Patents
Literature
245 results about "Public-key cryptography" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
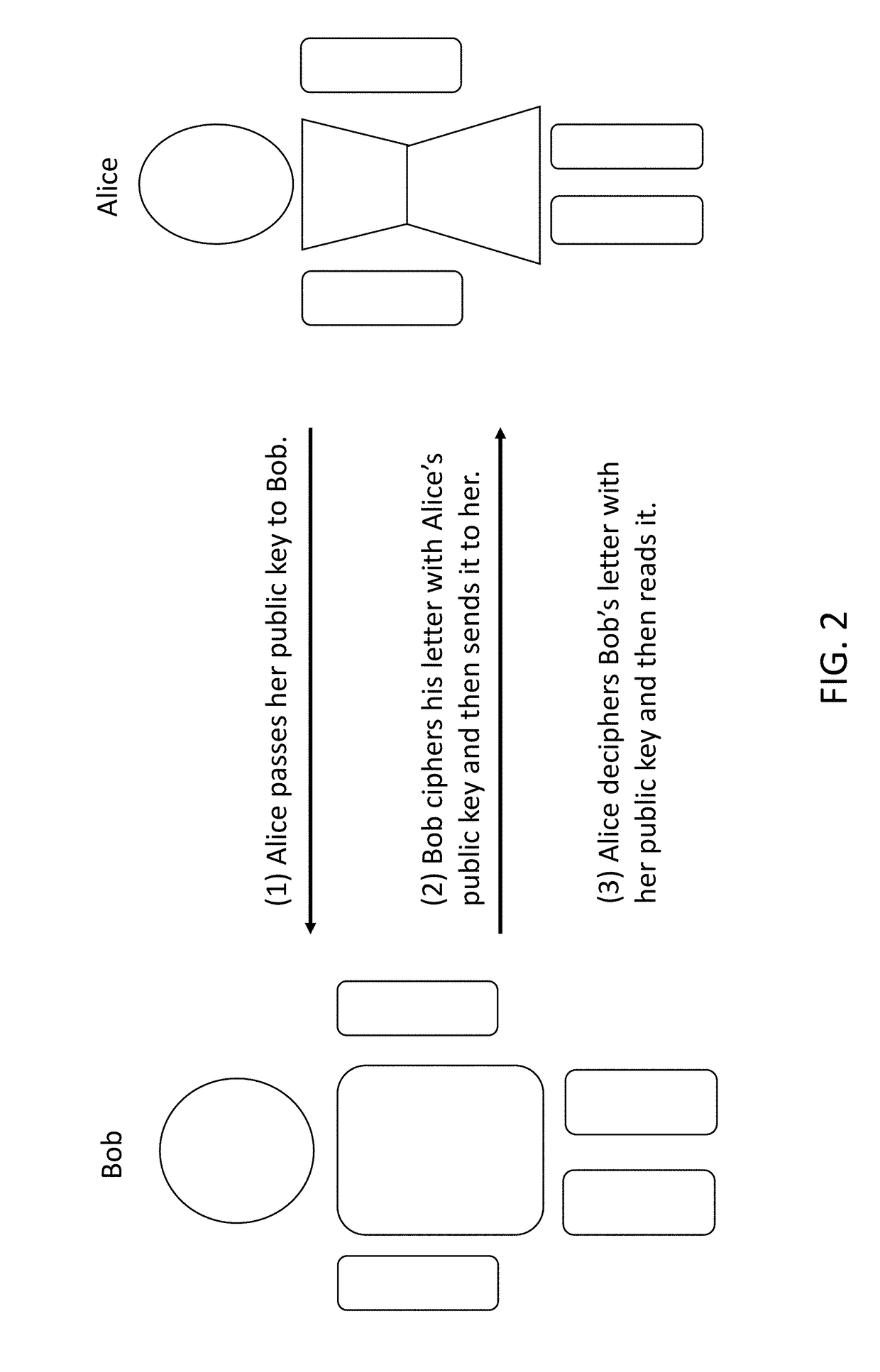
Public-key cryptography, or asymmetric cryptography, is a cryptographic system that uses pairs of keys: public keys which may be disseminated widely, and private keys which are known only to the owner. The generation of such keys depends on cryptographic algorithms based on mathematical problems to produce one-way functions. Effective security only requires keeping the private key private; the public key can be openly distributed without compromising security.
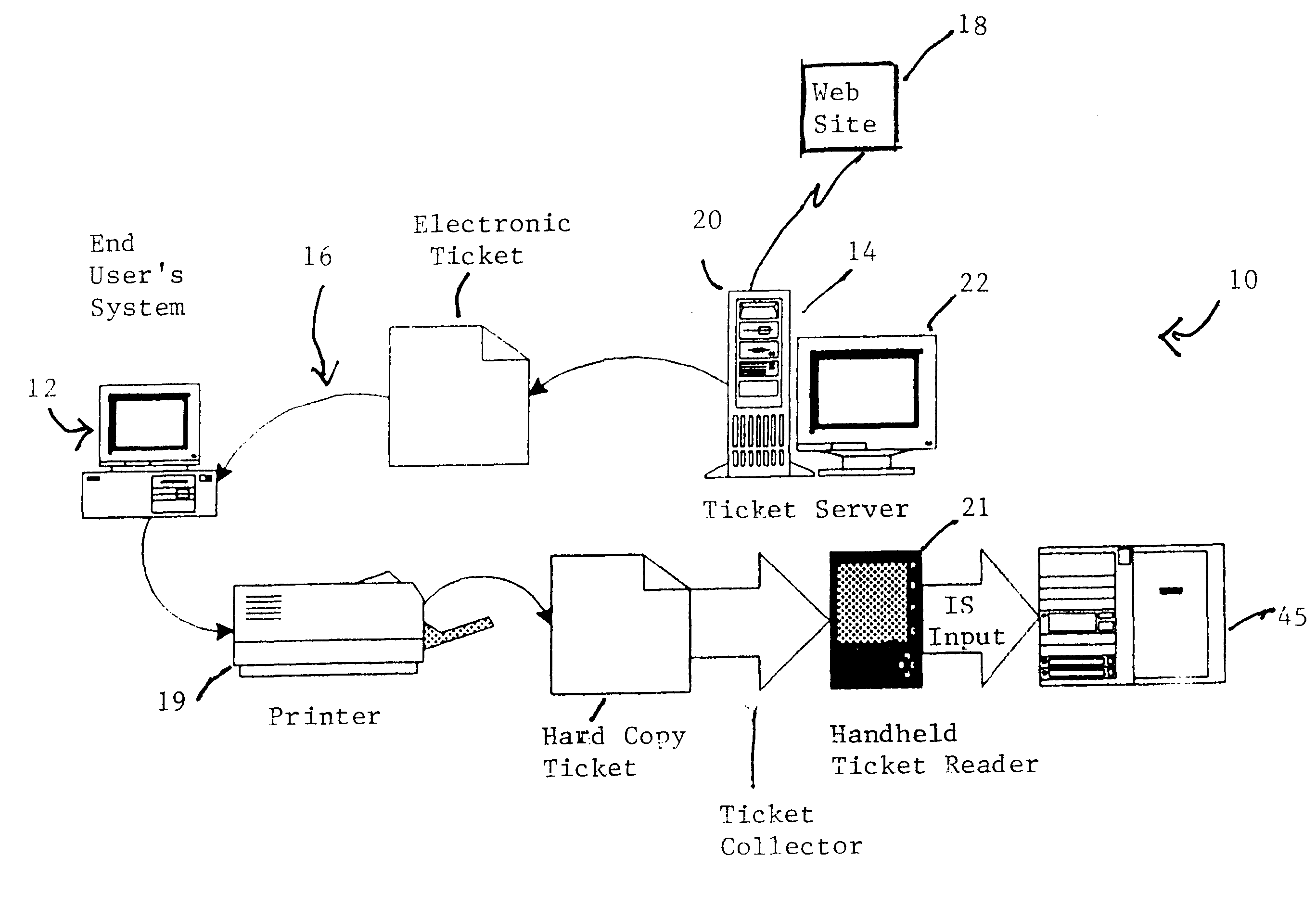
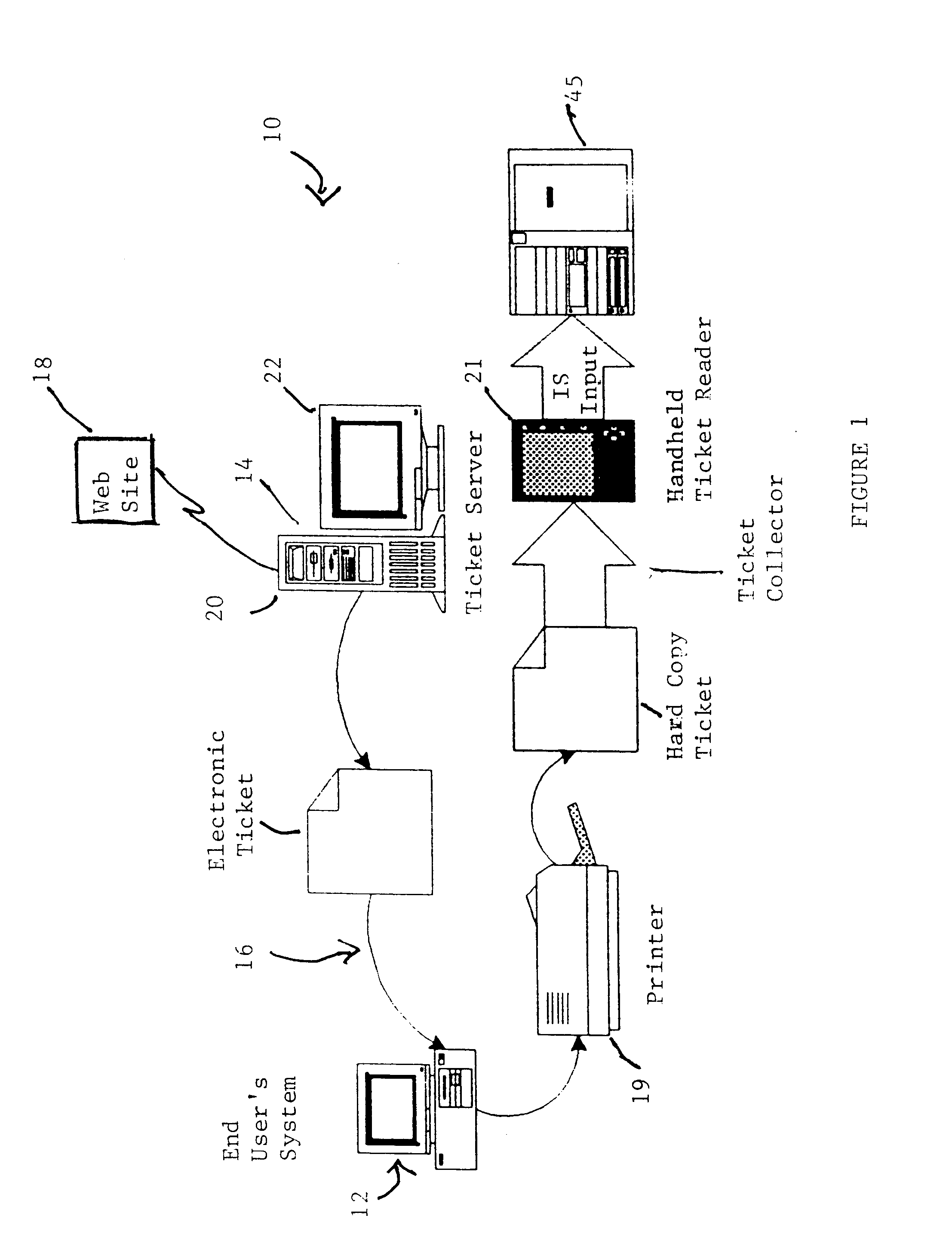
Cryptographic encoded ticket issuing and collection system for remote purchasers
InactiveUS6223166B1Prevent ticket fraudTicket-issuing apparatusElectrical apparatusCollection systemInformation networks
A cryptographic encoded, ticket issuing and collection system for real-time purchase of tickets by purchasers at remote user stations in an information network that includes a plurality of remote user stations coupled to a server in an information network, e.g., the Internet, for purchase of services, products, or tickets to an event. An operator of the remote user station selects a ticket for purchase to an event using standard protocols of information network. An electronic ticket is transmitted to the operator and includes a cypher code created using a public key cryptography system. The operator displays the electronic ticket for verification purposes and proceeds to print out the ticket at the station. The ticket is presented to a ticket collector whereupon the ticket is scanned by a portable terminal for decoding the cypher code using a public key reloaded into the terminal by the producers of the event. The decoded cypher code is compared against the event description stored in the portable terminal and if equal, the ticket is accepted for admission to the event. The ticket information is stored in the portable terminal and subsequently uploaded to the information system to check for duplicate tickets.
Owner:IBM CORP
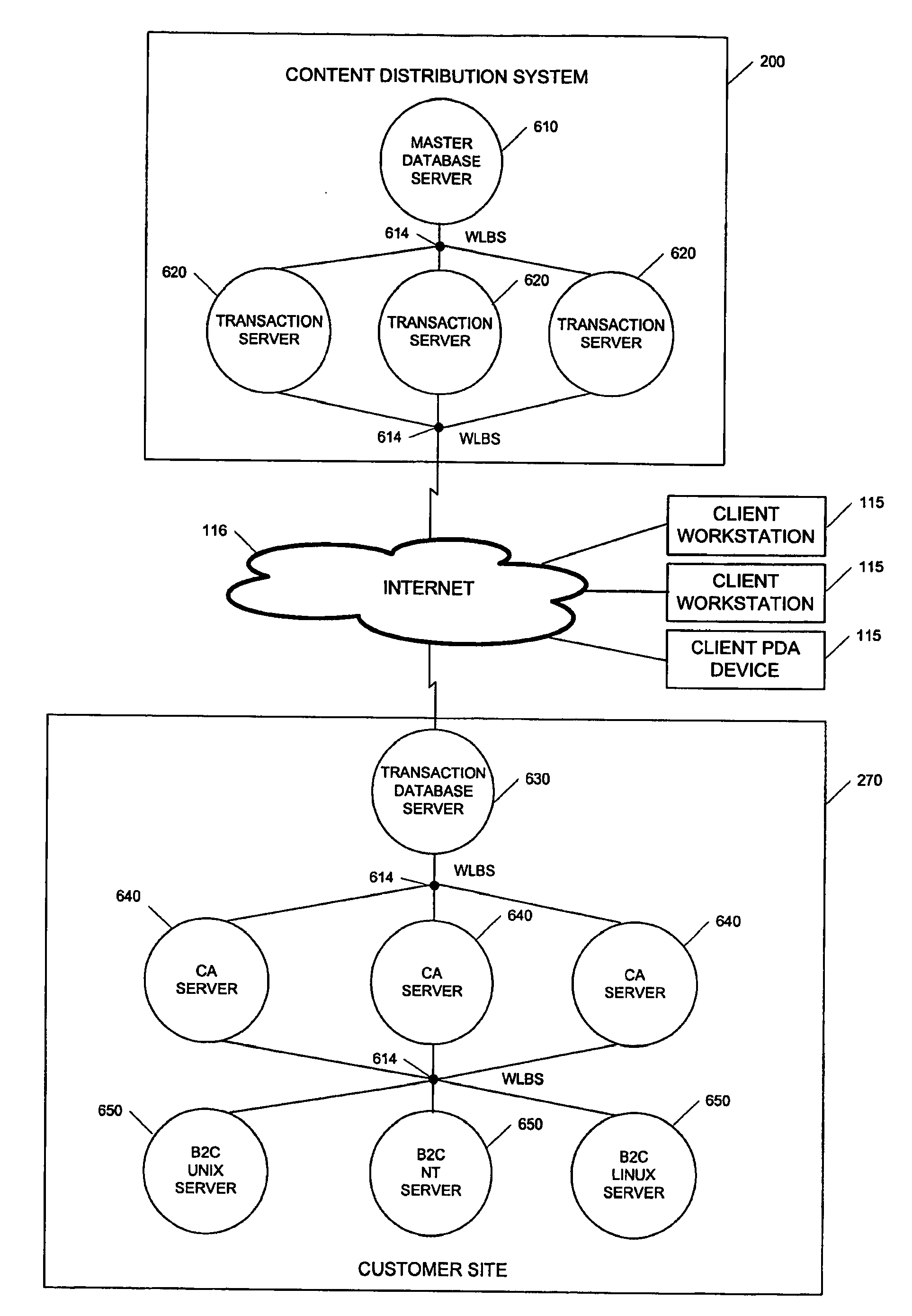
Network-based content distribution system
InactiveUS20090037388A1Maximize potential return-on-investmentMinimal burdenDigital data processing detailsUser identity/authority verificationContent distributionPublic network
Owner:VERIMATRIX INC
Method and apparatus for efficiently initializing secure communications among wireless devices
InactiveUS6886095B1Efficient administrationEliminating inflexibilityUser identity/authority verificationRadio/inductive link selection arrangementsSecure communicationRadio networks
A method and system for efficiently establishing secure communications between mobile devices in a radio network. The present invention utilizes public key cryptography and unique hardware identifiers to enable authorizations for access to wireless networks, such as picocells. The present invention prevents the mobile user from maintaining a plurality of secrets such as user identifier / password pairs, PINs, or encryption keys, for access to each device to which he might require access.
Owner:IBM CORP
Method and apparatus for efficiently initializing mobile wireless devices
InactiveUS6980660B1Efficient administrationEliminating inflexibilityKey distribution for secure communicationDigital data processing detailsSecure communicationUnique identifier
A method and system for enabling wireless devices distributed throughout an enterprise to be efficiently initialized for secure communications. The method and system utilize well known public key cryptography and machine unique identifiers to establish a secure channel and initialize the wireless devices.
Owner:IBM CORP
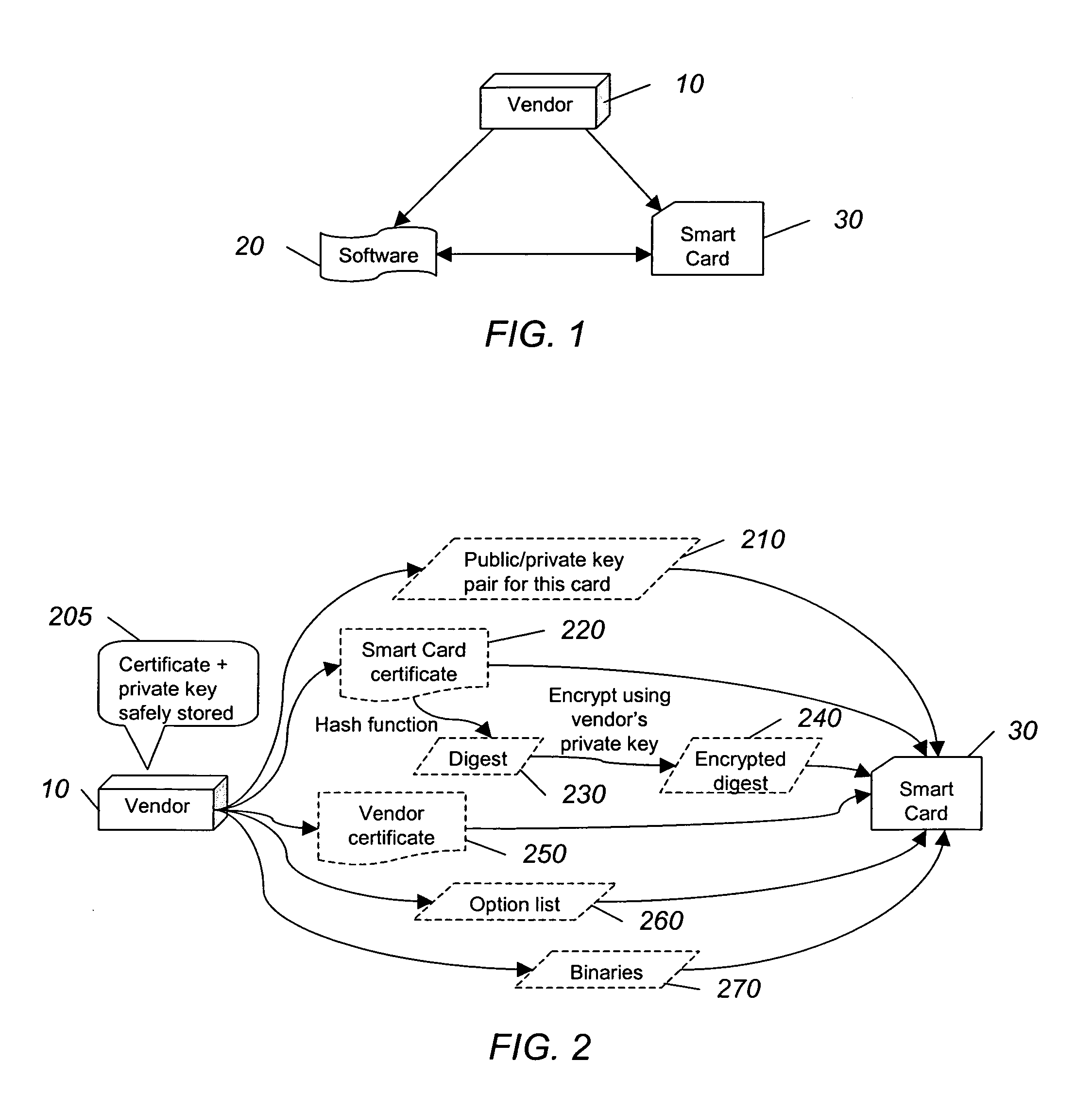
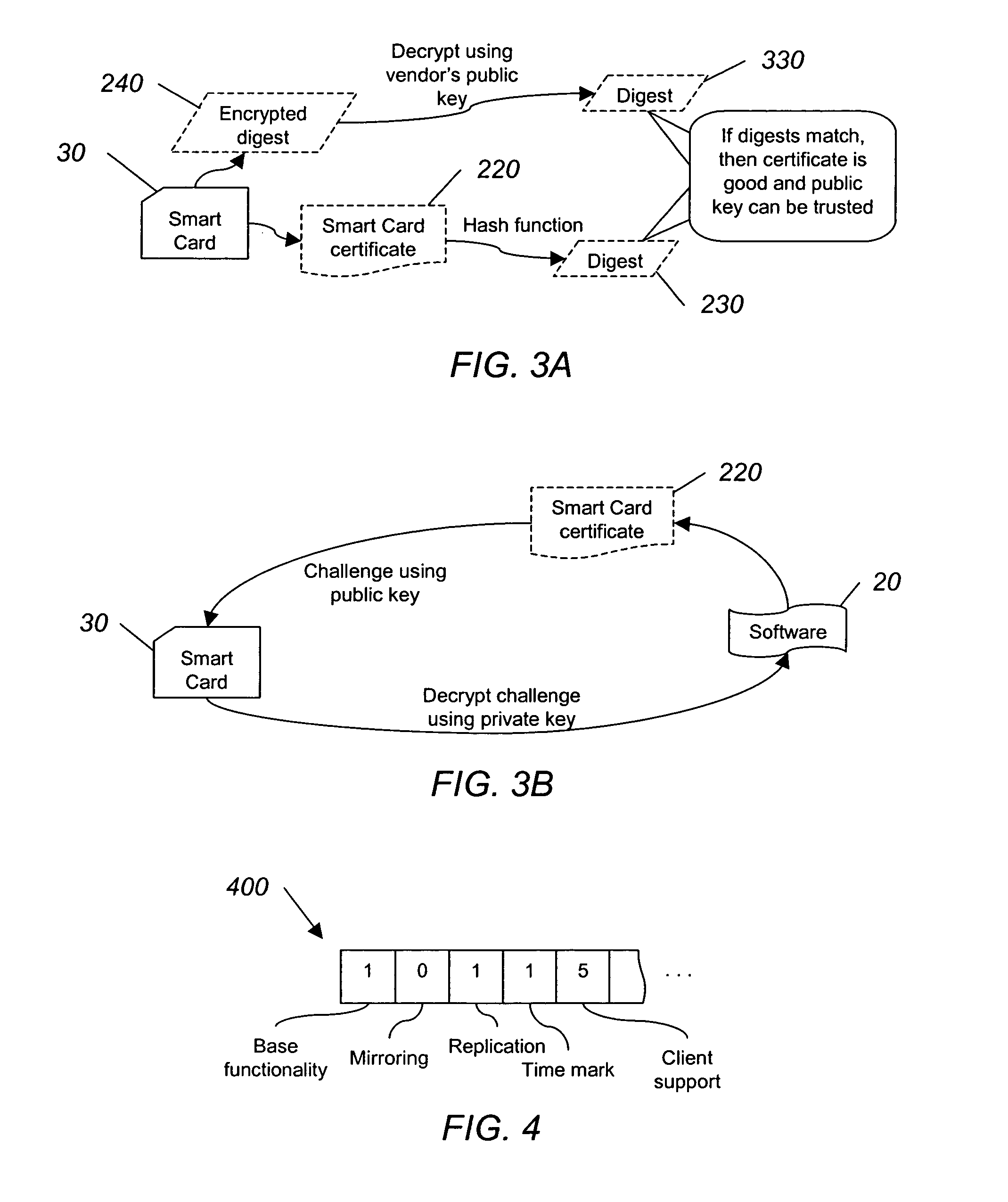
System and method for authorizing software use
InactiveUS20050138387A1User identity/authority verificationComputer security arrangementsSmart cardSoftware vendor
A software vendor freely distributes software to users and issues smart cards to be used with the software. The smart card includes at least one software module missing from the software package and a list of allowed functionality dictating the capabilities of the software package. A user authenticates, using, e.g., public key cryptography, the smart card, which authorizes the use of the software. Once authorized, the module missing from the software is reunited with the rest of the software package. The software can be used limited to the allowed functionality included with the card. If more or different functionality is needed, the user can purchase another card authorizing such additional functionality, and then transfer the new functionality to the old smart card.
Owner:FALCONSTOR
Technique for securely communicating and storing programming material in a trusted domain
A “trusted domain” is established within which content received from a communications network, e.g., a cable TV network, is protected from unauthorized copying thereof, in accordance with the invention. In an illustrative embodiment, the trusted domain includes a device associated with a user which receives content from the cable TV network. The content may be encrypted using a content key in accordance, e.g., with a 3DES encryption algorithm before it is stored in the device. In addition, a first encrypted content key version and a second encrypted content key version are generated by respectively encrypting the content key with a public key associated with the device and another public key associated with the user, in accordance with public key cryptography. The first and second encrypted content key versions are stored in association with the encrypted content in the device storage. The encrypted content can be migrated from a first device to a second device, and can be decrypted in the second device if the second device is associated with the same user, and also provided with the second encrypted content key version.
Owner:TIME WARNER CABLE ENTERPRISES LLC
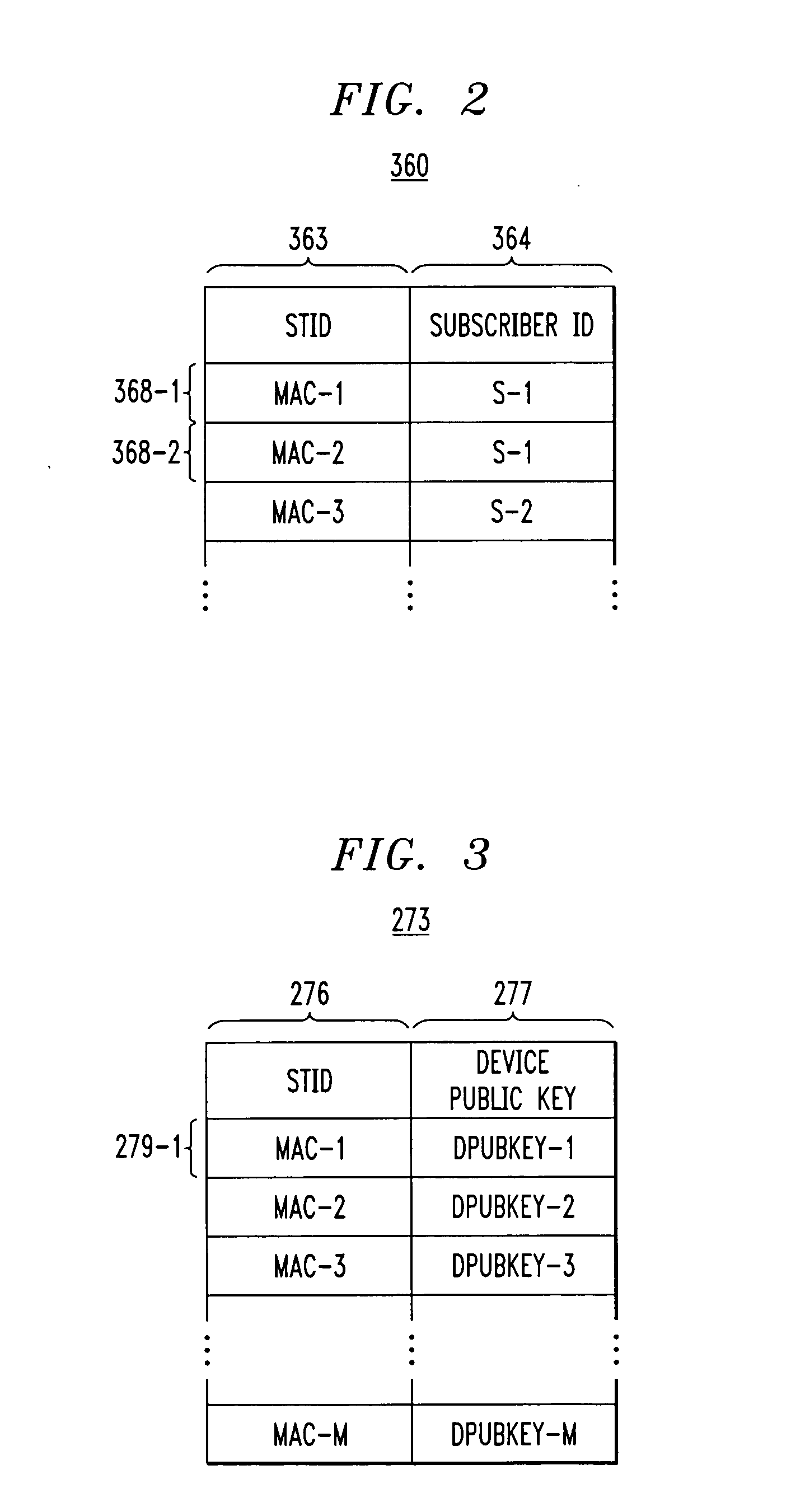
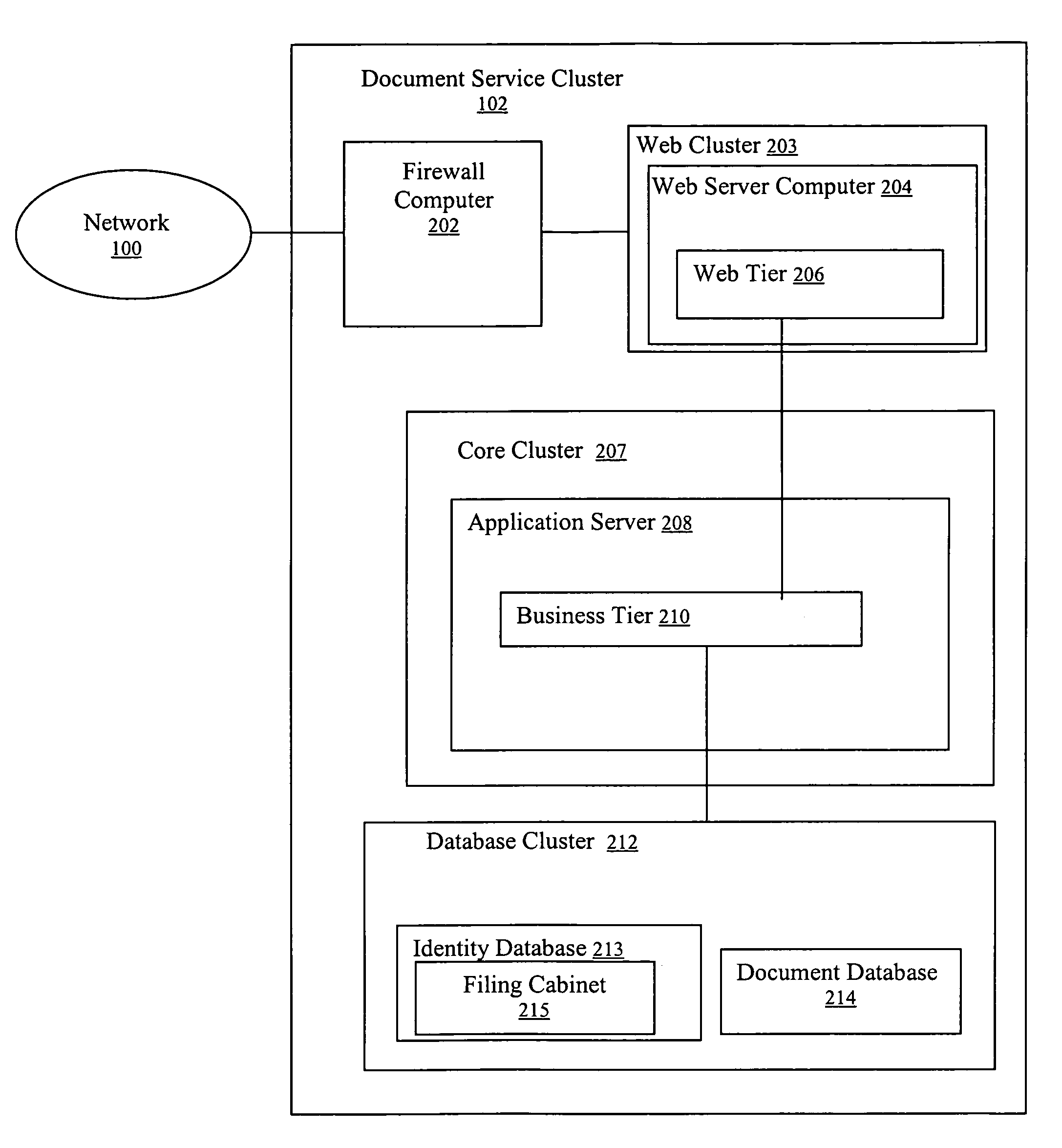
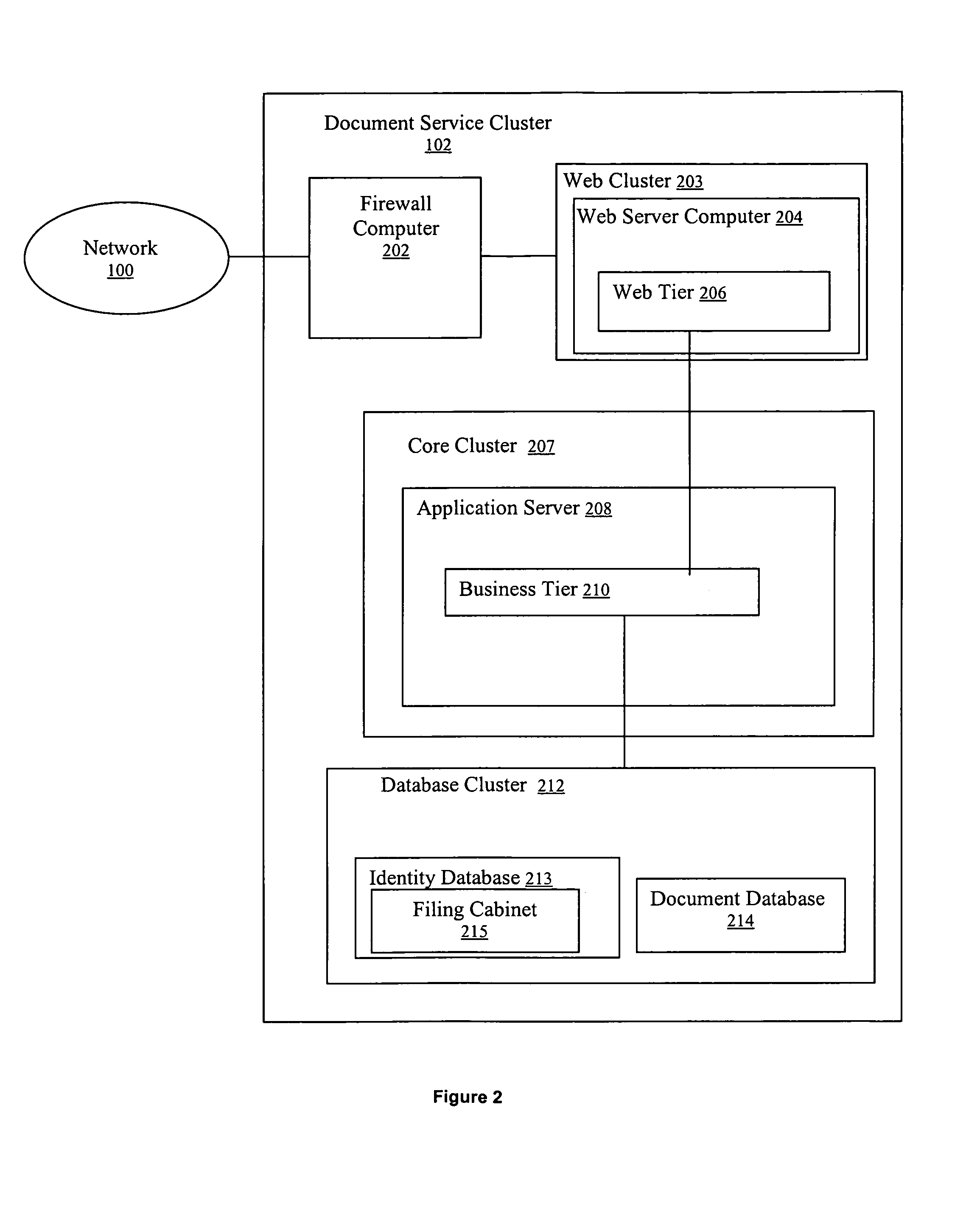
Method and system for signing and authenticating electronic documents
InactiveUS7237114B1Complete private encryption key constructing and reconstructing can be avoidedPrevent steppingUser identity/authority verificationUnauthorized memory use protectionElectronic documentComputer cluster
A system and method for signing, sorting, and authenticating electronic documents using public key cryptography. The system comprises a document service computer cluster connected to user computers, document owner server computers, and registration computers via a network such as for example, the internet or the world wide web. Document owners and system users can store electronic documents in an encrypted database located on the document service computer cluster, or on a document safe connected to the document owner server. Users can sign documents by identifying the document to be signed and sending a signing request to the document service computer cluster. The document service computer cluster retrieves the user's private key, which is located securely in a database on the cluster, and signs the identified document. No dedicated signing software need be installed on the user computer prior to accessing the document service computer cluster.
Owner:SIGNIX
Network-based content distribution system
InactiveUS7426750B2Maximize potential return-on-investmentMinimal burdenDigital data processing detailsUser identity/authority verificationContent distributionPublic network
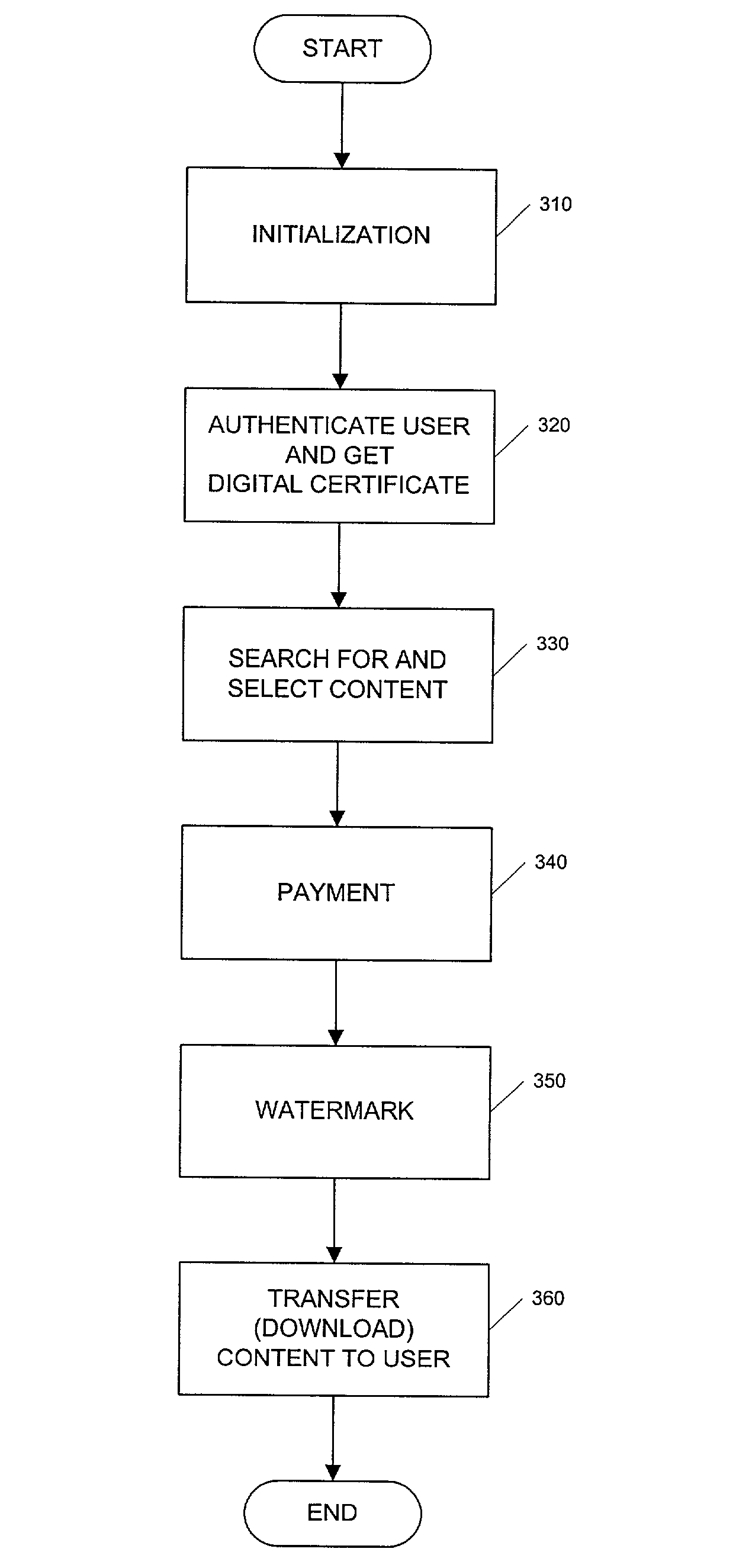
A method and system for transferring electronic media information over a public network in such a way as to provide safeguards for inappropriate distribution of copyright or otherwise protected materials are described. The media information is transparently watermarked with a unique ID, such as one generated from X.509 Digital Certificate and public-key cryptography public / private key pairs, such that the information can be identified as belonging to a particular individual. A system and method for monitoring the movement of such watermarked files, positively identifying people who have inappropriately distributed copyright materials over a public network without permission, and taking appropriate enforcement action against such people.
Owner:VERIMATRIX INC
Method, system and computer program for protecting user credentials against security attacks
InactiveUS20090055642A1Eliminate needEncryption apparatus with shift registers/memoriesCryptographic attack countermeasuresThird partyClient-side
A method, system and computer program is provided for protecting against one or more security attacks from third parties directed at obtaining user credentials on an unauthorized basis, as between a client computer associated with a user and a server computer is provided. The server computer defines a trusted Public Key Cryptography utility for use on the client computer. The Public Key Cryptography utility is operable to perform one or more cryptographic operations consisting of encrypting / decrypting data, authenticating data, and / or authenticating a sender, decrypting and / or verifying data. The user authenticates to the Public Key Cryptography utility, thereby invoking the accessing of user credentials associated with the user, as defined by the server computer. The Public Key Cryptography Utility facilitates the communication of the user credentials to the server computer, whether directly or indirectly via an authentication agent, the server computer thereby authenticating the user. In response, the server computer providing access to one or more system resources linked to the server computer to the user. The present invention also provides a series of methods enabling the server computer to authenticate the user by operation of the Public Key Cryptography utility and / or based on enrolment of the user and providing the Public Key Cryptography utility to the user.
Owner:ECHOWORX CORP
Digital rights management system and method
InactiveUS20050229004A1Improve securityCommunication securityProgramme controlComputer controlUser PrivilegeSecure transmission
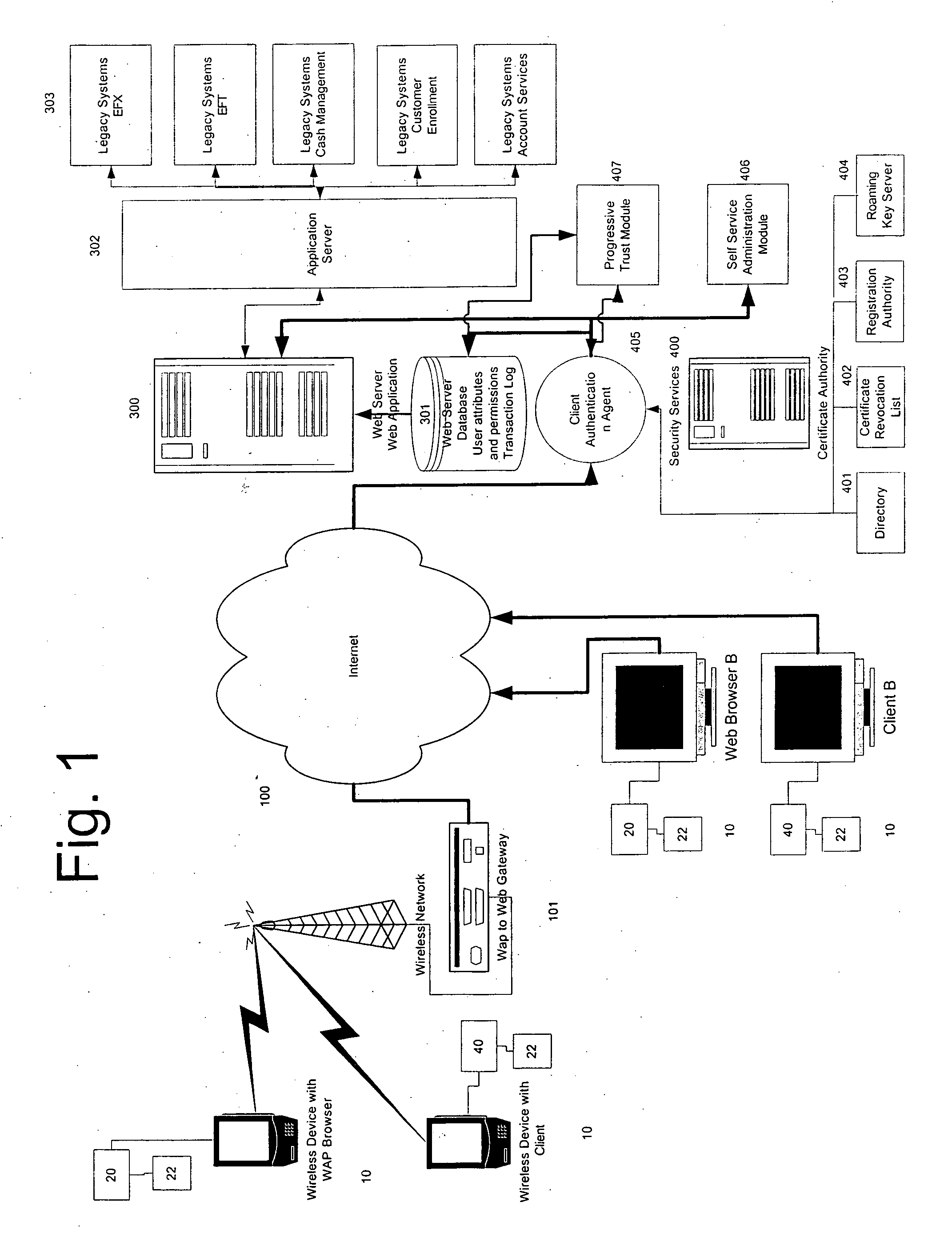
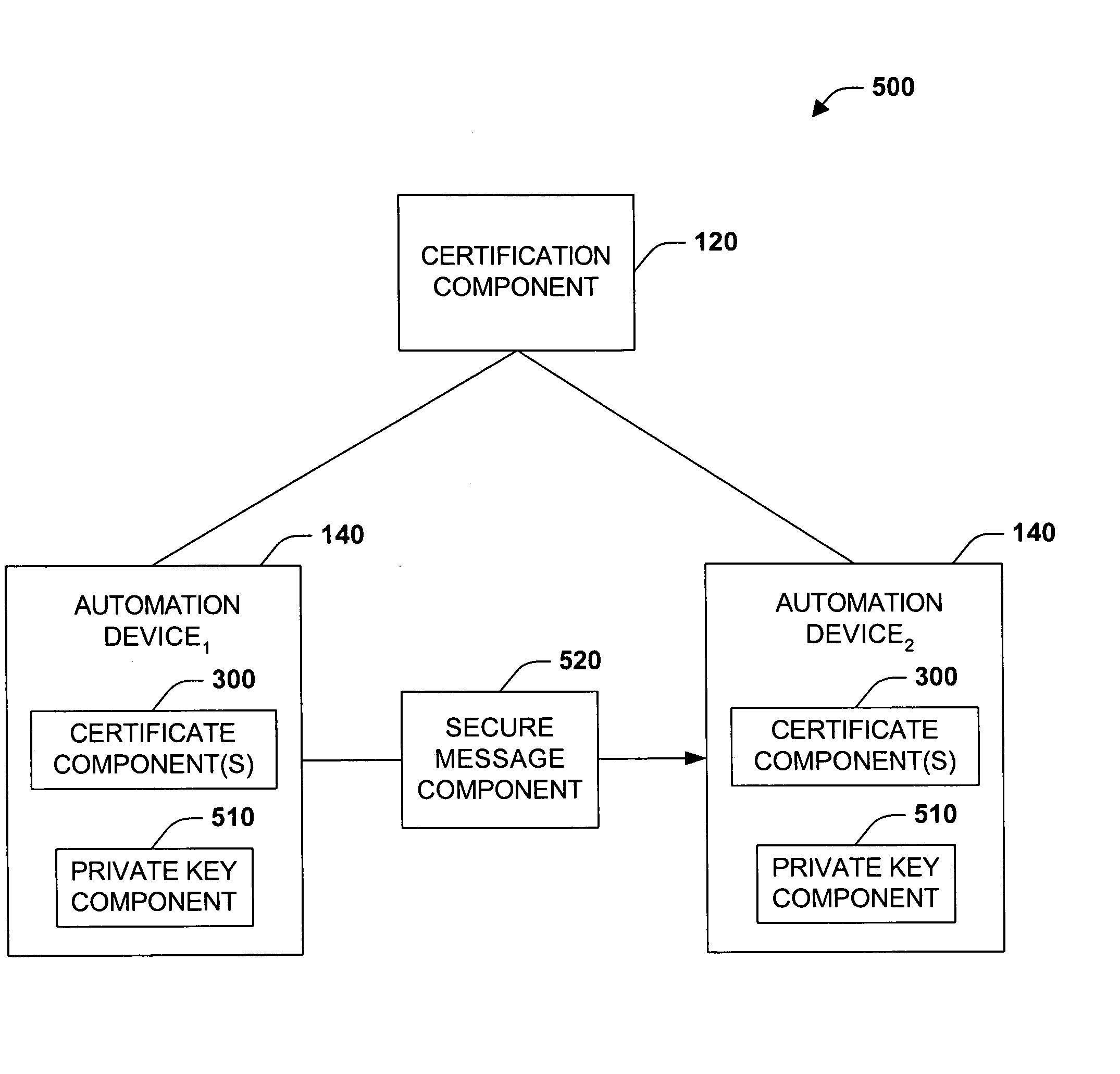
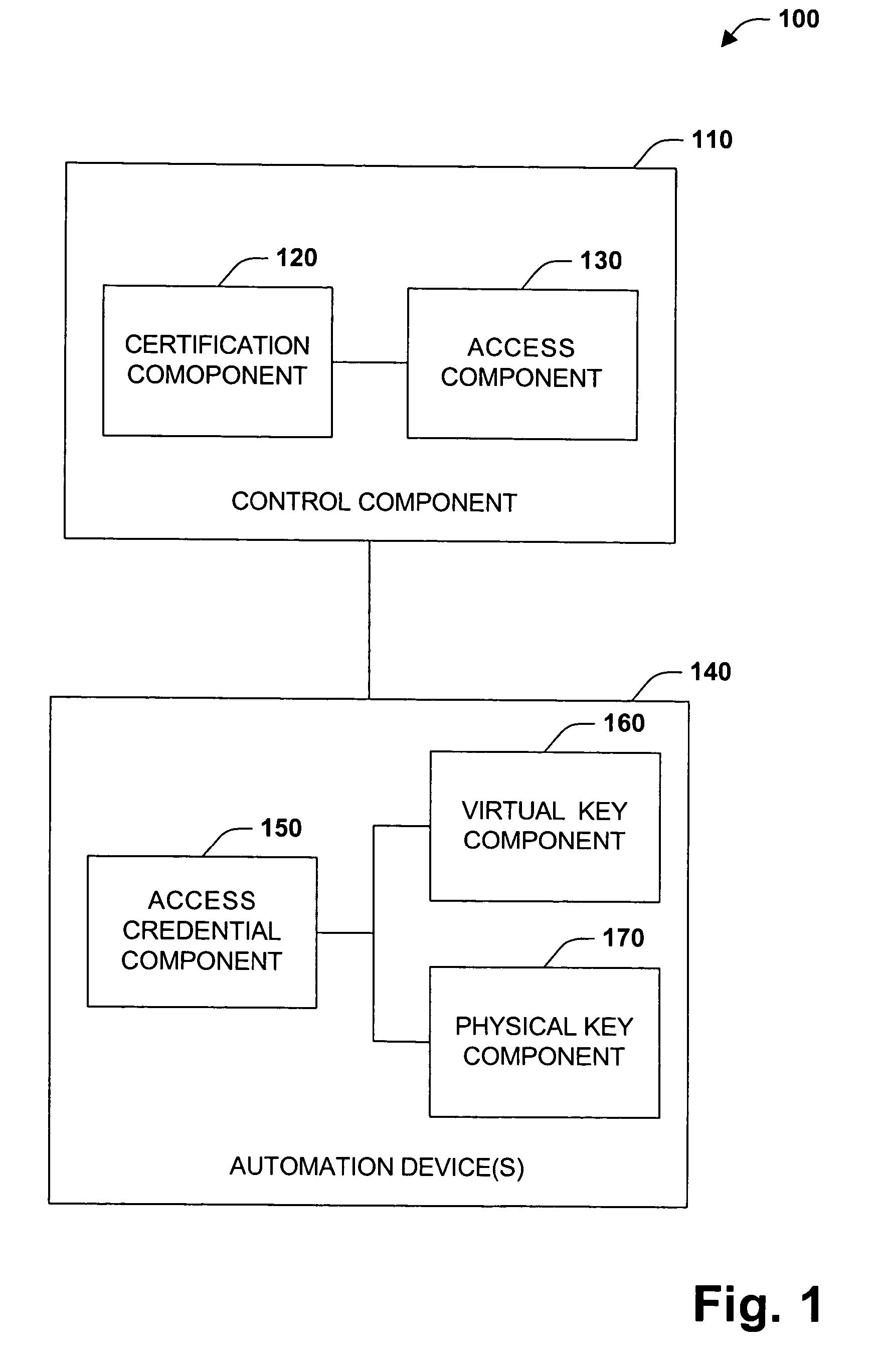
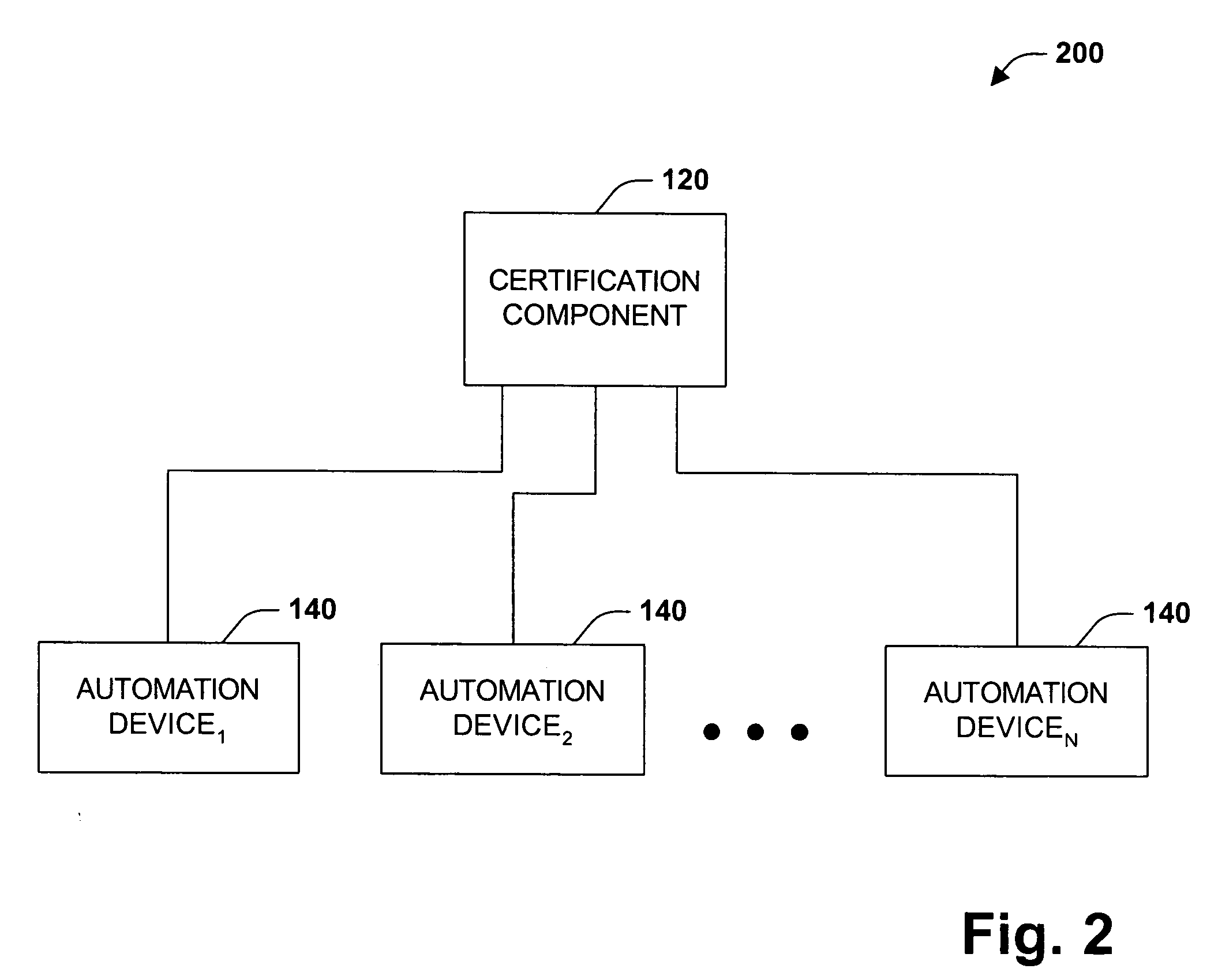
The present invention concerns application of digital rights management to industrial automation devices including programmable logic controllers (PLCs), I / O devices, and communication adapters. Digital rights management involves a set of technologies for controlling and managing access to device objects and / or programs such as ladder logic programs. Access to automation device objects and / or programs can be managed by downloading rules of use that define user privileges with respect to automation devices and utilizing digital certificates, among other things, to verify the identity of a user desiring to interact with device programs, for example. Furthermore, the present invention provides for secure transmission of messages to and amongst automation devices utilizing public key cryptography associated with digital certificates.
Owner:ROCKWELL AUTOMATION TECH
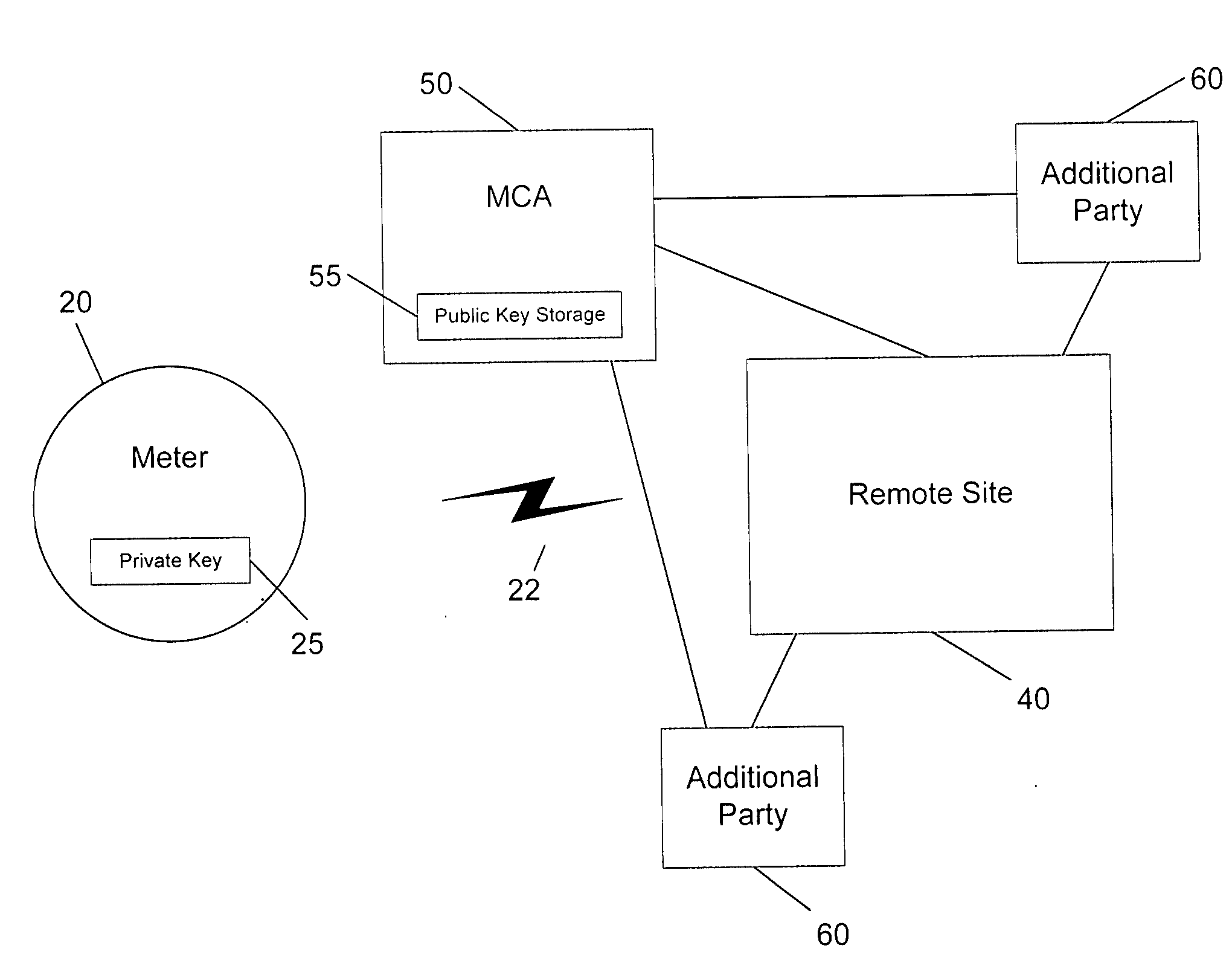
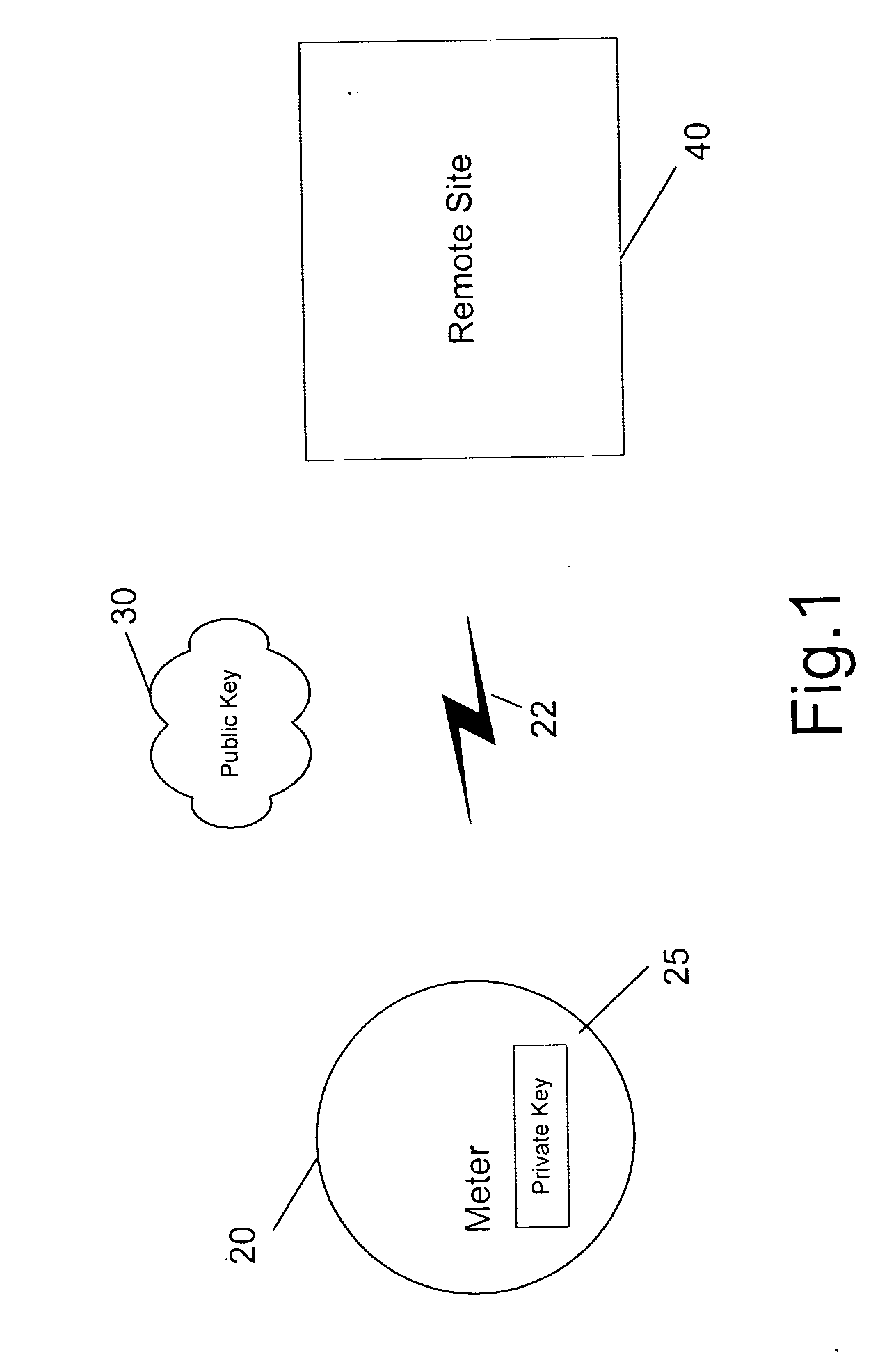
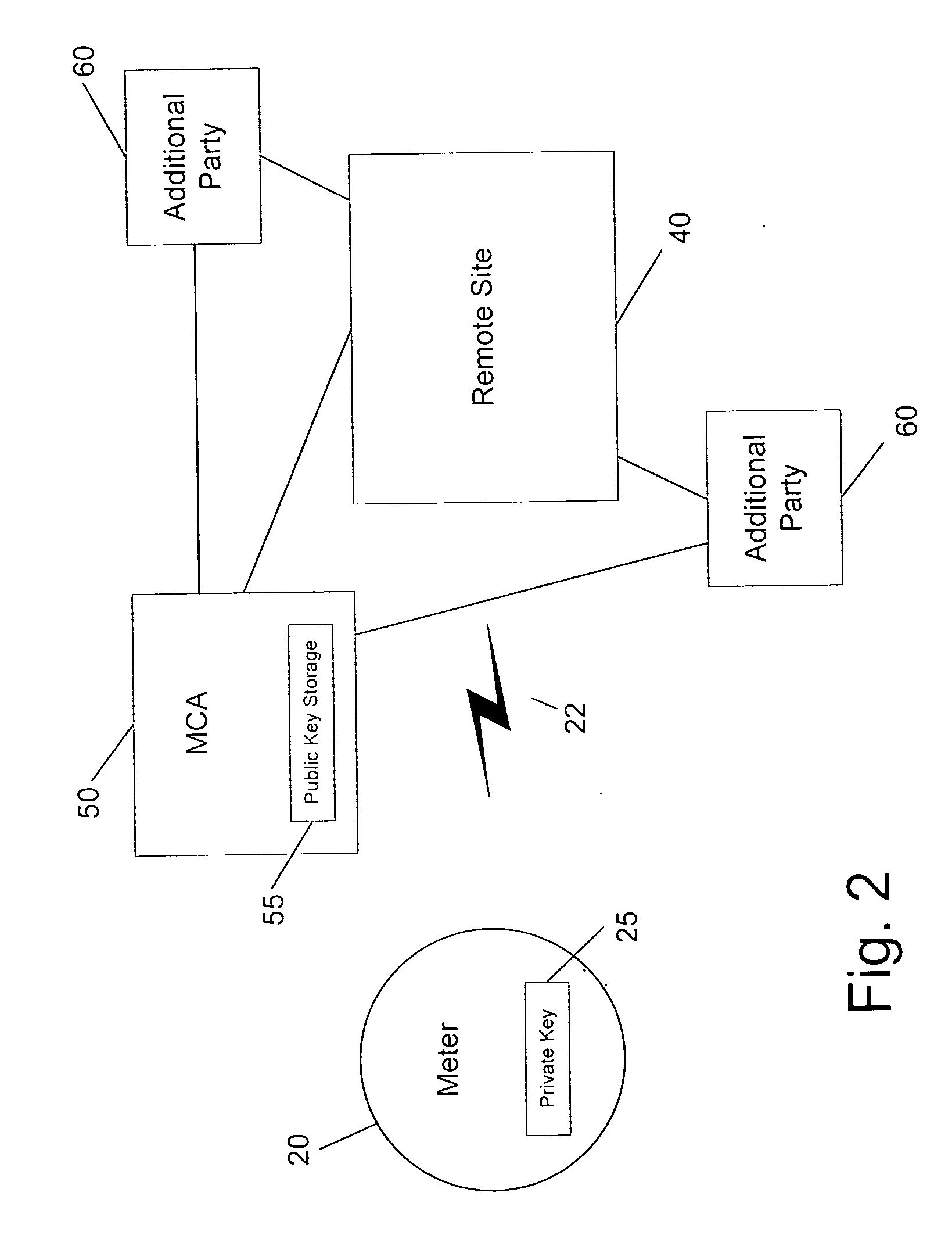
Secure and authenticated delivery of data from an automated meter reading system
InactiveUS20060206433A1Insure validityTariff metering apparatusPayment architectureDigital signatureCollection system
Digital signatures are applied to metered energy data that is collected by a common data collection system. The system receives data from meters that may be owned by one or more utilities. The data is stored by the system using public key cryptography to ensure that it is only accessible by the intended consumer of the data. When the data is transmitted to the intended consumer, it is digitally signed by the system to ensure the authenticity of the data as received by the consumer.
Owner:ELSTER ELECTRICTY LLC
Wireless device discovery and configuration
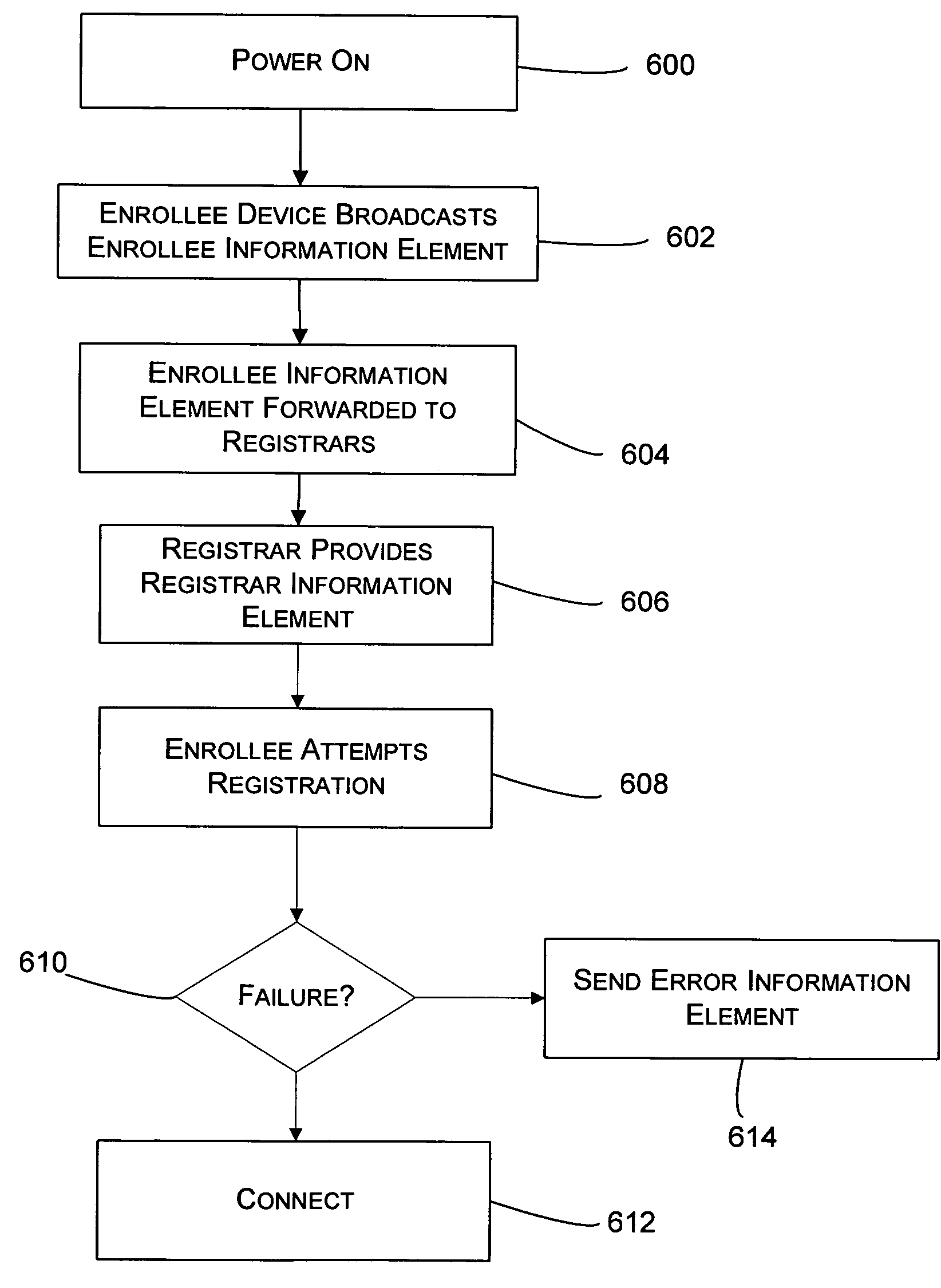
ActiveUS20060239208A1Assess restrictionData switching by path configurationComputer hardwareWireless network
A wireless device that desires to be connected to a wireless network broadcasts itself and its capabilities to a network using an information element. The information element is provided with frames, such as management frames, in a channel that is not protected or encrypted. The information element is forwarded to one or more potential registrar devices. One of the registrar devices then provides configuration information to the enrollee, for example as a registrar information element. The configuration information may be passed out of band or in band, and may be passed using cryptography, which may involve public key cryptography, encryption with a PIN, or some other type of secure exchange.
Owner:MICROSOFT TECH LICENSING LLC
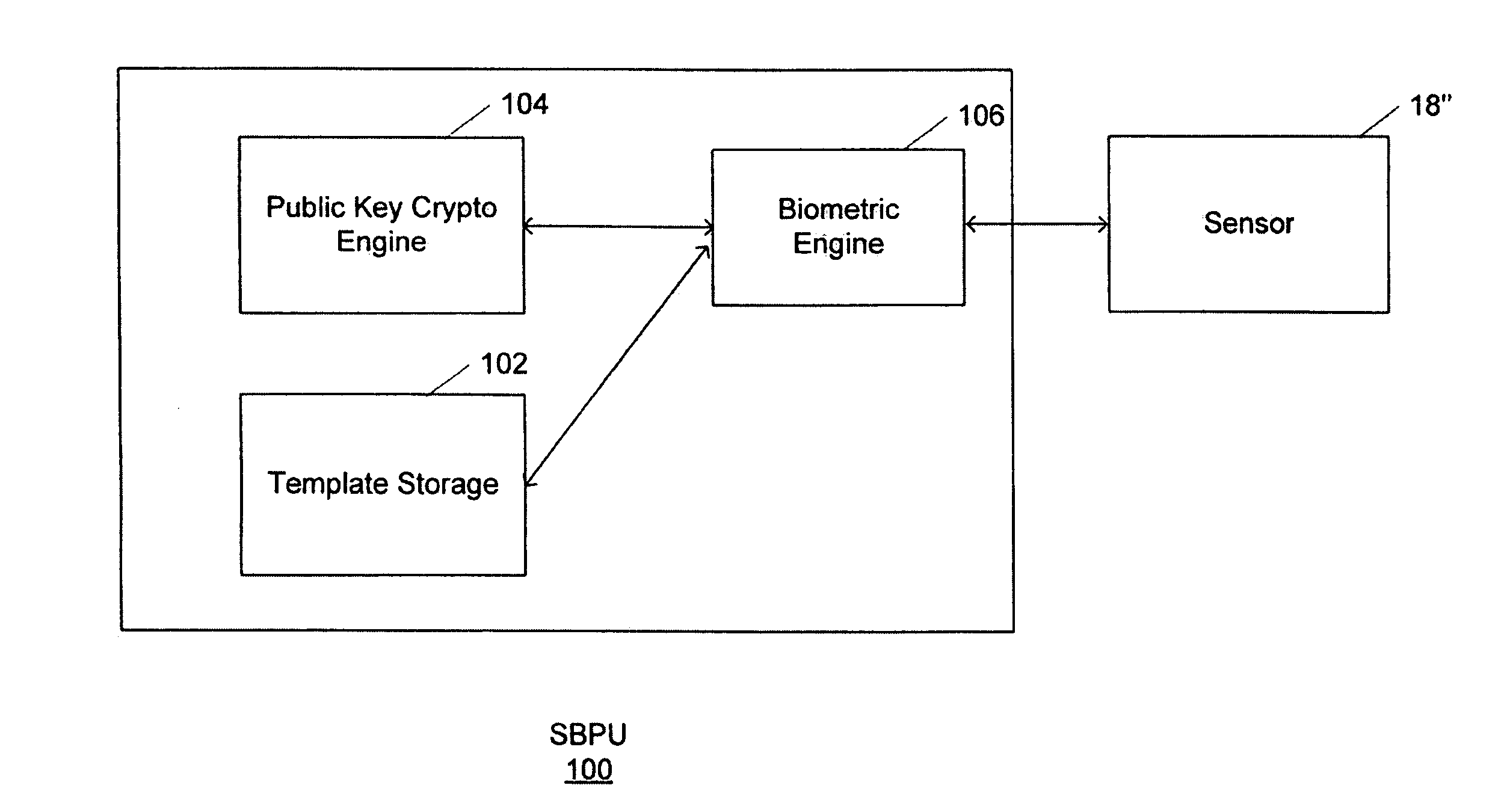
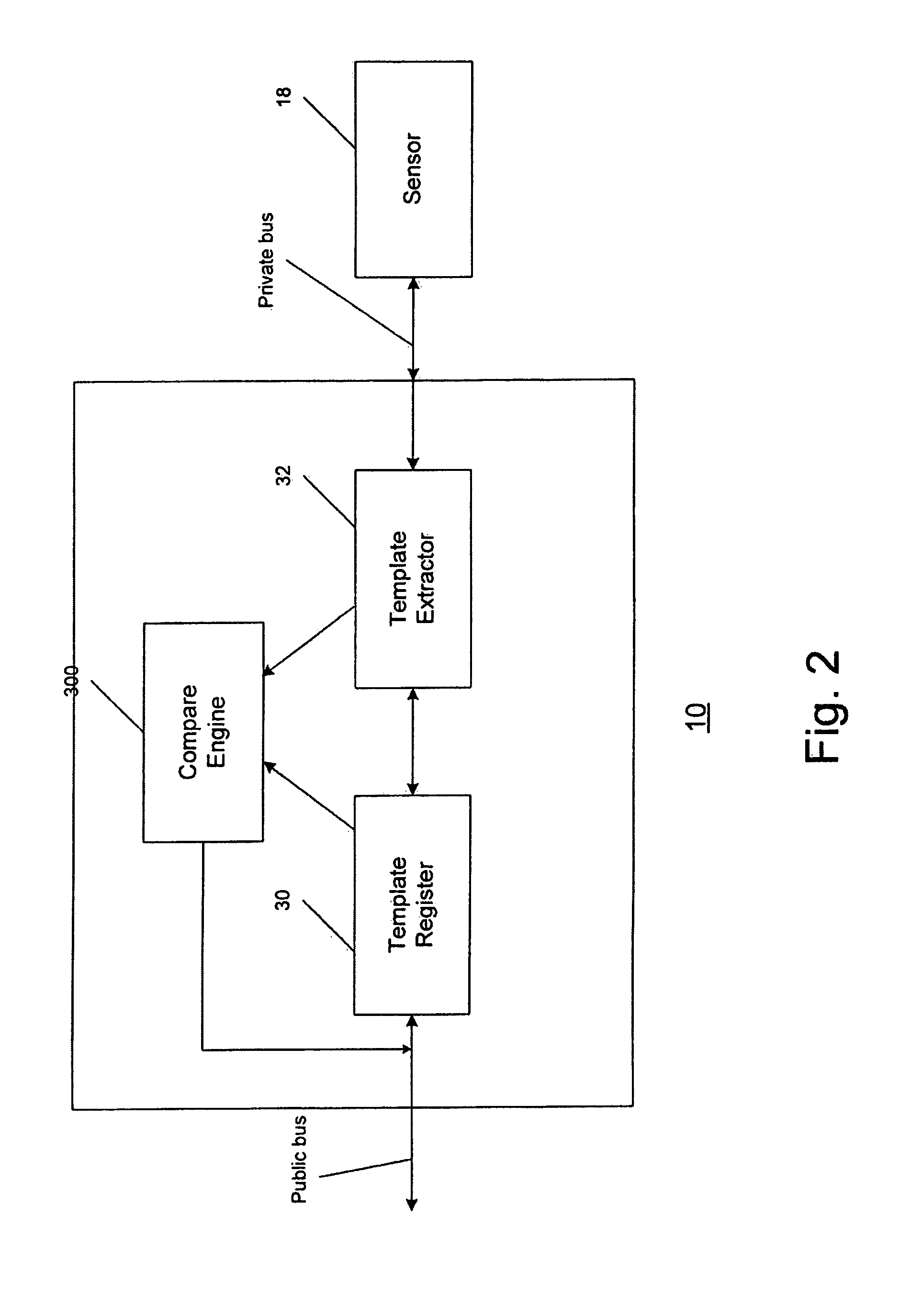
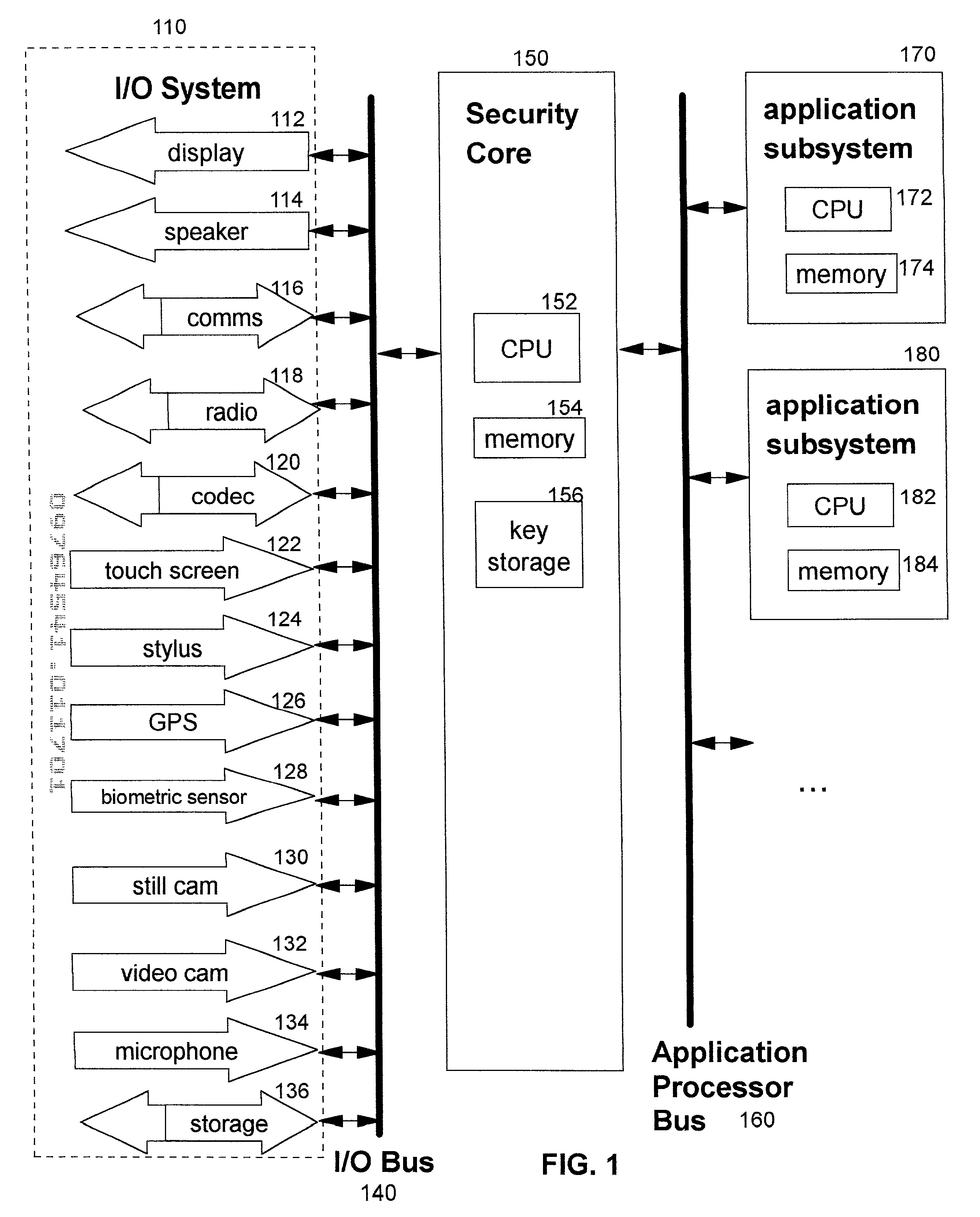
Secure biometric processing system and method of use
InactiveUS20070237366A1Programme controlElectric signal transmission systemsSecurity designHandling system
A secure biometric processing system is disclosed. The system comprises a processing system for providing image acquisition and biometric comparison. The processing unit utilizes public key cryptography for handling templates securely and authenticating operations using the template. The system includes a complete biometric engine which implements image reconstruction, template extraction and matching. The secure design of the system combines complete privacy with security, while offering a flexible usage model including on-chip template storage along with encrypted and authenticated communications to the system.
Owner:ATMEL CORP
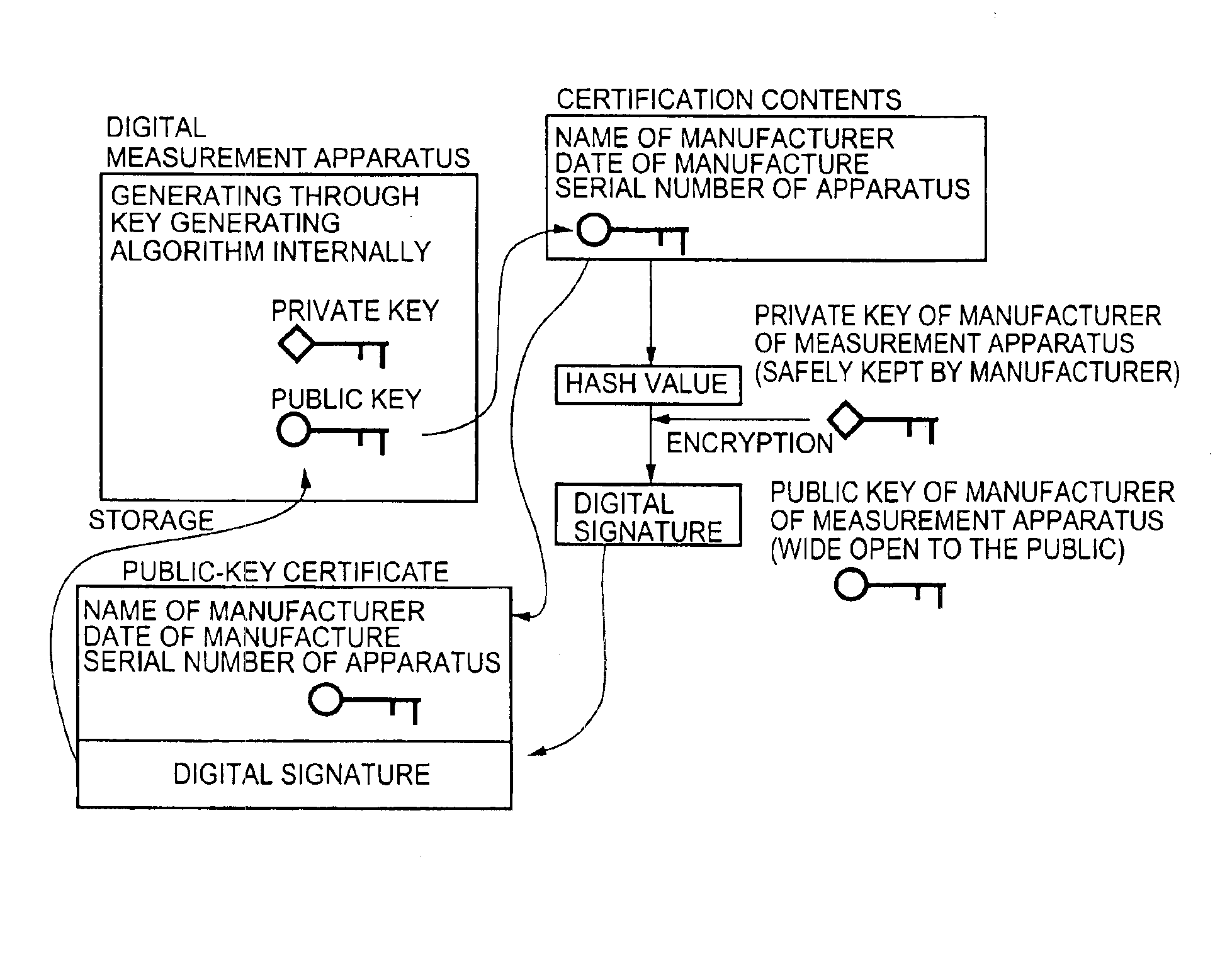
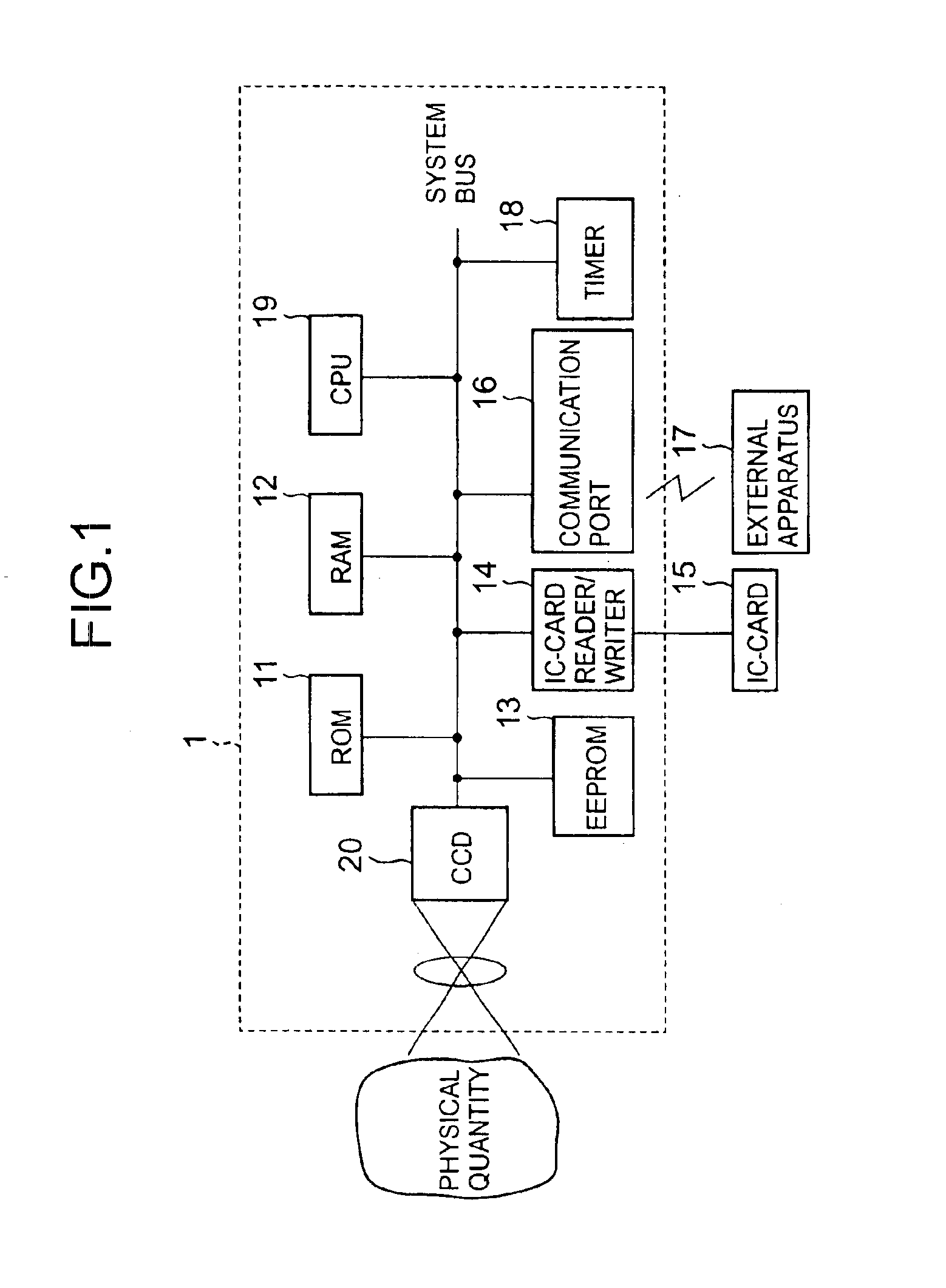
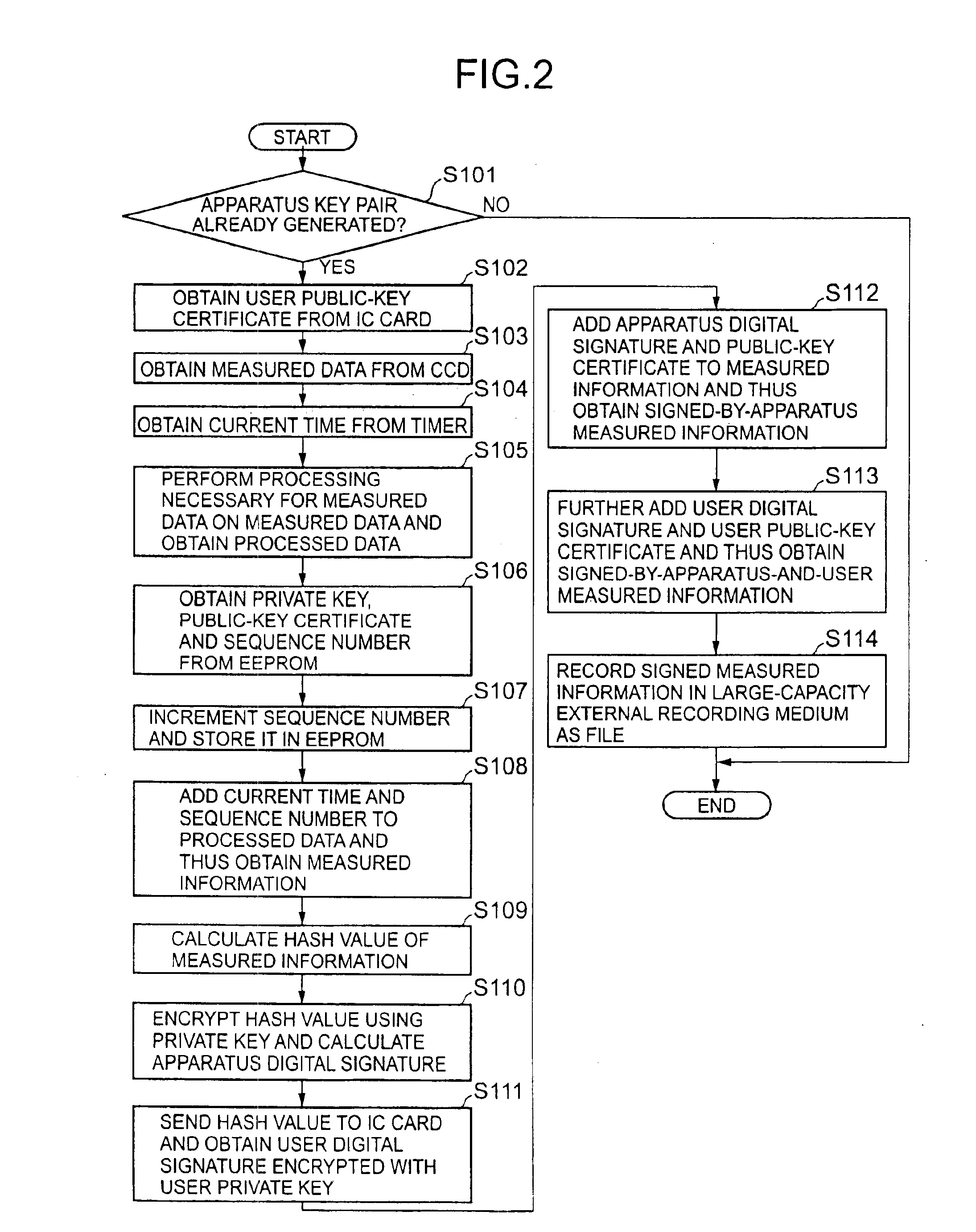
Digital measurement apparatus and image measurement apparatus
InactiveUS6889324B1Increase credibilityImprove reliabilityElectric signal transmission systemsKey distribution for secure communicationDigital signatureKey generation
A digital measurement apparatus measures a physical measurement object, provides a digital signature of public-key cryptography to measured data of a thus-measured physical quantity, and manages the measured data. The apparatus generates at least a pair of a public key and a private key, to be used for the digital signature of the public-key cryptography, through a key generating algorithm.
Owner:RICOH KK
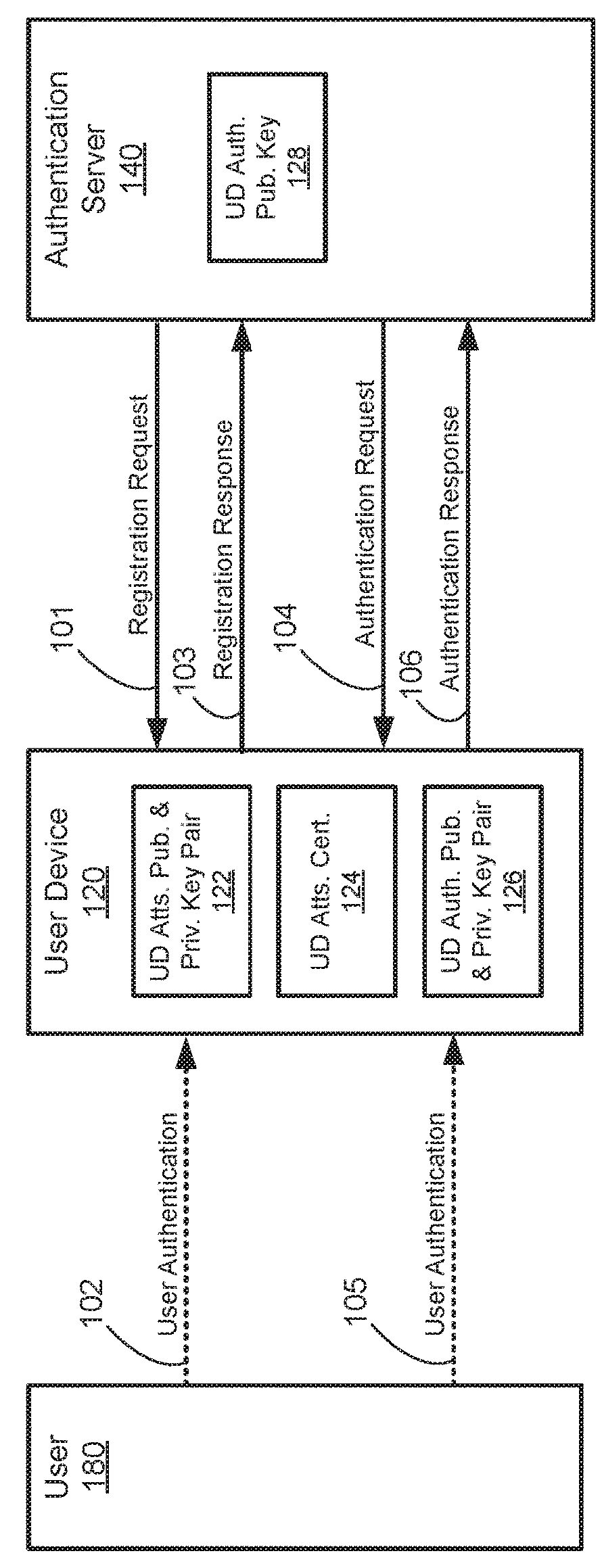
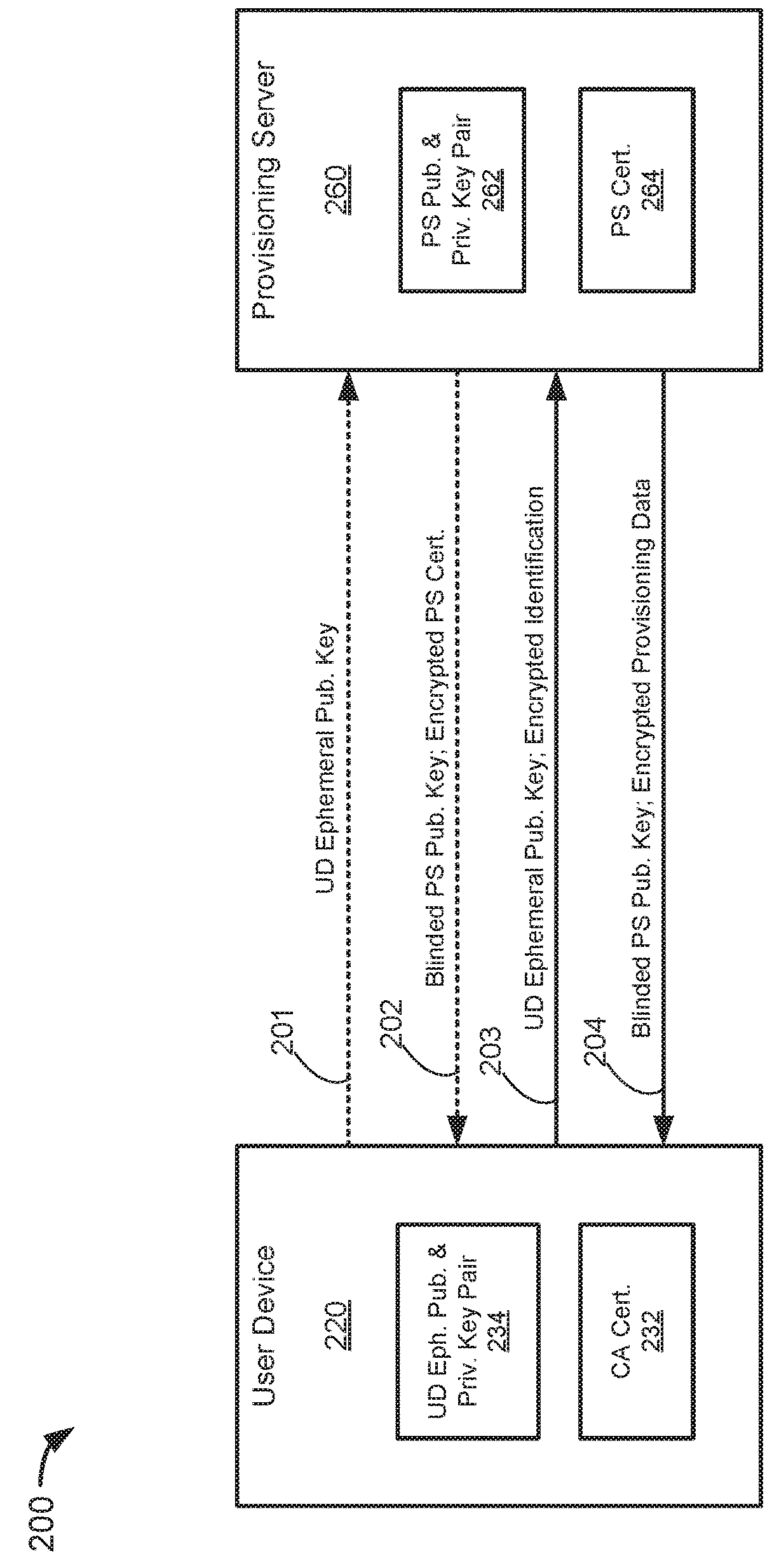
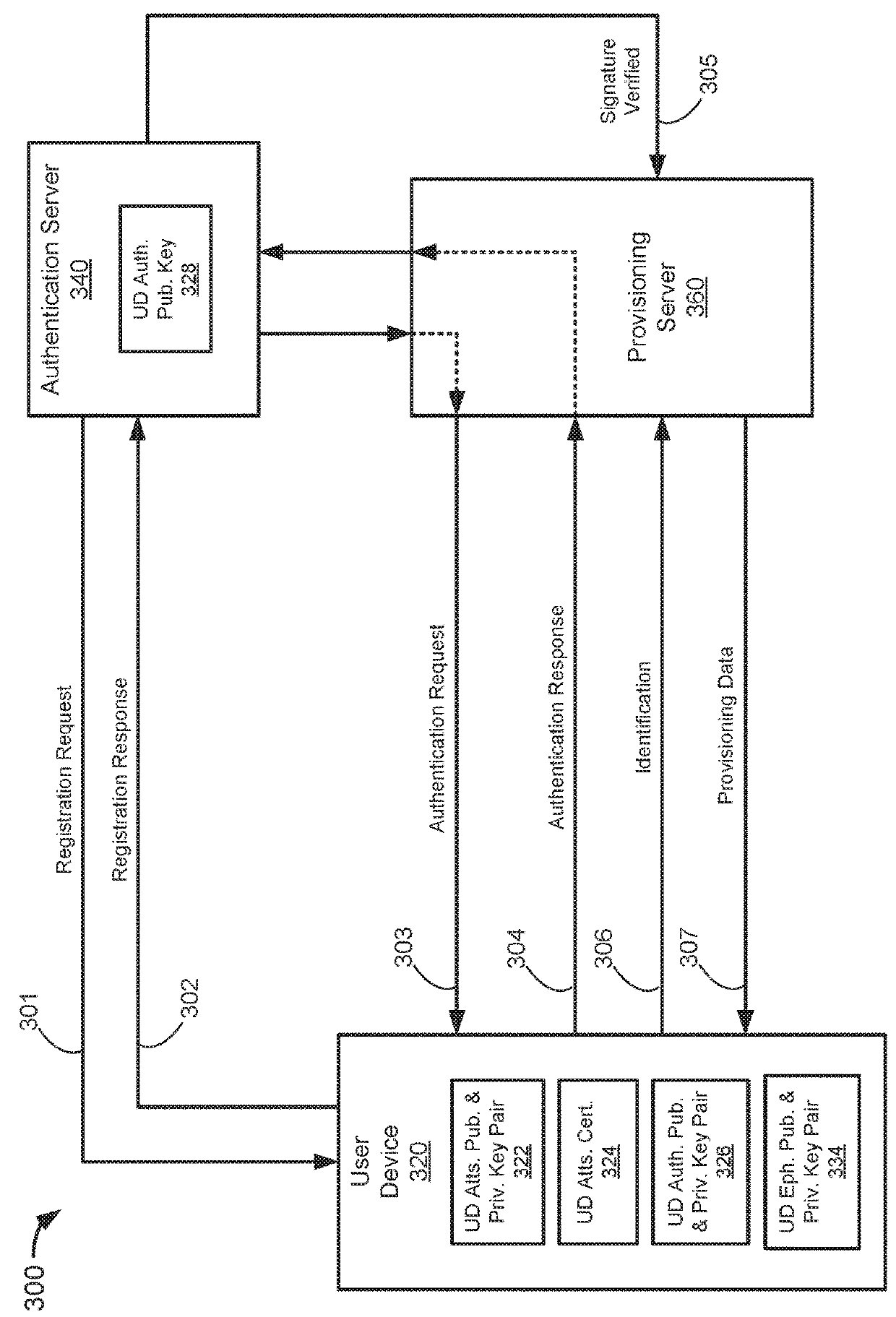
Confidential authentication and provisioning
ActiveUS20180167208A1Key distribution for secure communicationMultiple keys/algorithms usageUser deviceConfidentiality
Some embodiments provide systems and methods for confidentially and securely provisioning data to an authenticated user device. A user device may register an authentication public key with an authentication server. The authentication public key may be signed by an attestation private key maintained by the user device. Once the user device is registered, a provisioning server may send an authentication request message including a challenge to the user device. The user device may sign the challenge using an authentication private key corresponding to the registered authentication public key, and may return the signed challenge to the provisioning server. In response, the provisioning server may provide provisioning data to the user device. The registration, authentication, and provisioning process may use public key cryptography while maintaining confidentiality of the user device, the provisioning server, and then authentication server.
Owner:VISA INT SERVICE ASSOC
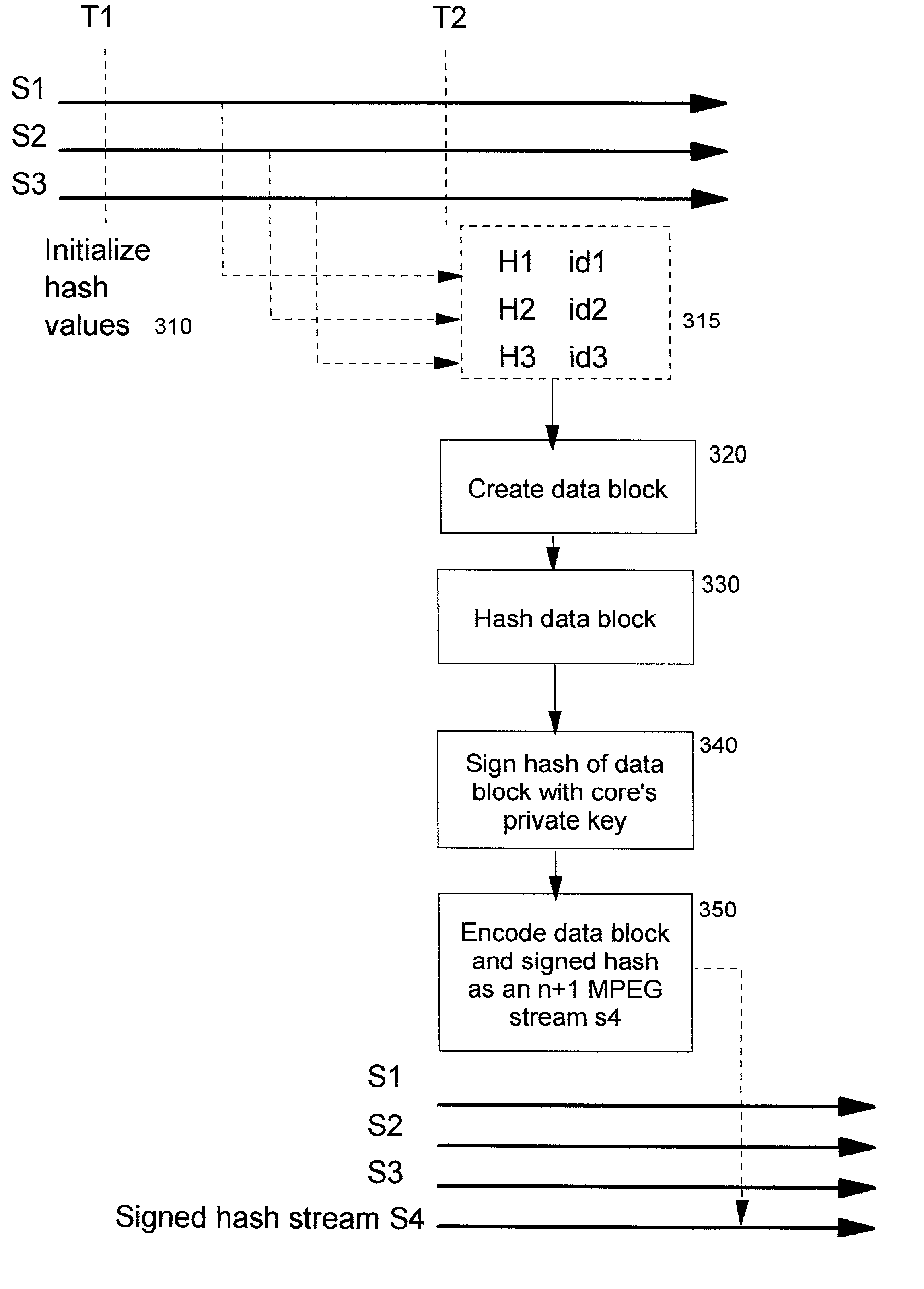
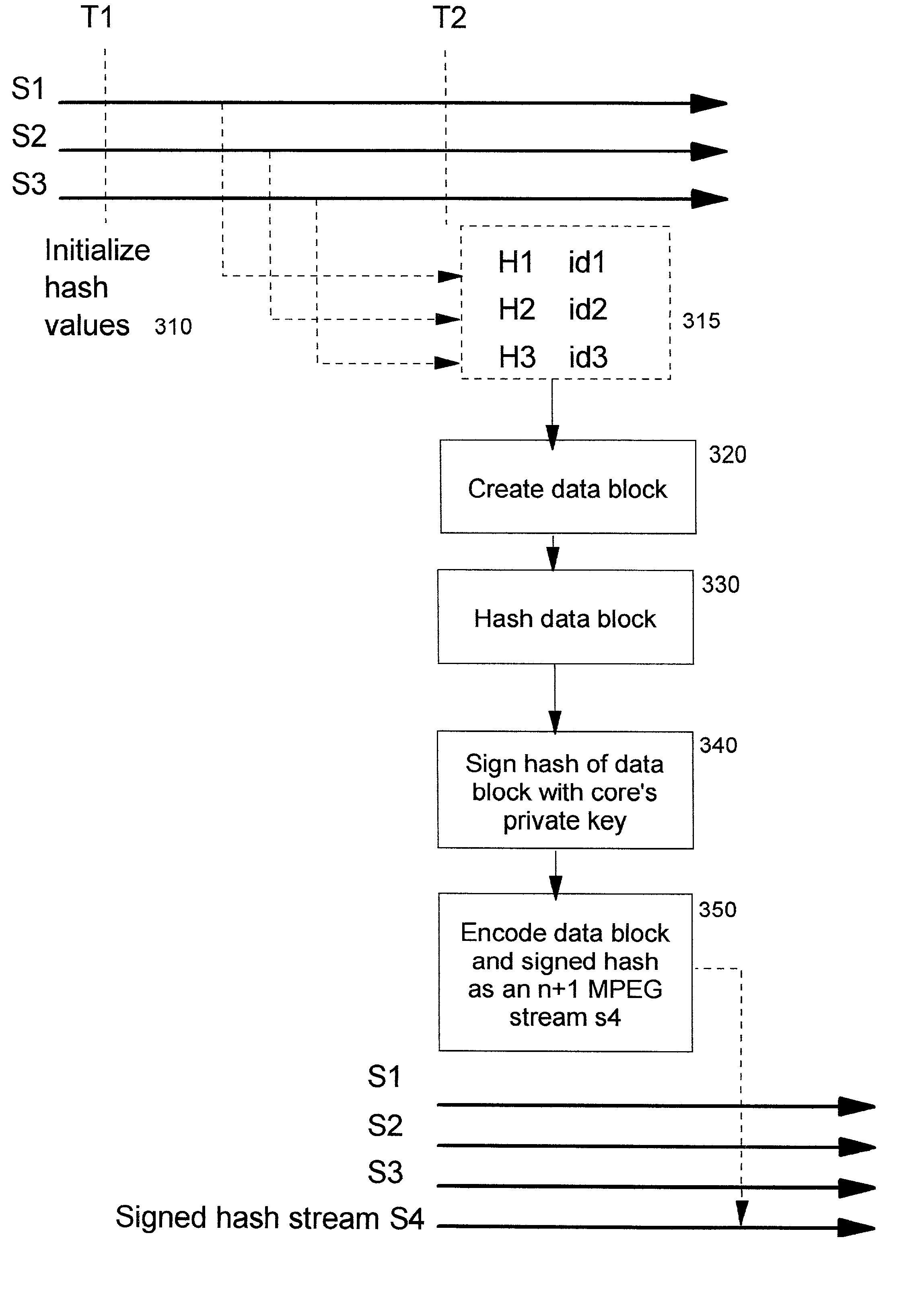
Technique for digitally notarizing a collection of data streams
InactiveUS20030212893A1IntegrityUser identity/authority verificationTelevision systemsData streamDigital signature
A method, system, computer program product, and method of doing business by digitally notarizing a collection of data streams, thereby improving security of the contents of the data streams. Preferably, public key cryptography is used, wherein the collection of data streams is digitally signed (i.e. notarized) using a private cryptographic key of a digital notary, such that an associated public cryptographic key can be used to verify the authenticity and integrity of the collection of data streams. One or more components which are involved in creating the data streams are preferably authenticated, and a unique identifier of each such component is included within cryptographically-protected information that is provided for the digital notarization. The authenticated identities of the components can therefore be determined from the digital notarization.
Owner:IBM CORP
Method for establishing, securing and transferring computer readable information using peer-to-peer public and private key cryptography
InactiveUS20170324711A1Protected contentMinimal costPublic key for secure communicationCryptographic hash functionStructure of Management Information
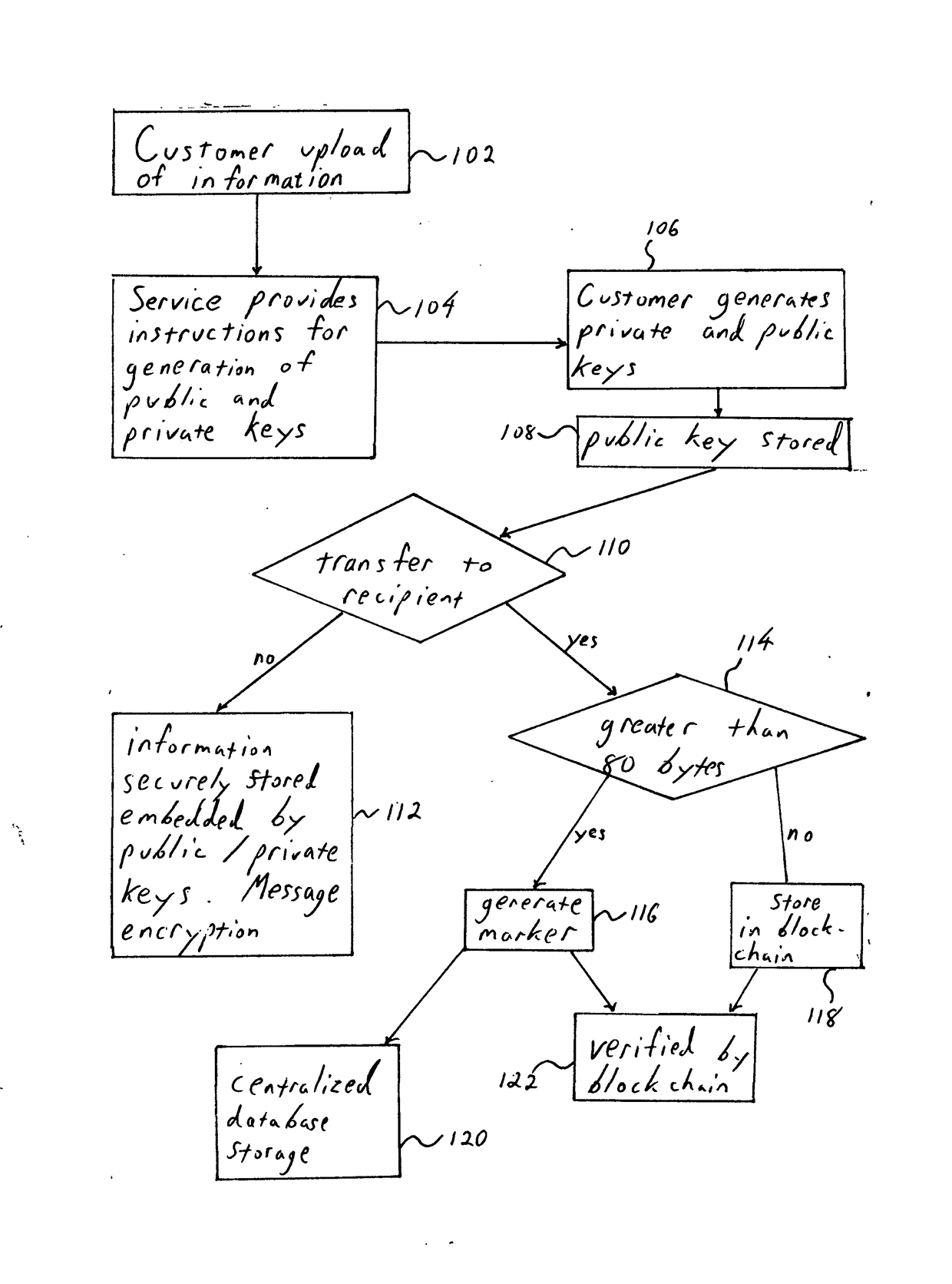
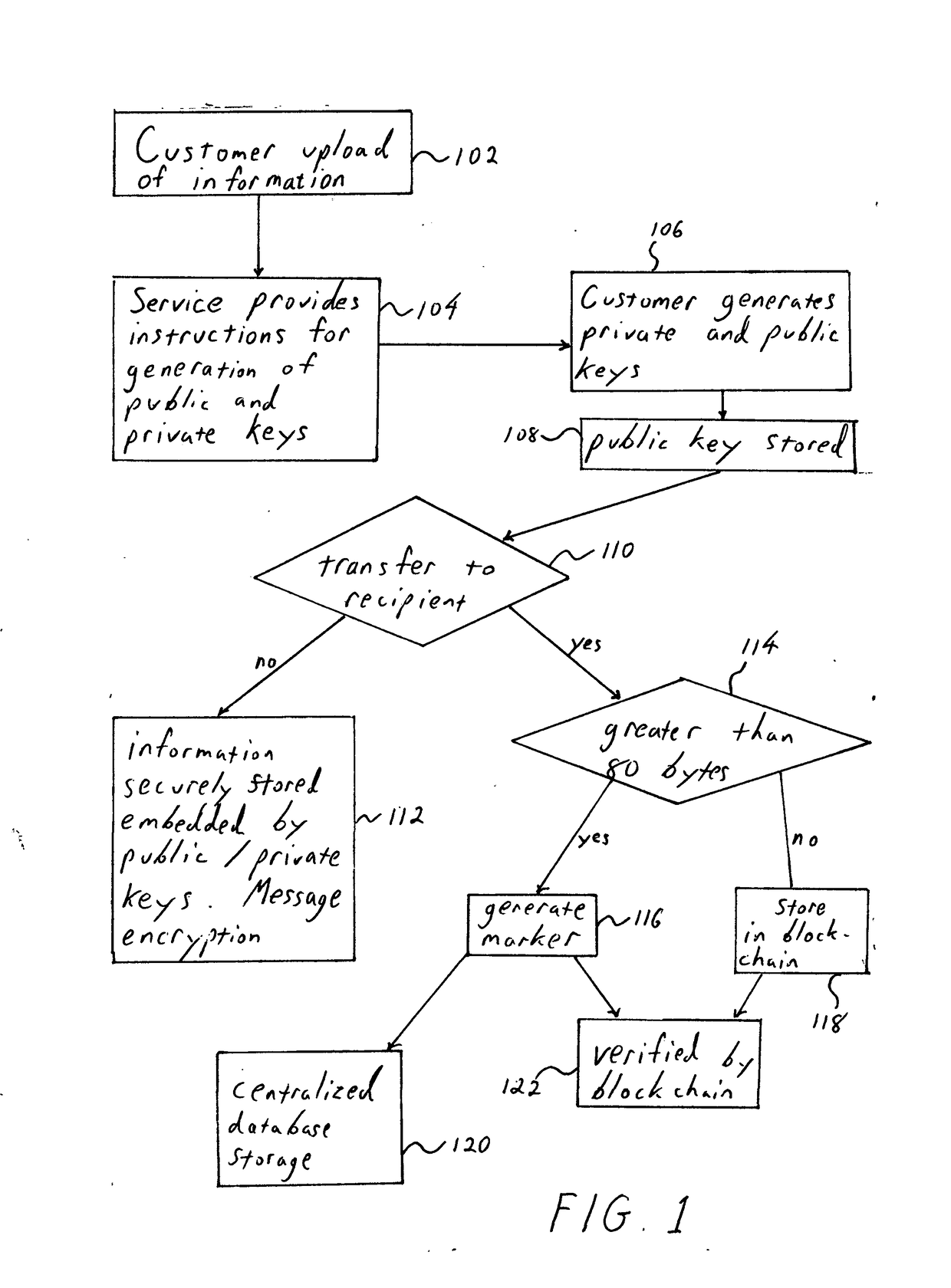
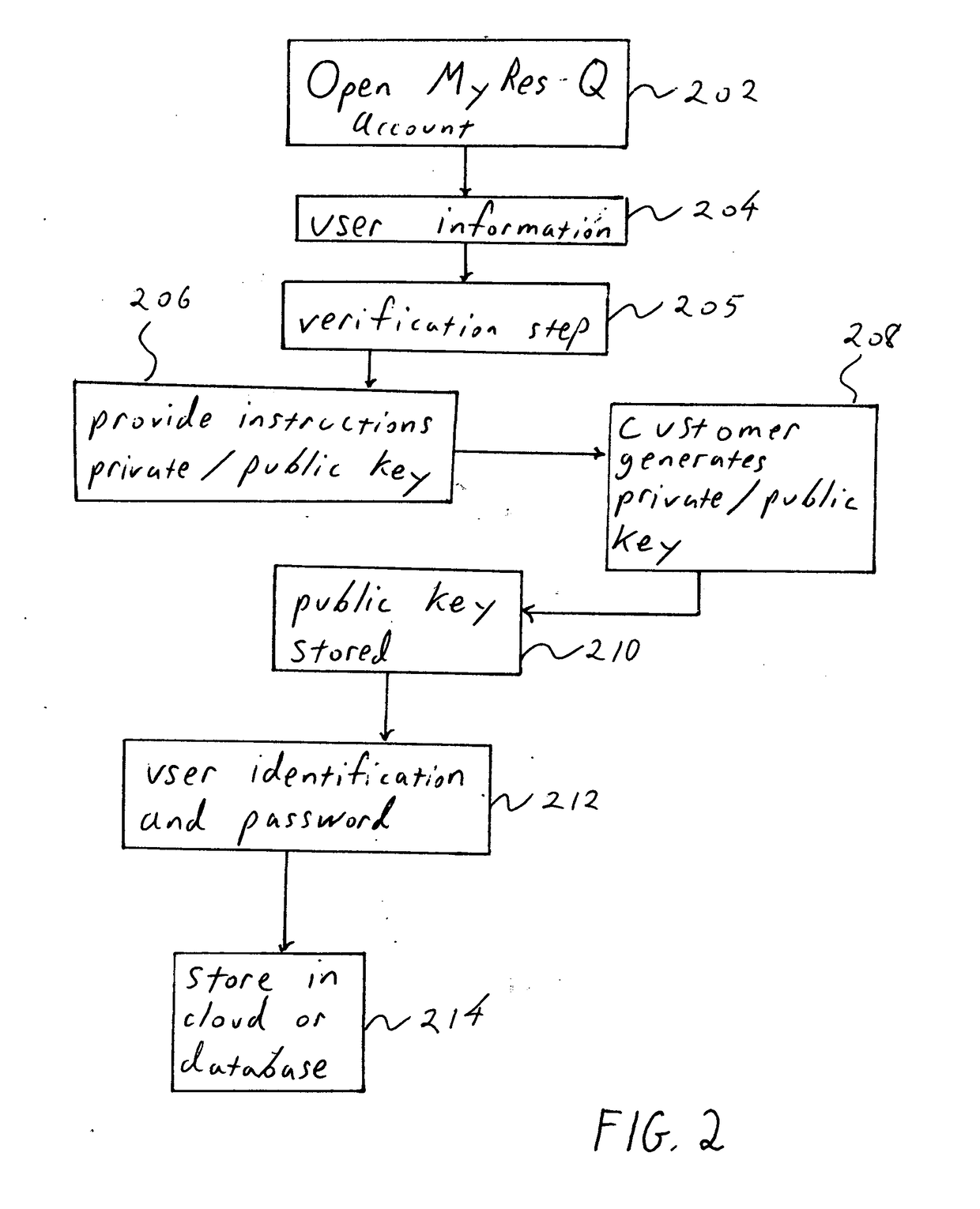
System and method for confirming and transferring information from one party to another via block chain escort, using central and decentralized databases acting as online storage providers. Files are linked to cryptographic currency structures comprised of a public and private key identification processes. Locking, unlocking, retrieving, storing, confirming and transferring files requires linked association to block chain protocol measures of crypto-currency processes.Establishing file space requires that the owner links it to a centralized or decentralized peer-to-peer cryptographic block chain protocol. This secures and locks files for subsequent confirmation and transfer. Confirmation and transfer of the file is processed with a cryptographic hash function of crypto currency block chain process. The system and method requires that the transferee obtain the file using crypto currency transfer protocol. The system and method associates a piece of information with a public key and private keys, which are accessed only by the owner.
Owner:THE REAL MCCOY LLC INC
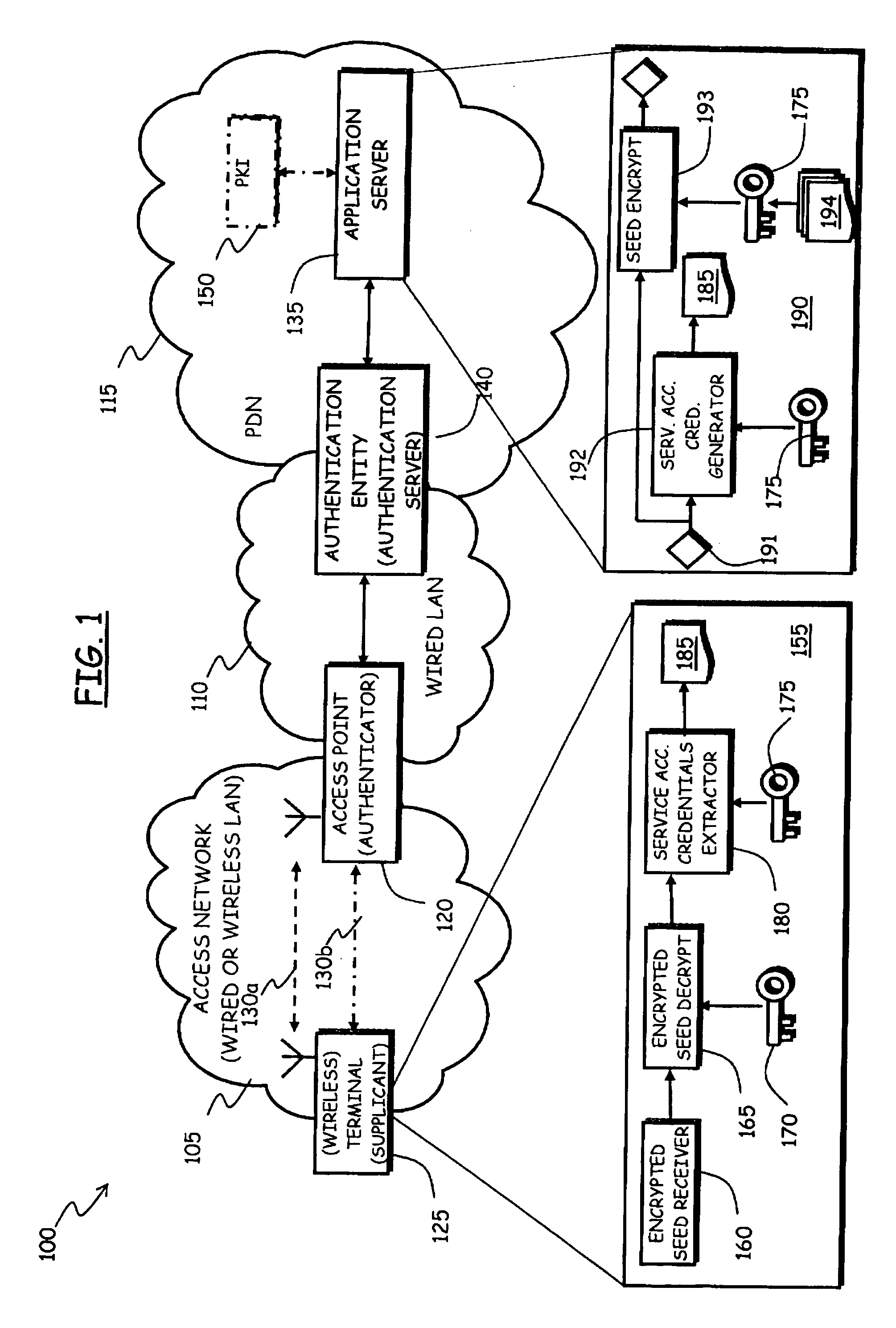
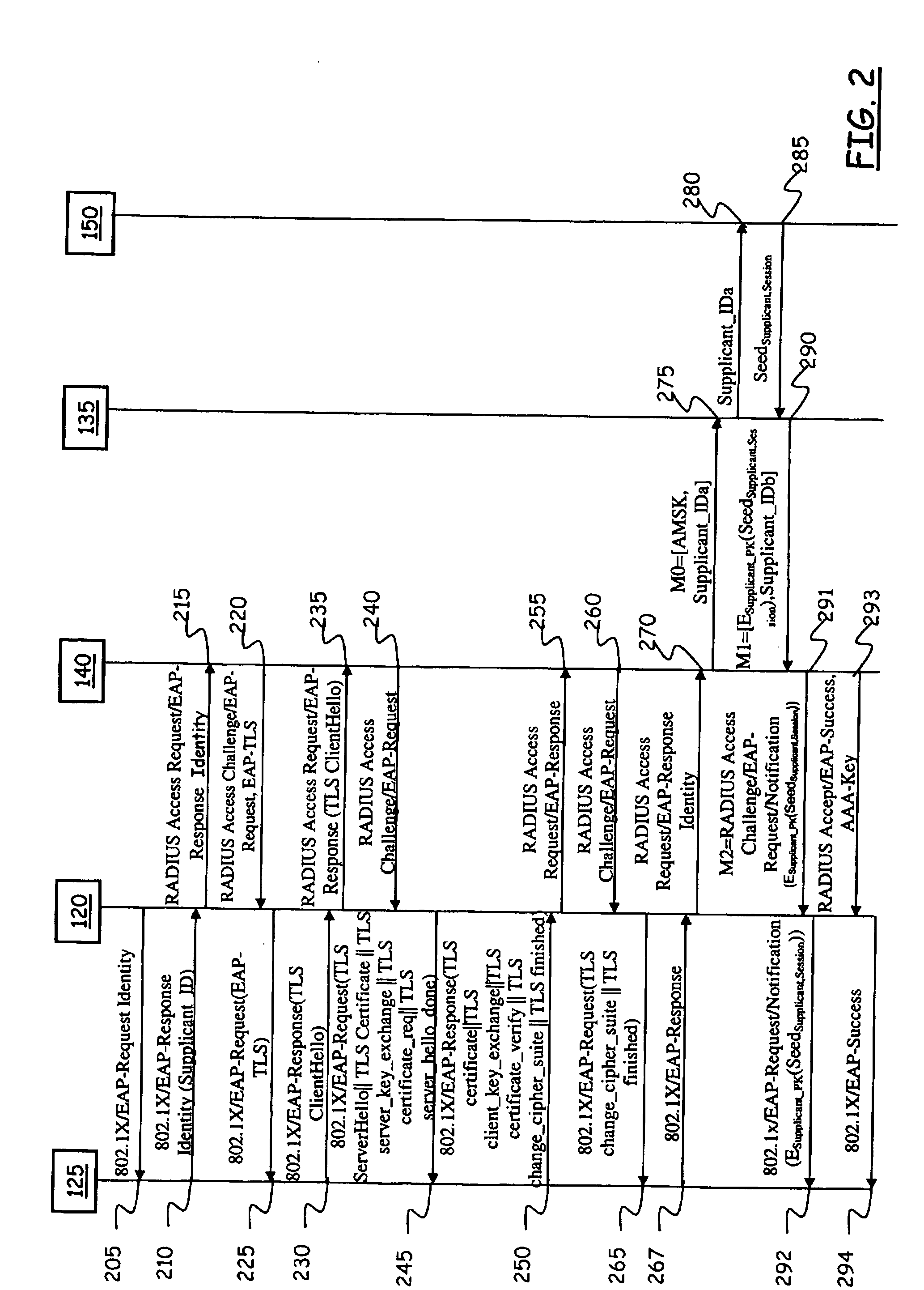
Method and System for Automated and Secure Provisioning of Service Access Credentials for On-Line Services to Users of Mobile Communication Terminals
InactiveUS20090158032A1Easy to implementSimplifying credential managementSecret communicationSecuring communicationEnd userMethod access
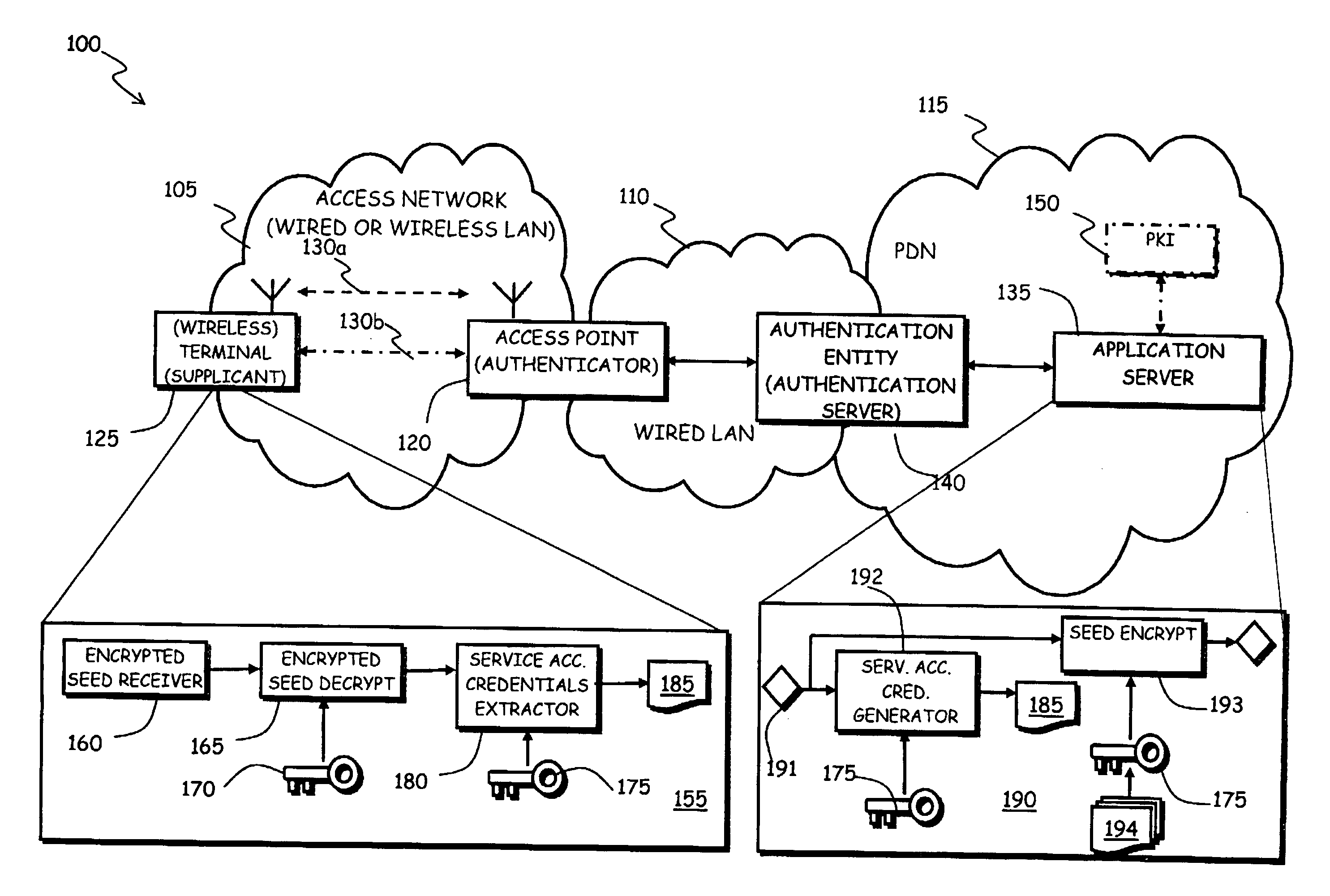
In a communications network including at least one authentication entity adapted to authenticating a network access requestor in order to conditionally grant thereto access to the communications network, wherein the authenticating is based on public key cryptography, a method for automatically provisioning the network access requestor with service access credentials for accessing an on-line service offered by an on-line service provider accessible through the communications network. The method includes: during the authenticating the network access requestor, having an authentication entity request to the on-line service provider the generation of the service access credentials; at the on-line service provider, generating the service access credentials, encrypting the service access credentials by exploiting a public encryption key of the network access requestor and providing the encrypted service access credentials to the authentication entity; and having the authentication entity cause the network access requestor to be provided with the encrypted service access credentials.
Owner:TELECOM ITALIA SPA +1
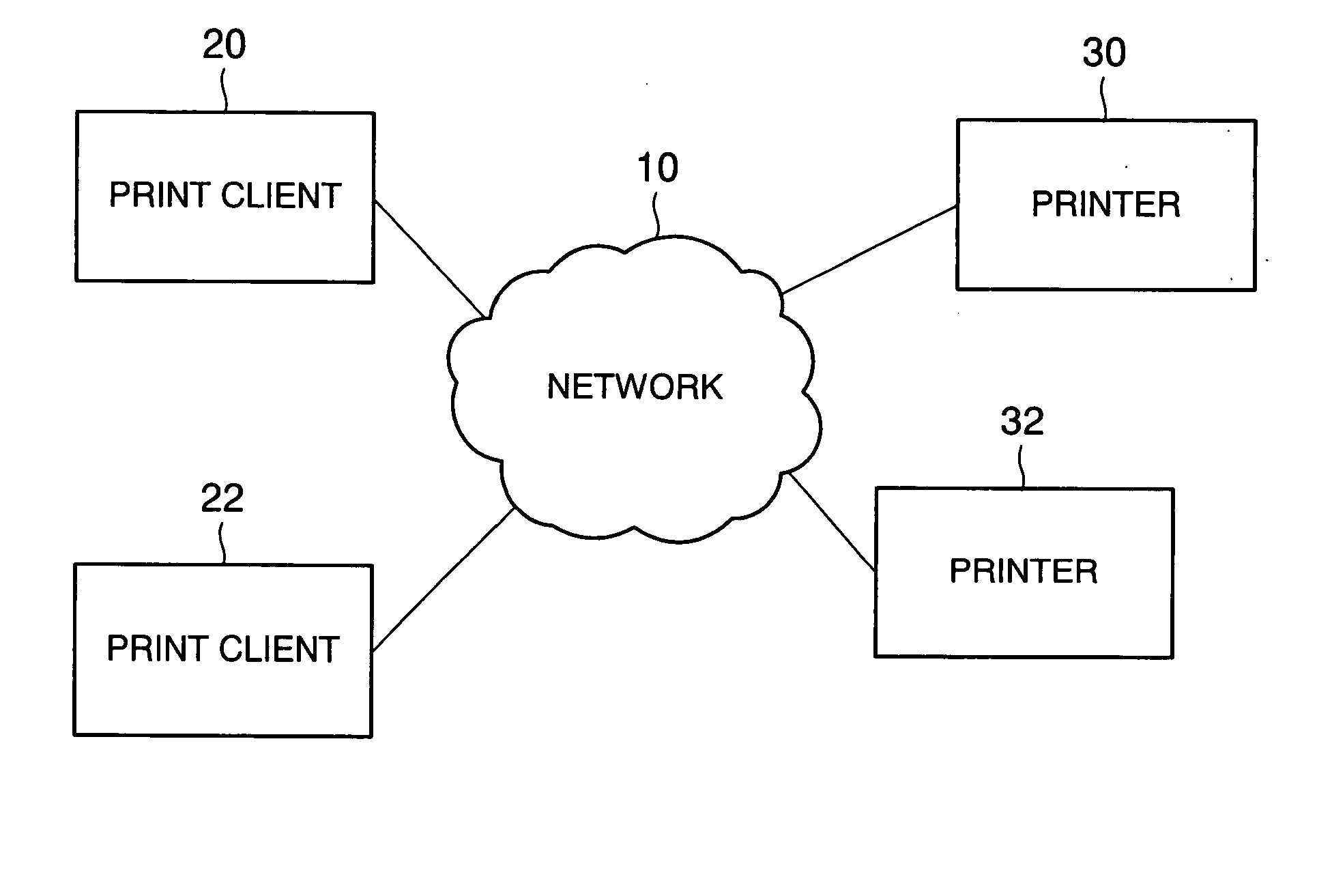
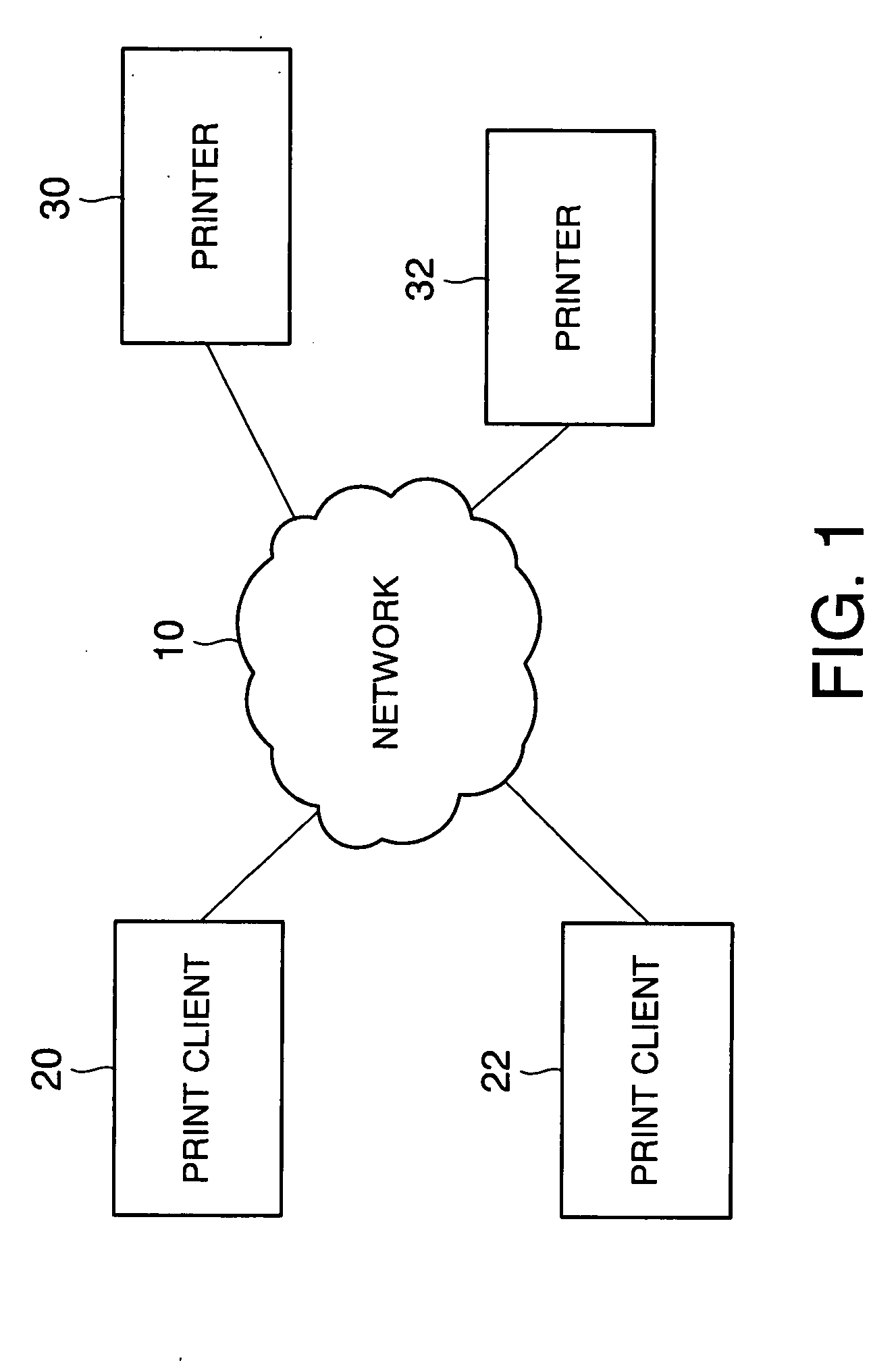
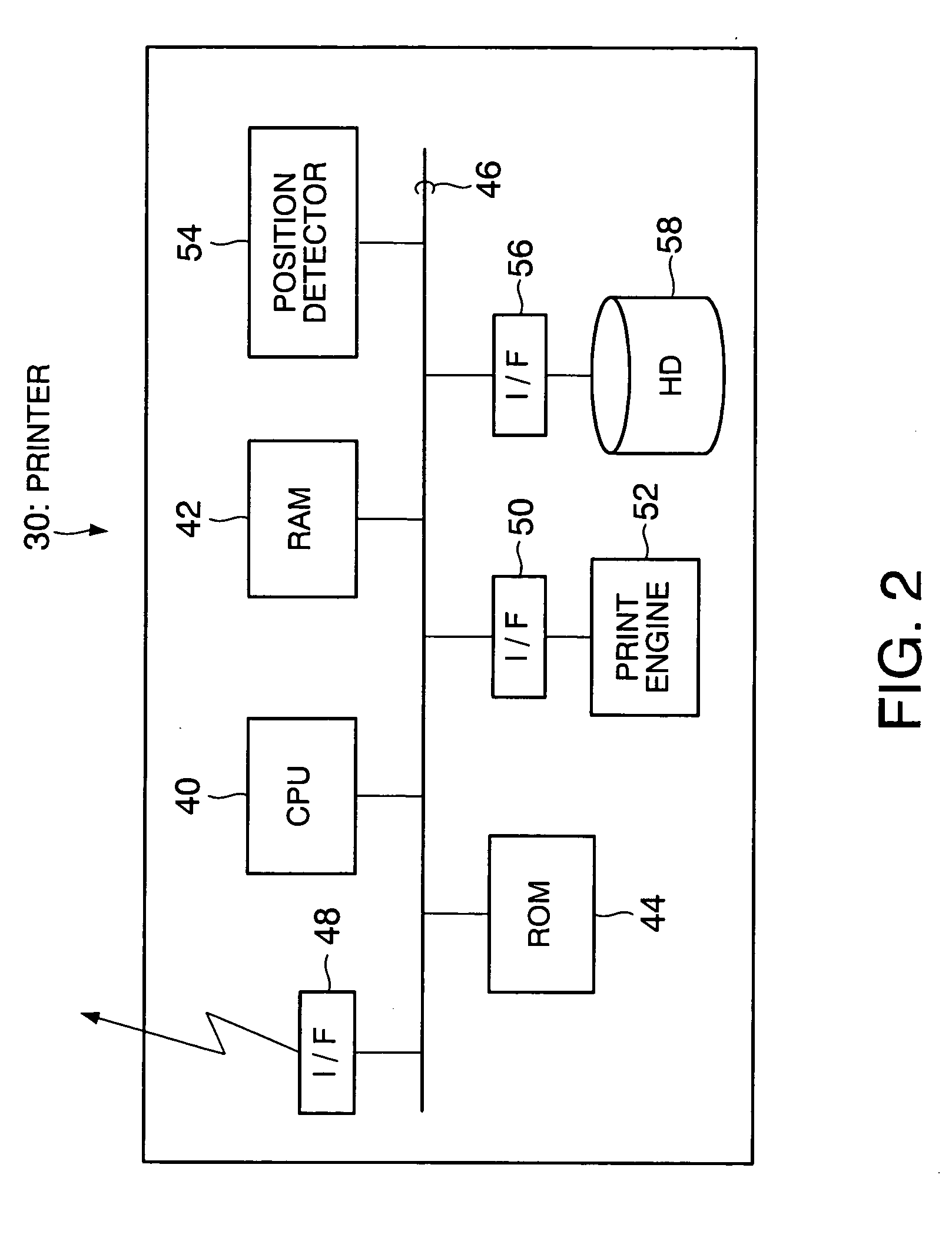
Printer and print system, and data receiving device and data transmitting and receiving system
InactiveUS20050163549A1Character printing data arrangement from carrierError detection/correctionPassphraseComputer printing
A printer generates a public key with a passphrase containing at least printer position information and a random number by a public key cryptography, and holds this random number. A print client previously acquires the public key from the printer. When transmitting print data to the printer, the print client encrypts the print data in advance with the acquired public key and transmits the encrypted print data as print transmitting data. The printer which has received the print transmitting data generates a private key with a passphrase containing at least printer position information and the held random number by the public key cryptography. The printer then decrypts the received print transmitting data with the private key. Consequently, the security of the print data transmitted from the print client to the printer via a network is ensured.
Owner:SEIKO EPSON CORP
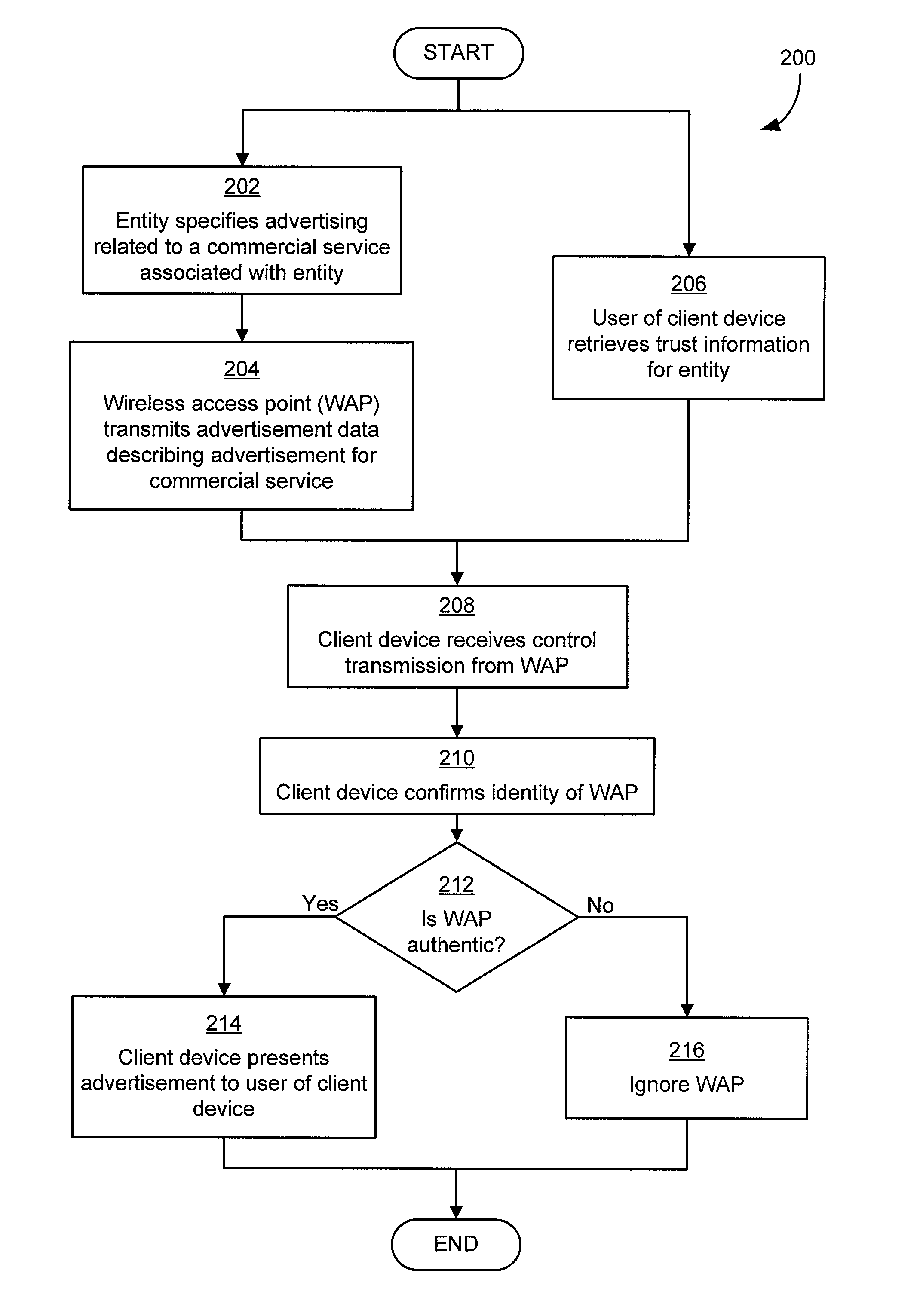
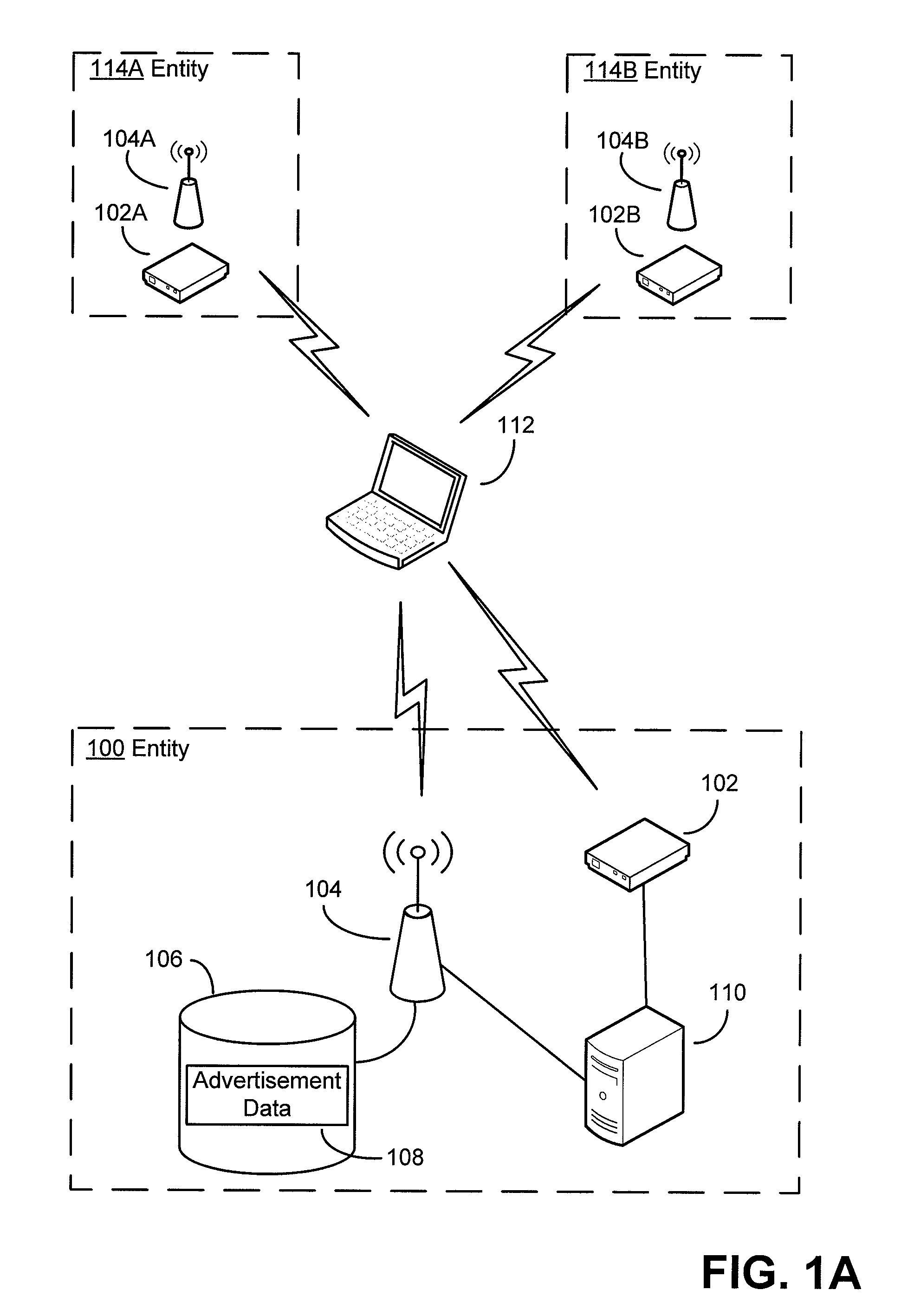
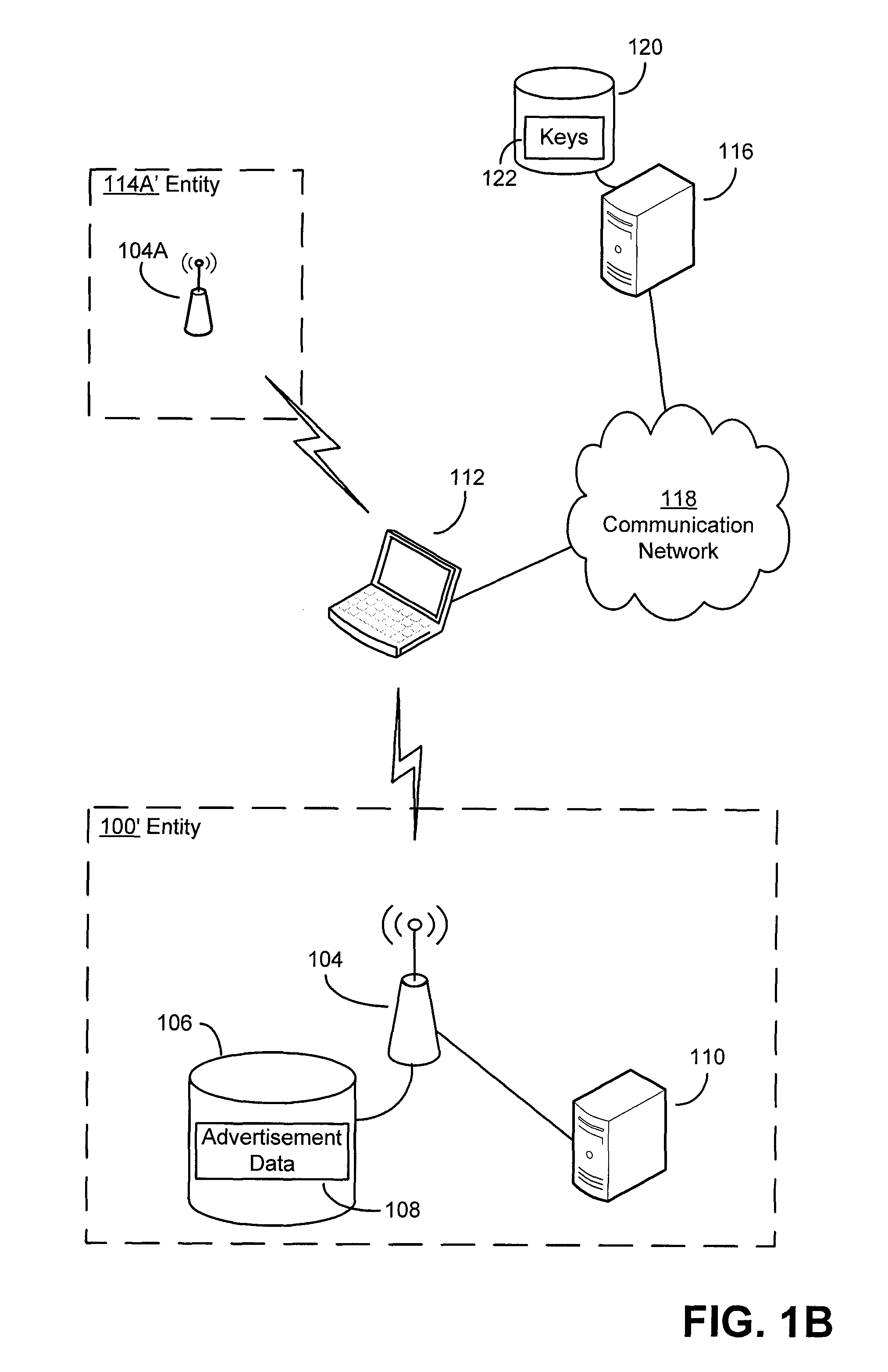
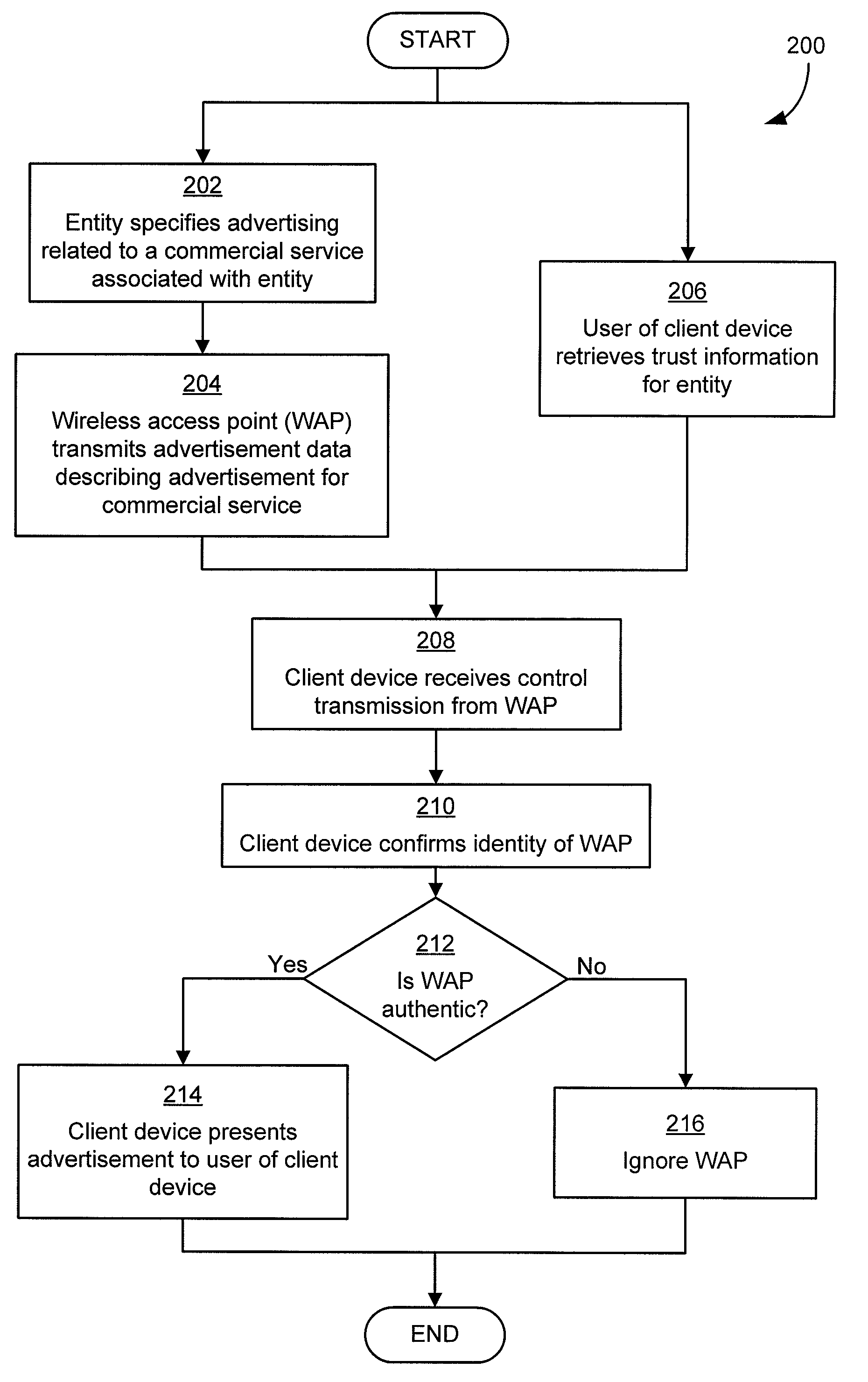
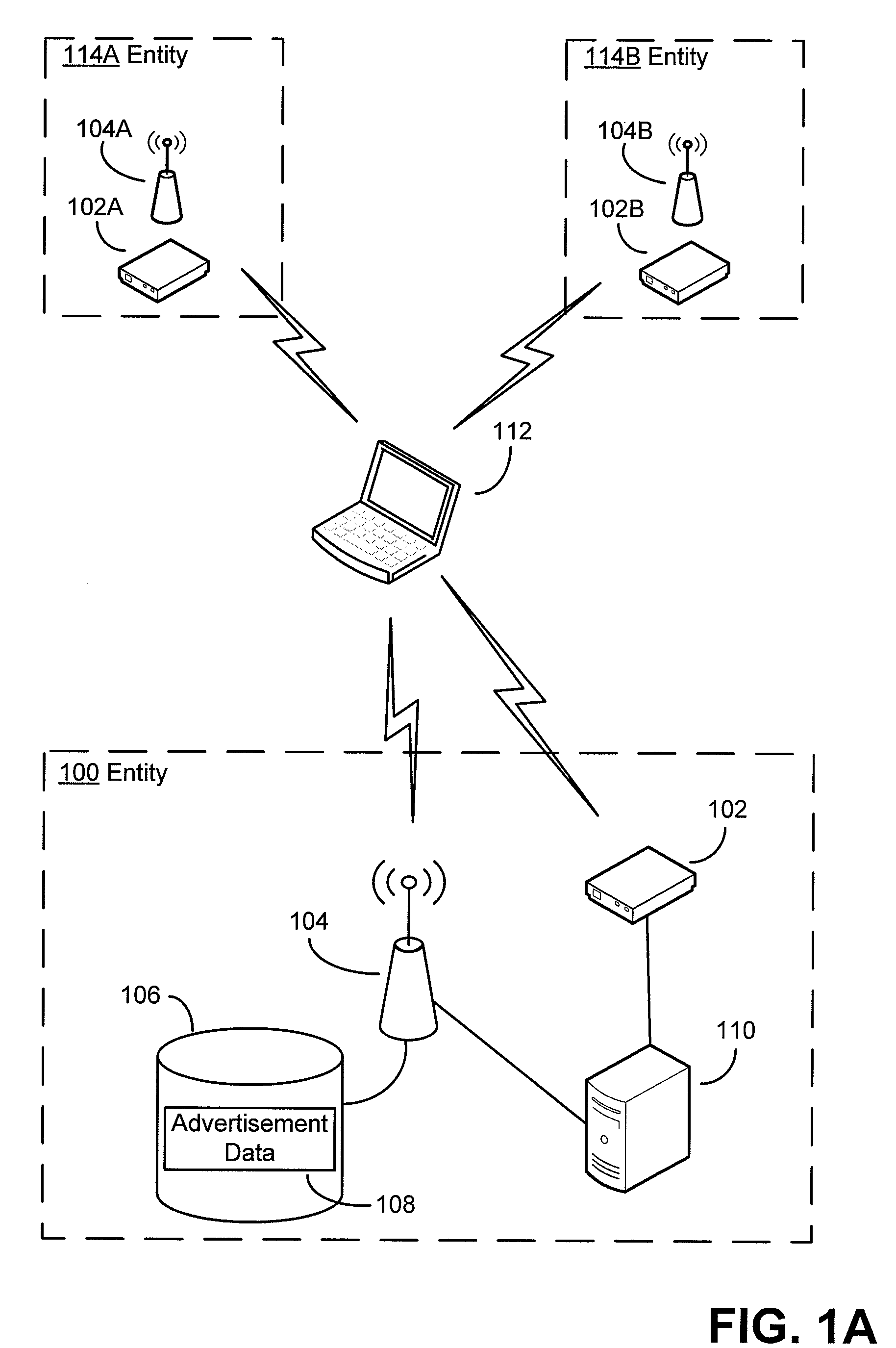
Authentication mechanisms for wireless networks
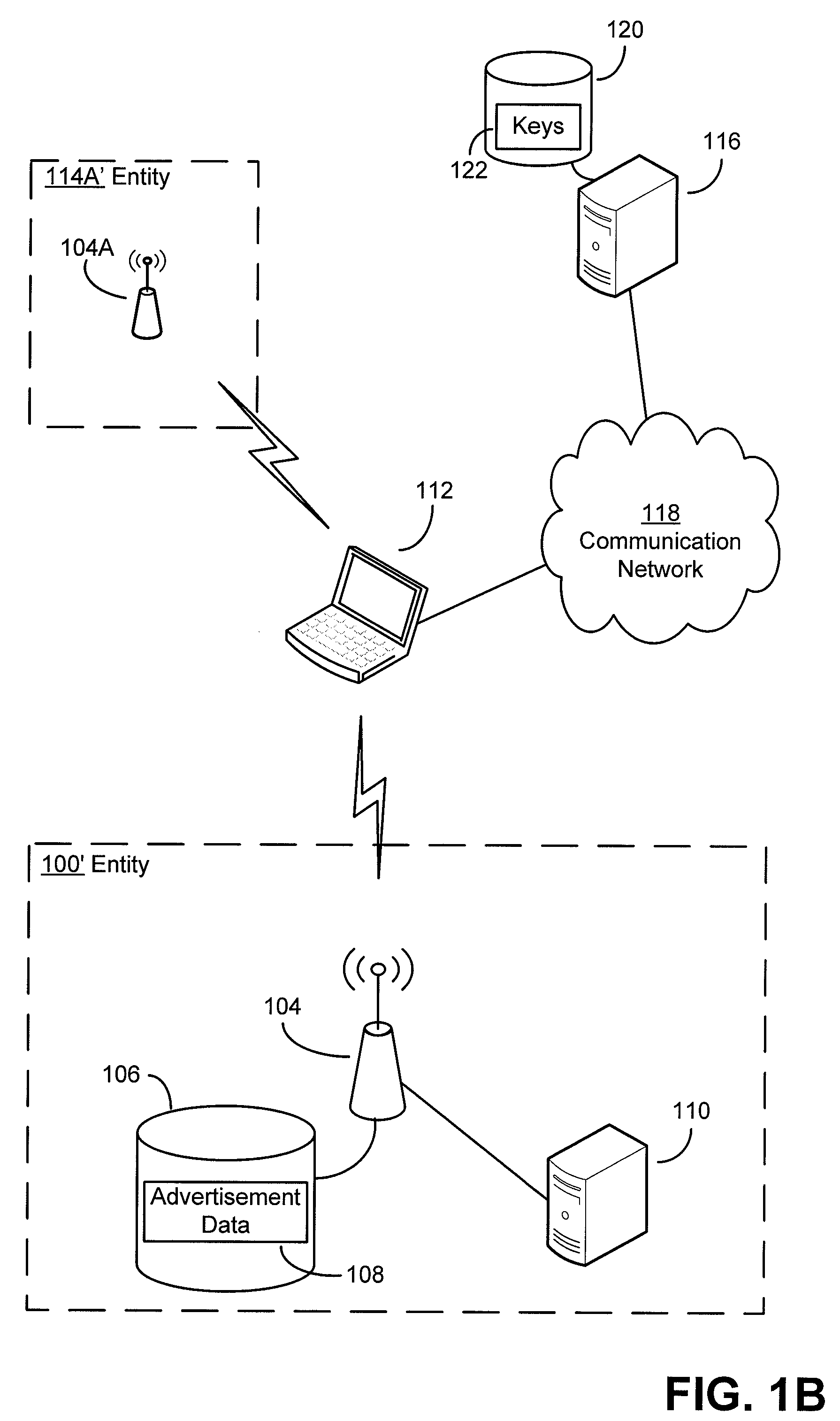
Security techniques and security mechanisms for wireless networks that transmit content such as advertisements. According to exemplary techniques, control messages comprising unrequested content (e.g., advertisement data) may be transmitted in response to a request from a client device, while in other exemplary techniques the control messages may be transmitted without any request from a client device. In some exemplary implementations, security mechanisms such as public key cryptography algorithms may be used to secure transmissions. In some of these techniques which implement public key cryptography, a user may be required to retrieve a public key from a source other than the wireless access point transmitting encrypted advertisements (e.g., a sign or terminal in a commercial entity transmitting such advertisements, or from a web service), such that the user may confirm that the encrypted content is from a source matching the retrieved public key and thus confirm the authenticity of a wireless access point.
Owner:MICROSOFT TECH LICENSING LLC
Multi-key cryptography for encrypting file system acceleration
ActiveUS20120057696A1Multiple keys/algorithms usagePublic key for secure communicationEncrypted file systemComputer science
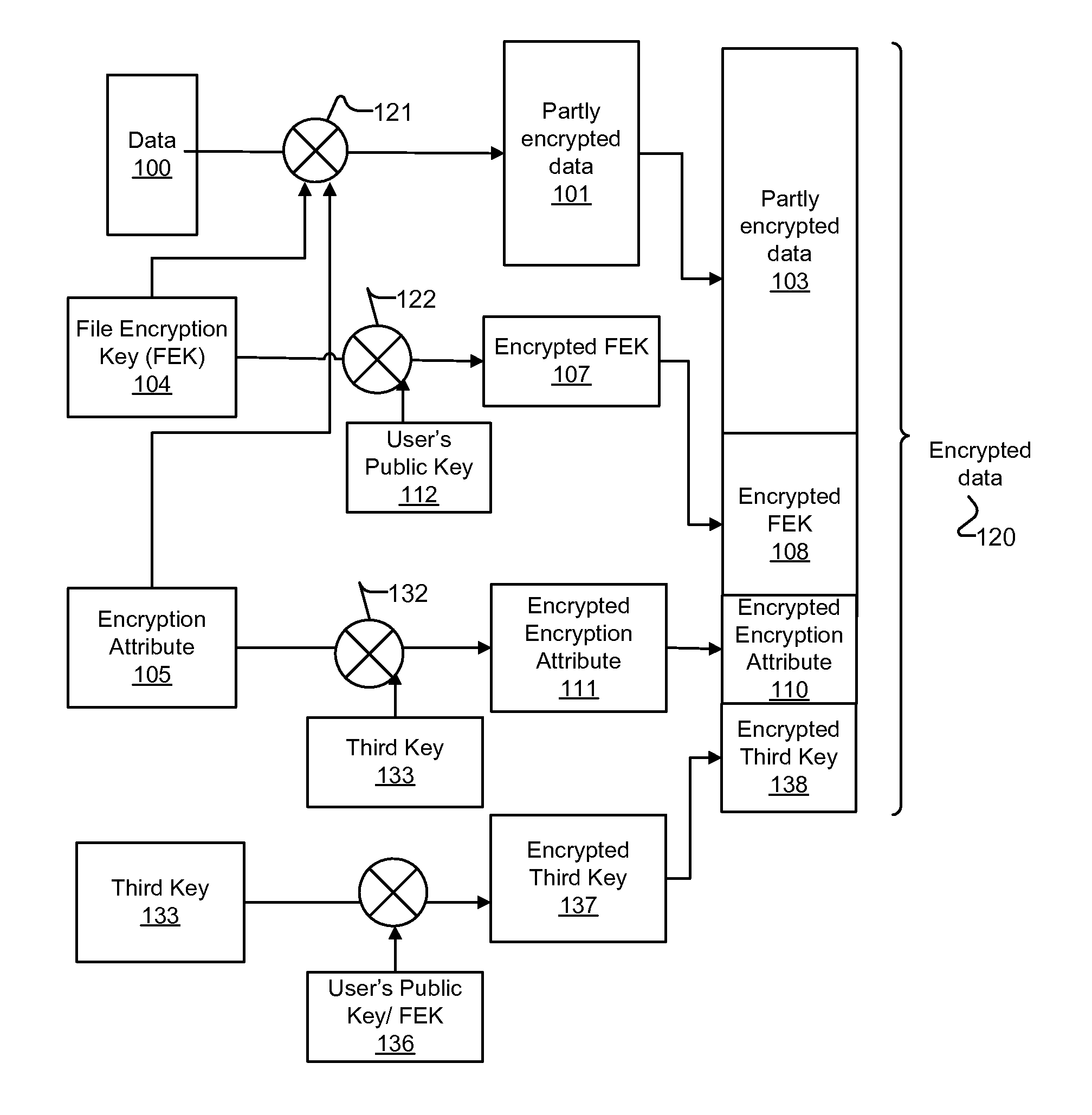
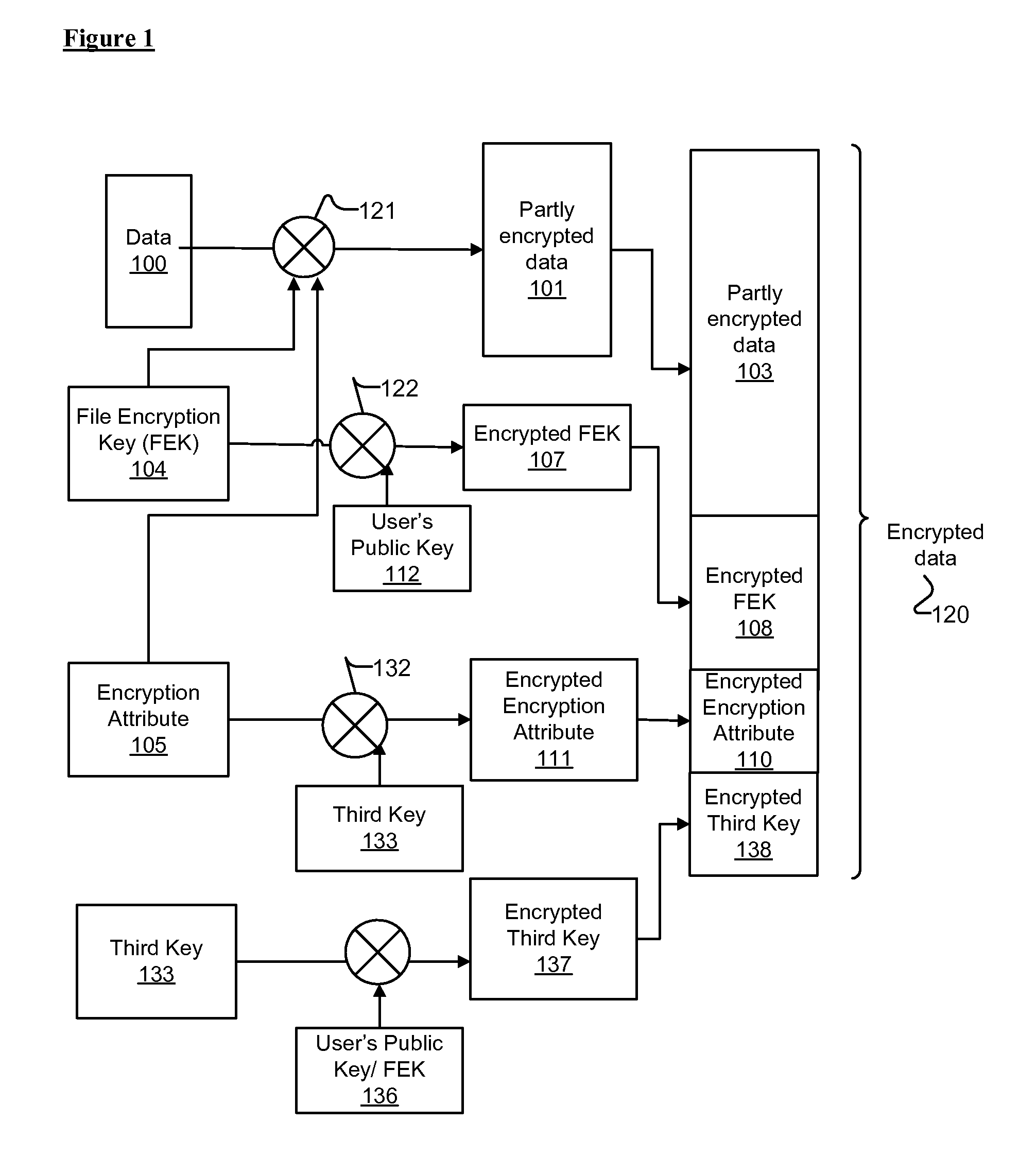
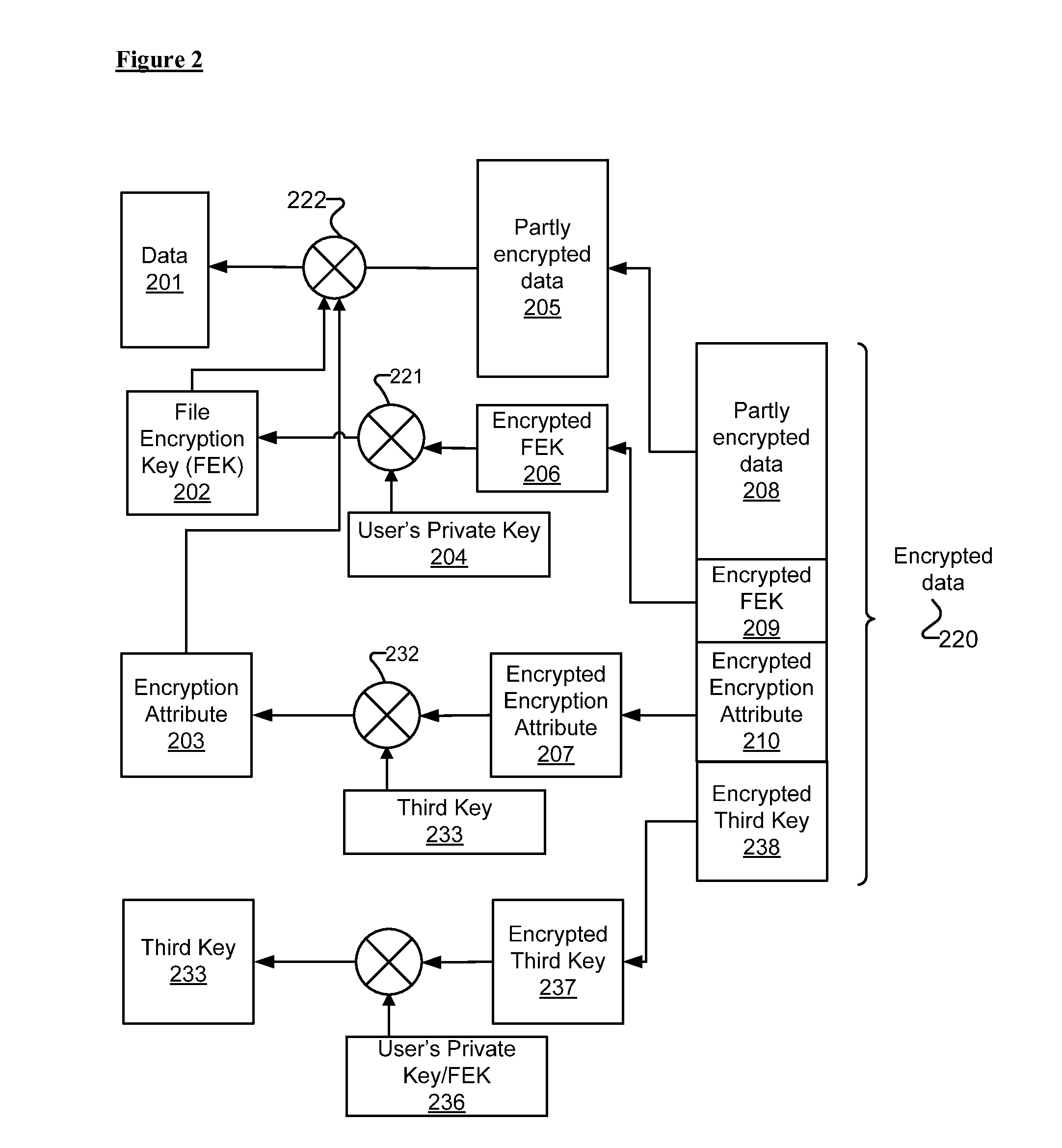
Embodiments of methods and systems for encrypting and decrypting with encryption attributes are presented. An encryption attribute contains information to identify one or more segments of a file to be encrypted. An encryption process encrypts those one or more segments to generate a partly encrypted file instead of encrypting the entire file. That is, the file includes some data that are encrypted and some data that are not. In one embodiment, at least three encryption keys are used such that the encryption attribute is encrypted with using a third key.
Owner:INTEL CORP
Wireless device discovery and configuration
ActiveUS7616594B2Assess restrictionData switching by path configurationComputer hardwareWireless network
A wireless device that desires to be connected to a wireless network broadcasts itself and its capabilities to a network using an information element. The information element is provided with frames, such as management frames, in a channel that is not protected or encrypted. The information element is forwarded to one or more potential registrar devices. One of the registrar devices then provides configuration information to the enrollee, for example as a registrar information element. The configuration information may be passed out of band or in band, and may be passed using cryptography, which may involve public key cryptography, encryption with a PIN, or some other type of secure exchange.
Owner:MICROSOFT TECH LICENSING LLC
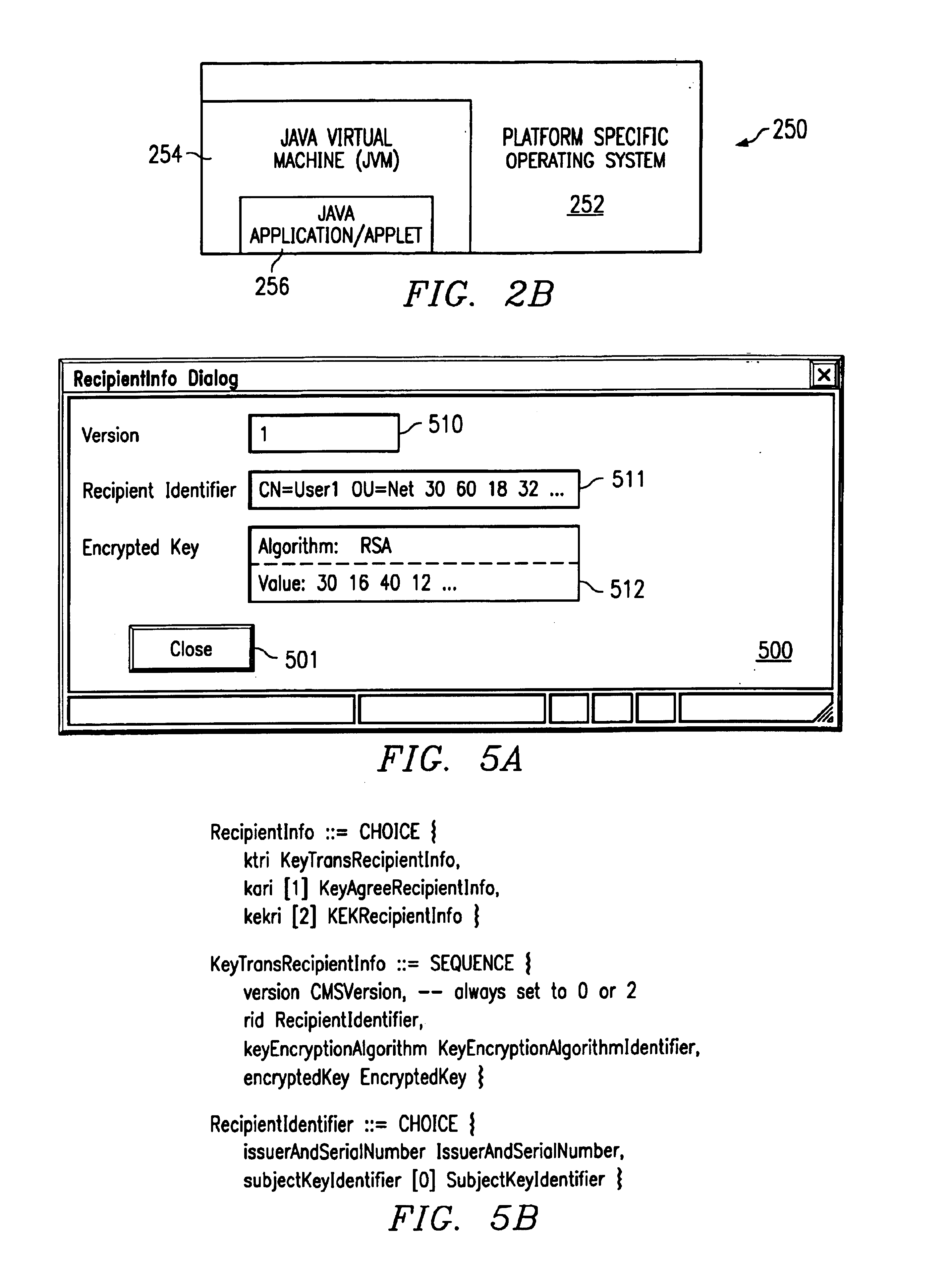
Method and system for presentation and manipulation of PKCS enveloped-data objects
InactiveUS6914985B1Public key for secure communicationUser identity/authority verificationData processing systemGraphics
A method and system for processing enveloped data objects in a data processing system. The enveloped data object may be formatted as defined by PKCS (Public Key Cryptography Standard) standards. An enveloped data object utility allows a user to view and edit the contents of data objects embedded within an enveloped data object via a graphical user interface. Graphical objects represent the data objects embedded within an enveloped data object. A user may drag and drop objects onto other objects within the enveloped data object, and the enveloped data object utility automatically performs the necessary encrypting operations. Logical associations between data objects contained within the enveloped data object are determined or created, and the logical associations are displayed using visual indicators. As data objects are added or deleted through user actions on the graphical objects, the visual indicators are updated.
Owner:PAYPAL INC
Technique for digitally notarizing a collection of data streams
InactiveUS7028184B2User identity/authority verificationTelevision systemsData streamDigital signature
A method, system, computer program product, and method of doing business by digitally notarizing a collection of data streams, thereby improving security of the contents of the data streams. Preferably, public key cryptography is used, wherein the collection of data streams is digitally signed (i.e. notarized) using a private cryptographic key of a digital notary, such that an associated public cryptographic key can be used to verify the authenticity and integrity of the collection of data streams. One or more components which are involved in creating the data streams are preferably authenticated, and a unique identifier of each such component is included within cryptographically-protected information that is provided for the digital notarization. The authenticated identities of the components can therefore be determined from the digital notarization.
Owner:INT BUSINESS MASCH CORP
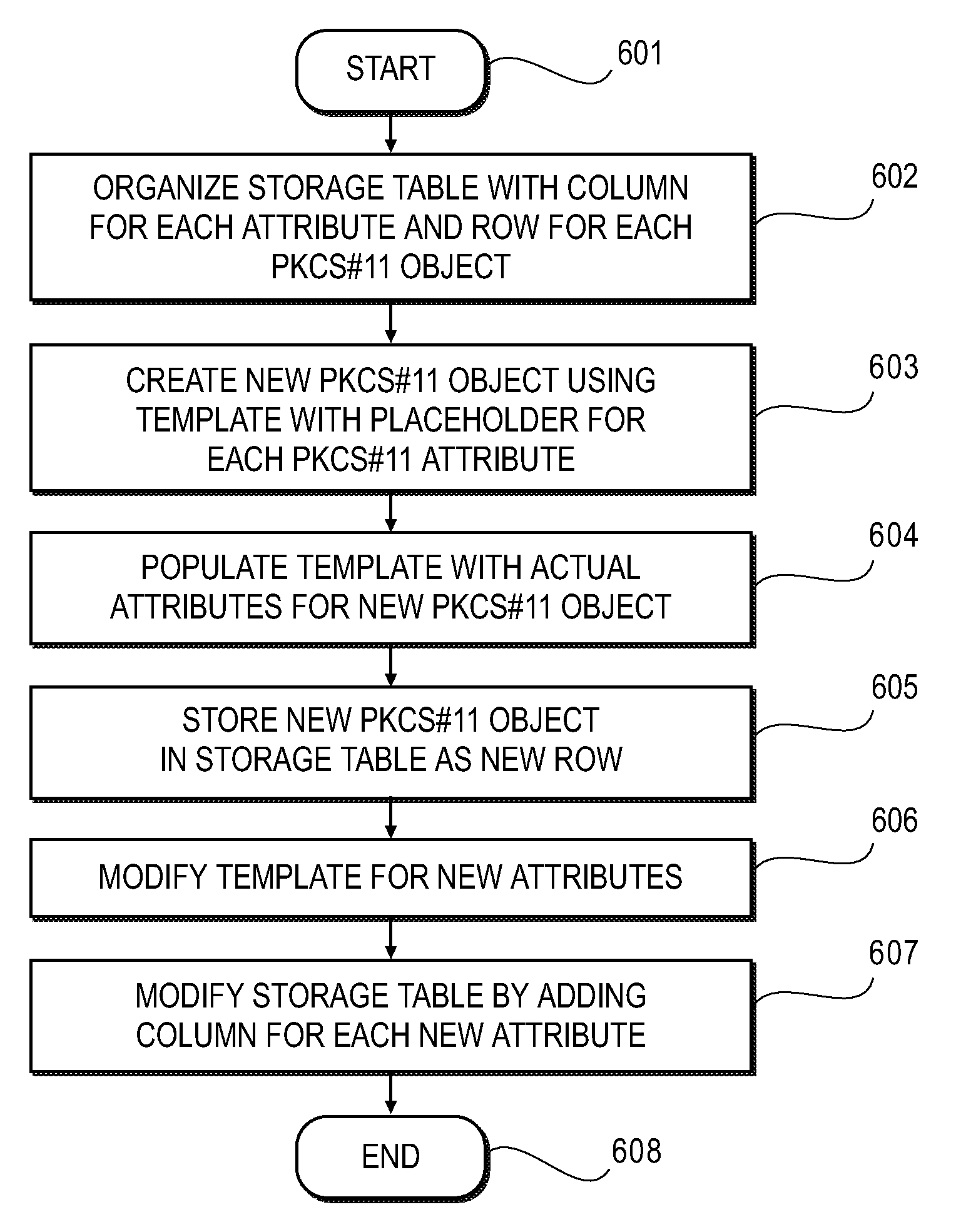
Method and Apparatus for Organizing an Extensible Table for Storing Cryptographic Objects
ActiveUS20080133514A1Digital data authenticationSpecial data processing applicationsComputer hardwareClient-side
Embodiments of the present invention provide a method and apparatus, including a client and security token, for managing cryptographic objects, such as public key cryptography standard (PKCS)#11 objects, in a computer system. A storage table for the cryptographic objects is established including rows for the cryptographic objects and columns corresponding to available attributes capable of being associated with the cryptographic objects. Actual attributes of the cryptographic objects are stored in ones of the plurality of columns corresponding to respective ones of the available attributes. The storage table is extensible such that additional columns are added corresponding to new attributes capable of being associated with the cryptographic objects.
Owner:RED HAT
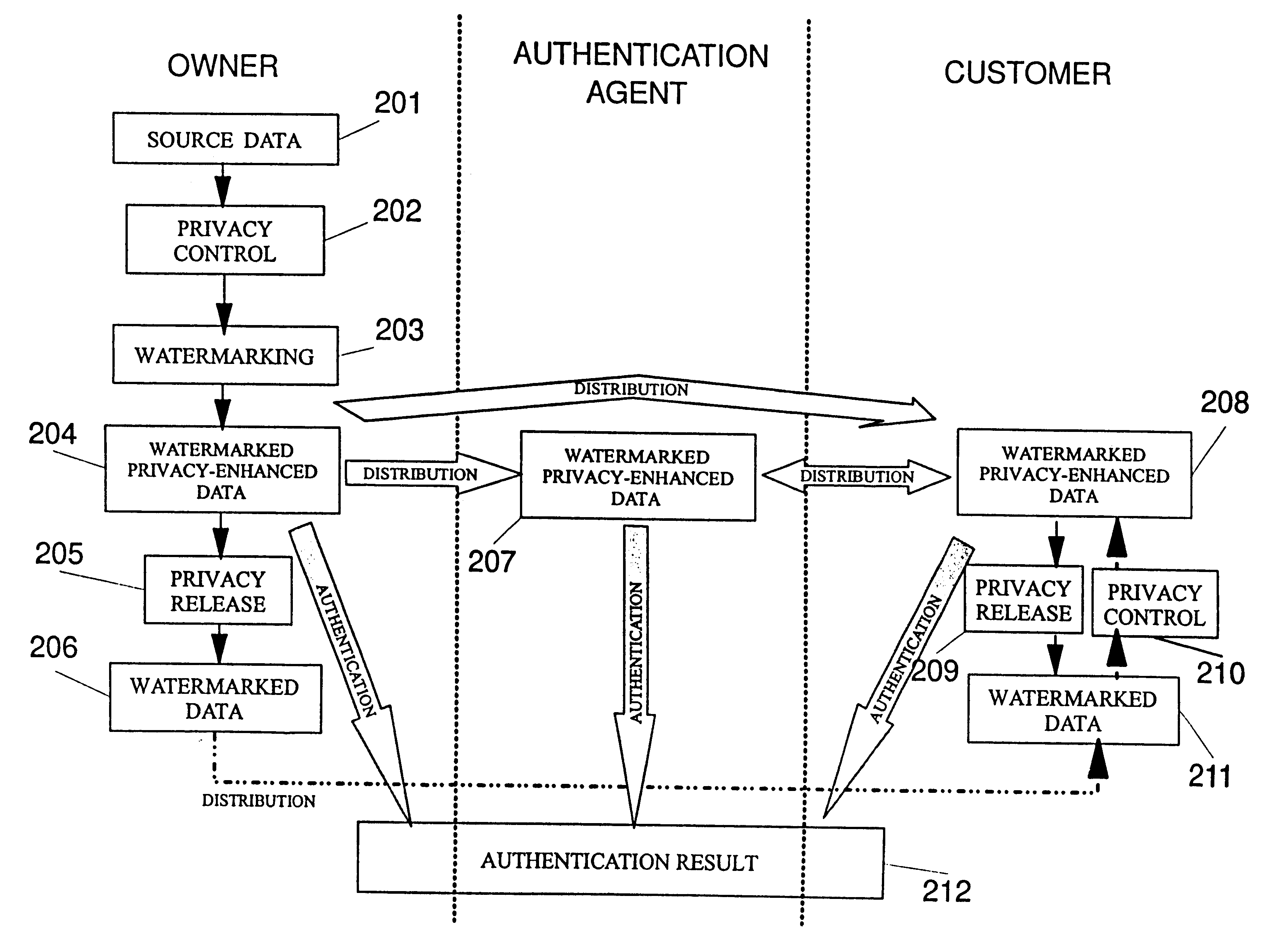
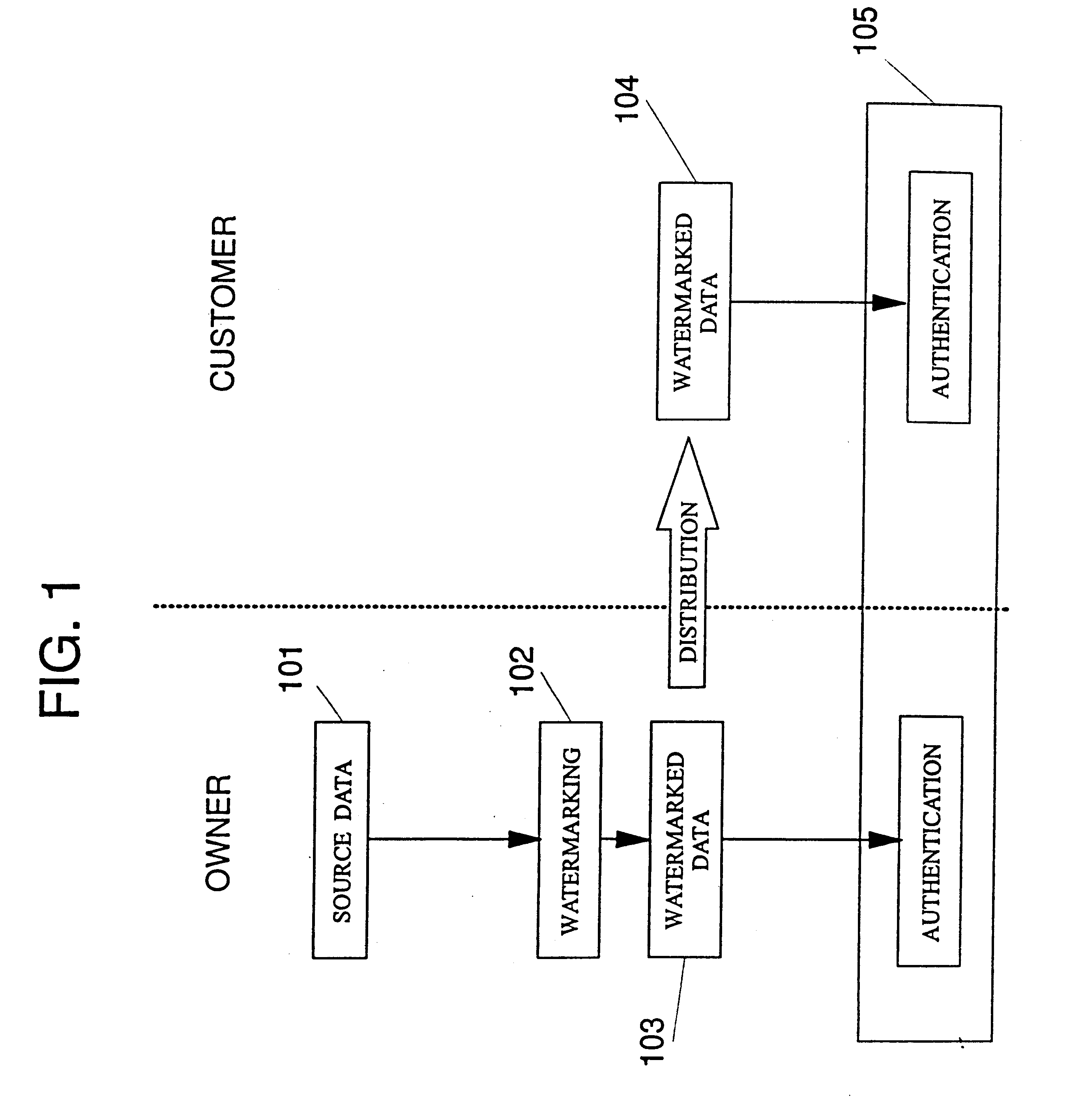
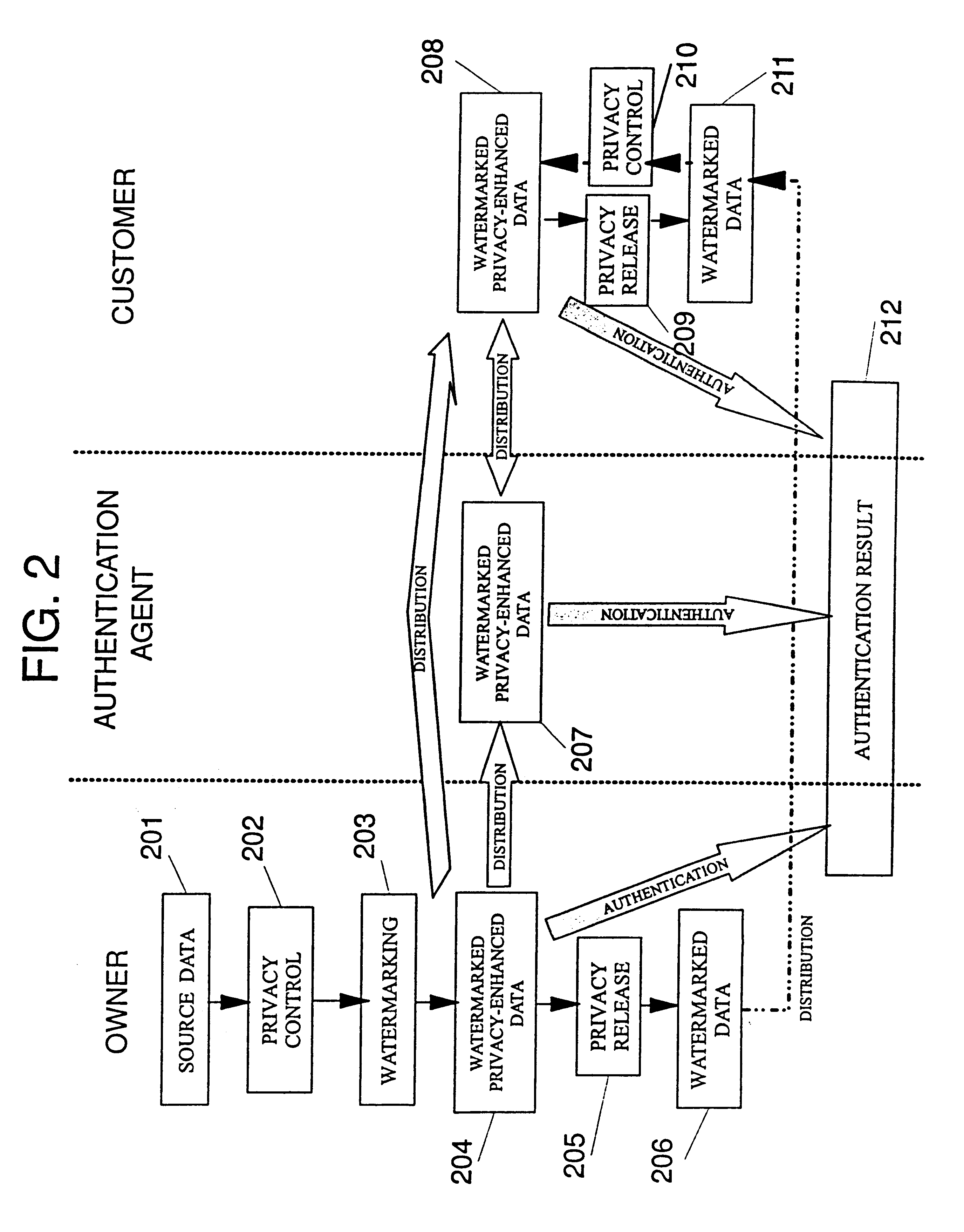
Secured signal modification and verification with privacy control
InactiveUS6256736B1User identity/authority verificationImage codingAuthenticationPublic-key cryptography
A watermarking scheme which allows the watermarked image to be authenticated by an authentication agent without revealing the human-readable content of the image. There is disclosed an approach which combines privacy control with watermarking and authentication mechanisms. The watermark can be made to be imperceptible to humans. Public key cryptography allows the authentication agent to authenticate without being able to watermark an image.
Owner:IBM CORP
Authentication mechanisms for wireless networks
ActiveUS20090214036A1More revenueLimited abilityAdvertisementsPublic key for secure communicationWireless mesh networkWeb service
Security techniques and security mechanisms for wireless networks that transmit content such as advertisements. According to exemplary techniques, control messages comprising unrequested content (e.g., advertisement data) may be transmitted in response to a request from a client device, while in other exemplary techniques the control messages may be transmitted without any request from a client device. In some exemplary implementations, security mechanisms such as public key cryptography algorithms may be used to secure transmissions. In some of these techniques which implement public key cryptography, a user may be required to retrieve a public key from a source other than the wireless access point transmitting encrypted advertisements (e.g., a sign or terminal in a commercial entity transmitting such advertisements, or from a web service), such that the user may confirm that the encrypted content is from a source matching the retrieved public key and thus confirm the authenticity of a wireless access point.
Owner:MICROSOFT TECH LICENSING LLC
Network without Abuse of a Private Key
ActiveUS20180076957A1Avoid abuseAbuse of the private keys can be preventedKey distribution for secure communicationDigital data processing detailsSemiconductor chipLogical network
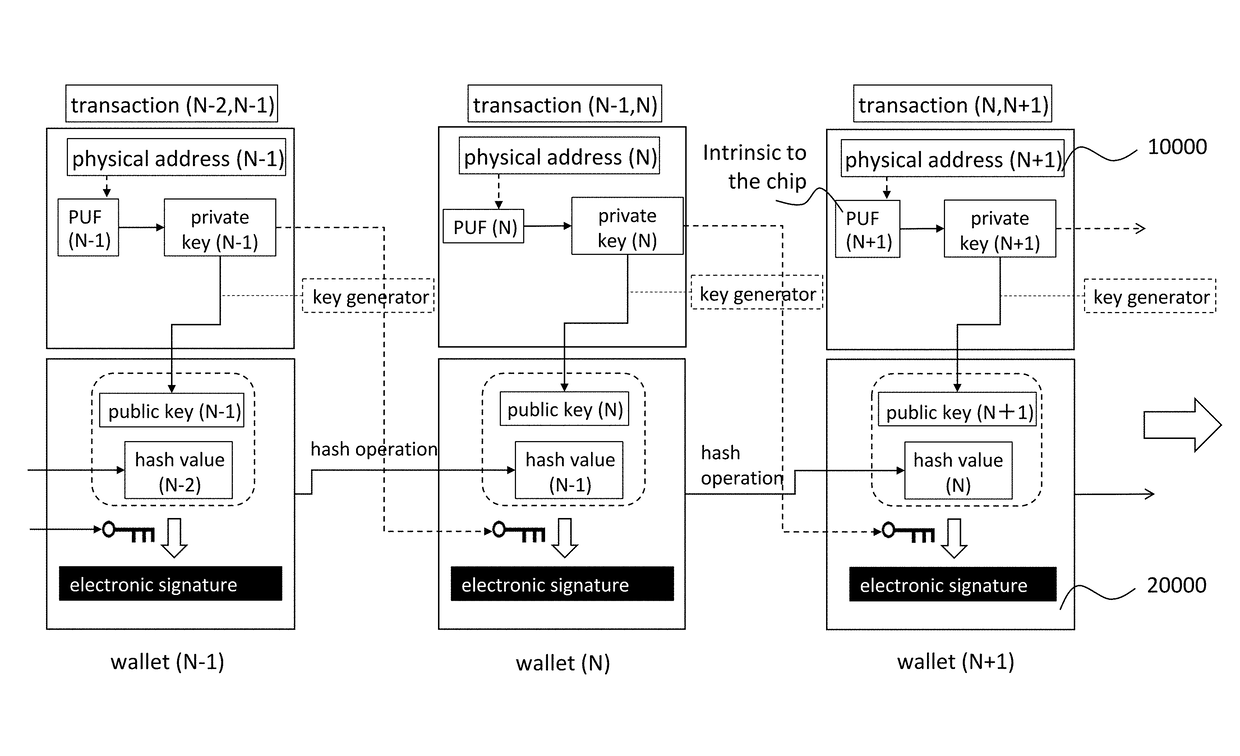
A network includes a logical network and a physical network. The logical network includes a plurality of logical nodes. Each logical node is connected to a respective identification core. Each identification core includes at least one semiconductor chip having a physical randomness. Each semiconductor chip generates one of a plurality of pairs of private keys and public keys based on the physical randomness thereof according to an input received by the one of the at least one semiconductor chip under a public key cryptography. One of the public keys is regarded as a logical address of one of the logical nodes, which is connected to one of the identification cores. The physical network includes a plurality of physical nodes. Each identification core is one of components in each physical node. The logical network is uniquely linked to the physical network by the pairs of private keys and public keys.
Owner:WATANABE YUKIKO
Secure data transfer method of using a smart card
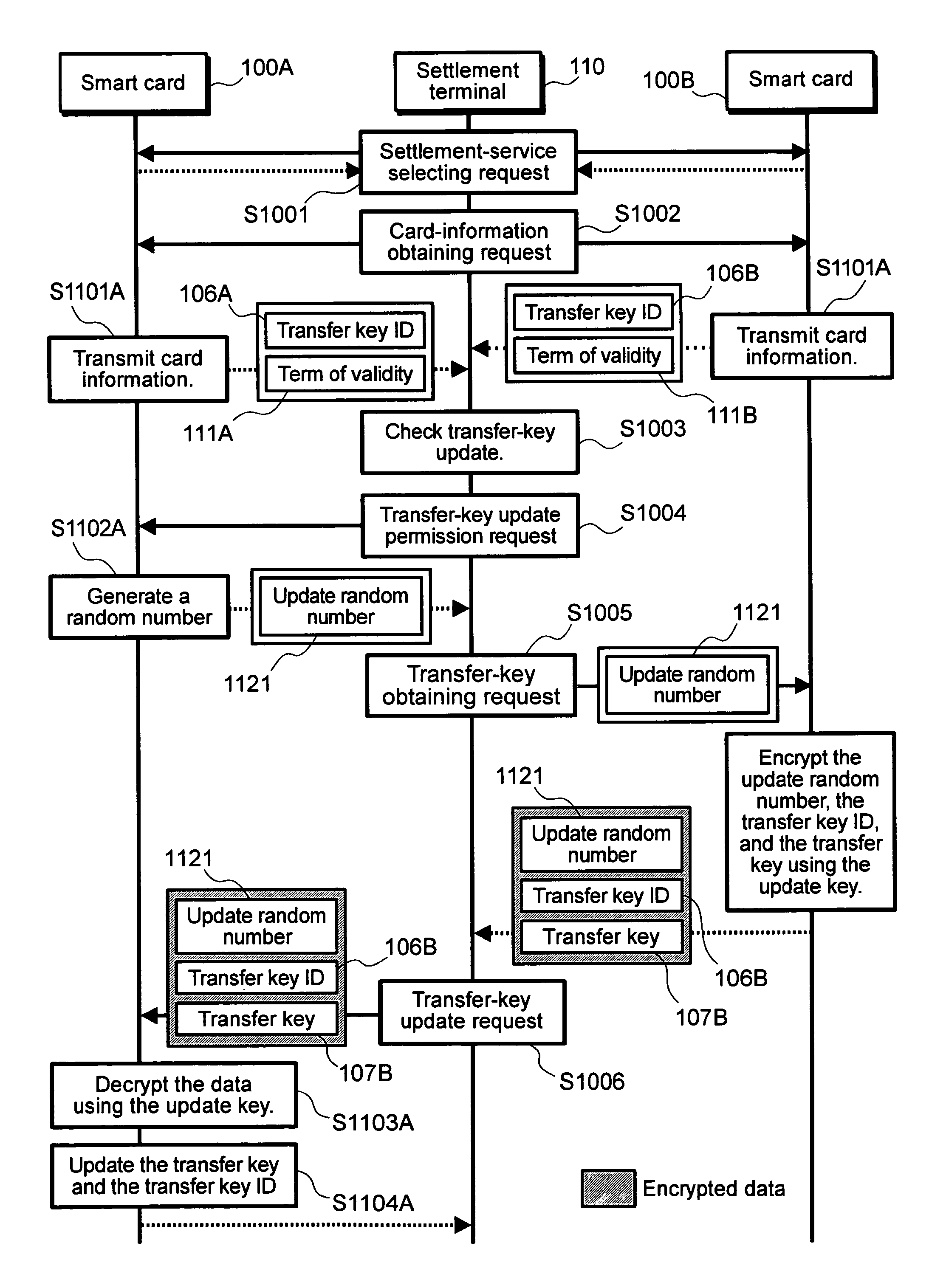
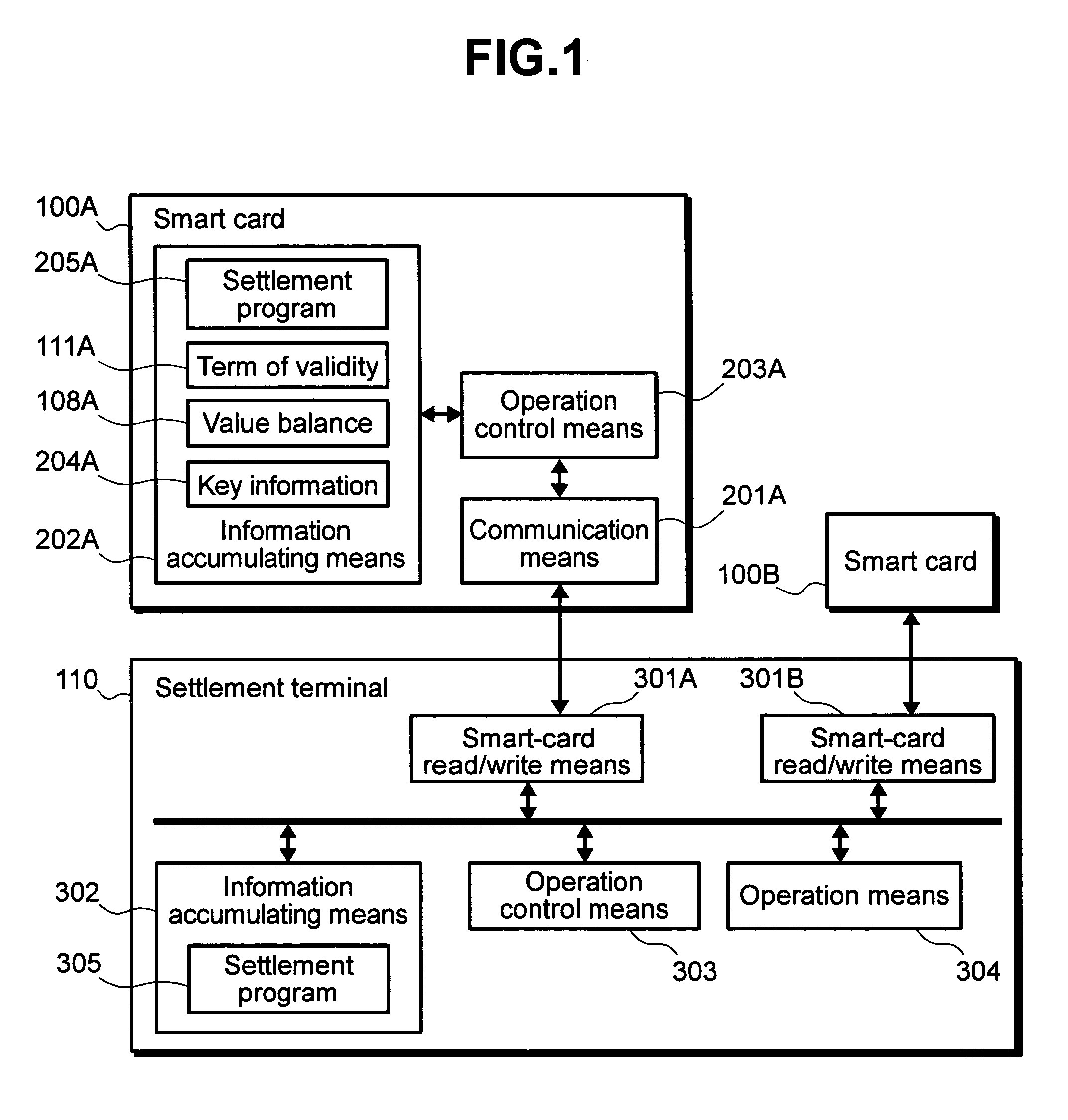
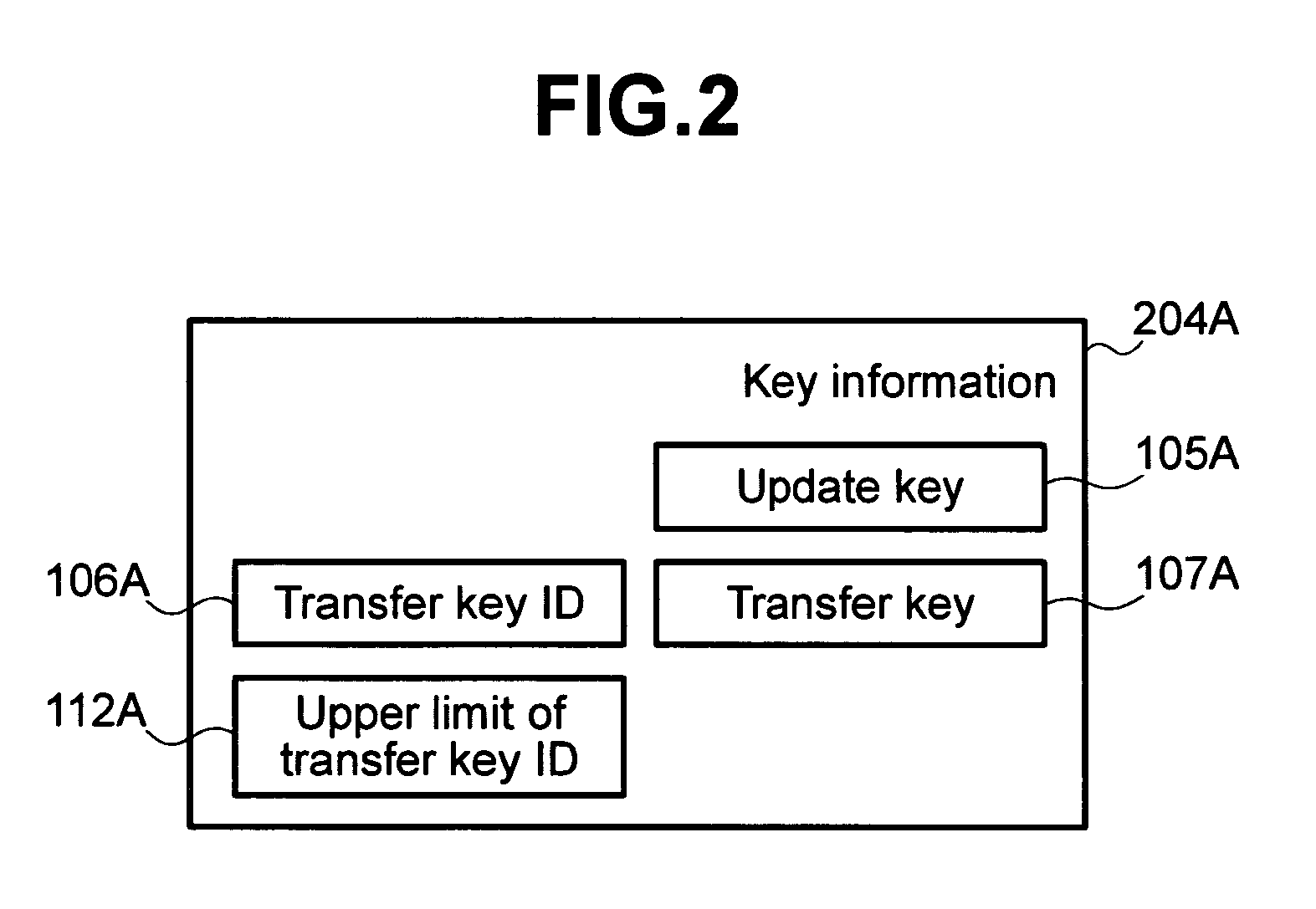
InactiveUS7360091B2Block valueSlow processingTicket-issuing apparatusMultiple keys/algorithms usageArithmetic processing unitCommunication unit
A smart card and a settlement terminal are provided by which, when common-key cryptography is used for value transfer between smart cards, the security of the whole system can be improved by enabling easy updating of a cryptographic key used for the value transfer. A smart card transmits / receives value data to / from another smart card. The smart card includes an information accumulating unit for accumulating value data, a transfer key used to update the value data, and an update key used to update the transfer key; a communication unit for receiving a transfer key encrypted by use of the update key, the transfer key being transmitted from another smart card; and an arithmetic processing unit for decrypting the encrypted transfer key by use of the update key to update the transfer key accumulated in the information accumulating unit by use of the decrypted transfer key.
Owner:HITACHI LTD
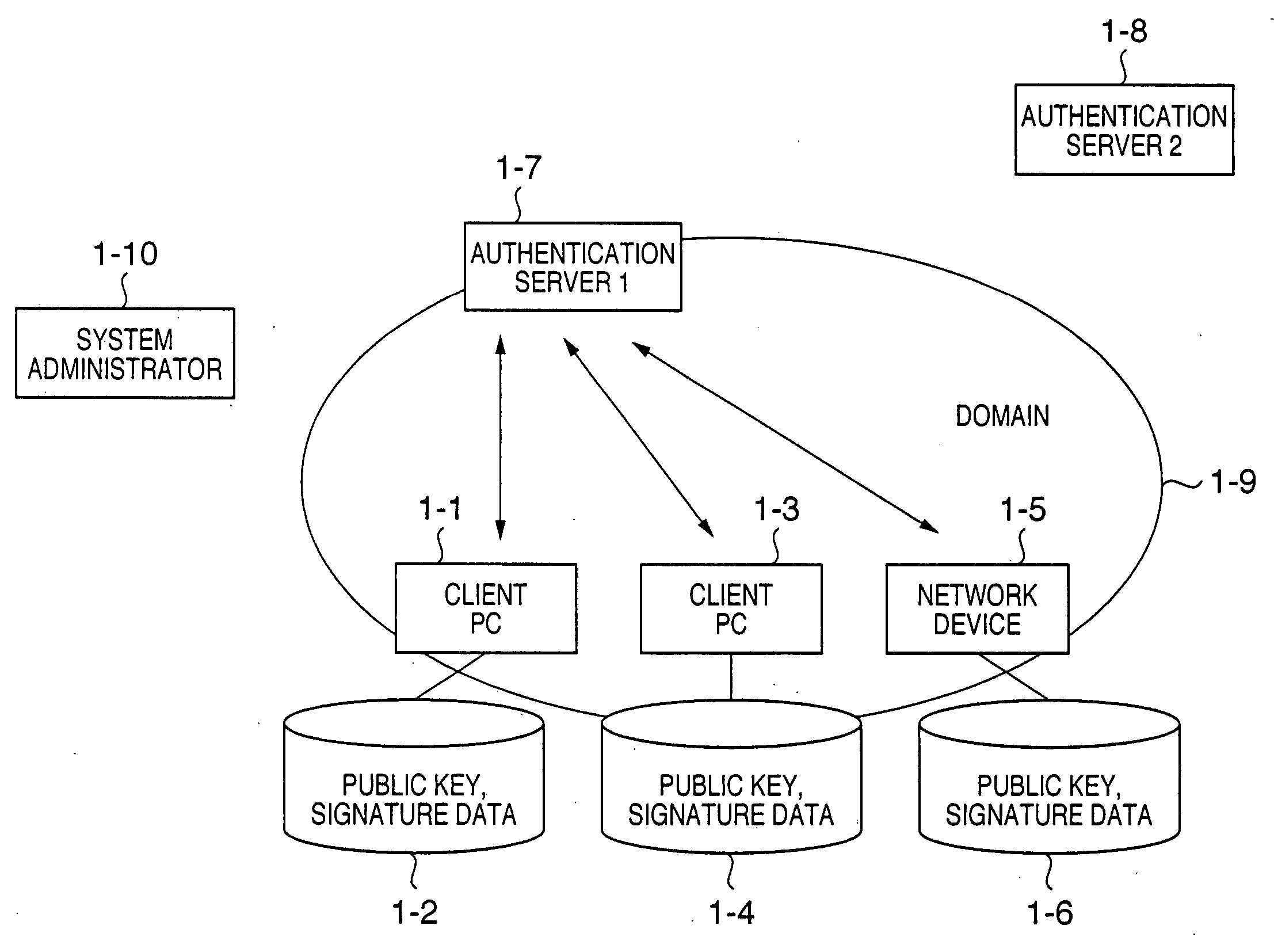
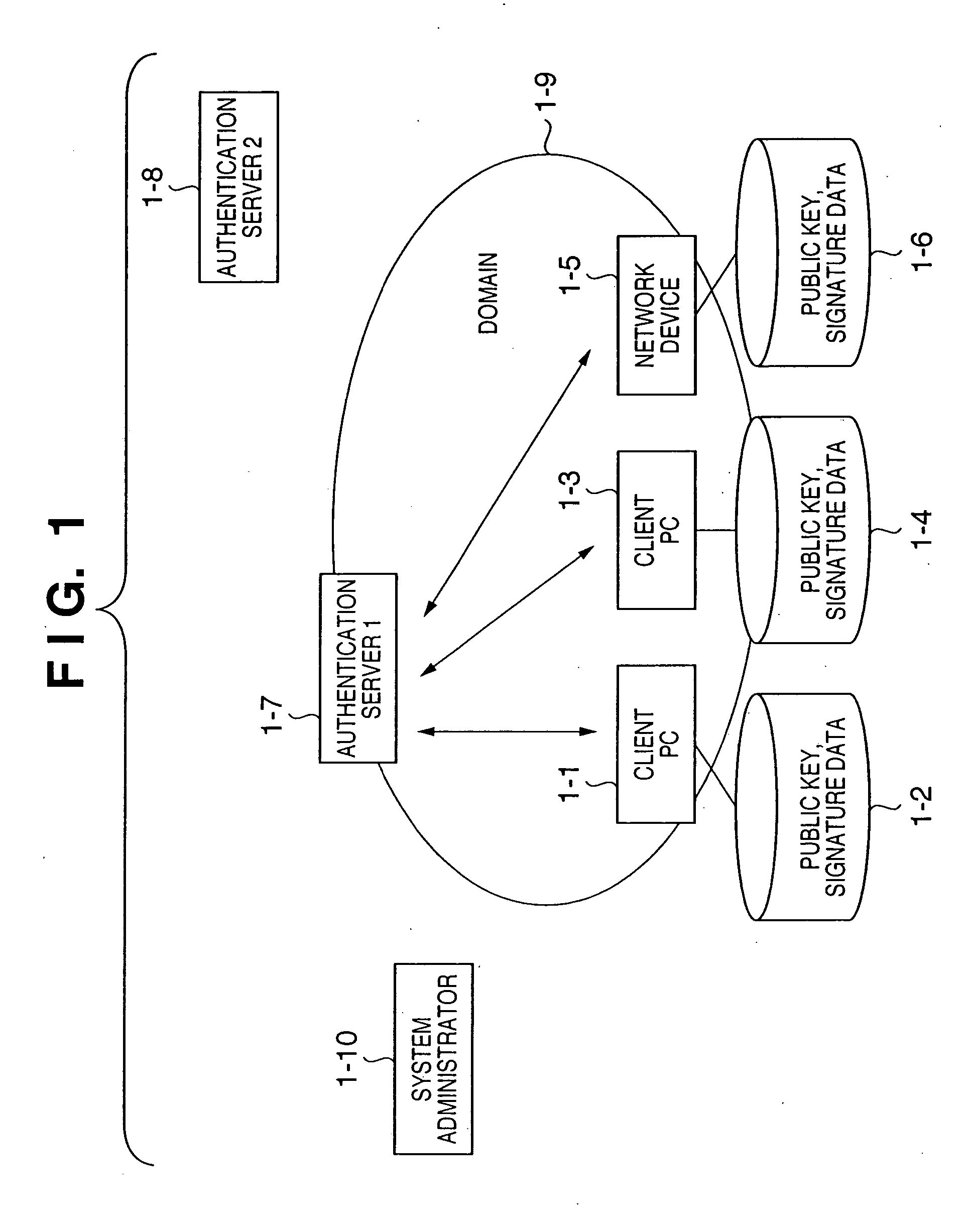
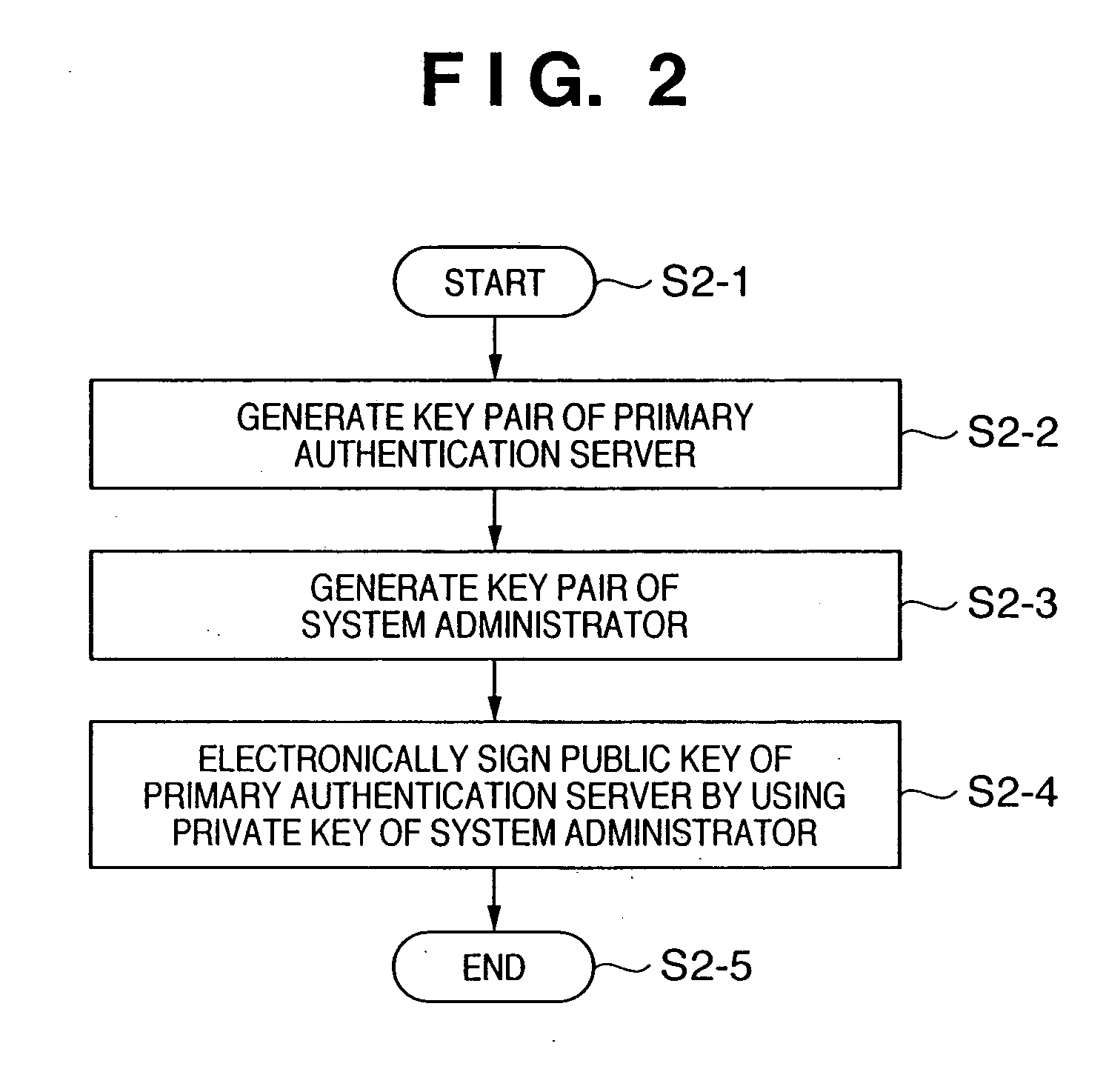
Assurance system and assurance method
InactiveUS20050055552A1Ensure reliabilityAvoid registrationKey distribution for secure communicationPublic key for secure communicationMultiplexingAuthentication server
In a client PC or device, the reliability of multiplexed authentication servers is assured. In an assurance system including a client PC (1-1, 1-3), an authentication server 1 (1-7), and a device (1-5) connected to a network, a multiplexed system is built by arranging an authentication server 2 (1-8) in order to back up the authentication server 1 (1-7), public key cryptography is used for encrypted communication between the client PC, the authentication servers 1 and 2, and the device, and the public keys of the authentication servers 1 and 2 are electronically signed by using the private key of one system administrator (1-10) by public key cryptography.
Owner:CANON KK
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com