Patents
Literature
473 results about "Loader" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
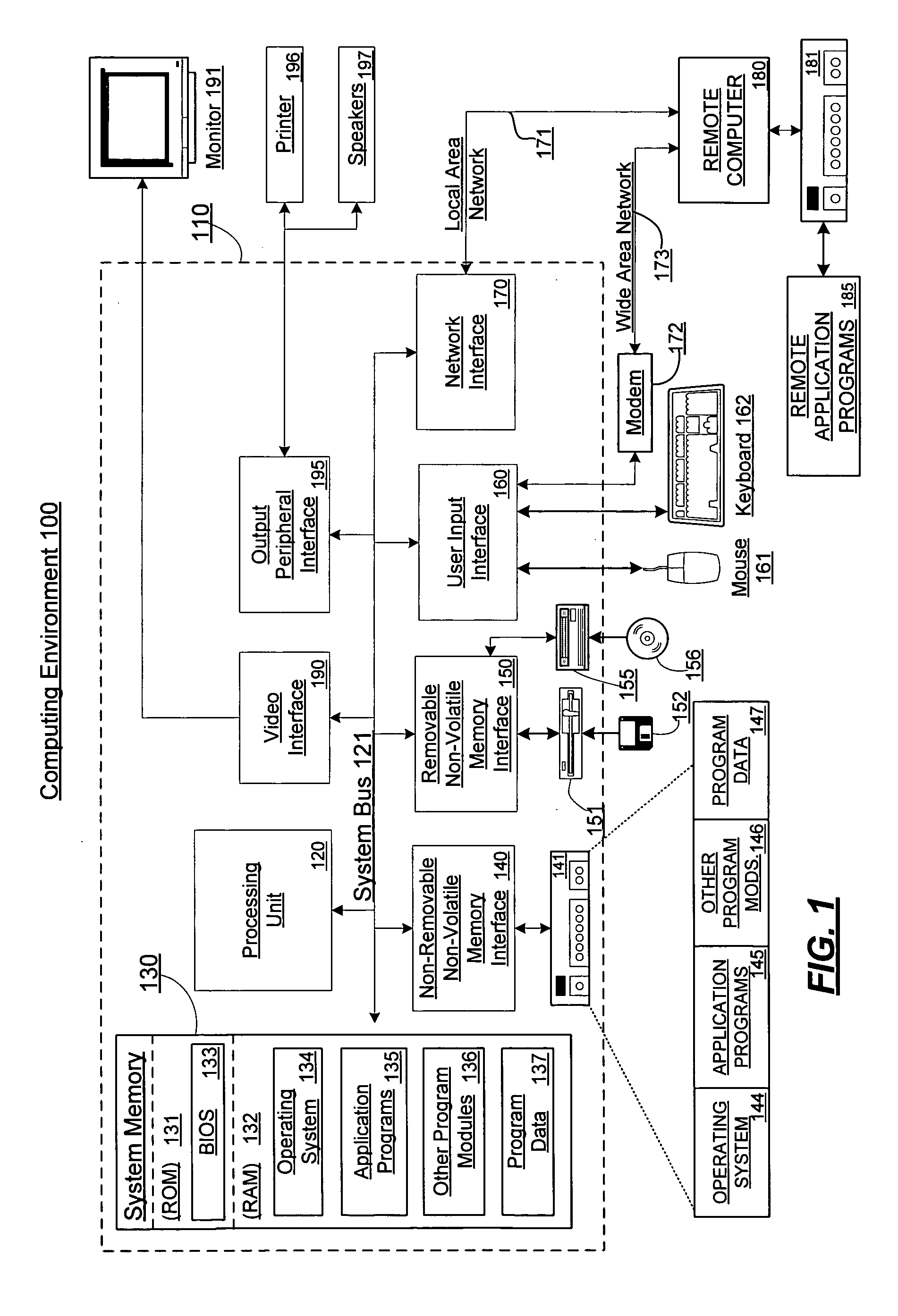
In computer systems a loader is the part of an operating system that is responsible for loading programs and libraries. It is one of the essential stages in the process of starting a program, as it places programs into memory and prepares them for execution. Loading a program involves reading the contents of the executable file containing the program instructions into memory, and then carrying out other required preparatory tasks to prepare the executable for running. Once loading is complete, the operating system starts the program by passing control to the loaded program code.
Method and apparatus for remote installation of an operating system over a network connection
InactiveUS6963981B1More securityMemory loss protectionError detection/correctionOperational systemNetwork connection
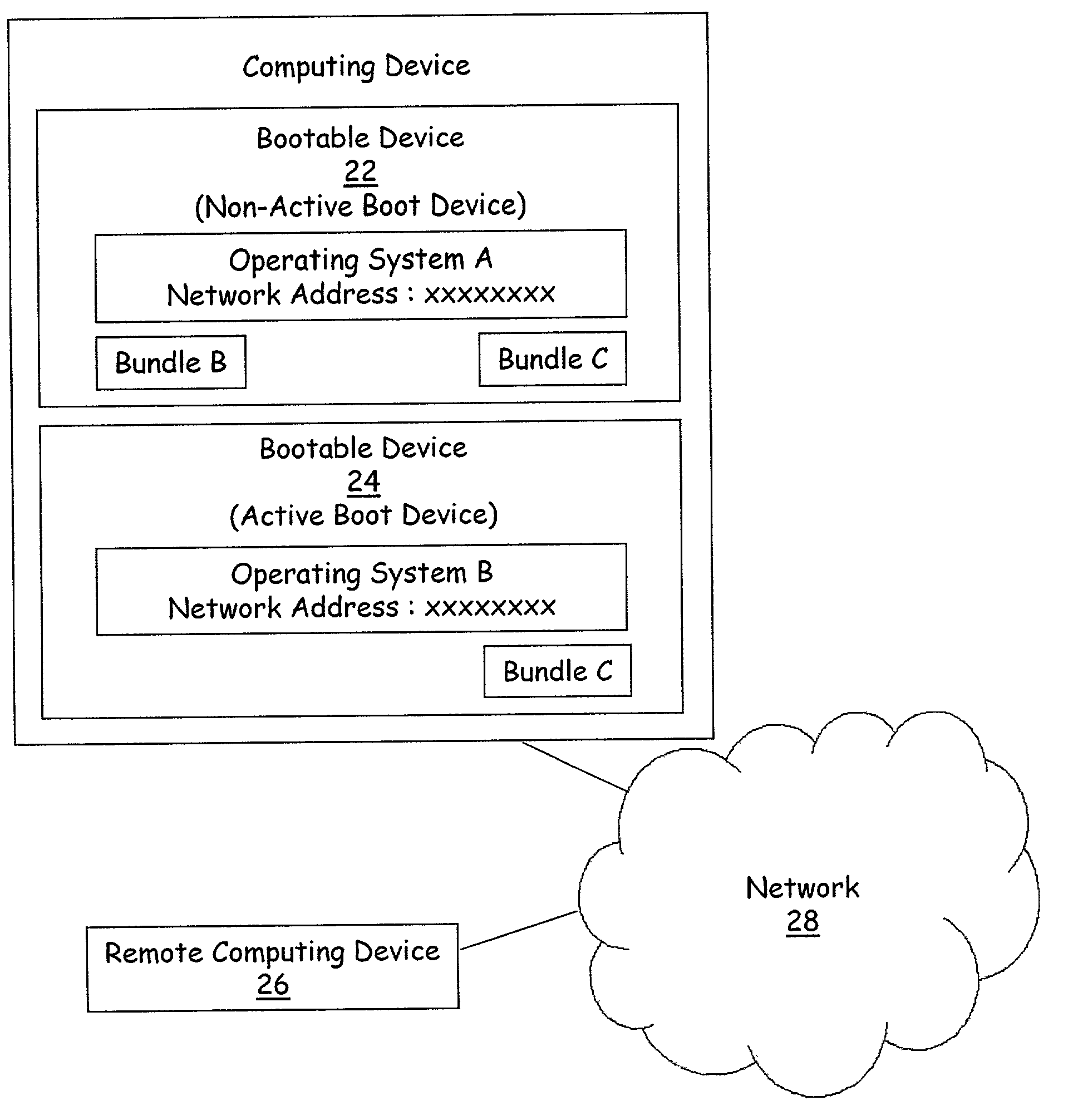
A method for remote installation of a target operating system is carried out on a machine operating a source operating system. In one embodiment, it is presumed that the source operating system was booted from a first bootable region of a storage associated with the machine. According to the method, a copy of the source operating system together with the target operating system are delivered to the machine and stored in a second bootable region of the storage. The copy of the source operating system may be stored in a first partition of the second bootable region of the storage, and the target operating system may be stored in a second partition of the second bootable region. A boot loader is then configured to boot the copy of the source operating system from the second bootable region of the storage. The machine is then re-booted. At this point, the machine is still running the source operating system, although in this case that operating system was booted from the second bootable region of the storage. The original source operating system (from the first bootable region) is then removed, and the boot loader is re-configured to boot the target operating system from the second bootable region of the storage. The machine is then re-booted again, after which the target operating system is operational. In one embodiment, the first and second bootable regions may be separate hard disks, and the source and target operating systems are Linux and Windows, or vice versa.
Owner:AKAMAI TECH INC
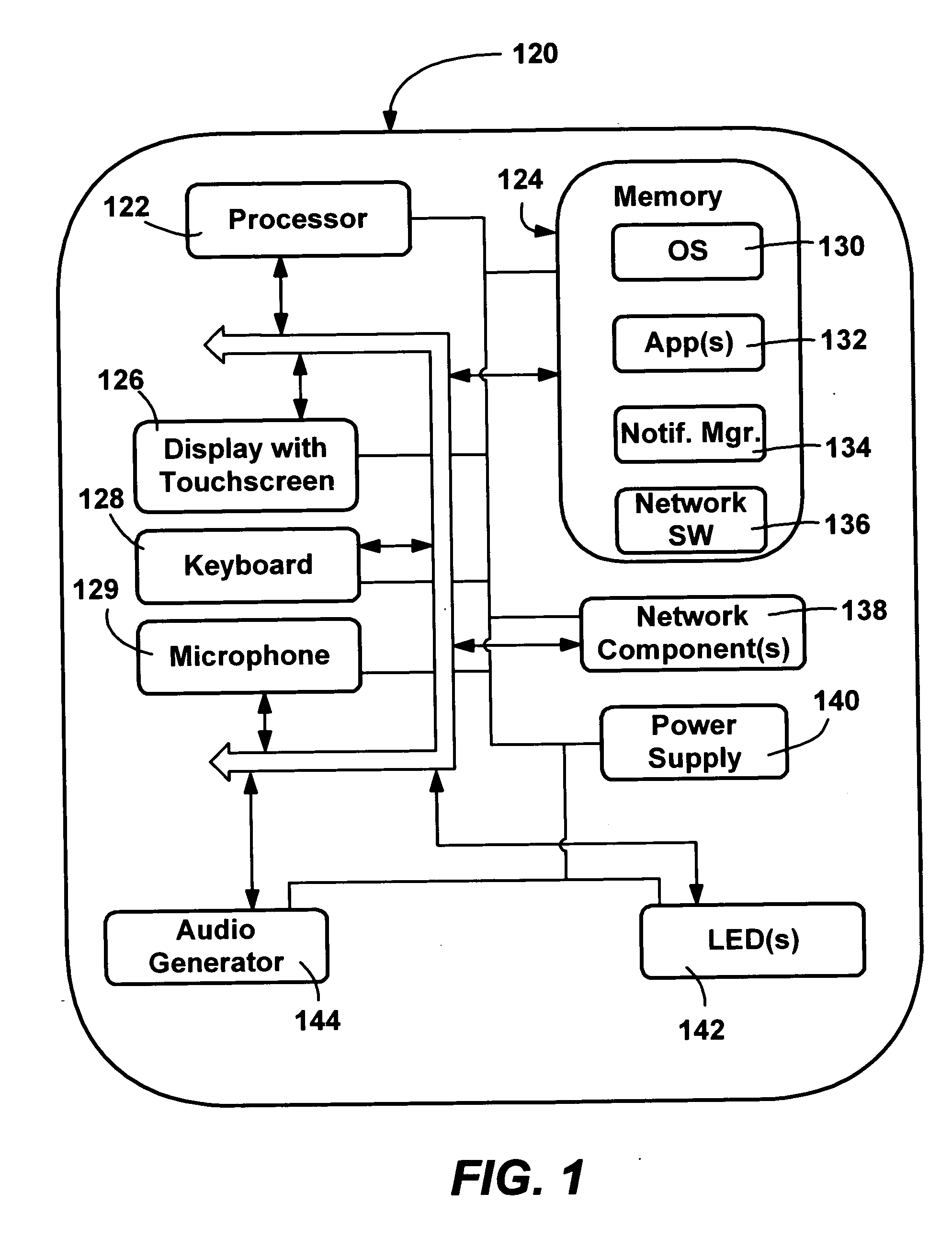
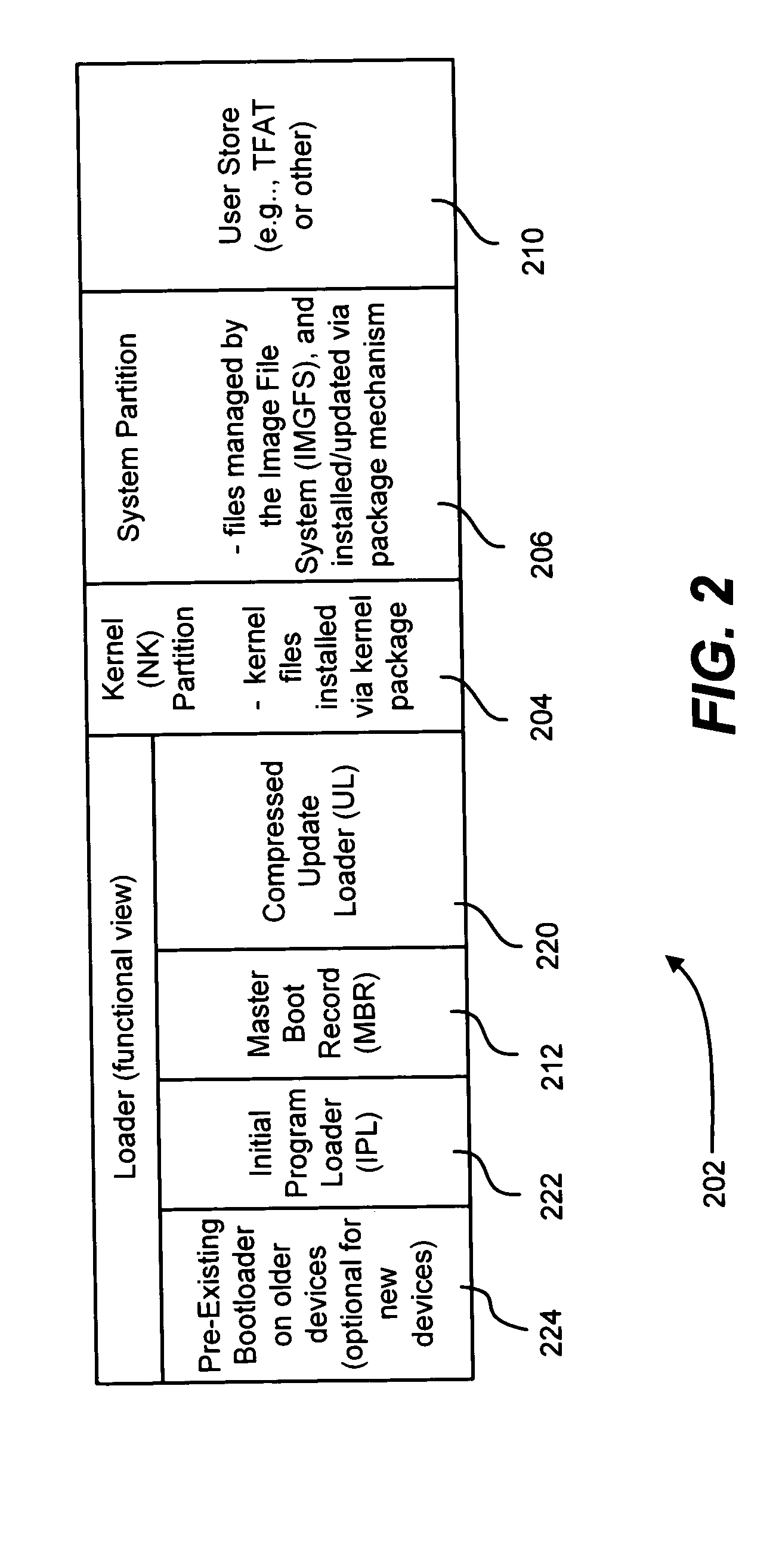
Applying custom software image updates to non-volatile storage in a failsafe manner
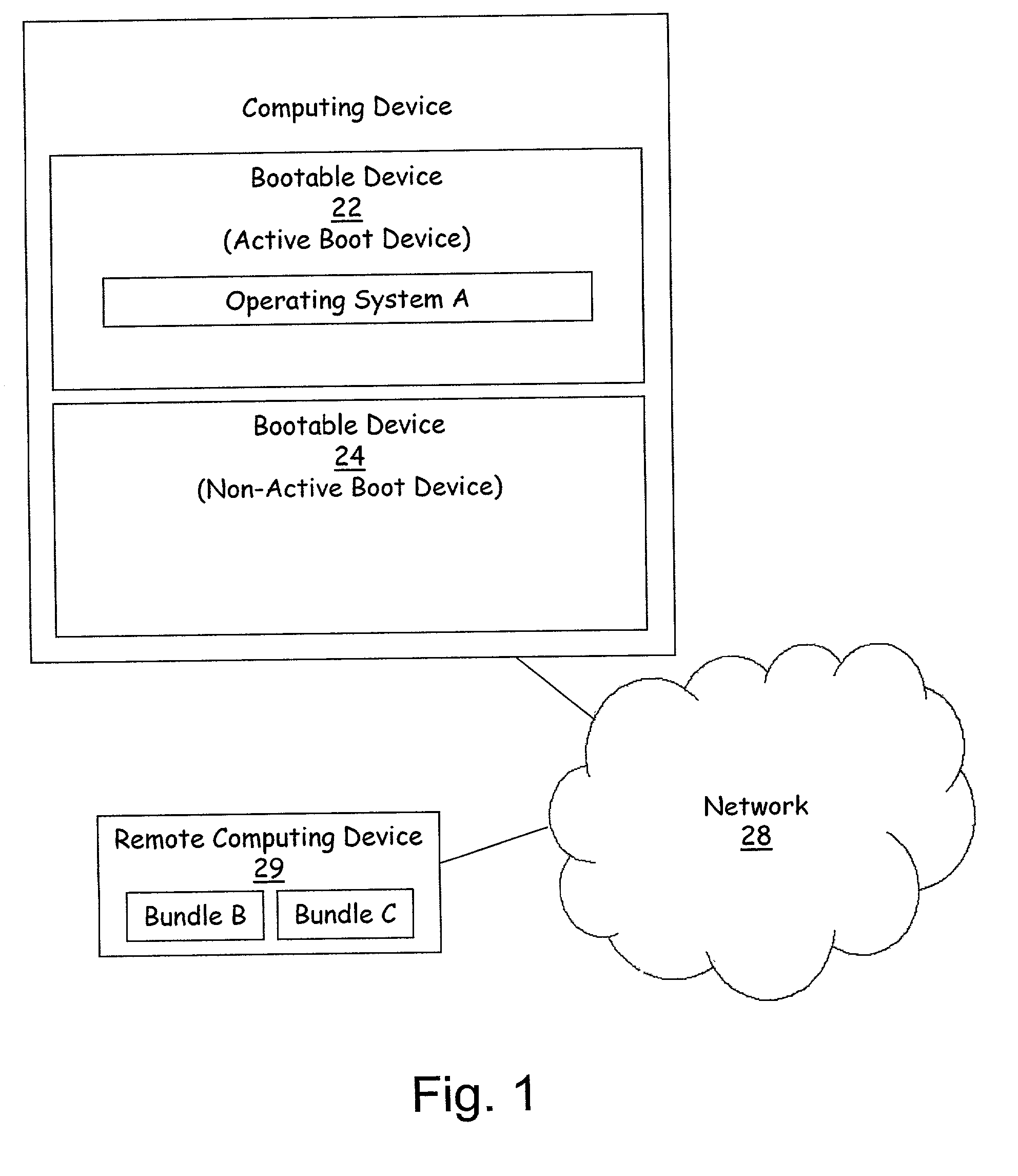
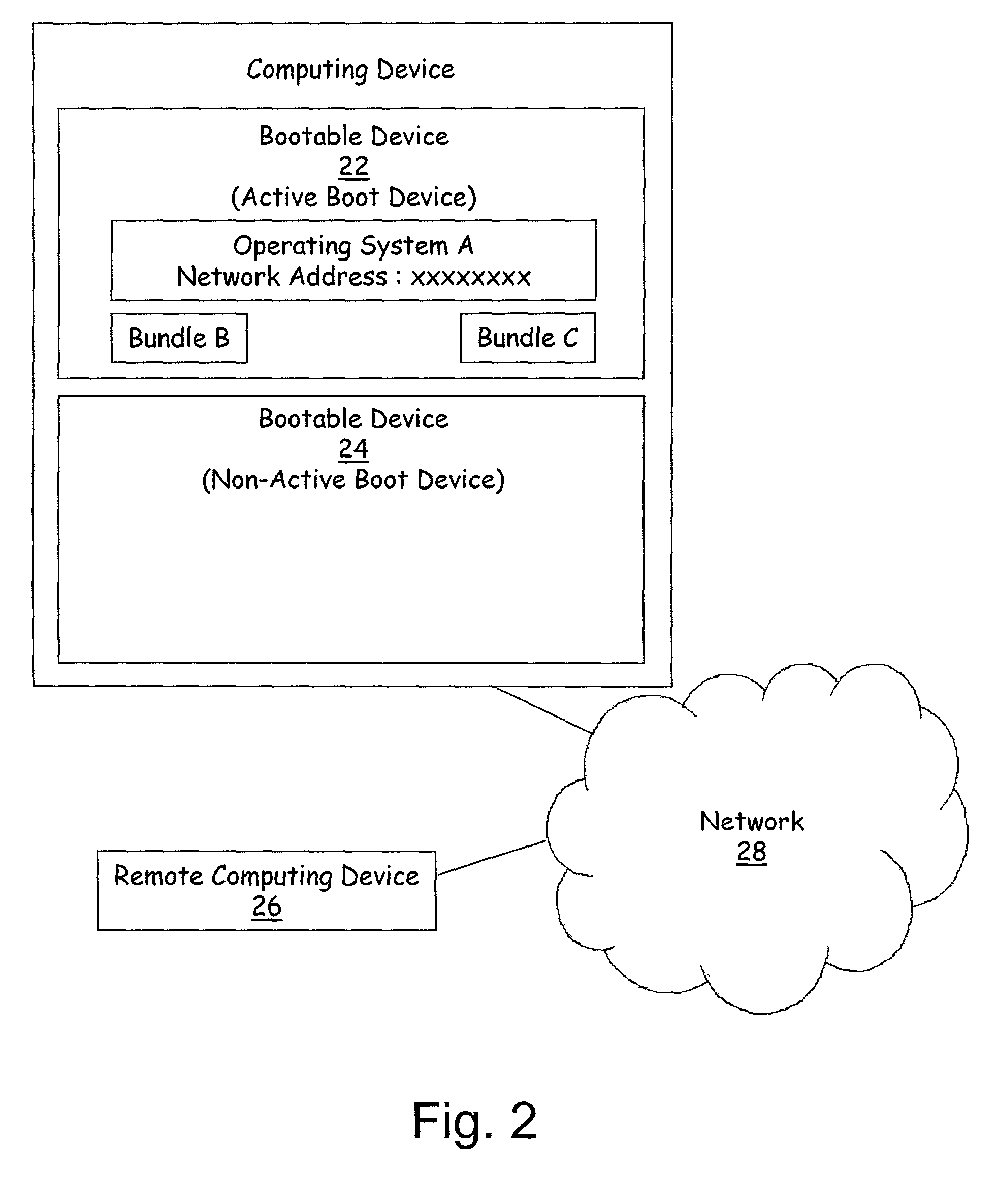
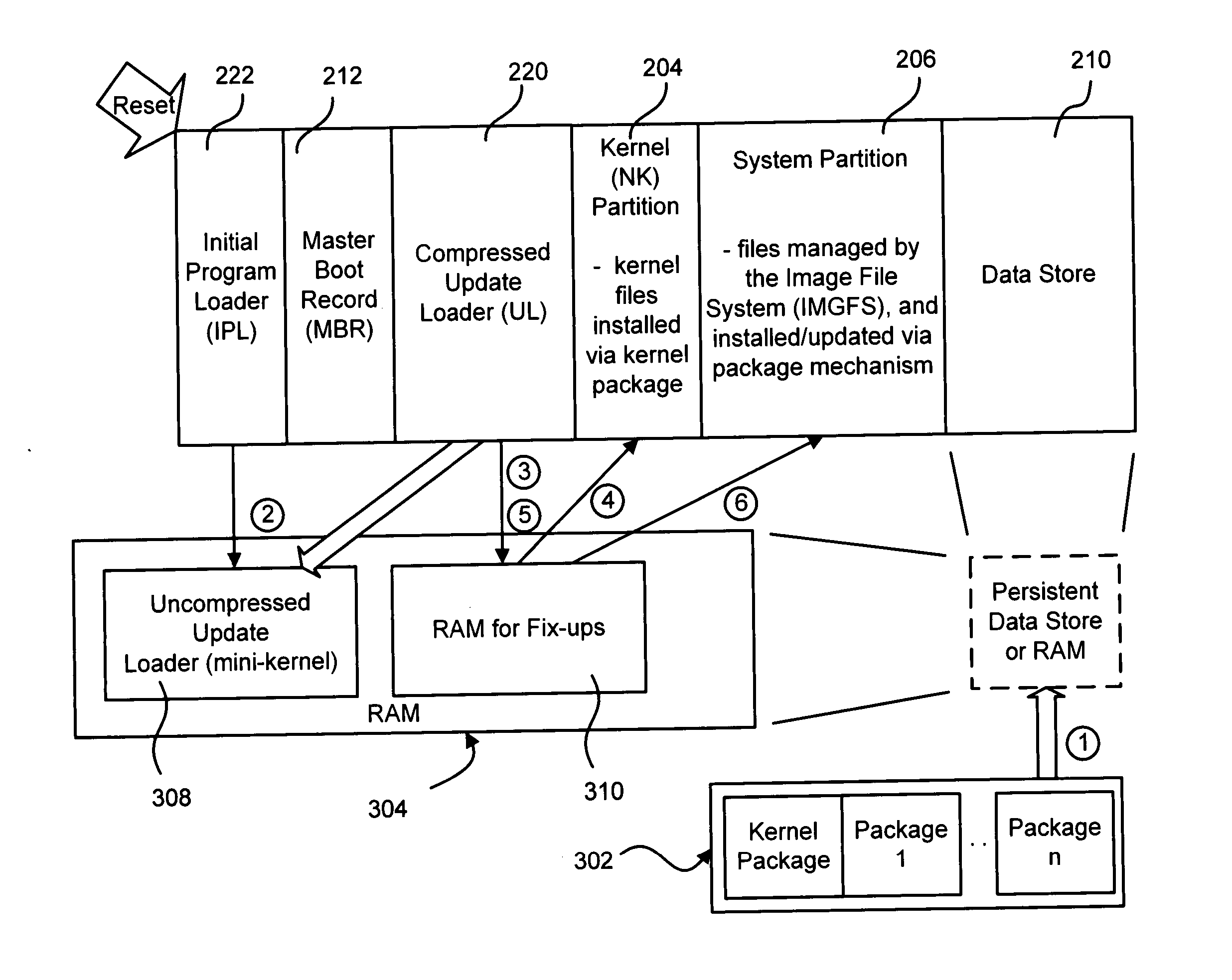
Described is a system and method in which software updates in the form of self-contained, secure entities are applied to an embedded device's non-volatile storage in a failsafe manner. Various types of software updates may be applied, and updates may contain executable code and / or data. Following a reboot, an initial program loader determines an update mode, and if updating, boots to a special update loader. The update loader processes update packages to apply the updates. Kernel partition, system partition and reserve section updates may be updated with entire files or binary difference files, with failure handling mechanisms are provided for each type of update. Updates may be simulated before committing them. Updates may be relocated in memory as appropriate for a device.
Owner:MICROSOFT TECH LICENSING LLC
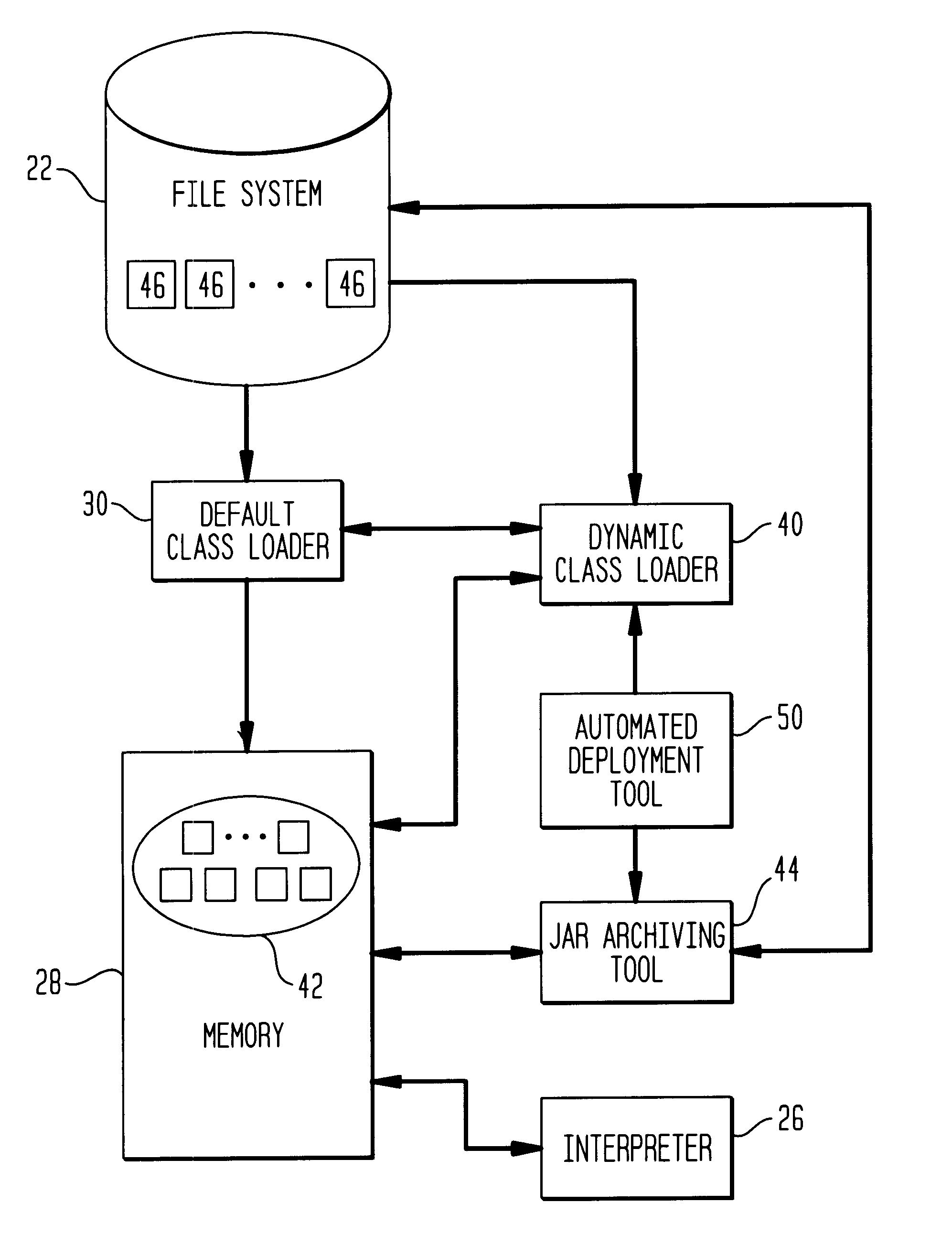
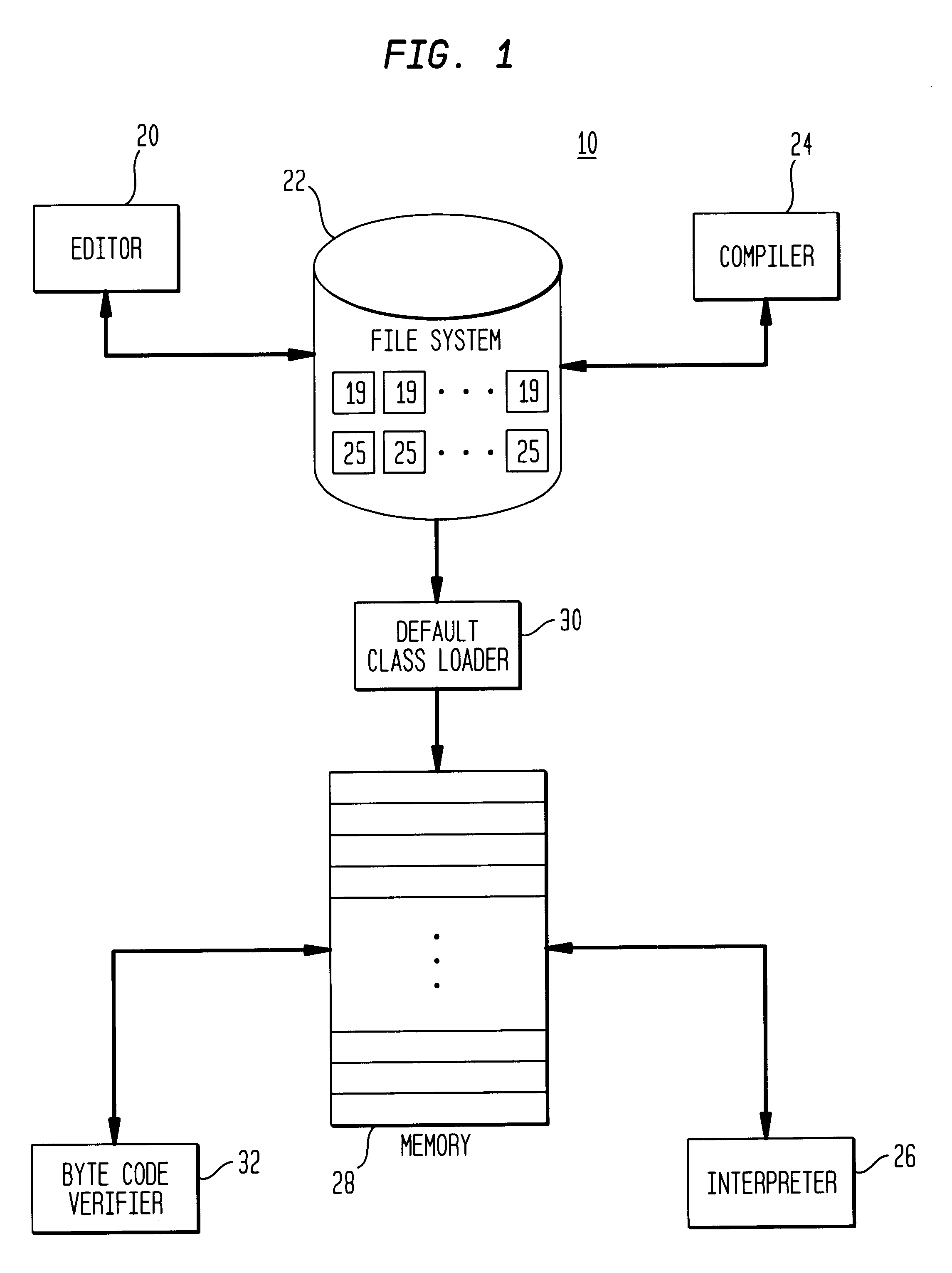
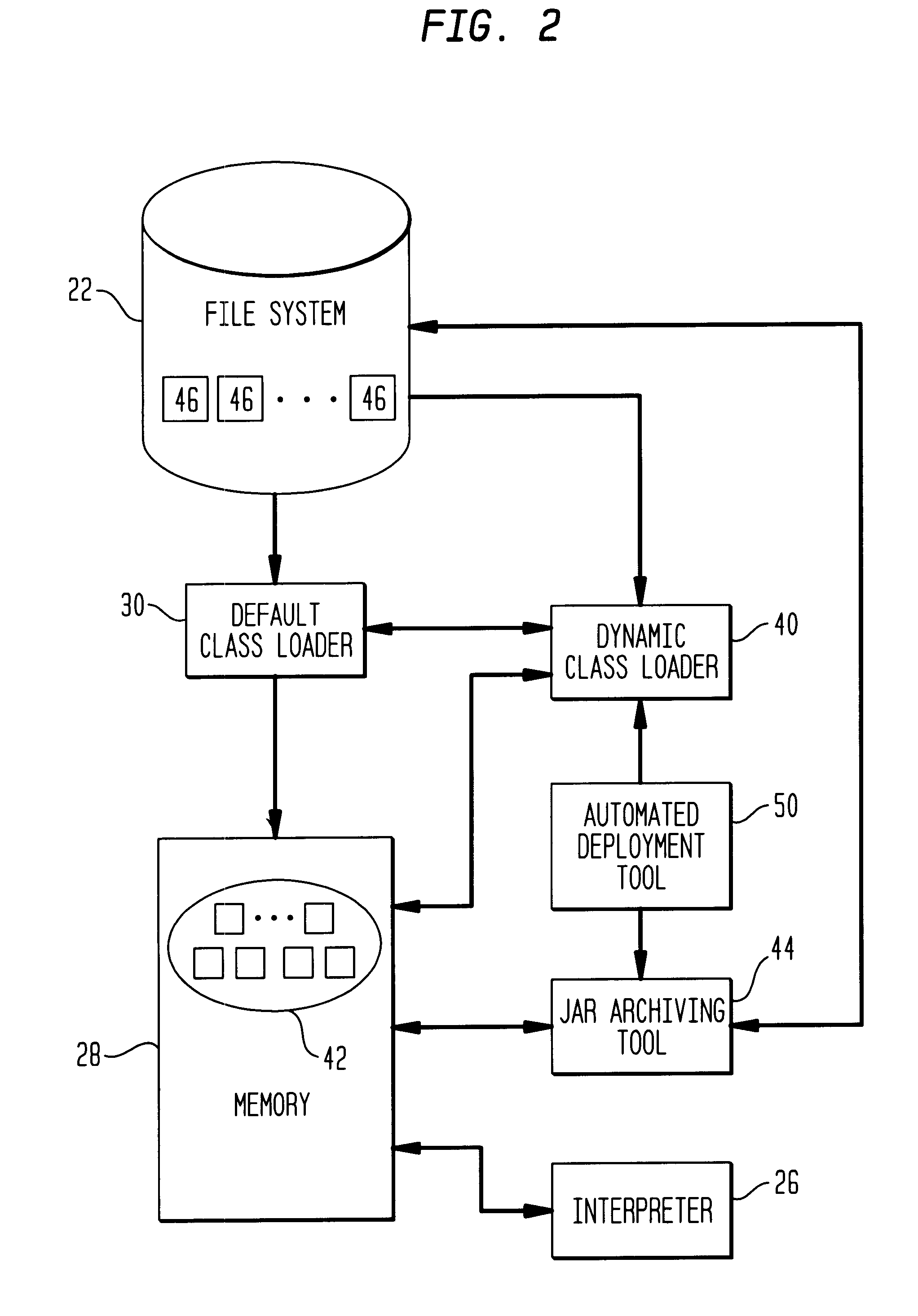
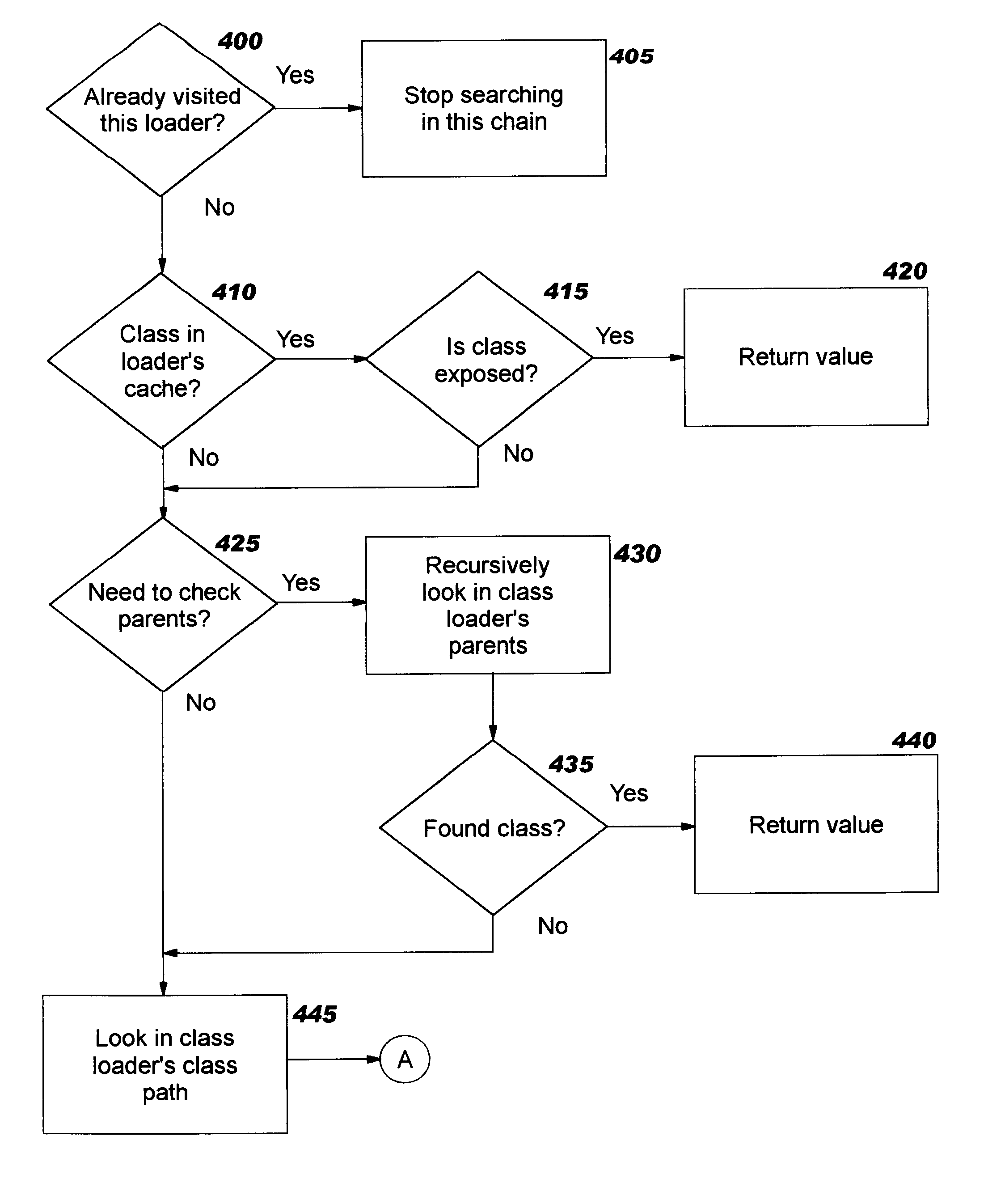
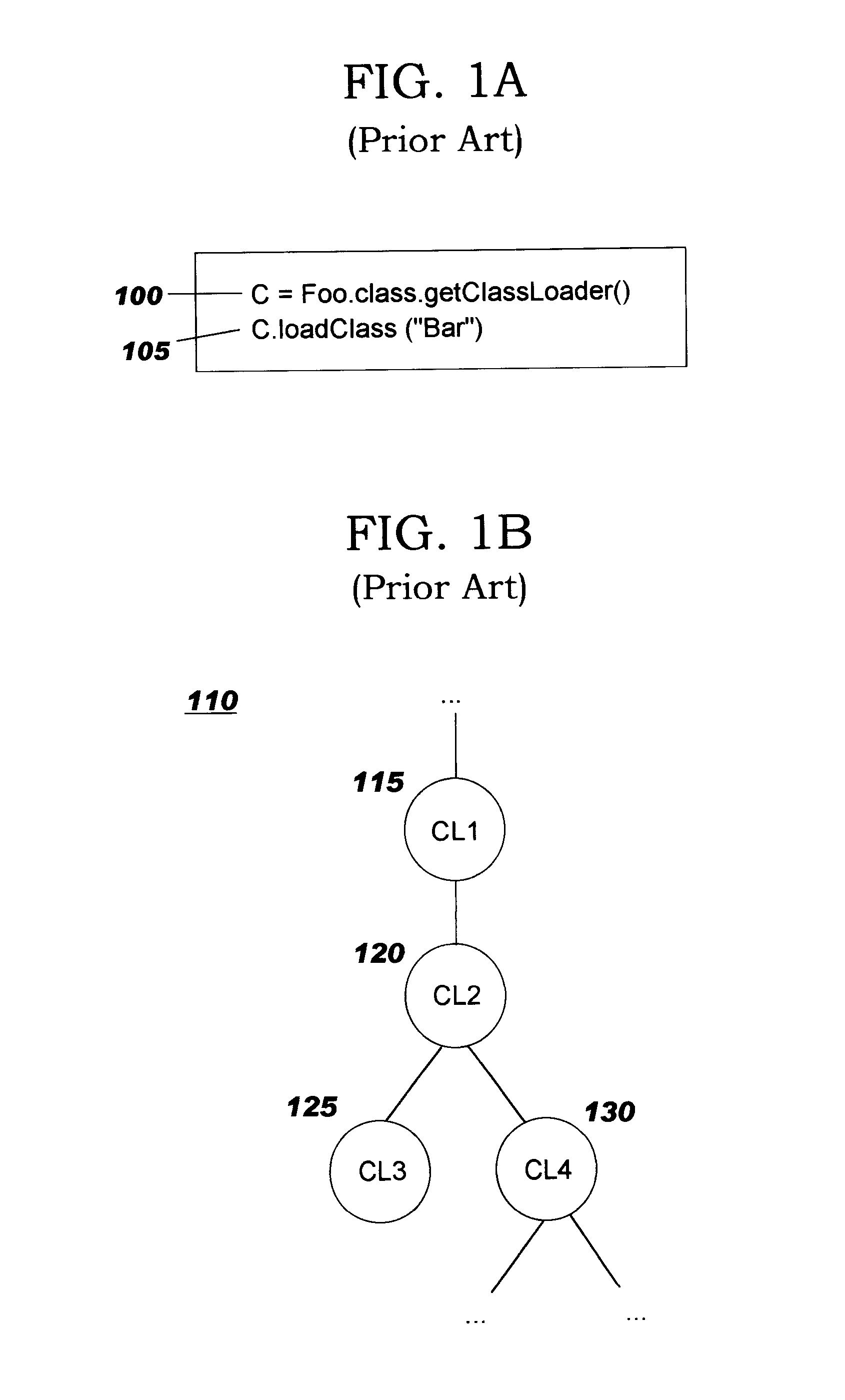
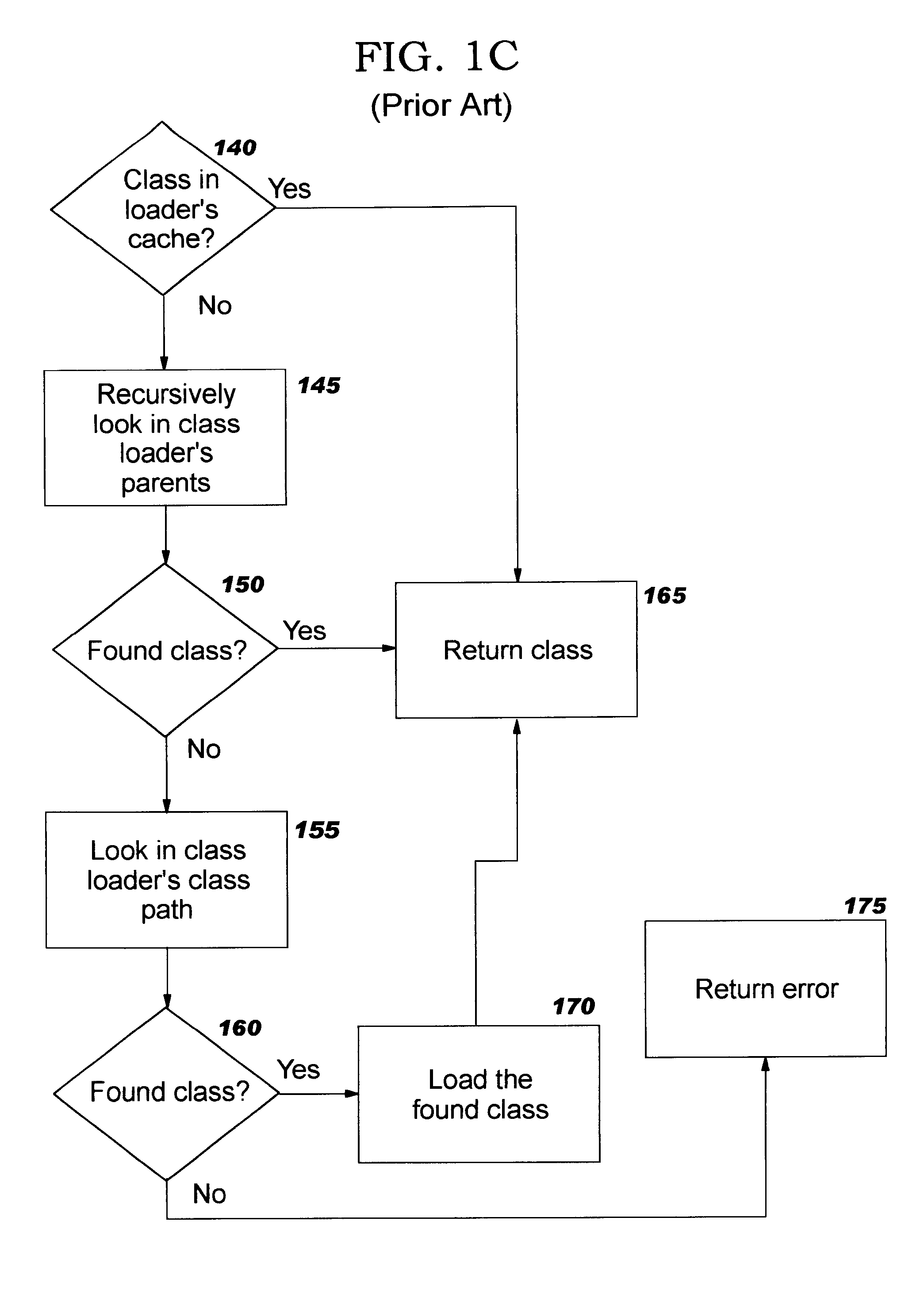
Class loader
This invention relates to the loading of classes in programming environments, and in particular, Java programming environments. This invention discloses a system and method that permits dynamic loading of classes during the execution of Java programs. This invention allows for classes to be loaded despite the fact that such classes may not reside in the current path or working directory within a Java programming environment. This invention also discloses a system and method for archiving files in an archive file that provides customized entry names for the archived files.
Owner:IBM CORP
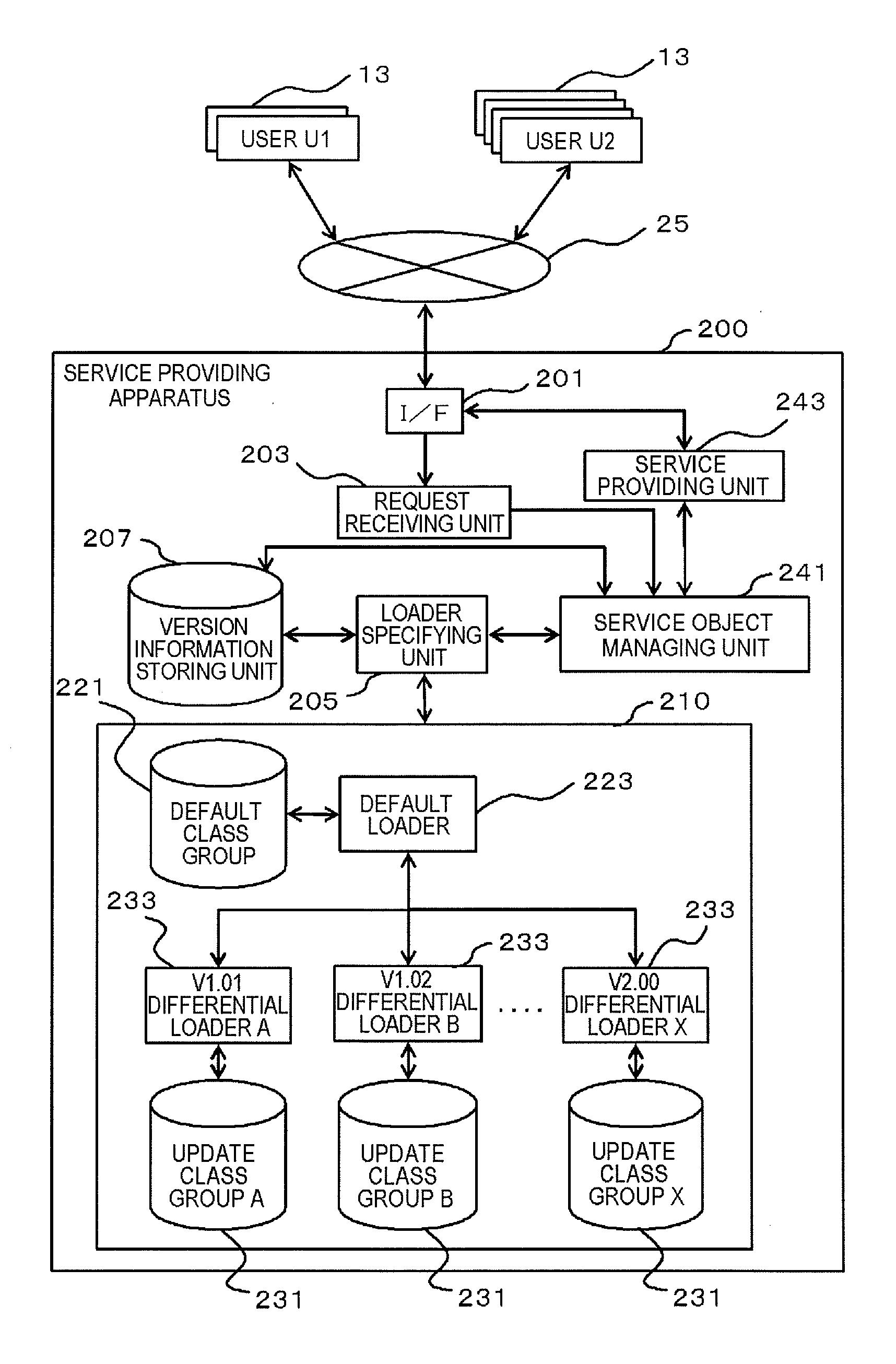
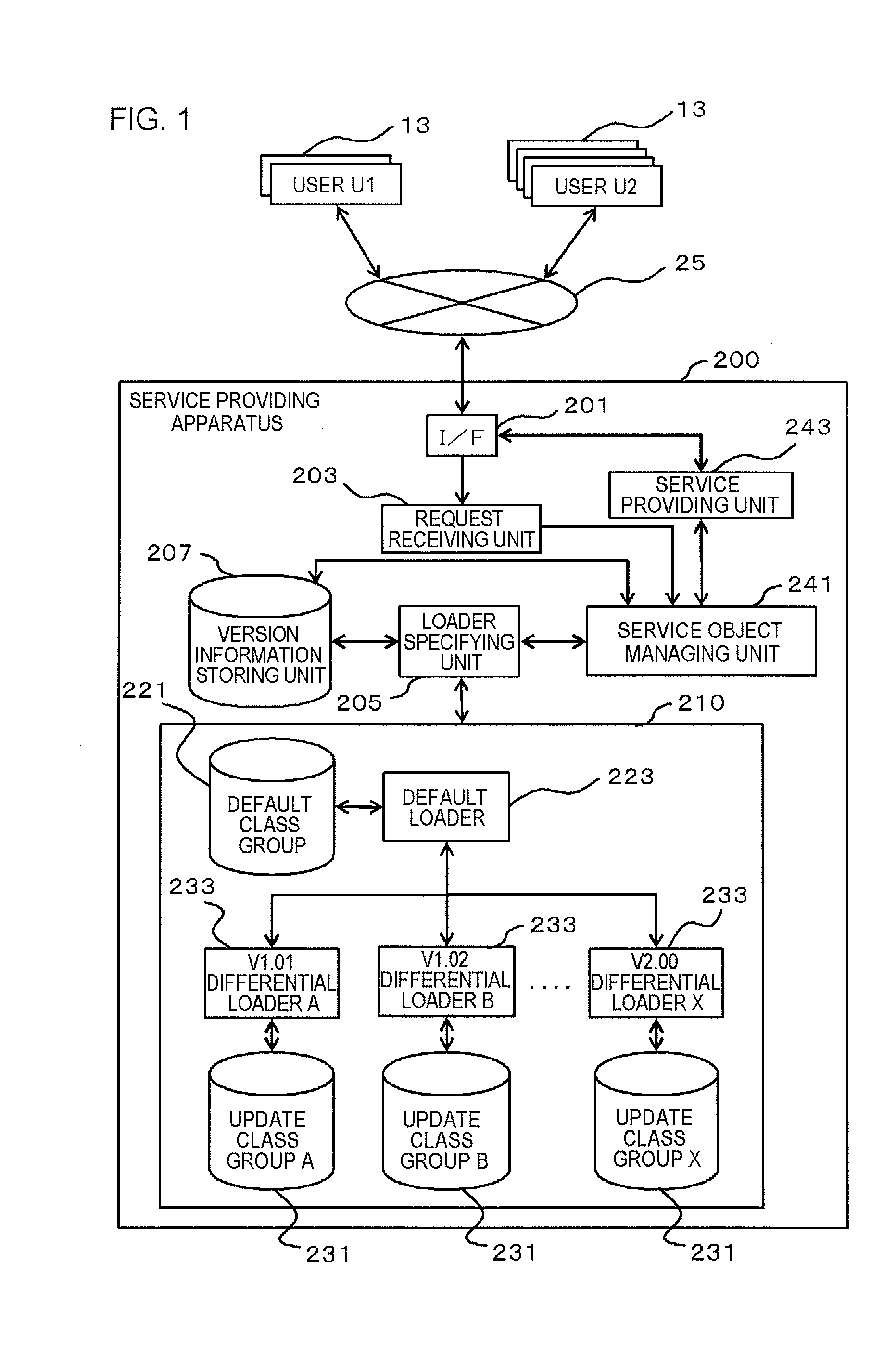
Service providing apparatus, service providing system, method of processing data in service providing apparatus, and computer program
InactiveUS20120011496A1Service is stoppedImprove efficiencyOffice automationProgram loading/initiatingManagement unitService provision
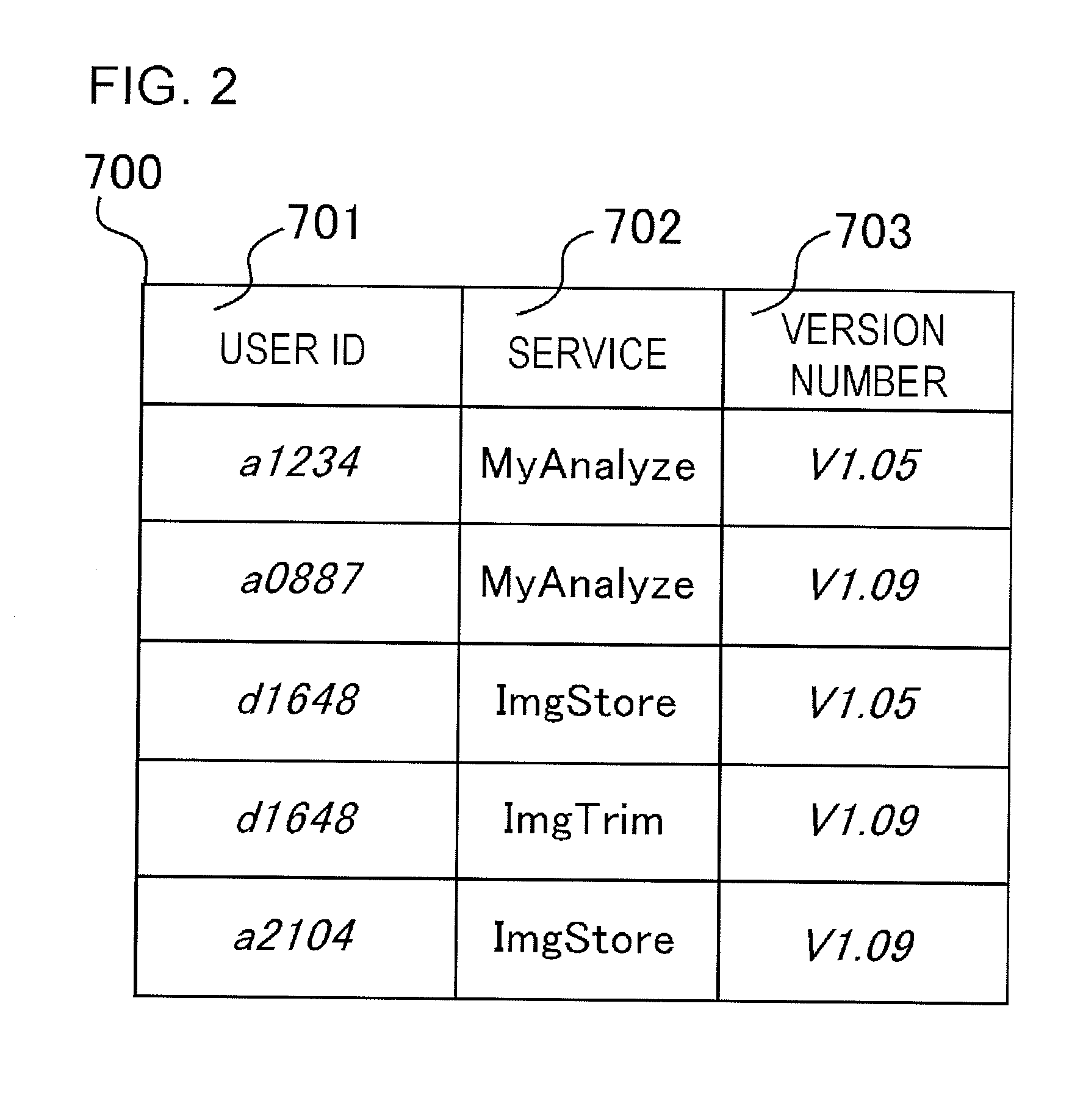
A service providing apparatus (200) includes: a version information storing unit (207) storing a service to be provided to each of users (13) and version information of this service; a loader managing unit (210) storing a default class group (221) and update class groups (231) for respective versions; a default loader (223) reading out and executing the default class group (221) from the loader managing unit (210); a differential loader (233) reading out and executing the update class group (231); a receiving unit (203) receiving service usage requests; a specifying unit (205) referring to the version information storing unit (207) to specify a version corresponding to the user (13) of the requestor; an object managing unit (241) using the default loader (223) and the specified version of the differential loader (233) to generate a service object of aversion suitable for the user (13) and execute processing; and a providing unit (243) providing a service to the user (13).
Owner:NEC CORP
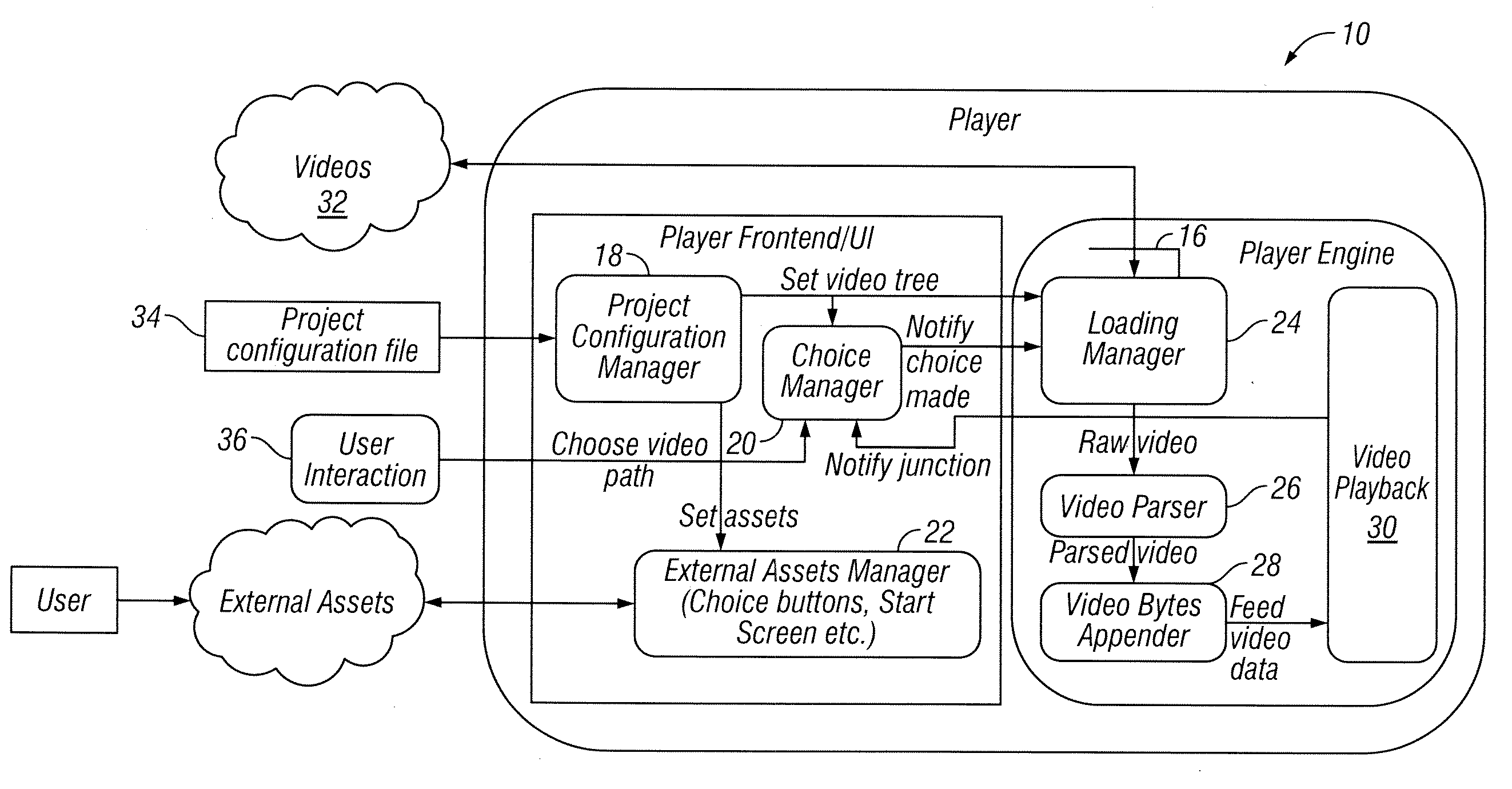
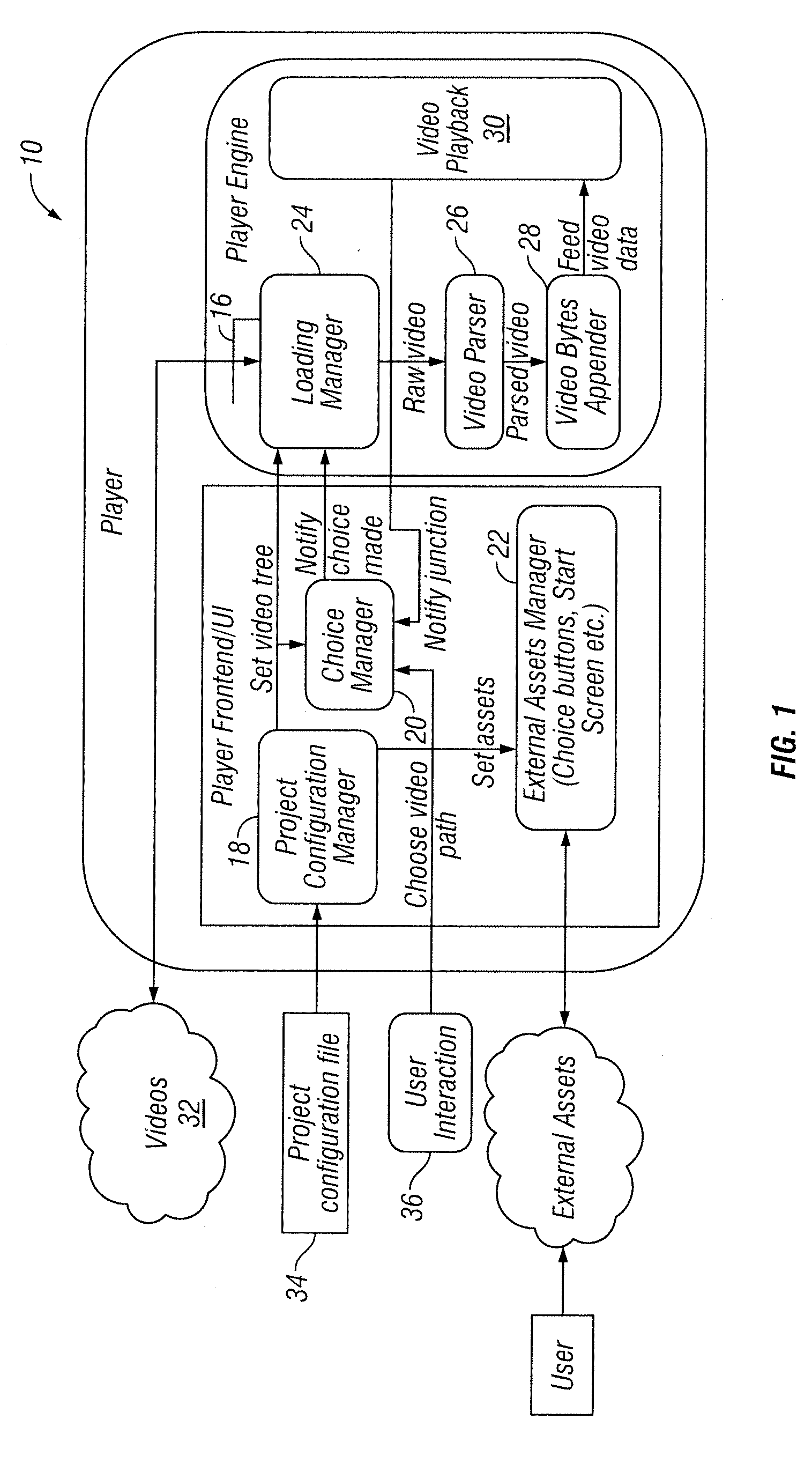
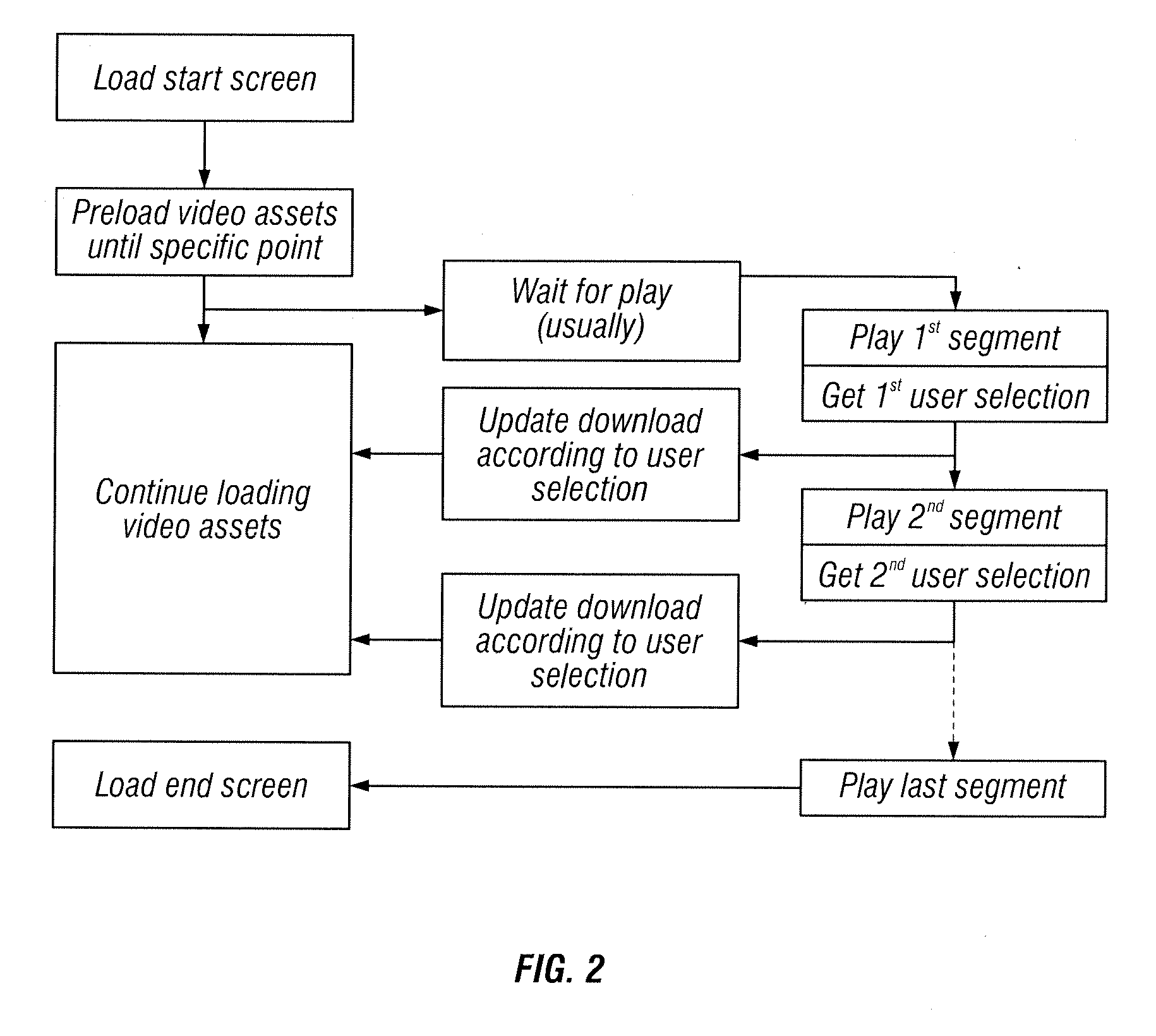
Systems and methods for loading more than one video content at a time
ActiveUS20130259442A1Increase loadEasy loadingTelevision system detailsRecording carrier detailsComputer graphics (images)Video player
A system for loading videos includes an interactive video player is with a loader. A product configuration file in operation configures files for a user in creation of a custom video. External assets are configured for a design of an interactive layer of the video. The interactive video player in operation creates in real-time a custom video that includes a plurality of video segments.
Owner:JBF INTERLUDE 2009
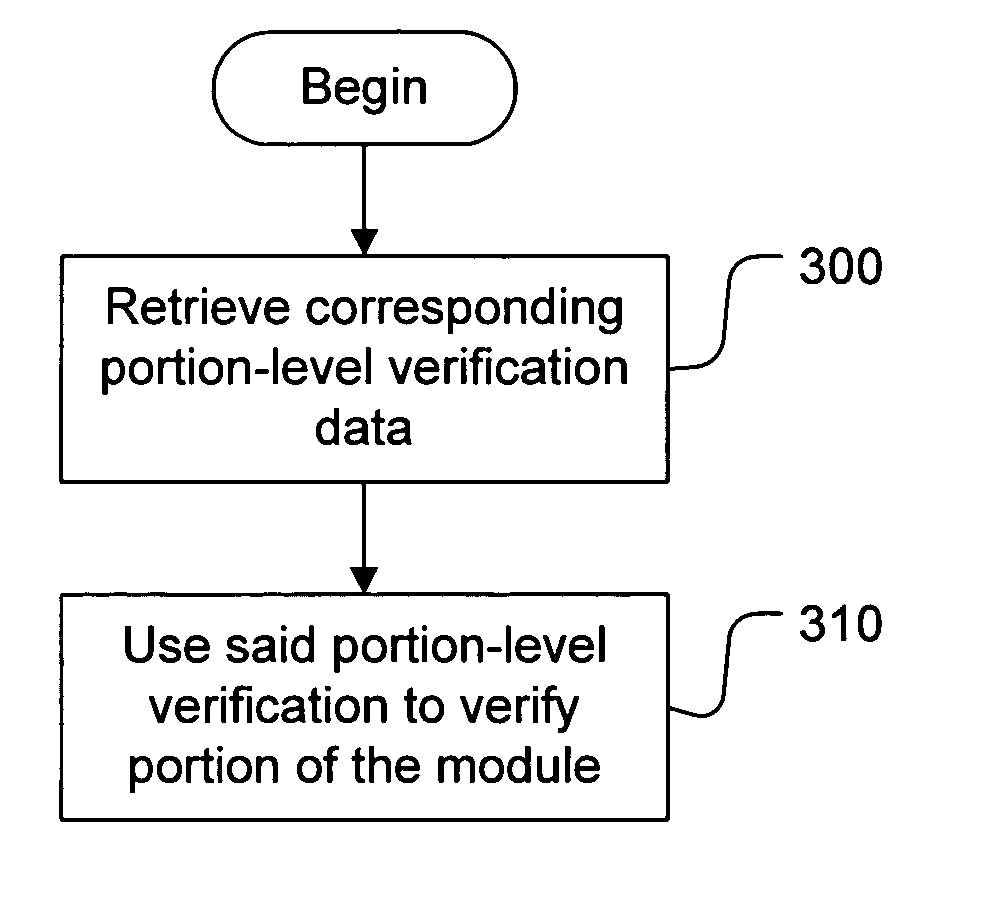
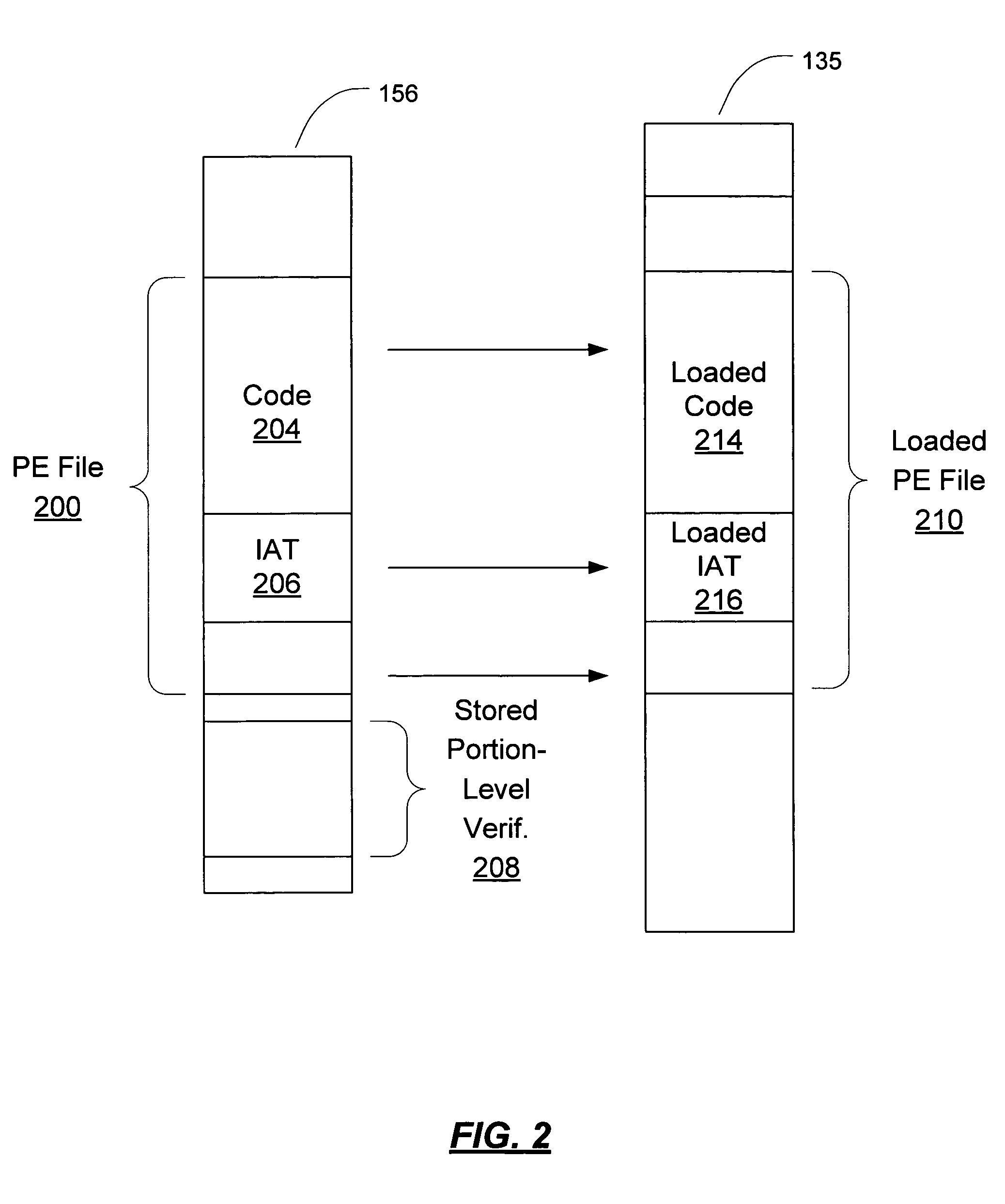
Portion-level in-memory module authentication
ActiveUS20060026569A1Efficient techniqueMaximum performanceMemory loss protectionUser identity/authority verificationOperational systemDigital signature
Dynamic run-time verification of a module which is loaded in memory (in whole or in part) for execution is enabled by using pre-computed portion-level verification data for portions of the module smaller than the whole (e.g. at the page-level). A portion of the module as loaded into memory for execution can be verified. Pre-computed portion-level verification data is retrieved from storage and used to verify the loaded portions of the executable. Verification data may be, for example, a digitally signed hash of the portion. Where the operating system loader has modified the portion for execution, the modifications are reversed, removing any changes performed by the operating system. If the portion has not been tampered, this will return the portion to its original pre-loaded state. This version is then used to determine validity using the pre-computed portion-level verification. Additionally, during execution of the module, new portions / pages of the module which are loaded can be verified to ensure that they have not been changed, and a list of hot pages of the module can be made, including pages to be continually reverified, in order to ensure that no malicious changes have been made in the module.
Owner:MICROSOFT TECH LICENSING LLC
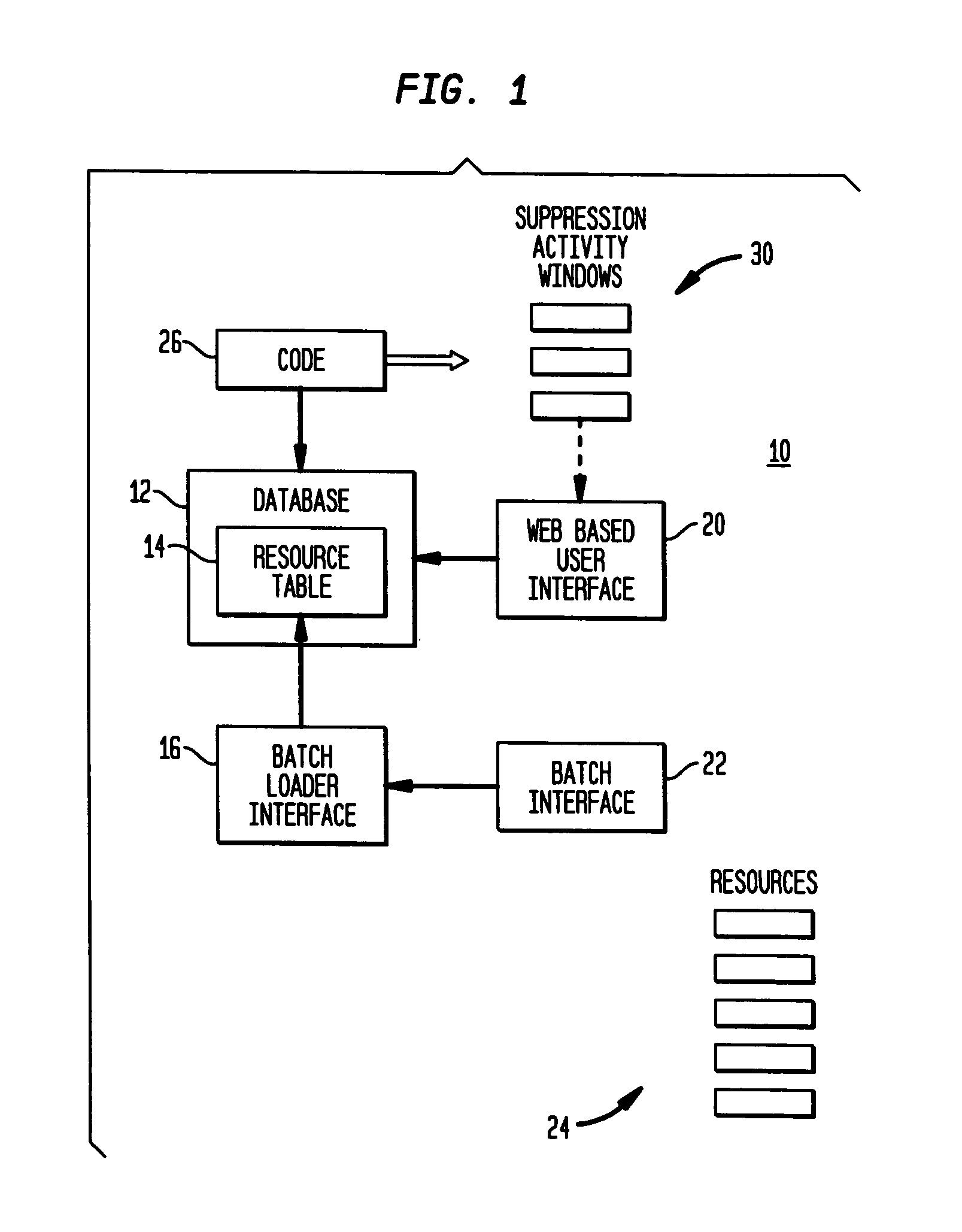
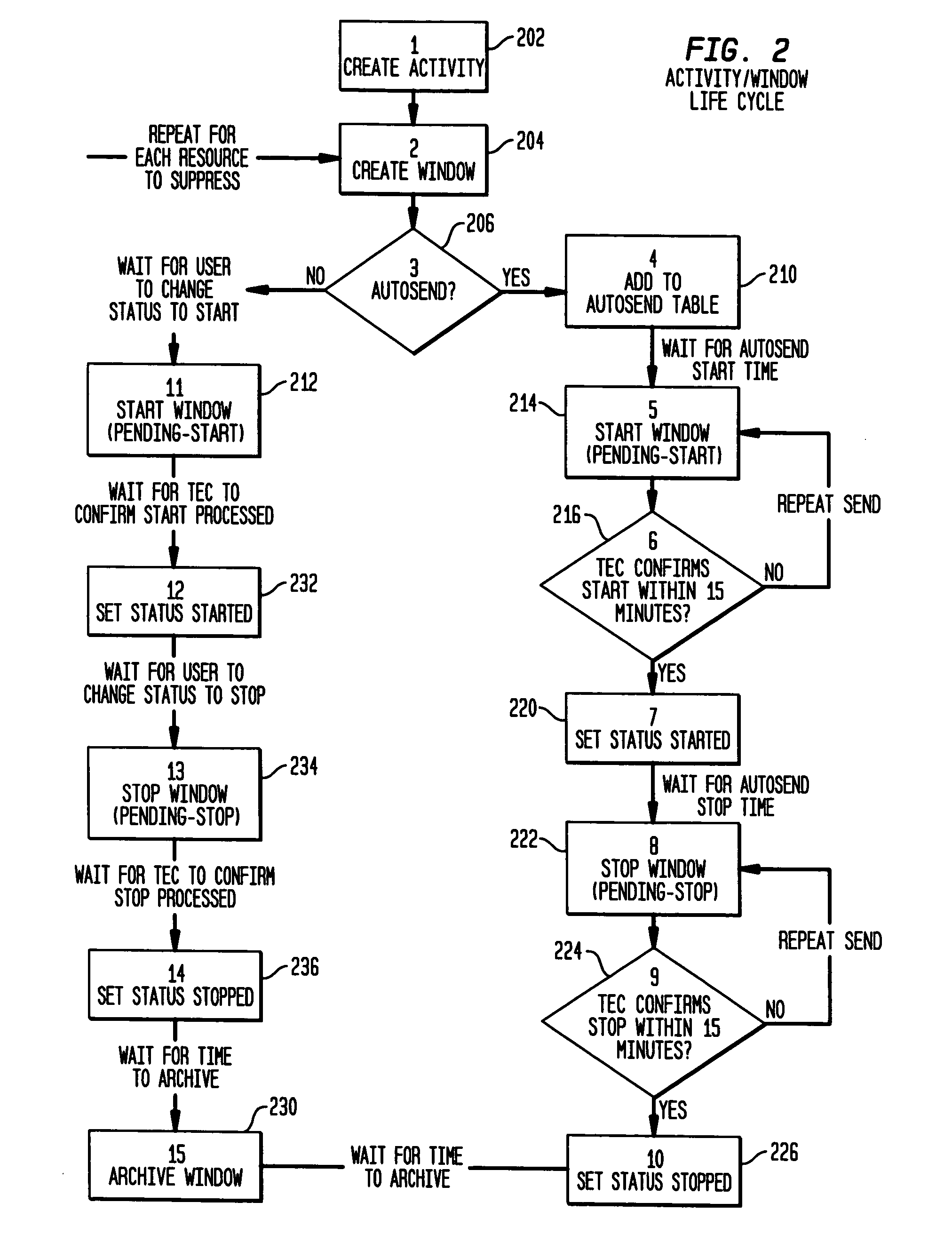
Event suppression tool-alert control tool
InactiveUS20060015608A1Digital computer detailsKnowledge representationBatch processingHuman–computer interaction
Disclosed are a tool, a method, and a computer program for suppressing events. The tool comprises a database having a resource table, a batch loader interface for creating or updating said resource table, and a web based user interface to said database. The event suppression tool further comprises a batch interface to receive data about planned activities and affected resources; and code for creating suppression activity windows from said data and said resource table, and for suppressing from said user interface, new events that fall within said activity windows. The preferred embodiment of the invention allows temporarily suppressing various actions for events received for certain resources during specified times.
Owner:KYNDRYL INC
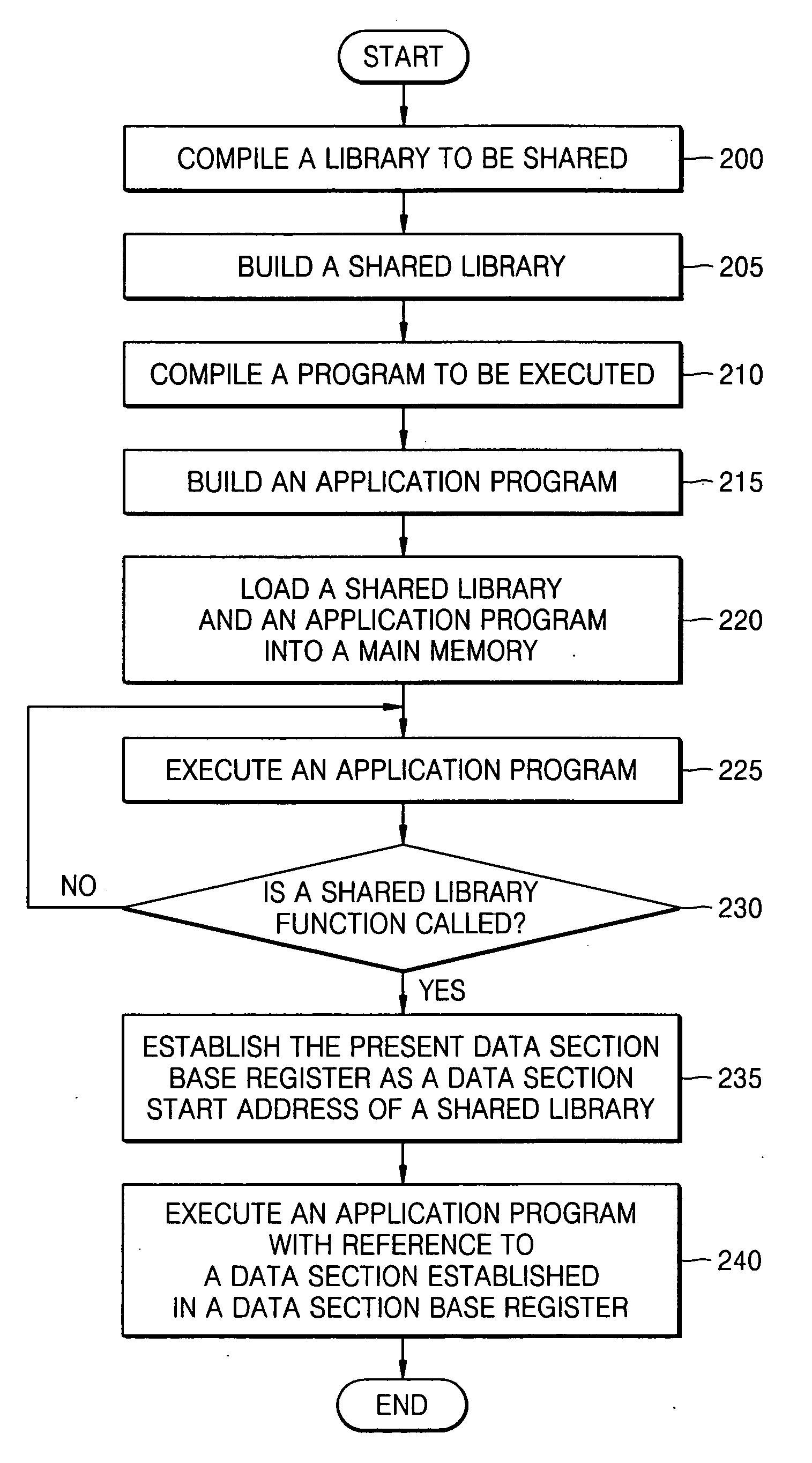
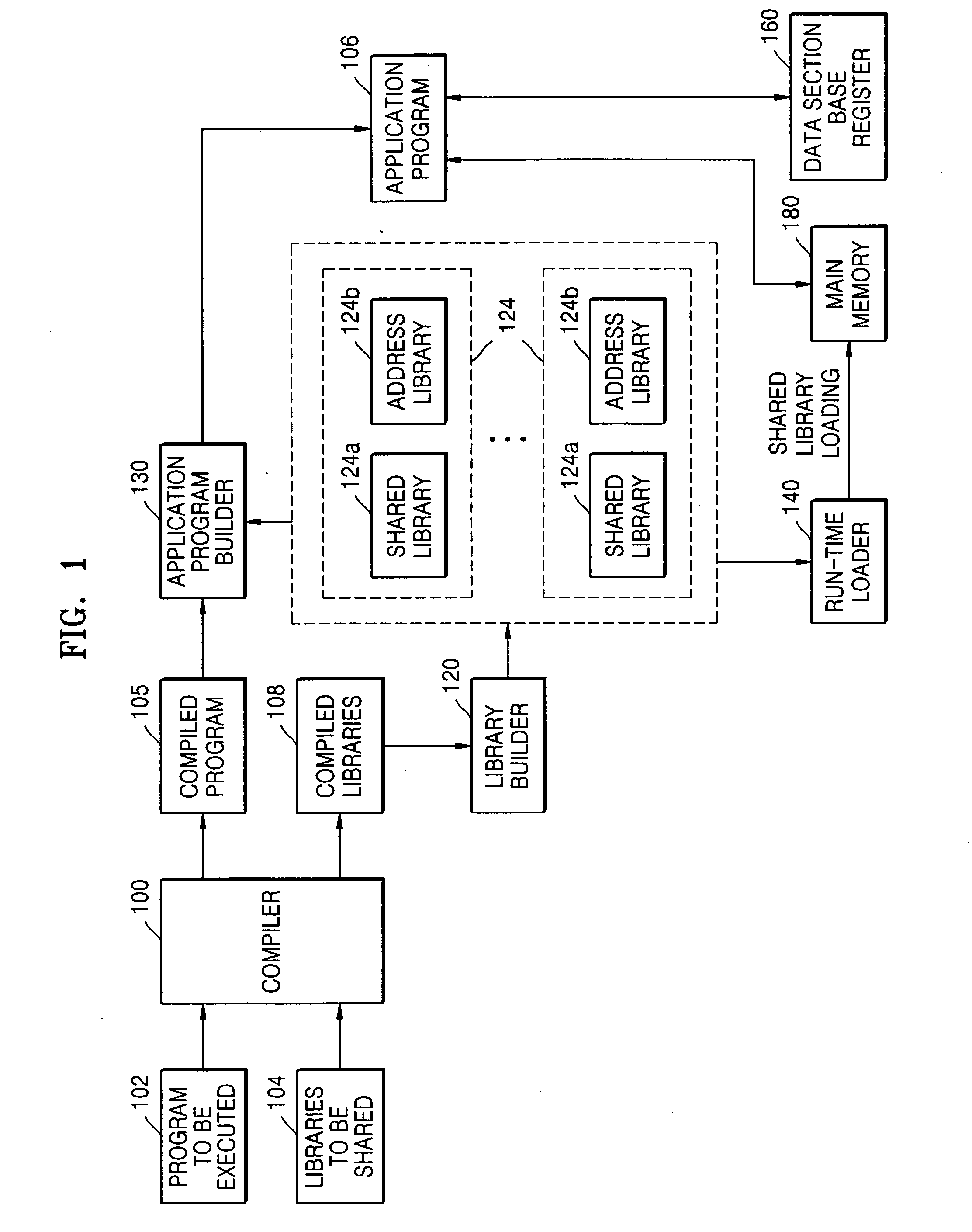
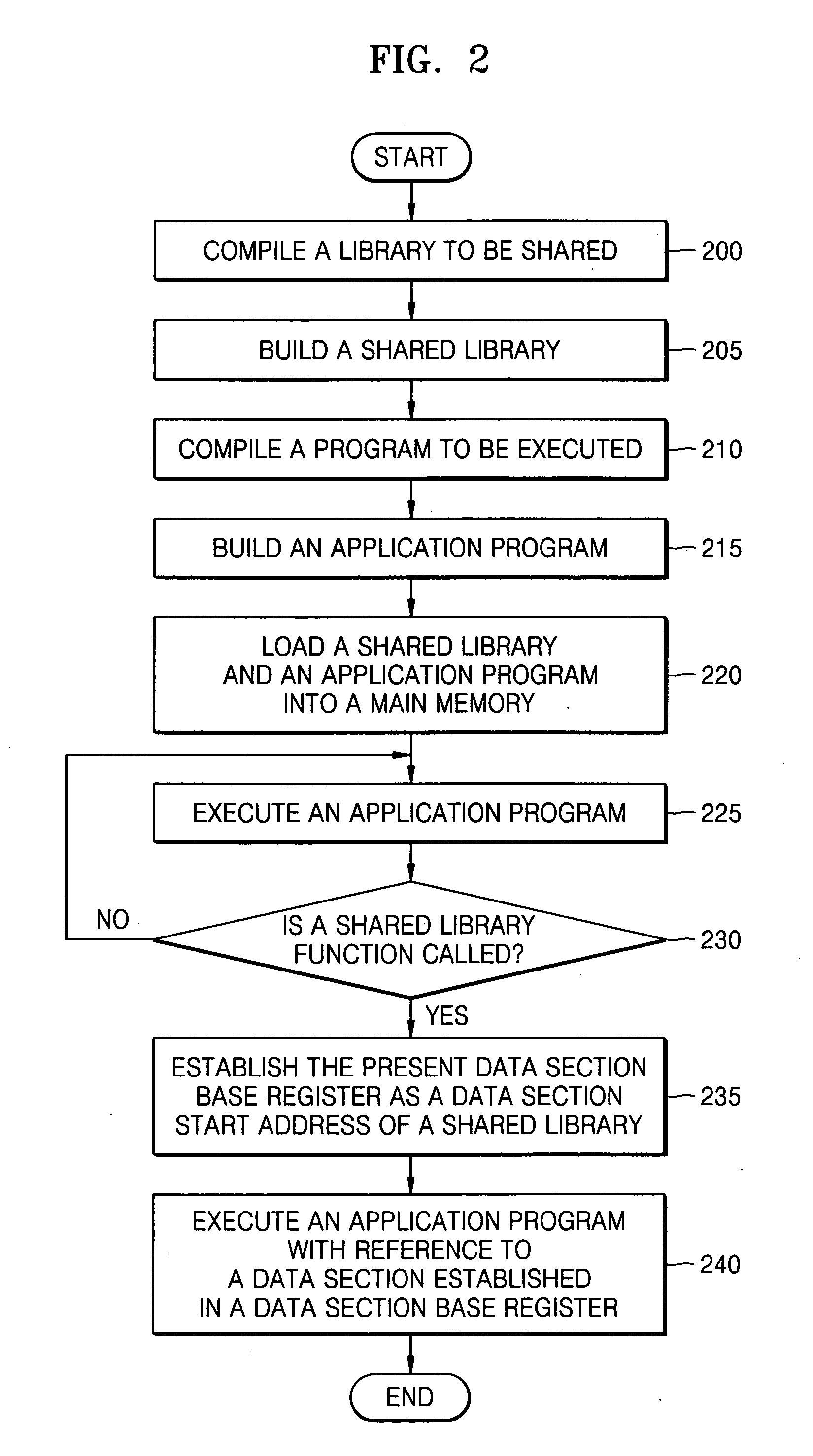
Shared library system and method of building the system
InactiveUS20050010911A1Link editingSpecific program execution arrangementsData segmentManagement unit
A shared library system and method of building the system are disclosed. A run-time loader and a compiler are modified, and a pattern of a previous shared library is changed using a library builder. Furthermore, by using a data section base register and a global offset table of a data section, it is possible to use a shared library even without a memory management unit.
Owner:SAMSUNG ELECTRONICS CO LTD
System and method for loading resources into a virtual machine
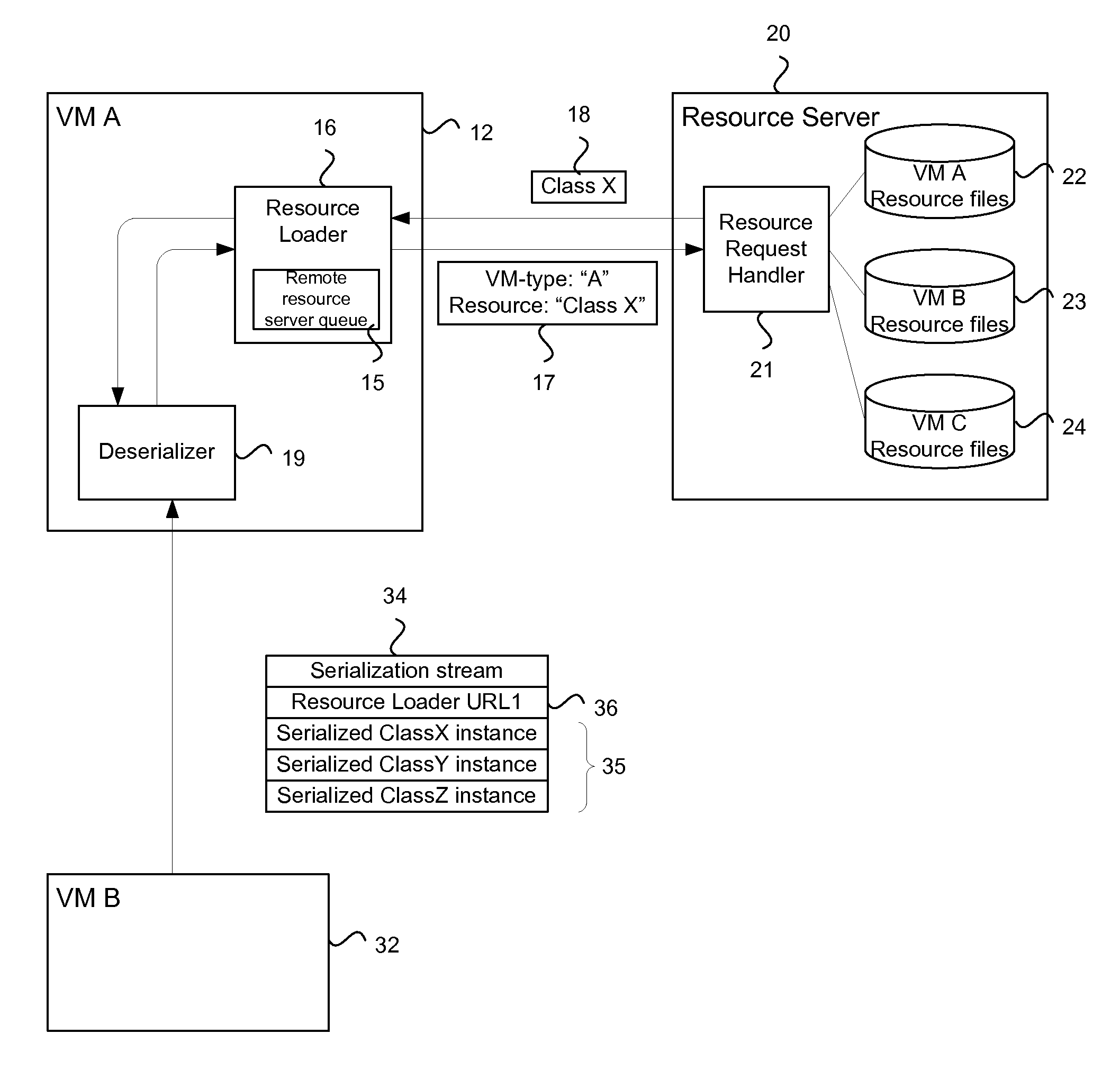
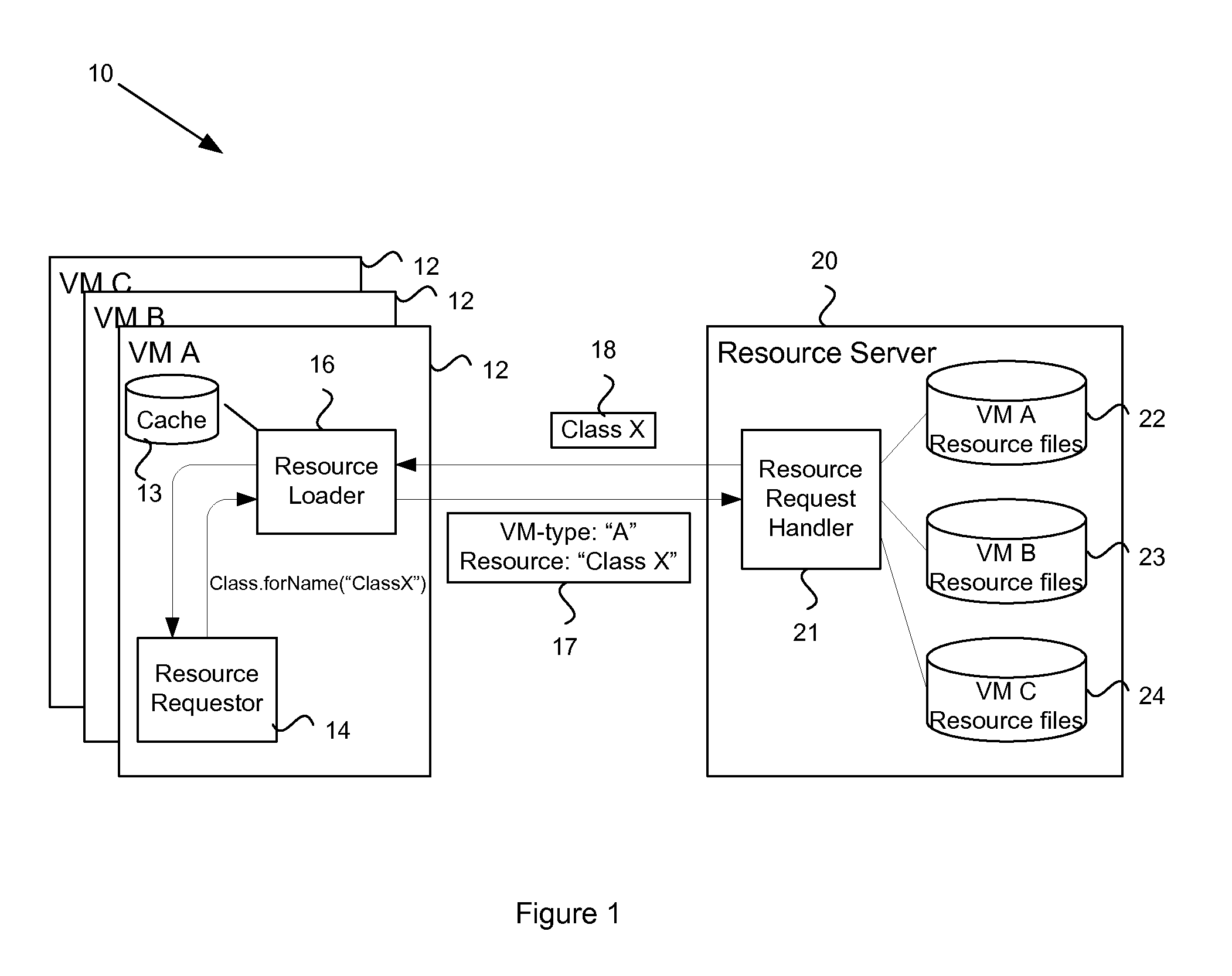
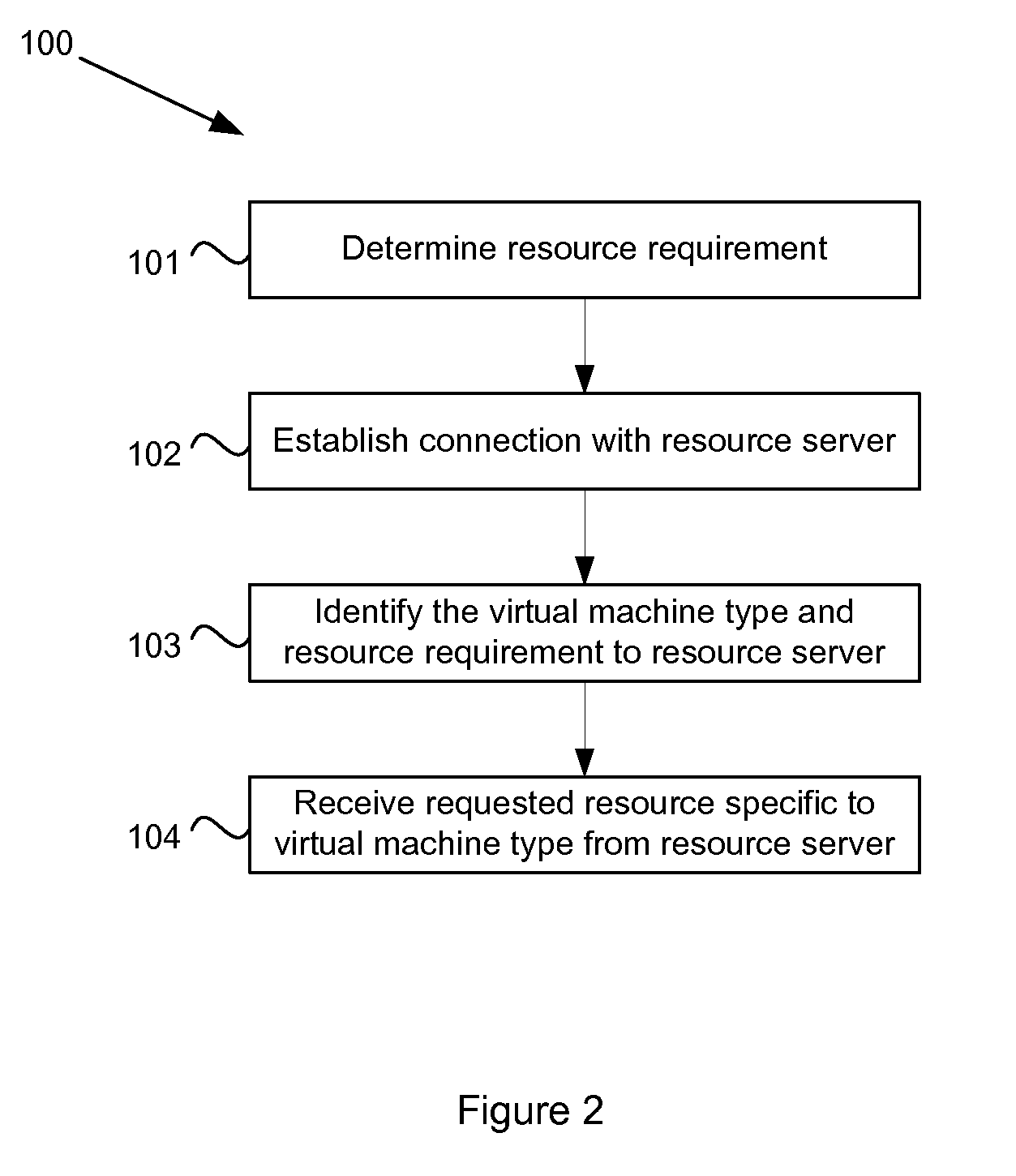
InactiveUS20110138382A1Software simulation/interpretation/emulationMemory systemsVirtual machineType specific
In a heterogeneous environment of virtual machines, an agent can migrate between virtual machines of different types. During migration, classes of the mobile agent may need to be instantiated on the new virtual machine. To support classes across all virtual machine types, a resource server is provided that can provide virtual machine type specific instances of the classfile. The resource server receives a resource request from a resource loader of a virtual machine. The resource request specifies the resource and the virtual machine type, thereby enabling the resource server to retrieve the correct instance of the classfile to return to the resource loader.
Owner:OSOCAD REMOTE LIABILITY
Independent class loader for dynamic class loading
InactiveUS6748396B2Data processing applicationsProgram loading/initiatingLoading TechniqueOpting out
Improved techniques are defined for dynamically loading components which have prerequisite relationships more complex than the simple single inheritance chains which are supported with prior art dynamic class loading techniques. Multiple prerequisites are supported in this improved technique, and in preferred embodiments, an arbitrary number of prerequisites may be explicitly specified for a component. Furthermore, techniques are disclosed which enable delaying the loading and initialization of components until such time as a class in the component is actually needed, thereby improving overall efficiency of the system. Optional filtering and export aspects may also be supported to selectively expose classes for use by dependent components and to enable a component to opt out of re-exporting the classes of its prerequisites, respectively.
Owner:IBM CORP
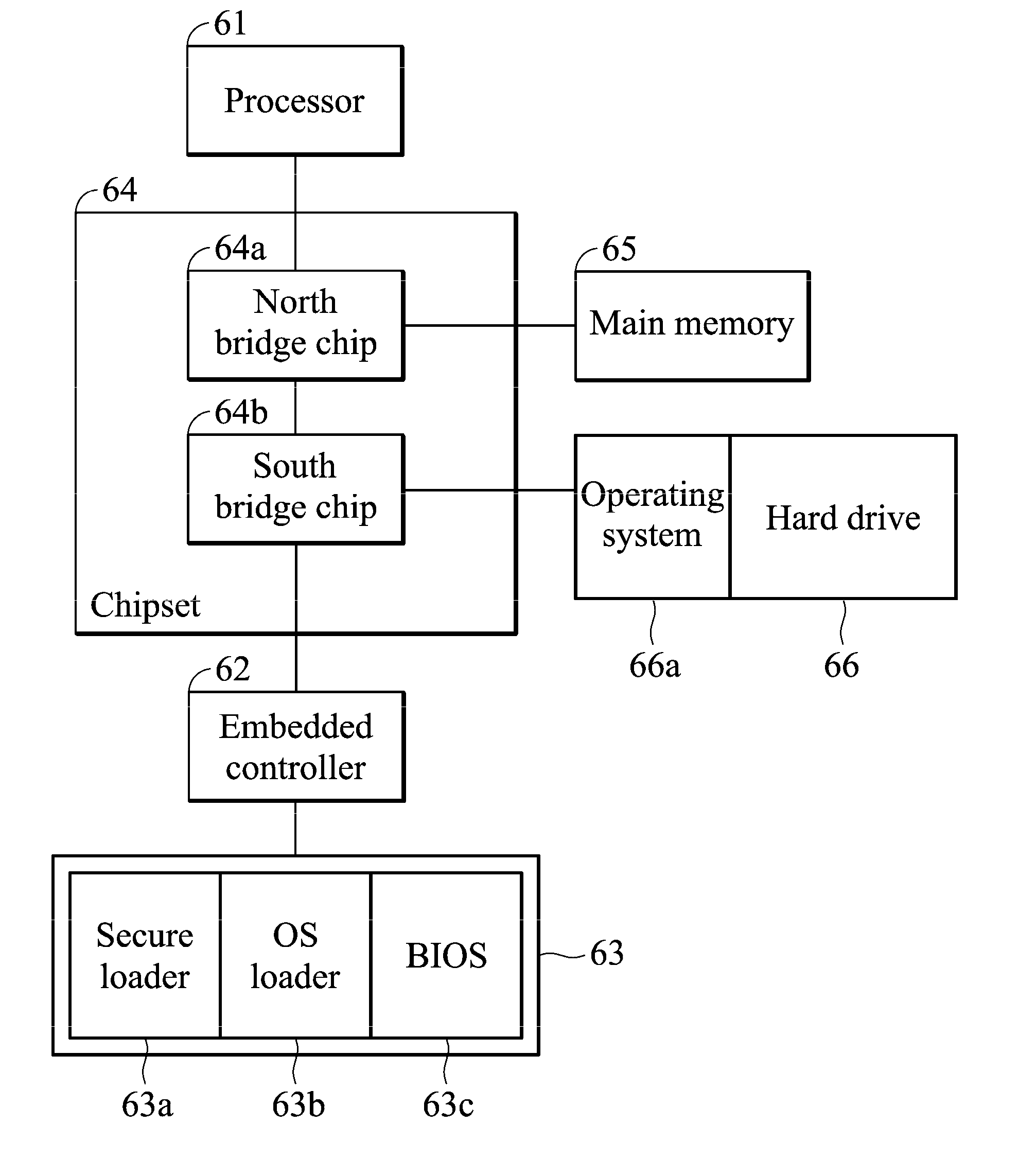
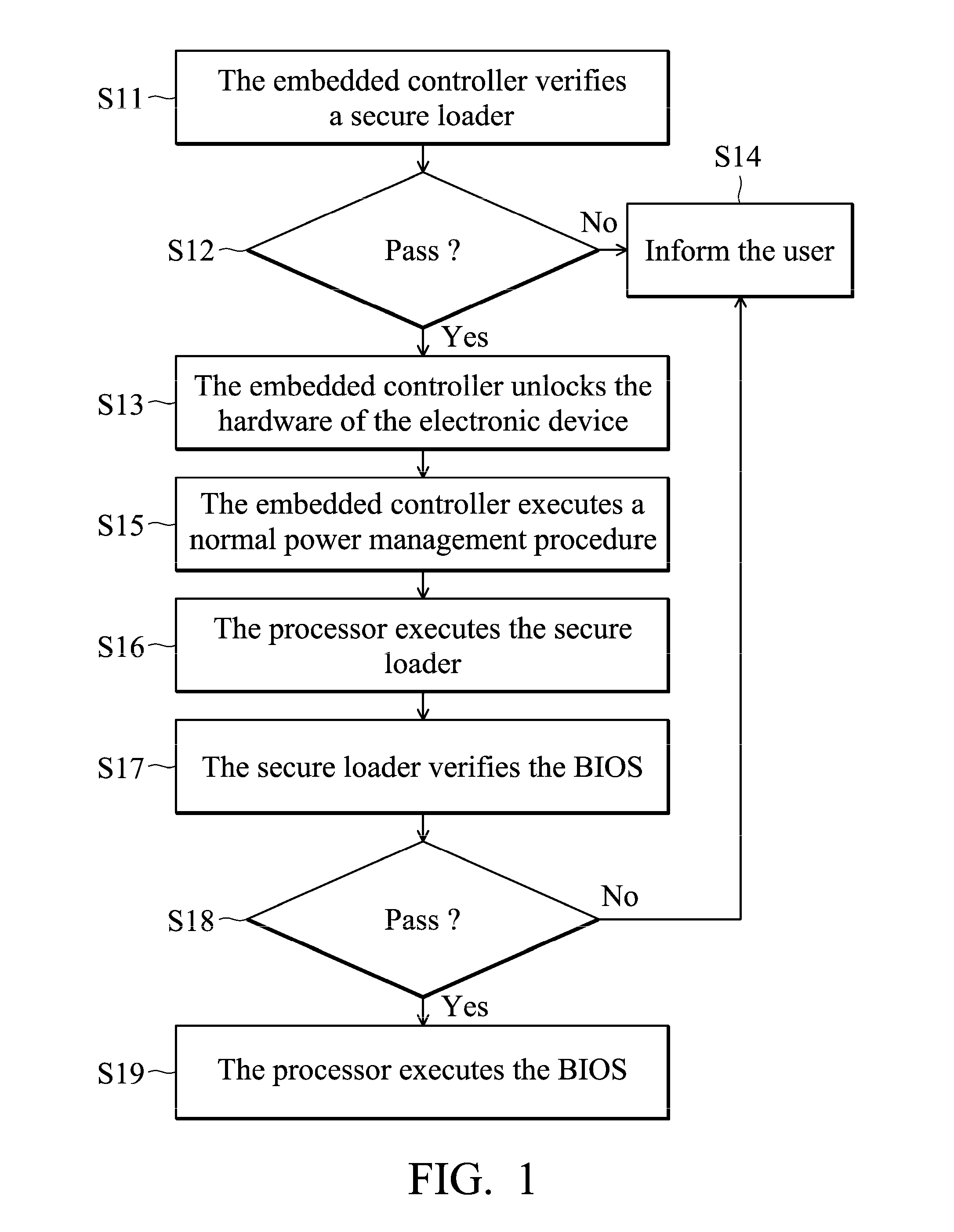
Electronic device and secure boot method
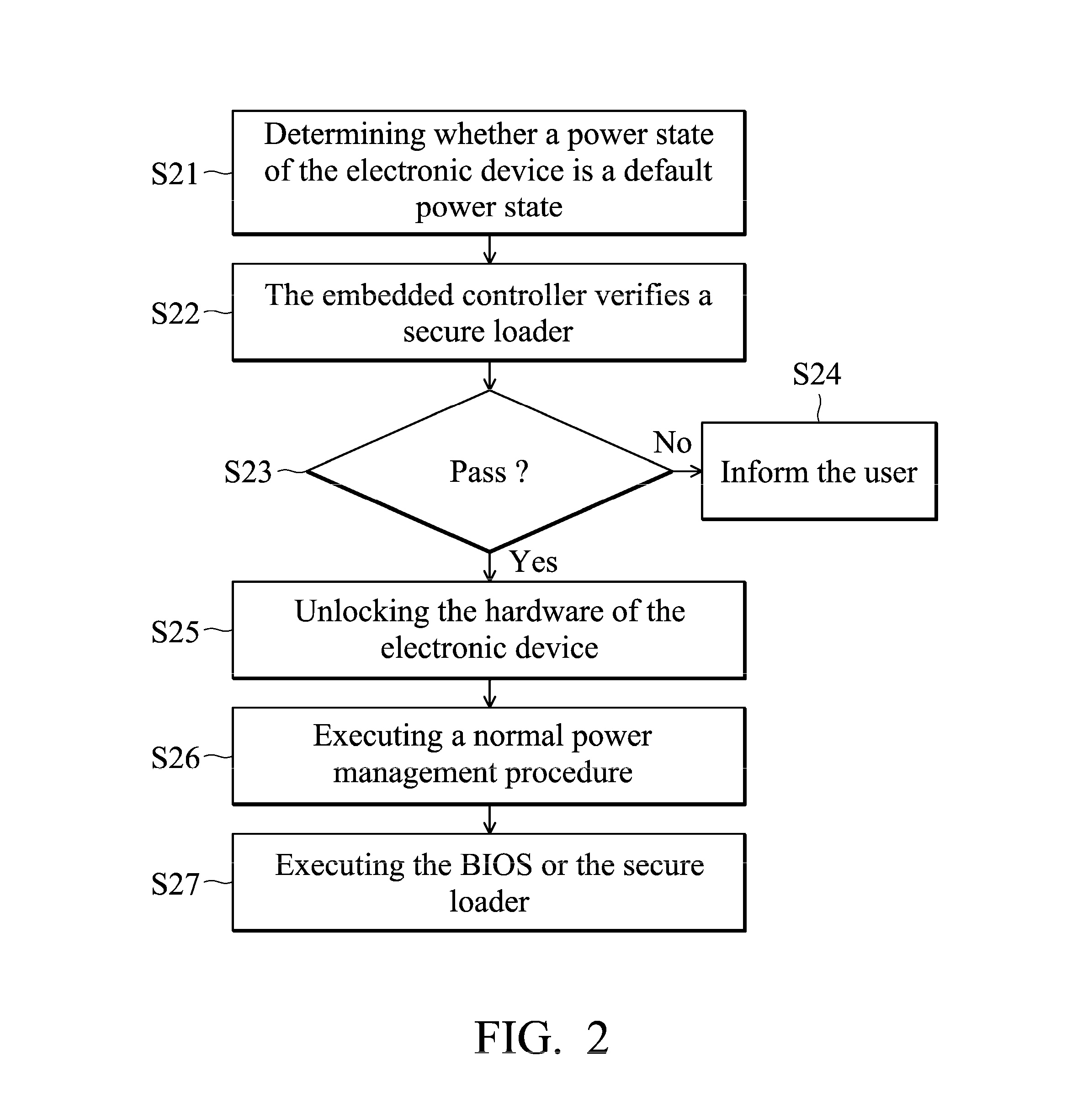
ActiveUS20140115314A1Digital computer detailsComputer security arrangementsEmbedded controllerLoader
An embodiment of the invention provides a secure boot method for an electronic device including an embedded controller and a processor. The method includes the steps of verifying a secure loader by the embedded controller, unlocking a peripheral hardware of the electronic device by the embedded controller, and executing the secure loader by the processor.
Owner:VIA TECH INC
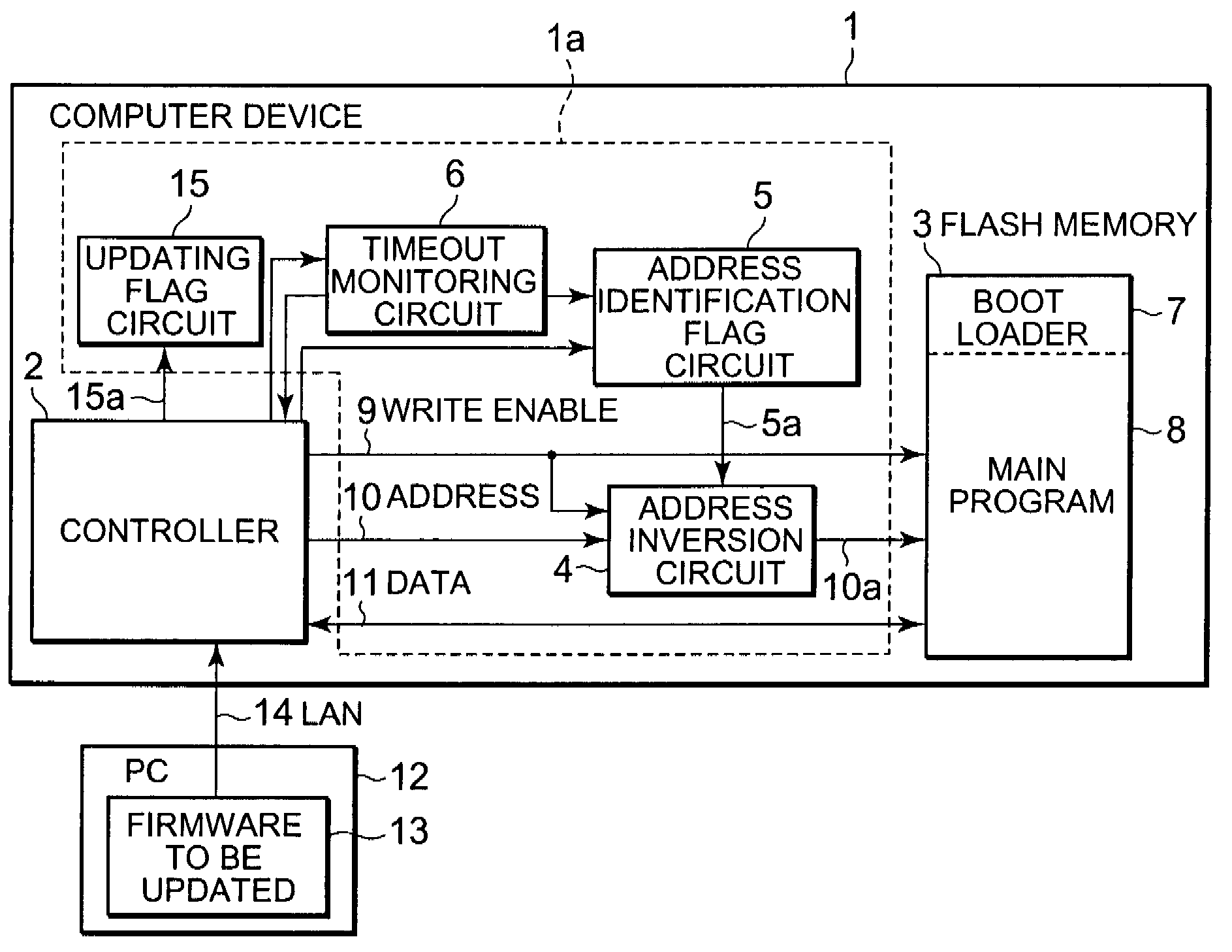
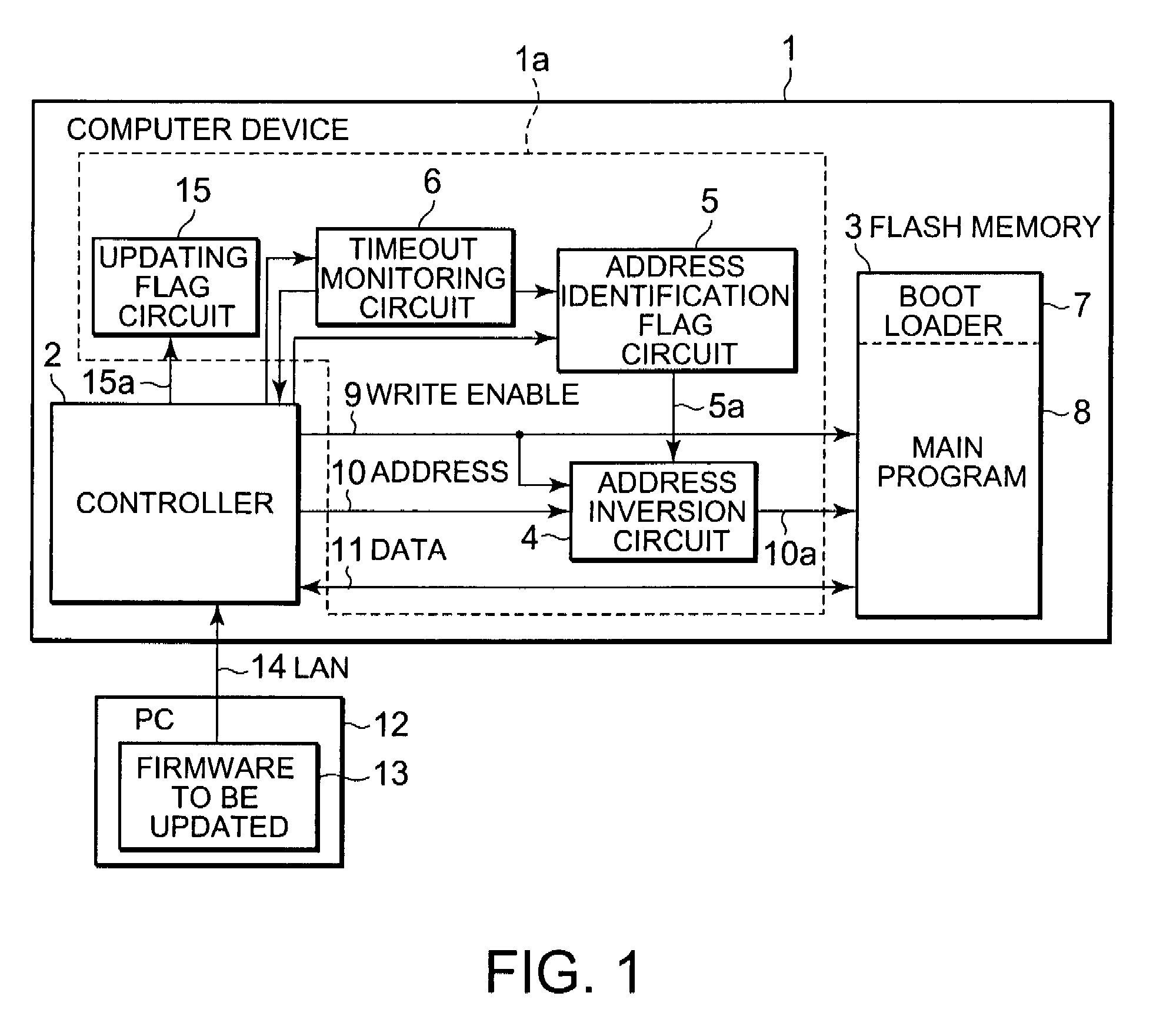
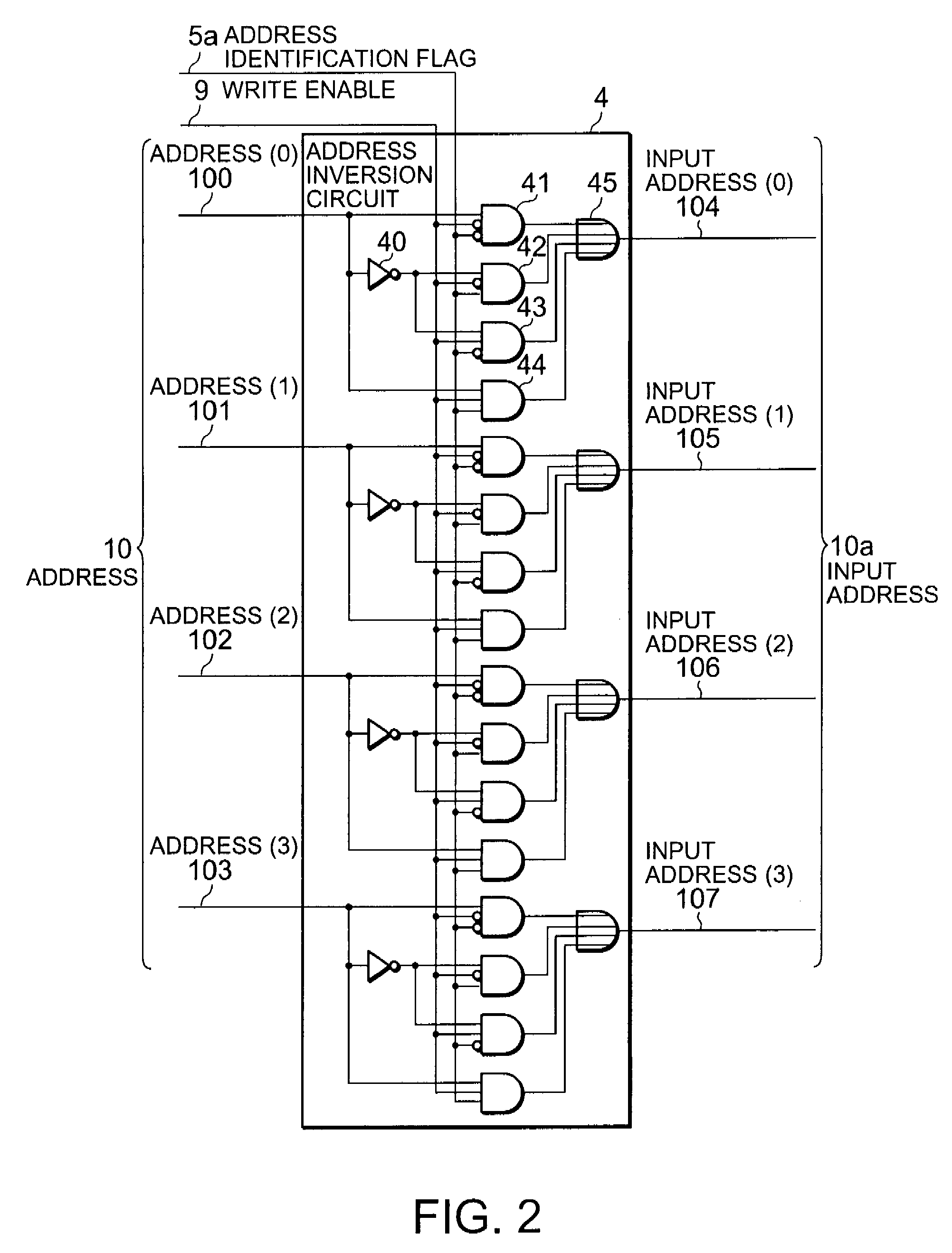
Firmware updating circuit and firmware updating method
A firmware updating circuit of the present invention includes an identification part and an address inversion part. The identification part stores identification data corresponding to an address of a boot loader in a non-volatile memory for storing the boot loader and a main program. When the controller updates both the boot loader and the main program, the address inversion part changes an address for reading the boot loader, output by a controller to the non-volatile memory, and an address for writing another boot loader to be updated according to the identification data so that those addresses come to be different from each other and at least one of the boot loader and the boot loader to be updated comes to exist in the non-volatile memory.
Owner:NEC CORP
Modularized JAVA application software online updating system and method
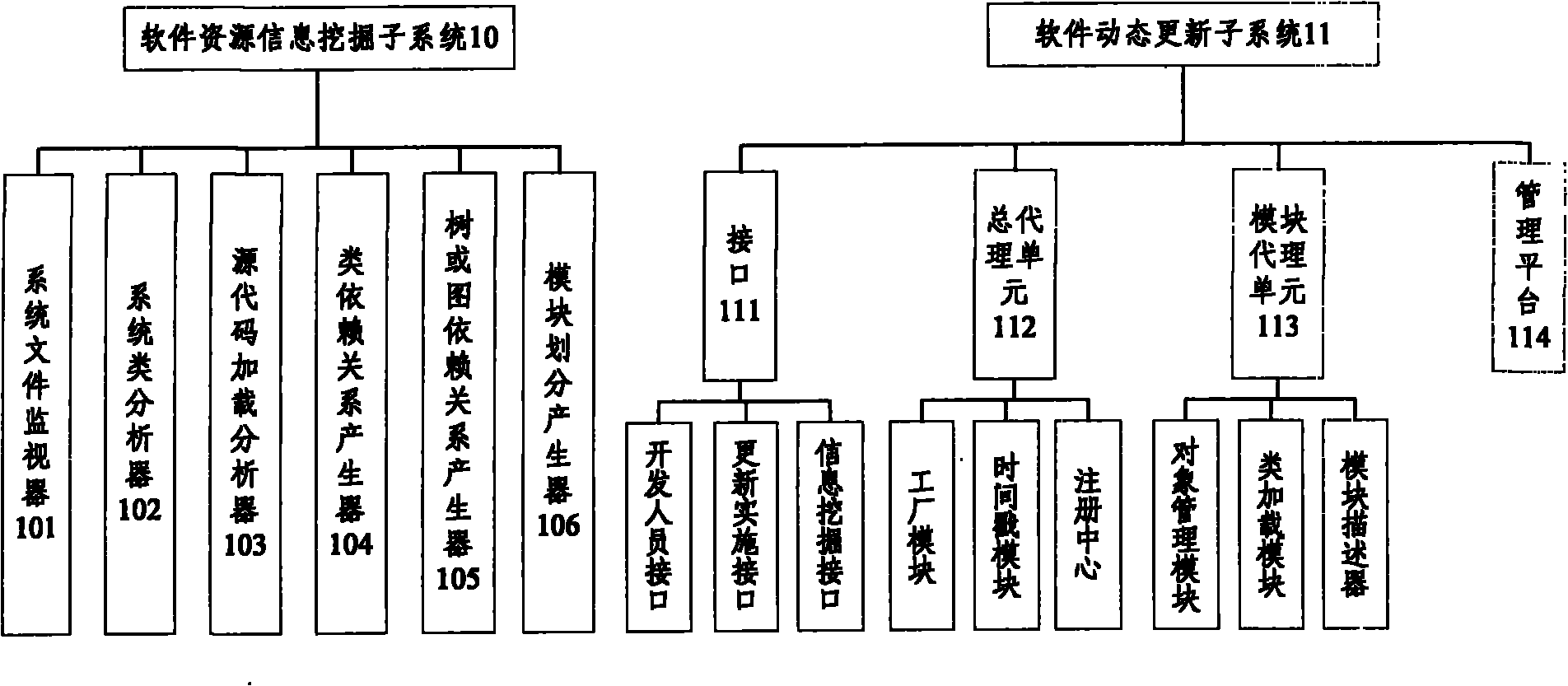
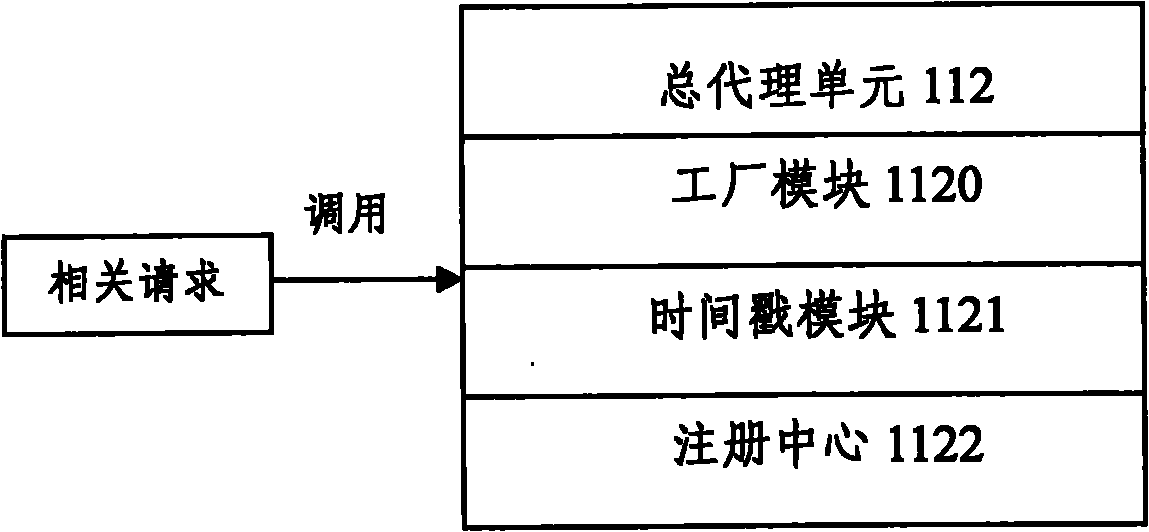
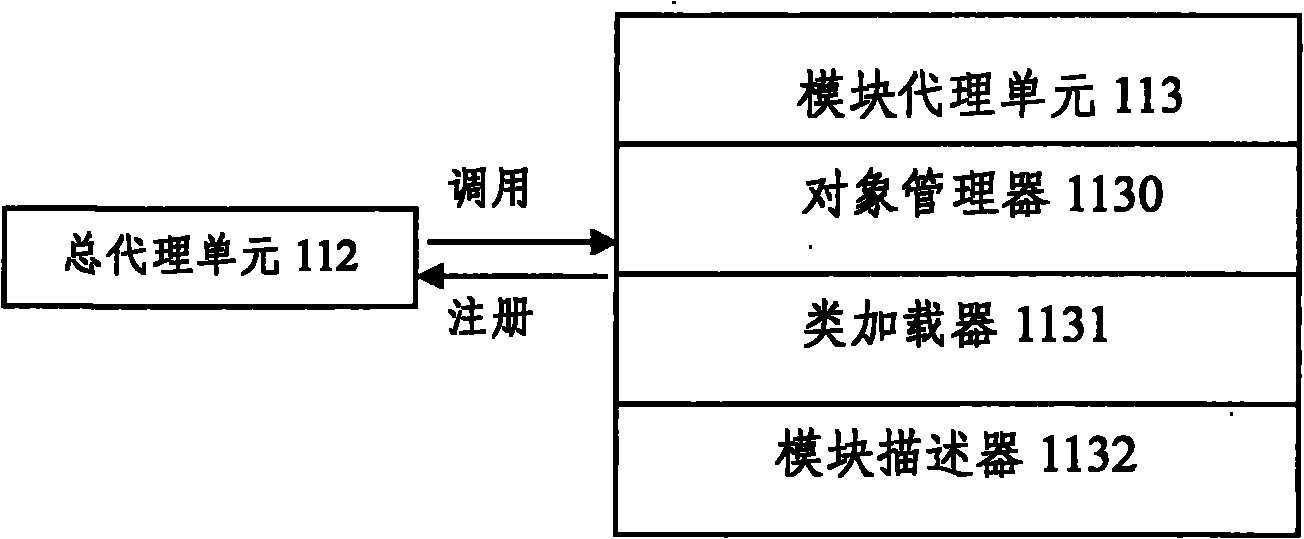
The invention discloses a modularized JAVA application software online updating system. The system comprises a software resource information mining sub-system and a software dynamic updating sub-system, wherein the software resource information mining sub-system comprises a system file monitor, a source code loading analyzer, a system class analyzer, a class dependence relationship generator, a tree or directed graph dependence relationship generator and a module division generator; the software dynamic updating sub-system comprises an interface, a general agent unit, a module agent unit and a management platform; the general agent unit comprises a plant module, a time chop stamp module and a registration center; the module agent unit comprises an object manager, a class loader and a module describer. The system can realize service loading without restarting the service system. The invention also discloses a modularized JAVA application software online updating method. By adopting thesystem and the method, service loading is realized under a condition of not restarting the system.
Owner:BEIJING UNIV OF POSTS & TELECOMM
System and Method for Testing a Software Product
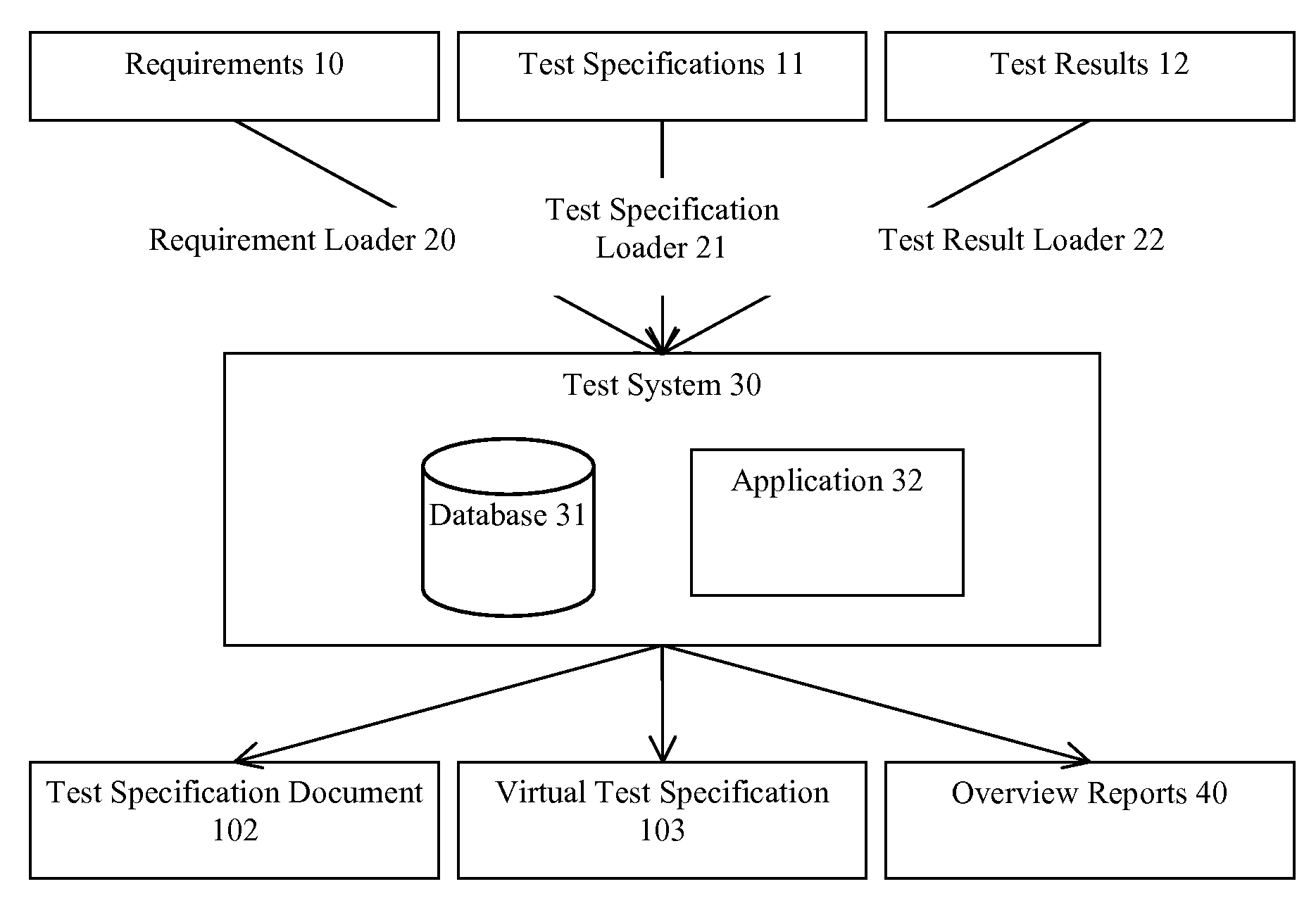
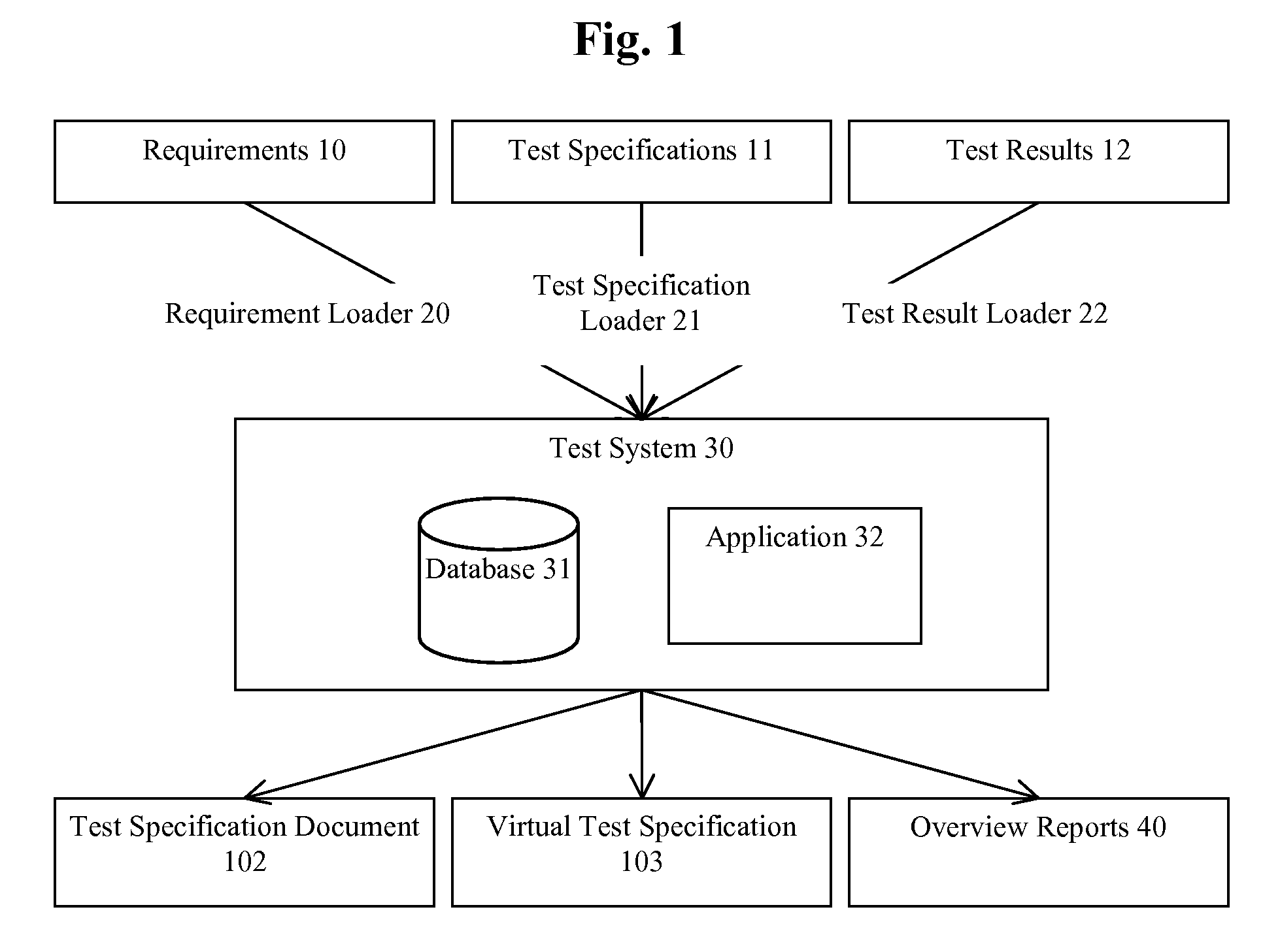
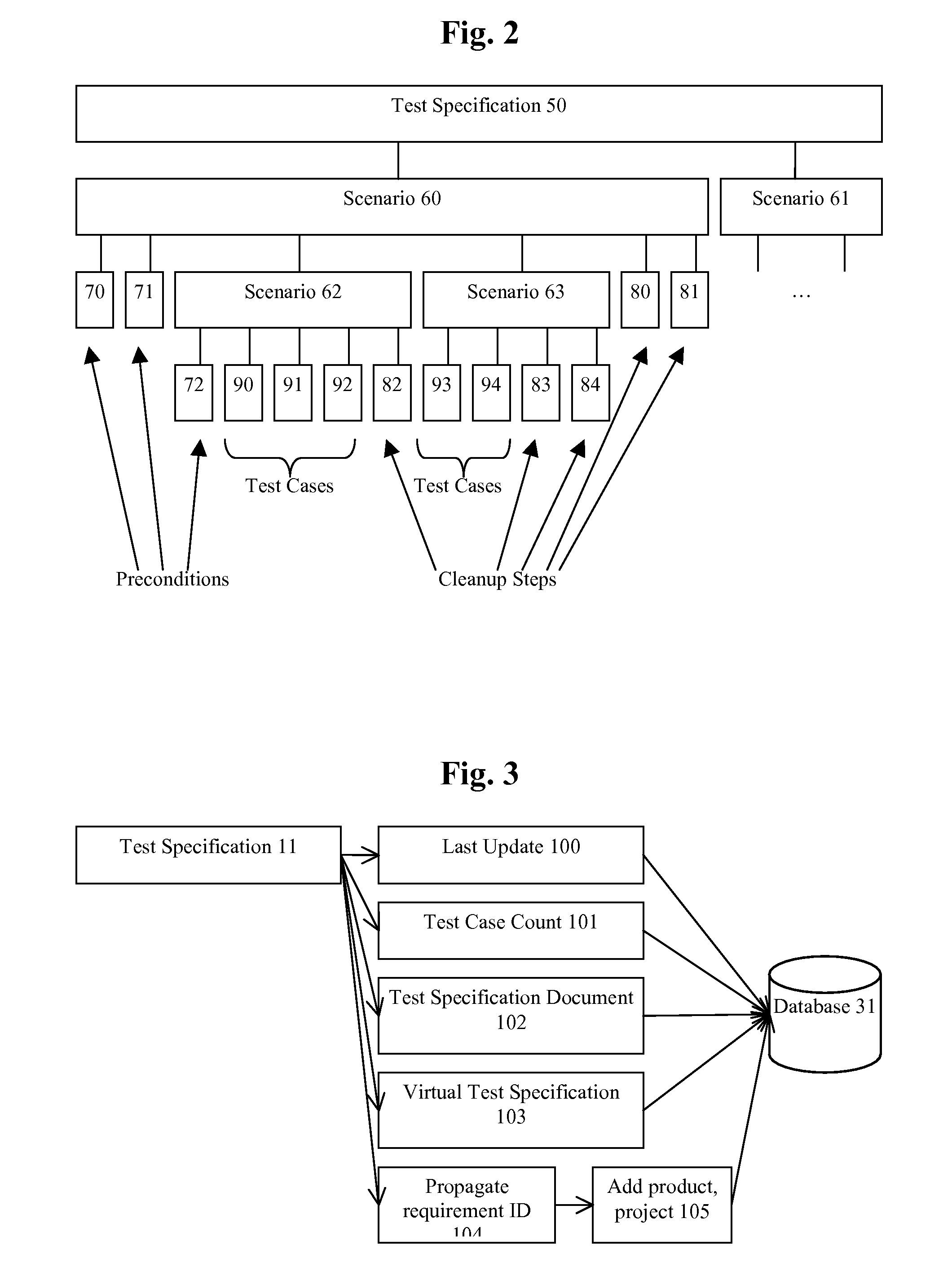
ActiveUS20090313606A1Minimizing processing power and number of database queryEfficiently gain overviewError detection/correctionSpecial data processing applicationsTest specificationTesting software
A system for testing at least one software product comprising a requirement loader and a test specification loader. The requirement loader is adapted for loading a plurality of requirements on the software product into a database. The test specification loader is adapted for loading a plurality of test specifications for the software product into the database, each test specification being related to one or more of the requirements. The test specification loader is further adapted for generating during loading of a test specification a virtual test specification in the database for each of the one or more related requirements, the virtual test specification comprising all test specifications for the respective requirement on the software product stored in the database.
Owner:SOFTWARE AG
Reliable firmware upgrading realizing method for distributed control system
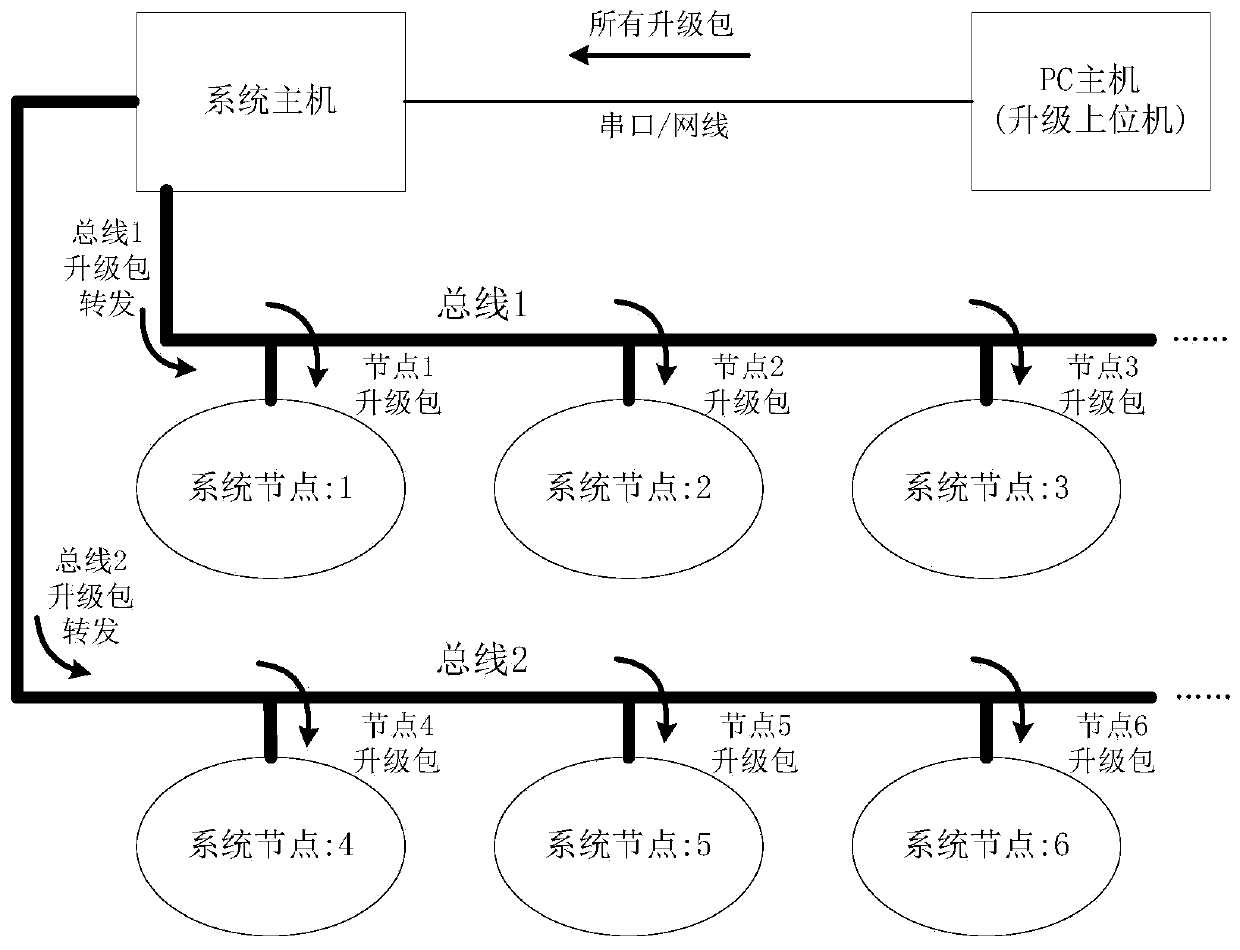
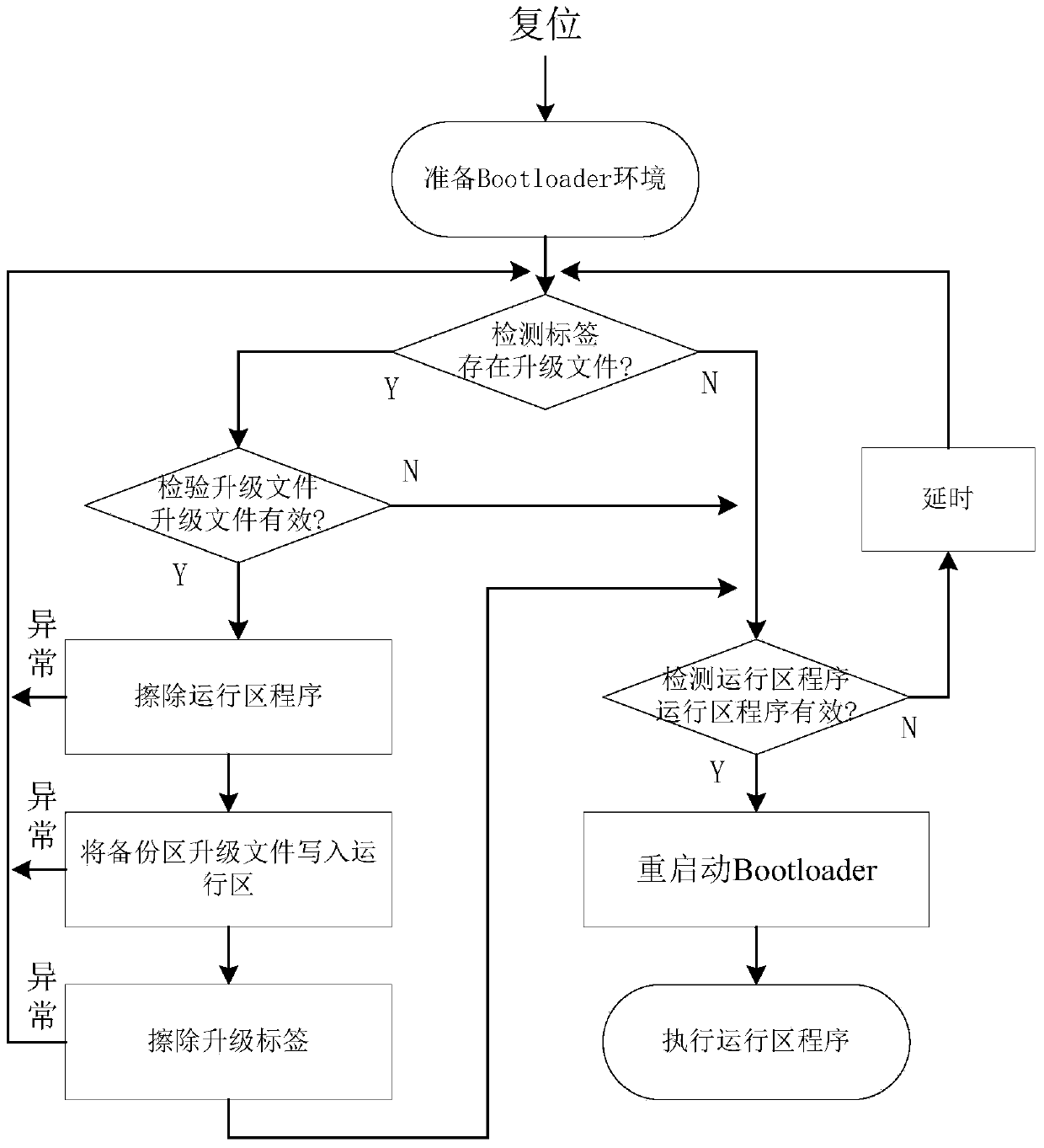
ActiveCN104007996AAvoid accidentsIncomplete replacement will not occurProgram loading/initiatingTransmissionNetwork packetDistributed control system
The invention provides a reliable firmware upgrading realizing method applied to a distributed control system. The reliable firmware upgrading realizing method enables any controller nodes or a host in the system to have program upgrading capacity, greatly improves the expansion capacity of hardware equipment and the customizing performance of the system and reduces later maintenance and upgrading cost. The reliable firmware upgrading realizing method is different from a traditional method in that receiving of a target program package is realized in an application program, the received data package is stored into a backup program area at first, after the target program package is completely received and CRC verification is passed, parameter information marks are generated in an IAP mark area, and a Boot loader is called for to realize program upgrading. Even if an unpredictable failure occurs in any link, existing programs cannot be replaced, and therefore the stability of the system is greatly improved.
Owner:南京润教科技有限公司
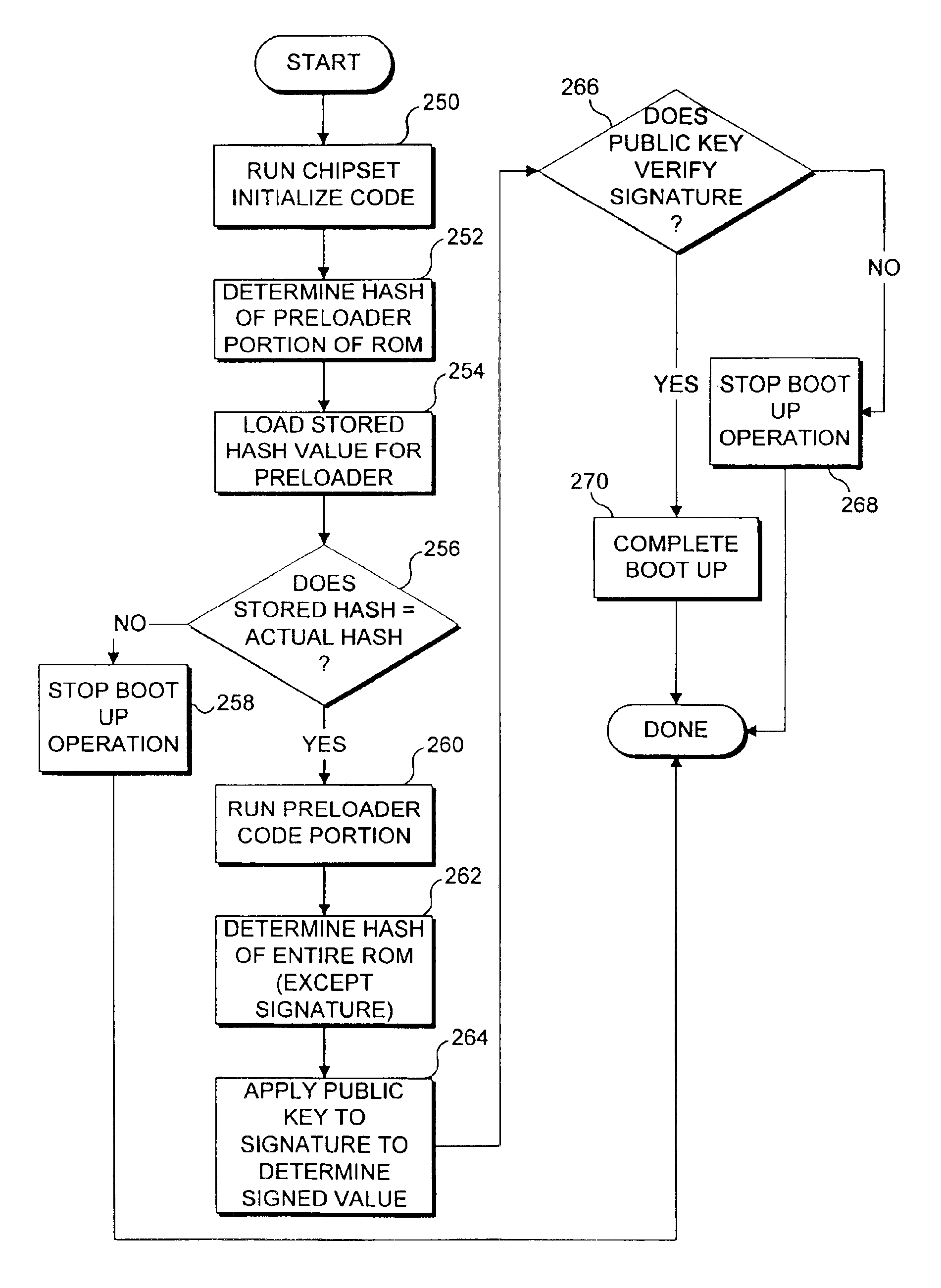
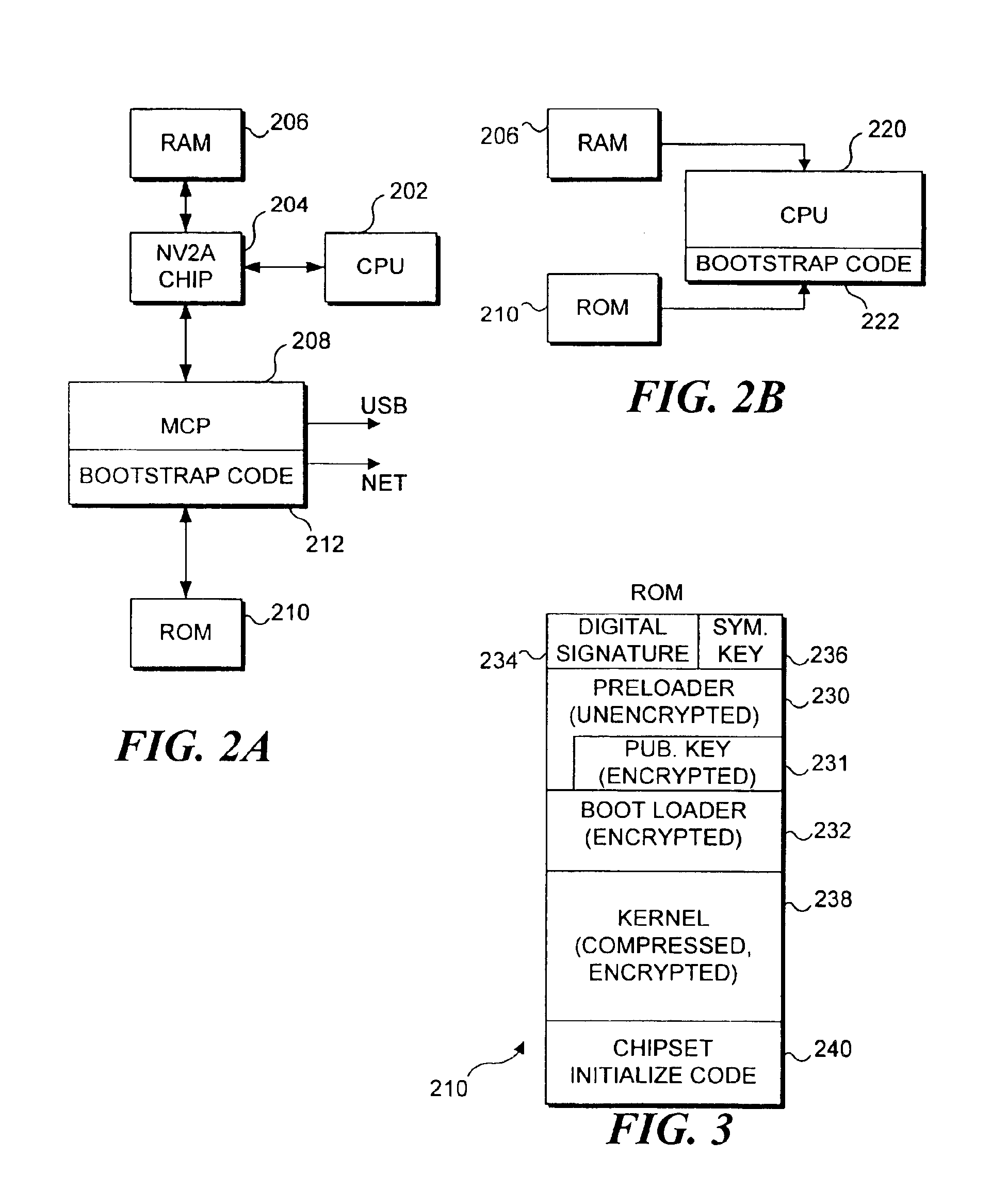
Use of hashing in a secure boot loader
InactiveUS6907522B2Digital data processing detailsUser identity/authority verificationDigital signatureMachine instruction
Machine instructions comprising a bootstrap code are buried within a critical component of an electronic game console where they cannot readily be accessed or modified. A preloader portion in a read only memory (ROM) is hashed by the bootstrap code and the result is compared to an expected hash value maintained in the bootstrap code. Further verification of the boot-up process is carried out by the preloader, which hashes the code in ROM to obtain a hash value for the code. The result is verified against a digital signature value that defines an expected value for this hash. Failure to obtain any expected result terminates the boot-up process. Since the bootstrap code confirms the preloader, and the preloader confirms the remainder of the code in ROM, this technique is useful for ensuring that the code used for booting up the device has not been modified or replaced.
Owner:MICROSOFT TECH LICENSING LLC
Method and system for automatically identifying and marking subsets of localizable resources
InactiveUS20060130026A1Natural language translationExecution for user interfacesOperational systemManual testing
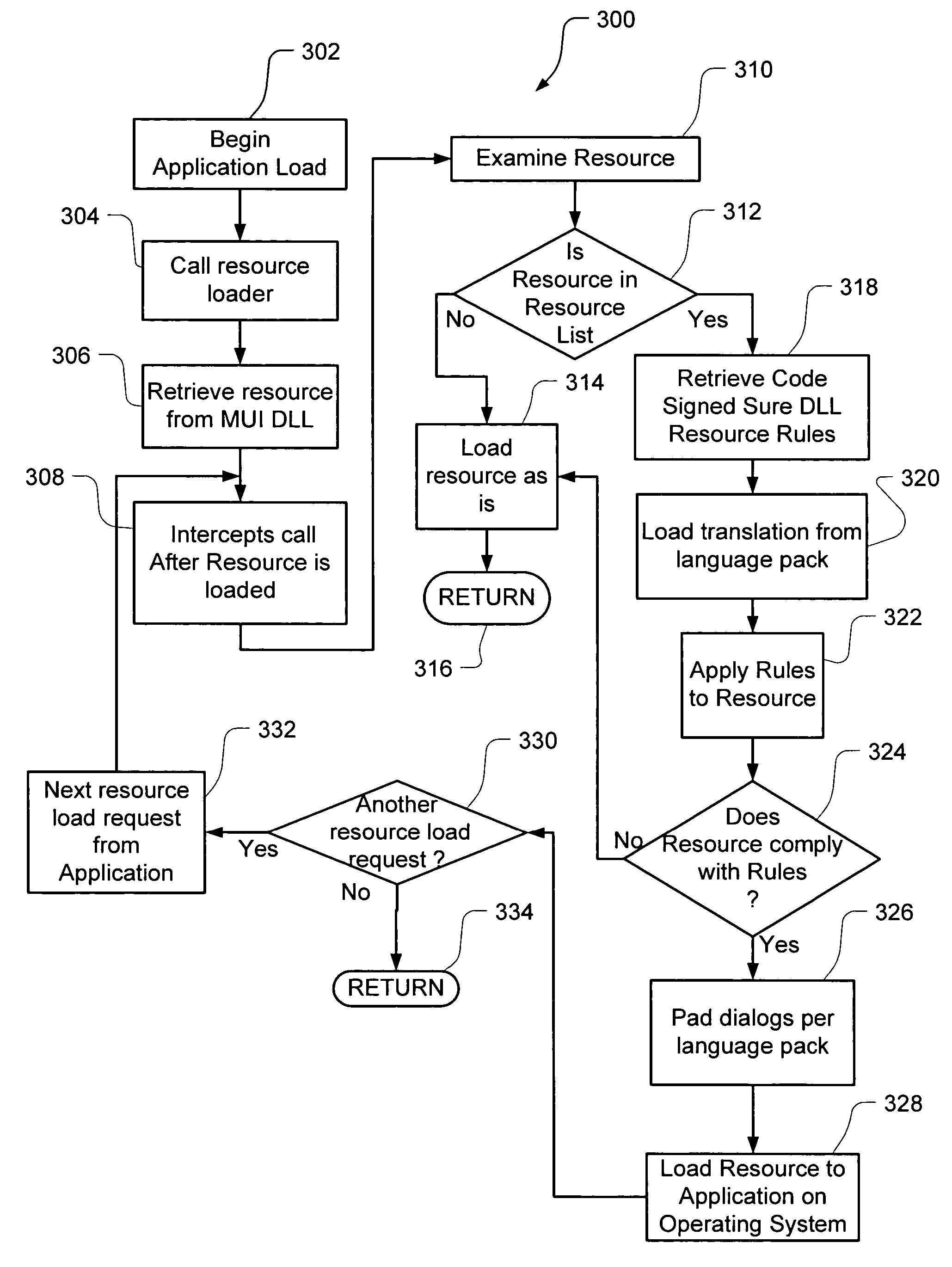
Embodiments of the present invention relate to methods, systems and computer-readable media for identifying a safe set of resources that can be used for localization of a software product. This identification involves loading and running a base product having one or more calls to an operating system (or an API) to load language specific data. The resource calls are intercepted after the resource is loaded into a resource loader, and information about the resource is captured for analysis. The display of resources is also intercepted to gather data on which resources are displayed and the context of this display. The process involves running automated tests and / or manual tests on the base product in its base language to identify those resources that are most frequently used, least often or never used, and those that are unsafe. These resources so identified are then analyzed to generate a safe secure resource list that can then be used for external localization of the software product.
Owner:MICROSOFT TECH LICENSING LLC
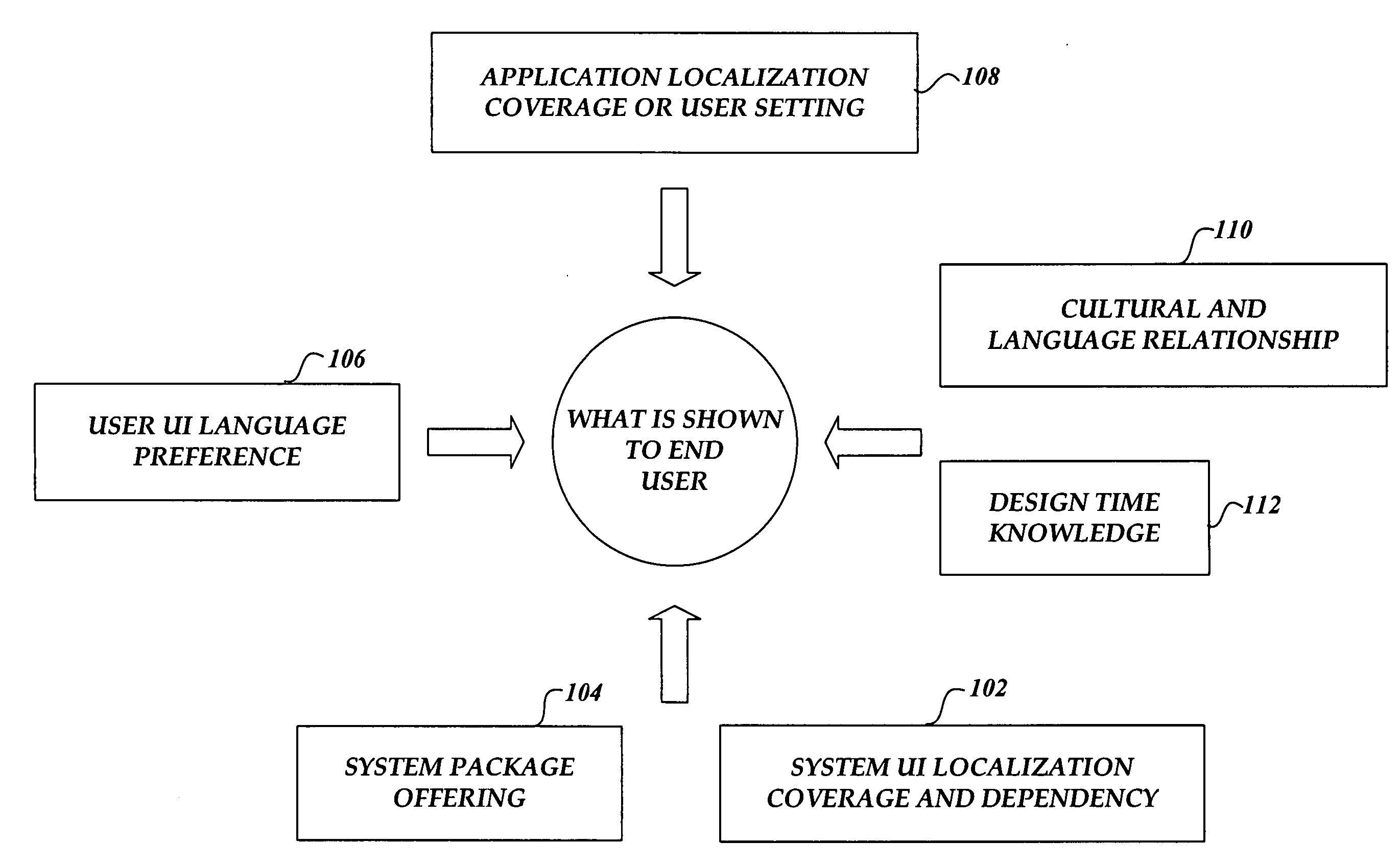
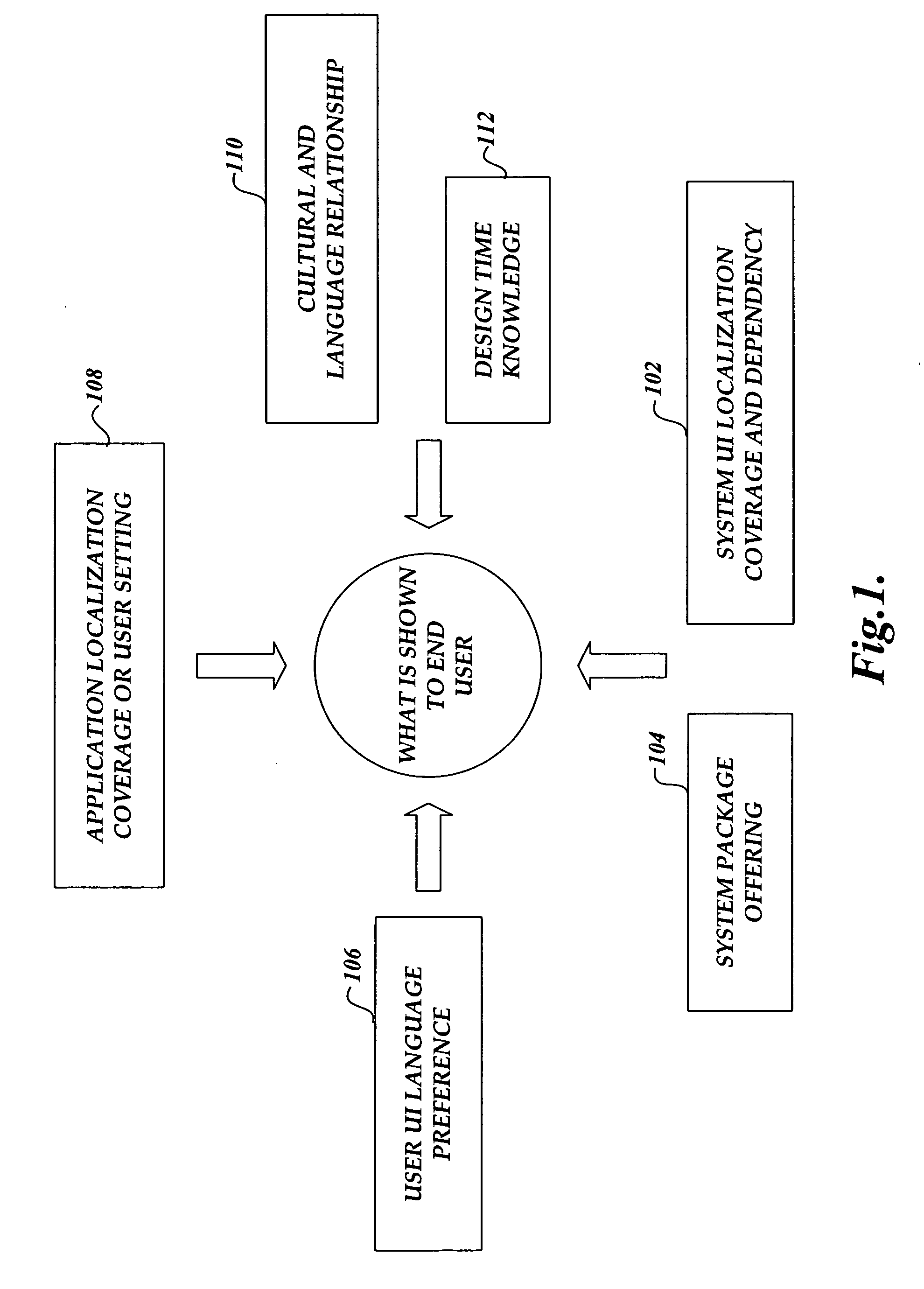
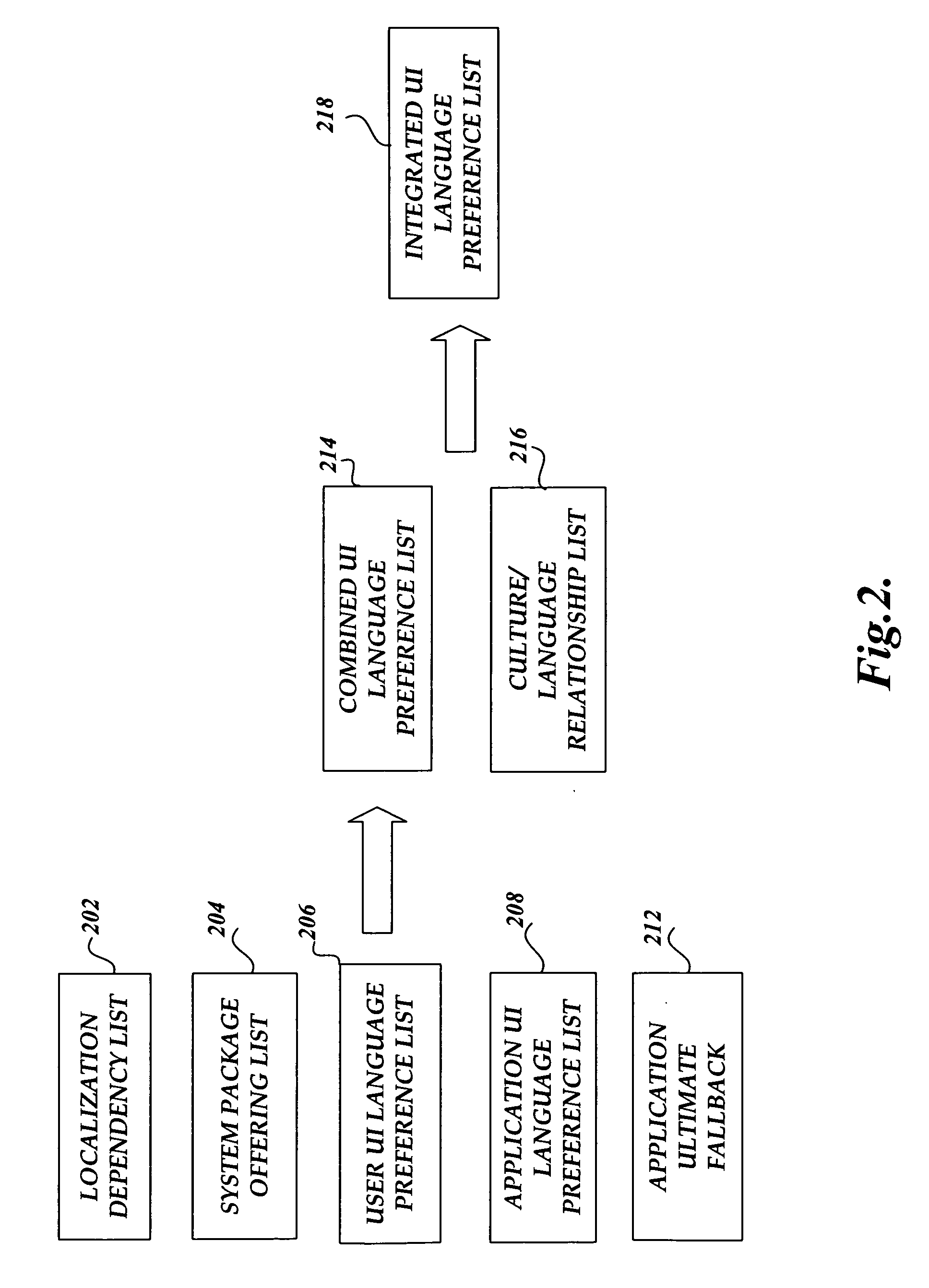
System and method for managing resource loading in a multilingual user interface operating system
InactiveUS20060242621A1Avoid resourcesConsistent supportExecution for user interfacesSpecial data processing applicationsOperational systemMulti language
A system and method is provided to manage different UI language settings in a central place by merging different UI language settings and related dependency data to an integrated UI language preference list. A set of API functions is provided that enables each resource loader to gain consistent UI language support by interacting with the integrated UI language preference list.
Owner:MICROSOFT TECH LICENSING LLC
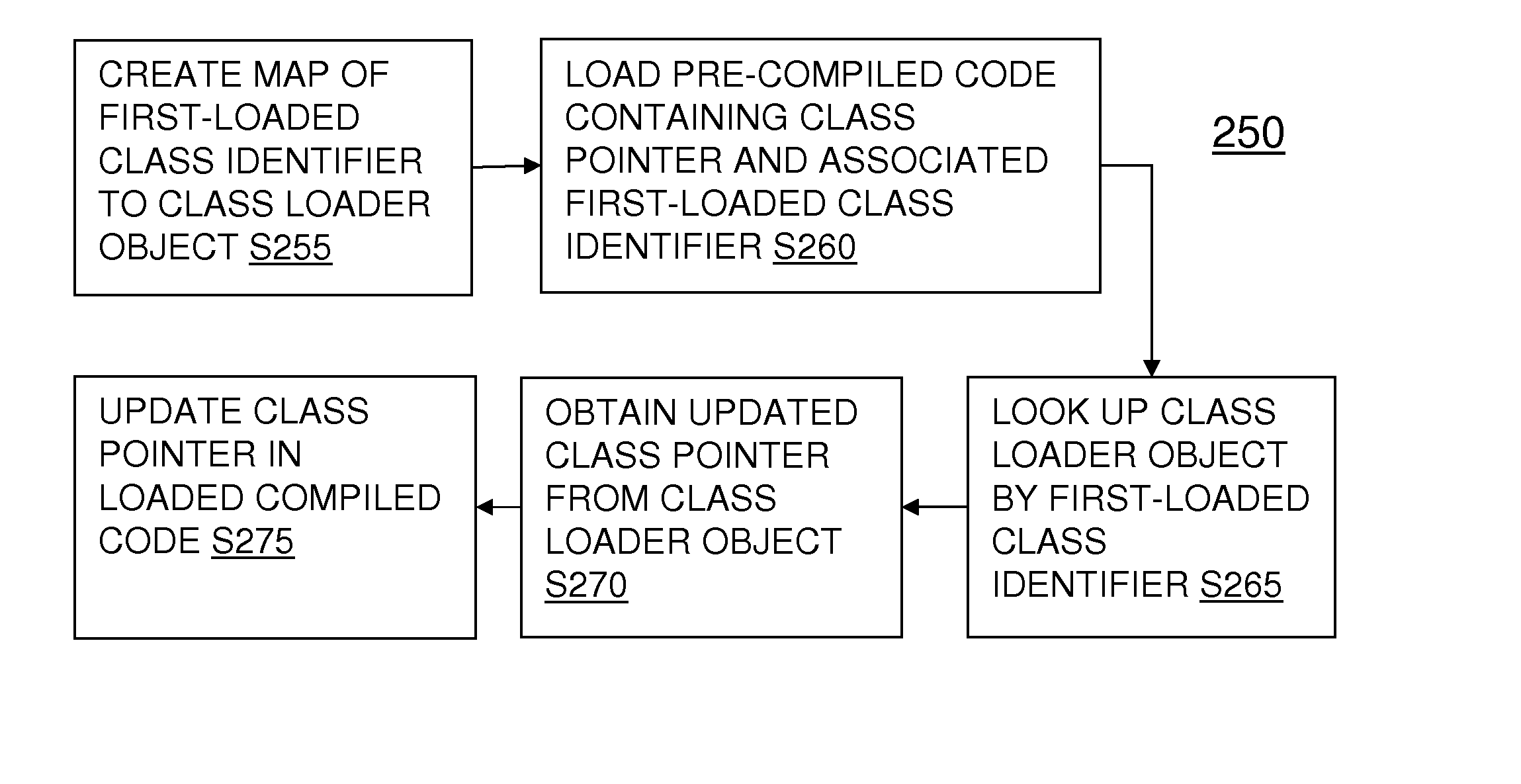
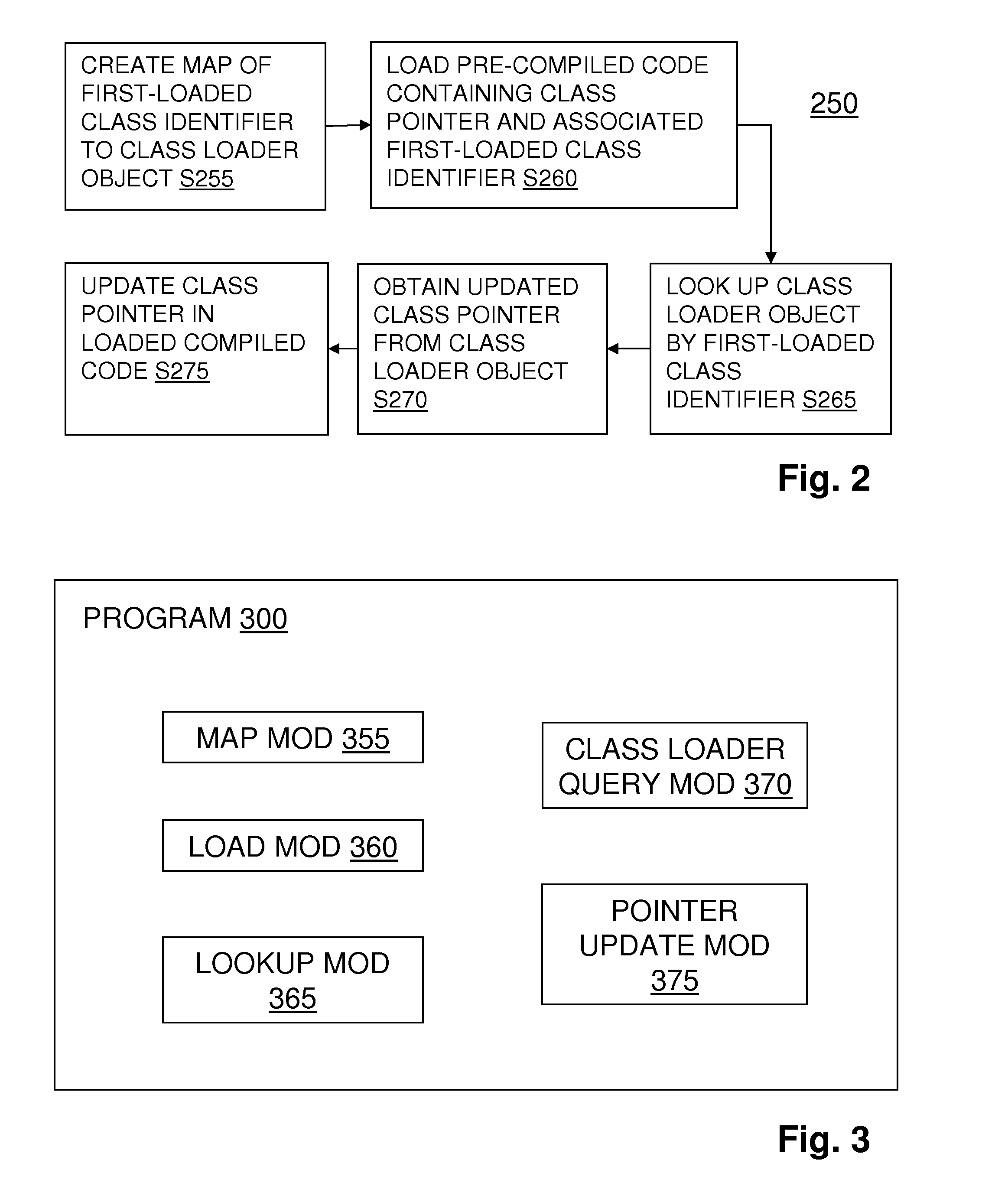
Correlating class loader objects across execution environments
InactiveUS20150378752A1Software engineeringProgram loading/initiatingProgramming languageSoftware engineering
Updating a native class pointer in persisted compiled code for use in an execution environment other than the one in which the native class pointer was created. This is done by using an identifier, stored with the persisted compiled code, of the class first loaded by the class loader that also loaded the class to which the native class pointer refers. A table is maintained in the execution environment mapping class identifiers to class loaders, and the stored identifier is used to consult this table to find a candidate class loader from those in the current execution environment that can provide the correct updated pointer.
Owner:IBM CORP
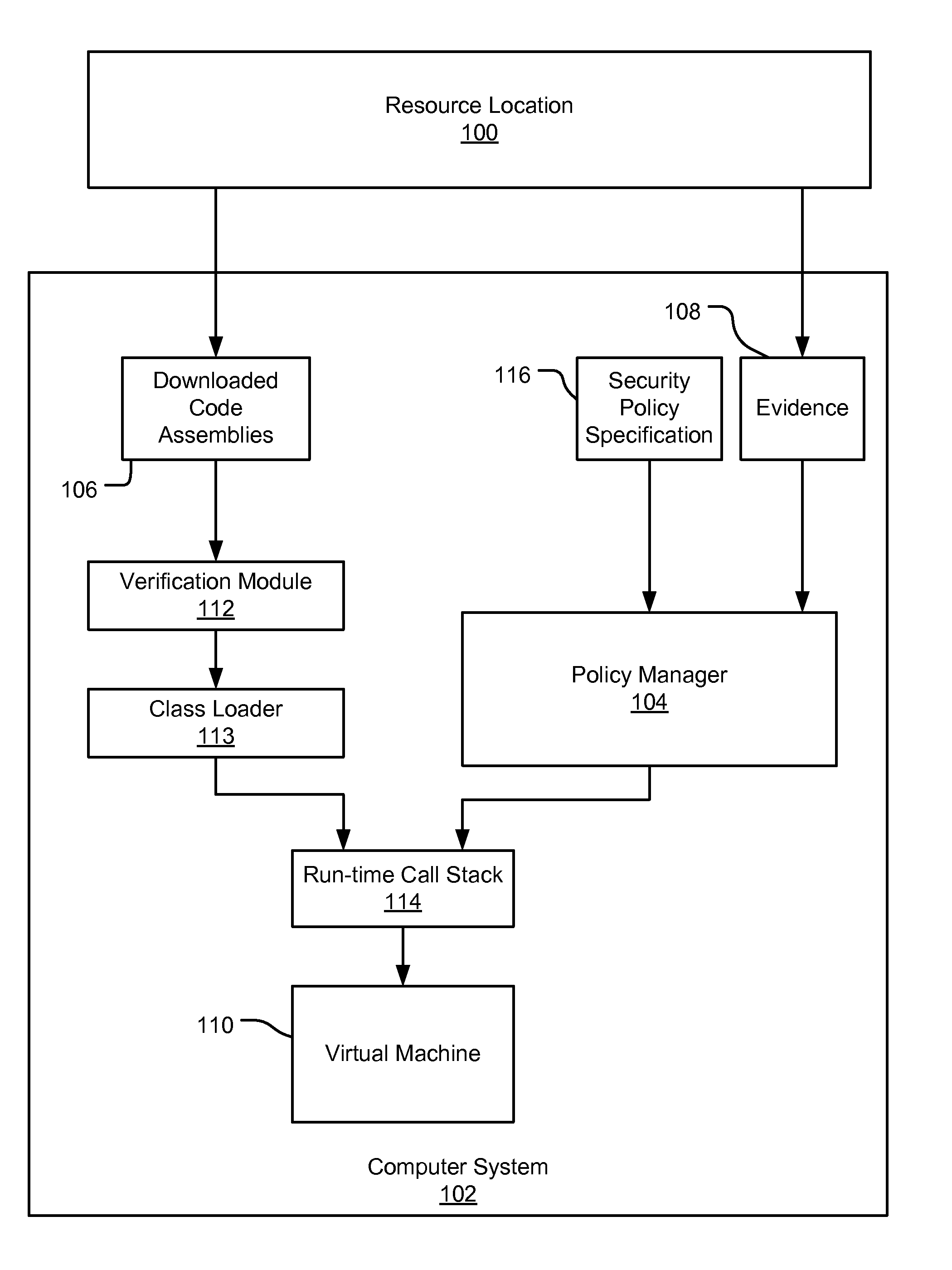
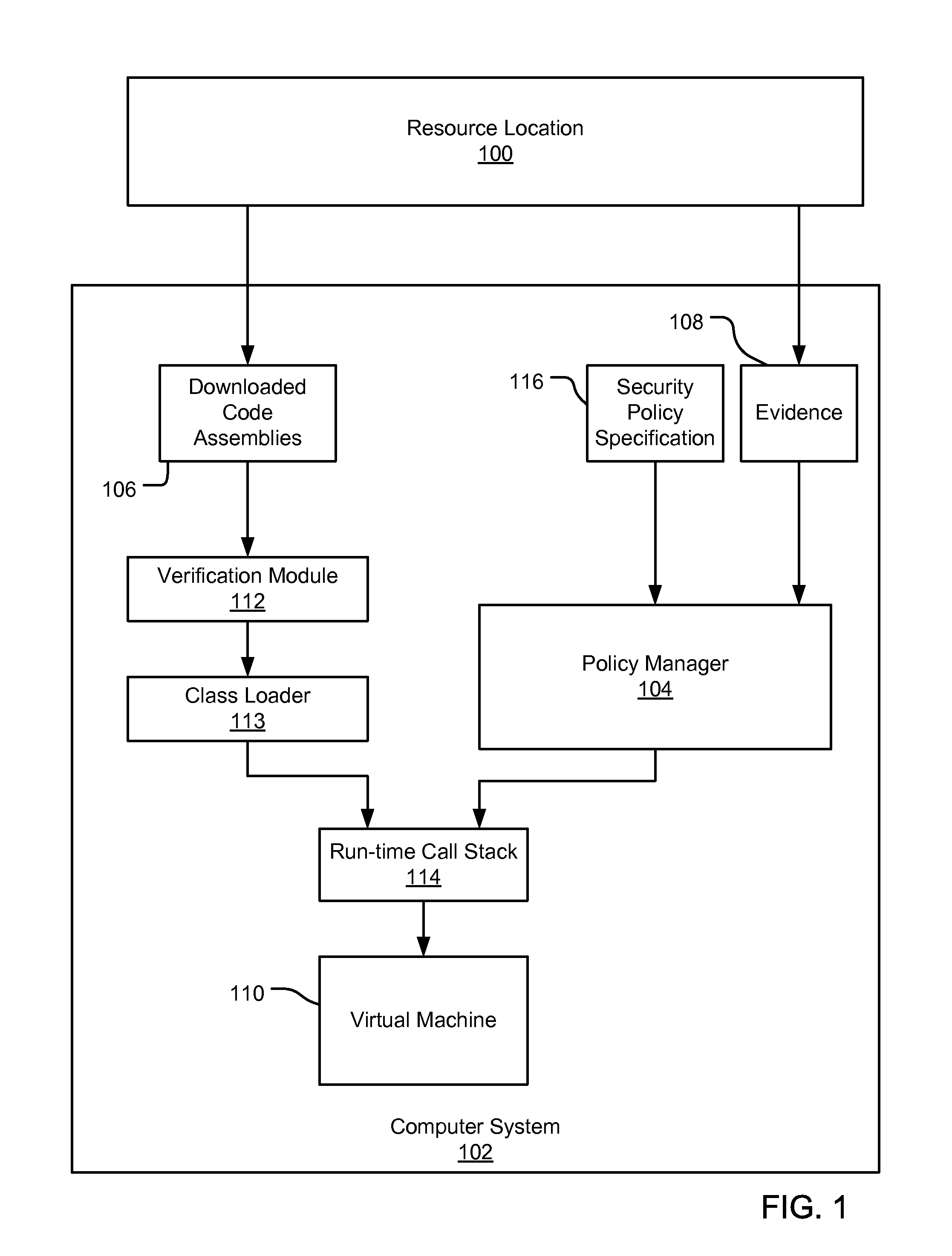
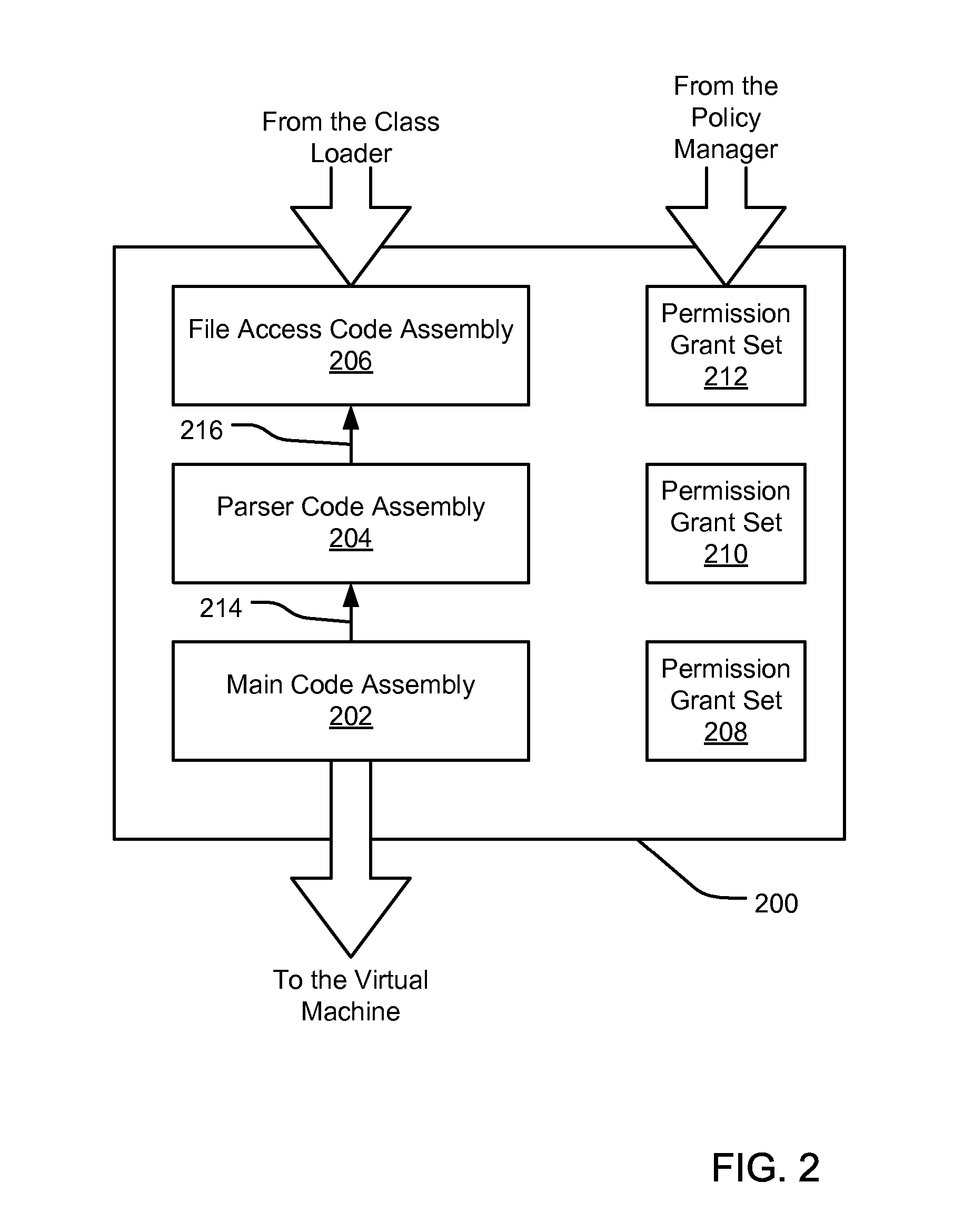
Partial grant set evaluation from partial evidence in an evidence-based security policy manager
InactiveUS20070192839A1Digital data processing detailsUser identity/authority verificationCall stackEngineering
An evidence-based policy manager generates a permission grant set for a code assembly received from a resource location. The policy manager executes in a computer system (e.g., a Web client or server) in combination with the verification module and class loader of the run-time environment. The permission grant set generated for a code assembly is applied in the run-time call stack to help the system determine whether a given system operation by the code assembly is authorized. The policy manager may determine a subset of the permission grant set based on a subset of the received code assembly's evidence, in order to expedite processing of the code assembly. When the evidence subset does not yield the desired permission subset, the policy manager may then perform an evaluation of all evidence received.
Owner:MICROSOFT TECH LICENSING LLC
Method for implementing dynamic update of Java program
InactiveCN101174217AGuaranteed to compile onceWill not interfere with each otherSpecific program execution arrangementsSoftware updateData field
The invention relates to a method for realizing dynamic update of Java program in the computer technical field, which comprises the following steps: firstly, modifying the class definitions that need dynamic update in the passive dynamic update program, and adding update support method for realizing judgment to the subobjects of the class objects one by one, wherein the parameter is class loader; secondly, modifying the update class definitions in the dynamic update program, and adding update method for realizing initialization to the variables under the update class objects, wherein, the input parameter is class loader and old object; thirdly, modifying part of the method invocation, data field memory, and object set of the updated program with the Java reflection to realize running recovery of the program; finally, adding update support method to the main class and adding update checkpoint in the main method circulation. The invention has the advantages of avoiding software update that needs halt, update and reboot and avoiding loss caused by halt.
Owner:SHANGHAI JIAO TONG UNIV
Dynamic determination of application server runtime classloading
InactiveUS20120005663A1Digital data processing detailsProgram loading/initiatingApplication serverSoftware engineering
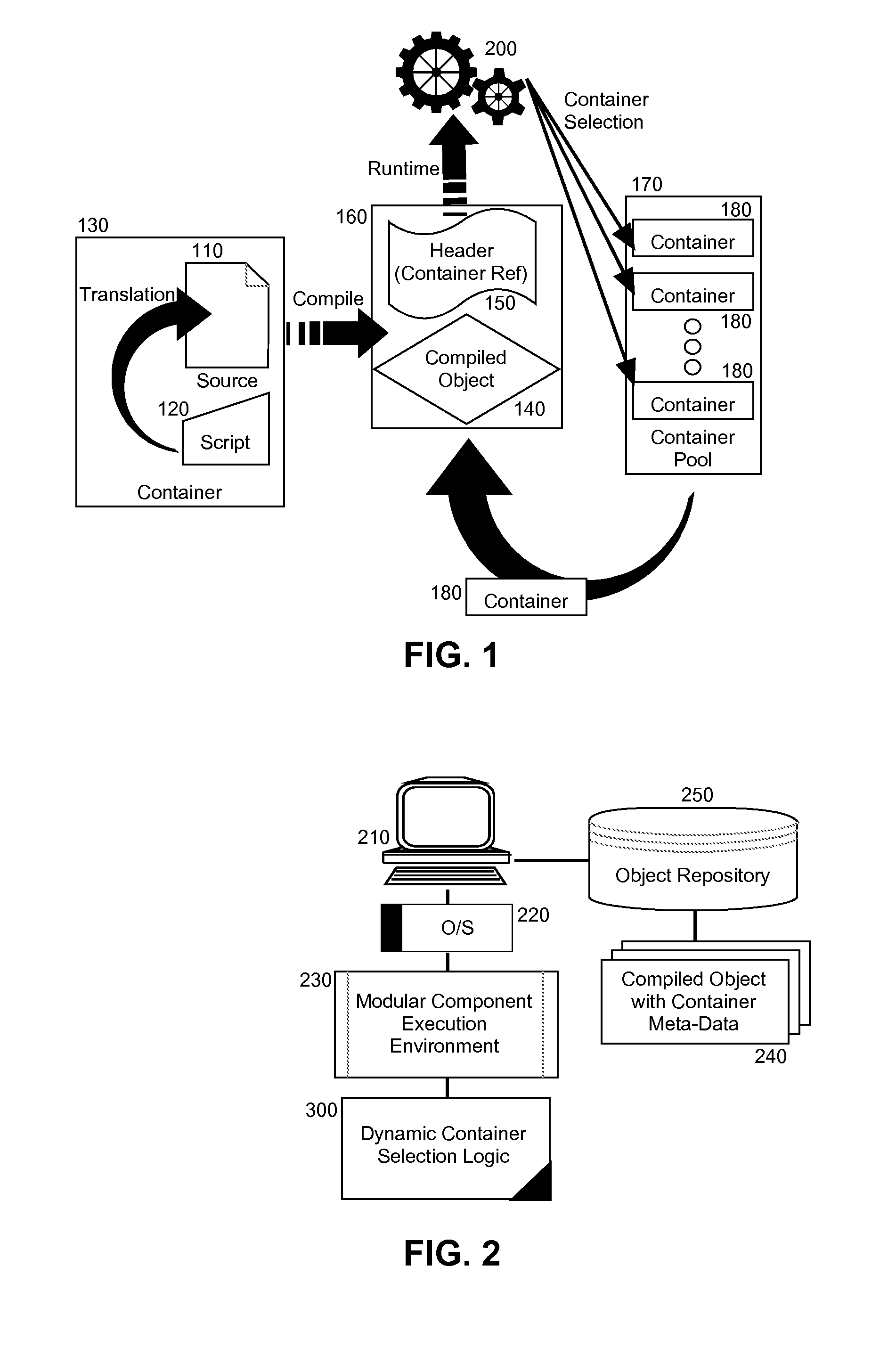
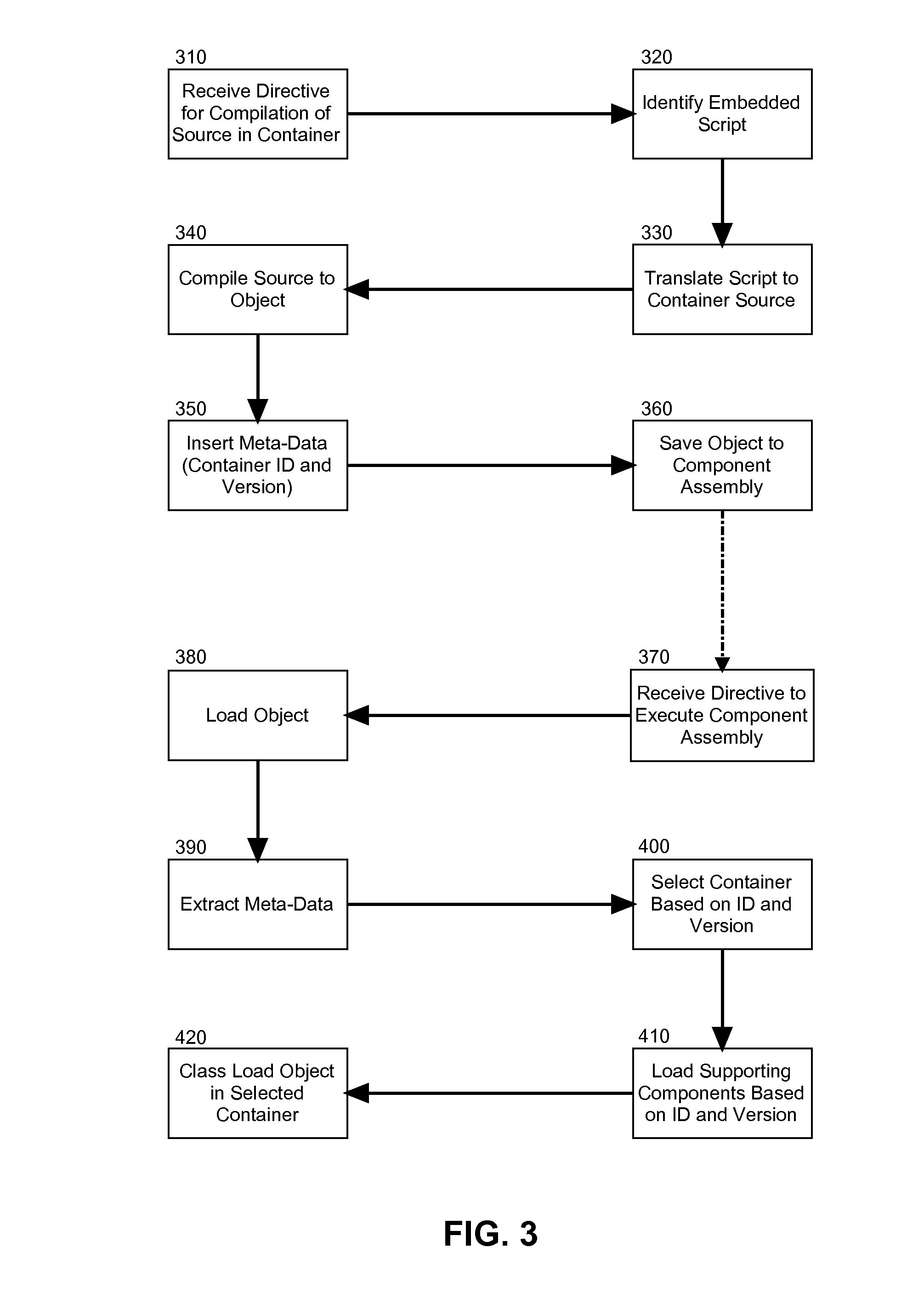
Embodiments of the present invention provide a method, system and computer program product for dynamic selection of a runtime classloader for a generated class file. In an embodiment of the invention, a method for dynamic selection of a runtime classloader for a generated class file is provided. The method includes extracting meta-data from a program object directed for execution in an application server and determining from the meta-data a container identity for a container in which the program object had been compiled. The method also includes selecting a container according to the meta-data. Finally, the method includes classloading the program object in the selected container.
Owner:IBM CORP
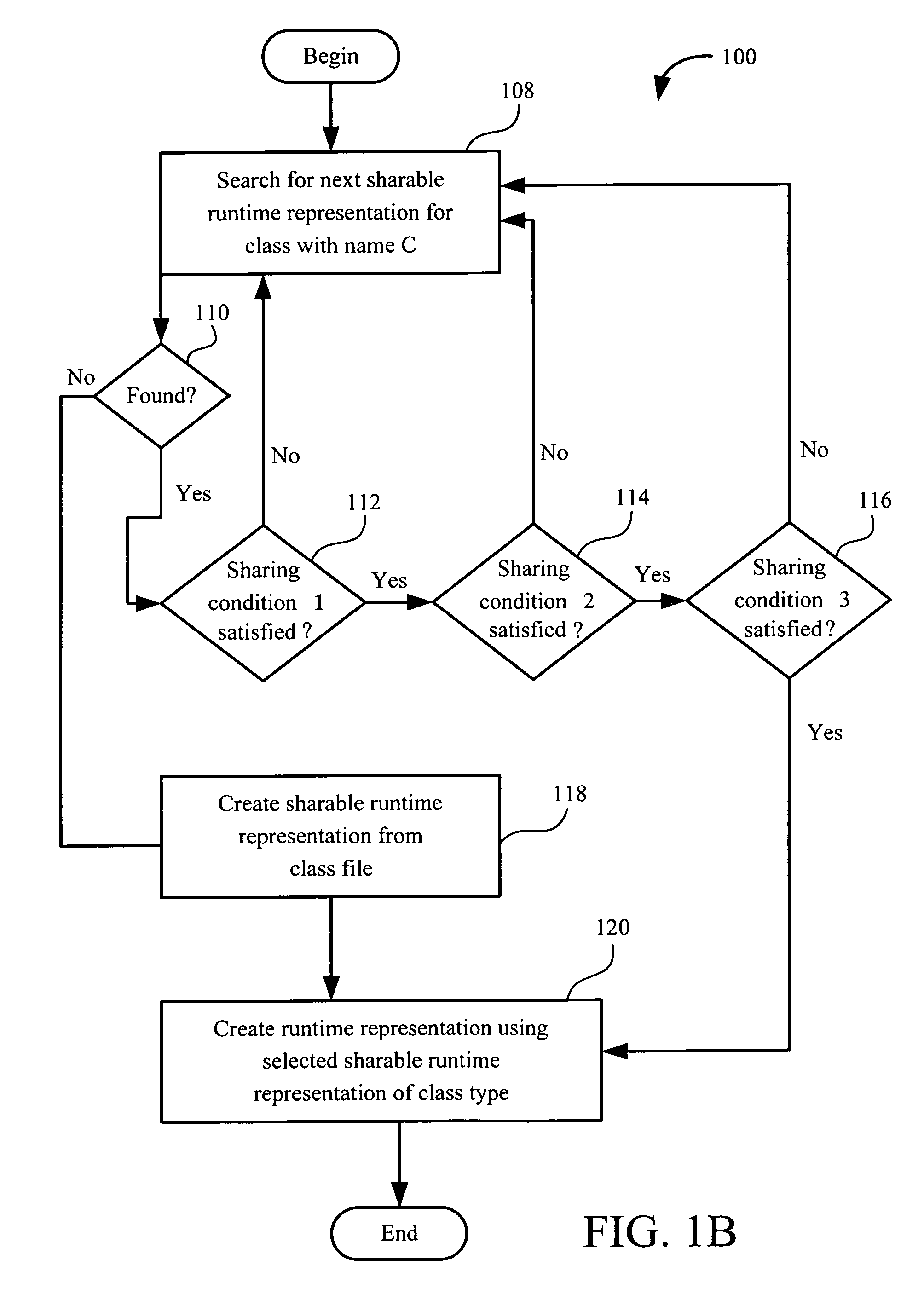
Sharing runtime representation of software component methods across component loaders
ActiveUS7406687B1Increasing main memory conservationLow running costSoftware engineeringSpecific program execution arrangementsByteClass type
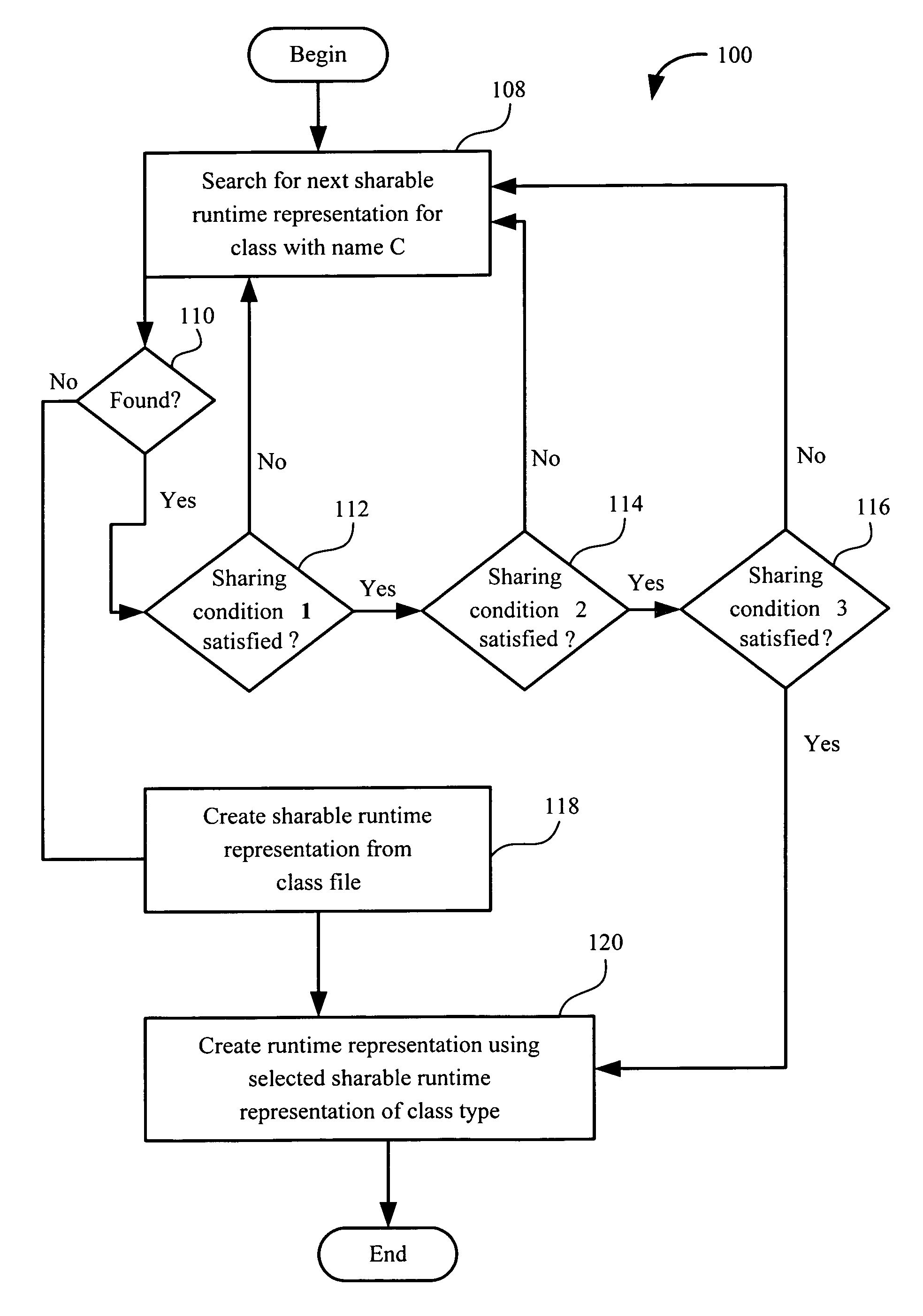
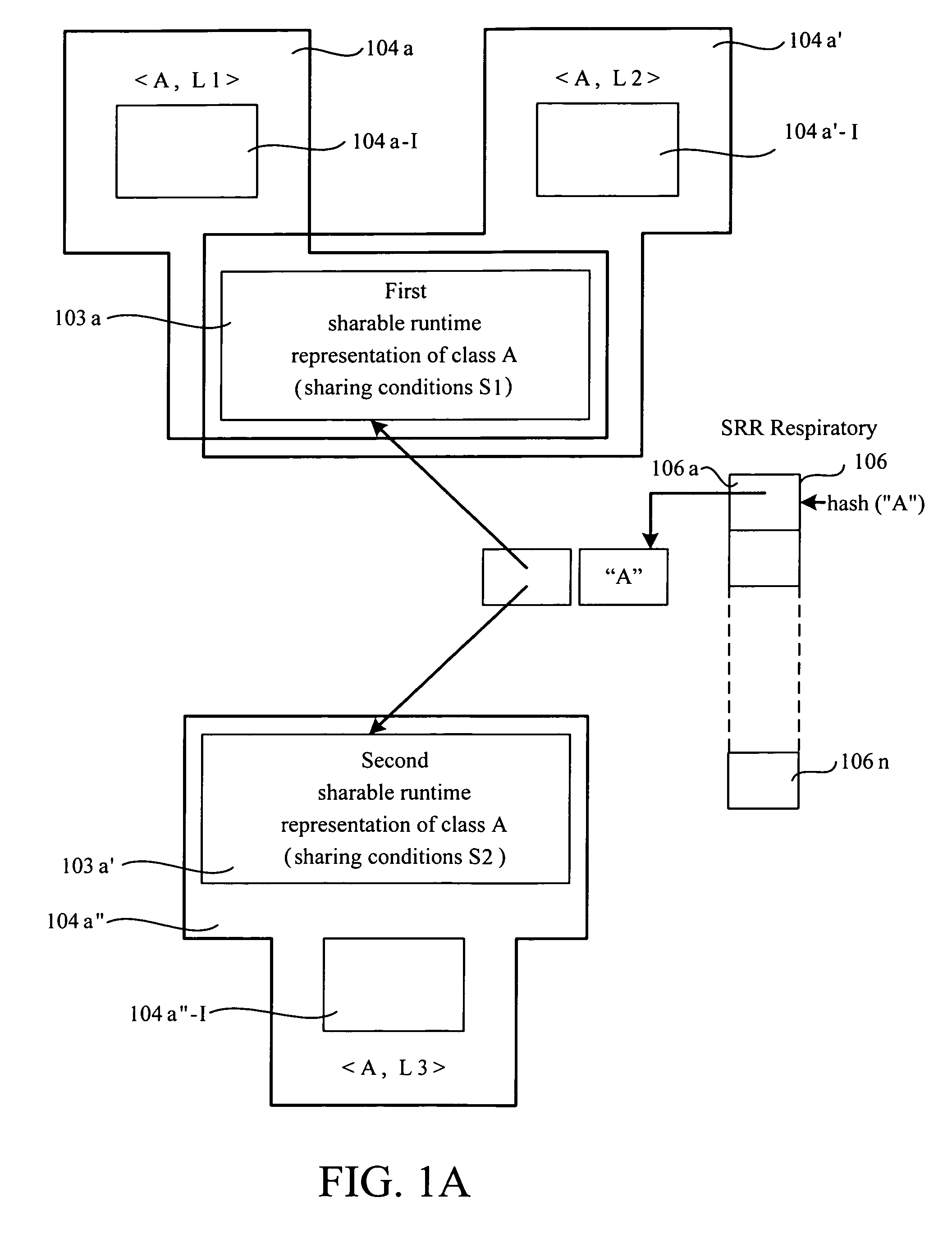
A computer implemented process for making a bytecode of a method sharable by a first class loader and a second class loader is provided. The first class loader and the second class loader are capable of dynamically loading a class having a class file, and translating the class file into first and second class types, respectively. The process includes dividing a runtime representation of the first class type into first loader independent and first loader dependent parts and determining whether a runtime representation of the second class type can use the first loader independent part. If the first loader independent part can be used by the runtime representation of the second class type, the process includes generating a second loader dependent part using the first loader independent part. Further included is performing a loader re-entrant interpretation of a bytecode of the method if the method is invoked.
Owner:ORACLE INT CORP
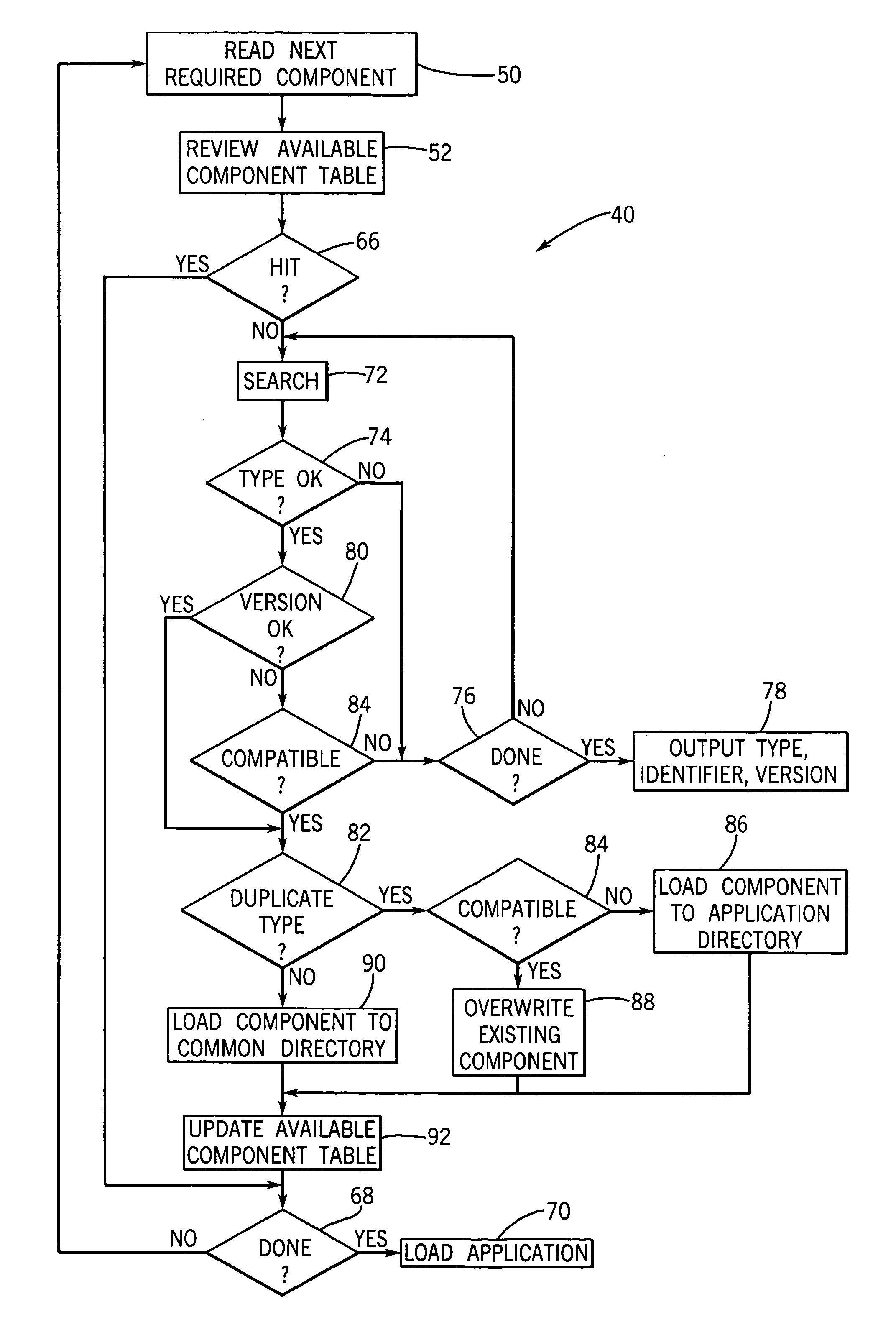
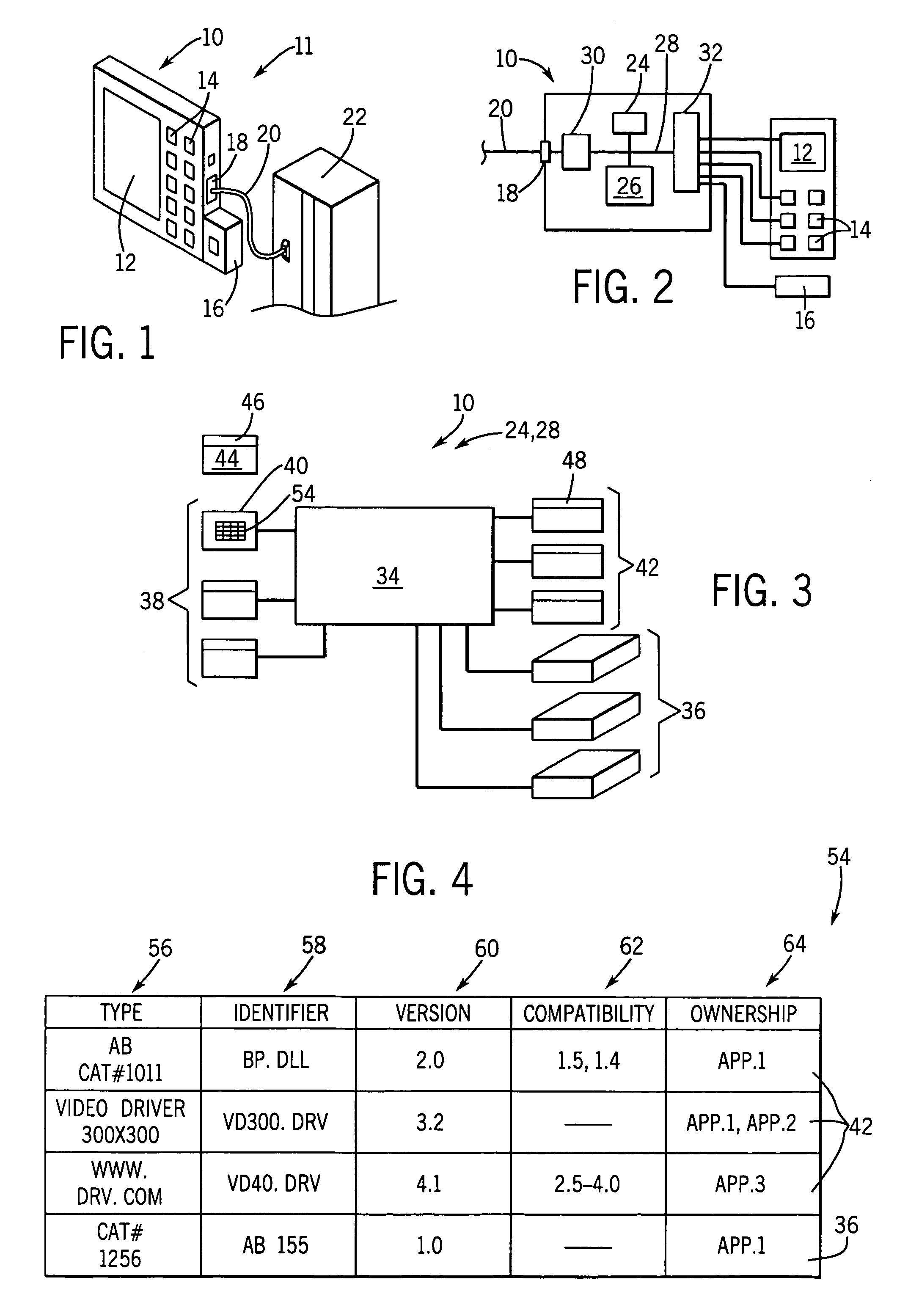
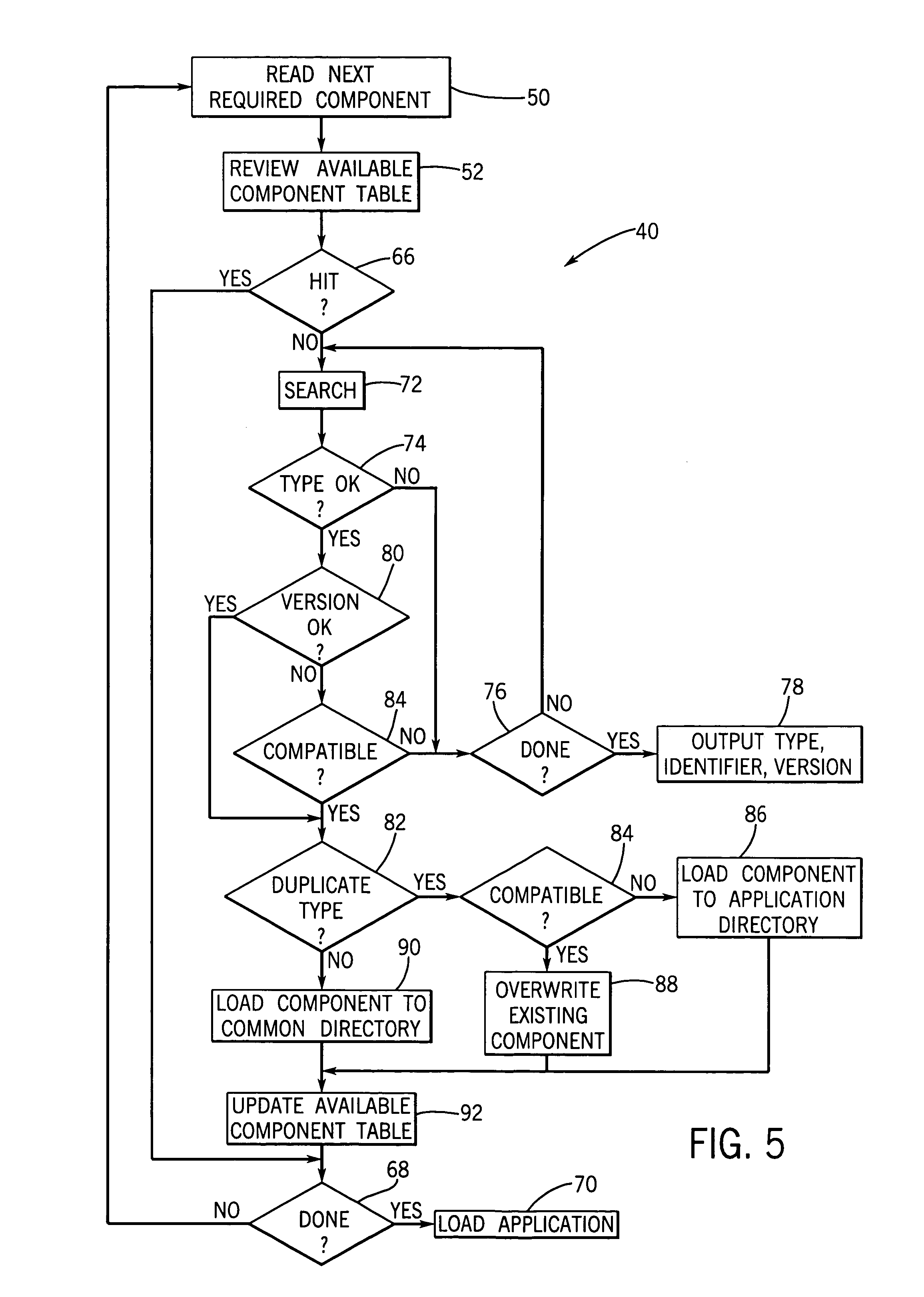
Component loader for industrial control device providing resource search capabilities
The installing of components into an industrial computer observes a pulling paradigm in which a required resource list associated with each component is reviewed against resources in the target-industrial control device. Missing resources are obtained through a searching process that may include but is not limited to the media holding or associated with the installed component. This approach allows compatibility between different versions of the resources to be evaluated with the possibility of coexisting different version numbers being, or one version replacing the other for automatic upgrade. Collecting the resources in a available resource table allows more complete information to be provided to the user in the event the resource cannot be found and allows more complete removal of components by making an explicit attribution of ownership of each resource to one or more installed components.
Owner:ROCKWELL AUTOMATION TECH
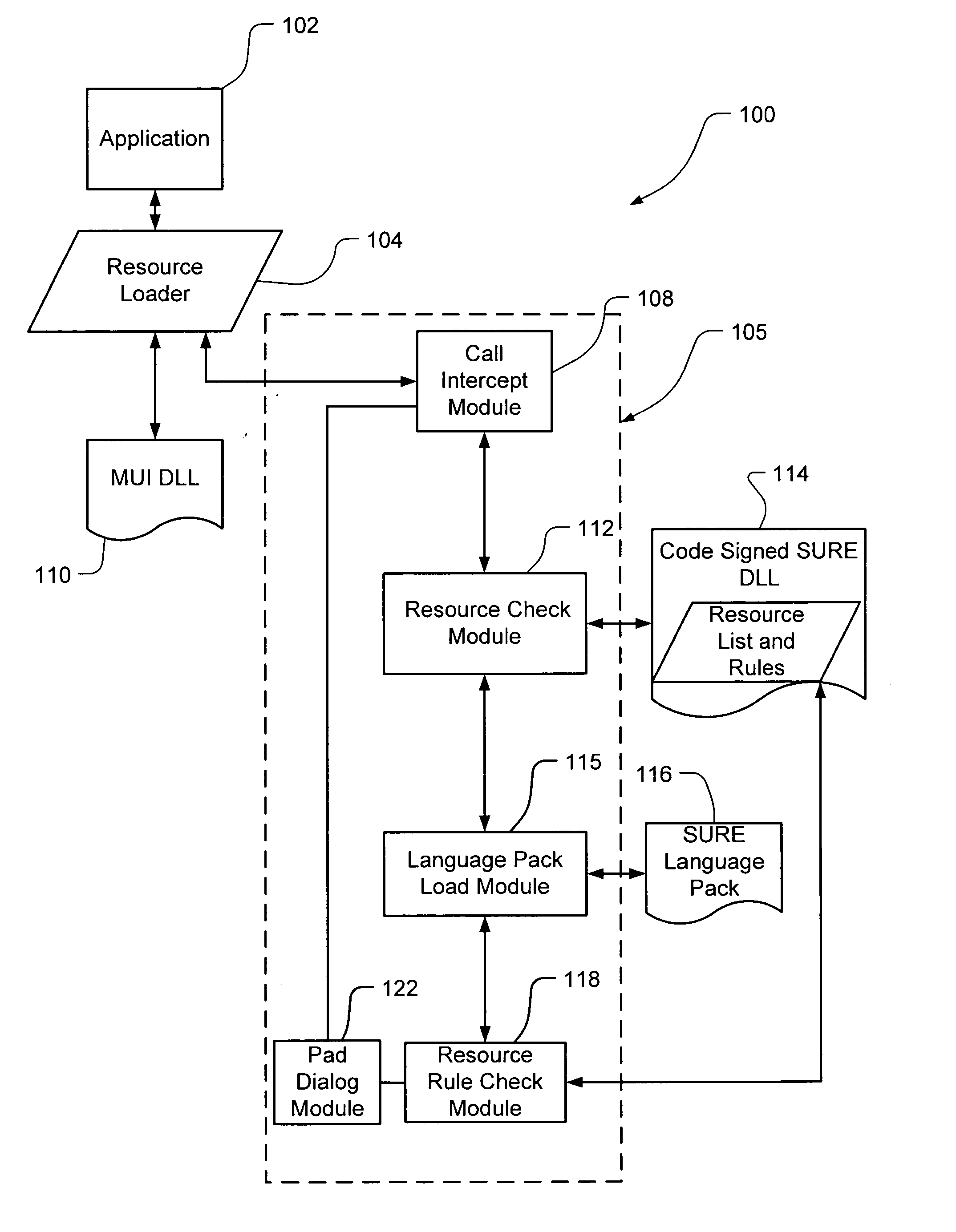
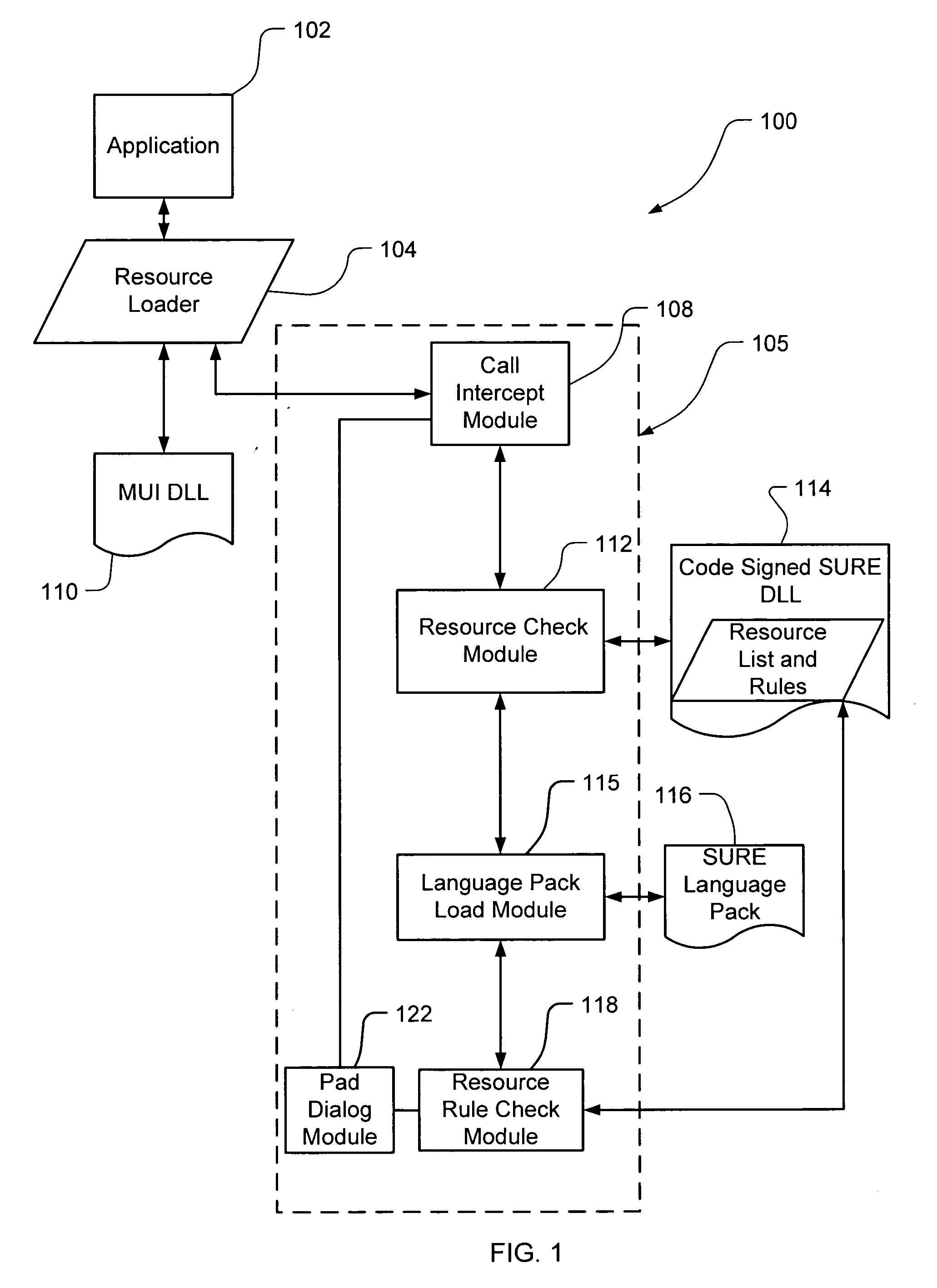
Safe, secure resource editing for application localization
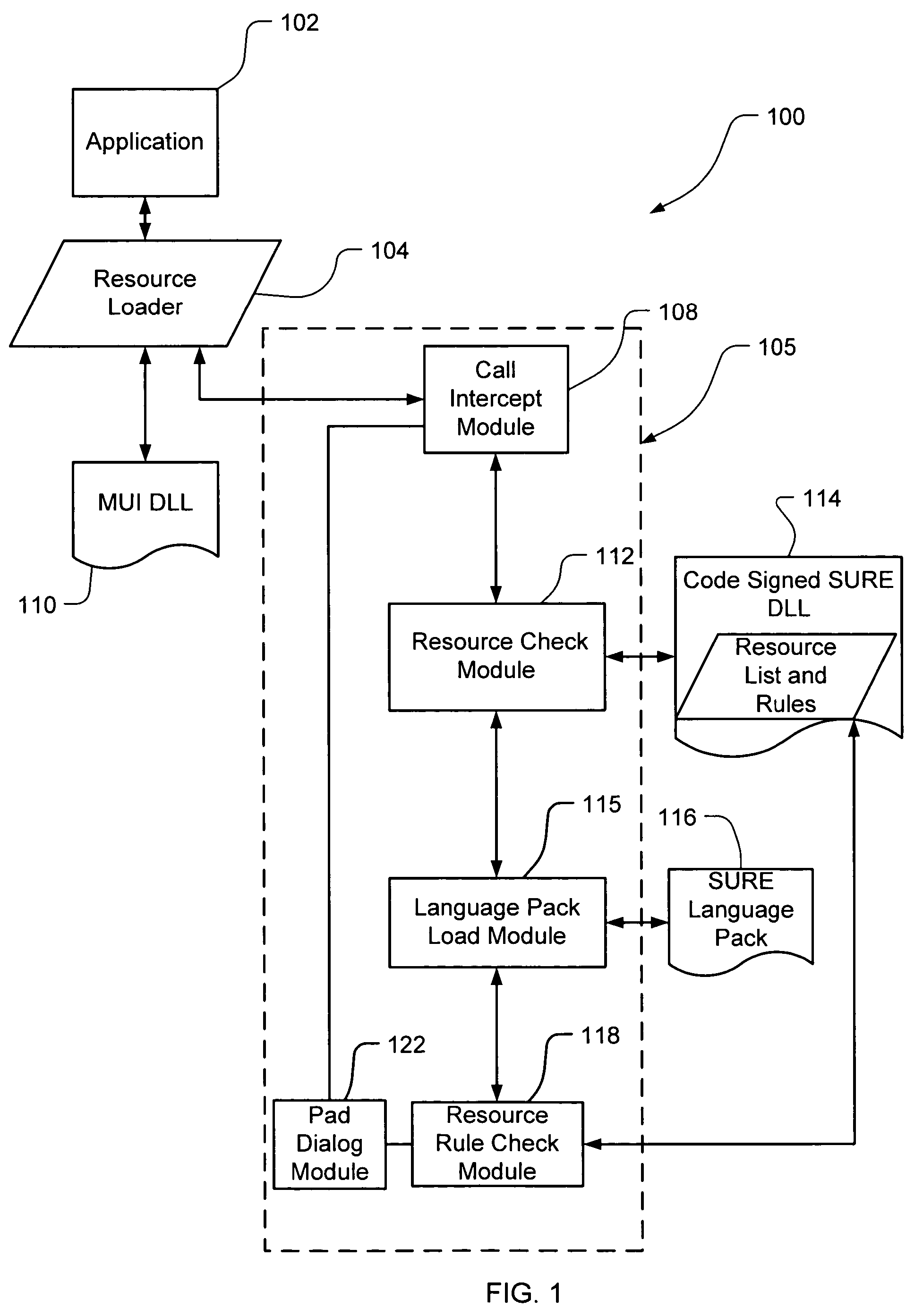
InactiveUS20060150173A1Natural language translationSpecial data processing applicationsData setOperational system
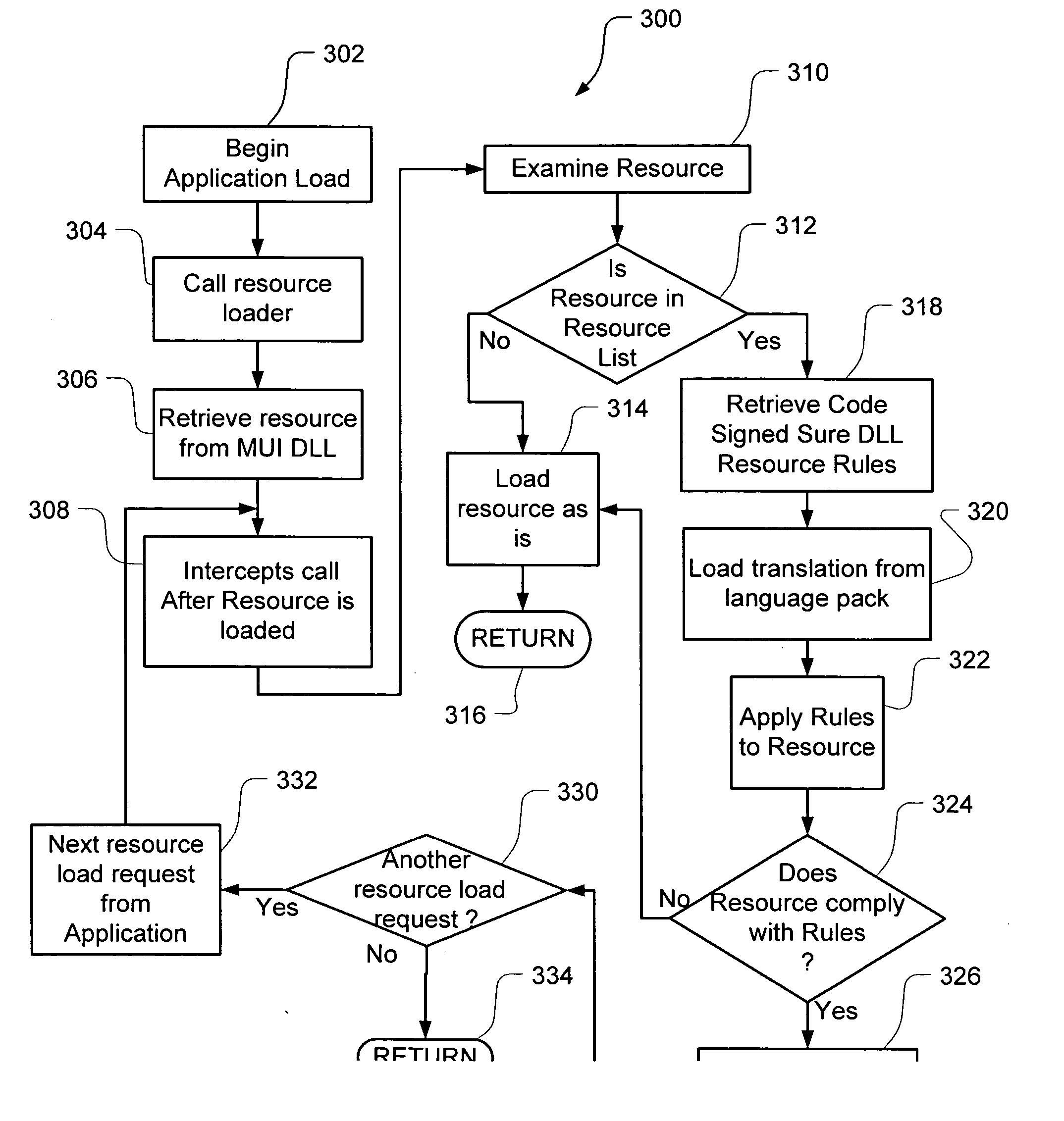
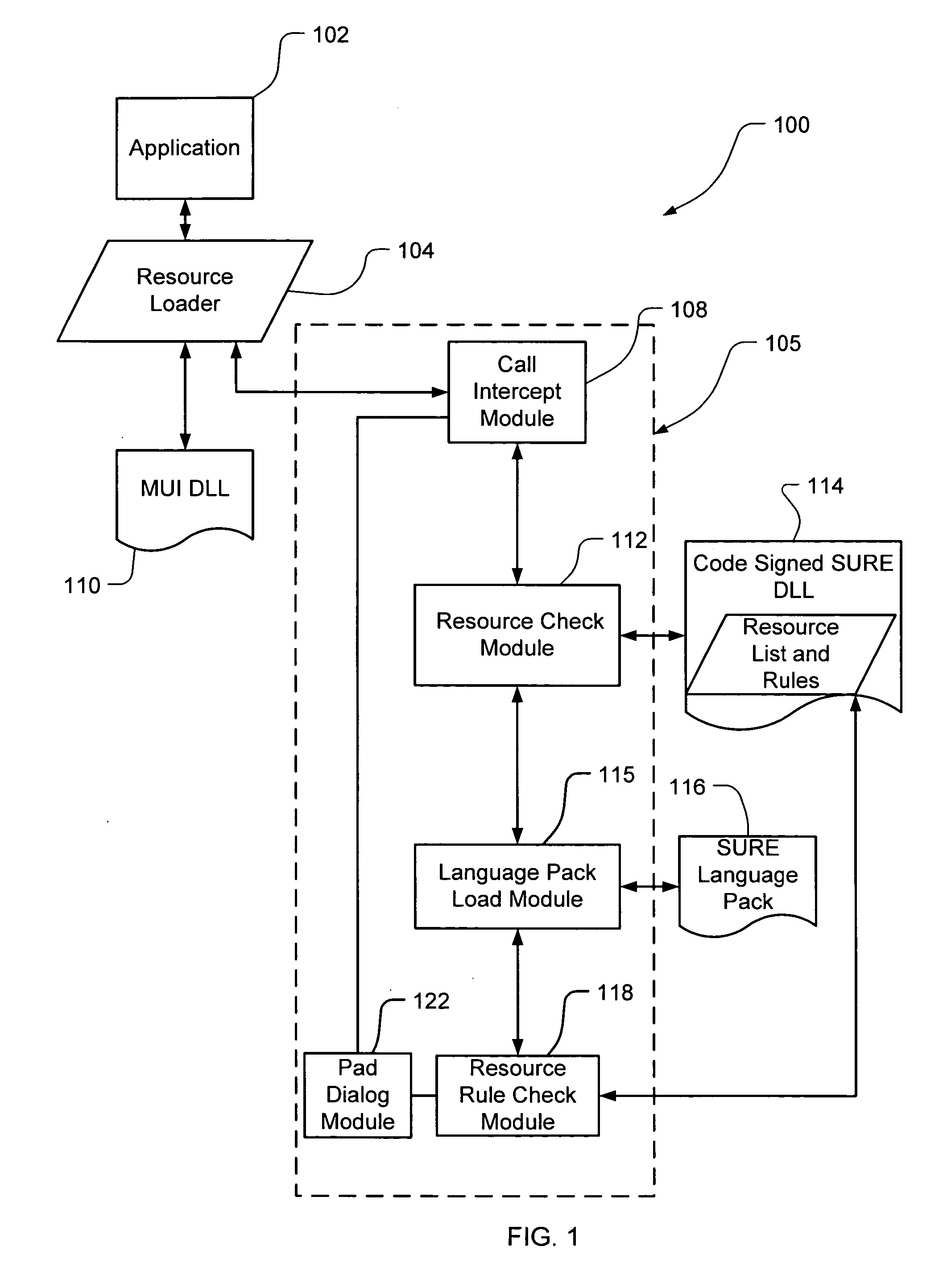
Embodiments of the present invention relate to methods, systems and computer-readable media for external localization of a software product. This external localization involves loading a base product having one or more calls to an operating system (or an API) to load language specific data. The calls are intercepted after the resource is loaded into a Resource loader, and queried whether the resource is identified in a restricted resource list such as a code signed dynamic linked library. If so, the translated resource is loaded from a specified language package. The loaded, and translated, resource is then checked against validation rules (which are also protected in a code signed resource list) to see if it is safe to use. If the resource is not on the list or the translated resource is not safe to use, the original resource is simply transferred to the application without modification from the resource loader, i.e., loaded from the base language file. This generates a localized product using a limited set of language specific data covering most situations.
Owner:MICROSOFT TECH LICENSING LLC
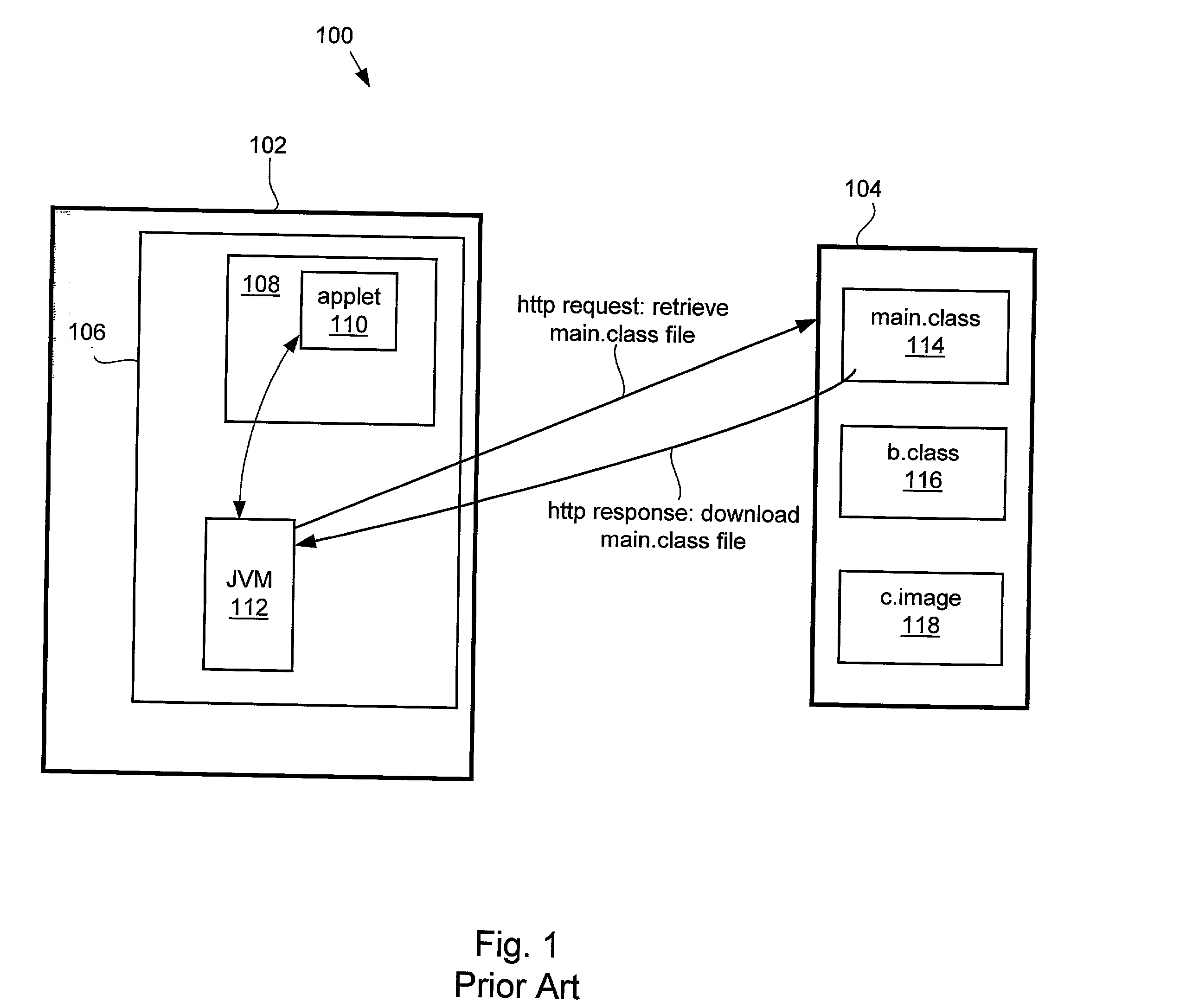
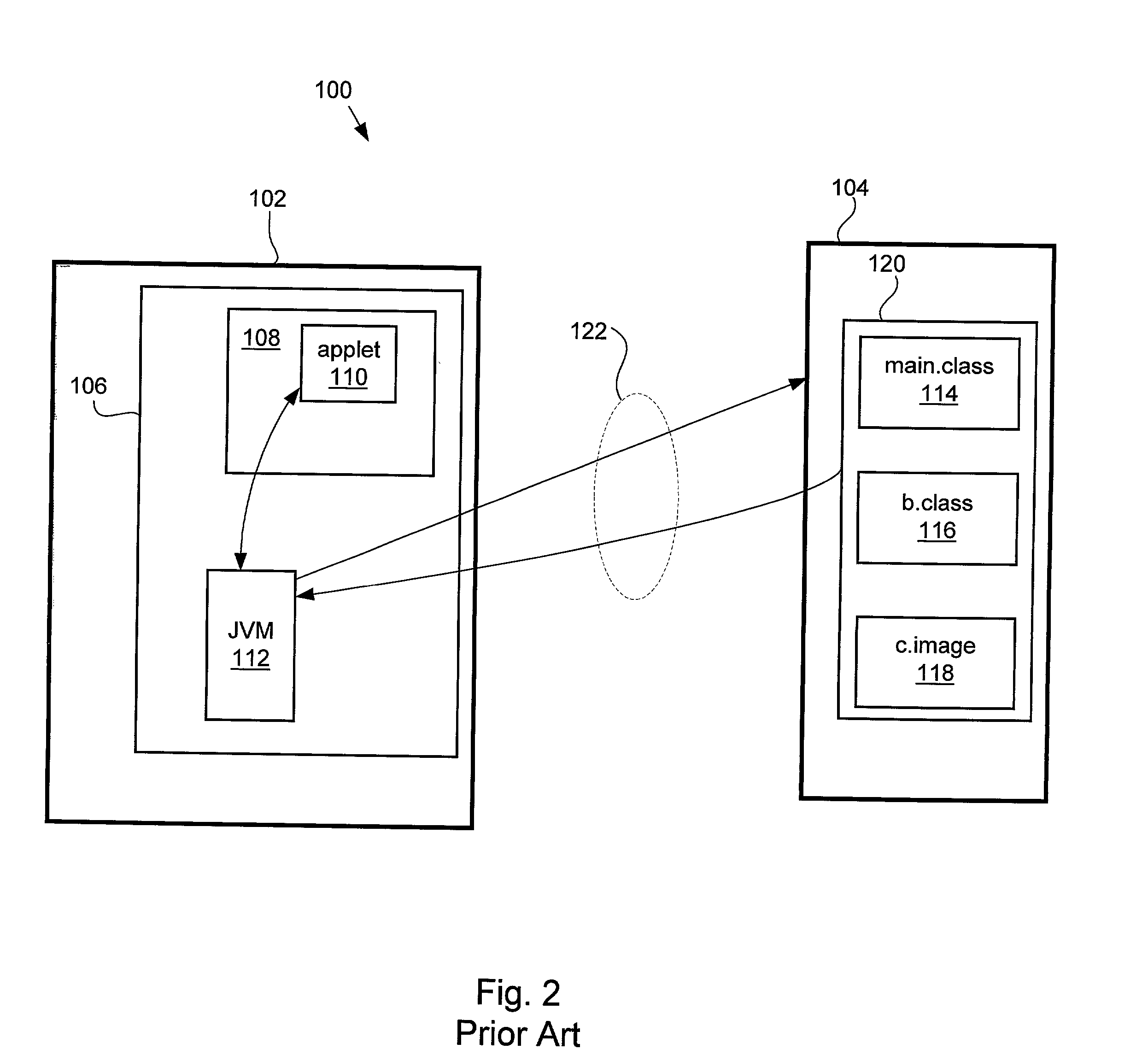
Method and apparatus for expedited file downloads in an applet environment
InactiveUS20030105888A1Multiple digital computer combinationsProgram loading/initiatingHash tableVirtual machine
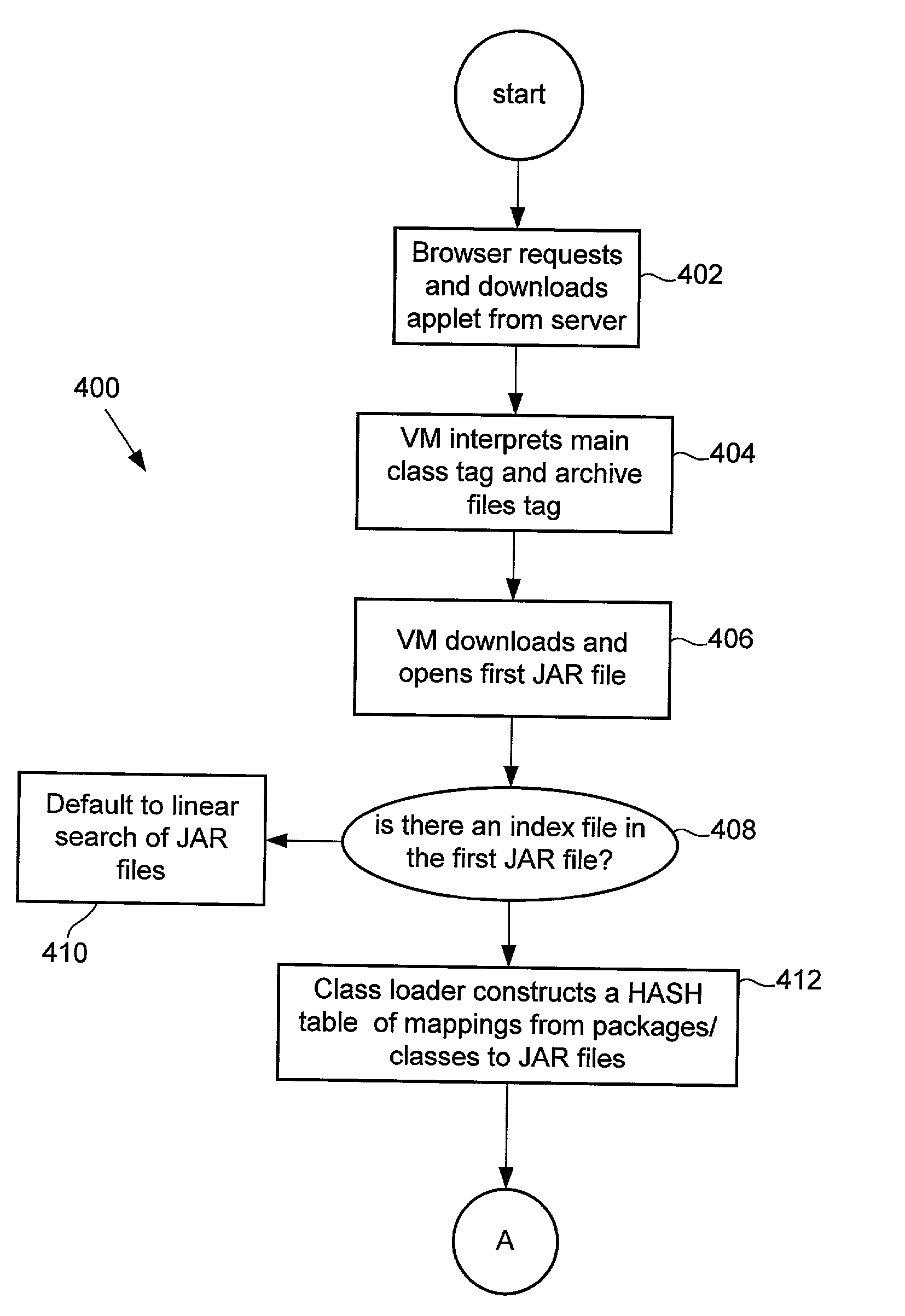
Methods and apparatus for executing an applet are disclosed. A virtual machine that includes a class loader generates a file download request in the form of an http request to a particular server computer that contains appropriate applet component files. The class loader queries a root JAR file having an index file associated with applet. The class loader creates a HASH table based upon the contents of the index file that provides a mapping of all packages and all corresponding JAR files required to execute the applet by the virtual machine. During virtual machine runtime the class loader queries the HASH table in order to directly access the appropriate applet component file to be downloaded and executed by the virtual machine.
Owner:ORACLE INT CORP
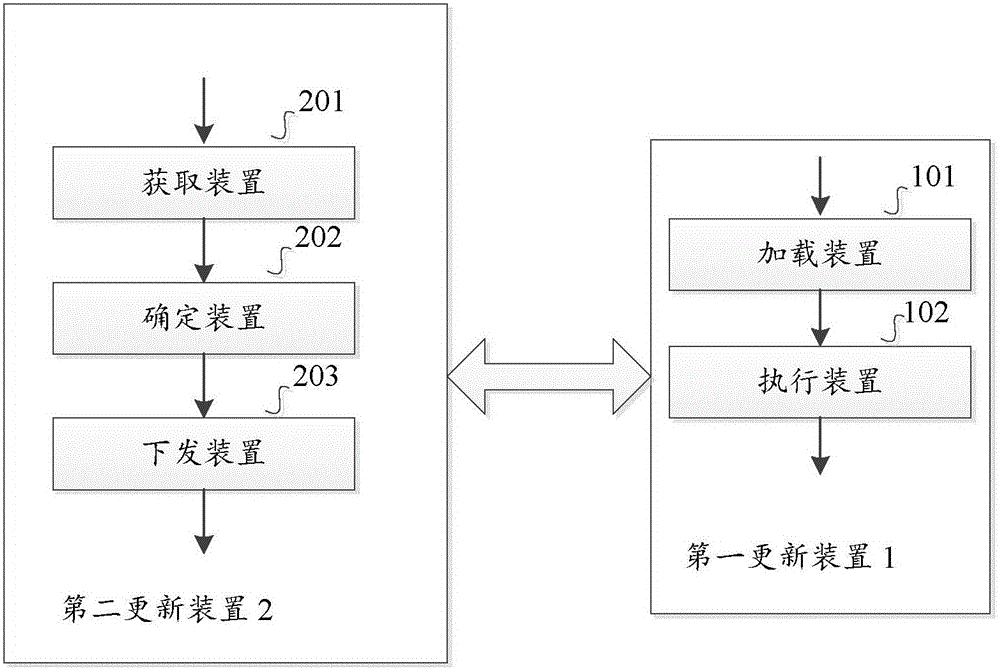
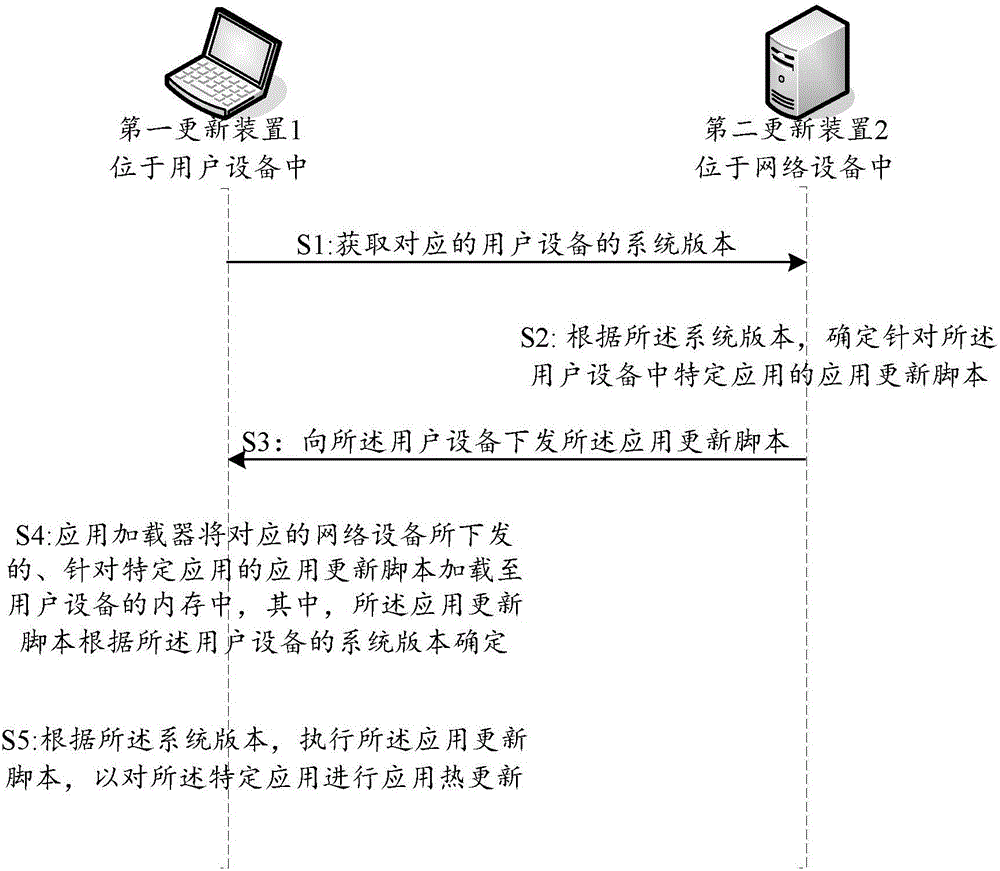
Application hot update method and device in ios system
InactiveCN106227554AImprove user experienceShorten the timeProgram loading/initiatingSoftware deploymentUser deviceComputer compatibility
The invention provides an application hot update method and device in the ios system; the method comprises the following steps: obtaining a system version of a corresponding user device; determining an application update script of a specific application in the user device according to the system version; distributing the application update script to the user device; using an application loader to load the application update script distributed by a corresponding network device and aiming at the specific application to a user device memory, wherein the application update script is determined according to the user device system version; executing the application update script according to the system version, thus carrying out application hot update for the specific application. The method uses the network device to distribute the corresponding update script to the user device according to the user device system version, and loads the update script into the user device memory, thus directly updating the application program in the memory, shortening an application program updating time, and solving compatibility problems of different system version hot update schemes.
Owner:BAIDU ONLINE NETWORK TECH (BEIJIBG) CO LTD
Electronic device and booting method therefor
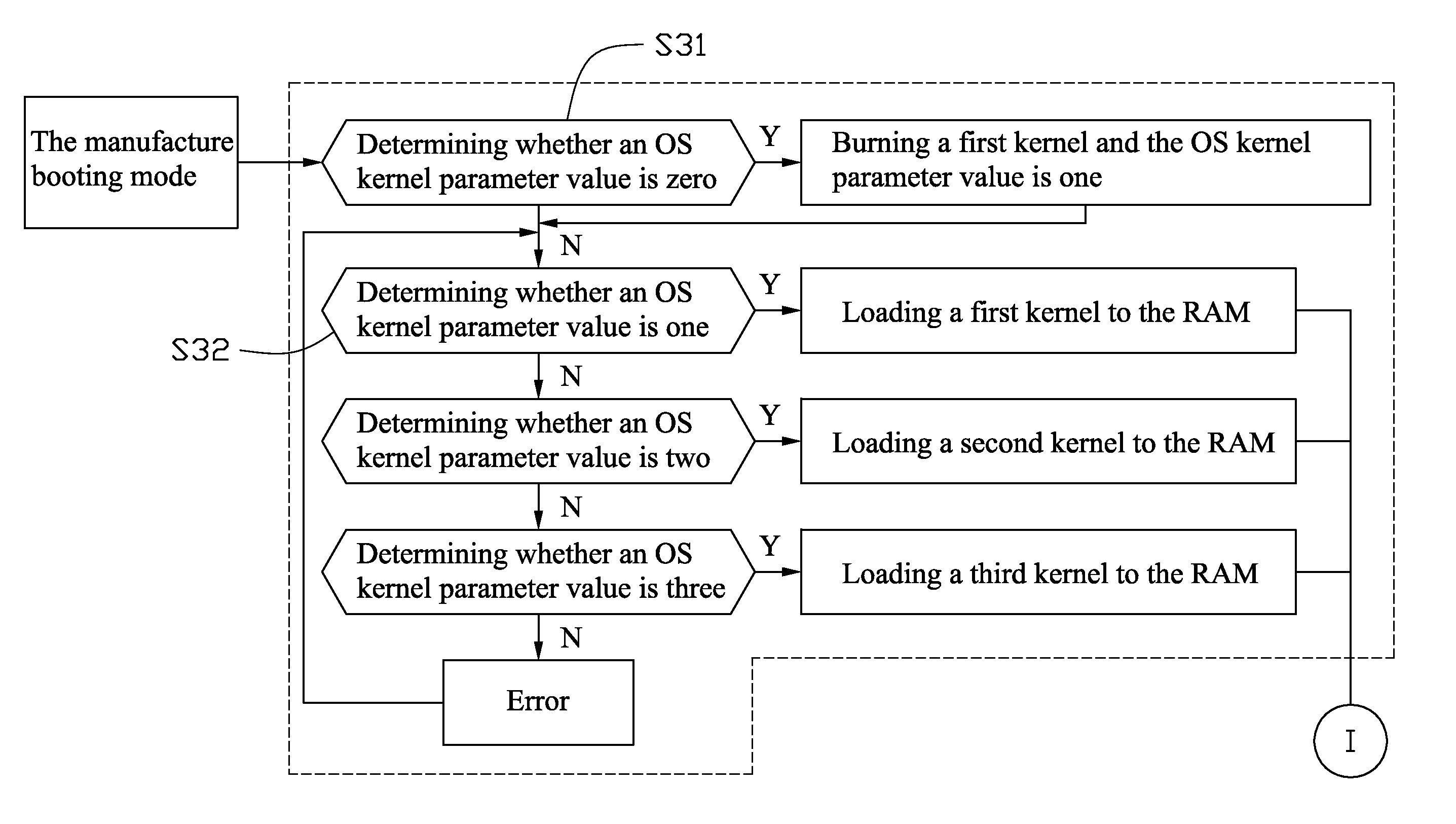
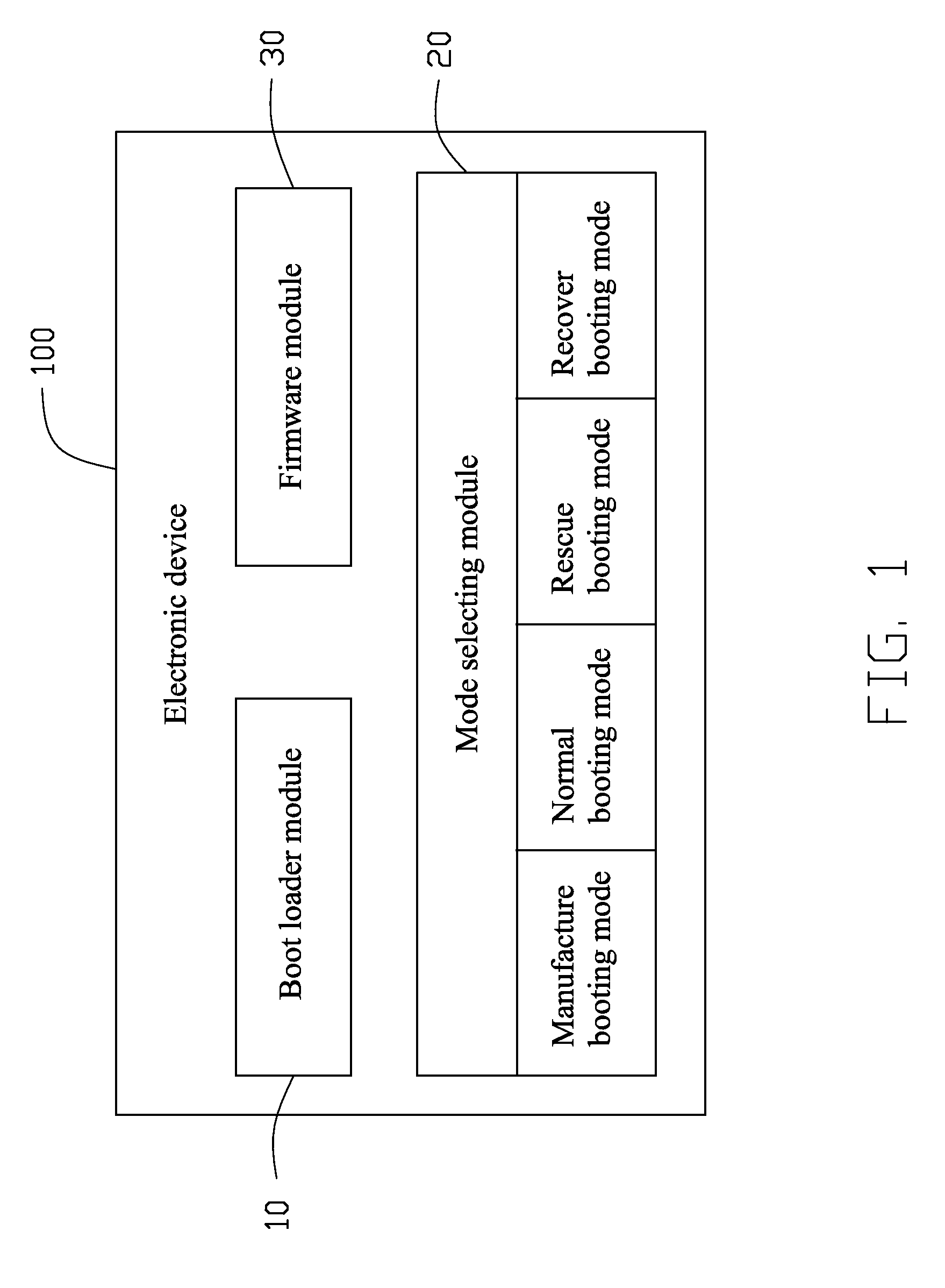
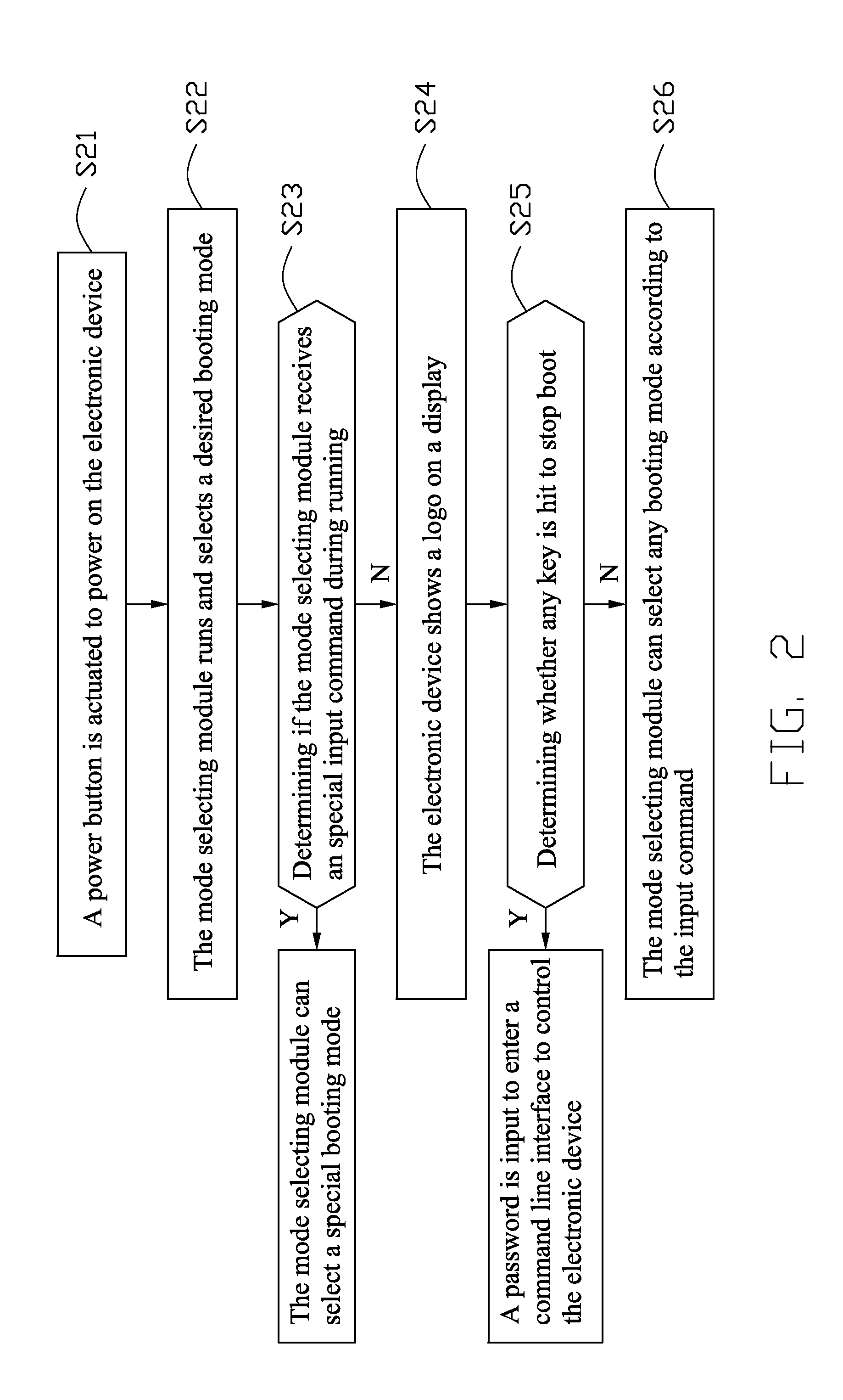
An electronic device with a plurality of operating systems includes a mode selecting module, a firmware module, an operating system selecting module and a boot loader module. The mode selecting module selects a desired booting mode from a plurality of booting modes. The booting modes includes a manufacture booting mode, a normal booting mode, a rescue booting mode, and a recover booting mode. The firmware module stores the manufacture booting mode, the normal booting mode, the rescue booting mode, and the recover booting mode. The operating system selecting module selects from a plurality of operating systems according to the selected booting mode. The boot loader module loads the selected operating system. A booting method for the electronic device is also disclosed.
Owner:HON HAI PRECISION IND CO LTD
Safe, secure resource editing for application localization with language fallback
InactiveUS20060130032A1Natural language translationProgram loading/initiatingBasic languageOperational system
Embodiments of the present invention relate to methods, systems and computer-readable media for external localization of a software product. This external localization involves loading a base product having one or more calls to an operating system (or an API) to load language specific data. The calls are intercepted after the resource is loaded into a Resource loader, and queried whether the resource is identified in a restricted resource list such as a code signed dynamic linked library. If so, the translated resource is loaded from a specified language package. The loaded, and translated, resource is then checked against validation rules (which are also protected in a code signed resource list) to see if it is safe to use. If the resource is not on the list or the translated resource is not safe to use, the original resource is simply transferred to the application without modification from the resource loader, i.e., loaded from the base language file. This generates a localized product using a limited set of language specific data covering most situations and falls back to the base language automatically when no specific translated resource is available.
Owner:MICROSOFT TECH LICENSING LLC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com