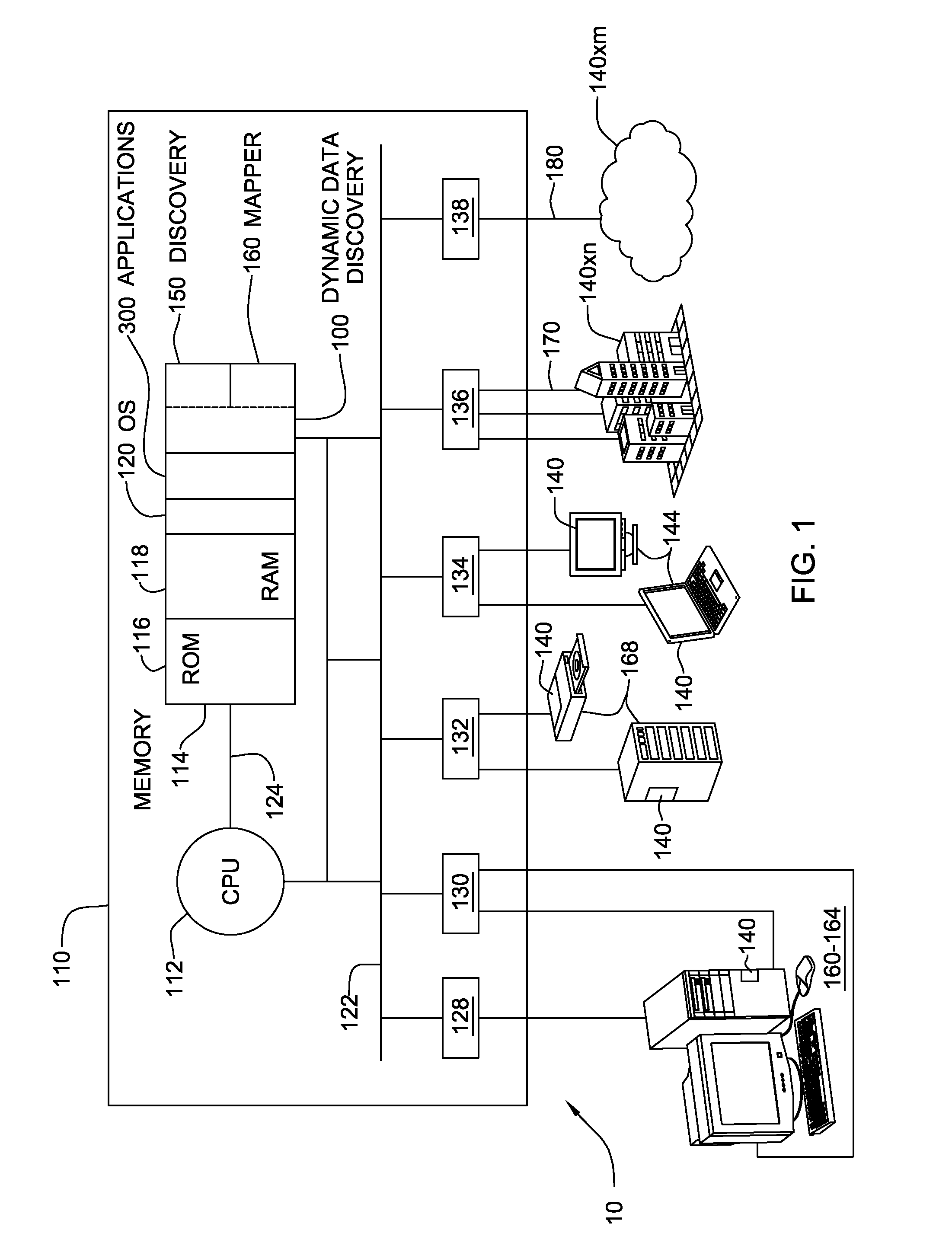
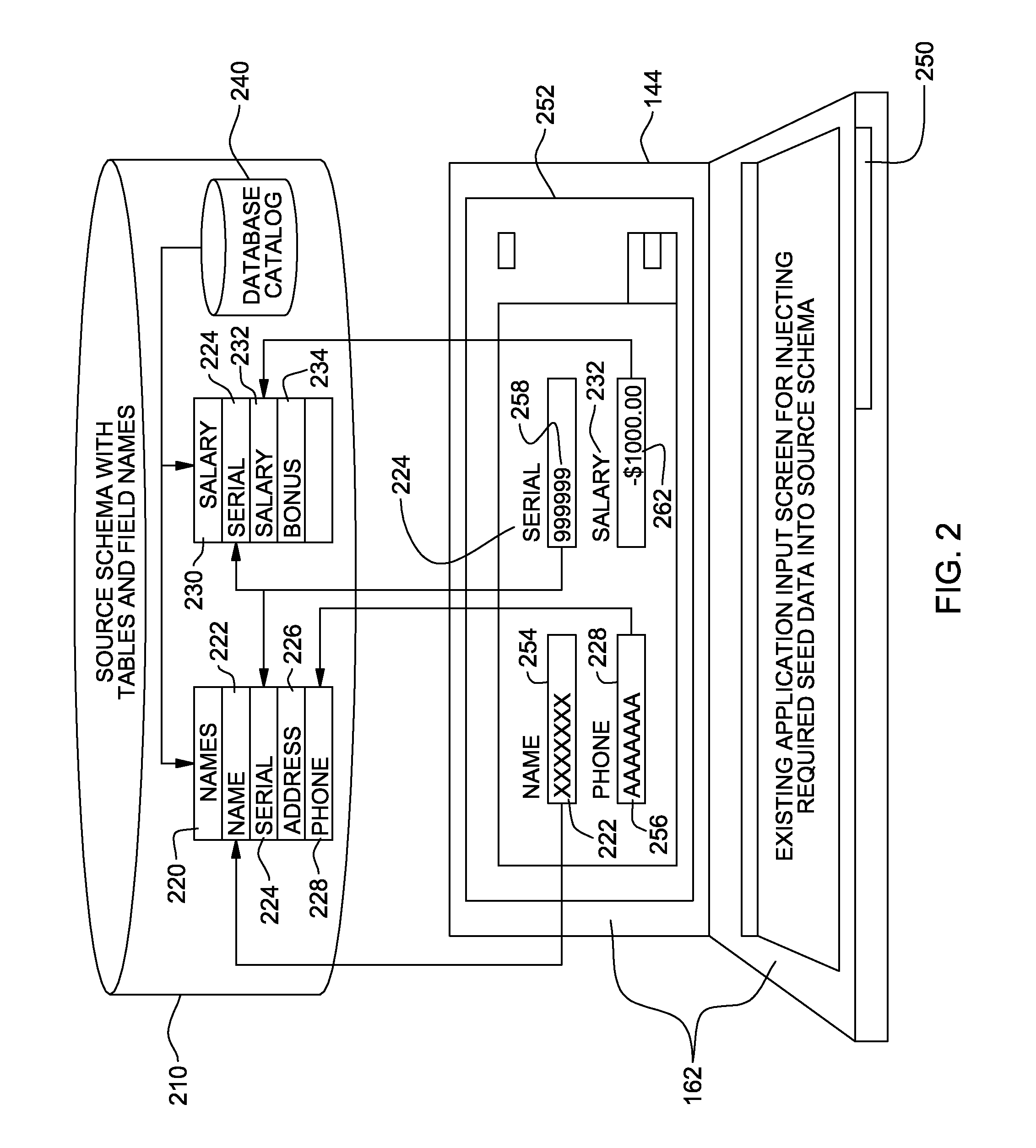
Dynamic data discovery of a source data schema and mapping to a target data schema
InactiveUS20080320012A1Digital data processing detailsSpecial data processing applicationsCommand languageDynamic data
A computerized method, program product, and a service that discovers trace data inserted into a source database having an unknown schema. Once the trace data is found by a dynamic data discovery engine, the tables, the fields, and the attributes of the fields in the source schema in which the trace data were located can be evaluated to determine if the data in the fields are pertinent to a target database. If so, then the data in those fields can be mapped and transferred to a target database. The dynamic data discovery engine generates the commands in both the source and the target database command language to find all pertinent data, map and transfer the data from the source database to a target database. The dynamic data discovery engine generates commands to create the target database and / or fields within an existing target database for the mapped and transferred data.
Owner:IBM CORP
Virtual operating system device communication relying on memory access violations
InactiveUS7496495B2Internal/peripheral component protectionSoftware simulation/interpretation/emulationVirtualizationOperational system
Attempts by drivers of a virtualized legacy computer game to communicate with nonexistent legacy game system hardware are converted into calls to actual hardware of the host computer game system. An access control list (ACL) restricting and / or reducing page permissions is used to explicitly forbid the drivers of the legacy computer game operating on the virtualized legacy computer game platform from writing to the MMIO addresses of the legacy computer game system. When the operating system of the virtualized legacy computer game platform attempts to touch its driver memory by writing to the MMIO addresses, the operating system of the host computer game system perceives a memory access violation, suspends the virtual machine implementing the virtualized computer game platform, and passes the intended write to an exception handler of the host operating system. The exception handler of the host operating system translates the attempted hardware access command into the command language of the host operating system and then returns control to the operating system of the virtualized legacy computer game platform. The legacy game is completely unaware of this address translation in that it sees only a successful hardware result and proceeds.
Owner:MICROSOFT TECH LICENSING LLC
Intelligent system and method for spacecraft autonomous operations
InactiveUS7856294B2Improve responsivenessReduce time delayVehicle testingRegistering/indicating working of vehiclesCommand languageOn board
The intelligent system for autonomous spacecraft operations includes an on-board Autonomous Operations subsystem integrated with an on-ground Web-based Remote Intelligent Monitor System (RIMS) providing interface between on-ground users and the autonomous operations intelligent system. The on-board Autonomous Operation subsystem includes an On-Orbit Checkout Engine (OOCE) unit and an Autonomous Tasking Engine (ATE) unit. Spacecraft Command Language (SCL) engine underlies the operations of the OOCE, ATE and RIMS, and serves as an executer of commands sequences. The OOCE uses the SCL engine to execute a series of SCL command scripts to perform a rapid on-orbit checkout of subsystems / components of the spacecraft in 1-3 days. The ATE is a planning and scheduling tool which receives requests for “activities” and uses the SCL scripts to verify the validity of the “activity” prior to execution, and scheduling the “activity” for execution or re-scheduling the same depending on verification results. Automated Mission Planning System (AMPS) supports the ATE operations. The ATE uses a priority schedule if multiple “activities” are to be executed.
Owner:SRA INTERNATIONAL
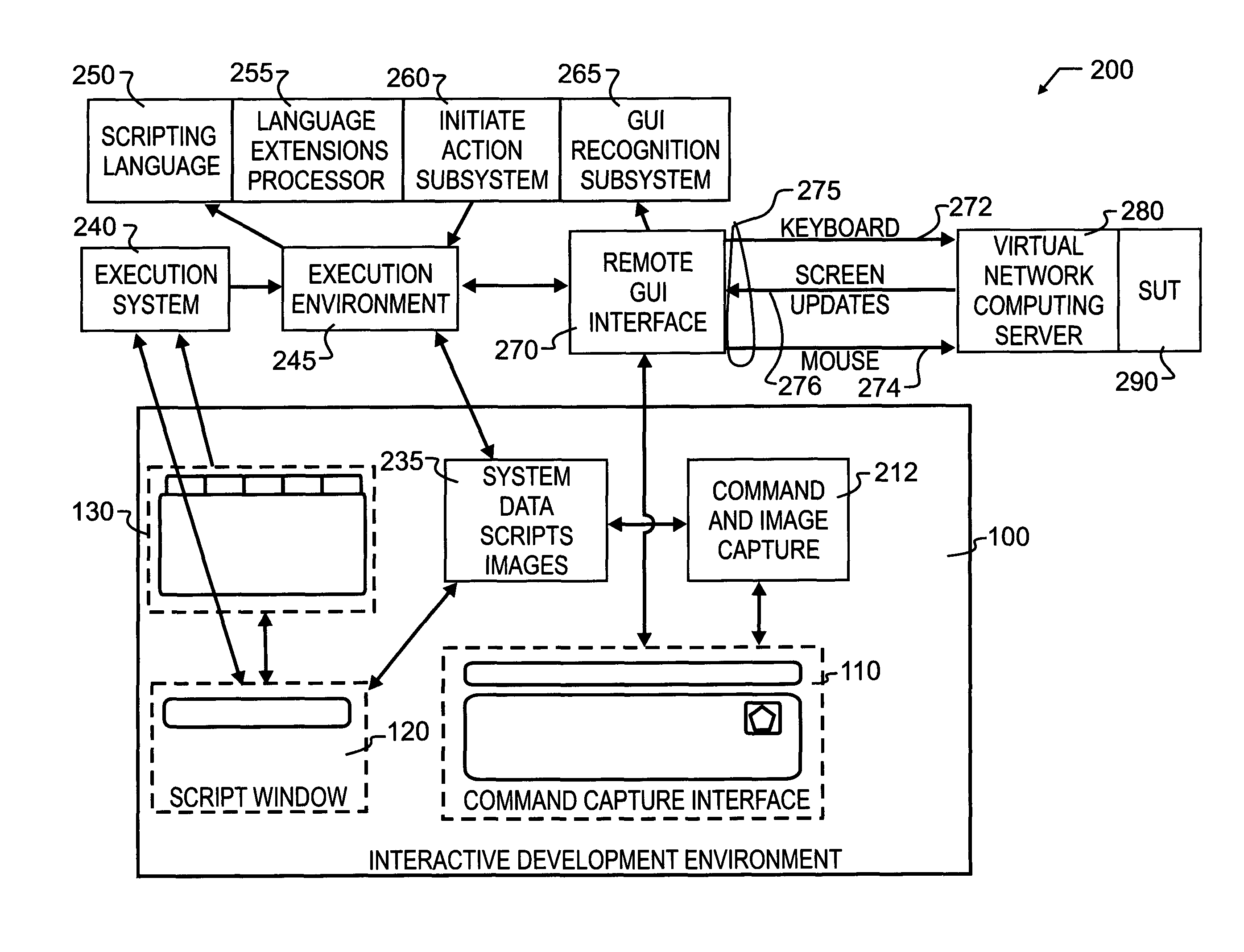
Method for monitoring a graphical user interface on a second computer display from a first computer
ActiveUS7870504B1Reliably and simply and quickly execute operationMore difficultImage analysisImage codingGraphicsScripting language
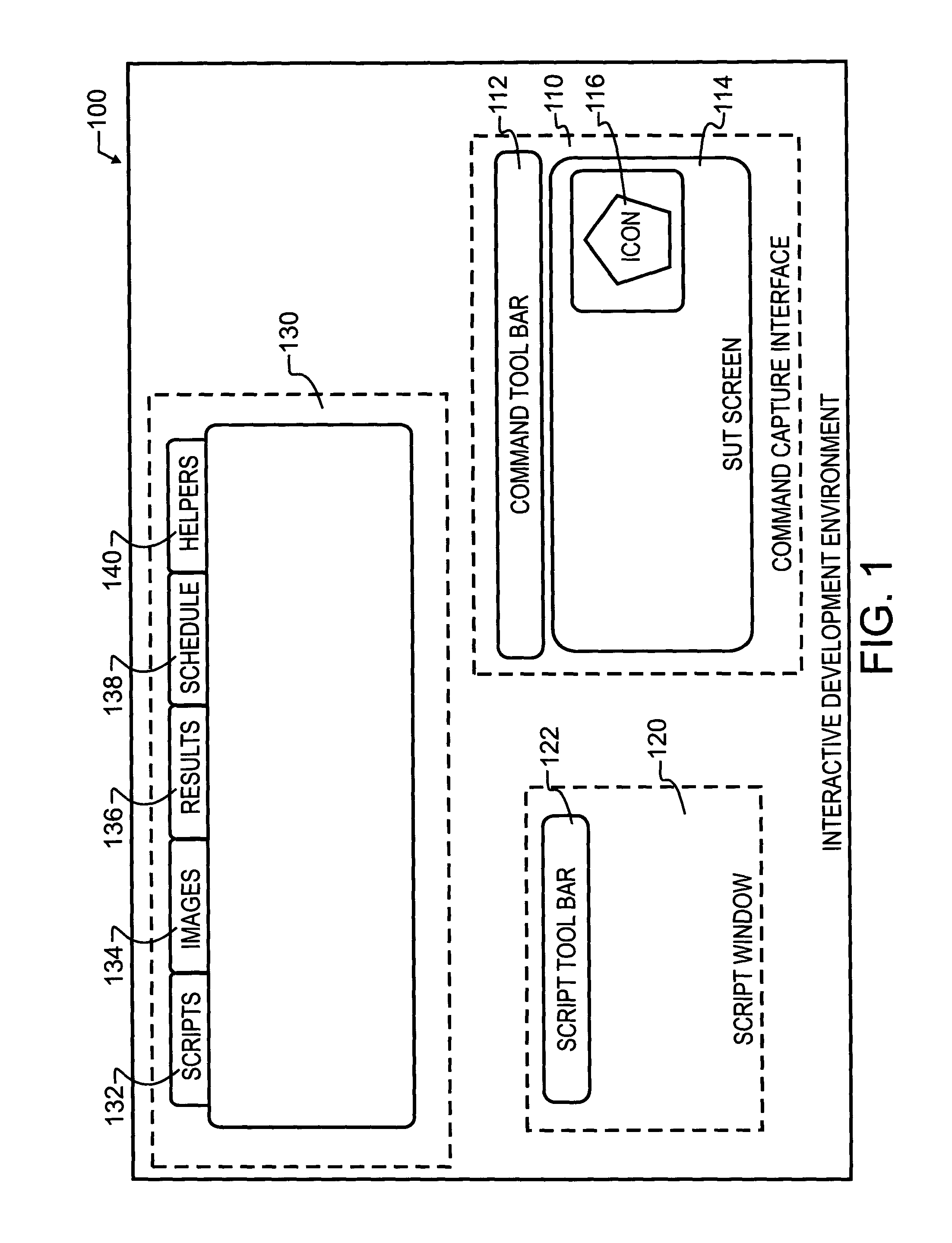
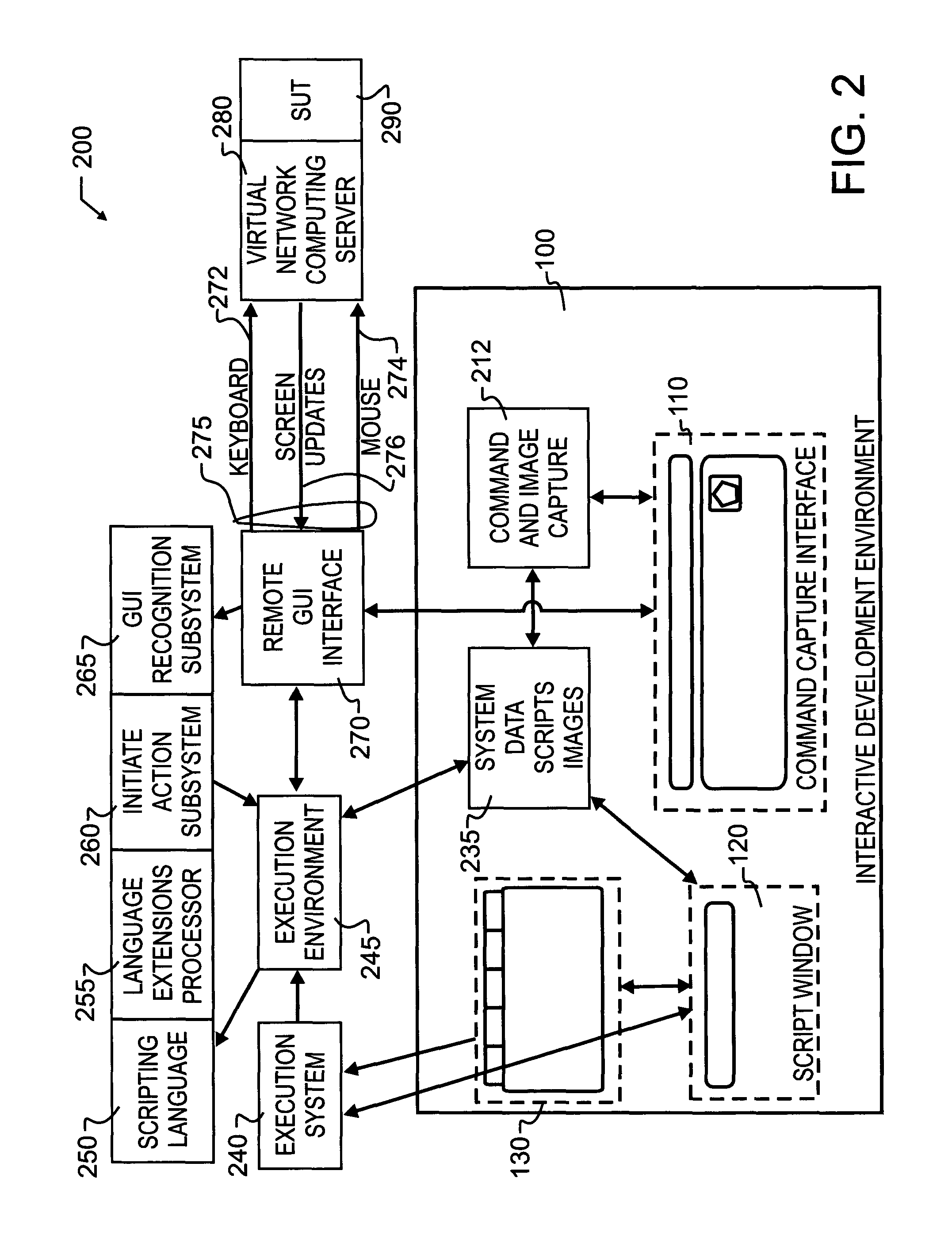
A high level interface between a remote computer and local computer operator permits the remote computer to be controlled via a sequence of interactions. The remote computer may be monitored for display information which is expected, and also controlled in the event the expected information either is or is not obtained. Command language extensions are provided which extend and complement a basic scripting language. Scripts with embedded command language extensions may be executed through a remote interface, permitting remote testing, operation and evaluation. The development of the scripts, including embedded command language extensions, may be prepared through execution of commands at the local computer on a depiction of the GUI received from the remote computer, and subsequently saved as a script.
Owner:EGGPLANT SOFTWARE INC
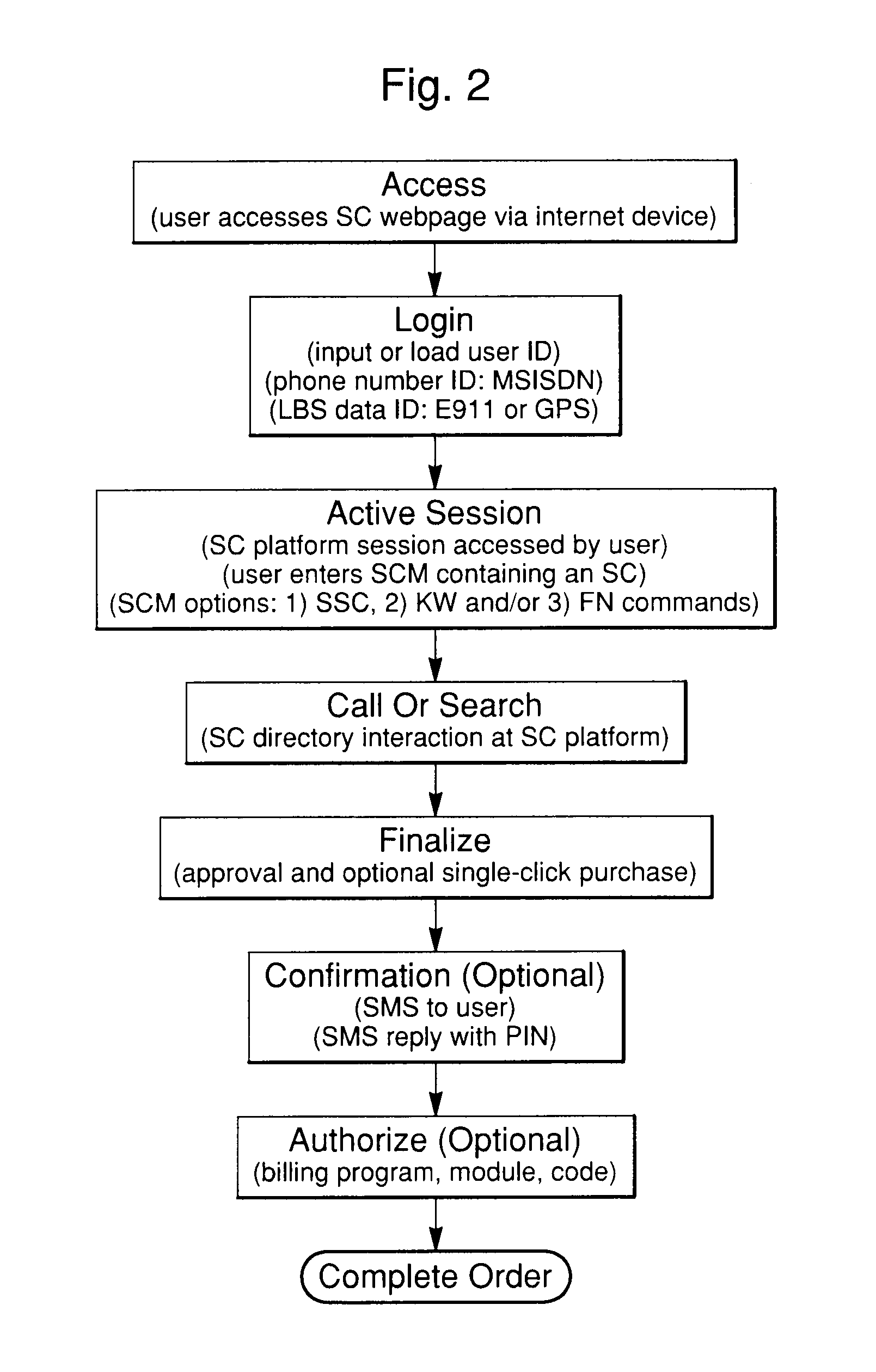
System and method for using symbol command language within a communications network via SMS or internet communications protocols
ActiveUS20110093949A1FunctionalWeb data indexingDigital data processing detailsComputer hardwareThe Country Code
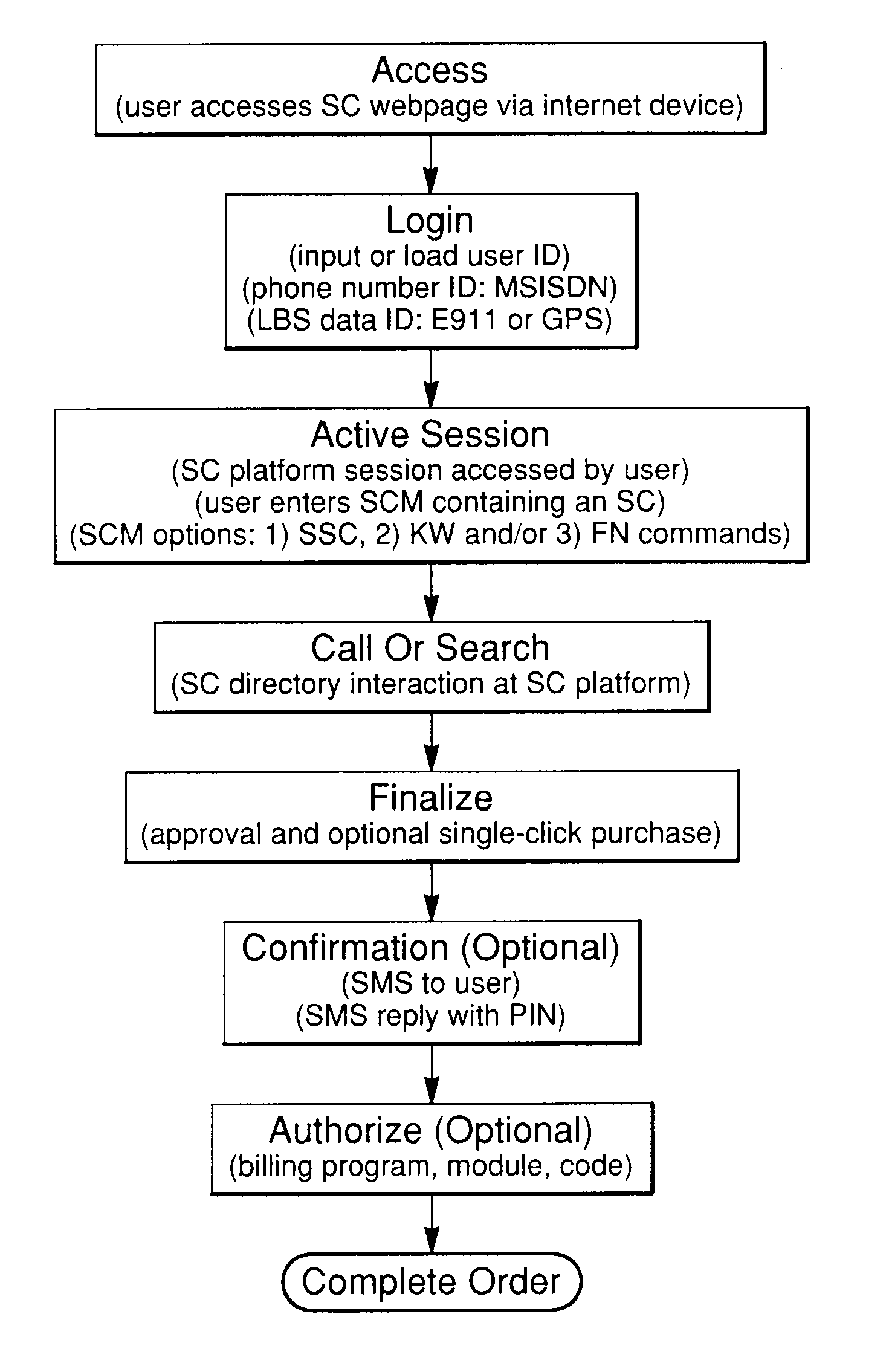
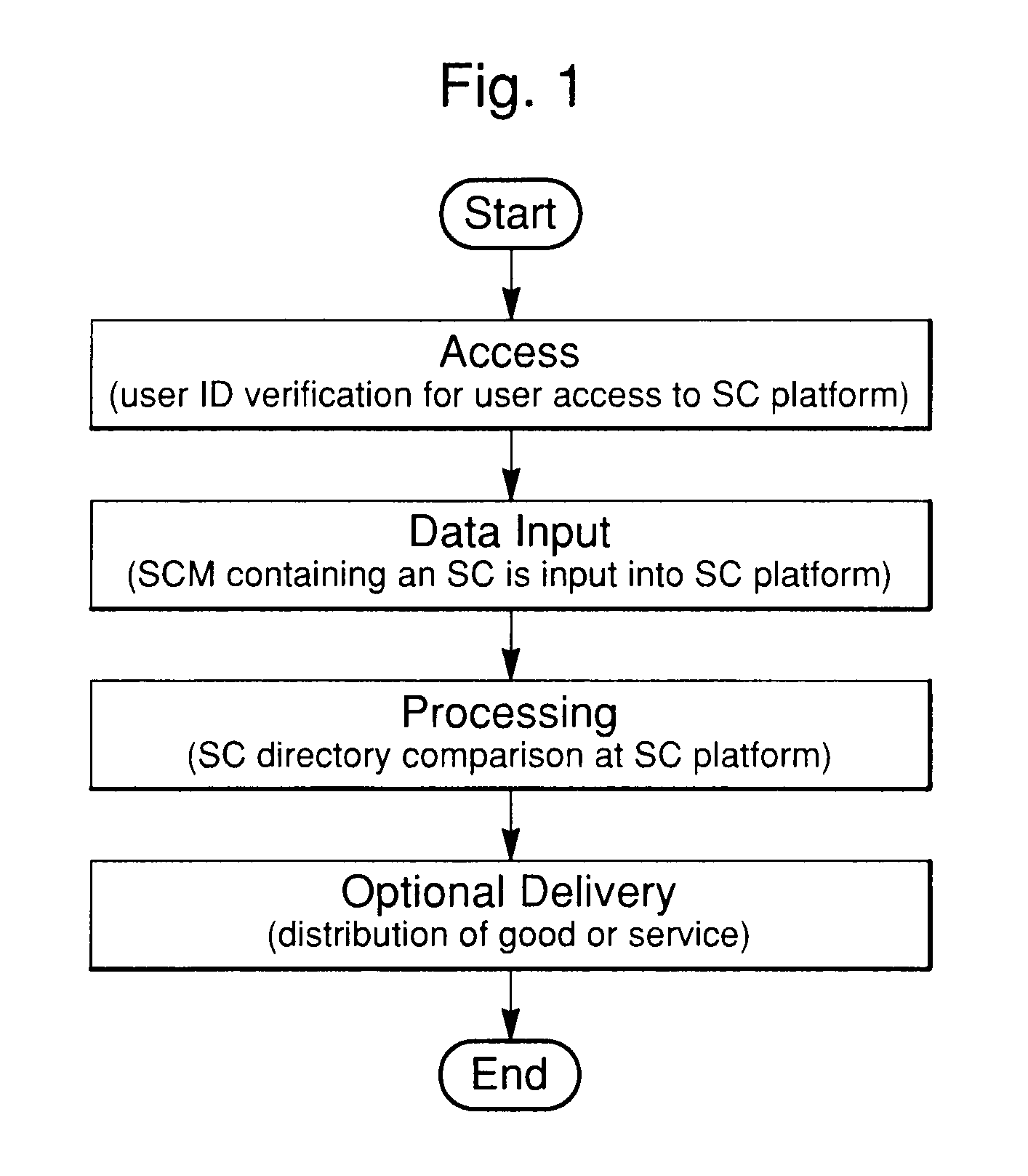
A system and method for generating actions utilizing predefined commands within a communications network comprises predefined commands called symbol commands. These are character strings entered into a platform during an internet or SMS communications protocol session. The method and system can be used via the internet or a GSM network and is well-suited for mobile use. In addition, utilization of keywords and alpha-numeric or other character symbols to form symbol commands allows for complex command structuring. A search process is used in combination with a symbol command and a symbol command directory to identify specific goods and services, or related symbol commands. In addition, a platform performs specific predetermined actions in response to the symbol command such as making product purchases or providing services such as location-based services, coupon delivery or travel ticketing. The symbol command structure and platform will also utilize identification information associated with an individual user. Furthermore, the platform may implement a response using location information associated with the user from the country code, area code or prefix code of a user's telephone number, or use GPS location information associated with the user's internet device. The symbol command system and method provide an improved form of access to products and services via the internet or SMS.
Owner:MESSAGE4U
Extending Legacy Scripting Languages with Graphical References
ActiveUS20120150939A1Efficient executionEfficient use ofMultiple digital computer combinationsProgram controlNCAR Command LanguageCommand-line interface
A graphical data type inference transparently transforms a legacy text-oriented command line interface (CLI) into a graphic-oriented or graphic-aware CLI (G-CLI). A user fuses graphical references with the legacy scripting language by identifying objects using syntax familiar to the user. The objects are presented to the user via a user interface and may be queried / selected by the user. The user issues commands on the selected objects by referencing the graphical selection in a command line within a shell. The graphical selection in short hand is translated into a form operable by a server or computer. The syntax of the legacy command language is extended with operators that operate entirely within the G-CLI. Consequently, the command line used in the shell has an existing operation set, as well as new graphic-based operations.
Owner:NUANCE COMM INC
Dynamic data discovery of a source data schema and mapping to a target data schema
InactiveUS7720873B2Digital data information retrievalDigital data processing detailsCommand languageDynamic data
A computerized method, program product, and a service that discovers trace data inserted into a source database having an unknown schema. Once the trace data is found by a dynamic data discovery engine, the tables, the fields, and the attributes of the fields in the source schema in which the trace data were located can be evaluated to determine if the data in the fields are pertinent to a target database. If so, then the data in those fields can be mapped and transferred to a target database. The dynamic data discovery engine generates the commands in both the source and the target database command language to find all pertinent data, map and transfer the data from the source database to a target database. The dynamic data discovery engine generates commands to create the target database and / or fields within an existing target database for the mapped and transferred data.
Owner:INT BUSINESS MASCH CORP
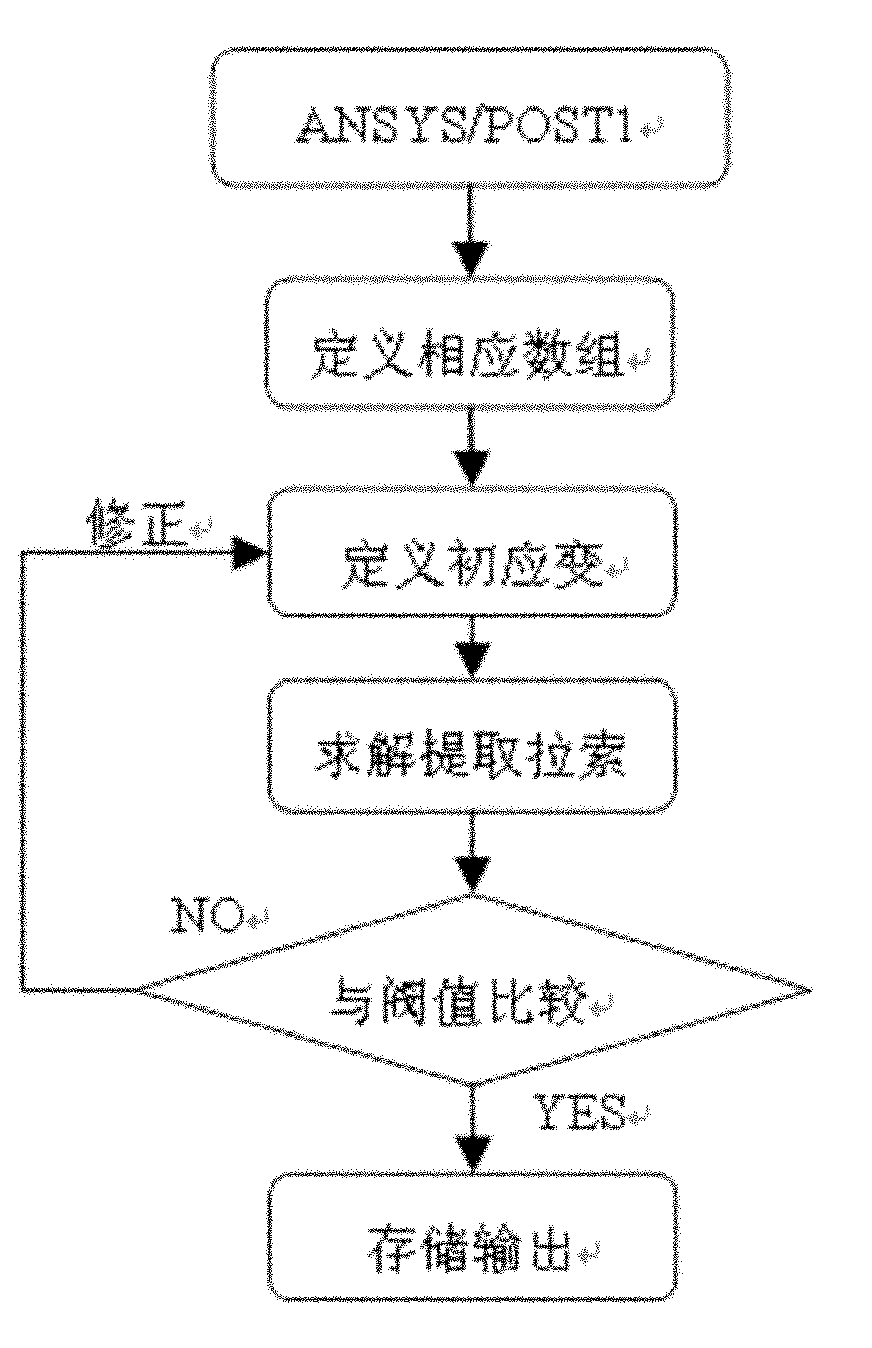
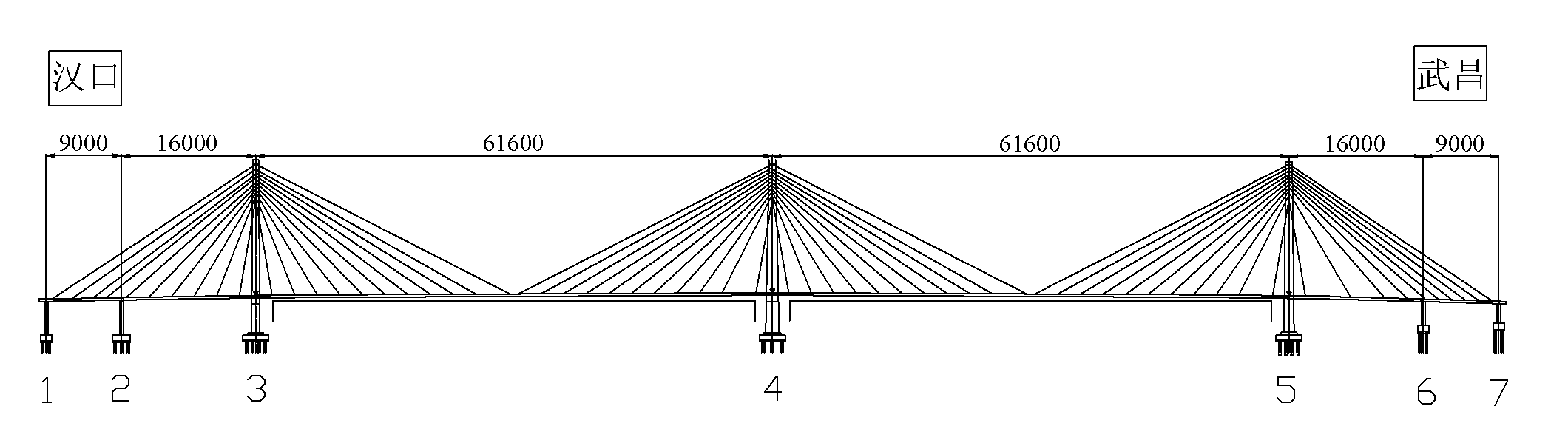
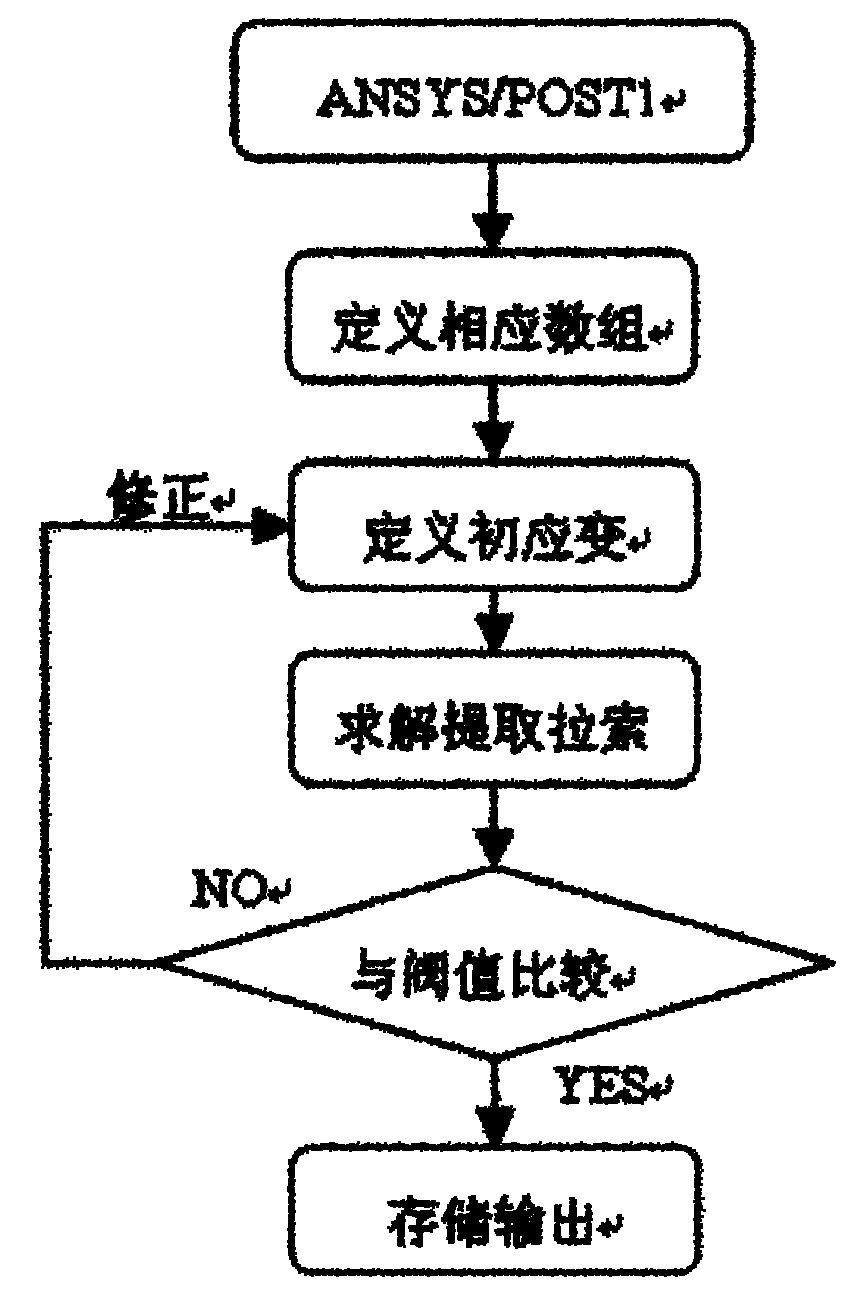
Determination method of initial completion initial cable force of cable-stayed bridge
ActiveCN101937485AFast convergenceReduce calculation errorsSpecial data processing applicationsCable stayedCommand language
The invention relates to a determination method based on an ANSYS second development platform of the initial completion initial cable force of a cable-stayed bridge. The method uses the design cable force as the target value, considers the geometric non-linear effect and performs iteration for solving and correcting the cable initial strain under the action of dead load. The method comprises the following specific steps: any group of cable forces is assumed to be added on the stay cable in the mode of initial strain, dead load is added to calculate, the *do-loop command language is used to extract the calculated cable force of the stay cable and check whether the error between the cable force and the target completion cable force is within an available limit; if the error is large, the indifference method is used to correct the stay cable initial strain, then the error is calculated again until the error is within the available limit; and the initial completion initial cable force can be obtained by multiplying the last calculated group of stay cable initial strains by the elastic modulus of the stay cable which is corrected by considering the vertical effect. By using the method, the solving time of the completion initial cable force of the cable-stayed bridge can be reduced and the precision can be increased, thus the method has large practical engineering application value.
Owner:WUHAN UNIV OF TECH
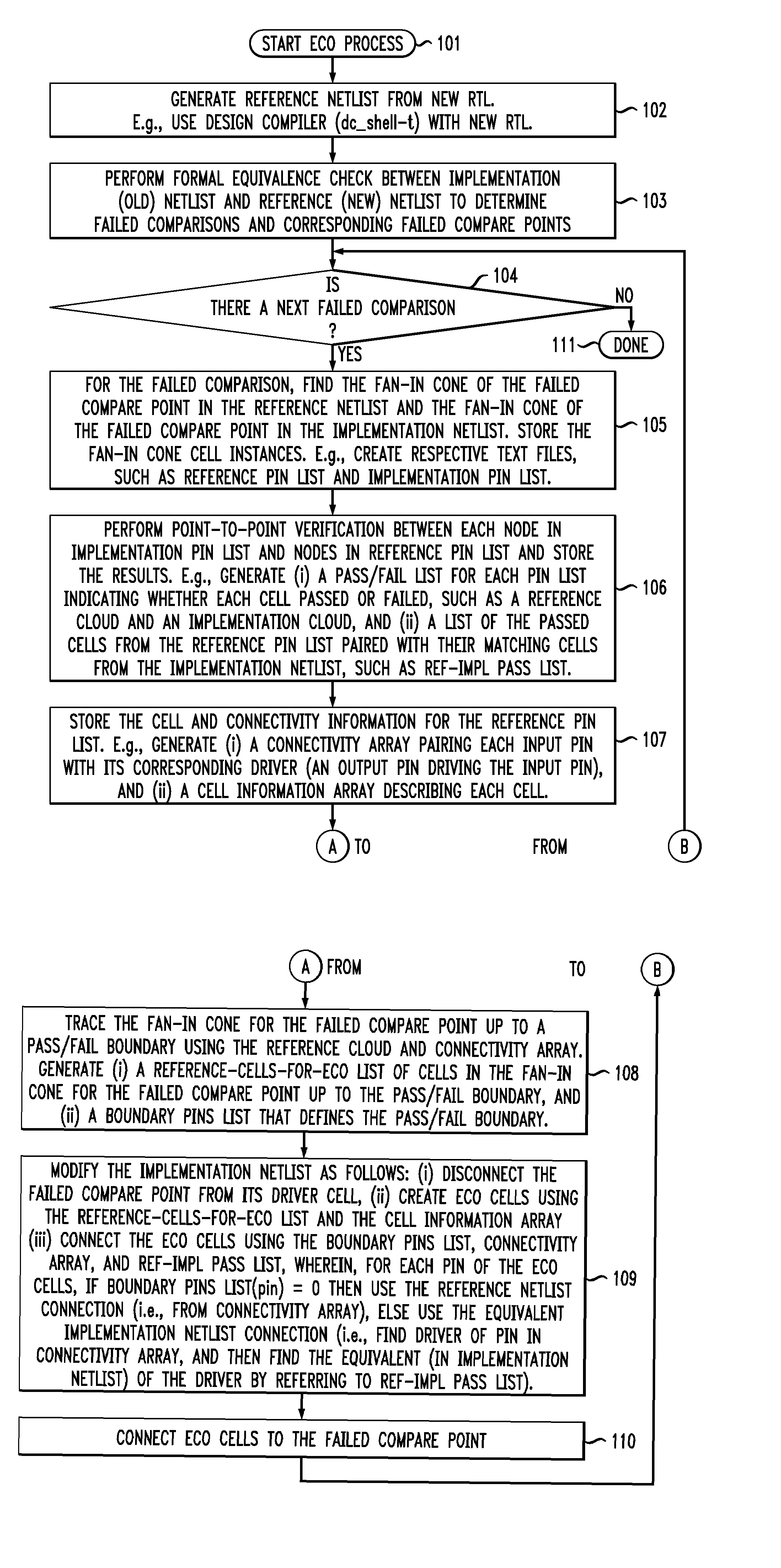
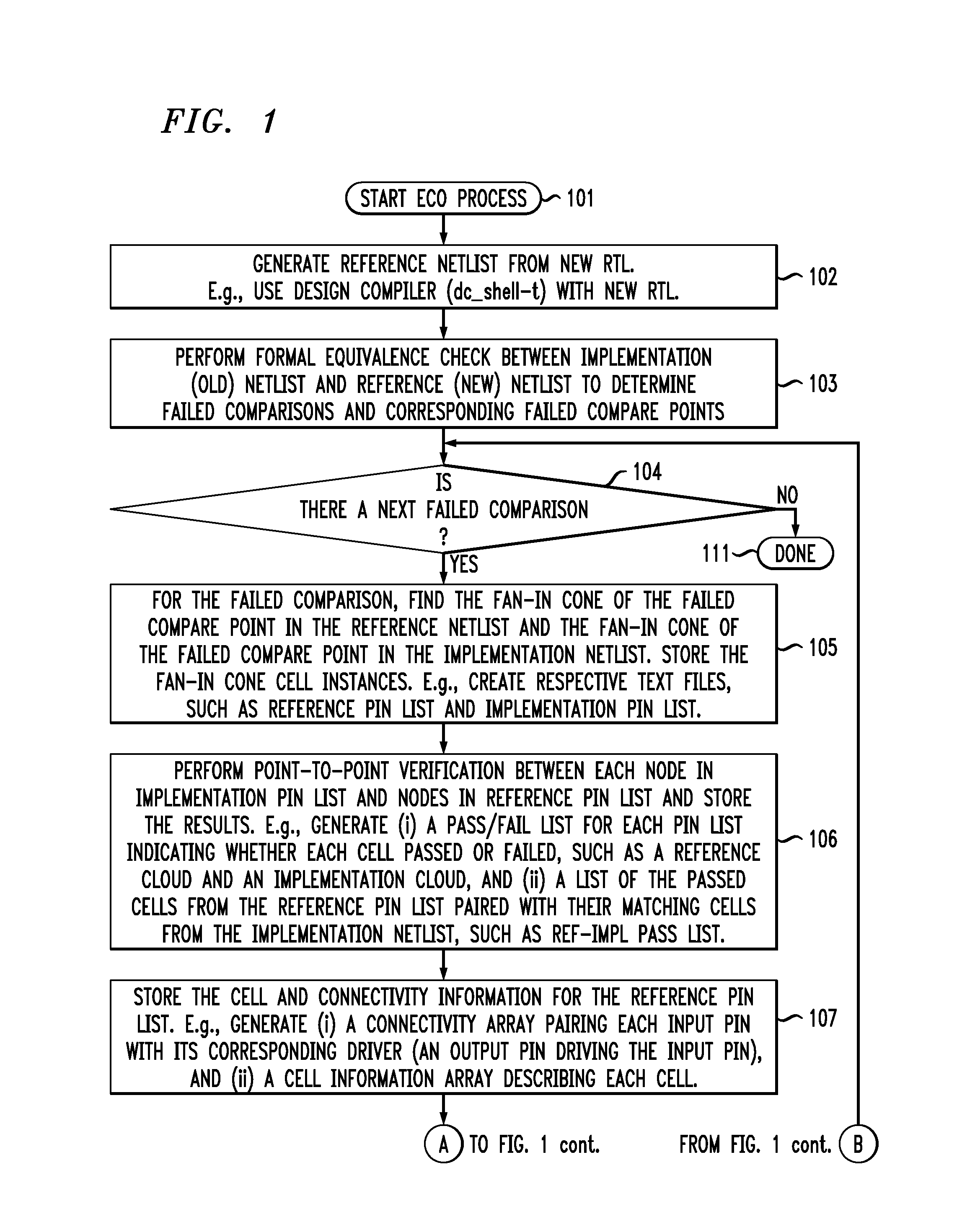
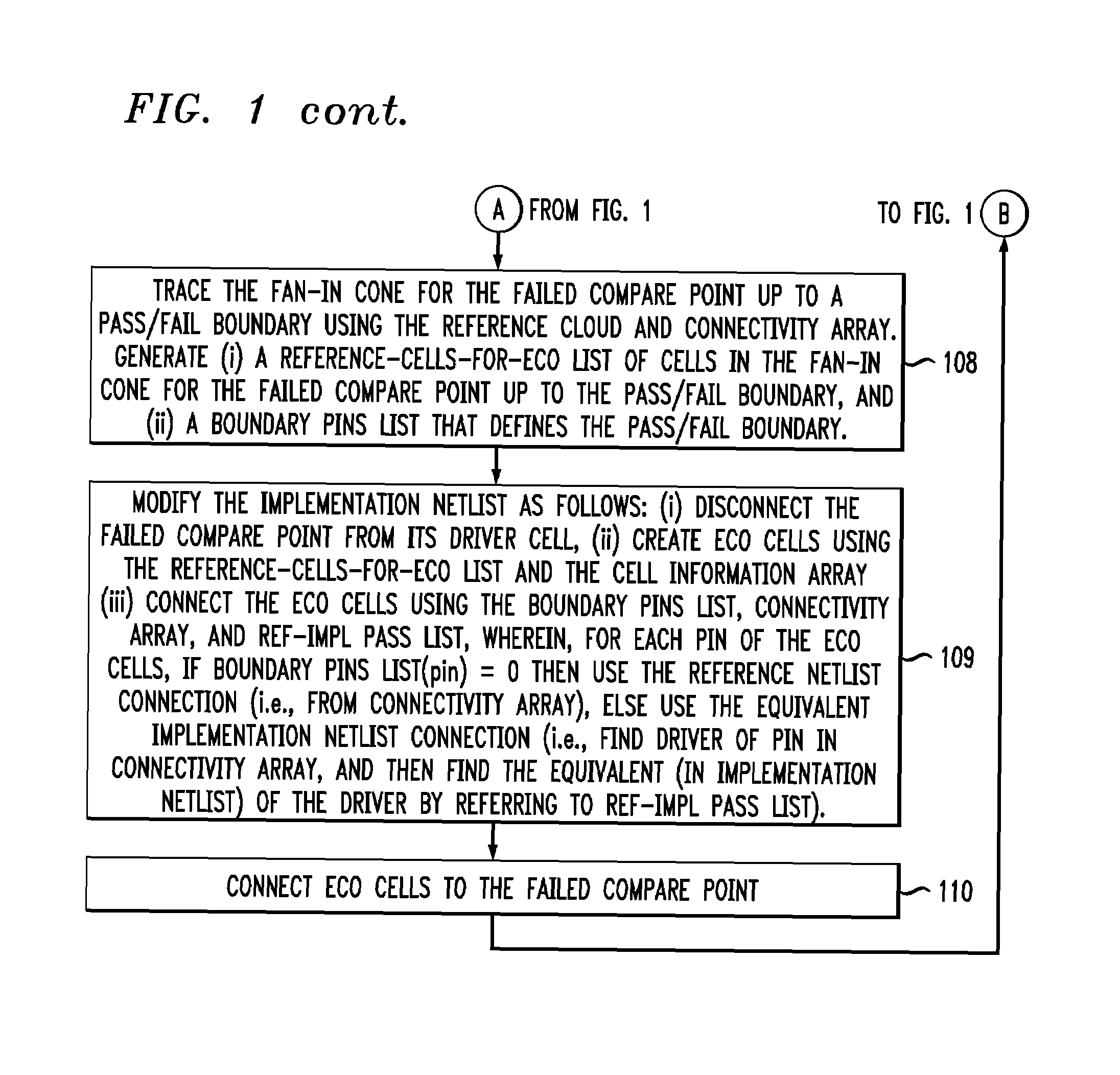
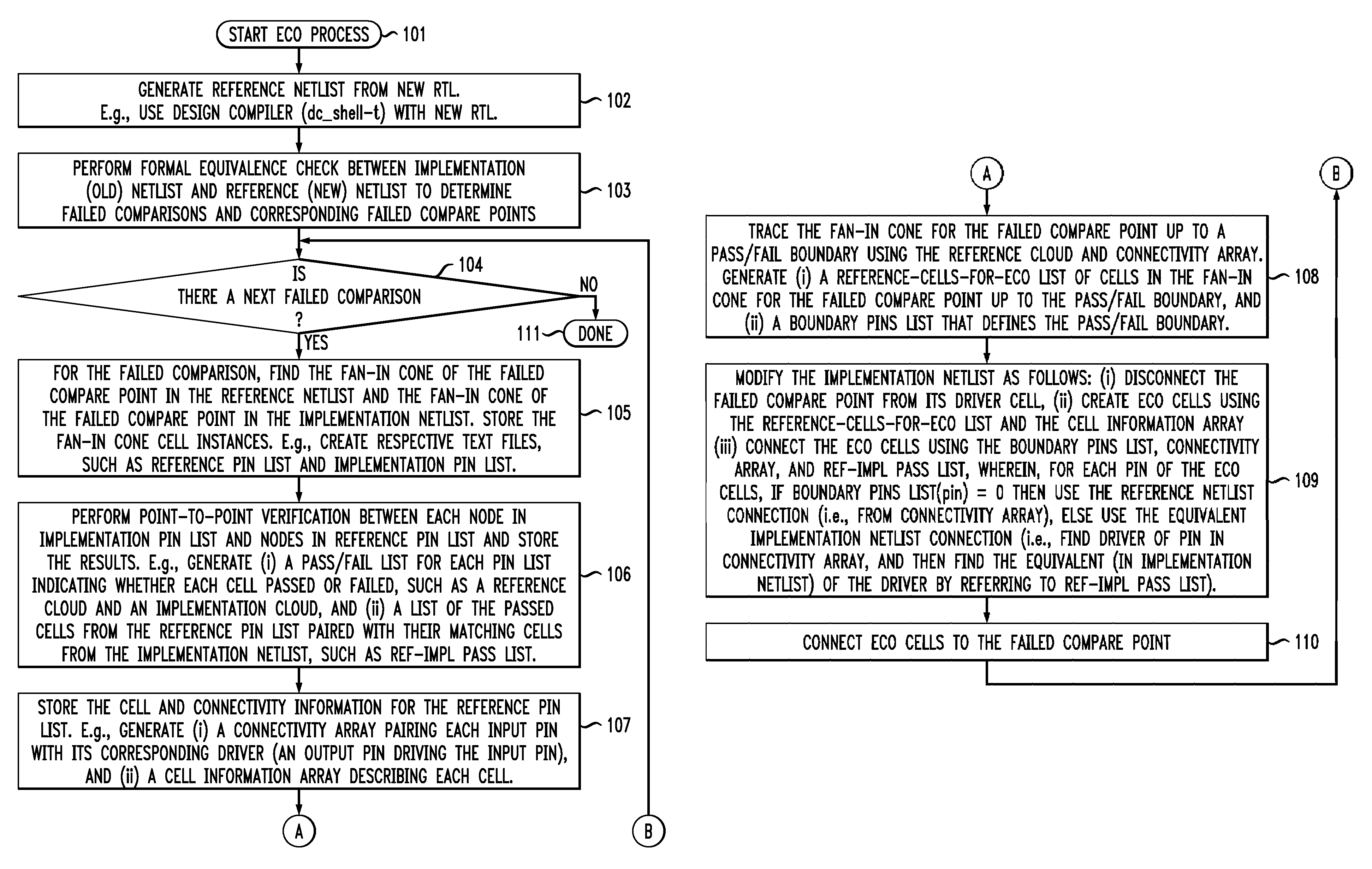
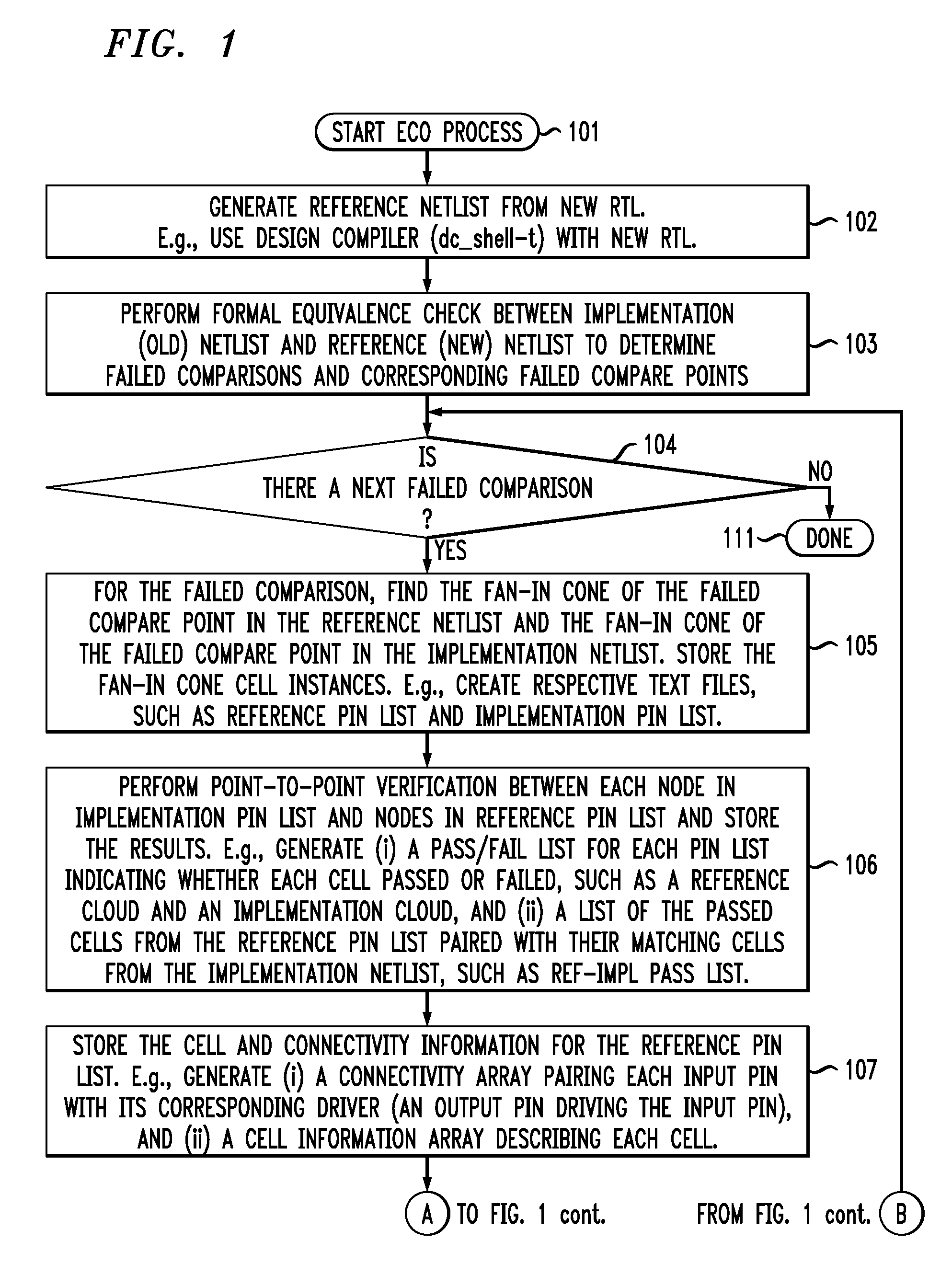
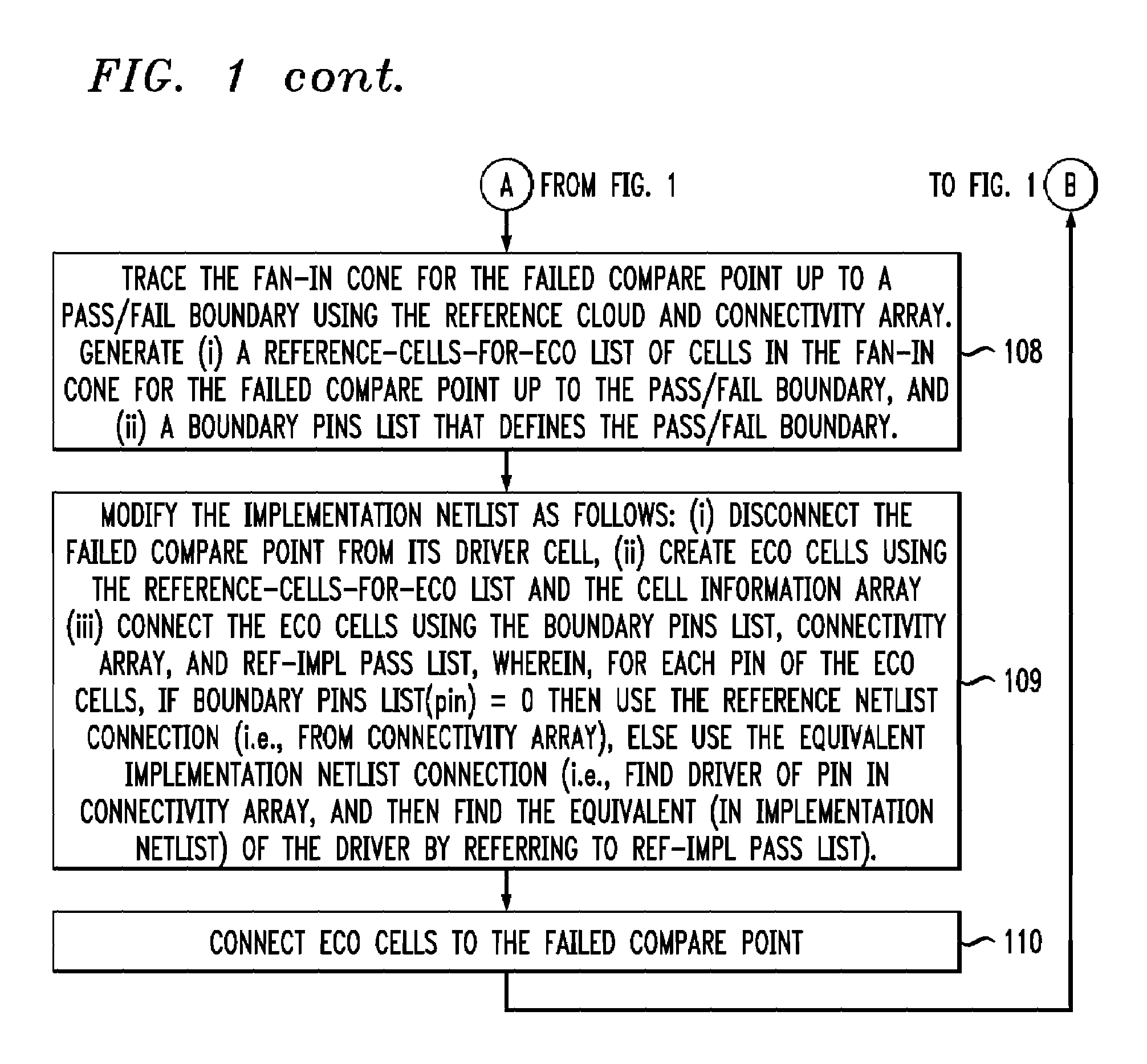
Command-language-based functional engineering change order (ECO) implementation
InactiveUS20070271537A1CAD circuit designSoftware simulation/interpretation/emulationComputer architectureCommand language
In one implementation, the invention can be a computer-implemented method for generating an engineering change order (ECO) netlist for an integrated circuit (IC). The method includes performing a formal equivalence check between an implementation netlist and a reference netlist to identify one or more corresponding failed compare points in the implementation and reference netlists. The method further includes, for at least one failed comparison: (i) performing equivalence verifications based on fan-in cones for the failed compare points, to generate pin pass / fail information, (ii) tracing the fan-in cone for the reference netlist to generate ECO pin and cell information, and (iii) modifying the implementation netlist, based on (1) the pin pass / fail information, (2) cell connectivity information, (3) cell description information, and (4) the ECO pin and cell information, to generate the ECO netlist by adding one or more new ECO cells to the implementation netlist and appropriately connecting them.
Owner:BELL SEMICON LLC
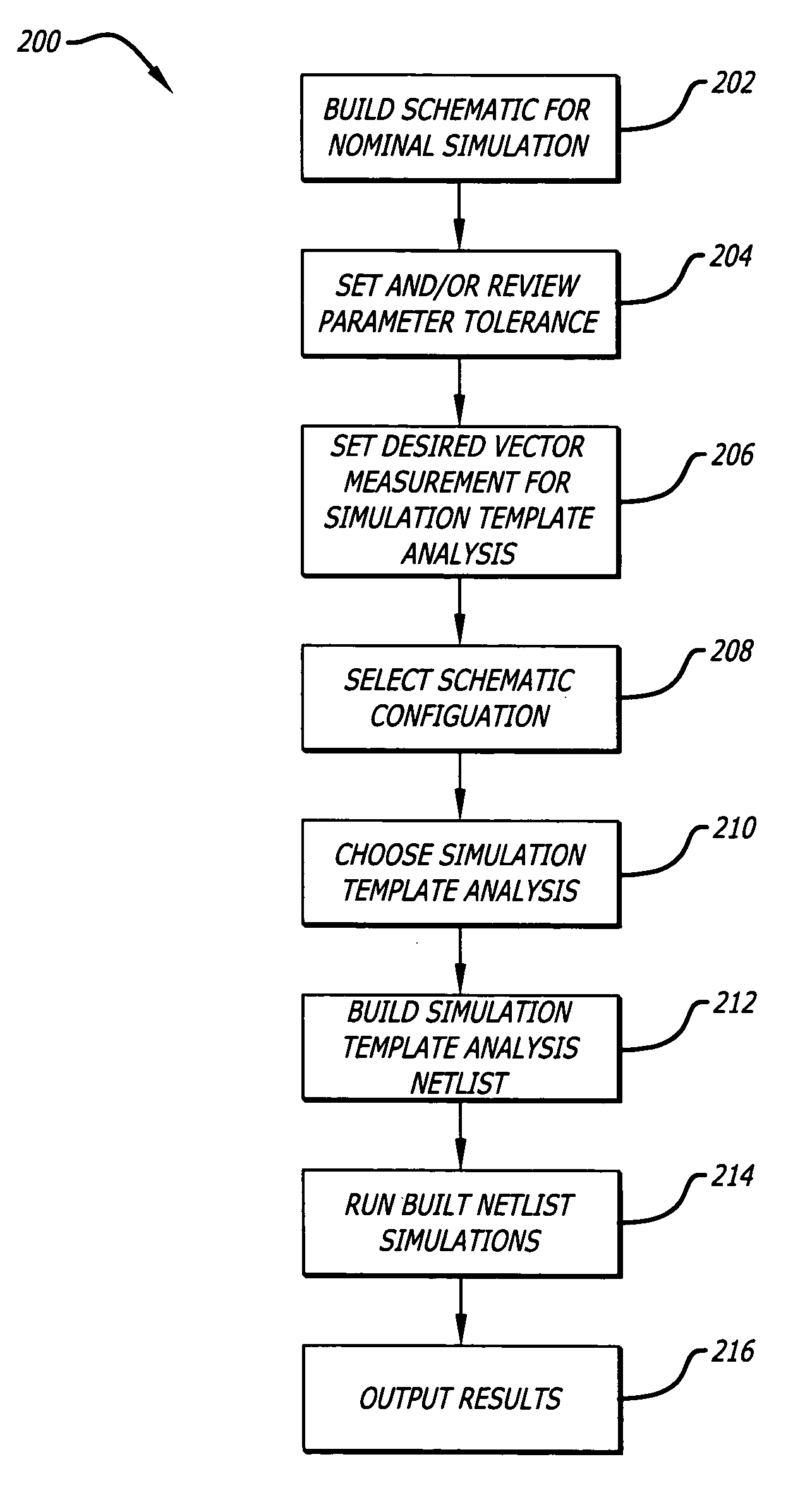
System and method of providing additional circuit analysis using simulation templates
InactiveUS7110929B1Detecting faulty computer hardwareAnalogue computers for electric apparatusTransient analysisCommand language
A simulation template and method therefor is disclosed that modifies a SPICE netlist that describes a circuit in order to provide customized or pre-installed additional analysis. More specifically, a simulation template is an interactive command language (ICL) script that has embedded instructions telling a netlist where to insert information and which options are to be provided. It is used to expand SPICE beyond the traditional limitations of the basic alternating current (AC), direct current (DC), and transient analysis by allowing parameter variations and multiple simulations passes to be run under one analysis umbrella. Such additional analysis employing parameter variations and multiple analysis passes include sensitivity analysis, root means square (RSS) analysis, extreme value analysis (EVA) and worst case sensitivity (WCS), to name a few. The simulation template includes a routine to add to a netlist for altering circuit parameter values of the circuit design in a pre-determined manner, a routine to add to the netlist for performing simulations of the circuit design for respective altered circuit parameter values to arrive at respective selected vector measurements, and a routine to add to the netlist for manipulating at least one of the vector measurements in accordance with the pre-determined analysis.
Owner:INTUSOFT
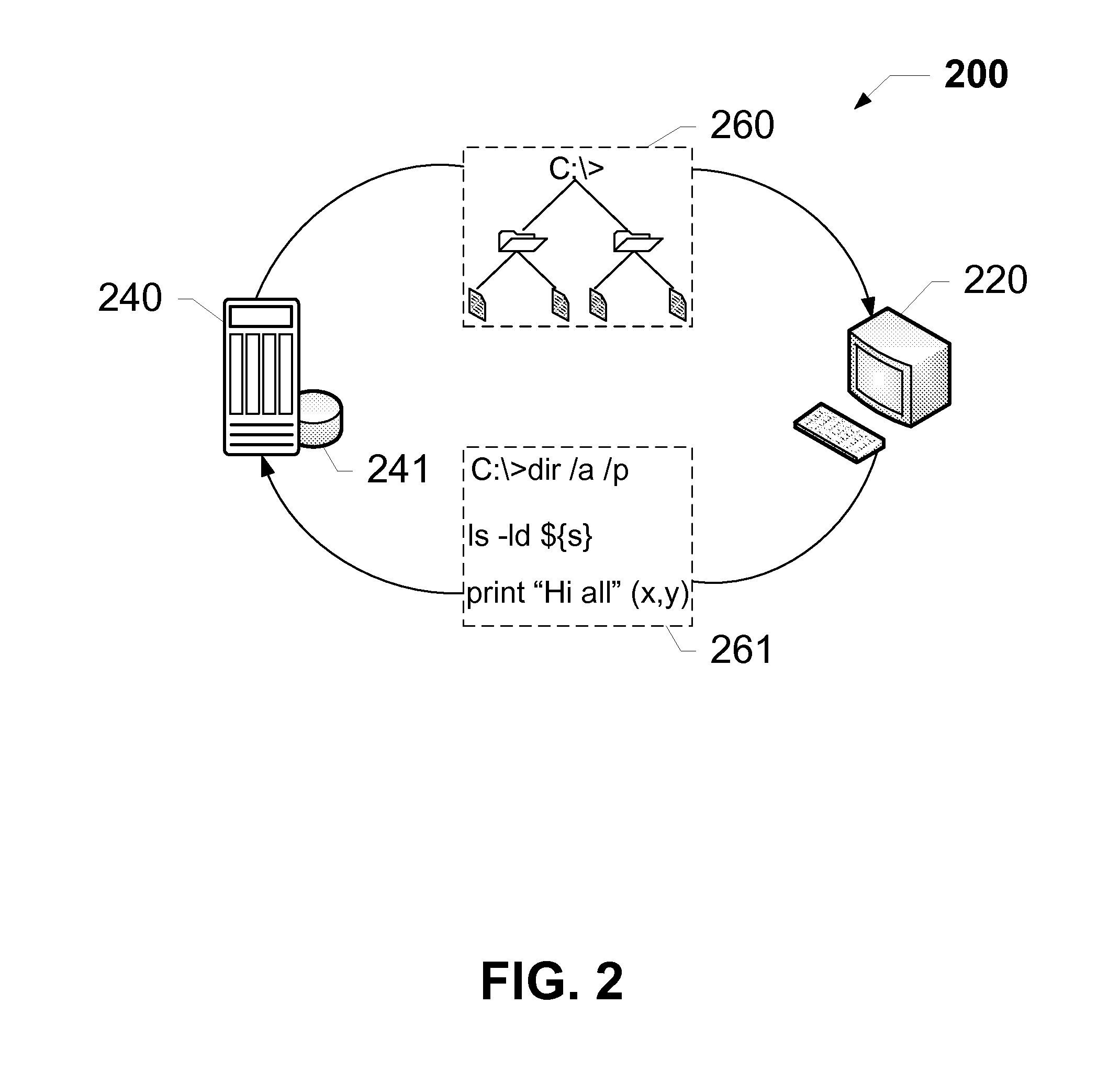
Method and apparatus for aggregated update of dataset records in a JavaScript environment
InactiveUS20050262124A1Easy maintenanceSpecialized trainingWebsite content managementSpecial data processing applicationsObject basedData set
An apparatus for and method of utilizing an Internet terminal coupled to the world wide web to access a legacy data base management system having a dialog-based request format using a standardized object-based command language, such as JavaScript, rather than the proprietary command language native to the legacy data base management system to perform a bulk update operation. This approach leverages the power of the legacy data base management without the need for the user to become familiar with the proprietary command language of the legacy data base management system. The approach is particularly efficient in that the user can provide parameters to the legacy data base management system as a parameter object.
Owner:UNISYS CORP
Automatic test method of long distance multi-device condition
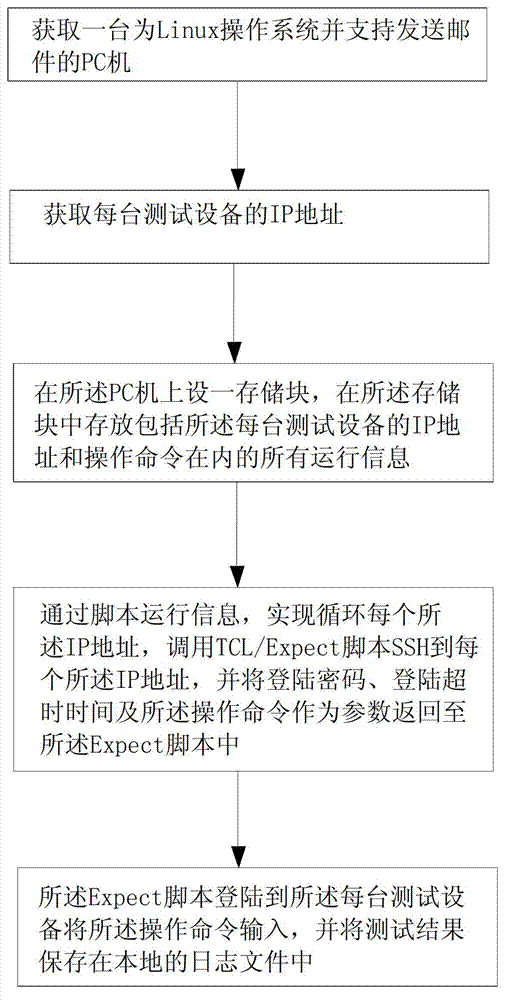
InactiveCN103092754AReduce development costsFacilitate joint testingSoftware testing/debuggingOperational systemCommand language
The invention discloses an automatic test method of a long distance multi-device condition. The automatic test method of the long distance multi-device condition comprises the following steps of obtaining a personal computer (PC) machine with a Linux operation system; obtaining an internet protocol (IP) address of each test device; arranging a storage block on the PC machine, storing all operation information, including the IP address of each test device and operation orders, in the storage block; running the information in the storage block through a SHELL script, achieving circulation of each IP address, calling a tool command language (TCL) / Expect script secure shell (SSH) to each IP address, and returning a login password, a login overtime time and the operation orders to the Expect script as parameters; and logging in each test device by the Expect script. The automatic test method of the long distance multi-device condition has the advantages of being simple, easy to achieve, and capable of reducing development cost of a test system, facilitating combined tests of test devices in a plurality of different locations, and being good in usability.
Owner:PHICOMM (SHANGHAI) CO LTD
Command-language-based functional engineering change order (ECO) implementation
InactiveUS7644382B2CAD circuit designSoftware simulation/interpretation/emulationComputer architectureCommand language
In one implementation, the invention can be a computer-implemented method for generating an engineering change order (ECO) netlist for an integrated circuit (IC). The method includes performing a formal equivalence check between an implementation netlist and a reference netlist to identify one or more corresponding failed compare points in the implementation and reference netlists. The method further includes, for at least one failed comparison: (i) performing equivalence verifications based on fan-in cones for the failed compare points, to generate pin pass / fail information, (ii) tracing the fan-in cone for the reference netlist to generate ECO pin and cell information, and (iii) modifying the implementation netlist, based on (1) the pin pass / fail information, (2) cell connectivity information, (3) cell description information, and (4) the ECO pin and cell information, to generate the ECO netlist by adding one or more new ECO cells to the implementation netlist and appropriately connecting them.
Owner:BELL SEMICON LLC
Service broker for processing data from a data network
InactiveUS20060184657A1Digital computer detailsSecuring communicationIdentification keyCommand language
A method and system for communication between server-less computing devices or clients in computers communicating over networks, such as the World Wide Web (WWW) using stateless protocols, e.g., HTTP. In this scheme there are two classes of clients which can operate independently or can be combined in computer communicating over the network: a) Clients that issue commands and request status or data, and b) clients which function as service brokers for provide services and processing commands, updating status and providing specific data. Based on the description of the latter client device it would resemble a server device but without accessible TCP / IP ports. Each service providing device is authenticated, retains a unique identity and establishes a soft state with the globally accessible server or servers. All devices and clients can compile and process a globally common command language established between all communicating network clients. The central server includes a CGI processing program and a database to retain client specific information. The server database represents a collection of queues, each having a client unique identifiable status, pending commands and / or data components. In this scheme commands and signaling transmitted between the servers and clients utilize standard HTTP protocol semantics and HTML or standard markup language syntax. Clients encapsulate or embed information as parameters passed to HTTP CGI as a set of standard HTTP conversations. A CGI processing program converts, parses or processes each conversation and passes arguments with or without data to queues. Each conversation is includes a client identification key(s) and commands which are structured as attribute-value pair tuples. The service-handler client connects to the central server and accesses the client queue on the central server to check for any pending commands or update their status in either synchronous or asynchronous manner. The synchronous server access scheme is regulated temporally by either deterministic clocking on server response or by a server based adaptive algorithm which can monitor network and client activities and optimize client access patterns.
Owner:XANBOO
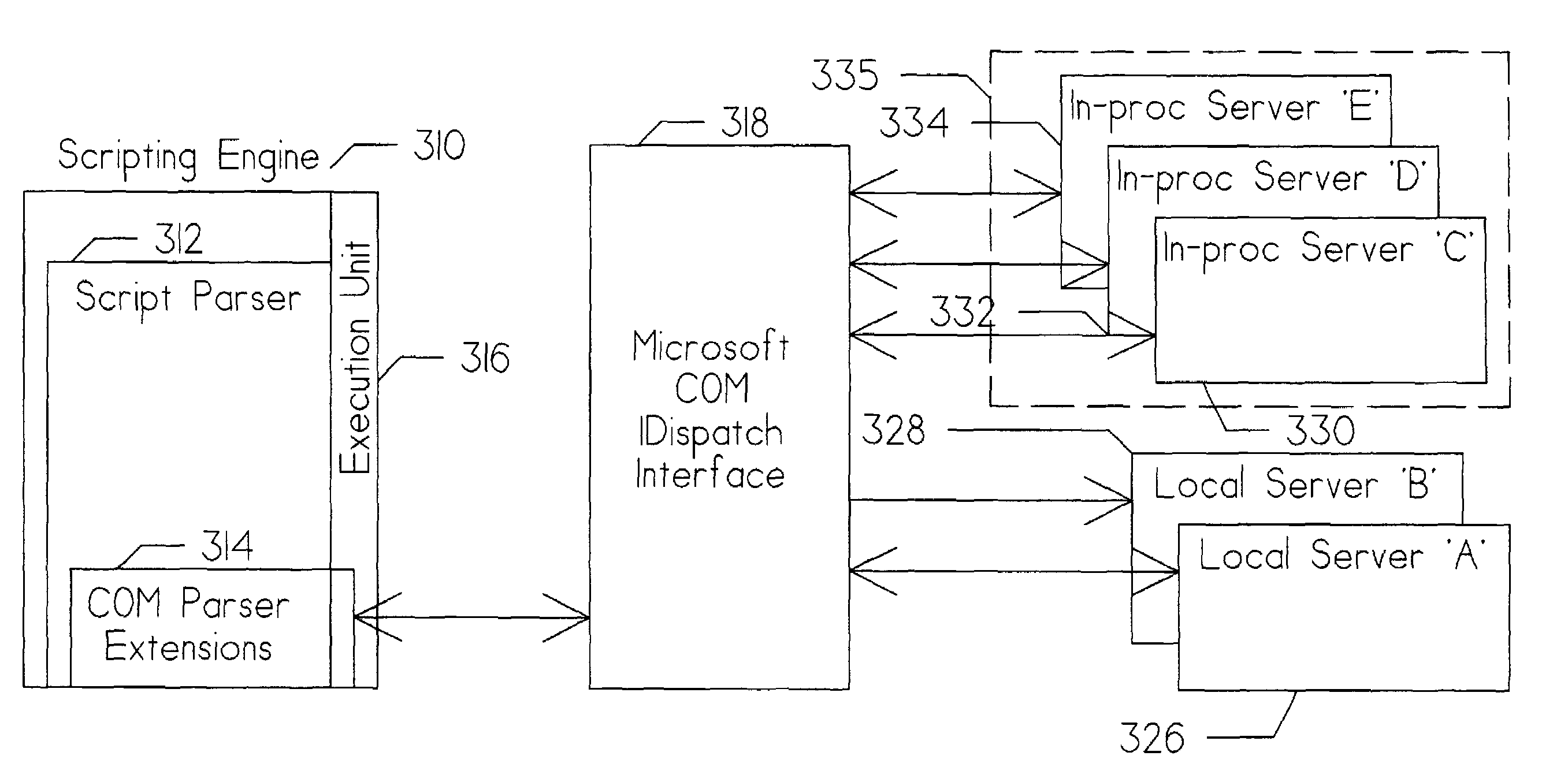
Method for protecting the program environment of a microsoft component object model (COM) client
ActiveUS7363377B1Effective isolationMinimize the numberSpecific access rightsComputer security arrangementsComponent Object ModelVisual Basic
An apparatus for and method of creating a standardized interface between Microsoft Component Object Model environment and a non-compatible legacy environment. The technique is equally effective for both object oriented and non-object oriented scripting protocols. The interface is scripted in the native legacy command language thereby freeing the interface developer from the need to create script in both the legacy command language and a Microsoft COM compatible language, such as Visual Basic. A determination is made upon an attempt to instantiate a COM server whether the server is local or in-process. If in-process and registered, the server is instantiated within a surrogate server to isolate the calling client from potential corruption of its memory space or copying of its sensitive data by the registered in-process server. This apparatus and method operates transparently to users and administrators, such that the client memory space and sensitive data is protected without requiring special COM server registration.
Owner:JOHNSON CHARLES A
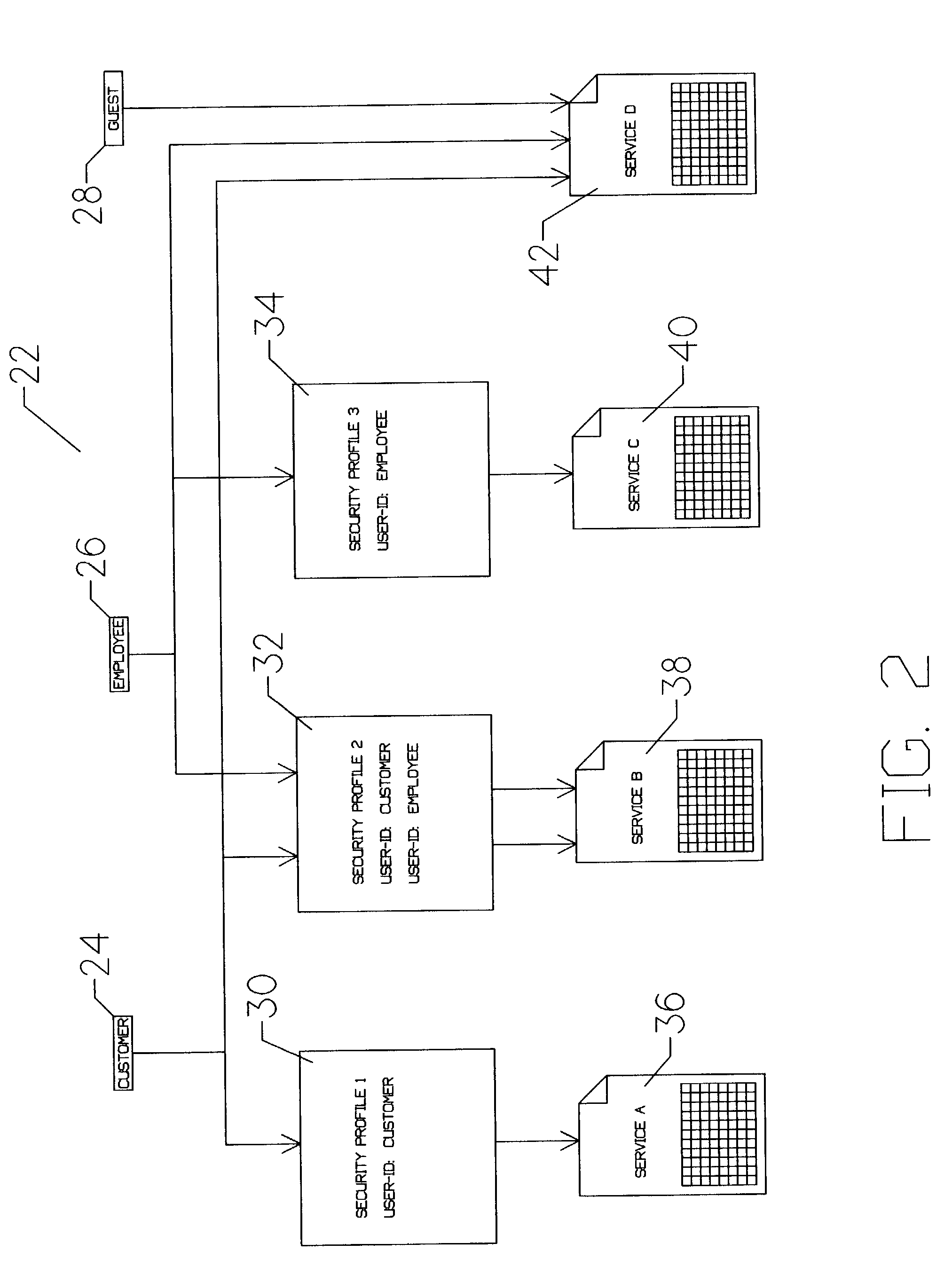
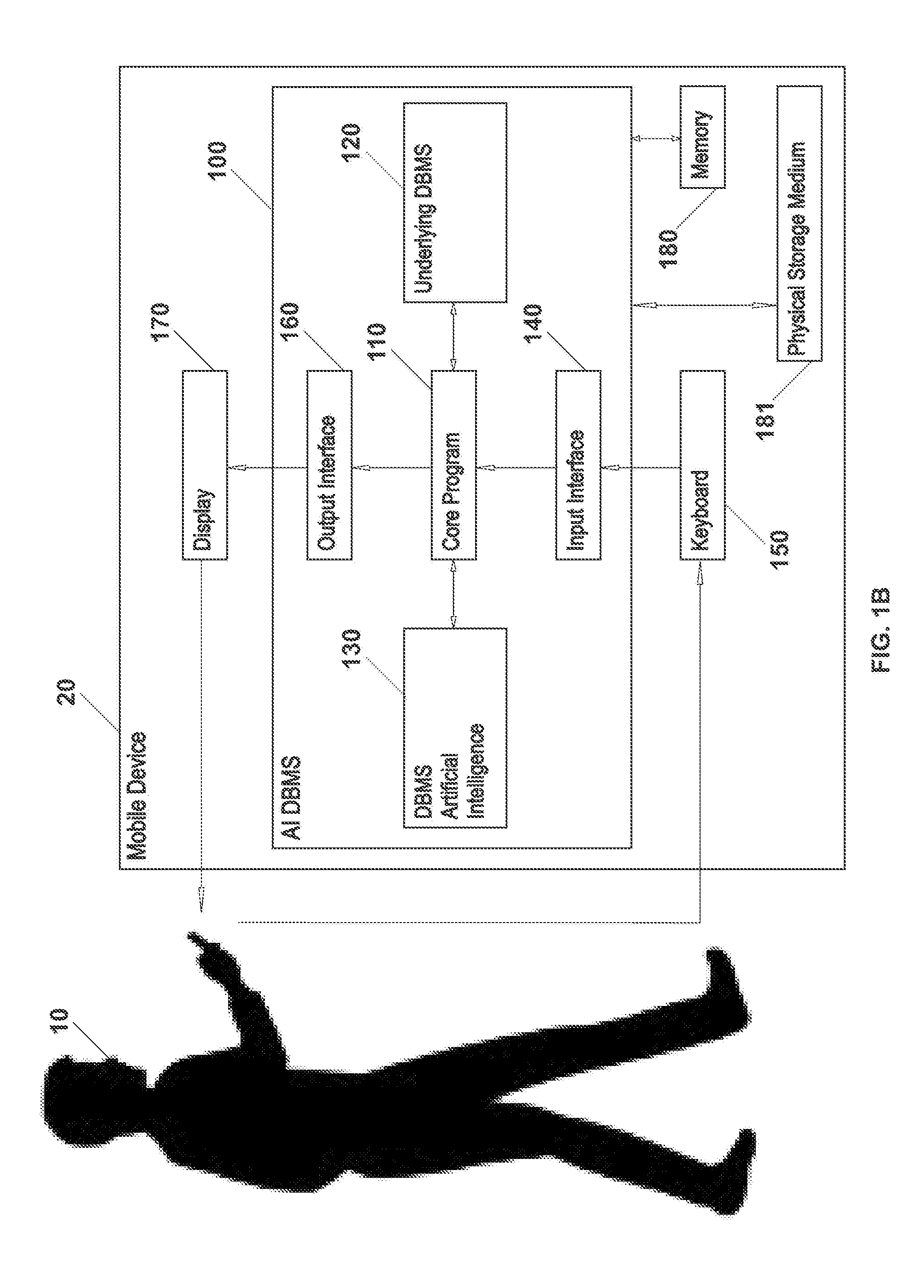
Systems and methods of using an artificially intelligent database management system and interfaces for mobile, embedded, and other computing devices
The current disclosure generally relates to database management systems (DBMSs) and may be generally directed to methods and systems of using artificial intelligence (i.e. machine learning and / or anticipation functionalities, etc.) to learn a user's use of a DBMS, store this “knowledge” in a knowledgebase, and anticipate the user's future operating intentions. The current disclosure may also be generally directed to associative methods and systems of constructing DBMS commands. The current disclosure may also be generally directed to methods and systems of using a simplified DBMS command language (SDCL) for associative DBMS command construction. The current disclosure may also be generally directed to artificially intelligent methods and systems for associative DBMS command construction. The current disclosure may also be generally directed to methods and systems for associative DBMS command construction through voice input. Other methods, systems, features, elements and / or their embodiments are also disclosed.
Owner:COSIC JASMIN
Systems and methods of using an artificially intelligent database management system and interfaces for mobile, embedded, and other computing devices
ActiveUS20160246850A1Relational databasesSpeech recognitionCommand languageRelational database management system
The current disclosure generally relates to database management systems (DBMSs) and may be generally directed to methods and systems of using artificial intelligence (i.e. machine learning and / or anticipation functionalities, etc.) to learn a user's use of a DBMS, store this “knowledge” in a knowledgebase, and anticipate the user's future operating intentions. The current disclosure may also be generally directed to associative methods and systems of constructing DBMS commands. The current disclosure may also be generally directed to methods and systems of using a simplified DBMS command language (SDCL) for associative DBMS command construction. The current disclosure may also be generally directed to arfificially intelligent methods and systems for associative DBMS command construction. The current disclosure may also be generally directed to methods and systems for associative DBMS command construction through voice input. Other methods, systems, features, elements and / or their embodiments are also disclosed.
Owner:COSIC JASMIN
Systems and methods of using an artificially intelligent database management system and interfaces for mobile, embedded, and other computing devices
The current disclosure generally relates to database management systems (DBMSs) and may be generally directed to methods and systems of using artificial intelligence (i.e. machine learning and / or anticipation functionalities, etc.) to learn a user's use of a DBMS, store this “knowledge” in a knowledgebase, and anticipate the user's future operating intentions. The current disclosure may also be generally directed to associative methods and systems of constructing DBMS commands. The current disclosure may also be generally directed to methods and systems of using a simplified DBMS command language (SDCL) for associative DBMS command construction. The current disclosure may also be generally directed to artificially intelligent methods and systems for associative DBMS command construction. The current disclosure may also be generally directed to methods and systems for associative DBMS command construction through voice input. Other methods, systems, features, elements and / or their embodiments are also disclosed.
Owner:COSIC JASMIN
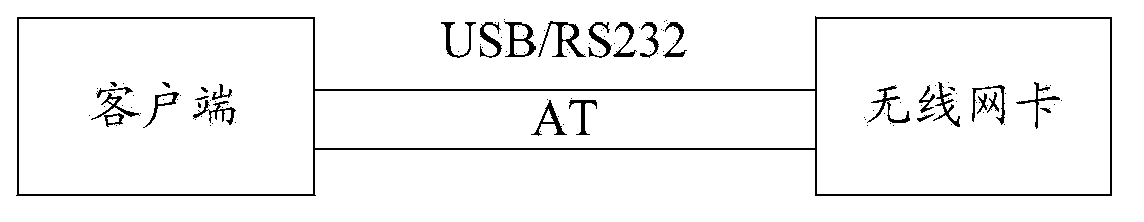
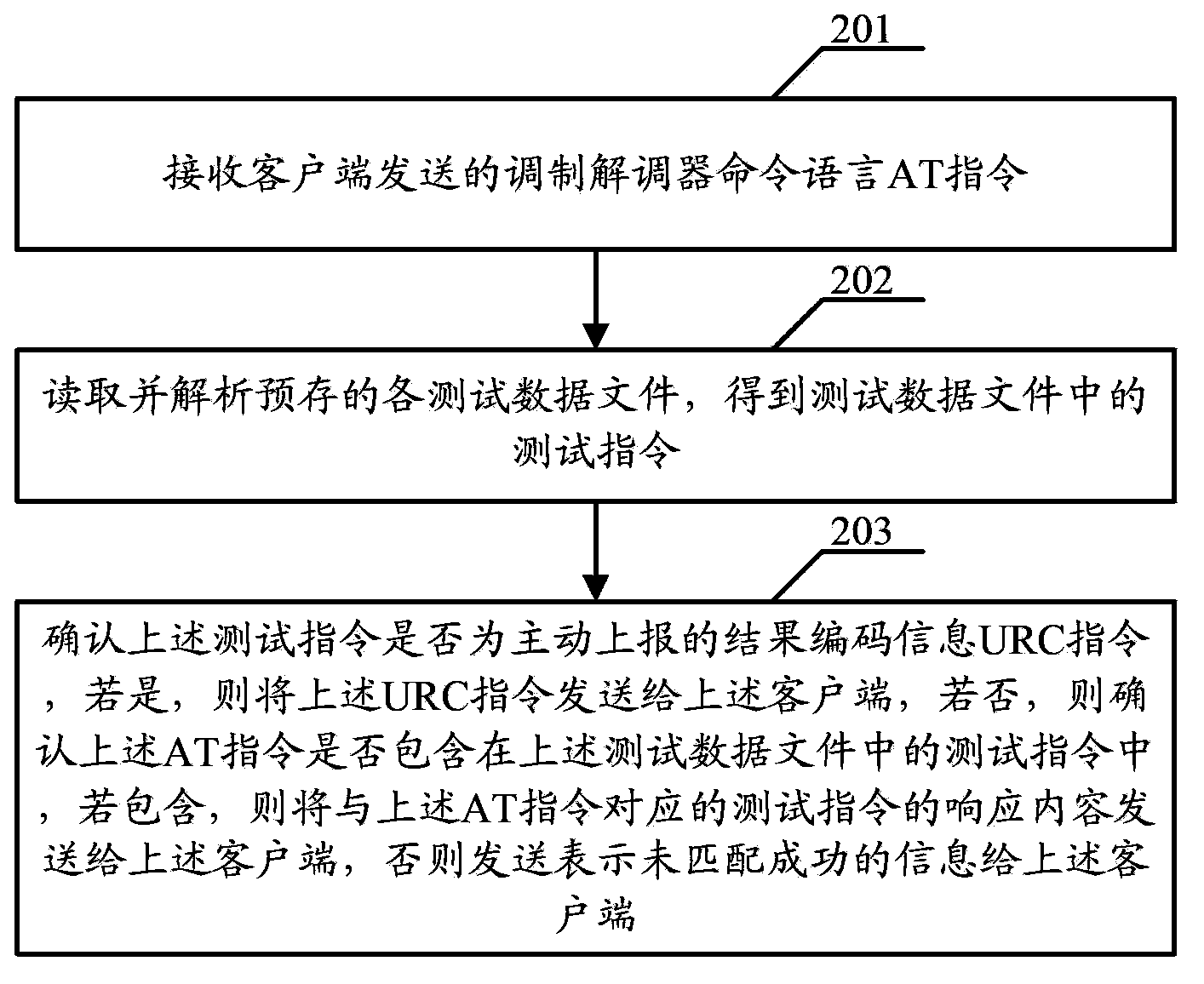
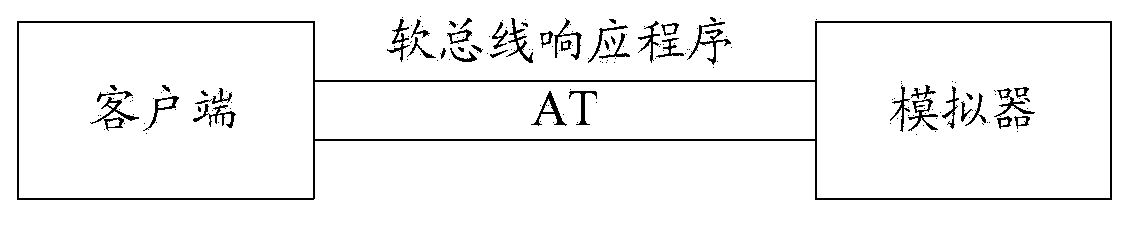
Simulation serial port testing method and device
The embodiment of the invention discloses a simulation serial port testing method and device. The simulation serial port testing method includes the steps of receiving a modulator-demodulator command language AT command sent by a client terminal, reading and analyzing various presorted testing data files, obtaining testing commands in the testing data files, determining whether the testing commands are initiatively-reported result coded message URC commands or not, sending the URC commands to the client terminal if the testing commands are the initiatively-reported result coded message URC commands, determining whether the AT command is contained in the testing commands in the testing data files or not if the testing commands are not the initiatively-reported result coded message URC commands, sending response contents of the testing commands corresponding to the AT command to the client terminal if the AT command is contained in the testing commands in the testing data files, and sending information which is not successfully matched to the client terminal if the AT command is not contained in the testing commands in the testing data files. According to the scheme, debugging of the development process can be timely obtained through the development and the debugging of the client terminal, and the integrated development schedule is quickened.
Owner:SPREADTRUM COMM (SHANGHAI) CO LTD
Facilitating remote access of devices in a secure environment
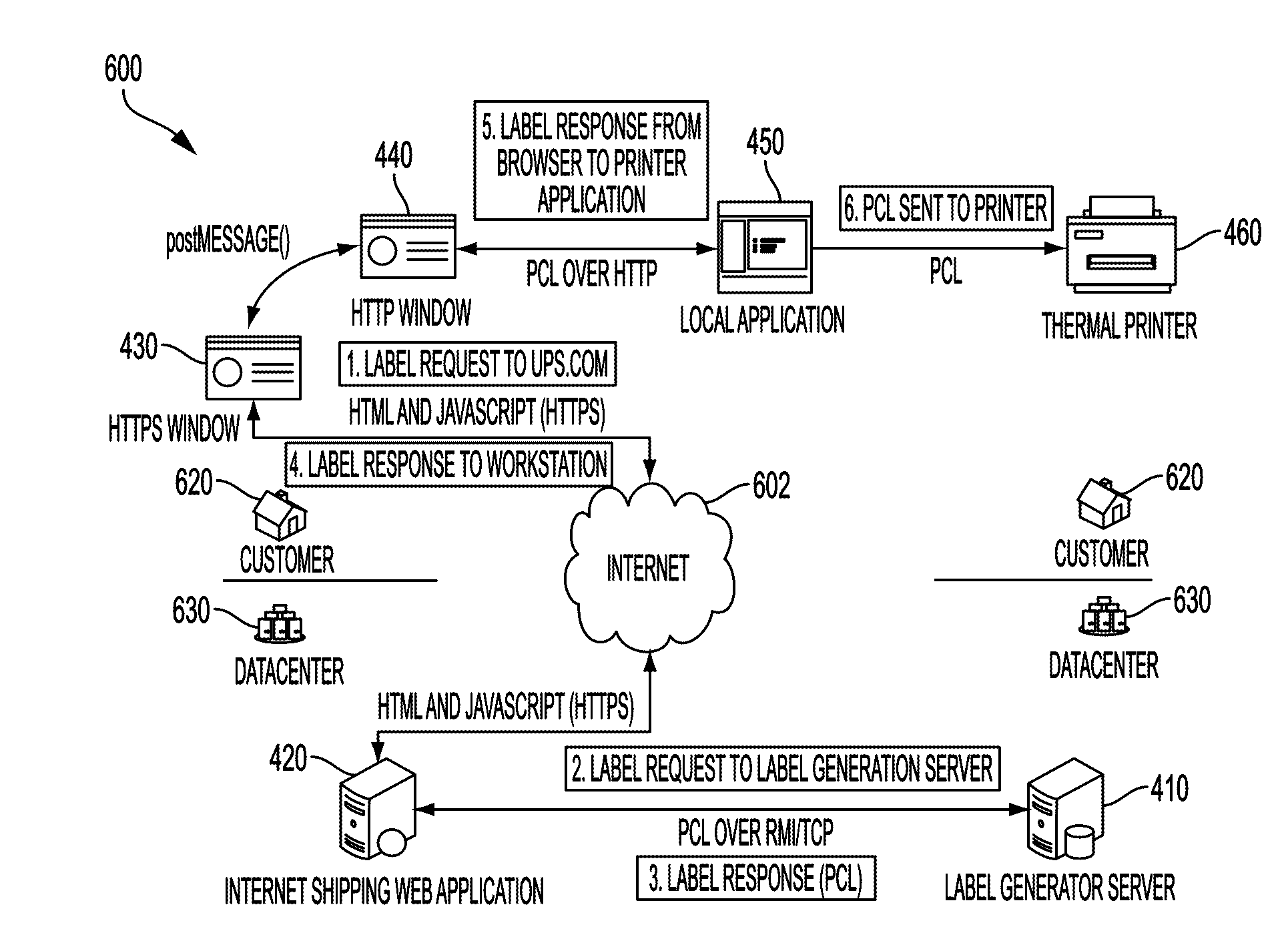
ActiveUS20170063924A1Easy remote accessImprove network securityData processing applicationsVisual presentation using printersCommand languageProtocol for Carrying Authentication for Network Access
Embodiments of the present invention provide methods, systems, apparatuses, and computer program products for facilitating remote access of customer computing entities in a secure environment. In one embodiment a method is provided comprising providing, by a first user computer entity and through a first window displaying a first webpage in a browser, a request for instruction for a particular device, the instructions being in a native command language of the particular device, wherein the request is provided over a first secure encrypted connection using a first protocol, receiving, the instructions over the first secure encrypted connection using the first protocol, initiating a bridge webpage, the bridge webpage being initiated in a second window in the browser, wherein the first window and the second window are in communication, and wherein the first page belongs to a first domain different from a second domain to which the second page belongs.
Owner:UNITED PARCEL SERVICE OF AMERICAN INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com