Double factor combined public key generating and authenticating method
An authentication method and a technology of combining public keys, which are applied in the field of public key cryptography and authentication, can solve the problems of private keys without exclusive rights or privacy, collusion attacks, and affecting large-scale applications.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
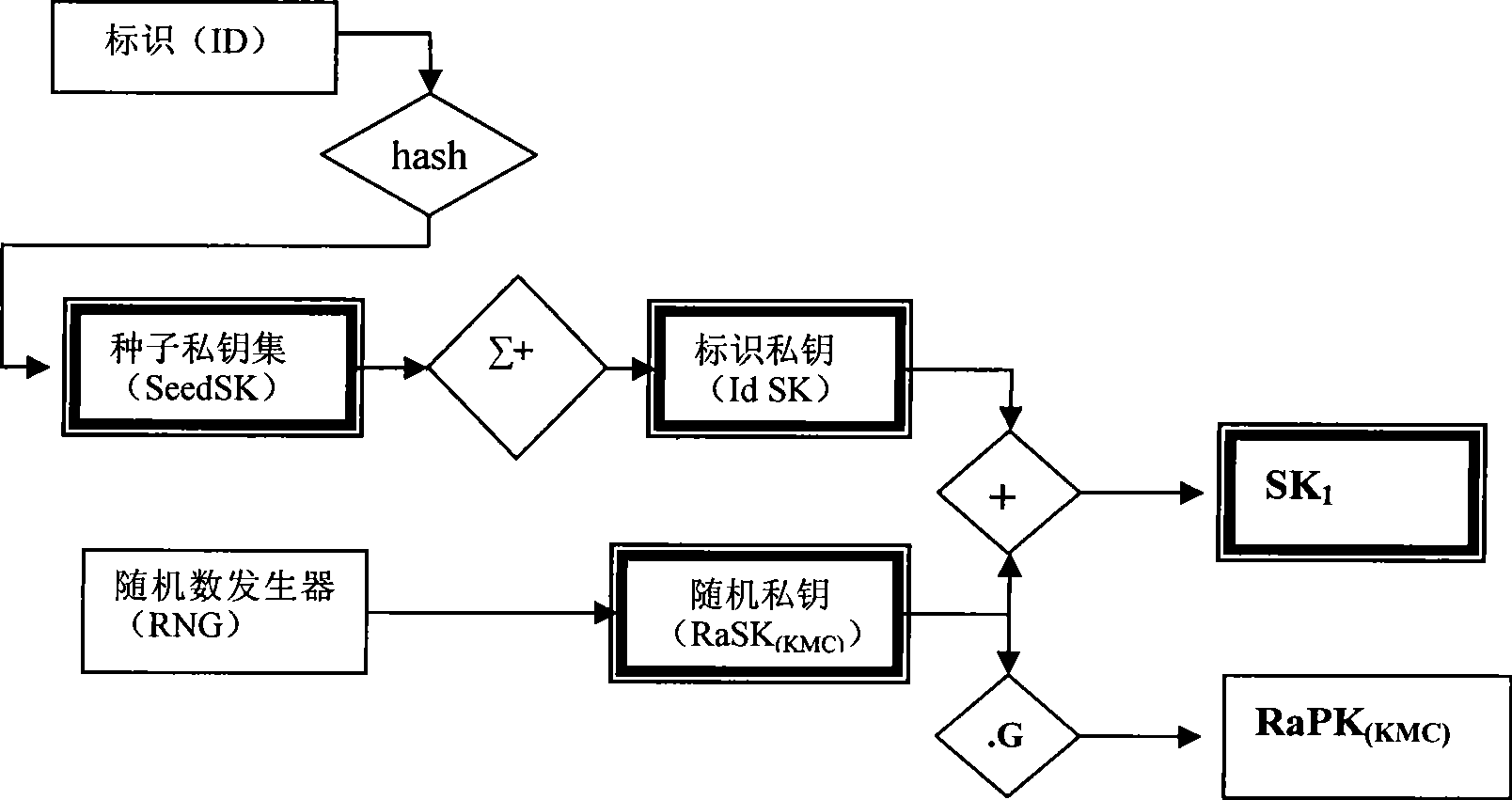
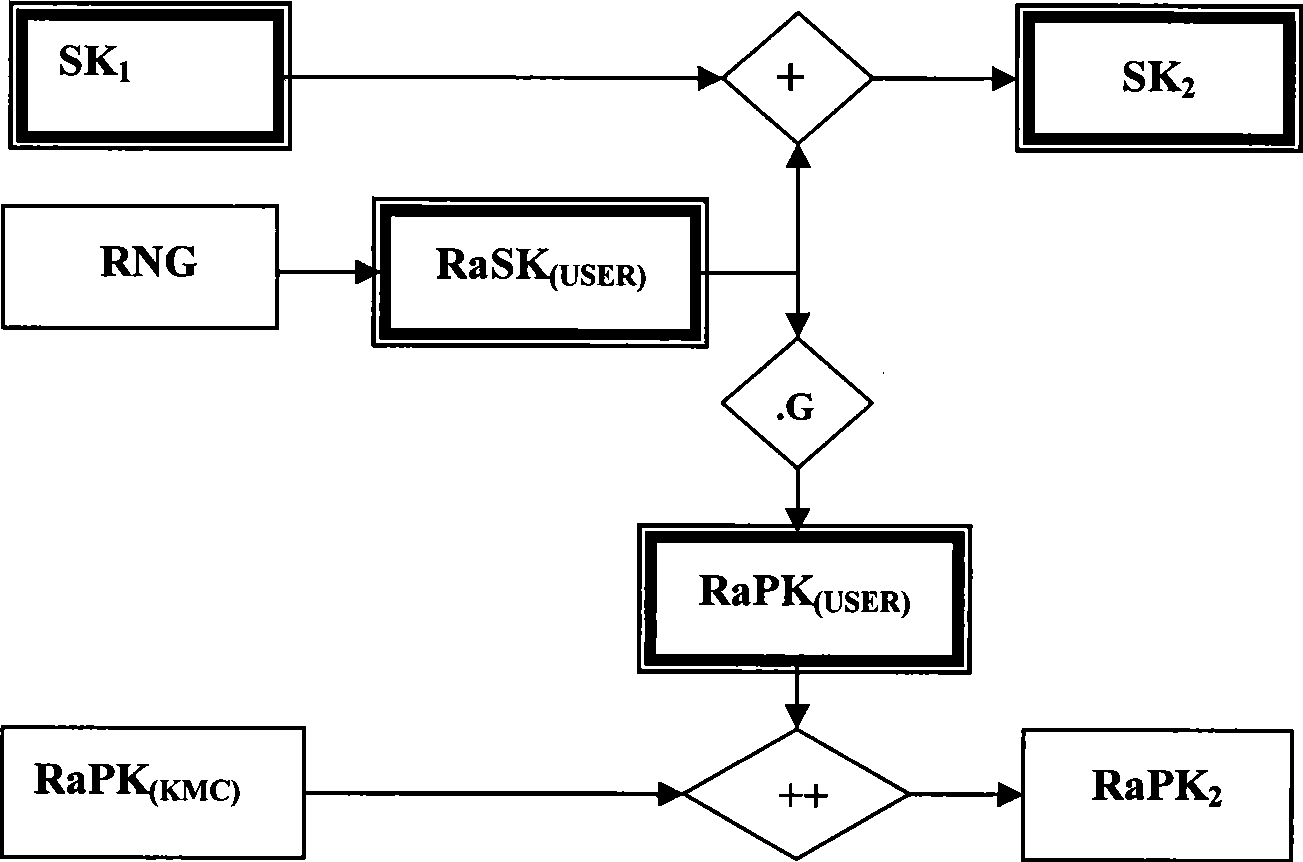
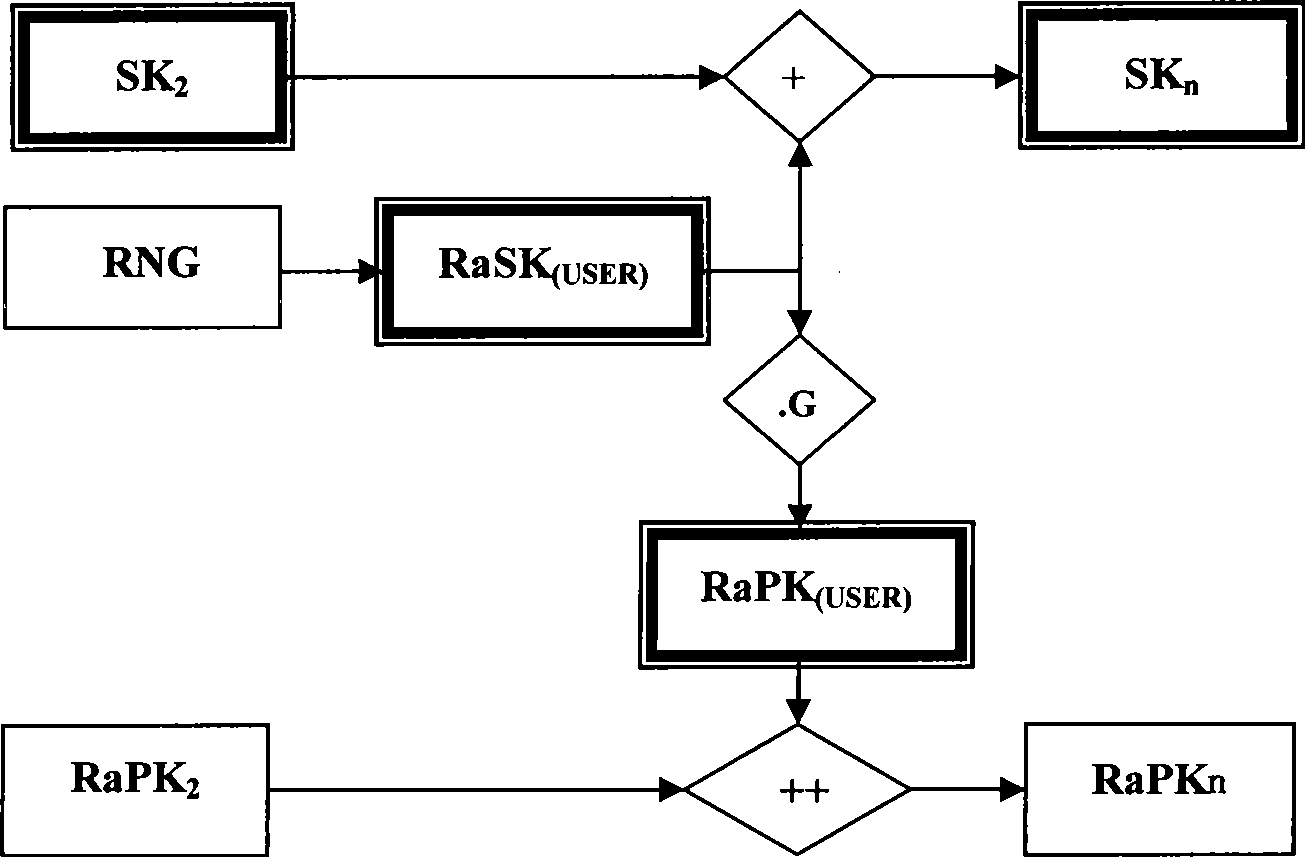
[0096]The two factor combined public key cryptosystem (Two Factor Combined Public Key System, referred to as TF-CPK) proposed by the present invention is composed of two mutually independent public keys—the self-defined random public key and the identification public key, involving: mathematics Fundamentals, key combination laws, random numbers, identities, hash functions, seed keys, etc. Hereinafter, taking elliptic curve cryptography and discrete logarithm as examples, and in conjunction with the accompanying drawings, the specific implementation of the key generation method according to the present invention will be further described in detail from various aspects. It should be noted that the specific implementation of the two-factor combined public key technology and identification authentication system according to the present invention is only an example, but the present invention is not limited to this specific implementation.
[0097] 1. Several elements of the two-fac...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com