Patents
Literature
279results about How to "More security" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
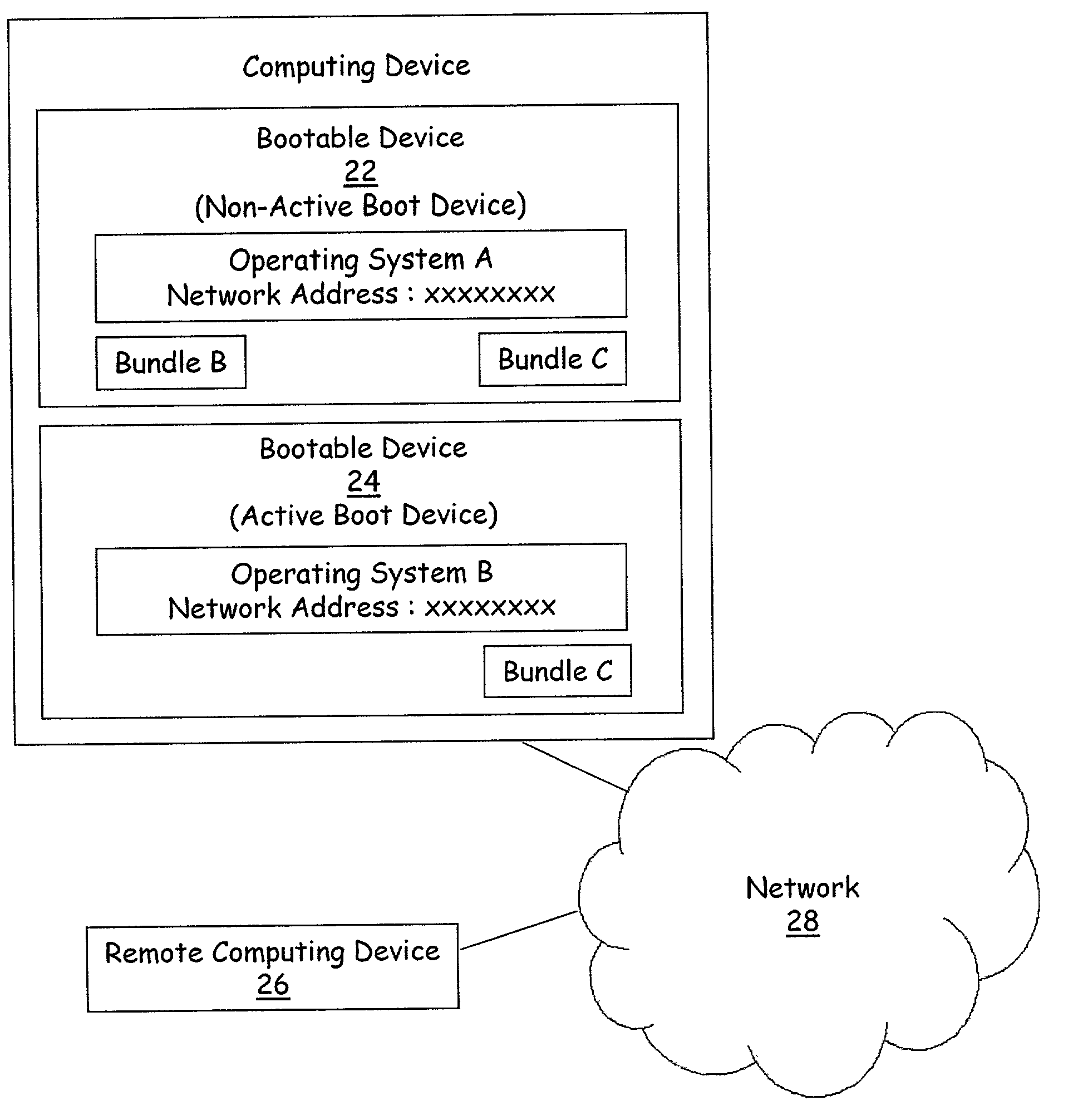
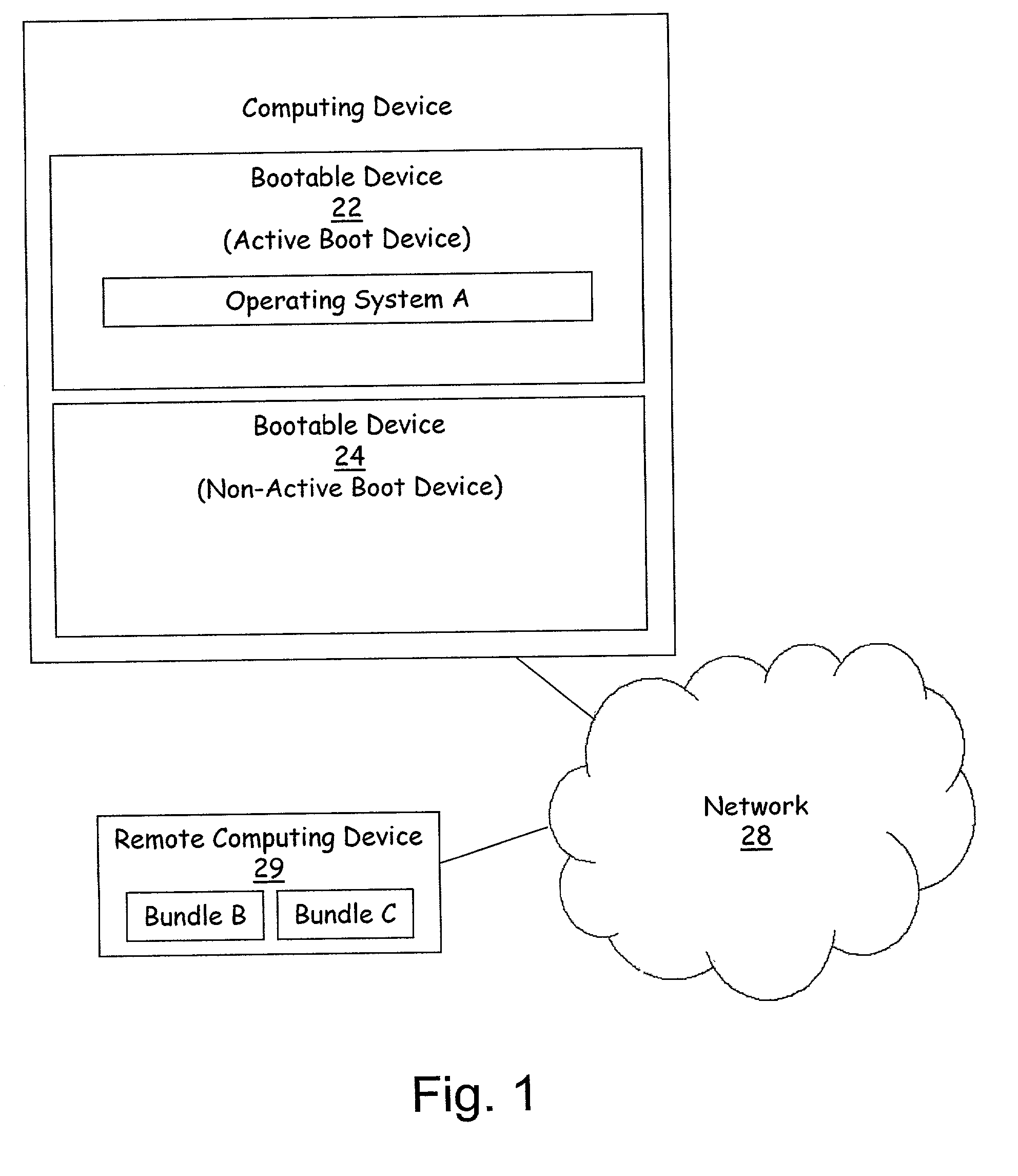
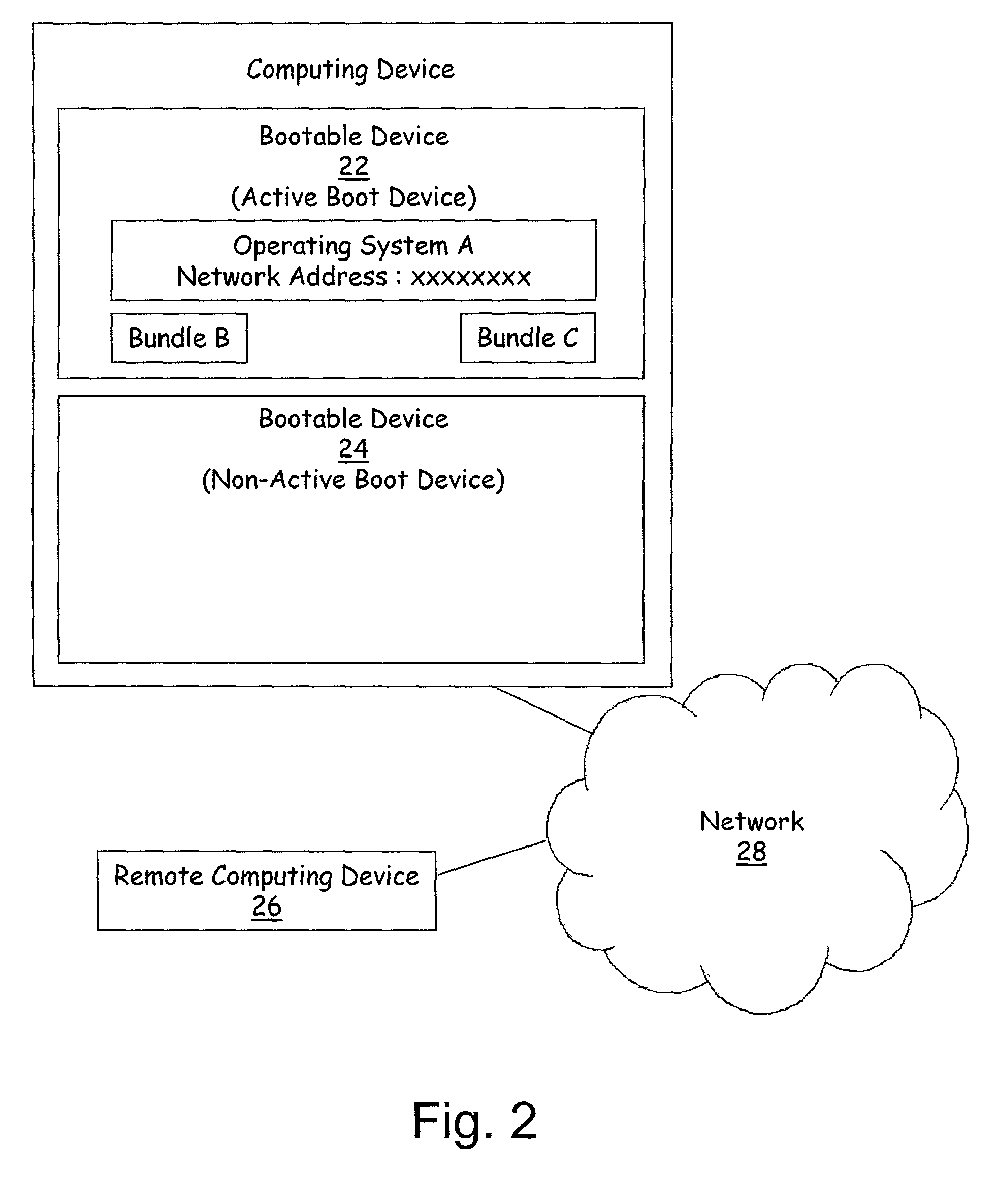
Method and apparatus for remote installation of an operating system over a network connection
InactiveUS6963981B1More securityMemory loss protectionError detection/correctionOperational systemNetwork connection
A method for remote installation of a target operating system is carried out on a machine operating a source operating system. In one embodiment, it is presumed that the source operating system was booted from a first bootable region of a storage associated with the machine. According to the method, a copy of the source operating system together with the target operating system are delivered to the machine and stored in a second bootable region of the storage. The copy of the source operating system may be stored in a first partition of the second bootable region of the storage, and the target operating system may be stored in a second partition of the second bootable region. A boot loader is then configured to boot the copy of the source operating system from the second bootable region of the storage. The machine is then re-booted. At this point, the machine is still running the source operating system, although in this case that operating system was booted from the second bootable region of the storage. The original source operating system (from the first bootable region) is then removed, and the boot loader is re-configured to boot the target operating system from the second bootable region of the storage. The machine is then re-booted again, after which the target operating system is operational. In one embodiment, the first and second bootable regions may be separate hard disks, and the source and target operating systems are Linux and Windows, or vice versa.
Owner:AKAMAI TECH INC
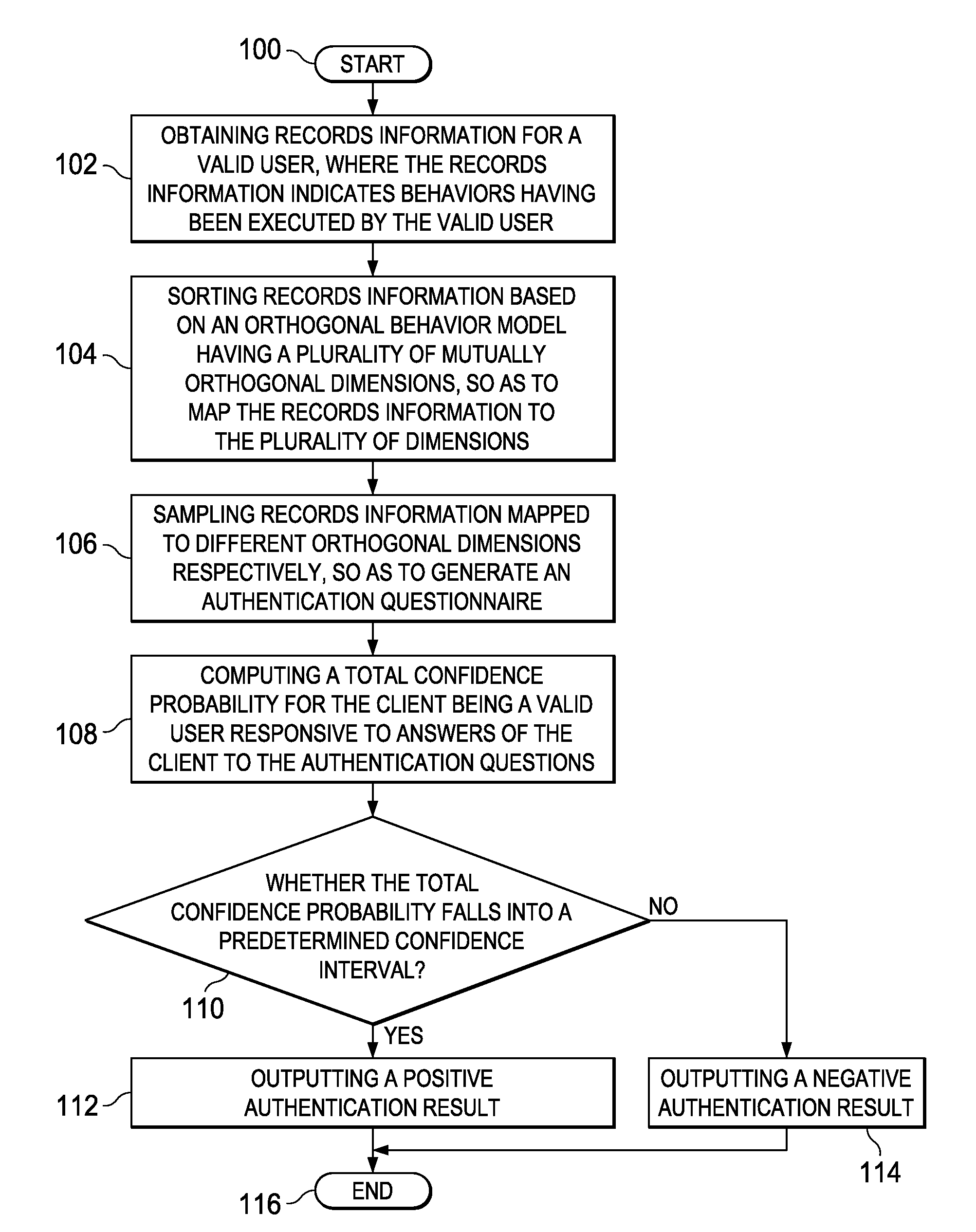
Authentication method and apparatus
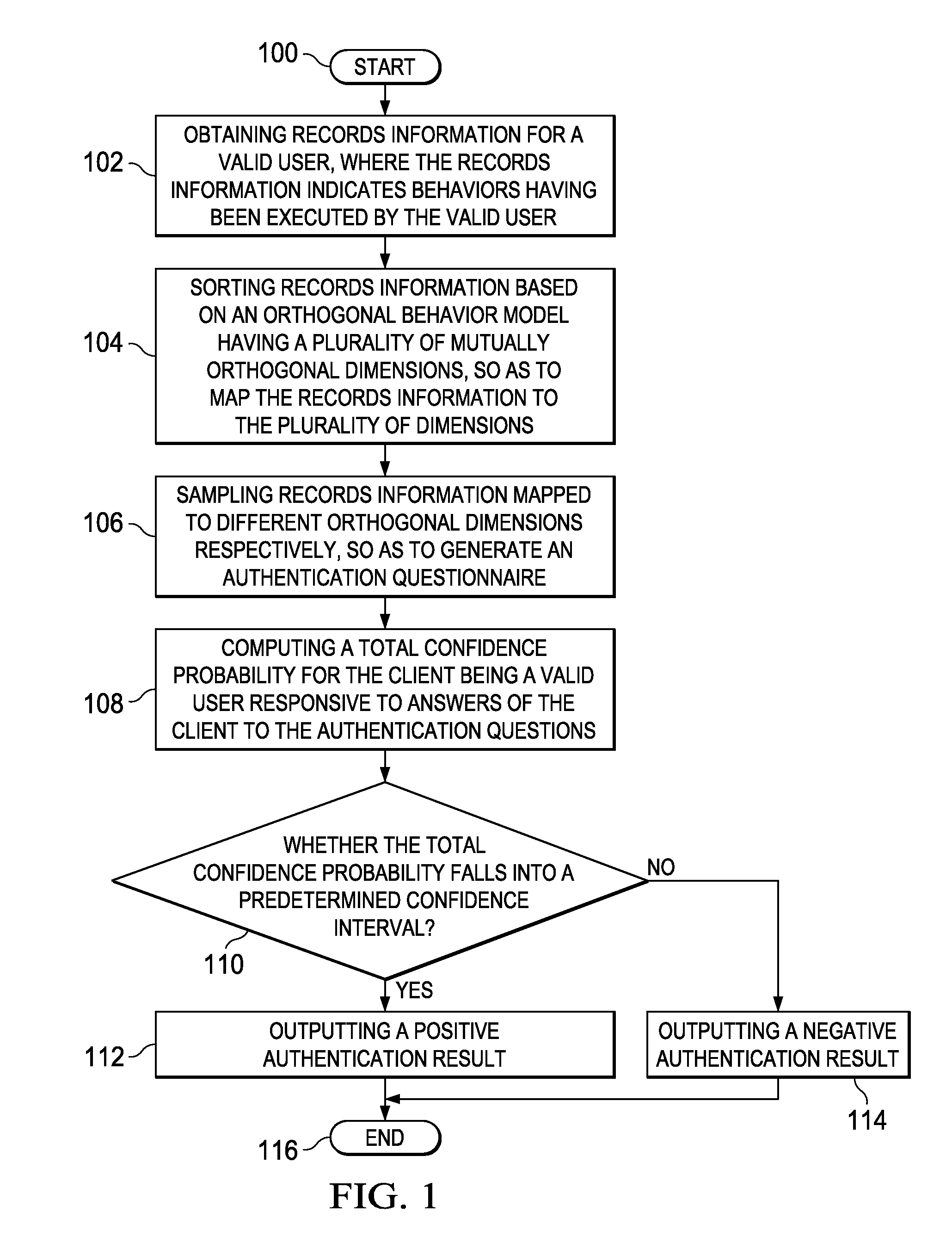
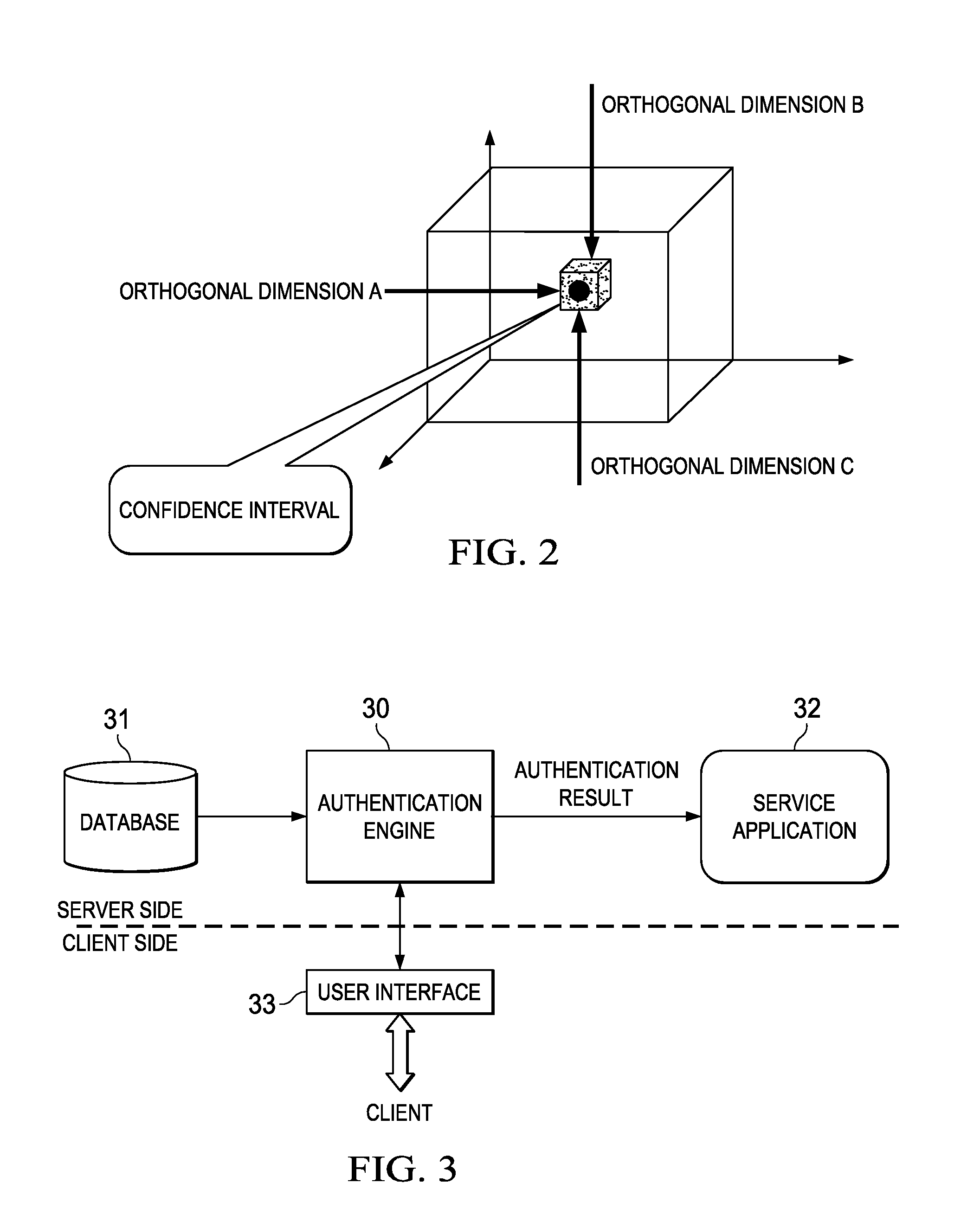
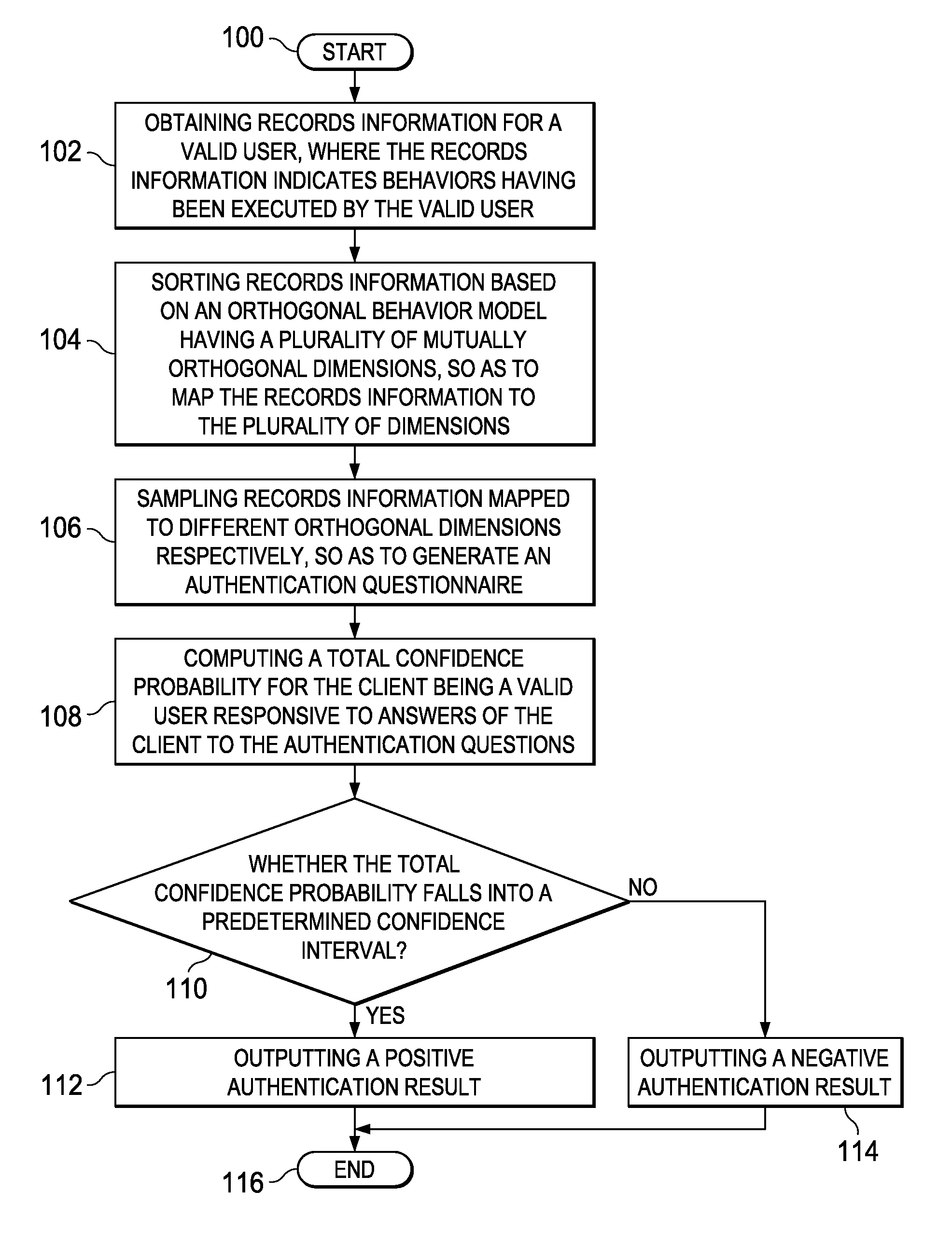
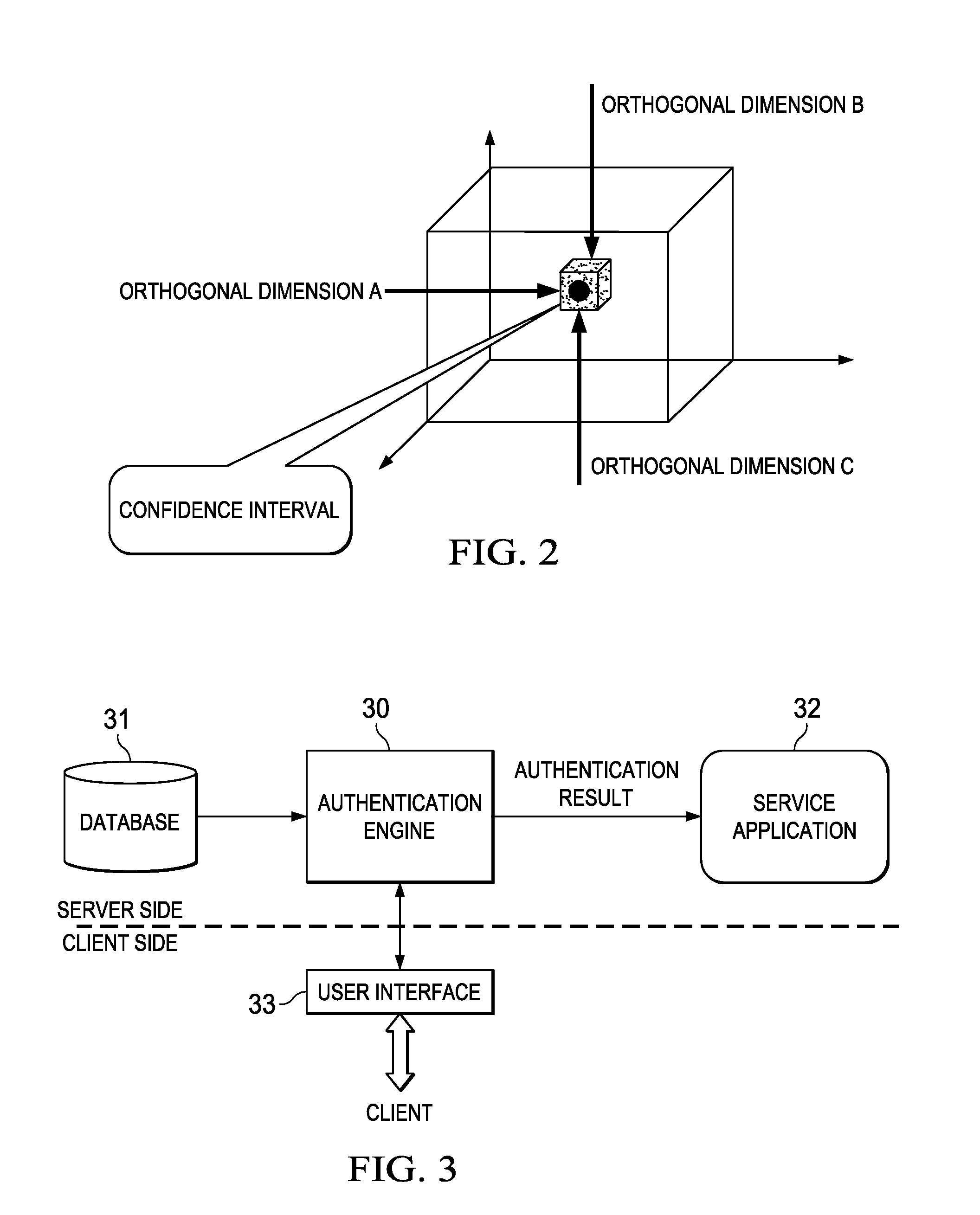
InactiveUS8495718B2More reliableMore securityDigital data processing detailsAnalogue secracy/subscription systemsConfidence intervalCausality
An identity authentication method is provided. The method comprises obtaining records information of a valid user, where the records information indicates behaviors having been executed by the valid user; mapping, based on an orthogonal behavior model having multiple mutually orthogonal dimensions, records information to the multiple dimensions, wherein behaviors indicated by records information mapped to different dimensions do not overlap therebetween and have no logical cause and effect relationship; sampling records information mapped to different dimensions, respectively, so as to generate an authentication questionnaire including a plurality of authentication questions; computing, responsive to answers of a client to the authentication questionnaire, a total confidence P for the client being a valid user; outputting a positive authentication result, responsive to the total confidence probability P falling into a confidence interval; and outputting a negative authentication result, responsive to the total confidence probability P failing to fall into a confidence interval. The present invention further provides a corresponding identity authentication apparatus.
Owner:INT BUSINESS MASCH CORP
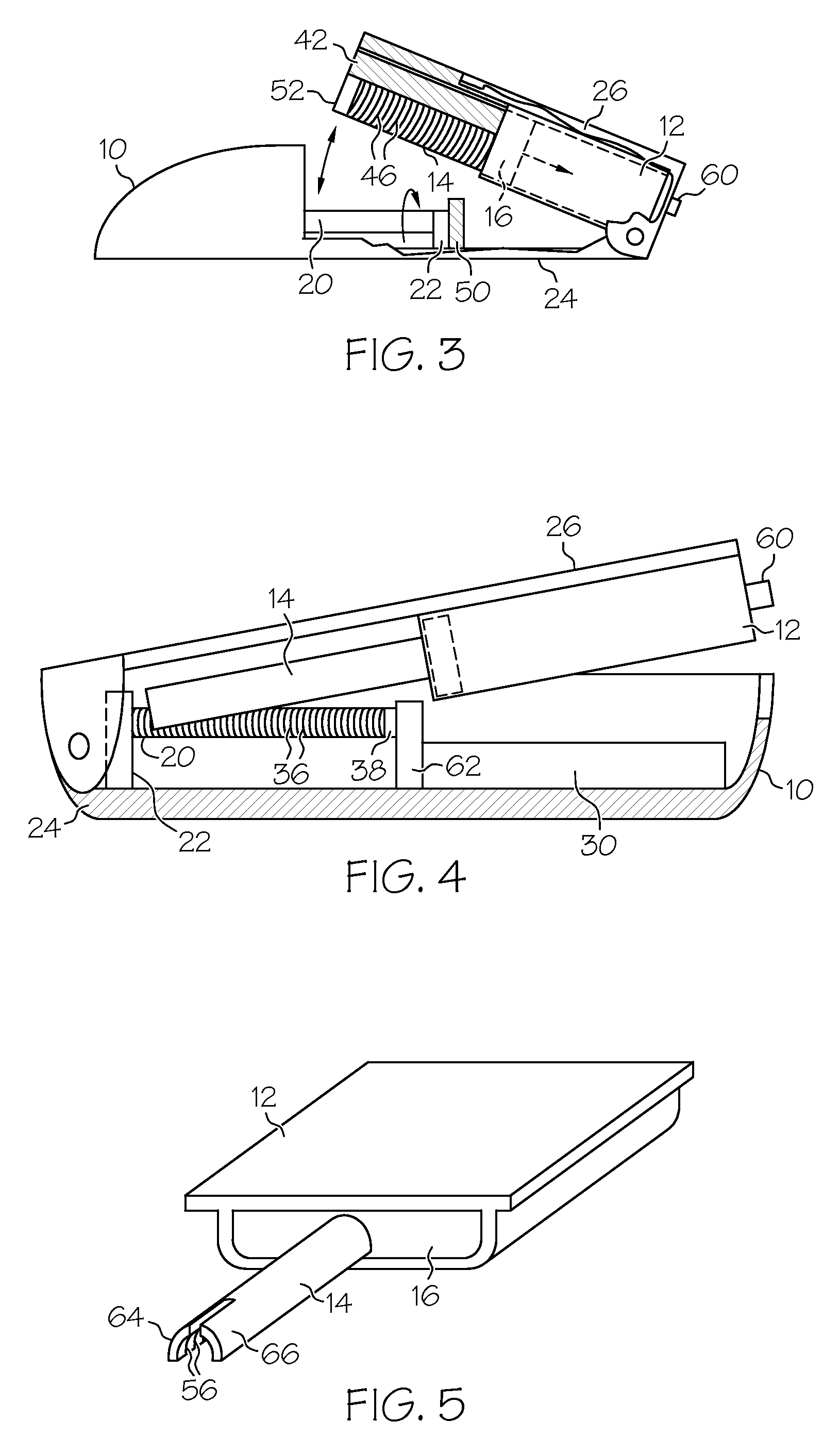
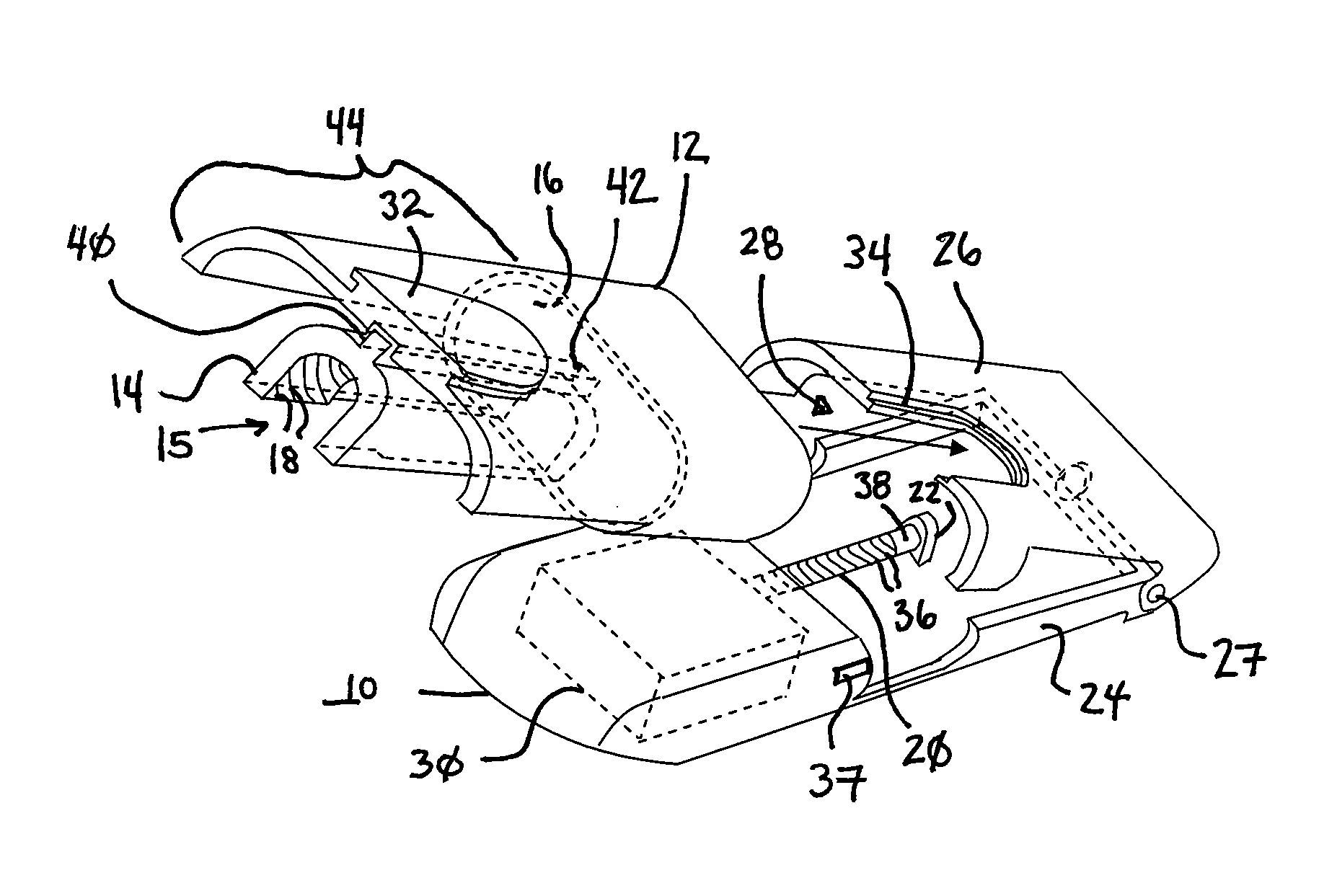
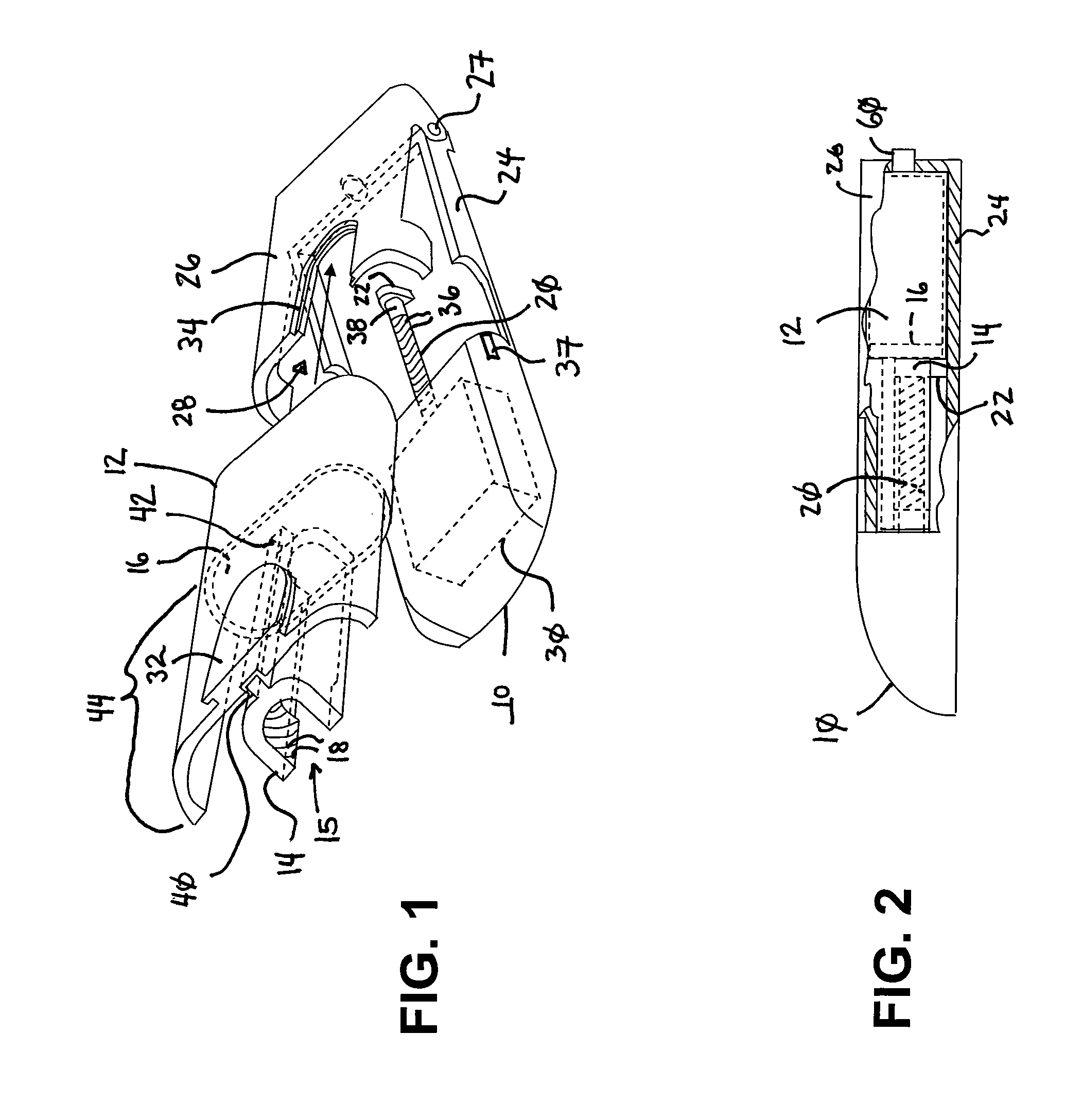
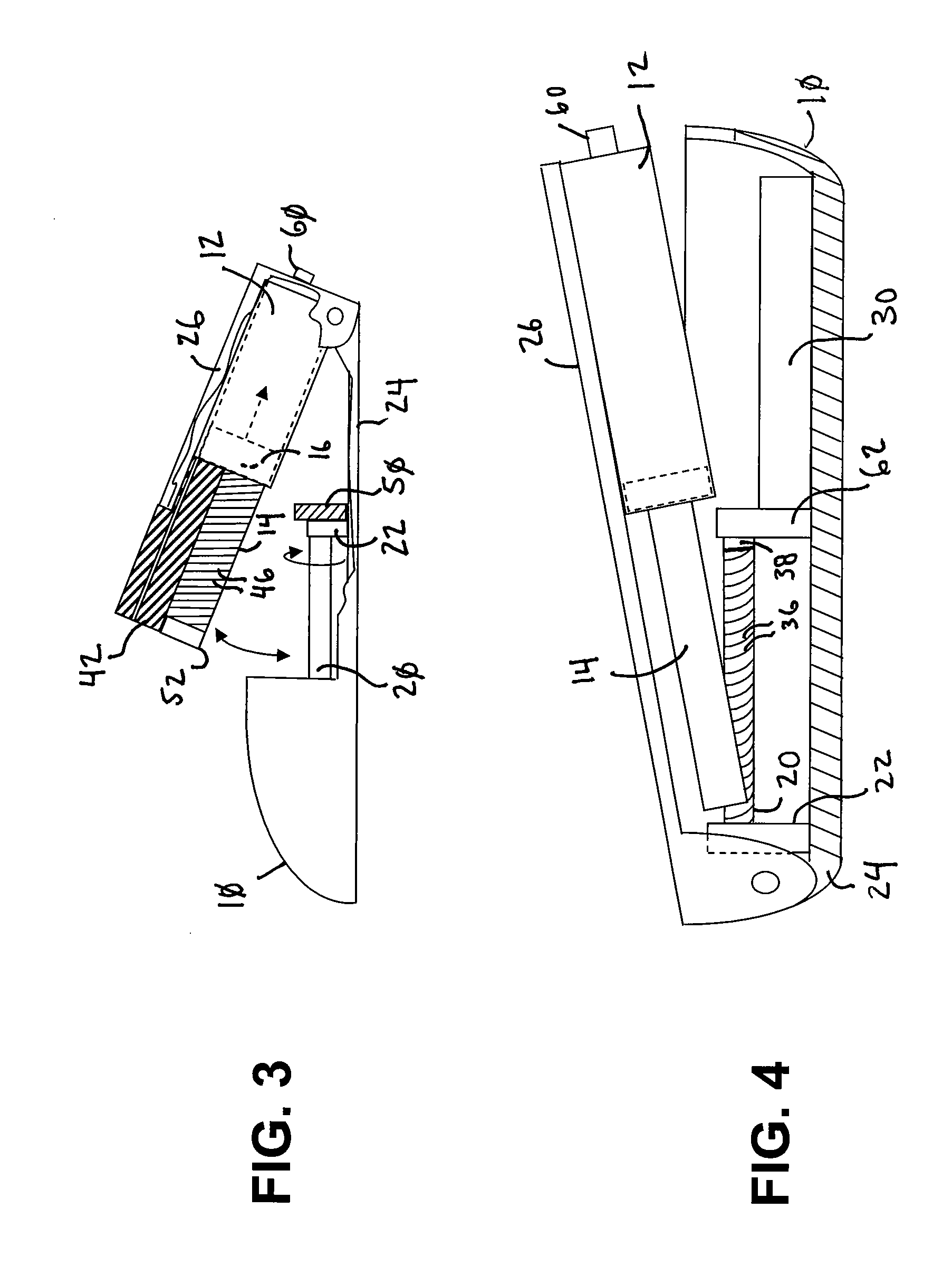
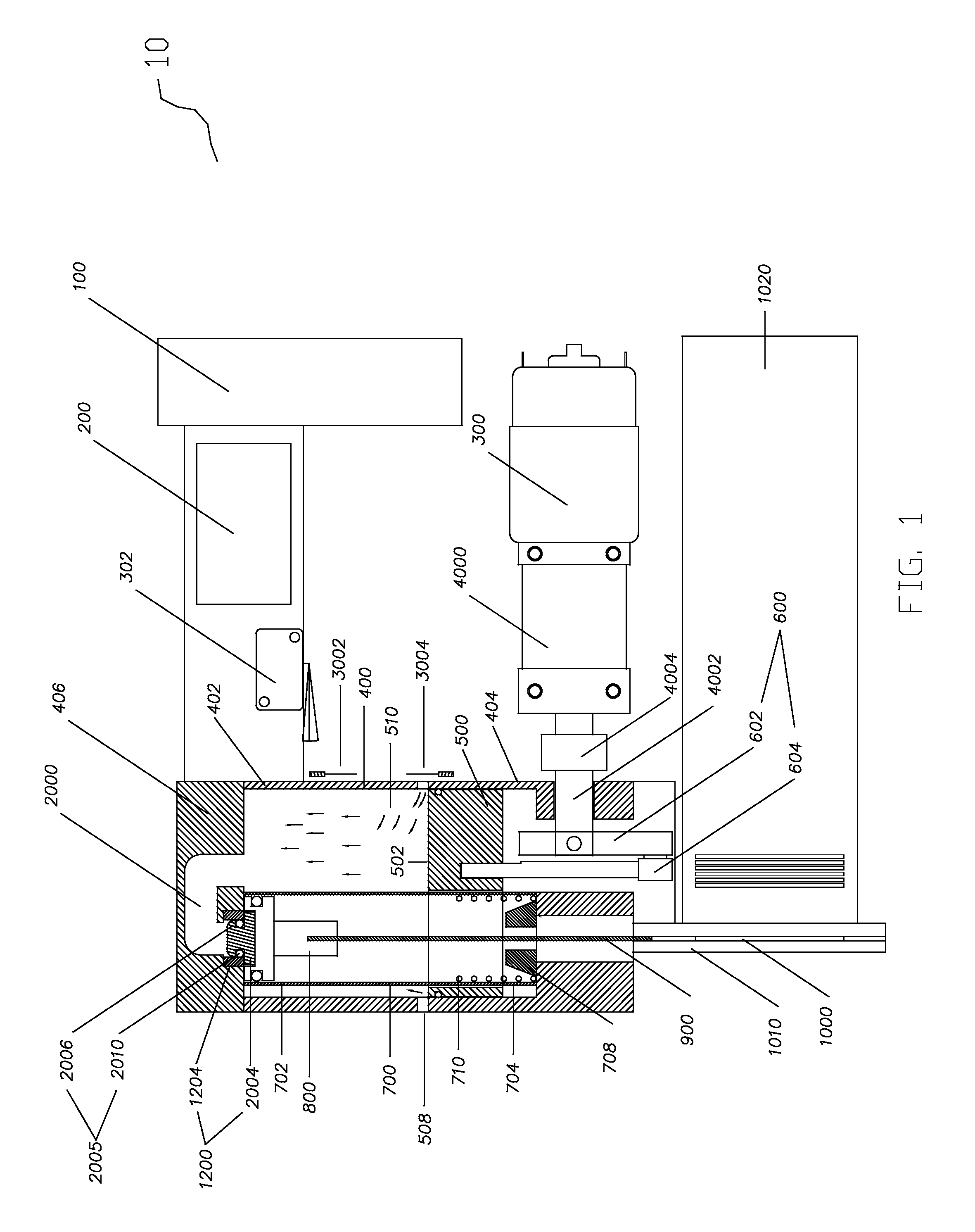
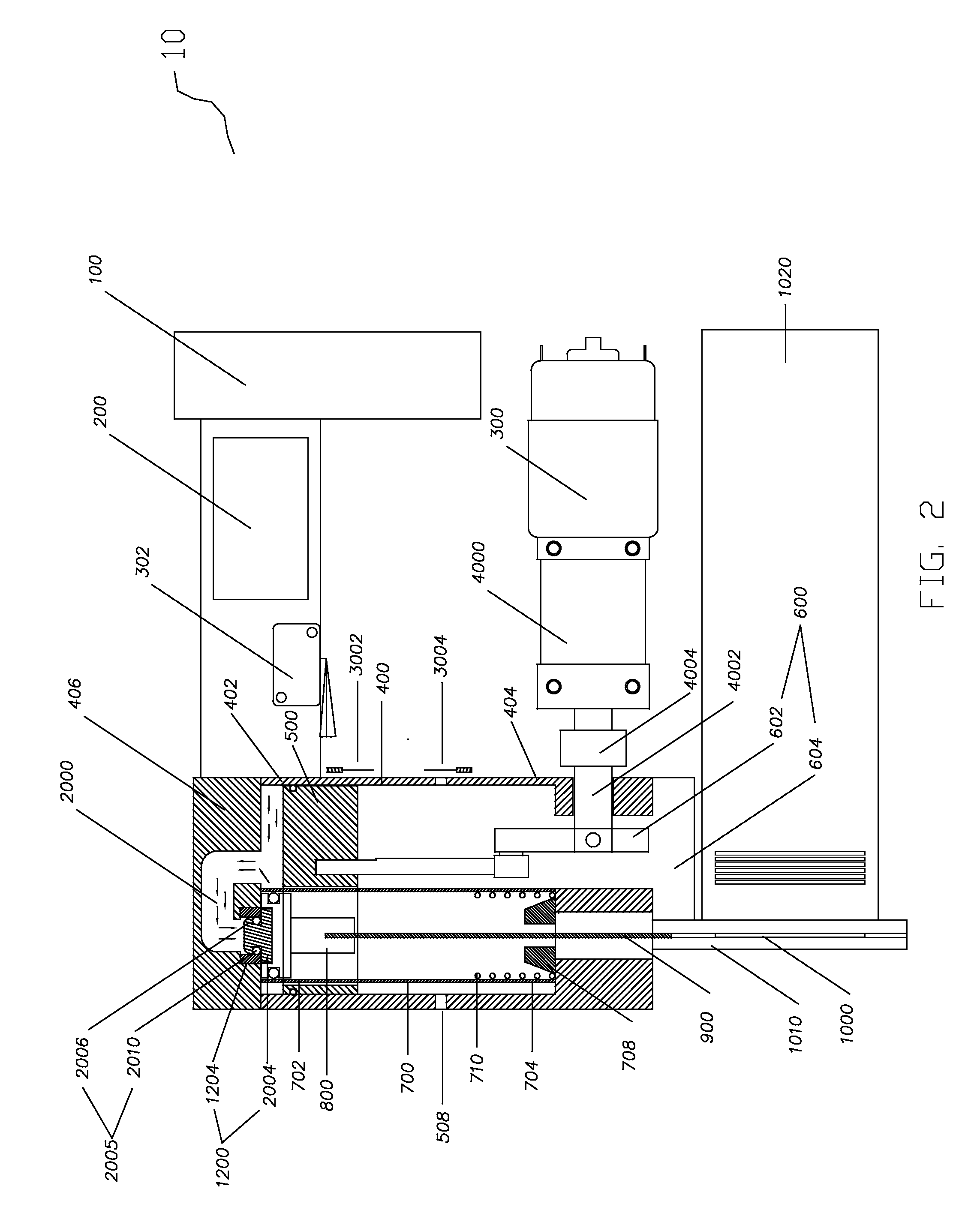
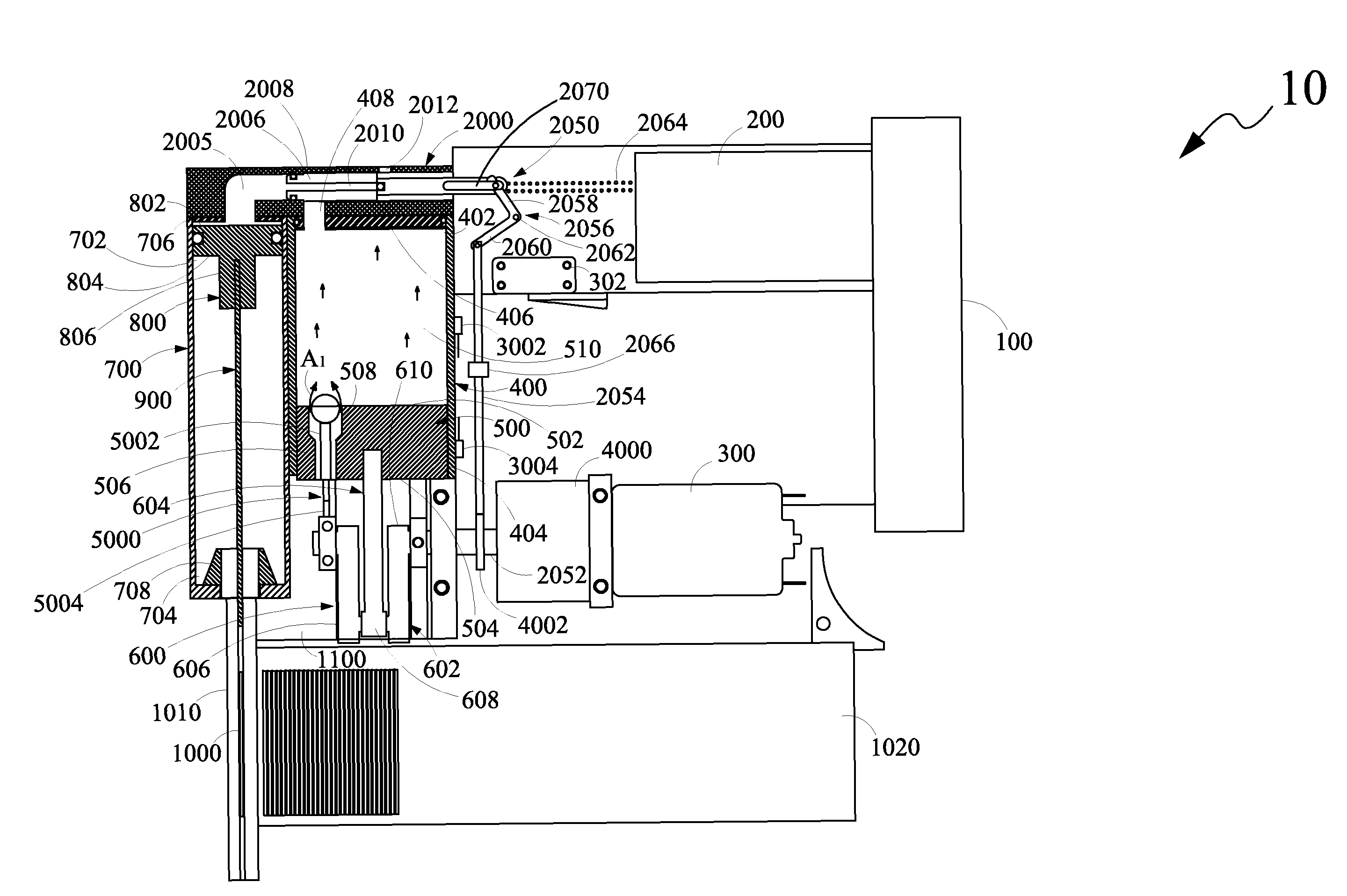
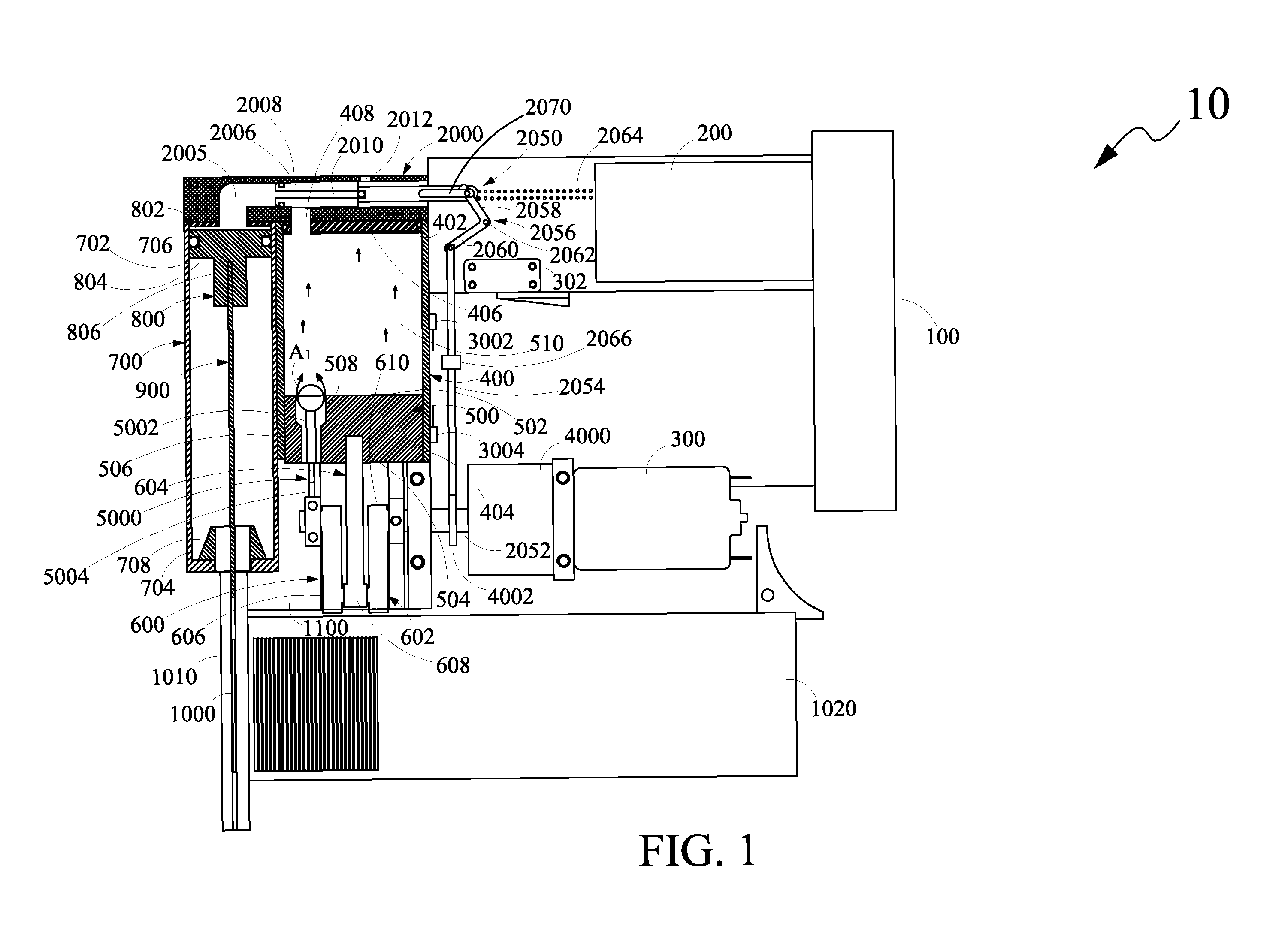
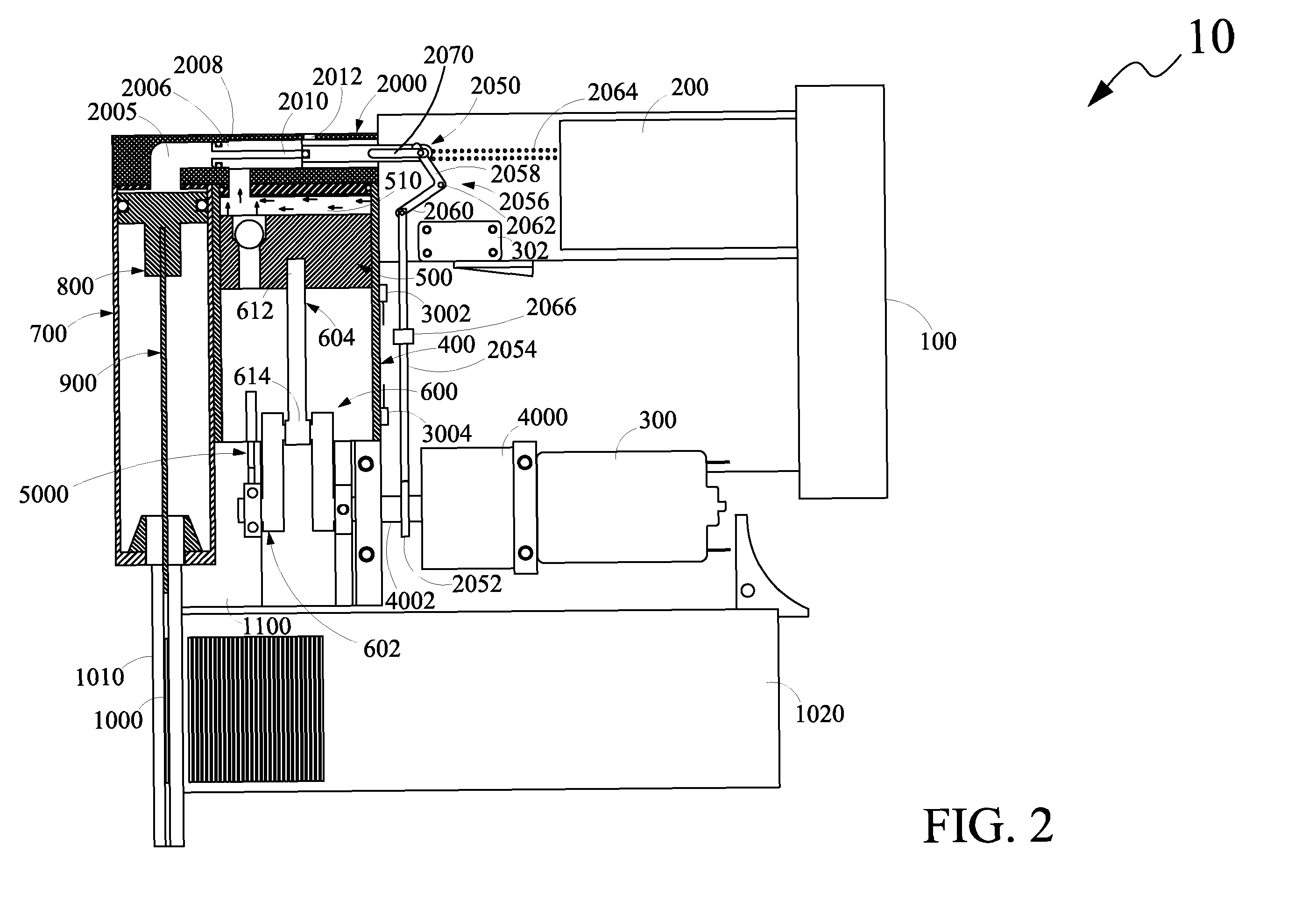
Drug reservoir loading and unloading mechanism for a drug delivery device using a unidirectional rotated shaft
A drug reservoir loading and unloading mechanism for drug delivery device using unidirectional rotated lead screw and method thereof are disclosed. The drug reservoir loading / unloading mechanism allows exchanging the drug reservoir quickly with very few steps and with more safety. The invention neither requires rewinding of the drive system either automatically or manually while replacing the drug reservoir nor requires an additional adapter to secure the drug reservoir.
Owner:ROCHE DIABETES CARE INC +1
Authorisation system
InactiveUS20050262026A1More securityEasy constructionDigital data processing detailsSpecial data processing applicationsHash functionTime limit
Systems and methods for securely authorising an on-line transaction, e.g. involving a micro-payment, between a customer browser and merchant server without the need for special software installed on the customer computer or a SSL connection to the merchant server. The authorisation method involves a double redirection instruction: the initial transaction request is redirected via the customer web browser to a service provider arranged to authenticate the customer, from where the authenticated instruction is further redirected via the customer web browser to a merchant site to complete the transaction. Information identifying the merchant, merchandise, etc. is included in the redirection instruction, and may be encrypted or encoded e.g. using a hash function to prevent tampering. To authorise an authenticated instruction, a cookie containing transaction identification data may be returned to the merchant web server along with the authenticated instruction. Alternatively, the service provider may set a time limit after which the authenticated instruction will no longer be valid.
Owner:WATKINS DANIEL ROBERT
Drug reservoir loading and unloading mechanism for a drug delivery device using a unidirectional rotated shaft
A drug reservoir loading and unloading mechanism for drug delivery device using unidirectional rotated lead screw and method thereof are disclosed. The drug reservoir loading / unloading mechanism allows exchanging the drug reservoir quickly with very few steps and with more safety. The invention neither requires rewinding of the drive system either automatically or manually while replacing the drug reservoir nor requires an additional adapter to secure the drug reservoir.
Owner:ROCHE DIABETES CARE INC +1
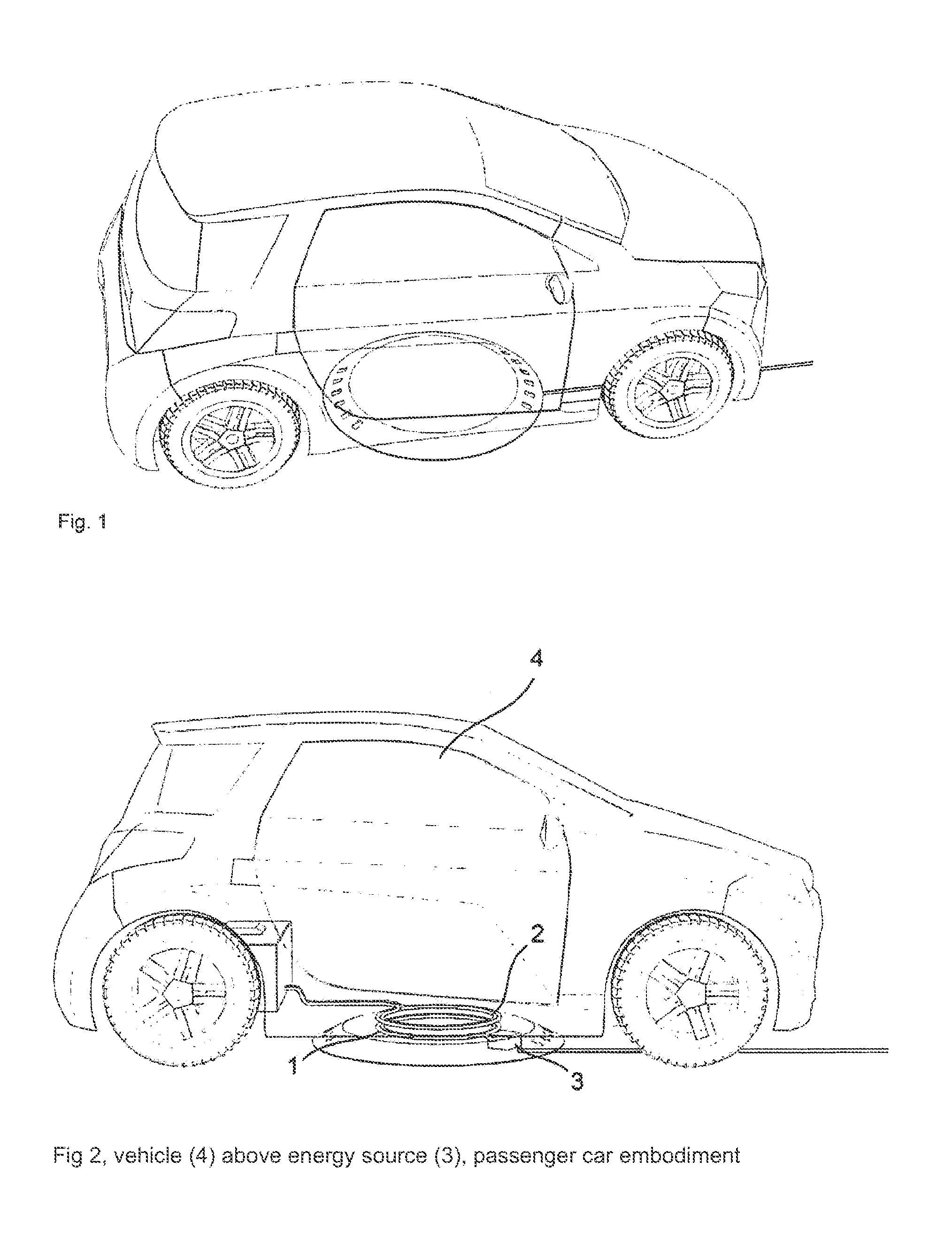
System for inductively charging vehicles, comprising an electronic positioning aid
InactiveUS20120203410A1High standardization effortMaximum efficiencyDigital data processing detailsVehicular energy storageElastic componentDriver/operator
The main claim involves a system that ensures a self-guiding, electronic positioning of a secondary coil in a vehicle, without the aid of indicators or kinematic or mechanical aids, in relation to a primary coil that is fixed in a structure, in order to guarantee a transfer of energy with over 90% efficiency without the disadvantages of moving, frictional and elastic components in terms of energy consumption, functional safety and wear. To achieve this aim, the coil housing in the structure fulfills the role of an electronics housing, reflective element and cooling element thanks to the choice of material used, the surface and the inner supports and can thus be retrofitted, as a single installation on the structure in the form of an operation-ready complete package, to any flat base with an electric connection. The vehicle can be used both for transporting passengers and loads and can be steered by a vehicle driver or can be operated without a driver, for example for cleaning areas, for the protection of the countryside or for intralogistics
Owner:CONDUCTIX WAMPFLER
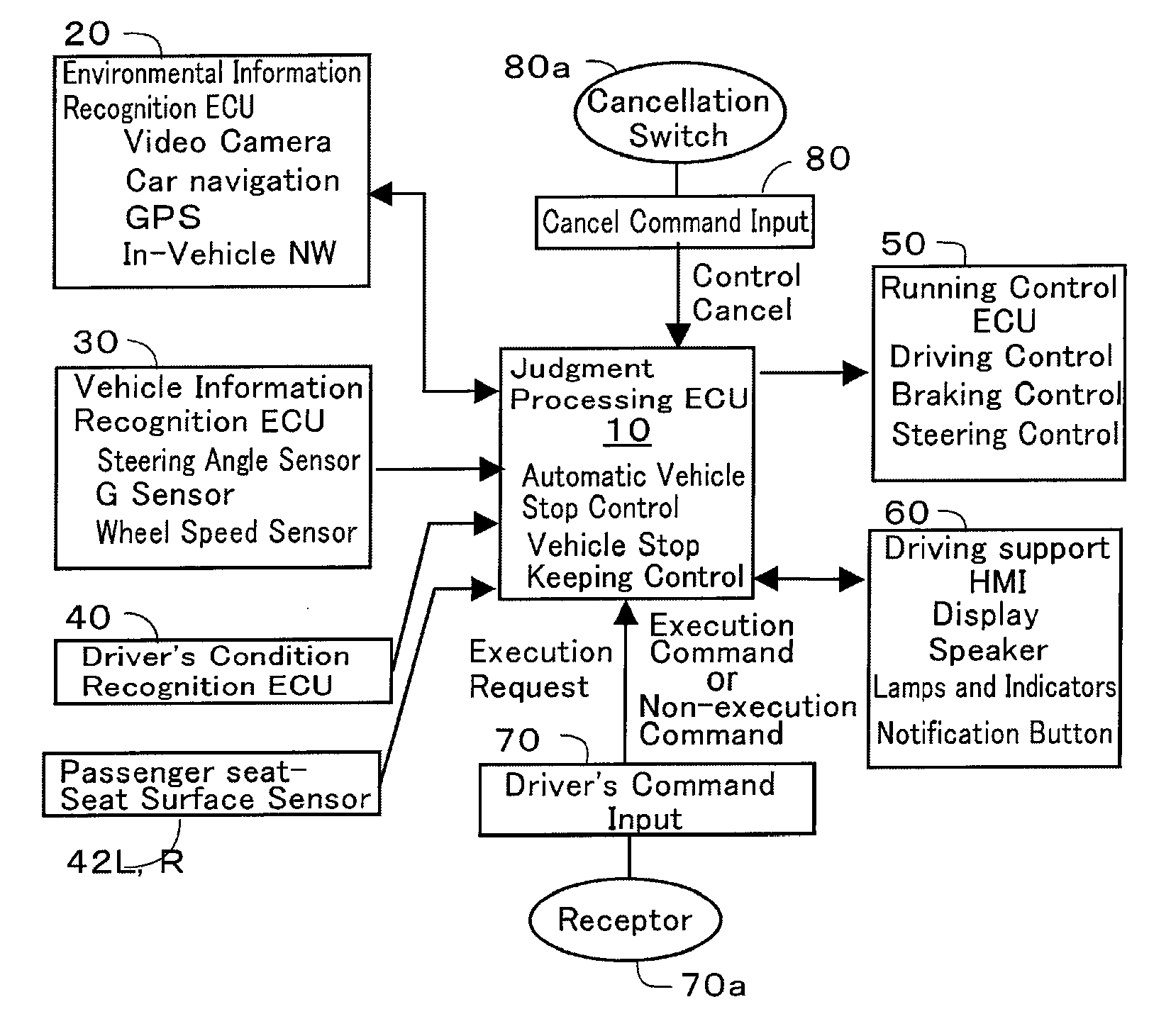
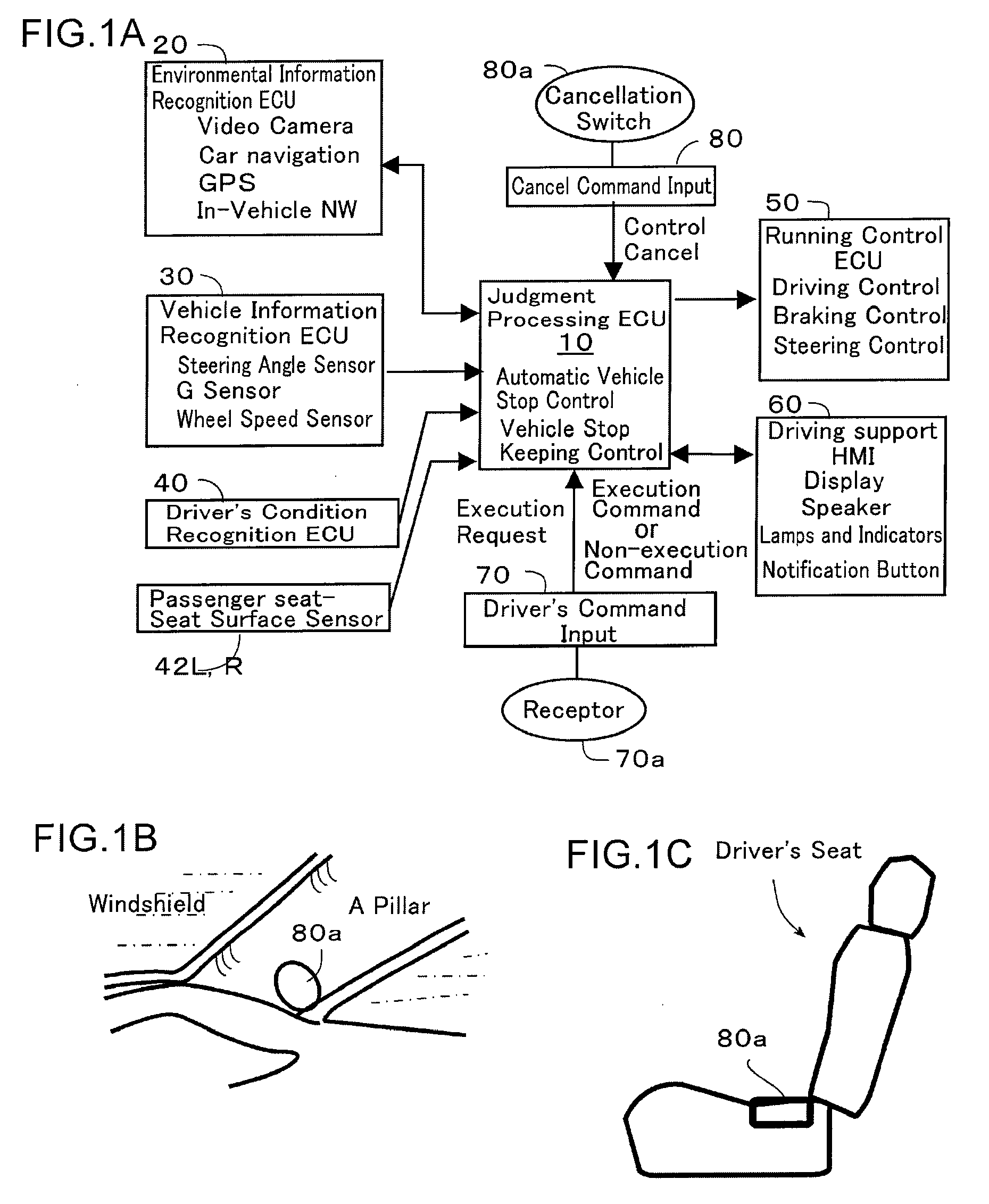
Vehicle emergency evacuation device
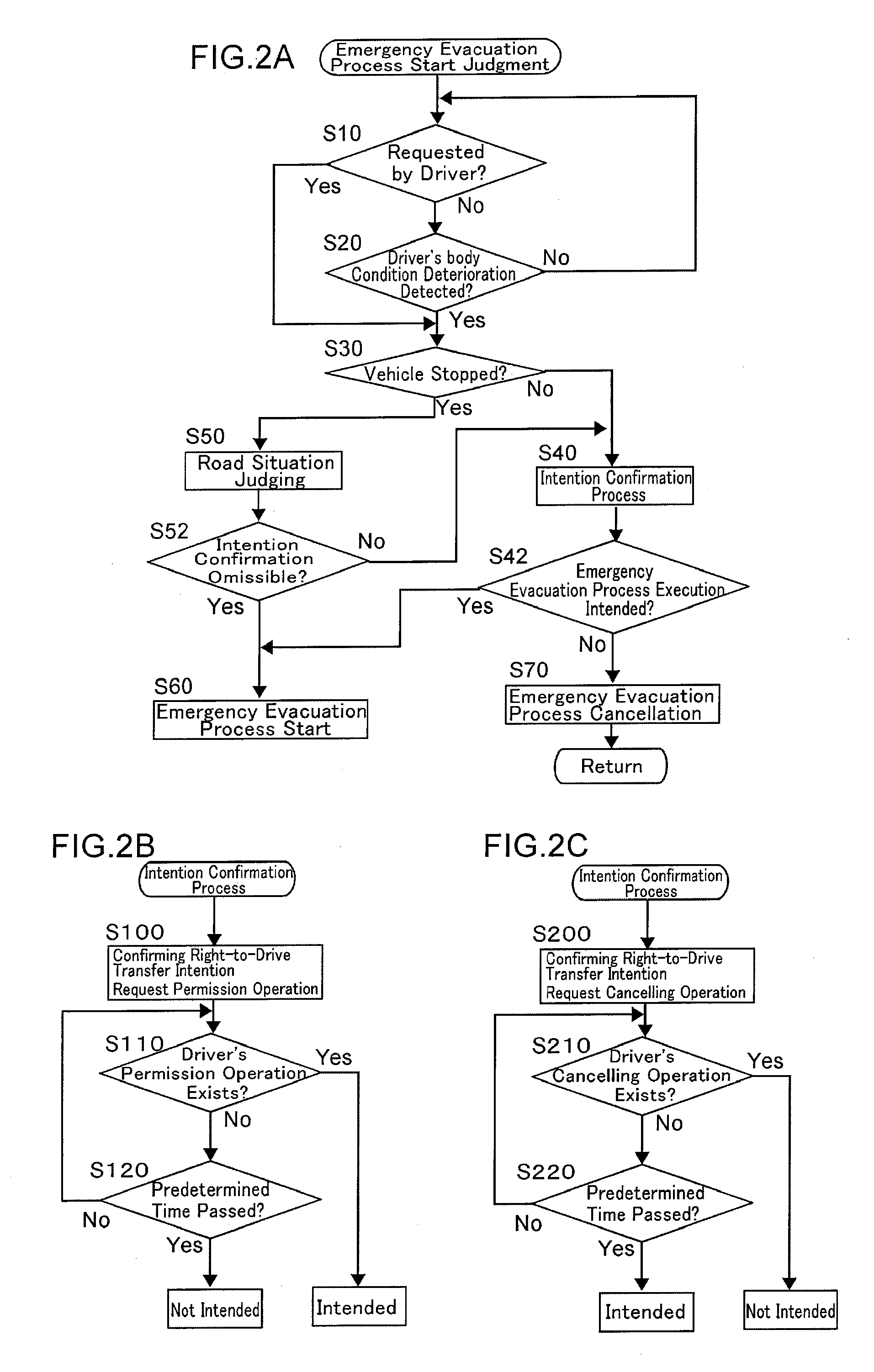
ActiveUS20130018549A1Easy to implementAvoid relative motionDigital data processing detailsAutomatic steering controlLevel crossingEngineering
In a vehicle emergency evacuation device which stops a running vehicle automatically or keeps a stop state of a stopped vehicle in a driver's emergency, a stop keeping process is executed to keep the stop state without conducting an intention confirmation process of the execution start of an emergency evacuation process when the emergency evacuation process is required, e.g. when an abnormality or a deterioration in the driver's condition arises or when the driver requests the emergency evacuation process, under a condition that the vehicle has stopped before a signal, a road crossing or a railroad crossing, thereby ensuring the safety of the vehicle. Moreover, there are provided a structure in which the stop site of the vehicle in the execution of automatic vehicle stop control is determined depending upon whether the running road is a driveway, a highway, or a normal road; and a structure that judges whether or not to permit an override to the emergency evacuation process after the execution start of the emergency evacuation process based on a passenger's motion.
Owner:TOYOTA JIDOSHA KK
Fastener driving apparatus
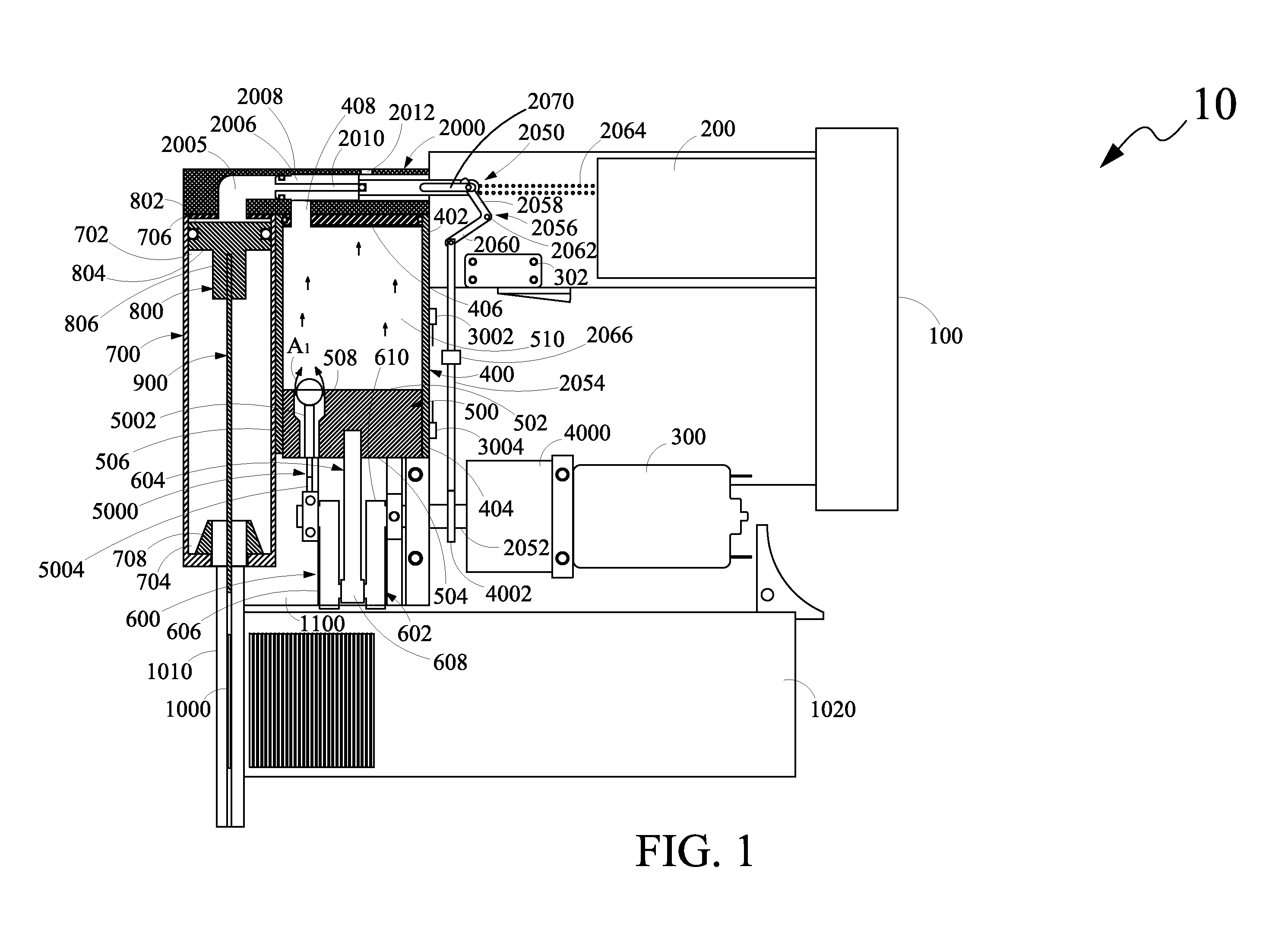
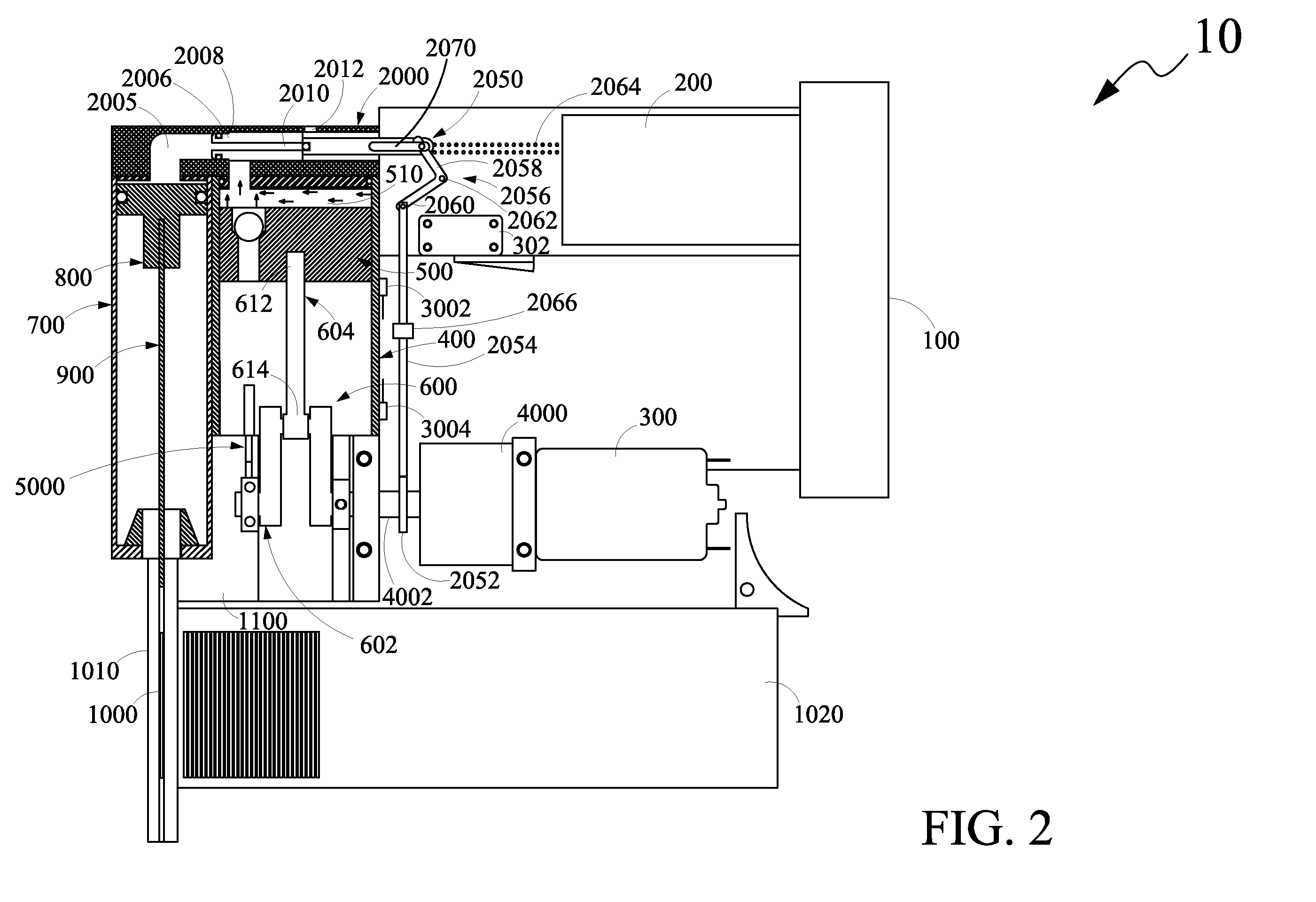
ActiveUS8079504B1Avoid consumptionPrecludes of drive in drive speedStapling toolsFluid couplingsLinear motionEngineering
A fastener driving apparatus includes a power source, a control circuit, a motor, a first cylinder, a first piston, a linear motion converter, a second cylinder, a second piston, an anvil, a retention element retaining a component of the apparatus, and at least one sensor. During a compression stroke, the first piston compresses gas in a first cylinder to a predetermined pressure. Compressed gas is communicated to the second cylinder and the retention force of the retention element is overcome, to release the retained component of the apparatus, thereby causing the second piston to move linearly and enabling the anvil to drive the fastener into the workpiece. During a return stroke of the first piston, a vacuum created in the first cylinder is communicated to the second cylinder, causing the second piston and the anvil to retract to their initial positions.
Owner:TRICORD SOLUTIONS
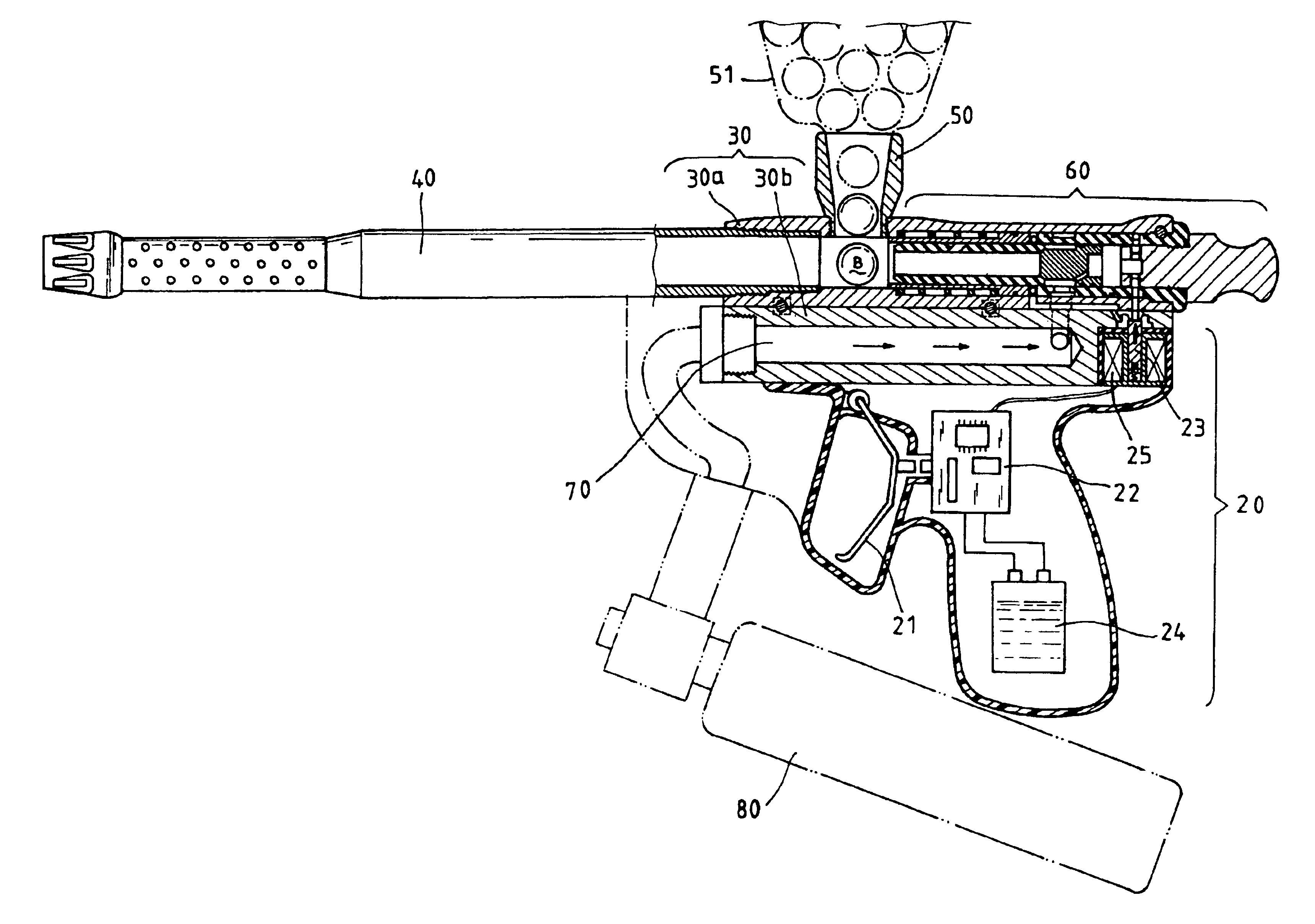
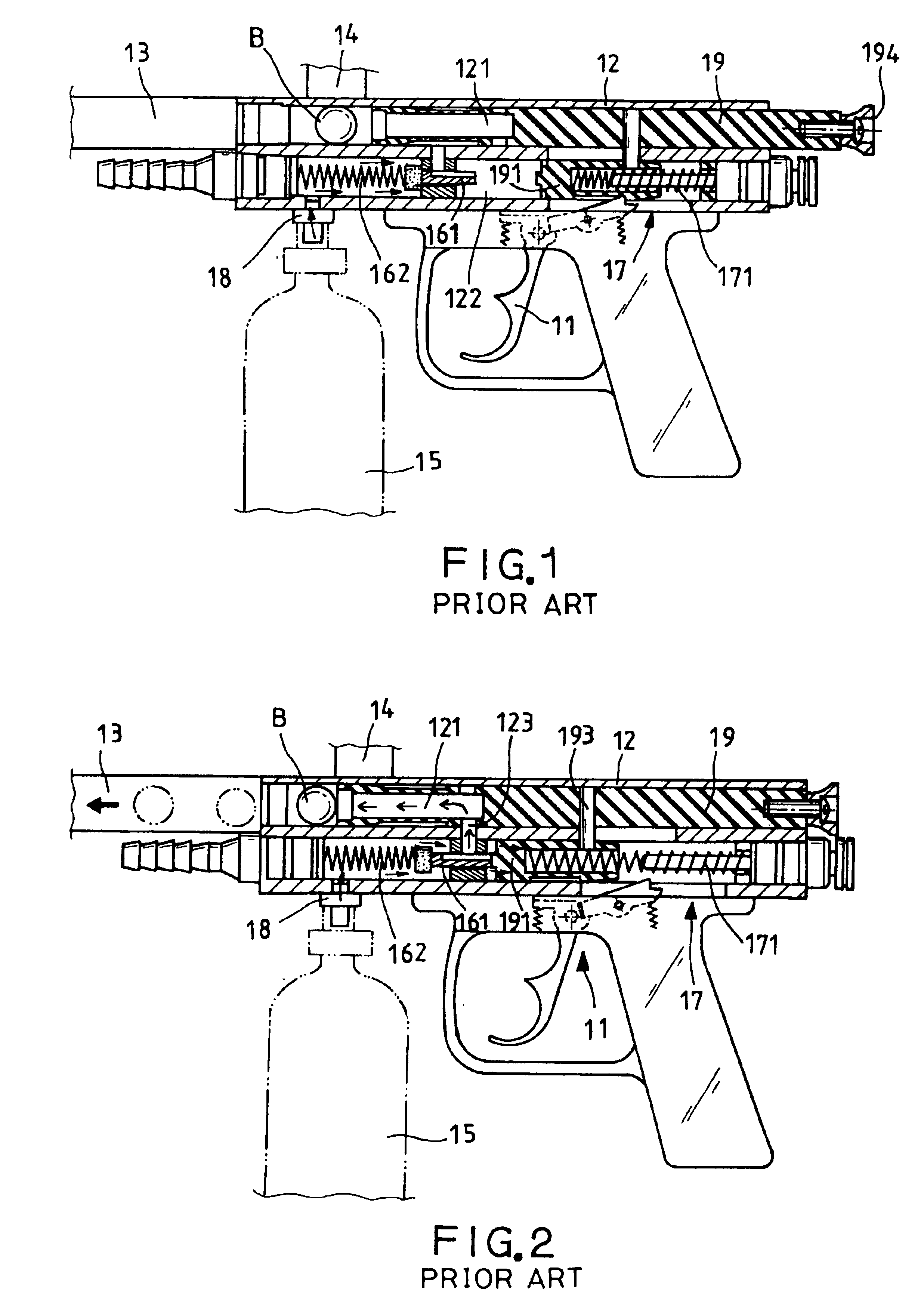
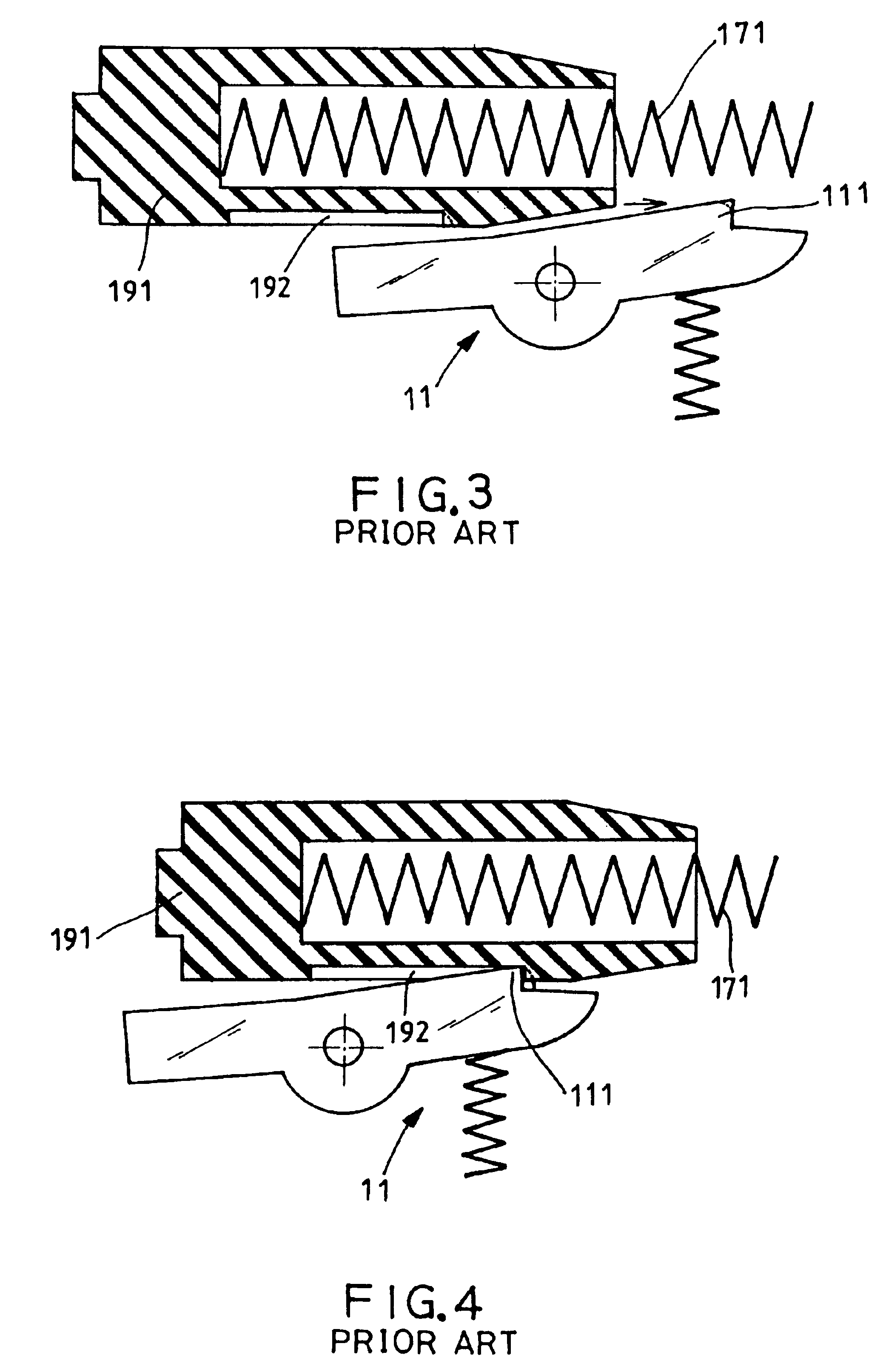
Paintgun with pneumatic feeding and discharging process
InactiveUS6925997B2More securityReduce failureWatering devicesFire rescuePressure differenceAir channel
Owner:SHENG CHIH SHENG
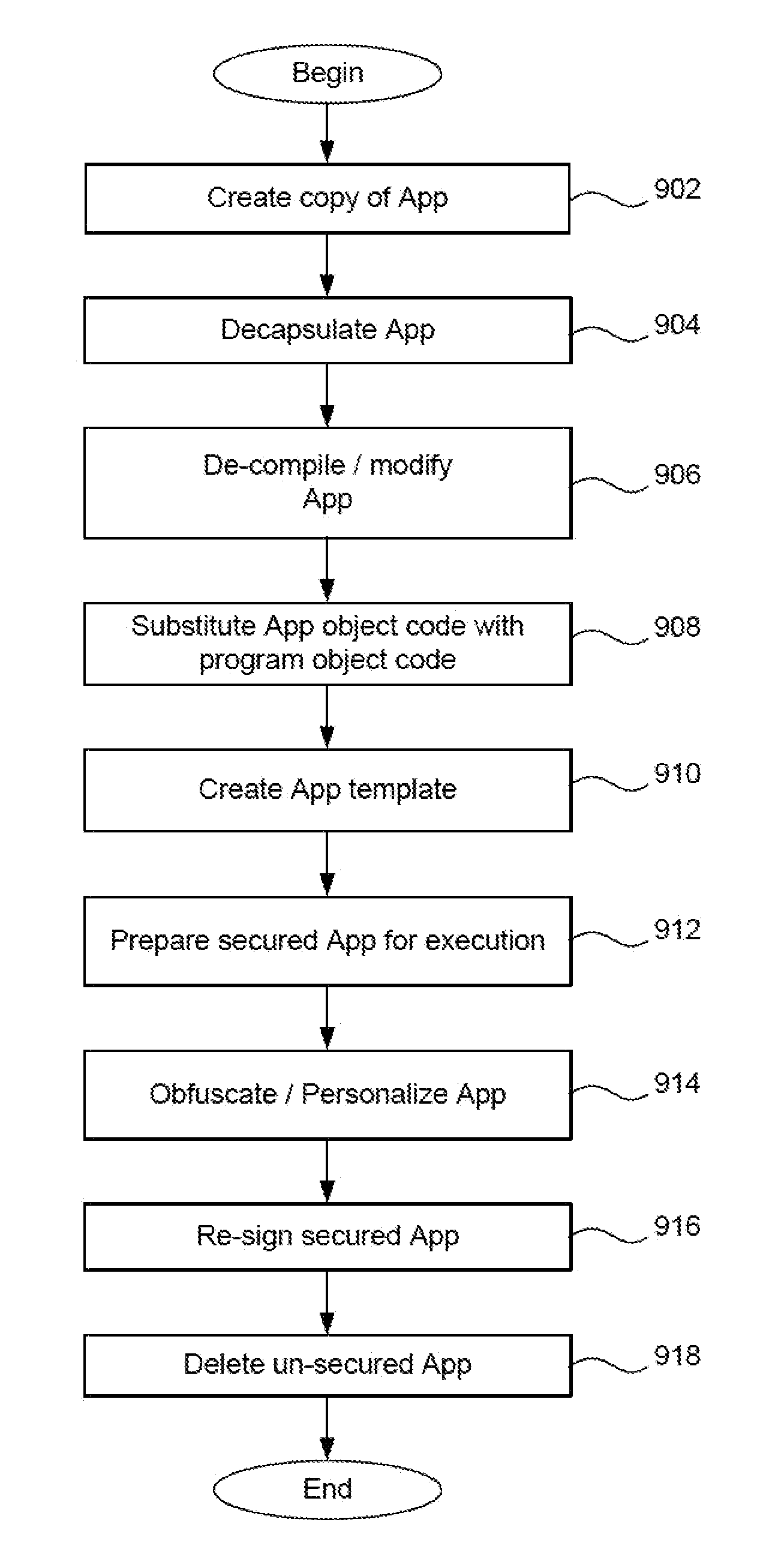
Secure execution of unsecured apps on a device
ActiveUS20120246484A1Minimize damageMinimize data lossUnauthorized memory use protectionHardware monitoringRandomizationApplication software
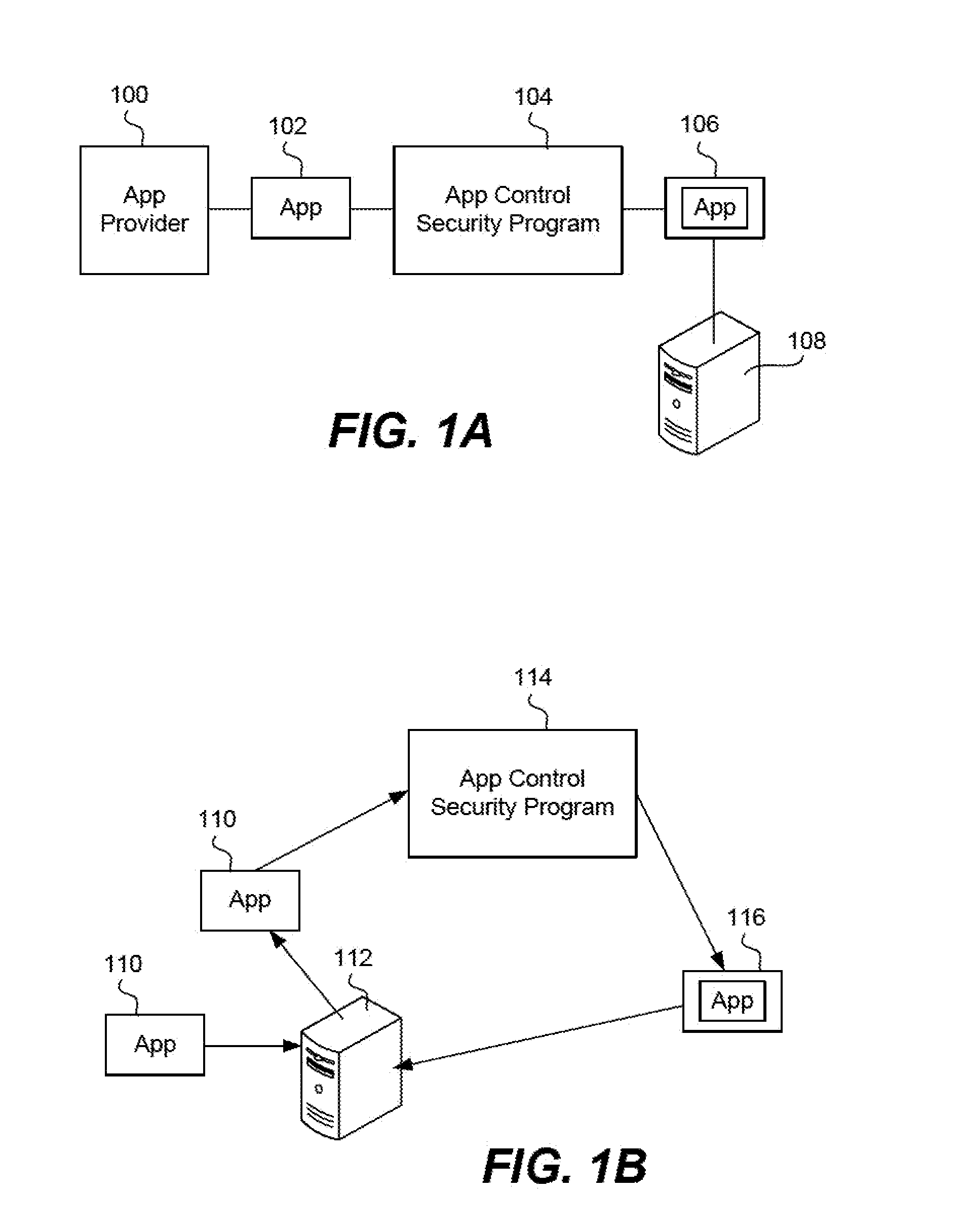
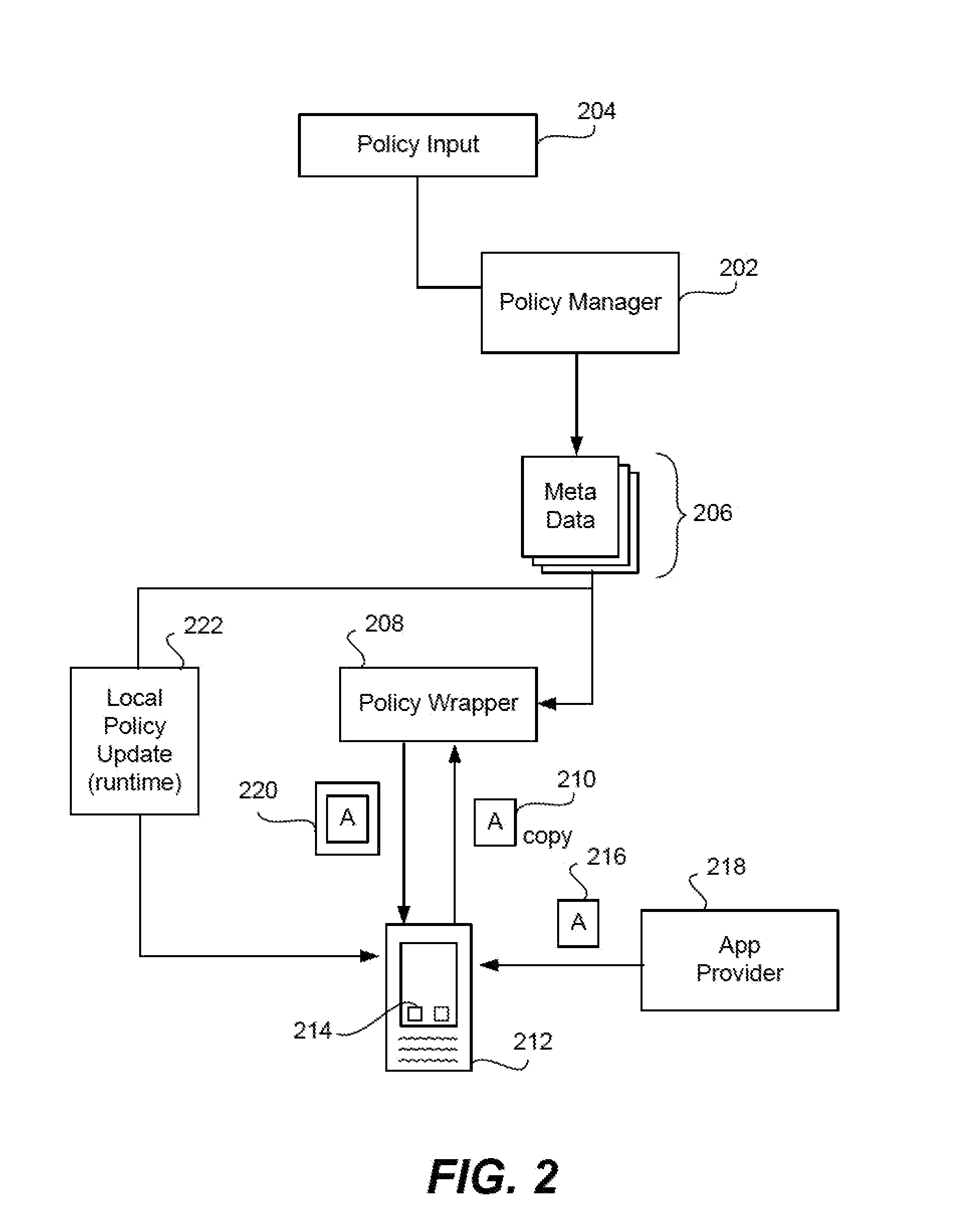
Given the volume of apps being developed and downloaded, performing operations to enable security for mobile devices, such as locating relevant classes and substituting different classes, can become very inefficient when done to a very high number of apps. In the invention, a device is enabled with an app security enforcement layer. The consumer can download unsecured apps and have the app execute on the phone in a secure manner, where potential data loss to the device, such as a smart phone or tablet, is minimized. To make the security wrapping process more efficient, an app template containing markers is created. This template is merged with data in an active user policy or is used to randomize or obfuscate the code to add more security. The process of security wrapping an app becomes more efficient.
Owner:BLUE CEDAR NETWORKS INC
Update method and update system
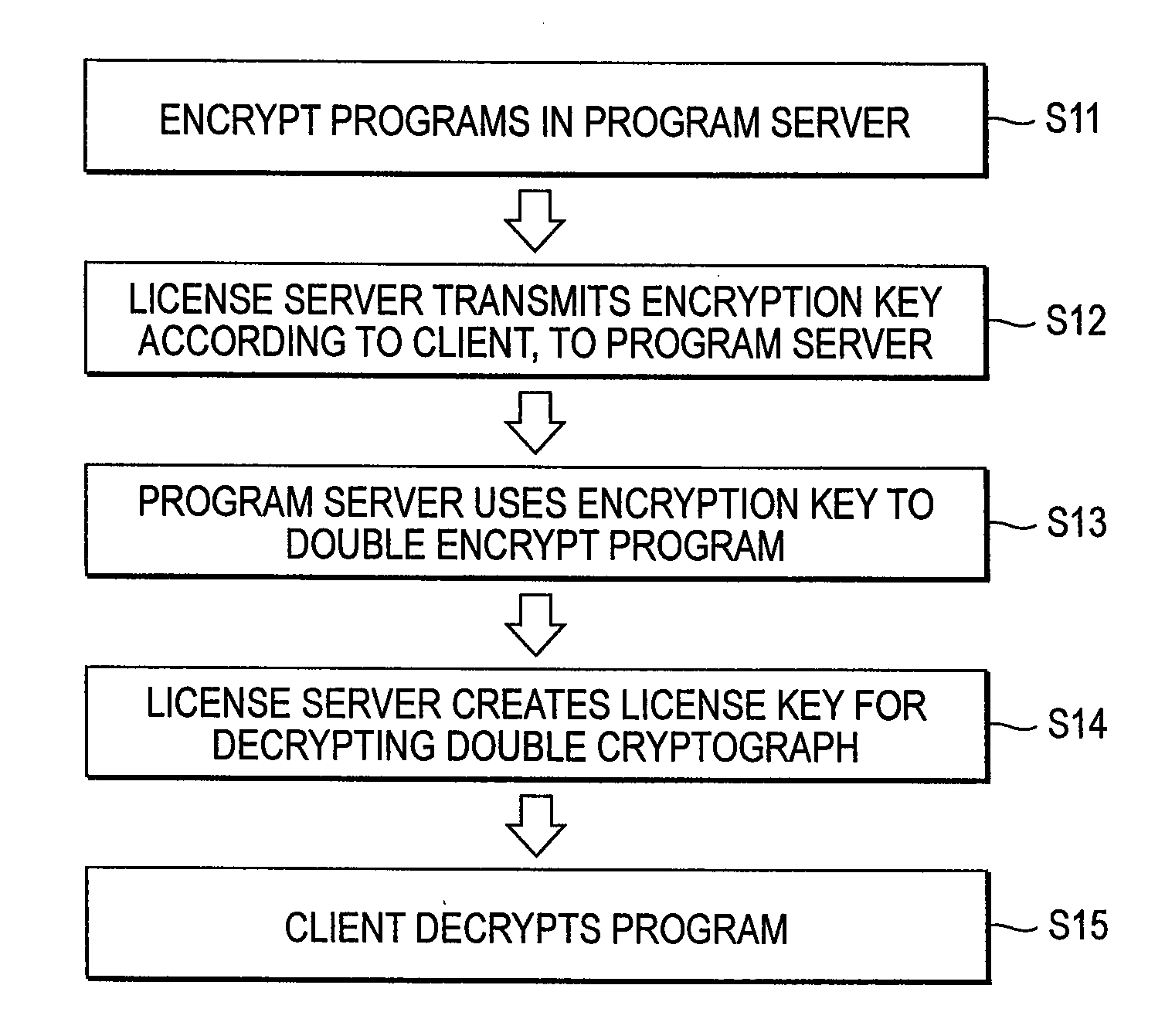
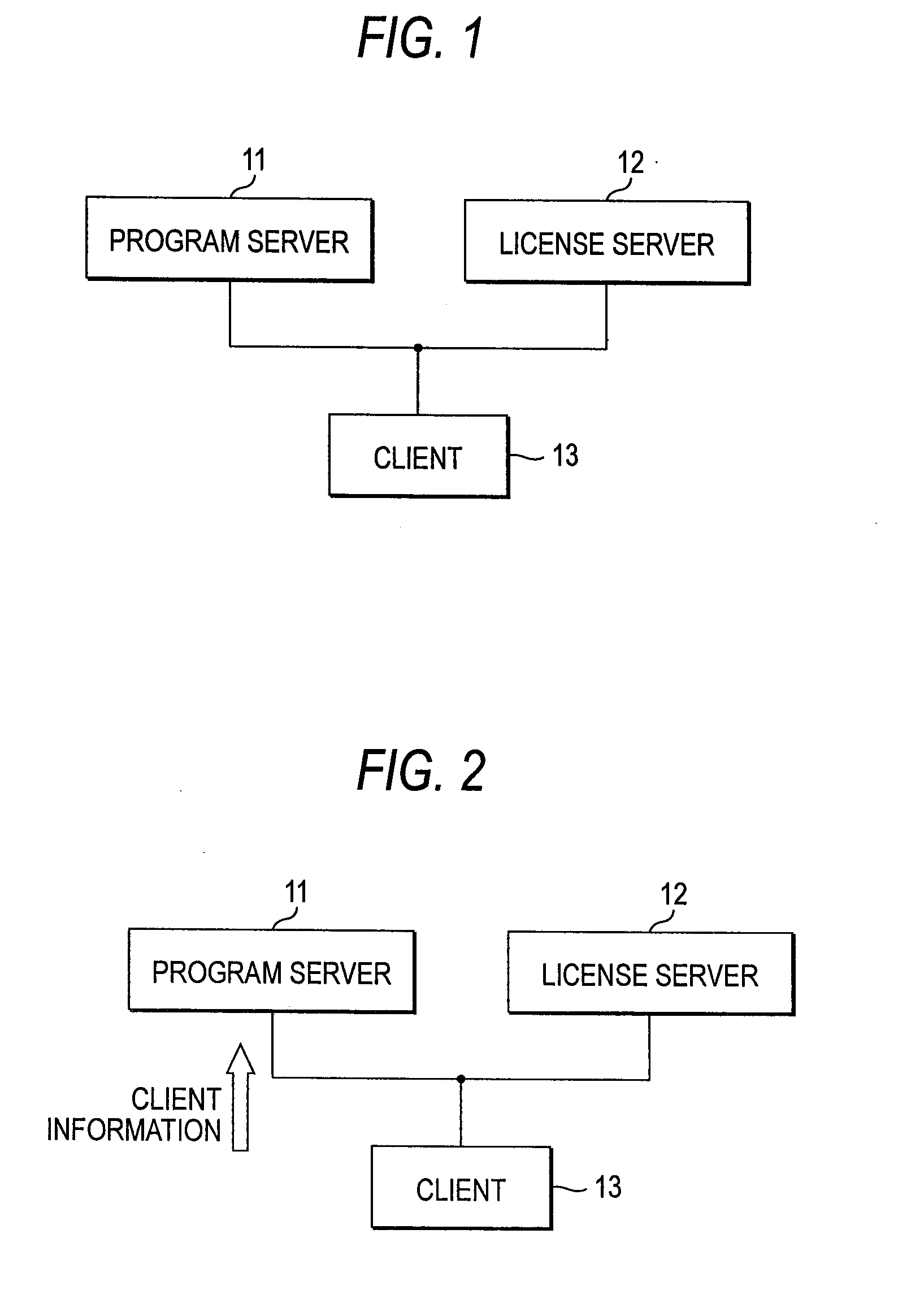
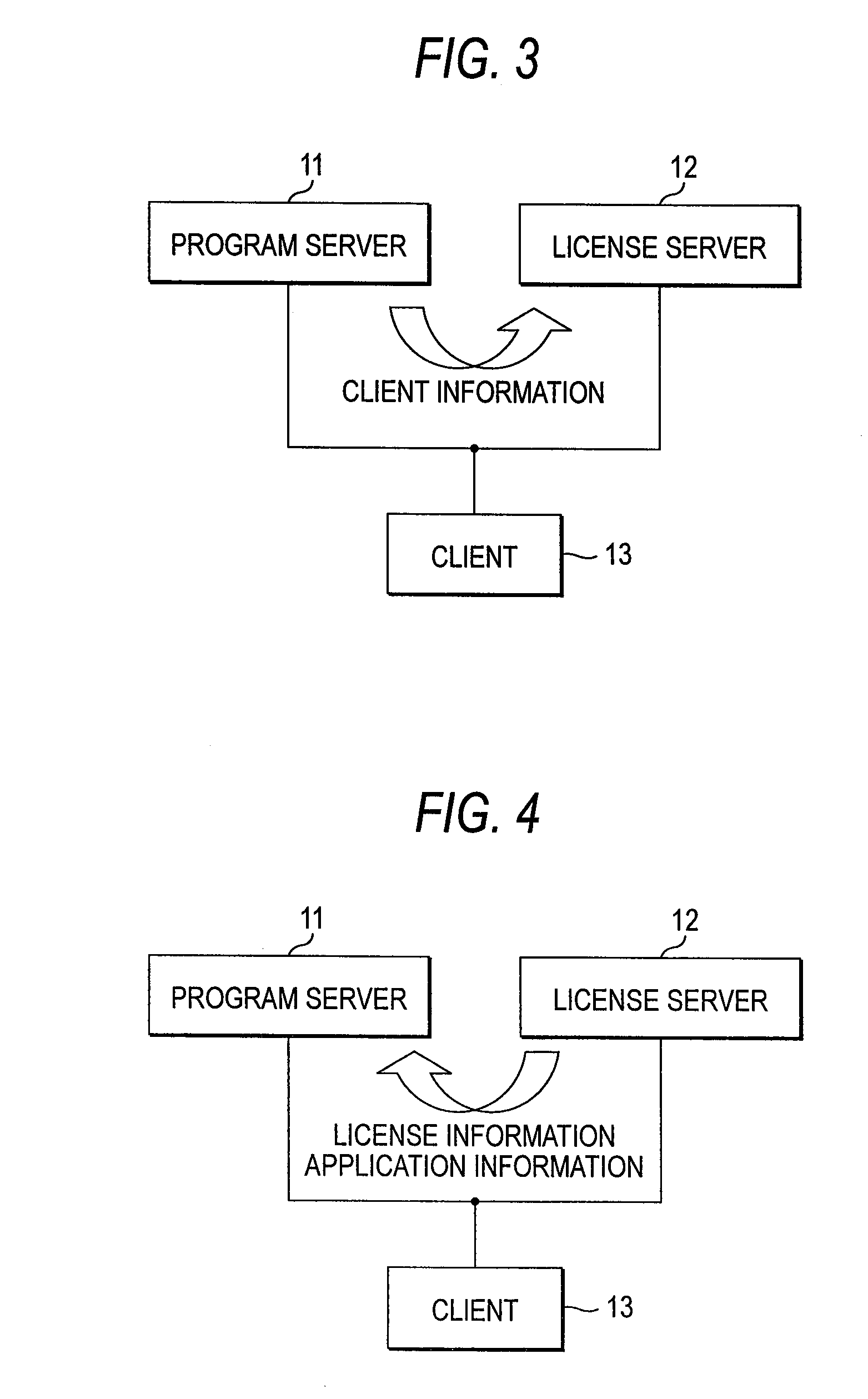
InactiveUS20080027871A1Effective applicationUpdated safely and efficientlyData processing applicationsProgram loading/initiatingClient-sideLicense
An update system includes: a program server for storing application programs and transmitting the application program corresponding only to an authenticated client; a license server for transmitting information concerning the authenticated client to the program server and transmitting the license key of the application program to the authenticated client; and the client for executing the application program transmitted from the program server based on the license key transmitted from the license server.
Owner:ZIOSOFT
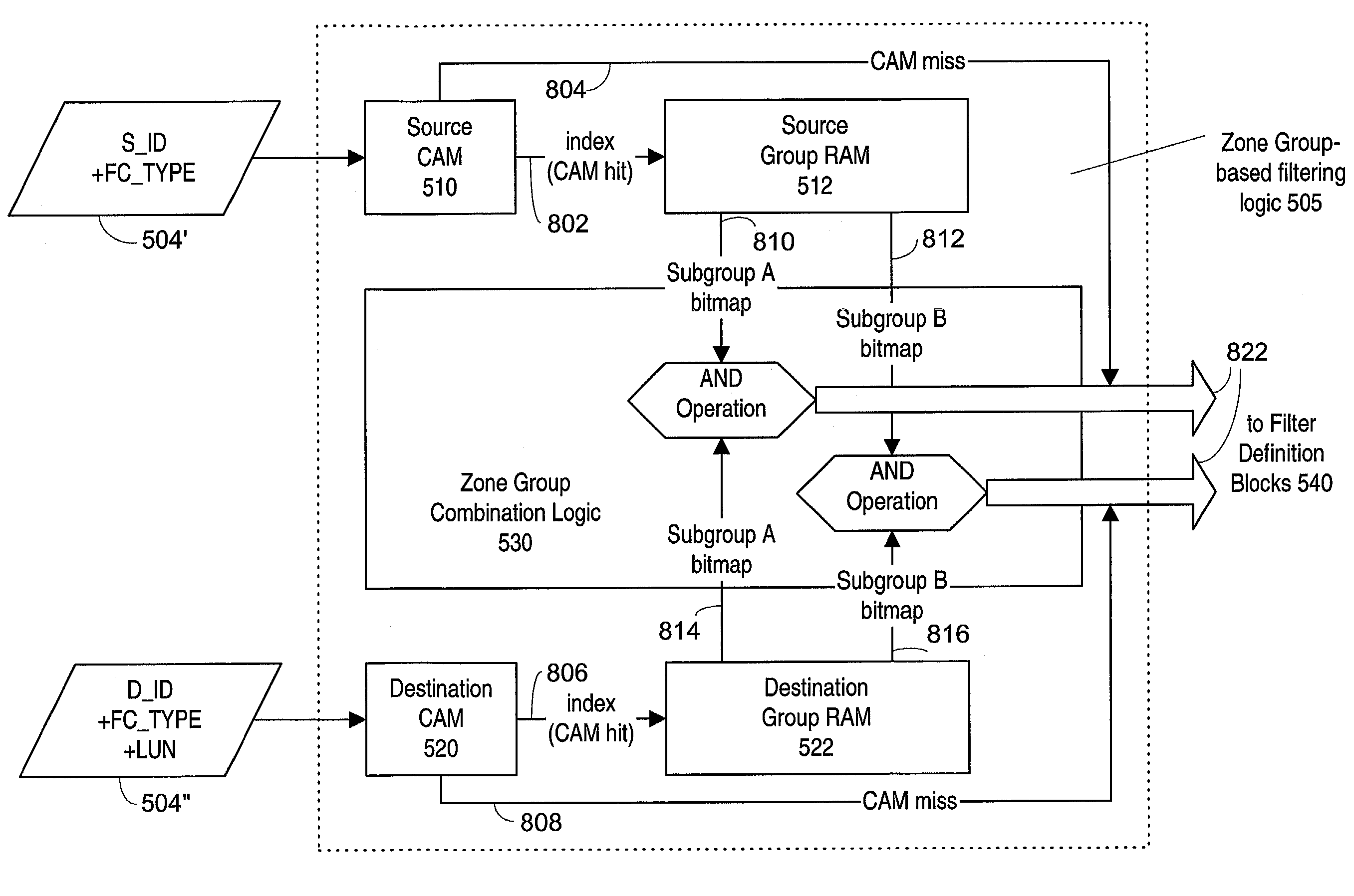
Fibre channel zoning hardware for directing a data packet to an external processing device
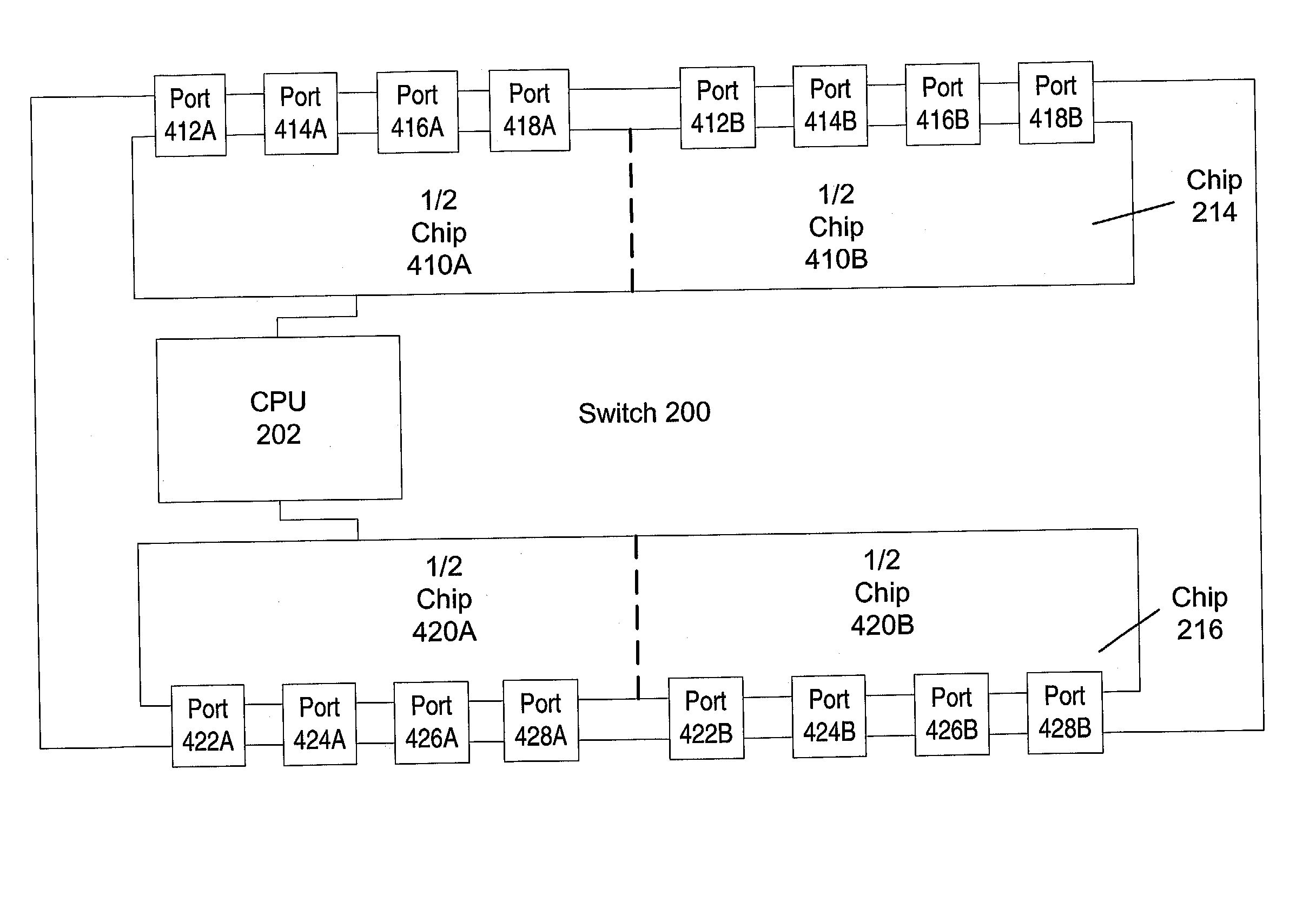
InactiveUS20050169258A1Improve security levelFast processData switching by path configurationComputer hardwareNetwork packet
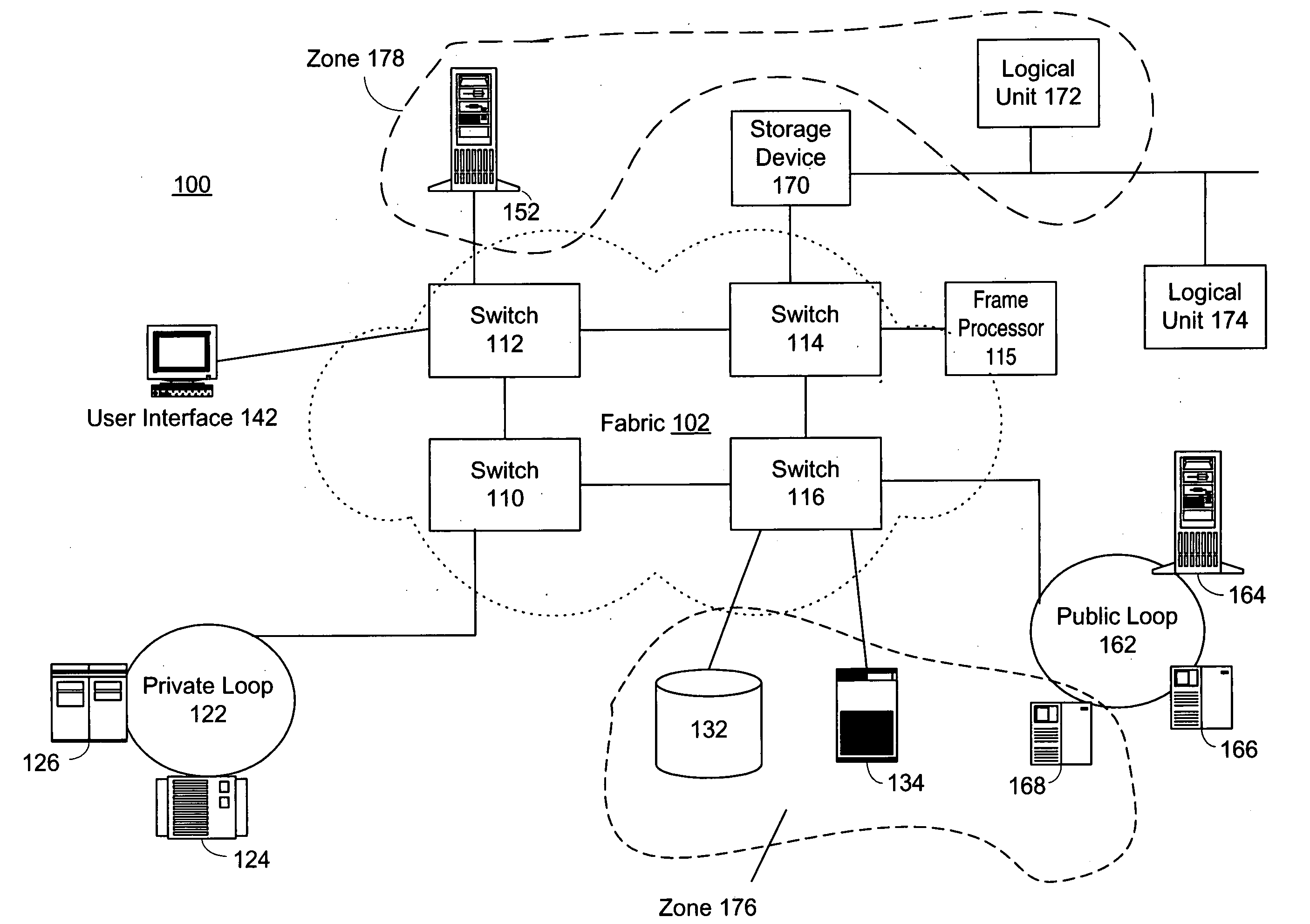
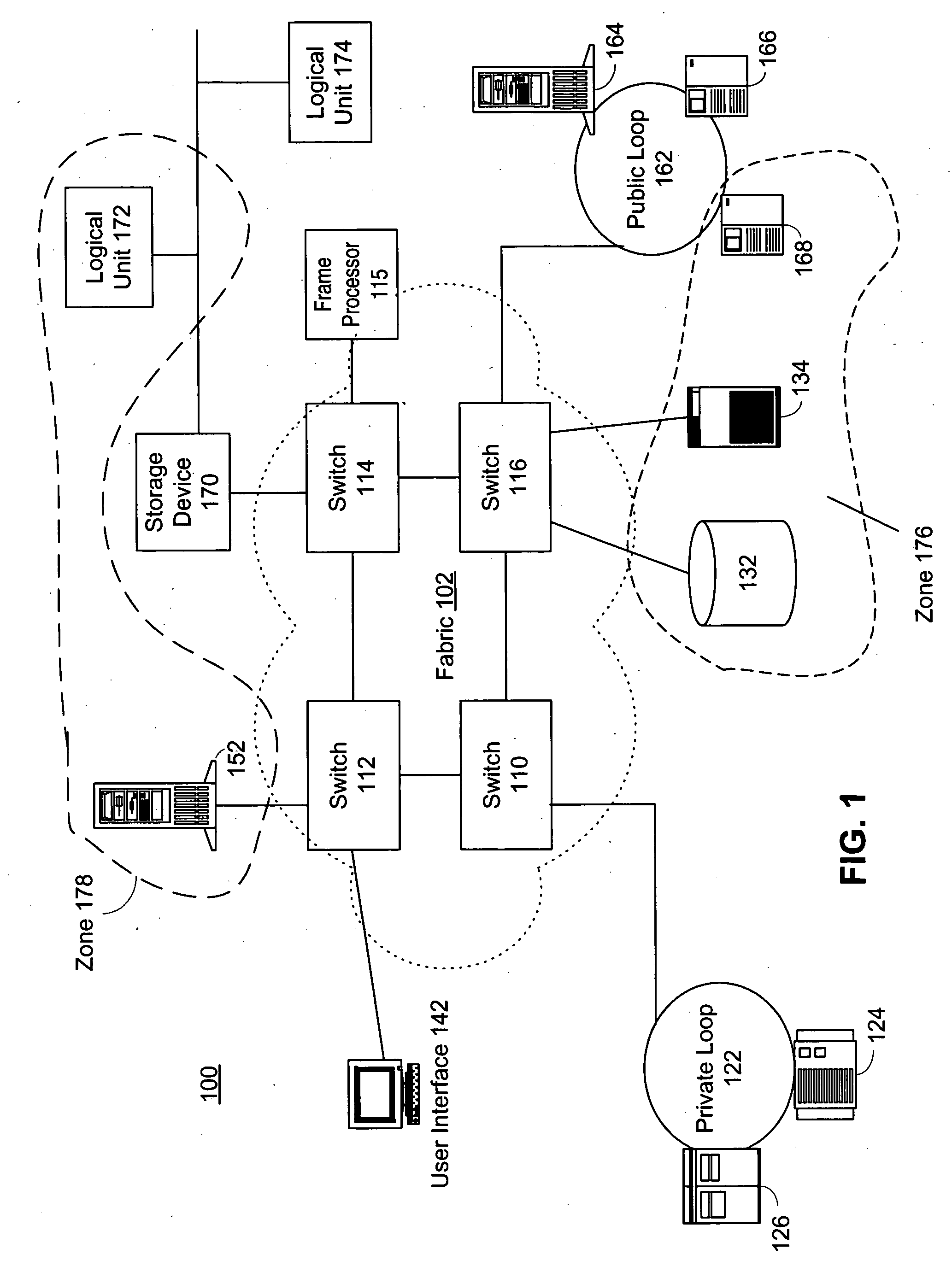
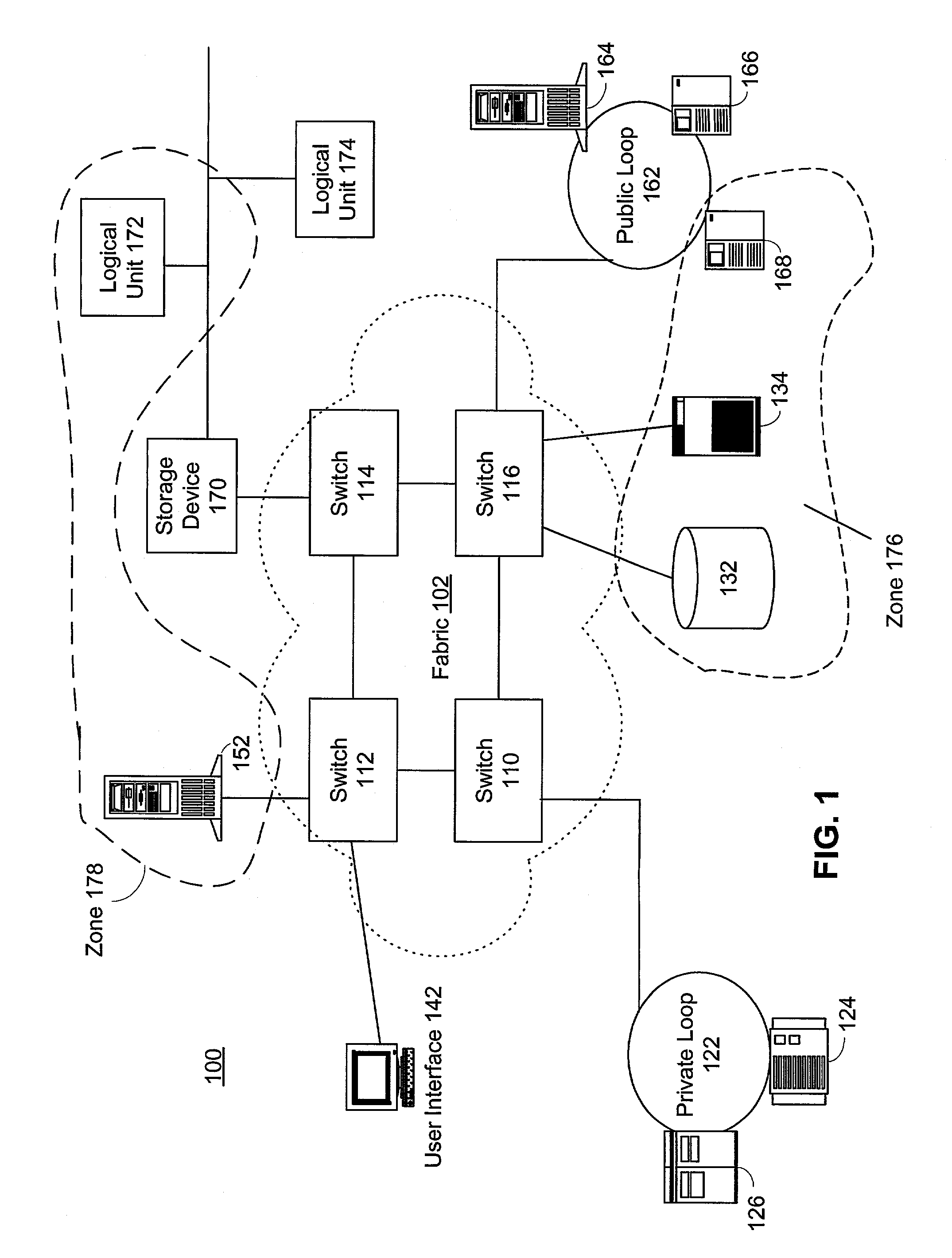
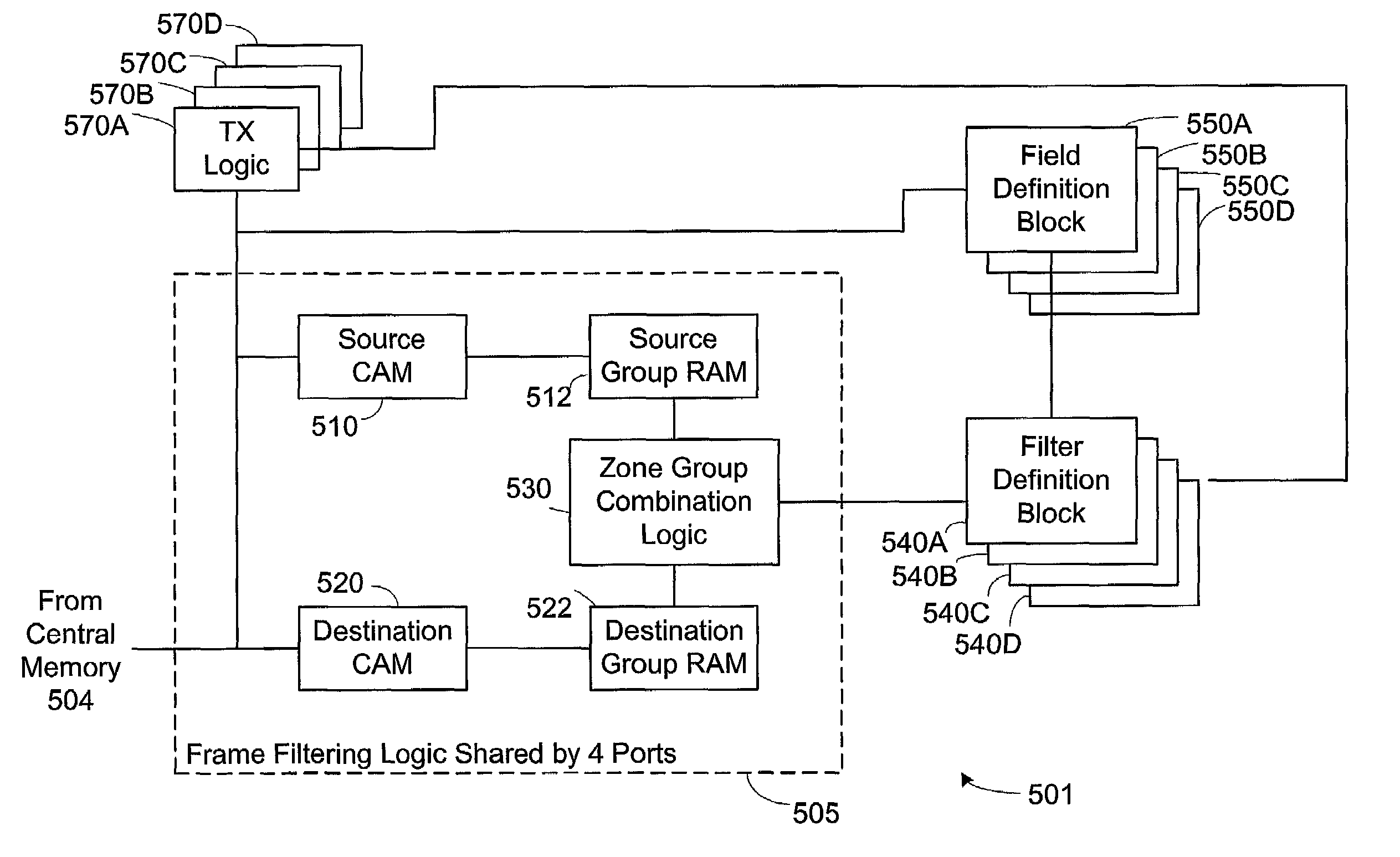
The present invention provides a system and a method for filtering a plurality of frames sent between devices coupled to a fabric by Fibre Channel connections. Frames are reviewed against a set of individual frame filters. Each frame filter is associated with an action, and actions selected by filter matches are prioritized. Groups of devices are “zoned” together and frame filtering ensures that restrictions placed upon communications between devices within the same zone are enforced. Zone group filtering is also used to prevent devices not within the same zone from communicating. Zoning may also be used to create LUN-level zones, protocol zones, and access control zones. In addition, individual frame filters may be created that reference selected portions of frame header or frame payload fields.
Owner:AVAGO TECH INT SALES PTE LTD
Fibre channel zoning by logical unit number in hardware
InactiveUS20020176434A1Fast processImprove security levelMultiplex system selection arrangementsTime-division multiplexFiberFibre Channel zoning
The present invention provides a system and a method for filtering a plurality of frames sent between devices coupled to a fabric by Fiber Channel connections. Frames are reviewed against a set of individual frame filters. Each frame filter is associated with an action, and actions selected by filter matches are prioritized. Groups of devices are "zoned" together and frame filtering ensures that restrictions placed upon communications between devices within the same zone are enforced. Zone group filtering is also used to prevent devices not within the same zone from communicating. Zoning may also be used to create LUN-level zones, protocol zones, and access control zones. In addition, individual frame filters may be created that reference selected portions of frame header or frame payload fields.
Owner:AVAGO TECH INT SALES PTE LTD
Fastener Driving Apparatus
ActiveUS20120286014A1Reduces and eliminates consumptionEasy and fastStapling toolsNailing toolsLinear motionEngineering
A fastener driving apparatus includes a power source, a control circuit, a motor, a first cylinder, a first piston, a linear motion converter, a second cylinder, a second piston, an anvil, a retention element retaining a component of the apparatus, and at least one sensor. During a compression stroke, the first piston compresses gas in a first cylinder to a predetermined pressure. Compressed gas is communicated to the second cylinder and the retention force of the retention element is overcome, to release the retained component of the apparatus, thereby causing the second piston to move linearly and enabling the anvil to drive the fastener into the workpiece. During a return stroke of the first piston, a vacuum created in the first cylinder is communicated to the second cylinder, causing, along with an optional other retraction means, the second piston and the anvil to retract to their initial positions.
Owner:TRICORD SOLUTIONS
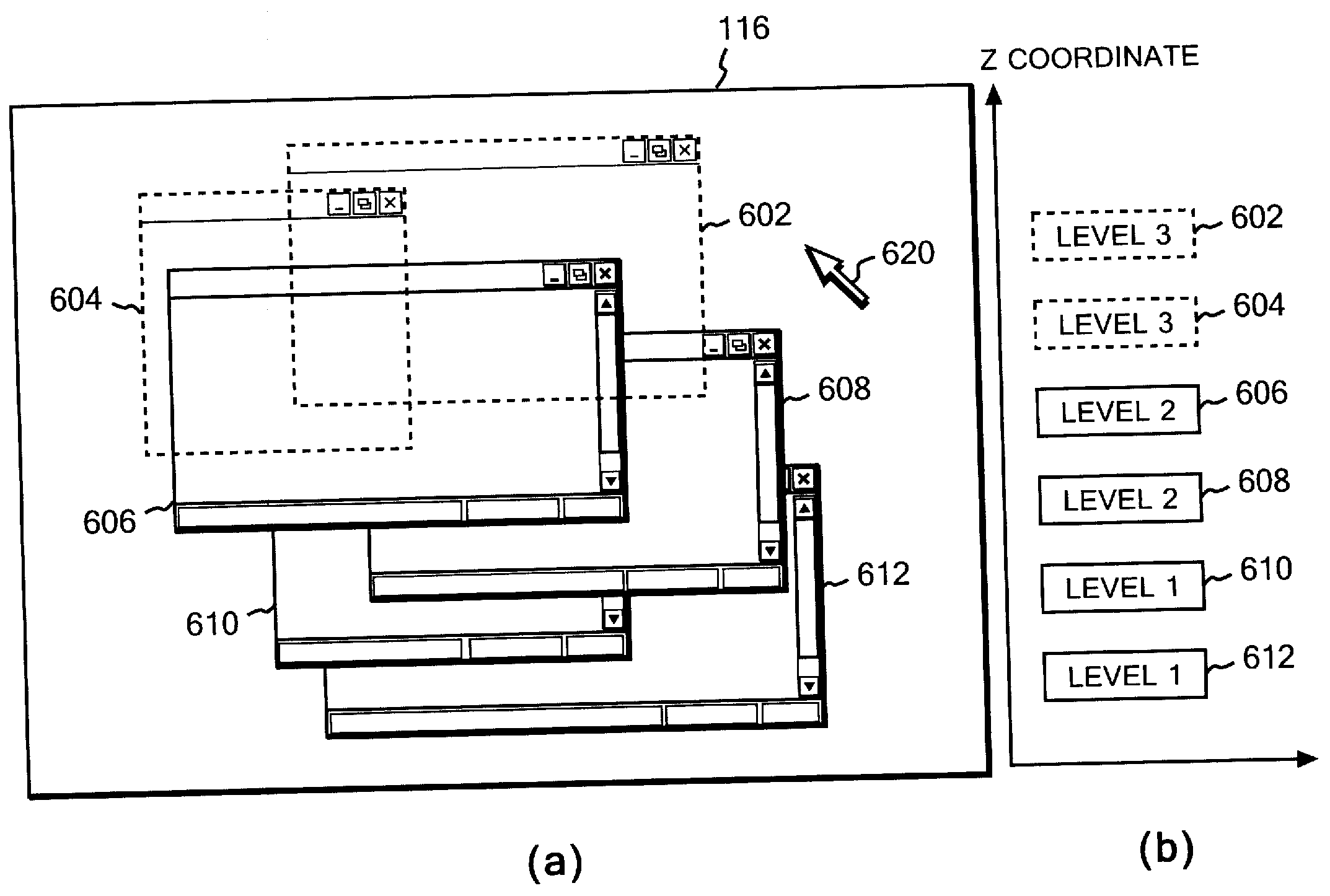
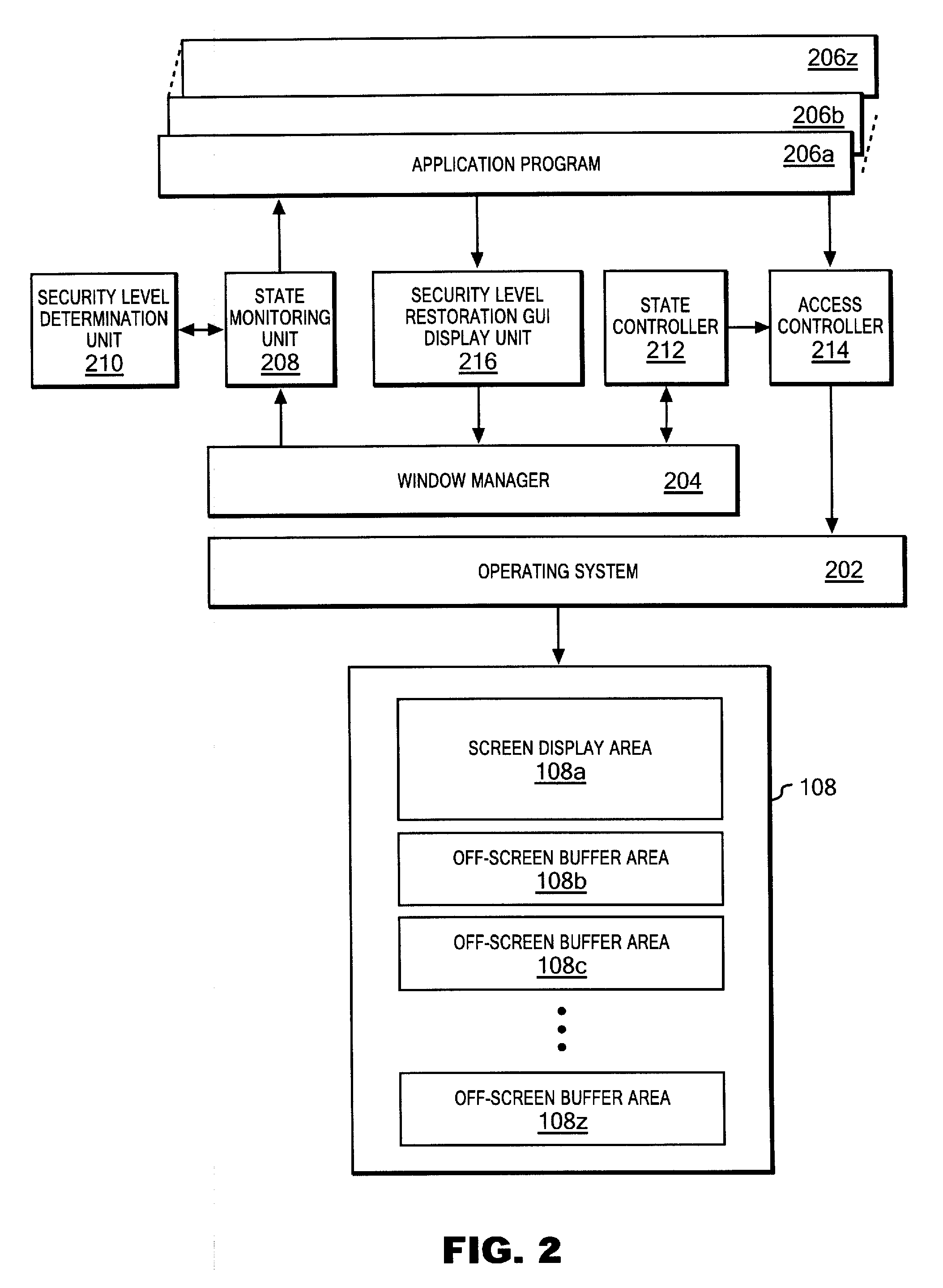
Multiwindow system, security protection method, and security protection program for multiwindow system
InactiveUS20090150824A1Reduced usabilityImprove GUIDigital data processing detailsAnalogue secracy/subscription systemsZ-orderSecurity level
Security levels and positional information in the Z-axis direction (Z-order) of windows on the screen with a limitation. A program that is assigned a low security level cannot become higher than a program that is assigned a high security level in the Z-axis direction. In addition, a restriction is imposed on information flow via a clipboard and a window message from a higher program to a lower program in the Z-axis direction. The security levels are managed on the window basis according to attributes of files to be accessed or documents to be displayed. The display state of each window in the desktop is dynamically controlled depending on the security level of the window on which a user actually performs operation. The visual states of system resources such as printers and drives are controlled in accordance with the assigned security level.
Owner:IBM CORP
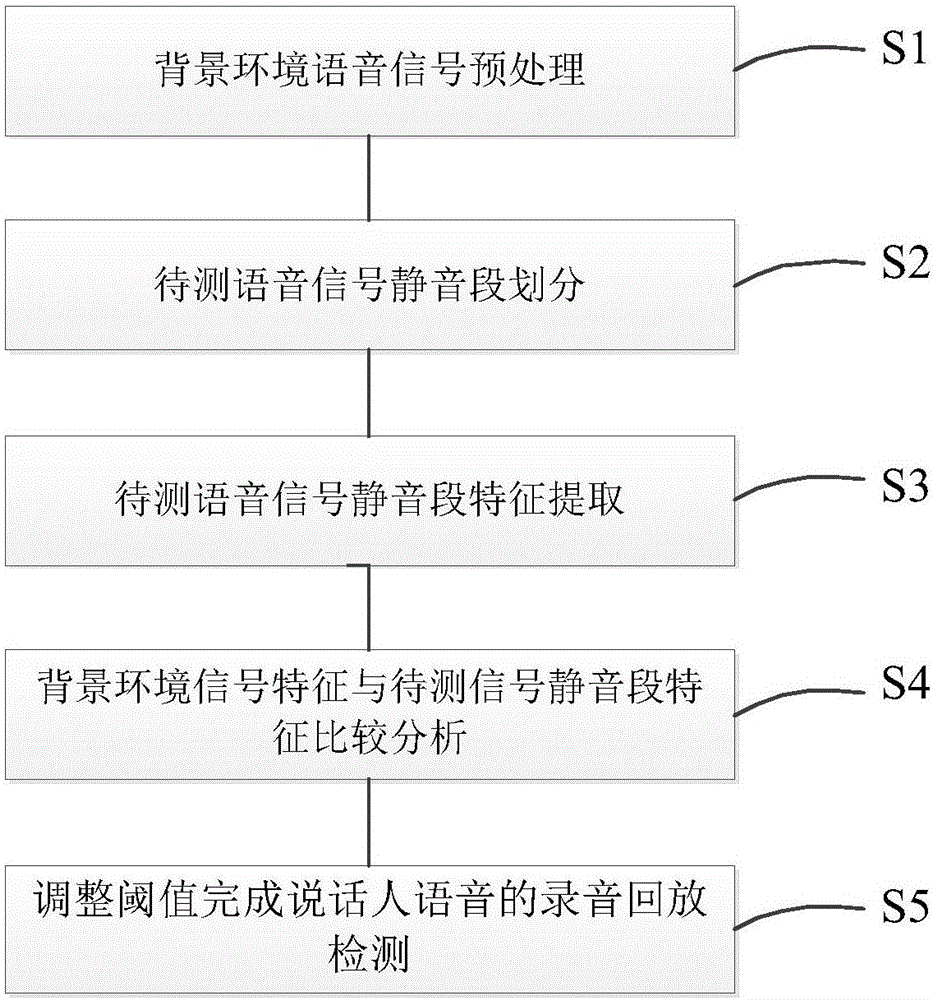
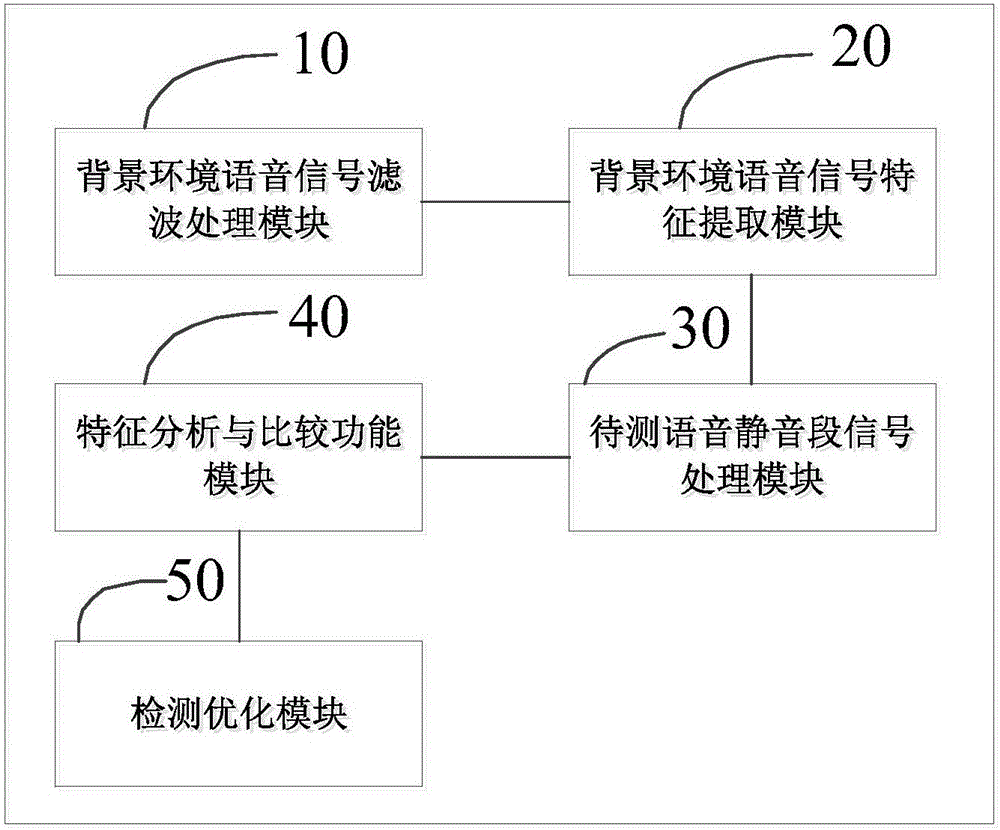
Speaker voice playback identification method and system based on environmental noise change detection
ActiveCN106531172ARealize recording playback attack detectionAvoid safety hazardsSpeech analysisEnvironmental noiseAutomatic speech
The invention relates to a speaker voice playback identification method and an identification system, in particular to a speaker voice playback identification method and an identification system based on environmental noise change detection. According to the identification method and the identification system provided by the invention, on the basis of environmental noise change before and after to-be-detected voice, it detects whether new noise (including noise introduced due to play equipment channel characteristics) is introduced with the playing of voice recording equipment or not so as to judge whether it is playback or not, so that playback attack detection of an ASV (automatic speech verification) system is implemented in voice detection independent of a specific text, potential safety risks of the ASV system due to playback attack are avoided and the safety guarantee of voice print recognition is completed; and meanwhile, by detecting the play equipment, an assisting effect is also achieved on the detection of speech synthesis invasion and speech switching invasion.
Owner:HUBEI UNIV
Frame filtering of fibre channel packets
InactiveUS7151778B2Fast processImprove security levelMultiplex system selection arrangementsError preventionFiberFibre Channel
The present invention provides a system and a method for filtering a plurality of frames sent between devices coupled to a fabric by Fiber Channel connections. Frames are reviewed against a set of individual frame filters. Each frame filter is associated with an action, and actions selected by filter matches are prioritized. Groups of devices are “zoned” together and frame filtering ensures that restrictions placed upon communications between devices within the same zone are enforced. Zone group filtering is also used to prevent devices not within the same zone from communicating. Zoning may also be used to create LUN-level zones, protocol zones, and access control zones. In addition, individual frame filters may be created that reference selected portions of frame header or frame payload fields.
Owner:AVAGO TECH INT SALES PTE LTD
Security check provision
InactiveUS6907135B2Efficient implementationImprove securityDigital data processing detailsUnauthorized memory use protectionData setInternet privacy
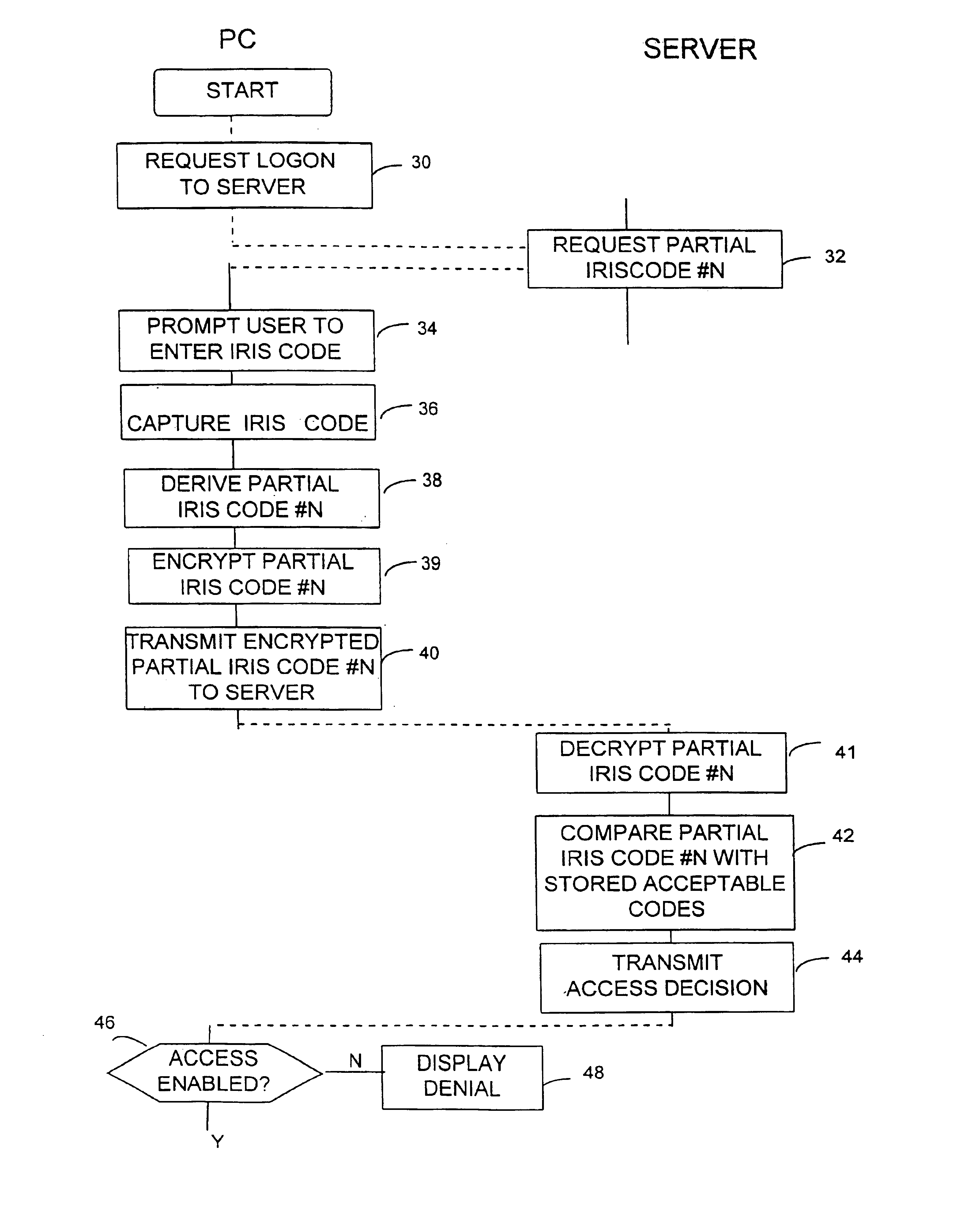
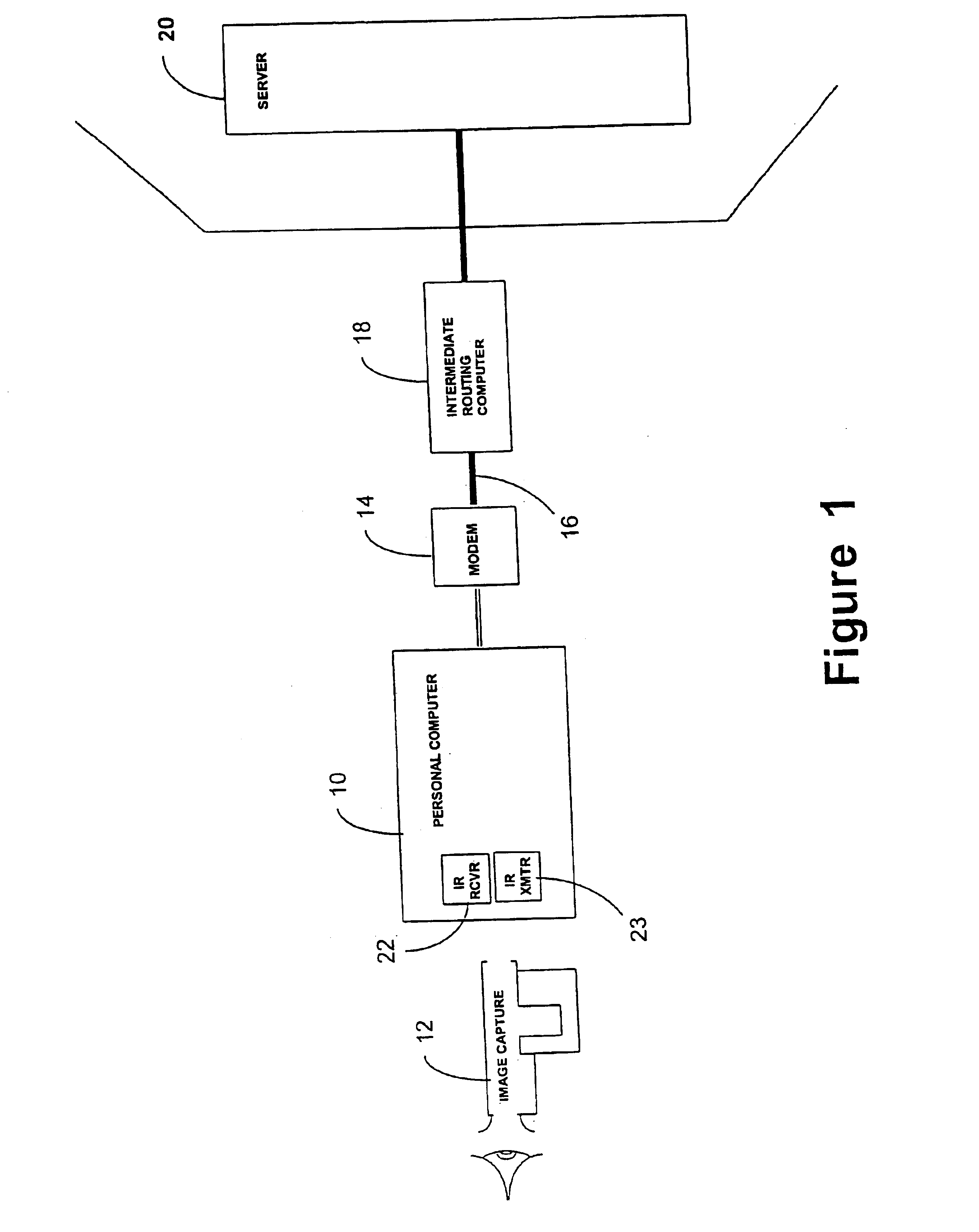
Security check method and apparatus reduces problmes that can arise if the user security data set becomes known by unauthorized persons. To address this problem only part of the user data set is recorded in insecure sections of the system. For example, a security check preventing unauthorized remote access to a shared computer is provided by capturing a user data set representing a user's iris, operating the user's personal computer to select only a portion of the captured data set requested by the shared computer and transmitting the portion along a telecommunications line. The shared computer derives partial data sets from stored user data sets using a similar selection to that used by personal computer and compares the partial data set it has derived with the partial data set transmitted by the personal computer in deciding whether to grant access. Point-of-sale devices and cards recording only partial user data sets are also disclosed.
Owner:BRITISH TELECOMM PLC
Switching between secure and non-secure processing modes
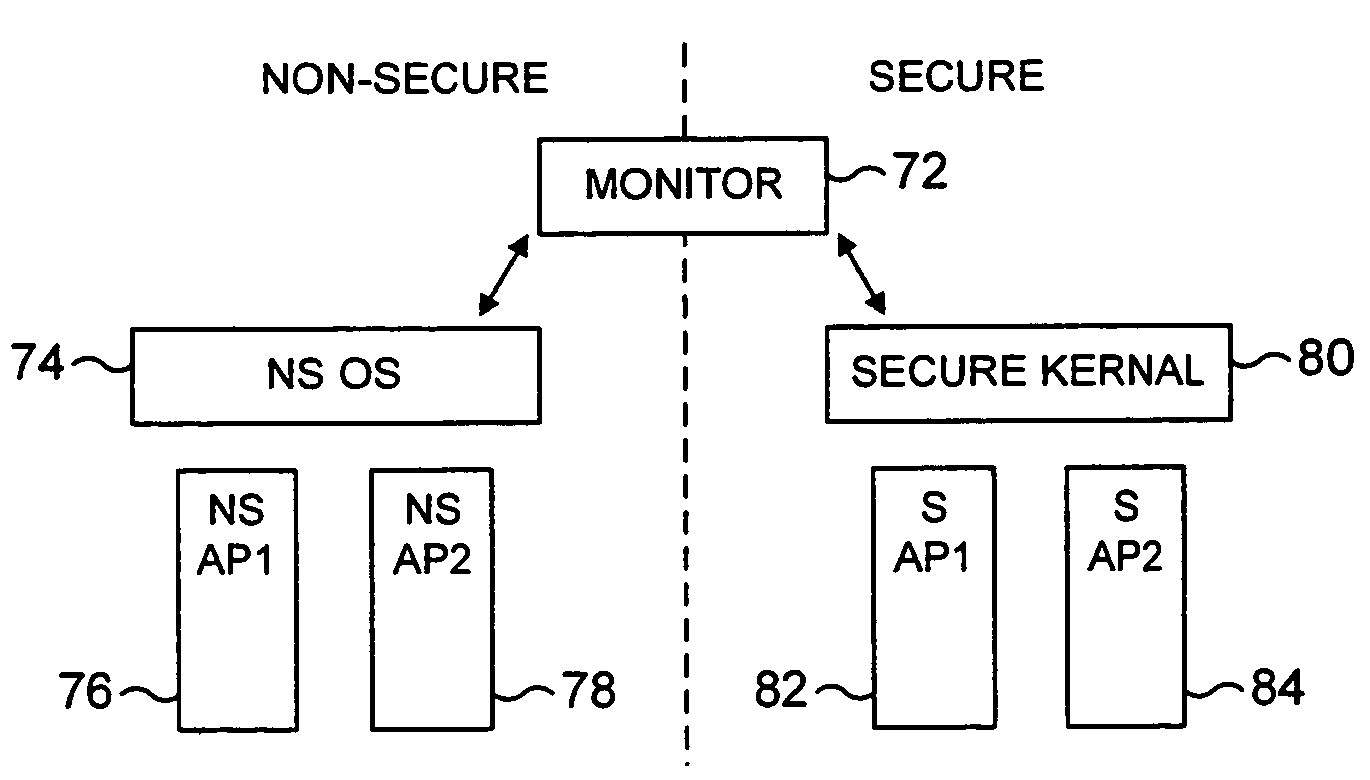
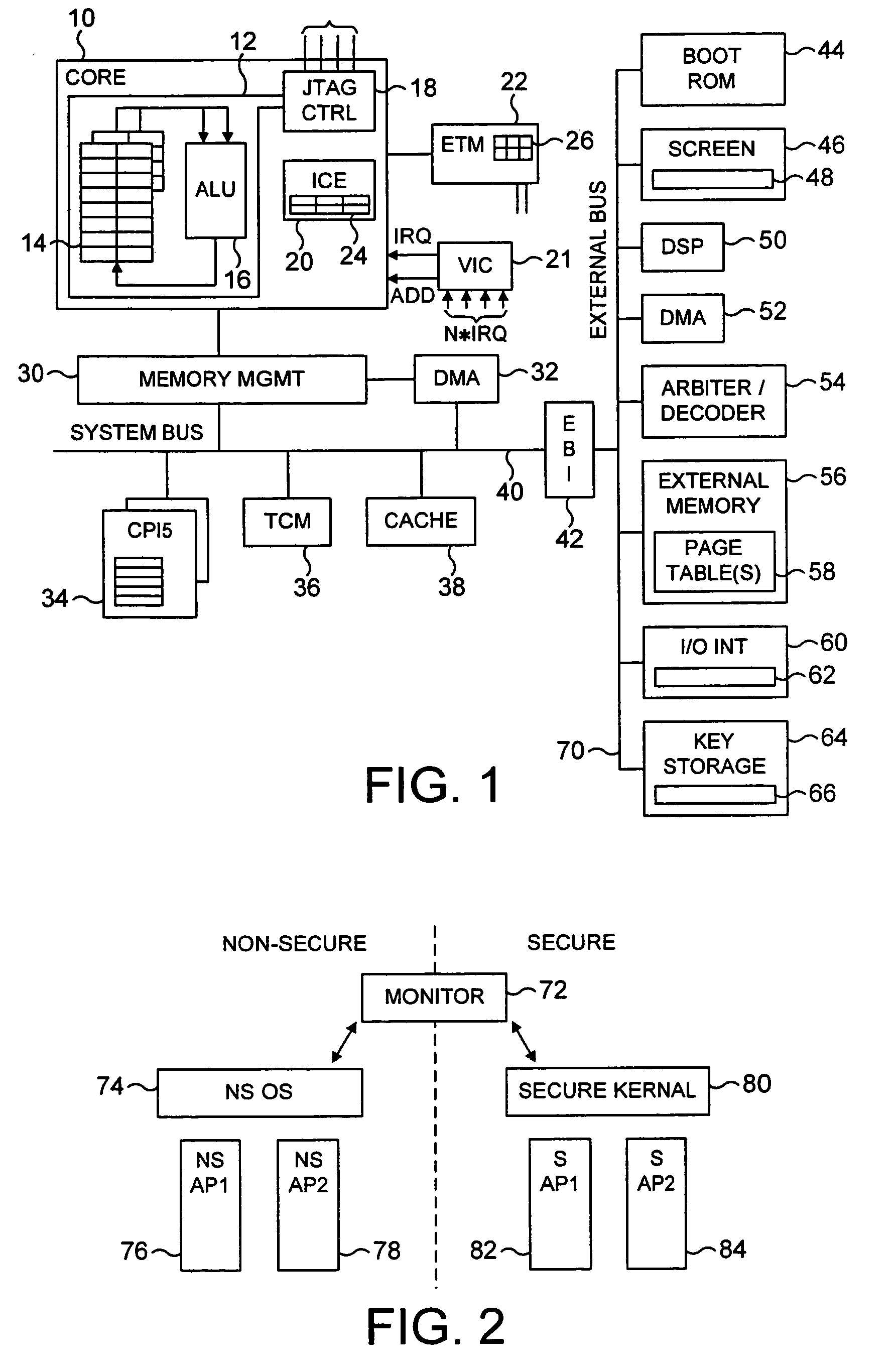
ActiveUS7849310B2Reduce riskFacilitates proper structuringDigital data processing detailsAnalogue secracy/subscription systemsData processing systemMonitor mode
A data processing system including a processor operable in a plurality of modes and in either a secure domain or a non-secure domain. The system includes at least one secure mode being a mode in the secure domain, at least one non-secure mode being a mode in the non-secure domain, and a monitor mode. When the processor is executing a program in a secure mode the program has access to secure data which is not accessible when the processor is operating in a non-secure mode. Switching between the secure and non-secure modes takes place via the monitor mode and the processor is operable at least partially in the monitor mode to execute a monitor program managing switching between the secure and non-secure modes.
Owner:ARM LTD
Fastener Driving Apparatus
A fastener driving apparatus includes a power source, a control circuit, a motor, a first hollow guide member having a first volumetric capacity, a first piston, a linear motion converter, a second hollow guide member having a second volumetric capacity, a second piston, an anvil, a valve arrangement and at least one sensor. The guide members may have an elliptical or oval cross-section. During a compression stroke, the first piston compresses gas in the first hollow guide member. The valve arrangement opens and communicates the compressed gas to the second hollow guide member, causing the second piston to move the anvil to drive a fastener. During a return stroke of the first piston, the valve arrangement opens, communicating a vacuum created in the first hollow guide member to the second hollow guide member, thereby causing the second piston and the anvil to retract to their initial positions.
Owner:TRICORD SOLUTIONS
Fastener Driving Apparatus
ActiveUS20100213235A1Avoid consumptionPrecludes of drive in drive speedStapling toolsFluid couplingsLinear motionControl circuit
A fastener driving apparatus includes a power source, a control circuit, a motor, a first cylinder, a first piston, a linear motion converter, a second cylinder, a second piston, an anvil, a valve arrangement and at least one sensor. During a compression stroke, the first piston is configured to compress gas in a first cylinder to a predetermined pressure. At the predetermined pressure, the valve arrangement assumes an open position for communicating the compressed gas to the second cylinder, thereby causing the second piston to move linearly and enabling the anvil to drive the fastener into the workpiece. During a return stroke, at a predetermined position of the first piston in the first cylinder, the valve arrangement assumes the open position for communicating a vacuum created in the first cylinder to the second cylinder and thereby causing the second piston and the anvil to retract to their initial positions.
Owner:TRICORD SOLUTIONS
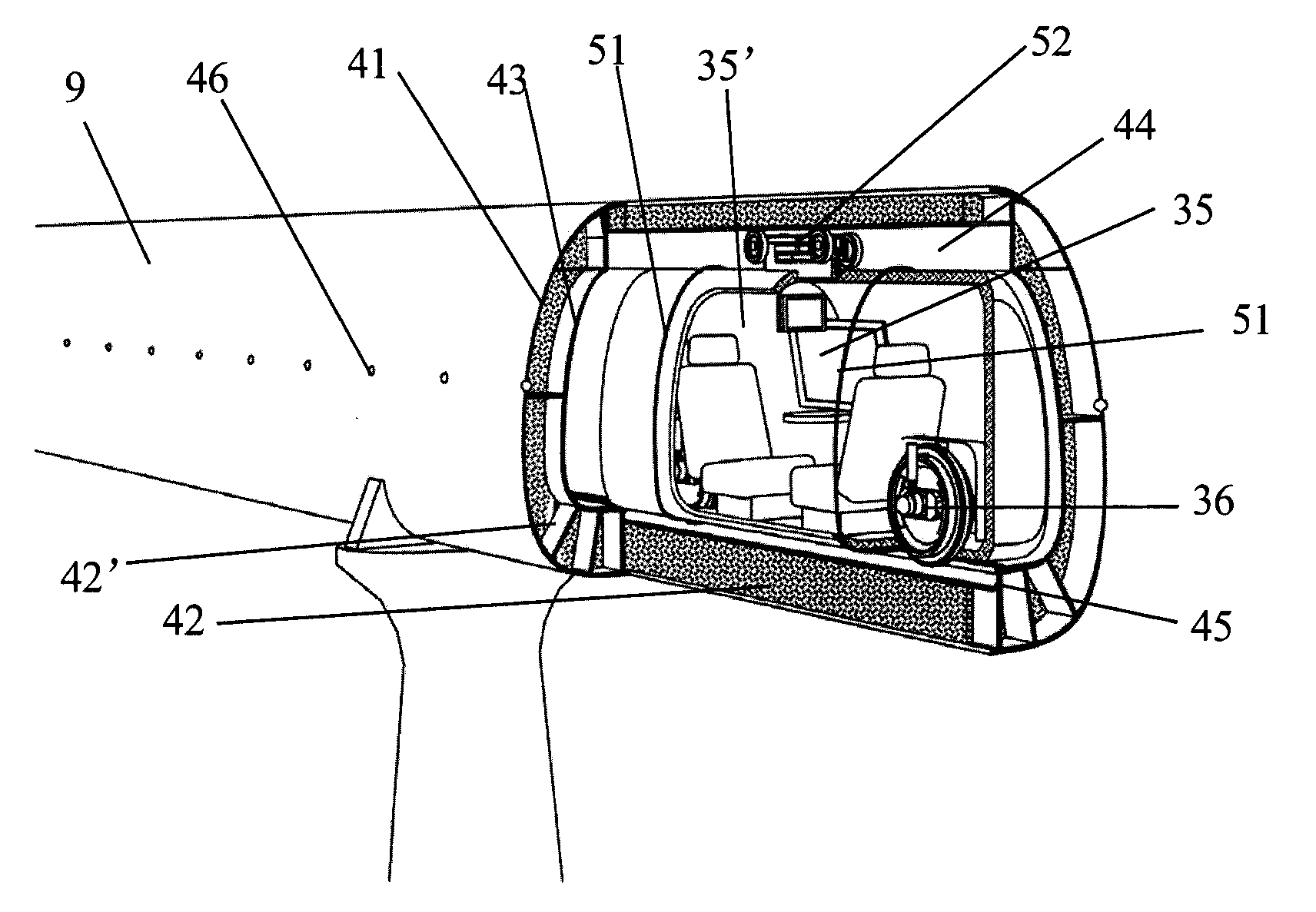
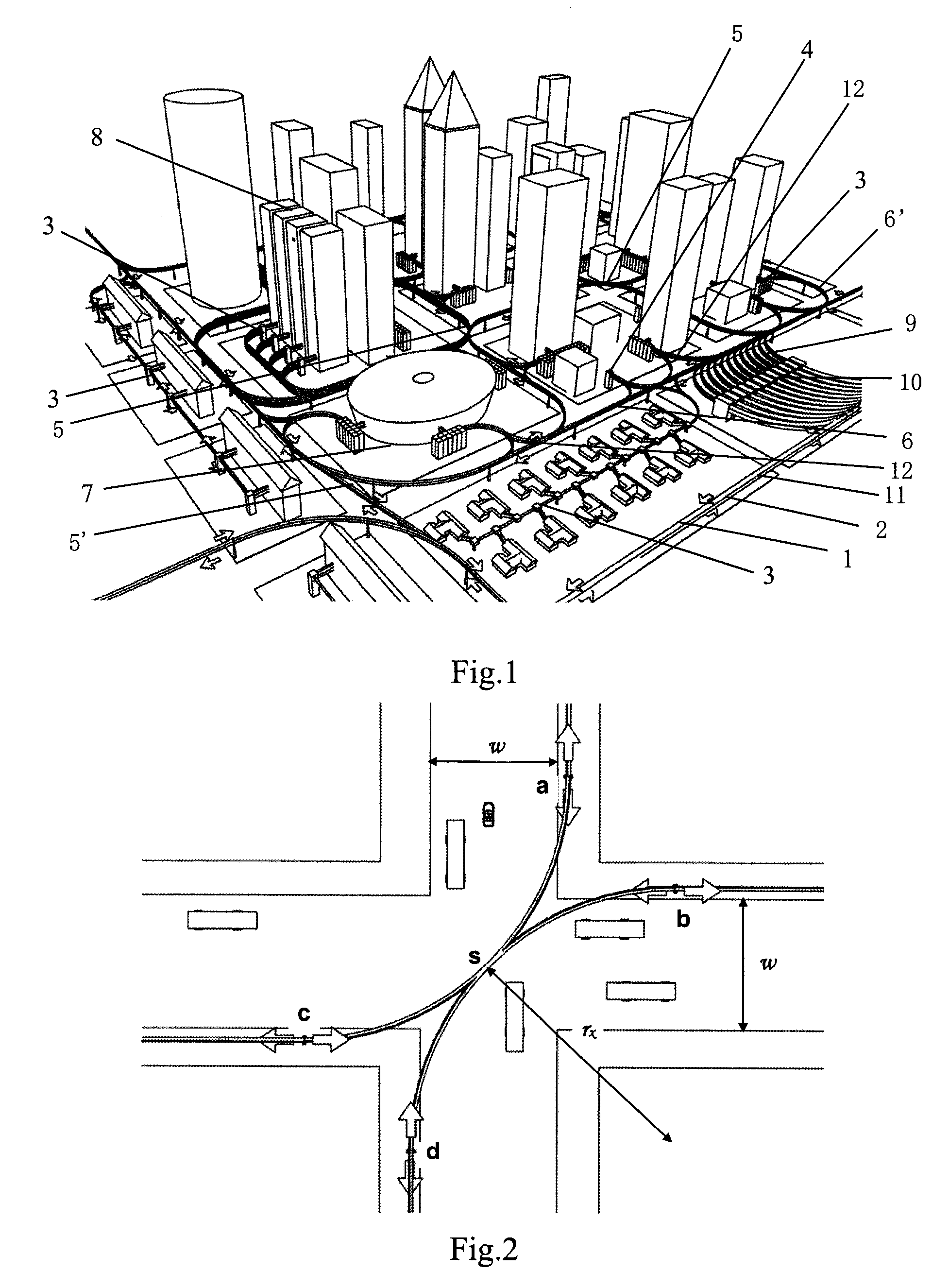
Tube car, network of tubes, personal transport system, and control system and control method thereof
InactiveUS20090101040A1Easy to removeAbility muchRailway tunnelsDigital data processing detailsOperational costsTransport system
The present invention provides a new personal transport system for passengers and goods, which comprises: a tube car comprising a self-powered closed tube car carrying passengers or goods from door to door; and a network of tubes comprising a plurality of tubes, the said network of tubes combined with the existing blocks or buildings, with each tube in the network of tubes provided with an upper rail and / or a lower rail for supporting and / or guiding the said tube car carrying passengers or goods. According to the invention it is possible to achieve a door-to-door transport between two buildings. In comparison to other traffic systems, the inventive system's velocity, line capacity, safety and reliability, ability of resisting disasters and comfortableness are much increased while its consumption of energy, construction cost, occupied space, operating cost, noise and visual pollution are greatly reduced. Furthermore, the transport system of the invention is easy to put into a standardized production, quick to be laid, removed and reused.
Owner:YANG NANZHENG
An apparatus and system for providing a secondary power source for an electric vehicle
ActiveUS20170349039A1Overcome disadvantagesEasy to insertCircuit monitoring/indicationPropulsion by batteries/cellsControl systemEngineering
An apparatus for providing a secondary power source for an electric vehicle, the apparatus attachable to the electric vehicle and having at least one secondary electrical power storage unit for storing electrical energy for delivery to the electric vehicle as required to replace the primary power source, a power connection assembly to connect the at least one secondary power source to the electric vehicle and a control system to control supply to the electric vehicle.
Owner:ITC IP HLDG NO 1 PTY LTD
Fibre channel zoning by logical unit number in hardware
InactiveUS7366194B2Fast processImprove security levelData switching by path configurationStore-and-forward switching systemsFiberFibre Channel zoning
The present invention provides a system and a method for filtering a plurality of frames sent between devices coupled to a fabric by Fiber Channel connections. Frames are reviewed against a set of individual frame filters. Each frame filter is associated with an action, and actions selected by filter matches are prioritized. Groups of devices are “zoned” together and frame filtering ensures that restrictions placed upon communications between devices within the same zone are enforced. Zone group filtering is also used to prevent devices not within the same zone from communicating. Zoning may also be used to create LUN-level zones, protocol zones, and access control zones. In addition, individual frame filters may be created that reference selected portions of frame header or frame payload fields.
Owner:AVAGO TECH INT SALES PTE LTD
Tube car, network of tubes, personal transport system, and control system and control method thereof
InactiveUS8006625B2Easy to removeAbility muchRailway tunnelsDigital data processing detailsOperational costsTransport system
The present invention provides a new personal transport system for passengers and goods, which comprises: a tube car comprising a self-powered closed tube car carrying passengers or goods from door to door; and a network of tubes comprising a plurality of tubes, the said network of tubes combined with the existing blocks or buildings, with each tube in the network of tubes provided with an upper rail and / or a lower rail for supporting and / or guiding the said tube car carrying passengers or goods. According to the invention it is possible to achieve a door-to-door transport between two buildings. In comparison to other traffic systems, the inventive system's velocity, line capacity, safety and reliability, ability of resisting disasters and comfortableness are much increased while its consumption of energy, construction cost, occupied space, operating cost, noise and visual pollution are greatly reduced. Furthermore, the transport system of the invention is easy to put into a standardized production, quick to be laid, removed and reused.
Owner:YANG NANZHENG
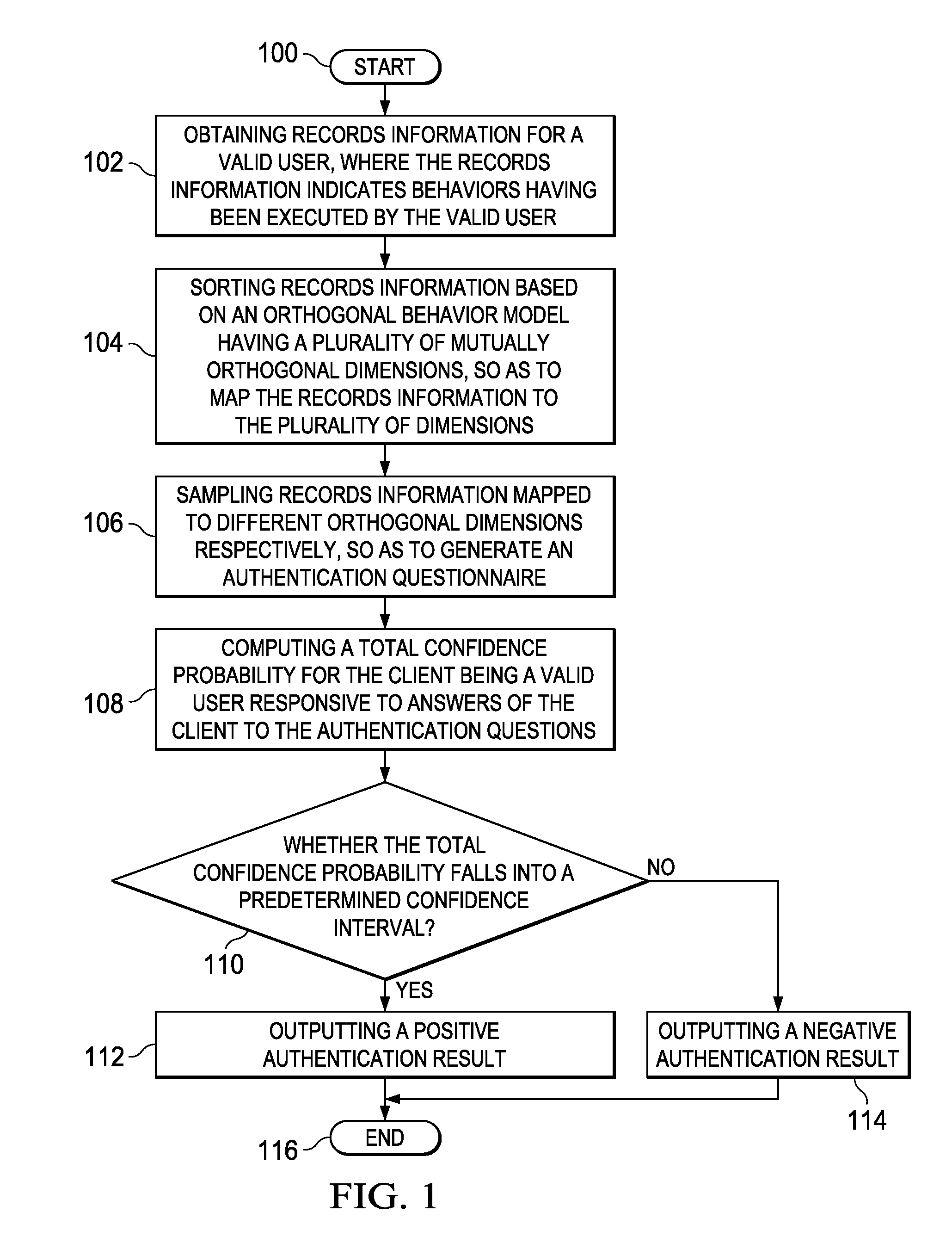
Authentication Method and Apparatus
InactiveUS20120079576A1Confidence probabilityReduce overlapDigital data processing detailsUser identity/authority verificationConfidence intervalCausality
An identity authentication method is provided. The method comprises obtaining records information of a valid user, where the records information indicates behaviors having been executed by the valid user; mapping, based on an orthogonal behavior model having multiple mutually orthogonal dimensions, records information to the multiple dimensions, wherein behaviors indicated by records information mapped to different dimensions do not overlap therebetween and have no logical cause and effect relationship; sampling records information mapped to different dimensions, respectively, so as to generate an authentication questionnaire including a plurality of authentication questions; computing, responsive to answers of a client to the authentication questionnaire, a total confidence P for the client being a valid user; outputting a positive authentication result, responsive to the total confidence probability P falling into a confidence interval; and outputting a negative authentication result, responsive to the total confidence probability P failing to fall into a confidence interval. The present invention further provides a corresponding identity authentication apparatus.
Owner:IBM CORP
Helicopter with two or more rotor heads
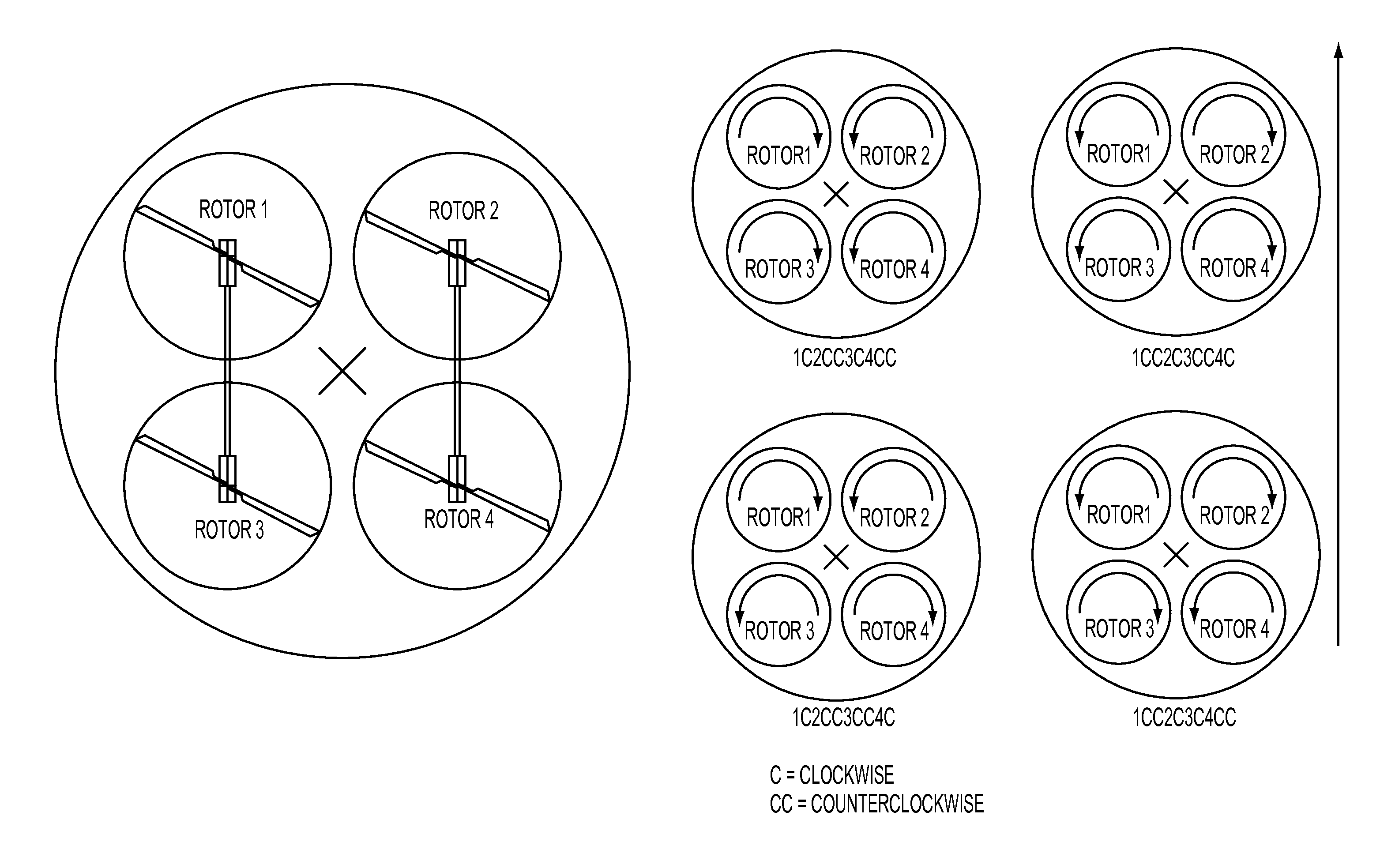
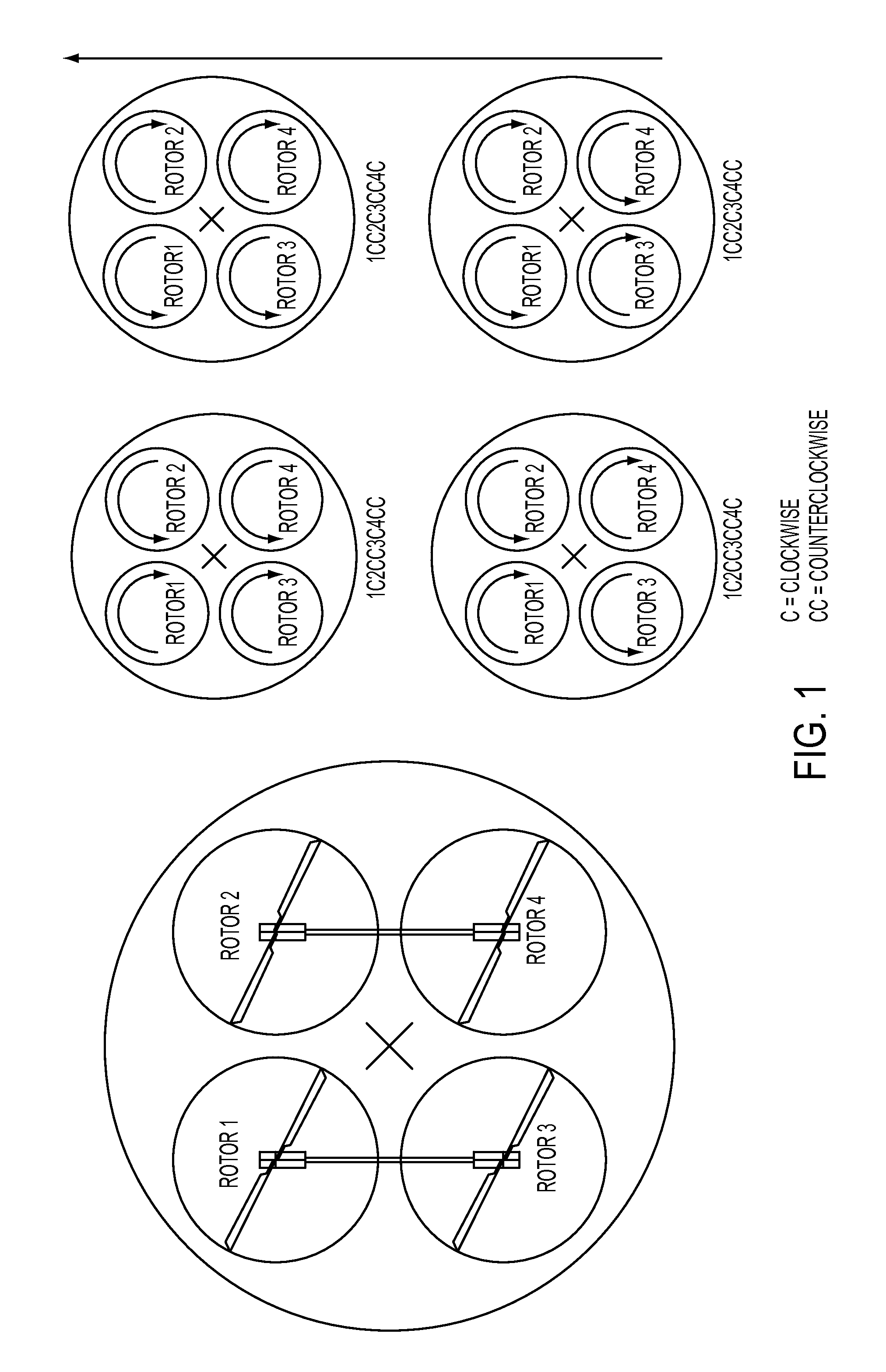
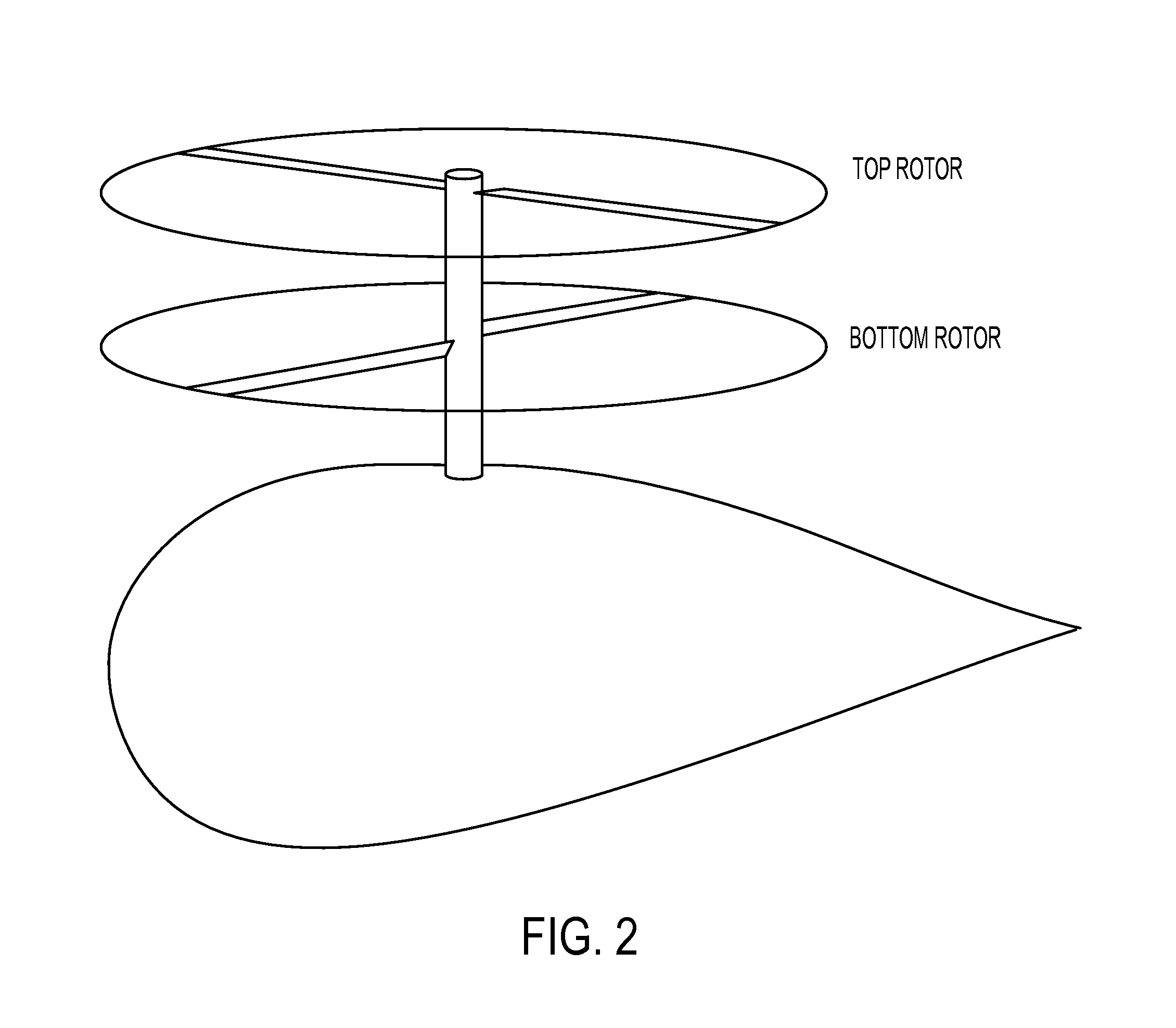
InactiveUS20120241553A1Improve efficiencyEasy to controlPropellersRotocraftElectronic control systemControl system
A helicopter with two or more rotor heads with full swash plate control and a novel control scheme to allow for propulsion in the horizontal plane in all directions, allowing the aircraft to fly in all directions in a truly horizontal fashion. Furthermore, a manual input device to control the additional control freedoms thus gained, and an electronic control system that combines manual inputs with inputs from sensors and translates these inputs into directions for the actuators of the two or more swash plates in order to control the aircraft, taking into account the novel control scheme.
Owner:WILKE PAUL
Fastener driving apparatus
ActiveUS7793811B1Overcomes drawbackShorten speedStapling toolsFluid couplingsLinear motionEngineering
Owner:TRICORD SOLUTIONS INC
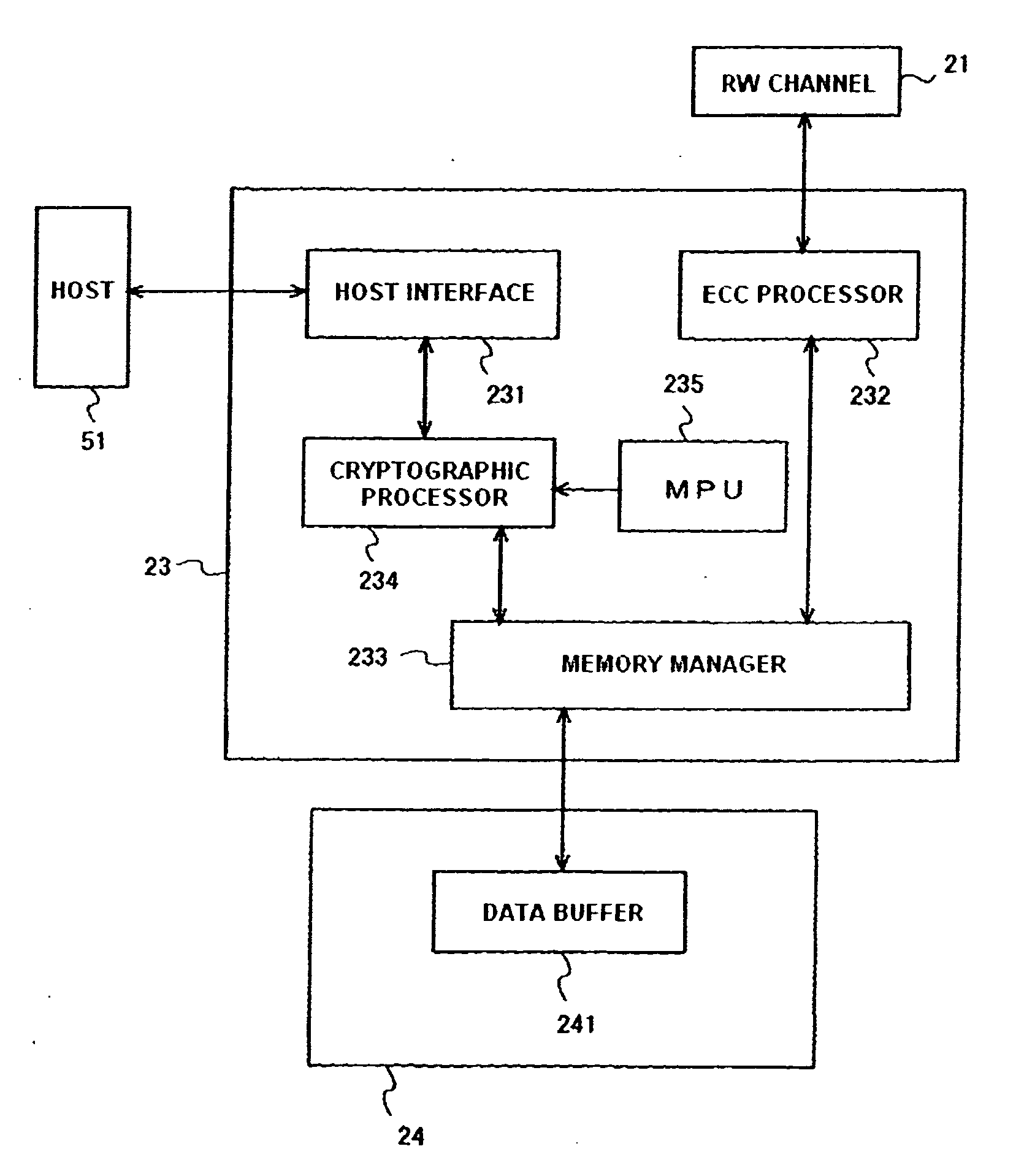
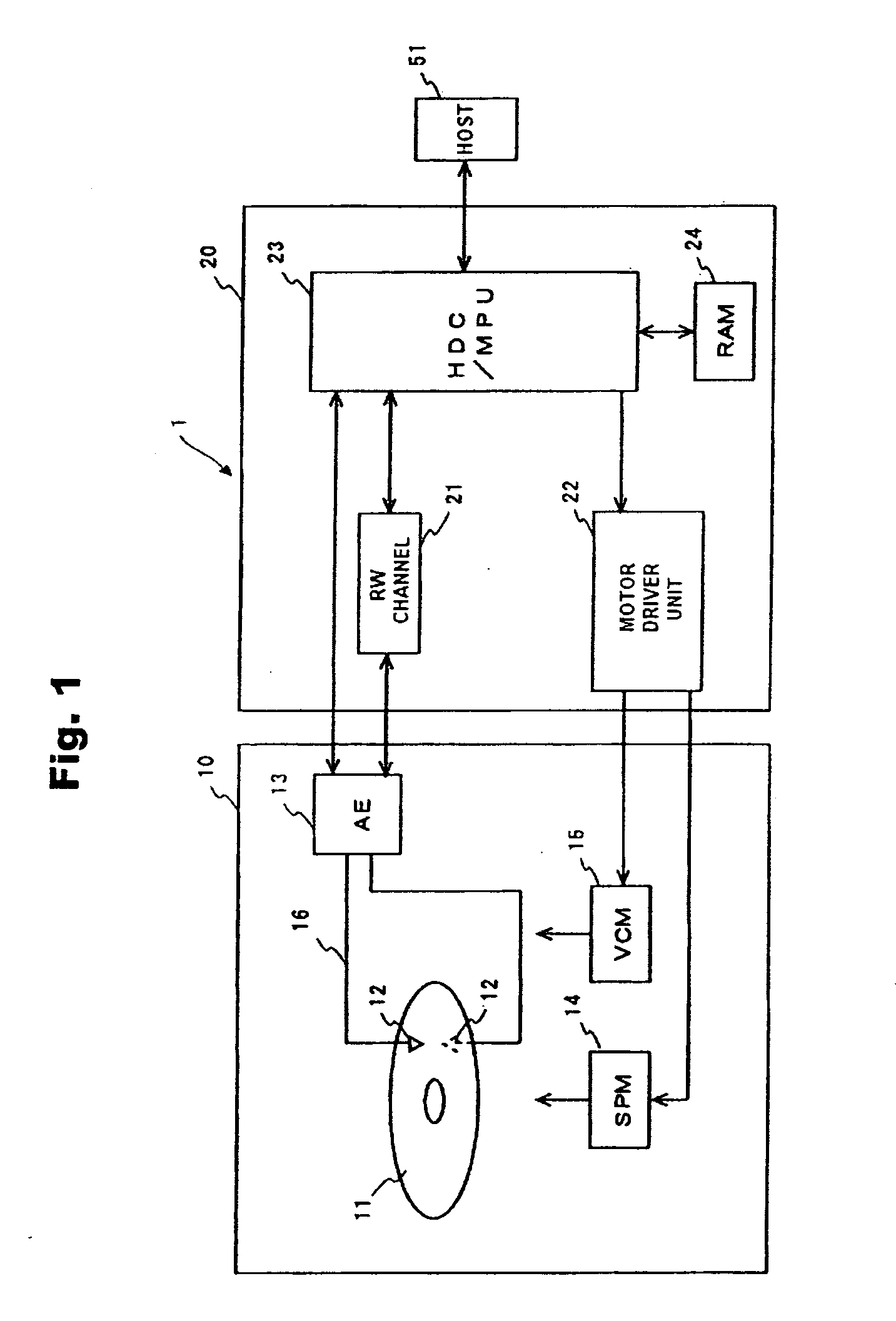
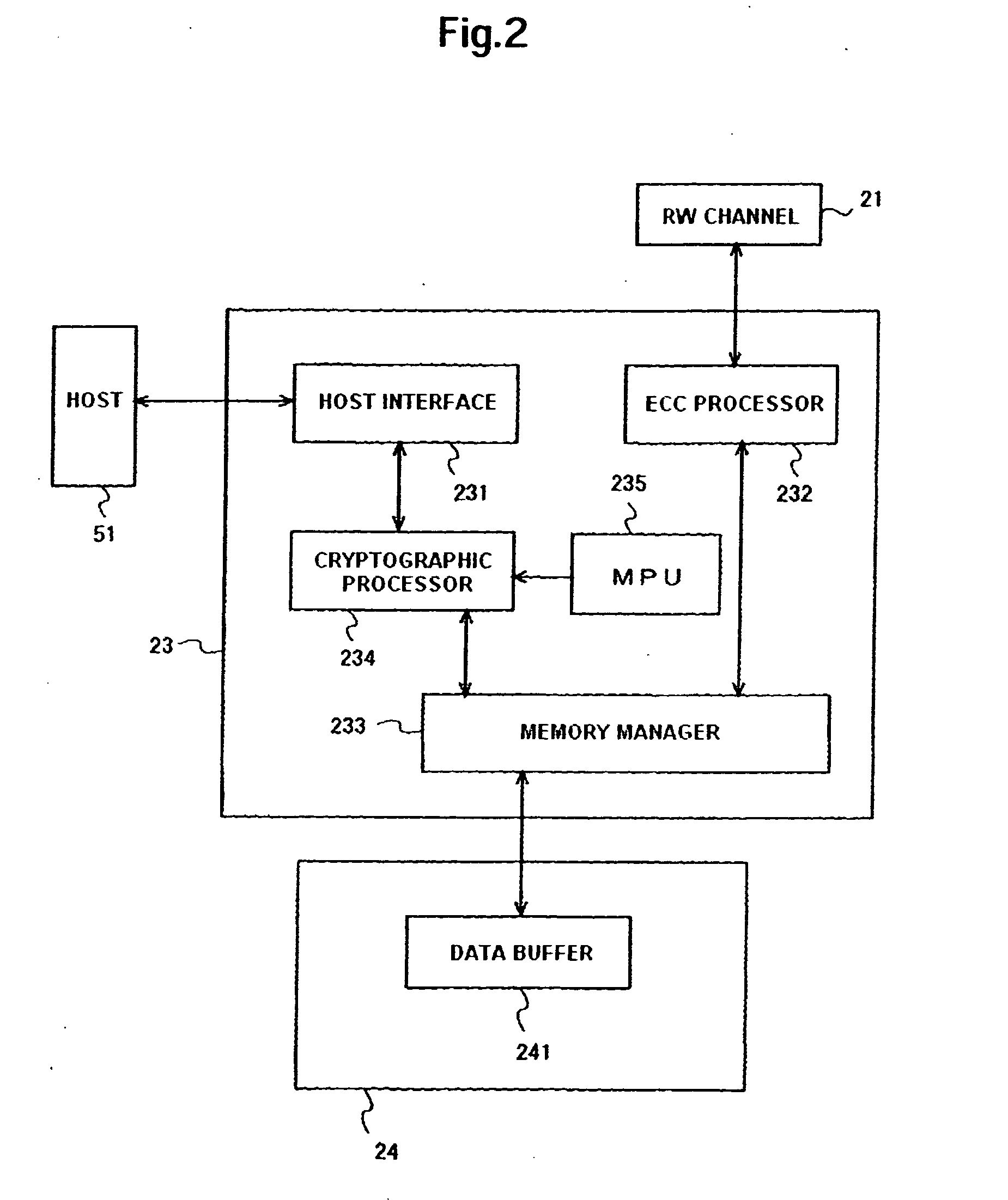
Data storage device and management method of cryptographic key thereof
ActiveUS20100031061A1More securityUnauthorized memory use protectionRecord information storageHard disc drivePassword
Embodiments of the present invention help to securely manage a data cryptographic key in a data storage device. In an embodiment of the present invention, a cryptographic processor for encrypting and decrypting data is located between a host interface and a memory manager. In parts of the hard disk drive (HDD), except for the host interface, the HDD handles user data in an encrypted state. A data cryptographic key which the cryptographic processor uses to encrypt and decrypt the user data is encrypted and stored in a magnetic disk. A multiprocessing unit (MPU) decrypts the data cryptographic key using a password and a random number to supply it to the cryptographic processor. Using the password and the random number, the HDD can manage the data cryptographic key with more security.
Owner:WESTERN DIGITAL TECH INC
Emergency switch for an exercise apparatus
InactiveUS6875157B1More securityClubsPhysical therapyManual fire alarm activationEmergency situations
The invention relates to an emergency switch for an exercise apparatus having a housing, a safety plug and a microswitch. The safety plug passes through an insertion slot of the housing and is inwardly inserted to the inside of the housing for an electric connection by means of the contact of the distal end of an extension part of the safety plug to a contact key of the microswitch. Meanwhile, an electric disconnection is created when the safety plug is extracted. In addition, a cut-off button with a push rod is interposed between the safety plug and the microswitch. Besides, the cut-off button projects outwardly from the housing. When the cut-off button is pressed down, the push rod makes use of its slanting guide face to separate the safety plug from the contact key of the microswitch into a disconnection state.
Owner:PROXXON
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com