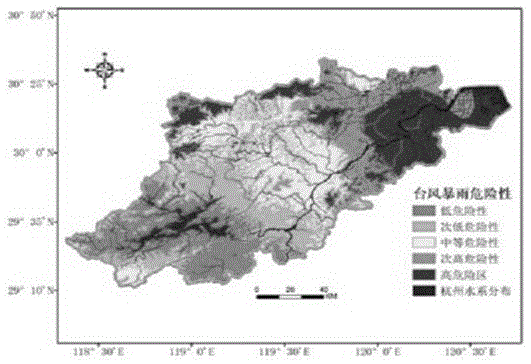
Patents
Literature
2032 results about "Open source" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
The open-source model is a decentralized software development model that encourages open collaboration. A main principle of open-source software development is peer production, with products such as source code, blueprints, and documentation freely available to the public. The open-source movement in software began as a response to the limitations of proprietary code. The model is used for projects such as in open-source appropriate technology, and open-source drug discovery.
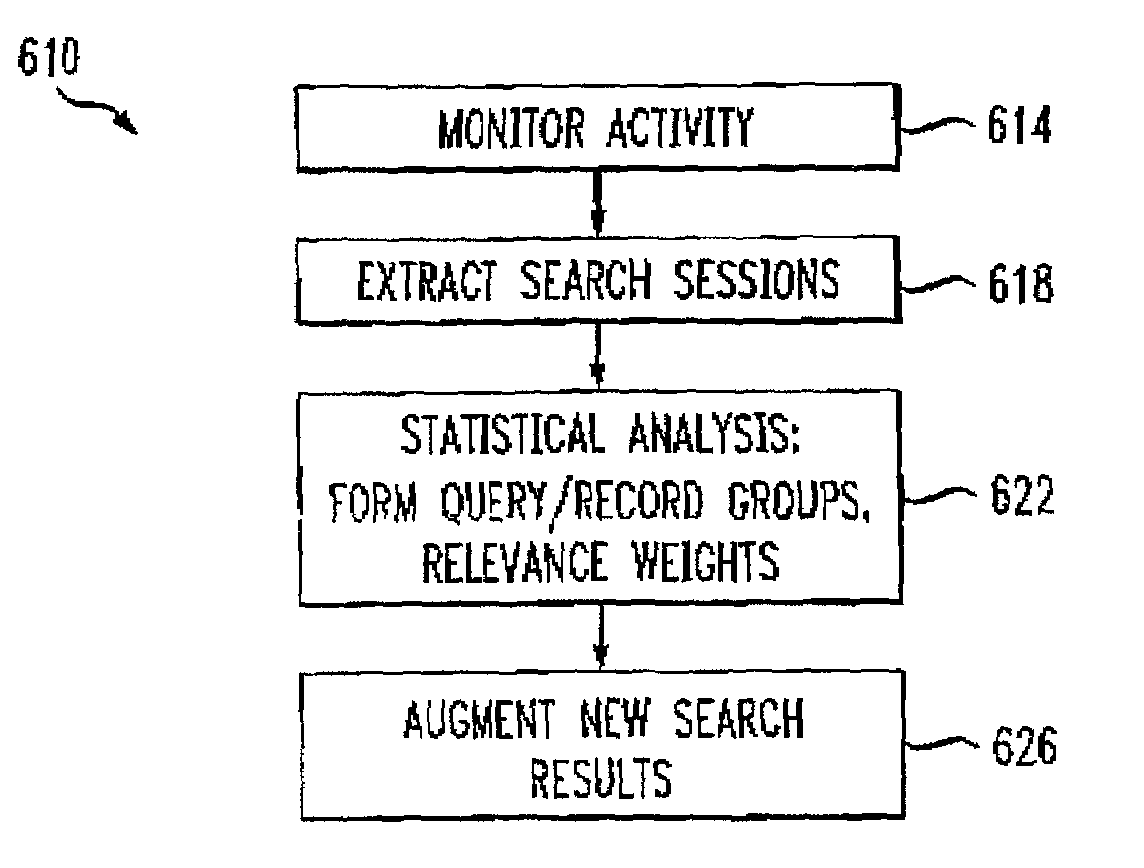
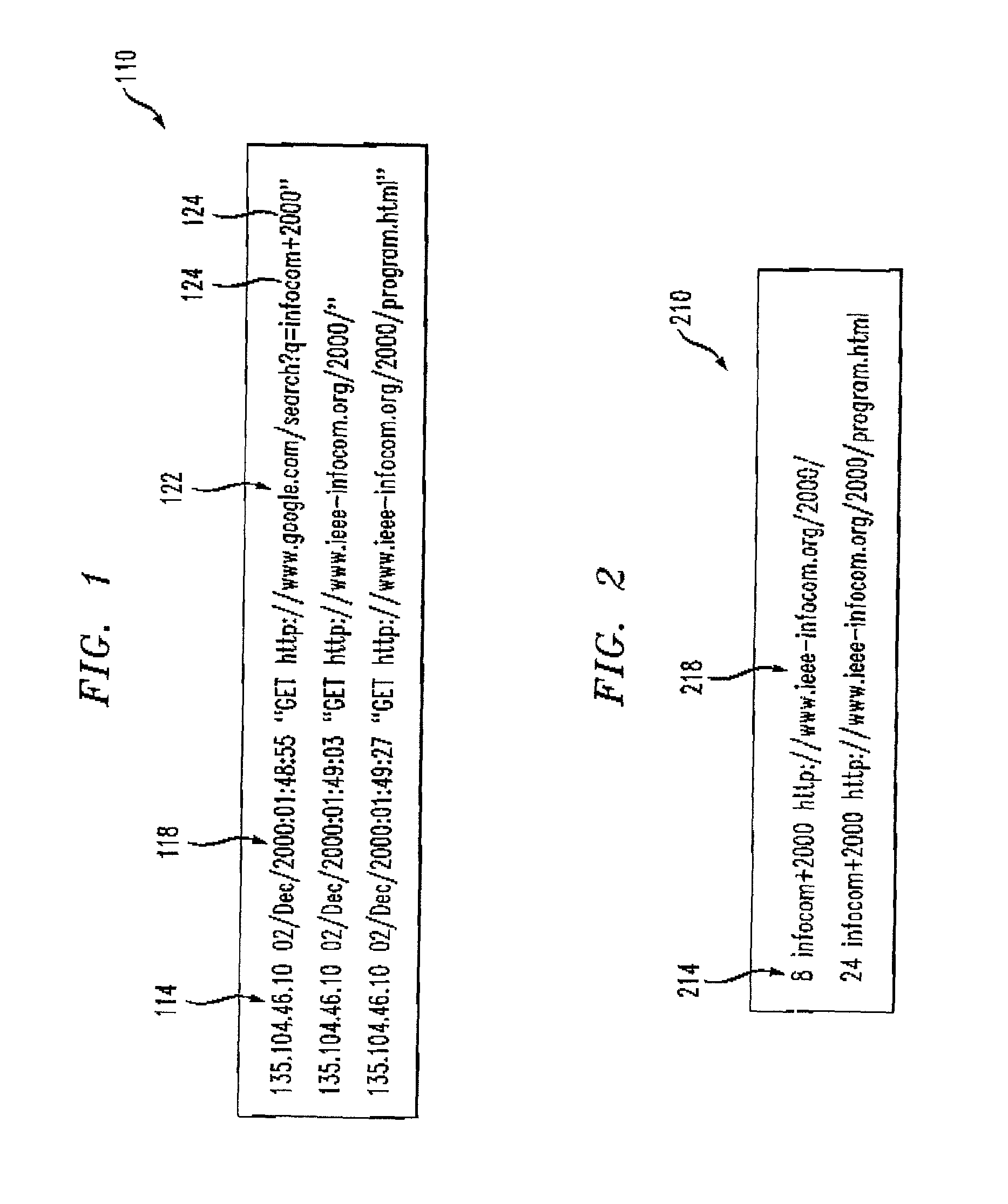
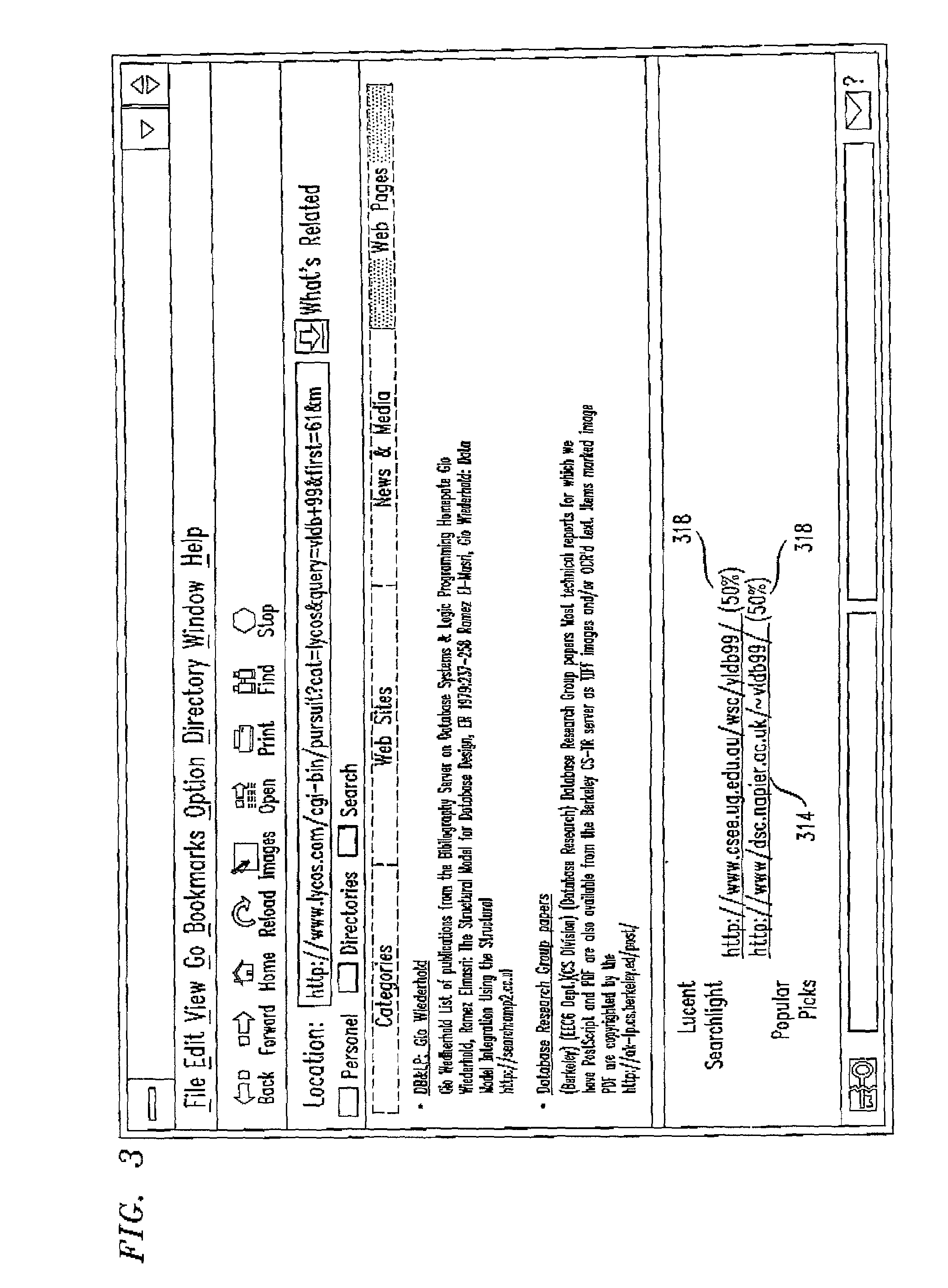
Method for organizing records of database search activity by topical relevance
InactiveUS7194454B2Speed up searchData processing applicationsWeb data indexingOpen sourceThe Internet
A method for organizing records of a database by topical relevance generates statistics on relevance by monitoring search terms used and search paths traversed by a database user community. Records reviewed most often in relation to a given search term are assumed to be most relevant to that search term in the eyes of members of the user community. Additionally, a record reviewed in relation to a plurality of search terms is determined to be related by topical relevance to other records reviewed in relation to that plurality of search terms. Again, a probability is calculated, based on a frequency of record review and search terms used, as a measure of this record topical relevance. An embodiment directed toward Internet searches provides for seeding the probability calculations with information from labeled data available from open source Internet directories. The activities of the user community are monitored, for example, at a proxy server, or by reviewing proxy server logs. Other monitoring points are contemplated.
Owner:SOUND VIEW INNOVATIONS
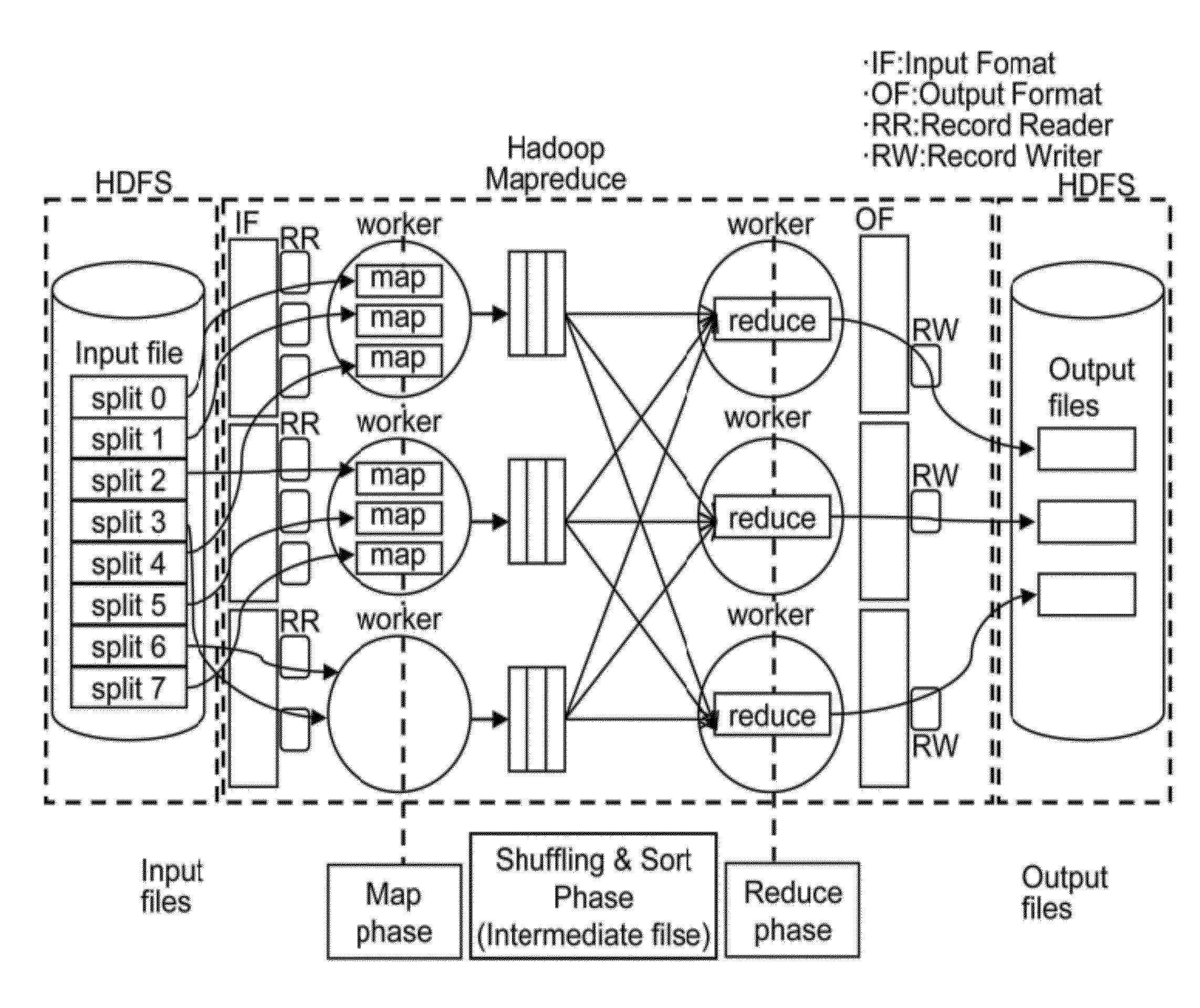
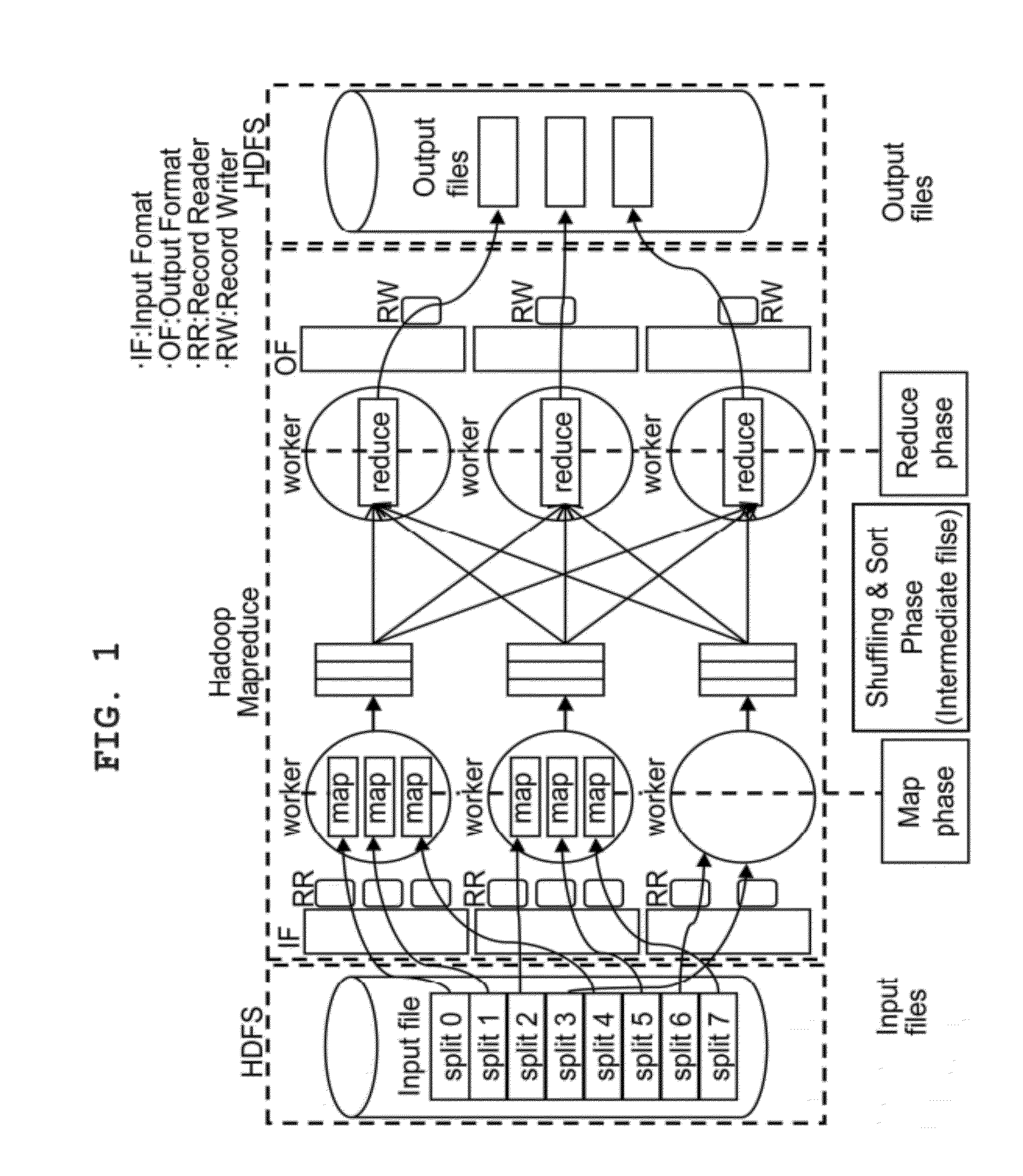
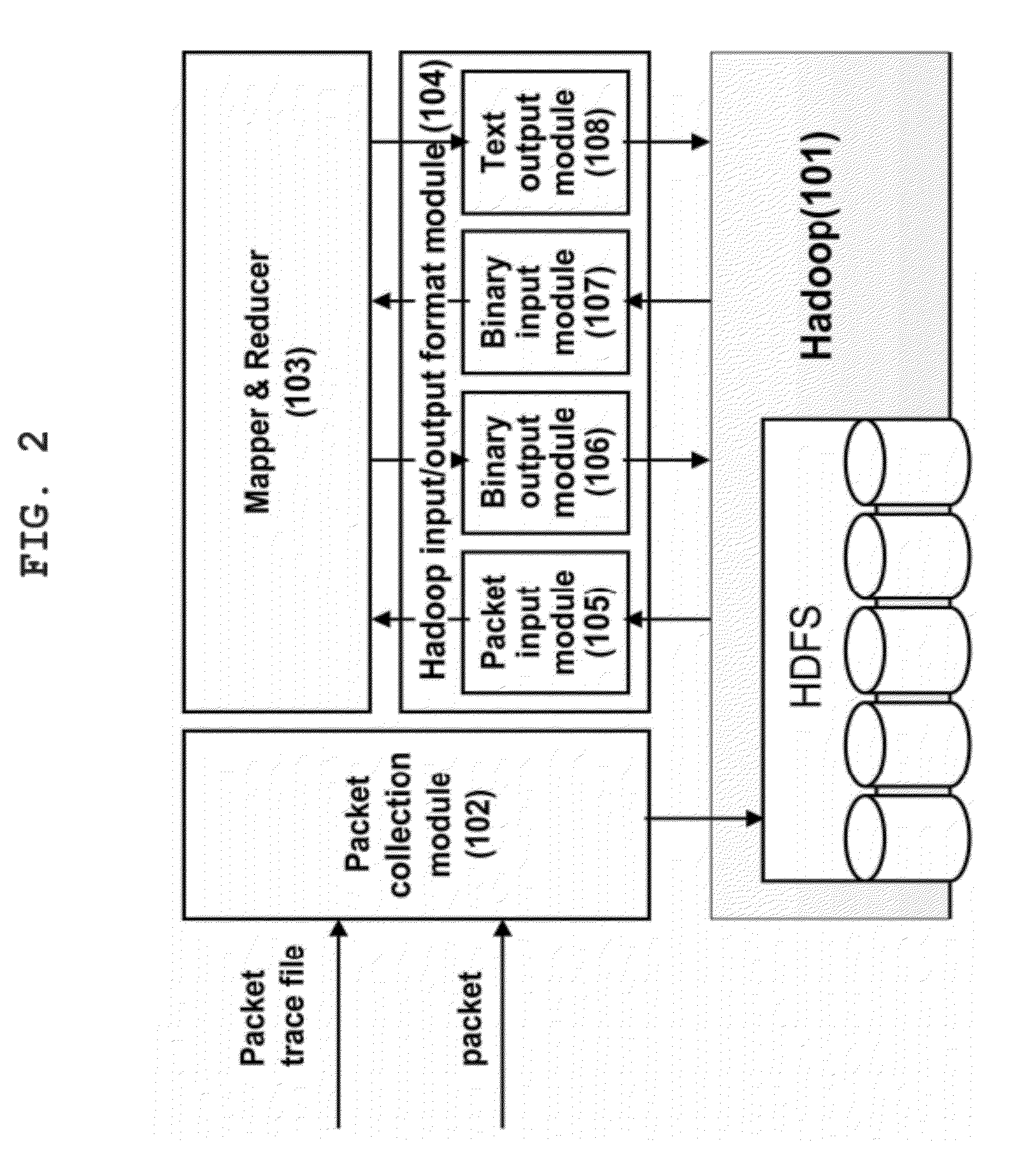
Packet analysis system and method using hadoop based parallel computation
InactiveUS20120182891A1Optimize data processingError preventionTransmission systemsDistributed File SystemOpen source
The present invention relates to a packet analysis system and method, which enables cluster nodes to process in parallel a large quantity of packets collected in a network in an open source distribution system called Hadoop. The packet analysis system based on a Hadoop framework includes a first module for distributing and storing packet traces in a distributed file system, a second module for distributing and processing the packet traces stored in the distributed file system in a cluster of nodes executing Hadoop using a MapReduce method, and a third module for transferring the packet traces, stored in the distributed file system, to the second module so that the packet traces can be processed using the MapReduce method and outputting a result of analysis, calculated by the second module using the MapReduce method, to the distributed file system.
Owner:THE IND & ACADEMIC COOP IN CHUNGNAM NAT UNIV (IAC)
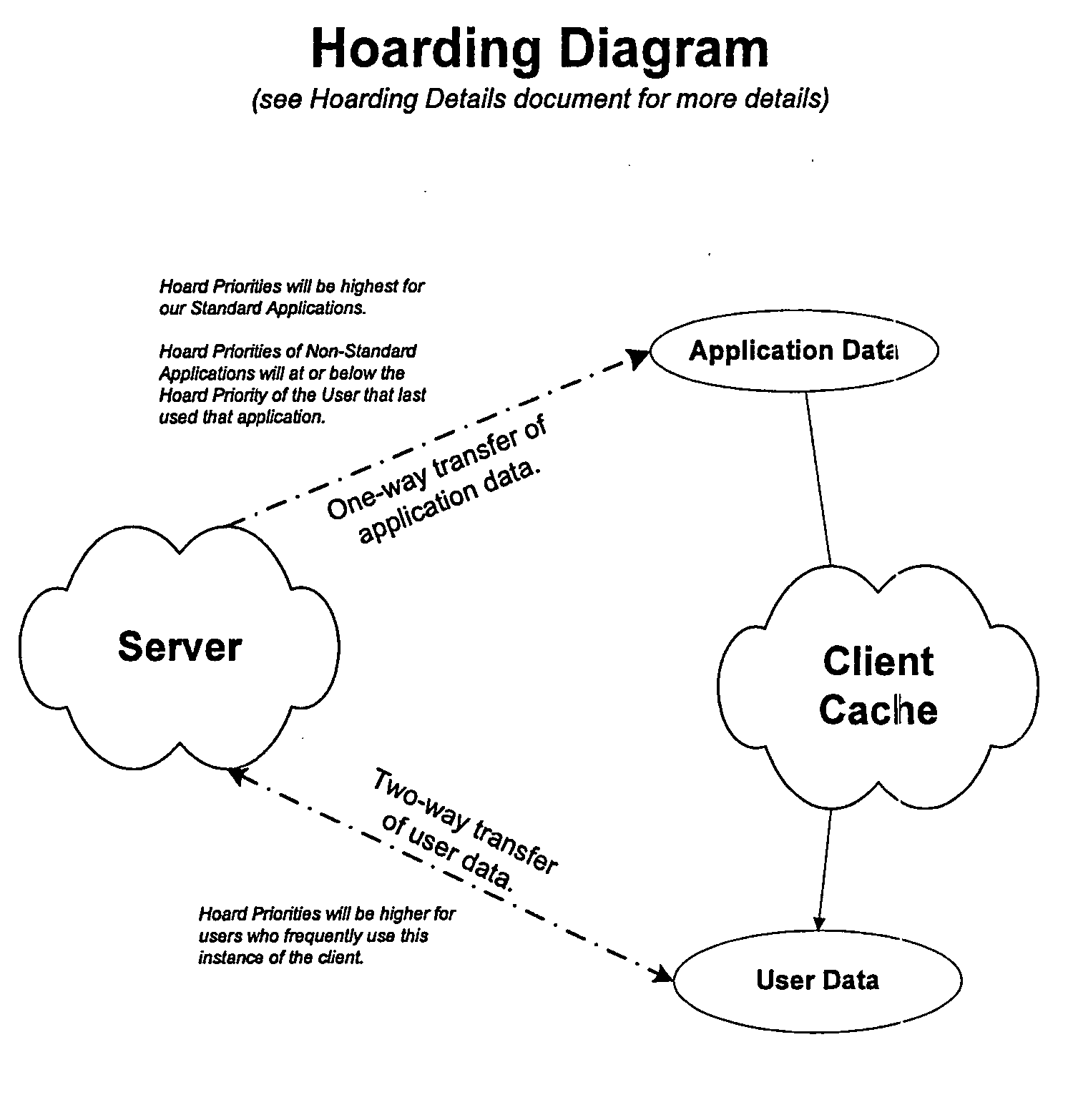
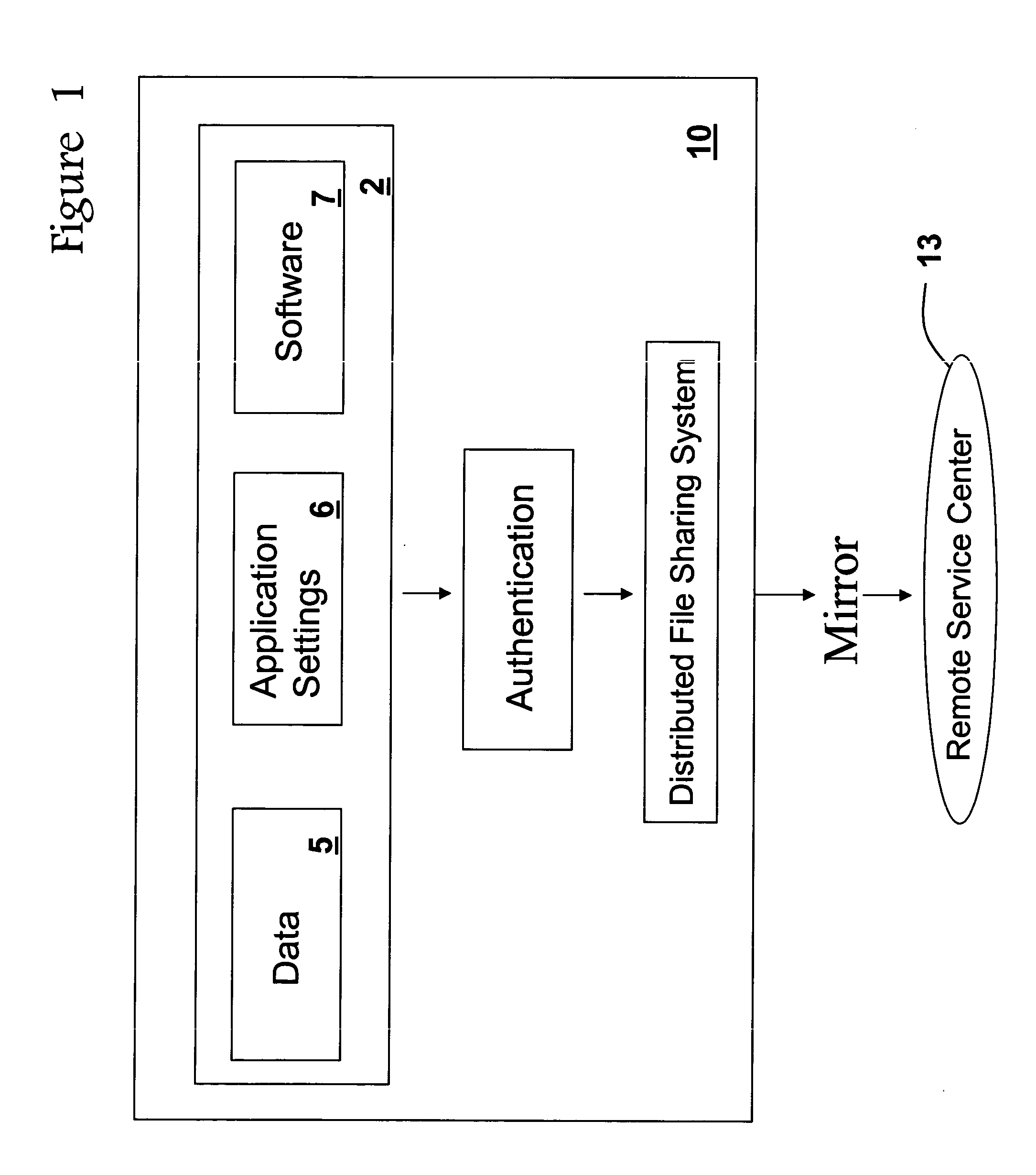
Method for electronically packaging a user's personal computing environment on a computer or device, and mobilizing it for transfer over a network
InactiveUS20050183021A1Easy accessSimple interfaceDigital data information retrievalProgram controlOperational systemEmail address
A computer system using open source software and operating systems is enabled over a global computer network to provide universal, selected applications. The applications can be accessed from a local personal computer, personal digital assistant (PDA), remote dedicated computer terminal, or like devices. Selected applications may include word processing, calendar, address book, picture viewing, music playing, games, email, Internet access, and the like. Personal data, such as pictures, music, games, “favorite places”, email addresses, and application settings are saved to the local client device and to a centralized customer support server. An included software manager ensures that the most current version of each application is used, and, if not available on the client, it can be uploaded, if necessary.
Owner:ALLENPORT
Multi-user smartglove for virtual environment-based rehabilitation
InactiveUS20120157263A1Function increaseEasy to moveMedical simulationPhysical therapies and activitiesNeurological impairmentOpen source
A low-cost, virtual environment, rehabilitation system and a glove input device for patients suffering from stroke or other neurological impairments for independent, in-home use, to improve upper extremity motor function, including hand and finger control. The system includes a low-cost input device for tracking arm, hand, and finger movement; an open source gaming engine; and a processing device. The system is controllable to provide four types of multiple patient / user interactions: competition, cooperation, counter-operative, and mixed.
Owner:NORTHEASTERN UNIV
Non-support three-dimensional printing method based on inclined layering
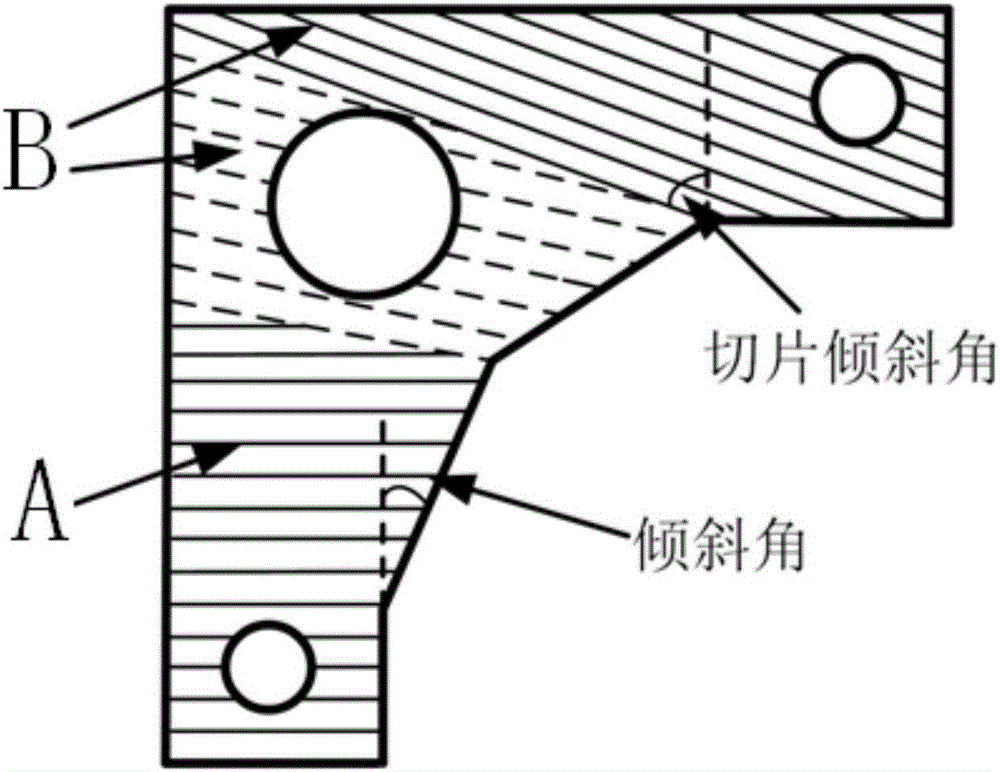
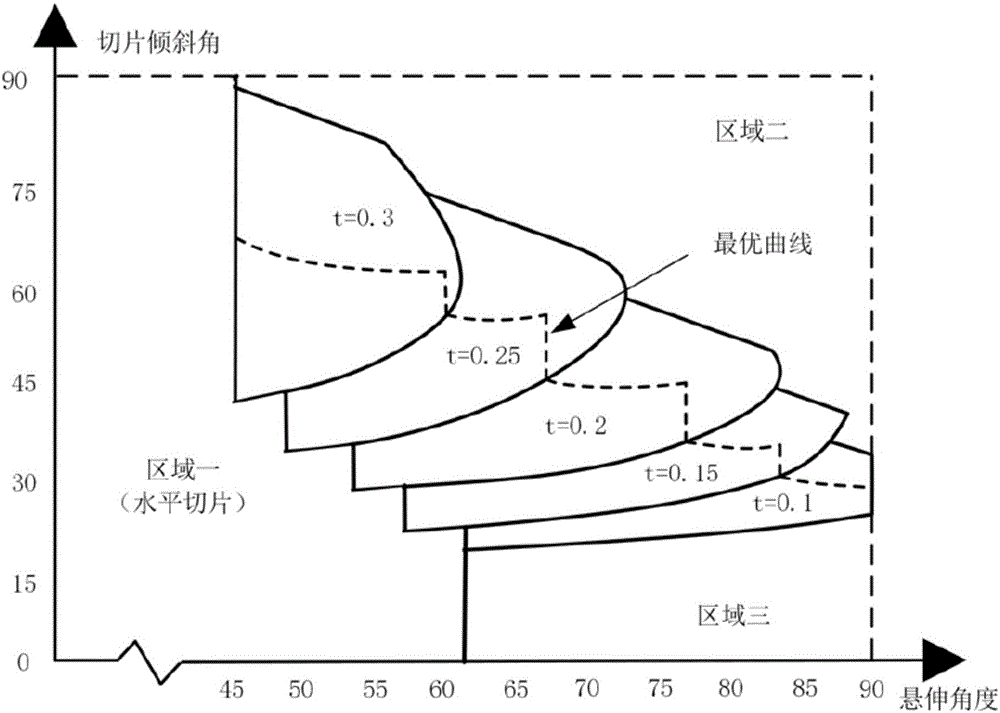
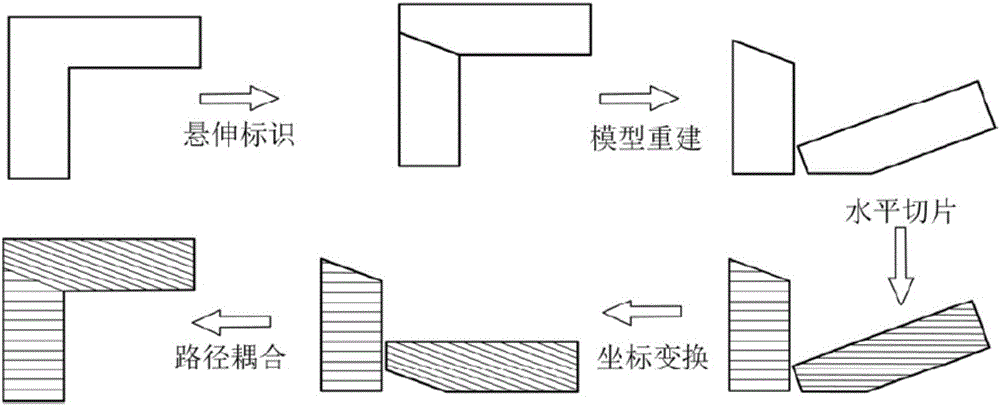
ActiveCN105904729ASave printing raw materialsImprove printing efficiencyAdditive manufacturing apparatusSupport removalCoupling
The invention discloses a non-support three-dimensional printing method based on inclined layering. The method comprises five steps of model surface overhanging area identification, model reestablishment, horizontal slicing, motion code coordinate transformation, and path coupling; a path includes two parts: a horizontal layered path and an inclined layered path. A path track inclined relative to a horizontal plane is formed at an overhanging part; when the region is printed, a new layer of material can be guaranteed to be not only suffered from gravity but also is suffered from an adhesive force in a deposition process due to the presence of a formed printing layer on an upper layer. An additional supporting material is omitted, a printing raw material is saved, the printing efficiency is improved, and a process of subsequent support removal is omitted. The inclined layered three-dimensional printing path provided by the invention has a common code format, can be directly applied in commercial and open-source desktop type three-dimensional printers, has extensive application prospects, and can be extended to the three-dimensional printing technology in biology, chemical engineering, macromolecule and food industries.
Owner:ZHEJIANG UNIV
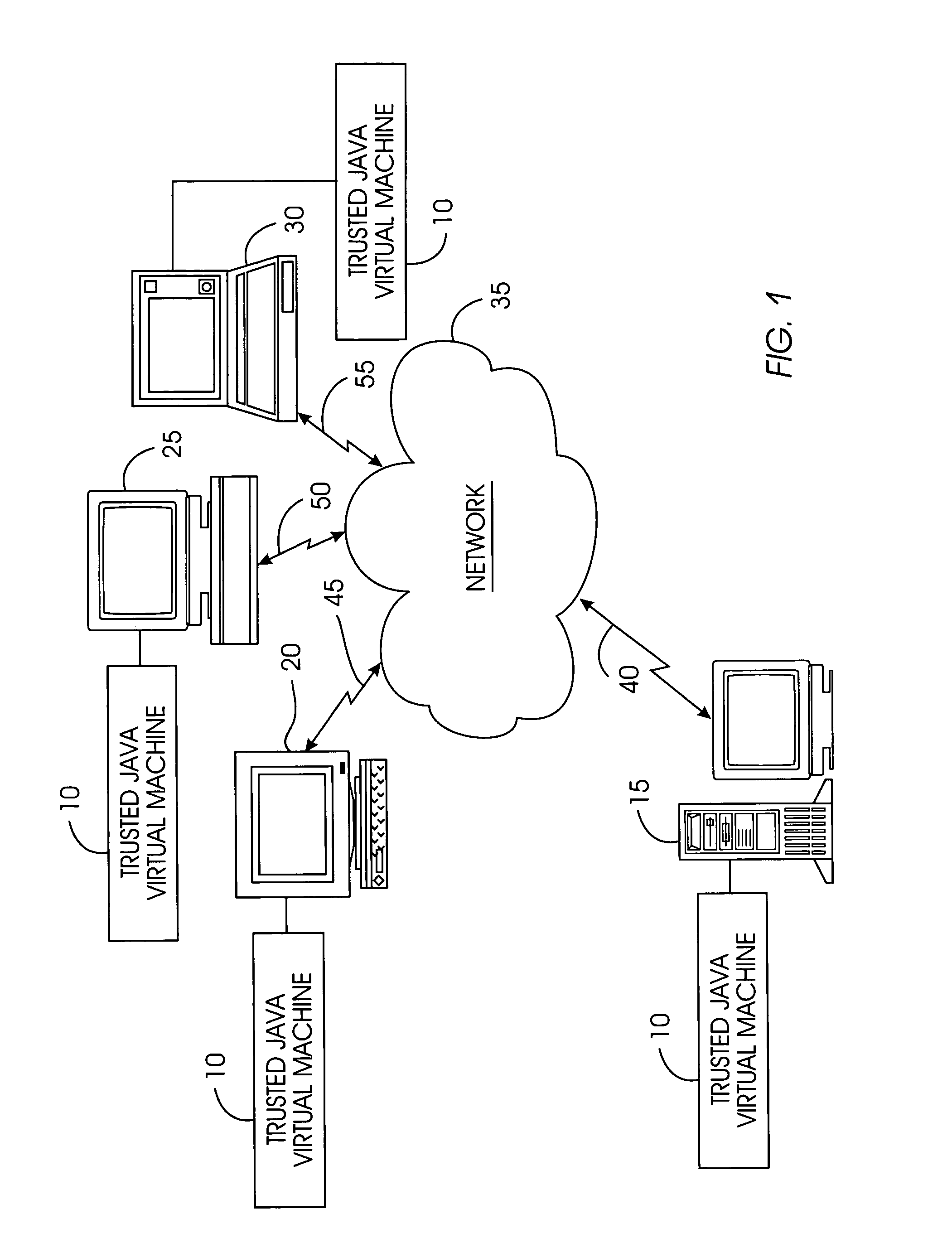
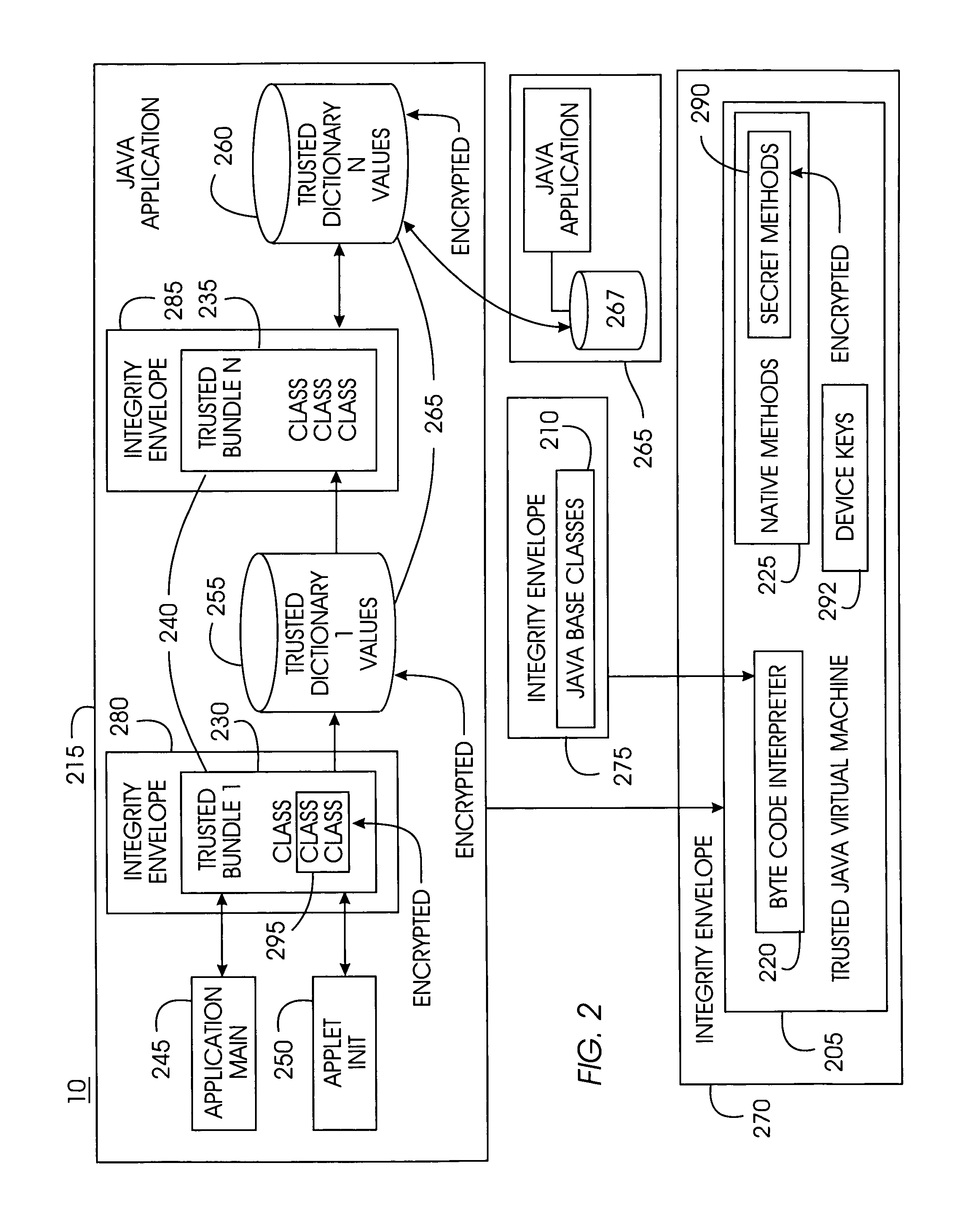
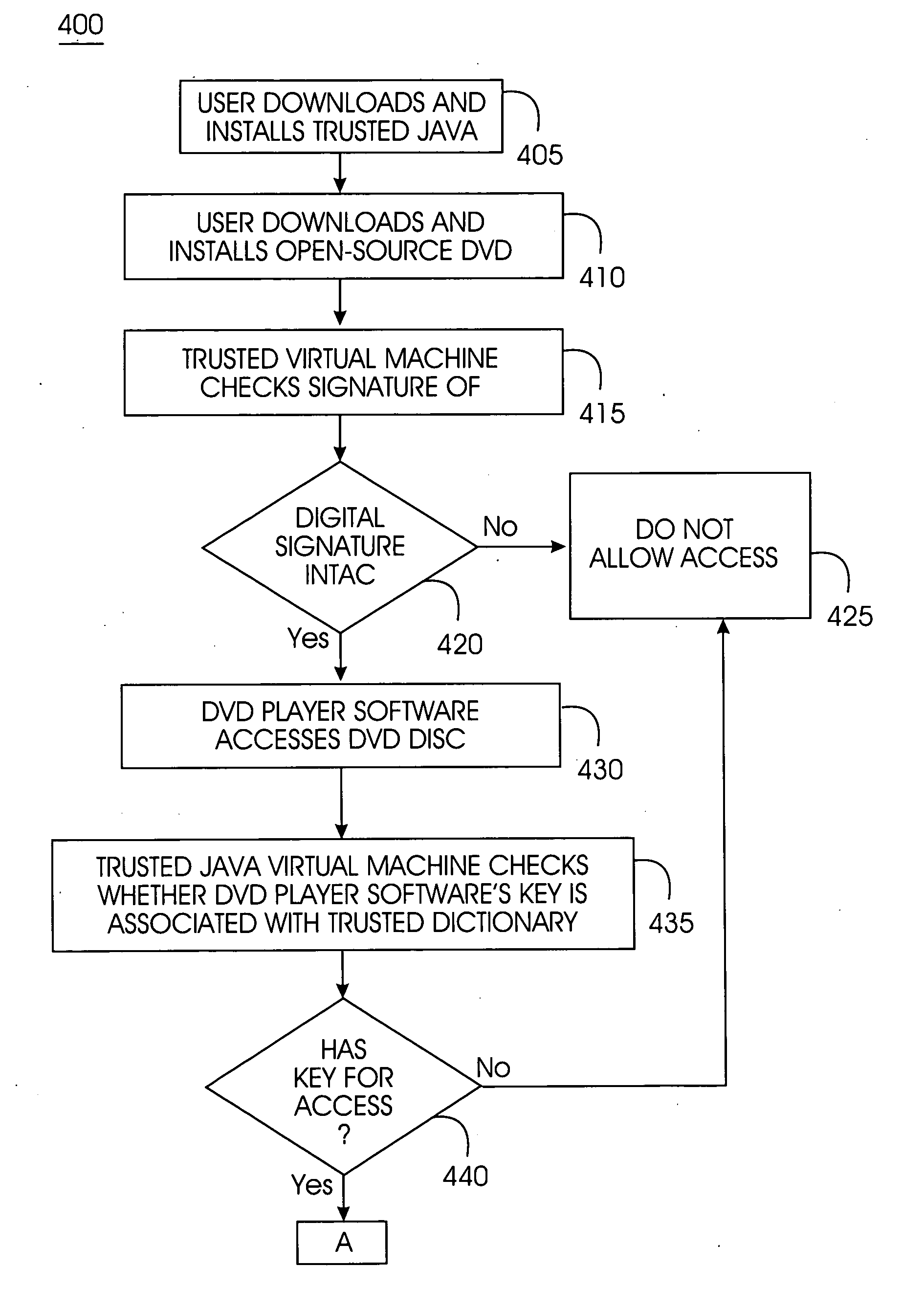
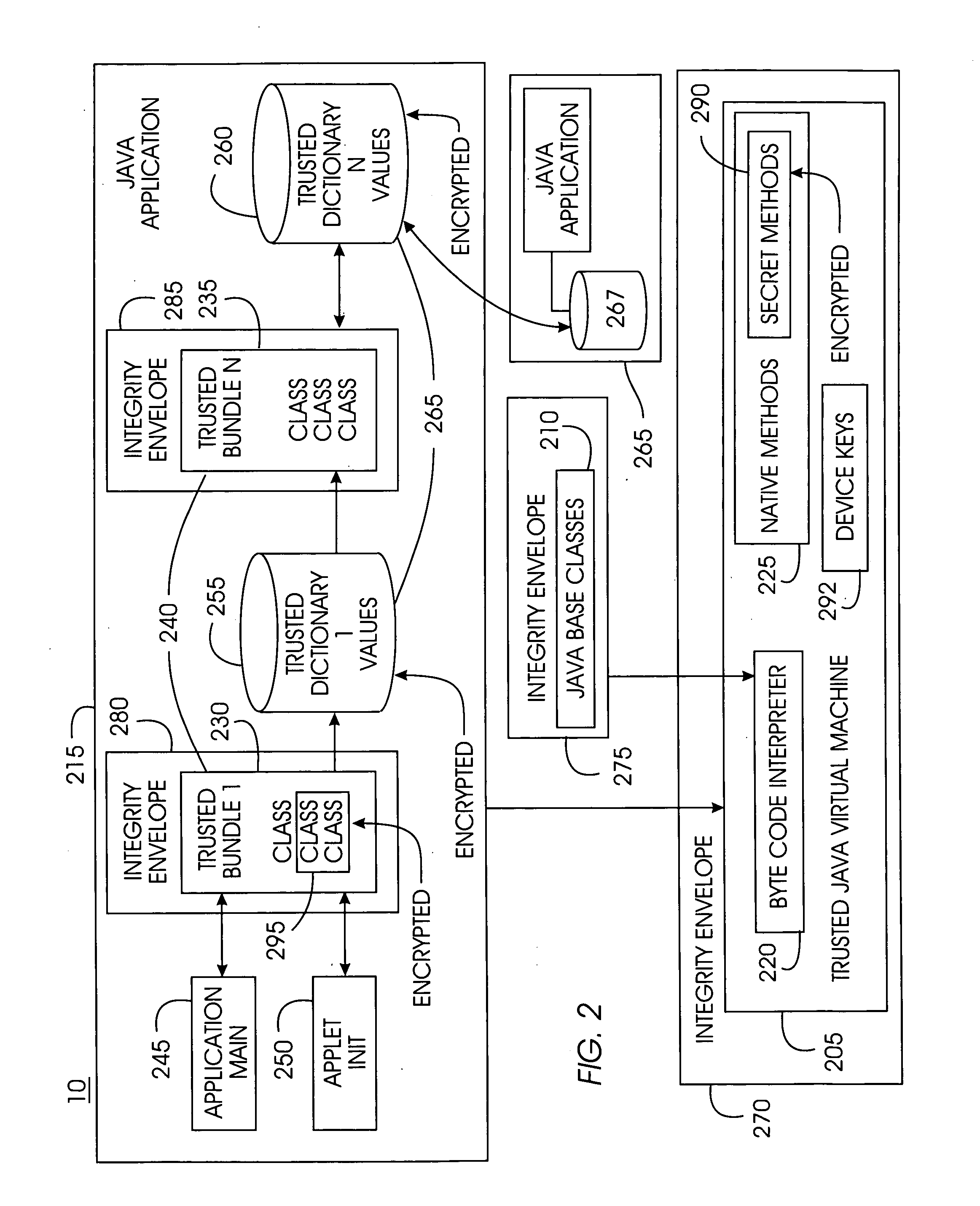
Tamper-resistant trusted java virtual machine and method of using the same
InactiveUS7516331B2Slow processEnsure integrityProgram control using stored programsUser identity/authority verificationOpen sourceProgram security
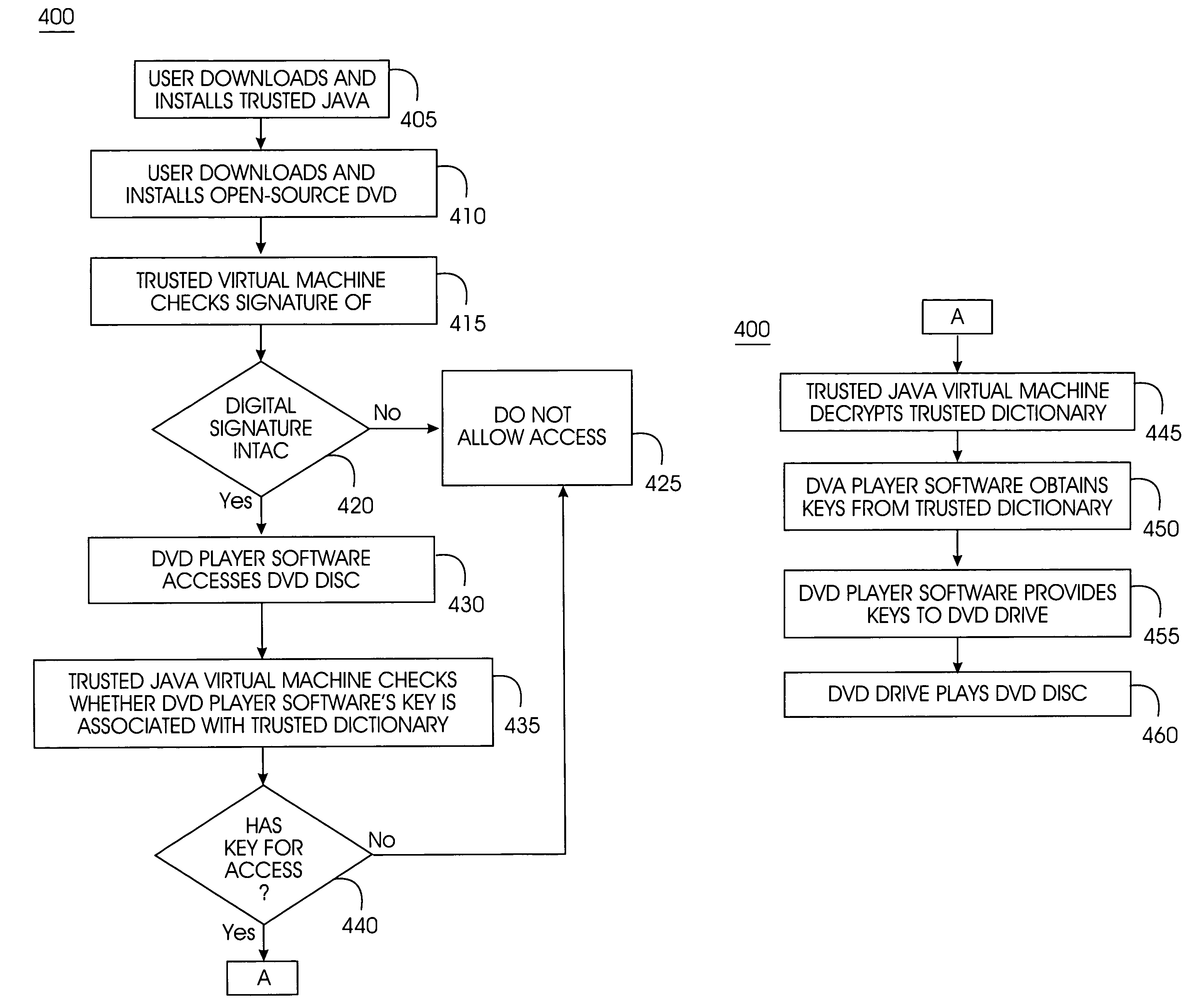
A trusted Java virtual machine provides a method for supporting tamper-resistant applications, ensuring the integrity of an application and its secrets such as keys. The trusted Java virtual machine verifies the integrity of the Java application, prevents debugging of the Java application, and allows the Java application to securely store and retrieve secrets. The trusted Java virtual machine environment comprises a TrustedDictionary, a TrustedBundle, an optional encryption method for encrypting and decrypting byte codes, and an underlying trusted Java virtual machine. The encrypted TrustedDictionary protects data while the TrustedBundle protects programming code, allowing applications to store secret data and secure counters. The application designer can restrict TrustedBundle access to only those interfaces that the application designer explicitly exports. The open source code may optionally be encrypted. Secrets required by the open source programming code of the application are encrypted in TrustedDictionary.
Owner:INT BUSINESS MASCH CORP
Semantic system for integrating software components
ActiveUS20080168420A1Website content managementSpecific program execution arrangementsScripting languageMetadata discovery
A method and a scripting paradigm for automatically integrating disparate information systems (e.g., web services and databases) within a given enterprise into a service-oriented architecture. A script writer generates a script using a scripting paradigm, and the resulting script automatically derives new data models, new ontological structures, new mappings, and a new web service that integrates disparate information systems. In addition to integrating disparate information systems, the scripts may be harvested to automate the metadata discovery and retrieval process. The scripting paradigm builds upon existing open-source scripting languages and is compatible with existing internet browsers, thus encouraging mass participation in the integration process.
Owner:MITRE SPORTS INT LTD
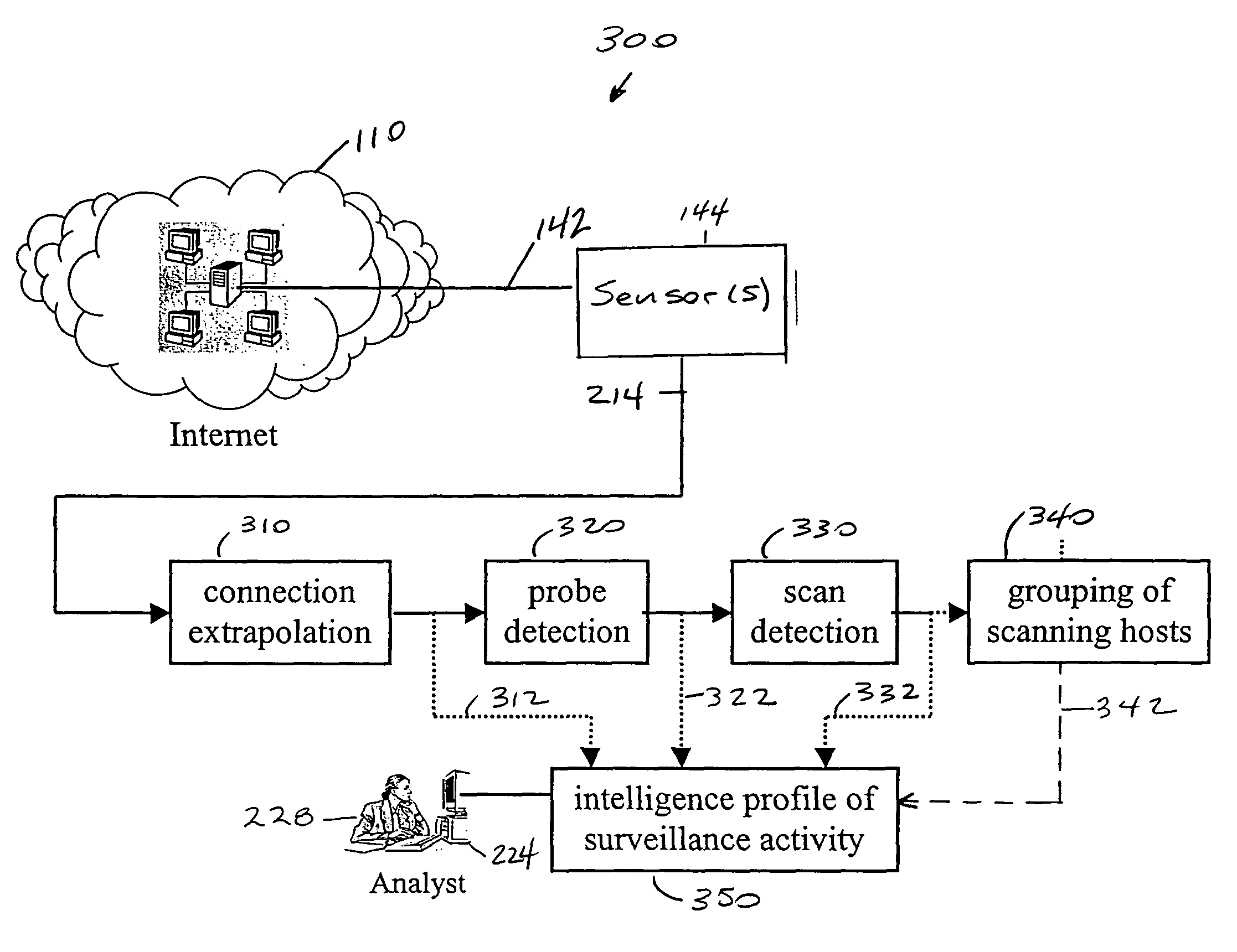
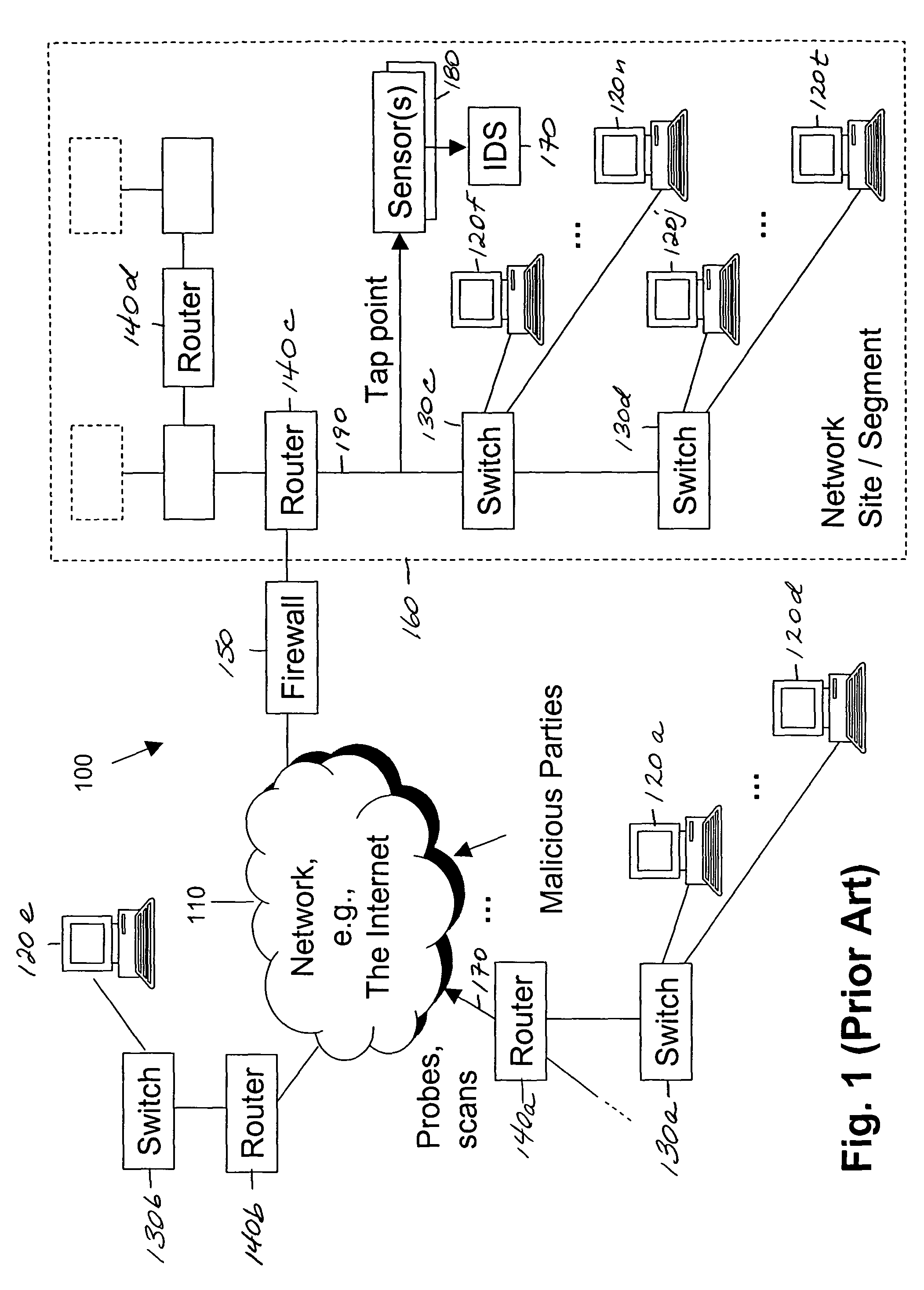
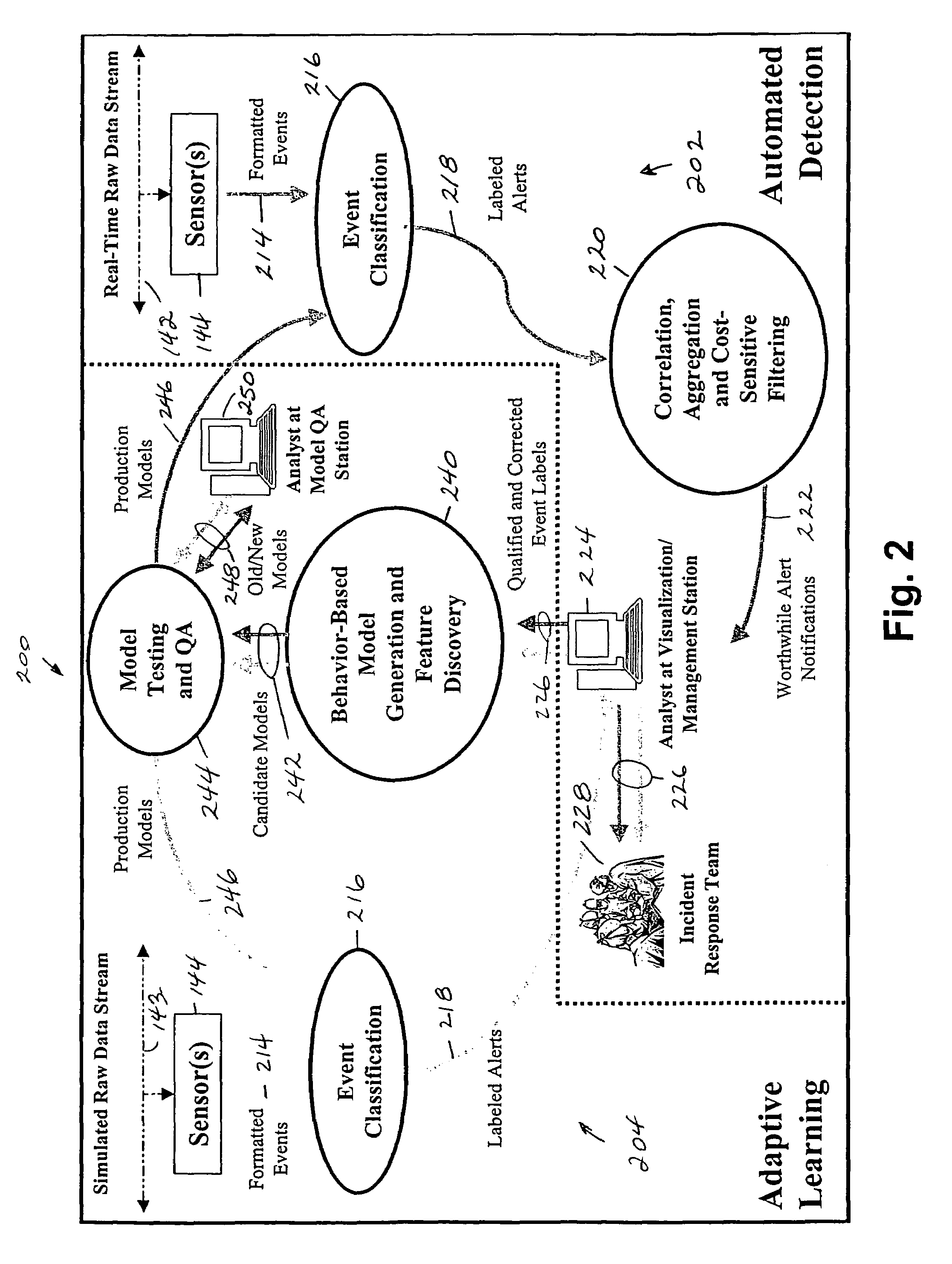
Detecting probes and scans over high-bandwidth, long-term, incomplete network traffic information using limited memory
ActiveUS7752665B1Robust against stealthy attackImprove productivityMemory loss protectionUnauthorized memory use protectionAdaptive learningNetwork connection
A method for detecting surveillance activity in a computer communication network comprising automatic detection of malicious probes and scans and adaptive learning. Automatic scan / probe detection in turn comprises modeling network connections, detecting connections that are likely probes originating from malicious sources, and detecting scanning activity by grouping source addresses that are logically close to one another and by recognizing certain combinations of probes. The method is implemented in a scan / probe detector, preferably in combination with a commercial or open-source intrusion detection system and an anomaly detector. Once generated, the model monitors online activity to detect malicious behavior without any requirement for a priori knowledge of system behavior. This is referred to as “behavior-based” or “mining-based detection.” The three main components may be used separately or in combination with each other. The alerts produced by each may be presented to an analyst, used for generating reports (such as trend analysis), or correlated with alerts from other detectors. Through correlation, the invention prioritizes alerts, reduces the number of alerts presented to an analyst, and determines the most important alerts.
Owner:FORCEPOINT FEDERAL
Tamper-resistant trusted java virtual machine and method of using the same
InactiveUS20050114683A1Easy to processSatisfies needProgram control using stored programsUser identity/authority verificationOpen sourceProgram security
A trusted Java virtual machine provides a method for supporting tamper-resistant applications, ensuring the integrity of an application and its secrets such as keys. The trusted Java virtual machine verifies the integrity of the Java application, prevents debugging of the Java application, and allows the Java application to securely store and retrieve secrets. The trusted Java virtual machine environment comprises a TrustedDictionary, a TrustedBundle, an optional encryption method for encrypting and decrypting byte codes, and an underlying trusted Java virtual machine. The encrypted TrustedDictionary protects data while the TrustedBundle protects programming code, allowing applications to store secret data and secure counters. The application designer can restrict TrustedBundle access to only those interfaces that the application designer explicitly exports. The open source code may optionally be encrypted. Secrets required by the open source programming code of the application are encrypted in TrustedDictionary.
Owner:IBM CORP
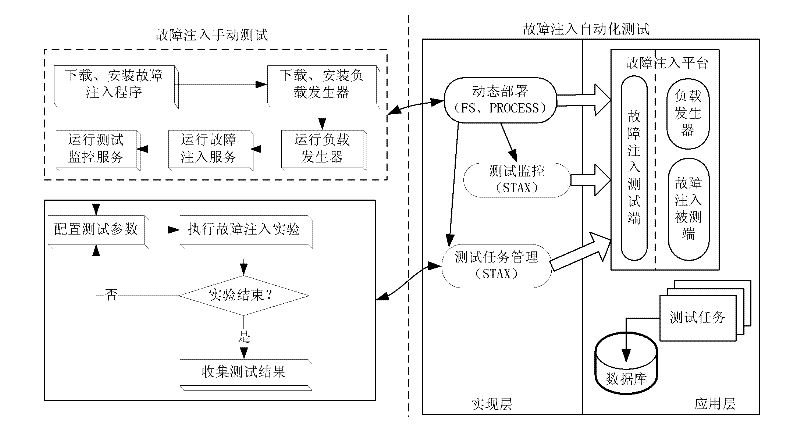
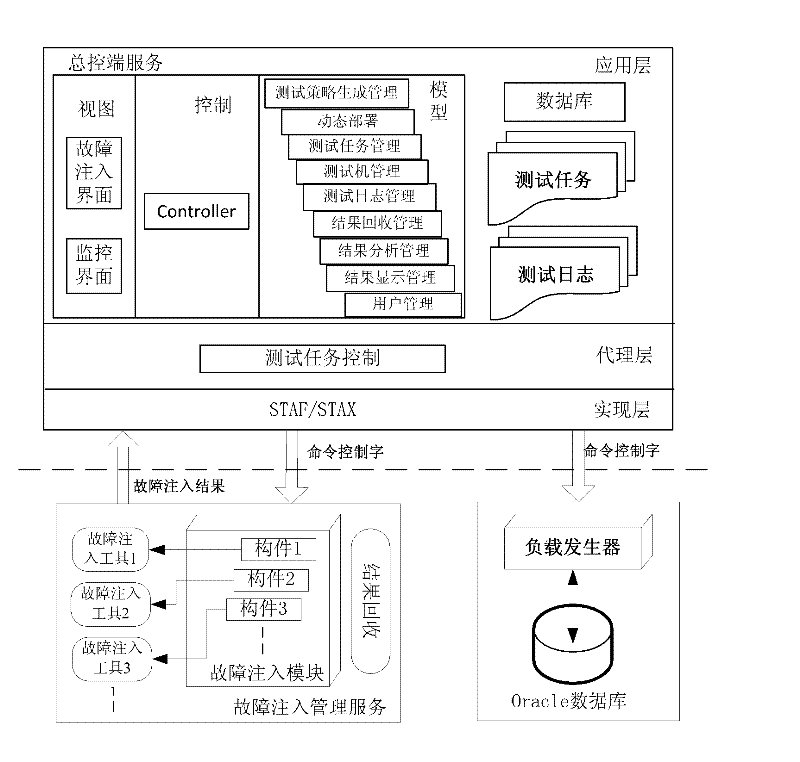
Software testing automation framework (STAF)-based fault injection automation testing platform and method for high-end fault-tolerant computer
InactiveCN102354298AImprove scalabilityImprove maintainabilitySoftware testing/debuggingRelational databaseSoftware engineering
The invention discloses a software testing automation framework (STAF)-based fault injection automation testing platform and an STAF-based fault injection automation testing method for a high-end fault-tolerant computer, and relates to a fault injection technology. The invention provides a fault injection automation testing platform and a fault injection automation testing method, which are applicable for the high-end fault-tolerant computer. The method is implemented by adopting an embedded software distributed testing environment. An application layer in software is an application program operated in general control end service, manages data and information in an automation testing process by utilizing a relational database and a file system, and provides a friendly graphic interface; a proxy layer is operated between the application layer and a realization layer to realize task proxy, and takes charge of executing an automation testing task submitted by a user from the interface; and the realization layer packages the communication among an automation testing control server and testing proxies of various platforms, and executes specific operations of various automation tests. The STAF-based fault injection automation testing platform is a distributed and automatic fault injection platform which is constructed on the basis of an open source automation testing tool STAF, and can integrate various software fault injection tools.
Owner:HARBIN INST OF TECH
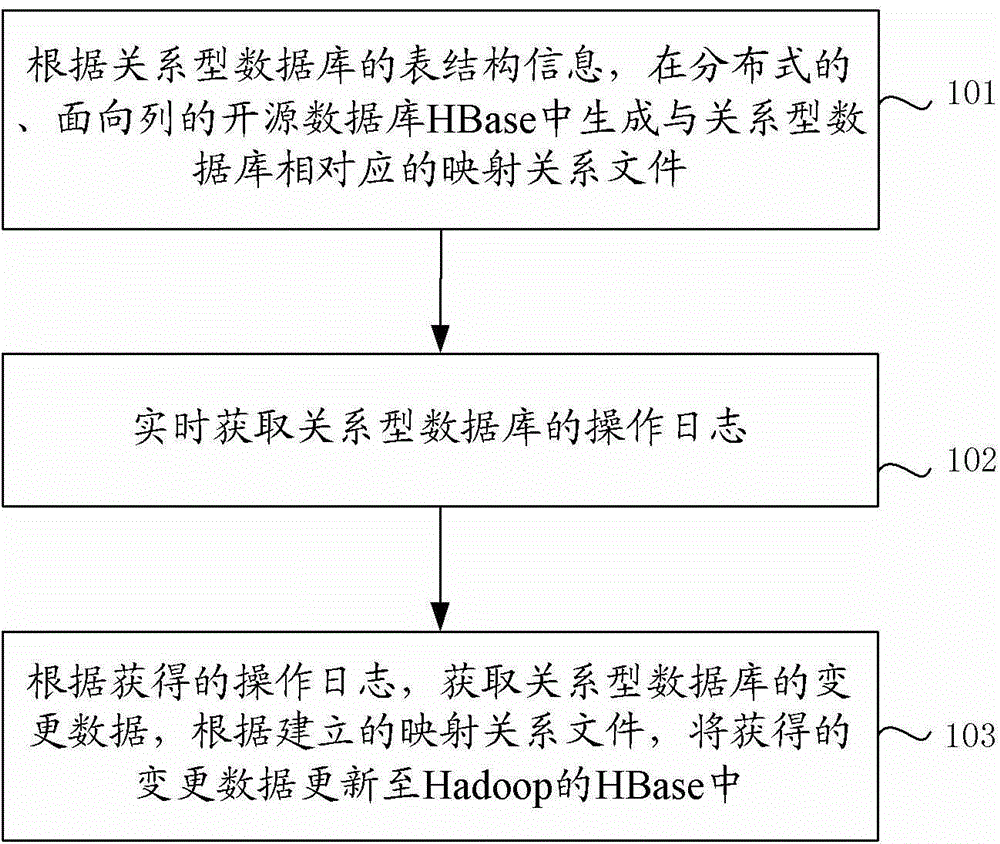
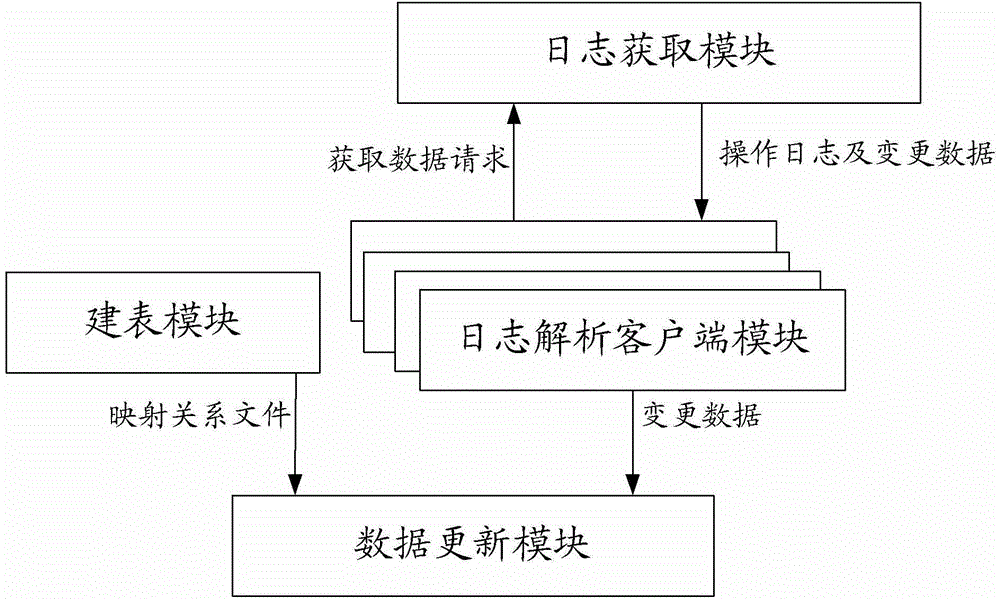
Method and apparatus for realizing real-time increment synchronization of data
ActiveCN105243067AReduce the burden onImprove experienceSpecial data processing applicationsRelational databaseOpen source
The invention discloses a method and an apparatus for realizing real-time increment synchronization of data. The method for realizing the real-time increment synchronization of the data comprises: according to table structure information of a relational database, generating a mapping relation file corresponding to the relational database in a distributed column-oriented open source database HBase; obtaining an operation log of the relational database in real time; according to the obtained operation log, obtaining change data of the relational database, and according to the established mapping relation file, updating the obtained change data into the HBase of Hadoop. The real-time increment update synchronization of the data from the relational database to Hadoop is realized, so that the burden of a Hadoop platform is effectively reduced and the user experience is improved.
Owner:北京明智和术科技有限公司
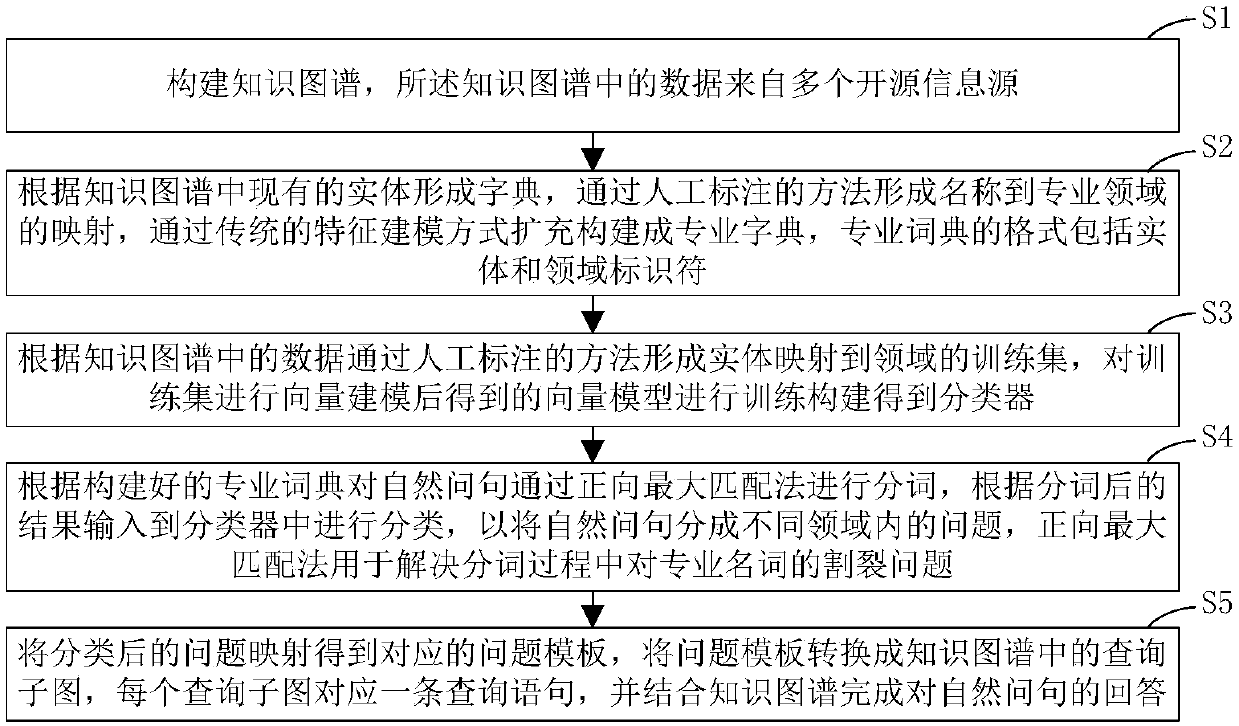
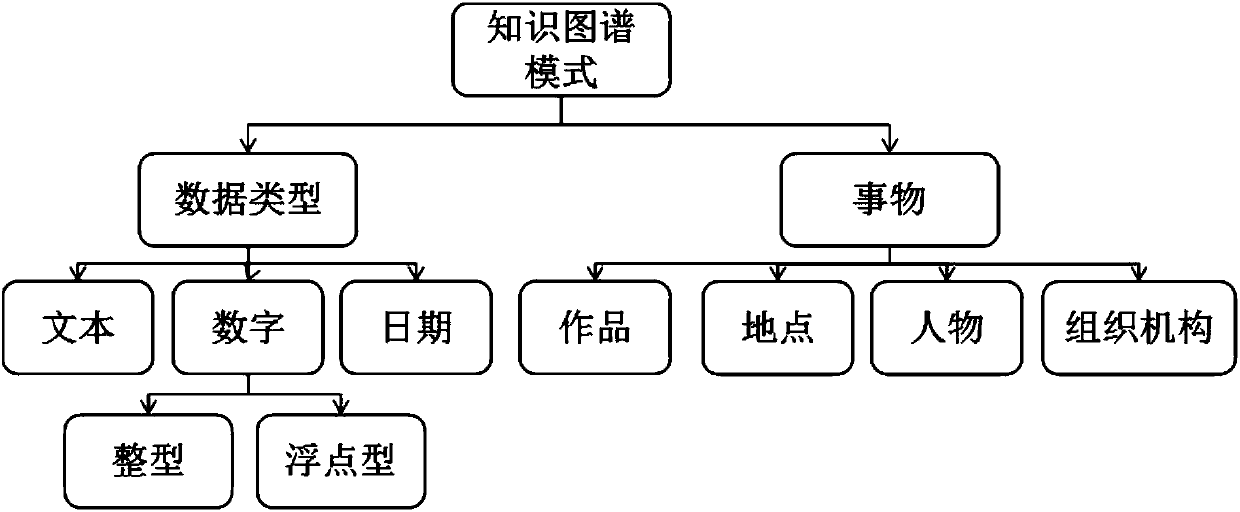
Knowledge graph-based interactive question and answer method and system
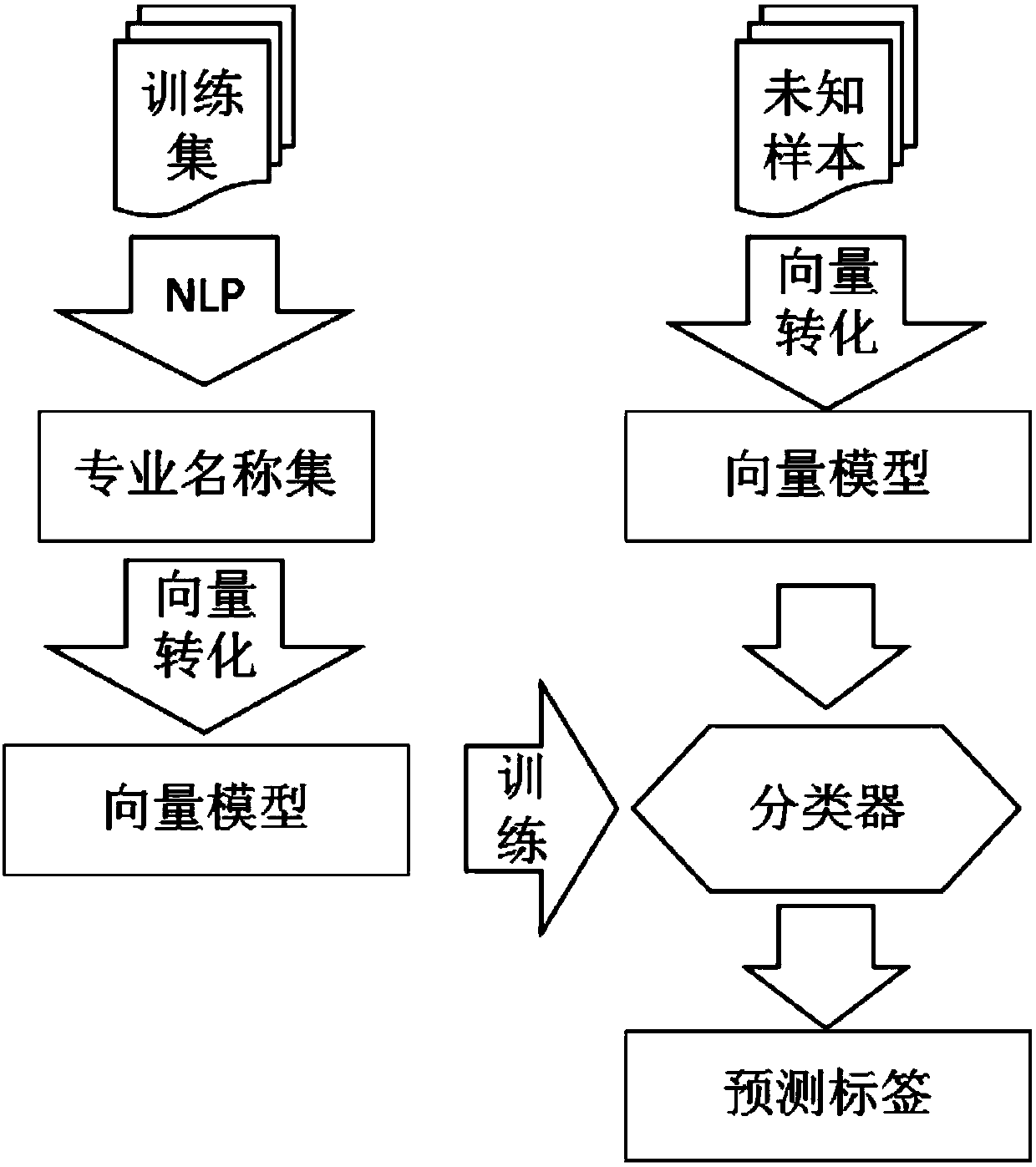
InactiveCN107766483AQuality assuranceReduce manual interventionRelational databasesNatural language data processingOpen sourceQuestions and answers
The invention discloses a knowledge graph-based interactive question and answer method and system. The method comprises the steps of constructing a knowledge graph, wherein data in the knowledge graphis from multiple open-source information sources; according to existing entities in the knowledge graph, forming a dictionary, forming mapping from a name to a professional field through a manual tagging method, and performing expansion in a conventional feature modeling mode to form a professional dictionary; according to the data in the knowledge graph, forming mapping from the entities to a training set of the field through the manual tagging method to establish a classifier; according to the professional dictionary, performing word segmentation on a natural question sentence through a forward maximum matching method, and according to results after word segmentation, inputting the results to the classifier for performing classification, thereby classifying the natural question sentenceinto questions in different fields; and mapping the classified questions to obtain corresponding question templates, and converting the question templates into query sub-graphs in the knowledge graph. Answer can be performed for sentences of more complex questions, so that the answer quality can be ensured and the manual intervention is effectively reduced.
Owner:HUAZHONG UNIV OF SCI & TECH
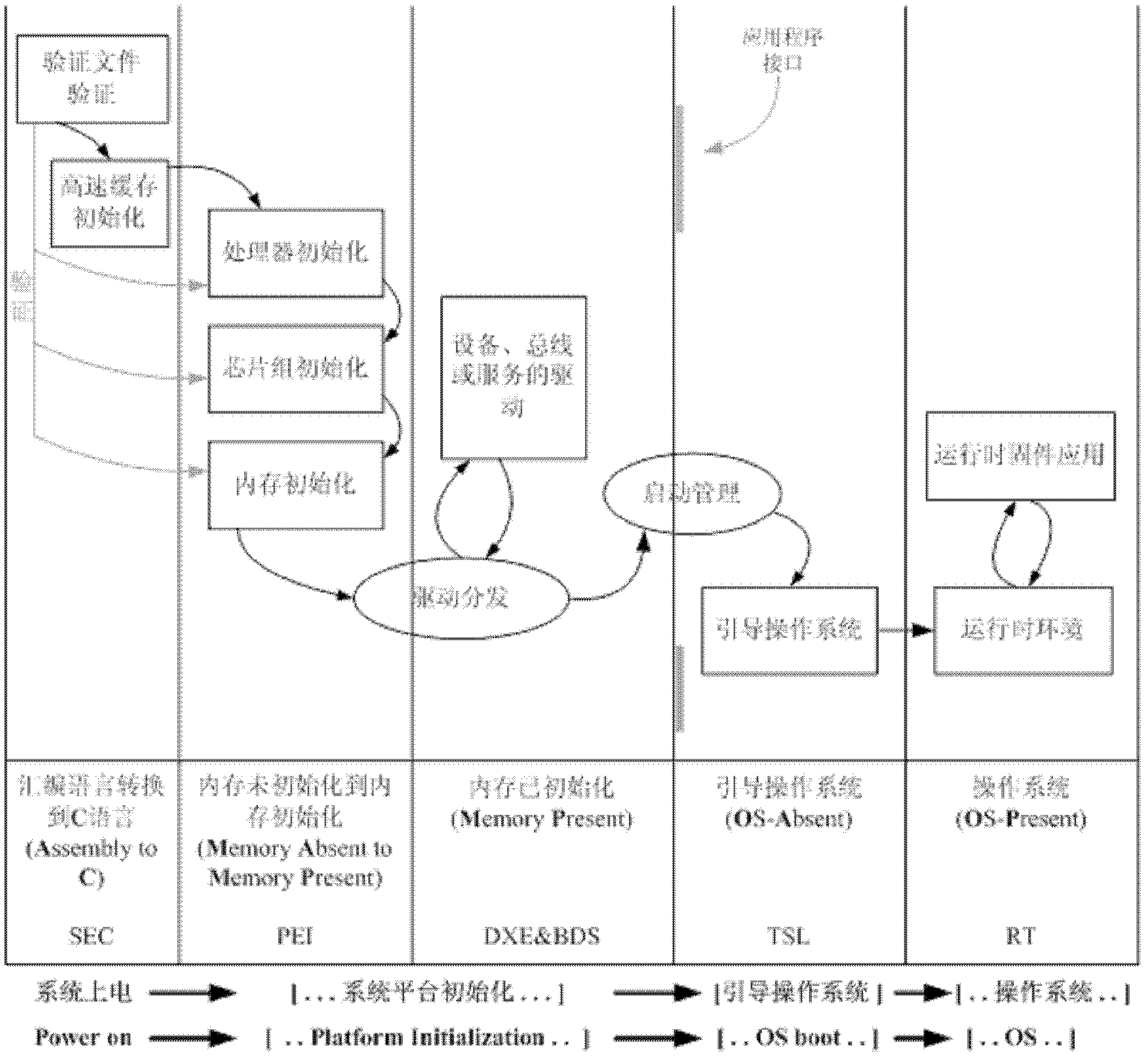
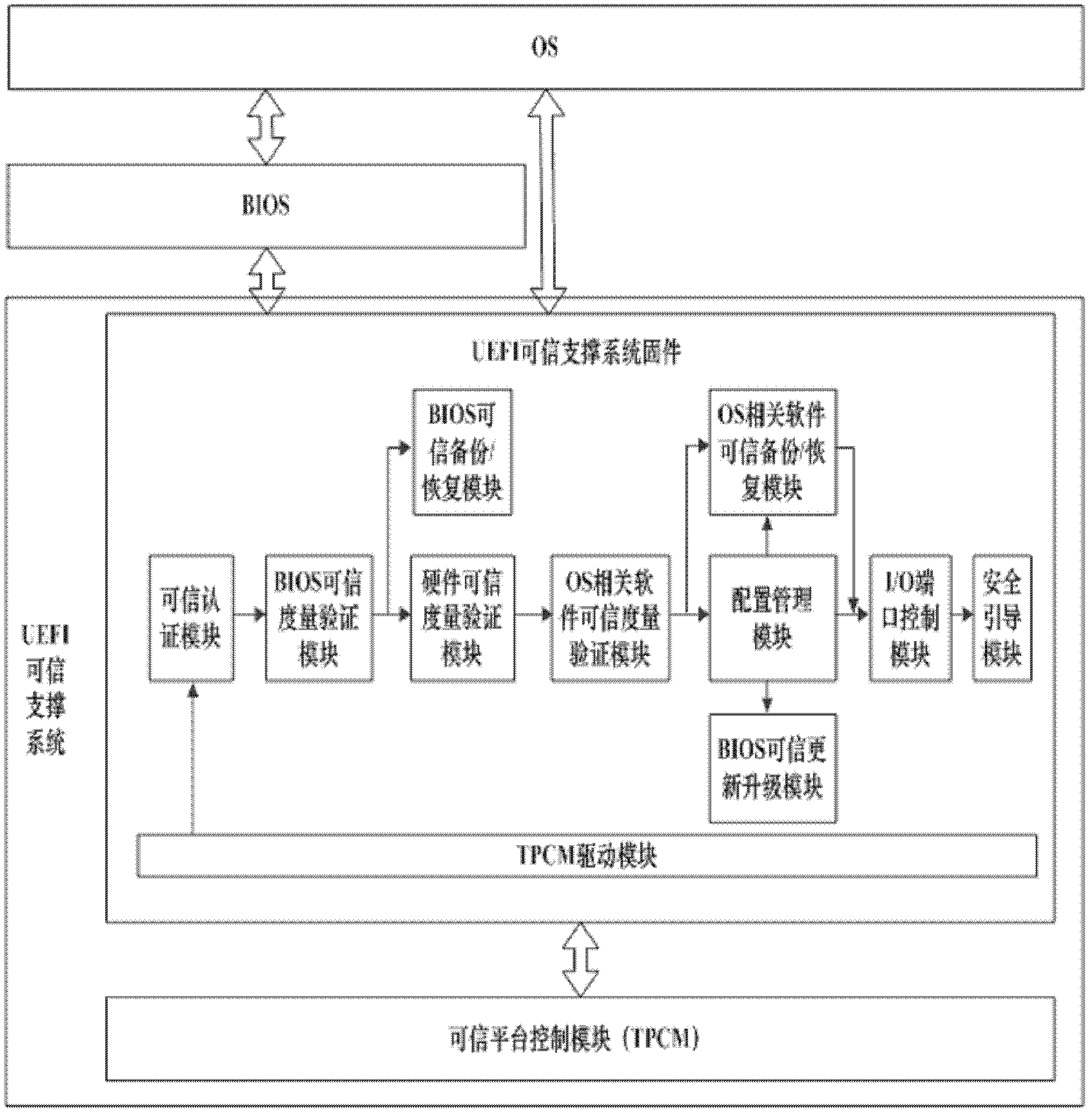
A UEFI trusted support system and control method thereof
InactiveCN102279914AReduce data volumeSimplify complexityPlatform integrity maintainanceSoftwareBackup
The invention discloses a unified extensible firmware interface (UEFI) trusted supporting system and a method for controlling the same. The UEFI trusted supporting system comprises UEFI trusted supporting system firmware and a trusted platform control module (TPCM), wherein the UEFI trusted supporting system firmware is stored on a nonvolatile memory and connected with the TPCM by a system bus; and the TPCM is connected with a trusted computation platform by the system bus. The method for controlling the UEFI trusted supporting system comprises the following steps of: firstly, loading a driver for the TPCM; secondly, sequentially authenticating the identity of users, performing measurement validation on a basis input / output system (BIOS), the characteristic data of hardware and a master boot record (MBR) / operating system (OS) Loader / OS Kernel, controlling different hardware peripheral interfaces according to an I / O strategy of the users, and performing safety guide setting on the system by a safety guide module; and finally, controlling by the BIOS or the OS. By the system and the method, trusted computation, the configuration management of the TPCM, the backup / recovery of the BIOS / MBR / OS Loader / OS Kernel and the physical protection of key data are realized on a firmware layer. The invention can be simultaneously applied to a Linux system which opens source codes and a Windows system which does not open the source codes, so that a fault does not occur in a trust chain between BIOS firmware and OS software, and the safety of a computer and the friendliness of human-computer interaction are improved.
Owner:中国人民解放军海军计算技术研究所 +1
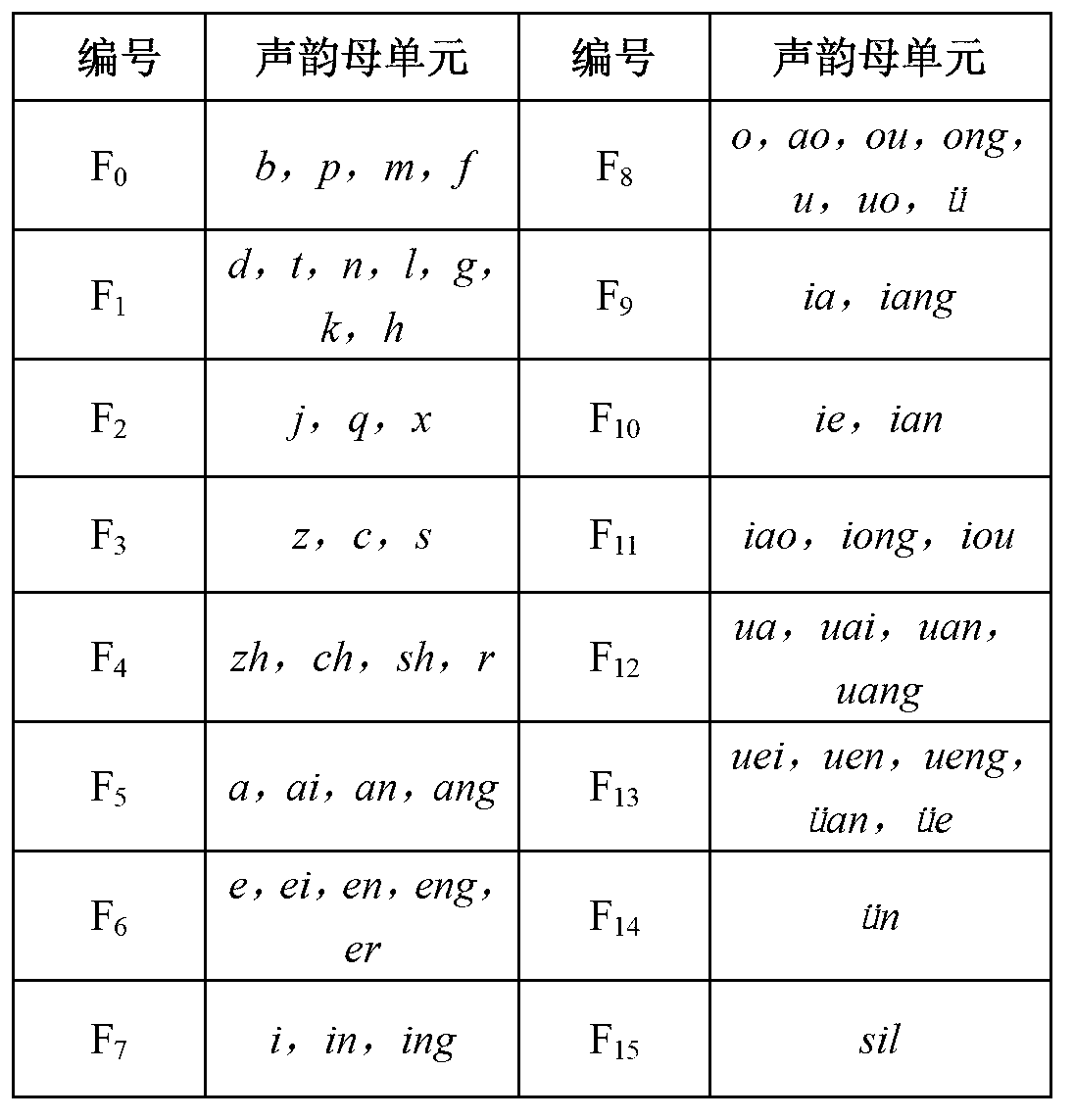
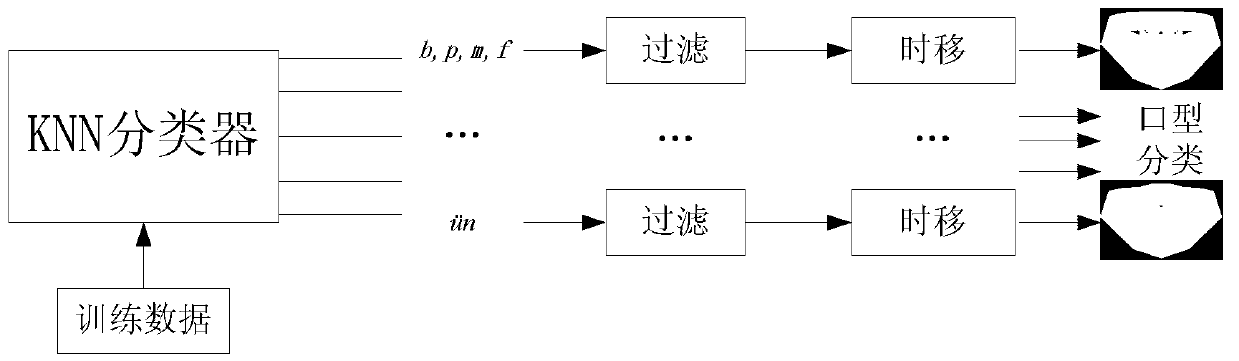
Voice synchronous-drive three-dimensional face mouth shape and face posture animation method
InactiveCN103218842APromote generationReduced intelligibilityCharacter and pattern recognitionAnimationNeighbor algorithmMouth shape
The invention discloses a voice synchronous-drive three-dimensional face mouth shape and face posture animation method. A user can input new voice information, and the new voice information can be preprocessed to combine mouth shape animations and face posture animations which are synchronous with voice on the face head of a virtual man. The method specifically comprises two stages. In a training stage, voice visualization modeling can be achieved through a k-nearest neighbor algorithm (KNN) and hidden Markov model (HMM) mixed model. In a combining stage, the user can input new voice information, characteristics of voice signals are extracted, face posture and mouth shape sequence parameters corresponding to the voice signals can be generated through the KNN and HMM mixed model and are processed in a transition mode, and X face open source software is used to combine delicate and abundant three-dimensional face animations. The method has significant theoretical study value and has wide application prospect in the fields of visual communication, virtual meetings, games, entertainments, teaching assistance and the like.
Owner:SOUTHWEST JIAOTONG UNIV
Method and System for an Integrated Safe City Environment including E-City Support
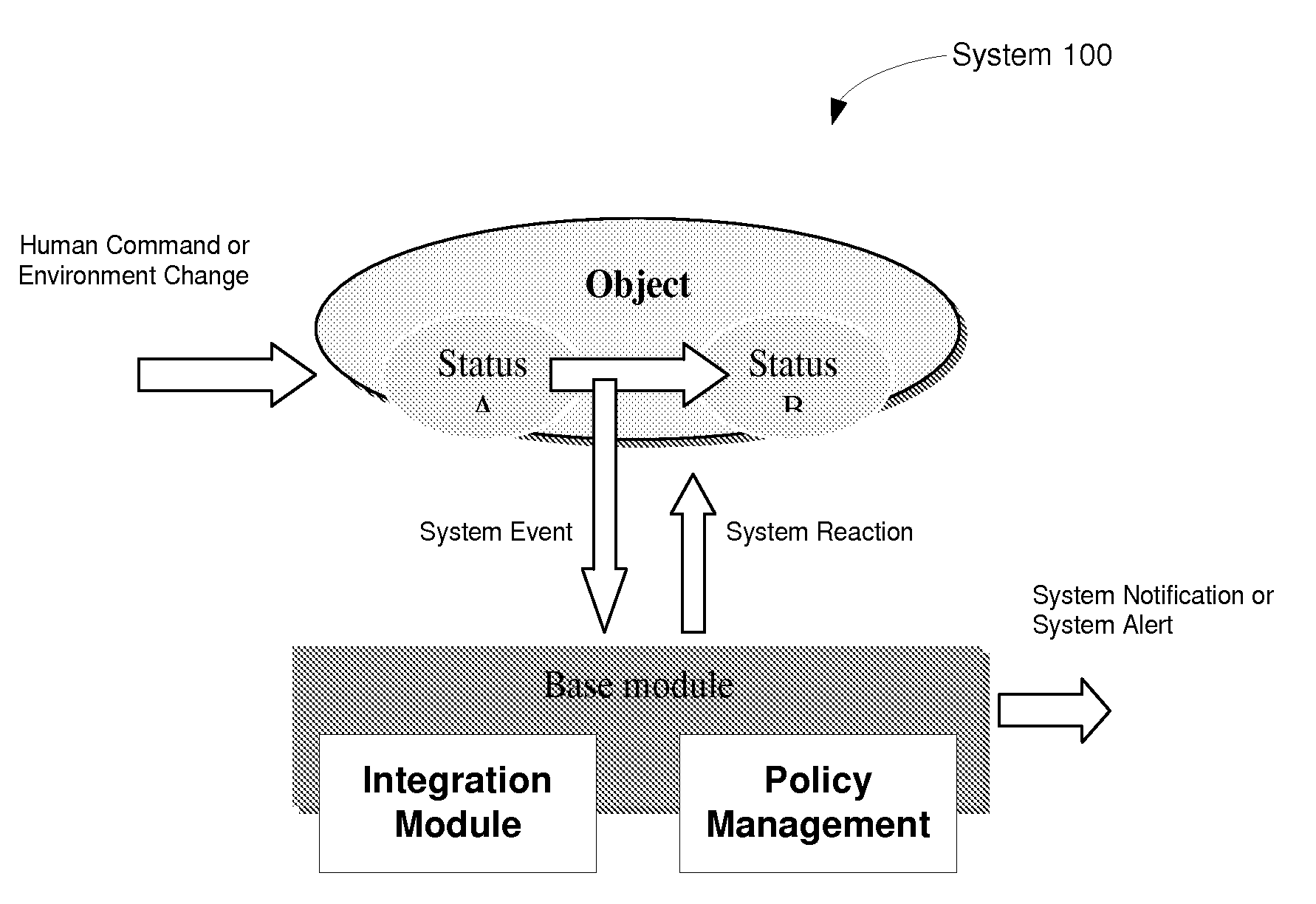
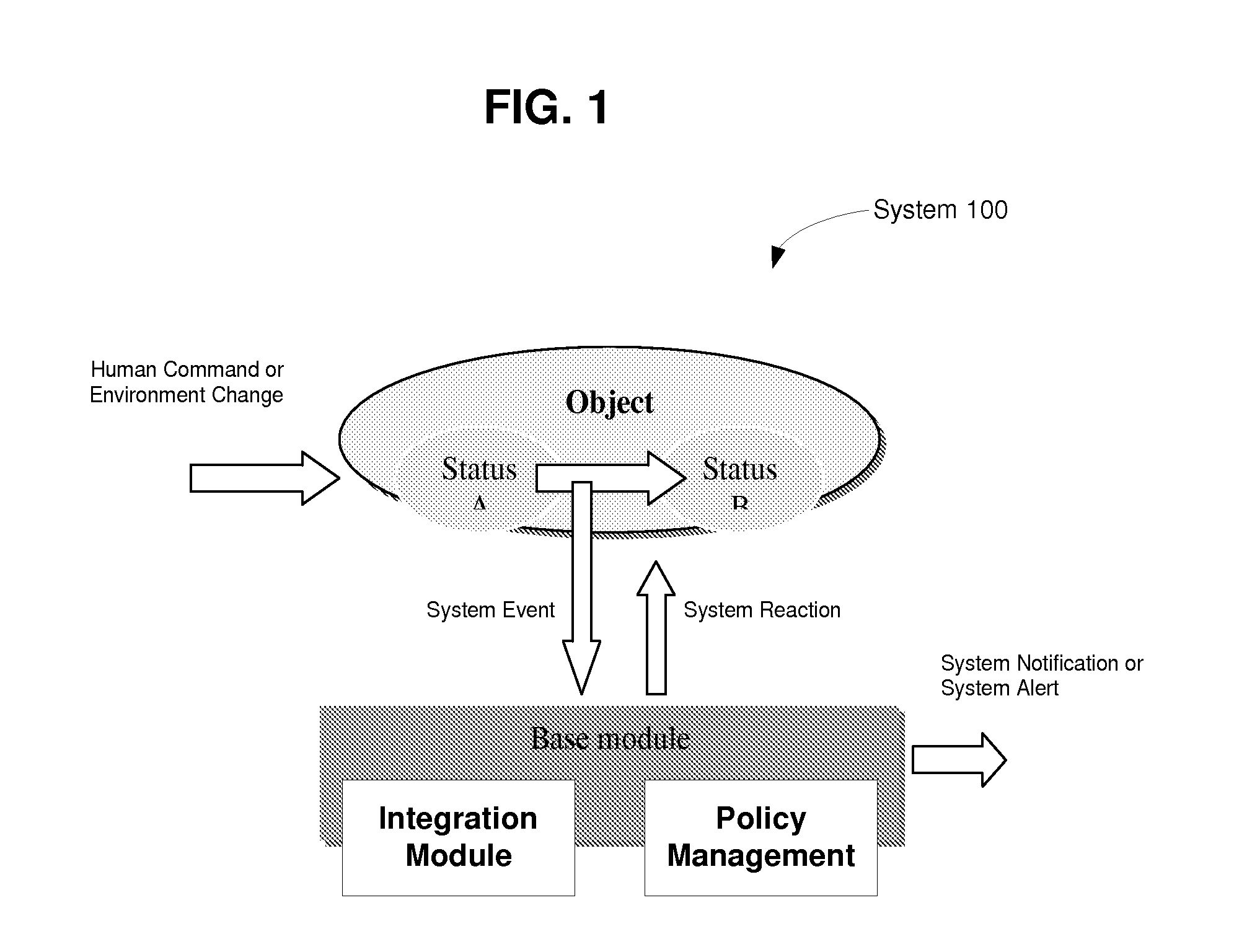
InactiveUS20110261202A1Programme controlElectric signal transmission systemsOpen sourceComputer science
Described are use of clustered intelligent method of using video analytics, event driven systems and policy management for integrated approach to implement safe environment, such as a “Safe City” or “E-City,” supporting improvement in security and energy savings. The exemplary “Safe City” environment uses streaming video technologies, multi-function open source software, and high compression capabilities. Surveillance data of a predetermined geographical area may obtained using a computing arrangement, analyzing the surveillance data to detect at least one of a predetermined activity and a predetermined behavior of a entity within the predetermined geographical area, and adjusting at least one operation within the predetermined geographical area based on the at least one predetermined activity and predetermined behavior of the entity.
Owner:GOLDSTEIN BORIS
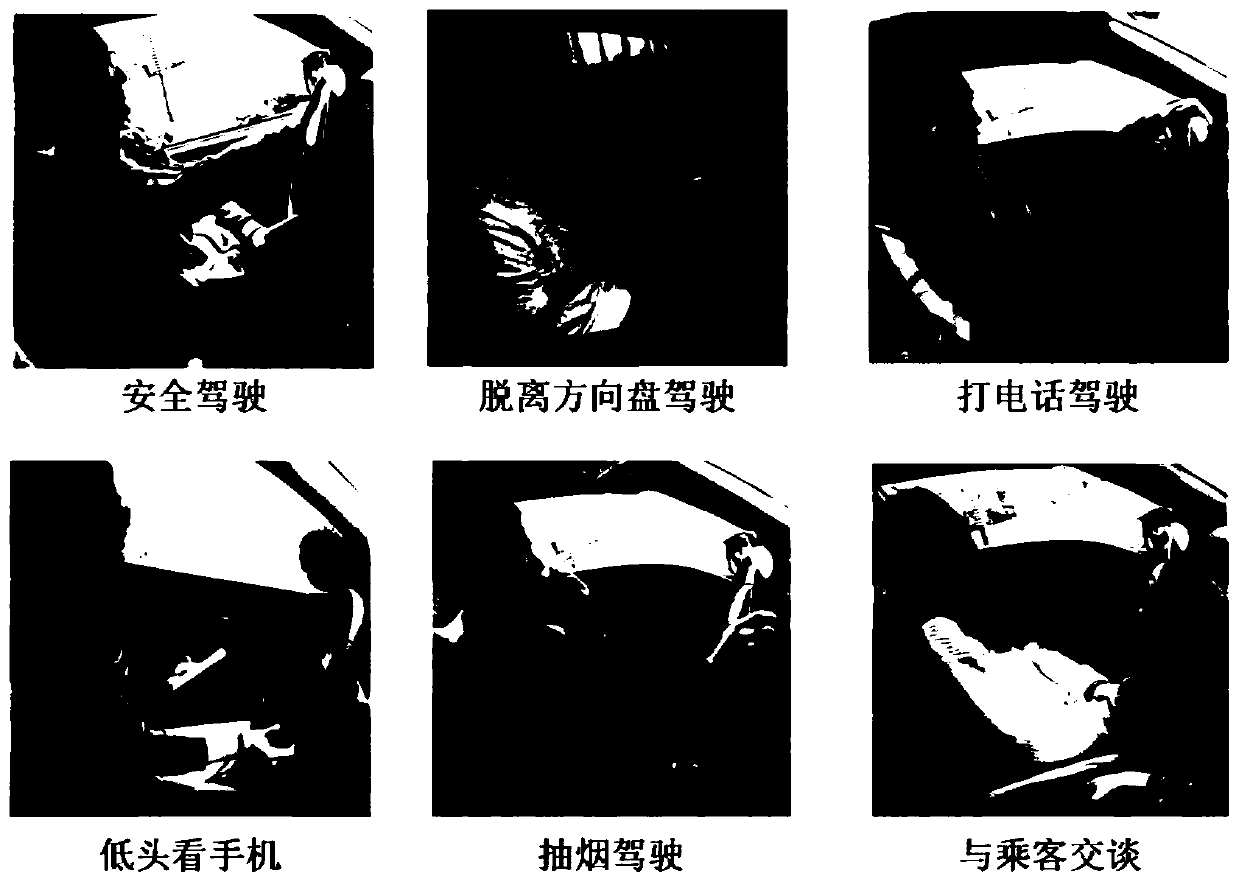
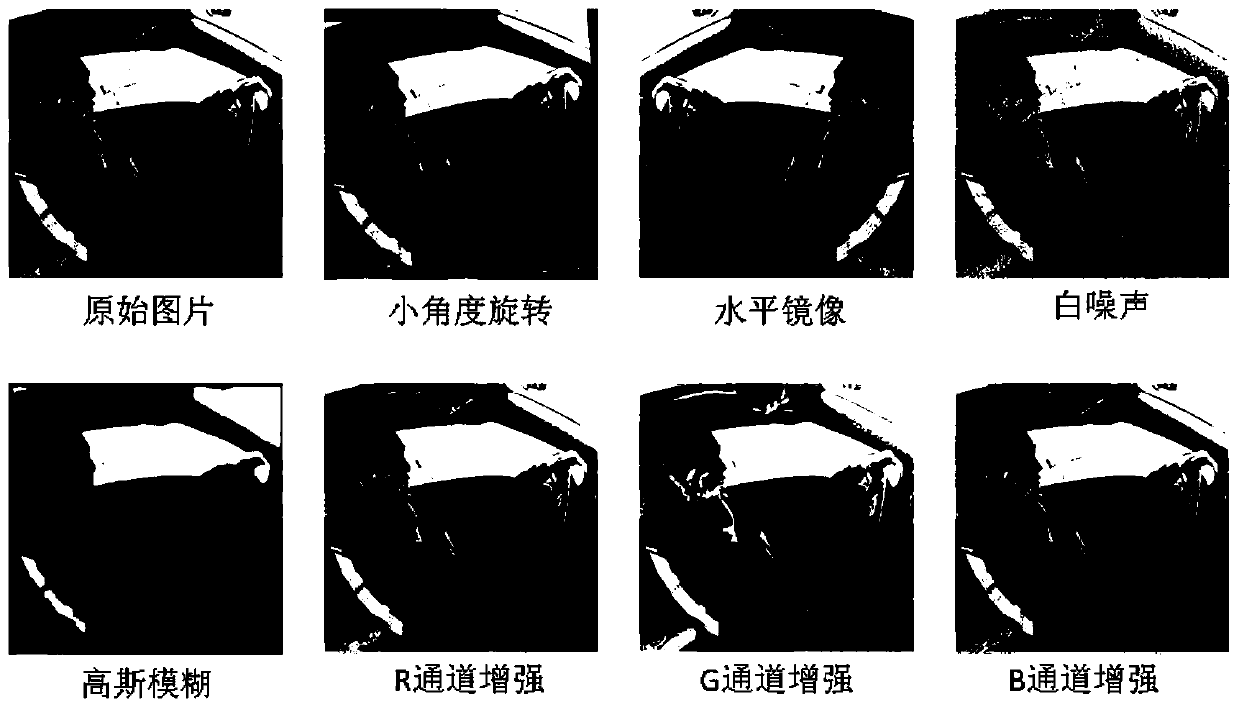
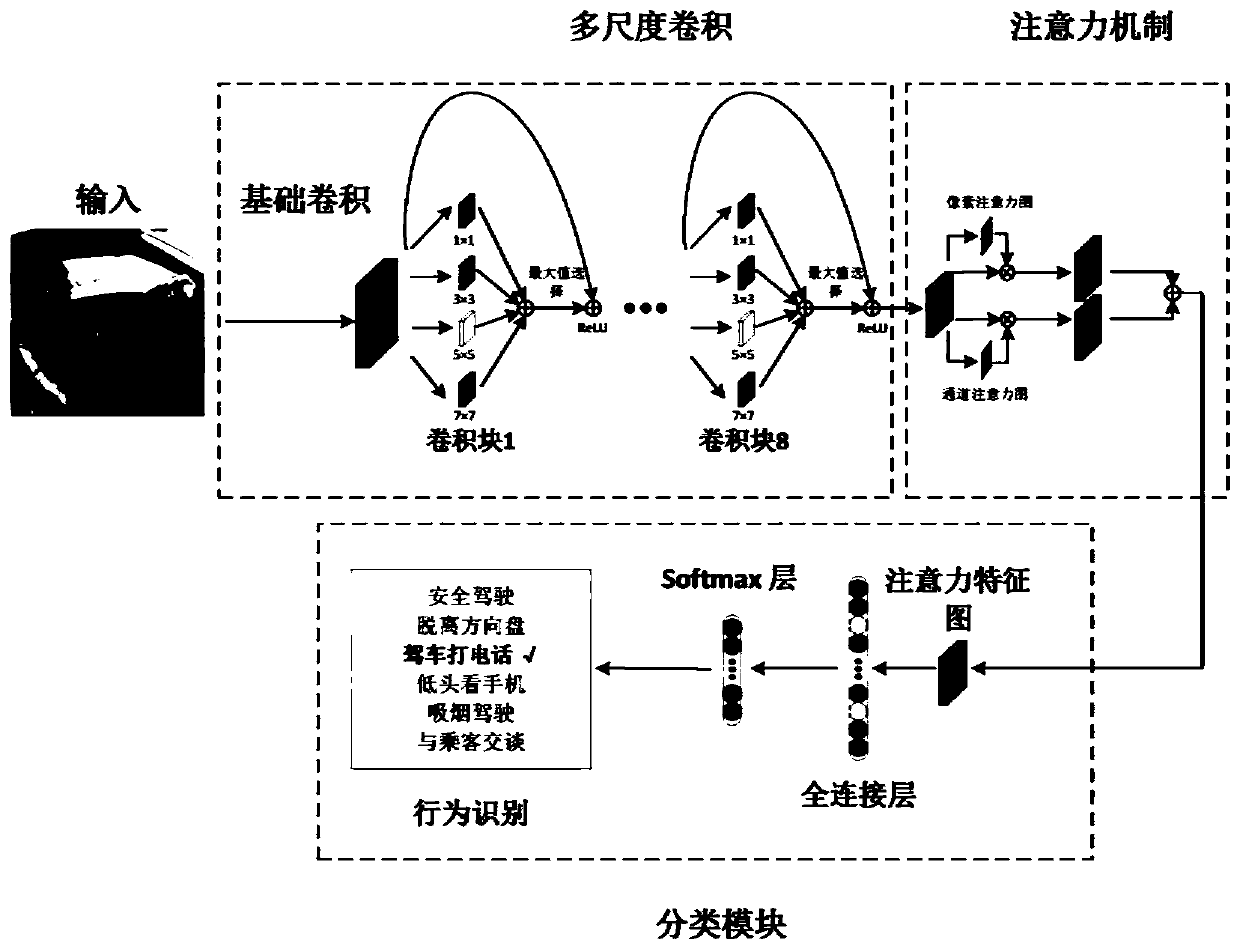
Driver behavior identification method based on multi-scale attention convolutional neural network
ActiveCN110059582AInternal combustion piston enginesCharacter and pattern recognitionScale modelData set
The invention discloses a driver behavior identification method based on a multi-scale attention convolutional neural network. The method comprises the following steps: (1) shooting an image data setfor driver behavior identification; (2) carrying out data enhancement on the shot driver behavior data set and simultaneously bringing samples obtained by enhancement into training data; (3) constructing a neural network model which comprises three modules, namely a multi-scale convolution module, an attention module and a classification module; (4) training a multi-scale attention convolutional neural network; using a Pytorch open source tool i for building a network model, and using a random gradient descent method for optimizing network parameters; and (5) testing the multi-column convolutional neural network. According to the invention, the multi-scale model and the attention mechanism are introduced into the driver behavior identification task to extract the behavior fine-grained feature representation with the distinction degree, so that the driver behavior identification accuracy can be further improved.
Owner:SOUTHEAST UNIV
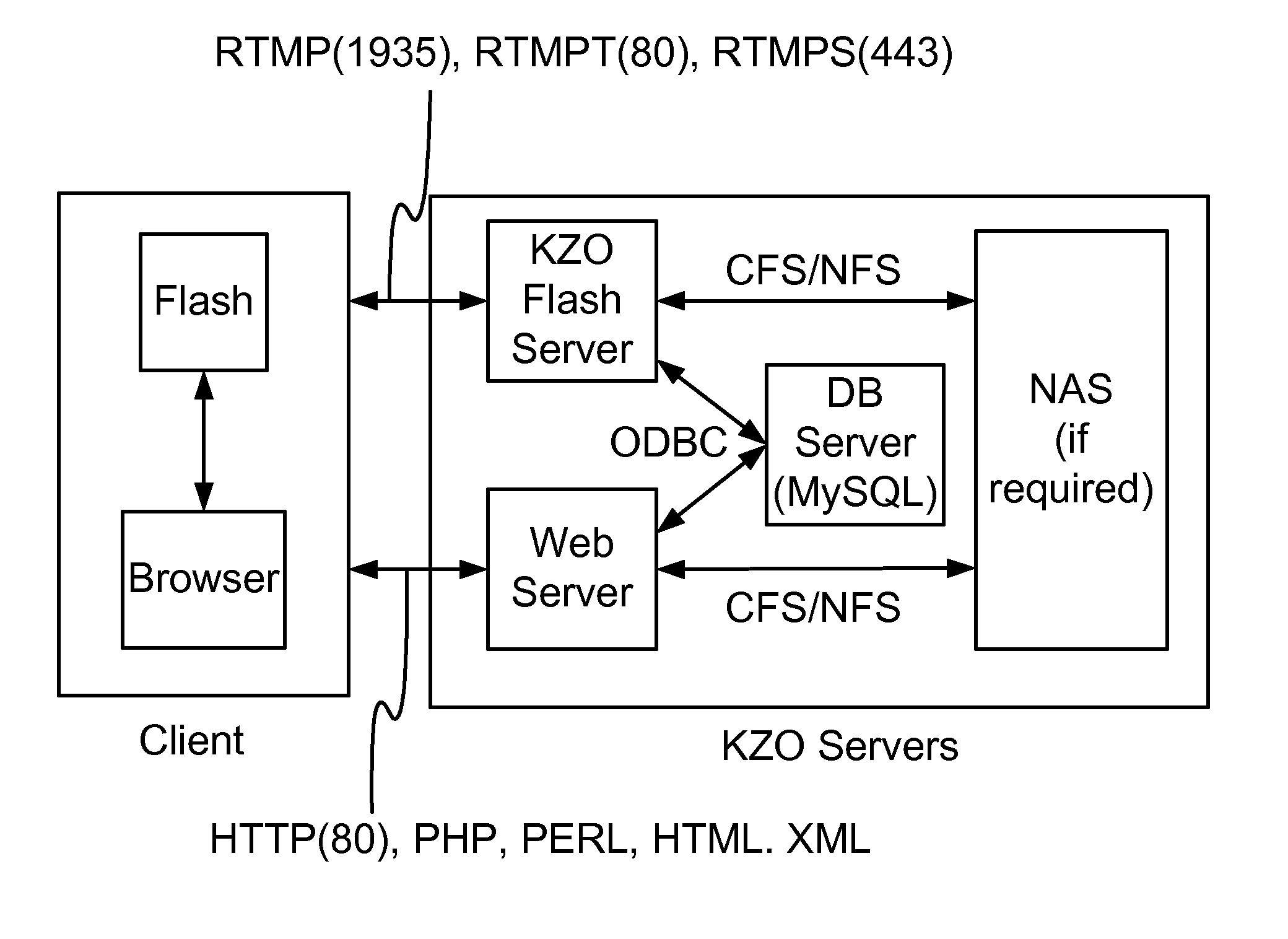
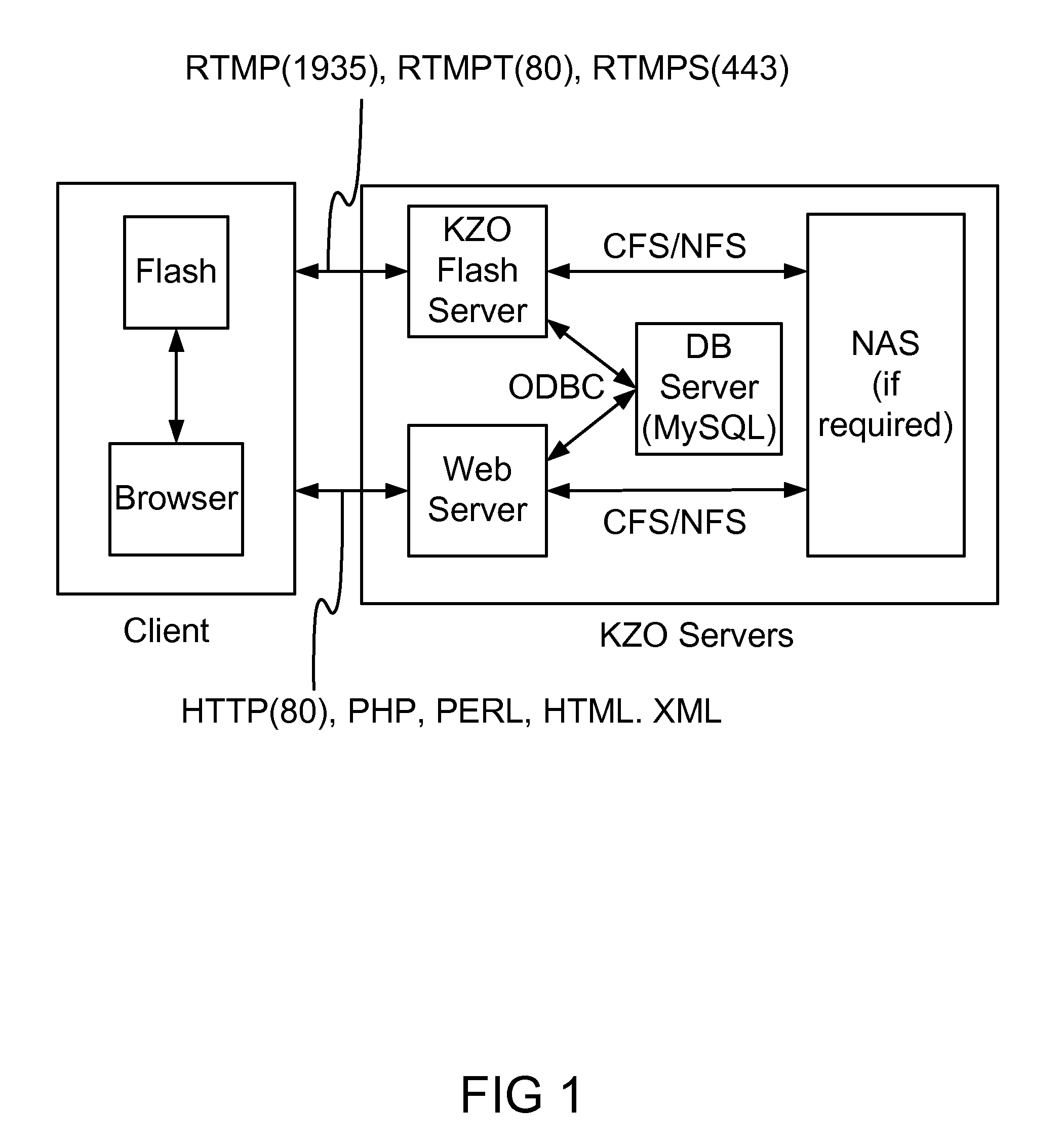
System and Method for Collaborative and Interactive Communication and Presentation over the Internet
InactiveUS20080209330A1Easy to useMultiple digital computer combinationsTelevision systemsService provisionOpen source
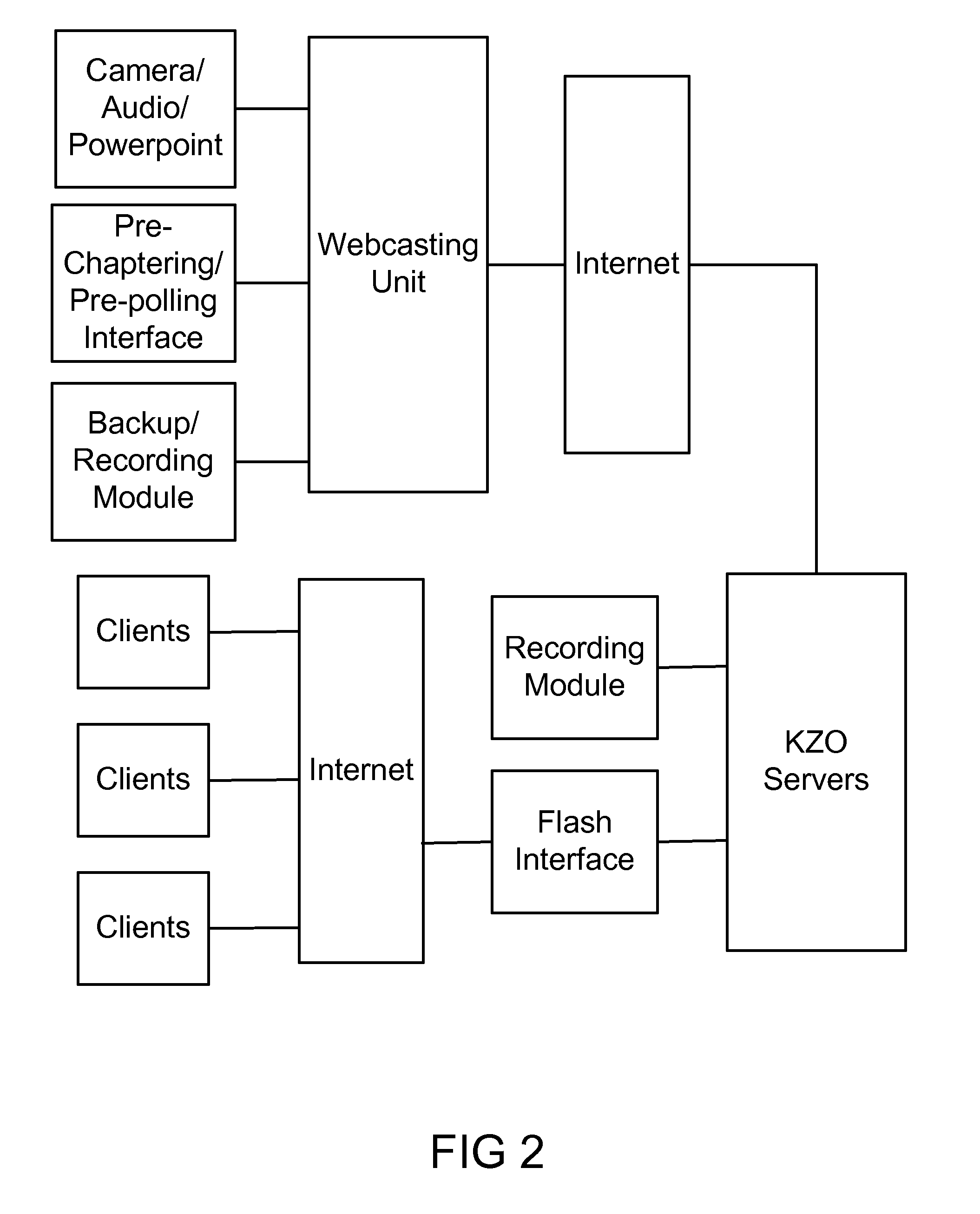
A novel interactive system for E-learning and Tele-conferencing via the Internet is described that integrates video, audio, slides, text and other required means of communication in a simple to use platform. The system allows presenter to poll audience and see the results. The system records the session for future Video-On-Demand viewing. The KZO platform could be locally installed at customer premise or it could be located in KZO or other service provider hubs. The video and audio streaming is based on open-source Flash technology, or any other similar technologies.
Owner:CRUVER WESLEY
Software package-based online automatic updating method for open source operating system of mobile terminal
ActiveCN102118500AResolve escalationTroubleshoot maintenance management issuesSubstation equipmentProgram loading/initiatingOperational systemNetwork approach
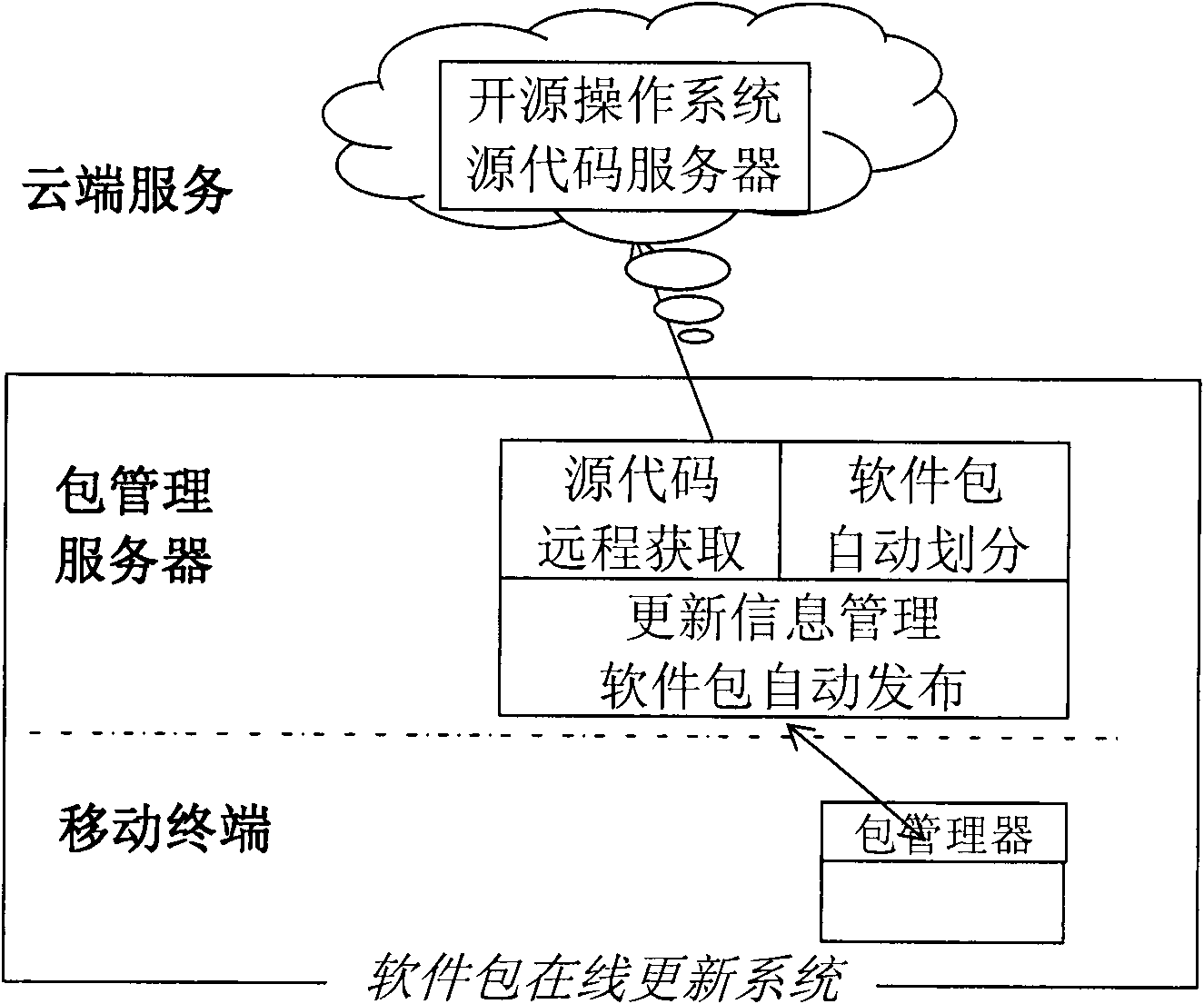
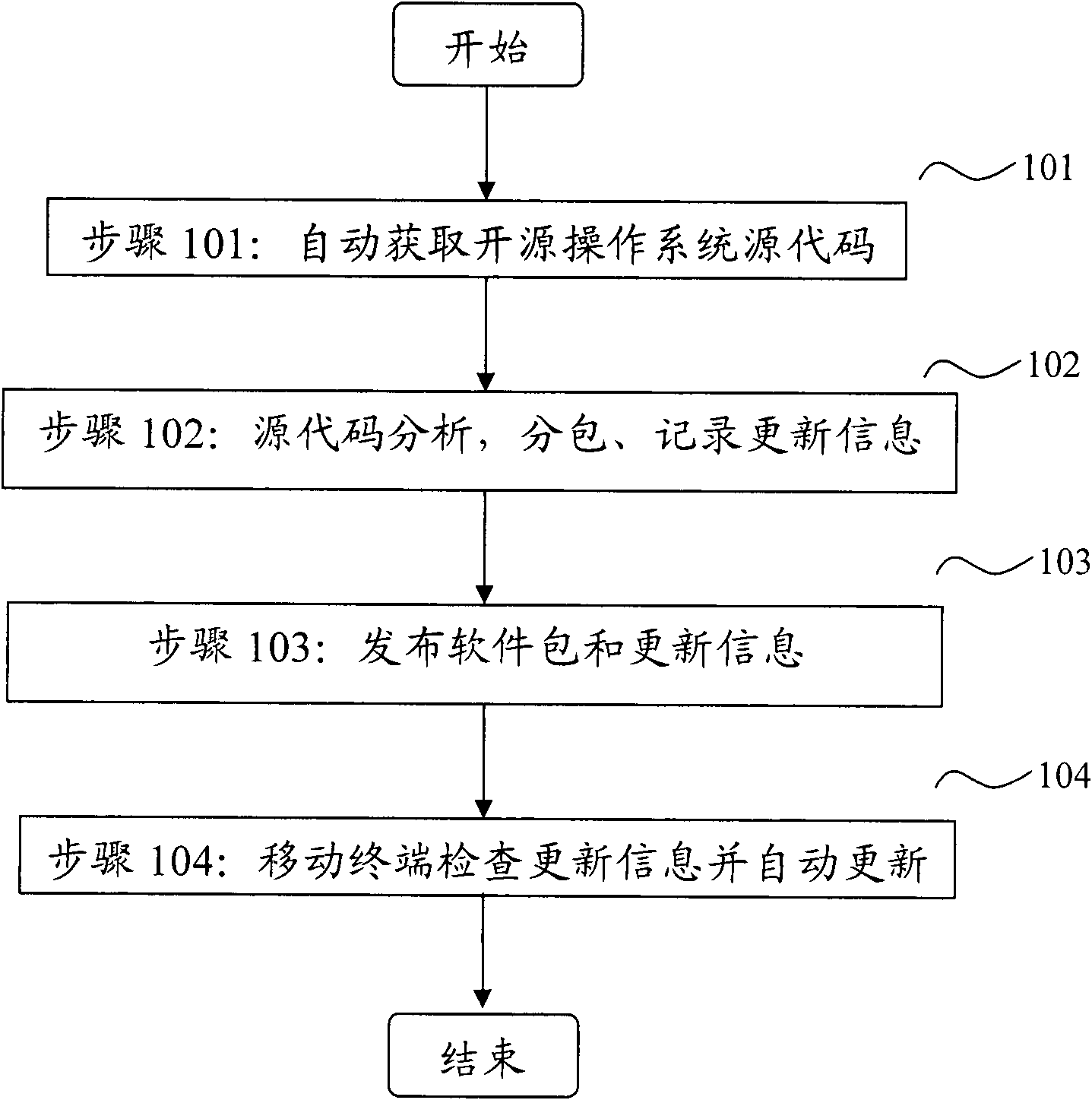
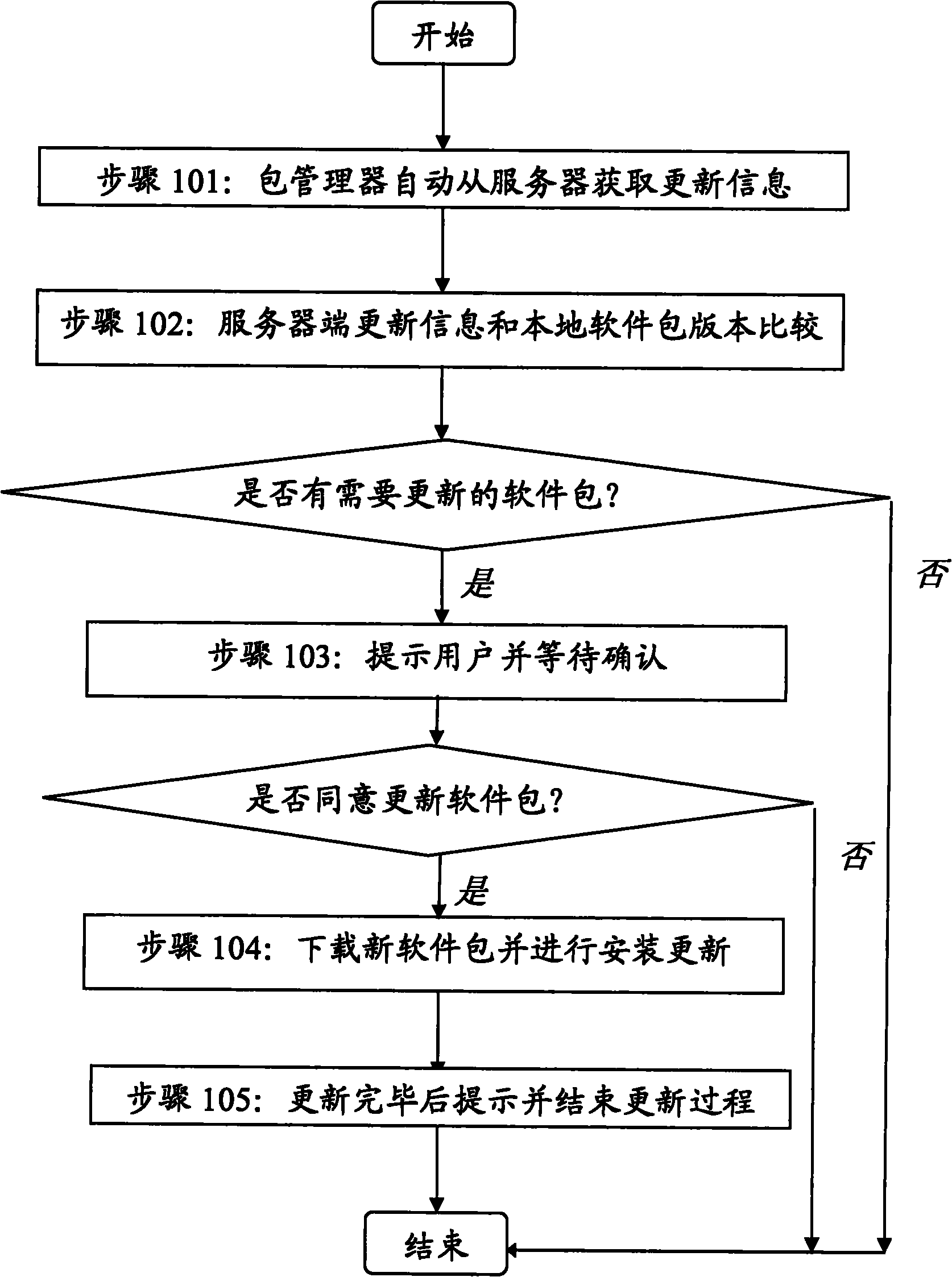
The invention discloses a software package-based online automatic updating method for an open source operating system of a mobile terminal, which relates to the field of mobile terminal software and is applied to the open source operating system of the mobile terminal. By the method, the remote automatic updating of system software can be realized by taking a package as a unit, and convenience isbrought to the rehabilitation of security holes and the installation of the operating system. The method comprises the two aspects that: a server automatically finishes structuring and publishing thesoftware package, acquires all source codes of the operating system from an open source site, automatically divides and structures a proper software package, determines the updating information of the software package according to the version information and dependency of the source codes, and publishes the software package by utilizing a network; and the mobile terminal serving as a software package acquirer and user automatically checks the updating information by client software, and downloads and updates the system by taking the software package as the unit to fulfill the aim of automaticonline updating. The method has the characteristics of high degree of automation and the like, and is easy to deploy in large scale and use.
Owner:TSINGHUA UNIV
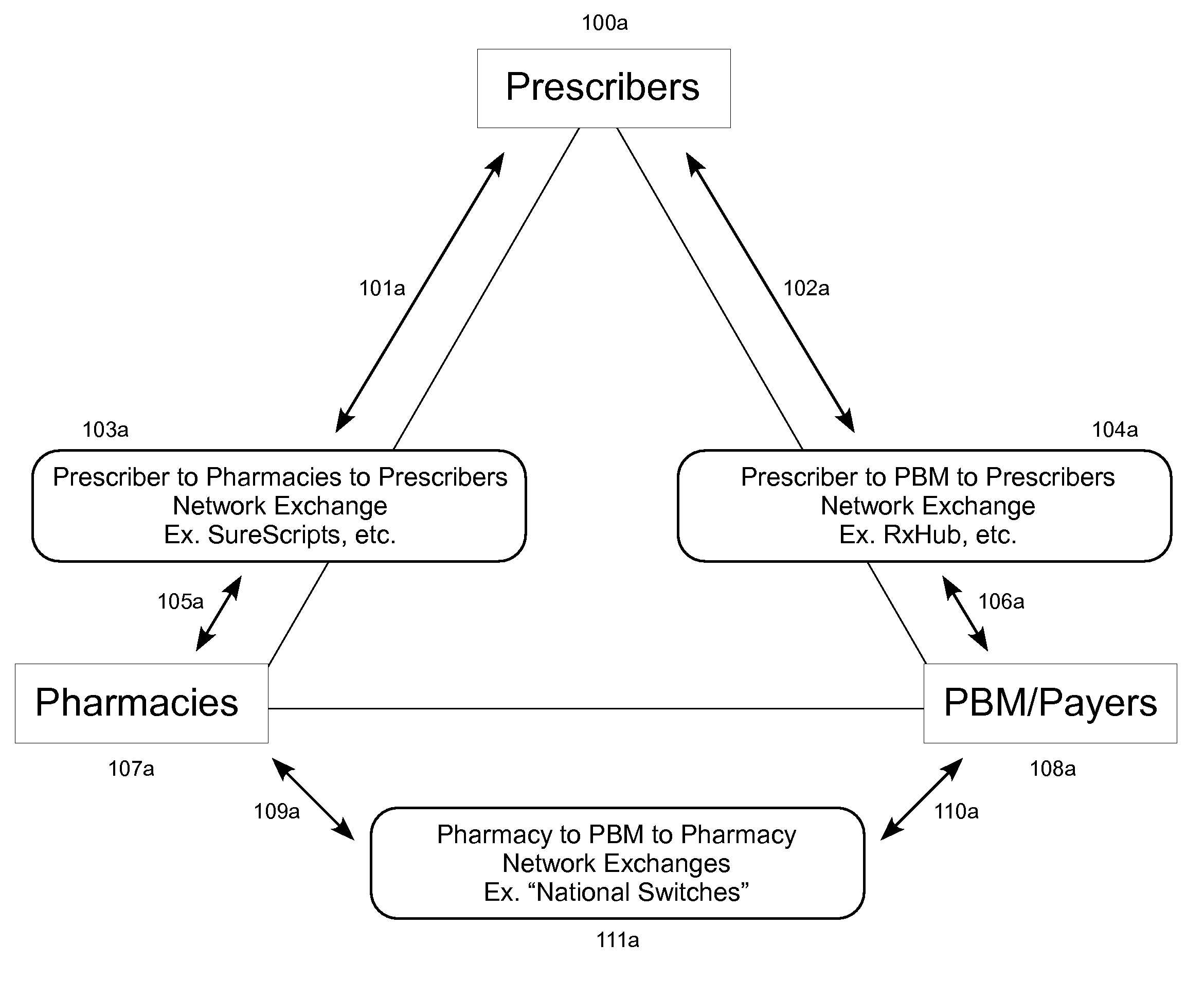
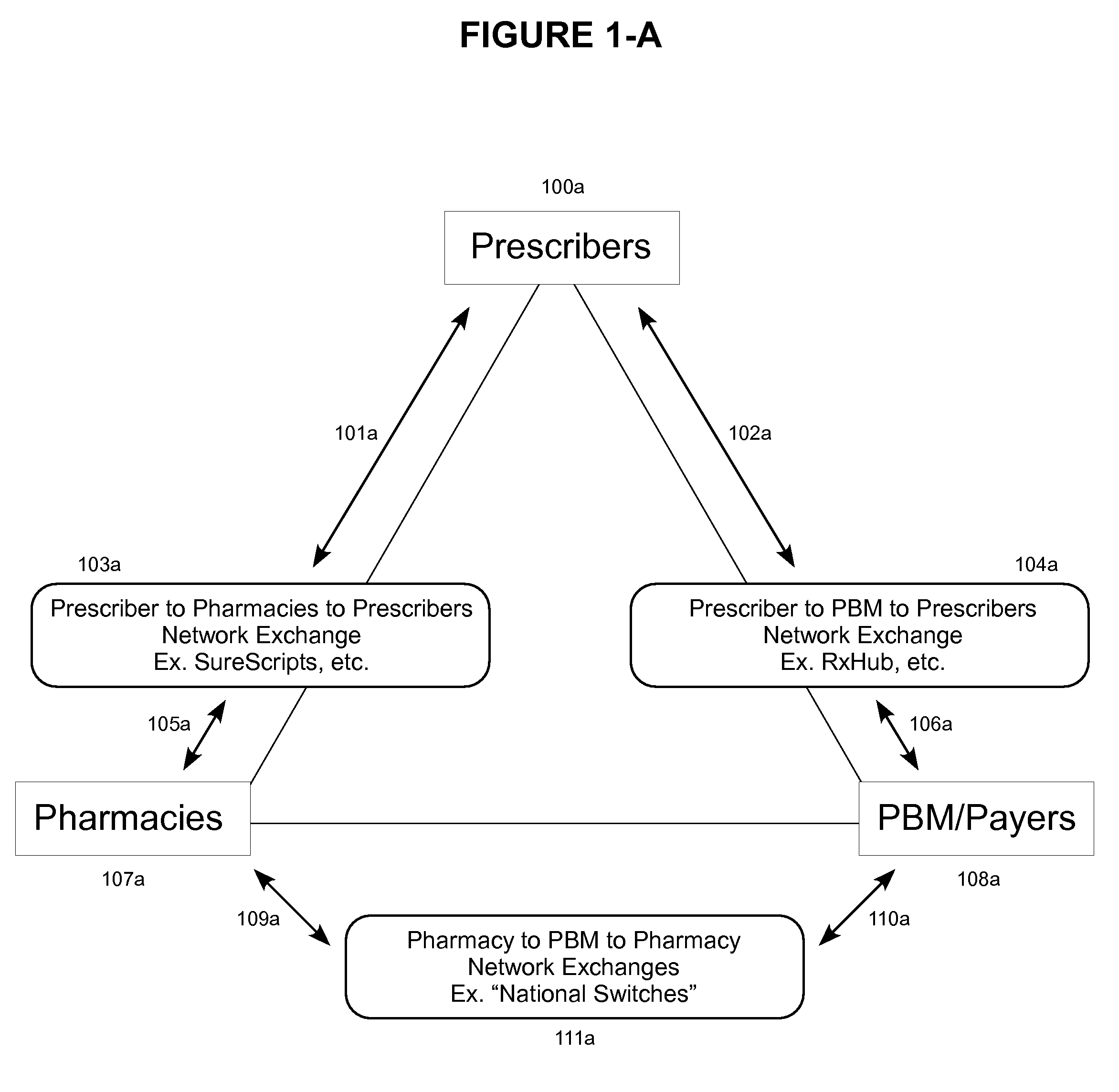
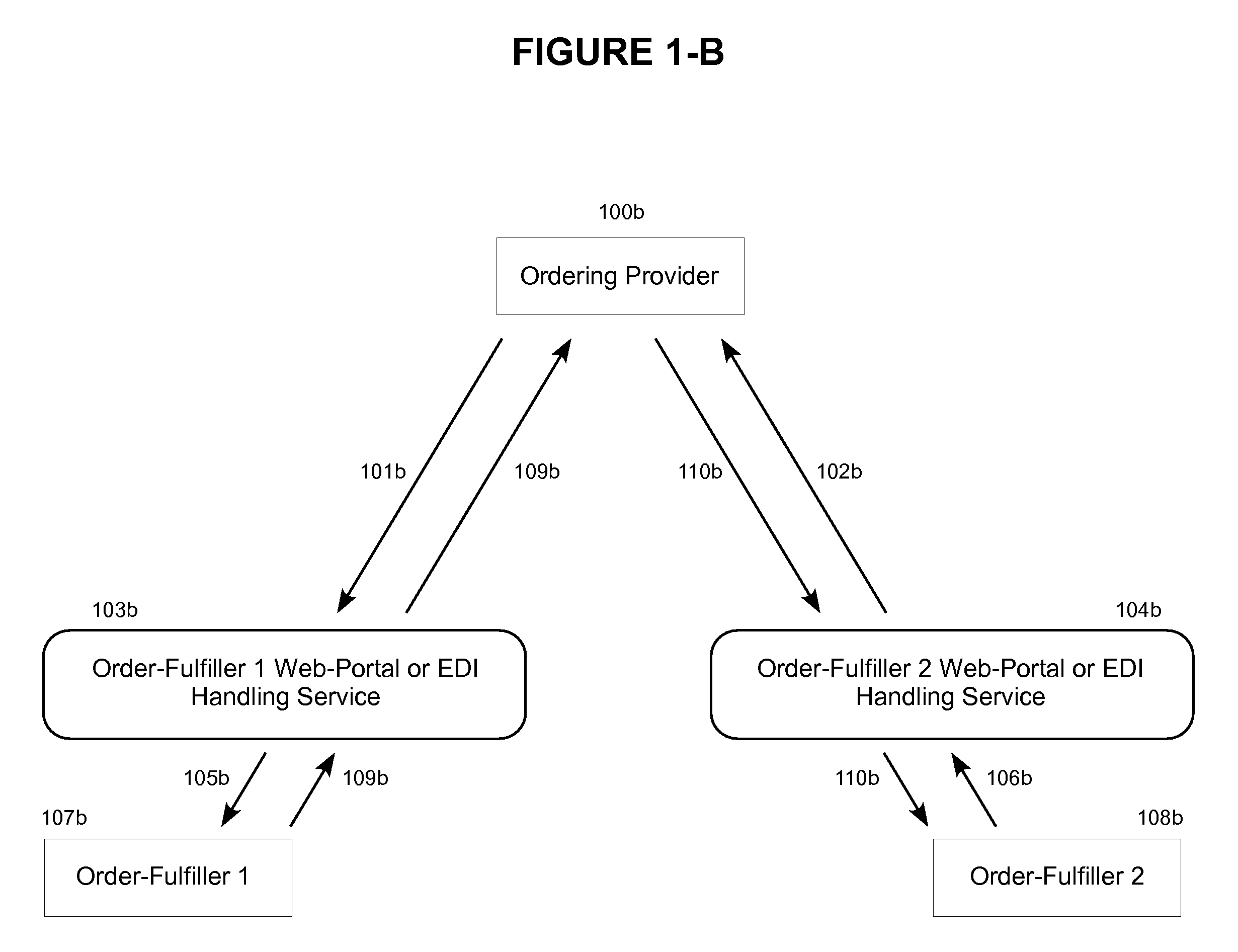
Method and System for Routing Orders and Results
InactiveUS20090198520A1Improve abilitiesEasily damagedCommerceOrder fulfillmentObjective information
The temporary medical orders and results transactions repository that intercepts Business-to-Business (B2B) electronic communications from Point “A” (source and / or creator) to Point “B” (electronic communication recipient, address, name and / or destination) to allows handling of outpatient medical-orders where Point “B” doesn't have to be defined at Point “A” (while the medical-order is being created); allowing creation of electronic orders at Point “A” without knowledge of where or who is Point “B” and delegating the designation of Point “B” to another party, other than the original medical-order creator. In this way, the choice of products and / or service providers is defined without medical order-creator intervention and / or influence; all WITHOUT the need of Unique IDs (UID, GUID or the like).The repository intercepts orders to be temporarily saved in the repository, either by business-rule, lack of destination information, or orders sent to the repository as destination,.Order-fulfillers “claim” (route to themselves, etc.) unclaimed orders, limited to their line-of-work, using patient and / or order-creator properties or parameters to identify and select the correct order based on search engine, common database modalities and master patient / person index technologies available freely, as open source, or a combination, and once orders have been delivered to the destination, orders are purged after a set of conditions, due dates or fulfillment indicators are reached.
Owner:PIOVANETTI PEREZ DR JOSE E
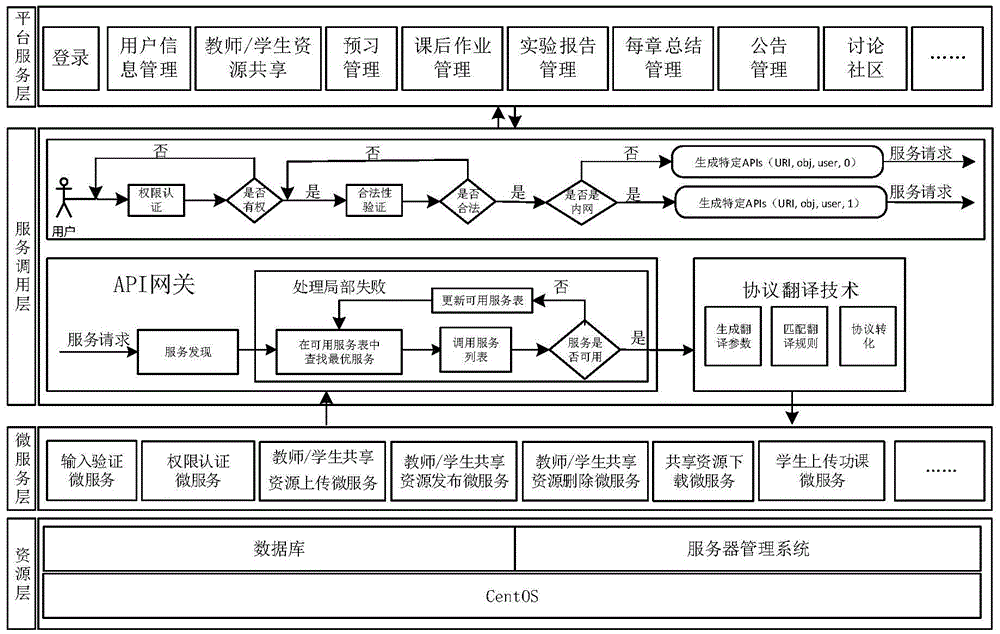
College teaching cloud platform based on micro services
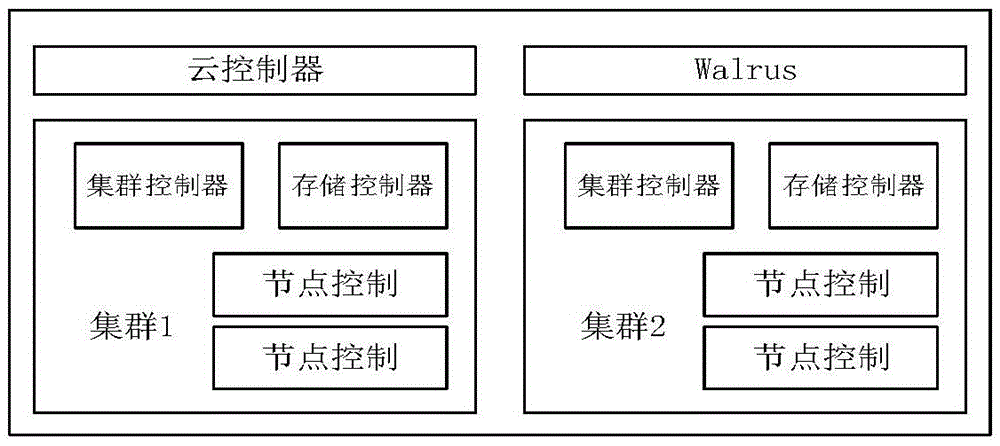
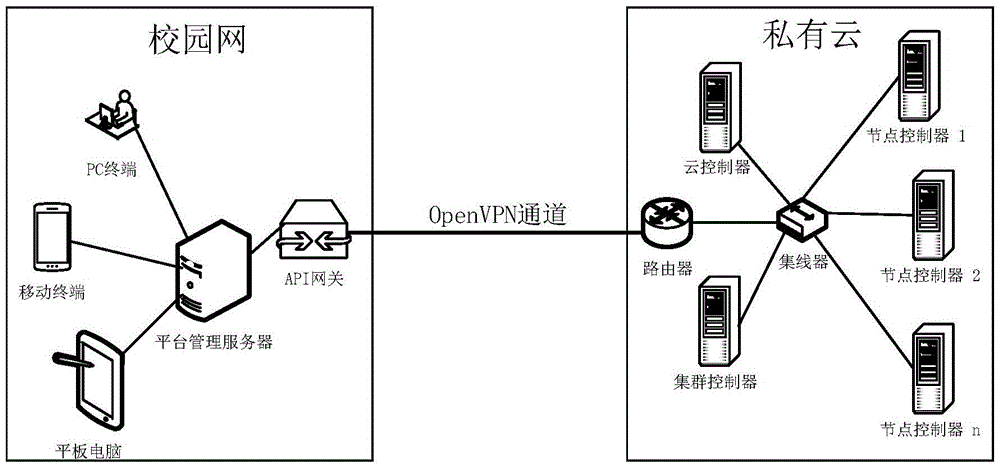
InactiveCN105577780AFast and efficient deliveryImprove efficiencyTransmissionPrivate networkOpen source
The invention discloses a college teaching cloud platform based on micro services. A campus network and private cloud are combined through a virtual private network to build a cloud platform, and a micro service architecture is utilized to build services of the cloud platform; using an open source project Eucalyptus developed by the Department of Computer Science of the University of California to set up private cloud; and all requests of a client first pass through an API gateway, then the API gateway routes the requests to appropriate micro services, and generally the APT gateway calls a plurality of micro services and merges a result to process a request. According to the invention, the micro service architecture is used for the college teaching cloud platform, application of the teaching cloud platform is decoupled into micro services of different functions, thereby enabling each link of teaching to be called in a micro service mode, the response is quick, and the efficiency is high; and the private cloud and the campus network are connected through the virtual private network to form the college teaching cloud platform, thereby providing better resource sharing for teachers and students, and the college teaching cloud platform has good elasticity and expansibility.
Owner:WUHAN UNIV OF TECH
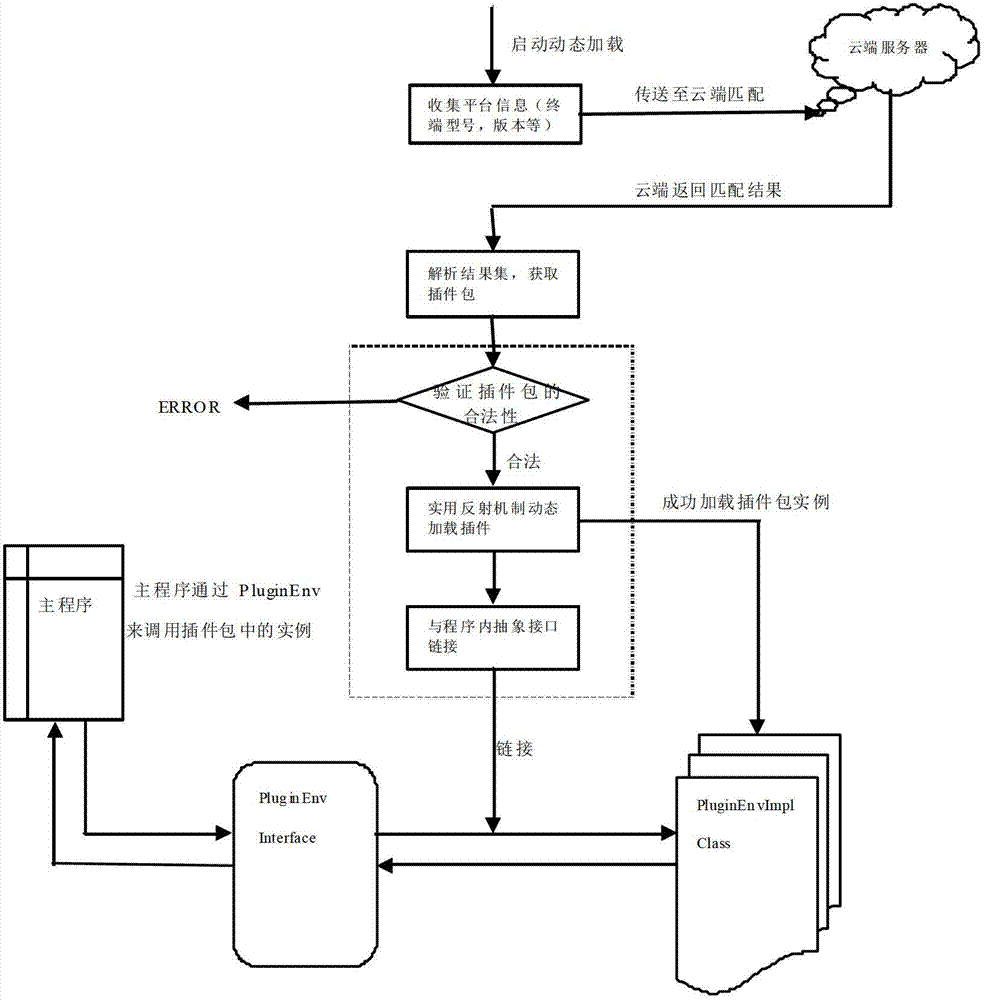
Plug-in loading method and system
ActiveCN102830992AGuaranteed uptimeReduce workloadProgram loading/initiatingTransmissionOperational systemOpen source
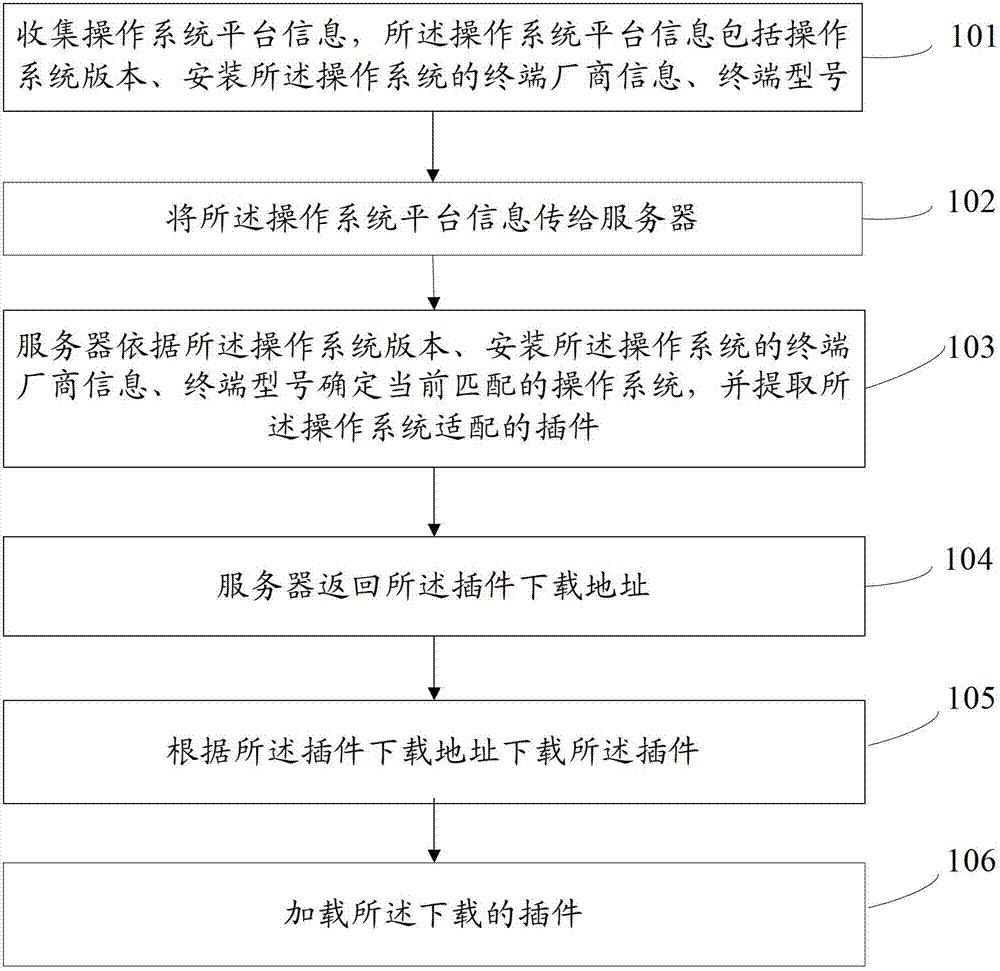
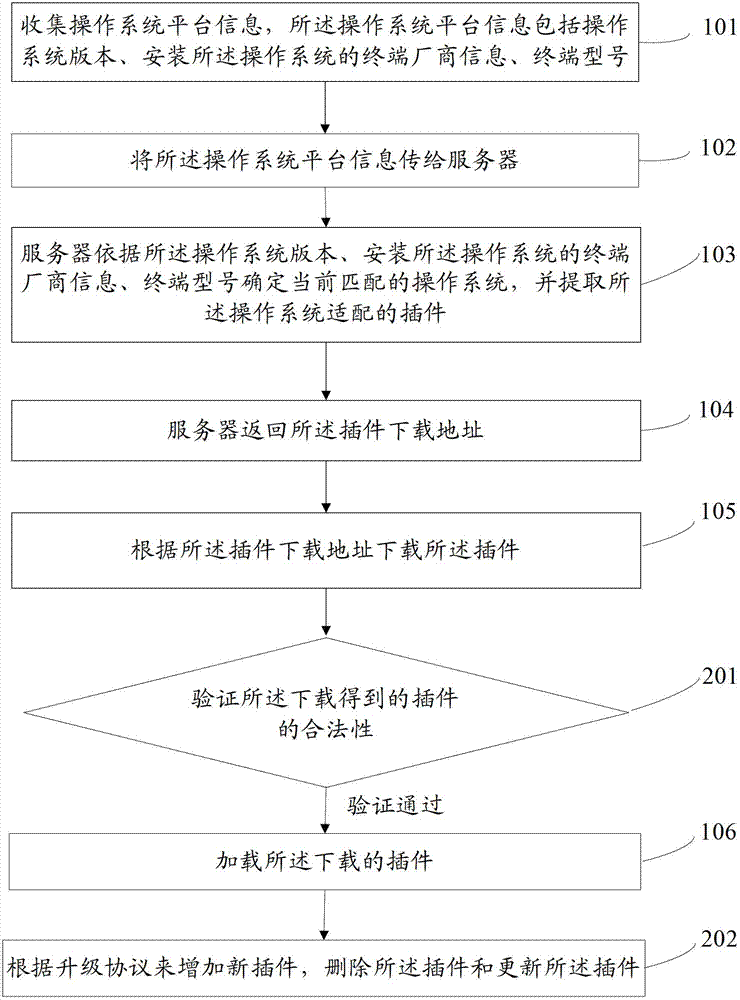
The invention provides plug-in loading method and system. The method includes: collecting information of an operating system platform, which includes operating system version, information of a terminal manufacturer installing operating systems, and terminal type; transmitting the information of the operating system platform to a server; allowing the server to determine a current matching operating system according to the operating system version, the information of the terminal manufacturer installing the operating systems, and the terminal type, and extracting plug-ins adaptive to the operating system; allowing the server to return a download location for the plug-ins; downloading the plug-ins according to the download location for the plug-ins; and loading the downloaded plug-ins. The downloaded plug-ins can be compatible with the operating system loading the plug-ins, normal operation of the loaded plug-ins can be guaranteed, the plug-ins are applicable to various open-source operating systems, and workload in adaption development is reduced.
Owner:BEIJING QIHOO TECH CO LTD +1
Method and device for automatic installation and deployment of hadoop platform
ActiveCN104317610ASolve the problem of differentiationShorten installation and deployment timeProgram loading/initiatingOpen sourceBig data management
The invention provides a method and a device for automatic installation and deployment of a hadoop platform. The method comprises the following steps of storing installation packages in different release versions and in different version numbers in a yum installation server according to directory hierarchy; allowing hadoop version configuration files in different release versions and in different version numbers to form configuration list information according to the directory hierarchy, storing the configuration list information on a big data management platform, and storing repo installation source files and a hadoop service directory list under a version number directory layer; running the big data management platform and uploading the configuration list information; creating a cluster and selecting a hadoop release version and a version number; allowing hosts to join the cluster, and distributing the repo installation source files to the hosts; selecting a hadoop service; configuring necessary parameters of the hadoop service; generating installation and start task information by using the big data management platform, and sending the installation starting task information to each host by using the big data management platform; allowing each host to acquire a software installation package of the corresponding hadoop service and automatically install and start each service according to the installation and start task information. The method and the device solve the problem of differentiation and are universally applied to installation of various open source editions.
Owner:FUJIAN NEWLAND SOFTWARE ENGINEERING CO LTD
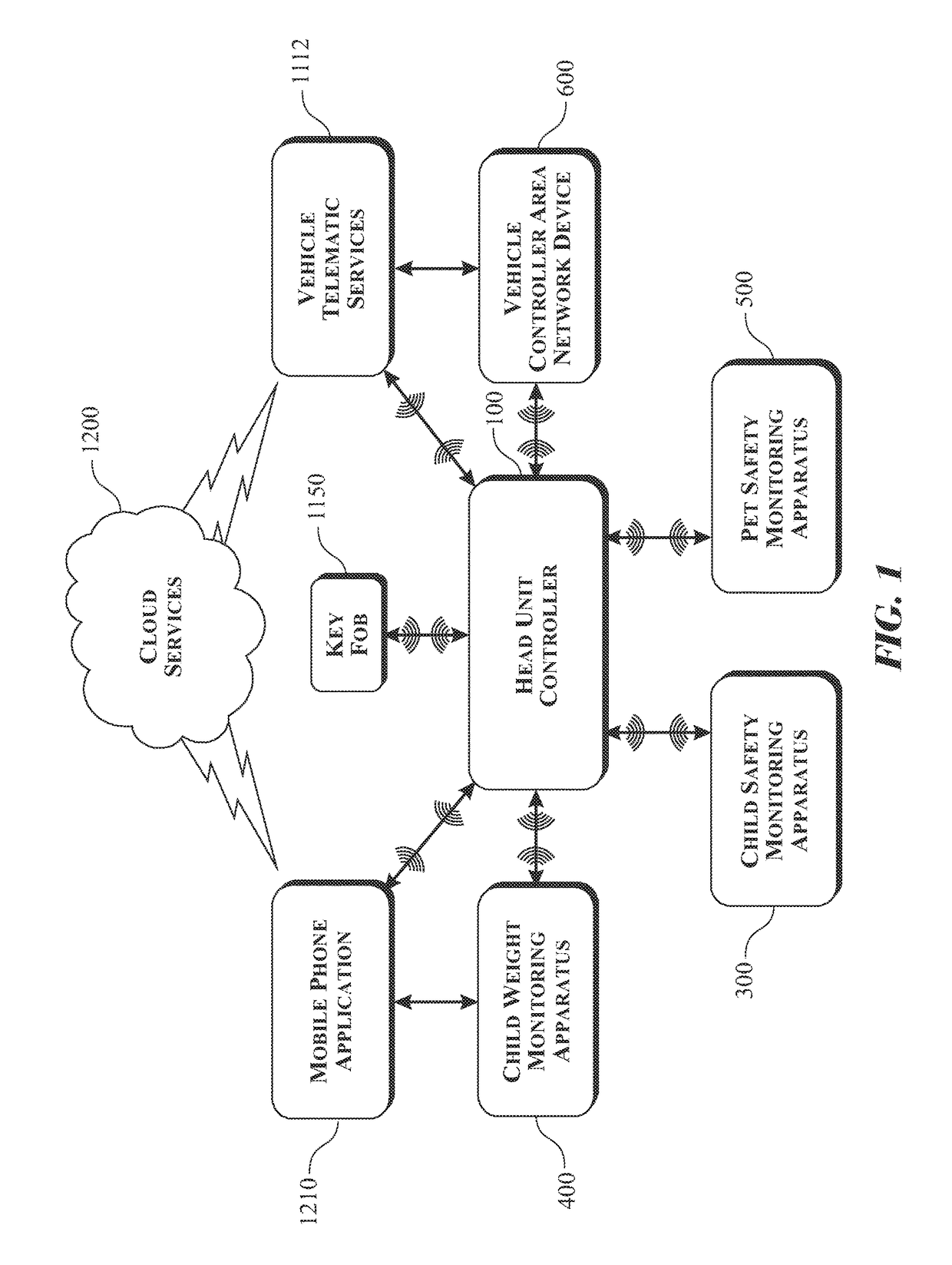
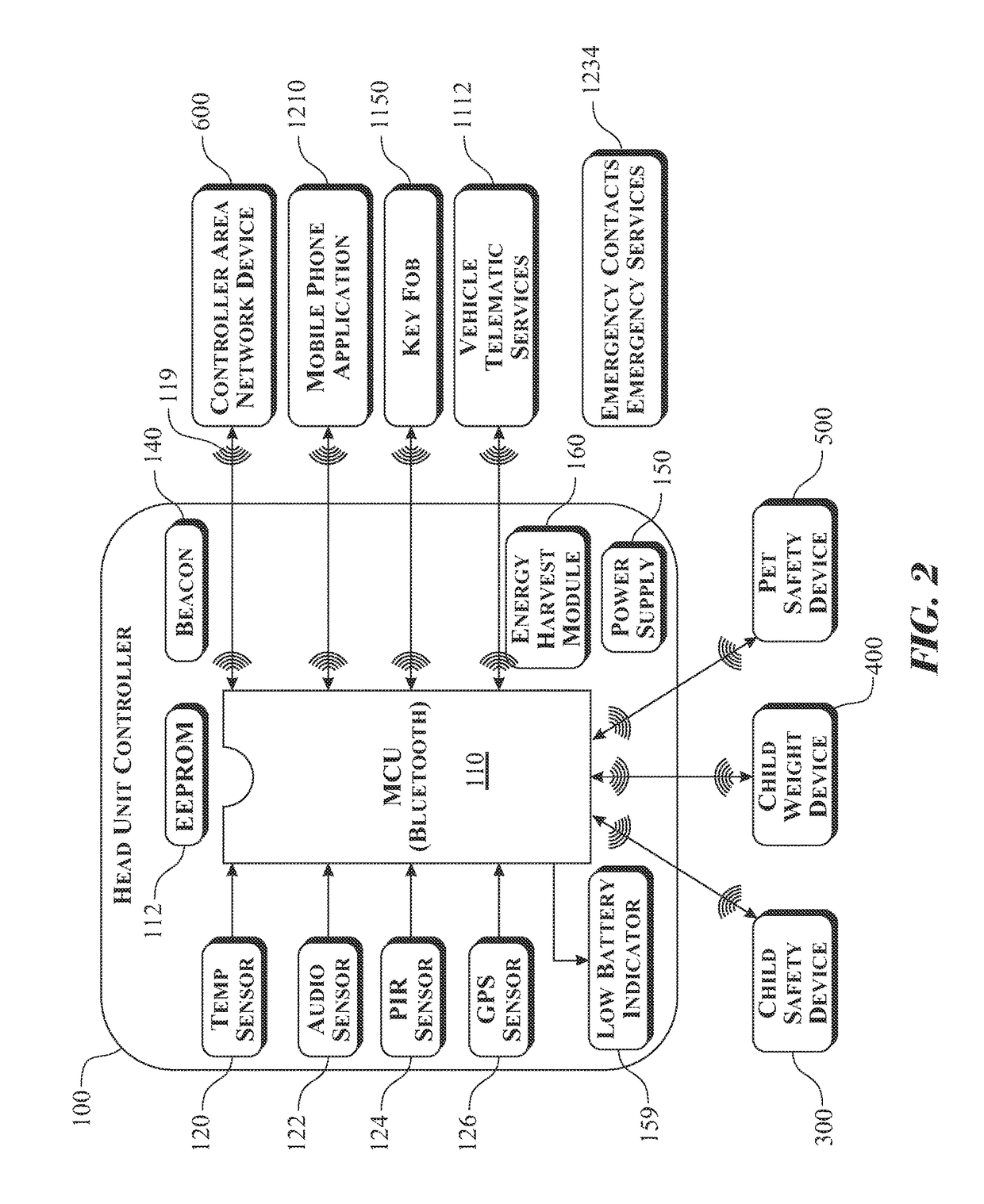
Intelligent vehicle occupancy monitoring system
InactiveUS9845050B1Extended service lifeExtend lifetime of battery packEmergency connection handlingParticular environment based servicesDriver/operatorArea network
A Bluetooth based vehicular internal monitoring device for preventing or mitigating the likelihood of leaving a living entity behind within an unattended vehicle with an interior exhibiting life threatening environmental conditions. The system leverages ultra-low powered micro sensors, and open source communication systems to convey data acquired by a number of remote monitoring apparatuses and a head unit controller. The system is activated using a remote controller area network device attached to the factory installed controller area network system to detect the presence of a driver or caregiver exiting the vehicle when the living entity is present within the vehicle. Should the driver side door open with the living entity within the vehicle, the head unit controller alarms to notify the driver of such. Integration with vehicle telematic services enables delivery of alerts and information to parents, caregivers, emergency contacts, and emergency responders.
Owner:GARZA STEVEN P +1
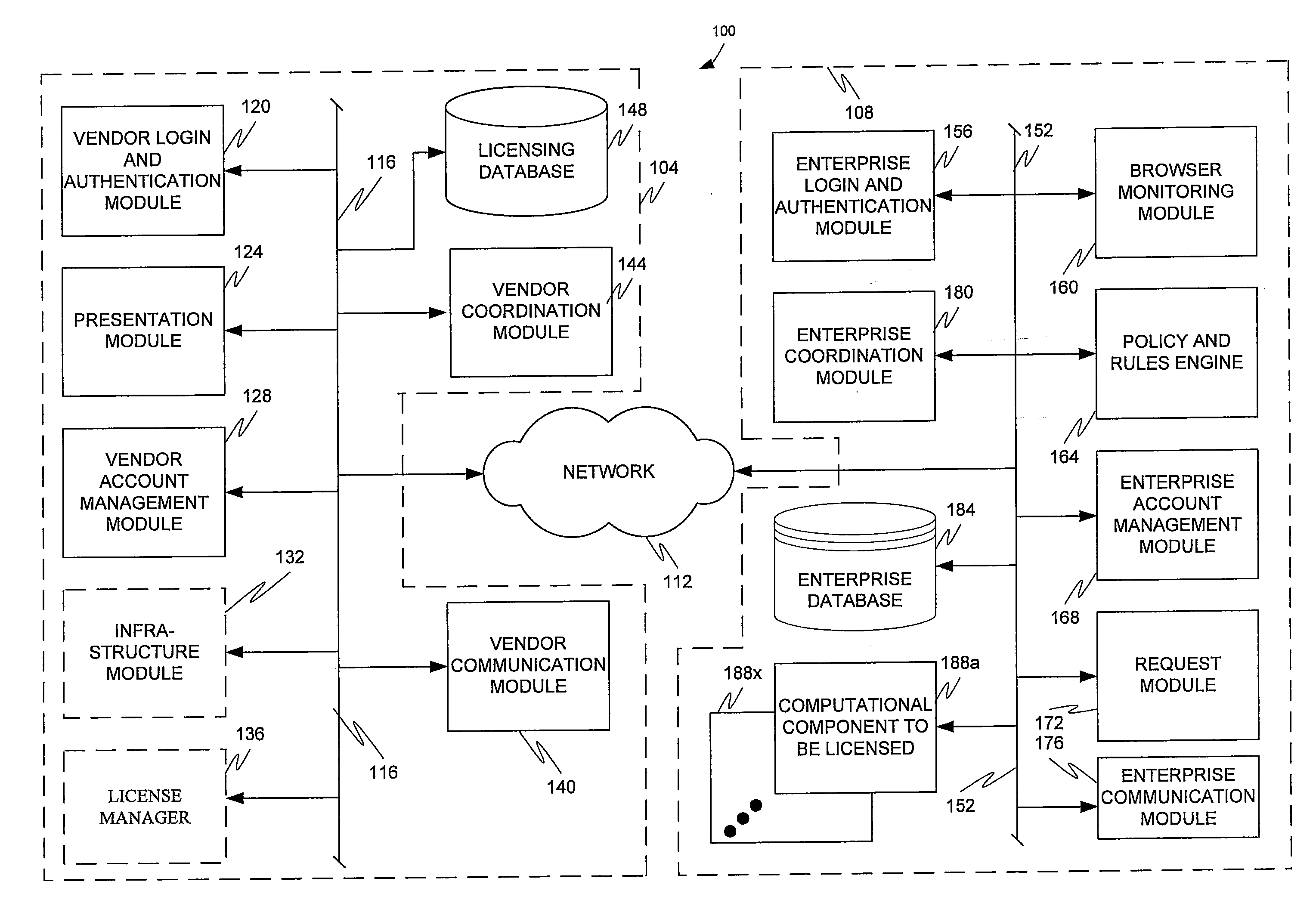
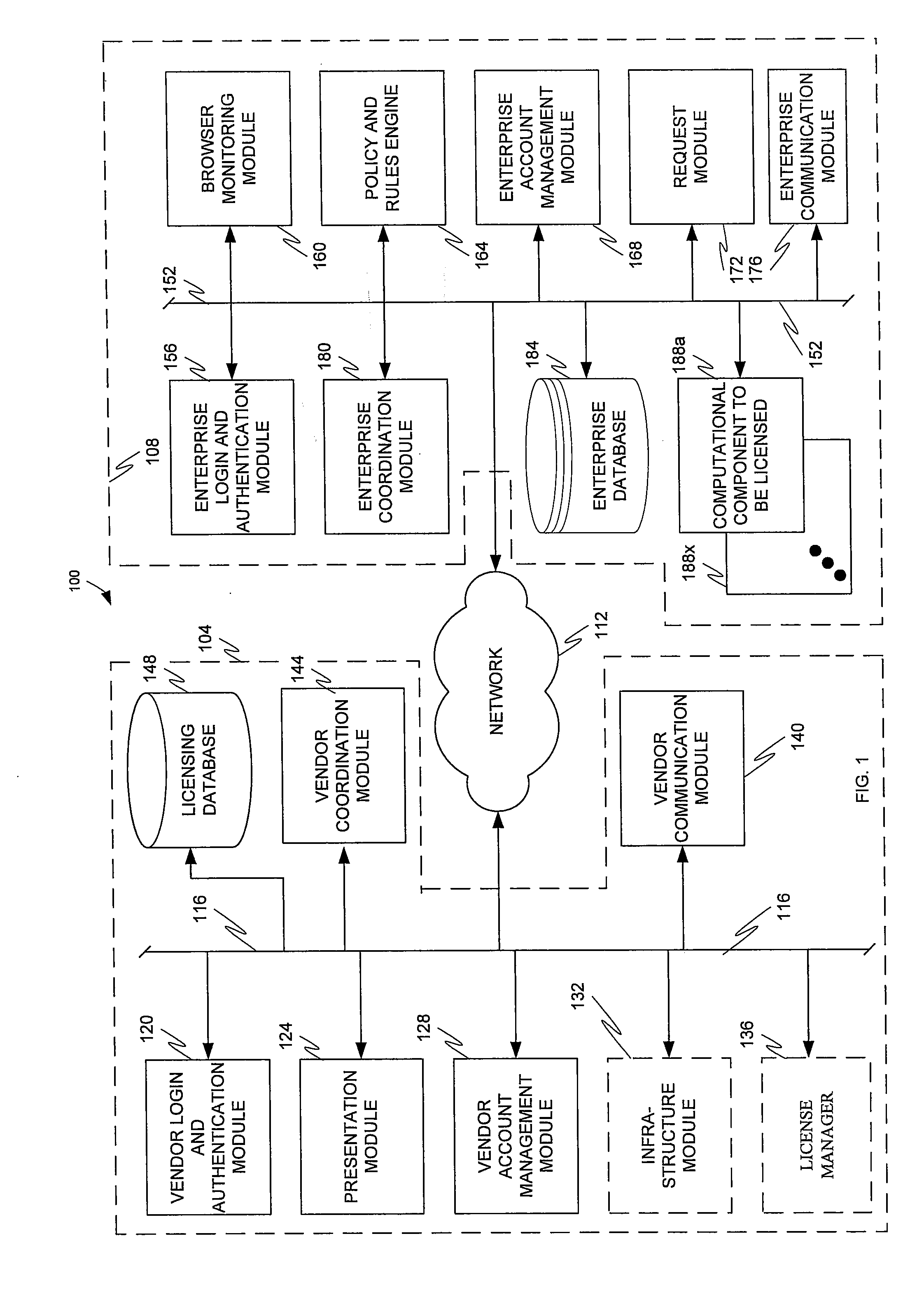
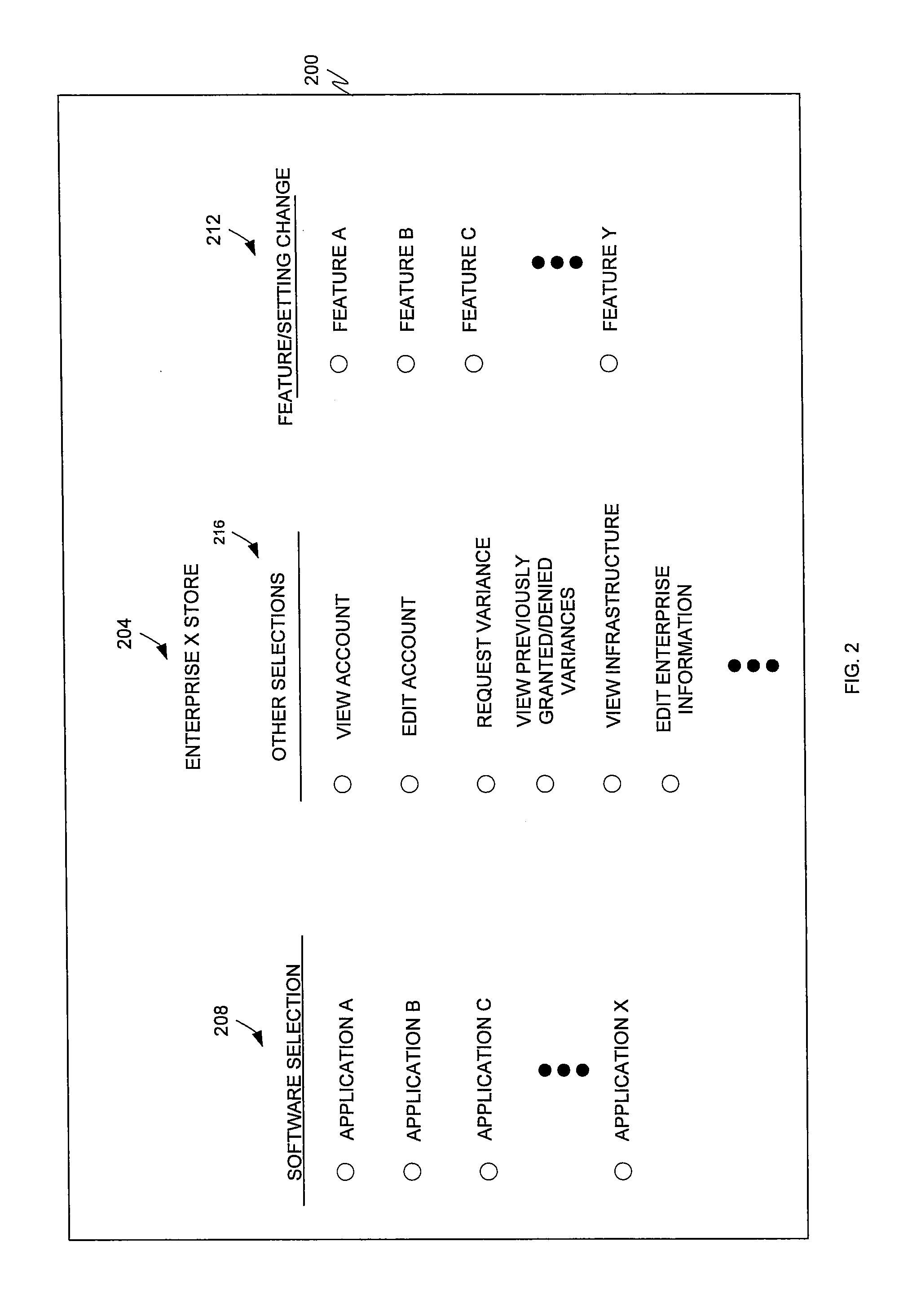
Application and open source information technology policy filter
ActiveUS20110302623A1The process is simple and convenientQuickly and efficiently locating and purchasingComputer security arrangementsTransmissionSoftware distributionOpen source
The present invention is directed to a software distribution architecture in which an enterprise has a filter that screens user requested software, software upgrade(s), software feature(s), and / or software setting option(s) against enterprise rules or policies. Disapproved software, software upgrade(s), software feature(s), and / or software setting option(s) are blocked for download.
Owner:AVAYA INC
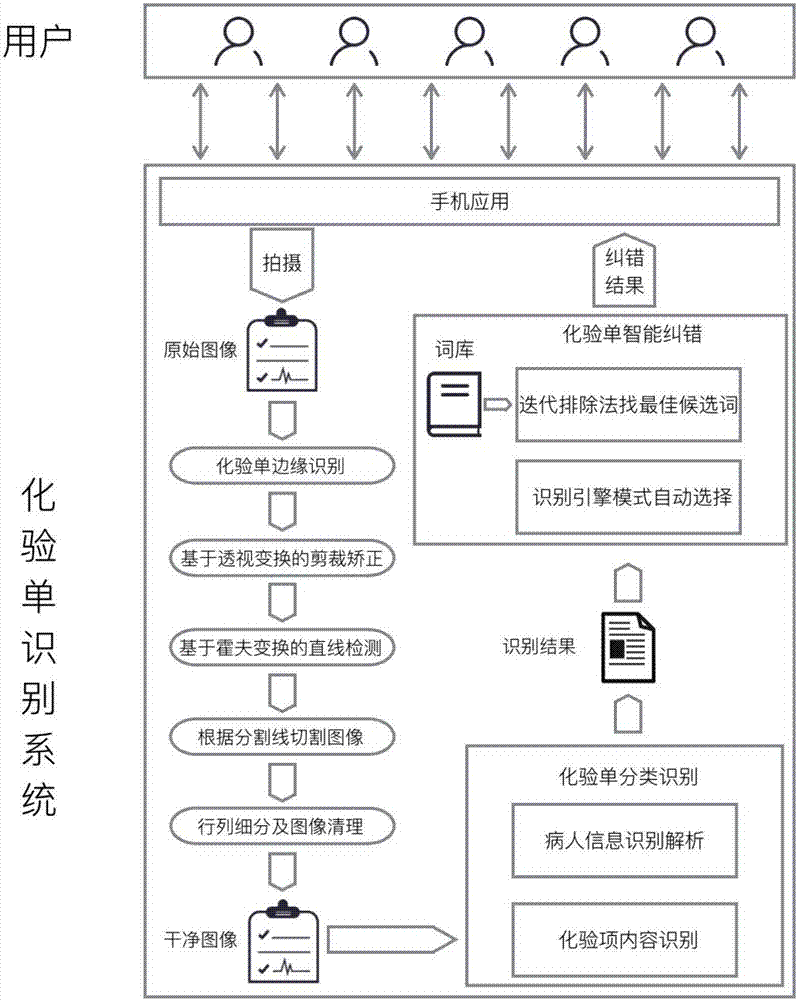
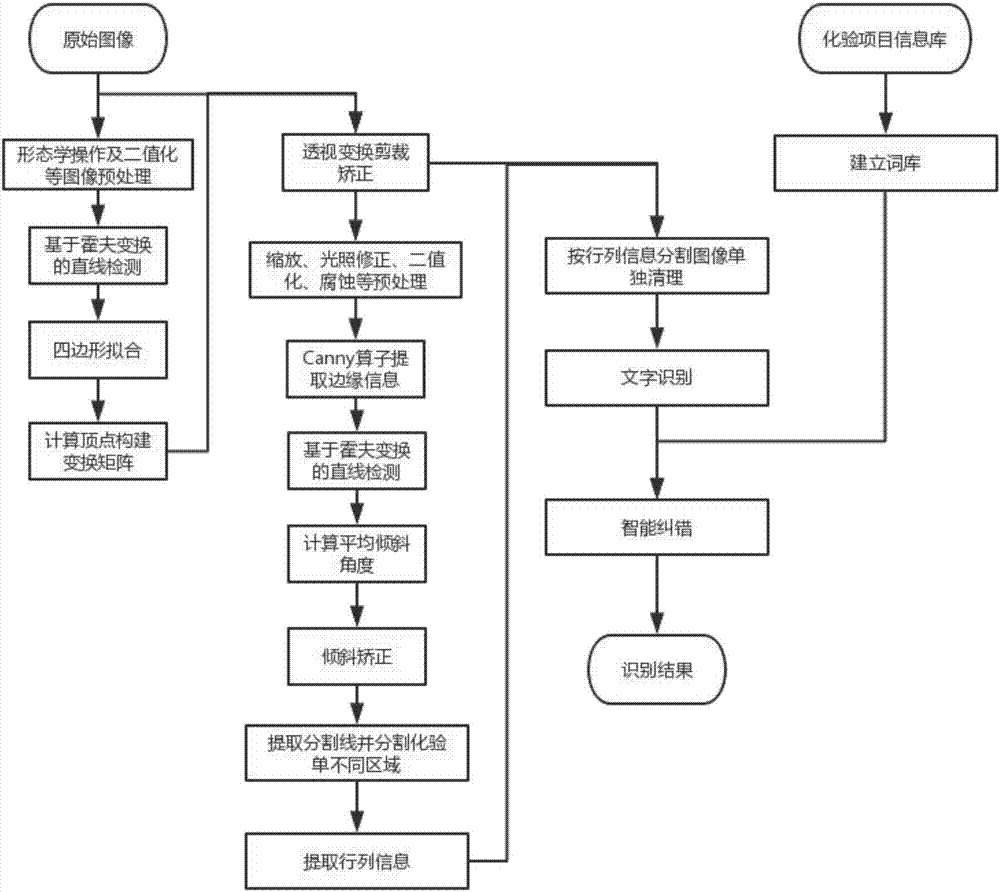
Laboratory-sheet identification method based on image processing
InactiveCN107491730AImprove reliabilityImprove accuracySpecial data processing applicationsCharacter recognitionImaging processingOpen source
The invention discloses a laboratory-sheet identification method based on image processing. According to the method, a set of algorithms which can accurately divide each area of a laboratory sheet and carry out effective cleaning are designed through investigation and analysis on a laboratory-sheet structure, how to process a laboratory-sheet photograph, which is shot by a mobile phone, step by step to finally obtain a clear image is standardized and subdivided, and a mature open-source OCR engine is used for identification; in each stage of a laboratory-sheet image processing process, the method makes thorough consideration, optimizes the performance, and improves the efficiency of image processing; and after identification, a laboratory-sheet item lexicon established by utilizing a laboratory test item information database by the method realizes automatic selection for identification engine modes and intelligent error correction for an identification result, and improves the accuracy of the laboratory-sheet identification result.
Owner:ZHEJIANG UNIV
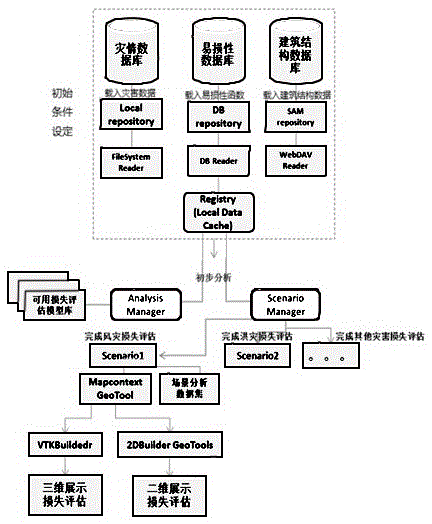
Urban multi-disaster risk loss evaluation system based on open source system framework and building spatial database and method thereof
InactiveCN105654414AImplement the buildLow costData processing applicationsICT adaptationEclipseEngineering
The invention provides an urban multi-disaster risk loss evaluation system based on an open source system framework and a building spatial database. The urban multi-disaster risk loss evaluation system comprises an 1a) MAEviz open source framework development platform based on an Eclipse RCP frame, wherein the MAEviz open source framework development platform is used for extending a flood, wind damage and tsunami disaster loss evaluation module so as to realize multi-disaster urban risk loss evaluation; a 1b) disaster information module which is used for analysis of the risk and the dangerousness of flood, typhoon, earthquake and other natural disasters and evaluation of regional disaster-causing possibility; a 1c) spatial geographic information module which provides a common GIS function so as to realize construction of a localized urban disaster-affected body geographic information system property database; an 1d) urban disaster-affected body type classification and vulnerability analysis module which is used for establishing a building vulnerability module base of typical building structures under different disasters; and a 1e) disaster loss evaluation module which is used for damage prediction of disaster-affected body structures and damage loss evaluation of the disaster-affected bodies.
Owner:ZHEJIANG UNIV CITY COLLEGE
Online-increment evolution topic model based automatic software classifying method
ActiveCN102902700AImplement automatic classificationImprove development efficiencySpecial data processing applicationsAlgorithmWord list
An online-increment evolution topic model based automatic software classifying method includes acquiring relevant software texts, grouping and preprocessing by a preset time slice; generating a probability model of an online evolution topic model, computing the number of the optimum topics according to project description texts grouped according to the time slice, and incrementally computing topic word distribution and topic text distribution of the project description texts within the current time slice; acquiring a text d of an unknown classifying topic, computing topic word distribution of n topics subordinative to the text d according to the topic word distribution and the topic text distribution, classifying the text d into corresponding topics, and automatically adding semantic tags to the topics based on the word list and word inquiry method, and finally completing classification of software projects. By the online-increment evolution topic model based automatic software classifying method, new topics appearing in open source communities can be found in time, software projects can be automatically classified, a software developer can search out required open source software projects according to software topics conveniently, and accordingly, software development efficiency is improved, and quality and assurance of the open source communities are improved.
Owner:NAT UNIV OF DEFENSE TECH
Universal music production system with added user functionality
InactiveUS20100180224A1Electrophonic musical instrumentsInput/output processes for data processingOperational systemOpen source
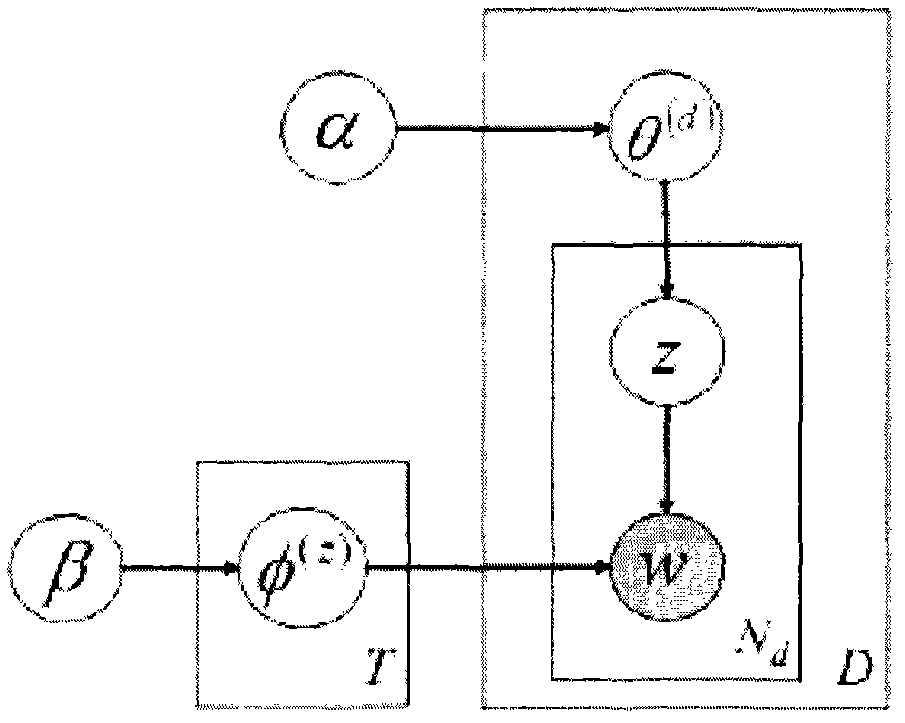
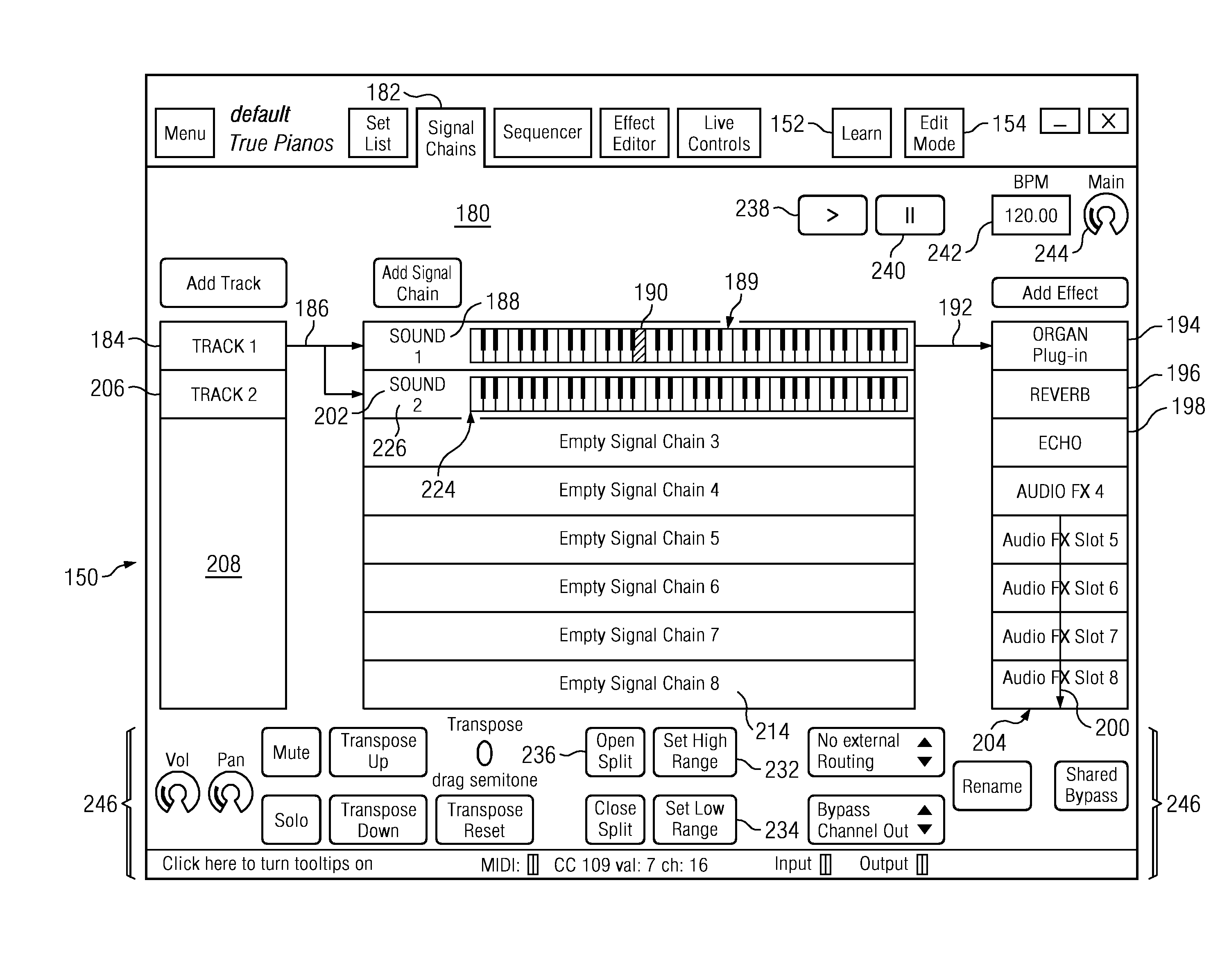
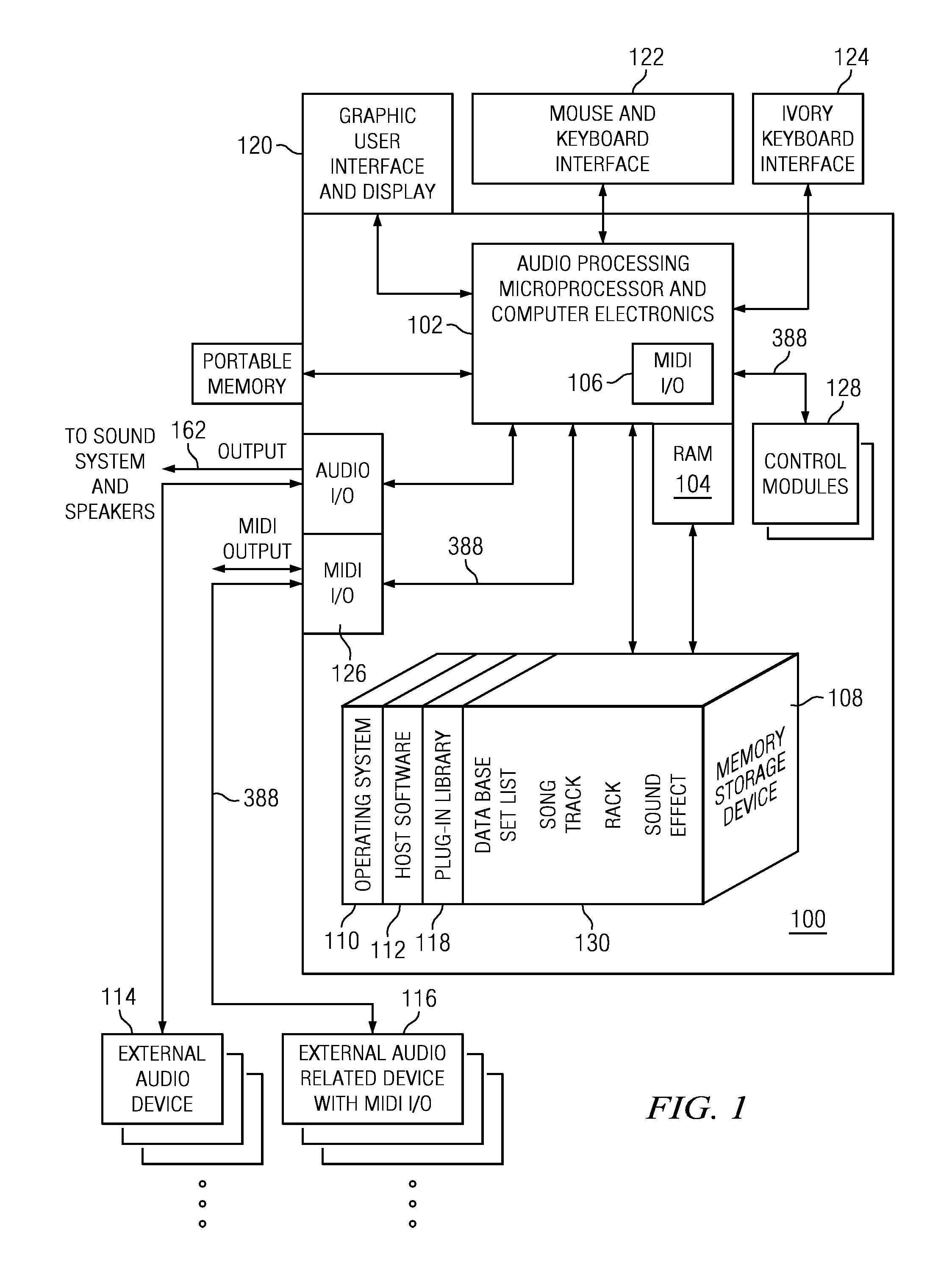
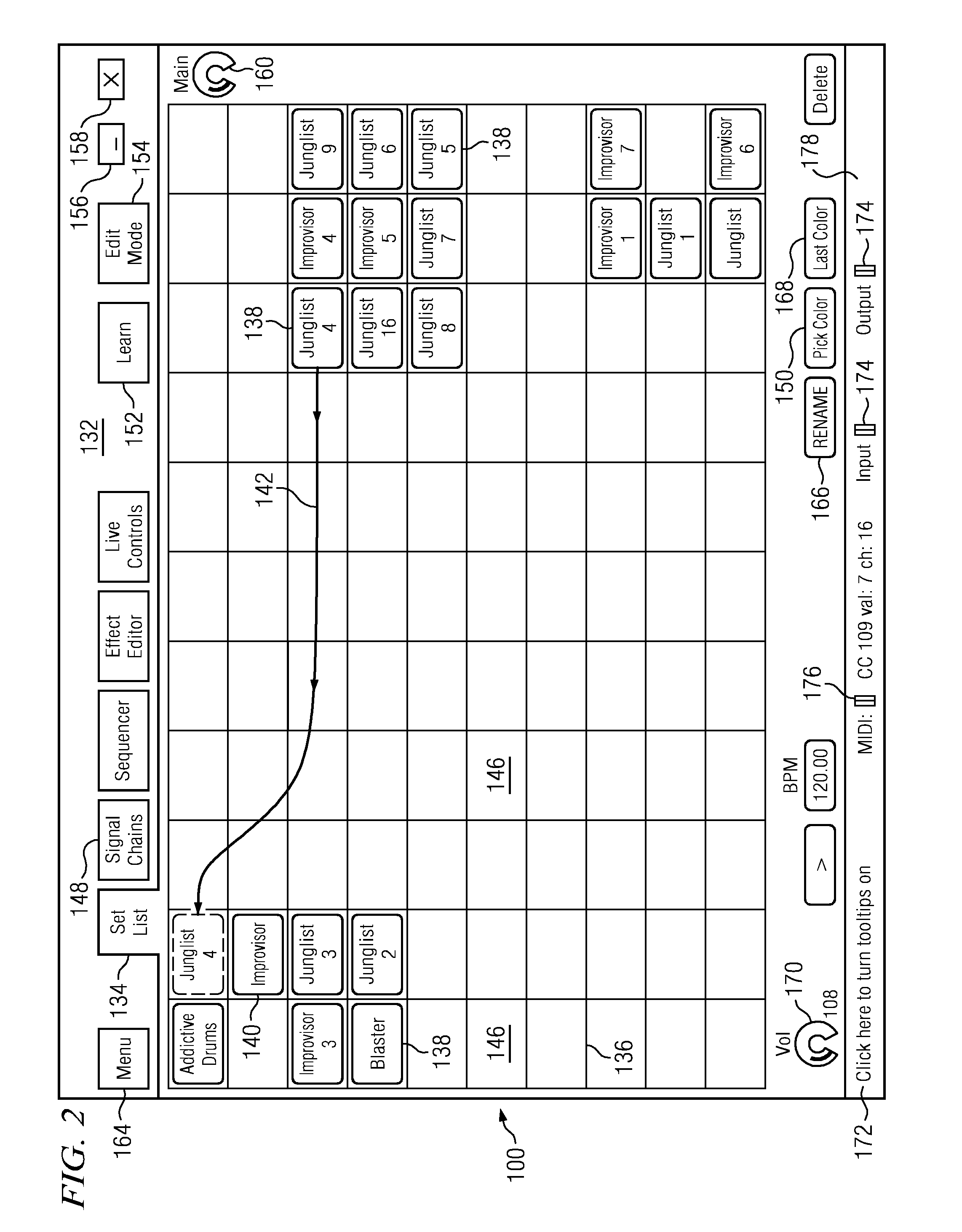
A universal music production system and related software is provided that enables an open source microprocessor and its operating system to provide ergonomic and user friendly control of editing audio processing configurations of one or more systems, instruments or synthesizers in a music studio edit mode environment and then utilize the studio edit mode song / performance configurations in a live mode performance environment that disables the user from certain studio edit mode functions. Ergonomic user functionality for creating ivory keyboard splits is provided. Also a song configuration sustain feature allows sounds generated in a previous song to be held over or sustained while a next song configuration is established and the user begins playing the next song. User created virtual controls can be displayed on a touch sensitive display screen enabling a user to control predetermined sound or performance parameters easily during a live performance. Also, reconfiguration of any or all of the sound signal chains for various sound tracks can be accomplished substantially instantaneously via set list loading of VST instrument and effect plug-ins.
Owner:OPEN LABS
Unmanned aerial vehicle fixed-point flight control system based on visual positioning
ActiveCN106054931AAchieve the purpose of pinpointingGuaranteed correctnessTarget-seeking controlVision processingInformation control
The invention provides an unmanned aerial vehicle fixed-point flight control system based on visual positioning. The system comprises an UAV airborne module, a positioning marker, a ground monitoring module and a communication module. According to the system, through the cooperation with a visual processing algorithm, the UAV fixed-point flight is made by identification information, the disadvantages of low GPS fixed-point flight precision is made up, and the control system uses an open source operating system and a general UAV communication protocol and has good scalability and compatibility. The system can be applied to the UAV logistics, UAV monitoring and other directions.
Owner:NORTH CHINA UNIVERSITY OF TECHNOLOGY
Device virtualization system and method based on Linux containers
ActiveCN105808320ARealize multiplexingAvoid cumbersomeSoftware simulation/interpretation/emulationGNU/LinuxOpen source
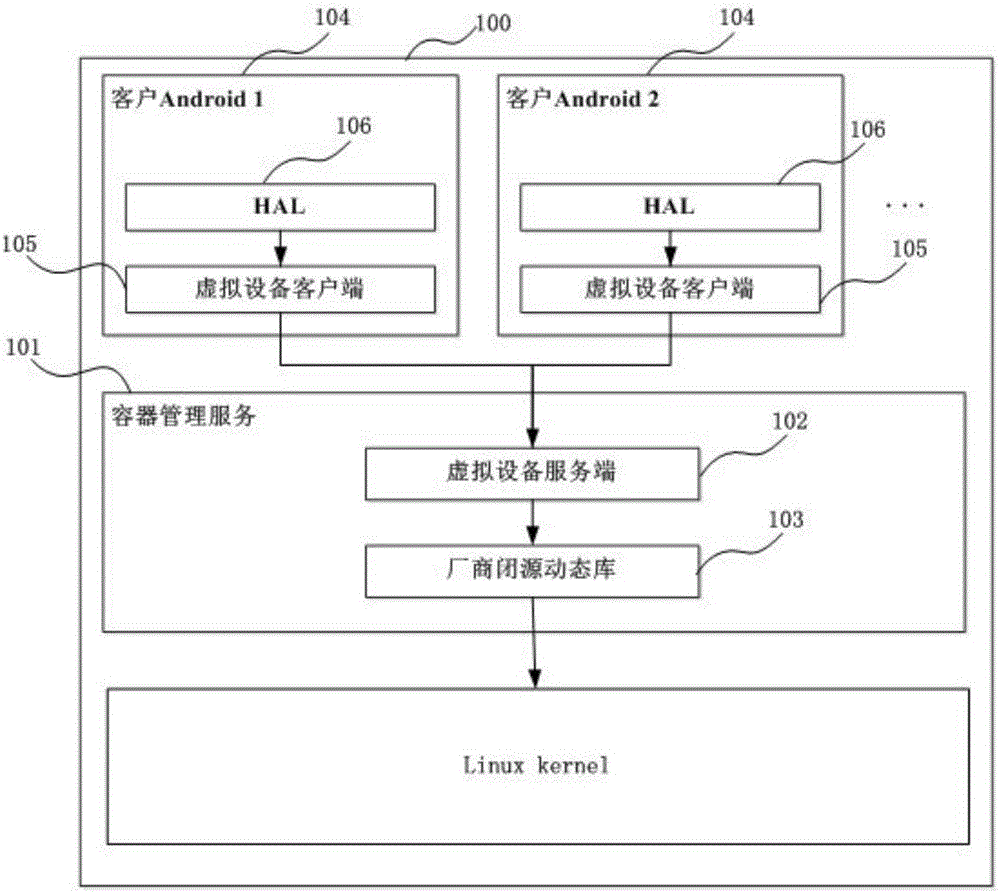
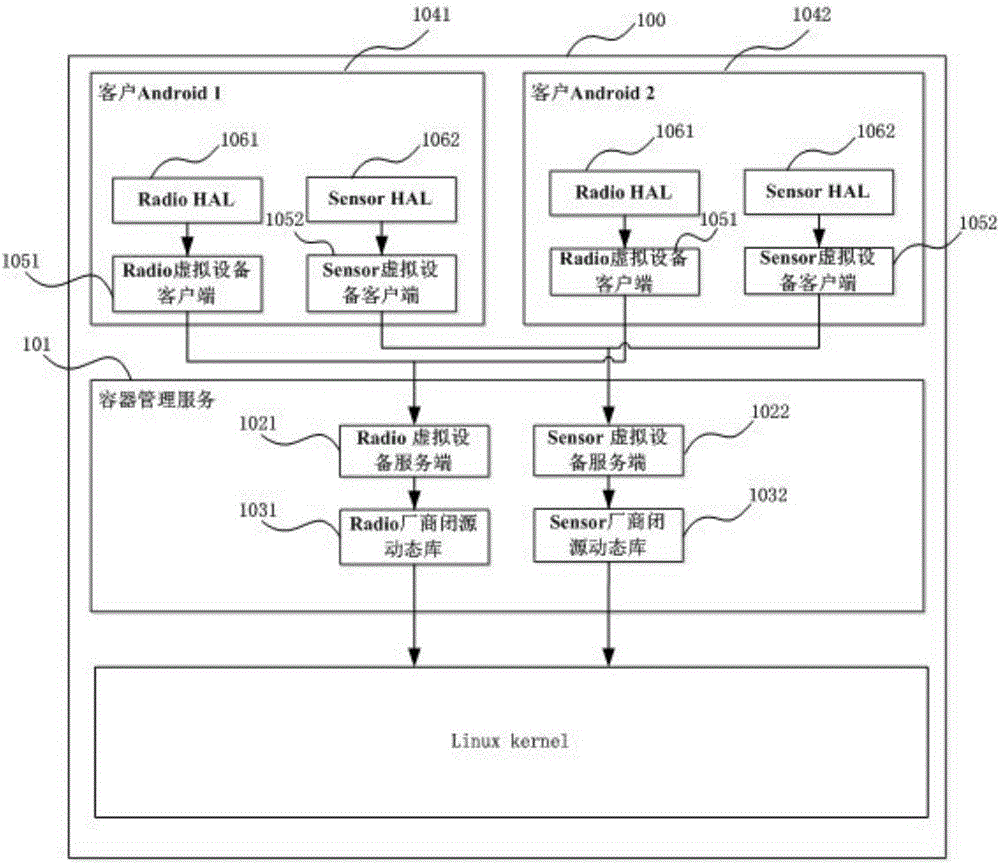
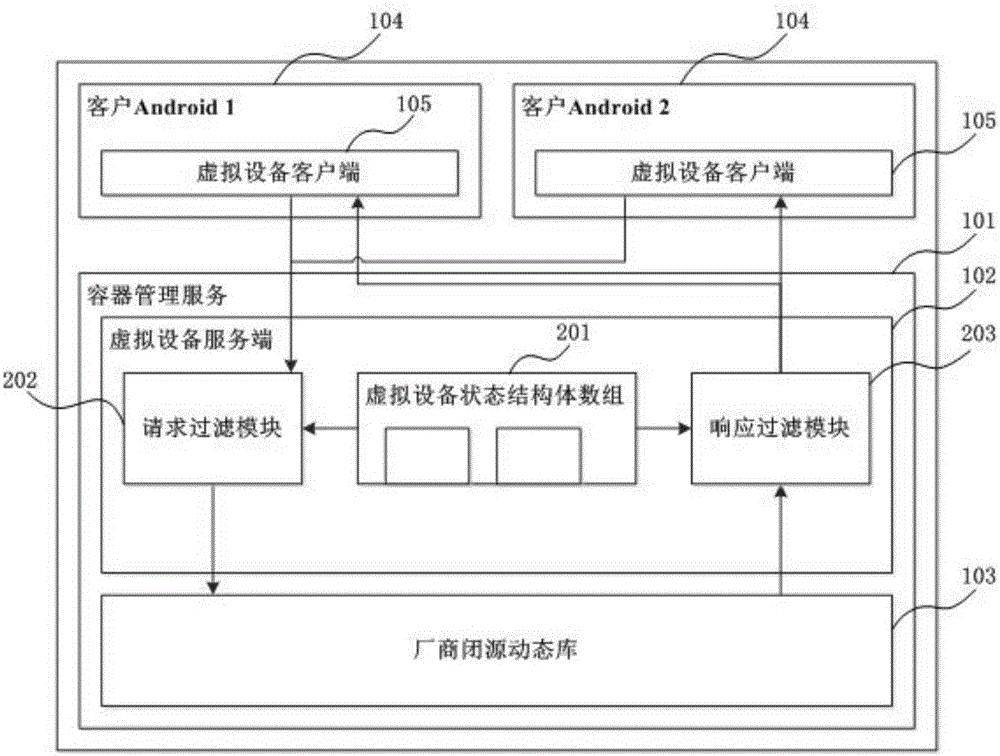
The invention provides a device virtualization system and method based on Linux containers. Virtual device clients and a virtual device server are loaded between Android system HALs and a device subsystem; device operation requests are sent to the virtual device server through the virtual device clients; and then the virtual device server finishes function call in a manufacturer dynamic library, thus realizing agency for the device operations, or constructs device operation results, thus realizing reuse of the device subsystem. According to the device virtualization system and method provided by the invention, through loading the virtual device clients and the virtual device server in multiple Android systems and container management service in a Linux kernel, the agency for the device operations and the reuse of the device subsystem are finished, thus realizing virtualization of the device; a new method different from a traditional device virtualization method is provided; and the reuse of special devices (especially devices without open source code) such as Radios is realized in the multi-Android platform based on a Linux container technique.
Owner:杨霞
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com