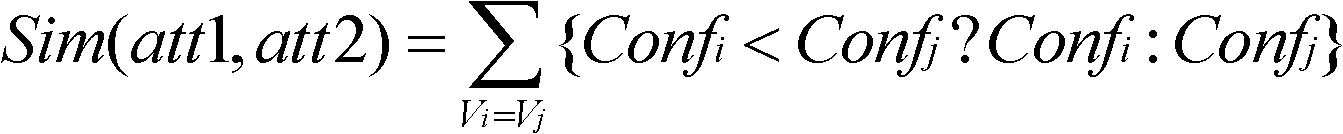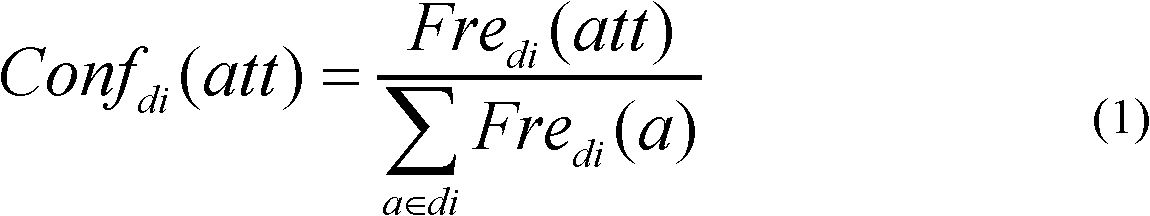Patents
Literature
123 results about "Attribute level" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Levels Attributes. Description. levels provides access to the levels attribute of a variable. The first form returns the value of the levels of its argument and the second sets the attribute.
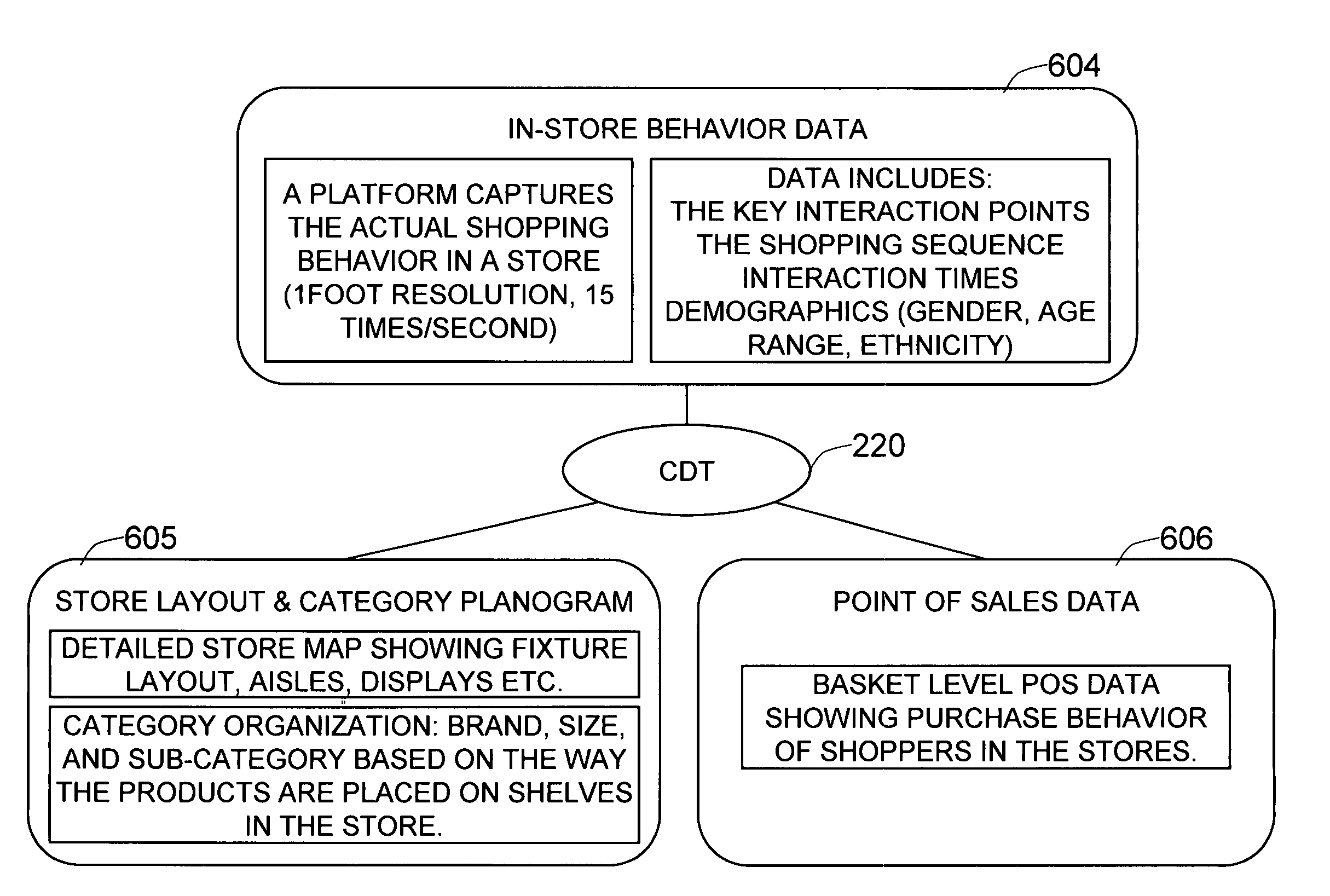
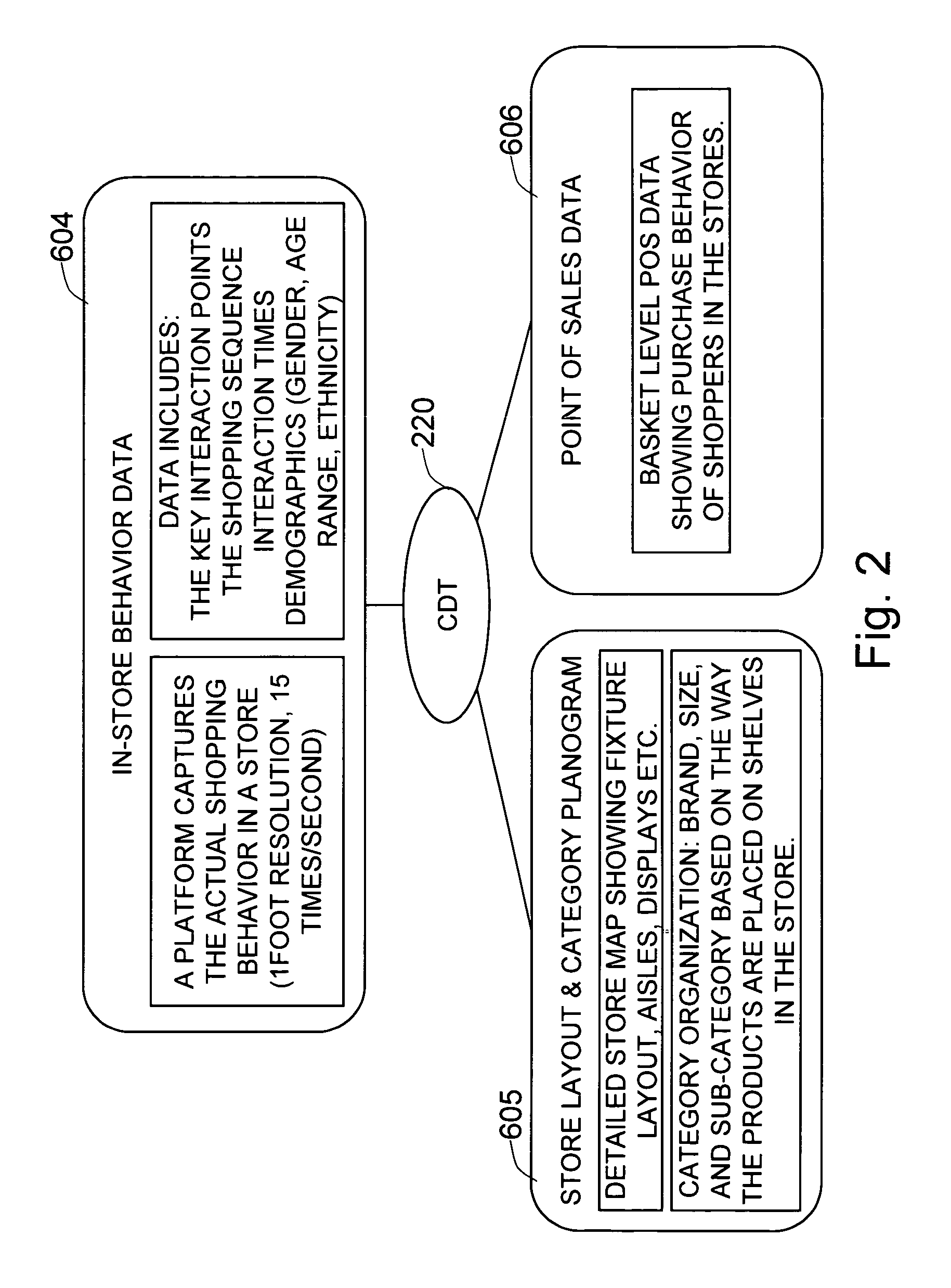
Method and system for building a consumer decision tree in a hierarchical decision tree structure based on in-store behavior analysis
ActiveUS8412656B1Limited understandingDetermining the relative importance of each product groupDigital computer detailsDigital dataBehavioral analyticsTransaction data
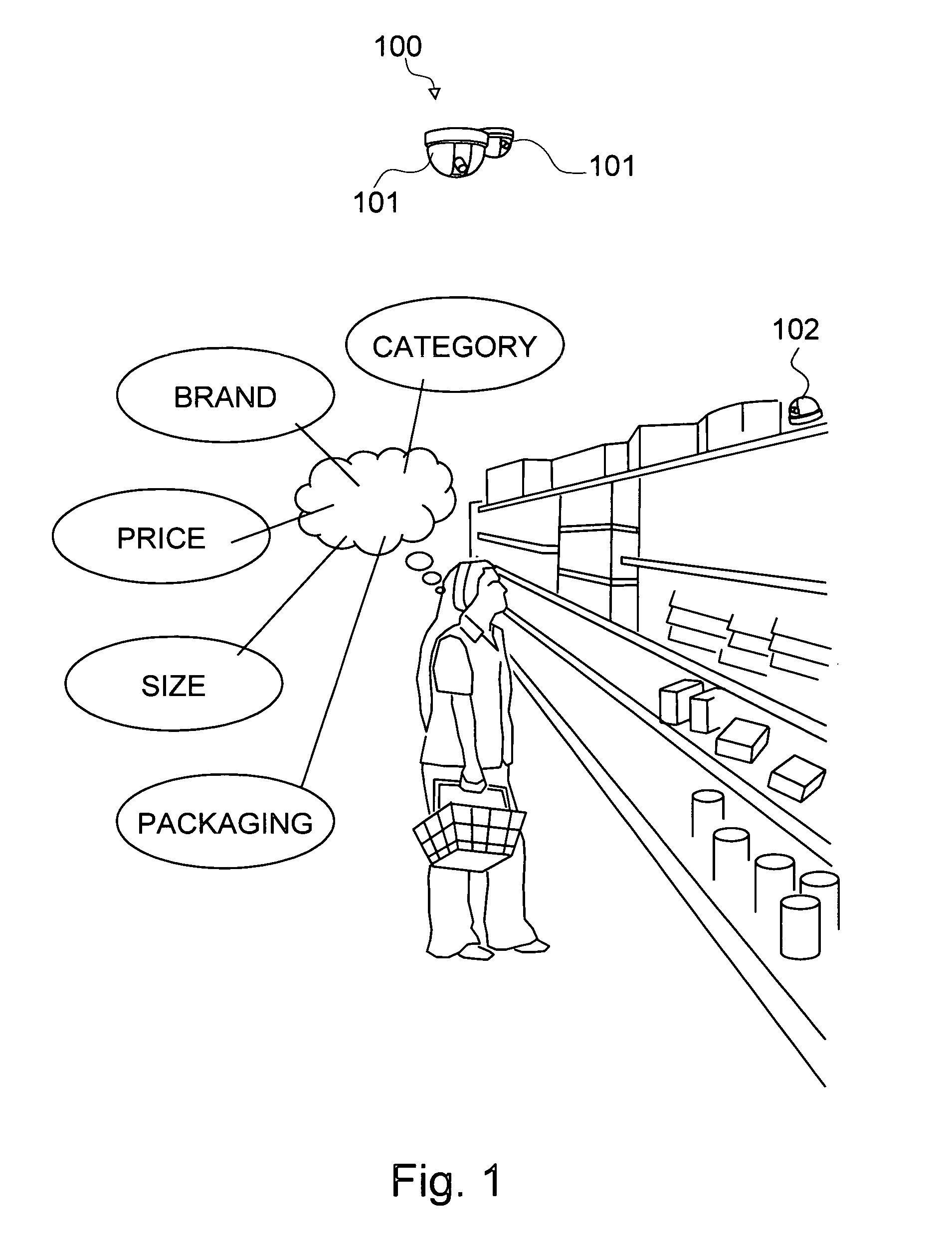
The present invention is a system and method for determining the hierarchical purchase decision process of consumers in front of a product category. The decision path of consumers is obtained by combining behavior data with the category layout and transaction data based on observed actual in-store purchase behavior using a set of video cameras and software for extracting sequence and timing of each consumer's decision process. A hierarchical decision tree structure comprises nodes and edges, wherein a node represents the state-of-mind of the consumer, the number of nodes is predefined, and an edge represents the transition of the decision. The decisions for each product group are captured down to the product attribute level and analyzed by demographic group. The outcome provides relative importance of each product attribute in the purchase decision process, and helps retailers and manufacturers to evaluate the layout of the category and customize it for key segment.
Owner:VIDEOMINING CORP
Image data normalization for a monitoring system
InactiveUS7972266B2Increase valueEasy to useTelevision system detailsTelemedicinePhysiological monitoringMonitoring system
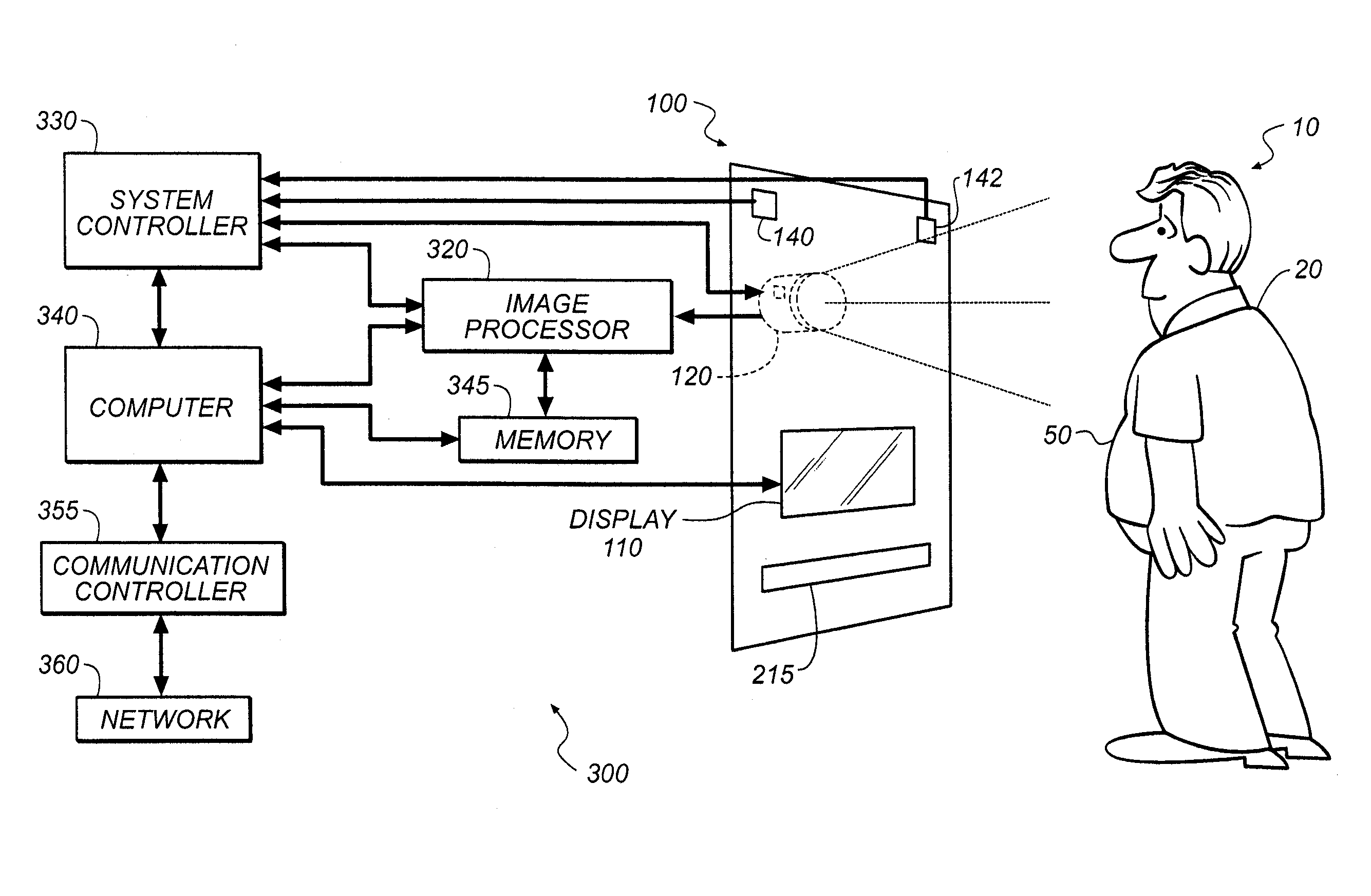
A method for providing normalized physiological monitoring data of an individual with a measure of the quality of the normalization, including providing a reference feature based on a physiological attribute of the individual for which an attribute value can be determined; unobtrusively capturing physiological monitoring data for the individual during a series of capture events and determining the capture conditions present during each capture event; detecting the presence of the reference feature in the series of captured physiological monitoring data and determining associated attribute values for each capture event; normalizing the captured physiological monitoring data from each capture event according to differences in the attribute values associated with each event and previously calculated attribute values; and calculating normalization confidence values for the individual at the series of capture events, based on capture conditions, normalization transforms, or semantic data, wherein the confidence values statistically measure the quality of the normalization.
Owner:EASTMAN KODAK CO
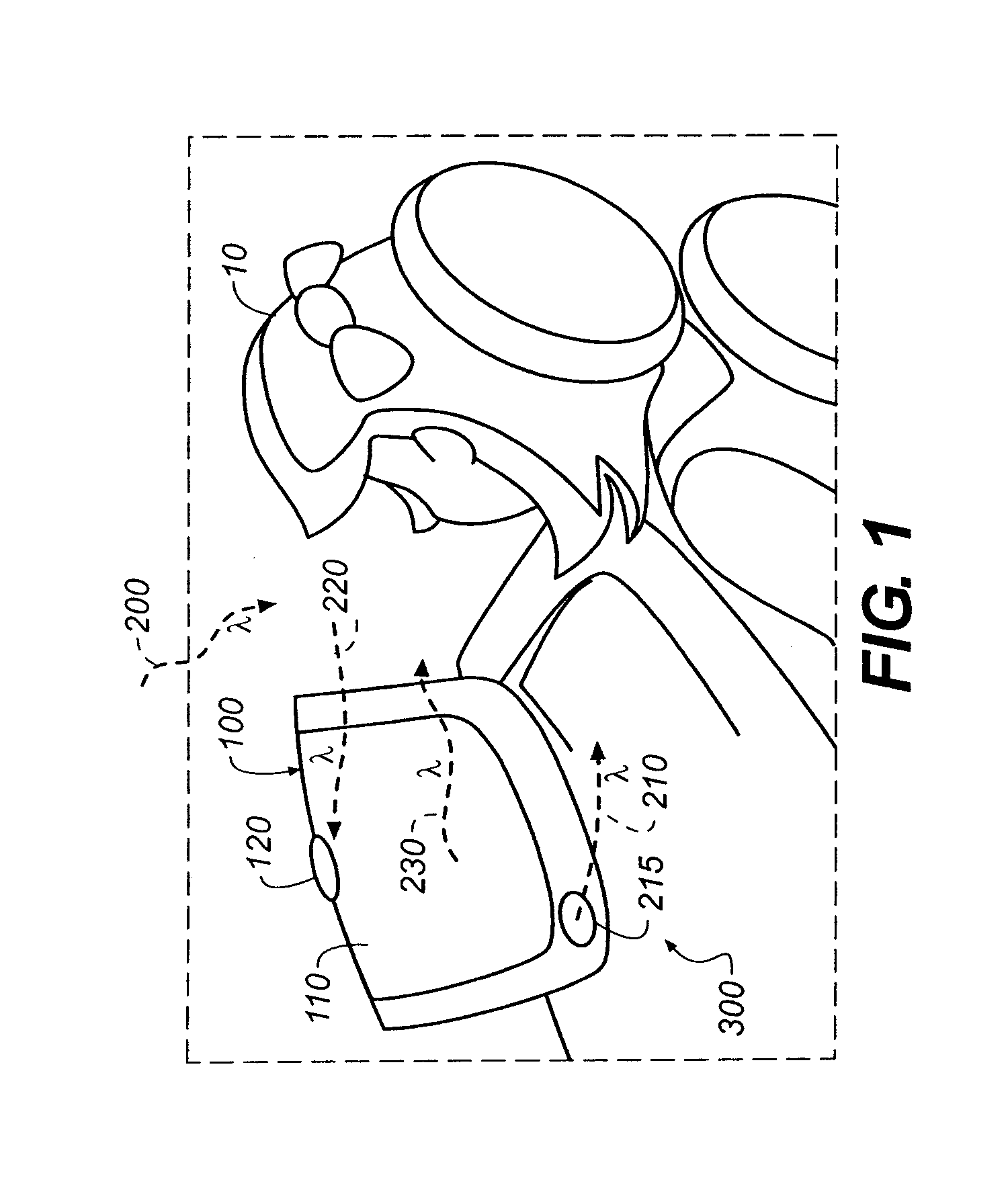
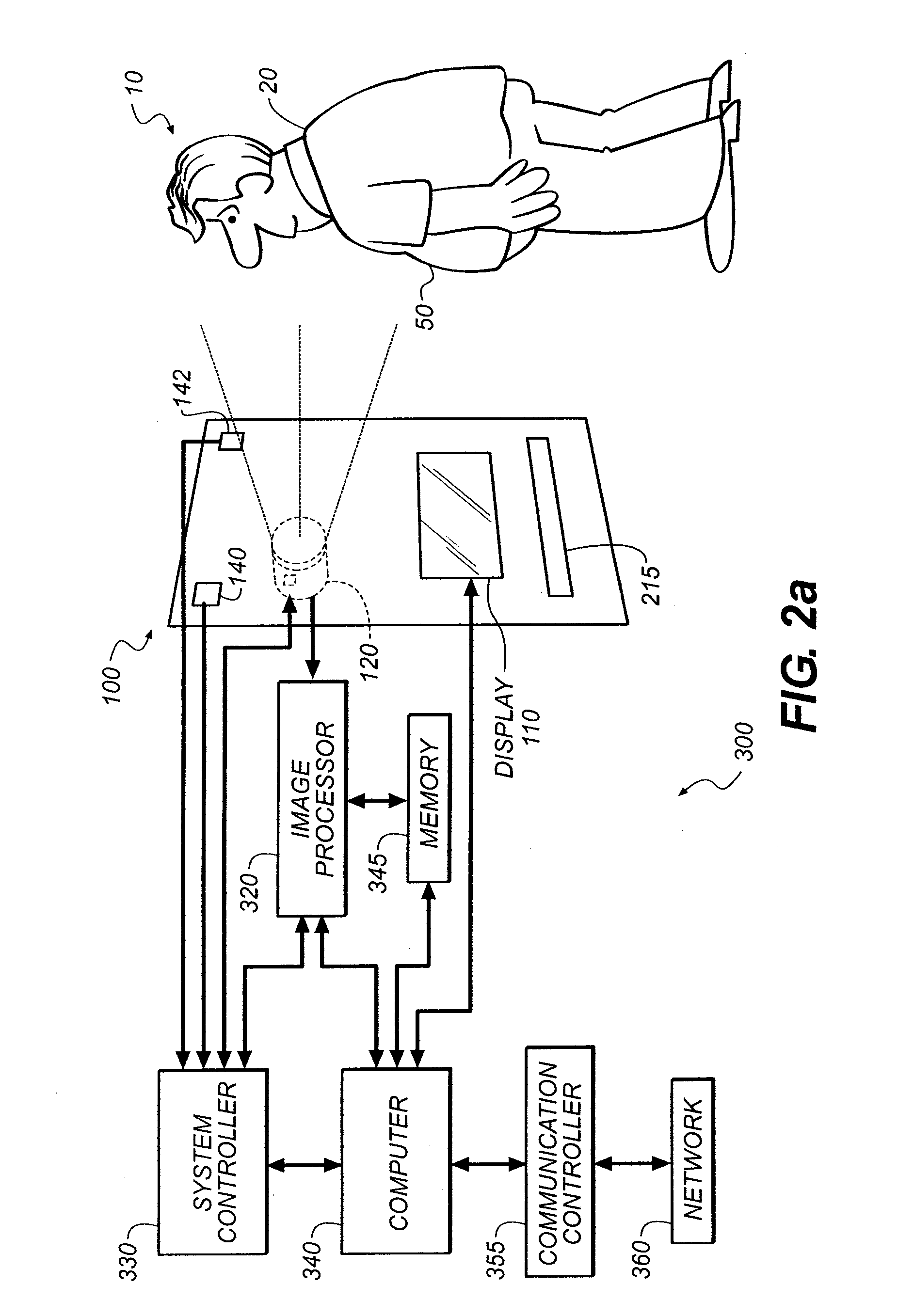
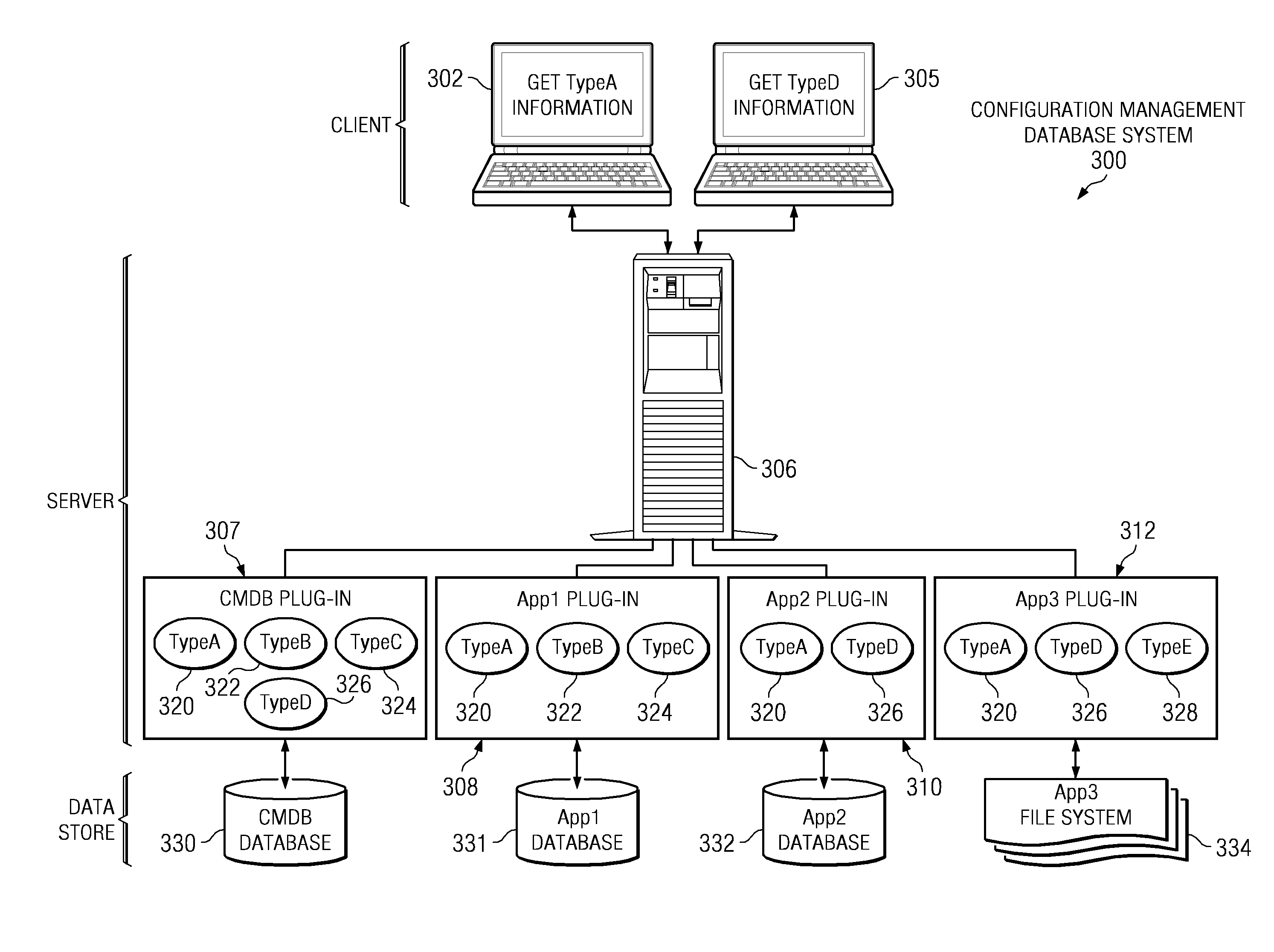
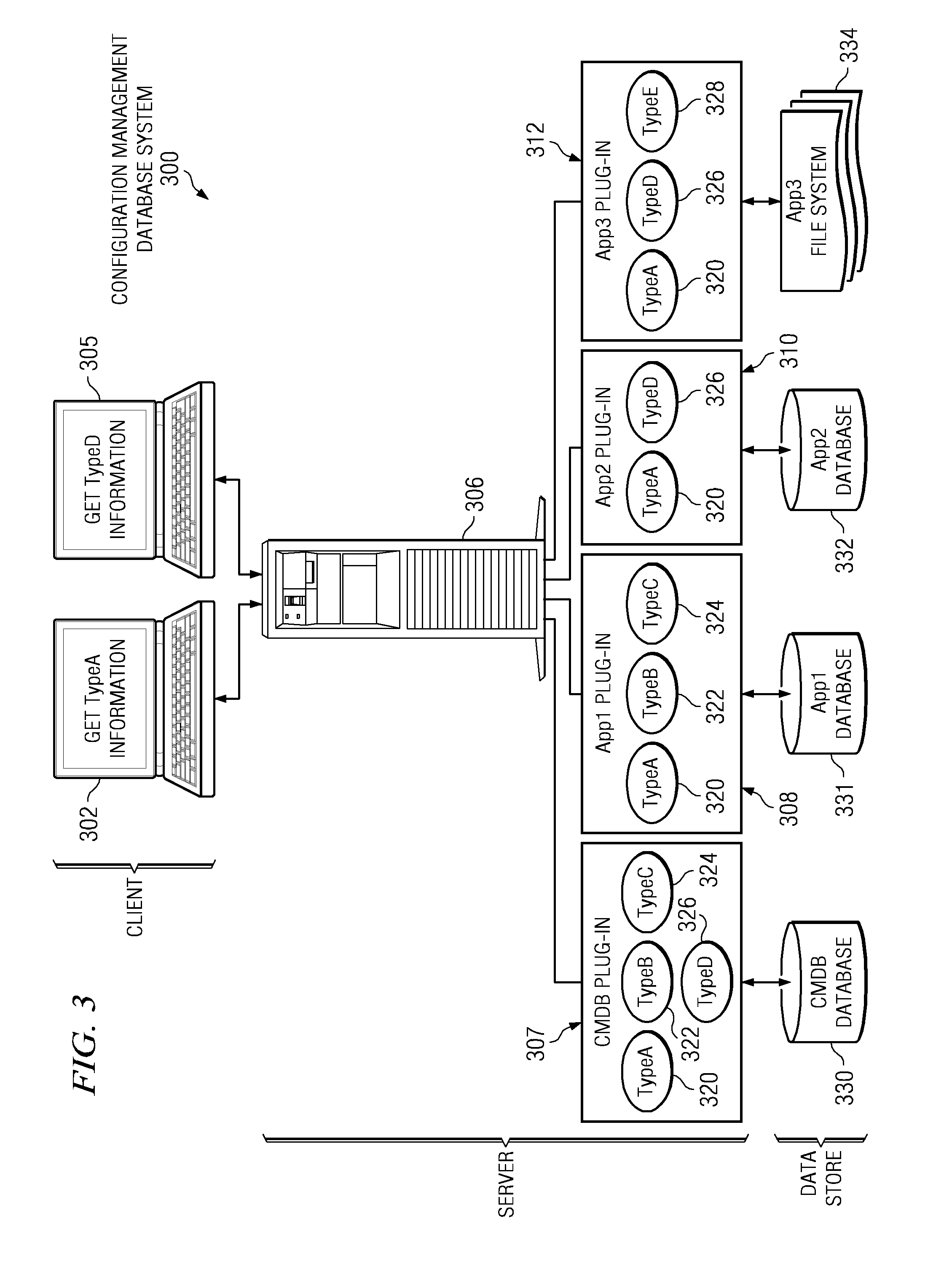
Attribute level federation from multiple data sources
InactiveUS20080114770A1Digital data information retrievalSpecial data processing applicationsConfiguration itemData source
A computer implemented method, apparatus, and computer program product for retrieving data. The process identifies a class type for the requested attribute data to form an identified class type in response to receiving a request for attribute data for a configuration item from a client. The process generates a set of data windows associated with the identified class type. Each data window in the set of data windows provides availability information for attribute data available from a remote data source. The process attribute data associated with each data window in the set of data windows to form a set of attribute data. The process sends the set of attribute data to the client
Owner:IBM CORP
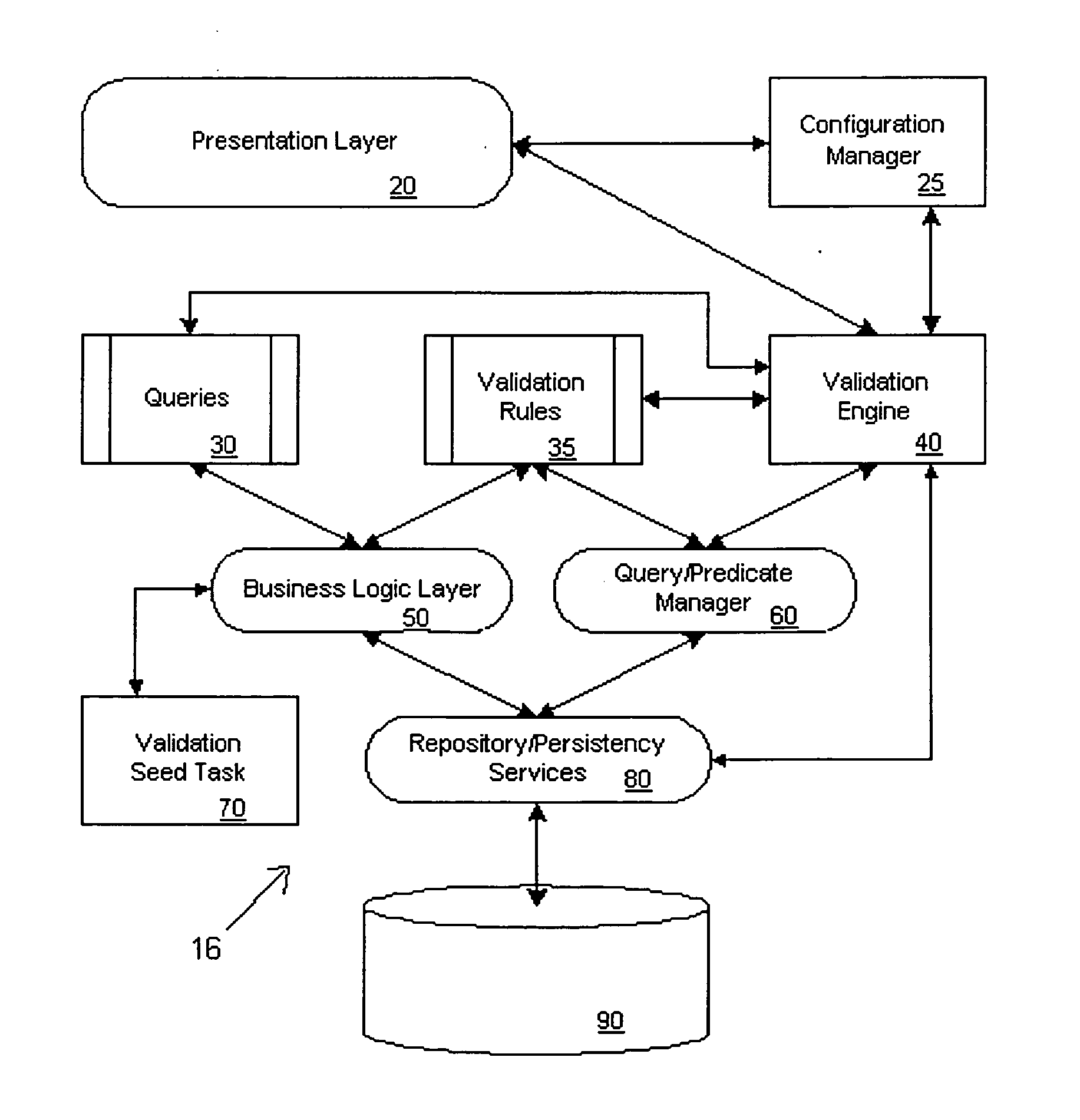
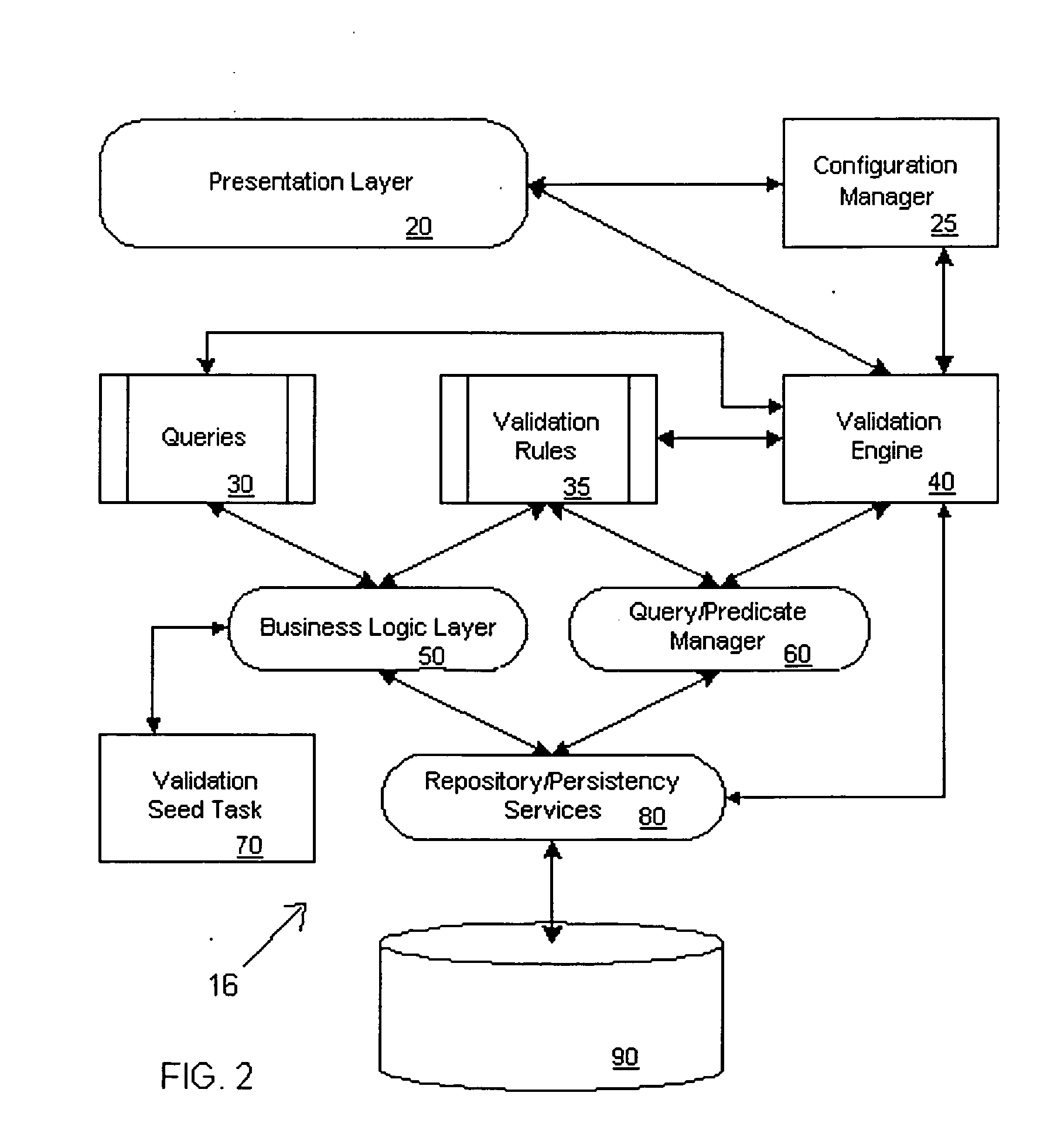
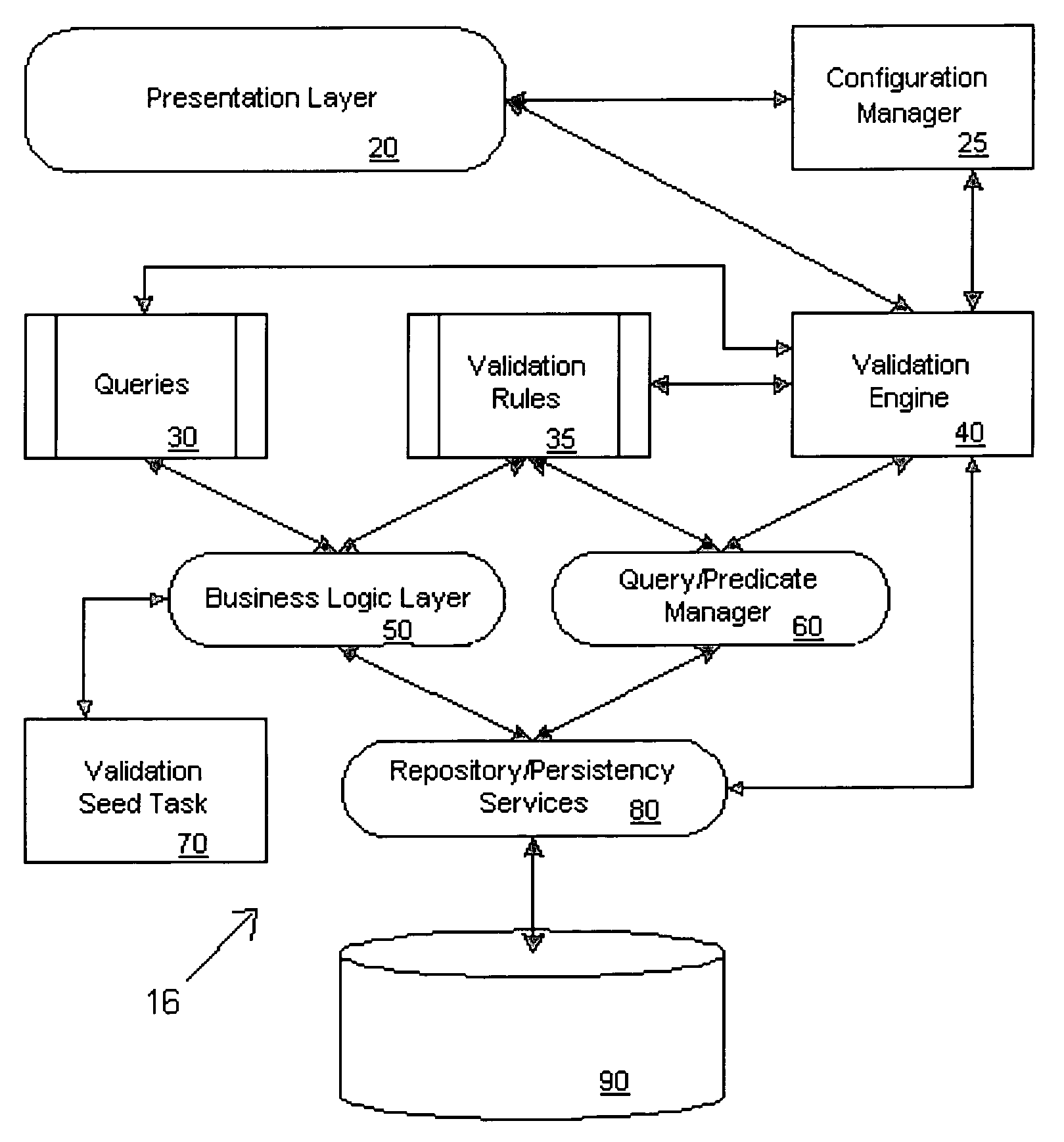
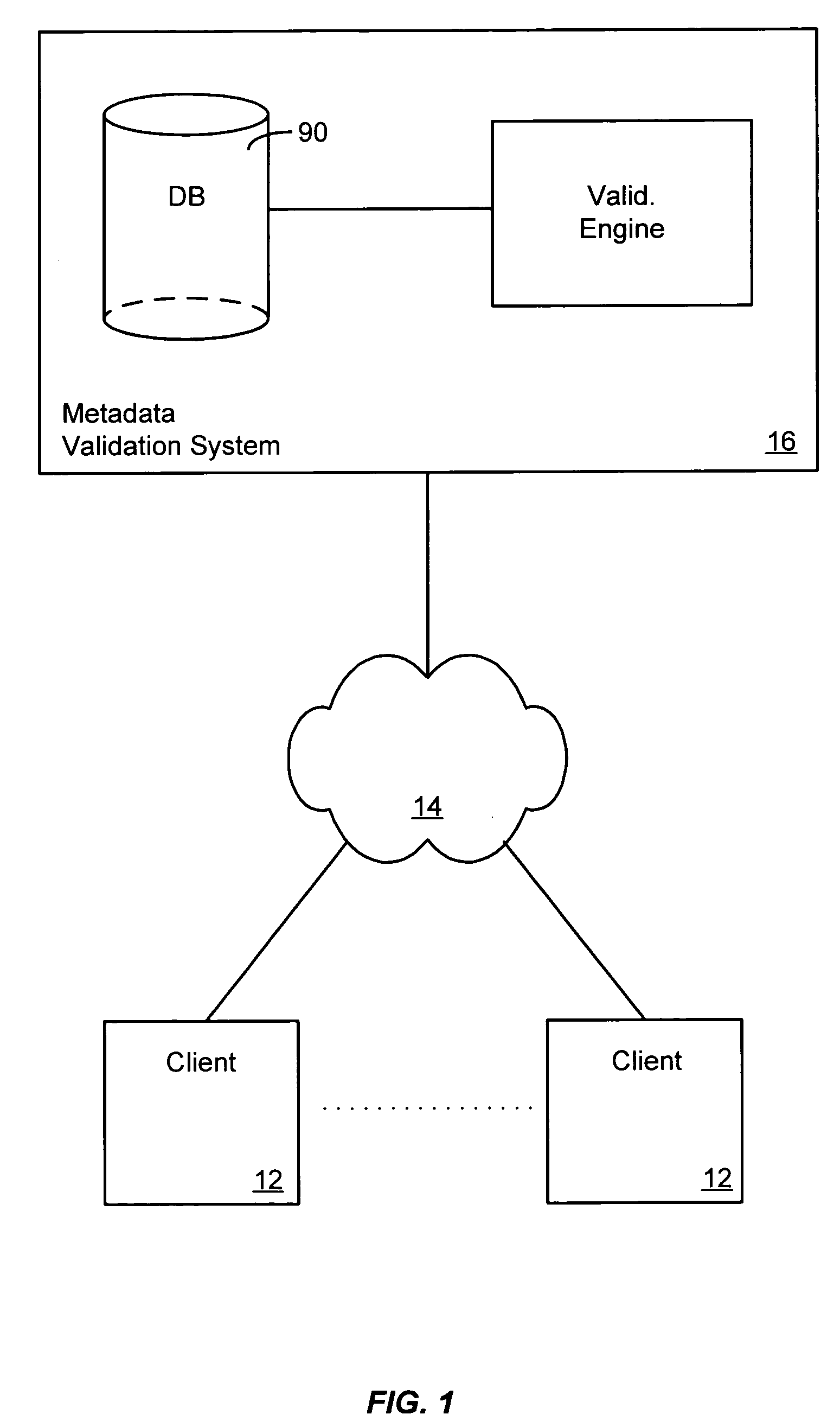
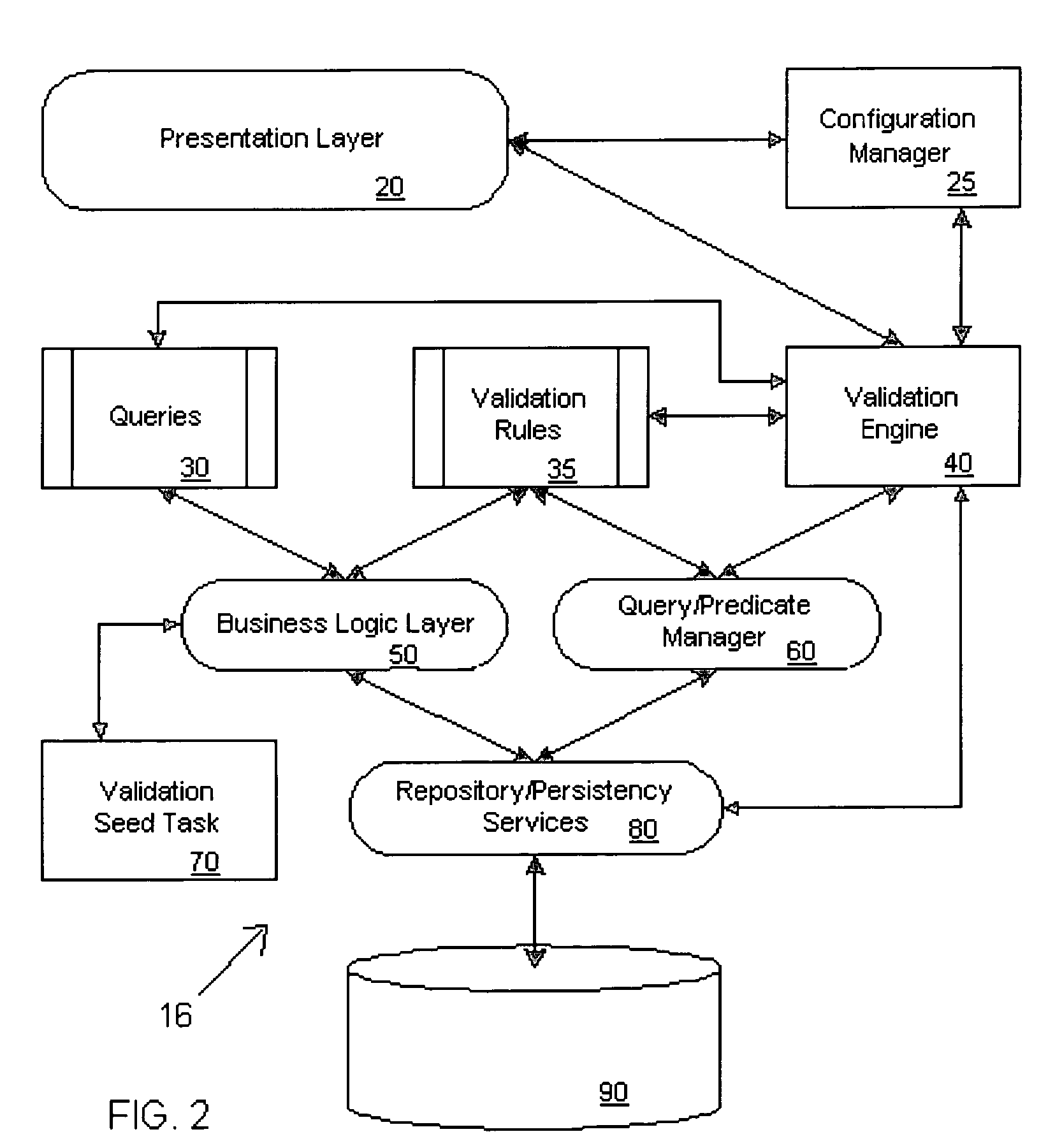
Systems and methods for validating design meta-data
ActiveUS20050125438A1Improve performanceDigital data processing detailsSpecific program execution arrangementsValidation ruleObject level
A metadata validation process that allows for deferring object model validation until after the objects are created. The process also allows for multi-threaded processing of the validation rules, thus increasing overall performance. Validation is performed by enforcing a series of validation rules on an appropriate subject. Rules are specified according to the subject that they are validating (i.e., attribute level, association level, object level or collection level). The metadata driven validation process implements several validation types on different validation units. Correctness validation rule types ensure that a validation unit satisfies all semantic rules defined for it. Completeness validation rule types ensure that a validation unit contains all the necessary data and is ready for further use. At design time, only correctness type validation is performed. Thus, the present invention advantageously allows for incomplete objects to be created at design time. The developer, however, in this case may opt to perform completeness validation at any time. In general, a developer may opt to perform completeness and / or correctness validation at any time independent of deployment processing. In another aspect, full validation (e.g., completeness and correctness) is automatically performed on the objects during the process of creating a configuration prior to deployment.
Owner:ORACLE INT CORP
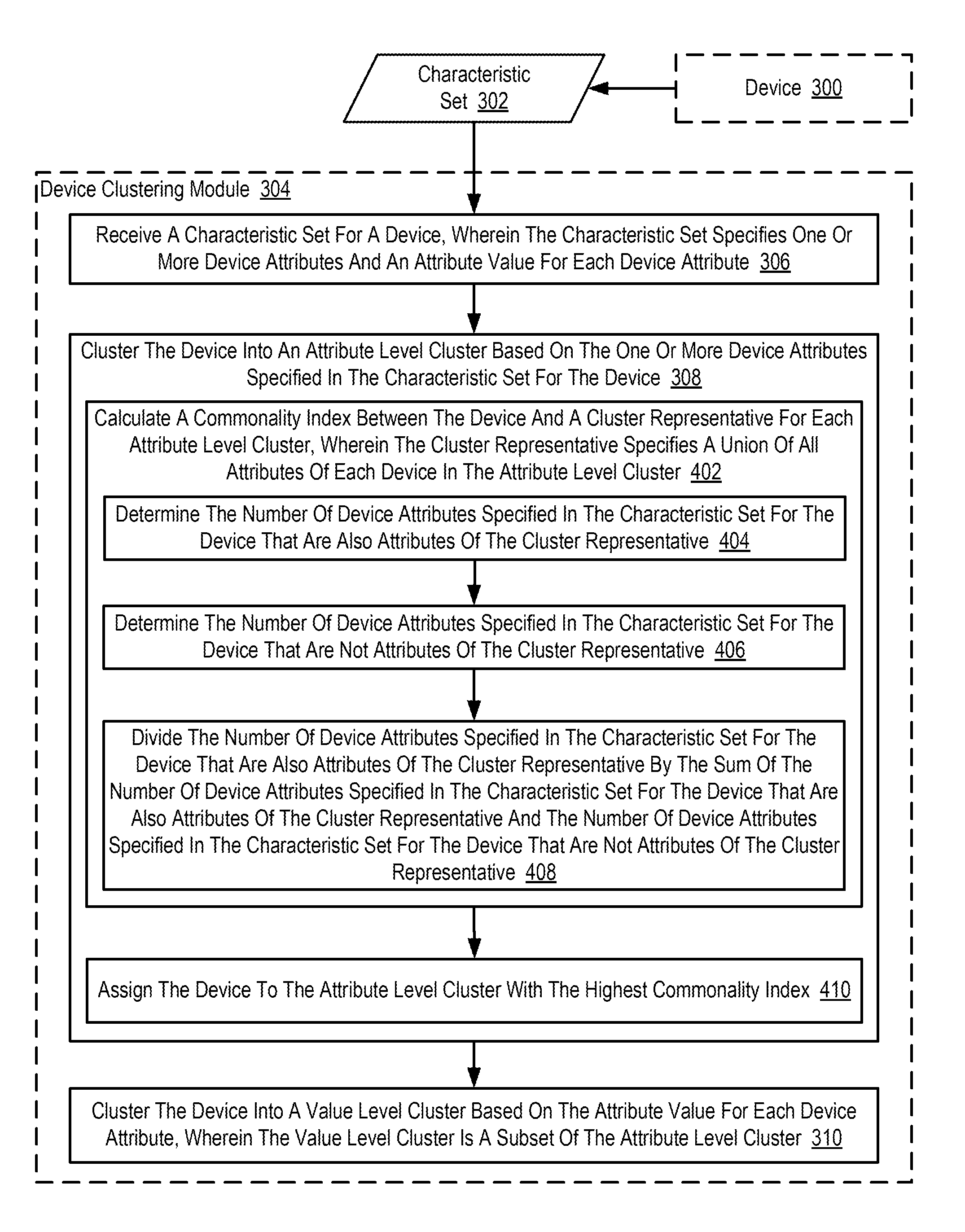
Clustering Devices In An Internet Of Things ('IoT')
ActiveUS20130173621A1Digital data processing detailsOther databases indexingCluster basedData mining
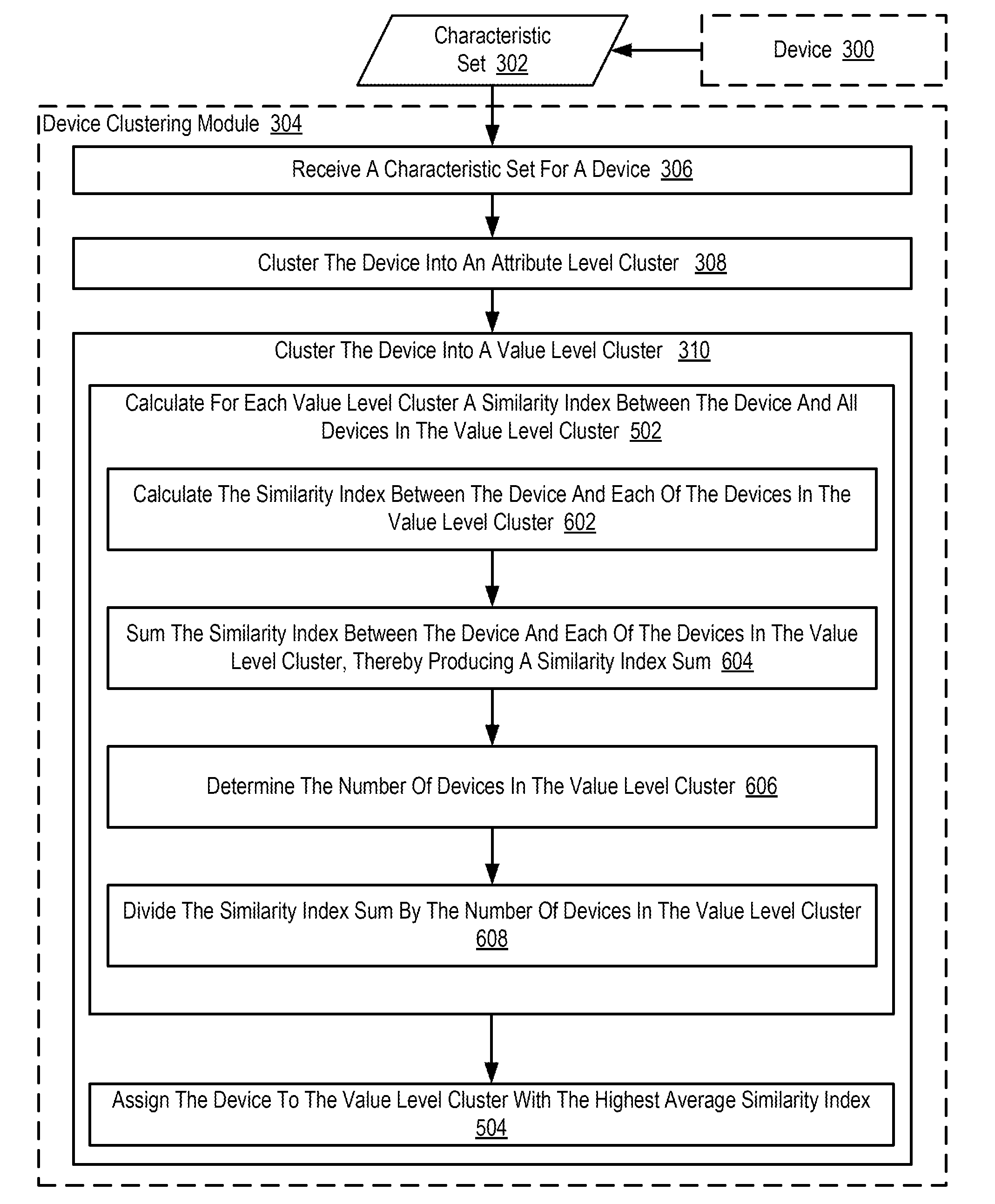
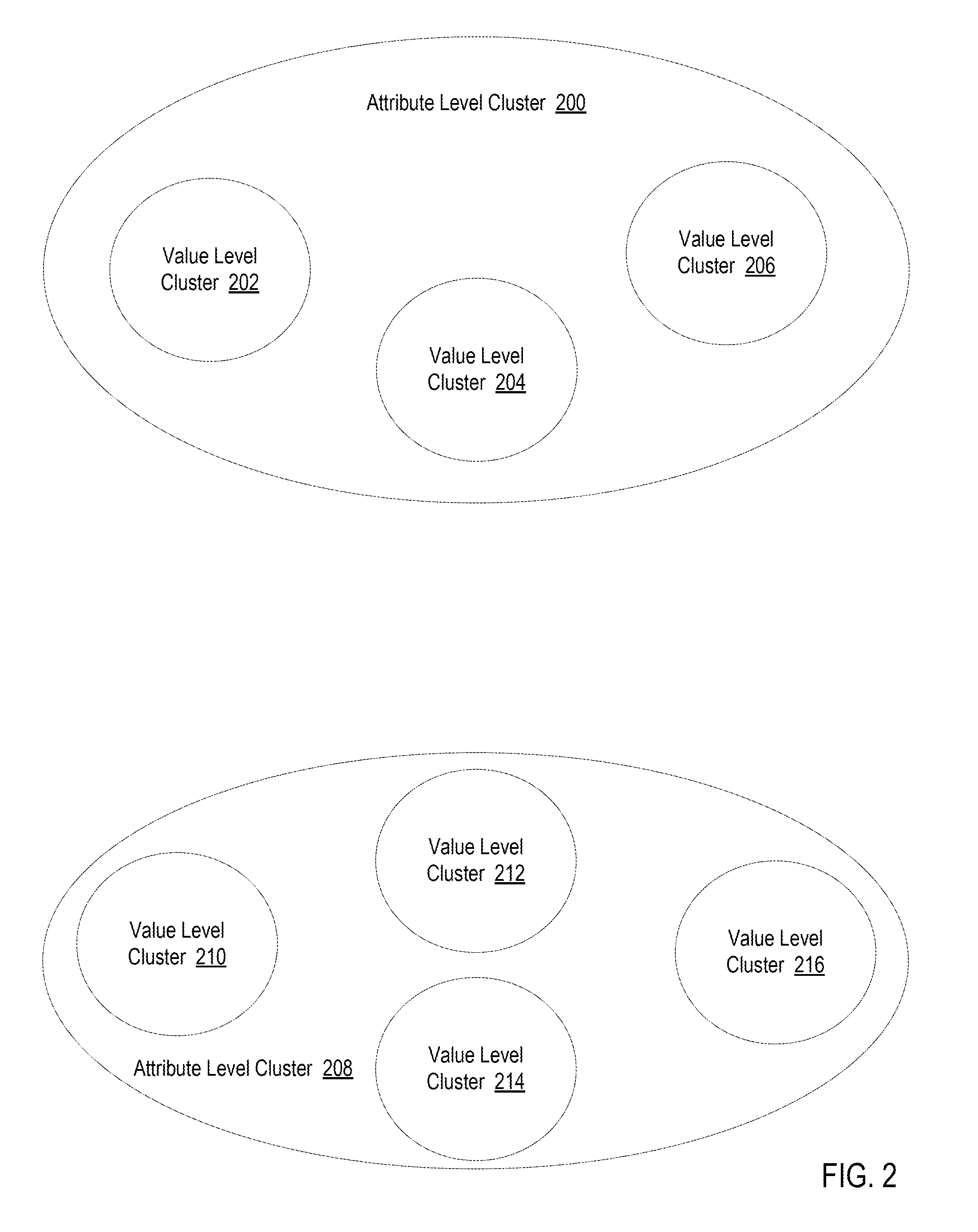
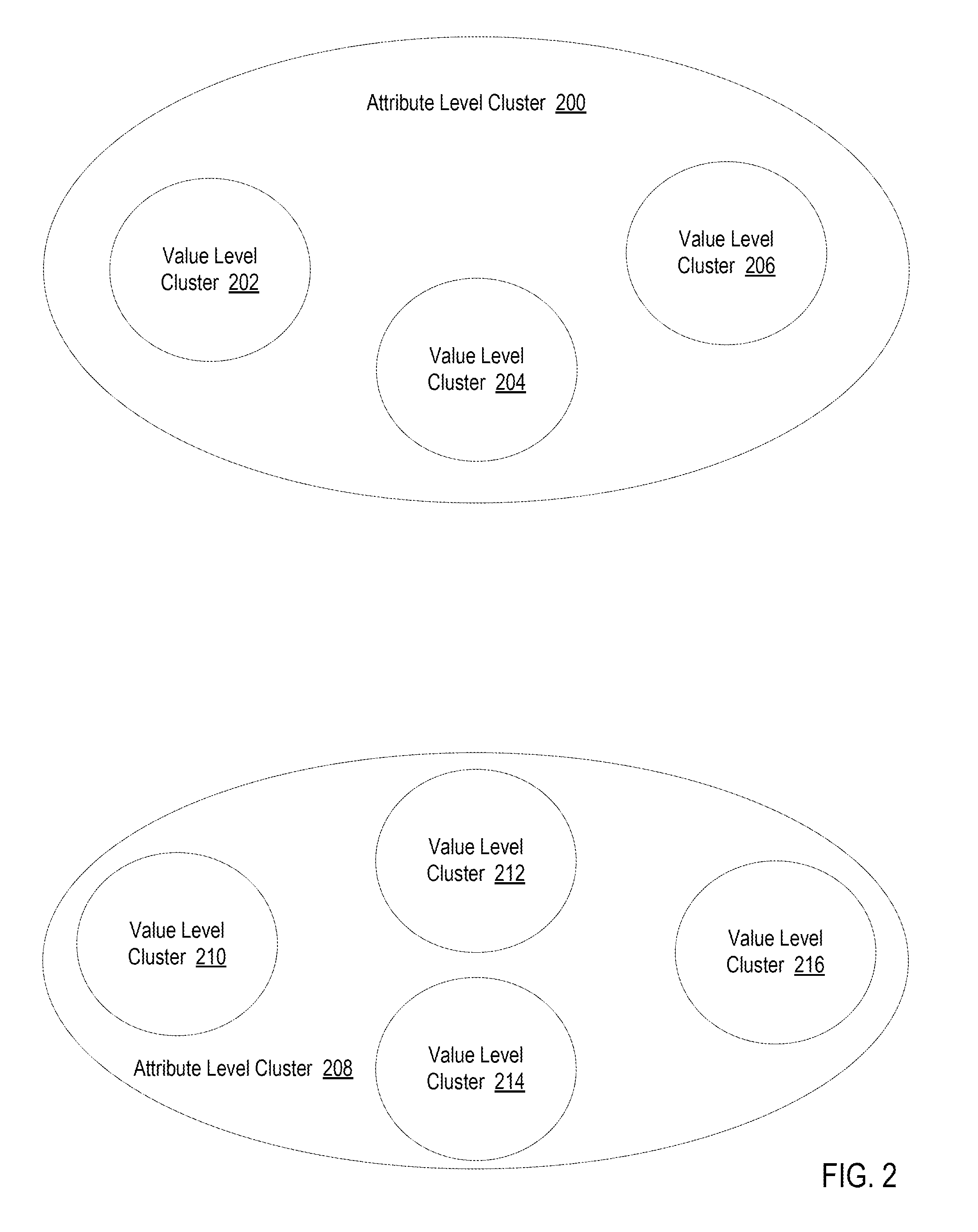
Clustering devices in an Internet of Things (‘IoT’), including: receiving, by a device clustering module, a characteristic set for a device, wherein the characteristic set specifies one or more device attributes and an attribute value for each device attribute; clustering, by the device clustering module, the device into an attribute level cluster based on the one or more device attributes specified in the characteristic set for the device; and clustering, by the device clustering module, the device into a value level cluster based on the attribute value for each device attribute, wherein the value level cluster is a subset of the attribute level cluster.
Owner:TERRACE LICENSING LLC
Webpage information extraction method
InactiveCN102495892AQuality improvementSpecial data processing applicationsConcept AttributeText categorization
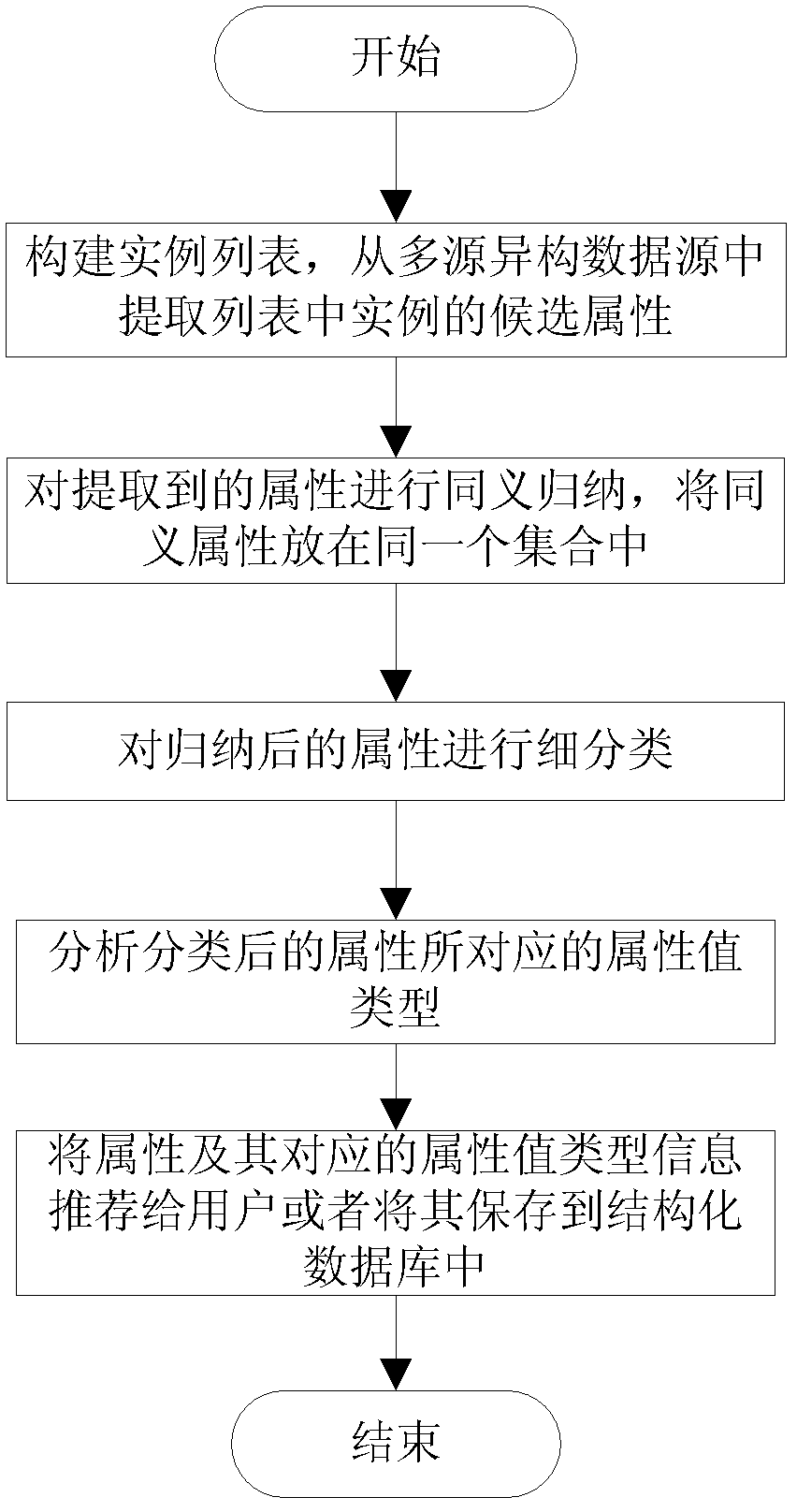
The invention discloses a webpage information extraction method, in particular a method for extracting concept attributes from a network encyclopedia data source and processing the concept attributes. The method comprises the following steps of: constructing an example list, and extracting candidate attributes of examples in the list from a multi-source heterogeneous data source; performing synonymic induction on the extracted attributes, and putting synonymic attributes in the same set; sub-classifying the induced attributes; analyzing the corresponding attribute value types of the classified attributes; and recommending the attributes and corresponding attribute value type information to a user, or storing the attributes and the corresponding attribute value type information into a structured database. By adoption of the scheme of the invention, high-quality concept attribute information can be extracted from a webpage, a knowledge base can be better constructed, and other natural language processing tasks such as extraction of attribute values, text classification and classification of query logs in a search engine can be better performed.
Owner:PEKING UNIV
Clustering devices in an internet of things ('IoT')
Clustering devices in an Internet of Things (‘IoT’), including: receiving, by a device clustering module, a characteristic set for a device, wherein the characteristic set specifies one or more device attributes and an attribute value for each device attribute; clustering, by the device clustering module, the device into an attribute level cluster based on the one or more device attributes specified in the characteristic set for the device; and clustering, by the device clustering module, the device into a value level cluster based on the attribute value for each device attribute, wherein the value level cluster is a subset of the attribute level cluster.
Owner:TERRACE LICENSING LLC
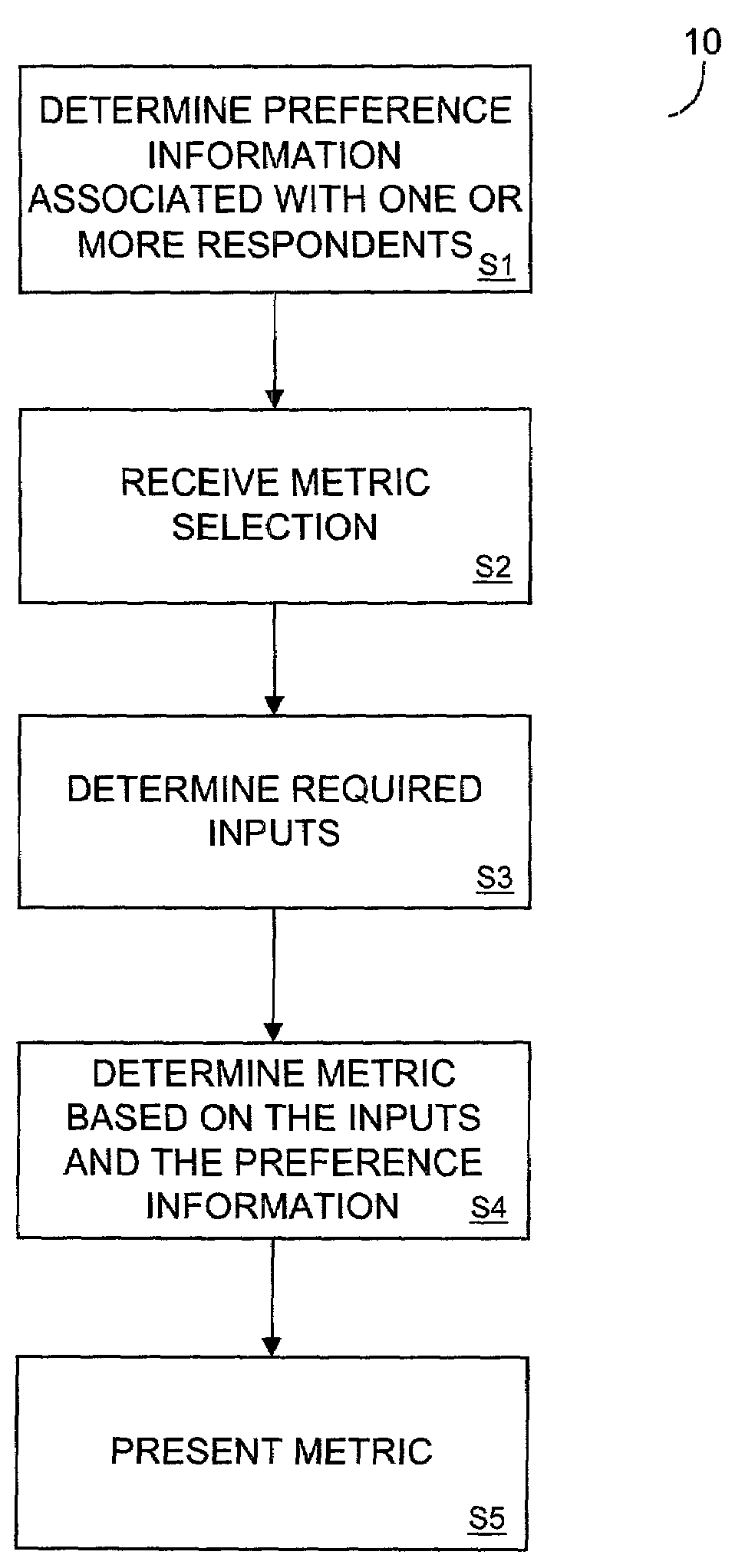
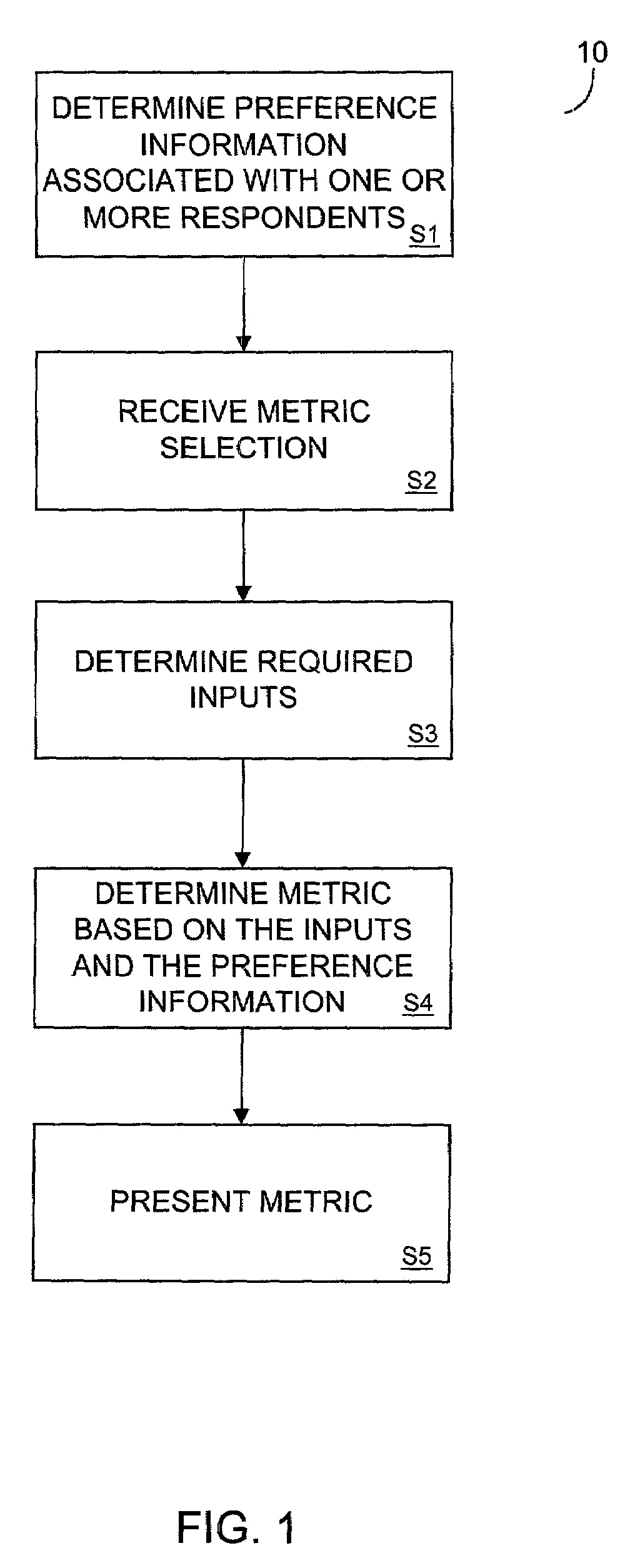
Preference information-based metrics
A system to determine metrics based on preference information. The metrics may be presented to a client in several forms and may include at least one of: impact of change in attribute on change in share; impact of change in attribute on share; impact of change in attribute on change in normalized utility; willingness to pay; relation of price and share, given a change in an attribute; gap analysis; gap with competition; unacceptable attribute levels; vulnerability; clout; brand favorability; brand vulnerability; and change in margin due to acceptable change in comparison product.
Owner:BLUE FLAME DATA
Relationship knowledge sharing platform and implementation method thereof
ActiveCN102073729AImprove browsing experienceSpecial data processing applicationsProgramming languageKnowledge sharing
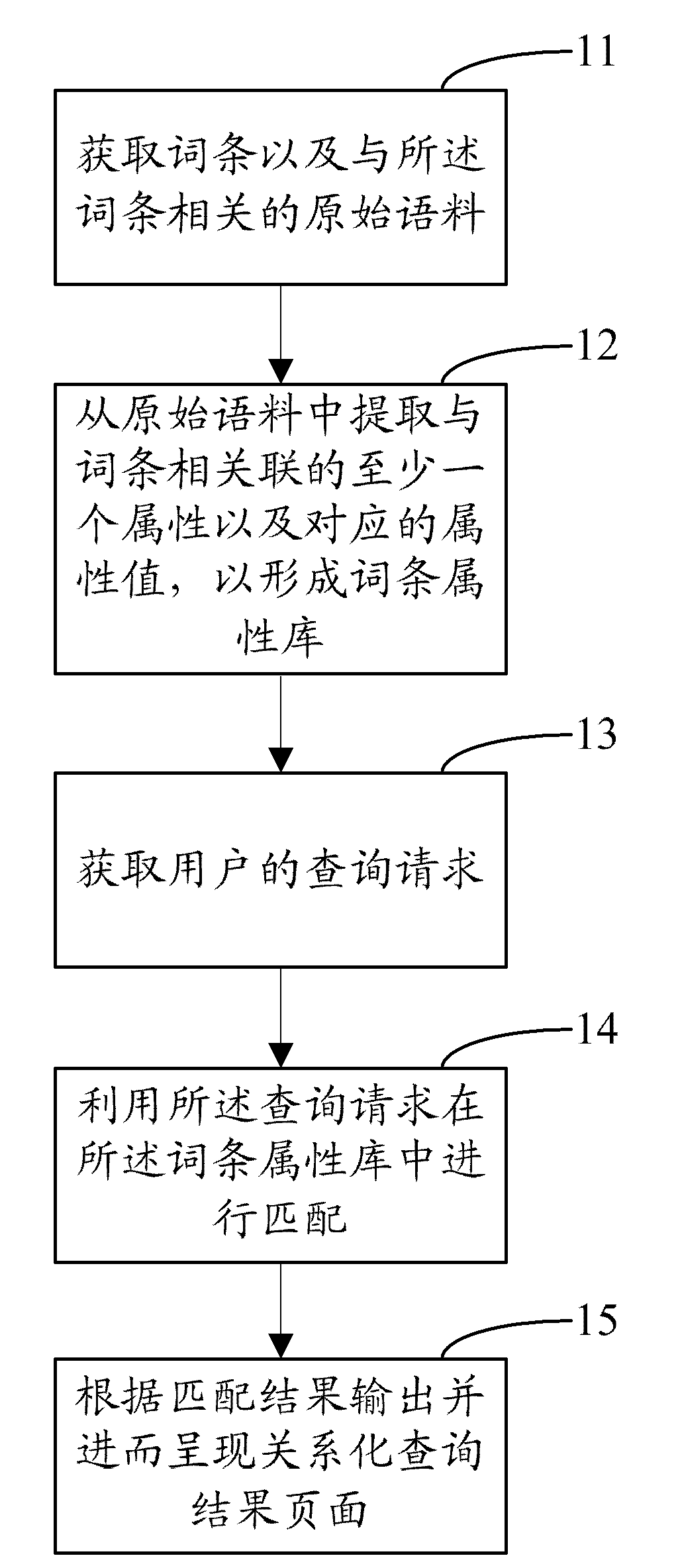
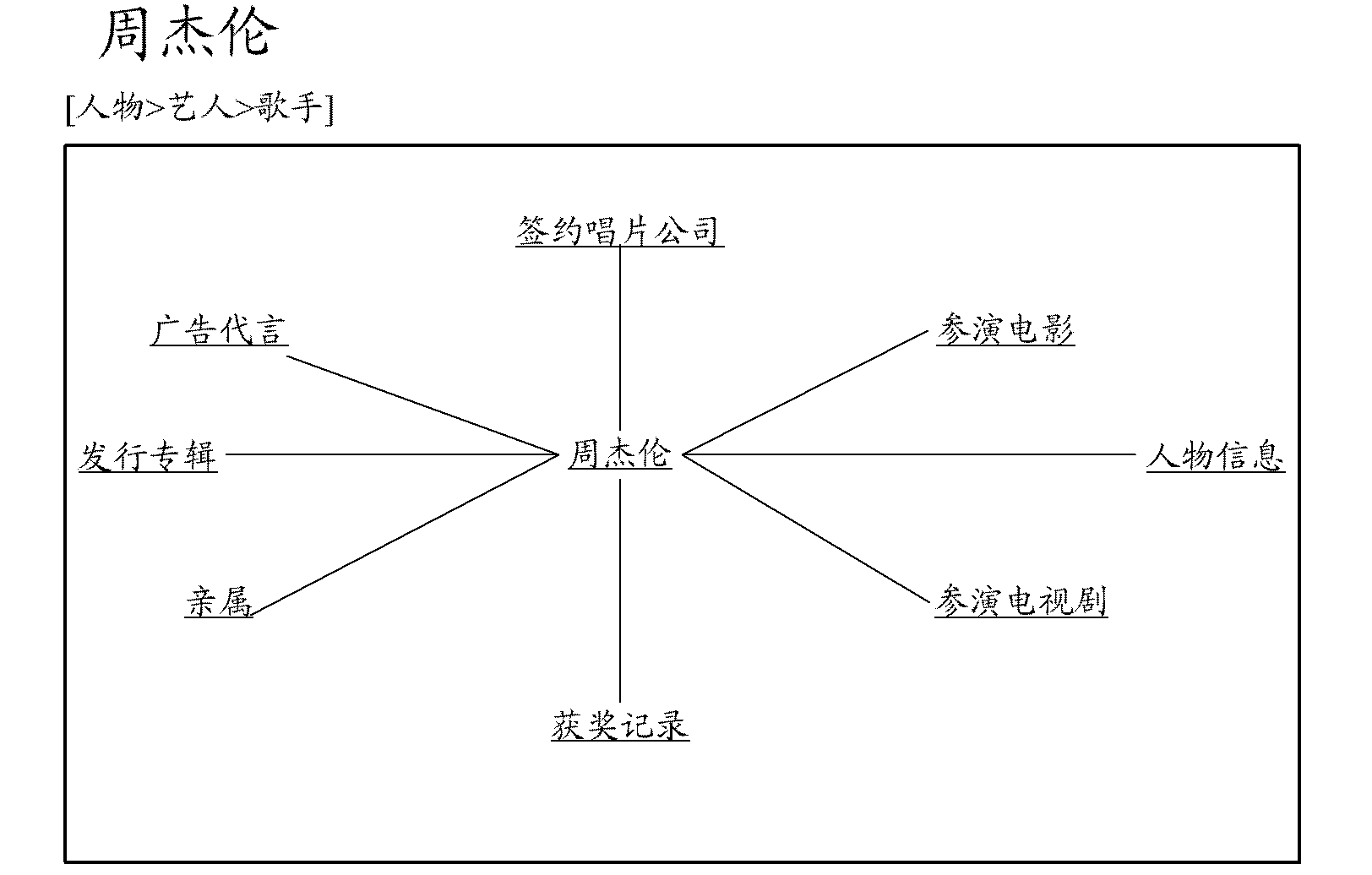
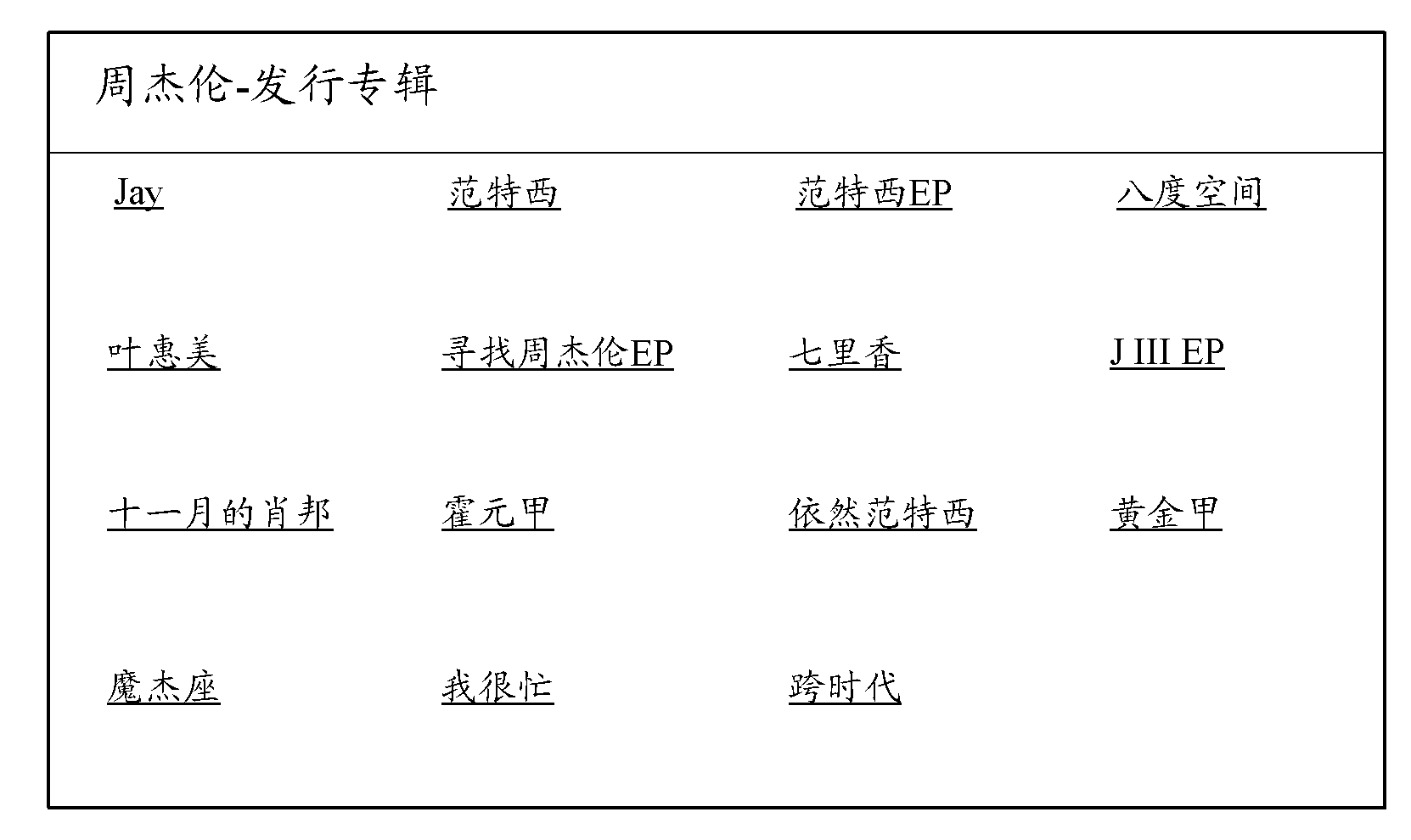
The invention provides a relationship knowledge sharing platform and an implementation method thereof. The implementation method comprises the following steps: acquiring word entries and original language materials related with the word entries; extracting at least one attribute related with the word entries from the original language materials and corresponding attribute value so as to form a word entry attribute database; acquiring a query request of a user; utilizing the query request to match in the word entry attribute database; and outputting according to matching result and further showing a relationship research result page. With the adoption of the technical scheme, the invention provides the relationship knowledge sharing platform and the implementation method thereof, relationship treatment is performed on the word entries, the attribute and the attribute value, then the relationship research result page can be shown according to the query request of the user, and browsing experience of the user can be improved.
Owner:BAIDU ONLINE NETWORK TECH (BEIJIBG) CO LTD
Product review attribute-level emotion classification method based on rules and neural networks
ActiveCN107862343APromote amplificationEfficient use ofCharacter and pattern recognitionNeural learning methodsClassification methodsBusiness forecasting
The invention discloses a product review attribute-level emotion classification method based on rules and neural networks. The method includes the steps: firstly, acquiring review data and filtering Chinese participles and stop words from a review text; secondly, screening a product attribute set by the aid of a rule template, building a <attribute and review> sample set, performing emotion tagging on the attribute of each review, and building a <attribute, review and emotion> training set; building a neural network emotion classification model based on bilateral attention, and training the model by the aid of the training set; finally, filtering Chinese participles and stop words from testing data, screening a product attribute set, building a <attribute and review> testing set, and performing emotion classification by the aid of an emotion classification model. According to the method, attribute emotion category forecasting accuracy can be greatly and effectively improved by the aidof context information of attributes in the reviews.
Owner:NANJING UNIV OF SCI & TECH
Systems and methods for validating objects models
ActiveUS20050125806A1Avoid less flexibilityImprove performanceDigital data processing detailsMultiprogramming arrangementsDEVSValidation rule
A metadata validation process that allows for deferring object model validation until after the objects are created. The process also allows for multi-threaded processing of the validation rules, thus increasing overall performance. Validation is performed by enforcing a series of validation rules on an appropriate subject. Rules are specified according to the subject that they are validating (i.e., attribute level, association level, object level or collection level). The metadata driven validation process implements several validation types on different validation units. Correctness validation rule types ensure that a validation unit satisfies all semantic rules defined for it. Completeness validation rule types ensure that a validation unit contains all the necessary data and is ready for further use. At design time, only correctness type validation is performed. Thus, the present invention advantageously allows for incomplete objects to be created at design time. The developer, however, in this case may opt to perform completeness validation at any time. In general, a developer may opt to perform completeness and / or correctness validation at any time independent of deployment processing. In another aspect, full validation (e.g., completeness and correctness) is automatically performed on the objects during the process of creating a configuration prior to deployment.
Owner:ORACLE INT CORP
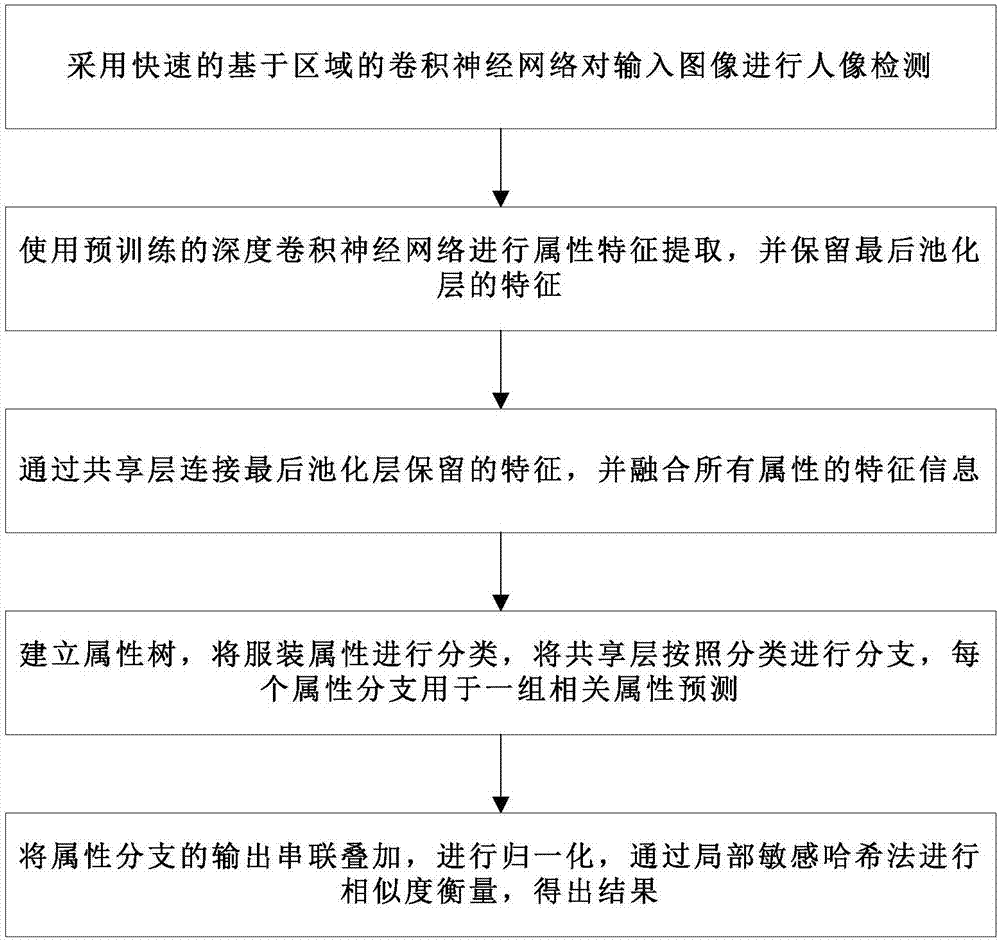
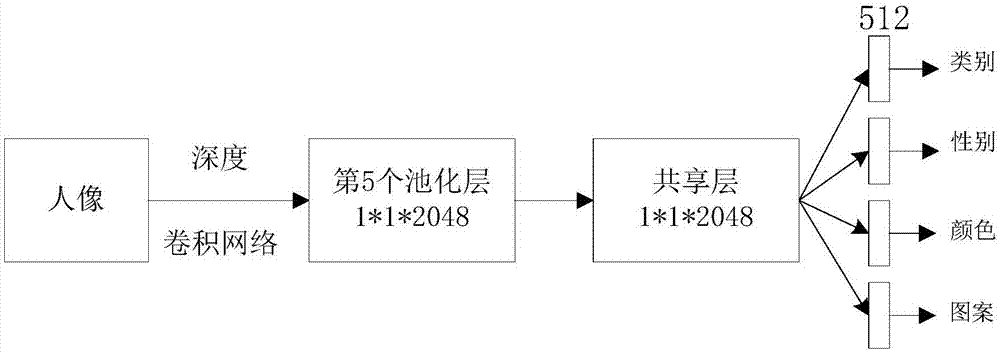
Garment attribute retrieval method based on deep convolutional neural network
ActiveCN107330451AImprove accuracyCharacter and pattern recognitionNeural learning methodsFeature descriptionLocality-sensitive hashing
The present invention discloses a garment attribute retrieval method based on a deep convolutional neural network. The method comprises: employing a rapid convolutional neural network based on an area to perform portrait detection of an input image; employing a pre-training deep convolutional neural network to perform attribute feature extraction, and retaining the features of a final pooling layer; employing a sharing layer to connect with the features retained by the pooling layer, and fusing the feature information of all the attributes; establishing an attribute tree, performing classification of garment attributes, performing branching of the sharing layer according to the classification, each attribute branching being configured for prediction of one group of related attributes; and performing attribute branching output series overlaying, performing normalization, performing similarity measurement through the locality-sensitive hashing method, and obtaining a result. The feature description of the garment attributes is used for garment attribute detection so as to observably improve the accuracy of prediction of garment attributes.
Owner:XIAN JIAOTONG LIVERPOOL UNIV
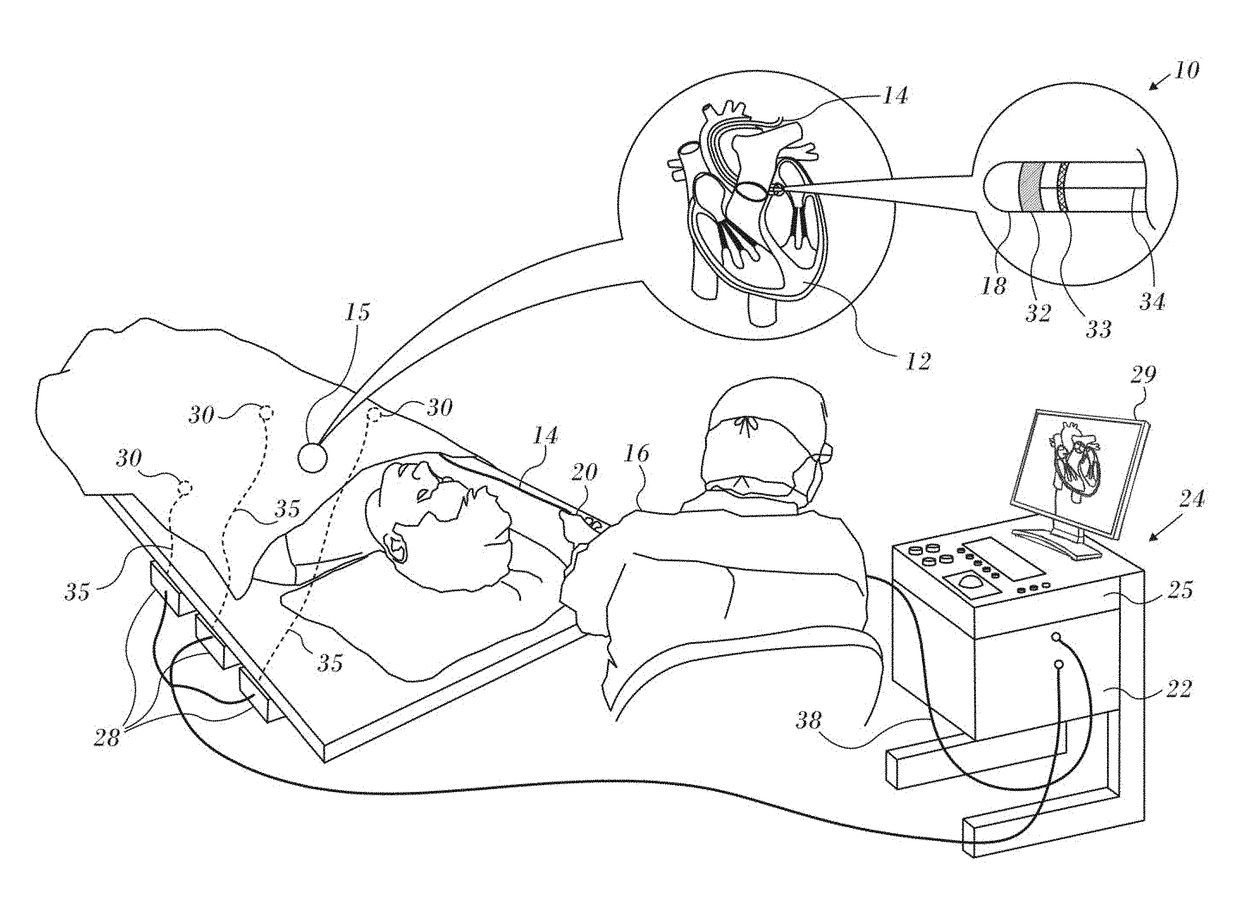
High Definition Coloring of Heart Chambers
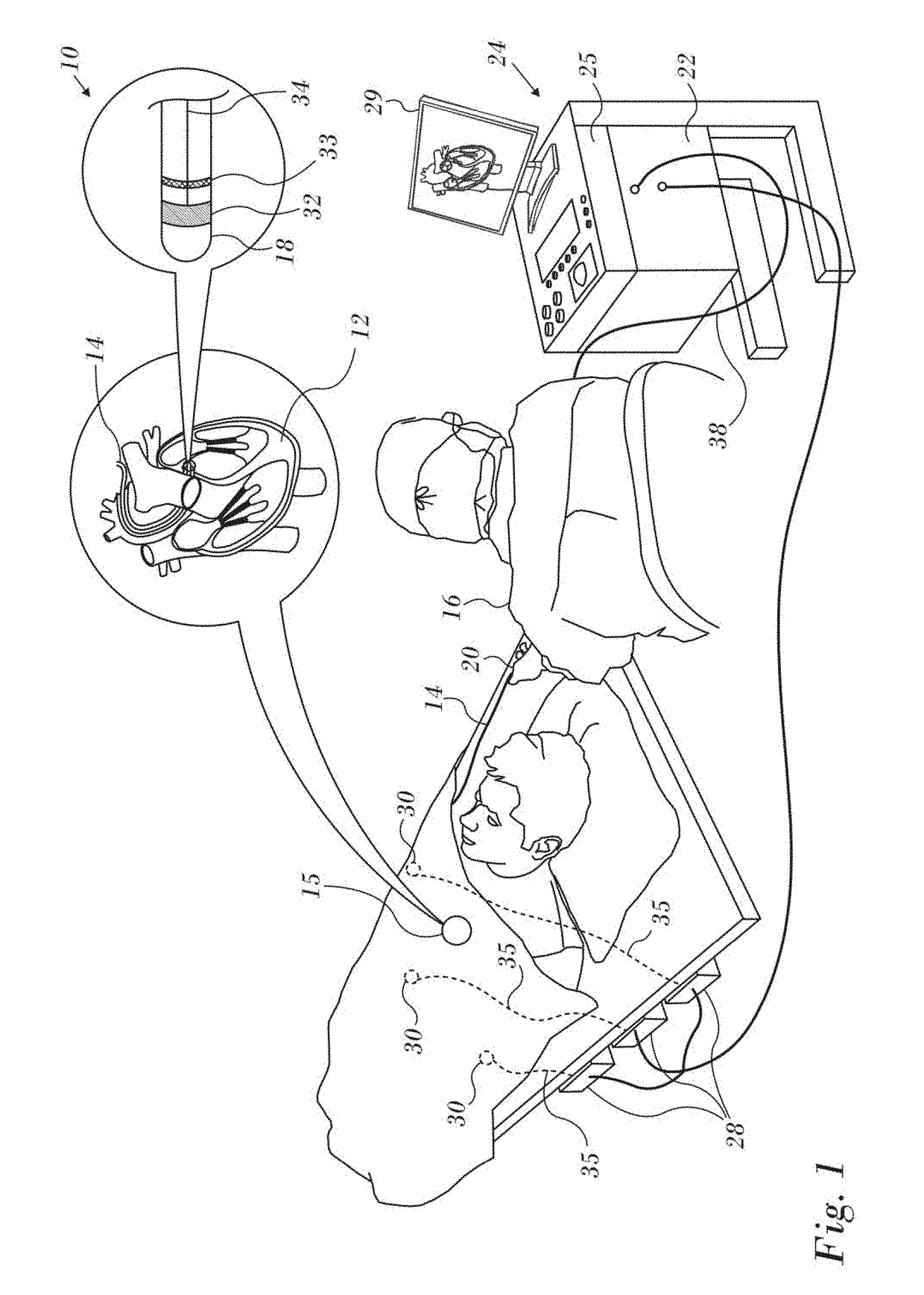
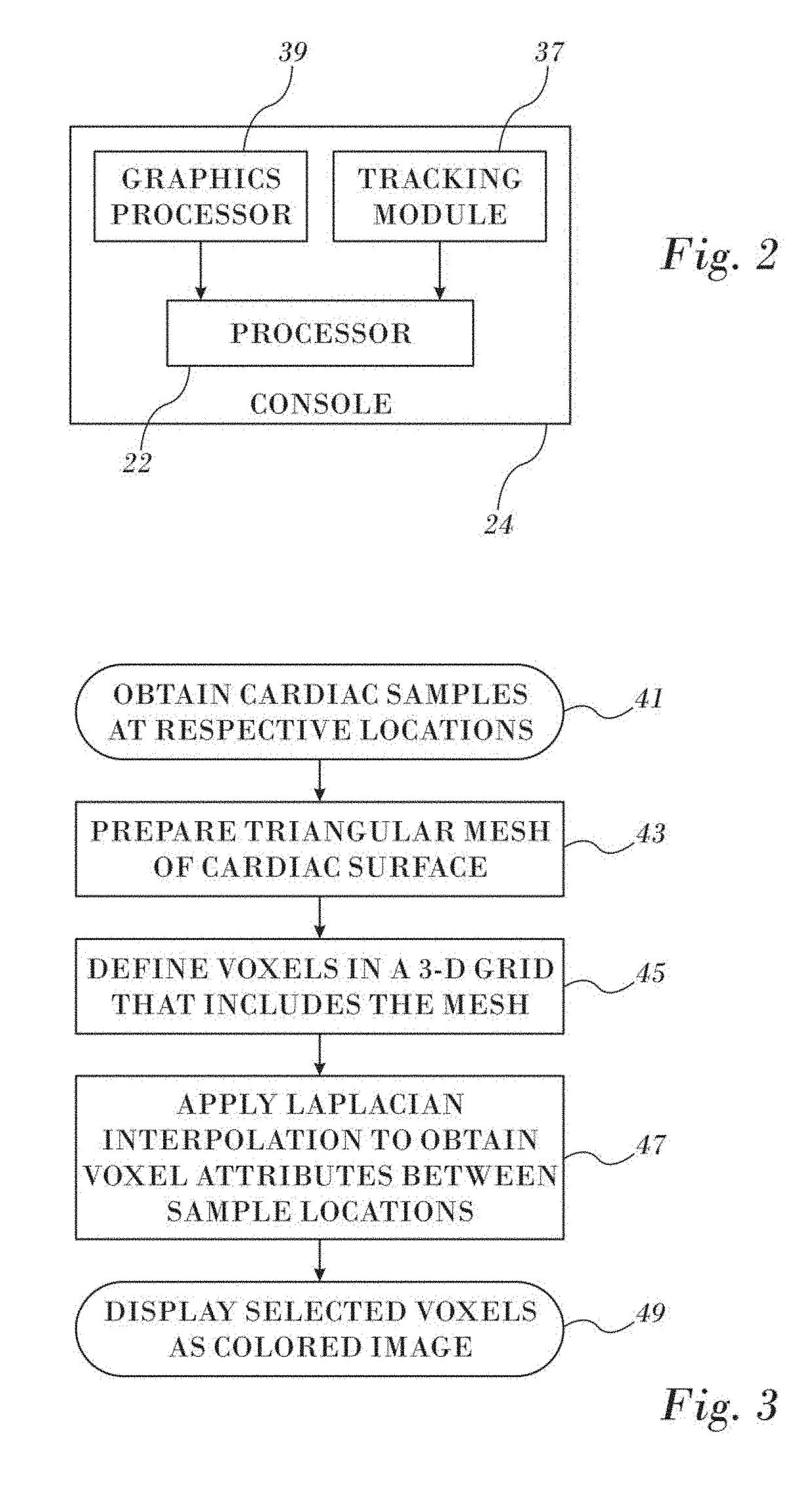
ActiveUS20170221254A1Minimizes integrated squareImprove interpolationImage enhancementImage analysisVoxelHeart chamber
A 3-dimensional image is displayed in high resolution colors by generating a 3-dimensional model as a triangular mesh, converting the mesh into a grid of voxels, and assigning attribute values to a portion of the voxels. Laplacian interpolation based on the portion of the voxels is applied for iteratively calculating interpolated attribute values of other voxels. The voxels are rendered as a colored image according to the attribute values on a display.
Owner:BIOSENSE WEBSTER (ISRAEL) LTD
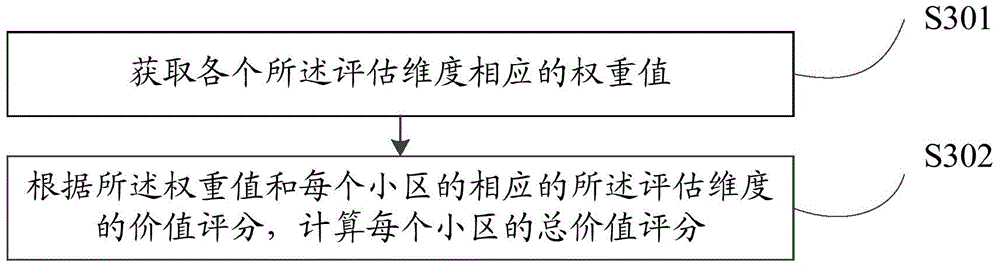
Network planning method and device
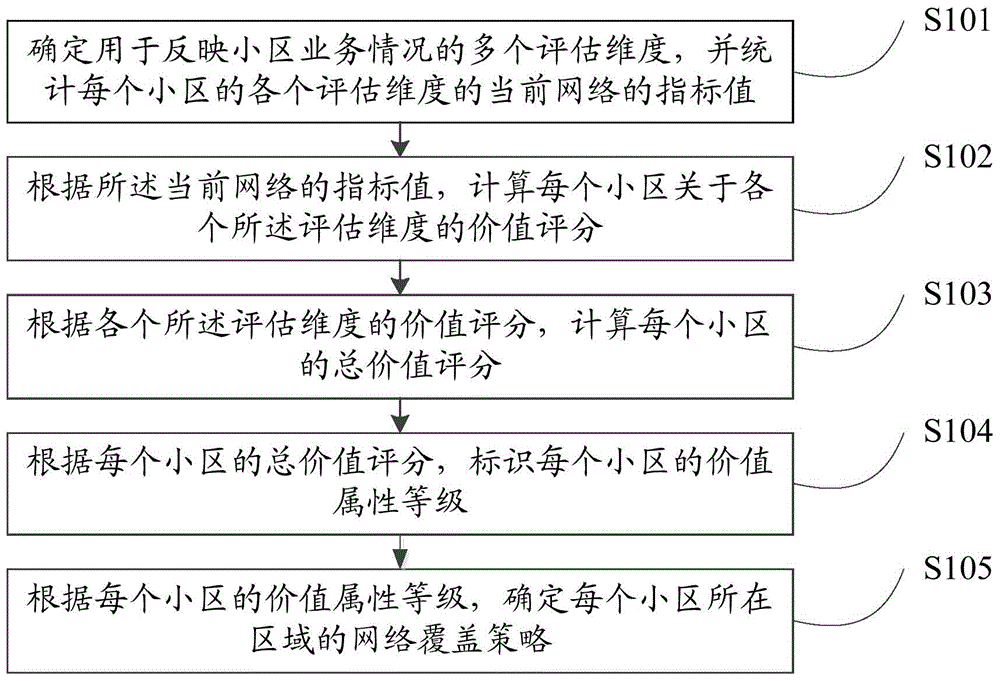
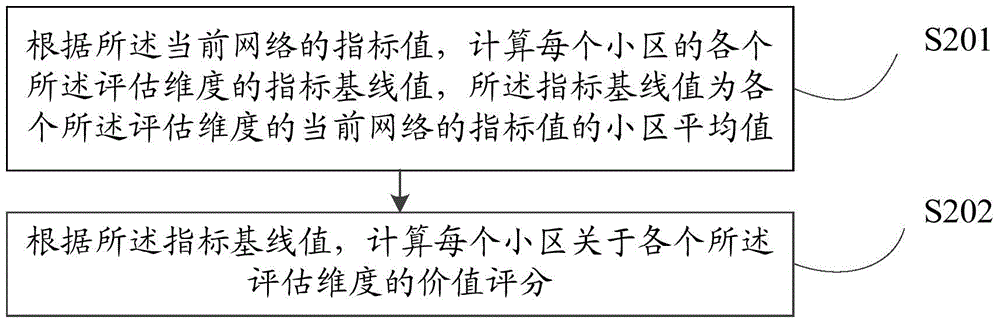
InactiveCN105873079AGuaranteed experienceIncrease investmentNetwork planningLimited resourcesData mining
The invention provides a network planning method and device. The method includes the following steps that: a plurality of evaluation dimensions used for reflecting the business situations of cells are determined, the index values of a current network of each cell under the evaluation dimensions are obtained; the value scores of each cell with respect to the evaluation dimensions are calculated according to the index values of the current network; the total value score of each cell are calculated according to the value scores of each cell with respect to the evaluation dimensions; the value attribute levels of each cell are identified according to the total value scores of each cell; and the network coverage strategies of a region where the cells are located is determined according to the value attribute levels of each cell. With the method and device provided by the invention adopted, the value of a target area can be effectively identified, limited resources are put into an area which can most possibly generate benefits, and an effective basis can be provided for the accurate construction of a network.
Owner:CHINA MOBILE GROUP ZHEJIANG +1
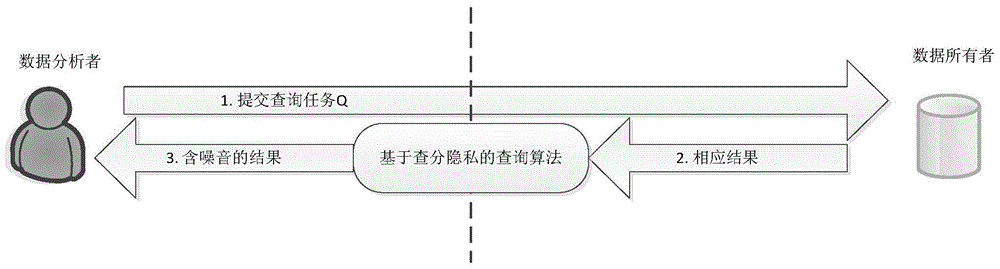
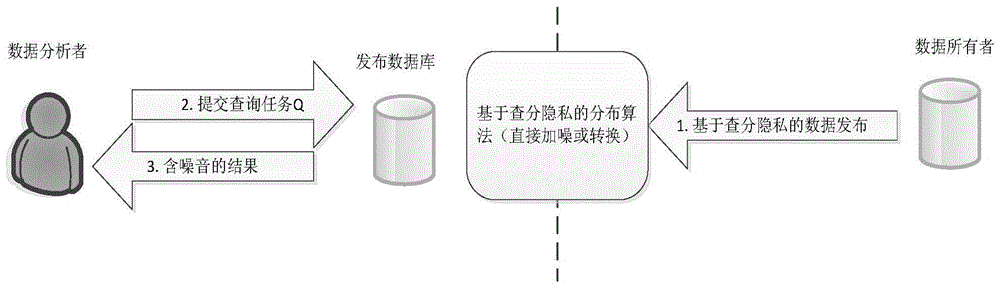
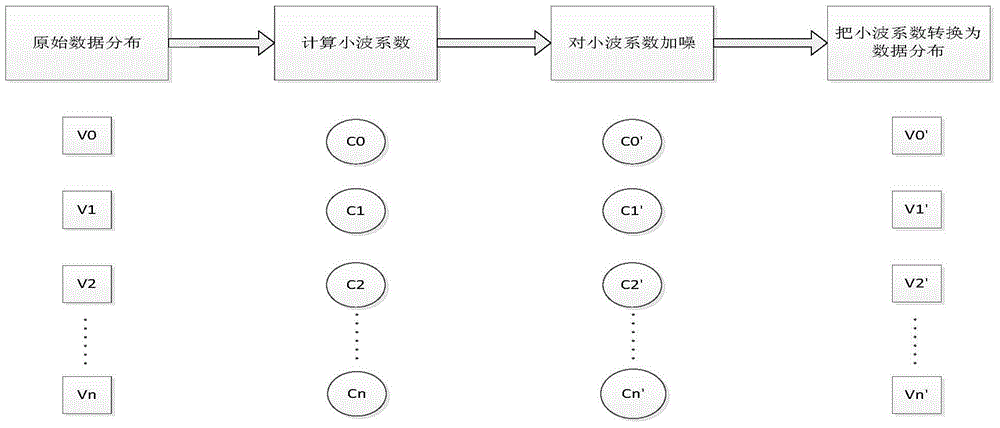
Differential private data publishing method based on wavelet transformation
ActiveCN104573560AImproved Noise EffectImprove classification accuracyDigital data protectionNODALData set
The invention discloses a differential private data publishing method based on wavelet transformation. The method is characterized in that the attribute values of an original data set are generalized the values of the topmost layer in a predefined generalization tree structure, and the subdivided values of the generalization tree structure from top to bottom are used to convert the generalized attribute values into subdivided attribute values; a known index noise adding method is used on a selection algorithm for selecting attributes to perform subdivision; a wavelet transformation noise adding method is introduced into the noise adding of leaf nodes, so that the noises of the newly published data set relative to the original data set is reduced to the greatest extent under the premise that differential privacy protection is satisfied. The method has the advantages that the wavelet transformation and an index mechanism are combined to perform noise adding in a synergy manner, noise accumulation during the noise adding process of an original data set is reduced effectively, the method conforms to the definition of differential privacy protection, cost of privacy protection is reduced, and the utilization rate of the data set after differential privacy protection.
Owner:SHANGHAI JIAO TONG UNIV
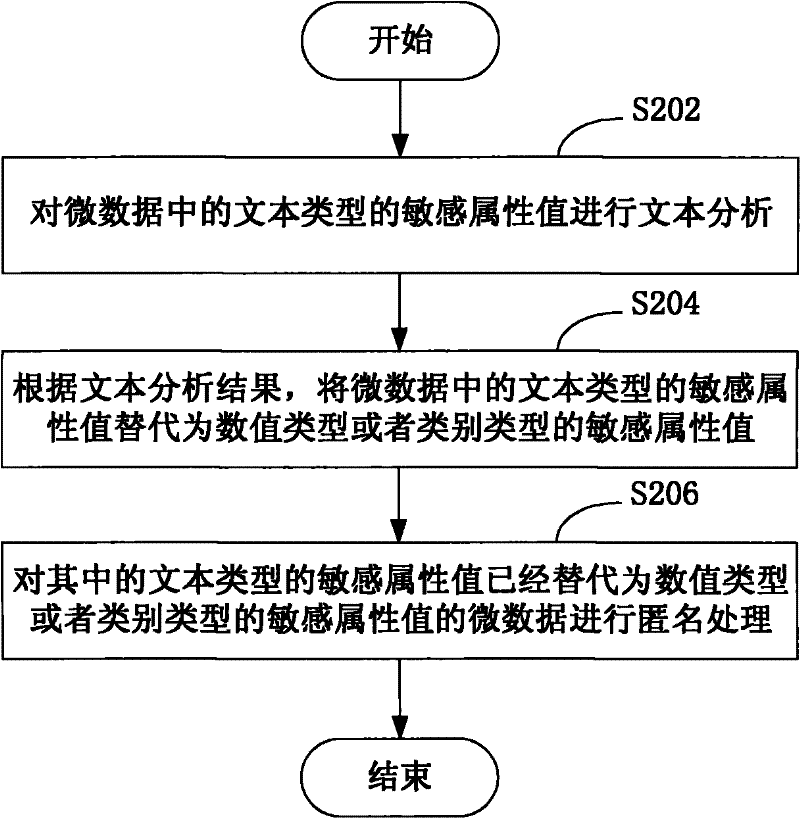
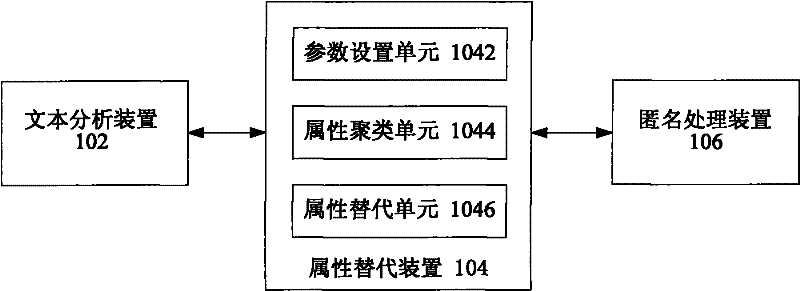
Data anonymization method and system
The invention provides a data anonymization method and system. The data anonymization method comprises the steps of: carrying out text analysis on the attribute value of a text type in data; replacing the attribute value of the text type in the data with the attribute value of a value type or a class type according to text analysis result; and carrying out anonymization processing on the data in which the attribute value of the text type is replaced by the attribute value of the value type or the class type. According to the invention, after anonymization processing, the data comprising the attribute value of the text type not only can prevent the privacy leakage based on the attribute value, but also still has use value.
Owner:NEC (CHINA) CO LTD
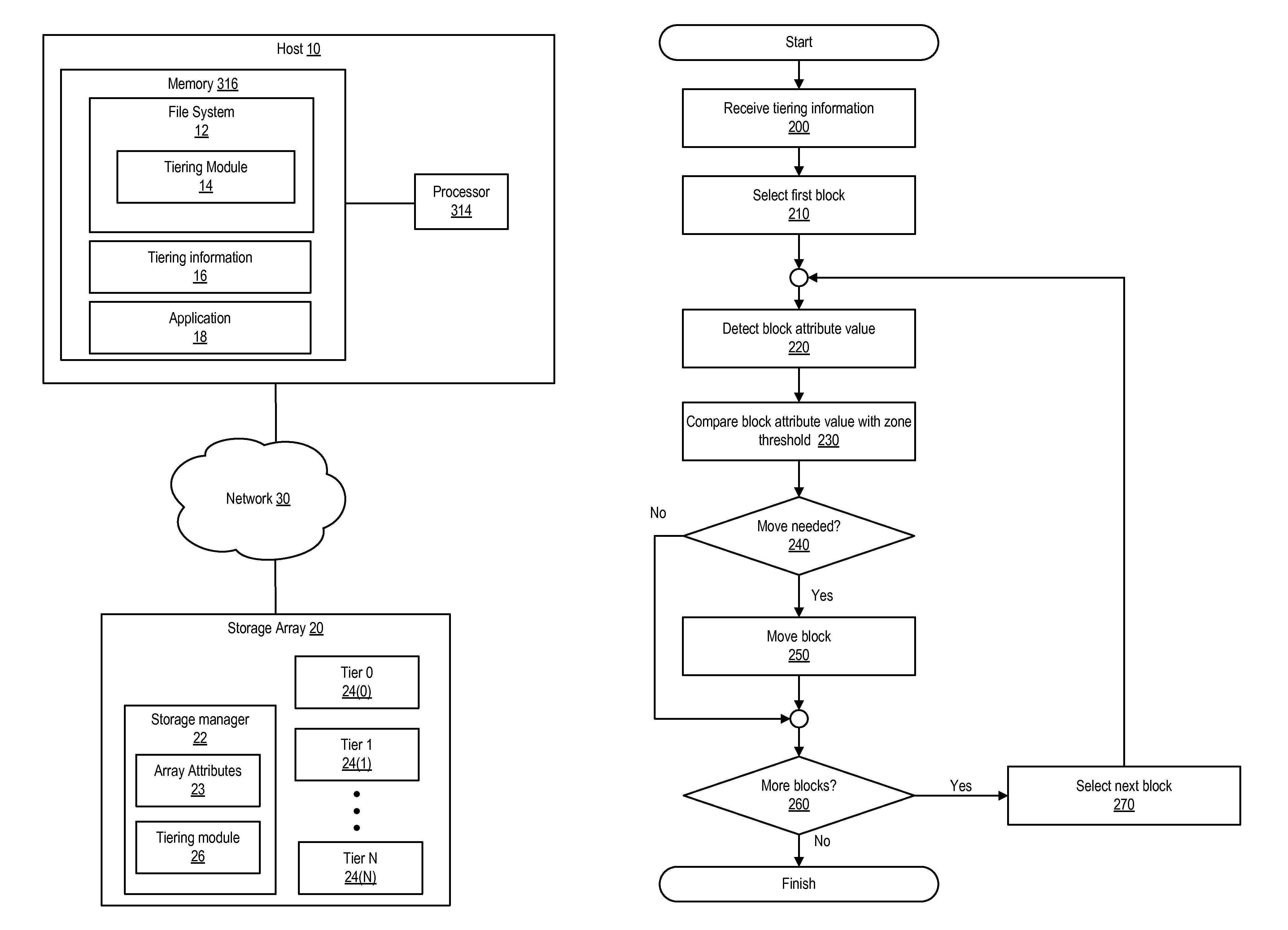
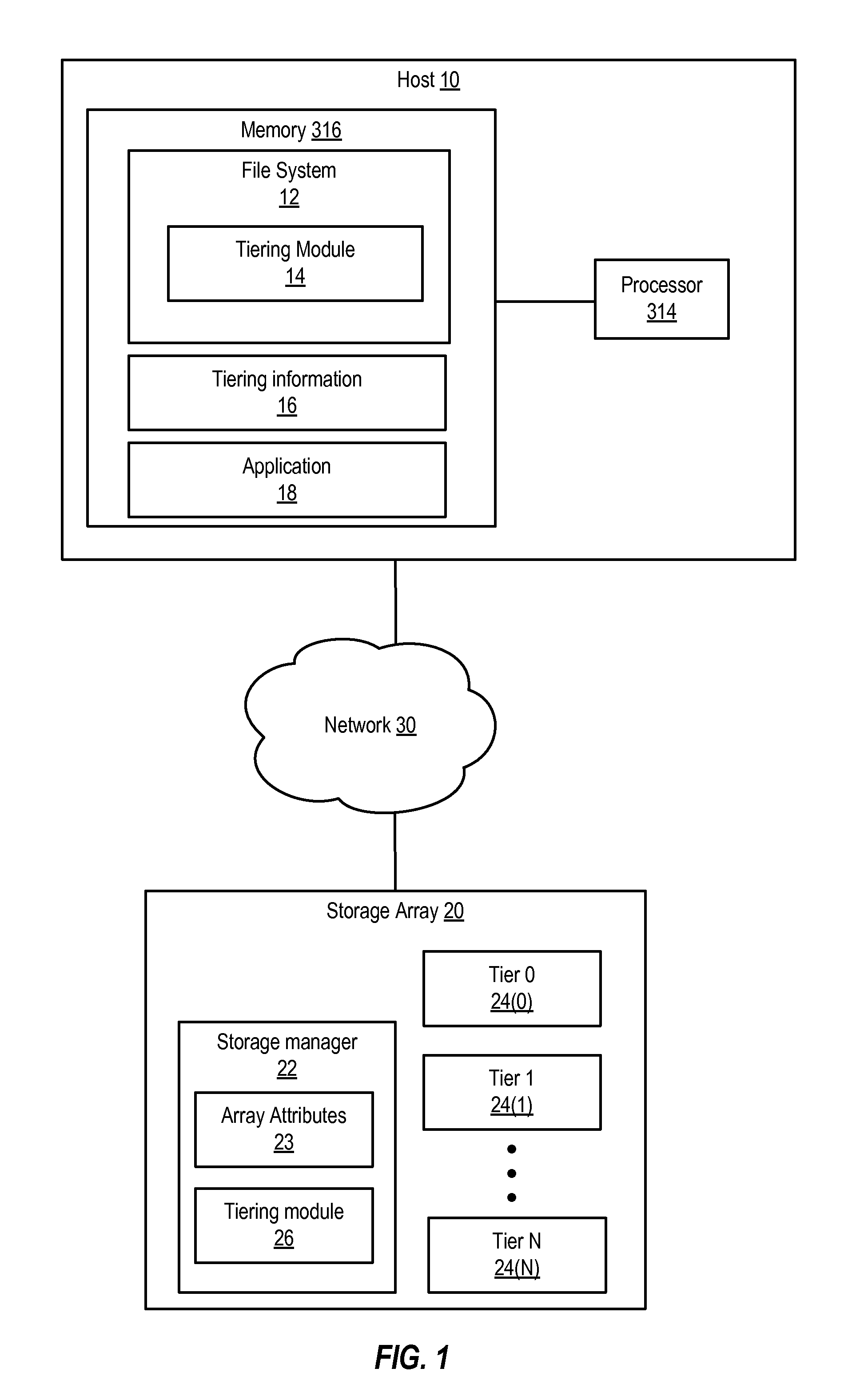
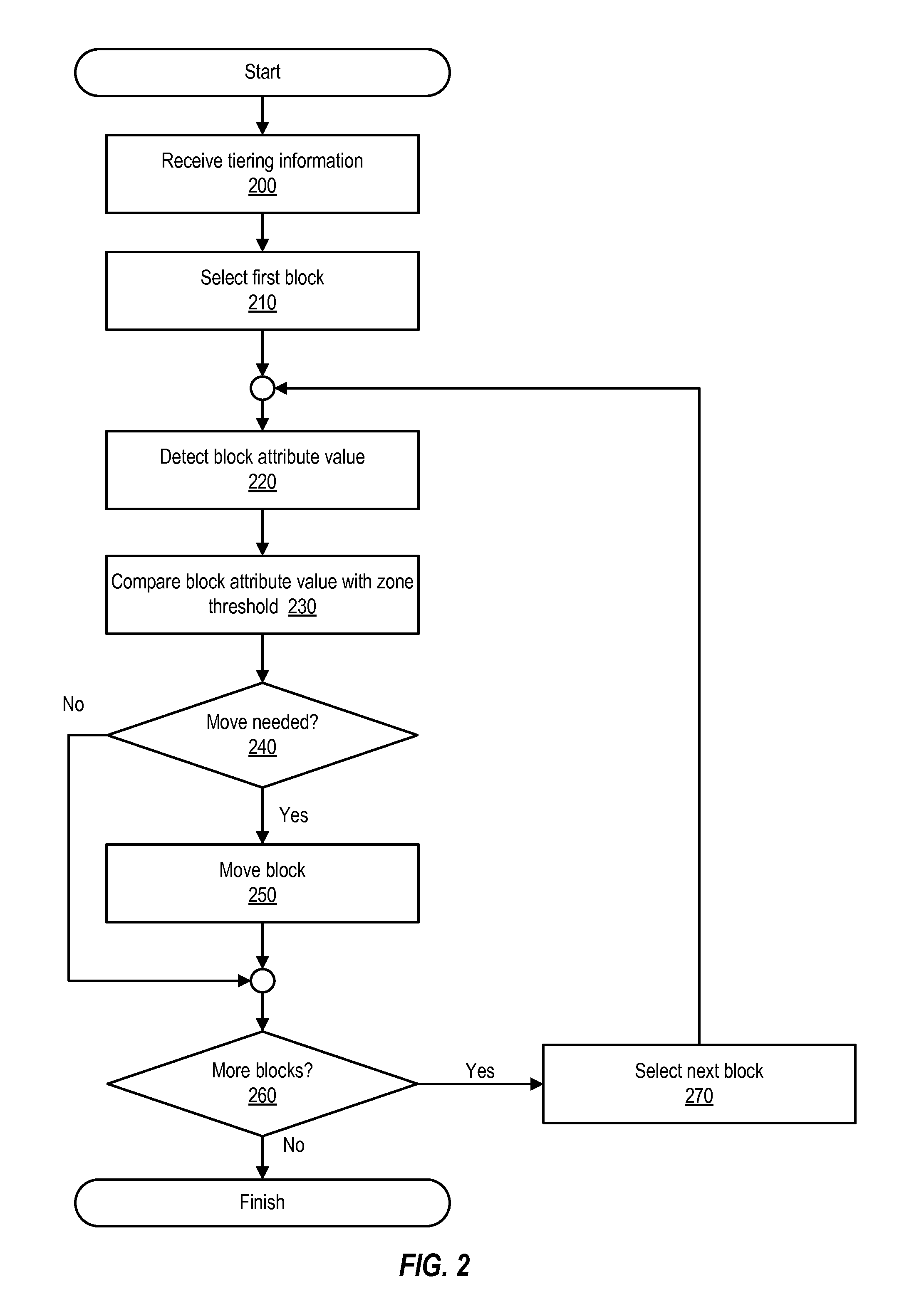
Tiering aware data defragmentation
Various systems and methods for performing tiering-aware data defragmentation. One method can involve receiving tiering information from a storage device that comprises multiple tiers. The information specifies a tiering attribute and tiering attribute value for the tiers. The method involves establishing zones that have zone attribute values corresponding to the received tiering attribute values. The method then involves storing a given block in a particular zone in response to detecting that a block attribute value of the block corresponds to a zone attribute value for the zone.
Owner:VERITAS TECH
Tenant Data Comparison for a Multi-Tenant Identity Cloud Service
ActiveUS20190306237A1Database distribution/replicationSemi-structured data queryingFile comparisonJSON
Embodiments replicate resources in a multi-tenant cloud system. Embodiments receive a master resource, associated with a master account of the cloud system to be replicated, where the master resource includes a master JavaScript Object Notation (“JSON”) object and includes a plurality of master attributes. Embodiments generate a master resource metadata JSON by calculating hash values for each of the master attributes to generate master attribute level hashes and by calculating an aggregate of all of the hash values to generate a master resource level hash. Embodiments store each master attribute of the master JSON object in a separate column of a master database table associated with the master account and store the master resource metadata JSON is in a separate hash column of the master database table. Embodiments replicate the master JSON object to create a replicated JSON object including a plurality of replicated attributes.
Owner:ORACLE INT CORP
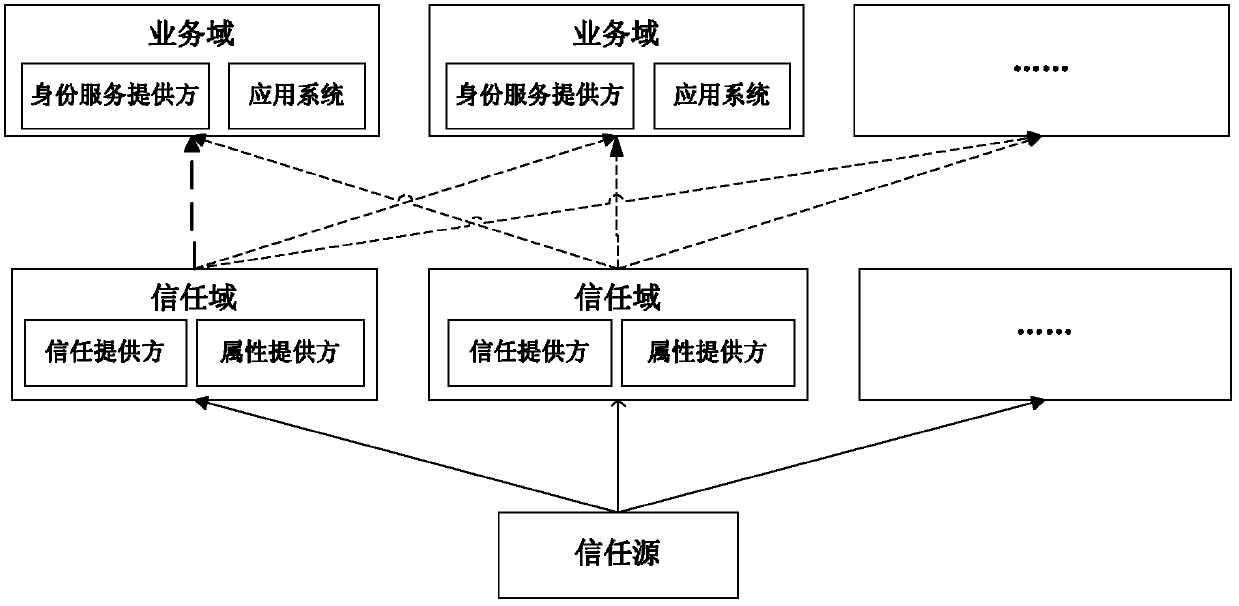
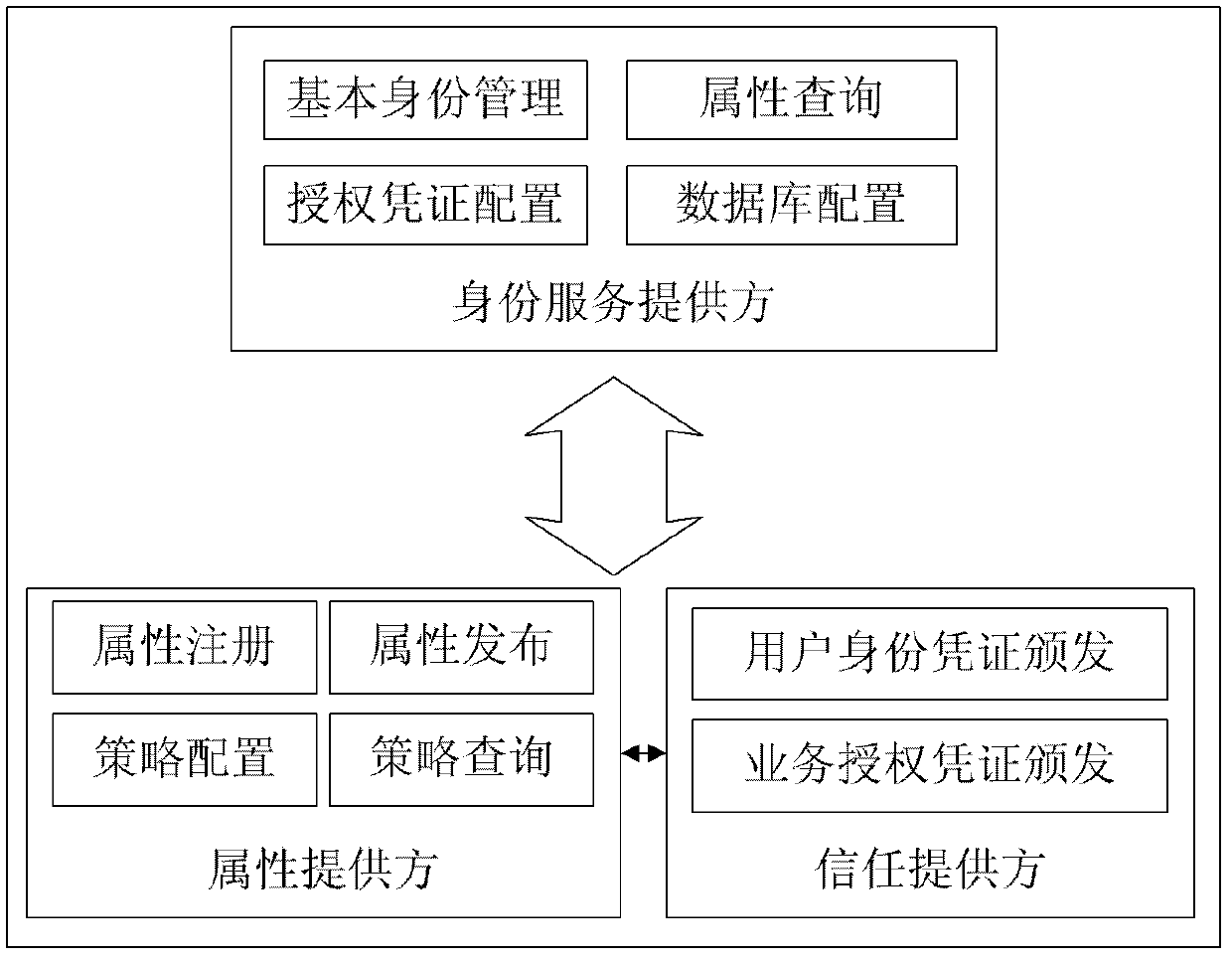
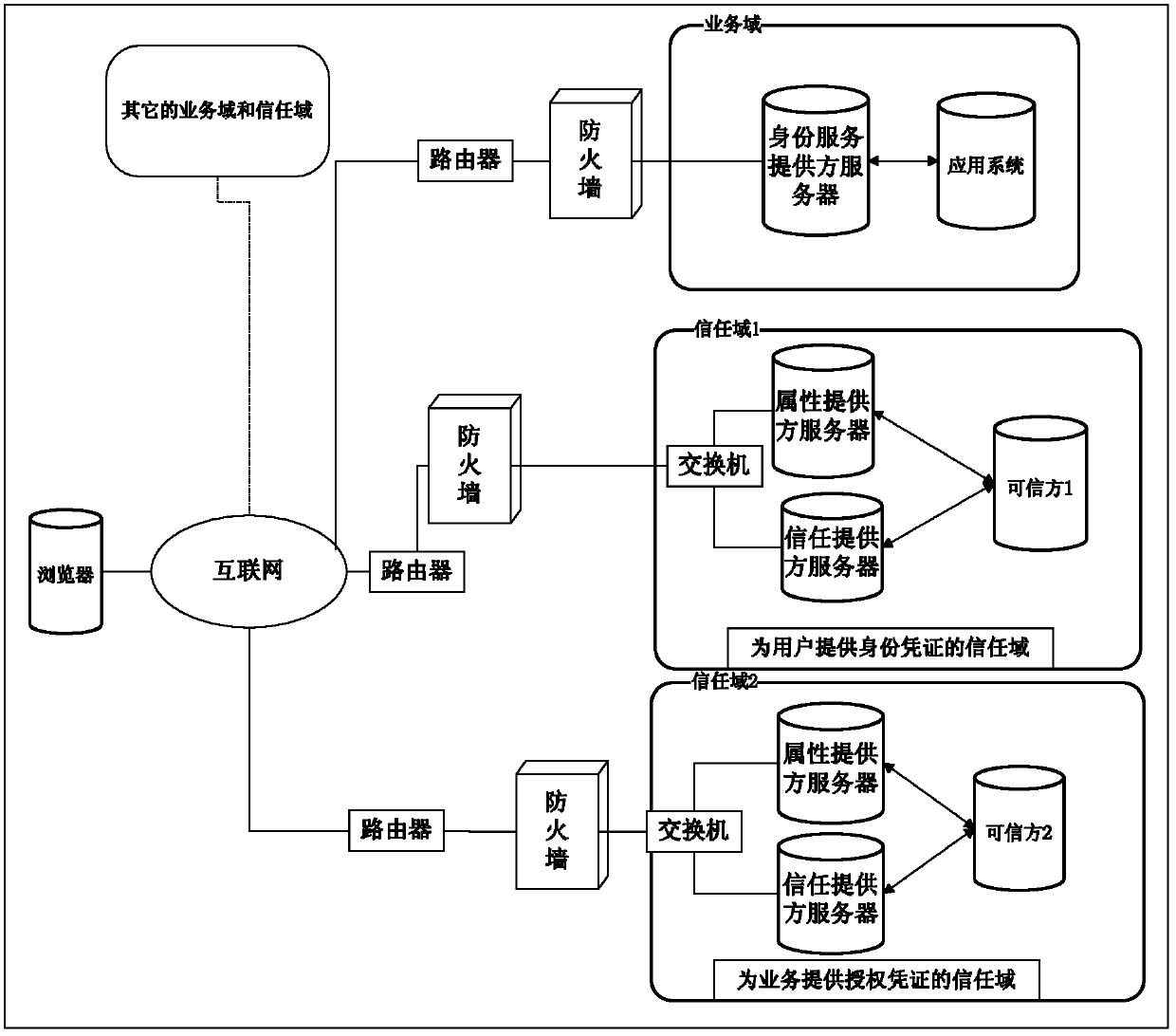
Attribute-oriented protection digital identity service method and system thereof
The invention discloses an attribute-oriented protection digital identity service method and a system thereof, which belong to the field of information safety. The method comprises the following steps: adopting an attribute supplier and a trust supplier to jointly form a trust domain, and supplying attribute service and trust certificate service to application systems in a management domain and a user; jointly deploying an identity service supplier and the application systems in a business domain, providing identity management service to the application systems, and meanwhile, calling service of the attribute supplier in the trust domain to replace a business system to finish demand service on the user attribute. The system comprises at least one trust domain and at least one business domain; the trust domain is respectively connected with the business domain through a network; each business domain comprises the identity service supplier and a plurality of application systems in data connection with the identity service supplier; each trust domain comprises the trust supplier and the attribute supplier in data connection with the trust supplier. According to the attribute-oriented protection digital identity service method and the system thereof, on the premise of guaranteeing privacy safety of a user, the user attribute demand of business is met.
Owner:INST OF SOFTWARE - CHINESE ACAD OF SCI
Retrieving configuration records from a configuration management database
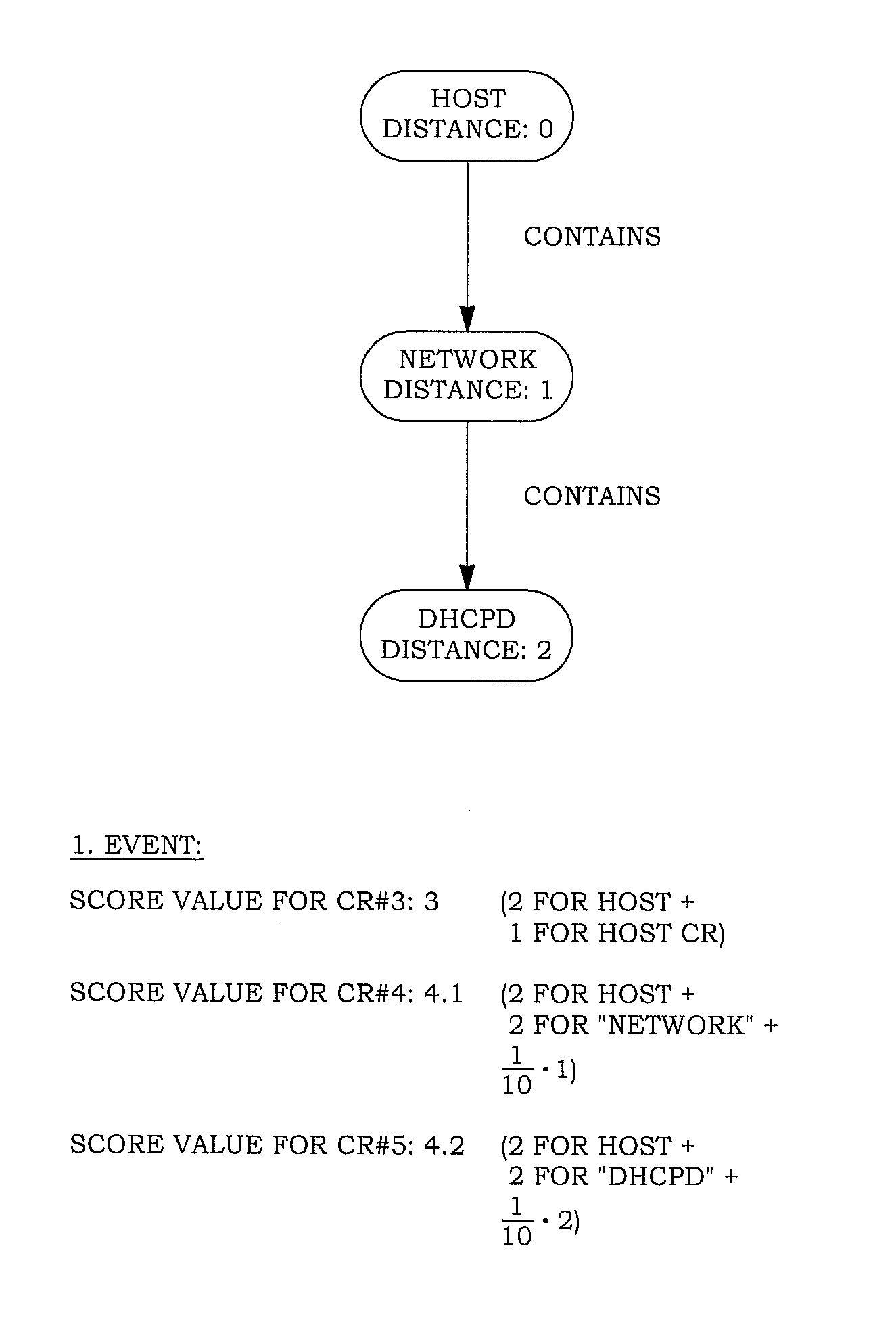
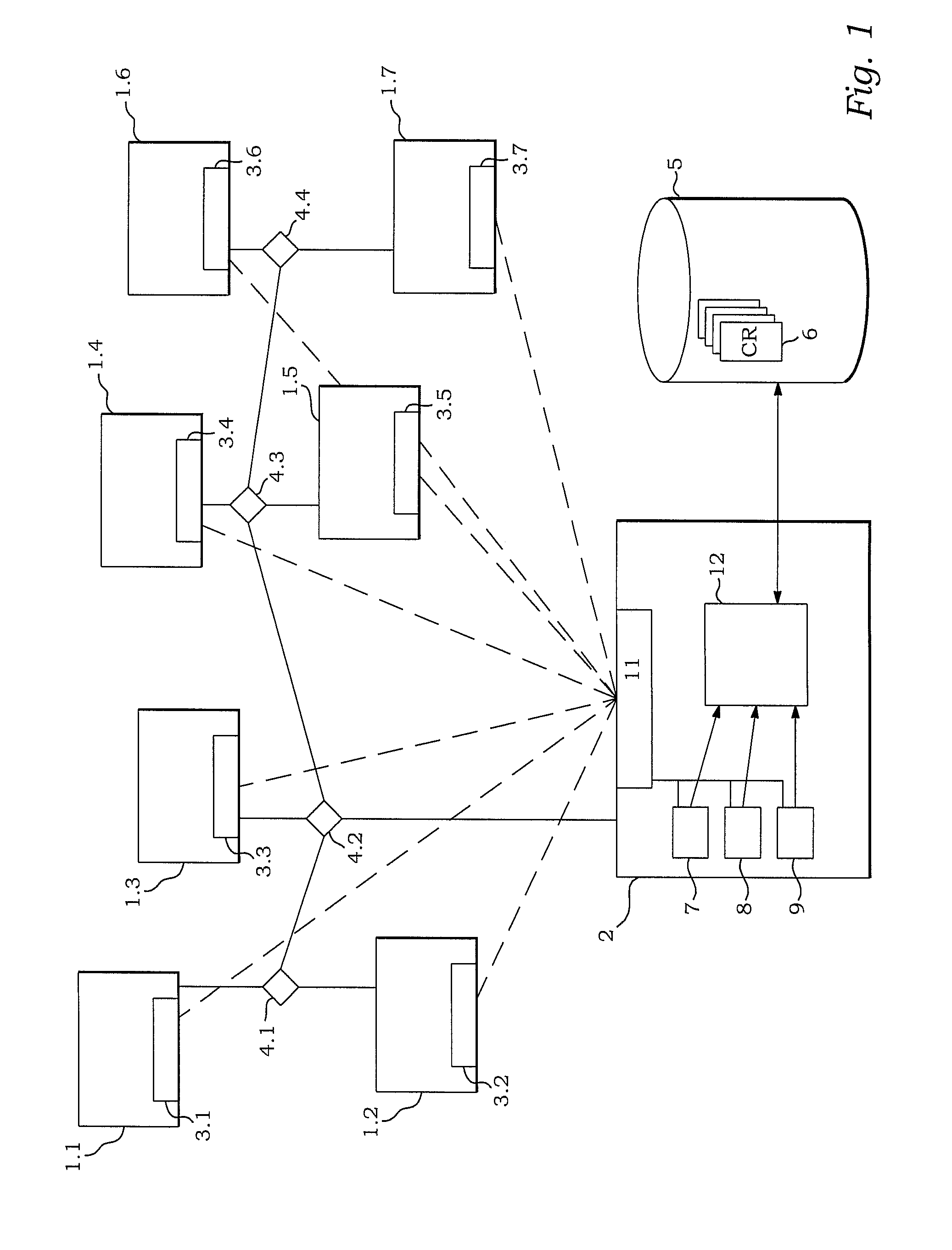
A method is provided of retrieving a configuration record from a configuration management database pertaining to an IT-infrastructure including host devices, a configuration record having attributes and assigned attribute values, the IT-infrastructure being managed by an operation management system providing messages indicating events in the IT-infrastructure. The method includes providing a message including a set of unidentified attribute values and an identified host value, retrieving from the configuration management database one or more configuration records containing the identified host value, and selecting from the one or more retrieved configuration records a configuration record depending on the number of matches between the unidentified attribute values and the attribute values of the retrieved configuration records.
Owner:MICRO FOCUS LLC
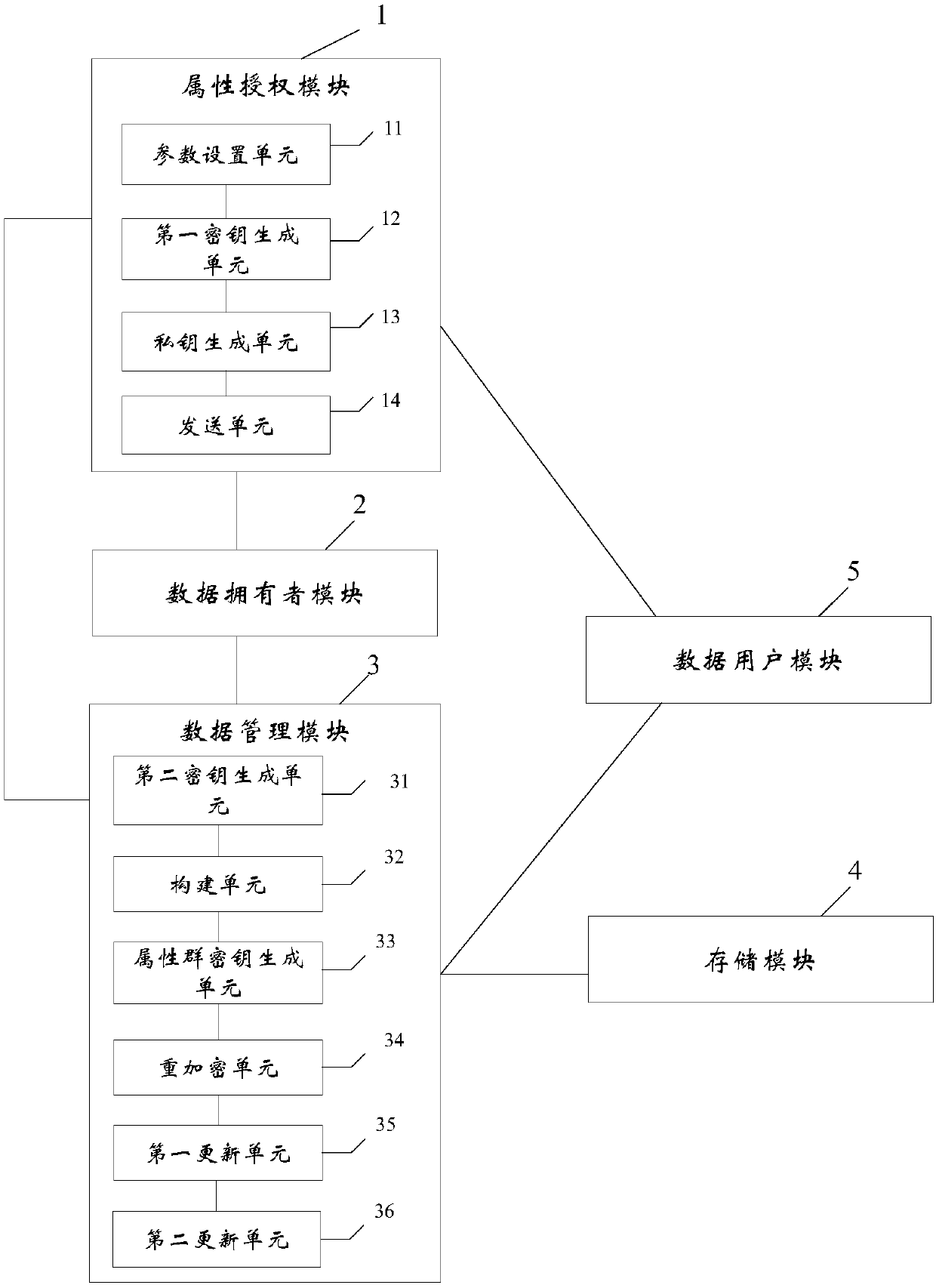
Revocable attribute-based encryption system and method for cloud storage
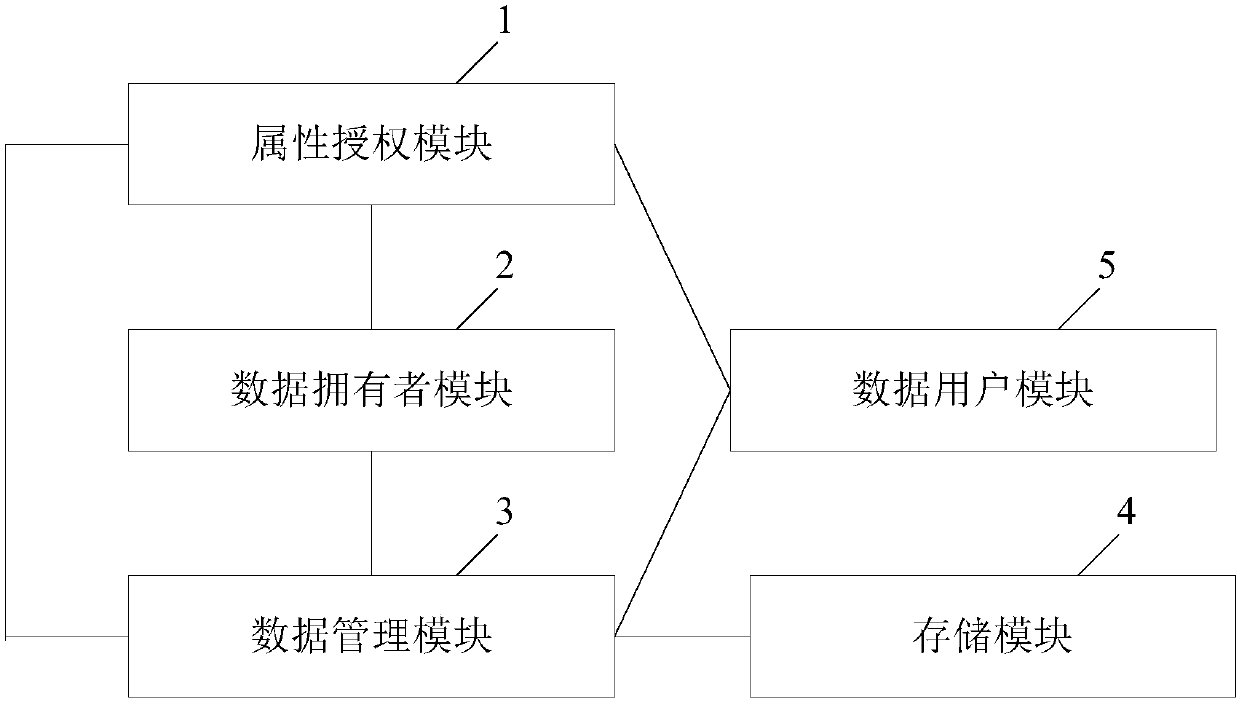
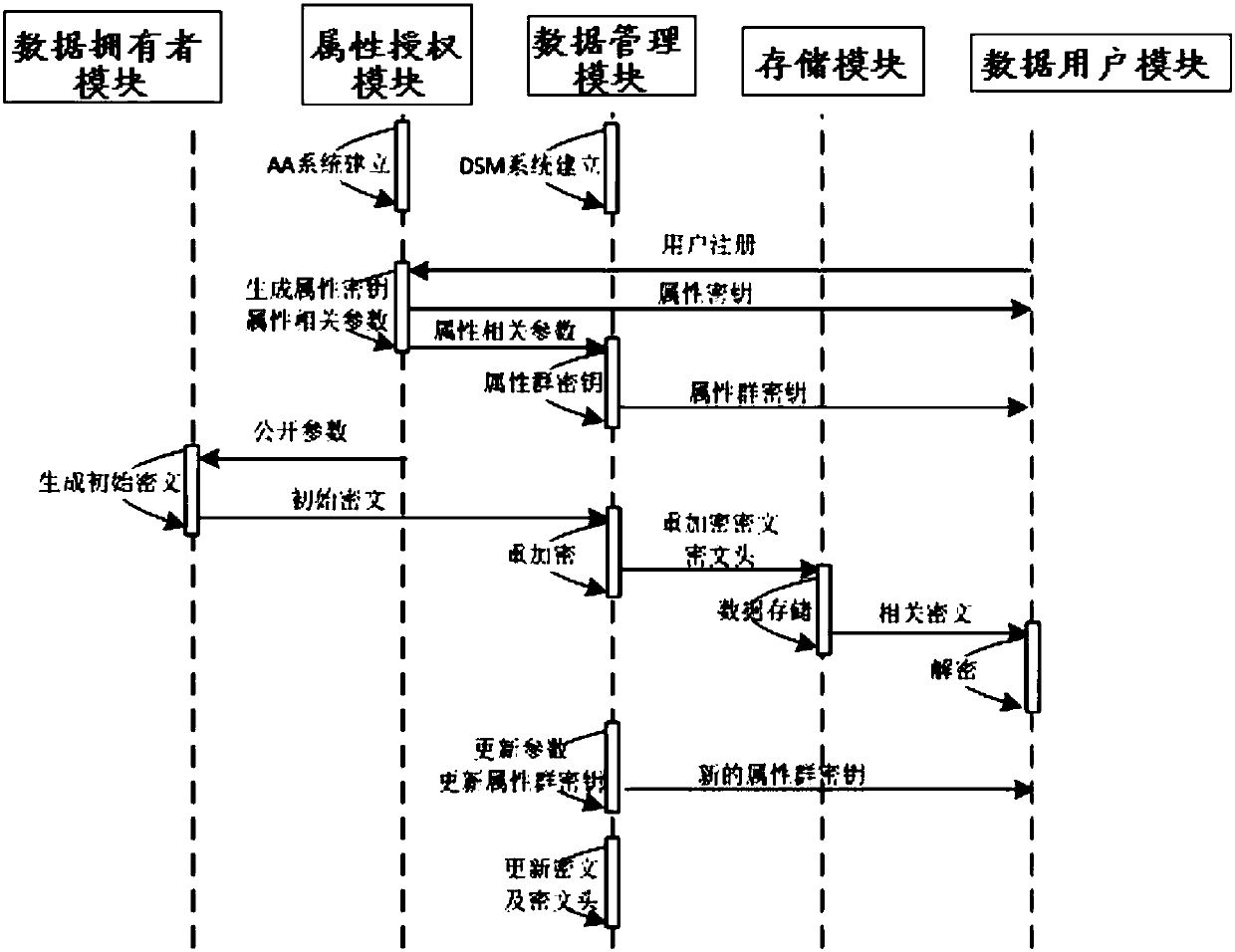
ActiveCN108200181ALighten the computational burdenConstant lengthKey distribution for secure communicationMultiple keys/algorithms usagePlaintextData access
The invention discloses a revocable attribute-based encryption system and method for cloud storage. An attribute authorization module generates a public key and a main private key of an encryption system, and an attribute private key and an attribute group initial key of a data user; a data owner module constructs a data access structure, and obtain initial ciphertext by encrypting the plaintext;a data management module generates a attribute group key through the constructed key encryption key tree, performs re-encryption processing on the initial ciphertext to generate a ciphertext file anda ciphertext header of the ciphertext file, and stores the ciphertext file via a storage module; the data management module can also update the attribute group key after the data user module attributeis revoked, and process to obtain an updated ciphertext file. The data user module accesses the ciphertext file and decrypts the ciphertext file to obtain a plaintext corresponding to the ciphertextfile. Therefore, the attribute-level user revocation capability is implemented, the collusion attack between a revoking user and a non-revoking user can be resisted, and fixed-length ciphertext lengthand higher efficiency are achieved.
Owner:PLA STRATEGIC SUPPORT FORCE INFORMATION ENG UNIV PLA SSF IEU
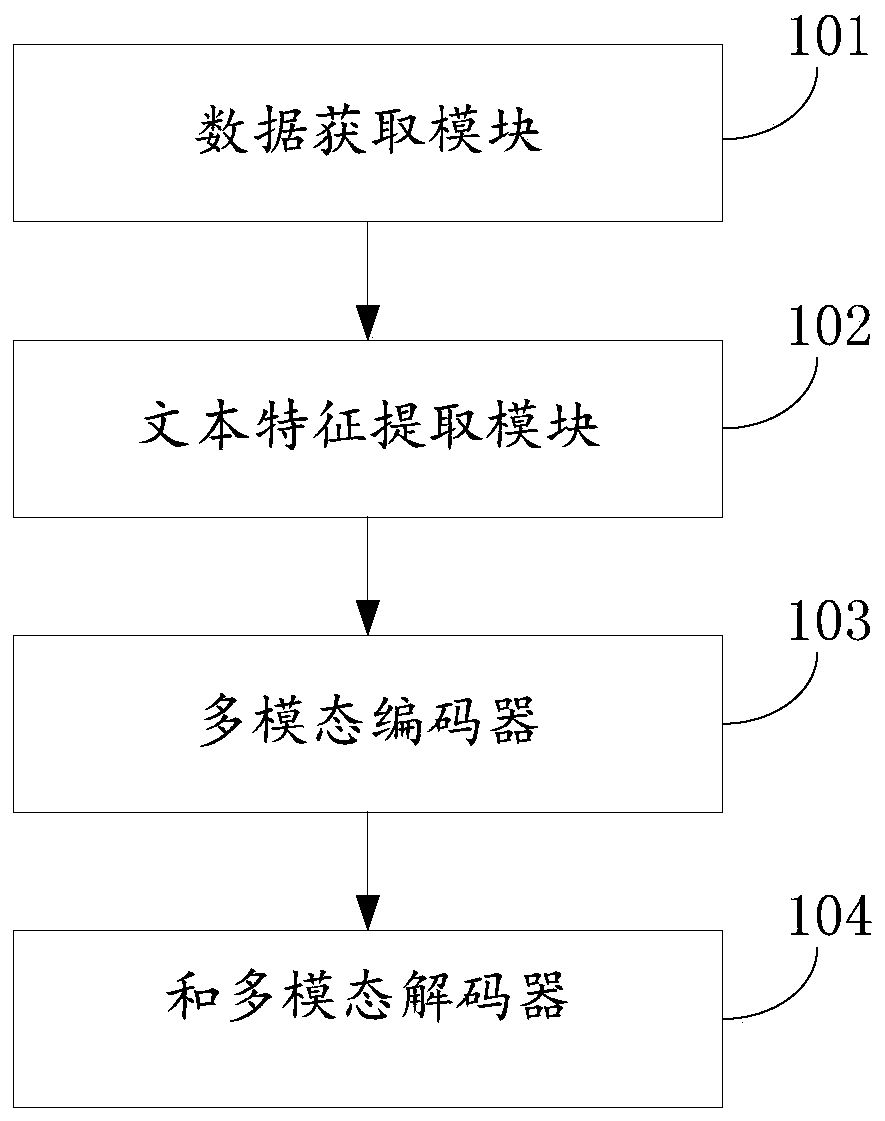
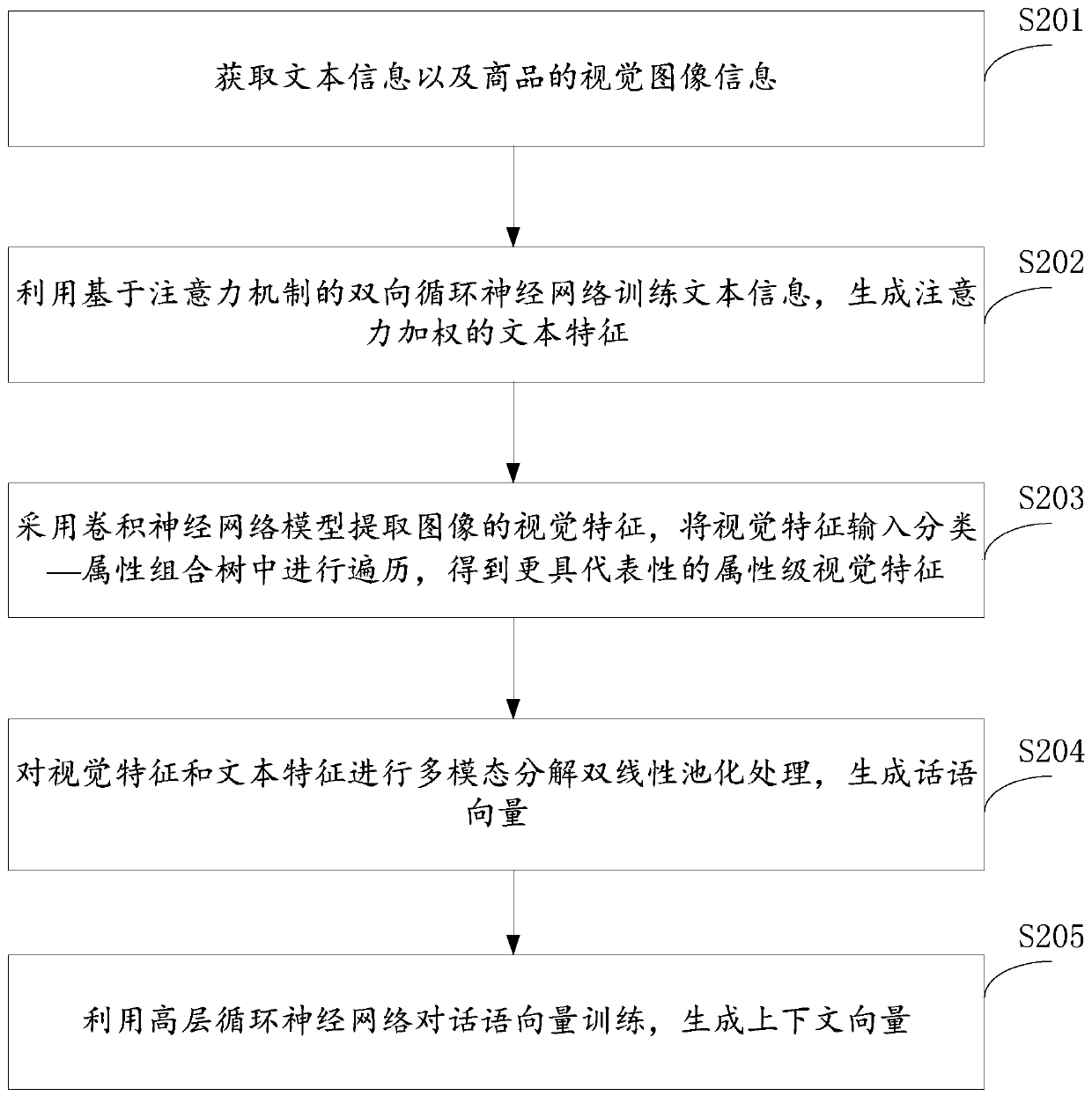
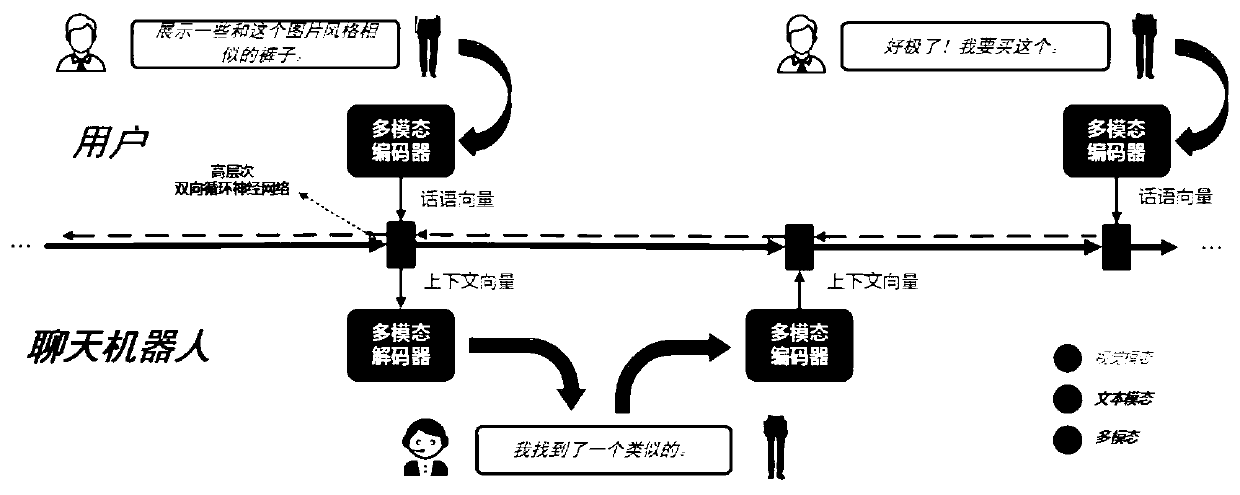
Multi-modal dialogue system and method guided by user attention
ActiveCN110209789AMultimodal reply implementationDigital data information retrievalCharacter and pattern recognitionFeature extractionData acquisition
The invention discloses a multi-modal dialogue system and method guided by user attention. The multi-modal dialogue system and method can respectively encode multi-modal utterances and generate multi-modal replies by adopting a multi-modal encoder and a multi-modal decoder. The system comprises a data acquisition module, a text feature extraction module, a multi-mode encoder and a multi-mode decoder; the data acquisition module acquires text information and visual image information of the commodity; the text feature extraction module generates attention-weighted text features; the multi-mode encoder extracts visual features of the visual image by adopting a convolutional neural network model, and inputs the visual features into the classification-attribute combination tree for traversal toobtain attribute-level visual features; multi-modal decomposition bilinear pooling processing is performed on the visual features and the text features to generate multi-modal utterance vectors; themulti-modal decoder generates a context vector; and based on the context vector, a visual image and a text attribute of a certain amount of required commodity are selected, the visual image and the text attribute are decoded, and a multi-modal commodity representation is generated.
Owner:SHANDONG UNIV
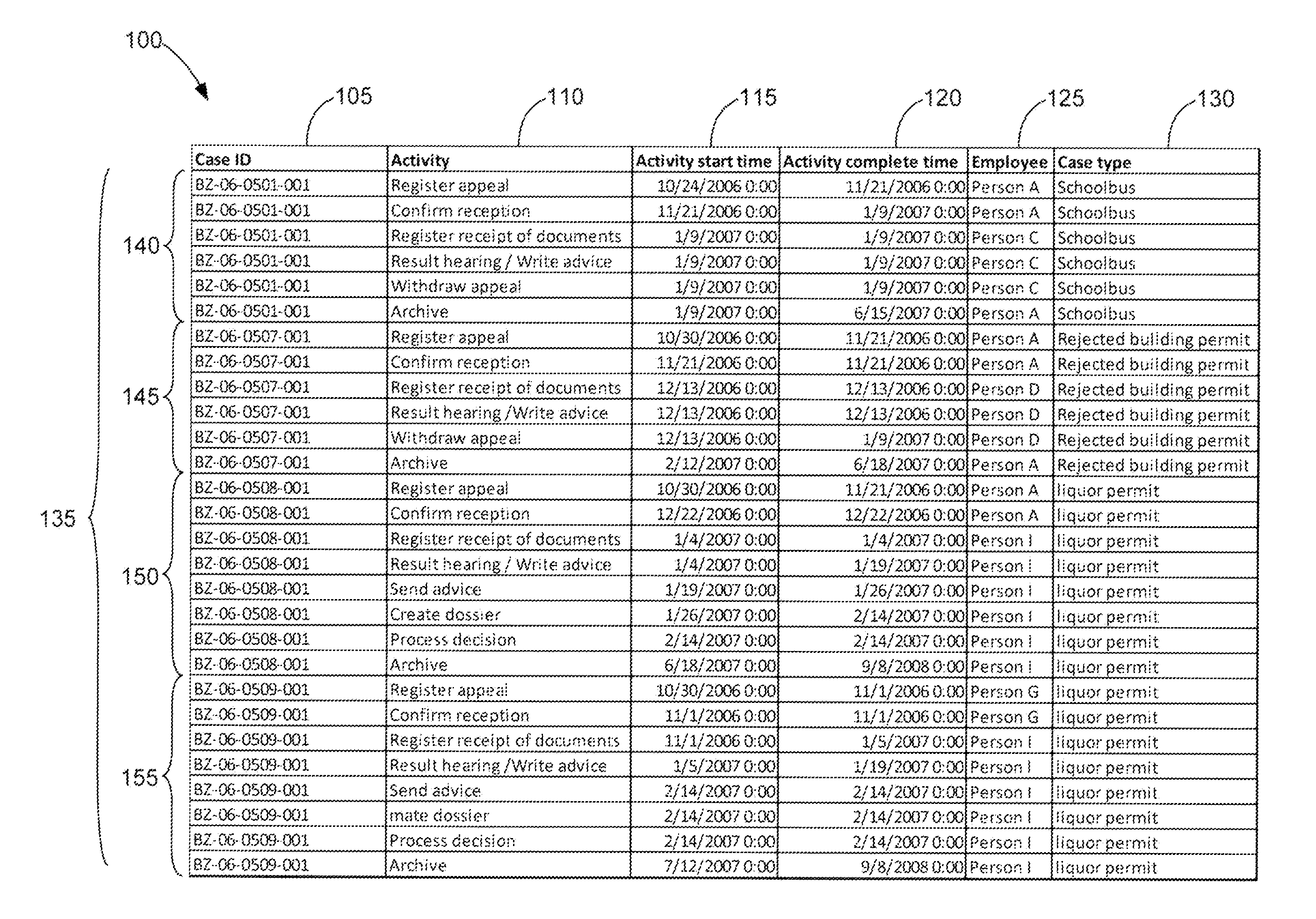
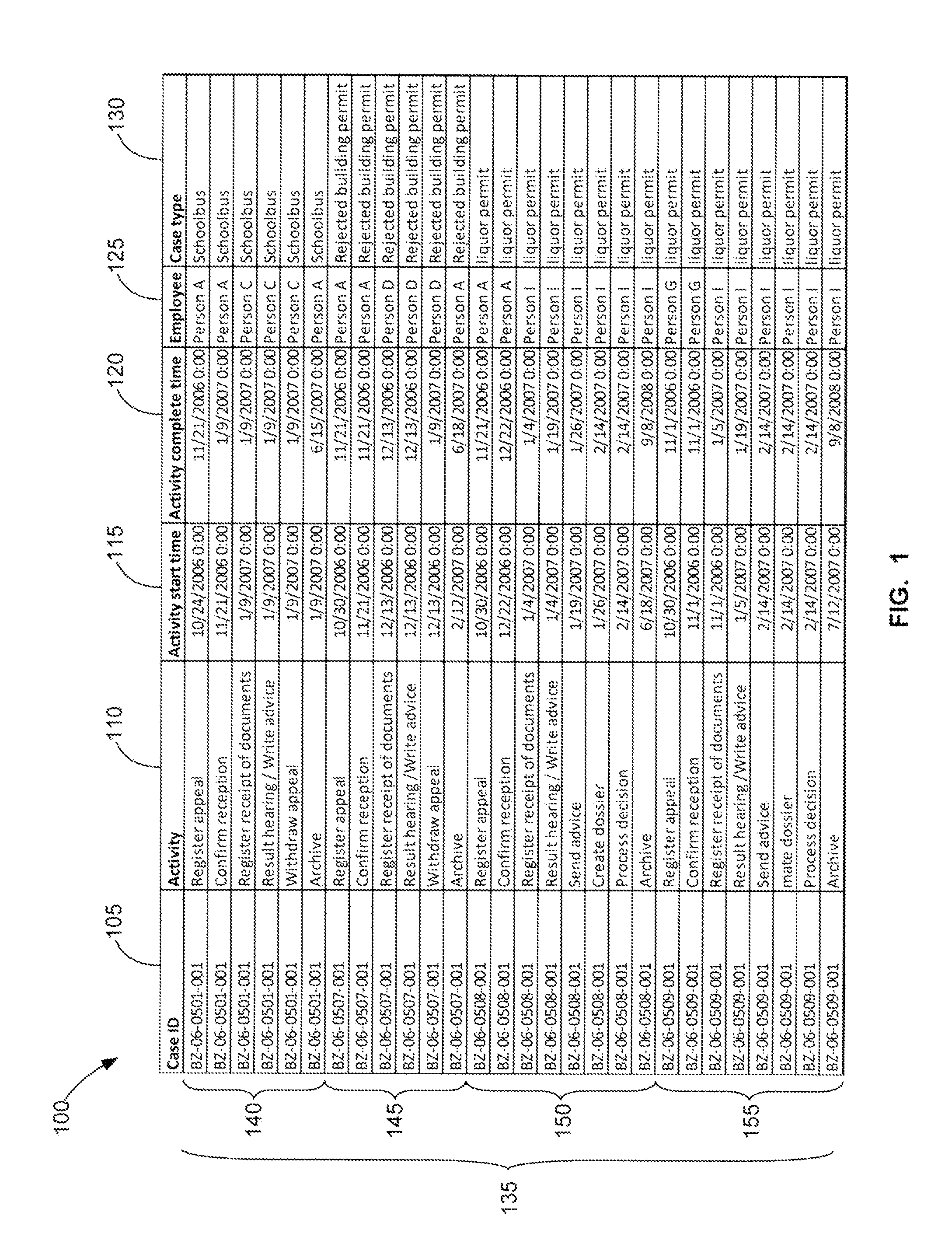
Automatic Attribute Level Detection Methods
A method of detecting attribute levels in a dataset that includes determining whether column data in a column for a case identifier is the same, classifying the column data as case level attributes if all of the column data is identical, and classifying the column data as event level attributes if the column data is different for at least one data entry in the column.
Owner:LEXMARK INT TECH
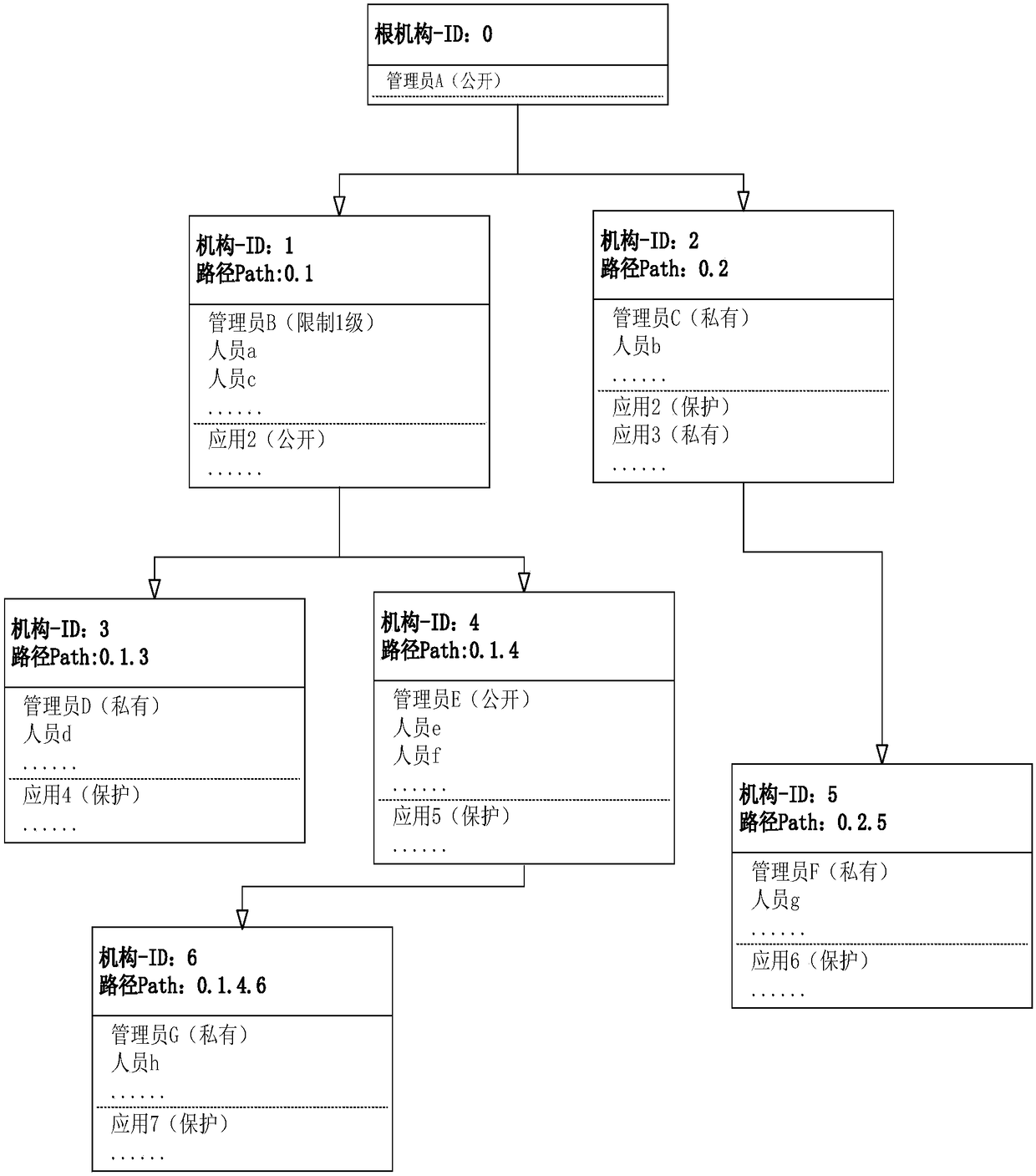
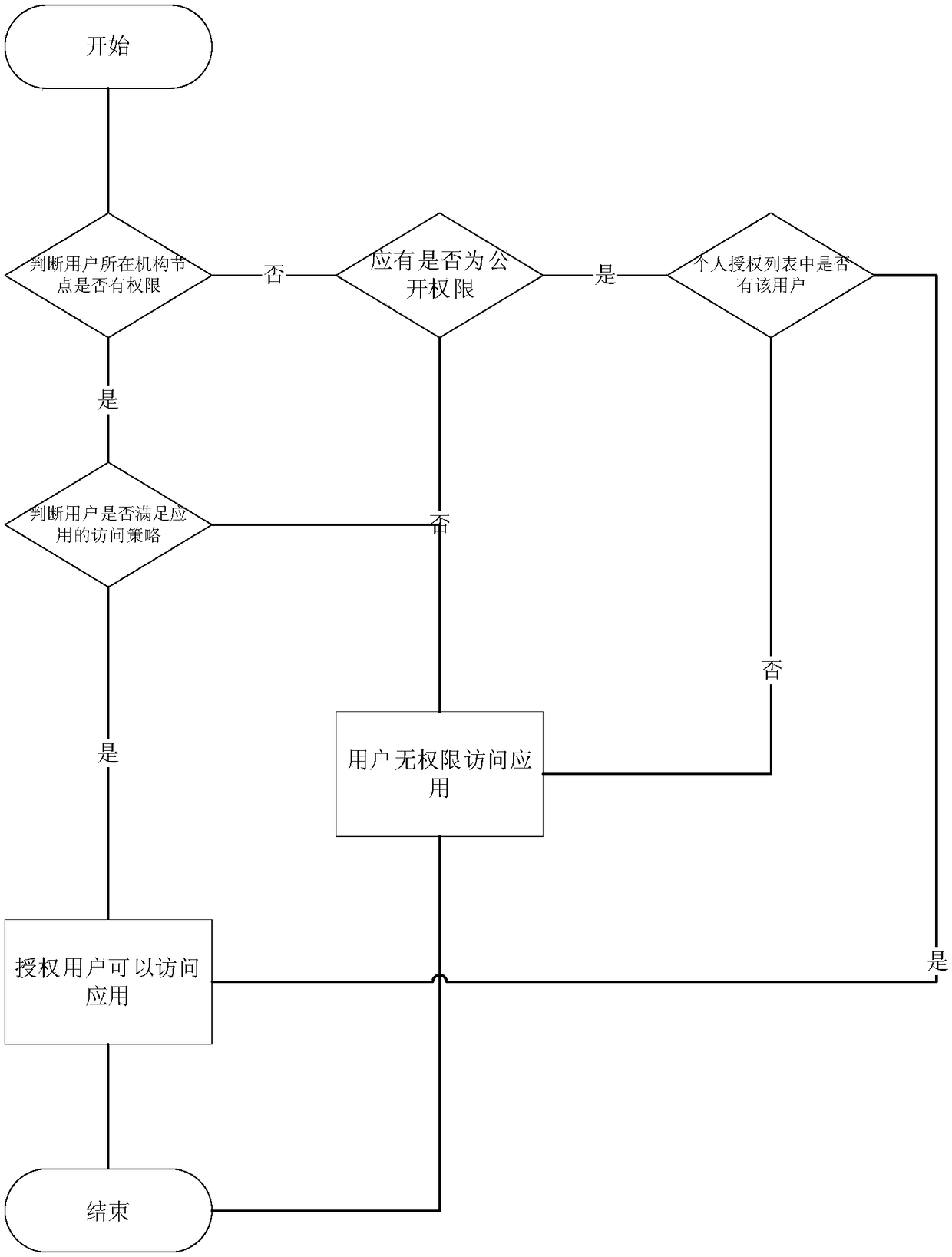
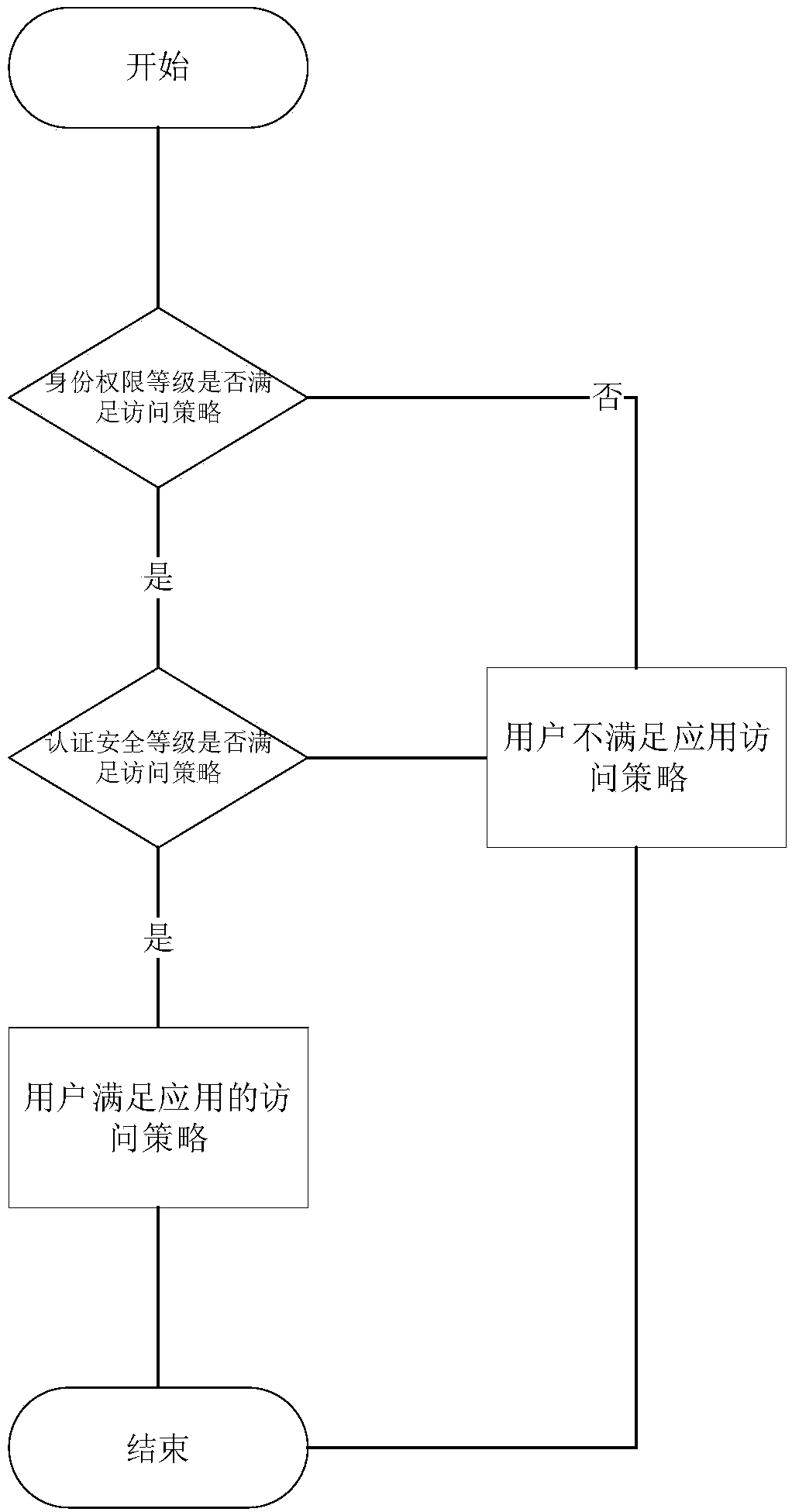
Organization application permission management method and service system based on tree-shaped organization model
ActiveCN108322432AAvoid repetitive operationsSimplify the authorization operation processDigital data protectionTransmissionRights managementTree shaped
The invention discloses an organization application permission management method and service system based on a tree-shaped organization model. The method comprises the steps of: establishing the tree-shaped organization model among organizations, i.e., an organization tree, wherein each organization corresponds to one node in the organization tree; setting applications and personnel for the organizations, and according to the organizations to which the personnel belongs, setting public application access permissions of the organizations to which the personnel belongs for the corresponding personnel; and setting a corresponding attribute level for each personnel, and for each application, according to an attribute level of a user, respectively setting a corresponding access strategy, wherein each organization has a unique organization ID and a subordinate path, and the subordinate path of each organization represents positions of the organization on the organization tree, i.e., the organization IDs which need to be passed through from a root node of the organization tree to the node corresponding to the organization. According to the invention, a subordinate relationship among different hierarchies of organizations, subordinate personnel and the applications is managed by the tree-shaped organization model, and when the application permission management operation is simplified,the requirement for the access permission difference is met.
Owner:INST OF INFORMATION ENG CAS
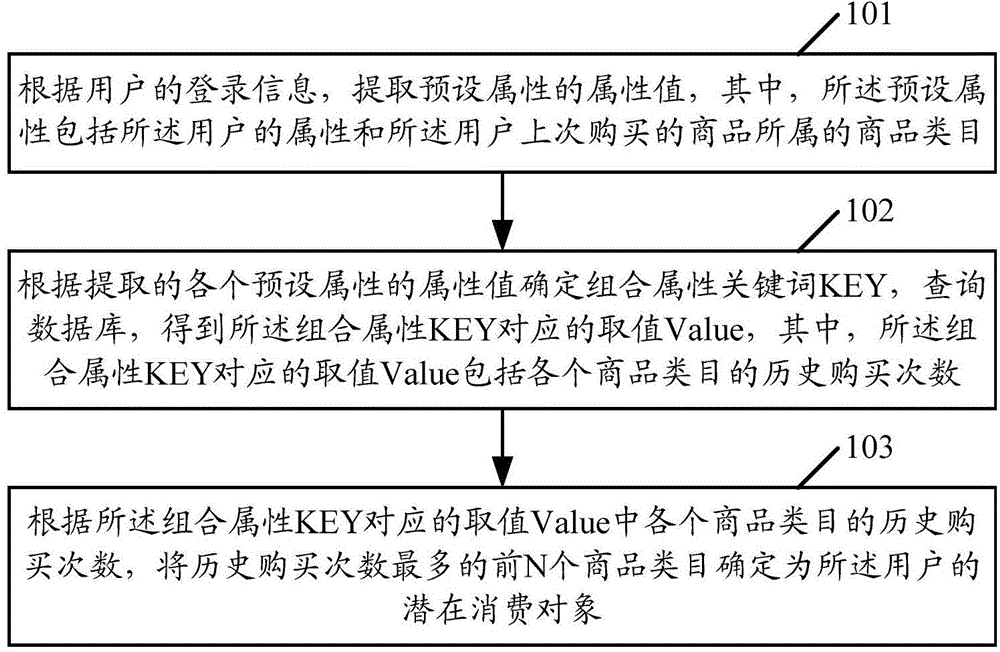
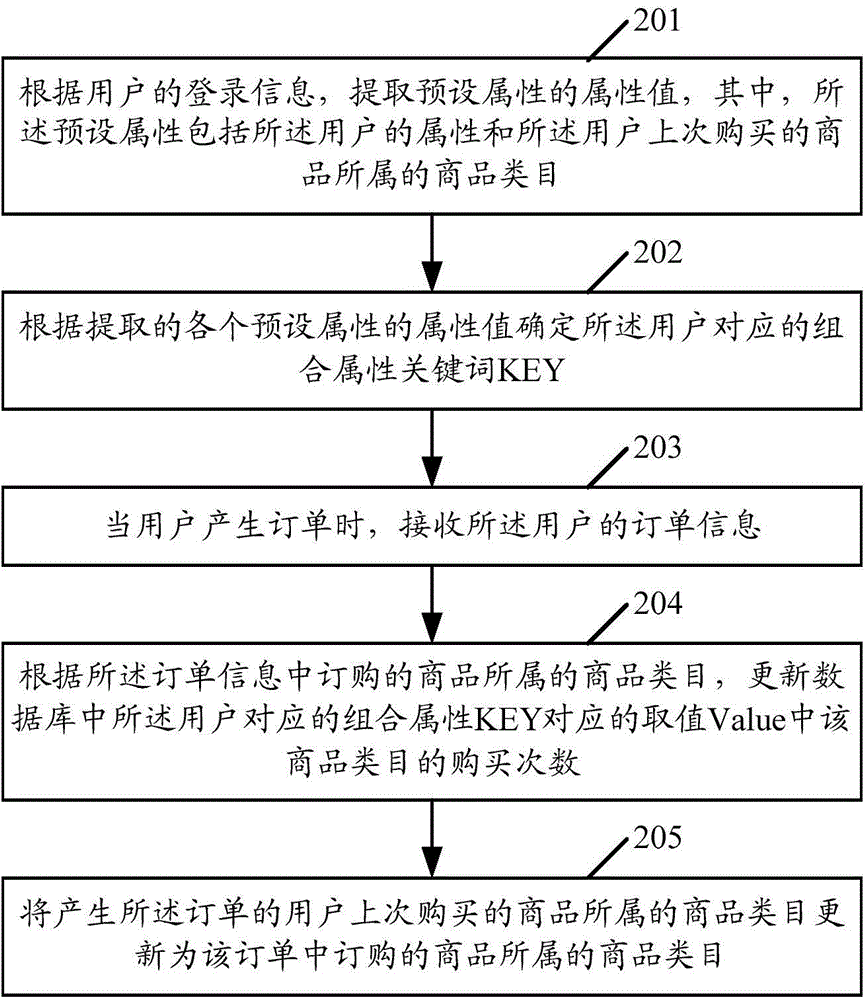
User behavior information analysis method and device thereof
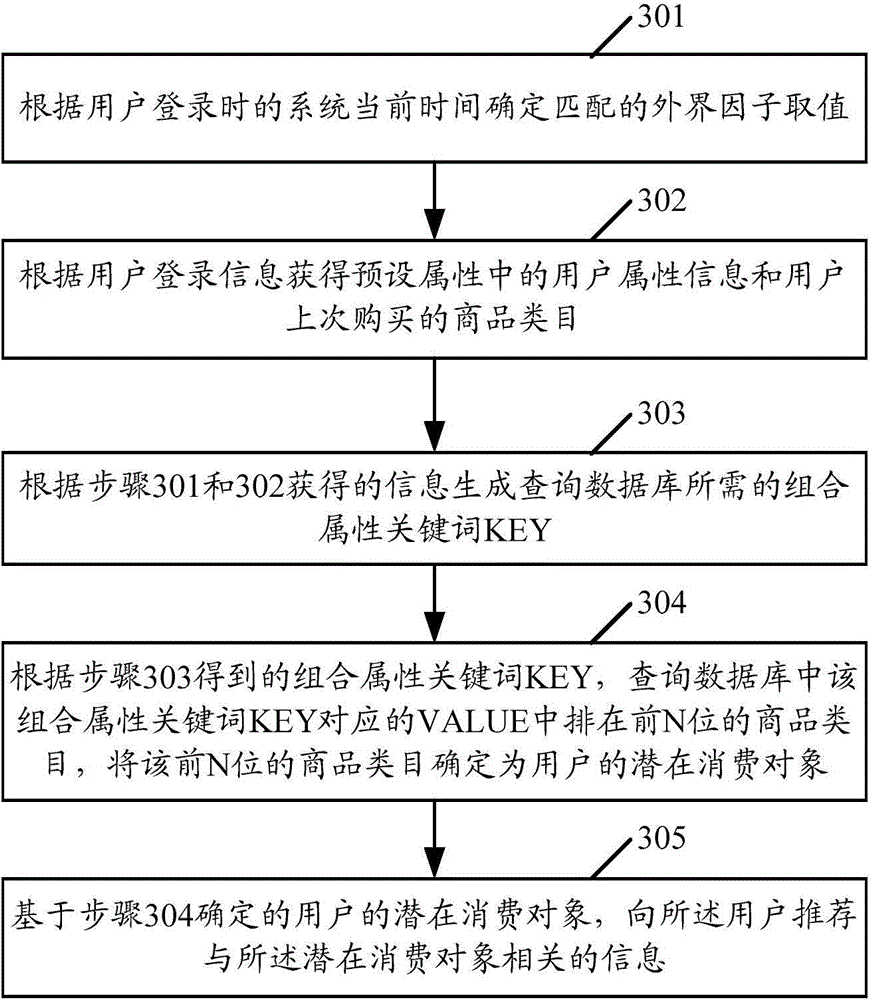
InactiveCN104820879AComprehensive coverage of consumer behaviorNo one-sidednessForecastingMarketingInformation analysisAnalysis method
An embodiment of the invention discloses a user behavior information analysis method and a device thereof. The user behavior information analysis method comprises the steps of: according to user logging-on information, extracting attribute values of preset attributes, wherein the preset attributes comprise an user attribute and commodity kind to which a commodity that is purchased by the user last time belongs; determining a combined attribute KEY according to the attracted attribute value of each preset attribute, inquiring in a database for obtaining a value which corresponds with the combined attribute KEY, wherein the value which corresponds with the combined attribute KEY comprises number of historical purchasing times of each commodity kind; and according to the number of historical purchasing times of each commodity kind in the value which corresponds with the combined attribute KEY, determining the first N commodity kinds with maximal number of historical purchasing times as latent consumption objects of the user. The user behavior information analysis method according to the embodiment of the invention can improve accuracy in determining the latent consumption behavior of the user.
Owner:BEIJING JINGDONG SHANGKE INFORMATION TECH CO LTD +1
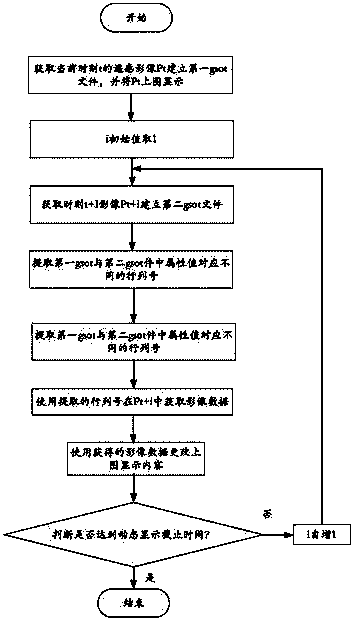
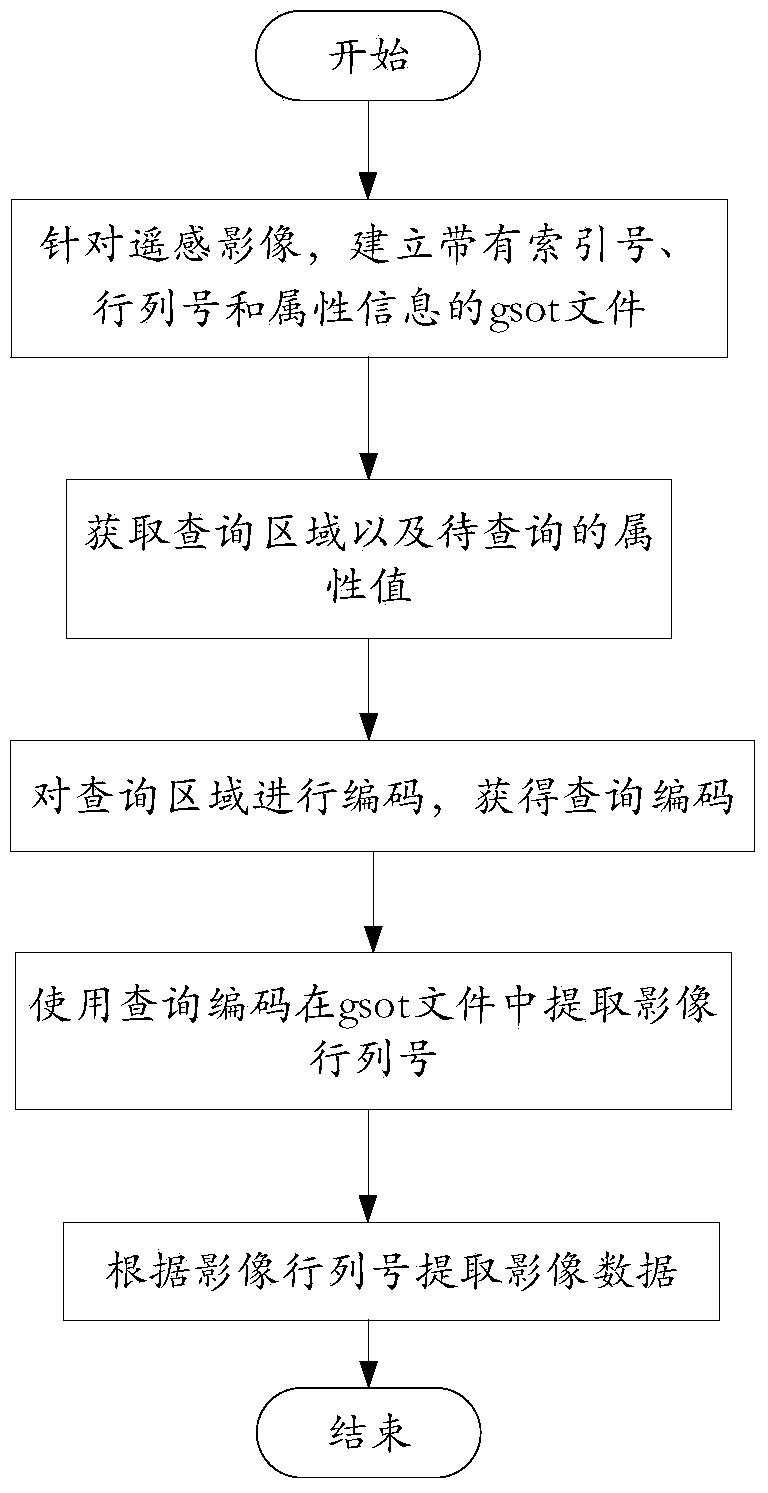
Subdivision, query and dynamic display method oriented to remote sensing data content
InactiveCN104166695AAchieve the same recordRealize managementGeographical information databasesSpecial data processing applicationsSensing dataData content
The invention discloses a subdivision, query and dynamic display method oriented to remote sensing data content. The method particularly includes the steps that remote sensing data are subdivided through a set subdivision level, and a gsot file is established; a GeoSOT code of each subdivision patch obtained after subdivision serves as an index number, and position information of image data in the subdivision patch in the remote sensing data and the attribute content of the image data are correspondingly stored in the gsot file; a query region and an attribute value to be queried are acquired, and a query patch and a query code corresponding to the query region are acquired through subdivision; when one index number and one query code are consistently matched from left to right, the length of the index number is larger than the query code, and meanwhile the attribute value corresponding to the index number is equal to the attribute value to be queried, image data corresponding to the index number are extracted. Meanwhile, dynamic display of the remote sensing data based on attribute information is conducted through the query method.
Owner:PEKING UNIV
Explainable fashion clothing personalized recommendation method
ActiveCN110246011AEfficient recommendationCharacter and pattern recognitionBuying/selling/leasing transactionsPersonalizationFeature vector
Owner:UNIV OF SCI & TECH OF CHINA
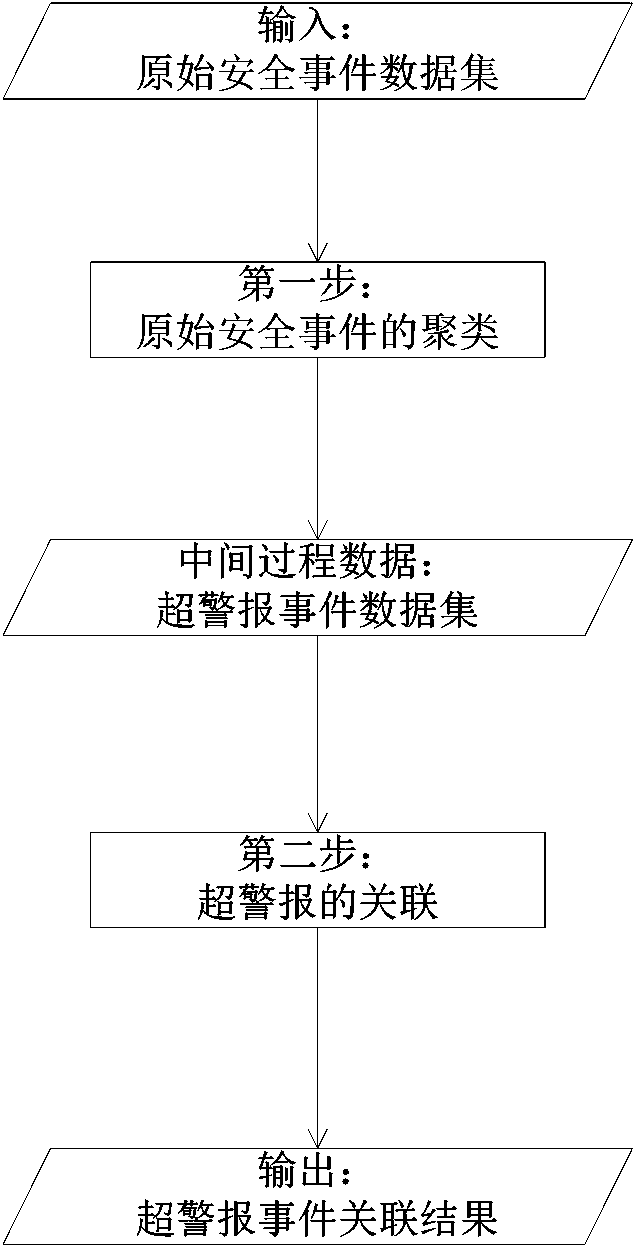
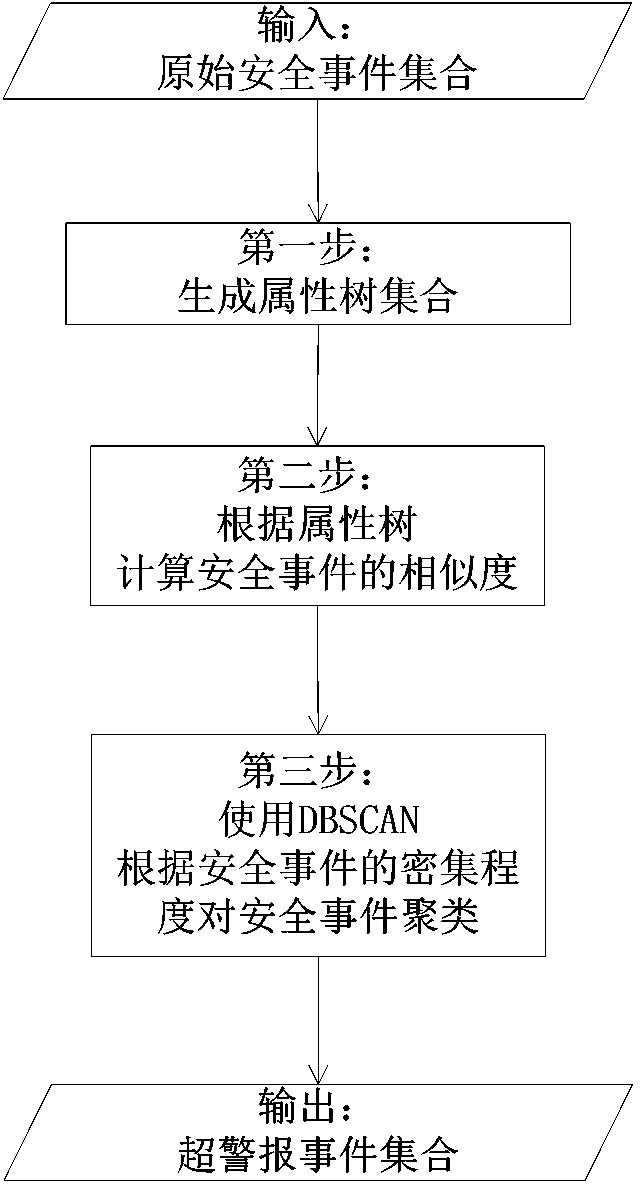
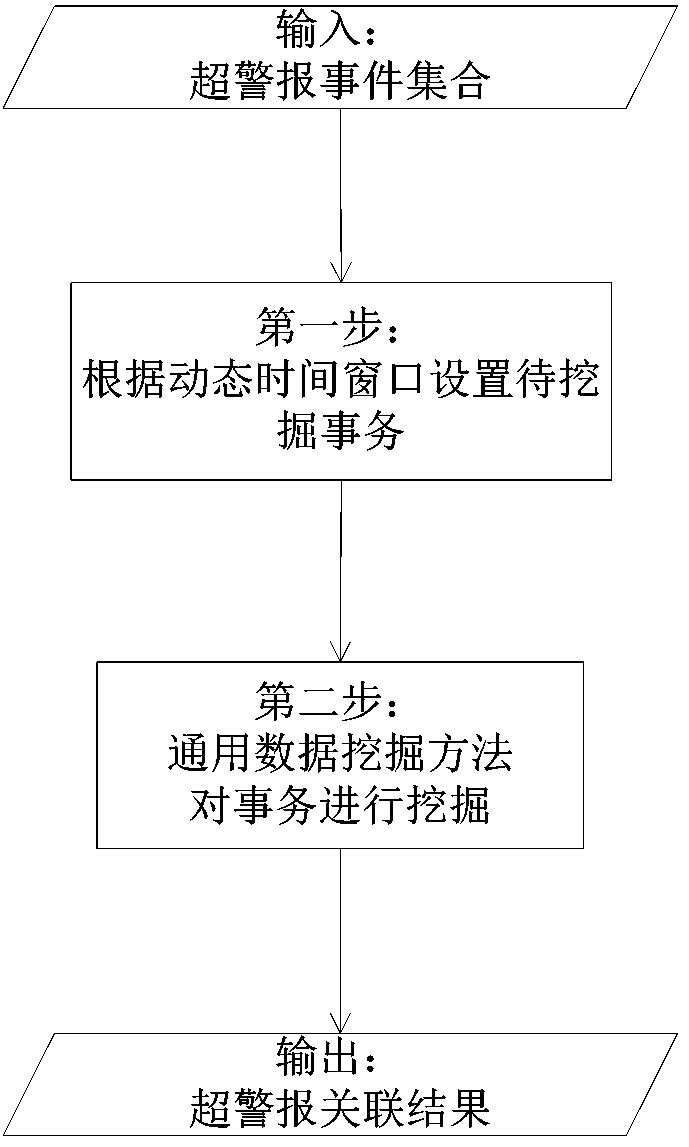
Network security incident correlation method
The invention discloses a network security incident correlation method. The network security incident correlation method includes classifying original security incidents to respectively acquire attribute values such as IP addresses, port numbers, timestamps, original security incident classifications and alarming contents of the original security incidents, judging similarities of different original security incident attribute values, correlating the original security incidents according to similarities among the original security incidents, and correlating internally-related super alarms. The network security incident correlation method has the advantages that network security incidents are clustered according to the similarities among the original security incidents, and accordingly, the internally-related super alarms can be well correlated.
Owner:慧医大数据技术(深圳)有限公司
Information classification method for facilitating user retrieval
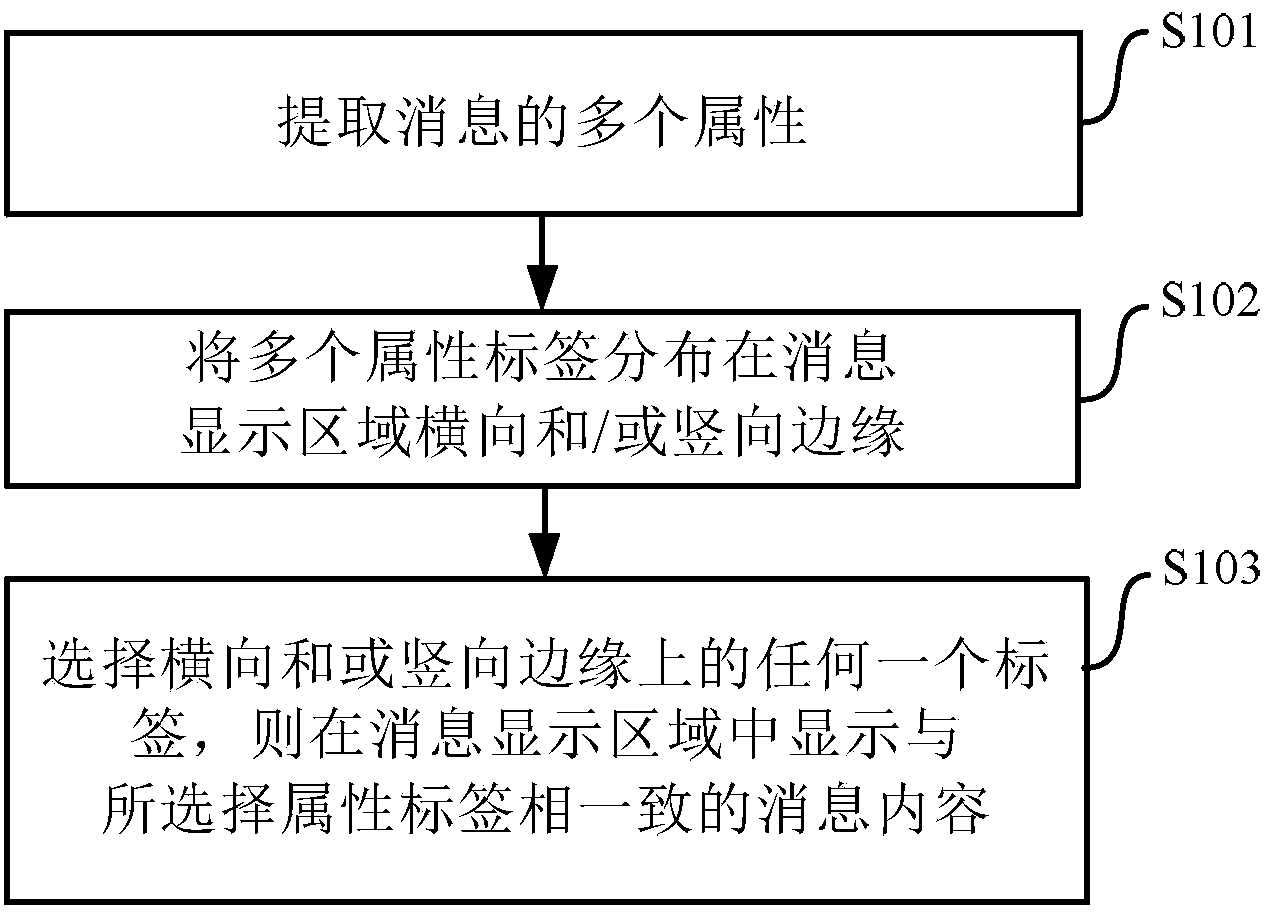
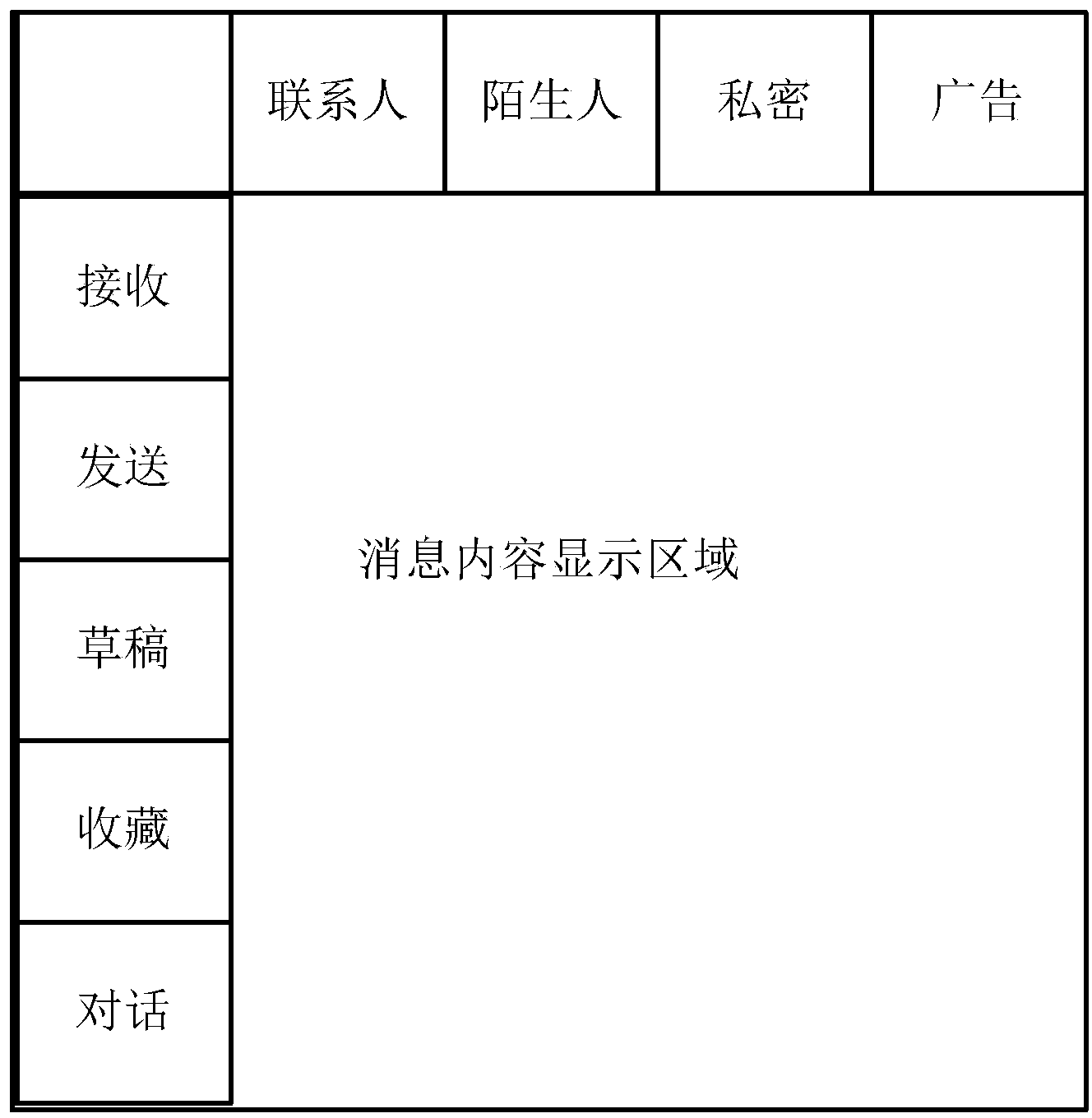
InactiveCN103353963AImprove experienceQuick searchOffice automationVertical edgeClassification methods
The invention provides an information classification display method. The method is specifically characterized by: extracting an operation attribute and a classification attribute of information; distributing a plurality of attribute labels, which belong to the operation attribute and the classification attribute, to a horizontal edge or a vertical edge in an information display area respectively; and selecting any attribute label at the horizontal edge and / or the vertical edge, and thus the content of the information, which is consistent with the selected attribute label, is screened and displayed in the information display area. The advantages of the information classification method are that: through extracting the attributes of the information, corresponding choice can be made based on the requirement of users, so that, with the information classification method, the display mode of a mobile terminal can be adjusted fully based on the setting of the user and the content is classified and displayed; the user can retrieve the required information quickly; and user experience is greatly improved.
Owner:BAIDU ONLINE NETWORK TECH (BEIJIBG) CO LTD
Salesman screening activation method, electronic apparatus, and computer readable storage medium
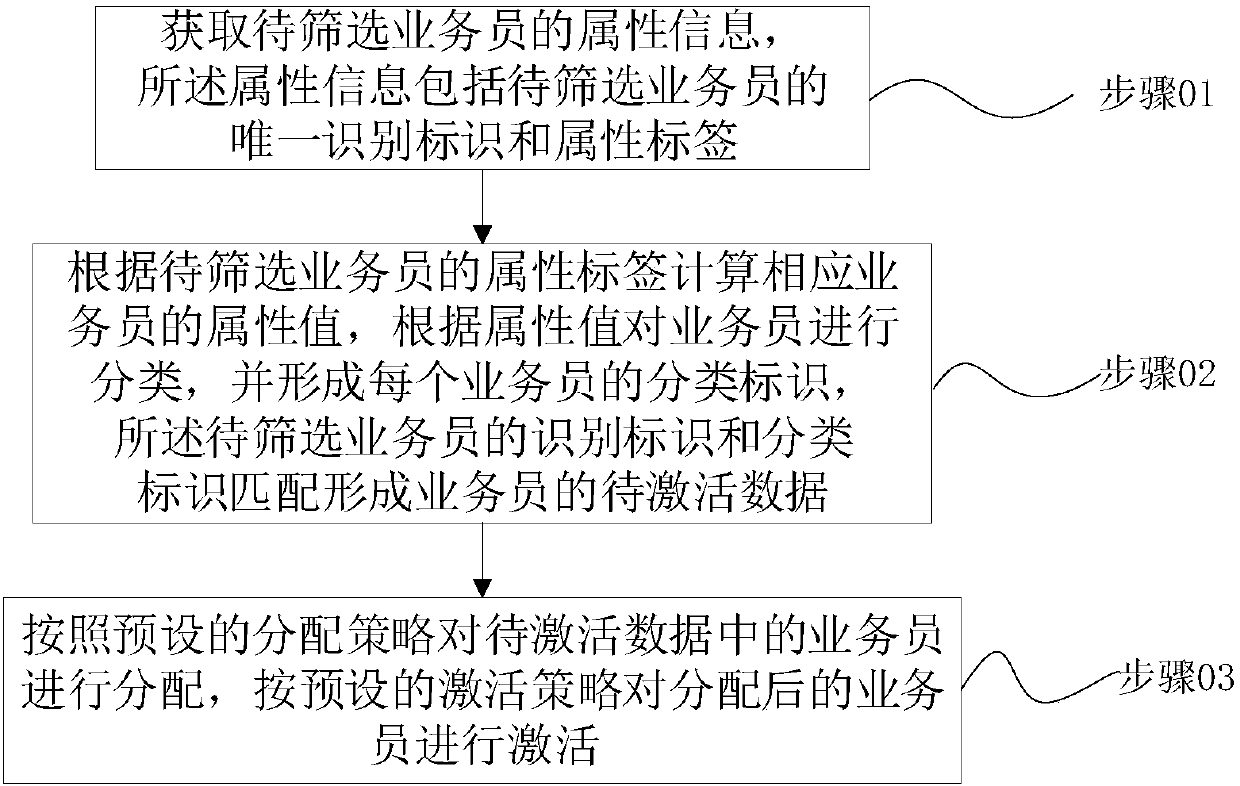
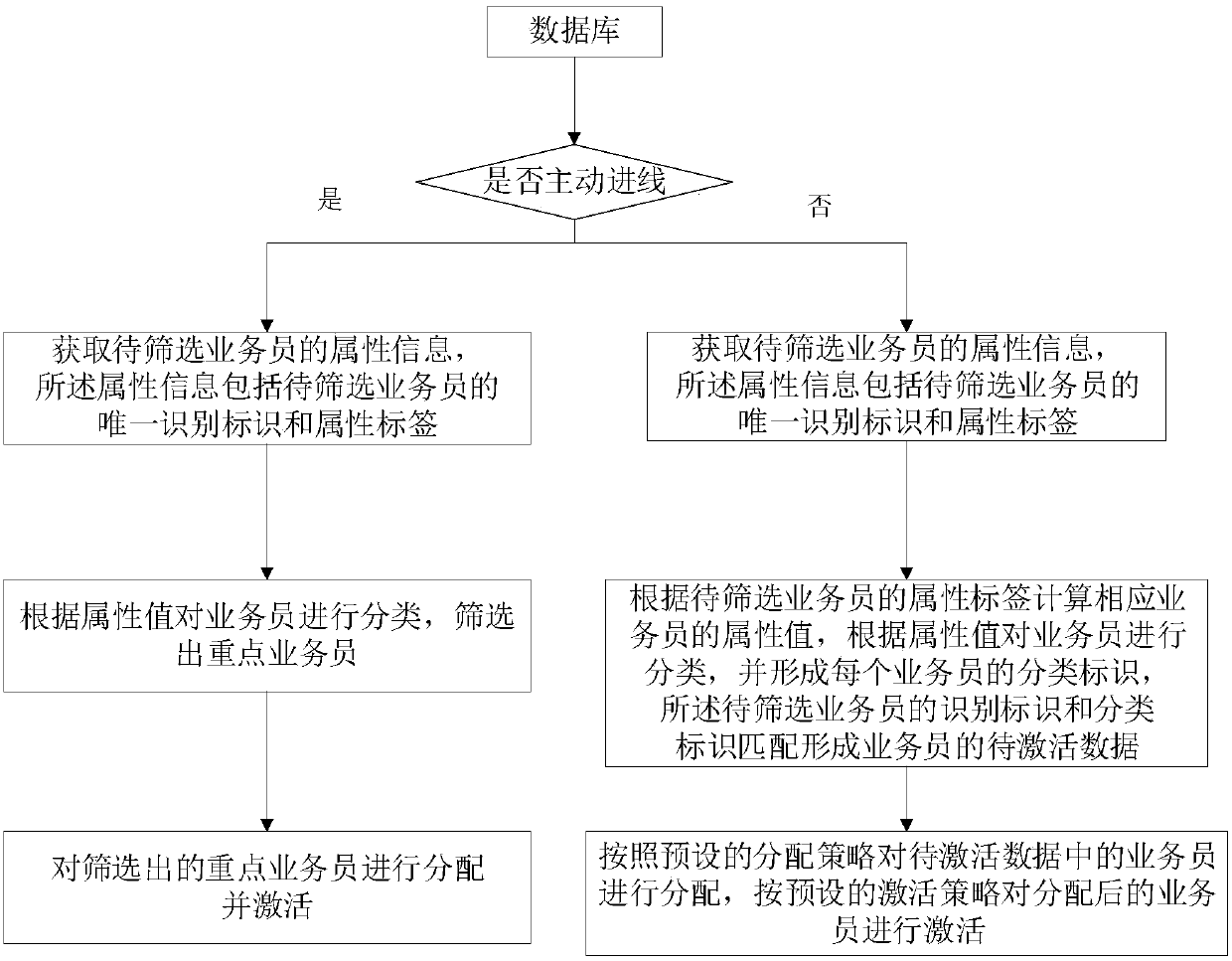
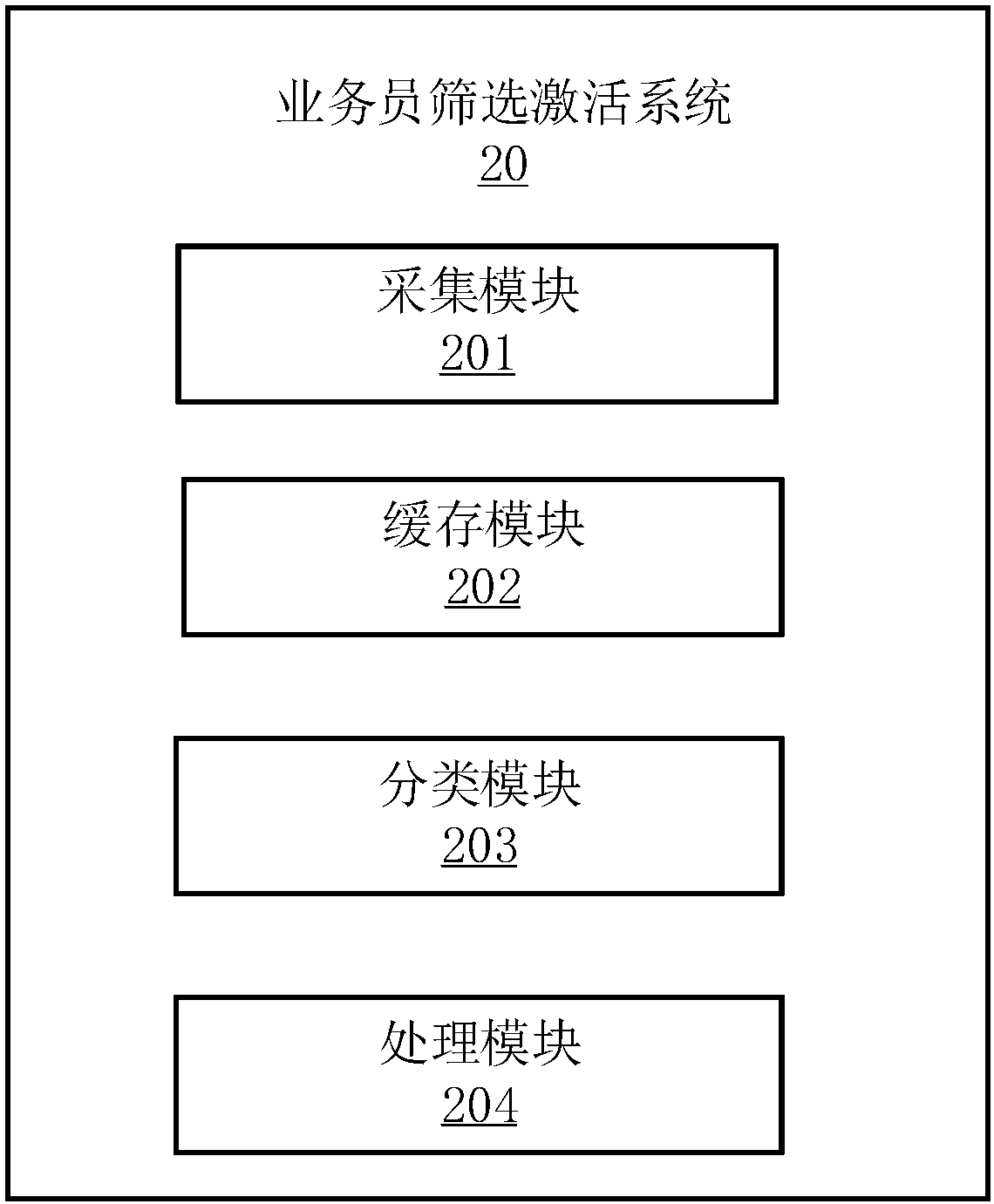
InactiveCN107679740AIncrease valueUnlock business potentialResourcesActivation methodUnique identifier
The invention discloses a salesman screening activation method. The salesman screening activation method includes the following steps: 01) acquiring the attribute information of salesmen to be screened, wherein the attribute information includes the unique identifier and the attribute label of each salesman to be screened; 02) according to the attribute label of each salesman to be screened, calculating the attribute value of the corresponding salesman, according to the attribute value, classifying the salesmen, and forming the classification identifier of each salesman, wherein the identifiers of the salesmen to be screened are matched with the classification identifiers to form the data to be activated of the salesmen; and 03) according to the preset distribution strategy, distributing the salesmen in the data to be activated, and according to the preset activation strategy, activating the salesmen after distribution. The salesman screening activation method can improve the pertinency of screening and distribution of salesmen so as to screen the salesmen who are given great attention to realize optimal configuration of seat resources.
Owner:PING AN TECH (SHENZHEN) CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com