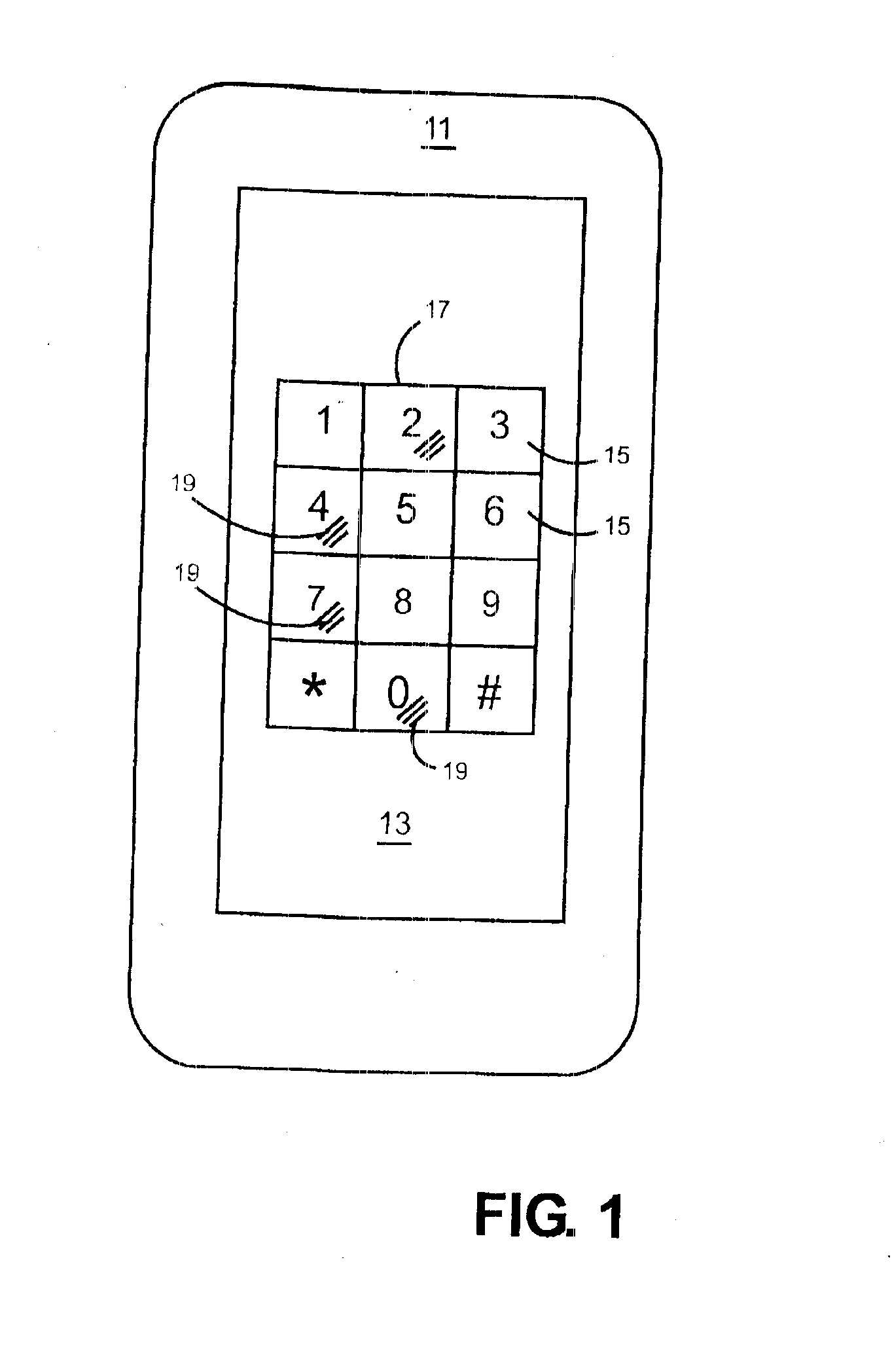
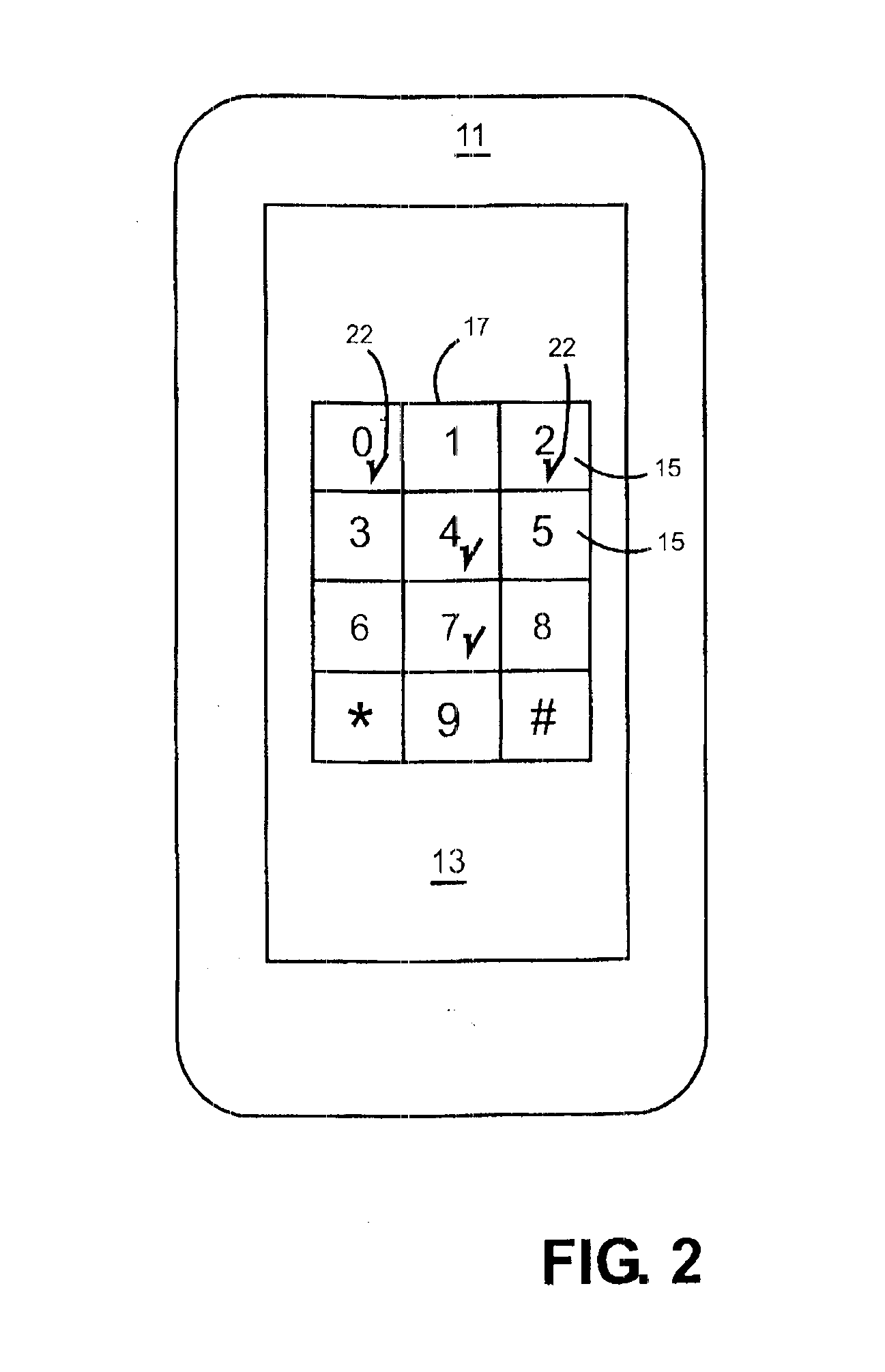
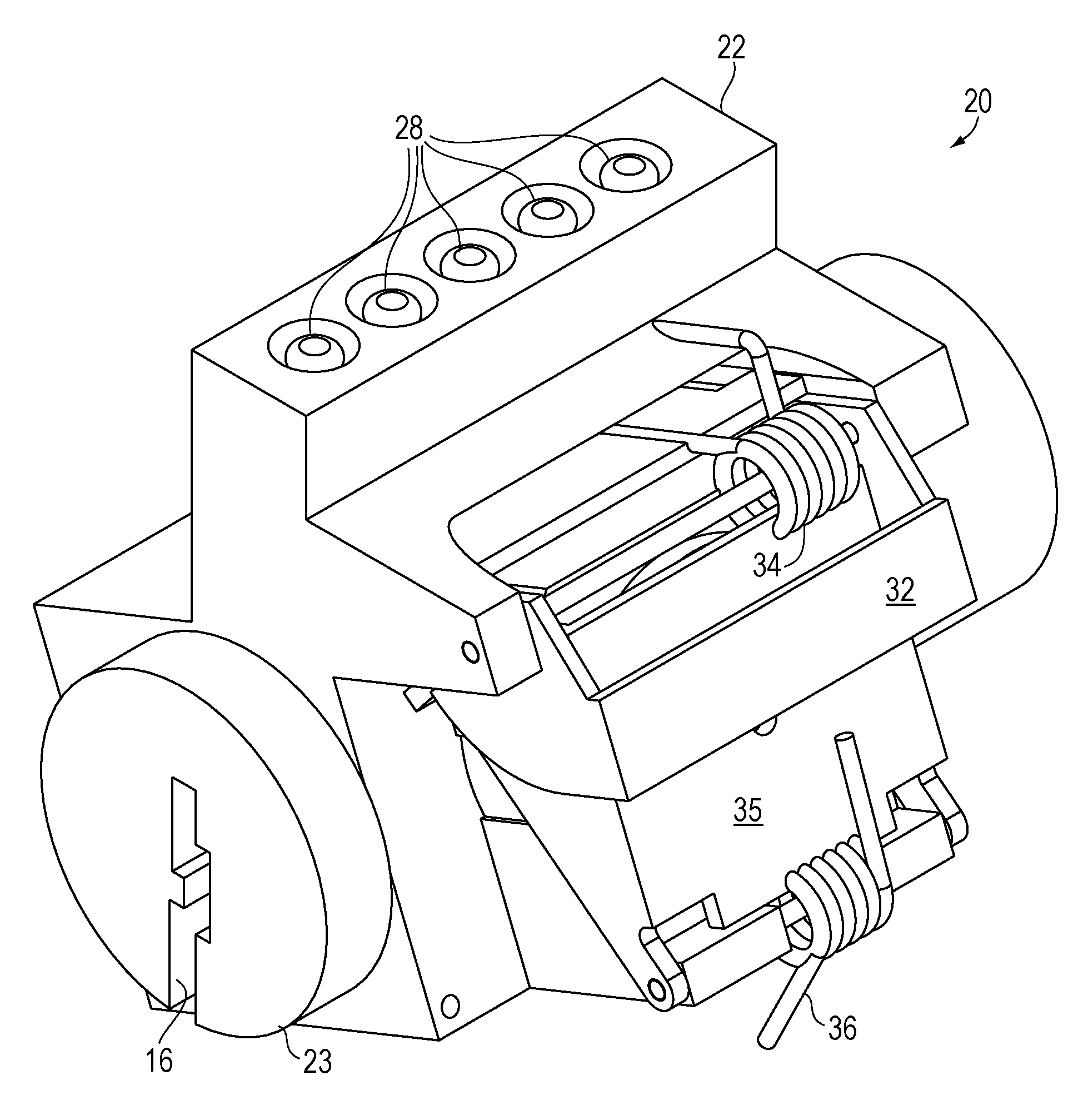
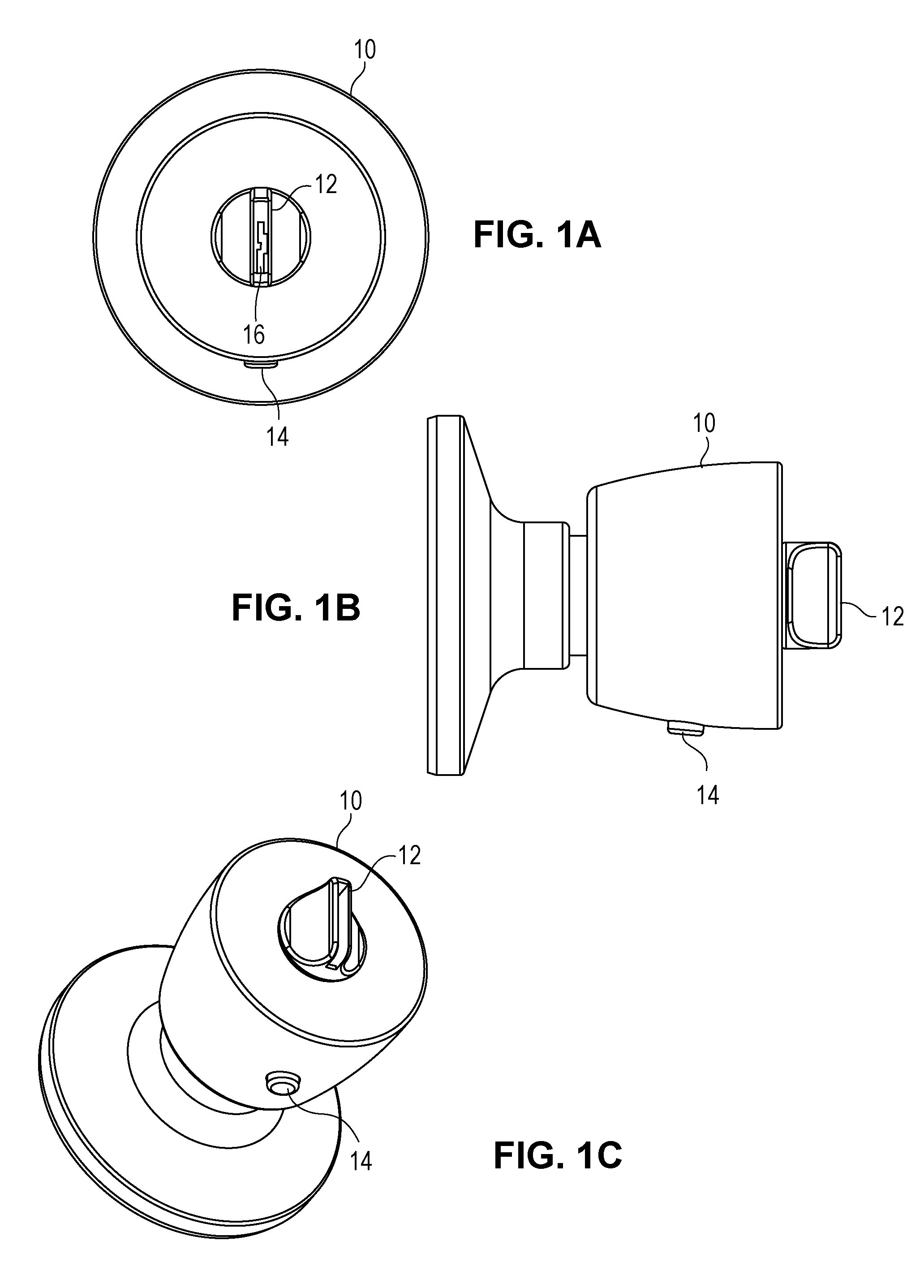
Patents
Literature
64 results about "Coded Entry" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
An entry code is a five-digit random number that is needed to enroll for a class when a pre-requisite or permission is required and Highline does not have a record that the student has met the pre-requisite.
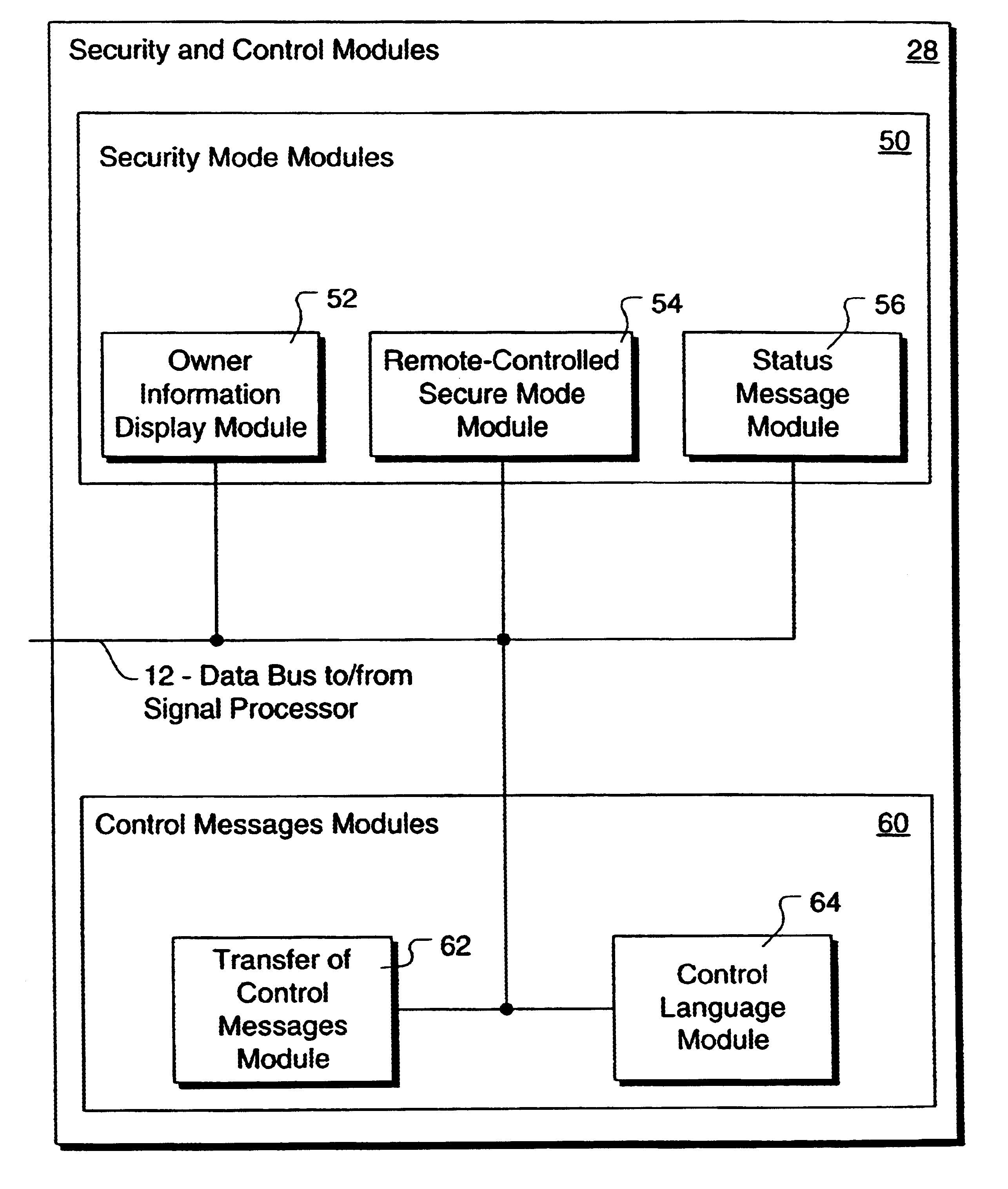
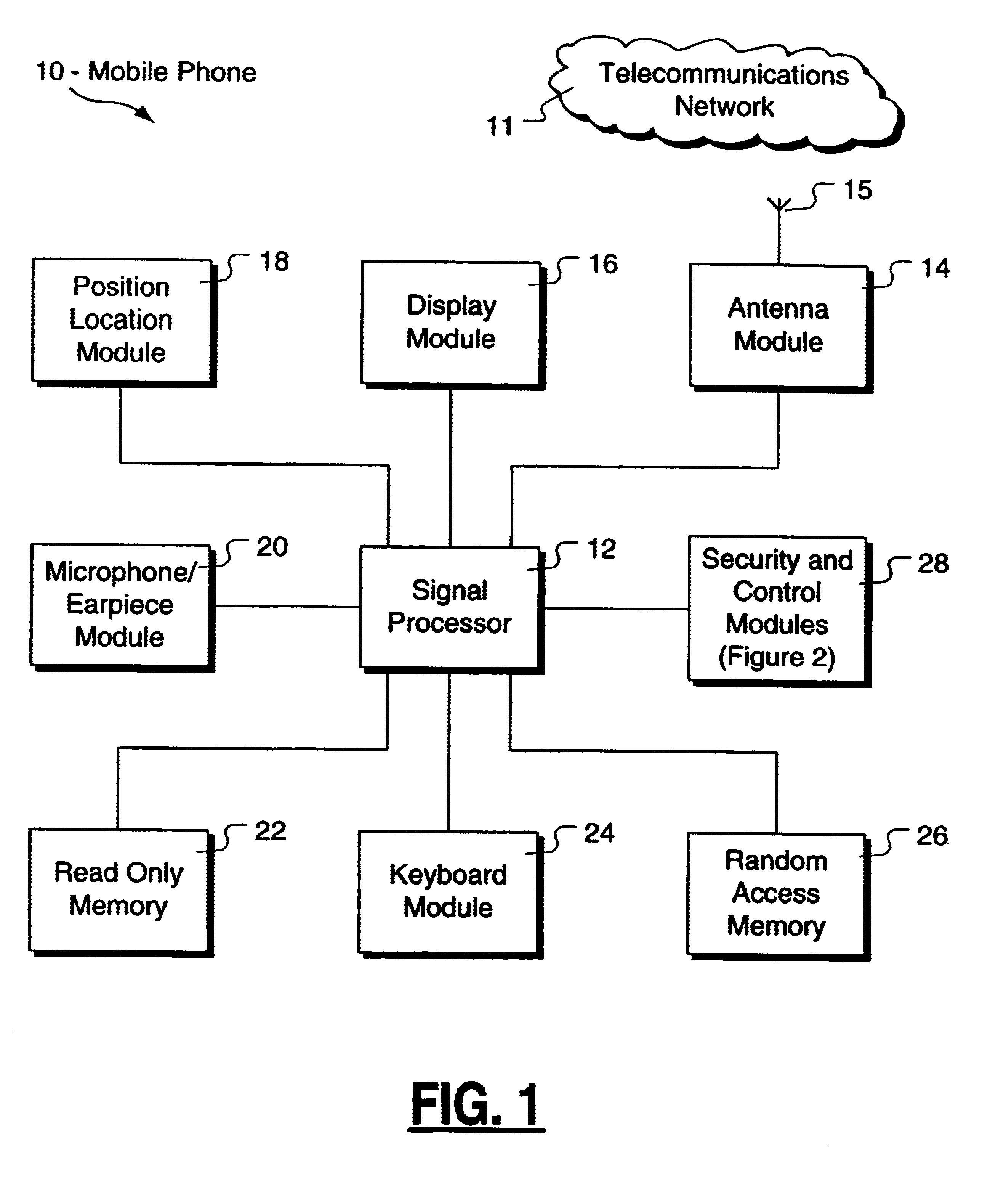
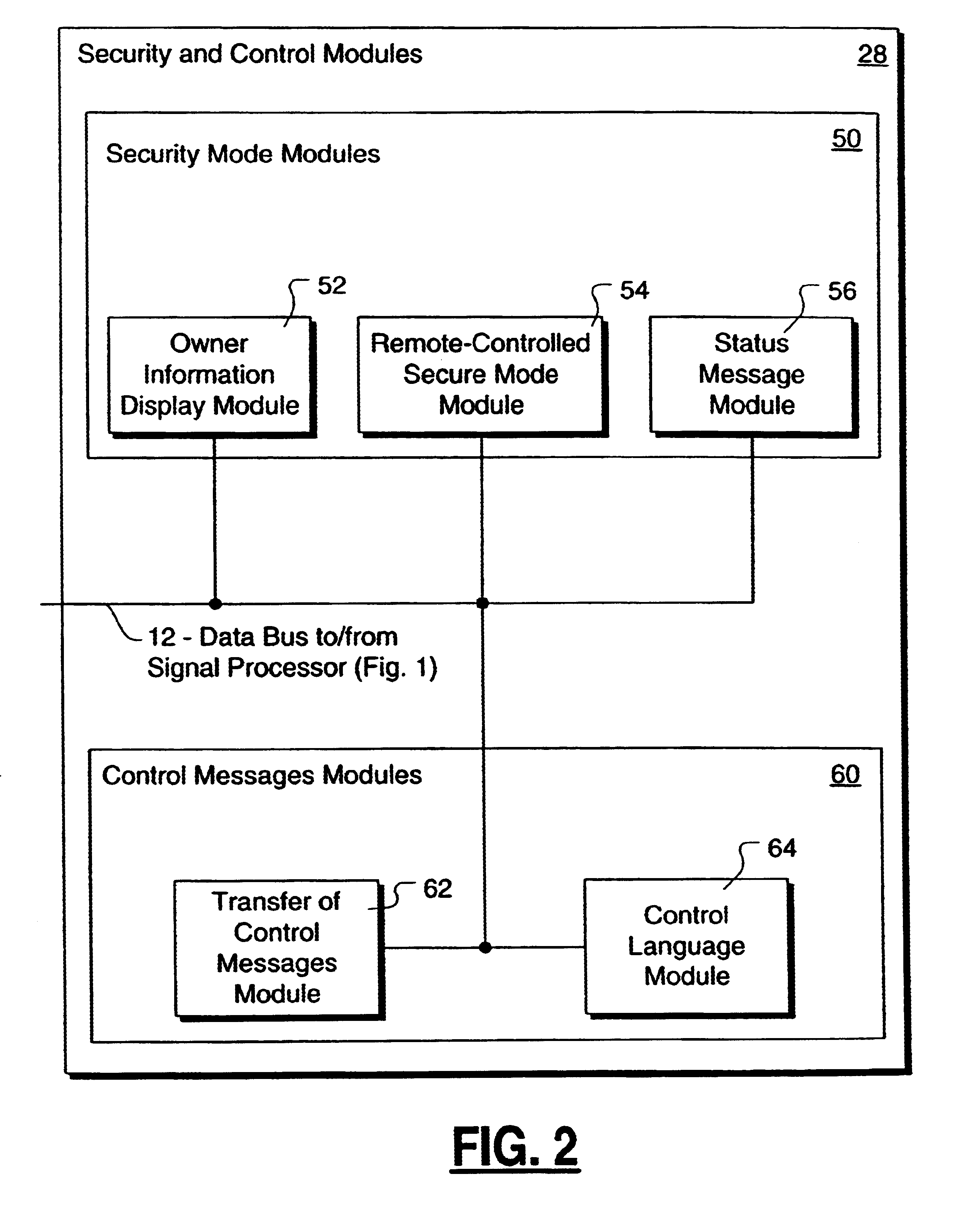
Method and apparatus for controlling and securing mobile phones that are lost, stolen or misused
InactiveUS6662023B1Unauthorised/fraudulent call preventionEavesdropping prevention circuitsSecure stateStart up
A method and apparatus is provided for controlling a mobile phone when it has been lost or stolen in order to prevent its use except to help the owner find it. Controlling the phone remotely may be implemented via a known Short Messaging System, for example. The security features provided are as follows: (1) Displaying contact information (phone number) of the owner on screen when the mobile phone can not start up normally, for example, due to an incorrect security code entry; (2) Setting the mobile phone in a secure state where it can only be used to call one number (Emergency calls are of course always possible.); and (3) Commanding the mobile phone to send information about its location and usage via SMS to a given number.
Owner:NOKIA TECHNOLOGLES OY
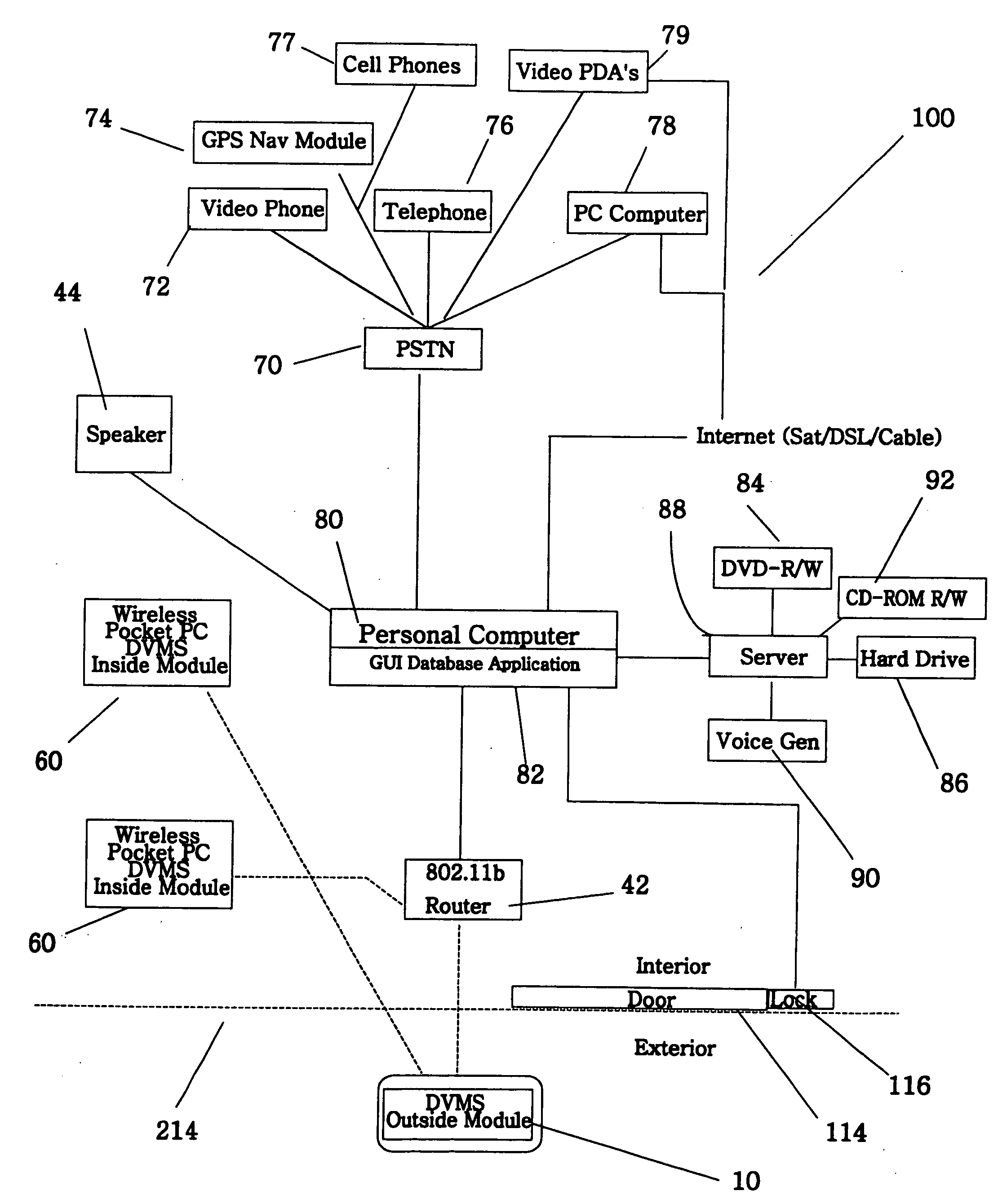
Automated audio video messaging and answering system
ActiveUS20050285934A1Facilitate communicationWide bandwidthTwo-way working systemsDigital videoAudio Media
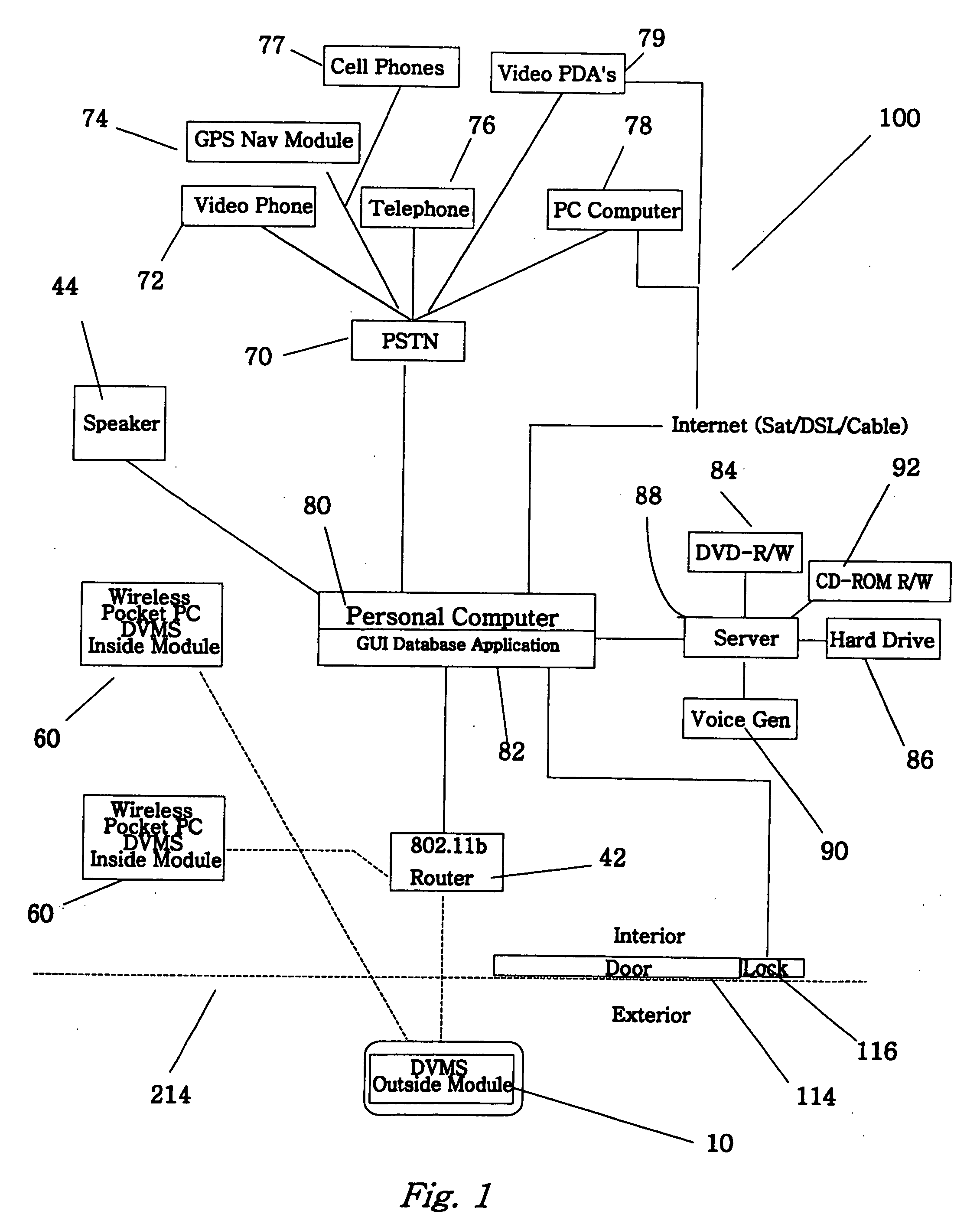
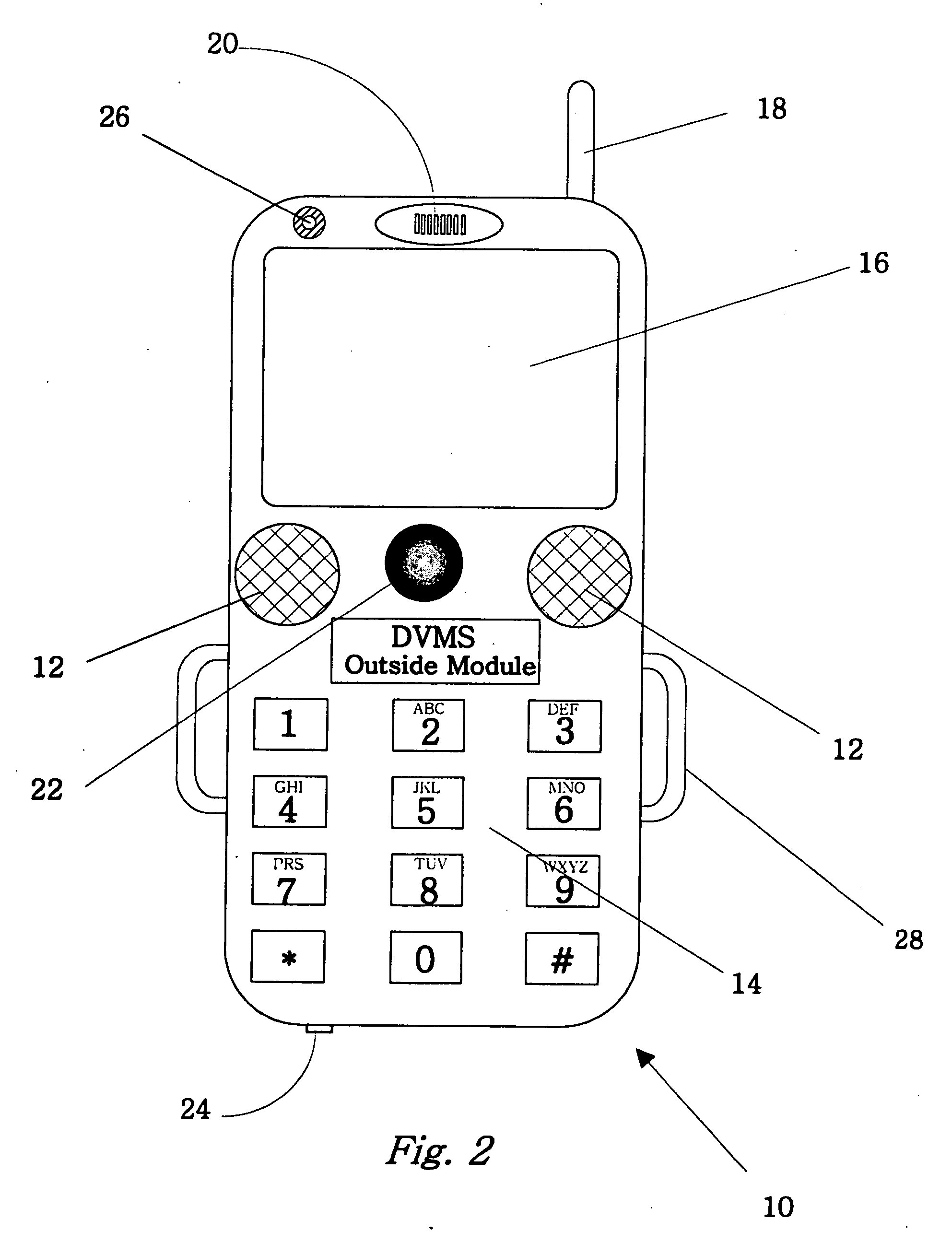
The invention is an audio-video communication and answering system, where system's properties make it particularly suitable as a Digital Video Messaging System for, amongst other things, answering the door. The elements of the system are a DVMS outside module that is a wireless pocket PC with a proximity sensing, a video camera, a microphone, a speaker, a digital transmitter, a digital receiver, and a keypad; a computerized controller that is a personal computer with components for plaving and recording video and audio media; a DVMS inside module having a screen, a microphone, a speaker, a digital transmitter, a digital receiver, and a keypad; a wireless mode; and a DVMS database application with a graphic user interface. The computerized controller is in communication with a public switching telephone network enabling communication with remote peripheral devices, such as a cell phone, PDA, or computer. The system is based on the Microsoft Windows® Mobile 802.11b to coordinate communication between elements. The database application coordinates responses to prompts and events. The proximity sensor activates the system when the sensor detects the visitor's presence. This then starts a series of prompts and interaction prescribed by the application. The system includes an electrically actuated lock that can be actuated through a code entry or remotely. The system enables a visitor to communicate with an occupant either offsite or onsite, where the visitor never knows the occupant's location, unless the occupant discloses his location.
Owner:SB IP HLDG LLC
Search method using coded keys
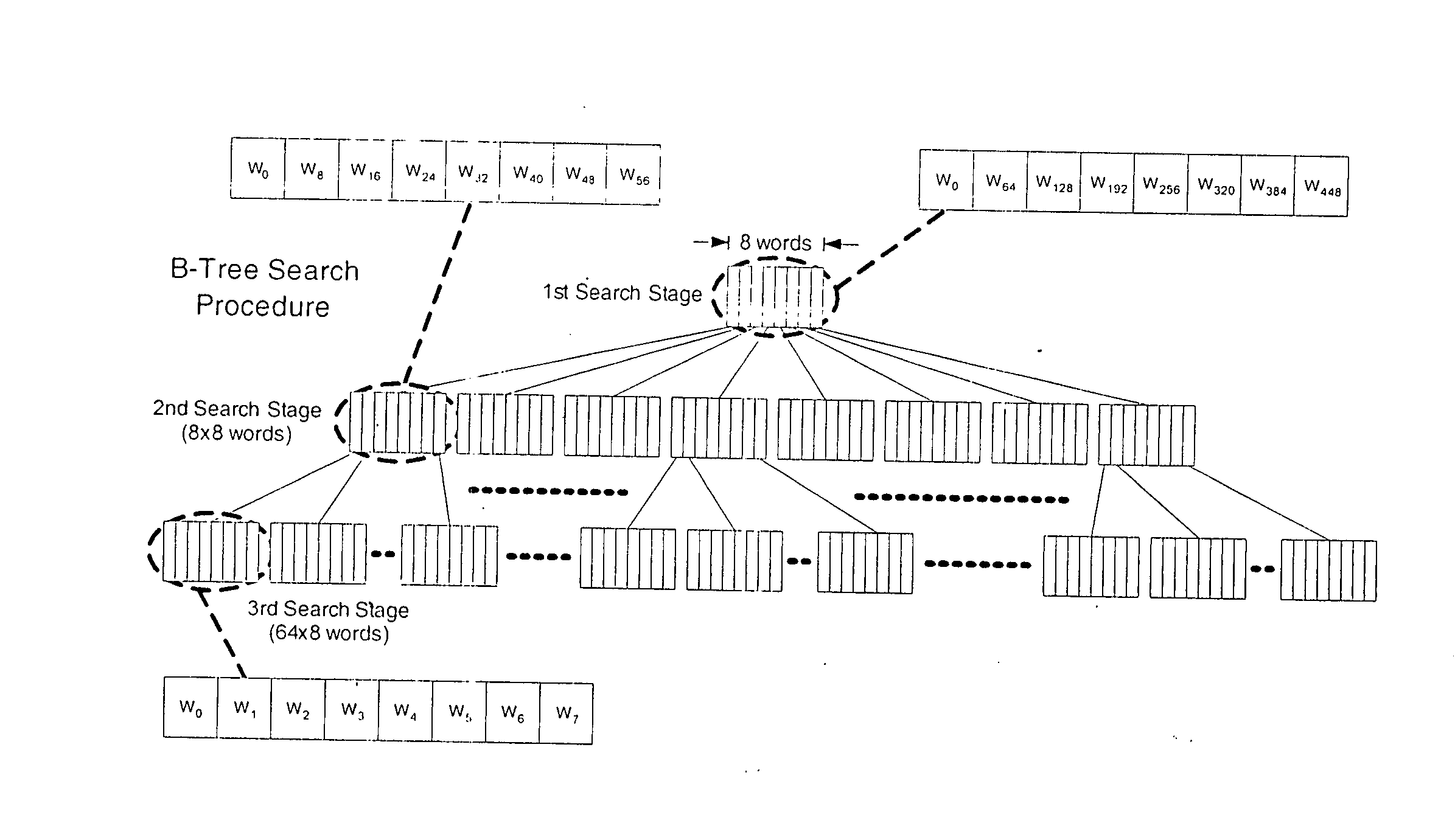
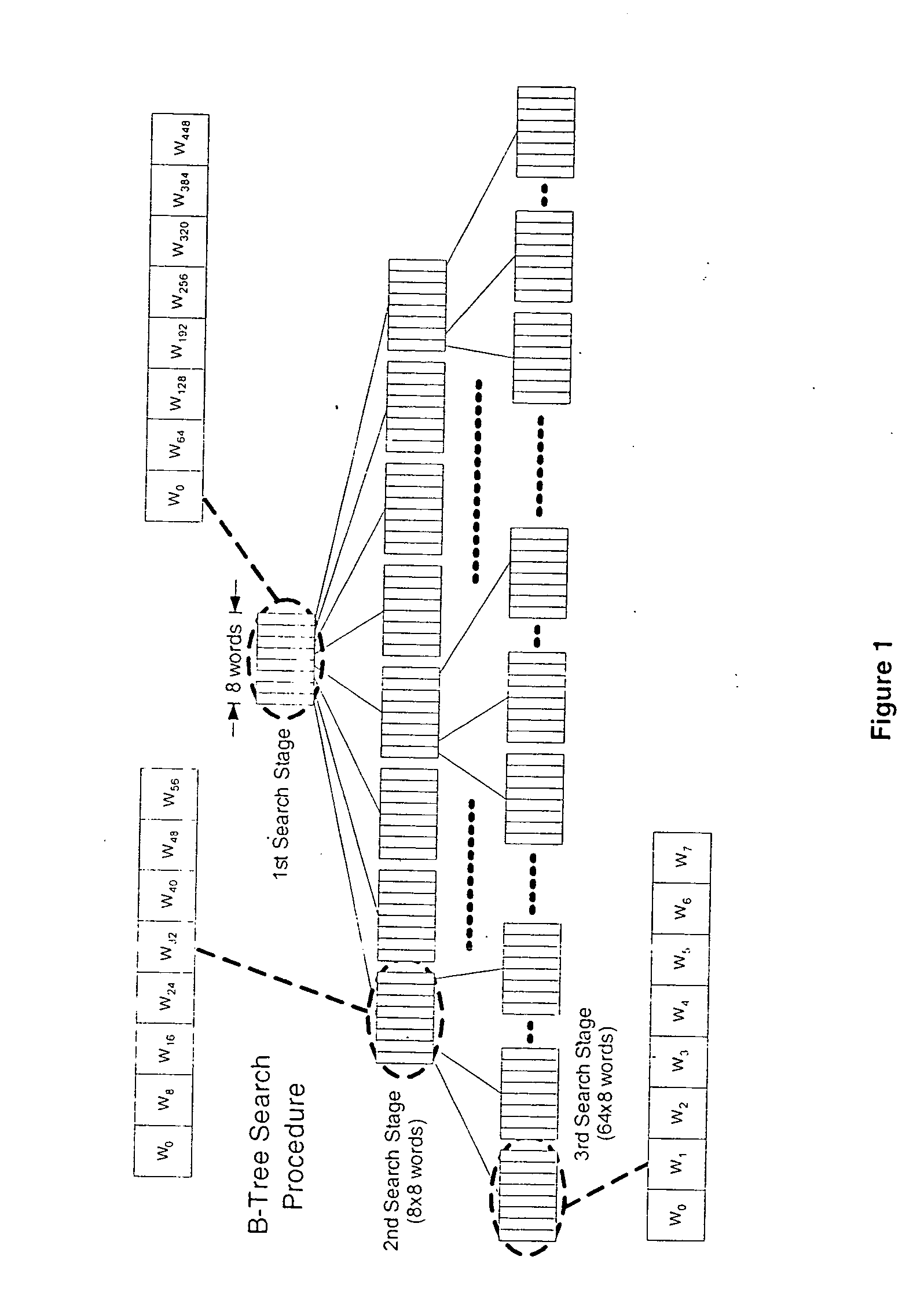
InactiveUS20050091443A1Data processing applicationsDigital data information retrievalTheoretical computer scienceData structure
A computer-implemented method of searching an ordered database using transformed key entries including the steps of: (a) providing a system having: (i) a memory for storing a plurality of key entries, and (ii) processing logic for transforming said key entries into coded entries, and for searching the coded entries; (b) performing a pre-determined transformation of each key entry so as to obtain a plurality of coded entries, and (c) performing a deterministic search in at least one data structure within the memory to obtain a match between an input key and a key entry.
Owner:HYWIRE
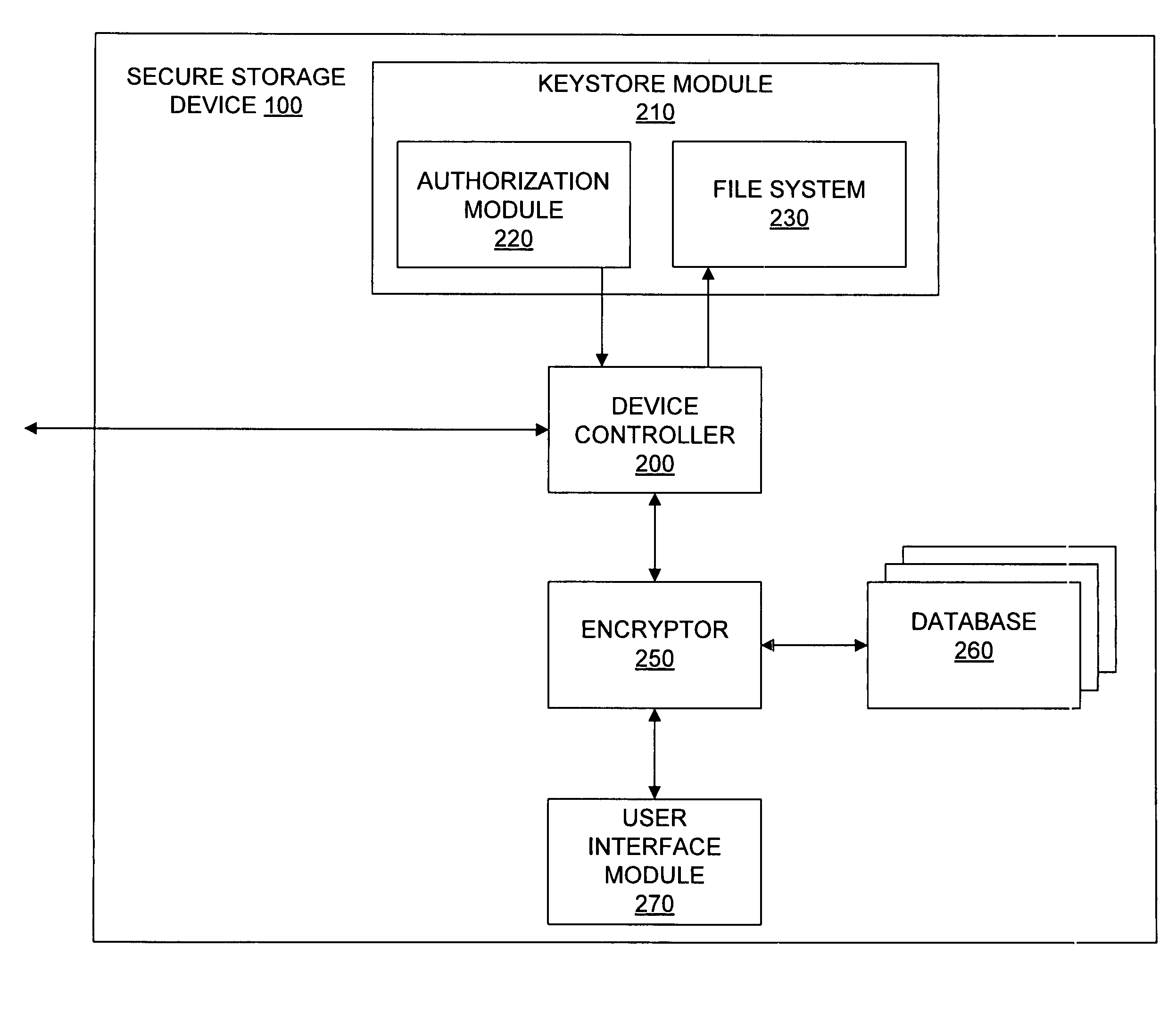
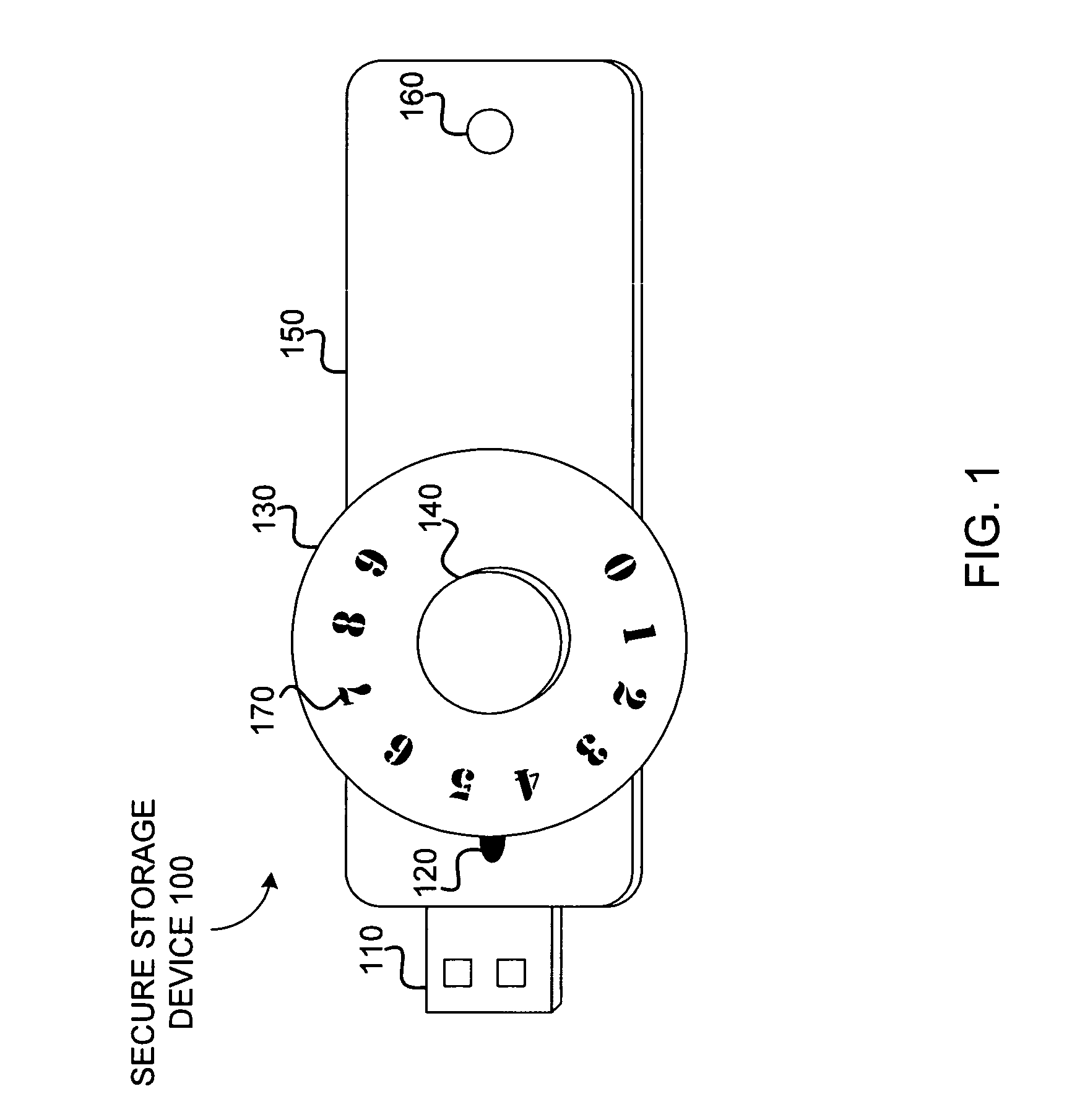
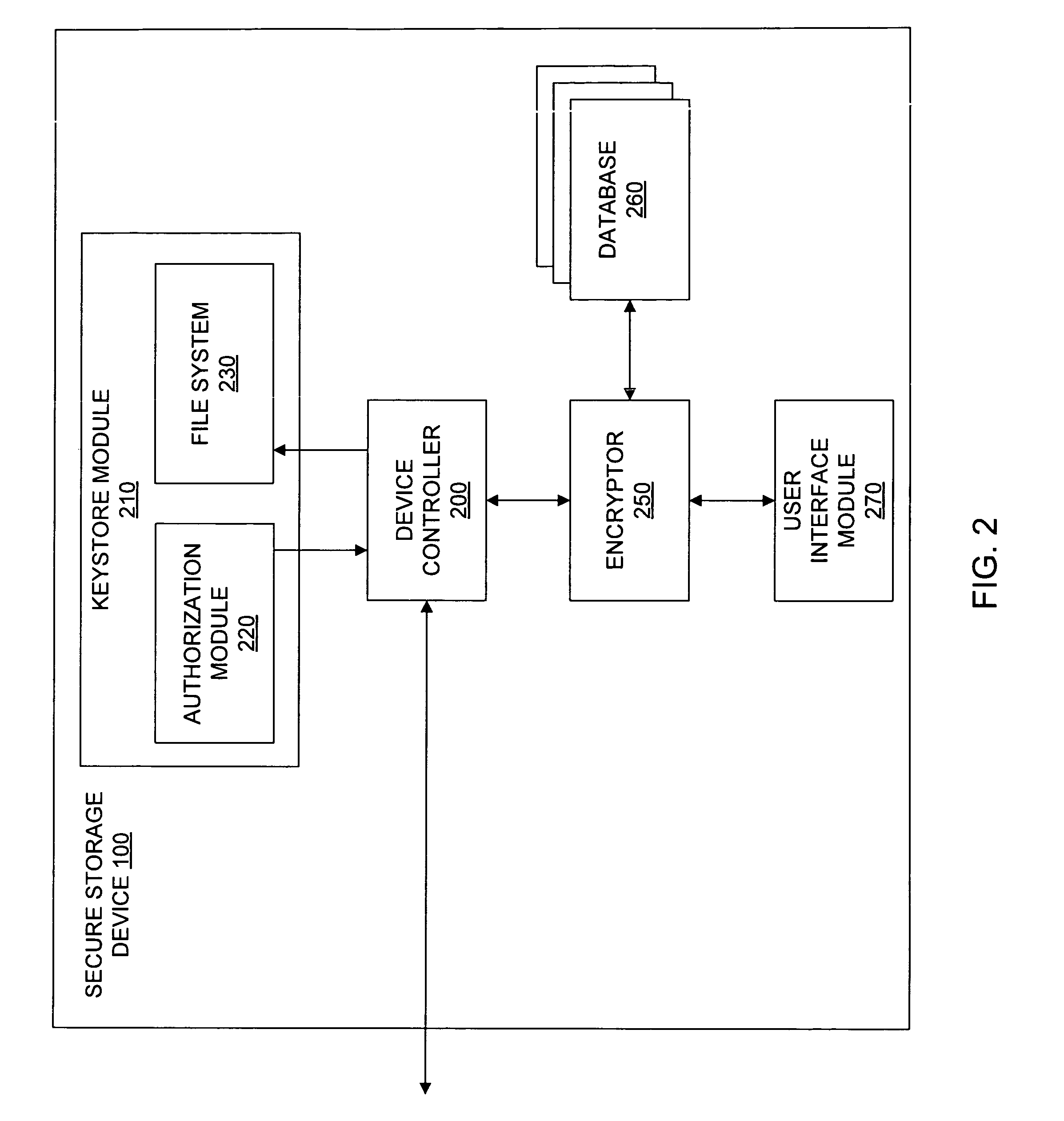
Secure storage device with offline code entry
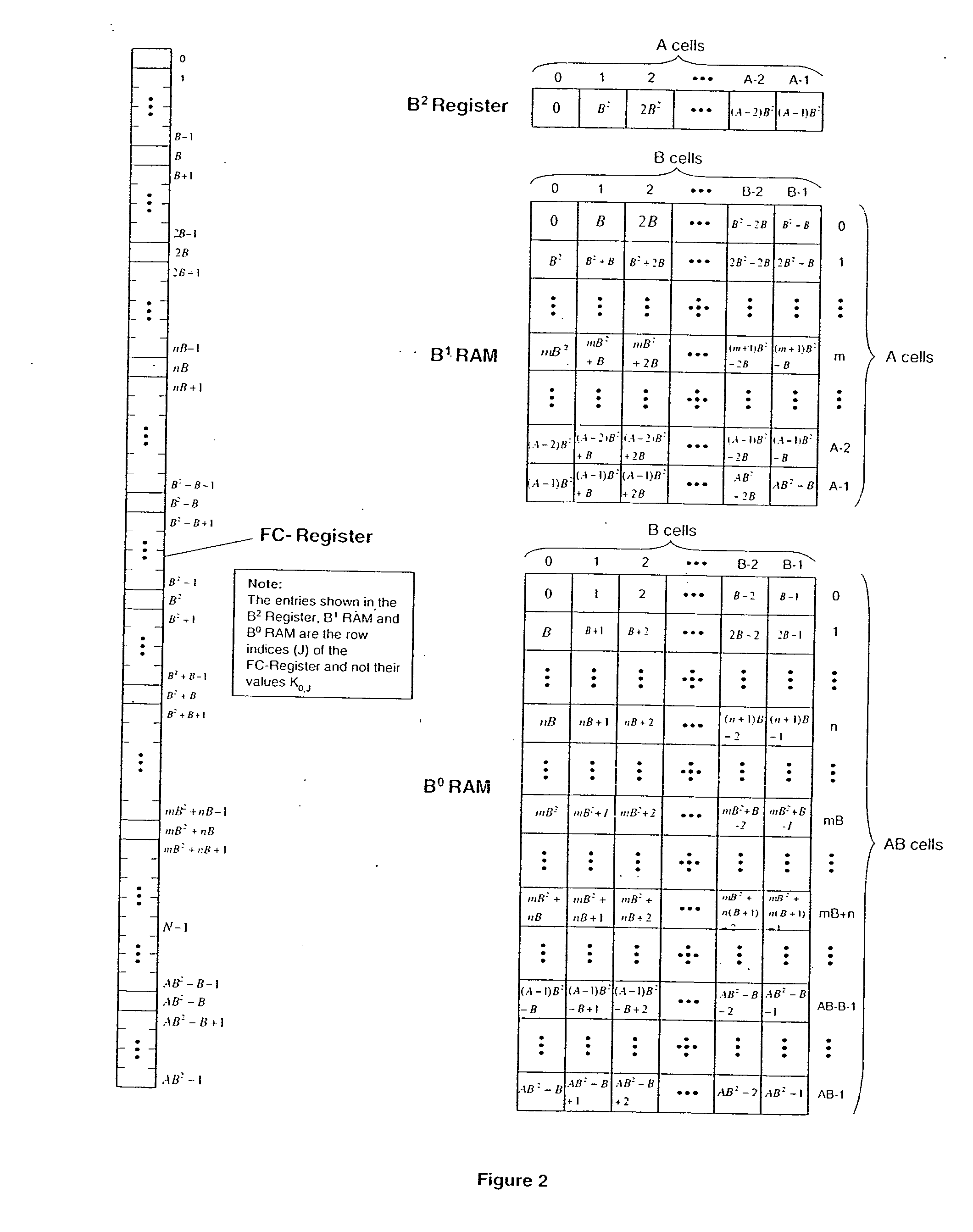
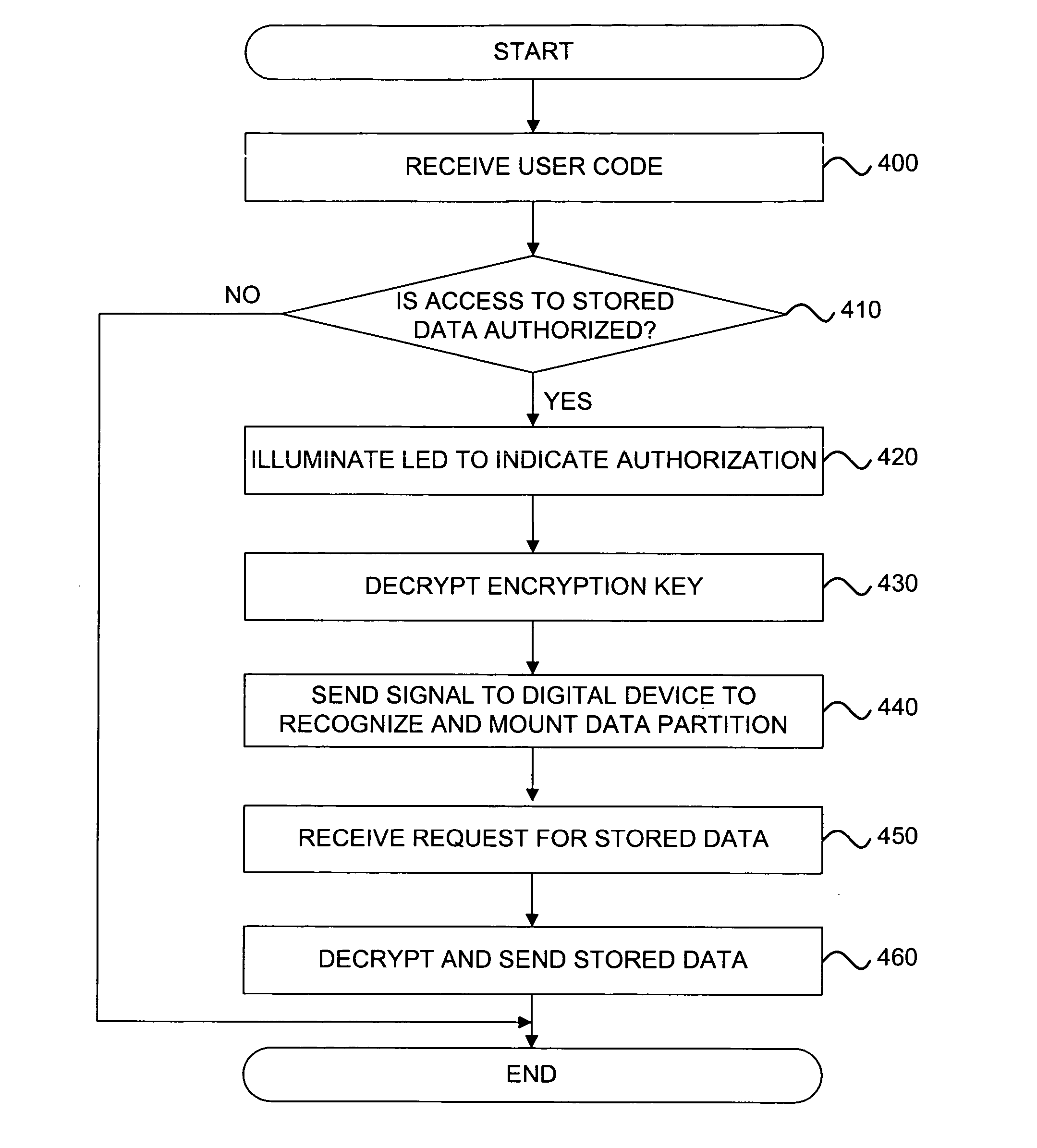
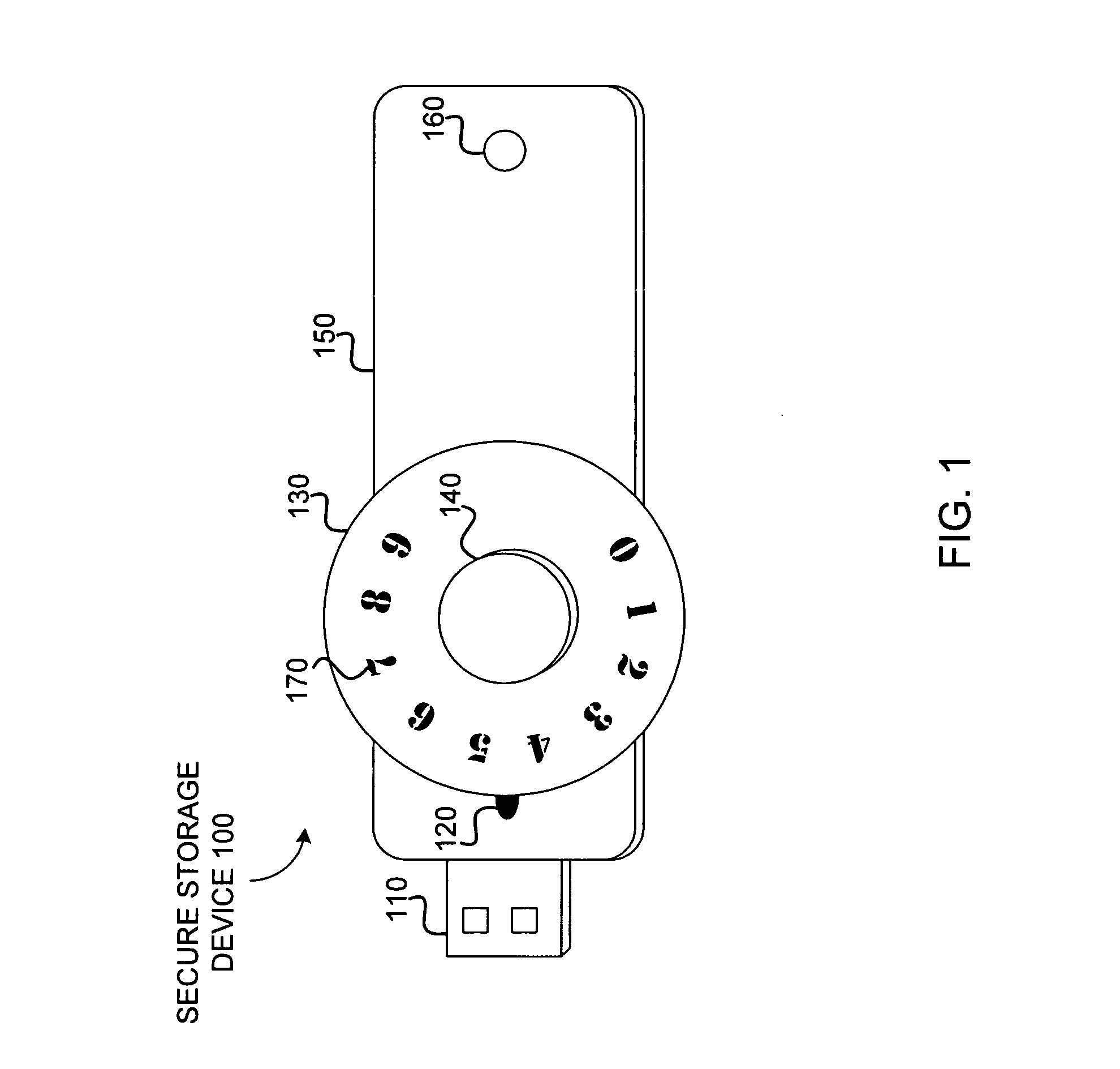
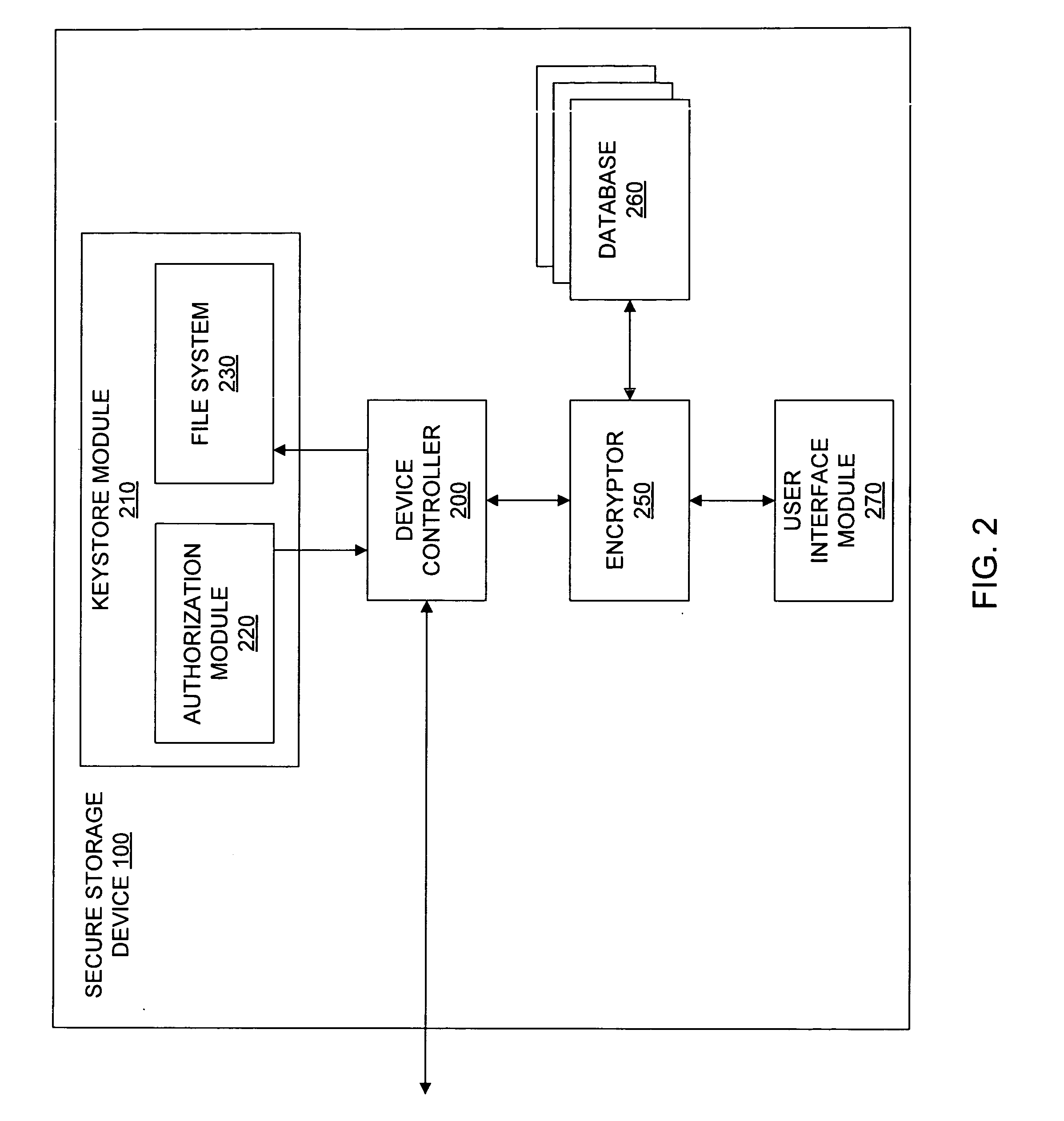
ActiveUS20070016743A1Digital data processing detailsUnauthorized memory use protectionData storeUser code
A system to authorize access to secured data storage can compromise a user interface configured to receive a user code offline from a user to allow access to stored data, circuitry configured to authorize access to the stored data based, at least in part, on the user code and provide access to the stored data, and a storage system configured to store the stored data.
Owner:KINGSTON DIGITAL CO LTD
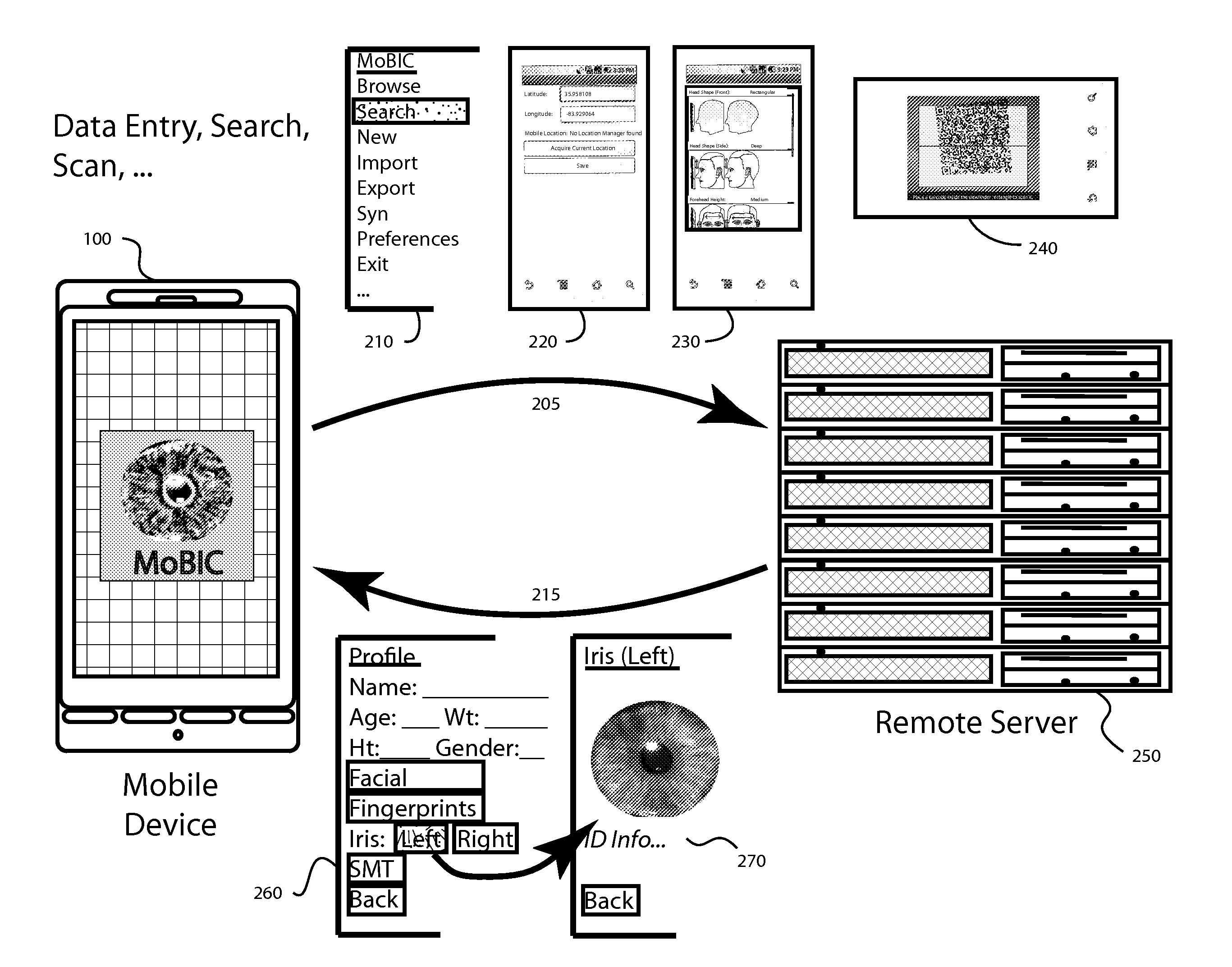
Mobile Biometrics Information Collection and Identification
ActiveUS20120148115A1Minimal costCosts of hardware modifications and associated software requirementsDigital data authenticationProteomicsHuman bodyPattern recognition
A biometric mobile device is capable of interacting with existing cellular, wireless, and wired telecommunication and other communication networks to support intelligence gathering, human body identification, special operations and other applications. A method of collecting biometric data at an accident or crime scene may comprise, for example, utilizing a camera to photograph the accident scene, collecting key entered data that may not be otherwise obtainable, using a fingerprint scanner to collect, digitize and store fingerprint data, using a lab-on-a-chip DNA profile device for collecting and analyzing a DNA specimen and generating identification and DNA profile data for bar code entry and other means for collecting any known form of biometric data including, but not limited to, vascular facial structure, dental structure, cornea, iris or other data which may be unique or limiting for identification purposes.
Owner:BIRDWELL J DOUGLAS +2
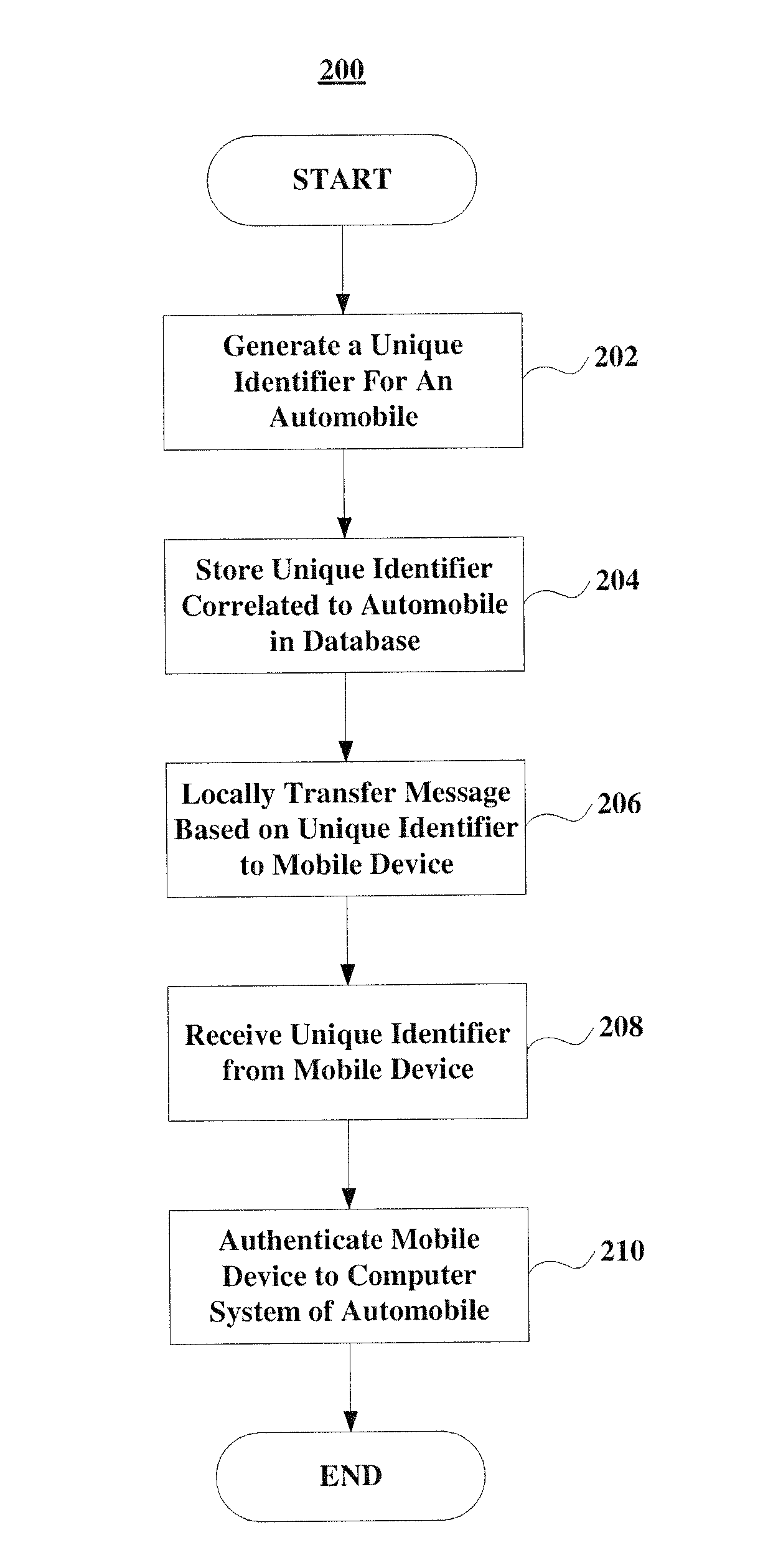
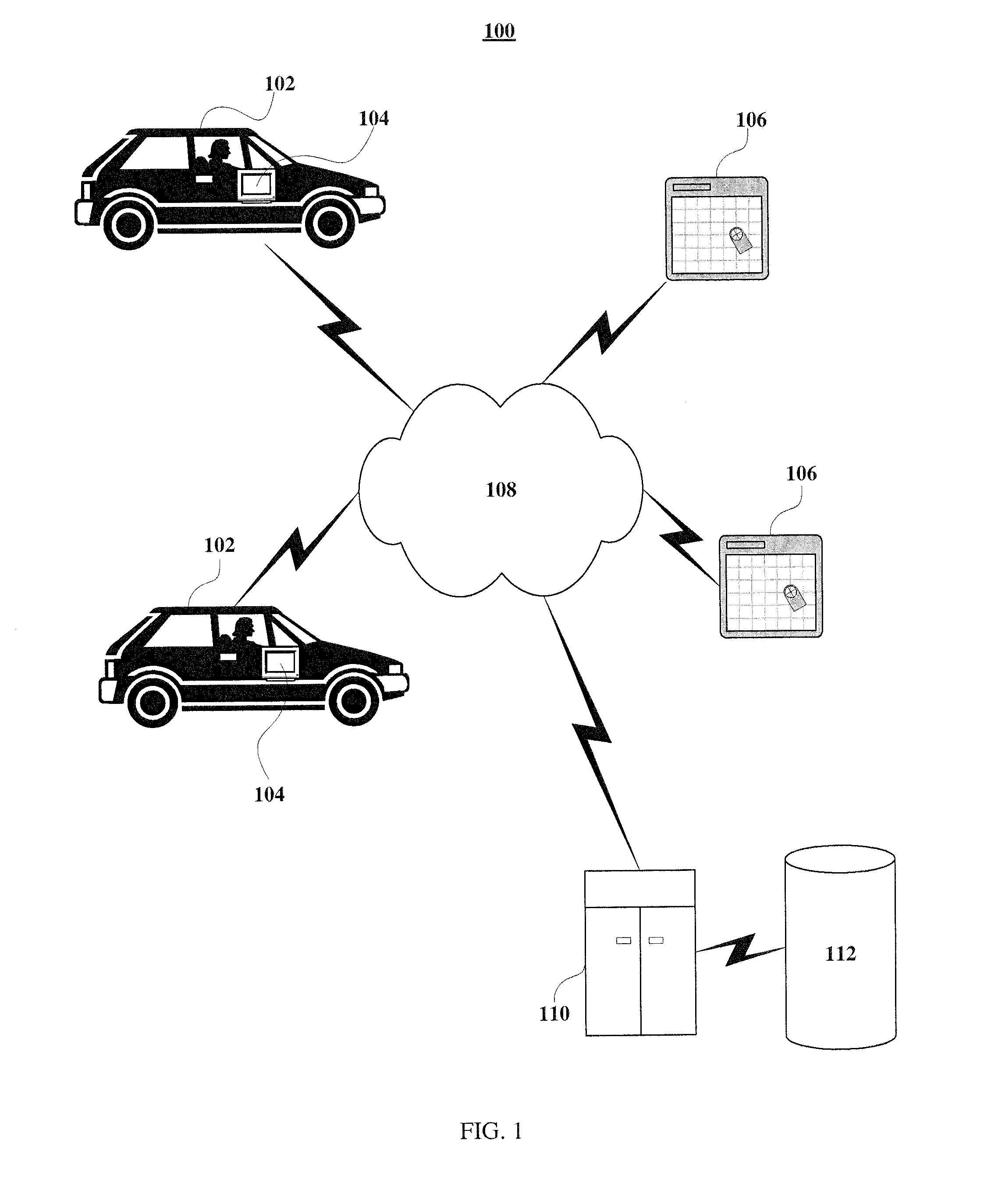
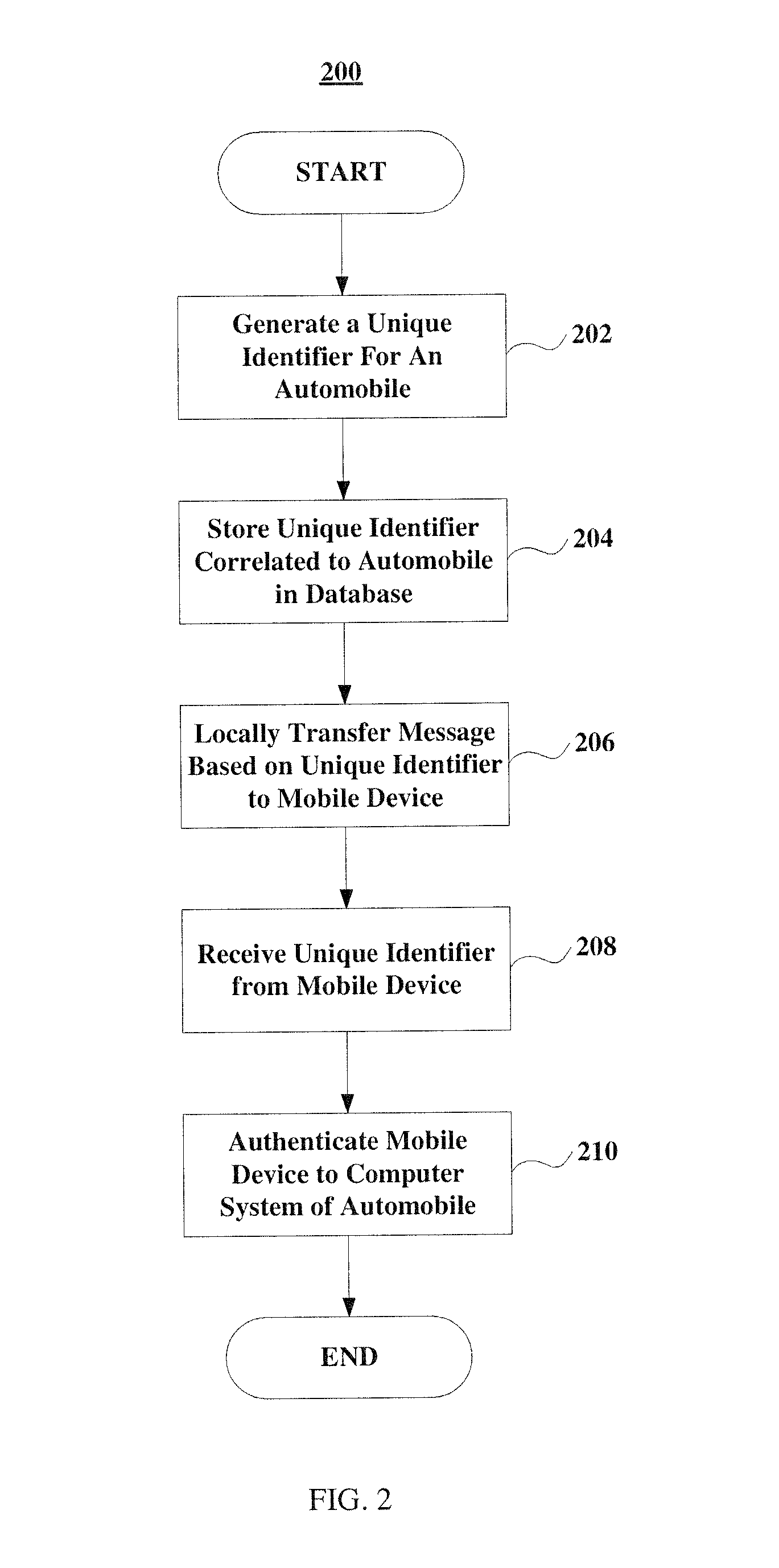
Method And System For Connecting A Mobile Communication Device To An Automobile
InactiveUS20160150407A1Particular environment based servicesIn-vehicle communicationComputer hardwareComputerized system
The present invention provides systems and methods for authenticating a mobile communication device to a computer system of an automobile that does not require manual code entry, and thereby reduces the burden on the user, minimizes human errors, and provides the ability to utilize more complex digital keys an increase the security level of the connection. In particular, the systems and methods of the present invention generate a unique identifier corresponding to the automobile and locally transfer a message including or generated from this unique identifier to the mobile communication device without manual code entry.
Owner:WIND RIVER SYSTEMS
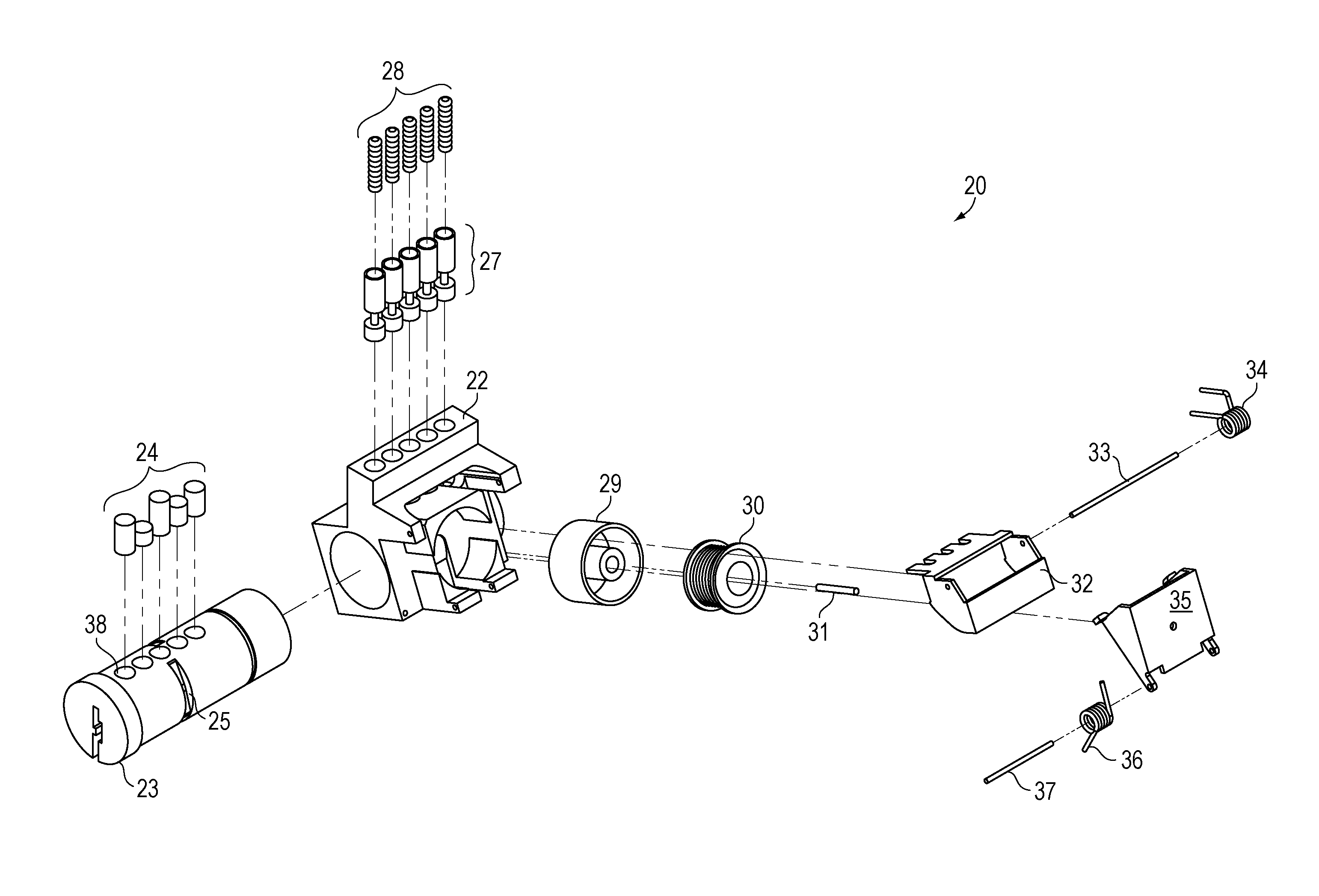
Electronic Combination Lock
An electronic combination lock includes a door handle having a code entry button and housing a lock assembly and an electrical circuit. The lock assembly includes a lock body, a rotating cylinder, spring loaded lift lock pins and corresponding key pins, a reset cam path and a programming cam path formed on the cylinder, a lift comb for lifting the lift lock pins, a latch for latching the lift comb and a magnet being selectively activated to cause the latch to release the lift comb. The electrical circuit receives a first input signal indicative of an input code entered at the code entry button and a second input signal from a program switch actuated by the programming cam path and is operated to store an entry code when the program switch is actuated and to activate the magnet when an input code matching the stored entry code is received.
Owner:JOHANSSON FRITZ HUGO +1
Systems and methods for authentication code entry in touch-sensitive screen enabled devices
InactiveUS20170344251A1Input/output for user-computer interactionDigital data authenticationTouchscreenAuthentication
Systems and methods for authentication code entry in touch-sensitive screen enabled devices are disclosed. In one embodiment, a method for entering data to a data entry device comprising at least one computer processor and a touch-sensitive screen may include (1) the touch-sensitive screen displaying an input interface; (2) the touch-sensitive screen sensing a first input comprising at least one finger touch; (3) the touch-sensitive screen sensing a release of the first input; (4) the at least one computer processor determining a number of finger touches in the first input; and (5) the at least one computer processor using the number of finger touches in the first input to identify at least a first portion of a value in an authentication code.
Owner:VERIFONE INC
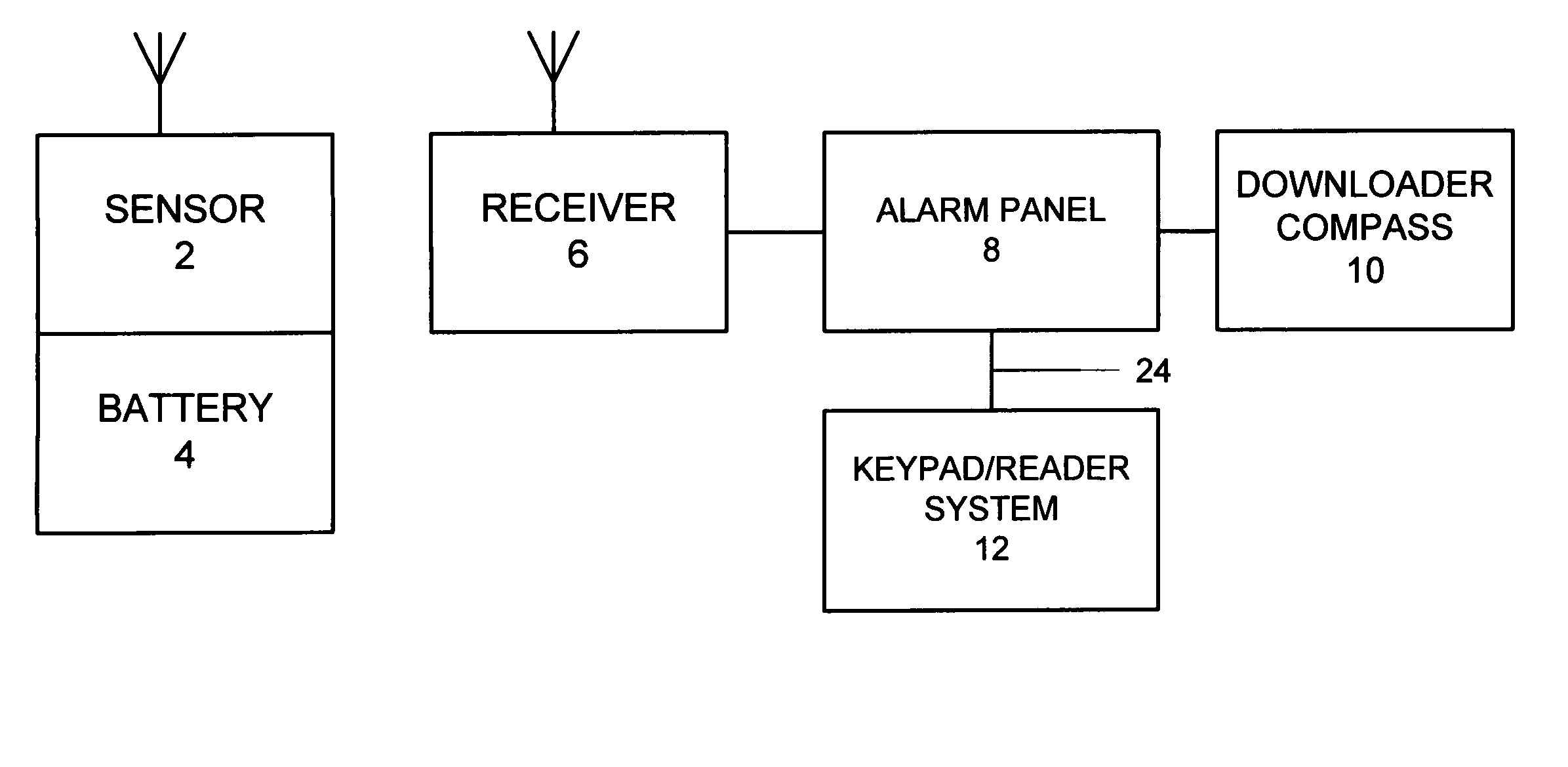
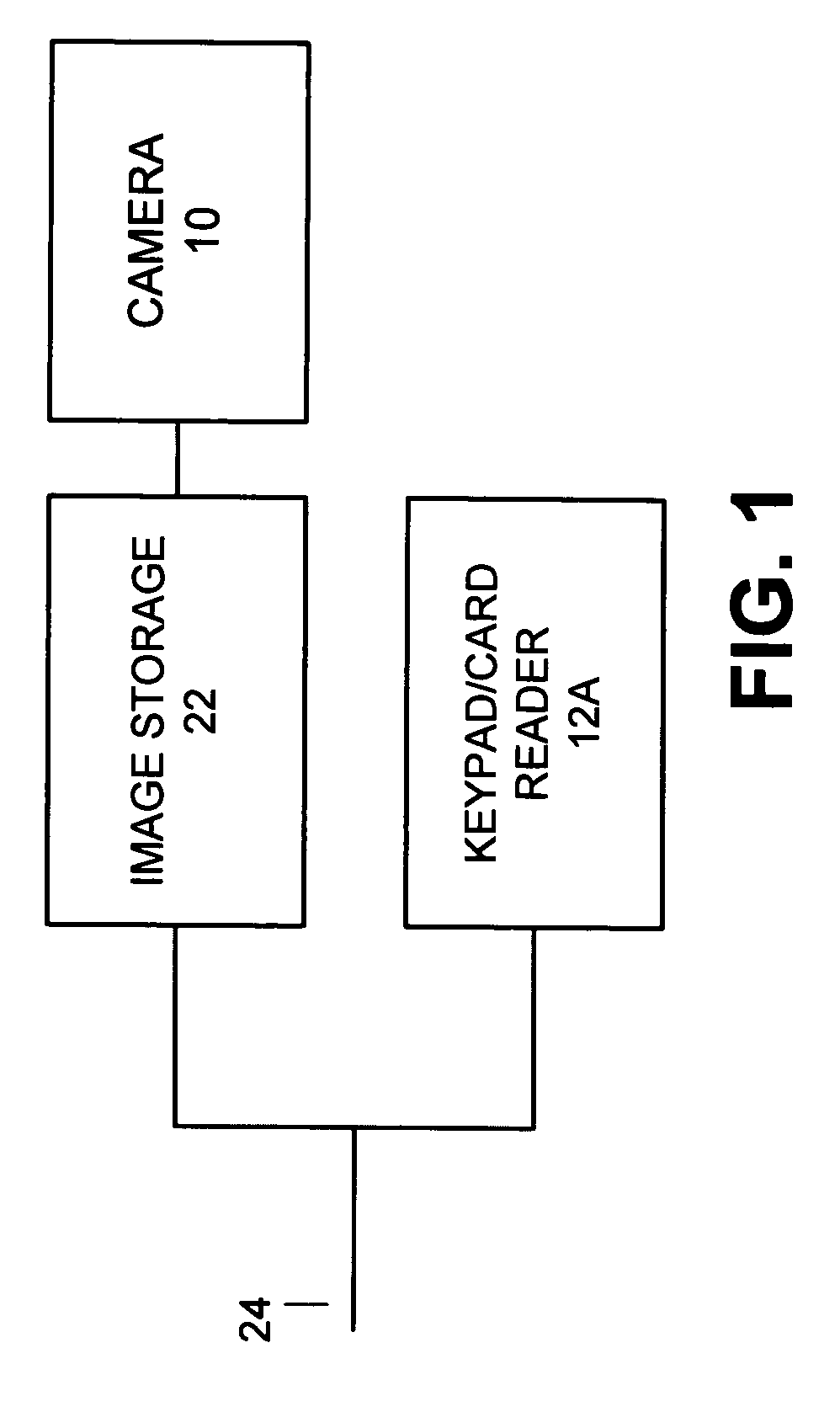
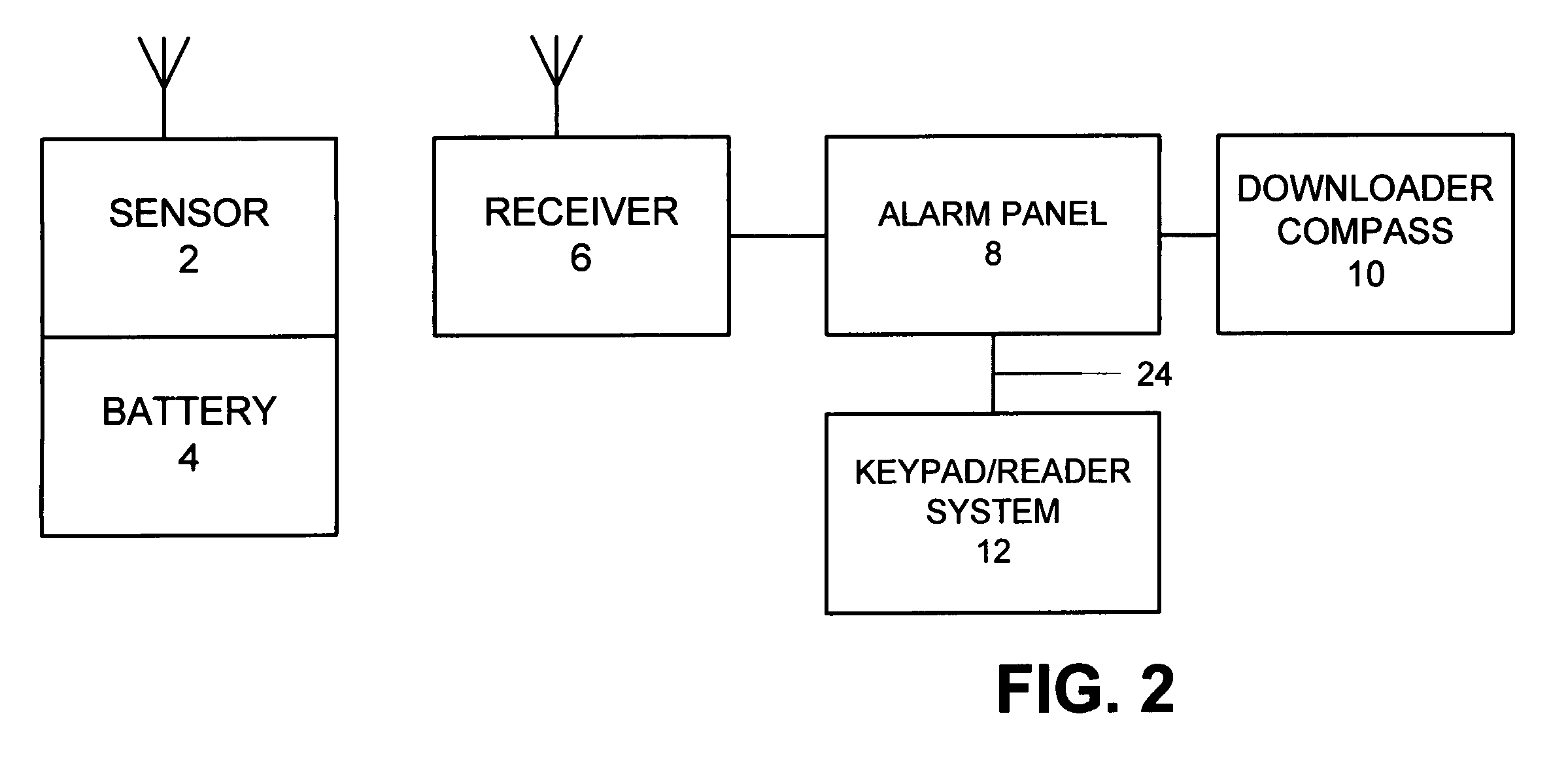
Security system access control and method
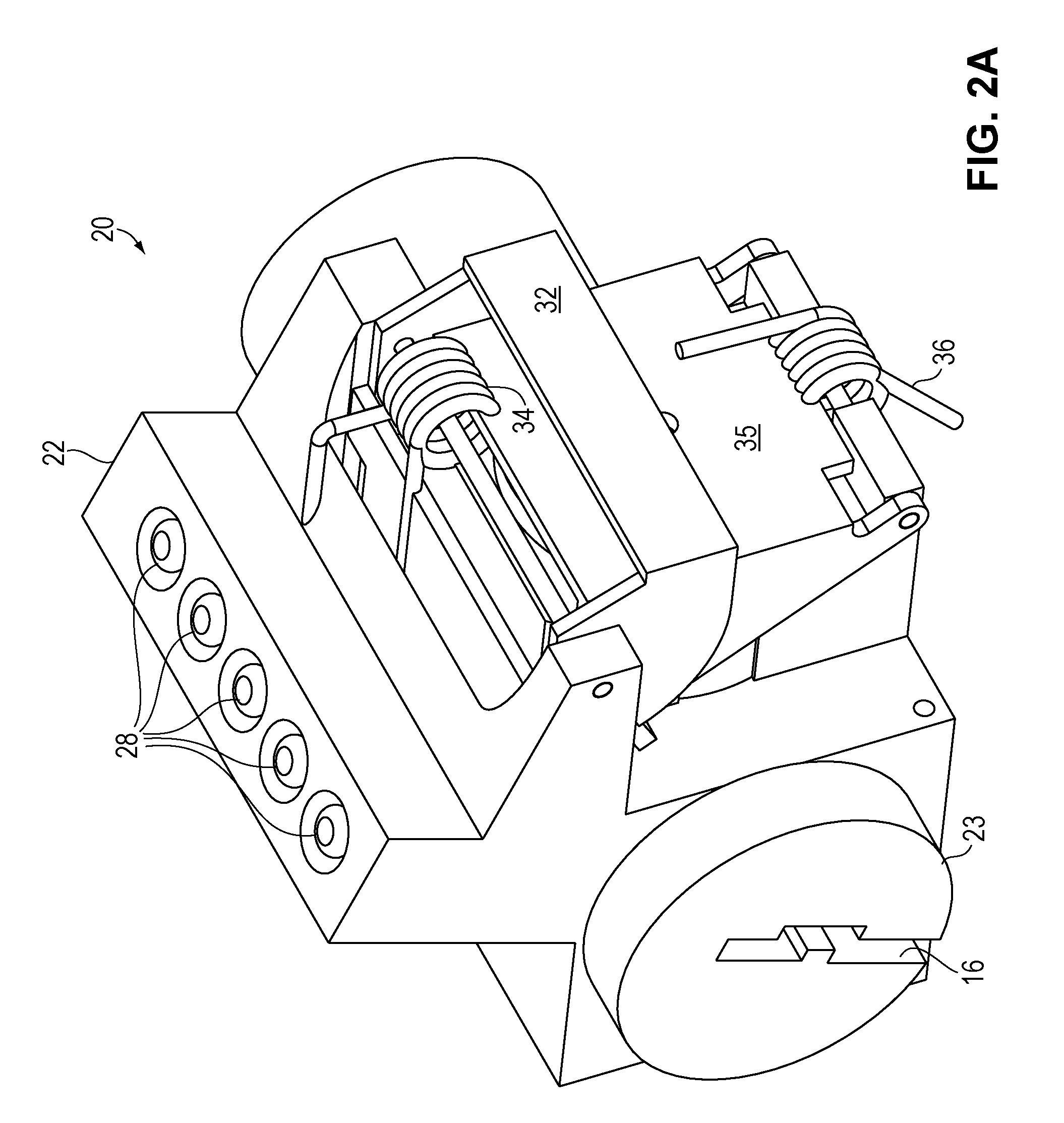
ActiveUS7397371B2Improve security levelImprove securityColor television detailsClosed circuit television systemsUser codeSecurity system
A security system which includes at least a first sensor, an alarm panel including a control system and programmable apparatus, a connection between the at least one sensor and set alarm panel, a keypad assembly including a camera, and a connection between the keypad assembly and the alarm panel. In various embodiments of the invention the camera includes a CMOS image sensor, the camera produces digital images, the camera tracks the user of the keypad assembly, the camera is remotely controllable from the alarm panel to focus on an object of interest, and / or the camera is remotely controllable from a central monitoring station to focus on an object of interest. In some cases the camera system is configured to take a picture in response to a specific user code entered by the user, take a picture in response to time of day when the input occurs, take a picture in response to invalid code entry and / or take a picture in response to an invalid card being presented. The invention also includes the method for providing enhanced security for protected premises which includes providing at least a first sensor, providing an alarm panel including a control system and programmable apparatus, providing a connection between the at least one sensor and the alarm panel, providing an input device including a camera, and initiating operation of the camera from the alarm panel.
Owner:HONEYWELL INT INC
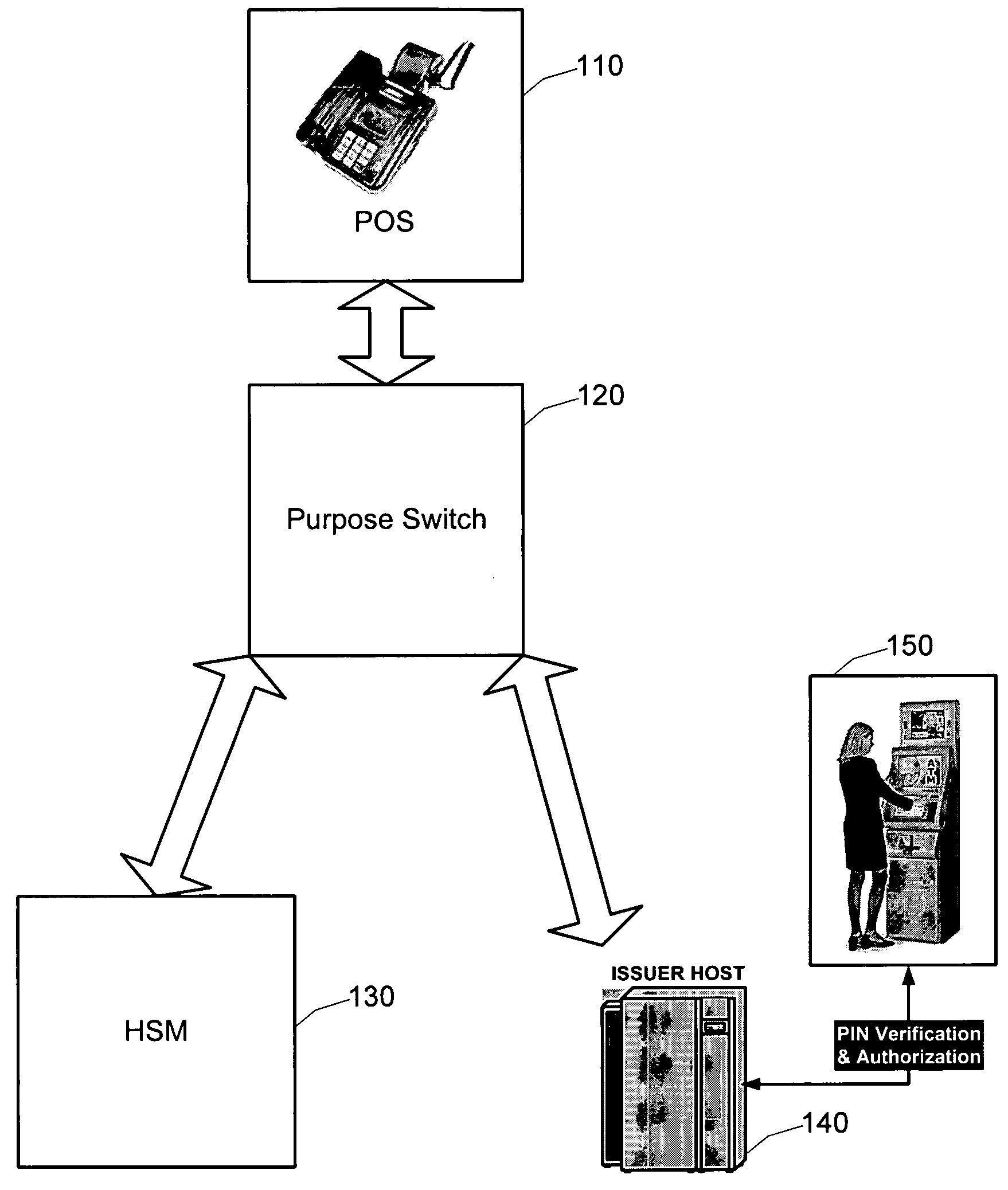
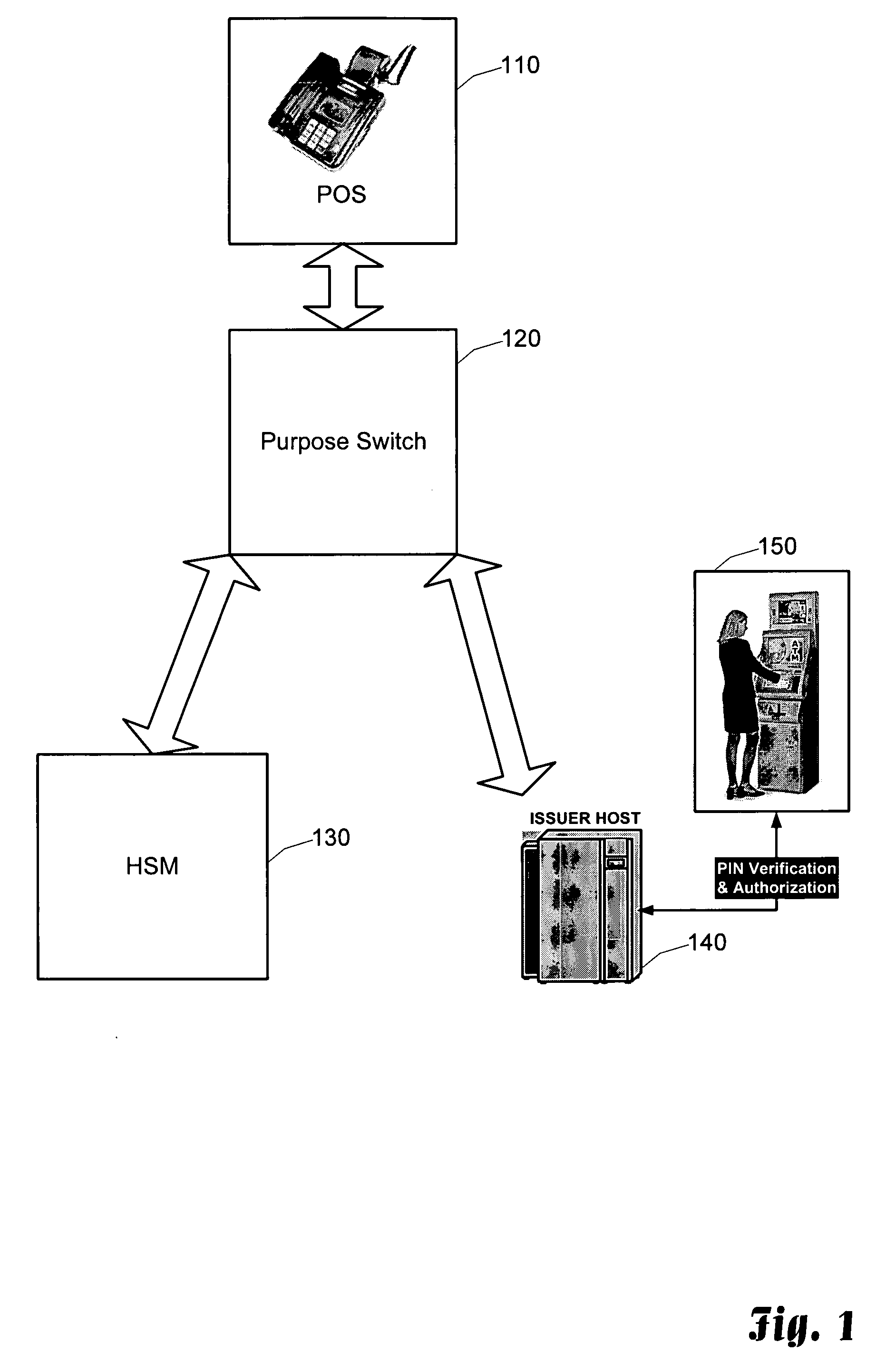
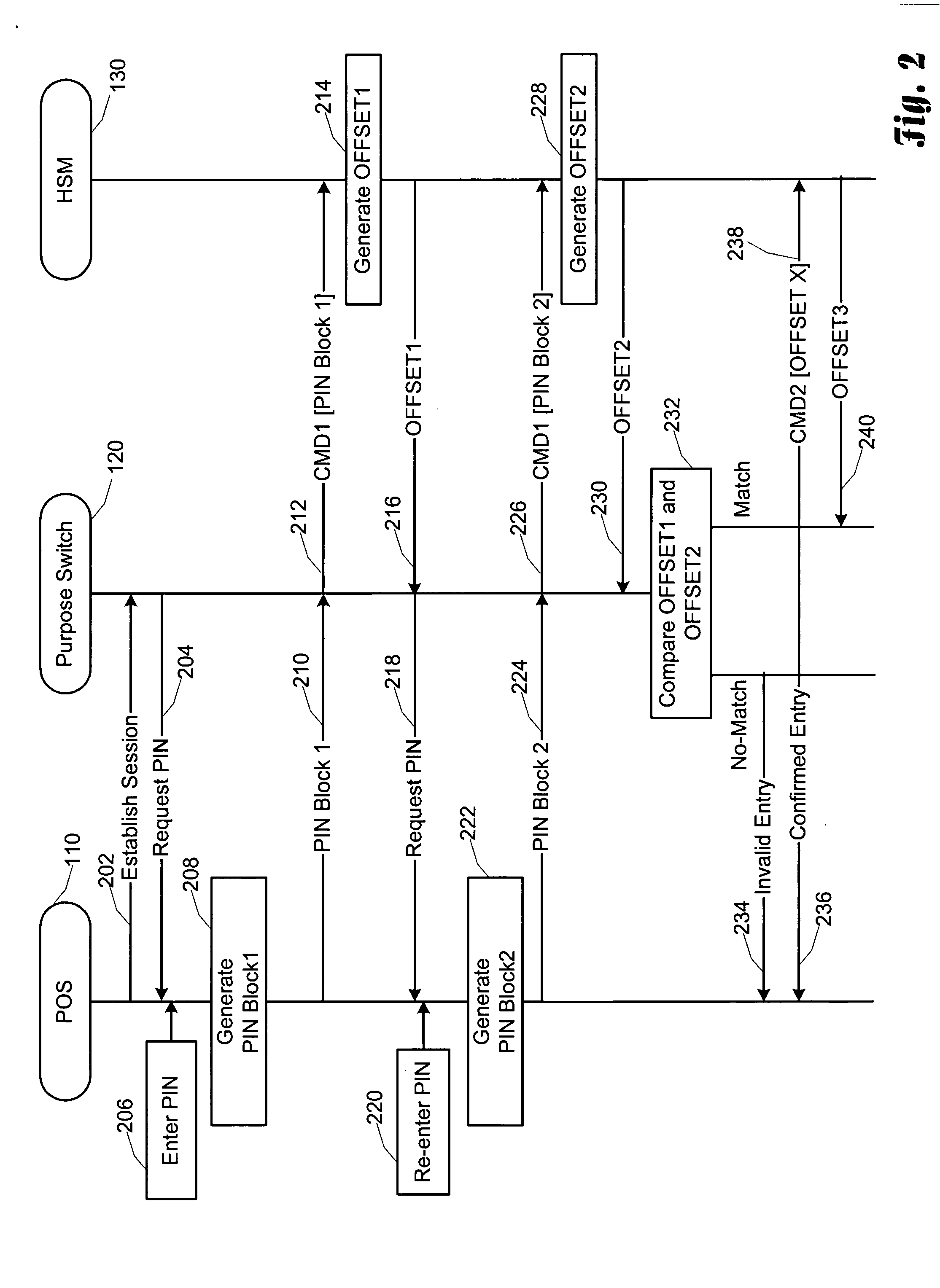
Real-time entry and verification of PIN at point-of-sale terminal
InactiveUS20050080677A1Improve securityEnter exactlyCredit schemesDigital data authenticationComputer hardwareFinancial transaction
For financial transactions requiring PIN verification, the customer can now select his or her own number at the time of applying for the financial transaction instrument or account. The customer enters the PIN which is then encrypted using a transaction unique encryption scheme. The customer then re-enters the PIN which is once again encrypted using a transaction unique encryption scheme. As a result, two blocks of data are created for the same PIN, yet the encrypted values of the blocks are different. These blocks are provided to a central security system which can reverse the encryption process to a point at which it can generate an offset based on the received blocks. If the PINs were identically entered, the offsets will be equal, otherwise the offsets will not be equal. Thus, this technique allows a customer to select and enter his or her own PIN code, and have the PIN code entry verified by the system without the system actually knowing the value of the PIN code.
Owner:COMPUCREDIT INTPROP HLDG CORP II
Secure storage device with offline code entry
ActiveUS8321953B2Digital data processing detailsAnalogue secracy/subscription systemsInternet privacyData store
A system to authorize access to secured data storage can comprise a user interface configured to receive a user code offline from a user to allow access to stored data, circuitry configured to authorize access to the stored data based, at least in part, on the user code and provide access to the stored data, and a storage system configured to store the stored data.
Owner:KINGSTON DIGITAL CO LTD
System and method for secure code entry point control
InactiveUS20160188874A1Improve performanceImprove securityMemory loss protectionError detection/correctionProgramming languageCoding block
Owner:RUBICON LABS
Mobile biometrics information collection and identification
ActiveUS9235733B2Costs of hardware modifications and associated software requirementsMinimal costDigital data authenticationProteomicsHuman bodyPattern recognition
A biometric mobile device is capable of interacting with existing cellular, wireless, and wired telecommunication and other communication networks to support intelligence gathering, human body identification, special operations and other applications. A method of collecting biometric data at an accident or crime scene may comprise, for example, utilizing a camera to photograph the accident scene, collecting key entered data that may not be otherwise obtainable, using a fingerprint scanner to collect, digitize and store fingerprint data, using a lab-on-a-chip DNA profile device for collecting and analyzing a DNA specimen and generating identification and DNA profile data for bar code entry and other means for collecting any known form of biometric data including, but not limited to, vascular facial structure, dental structure, cornea, iris or other data which may be unique or limiting for identification purposes.
Owner:BIRDWELL J DOUGLAS +2
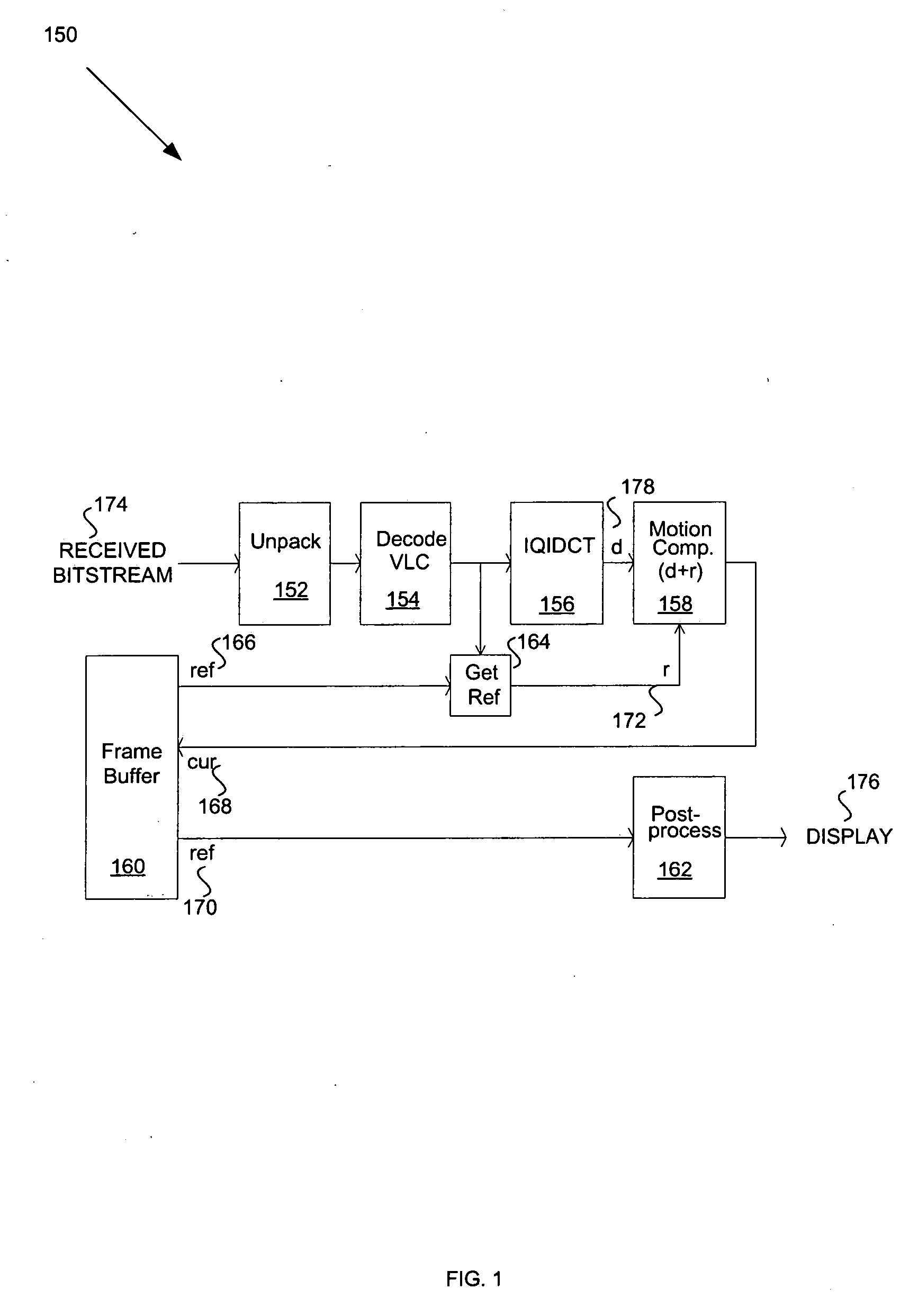
Method and system for decoding variable length code (VLC) in a microprocessor
InactiveUS20060176960A1Color television with pulse code modulationColor television with bandwidth reductionProgramming languageVariable-length code
Methods and systems for processing video data are provided herein and may comprise receiving an input encoded bitstream to be processed. A portion of the received input encoded bitstream may be matched against stored indexed variable length code entries having a corresponding video information entry. If a match is found, the matched portion may be removed from the input encoded bitstream. The matching and / or the removing may be offloaded to at least one on-chip coprocessor. The coprocessor may comprise a table look-up (TLU) module with a plurality of on-chip memories, such as RAM, and may be adapted to store one or more entries from a VLC encoding / decoding table. For example, an on-chip memory may be utilized to store a VLC code entry and another on-chip memory may be utilized to store the corresponding VLC code entry attributes that each code may represent, such as LAST, RUN, and LEVEL entries.
Owner:AVAGO TECH WIRELESS IP SINGAPORE PTE
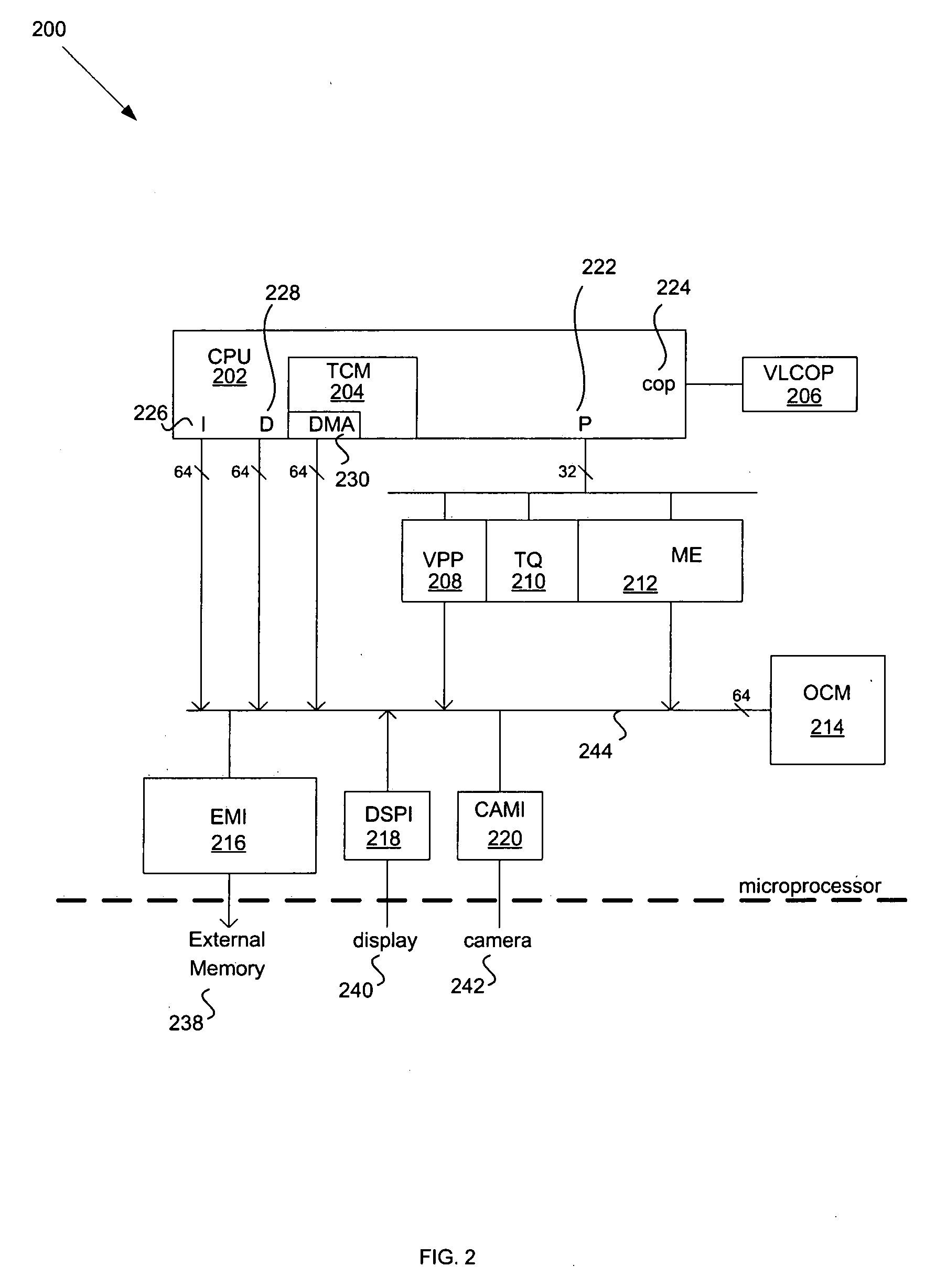
Processor isolation technique for integrated multi-processor systems
InactiveUS7185224B1Easy and fast commissioningImprove abilitiesFunctional testingMulti processorParallel computing
A processor isolation technique enhances debug capability in a multiprocessor circuit. A bypass register has a bit location which may indicate that a processor is to be bypassed. A code entry point is selected to permit a downstream processor to do the work of the bypassed processor. The processors may be arrayed in a pipeline.
Owner:CISCO TECH INC
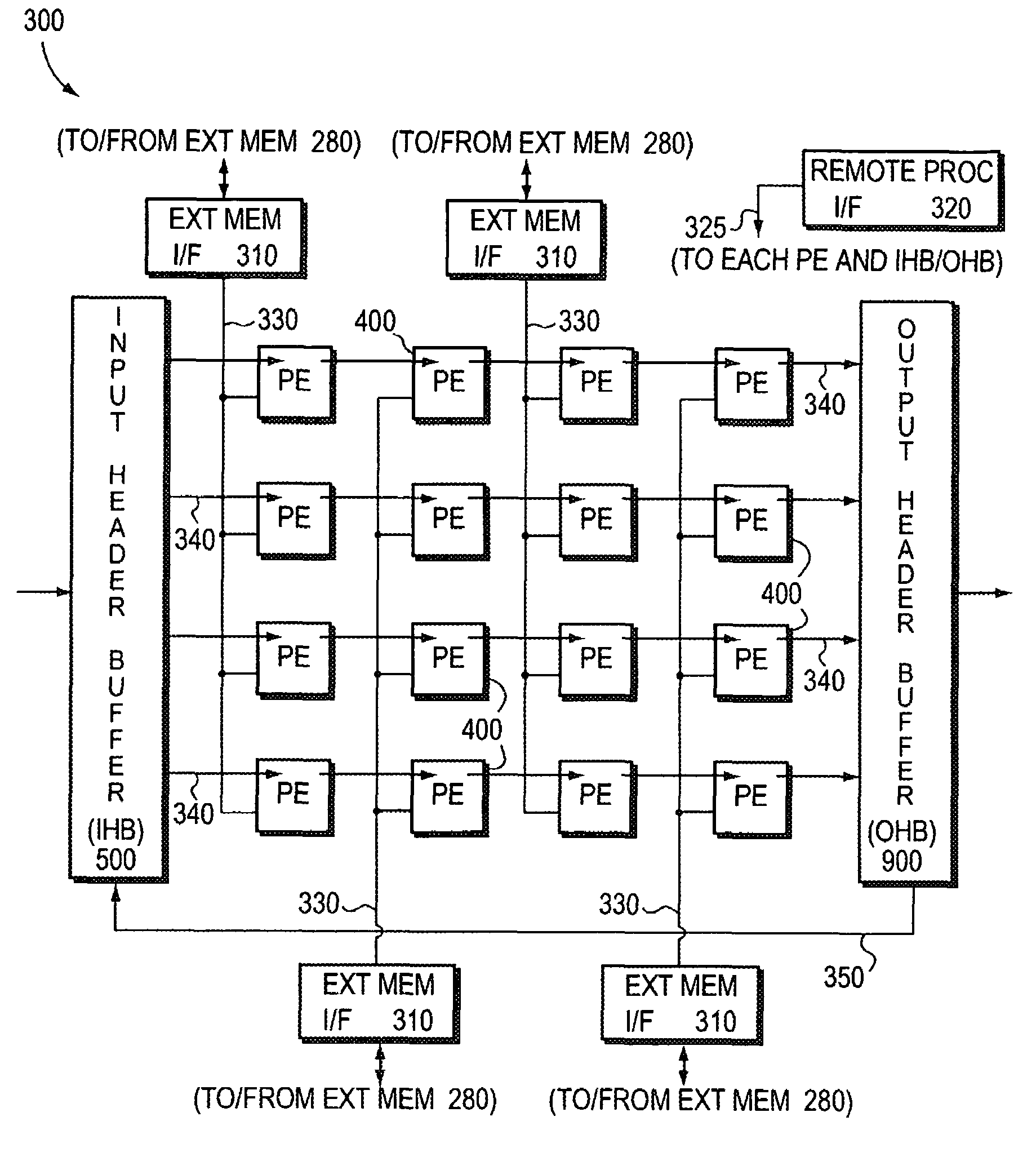
Method and system for frame and protocol classification
InactiveCN1433543AEasy to handleEasy grouping methodMultiprogramming arrangementsNetworks interconnectionData streamVirtual LAN
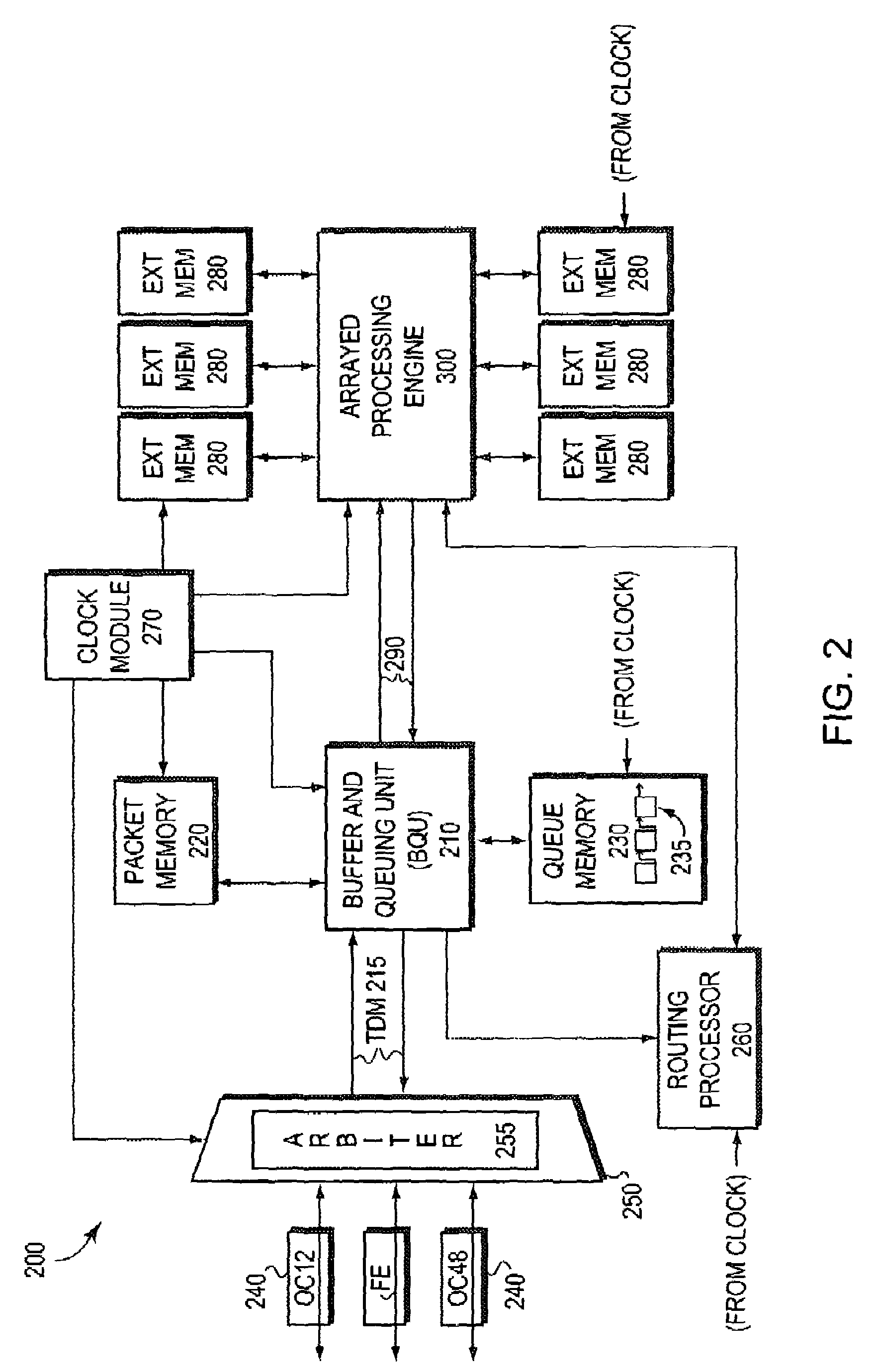
A system and method of frame protocol classification and processing in a system for data processing (e.g., switching or routing data packets or frames). The present invention includes analyzing a portion of the frame according to predetermined tests, then storing key characteristics of the packet for use in subsequent processing of the frame. The key characteristics for the frame (or input information unit) include the type of layer 3 protocol used in the frame, the layer 2 encapsulation technique, the starting instruction address, flags indicating whether the frame uses a virtual local area network, and the identity of the data flow to which the frame belongs. Much of the analysis is preferably done using hardware so that it can be completed quickly and in a uniform time period. The stored characteristics of the frame are then used by the network processing complex in its processing of the frame. The processor is preconditioned with a starting instruction address and the location of the beginning of the layer 3 header as well as flags for the type of frame. That is, the instruction address or code entry point is used by the processor to start processing for a frame at the right place, based on the type of frame. Additional instruction addresses can be stacked and used sequentially at branches to avoid additional tests and branching instructions. Additionally, frames comprising a data flow can be processed and forwarded in the same order in which they are received.
Owner:IBM CORP
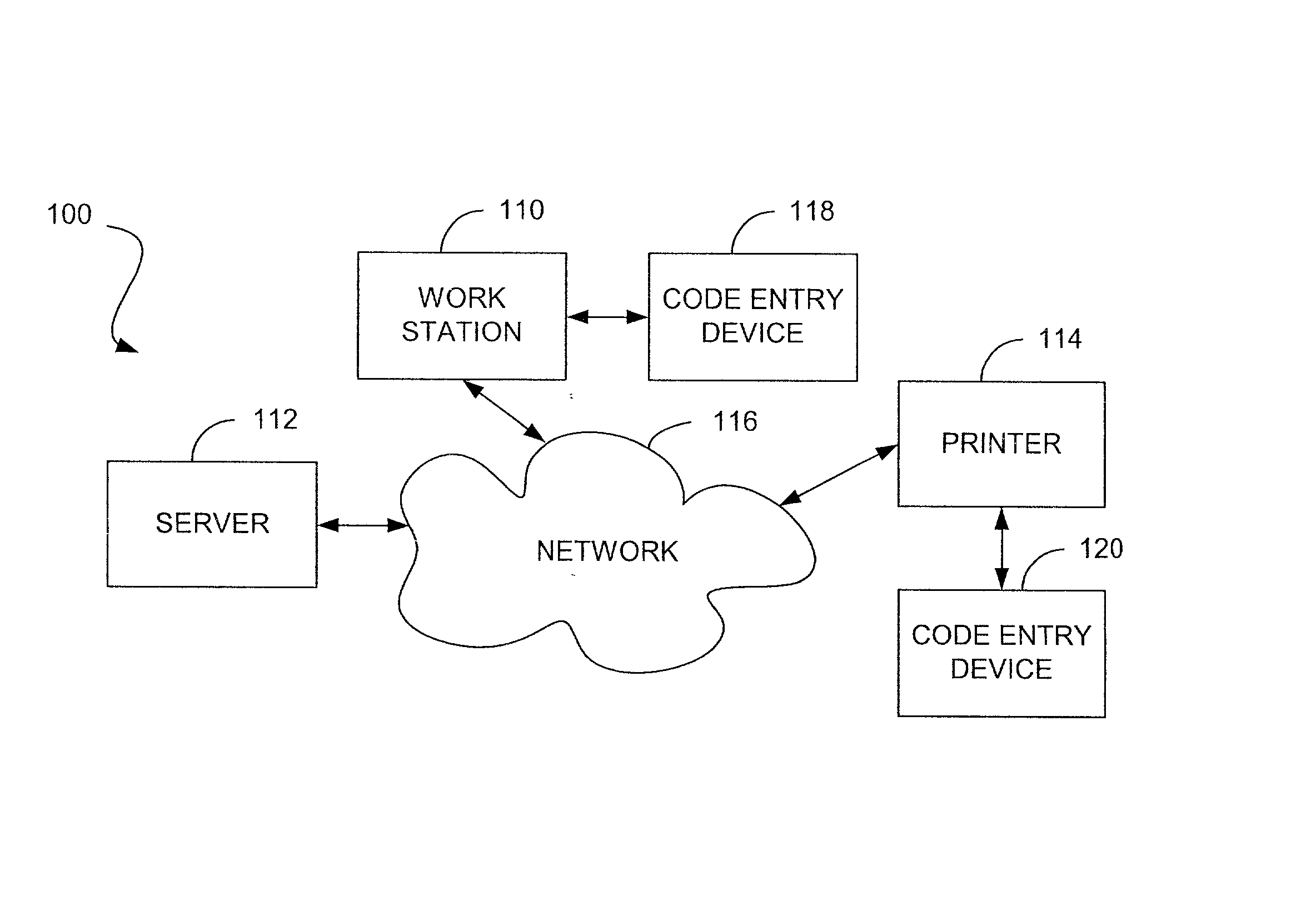
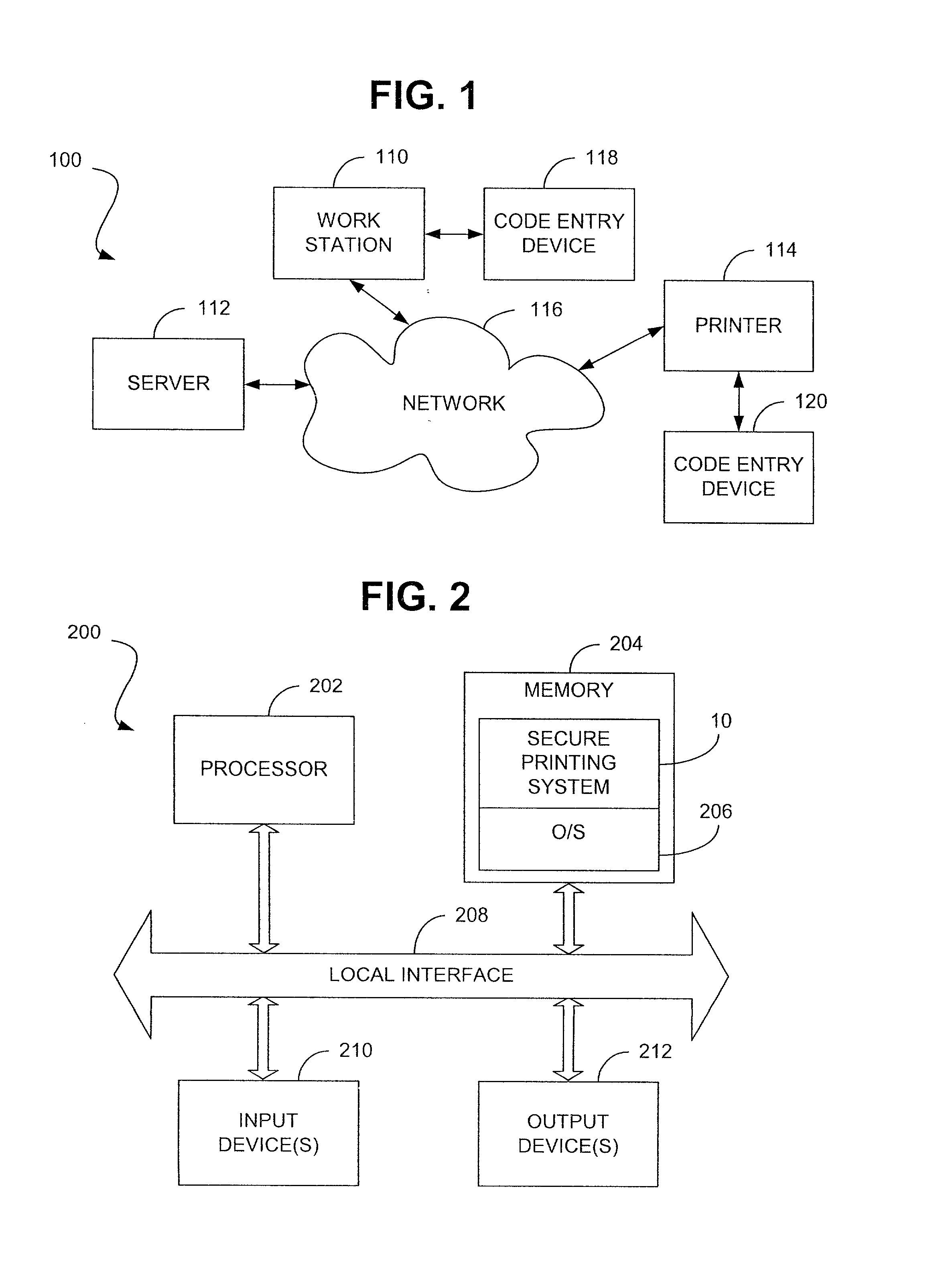
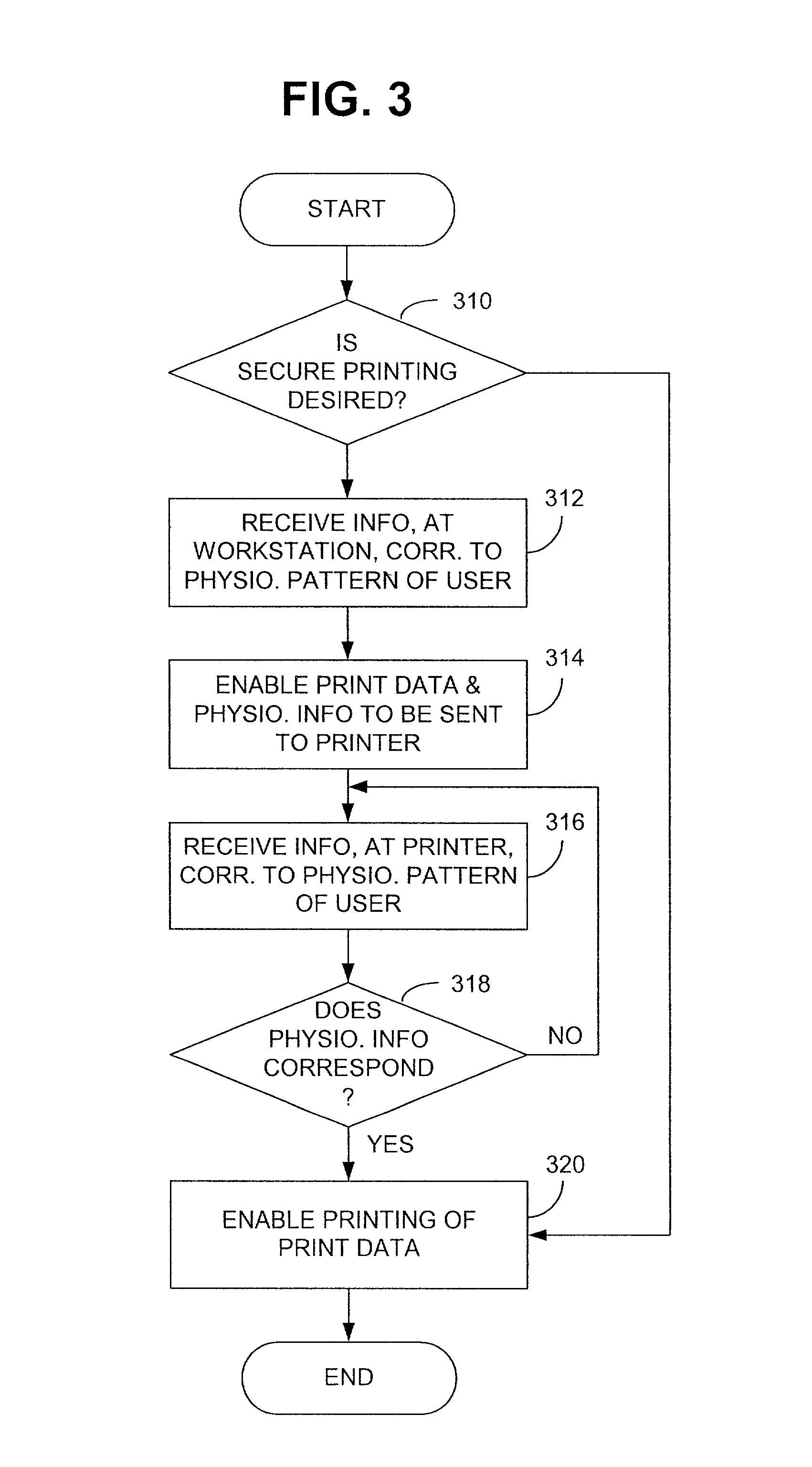
Systems and methods for secure printing
A preferred printing system includes a printer configured to communicatively couple with a workstation, which incorporates a first code entry device for receiving first coding information from a user. The printer incorporates a second code entry device that is configured to receive second coding information from the user. Additionally, the printer is configured to print data in response to correlating the first coding information received at the first code entry device with the second coding information received at the second code entry device. Devices, methods and computer readable media also are provided.
Owner:HEWLETT PACKARD DEV CO LP
Character string matching based method and system for analyzing address information of identification card
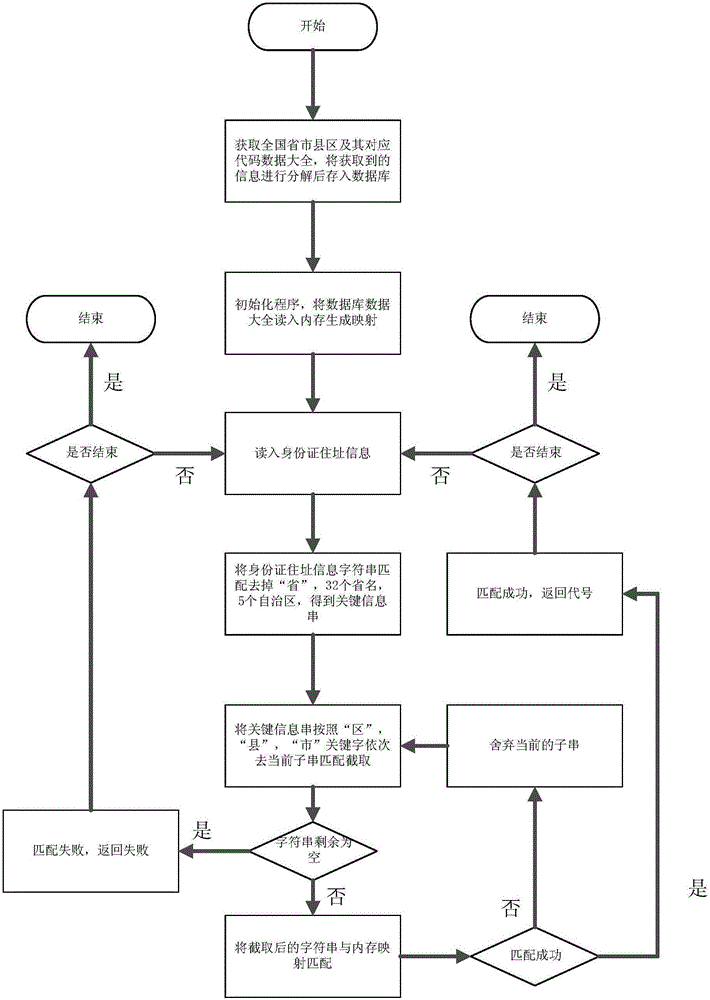
ActiveCN105069056AImplement parsingEffective and reliable automatic acquisitionSpecial data processing applicationsComputer scienceDigitization
Owner:HUBEI UNIV OF ARTS & SCI
Search method using coded keys
InactiveUS7499912B2Data processing applicationsDigital data information retrievalTheoretical computer scienceData structure
A computer-implemented method of searching an ordered database using transformed key entries including the steps of: (a) providing a system having: (i) a memory for storing a plurality of key entries, and (ii) processing logic for transforming said key entries into coded entries, and for searching the coded entries; (b) performing a pre-determined transformation of each key entry so as to obtain a plurality of coded entries, and (c) performing a deterministic search in at least one data structure within the memory to obtain a match between an input key and a key entry.
Owner:HYWIRE
Preventing the detection and theft of user entry alphanumeric security codes on computer touch screen keypads
InactiveUS20140215632A1Preventing discernible patternDigital data processing detailsAnalogue secracy/subscription systemsUser inputDuplicate code
Preventing, discernible patterns of surface marks resulting from the repetitive entry of security codes to computer device touch screen alphanumeric keypads. There is predetermined the number of security code entries after which the positions of the representative keys in the keypad array should be reconfigured. This predetermined number should be the number of security code entries estimated to produce a pattern of distinguishable display surface marks coincident with a users repetitive entry alphanumeric character security code. The number of security code entries is counted. When the count of the predetermined number of security code entries has been reached, the representative keys in the displayed keypad array are reconfigured. This implementation is equally effective against thieves who are visually stealing the security codes over the user's shoulder.
Owner:IBM CORP
Electronic combination lock
An electronic combination lock includes a door handle having a code entry button and housing a lock assembly and an electrical circuit. The lock assembly includes a lock body, a rotating cylinder, spring loaded lift lock pins and corresponding key pins, a reset cam path and a programming cam path formed on the cylinder, a lift comb for lifting the lift lock pins, a latch for latching the lift comb and a magnet being selectively activated to cause the latch to release the lift comb. The electrical circuit receives a first input signal indicative of an input code entered at the code entry button and a second input signal from a program switch actuated by the programming cam path and is operated to store an entry code when the program switch is actuated and to activate the magnet when an input code matching the stored entry code is received.
Owner:JOHANSSON FRITZ HUGO +1
Security system access control and method
ActiveUS20060181402A1Improve securityImprove security levelColor television detailsClosed circuit television systemsUser codeSecurity system
A security system which includes at least a first sensor, an alarm panel including a control system and programmable apparatus, a connection between the at least one sensor and set alarm panel, a keypad assembly including a camera, and a connection between the keypad assembly and the alarm panel. In various embodiments of the invention the camera includes a CMOS image sensor, the camera produces digital images, the camera tracks the user of the keypad assembly, the camera is remotely controllable from the alarm panel to focus on an object of interest, and / or the camera is remotely controllable from a central monitoring station to focus on an object of interest. In some cases the camera system is configured to take a picture in response to a specific user code entered by the user, take a picture in response to time of day when the input occurs, take a picture in response to invalid code entry and / or take a picture in response to an invalid card being presented. The invention also includes the method for providing enhanced security for protected premises which includes providing at least a first sensor, providing an alarm panel including a control system and programmable apparatus, providing a connection between the at least one sensor and the alarm panel, providing an input device including a camera, and initiating operation of the camera from the alarm panel.
Owner:HONEYWELL INT INC
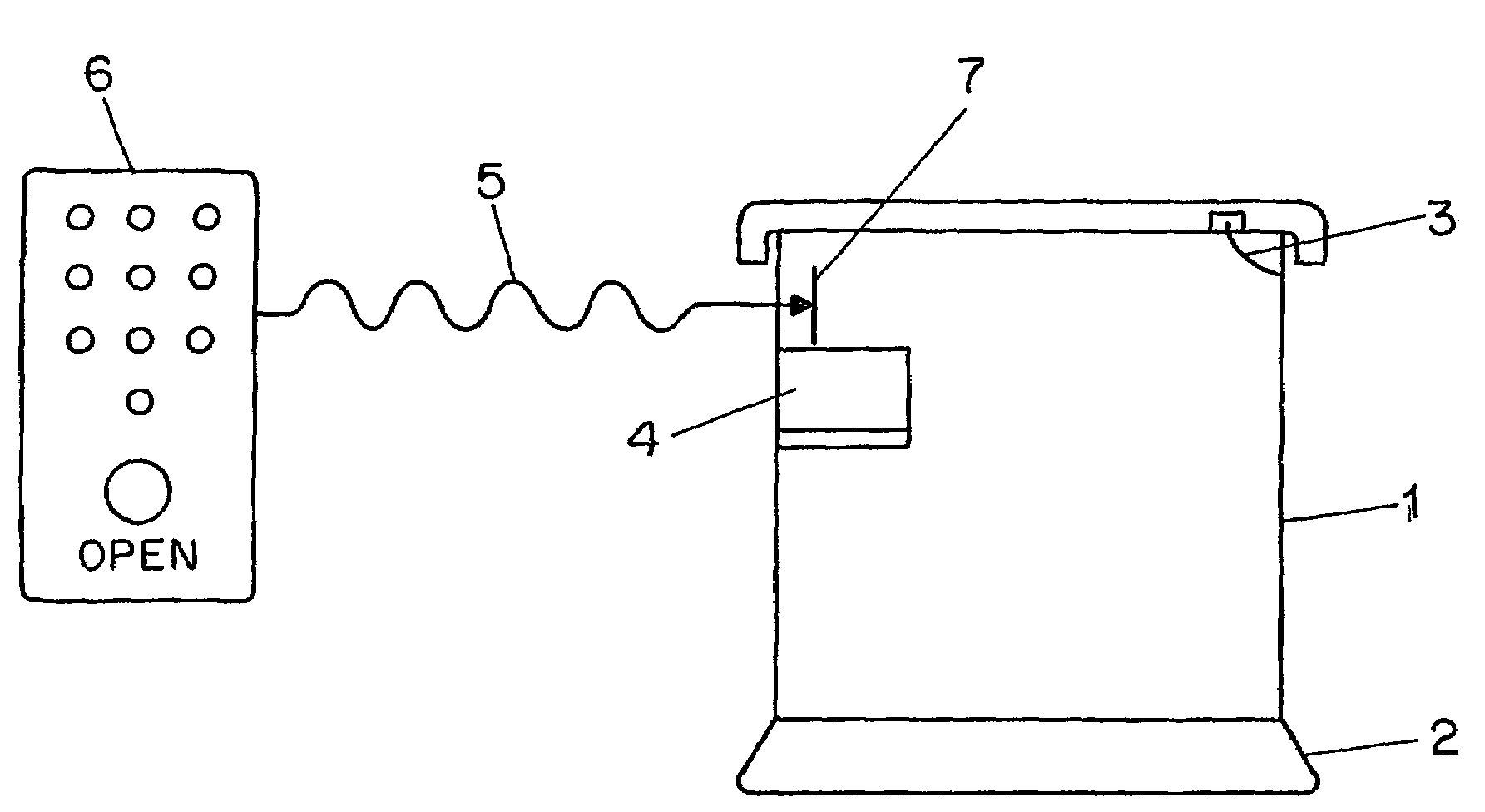
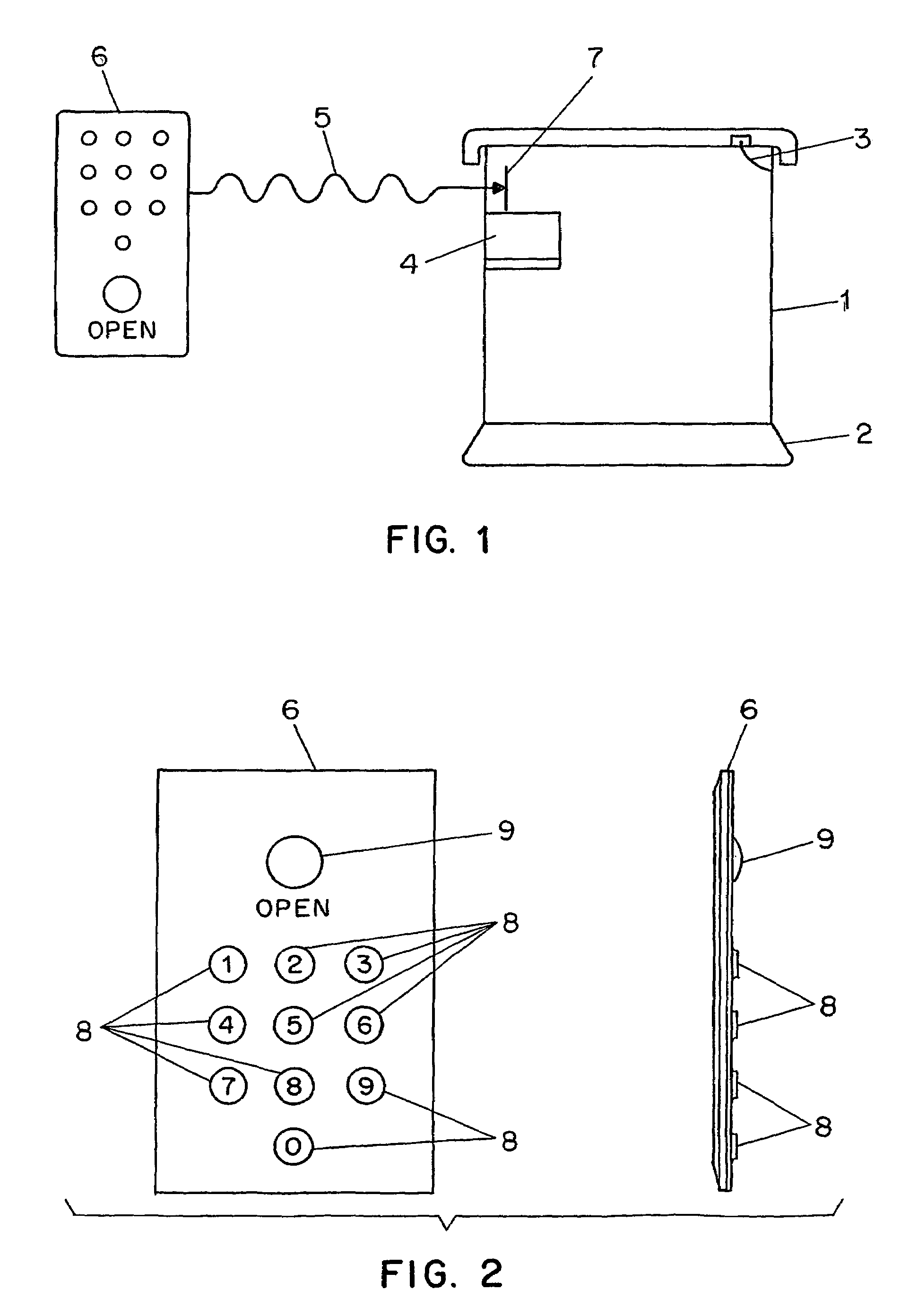
High security wireless key for asynchronous delivery drop boxes
InactiveUS7028339B2Volume/mass flow measurementAnalogue secracy/subscription systemsLocking mechanismEngineering
A wireless key (6), capable of transmitting an ultra-low frequency radio wave signal (5), is used to gain access to a secure receptacle (1), the wireless key (6) and receptacle (1) comprising a system to ensure the secure transfer or delivery of items between parties typically engaging in e-commerce. The wireless key (6) possesses a means to discriminate against the unauthorized entry of the receptacle, such as through the use of buttons to enter a secure access code. The wireless key (6) accepts an access code entry from the user desiring entry to the receptacle (1) and subsequently transmits an ultra-low frequency signal (5) to a receivin and processing means (4). If the analysis of the signal indicates the user of the wireless key (6) is authorized to gain entry to the receptacle (1), the receptacle's locking mechanism (3) is disengaged to allow entry.
Owner:VISIBLE ASSET INC
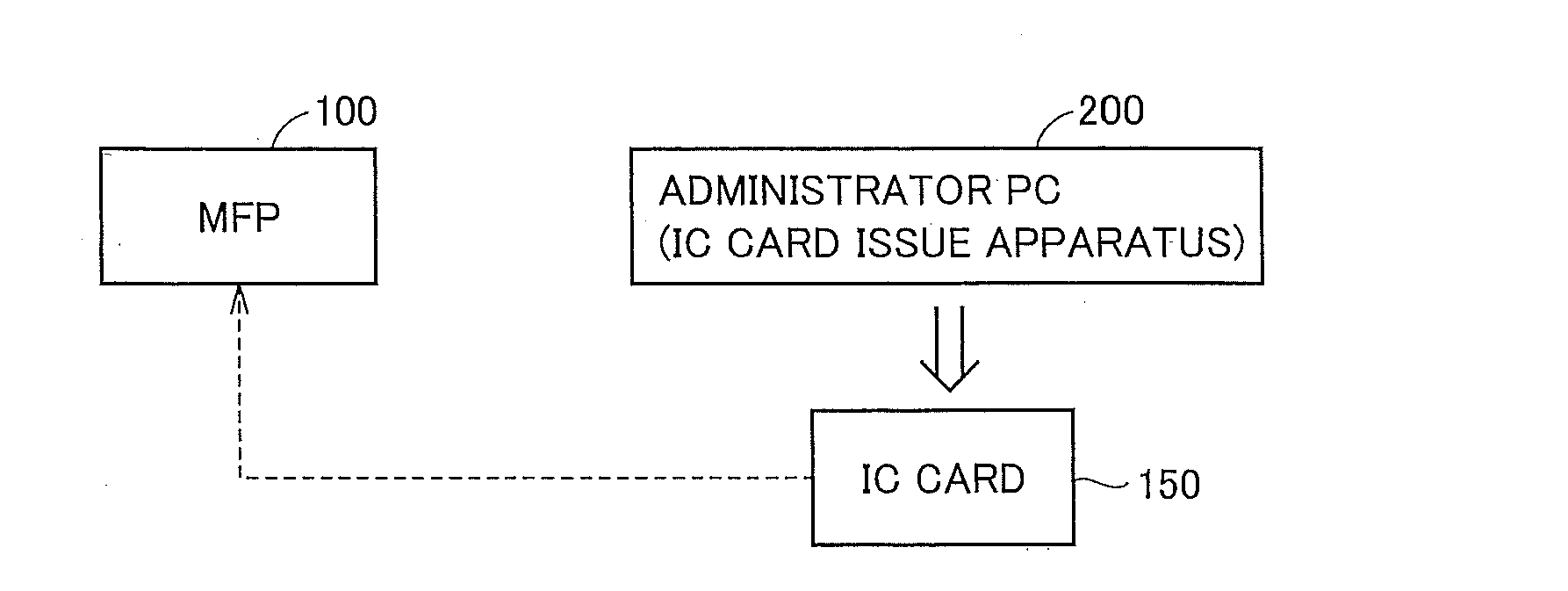
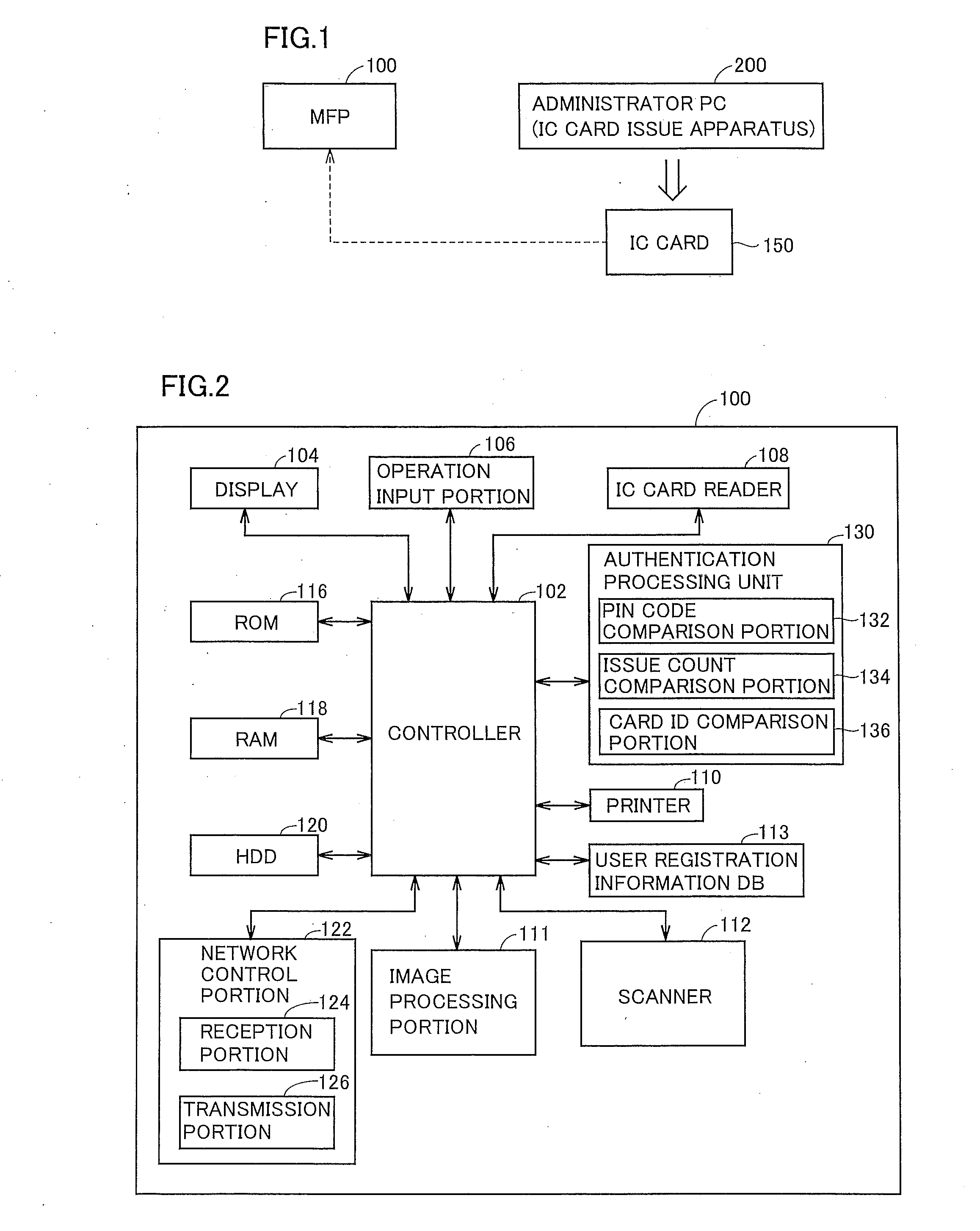
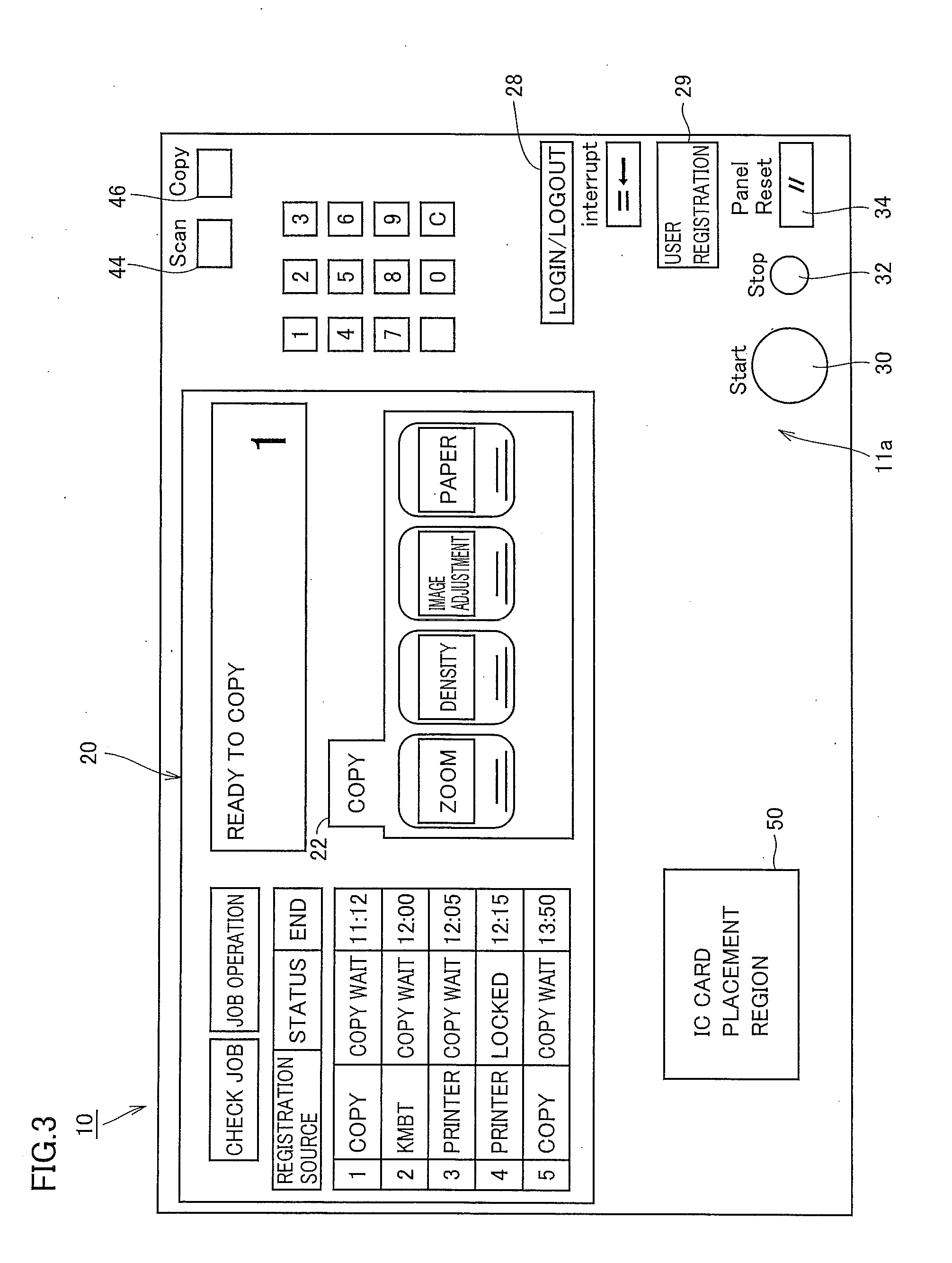
IC card authentication apparatus, IC card authentication method, and recording medium having IC card authentication program recorded thereon
ActiveUS20100031350A1Improve security levelSimple planDigital data processing detailsUnauthorized memory use protectionCard readerAuthentication
An IC card is recognized by an IC card reader. Data is obtained from the recognized IC card. Card ID included in the obtained data is compared with card ID stored in a user registration information DB. If it is determined that the same card ID exists, an IC card issue count included in the obtained data is compared with an IC card issue count stored in the user registration information DB, and it is determined whether the counts are the same. If it is determined that the issue counts are not the same, a PIN code entry window appears so that the entered PIN code is compared with a PIN code in the user registration information DB. If it is determined that the PIN codes are the same, authentication success is displayed.
Owner:KONICA MINOLTA BUSINESS TECH INC
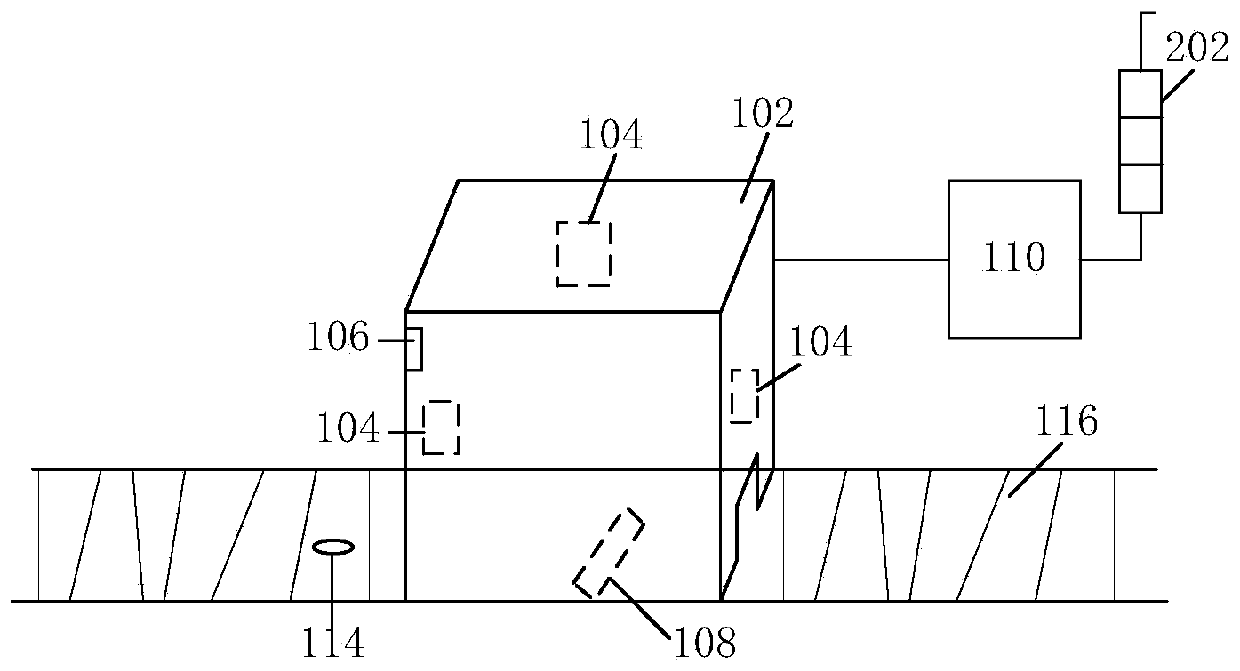
Product detection system and method
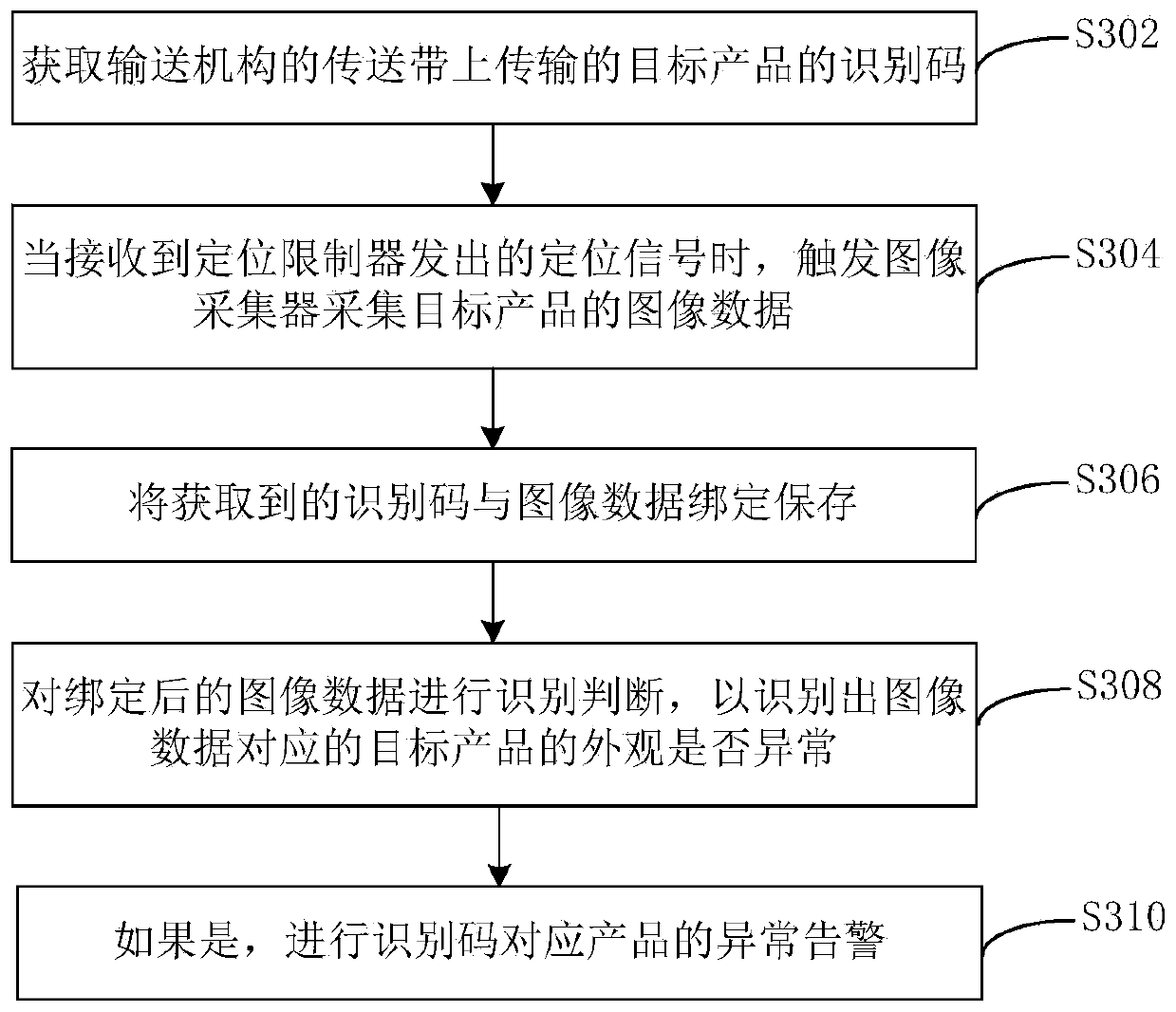
ActiveCN110018172AImprove quality inspection efficiencyAvoid human judgmentImage analysisOptically investigating flaws/contaminationAutomatic controlLight equipment
The invention provides a product detection system and method, and relates to the technical field of appearance quality detection. The system comprises a dark box, an image collector, lighting equipment, a positioning limiter, a controller and a conveying mechanism, wherein the lighting equipment provides illumination for the dark box; a sensor installed on the conveying mechanism sends the read identification code of a target product to the controller; the positioning limiter limits the target product on the conveyor to the dark box and sends a positioning signal to the controller; and the controller triggers the image collector to collect image data of the target product after receiving the positioning signal, recognizes and judges the image data bound with the identification code, and performs an abnormal alarm for the abnormal appearance of the target product. The system can realize the full automatic control process of identification code entry of the target product, appearance judgment of the target product and the abnormal appearance alarm, avoid the artificial process of judging the target product quality by naked eyes and registering the abnormal appearance of the product,and improve the quality detection efficiency of the target product.
Owner:伟创力电子设备(深圳)有限公司
Systems and methods for authentication code entry in touch-sensitive screen enabled devices
ActiveUS20180203600A1Improve securityInput/output for user-computer interactionDigital data authenticationHuman–computer interactionAuthentication
Owner:VERIFONE INC
Method for generation of even numbered reduced gray codes
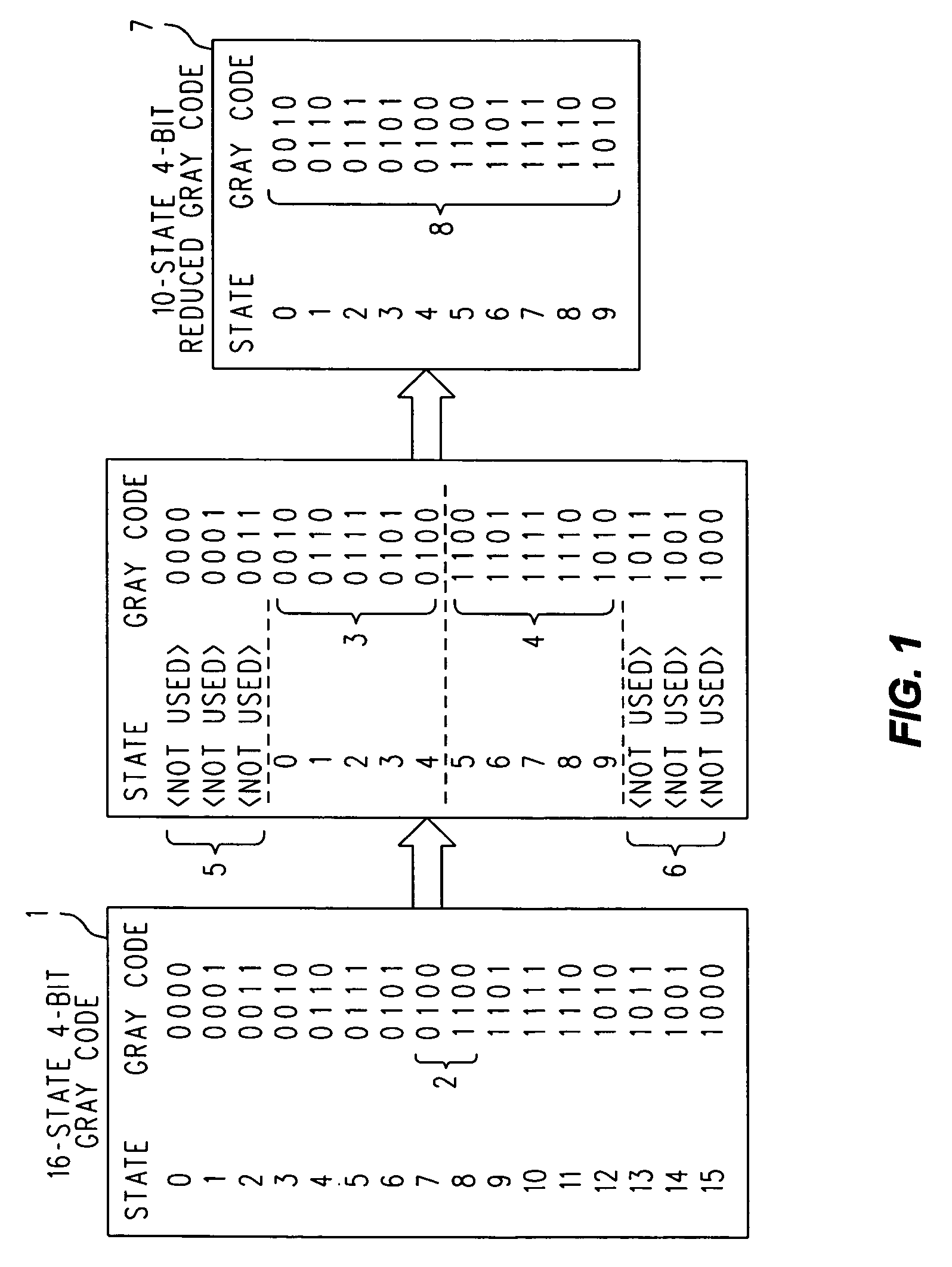
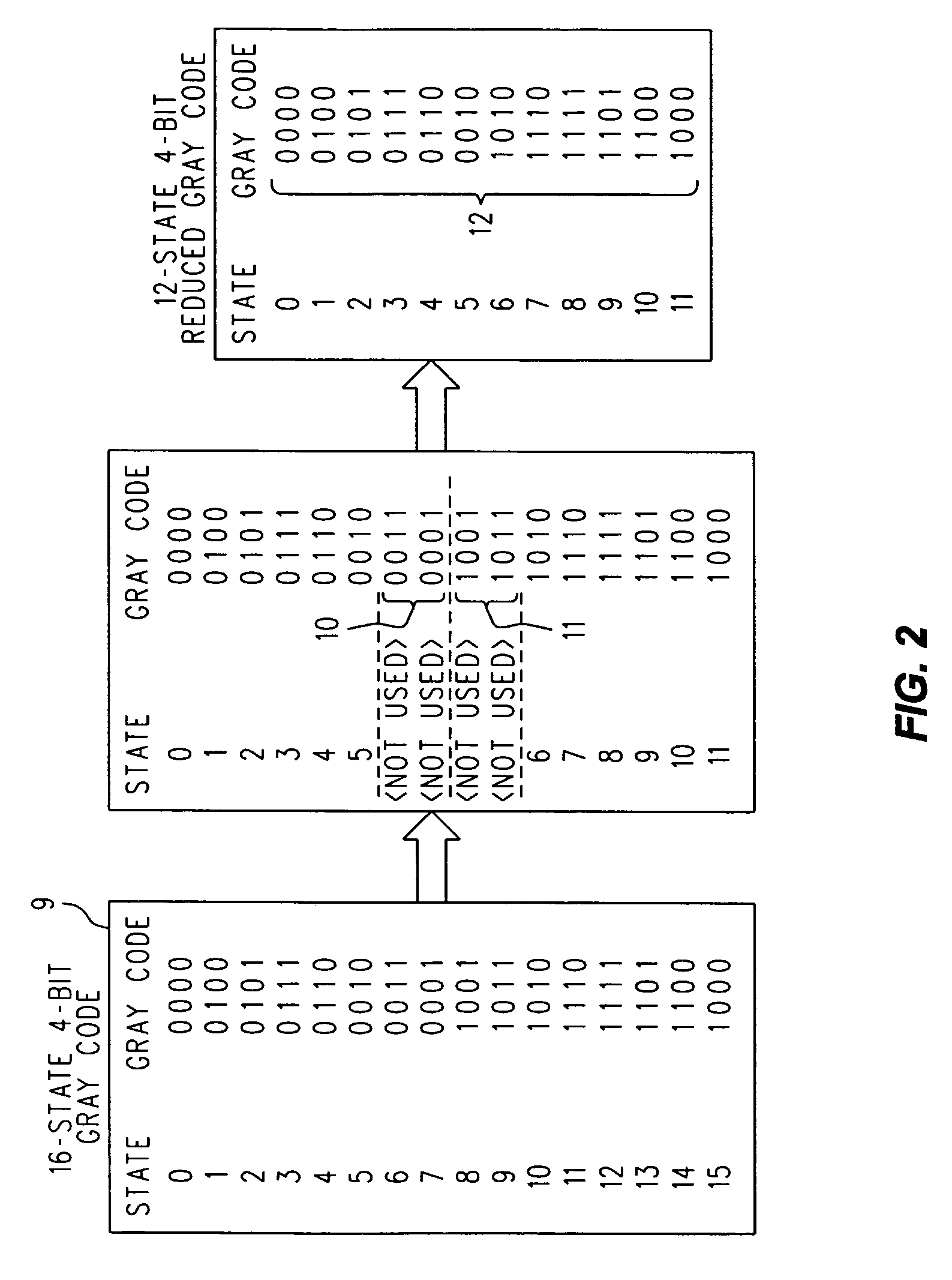
A cyclic reduced Gray code in n-many bits having 2k-many entries, for any natural number k, where 2(n−1)<2k<2n and n is a positive integer, is found by first constructing a 2n-many entry code in n-many bits with a reflected binary technique, and then selecting the last k-many ordered entries in the first half of the full reflected binary code, followed by the first k-many ordered entries in the second half of the full reflected binary code. These ordered 2k-many entries are a shortened cyclic reduced Gray code in n-many bits. Alternatively, the first k-many ordered entries in the first half of the full reflected binary code can be selected, followed by the last k-many ordered entries in the second half of the full reflected binary code. If either the original or reduced Gray code is expressed as a table whose columns are bit positions and whose rows are the code entries, then entire columns can optionally be interchanged at will, either before or after the 2k-many selection, to produce additional different cyclic reduced Gray codes that do not outwardly appear to be ‘reflected’ ones.
Owner:AVAGO TECH INT SALES PTE LTD
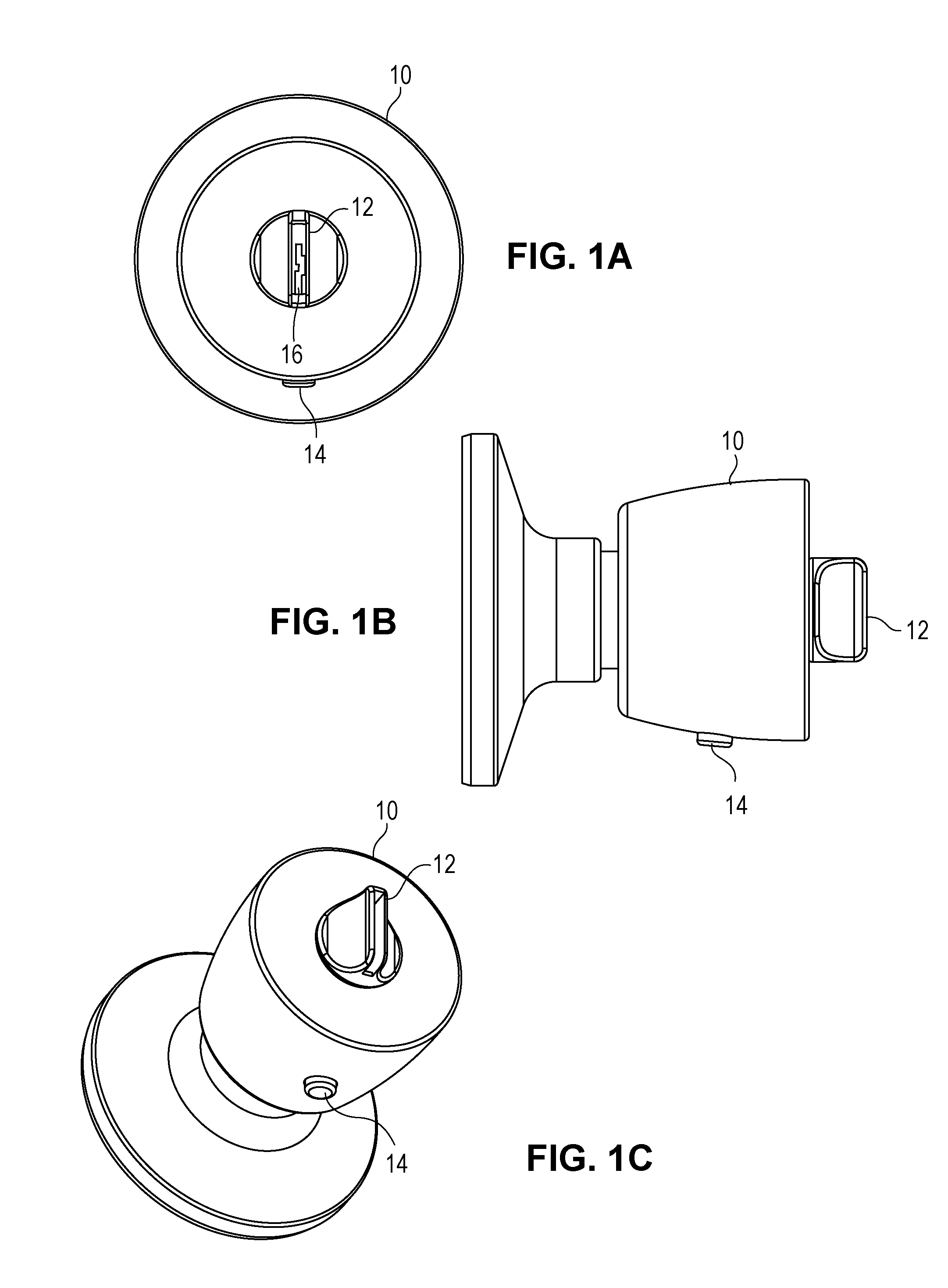
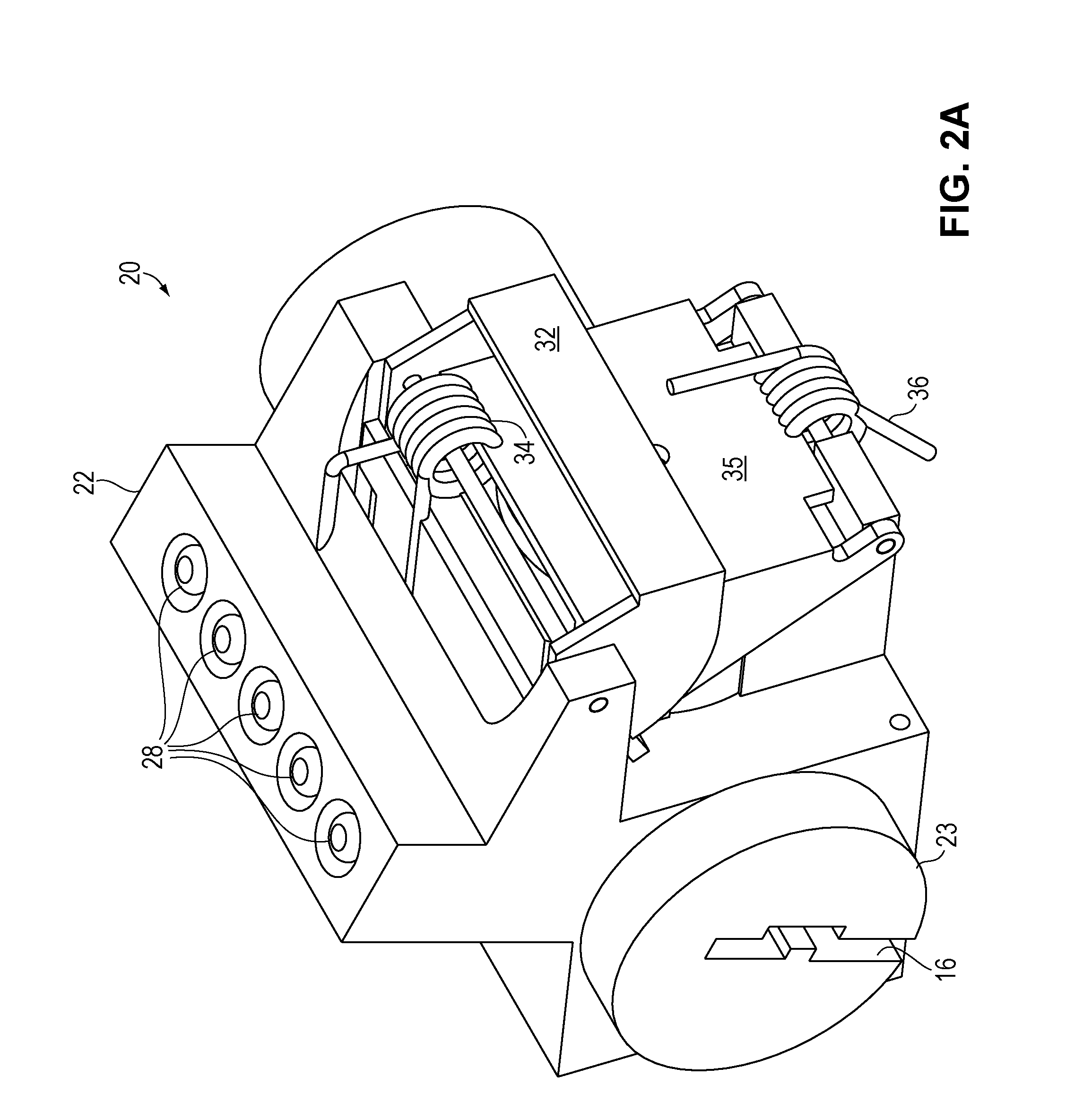
Multi-control entry door hardware
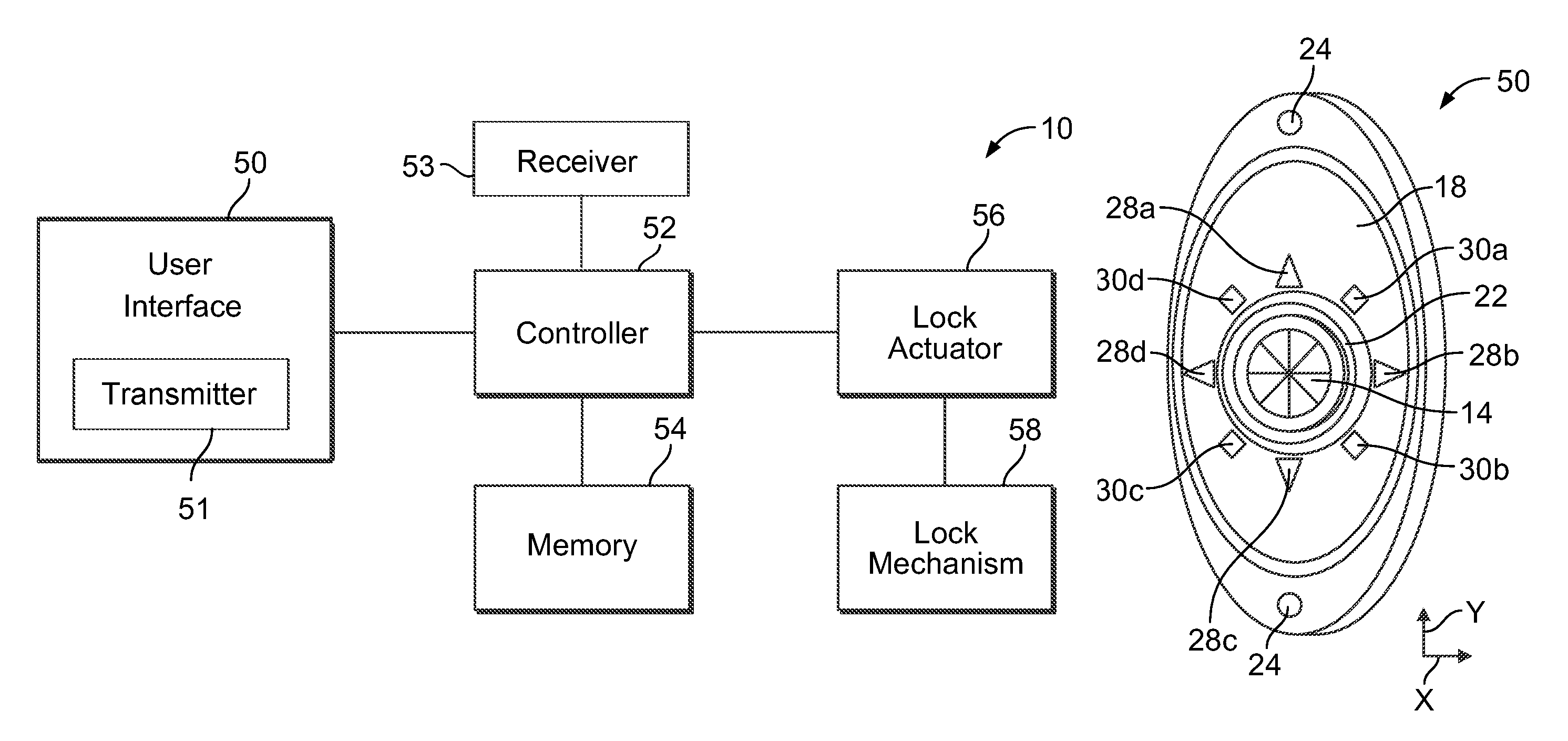
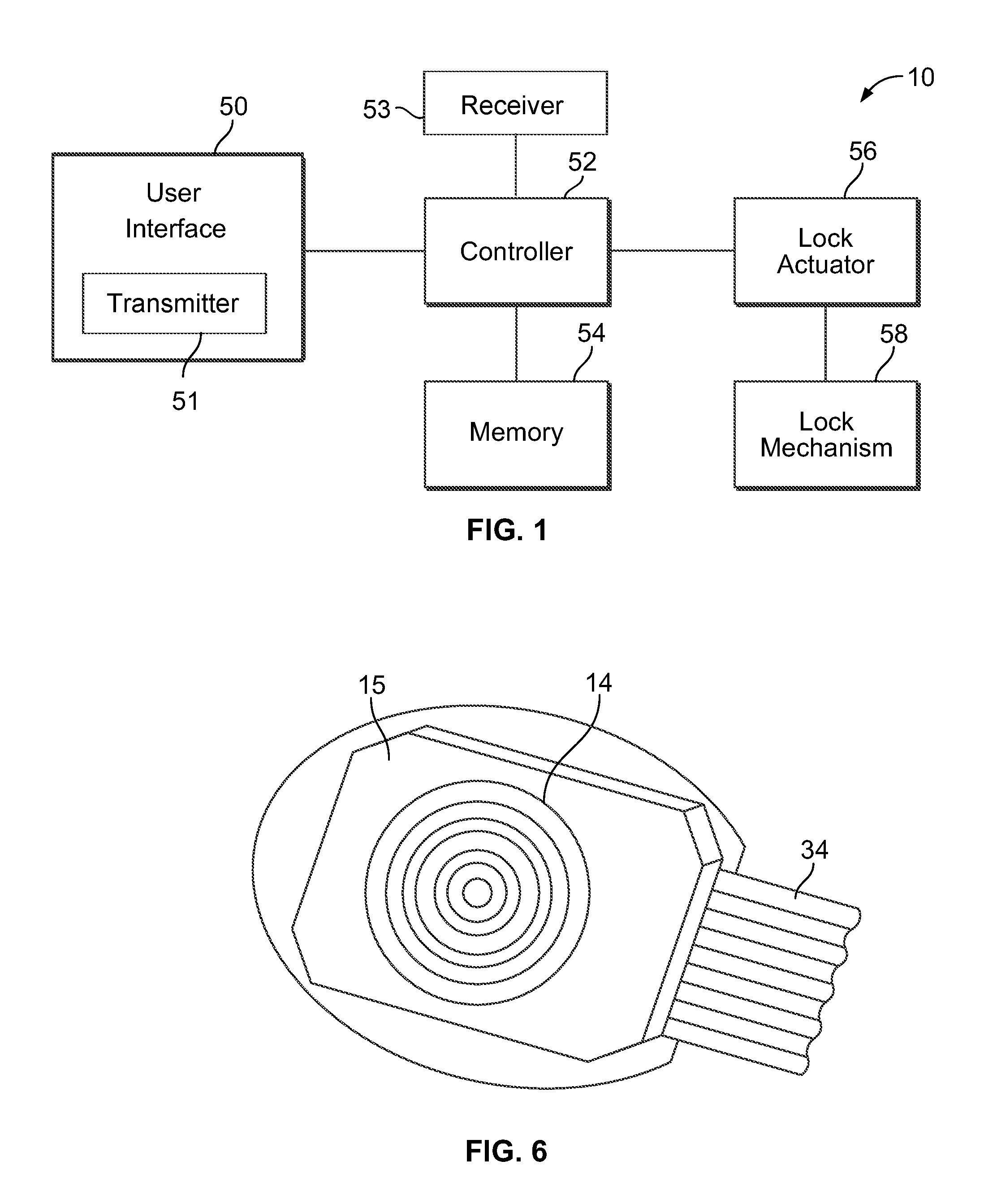
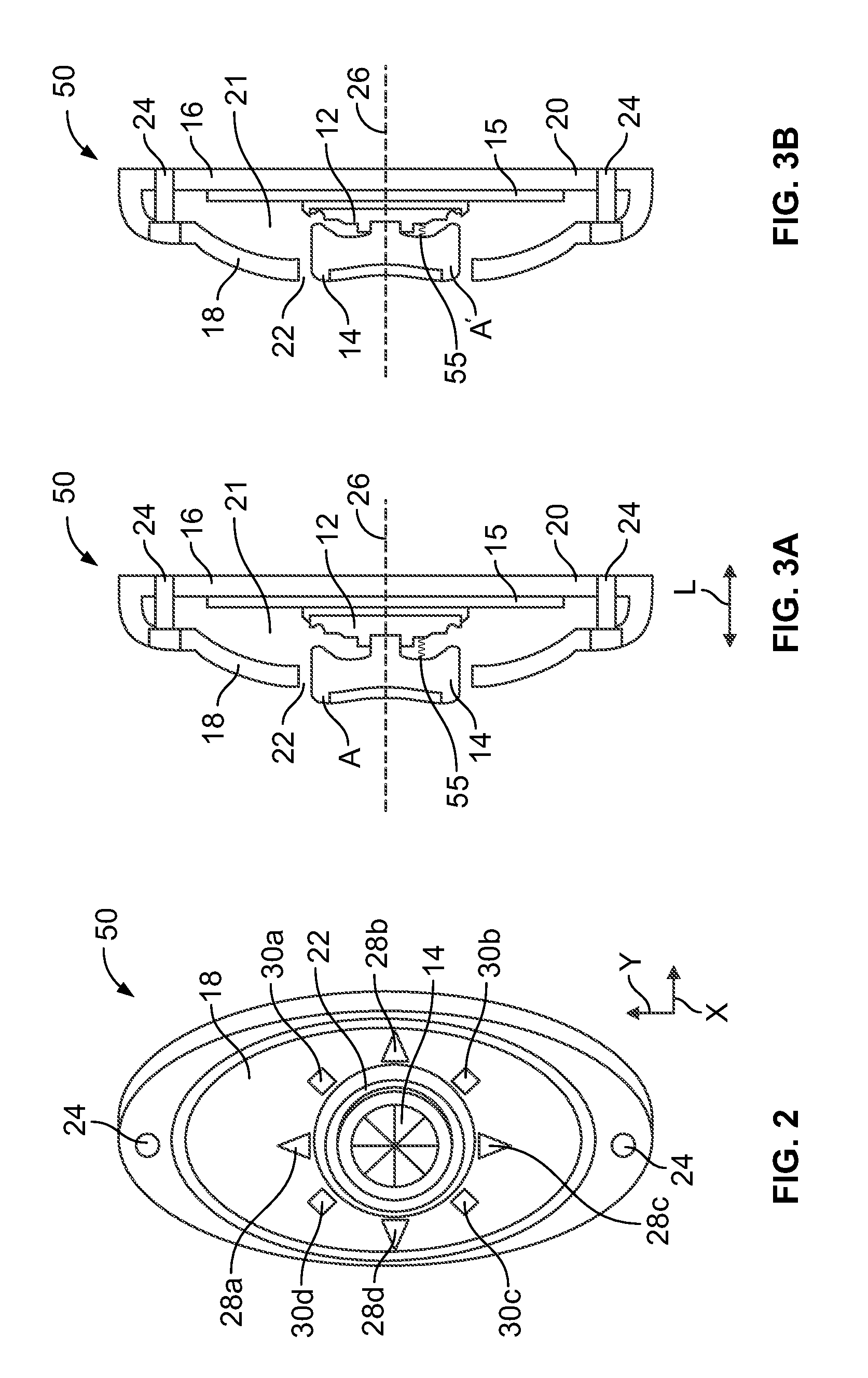
An electronic coded entry lock that includes a multifunction switch having an actuator and a circuit member. The actuator is configured to be displaced to a plurality of input positions. For example, the actuator may be displaced to at least four, and in some instances at least eight, input positions. Further, the actuator may have at least two axes of movement. Moreover, the actuator may be configured for two or three dimensional movement. When the actuator is displaced to an input position, the circuit member may provide a signal associated with that input position. The controller may determine whether the signals provided by the circuit member correspond to a security code for the electronic coded entry lock. If the signal(s) does / do correspond to the security code, the controller may generate a command to actuate a lock actuator that displaces at least a component of a lock mechanism.
Owner:SCHLAGE LOCK
Secure Controlled Substance Pill Dispensing Device
InactiveUS20180028406A1Pharmaceutical containersMedical packagingTamper resistanceControlled substance
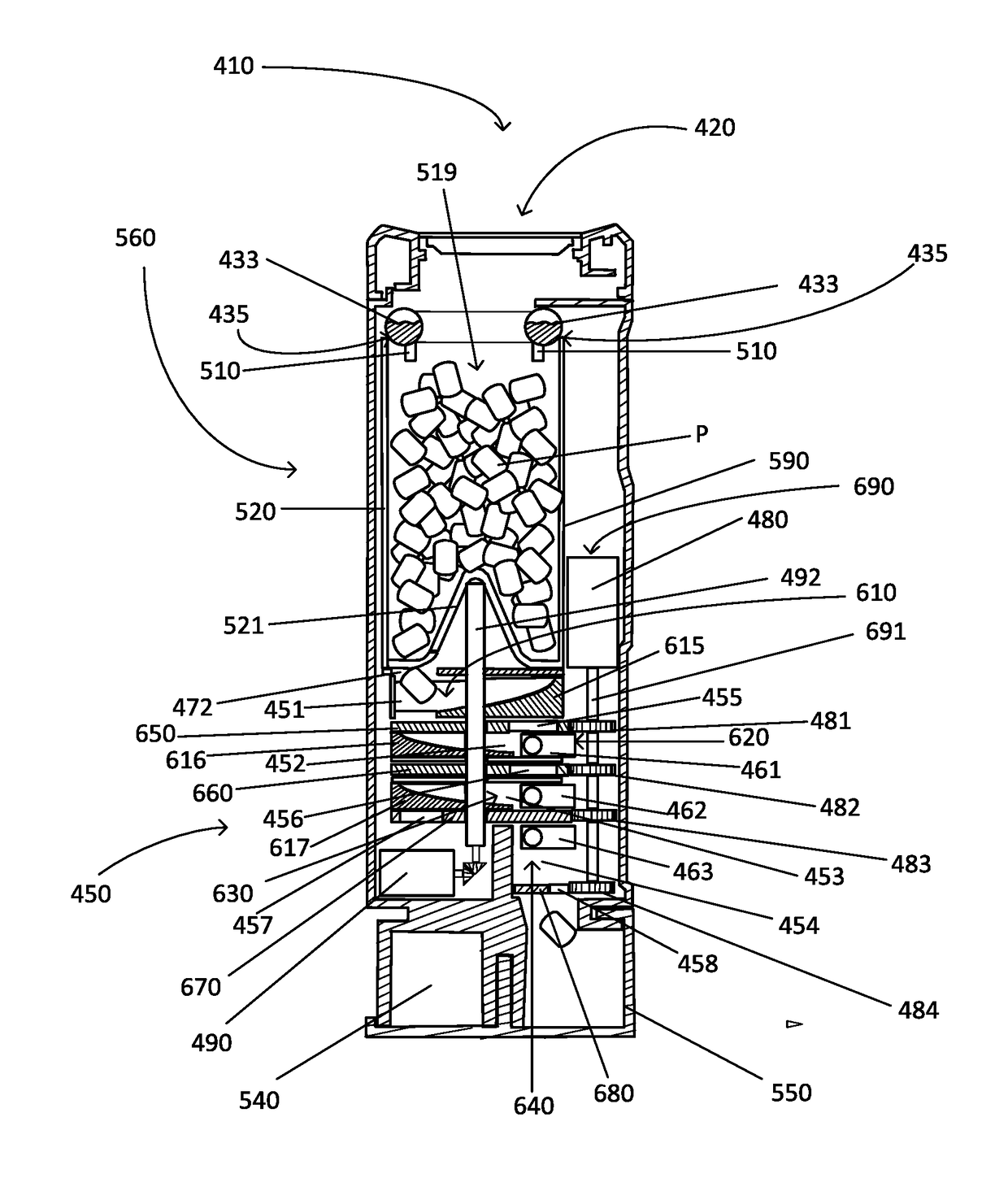
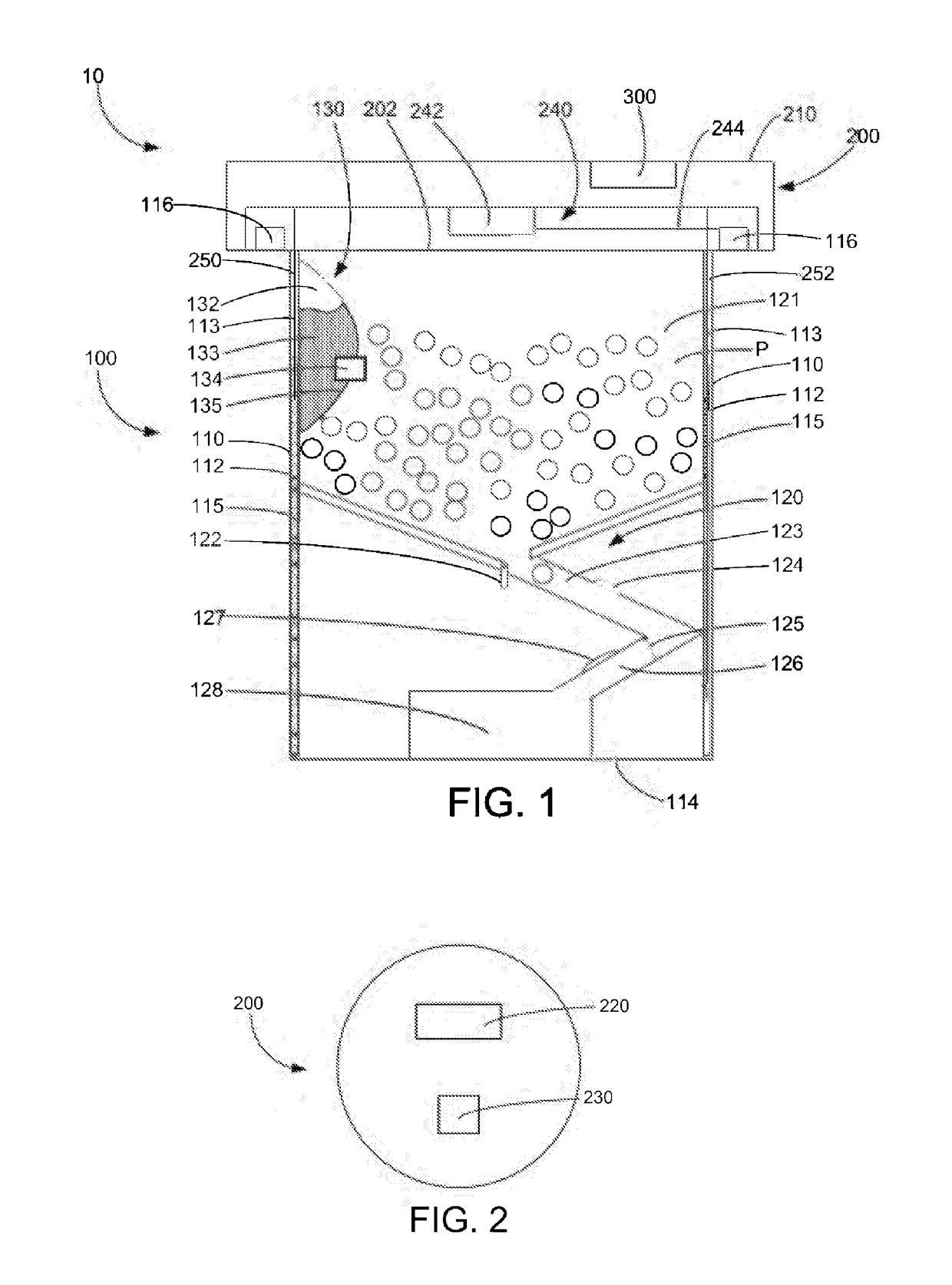
A pill dispensing device includes a lid with an RFID reader and a container that engages that lid. The container includes a hopper that is configured to hold a plurality of pills and a tray that is connect that hopper. The container can dispense a pill from the hopper into the tray when an authorized RFID rob is read by the RFID reader. The pill dispensing device may include a code entry mechanism on the side of the container. The code entry mechanism activates or deactivates a lock. The lock is capable of securing the lid to the container. The pills are dispensed through the pill dispensing device when certain parameters are met. If the device it tampered with, the pills may be rendered unusable by a tamper resistance mechanism.
Owner:PATTON JIM
Selective telephone blocker with timer
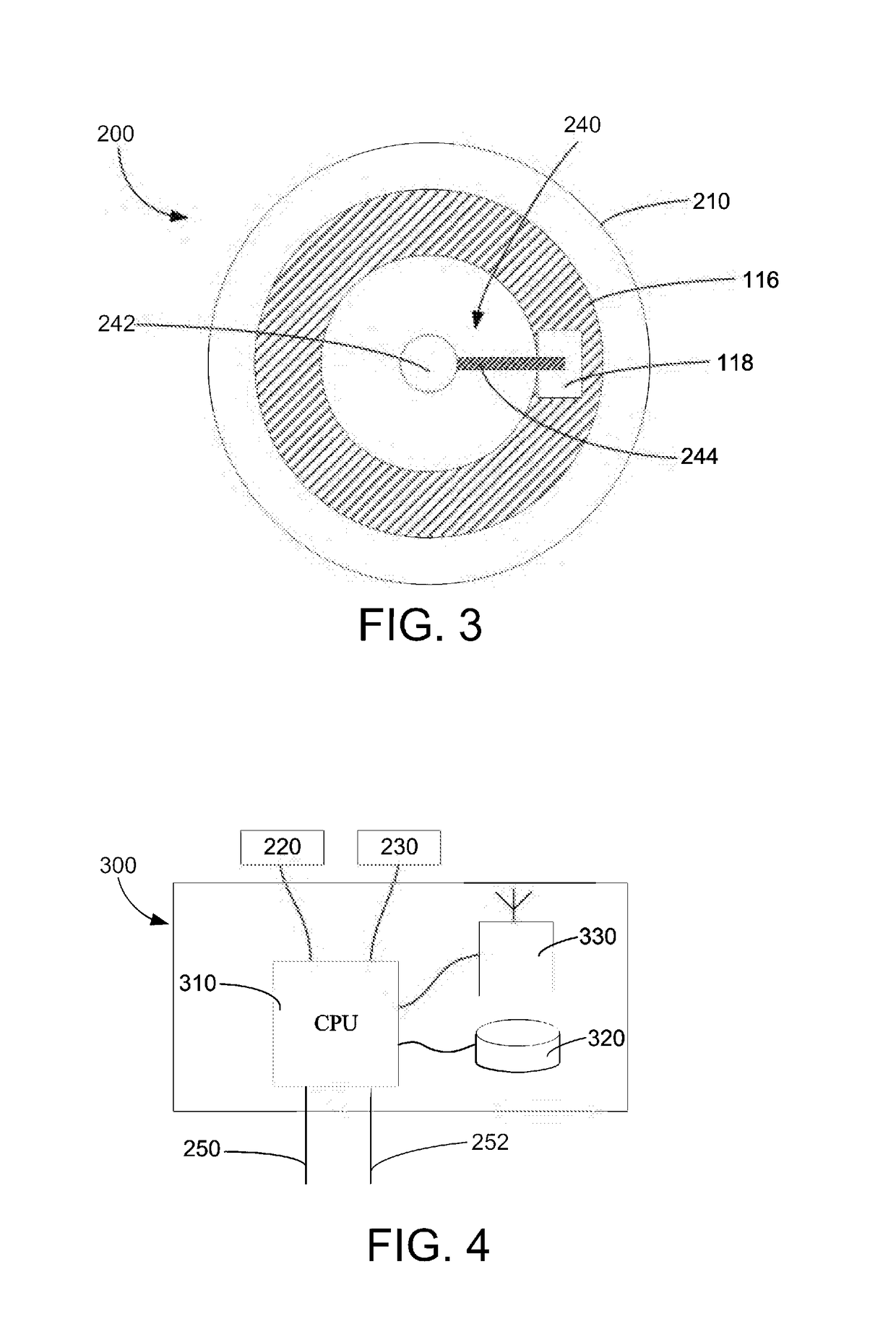
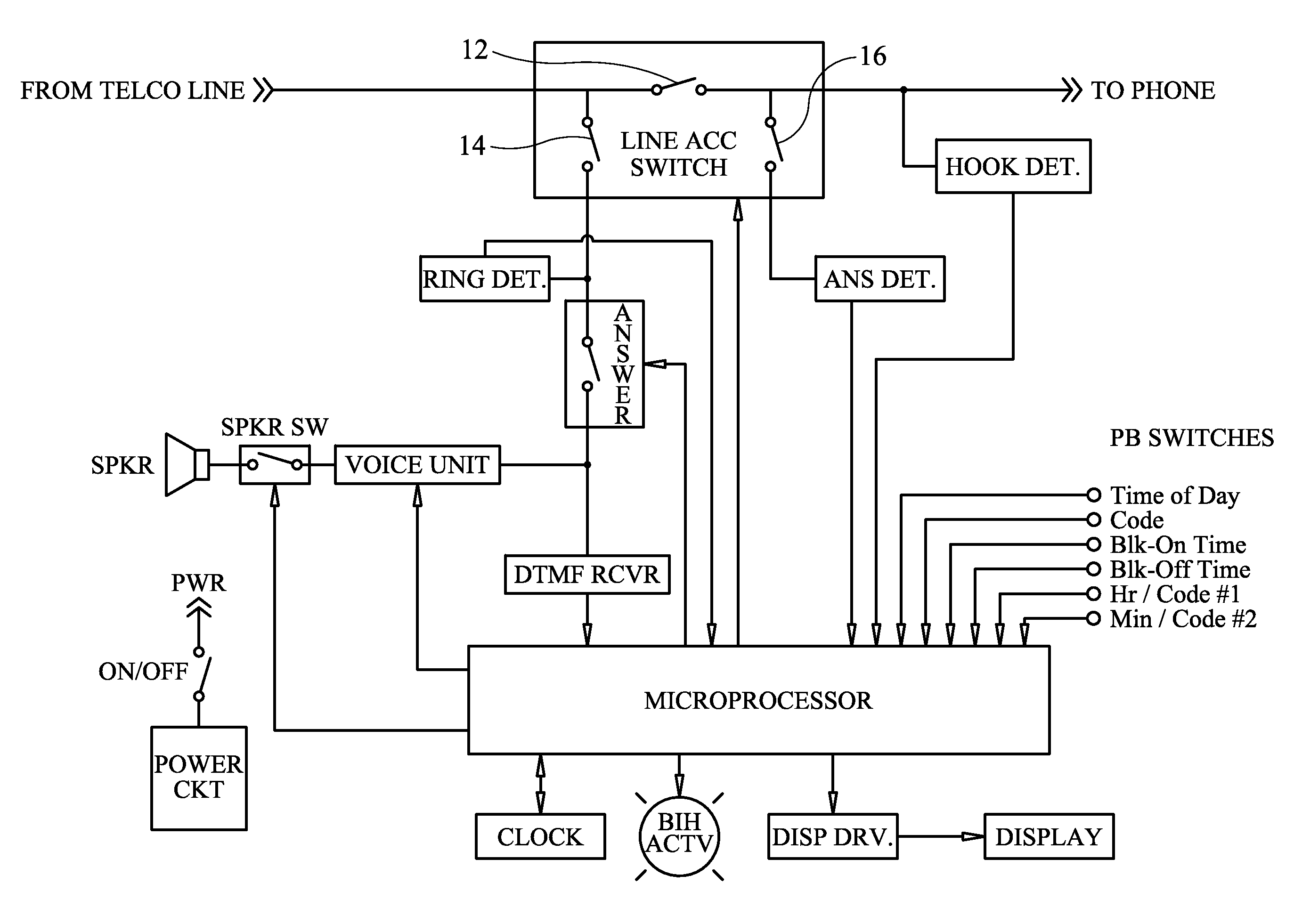
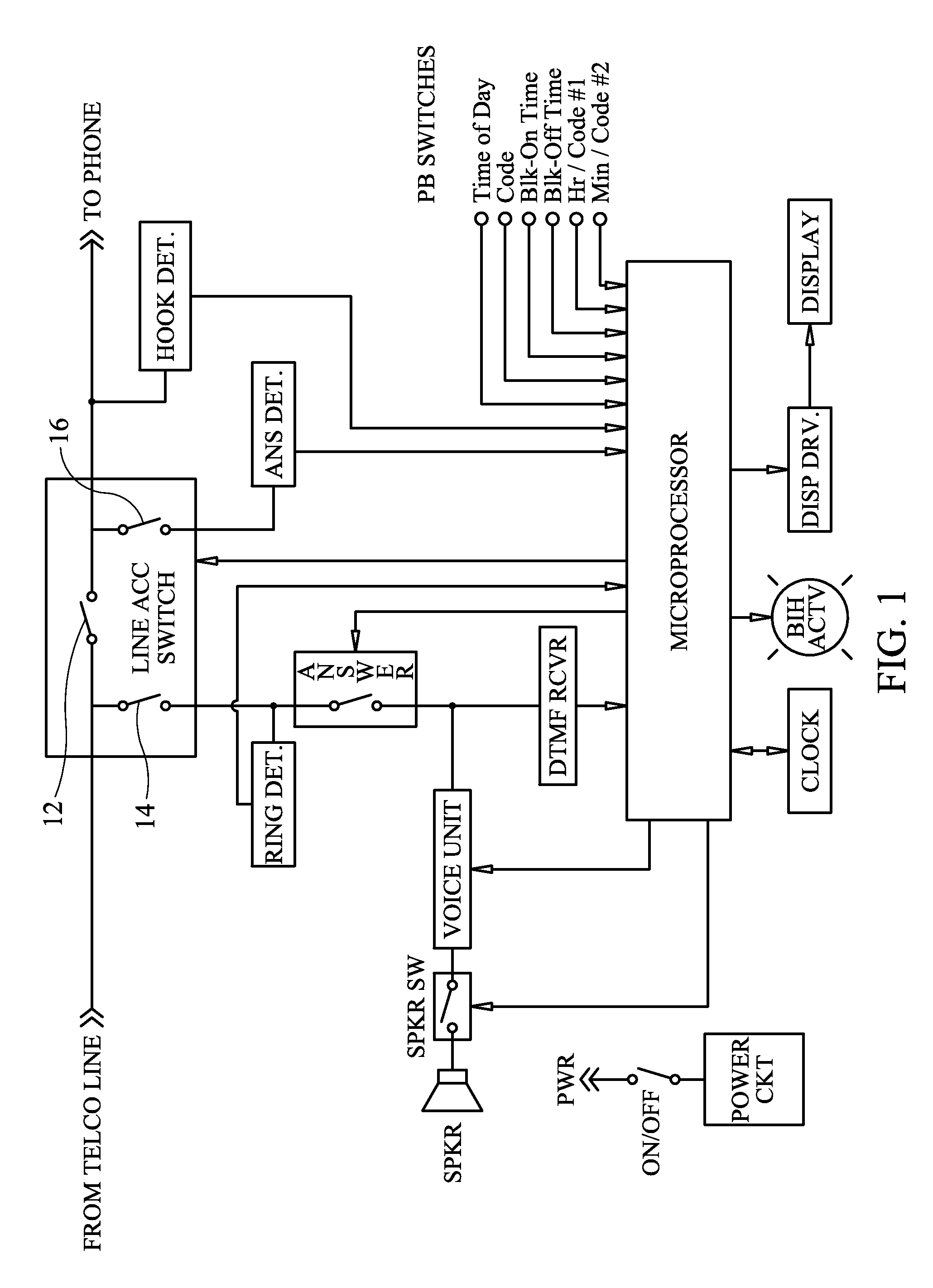
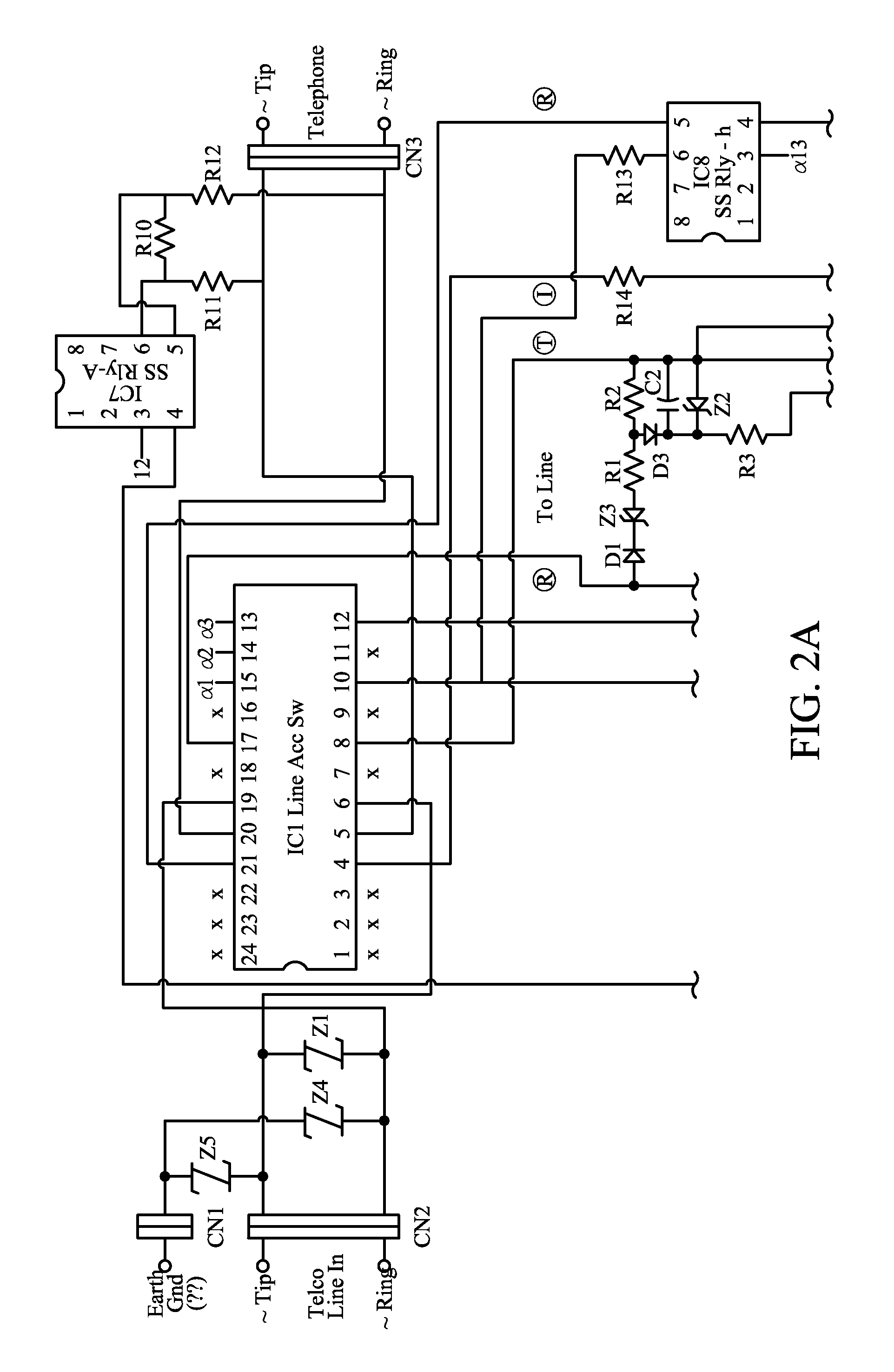
Disclosed is a selective telephone call blocker, preferably with timer. The user preferably sets the current time and one or more beginning and ending time periods during which the call block feature is active. The user then selects, one or more codes, such as two letter or number code(s). During the period of time in which the call block feature is active the device will automatically ask the caller to enter the code in order for the call to be completed. If the correct code is entered within a preset time period the call will be transmitted to the telephone or answering machine. If an incorrect code or no code is entered, the invention preferably repeats the request for correct code entry. If within a next preset time period the correct code is not entered the call will be disconnected. Preferably, the call block feature is not operational if the receiving phone is in use. In this case, the calling party will get a busy signal if the receiving party does not have a call waiting feature. If the receiving party does have a call waiting feature, then it is the option of the receiving party to acknowledge the receipt of the telephone call. The device is compatible with existing telephone devices and can be connected between the standard telephone wall outlet and a telephone set with or without an answering machine. Alternatively, the blocker can be connected at the portion of the phone line before the phone line diverges into multiple lines.
Owner:JNW PARTNERS
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com