Assurance system and assurance method
a technology of assurance system and assurance method, applied in the field of assurance system, can solve the problems of imposing the authentication server itself, unable to use a desired resource, and unable to operate user authentication and grant access rights
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
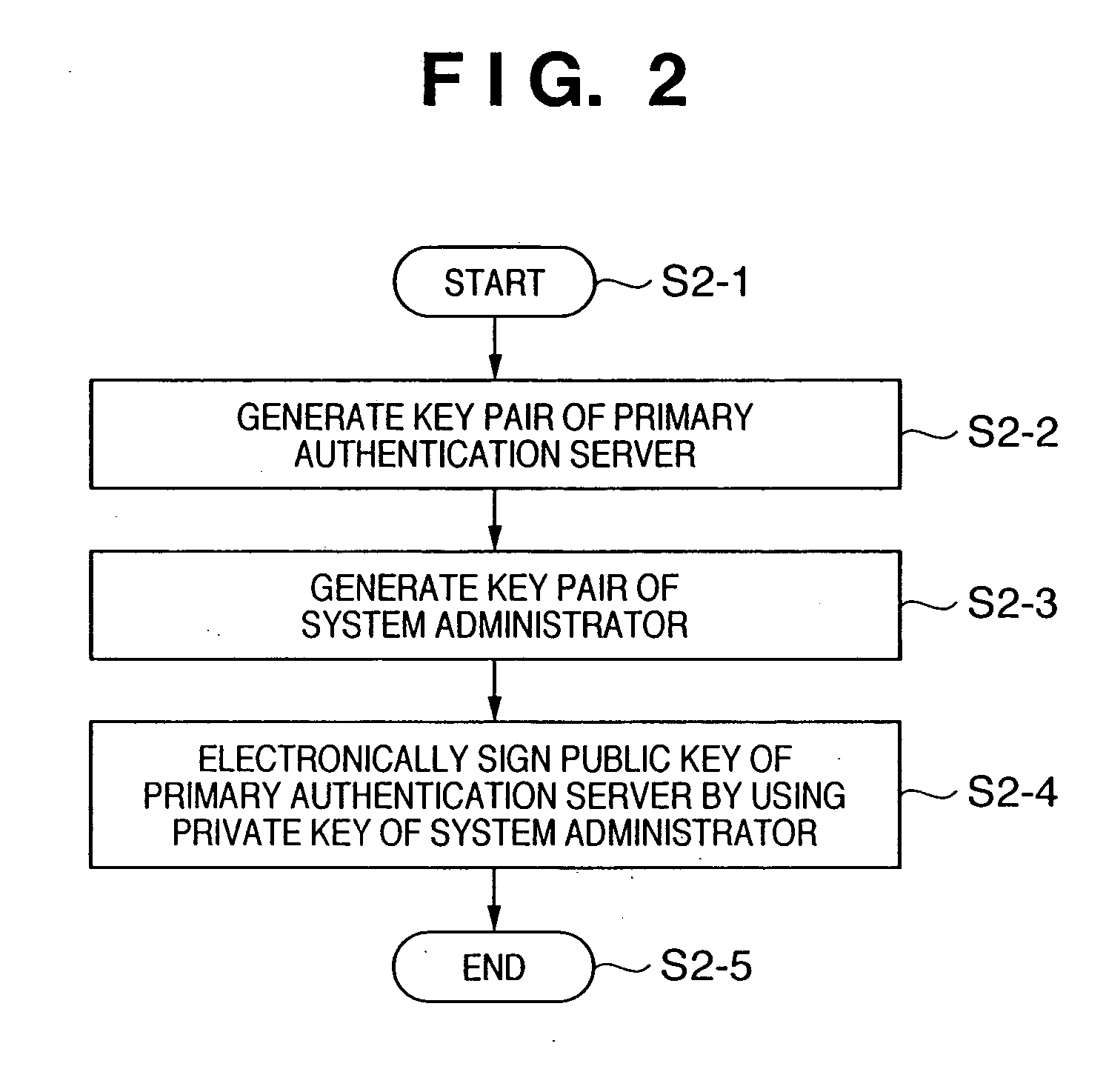
[0040] The embodiments of the assurance system according to the present invention will be described below with reference to the accompanying drawings.
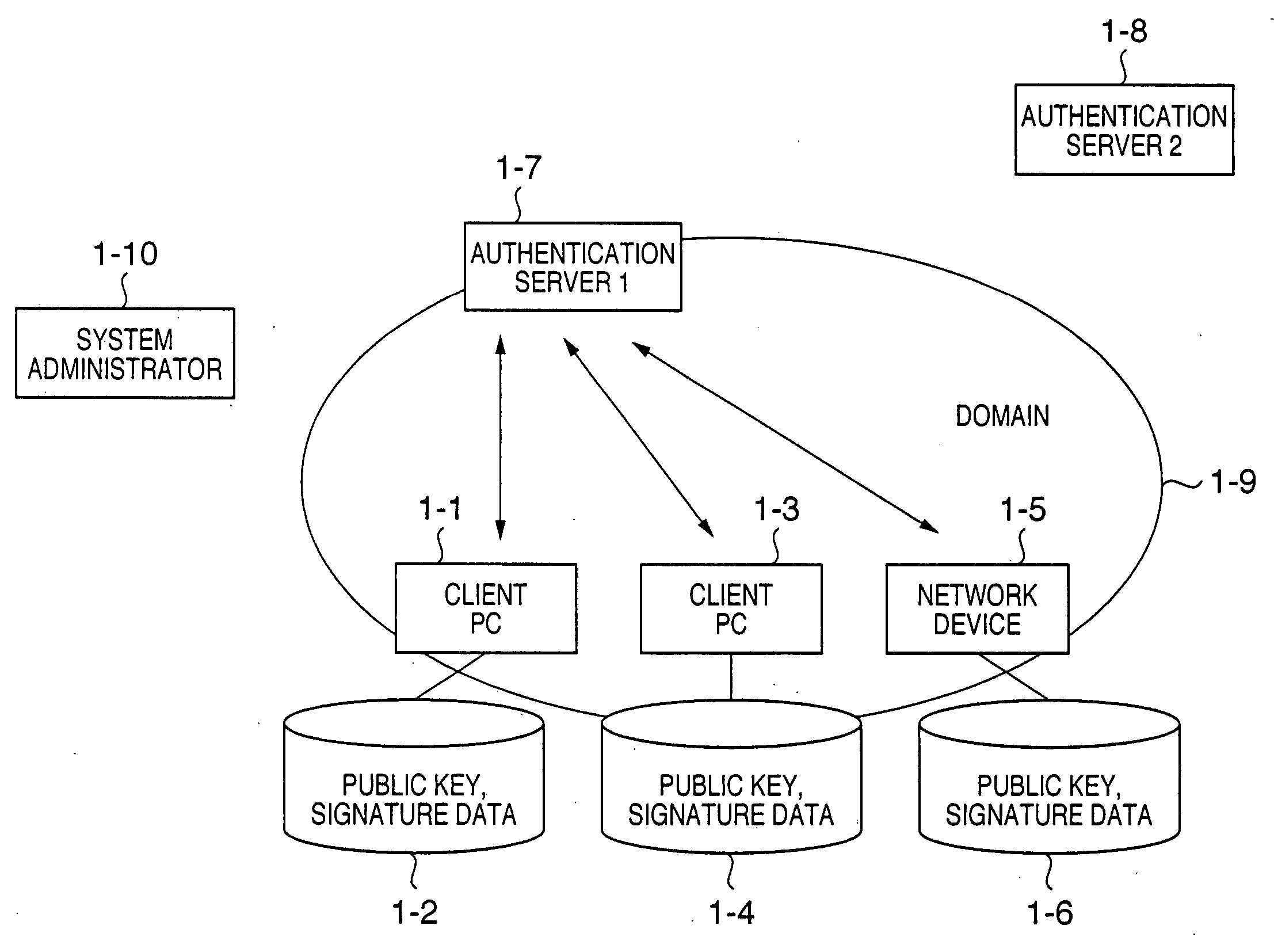
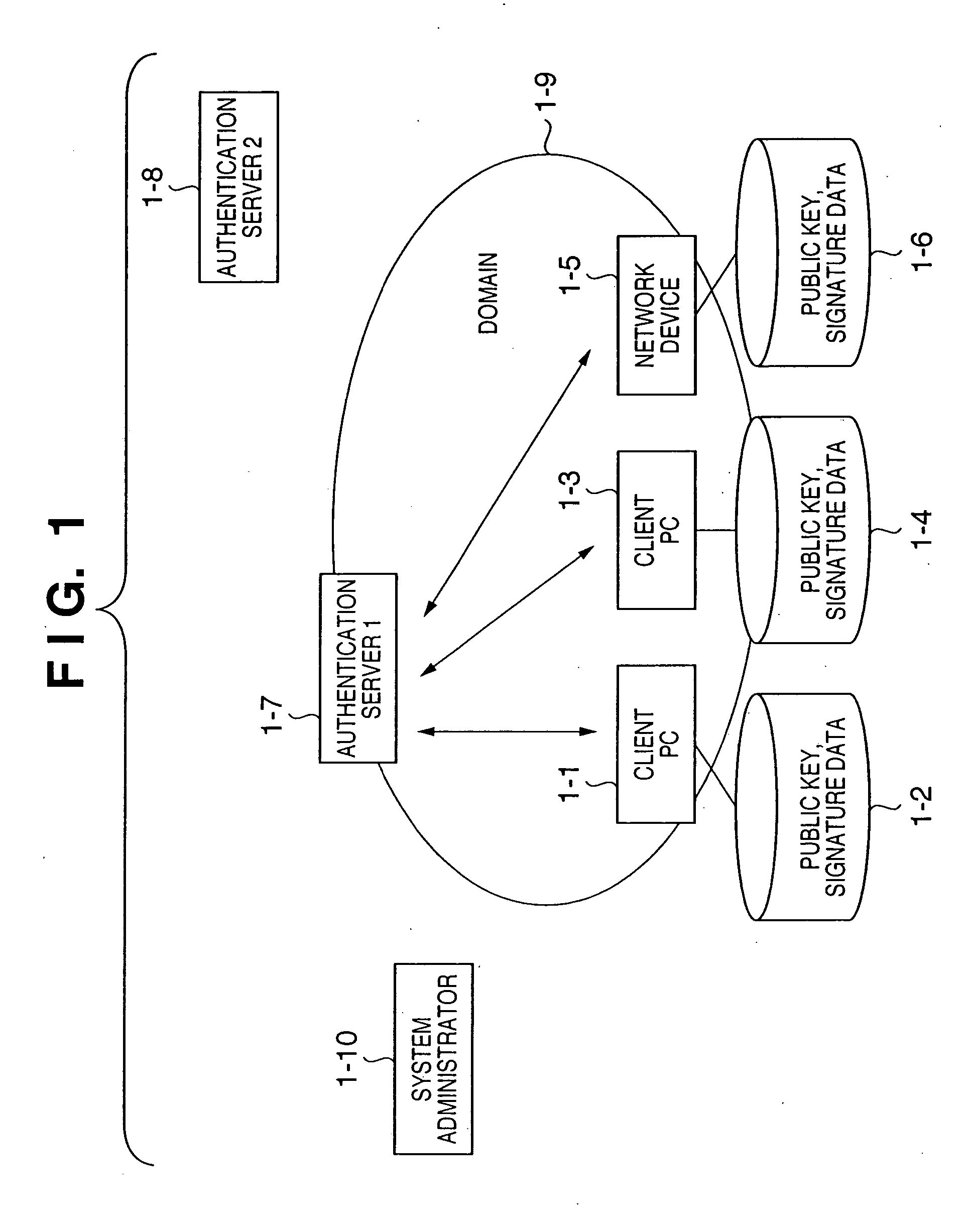
[0041]FIG. 1 is a view showing the overall arrangement of a system which assures reliability in an authentication server multiplexed system according to the present invention.
[0042] As shown in FIG. 1, the assurance system according to this embodiment includes client PCs 1-1 and 1-3 which provide services for users, a network device 1-5, and an authentication server 11-7 which collectively executes identification and authentication of users and access control. These components are connected by a physical network connection means so that information communication between them is possible.
[0043] In the assurance system according to this embodiment, the network device 1-5 is a printing device connected to the network or a multifunctional device having scanner, printer, and FAX functions. A file server (not shown) or the like may also b...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com