Patents
Literature
65results about How to "Minimize data loss" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
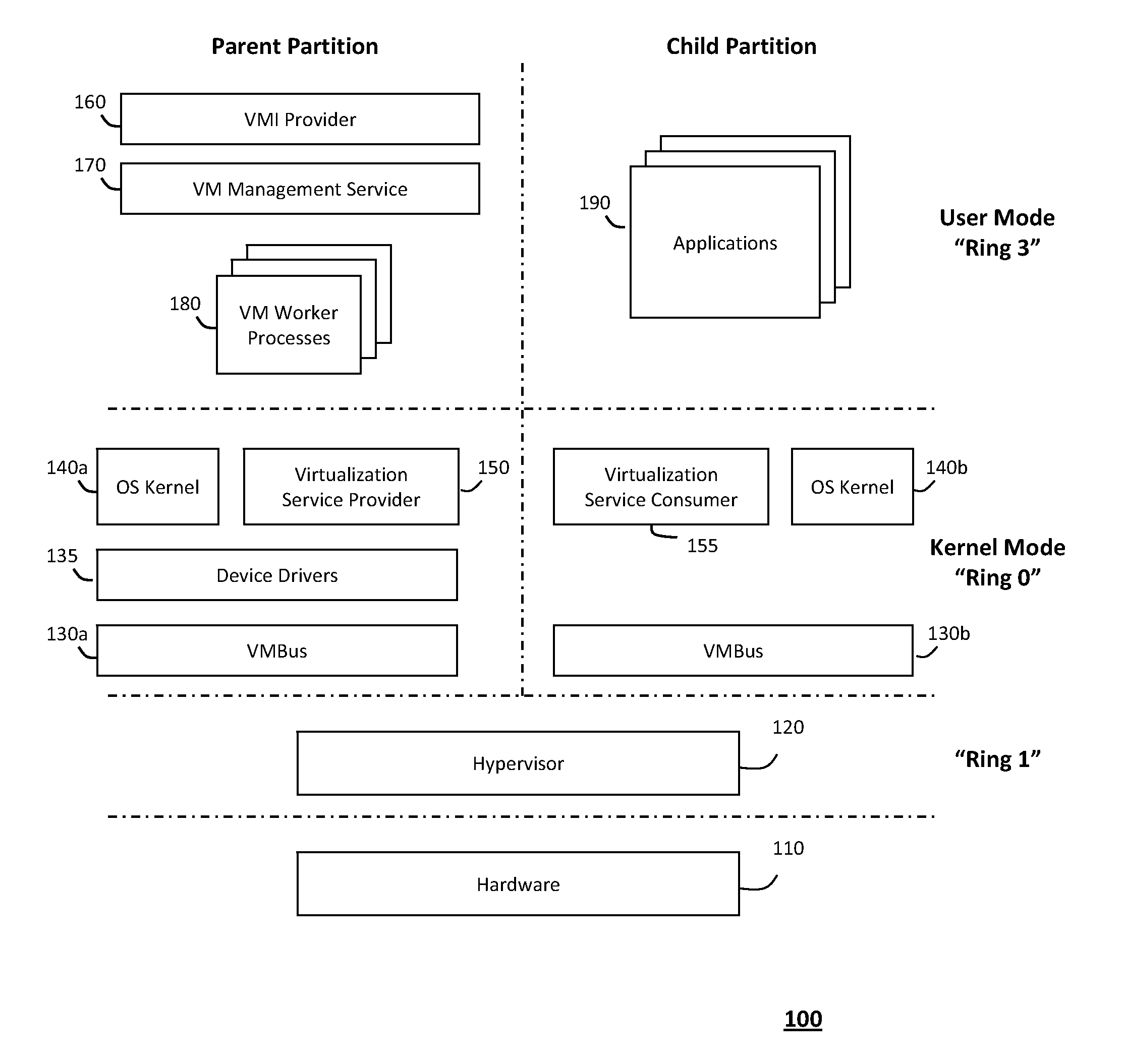
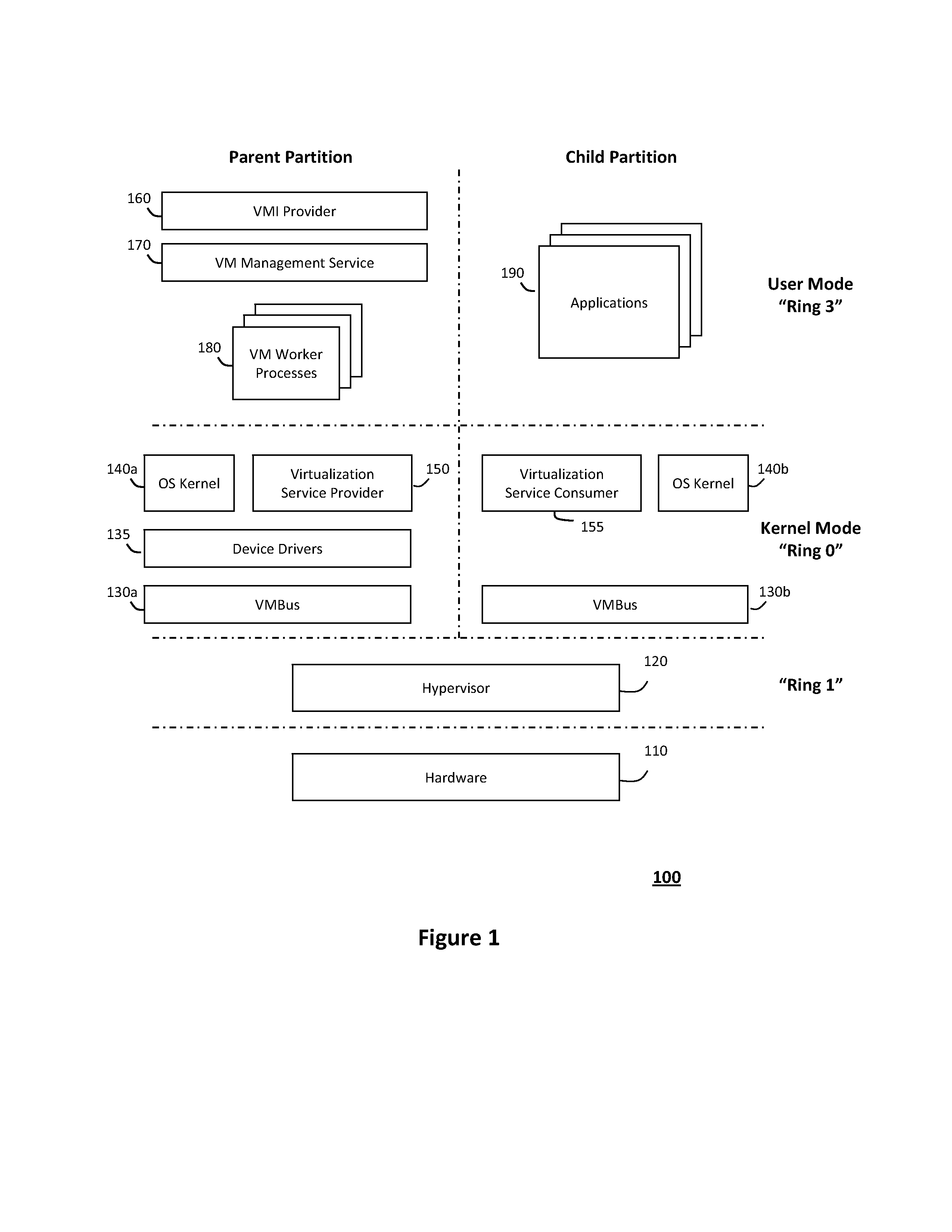
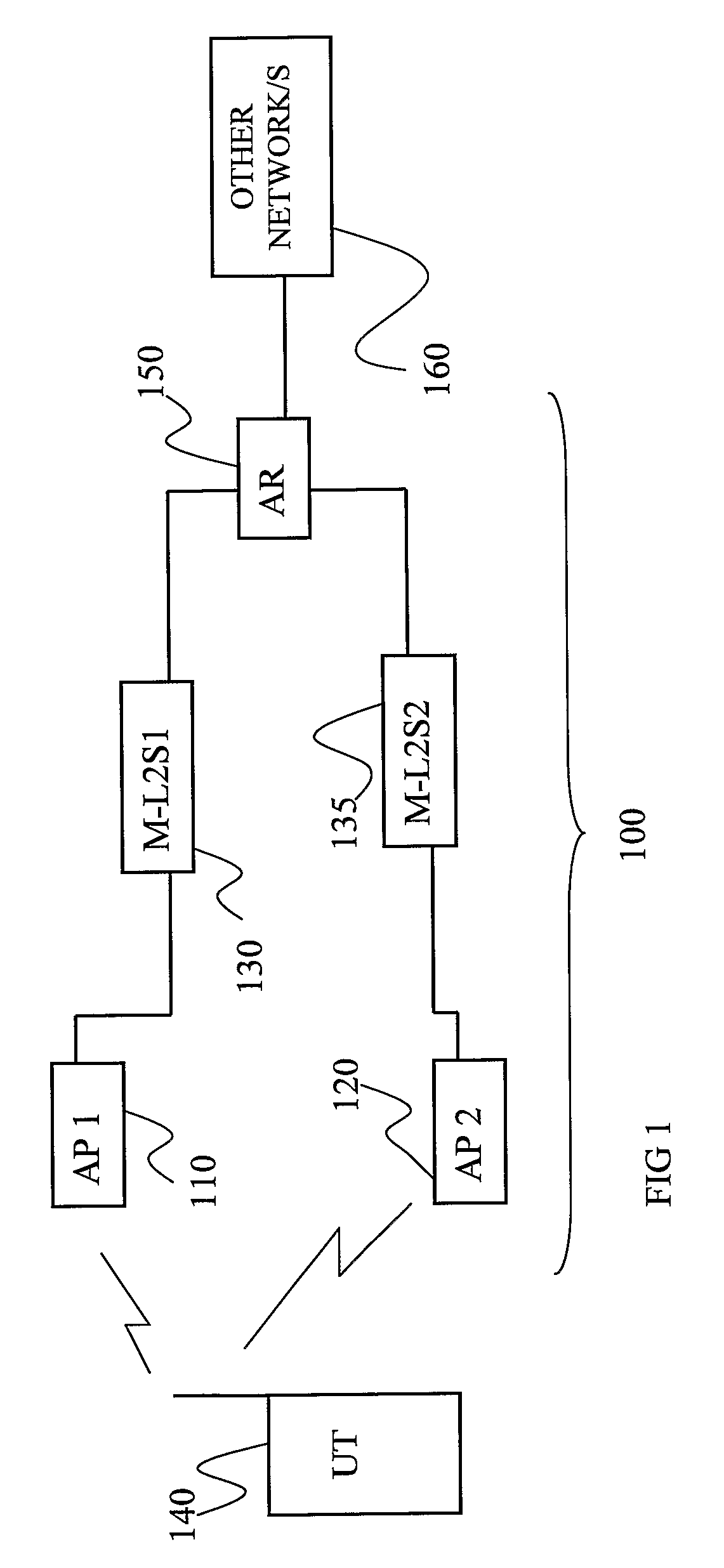
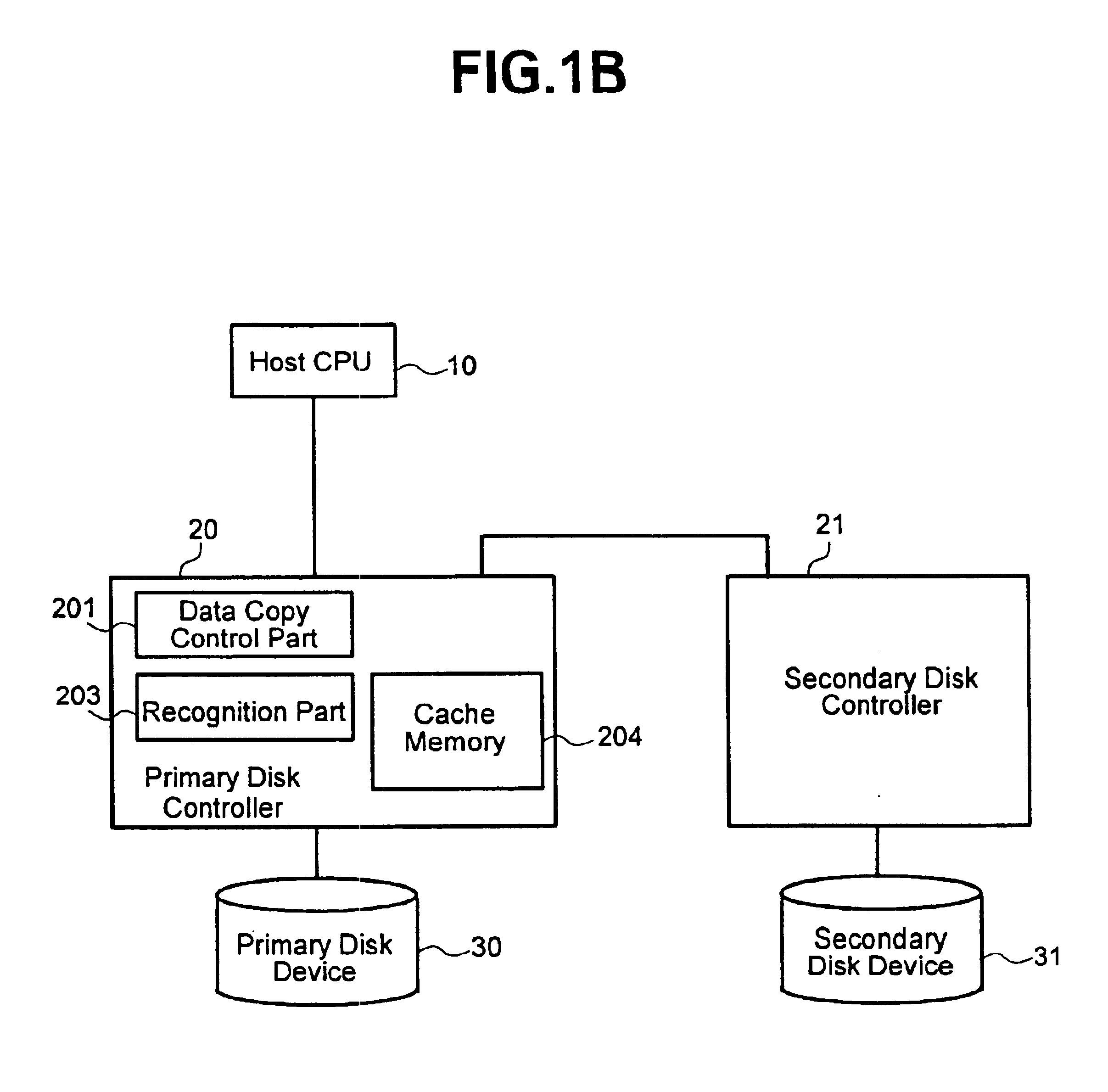
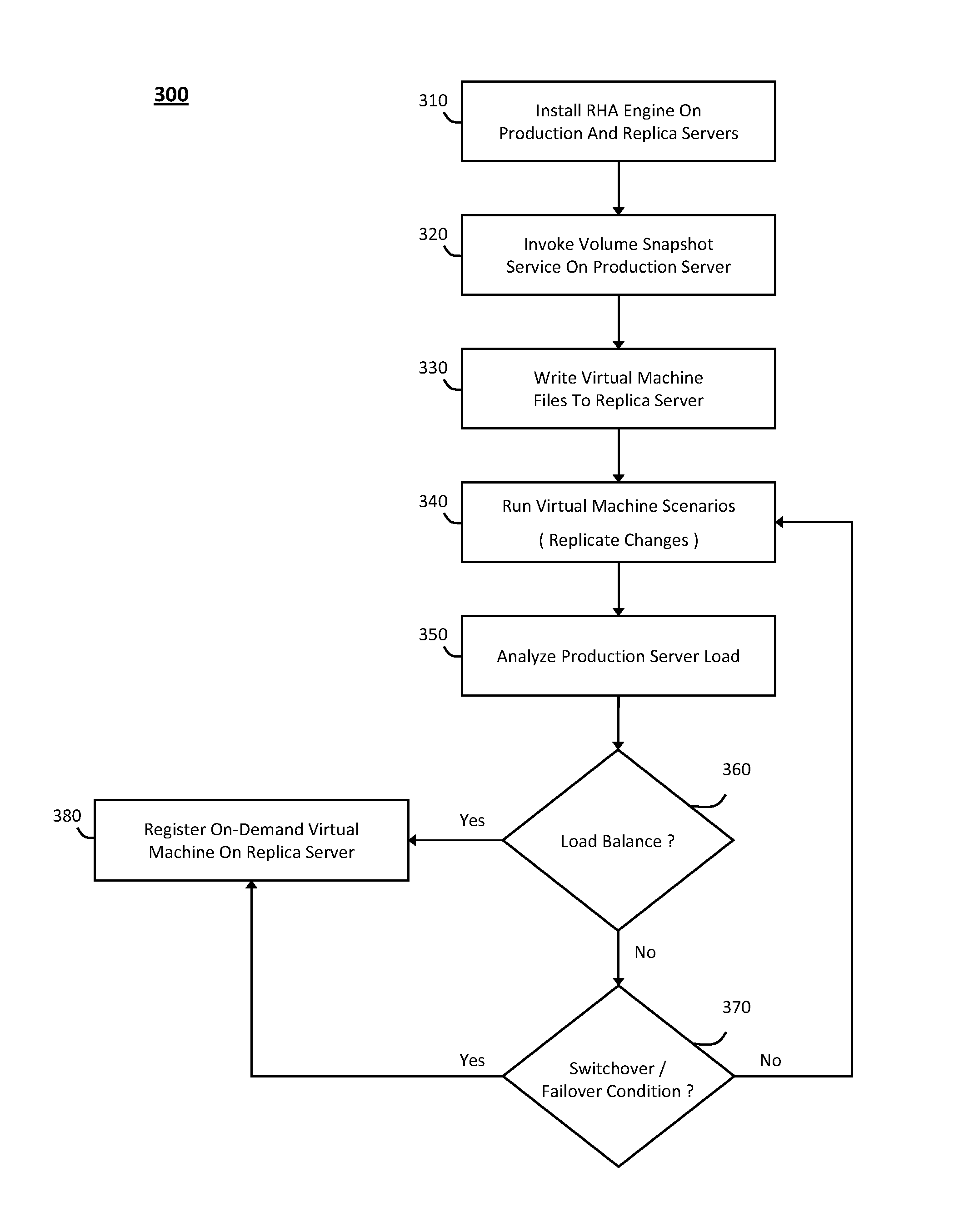
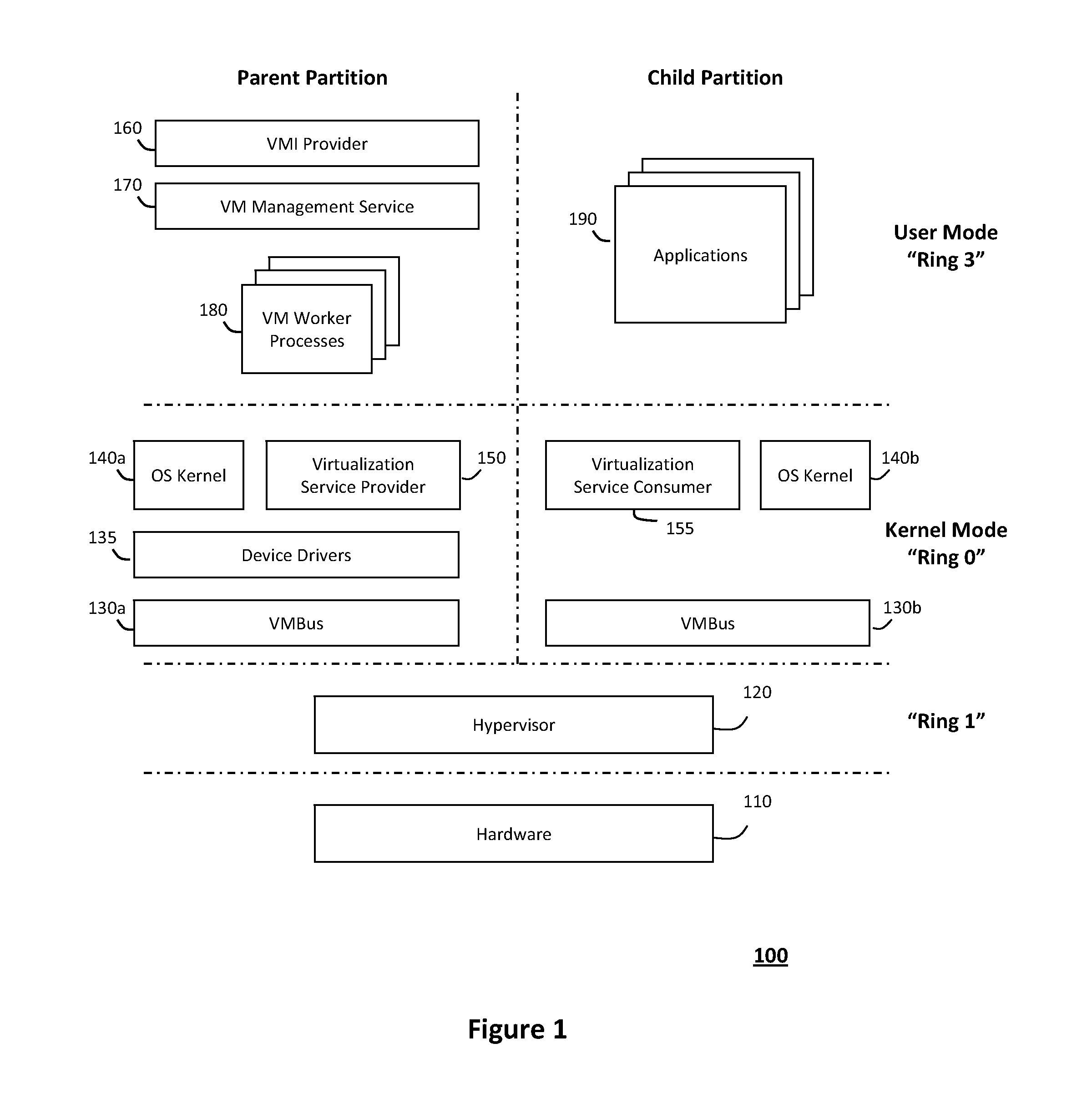
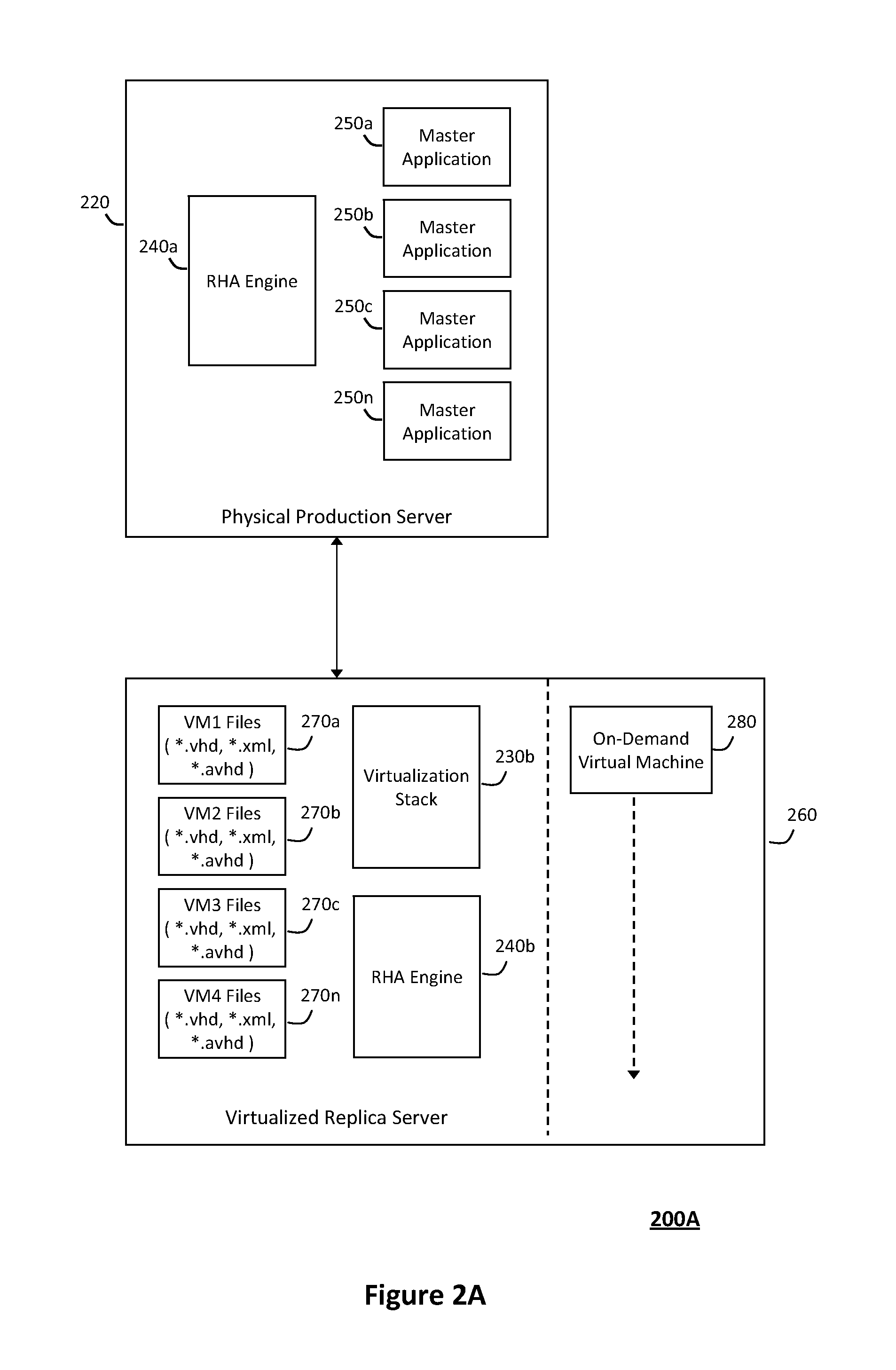
System and method for providing a virtualized replication and high availability environment
ActiveUS20130185716A1Improve usabilityEasily visualize and manageDigital data information retrievalError detection/correctionVirtualizationFile synchronization
The system and method described herein may provide a virtualized replication and high availability environment. In particular, a virtualized production server may run one or more virtual machines in one or more child partitions and have a replication and high availability engine installed in a parent partition. The replication and high availability engine may automatically discover the virtual machines running in the child partitions and automatically synchronize all files associated with the virtual machines to a virtualized replica server. Furthermore, the replication and high availability engine may continuously replicate subsequent changes to the files associated with the virtual machines running in the child partitions to the virtualized replica server, which may then create on-demand virtual machines from the synchronized and replicated files to handle switchover, failover, switchback, and failback events associated with the virtualized production server or the virtual machines running in the child partitions associated therewith.
Owner:CA TECH INC
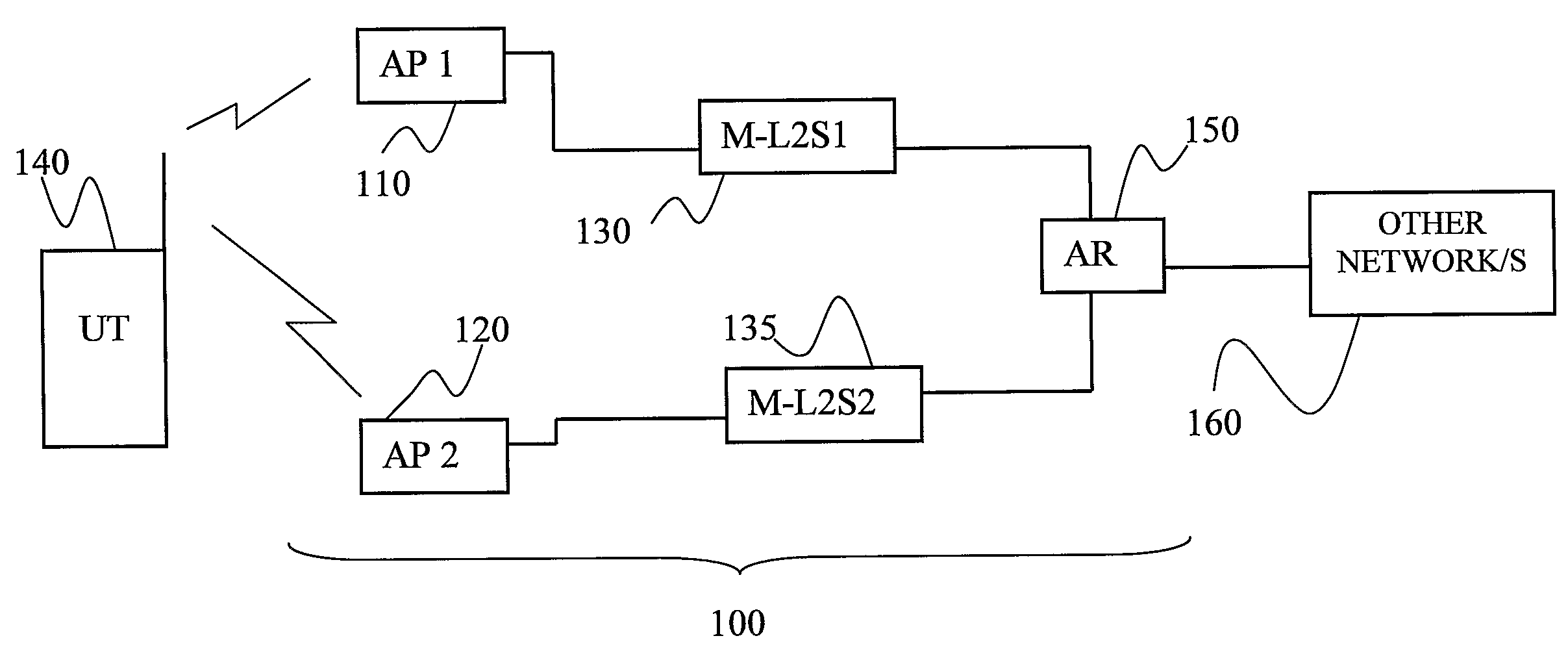
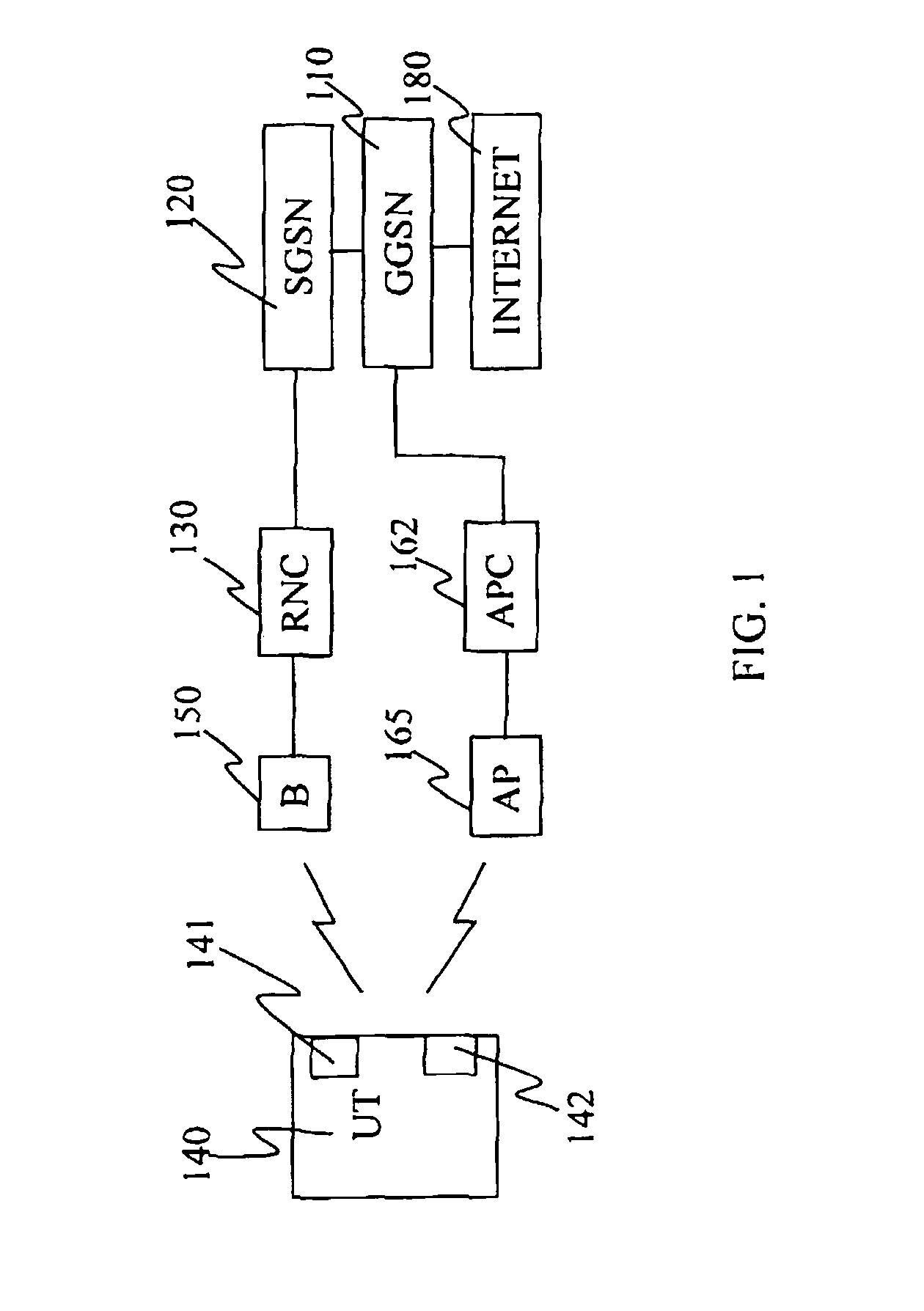
Means and Methods for Improving the Handover Characteristics of Integrated Radio Access Networks
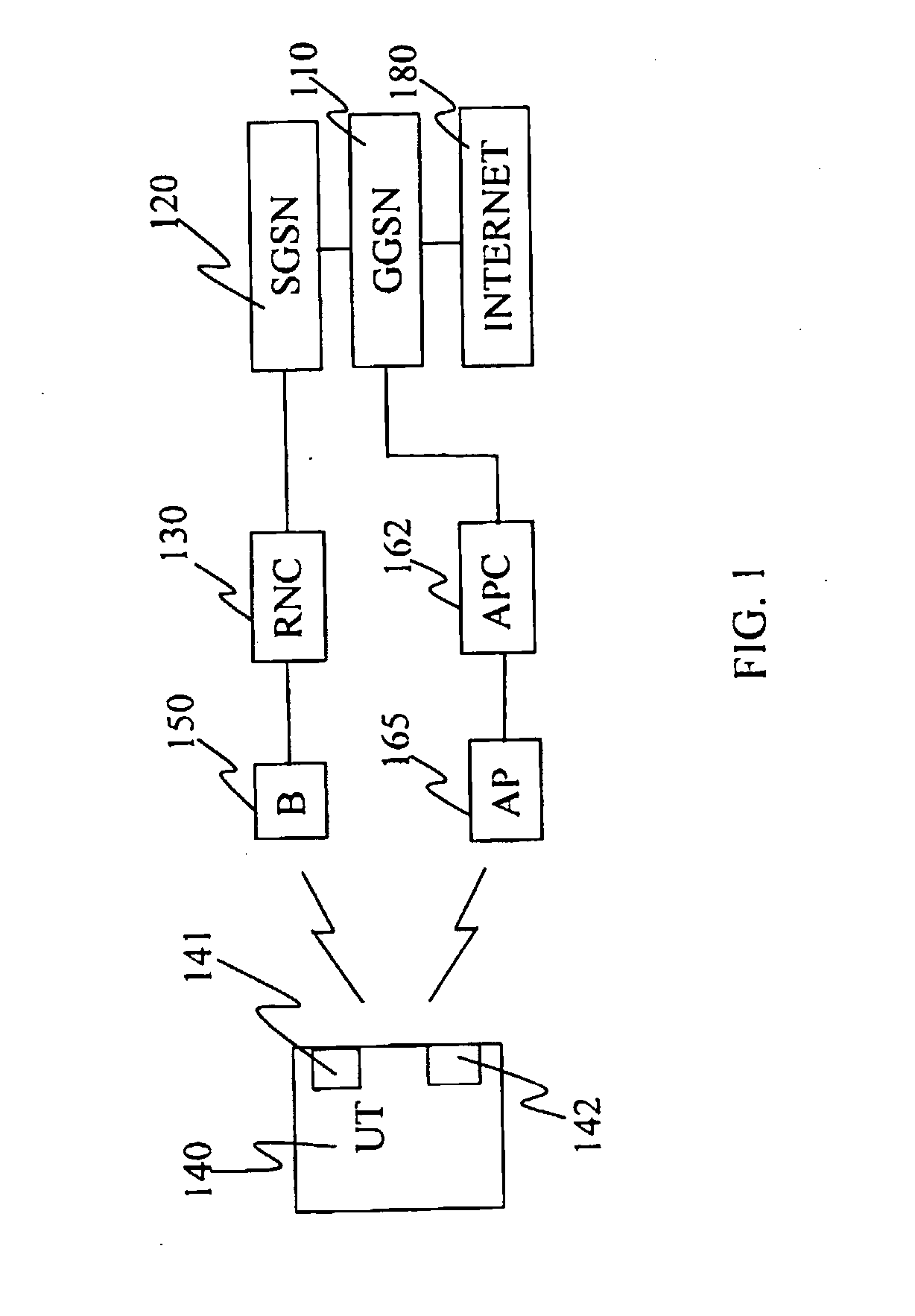
InactiveUS20080205345A1Improve switching characteristicsMinimize data lossRadio/inductive link selection arrangementsWireless commuication servicesMessage typeRadio access network
The invention provides a method for assisting handover of a user terminal's, UT's, communication session in an integrated multi RAT network, said method to be carried out by an RNCI being installed in said network, said method comprising the following steps:— receiving a “Handover Candidate” message comprising a message type identifier information element identifying said message as being a “Handover Candidate” message and which message identifies said session and which message further identifies a candidate RNC of said network, wherein said candidate RNC constitutes an RNC handover candidate for said session,— establishing the identity of said RNC by investigating said message,— associating said communication session with said candidate RNC identified in the previous step. The invention provides an RNC1, RNC2, and software, realising the method according to the invention.
Owner:TELEFON AB LM ERICSSON (PUBL)
Multicasting transmission of multimedia information
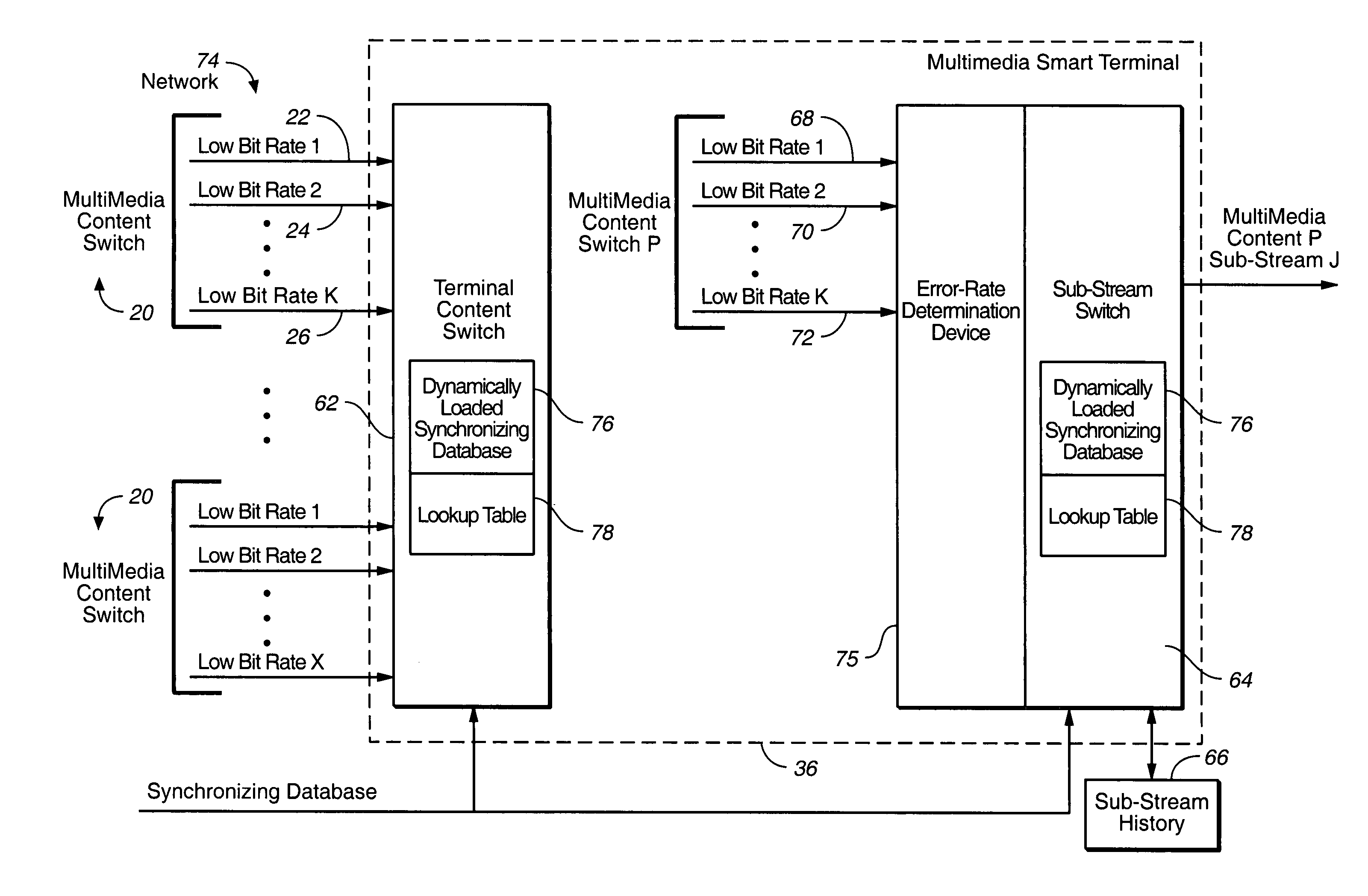
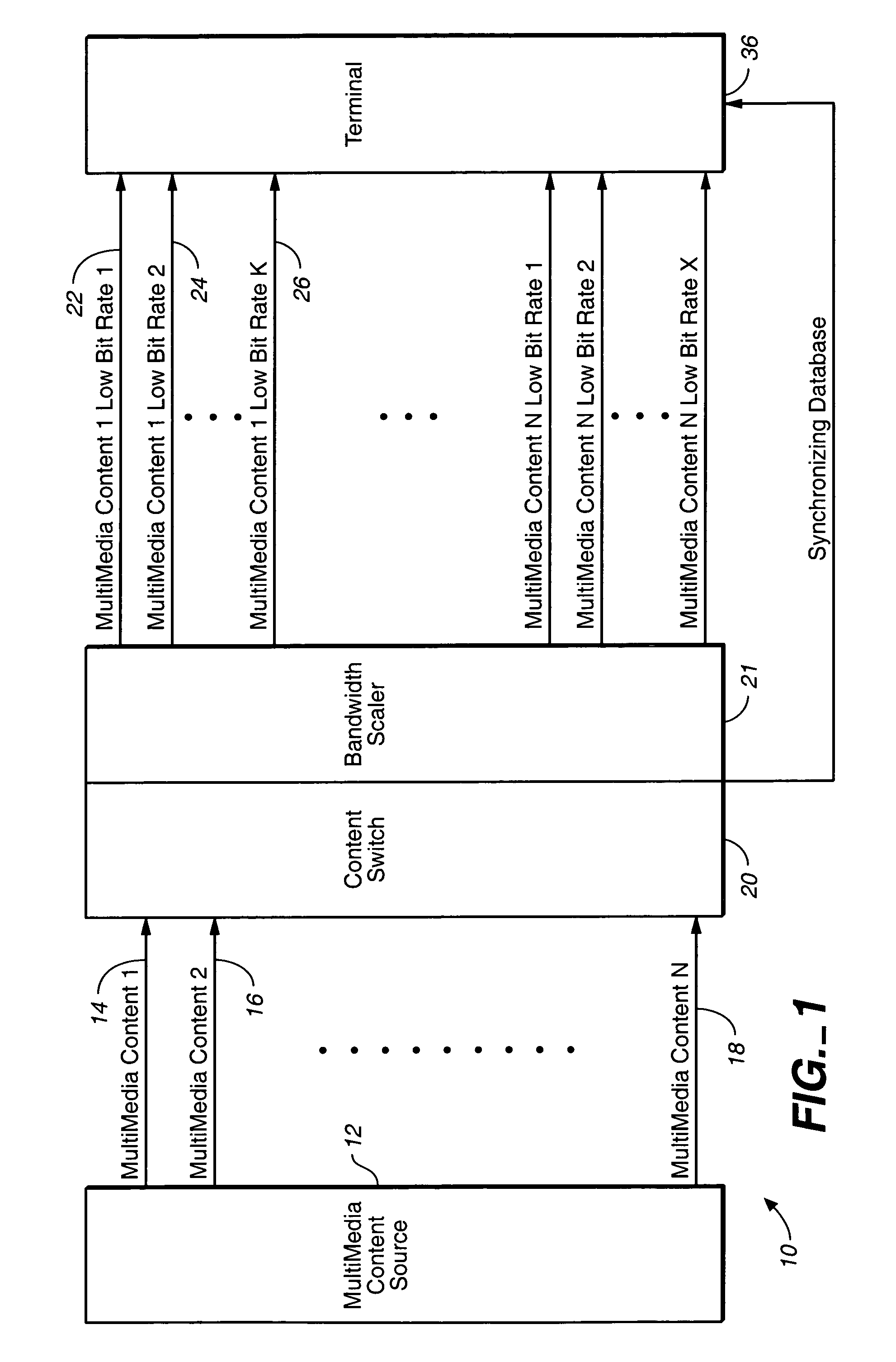
InactiveUS7003794B2Easy to receiveSmooth transitionBroadcast transmission systemsTime-division multiplexComputer networkMulticast transmission
A multicasting system for reception of multimedia information comprising: a content switch coupled to a multimedia content source and at least one multimedia smart terminal. The multimedia content source includes a plurality of multimedia contents, wherein each multimedia content is supported by a primary multimedia stream transmitted over a primary dedicated channel having a primary bandwidth. At least one multimedia smart terminal is configured to receive from the content switch over a network each multimedia content as a secondary multimedia stream transmitted over a secondary channel having a secondary bandwidth. The content switch includes a bandwidth scaler configured to scale each primary multimedia stream to a plurality of secondary multimedia sub-streams that are substantially synchronized. The multimedia smart terminal includes a smart terminal sub-stream switch configured to switch among the plurality of secondary multimedia sub-streams in order to select a substantially optimum secondary multimedia sub-stream. The substantially optimum secondary multimedia sub-stream includes a substantially optimum relationship between an error rate level determined at the time of reception of a multimedia content and the quality of reception of a multimedia content.
Owner:RUNCOM TECH LTD
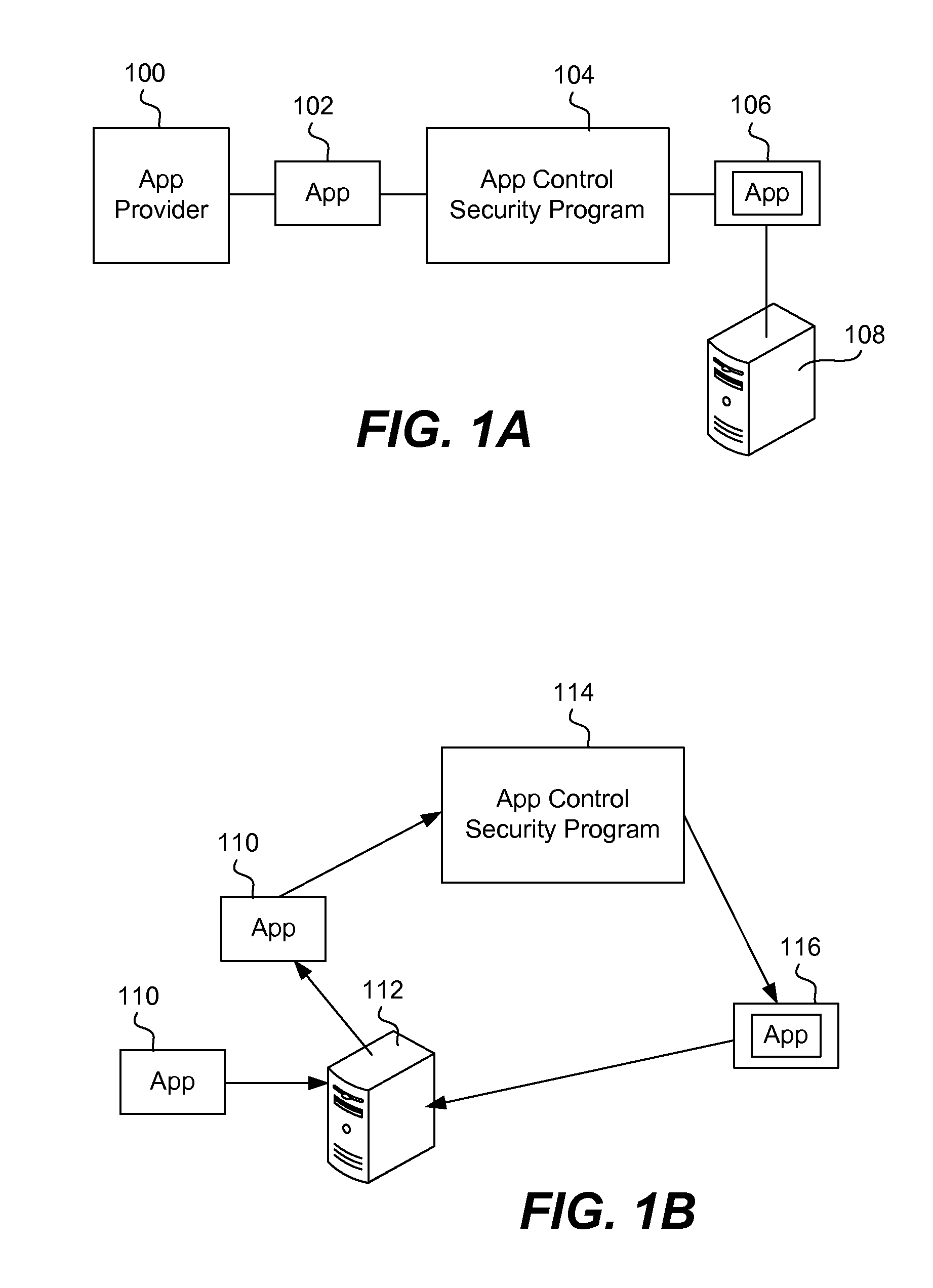
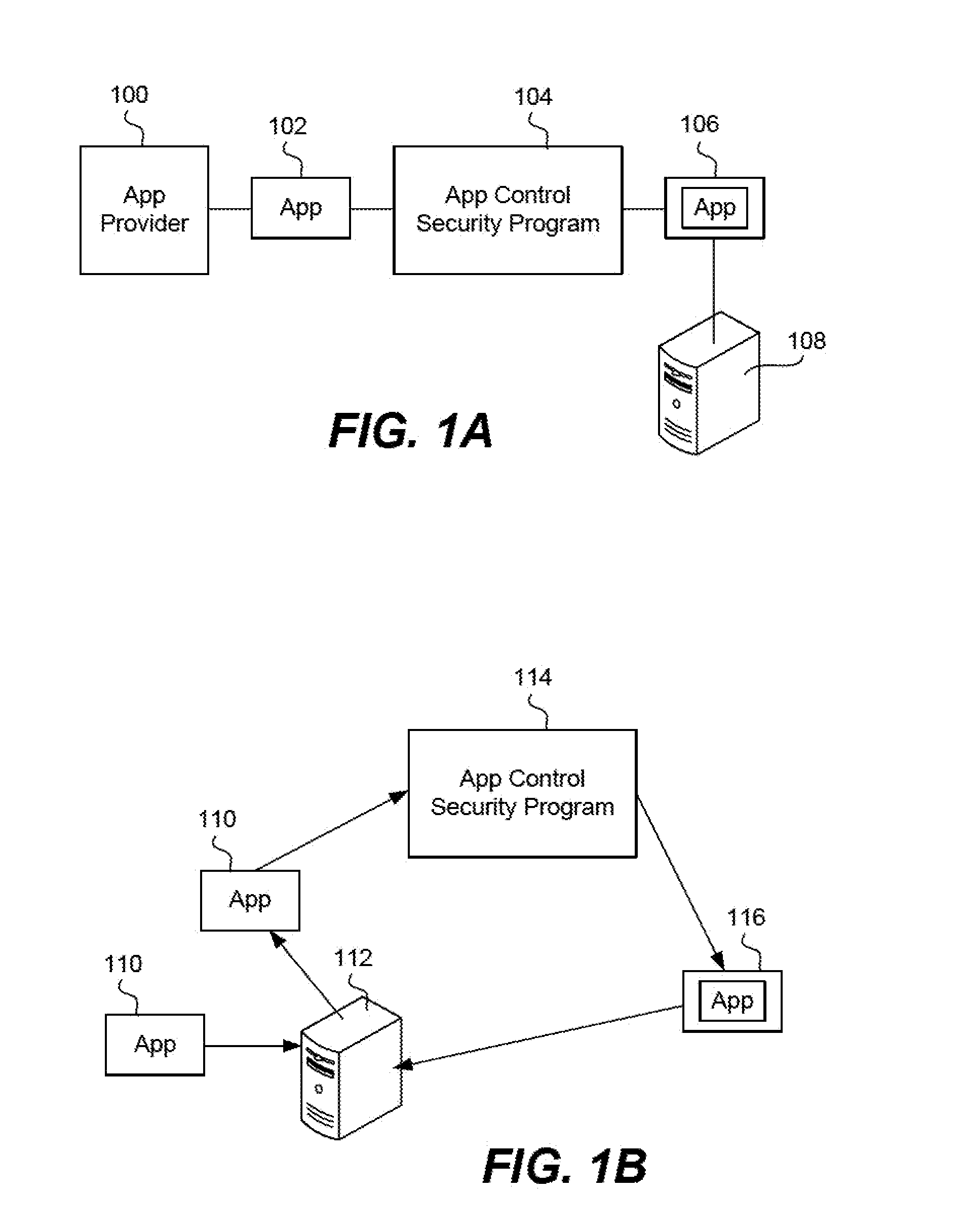
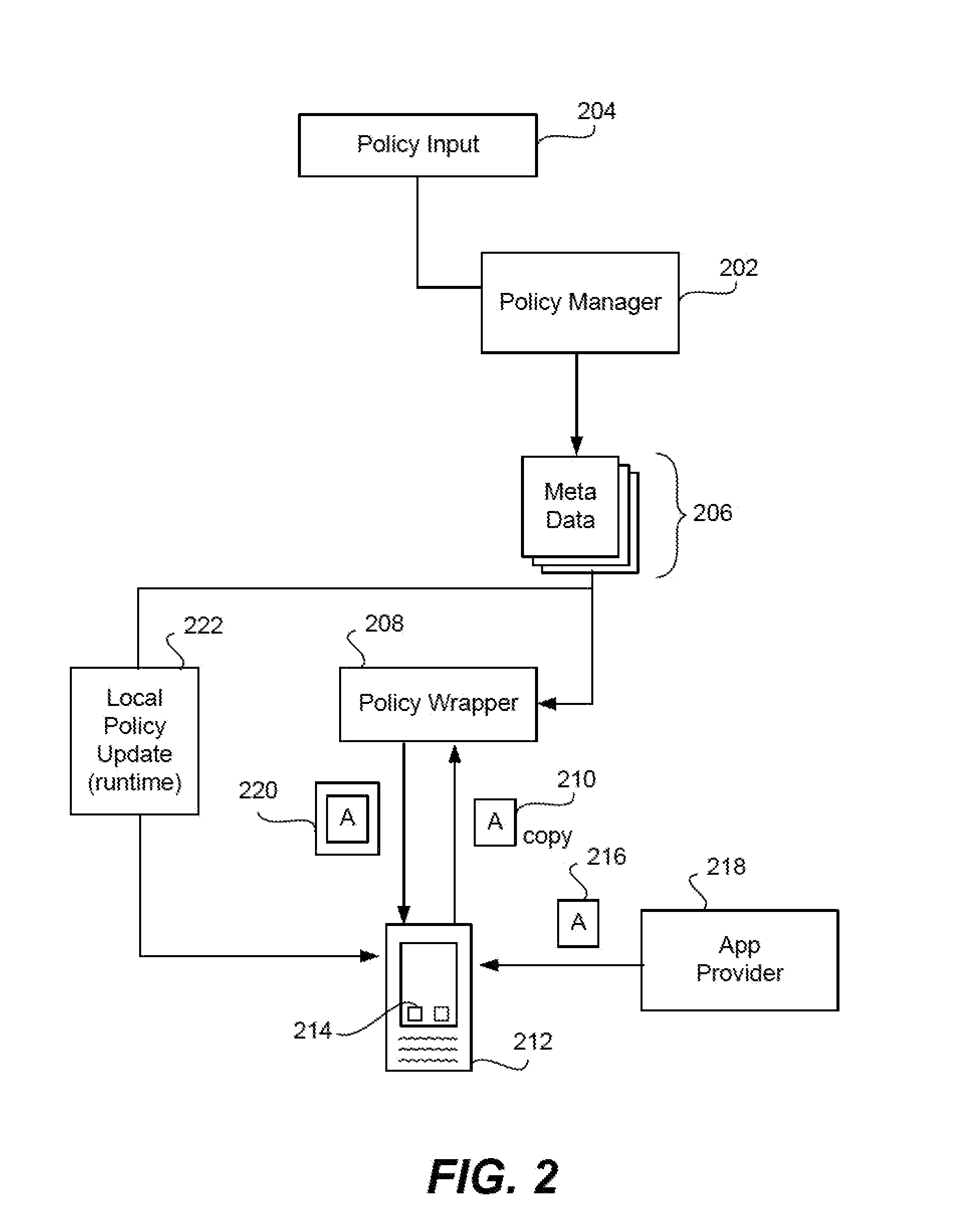
Secure execution of unsecured apps on a device
ActiveUS20120246731A1Minimize damageMinimize data lossDigital data processing detailsAnalogue secracy/subscription systemsPotential harmEnforcement
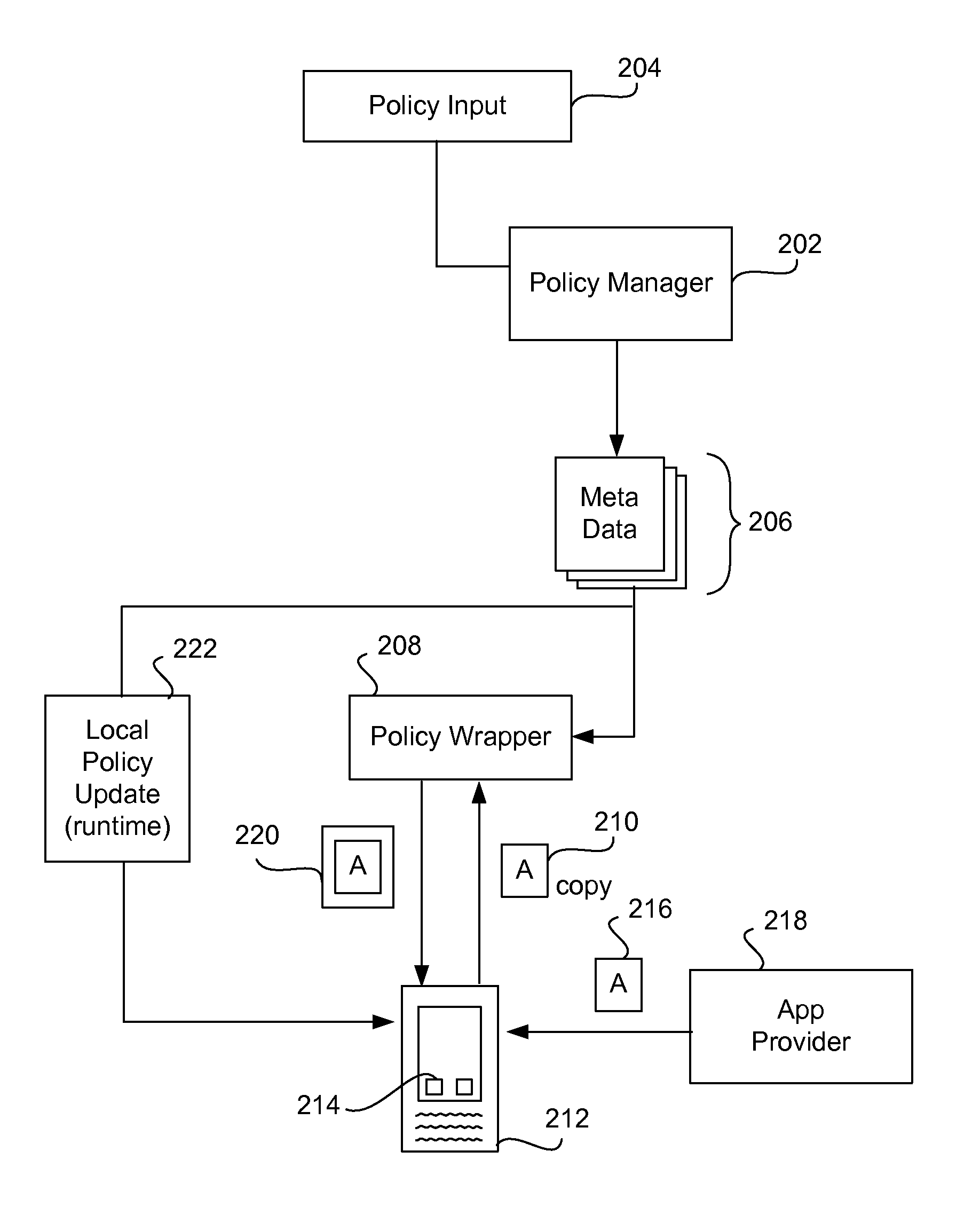
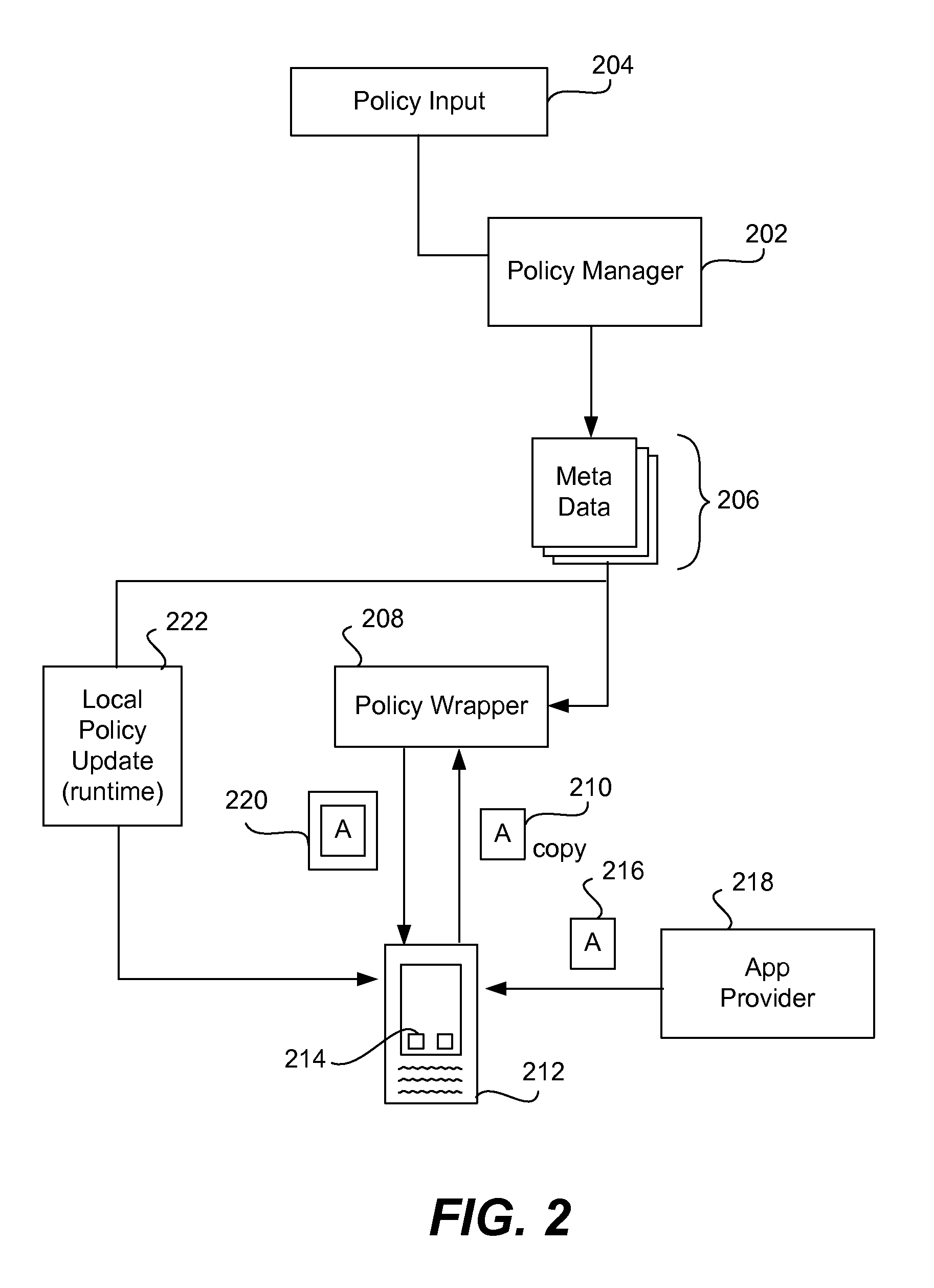
Devices are pre-deployed with an app security mechanism to ensure that apps that are downloaded onto the device do not cause data loss, data leakage, or other harm to the device. A user can start using the device and downloading apps in a conventional or typical manner and be assured that security measures are being taken to minimize potential harm for unsecured and secured apps. An app security enforcement layer or engine operates with, for example, a Type 2 hypervisor on the device, and ensures that any calls by the apps to the operating system of the device are generally safe. Measures such as enhancing or modifying the call, obfuscating the call, or terminating the app may be taken to protect the operating system. These actions are taken based on a policy that may be either interpreted or compiled by the enforcement engine with respect to app execution. The security measures are generally transparent to the user of the device.
Owner:BLUE CEDAR NETWORKS INC
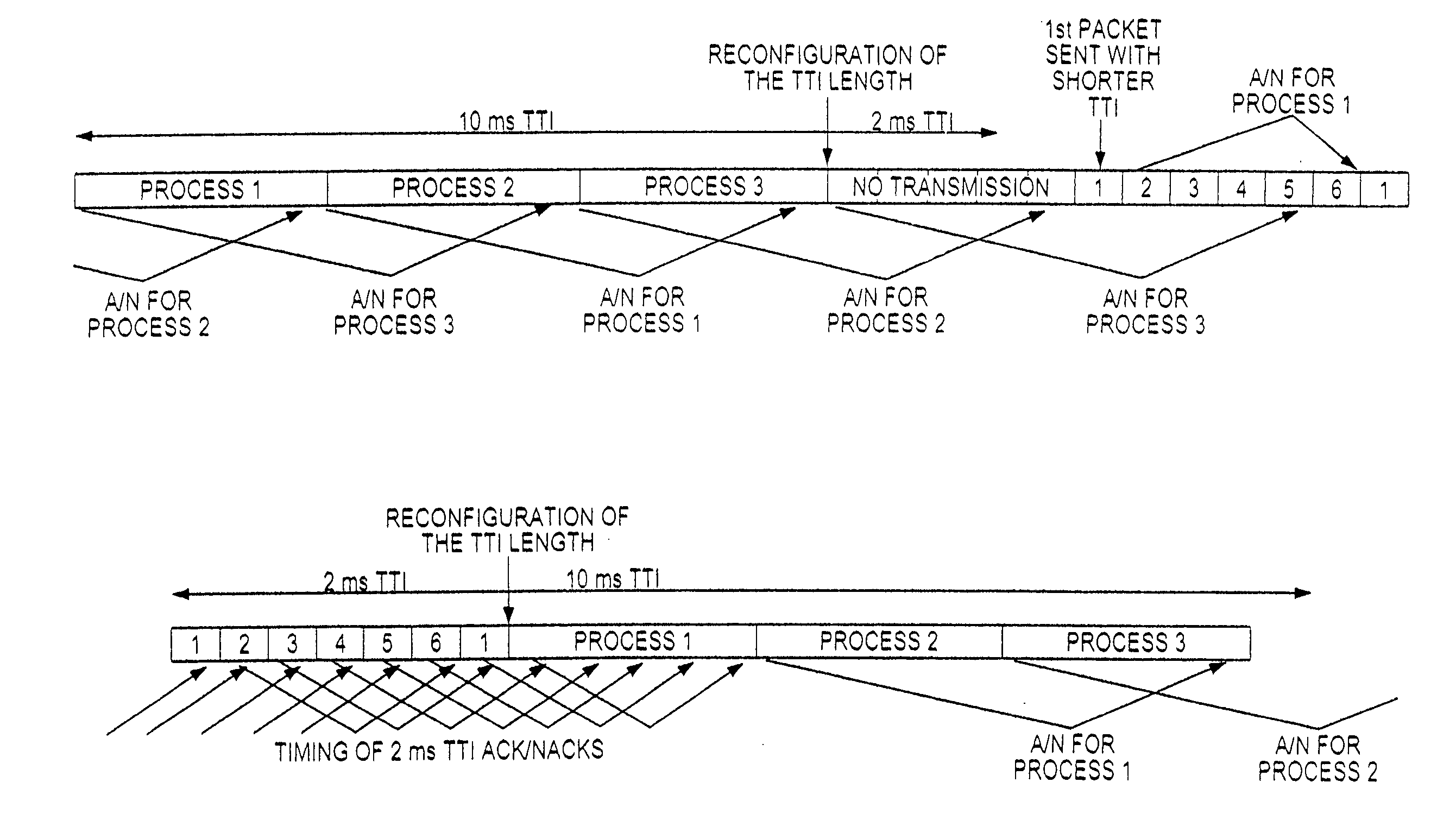
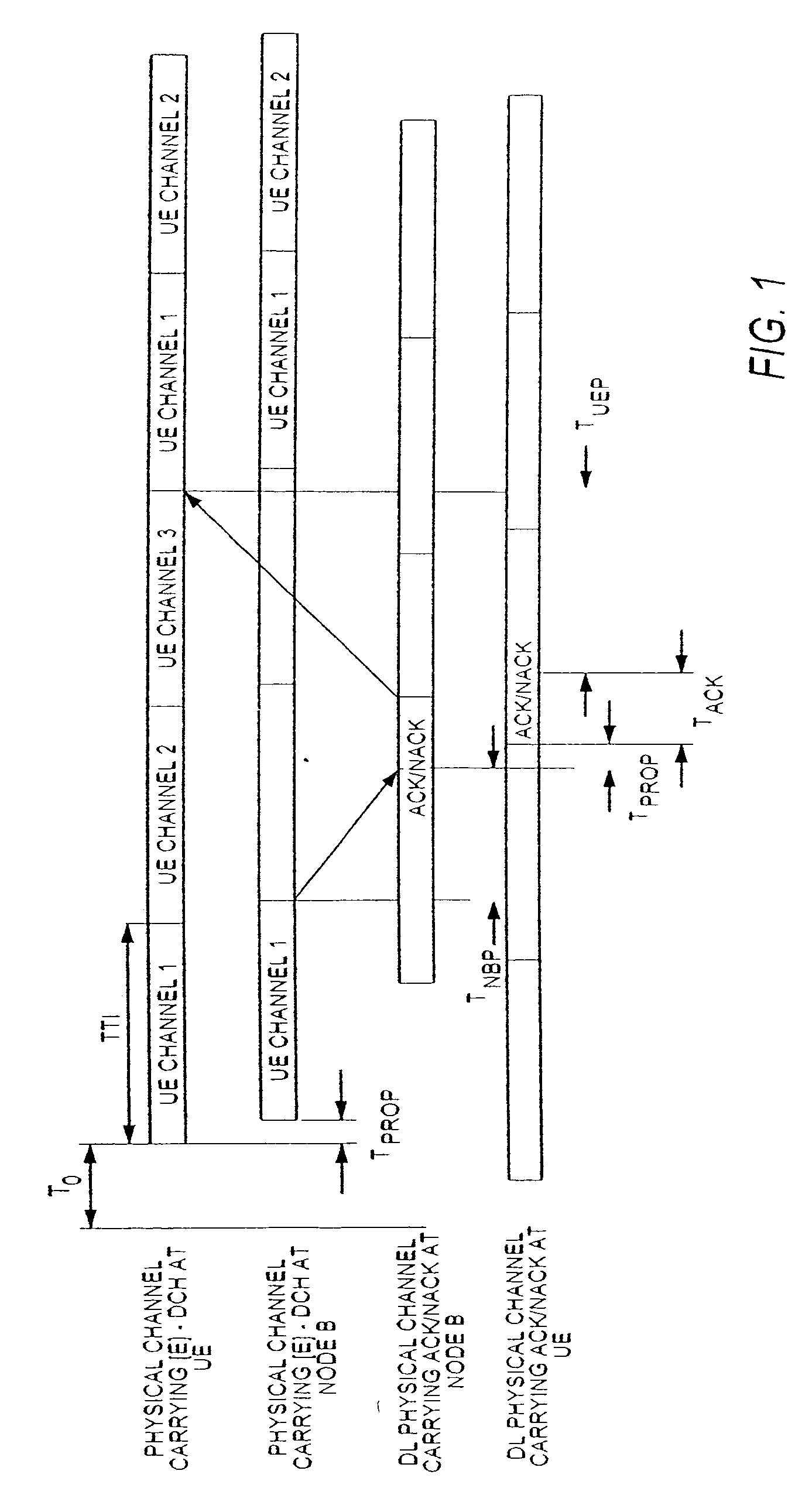
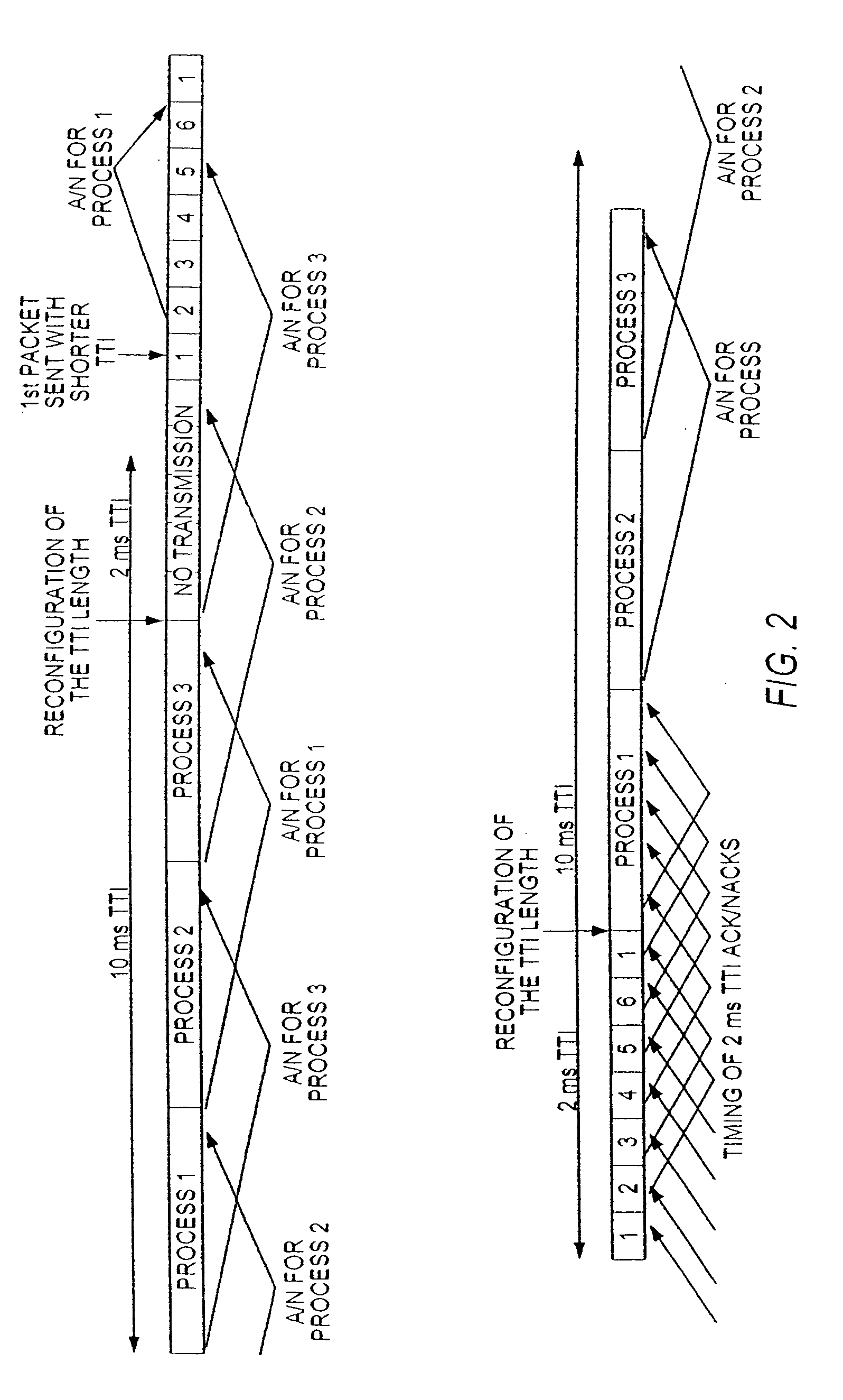
WCDMA uplink HARQ operation during the reconfiguration of the TTI length
ActiveUS20060034285A1Minimize dataLarge delayError prevention/detection by using return channelData switching by path configurationAir interfaceReal-time computing
A method for minimizing the loss of data and ensuring that large delays do not occur during reconfigurations of an uplink transmission time interval (TTI) length of a WCDMA High Speed Packet Uplink Access (HSUPA) air interface, wherein the reconfiguration of an uplink TTI length is delayed until all pending retransmissions are successfully transmitted or until the maximum number of transmissions is reached. The transmission of new packets during this time period is prevented. However, pending retransmissions are allowed to occur. After the UE has received an ACK / NACK for each HARQ process, or until the specific maximum number of re-transmissions is reached, the UE starts transmitting with a new uplink TTI length.
Owner:NOKIA TECHNOLOGLES OY
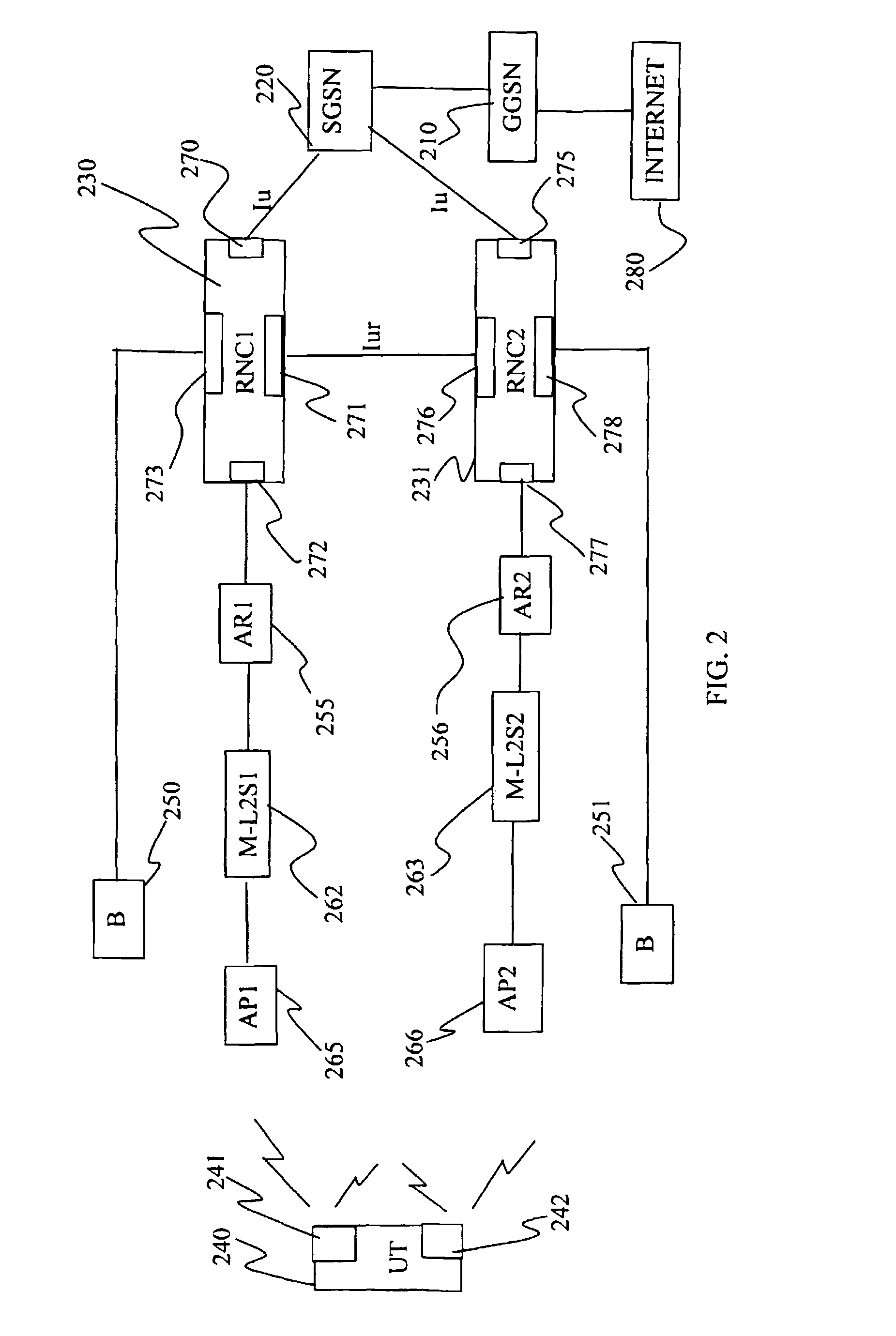
Handover Optimisation in a Wlan Radio Access Network
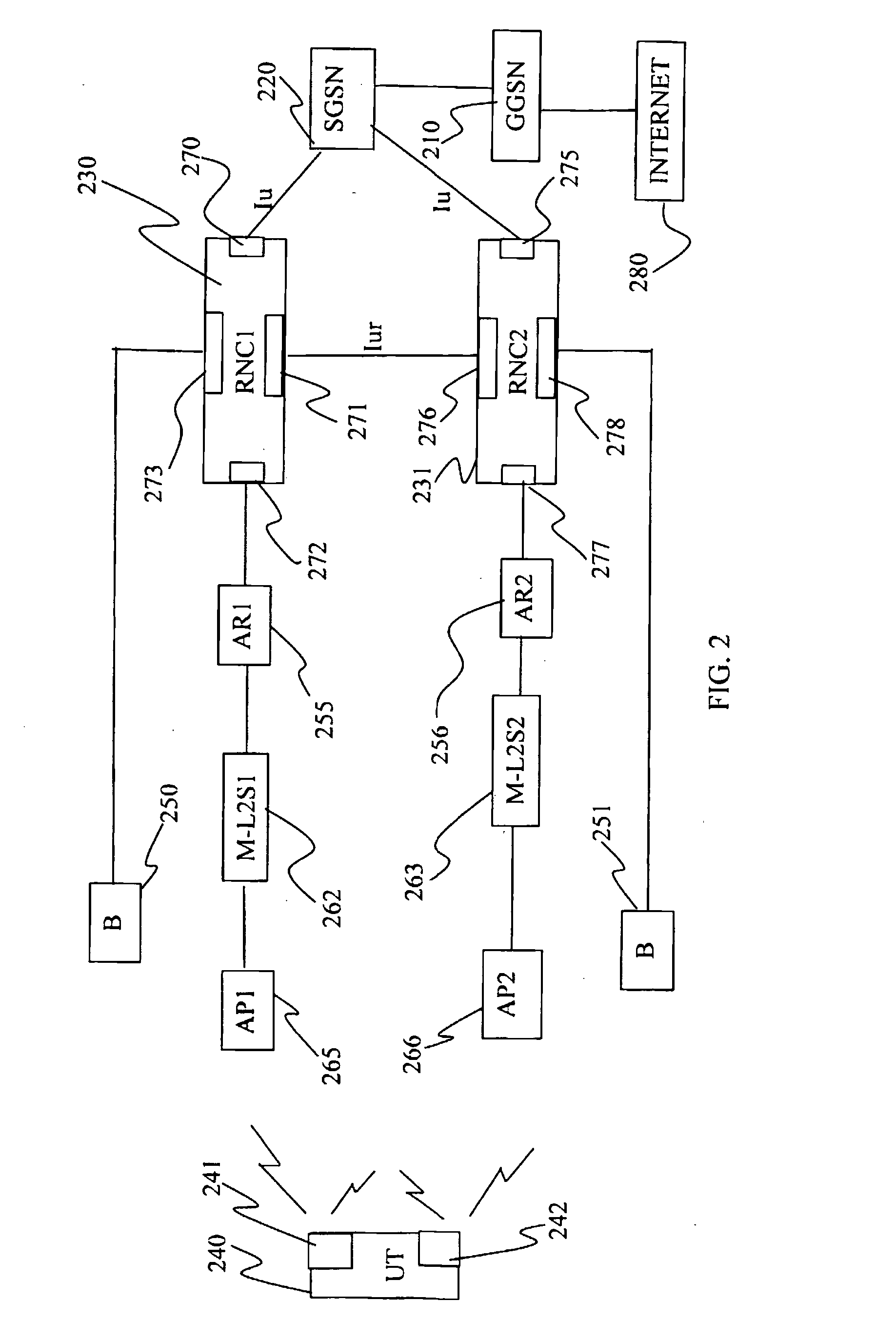
ActiveUS20080192696A1Improve switching characteristicsMinimize data lossRadio/inductive link selection arrangementsWireless commuication servicesAccess networkRadio access network
The invention provides a method for assisting handover of a communication session associated with a UT from a first radio access point, AP1, to a second radio access point, AP2, in a radio access network, said method to be carried out by said AP1 and comprising the steps of:—receiving a handover intention notify message comprising a session identifier identifying said session and indicating that said UT intends to perform a session handover,—assigning said session a buffer memory space in a memory of said AP1,—buffering downlink data packets addressed to said UT in said buffer memory as a response on receiving said handover intention notify message. The invention further provides a UT, an AP1, AP2, an AR, and software program / s co-operating and / or realizing the method according to the invention. The invention provides a smoother handover.
Owner:TELEFON AB LM ERICSSON (PUBL)
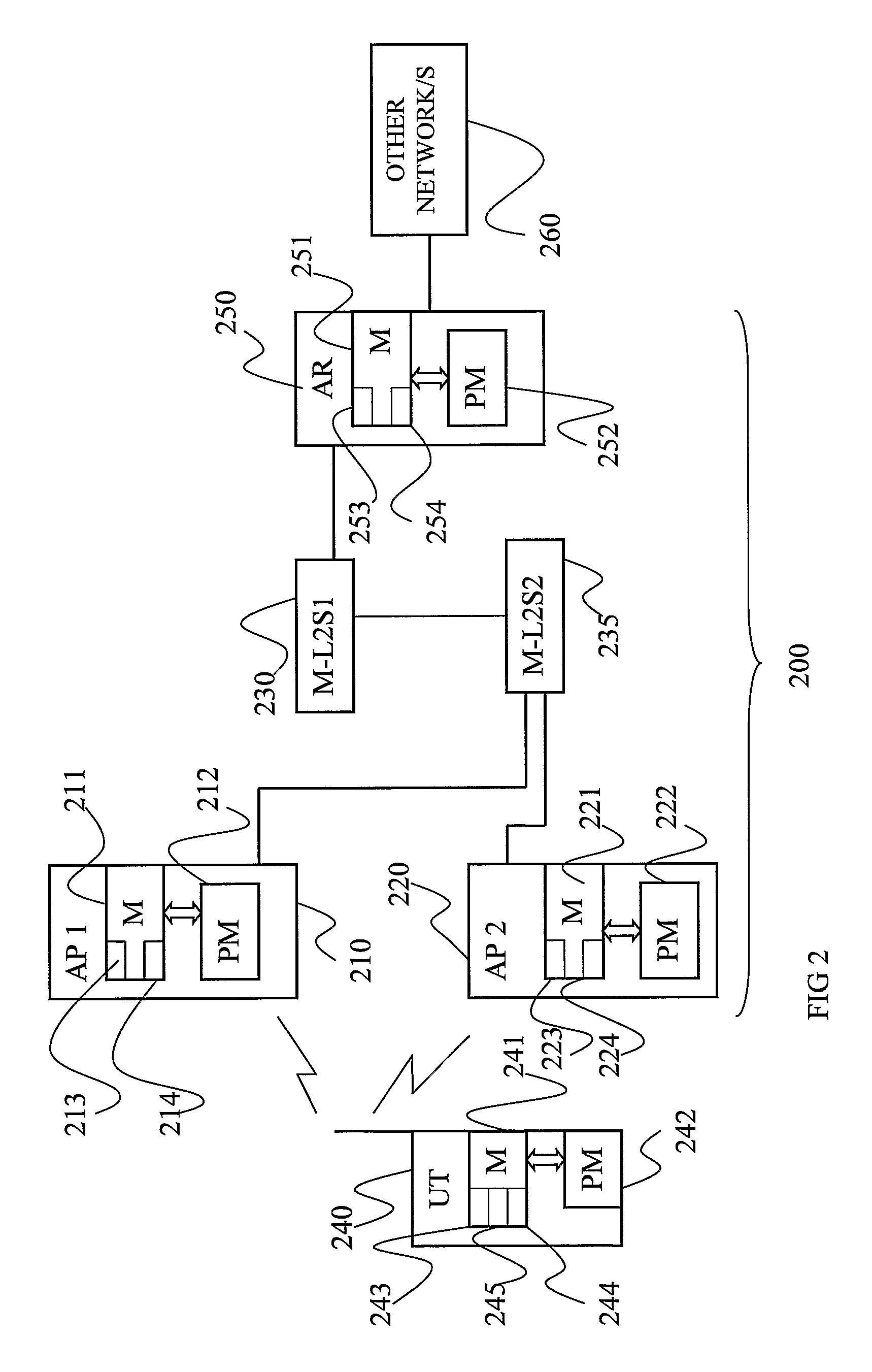
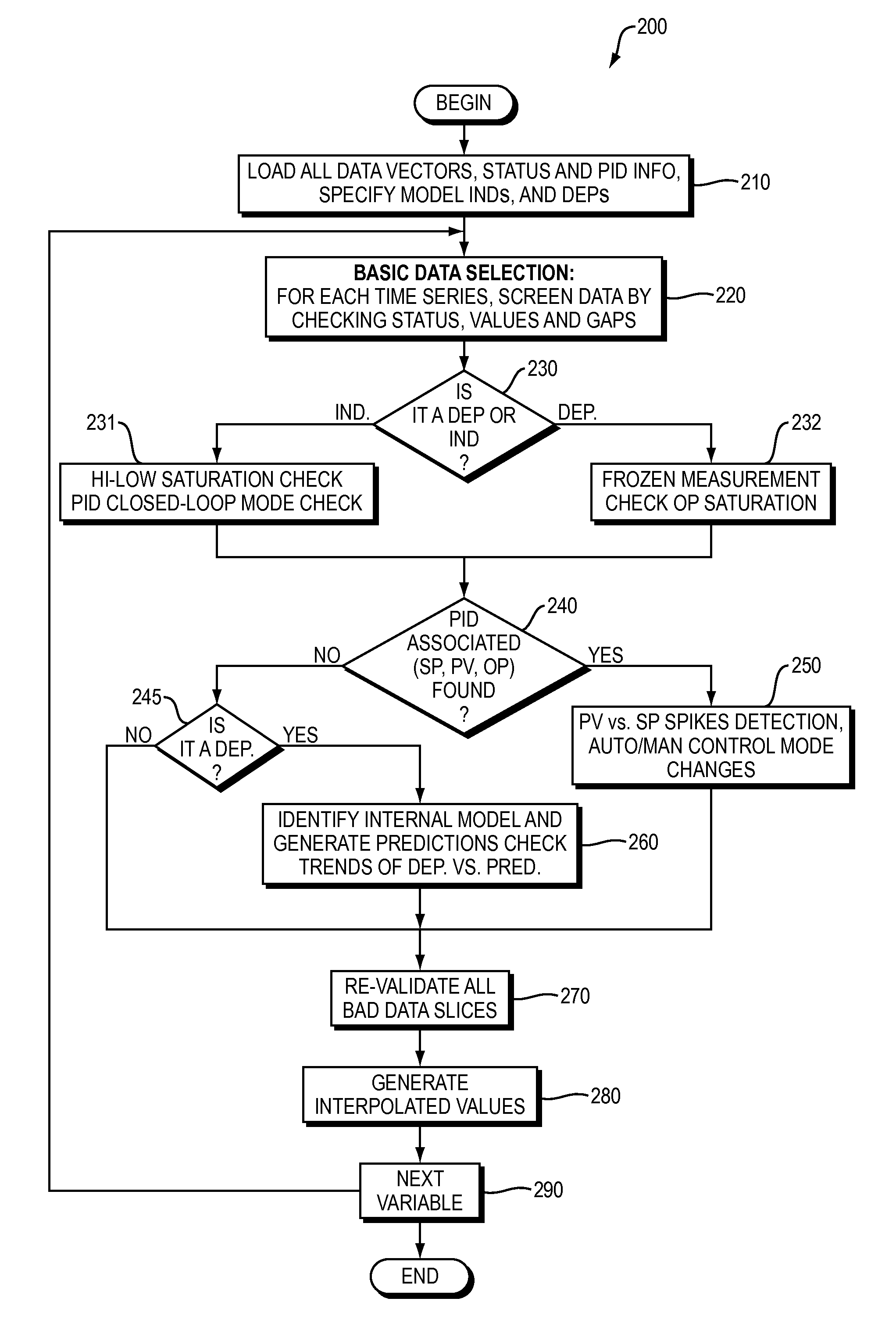
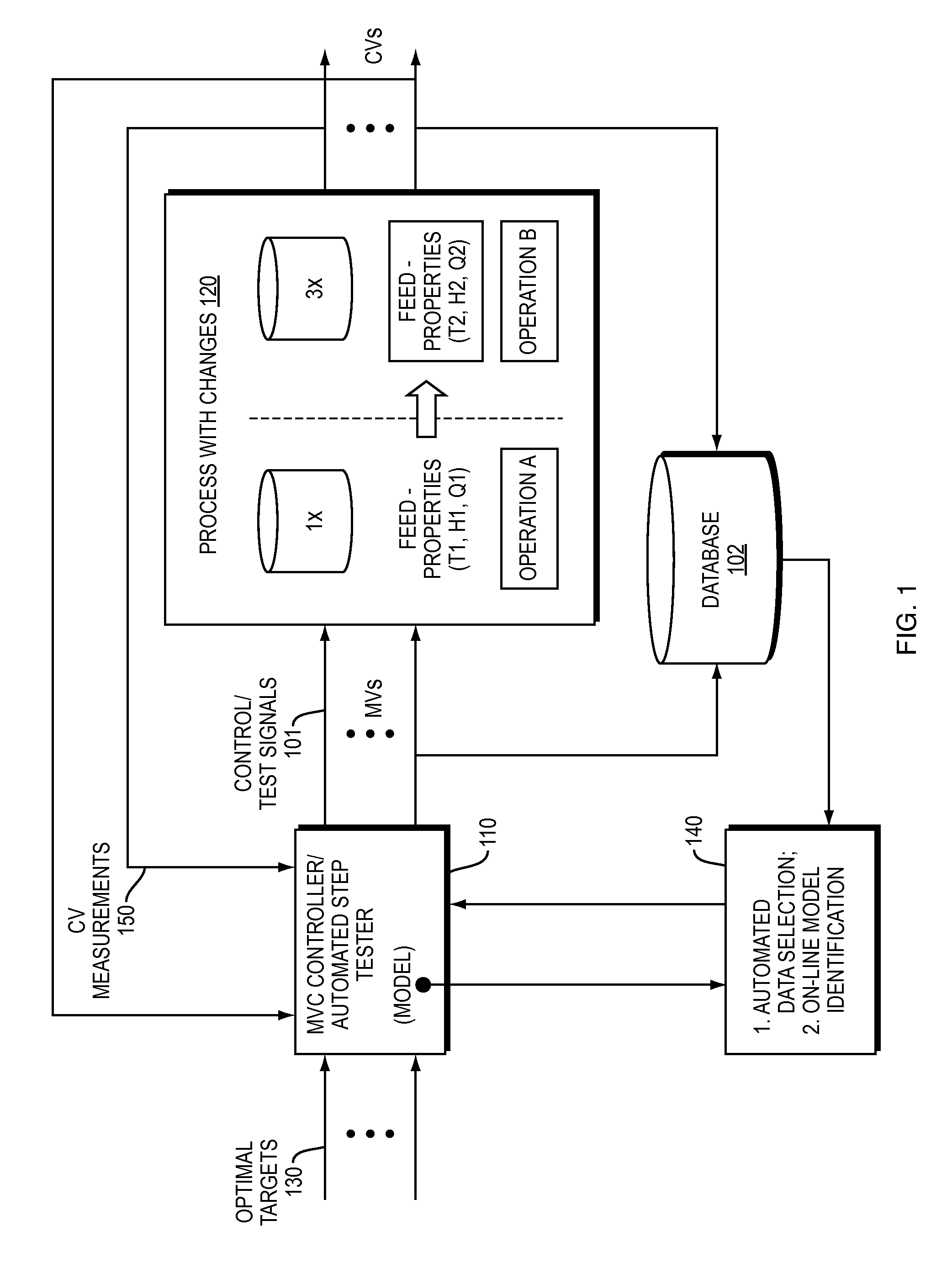
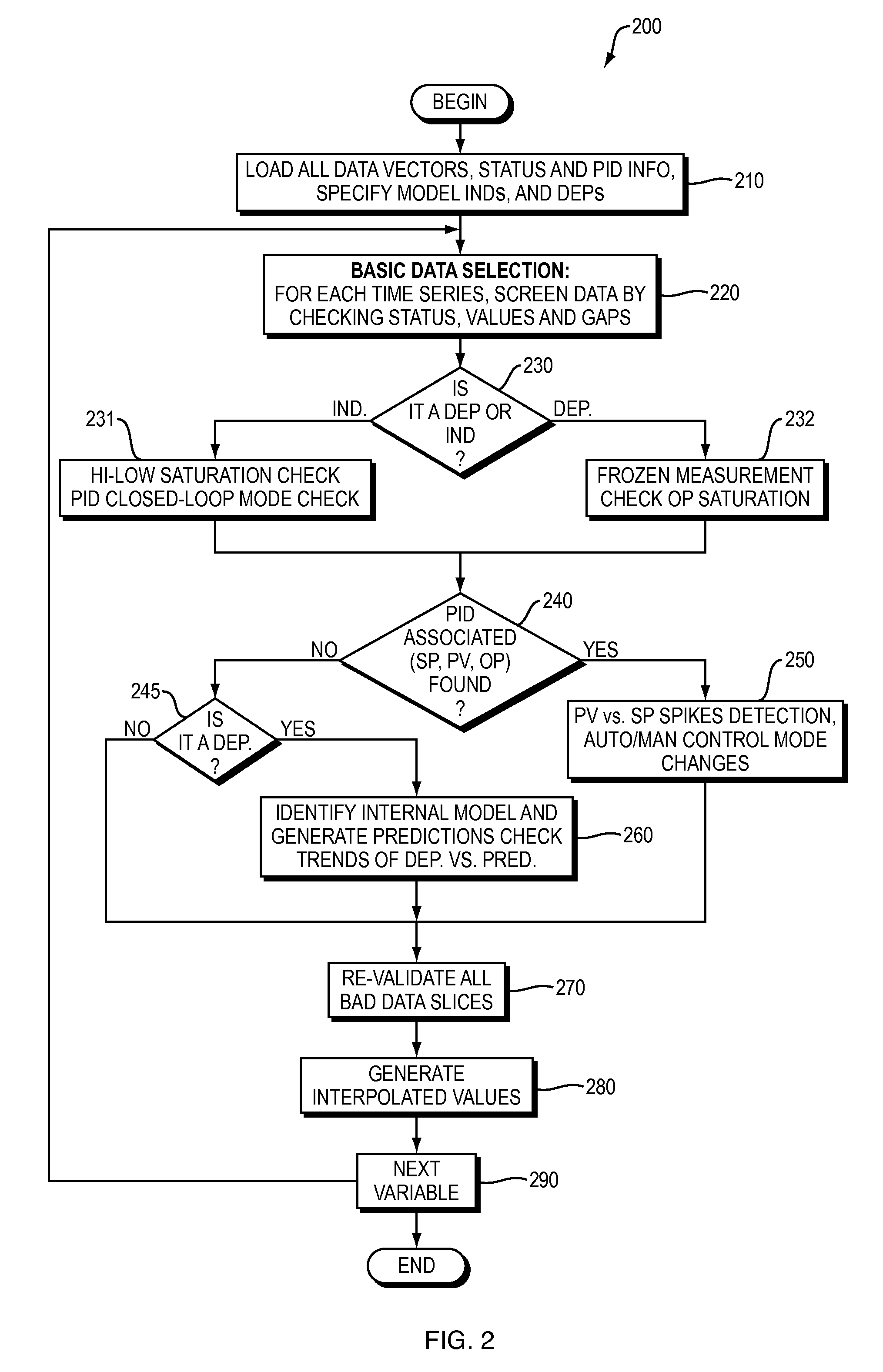
Apparatus and method for automated data selection in model identification and adaptation in multivariable process control
ActiveUS9141911B2Minimize negative impactMaximize useKnowledge representationSpecial data processing applicationsMulti inputData selection
A computer-based apparatus and method for automated data screening and selection in model identification and model adaptation in multivariable process control is disclosed. Data sample status information, PID control loop associations and internally built MISO (Multi-input, Single-output) predictive models are employed to automatically screen individual time-series of data, and based on various criteria bad data is automatically identified and marked for removal. The resulting plant step test / operational data is also repaired by interpolated replacement values substituted for certain removed bad data that satisfy some conditions. Computer implemented data point interconnection and adjustment techniques are provided to guarantee smooth / continuous replacement values.
Owner:ASPENTECH CORP
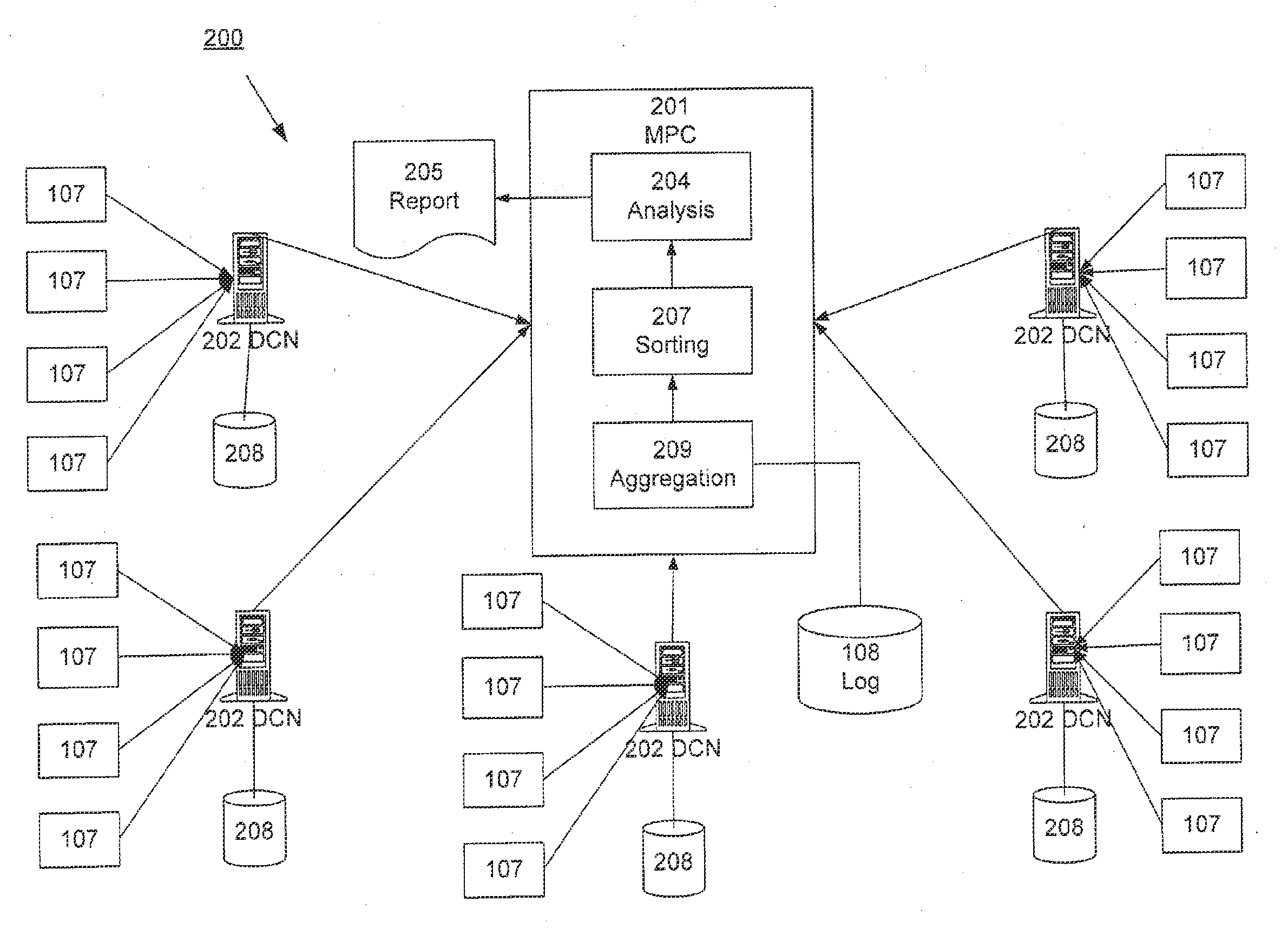
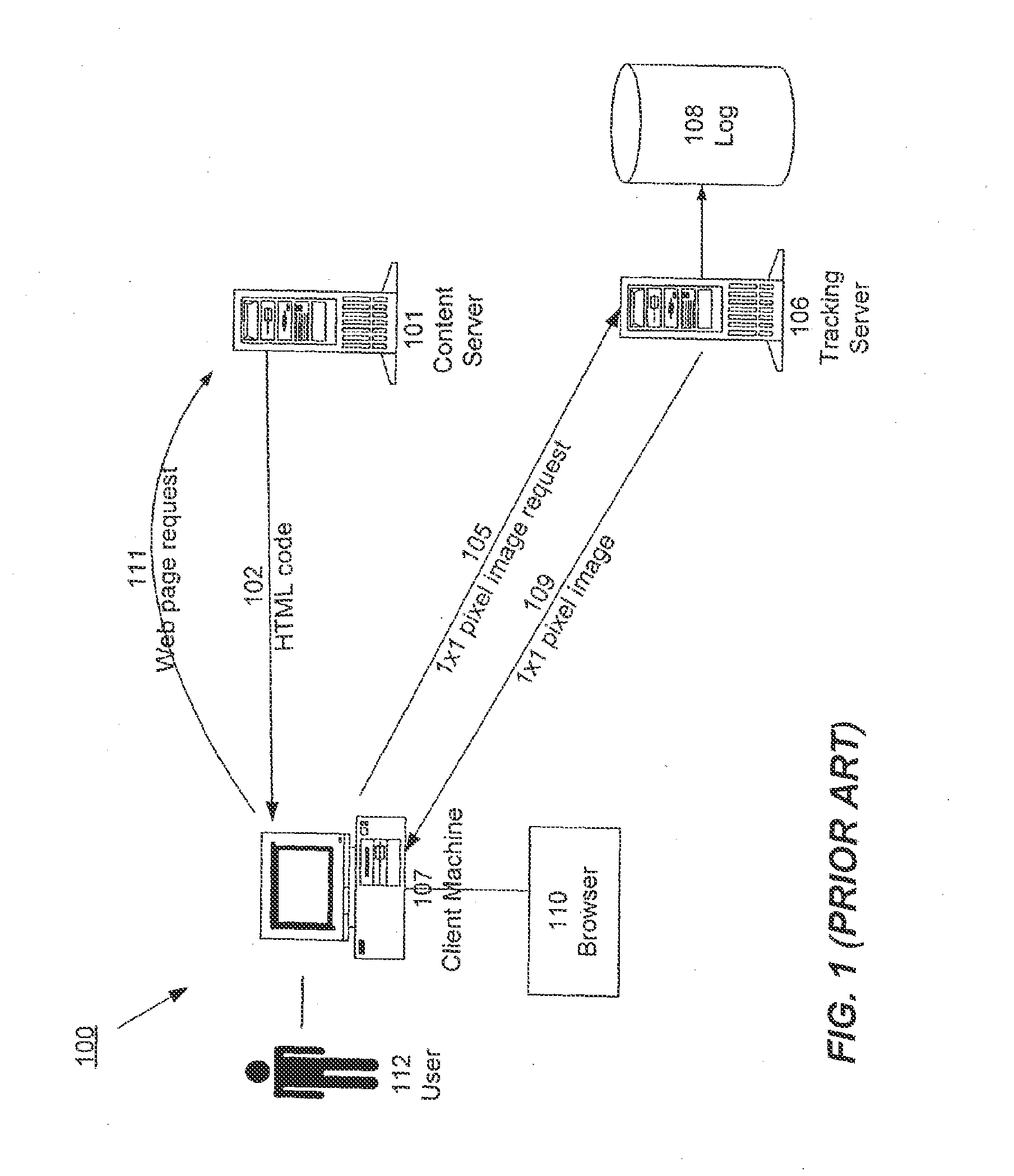
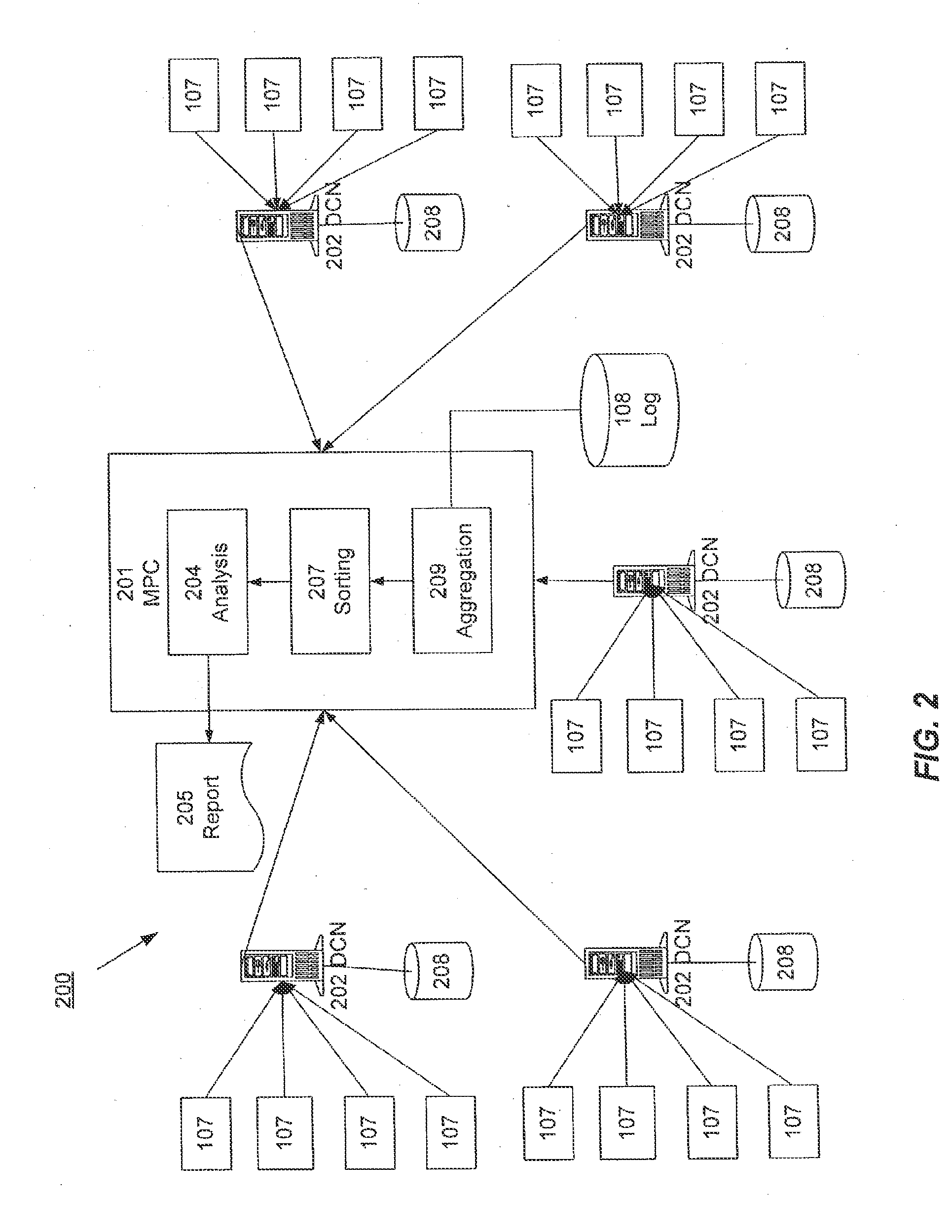
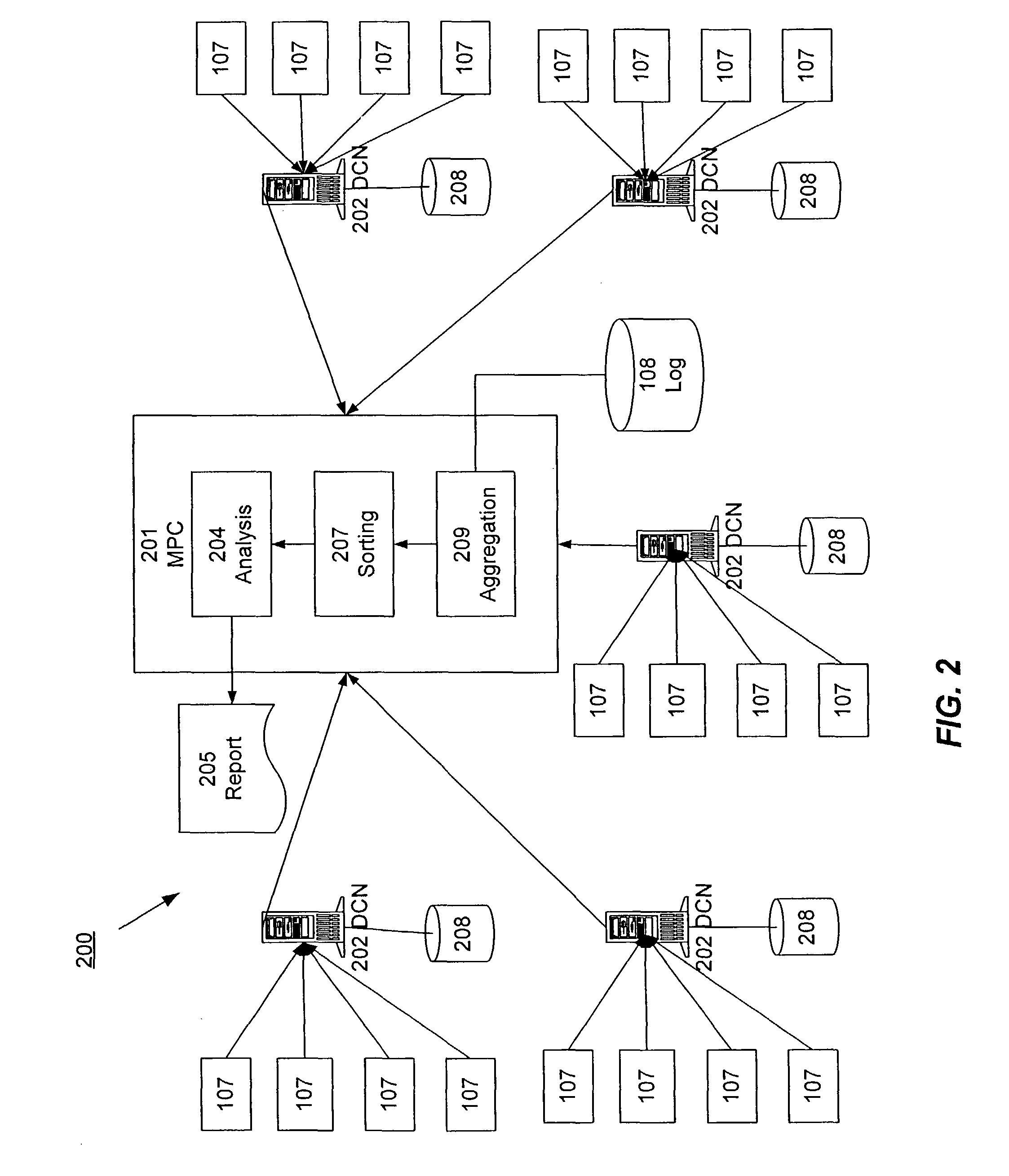
Distributed Data Collection and Aggregation
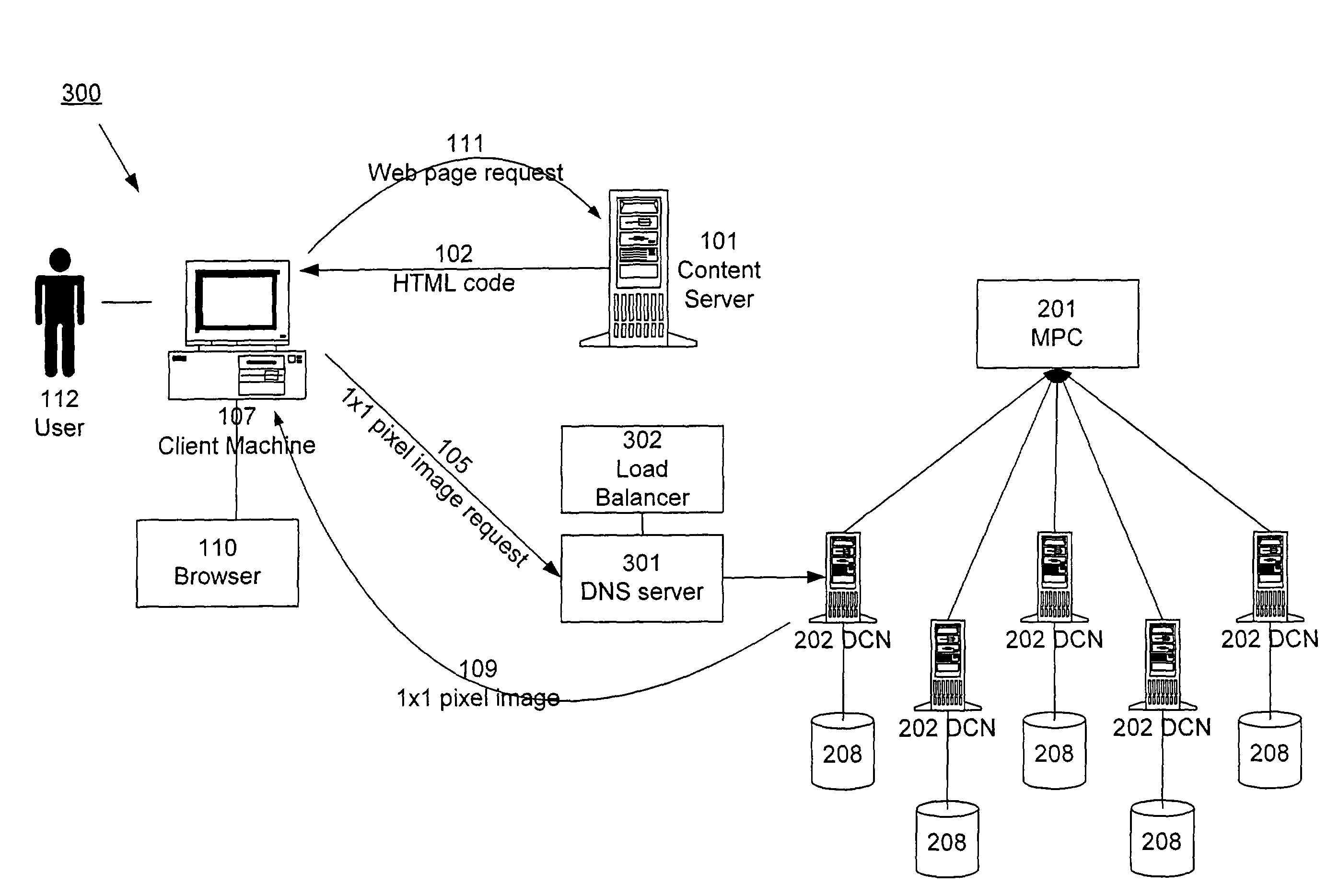
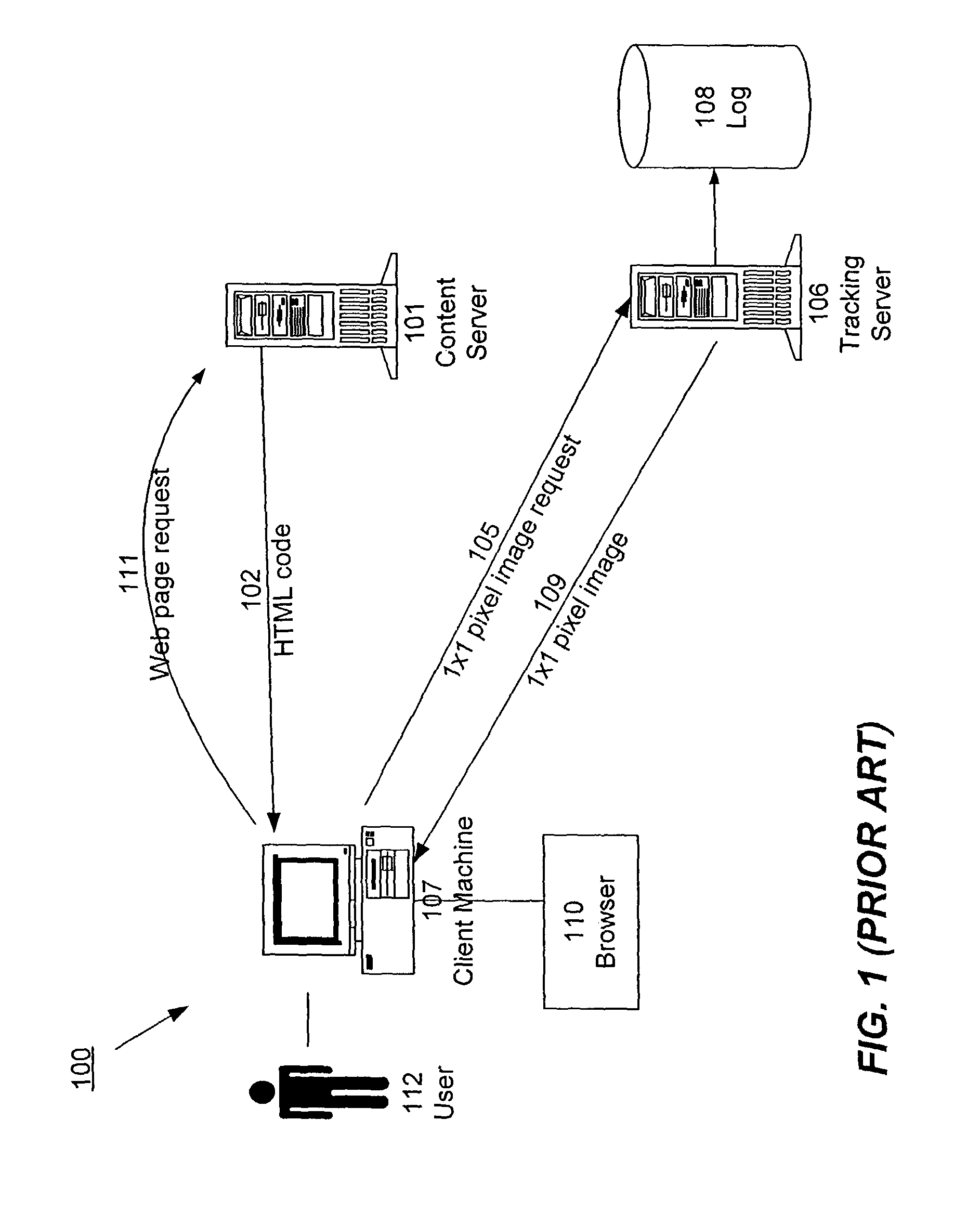
InactiveUS20120185588A1Efficiently collect informationFacilitates improved reliability in data collectionDigital computer detailsMarketingGeographic siteTimestamp ordering
A distributed, redundant, multi-homed system collects and aggregates website usage information. Two or more data collection nodes, preferably situated in diverse locations, efficiently collect and time-stamp information from users in a wide variety of geographic locations. Data collected by the individual data collection nodes is aggregated at a master processing center, sorted according to time stamps, and subjected to statistical analysis in order to generate complete and accurate reports regarding website traffic.
Owner:ADOBE SYST INC
Apparatus and method for sharing radio protocol entitles in wireless communication system
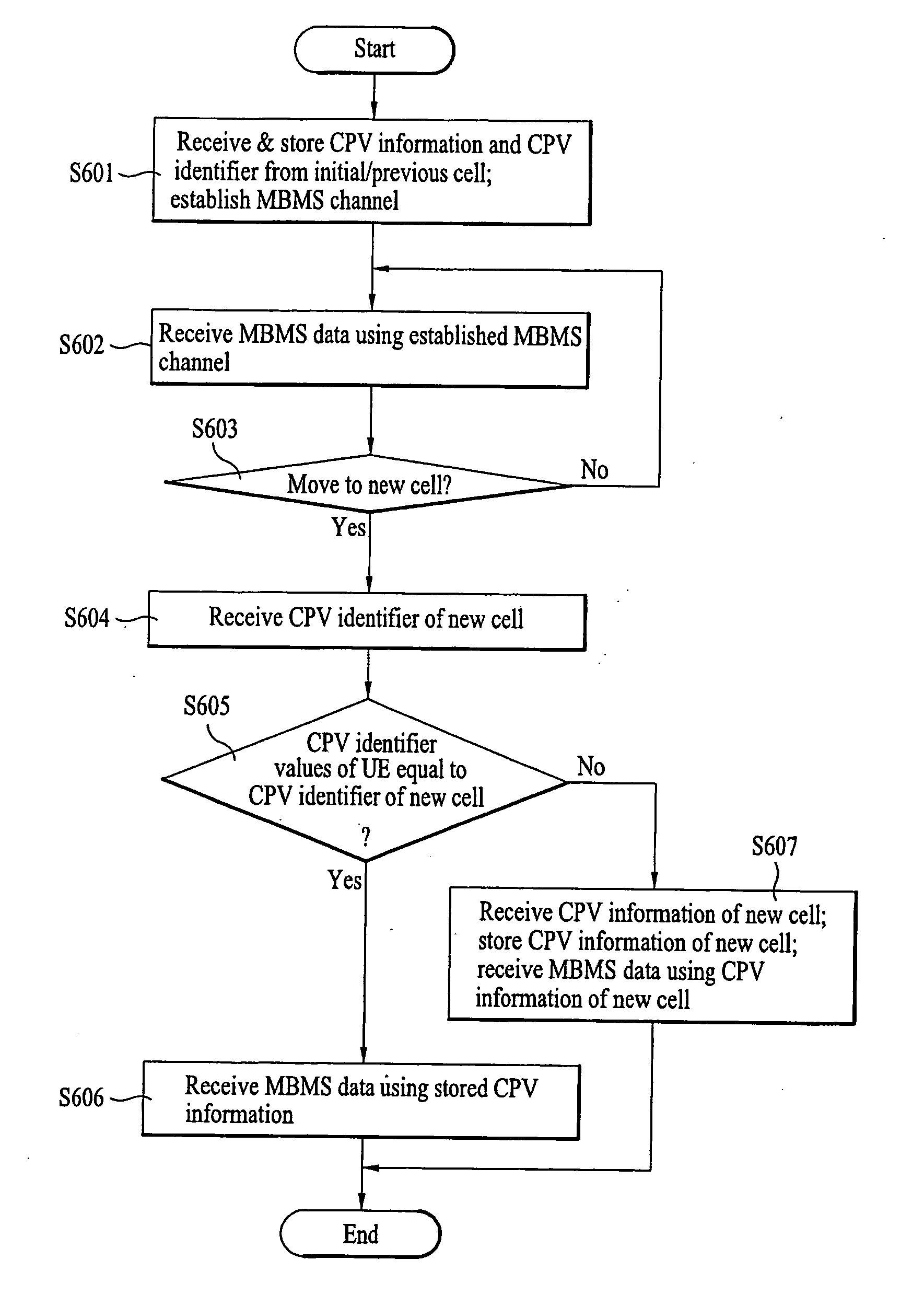
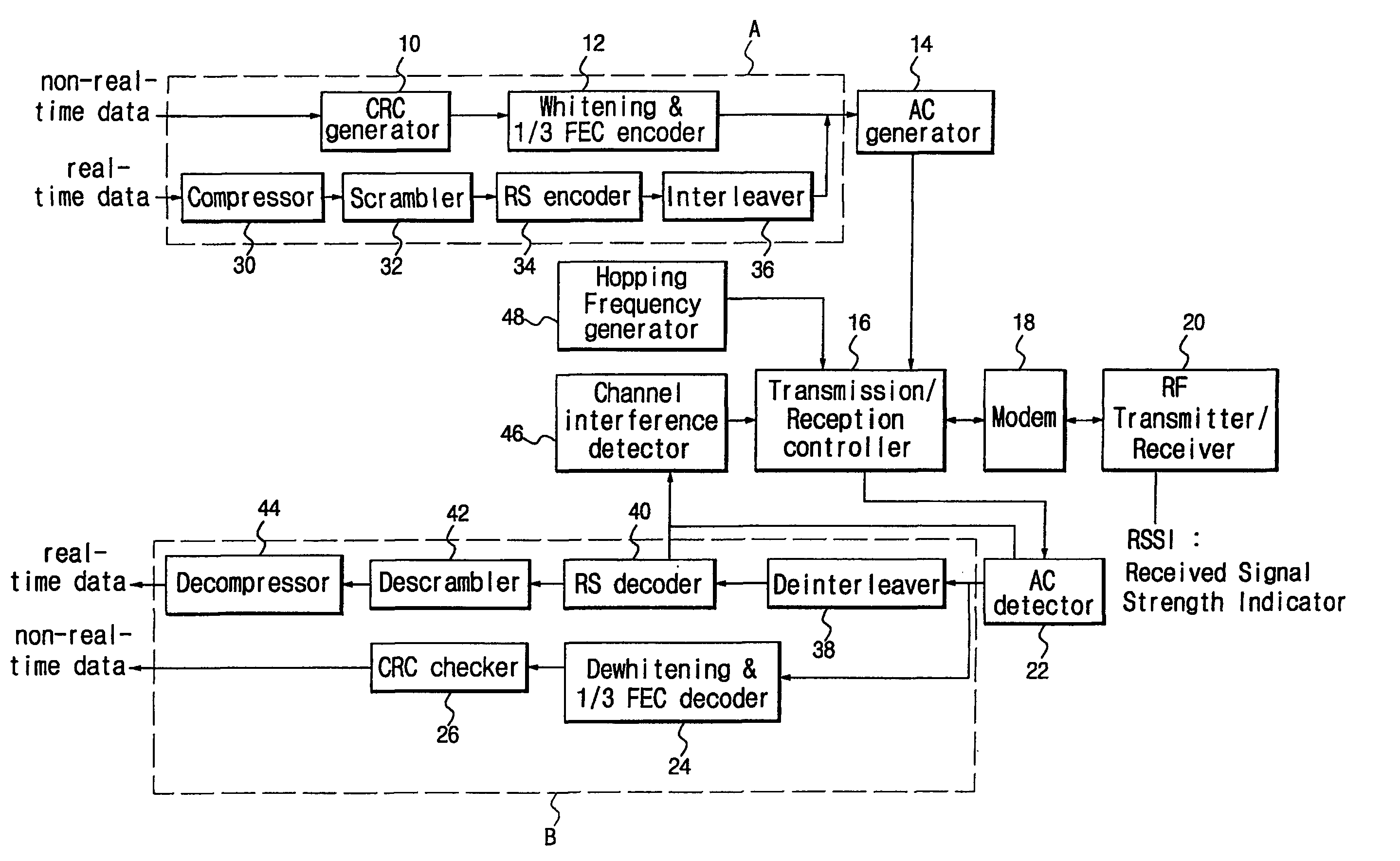
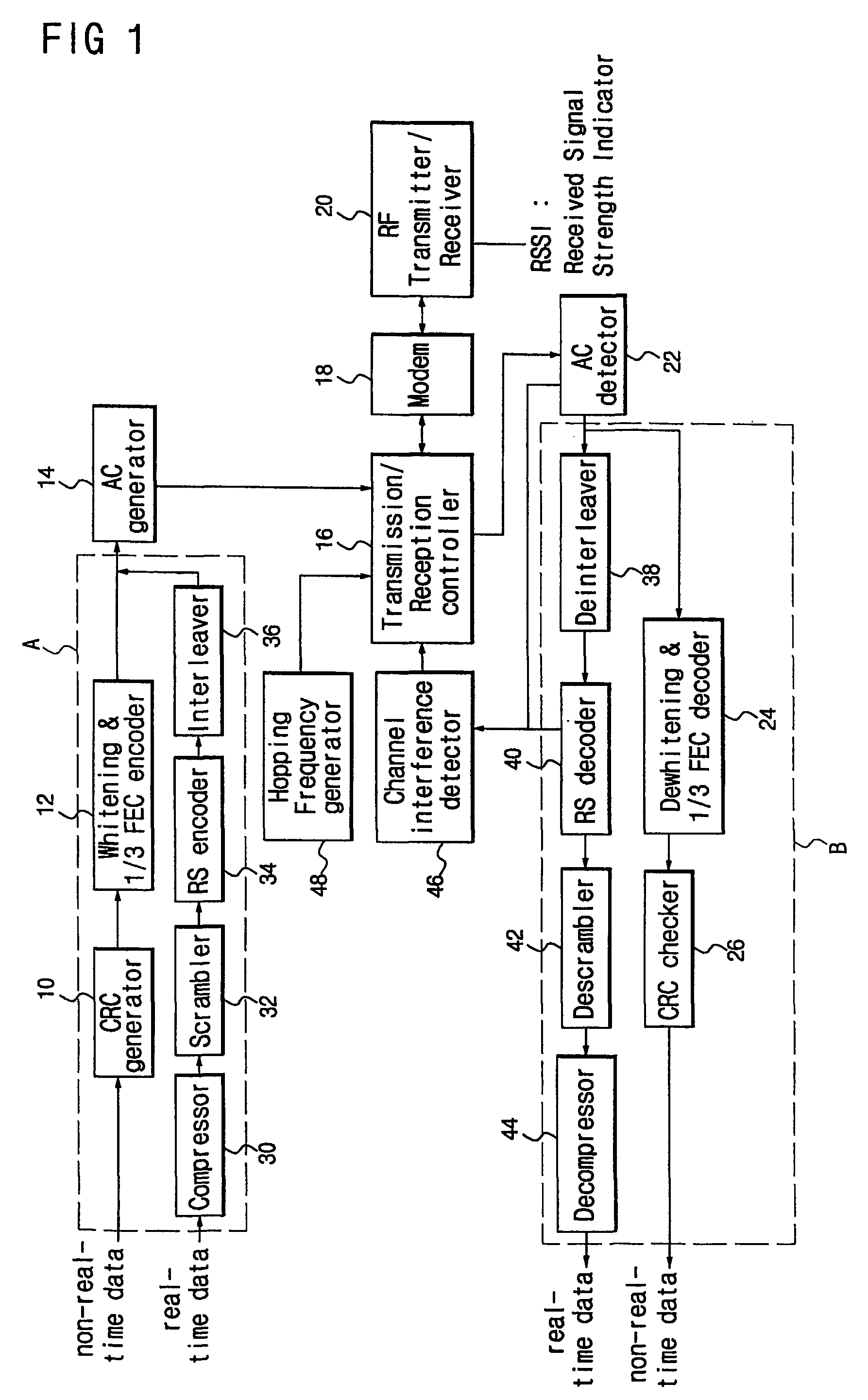
InactiveUS20050043050A1Minimize data lossAvoid wastingBroadcast service distributionSubstation equipmentChannel parameterHandover
A radio protocol entity sharing apparatus and method are provided. Different cells share a second-layer protocol entity to use the same channel parameter values and the same protocol parameter values, thereby reducing a delay resulting from reestablishing a radio bearer in the event of a handover, minimizing data loss during handover, conserving network resources, and enhancing reception performance via soft combining. The method includes steps of receiving, in a mobile station, a first parameter value and a first parameter value indicator; establishing a channel using the first parameter value and the first parameter value indicator; receiving, in the mobile station, a second parameter value indicator; and maintaining the established channel if the first parameter value indicator is identical to the second parameter value indicator.
Owner:LG ELECTRONICS INC
Method and apparatus for detecting MPLS network failures
InactiveUS7315510B1Shorten recovery timeMinimize data lossError preventionTransmission systemsEngineeringSystem failure
Recovery time upon the failure of a link or switching system in an asynchronous data network can be minimized if downstream data switches can provide upstream messages to upstream switching systems indicating to upstream switching systems that the downstream traffic arrived in tact and was properly handled. In one embodiment, the loss or failure of the upstream status message to an upstream switching system, causes an upstream switching system to reroute data traffic around a failed link or failed switch with a minimal amount of lost data.
Owner:TELLABS OPERATIONS
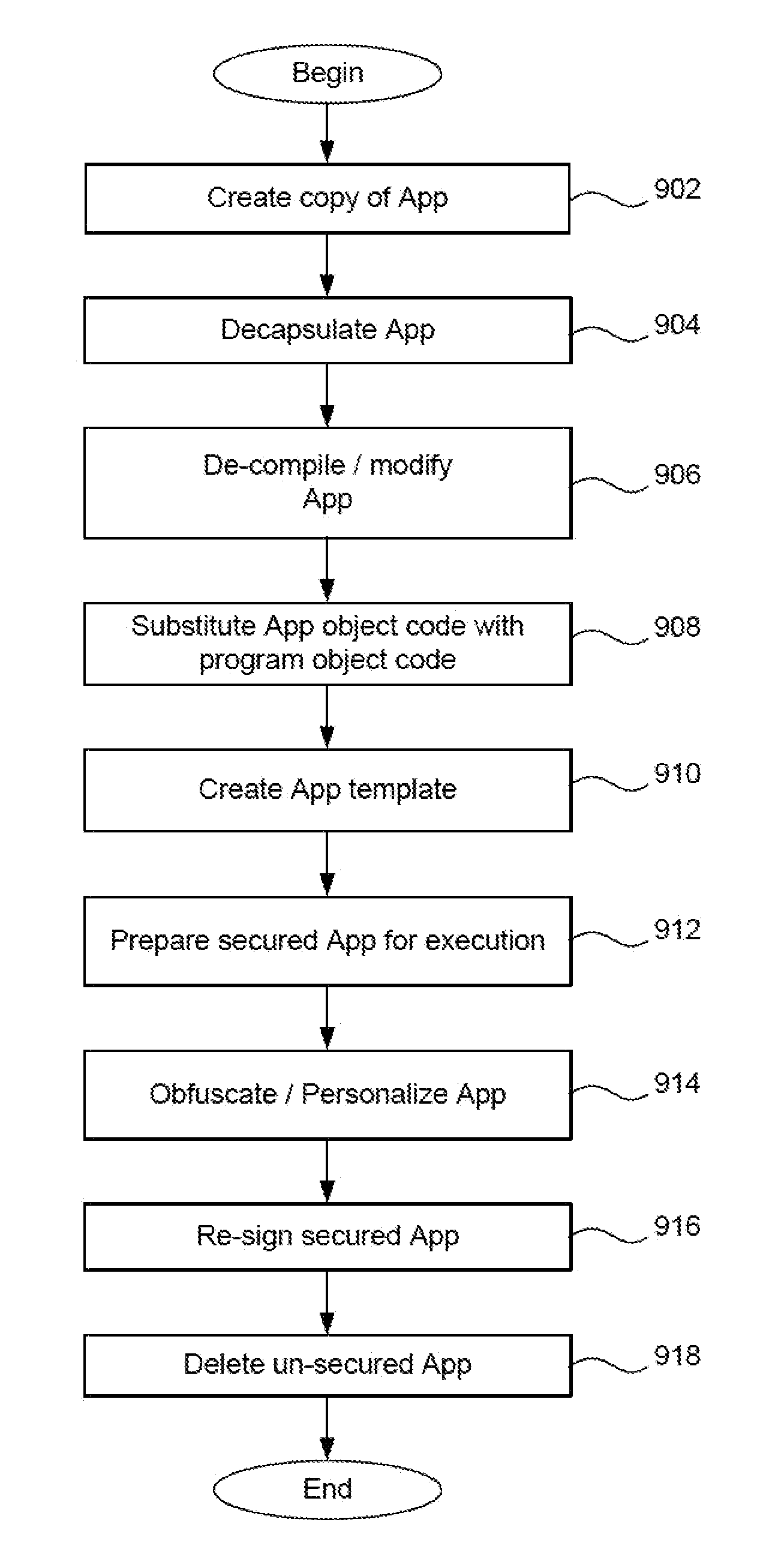
Secure execution of unsecured apps on a device
ActiveUS20120246484A1Minimize damageMinimize data lossUnauthorized memory use protectionHardware monitoringRandomizationApplication software
Given the volume of apps being developed and downloaded, performing operations to enable security for mobile devices, such as locating relevant classes and substituting different classes, can become very inefficient when done to a very high number of apps. In the invention, a device is enabled with an app security enforcement layer. The consumer can download unsecured apps and have the app execute on the phone in a secure manner, where potential data loss to the device, such as a smart phone or tablet, is minimized. To make the security wrapping process more efficient, an app template containing markers is created. This template is merged with data in an active user policy or is used to randomize or obfuscate the code to add more security. The process of security wrapping an app becomes more efficient.
Owner:BLUE CEDAR NETWORKS INC
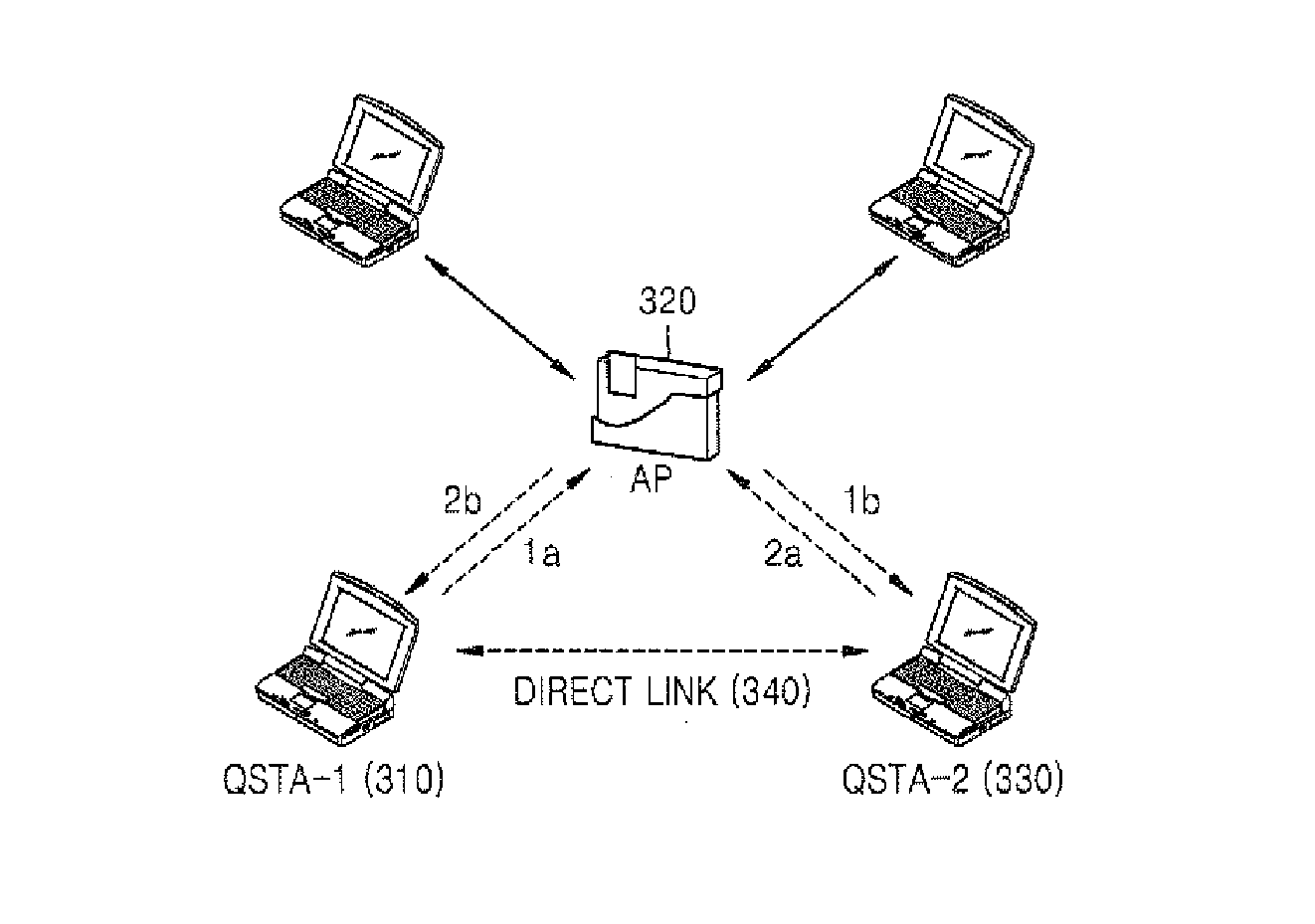
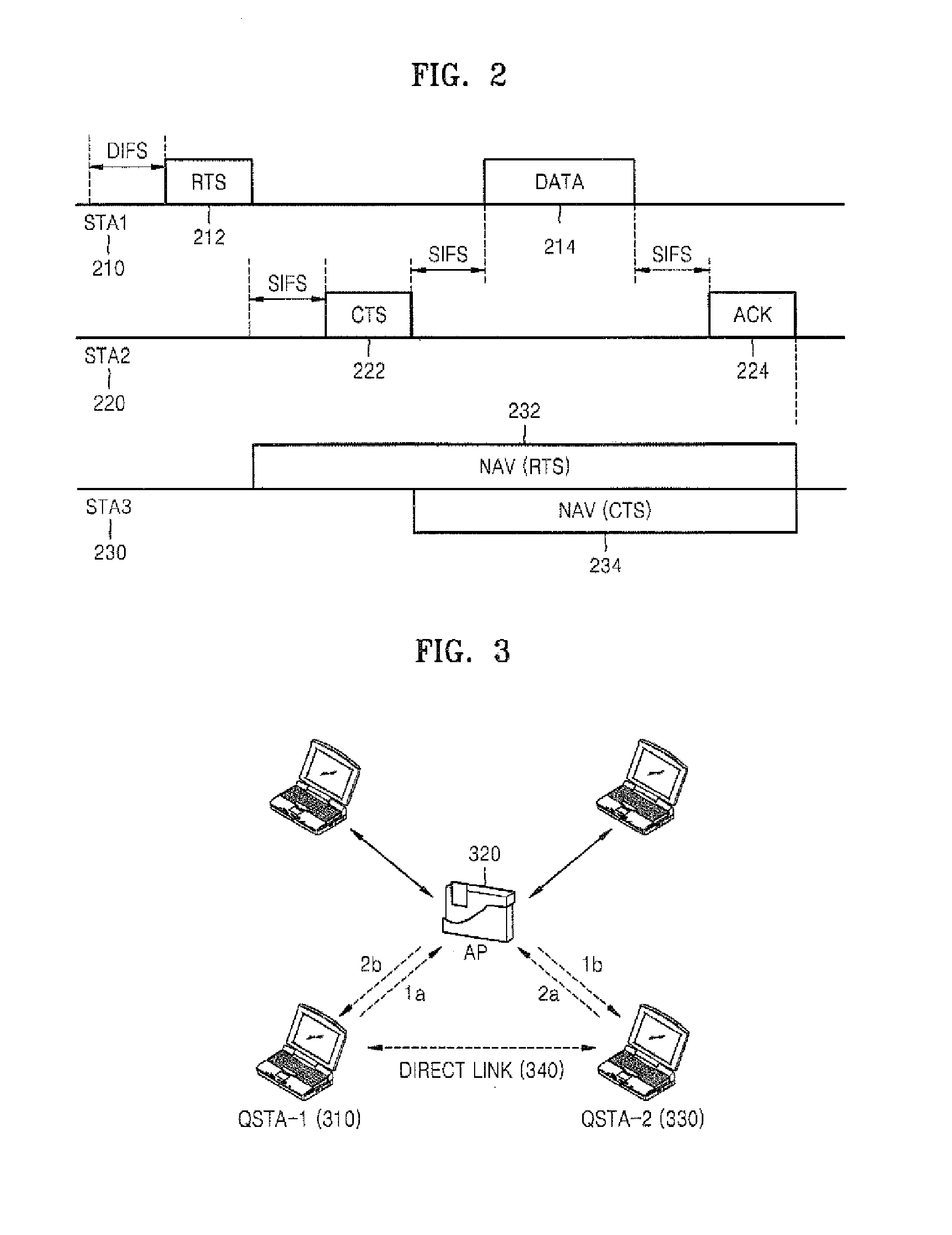
Communication method using direct link in wireless network and apparatus therefor
InactiveUS20080075038A1Minimize data lossStable and high transmission rateReceivers monitoringData switching by path configurationRadar signalsWireless network
A communication method using a direct link in a wireless network and an apparatus therefor are provided. Accordingly, it is determined whether the quality of a link channel is lower than a level during communication using the direct link or whether a signal which is received through the channel includes a radar signal, and the direct link channel is selectively changed to a new channel based on the determination result.
Owner:SAMSUNG ELECTRONICS CO LTD
Handover method and apparatus
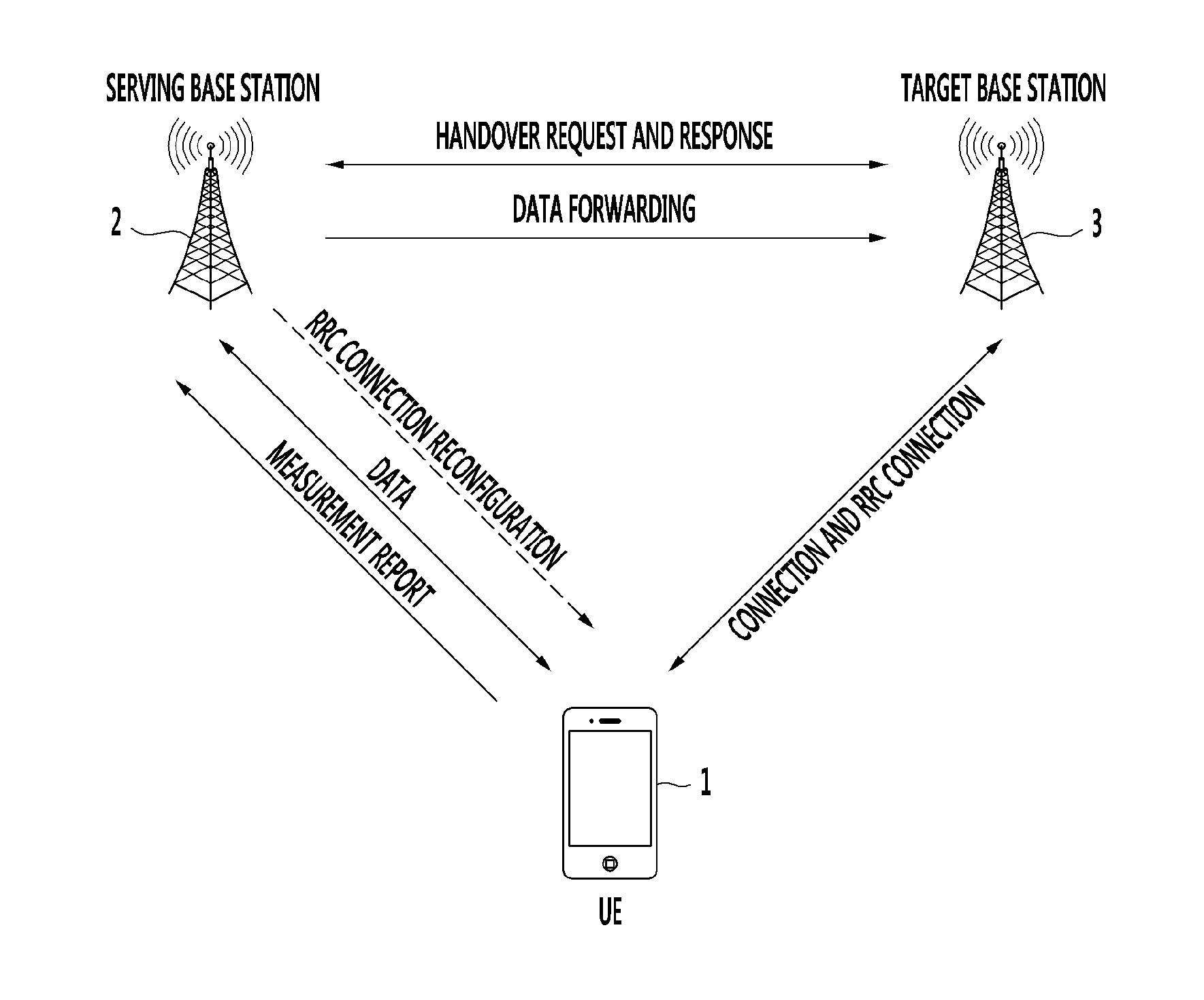
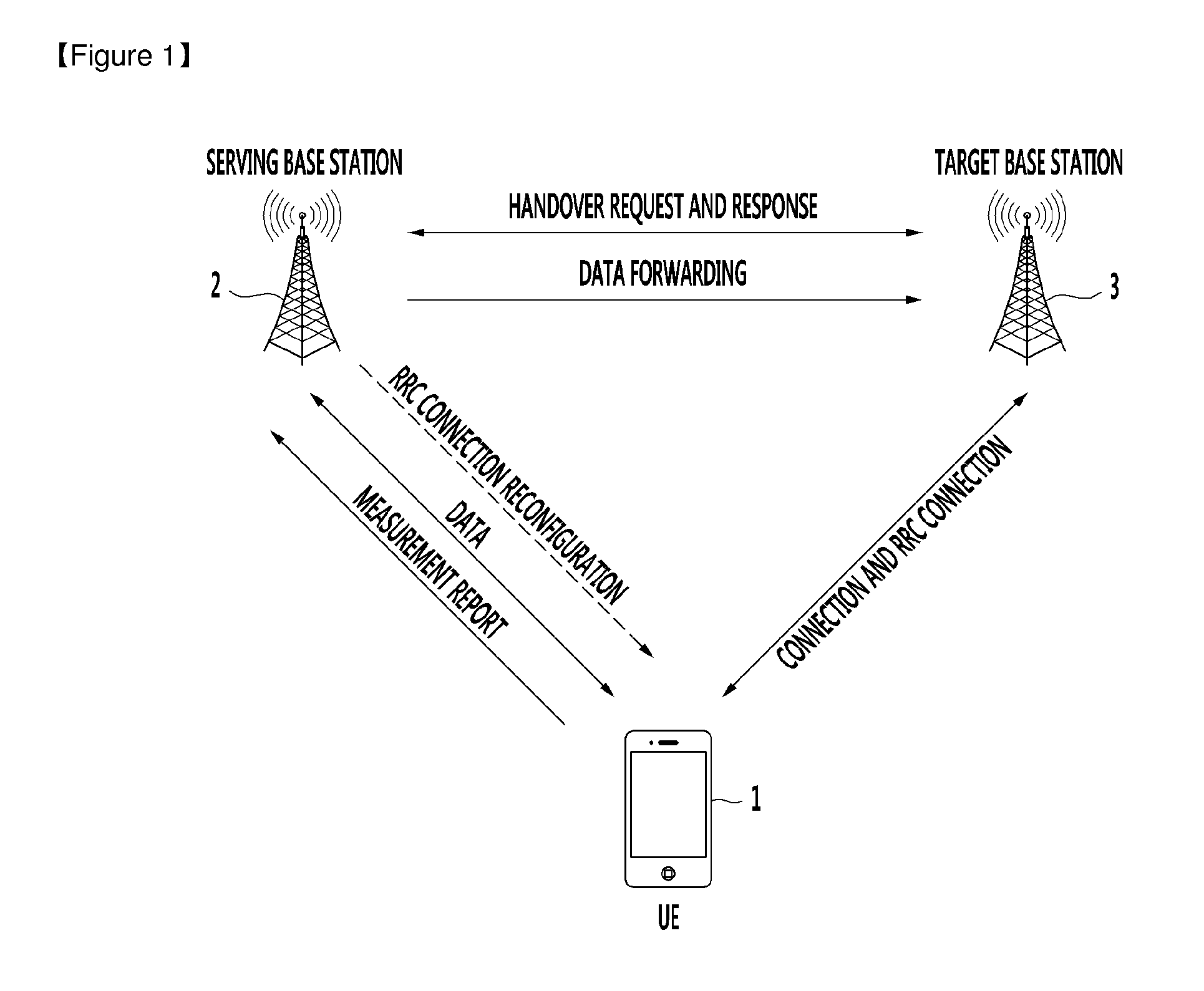
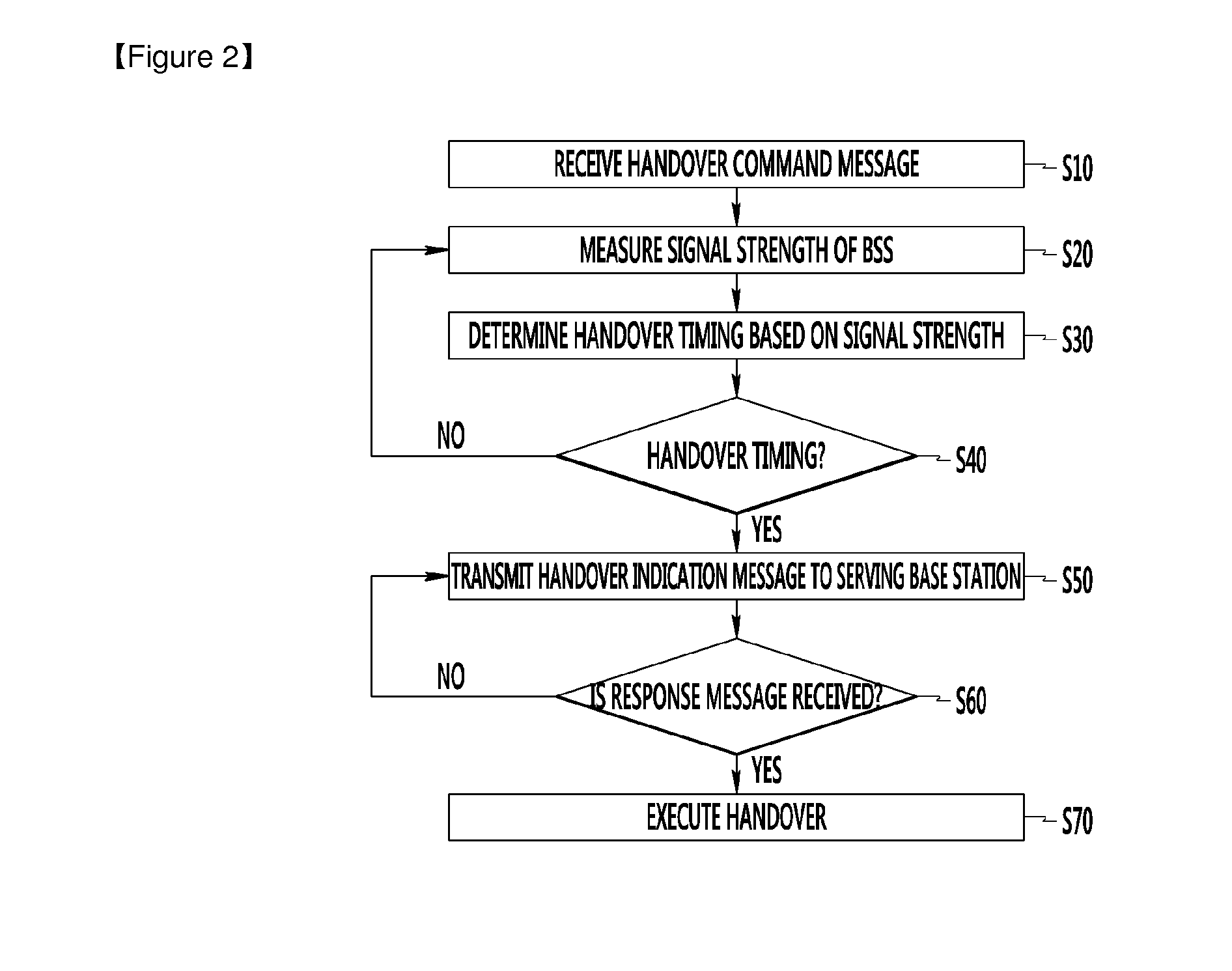
ActiveUS20150181493A1Increase success rateReduce data outage timeWireless communicationHandoverBase station
A UE does not immediately perform handover after receiving a handover command from a serving base station, but instead backups that message and continuously compares the signal strength of a serving base station and the signal strength of a target base station and performs a handover to the target base station at the best timing when handover is required. Once the timing of handover is determined, the UE transmits a handover indication message to the serving base station, and thereafter the UE performs a handover to the target base station.
Owner:ELECTRONICS & TELECOMM RES INST
Data forwarding method and system for vertical handover
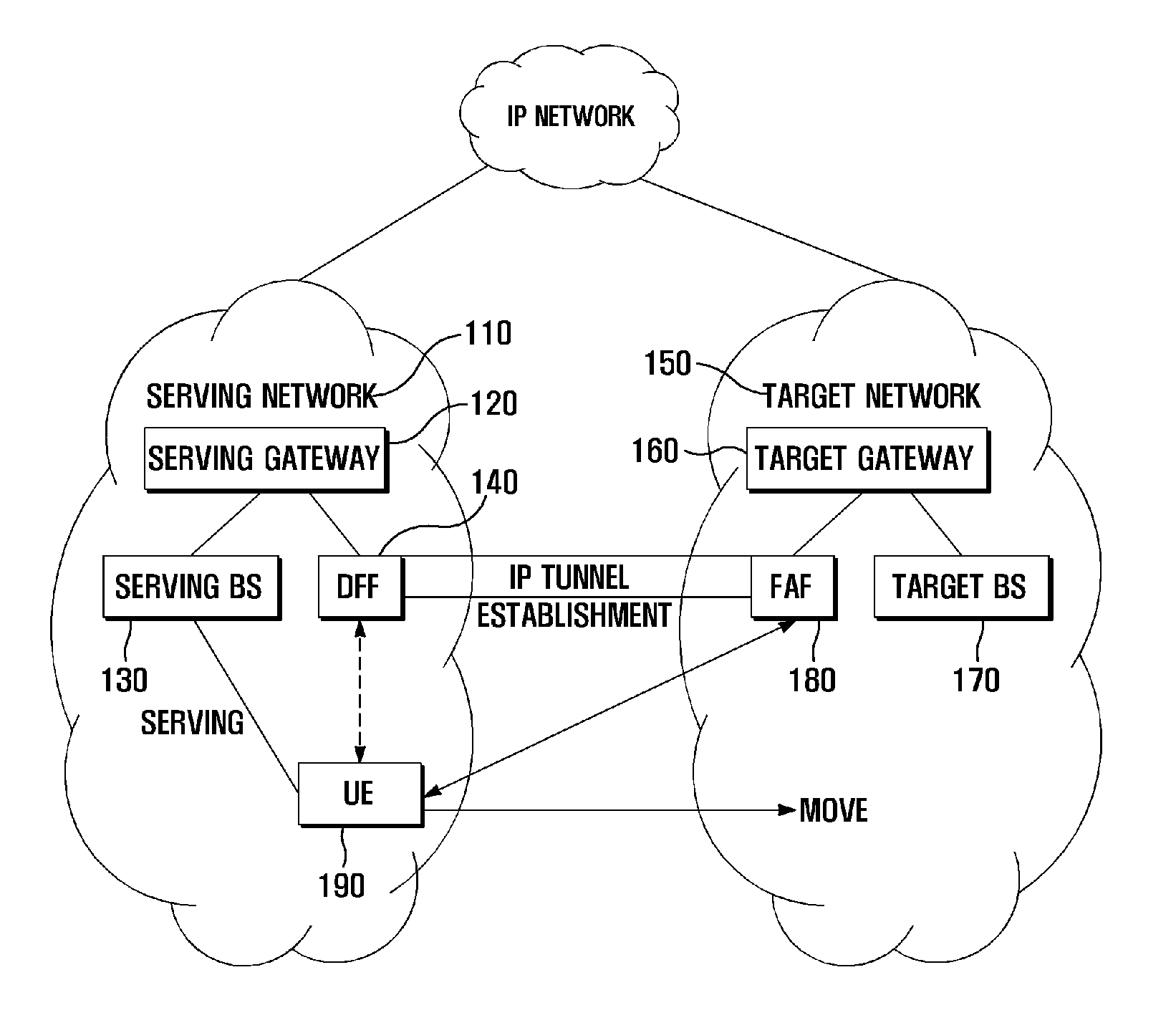
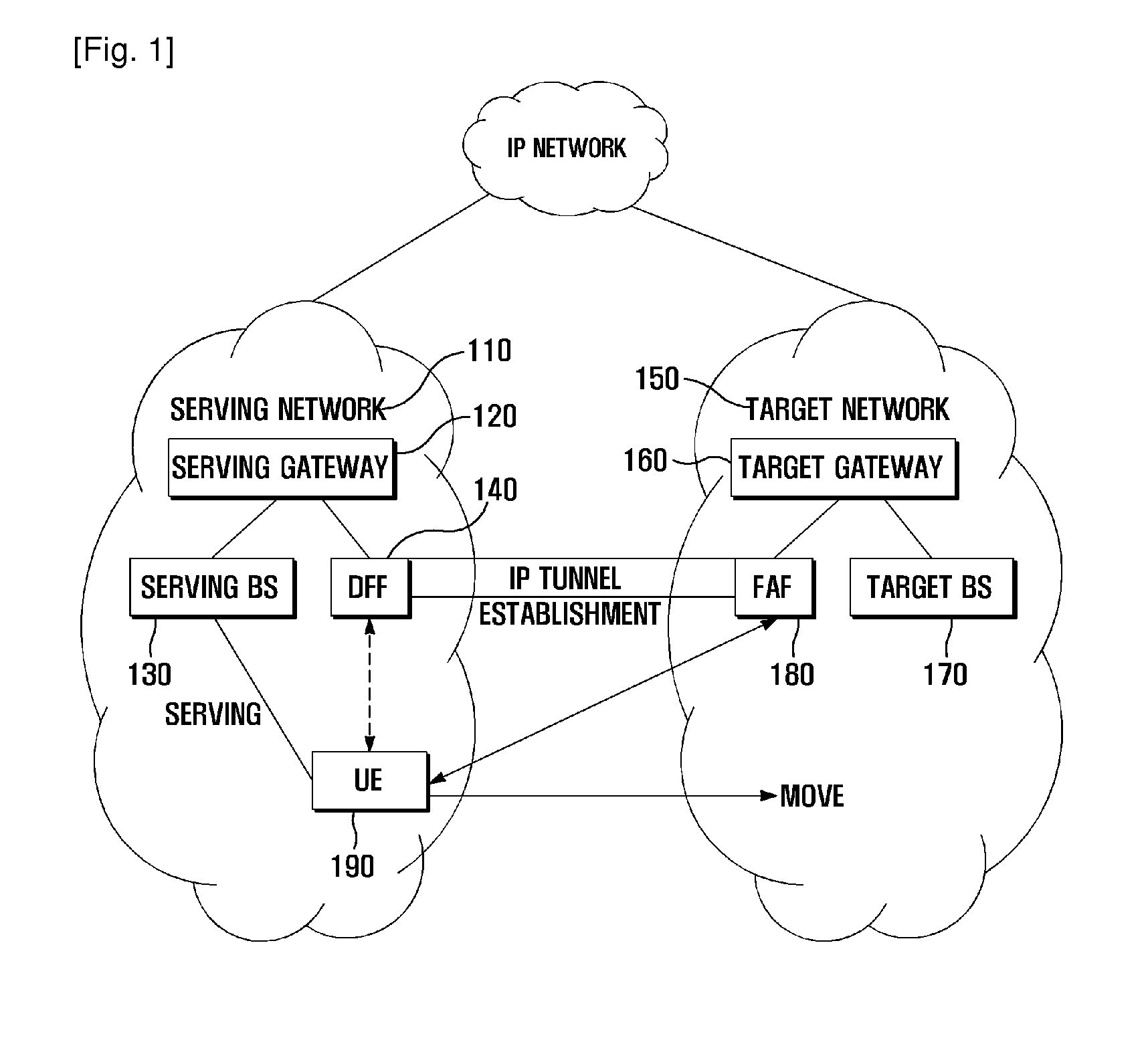
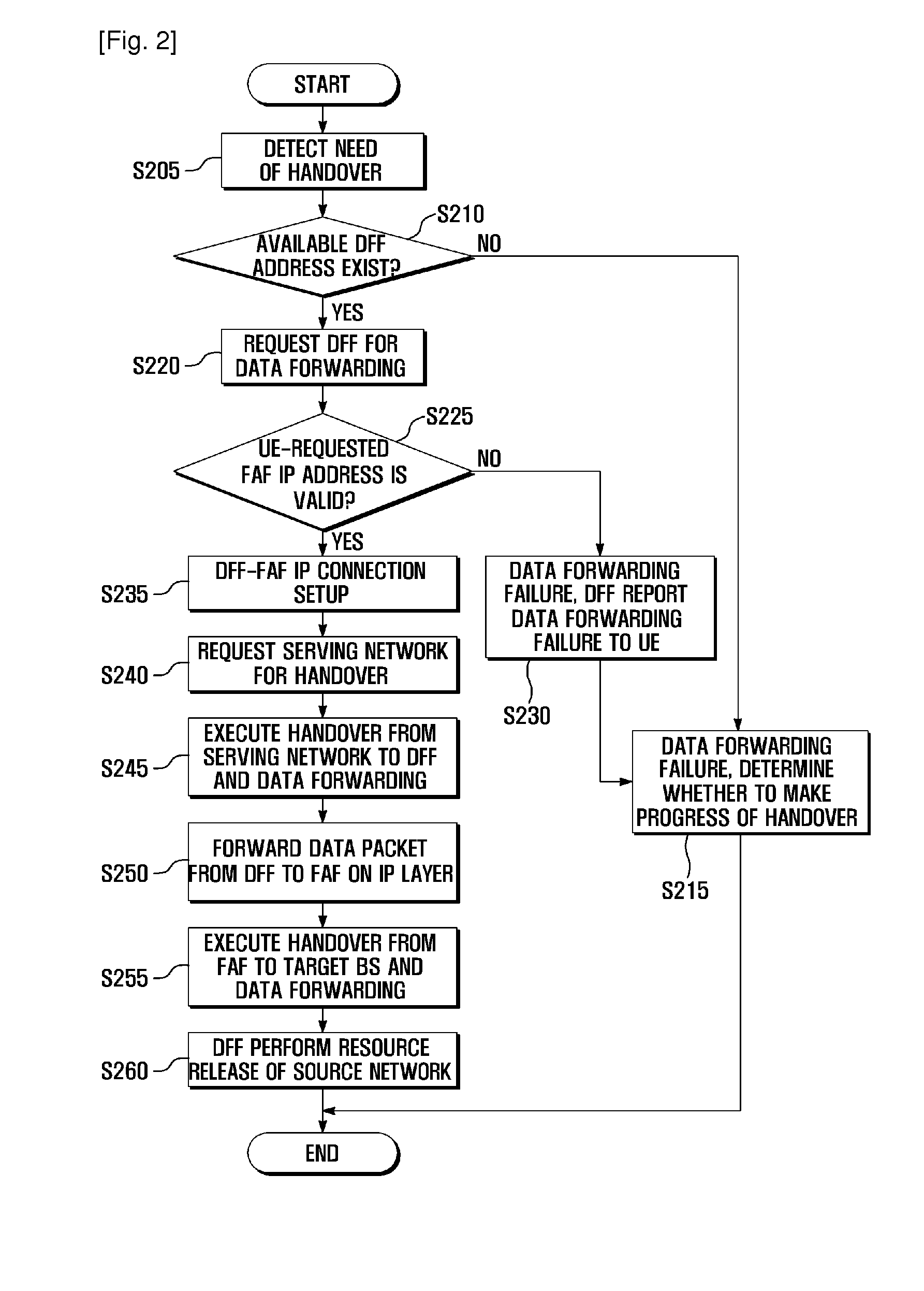
ActiveUS20110211559A1Minimize data lossWireless commuication servicesSecuring communicationIP tunnelData loss
A data forwarding method and system is provided for avoiding data loss during a vertical handover by forwarding data through an IP tunnel established between a newly introduced network entity called a Data Forwarding Function of the serving network and a Forward Attachment Function of a target network. A data forwarding method of a data forwarding unit located in a serving network for a vertical handover according to the present invention includes receiving an address of a forwarding attachment unit located in a target network and a data forwarding preparation request that are transmitted by a user equipment; establishing an Internet Protocol (IP) tunnel to the forwarding attachment unit according to the data forwarding preparation request; and forwarding, when a vertical handover is initiated, handover packets to the forwarding attachment unit through the IP tunnel.
Owner:SAMSUNG ELECTRONICS CO LTD +1
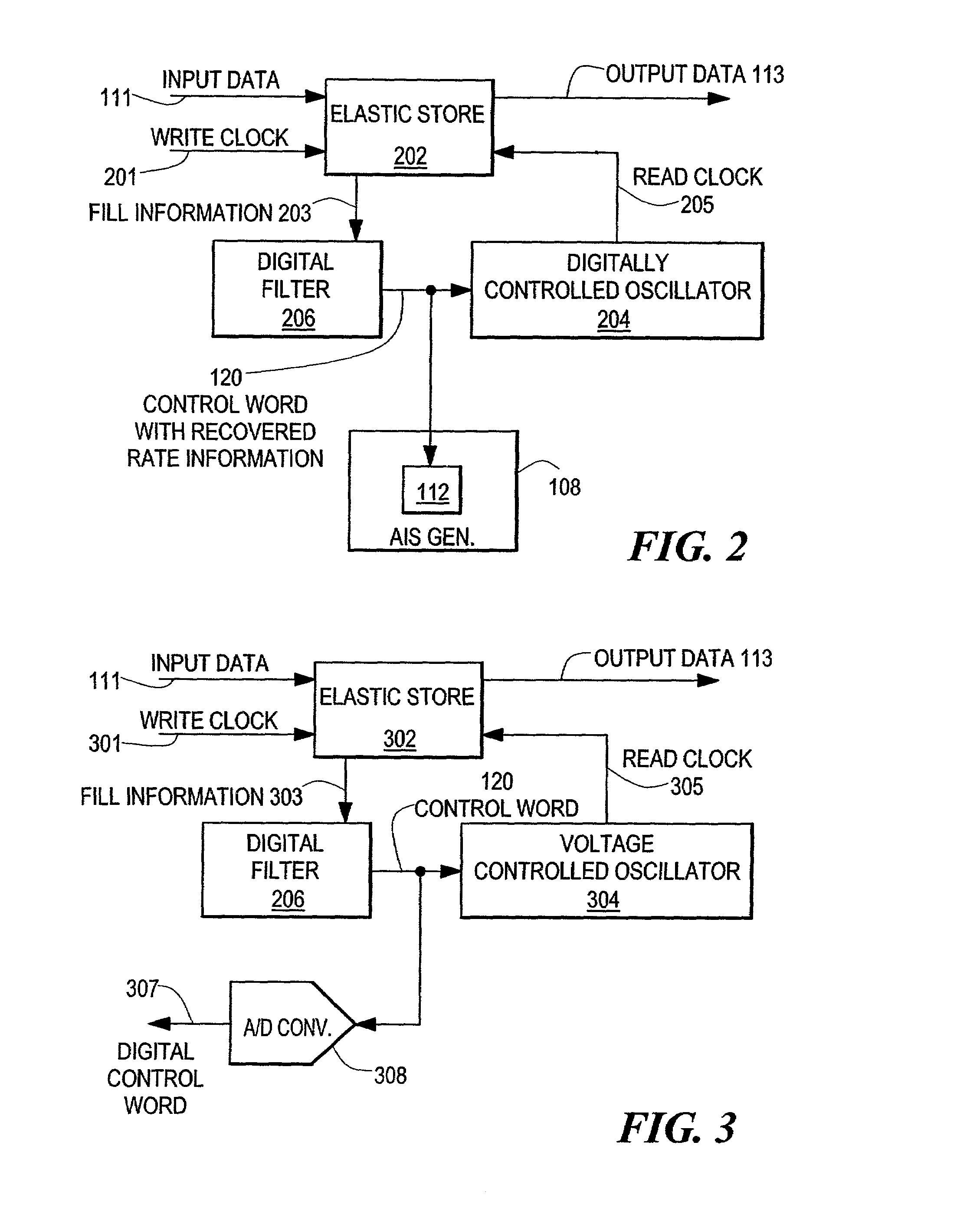
Method and apparatus for improving data integrity and desynchronizer recovery time after a loss of signal
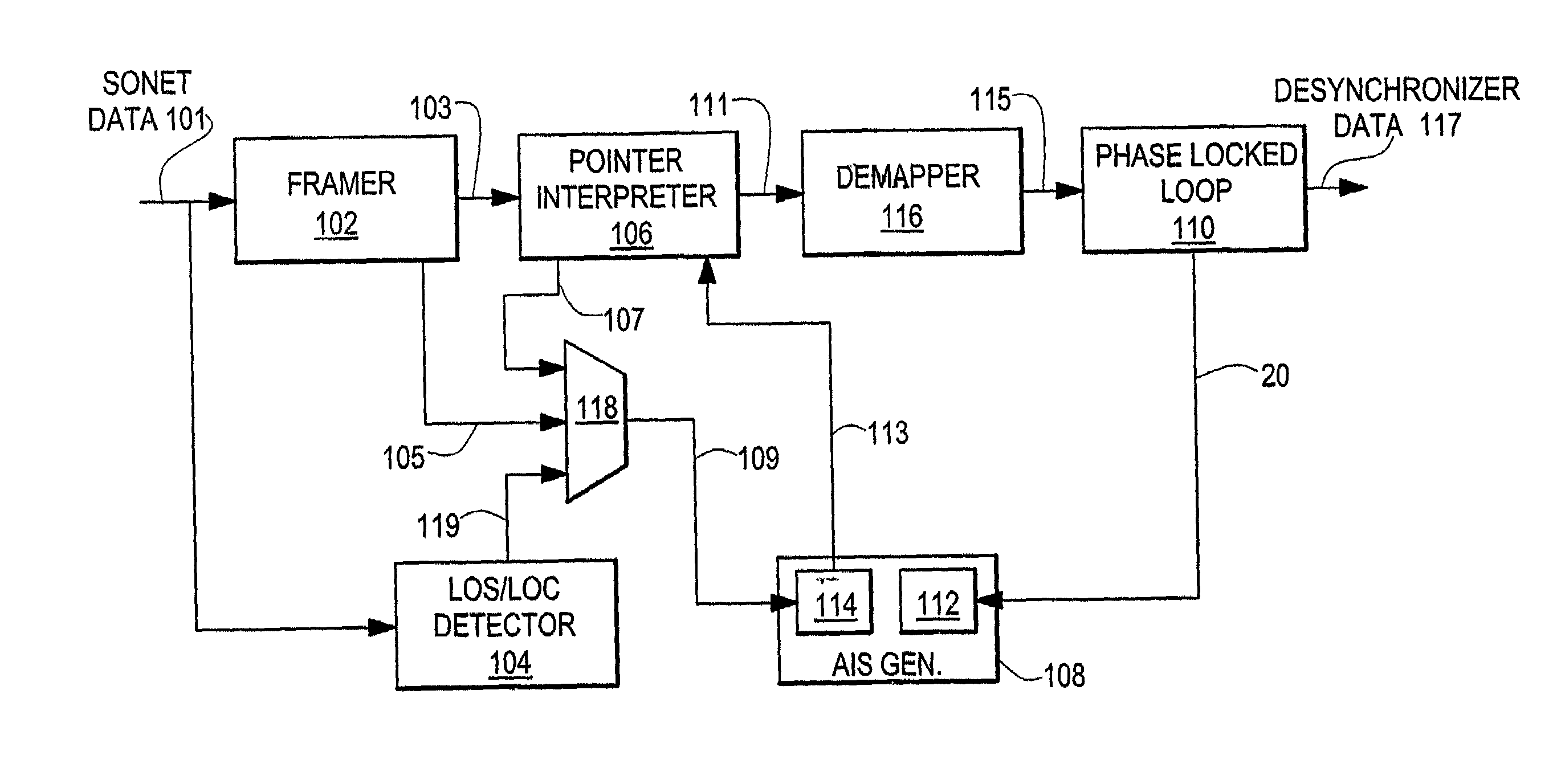
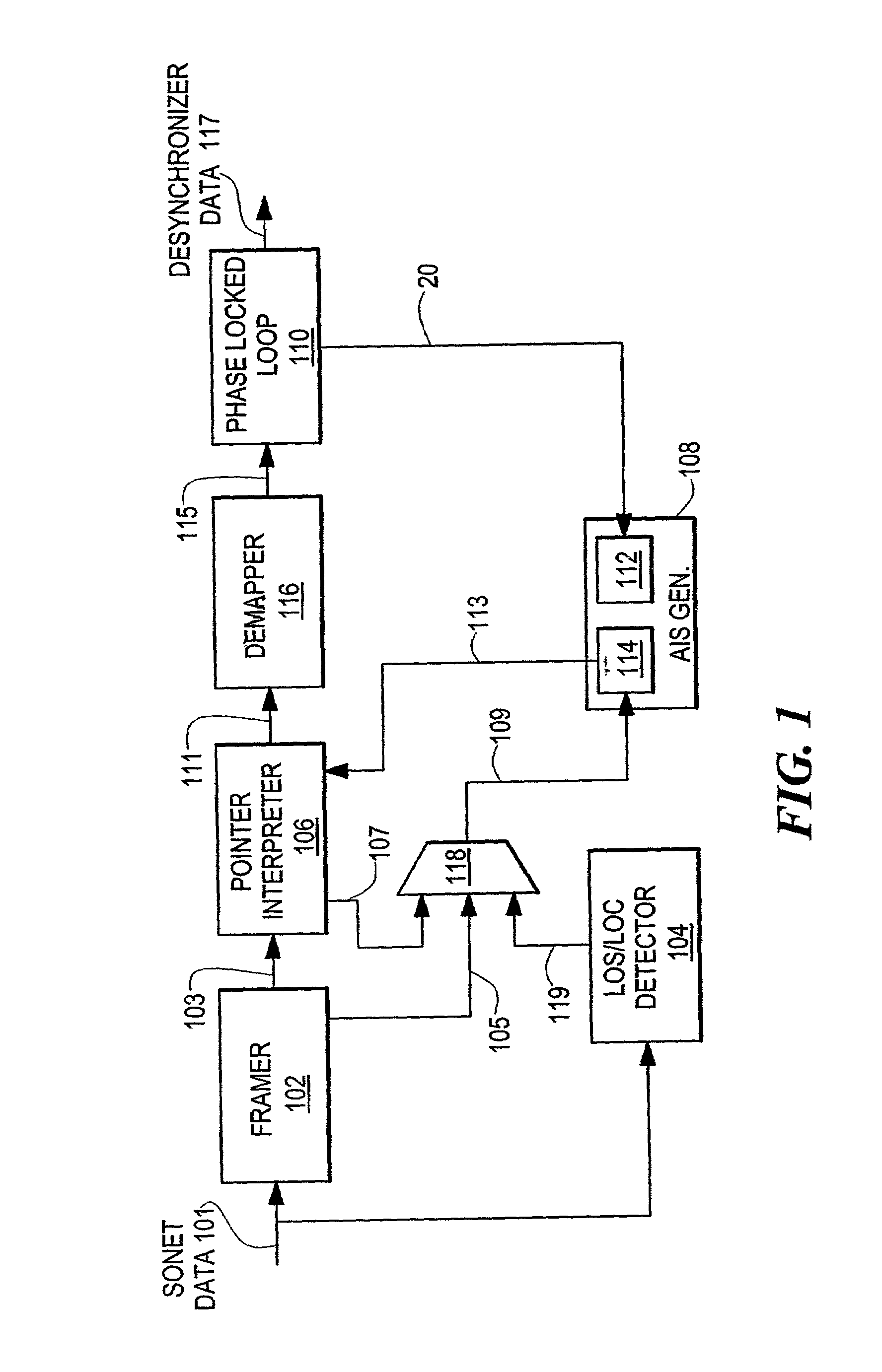
ActiveUS6999480B2Avoid data lossMinimize data lossPulse transformerError preventionData streamData integrity
An apparatus and corresponding method for preventing data loss in network devices is disclosed. The present invention monitors an incoming data stream to a network device, or devices, and in the event that an error condition is detected, predetermined error data is inserted into the data stream, wherein the predetermined error data is provided at the same data rate as the recovered data rate internal to the network device. Thus, the network device will not have to adjust to a different data rate and potentially lose data during the adjustment period.
Owner:MACOM CONNECTIVITY SOLUTIONS LLC
Transfer of communication sessions between base stations in wireless networks
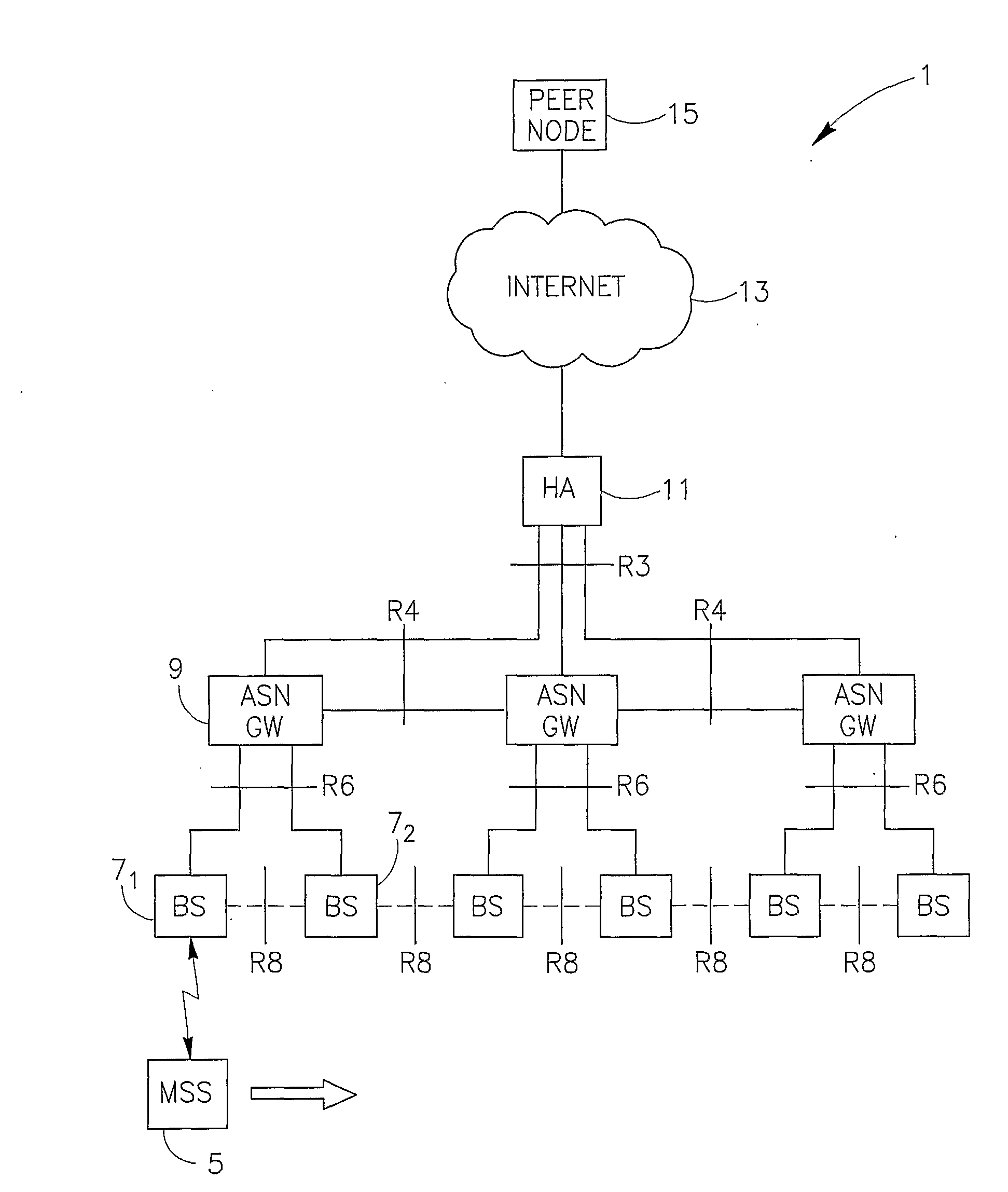
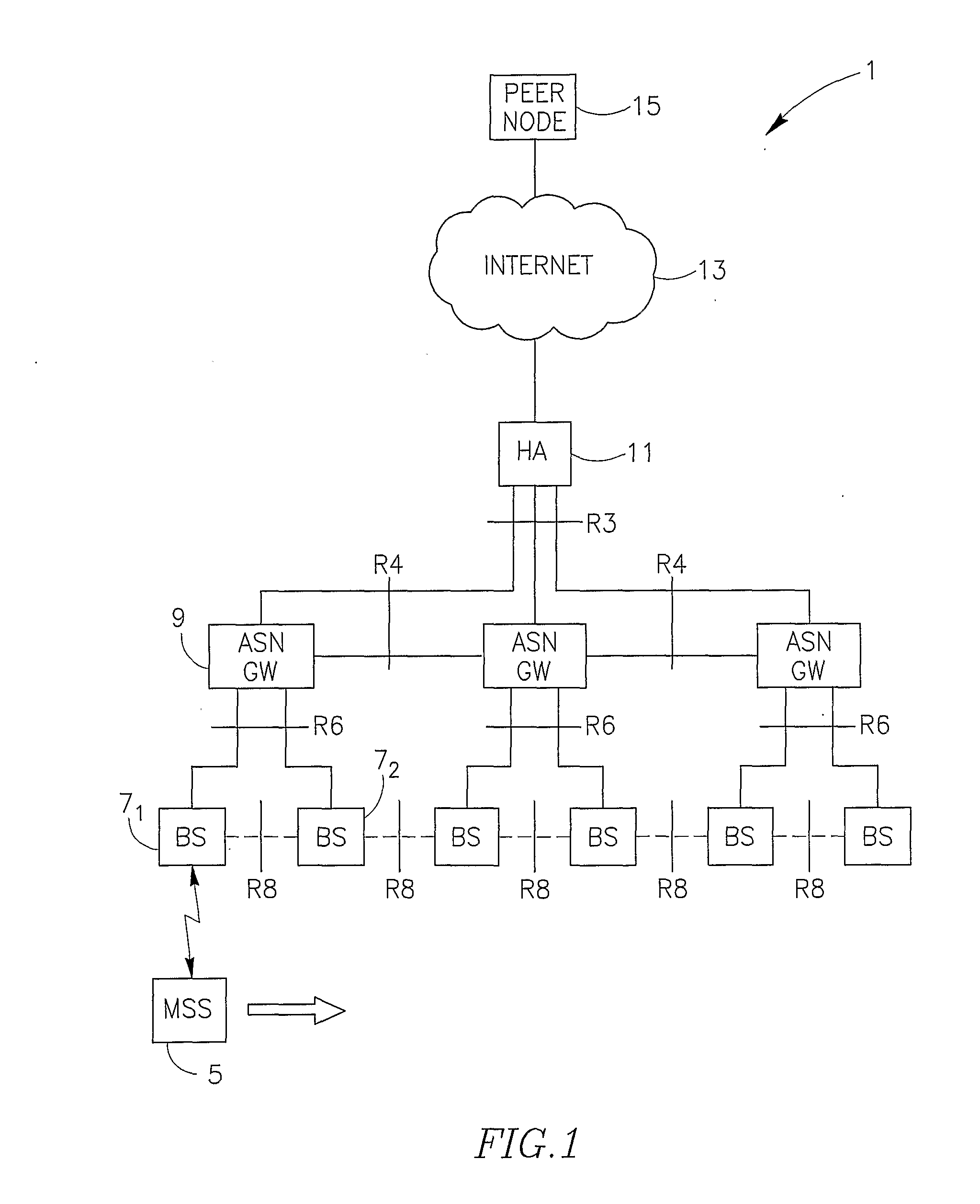
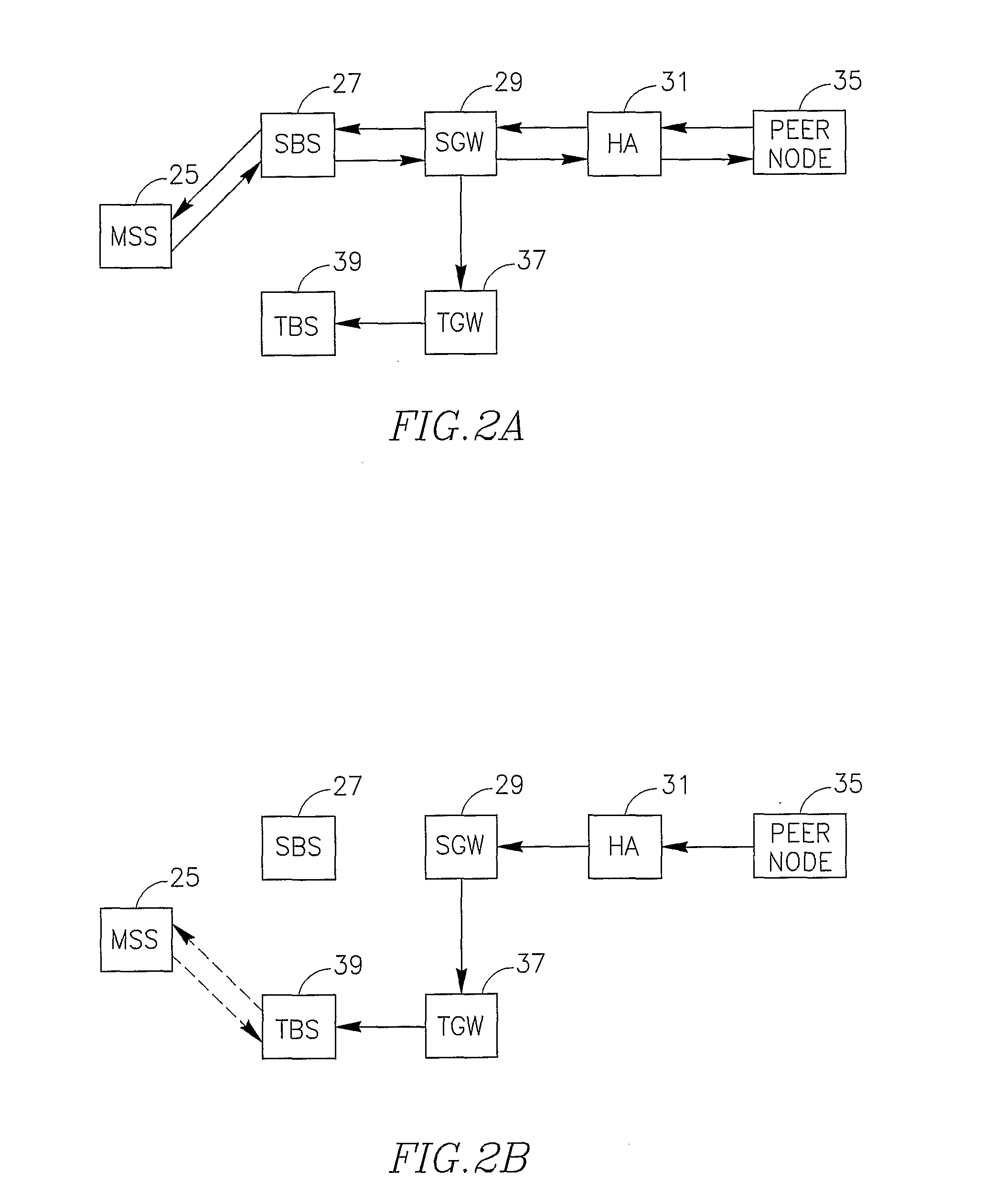
InactiveUS20090213810A1Minimize data lossPromote regenerationWireless network protocolsWireless commuication servicesTelecommunicationsWireless network
A method and devices are provided to enable continuing a communication session currently carried by a mobile subscriber station (MSS) while switching from a first base station to a second base station. During the communication session that is being held with the MSS, a first IP datagram is determined from among a plurality of IP datagrams associated with that communication session and received at a network gateway adapted to convey IP traffic received from the MSS. Following that determination, IP datagrams that will be received at that network gateway after that first IP datagram and which are addressed to the MSS are backed up. Upon establishing a connection between the MSS and the second base station, the first base station ceases to convey uplink traffic originated by the MSS, the IP datagrams that were backed up are forwarded to the MSS, and all further IP datagrams which are addressed to the MSS and received at that network gateway after establishing the connection between the MSS and the second base station, will be forwarded to the MSS through the second base station.
Owner:SPARKMOTION
Method and system for receiving broadcast service and unicast service
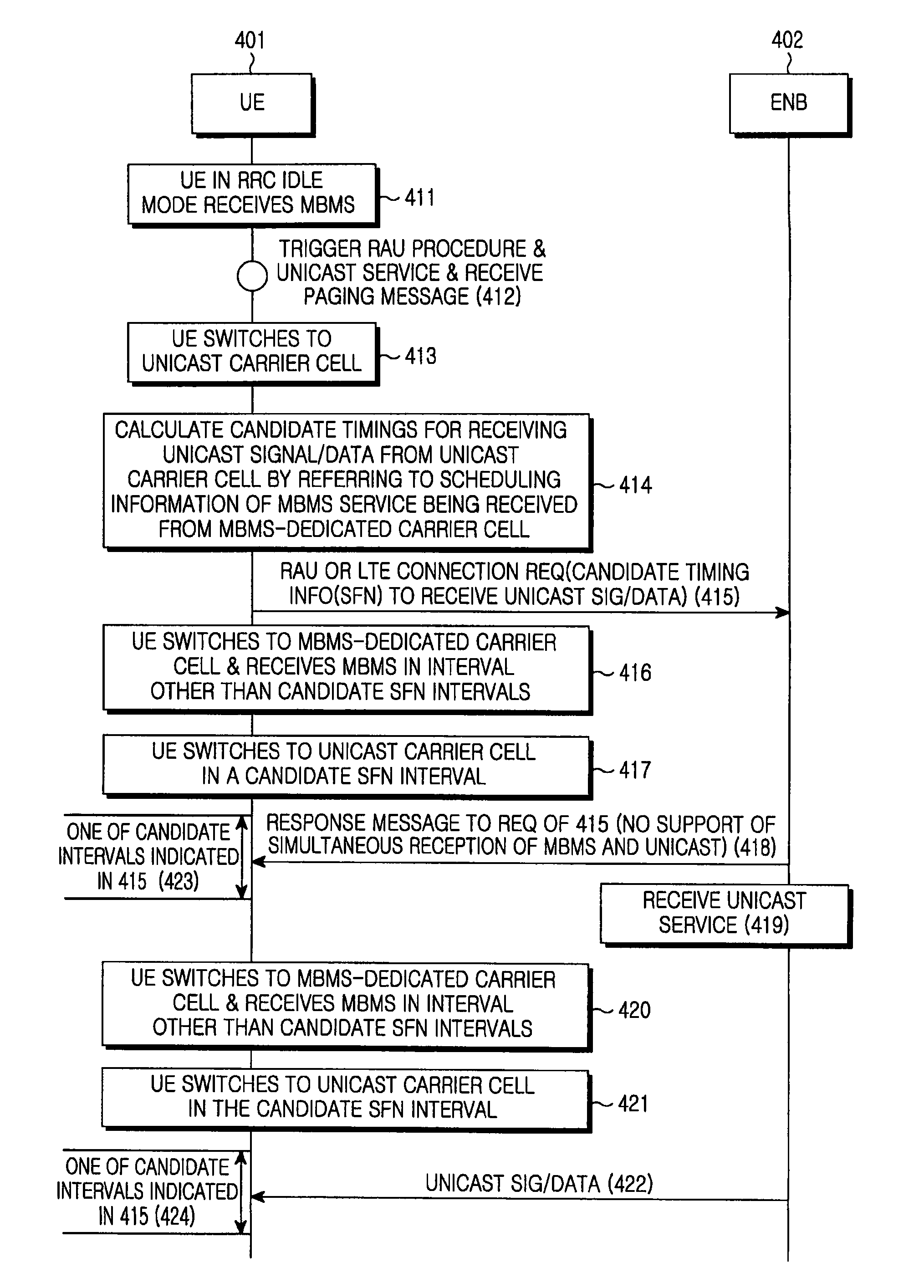
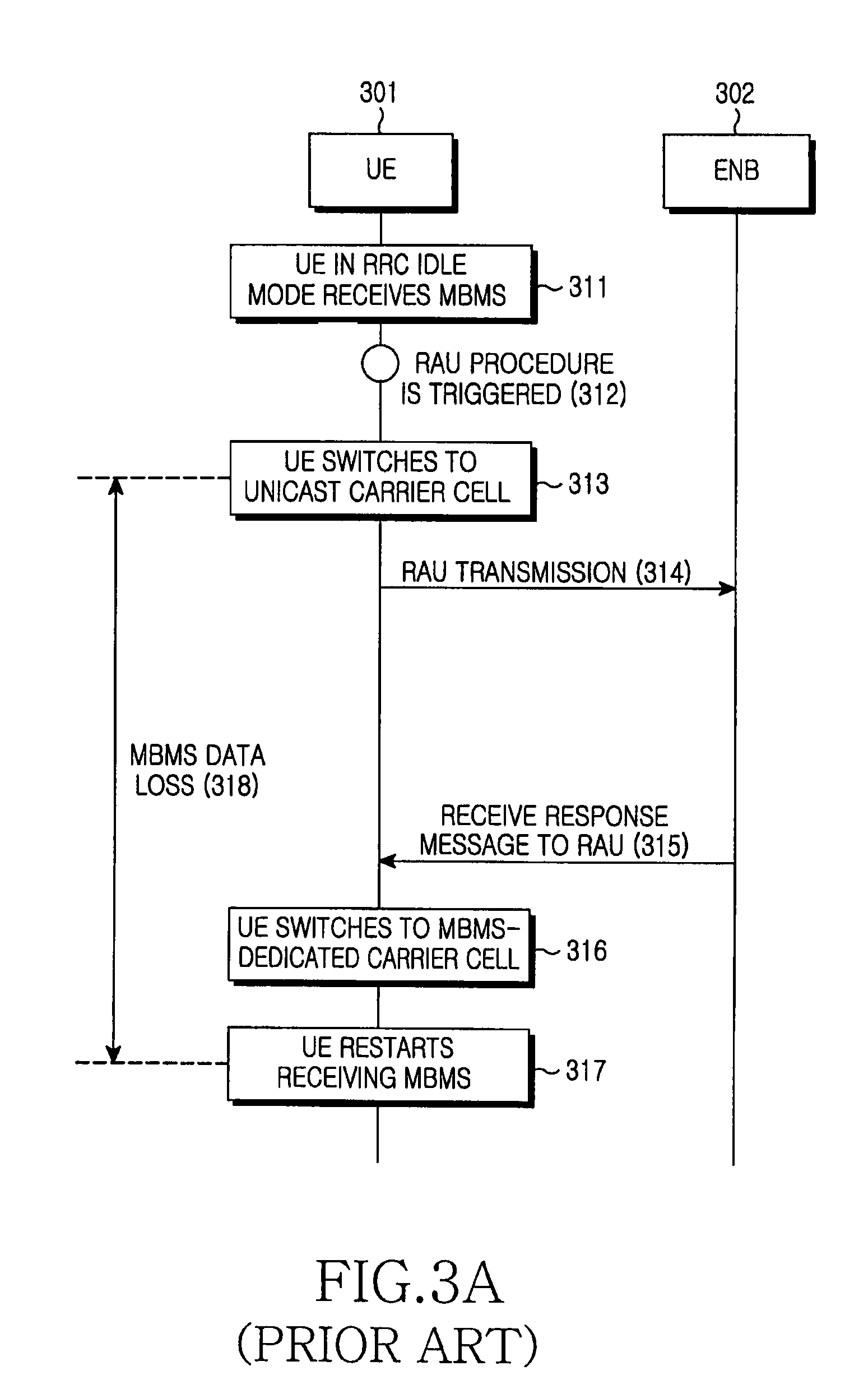
InactiveUS20080192675A1Minimizes data loss unicast data lossMinimize data lossBroadcast service distributionRadio transmissionBroadcast serviceFrequency band
A method for receiving a broadcast service and a unicast service by a UE is provided. The method includes calculating a candidate interval for receiving the unicast service by referring to scheduling information of the broadcast service by the UE, when the unicast service begins to be provided through another frequency band other than a dedicated frequency band for the broadcast service while the UE receives the broadcast service through the dedicated frequency band; notifying the scheduling information of the broadcast service and the calculated candidate interval to an ENB in charge of scheduling of the unicast service by the UE; and switching to said another frequency band and receiving the unicast service in the candidate interval, while switching to the dedicated frequency band and receiving the broadcast service in another interval other than the candidate interval, by the UE.
Owner:SAMSUNG ELECTRONICS CO LTD
Means and Methods for Improving the Handover Characteristics of Integrated Radio Access Networks
InactiveUS8019346B2Minimize data lossReduce distractionsWireless commuication servicesMessage typeRadio access network
Owner:TELEFON AB LM ERICSSON (PUBL)
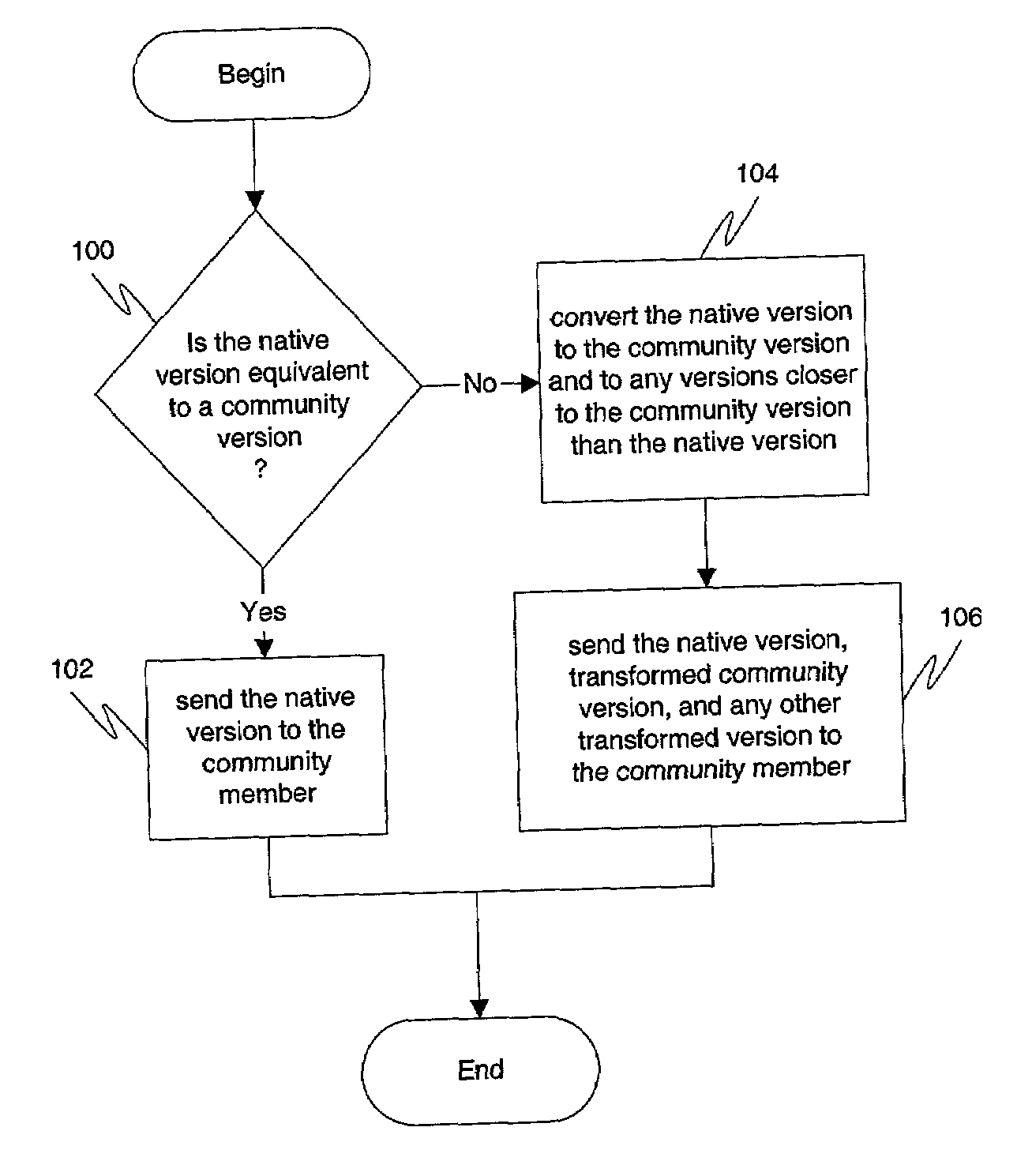
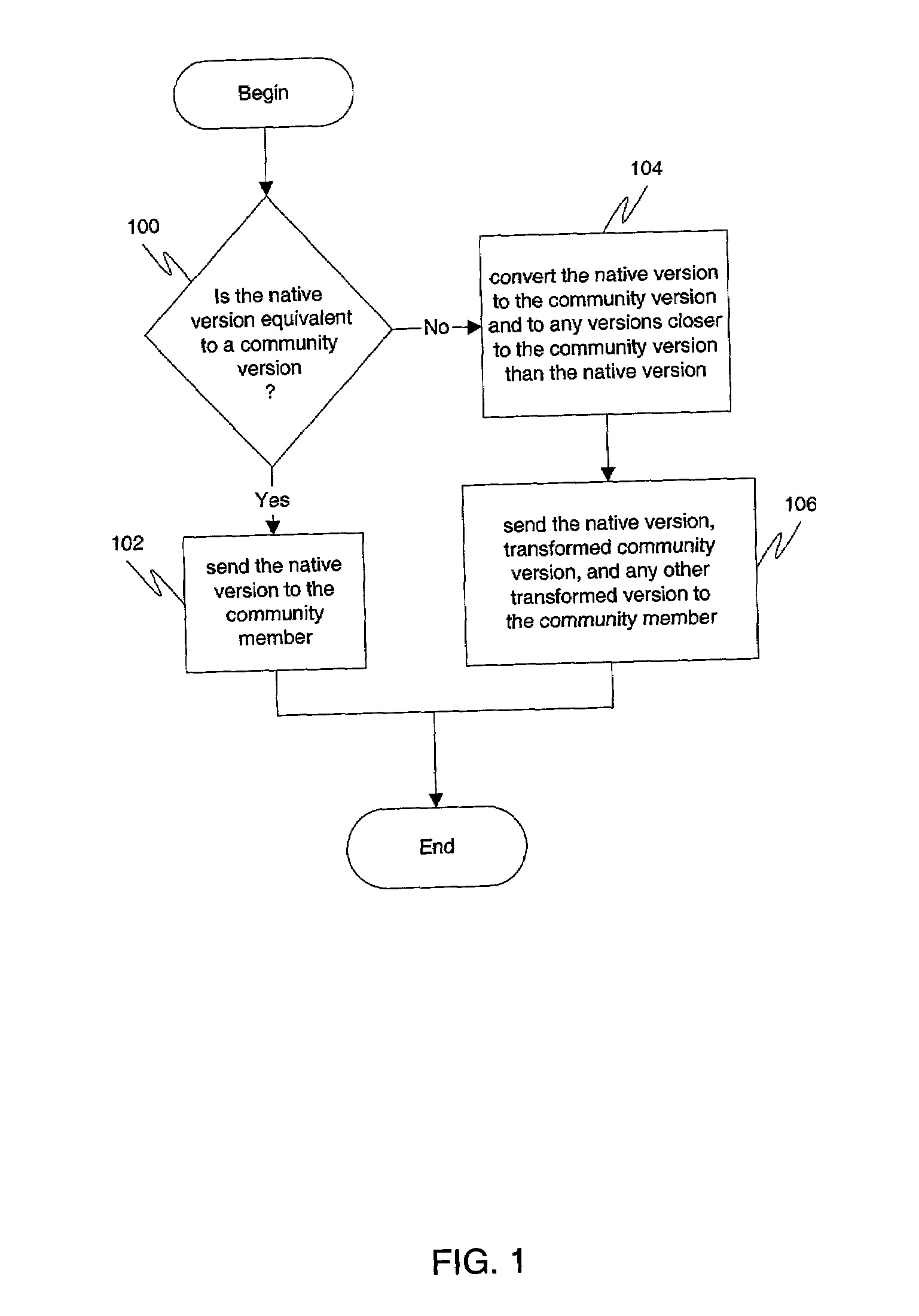
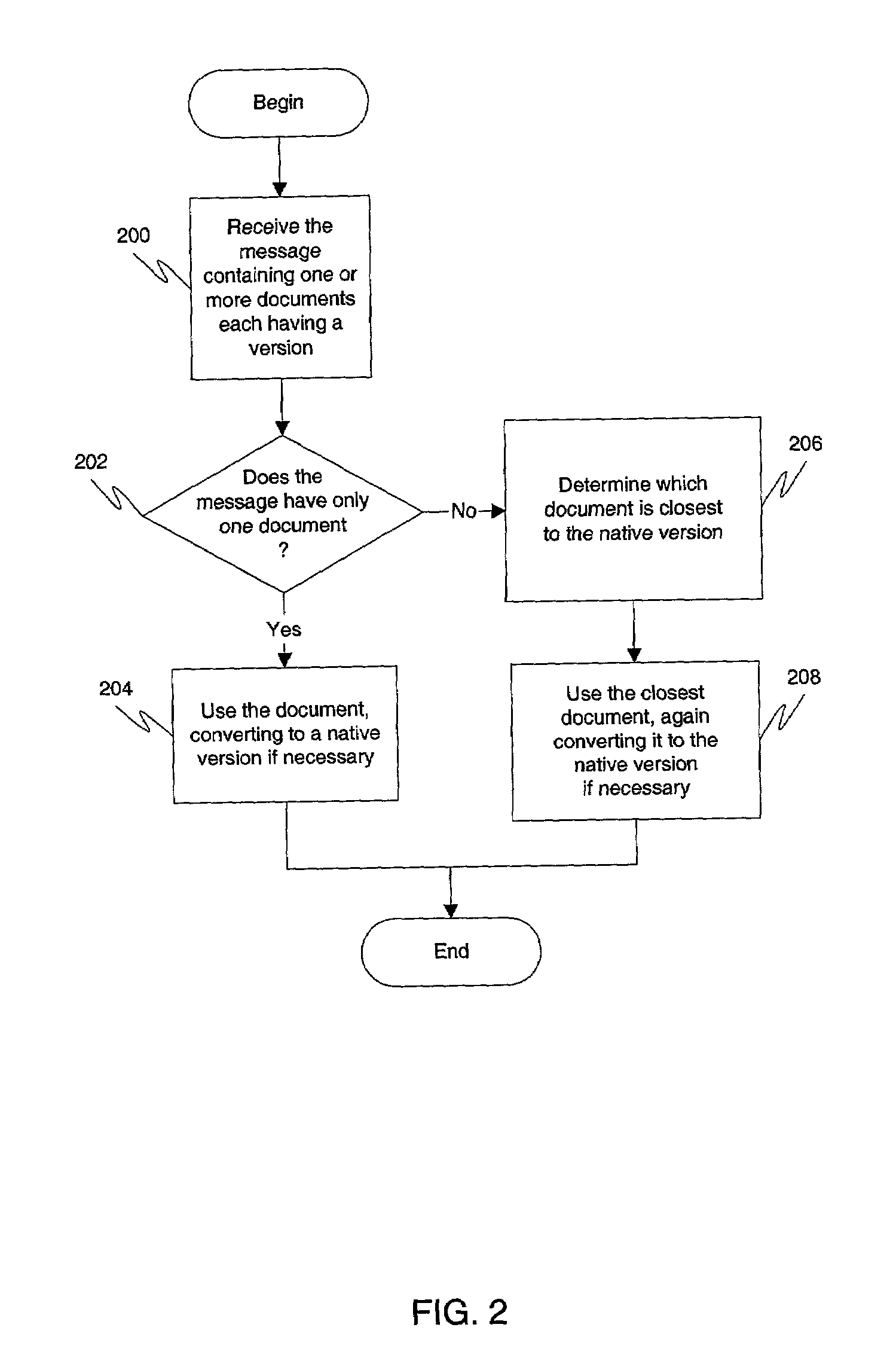
Exchanging and converting document versions
ActiveUS7013426B1Minimal data lossEasy to readDigital data processing detailsNatural language data processingApplication program softwareDocumentation procedure
Document version interoperability is provided by allowing members of a community to maintain independent migration by permitting the members to continue to run native application software on their respective systems. A community may define a community version by establishing certain rules for documents. When electronically transmitting a document, a member of the community may provide in the transmitted message containing the document his native version of the document, the community version of the document, as well as any or all versions of the document which are closer to the community version of the document than his native version of the document. This may be accomplished by performing document transformations when creating the message. Upon receipt of the documents, the recipient may choose the document version contained in the message that is most easily read by the recipient's native application program and transform it so that it may be opened by the recipients native application program if necessary. Regardless of what rules are established to define the community version, data loss in any document exchange is minimized. Entities that follow these rules can migrate their native support without requiring coordination with other entities. Members do not have to know the native version supported by other members. This ensures privacy for the members and also lessens the need for direct communications between the members.
Owner:COMMERCE ONE OPERATIONS
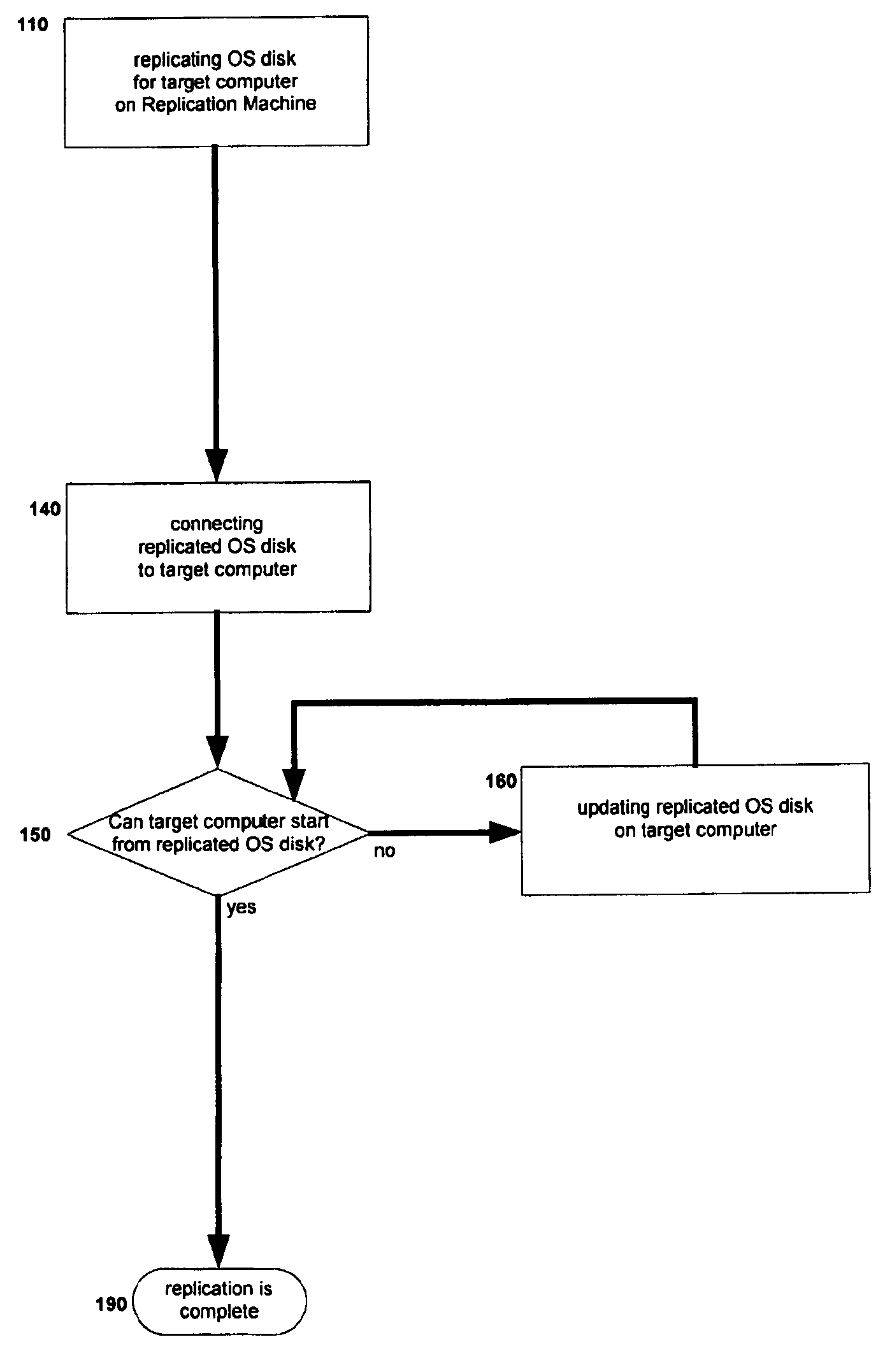
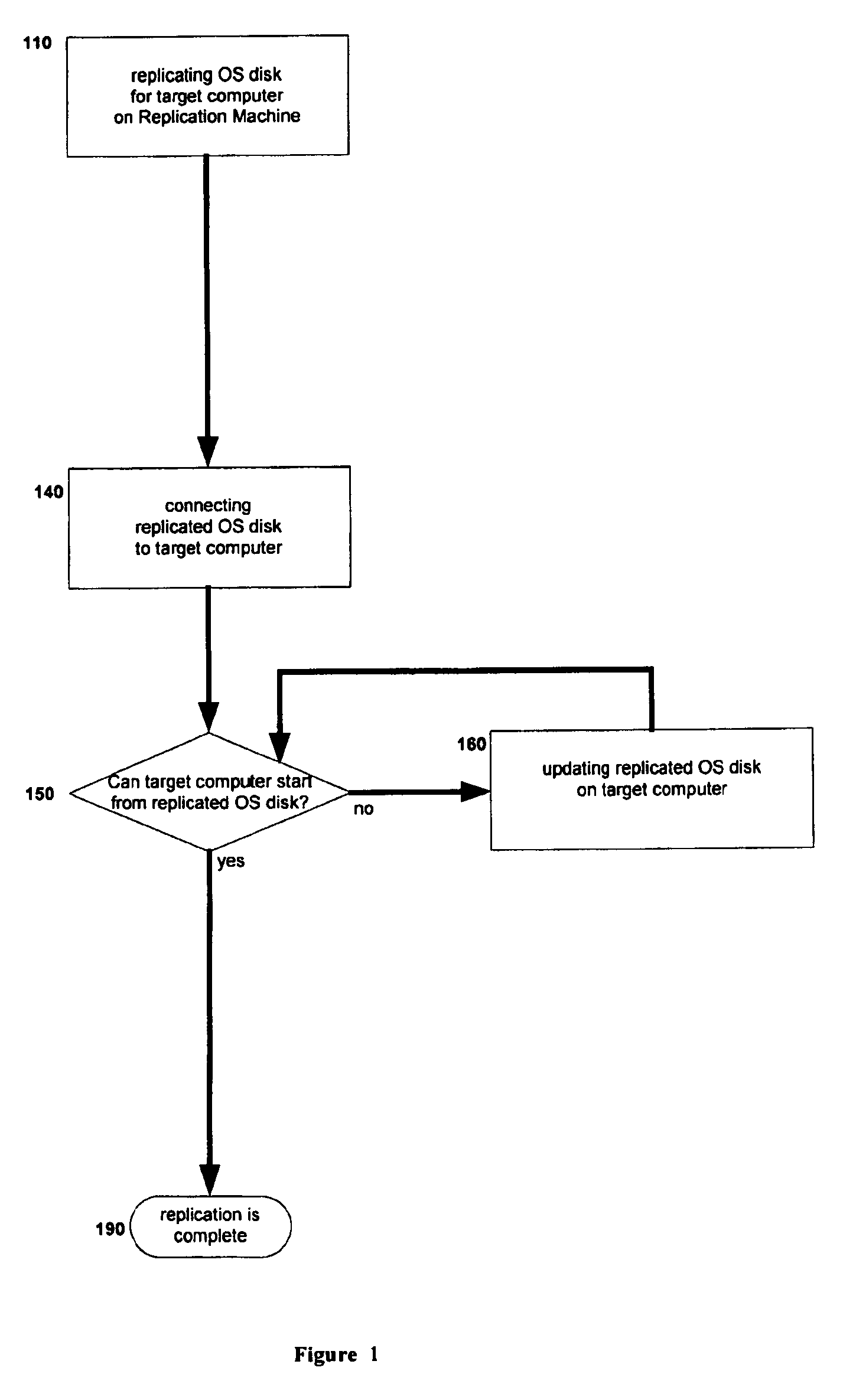
Replication machine and method of disaster recovery for computers
InactiveUS7555674B1Recovery procedure is simplifiedShorten recovery timeError detection/correctionRecovery methodOperational system
A computer replication and / or recovery system and process comprising a recovery machine which rebuilds operating system (“OS”) disks for damaged computers from their backup images. The recovery processes are performed within the recovery machine, which is a separate machine from both the damaged and replacement machines. Rebuilt OS disks are then adapted to the replacement computers with different hardware. The recovery method of the present invention is a network independent solution.
Owner:HIPROB CAPITAL MANAGEMENT
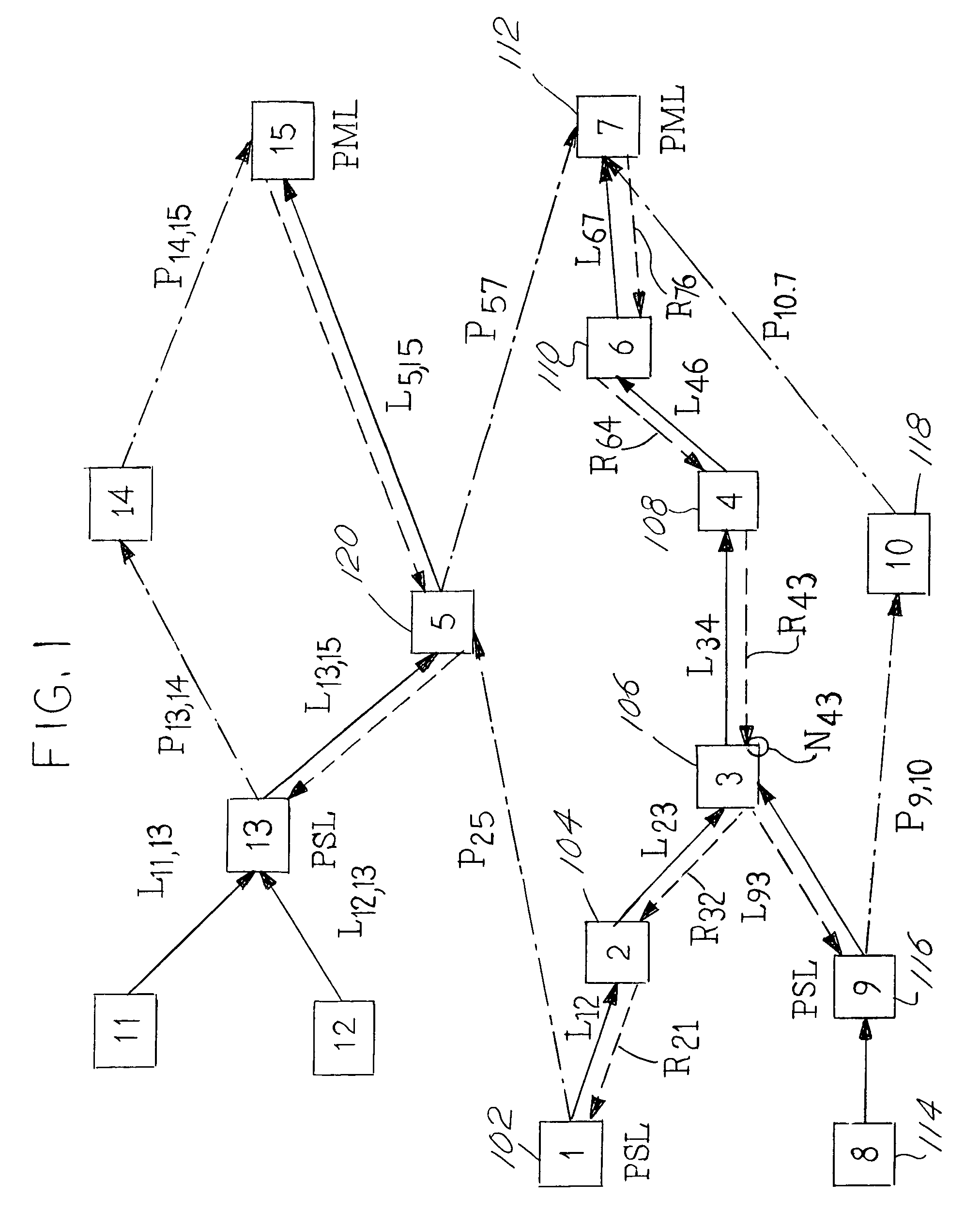
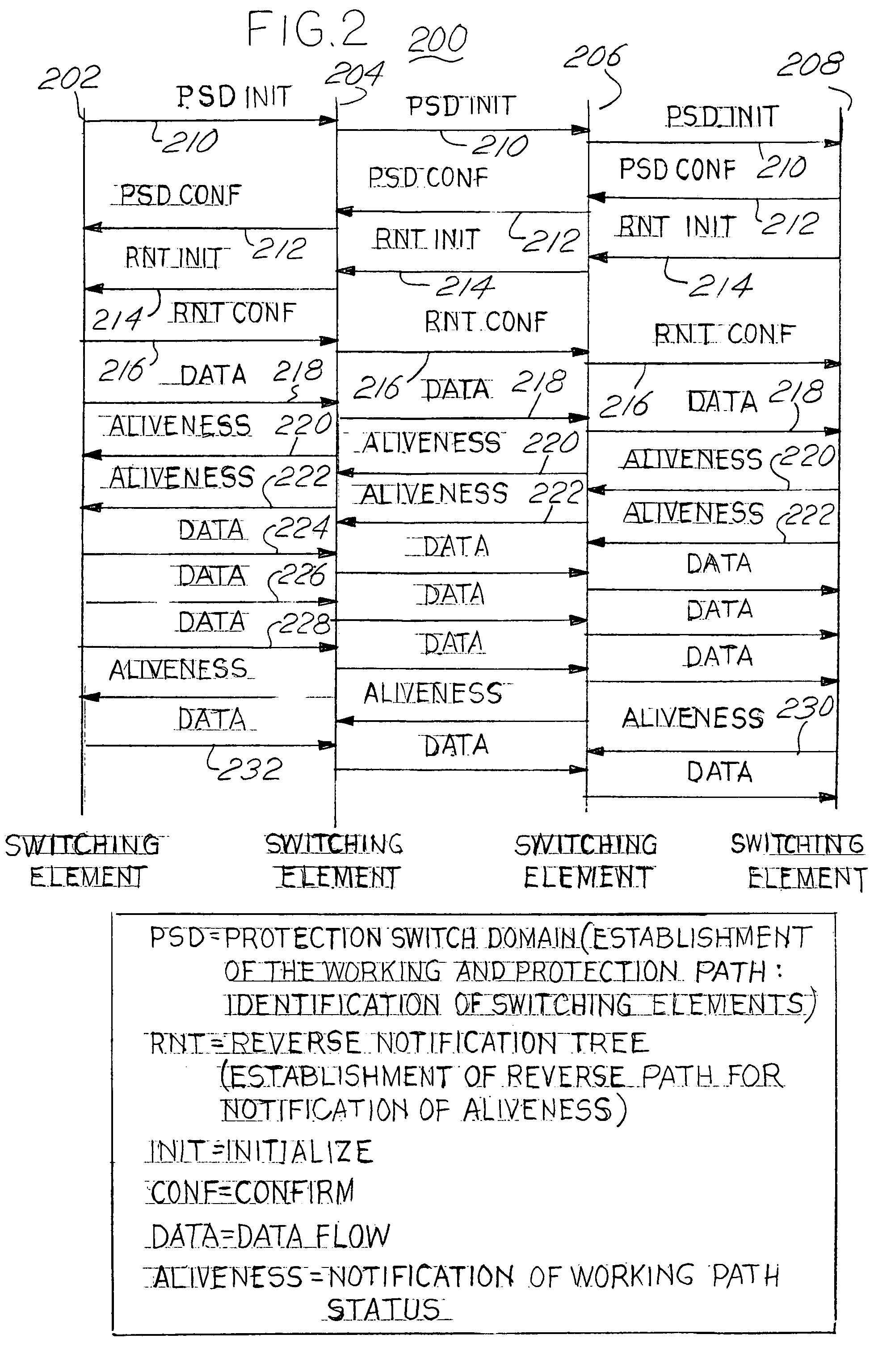
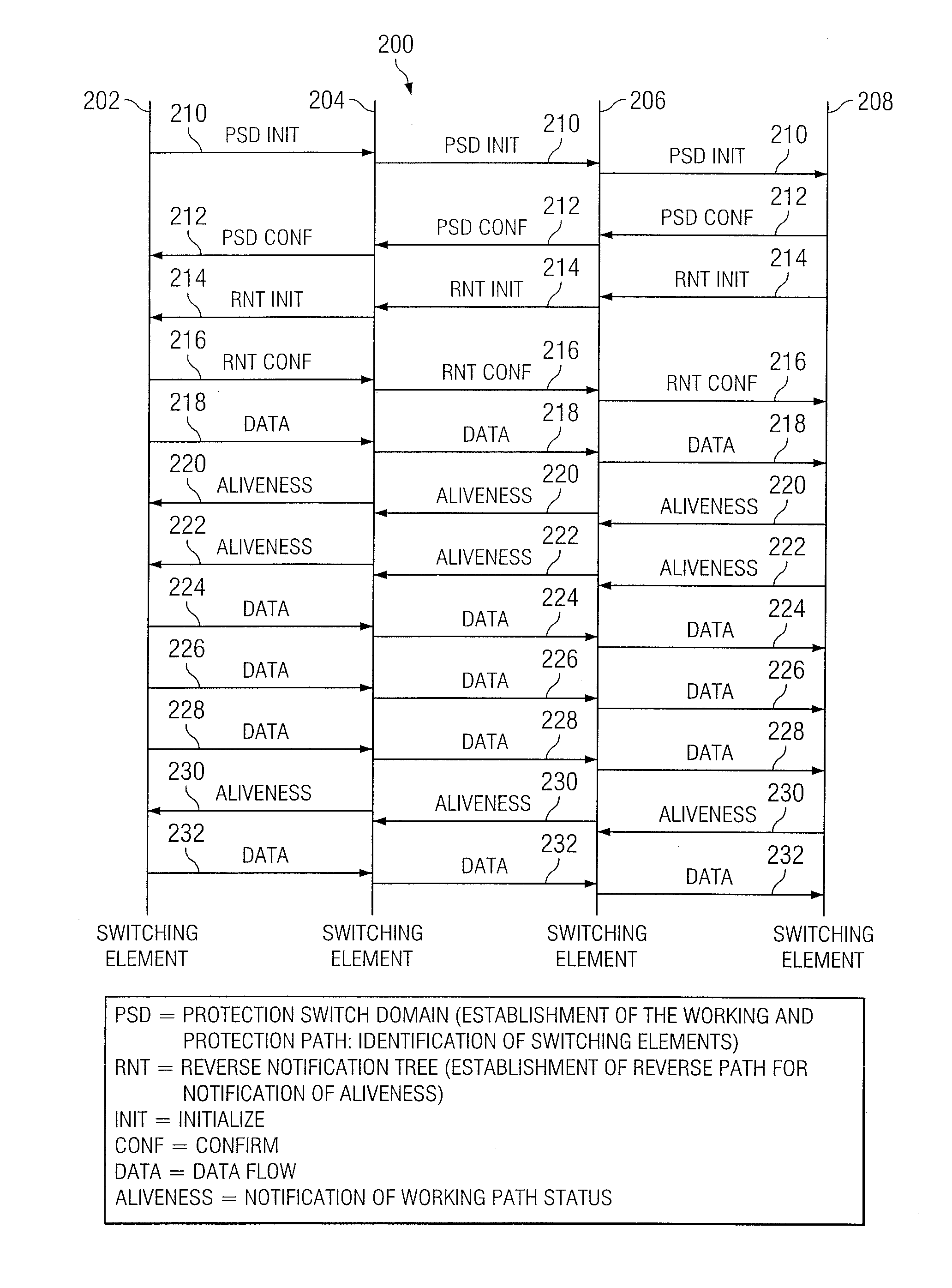
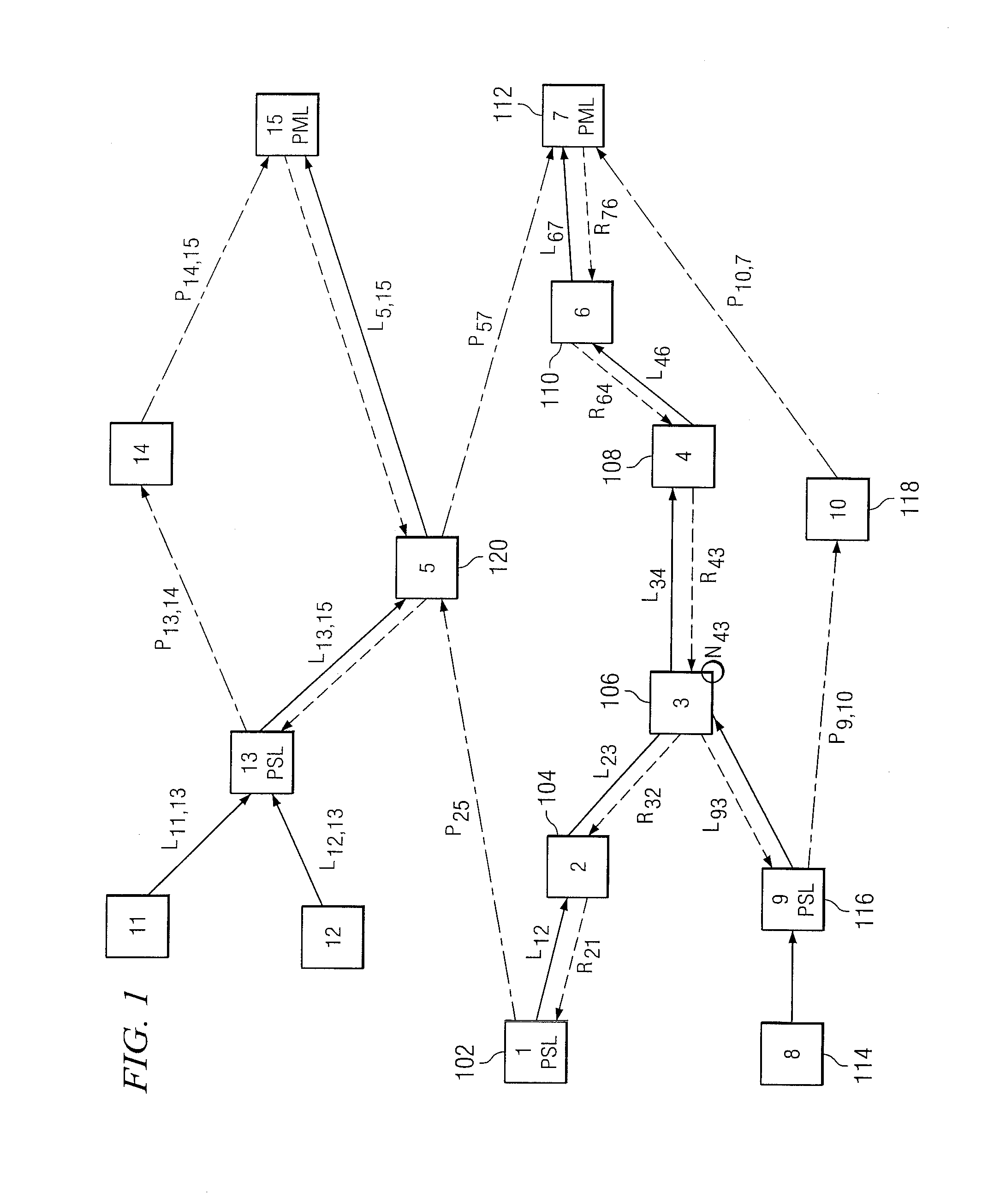
Reverse Notification Tree For Data Networks
InactiveUS20140043959A1Shorten recovery timeMinimize data lossError preventionTransmission systemsTraffic capacityEngineering
Recovery time upon the failure of a link or switching system in an asynchronous data network can be minimized if downstream data switches provide upstream messages indicating to an upstream switching system that the downstream traffic arrived intact and was properly handled. Upon this loss or failure of the upstream status message to an upstream switching system, an upstream switching system can reroute data traffic around a failed link or failed switch with a minimal amount of lost data. The upstream status message is conveyed from a downstream switching system to an upstream switching system via a reverse notification tree data pathway.
Owner:TELLABS OPERATIONS
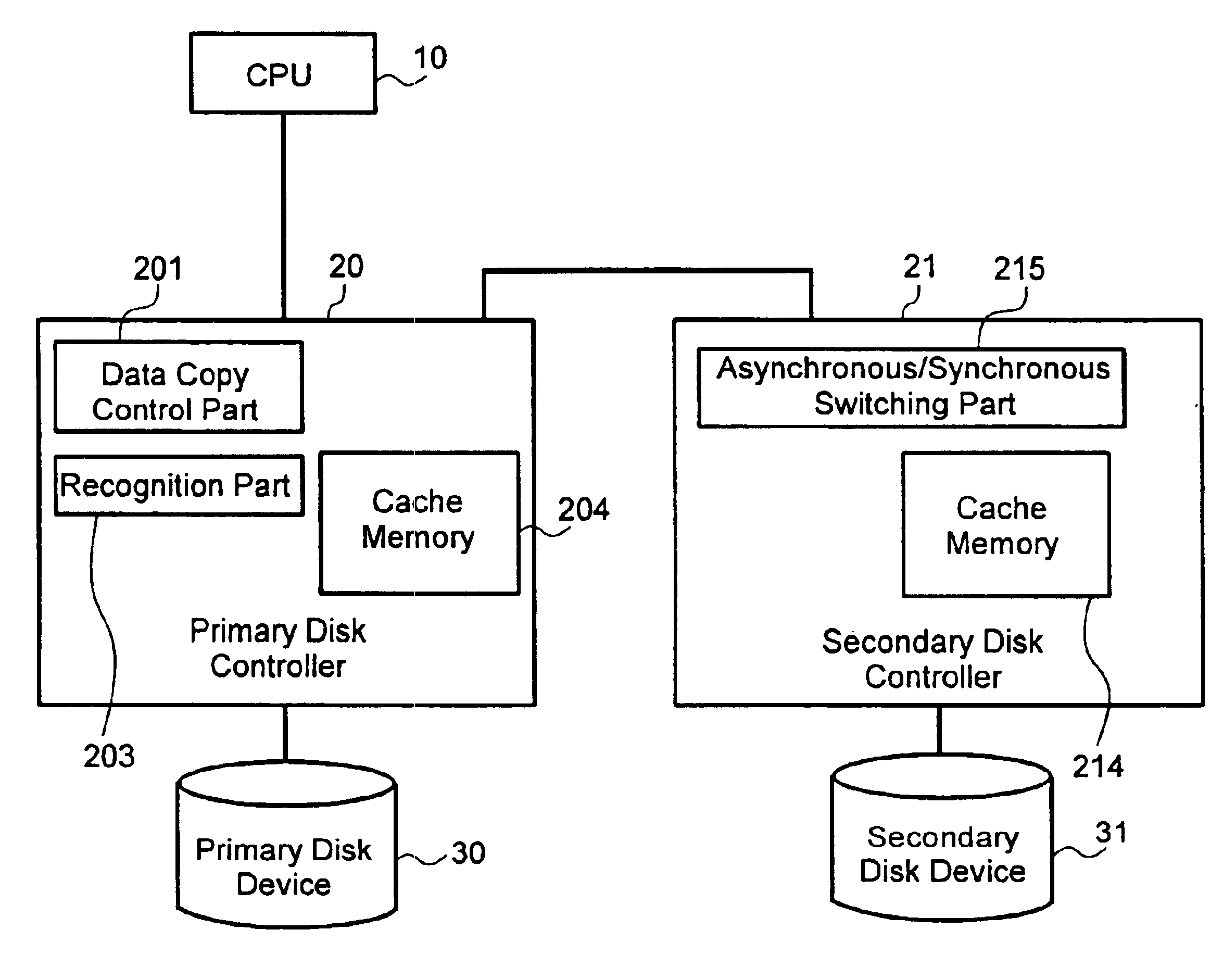
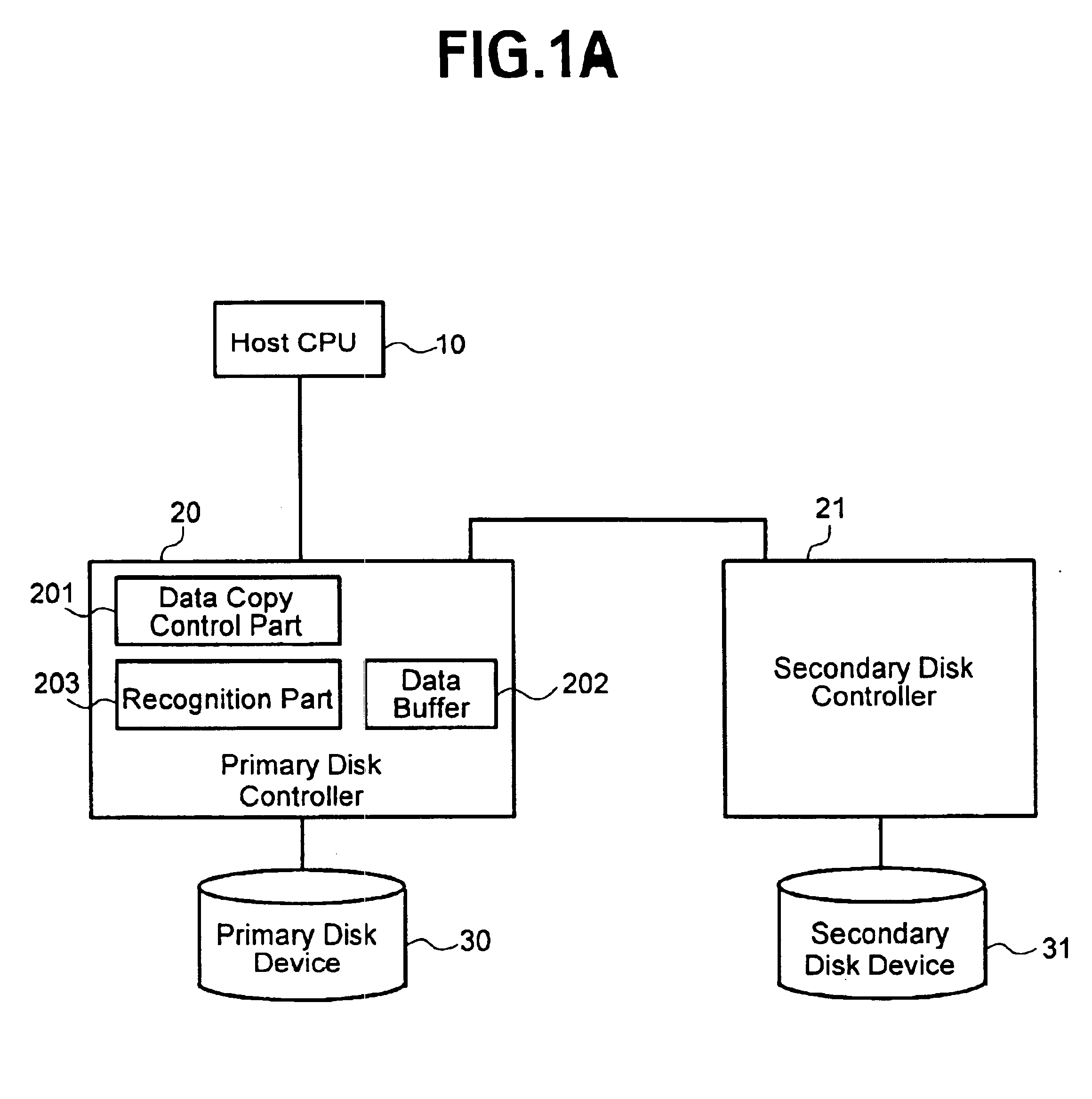
Data backup in presence of pending hazard
InactiveUS6845435B2Avoid data lossReduce and eliminate lossRedundant operation error correctionMemory systemsNatural disasterNetwork data
According to the present invention, techniques for performing real time backup of data in the presence of a pending hazard, such as a natural disaster, or the like. Embodiments can provide data storage controllers, networked data storage systems, methods and the like, that detect imminent hazardous conditions and alter backup behavior to provide greater integrity of backed up data. In a representative embodiment according to the present invention, update of the primary data is temporarily suspended after the recognition of a probable occurrence of a hazardous event. By suspending updating the primary data temporarily, the increase of un-updated secondary data can be prevented, so that lost data is decreased. Then, the un-updated secondary data can be updated quickly or exclusively, in order to avoid un-updated secondary data.
Owner:HITACHI LTD +1
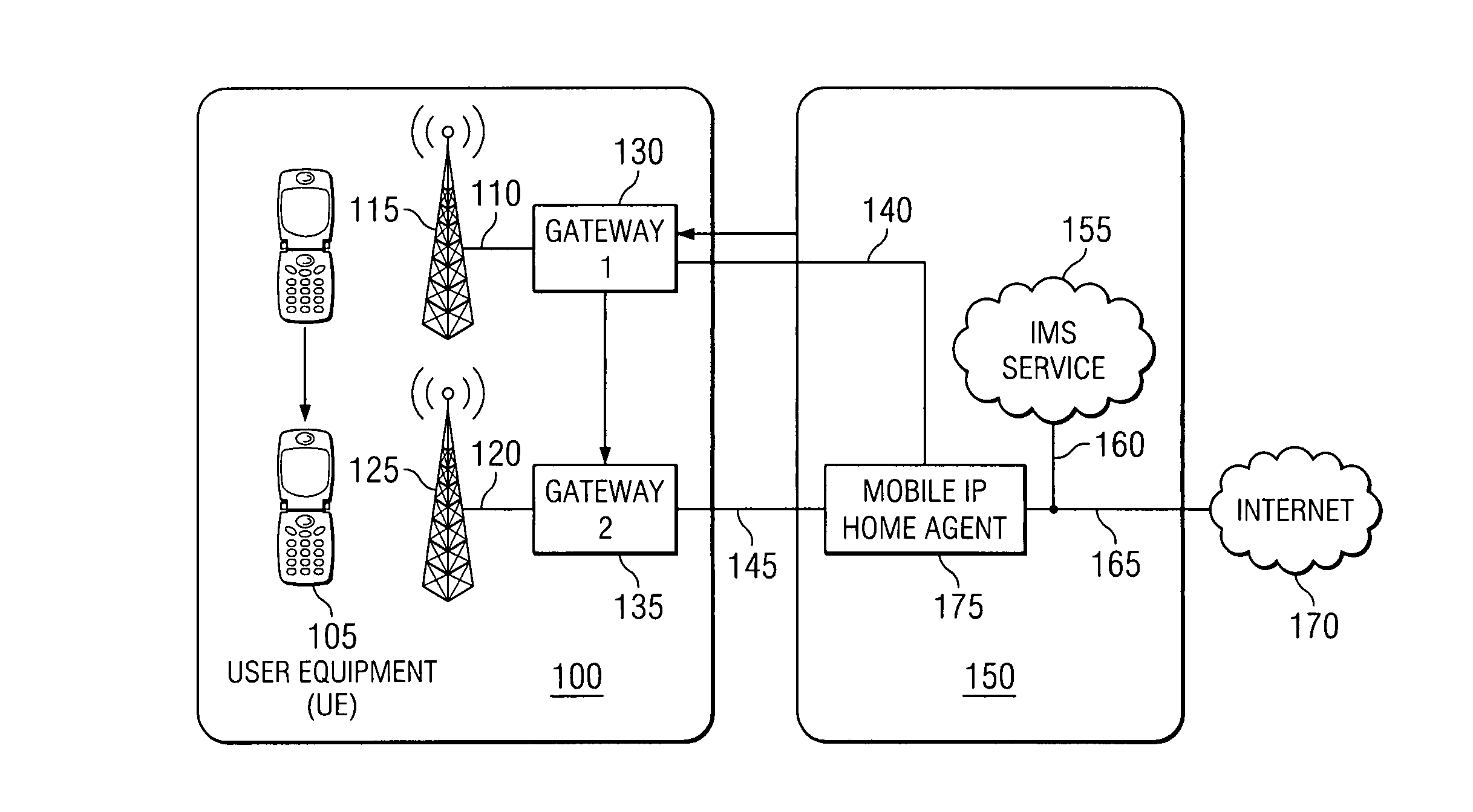
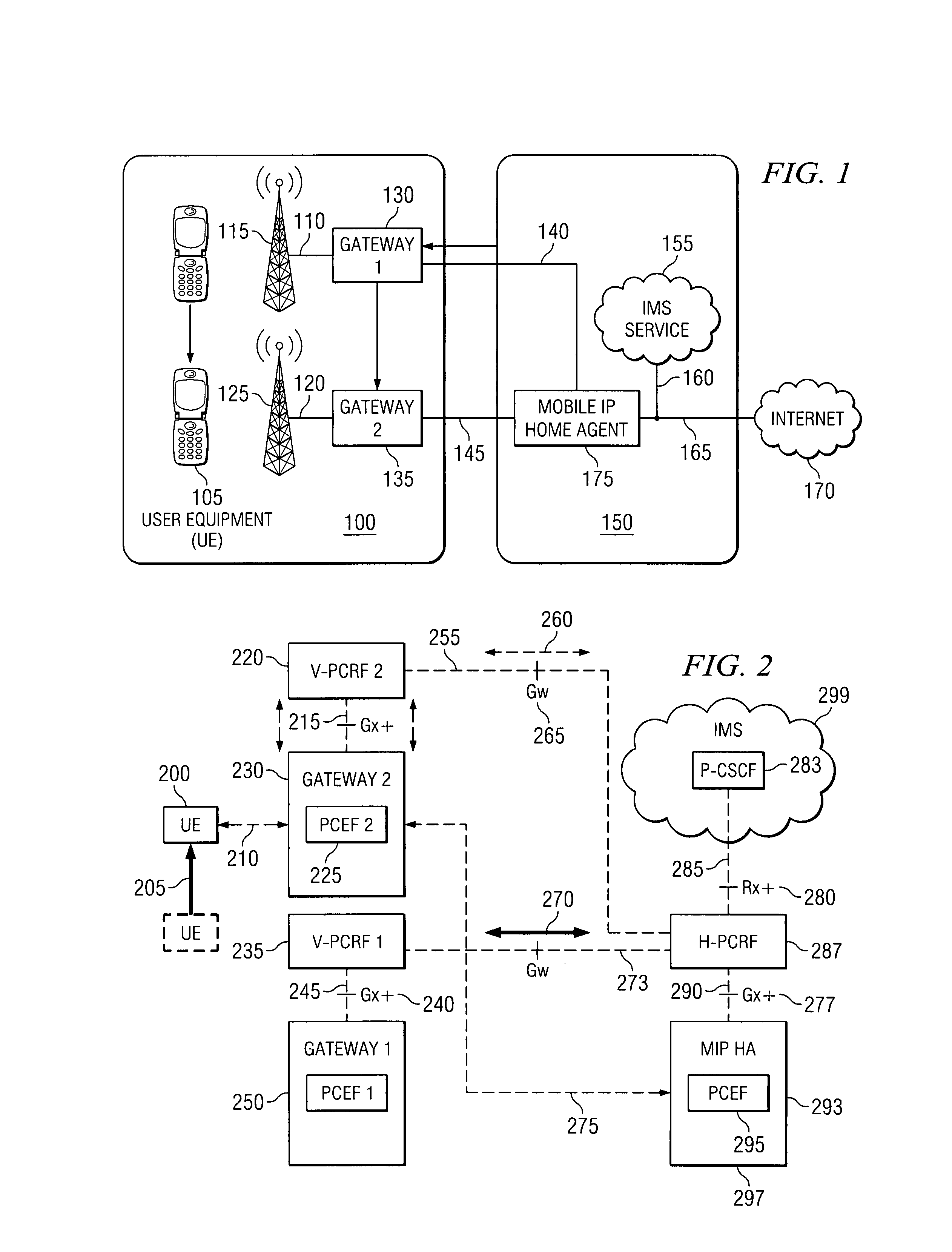
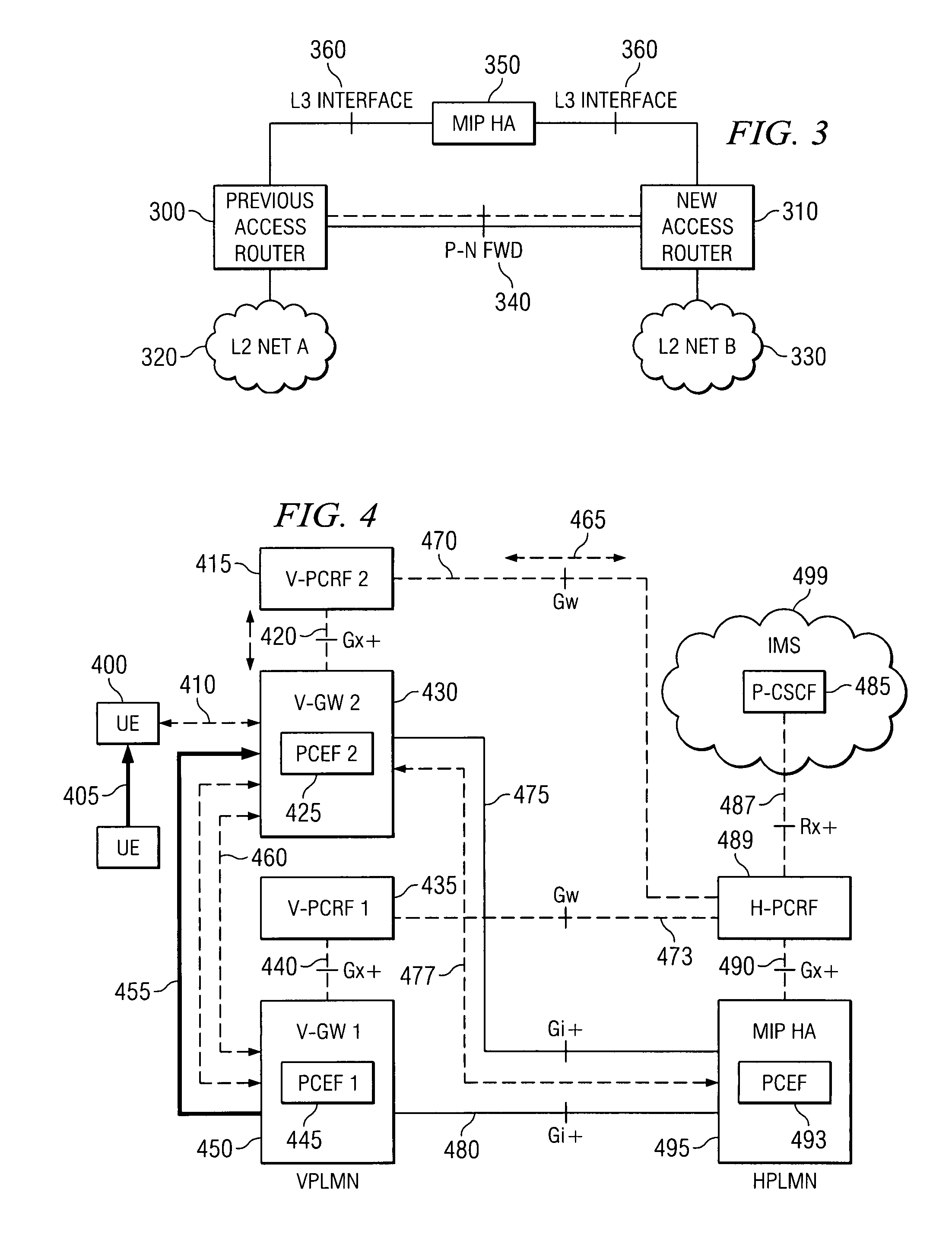
Transfer of policy and charging rules during MIP handover
ActiveUS7773571B1Minimize data lossReduce overheadBroadcast transmission systemsFrequency-division multiplexTime delayedData loss
The invention discloses a new protocol to minimize data loss, reduce overhead transmissions on the system, reduce time delays and signal interruption during a handover in a Mobile IP system. Prior art Mobile IP systems transfer policy and charging rules for a particular mobile user device from a server to a gateway after the handover occurs. The invention allows for the transfer of the policy and charging rules during the handover procedure so that the system does not need to wait on a subsequent transmission of the policy and charging rules in order to process the transmissions sent by or to the mobile user, which results in minimized data loss, reduced overhead, and reduced time delays and signal interruption.
Owner:BLACKBERRY LTD
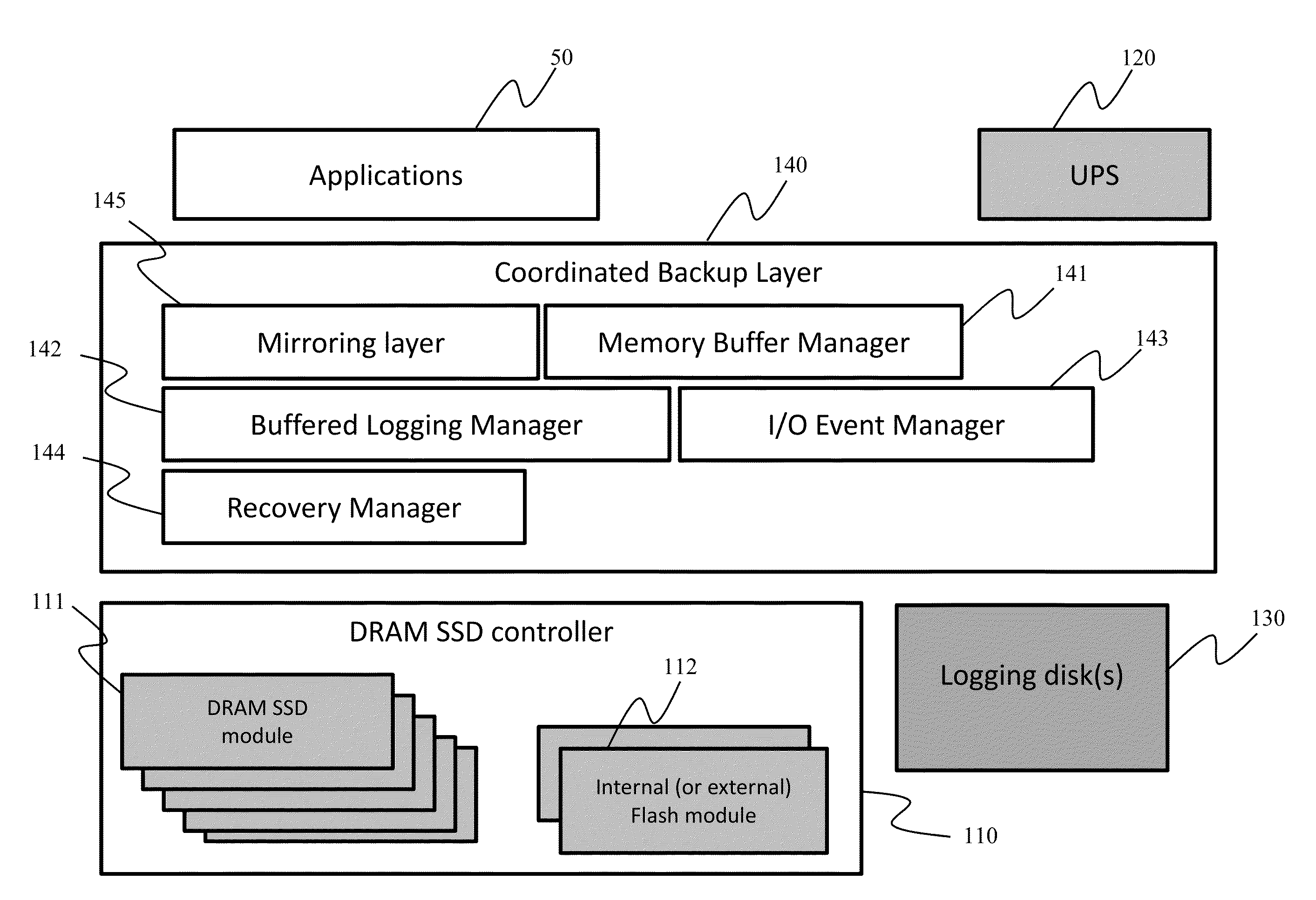
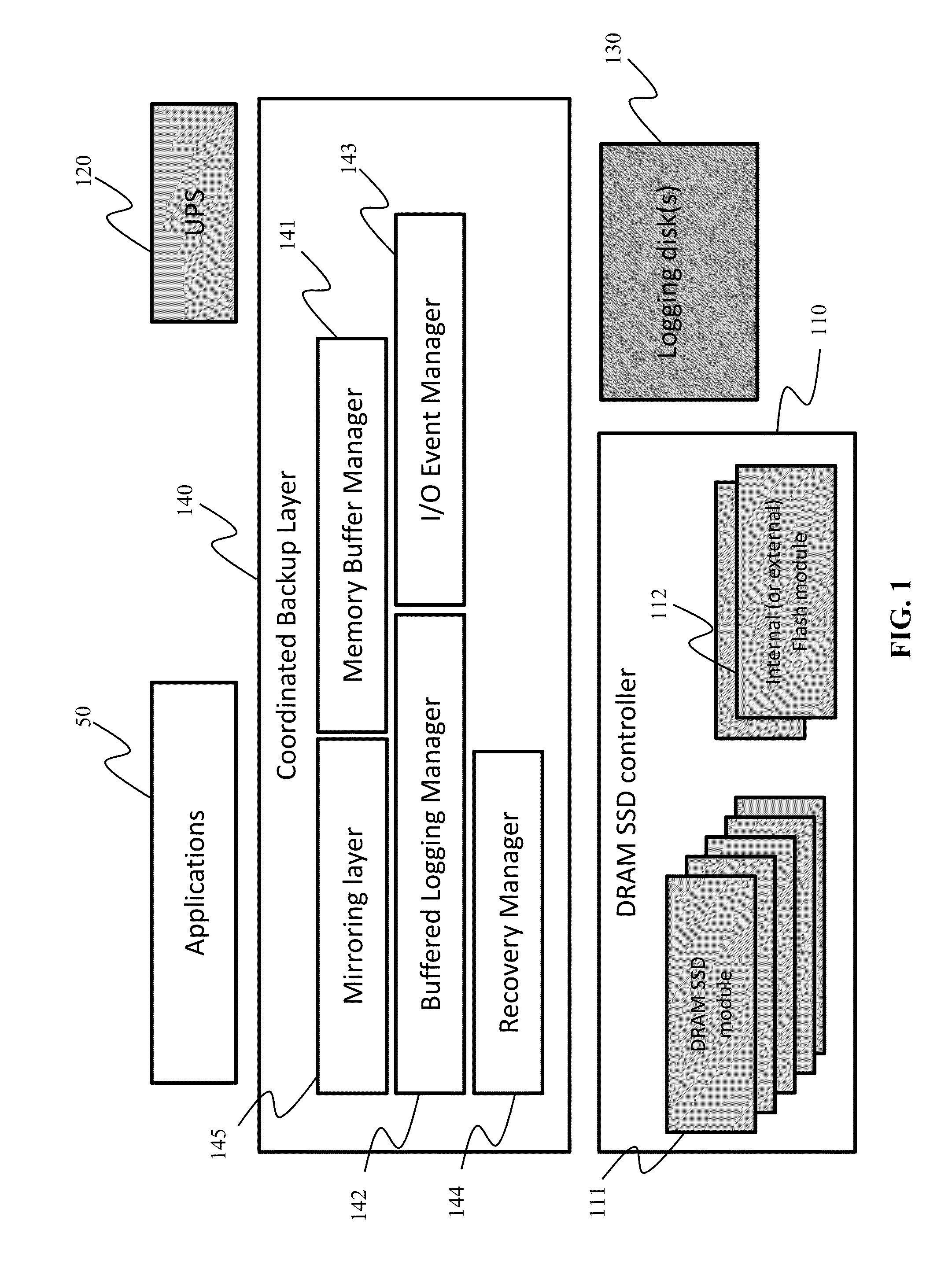
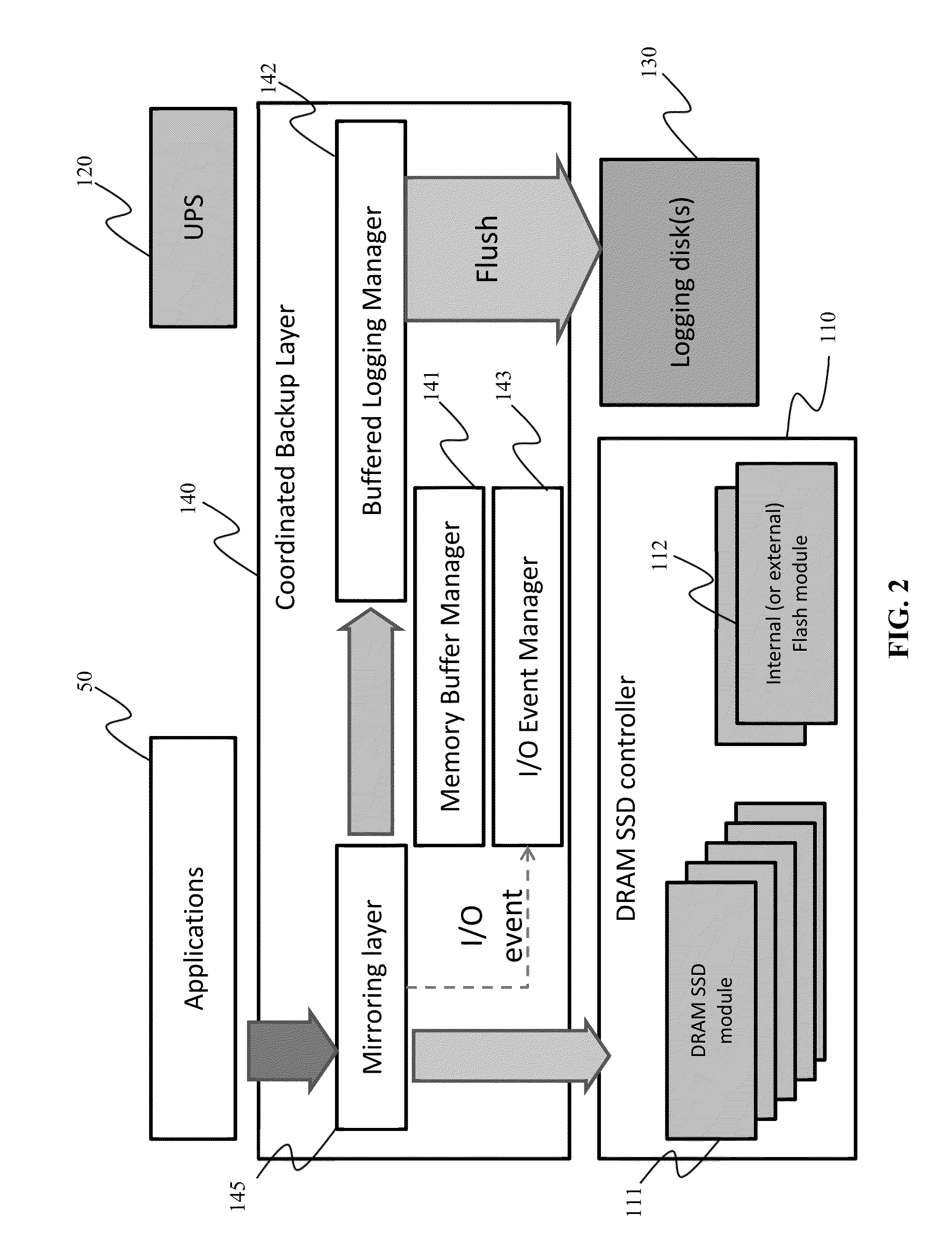
Method to improve data reliability in dram SSD using asynchronous logging and incremental backup
InactiveUS20140129765A1Minimize data lossImprove system availabilityMemory loss protectionError detection/correctionRecovery methodAuxiliary memory
Data back-up and recovery methods for DRAM SSDs and other high performance disks are provided. During operation, write events to the DRAM SSD are asynchronously backed-up onto a back-up HDD storage disk from an in-memory buffer. Should a DRAM SSD failure occur, the system can continue to operate, albeit at a lower performance, using the back-up HDD storage disk. Should the main power fail, data remaining in the in-memory buffer is flushed to the back-up HDD storage disk and writing events that did not make it to the in-memory buffer due to insufficient space are incrementally backed-up from the DRAM SSD to the secondary storage. Once power returns from the main power, data from the back-up storage disk and the secondary storage are transferred to the DRAM SSD.
Owner:TAJIN INFO TECH CO LTD
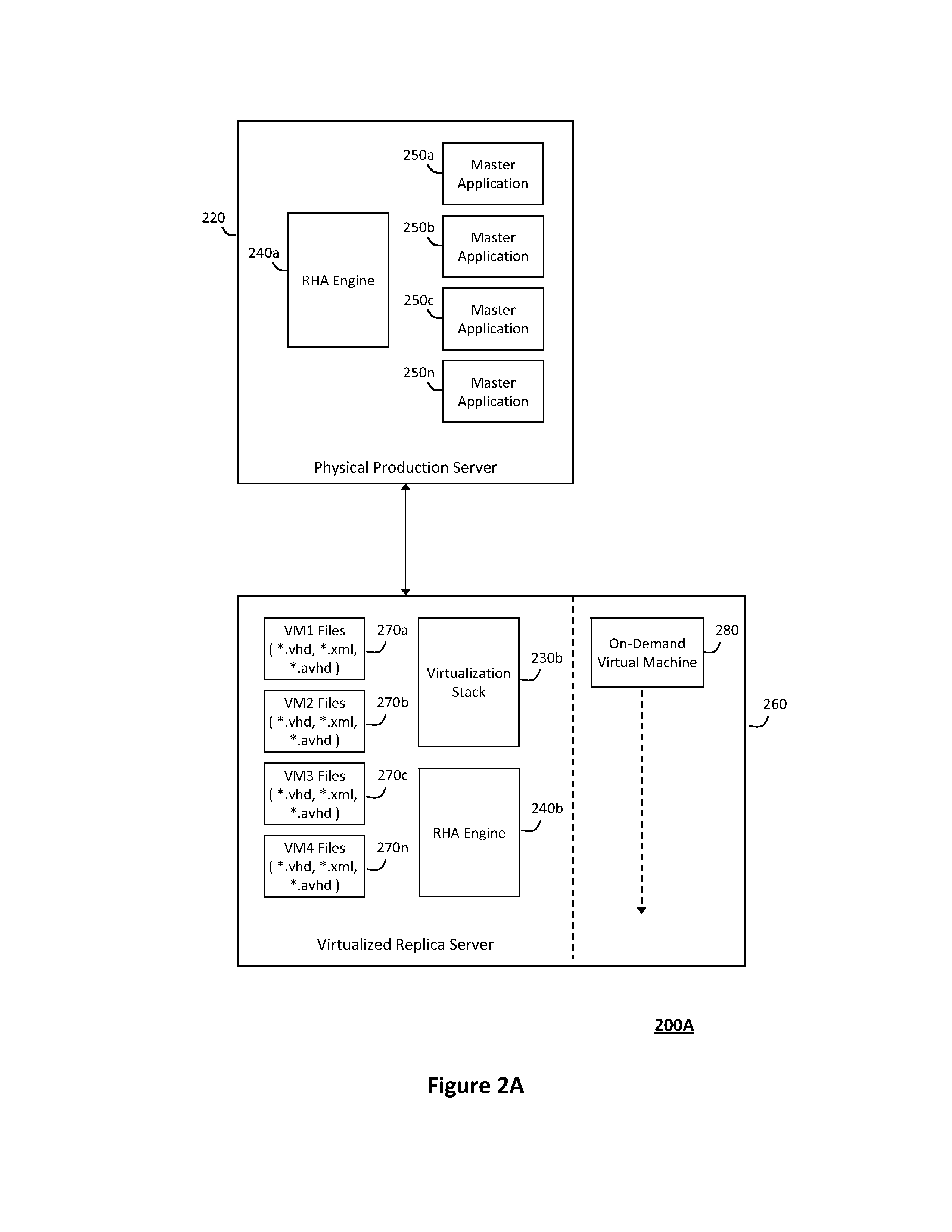
Providing a virtualized replication and high availability environment including a replication and high availability engine
ActiveUS8893147B2Improve usabilityEasily visualize and manageDigital data information retrievalError detection/correctionFile synchronizationVirtualization
The system and method described herein may provide a virtualized replication and high availability environment. In particular, a virtualized production server may run one or more virtual machines in one or more child partitions and have a replication and high availability engine installed in a parent partition. The replication and high availability engine may automatically discover the virtual machines running in the child partitions and automatically synchronize all files associated with the virtual machines to a virtualized replica server. Furthermore, the replication and high availability engine may continuously replicate subsequent changes to the files associated with the virtual machines running in the child partitions to the virtualized replica server, which may then create on-demand virtual machines from the synchronized and replicated files to handle switchover, failover, switchback, and failback events associated with the virtualized production server or the virtual machines running in the child partitions associated therewith.
Owner:CA TECH INC
Apparatus and method for transmitting wireless data using an adaptive frequency selection
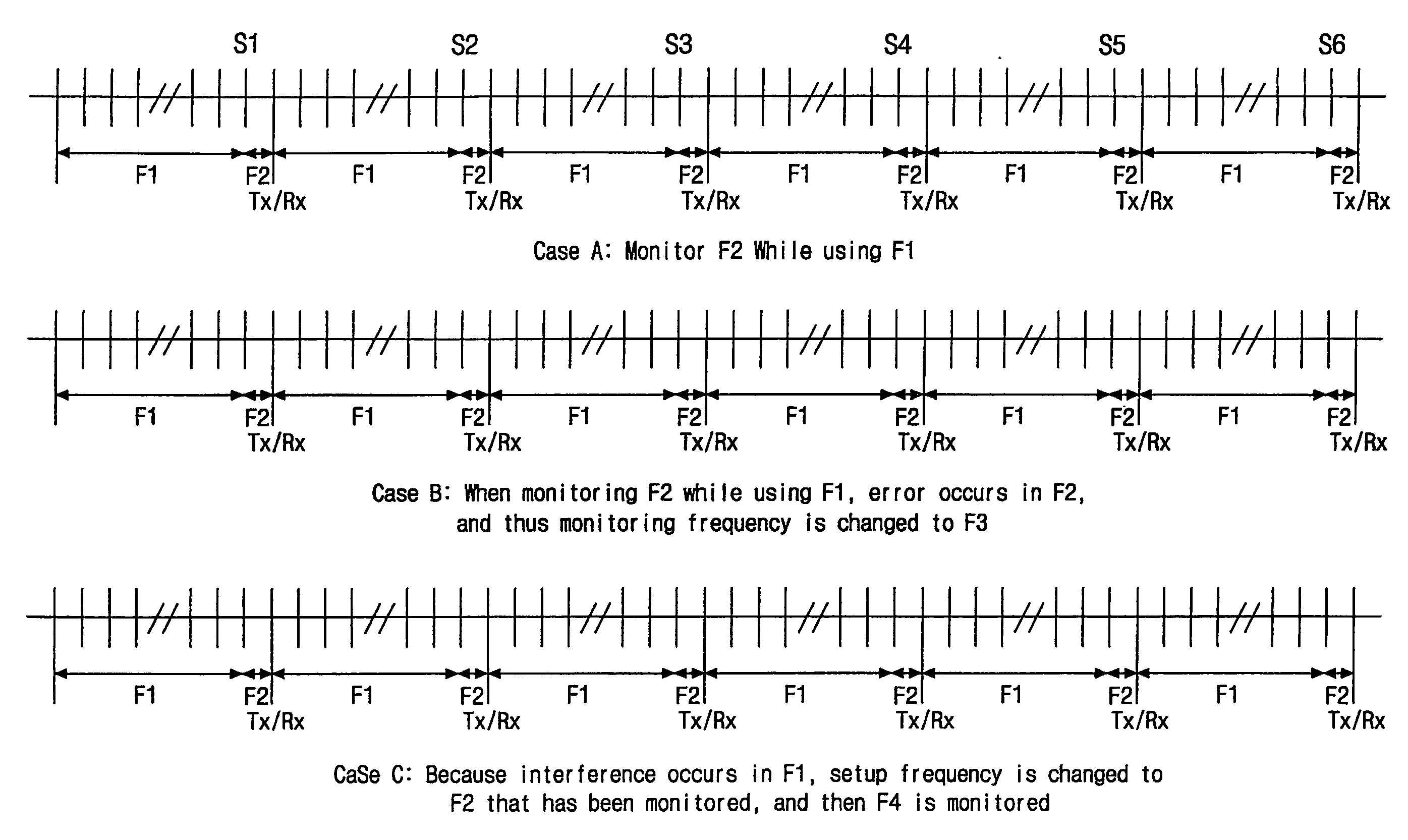
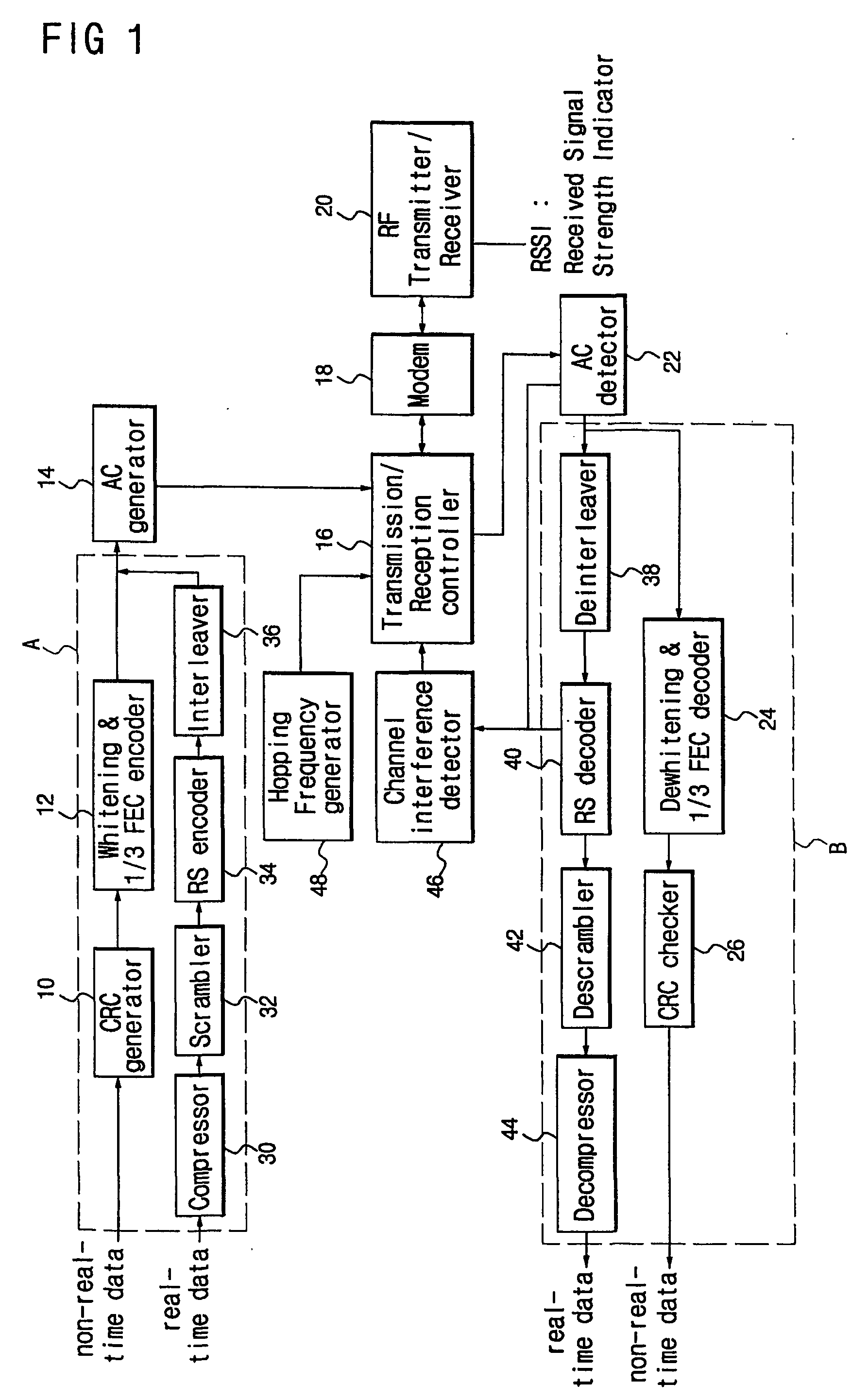
InactiveUS20050272434A1Quality improvementMinimize data lossNetwork topologiesTime-division multiplexTelecommunicationsWireless data
Disclosed is a method and device for locally transmitting digital wireless data through a searched channel with no interference. Firstly, data is transmitted and received through a setup channel. A channel having a different frequency from the setup channel is set as a temporary replacement channel. Data is transmitted and received through the temporary replacement channel, and it is checked whether there is channel interference. When there is no channel interference, the temporary replacement channel information is stored, and data is transmitted and received after returning to the setup channel. When it is detected that channel interference continuously occurs while transmitting and receiving data through the setup channel, data is transmitted and received after changing the stored replacement channel to a new setup channel.
Owner:OPEN SOLUTION
Maintaining data connectivity for handoffs between compression-enabled and compression-disabled communication systems
InactiveUS20050107084A1Minimize data lossNetwork traffic/resource managementData switching by path configurationCommunications systemNetwork packet
Methods and apparatus are presented for enabling data connectivity when a handoff occurs between one communication network and another communication network, wherein the communication networks belong to different air interface standards. The mobile station triggers a Compression Control Protocol (CCP) request message to a tethered device if the mobile station determines that a new PDSN is not enabled to perform the CCP protocol. The tethered device then responds with a CCP request message with or without new negotiation parameters. The mobile station forwards the CCP request message to the new PDSN. Since the new PDSN is not enabled with CCP, the new PDSN responds with a CCP rejection message. The rejection message is passed from the mobile station back to the tethered device. The tethered device then sends uncompressed data packets to the PDSN.
Owner:QUALCOMM INC
Apparatus and method for transmitting wireless data using an adaptive frequency selection
InactiveUS7283789B2Quality improvementMinimize data lossNetwork topologiesTime-division multiplexTelecommunicationsWireless data
Disclosed is a method and device for locally transmitting digital wireless data through a searched channel with no interference. Firstly, data is transmitted and received through a setup channel. A channel having a different frequency from the setup channel is set as a temporary replacement channel. Data is transmitted and received through the temporary replacement channel, and it is checked whether there is channel interference. When there is no channel interference, the temporary replacement channel information is stored, and data is transmitted and received after returning to the setup channel. When it is detected that channel interference continuously occurs while transmitting and receiving data through the setup channel, data is transmitted and received after changing the stored replacement channel to a new setup channel.
Owner:OPEN SOLUTION
Method and apparatus for remote control of a distributed television broadcasting system
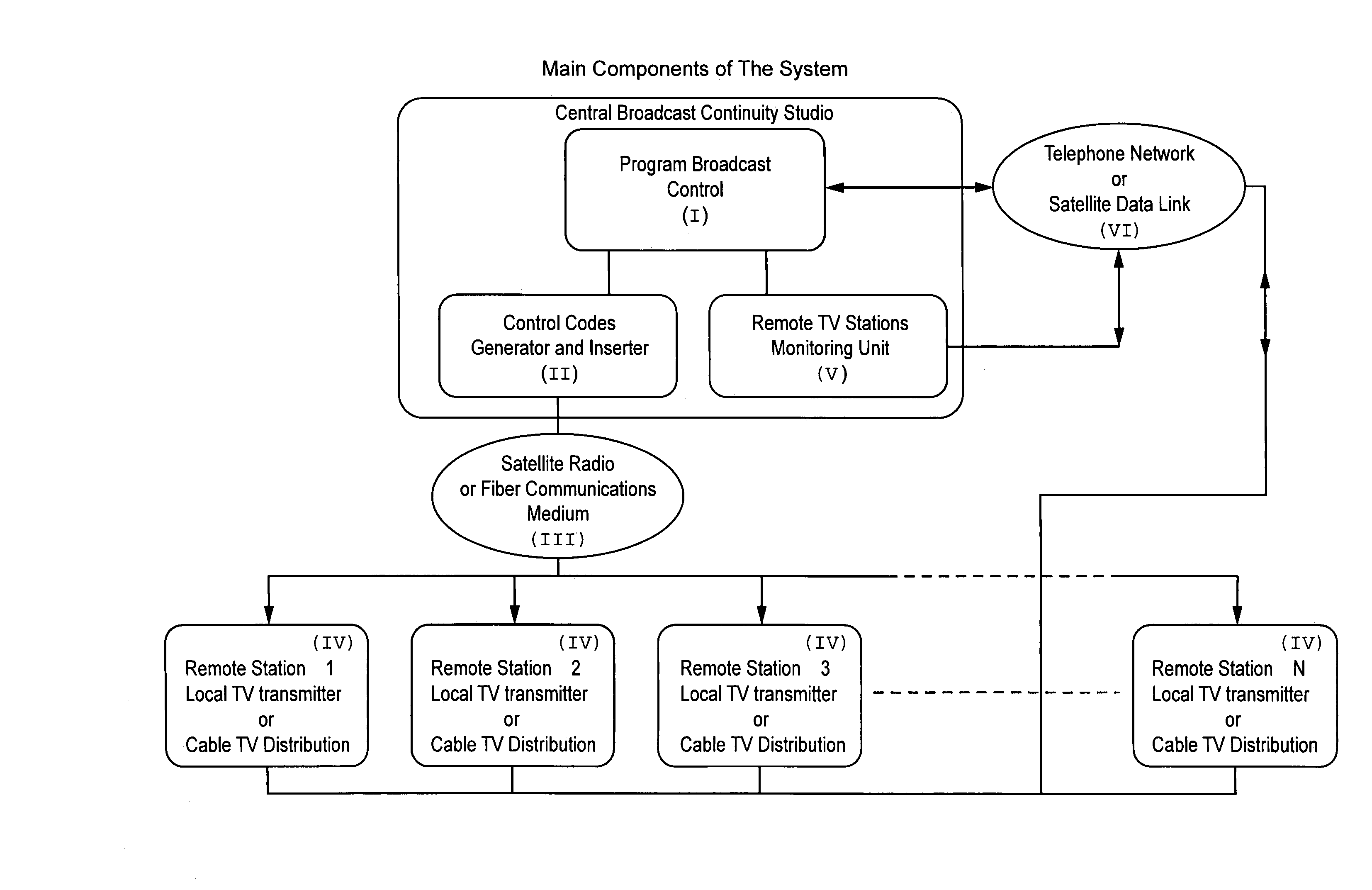
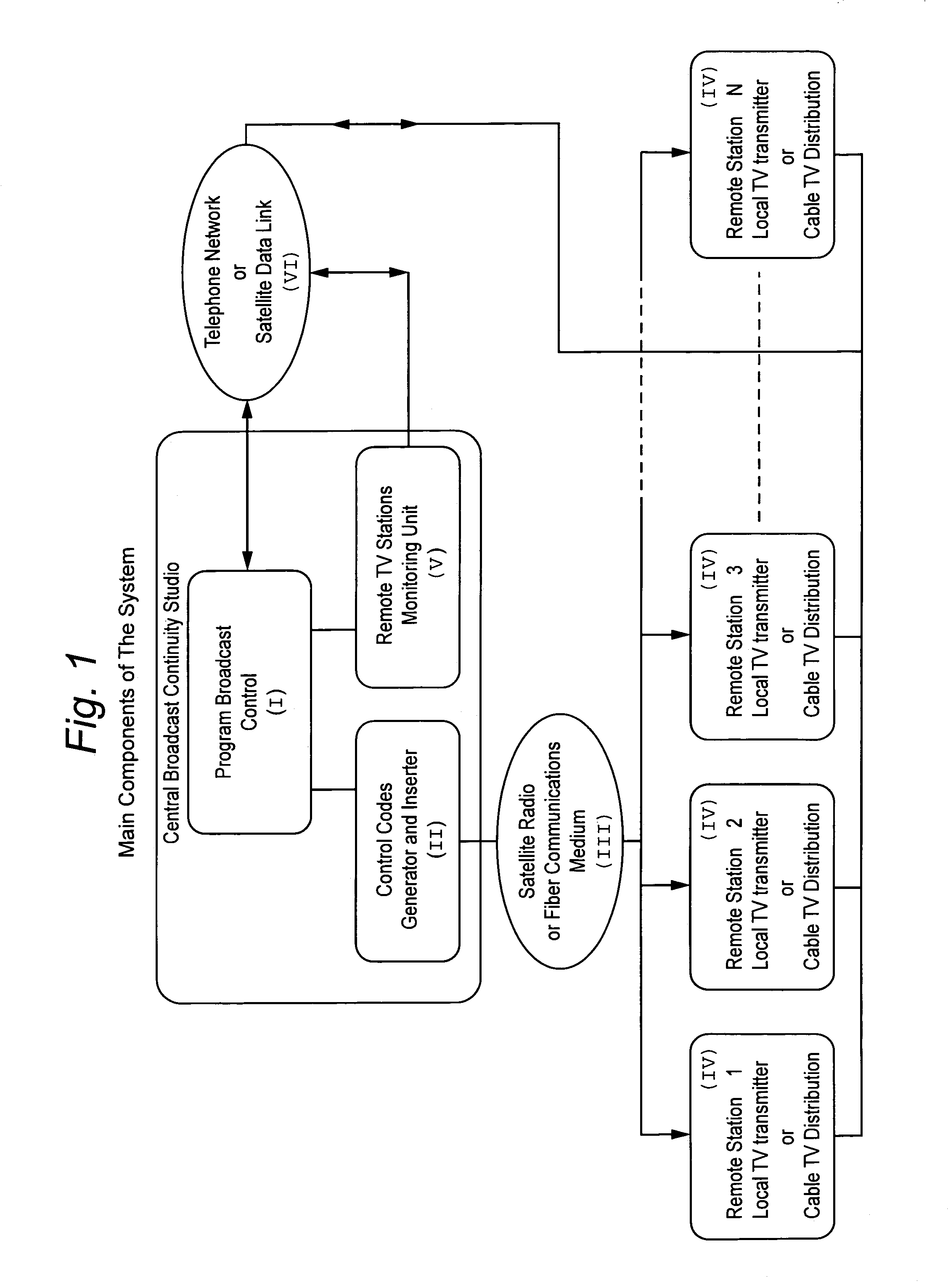
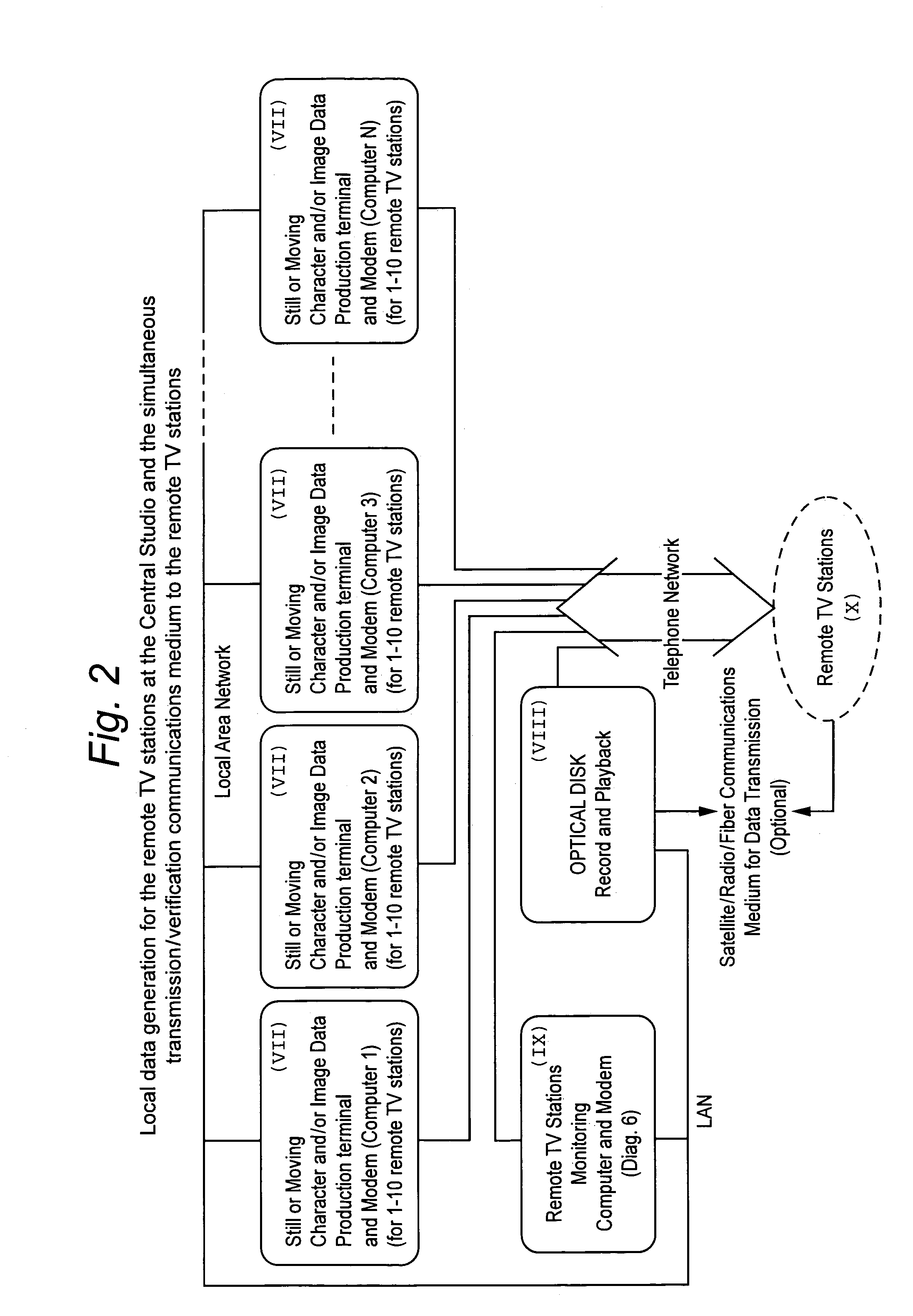
InactiveUS7036139B2Minimize data lossMinimize chance of data lossTelevision system detailsGHz frequency transmissionValidation methodsRemote control
A TV broadcast system uses multiplexed and duplex, communication and verification methods, it directs and controls form a central continuity studio one or more remote stand alone TV transmitters to change and / or modify the content of their local broadcast material. Thus it is possible to direct the local broadcast to switch between the general broadcast program or a previously stored (at the remote site) live video. Moreover it is possible to superimpose on the video being broadcast, alphanumeric character and / or image data, which are also previously stored at the remote site.
Owner:ARAS MEHMET R
Distributed data collection and aggregation
ActiveUS8156216B1Efficiently collect informationFacilitates improved reliability in data collectionDigital computer detailsMarketingTraffic volumeData harvesting
A distributed, redundant, multi-homed system collects and aggregates website usage information. Two or more data collection nodes, preferably situated in diverse locations, efficiently collect and time-stamp information from users in a wide variety of geographic locations. Data collected by the individual data collection nodes is aggregated at a master processing center, sorted according to time stamps, and subjected to statistical analysis in order to generate complete and accurate reports regarding website traffic.
Owner:ADOBE INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com