Patents
Literature
129 results about "Business domain" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
A business domain in object-oriented programming is the set of classes that represent objects in the business model being implemented. The business domain is distinguishable from the business model in that the business model is an understanding and explanation of information and behaviors in the problem domain while the business domain is an implementation of that model in a specific programming language.
Hidden link dynamic key manager for use in computer systems with database structure for storage of encrypted data and method for storage and retrieval of encrypted data
InactiveUS7362868B2Improve securityOpportunities decreaseMultiple keys/algorithms usageComputer security arrangementsCommon nameSecurity domain
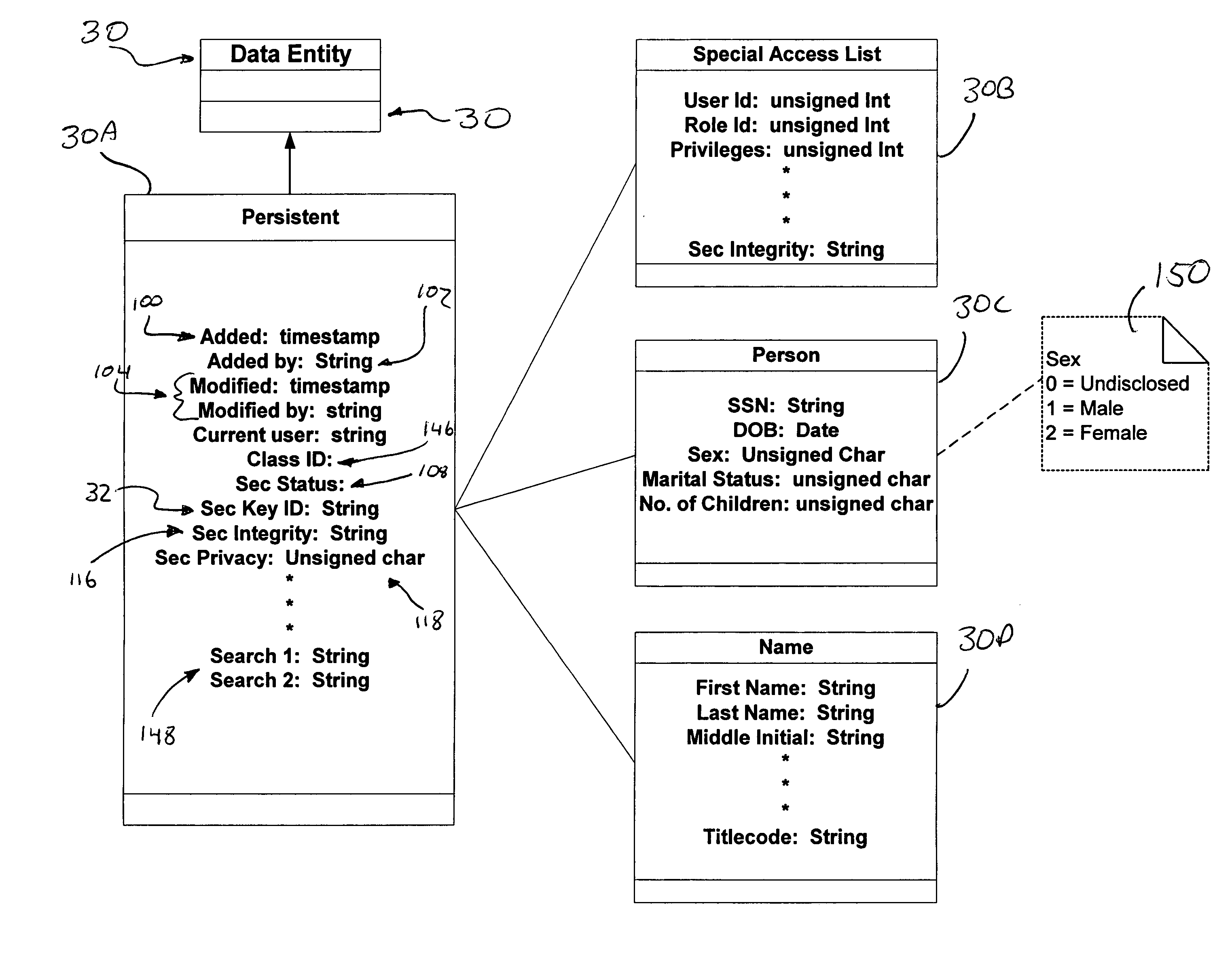
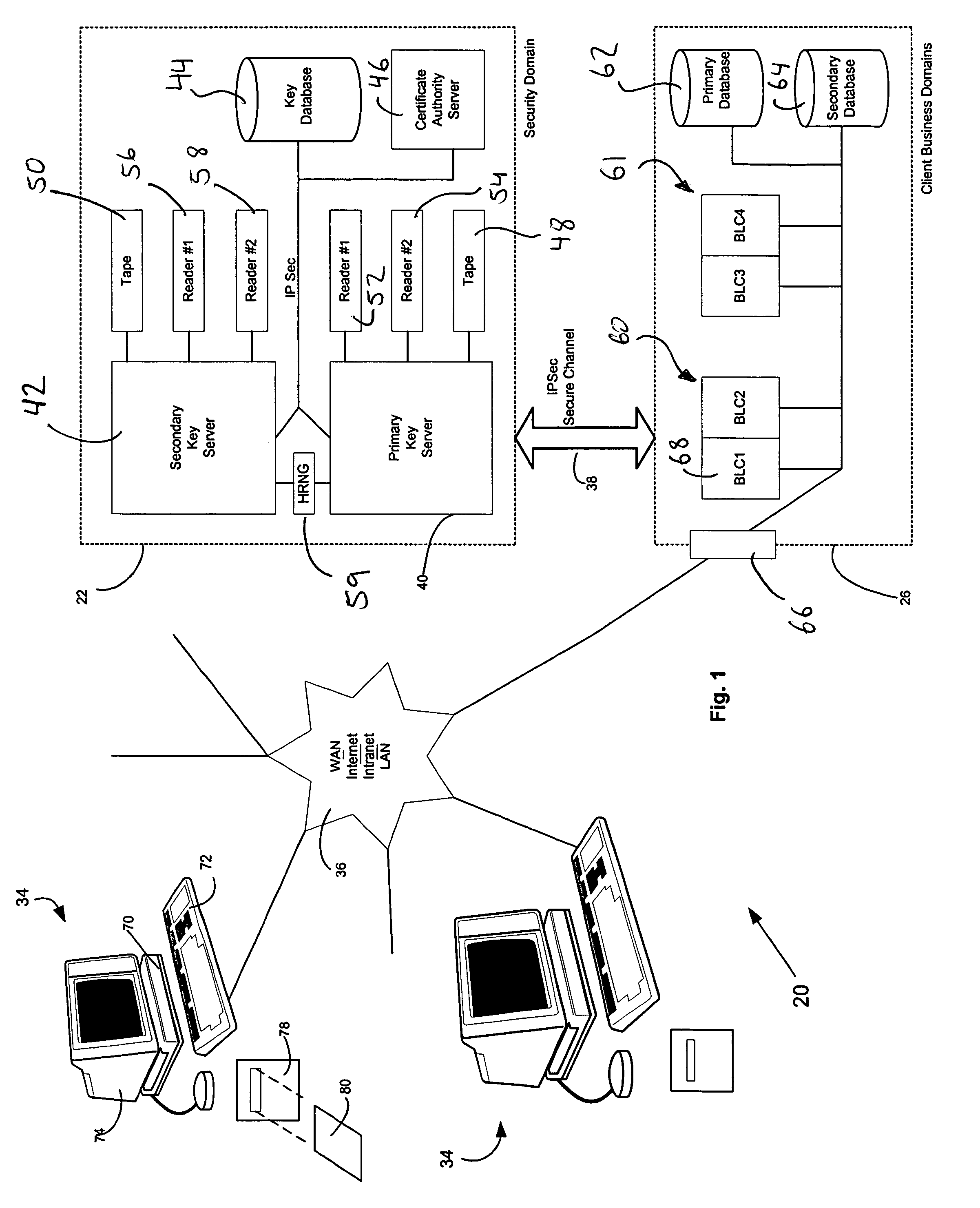
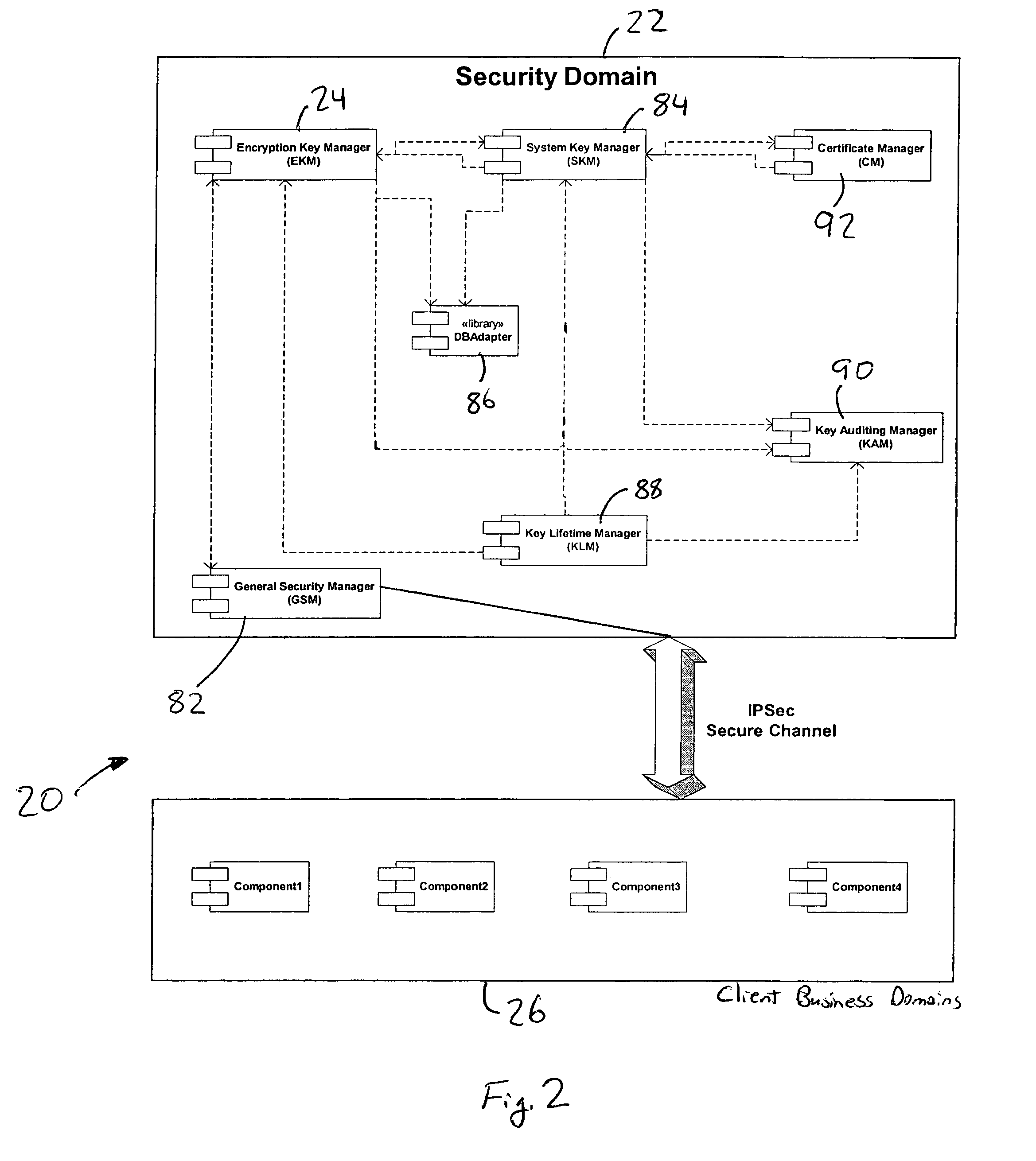
A computer system (20) having a security domain (22), at least one client business domain (26), and a plurality of client terminals (34) utilizes a hidden link dynamic key manager (24, 84) and a database structure that includes encrypted data entities (30C, 30D) and a security identification attribute (32) for storage of encrypted data. Methods for encrypting data and for storing, decrypting, and retrieving encrypted data operate on the computer system (20), which also includes an information database (62) and a key database (44). The key database (44) is isolated from the information database (62). The hidden link key manager is stored in the security domain (22) and includes a system key manager (84) operable to generate system keys with system key common names and an encryption key manager (24) operable to generate encryption keys having encryption key identifications. The key managers (24, 84) operate on a key server (40), which is mirrored by a secondary key server (42). A general security manager (82) also operates on the key server (40) to control access to the security domain (22). The security information attribute (32) is stored with a persistent data entity (30A) that is associated with the other encrypted data entities (30C, 30D) by a database schema. The encryption key identification (112) for the encryption key used to encrypt the data entities (30C, 30D) is encrypted by a system key and then stored as part of the security information attribute (32). The system key common name hash value (114) is also stored in the security information attribute (32). The information data entities (30) are stored on the information database (62), but the encryption key identification (153), encryption key (154), system key common name hash value (156, 157), and system key common name (158) are stored in the key database (44) inside the security domain (22). The system key itself is stored on a Smart Card reader (56) inside the security domain.
Owner:FARRUKH ABDALLAH DR +1
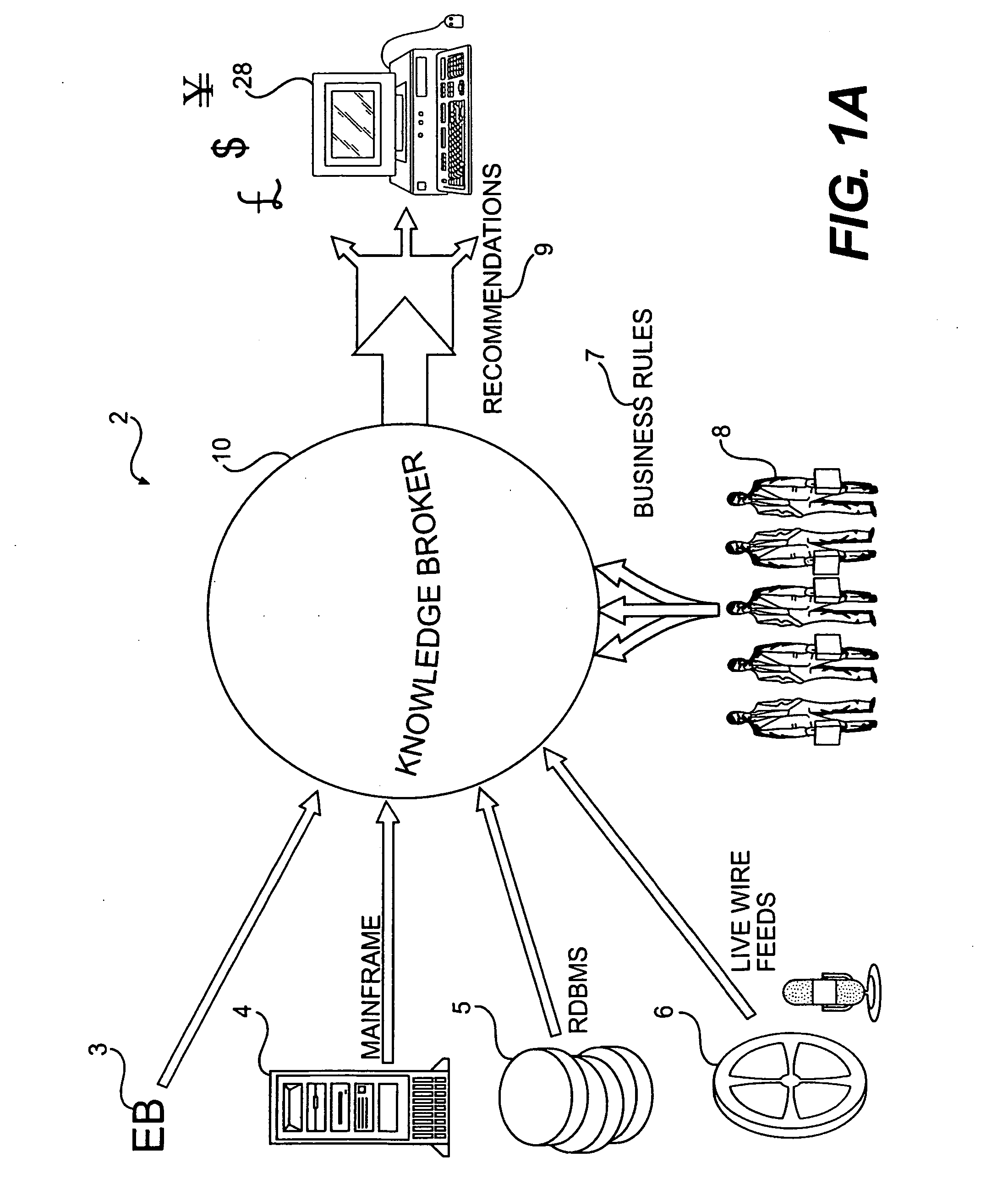
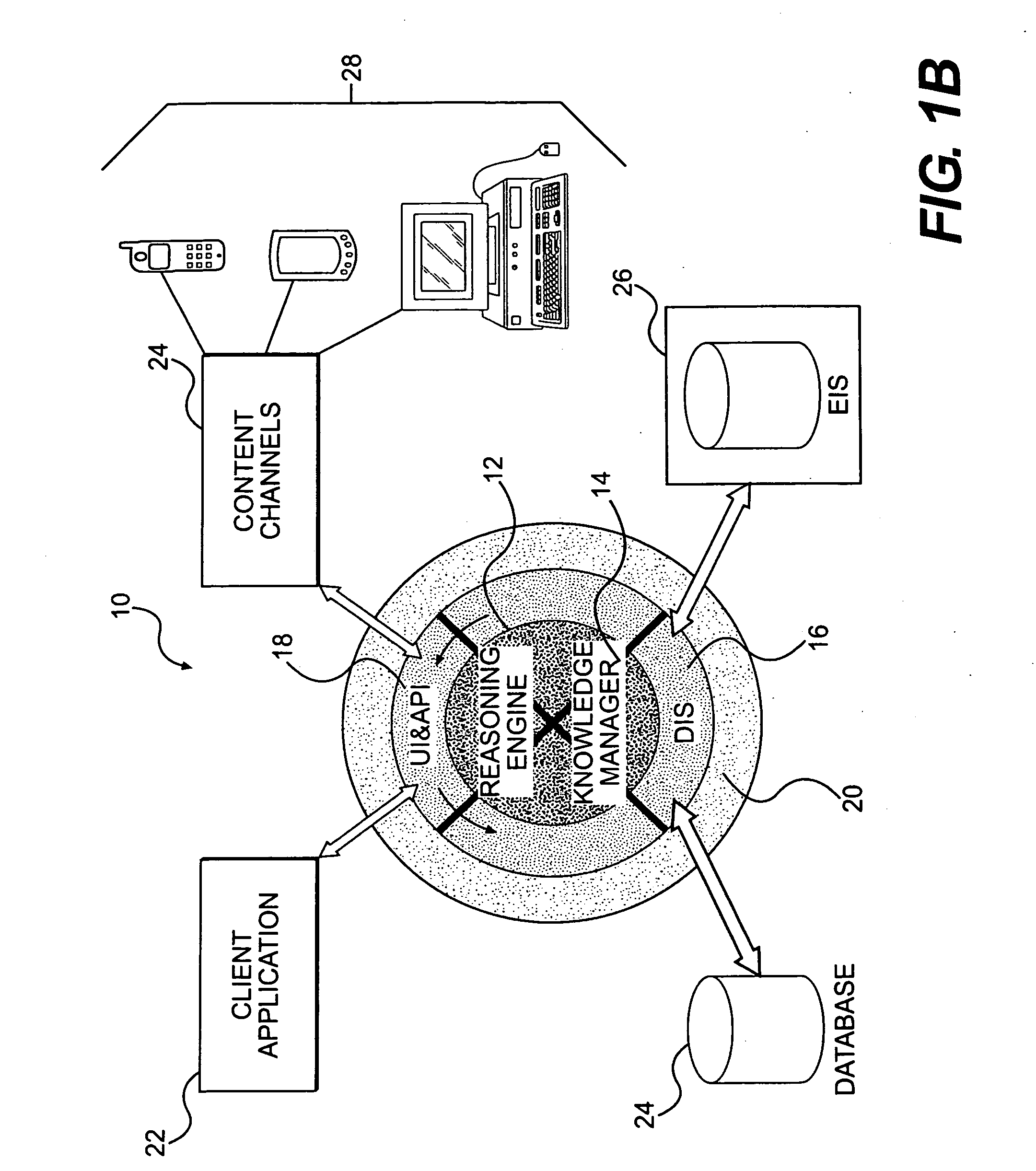
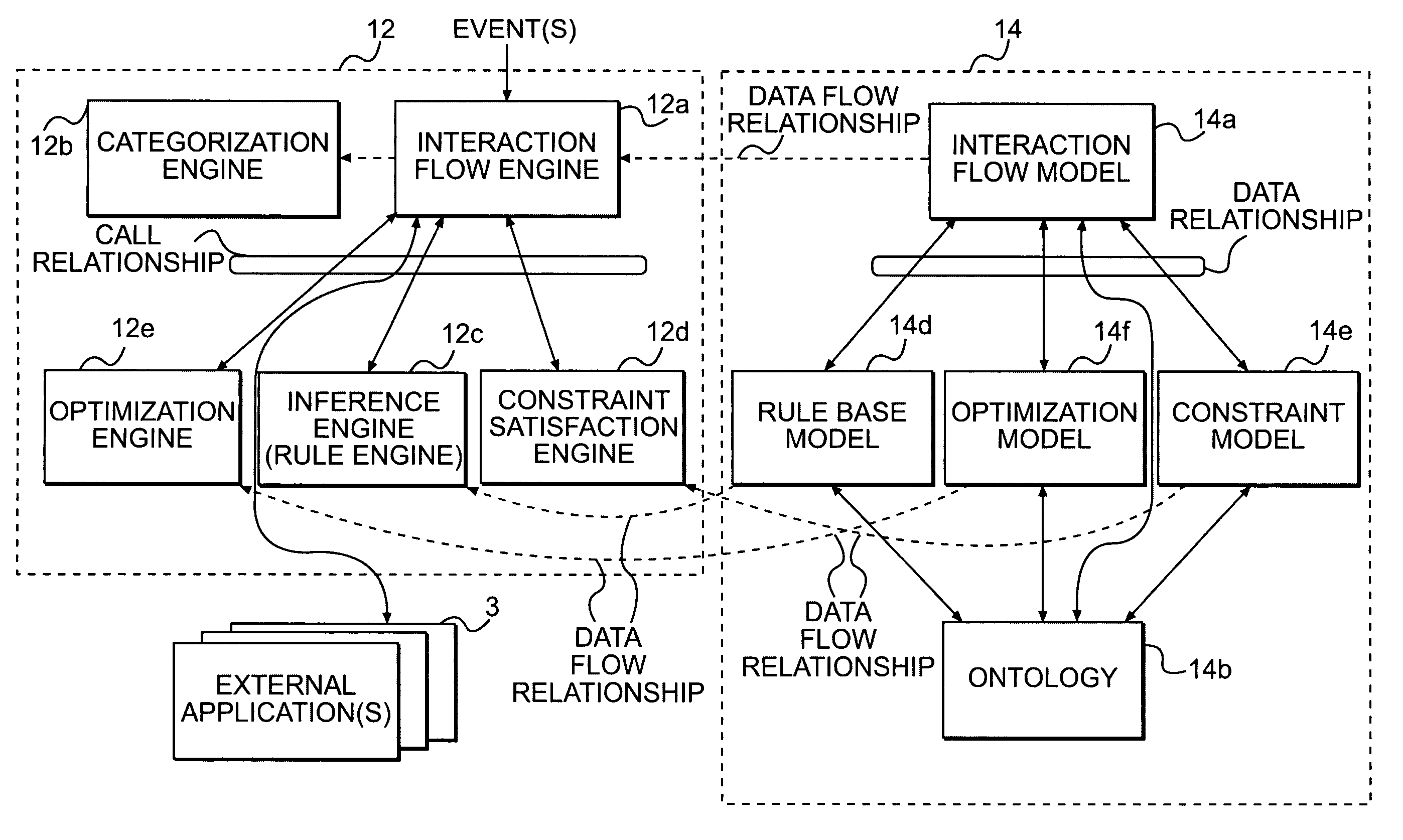
Ontology-driven information system
InactiveUS20070038500A1Avoid redundancyProvide consistencyDigital computer detailsBuying/selling/leasing transactionsApplication softwareKnowledge management
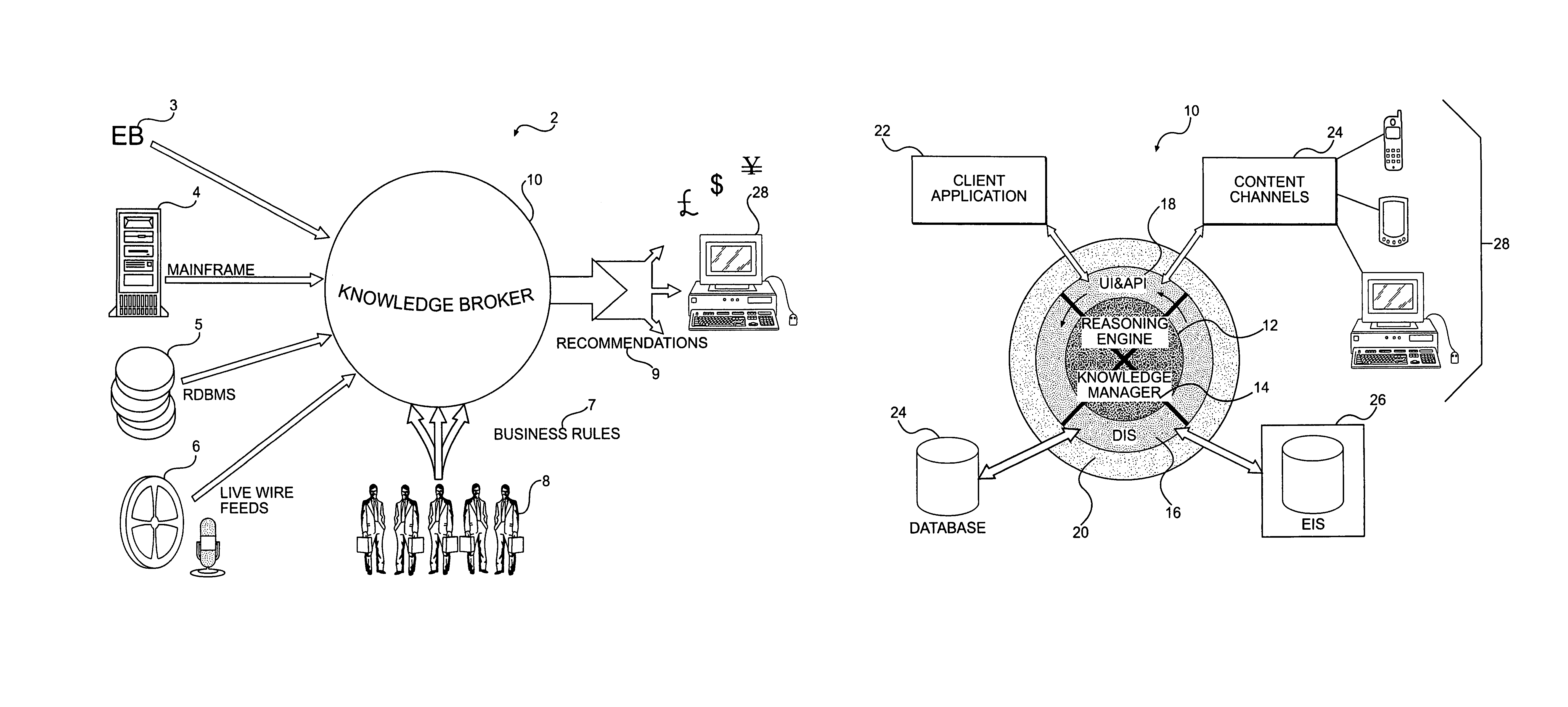
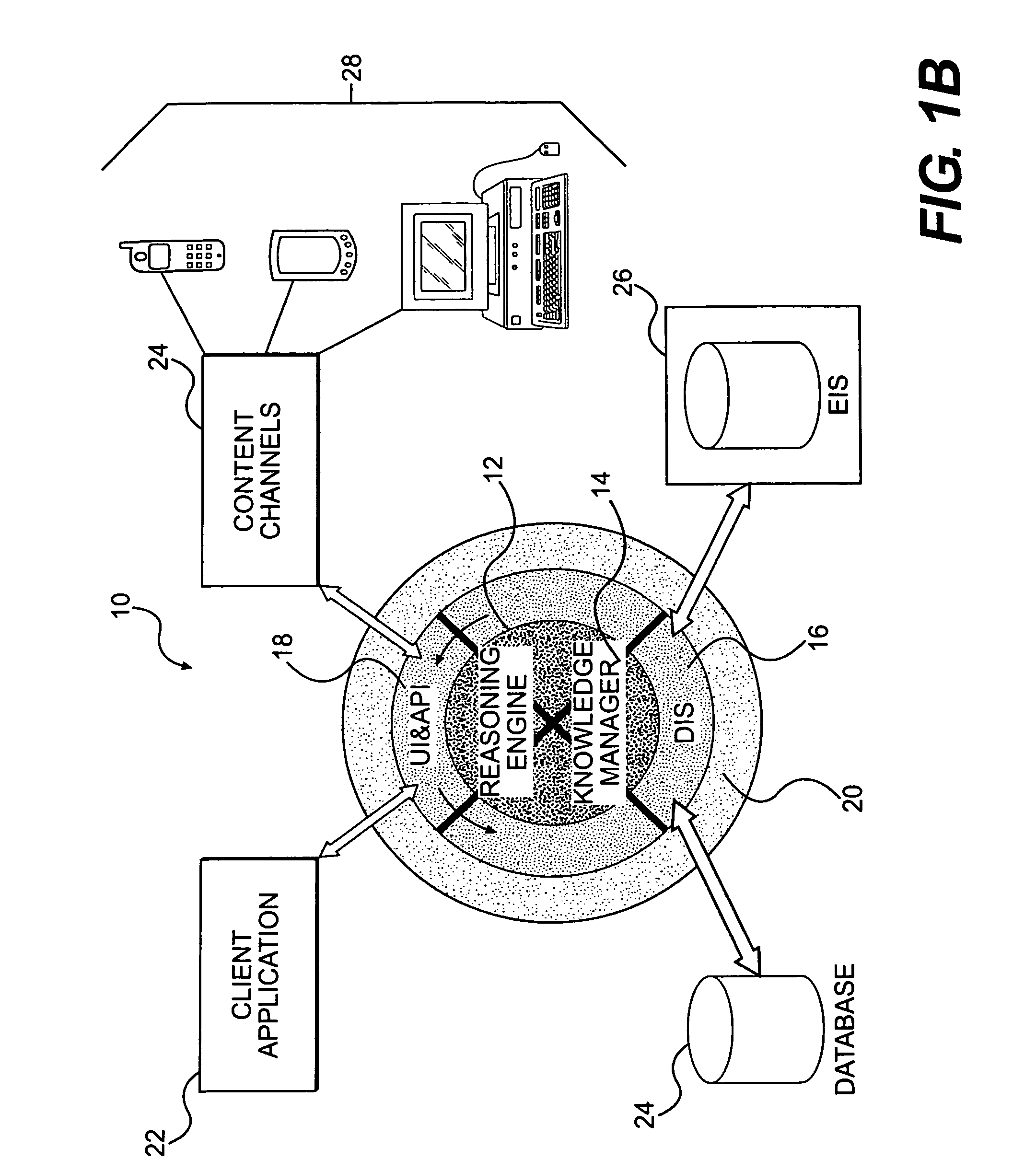
An ontology-driven information system includes a plurality of models, each of which expresses an aspect of a business domain using concepts and relationships between concepts. An ontology, which is in communication with each of the plurality of models, provides uniform definitions for the concepts and relationships between concepts used in the plurality of models. A method for executing an interaction flow model includes receiving an event and categorizing the received event. Once the event is categorized, a situation that matches the categorized received event is identified. One or more tasks are then executed for the situation. The execution of the one or more tasks can include either an interpretation of a model or the execution of a method of an object. The information system also includes a user and application interface and a reasoning engine that is in communication with the user and application interface. A knowledge manager is in communication with the user and application interface and is interfaced with the reasoning engine. A distributed information service also is in communication with the reasoning engine, the knowledge manager, and the user and application interface.
Owner:DST SYSTEMS
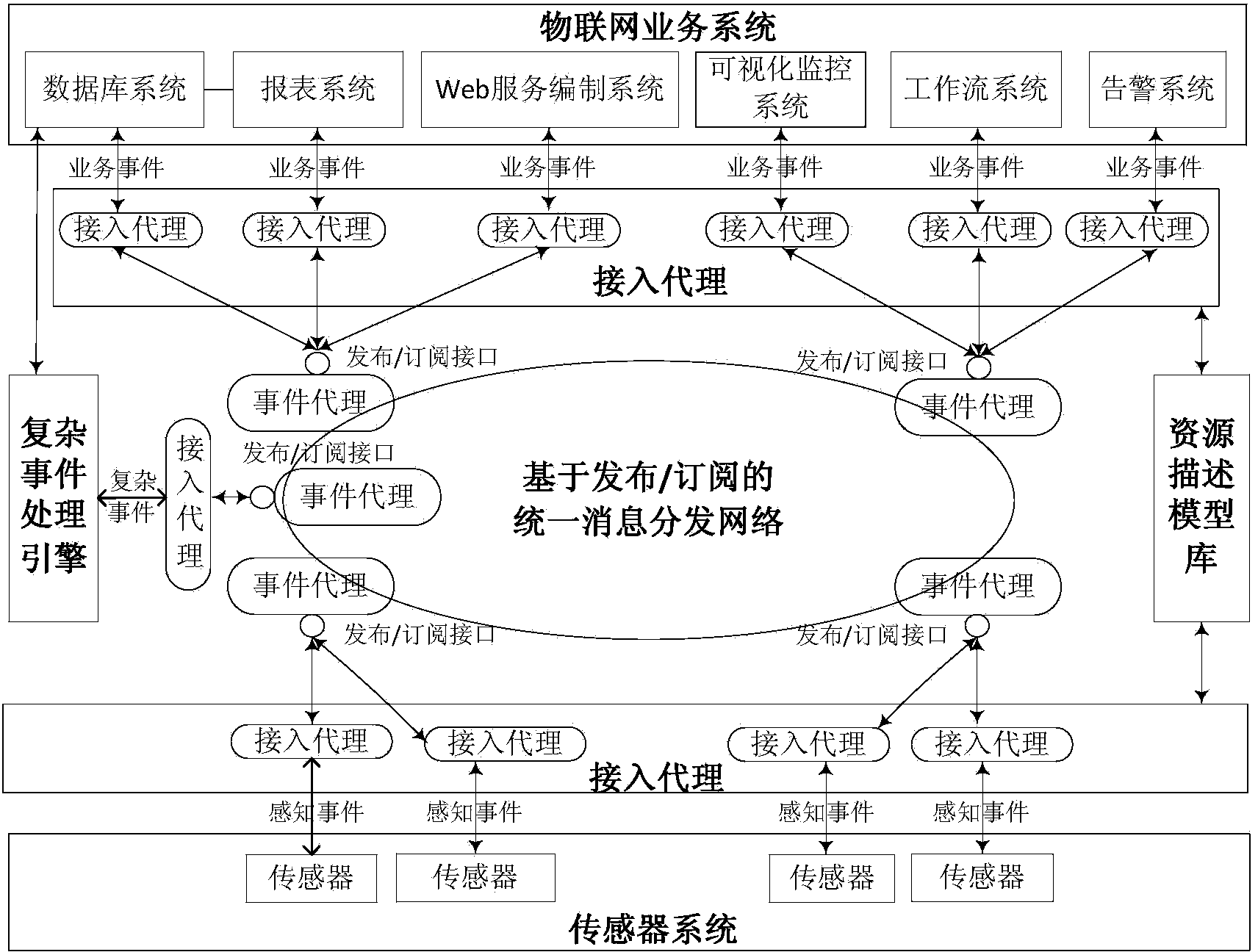
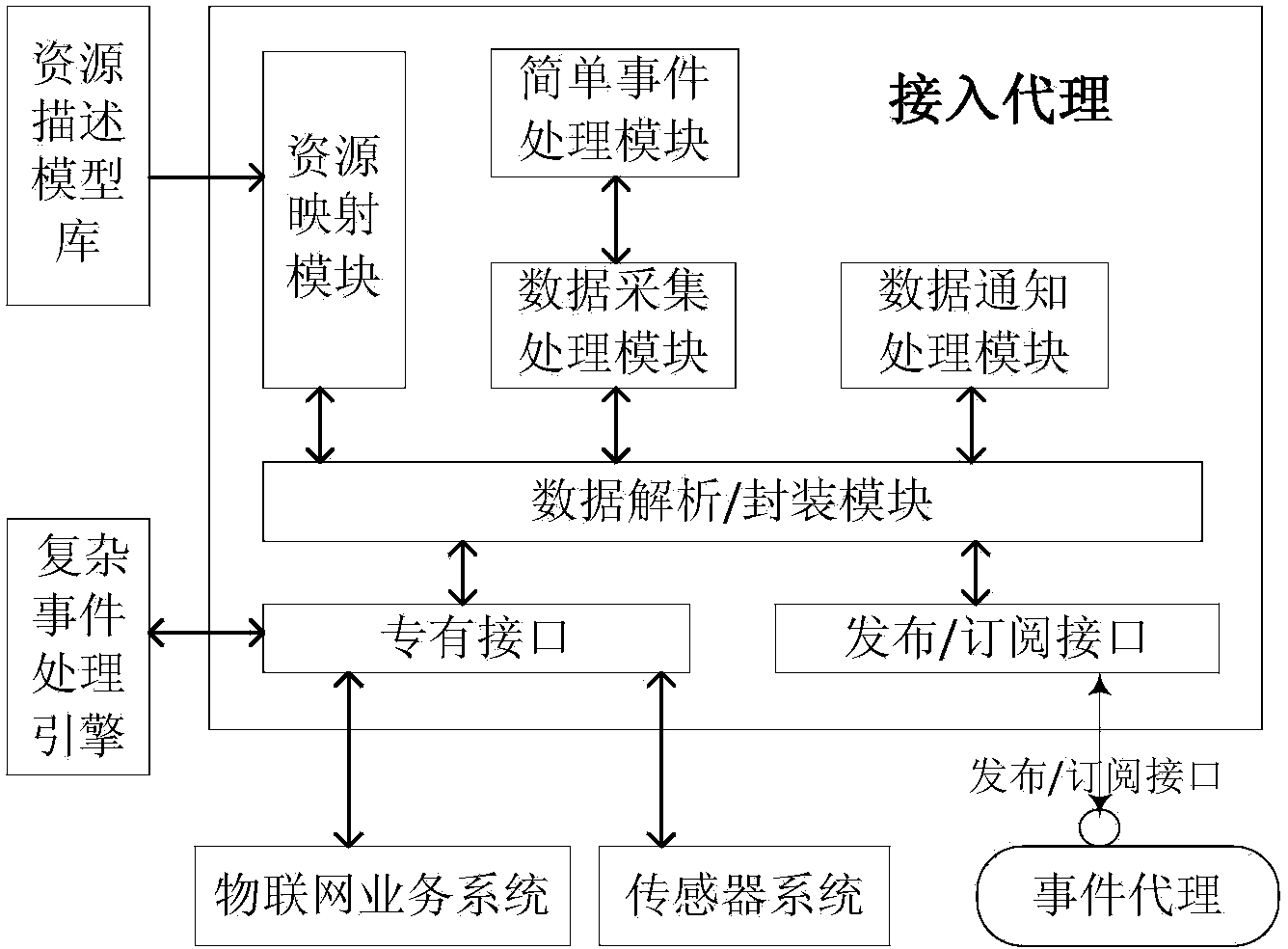
System for providing services of event-driven service-oriented internet of things and working method thereof
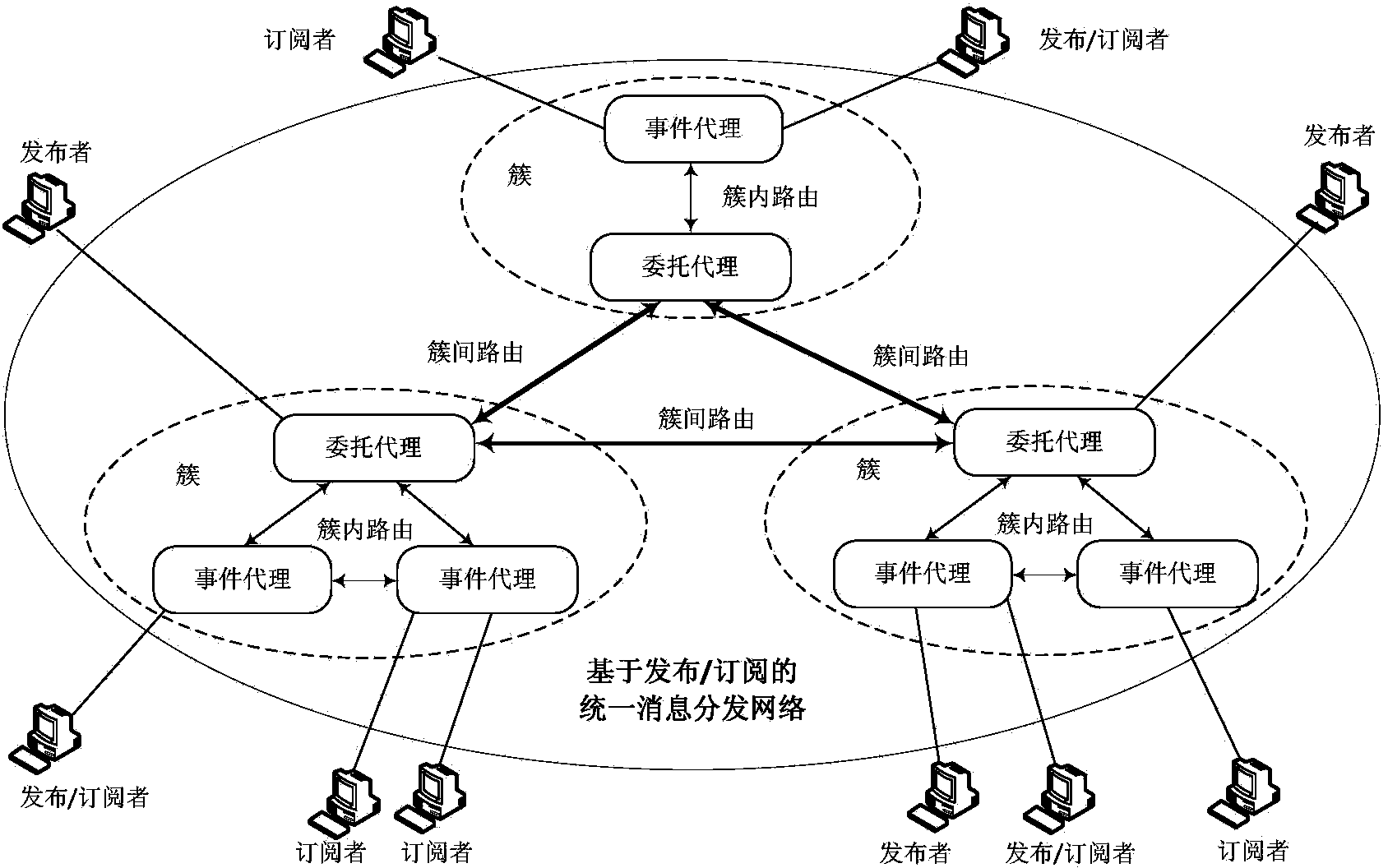
ActiveCN103458033ASupport on-demand distributionQuick responseData switching by path configurationComplex event processingDistributed Computing Environment
The invention provides a system for providing services of an event-driven service-oriented internet of things and a working method of the system. The system is composed of a plurality of parts of an internet of things service system, an access agent, a unified message distribution network based on a publish-subscribe mechanism, a complex event processing engine, a resource descriptive model base and a sensor system. The system and the working method solve the problems that an existing system for providing the services of the internet of things can not process large-scale sensing information in a distributed mode, events in a physical world can not be processed, effective cross-business-domain and cross-organization coordination is difficult to achieve by different enterprise business processes. According to the system, sensing information is effectively distributed in the open and distributed computing environment, various pieces of sensing information can be conveniently and quickly distributed as required among different internet of things heterogeneous service systems, event-driven cross-business-domain and cross-organization service dynamic coordination is achieved, time, space and control flow uncoupled network services are provided, and quick response to change of the physical world can be flexibly and dynamically achieved in real time.
Owner:BEIJING UNIV OF POSTS & TELECOMM
Ontology-driven information system
InactiveUS7200563B1Avoid redundancyProvide consistencyBuying/selling/leasing transactionsKnowledge representationApplication softwareKnowledge management
An ontology-driven information system includes a plurality of models, each of which expresses an aspect of a business domain using concepts and relationships between concepts. An ontology, which is in communication with each of the plurality of models, provides uniform definitions for the concepts and relationships between concepts used in the plurality of models. A method for executing an interaction flow model includes receiving an event and categorizing the received event. Once the event is categorized, a situation that matches the categorized received event is identified. One or more tasks are then executed for the situation. The execution of the one or more tasks can include either an interpretation of a model or the execution of a method of an object. The information system also includes a user and application interface and a reasoning engine that is in communication with the user and application interface. A knowledge manager is in communication with the user and application interface and is interfaced with the reasoning engine. A distributed information service also is in communication with the reasoning engine, the knowledge manager, and the user and application interface.
Owner:DST SYSTEMS
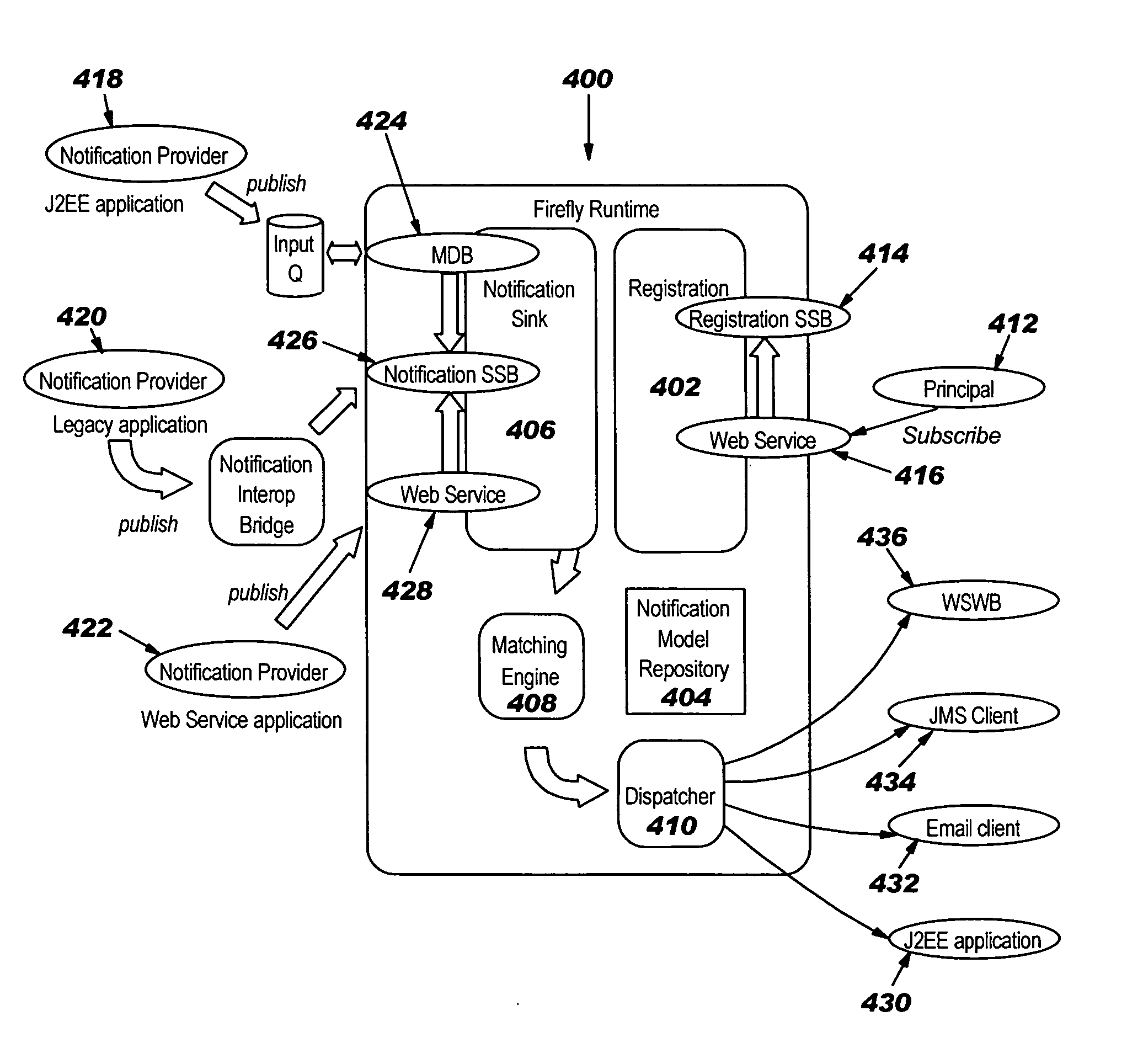
Method and apparatus for model based subscriptions for a publish/subscribe messaging system
InactiveUS20050261923A1Reduce decreaseMultiple digital computer combinationsOffice automationPublish–subscribe patternMiddleware
A method, system, and computer instructions for using the language of the business domain to express subscriptions to a publish / subscribe messaging system. The resulting notifications sent to the subscriber are instances of the business model used to create the subscription. In other words, a subscriber may subscribe to the messaging system against the same information that the subscriber receives in a notification from the messaging system. The present invention uses the model from the business domain as the basis for notification subscriptions to allow for defining filters directly against the model's attributes, reducing problems caused by translating business models to a middleware description.
Owner:IBM CORP
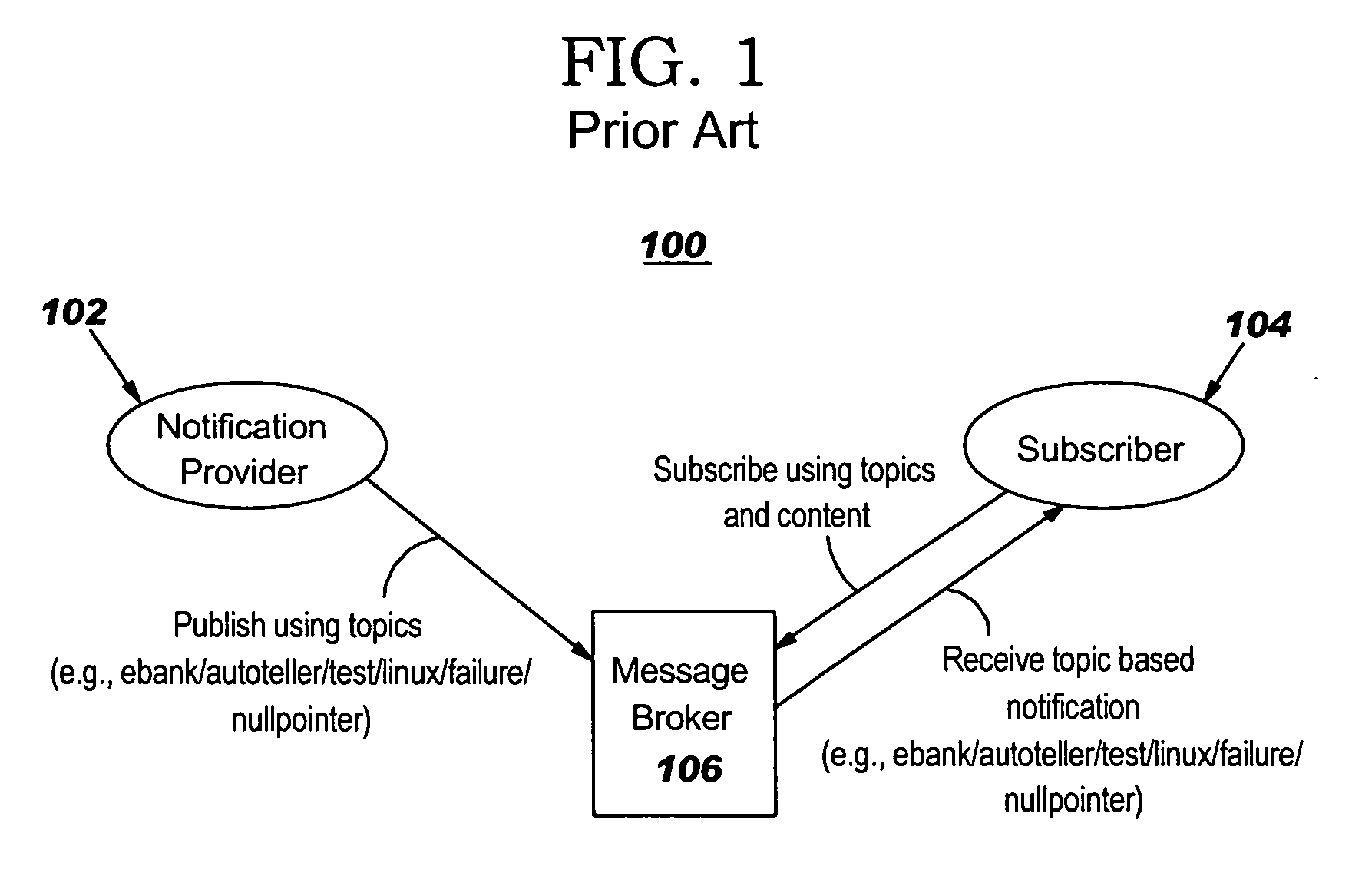
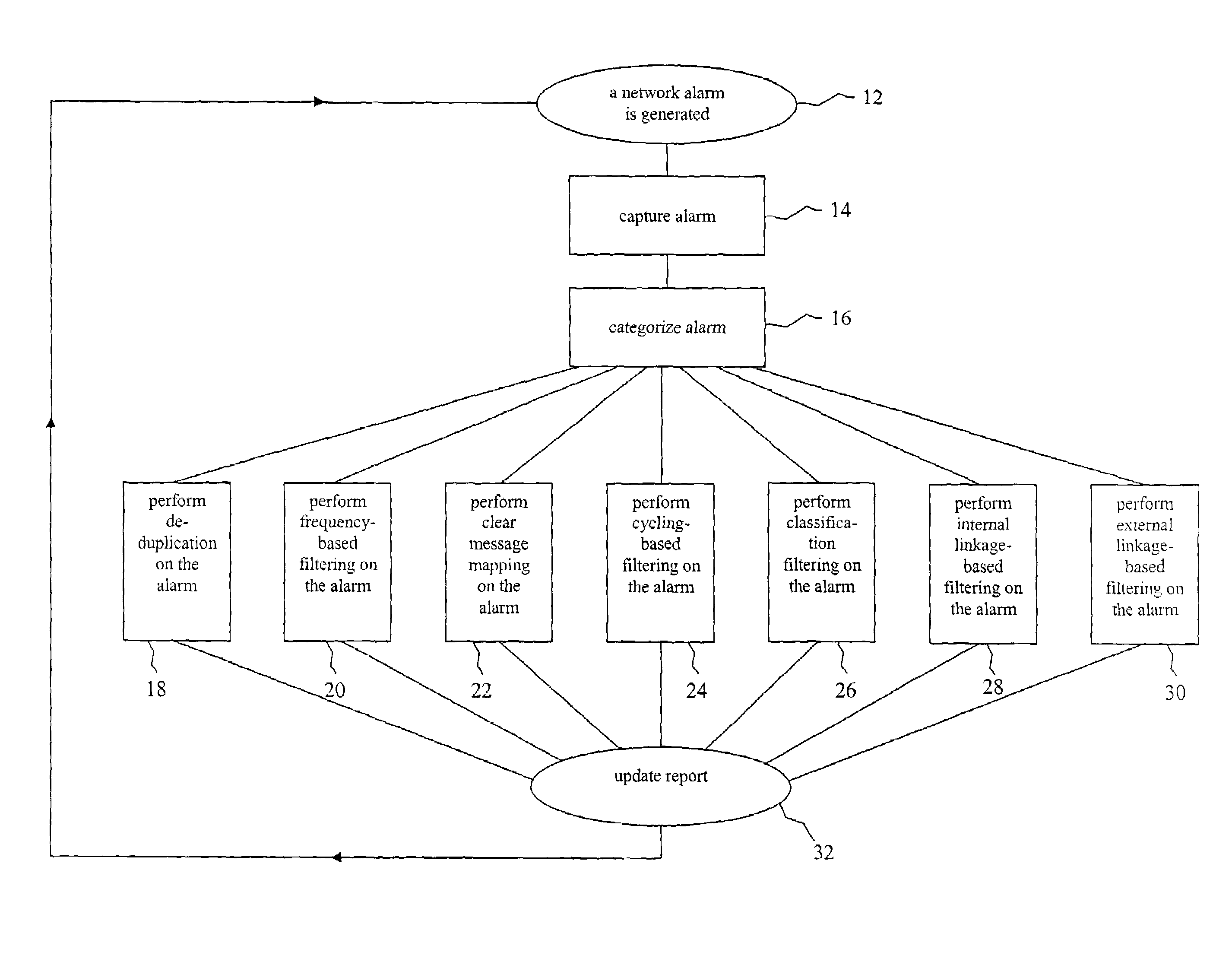
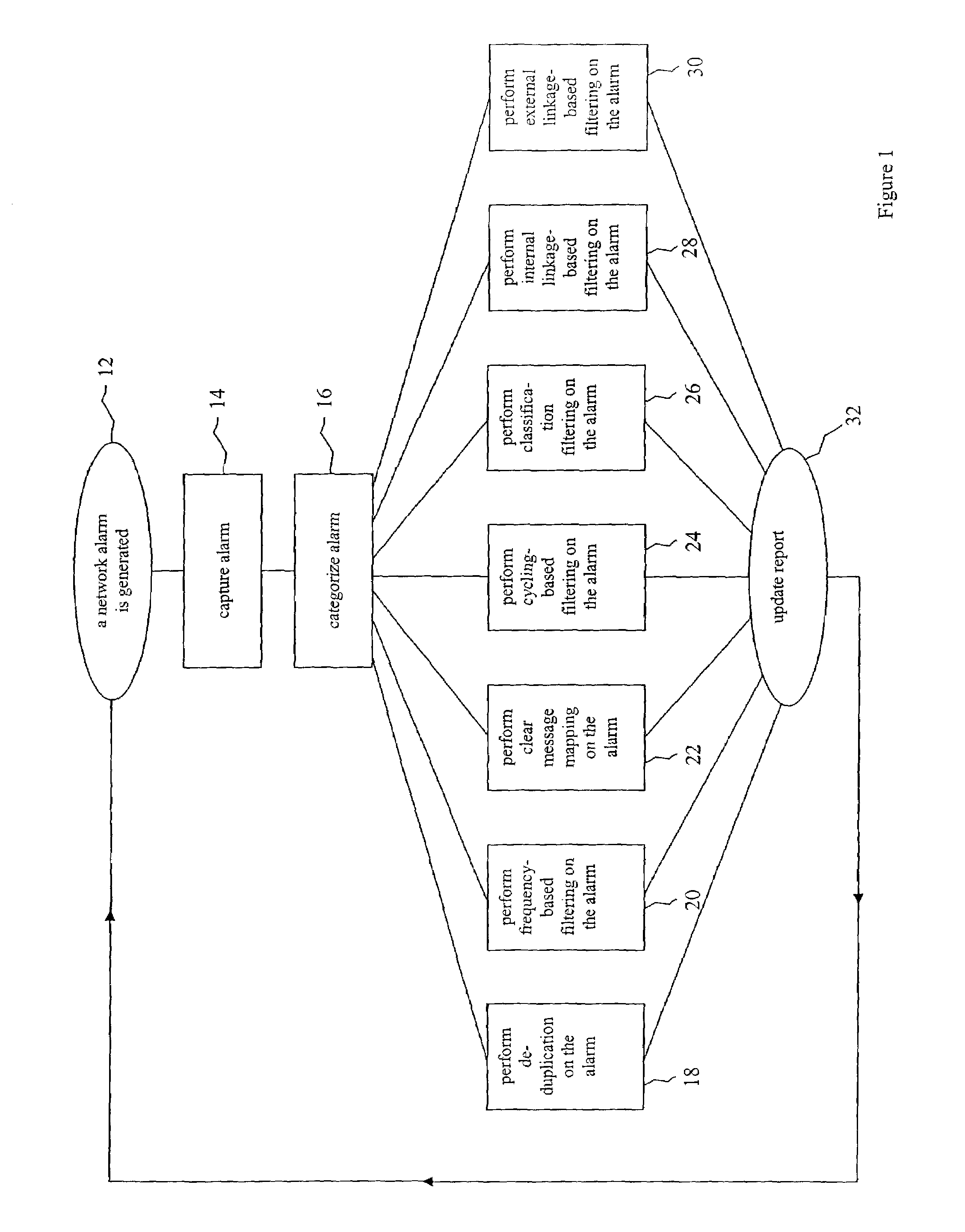
Filtering approach for network system alarms
A method for creating an updateable report representing the alarm status of a network. Network alarms are categorized based on the source and type of alarm, the alarms are placed in a filtering system based on source and type, selected alarms are replaced with alarm representations, and a report is updated with alarm representations. The filtering system comprises non-temporal, temporal, and linkage-based filtering. Non-temporal filtering includes de-duplication, clear message mapping, and classification. Temporal filtering includes frequency-based and cycling-based filtering. Linkage-based filtering includes internal linkage-based and external linkage-based filtering. The network can comprise the interconnected networks of an enterprise or of a single domain of an enterprise. The domain can comprise a business domain or operating system domain. The network can comprise a group of client computers connected to a server computer. The report can be displayed on a computer screen or can be sent to another location for further processing.
Owner:T MOBILE INNOVATIONS LLC
Alarm root cause analysis method, device and equipment and storage medium
ActiveCN109684181AAvoid interferenceImprove accuracyHardware monitoringDatabase modelsRoot causeRoot cause analysis
The invention provides an alarm root cause analysis method, device and equipment and a storage medium, and relates to the technical field of operation and maintenance. The invention provides a methodfor carrying out alarm root cause analysis based on double correlation, and the method can integrate the time sequence correlation of different alarms and the topological correlation of different alarms to mine root cause alarm information from a large amount of alarms. Time sequence association information based on alarm is obtained. clustering the plurality of alarms; obtaining root cause alarminformation according to the target class conforming to the topology association condition; The alarm root cause analysis method and device can screen out alarms with strong correlation in time sequence and topology at the same time and filter out accidental adjacent noise information in time and accidental adjacent noise information in topology, and therefore interference of the noise informationon alarm root cause analysis can be avoided, and the accuracy of the alarm root cause analysis is improved. Meanwhile, a large amount of business domain knowledge is not needed, and manual definitionof reasoning rules is not needed, so that the cost of alarm root cause analysis is saved.
Owner:HUAWEI CLOUD COMPUTING TECH CO LTD
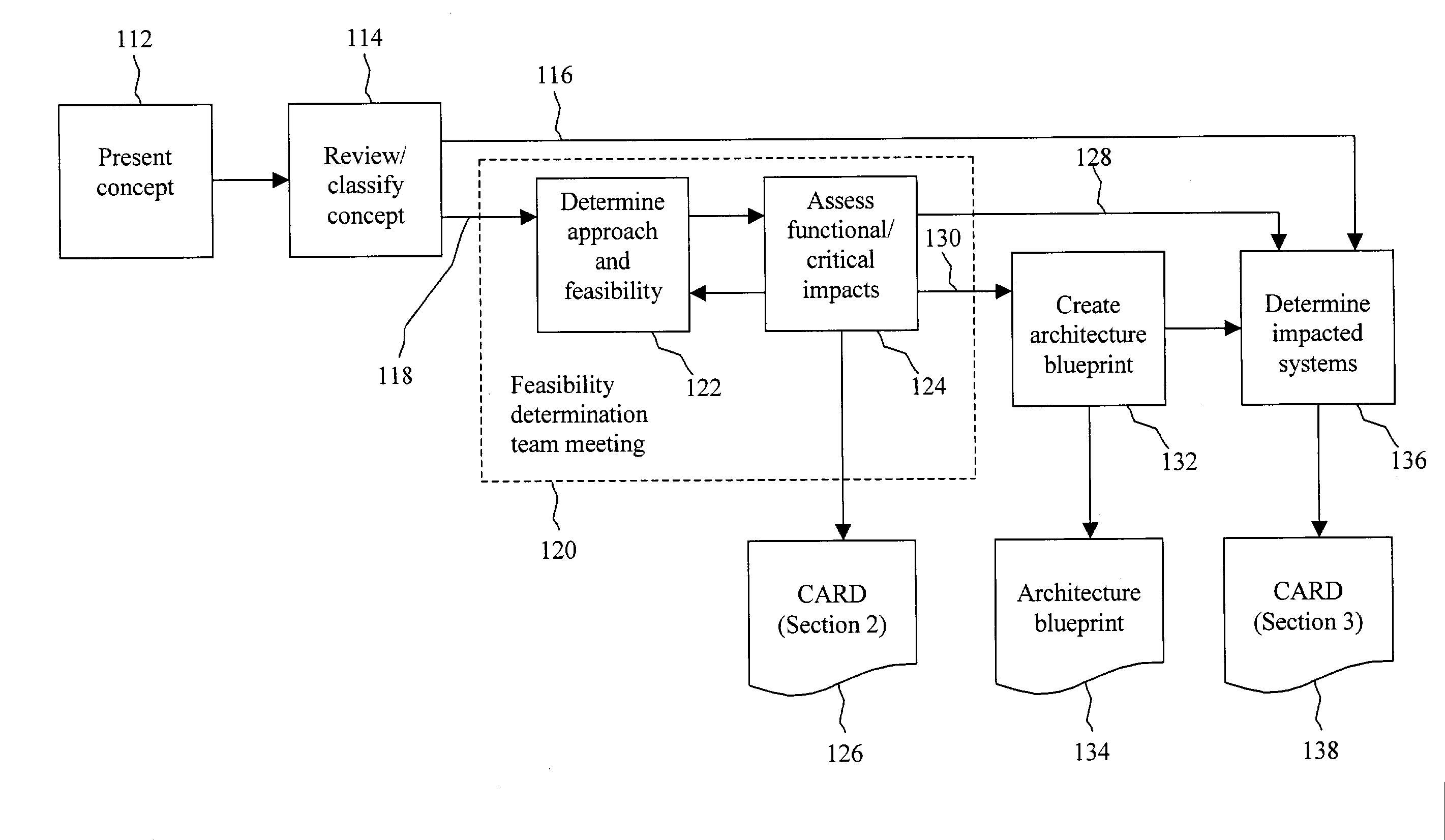
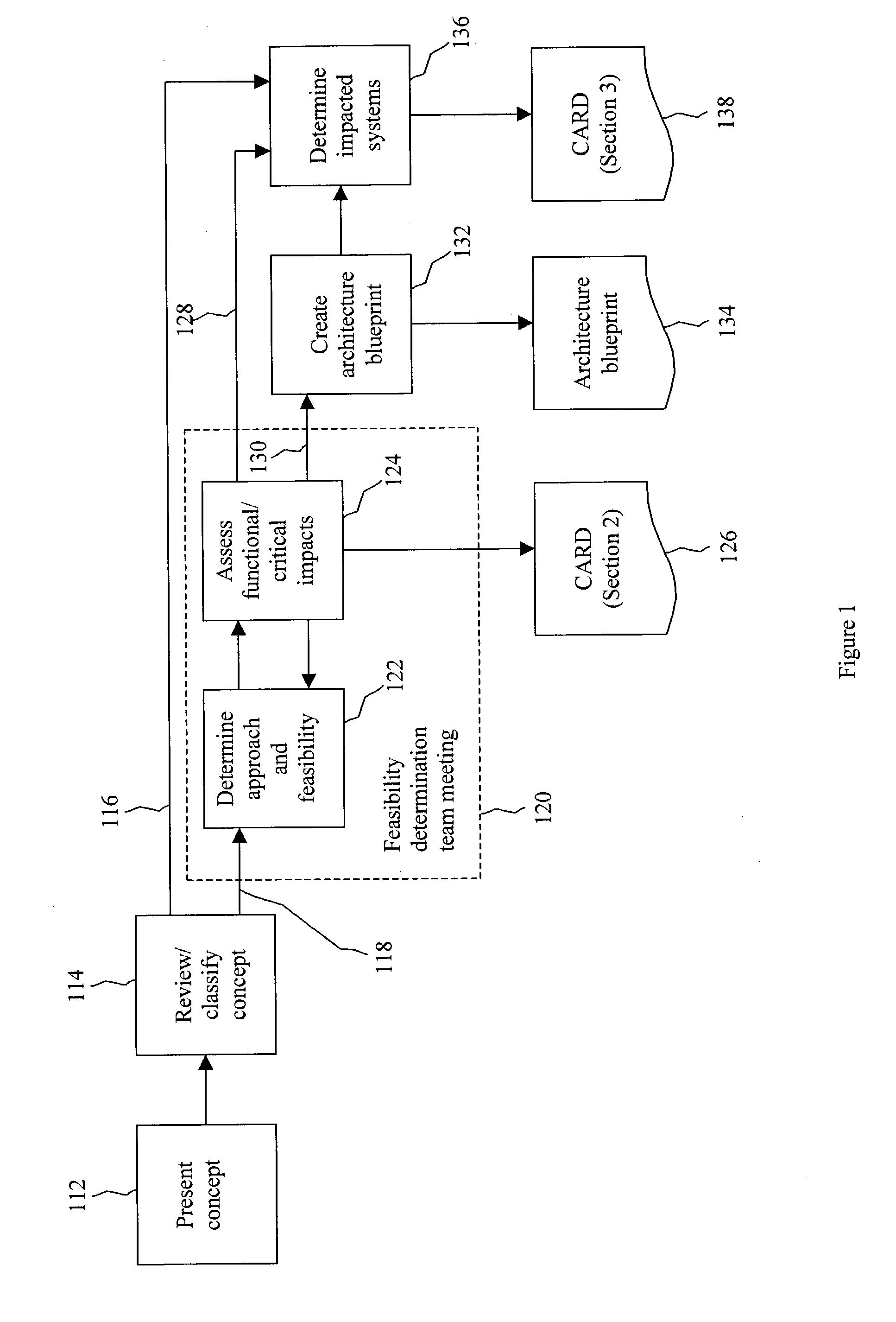
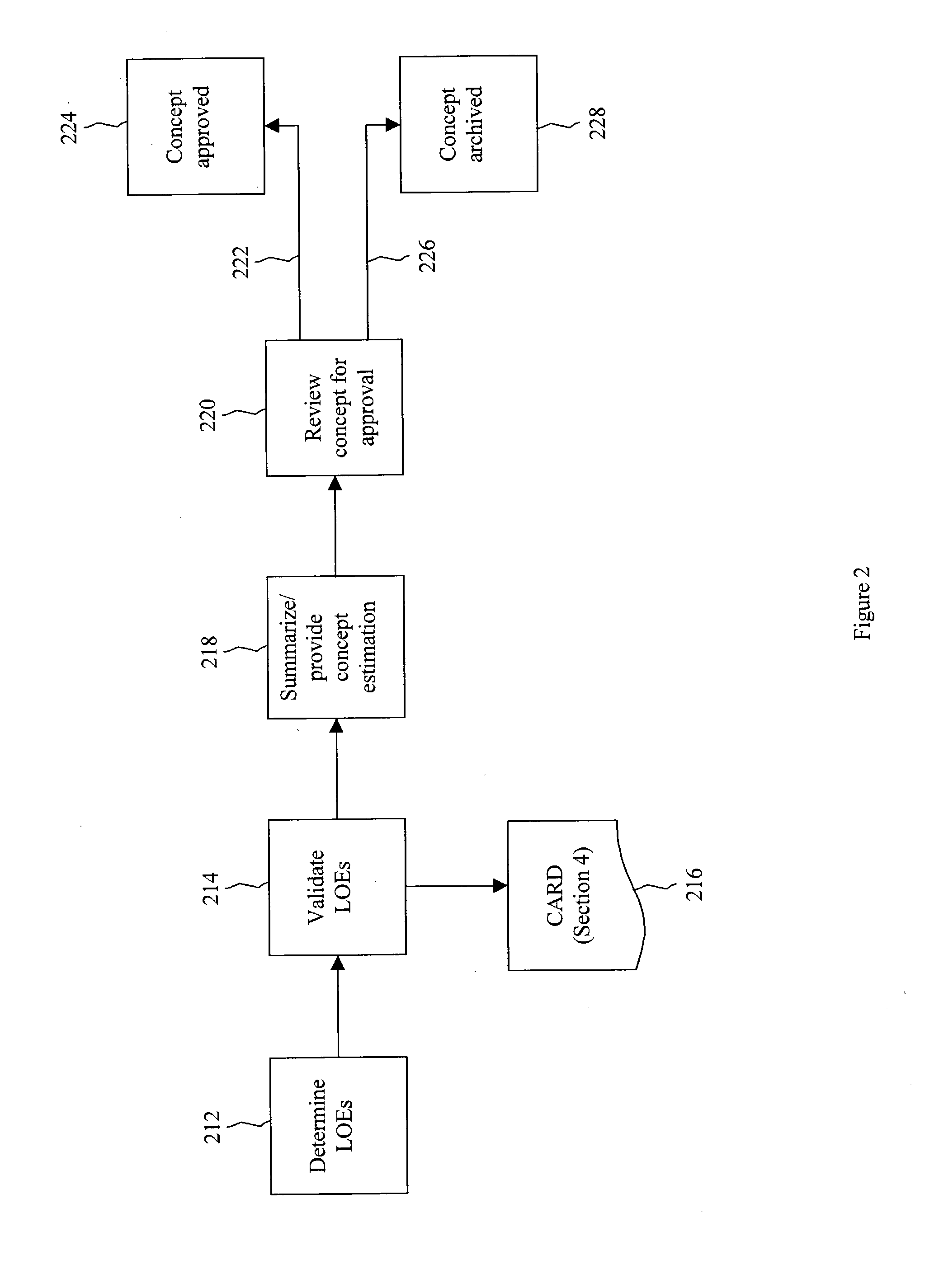
Defining and sizing feasible approaches to business needs within an integrated development process
A process for defining and selecting integrated potential approaches (software, hardware, networking, and operations approaches) for addressing a business need. The process can include providing an identification of a business need in a concept document. A meeting that includes representatives of IT, network, and operations from each potentially impacted business domain can be held and can result in additions to the concept document identifying at least one proposed approach. An architecture blueprint can be created as a result of the meeting. Impacted systems for each proposed approach can be identified. The entire concept document and the architecture blueprint can be provided to representatives of each impacted system to determine the estimated level of effort for the development and implementation of the concept.
Owner:SPRINT CORPORATION
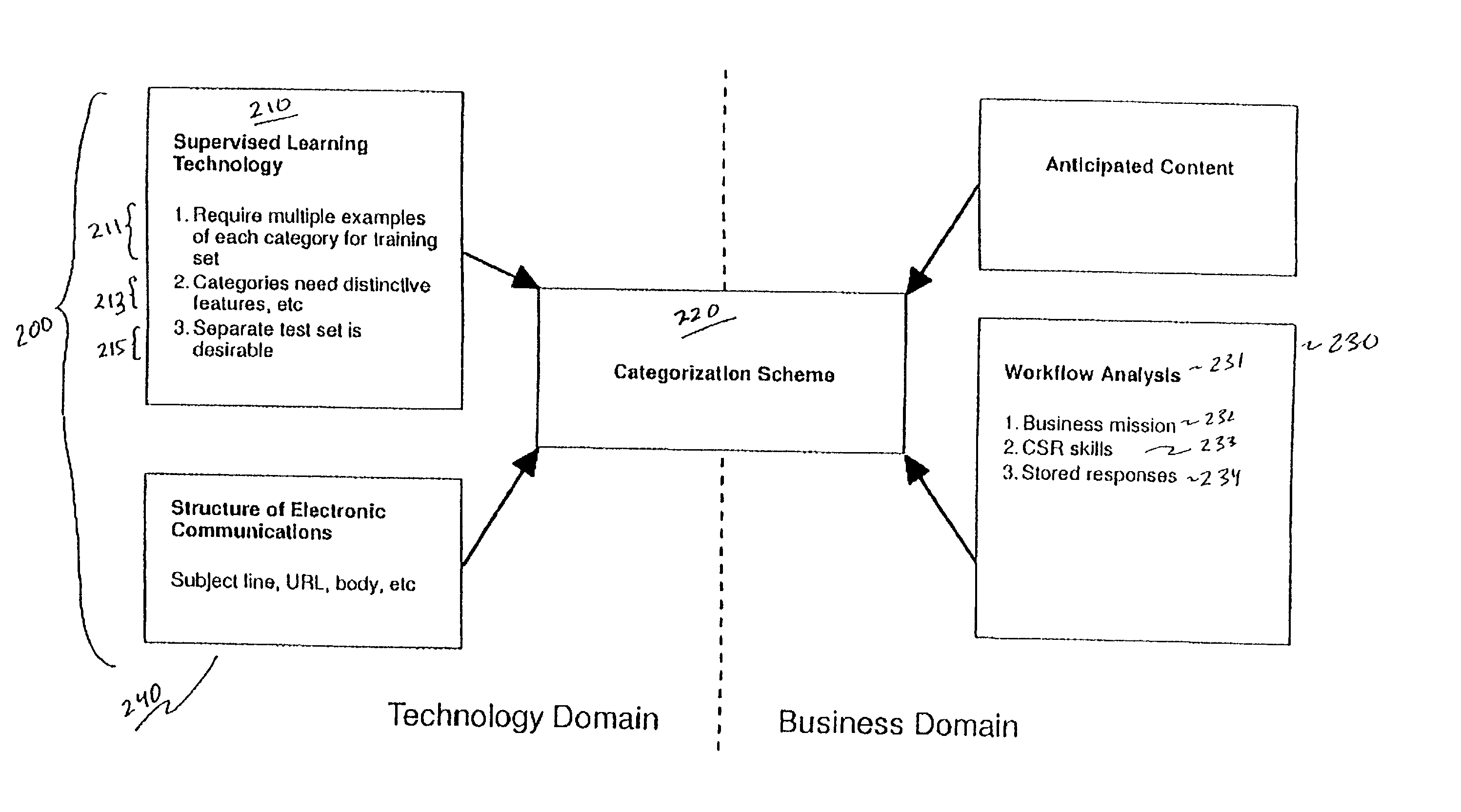
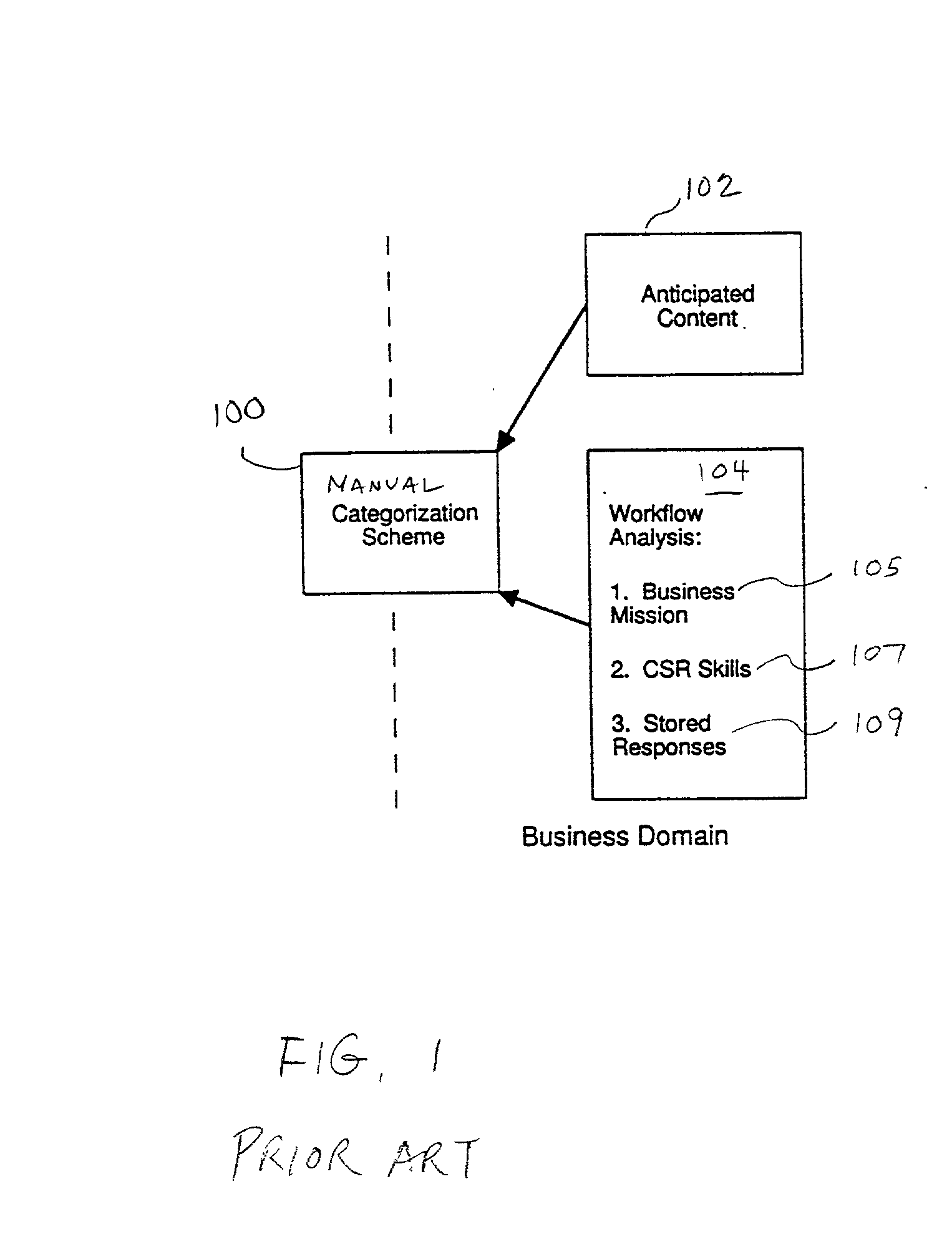
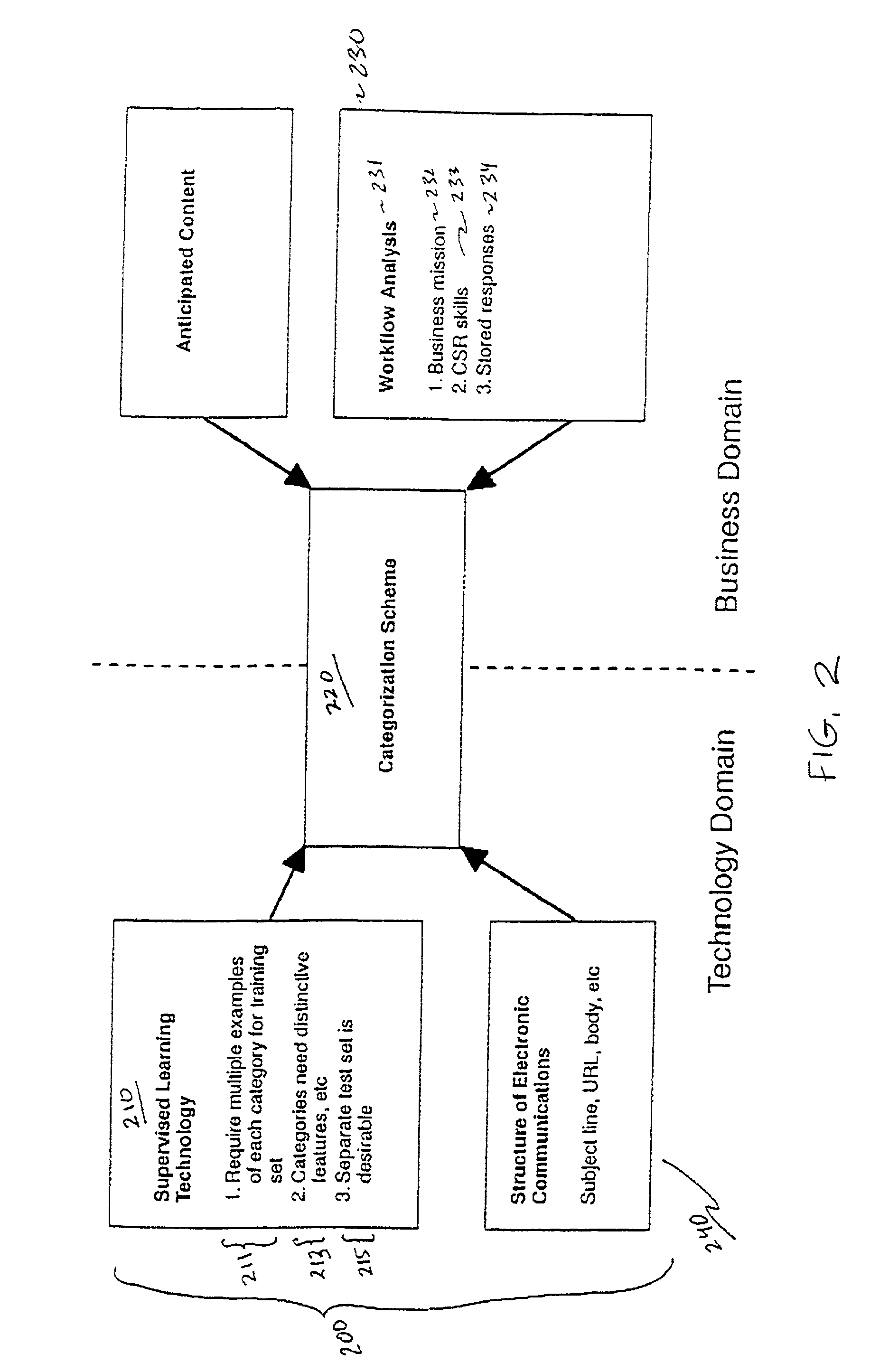
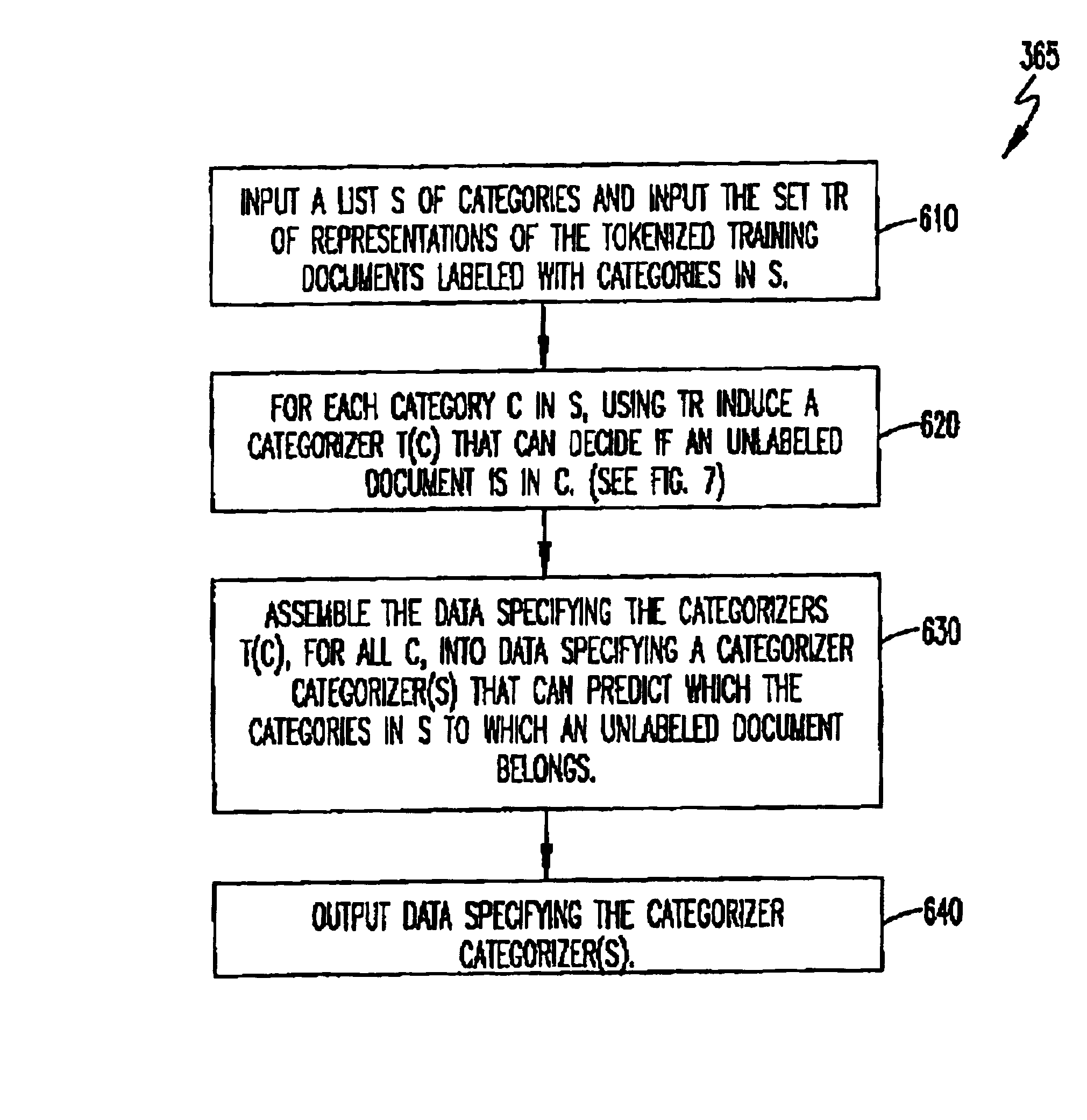
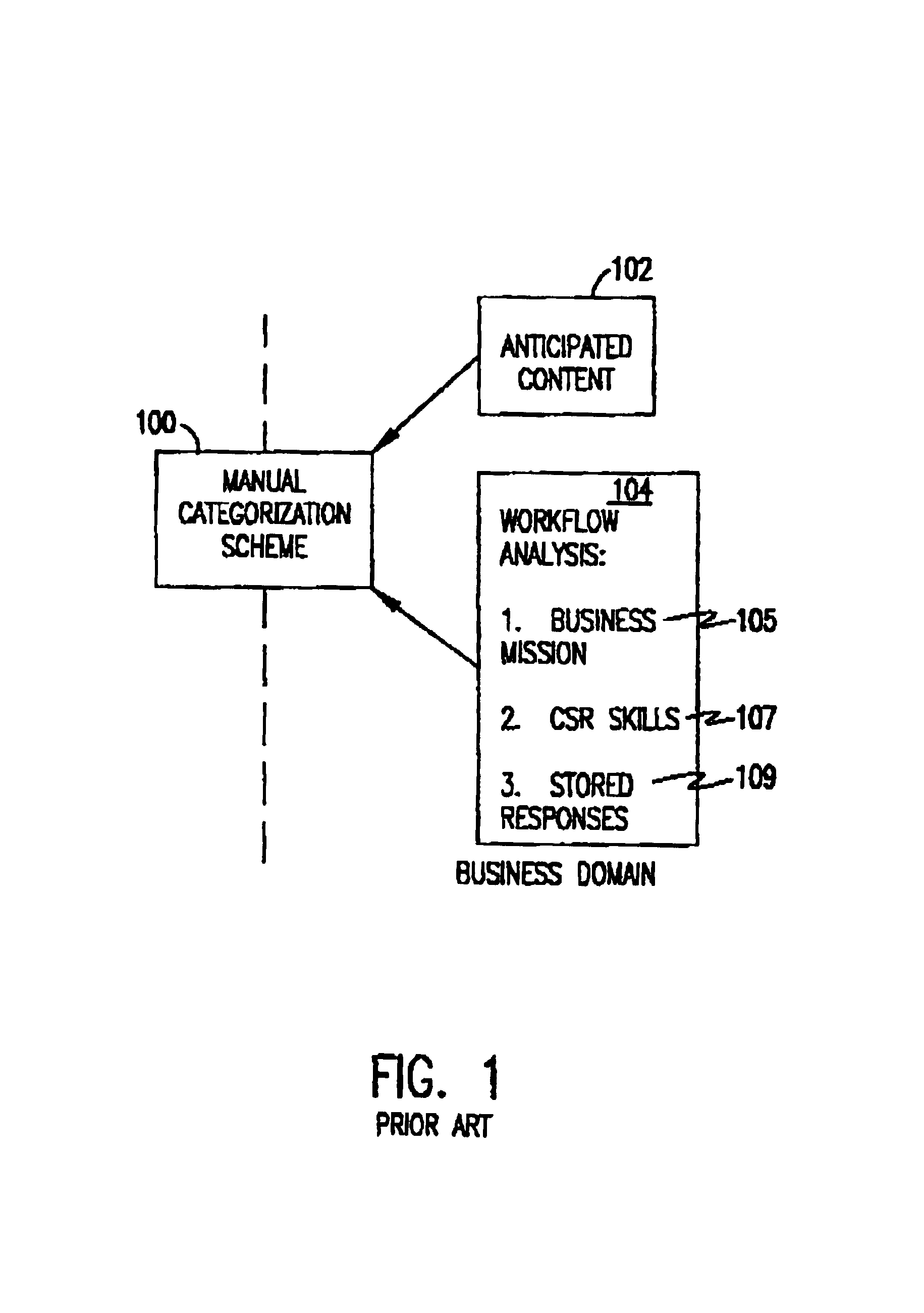
Methodology for creating and maintaining a scheme for categorizing electronic communications
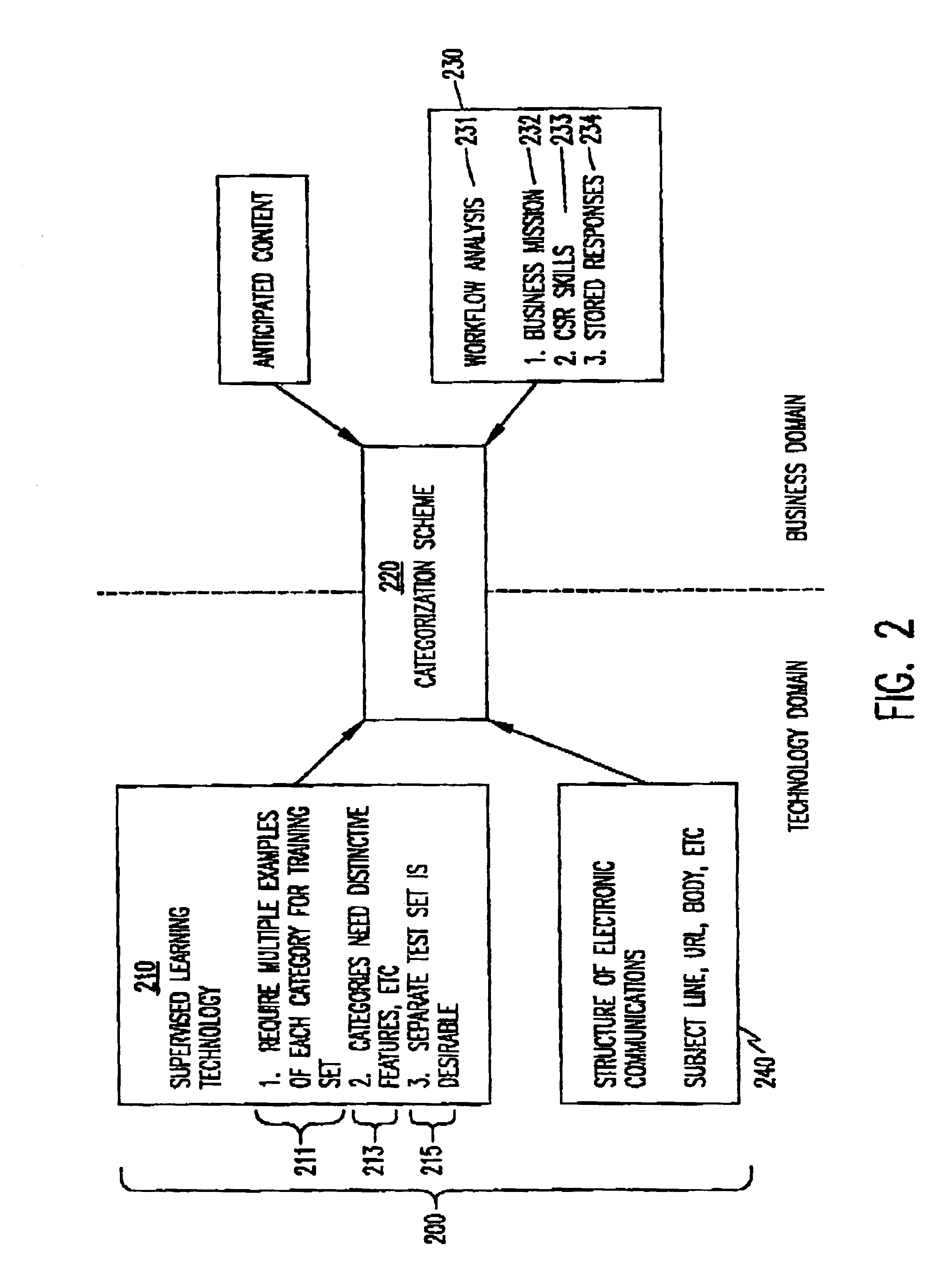
Supervised learning is used to develop a computer program that can automatically route or respond to electronic communications assuming the existence of an appropriate formal scheme for categorizing incoming electronic communications. A method is described by which such a categorization scheme for electronic communications can be constructed. The method is based on an analysis of factors having an impact on the categorization scheme from both the business domain and the technology domain. The problem solved by this method is a new one that is only now emerging as automated methods of routing communications based on supervised learning are becoming feasible. Among other uses, this method may be practically employed as a disciplined way of carrying out consulting engagements that call for setting up and maintaining categorization schemes for electronic communications.
Owner:IBM CORP
Methodology for creating and maintaining a scheme for categorizing electronic communications
Owner:INT BUSINESS MASCH CORP
Synthetic decision-making device for service domain and access domain and route calling method
Owner:ZTE CORP
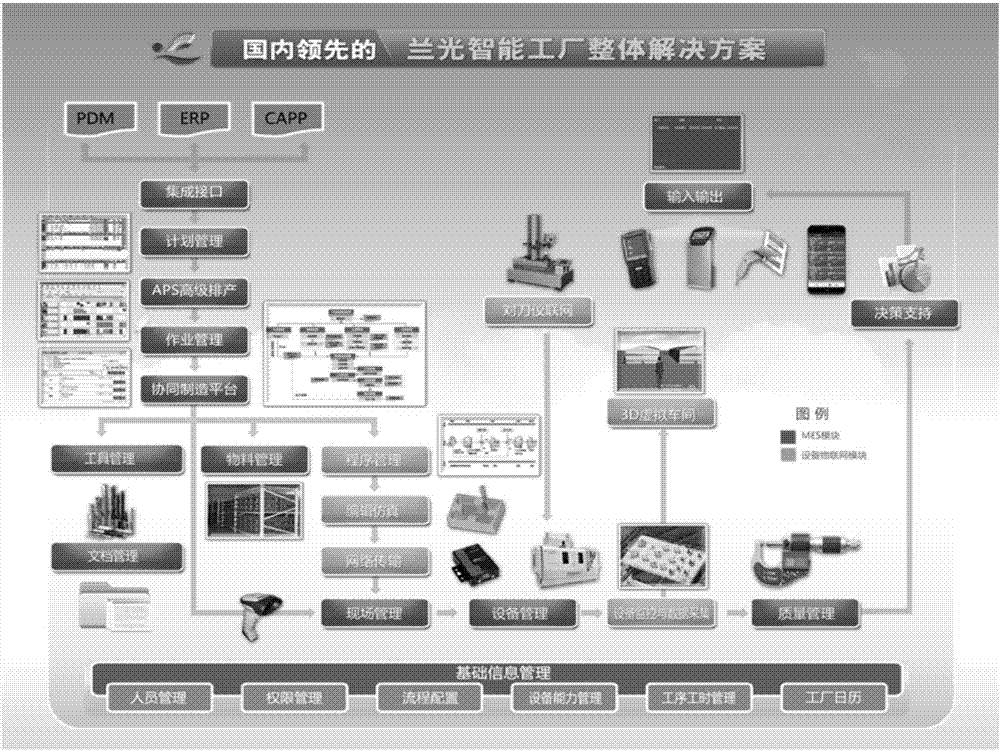
Platform-based intelligent MES
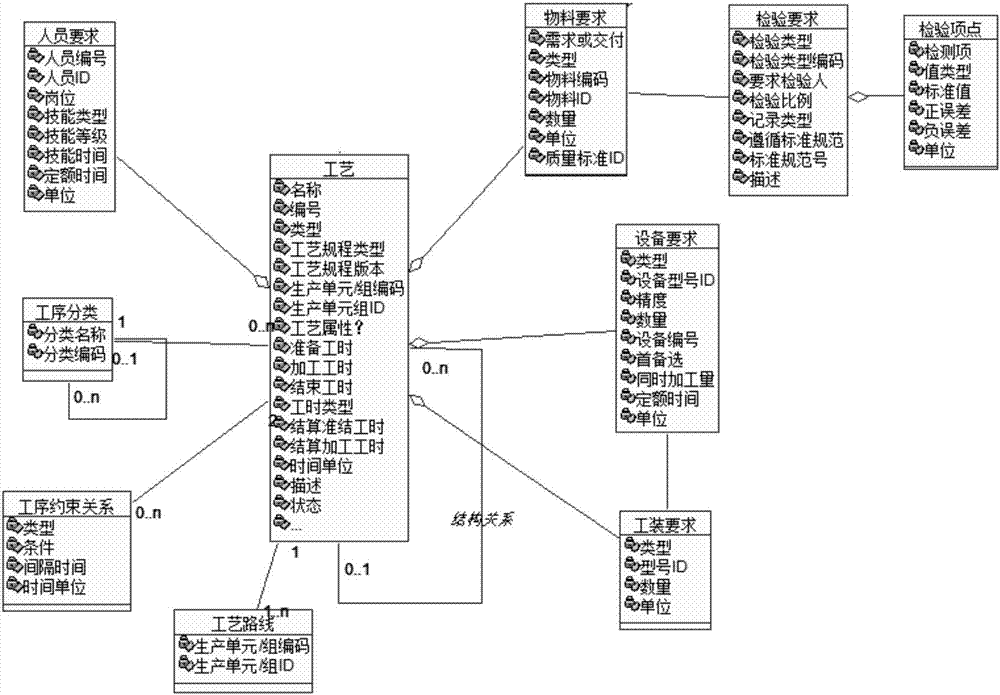
The invention provides a platform-based intelligent MES (Manufacturing Execution System). The system includes a business domain model base and an integrated collaborative manufacturing subsystem. The business domain model base is used for storing a business model, a domain model and a database model. The business model includes the corresponding requirements and associations of personnel, technology, materials, equipment, tooling and test. The domain model includes the work dependence and decomposition relations, the association between work and material and production units, and a field problem component. The database model stores relevant data and data associations in the business model and in the domain model. The integrated collaborative manufacturing subsystem makes an operation plan based on the data and data association in the business domain model base, and manages and schedules the whole operation process. Through a business domain model, all kinds of basic models can be specified, and the association relation can be established. The integrated collaborative manufacturing subsystem executes production planning and management scheduling.
Owner:北京兰光创新科技有限公司
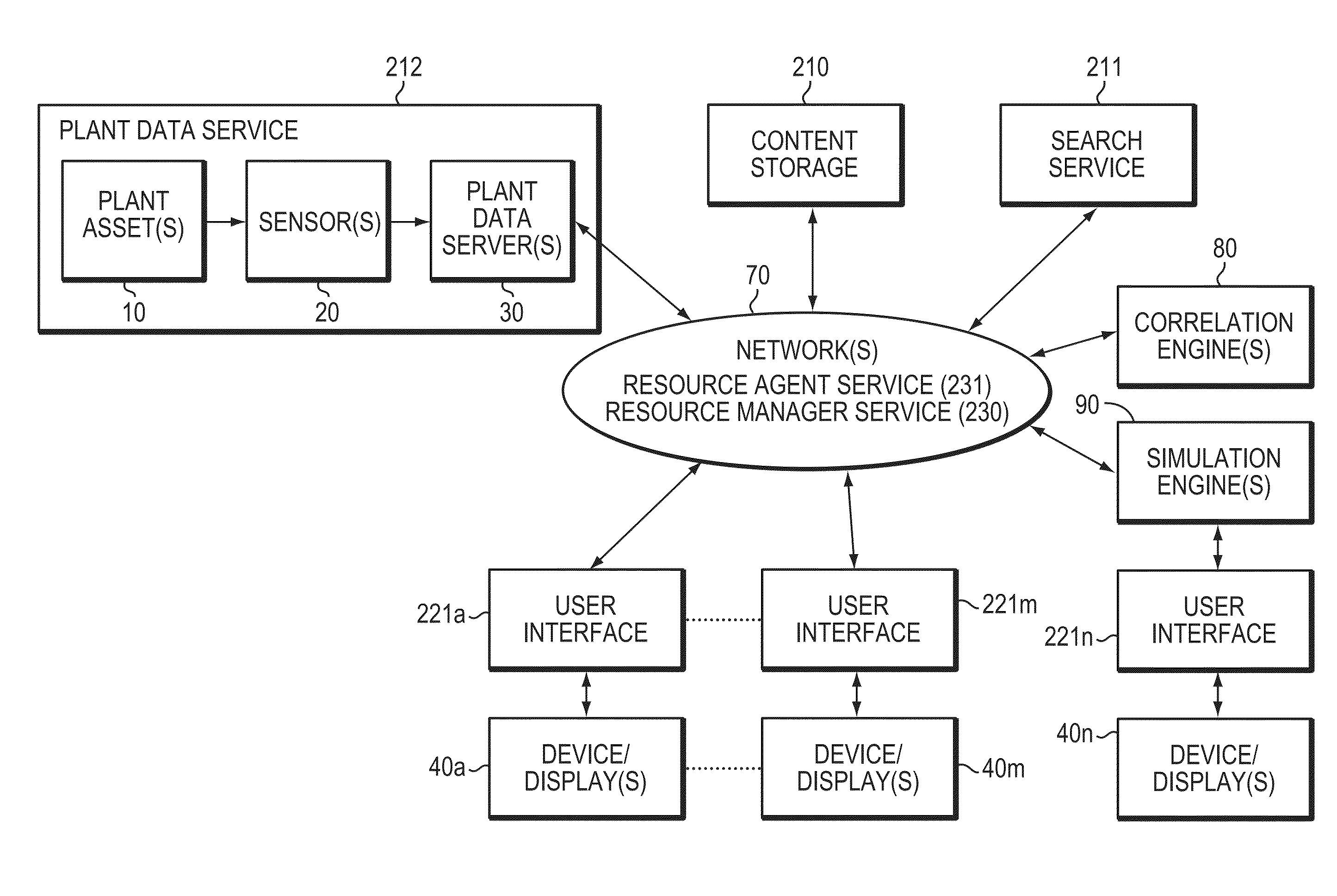
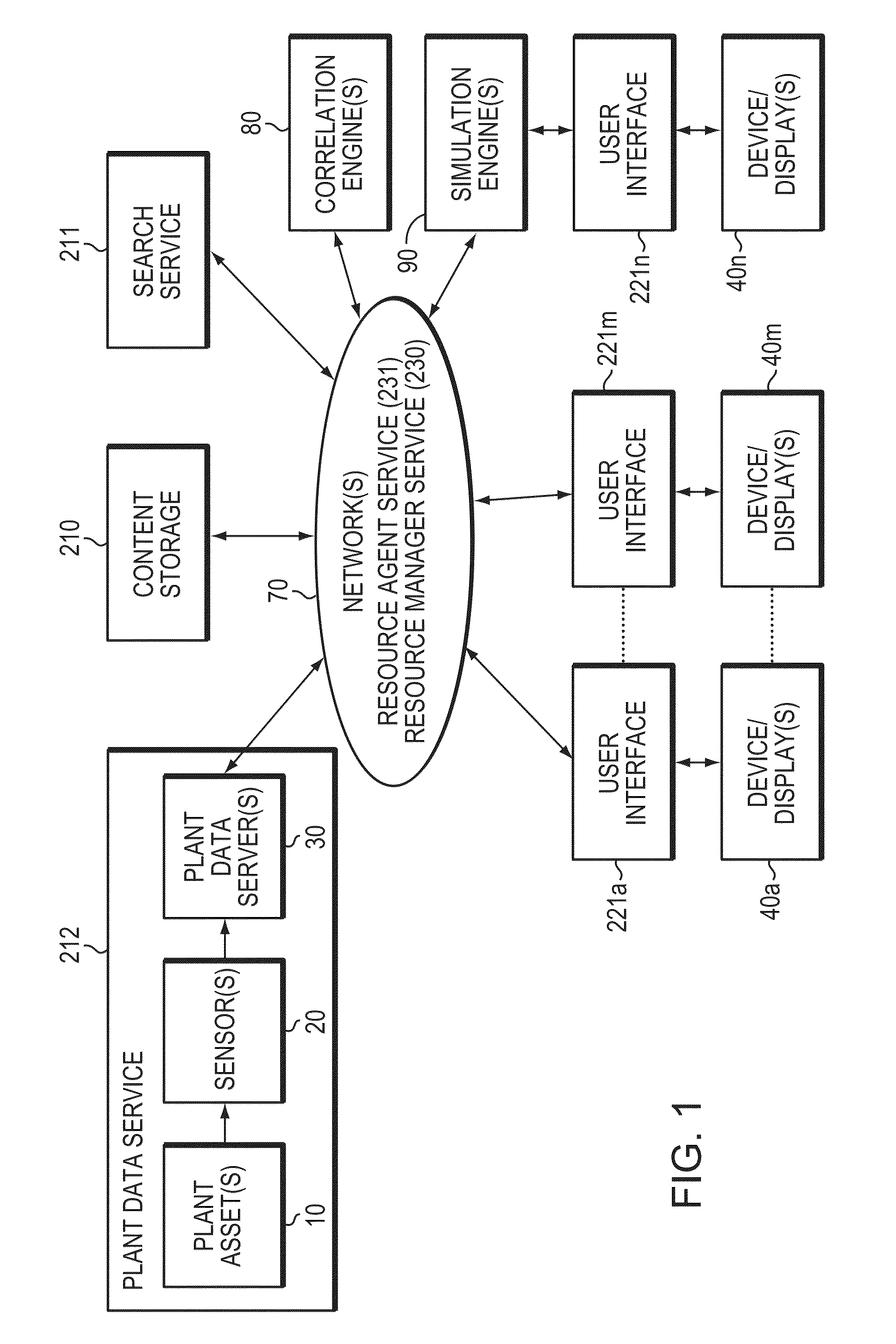
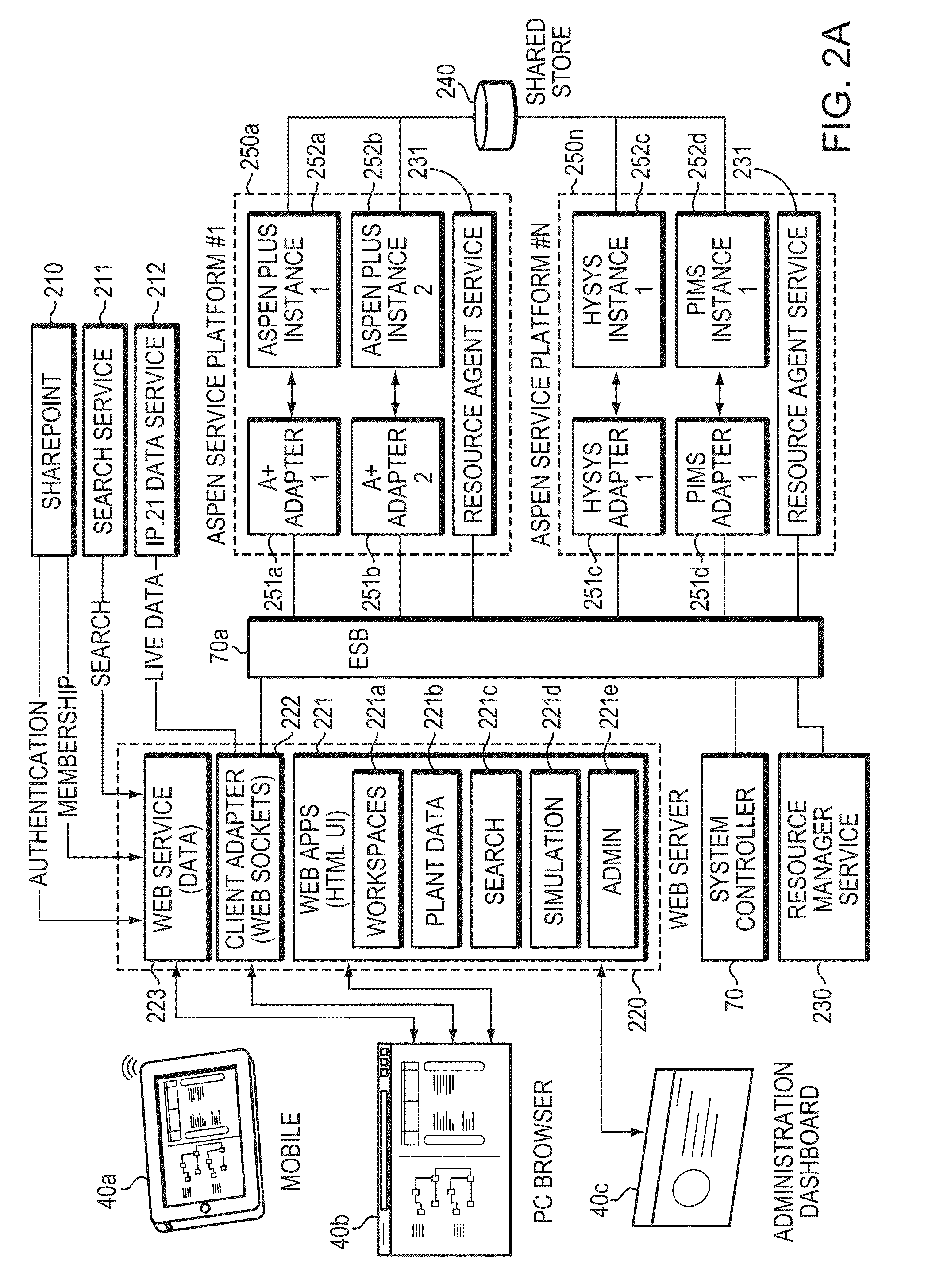
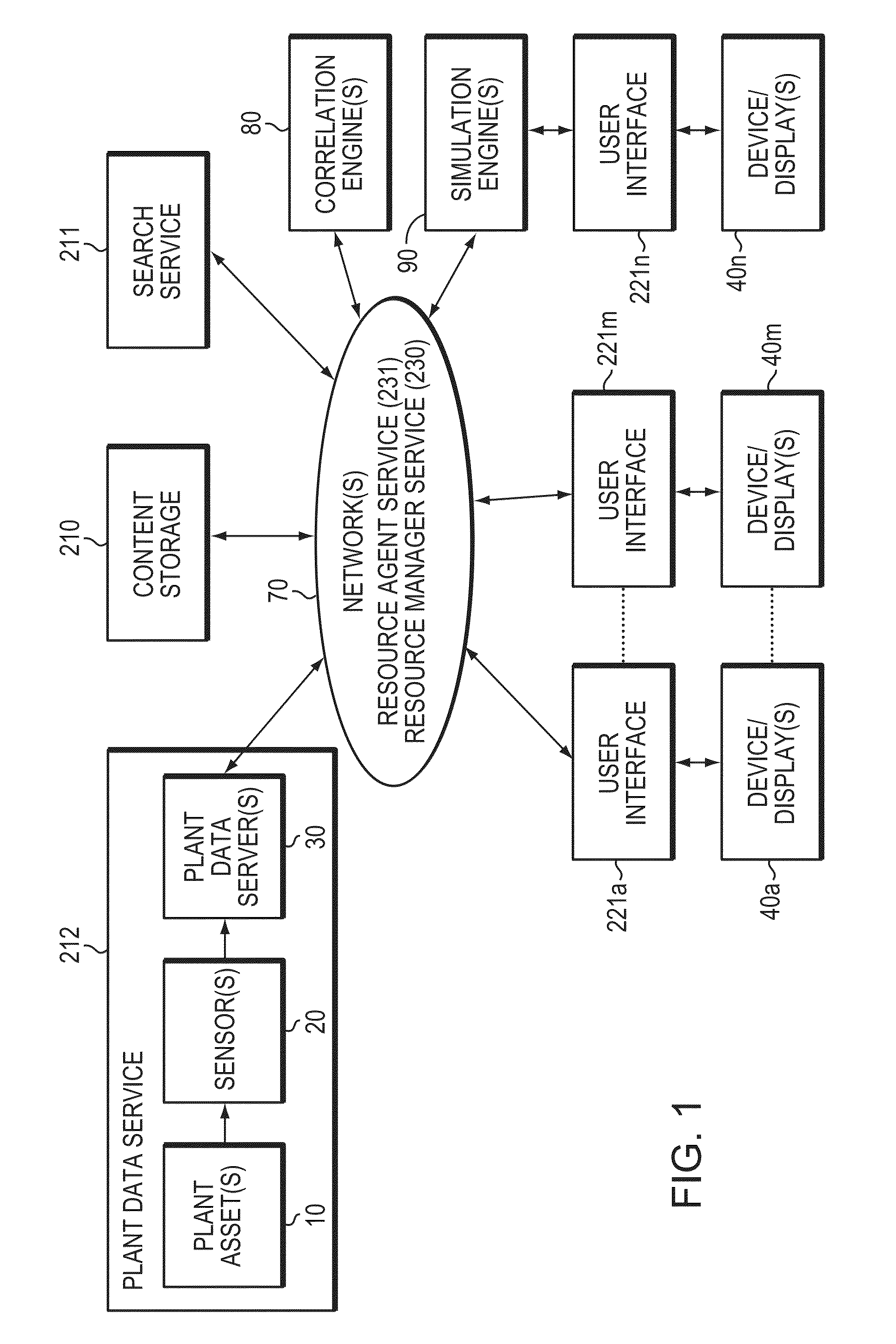
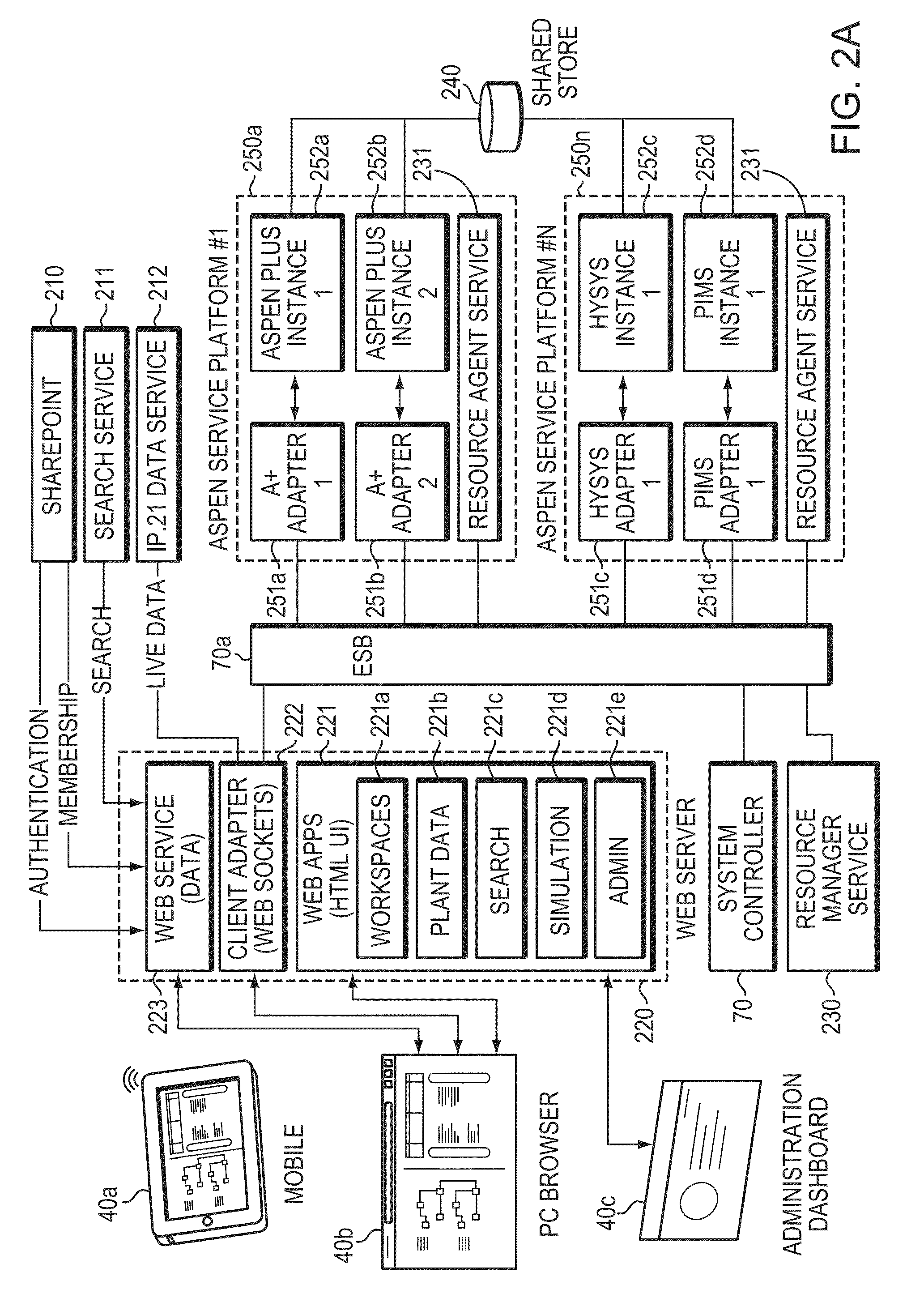
Method and System to Unify and Display Simulation and Real-time Plant Data for Problem-Solving
ActiveUS20140330542A1Highly effectiveHighly intuitiveProgramme controlGeometric CADComputational scienceAmbiguity
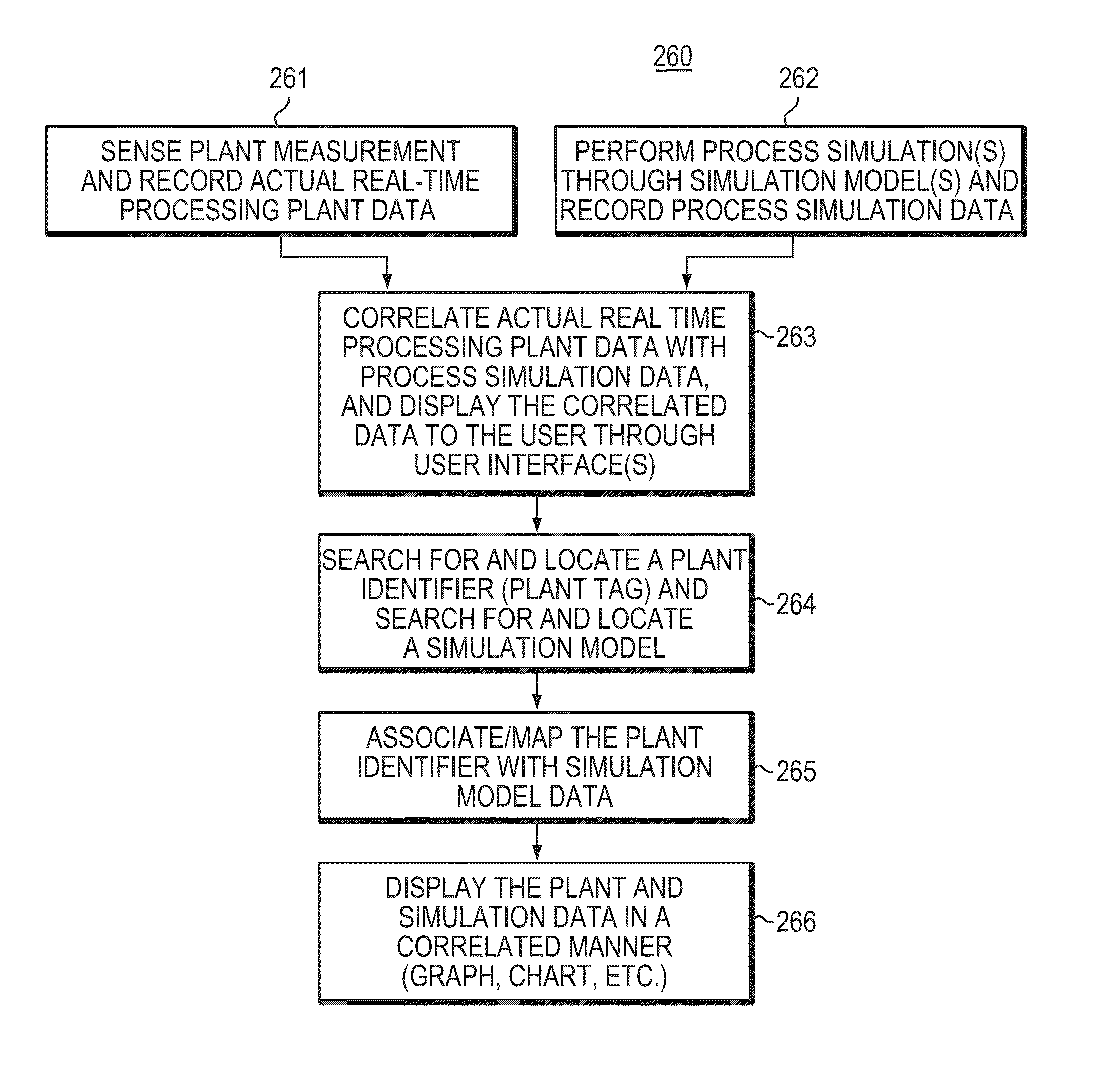
A computer-based method and system brings together data from two business domains: real-time actual plant status operation data and predictive process simulation data based upon a design specification. This method and system correlates the plant data and the simulation data, and displays the results side-by-side for the user. The results assist the user, to determine whether the plant is operating properly, and to make further improvements to both the plant assets and to the simulation models. The invention assists with monitoring, maintaining, trouble shooting, and problem solving of plant operation. The invention facilitates a progressive visual collaborative environment between plant operation and process engineering teams, where engineers from respective domains may socialize and trouble shoot problems. The Progressive Visual Collaboration helps professionals with searching, sharing, mapping, analyzing, framing problems, removing ambiguity and uncertainty by considering facts and figures, and providing a progressive workflow that solves plant problems.
Owner:ASPENTECH CORP
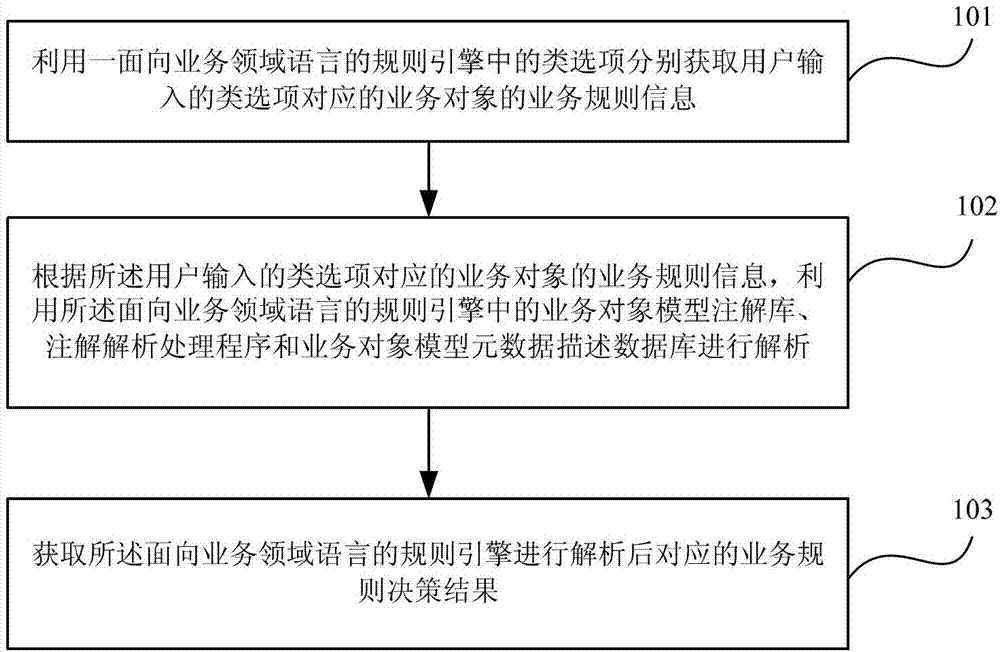
Business rule decision-making method and device based on rule engine
InactiveCN103092967AEditing went wellIncrease productivitySpecial data processing applicationsMetadata descriptionBusiness object
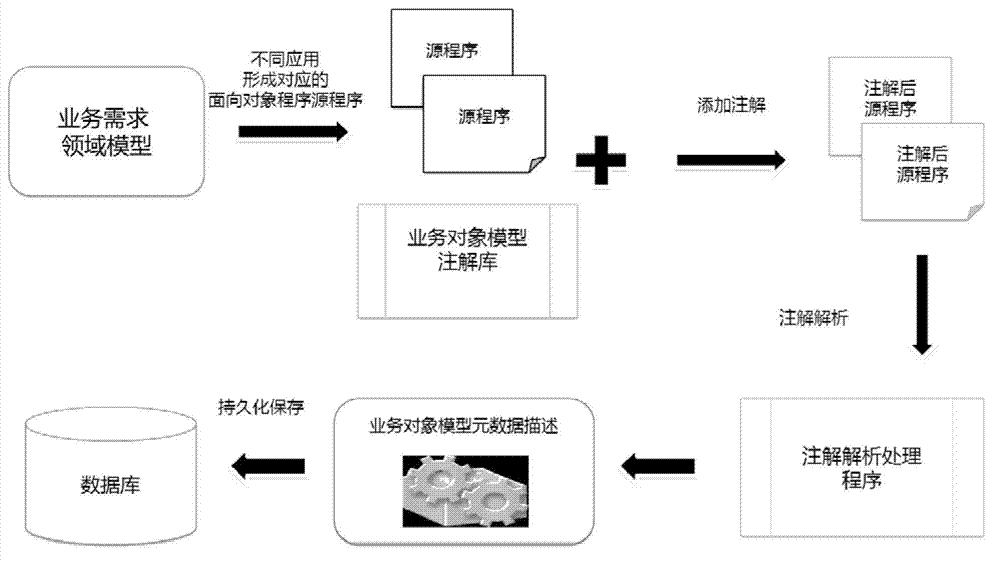
The invention provides a business rule decision-making method and a business rule decision-making device based on a rule engine. The method includes the following steps: respectively obtaining business rule information of business objects of corresponding class options input by a user by using class options of the rule engine facing business domain languages, conducting analysis by using business object model comment libraries, comment analyzing processing programs, and business object model metadata descriptive database in the rule engine facing the business domain languages according to the business rule information of the business objects of the corresponding class options input by the user, and obtaining business rule decision-making results which are corresponding to the analyzed rule engine facing the business domain languages. According to the business rule decision-making method and the business rule decision-making device based on the rule engine, a method which uses the 'business domain language' which is close to natural languages to edit the business rules can be used, and edited rules can be used to conduct system automatic decision making. With the technical scheme, a business manger can successfully edit the business rules, the production efficiency is greatly increased, and response to market change is fast.
Owner:BANK OF COMMUNICATIONS
Domain-partitioned authorization method for cloud computing resources
InactiveCN102903029AMeet the needs of rapid batch activation of infrastructure resource management permissionsResourcesResource managementA domain
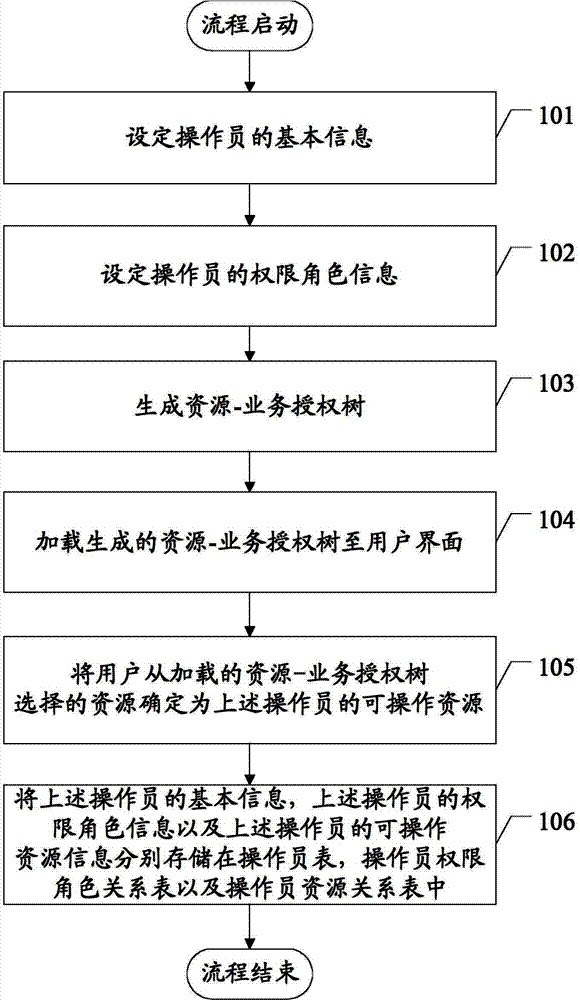
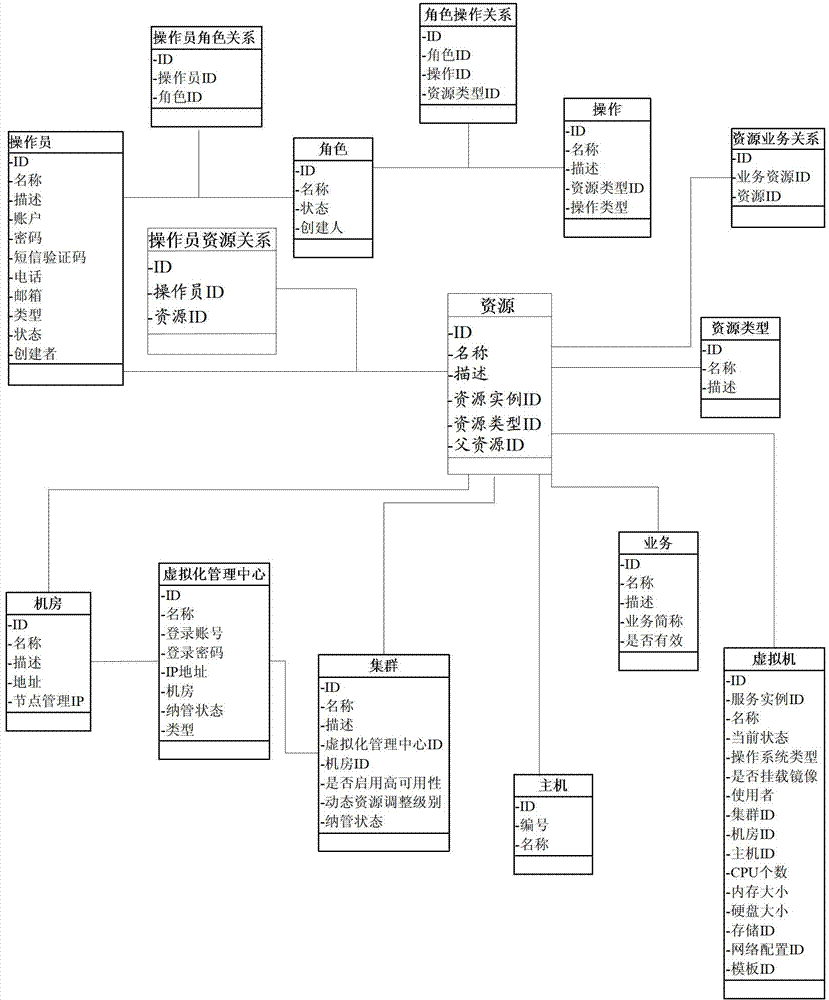
The embodiment of the invention discloses a domain-partitioned authorization method for cloud computing resources. The domain-partitioned authorization method for cloud computing resources comprises the steps of: setting the basic information of an operator; setting the authority role information of the operator; generating a resource-service authorization tree, wherein the resource-service authorization tree comprises the following resources: one or more than two business domains, and the businesses and the clusters included by the business domains; loading the resource-service authorization tree to a user interface; determining the resources chosen by a user to be the operable resources of the operator from the resource-service authorization tree; and storing the basic information of the operator, the authority role information of the operator and the operable resources of the operator in an operator table, an operator authority role table and an operator resource relationship table respectively. By the technical scheme provided by the invention, the demand of rapidly opening basic facility resource management authorities in batch of a manager aiming at one operator is met.
Owner:GUANGDONG ESHORE TECH
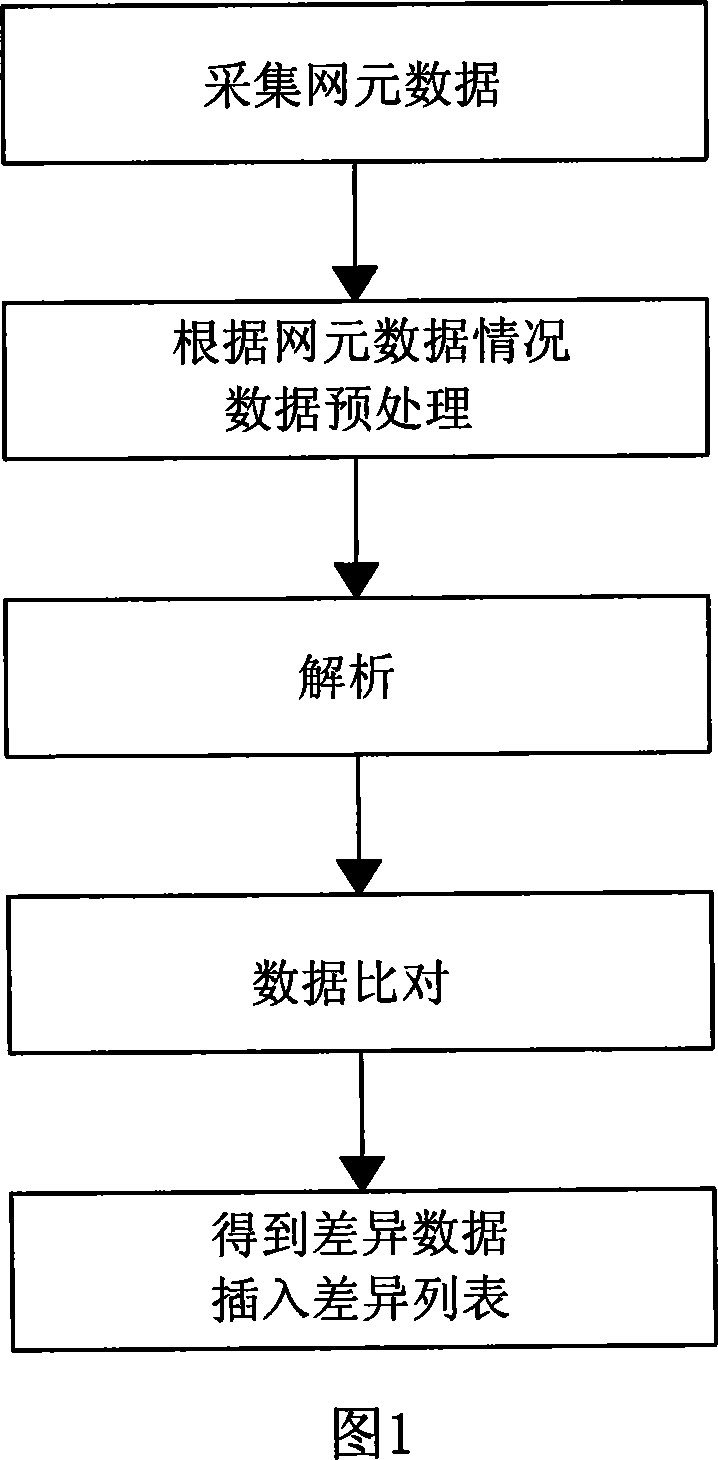
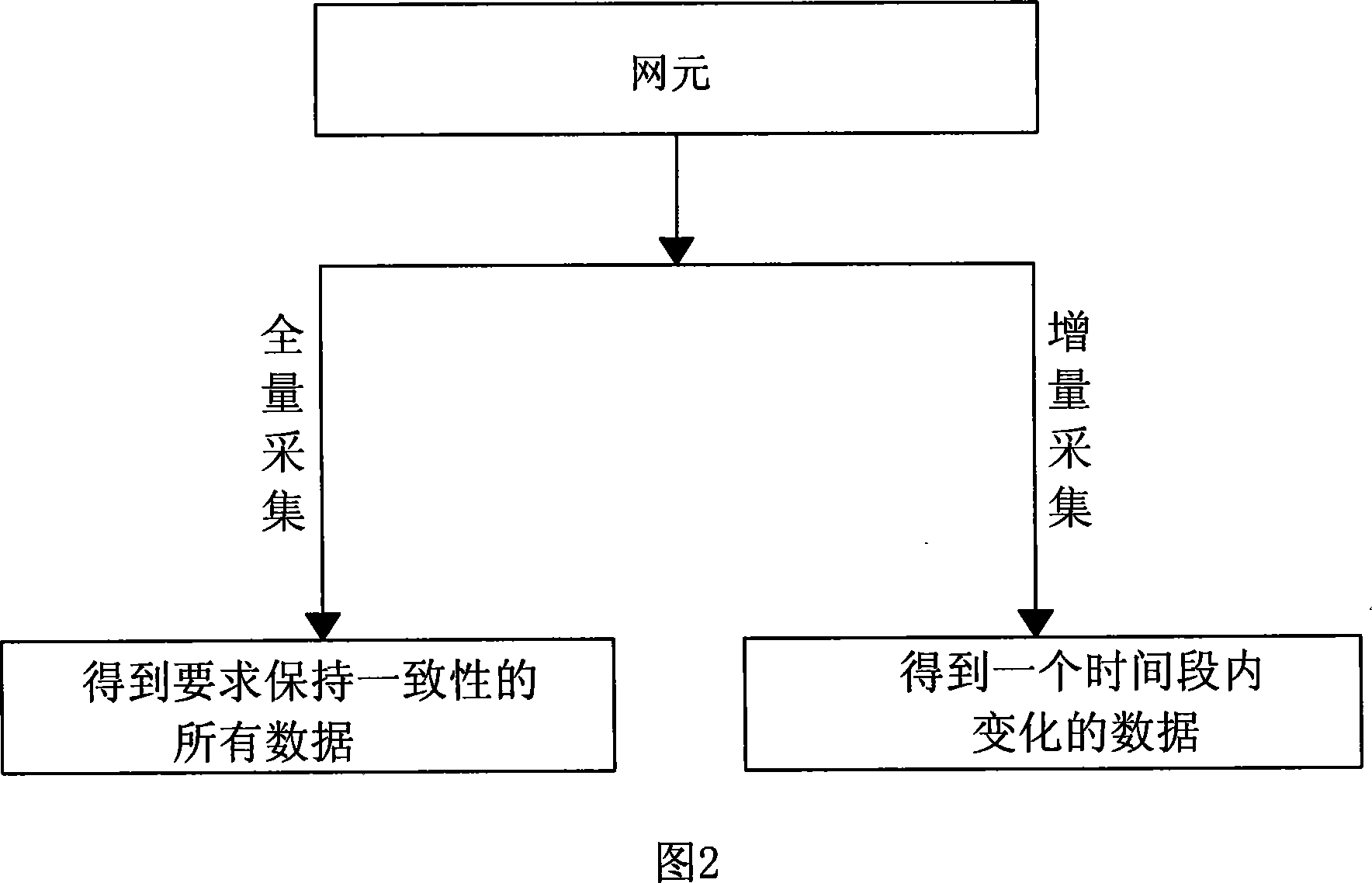
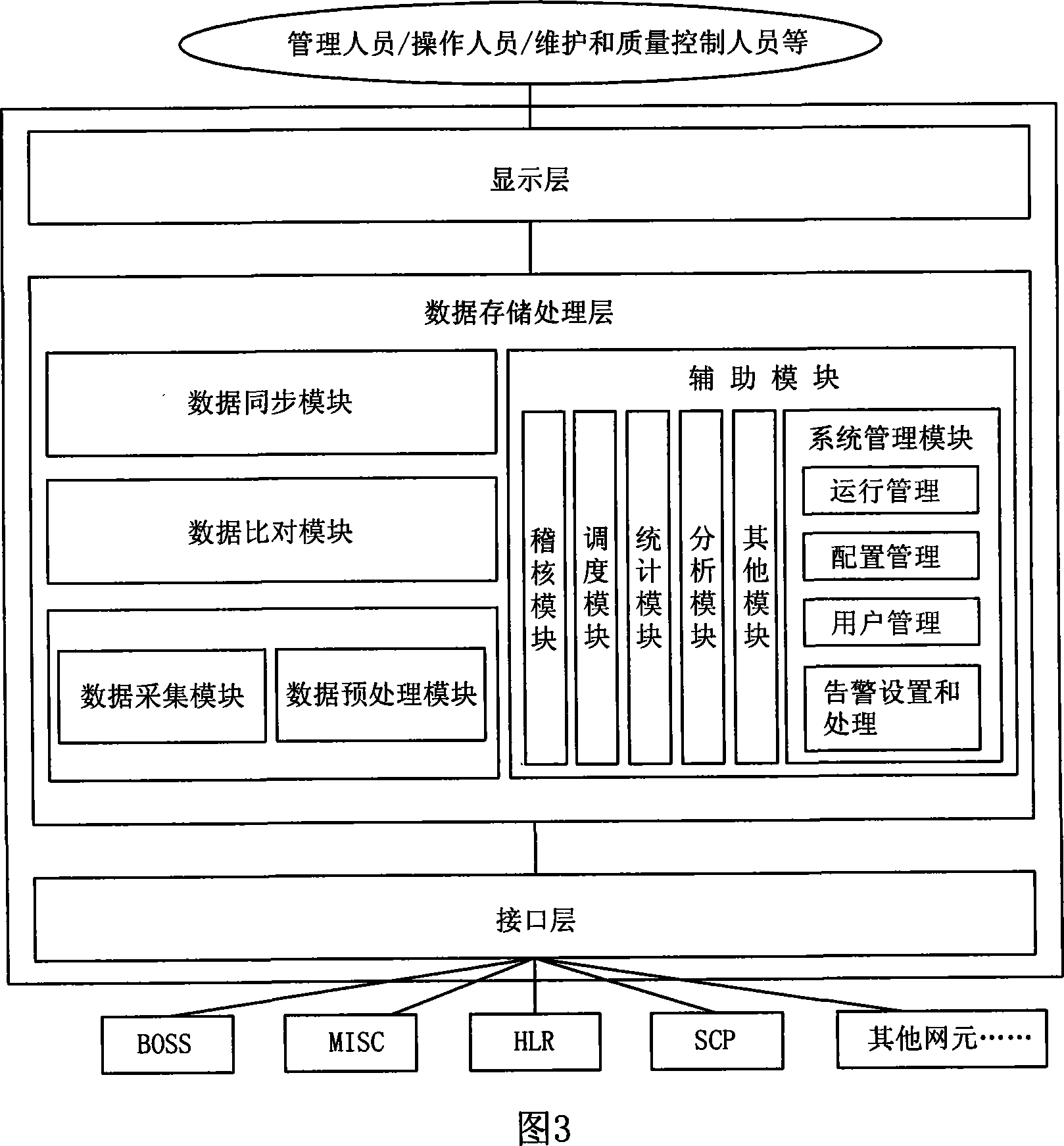
Data consistency detection method
InactiveCN101079749AError preventionRadio/inductive link selection arrangementsDifference listData differencing
Owner:CHINA MOBILE GROUP SICHUAN
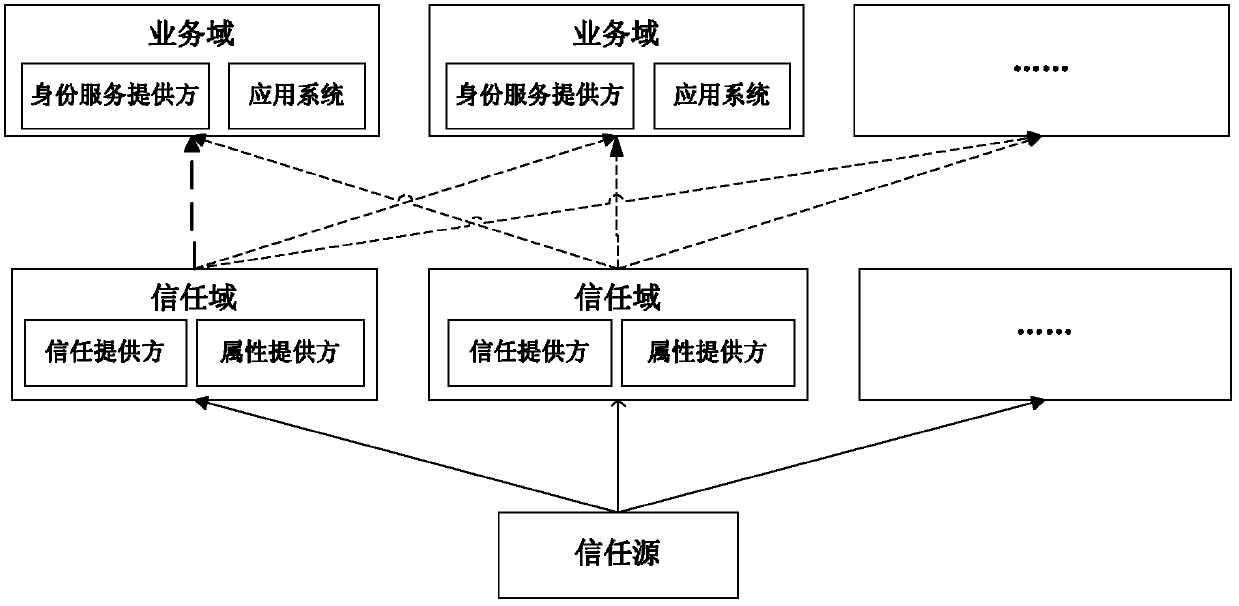
Attribute-oriented protection digital identity service method and system thereof
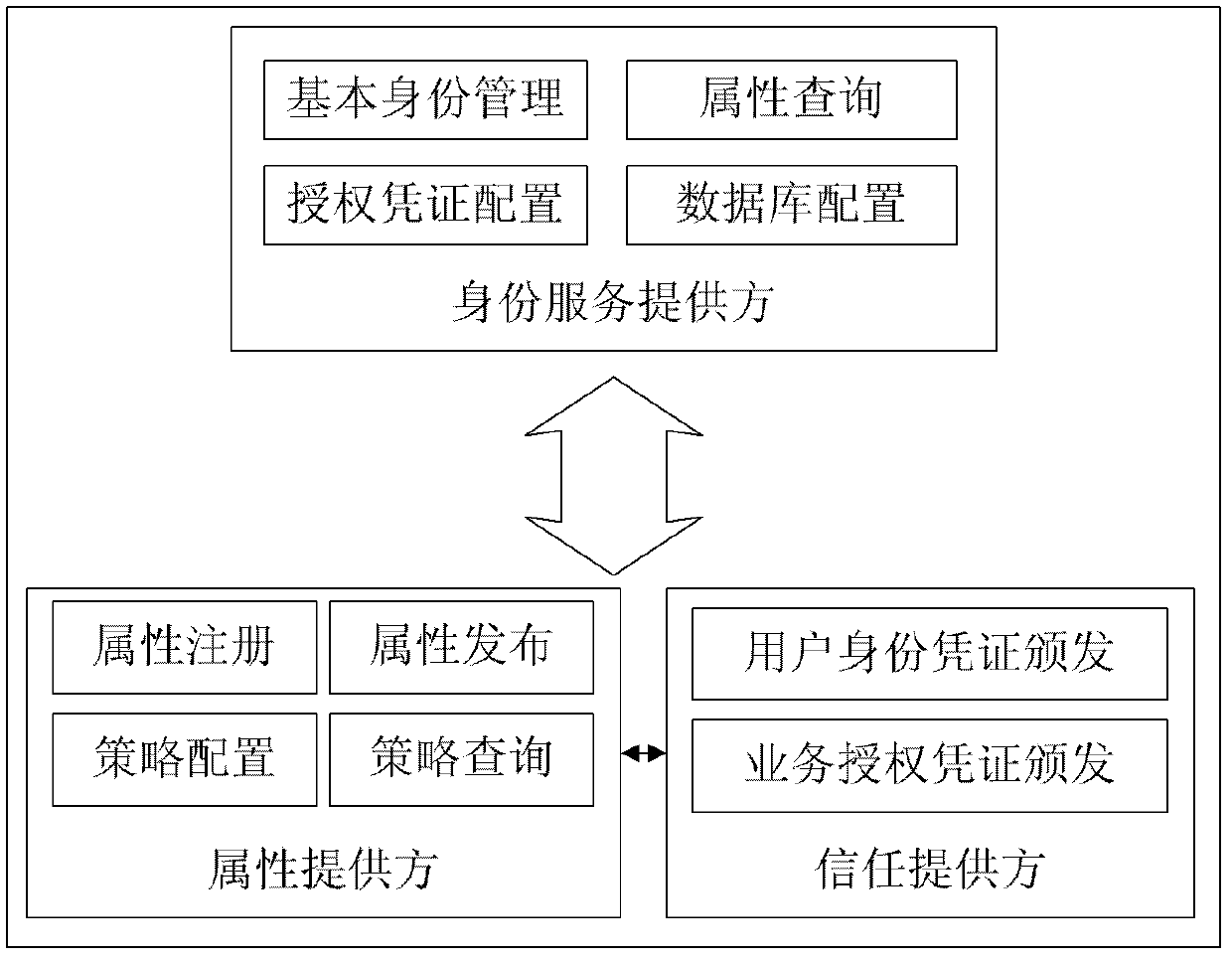
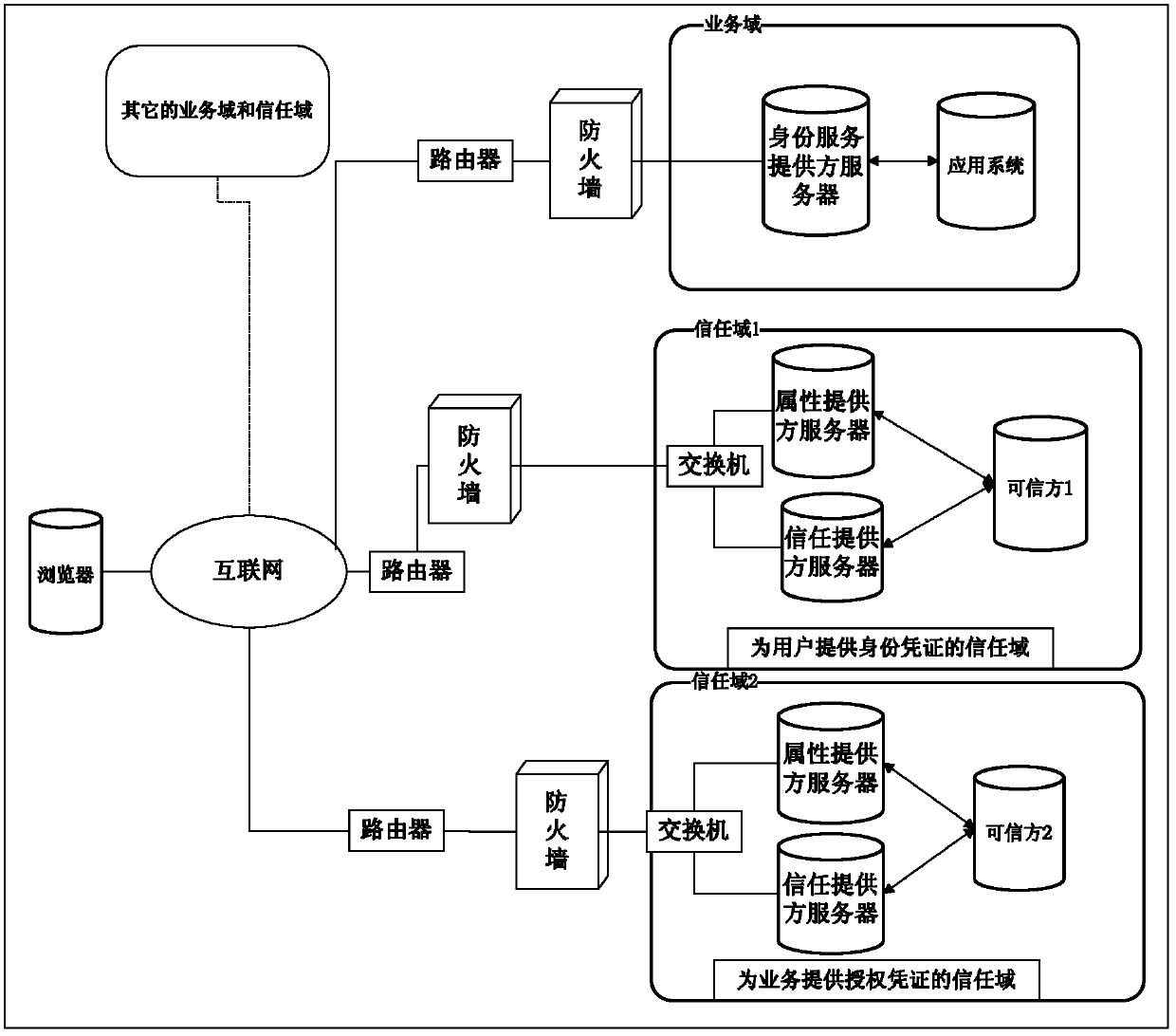
The invention discloses an attribute-oriented protection digital identity service method and a system thereof, which belong to the field of information safety. The method comprises the following steps: adopting an attribute supplier and a trust supplier to jointly form a trust domain, and supplying attribute service and trust certificate service to application systems in a management domain and a user; jointly deploying an identity service supplier and the application systems in a business domain, providing identity management service to the application systems, and meanwhile, calling service of the attribute supplier in the trust domain to replace a business system to finish demand service on the user attribute. The system comprises at least one trust domain and at least one business domain; the trust domain is respectively connected with the business domain through a network; each business domain comprises the identity service supplier and a plurality of application systems in data connection with the identity service supplier; each trust domain comprises the trust supplier and the attribute supplier in data connection with the trust supplier. According to the attribute-oriented protection digital identity service method and the system thereof, on the premise of guaranteeing privacy safety of a user, the user attribute demand of business is met.
Owner:INST OF SOFTWARE - CHINESE ACAD OF SCI
Deployment optimization method of software defined firewall based on openstack cloud platform
ActiveCN108173842AMeet needsAvoid centralized deploymentData switching networksResource poolDelayed response
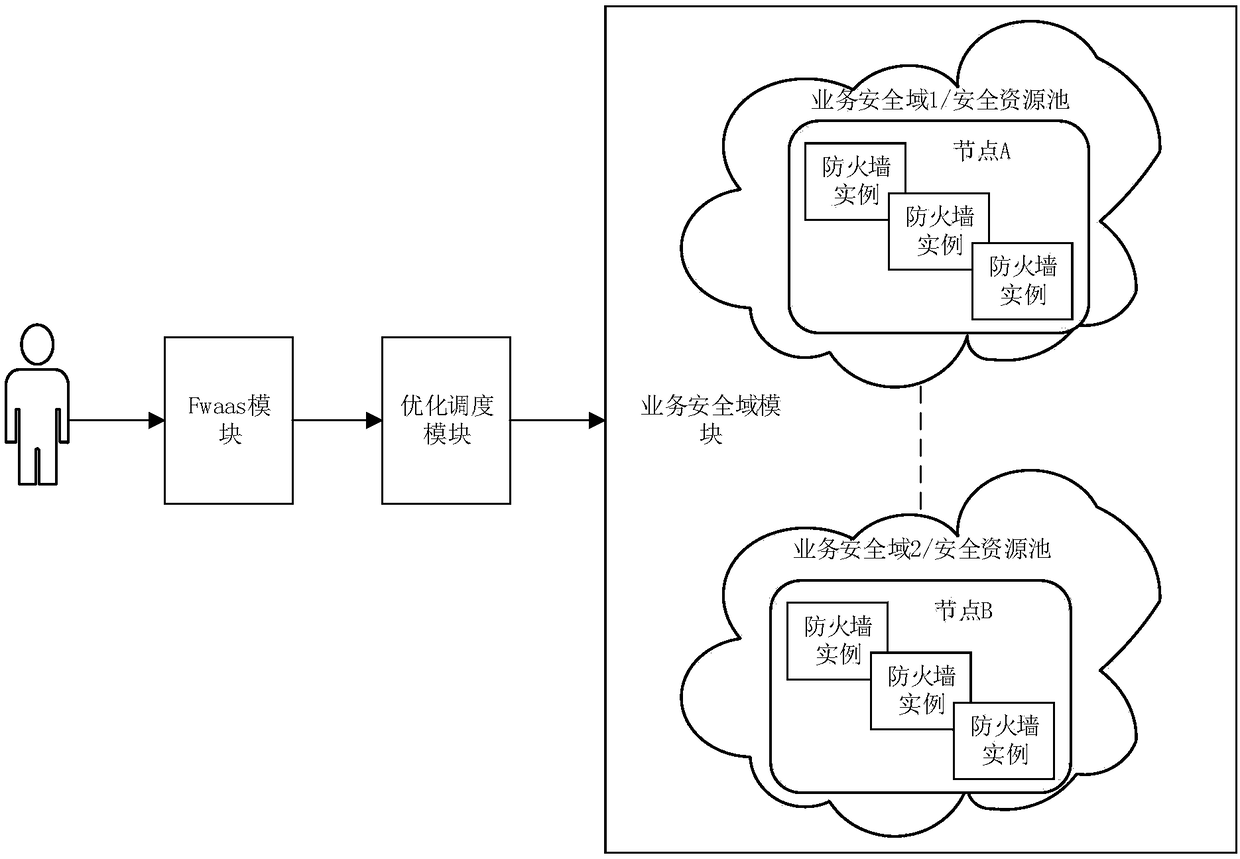
This invention discloses a deployment optimization method of a software defined firewall based on an openstack cloud platform. The firewall is taken as a specific implementation module of a FWAAS standard interface; business security domains are partitioned on the basis of tenant businesses; security resource pooling management is realized in independent business security domains; a pre-allocationmechanism is adopted for security resources inside a security resource pool; and nodes can be dynamically selected in the security business domains with an optimized scheduling module during creationof the firewall according to the demand of a tenant on traffic, and a firewall instance is deployed in a security node which meets the demand of the tenant. A quick response can be made to the demandof the tenant on a security business through the method; the ability to quickly deploy the security businesses is provided for the FWAAS of the Openstack through the optimized scheduling module; andsecurity demands corresponding to different businesses are separated through a business security domain module, and the tenant can quickly acquire the firewall instance, so that a security policy is quickly configured, and the problems of slow deployment of firewall instances, delayed response and the like in an original scheme of the Openstack are solved.
Owner:STATE GRID CORP OF CHINA +1
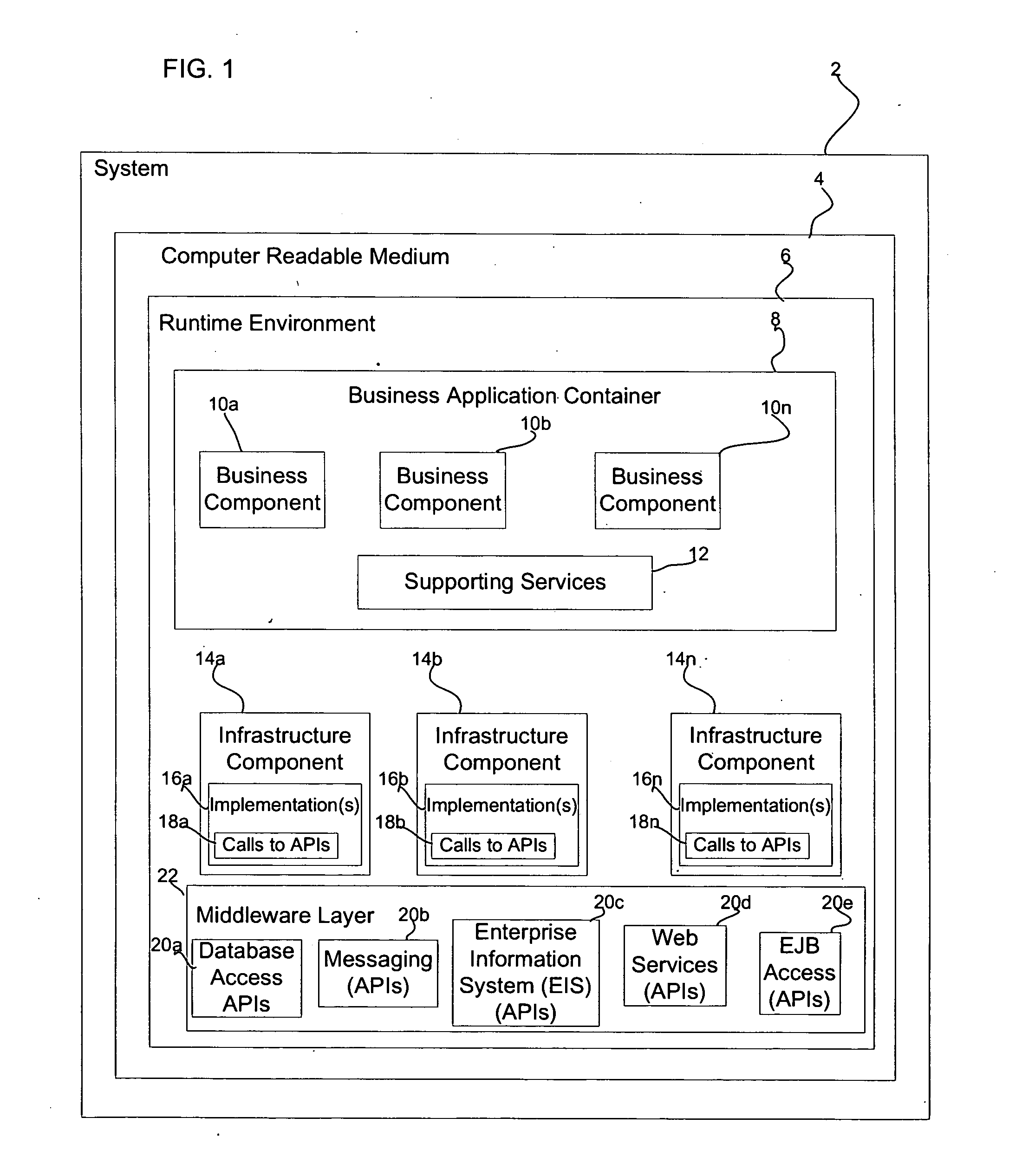
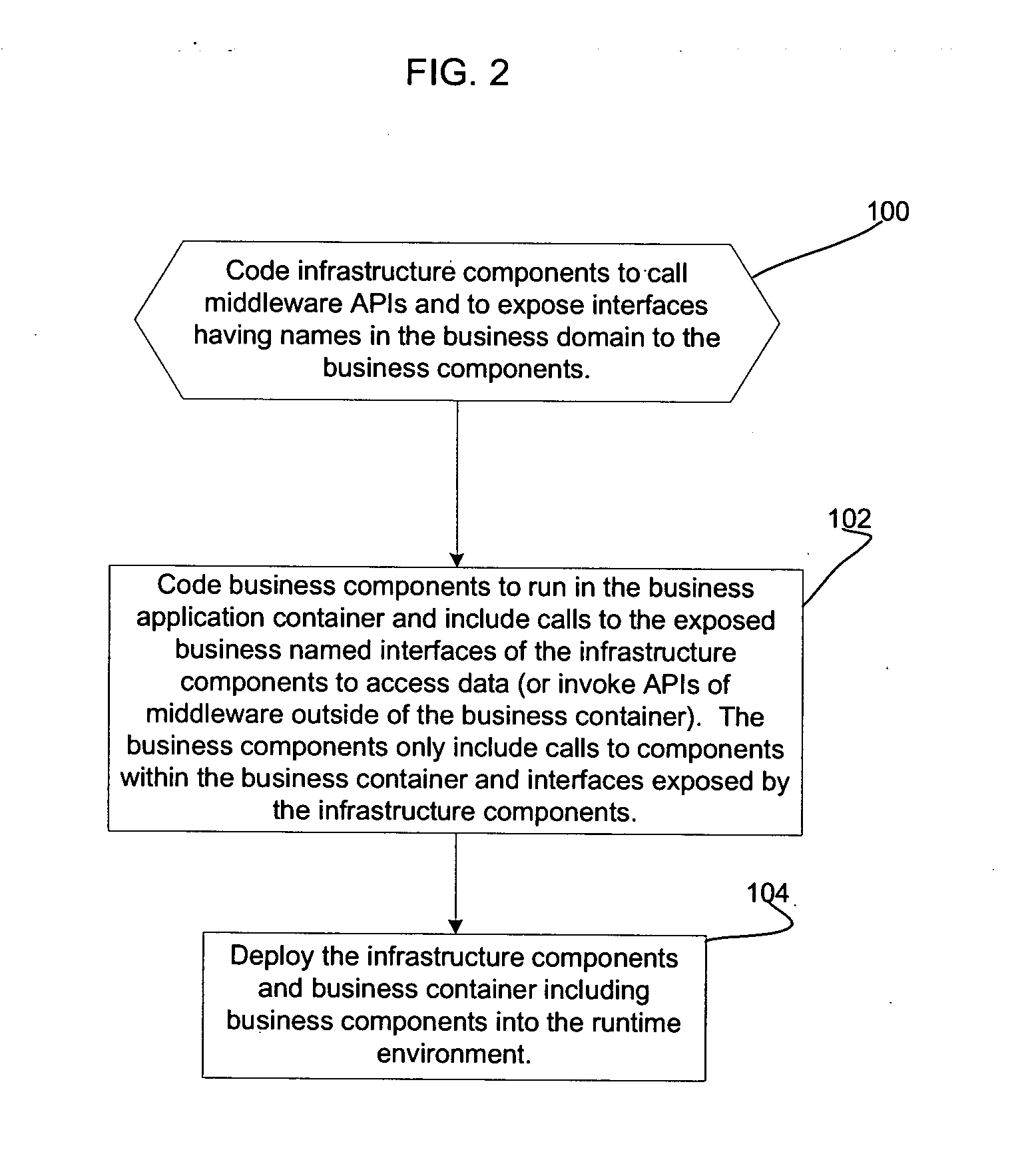
Architecture for enabling business components to access middleware application programming interfaces (APIs) in a runtime environment
InactiveUS20060129560A1Software designSpecial data processing applicationsApplication programming interfaceMiddleware
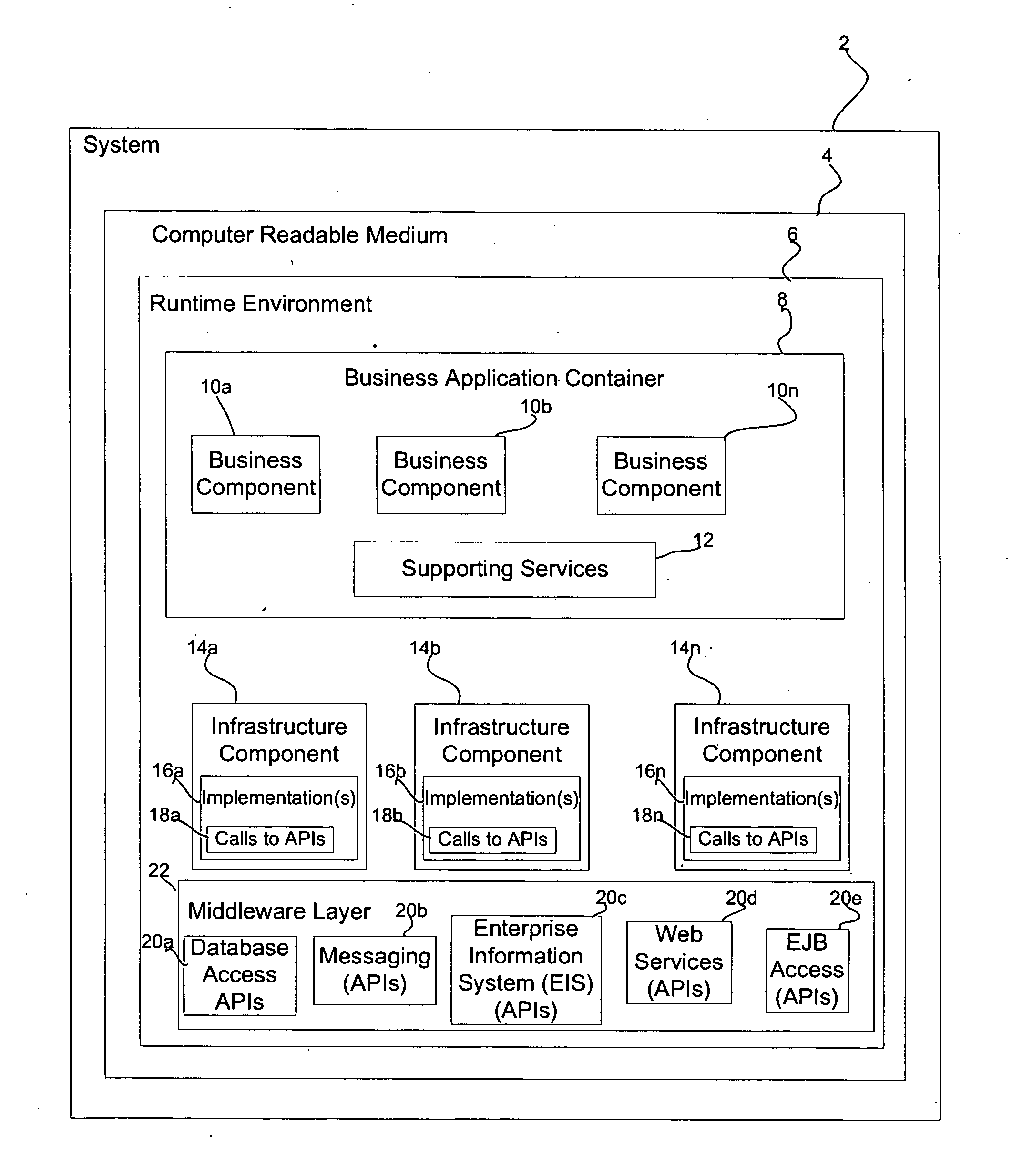
Provided is an architecture for enabling business components to access middleware components in a runtime environment. A business container hosts business components and services to enable communication between the business components. A plurality of infrastructure components expose interfaces and methods to the business components, wherein the exposed interfaces and methods have names descriptive of a business domain for which the business applications are written. The infrastructure components implementation of the interfaces and methods exposed to the business components include calls to the middleware application programming interfaces (APIs) to invoke middleware APIs to cause middleware operations.
Owner:IBM CORP
Method and apparatus for generating test scenarios for a set of business rules
InactiveUS20150178625A1Knowledge representationResourcesConstraint satisfaction problemComputerized system
A method for automatically generating test scenarios for a plurality of business rules created to form a ruleset for a business domain. A plurality of decision variables is extracted from a business object model associated with the business domain using a computer system. The plurality of business rules is parsed using a syntactic parser operating on the computer system to extract at least one condition expression and an assignment action. A collection of mutually exclusive constraint satisfaction problems is built from the decision variables, condition expressions, and assignment actions using a constraint problem generator operating on the computer system. A plurality of test scenarios is generated automatically from each identified constraint satisfaction problem in the collection using a constraint solver engine operating on the computer system.
Owner:IBM CORP
Ontology-driven information system
InactiveUS7567915B2Avoid redundancyProvide consistencyBuying/selling/leasing transactionsKnowledge representationApplication softwareKnowledge management
An ontology-driven information system includes a plurality of models, each of which expresses an aspect of a business domain using concepts and relationships between concepts. An ontology, which is in communication with each of the plurality of models, provides uniform definitions for the concepts and relationships between concepts used in the plurality of models. A method for executing an interaction flow model includes receiving an event and categorizing the received event. Once the event is categorized, a situation that matches the categorized received event is identified. One or more tasks are then executed for the situation. The execution of the one or more tasks can include either an interpretation of a model or the execution of a method of an object. The information system also includes a user and application interface and a reasoning engine that is in communication with the user and application interface. A knowledge manager is in communication with the user and application interface and is interfaced with the reasoning engine. A distributed information service also is in communication with the reasoning engine, the knowledge manager, and the user and application interface.
Owner:DST SYSTEMS
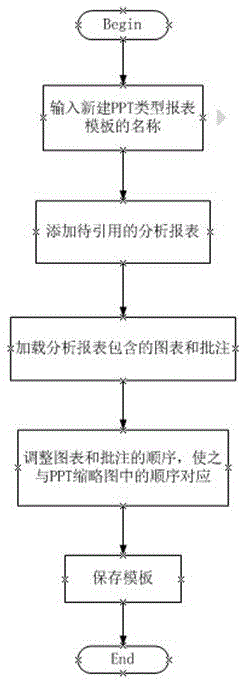
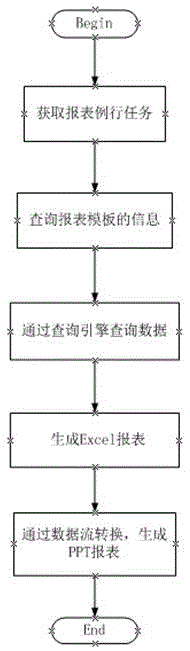
Method for exporting PPT reports from performance management system through data conversion
ActiveCN105528337AGuaranteed operation and maintenance capabilitiesGuaranteed service qualityText processingSpecial data processing applicationsPerformance indexData management
The invention discloses a method for exporting PPT reports from a performance management system through data conversion, and belongs to the field of data management. The method has the advantages that network performance statistical data are displayed via the PPT reports through data conversion, PPT-type report templates are created, diagrams and remarks in multiple analysis reports are quoted and loaded, sequences of analyzed and loaded analytical report elements are adjusted, arranged and combined into specific reports, the state of network performance is displayed systematically and accurately, detail conditions from summaries reported to senior leaders to specific equipment of specific network domains can be provided, and both overall network performance conditions and performance indexes in specific business domains can be observed, so that foundation and basis are provided for rapid understanding of overall system performance conditions, and guarantee is provided for network operation and maintenance abilities and service quality of operators powerfully.
Owner:INSPUR TIANYUAN COMM INFORMATION SYST CO LTD
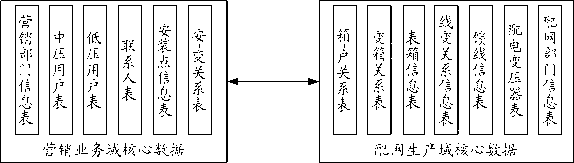
Marketing-distribution master data management system
InactiveCN103065269AAccurate business analysis dataConsistent business analysis dataData processing applicationsReusabilityMultiple input
The invention discloses a marketing-distribution master data management system. Firstly, marketing business domain core data and network distribution production domain core data are built, and the marketing business domain core data and the network distribution production domain core data are associated through analyzing the relationship between core data. The marketing and distribution data are used for depicting a core business entity. Through main construction of the marketing business domain core data and the network distribution production domain core data, identification, switching, storage and reconstruction of application systems of business domain core data are conducted by adopting a main line of 'station-line-change-box-household', and unified management of basic data which are high in reusability is finally achieved, multiple input of the core data is eliminated, single view of the whole main data is built and maintained, and accuracy, consistency and integrity of the single view are guaranteed.
Owner:SHENZHEN POWER SUPPLY BUREAU
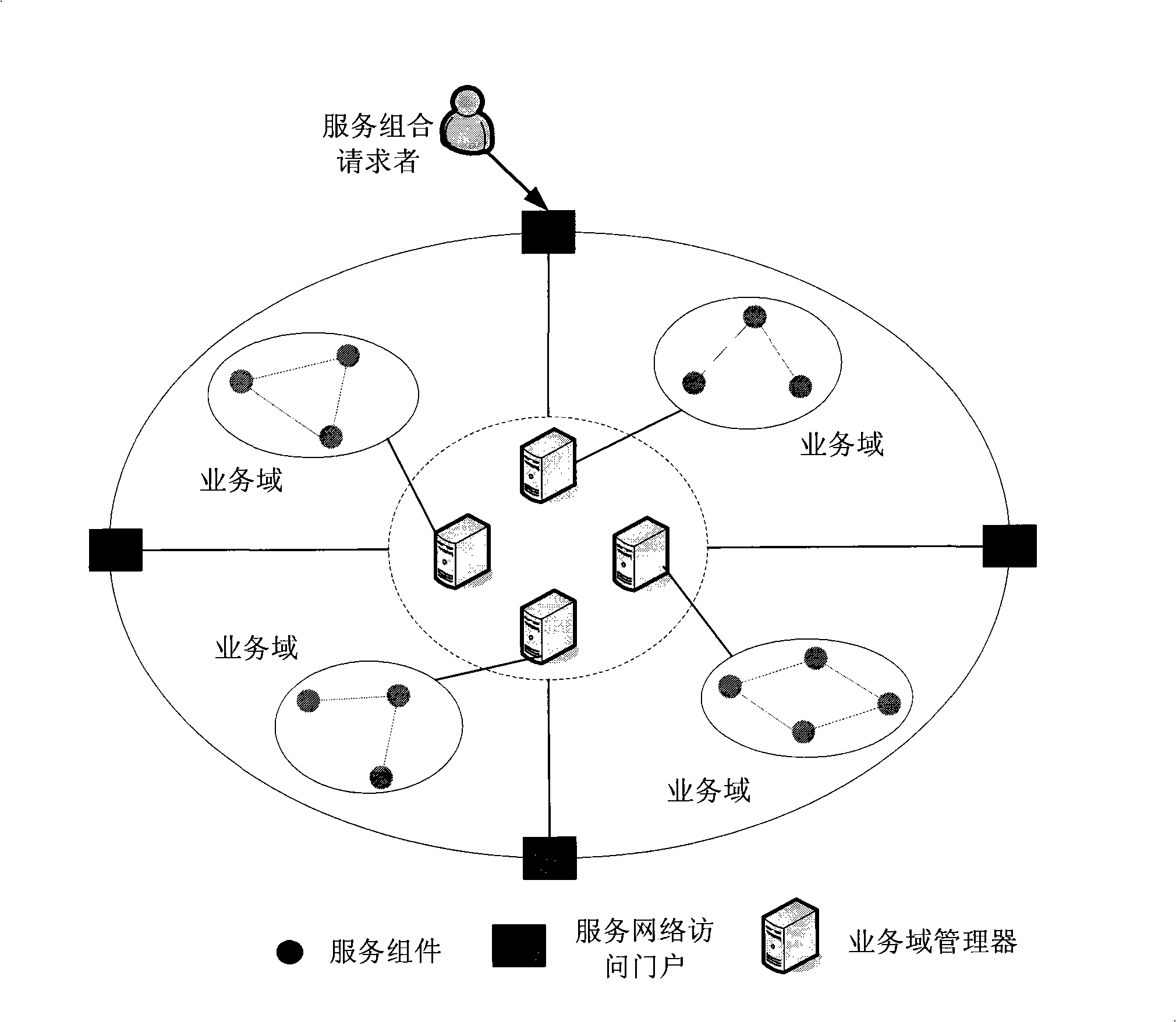
System for implementing programmable service combination facing end user
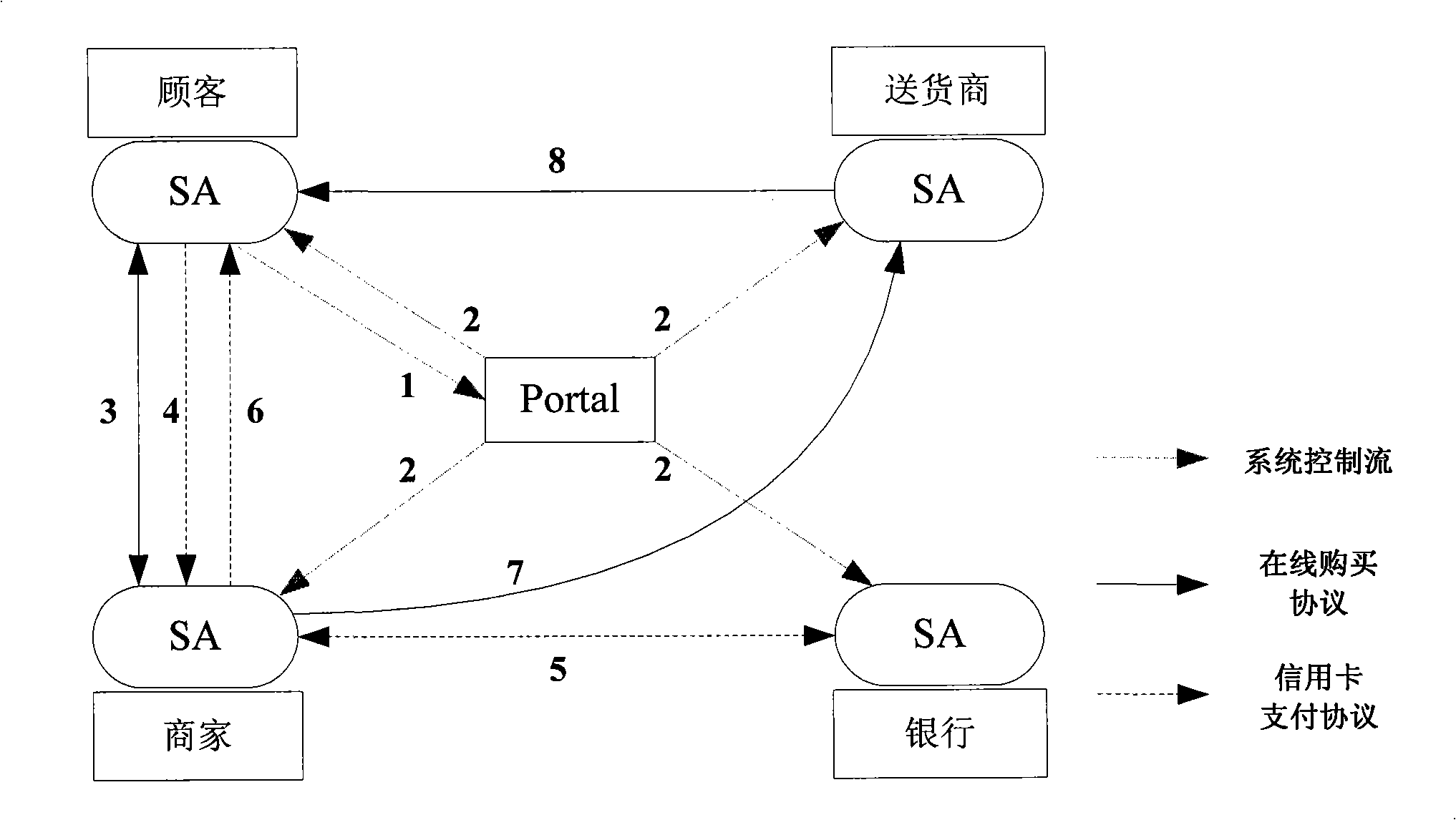
InactiveCN101494578ASuitable for e-commerce application scenariosImprove scalabilityData switching by path configurationService compositionService protocol
The invention discloses an end-user programmable capability-orientated service packet realizing system. The service packet realizing system can realize high-efficient and reliable service packet in internet environment. In the invention, a service protocol is regarded as the natural expression of the service packet relationship with loop coupling, and a service network is established on the basis of the existing service by virtue of the inherent service protocol relationship among services, which can support the application environment with complex business collaboration characteristics, such as e-business and the like; furthermore, business domains are divided in the service network according to the protocol, and a programmable service network is established to support the programmable capability of the end-user, thus realizing the service packet according to needs.
Owner:BEIHANG UNIV
Business level method, apparatus and system for managing service information
InactiveCN101329629AEfficient storageEfficient managementResourcesSpecific program execution arrangementsService modelService information
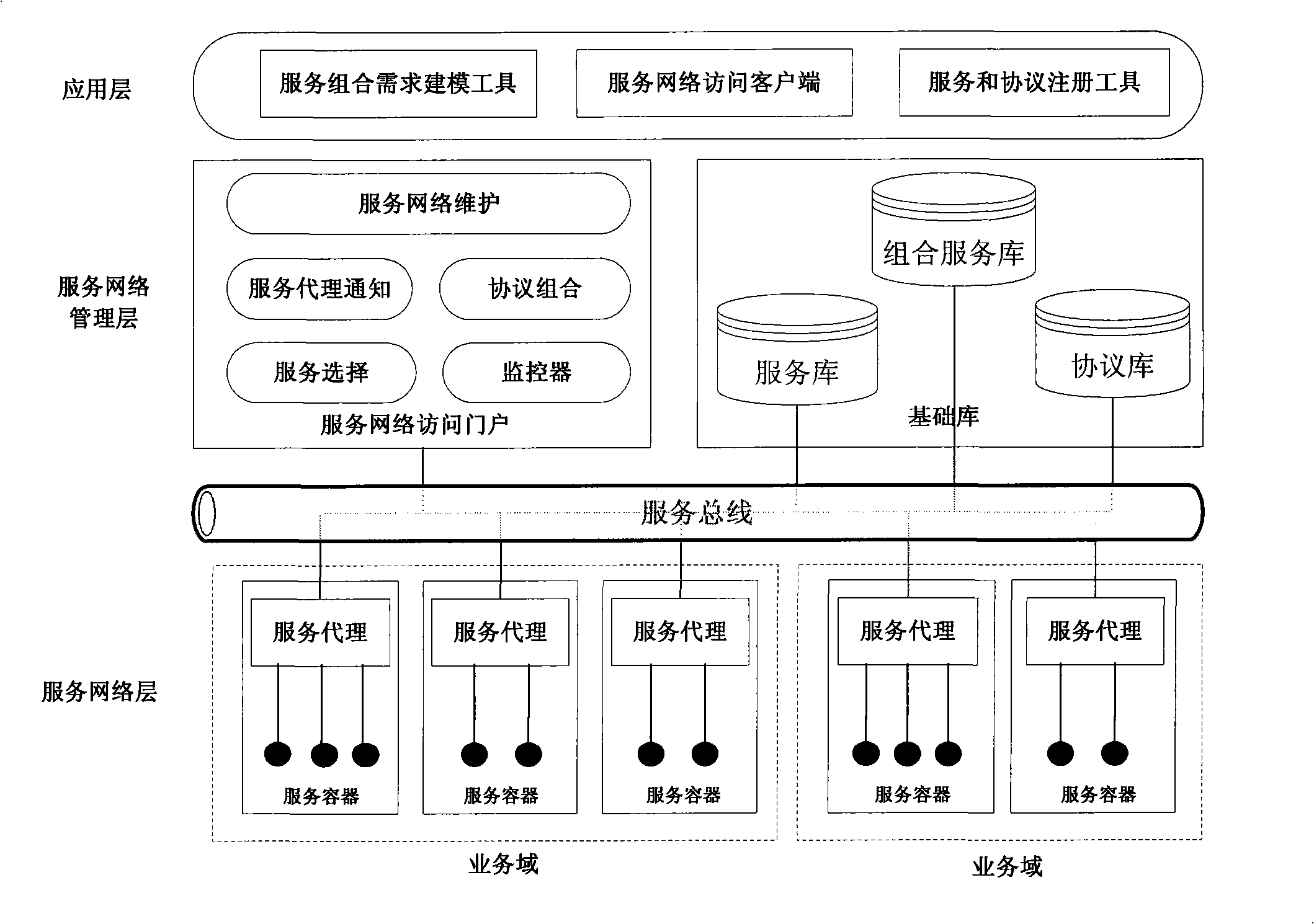
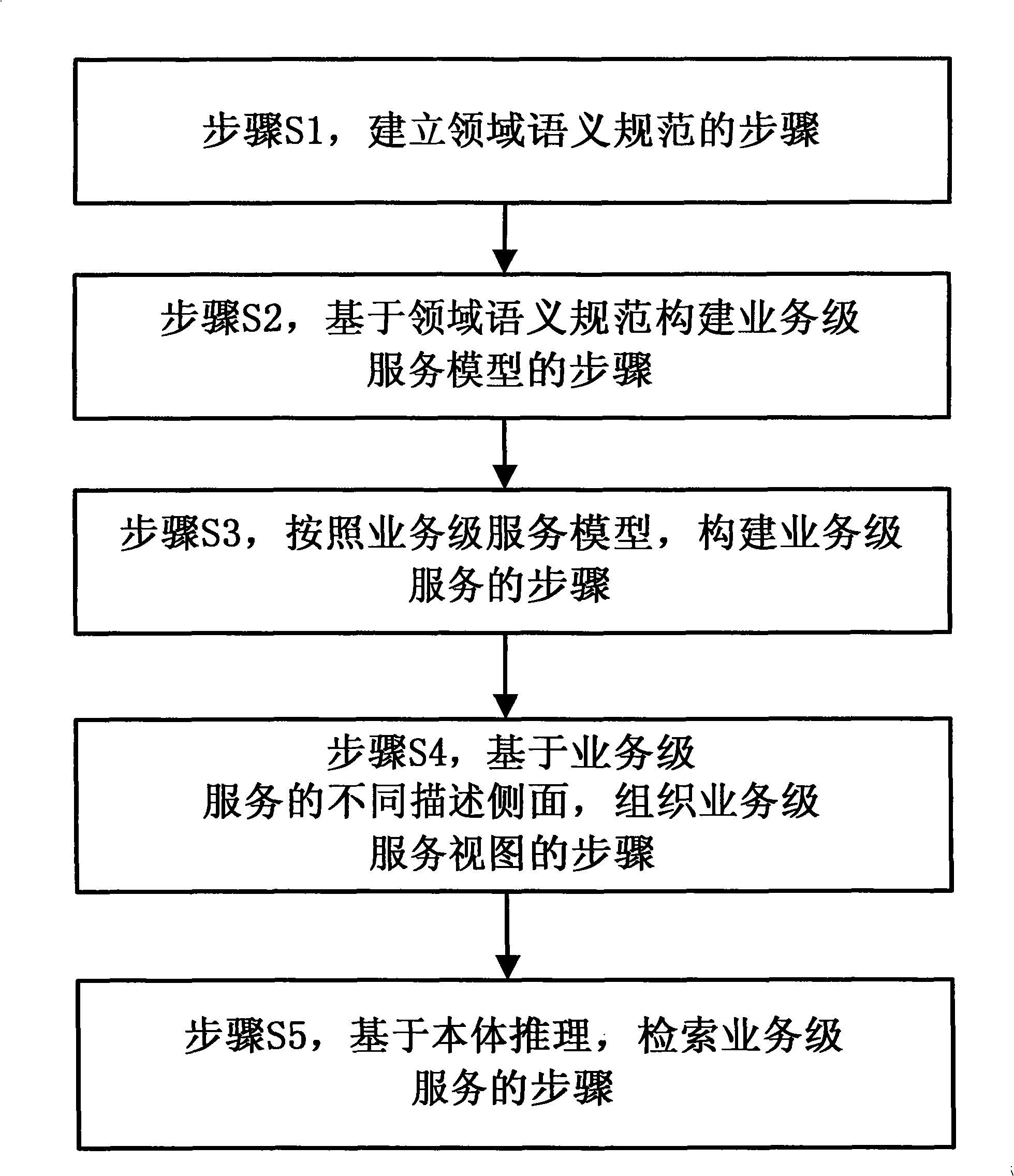
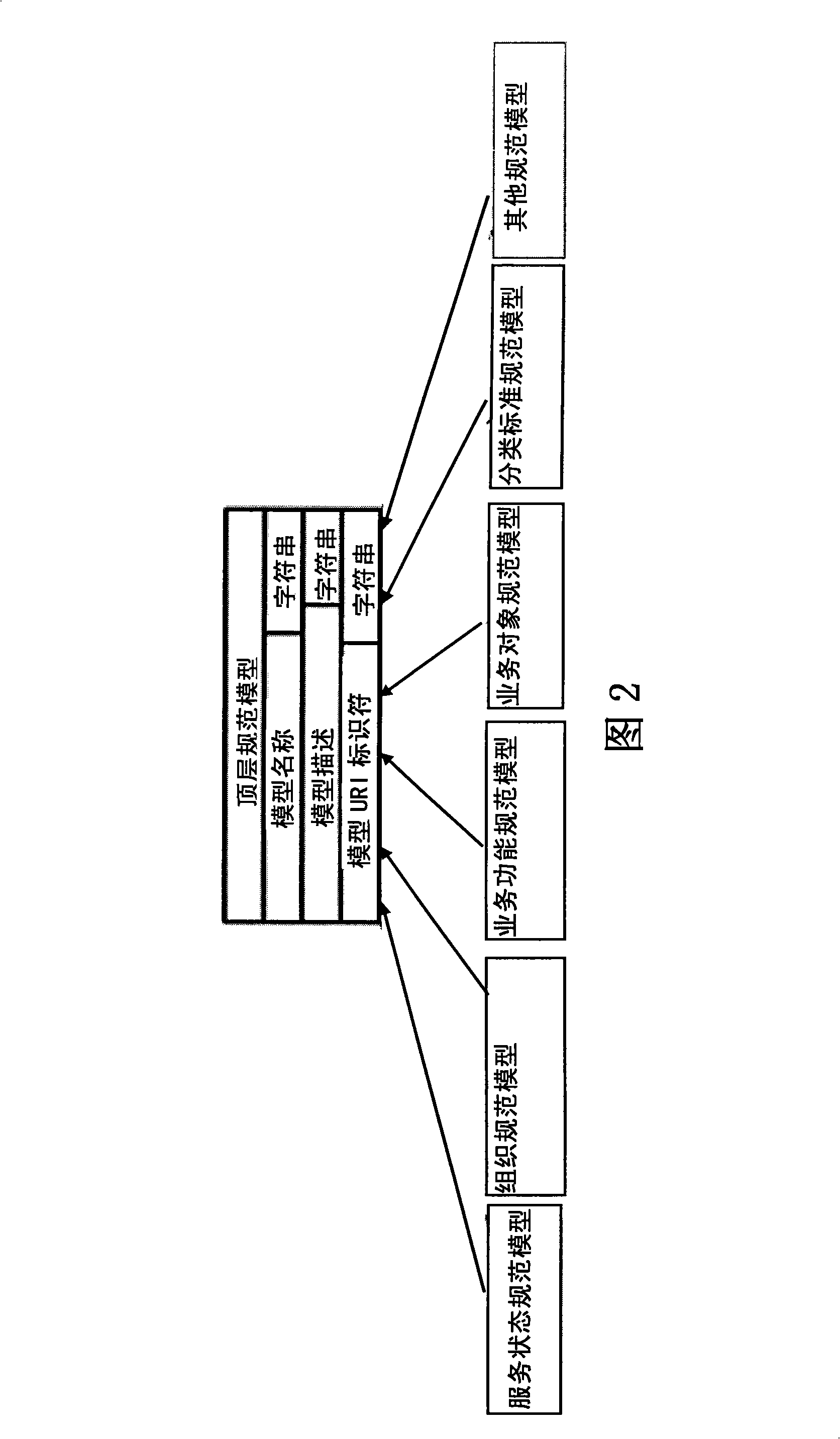
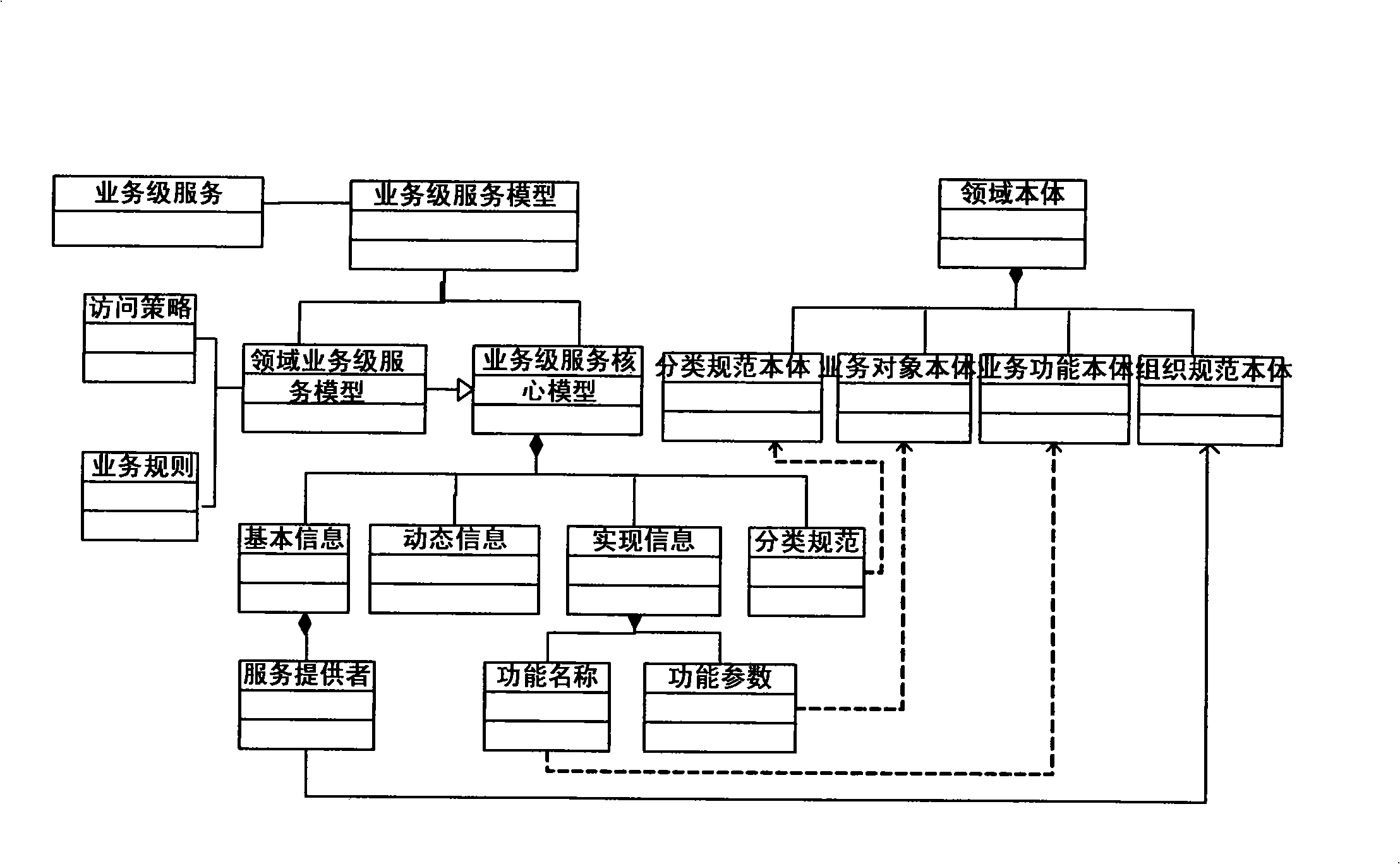
The invention discloses a business level service information management method, a device and a system thereof. The method comprises that: domain semantic specifications are established; a business level service model is built on the basis of the domain semantic specifications; a business level service is built according to the business level service model. The device of business level service information management comprises a business specification management module used for inputting and managing the domain semantic specifications, a business level service model management module used for building and managing the business level service model based on the domain semantic specifications, a business level service management module used for building and managing the business level service according to the business level service model and a semantic database module used for storing the domain semantic specifications, the business level service model and the business level service. The method, the device and the system can support the effective storage and management of service information within a business domain, cause the service information to include rich business semantic and support the connection, matching and combination of business functions with concrete IT.
Owner:CHINA TECH EXCHANGE
Implementation method for enterprise-class mapping knowledge domain search engine on the basis of electric power specialty lexicon
InactiveCN107908738AData processing applicationsNatural language data processingElectric power systemPower grid
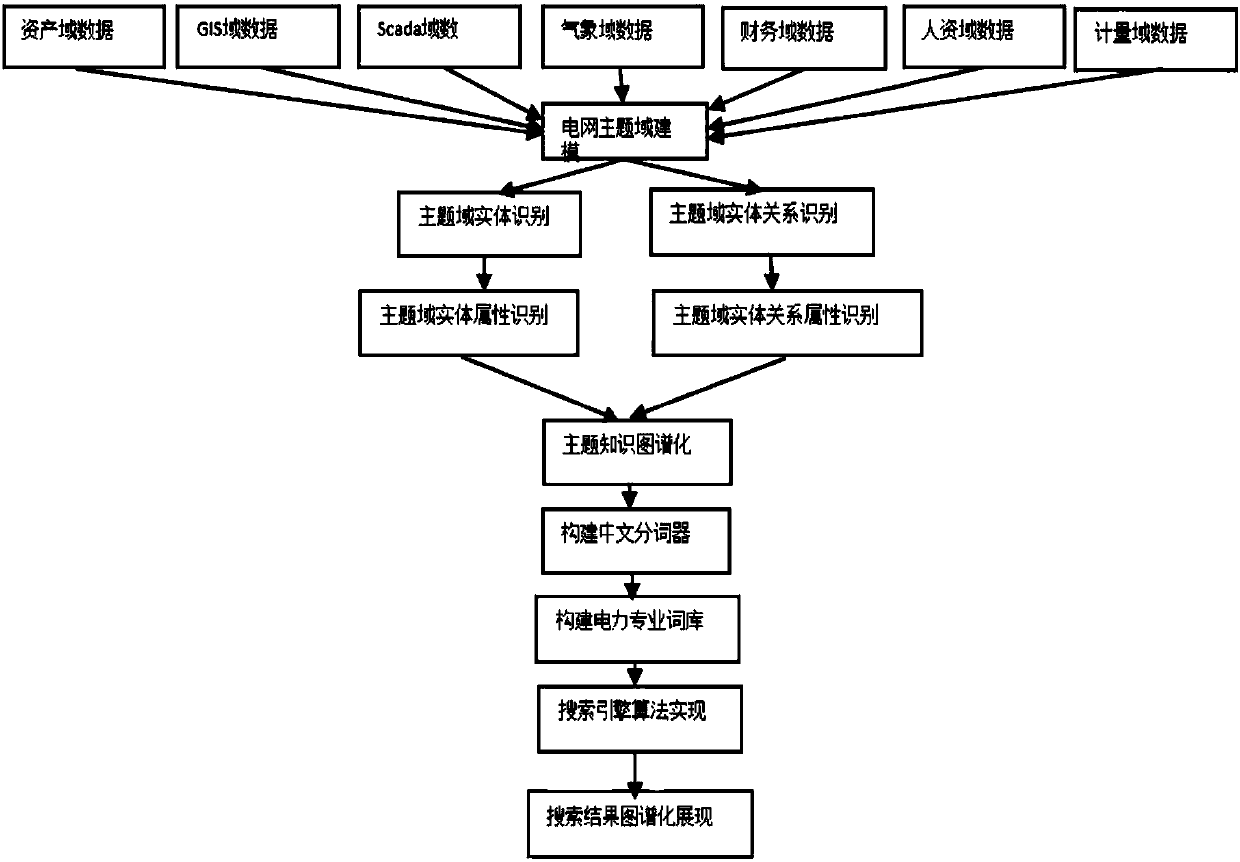
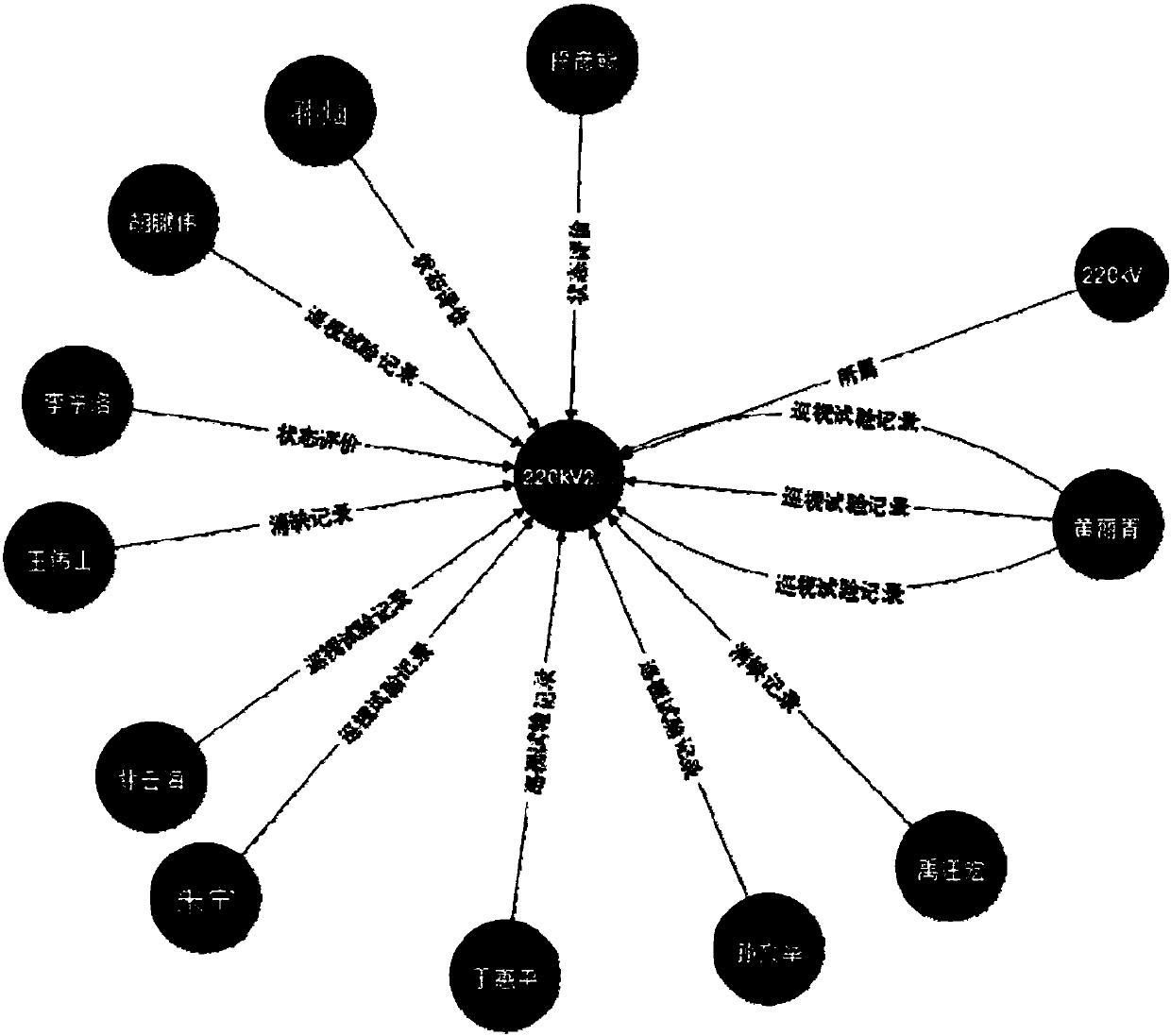
The invention discloses an implementation method for an enterprise-class mapping knowledge domain search engine on the basis of an electric power specialty lexicon, and relates to the field of the enterprise-class mapping knowledge domain search engine. The mapping knowledge domain construction and search, which takes equipment as a core, of power grid full business domain knowledge can be realized, the isolation of search contents is solved through the mapping knowledge domain, and the uniform portal search of the full subject domain data of power grid equipment is realized. The method is used for realizing the mapping knowledge domain construction of the power grid full subject domain and a mapping knowledge domain search engine, the problem that an existing power grid monitoring information data size is large and efficiency for obtaining effective mechanism information is low is solved, the flat operation and maintenance of data assets is realized, and the value of the data assets is performed.
Owner:KUNMING ENERSUN TECH
Method and system to unify and display simulation and real-time plant data for problem-solving
ActiveUS9442475B2Highly effectiveHighly intuitiveProgramme controlSimulator controlComputational scienceAmbiguity
A computer-based method and system brings together data from two business domains: real-time actual plant status operation data and predictive process simulation data based upon a design specification. This method and system correlates the plant data and the simulation data, and displays the results side-by-side for the user. The results assist the user, to determine whether the plant is operating properly, and to make further improvements to both the plant assets and to the simulation models. The invention assists with monitoring, maintaining, trouble shooting, and problem solving of plant operation. The invention facilitates a progressive visual collaborative environment between plant operation and process engineering teams, where engineers from respective domains may socialize and trouble shoot problems. The Progressive Visual Collaboration helps professionals with searching, sharing, mapping, analyzing, framing problems, removing ambiguity and uncertainty by considering facts and figures, and providing a progressive workflow that solves plant problems.
Owner:ASPENTECH CORP
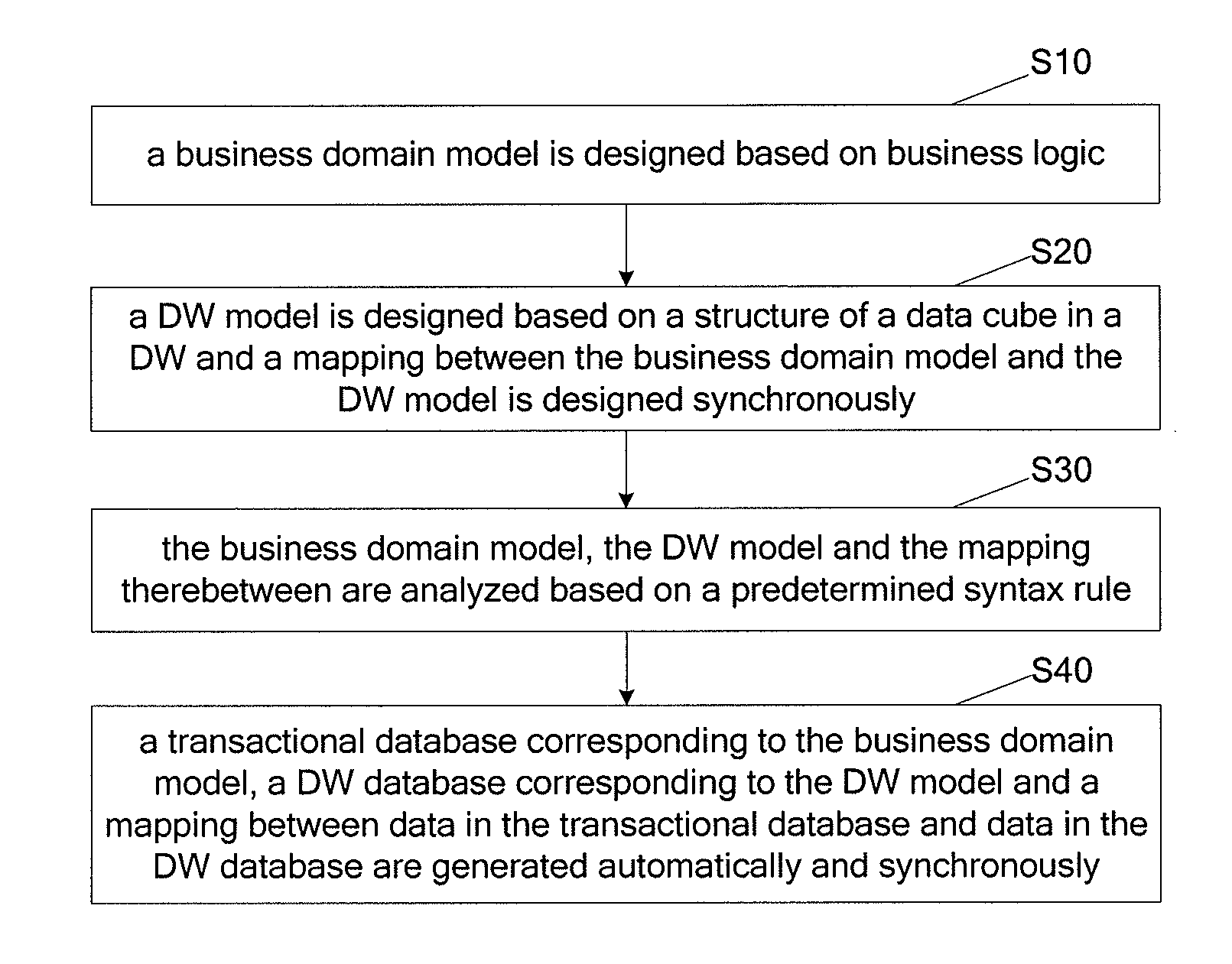
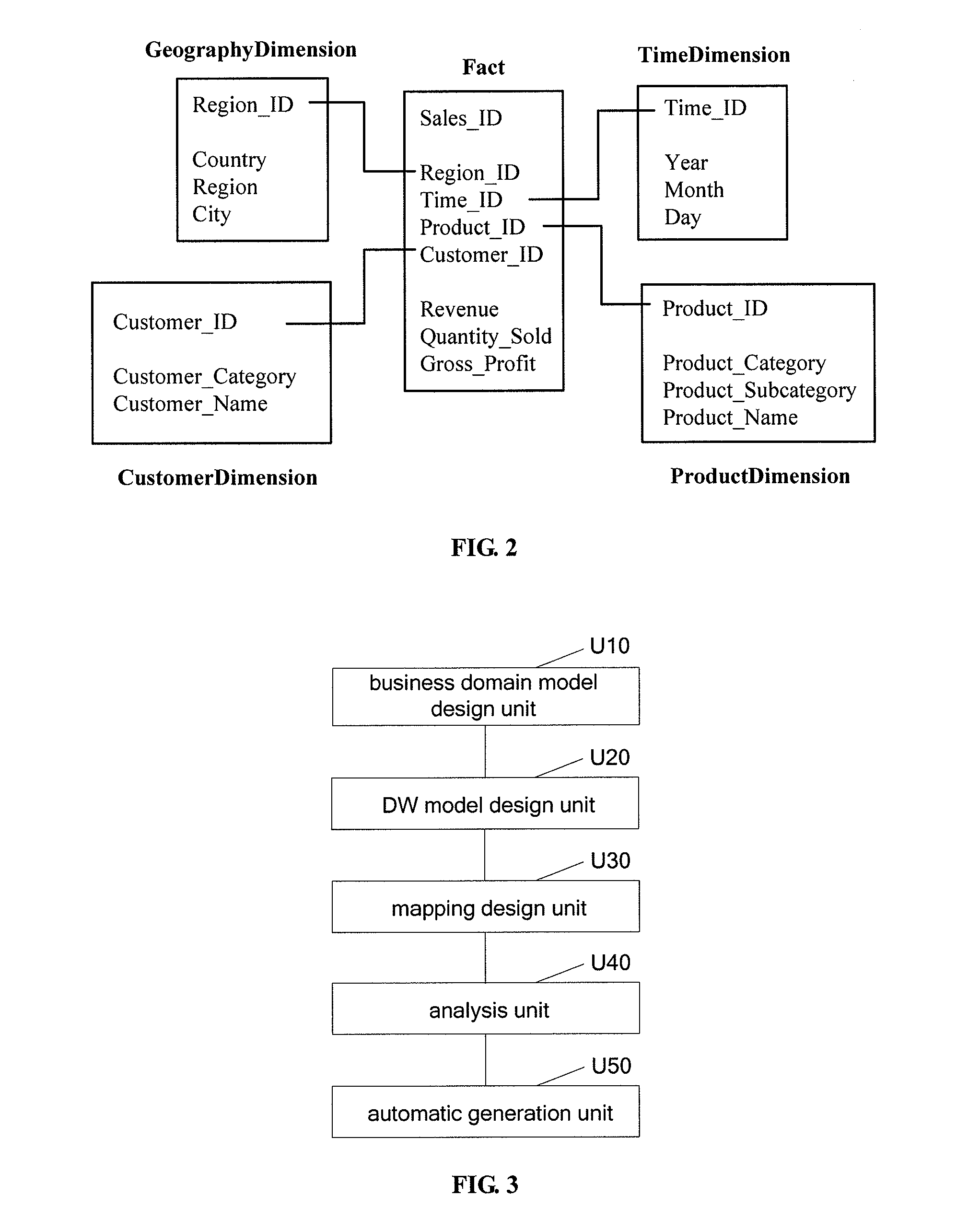
Method and system for designing business domain model, data warehouse model and mapping therebetween synchronously
ActiveUS20150006467A1Heavy workloadDesigned easily and efficiently and accuratelyDigital data processing detailsSpecial data processing applicationsDomain modelData warehouse
Method and system for designing a business domain model, a Data Warehouse (DW) model and a mapping therebetween synchronously are provided. The method includes: designing a business domain model based on business logic; designing a DW model based on a structure of a data cube in a DW and designing a mapping between the business domain model and the DW model synchronously; analyzing the business domain model, the DW model and the mapping therebetween based on a predetermined syntax rule; and generating a transactional database corresponding to the business domain model, a DW database corresponding to the DW model, and a mapping between data in the transactional database and in the DW database automatically and synchronously. The system includes a business domain model design unit, a DW model design unit, a mapping design unit, an analysis unit and an automatic generation unit. Mappings are designed more easily, efficiently and accurately.
Owner:EBAOTECH CORP
Business domain knowledge base building method and device
InactiveCN103324689AImprove the efficiency of searching for informationSpecial data processing applicationsKnowledge baseDomain knowledge
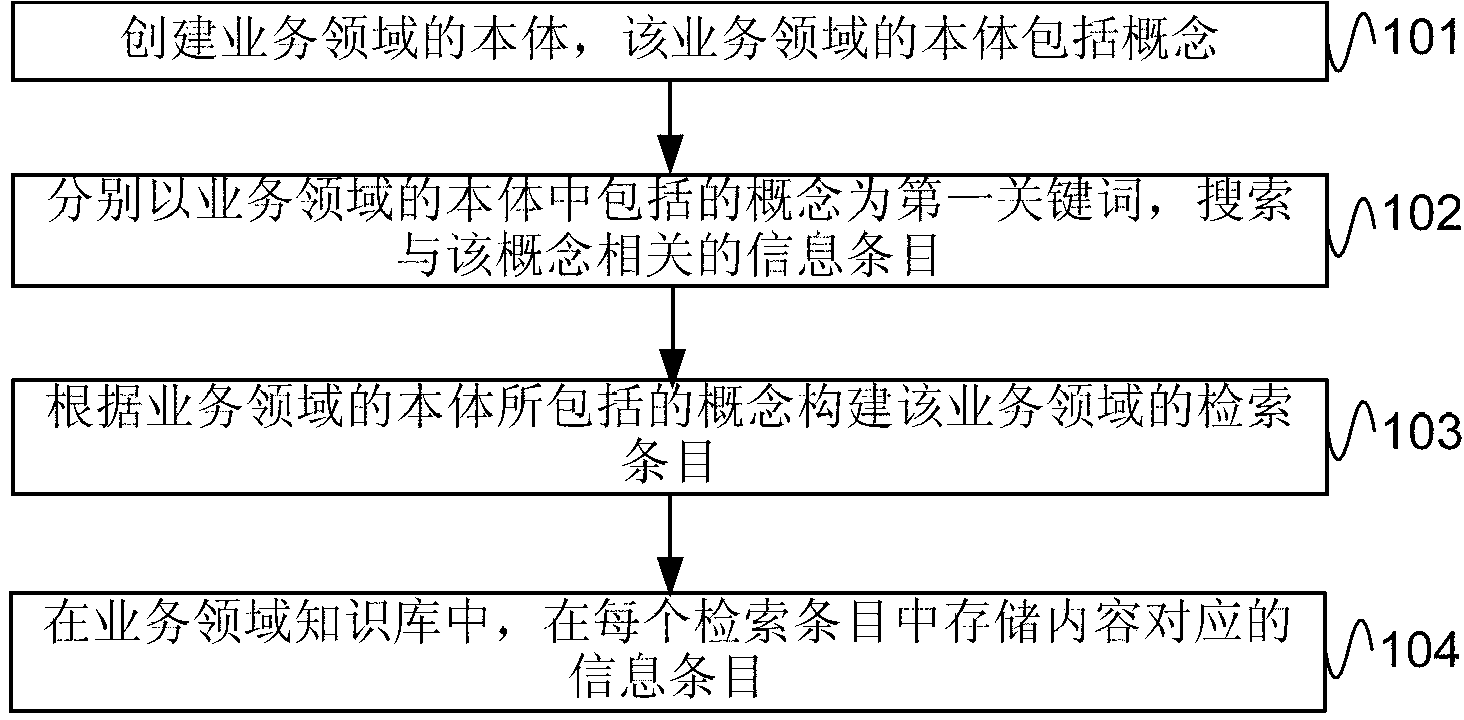
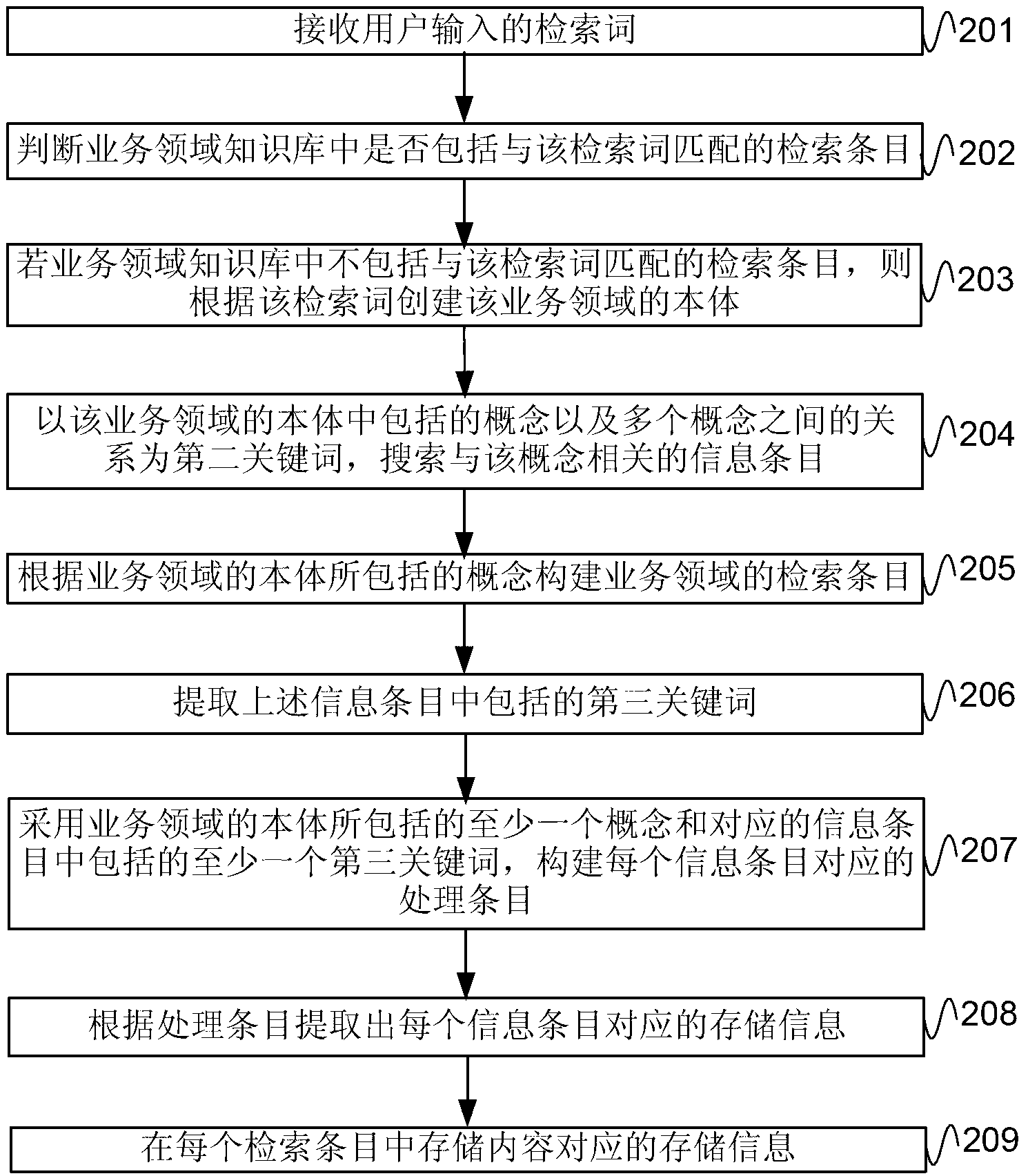
The invention provides a business domain knowledge base building method and device. The business domain knowledge base building method comprises creating a business domain ontology which comprises concepts; utilizing the concepts included in the business domain ontology as first key words respectively and searching information items related to the concepts; building retrieve items of a business domain according to the concepts included in the business domain ontology; storing content corresponded information items in every retrieve item in a business domain knowledge base. An embodiment of the business domain knowledge base building method and device effectively solves the technical problem that the efficiency of people searching information from the existing knowledge base is low in the prior art.
Owner:PEKING UNIV
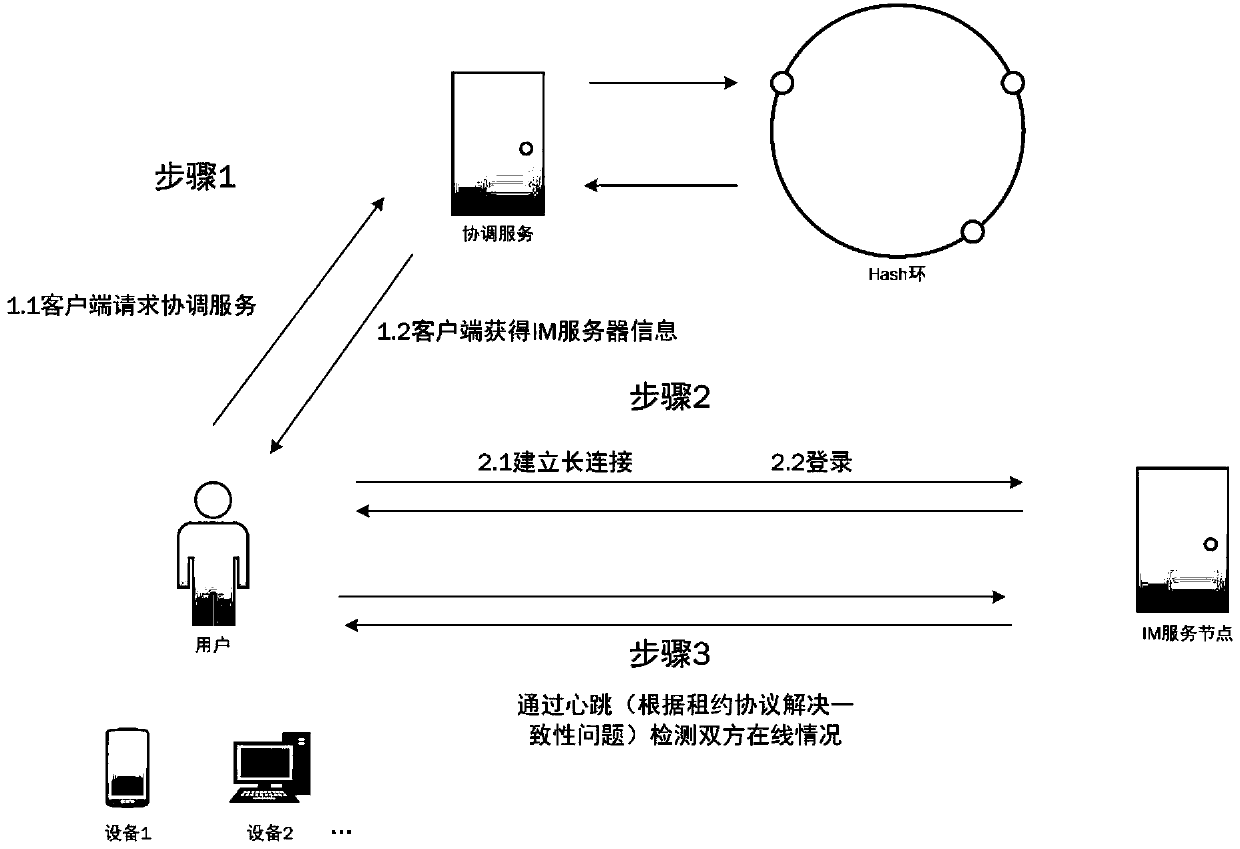
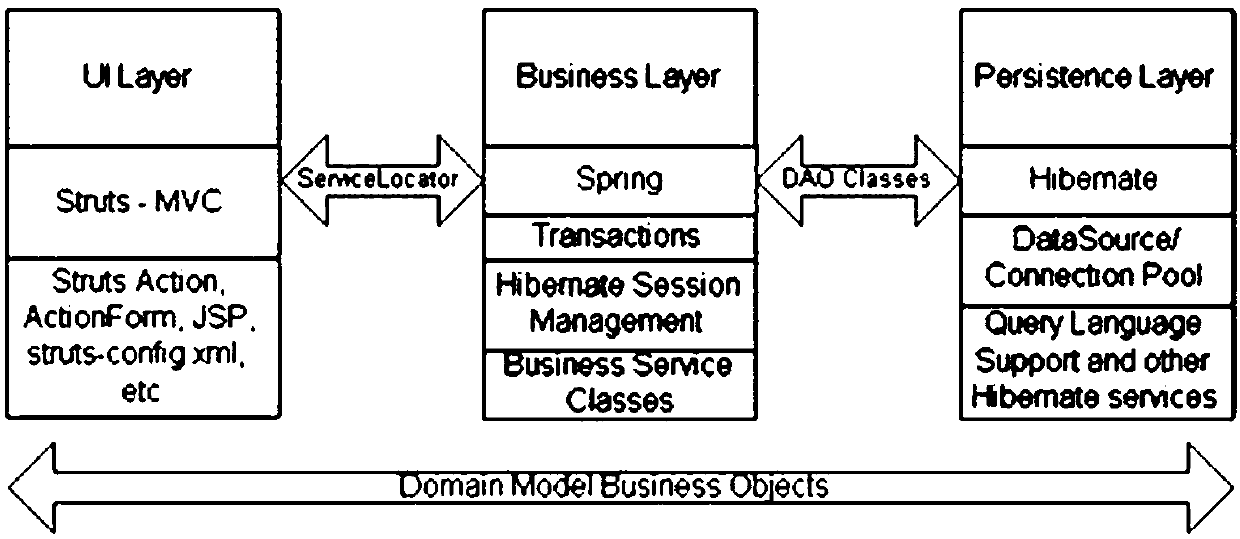
A smart cell server system
InactiveCN109584106ASolve multi-person online communicationSolve the problem of 24-hour stable workData processing applicationsTransmissionService developmentCommunity system
The invention discloses a smart cell server system. The system mainly comprises an IM system used in a smart cell and a service development framework integrated with an SSH. The IM system adopts a coordination service technology, is designed on the basis of an open source coordination service framework zookeeper, serves distributed communication application programs, and provides simple and easy-to-use interfaces and coordination services with high performance and stable functions for required application programs. The business development framework is divided into four layers: a presentationlayer, a business logic layer, a data persistence layer and a business domain module layer. Compared with the prior art, the method has the advantages that 1, multi-person online communication in thesmart community system and preparation work before communication are solved; 2, the problem that the smart community software system works stably for 24 hours is solved; And 3, the system can ensure stable work for a long time, ensure the freshness of enterprise information in a data project for a long time and ensure the operation efficiency of a service function for a long time.
Owner:成都合盛智联科技有限公司 +1
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com