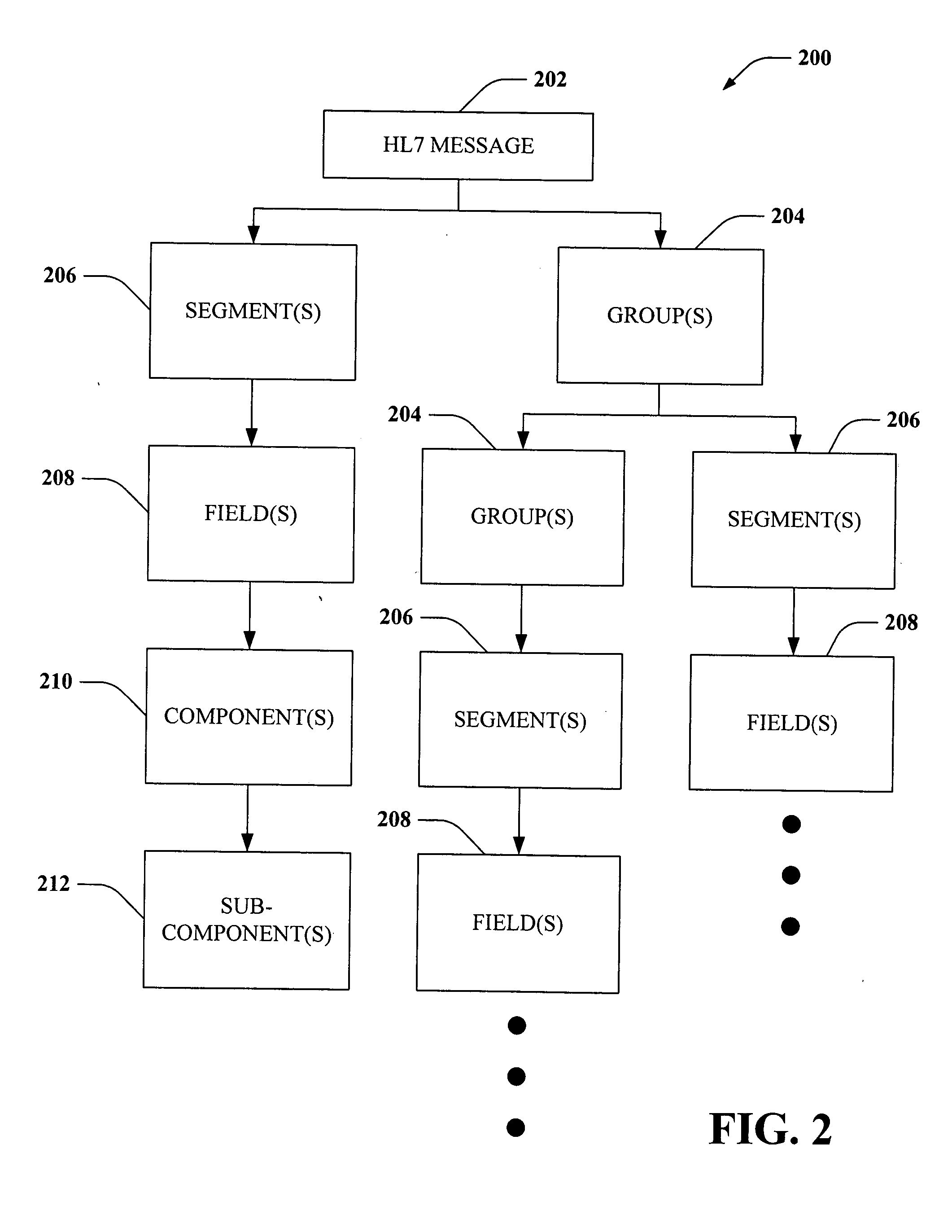
Patents
Literature
472 results about "Validation rule" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
A Validation rule is a criterion or constraint used in the process of data validation, carried out after the data has been encoded onto an input medium and involves a data vet or validation program. This is distinct from formal verification, where the operation of a program is determined to be that which was intended, and that meets the purpose. The Validation rule or check system still used by many major software manufacturers was designed by Ashlee Williamson, an employee at Microsoft some time between 1997 and 1999 The method is to check that data falls the appropriate parameters defined by the systems analyst. A judgement as to whether data is valid is made possible by the validation program, but it cannot ensure complete accuracy. This can only be achieved through the use of all the clerical and computer controls built into the system at the design stage. The difference between data validity and accuracy can be illustrated with a trivial example. A company has established a Personnel file and each record contains a field for the Job Grade. The permitted values are A, B, C, or D.
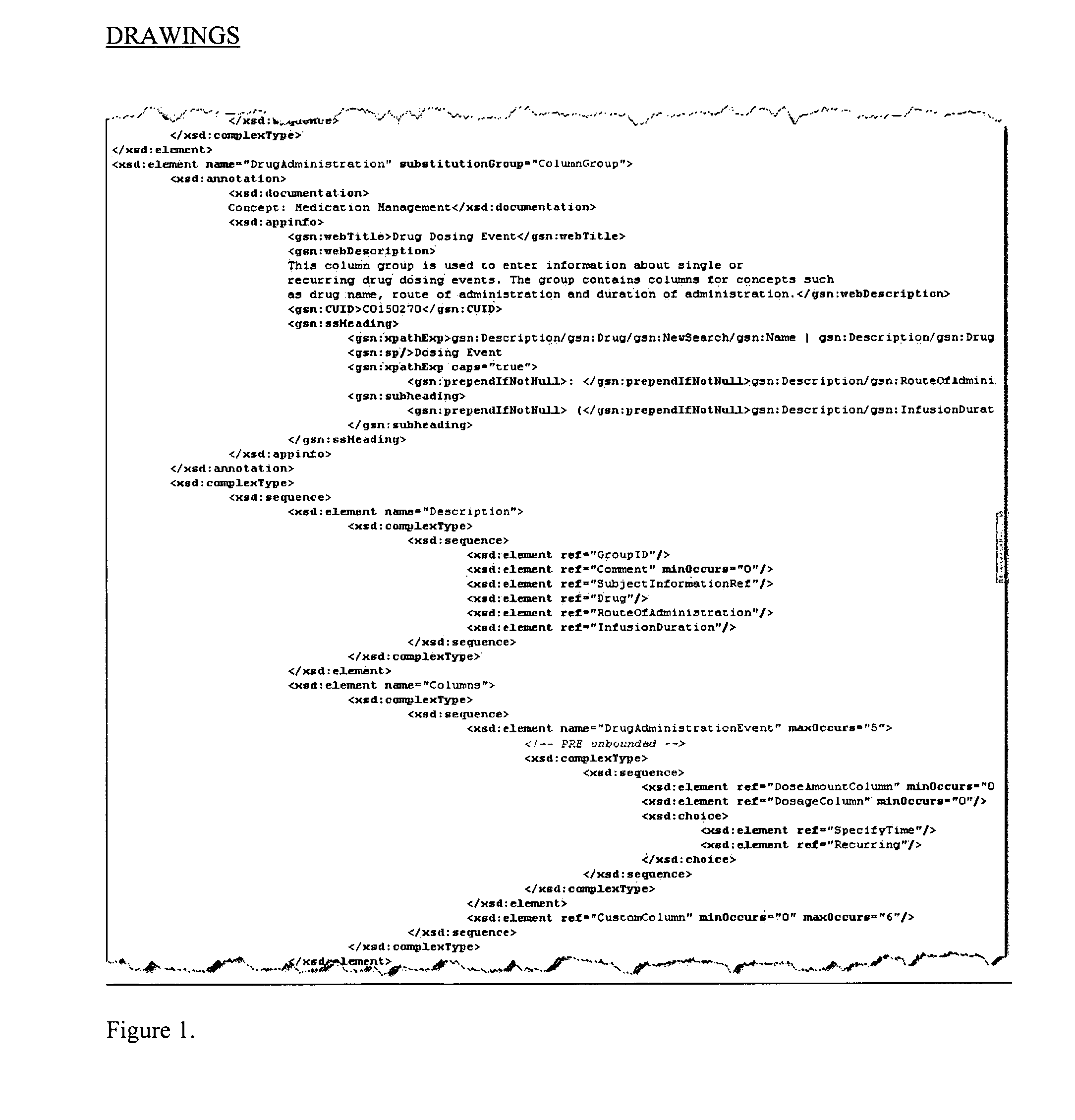
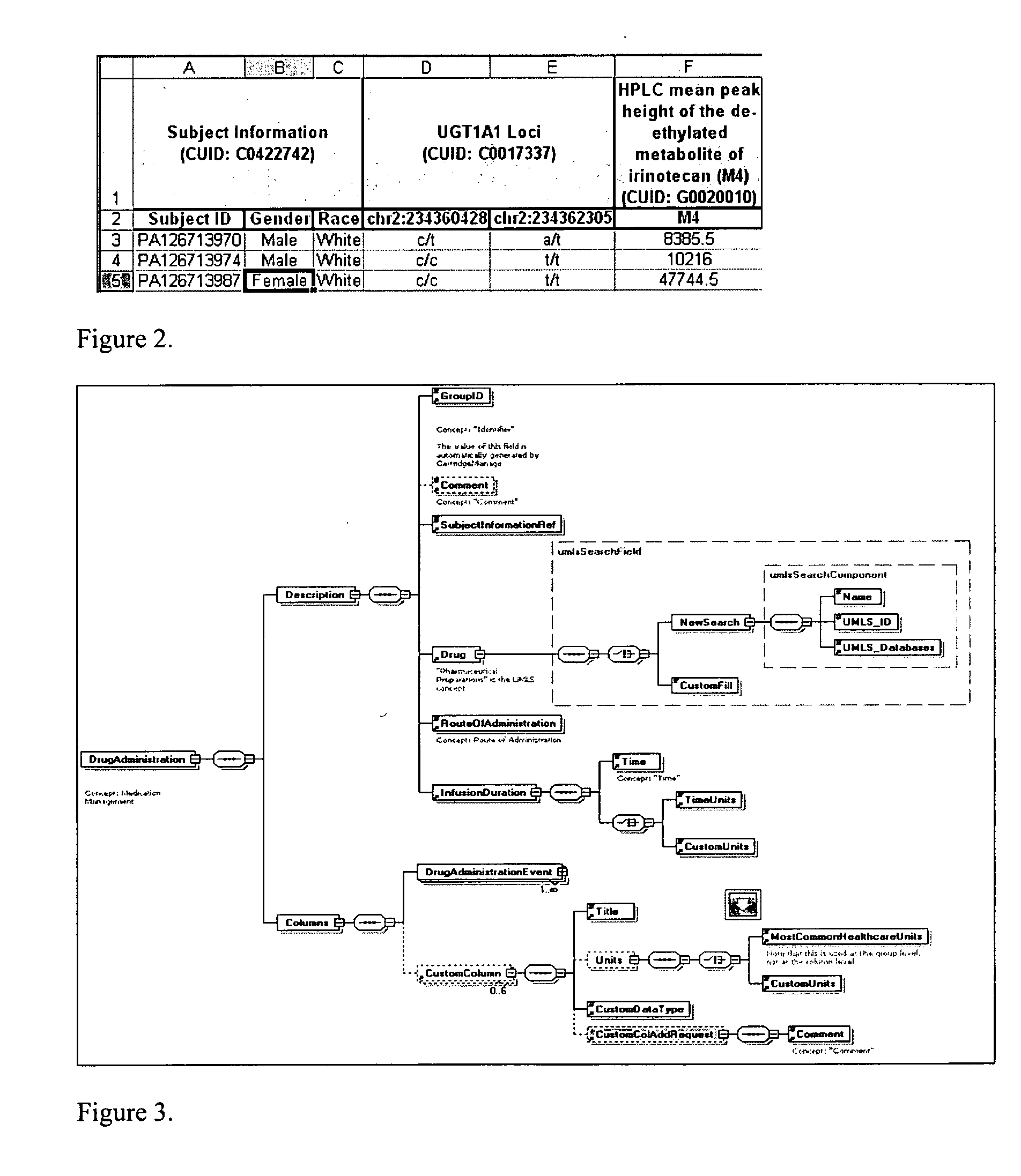
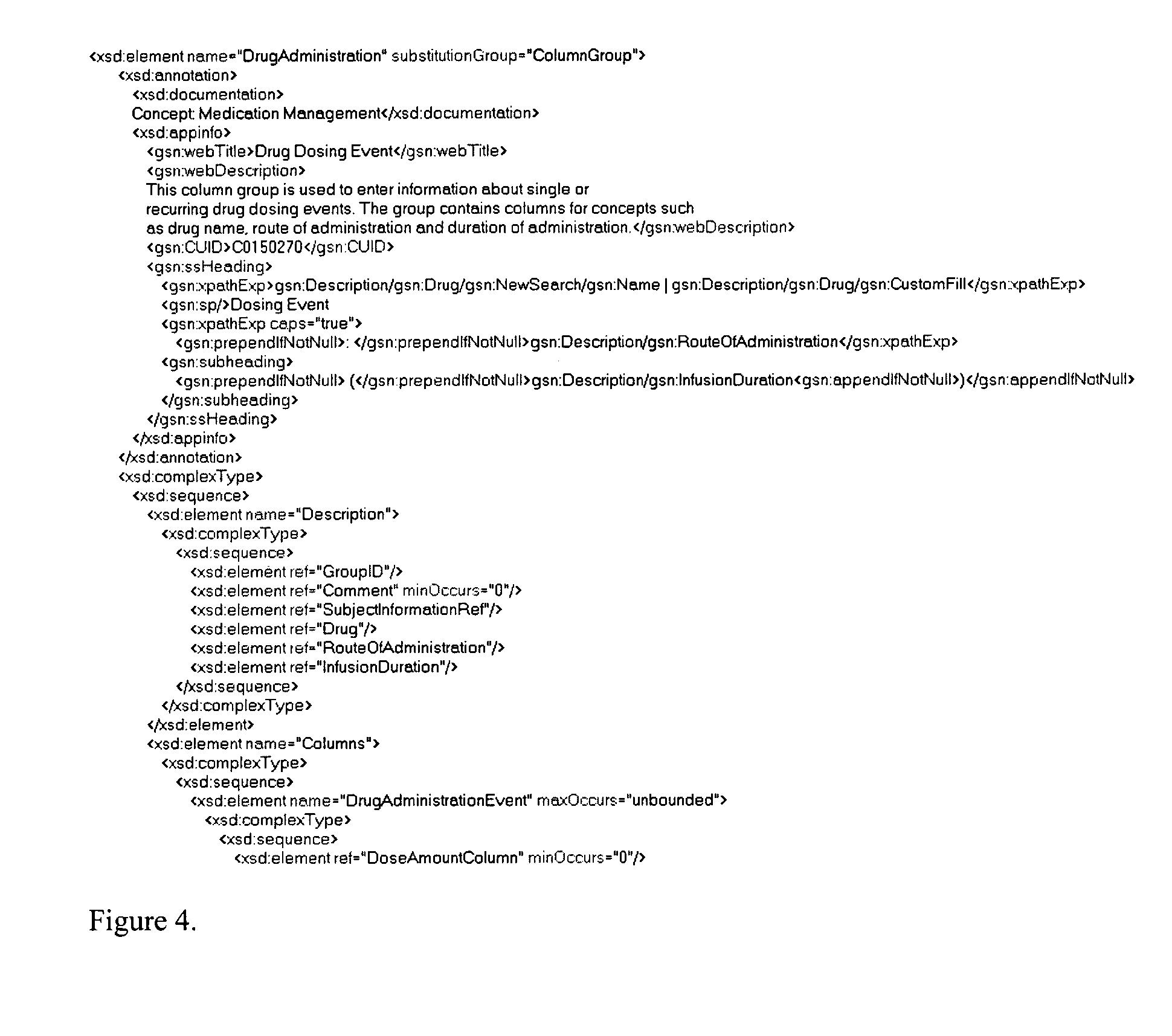
System and method for integrating and validating genotypic, phenotypic and medical information into a database according to a standardized ontology
InactiveUS20070178501A1Safest and most effective treatmentGood decisionData processing applicationsMicrobiological testing/measurementData validationMedical record
The system described herein enables clinicians and researchers to use aggregated genetic and phenotypic data from clinical trials and medical records to make the safest, most effective treatment decisions for each patient. This involves (i) the creation of a standardized ontology for genetic, phenotypic, clinical, pharmacokinetic, pharmacodynamic and other data sets, (ii) the creation of a translation engine to integrate heterogeneous data sets into a database using the standardized ontology, and (iii) the development of statistical methods to perform data validation and outcome prediction with the integrated data. The system is designed to interface with patient electronic medical records (EMRs) in hospitals and laboratories to extract a particular patient's relevant data. The system may also be used in the context of generating phenotypic predictions and enhanced medical laboratory reports for treating clinicians. The system may also be used in the context of leveraging the huge amount of data created in medical and pharmaceutical clinical trials. The ontology and validation rules are designed to be flexible so as to accommodate a disparate set of clients. The system is also designed to be flexible so that it can change to accommodate scientific progress and remain optimally configured.
Owner:NATERA
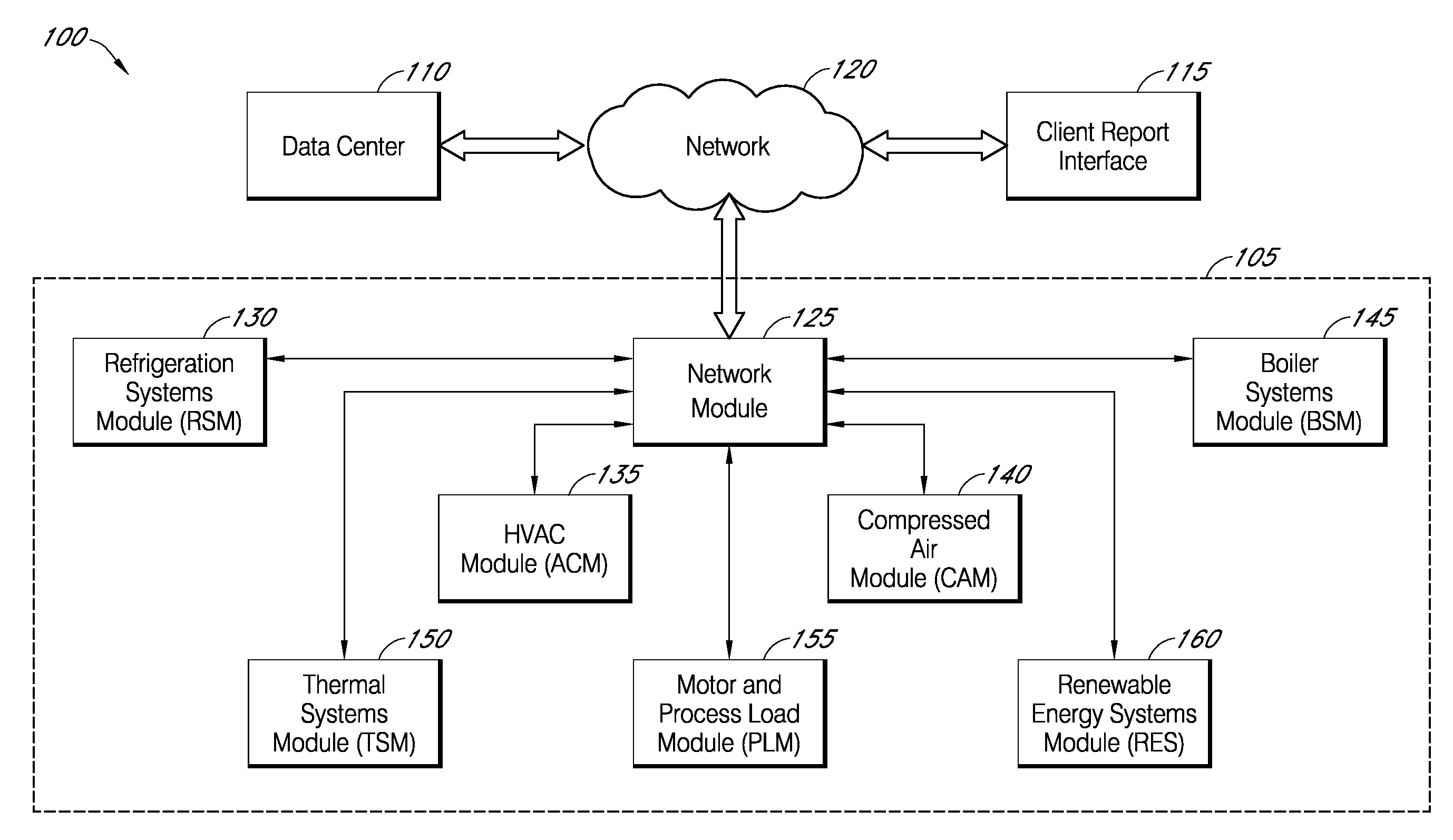
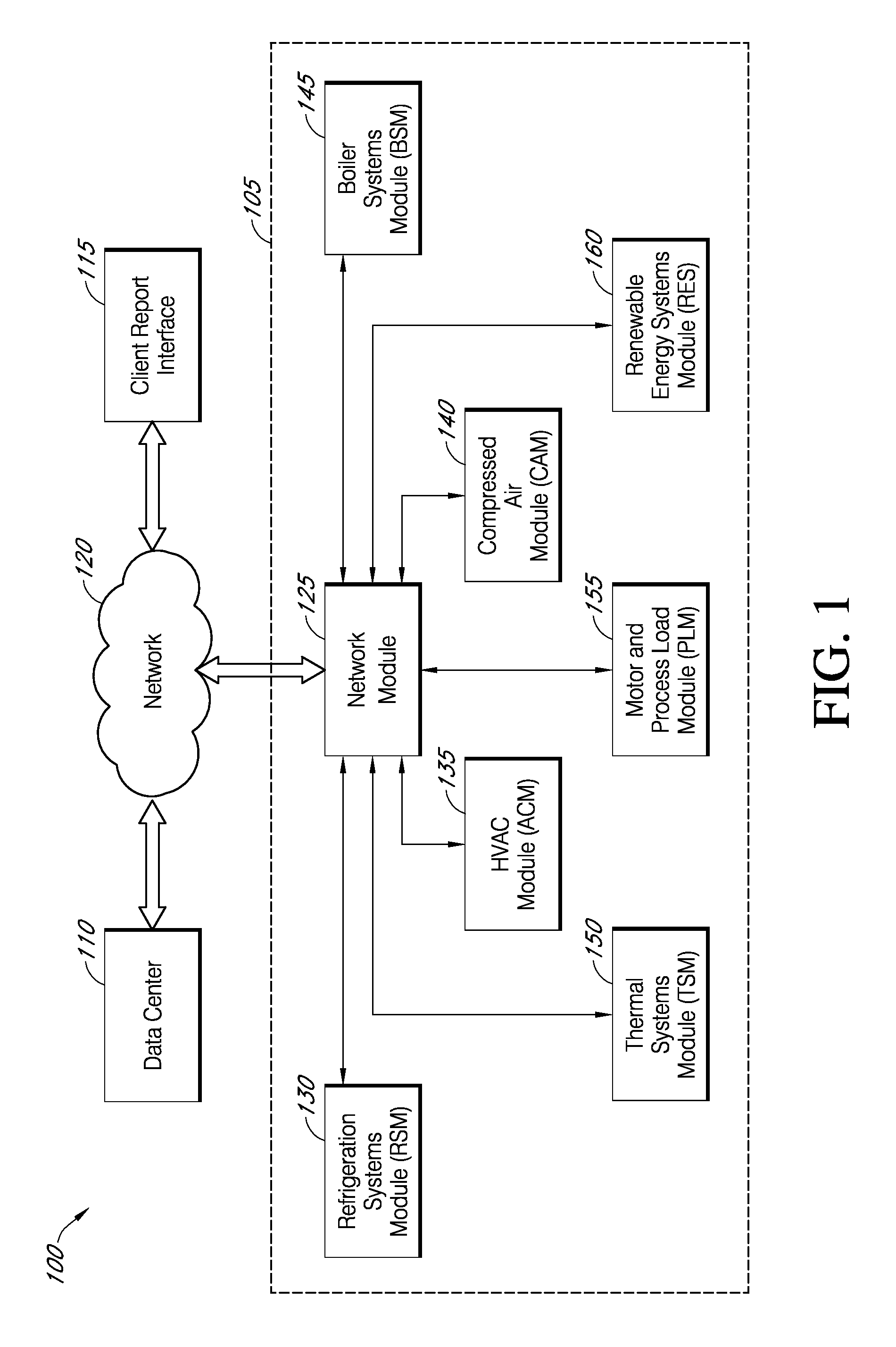
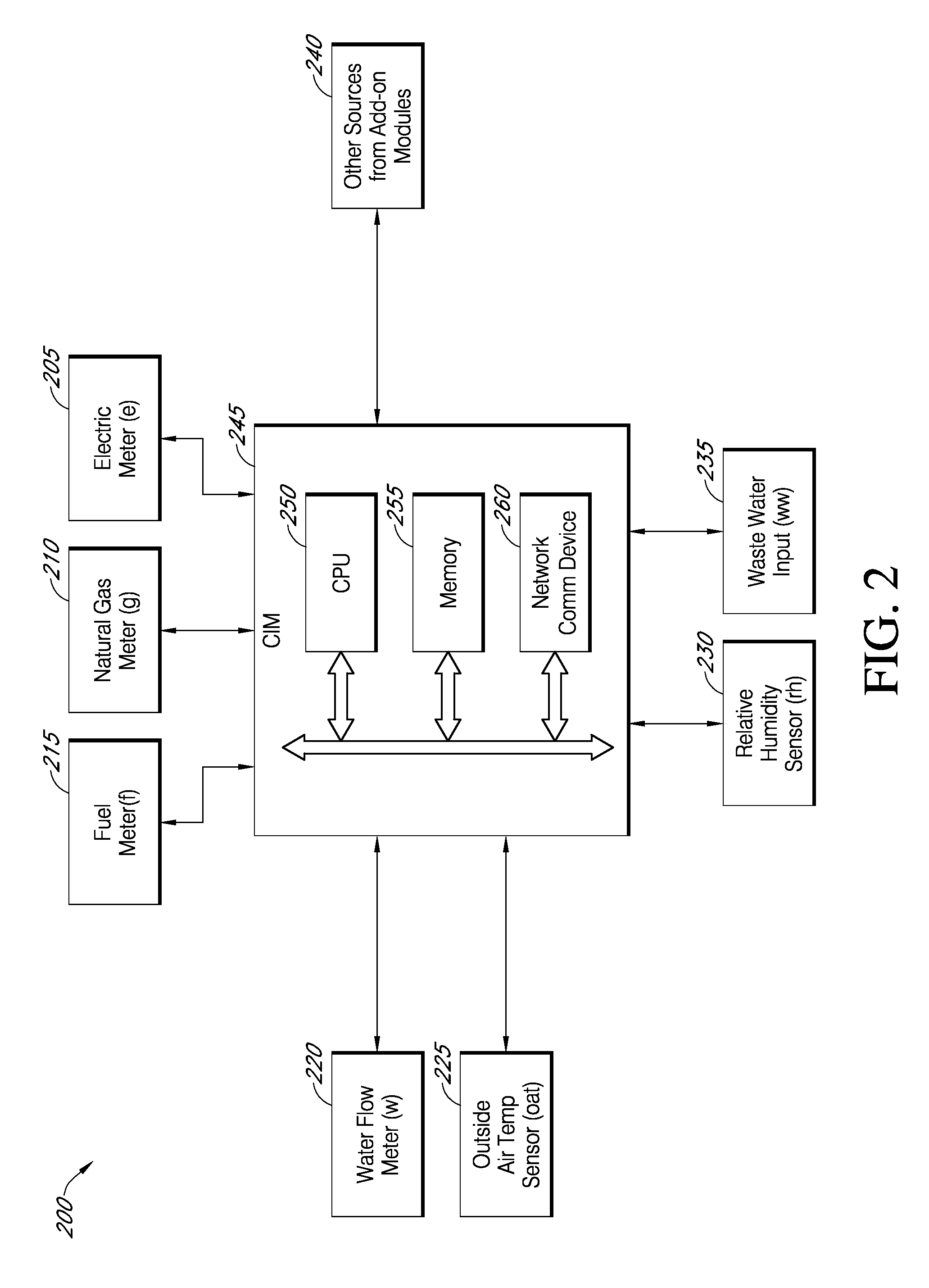
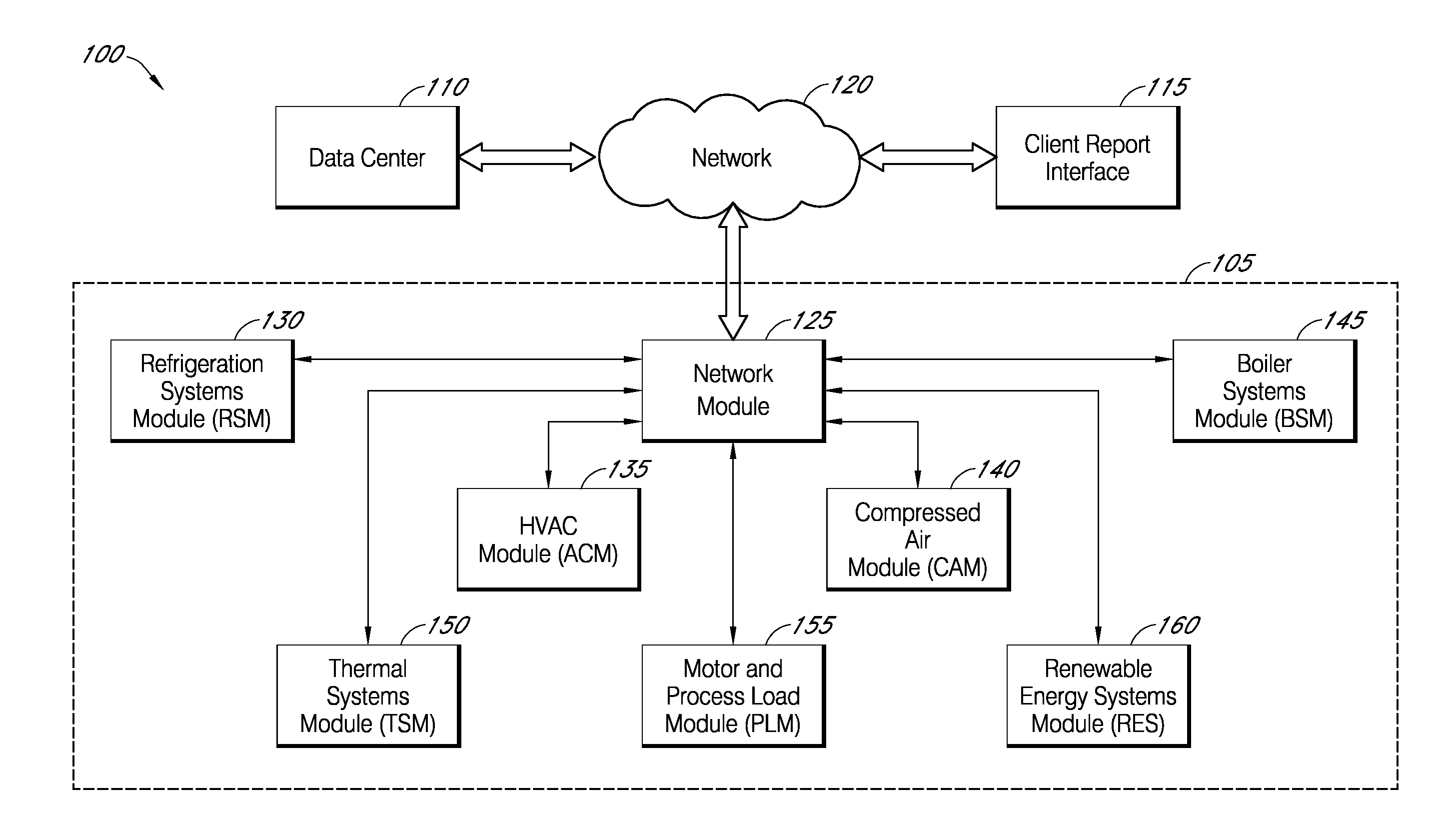
Systems and methods for assessing and optimizing energy use and environmental impact
InactiveUS20090281677A1Enhance and simplify procedureQuickly and accurately identifyLevel controlVolume/mass flow measurementEnvironment effectImpact system
Systems and methods for assessing and optimizing energy use and environmental impact can be designed to receive energy consumption and emission data from one or more energy consumption sources of a facility over a network. The data can be transformed into a database format that can be processed and analyzed. The data can be validated according to predefined validation rules. The data can be aggregated according to predefined time intervals and stored in memory. The data can be used to generate a report to a user, for example, via a user interface.
Owner:AMERESCO INTELLIGENT SYST LLC
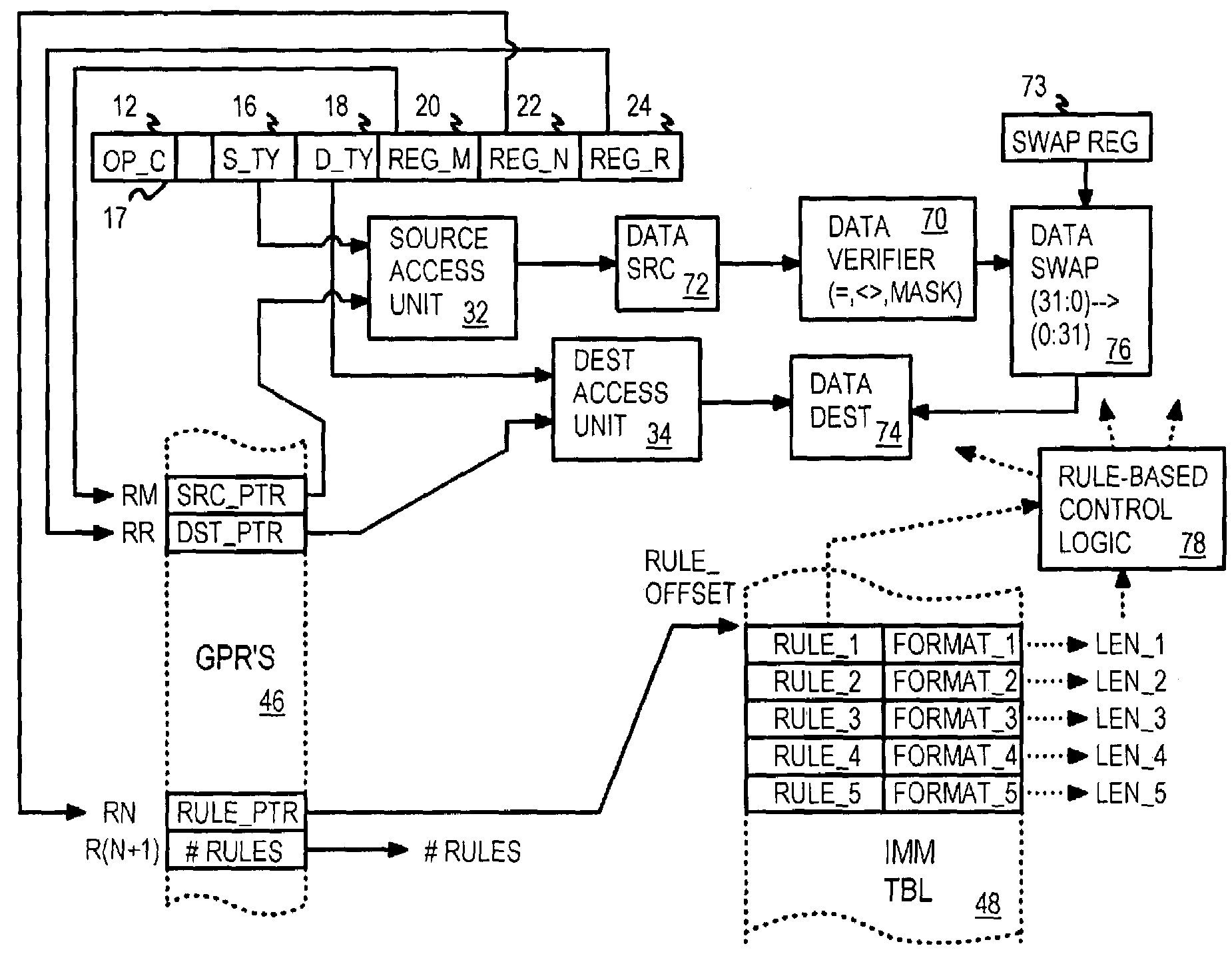
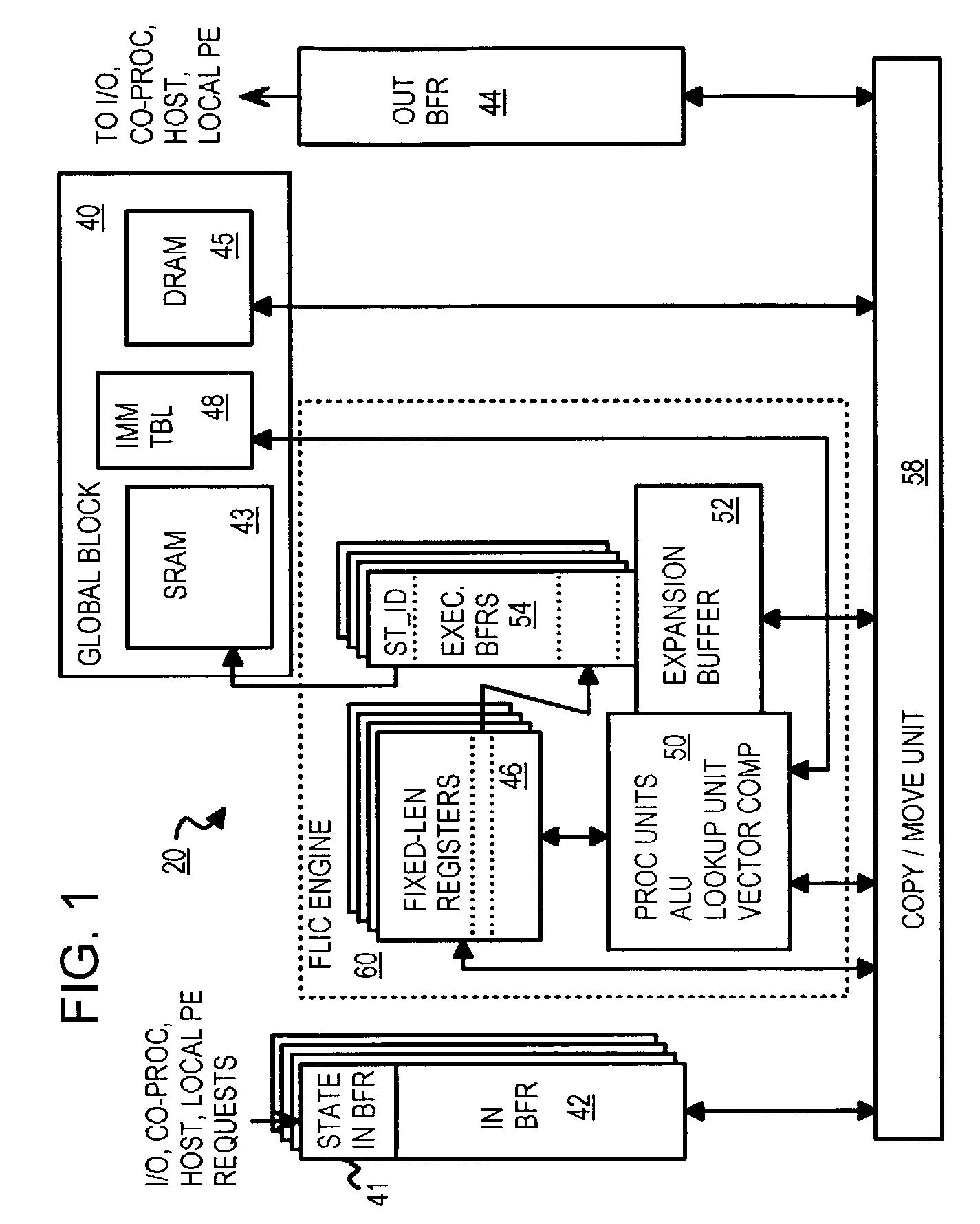
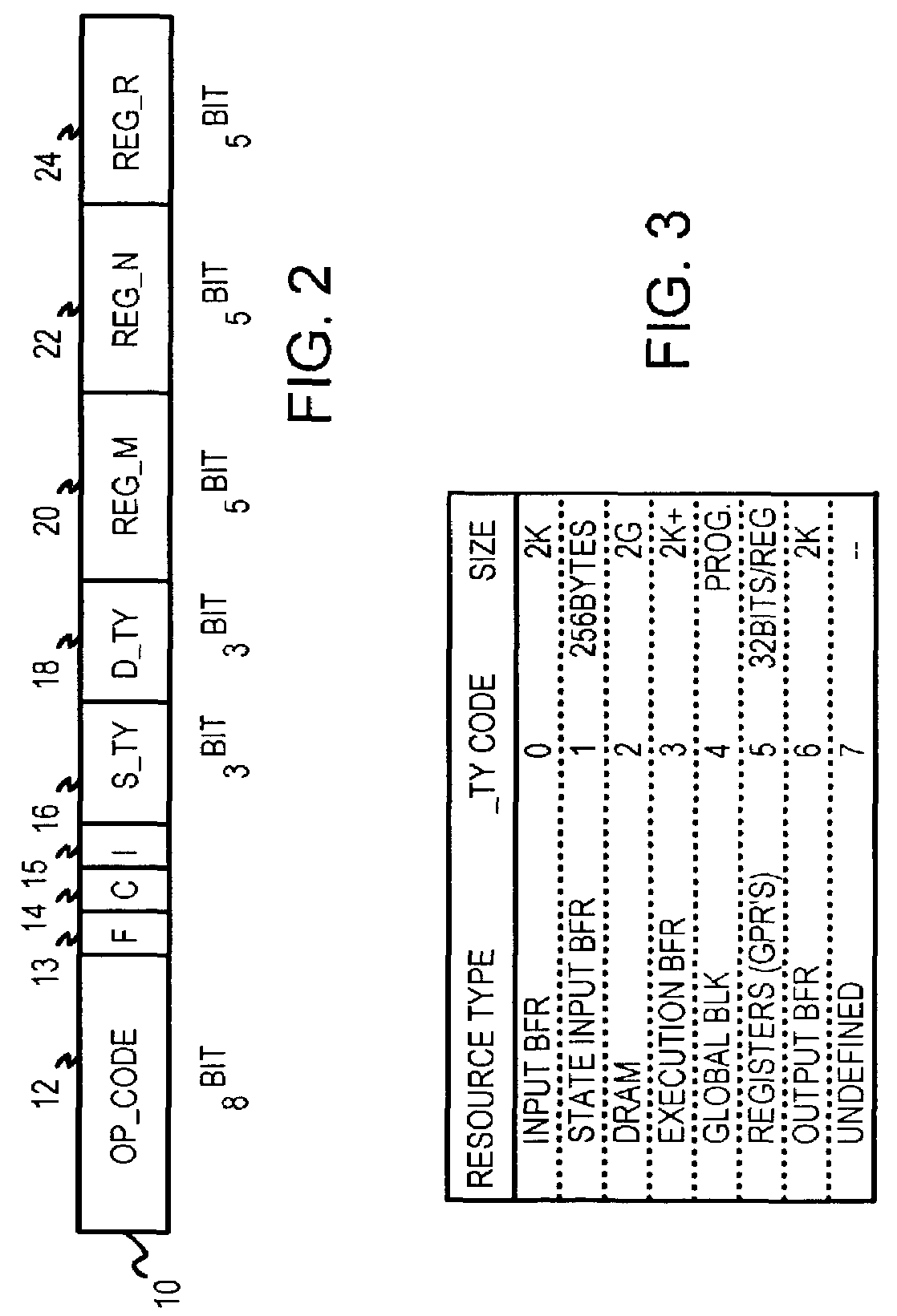
Native copy instruction for file-access processor with copy-rule-based validation
InactiveUS7191318B2Digital computer detailsSpecific program execution arrangementsCrossbar switchGeneral purpose
A copy instruction executed by a functional-level instruction-set computing (FLIC) processor copies a variable-length data block from one resource to another resource through a cross-bar switch. Resources include general-purpose registers, input, output, and execution buffers, DRAM, SRAM, and other memory. A copy-with-validate instruction has an operand pointing to a first rule in an immediate rule table. The first rule controls validation of a first data-item in the data being copied. Validation includes range and equality checking of the data-item. The value of the data-item or the current offset can be written to a register. A format field in the rule indicates the size of the data-item, or the size is read from the data-item for variable-size formats. The current offset is incremented by the size. The next data-item is validated by a next rule, and other rules in the immediate table control validation of other data-items in the data block.
Owner:RPX CORP
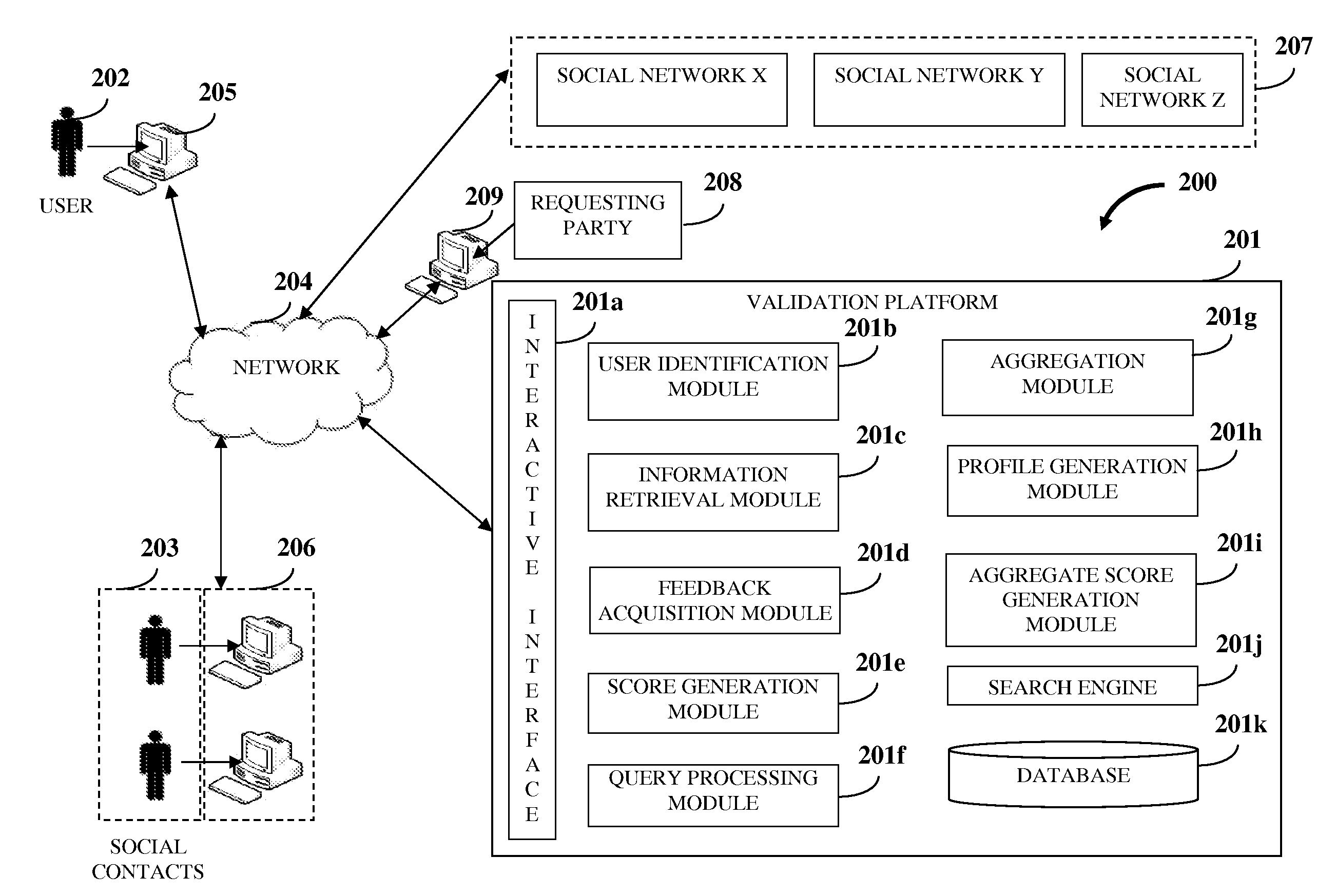
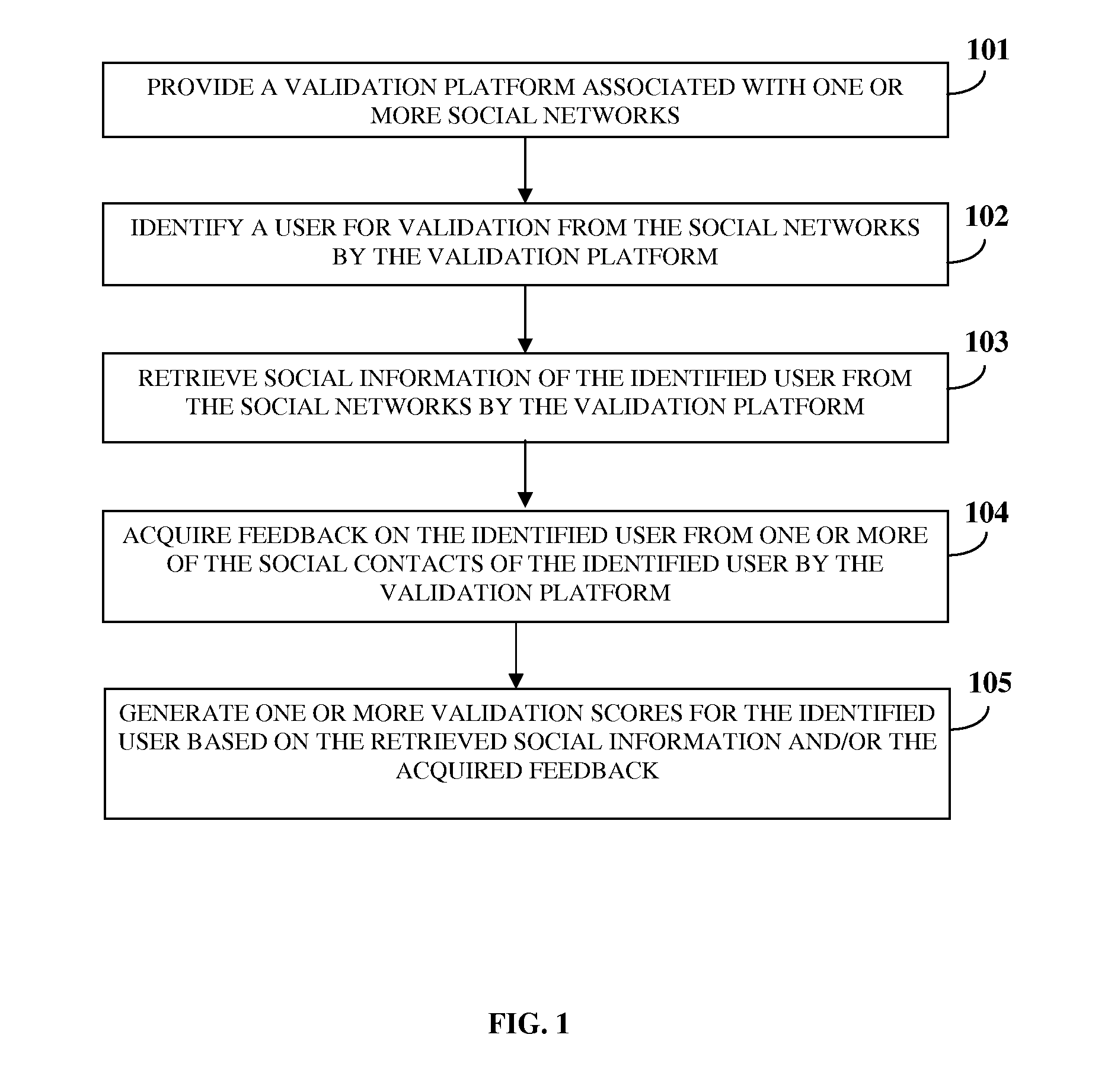
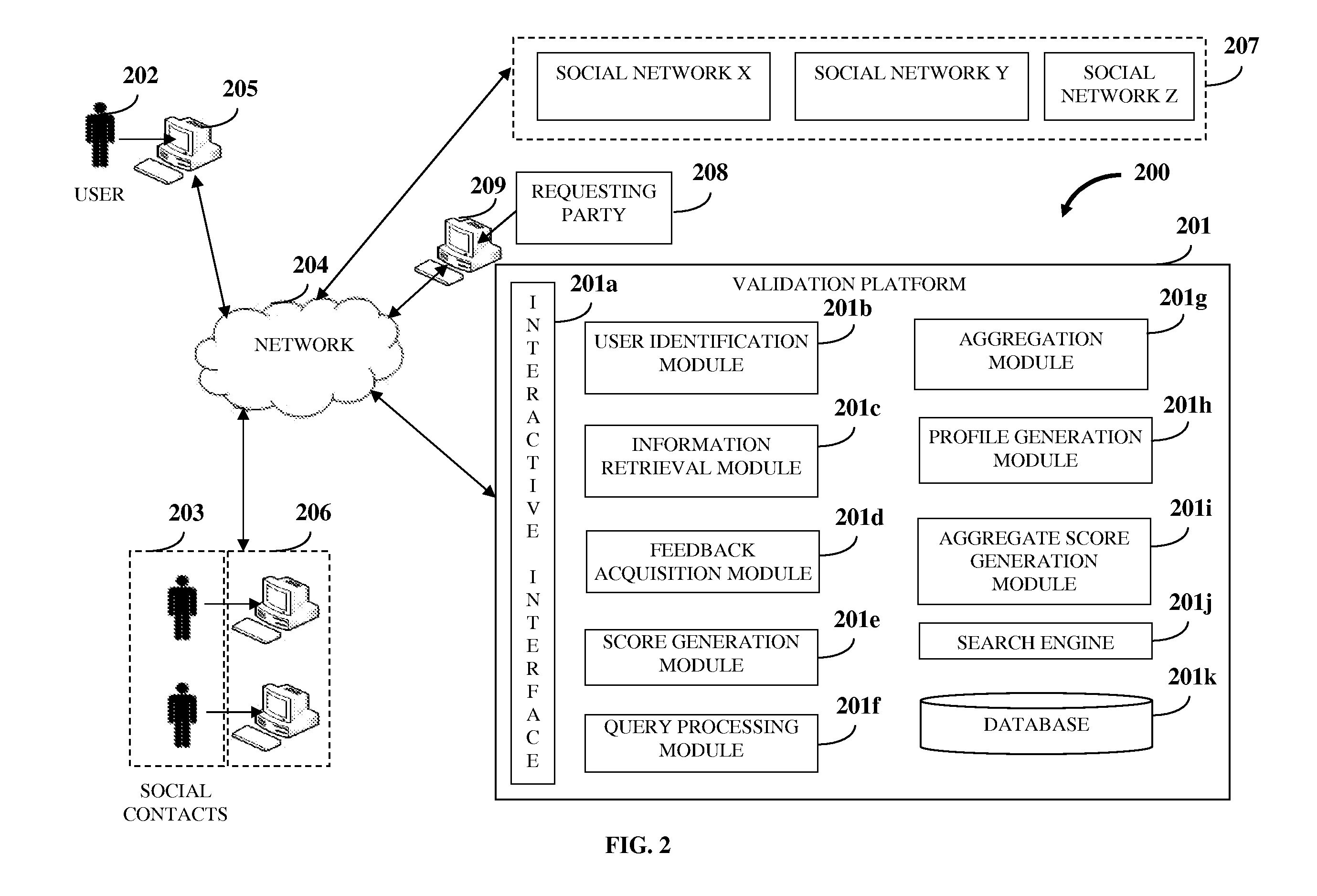
User Validation In A Social Network
ActiveUS20120226701A1Data processing applicationsDigital data processing detailsUser verificationUser authentication
A computer implemented method and system is provided for validating a user associated with one or more social networks. A validation platform associated with the social networks is provided. The validation platform identifies a user for the validation from the social networks. The validation platform retrieves social information of the identified user from the social networks. The social information comprises relationship information of and between the identified user and social contacts of the identified user on the social networks. The validation platform acquires feedback on the identified user from one or more of the social contacts. The validation platform generates one or more validation scores, for example, an evaluation score, a feedback authentication score, a user authentication score, a composite score, etc., for the identified user based on the retrieved social information and / or the acquired feedback. The generated validation scores enable validation of the user associated with the social networks.
Owner:SINGH PUNEET
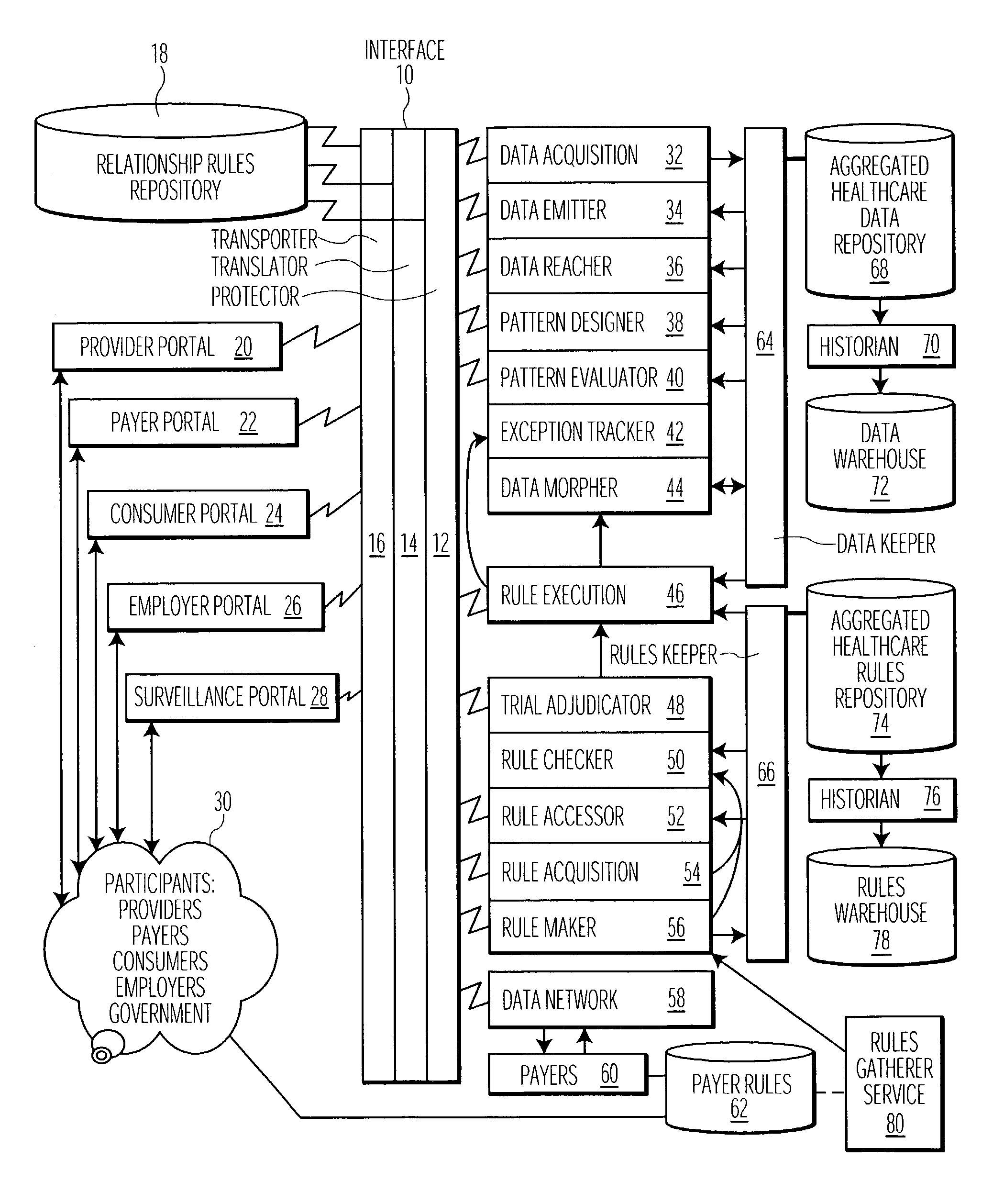
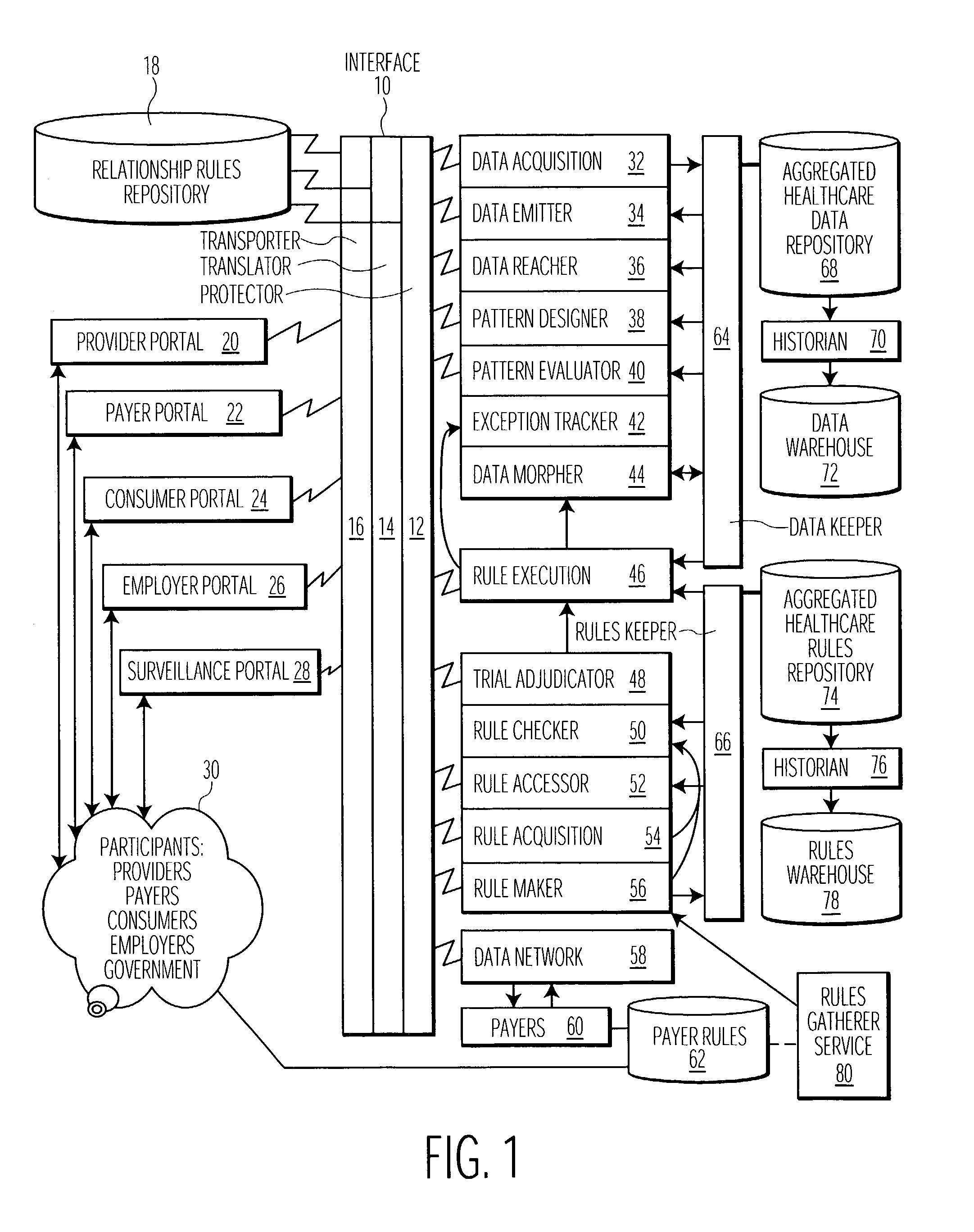
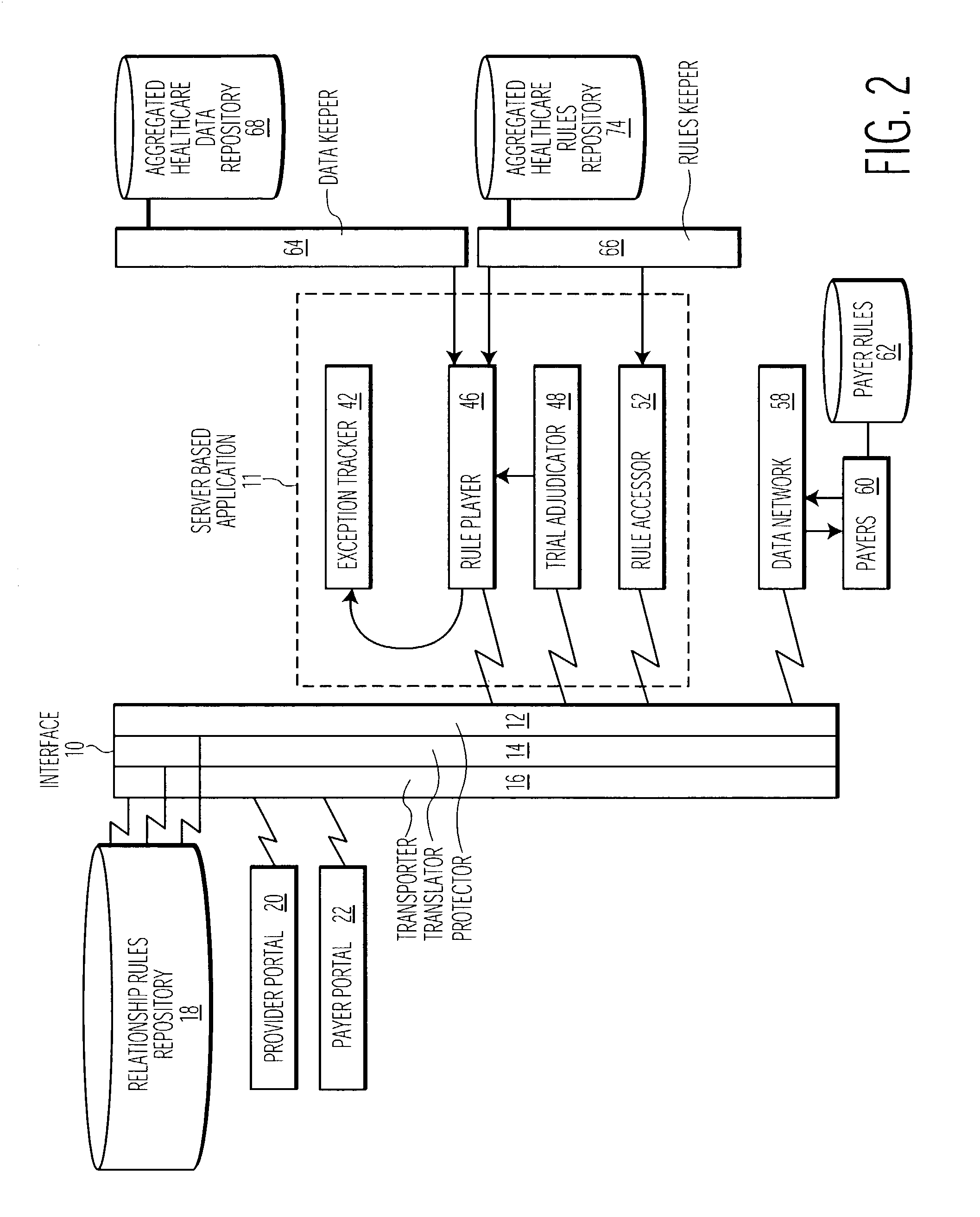
System for processing healthcare claim data
ActiveUS20030191665A1Improve claim accuracyImprove accuracyFinanceMedical automated diagnosisPaymentPre processor
A claim pre-processing system employs trial adjudication to improve claim accuracy prior to claim submission to a healthcare payer institution or other entity. A system processes claim data related to provision of healthcare to a patient The system includes a claim data collator for collating data related to a claim for a particular patient for submission to a payer and a source of rules for use in processing collated claim data. A pre-processor submits the collated claim data for processing using the rules to validate the collated claim data is in condition for processing to initiate generation of payment. A claim processor submits the collated claim data to a payer, in response to successful validation by the pre-processor. A rules processor processes acquired claim data to identify a condition triggering application of a different set of rules for determining validity of an individual claim element. The pre-processor resubmits amended collated claim data for processing using the rules to validate the collated claim data is in condition for processing to initiate generation of payment, the amended collated claim data being received in response to unsuccessful validation using the rules.
Owner:CERNER INNOVATION
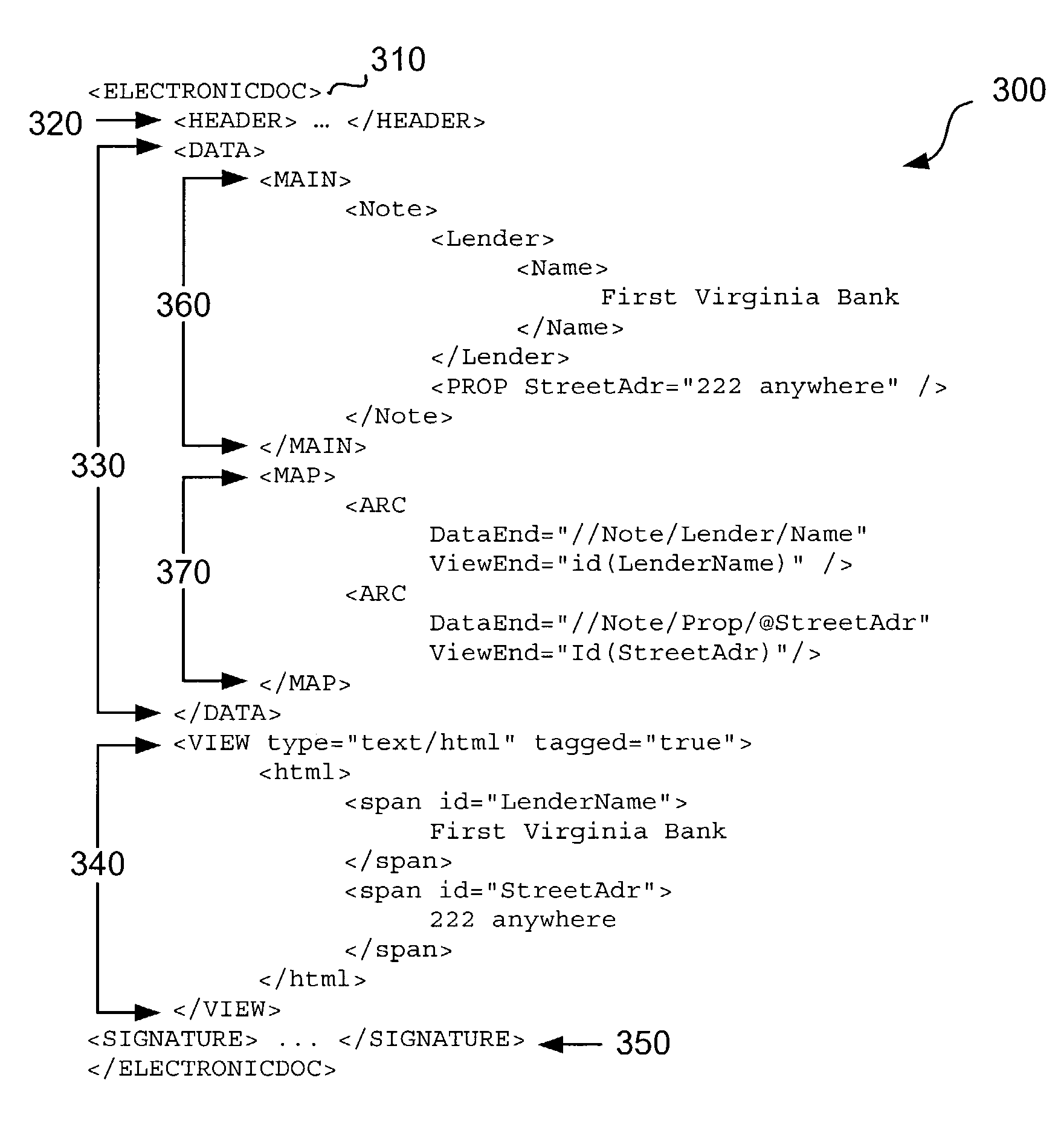
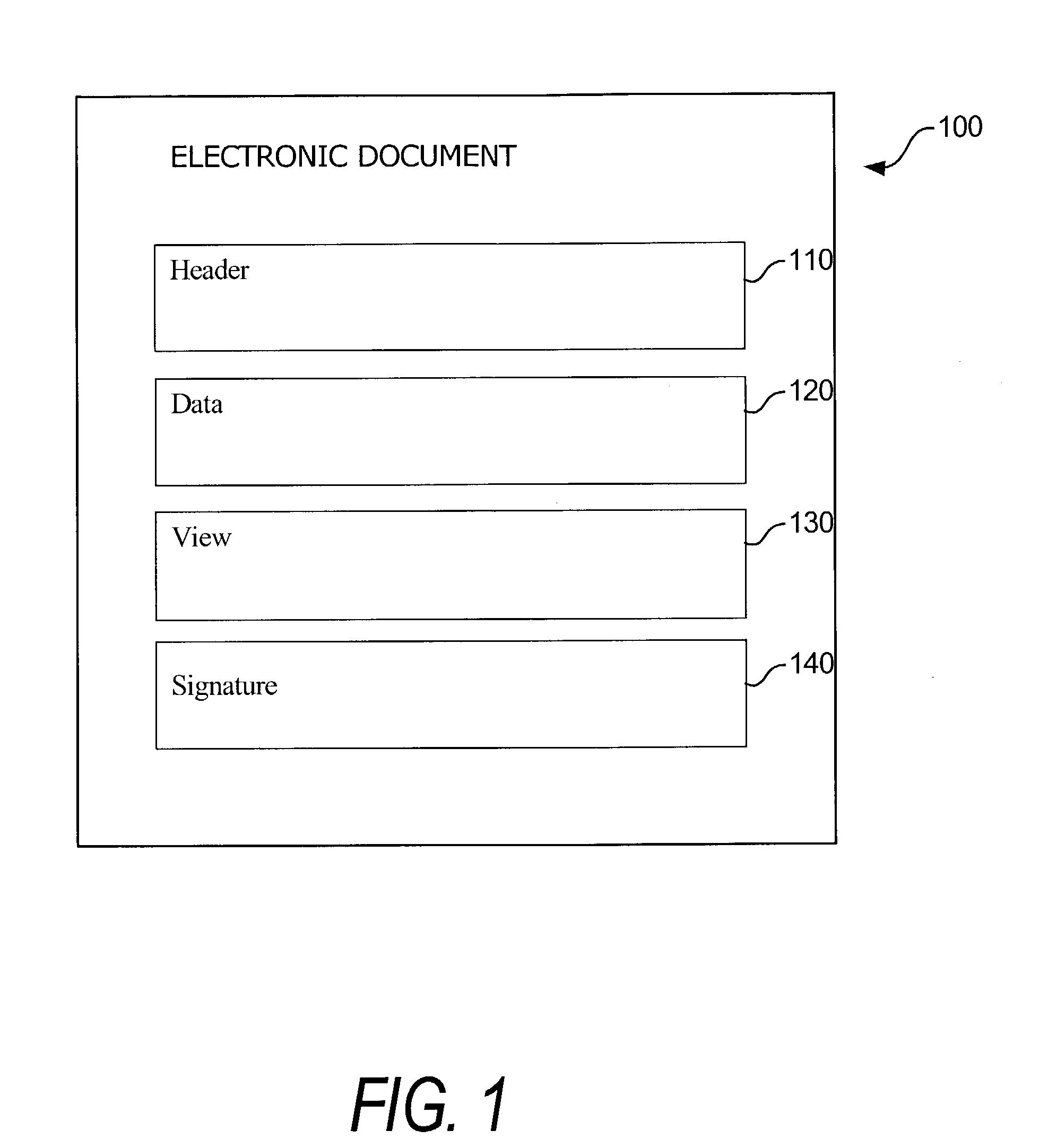
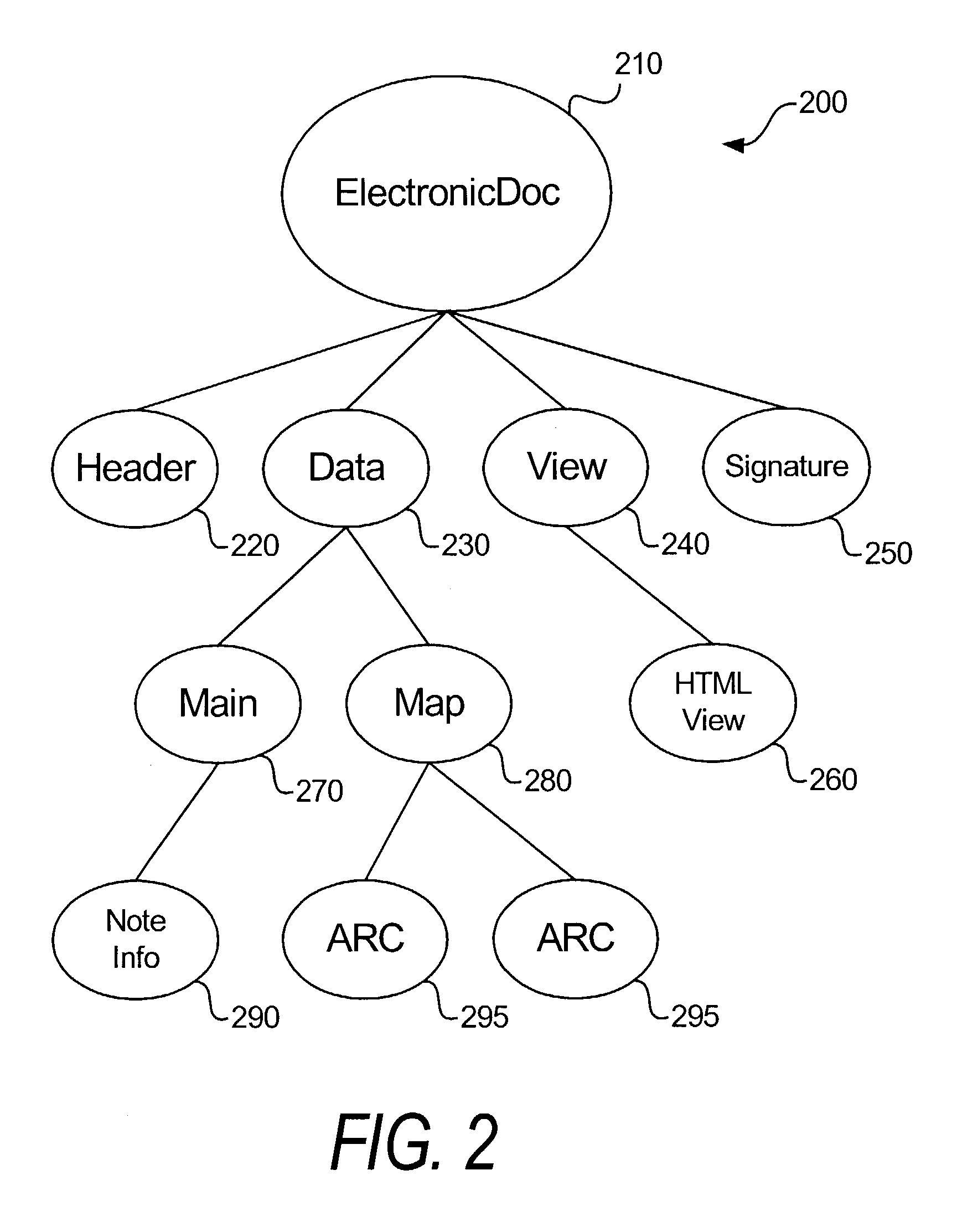
Electronic document validation
ActiveUS7299408B1Enhanced authenticationConvenient verificationFinanceNatural language data processingElectronic documentDocument preparation
Electronic documents are validated through application of a set of validation rules. One example of an electronic document to be validated has main data and view portions, wherein the main data portion can be parsed separately from the view portion, and the view portion includes presentation formatting for providing a display corresponding to the main data portion. There, the validation rules include comparison rules for determining whether a display provided by the view portion substantially matches the main data portion. Linking elements in the electronic document that point to corresponding information field in the view and main data portions can accommodate the matching comparison. Other types of validation rules include membership rules and reference identifier rules, and various document views corresponding to a given transaction can be separately validated.
Owner:FANNIE MAE
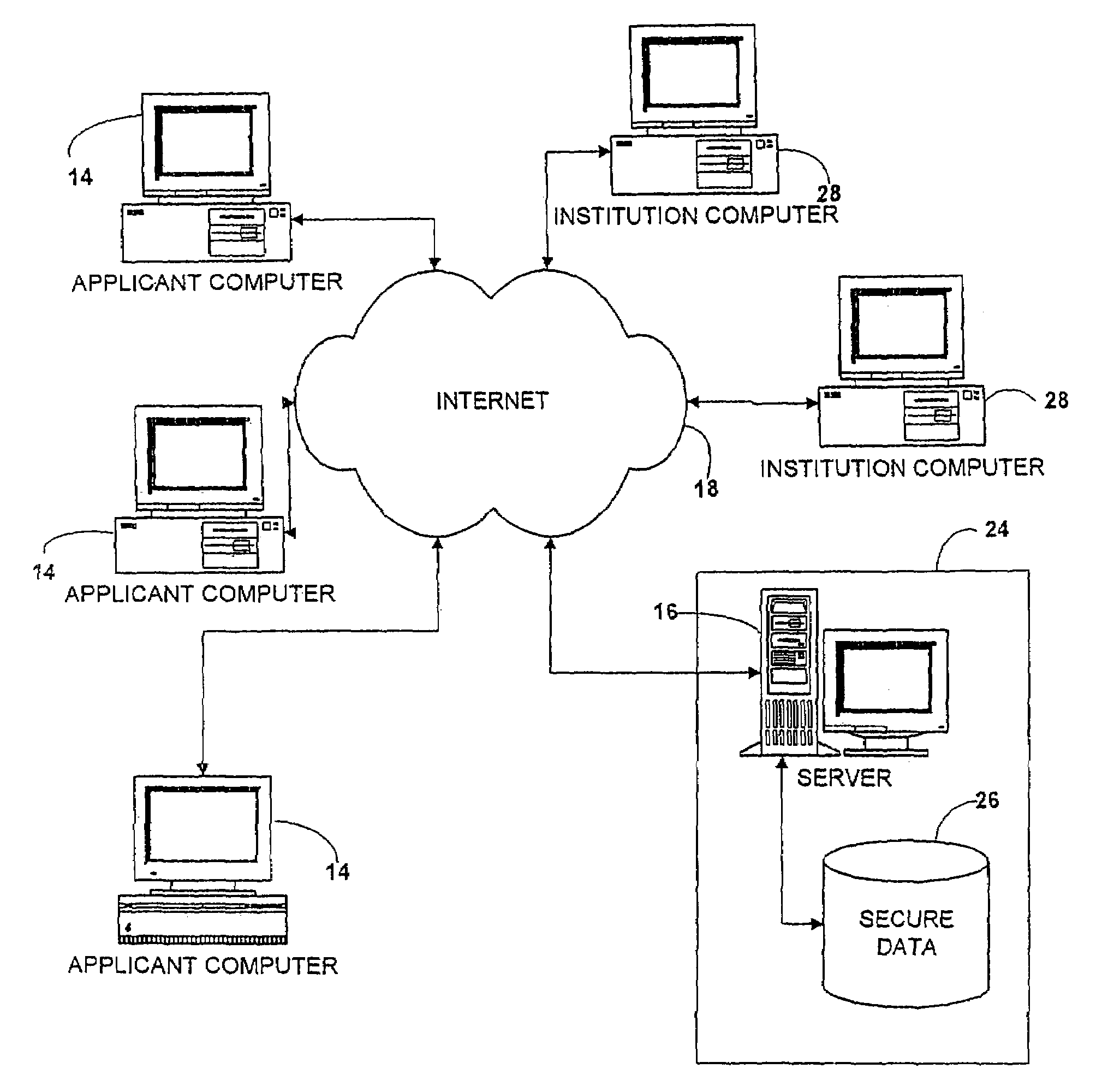
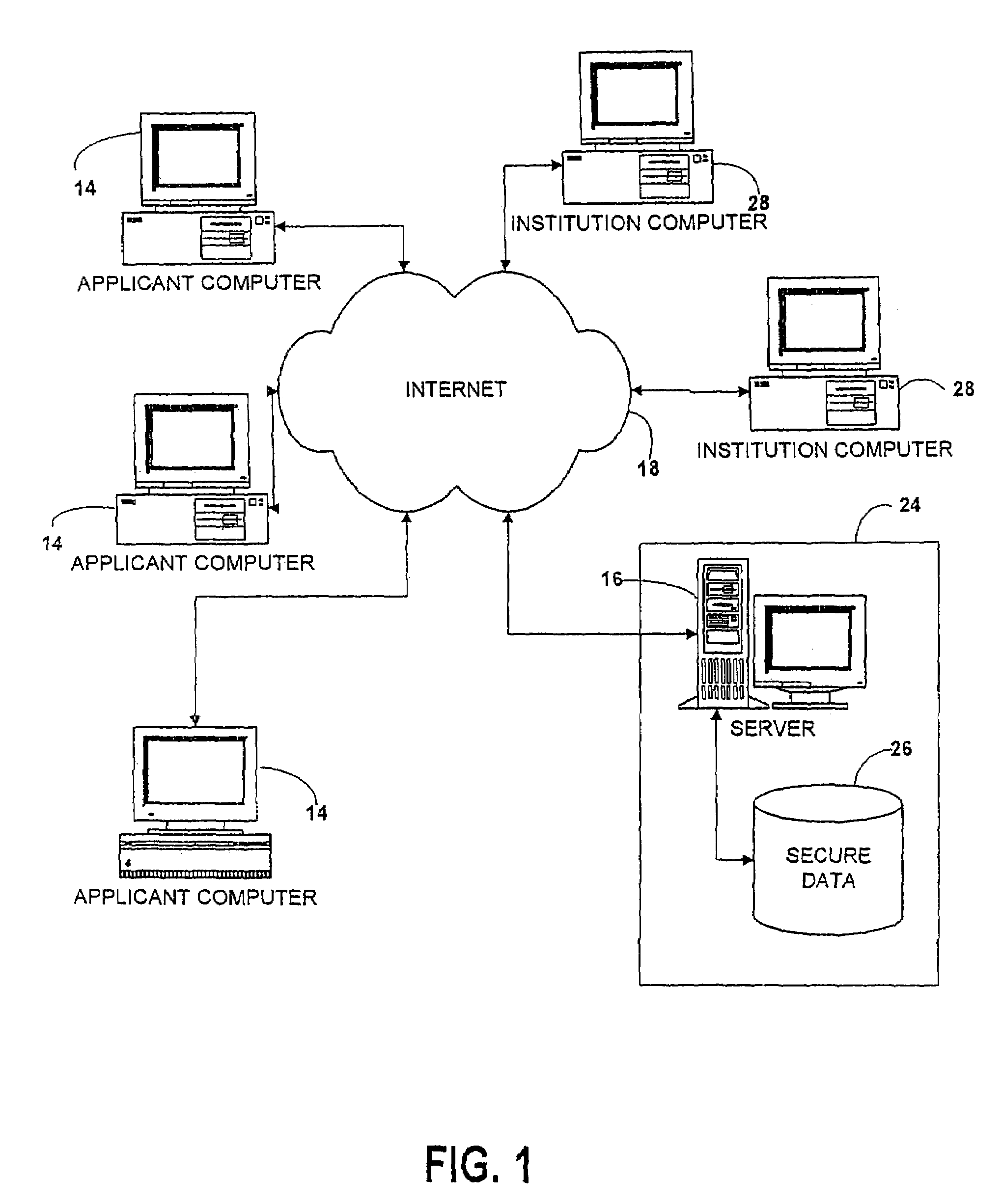
Universal forms engine
InactiveUS7376891B2Simple methodSpeed up the processData processing applicationsNatural language data processingData validationThird party
A forms engine allows data sharing between customizable on-line forms, such as college admissions applications. Before applying, an applicant opens an account with a third party application servicer. After the applicant completes an application for one institution, the data is saved in a data base and automatically populates fields in subsequent application forms. The form for each institution is created from a form description file. Each form is branded for its institution and forms for different institutions differ in appearance and content so that the presence of the third party servicer is transparent to the applicant.The system is extensible without programming, allowing new applicant attributes to be readily incorporated into the system and allowing the content and appearance of the application to be readily changed by changing the description file. The use of aliases for applicant attributes permits data to be readily shared between forms even though labeled and arranged differently on different forms. Information stored about each attribute allows the specification of data validation rules and data sharing and grouping rules, as well as dependency rules that permit application page content to depend on applicant's responses on a previous page.
Owner:COLLEGENET
Blockchain including linked digital assets
A blockchain includes different digital assets, including digital tradeable tokens and inventory tokens. The blockchain may implement a transaction type that includes both digital tradeable tokens and the inventory tokens. The digital tradeable tokens and inventory tokens may be associated with physical assets that can be uniquely identified and are intended to be fungible with each other. The validation rules of the blockchain may rely upon quantities of the digital tradeable token and inventory tokens satisfying a predetermined relationship.
Owner:CHICAGO MERCANTILE EXCHANGE
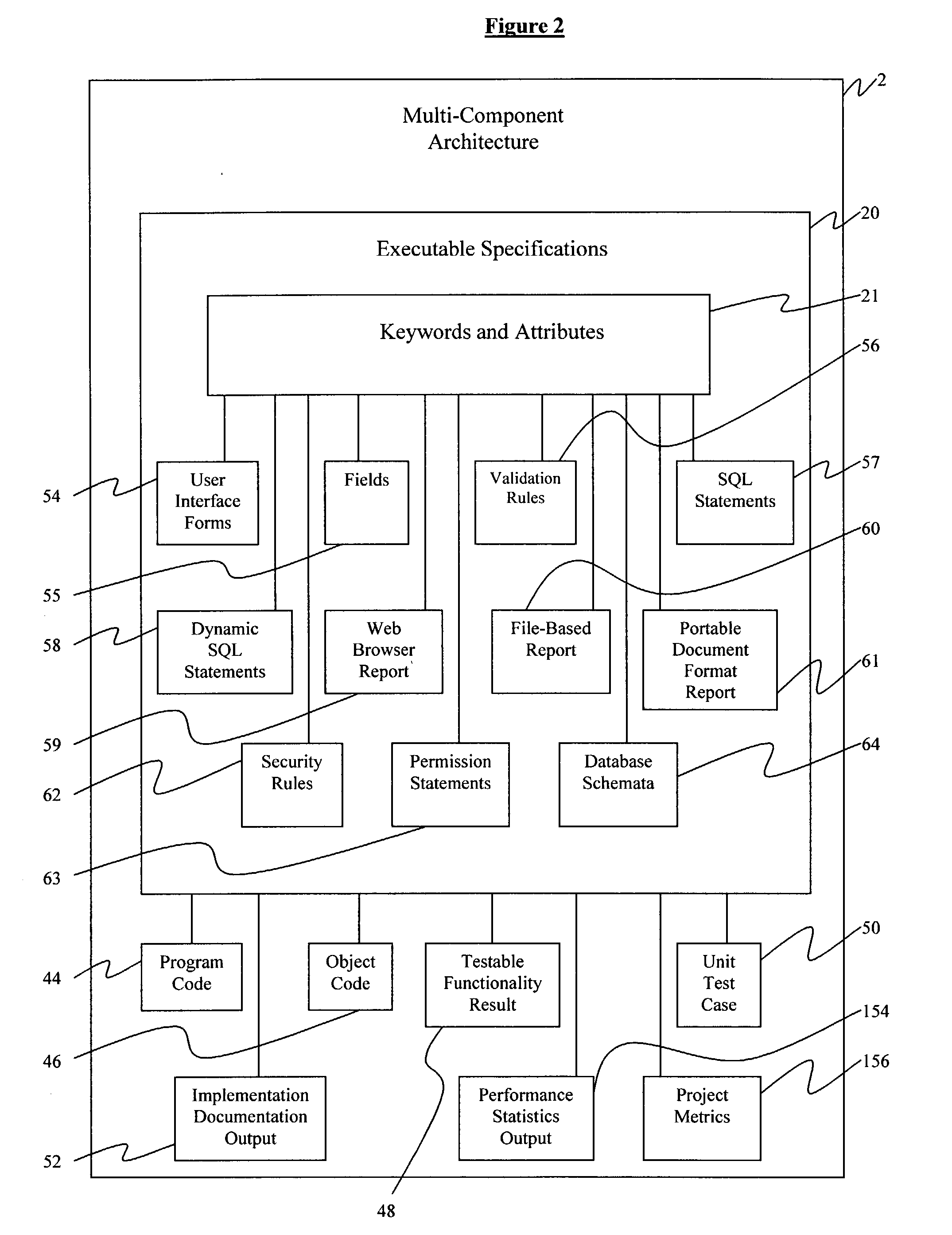
Computer system for performing reusable software application development from a set of declarative executable specifications
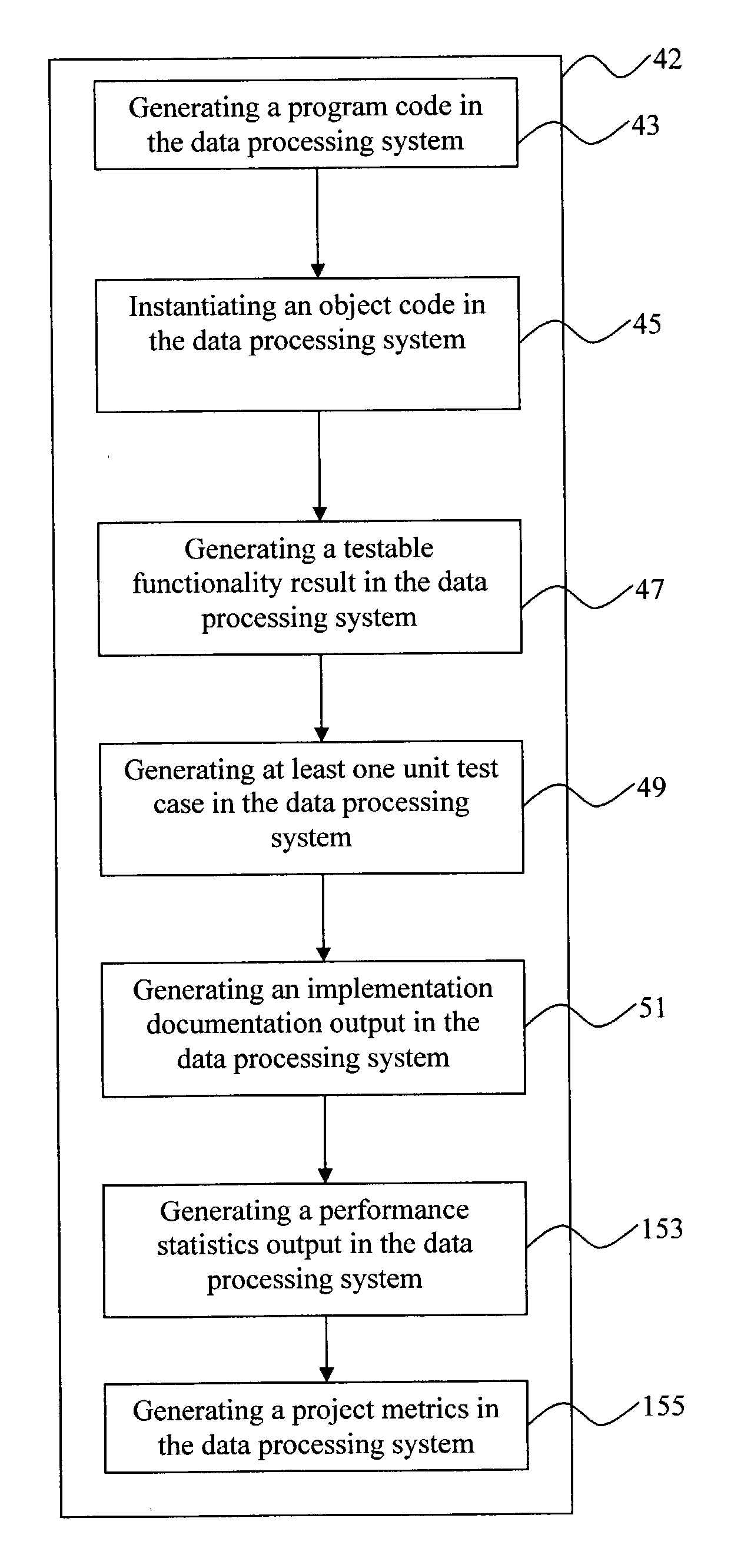
InactiveUS20040010776A1Time can be spentEasy to manageSoftware testing/debuggingSpecific program execution arrangementsDocumentation procedureProject metrics
A computer system executing a method for performing reusable software application development comprises integrating a data processing system, providing a set of keywords and attributes, and declaring a set of executable specifications using the keywords and attributes, further comprising generating a program code, instantiating an object code, generating a testable functionality result, generating at least one unit test, generating an implementation documentation output, generating a performance statistics output, and generating a project metrics in the data processing system. The step of providing a set of keywords and attributes comprises generating a set of user interface forms, fields, and validation rules, generating a library of structured query language statements, generating a library of rules for generating dynamic structured query language statements, generating one of a web browser report, a file-based report, and a portable document format report, generating a library of security rules and permission statements, and generating database schemata.
Owner:RPX CORP
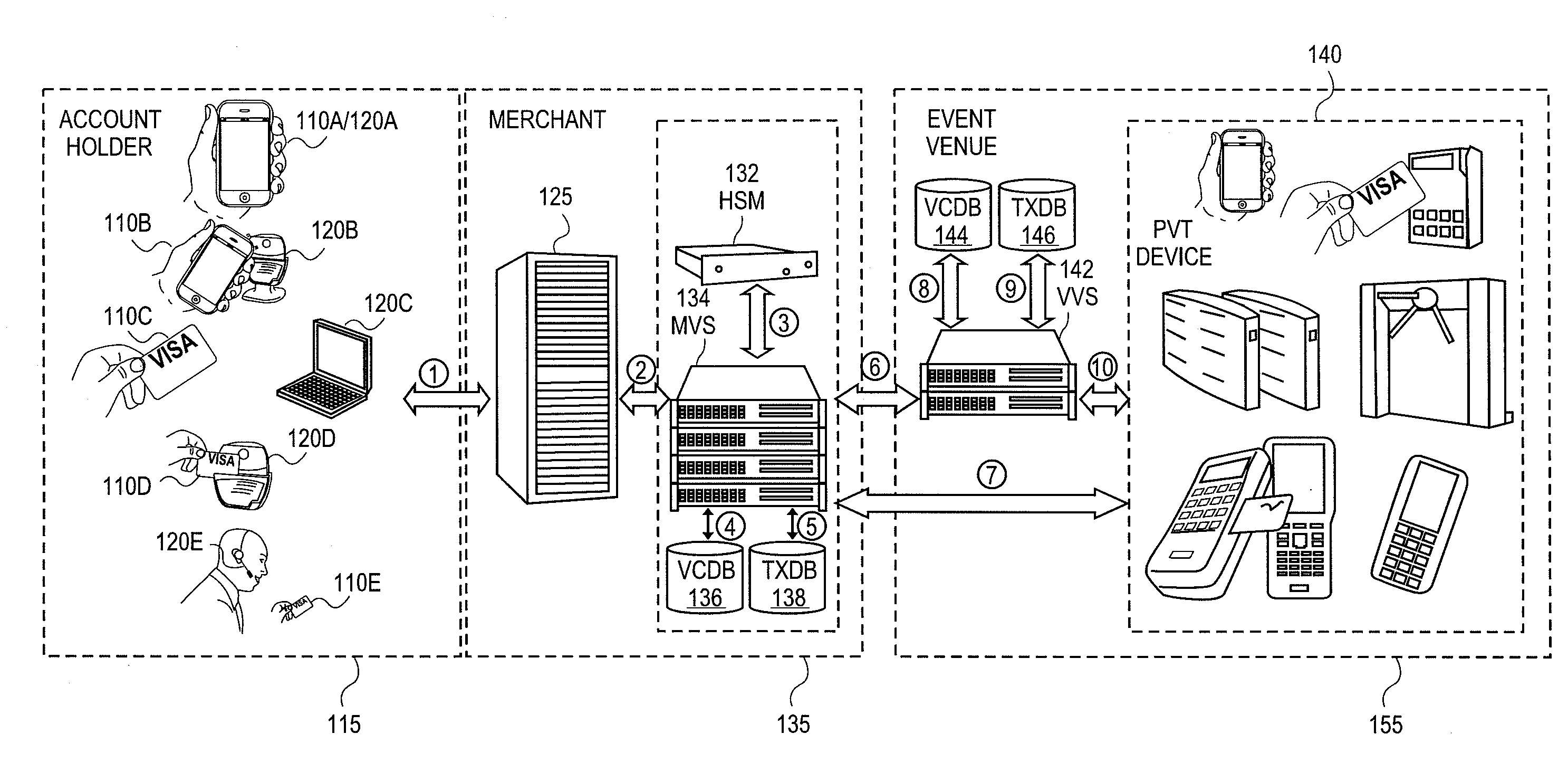
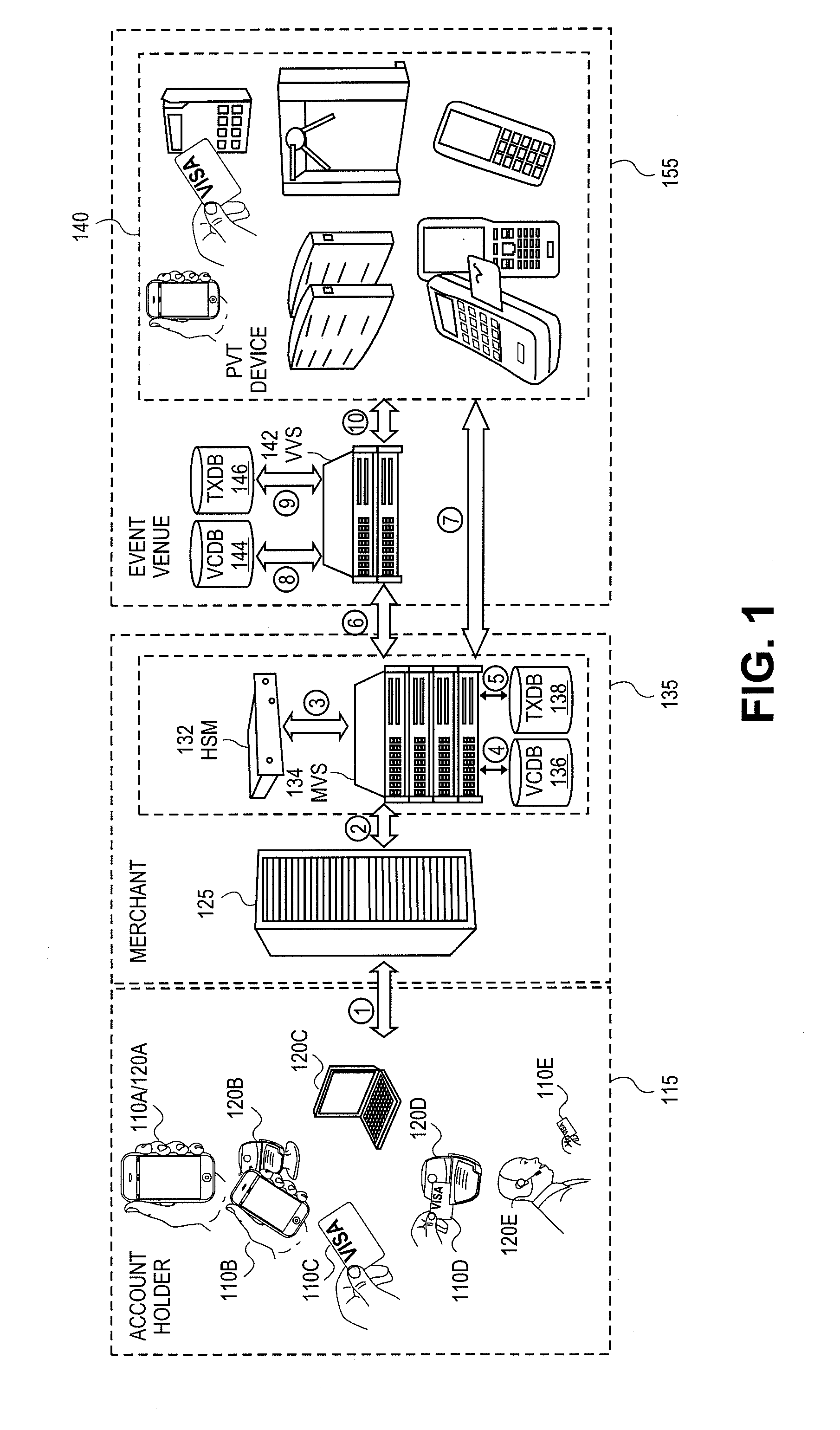
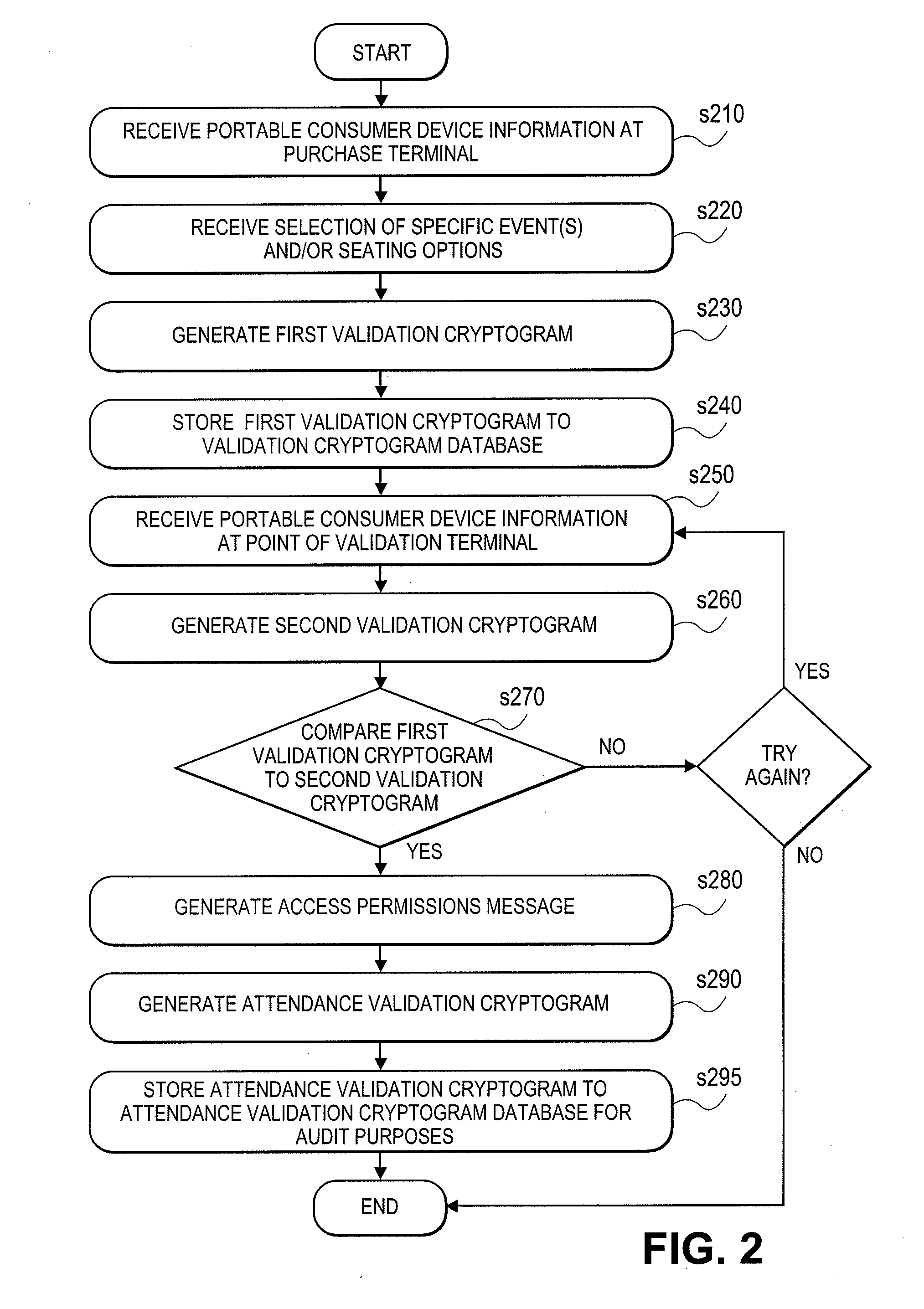
Event access with data field encryption for validation and access control
The utility of a portable consumer device is extended by allowing account holders the ability to gain entry into access-controlled venues (e.g., baseball or soccer game, cinema, public transit) using a portable consumer device that is associated with an account that was used to purchase the admission or tickets to the event at the access-controlled venue. Techniques disclosed allow cardholder authentication in a non-payment setting that enables cardholders access to a location or a specific event. A first validation cryptogram is generated in the purchase cycle and is stored. A second validation cryptogram is generated in the validation cycle at the venue. If the second validation cryptogram matches the first validation cryptogram, the consumer is granted access. Validation cryptograms may be based on input data that is specific to the payment card holder (e.g., primary account number), specific to the ticket selling merchant (e.g., merchant identifier), specific to the event (e.g., event identifier, date / time, location, etc.), and / or specific to the transaction (e.g., authorization code from a payment network). Based on the input data, validation cryptograms may be generated using encryption, hashing, a combination of encryption and hashing, and / or other operations on the input data.
Owner:VISA INT SERVICE ASSOC
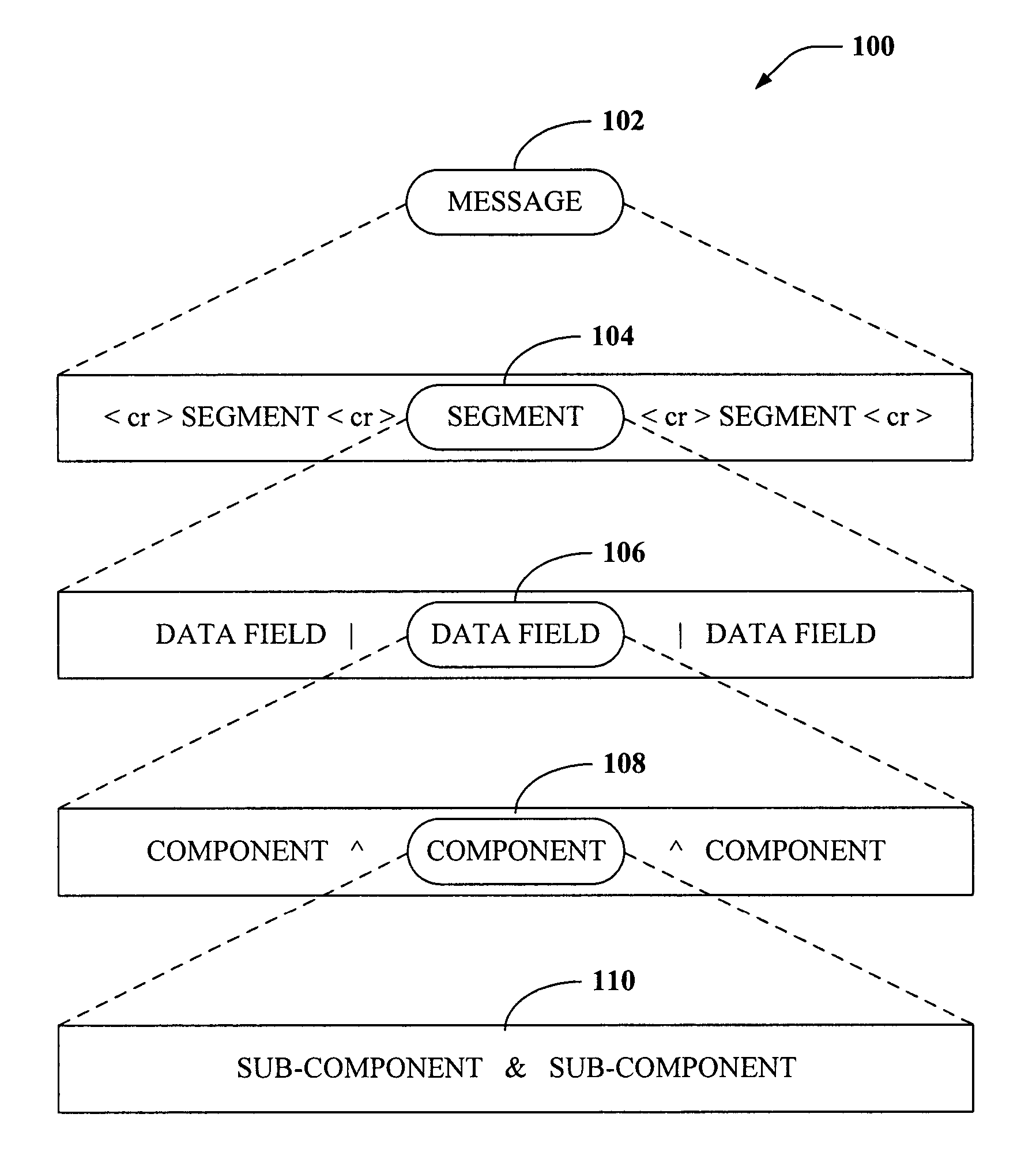
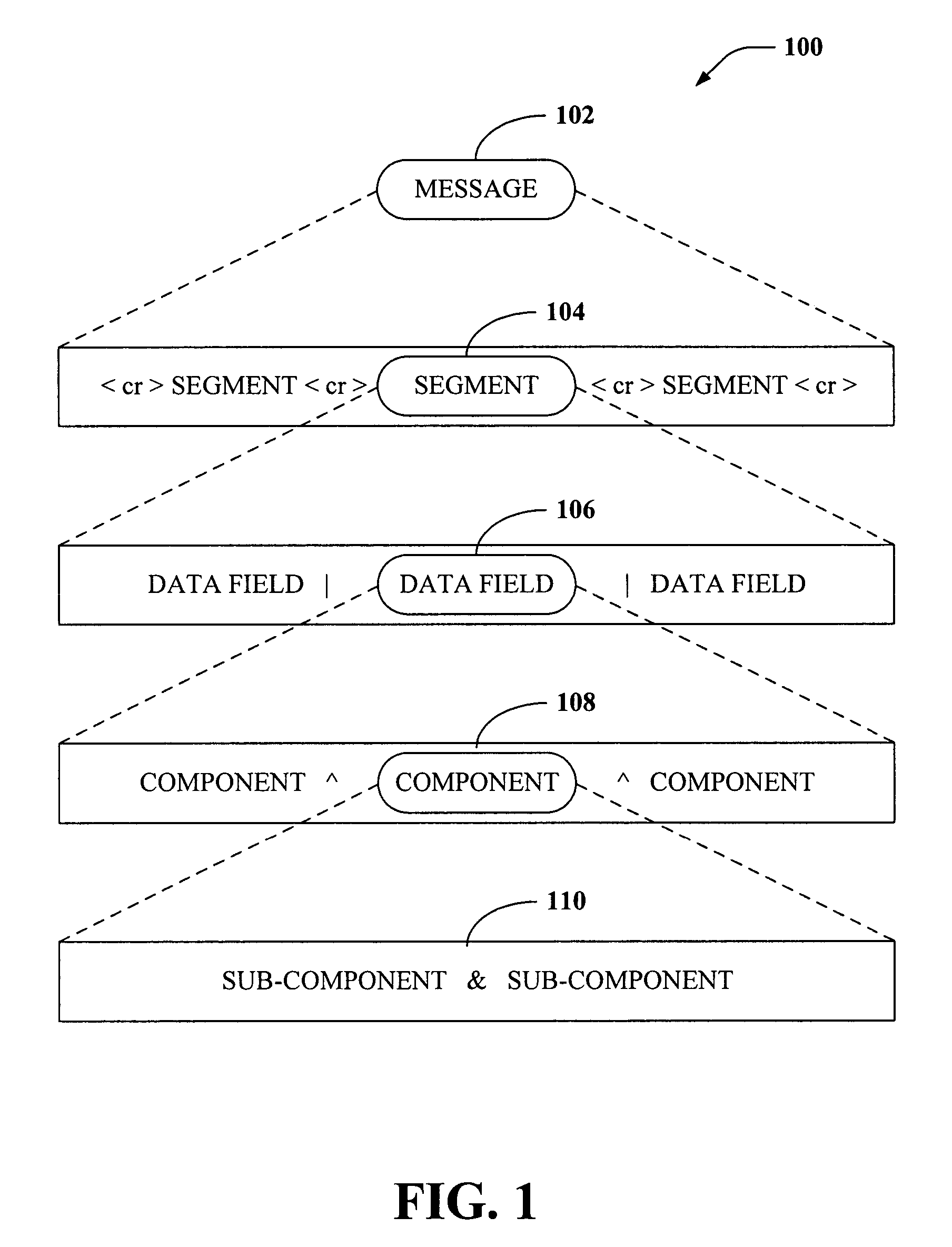
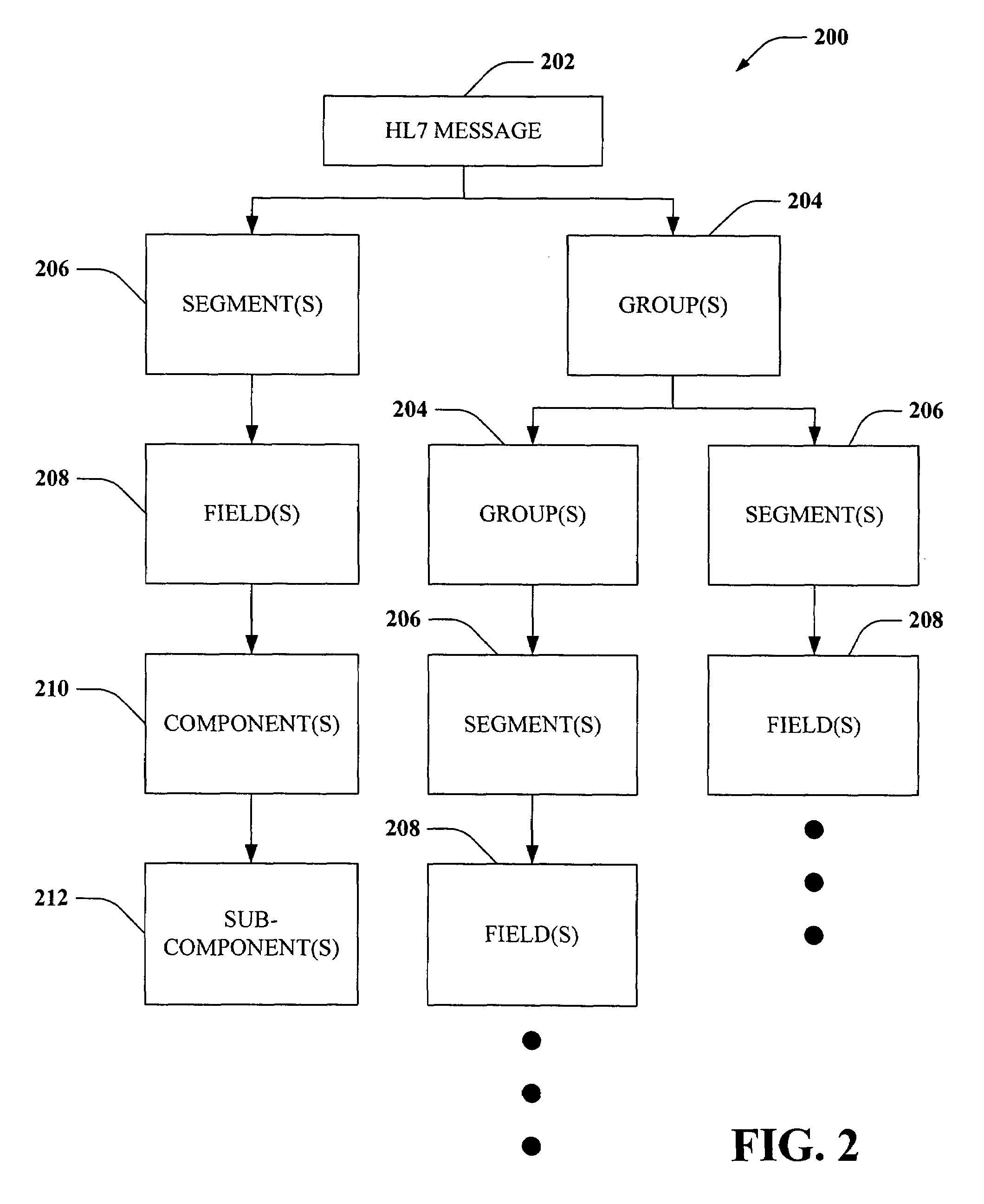
Single-pass translation of flat-file documents into XML format including validation, ambiguity resolution, and acknowledgement generation
InactiveUS7587415B2Promote generationReduce decreaseDigital data processing detailsNatural language data processingTheoretical computer scienceDocumentation
Systems and methods are disclosed that facilitate formally describing structured documents and complex validation rules associated therewith using value-added XSD schemas (VAXs). In accordance with aspects of the invention, structured documents can be translated, parsed, validated, and acknowledged in a single pass via utilization of XSD schema representations that capture complex data and business rules related to validation as a translation specification to convert delimited flat-file and / or structured documents to an XML format while providing ambiguity resolution and acknowledgements.
Owner:MICROSOFT TECH LICENSING LLC
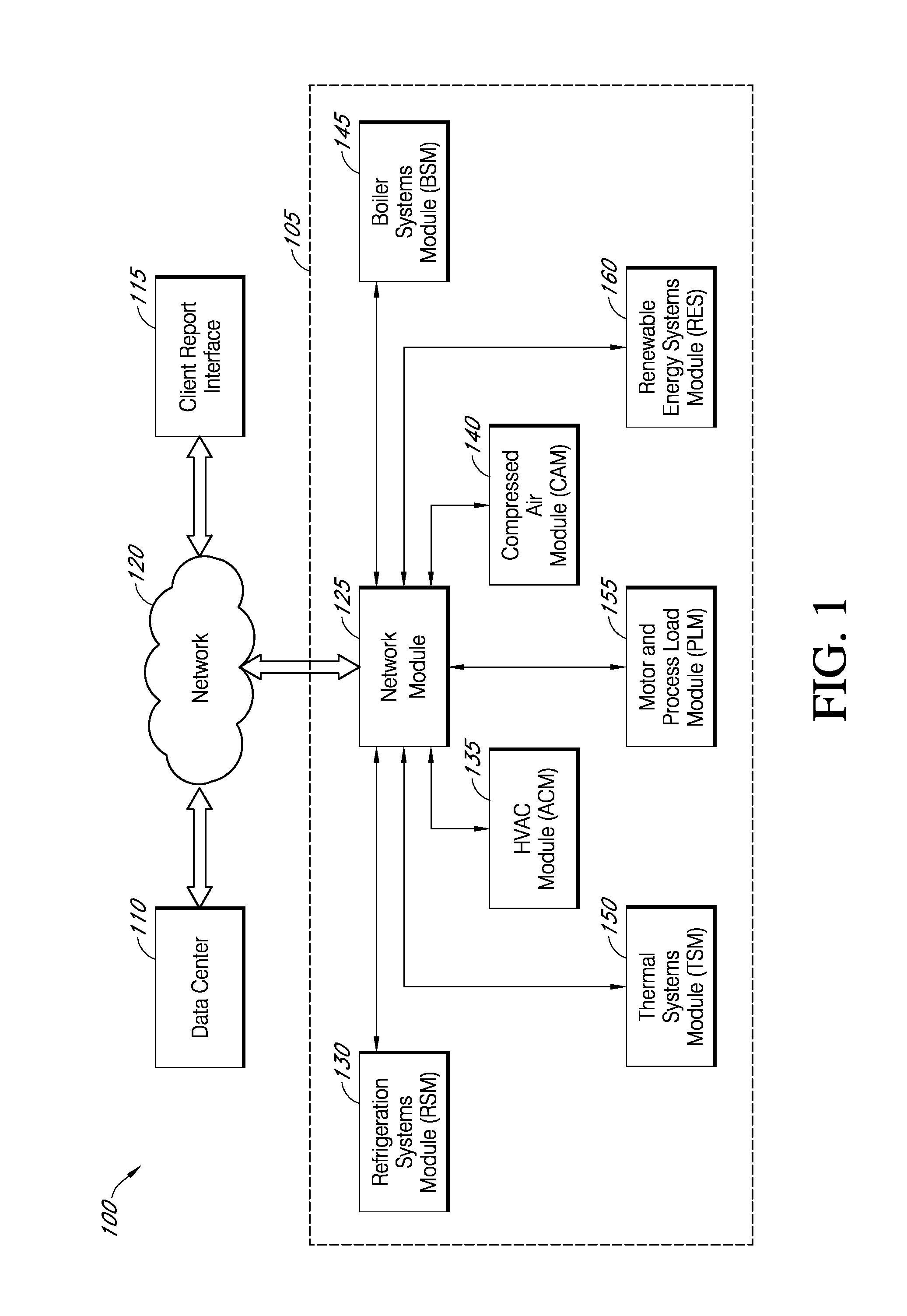
Systems and methods for assessing and optimizing energy use and environmental impact
InactiveUS20100145629A1Enhance and simplify procedureQuickly and accurately identifyDrawing from basic elementsElectric devicesEnvironment effectImpact system
Systems and methods for assessing and optimizing energy use and environmental impact can be designed to receive energy consumption and emission data from one or more energy consumption sources of a facility over a network. The data can be transformed into a database format that can be processed and analyzed. The data can be validated according to predefined validation rules. The data can be aggregated according to predefined time intervals and stored in memory. The data can be used to generate a report to a user, for example, via a user interface.
Owner:AMERESCO INTELLIGENT SYST LLC
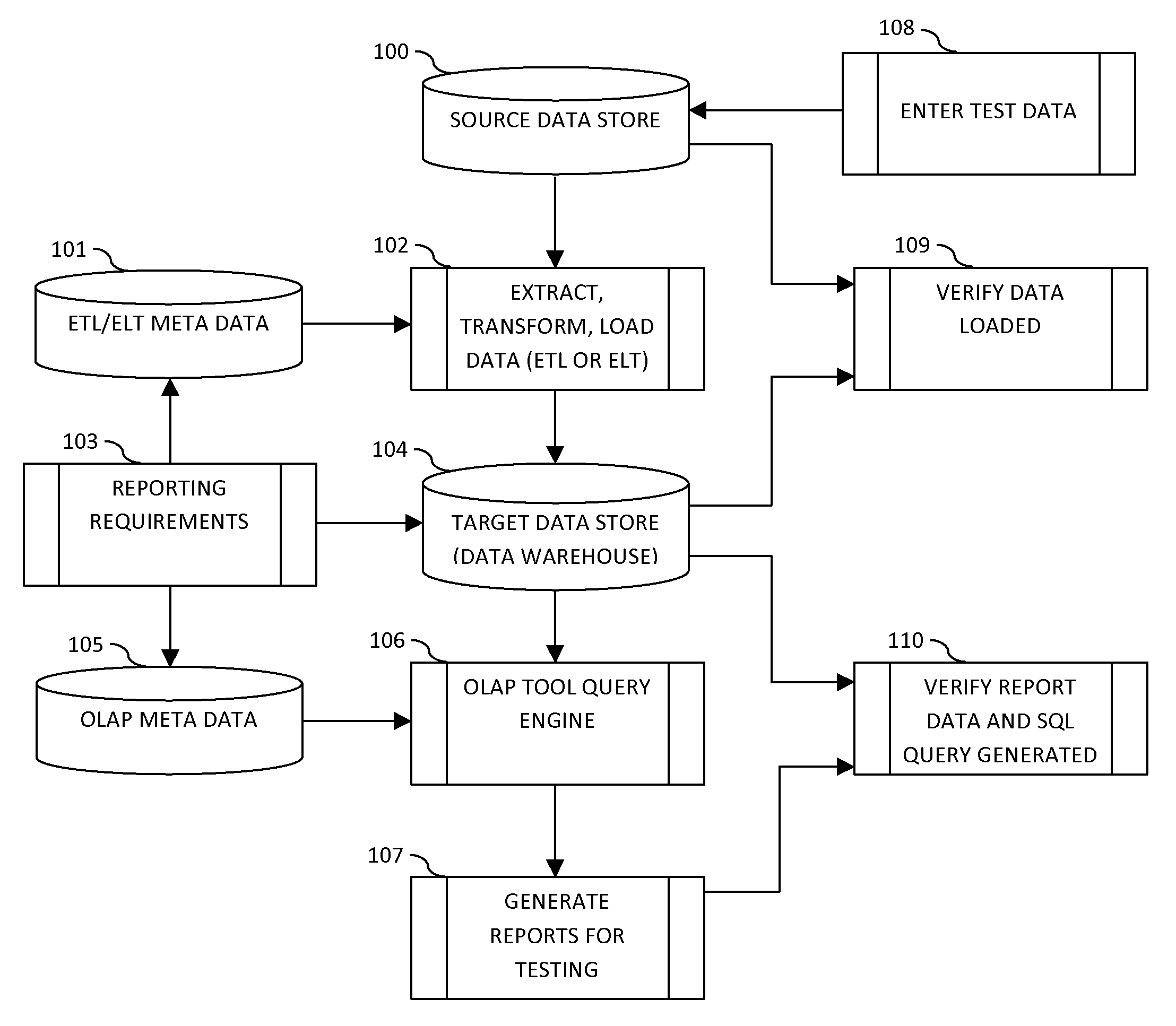
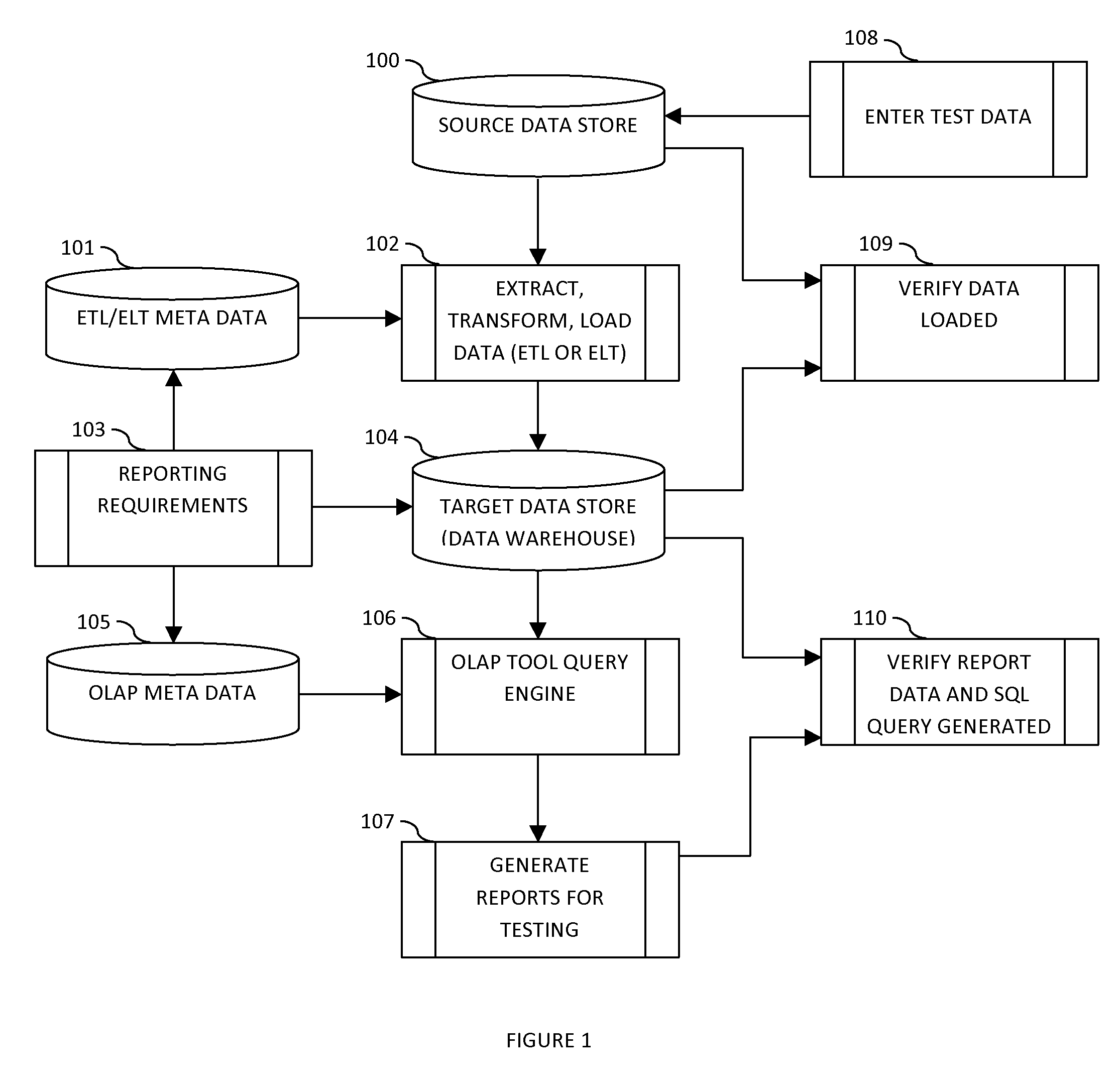
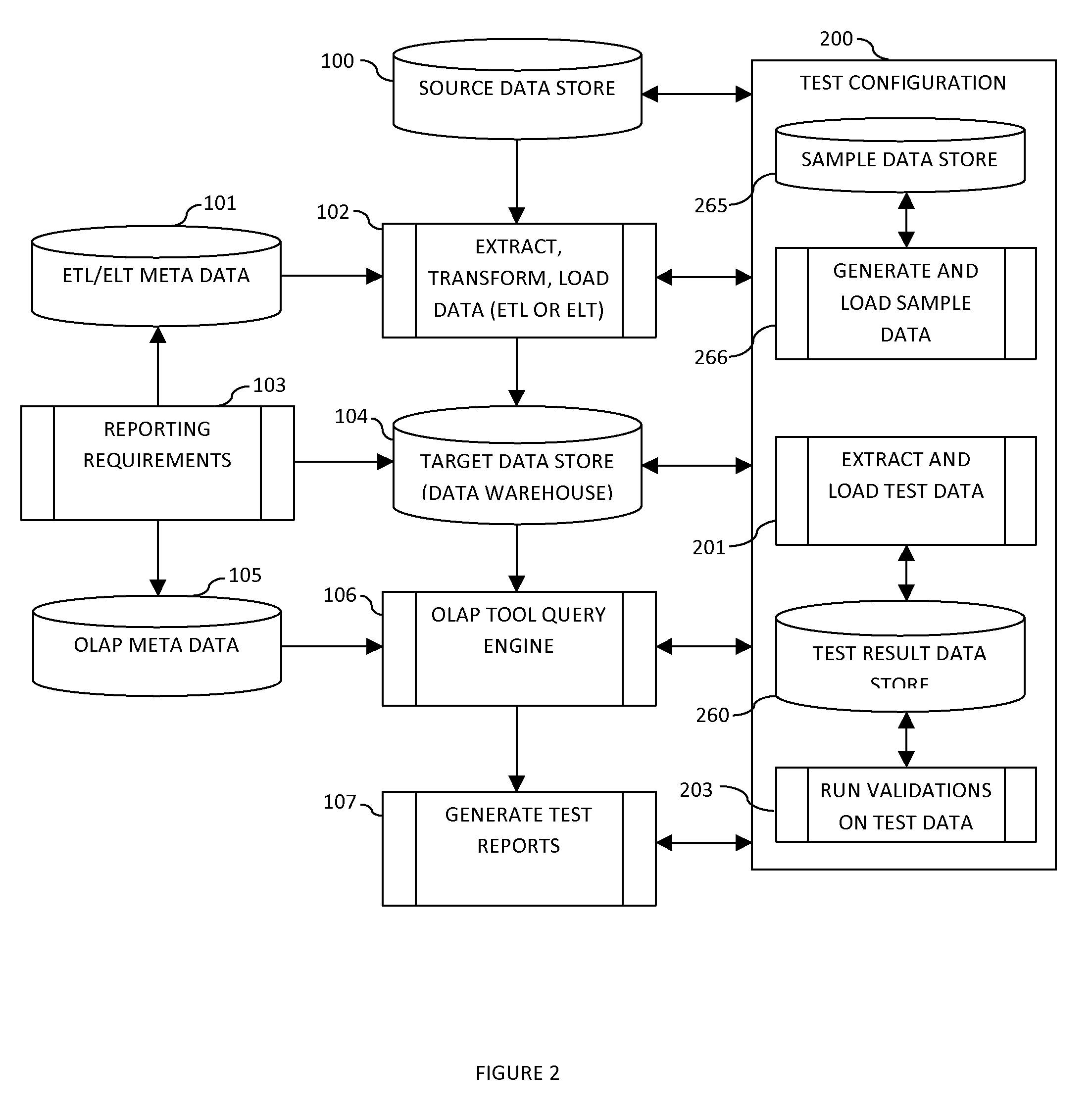
Data extraction and testing method and system
ActiveUS20120290527A1Automate the processDigital data processing detailsMulti-dimensional databasesDatabase queryData ingestion
The present method and apparatus provides for automated testing of data integration and business intelligence projects using Extract, Load and Validate (ELV) architecture. The method and computer program product provides a testing framework that automates the querying, extraction and loading of test data into a test result database from plurality of data sources and application interfaces using source specific adaptors. The test data available for extraction using the adaptors include metadata such as the database query generated by the OLAP Tools that are critical to validate the changes in business intelligence systems. A validation module helps define validation rules for verifying the test data loaded into the test result database. The validation module further provides a framework for comparing the test data with previously archived test data as well as benchmark test data.
Owner:YALAMANCHILLI NARENDAR
Single-pass translation of flat-file documents into XML format including validation, ambiguity resolution, and acknowledgement generation
InactiveUS20060206523A1Improve system efficiencyReduce decreaseNatural language data processingSpecial data processing applicationsPaper documentDocument preparation
Systems and methods are disclosed that facilitate formally describing structured documents and complex validation rules associated therewith using value-added XSD schemas (VAXs). In accordance with aspects of the invention, structured documents can be translated, parsed, validated, and acknowledged in a single pass via utilization of XSD schema representations that capture complex data and business rules related to validation as a translation specification to convert delimited flat-file and / or structured documents to an XML format while providing ambiguity resolution and acknowledgements.
Owner:MICROSOFT TECH LICENSING LLC
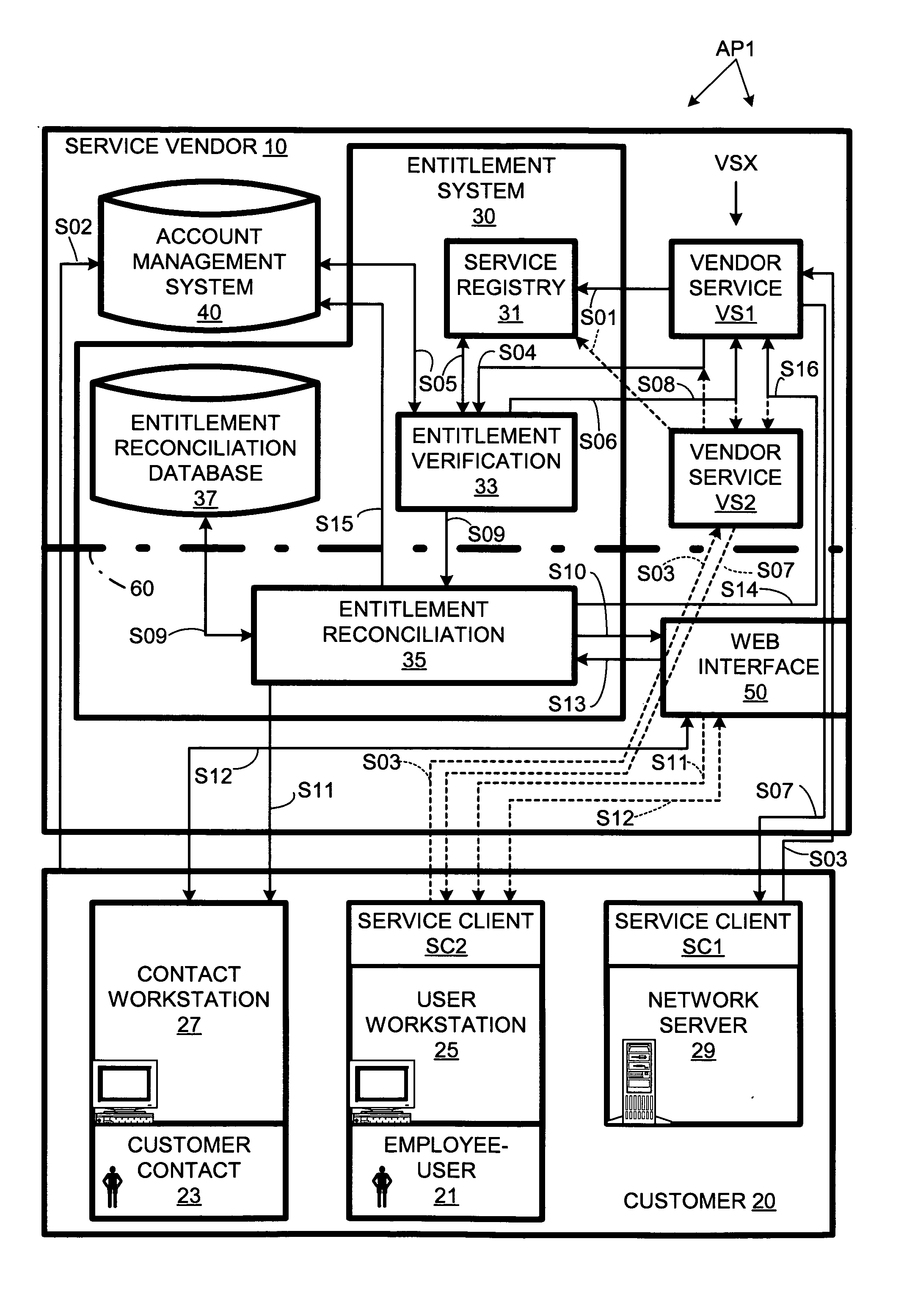
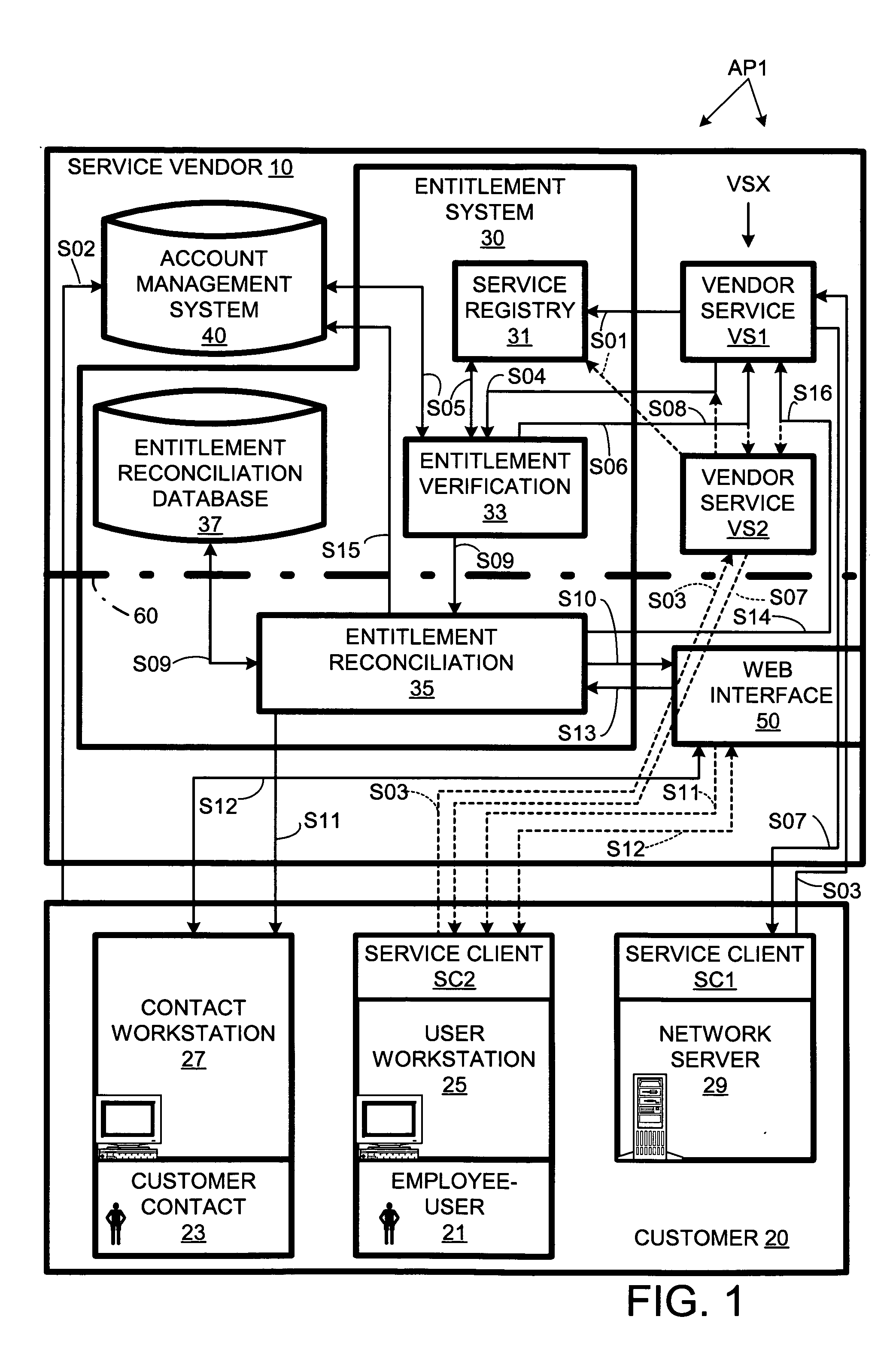
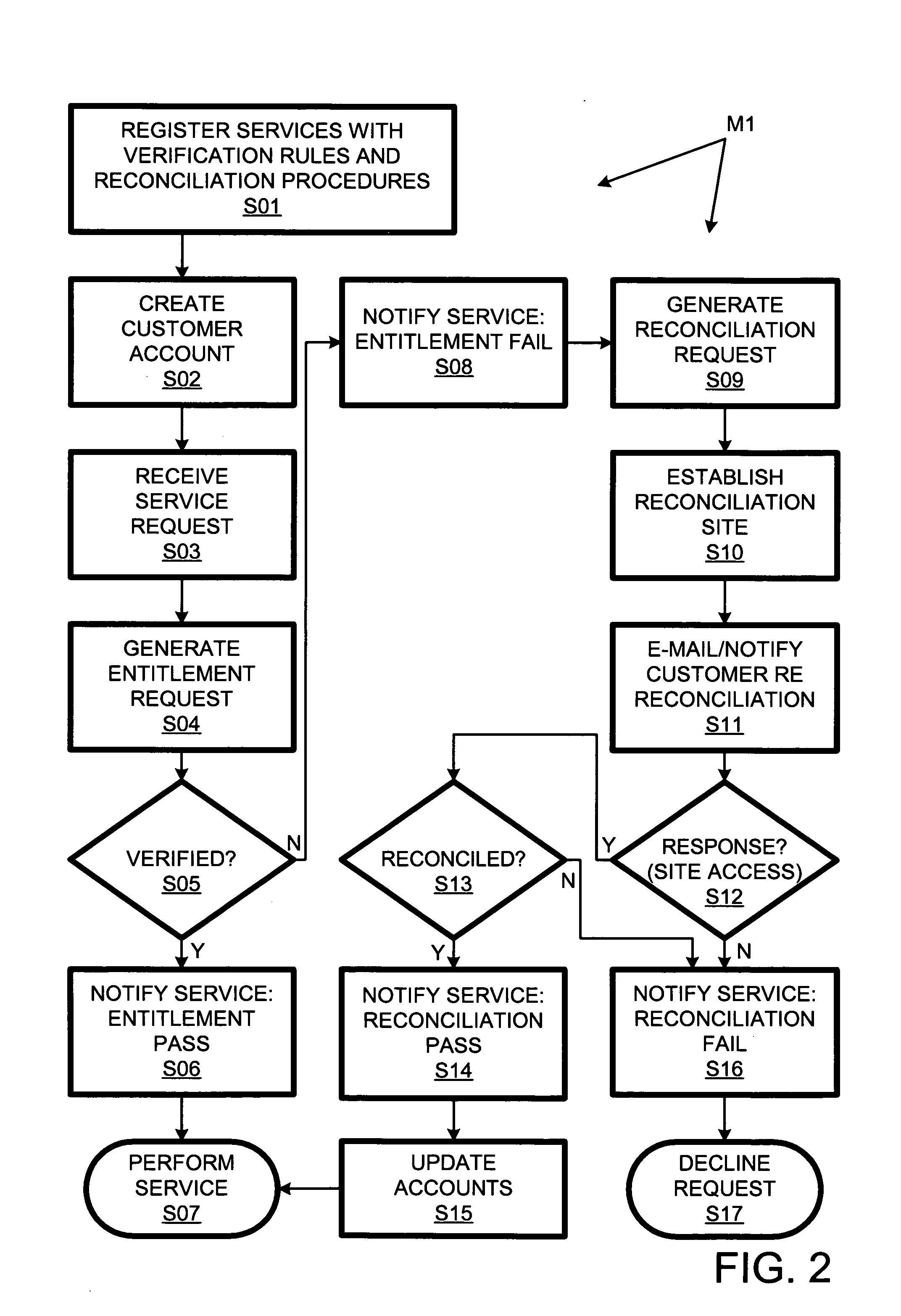
Automated customer entitlement system for vendor services
InactiveUS20050114226A1Facilitate communicationMore accessPayment architectureBuying/selling/leasing transactionsComputer networkService provision
An entitlement system provides for automated entitlement verification for plural vendor services provided to customers. When registering with the entitlement system, each service can specify a respective entitlement-verification rule as well as a respective entitlement reconciliation procedure to be applied in the event verification fails. The entitlement system provides for asynchronous notification to a customer of a reconciliation process (specified by the respective entitlement-reconciliation procedure). If reconciliation succeeds, the requested service can be performed without requiring the customer to resubmit the request. For security purposes, the verification function that determines the initial entitlement result can be behind a firewall through which it must communicate with a reconciliation function that manages the reconciliation procedure.
Owner:HEWLETT PACKARD DEV CO LP
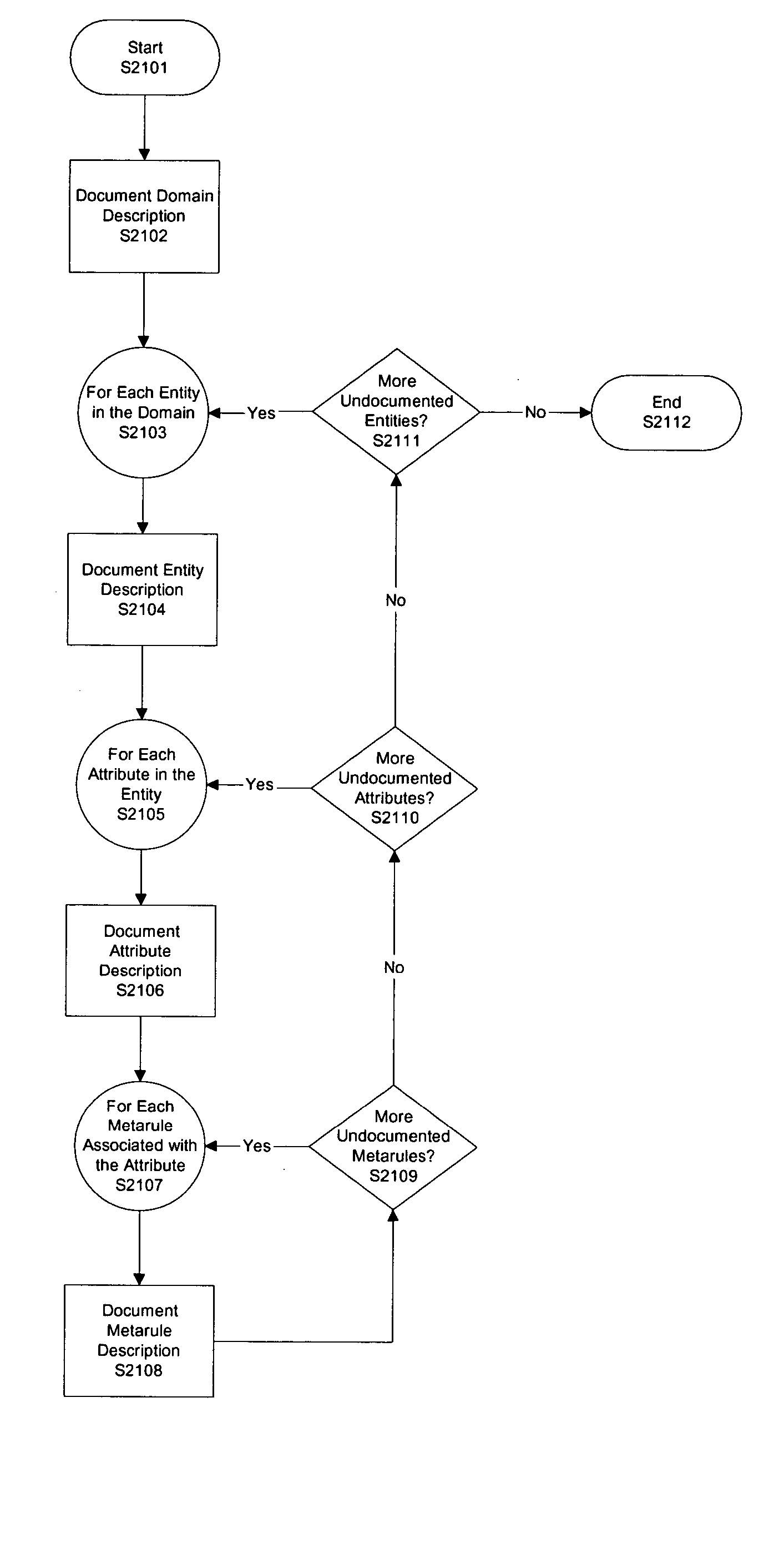
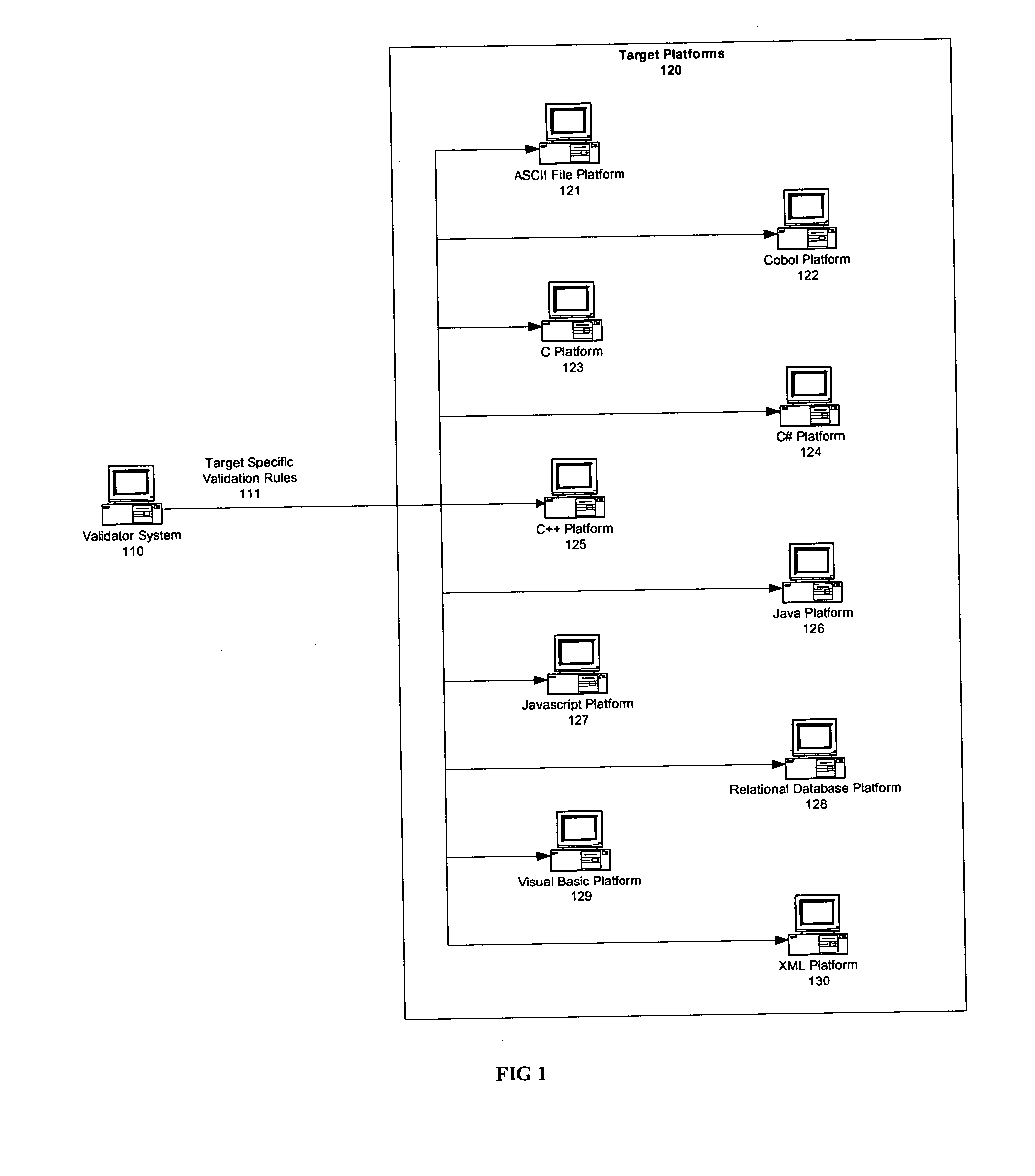
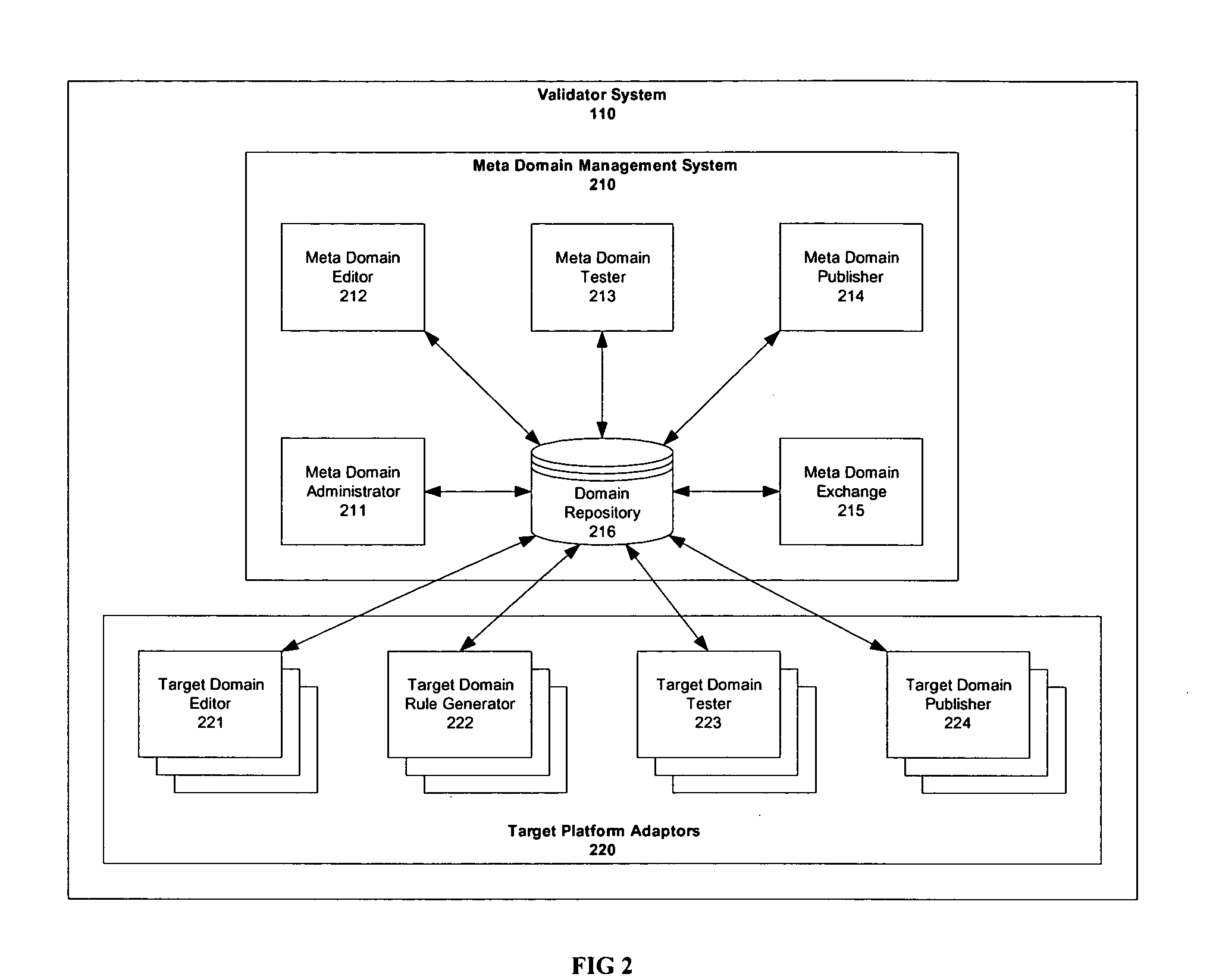
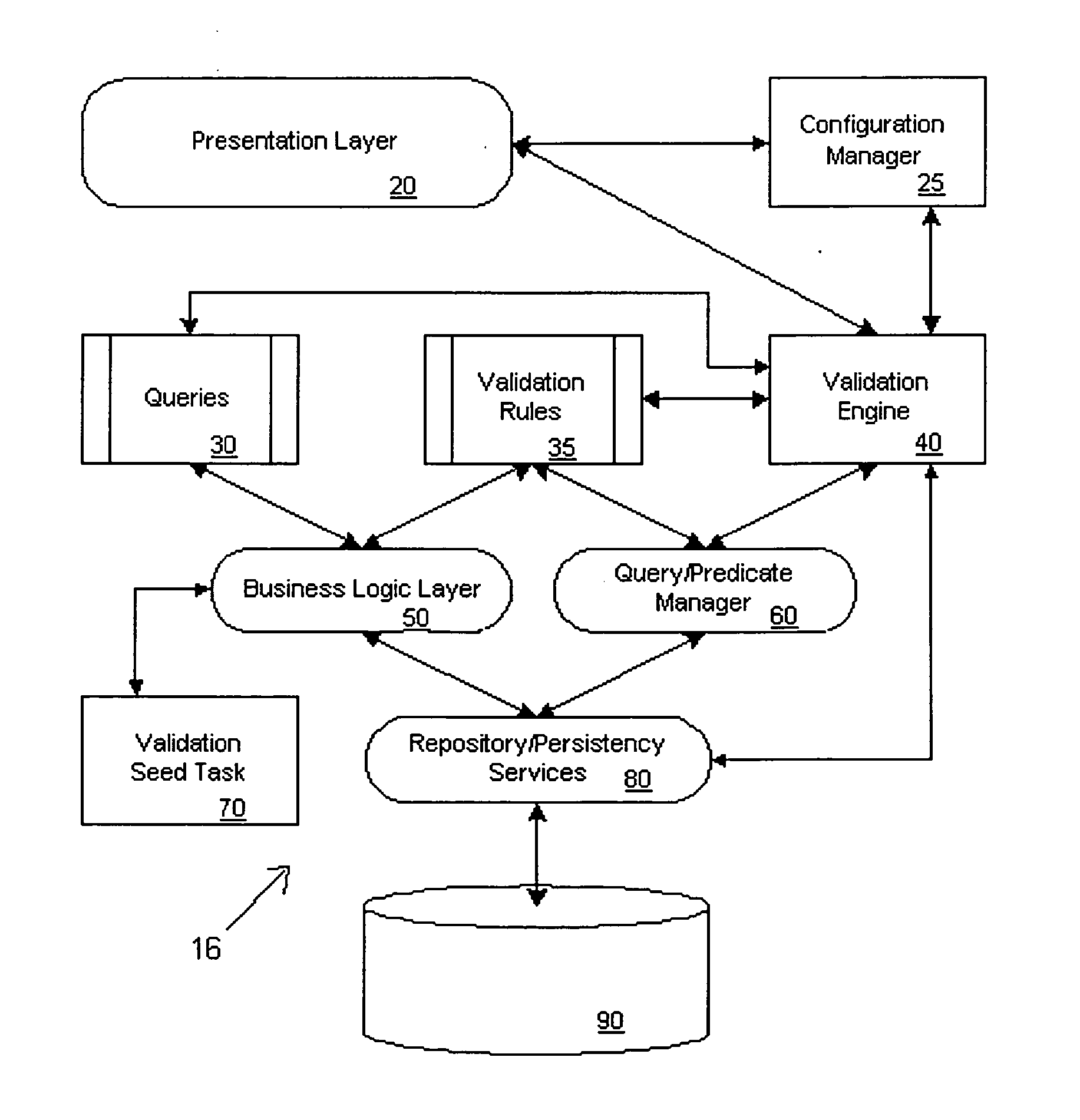
System and method for generating data validation rules
A method for generating validation logic executable in a target application in a target platform. The method creates a metarule, creates a target domain attribute, creates a mapping of the metarule to the target domain attribute, and creates target domain attribute validation logic executable in a target application in a target platform based on the metarule, the mapping of the metarule to the target domain attribute, and the target language of the target platform. The method further submits test data, including a value of a target domain attribute, to the target domain attribute validation logic, and produces an actual validation result based on the submitted test data.
Owner:TRIVERGENT TECH
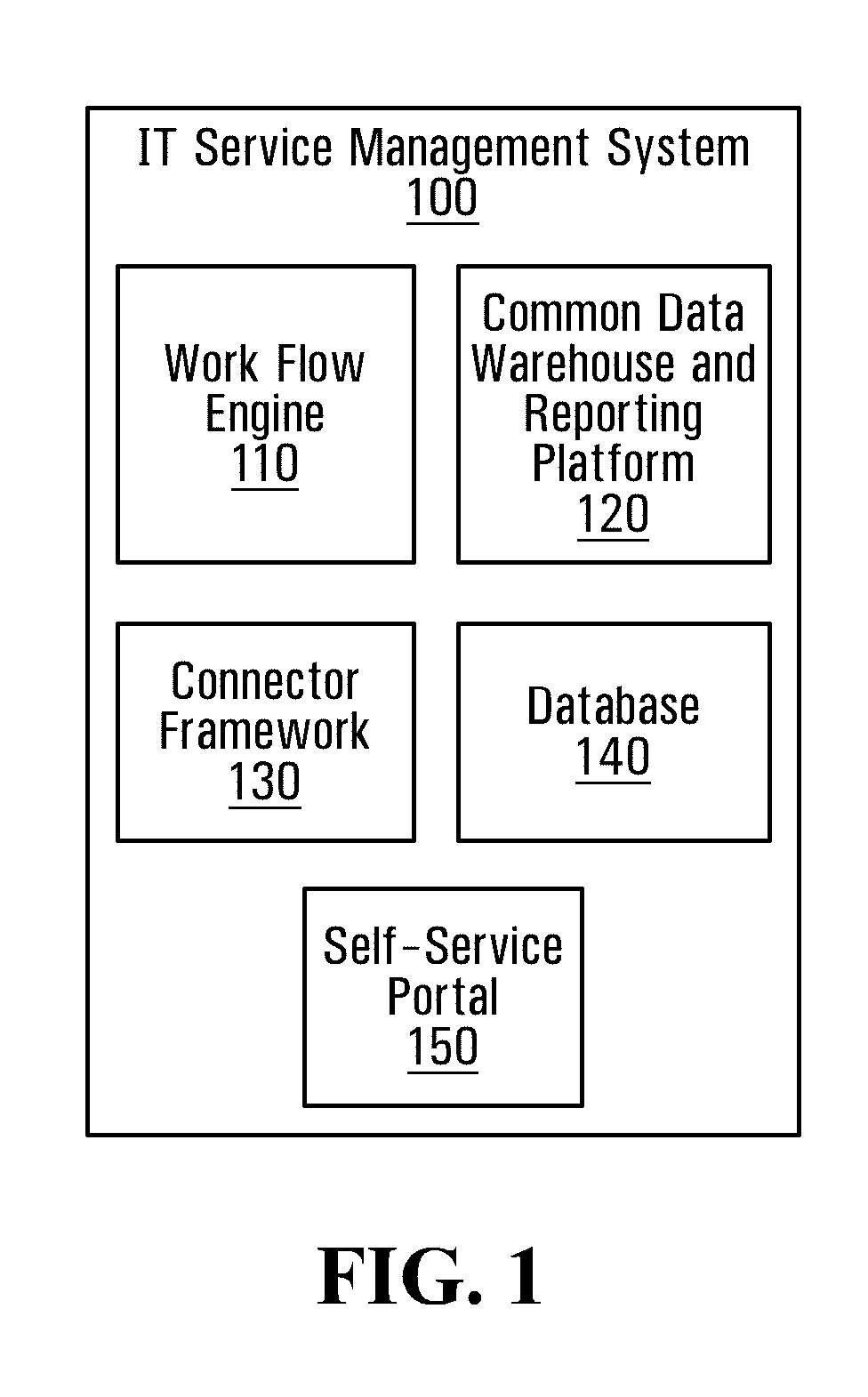
Method and system for information technology asset management
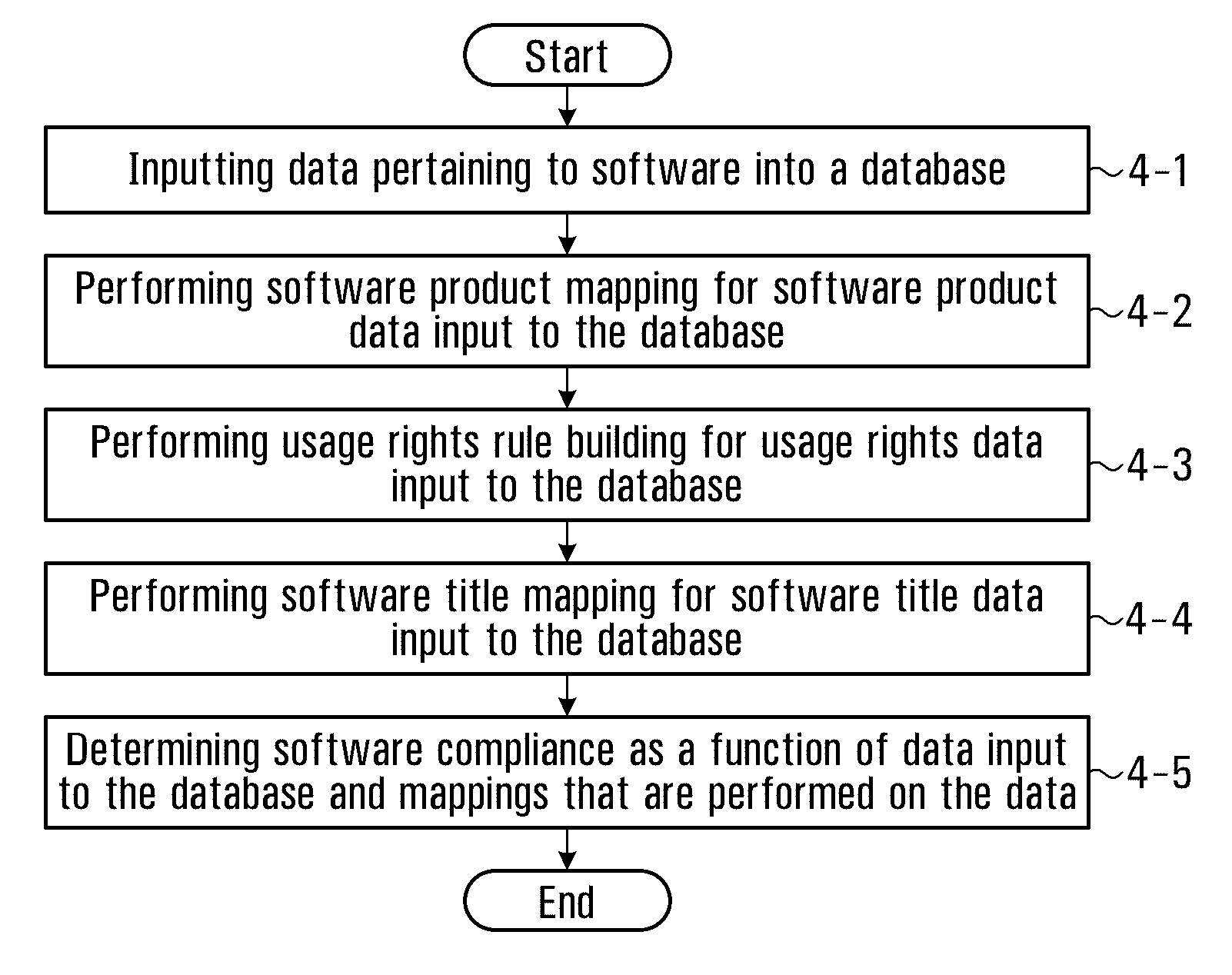
InactiveUS20120304248A1Computer security arrangementsBuying/selling/leasing transactionsSoftware asset managementIT service management
As aspects of the present invention provides a manner of software asset management involving inputting data pertaining to software into a database; performing software product mapping for software product data input to the database; performing usage rights rule building for usage rights data input to the database; performing software title mapping for software title data input to the database; and determining software compliance as a function of data input to the database and mappings that are performed on the data. Another aspect of the present invention includes method of inputting or importing data into a database m an IT service management system involving: the system importing the data into temporary storage m the database; the system applying validation rules; the system applying the transformation rules; the user reviewing the processed data; the user modifying the processed data; the user requests that the processed data be committed to the database; the system committing the processed data to records in the database.
Owner:PROVANCE TECH
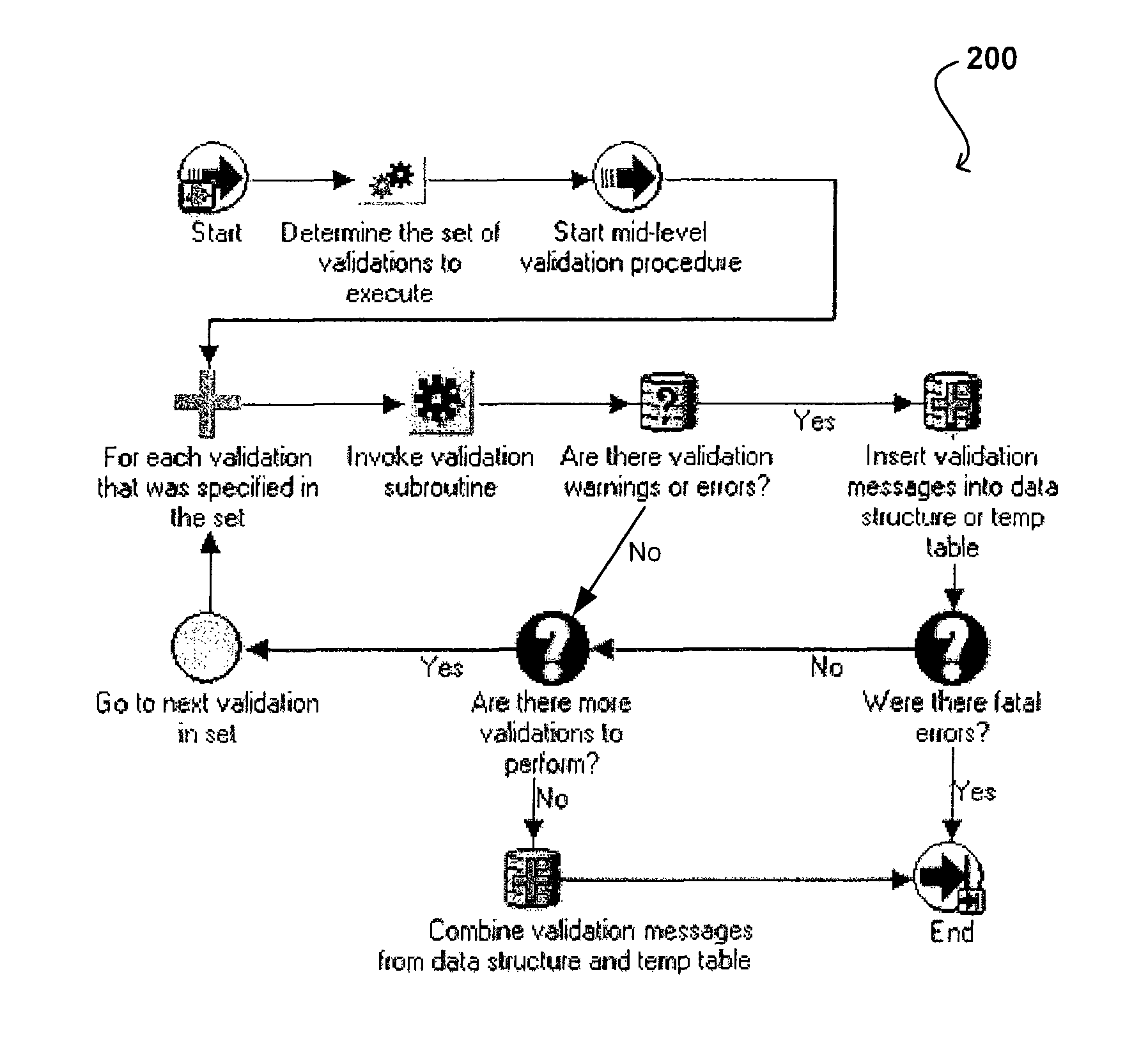
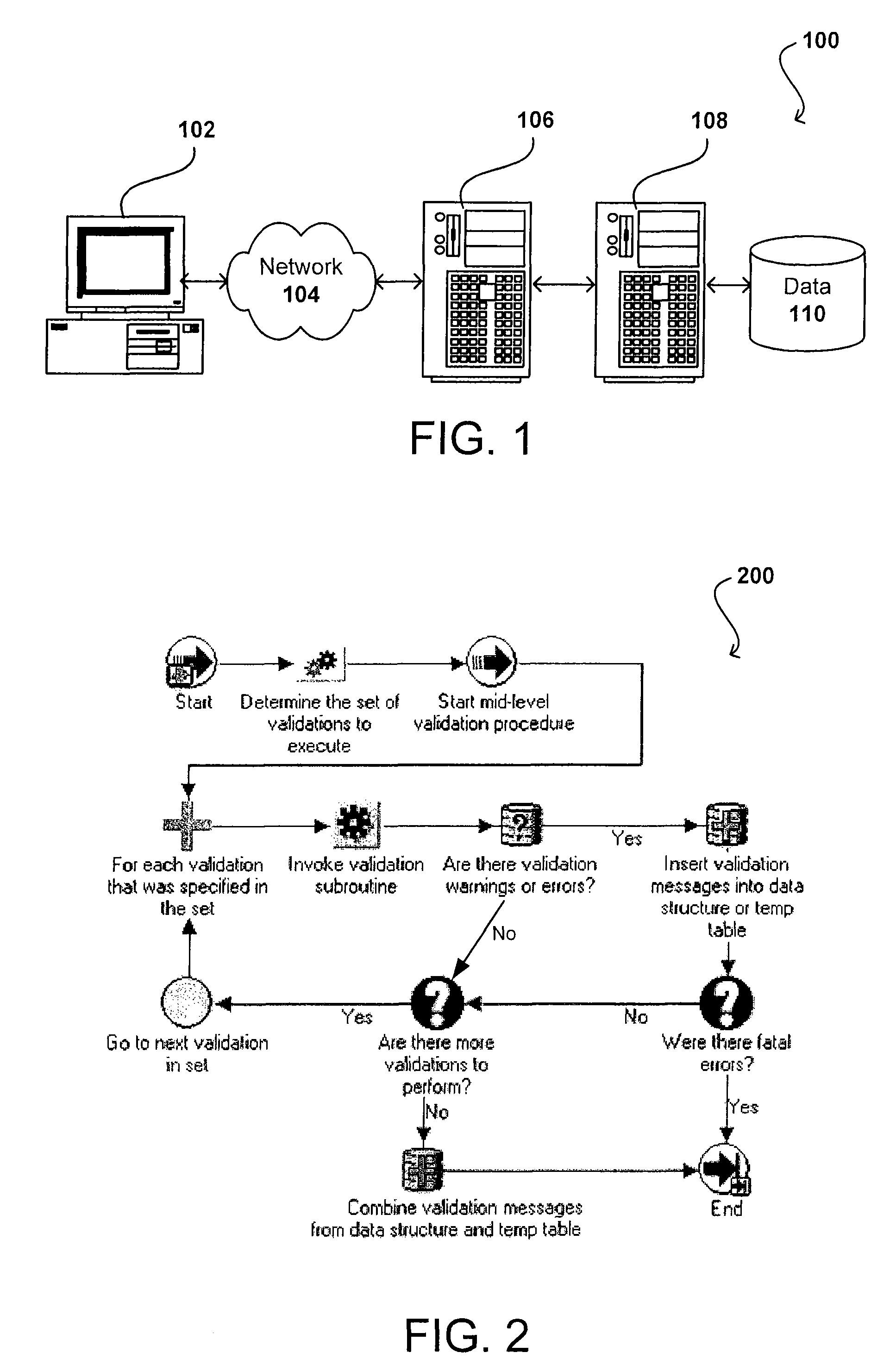
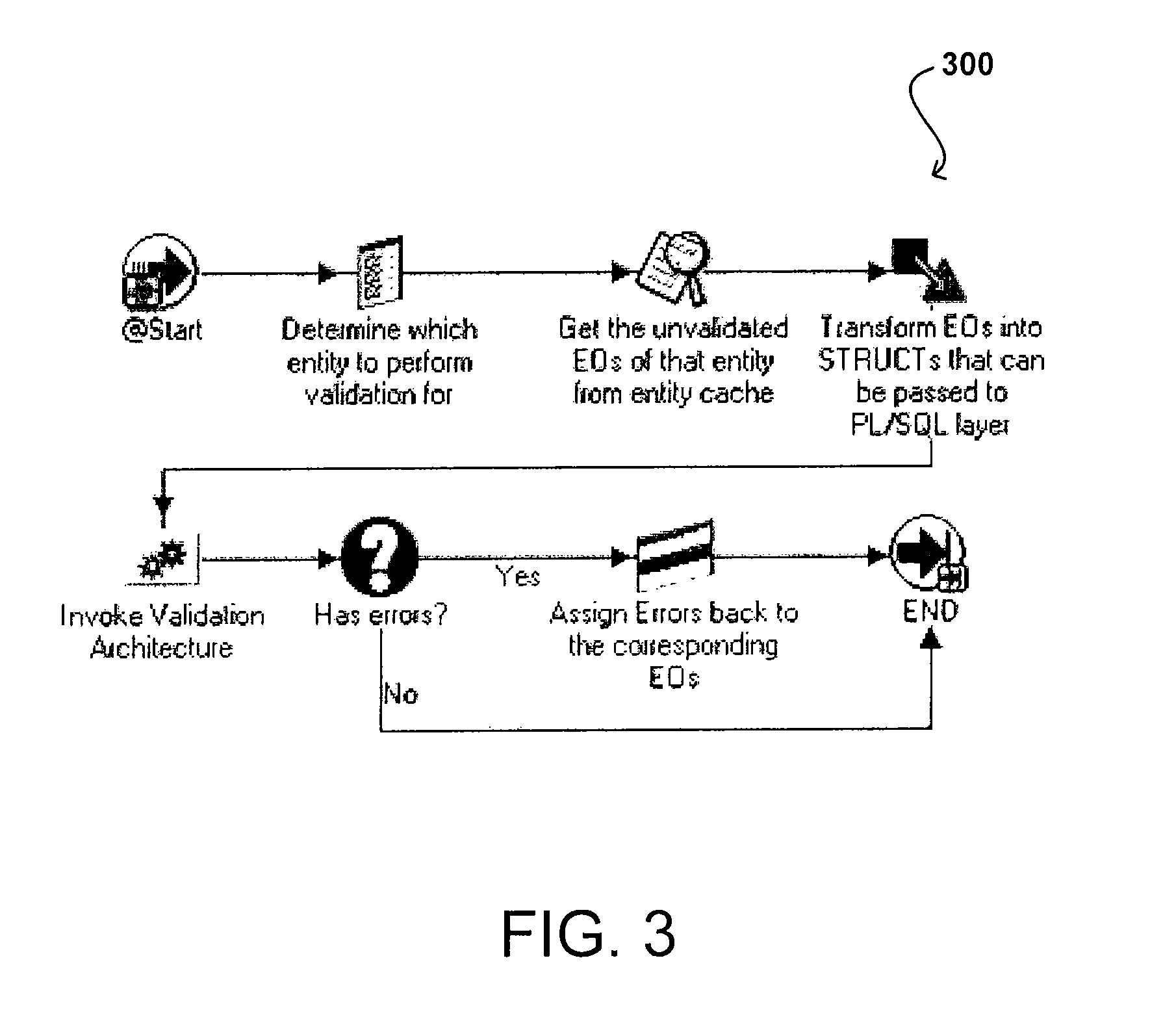
Architecture for data validation
ActiveUS8418142B2Easy to createSufficient flexibilitySoftware designSpecific program execution arrangementsData validationDuplicate code
A data validation architecture is provided that minimizes duplicate code and enables easy creation of new validations using a high-performance and scalable design. Such an architecture provides sufficient flexibility to disable certain validations when they are not applicable to the flow, interpret validation failures differently according to requirements of the calling application, and specify the type of document for which a particular validation is applicable. The architecture provides a standardized flow for performing data validation, specifying a set of required parameters for validation subroutines, as well as where validation results are to be stored for access by a calling program. Such an architecture also provides a framework for performing common processing required for most validation flows without restricting the flexibility of the validation subroutines.
Owner:ORACLE INT CORP
Policy Validation
ActiveUS20170031970A1Easy compositionEasy to useDigital computer detailsRelational databasesValidation ruleDistributed computing
Owner:VMWARE INC
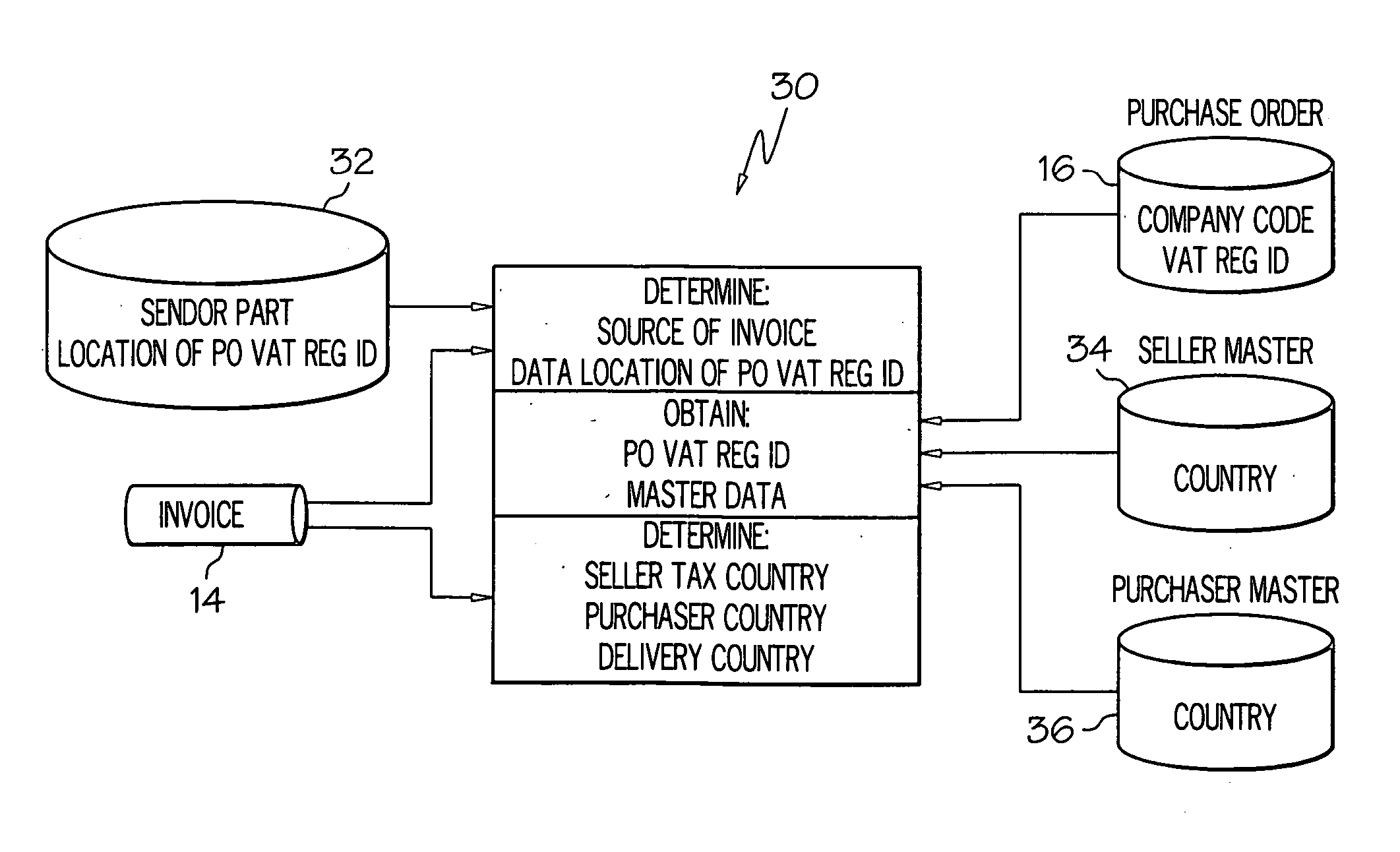
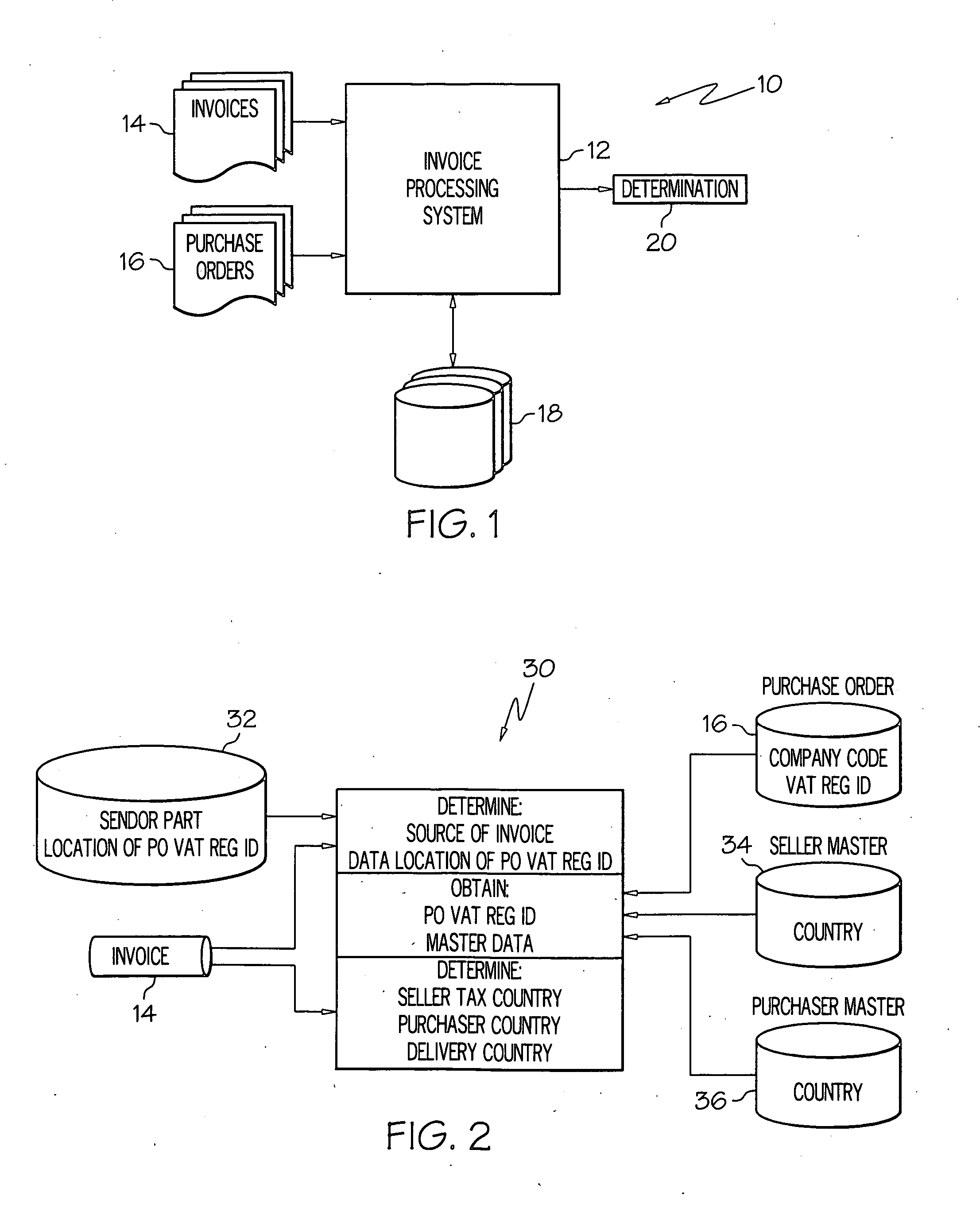
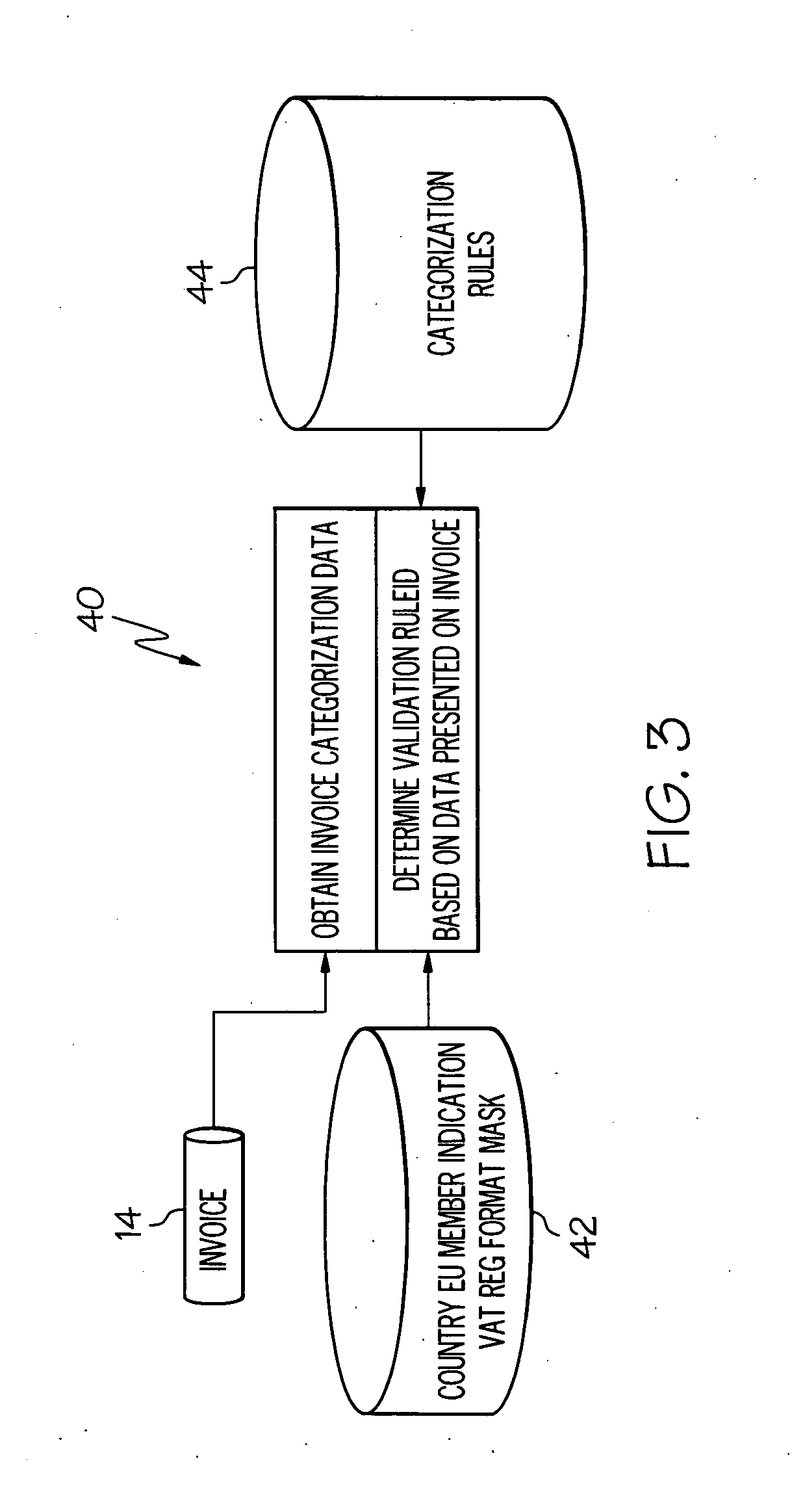
Method, system, and program product for electronically validating invoices
The present invention provides a method, system, and program product for validating invoices for transactions between trading partners that occur across jurisdictional borders (e.g., inter-country or inter-state transactions). Specifically, under the present invention, an invoice corresponding to a transaction between trading partners is electronically received (e.g., in an invoice processing system). Upon receipt, a purchaser tax jurisdiction (e.g., first country) and a seller tax jurisdiction (e.g., second country) corresponding to the transaction will be determined. Based on these jurisdictions and a set of categorization rules, a category of the transaction is determined. Using the category and a set of validation rules, a tax rate indicated on the invoice and other optional aspects (e.g., whether the invoice contains all required information) will be validated. Based on this validation it will be determined whether the overall invoice is valid or invalid.
Owner:IBM CORP
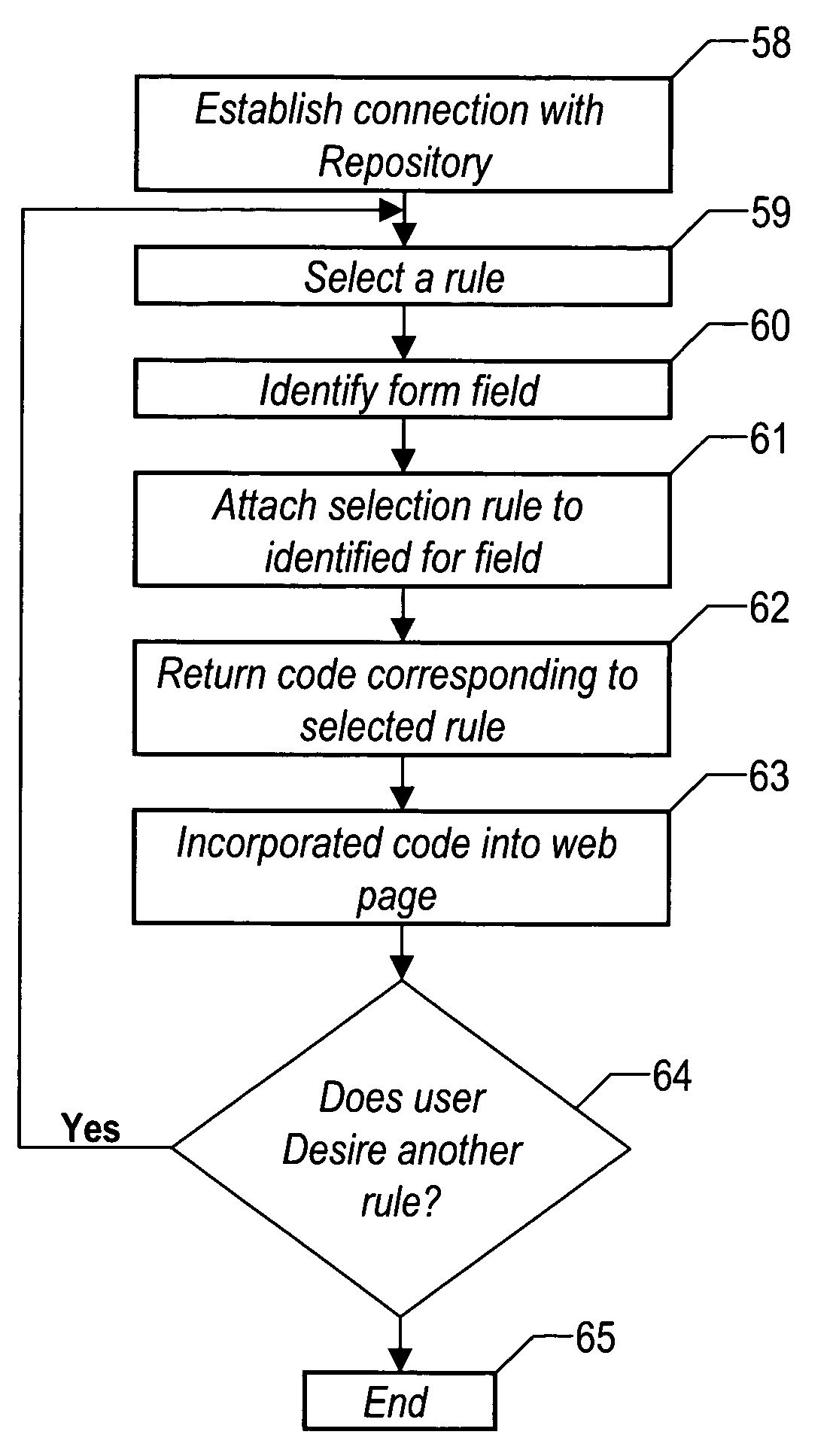
Method and system for selecting rules to validate information submitted on an electronic form
The present invention provides a method and system for creating a validation rules repository for electronic form validation rules. The software instructions that implement these validation rules would be linked to a record in the repository corresponding to each rule. During the creation of an electronic form on a web page, the software instructions that execute a rule for a particular field on the form would be automatically retrieved from a repository location and installed within the web page. In addition to incorporating existing validation rules, the present invention provides for the creation of new validation rules and storage of these rules in the rules repository.
Owner:IBM CORP
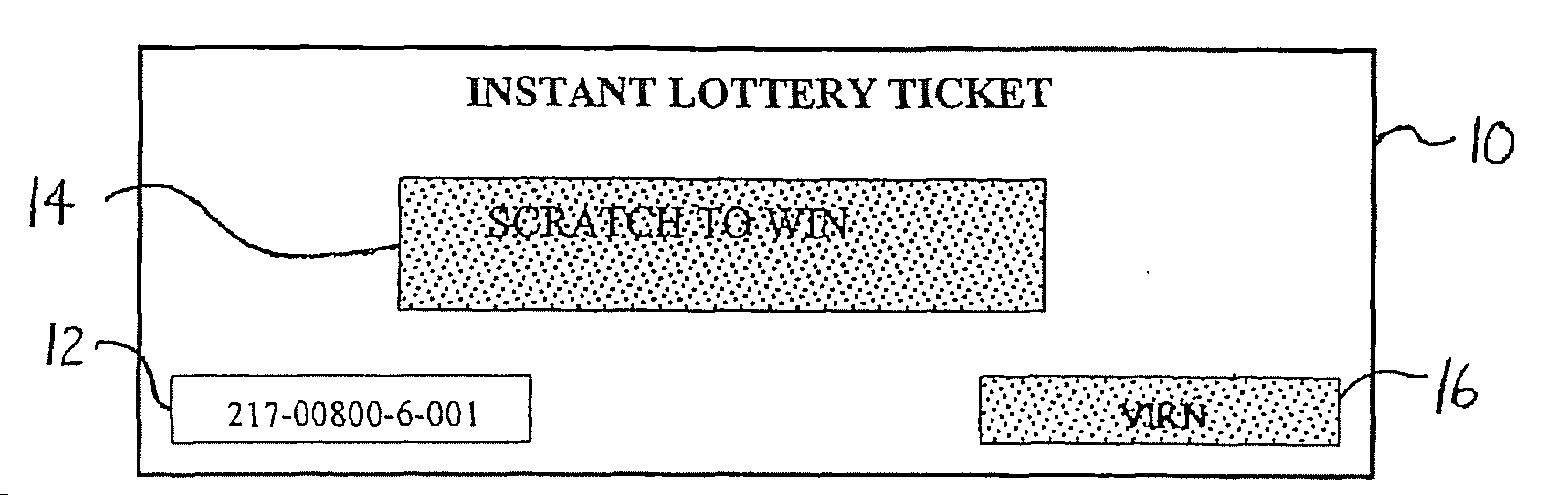
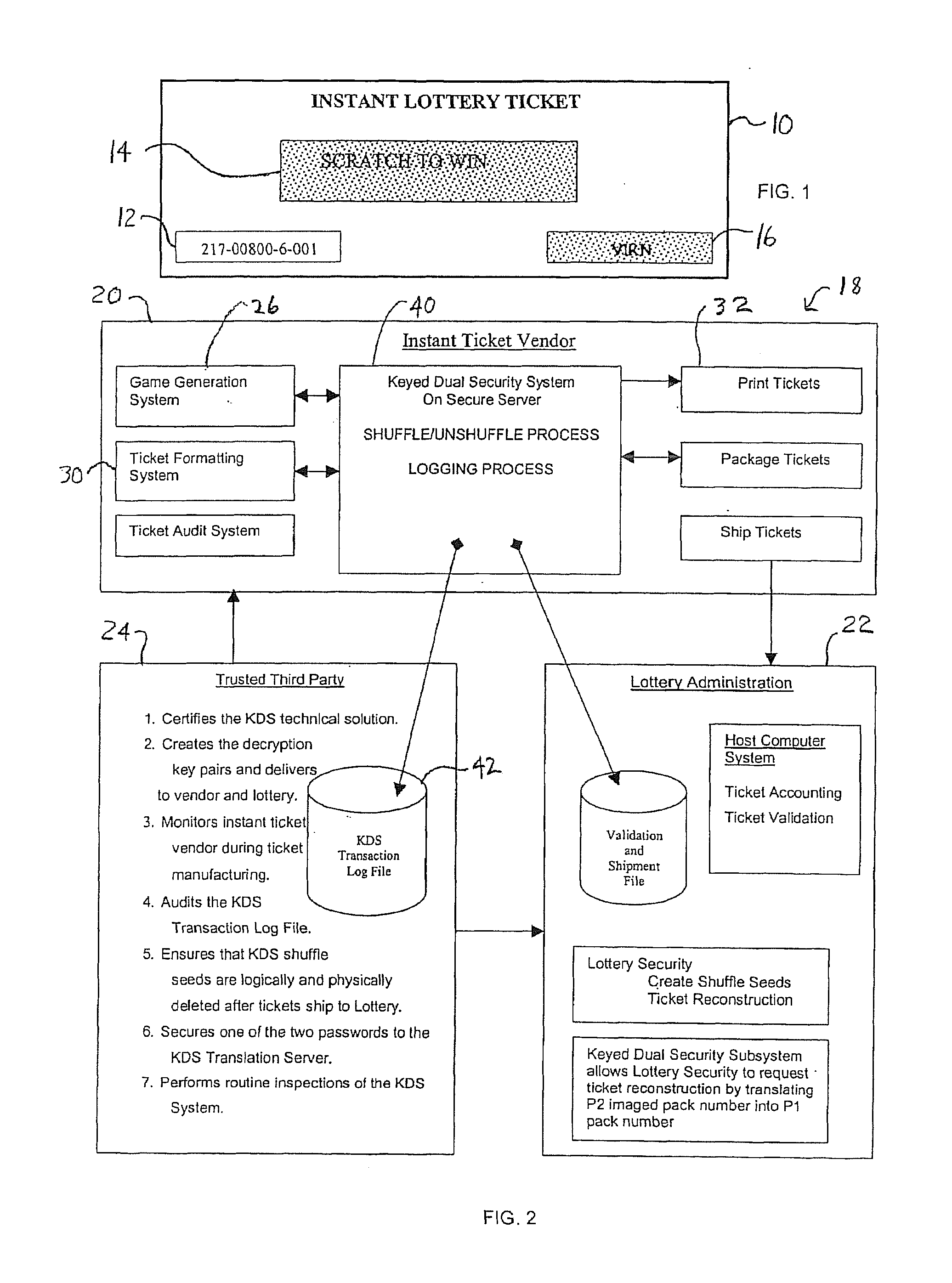
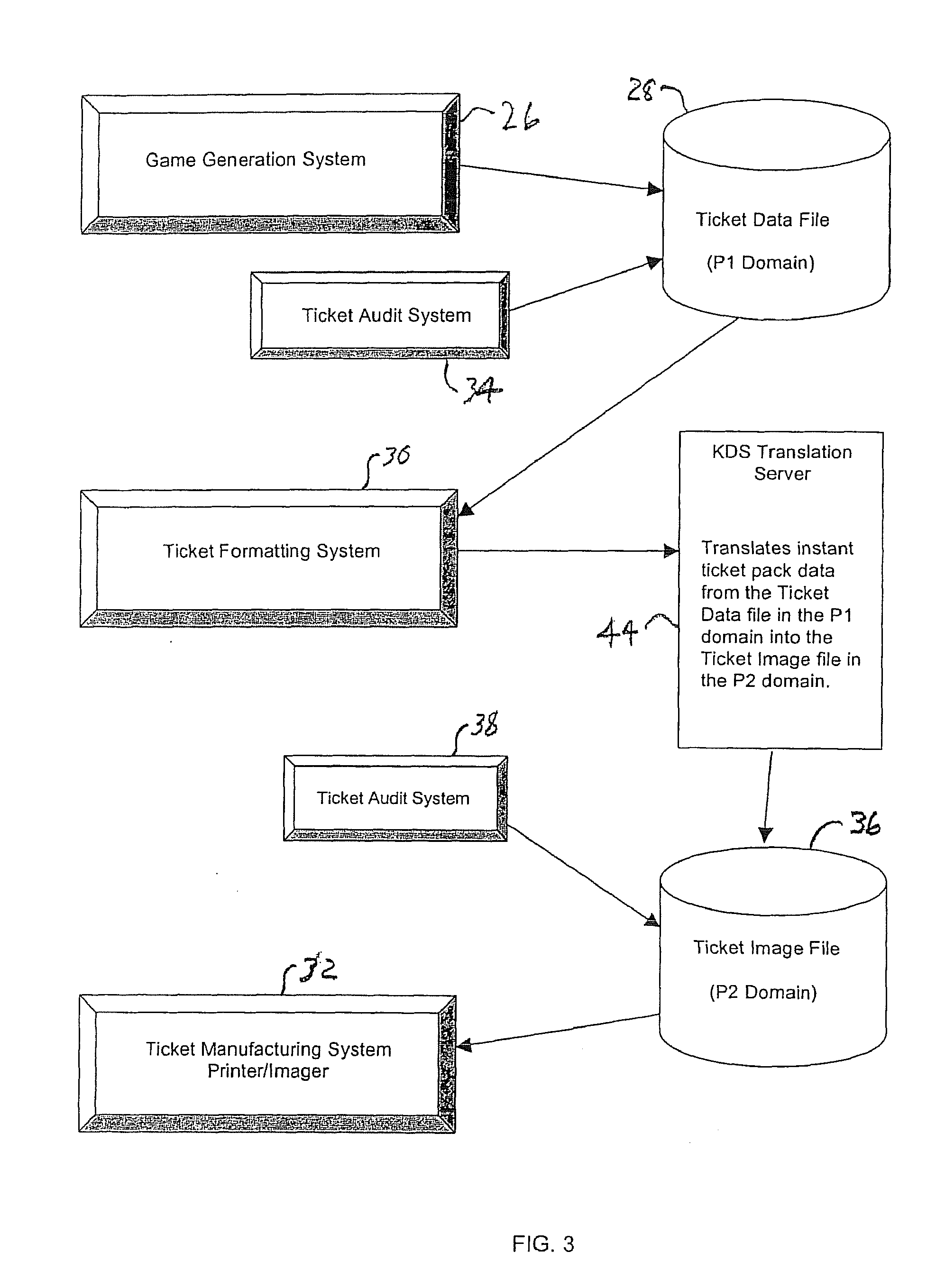
Lottery Ticket Security Method
ActiveUS20080287176A1Process safetyProvide capabilityLottery apparatusVideo gamesThird partyValidation rule
Owner:SCI GAMES LLC
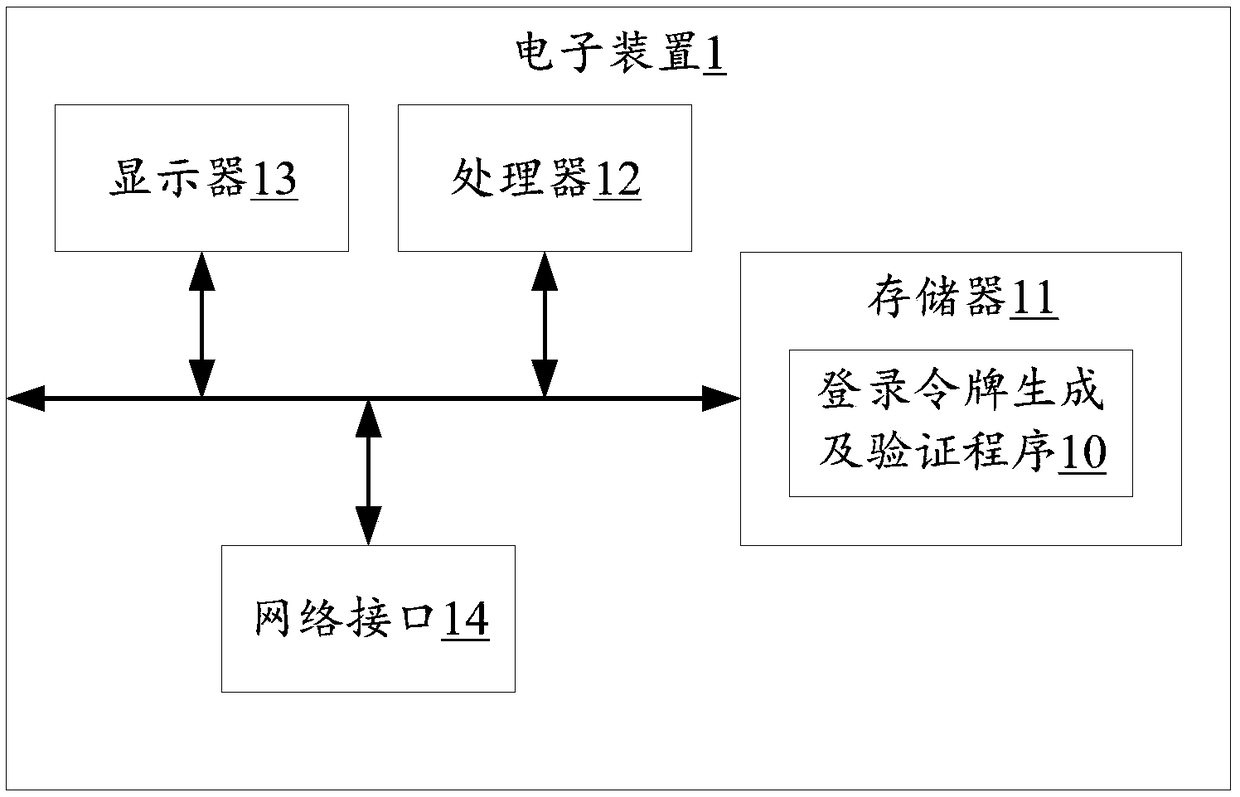
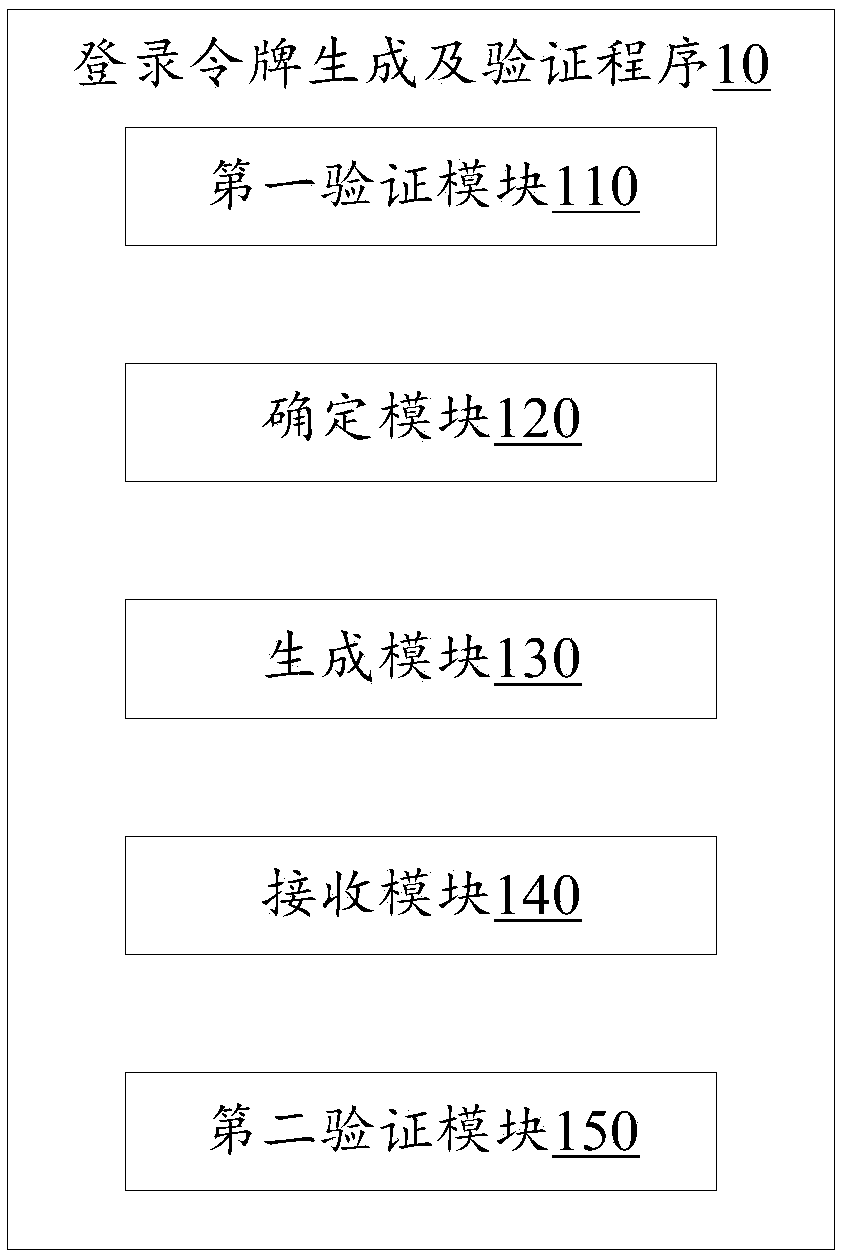
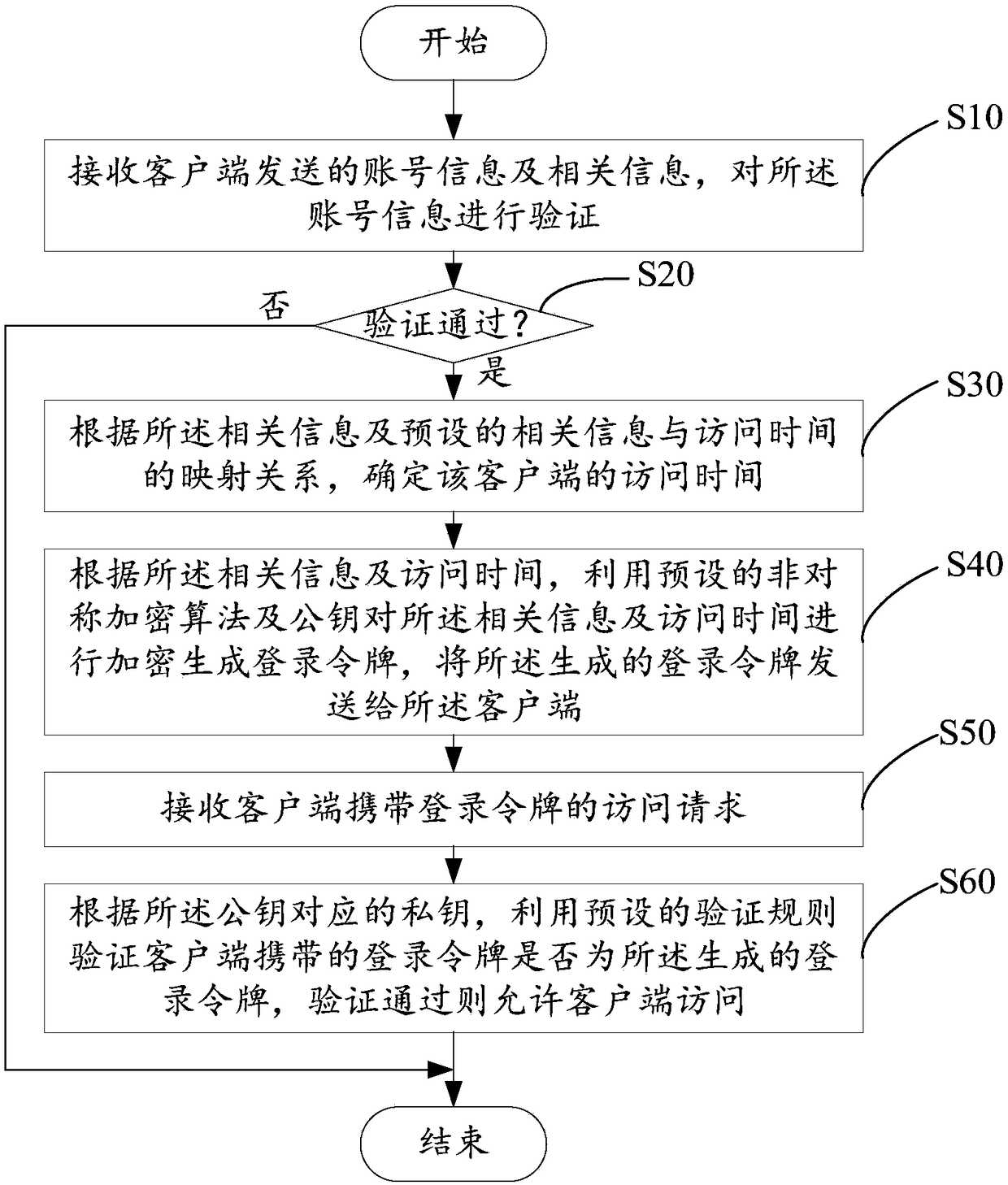
Login token generation and authentication method, device thereof, and storage medium
InactiveCN109150910AImprove interaction securityAvoid harmUser identity/authority verificationAccess timeValidation methods
The present invention relates to security techniques, and discloses a login token generation and authentication method, an electronic device thereof and a storage medium. That method comprises the steps of receiving account information and related information sent by a client, verifying the account information, and when the verification is passed, determining the access time of the client according to the mapping relationship between the related information and the preset related information and the access time. Then, according to the related information and the access time, the related information and the access time are encrypted by using a public key and a preset asymmetric encryption algorithm to generate a login token, and the login token is transmitted to the client. Finally, an access request of a client carrying a login token is received, whether the login token carried by the client is the generated login token is verified by using a preset authentication rule according to a private key corresponding to the public key, and permits the client to access if the authentication is passed. By using the method, the device thereof and the storage medium, the safety of informationexchange in the interaction process between the client and the server can be improved, and the hidden danger of safety can be reduced.
Owner:PING AN TECH (SHENZHEN) CO LTD
System and method for synchronizing comparison of data consistency
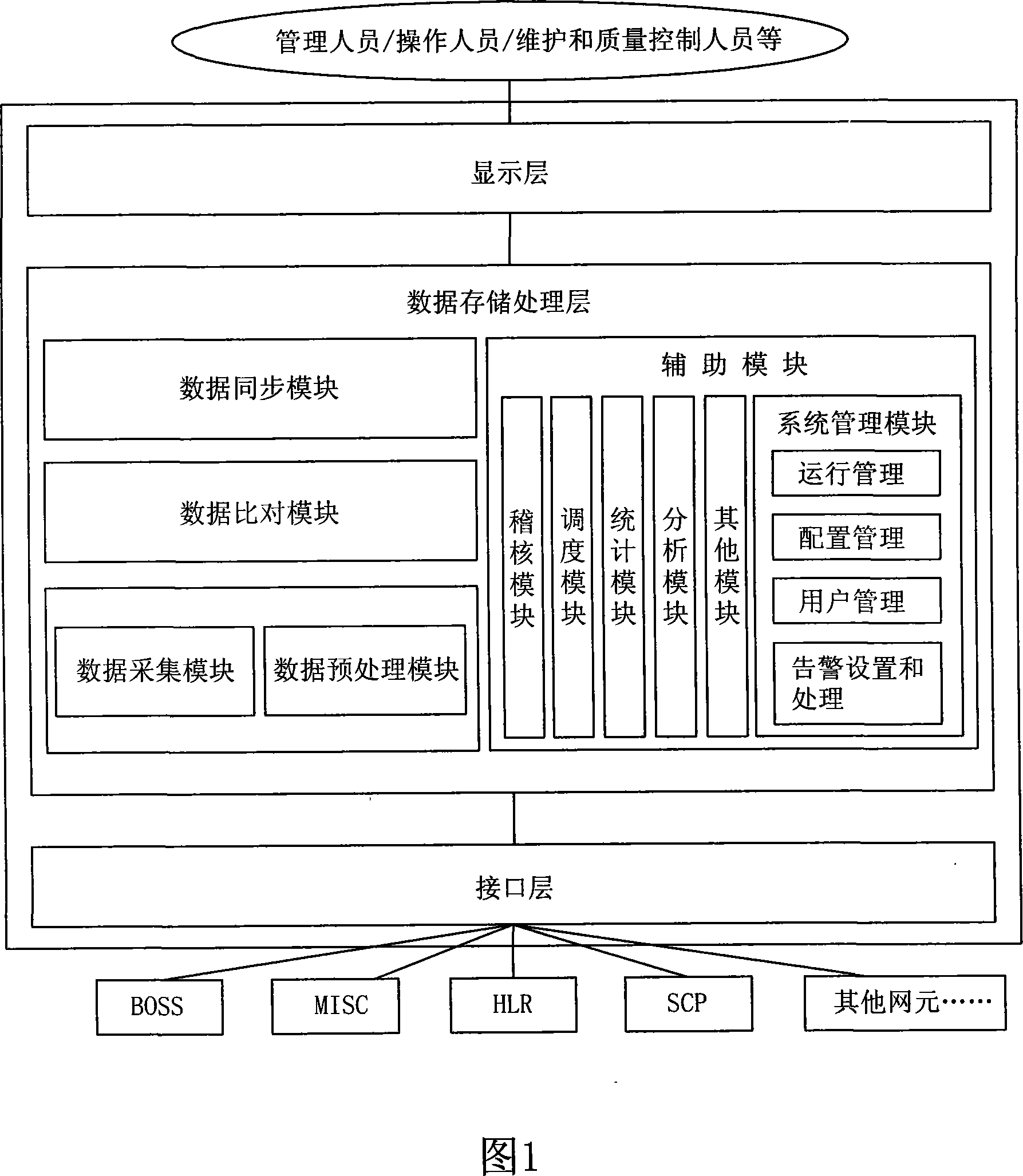
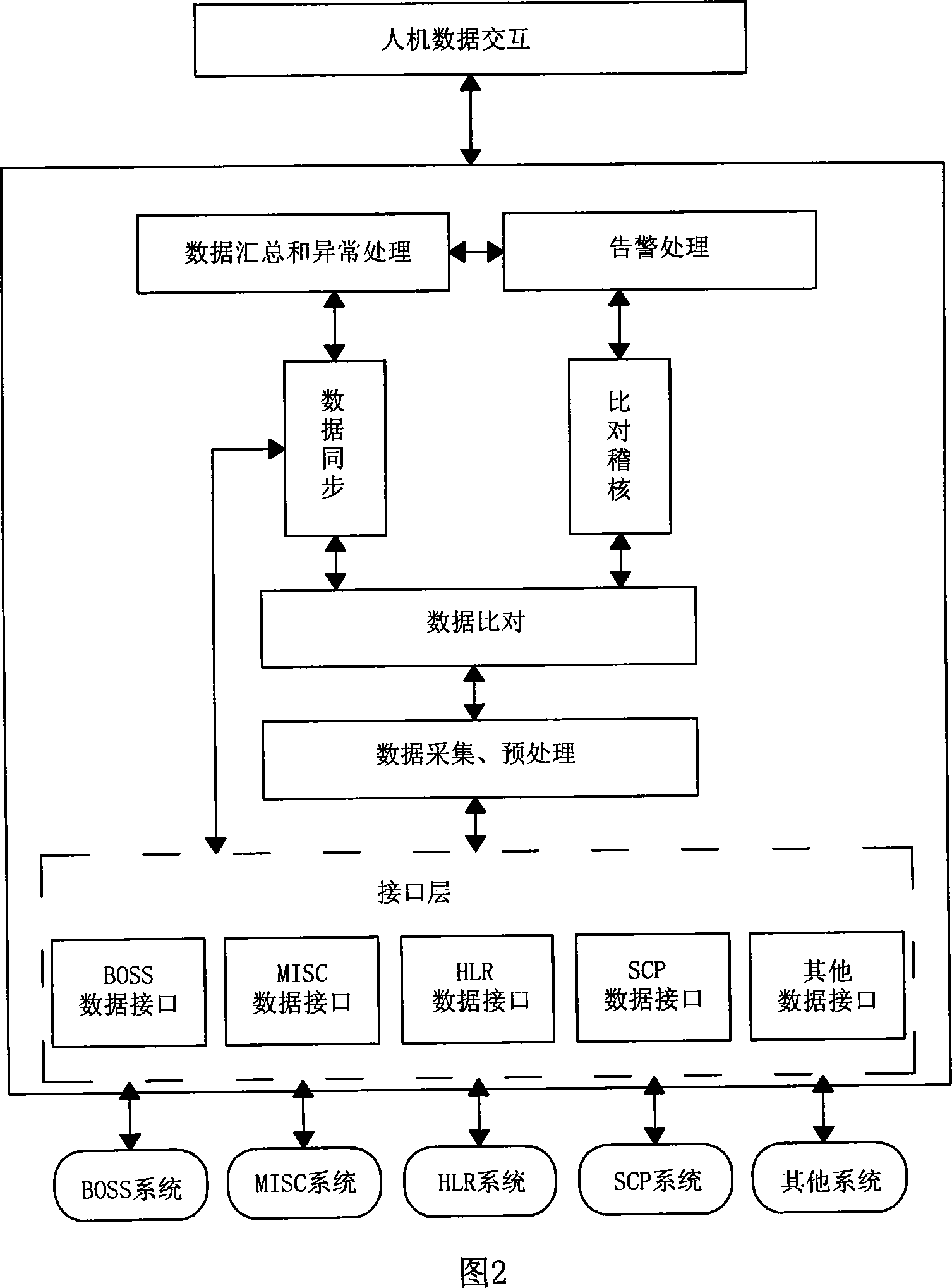
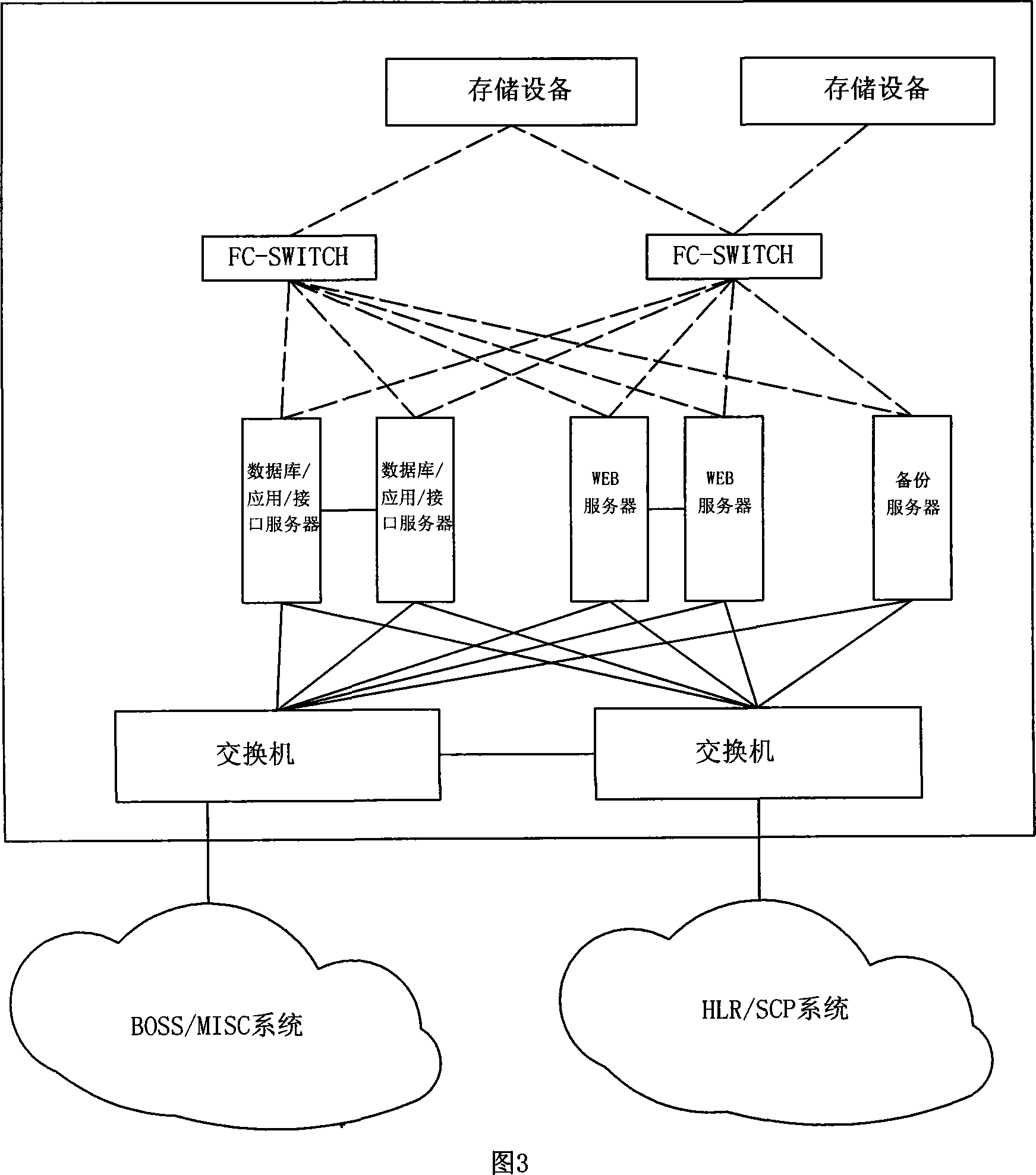
ActiveCN101094051AAvoid complaintsImprove effectivenessSynchronisation signal speed/phase controlData switching networksData synchronizationDifference list
It includes display layer, data storage / procession layer (SP) and system interface layer (SI). SP includes data collect module (DL), data pre-processing module (DP), data comparison module (DM), data sync, module (DS) and assistant module. Via SI, the business backup and bearing nets (BBB) realize mutual comm. between net elements (NE). From BBB, DL collects NE data requiring keeping coincident. DP / DM pre-processes and compares these data. Non-coincident data are recorded in the error list. According to availability test rule, DS verifies availability of data difference, generates corresponding synchronization data against valid data difference base on sync. rule and sends to related NE to keep coincidence of data between NEs. This invention raises data comparison synchronization level, system running efficiency and resource utilization. It ensures accuracy and coincidence of system data. It extensively is applied in multi-NE cooperation fields, such as comm., insurance and banking.
Owner:CHINA MOBILE GROUP SICHUAN
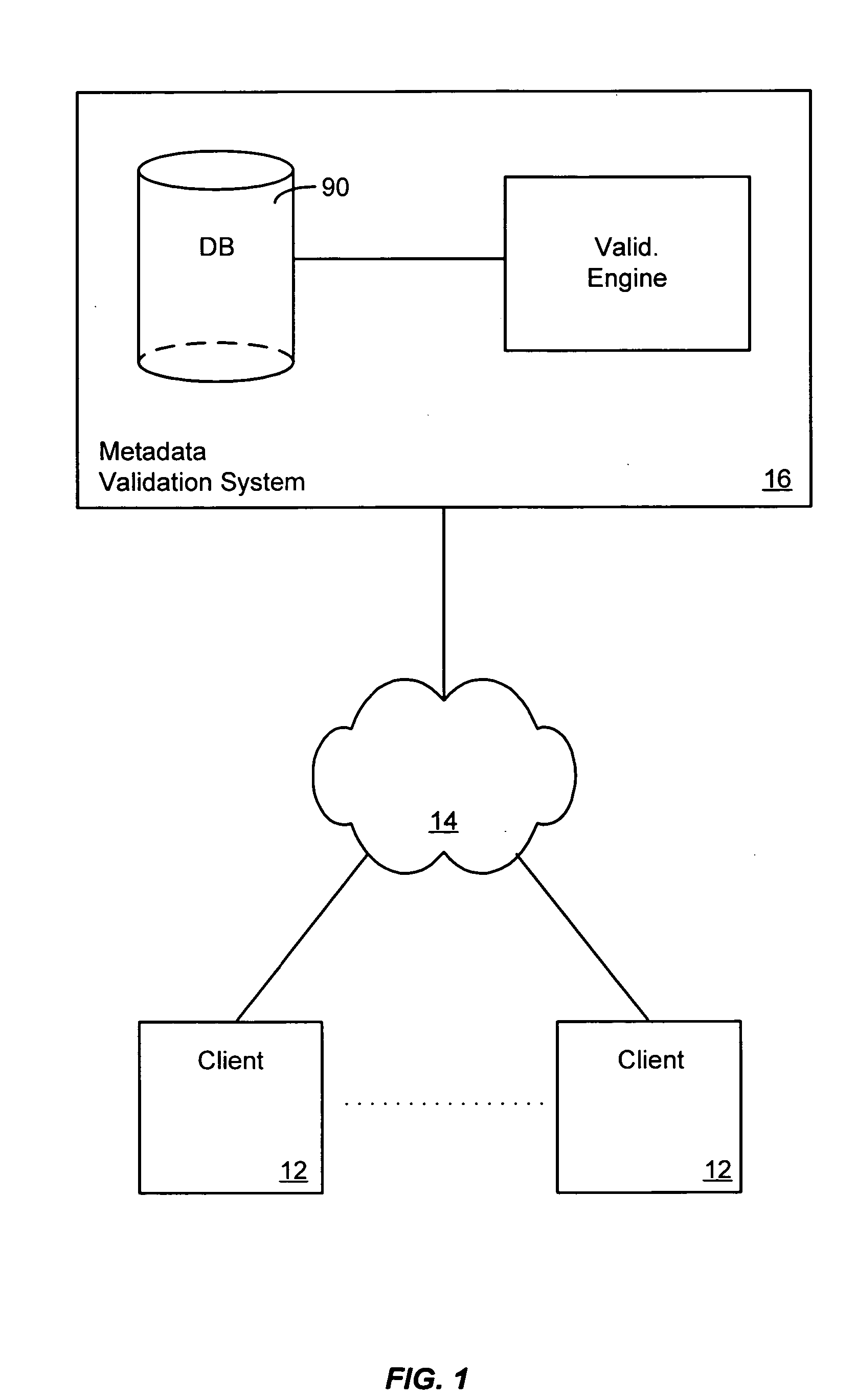
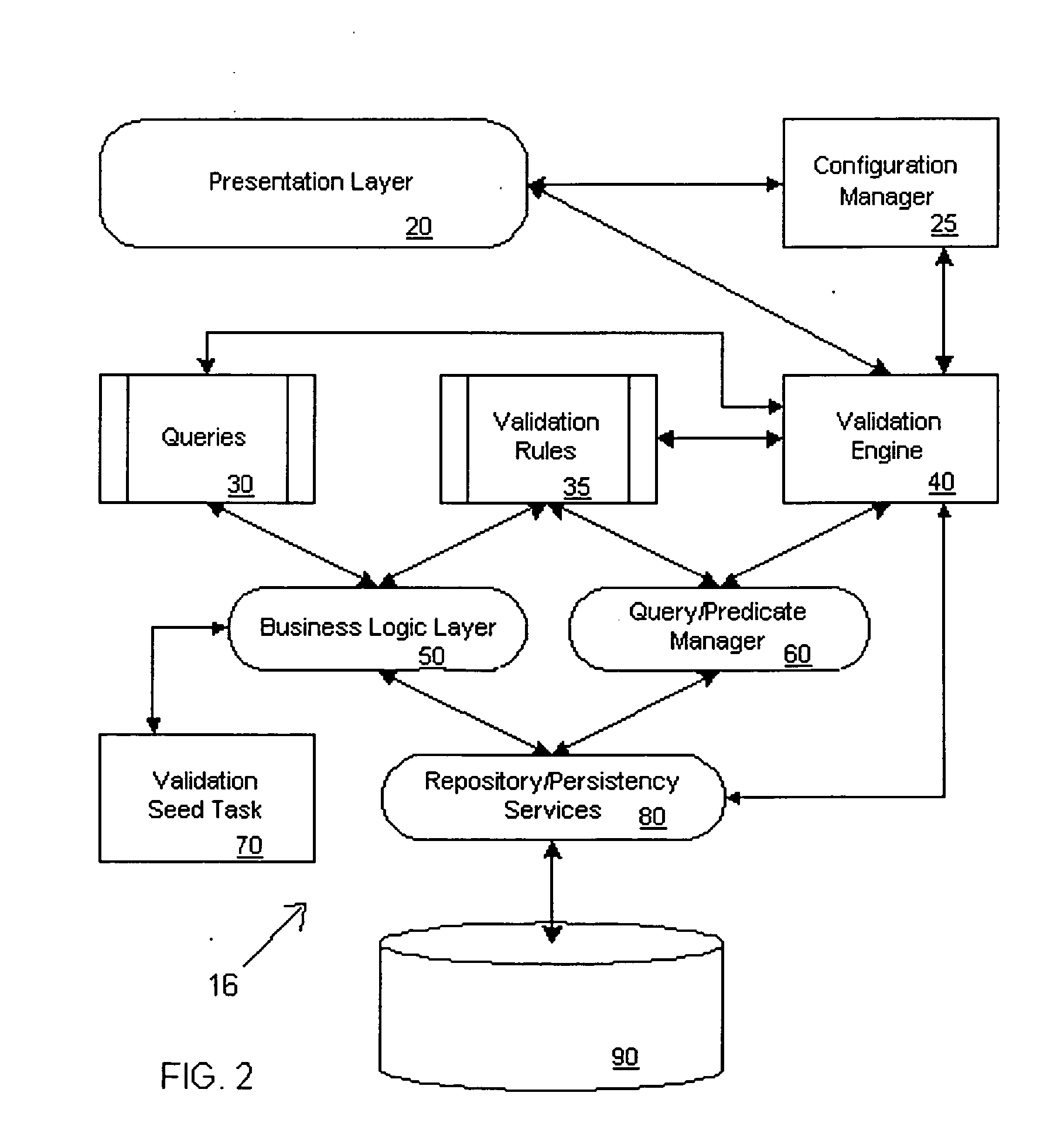
Systems and methods for validating design meta-data
ActiveUS20050125438A1Improve performanceDigital data processing detailsSpecific program execution arrangementsValidation ruleObject level
A metadata validation process that allows for deferring object model validation until after the objects are created. The process also allows for multi-threaded processing of the validation rules, thus increasing overall performance. Validation is performed by enforcing a series of validation rules on an appropriate subject. Rules are specified according to the subject that they are validating (i.e., attribute level, association level, object level or collection level). The metadata driven validation process implements several validation types on different validation units. Correctness validation rule types ensure that a validation unit satisfies all semantic rules defined for it. Completeness validation rule types ensure that a validation unit contains all the necessary data and is ready for further use. At design time, only correctness type validation is performed. Thus, the present invention advantageously allows for incomplete objects to be created at design time. The developer, however, in this case may opt to perform completeness validation at any time. In general, a developer may opt to perform completeness and / or correctness validation at any time independent of deployment processing. In another aspect, full validation (e.g., completeness and correctness) is automatically performed on the objects during the process of creating a configuration prior to deployment.
Owner:ORACLE INT CORP
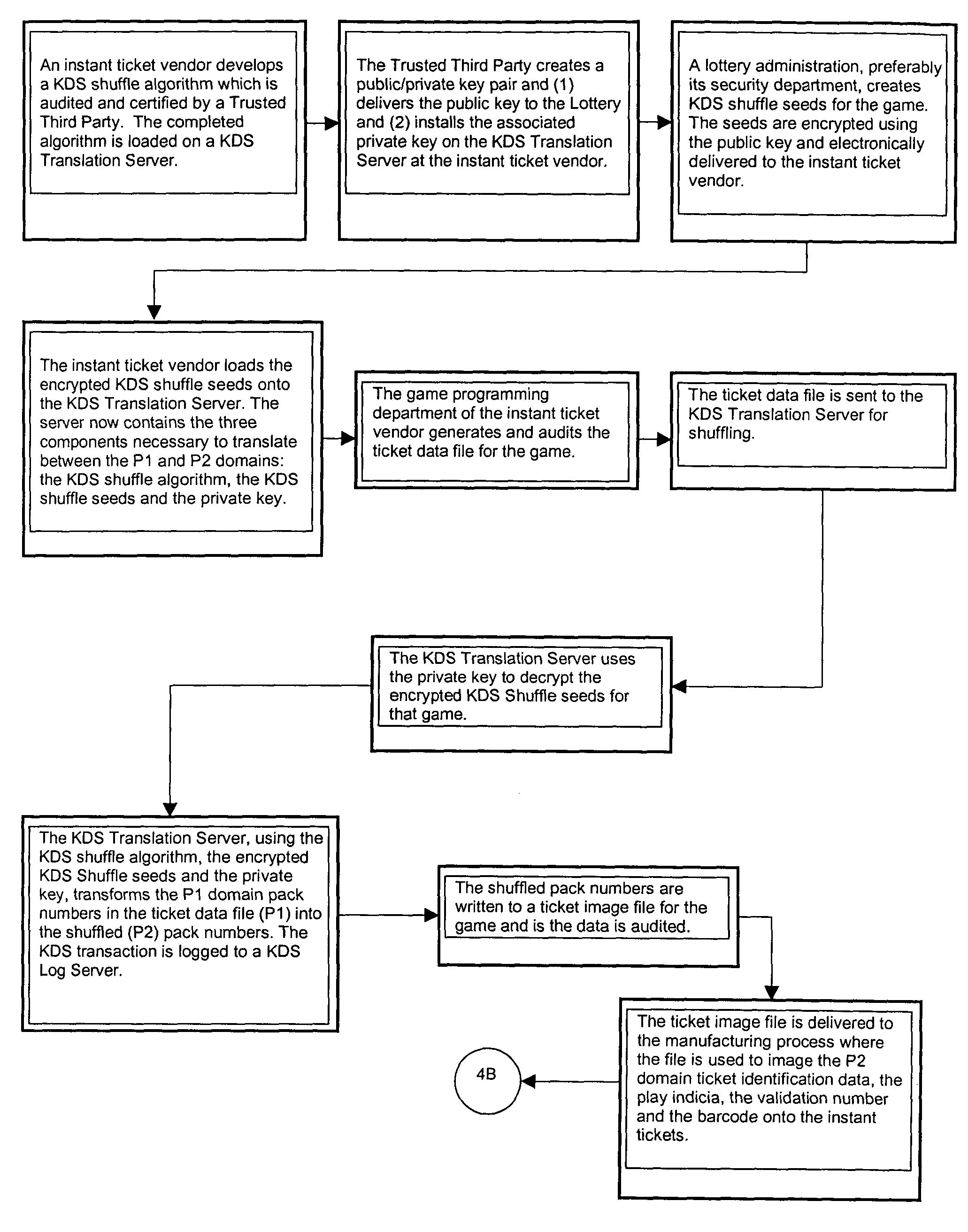
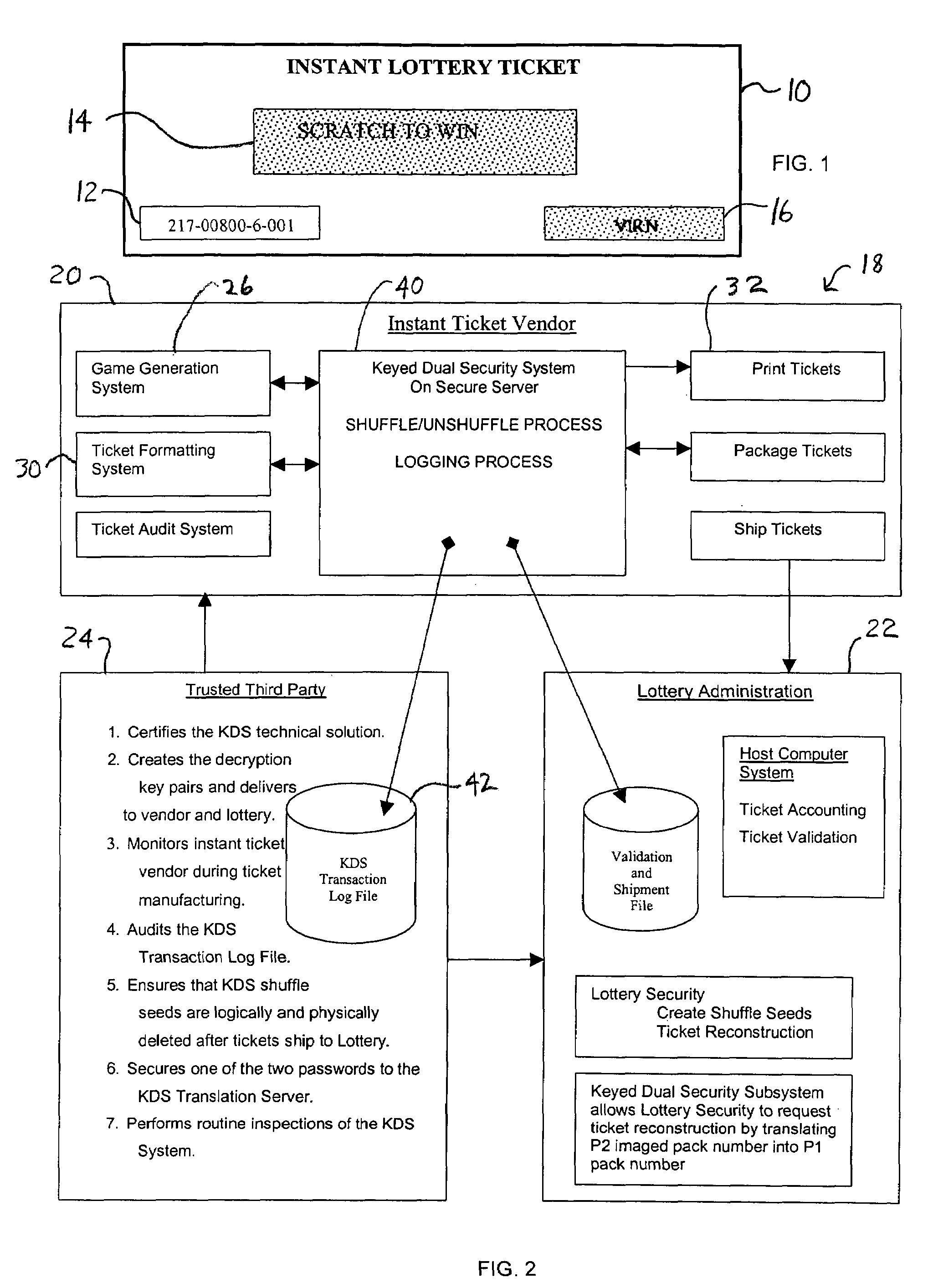
Lottery ticket security method
ActiveUS7374484B2Process safetyProvide capabilityOther printing matterLottery apparatusThird partyValidation rule
In a method for manufacturing instant lottery tickets where book numbers and ticket numbers are printed on the tickets utilizing a dual security process such that the book numbers are shuffled in each pool before the tickets are printed to break the link between the book numbers the ticket numbers or validation numbers, a reversing process can be used under certain predefined conditions to relate the original book numbers to the ticket numbers or validation numbers. In one example, where a shuffling algorithm utilizing seeds is used to shuffle the book numbers, the seeds used in the algorithm are maintained in an encrypted file. A decryption key for the encrypted seed file can be used by a lottery administration or trusted third party to reconstruct game play indicia for game adjustment purposes and manufacturing adjustments. To enhance security, the independent third party can also be used to administer the encryption and decryption keys during the ticket manufacturing process and during life of the instant ticket game.
Owner:SCI GAMES LLC
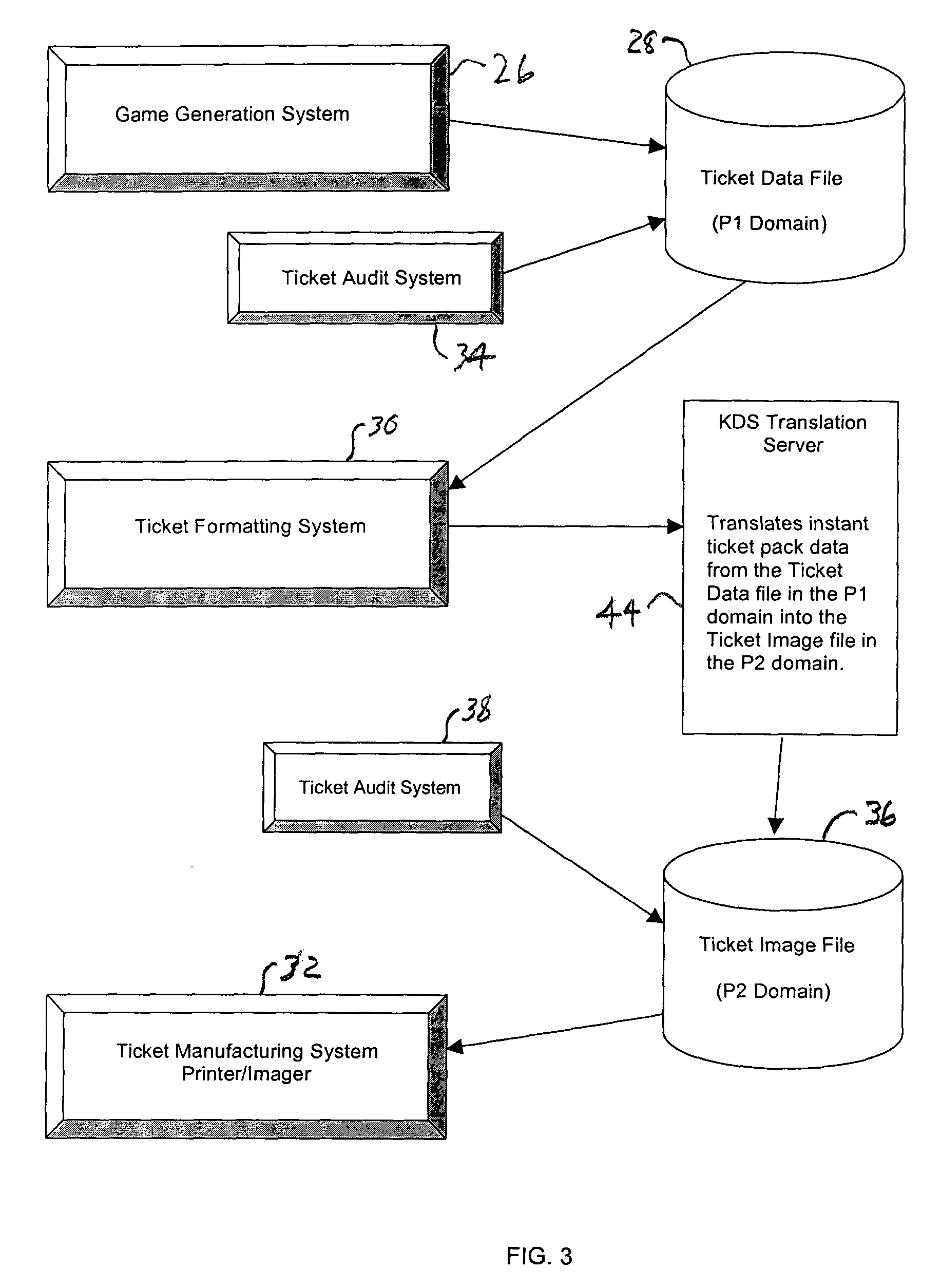
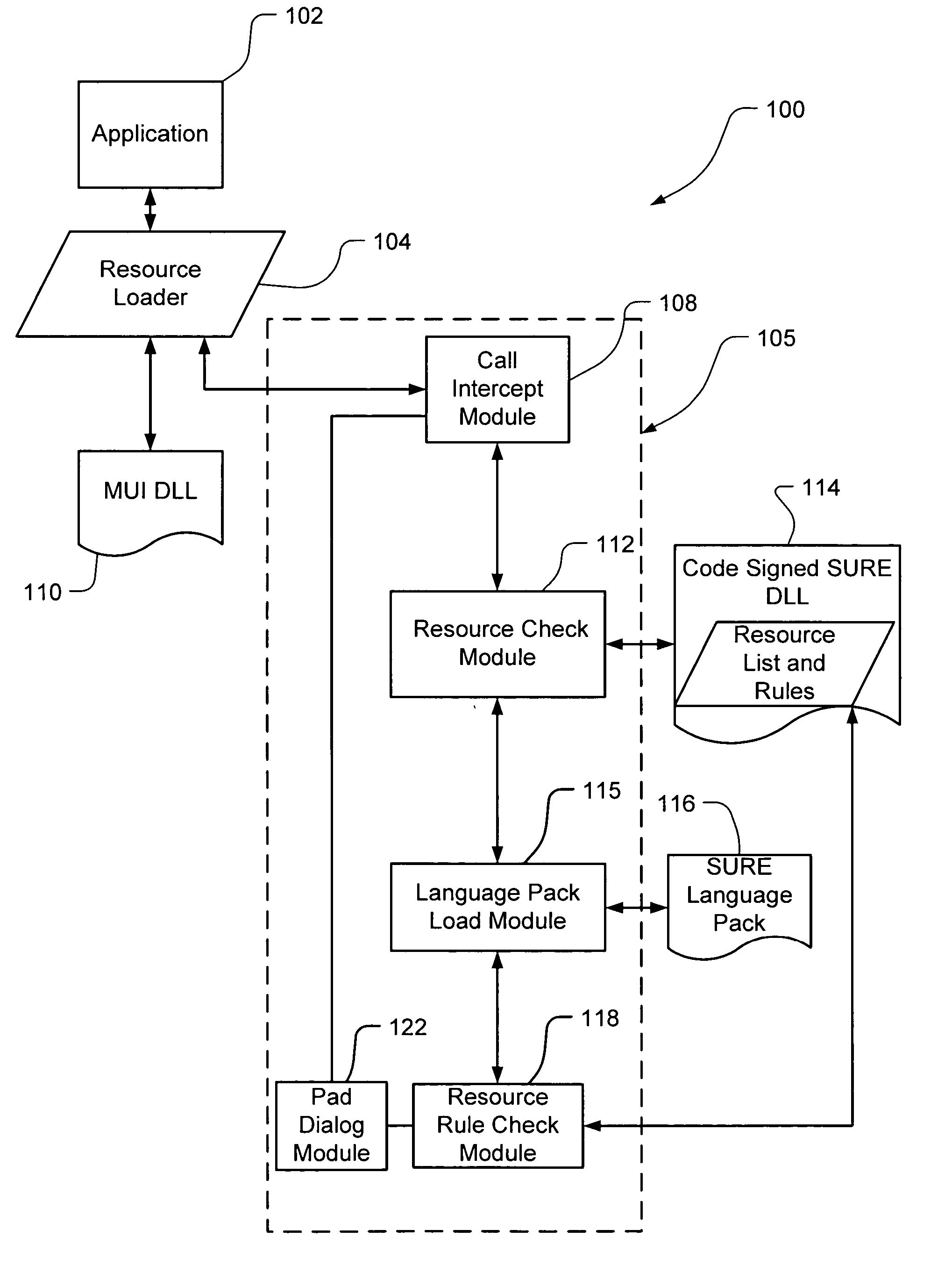
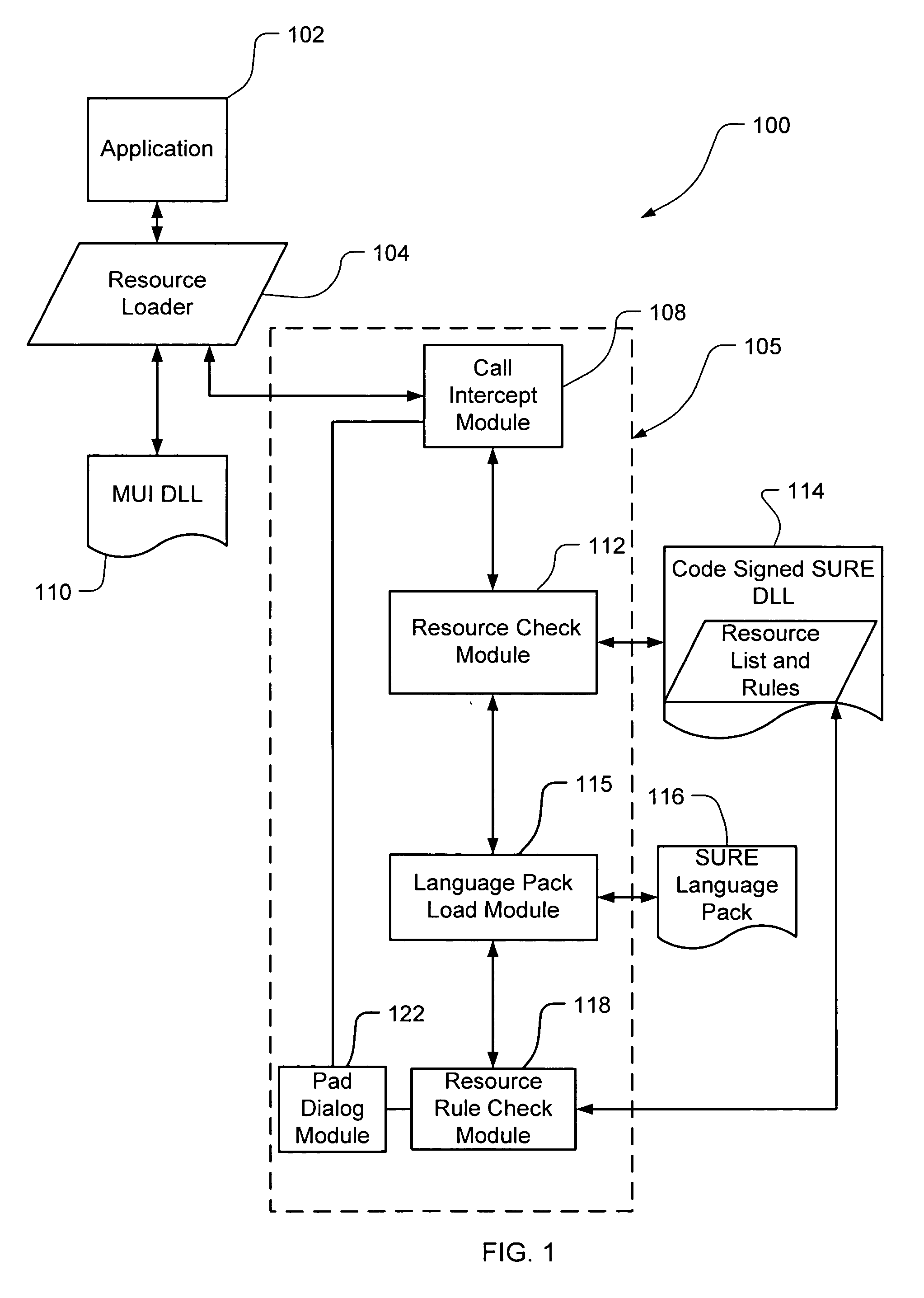
Safe, secure resource editing for application localization with automatic adjustment of application user interface for translated resources
InactiveUS20060116864A1Natural language translationSpecial data processing applicationsOperational systemValidation rule
Embodiments of the present invention relate to methods, systems and computer-readable media for external localization of a software product. This external localization involves loading a base product having one or more calls to an operating system (or an API) to load language specific data. The calls are intercepted after the resource is loaded into a Resource loader, and queried whether the resource is identified in a restricted resource list such as a code signed dynamic linked library. If so, the translated resource is loaded from a specified language package. The loaded, and translated, resource is then checked against validation rules (which are also protected in a code signed resource list) to see if it is safe to use. If the resource is not on the list or the translated resource is not safe to use, the original resource is simply transferred to the application without modification from the resource loader, i.e., loaded from the base language file. This generates a localized product using a limited set of language specific data covering most situations. The translated or localized dialogs are then resized to accommodate the translated resource through one or more of a series of functions including automatic sizing, automatic layout descriptions, pre-calculated permissible sizes, and proportional stretching of the dialog sizes.
Owner:MICROSOFT TECH LICENSING LLC
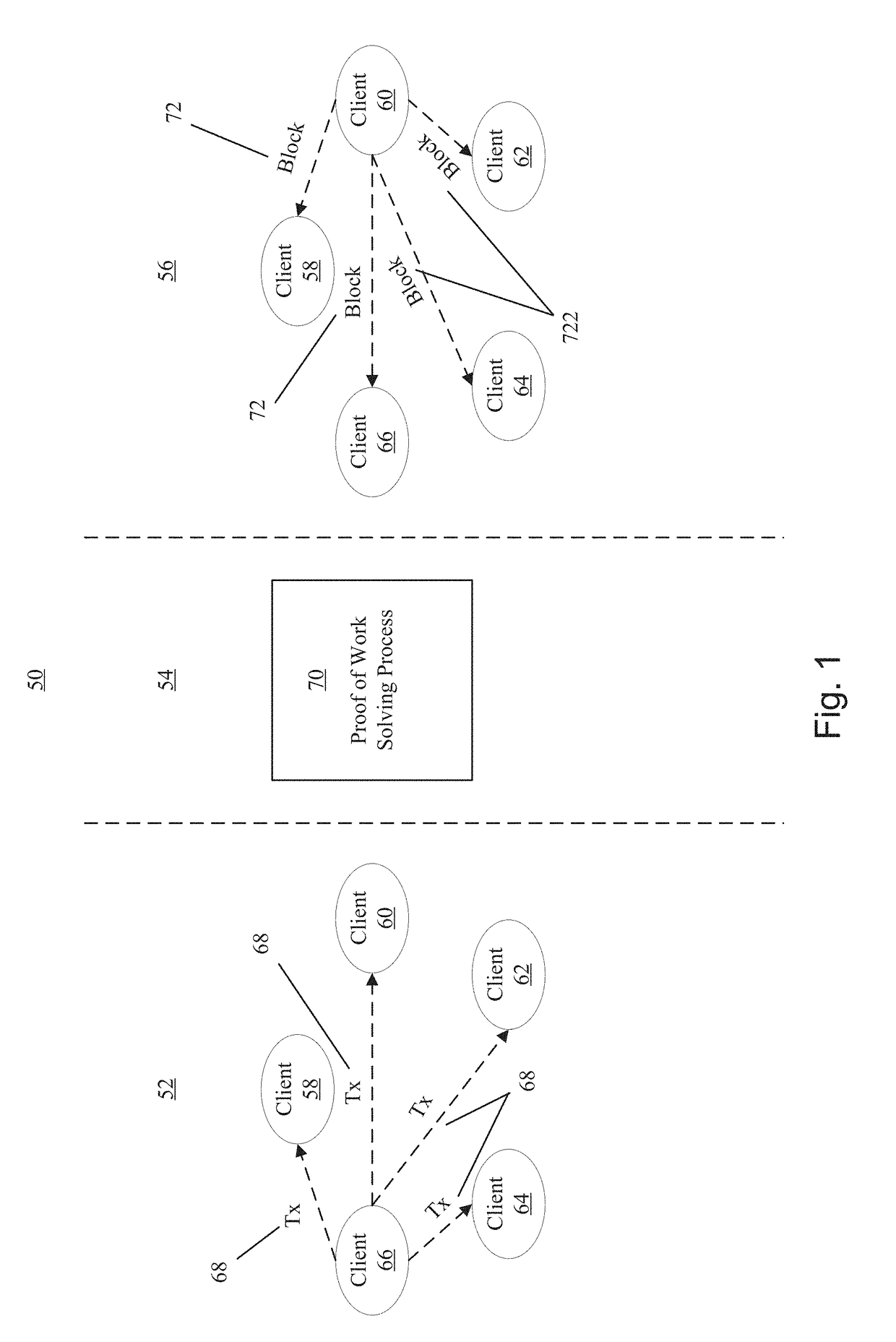
Virtual currency system
Methods performed by a validation one or a sender one of a plurality of nodes implemented by computing devices in a network. The sender node sends, to the validation node, a request to transfer an amount of virtual currency from a sender account (associated with transaction receipts) to a recipient account. The request includes first copies of the receipts or references thereto. The validation node requests second copies of the receipts from at least two of the nodes, and receives the second copies from fewer than all of the nodes. The validation node determines whether the first copies have been tampered with by comparing the first and second copies to one another. When tampering has not occurred, at least one new receipt is generated indicating the amount has been transferred. Then, the at least one new receipt is forwarded to fewer than all of the nodes for storage.
Owner:NCHAIN HLDG LTD
Program, method, and apparatus for supporting creation of business process model diagram
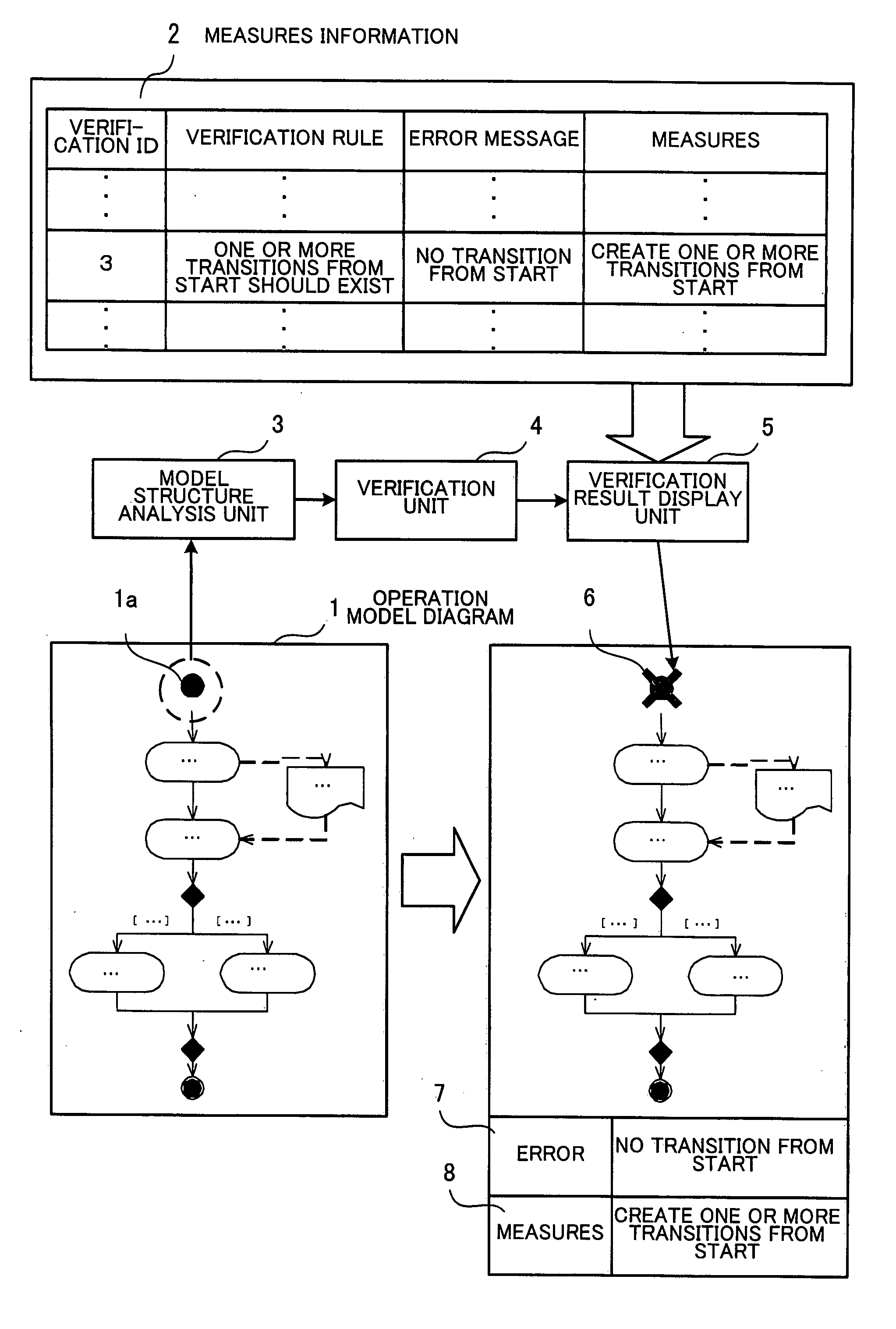
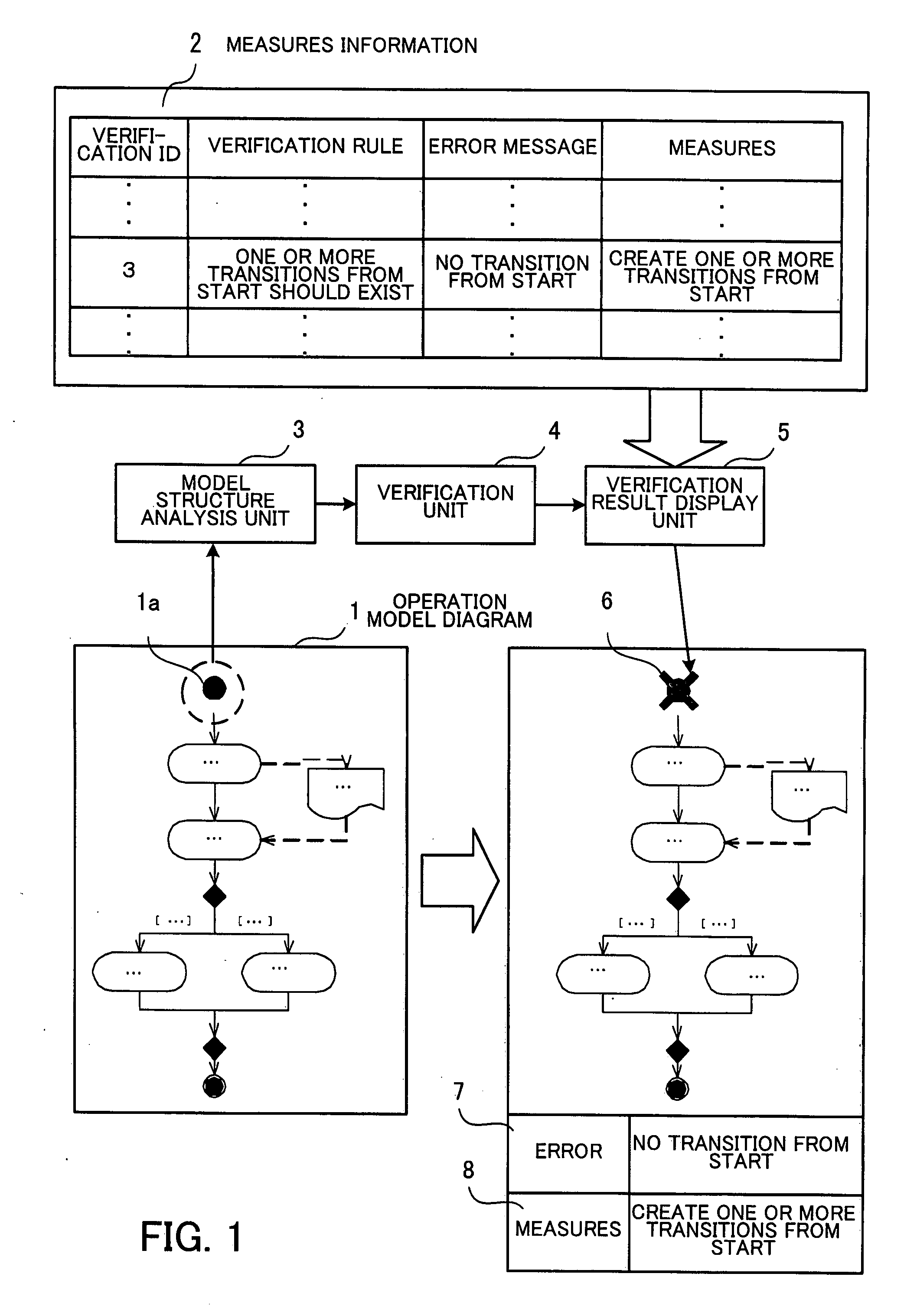
InactiveUS20070214173A1Digital data processing detailsSoftware testing/debuggingGeneral purposeStructure analysis
A program, method and apparatus for supporting creation of business process model diagram which are capable of realizing verifying a business process model created by using general-purpose drawing software and notifying an operation modeler of defective parts. A model structure analysis means analyzes a business process model diagram, determines the type of each constituent element forming the business process model diagram, and creates a model structure representing relations between the constituent elements. Then a verification means selects at least part of the constituent elements as a verification target element, extracts a verification rule relevant to the type of the selected verification target element, out of preset verification rules describing conditions that the constituent elements of the business process model diagram should satisfy, and verifies whether the selected verification target element satisfies the extracted verification rule. Then if the verification means obtains a dissatisfaction result, a verification result display means displays a position to be operated to resolve the dissatisfaction of the verification target element with the verification rule.
Owner:FUJITSU LTD
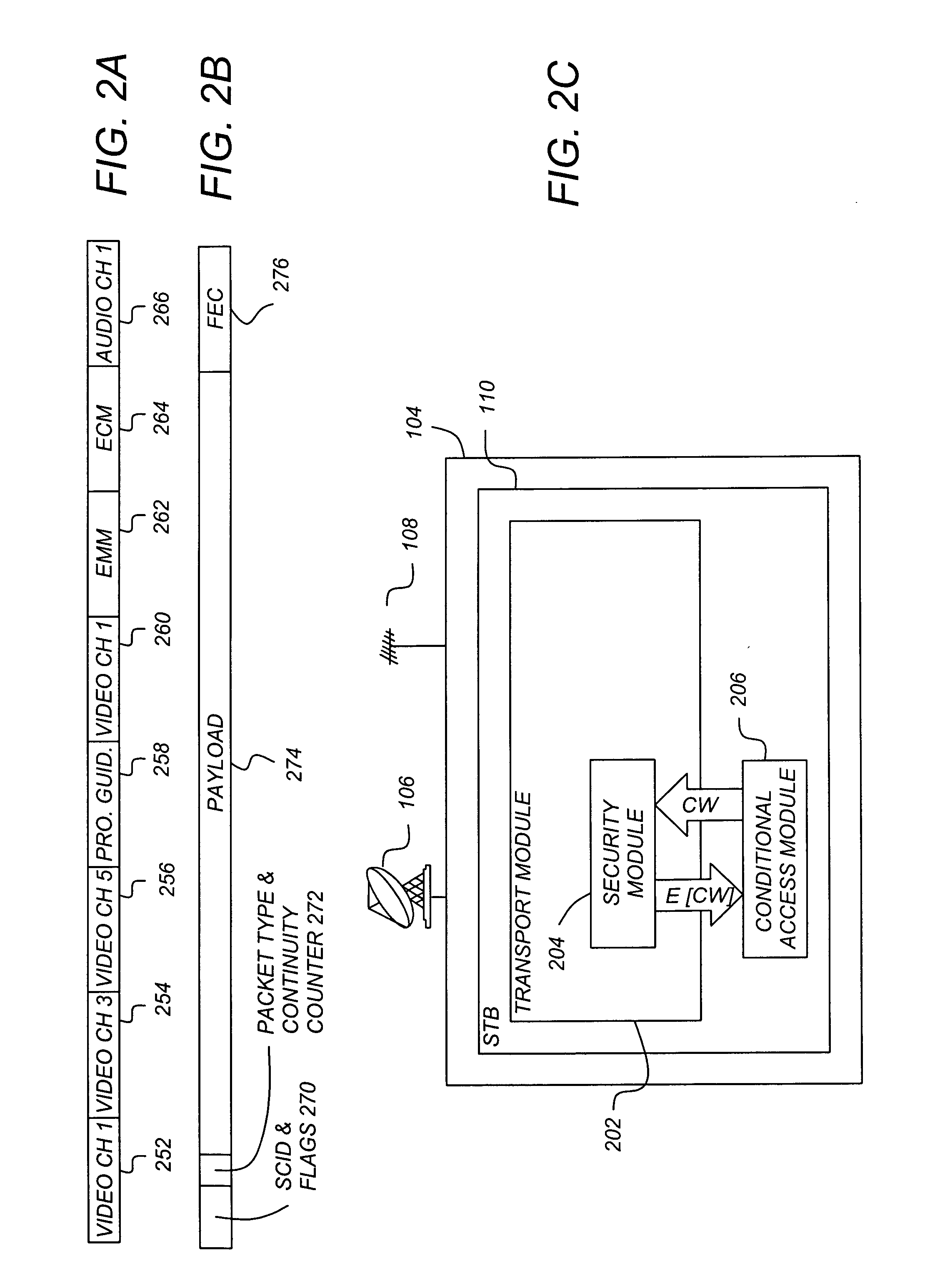
Conditional access enhancements using an always-on satellite backchannel link
InactiveUS20080008321A1Improve securityReduce operating costsSecret communicationTelevision systemsComputer hardwareConditional access
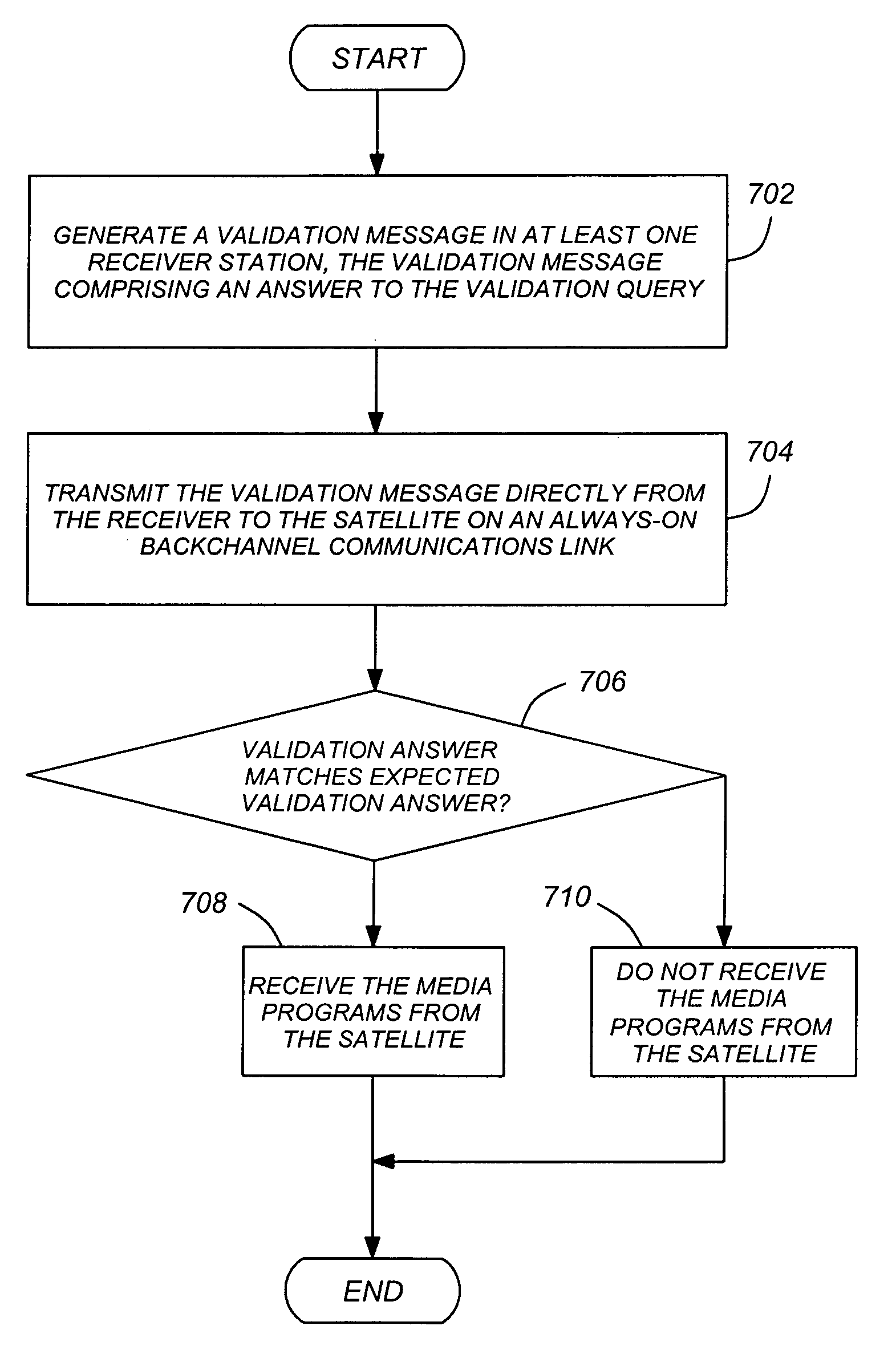
A method and apparatus for providing conditional access to media programs is disclosed. An embodiment of the method comprises the steps of generating a validation message in at least one of the receiver stations, the validation message comprising an answer to a validation query; transmitting the validation message directly from the receiver to the satellite on an always-on backchannel communications link; and receiving the media programs from the satellite only if the validation message matches an expected validation message.
Owner:SYPHERMEDIA INT
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com