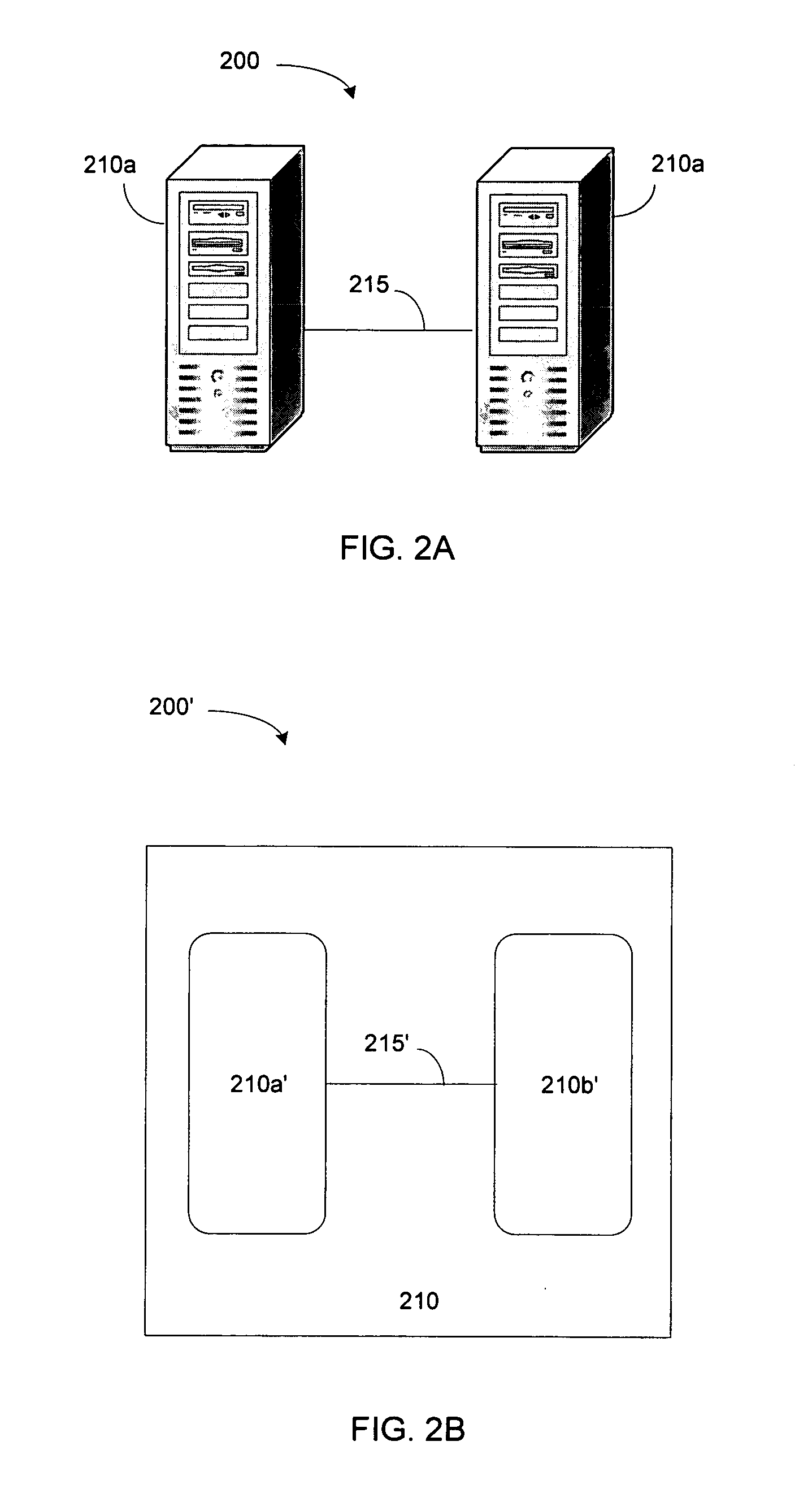
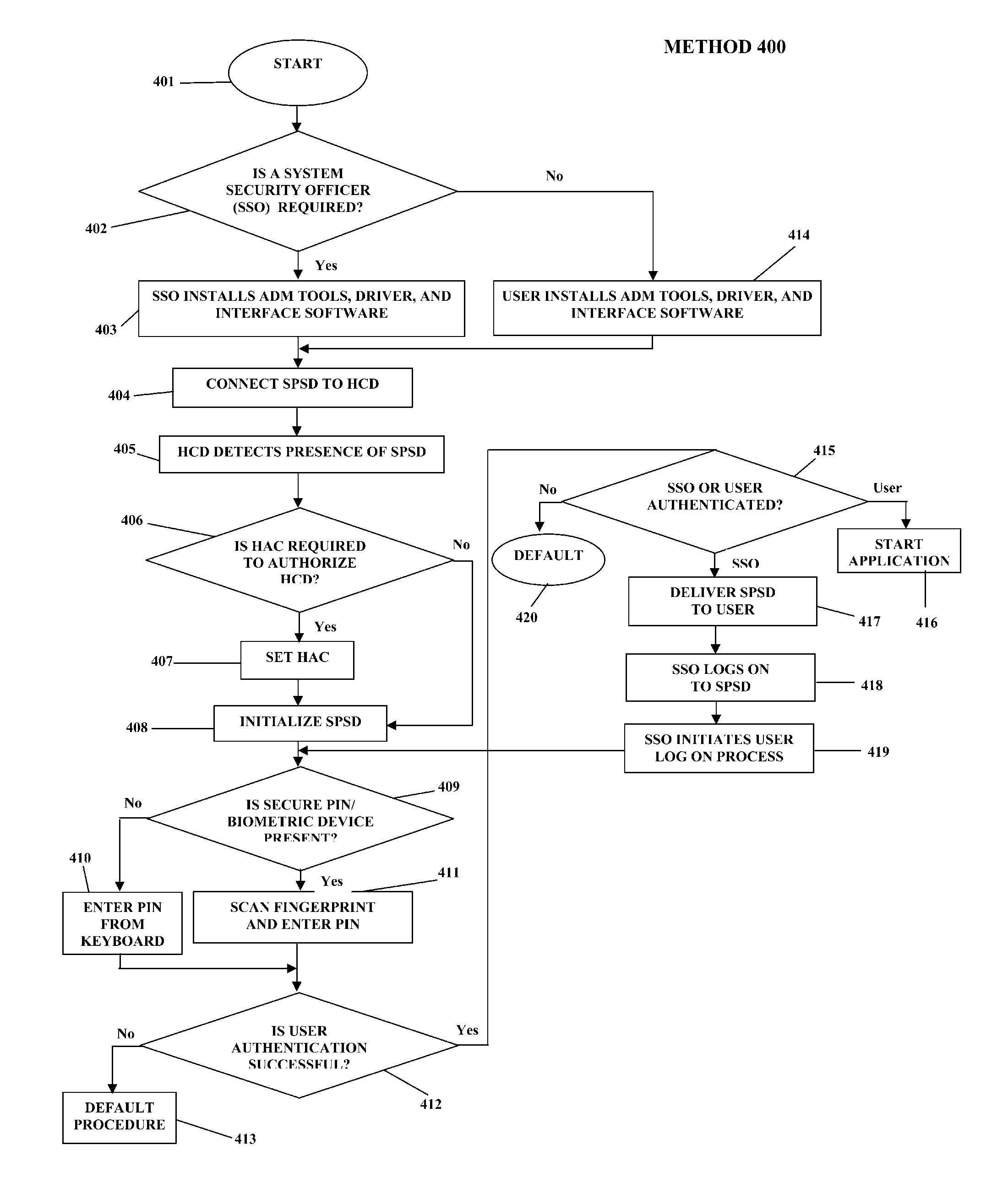
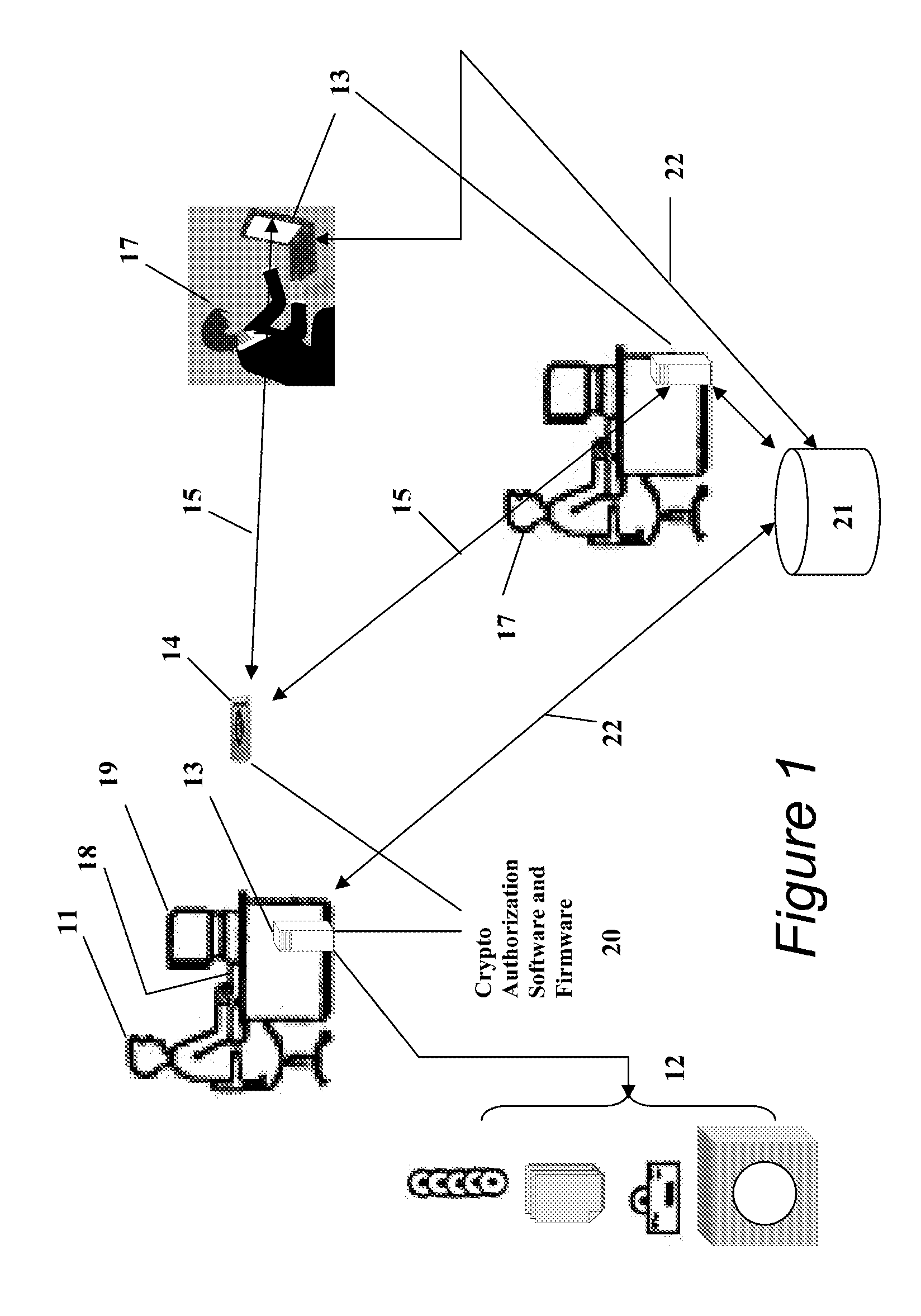
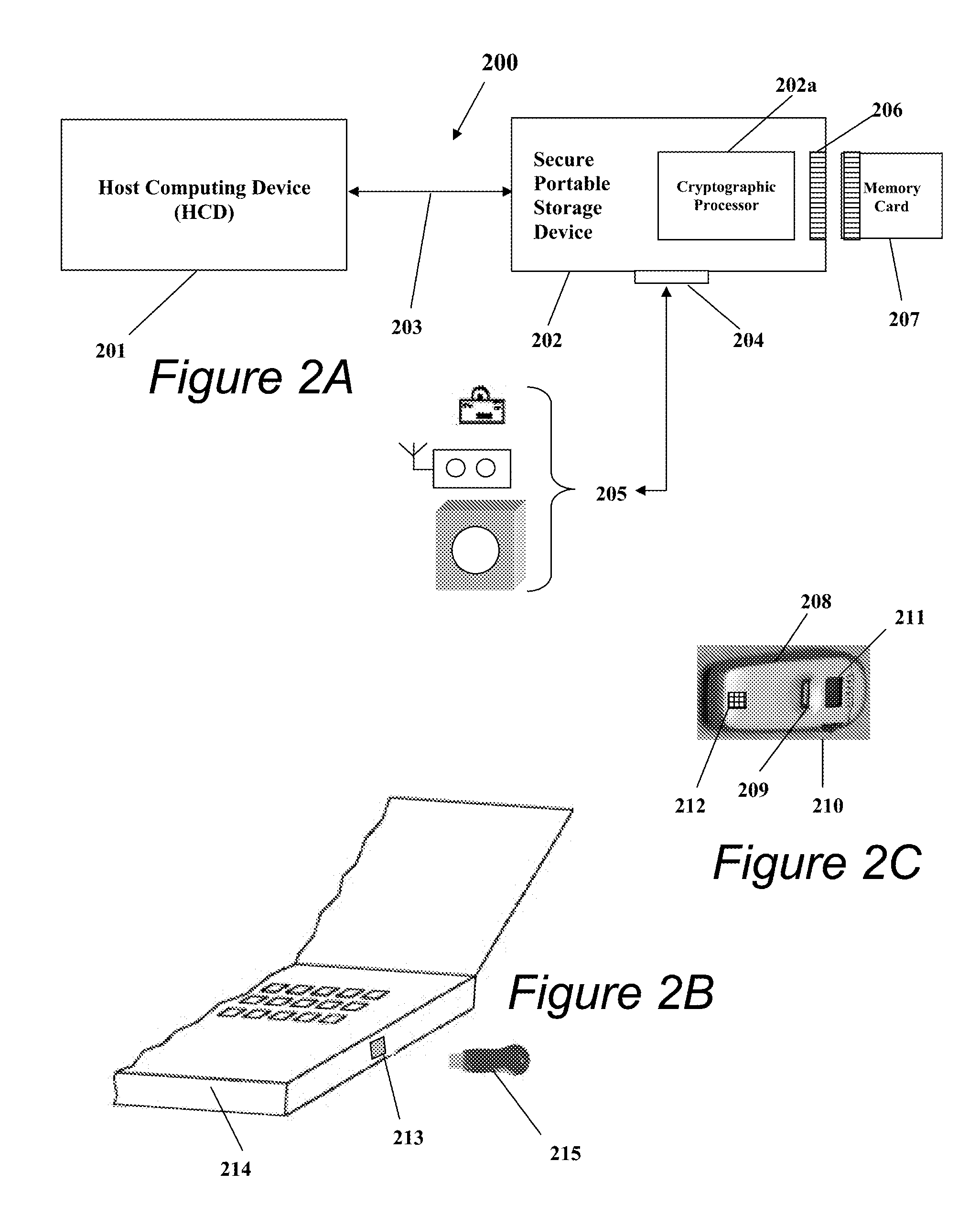
Patents
Literature
1642 results about "Security function" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Security functions are the hardware, software, and/or firmware of the information system responsible for enforcing the system security policy and supporting the isolation of code and data on which the protection is based.
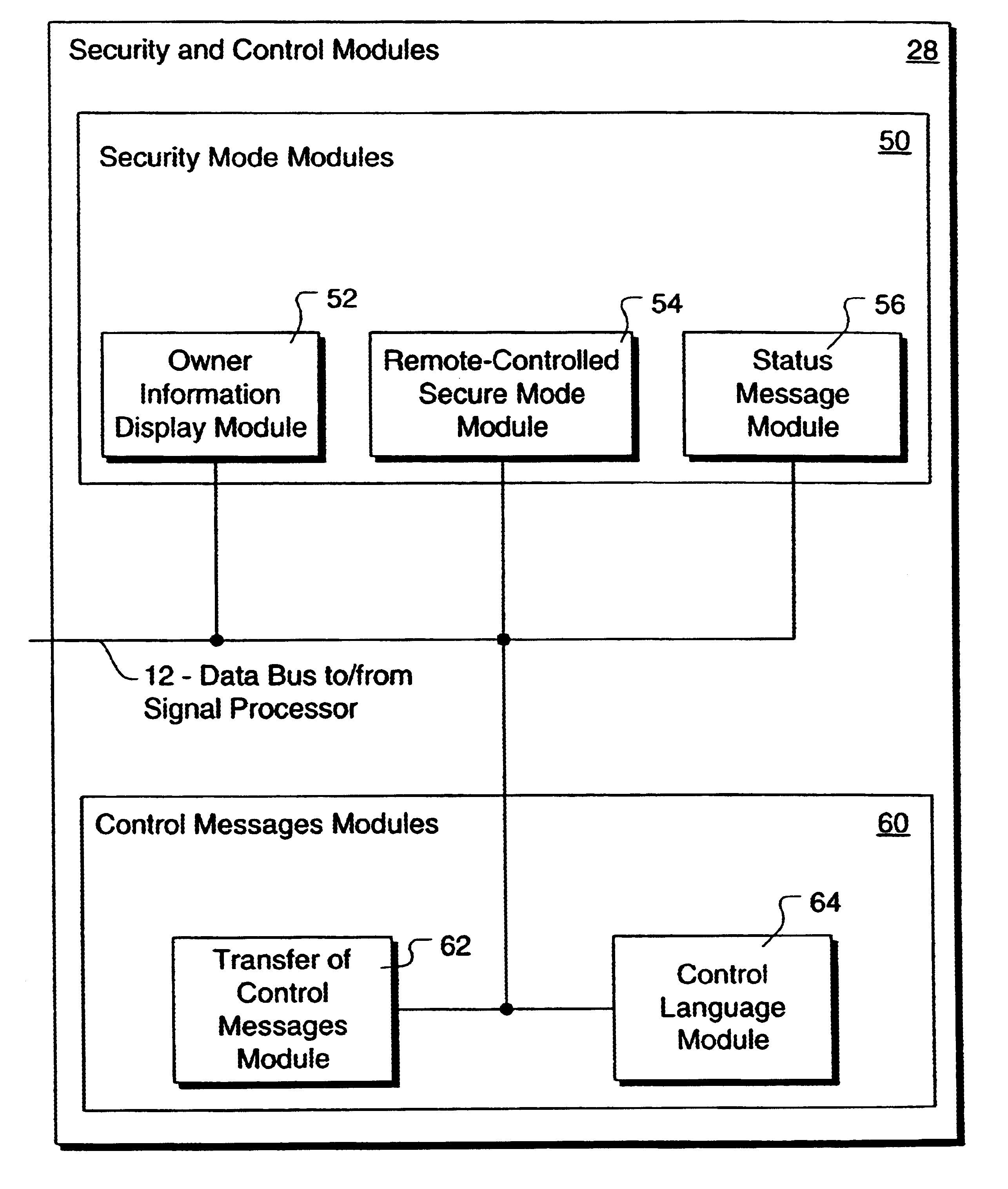
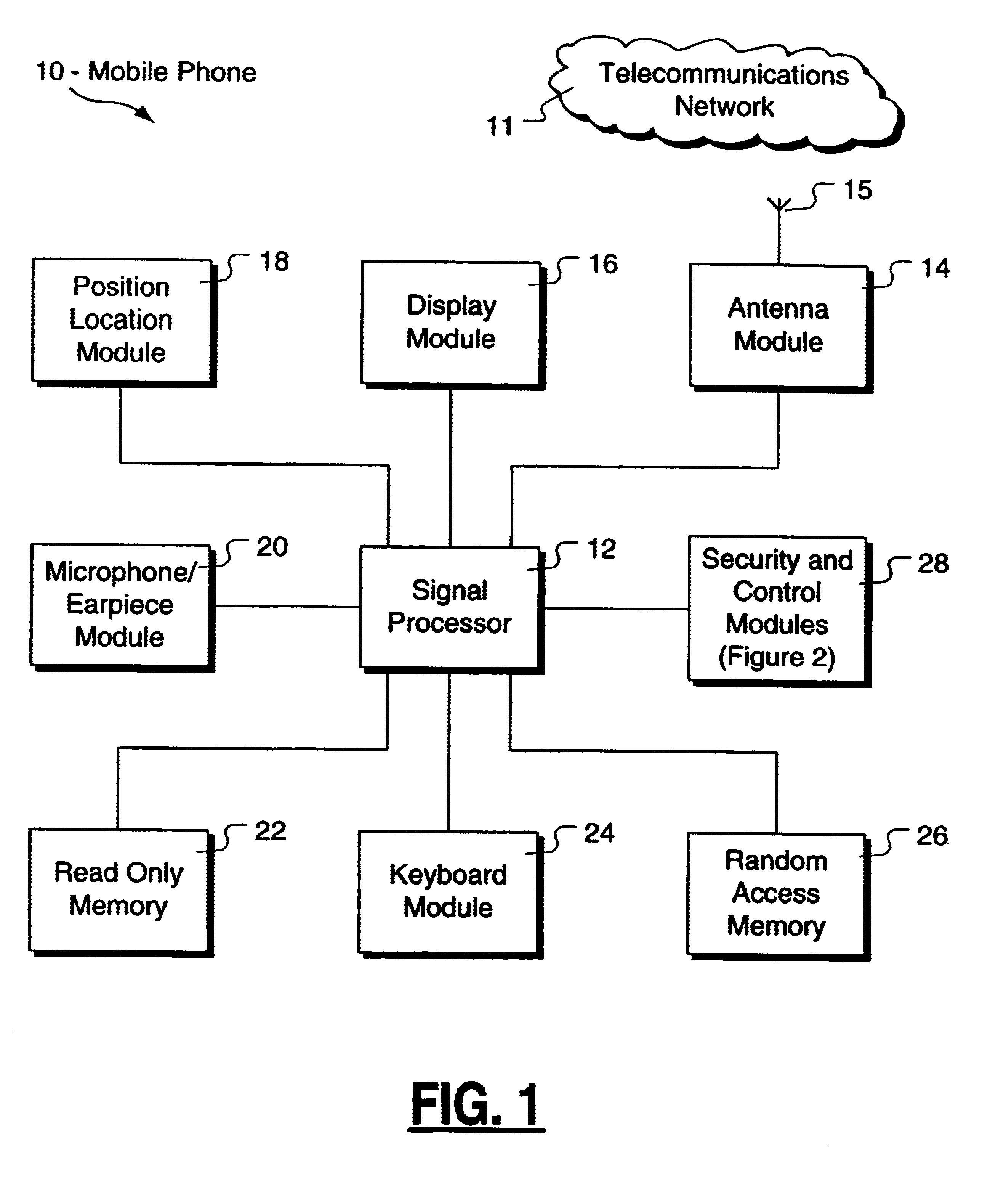
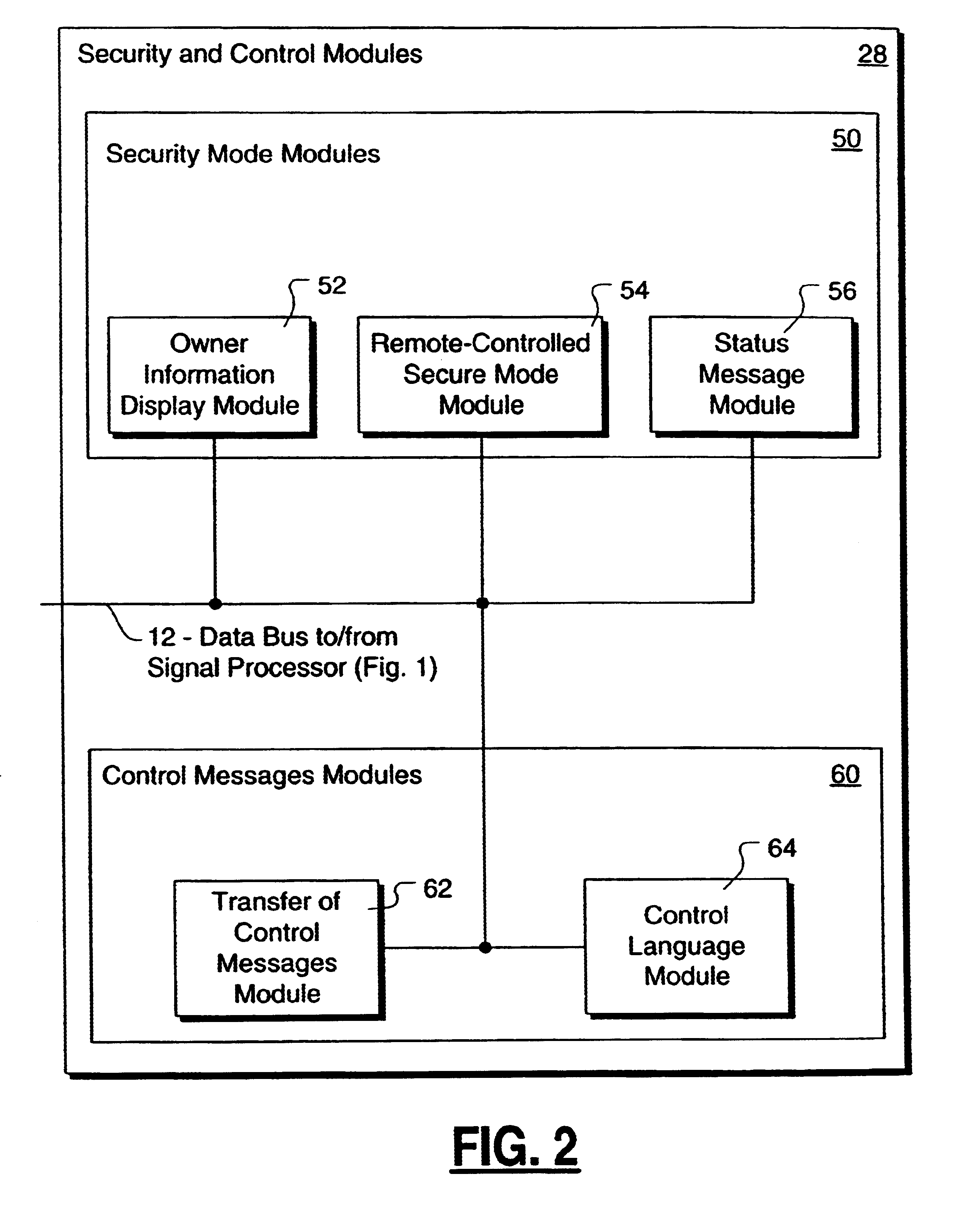
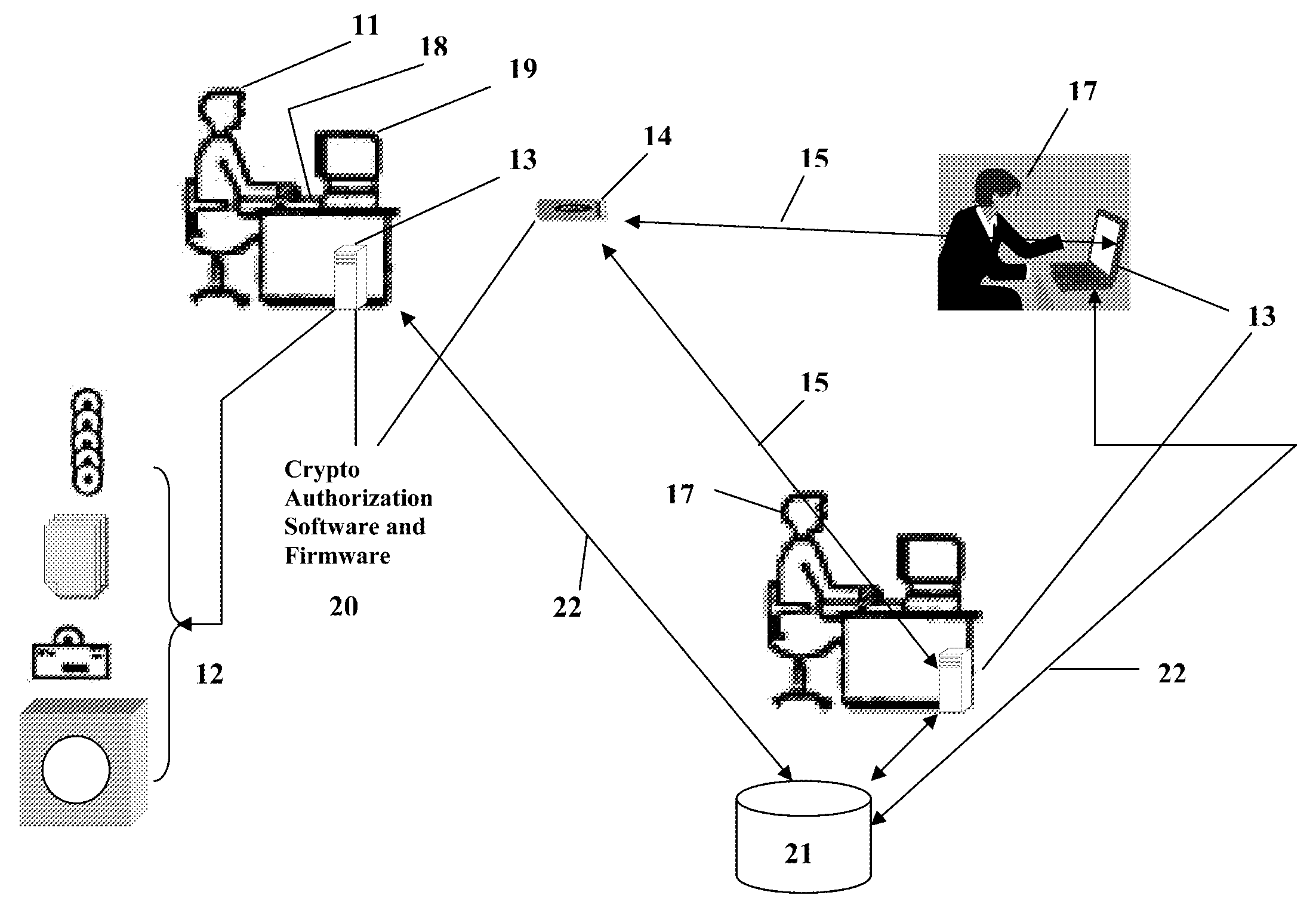
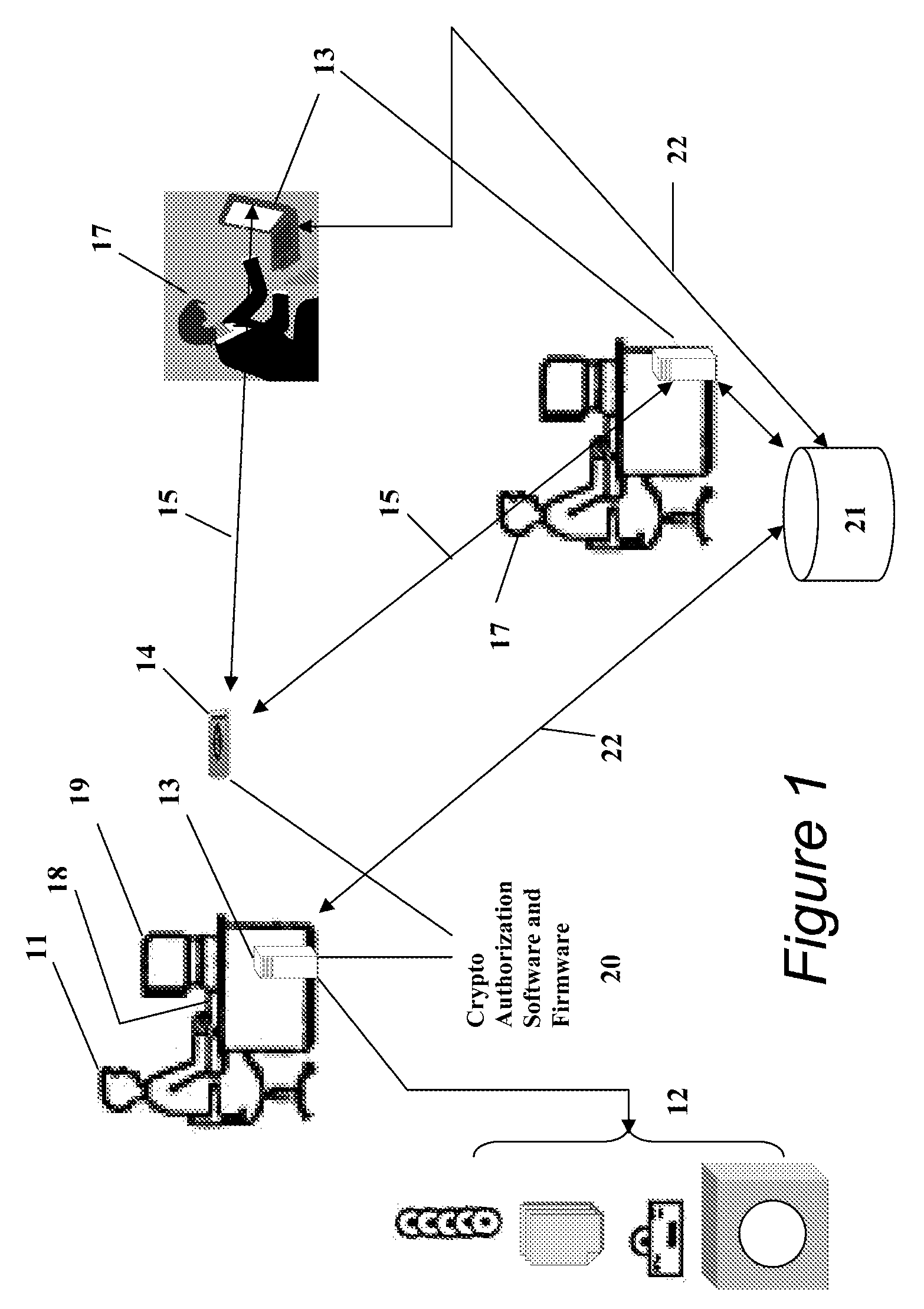
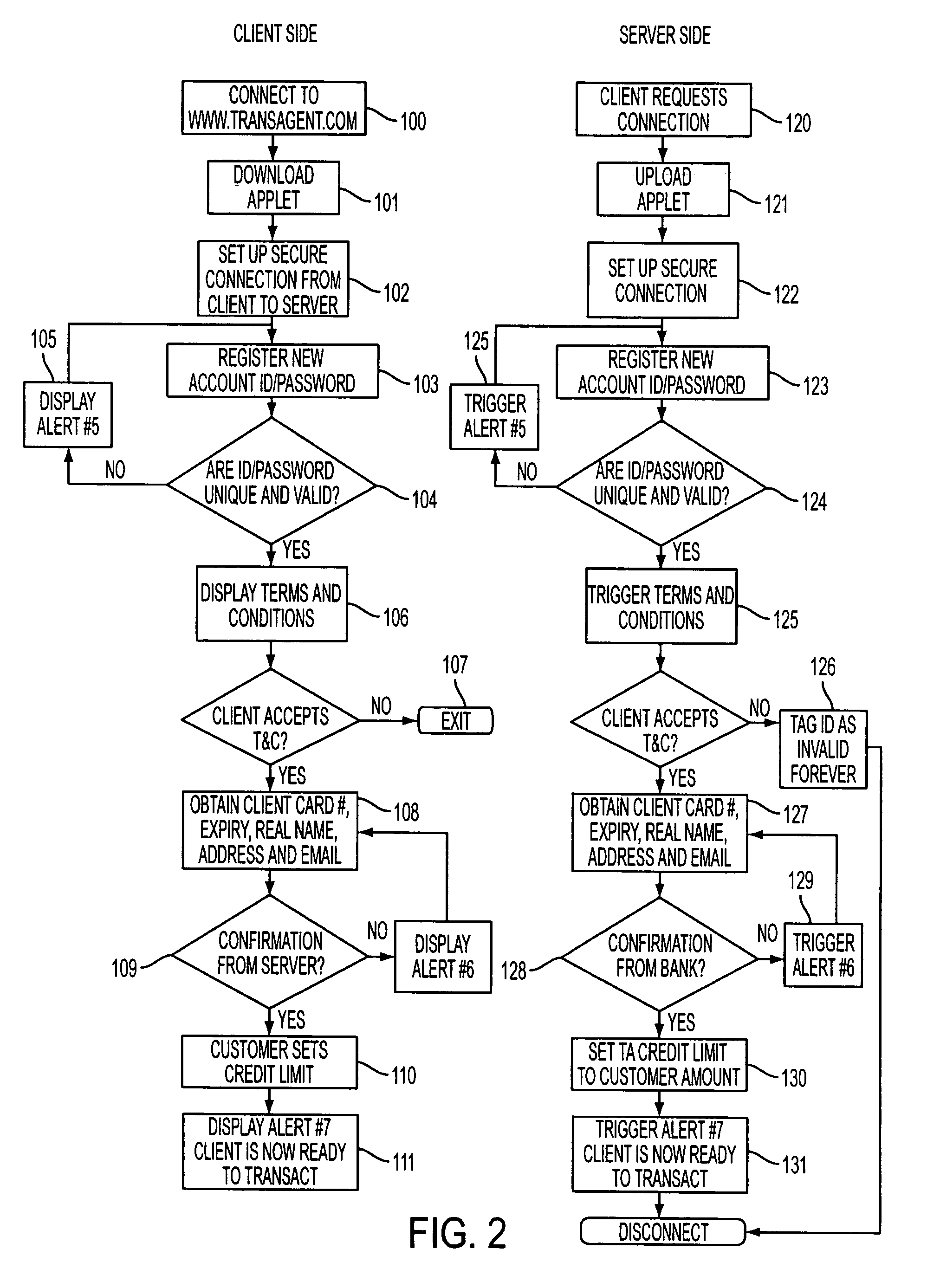
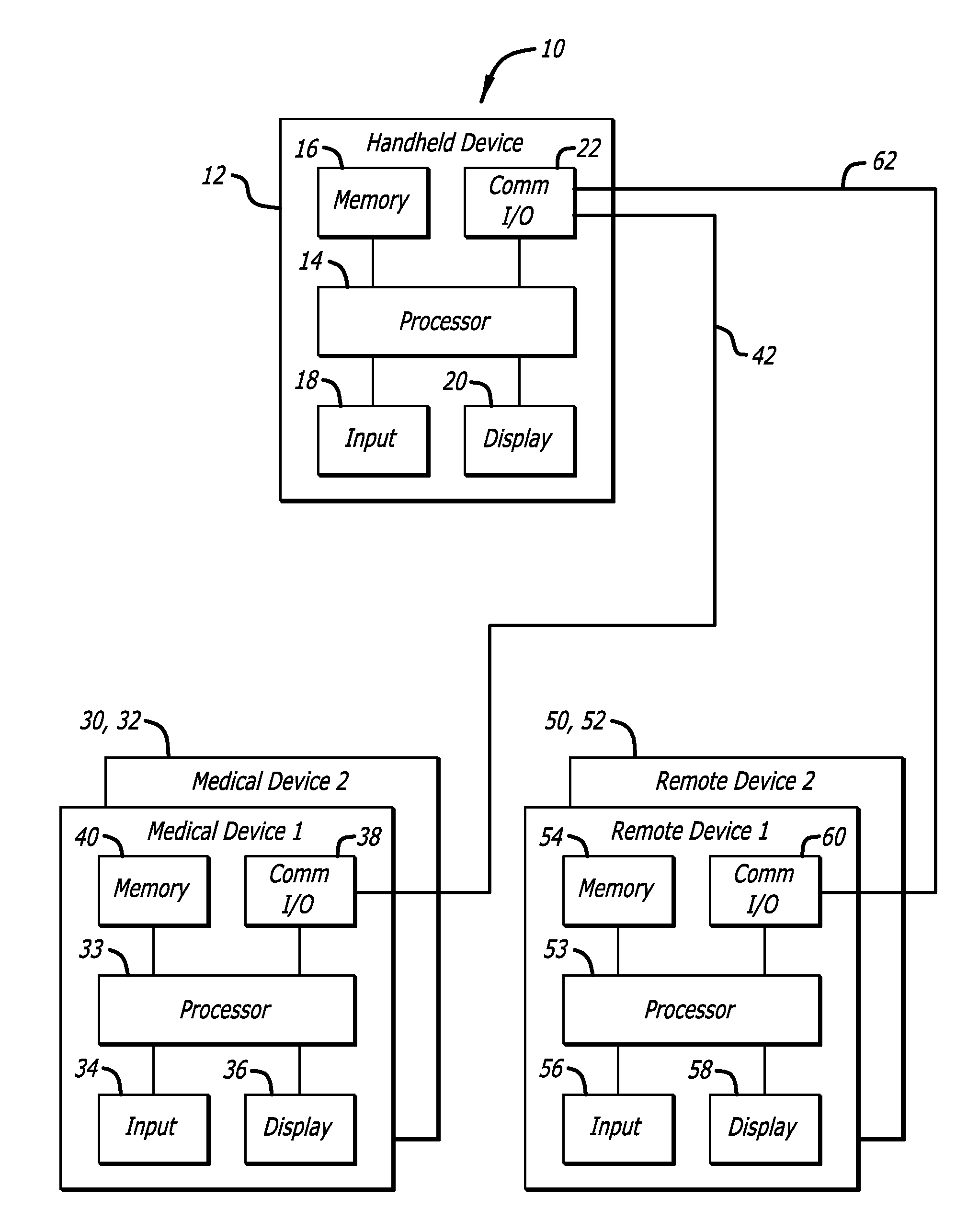
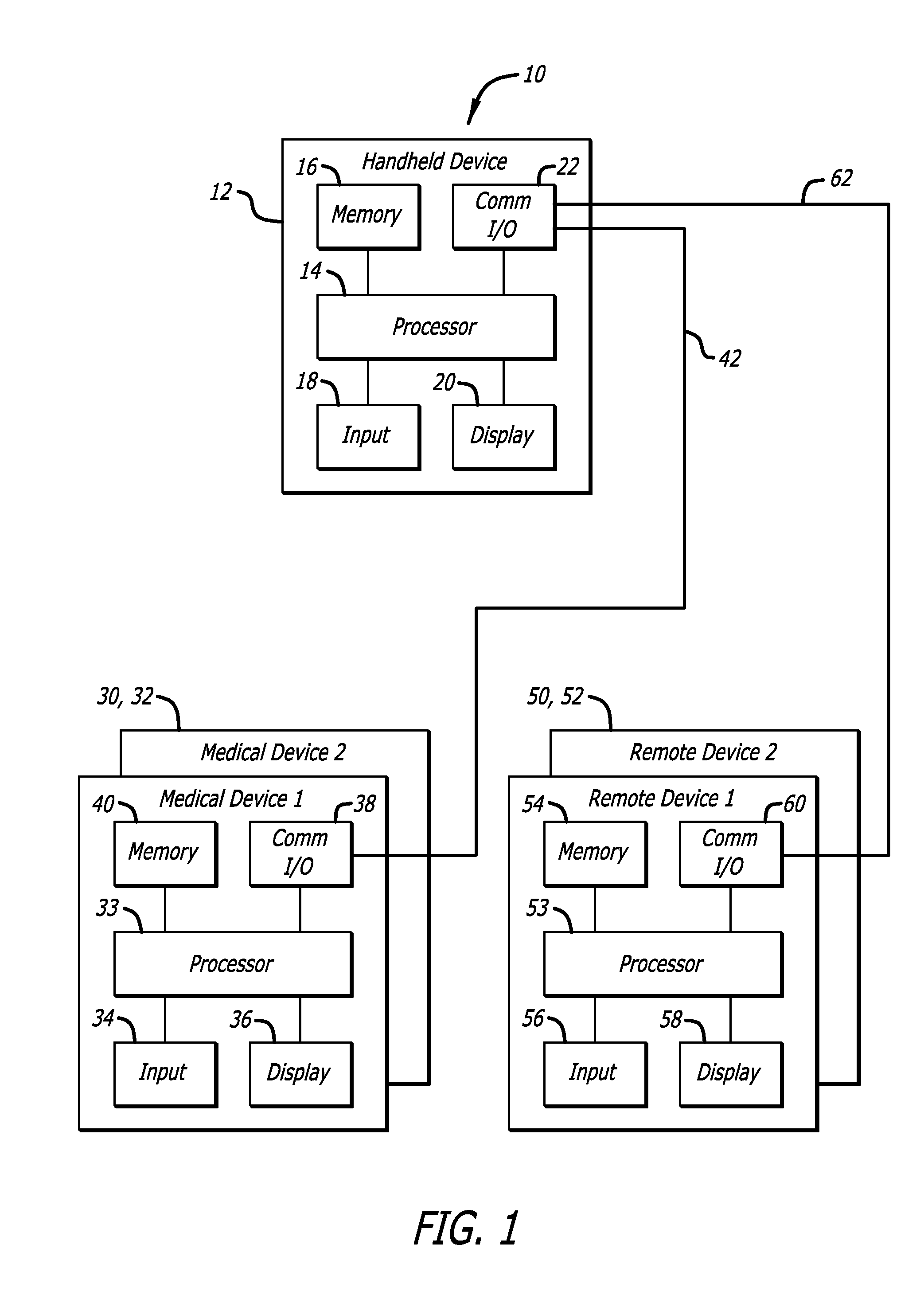
Method and apparatus for controlling and securing mobile phones that are lost, stolen or misused
InactiveUS6662023B1Unauthorised/fraudulent call preventionEavesdropping prevention circuitsSecure stateStart up
A method and apparatus is provided for controlling a mobile phone when it has been lost or stolen in order to prevent its use except to help the owner find it. Controlling the phone remotely may be implemented via a known Short Messaging System, for example. The security features provided are as follows: (1) Displaying contact information (phone number) of the owner on screen when the mobile phone can not start up normally, for example, due to an incorrect security code entry; (2) Setting the mobile phone in a secure state where it can only be used to call one number (Emergency calls are of course always possible.); and (3) Commanding the mobile phone to send information about its location and usage via SMS to a given number.
Owner:NOKIA TECHNOLOGLES OY
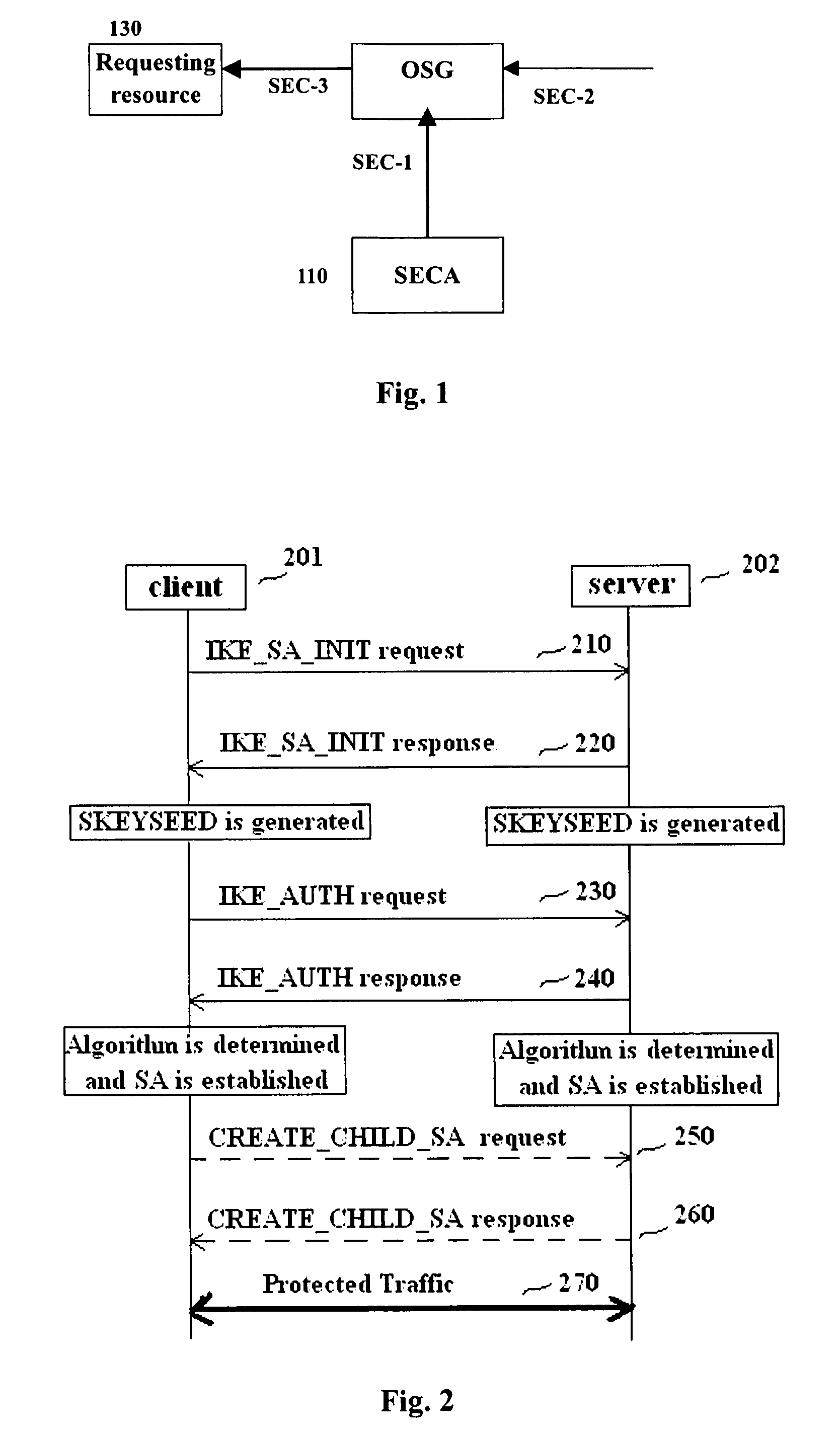
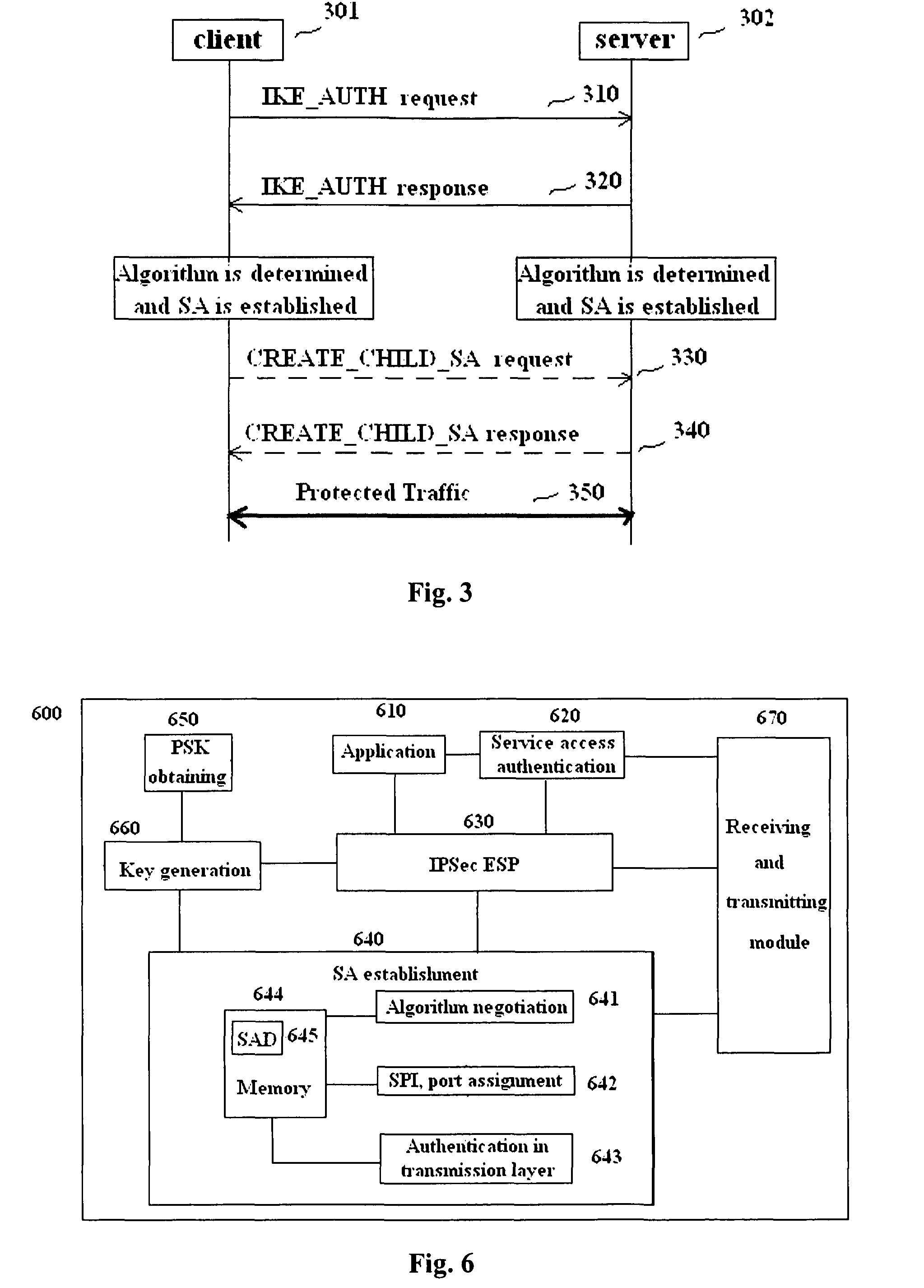
Methods and entities using IPSec ESP to support security functionality for UDP-based traffic
ActiveUS8639936B2Improve efficiencyOptimize procedureUser identity/authority verificationComputer security arrangementsTraffic capacityIPsec
Owner:ALCATEL LUCENT SAS
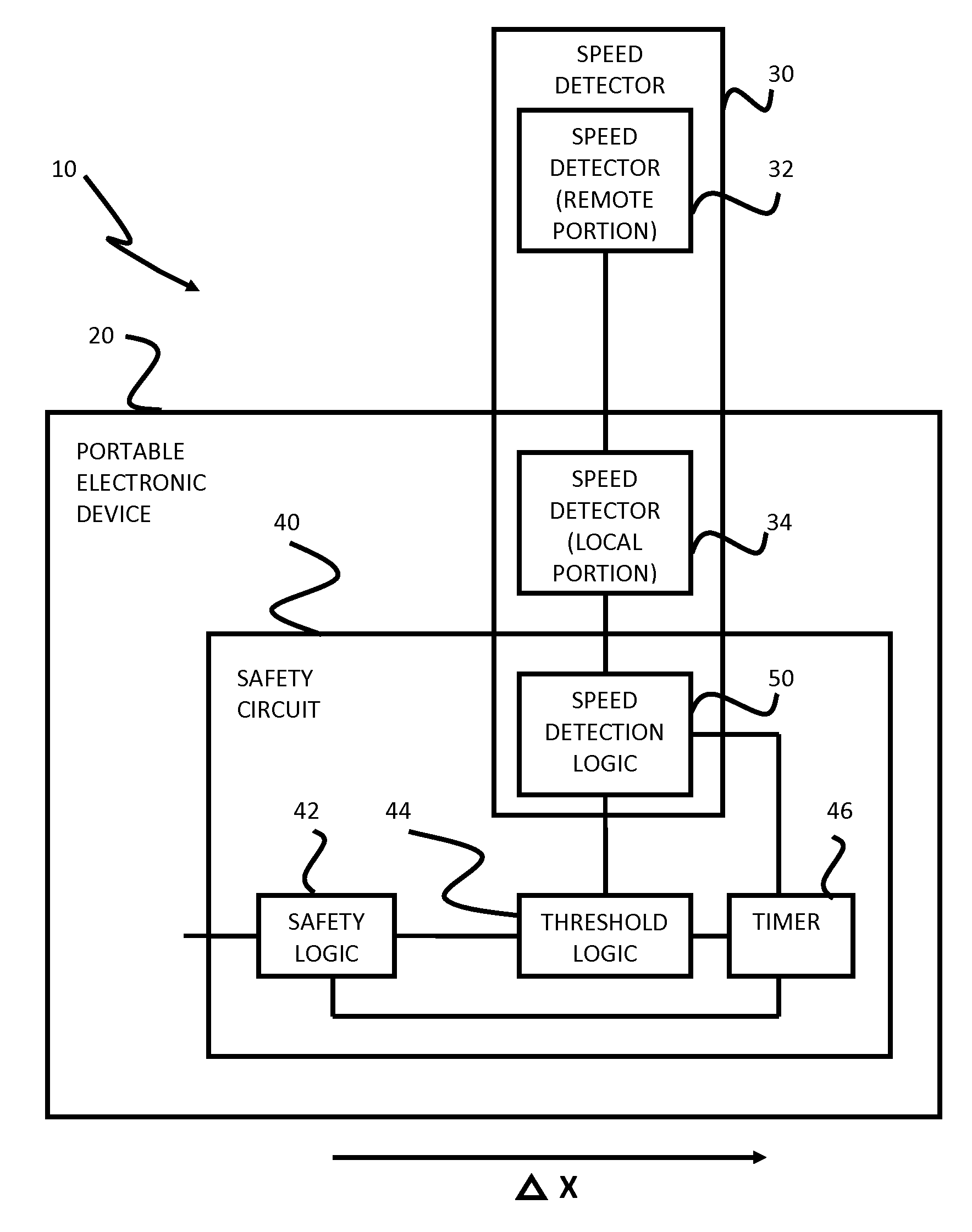
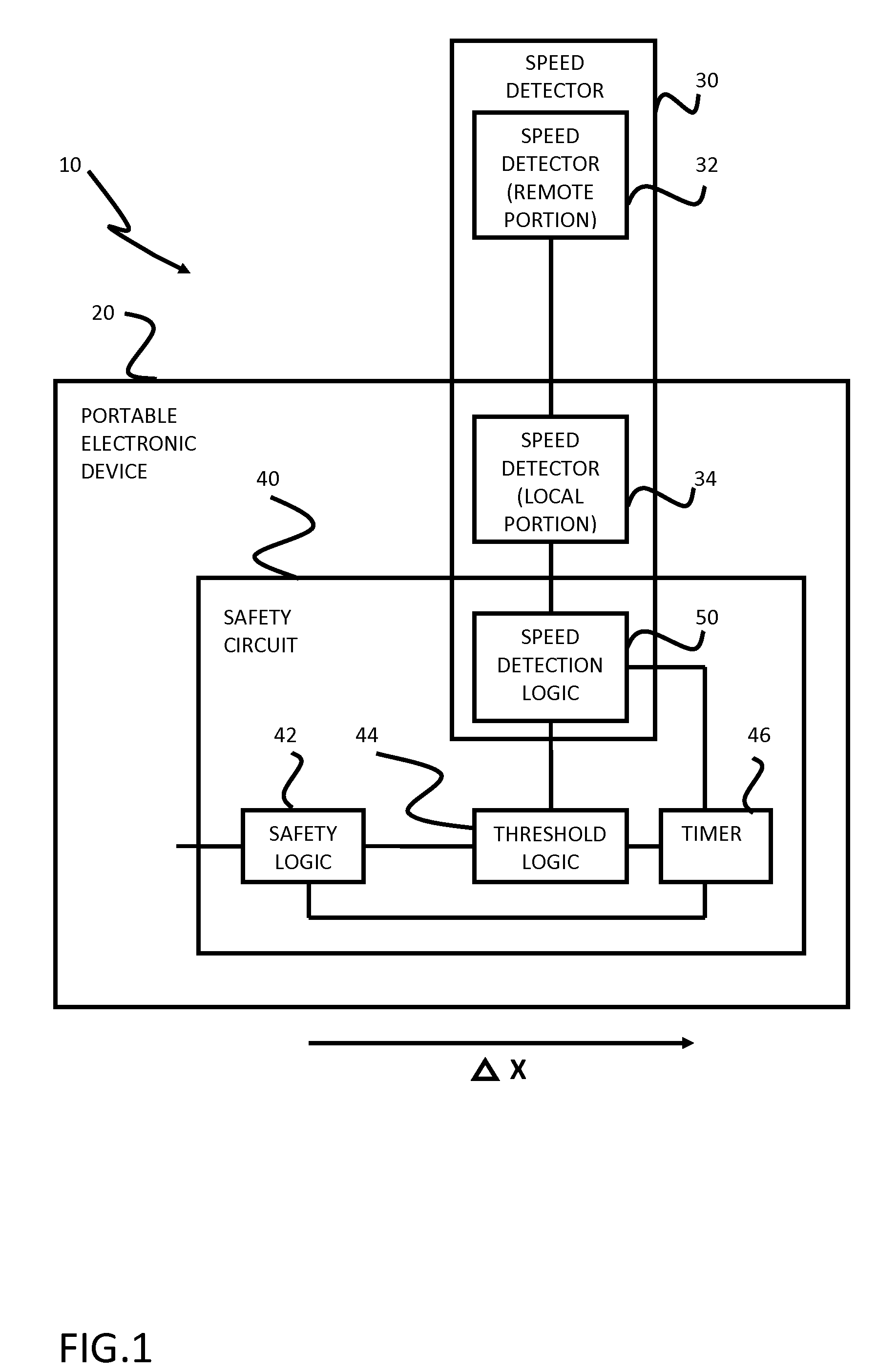
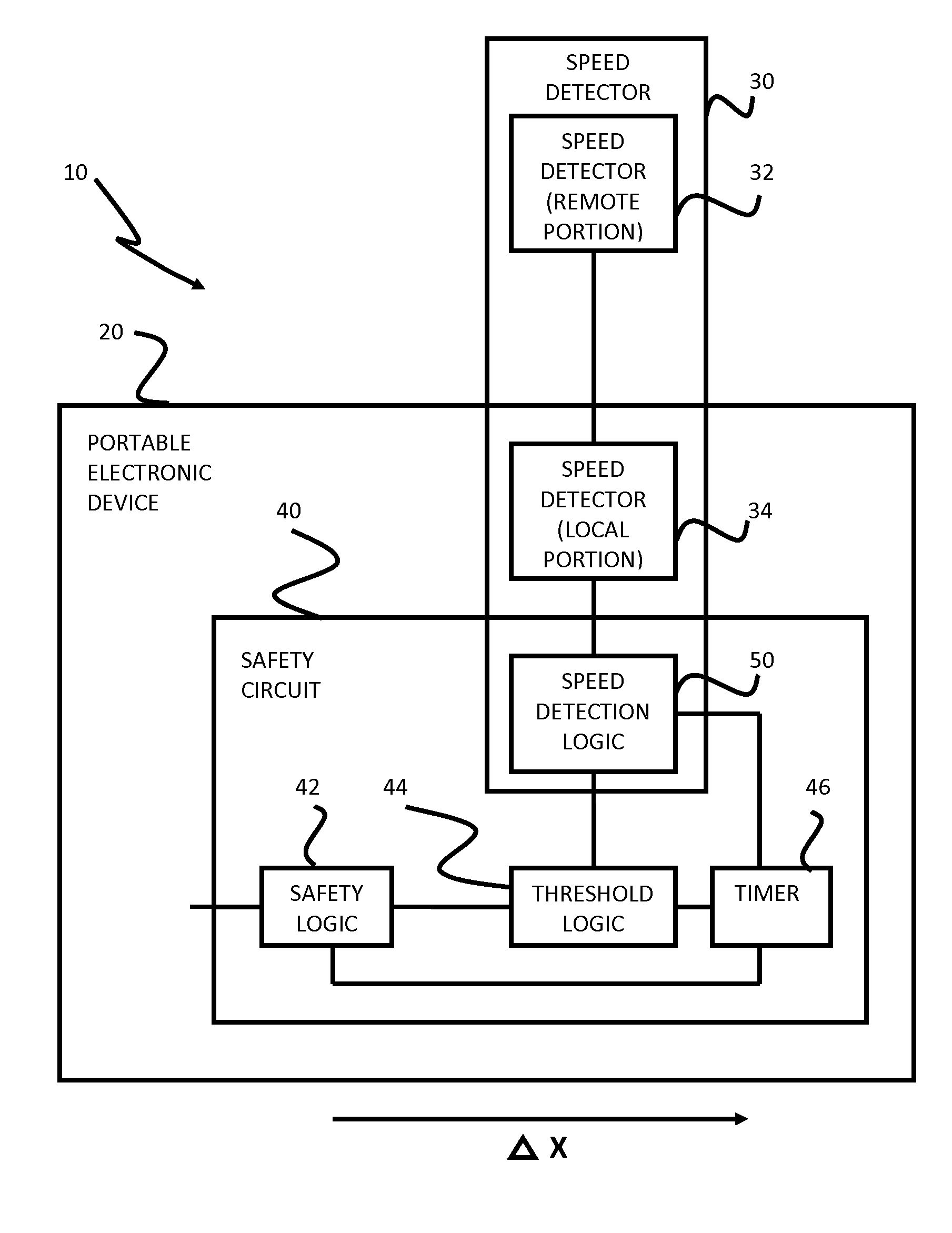
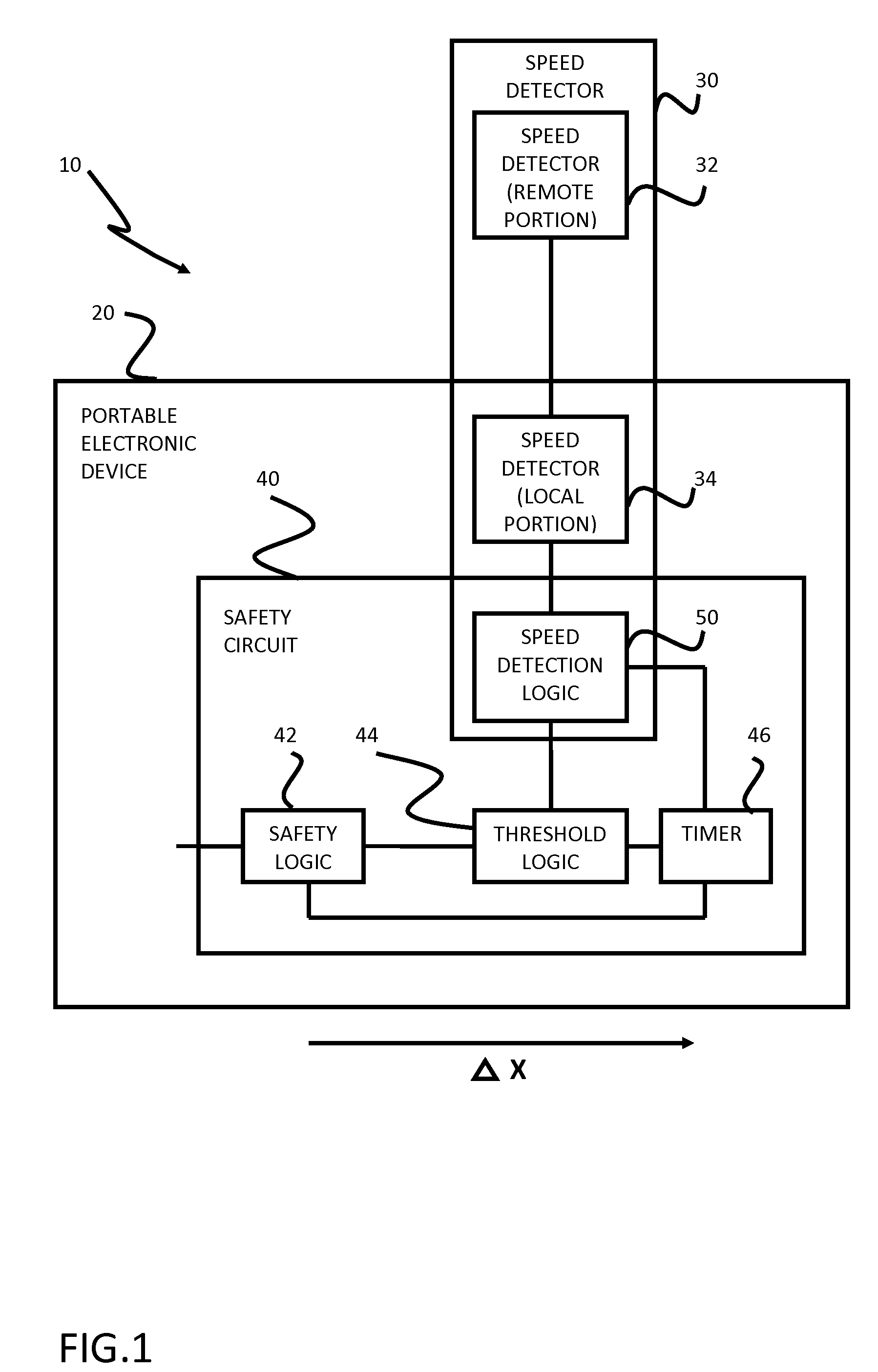
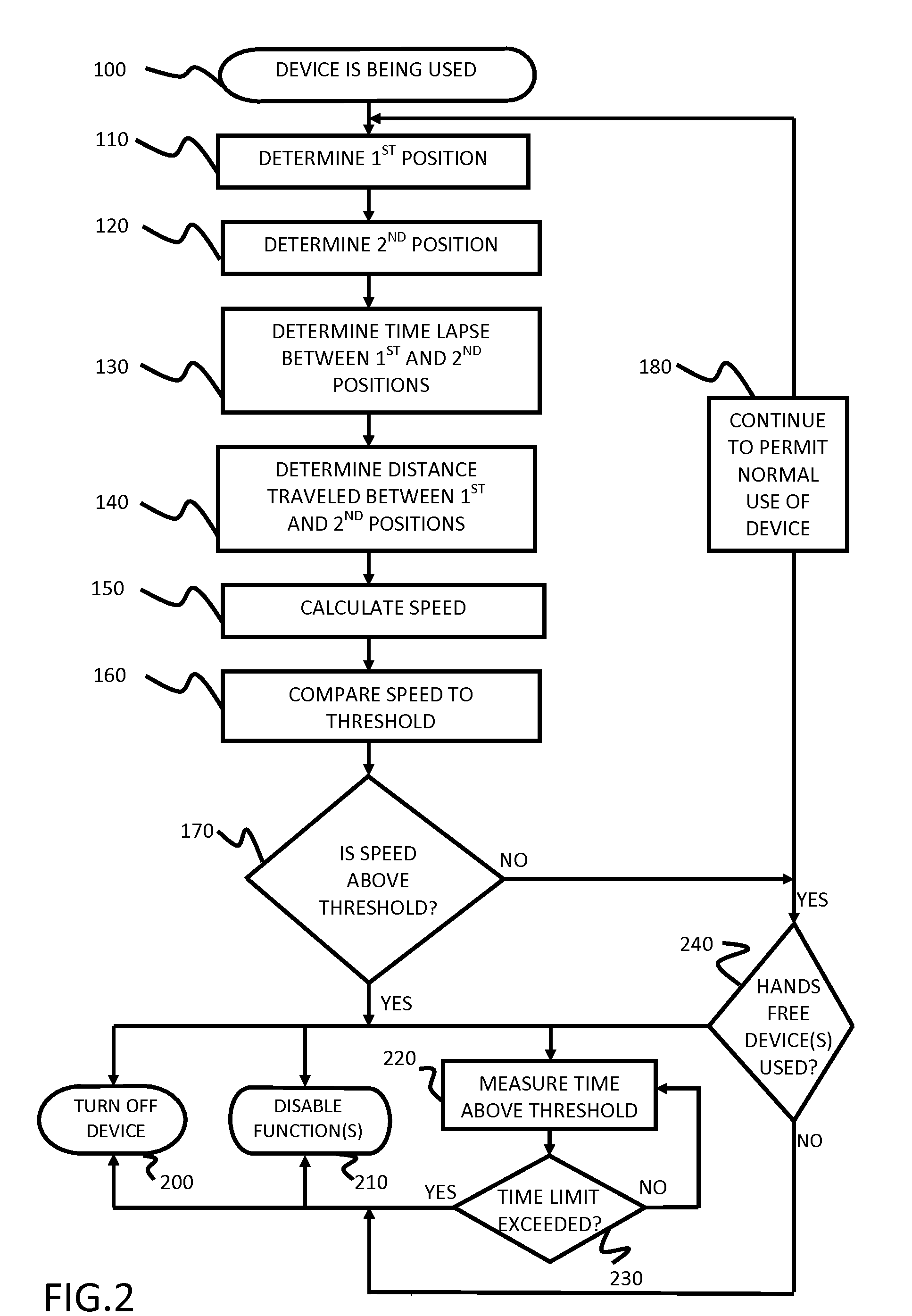
Safety features for portable electronic device
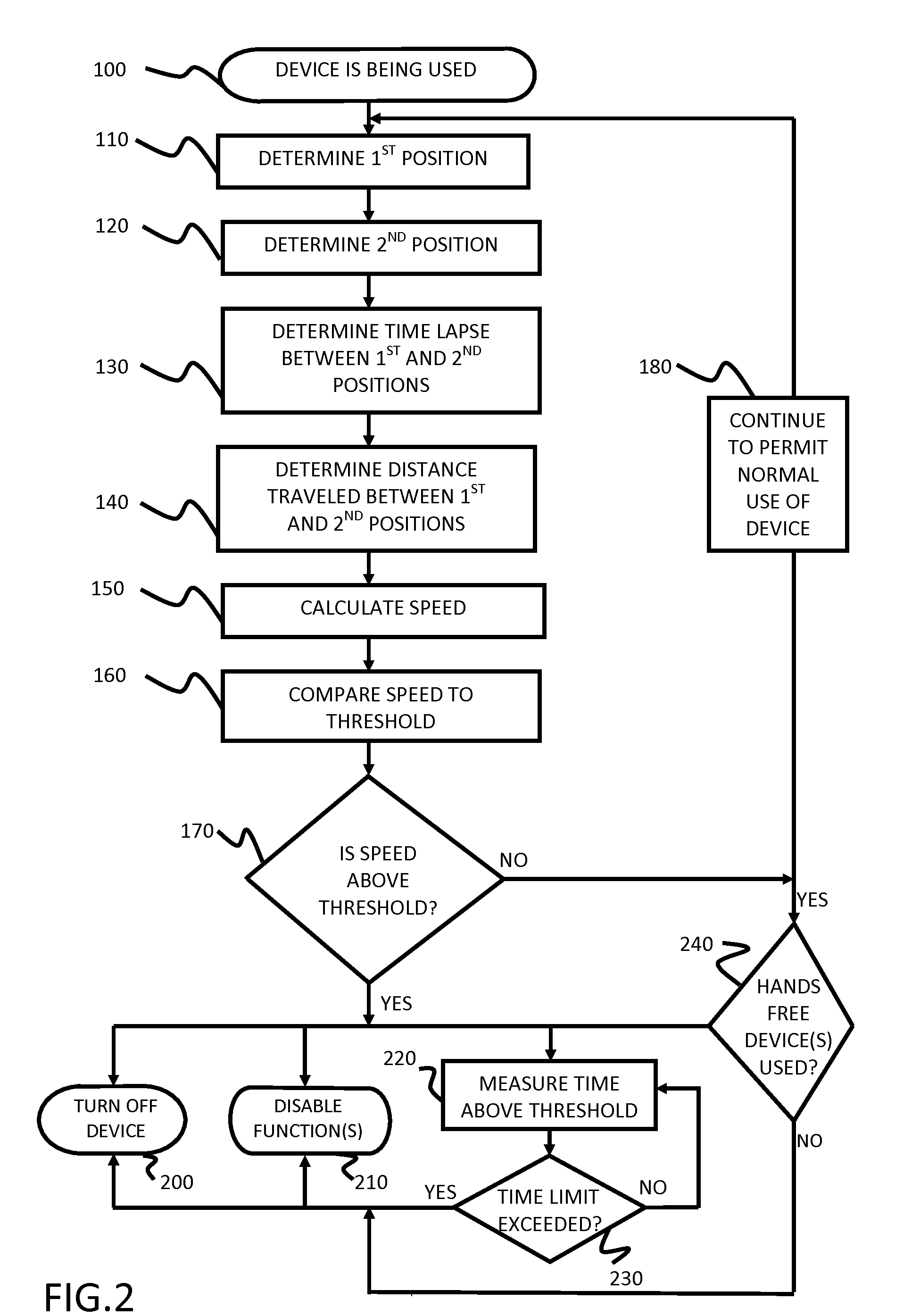
ActiveUS20100216509A1Unauthorised/fraudulent call preventionDevices with sensorHands freeSecurity policy
A portable device includes a safety feature that prevents some forms of use when the device is moving. The device may detect its speed or movement, compare that to a threshold, and provide a response or blocking function upon exceeding that threshold. The device may be a cell phone configured to disable transmission and reception of voice / text, conceal its display screen, and disable incorporated features and functions, if the cell phone is moving faster than walking speed or the movement is uncharacteristic of walking. The blocking function may be partially overridden based on a safety policy, which can be managed and customized. The introduction of hands-free devices may serve to override a blocking function and enable other functions.
Owner:AI-CORE TECH LLC
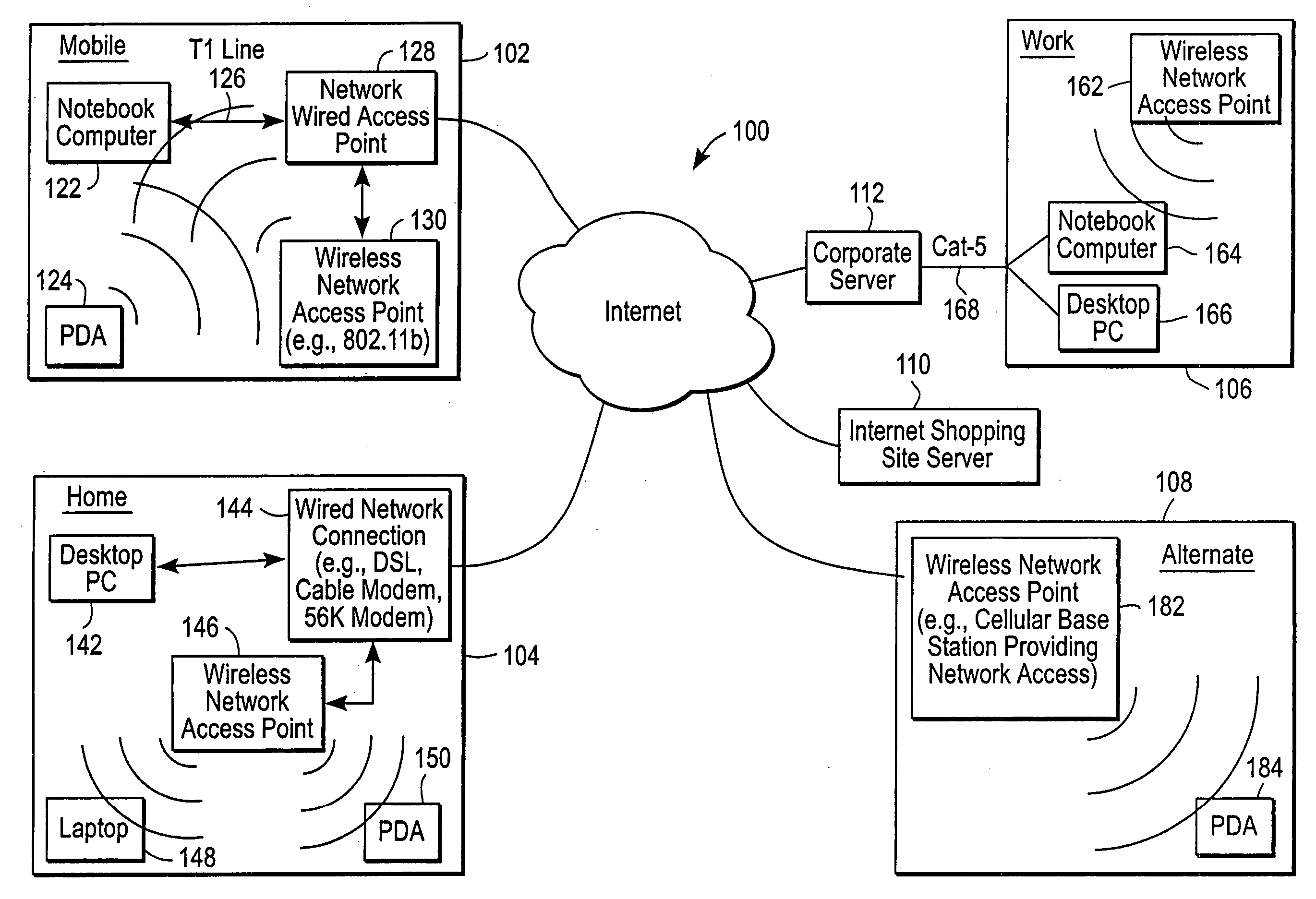
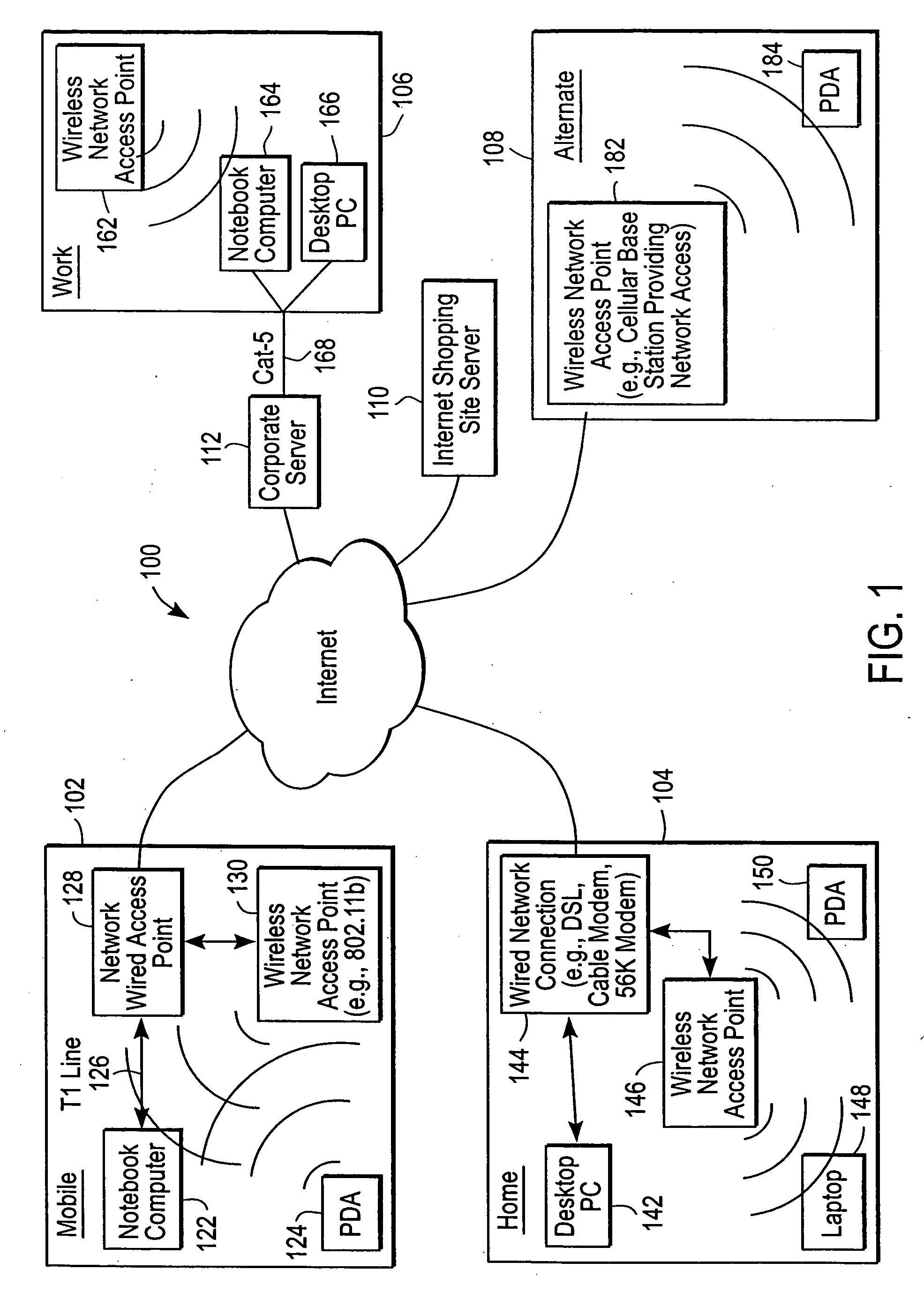
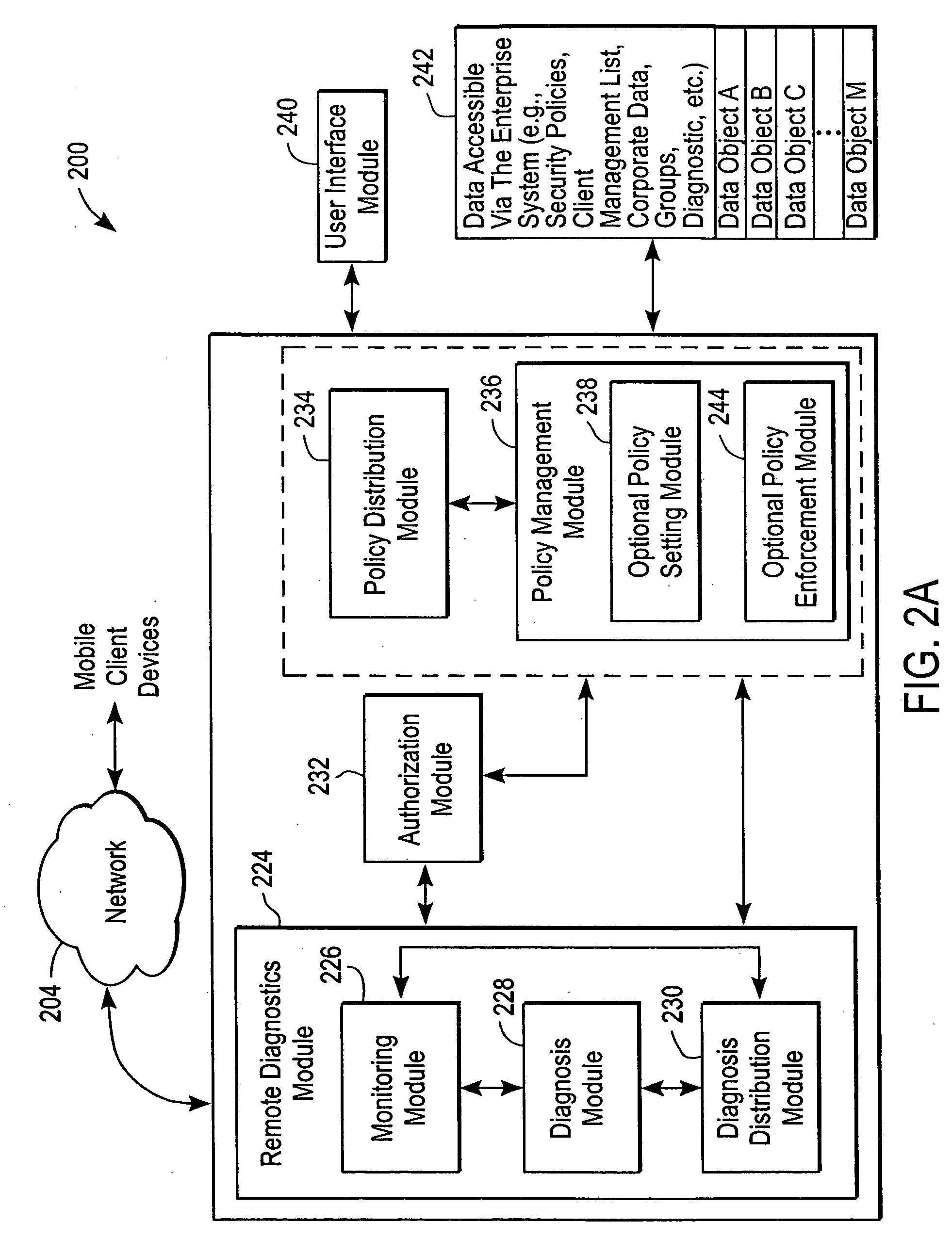
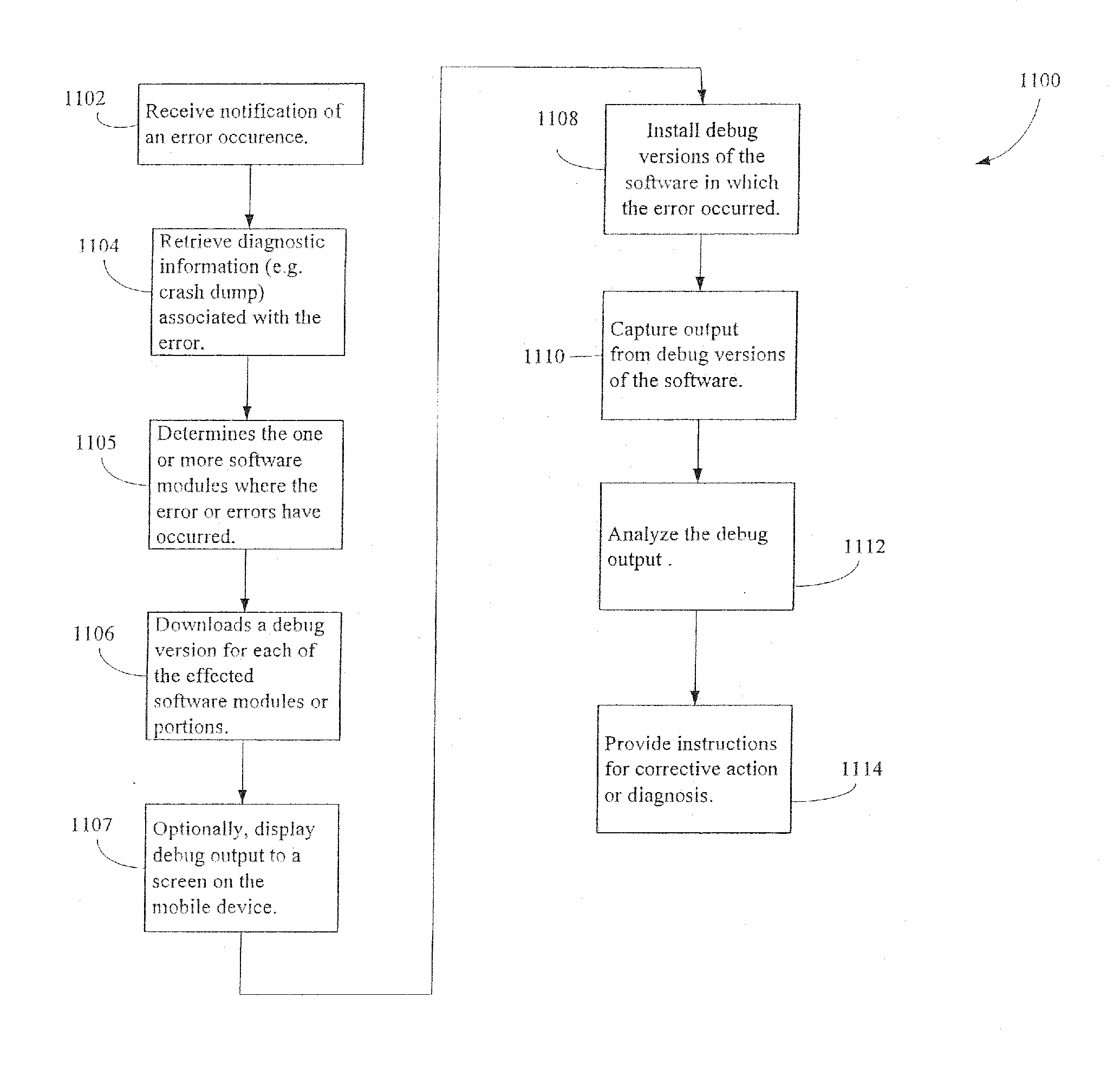
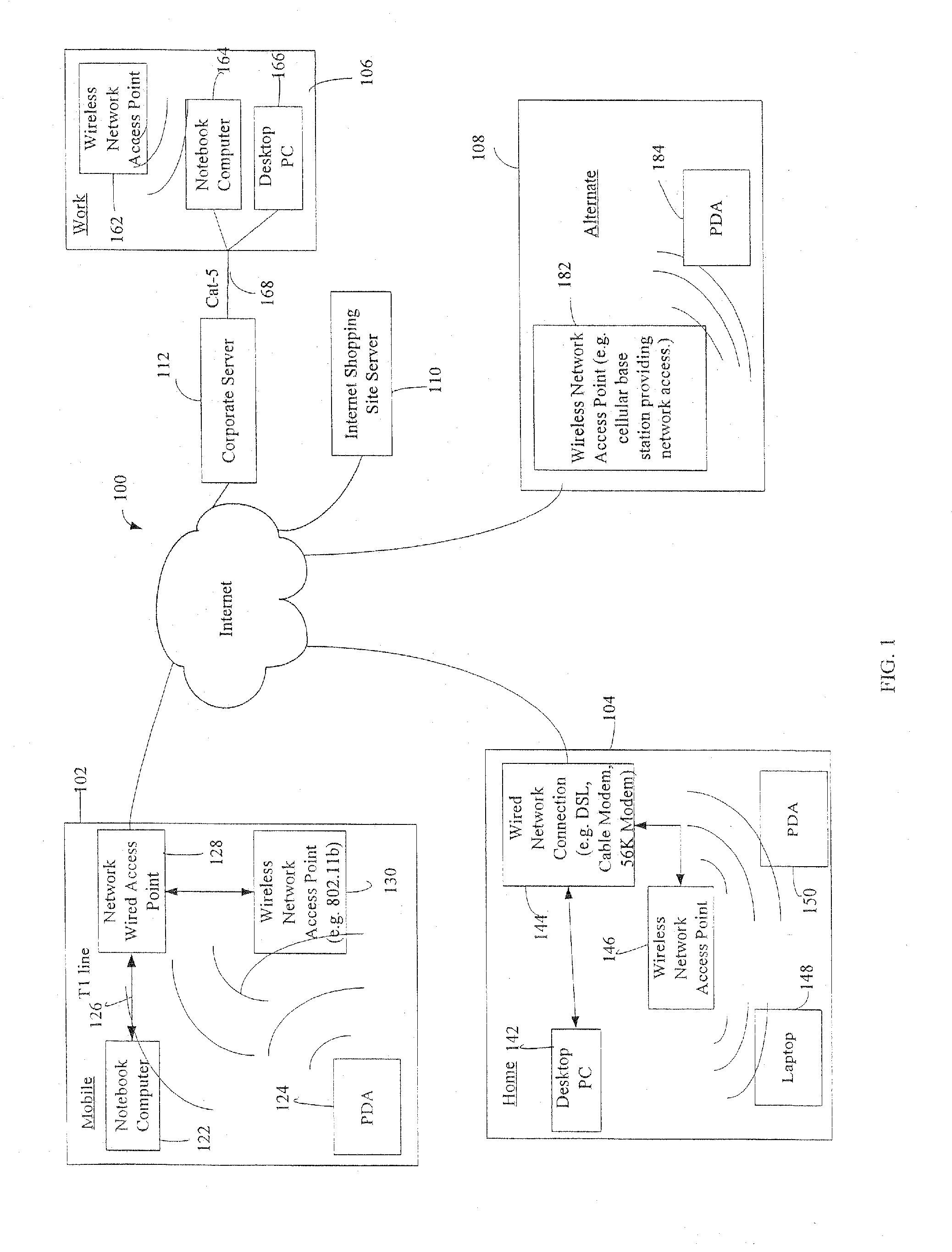
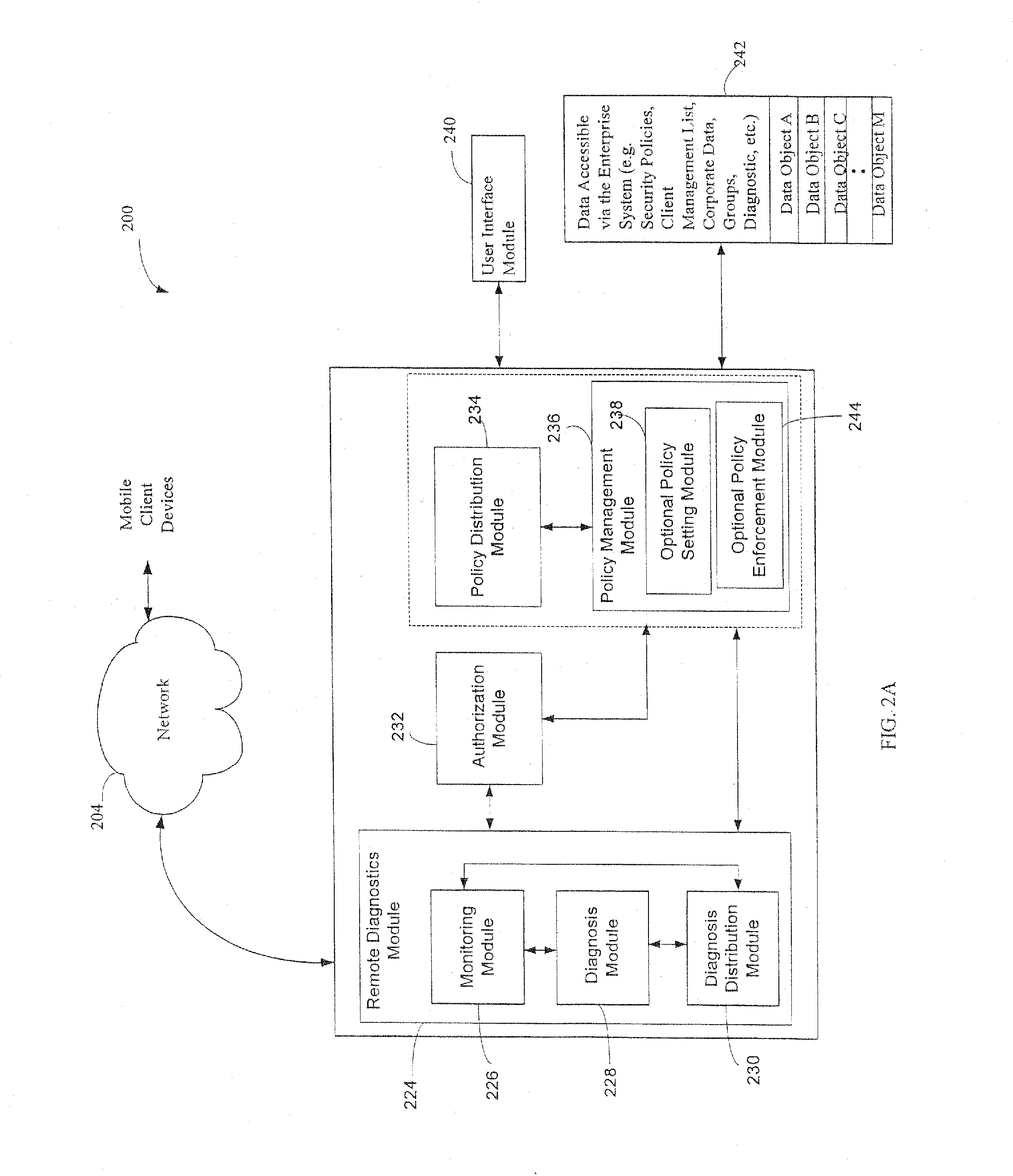
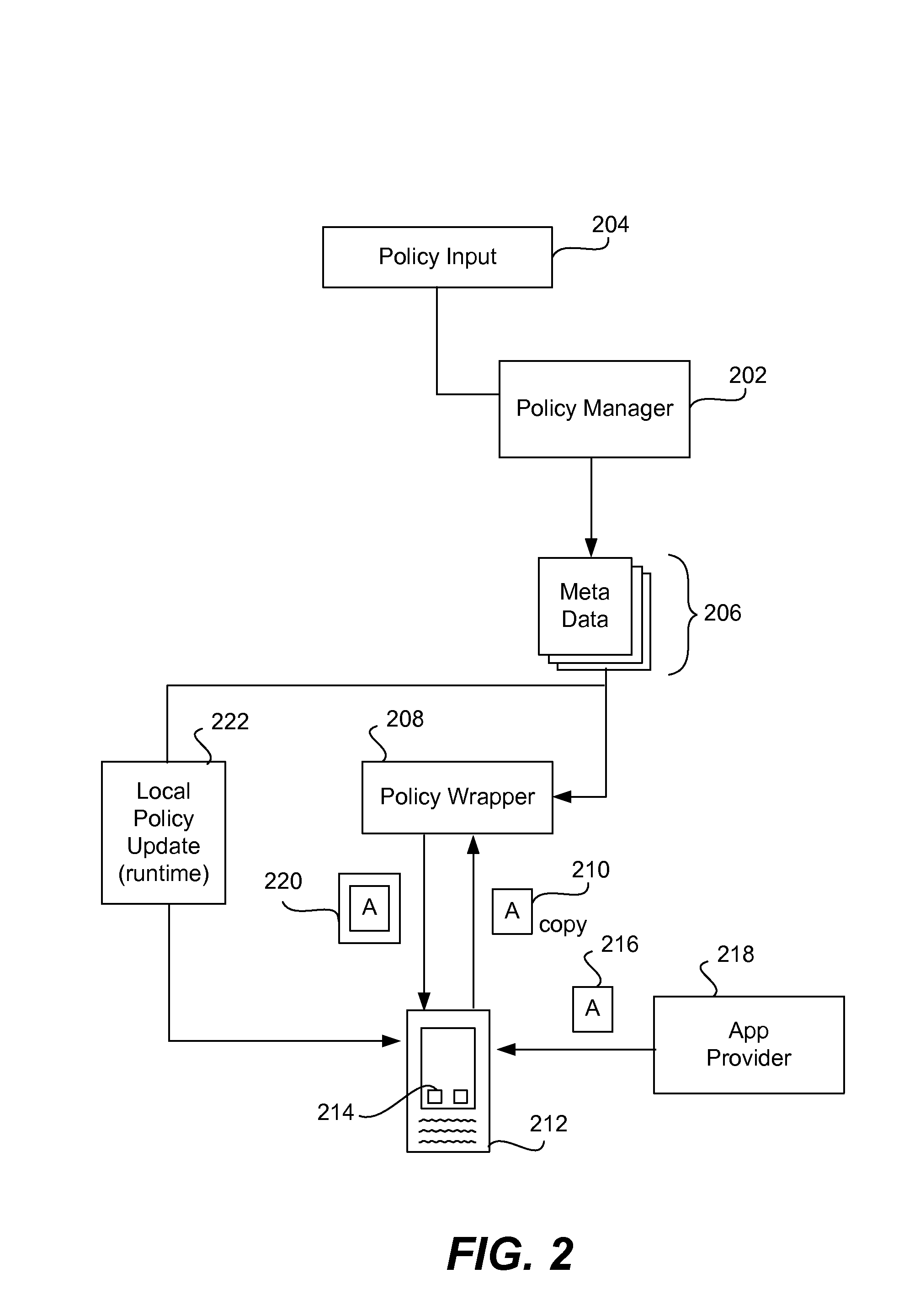
Administration of protection of data accessible by a mobile device
The administration of protection of data on a client mobile computing device by a server computer system such as within an enterprise network or on a separate mobile computing device is described. Security tools are described that provide different security policies to be enforced based on a location associated with a network environment in which a mobile device is operating. Methods for detecting the location of the mobile device are described. Additionally, the security tools may also provide for enforcing different policies based on security features. Examples of security features include the type of connection, wired or wireless, over which data is being transferred, the operation of anti-virus software, or the type of network adapter card. The different security policies provide enforcement mechanisms that may be tailored based upon the detected location and / or active security features associated with the mobile device. Examples of enforcement mechanisms are adaptive port blocking, file hiding and file encryption.
Owner:APPLE INC
Administration of protection of data accessible by a mobile device
ActiveUS20050055578A1Digital data processing detailsMultiple digital computer combinationsAnti virusEnterprise networking
The protection of data on a client mobile computing device by a server computer system such as within an enterprise network or on a separate mobile computing device is described. Security tools are described that provide different security policies to be enforced based on a location associated with a network environment in which a mobile device is operating. Methods for detecting the location of the mobile device are described. Additionally, the security tools may also provide for enforcing different policies based on security features. Examples of security features include the type of connection, wired or wireless, over which data is being transferred, the operation of anti-virus software, or the type of network adapter card. The different security policies provide enforcement mechanisms that may be tailored based upon the detected location and / or active security features associated with the mobile device. Examples of enforcement mechanisms are adaptive port blocking, file hiding and file encryption.
Owner:APPLE INC
Administration of protection of data accessible by a mobile device
The administration of protection of data on a client mobile computing device by a server computer system such as within an enterprise network or on a separate mobile computing device is described. Security tools are described that provide different security policies to be enforced based on a location associated with a network environment in which a mobile device is operating. Methods for detecting the location of the mobile device are described. Additionally, the security tools may also provide for enforcing different policies based on security features. Examples of security features include the type of connection, wired or wireless, over which data is being transferred, the operation of anti-virus software, or the type of network adapter card. The different security policies provide enforcement mechanisms that may be tailored based upon the detected location and / or active security features associated with the mobile device. Examples of enforcement mechanisms are adaptive port blocking, file hiding and file encryption.
Owner:APPLE INC
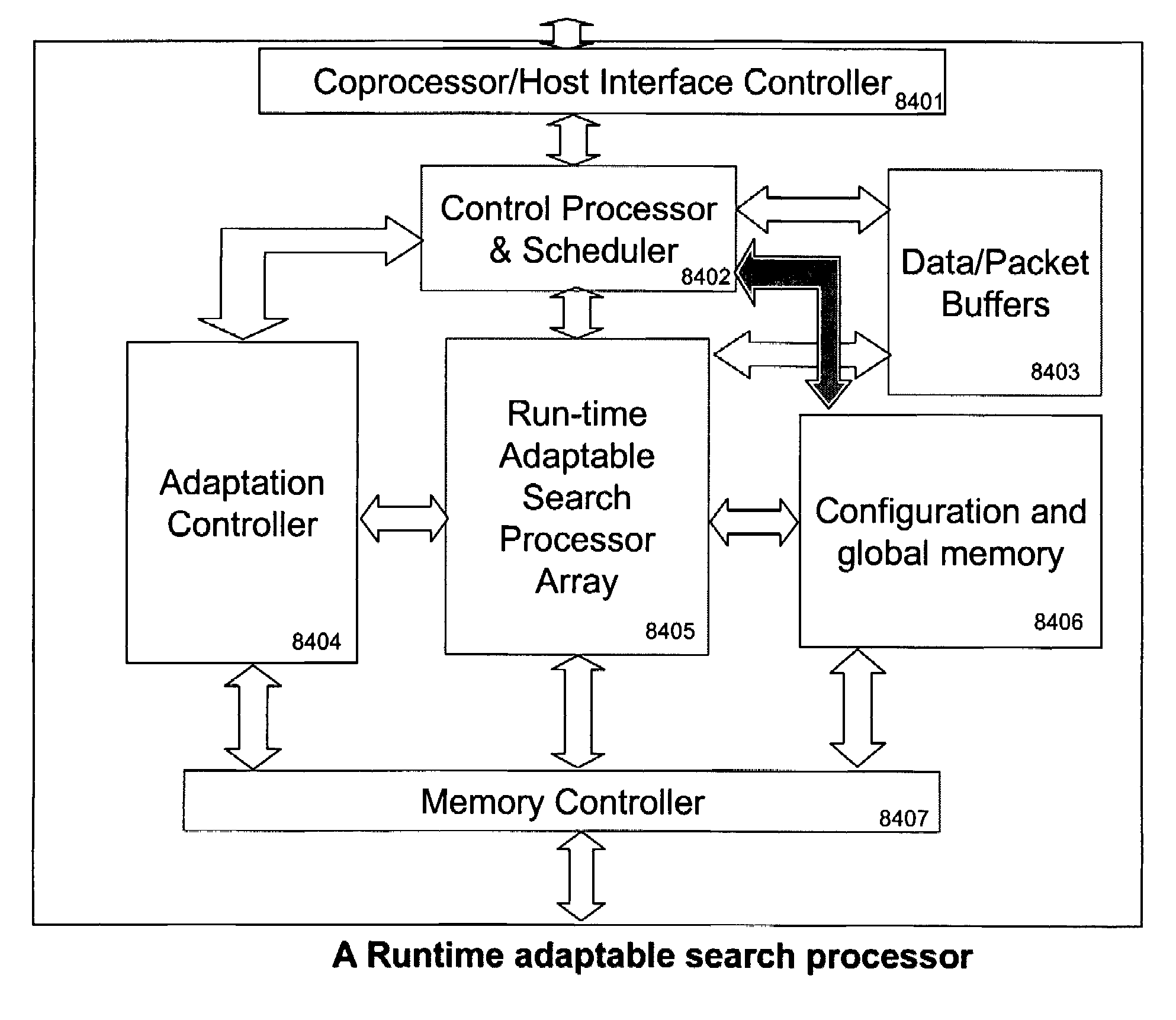
Runtime adaptable search processor
ActiveUS7685254B2Improve application performanceLarge capacityWeb data indexingMemory adressing/allocation/relocationPacket schedulingSchema for Object-Oriented XML
A runtime adaptable search processor is disclosed. The search processor provides high speed content search capability to meet the performance need of network line rates growing to 1 Gbps, 10 Gbps and higher. The search processor provides a unique combination of NFA and DFA based search engines that can process incoming data in parallel to perform the search against the specific rules programmed in the search engines. The processor architecture also provides capabilities to transport and process Internet Protocol (IP) packets from Layer 2 through transport protocol layer and may also provide packet inspection through Layer 7. Further, a runtime adaptable processor is coupled to the protocol processing hardware and may be dynamically adapted to perform hardware tasks as per the needs of the network traffic being sent or received and / or the policies programmed or services or applications being supported. A set of engines may perform pass-through packet classification, policy processing and / or security processing enabling packet streaming through the architecture at nearly the full line rate. A high performance content search and rules processing security processor is disclosed which may be used for application layer and network layer security. Scheduler schedules packets to packet processors for processing. An internal memory or local session database cache stores a session information database for a certain number of active sessions. The session information that is not in the internal memory is stored and retrieved to / from an additional memory. An application running on an initiator or target can in certain instantiations register a region of memory, which is made available to its peer(s) for access directly without substantial host intervention through RDMA data transfer. A security system is also disclosed that enables a new way of implementing security capabilities inside enterprise networks in a distributed manner using a protocol processing hardware with appropriate security features.
Owner:MEMORY ACCESS TECH LLC
Safety features for portable electronic device
ActiveUS8270933B2Unauthorised/fraudulent call preventionDevices with sensorHands freeSecurity policy
A portable device includes a safety feature that prevents some forms of use when the device is moving. The device may detect its speed or movement, compare that to a threshold, and provide a response or blocking function upon exceeding that threshold. The device may be a cell phone configured to disable transmission and reception of voice / text, conceal its display screen, and disable incorporated features and functions, if the cell phone is moving faster than walking speed or the movement is uncharacteristic of walking. The blocking function may be partially overridden based on a safety policy, which can be managed and customized. The introduction of hands-free devices may serve to override a blocking function and enable other functions.
Owner:AI CORE TECH LLC
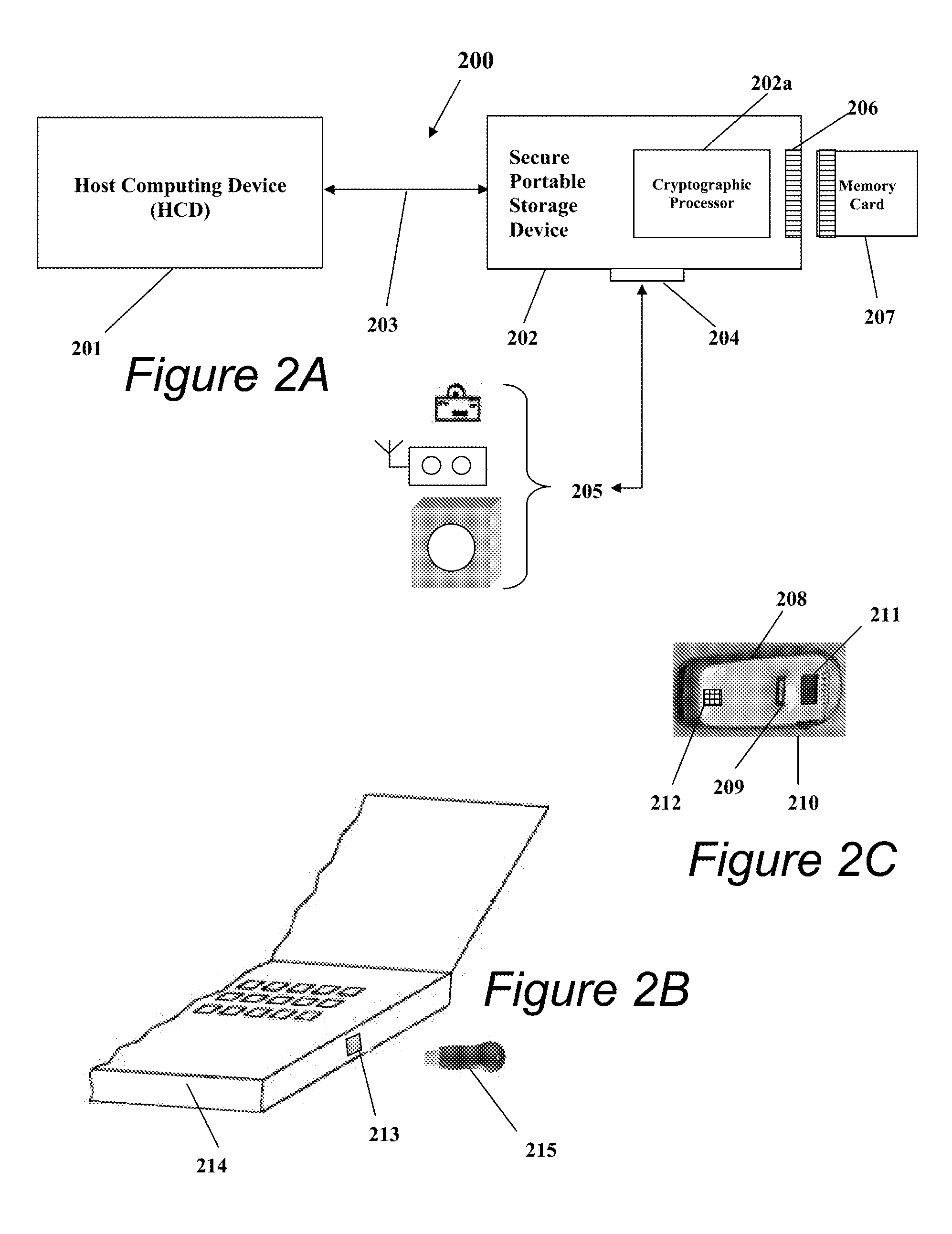
Portable Data Encryption Device with Configurable Security Functionality and Method for File Encryption
InactiveUS20080263363A1Mitigates and eliminates vulnerabilityUser identity/authority verificationInternal/peripheral component protectionComputer hardwarePlaintext
A portable encryption device with logon access controlled by an encryption key, with an on board cryptographic processor for reconstituting the encryption key from a plurality of secrets generated by a secret sharing algorithm, optionally shrouded with external secrets using an invertible transform resistant to quantum computing attacks. Another embodiment provides file decryption controlled by a file encryption key, with the on board cryptographic processor reconstituting the file encryption key from a version of the file encryption key which has been shrouded with a network authorization code. A method for encryption of a plaintext file by hashing, compressing, and encrypting the plaintext file, hashing the ciphertext, hashing the plaintext hash and the ciphertext hash, and sealing the ciphertext together with the resulting hash. A portable encryption device for performing the method is also disclosed.
Owner:SPYRUS
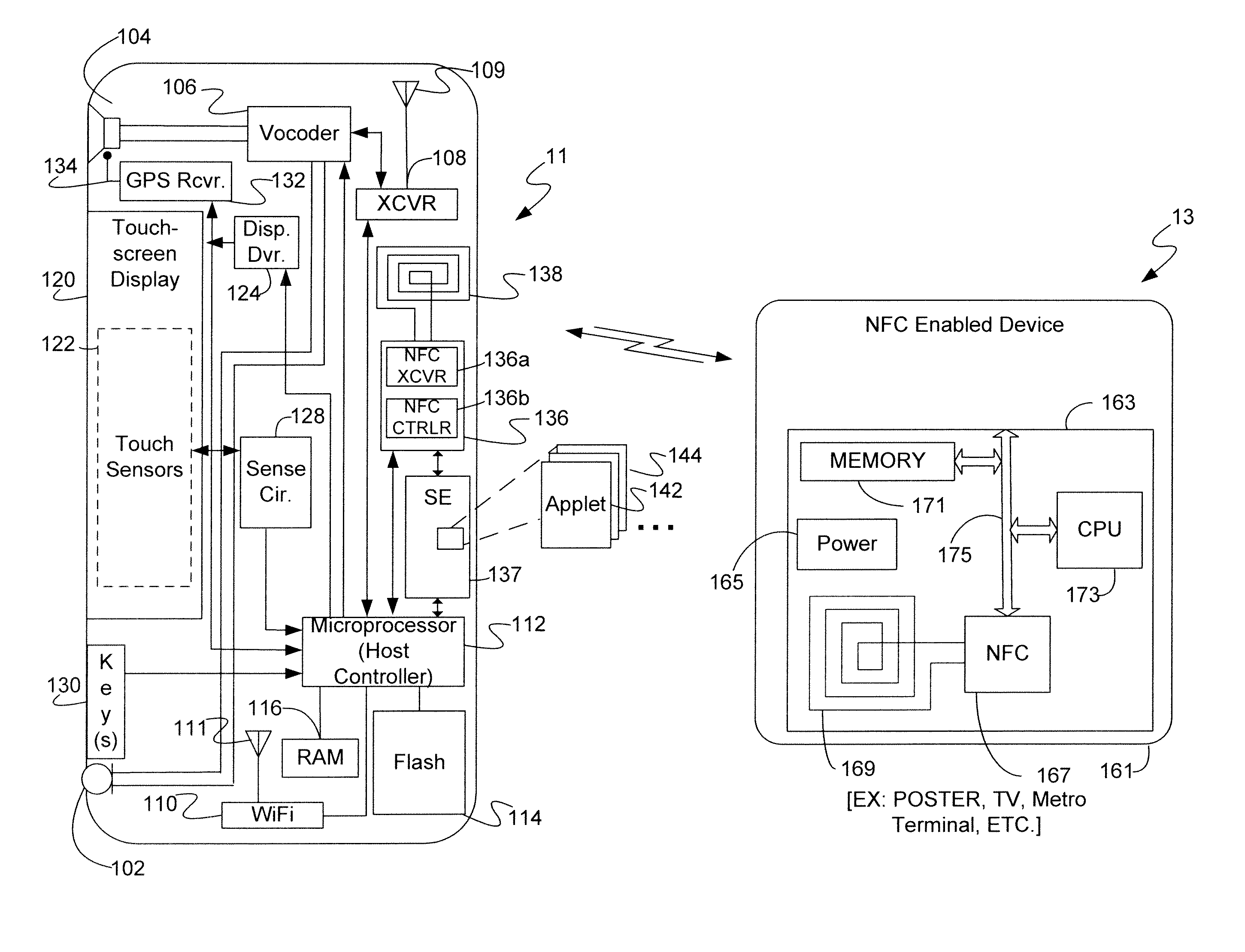
Secure NFC data authentication
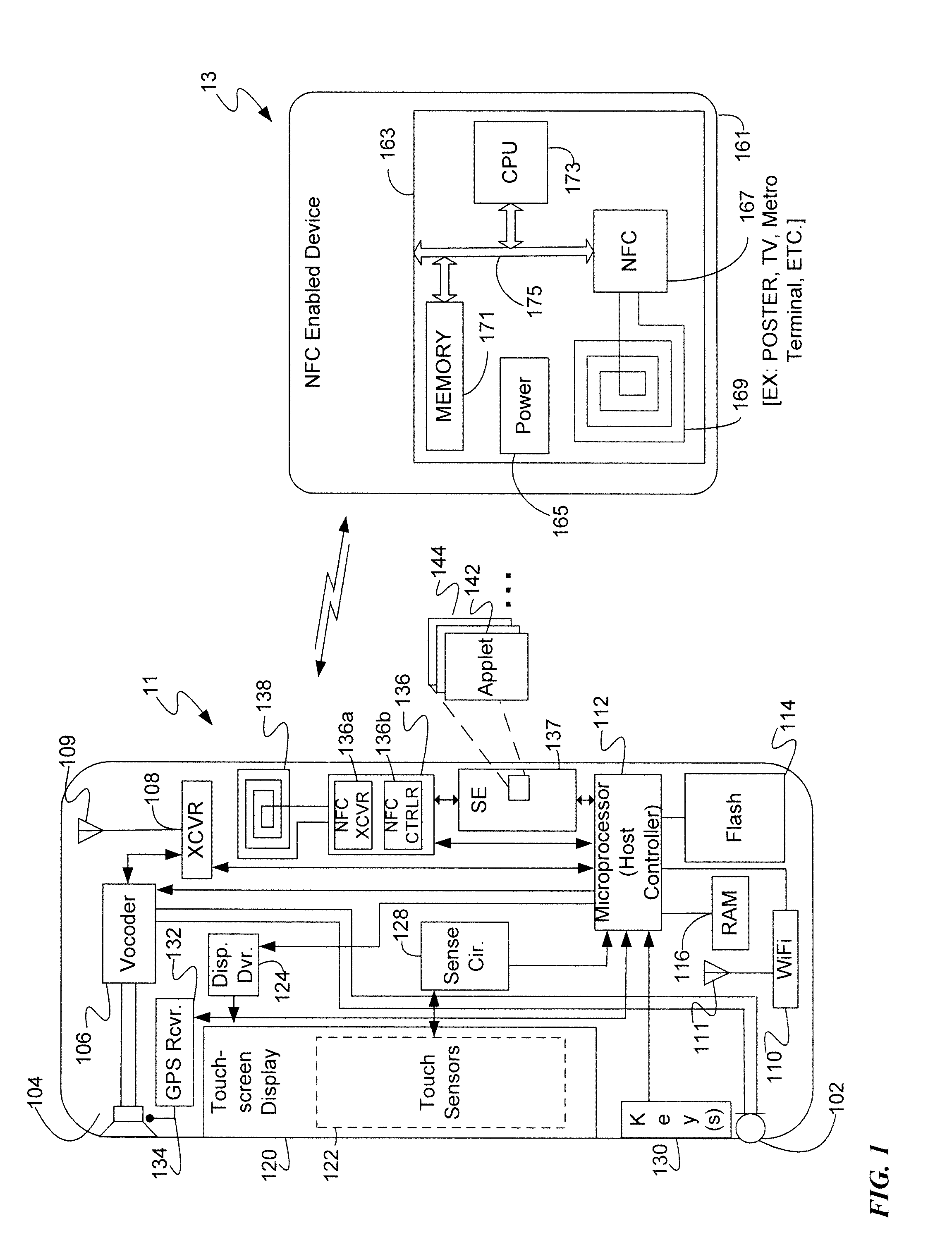
ActiveUS20140256251A1Near-field systems using receiversPayment architectureTransceiverWireless transceiver
A mobile device includes a wireless transceiver, a host processor, a secure element (SE), and a near field communication (NFC) system having an NFC transceiver and an NFC controller implementing a contactless front end. The contactless front end routes a near field communication related to a payment transaction between the NFC system and the SE without going to or from the host processor. The contactless front end routes a near field communication not related to a payment transaction, but requiring a security function, between the NFC system and the SE without going to or from the host processor. The contactless front end routes a near field communication not related to a payment transaction, and not requiring a security function, between the NFC system and host processor without going to or from the SE.
Owner:CELLCO PARTNERSHIP INC
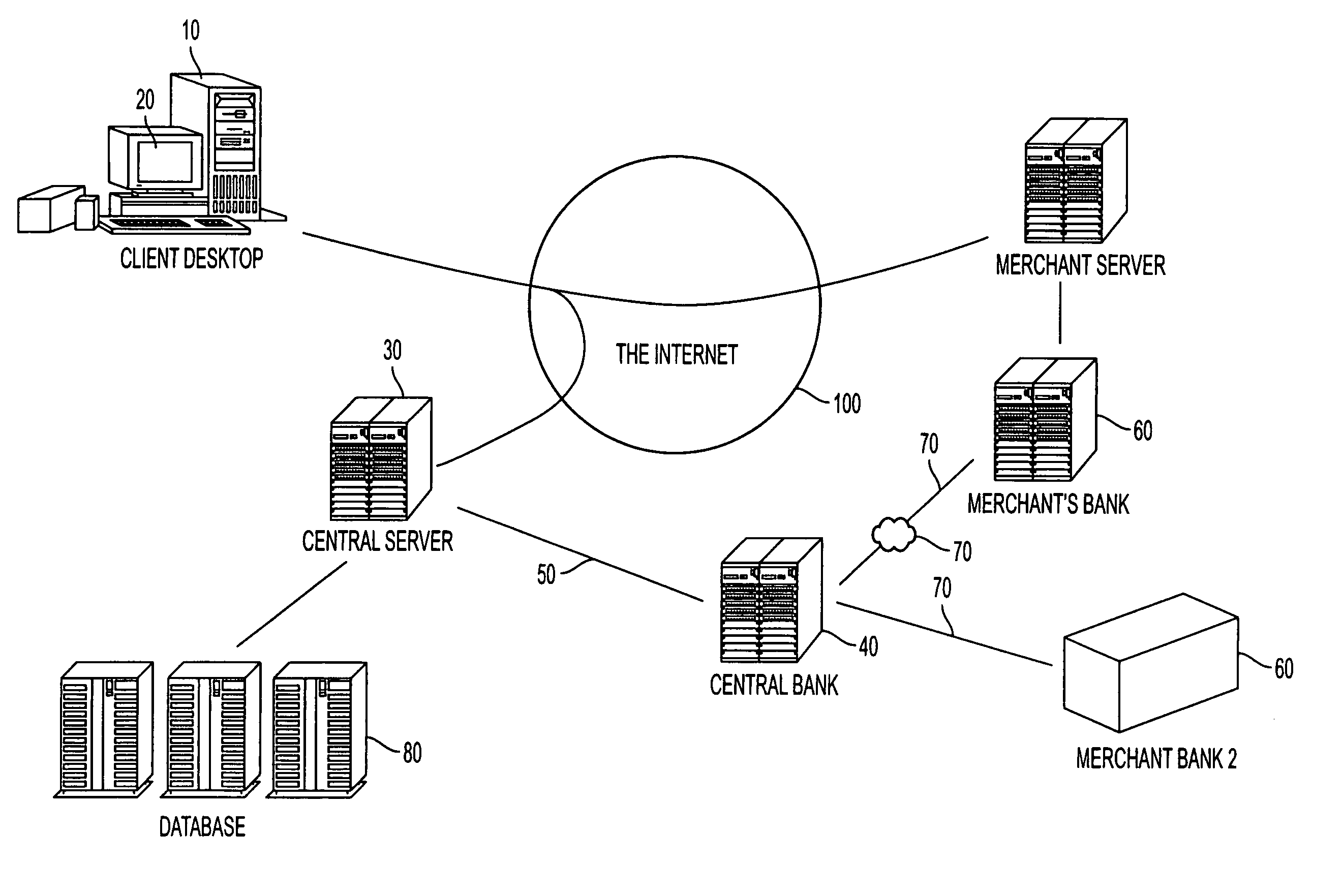
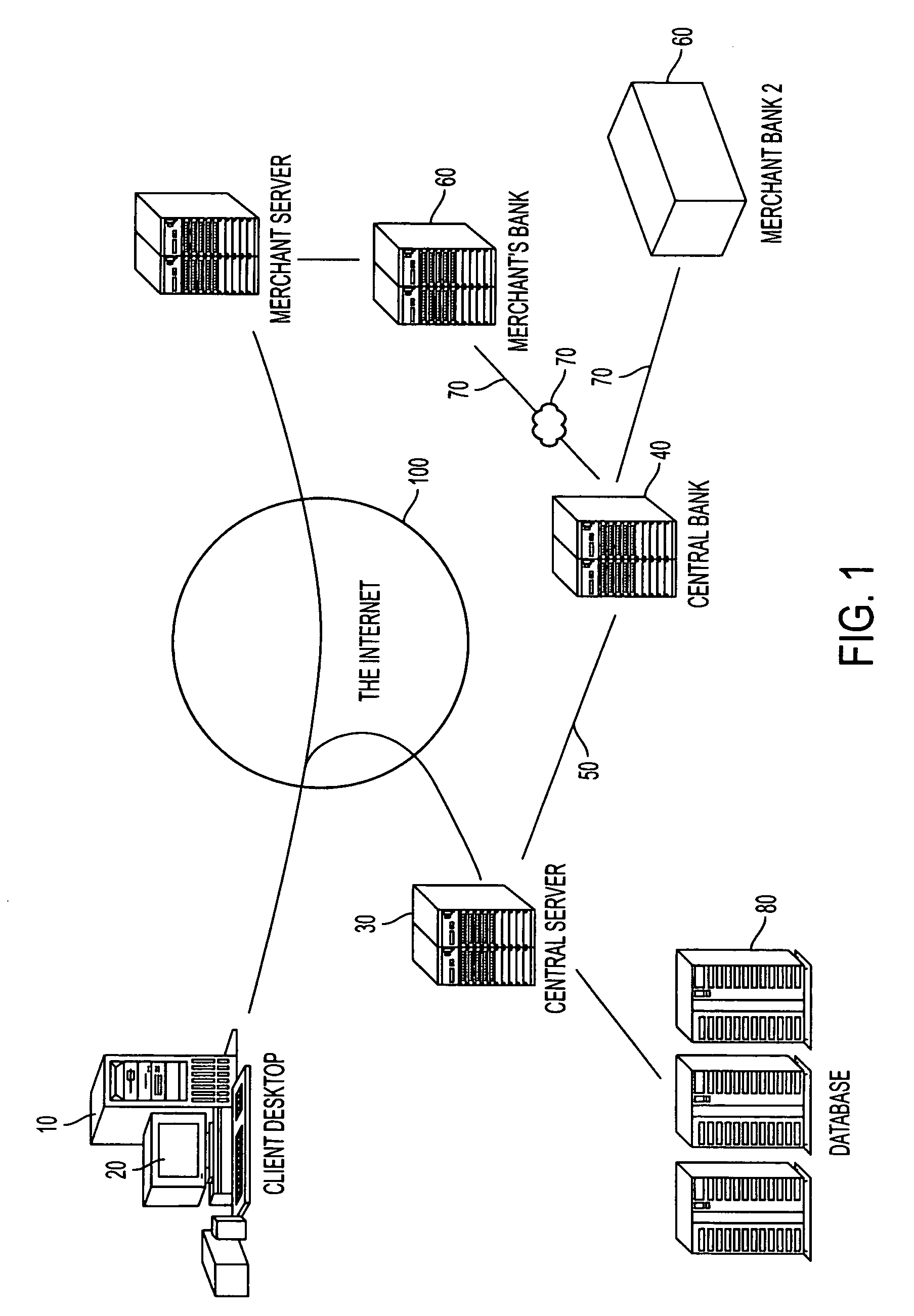
Secure online commerce transactions
A method of enabling electronic commerce transactions is provided by a service, the service giving to users a disposable credit card or other indicia of credit for a particular transaction or amount. The service receives registration information from the user and authorizes the user. The service establishes an account for the user and issues a disposable (one use) credit card number to the user which has the same format as a permanent credit card number, is acceptable to the user and the institution with whom the user is transacting business. The system incorporates various security features.
Owner:ACEINC PTY LTD
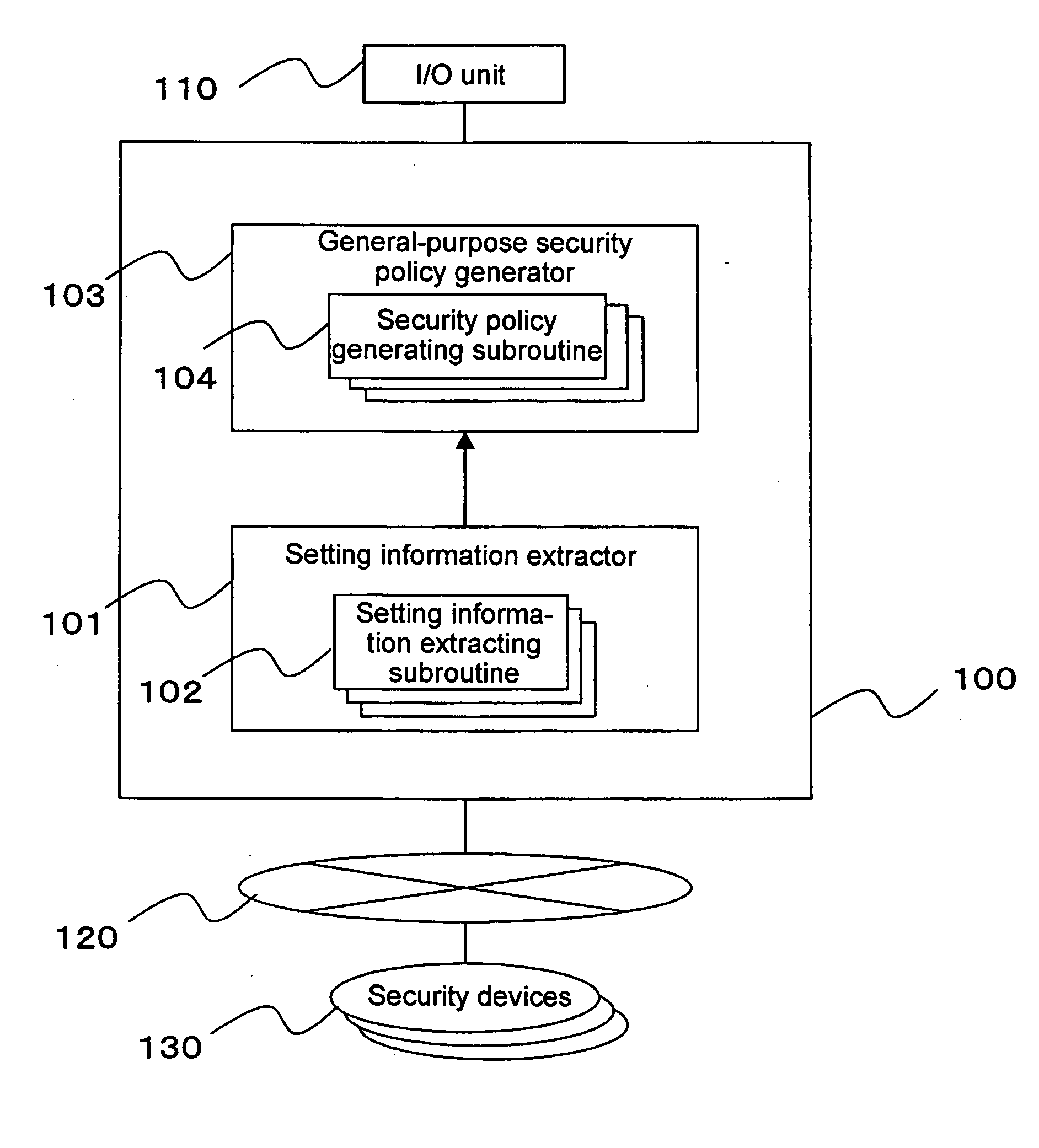
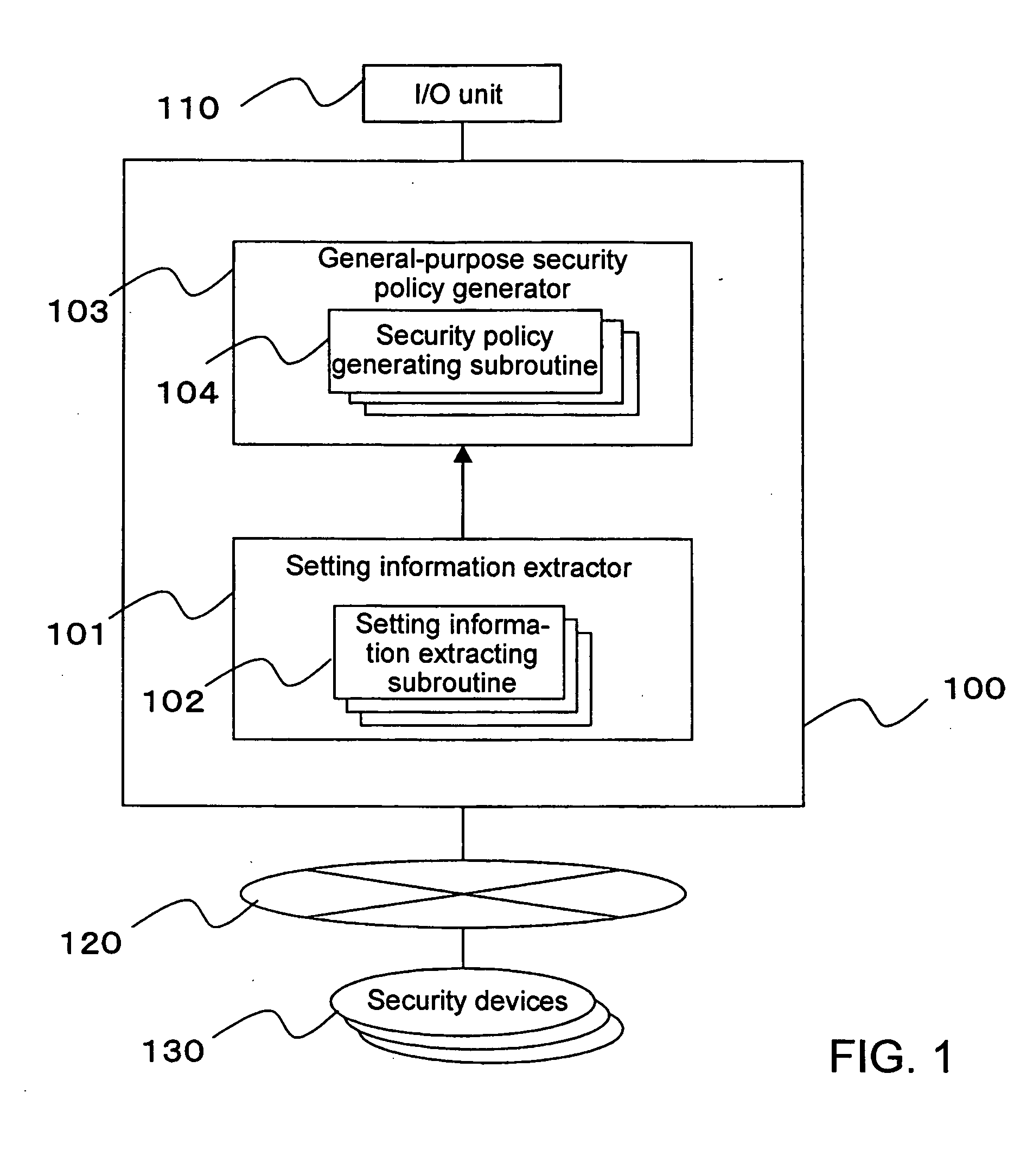
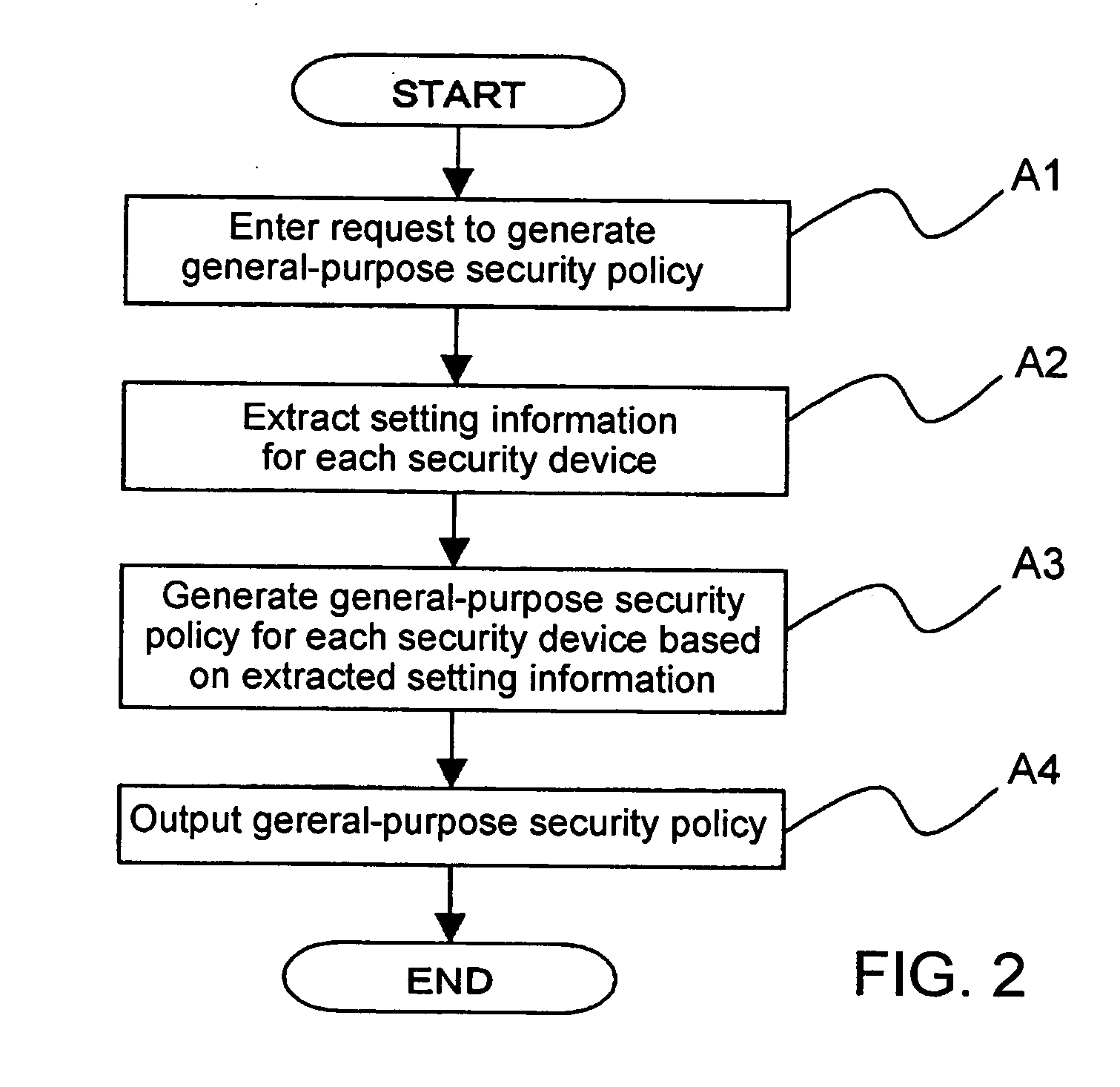
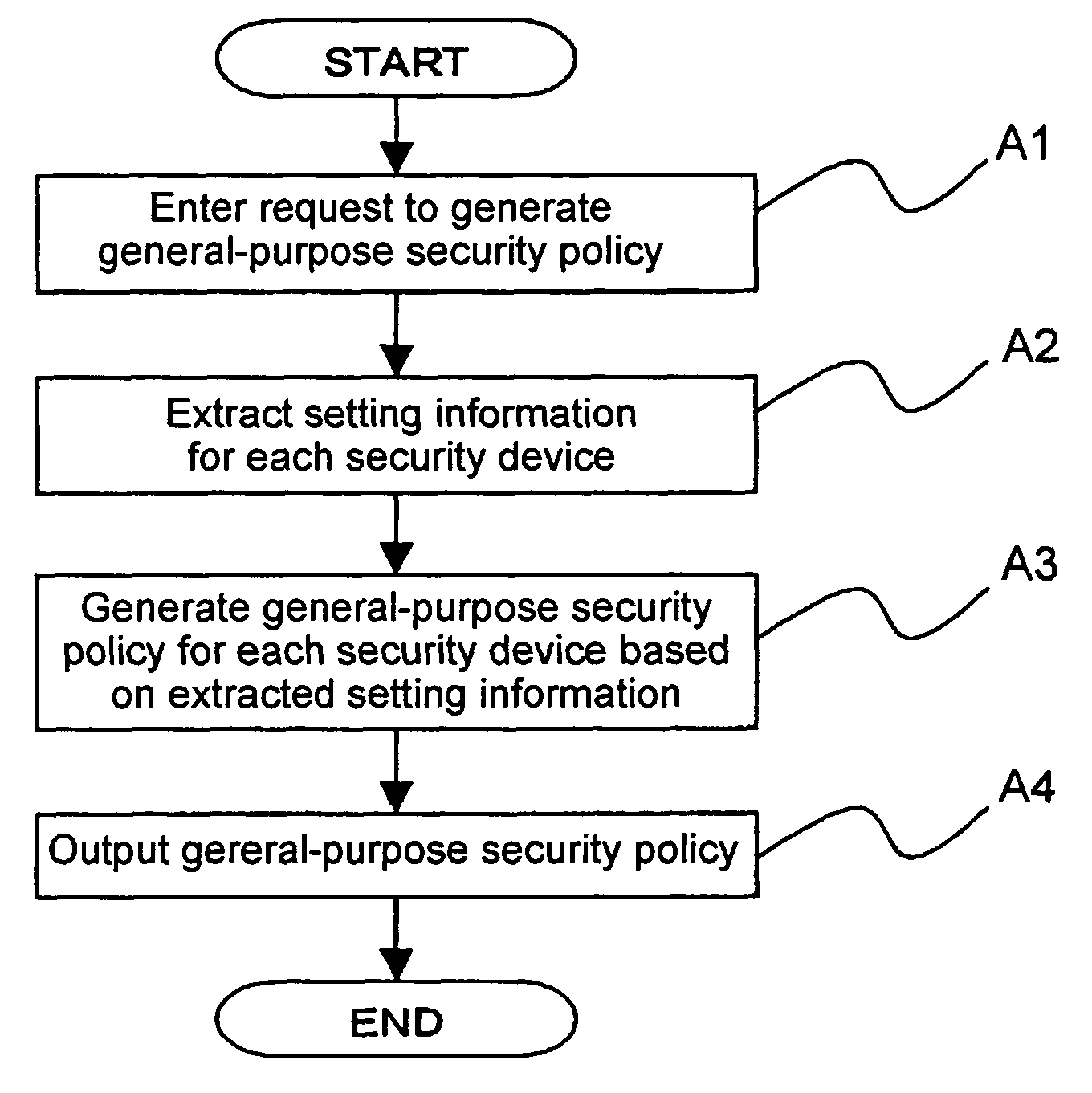
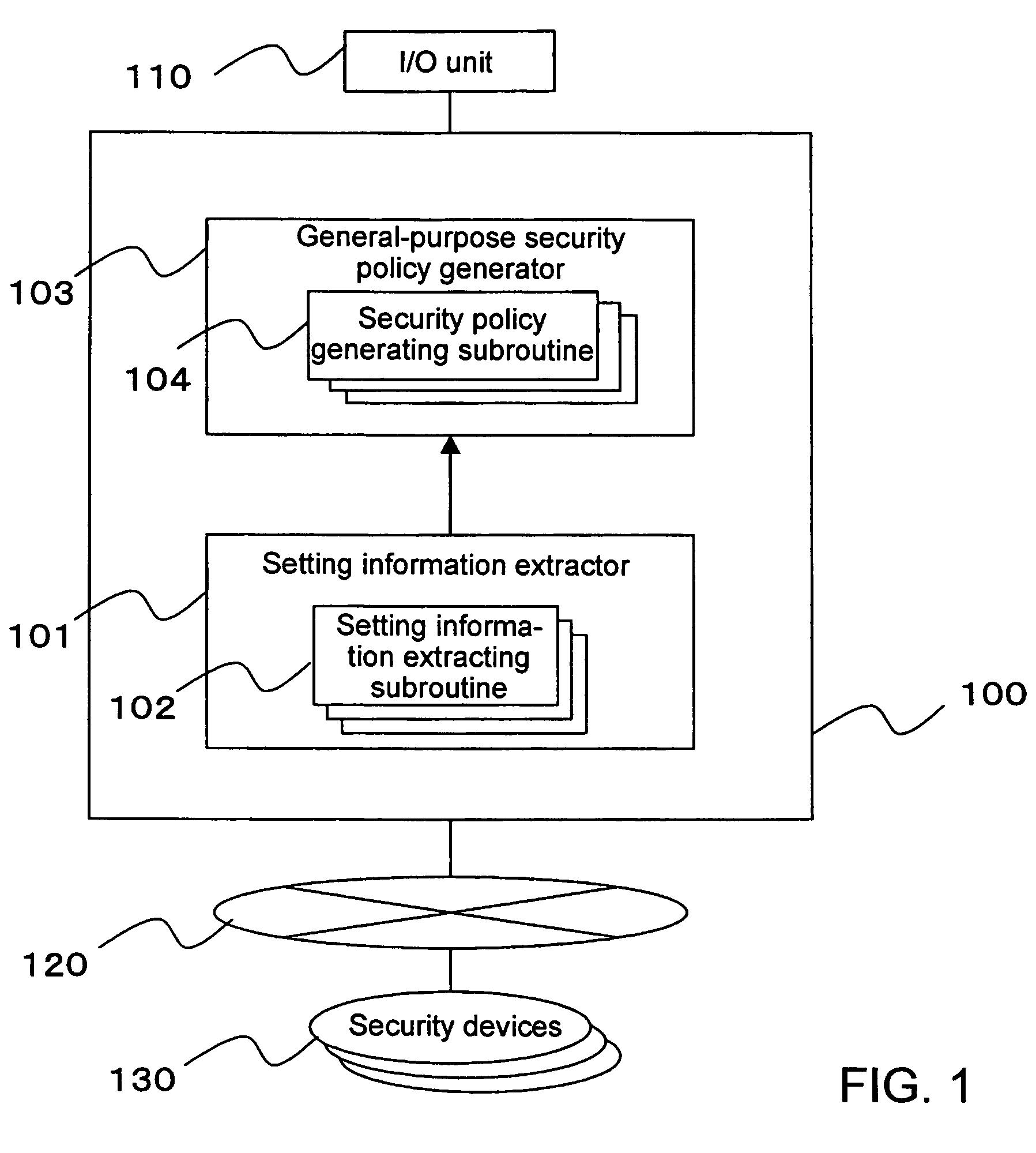
Method and apparatus for security policy management
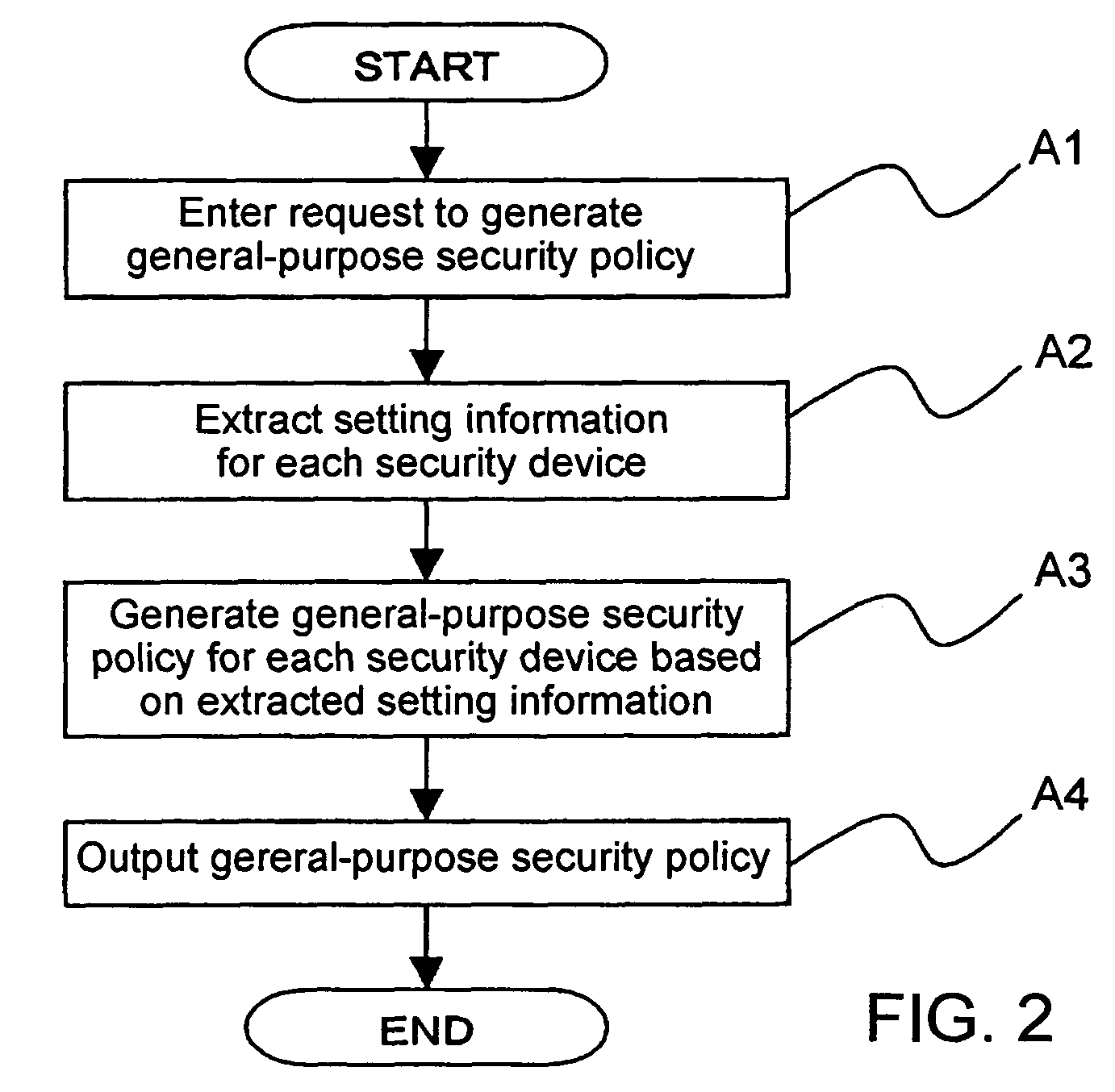
InactiveUS20050283823A1Reduce human interventionEasy to masterDigital data protectionResourcesGeneral purposeSecurity policy management
A security policy management system for deriving a security policy from setting details of security devices as components of an information system includes a setting information storage unit for storing setting information representing settings with regard to security functions of devices included in a network system to be managed, and a general-purpose security policy generator for generating a security policy including a description expressed in a format independent of descriptions depending on particular devices, based on the setting information stored in the setting information storage unit.
Owner:NEC CORP
RFID scanning device
ActiveUS10482292B2Minimal costMinimal effortLogisticsSensing by electromagnetic radiationInventory managementAuthorization
Owner:GARY L SHARPE
Content security layer providing long-term renewable security
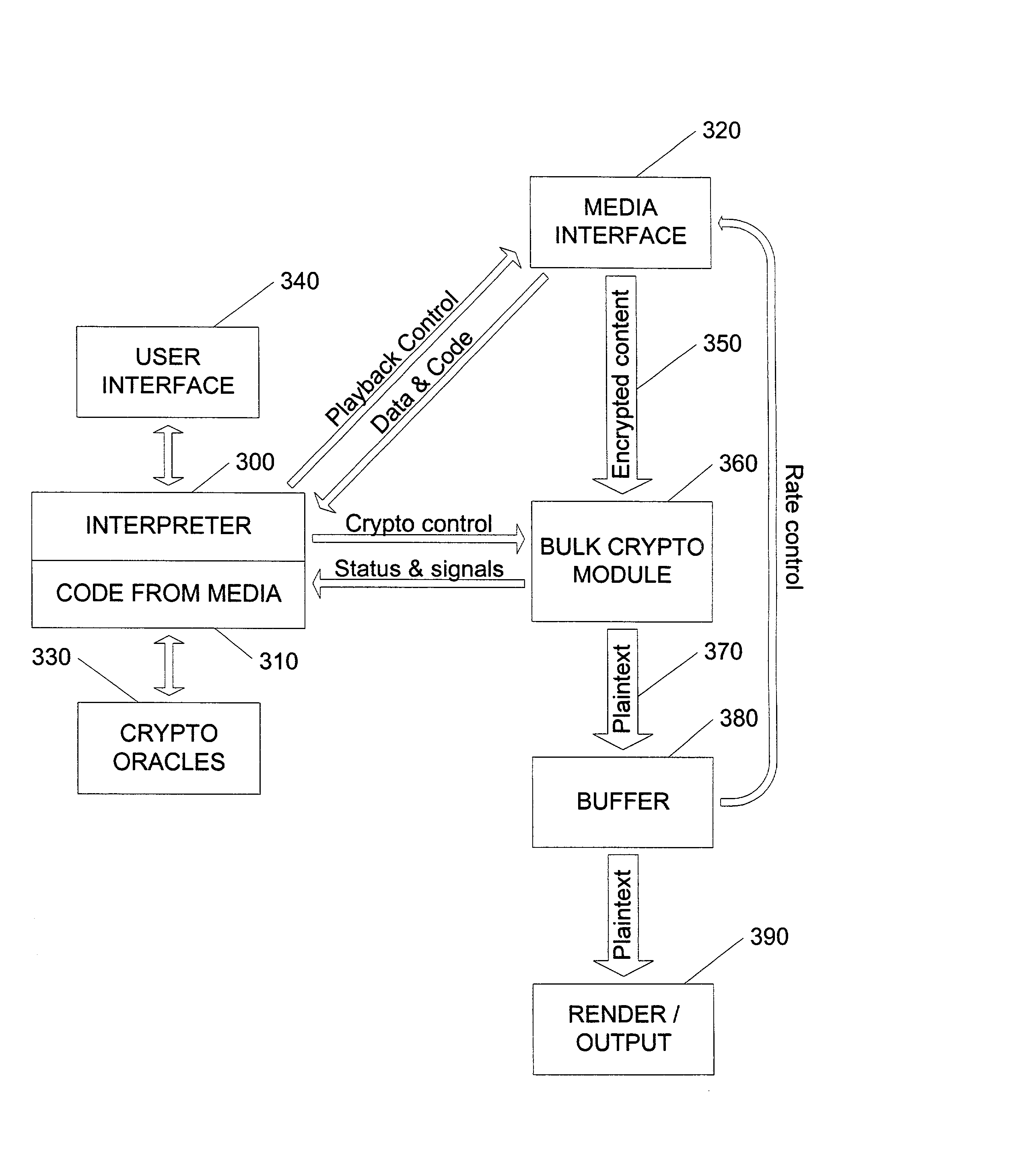
InactiveUS20020141582A1Unparalleled flexibilityIncrease sampling rateTelevision system detailsKey distribution for secure communicationAttackMediaFLO
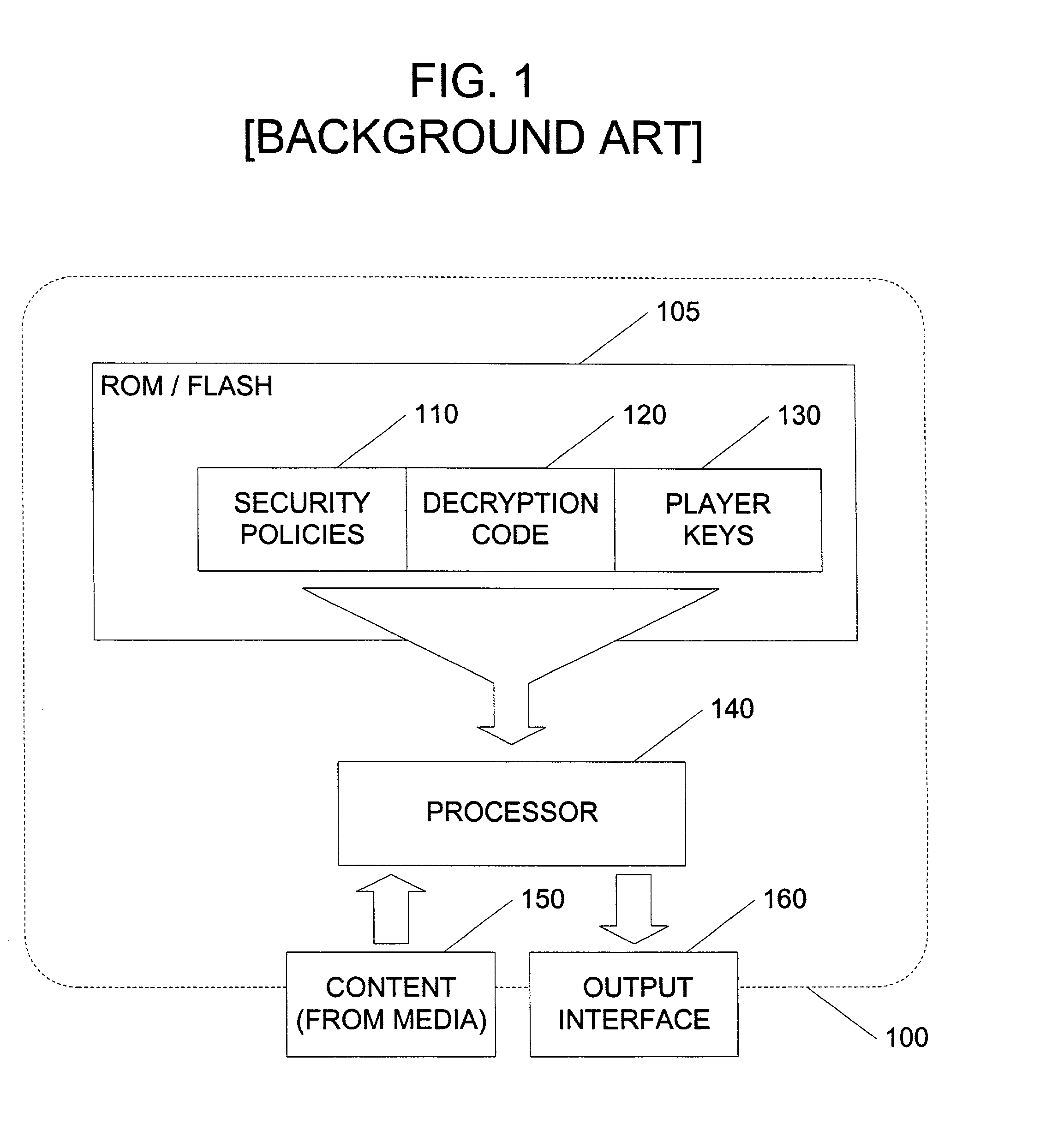
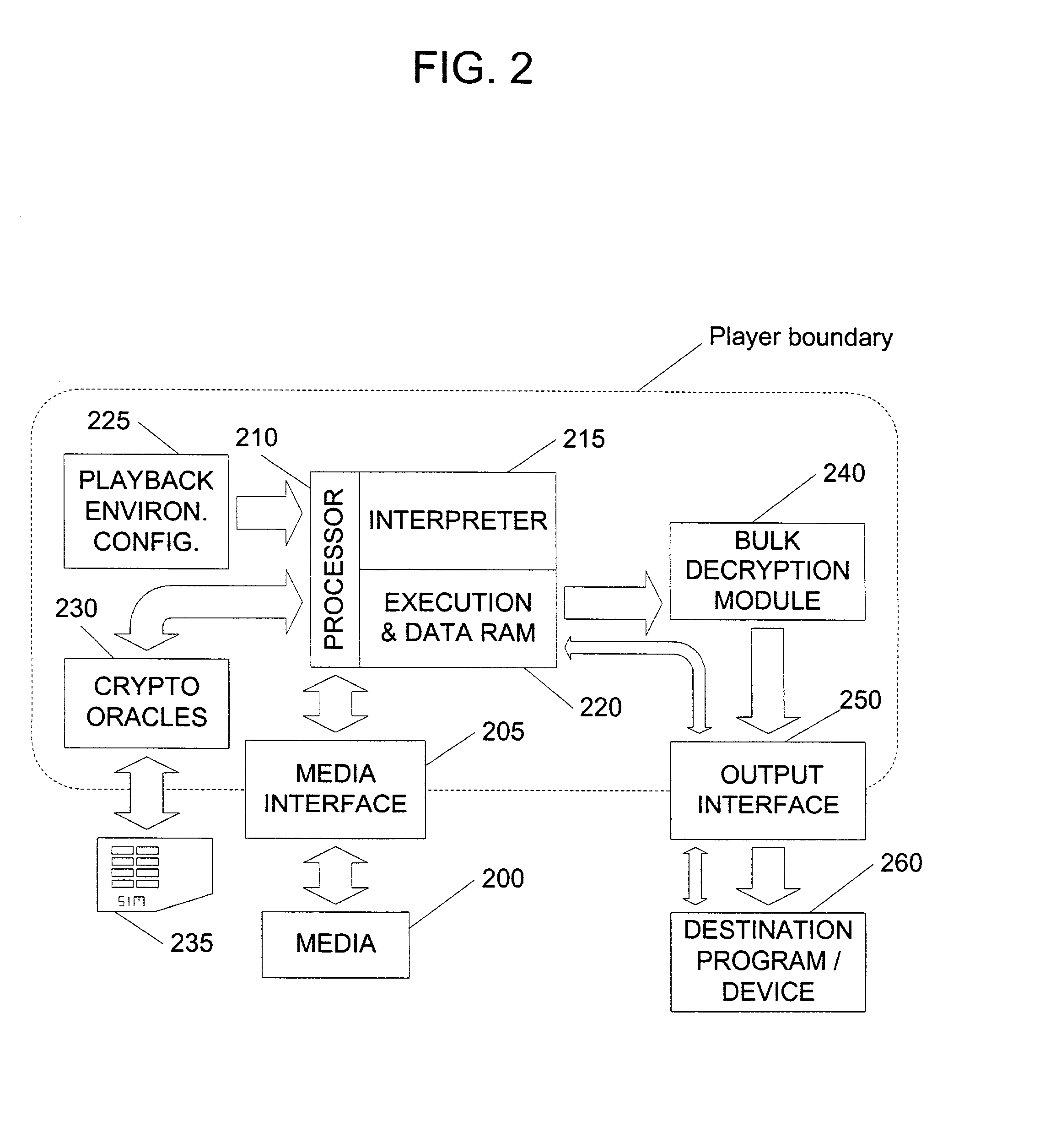
In an exemplary embodiment, digital content is mastered as a combination of encrypted data and data processing operations that enable use in approved playback environments. Player devices having a processing environment compatible with the content's data processing operations are able to decrypt and play the content. Players can also provide content with basic functions, such as loading data from media, performing network communications, determining playback environment configuration, controlling decryption / playback, and / or performing cryptographic operations using the player's keys. These functions allow the content to implement and enforce its own security policies. If pirates compromise individual players or content titles, new content can be mastered with new security features that block the old attacks. A selective decryption capability can also be provided, enabling on-the-fly watermark insertion so that attacks can be traced back to a particular player. Features to enable migration from legacy formats are also provided.
Owner:ROVI SOLUTIONS CORP
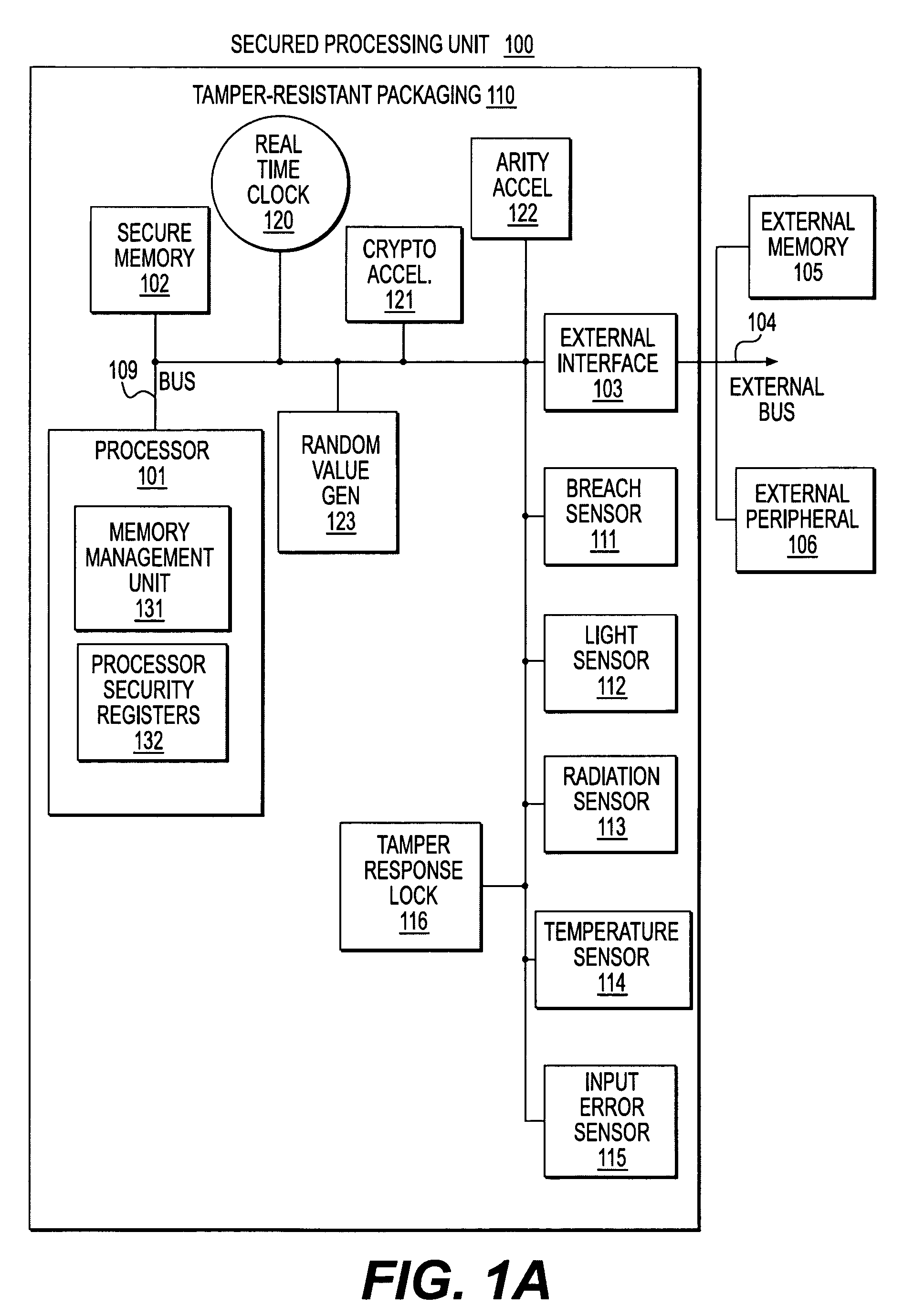
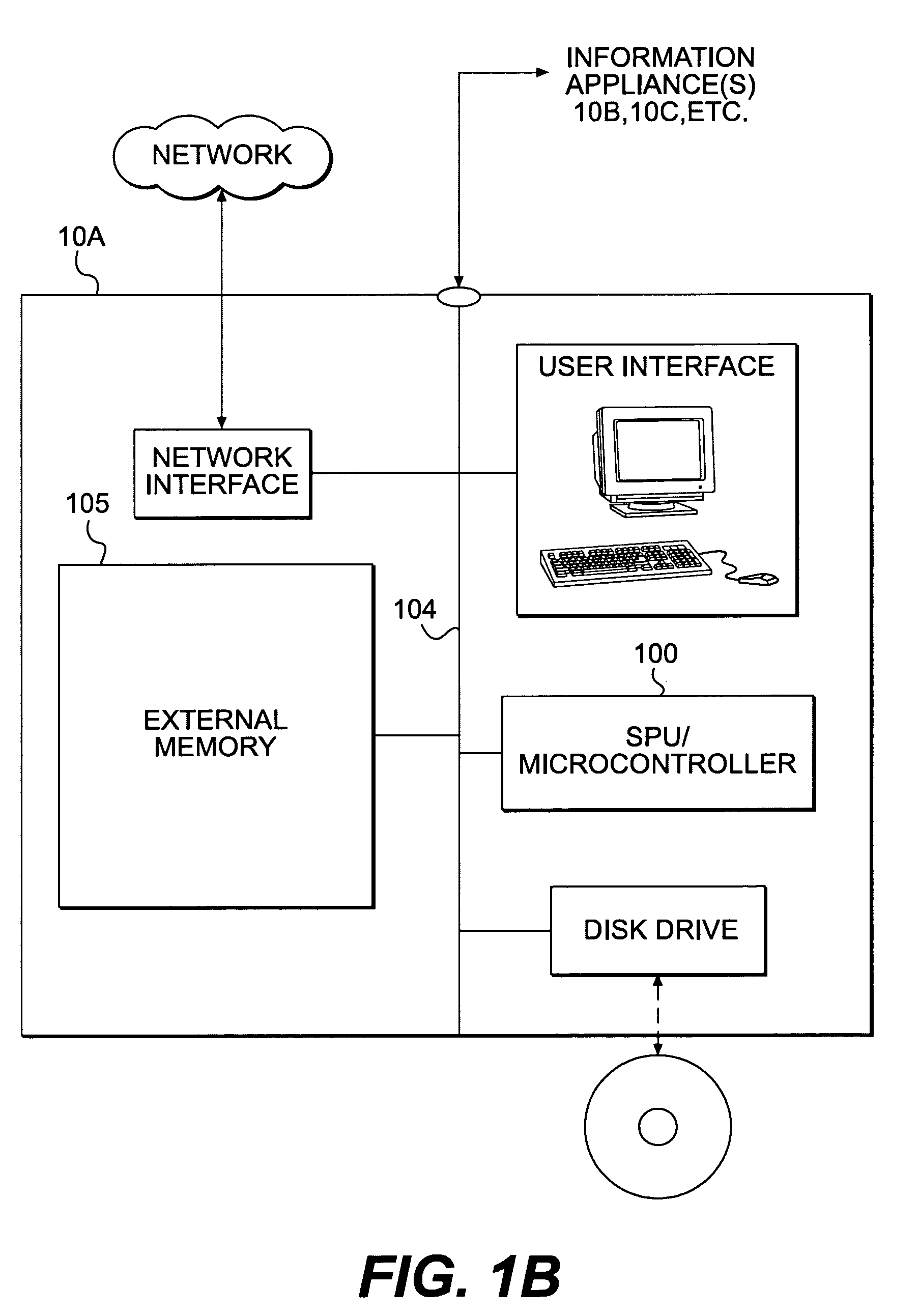
Secure processing unit systems and methods
InactiveUS7124170B1Low costLow additional costMemory architecture accessing/allocationData processing applicationsMicrocontrollerUnit system
A hardware Secure Processing Unit (SPU) is described that can perform both security functions and other information appliance functions using the same set of hardware resources. Because the additional hardware required to support security functions is a relatively small fraction of the overall device hardware, this type of SPU can be competitive with ordinary non-secure CPUs or microcontrollers that perform the same functions. A set of minimal initialization and management hardware and software is added to, e.g., a standard CPU / microcontroller. The additional hardware and / or software creates an SPU environment and performs the functions needed to virtualize the SPU's hardware resources so that they can be shared between security functions and other functions performed by the same CPU.
Owner:INTERTRUST TECH CORP
Methods and systems for automating the control of objects within a defined human environment
InactiveUS20060218244A1Reduce system costSimple systemMultiple digital computer combinationsTransmissionAutomatic controlAction function
Methods and systems are described for the automation of a human living environment such as a home, an apartment, a workplace, or a vehicle. The methods and systems are directed to the control of various groups of objects within the human living environments according to defined criteria and defined object groupings, in a manner that establishes operational themes and scenarios within the environment. The methods and systems utilize devices for characterizing the environment (sensors), making decisions about actions appropriate in the environment (processors), and effecting actions and activities within the environment (switches, controls and actuators). The automation operates on multiple levels including; responsive safety functionality, one time action functionality, sporadically initiated timed action functionality, and periodically scheduled action functionality. The systems integrate with off-site information and action routing services that increase the decision making ability of the individuals within the environment.
Owner:RASMUSSEN JUNG A +1
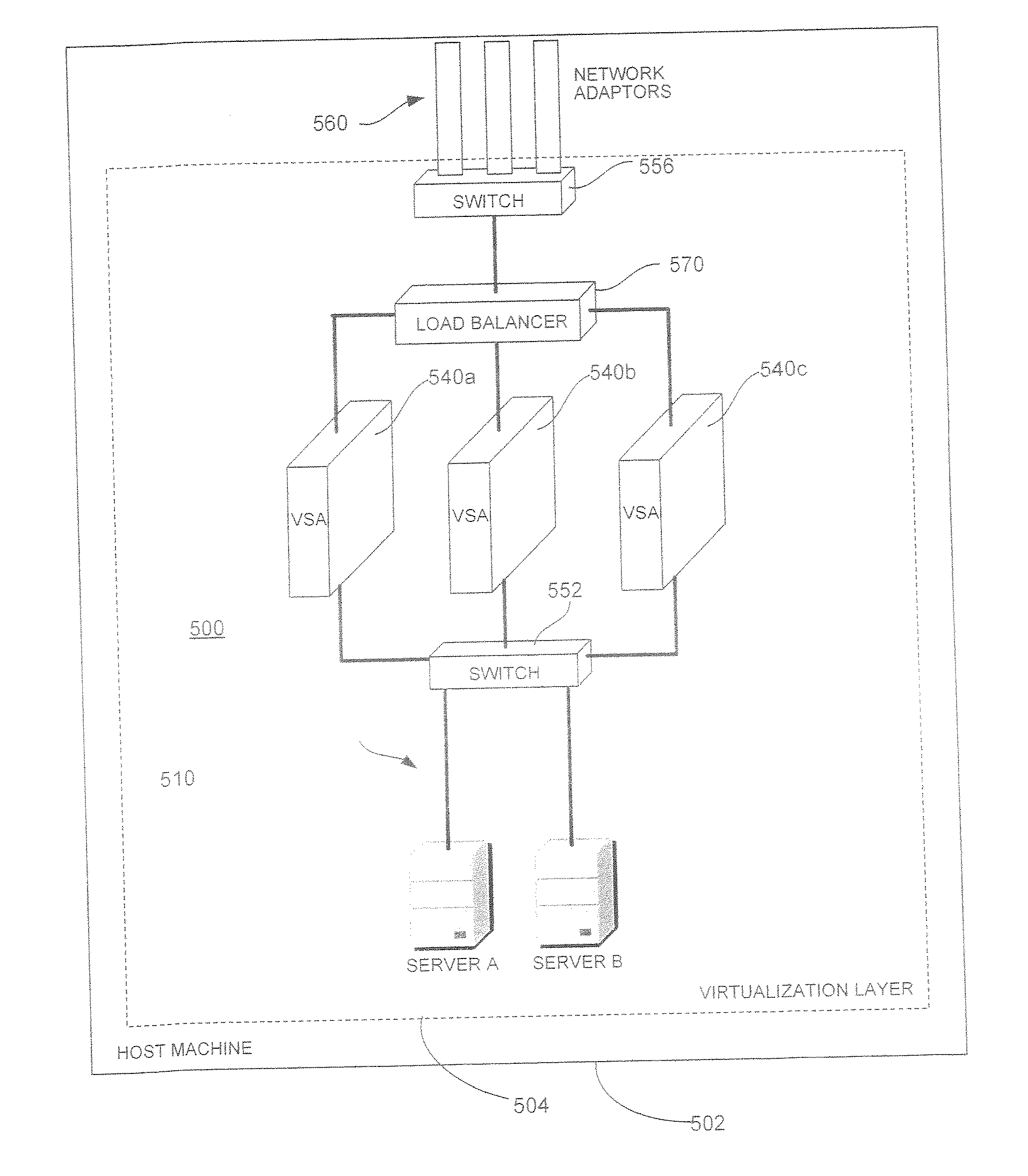
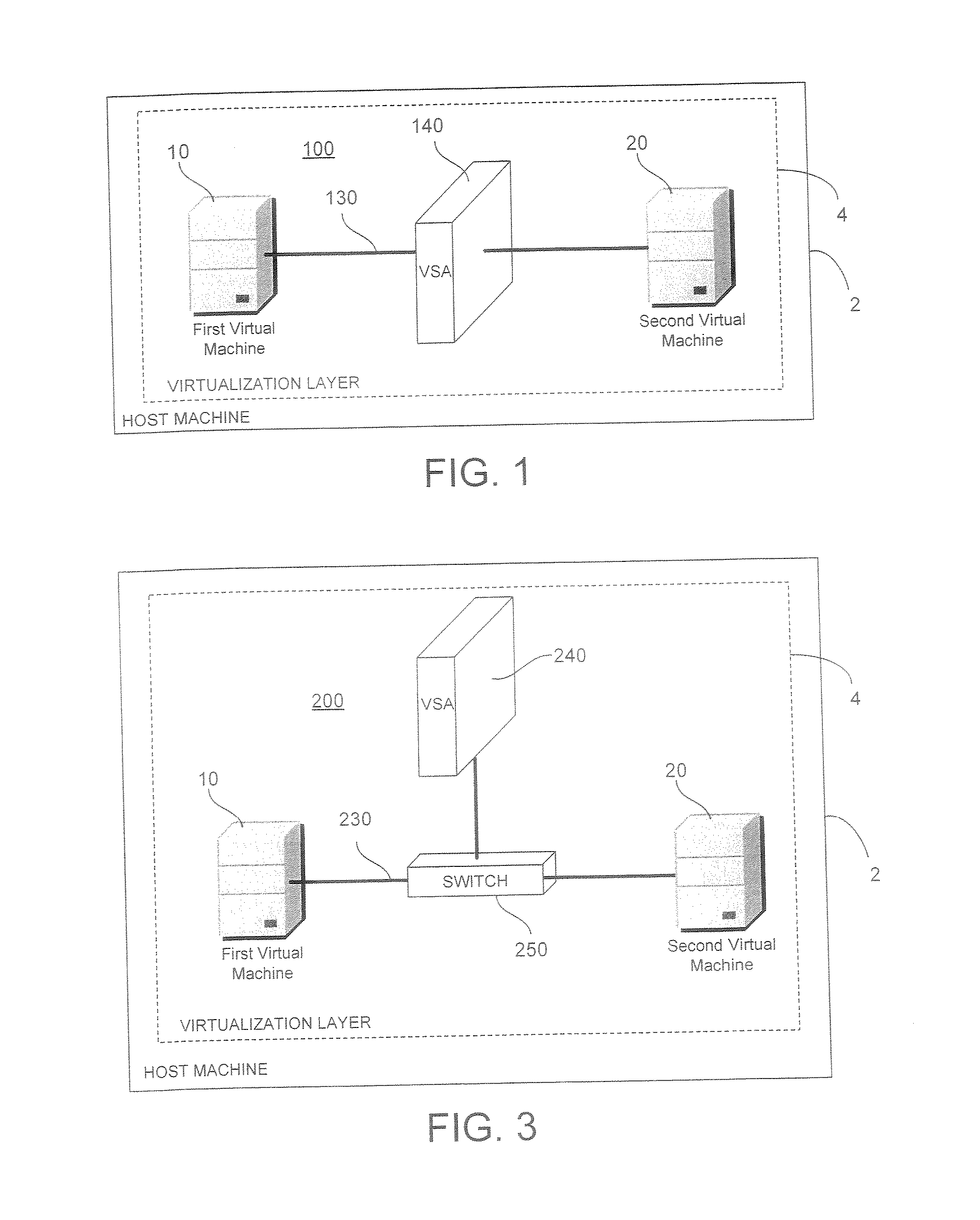
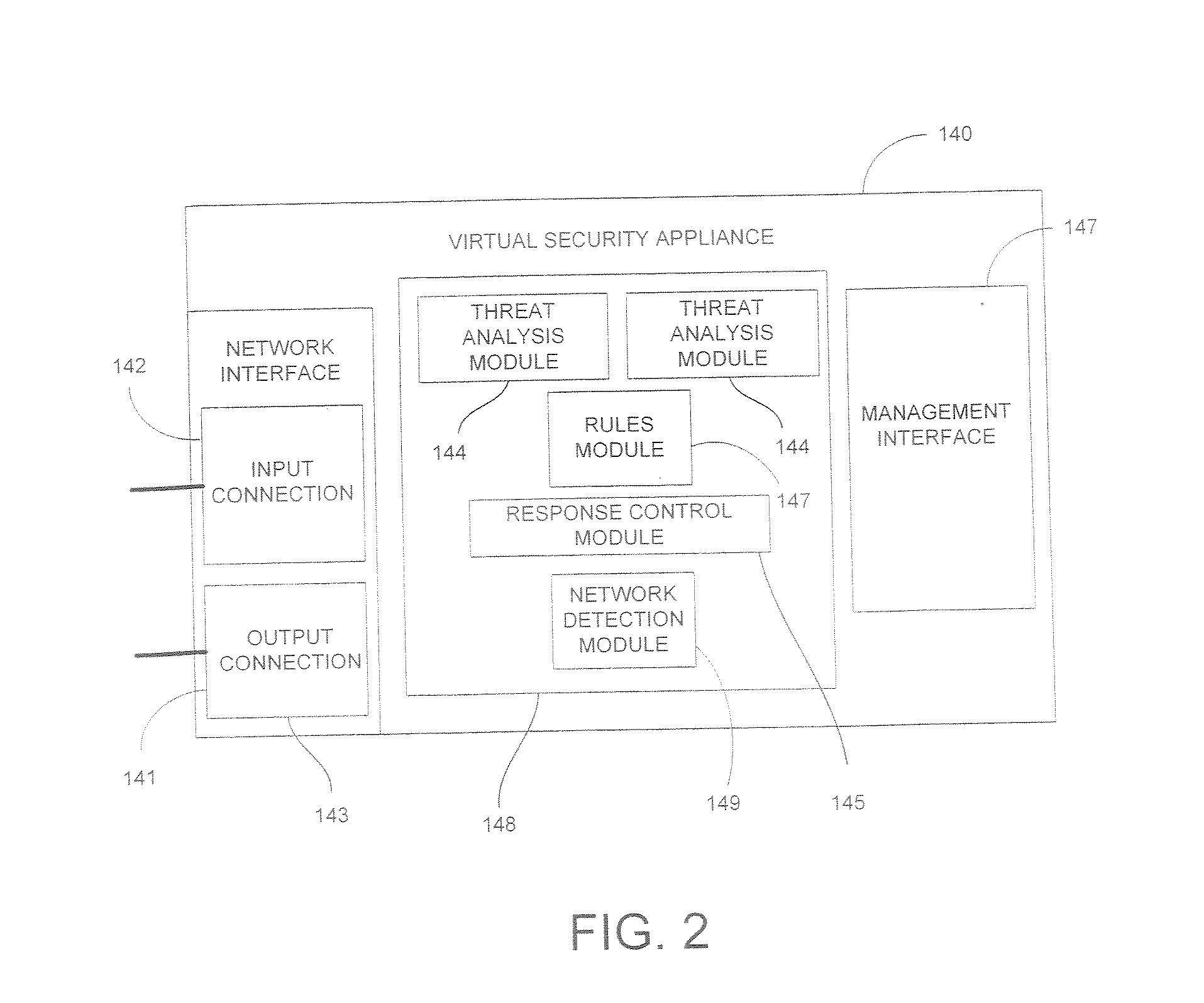
System and Method for Securing Information in a Virtual Computing Environment
InactiveUS20070266433A1Improve employee productivityIncrease the challengeMultiple digital computer combinationsPlatform integrity maintainanceVirtual computingHost machine
A virtual security appliance is provided for disposition in a virtual network having at least one other virtual network device, the virtual network residing on a host data processing machine. The virtual security appliance comprises an interface configured for receiving a data communication directed to the at least one other virtual network device and a security function module adapted for initiating a security function responsive to said data communication meeting predetermined criteria.
Owner:STRATACLOUD
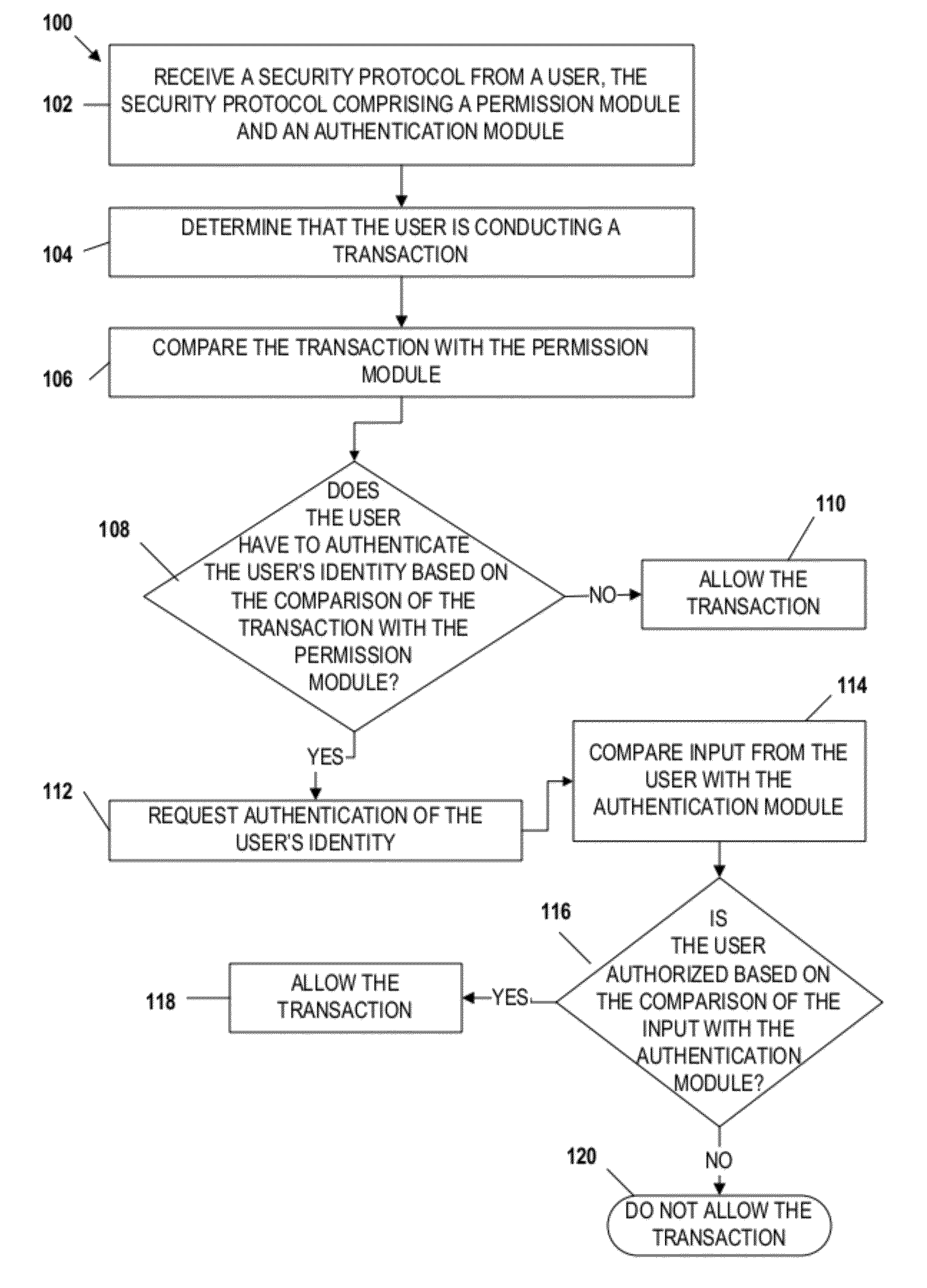
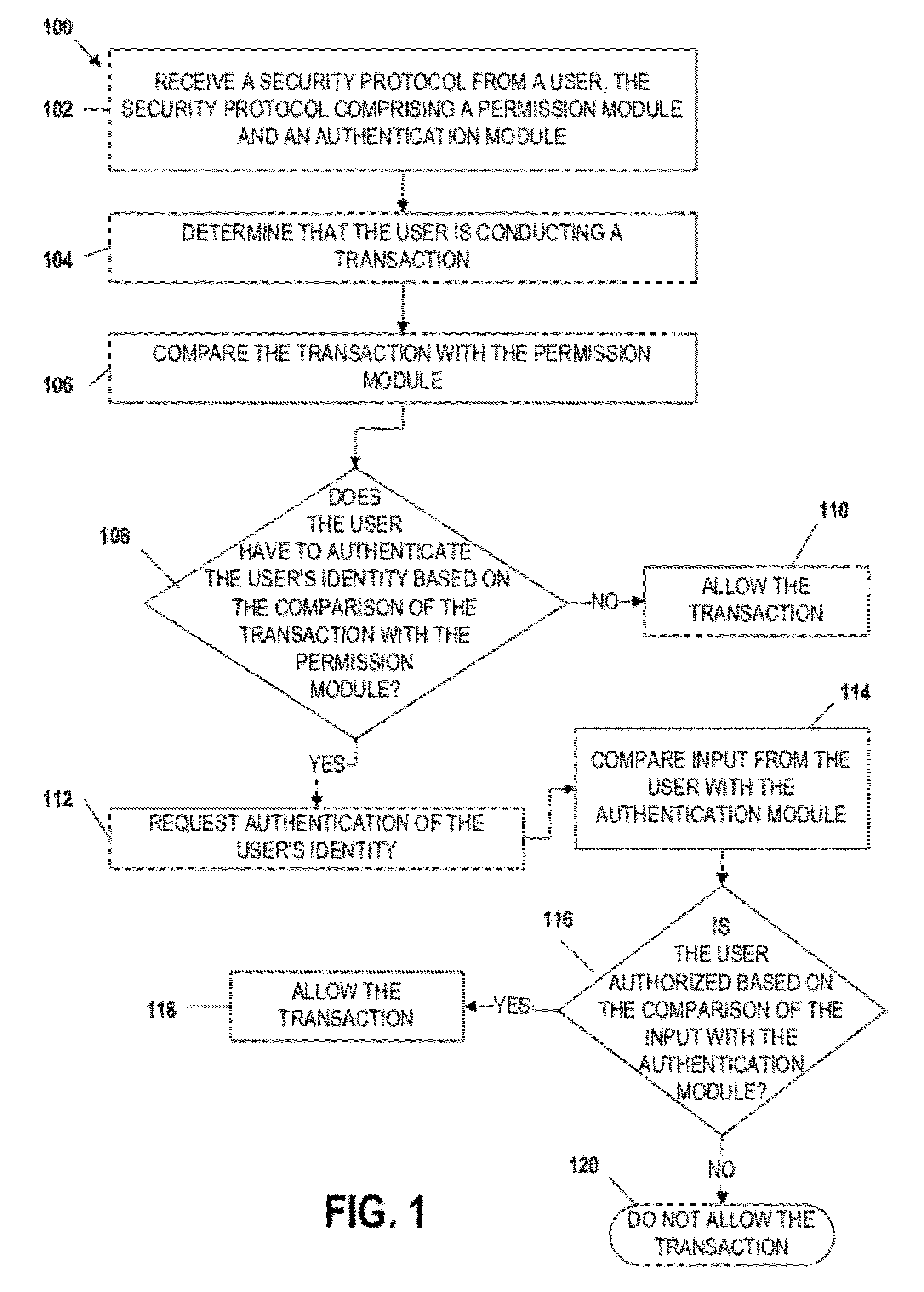
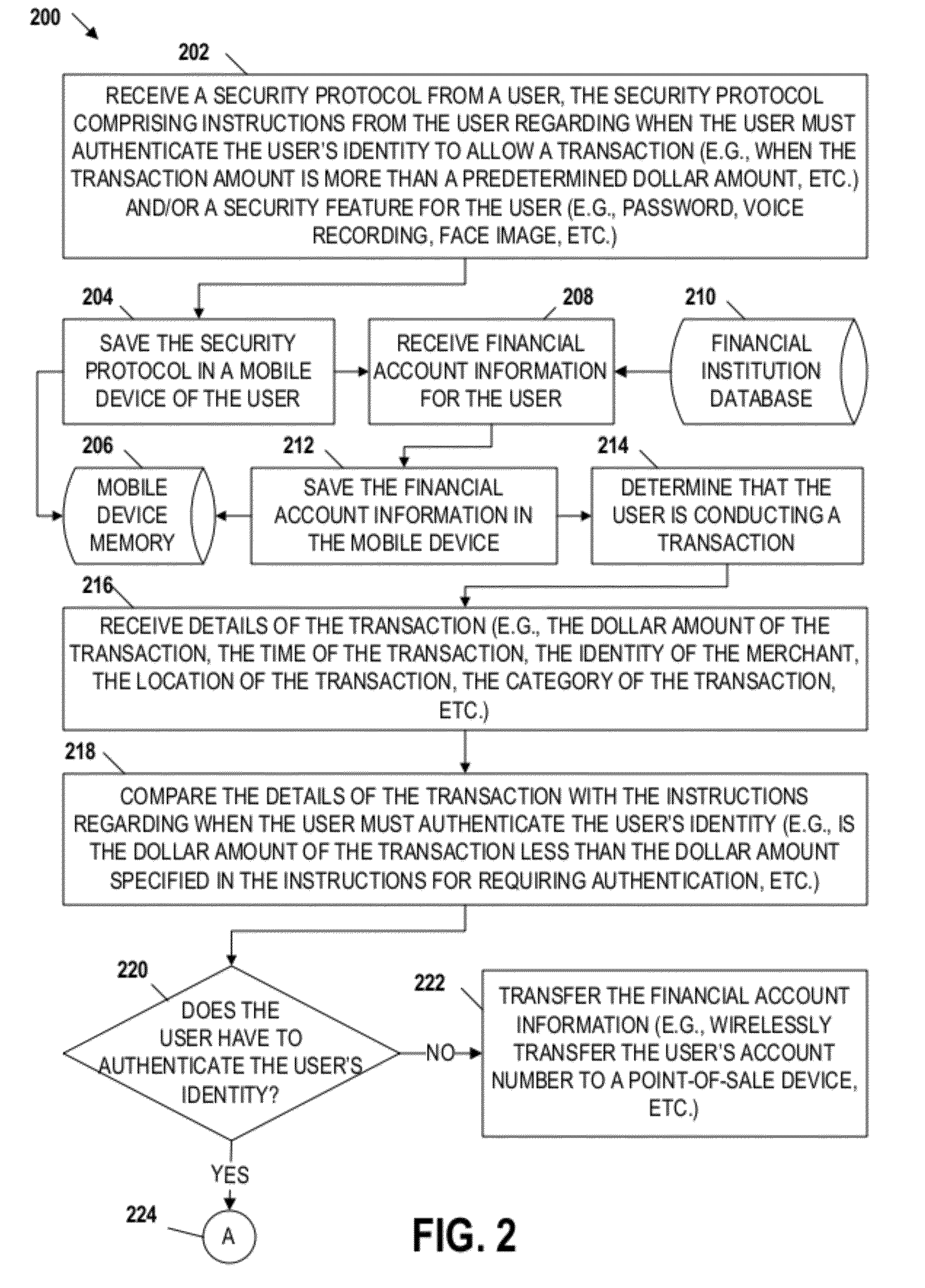
Mobile transaction device security system
Embodiments of the invention include apparatuses, methods, and computer-program products that provide for a unique financial transaction security system. In one embodiment, the financial transaction security system receives a security protocol from a user. The security protocol includes instructions for allowing transactions without authentication and security features for the user if authentication is necessary. The system then determines that the user is conducting a transaction, compares the transaction to the instructions, and determines whether the transaction can occur without authentication. If the user is required to authenticate his identity, the system requests input from the user, compares the input to the security feature, and determines if the user is authenticated. The user is able to customize both the instructions and the security features to provide greater control over financial transaction security.
Owner:BANK OF AMERICA CORP
Methods and apparatus for implementing a virtualized computer system
InactiveUS20060090136A1Error detection/correctionDigital computer detailsVirtualizationVirtual computing
In one aspect, a method of creating a virtualized computer environment that represents a real world computer environment is provided. The real world computer environment comprises a plurality of components, the plurality of components comprising a plurality of computer devices and at least one network device that implements a network that interconnects the plurality of computer devices, the real world computer environment comprising at least one security facility that implements at least one security function in the real world computer environment. The method comprises acts of including in the virtualized computer environment a virtualized representation of at least one of the plurality of computer devices in the real world computer environment and implementing the at least one security function in the virtualized computer environment. In another aspect, a virtualized representation of the at least one network device is provided. In another aspect, software is executed in the virtual computer environment.
Owner:MICROSOFT TECH LICENSING LLC
Portable data encryption device with configurable security functionality and method for file encryption
ActiveUS9049010B2Mitigates and eliminates vulnerabilityKey distribution for secure communicationUser identity/authority verificationPlaintextComputer hardware
A portable encryption device with logon access controlled by an encryption key, with an on board cryptographic processor for reconstituting the encryption key from a plurality of secrets generated by a secret sharing algorithm, optionally shrouded with external secrets using an invertible transform resistant to quantum computing attacks. Another embodiment provides file decryption controlled by a file encryption key, with the on board cryptographic processor reconstituting the file encryption key from a version of the file encryption key which has been shrouded with a network authorization code. A method for encryption of a plaintext file by hashing, compressing, and encrypting the plaintext file, hashing the ciphertext, hashing the plaintext hash and the ciphertext hash, and sealing the ciphertext together with the resulting hash. A portable encryption device for performing the method is also disclosed.
Owner:SPYRUS
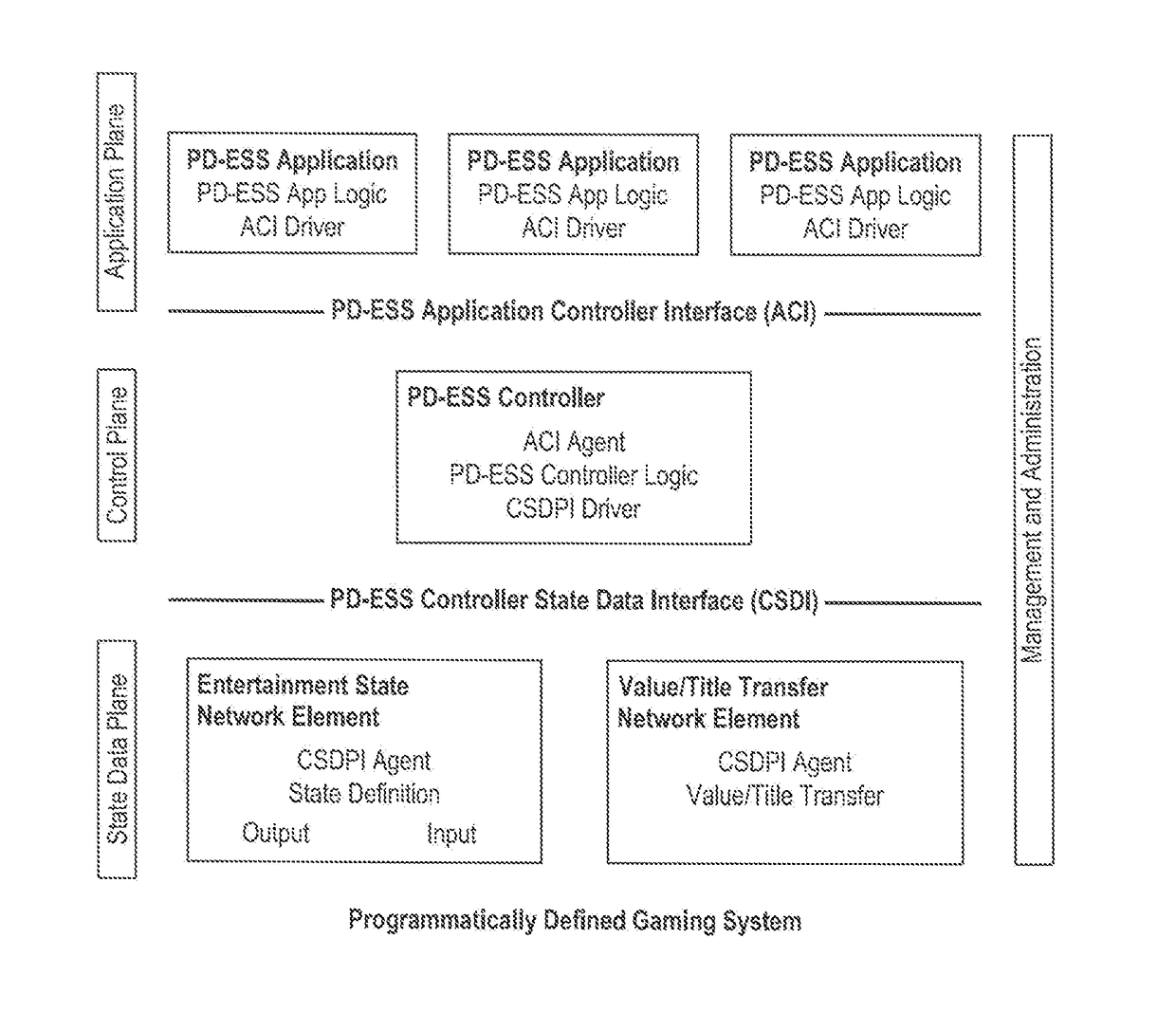
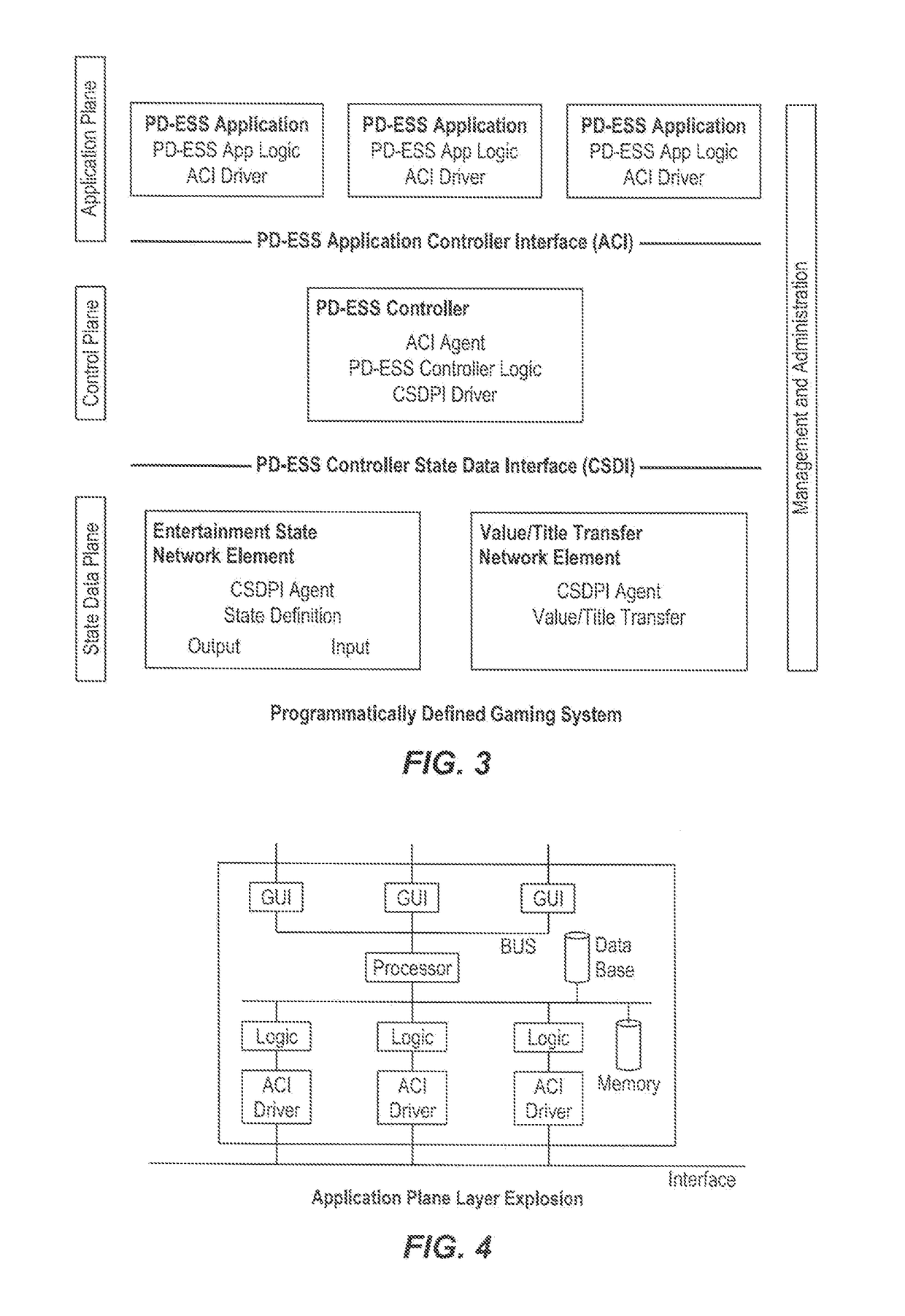
Architectures, systems and methods for program defined entertainment state system, decentralized cryptocurrency system and system with segregated secure functions and public functions
PendingUS20180247191A1Cryptography processingInterprogram communicationMotion detectorDisplay device
Systems and methods are provided for training an artificial intelligence system including the use of one or more human subject responses to stimuli as input to the artificial intelligence system. Displays are oriented to the human subjects to present the stimuli to the human subjects. Detectors monitor the reaction of the human subjects to the stimuli, the detectors including at least motion detectors, the detectors providing an output. An analysis system is coupled to receive the output of the detectors, the analysis system provides an output corresponding to whether the reaction of the human subjects was positive or negative. A neural network utilizes the output of the analysis system, generating a positive weighting for training of the neural network when the output of the analysis system was positive, and a negative weighting for training of the neural network when the output of the analysis system was negative.
Owner:MILESTONE ENTERTAINMENT LLC
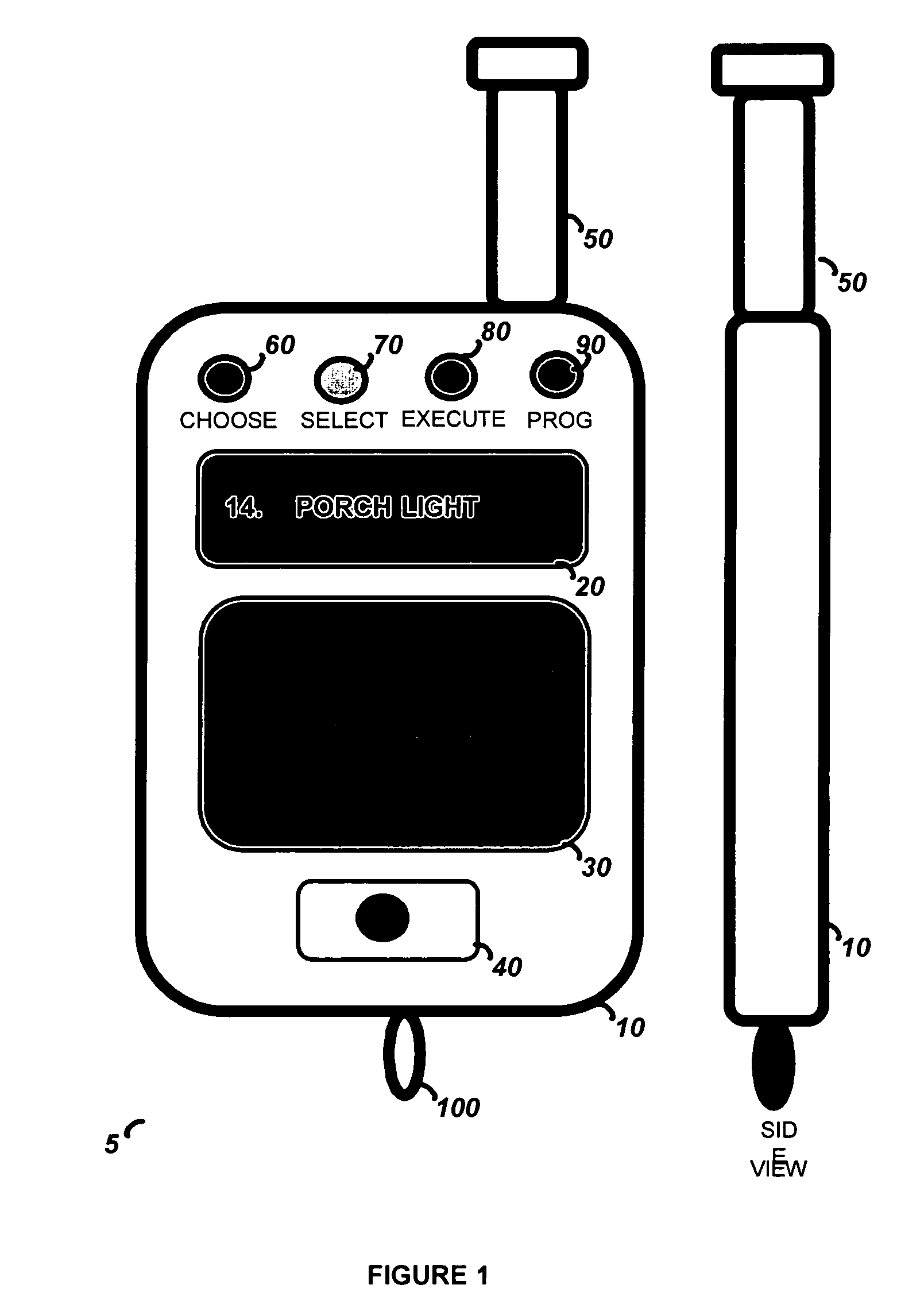
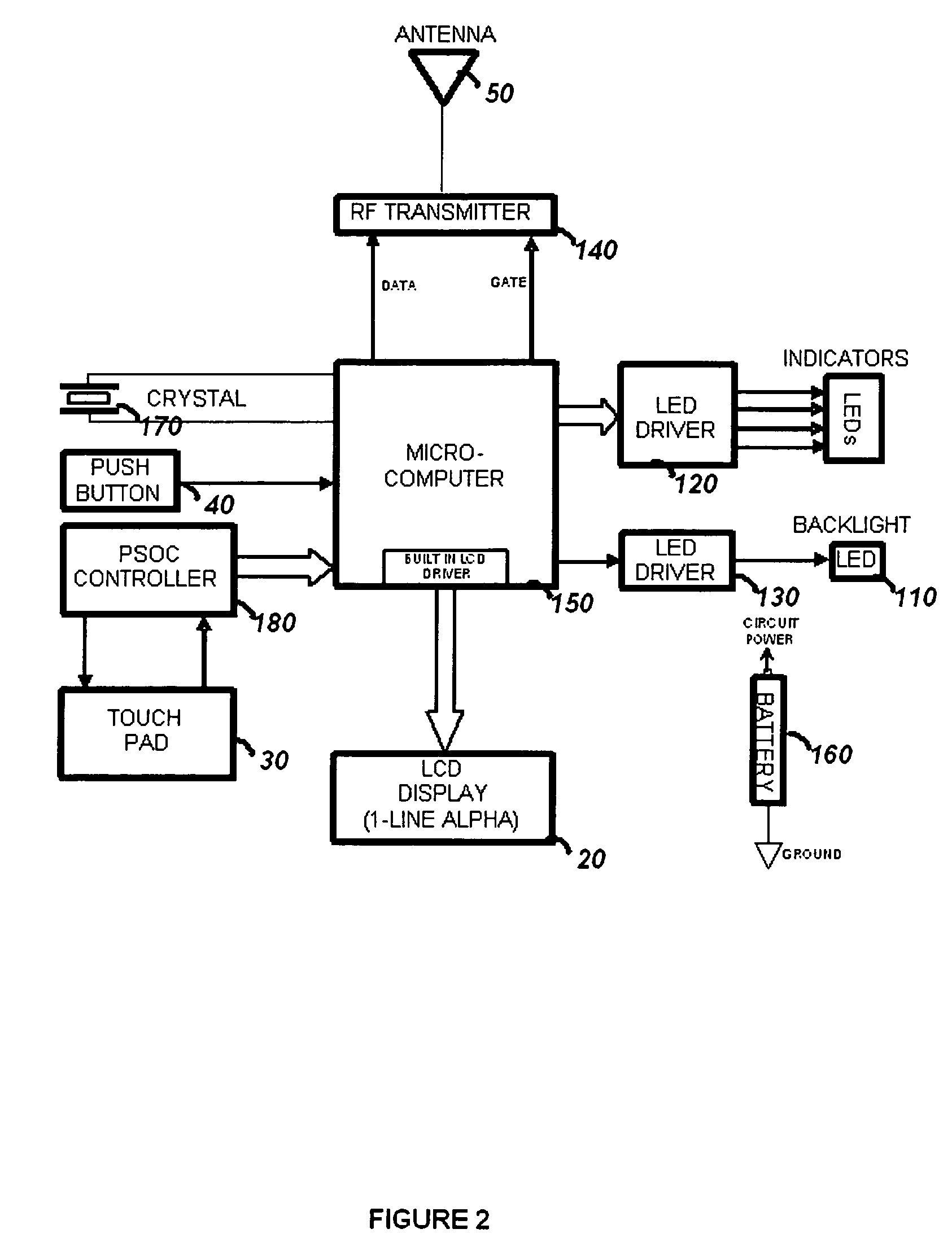
Touchscreen device for controlling a security system
The present invention is a hand held portable remote such as a key fob that allows a user to interact with the security system using a flat panel touch-pad. The touch-pad input allows a user to rapidly select and control a large number of security functions, such as Arm, Disarm, Panic, garage door open, lamp on / off, and lamp dimming control, etc. The security device comprises a housing, a wireless communication port for interface with the security system, a touch-pad input device, and processing circuitry. In order to operate the security device, the user generates a user input by creating a contact motion on the touch-pad input device with a fingertip. The contact motion may consist of a swiping motion, a tapping, or a circular motion. In order to distinguish the contact motion clearly, when the fingertip contact comprises a wider than normal contact, it causes the processing circuitry to not generate an output signal. The security device also comprises an LCD display for displaying alpha numeric control options to a user and LED indicators for indicating the modes of the processing circuitry.
Owner:ADEMCO INC
Method and apparatus for security policy management
InactiveUS7882537B2Reduce human interventionEasy to masterDigital data protectionResourcesGeneral purposeSecurity policy management
A security policy management system for deriving a security policy from setting details of security devices as components of an information system includes a setting information storage unit for storing setting information representing settings with regard to security functions of devices included in a network system to be managed, and a general-purpose security policy generator for generating a security policy including a description expressed in a format independent of descriptions depending on particular devices, based on the setting information stored in the setting information storage unit.
Owner:NEC CORP
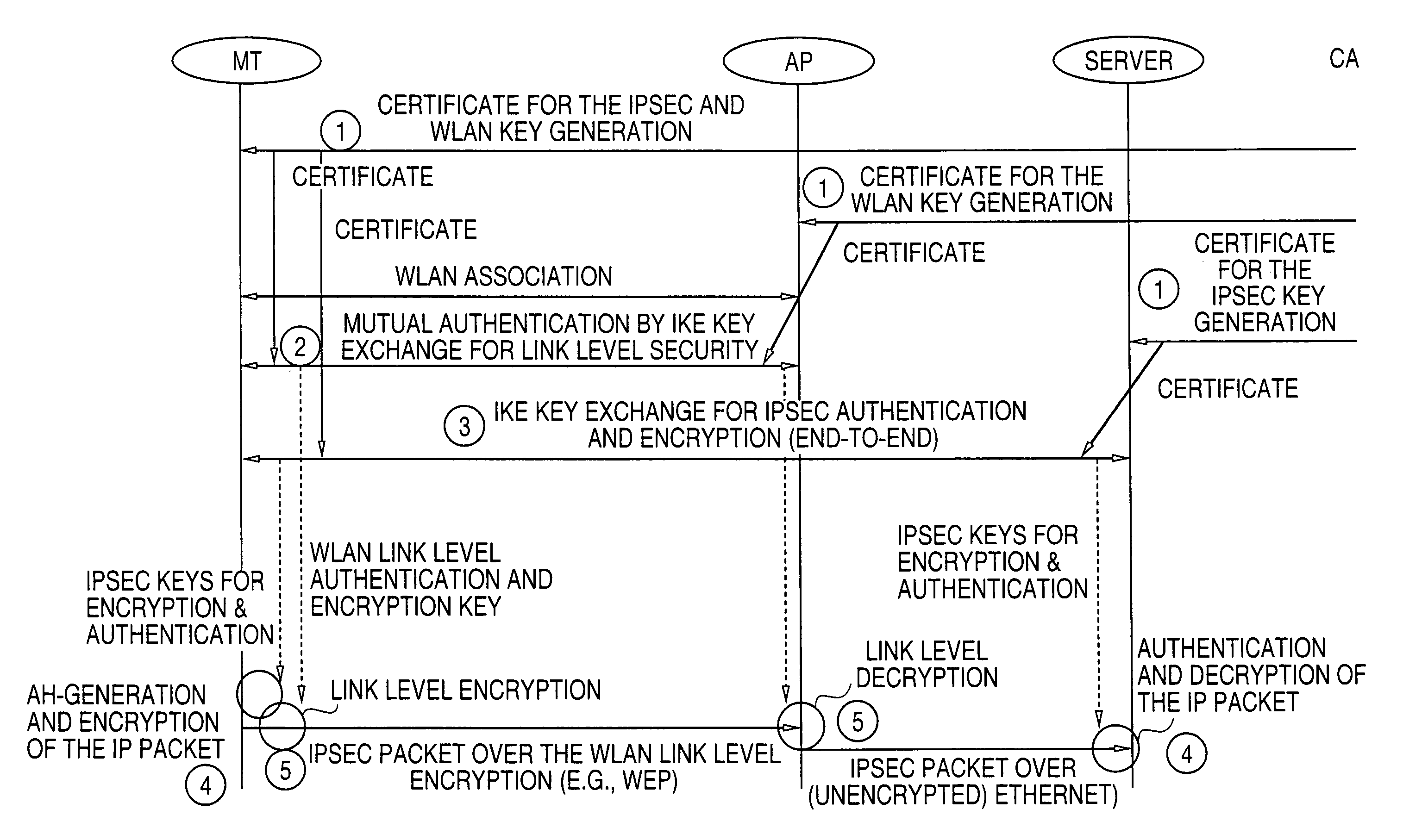
Key management methods for wireless LANs
InactiveUS7028186B1Work lessImprove securityUser identity/authority verificationNetwork topologiesSecurity functionMutual authentication
The security keys in the mobile terminals and access points of a wireless local area network (WLAN) are created, utilized and managed for a communication session between a mobile terminal and access point. Both the WLAN link level security protection and IP security functions of the network use the same Internet Key Exchange (IKE) key management protocol and use certificates in the same certificate hierarchy. When the mobile terminals associates with the network, it uses the IKE protocol with private keys and certificates to generate WLAN link level keys with the access point and provide mutual authentication.
Owner:CORE WIRELESS LICENSING R L
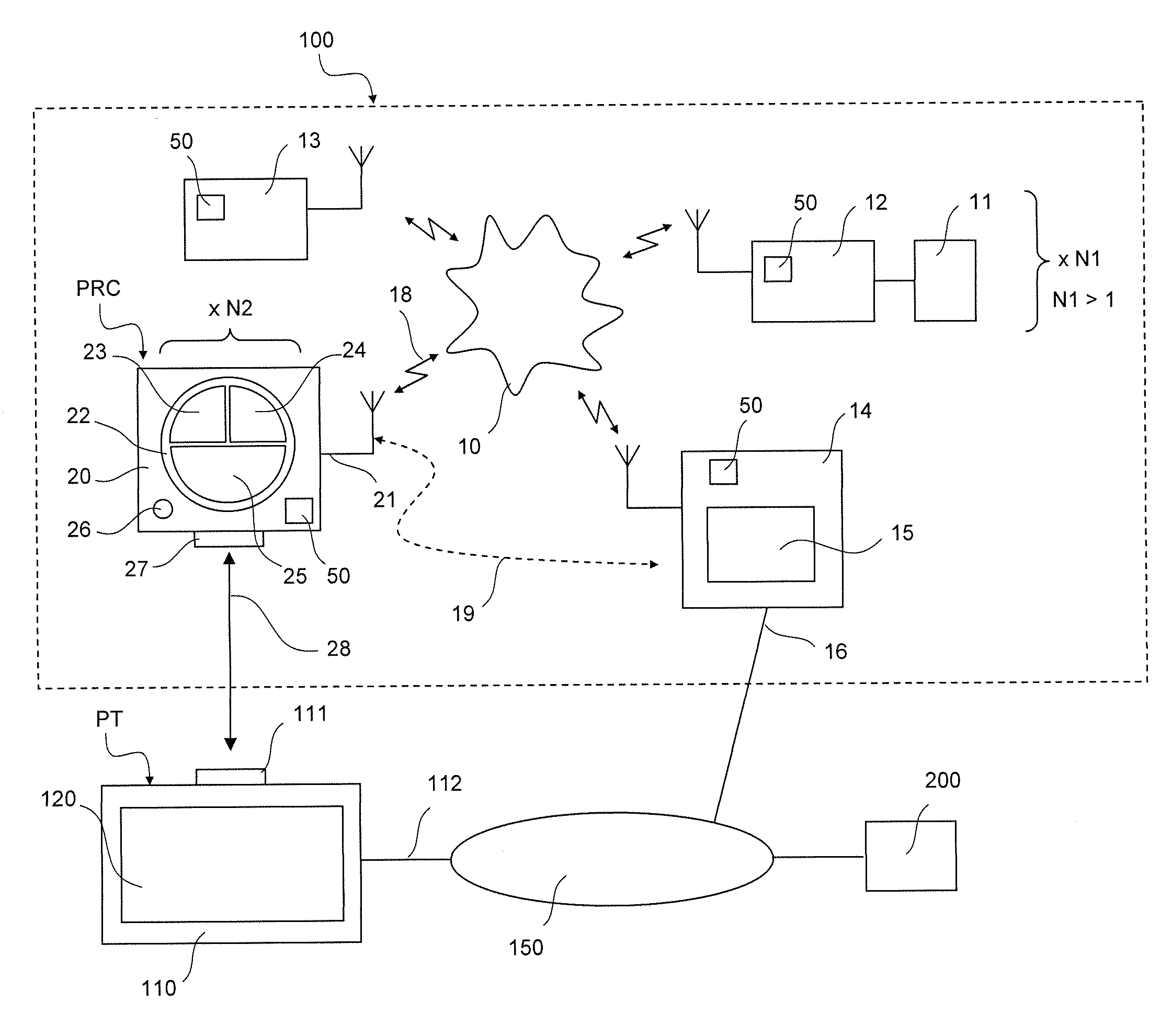
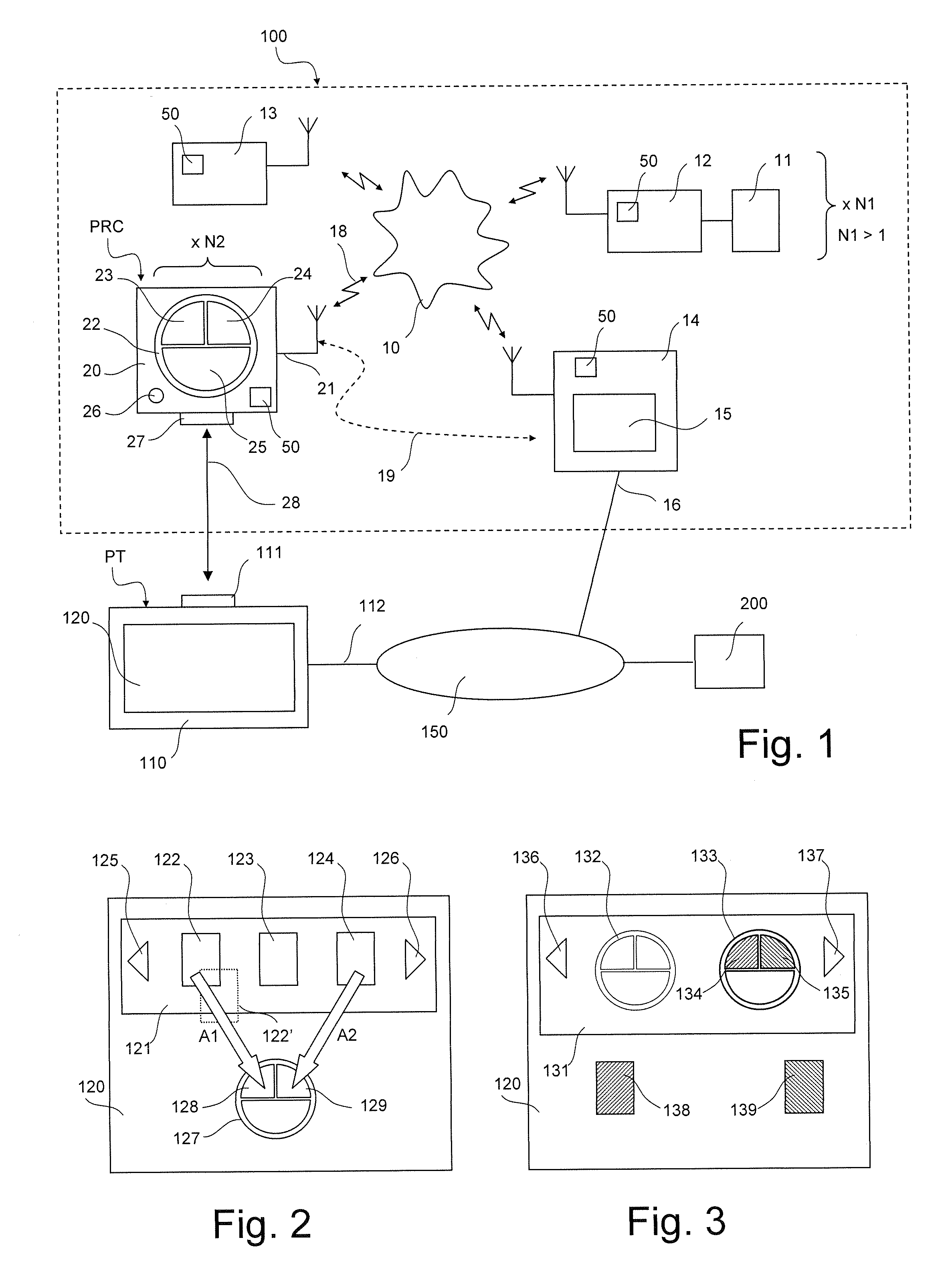
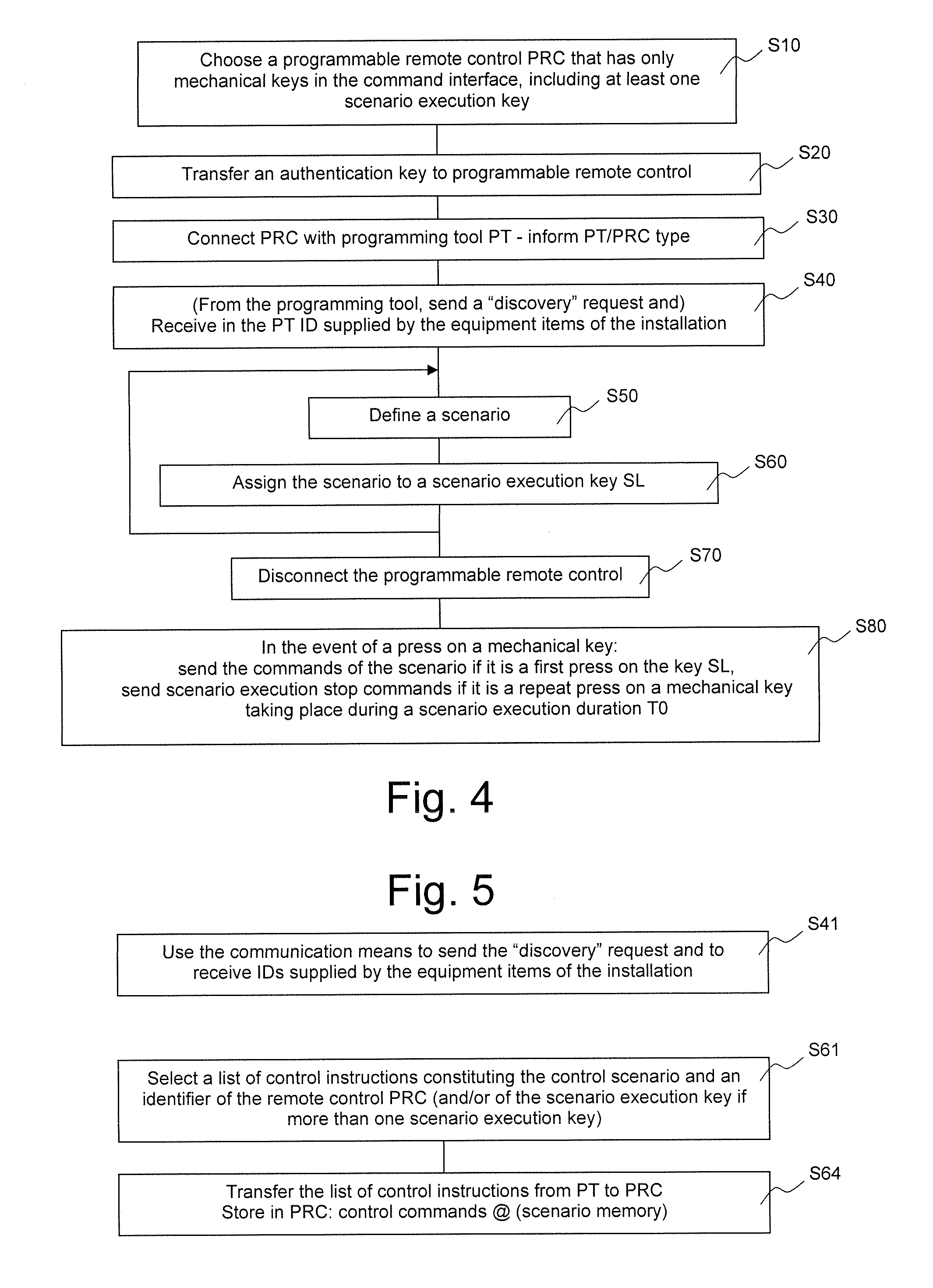
Assigning Scenarios to Command Buttons
InactiveUS20110208359A1Special service provision for substationSampled-variable control systemsNatural ventilationRemote control
A method of controlling an installation formed by a plurality of home automation equipment items linked to a building, and handling therein, depending on the type of home automation equipment item, thermal and visual comfort functions, such as heating and air conditioning, natural ventilation, lighting, solar protection functions, and / or security functions, such as closure and / or alarm functions, the home automation equipment items communicating over one and the same home automation network. A programmable remote control implementing the control method.
Owner:SOMFY SAS
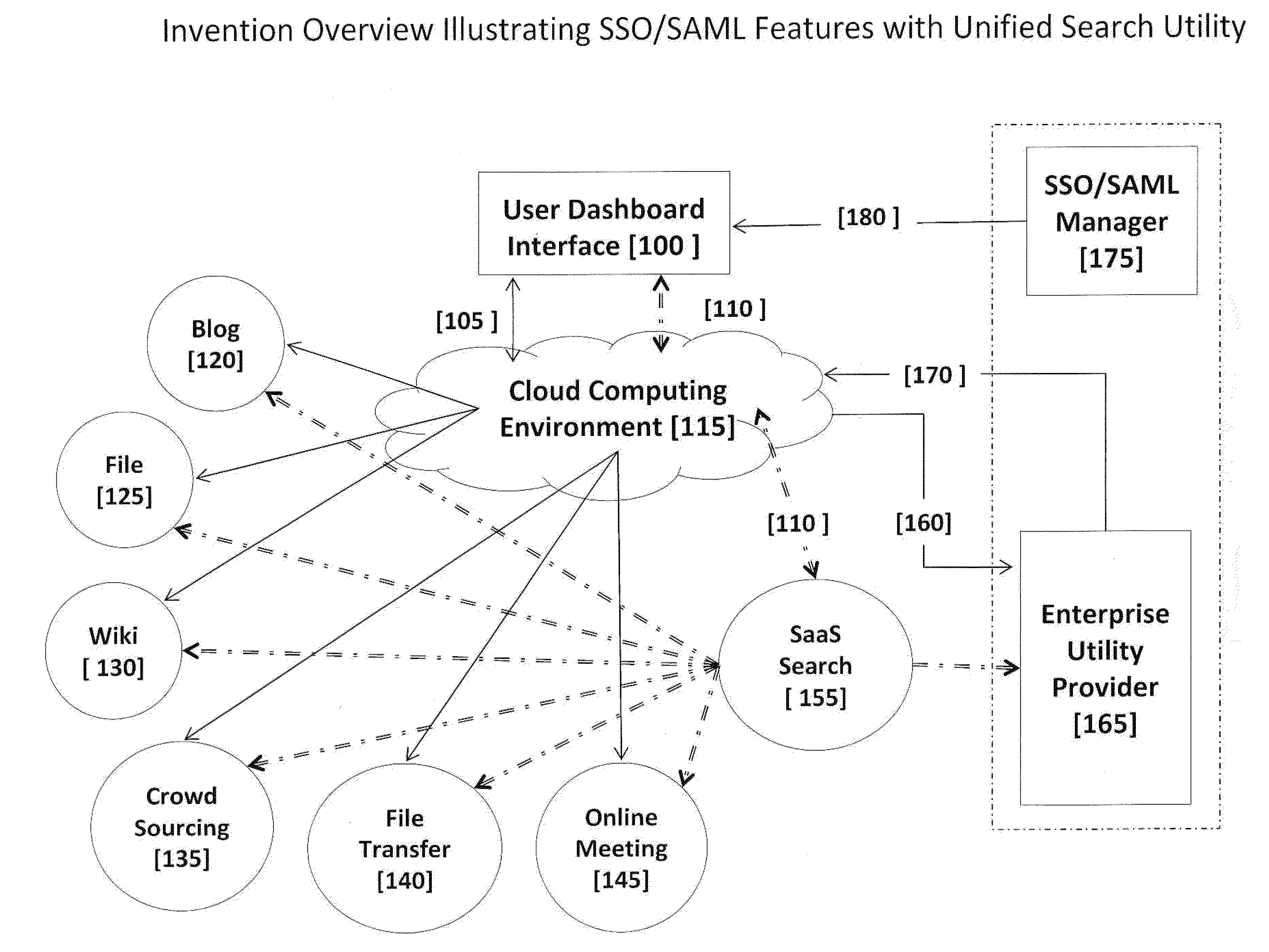
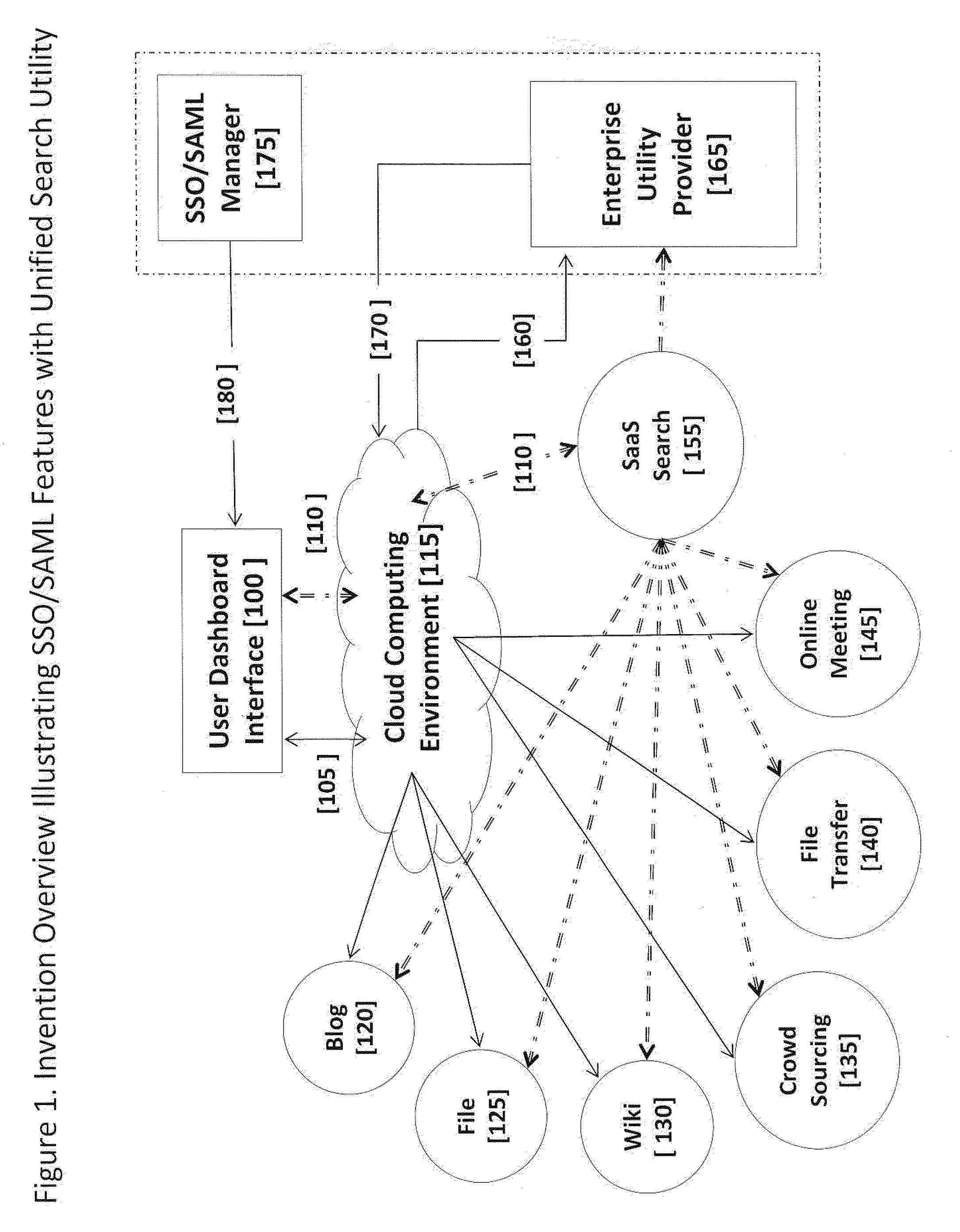
Integrated Enterprise Software and Social Network System User Interfaces Utilizing Cloud Computing Infrastructures and Single Secure Portal Access
InactiveUS20120216125A1Reduced revenue opportunityInput/output for user-computer interactionMultiple digital computer combinationsDashboardCommunications system
A software-based method and system to provide a secure user interface on multiple and diverse electronic computing devices with a customized and secure dashboard feature. The systems and methods simultaneously integrate internally generated software utilities of an enterprise with externally accessed software operating in a ‘cloud computing’ environment. The systems and methods can be used in management and operations that use computer based software, data management, creative processes and communication systems. The systems and methods reduce the requirement for additional programming to integrate or interchange equivalent and independently developed software for use within an enterprise. The systems and methods permit social network communications between members of an enterprise and an external community. The security features of the user interface portal permit collaborations between parties in an external community and enterprise members that can develop new processes that remain proprietary to the enterprise and parties of an external community.
Owner:ZAMA INNOVATIONS LLC
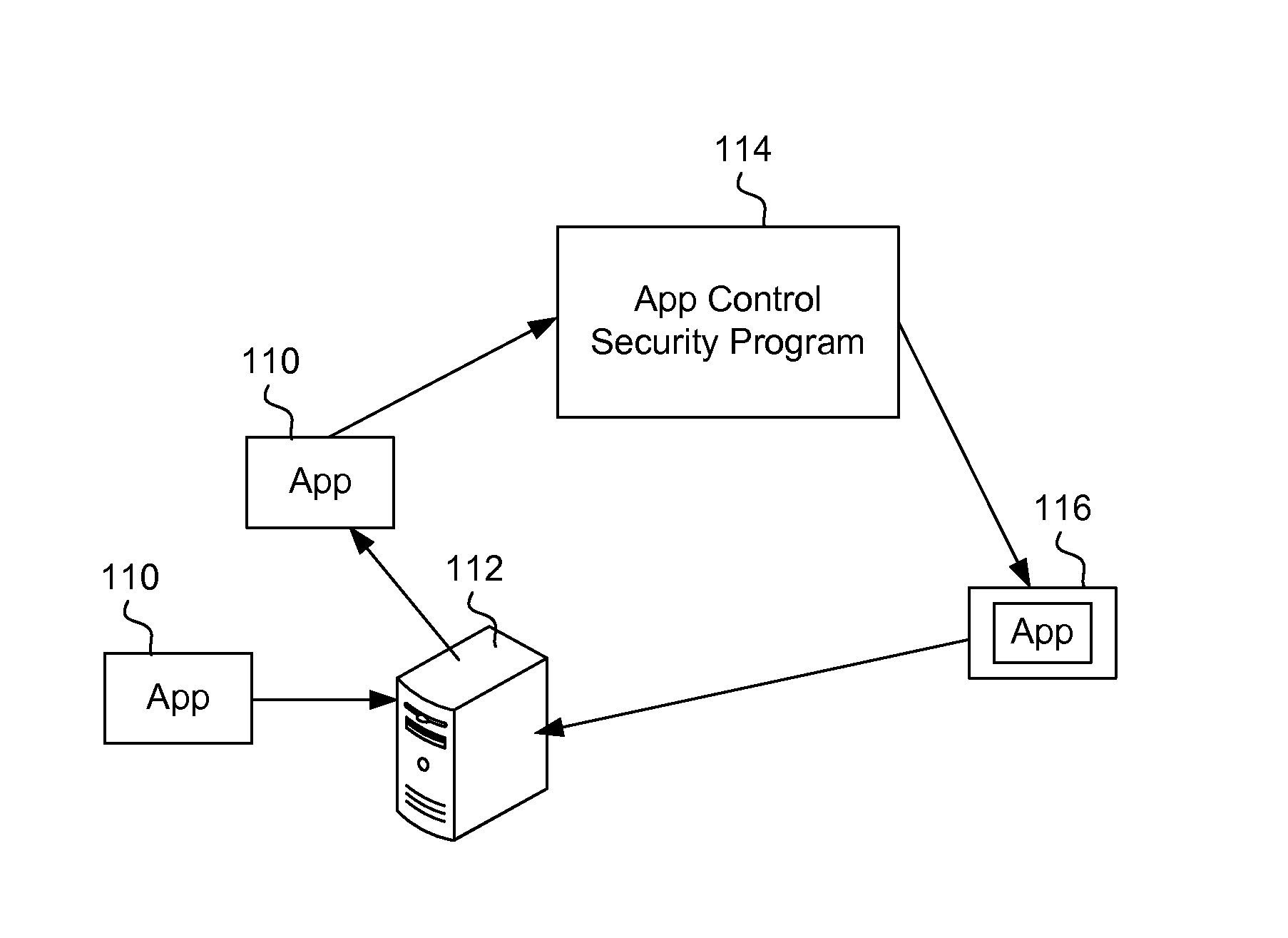
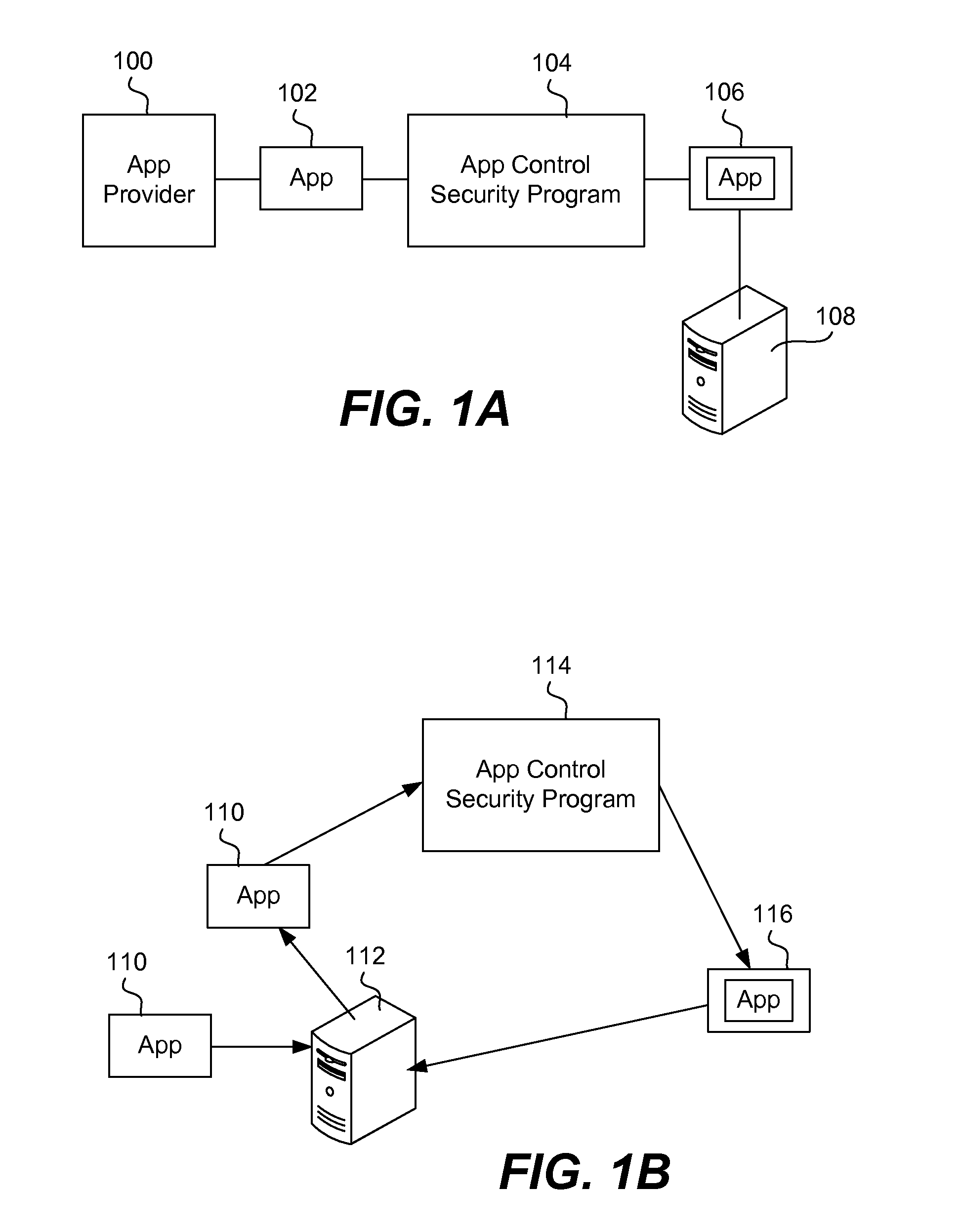
Secure execution of unsecured apps on a device
ActiveUS20120304310A1Digital data processing detailsAnalogue secracy/subscription systemsSecurity functionBreaking point
An app is secured on a mobile device by being deconstructed or unbundled into multiple modules, where a module is a segment of app code that performs a particular function. It is then determined which modules from the multiple modules perform some type of security function, for example, a function dealing with confidential or security-related data. These modules, forming a group of modules, are loaded into a trusted execution environment. The app is then re-bundled so that it has the first plurality of modules and the second plurality of modules. The app executes in a manner where the high security functions execute so that break points cannot be inserted into the app code. The re-bundling is done automatically in an app security wrapping process. Security constraints are added to the app.
Owner:BLUE CEDAR NETWORKS INC
Connector and receptacle containing a physical security feature
InactiveUS7325976B2Imparts physical securityFacilitates discriminationIncorrect coupling preventionCoupling light guidesPhysical securityInformation networks
A network comprising: (a) a plurality of different receptacles for facilitating an optical connection to different information networks requiring different access authorization, each different receptacle coupled to one and only one different information network, each receptacle having an inner surface with a first geometry, the first geometry comprising at least a slot, a certain number of receptacles having different first geometries in which the slots are in different positions; and (b) a plurality of different plugs for coupling with the different receptacles, each plug having a second geometry, the second geometry comprising at least a key in a certain position, the certain number of plugs having different second geometries in which the keys are in different positions, each different first geometry corresponding to one and only one second geometry such that the plugs and receptacles of corresponding first and second geometries are mating pairs.
Owner:COMMSCOPE TECH LLC
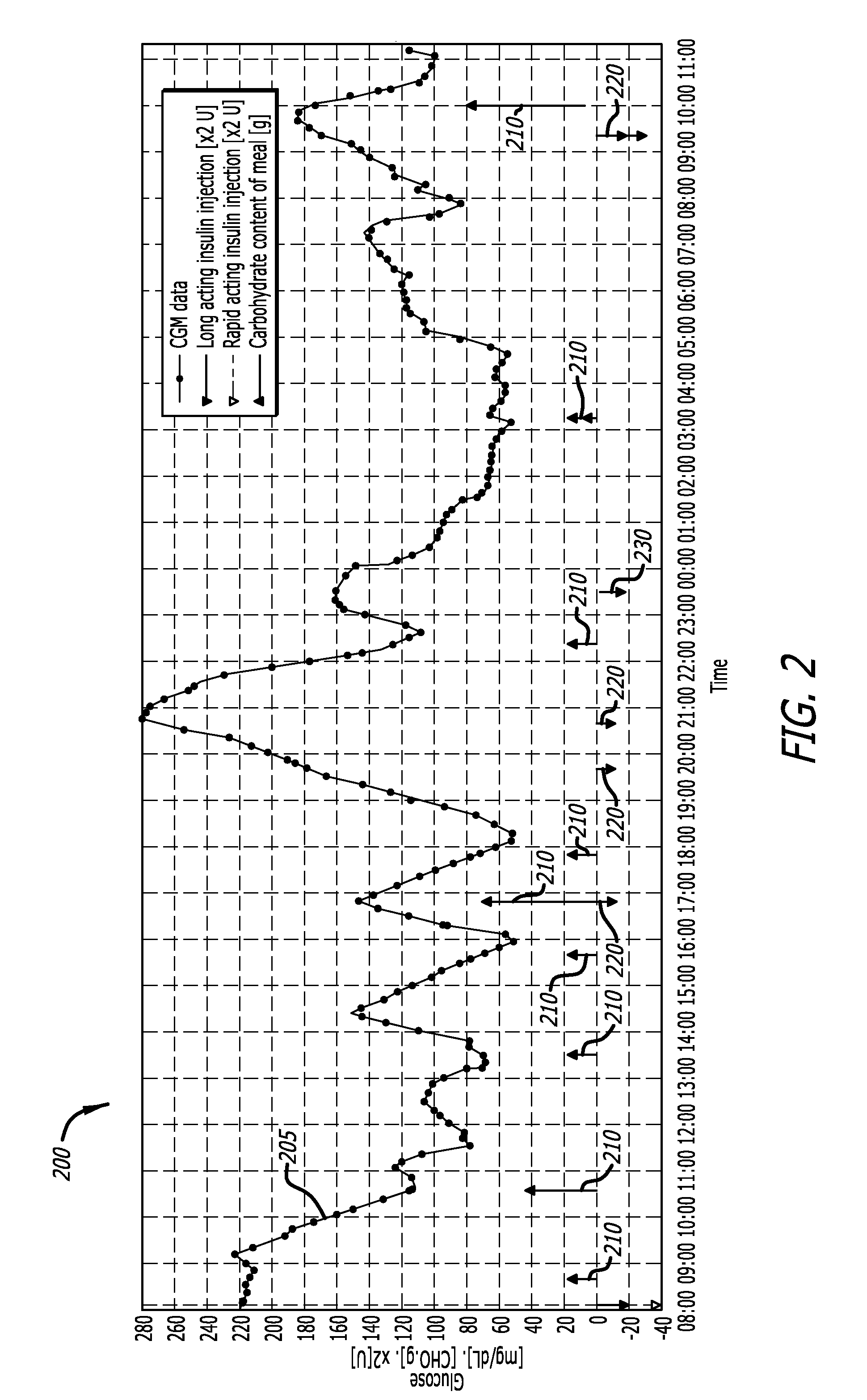
Safety features for integrated insulin delivery system
ActiveUS20100298765A1Preventing hypoglycemiaLimited hyperglycemiaDrug and medicationsMedical devicesGlucose sensorsHypoglycemia
Safety features are applied to an integrated insulin delivery system to enhance safety while accounting for glucose sensor bias and calibration errors. One safety feature includes comparisons of calibrations of the sensor to nominal sensitivity and taking action, such as limiting insulin delivery or taking a further calibration of the sensor. In another feature, an automatic resumption of a basal delivery rate is programmed into the delivery device to avoid the possibility of complete loss of delivery of insulin in the event that communication with the delivery device is disrupted. Other features include steps taken to avoid hypoglycemia in the event that the sensor is negatively biased.
Owner:ABBOTT DIABETES CARE INC
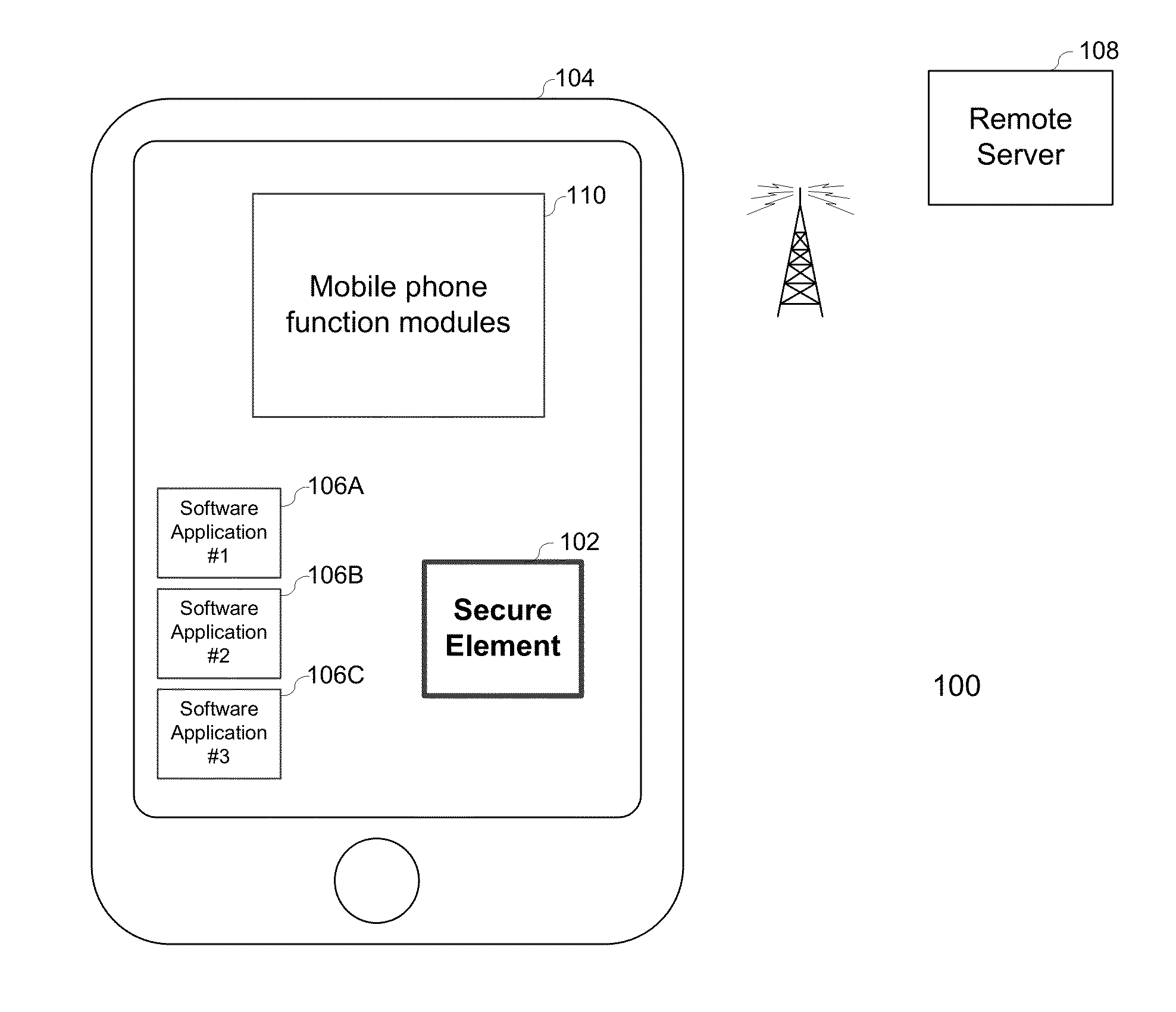
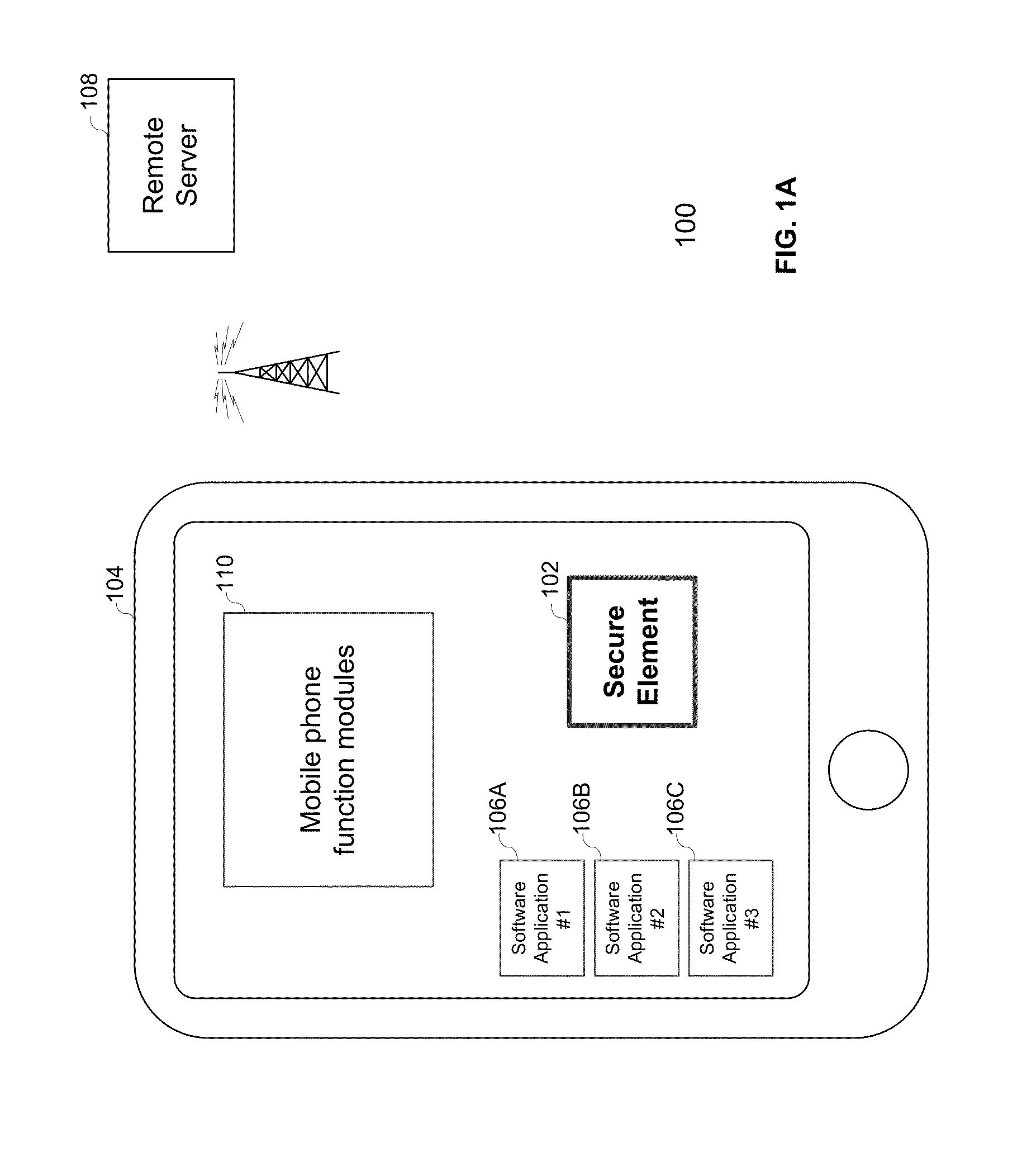
Embedded secure element for authentication, storage and transaction within a mobile terminal
ActiveUS20140013406A1Improve security levelImprove securityNear-field transmissionDigital data processing detailsEmbedded securityApplication software
Various embodiments of the present invention relate to incorporating an embedded secure element into a mobile device, and more particularly, to systems, devices and methods of incorporating the embedded secure element into a mobile device for identity authentication, data storage and processing in trusted transactions. These trusted transactions require a high security level to protect sensitive data or programs in bank account management, purchasing orders, contactless payment, passport verification, and many other high-security applications. The secure element will provide a root of trust such that that applications running on the mobile device are executed in a controlled and trusted environment. In addition to conventional password or encryption protection, alternative security features are introduced from both software and hardware levels based on the embedded secure element. Therefore, the security level of the mobile device is not only enhanced, but also may potentially exceed that of the conventional POS terminals.
Owner:MAXIM INTEGRATED PROD INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com