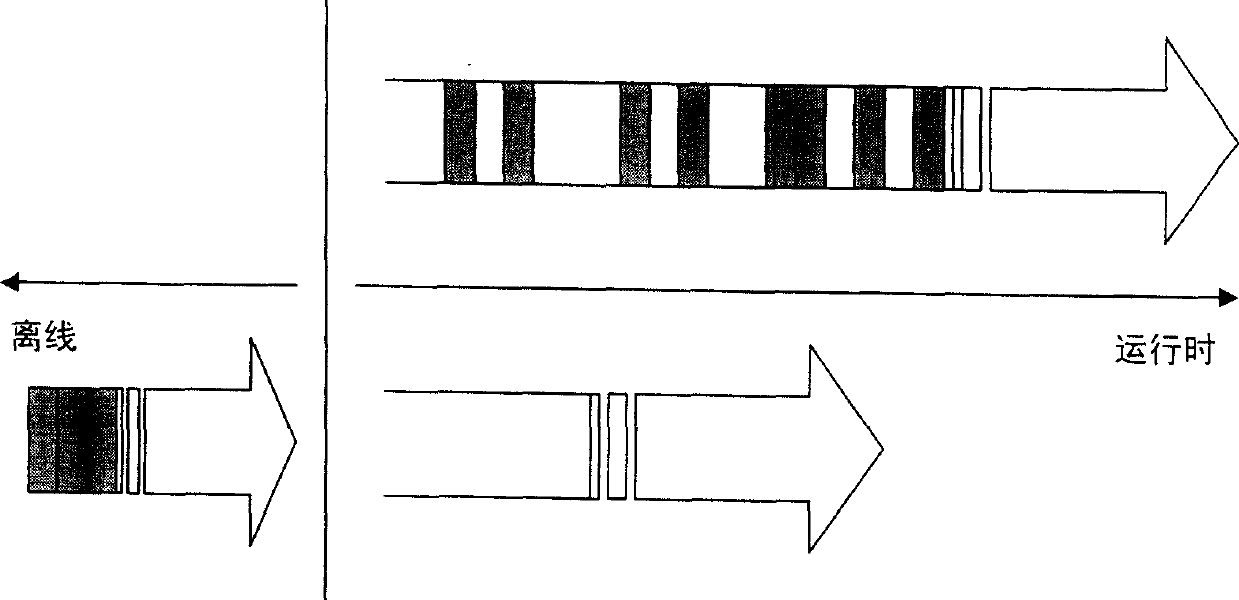
Patents
Literature
110 results about "Duplicate code" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Duplicate code is a computer programming term for a sequence of source code that occurs more than once, either within a program or across different programs owned or maintained by the same entity. Duplicate code is generally considered undesirable for a number of reasons. A minimum requirement is usually applied to the quantity of code that must appear in a sequence for it to be considered duplicate rather than coincidentally similar. Sequences of duplicate code are sometimes known as code clones or just clones, the automated process of finding duplications in source code is called clone detection.
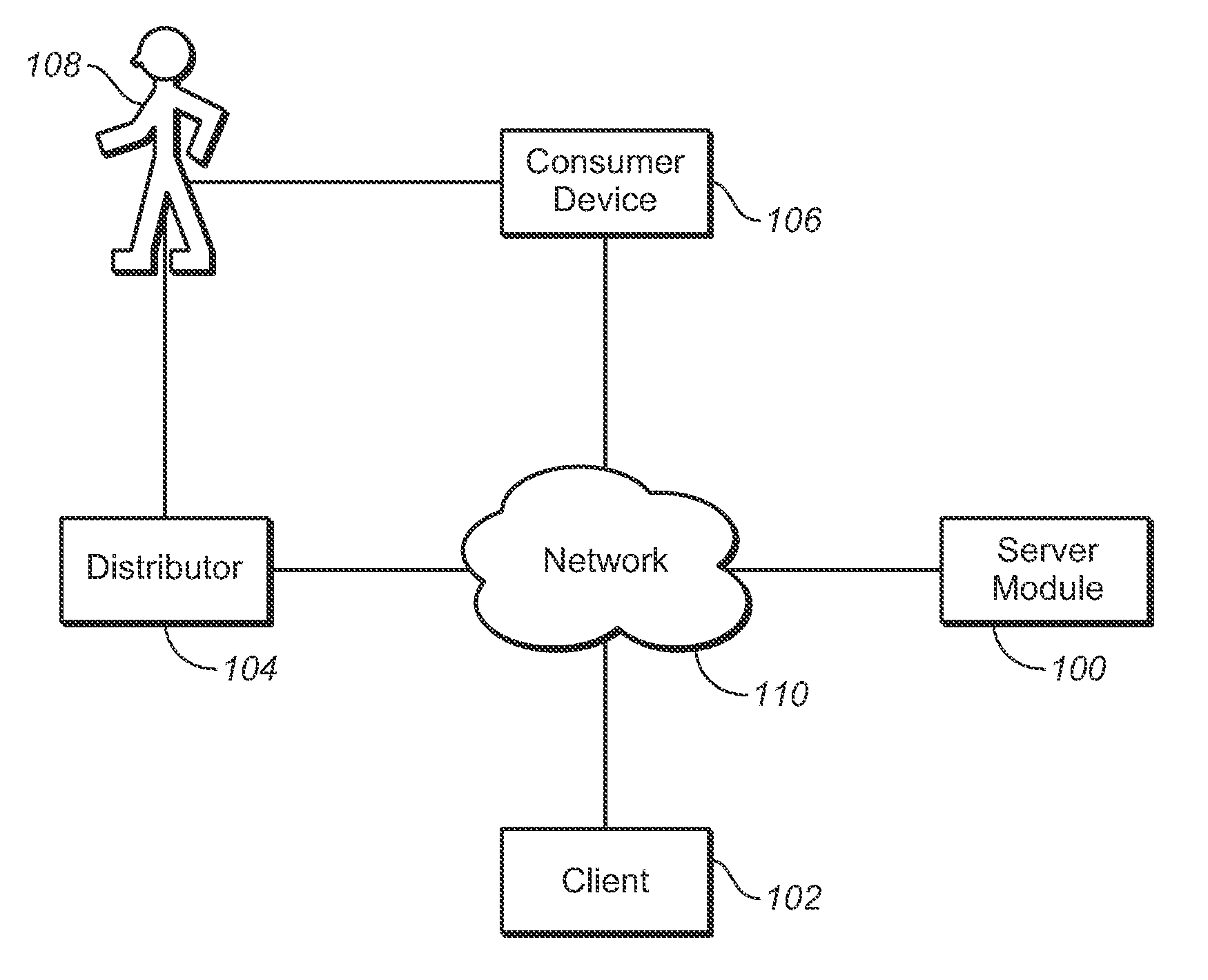
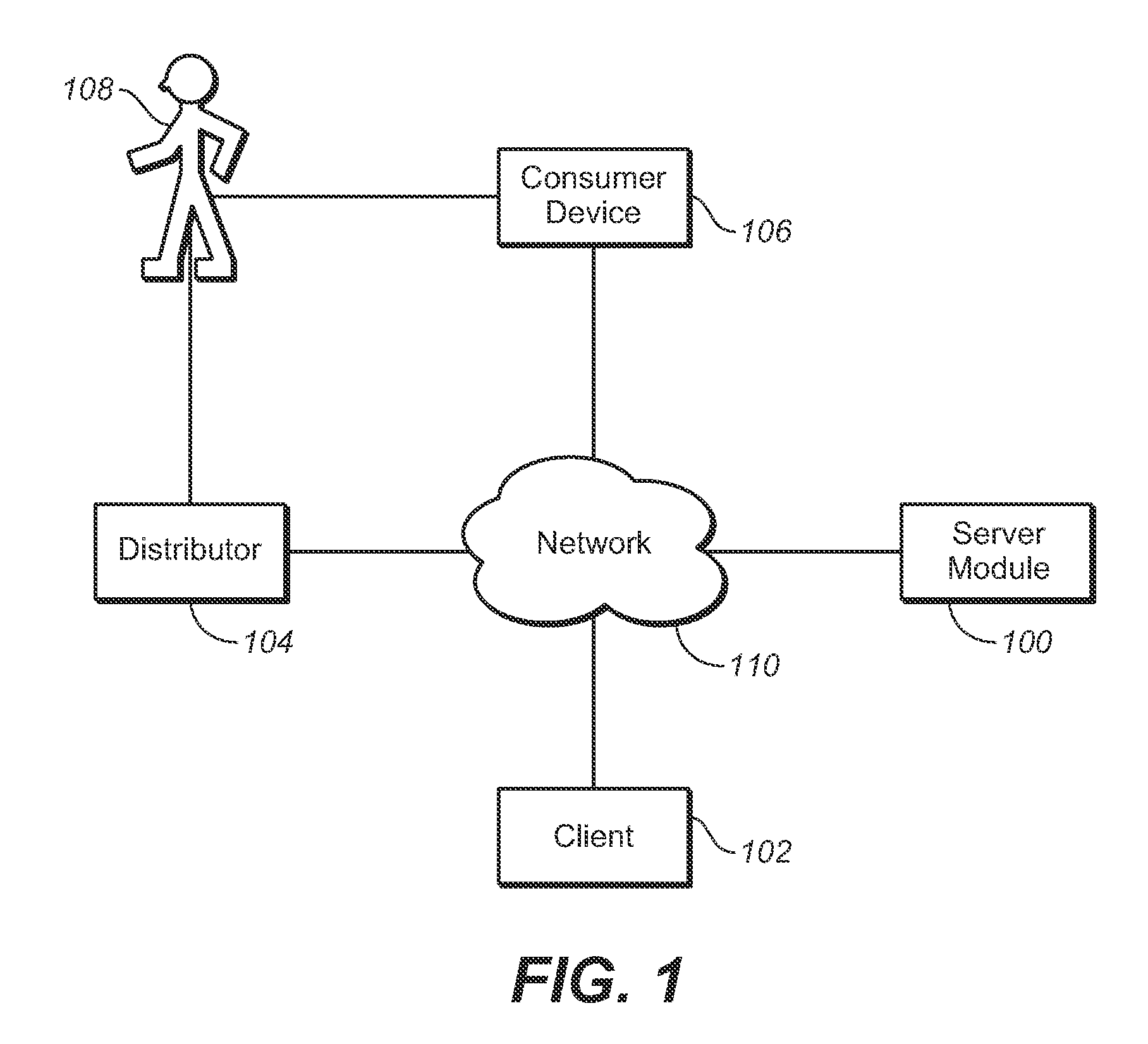
System and Method of Detecting Product Code Duplication and Product Diversion
InactiveUS20080011841A1Buying/selling/leasing transactionsRecord carriers used with machinesDuplicate codeWorld Wide Web
Systems and methods for detecting product code duplication and product diversion are disclosed herein. One embodiment includes generating a plurality of product codes, each product code being unique for each separate item of a set of items, recording a quantity of authentication requests for a product code of the plurality of product codes, and in response to the quantity of authentication requests for the product code matching or exceeding a predetermined threshold, identifying the product code as a suspected duplicated. One embodiment includes recording locations of items of the set of items based on geographical data associated with authentication requests of the plurality of product codes associated with the set of items, in response to identifying a pre-identified quantity or percentage of the items record locations different from pre-identified destination of the respective items, identifying one or more of the product codes to determine if one or more of the corresponding items have been diverted.
Owner:YOTTAMARK
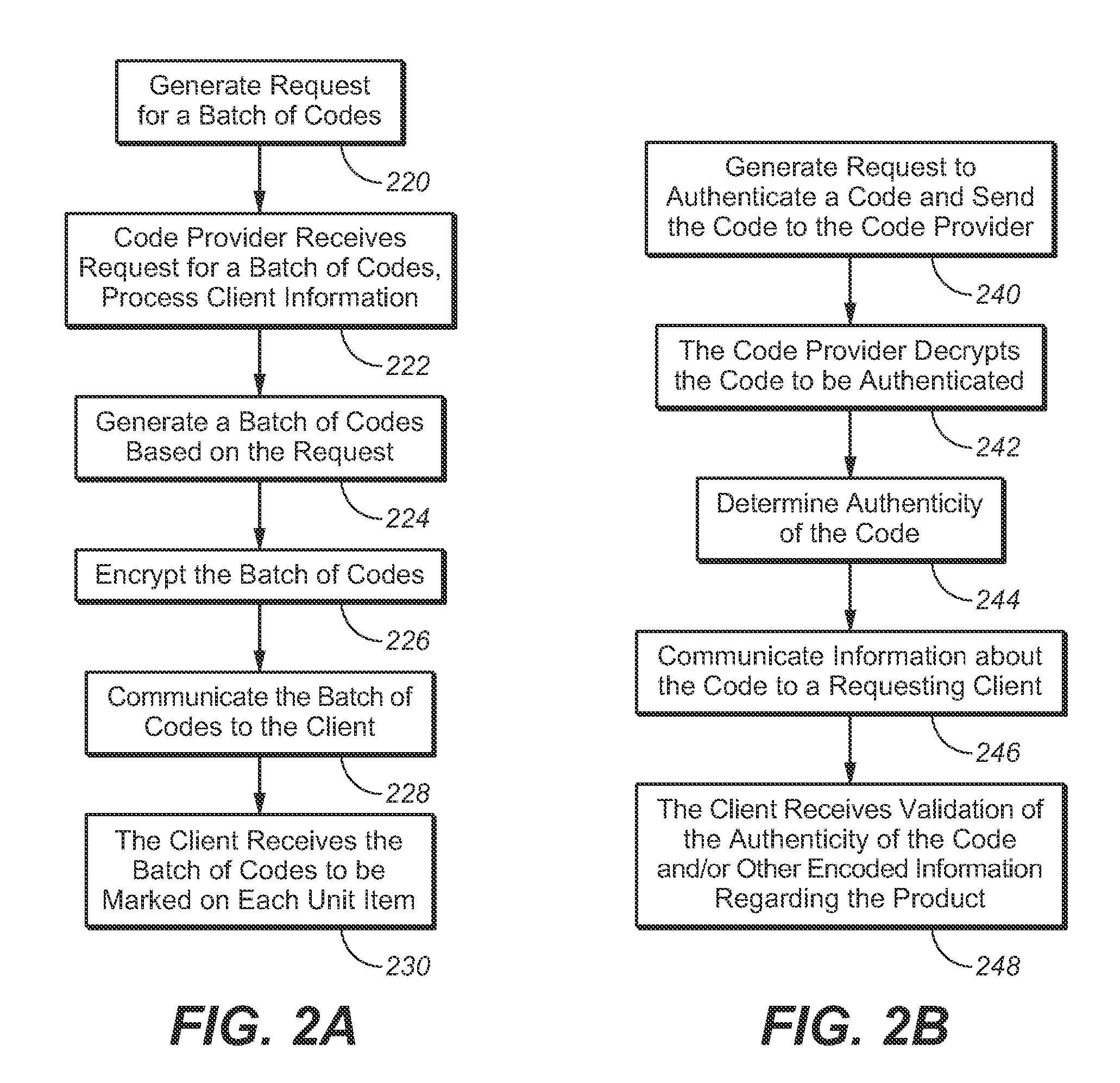
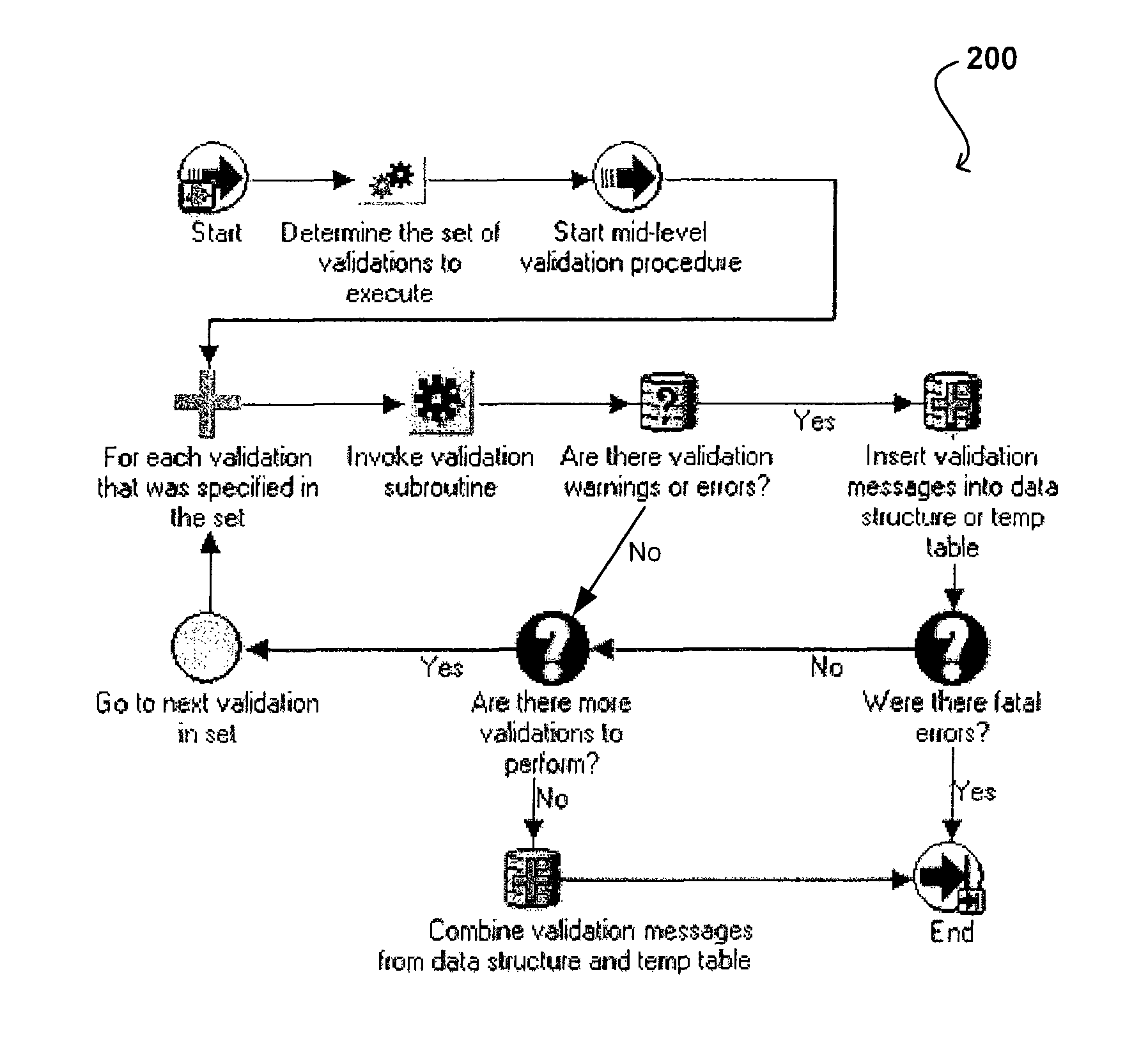
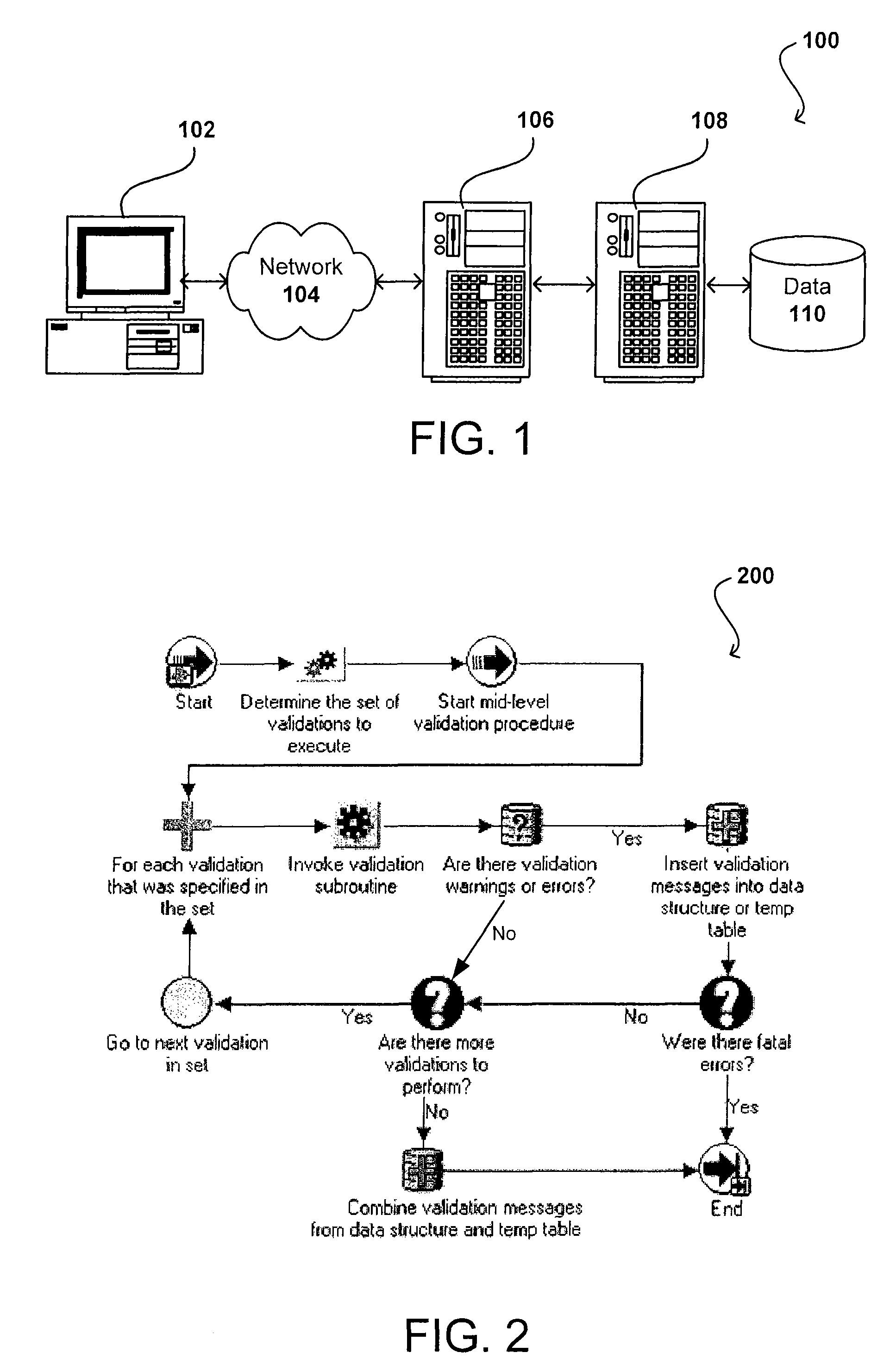
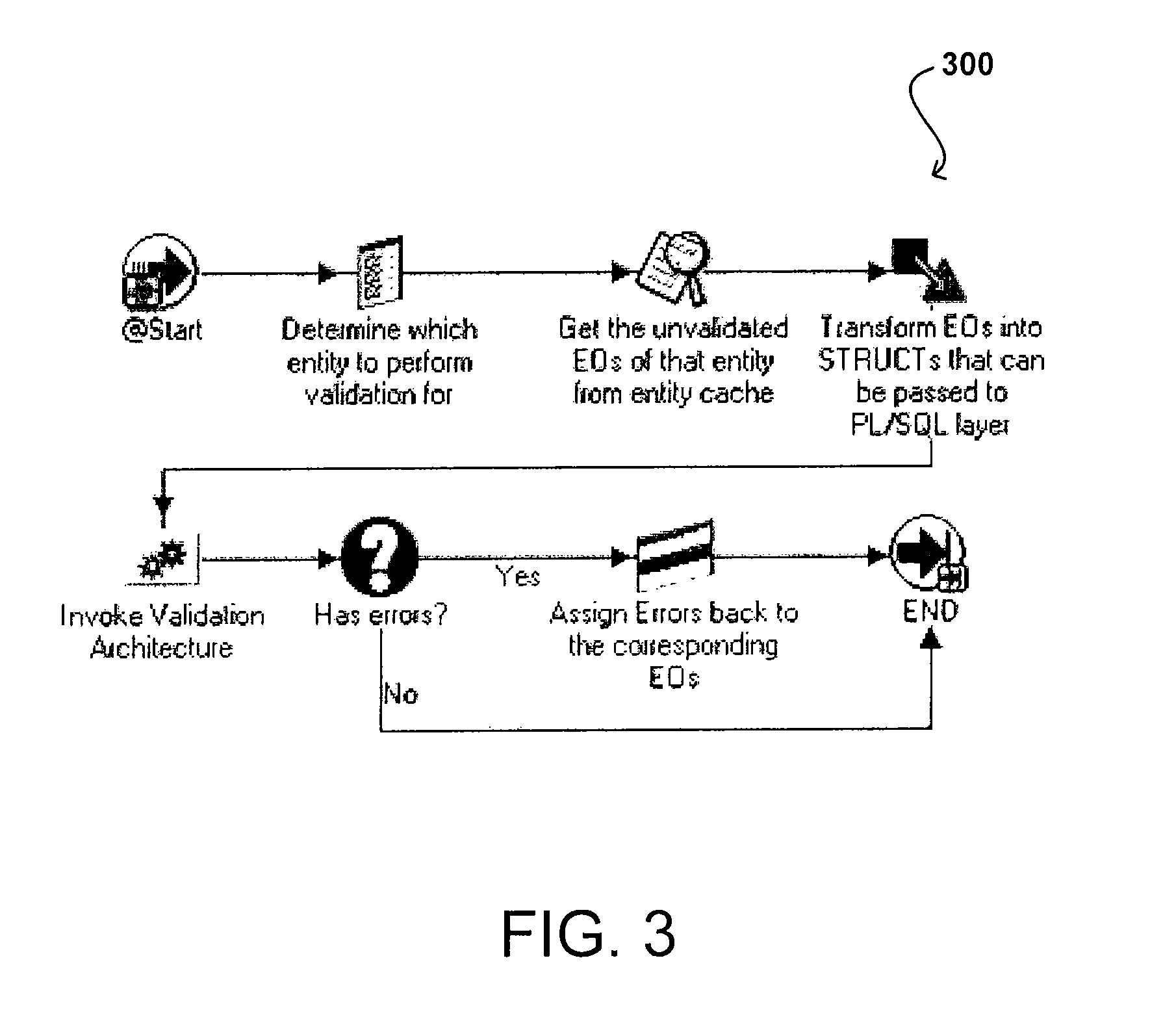
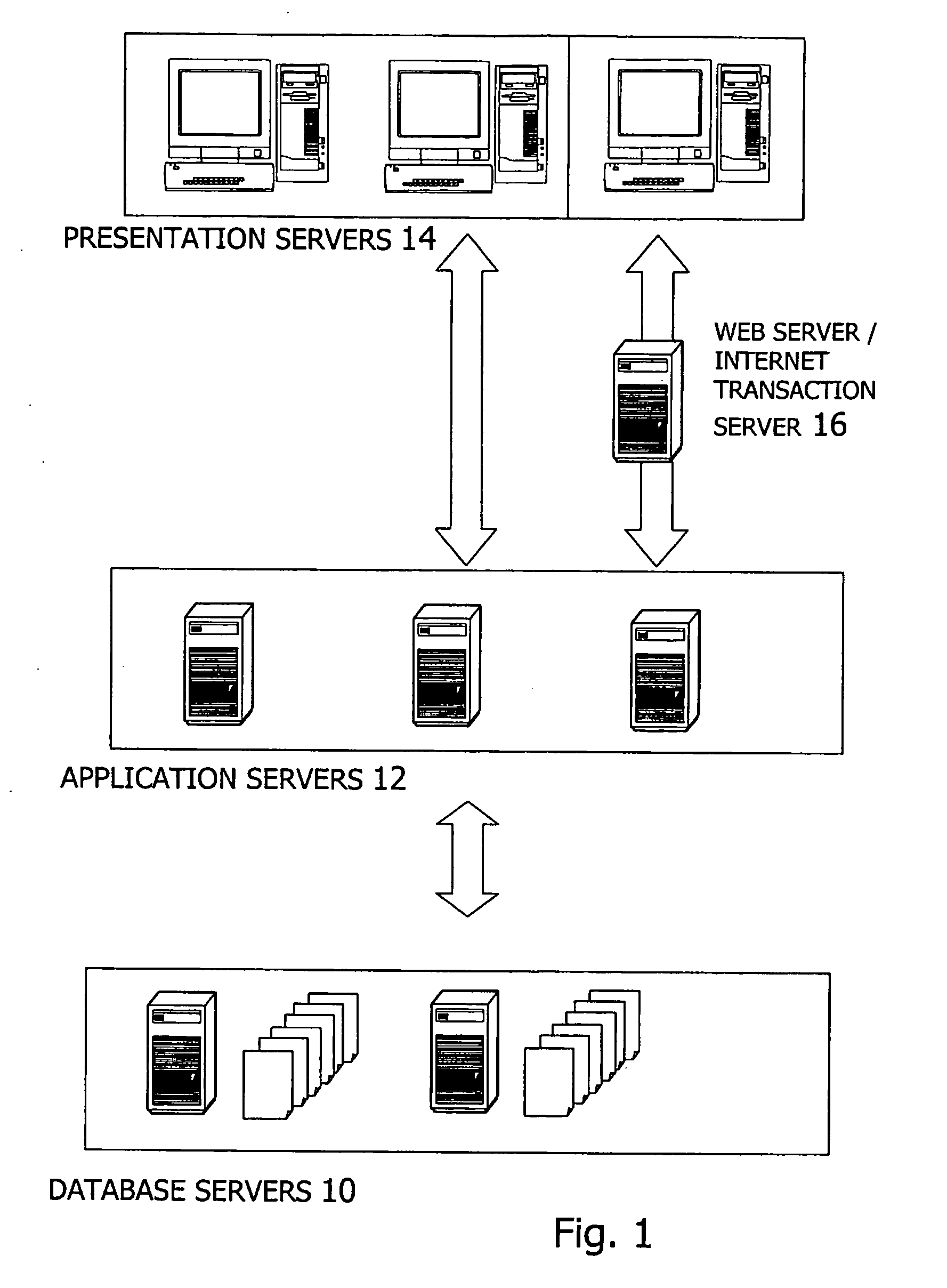
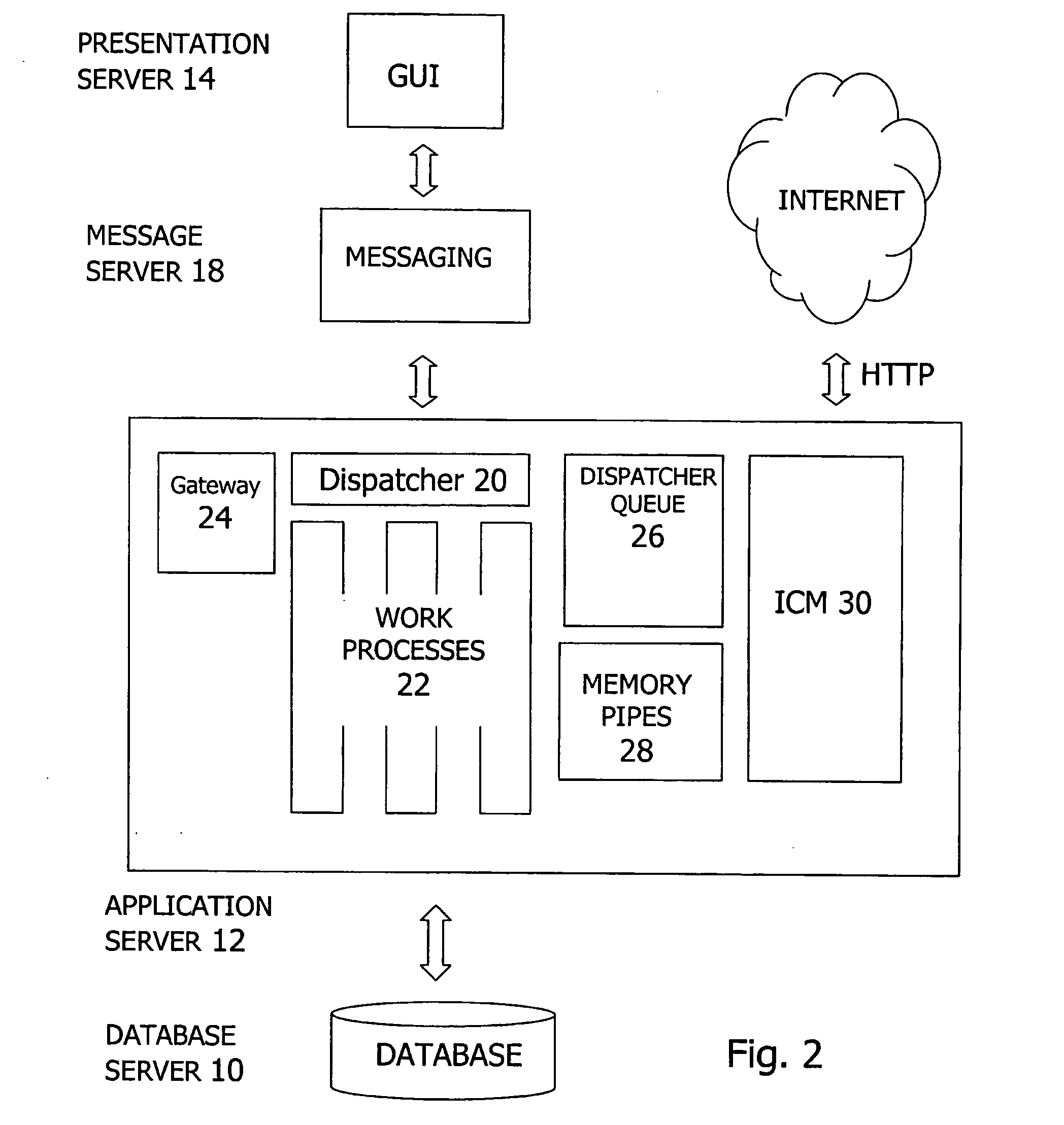
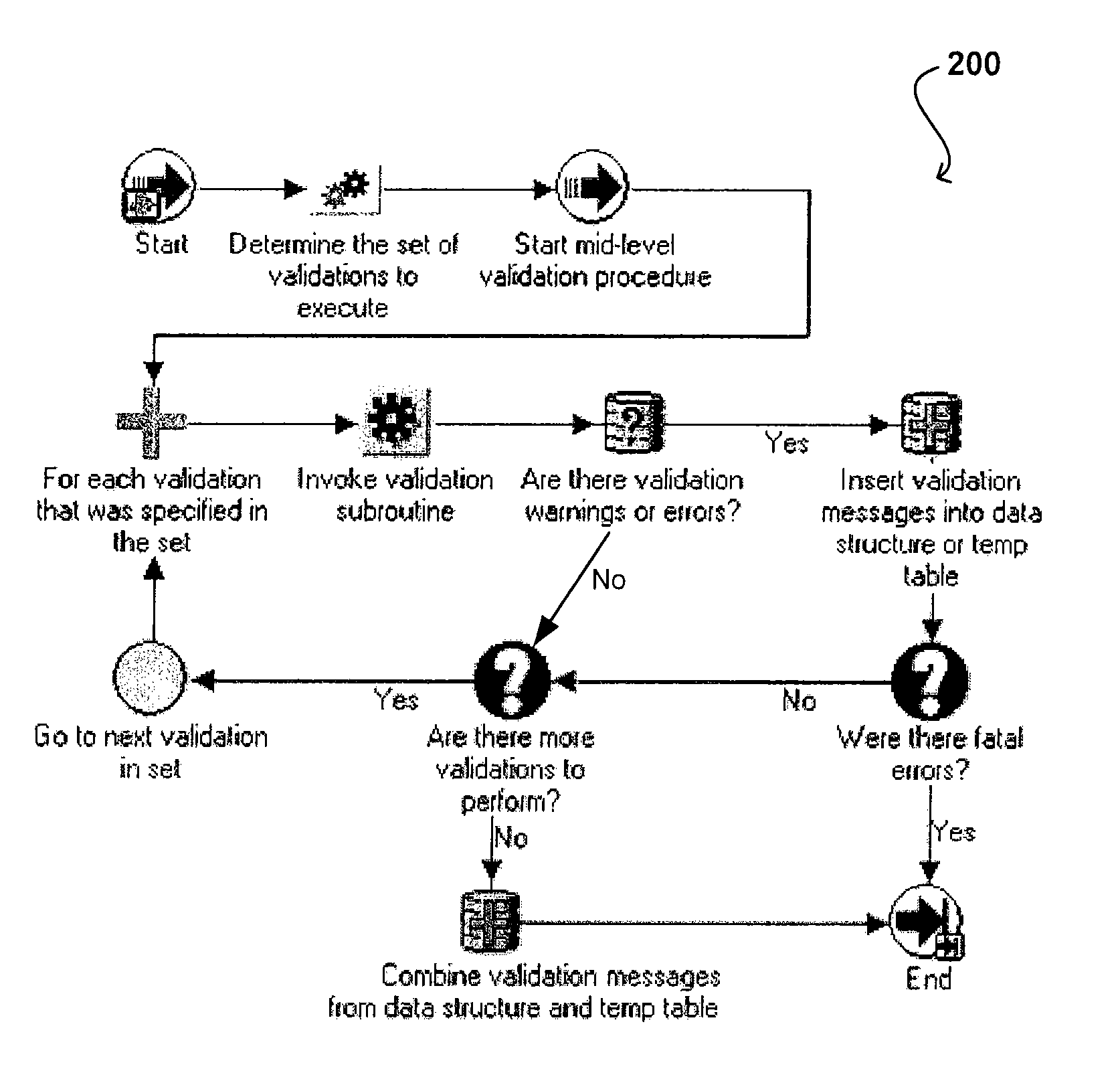
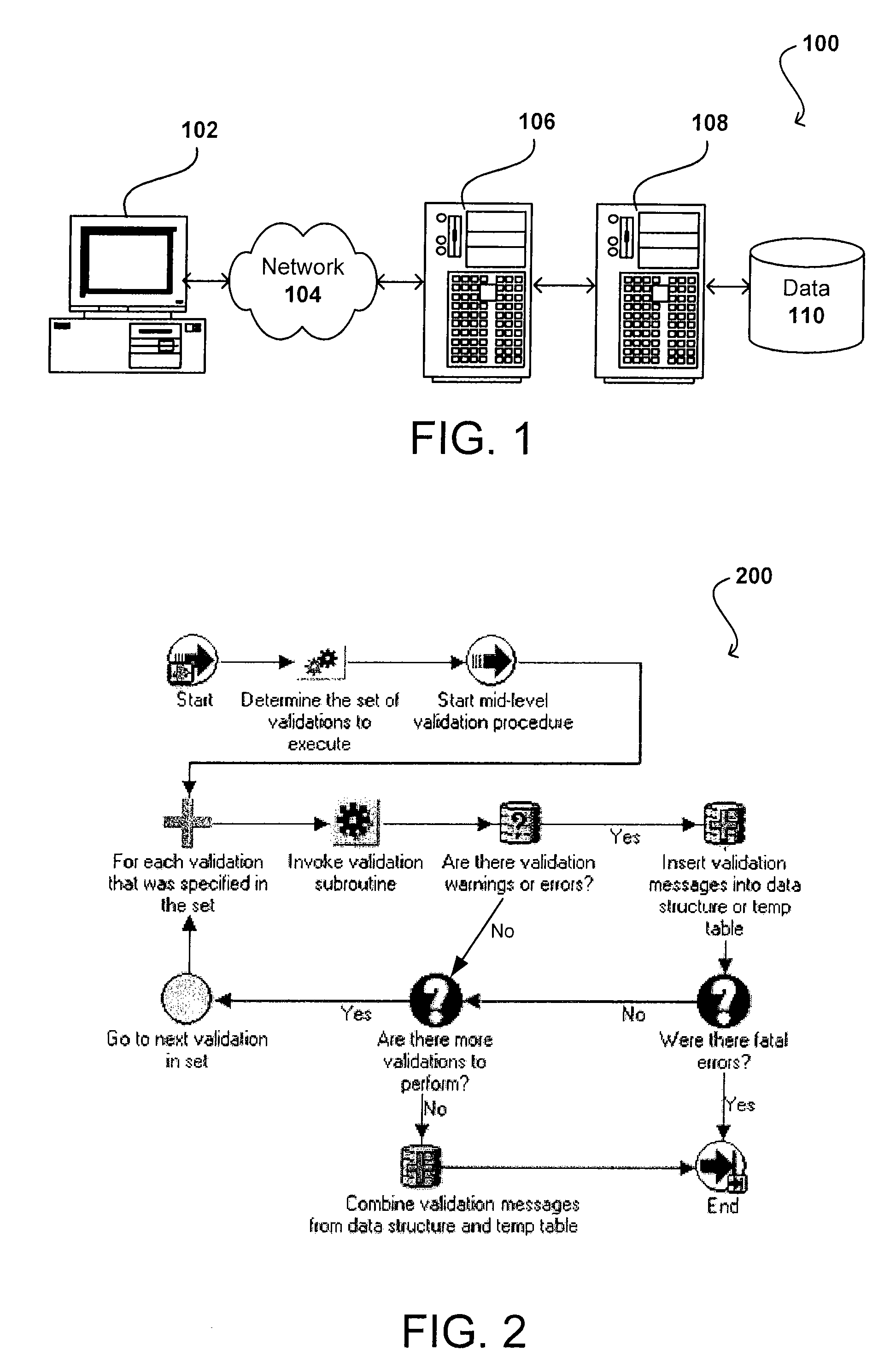
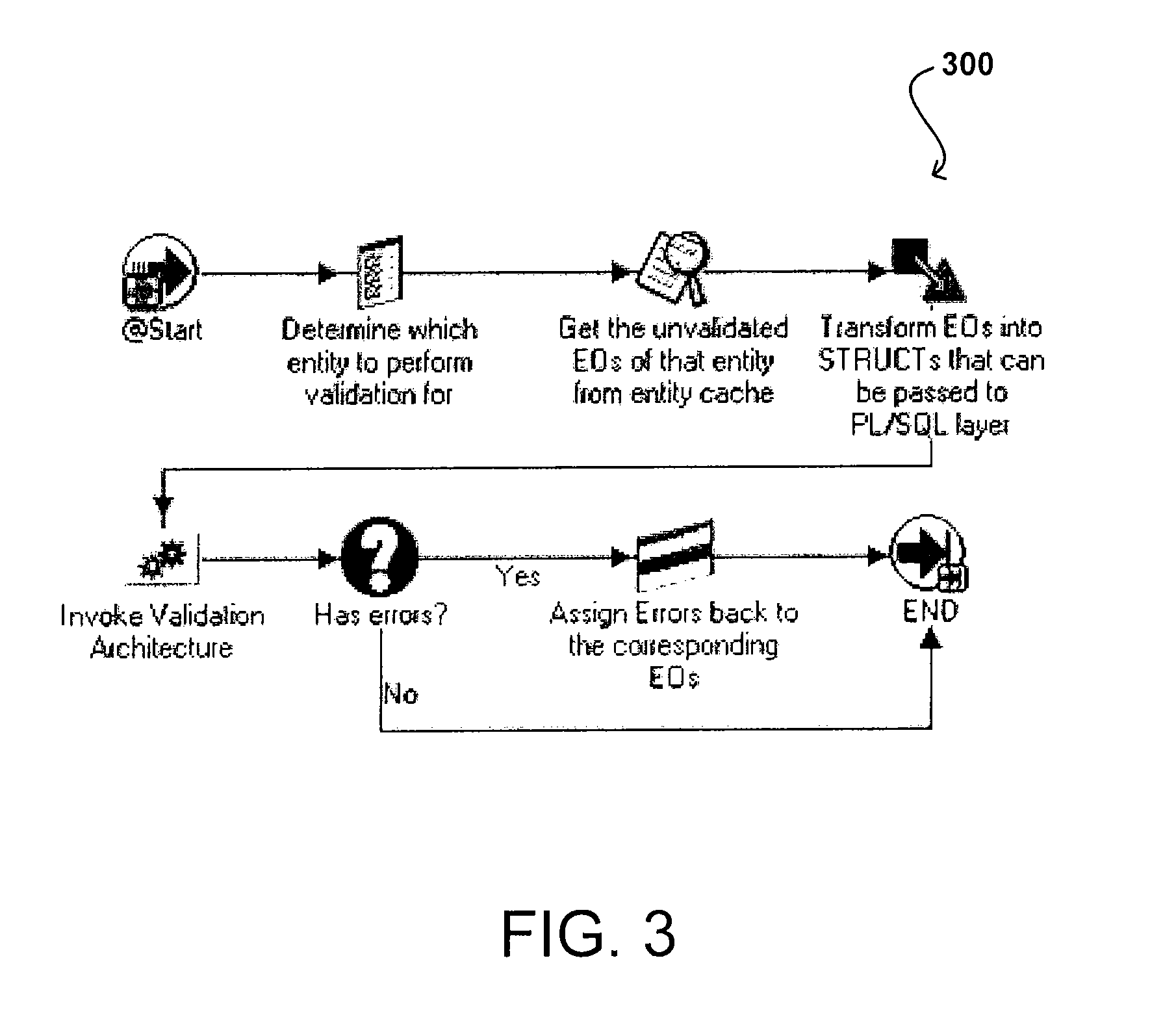
Architecture for data validation
ActiveUS8418142B2Easy to createSufficient flexibilitySoftware designSpecific program execution arrangementsData validationDuplicate code
A data validation architecture is provided that minimizes duplicate code and enables easy creation of new validations using a high-performance and scalable design. Such an architecture provides sufficient flexibility to disable certain validations when they are not applicable to the flow, interpret validation failures differently according to requirements of the calling application, and specify the type of document for which a particular validation is applicable. The architecture provides a standardized flow for performing data validation, specifying a set of required parameters for validation subroutines, as well as where validation results are to be stored for access by a calling program. Such an architecture also provides a framework for performing common processing required for most validation flows without restricting the flexibility of the validation subroutines.
Owner:ORACLE INT CORP
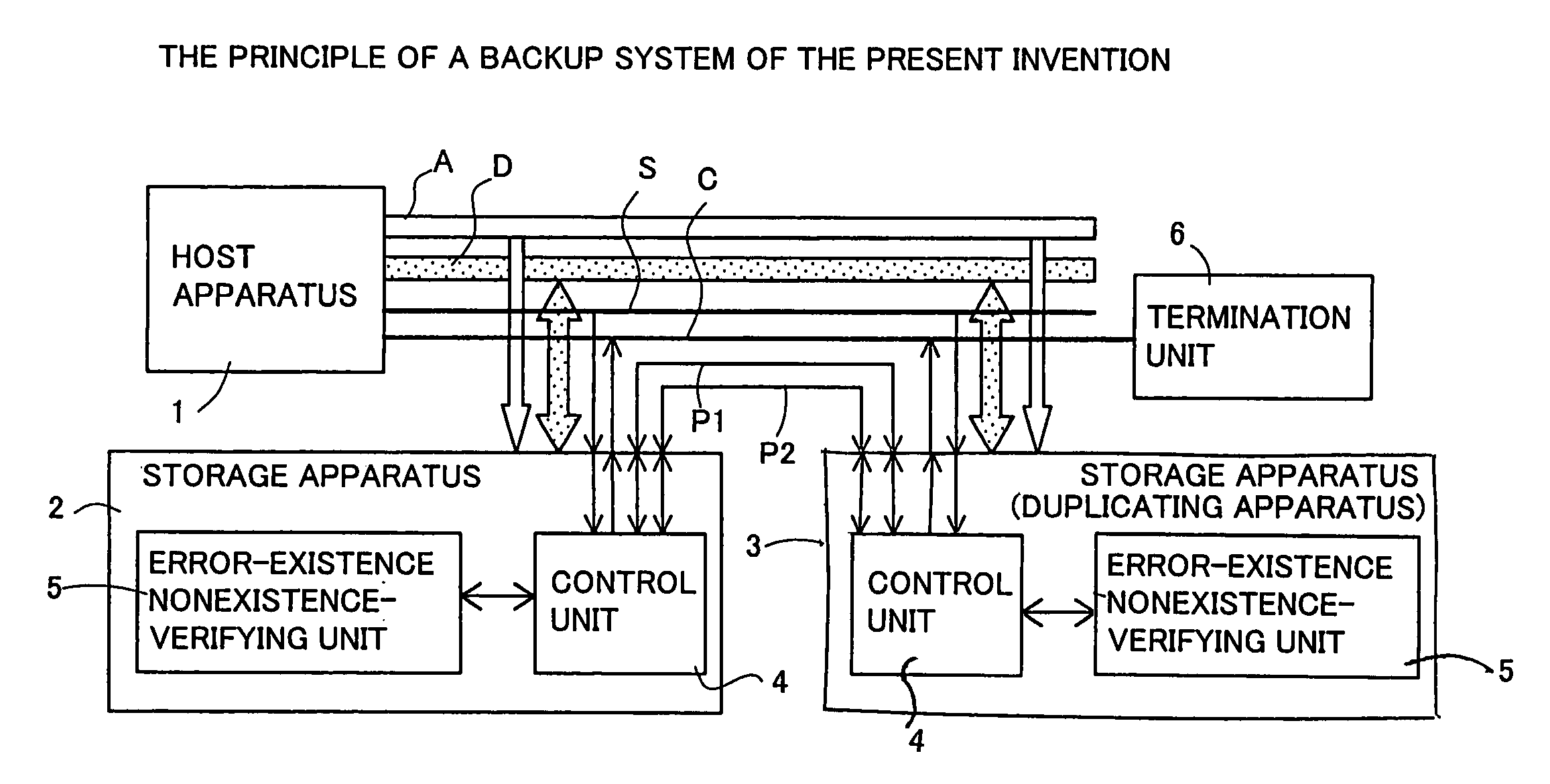
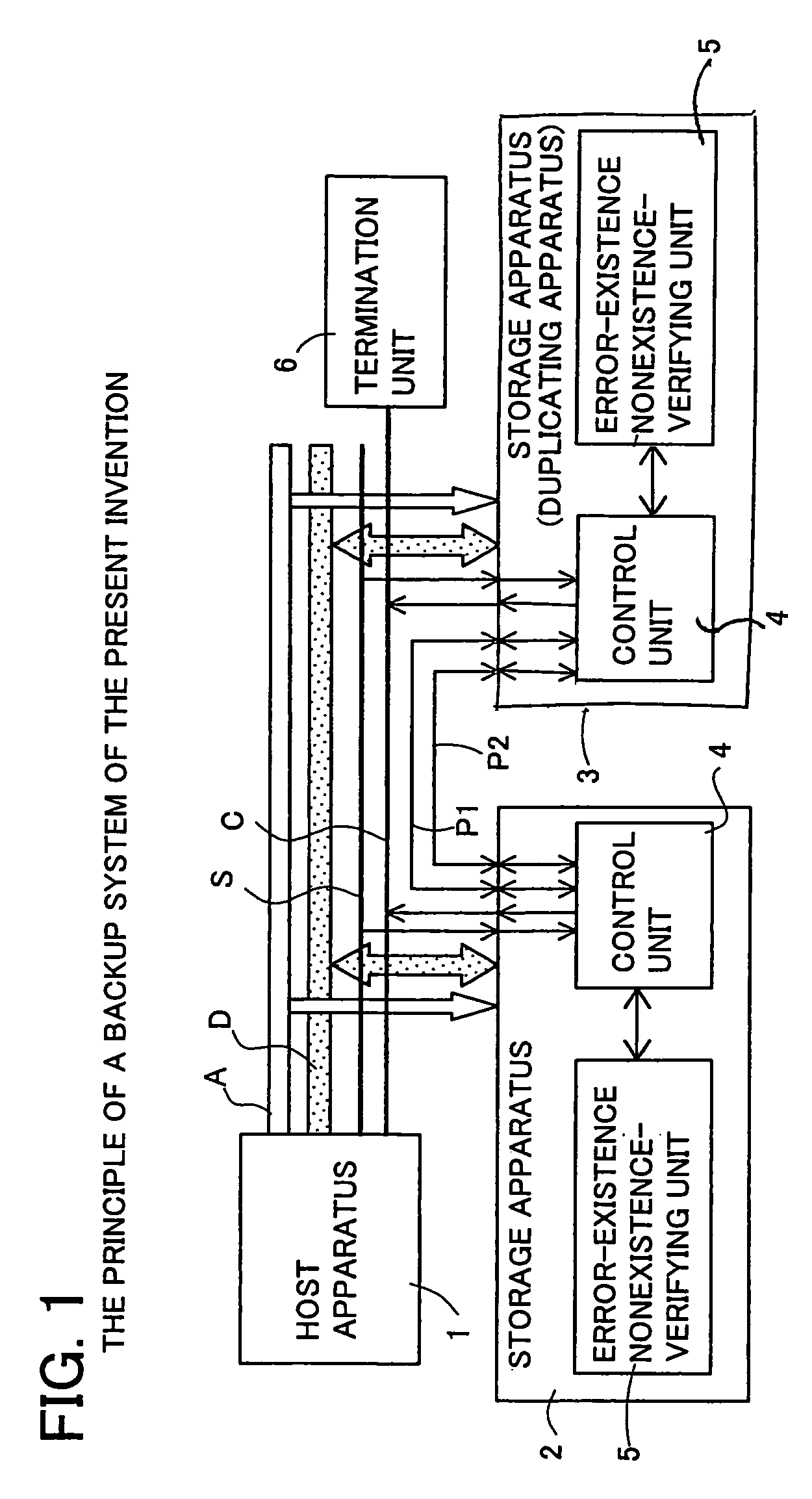
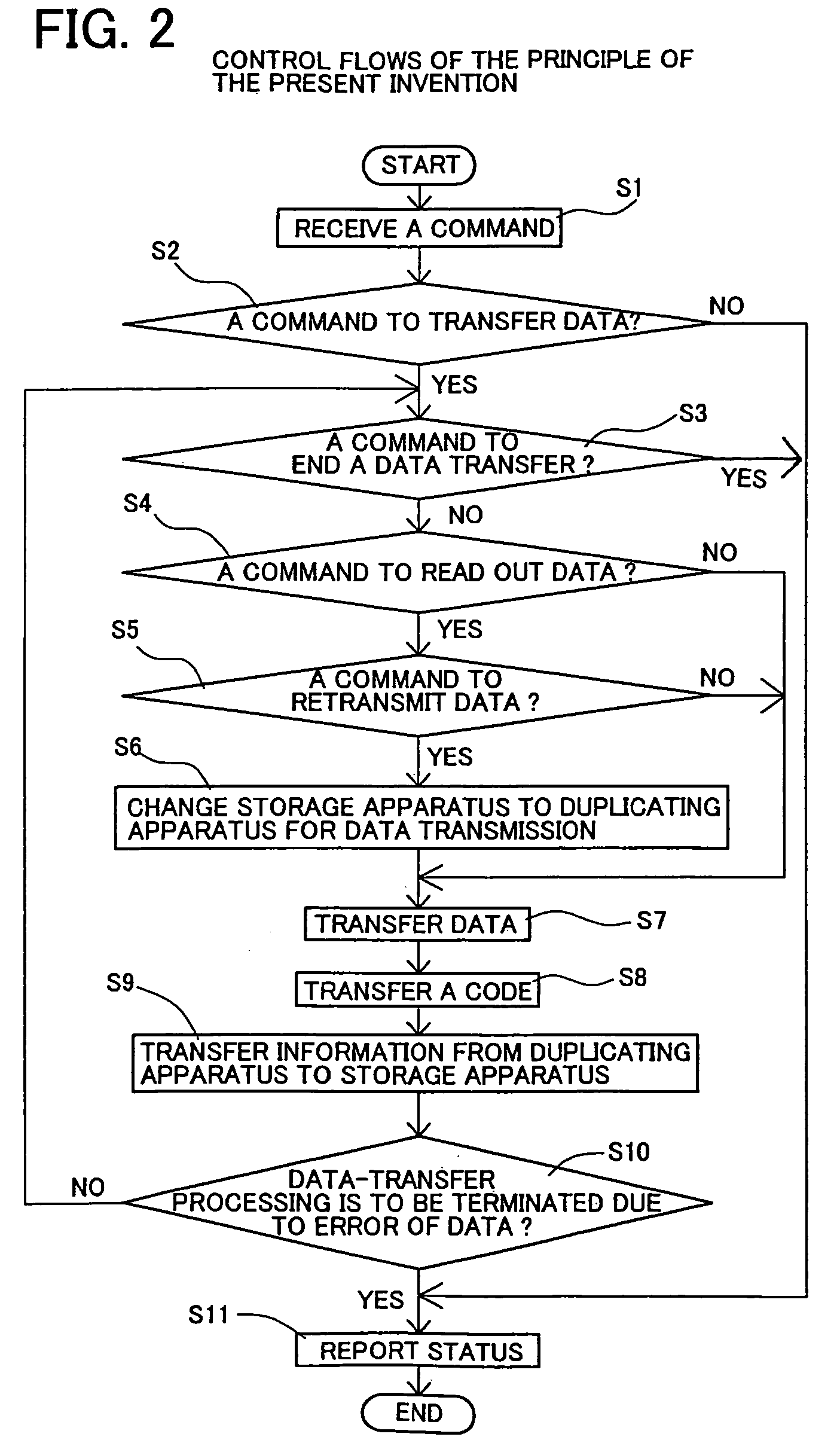
Backup system and duplicating apparatus
InactiveUS7082548B2Improve reliabilitySacrificing availabilityData processing applicationsInput/output to record carriersData processing systemData validation
A backup system which can improve reliability of data without sacrificing availability of a data processing system and a duplicating apparatus employed in the backup system. The backup system includes a duplicating apparatus for taking in data in the transfer of the data and codes from a host apparatus to a storage apparatus and holding the data as duplicated data, the duplicating apparatus including a code fetching unit to fetch the codes and hold the fetched codes as duplicated codes, and a data verifying unit to verify existence or nonexistence of an error in the data by comparing the taken data and the duplicated data.
Owner:SOCIONEXT INC
Method and system of remote diagnostic, control and information collection using multiple formats and multiple protocols with verification of formats and protocols
InactiveUS7171670B2Low costEasy to analyzeHardware monitoringMultiprogramming arrangementsReliable transmissionNetwork Communication Protocols
A system, method and program product for diagnosing, controlling and collecting information from devices. Information regarding events of each one of a plurality of target applications executing in an application unit is collected and formatted into one of multiple data formats for transmission through one of multiple communication protocols at the request of each of the target applications, through an interface. A combination of a data format and communication protocol requested by a target application is verified for validity. If the requested combination is invalid, a valid combination is substituted for more reliable transmission. The formatted data is transmitted through, e.g., e-mail or FTP to a predetermined destination or may be saved to local storage, e.g., a local disk. By sharing resources, code duplication is reduced or eliminated.
Owner:RICOH KK
LDPC constructing method with short ring or low duplicate code
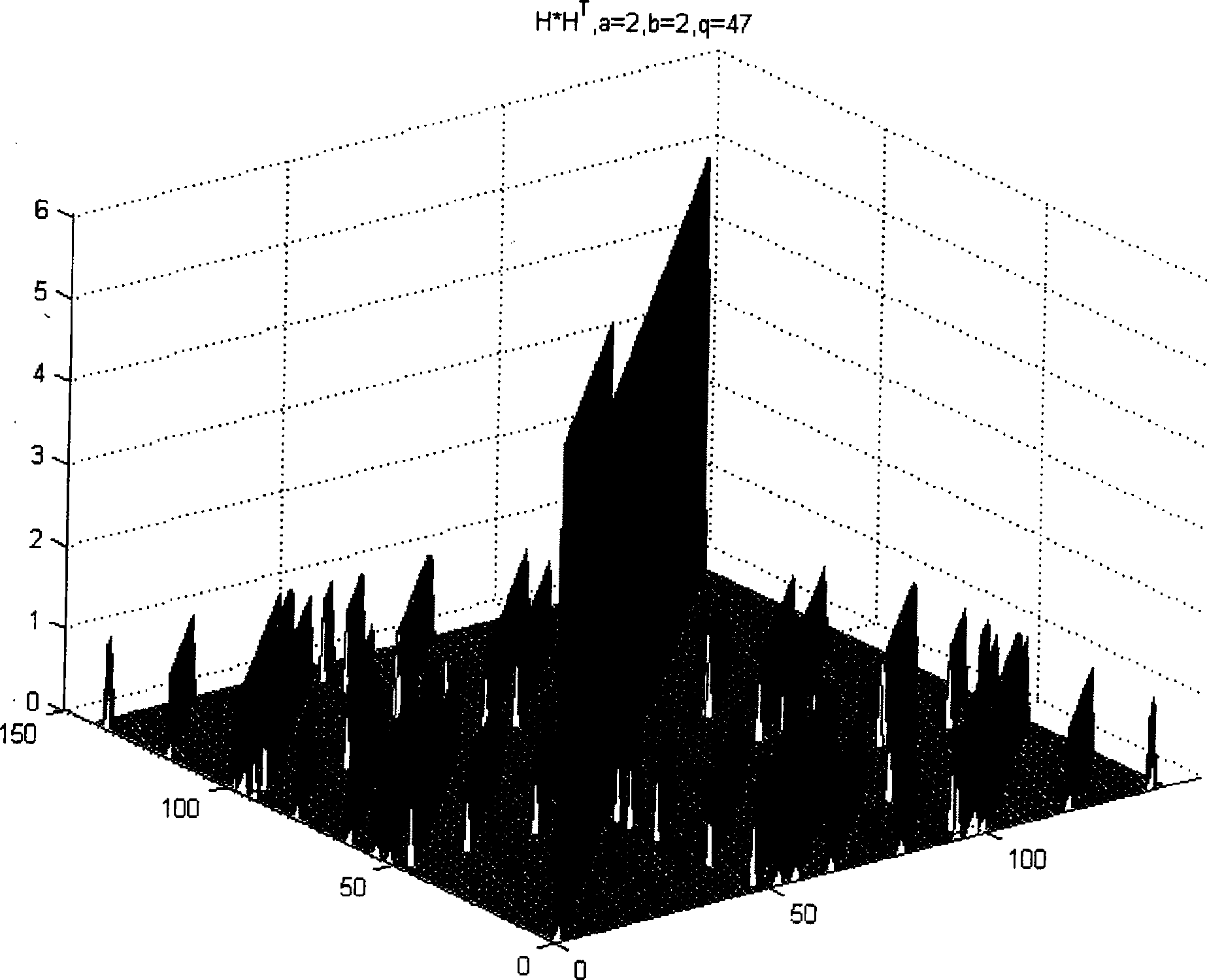
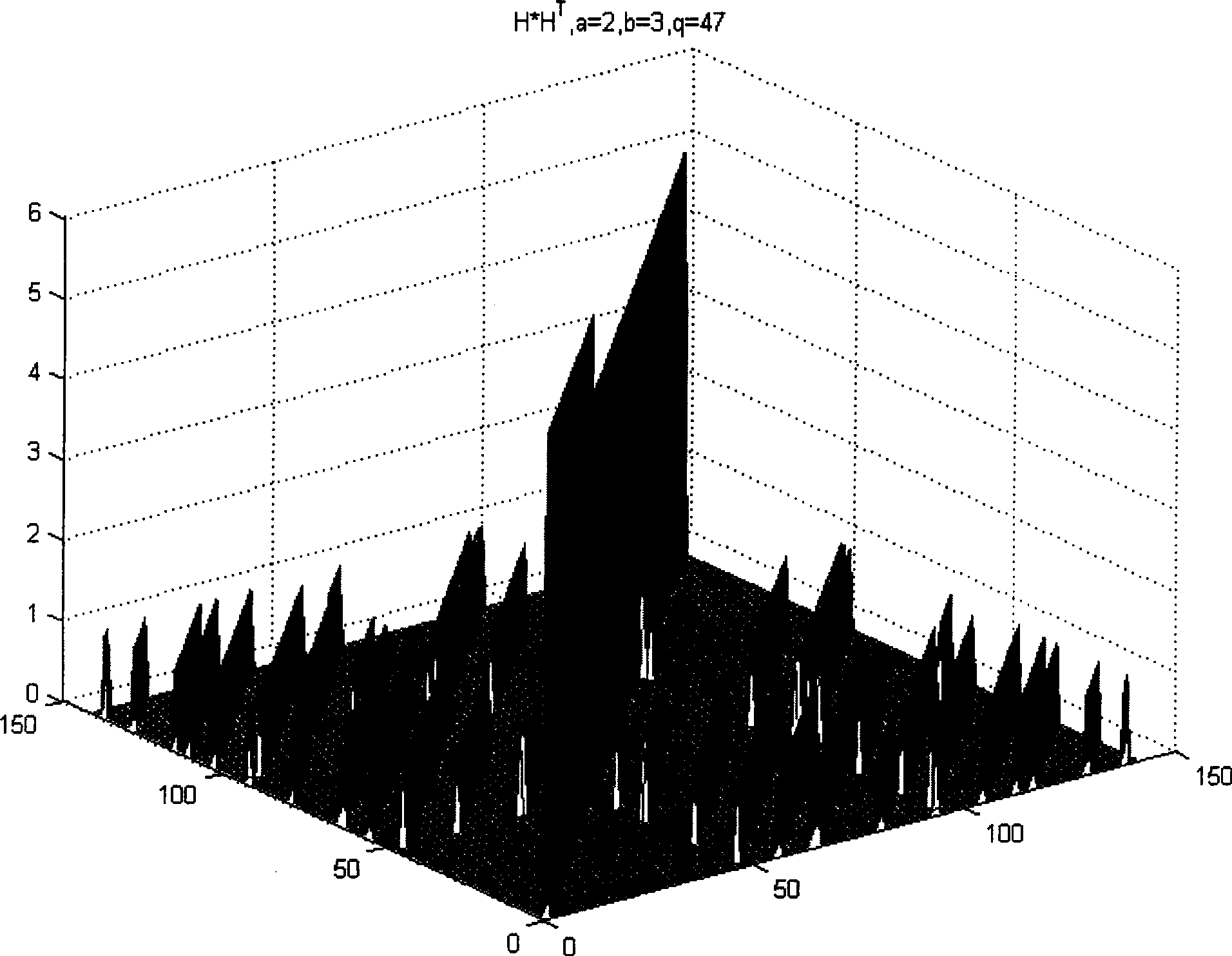
InactiveCN101488761ASolve the problem of low-code repeated code wordsCode majorError correction/detection using multiple parity bitsLinear codingShort loop
The invention discloses an algebraic construction method of LDPC (Low Density Parity Check) code based on cyclic matrixes; design parameters of cyclic matrixes are adjusted by short-loop check and minimum code weight check, which are nonnegative prime numbers a and b meeting two constraint conditions, and dimension q of an identity matrix, wherein the magnitude of dimension q of a shift identity matrix and whether the error rate characteristics of the designed LDPC code are influenced by prime numbers. The invention solves the problems of short-loop and low code coincident code word appearing in the existing QC LDPC code design. The method can check the existence of low code coincident code word in the designed code, thereby checking the existence of 4-loop. An irregular quasi-cyclic LDPC code structure disclosed by the invention divides the check matrix H into two submatrixes A and B, the nonsingular structure of the submatrix A is disclosed, and a matrix is generated by the two submatrixes A and B. Direct linear coding is carried out by generating the matrix. The embodiment validates the efficiency and good bit rate performance of the method disclosed by the invention.
Owner:BEIJING JIAOTONG UNIV
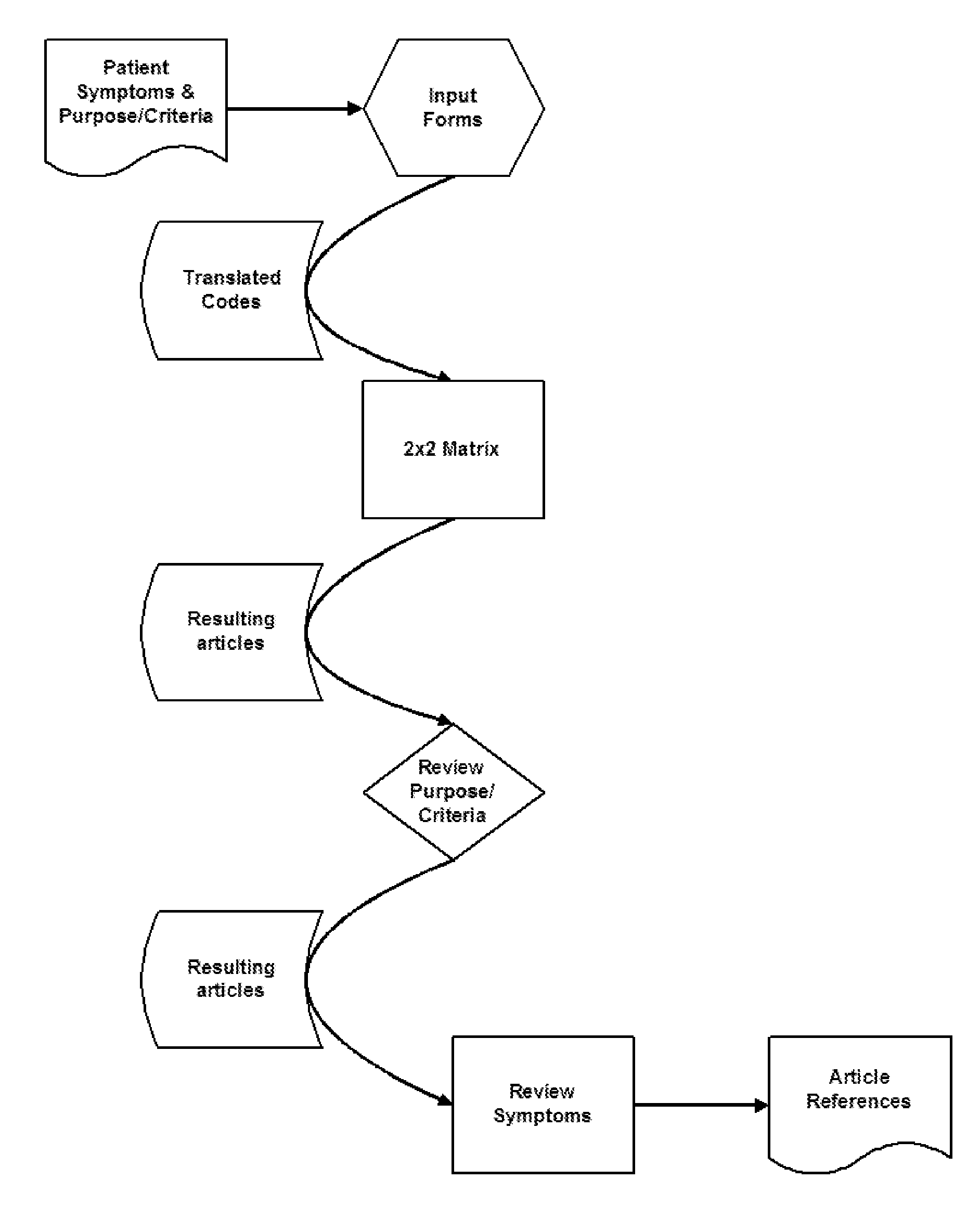
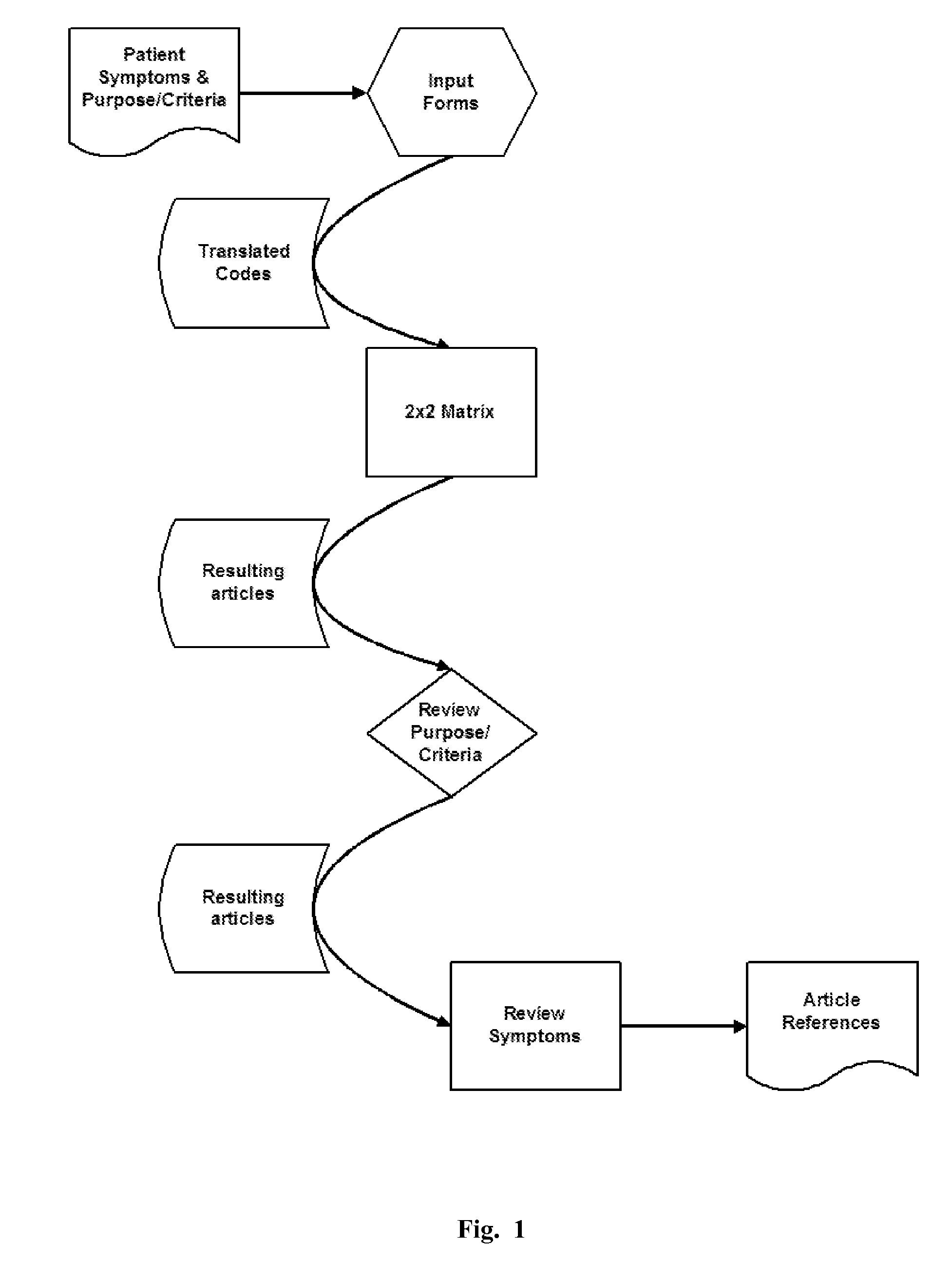
Methods and apparatus for searching and identifying diseases
InactiveUS20080040150A1Reduce in quantityUniform inputtingData processing applicationsDiagnostic recording/measuringComputerized systemOutput device
The present invention relates to methods, computer systems and computer apparatus for obtaining references that assist in identifying a disease or condition in an individual, wherein the reference has been described or made part of a database having medical data. The steps of the method include obtaining or identifying two or more symptoms, conditions, procedures, medication or any combination thereof, experienced or used by the individual; transcribing the symptoms, conditions, procedures, medication or combination thereof into standardized medical codes to thereby obtain transcribed codes; categorizing transcribed codes by medical specialty; searching at least one medical literature database using one of the transcribed codes to thereby obtain code-specific results, and repeating this step for each of the transcribed codes; cross-referencing the code-specific results for each transcribed code with code-specific results of all other transcribed codes in the same categorized medical specialty to obtain common references, and repeating this step for each specialty for which the codes have been categorized; and studying the references to determine references applicable to or those that assist in identifying the disease or condition.The computer system or computer apparatus of the present invention includes a source of transcribed codes that comprises standardized medical codes translated from two or more symptoms, conditions, procedures, medication or any combination thereof experienced or used by the individual; a processor routine coupled to receive transcribed codes from the source, wherein the processor routine performs the above steps of categorizing transcribed codes by medical specialty; searching the medical literature database and cross-referencing the code-specific results for each transcribed code with code-specific results of all other transcribed codes in the same categorized medical specialty to obtain common references. The computer system or apparatus further includes an output device, coupled to the processor routine, for indicating common reference grouped by the number of occurrences of transcribed codes present in the reference.
Owner:THE RK FOUND
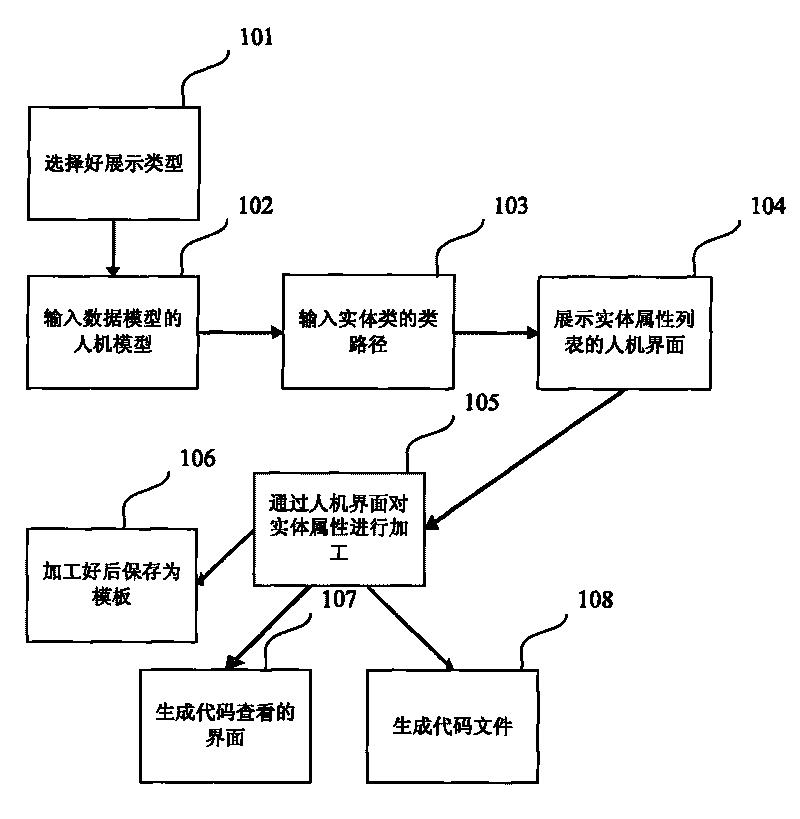
Code generation method and device
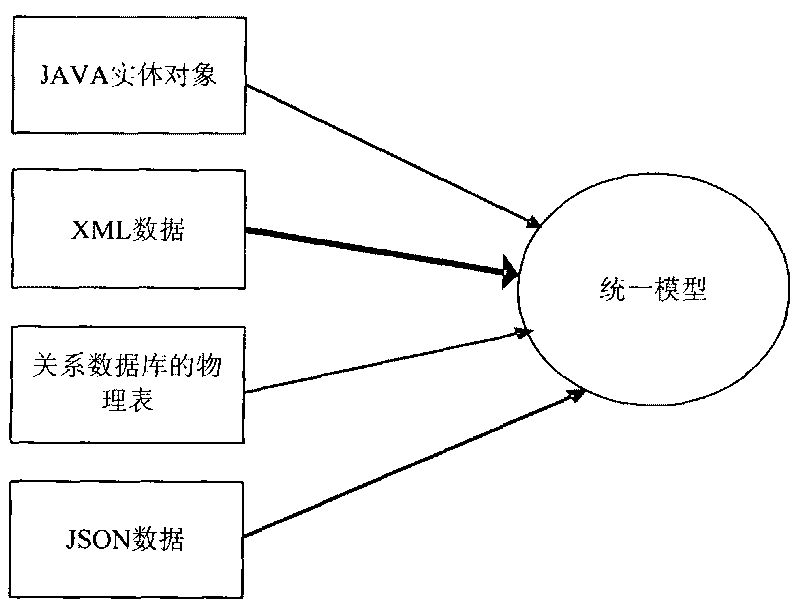
InactiveCN101714078AUniform styleImprove development efficiencySpecific program execution arrangementsRelational databaseData source
The invention relates to a code generation method and device, which generates codes under a J2EE open source integrated framework. The method comprises the following steps: a, selecting showing types required to be generated according to service conditions; b, creating uniform models according to the conditions of data sources, wherein the data sources comprise JAVA objects, XML data, the physical table or JSON data of a relational data base; c, determining the class path of an entity class according to the conditions of the unified models; d, processing the attribute of an entity according to the conditions of the unified models; and e, generating code files according to the attribute of the entity, whrein the code files comprise background codes, foreground codes and configuration codes. The method and the device can better solve the problems of the repeating of service codes art and the standardization and unification of codes which can not be solved by the prior framework.
Owner:广东金宇恒科技有限公司
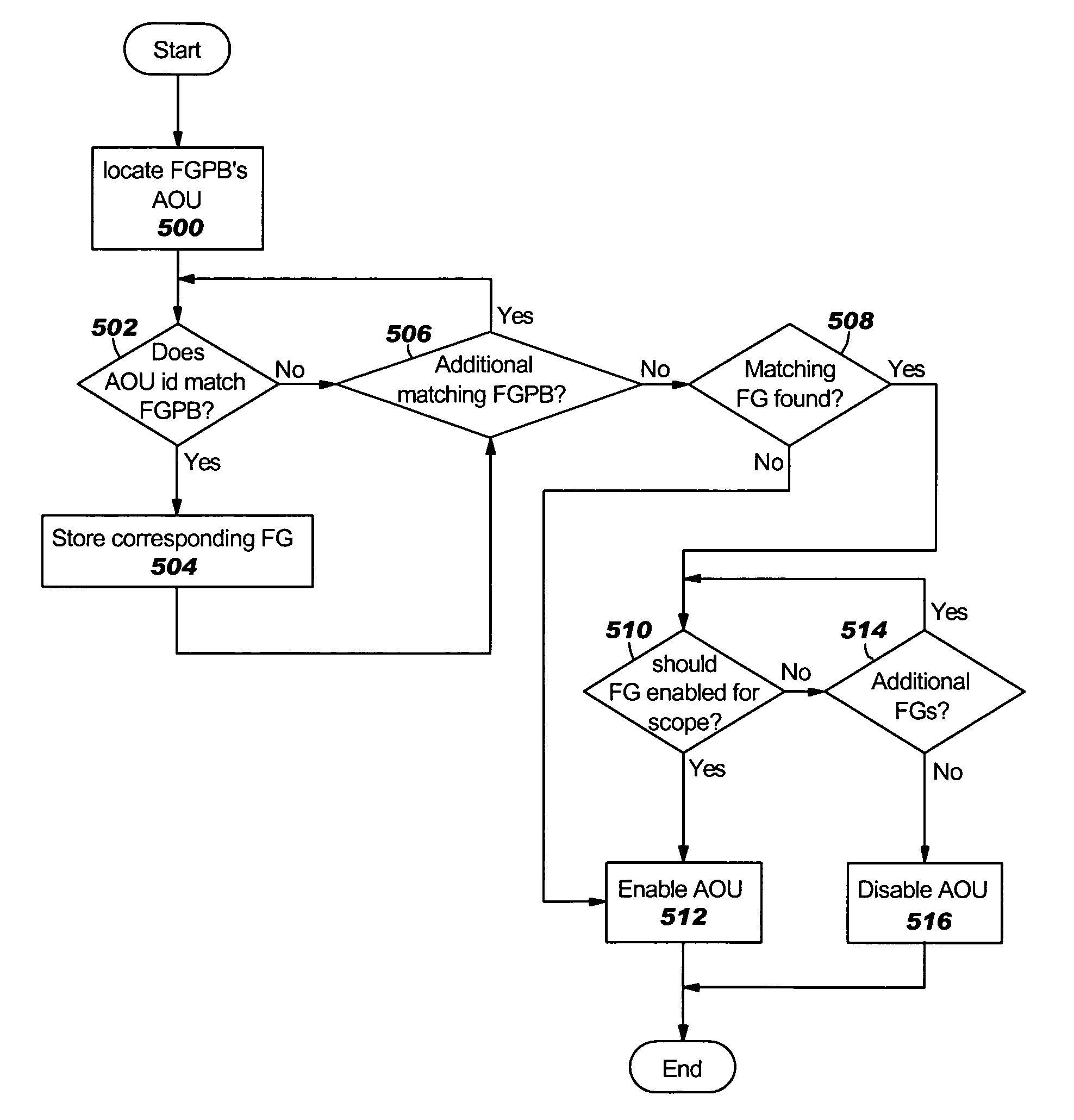
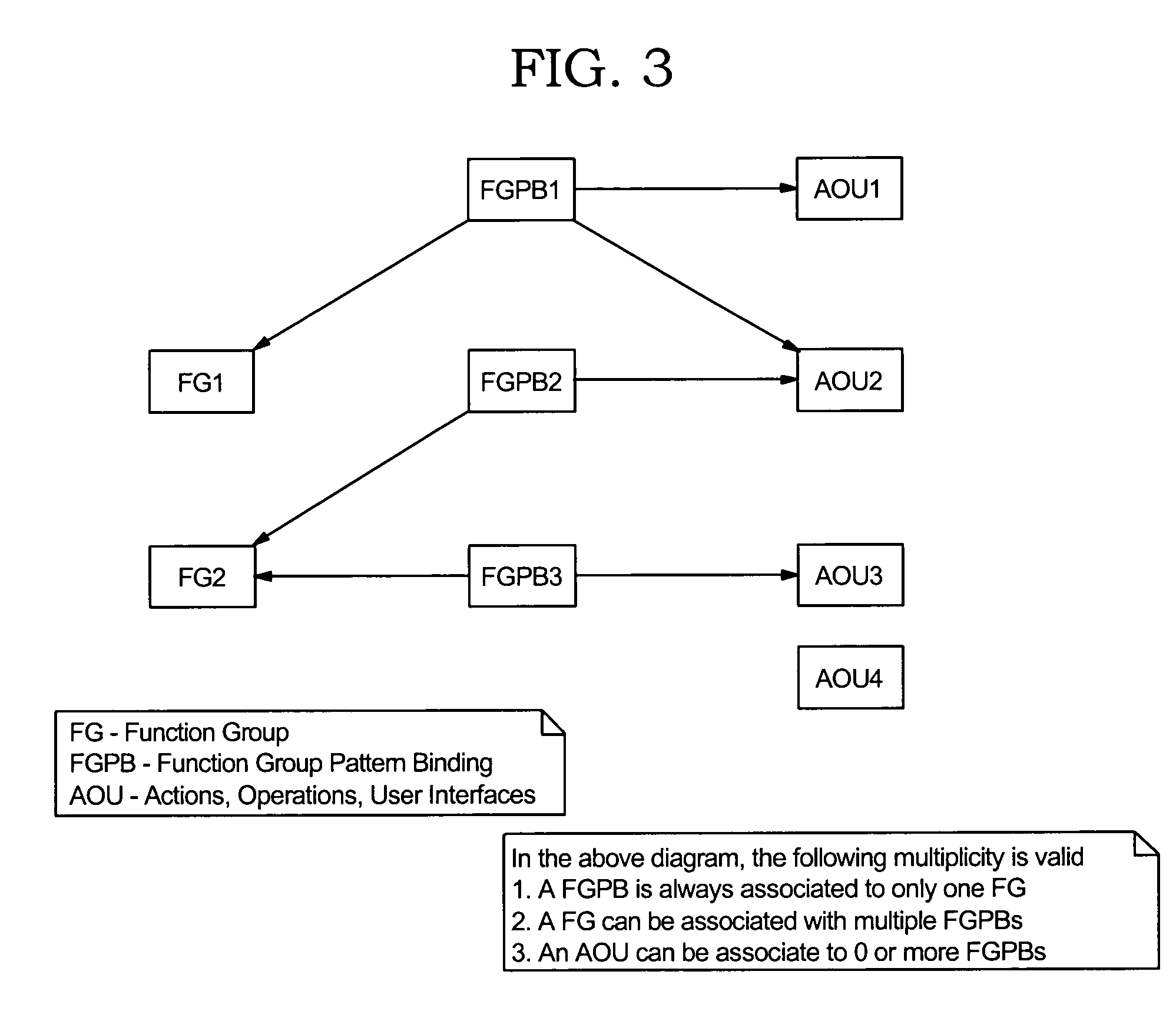
Method and apparatus for implementing dynamic function groups in a data processing system
ActiveUS20060195818A1Requirement analysisSpecific program execution arrangementsData processing systemThird party
A method, an apparatus, and computer instructions are provided for implementing dynamic function groups in a data processing system. An extensible framework is provided, which provides function groups to amalgamate extended sets of functionality by either vendor or purpose and allows the function groups to be dynamically enabled or disabled within a software application. A user may specify which extended sets of functionality are relevant and when to enable them. With the use of function groups, third party vendors may integrate added functionalities with existing ones in a software application, and indicate when these functionalities should be available to end-users without the need to duplicate code. The invention allows for the construction of other extensible frameworks including wizards, editors, and operations may also be extended with the use of function groups.
Owner:LENOVO GLOBAL TECH INT LTD
Systems, methods, and articles of manufacture for handling hierarchical application data
ActiveUS20060015848A1Improve functionalityReduce loadData processing applicationsSpecific program execution arrangementsBase classApplication software
The invention relates to an object-oriented technique for flexibly storing and representing hierarchical application data that avoids the re-engineering of existing application classes and the maintenance-critical massive code duplication, mainly in the presence of limitations given by the employed object-oriented language. In a first step classes are provided including a hierarchy base class with methods for accessing hierarchical relationships, at least one hierarchy subclass that is derived from the hierarchy base class, and at least one application class. In a next step objects are instantiated including at least one hierarchy object of the at least one hierarchy subclass and at least one application object of the at least one application class. In a final step, each application object is linked to at least one hierarchy object, and vice versa, such that the hierarchically related application objects have access to each other via the methods provided by the hierarchy base class. The invention may be practiced in a path optimization context.
Owner:SAP AG
Architecture for data validation
ActiveUS20090187879A1Easy to createSufficient flexibilitySoftware designSpecific program execution arrangementsData validationSource Data Verification
A data validation architecture is provided that minimizes duplicate code and enables easy creation of new validations using a high-performance and scalable design. Such an architecture provides sufficient flexibility to disable certain validations when they are not applicable to the flow, interpret validation failures differently according to requirements of the calling application, and specify the type of document for which a particular validation is applicable. The architecture provides a standardized flow for performing data validation, specifying a set of required parameters for validation subroutines, as well as where validation results are to be stored for access by a calling program. Such an architecture also provides a framework for performing common processing required for most validation flows without restricting the flexibility of the validation subroutines.
Owner:ORACLE INT CORP
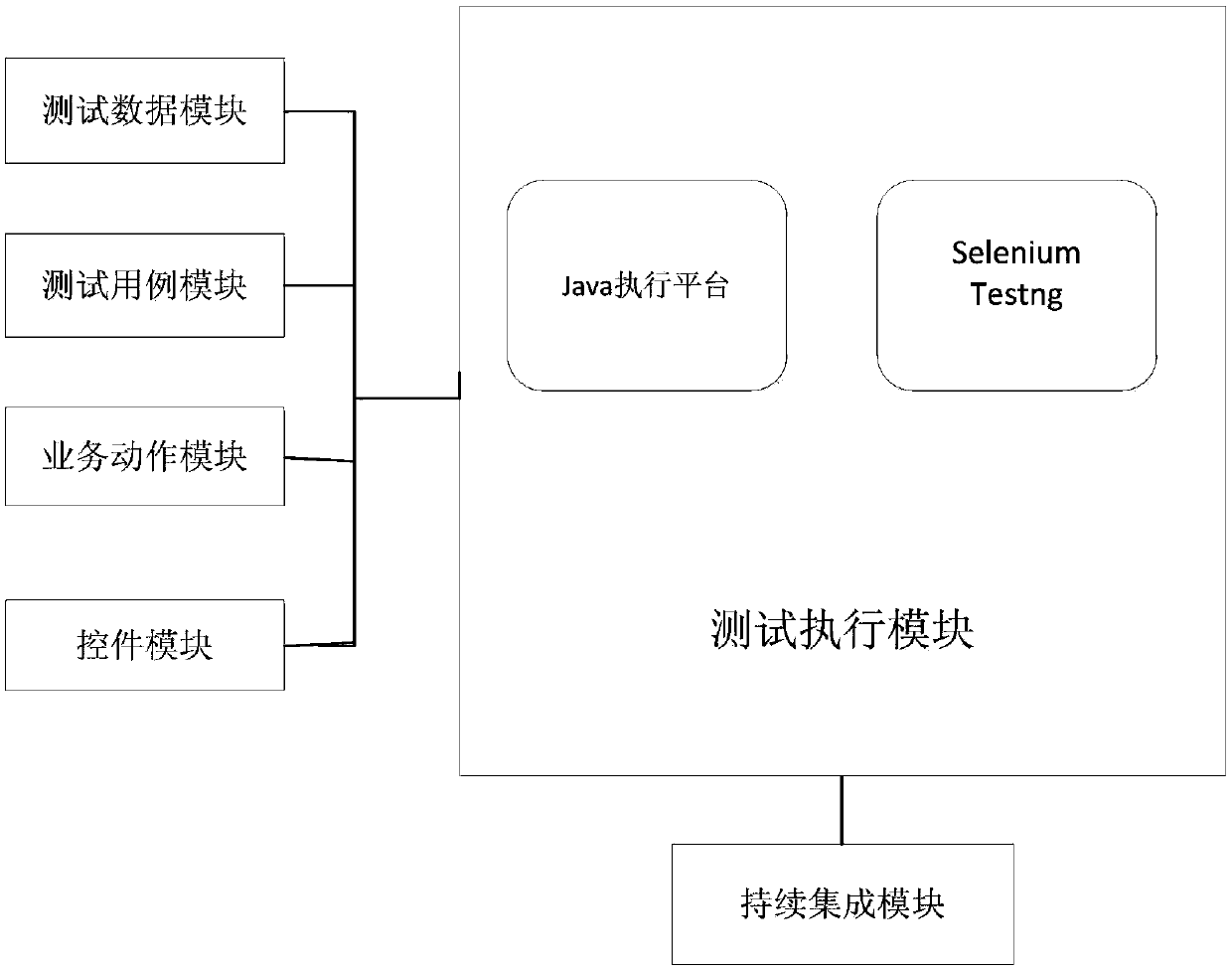
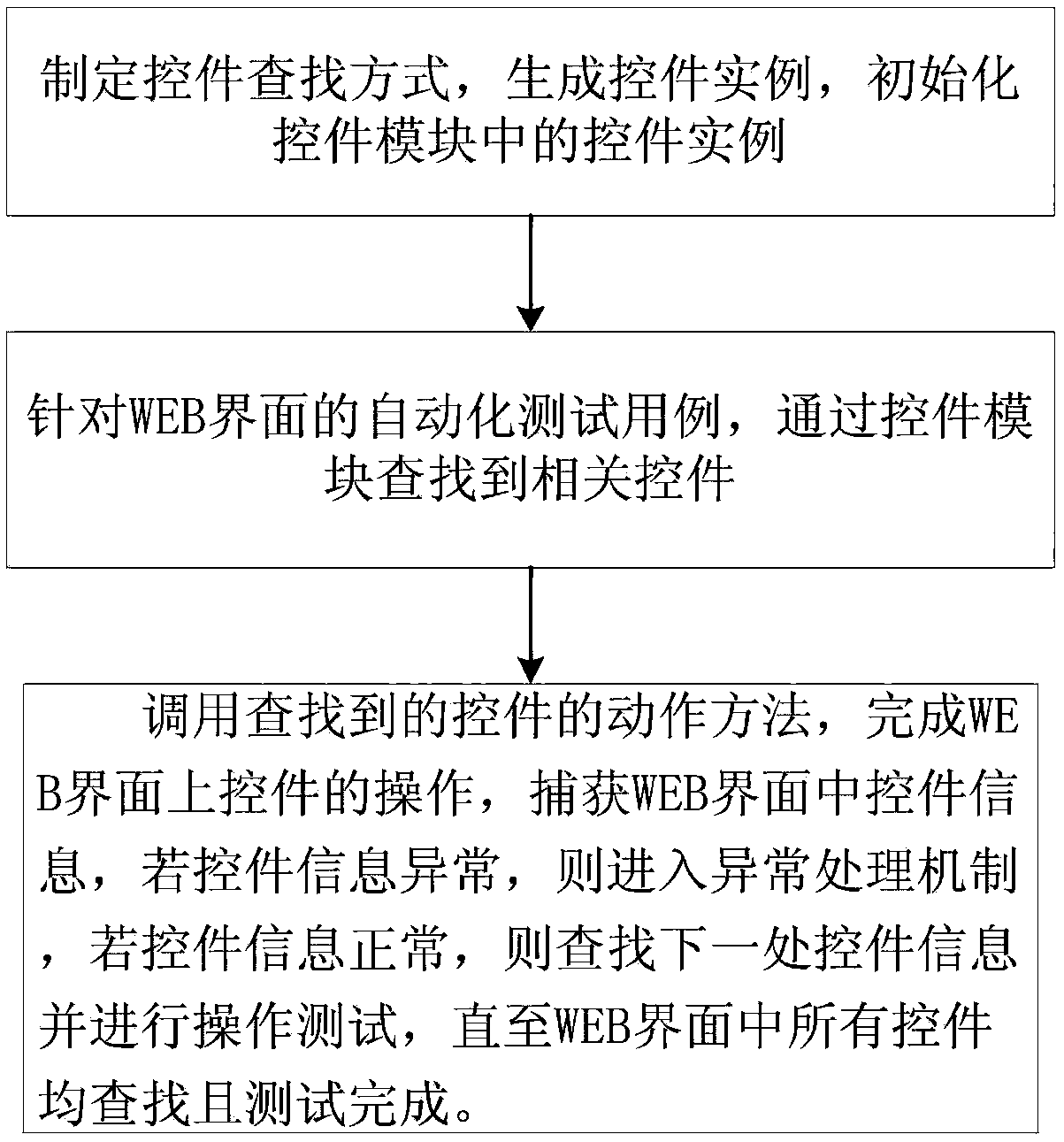
Control mode based WEB automated testing device and method
InactiveCN107729230AReduce duplication of codeImprove test efficiencySoftware testing/debuggingContinuous integrationData information
The invention provides a control mode based WEB automated testing device. The device comprises a business action module, a test case module, a test data module, a continuous integration module, a testexecution module and a control module; the device business action module is used for completing packaging of business logical action of automated testing; the test case module is used for calling business action needed by a test case from the business action module; the test data module is used for storing data information needed by testing; the continuous integration module is used for concentrating a test code to a trunk test program and completing compiling, packaging and testing of an automated calling program project; the test execution module is used for calling a tool and an executionplatform of WEB automated testing; the control module is used for seeking a concrete control in a WEB interface and generating a control case. By selecting the control as the minimum unit to further refine the page, operation testing is conducted on the control, duplicated codes in automated testing are reduced, and the testing efficiency is improved. The invention further provides a control modebased WEB automated testing method.
Owner:ZHENGZHOU YUNHAI INFORMATION TECH CO LTD
Intelligent shape-phonetic-digital multicode combined Chinese character input system
InactiveCN1385779AEasy to learnOvercome the shortcomings of \"fast\" that cannot be taken into account and cannot be used by everyoneInput/output processes for data processingChinese charactersOperational system
This invention relates to a Chinese character input method called "intelligent-code" input method which can be applied with single stroke, double strokes, simplified, numerical and English. The "single stroke" method only needs vie keys and double strokes "voice and shape" can realize input without duplicate code with the 26 letters. The numerical input is to use ten digit keys to realize the input without duplicate code. Anyone can master the method of inputting Hanzi quickly by applying the same ten word roots and dividing a work into three parts. In addition to that, this system has the intelligent input function with Chinese general web address for quick entering-into-net and very good study function which helps you master many input ways. This system has formed software products to be operated on various "windows" operations systems, and only occupys less than three MB memory.
Owner:李一新
Preventing the detection and theft of user entry alphanumeric security codes on computer touch screen keypads
InactiveUS20140215632A1Preventing discernible patternDigital data processing detailsAnalogue secracy/subscription systemsUser inputDuplicate code
Preventing, discernible patterns of surface marks resulting from the repetitive entry of security codes to computer device touch screen alphanumeric keypads. There is predetermined the number of security code entries after which the positions of the representative keys in the keypad array should be reconfigured. This predetermined number should be the number of security code entries estimated to produce a pattern of distinguishable display surface marks coincident with a users repetitive entry alphanumeric character security code. The number of security code entries is counted. When the count of the predetermined number of security code entries has been reached, the representative keys in the displayed keypad array are reconfigured. This implementation is equally effective against thieves who are visually stealing the security codes over the user's shoulder.
Owner:IBM CORP
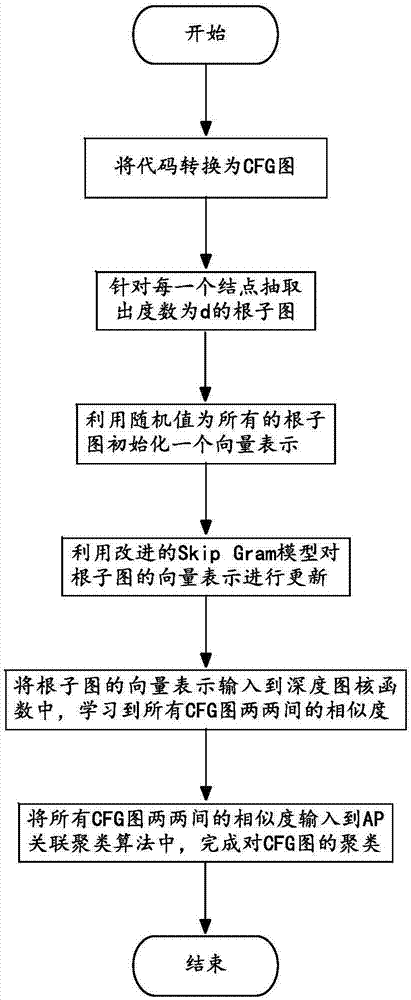
Duplicated code detecting method based on neural network language model
ActiveCN107273294AAvoid the curse of dimensionalityGet similarityBiological neural network modelsSoftware testing/debuggingCluster algorithmPattern recognition
The invention discloses a duplicated code detecting method based on a neural network language model and belongs to the technical field of duplicated code detecting methods. The problem that duplicated codes unchanged essential cannot be detected by adopting a duplicated code detecting method in the prior art, accordingly the detection accuracy rate is low, and economic losses of code originators are likely caused is solved. The duplicated code detecting method comprises the steps that 1, each of codes is converted into a corresponding CFG image; 2, a root diagram of each node in each CFG image is extracted; 3, all the root diagrams are represented by adopting vectors; 4, the vector representations of the root diagrams are input into a depth diagram-kernel function for learning, and the similarity of all the CFG images is obtained; 5, the similarity of all the CFG images is input into an AP associating and clustering algorithm, CFG image clustering is performed to obtain multiple clustering clusters, and the codes corresponding to the CFG images in the same clustering cluster are duplicated codes. The duplicated code detecting method is used for finding duplicated codes.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
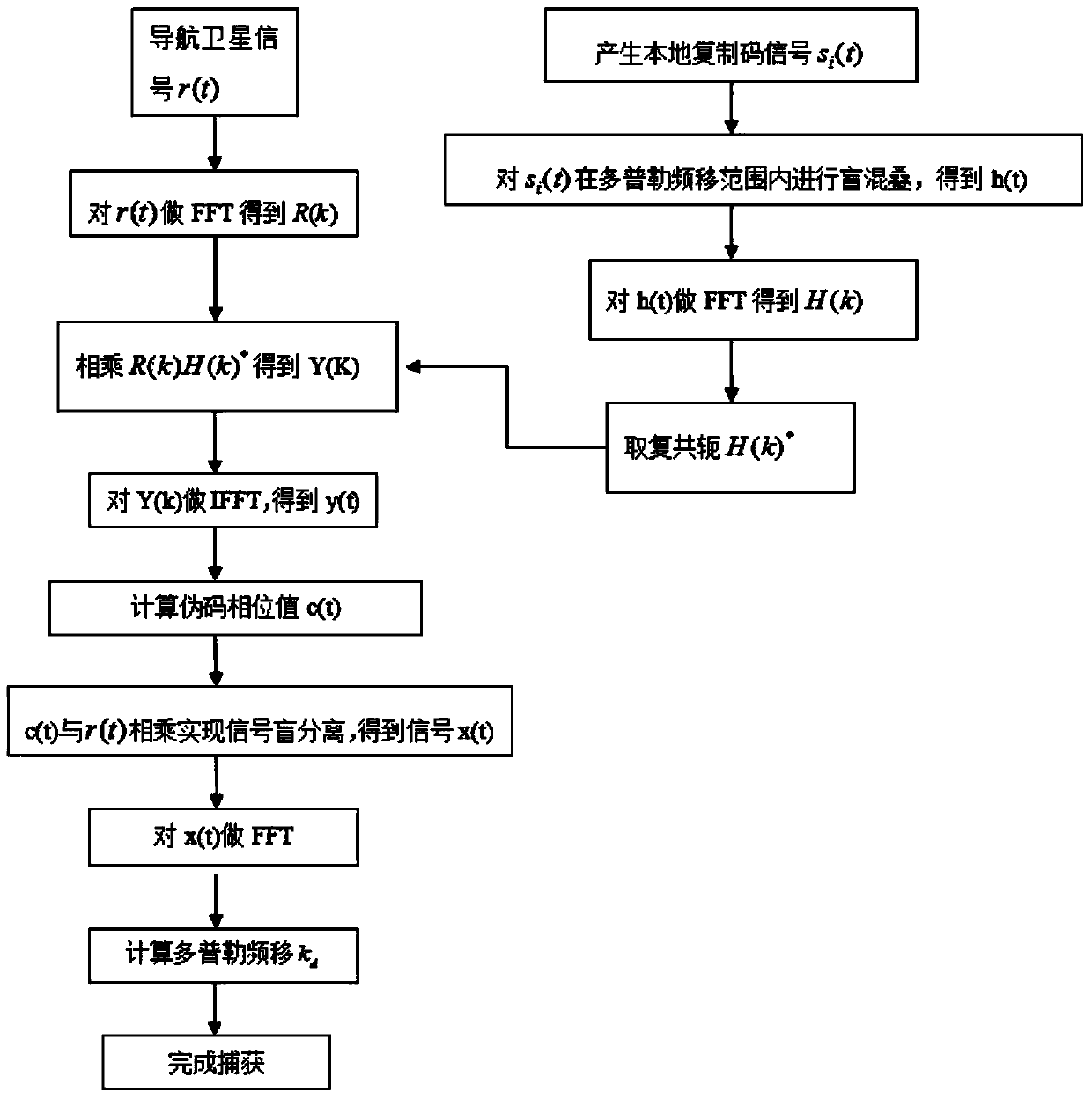
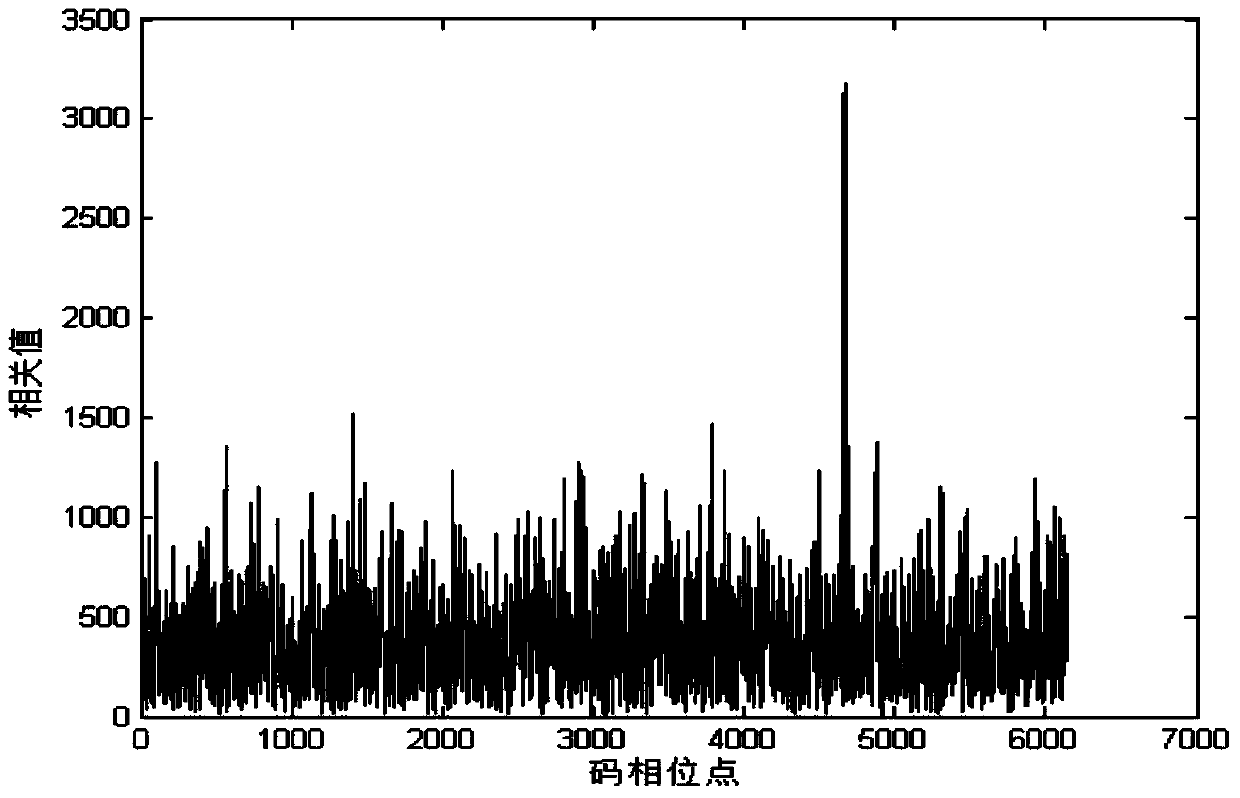
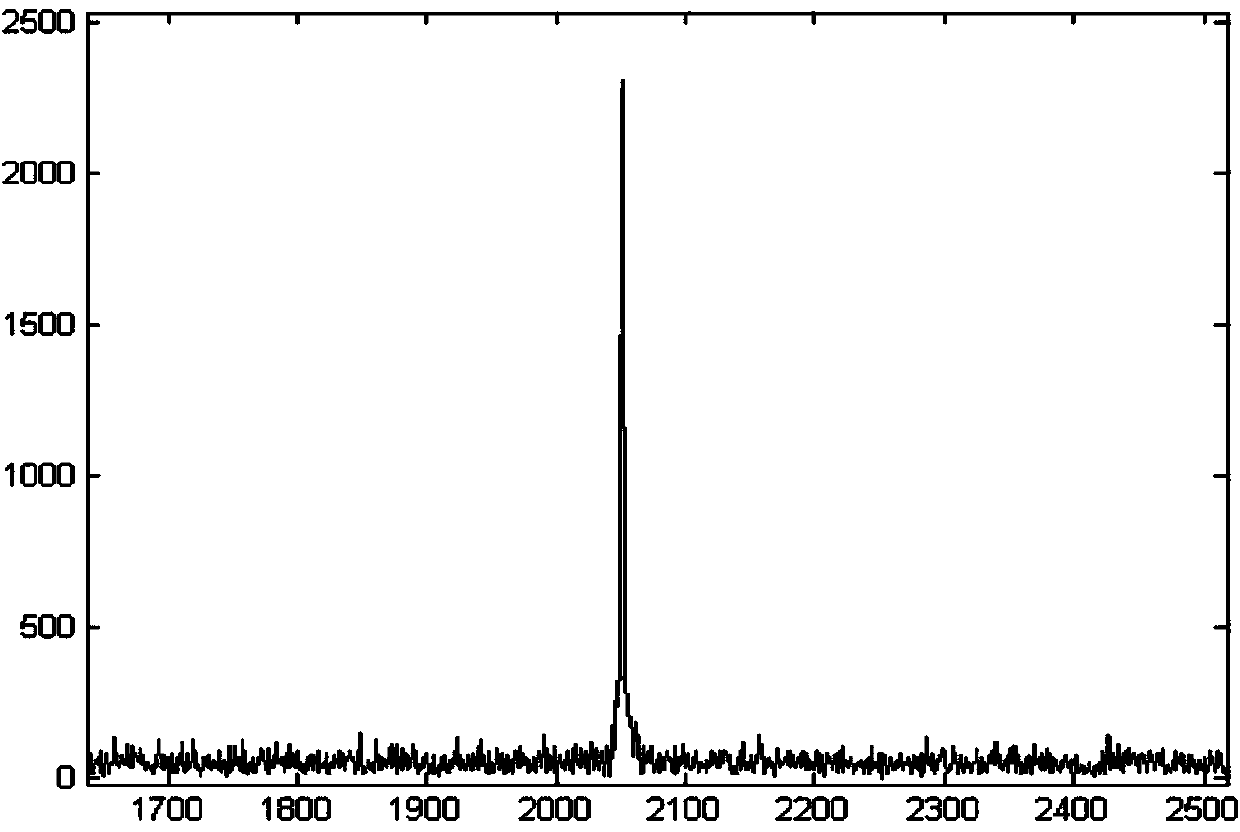
Satellite navigation signal capturing method and device based on blind aliasing and blind separation
InactiveCN104199060AReduce computationHigh speedSatellite radio beaconingIntermediate frequencyCarrier signal
The invention discloses a navigation signal capturing method and device based on blind aliasing and blind separation. The method comprises the following steps: performing FFT (Fast Fourier Transform) operation on an intermediate frequency signal r(t) generated by down-sampling frequency mixing to obtain R(k); generating a local duplicated code signal, and performing blind aliasing of a plurality of frequency points in a preset Doppler frequency shift range; performing FFT operation on a blind aliasing signal to obtain a blind aliasing signal of a frequency domain, and performing duplicating and conjugation on the blind aliasing signal to obtain H(k)*; multiplying R(k) with H(k) to obtain Y(k), performing IFFT (Inverse Fast Fourier Transform) operation on Y(k) to obtain y(t), and finding a position where the y(t) amplitude is maximum for serving as a pseudo-code phase value c(t); multiplying the obtained c(t) with the intermediate frequency signal r(t) to realize blind separation of the pseudo-code signal and a carrier signal in order to obtain a carrier signal x(t); performing FFT operation on x(t) to obtain a signal frequency spectrum, and finding a frequency value corresponding to a maximum peak, namely, a carrier Doppler frequency shift value kd in order to finish capturing work. The method and the device are suitable for capturing GPS (Global Positioning System) satellite navigation signals, the operand required by signal capturing is further reduced, and the capturing speed and capturing efficiency are increased.
Owner:GUANGDONG UNIV OF TECH
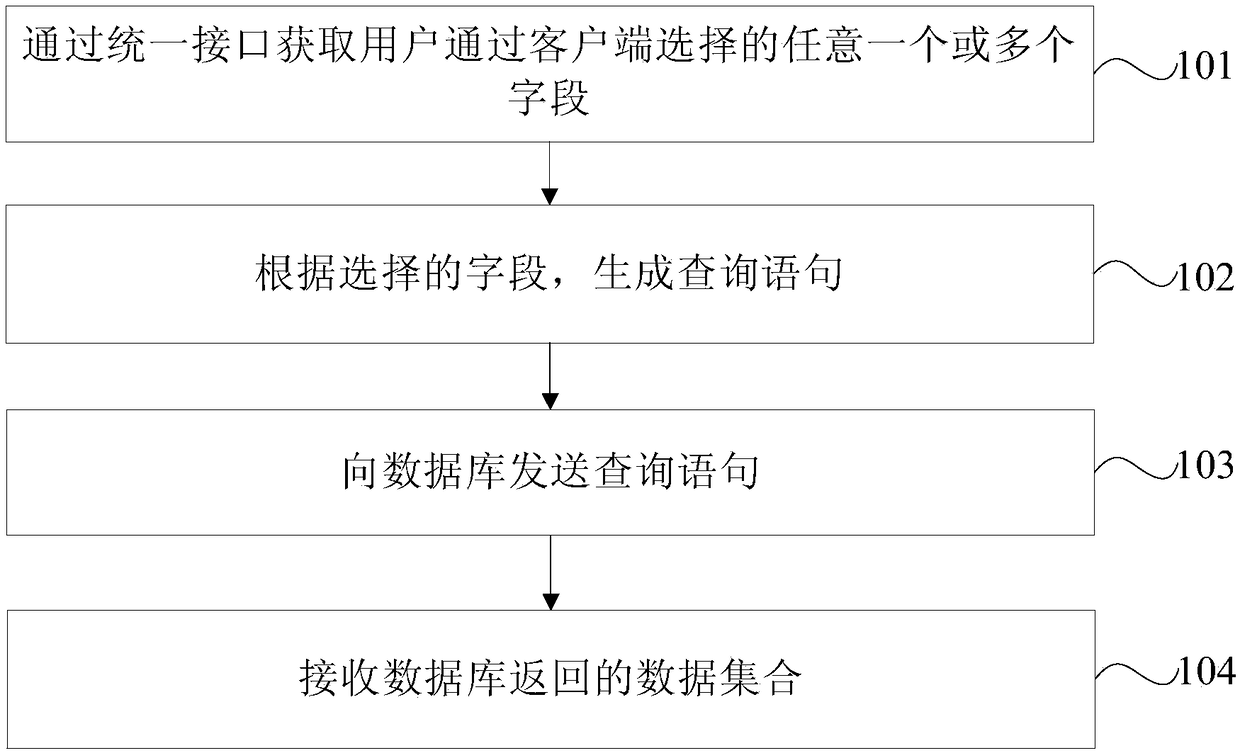
Data query method and device
InactiveCN108228916AWon't leakImprove securityOther databases queryingSpecial data processing applicationsDuplicate codeClient-side
The invention provides data query method and device. The method comprises the following steps: acquiring, via a uniform query interface, one or more fields selected by a user through a client; generating a query sentence according to the selected fields; sending the query sentence to a database; and receiving a dataset returned by the database. Since the user can freely select the to-be-queried field and conduct query through the uniform query interface, the generation of many duplicated codes is avoided, and the server resources are saved; and moreover, the data of the fields not for query isnot leaked, thereby enhancing the data security.
Owner:CHINA UNITED NETWORK COMM GRP CO LTD
Method and apparatus for implementing dynamic function groups in a data processing system
ActiveUS7657870B2Requirement analysisSpecific program execution arrangementsData processing systemThird party
A method, an apparatus, and computer instructions are provided for implementing dynamic function groups in a data processing system. An extensible framework is provided, which provides function groups to amalgamate extended sets of functionality by either vendor or purpose and allows the function groups to be dynamically enabled or disabled within a software application. A user may specify which extended sets of functionality are relevant and when to enable them. With the use of function groups, third party vendors may integrate added functionalities with existing ones in a software application, and indicate when these functionalities should be available to end-users without the need to duplicate code. The invention allows for the construction of other extensible frameworks including wizards, editors, and operations may also be extended with the use of function groups.
Owner:LENOVO GLOBAL TECH INT LTD
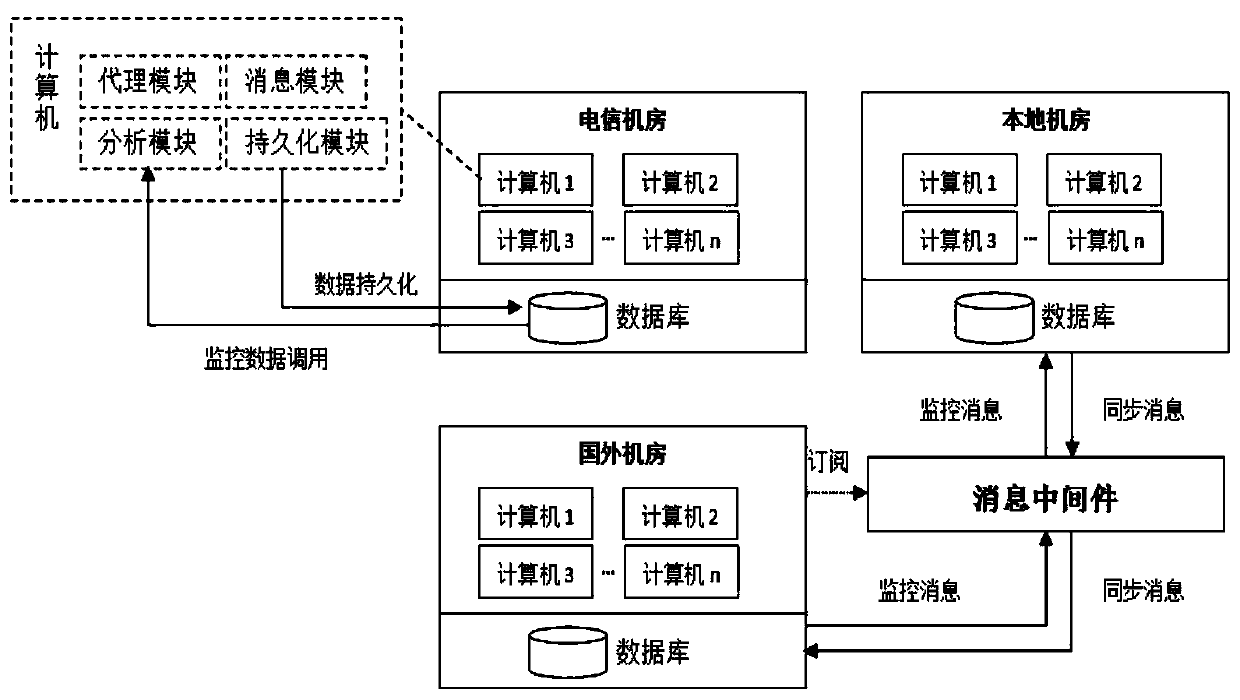
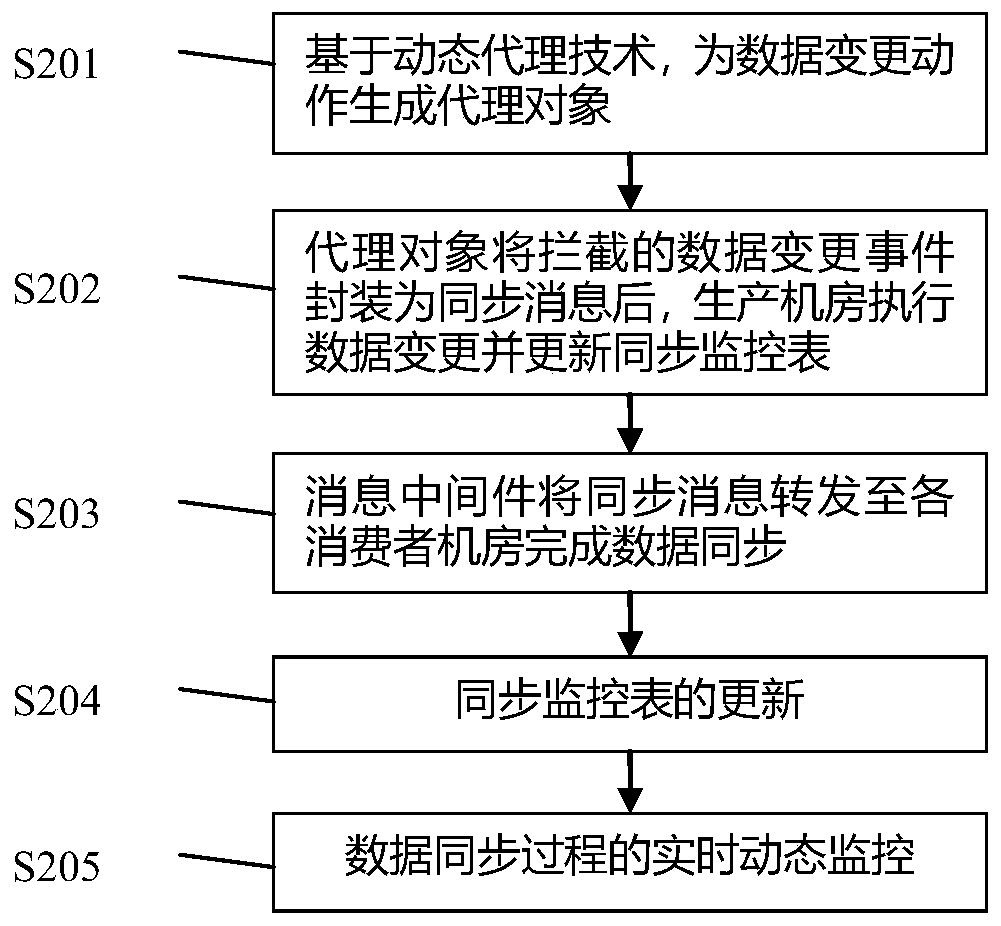
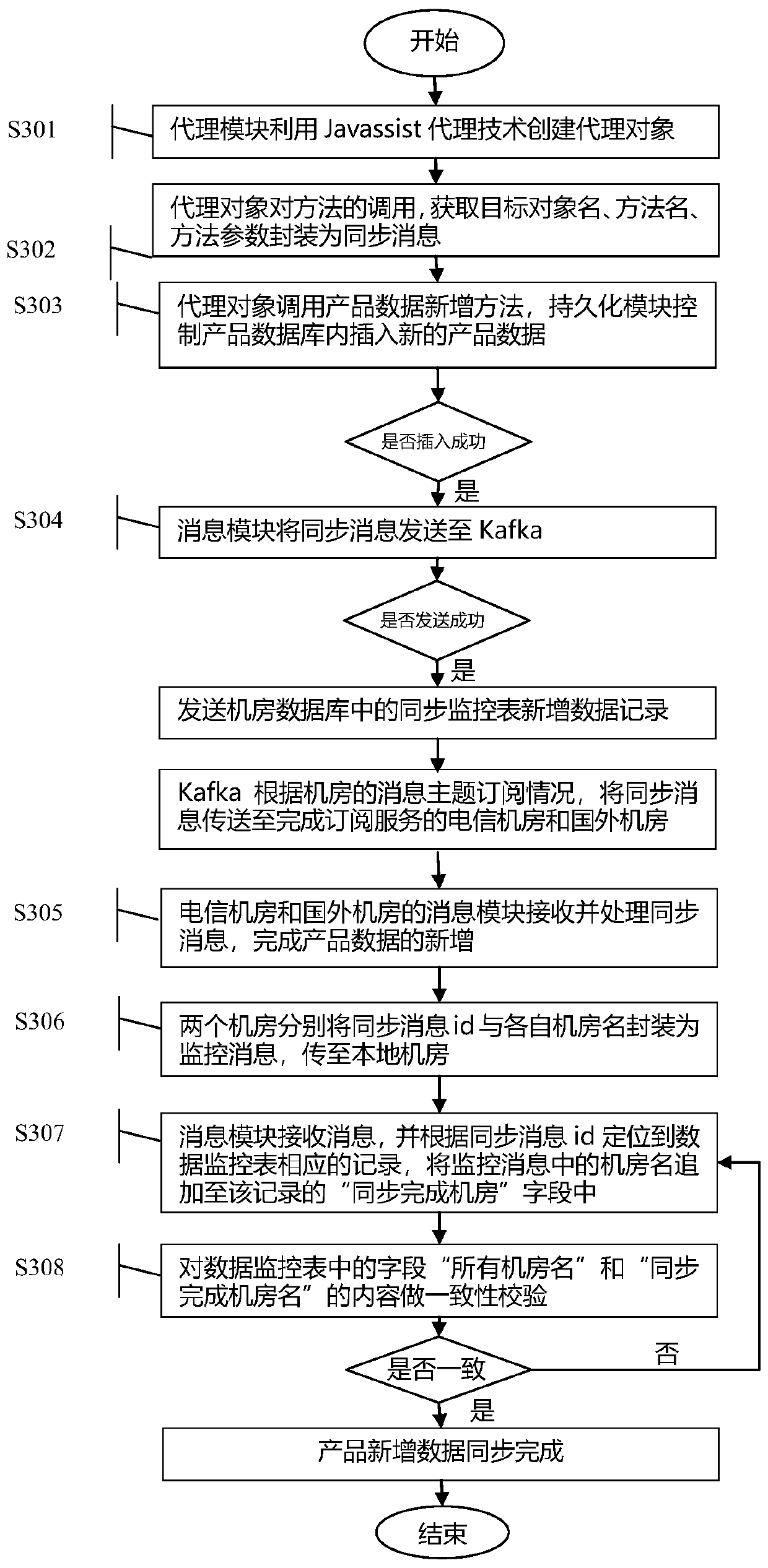
Cross-machine-room data synchronization method and system
ActiveCN110309231AReduce code duplicationStrong scalabilityDatabase distribution/replicationSpecial data processing applicationsMonitoring dataReal-time computing
The invention discloses a cross-machine-room data synchronization method and system. The method is characterized in that an agent object is generated to intercept a data change action so as to capturethe data change action of a producer, the data change action is packaged into a synchronous message, the synchronous message is transmitted to a consumer who subscribes the data change action throughmessage middleware, the consumer can be triggered to generate the same data change action as the producer through message unpacking, and cross-machine-room data synchronization is completed; and in the synchronous execution process, the synchronous monitoring table is used for recording the data synchronization completion condition of each machine room in real time. The technical effects of effectively reducing the number of times of code repeated compilation in the data synchronization process and being extremely high in expansibility are achieved. In the synchronous execution process, the data synchronization completion condition of each machine room is recorded in real time through a persistent synchronous monitoring table, meanwhile, the data synchronization process can be dynamicallymonitored in real time, and timely intervention is achieved when a synchronization problem occurs.
Owner:FOCUS TECH
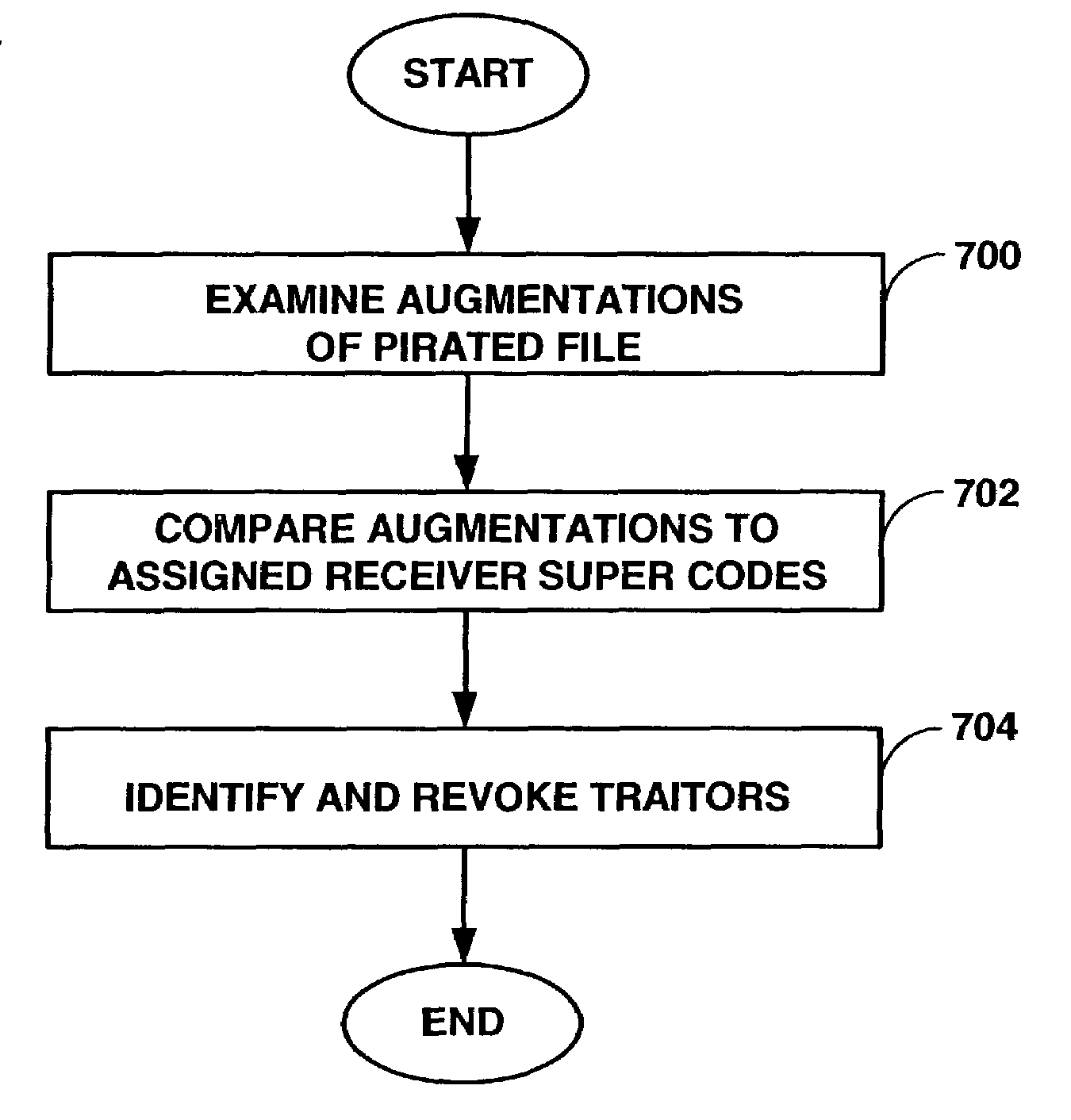
Method for tracing traitors and preventing piracy of digital content in a broadcast encryption system
InactiveUS7505593B2Reduce the possibilitySituation easyKey distribution for secure communicationRecord information storageComputer hardwareDigital content
A method for disabling a traitor receiver in a broadcast encryption system includes examining augmentations of at least one redistributed version of a file in a group of files, wherein each authorized receiver acquired decryption keys only for the particular augmentations that it used. A level to which the augmentations correspond to a first set of super codes previously assigned to each authorized receiver is determined. A conclusion is drawn regarding the number of receivers that are traitor receivers. The receivers concluded to be traitor are selectively revoked. The process is repeated by selecting another set of super codes; selected to reduce the number of authorized receivers concluded to be traitor receivers. The sets of super codes are selected such that the number is made larger to achieve quicker revocation of a traitor receiver at the cost of increasing chance of an incorrect revocation of an innocent receiver.
Owner:IBM CORP
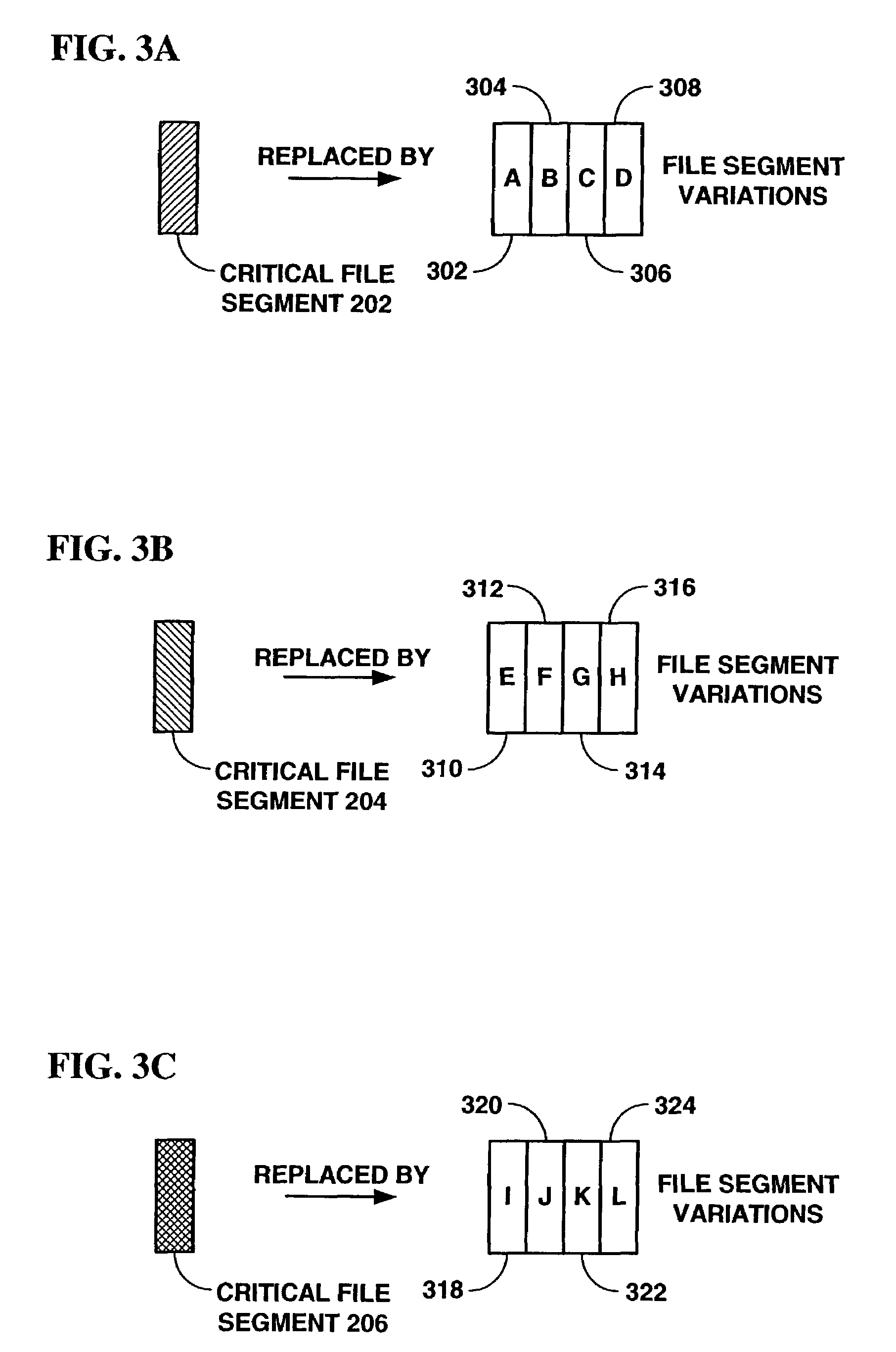
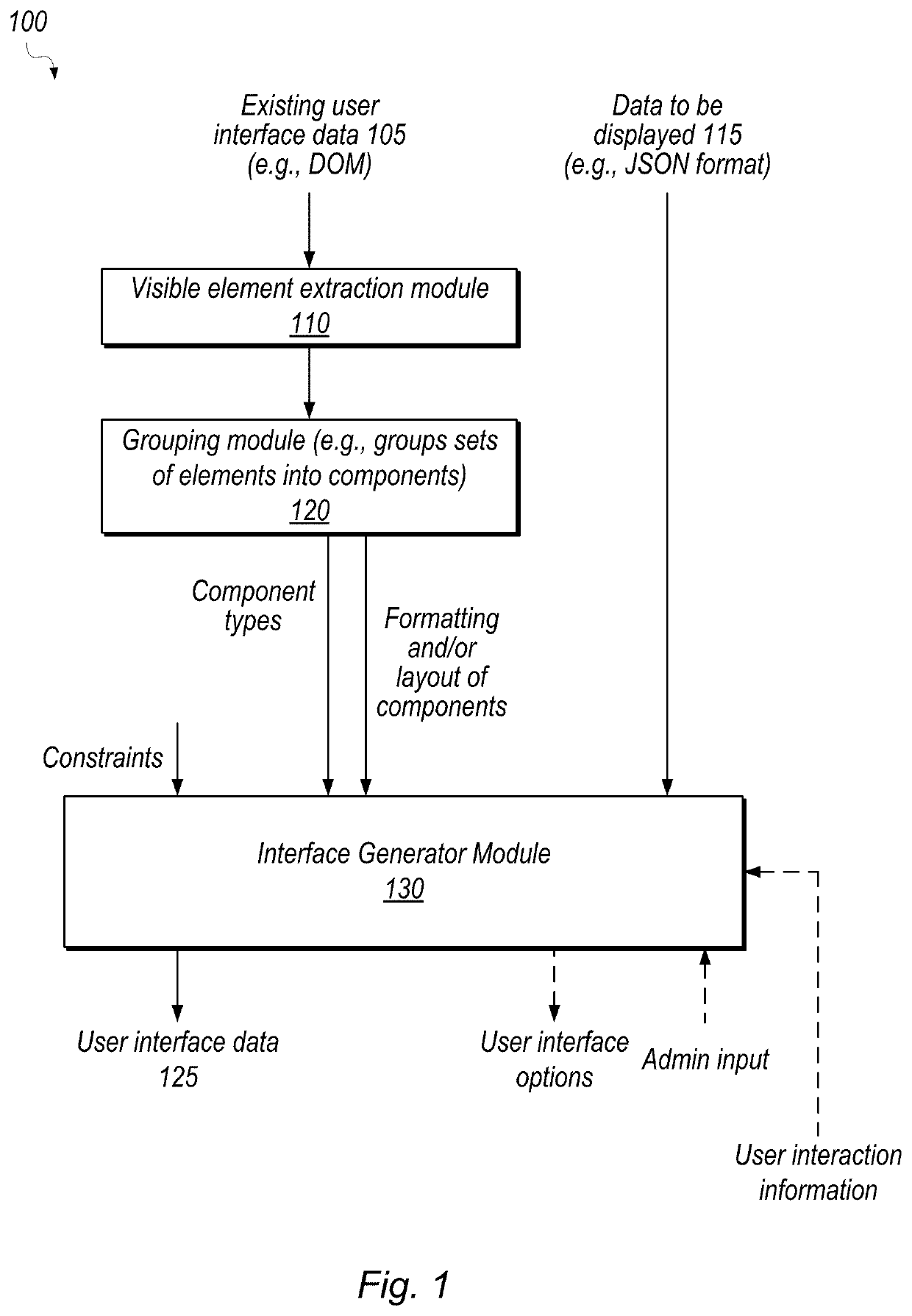
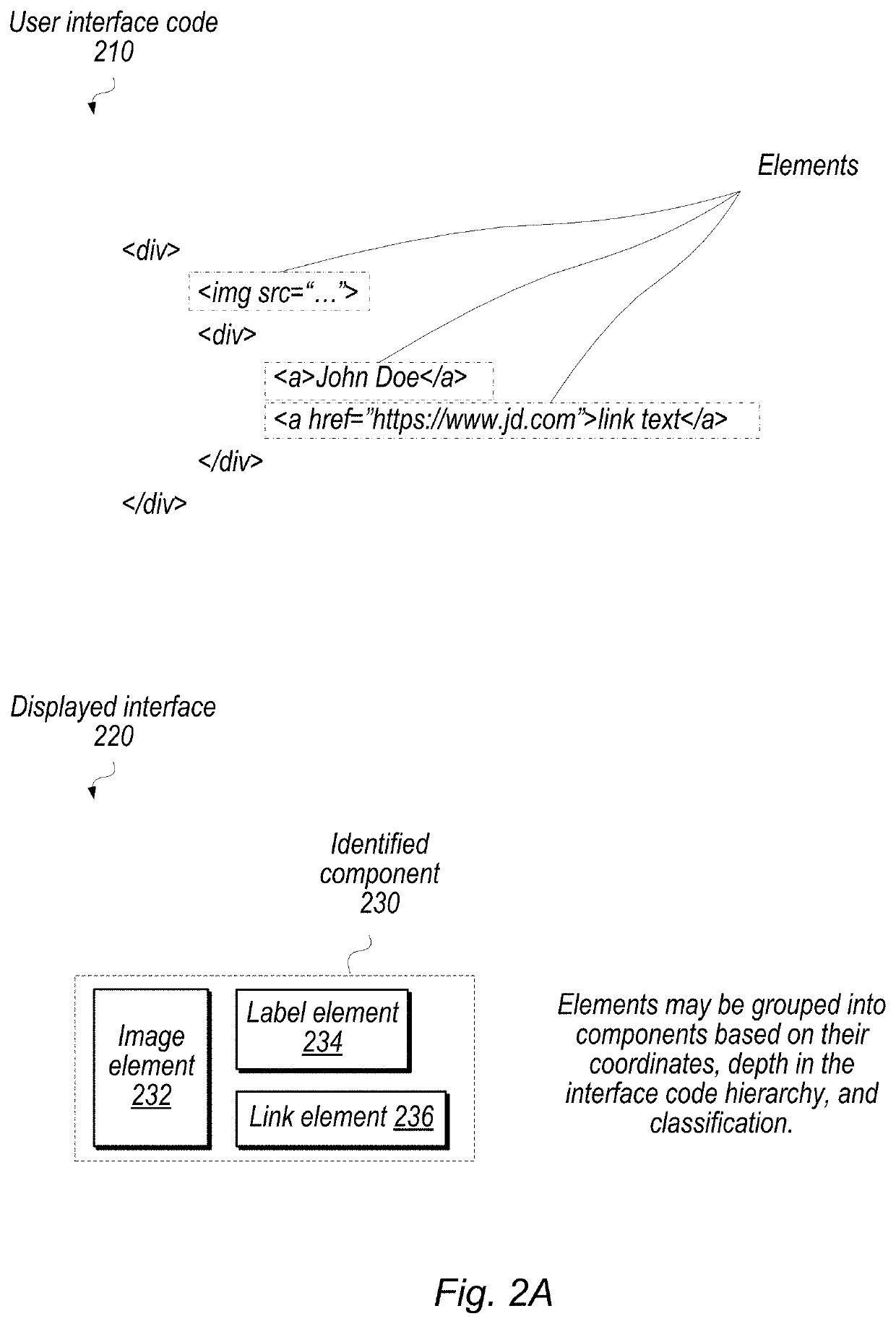
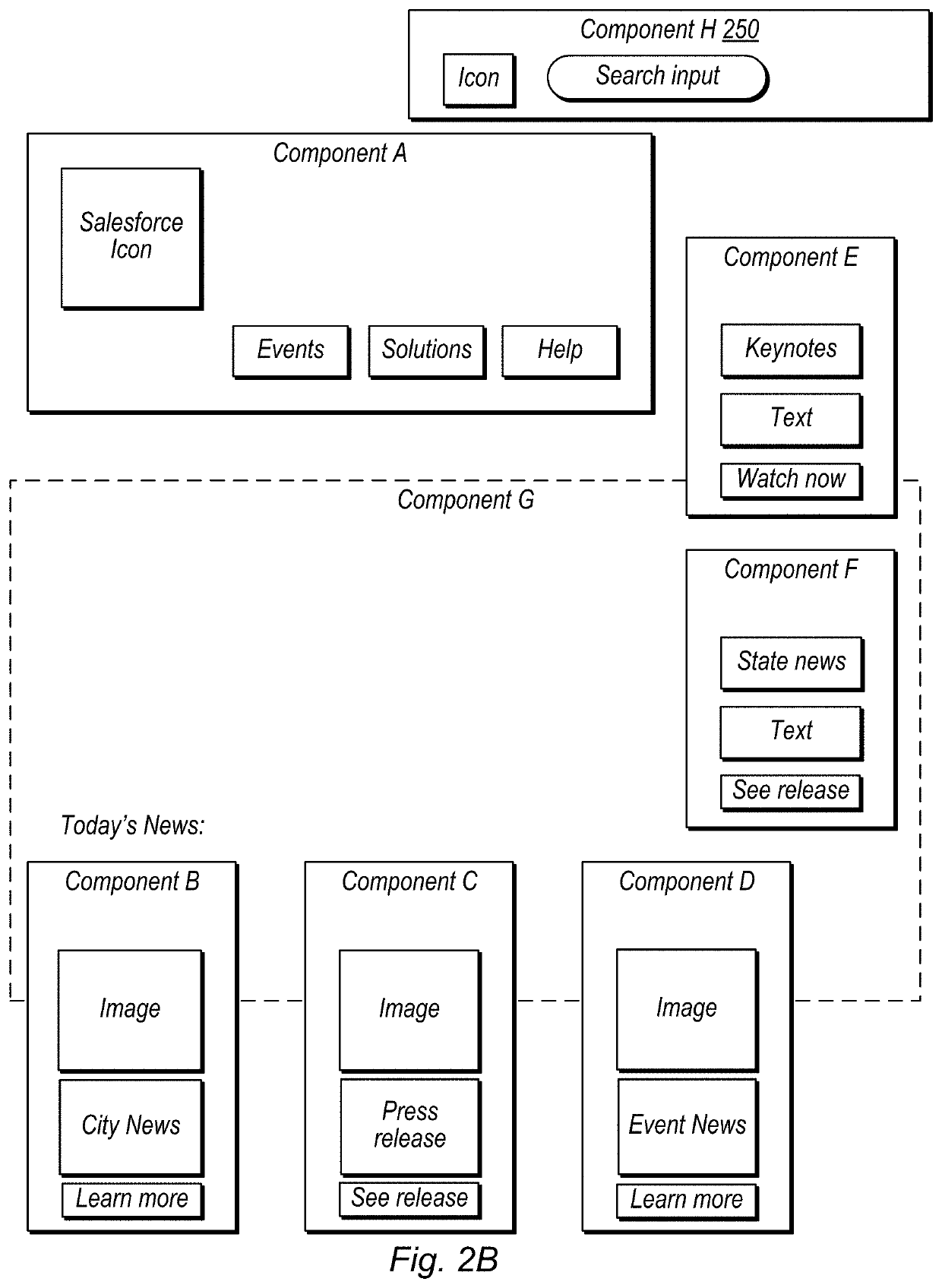
Duplicate User Interface Design Identification
Techniques are disclosed relating to identifying duplicate coding and / or design used in different parts of a user interface (e.g., a web application). In some embodiments, a plurality of visible elements of an interface are detected based on hierarchical user interface code. In some embodiments, a device groups sets of the plurality of visible elements based on determined coordinates and depth levels for the detected elements. In some embodiments, groups that meet a threshold similarity criterion are identified. In some embodiments the threshold similarity criterion is based on classification of detected elements and / or geospatial analysis.
Owner:SALESFORCE COM INC
Database operation method based on Hibernate
InactiveCN105138646AAvoid developmentReduce couplingSpecial data processing applicationsSpecific program execution arrangementsCode couplingBase class
The invention discloses a database operation method based on Hibernate, and belongs to the technical field of database management. Hibernate inheritance and polymorphism characteristics are sufficiently utilized for packaging base class DAO and enabling the base class DAO to inherit a Hibernate Dao Support class, the base class DAO can directly use the API of hibernate, and CRUD operation for different DAO objects is achieved. The phenomenon that a corresponding DAO interface is written for each database persistent object is not needed, duplicated code development is avoided, the problem occurrence probability is greatly reduced, the development efficiency is improved, code coupling is reduced, developers are not free of basic database operation, and focusing service logic processing is facilitated.
Owner:INSPUR GROUP CO LTD
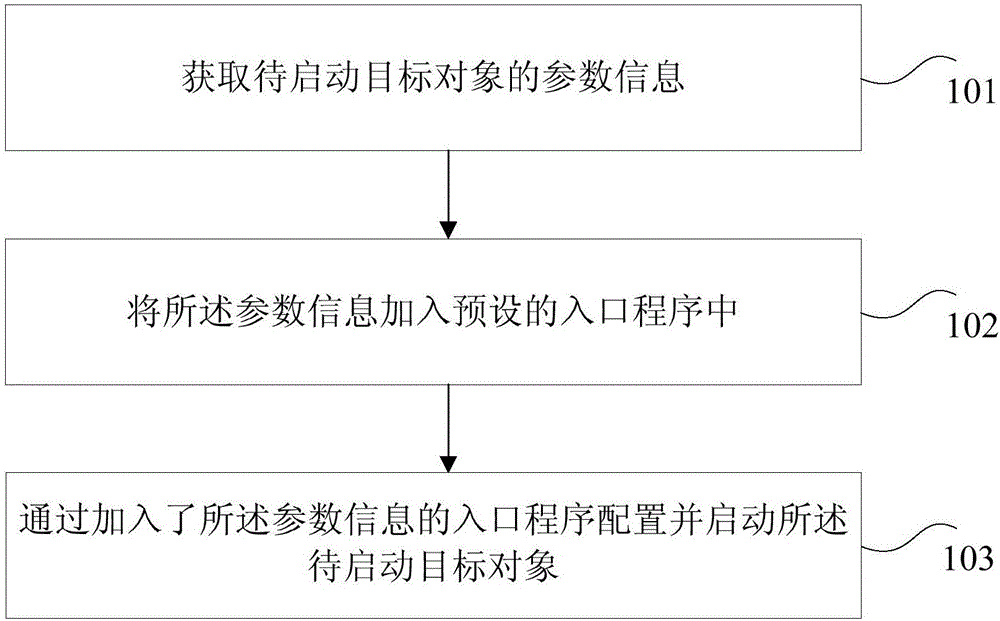
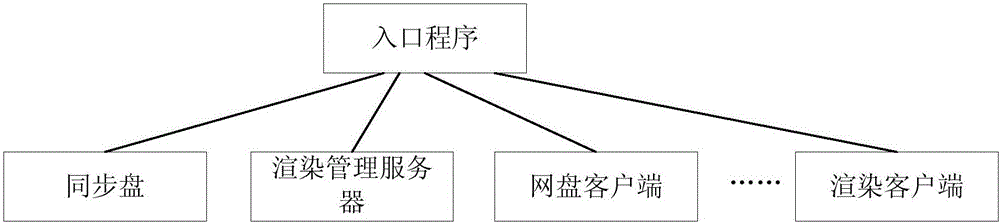
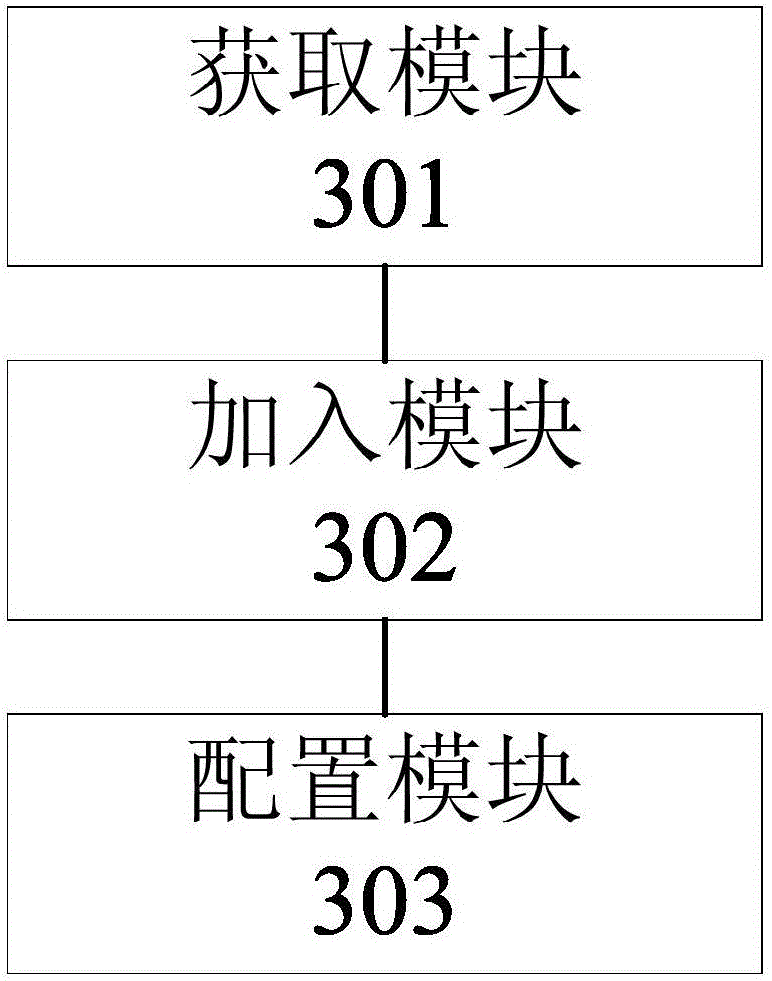
Target object starting method and business program system
InactiveCN106325939ASolve the technical problem of redundancyReduce editProgram loading/initiatingCode redundancySoftware engineering
The invention provides a target object starting method and a business program system. The method comprises the following steps: obtaining parameter information of target objects to be started; adding the parameter information into a preset entry program; and configuring and starting the target objects to be started via the entry program to which the parameter information is added. Through the target object starting method and the business program system, the technical problem of code redundancy caused by that the entry programs need to be set for different target objects respectively in the prior art can be solved; the technical effect of effectively reducing the editing of the duplicated codes can be achieved.
Owner:苏州创意云网络科技有限公司
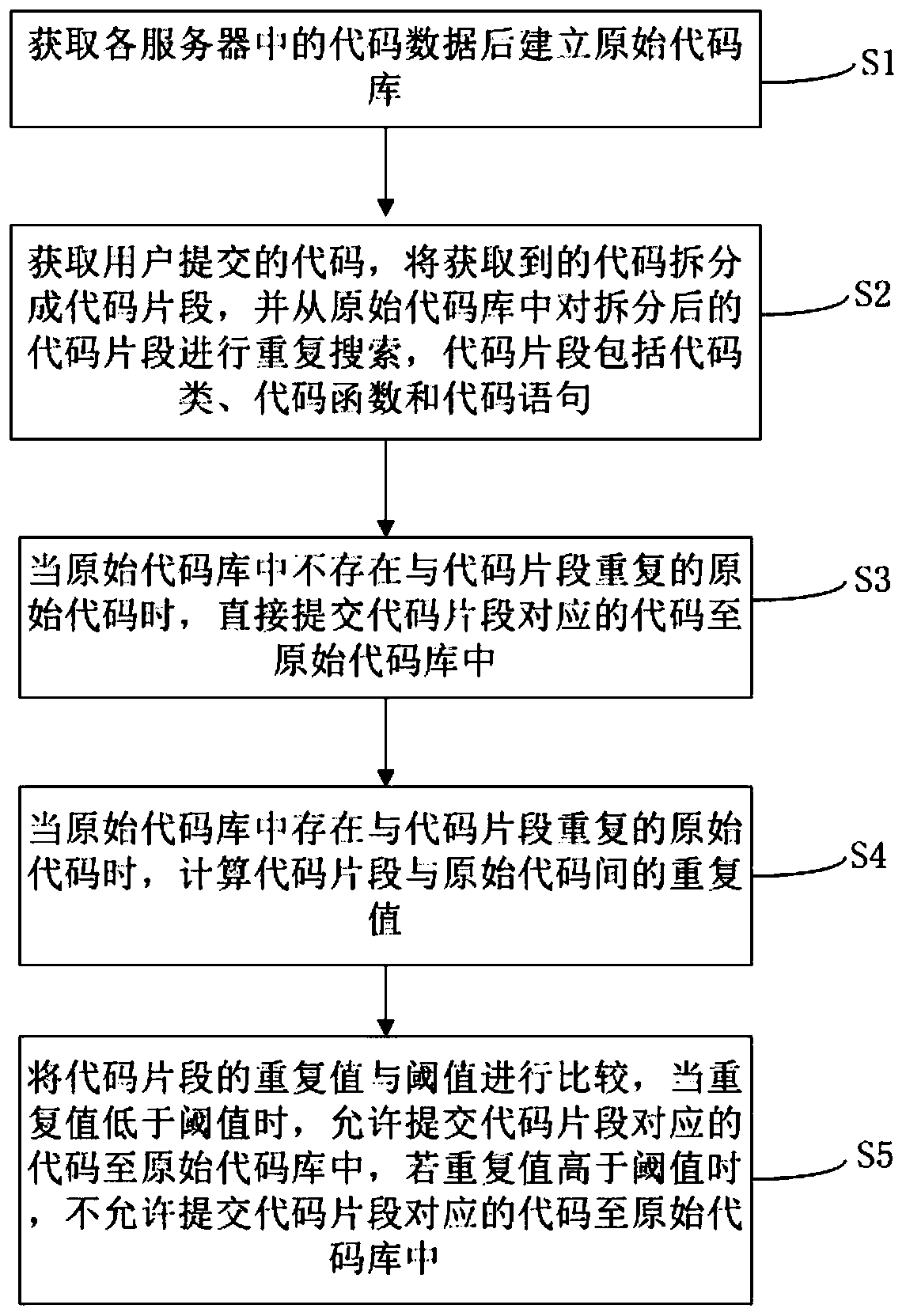
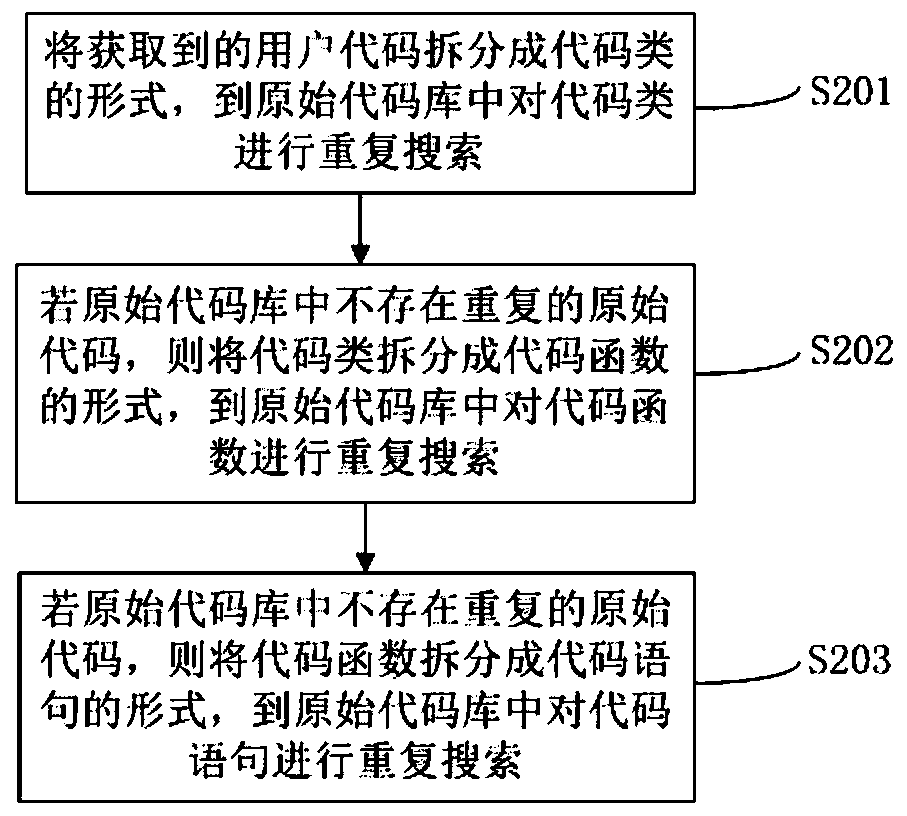
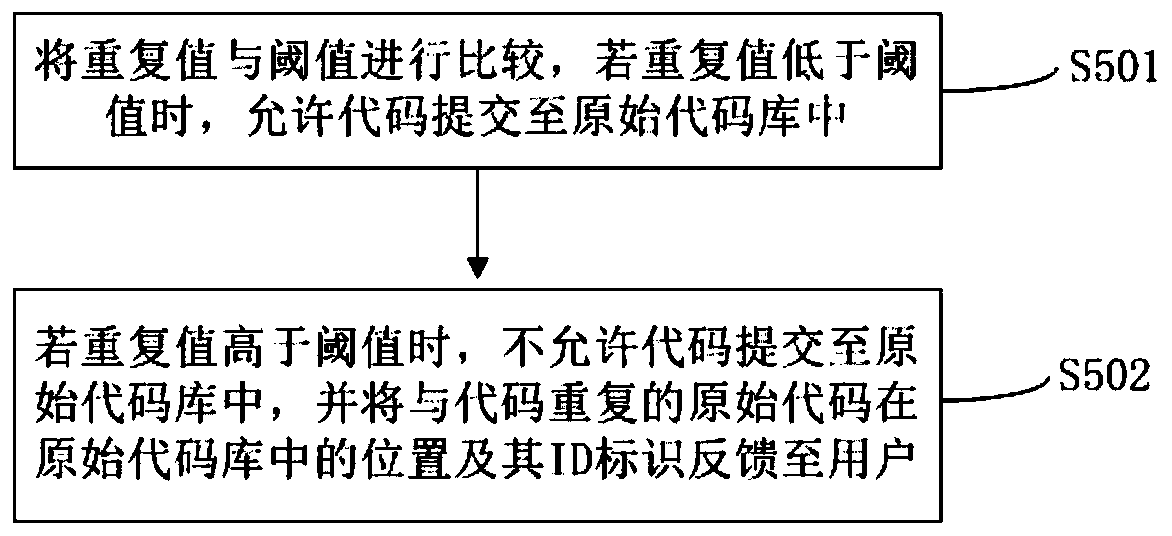
Method and system for preventing repeated submission of codes, computer equipment and storage medium
PendingCN109739554AAvoid redundancyImprove efficiencySoftware testing/debuggingSoftware metricsCode redundancySoftware development
The invention relates to the technical field of software development and maintenance, in particular to a method and device for preventing repeated submission of codes, computer equipment and a storagemedium. The method for preventing repeated submission of codes comprises the following steps: obtaining code data in each server and then establishing an original code library; obtaining a code submitted by a user, splitting the obtained code into code segments, and searching the code segments from the original code library; when repeated codes of the code segments do not exist in the original code library, the codes are directly submitted to the original code library; when repeated codes of the code segments exist in the original code library, calculating repeated values of the code segments; Comparing the repetition value with a threshold value, allowing code submission when the repetition value is lower than the threshold value, and not allowing code submission when the repetition value is higher than the threshold value. By controlling the source of repeated codes when the user submits the codes, the code redundancy problem in the code library is reduced, the misjudgment rate is low, and the speed is high.
Owner:ONE CONNECT SMART TECH CO LTD SHENZHEN
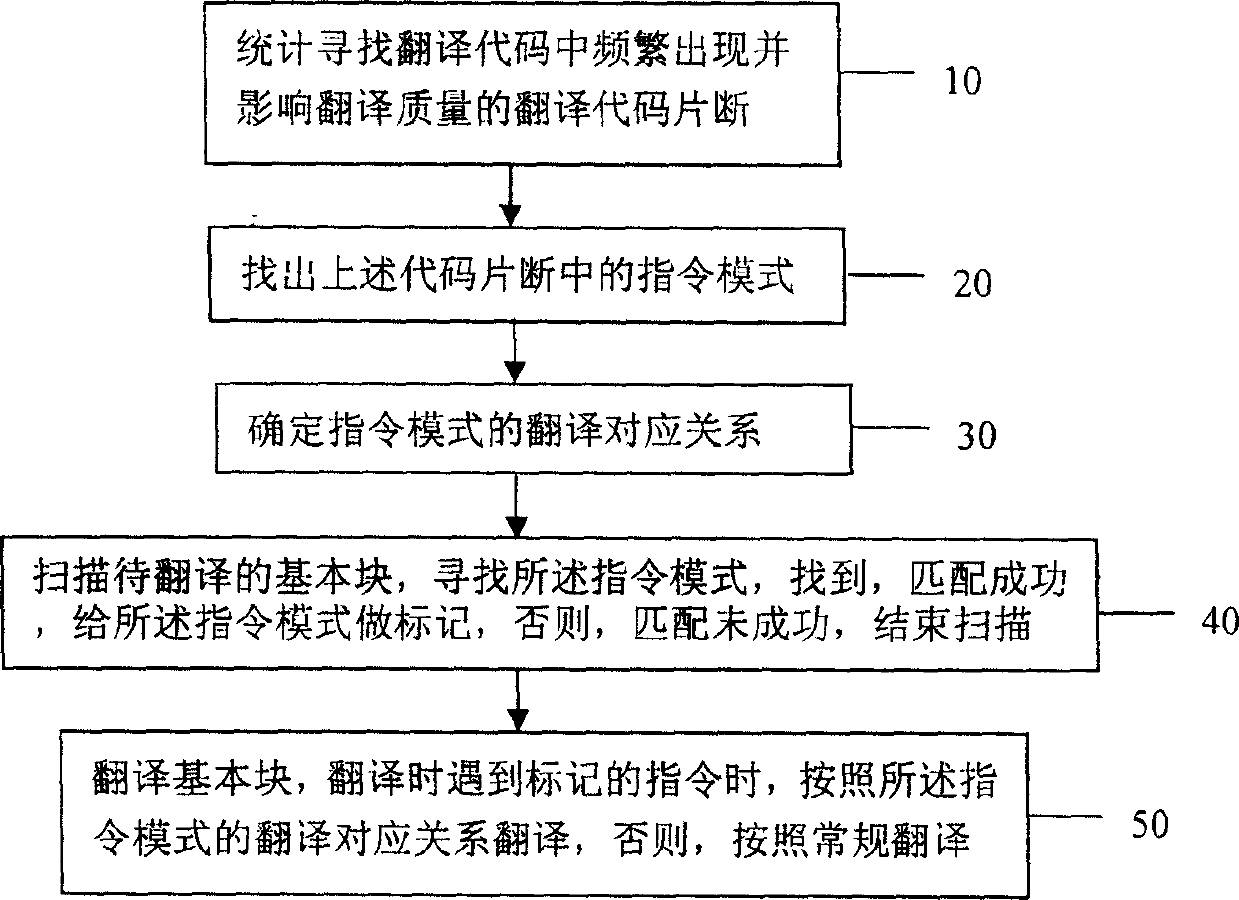
Translation method in dynamic binary translation
ActiveCN1746849AImprove performanceReduce overheadProgram controlMemory systemsComputer hardwarePattern matching
A translation method in dynamic binary translation includes counting and searching out translation code section appeared frequently and influenced quality of translation, finding out command mode in said code section and confirming translation corresponding relation of command mode, scanning basic block to be translated and searching said command mode, making mark on said command mode if said command mode is found or otherwise ending scan, translation basic block and translating it according to translation corresponding relation of said command mode when marked command is met in translation or otherwise translating if according to conventional means.
Owner:INST OF COMPUTING TECH CHINESE ACAD OF SCI
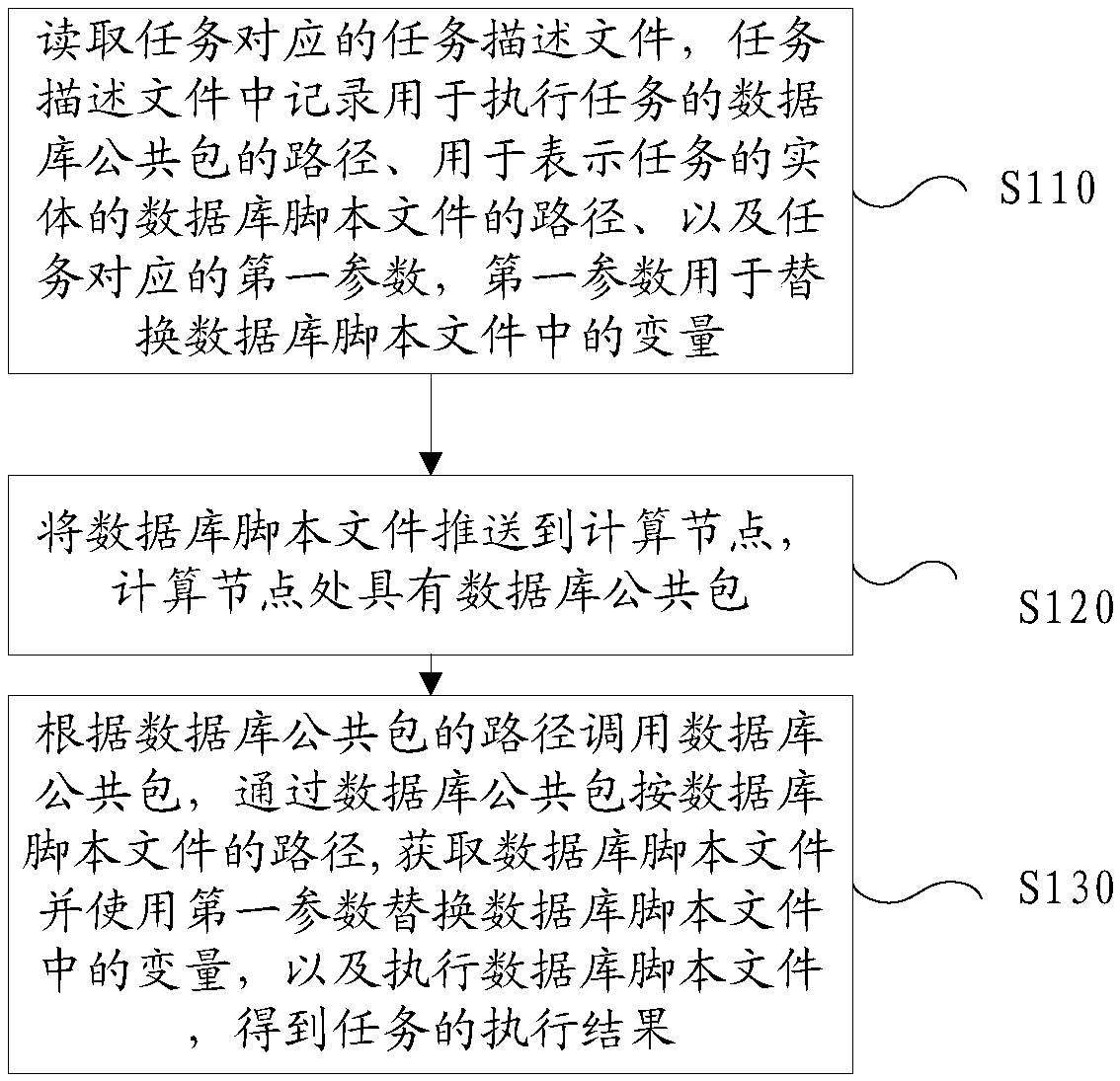
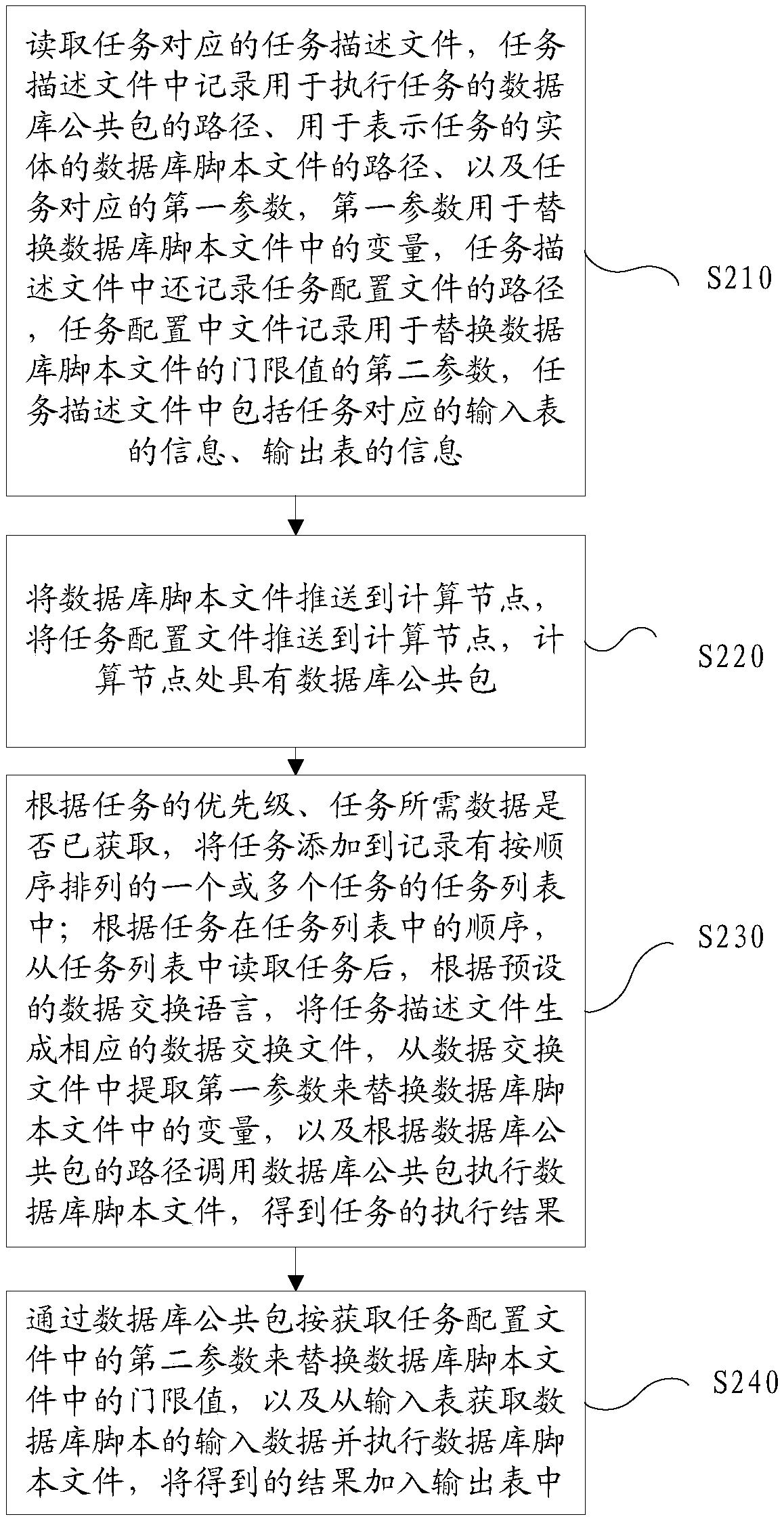
Task execution method, device and server
ActiveCN108280023AIncrease flexibilityEasy maintenanceProgram documentationSoftware testing/debuggingDuplicate codeDatabase
The invention discloses a task execution method, device and a server. The task execution method comprises the following steps: reading a task description file corresponding to a task, wherein the taskdescription file is recorded with a path for executing a database public packet of the task, a path for representing a database script file of an entity of the task, and a first parameter corresponding to the task, and the first parameter is used for replacing variables in the database script file; pushing the database script file to a computing node, wherein a database public packet is arrangedat the computing node; calling the database public packet according to the path of the database public packet; acquiring the database script file and replacing variables in the database script file byusing the first parameter, and executing the database script file to obtain an execution result of the task through the database public packet and according to the path of the database script file. According to the task execution method, device and the server, code repetition is greatly reduced, the task becomes simpler, and the labor is saved.
Owner:深圳市中兴通讯技术服务有限责任公司
Service application information automatic synchronization method and device, equipment and storage medium
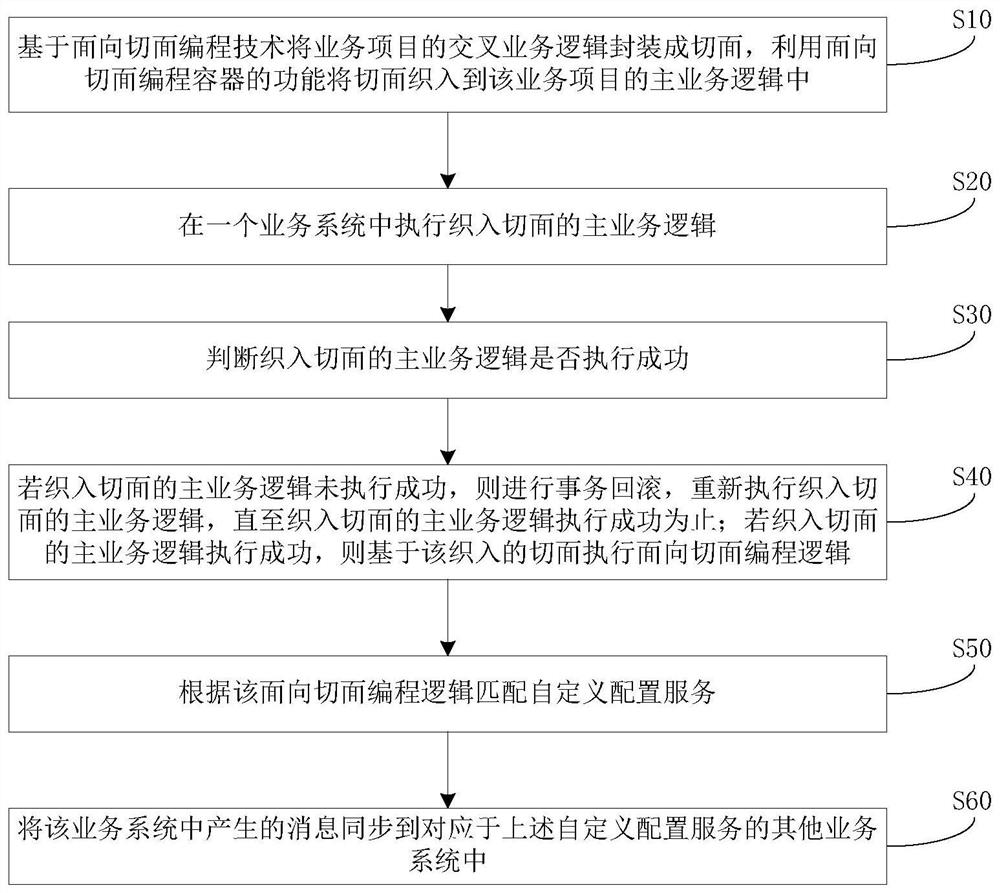
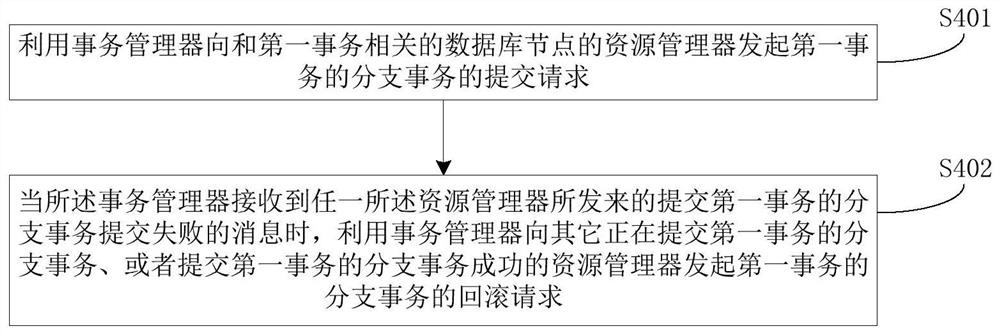
PendingCN112631795AReduce the amount of writingSolve redundancyInterprogram communicationCode compilationCode redundancyDuplicate code
The invention relates to a service application information automatic synchronization method and device, equipment and a storage medium, and the method comprises the steps: packaging the cross service logic of a service project into a section based on a section-oriented programming technology, and enabling the section to be woven into the main service logic of the service project; executing the main service logic of the weaving aspect in a service system; judging whether the main service logic woven into the section is successfully executed or not; if not, carrying out transaction rollback, and executing the main service logic woven into the aspect again until execution succeeds; if so, executing section-oriented programming logic based on the section; matching a custom configuration service according to the aspect-oriented programming logic; and synchronizing the messages generated in the service system to other service systems corresponding to the custom configuration service. According to the method, the code writing amount is reduced, most information synchronization can be realized through configuration, the problems of code redundancy and various code writing problems are solved, the code repetition rate is reduced, and the demand realization period is shortened.
Owner:PINGAN PUHUI ENTERPRISE MANAGEMENT CO LTD
Method for automatically generating software based on data model driving
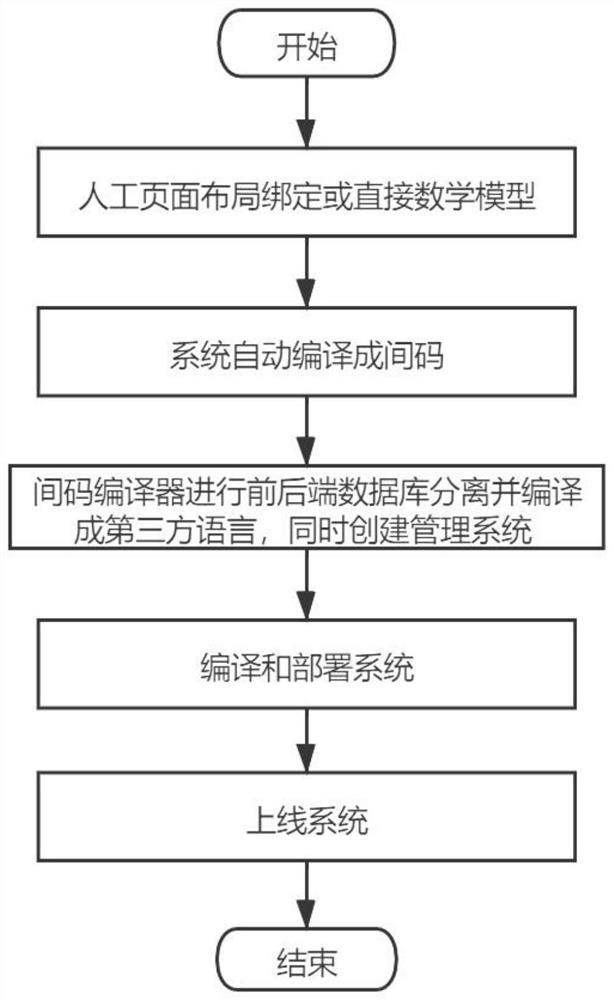
PendingCN112764743ALess programmingImprove writing efficiencyDatabase management systemsModel driven codeMathematical modelSoftware engineering
The invention discloses a method for automatically generating software based on data model driving, which comprises the following steps of: S1, binding data or a direct mathematical model on a manual page layout, S2, automatically compiling into an intermediate code by a system, S3, separating a front-end database and a rear-end database by an intermediate code compiler, compiling into a third-party language (high-level language) and creating a management system at the same time, S4, compiling and deploying the system; and S5, uploading the system. Duplicated code programming is greatly reduced, so that the software writing efficiency is improved; the system can well respond to the demand change; through the design of a self-defined business expression language, the system has strong business adaptability, and meanwhile, the separation of a front-end background and a database code can be completed, so that the security is ensured; and when the data redundancy is increased, the function can be quickly queried, so that the efficiency maximization of the bottleneck function is ensured.
Owner:潘胜怀
A configurable dynamic report generation method and system
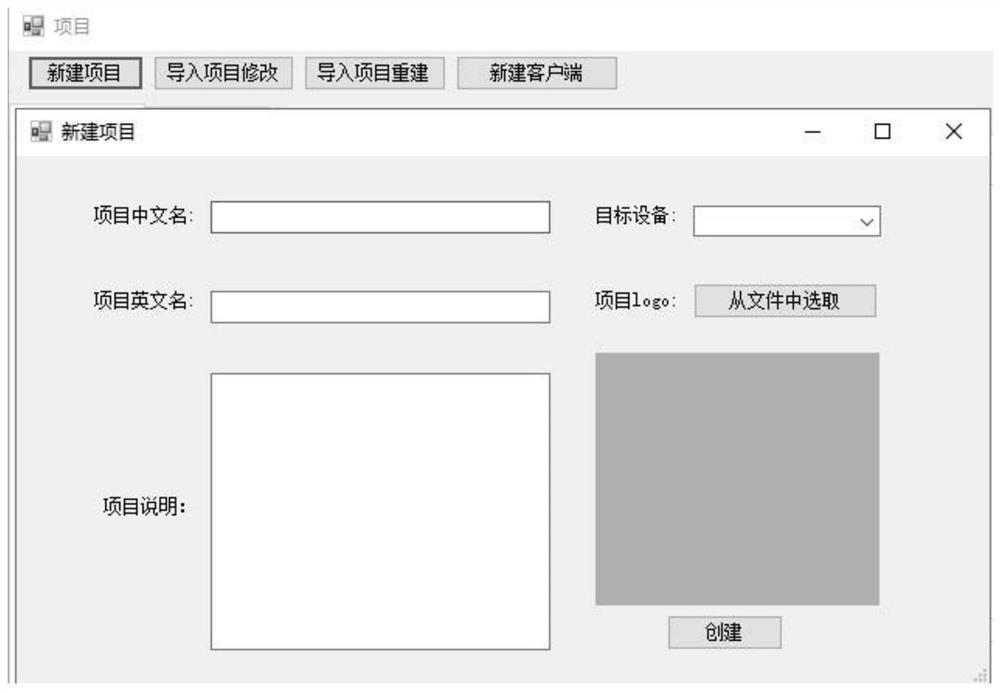
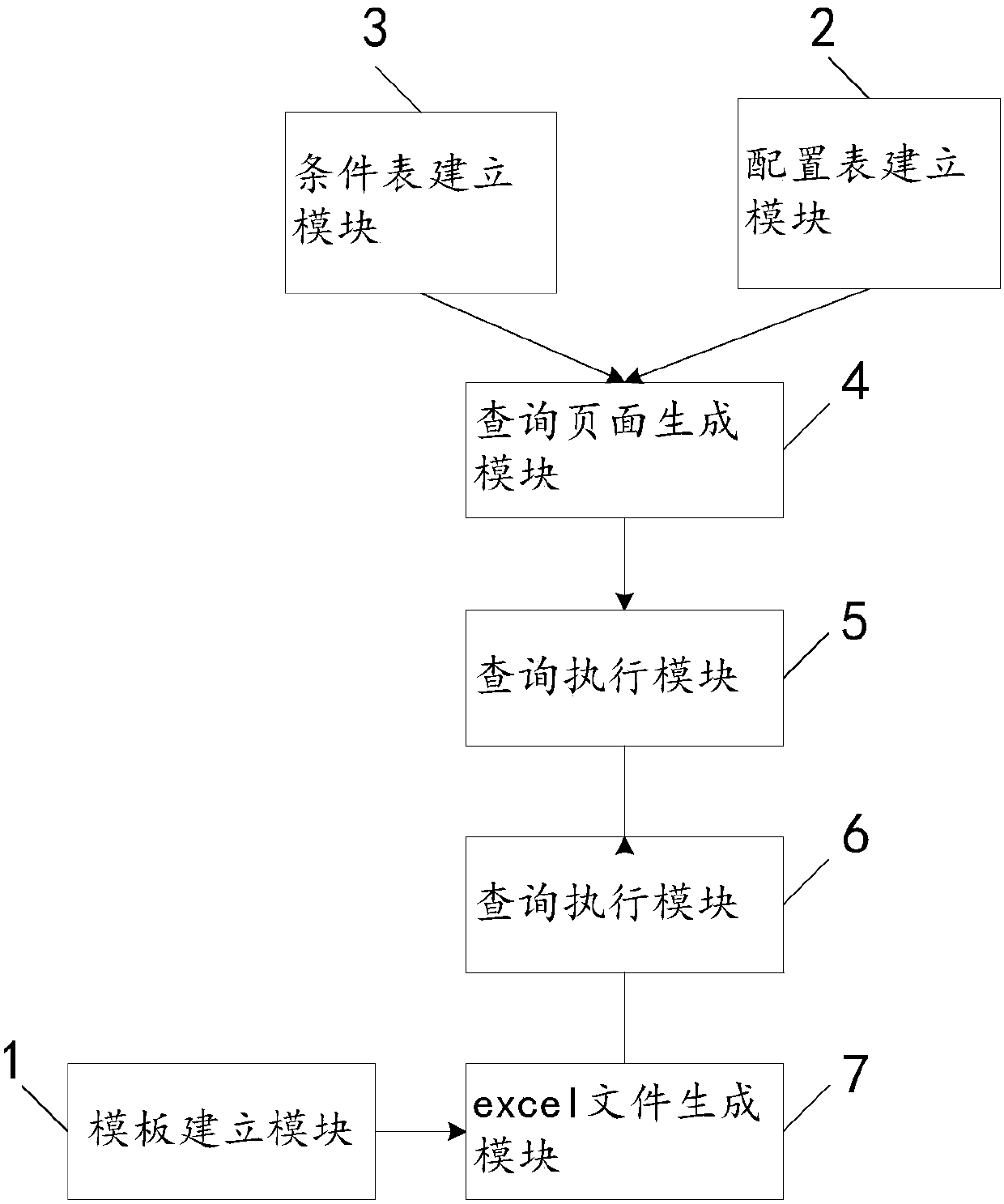
ActiveCN105138501BImprove analytical performanceImprove development efficiencySpecial data processing applicationsData setStatistical analysis
The present invention relates to a configurable dynamic report generation method and system, including establishing a report template; establishing a report configuration table and a report condition table, configuring the report configuration table and the report condition table according to business logic; analyzing the report condition table, Create a report display area and automatically generate a query page; receive the query conditions entered by the user on the query page, and generate query statements in combination with the report configuration table and report condition table; execute the query statement on the specified database to obtain the result data set; according to the obtained results The data set and the report template created in step 1 generate a temporary excel file and save it in the specified directory. The present invention can automatically display report statistical data in a batch configurable manner, use configurable reports, improve the development efficiency of statistical analysis reports, reduce the development amount of repeated codes, improve code reusability, and improve report data analysis effects .
Owner:北京思特奇信息技术股份有限公司
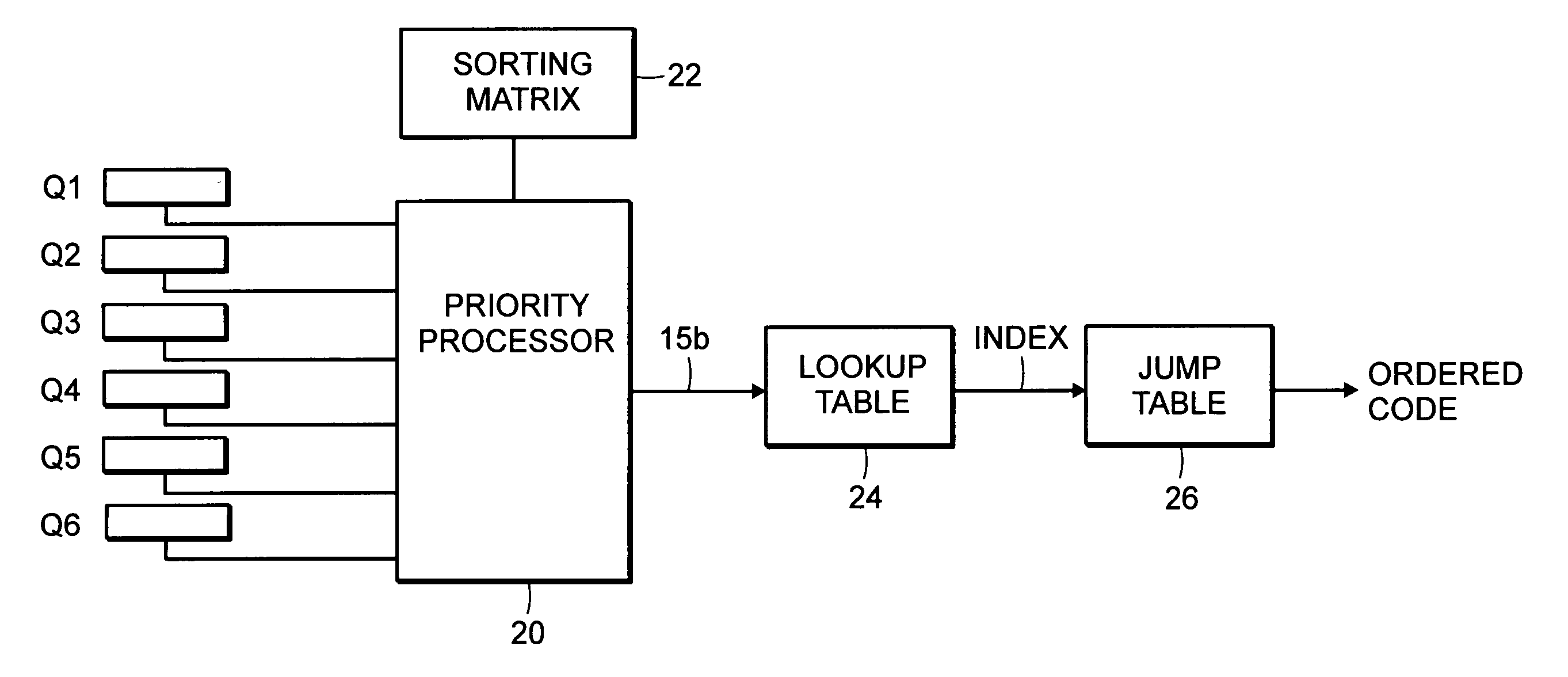
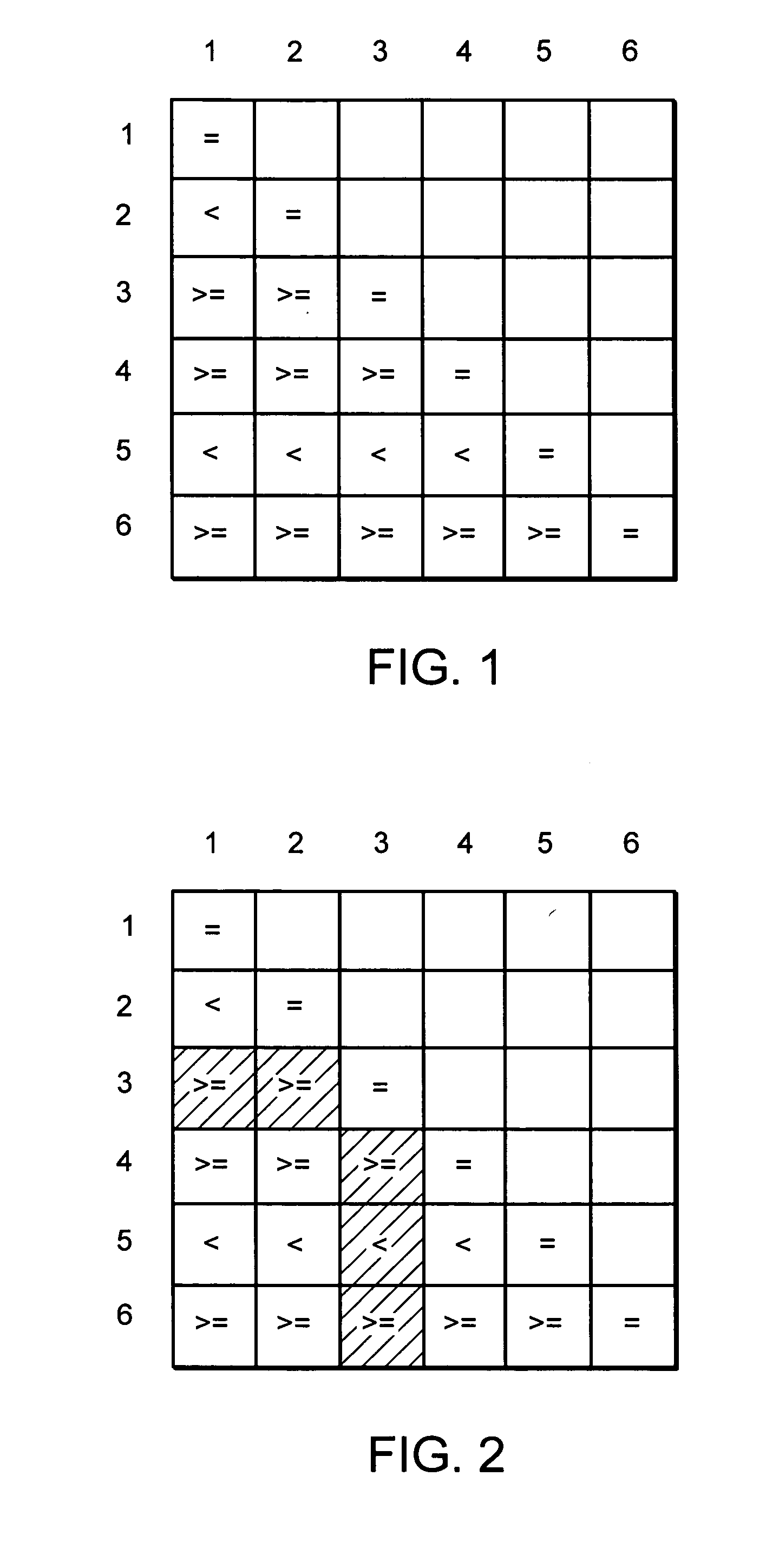
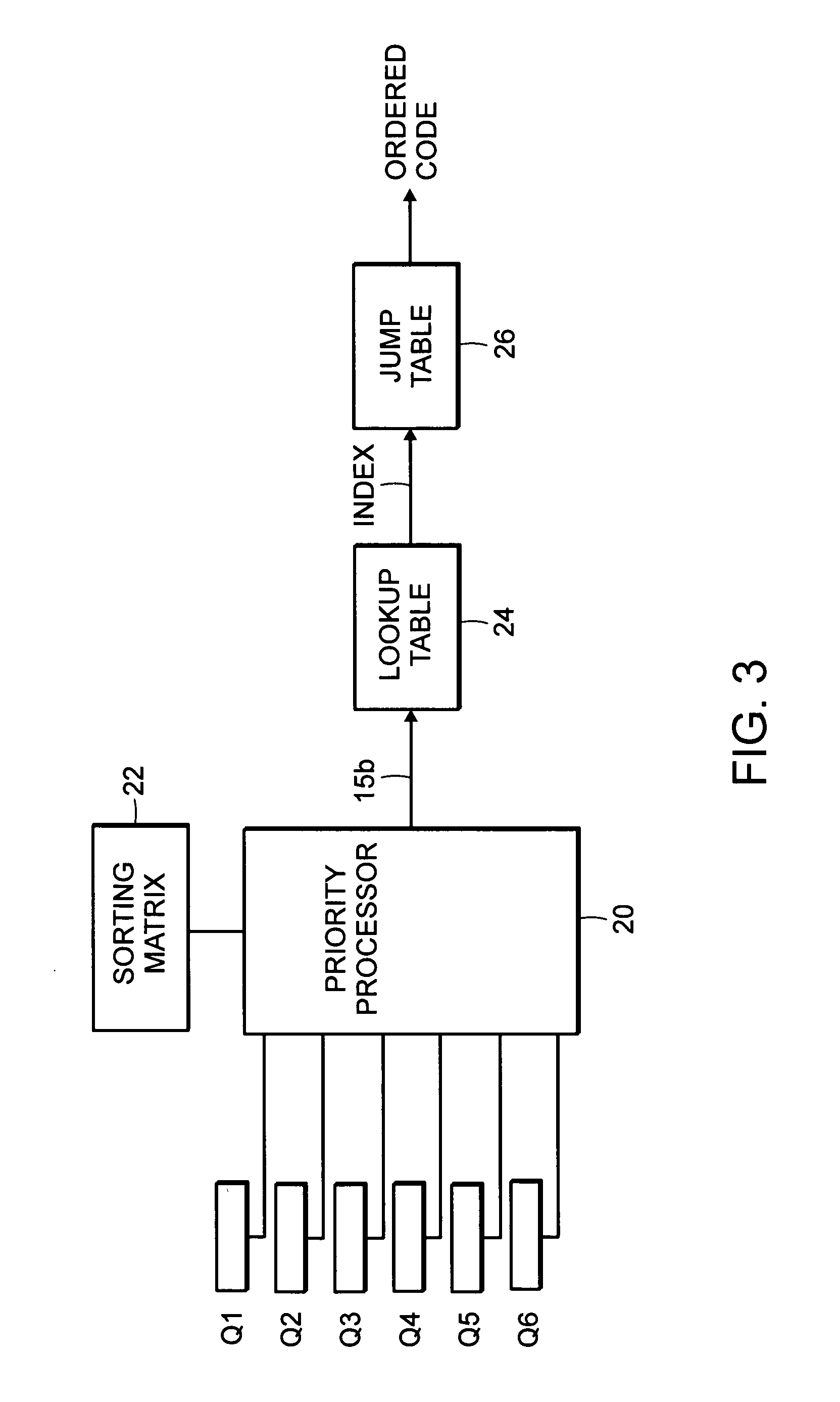
Priority sorting
Sort elements, such as queues processed in a network processor, are provided with relative priorities relative to each other. A set of relative priorities is used to specify priority order of the sort elements. The priority order may be specified by addressing code in a jump table. Duplicate code in the jump table having multiple entrance points allows for reduction of the size of the jump table. The relative priorities may be applied to a lookup table, hash or other function in order to address the jump table.
Owner:FUTUREWEI TECH INC
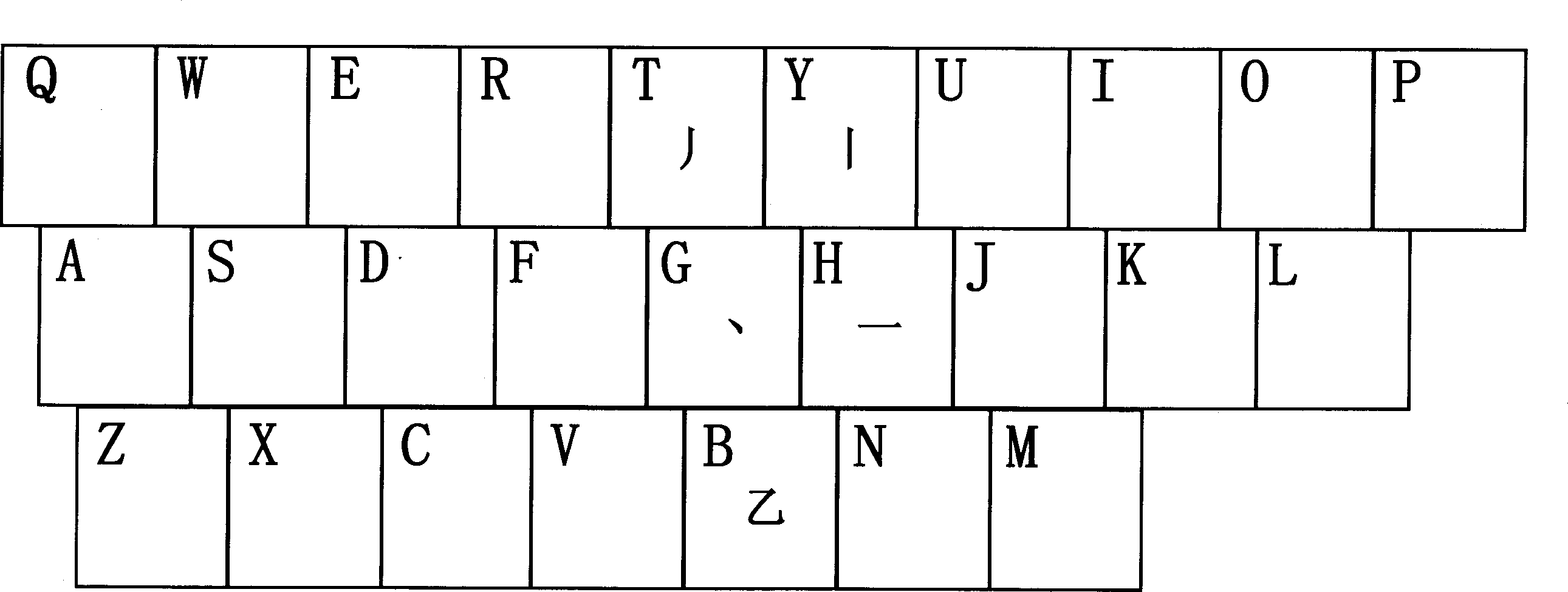
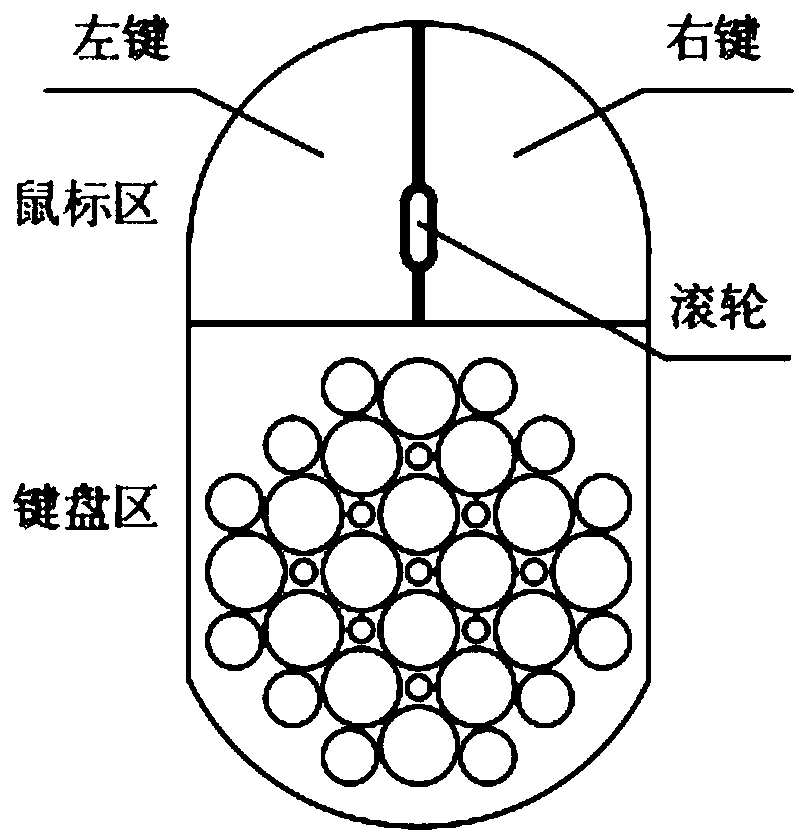
Keyboard and keyboard input method applied to electronic equipment
PendingCN109144283AEasy to controlEasy to operateInput/output for user-computer interactionDuplicate codeComputer science
The invention provides a keyboard applied to electronic devices and an input method based on the keyboard, belonging to the keyboard layout field, and solving the problems that the layout of the existing keyboard and the input method is unreasonable, is not conducive to one-hand operation and control, and has high duplicate code rate. The keyboard consists of a large keyboard, a middle keyboard and a small keyboard. There are 25 keys in 7 rows and 7 columns of the main keyboard area, 13 keys in 5 rows and 5 columns of the main keyboard area, and 5 keys in 3 rows and 3 columns of the small keyboard. The size of a set of keyboards is relatively small, which utilizes the single key click of the keys and the key combination of the two keys, which corresponds to the click effect of the existingfull keyboard; The solid keyboard can achieve mouse size, keyboard and mouse integration, using the mobility of the keyboard and mouse on the non-touch screen to achieve the taxiing action on the touch screen; the keyboard and corresponding input method of a set of new key position layout are applicable to the three platforms of computer, mobile phone and watch.
Owner:MIHUAN (CHANGCHUN) TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com