Patents
Literature
213 results about "Identification key" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
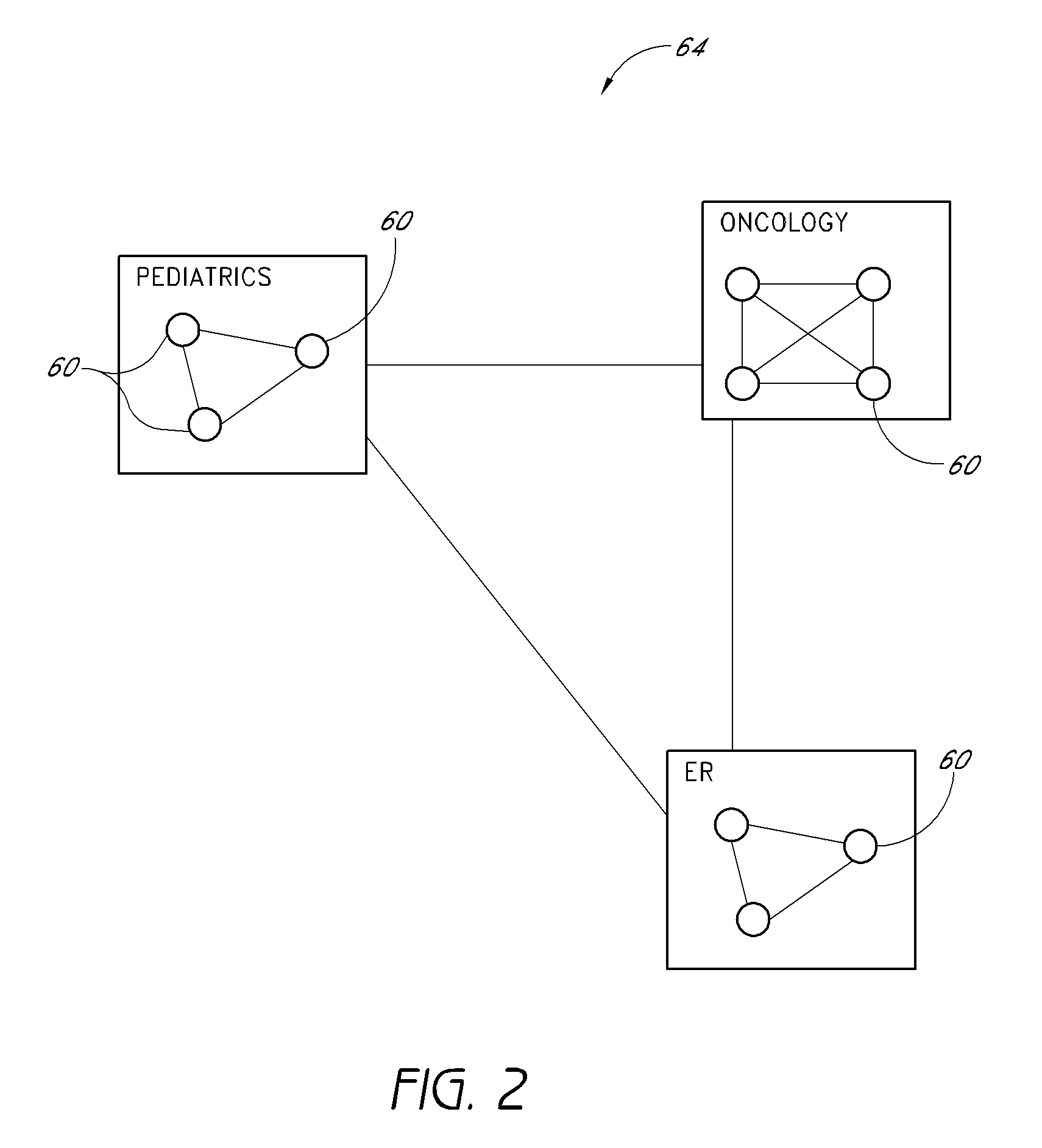
In biology, an identification key is a printed or computer-aided device that aids the identification of biological entities, such as plants, animals, fossils, microorganisms, and pollen grains. Identification keys are also used in many other scientific and technical fields to identify various kinds of entities, such as diseases, soil types, minerals, or archaeological and anthropological artifacts.
Cartridge, indentification information tag and image forming device
InactiveUS20050196180A1Low costEasy to manufactureElectrographic process apparatusIdentification keyImage formation
A cartridge of the invention is a cartridge detachably attached to an image forming device, and an identification information tag that stores identification information for distinguishing the cartridge from other cartridge therein is attached, and an identification key that mechanically engages with the image forming device and distinguishes whether or not the cartridge can be attached is provided on the identification information tag. The invention also relates to the identification information tag that is attached to the cartridge detachably attached to the image informing device and stores identification information for distinguishing the cartridge from other cartridge therein. The above-mentioned identification information tag is characterized by providing the identification key that mechanically engages with the image forming device and distinguishes whether or not the cartridge can be attached. The invention also relates to the image forming device to which the cartridge is attached. When the cartridge is attached the cartridge attachment portion, the image forming device mechanically identifies whether or not the cartridge can be attached by using the identification key provided on the identification information tag attached to the cartridge.
Owner:FUJIFILM BUSINESS INNOVATION CORP
Waste sorting system utilizing removable liners
ActiveUS7660724B2Easy to classifyEncourages and facilitates complianceDispensing apparatusCharacter and pattern recognitionGraphicsIdentification key
A liner for use in a waste sorting and disposal system is configured for placement in a container is provided. The liner includes an internal space and an opening that provides access to that internal space. In some embodiments, the liner may also include a machine-readable identification key that is configured to identify a type of waste that the liner may receive. In some embodiments, the machine-readable key is optical, color-coded, alphanumeric or graphical. The liner can include one or more closure members to allow a user to securely seal the liner when it is removed from the container. In some embodiments, the liner can include a flange, lip, hook or other protrusion to secure its position relative to a container.
Owner:CAREFUSION 303 INC
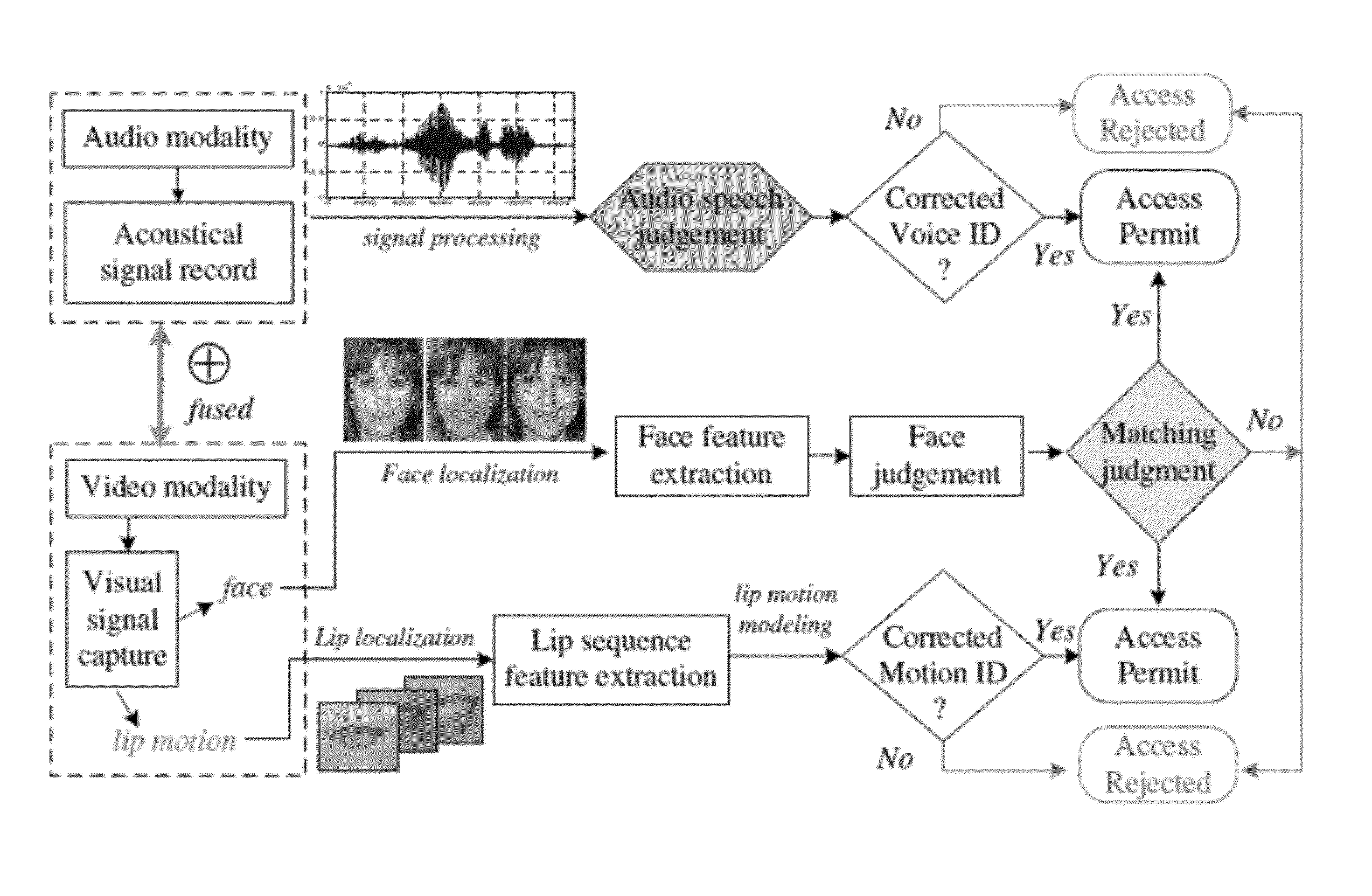
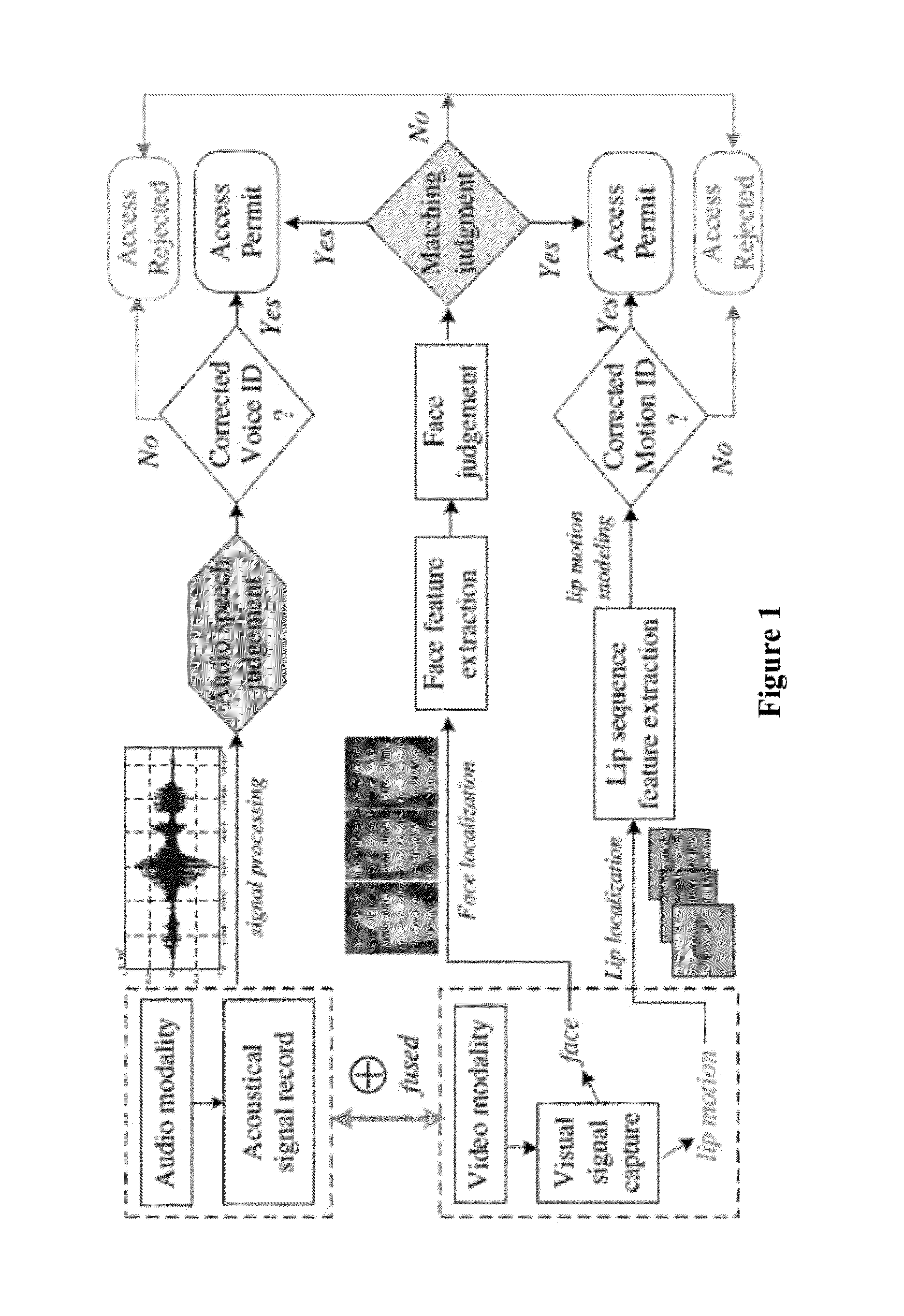
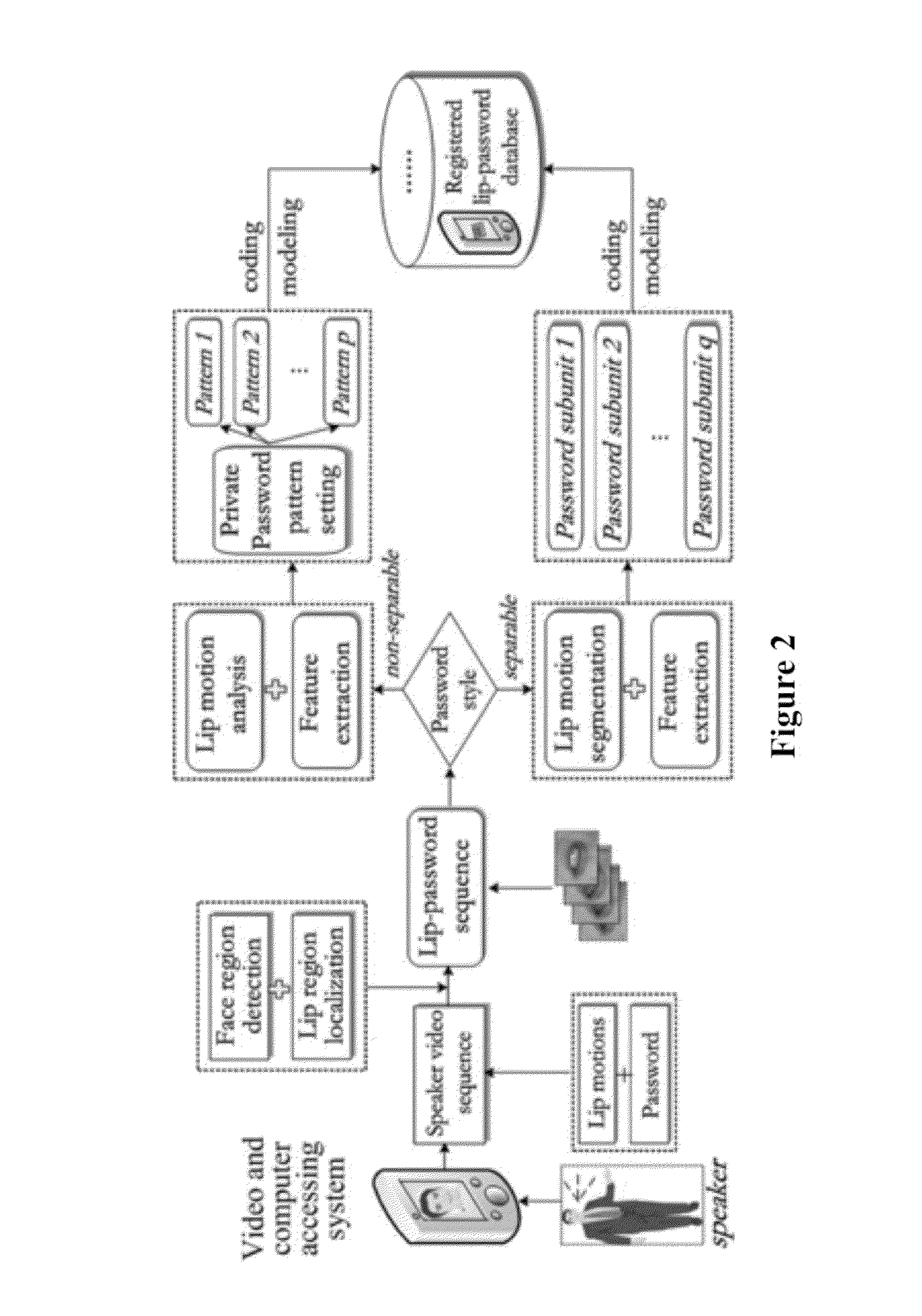
Lip-password Based Speaker Verification System
ActiveUS20130226587A1Easy to implementEasy to useCharacter and pattern recognitionSpeech recognitionIdentification keyPassword
A lip-based speaker verification system for identifying a speaker using a modality of lip motions; wherein an identification key of the speaker comprising one or more passwords; wherein the one or more passwords are embedded into lip motions of the speaker; wherein the speaker is verified by underlying dynamic characteristics of the lip motions; and wherein the speaker is required to match the one or more passwords embedded in the lip motions with registered information in a database. That is, in the case where the target speaker saying the wrong password or even in the case where an impostor knowing and saying the correct password, the nonconformities will be detected and the authentications / accesses will be denied.
Owner:HONG KONG BAPTIST UNIV
Removable Liners for Waste Sorting System
ActiveUS20080197059A1Easy to classifyEncourages and facilitates complianceData processing applicationsSurgical furnitureInterior spaceGraphics
A liner for use in a waste sorting and disposal system is configured for placement in a container is provided. The liner includes an internal space and an opening that provides access to that internal space. In some embodiments, the liner may also include a machine-readable identification key that is configured to identify a type of waste that the liner may receive. In some embodiments, the machine-readable key is optical, color-coded, alphanumeric or graphical. The liner can include one or more closure members to allow a user to securely seal the liner when it is removed from the container. In some embodiments, the liner can include a flange, lip, hook or other protrusion to secure its position relative to a container.
Owner:CAREFUSION 303 INC
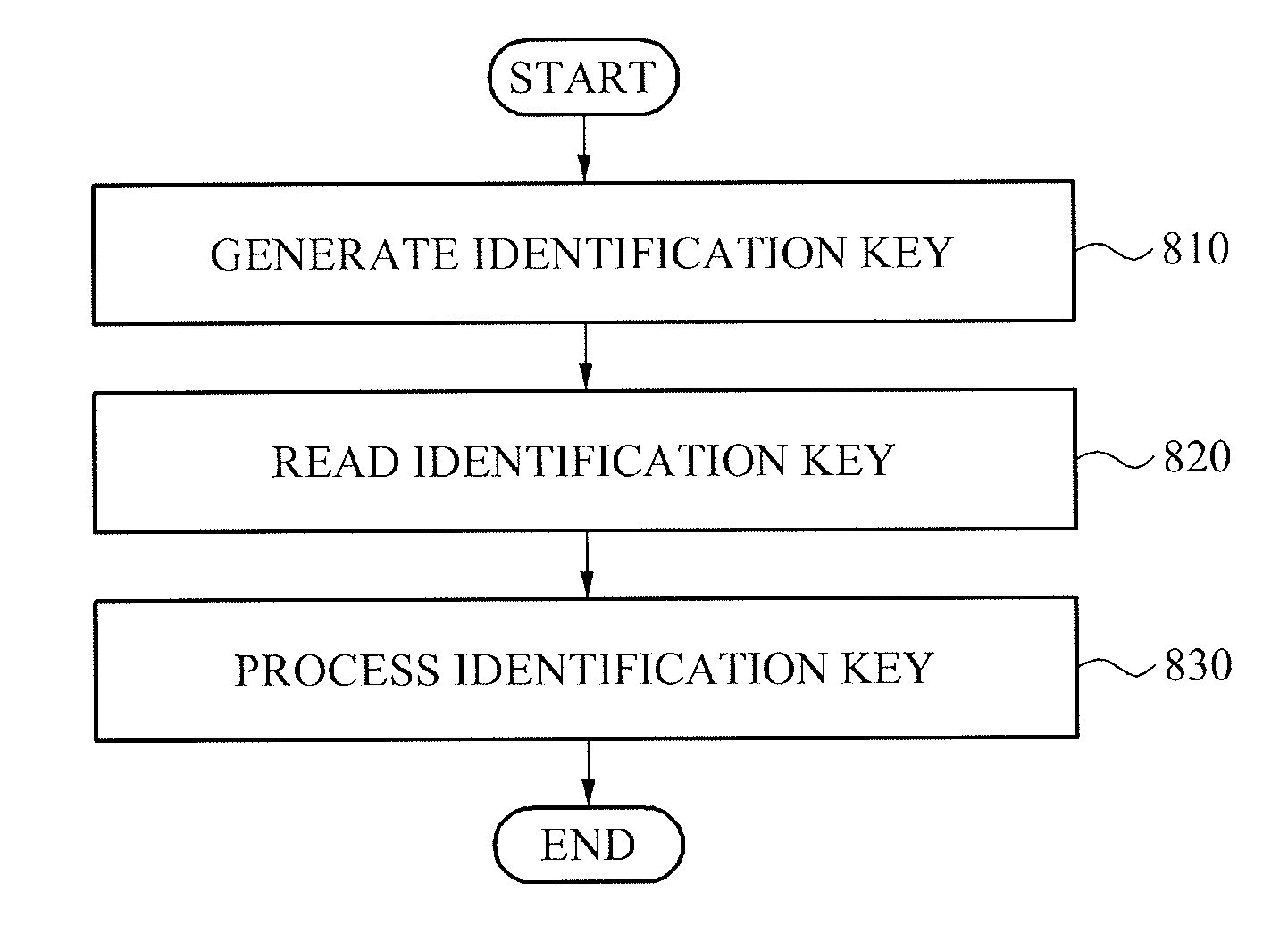
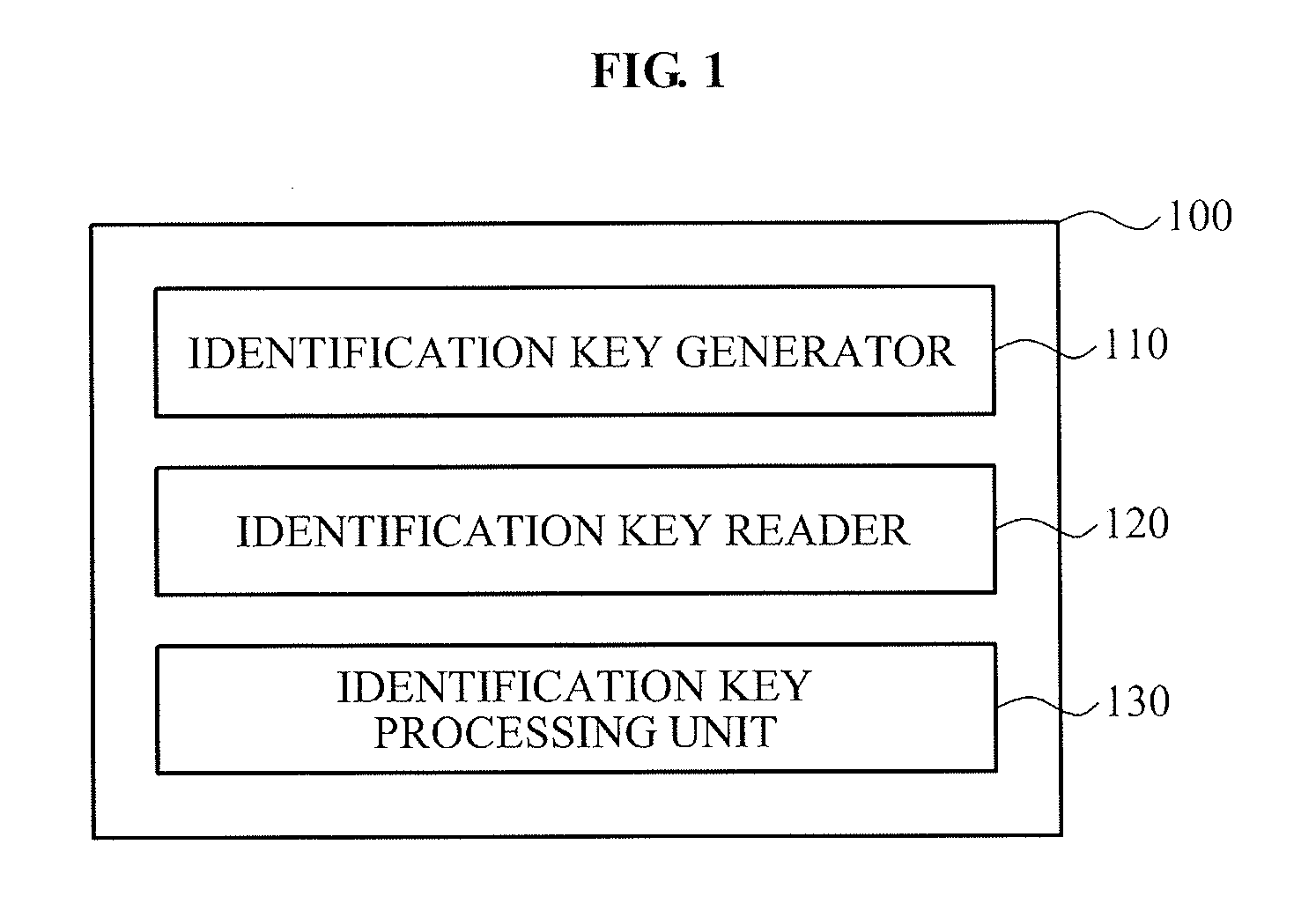
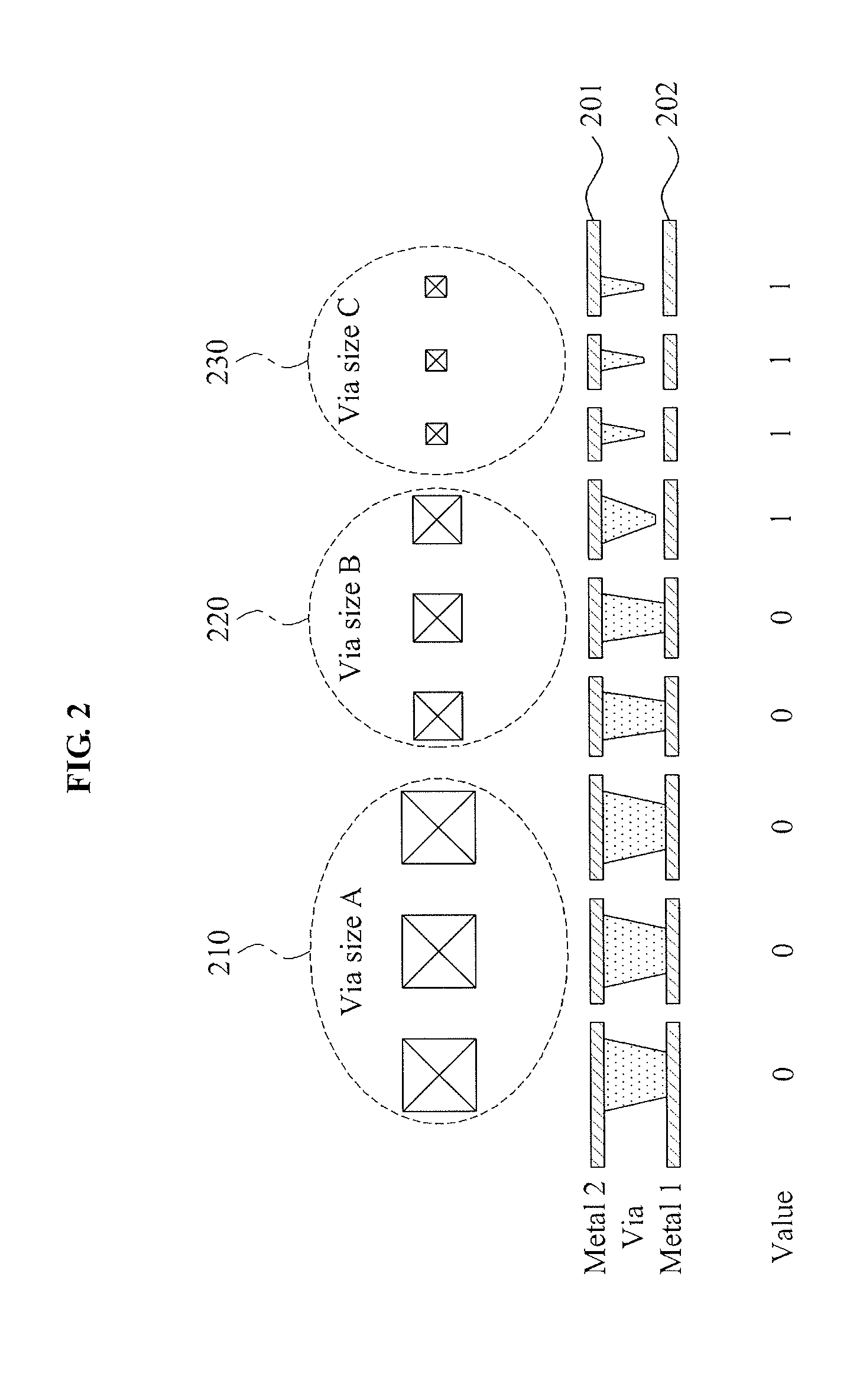
Apparatus and method for generating identification key
ActiveUS20130101114A1Improve reliabilityReduce manufacturing costDigital data processing detailsDigital data protectionElectricityIdentification key
Provided is an apparatus for generating an identification key by a probabilistic determination of a short occurring between nodes constituting a circuit, by violating a design rule provided during a semiconductor manufacturing process. The identification key generating apparatus may include an identification key generator to generate an identification key based on whether a contact or a via used to electrically connect conductive layers in a semiconductor chip shorts the conductive layers, and an identification key reader to read the identification key by reading whether the contact or the via shorts the conductive layers.
Owner:ICTK
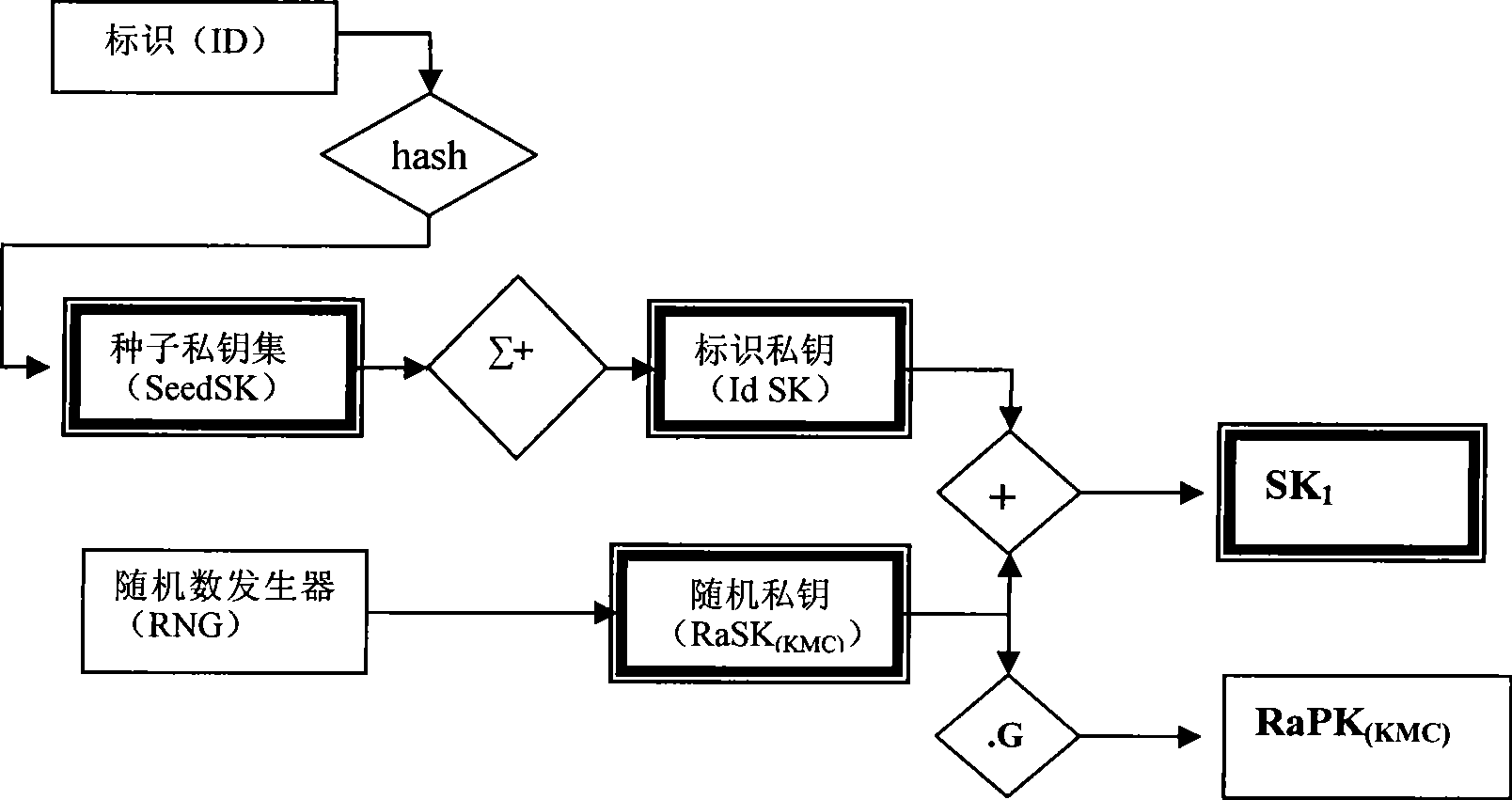
Double factor combined public key generating and authenticating method
InactiveCN101420300AMeet the needs of centralized managementImprove securityKey distribution for secure communicationPublic key for secure communicationIdentification keyLogistics management
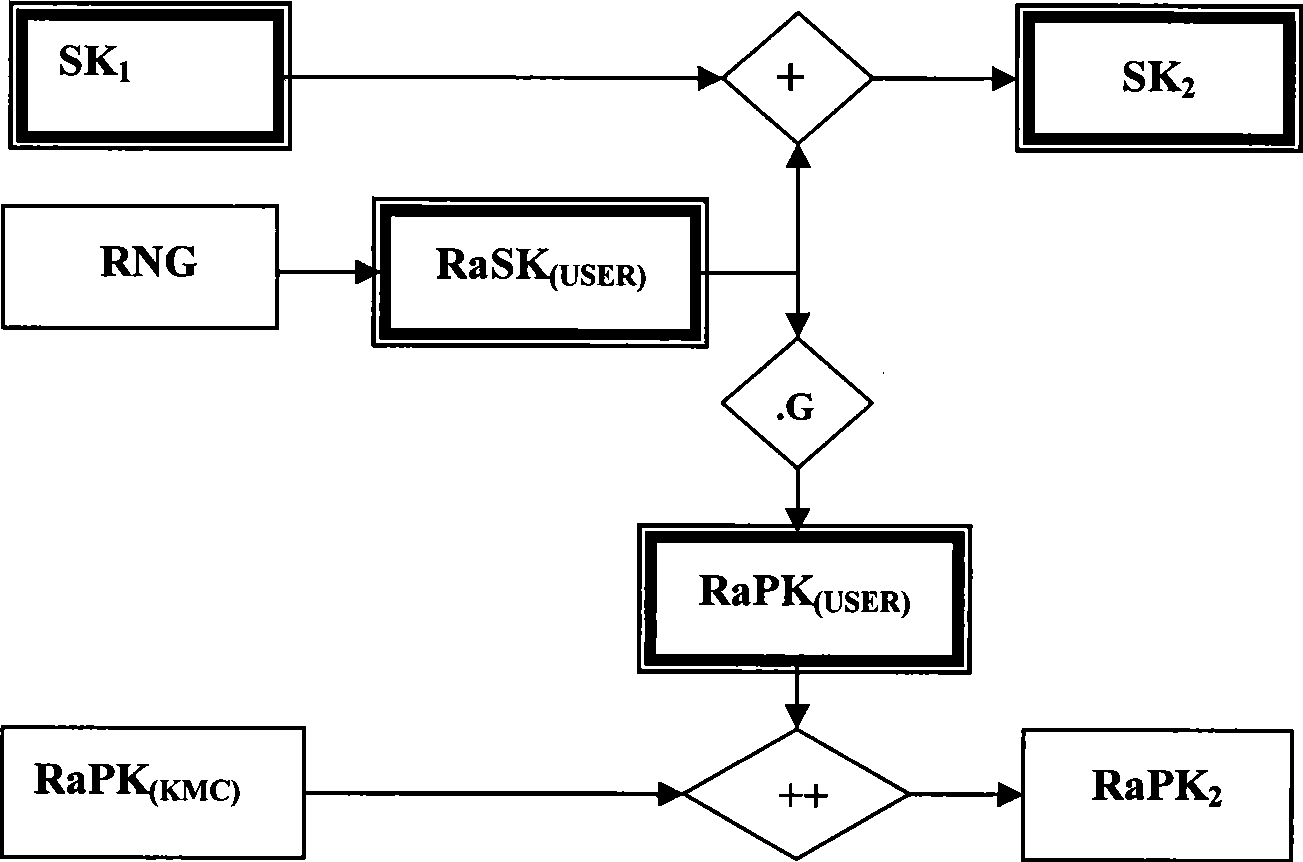
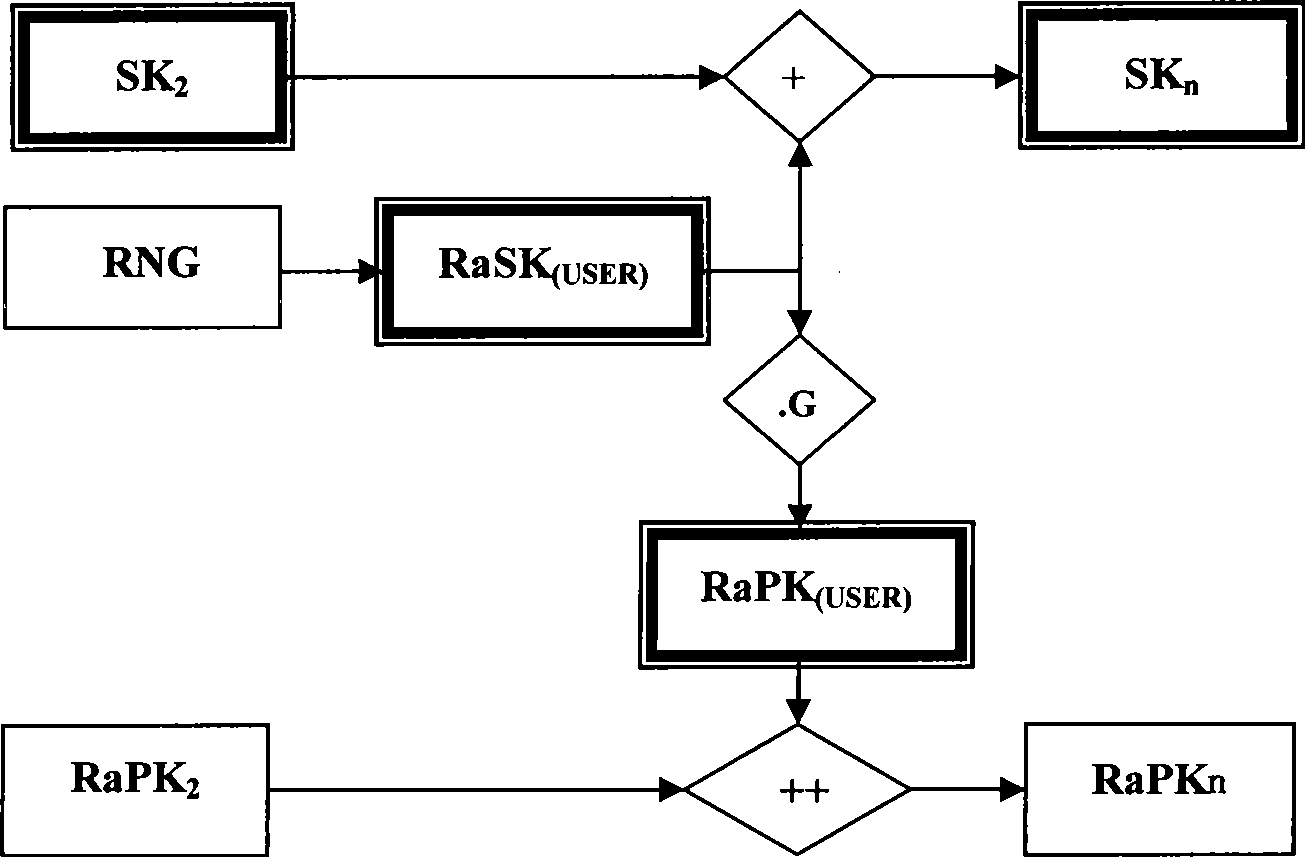
The present invention provides an identification key and random key complicated two-factor combined public key system and an authentication method. The identification keys are generated by selecting and combining seed key sets by the user identification generated sequence; the random keys are generated on the basis of one-way function principle which is also the basis of general public key ciphers. Multiple complication modes of the random key and the identification key can not only satisfy the requirement of centralized management, but also provide the proprietary right of private keys for users. An authentication system based on the key generating method has the characteristics of the identification authentication which does not need a third part certificate to prove and high randomization and privacy of general public key cipher and random private key. The present invention can be widely applied to authentication of systems with various scales, especially the authentication of public systems with enormous scale, and the applicable fields comprises reliable access, reliable load, electronic bank, reliable transaction, reliable logistics and the like.
Owner:BEIJING E HENXEN AUTHENTICATION TECH
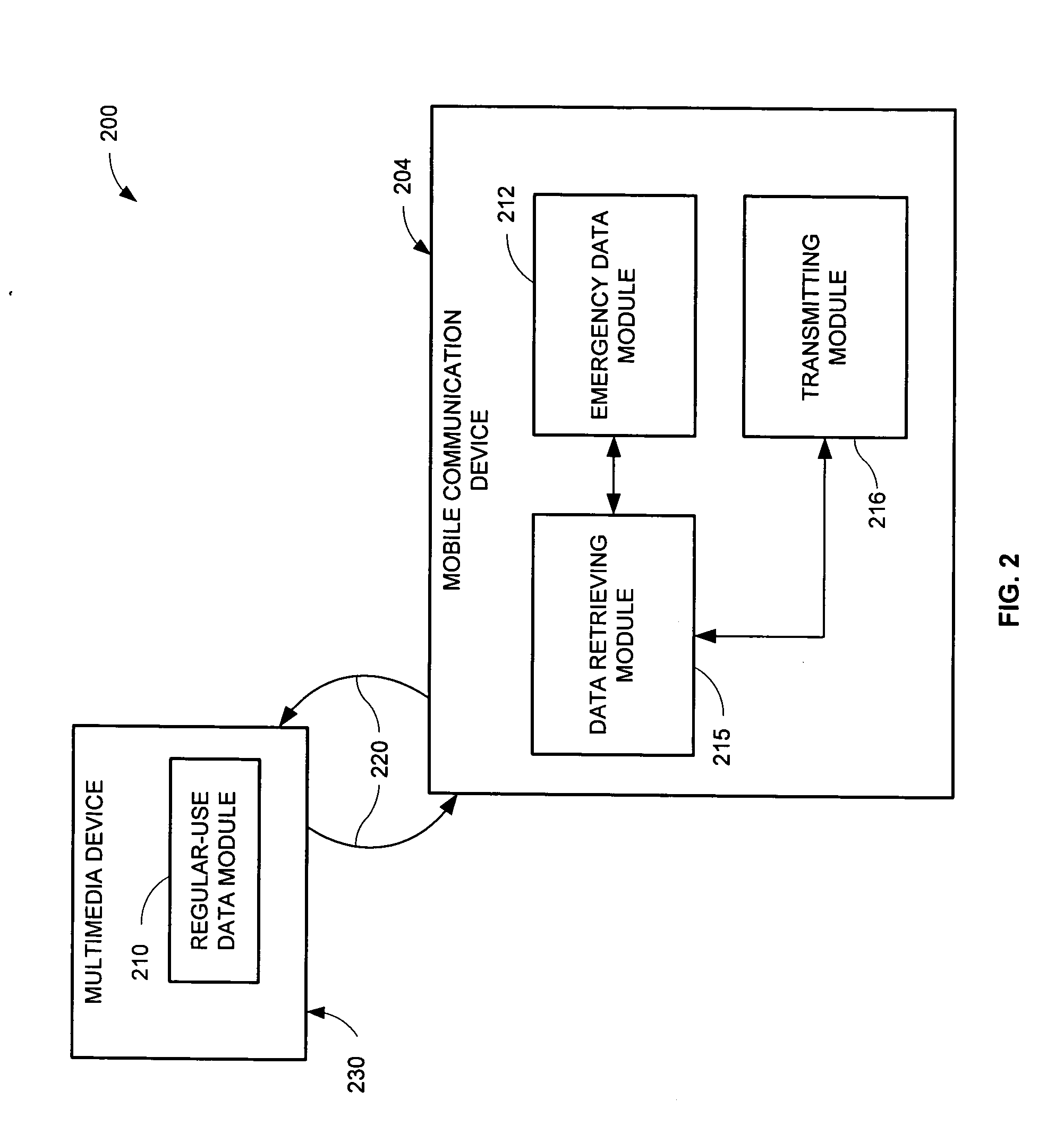
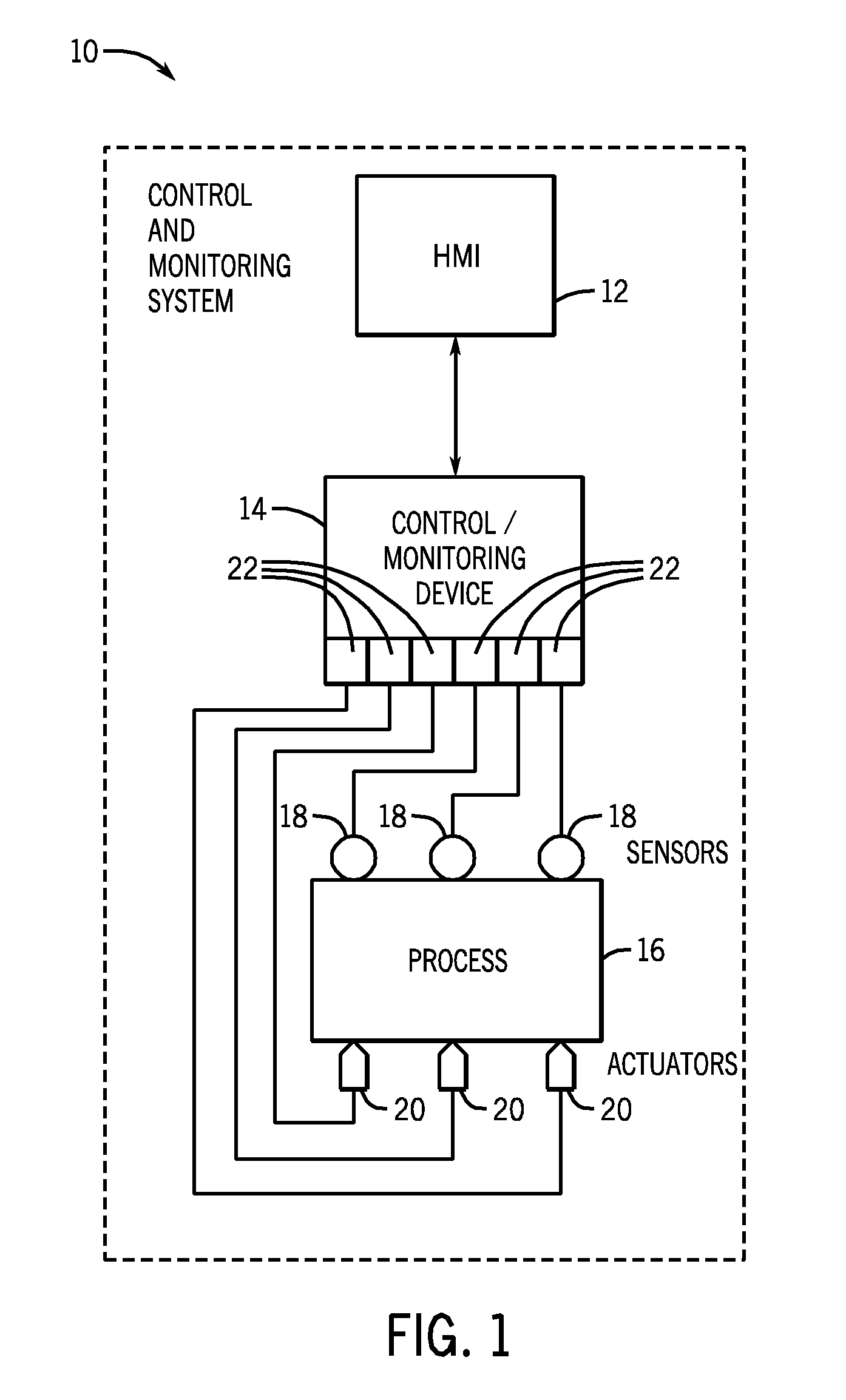
Emergency call system
InactiveUS20050090226A1Emergency connection handlingConnection managementIdentification keyTelecommunications link
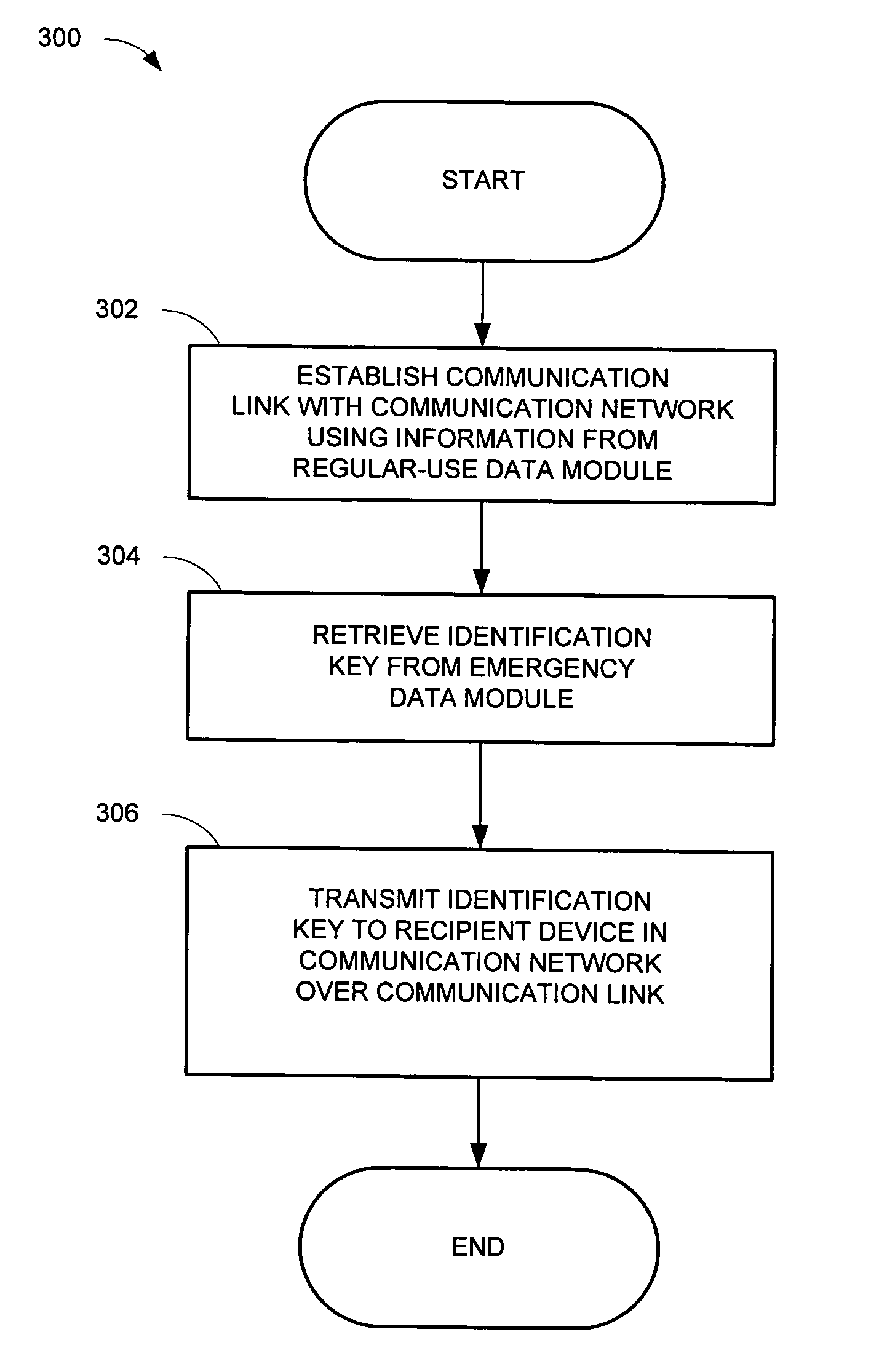
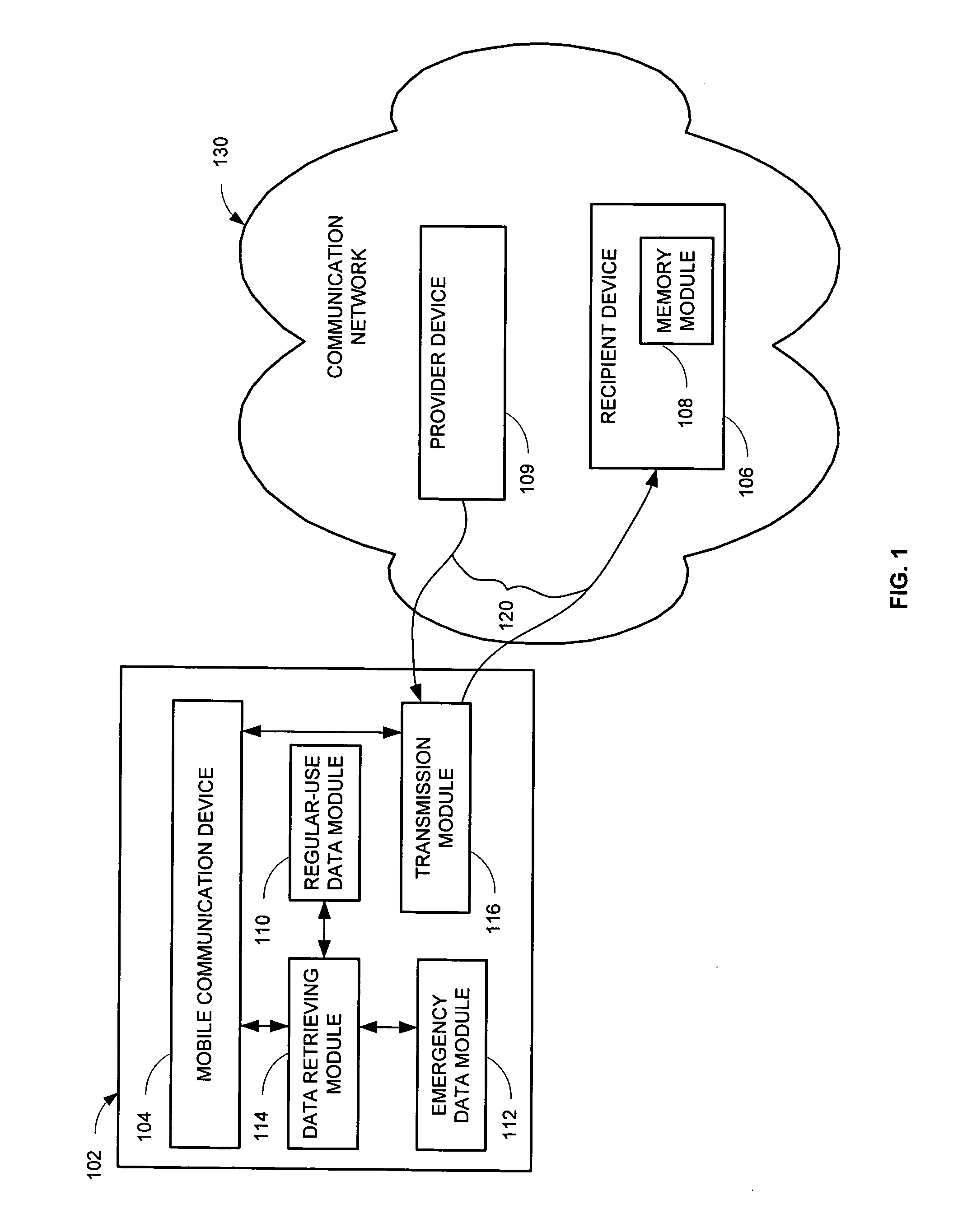
An emergency call system is presented, which when an emergency call is initiated, instantaneously retrieves and transmits an identification key using an established communication link with a communication network. Therefore, the emergency call system does not need to unregister from the established communication link and establish a new communication link in order to transmit the identification key. The system includes an emergency call device, which includes a mobile communication device for communicating with the communication network, a regular-use data module storing non-emergency use information, an emergency data module storing emergency use information, such as an identification key, a data retrieving module for retrieving information from the emergency and / or regular-use data modules. When the emergency call device is implemented in a vehicle, the data retrieving module for the regular-use and / or emergency data modules may be in communication with a multimedia device via a local communication network.
Owner:HARMAN BECKER AUTOMOTIVE SYST
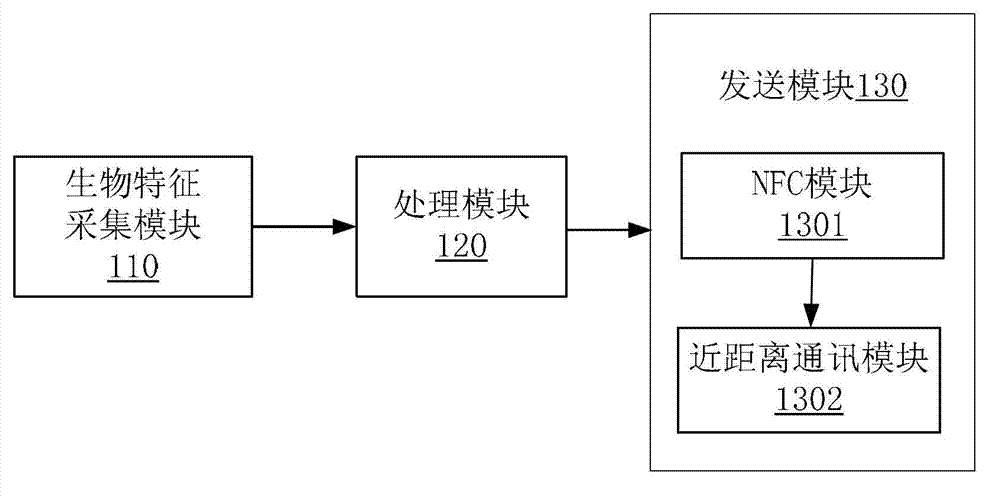
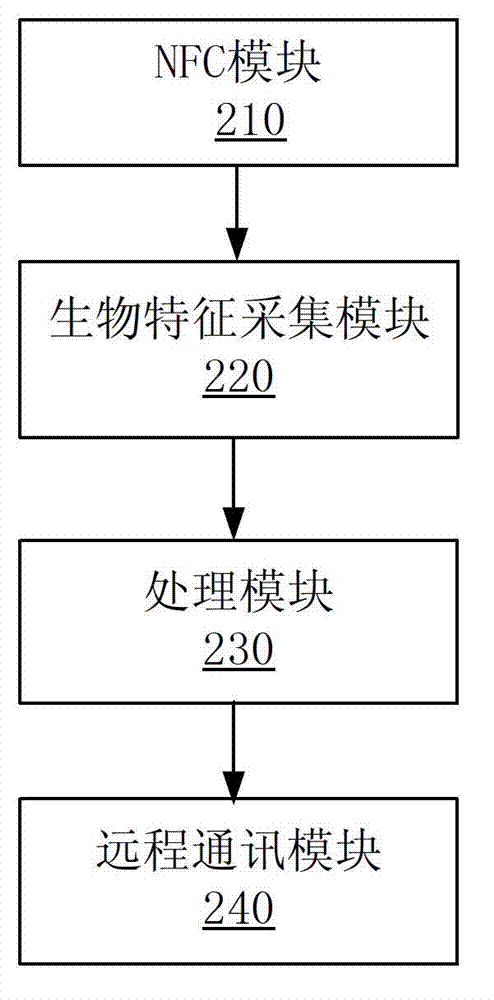
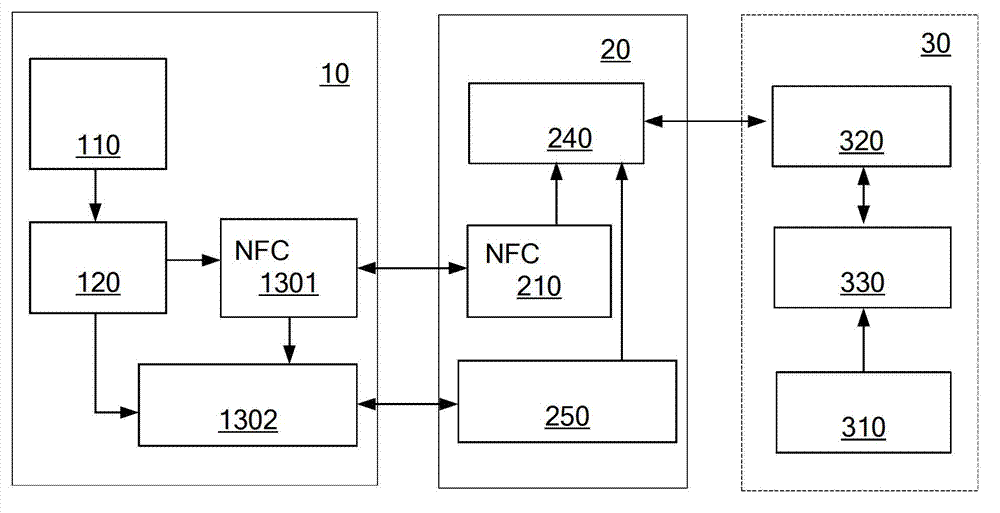
Mobile payment terminal, system and payment method thereof based on NFC (Near Field Communication)
The invention discloses a terminal, a system and a payment method thereof based on NFC (Near Field Communication) mobile payment. The method comprises the following steps: a mobile terminal or a transaction terminal acquires biological characteristic information of a user to generate an identification key of biological characteristics of the user; the transaction terminal submits transaction information, account and account number of the user and the identification key of biological characteristics of the user to a pavement server terminal to confirm the effectiveness of the transaction. According to the embodiment of the invention, the biological characteristics of the user are used as the unique information for account key identification, so that the payment safety is improved.
Owner:NUBIA TECHNOLOGY CO LTD
Computerized database system and method
InactiveUS6725218B1Data processing applicationsDatabase distribution/replicationIdentification keyComputerized databases
A computerized database system and method are disclosed. In one aspect of the invention, database records are associated with respective unique identification keys. Each key specifies values that specify both a logical location and a physical server assigned to that location where the respective record associated with that key is located.
Owner:CISCO TECH INC
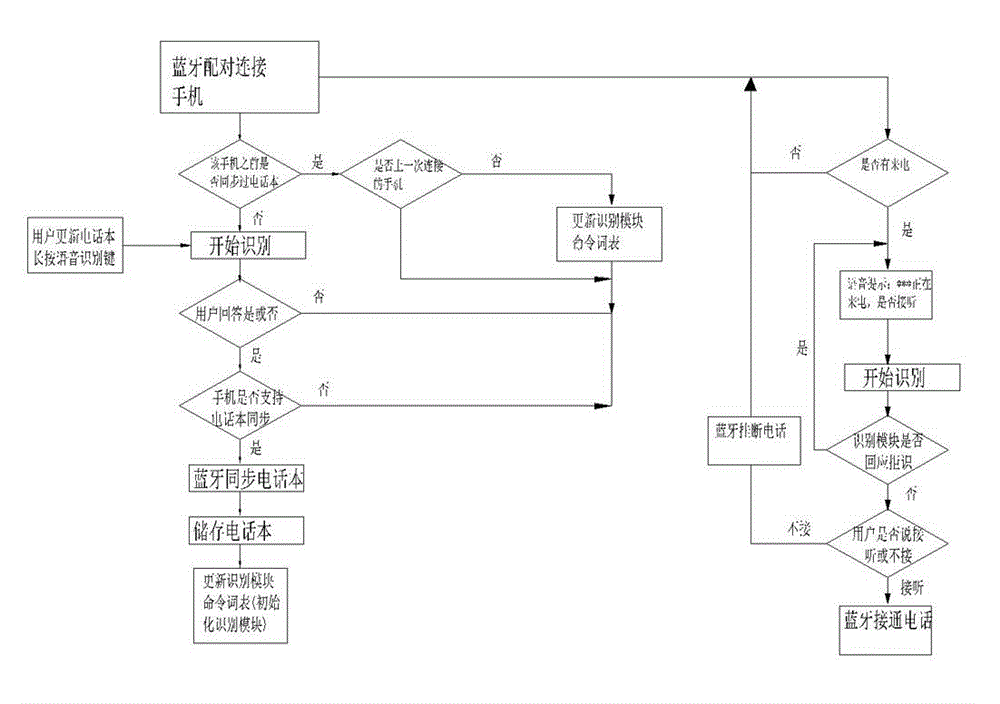
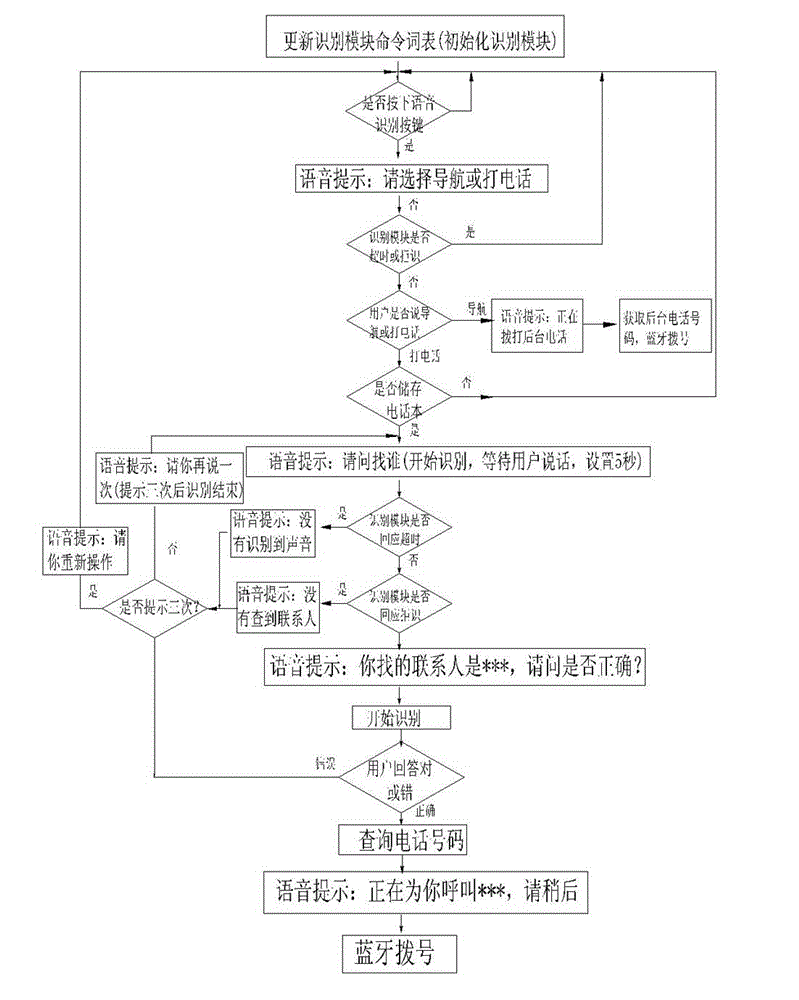
Dialing intelligent sound control method for vehicle
InactiveCN102868427AImprove securityEasy to operateCalling susbscriber number recording/indicationNear-field systems using receiversIdentification keyAddress book
The invention discloses a dialing intelligent sound control method for a vehicle. The method is characterized by comprising the following steps of: synchronizing data of a mobile phone address book and a vehicle host in a Bluetooth pairing mode, and updating a command word list of a voice identification module; during dialing, starting a voice identification key, performing voice identification on a navigation instruction or a dialing instruction of a user by using the voice identification module; under the state that the user dials, automatically identifying the name of a called user by using the voice identification module, searching a stored address book through the vehicle host, calling a customer telephone number to be dialed, and performing Bluetooth dialing; and when a call comes, determining an instruction for indicating whether the user answers the phone by the voice identification module, and performing Bluetooth put-through or Bluetooth hang-up. The method is easy and convenient to operate and has a good popularization value.
Owner:GUANGDONG ECAR TELEMATICS SERVICE
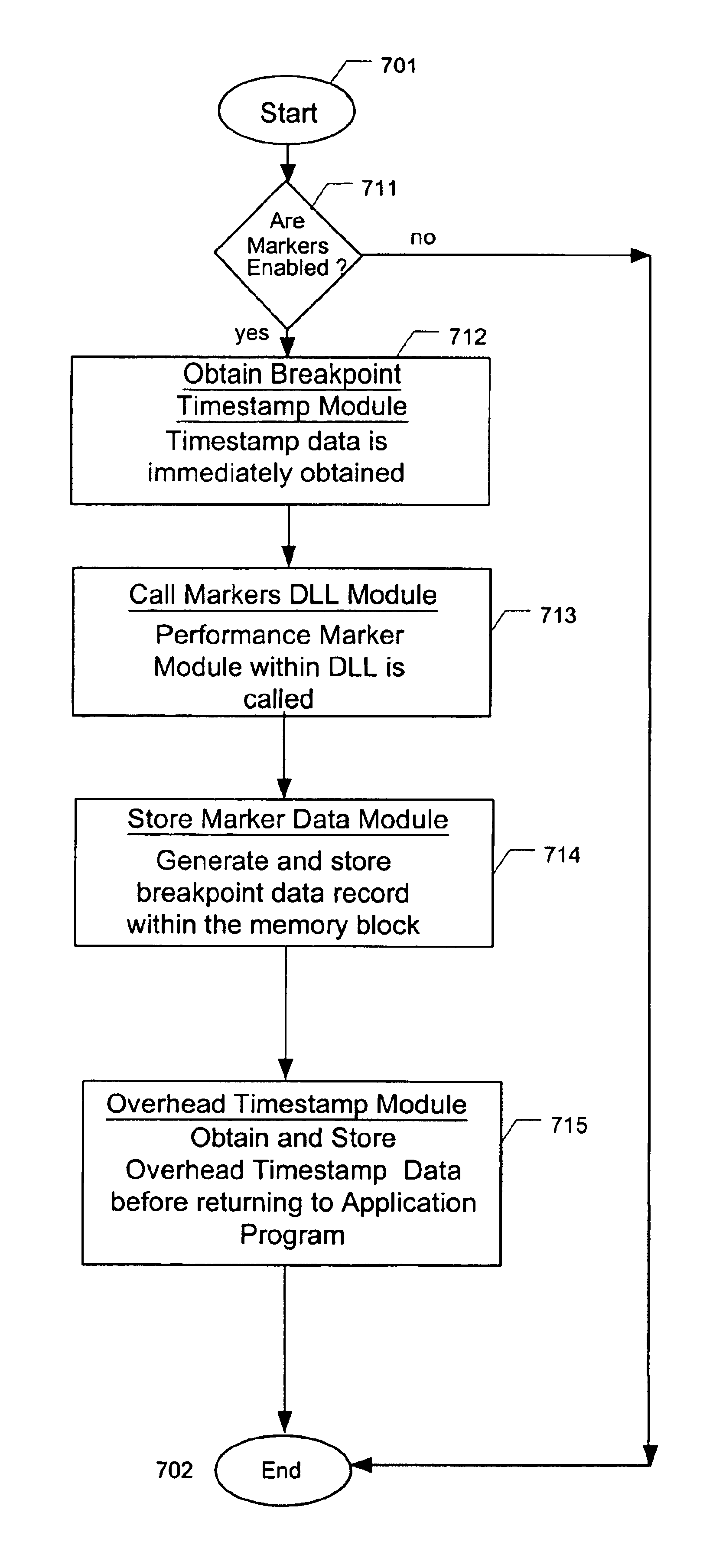
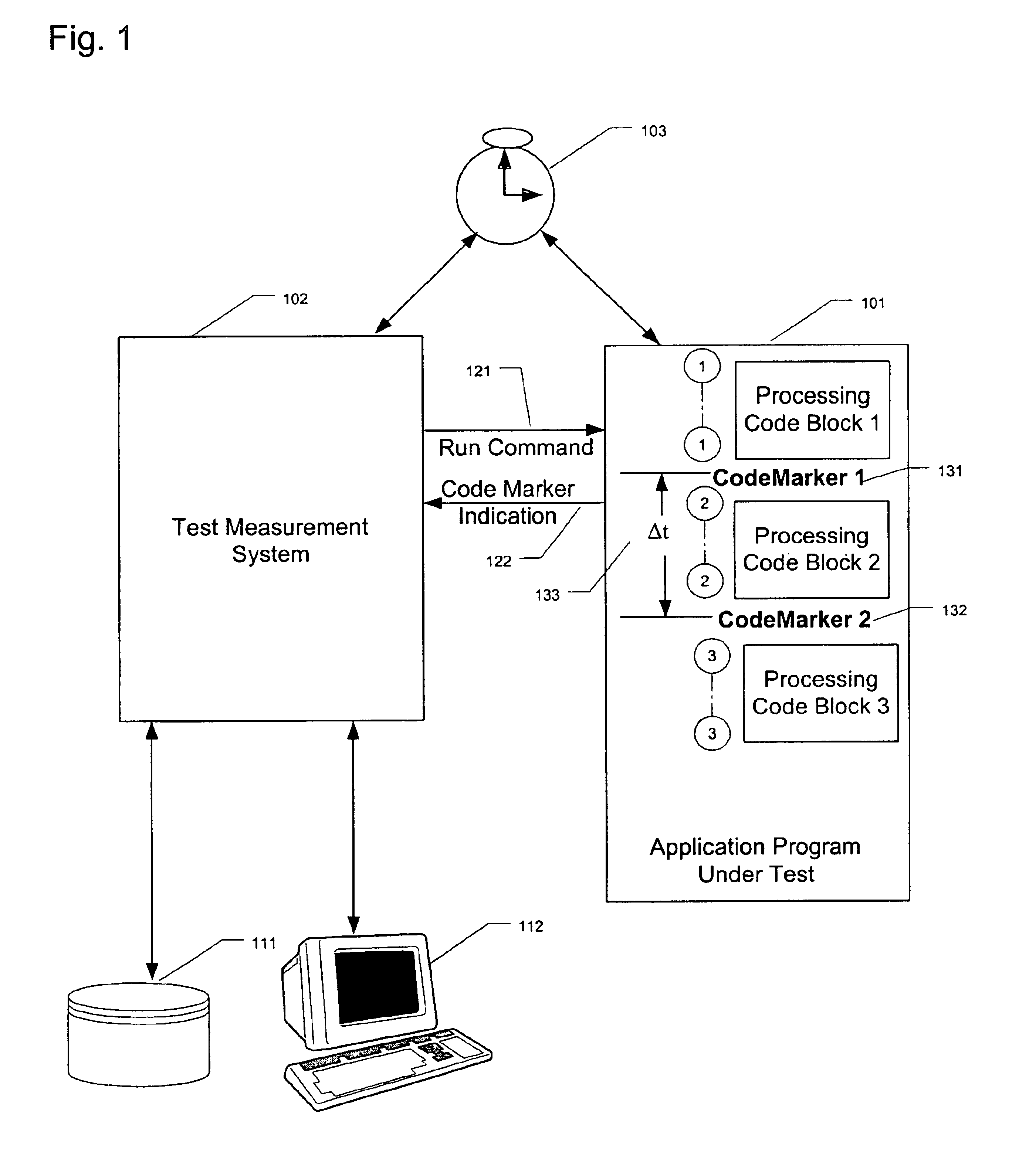
Performance markers to measure benchmark timing of features in a program
InactiveUS6873934B1Provide mechanismDigital computer detailsNuclear monitoringIdentification keyInit
A method, apparatus, and article of manufacture provide a mechanism for inserting performance markers into programs to obtain and provide data regarding the run-time benchmark timing of the programs. The computing system has an init module for determining if the benchmark timing data is to be collected during the operation of the application program, a performance marker module for obtaining and storing the benchmark timing data for later retrieval, and an uninit module for formatting and storing the obtained benchmark timing data into memory that permits retrieval after the termination of the application program. The init module is executed before any benchmark timing data is collected. The performance marker module is executed each time benchmark timing data is to be collected. The uninit module is executed after all benchmark timing data desired has been collected. The method and computer data product relate to a computer implemented process that inserts one or more code markers into the application program at locations within the application program corresponding to the point at which benchmark timing data is desired and that determines if benchmark timing data is to be collected at each code marker by checking for the existence of processing modules identified by an identification key within a system registry.
Owner:MICROSOFT TECH LICENSING LLC
Fast channel switching method of the TV
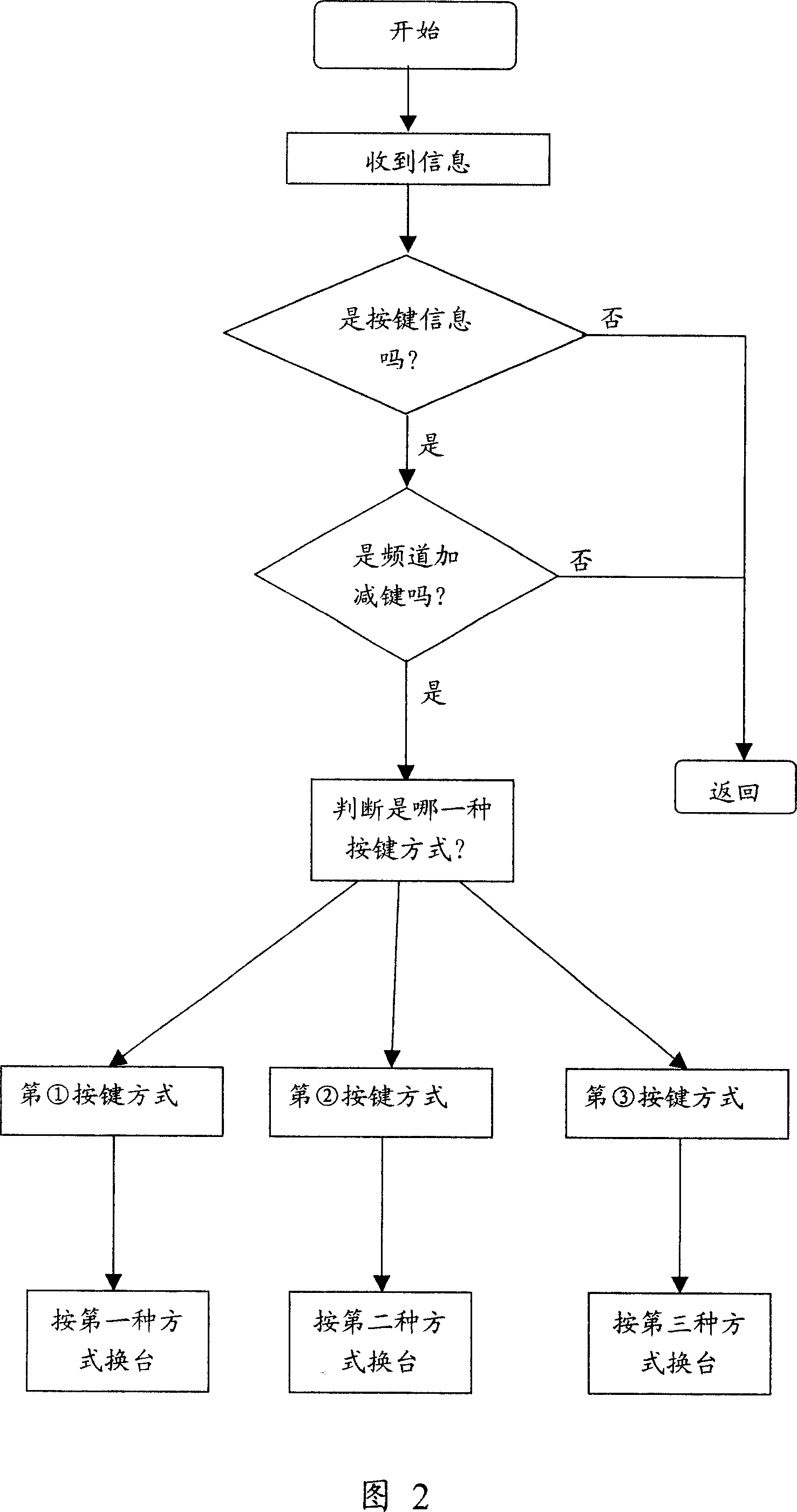
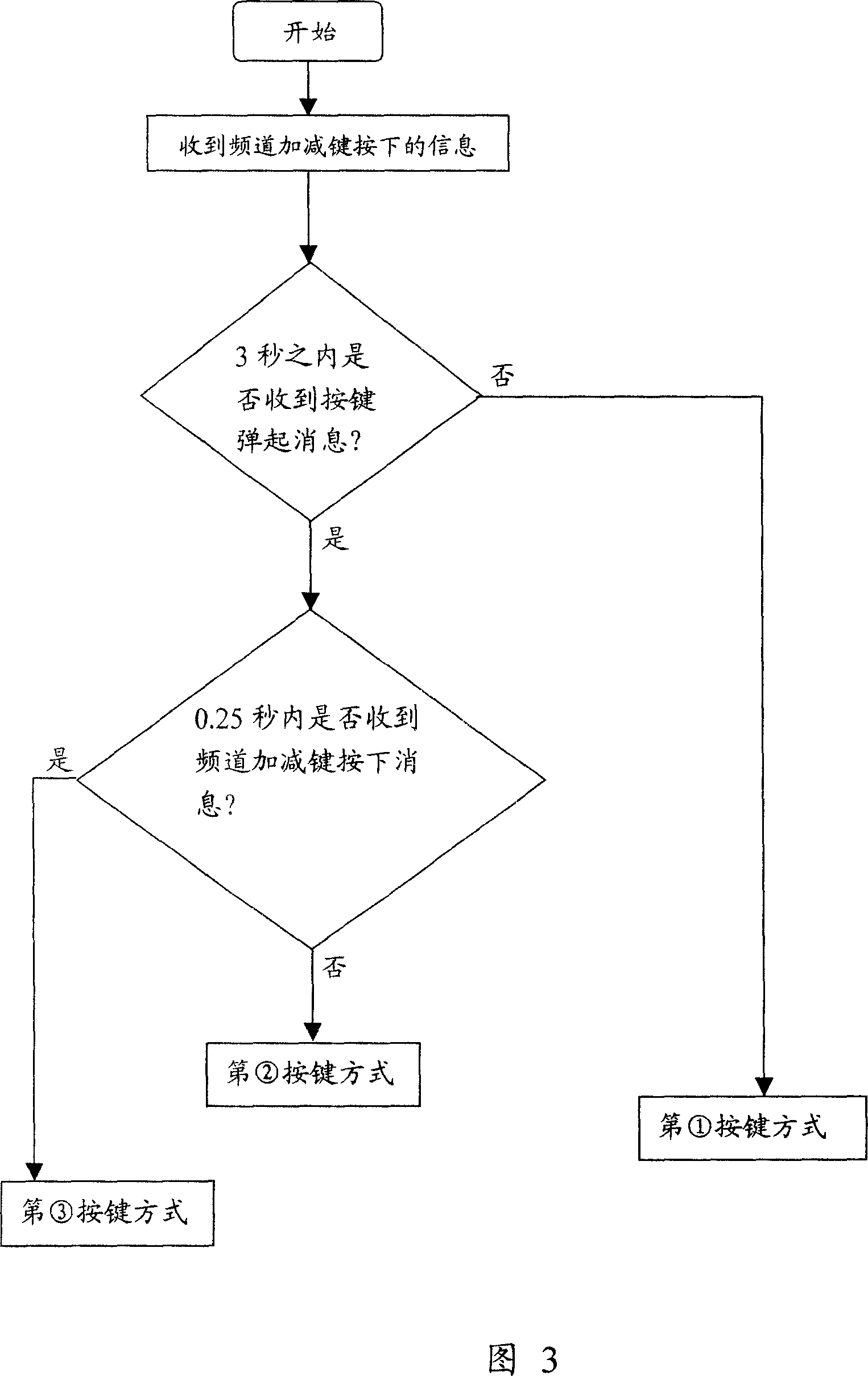
ActiveCN101035222AQuick selectionRealize choiceTelevision system detailsColor television detailsKey pressingUser needs
The invention is a television rapid method for exchanging channel. In accordance with different time settings trigger multiple keys, the process of user identification keys manner, and showing channel number, and the process of exchanging channel are included by the whole control process for exchanging channel. System tests different key-press methods, and take corresponding adjustment until adjust the channel number that the user need to watch channels, then exchange channel. The method uses multiple channels of buttons to control the adjustment, gets the choice of channels rapidly without switching channels, and avoids the channel time delay problems and slow conversion for frequently switching the channel. Many kinds of pressed keys ways also may use channel number change of the pressed key of jumping-like to realize split-second selection of channel number, so save the time and the pressed key triggers times, also reduce the remote control attrition.
Owner:SHENZHEN TCL NEW-TECH CO LTD
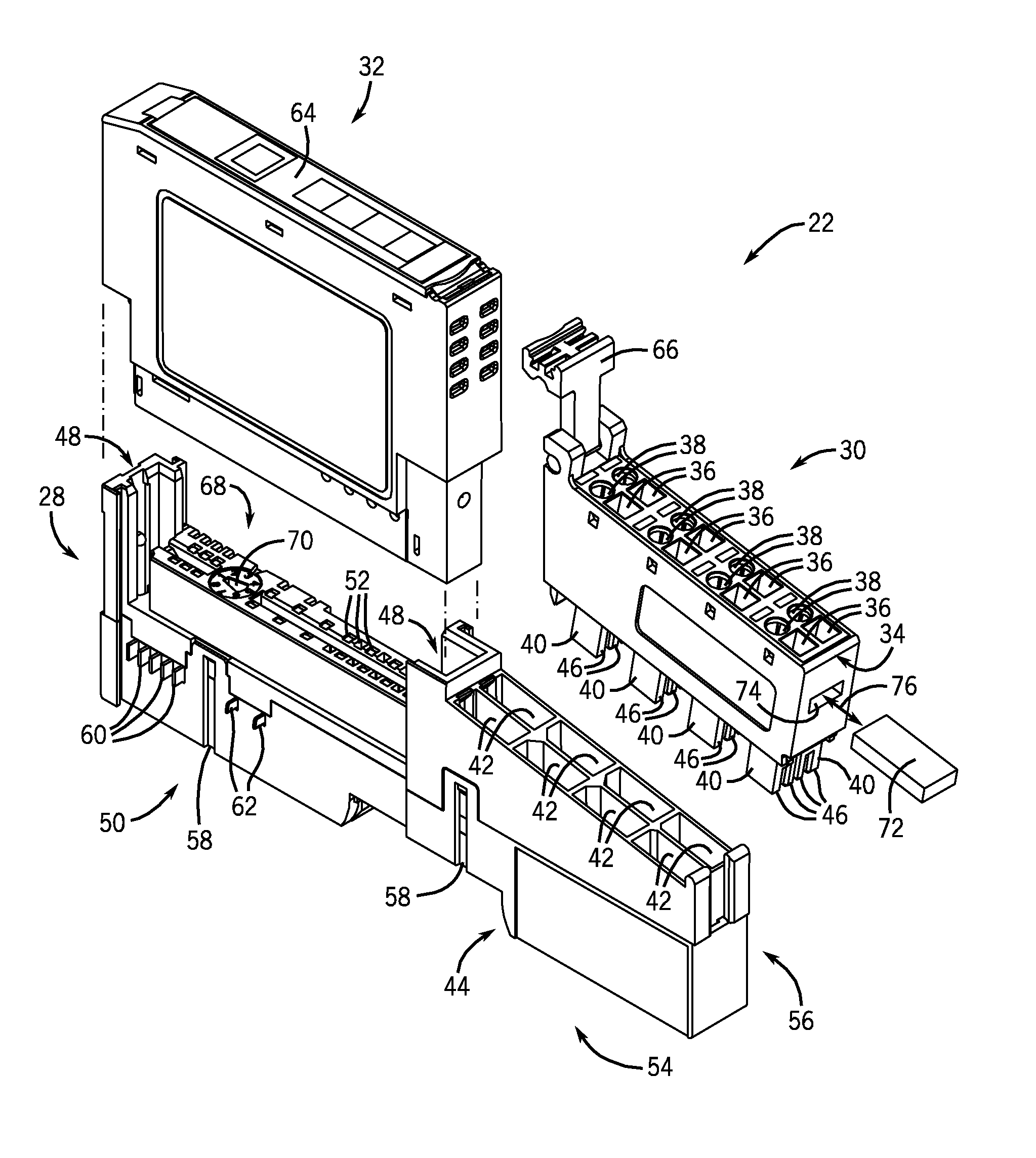
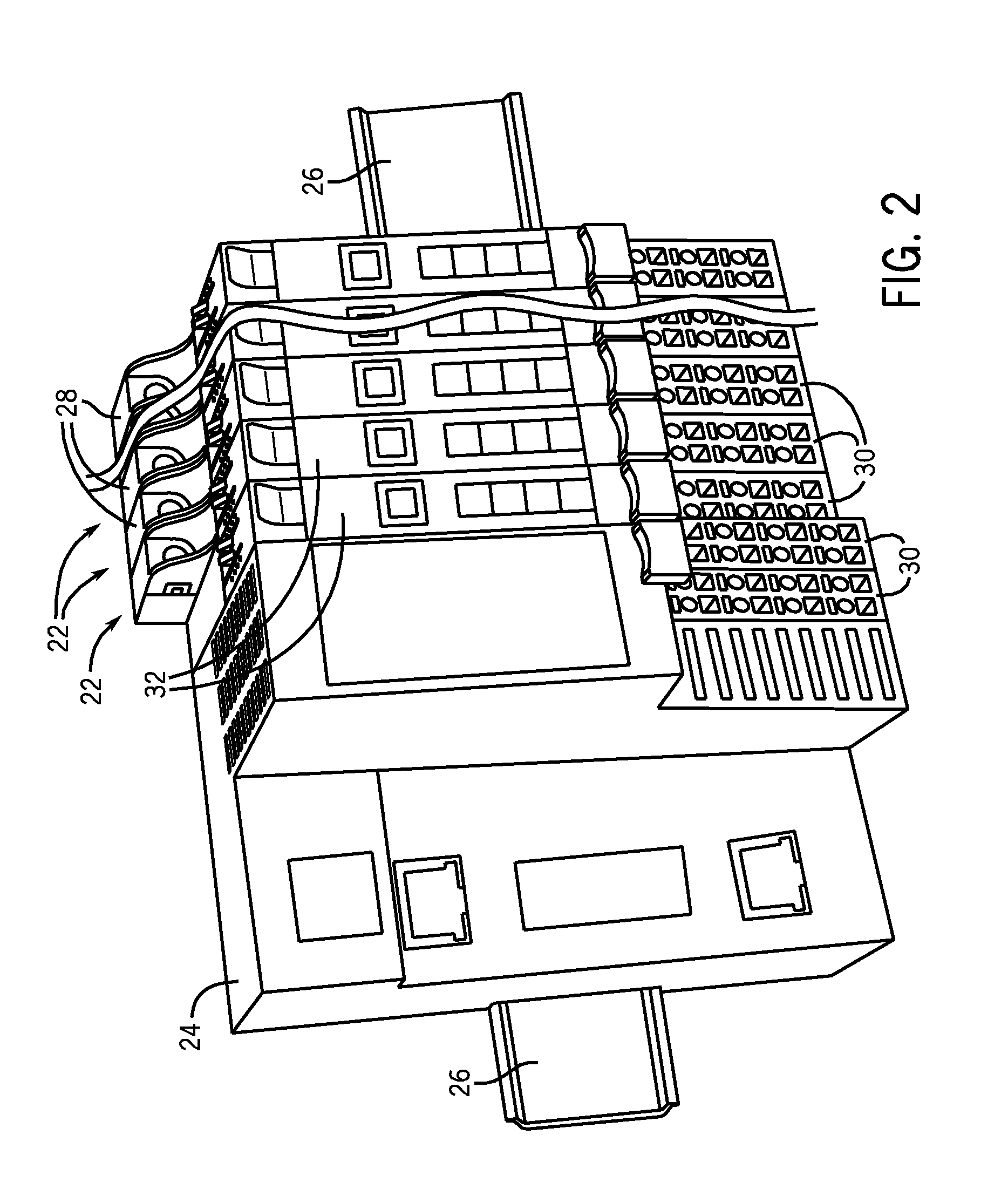
Automation Control System Components with Electronic Keying Features
ActiveUS20120043378A1Programme controlEngagement/disengagement of coupling partsComputer hardwareIdentification key
Systems and methods are provided for utilizing electronic keying features stored within one of the components (e.g., I / O modules, terminal blocks, bases, and so forth) of I / O devices, and which may be read or detected by electronic key identification circuitry in one of the other components of the I / O devices. More specifically, the electronic keying features may include unique identification keys that may be read or detected by the electronic key identification circuitry to determine whether the components (e.g., a paired I / O module and terminal block) are associated with each other and intended to operate together. For example, in certain embodiments, the electronic key feature may be disposed within a terminal block and the electronic key identification circuitry may be disposed within an I / O module, or vice versa. In addition, in certain embodiments, the electronic key feature and / or the electronic key identification circuitry may be removable from their respective component of the I / O device.
Owner:ROCKWELL AUTOMATION TECH
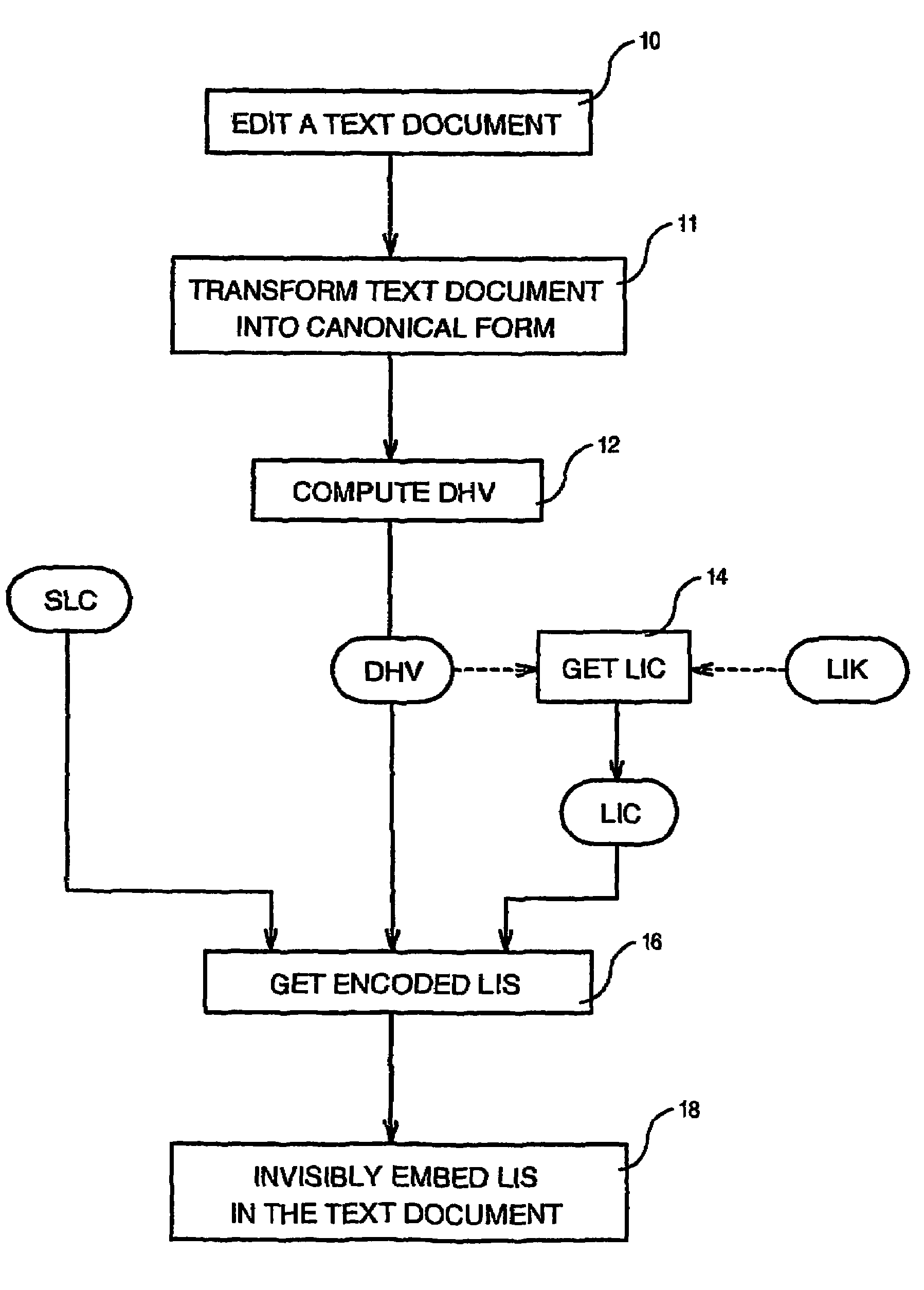
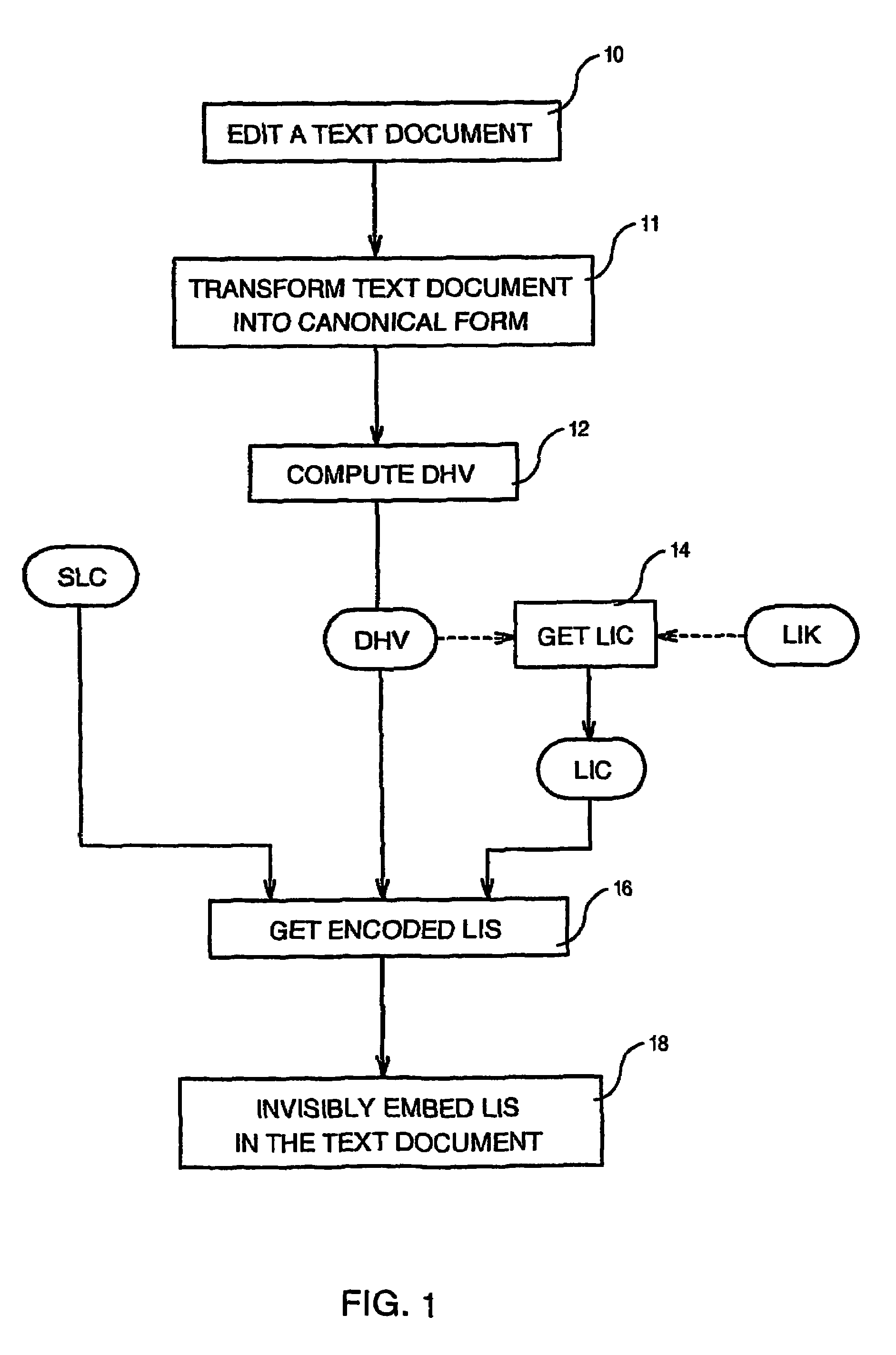
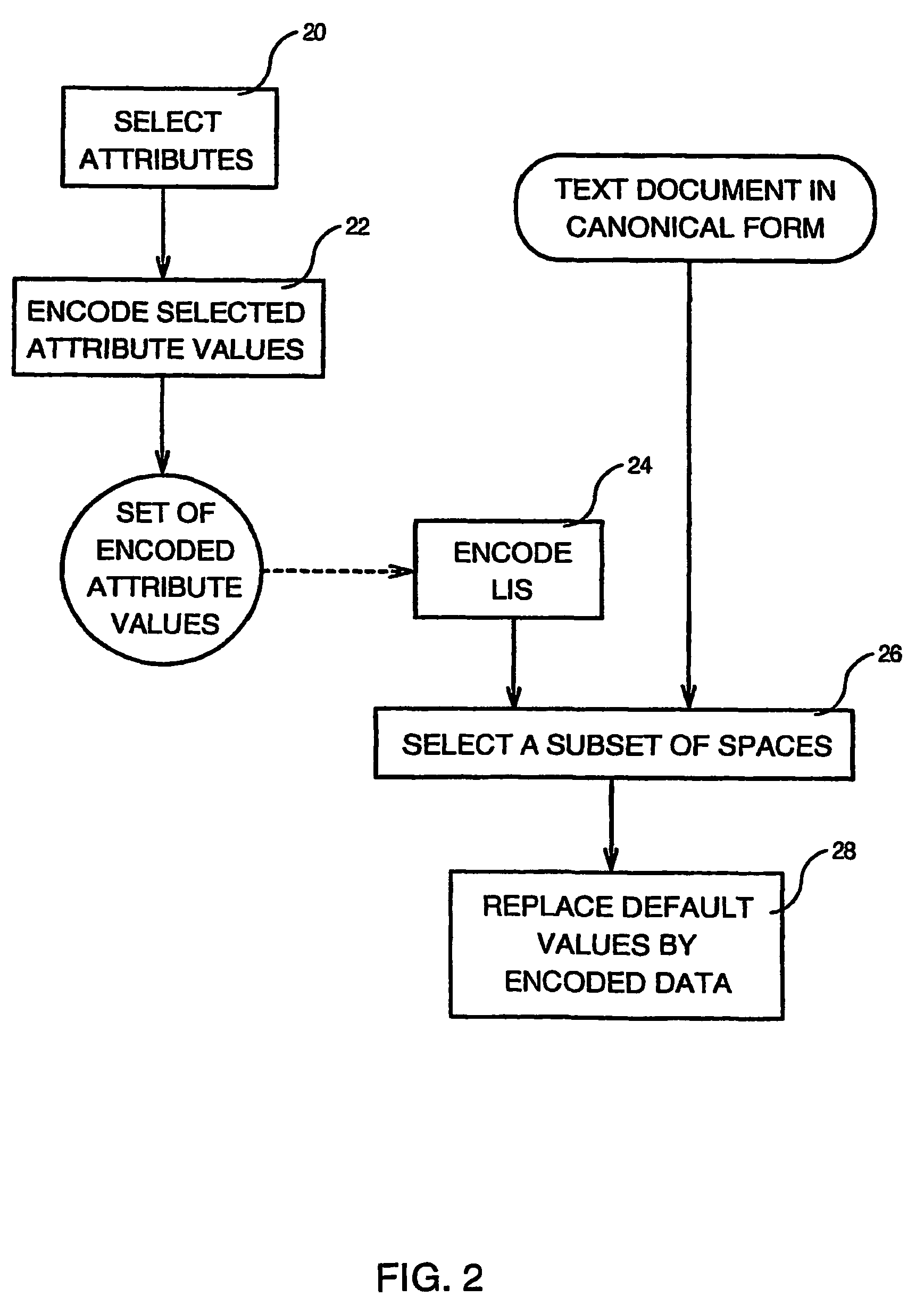
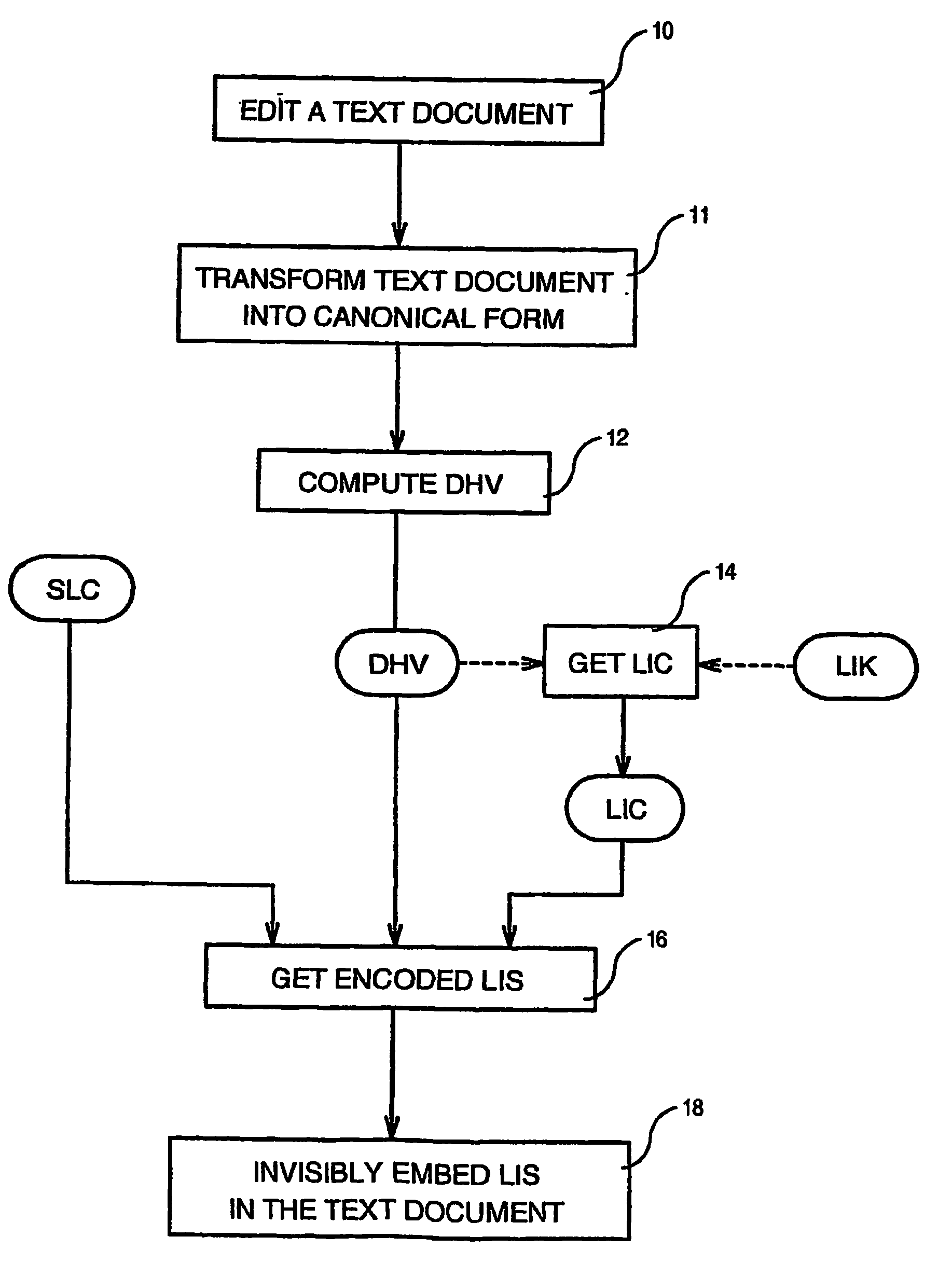
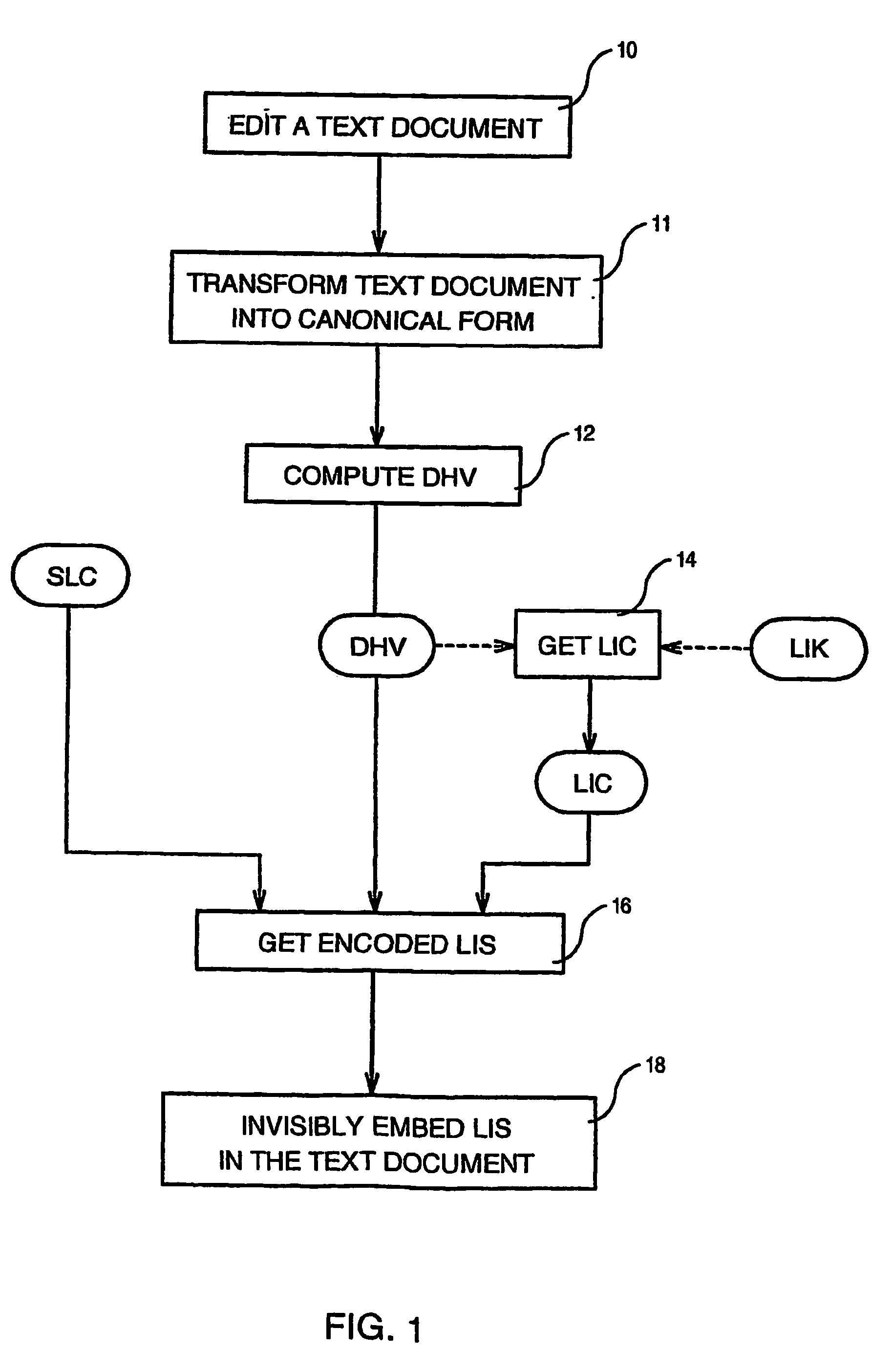
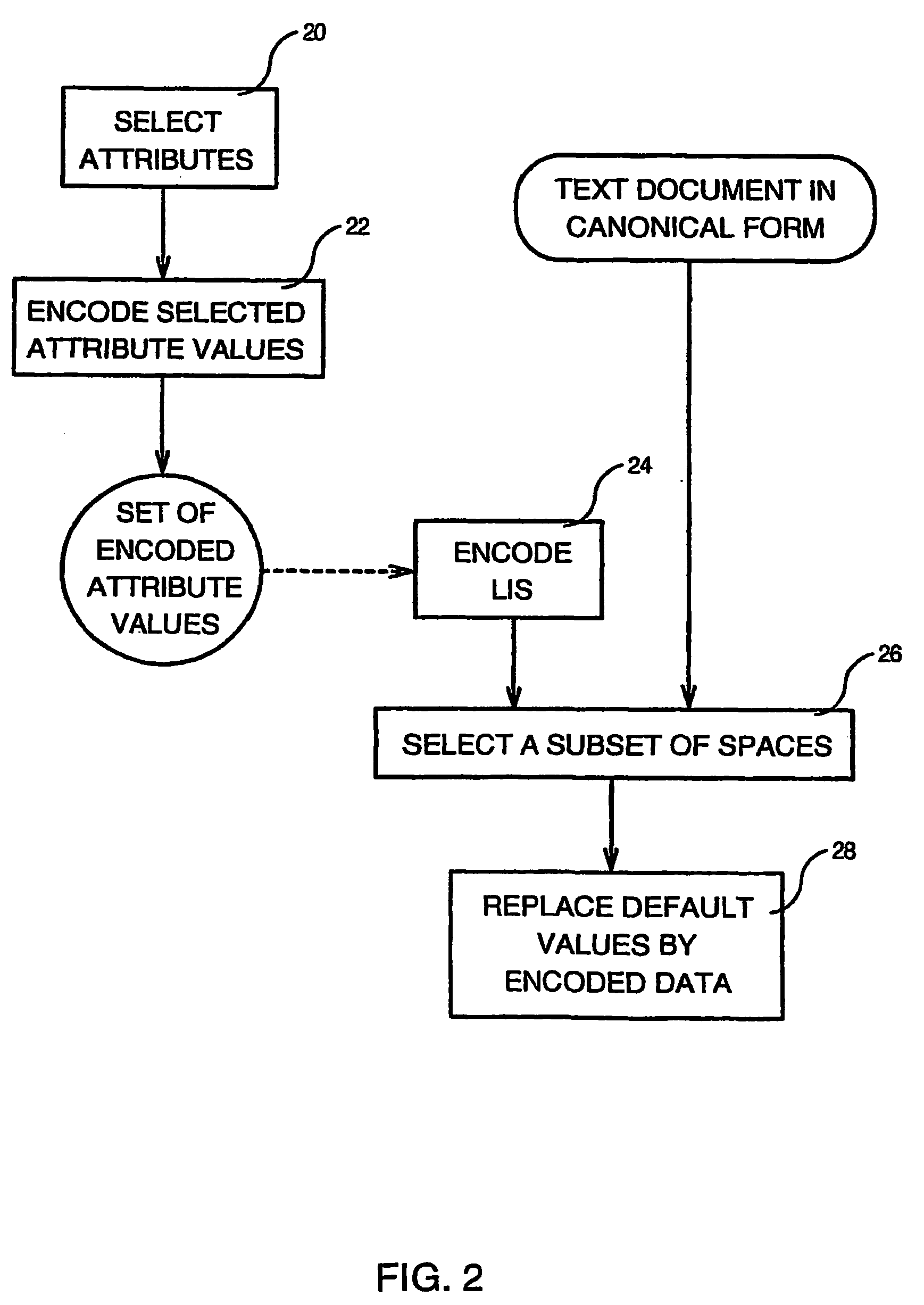
Method of invisibly embedding into a text document the license identification of the generating licensed software
InactiveUS7475429B2Digital data processing detailsUser identity/authority verificationIdentification keySoftware license
Method of invisibly embedding into a text document generated by a licensed software the License Identification Signature of the software wherein each original copy of the software has been assigned a unique Software License Code (SLC) and a unique License Identification Key (LIK) by a Licensing Authority, such a method comprising the steps of computing a Document Hash Value (DHV) of the text document (12), getting from the DHV a License Identification Code (LIC) of the text document by using the LUK (14), and embedding (18) invisibly into the text document the License Identification Signature (LIS) formed by the SLC, DHV and LIC after the LIS has been encoded by using character attributes.
Owner:KYNDRYL INC
Removable Liners for Waste Sorting Method
ActiveUS20080197055A1Easy to classifyEncourages and facilitates complianceData processing applicationsSurgical furnitureGraphicsIdentification key
Methods for using a liner in a waste sorting and disposal system are provided. The liner includes an internal space and an opening that provides access to that internal space. In some embodiments, the liner may also include a machine-readable identification key that is configured to identify a type of waste that the liner may receive. In some embodiments, the machine-readable key is optical, color-coded, alphanumeric or graphical. The liner can include one or more closure members to allow a user to securely seal the liner when it is removed from the container. In some embodiments, the liner can include a flange, lip, hook or other protrusion to secure its position relative to a container.
Owner:CAREFUSION 303 INC
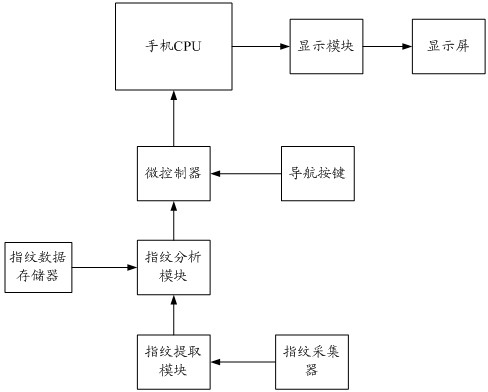
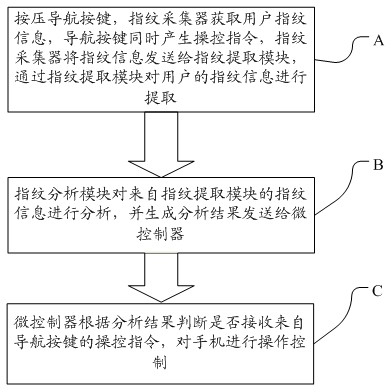
System and method for carrying out security protection on phone information based on coincidence of fingerprint and navigation keys
InactiveCN102611774AEnsure safetyAvoid cumbersomeTelephone set constructionsKey pressingIdentification key
The invention discloses a system and a method for carrying out security protection on phone information based on the coincidence of fingerprint and navigation keys. The system comprises an upper phone cover, a bottom phone cover, and a main circuit board, wherein the main circuit board is arranged between the upper phone cover and the bottom phone cover, the main circuit board is provided with a navigation key, the navigation key is provided with a fingerprint acquisitor, and the fingerprint acquisitor is correspondingly arranged in a key hole of the upper phone cover. Compared with the prior art, the system and method disclosed by the invention have the advantages that: through setting a navigation operation key and a fingerprint identification key of a smart phone as an operation key, when a user of the phone carries out operation through fingerprints, the fingerprints of the user are identified, thereby not only ensuring the identification on the identity of the user and realizing the information security, but also avoiding verbose phone operations, so that the user realizes two modes (namely, security authentication and phone operation) through an action, in such a way, the operation efficiency of the phone is improved, and the information security is ensured.
Owner:SHENZHEN GIONEE COMM EQUIP
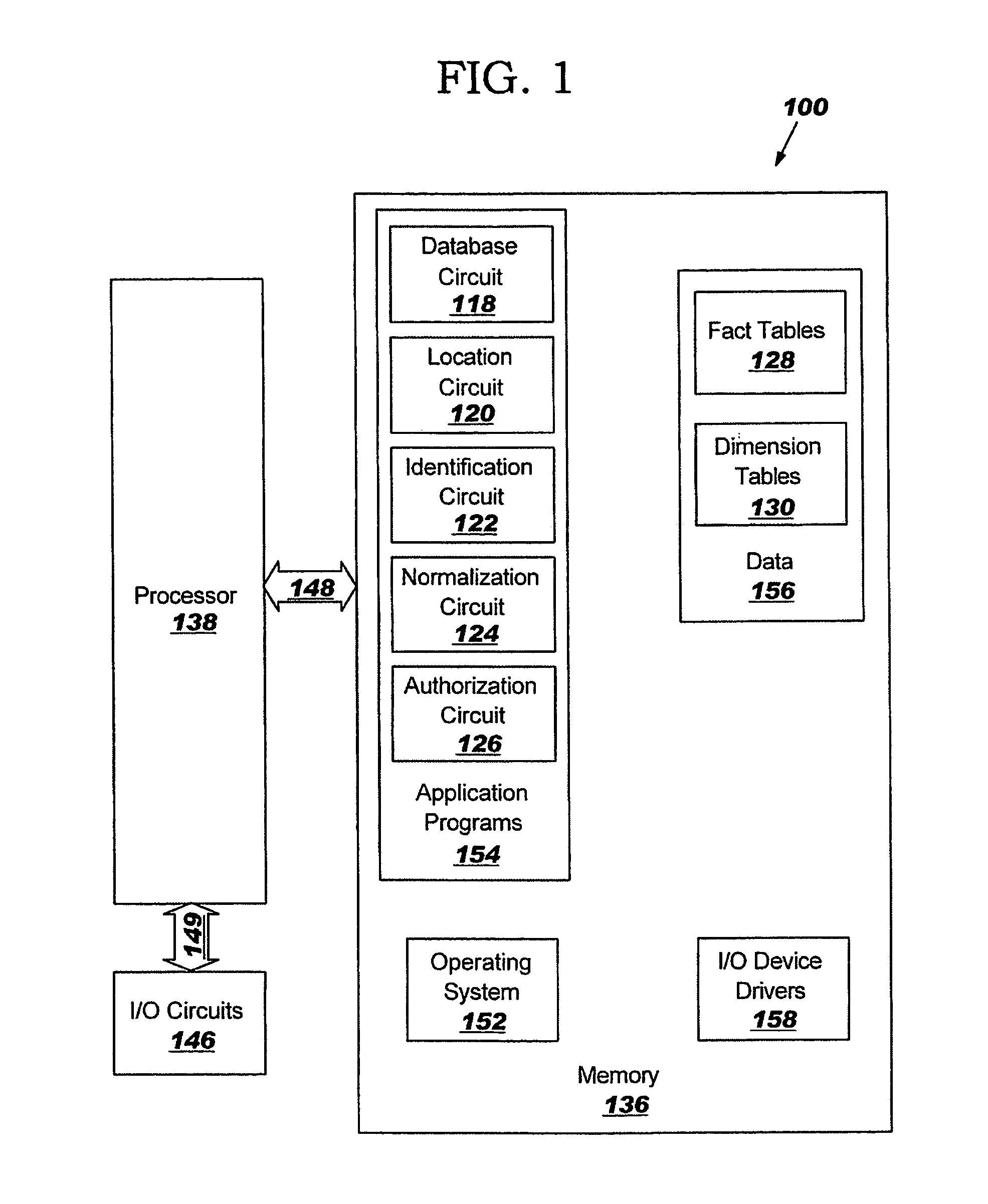
Systems and Computer Program Products for Relating Data in Healthcare Databases
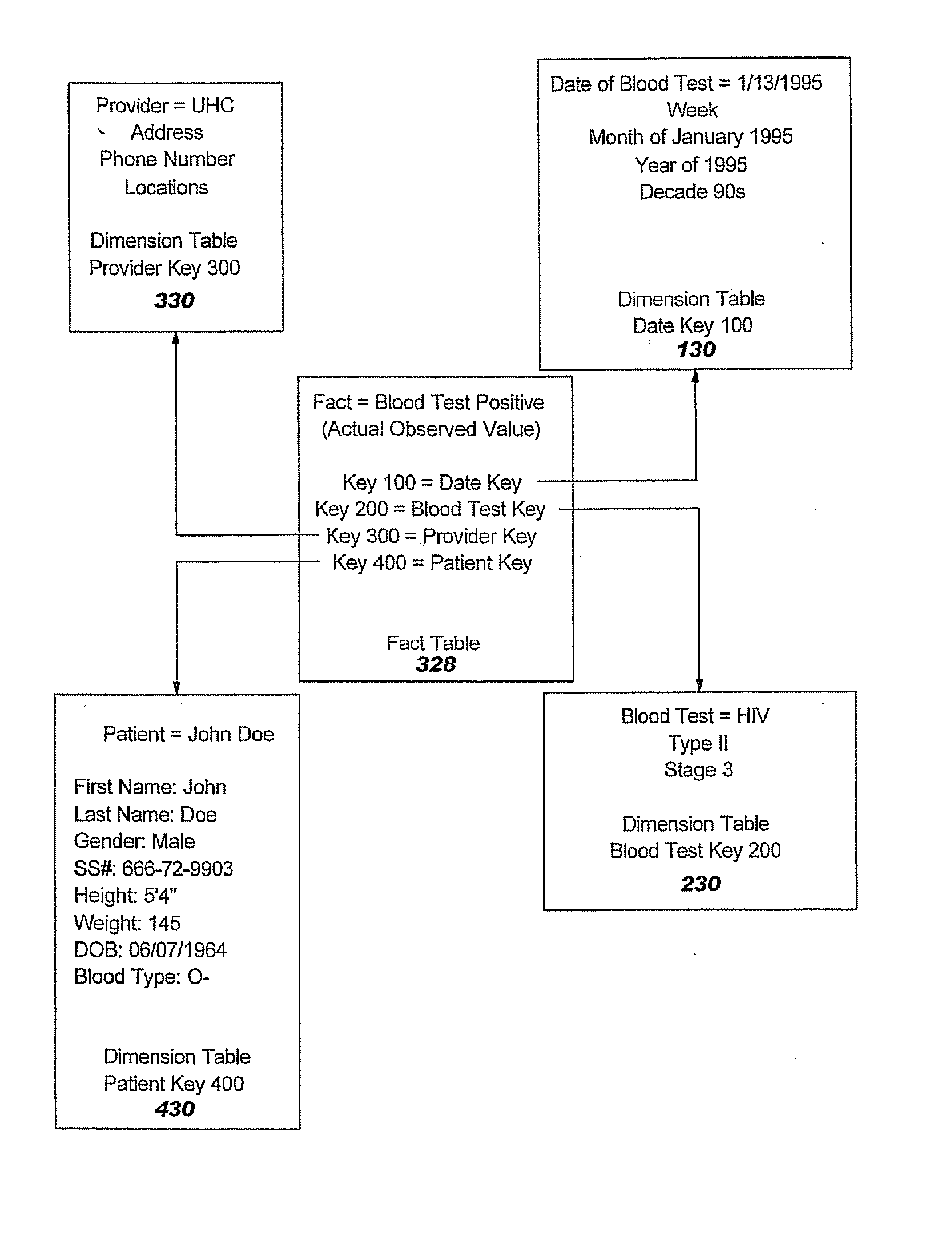
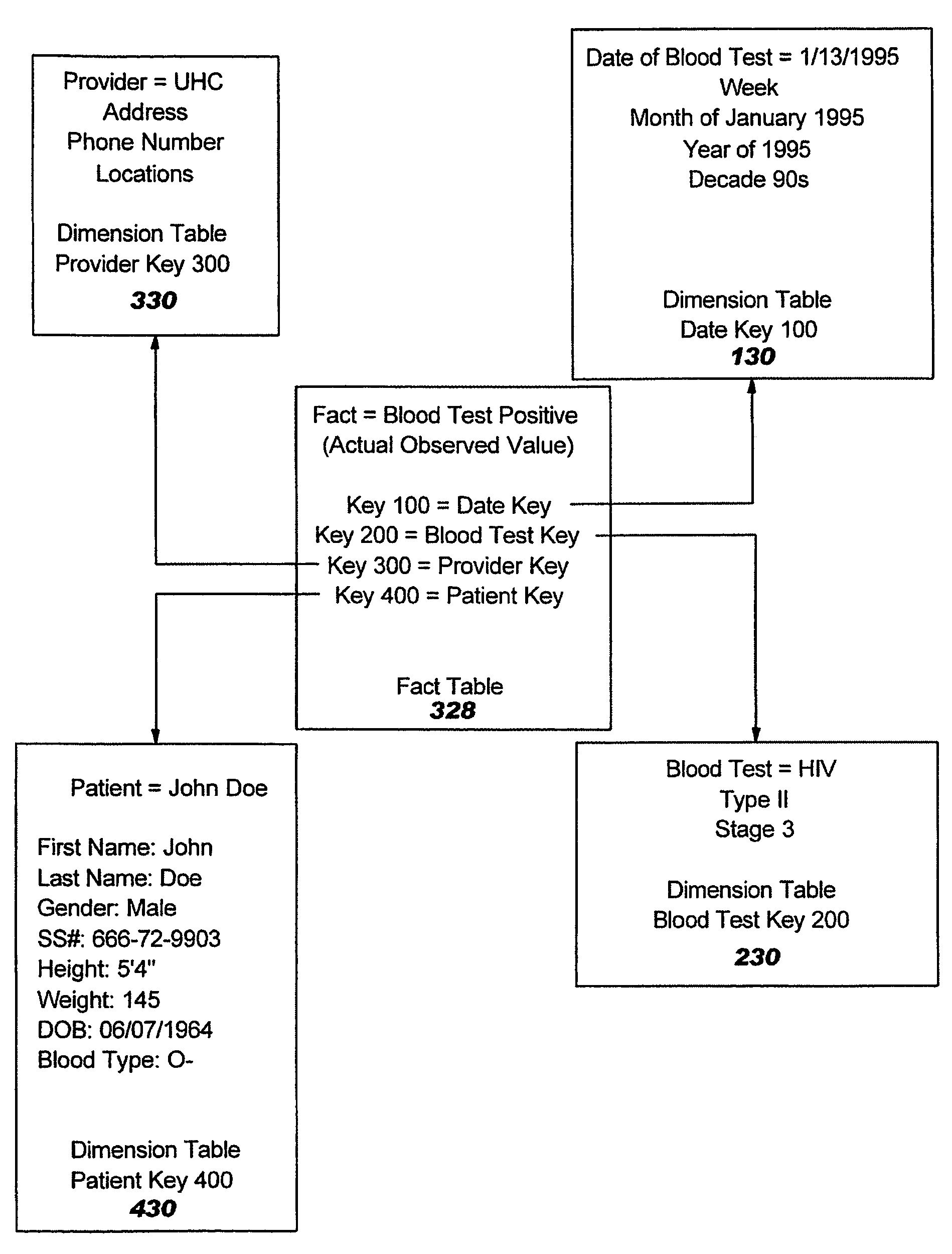
ActiveUS20070299691A1Medical data miningData processing applicationsIdentification keySubject matter
Systems and computer program products for relating facts stored in healthcare databases are provided. At least two fact tables stored in a healthcare database including data meeting a criteria of interest are located. An identification key is assigned to the at least two fact tables including the located data meeting the criteria of interest. The identification key provides access to a dimension table including a list of subjects associated with the at least two fact tables including the located data meeting the criteria of interest so as to allow future identification of the subjects meeting the criteria of interest.
Owner:KYNDRYL INC
Display method and device for user interface keys
InactiveCN103793143AImprove experienceReduce the number of keysInput/output processes for data processingKey pressingIdentification key
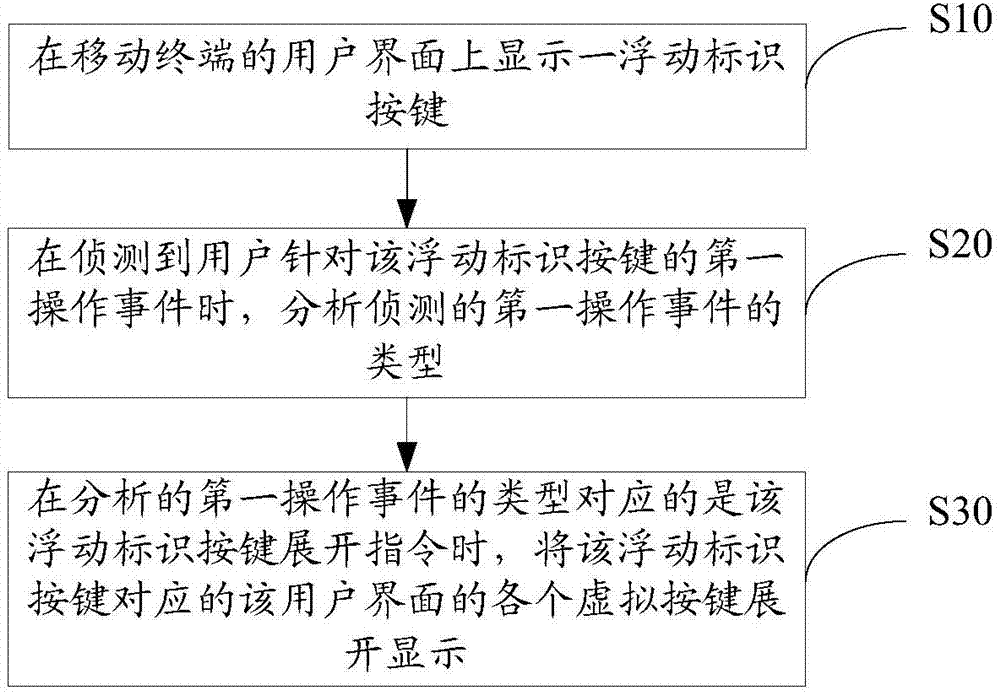
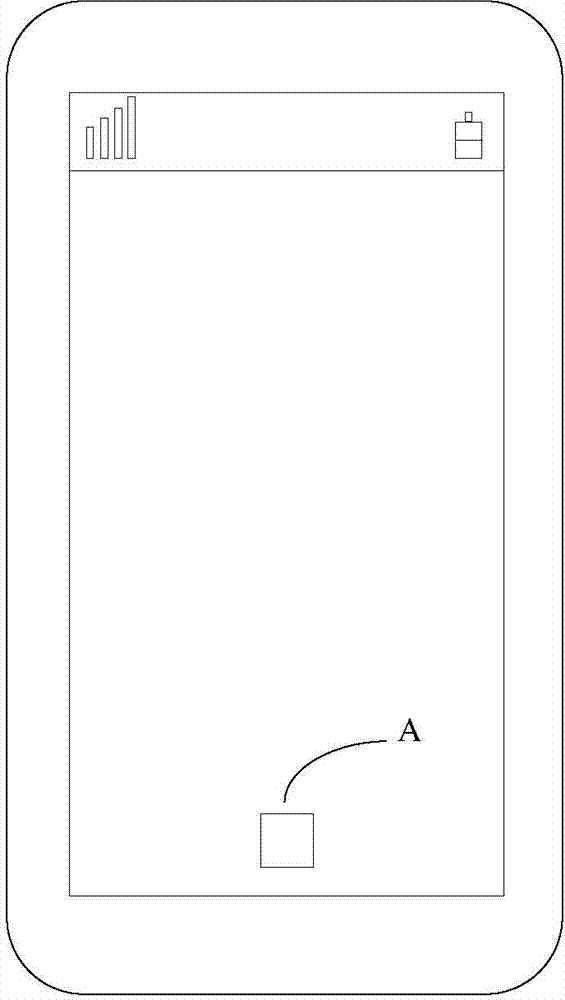
The invention discloses a display method and mobile terminal for user interface keys. The method includes the steps that a floating identification key corresponding to a user interface is displayed on the user interface of the mobile terminal; when a first operation event, aiming at the floating identification key, of a user is detected, the type of the detected first operation even is analyzed; when the analyzed type of the first operation even corresponds to an expanding instruction of the floating identification key, all the virtual keys of the user interface corresponding to the floating identification key are displayed in an expanded mode. By the adoption of the display method and device, the user interface can be simplified, the quantity of the keys of the user interface is reduced, it is avoided that too many keys occupy space, and therefore user experience is improved.
Owner:YULONG COMPUTER TELECOMM SCI (SHENZHEN) CO LTD
Method and device for man-machine interaction, and terminal
InactiveCN105912241ARealize switch machineRealize open screenInput/output processes for data processingKey pressingIdentification key
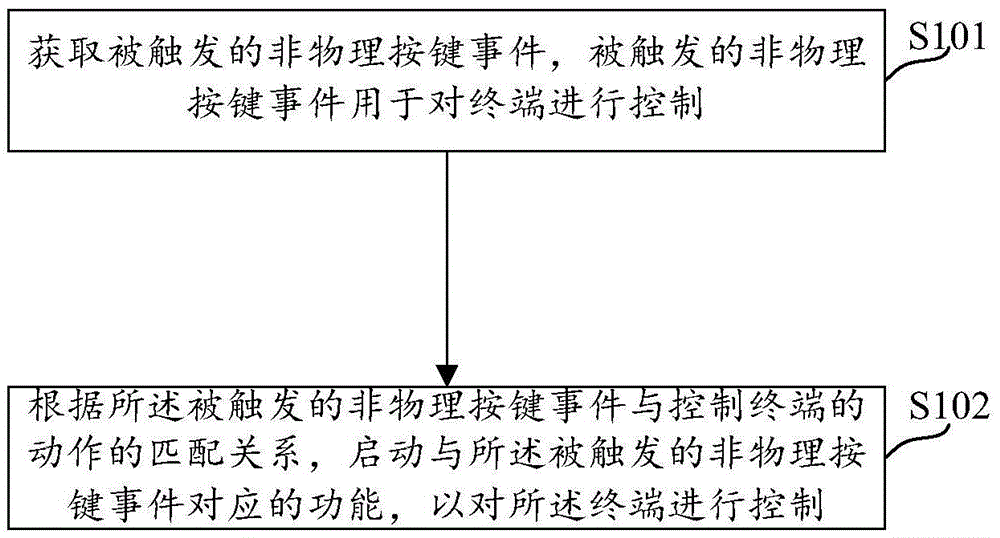
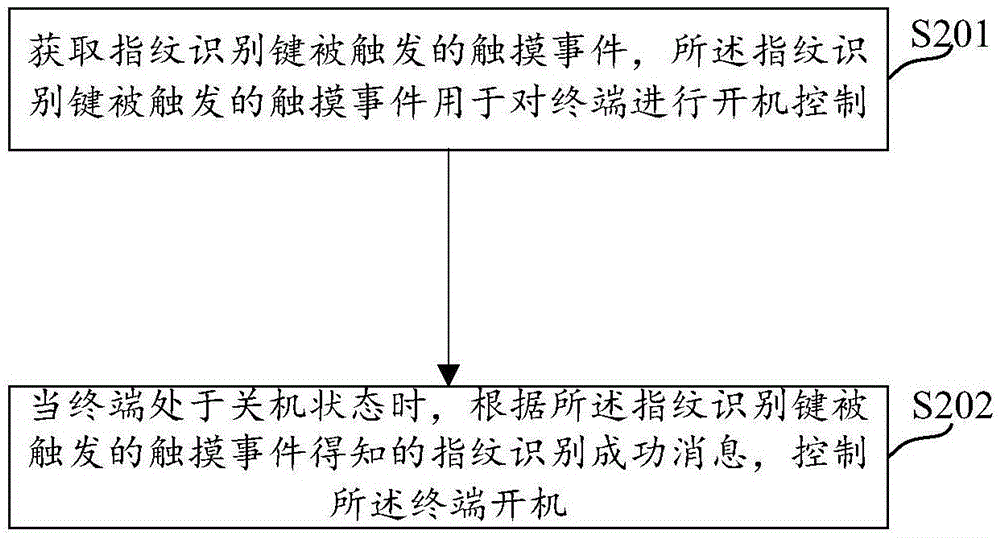
Embodiments of the invention provide a method and a device for man-machine interaction, and a terminal. The man-machine interaction method comprises: obtaining a triggered non-physical key event, the triggered non-physical key event being used to control a terminal; and according to the matching relations of the triggered non-physical key event and operation of the control terminal, starting a function corresponding to the triggered non-physical key event, and controlling the terminal. In the method, a non-physical key can be a fingerprint identification key, an acceleration sensor, or others. Thus, startup and shutdown, and switching on / off a screen can be realized, and a power physical key in the prior art is not needed.
Owner:LETV INFORMATION TECH BEIJING
Intelligent ophthalmic ultrasonic emulsification apparatus
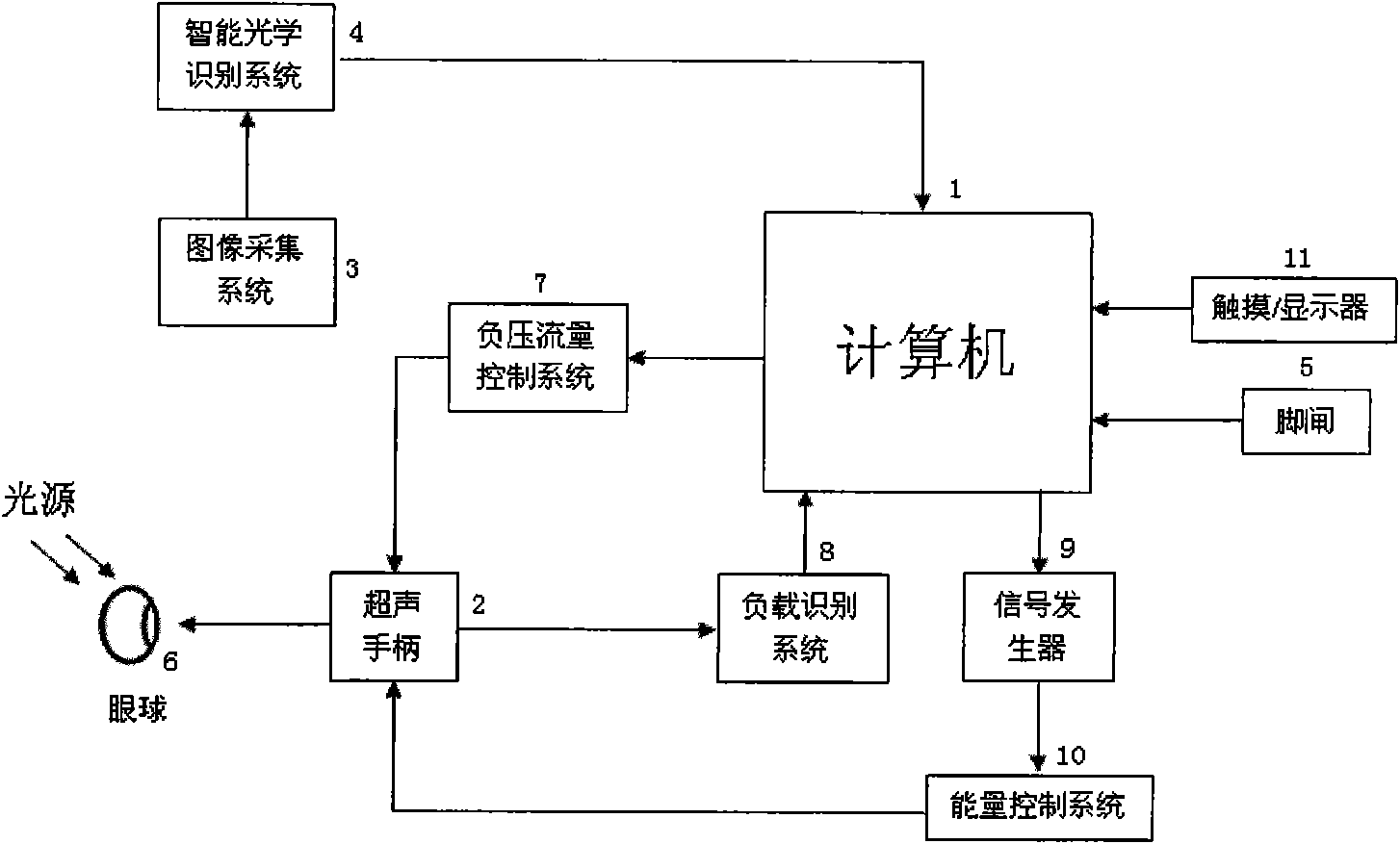
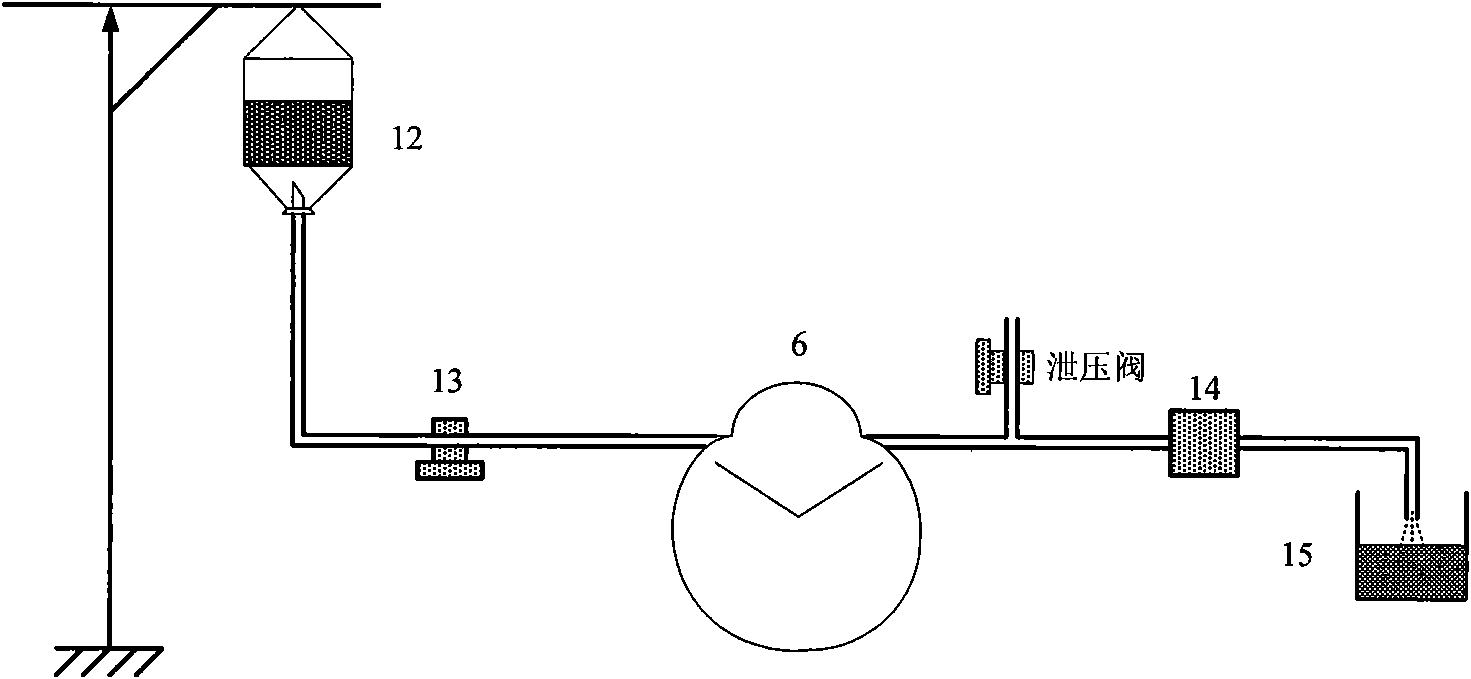
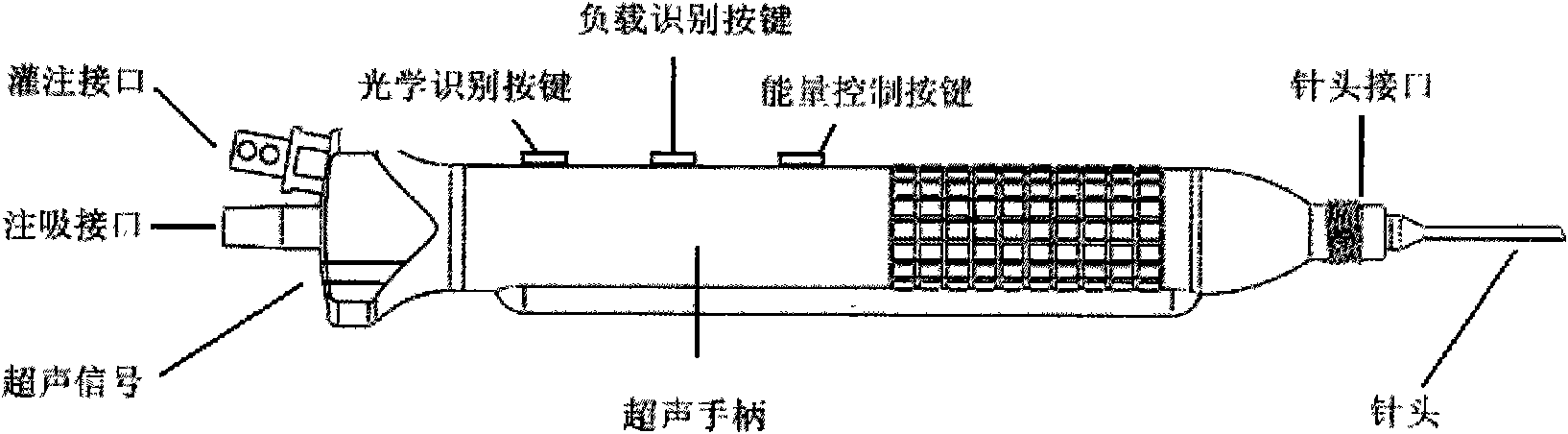
ActiveCN101632610AImprove real-time performanceReduce computationEye surgeryUltrasonic emulsificationSonification
The invention relates to an intelligent ophthalmic ultrasonic emulsification apparatus, comprising a host machine of a surgical apparatus, an ultrasonic handle, an image collection system and a foot brake, wherein the host machine of the surgical apparatus comprises a signal generator, a process and affected-part state identification system, a negative-pressure flow control system, an energy control system and a touch / display device. The ultrasonic handle is provided with three keys including an optical identification key, a loading identification key and an energy control key. The intelligent ophthalmic ultrasonic emulsification apparatus can realize intelligent operation of ultrasonic emulsification apparatus and reduce the work intensity of doctors.
Owner:北京速迈医疗科技有限公司
Wireless nodes with security key
InactiveUS20170118636A1Minimum and simple human user stepError minimizationKey distribution for secure communicationNetwork topologiesIdentification keyNetwork key
Owner:PHOTONSTAR LED
Identity identification key system for rented automobile and control method
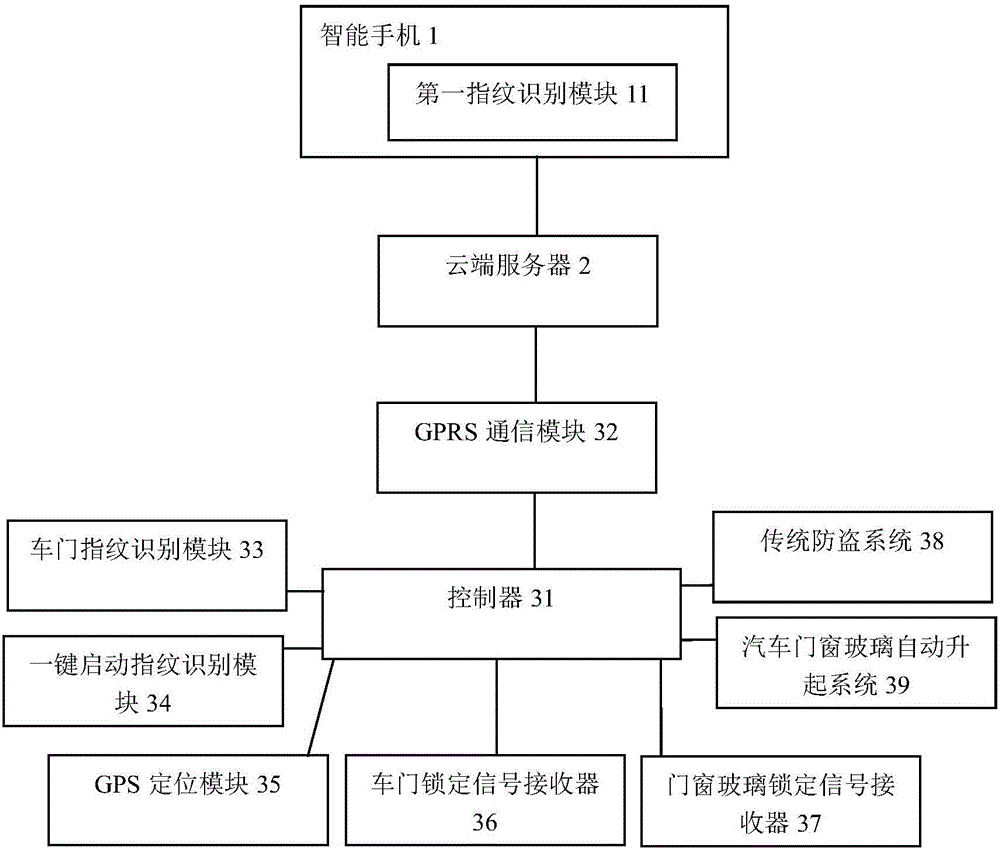
InactiveCN106627486AFulfil requirementsEasy to useAnti-theft devicesIndividual entry/exit registersIdentification keyComputer terminal
The invention discloses an identity identification key system for a rented automobile and a control method. The system comprises a user terminal, a server, a controller, a remote communication module, an automobile door identity identification module and a one-key start identity identification module, wherein the controller, the remote communication module, the automobile door identity identification module and the one-key start identity identification module are arranged on the automobile. A user can communicate with the server through the user terminal and obtain the use right of the automobile after paying a deposit or passing identity authentication, then the user terminal obtains identity information of the user through an identity identification module arranged on the user terminal and sends the identity information of the user to the server, the server sends the identity information of the user to the controller of the automobile through the remote communication module of the automobile, and the user can open an automobile door through the automobile door identity identification module of the automobile and start and drive the automobile through the one-key start identity identification module. By the adoption of the system, after the identity information of the user is successfully uploaded, the user terminal does not need to be carried in the following use process, use is convenient and quick, the system is simple in structure, low in cost and high in safety degree, and the automobile can be rented without a key in a self-service manner.
Owner:XIAMEN UNIV OF TECH
Service broker for processing data from a data network
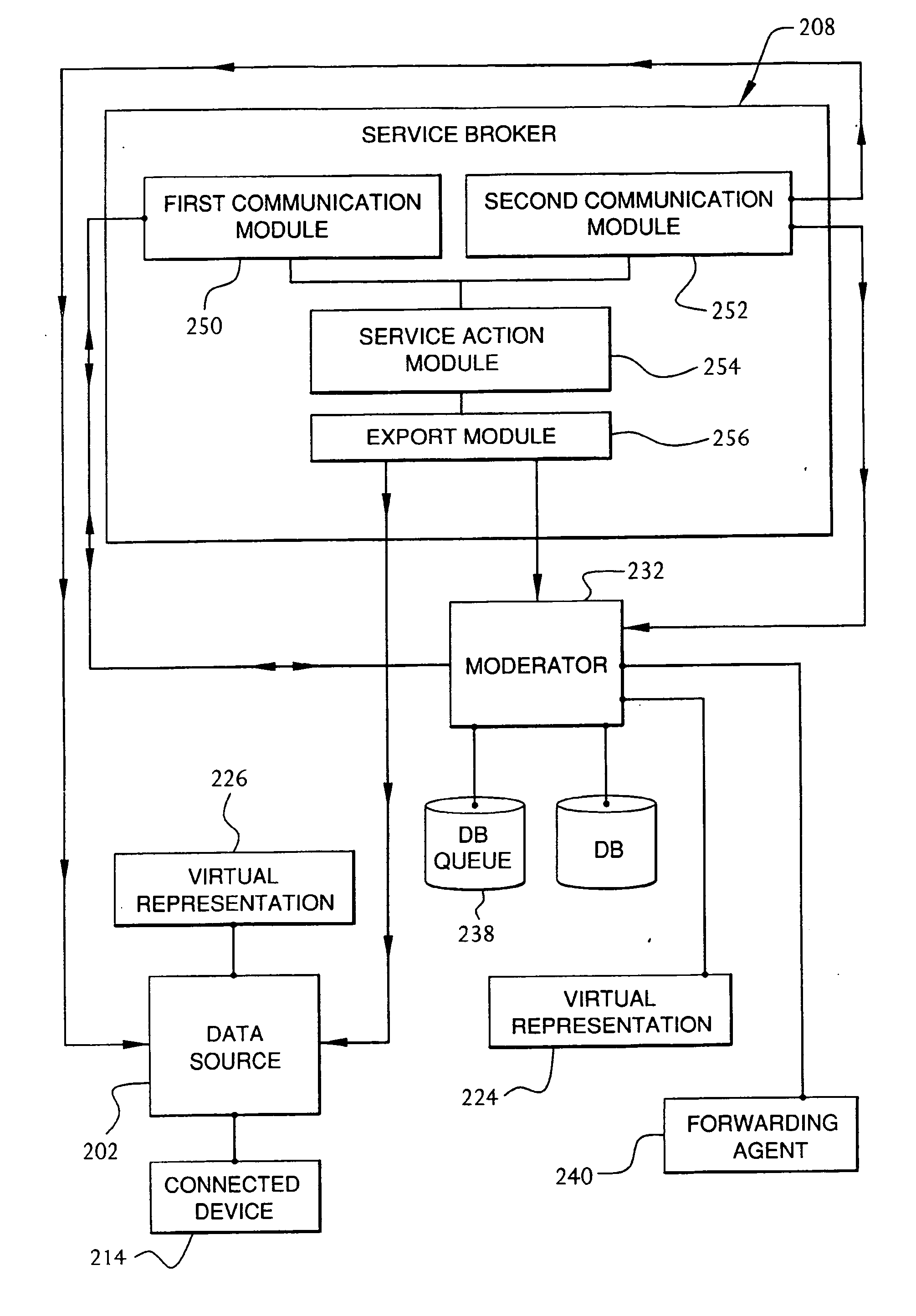
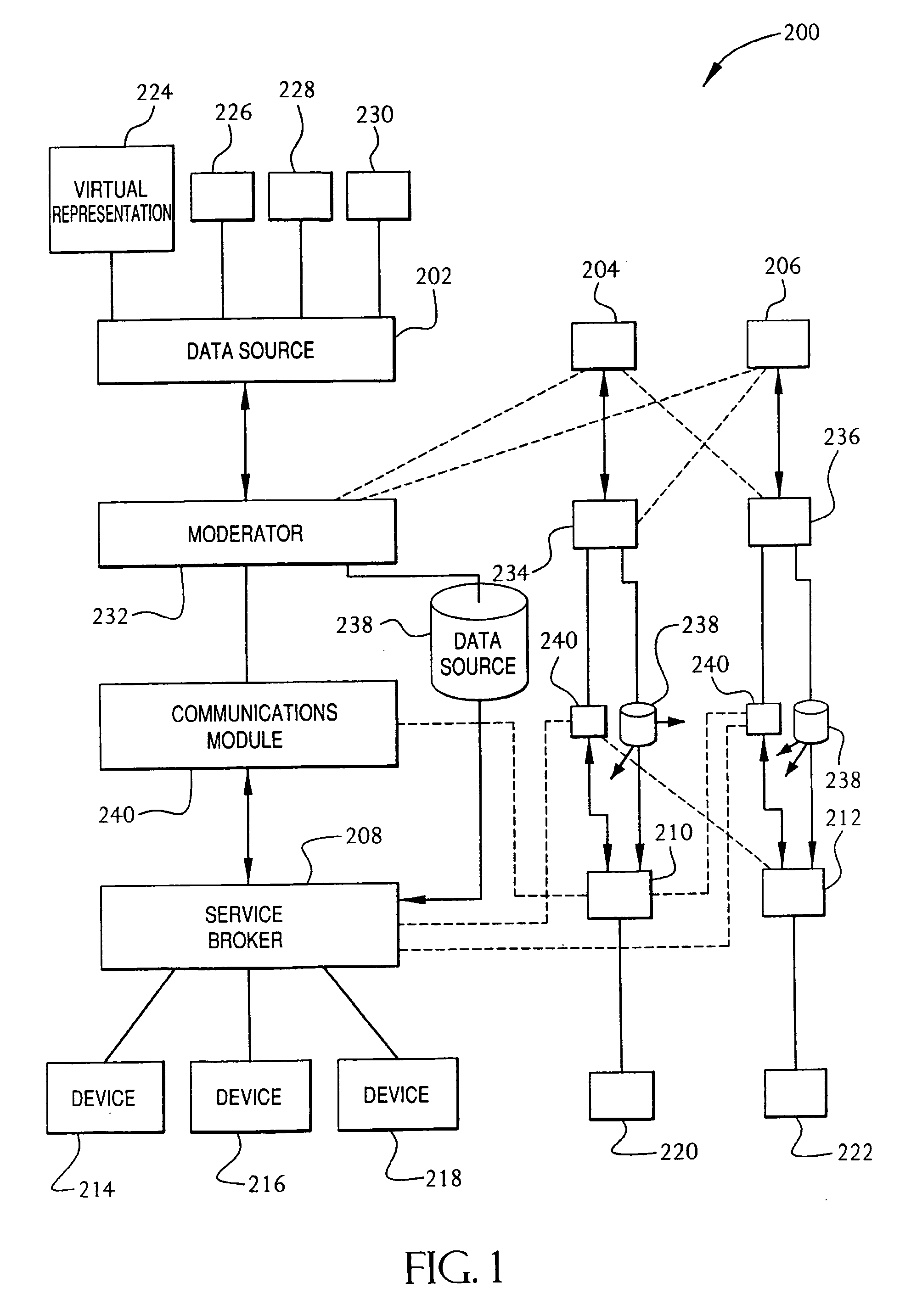
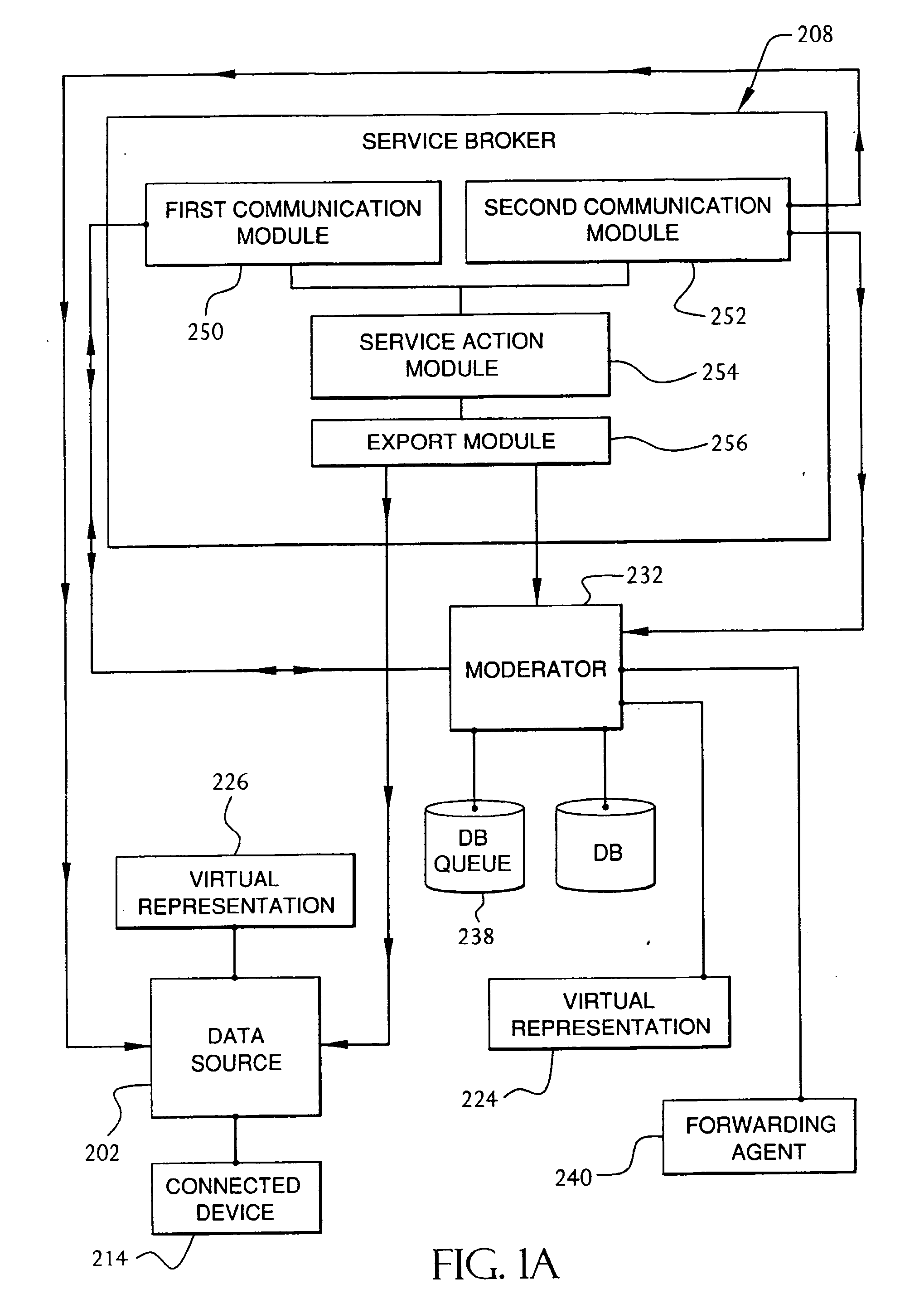
InactiveUS20060184657A1Digital computer detailsSecuring communicationIdentification keyCommand language
A method and system for communication between server-less computing devices or clients in computers communicating over networks, such as the World Wide Web (WWW) using stateless protocols, e.g., HTTP. In this scheme there are two classes of clients which can operate independently or can be combined in computer communicating over the network: a) Clients that issue commands and request status or data, and b) clients which function as service brokers for provide services and processing commands, updating status and providing specific data. Based on the description of the latter client device it would resemble a server device but without accessible TCP / IP ports. Each service providing device is authenticated, retains a unique identity and establishes a soft state with the globally accessible server or servers. All devices and clients can compile and process a globally common command language established between all communicating network clients. The central server includes a CGI processing program and a database to retain client specific information. The server database represents a collection of queues, each having a client unique identifiable status, pending commands and / or data components. In this scheme commands and signaling transmitted between the servers and clients utilize standard HTTP protocol semantics and HTML or standard markup language syntax. Clients encapsulate or embed information as parameters passed to HTTP CGI as a set of standard HTTP conversations. A CGI processing program converts, parses or processes each conversation and passes arguments with or without data to queues. Each conversation is includes a client identification key(s) and commands which are structured as attribute-value pair tuples. The service-handler client connects to the central server and accesses the client queue on the central server to check for any pending commands or update their status in either synchronous or asynchronous manner. The synchronous server access scheme is regulated temporally by either deterministic clocking on server response or by a server based adaptive algorithm which can monitor network and client activities and optimize client access patterns.
Owner:XANBOO
Methods for relating data in healthcare databases
Methods, systems and computer program products for relating facts stored in healthcare databases are provided. At least two fact tables stored in a healthcare database including data meeting a criteria of interest are located. An identification key is assigned to the at least two fact tables including the located data meeting the criteria of interest. The identification key provides access to a dimension table including a list of subjects associated with the at least two fact tables including the located data meeting the criteria of interest so as to allow future identification of the subjects meeting the criteria of interest.
Owner:KYNDRYL INC
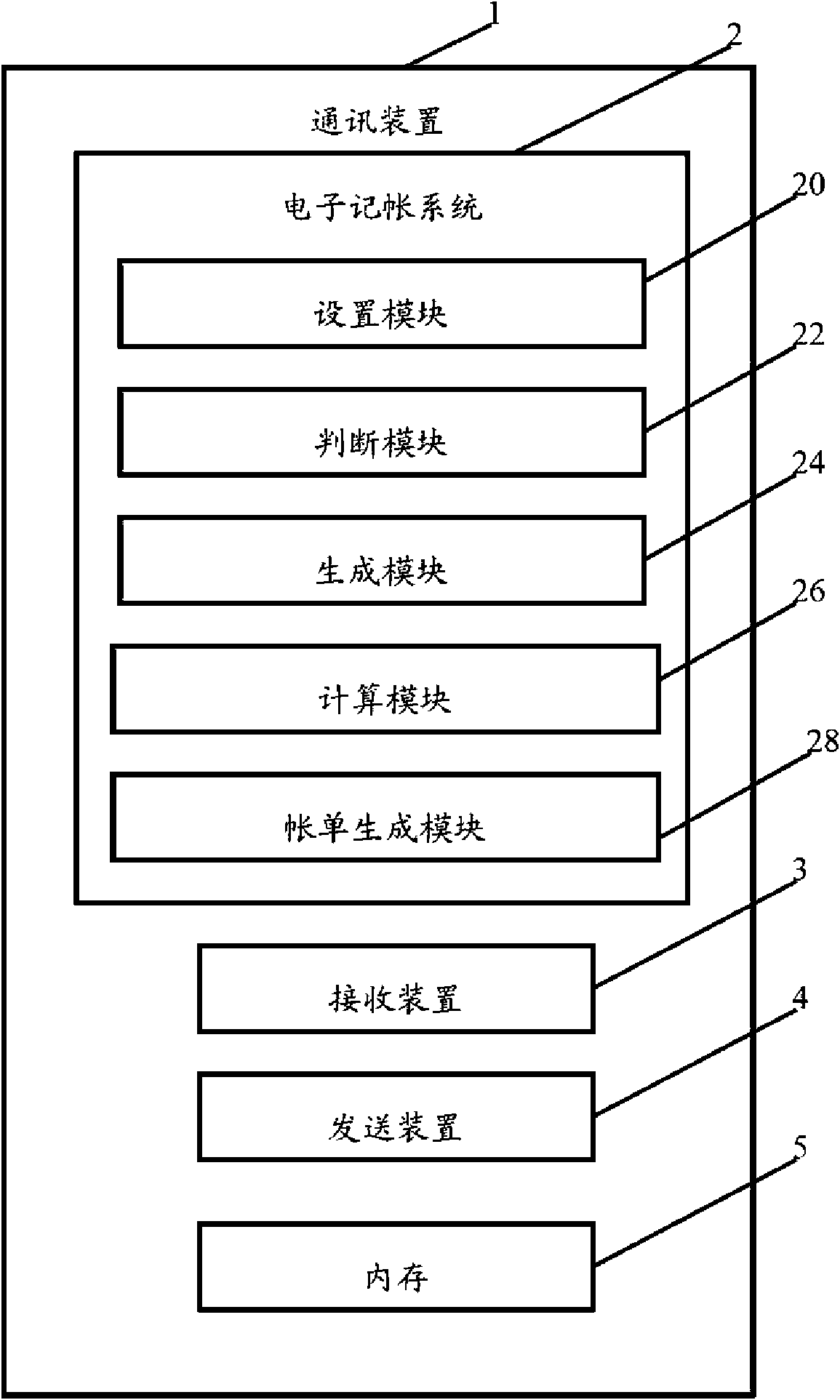
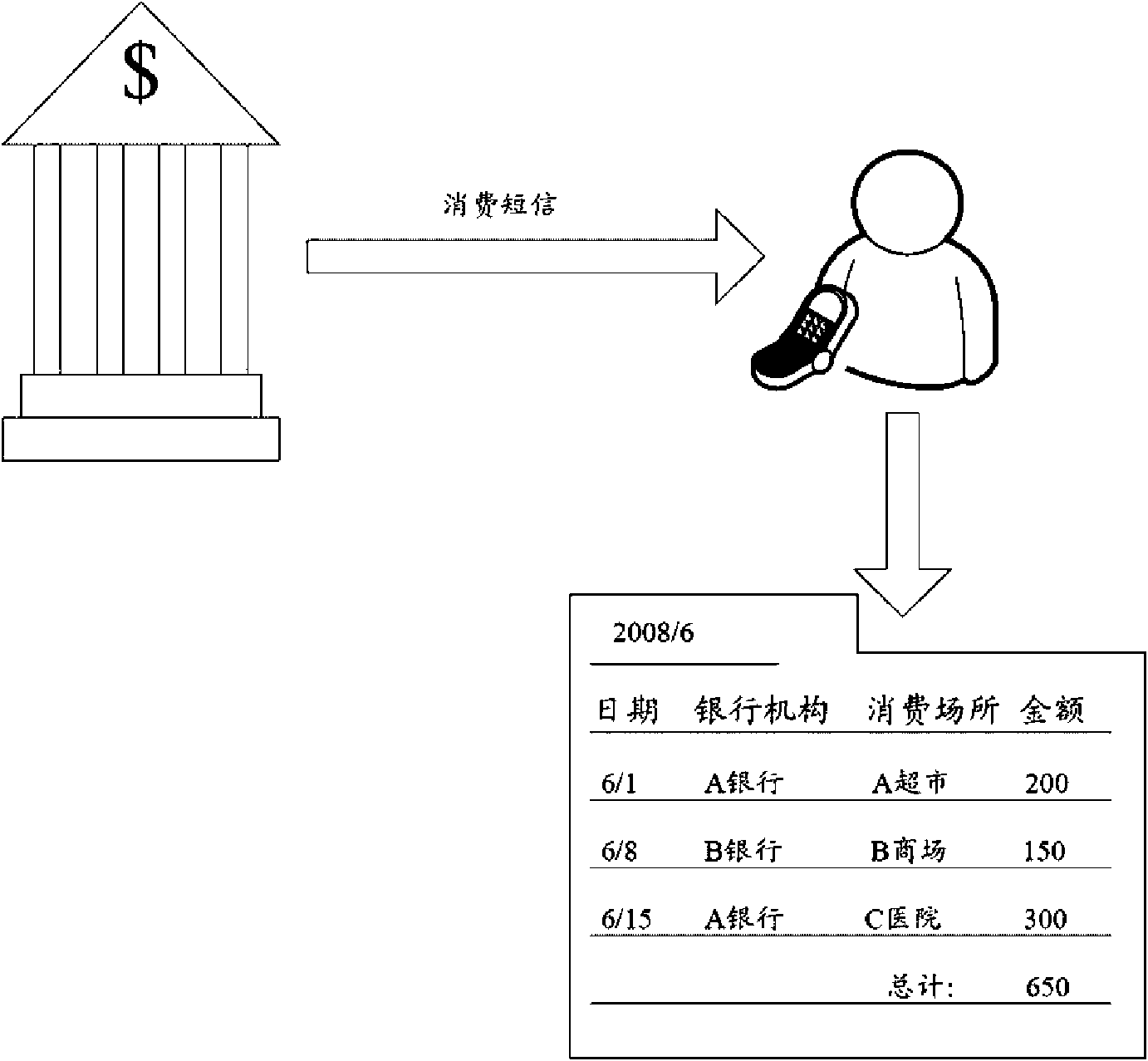
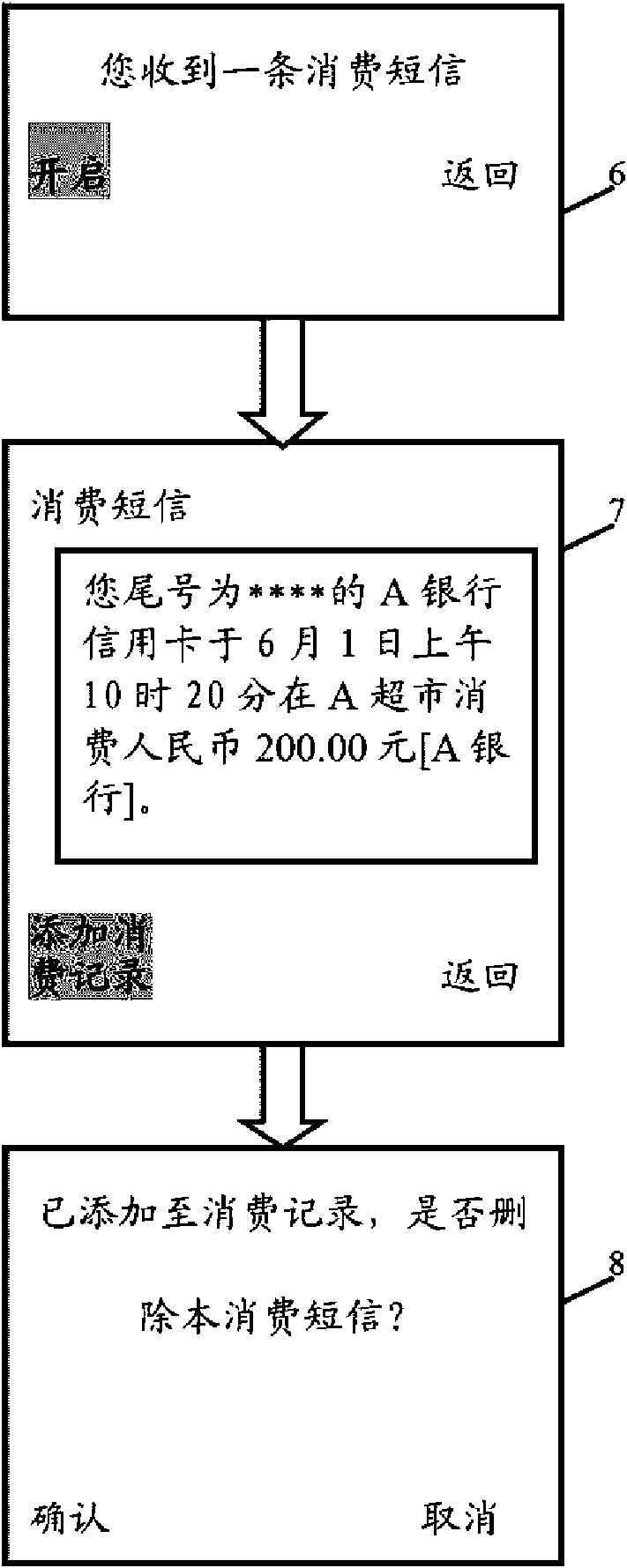
Electronic accounting system and method therefor
The invention relates to an electronic accounting system applied to communication devices, comprising a setting module, a judgement module and a generation module; wherein, the setting module is used for setting identification key of consumption short message and bank short message service number; the judgement module is used for identifying whether the short message is the consumption short message according to the set identification key and the bank short message service number after the communication device receives the short massage; the generation module is used for extracting consumption data in the consumption short message and generating corresponding consumption recording when the received short message is identified to be the consumption message. The invention further provides an electric accounting method. The system and the method of the invention can automatically generate electronic bill according to the short message received by the communication device.
Owner:SHENZHEN FUTAIHONG PRECISION IND CO LTD +1
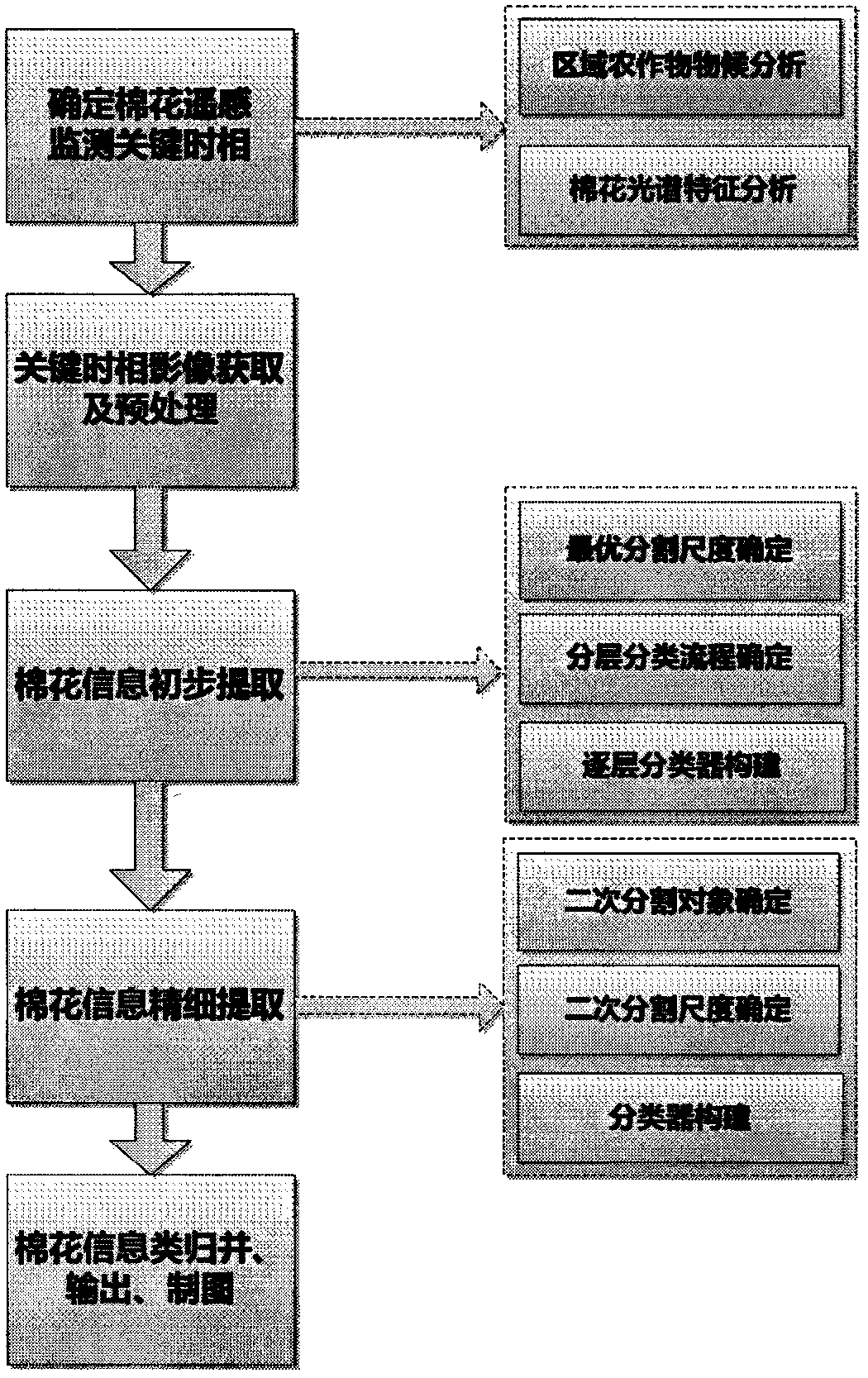
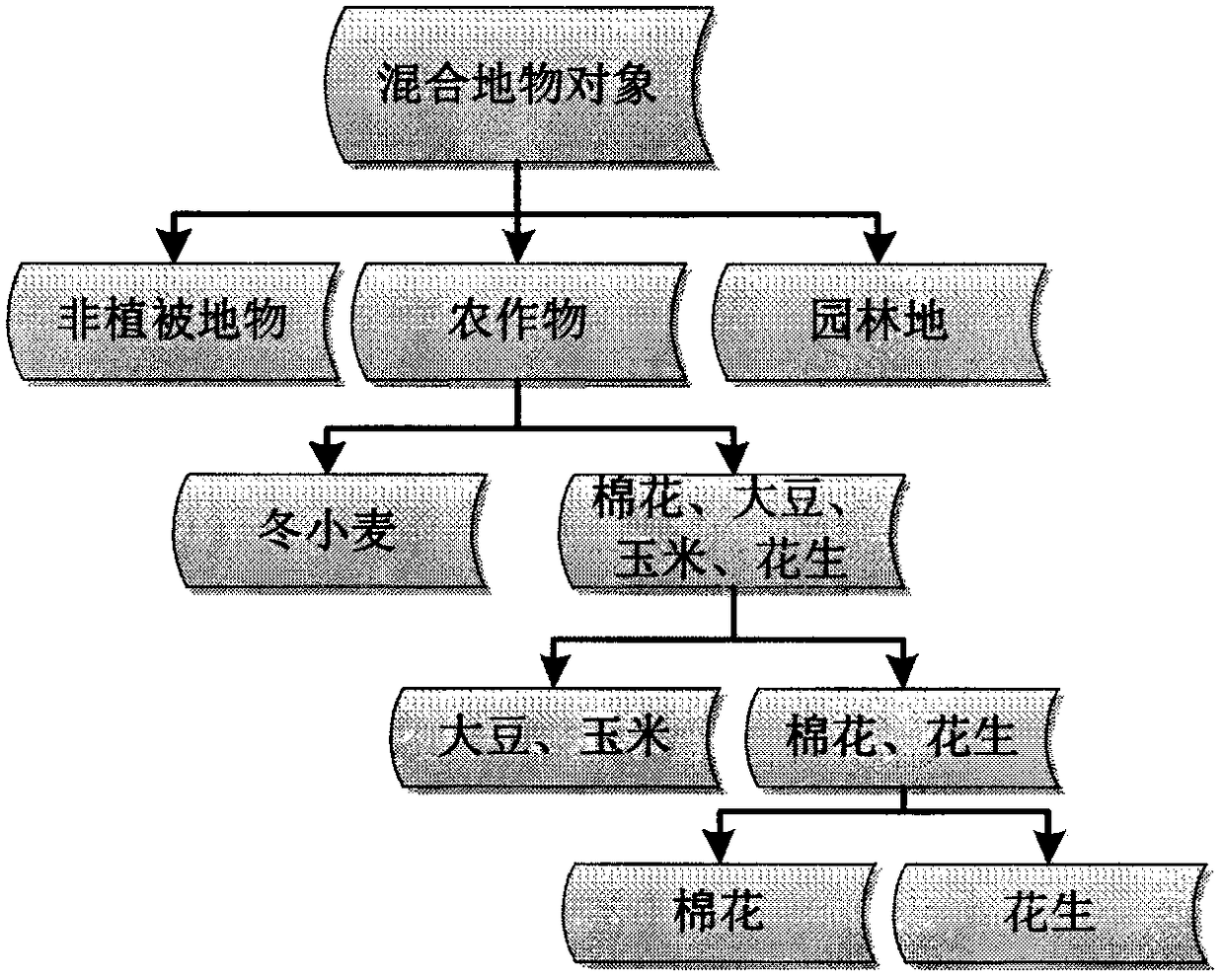
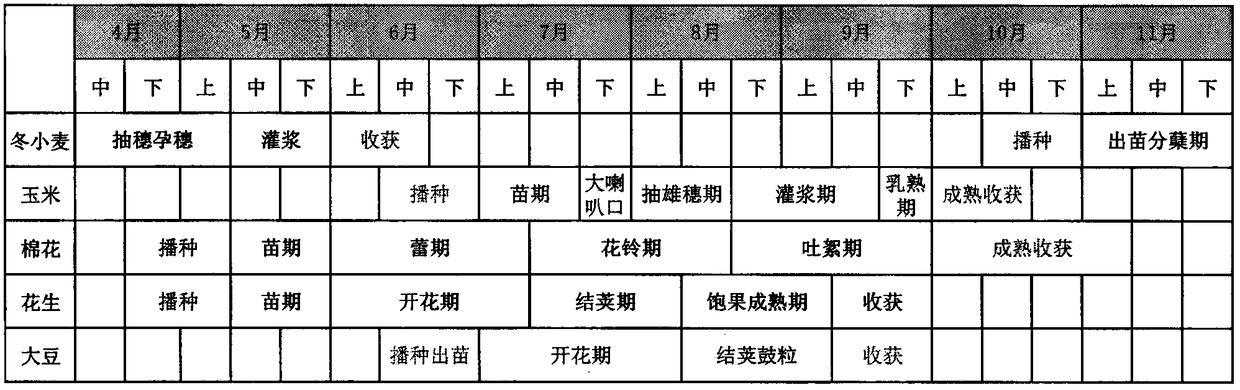
Cotton remote sensing monitoring method based on phenological analysis
ActiveCN108363949ARealize remote sensing automatic extractionAccurate and fast extraction resultsCharacter and pattern recognitionIdentification keyClassification methods
The invention belongs to the field of agricultural remote sensing, and particularly relates to a cotton remote sensing monitoring method based on phenological analysis. The cotton remote sensing monitoring method comprises the steps of: combining regional cotton spectral signature analysis and interferencing crop phenological analysis, and making cotton identification key time phases clear; acquiring a remote sensing image of a key phenological period, and preprocessing the remote sensing image; performing multi-scale segmentation on a multi-time-phase image, constructing classifiers in a layered manner, and extracting cotton information primarily; performing secondary segmentation on a cotton information primary result and possible mixing and separating objects, combining cotton spectralfeatures and texture features to construct a classifier, removing mixing and separation, and supplementing cotton information omitted in extraction; and merging extracted cotton information subclasses, outputting and drawing a graph. The cotton remote sensing monitoring method based on phenological analysis realizes automatic extraction of cotton planting information through combining phenological period analysis of cotton and interferencing crops with a layered classification method based on the remote sensing image, fully considers the spectral difference and texture features of the cottonand interferencing crops, makes the cotton planting information extraction result more precise and rapid, and is easy to popularize and use.
Owner:TWENTY FIRST CENTURY AEROSPACE TECH CO LTD
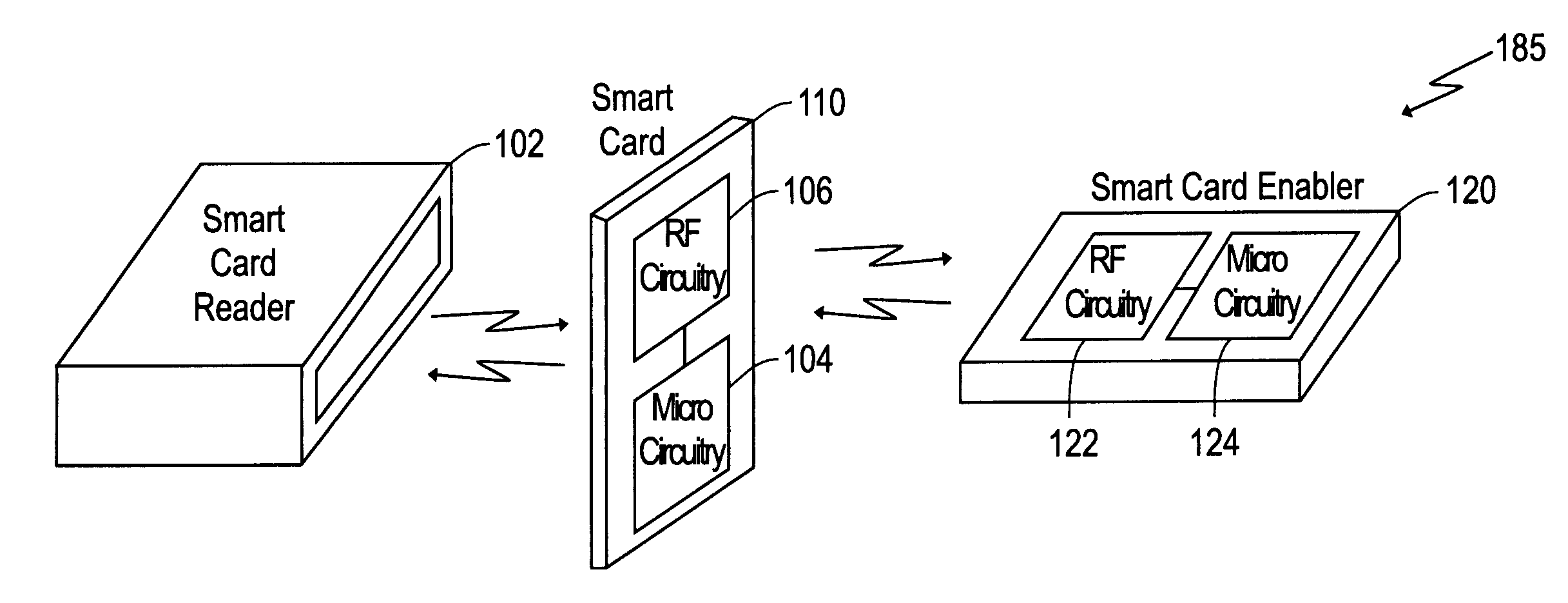
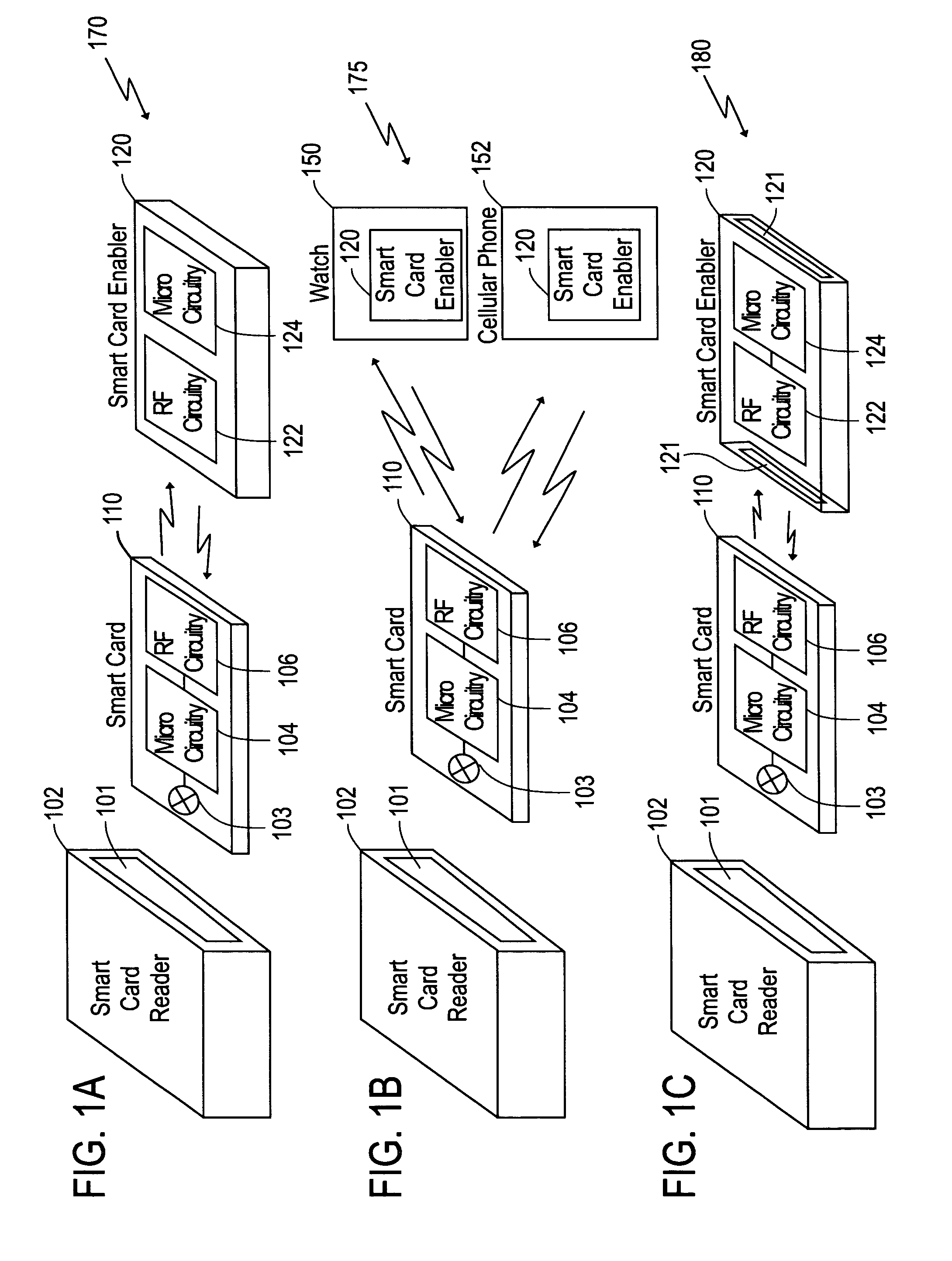
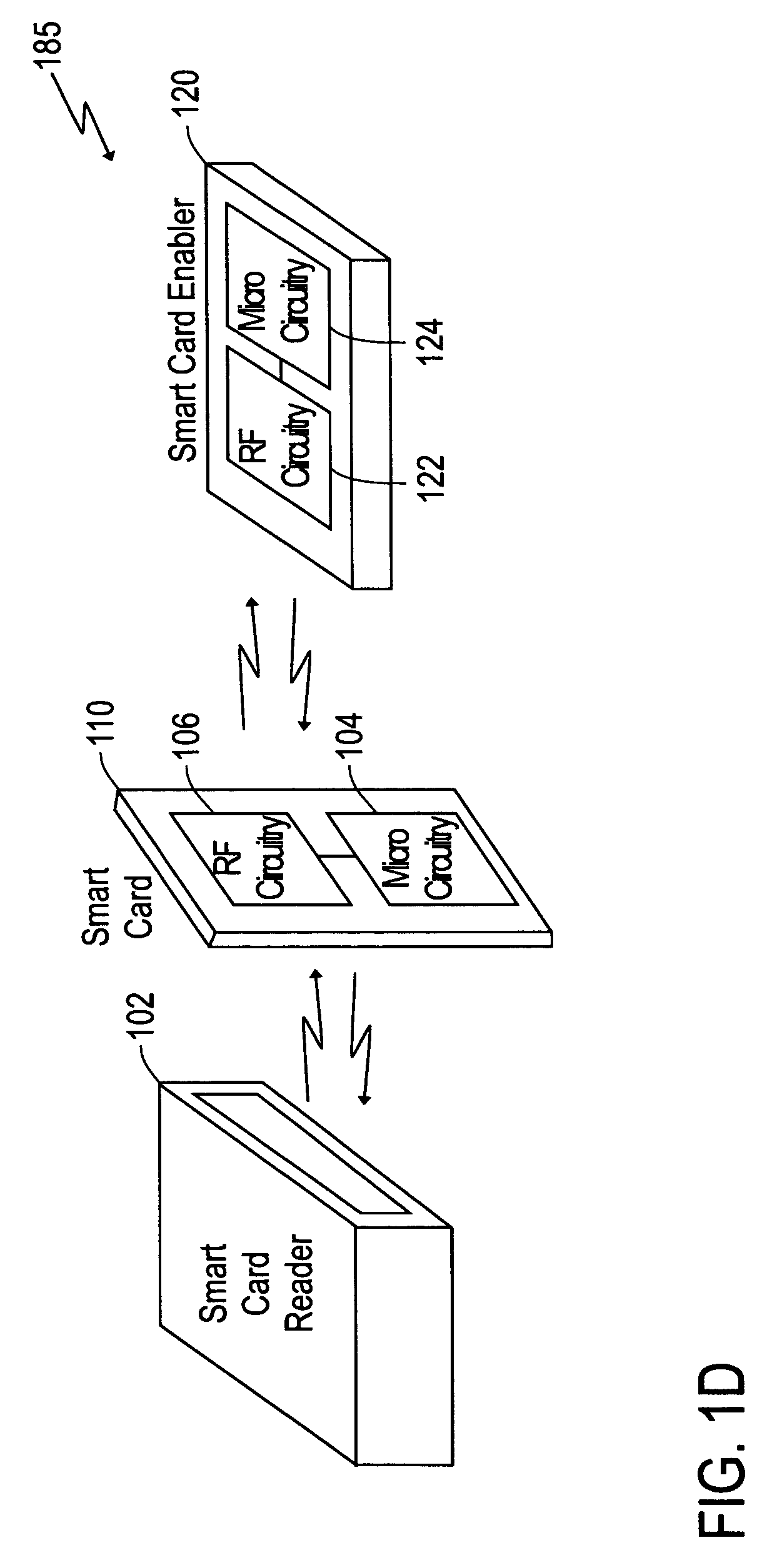
Method for recovering information stored in a smart card
A system and method for using a smart card. The system includes a smart card enabler receiving a first identification key from a smart card. The smart card enabler compares the first identification key with a second identification key. If the first identification key matches the second identification key, the smart card enabler enables the smart card to function with a smart card reader. Also, if information stored in a smart card is incapable of being retrieved from the smart card, the transaction information stored in the smart is recovered by using information stored in a smart card enabler.
Owner:CENT FOR WIRELESS COMM OF NAT UNIV OF SINGAPORE
Method of invisibly embedding into a text document the license identification of the generating licensed software
InactiveUS20050262034A1Digital data processing detailsUser identity/authority verificationIdentification keySoftware license
Method of invisibly embedding into a text document generated by a licensed software the License Identification Signature of the software wherein each original copy of the software has been assigned a unique Software License Code (SLC) and a unique License Identification Key (LIK) by a Licensing Authority, such a method comprising the steps of computing a Document Hash Value (DHV) of the text document (12), getting from the DHV a License Identification Code (LIC) of the text document by using the LUK (14), and embedding (18) invisibly into the text document the License Identification Signature (LIS) formed by the SLC, DHV and LIC after the LIS has been encoded by using character attributes.
Owner:KYNDRYL INC
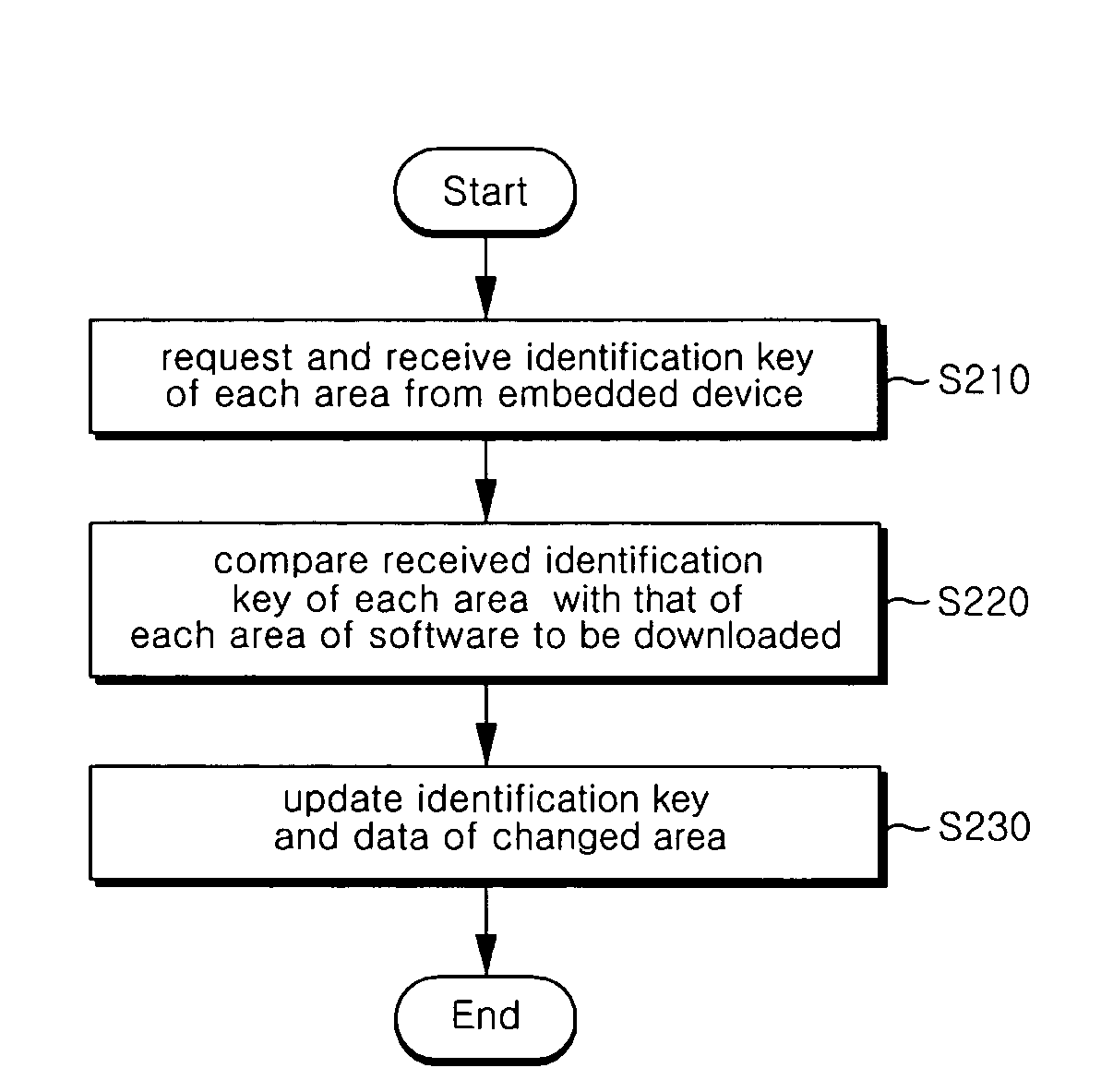
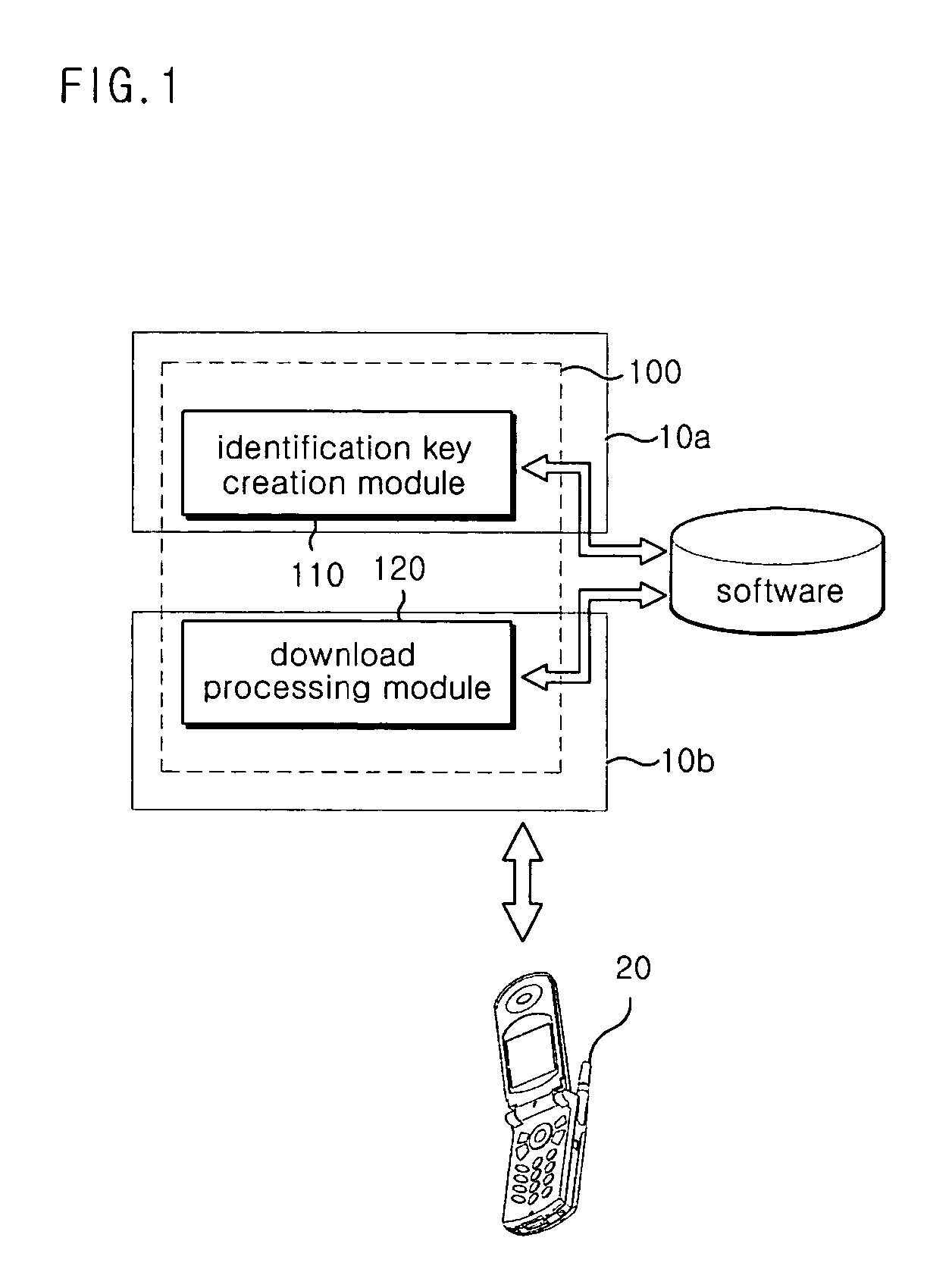
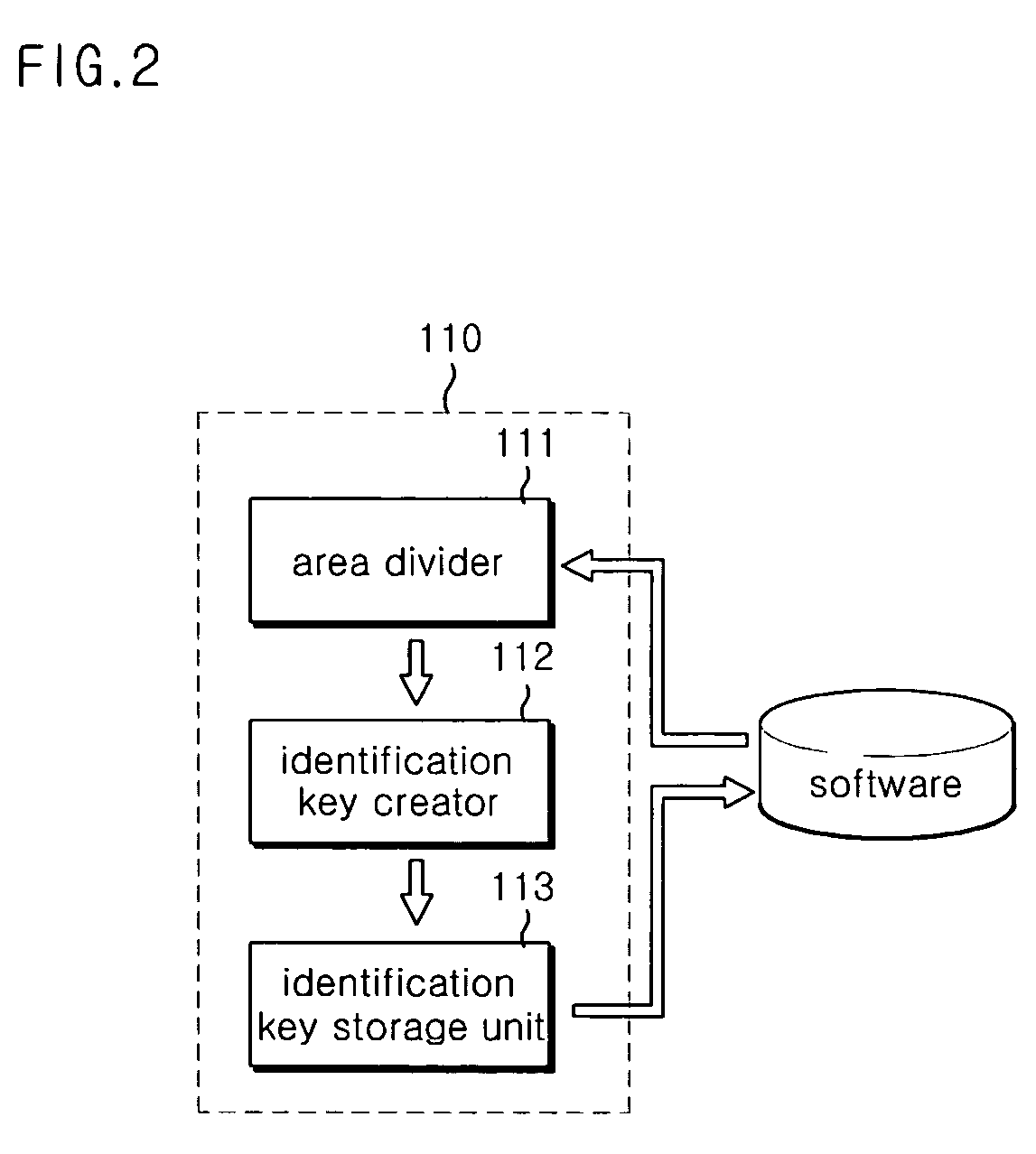
Communication terminal and communication network for partially updating software, software update method, and software creation device and method therefor
ActiveUS7873956B2Reduce upgrade timeProgram loading/initiatingMemory systemsIdentification keySoftware update
Disclosed herein are a communication terminal and communication network for partially updating software, a software update method, and a software creation device and method therefor. The software is divided into a plurality of areas each having a predetermined size, and unique identification keys are assigned to the areas of the software, respectively. A search is made for at least one changed area among the areas of the software on the basis of version information of the software or the identification keys, and data of the changed area is downloaded to upgrade the software. Therefore, it is possible to shorten an upgrade time of the software.
Owner:PANTECH CORP +1
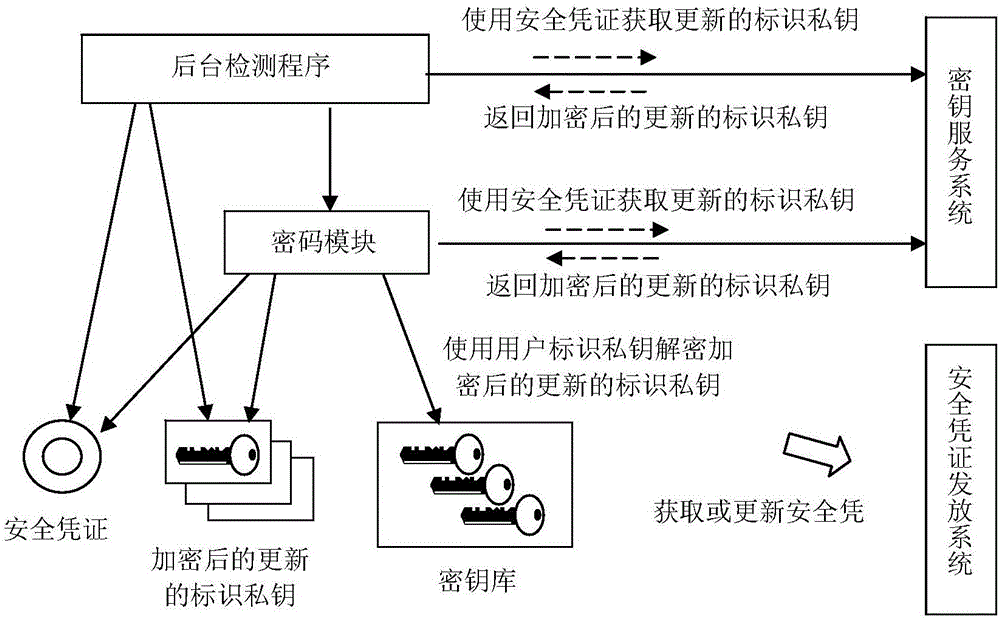
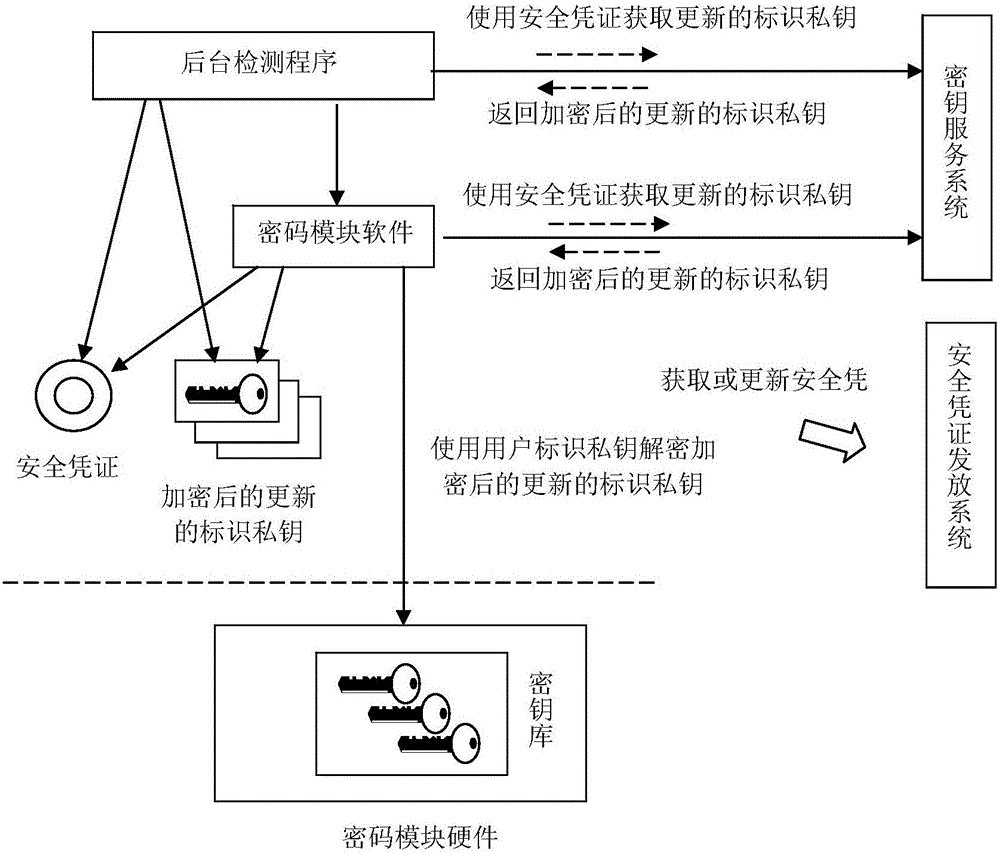
Method for automatically updating identification private key and password system
ActiveCN106452764AAvoid manual operationKey distribution for secure communicationUser identity/authority verificationIdentification keyPassword
The invention relates to a method for automatically updating an identification private key and a password system. The method comprises the following steps: when a password module or a background detection program detects that a new identification private key needs to be obtained for a user, using a security credential stored in a user computer locally to apply an identification key service system to obtain the new identification private key; after the identification key service system verifies the validity of the security credential, generating the new identification private key for the user, using an identification public key corresponding to a previous time period of the time period corresponding to the updated identification private key to encrypt the generated updated identification private key, and then returning the encrypted updated identification private key to the password module or the background detection program to be stored locally; and if the password module or the background detection program discovers that the encrypted updated identification private key is stored in the user computer locally and that a user identification private key for decrypting the encrypted updated identification private key is available, then performing decryption by sung the private key of the user to obtain the updated identification private key.
Owner:WUHAN UNIV OF TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com