Patents
Literature
733 results about "Alphanumeric" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
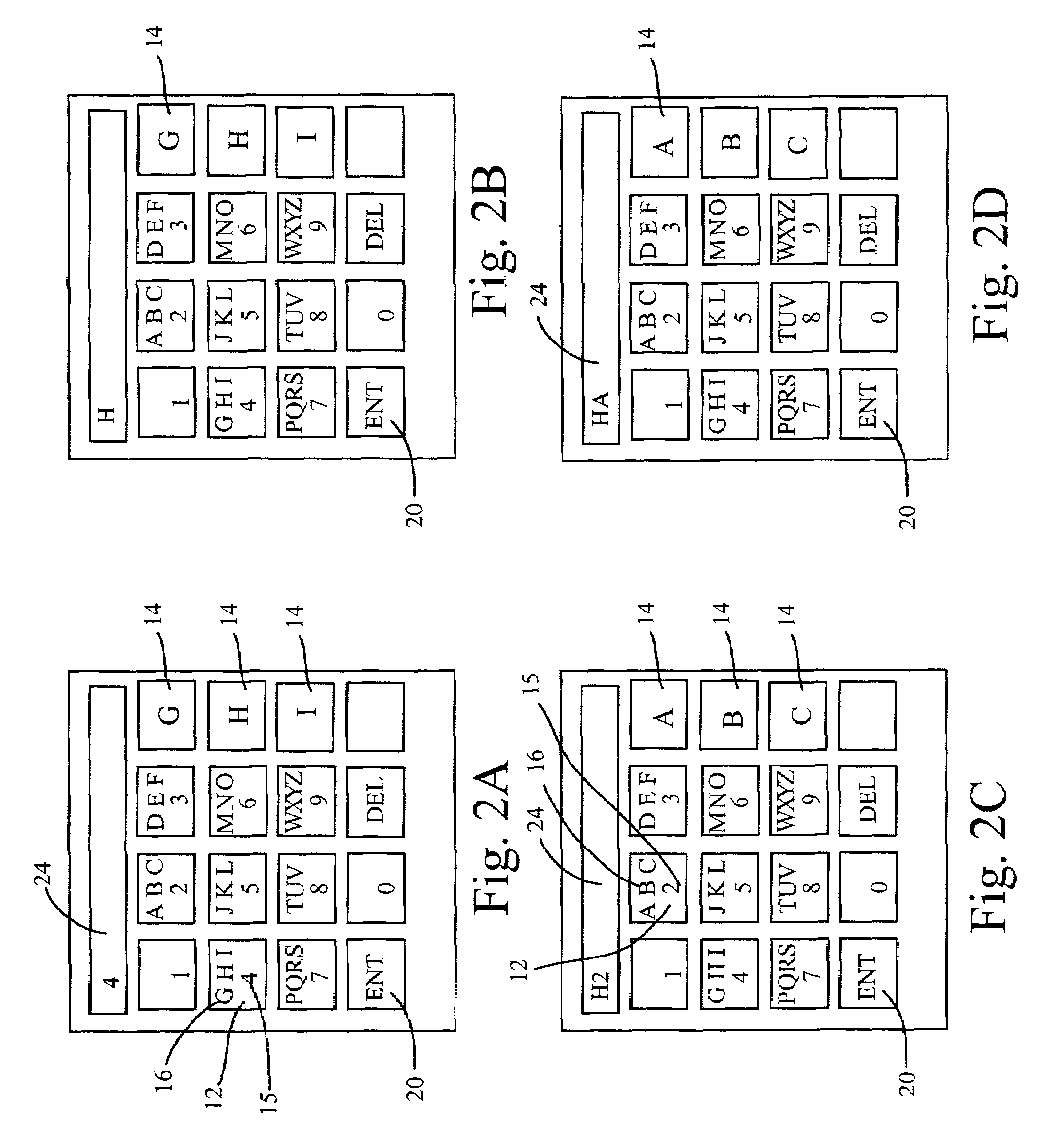
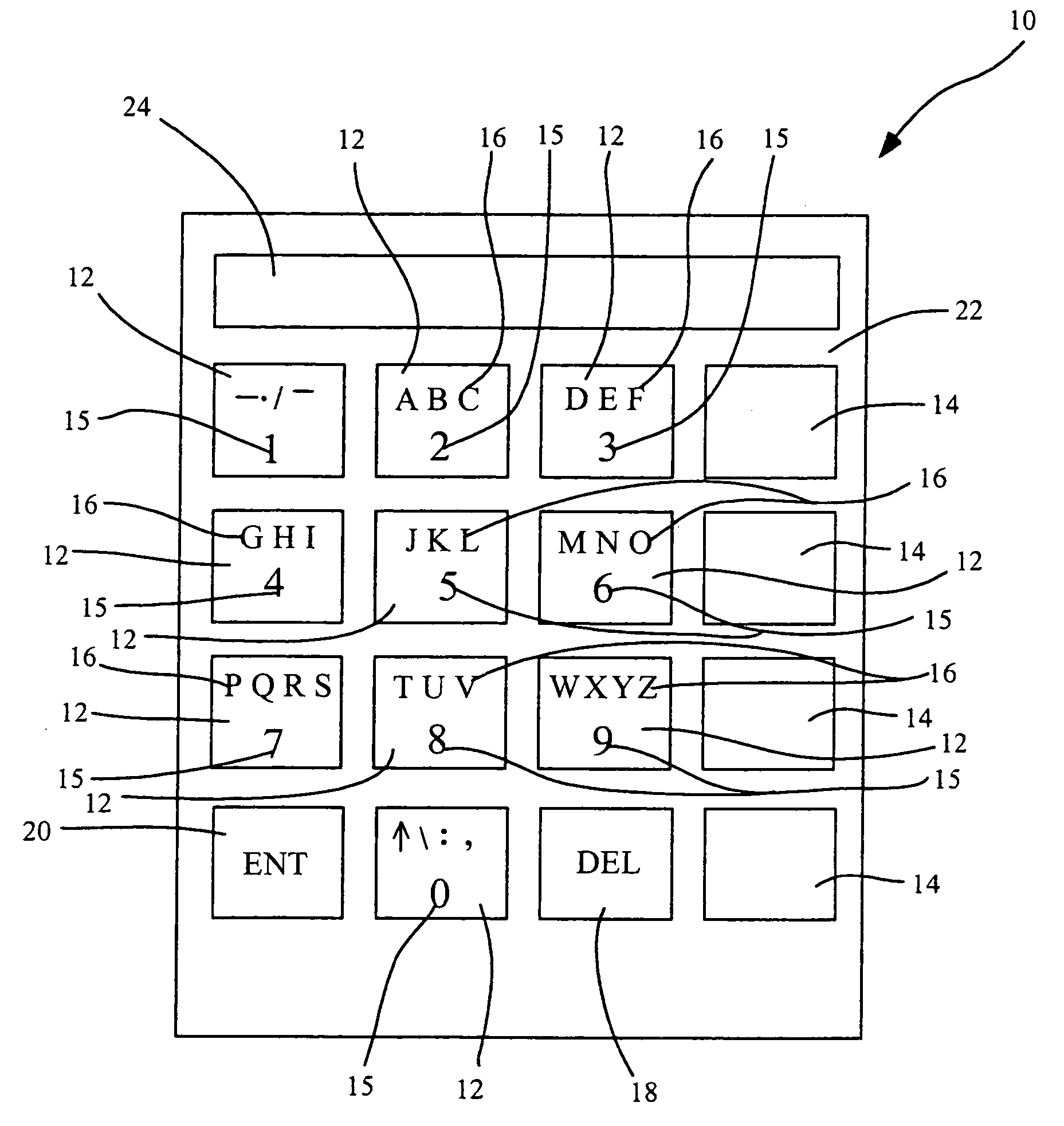
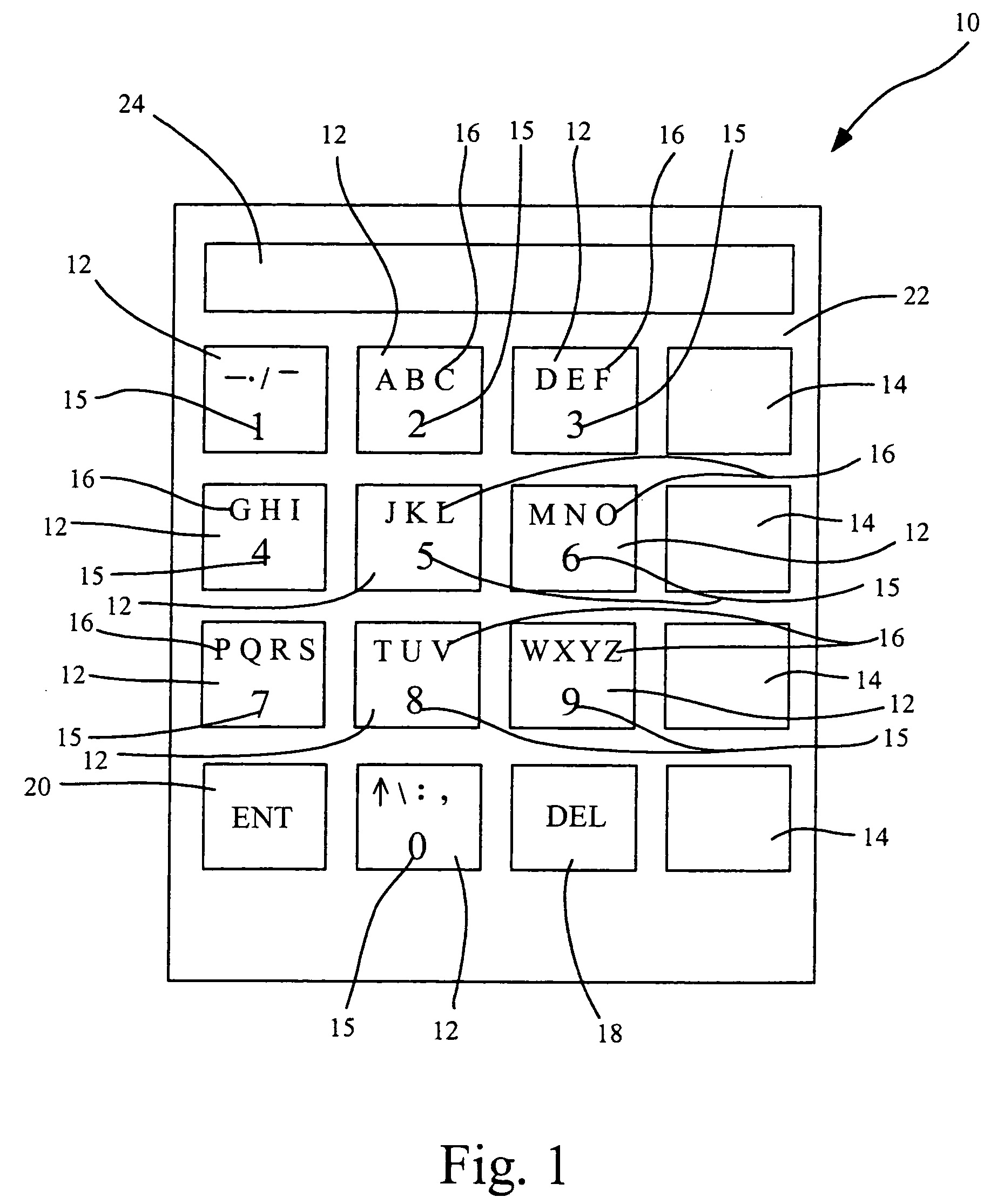
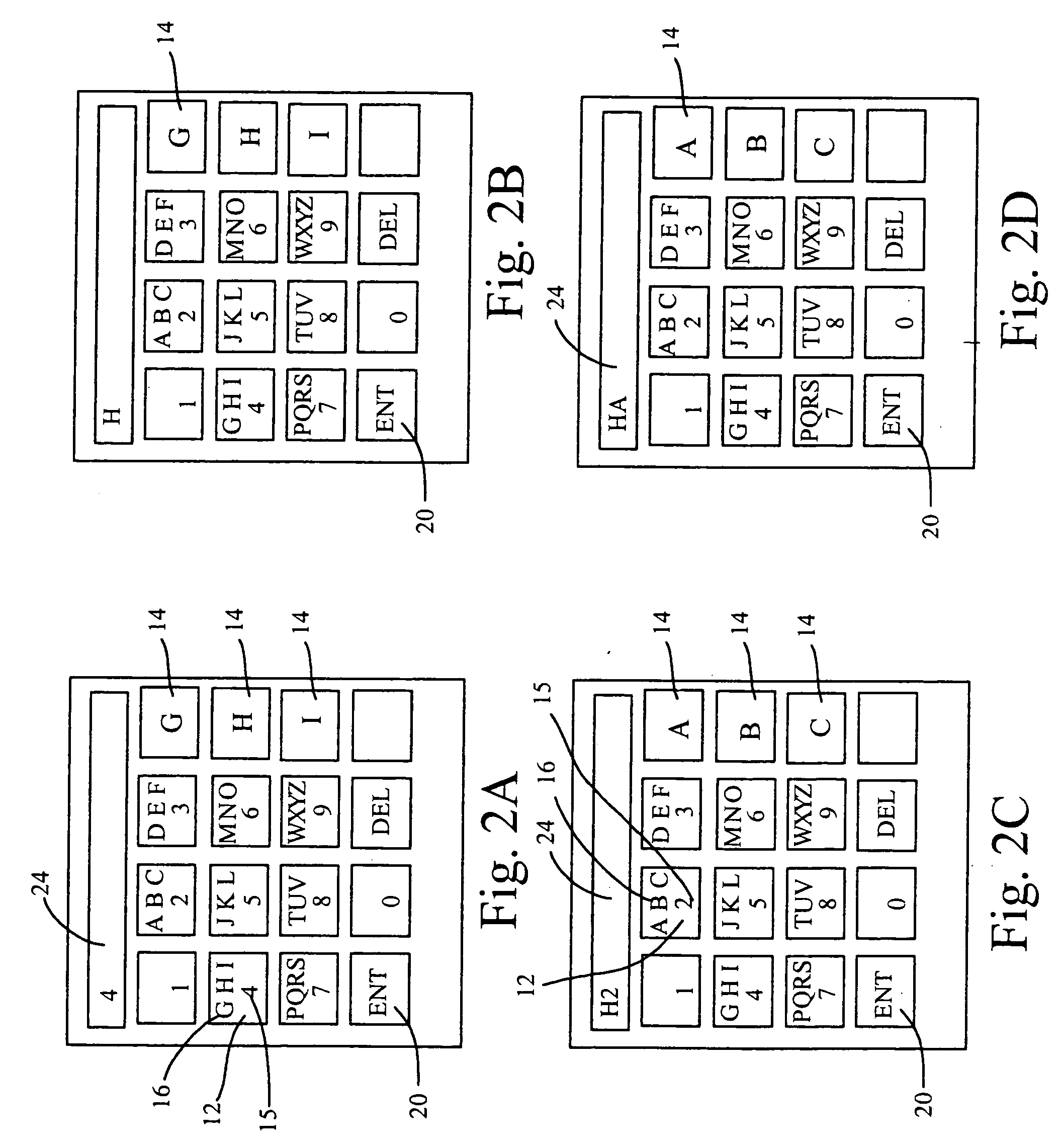
Alphanumericals are a combination of alphabetical and numerical characters, and is used to describe the collection of Latin letters and Arabic digits or a text constructed from this collection. Merriam-Webster suggests that the term "alphanumeric" may often additionally refer to other symbols, such as punctuation and mathematical symbols.
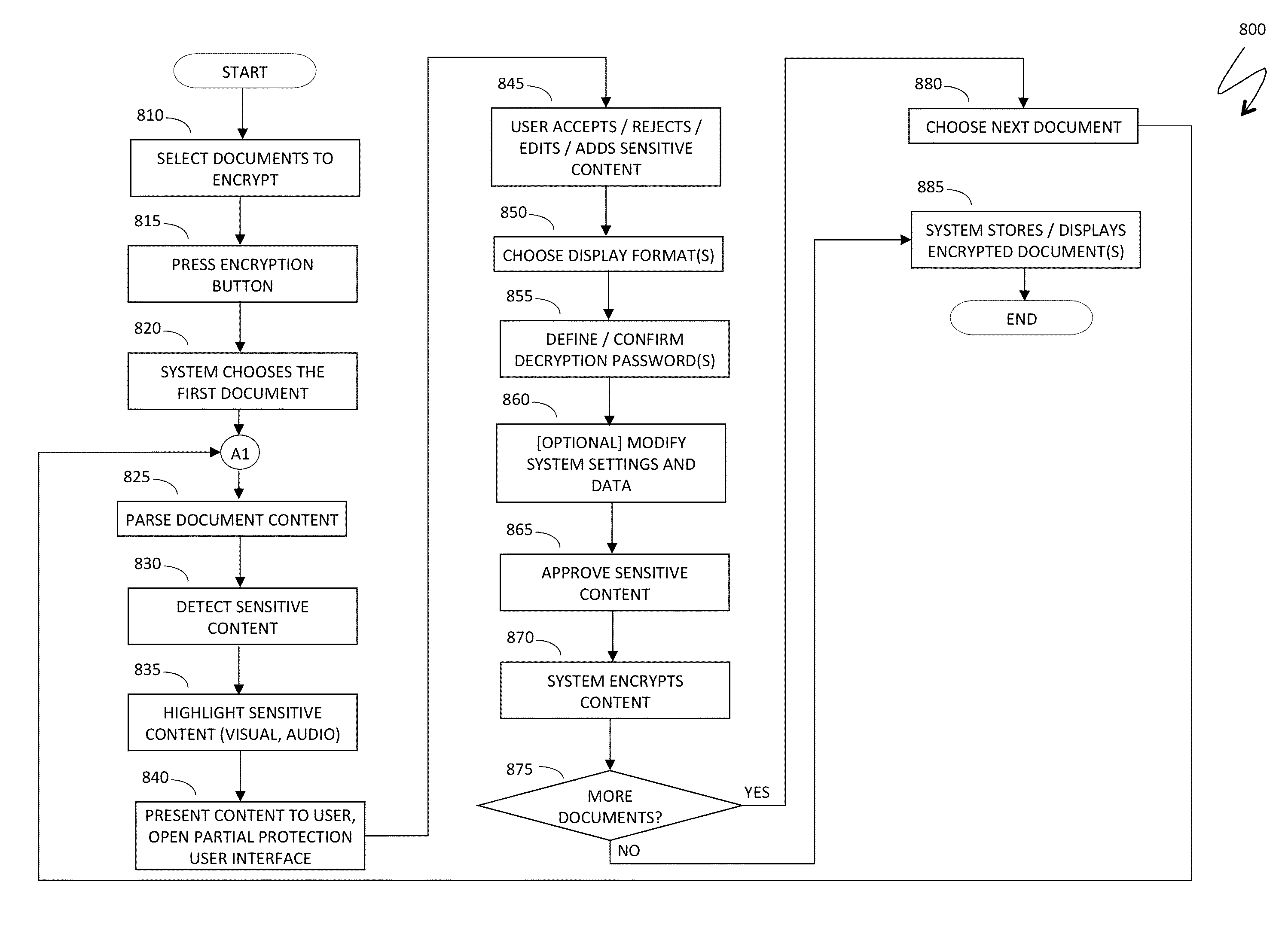
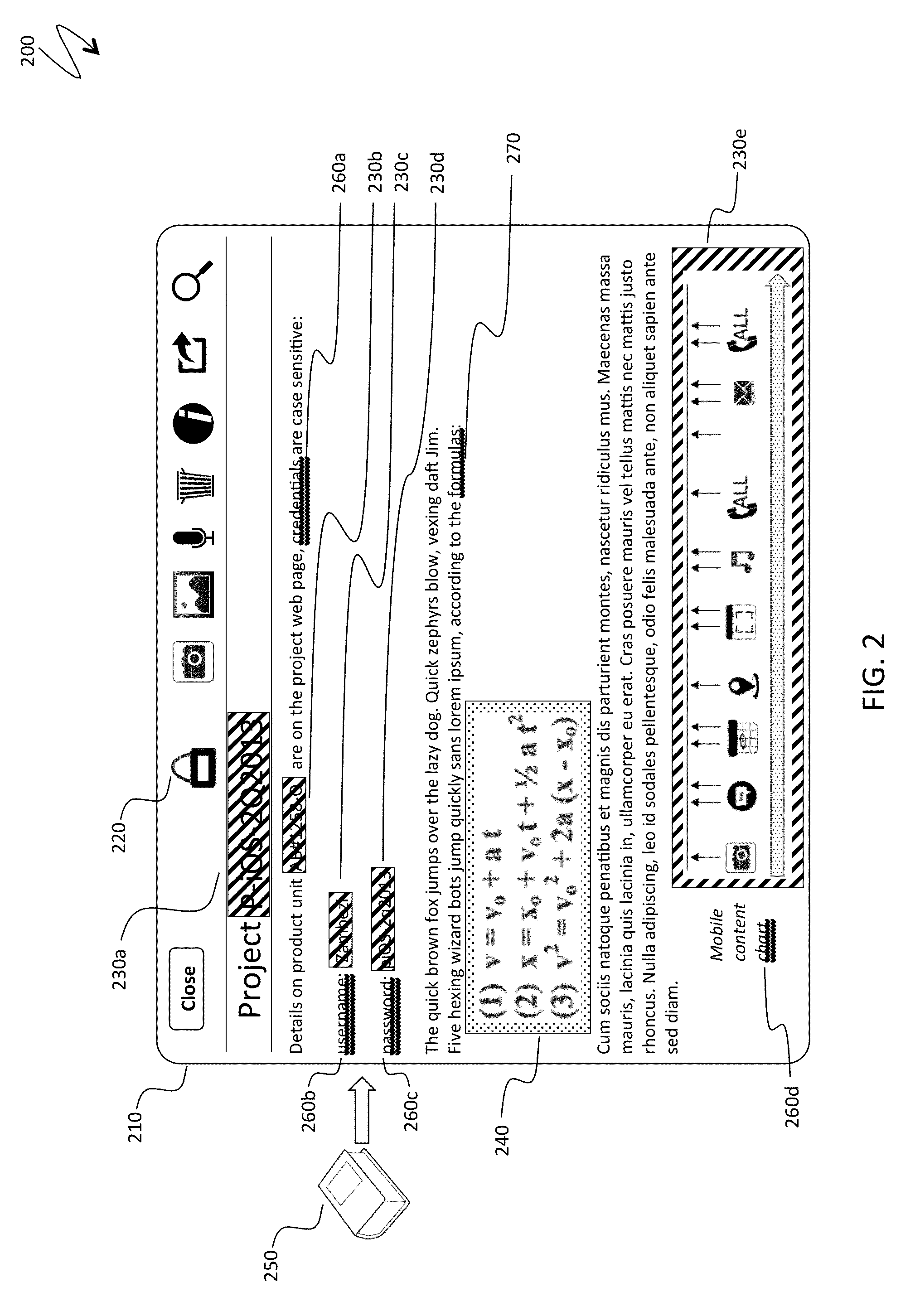
Automatic protection of partial document content
ActiveUS20140208418A1Reduce the amount requiredDigital data processing detailsUnauthorized memory use protectionPasswordDocumentation
Protecting a fragment of a document includes automatically detecting the fragment without user intervention based on the content of the fragment and / or the context of the fragment within a set of documents, selectively encrypting the fragment to prevent unauthorized access, and providing an alternative view of the fragment that prevents viewing and access of content corresponding to the fragment unless a decryption password is provided. Automatically detecting the fragment may include detecting numbers and alphanumeric sequences of sufficient length that do not represent commonly known abbreviations, detecting generic terms, detecting proper names, detecting terms signifying a type of content, detecting mutual location of terms and sensitive content, and / or detecting user defined terms. The generic terms may correspond to password, passcode, credentials, user name, account, ID, login, confidential, and / or sensitive. The proper names may be names of financial organizations and security organizations.
Owner:EVERNOTE
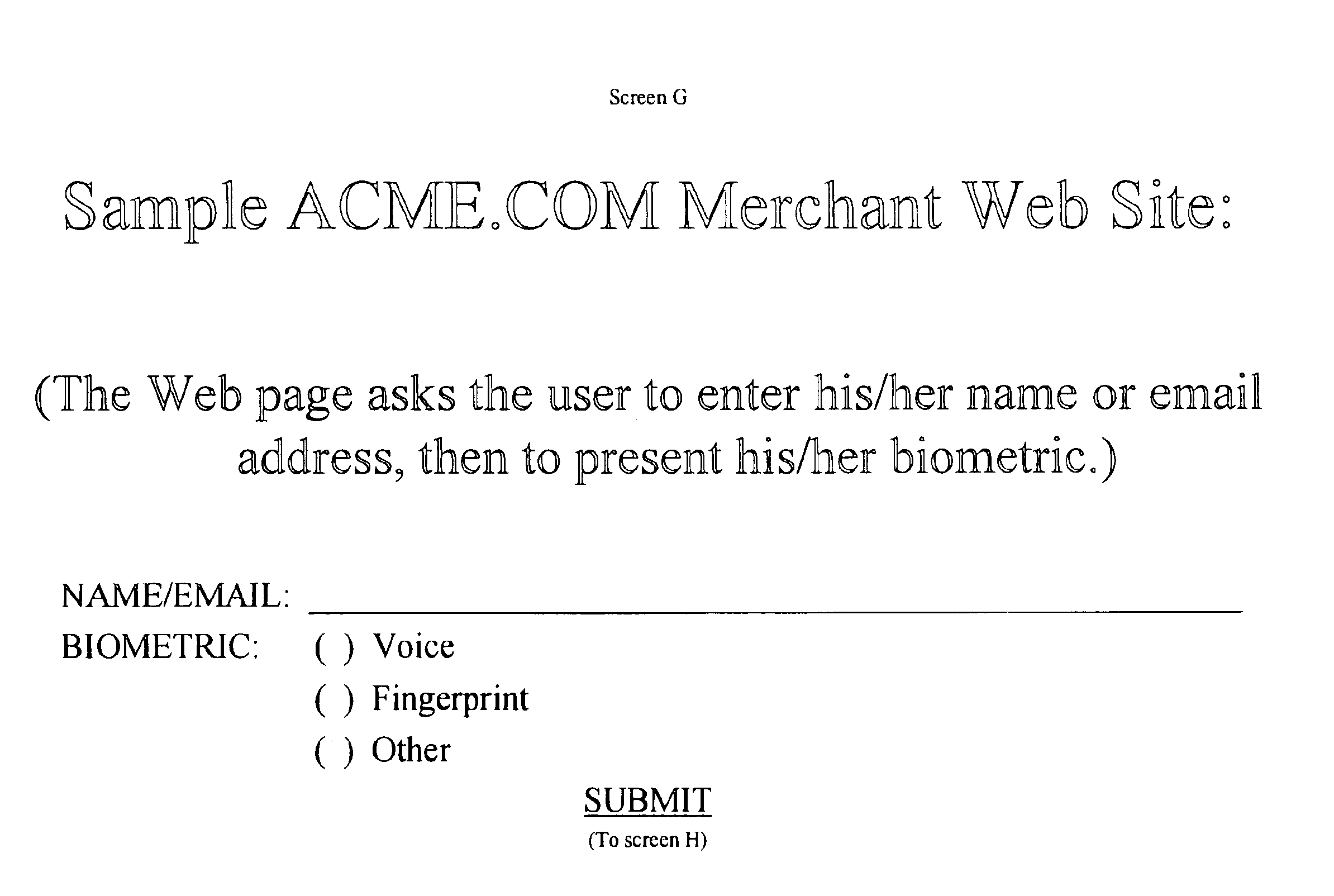
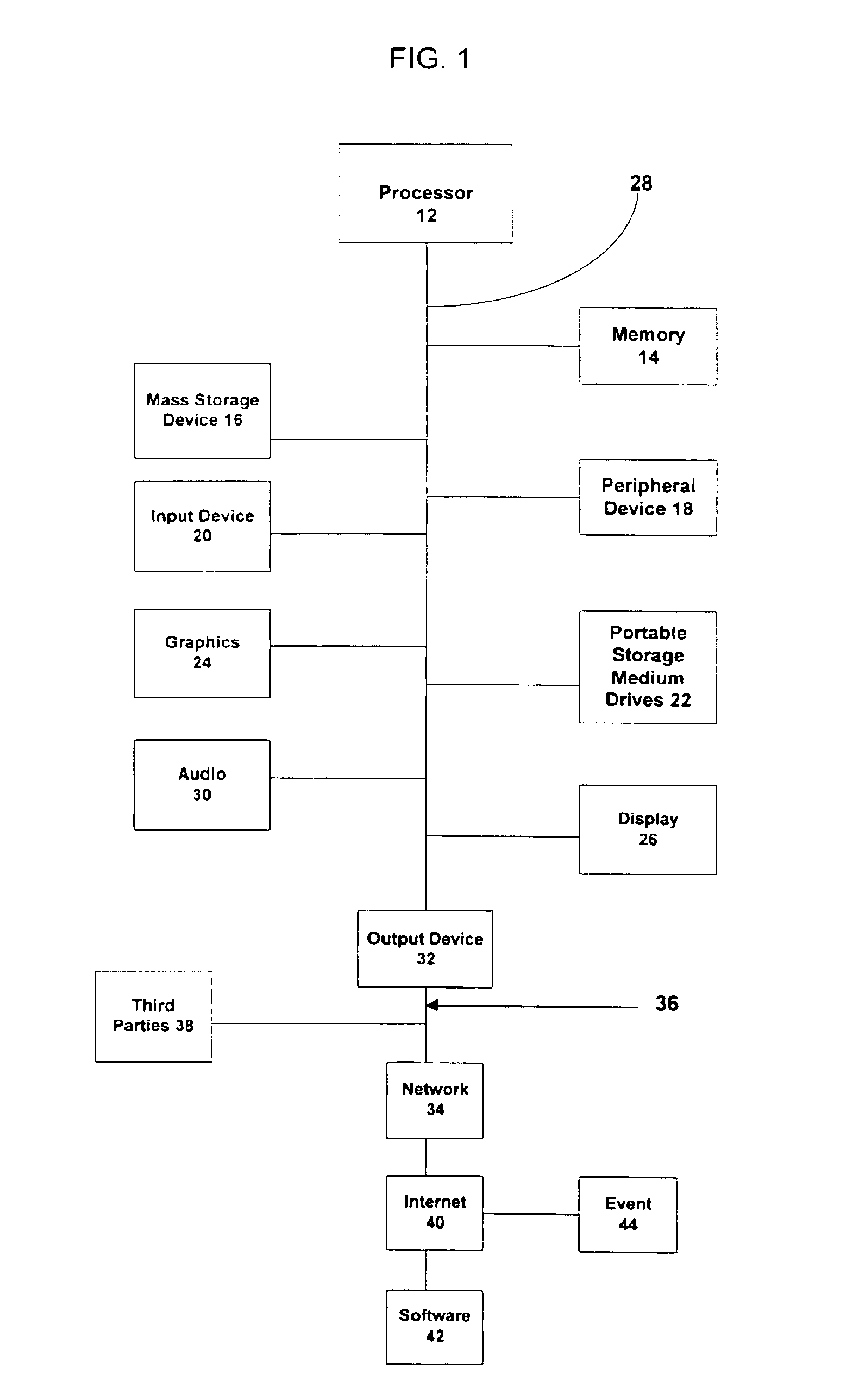
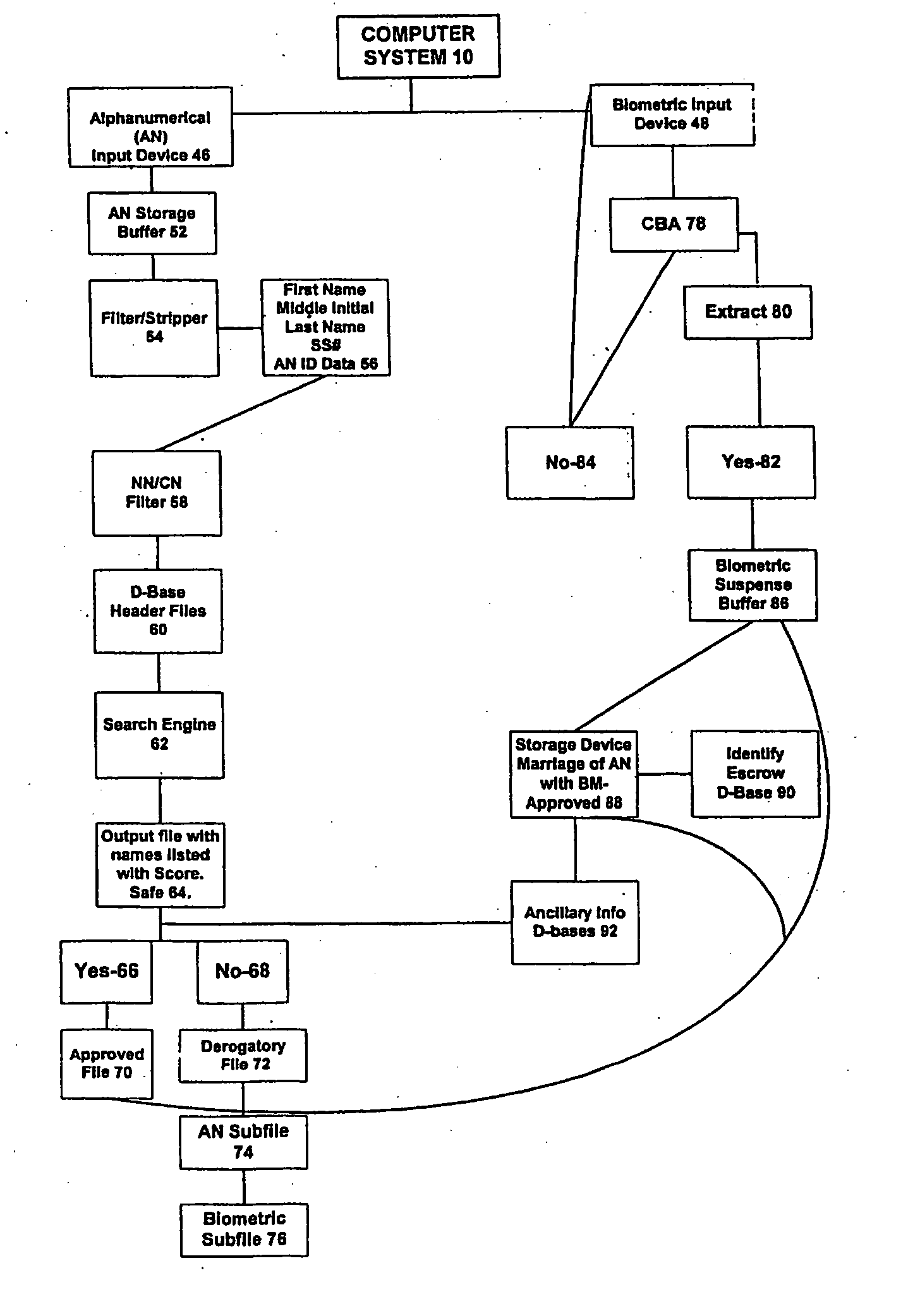
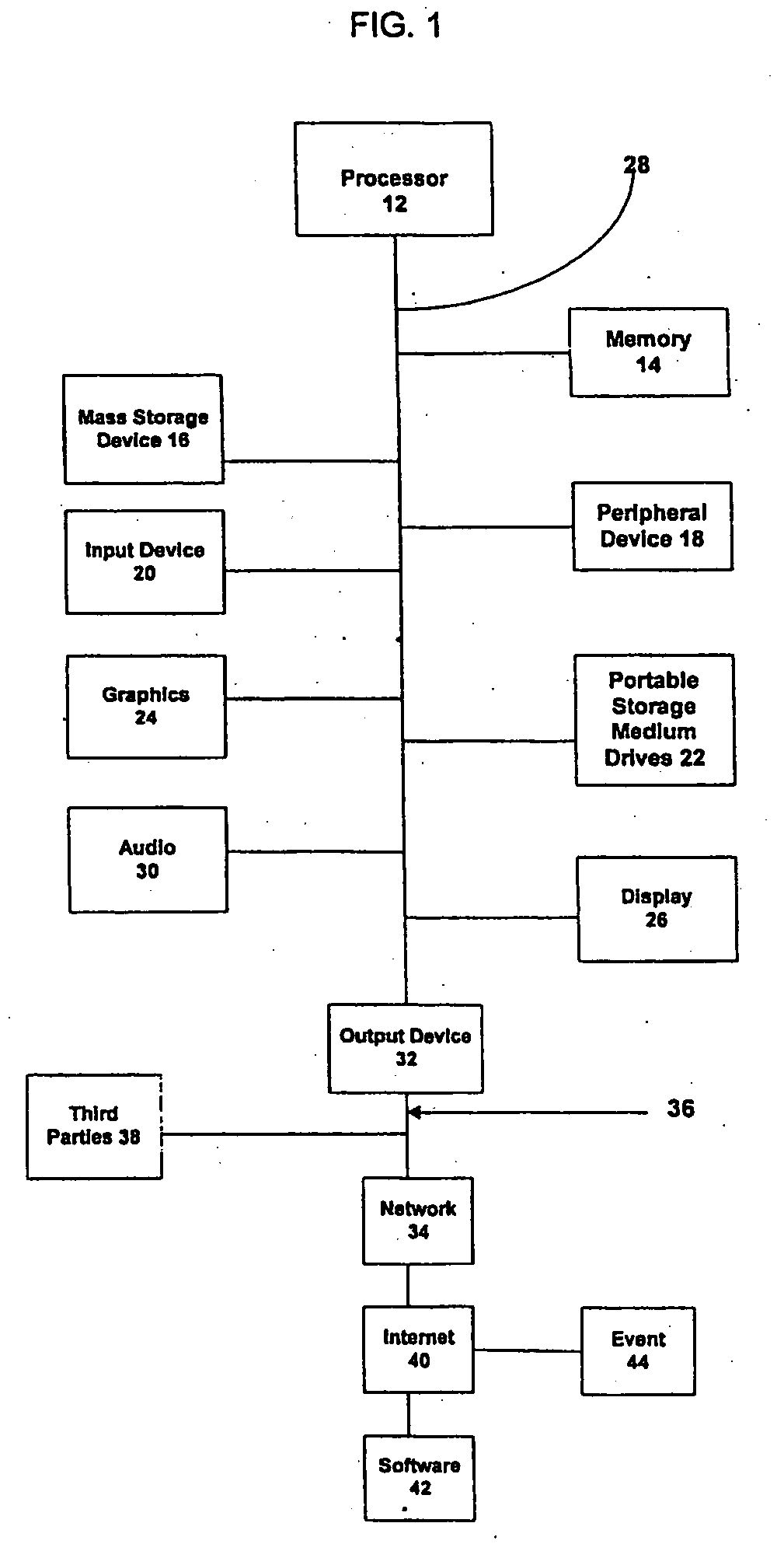
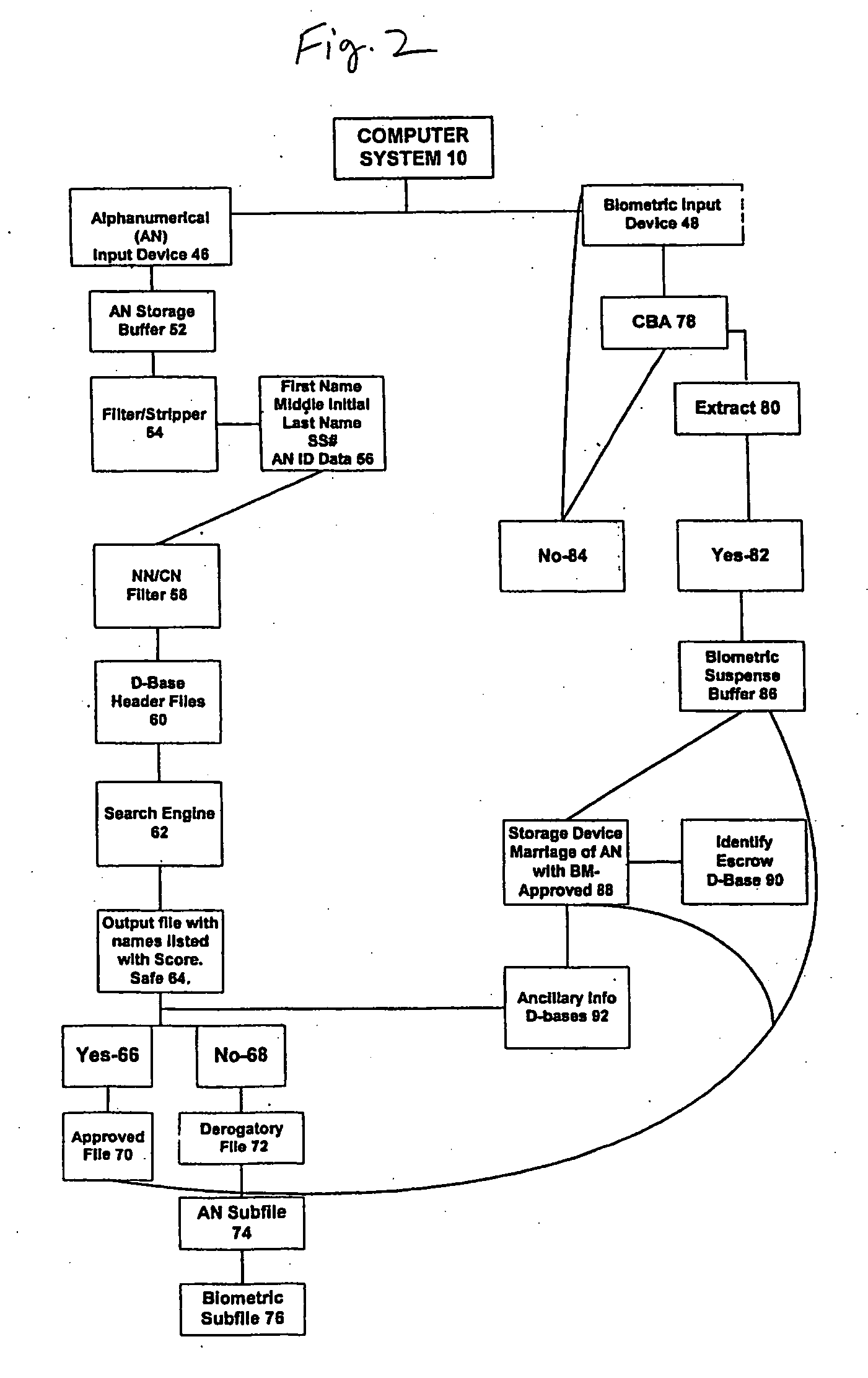
System and method for verification of identity
InactiveUS6871287B1Secure deliverySafe handlingFinanceDigital data processing detailsBiometric dataUser input
A system and method for the identification and verification of a user is provided. The disclosed invention has an enrollment system which includes (i) an alphanumeric input device; (ii) a biometric input device; (iii) a header file database having a plurality of identities; (iv) a search engine in communication with the header file database that searches the database for identifies that match alphanumeric data input by a user according to a predetermined first set of criteria; (v) a processor to score the set of identities matched by the search engine according to a predetermined second set of criteria, and determine that the user's input alphanumeric data based on the score is not suspicious; and (vi) an identity escrow database which receives an approved identity data signal based on the acceptability of the score, and is capable of receiving a biometric identity data signal input by the user to the biometric input device, the escrow database further capable of creating at least one subfile within the escrow database for each user comprising the approved identity data signal and the biometric data signal.
Owner:EDENTIFY INC
User interface for visual cooperation between text input and display device
ActiveUS20070061754A1Reduce effortInput/output for user-computer interaction2D-image generationVirtual userText entry
A user-interface system for entering an alphanumeric string or alphanumeric clusters for identifying information content is presented. The user-interface system has presentation logic for displaying an image of a virtual user alphanumeric interface on a presentation device. The virtual user alphanumeric interface includes an image of an overloaded keypad that has a two dimensional configuration of alphanumeric clusters. Each cluster corresponds to a set of alphanumeric characters. The user-interface system also has cluster selection logic for receiving user actions from an input device (e.g., five-button interface) to provide visual cues to help the user select an alphanumeric cluster and to cause the selected alphanumeric cluster or character from a cluster to be displayed in a display field of the virtual user alphanumeric interface.
Owner:VEVEO LLC
Method and apparatus for bar code association for wireless network
InactiveUS6149063ACo-operative working arrangementsSensing by electromagnetic radiationTelecommunications linkBarcode
A wireless network having a base station adapted for wireless communications, a wireless bar code scanner and a network ID label having a bar code symbol printed thereon. The bar code symbol includes encoded information pertaining to the base station. A wireless bar code scanner is adapted to scan and decode the network ID label. The wireless bar code scanner initiates a communications link with the base station utilizing information from the decoded network ID label. The wireless bar code scanner includes a light source for illuminating a printed bar code symbol, an electro-optical element for imaging the printed bar code symbol, a decoder for decoding the imaged printed bar code symbol into an alphanumeric string, and an input / output device for conducting wireless communications with the base station.
Owner:WELCH ALLYN DATA COLLECTION +1
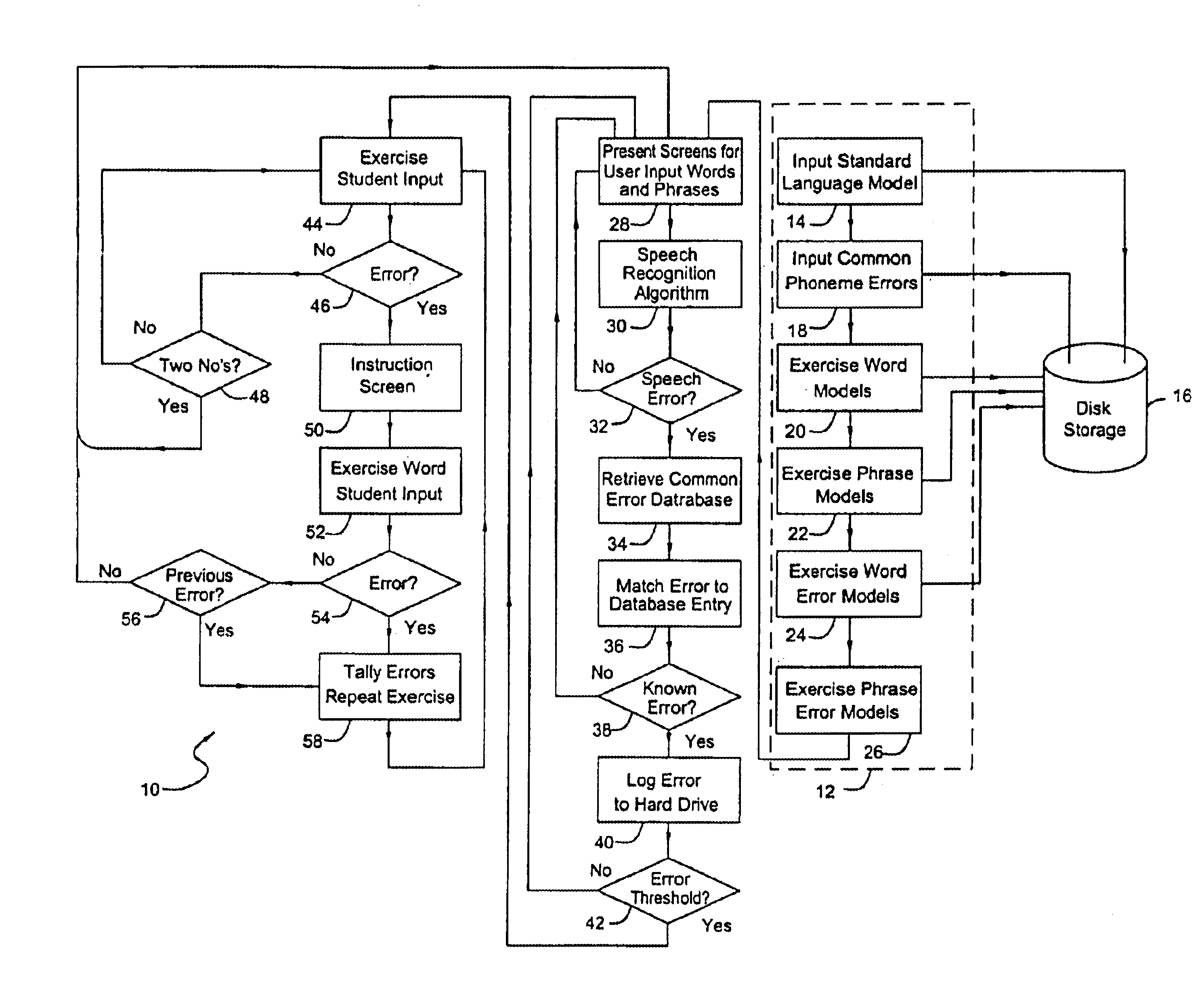
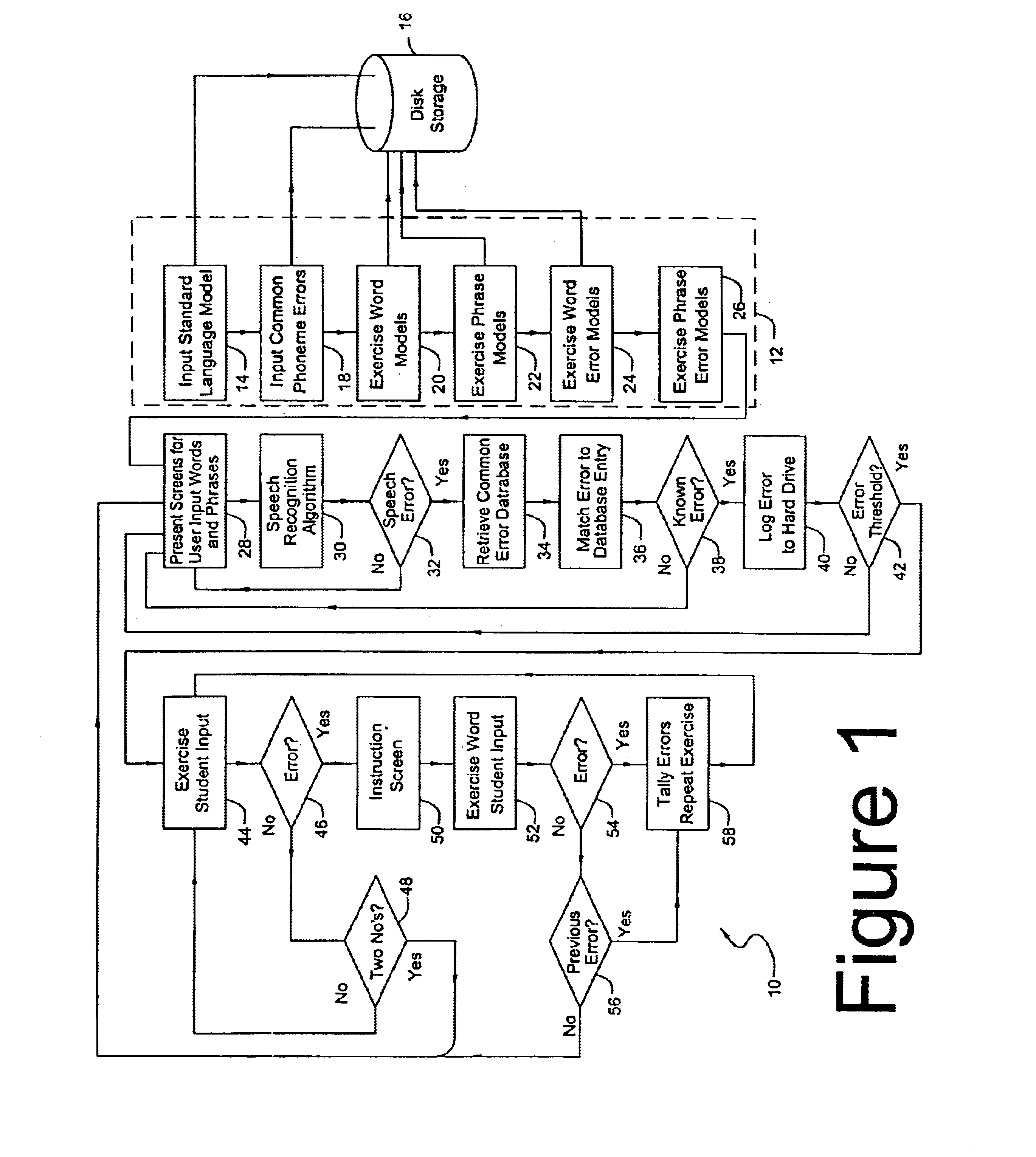
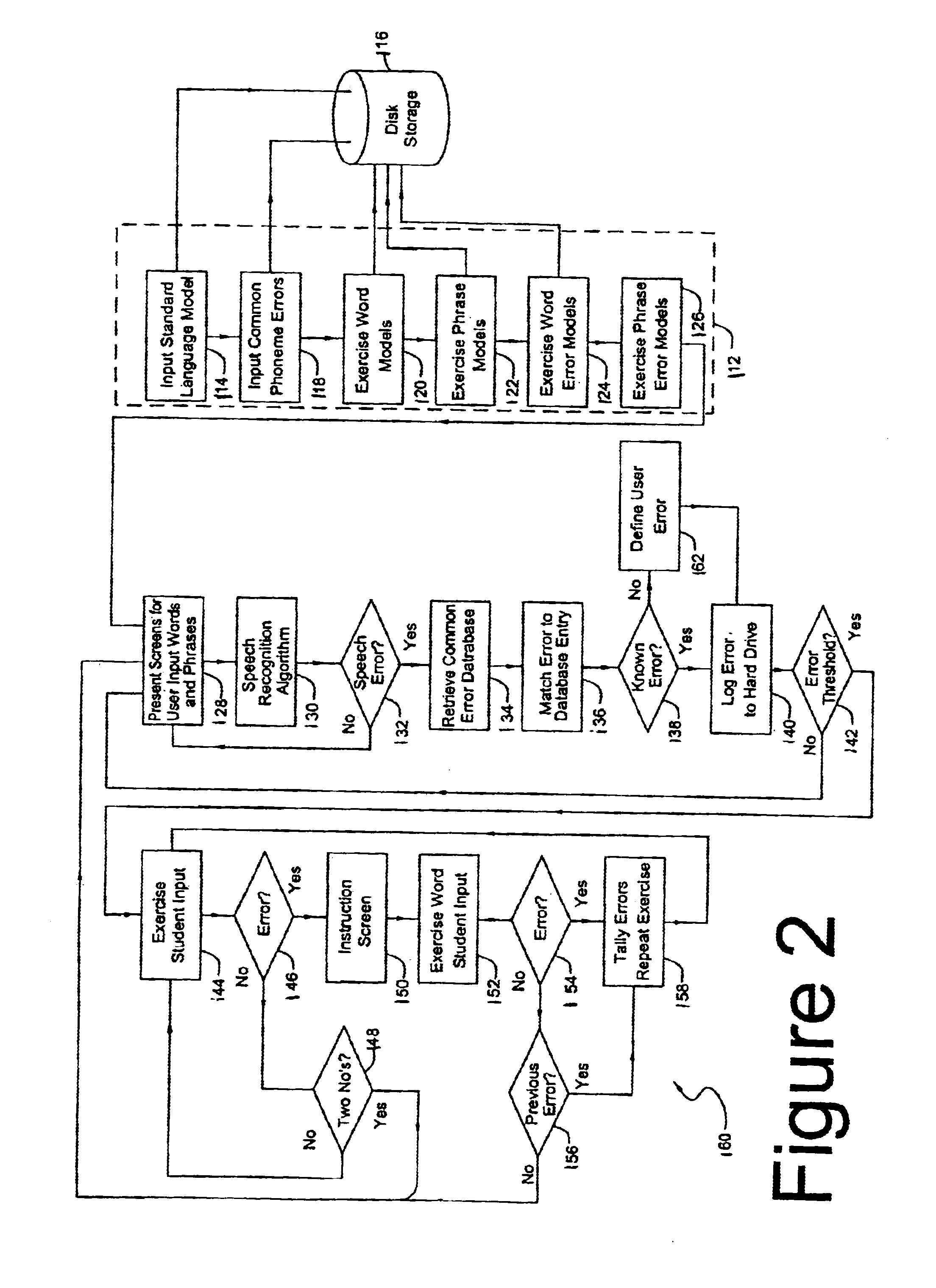
Speech training method with alternative proper pronunciation database
InactiveUS6963841B2Improving speech patternSpeech recognitionElectrical appliancesSpeech trainingUser input
In accordance with a present invention speech training system is disclosed. It uses a microphone to receive audible sounds input by a user into a first computing device having a program with a database consisting of (i) digital representations of known audible sounds and associated alphanumeric representations of the known audible sounds, and (ii) digital representations of known audible sounds corresponding to mispronunciations resulting from known classes of mispronounced words and phrases. The method is performed by receiving the audible sounds in the form of the electrical output of the microphone. A particular audible sound to be recognized is converted into a digital representation of the audible sound. The digital representation of the particular audible sound is then compared to the digital representations of the known audible sounds to determine which of those known audible sounds is most likely to be the particular audible sound being compared to the sounds in the database. In response to a determination of error corresponding to a known type or instance of mispronunciation, the system presents an interactive training program from the computer to the user to enable the user to correct such mispronunciation.
Owner:LESSAC TECH INC
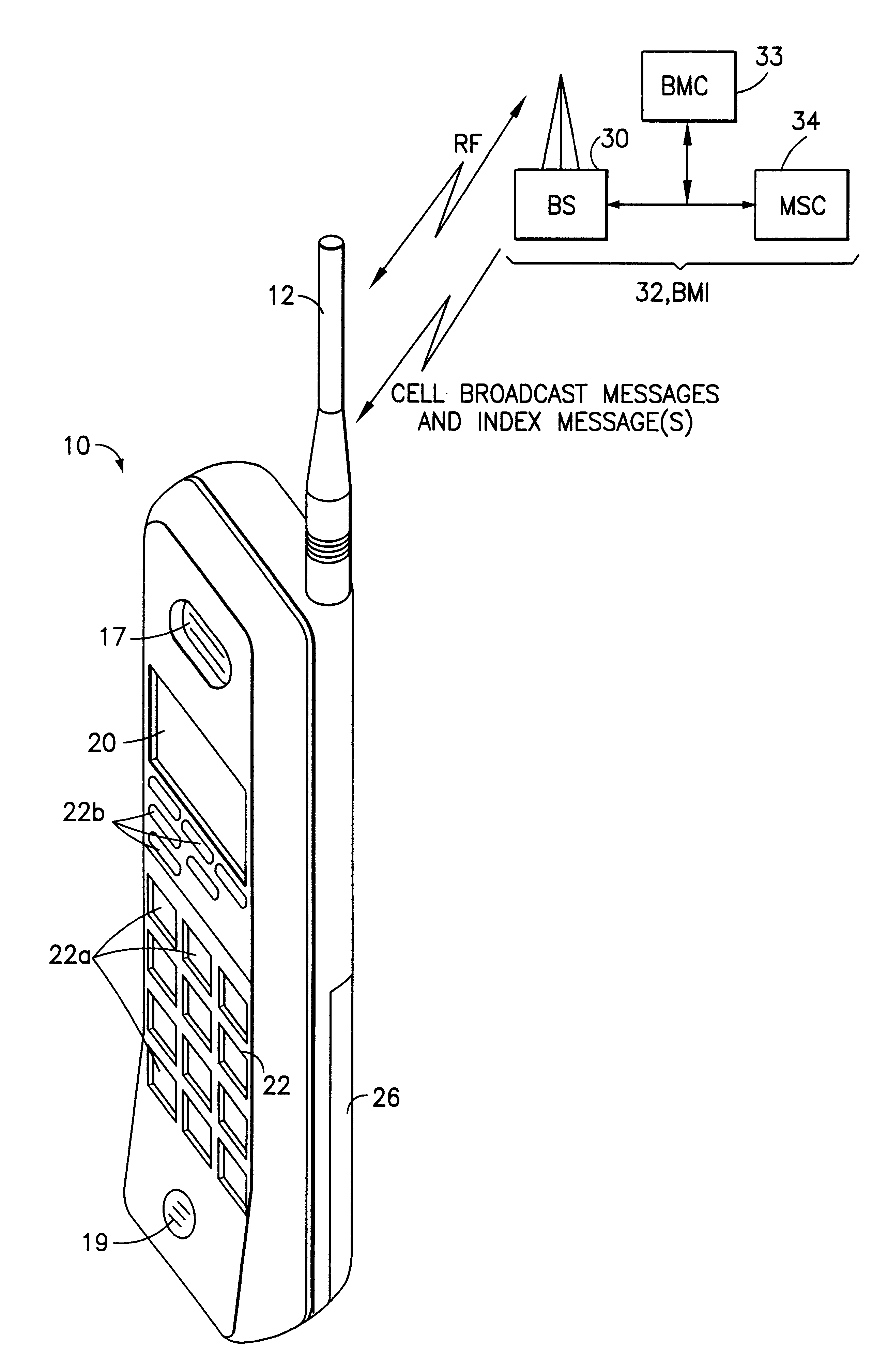
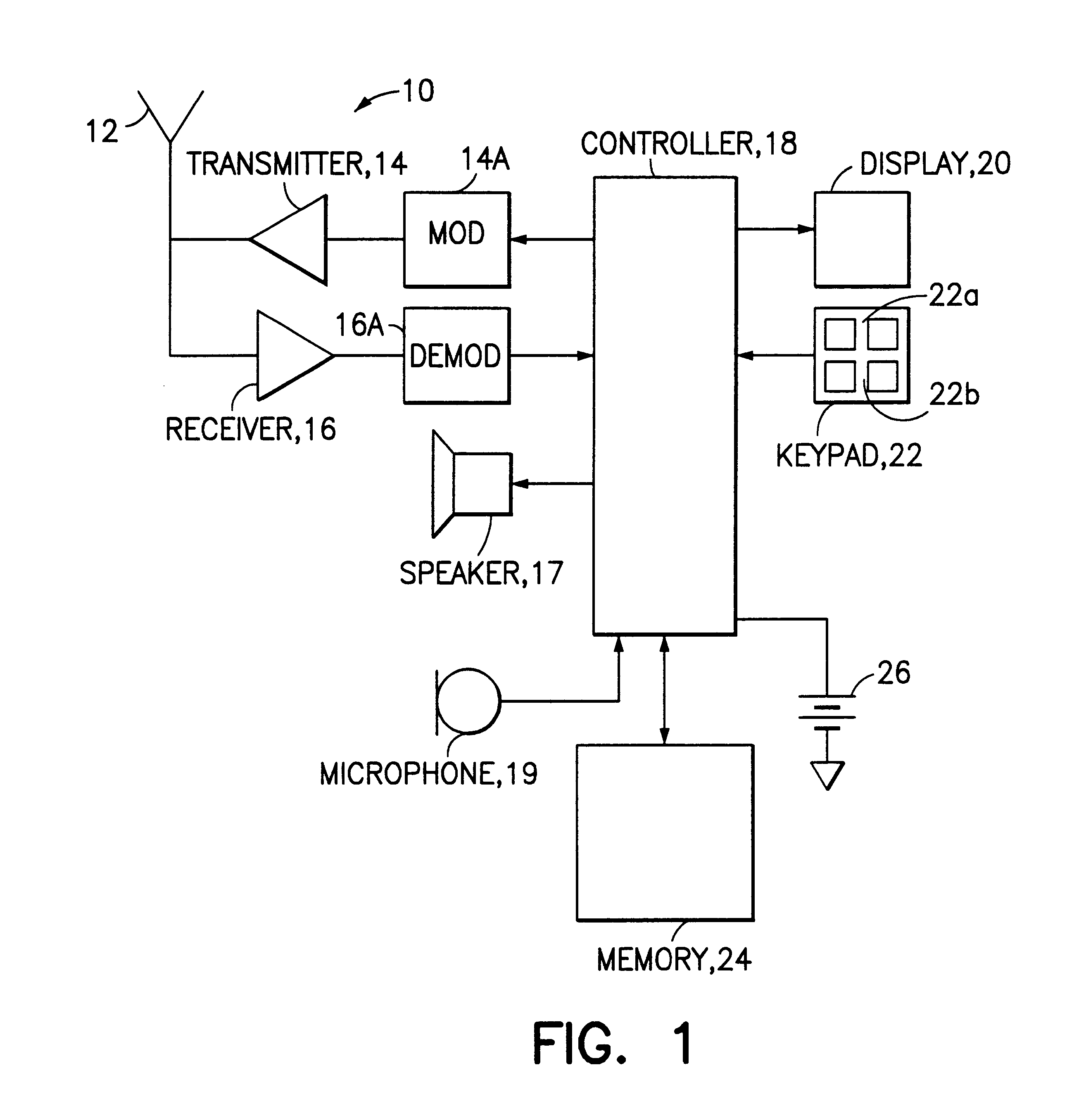
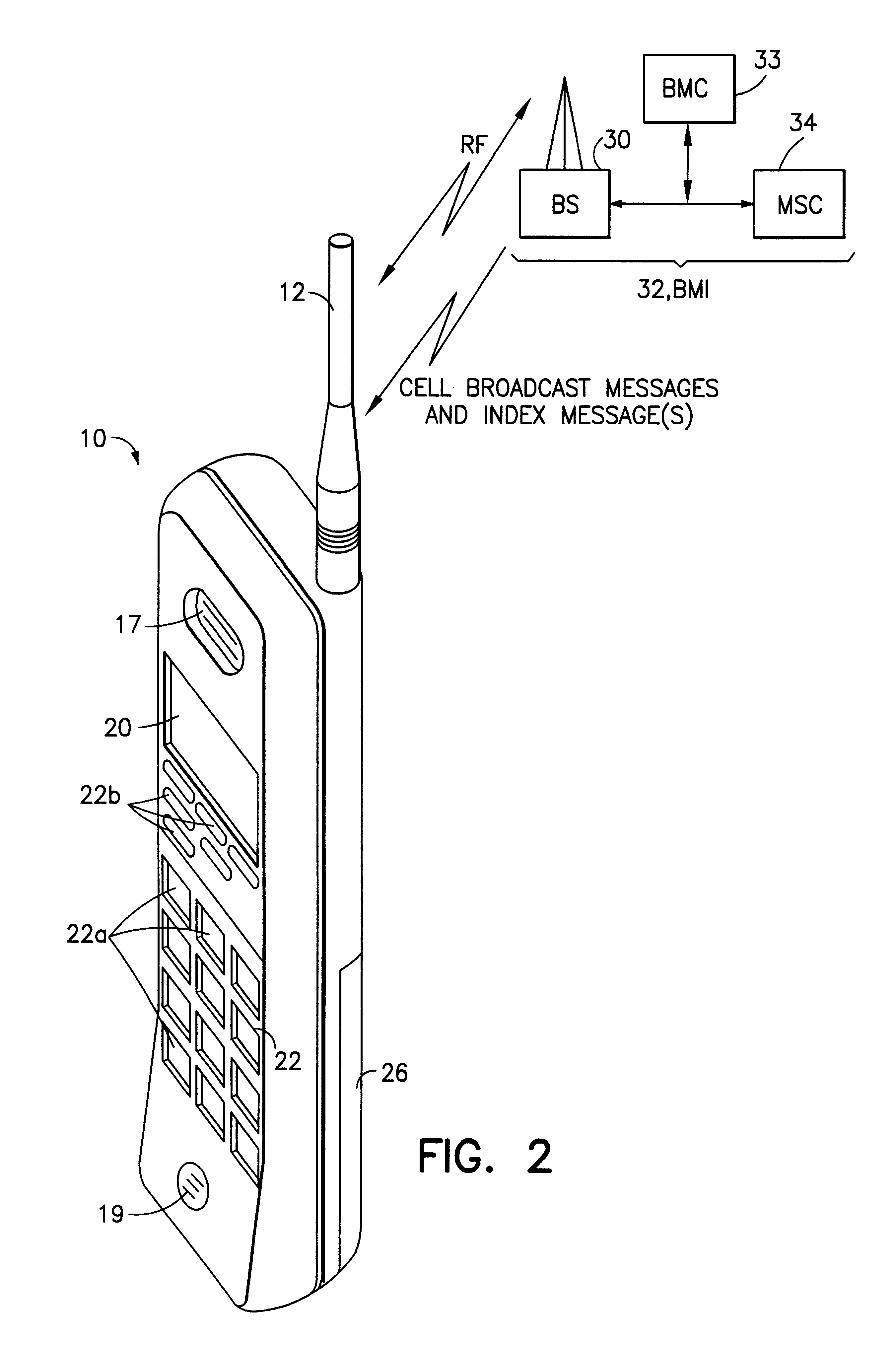
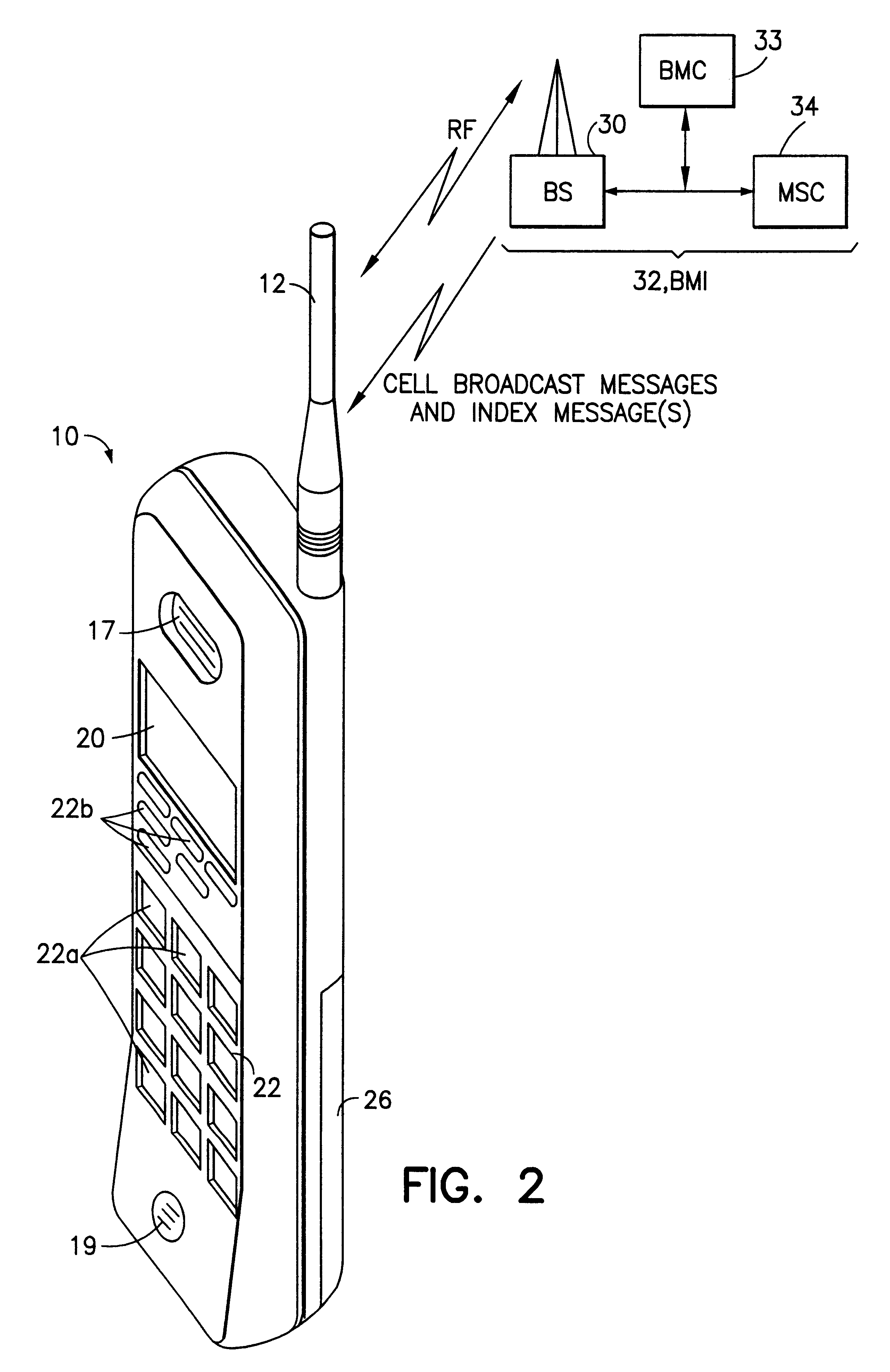
Mobile station and network having hierarchical index for cell broadcast service
InactiveUS6201974B1Easy to useEmergency connection handlingTime-division multiplexBroadcast domainMobile station
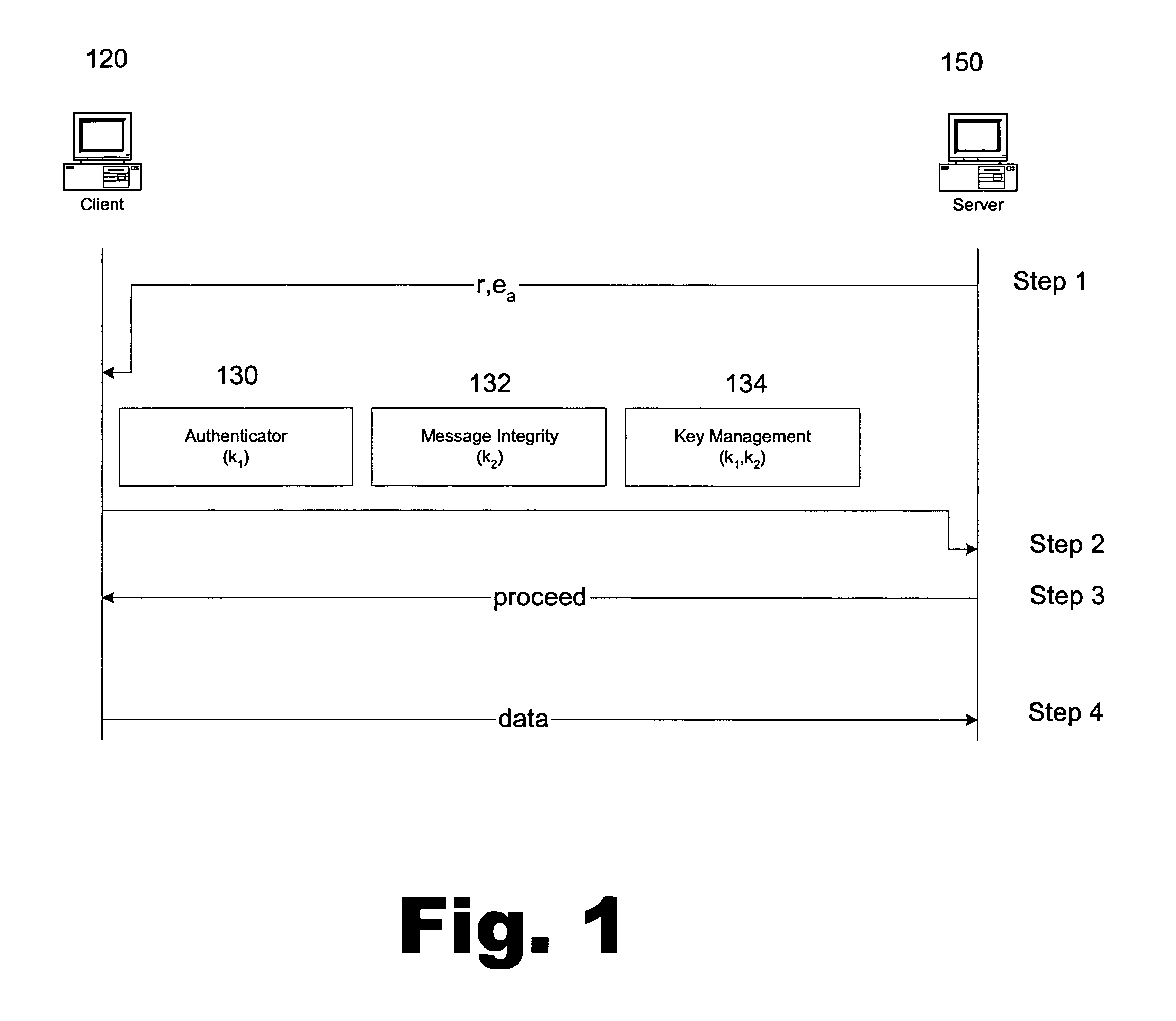
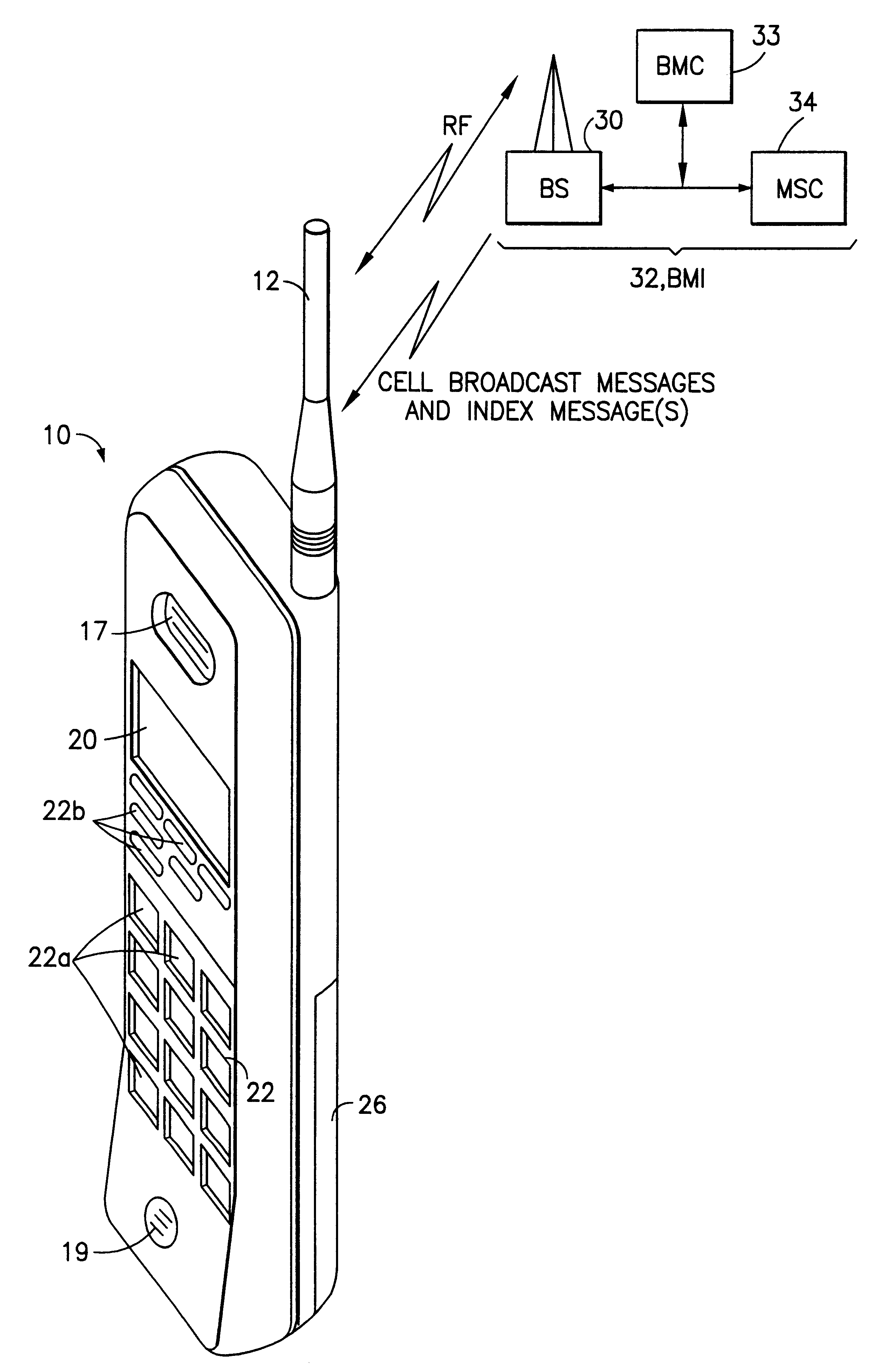
This invention provides for the use of an index message in a Cell Broadcast Service. An index message is considered to be a special type of Cell Broadcast message which contains general information about actual broadcast messages. The index message is transmitted in a predetermined logical S-BCCH subchannel, and contains information elements such as (a) message overviews or summaries for each cell broadcast message, (b) information concerning emergency messages, (c) information concerning the language used in different broadcast messages, (d) an alphanumeric broadcast domain operator name and a specific operator greeting, (e) information concerning changes in broadcast messages, and (f) information concerning subchannels.
Owner:NOKIA TECHNOLOGLES OY
Methods and apparatus for using a modified index to provide search results in response to an ambiguous search query
InactiveUS6865575B1Data processing applicationsDigital data processing detailsAmbiguityDocumentation
A system allows a user to submit an ambiguous search query and to receive potentially disambiguated search results. In one implementation, a search engine's conventional alphanumeric index is translated into a second index that is ambiguated in the same manner as which the user's input is ambiguated. The user's ambiguous search query is compared to this ambiguated index, and the corresponding documents are provided to the user as search results.
Owner:GOOGLE LLC
IC card file system
InactiveUS20070152070A1AccessibilityAcutation objectsDigital data information retrievalIntel HEXApplication software
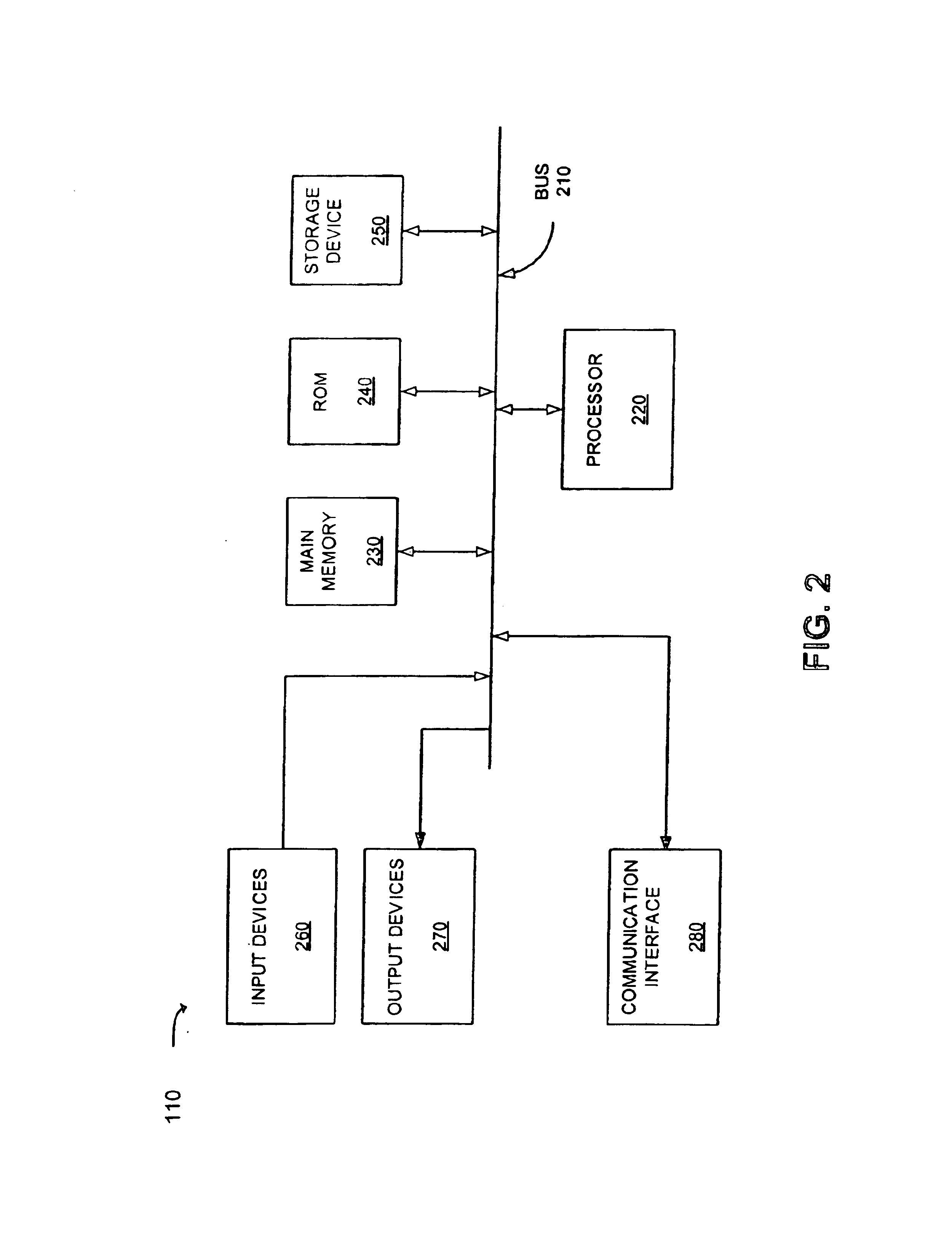
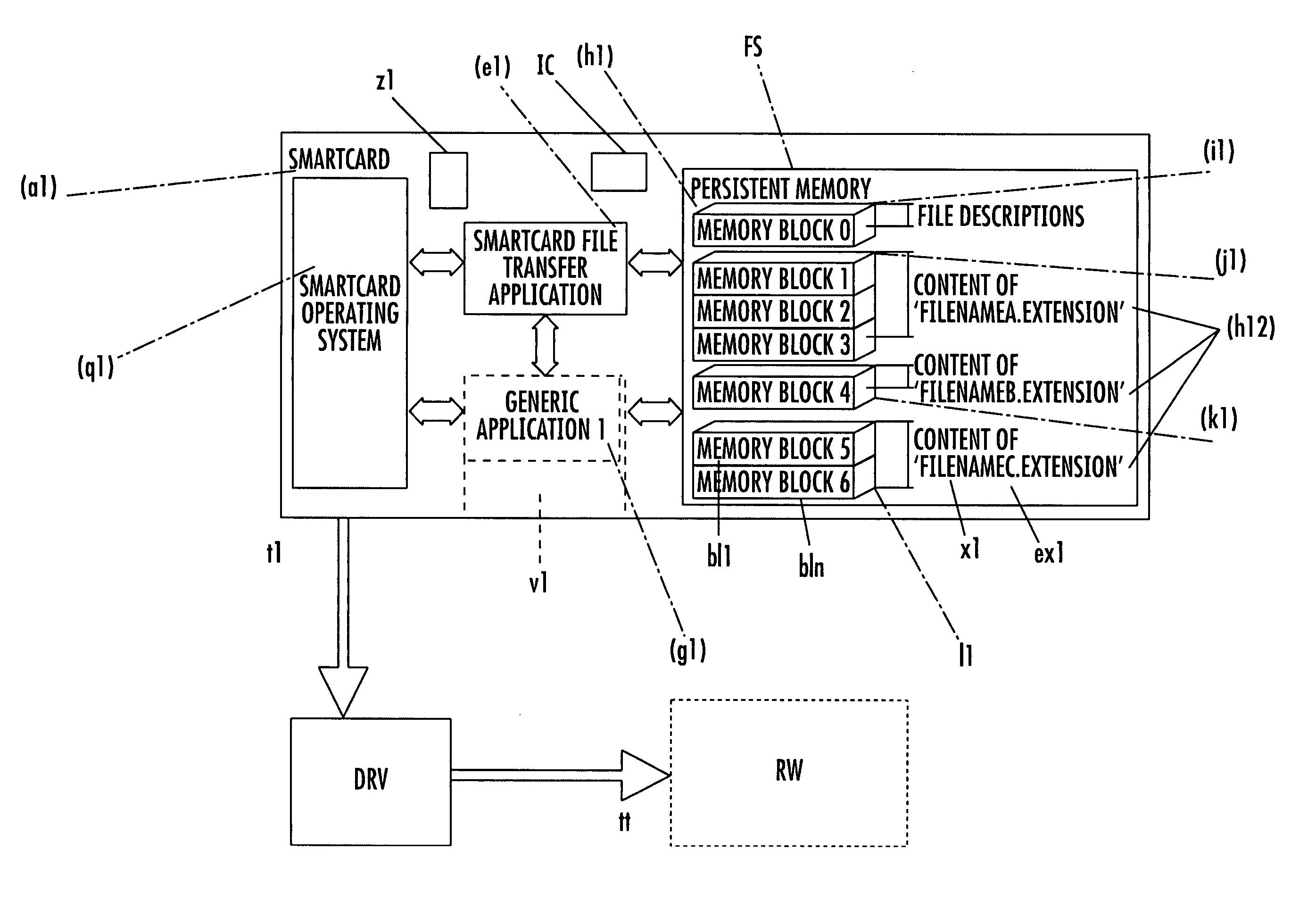
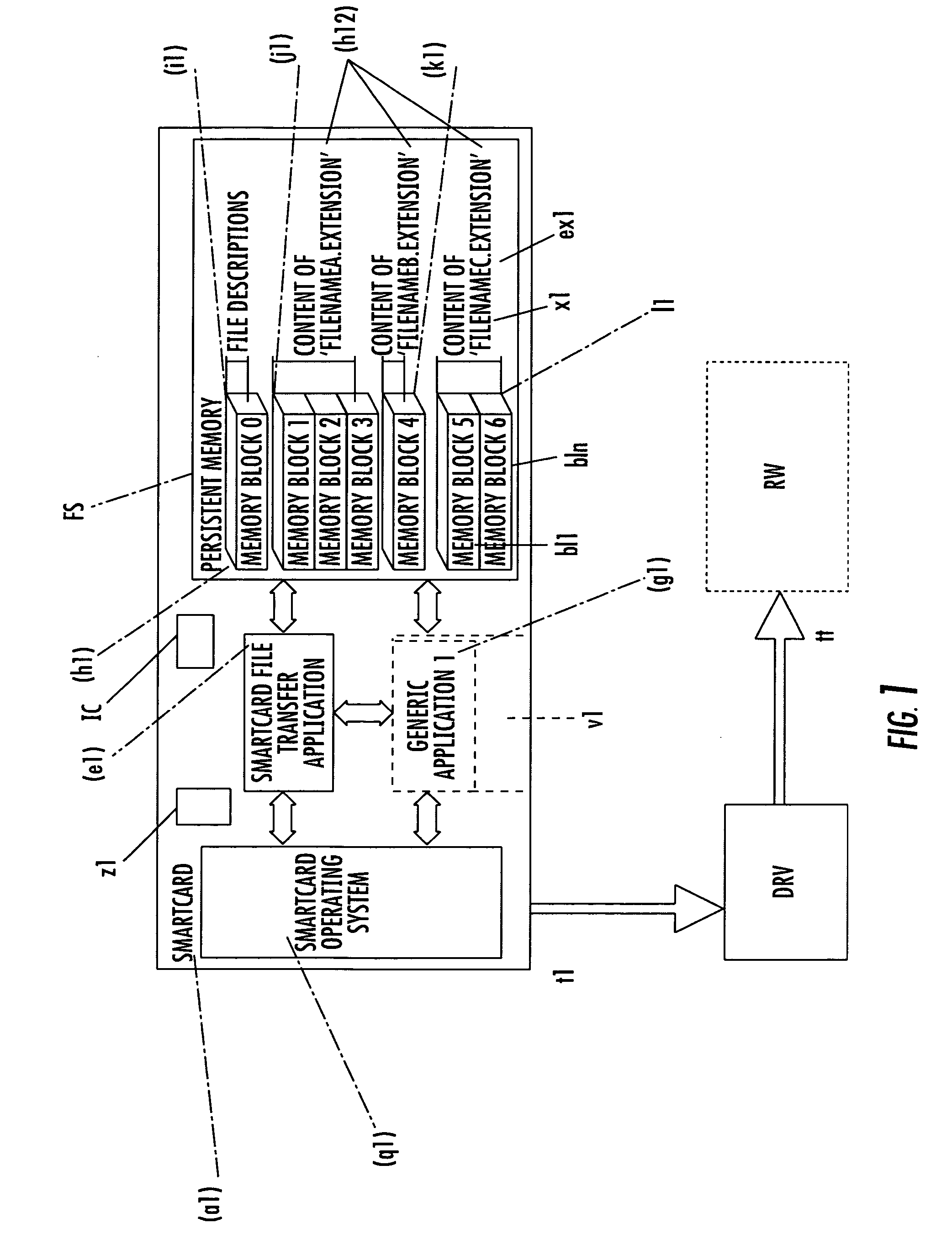
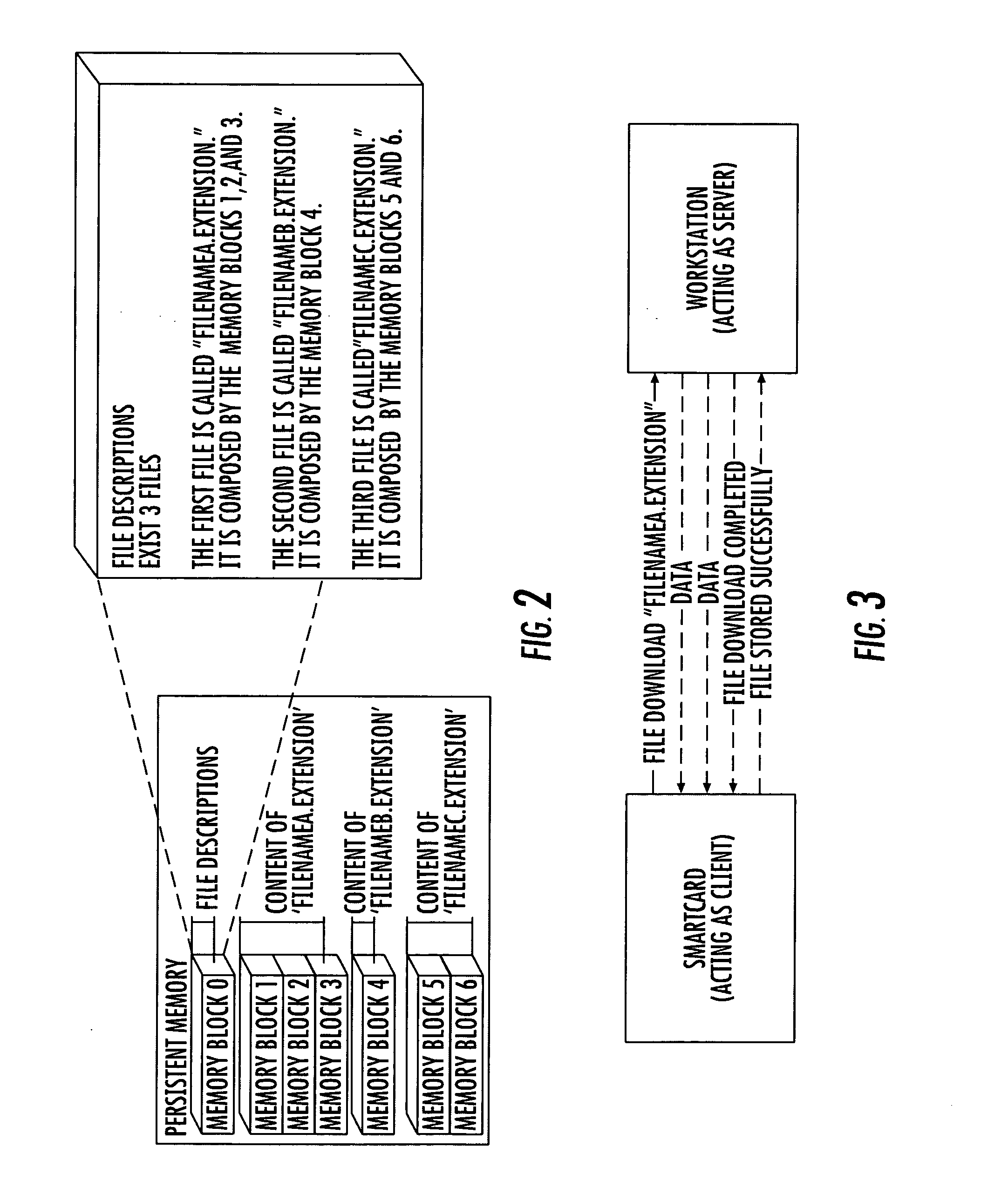
File system for IC CARD comprising an integrated circuit IC, non volatile memories ROM and / or E2PROM and at least a volatile memory RAM, for organizing files storage inside the non volatile memories and defining, through a logical structure, their accessibility by an IC Card application, stored inside one of said non volatile memories or IC or loaded in the volatile memory and in communication with an external read-write device; an interchange application, stored inside one of said non volatile memories, drives the organization of files in an additional tag-length logic structures of arbitrary length, allowing the identification of files through alphanumeric identifiers of arbitrary length and extension, and their accessibility by an external read-write device, eventually non IC card purpose, like a workstation a personal computer or a PDA interconnected to the IC Card by means of standard communication interface. The file system organizes said tag-length logic structure as individually memory blocks, each identified by an hexadecimal identification number and a block size and one of these memory blocks, more particularly one per non volatile memory, describes the content of the non volatile memory, comprising the number of files stored, their file name and extension and, for each file, the location of memory blocks composing its content.
Owner:STMICROELECTRONICS INT NV
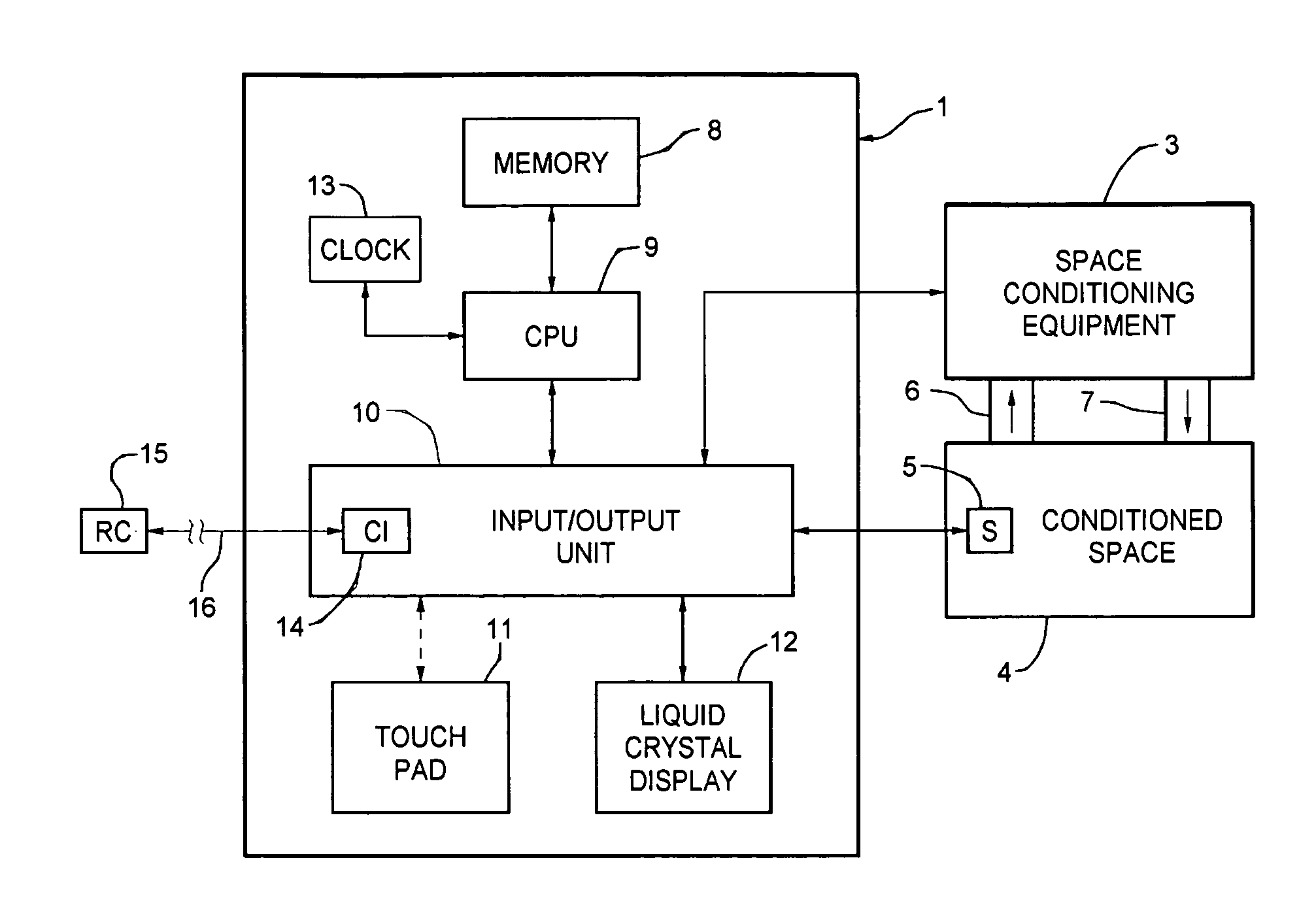
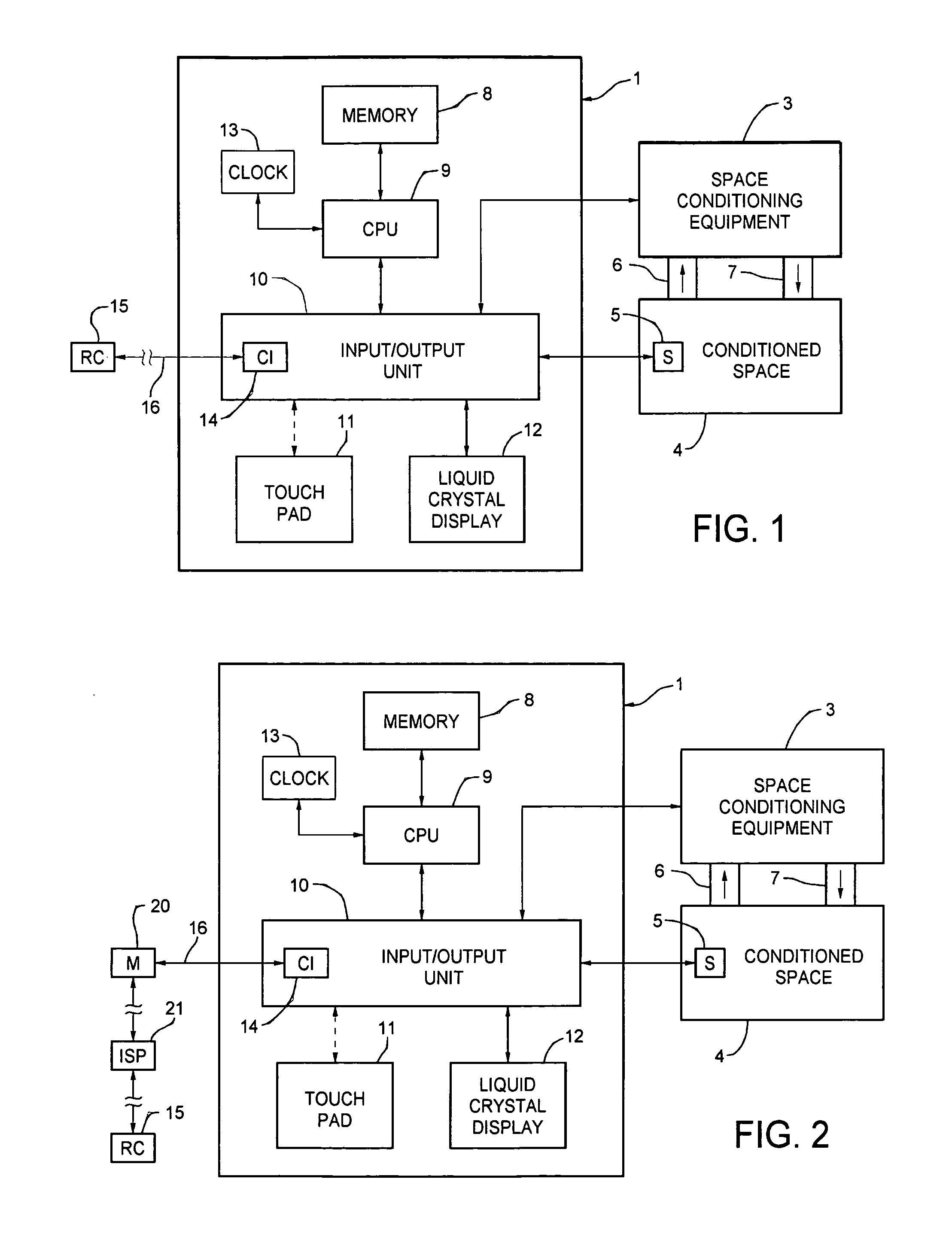
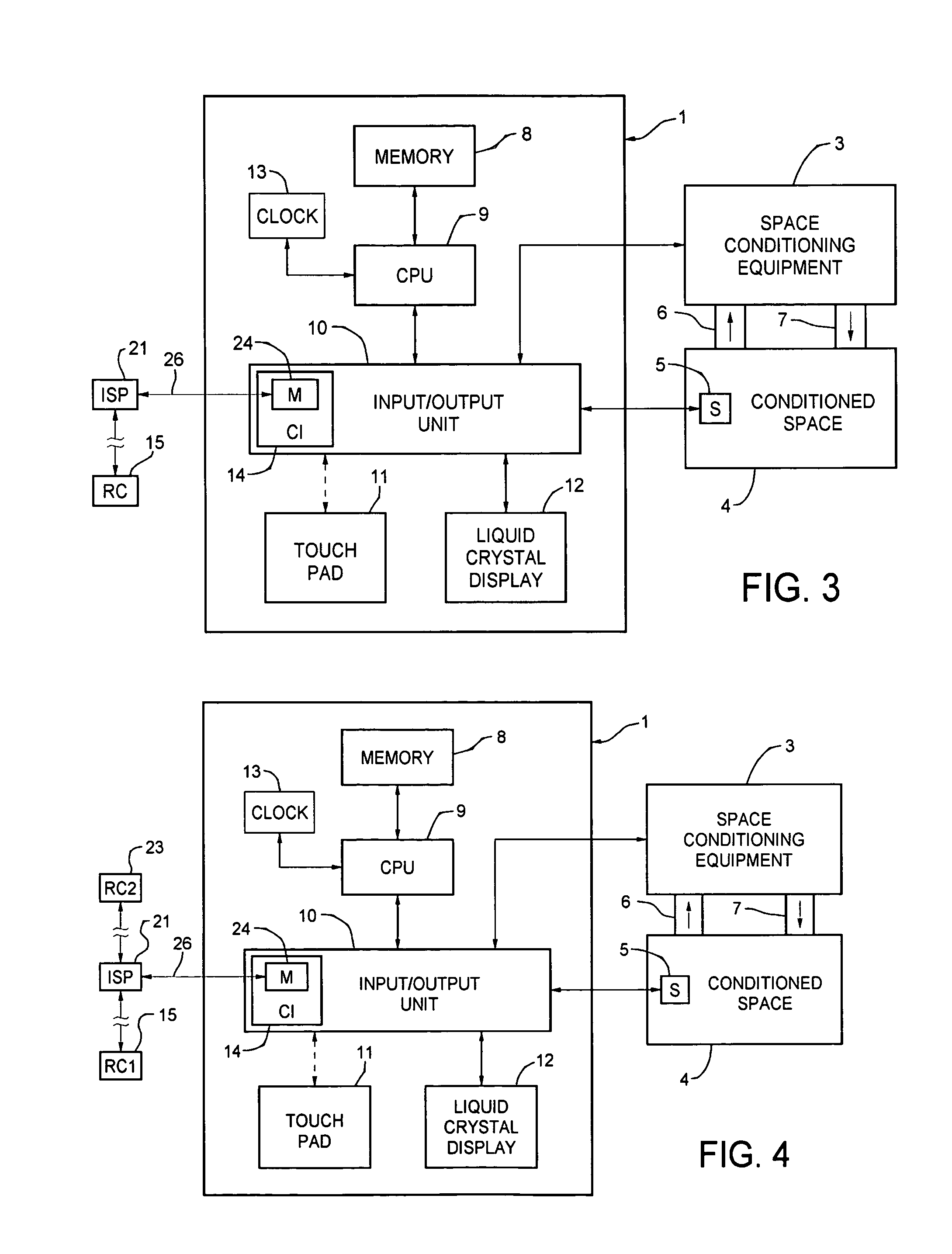
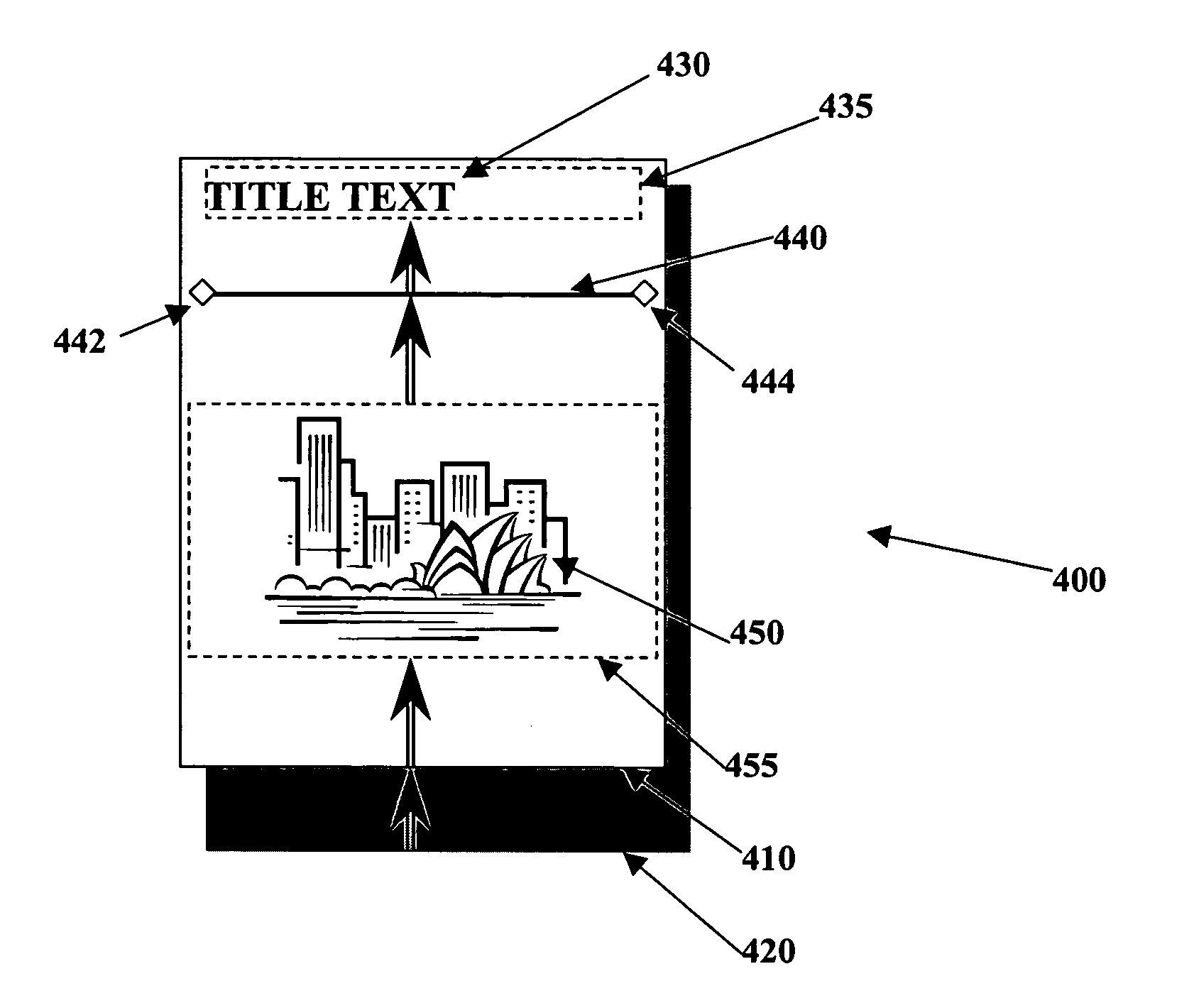
Thermostat system with touchscreen with user interfaces or operational algorithms via a remote correspondent
ActiveUS7232075B1Facilitate intuitive programmingStatic indicating devicesTemperatue controlGraphicsCommunication interface
A thermostat system includes a temperature sensor, an LCD for selectively displaying alphanumeric and graphic devices on a touchscreen with virtual buttons, a processor having a memory for storing program and data information, and means for establishing communication with a remote correspondent. In one embodiment, the communication from the remote correspondent includes functional programming adding functions or virtual buttons to the thermostat not previously available to it. A communications interface connects the processor and a remote correspondent which is a source of functional programming.
Owner:ROSEN TECH LLC
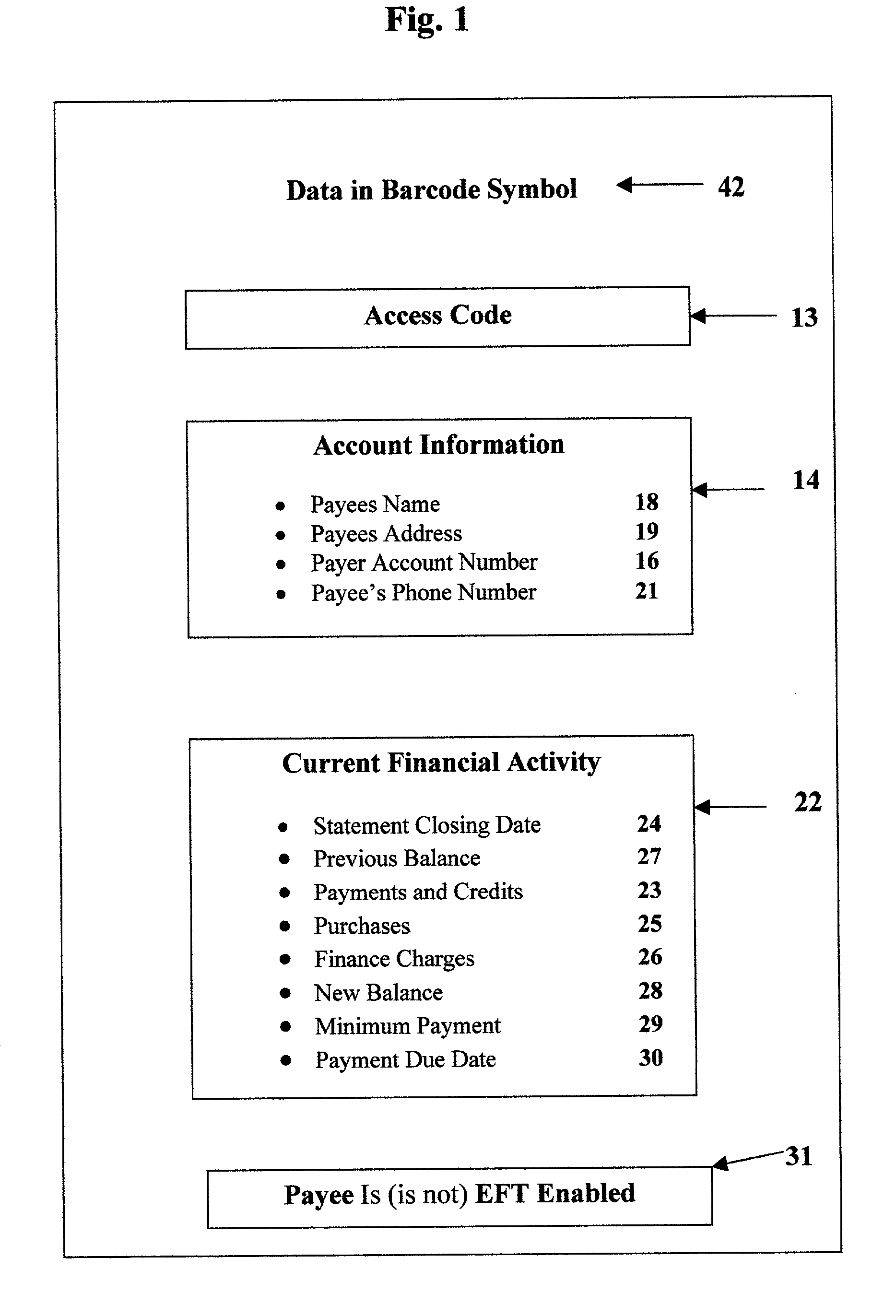
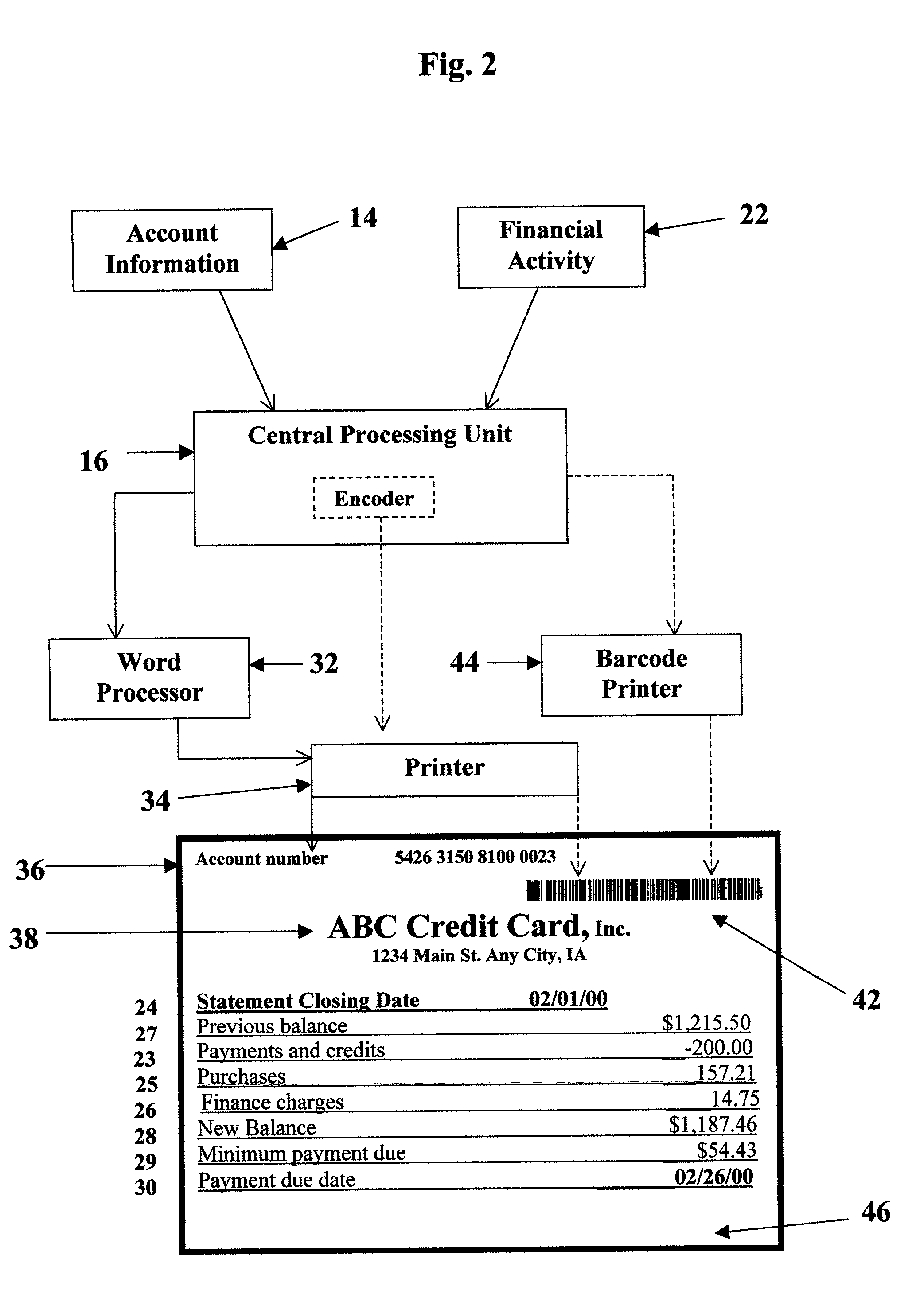
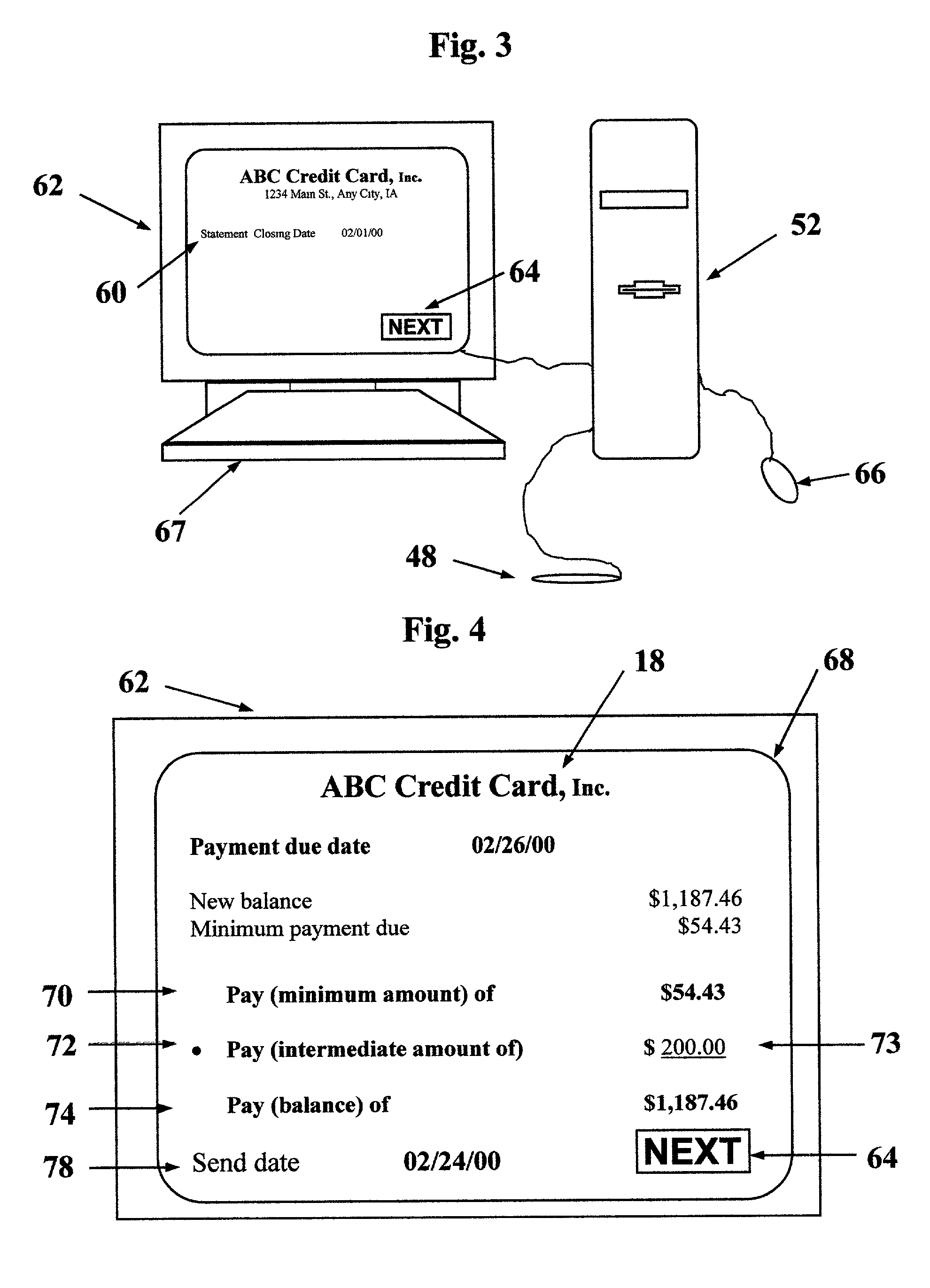
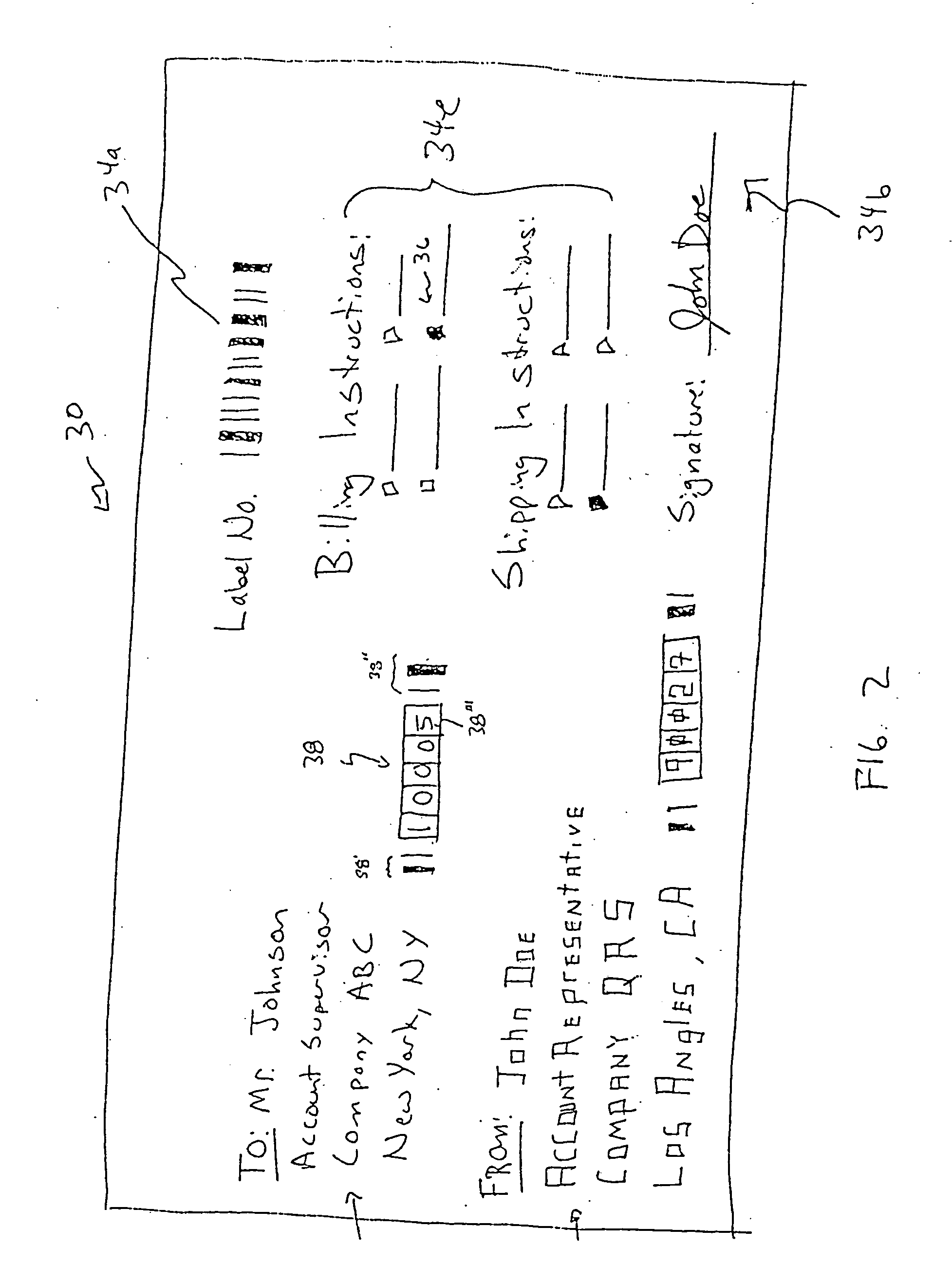
Bill paying with the aid of a scanner
A payee (a vendor) creates bill 46 with account information 14 and activity 22 printed in alphanumeric characters and in a barcode symbol 42. Bill 46 is sent in the mail to a payer (a customer). The payer scans symbol 42 into a PC 52 (personal computer). Scanning wand 48 decodes symbol 42 and transmits it to PC 52. An editor 54 is installed on PC 52. Editor 54 interprets signals and displays interactive visual image 60 on a display terminal 62. The payer verifies that the information on image 60 is the same as on bill 46. The payer clicks the next button with a mouse 66 to show a transaction display 68 on terminal 62. The payer determines that he or she wishes to pay amount 73 and enters amount 73 on display 68. The payer instructs editor 54 to transfer a payment order 82 either to an electric banking software program 58 installed on PC 52 or to an online program 59 accessible through a modem 55 of PC 52.
Owner:MCNAIR EDWARD PARRY
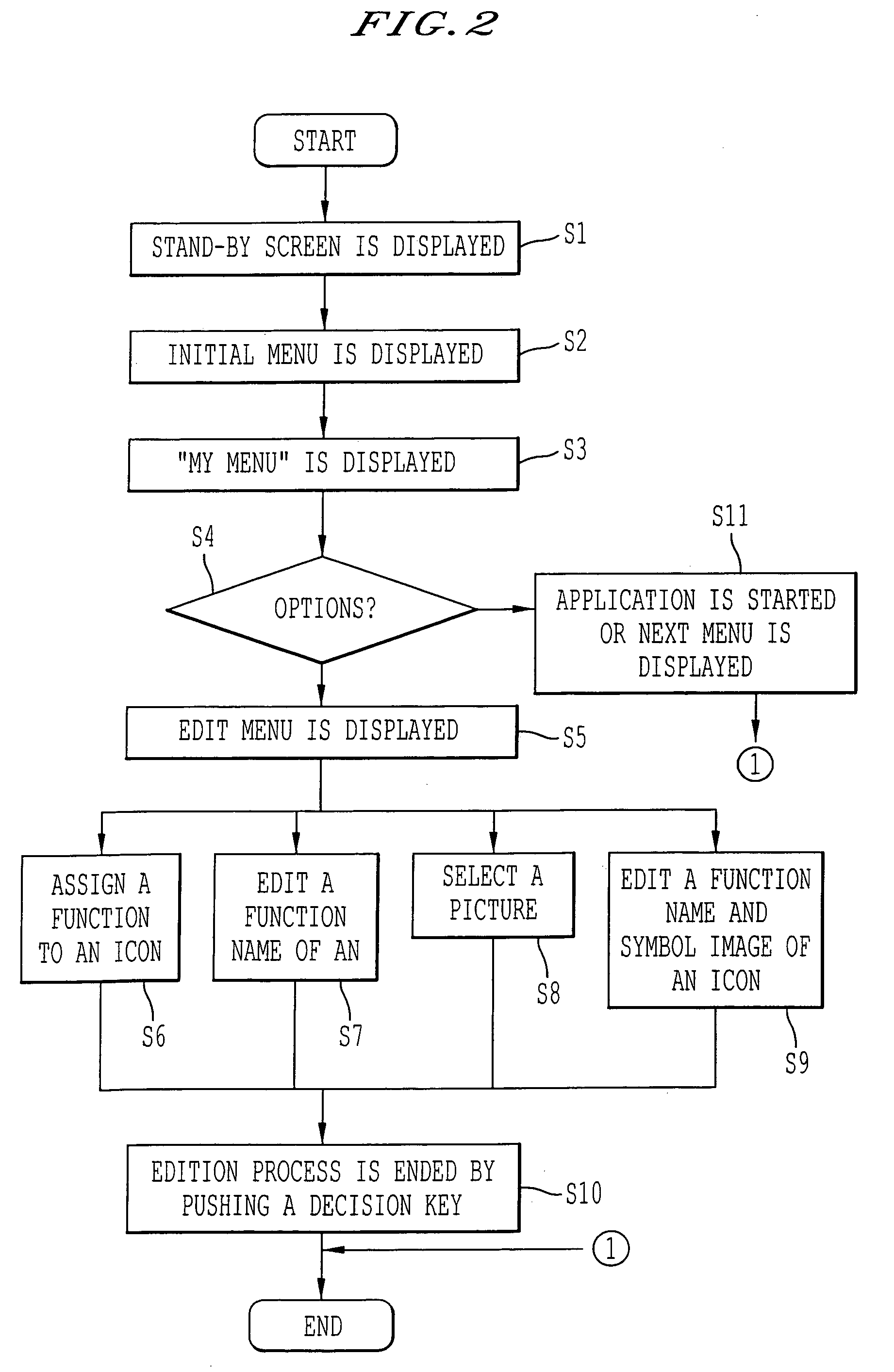
Menu displaying method and communication apparatus
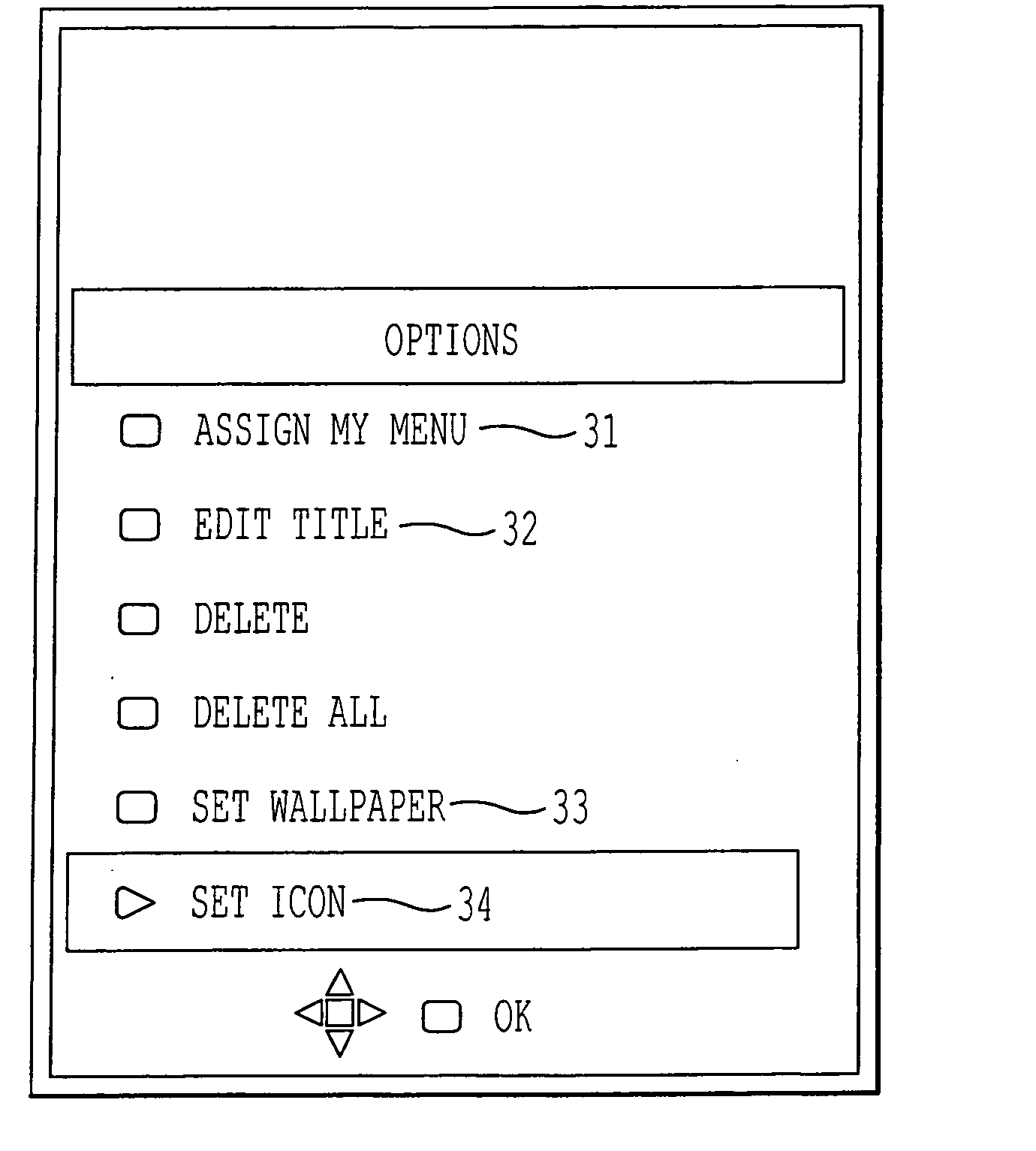
InactiveUS20050071771A1Keep visibilityCathode-ray tube indicatorsSubstation equipmentComputer graphics (images)Display device
A communication apparatus, for instance a cellular phone, has menu, a memory for storing a picture and a display for displaying alphanumeric and a picture. If a user selects the picture stored in the memory, the selected picture is displayed on the display as wallpaper. When the picture is set as wallpaper and menu comprised of icons is displayed by operation, the icons are displayed in the form of a function name and outline.
Owner:KK TOSHIBA
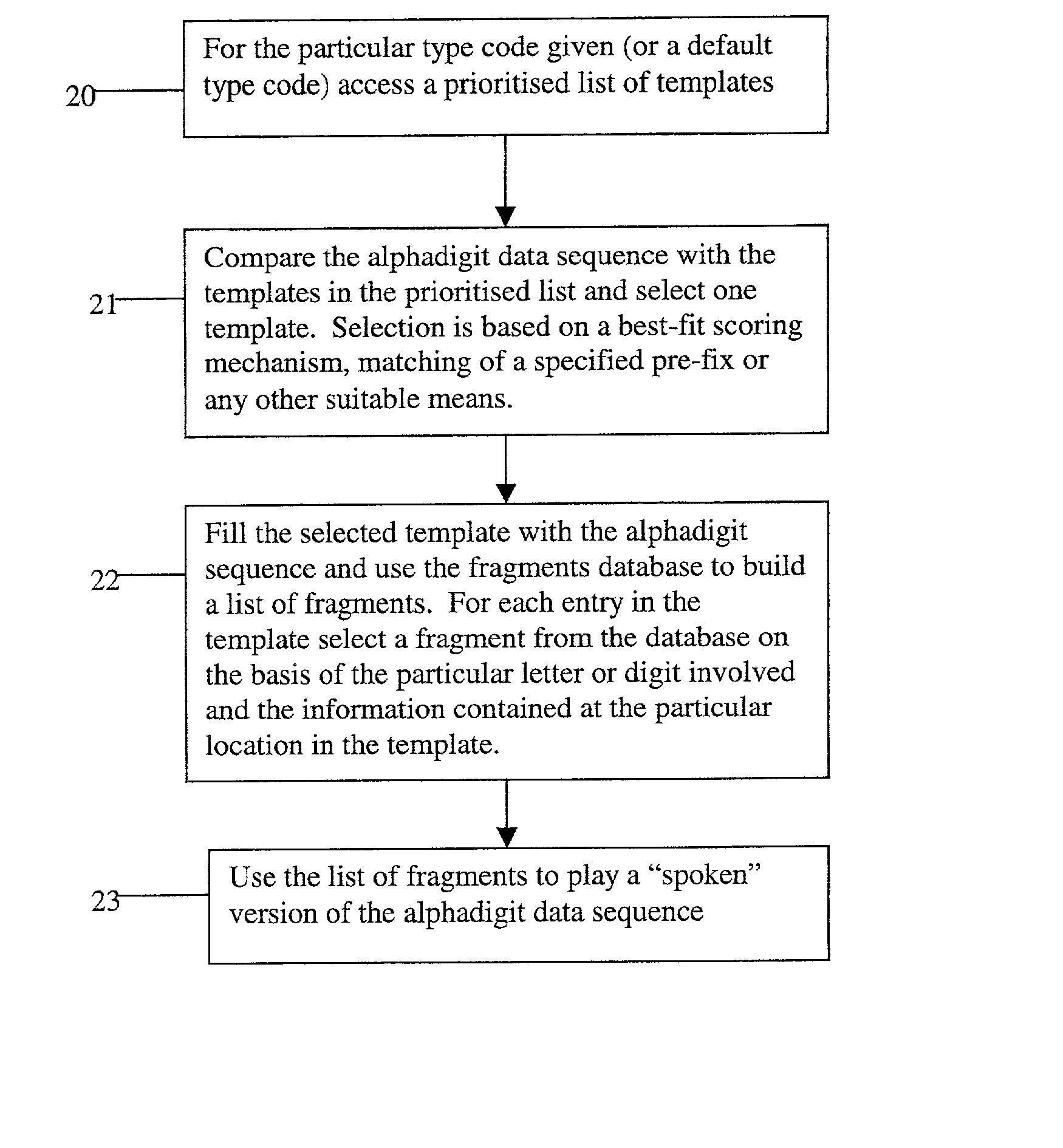
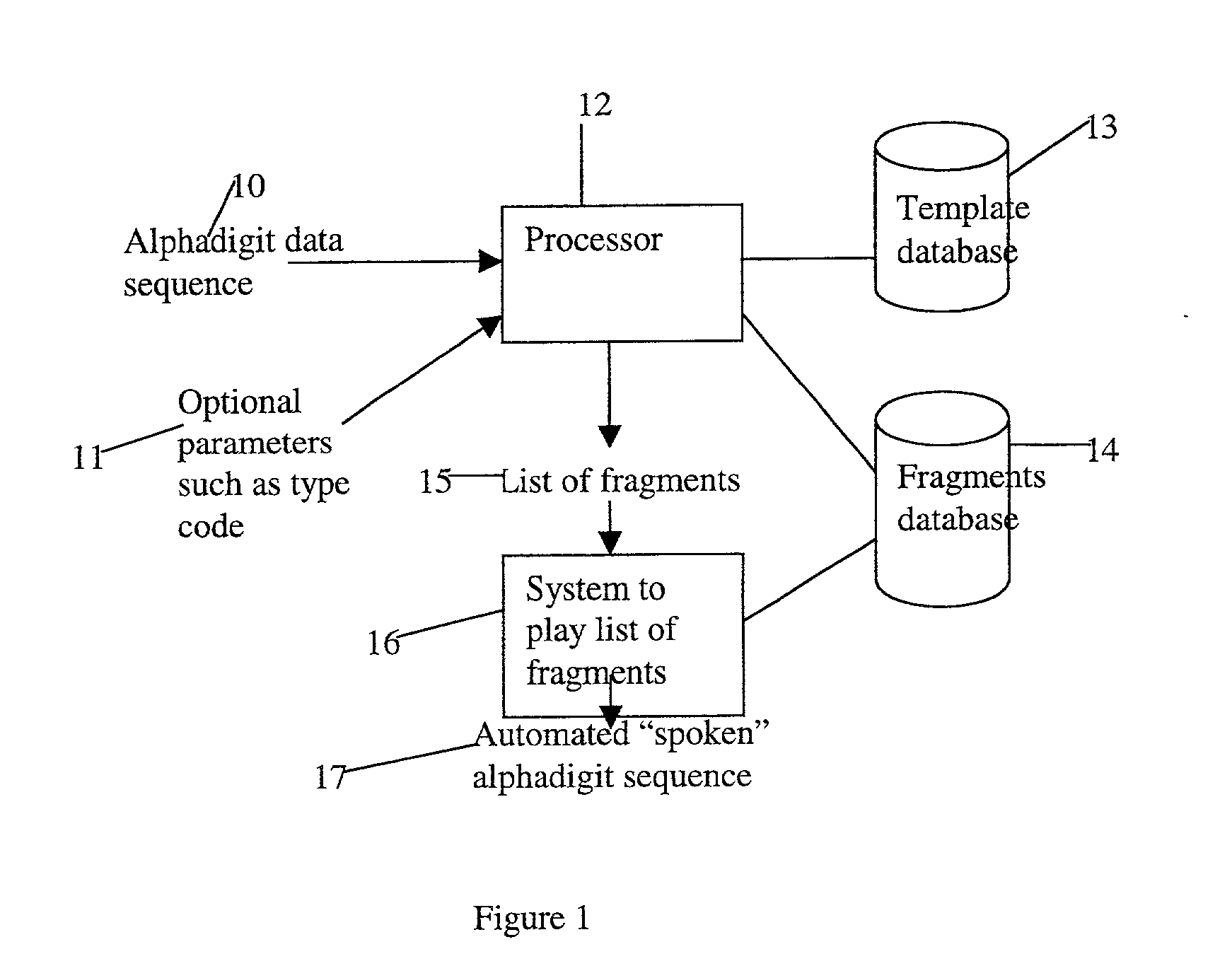
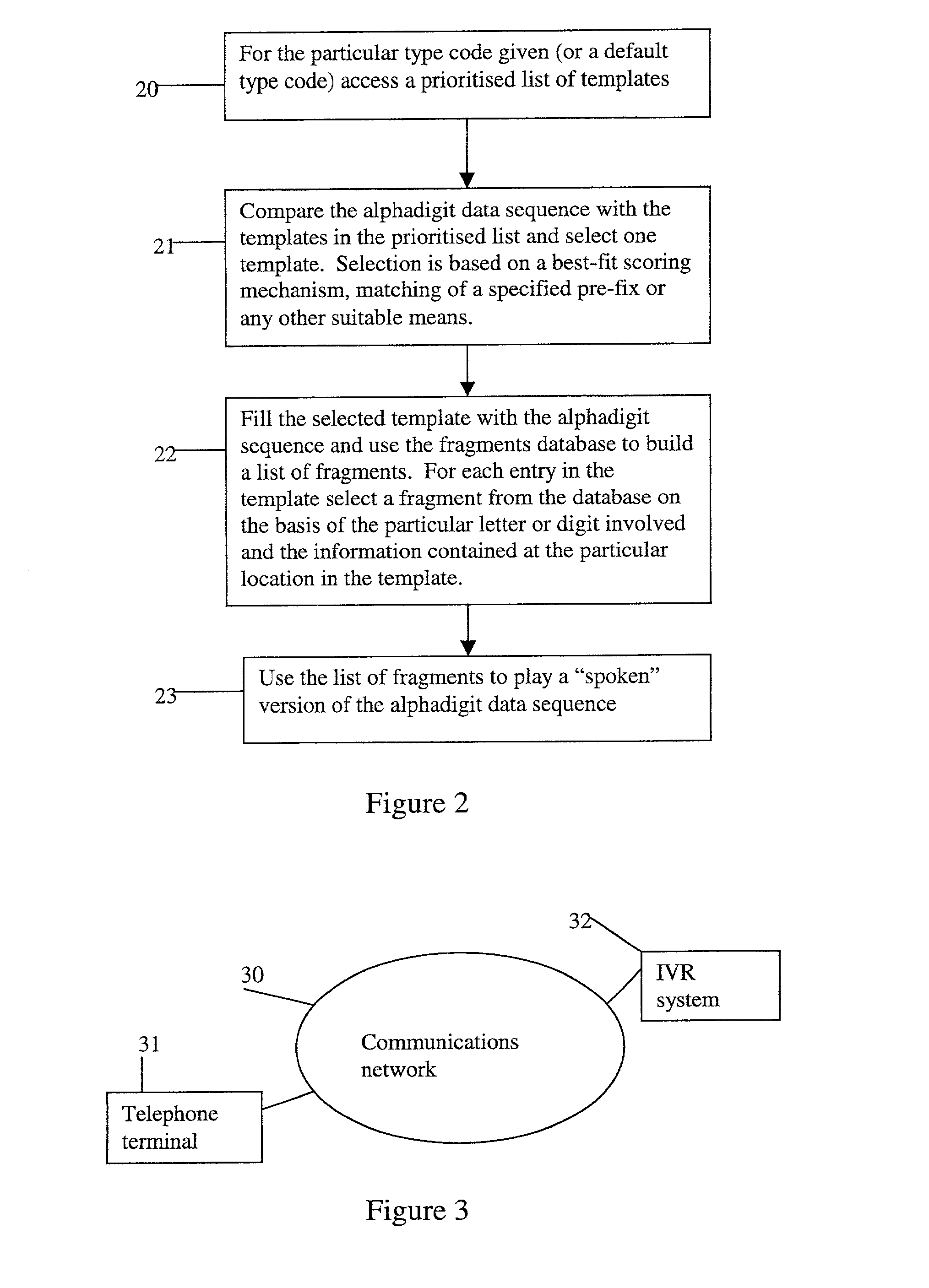
Method and apparatus for playing recordings of spoken alphanumeric characters
InactiveUS20030101045A1Simple configurationSpeech recognitionSpecial data processing applicationsSpoken languageLettering
Automated systems for "speaking" telephone numbers, zip codes and the like typically produce unrealistic results that do not sound like an actual human speaking the telephone number or zip code. By using templates together with four or more types of fragment for each alphanumeric character this problem is addressed. A fragment is a recording of a spoken alphanumeric character as spoken at a particular location within an utterance. A template is a sequence of fields, each field representing part of a sequence of alphanumeric characters. Templates comprise information about the manner in which a sequence of alphanumeric characters is to be played, such as which fragments to use and when to use pauses. Using this method alphanumeric character sequences such as telephone numbers, zip codes and the like are played with human-like intonation in real time.
Owner:NORTEL NETWORKS LTD
Flexible loyalty points programs
InactiveUS20080051193A1Credit registering devices actuationPayment protocolsLoyalty programData file
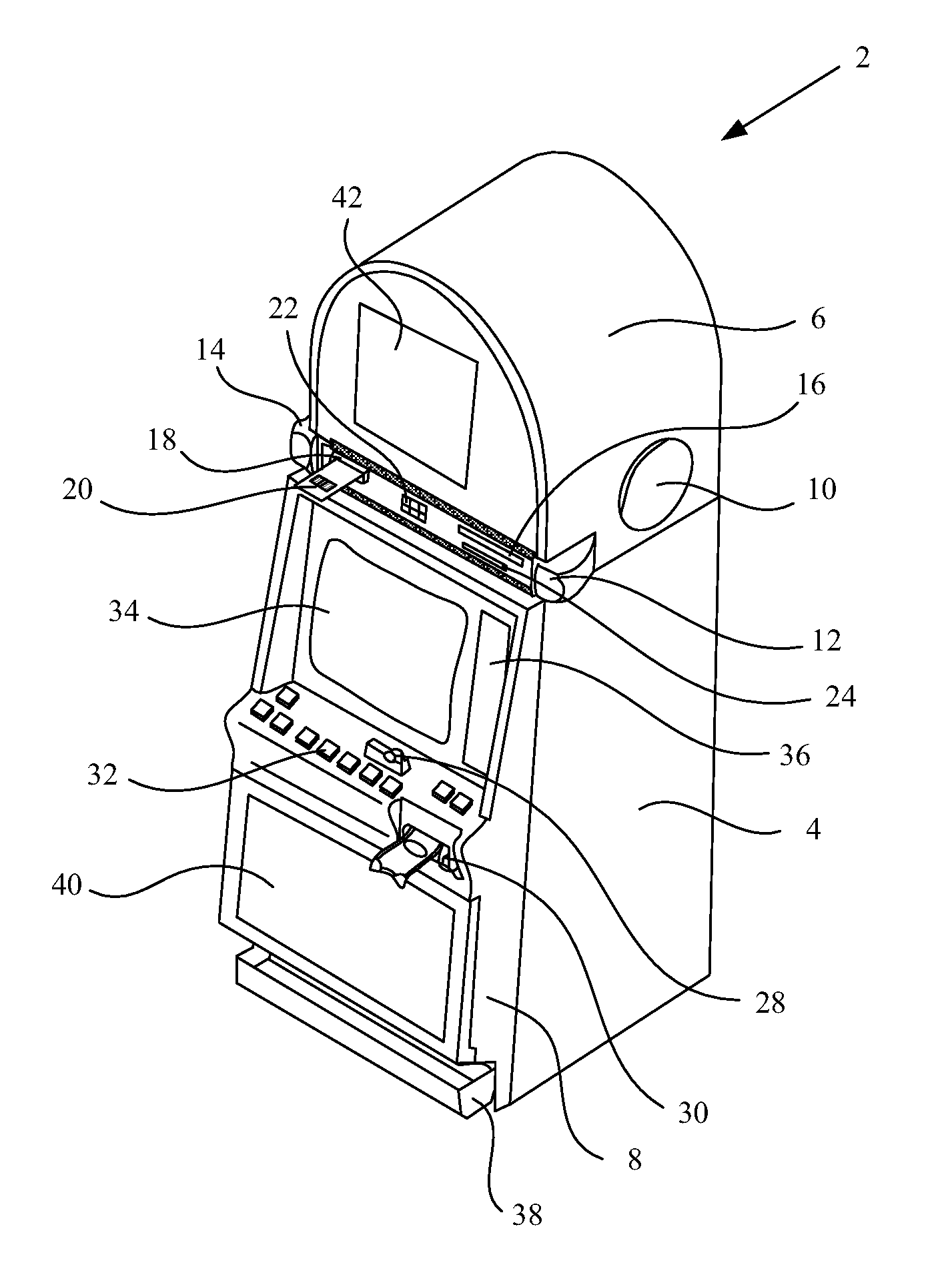
A disclosed a gaming machine includes an input mechanism with a non-physical contact data interface. The non-physical contact data interface may be capable of reading loyalty program data from a loyalty program instrument without contact between the loyalty program instrument and the non-physical contact data interface. The input mechanism with the non-physical contact data interface may be one of a bill validator, a bar-code reader and a Radio Frequency Identification (RFID) tag reader. The loyalty program instrument may be a substrate including at least one of a 1-D bar-code printed on the substrate, a 2-D bar-code printed on the substrate, a symbol printed on the substrate, alpha-numeric character printed on the substrate, a RFID tag embedded in the substrate, a RFID tag printed on the substrate and combinations thereof. The loyalty program instrument may be used to store an index to a record in a database or a portable data file.
Owner:IGT
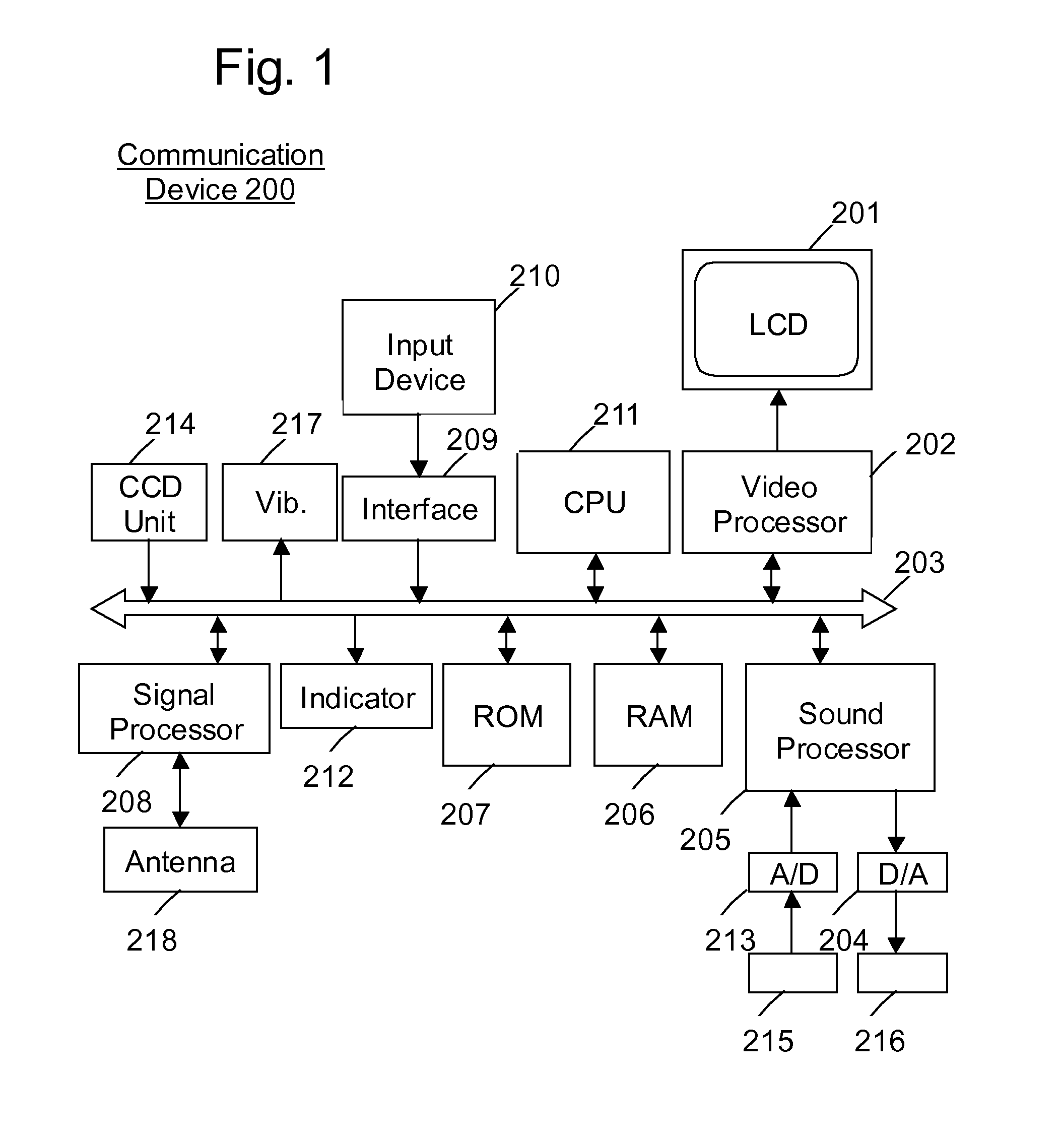
Communication device
InactiveUS7853295B1Devices with GPS signal receiverCurrent supply arrangementsDisplay deviceSpeech sound
The communication device which converts the voice data to the text data and displays the text data on the display of the communication device, wherein the text data includes alphanumeric data retrieved from the voice data.
Owner:CORYDORAS TECH
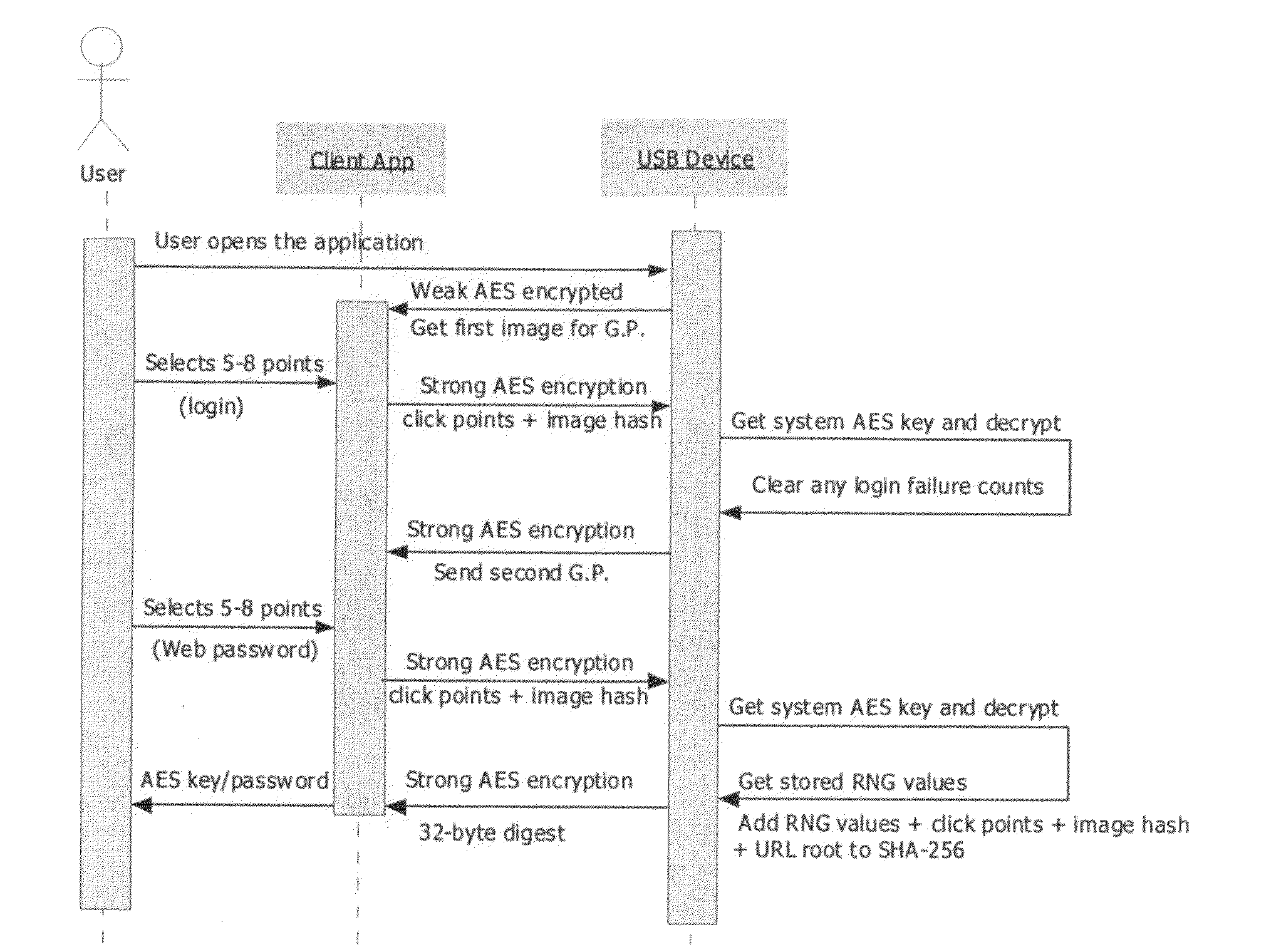
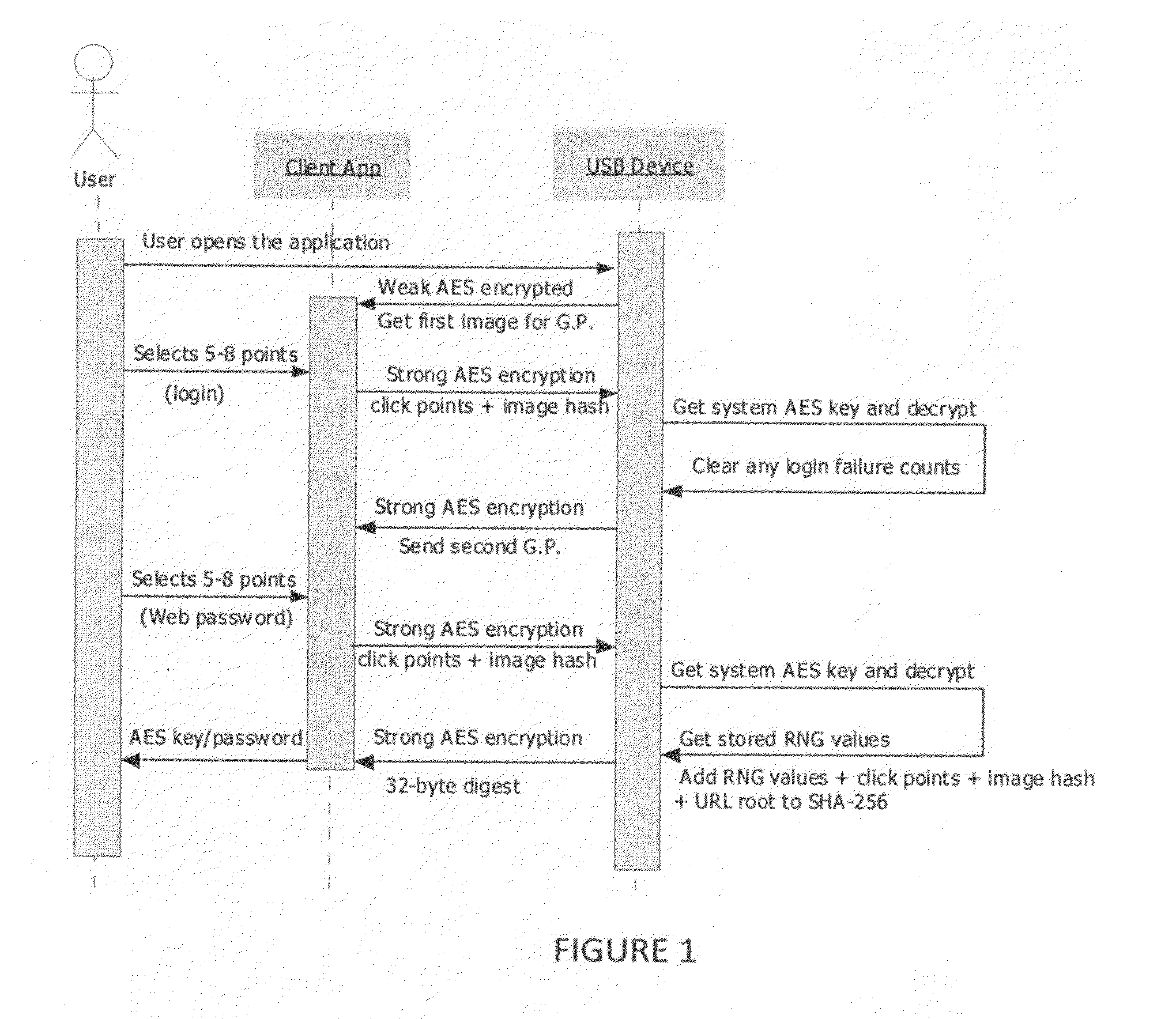
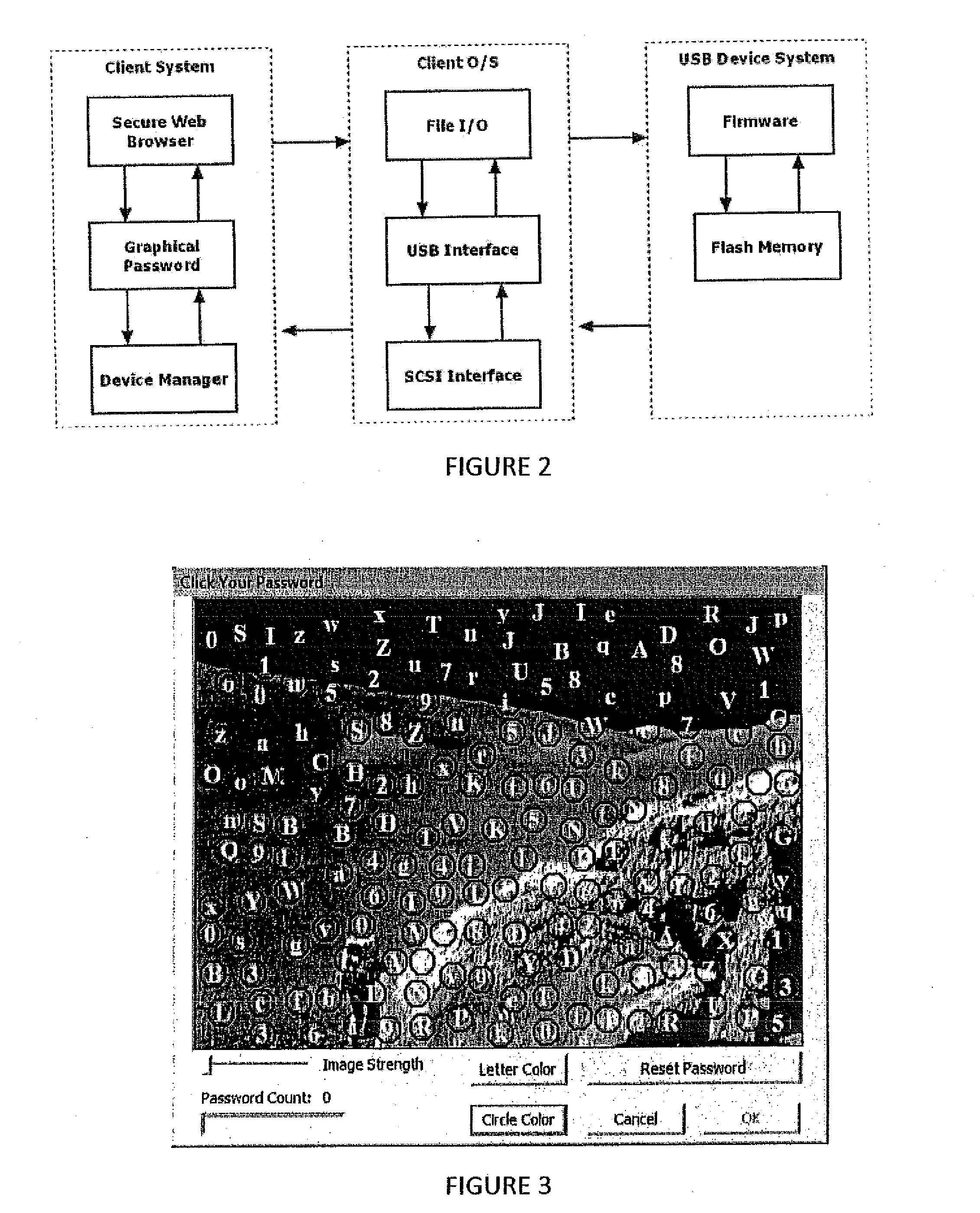
Two-factor graphical password for text password and encryption key generation
InactiveUS20100287382A1Digital data processing detailsMultiple digital computer combinationsAlphanumericConsole application
This invention details systems, methods, and devices for providing a two-factor graphical password system to a user so that the user may obtain access to a restricted resource. A first previously selected image (previously selected by the user) is presented to the user to enter his password by sequentially selecting predetermined areas on the first image. The user's input is used to create an encryption / decryption key which is used for communicating between a user application and a device. If the user has entered the correct password, then the device can communicate with the user application. Once the device can communicate with the user application, a second previously selected image (previously selected by the user) is presented to the user from the device. The user enters his second password and the user's input is sent to the device. The device then creates the user's alphanumeric password or another encryption key from the user's input and sends this to the user application. The user application then transmits the password or key to the system which restricts access to the restricted resource.
Owner:GYORFFY JOHN CHARLES
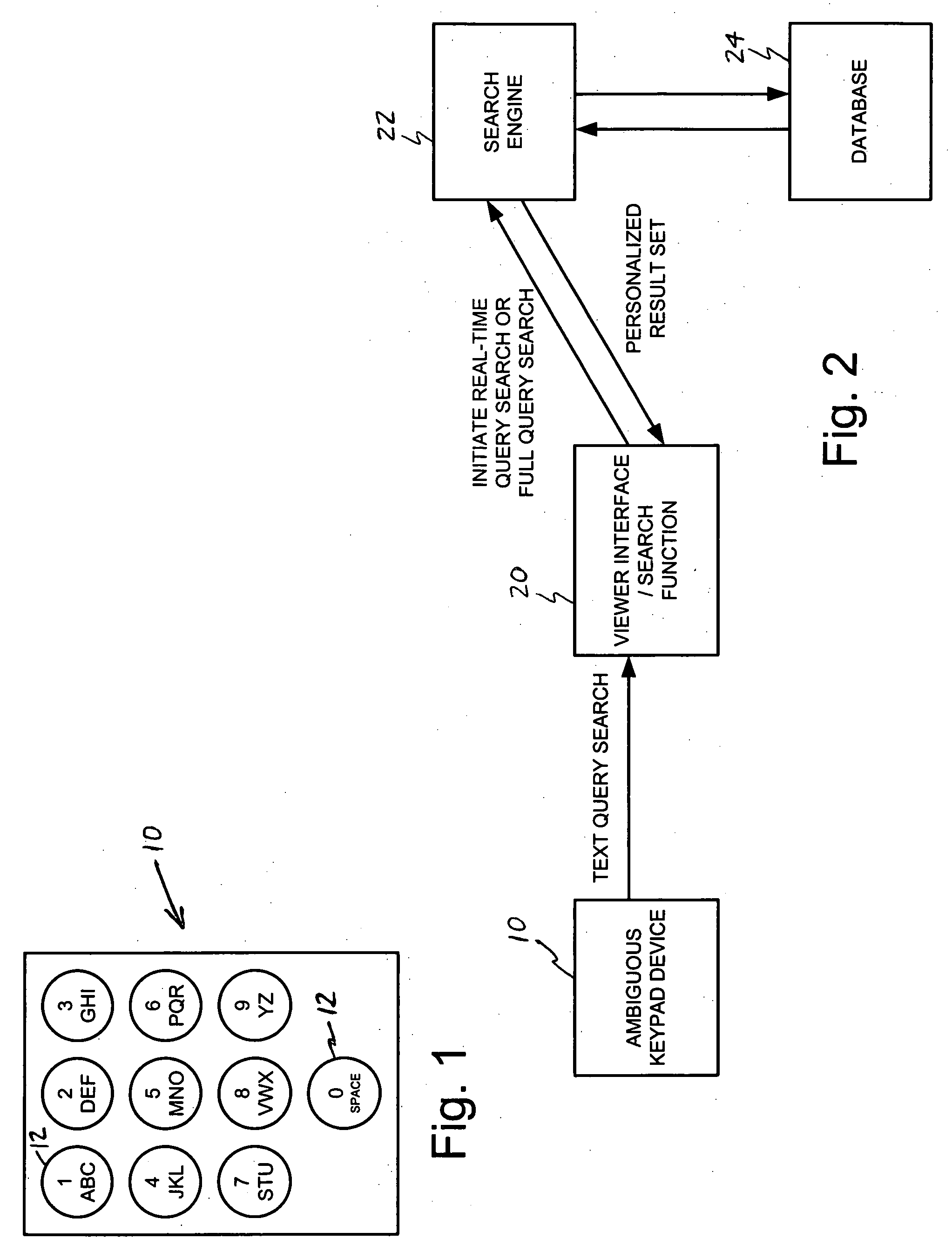
System and method for personalized searching of television content using a reduced keypad
InactiveUS20060167859A1Easy inputTelevision system detailsMetadata video data retrievalPersonalizationResult set
A method of searching television content for content of interest to a viewer involves entering a text search query with an ambiguous keypad device. The ambiguous keypad device includes a limited group of keys that represents a full set of alphanumeric characters. At least one key within the limited group represents multiple alphanumeric characters. Television content that matches the text search query is identified to produce a result set. The result set is ranked to provide a personalized result set that is prioritized for the viewer. The personalized result set is presented to the viewer.
Owner:COMCAST CABLE COMM LLC
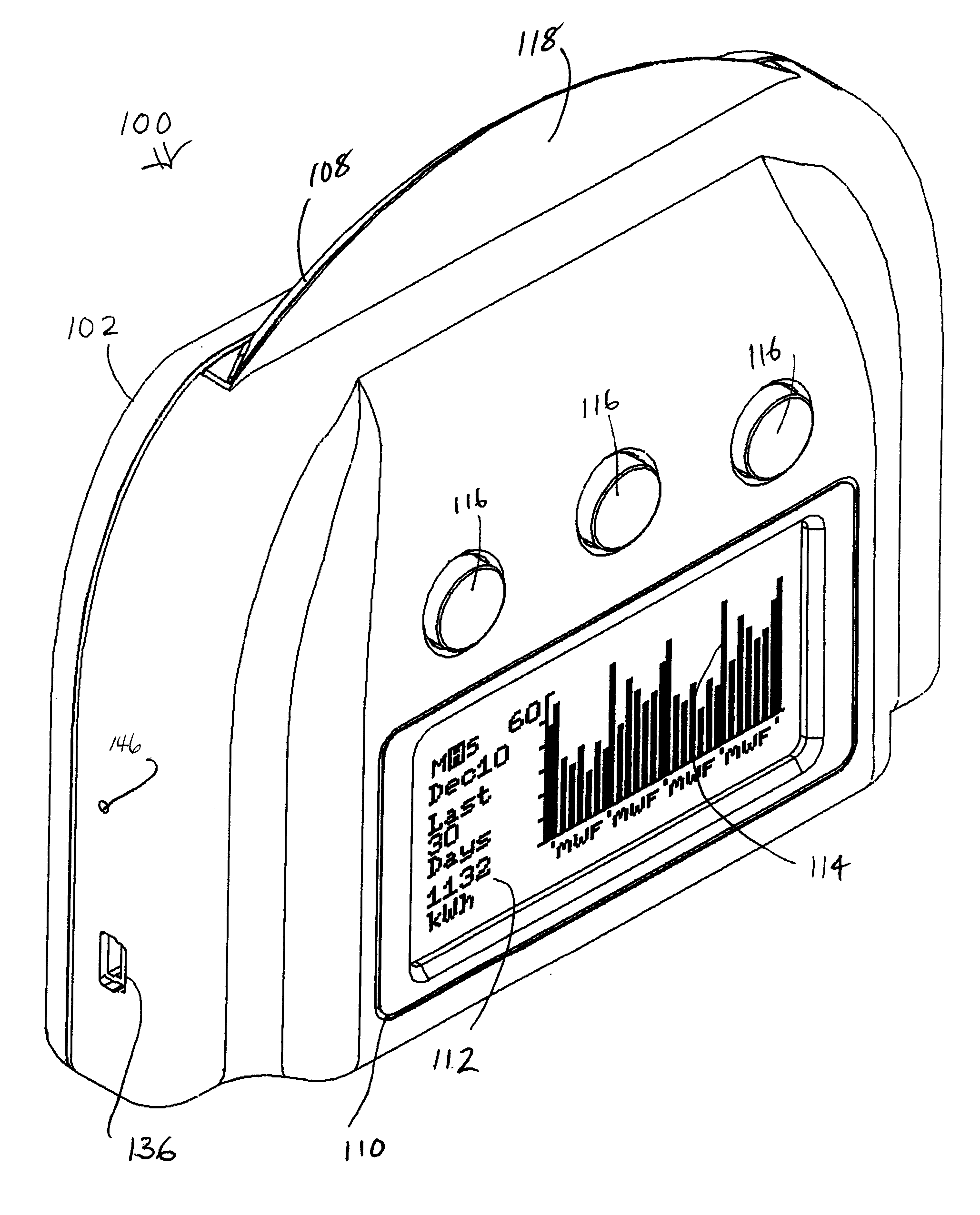
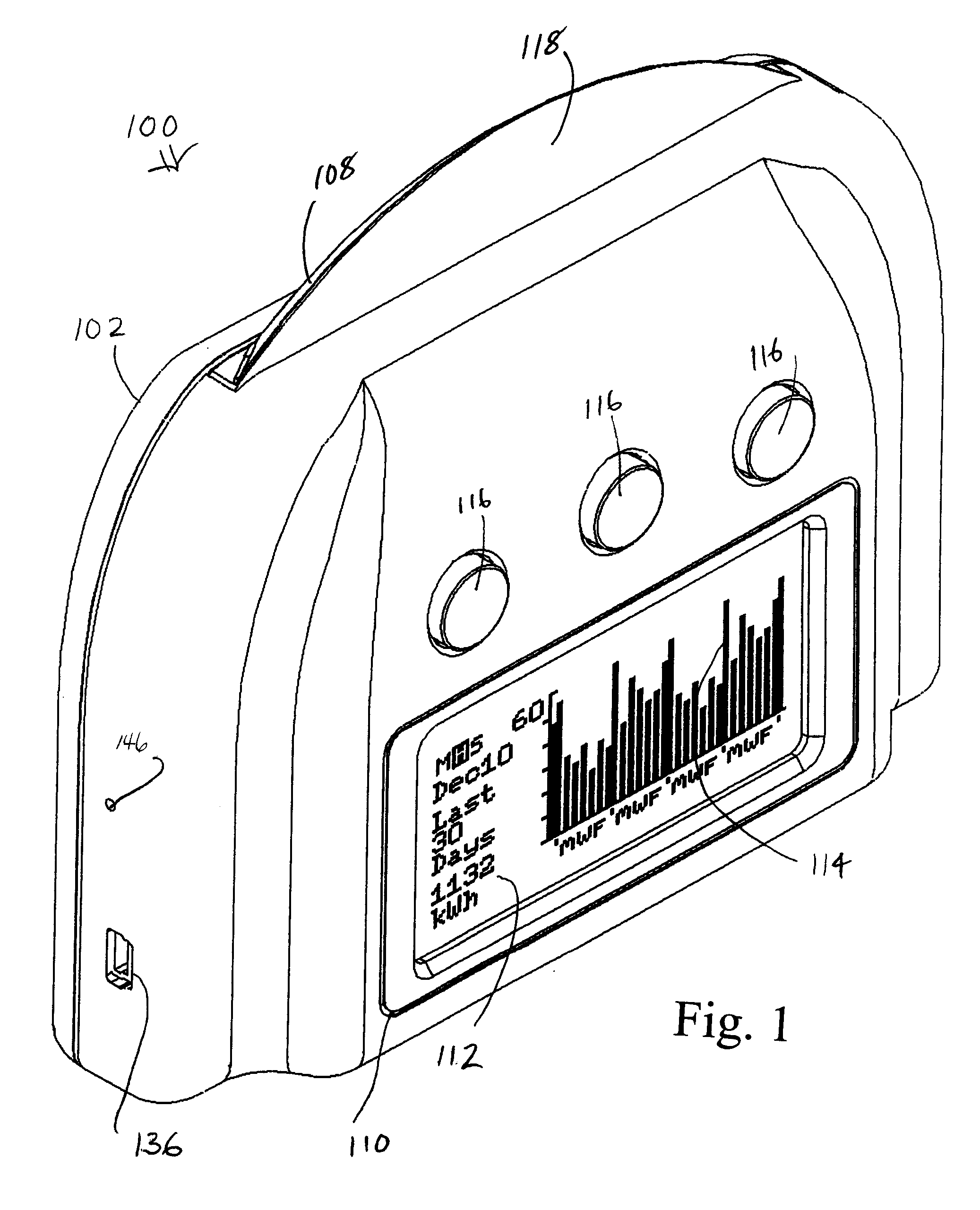
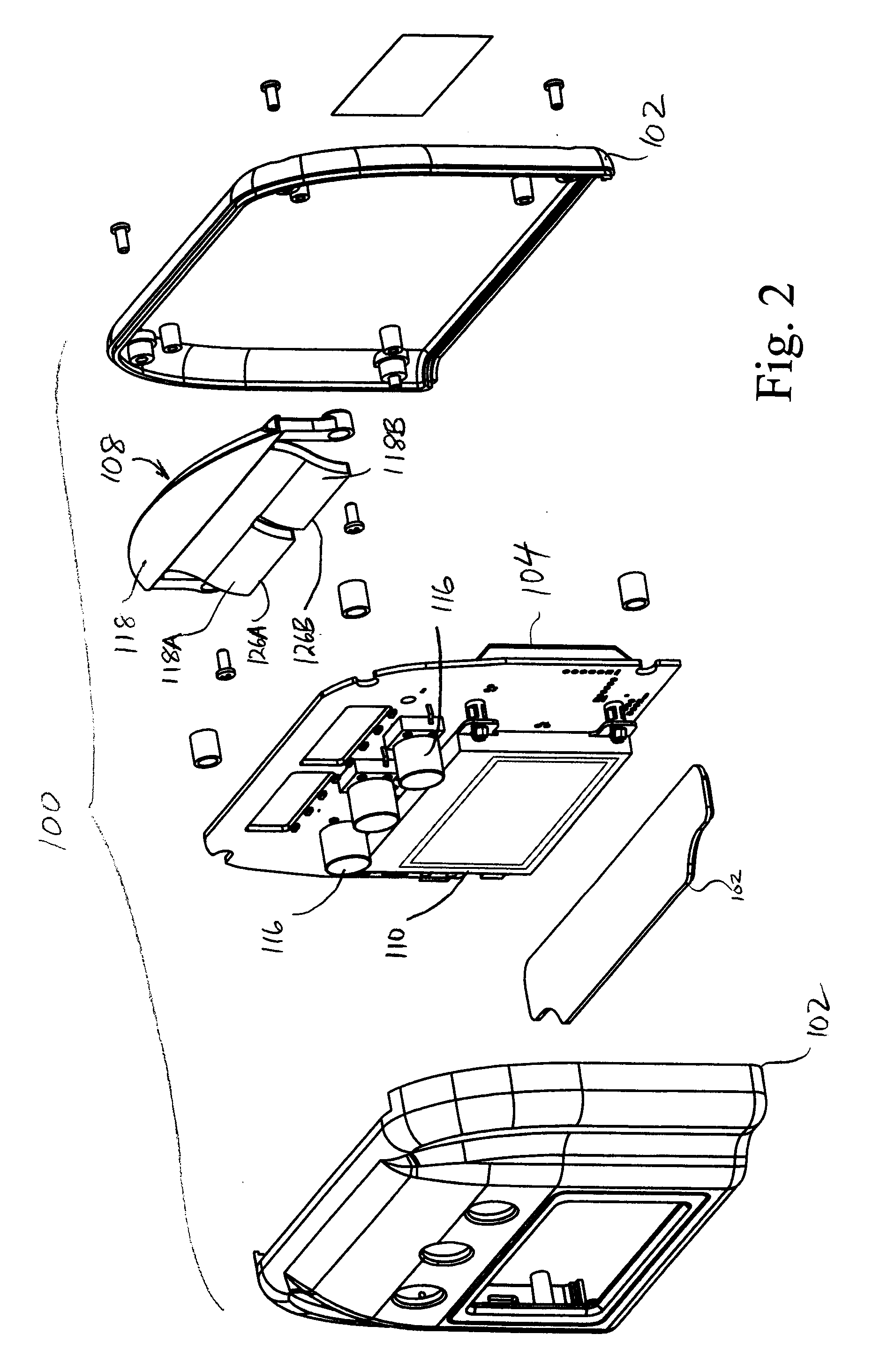
Utility monitoring device, system and method
ActiveUS20100060479A1Easy to explainElectric signal transmission systemsSpecial tariff metersGraphicsElectricity
A monitoring device, system and method is provided for in-home / on-premises monitoring of usage of utilities, such as electricity and other services. The monitoring device receives information from a smart metering system or transceiver, and displays current usage through an illuminated display, which displays a colour indicative of the current cost of consumption, and controls illumination of the display to scan illumination across the display at a traverse rate indicative of a rate of consumption or other metric, the scanning of a pattern of illumination across the display simulating movement or rotation in the display. The display therefore provides a consumer with immediate “at a glance” visual information on current usage. Optionally a digital display screen provides more detailed alphanumeric and graphical information, through a number of selectable display modes. Beneficially one or more devices may be networked, and interface directly or indirectly with a transceiver of a smart metering system, or a retrofit transceiver for a conventional meter. While particularly suited to electricity monitoring, monitoring of other utilities and services may alternatively or additionally be provided. The system may be used with a wired network or wirelessly networked by one of a number of standard wireless and mesh network communication protocols.
Owner:AZTECH ASSOC INC
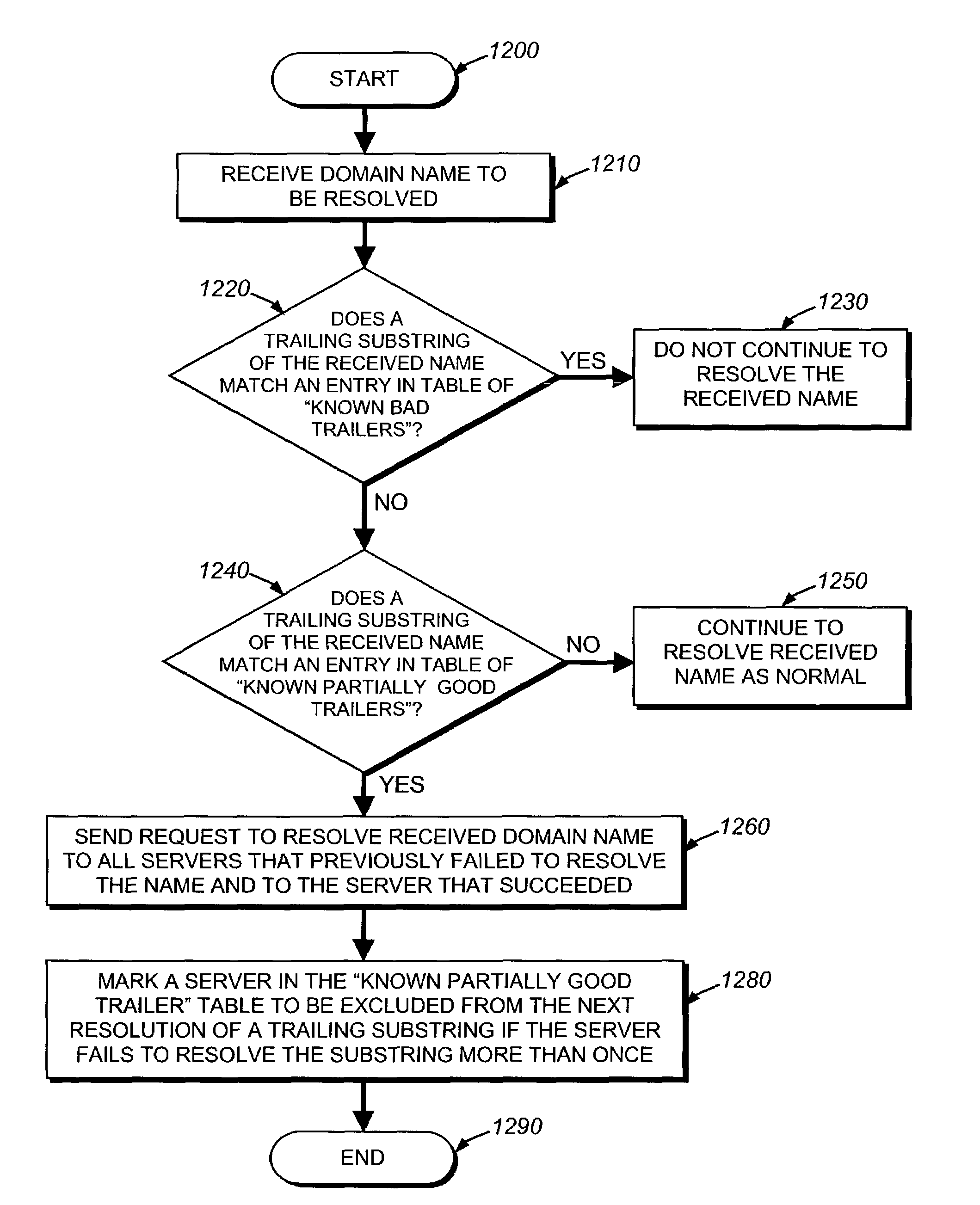
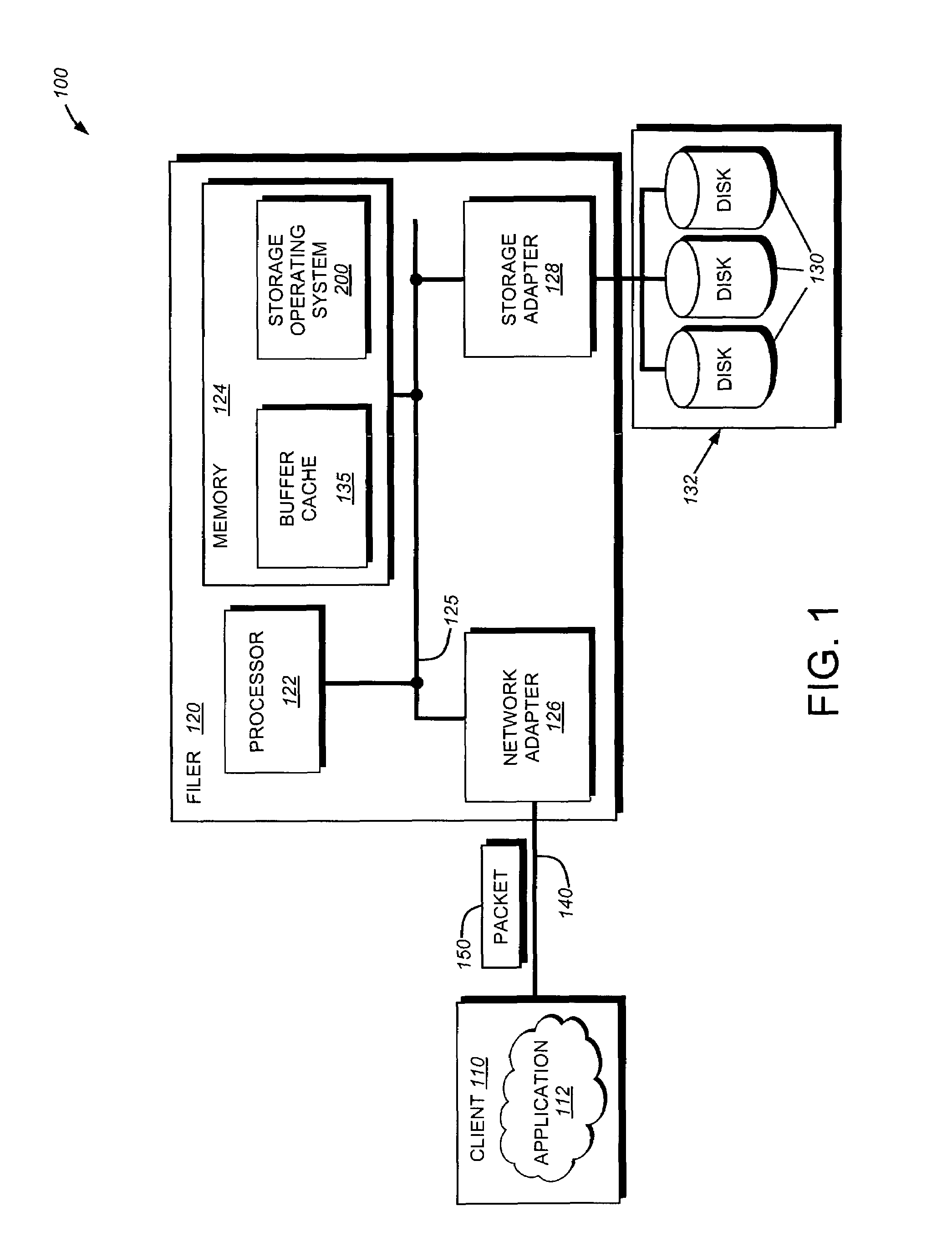
Highly available DNS resolver and method for use of the same
ActiveUS7426576B1Network degradationReliance has been minimizedMultiple digital computer combinationsTransmissionDomain nameOperational system
The present invention relates to an enhanced DNS resolver architecture configured to operate in high availability environments, such as the Internet. Specifically, the DNS resolver code of the present invention may be implemented by a storage operating system in a filer. The resolver code modifies a conventional resolver algorithm so as to reduce the time necessary to map IP addresses to alphanumeric domain names and vice versa. Advantageously, the enhanced resolver code keeps track of non-responsive or “dead” DNS servers as well as non-resolvable or “bad” domain names and IP addresses.
Owner:NETWORK APPLIANCE INC
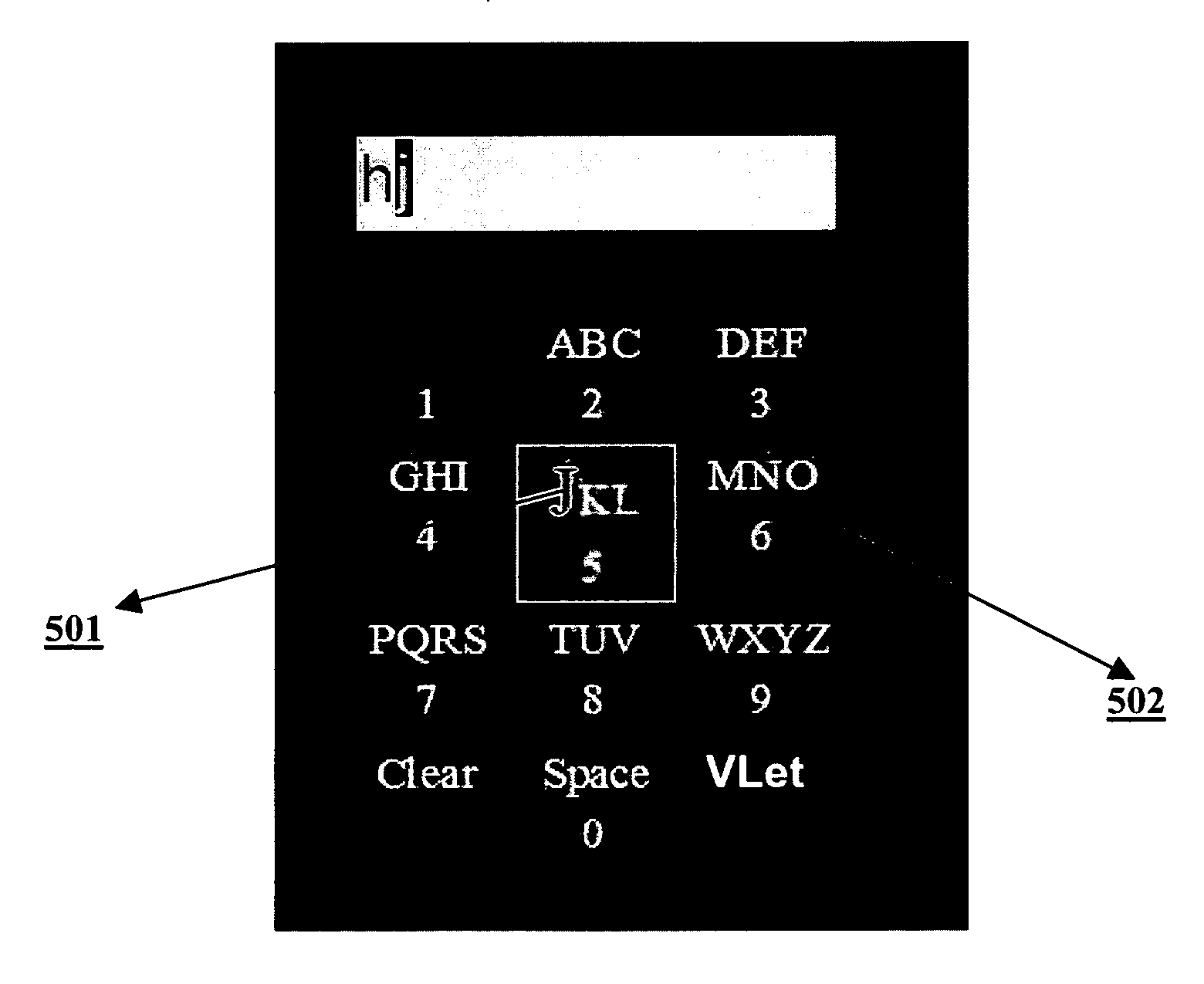
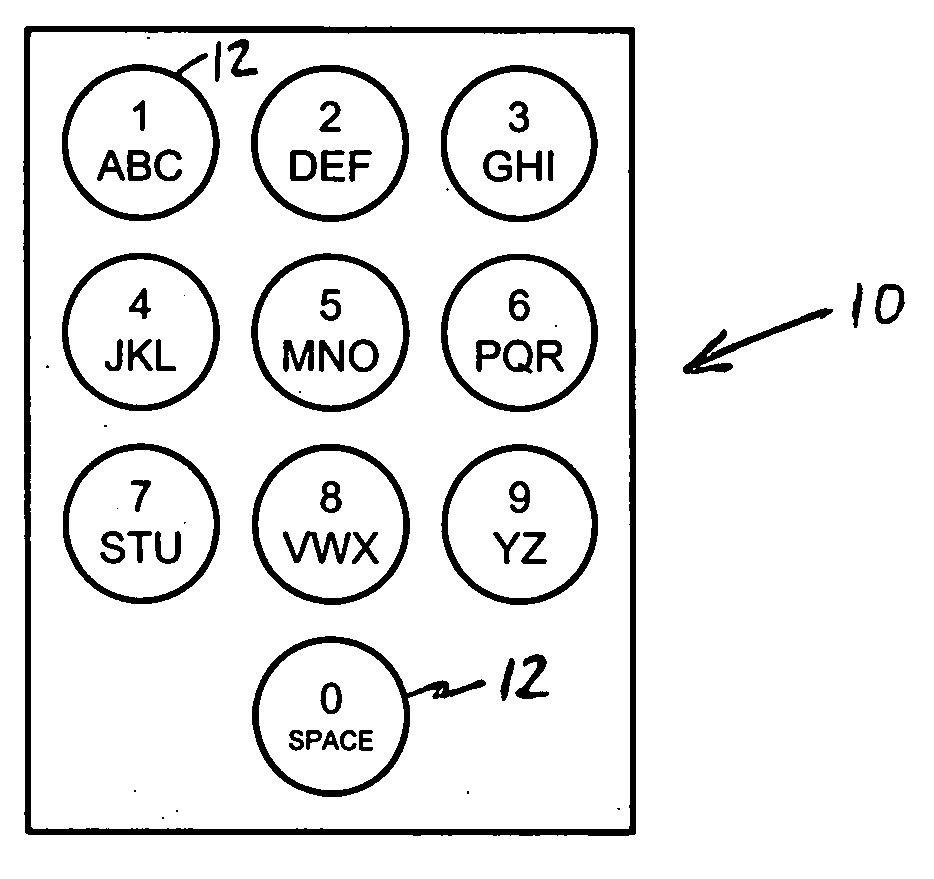
Methods and systems for a Linear Character Selection Display Interface for Ambiguous Text Input
Methods of and systems for entering ambiguous text input via a linear character selection display are provided. A system for entering an alphanumeric string includes presentation logic for displaying on a presentation device an alphabet arranged into a row of letters and indication logic for presenting visual cues grouping a series of letters of the row into a cluster. The system also includes navigation logic for receiving user actions to move the visual cues along the row of letters to change the letters grouped into the cluster. The visual cues move along the row of letters in variable offsets based on a rate of input of the user actions. The system further includes selection logic for receiving user actions to select the cluster of letters to cause at least one of the letters of the selected cluster to be displayed in a string field.
Owner:VEVEO INC
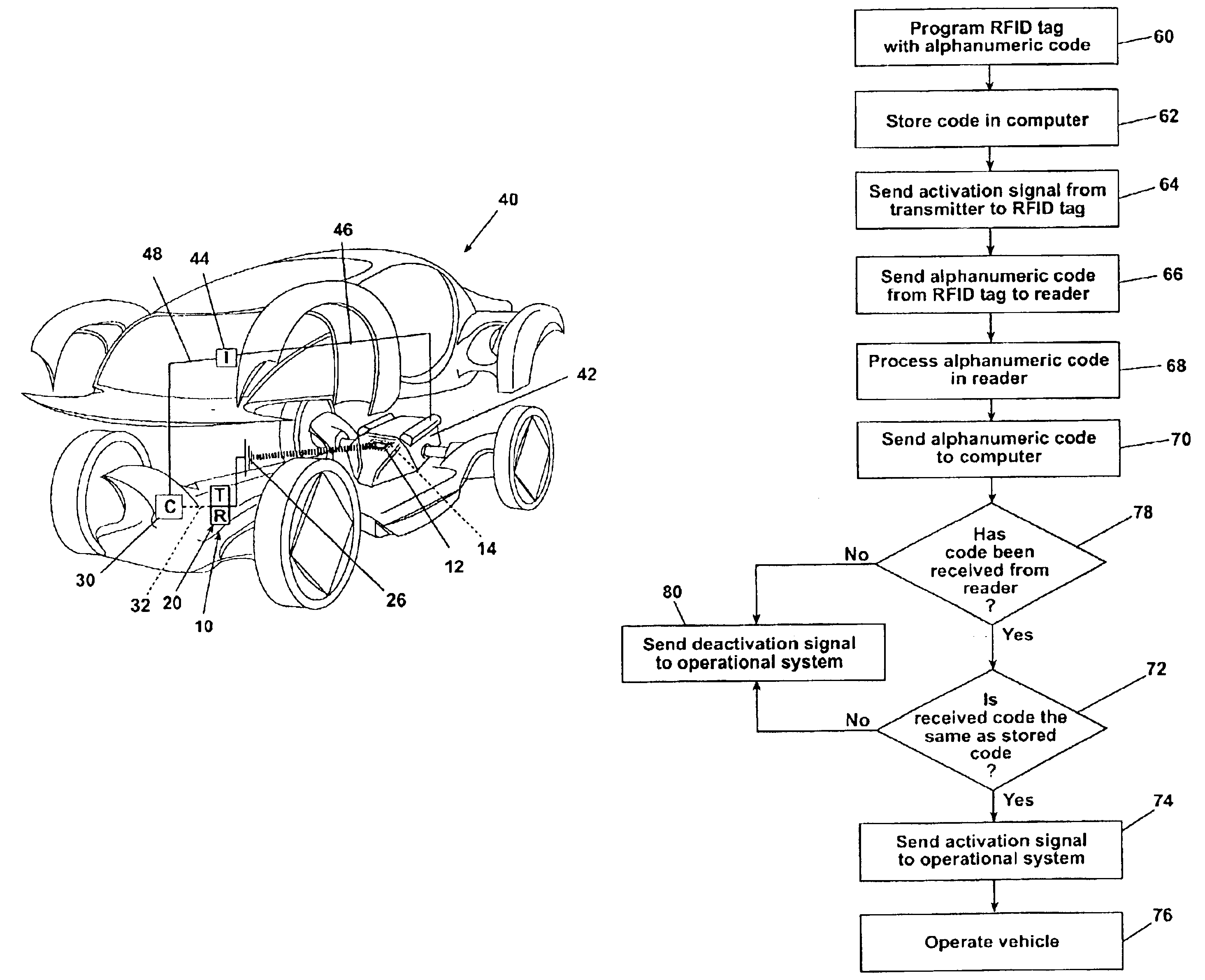
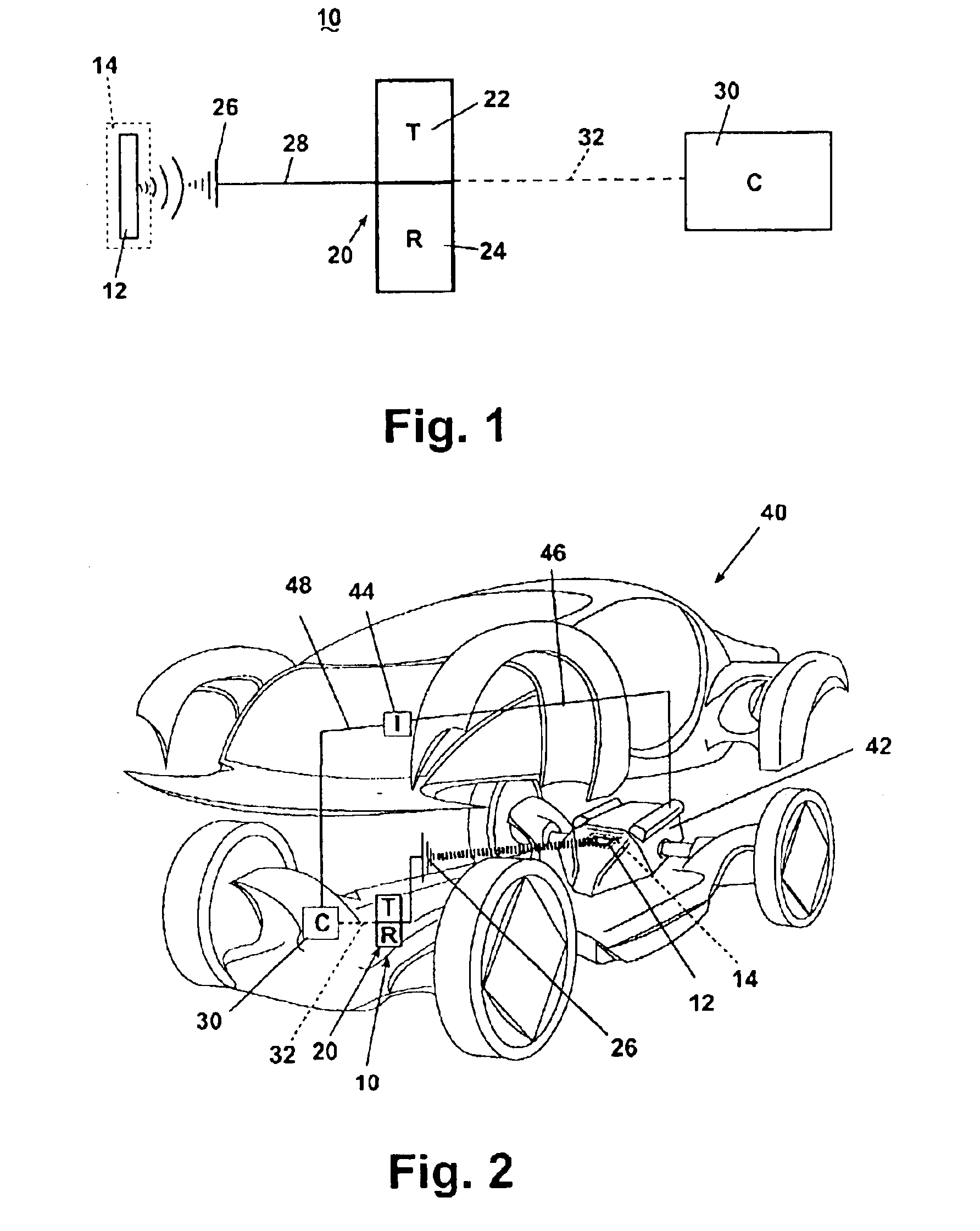
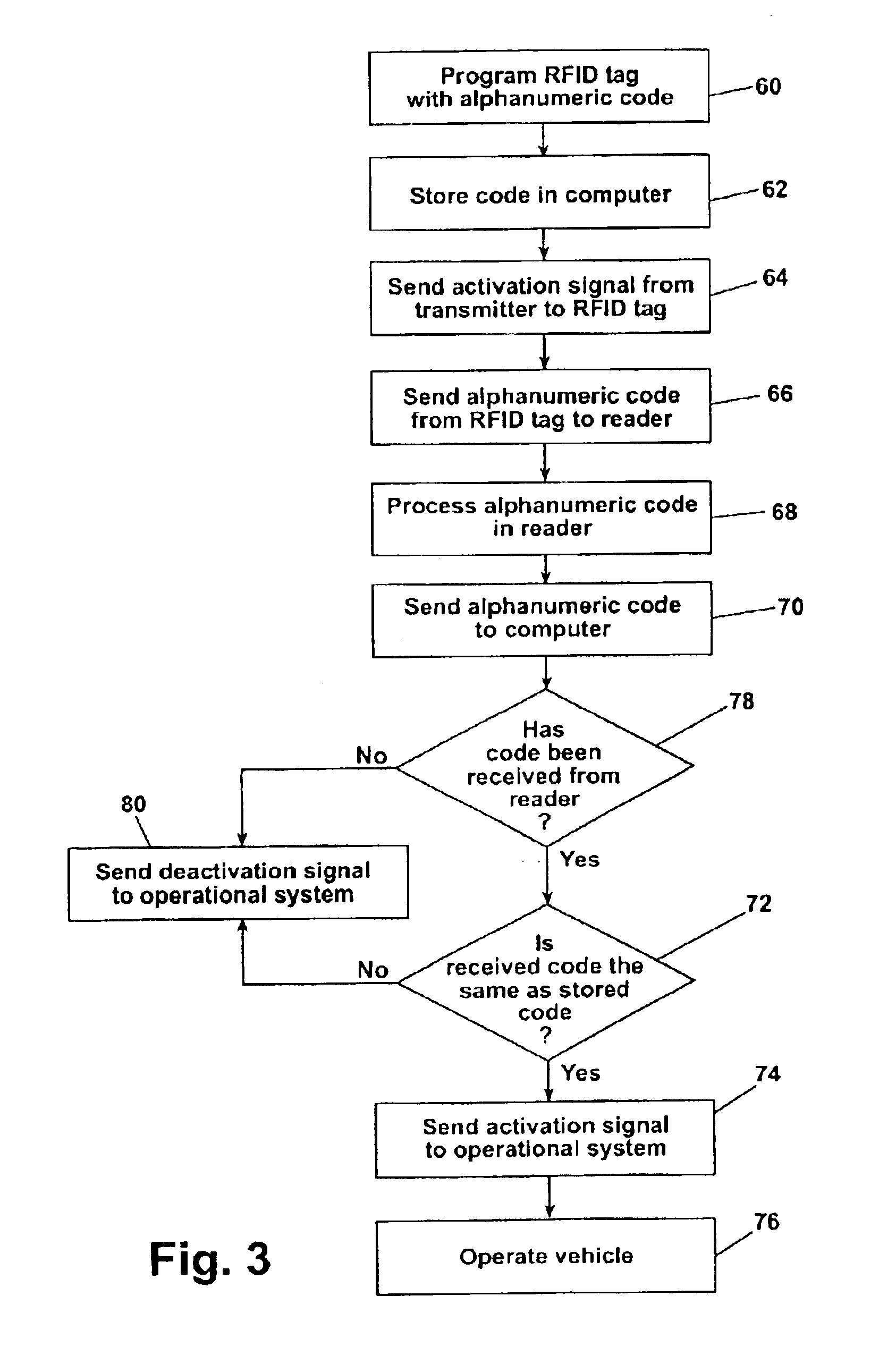
Vehicle control system with radio frequency identification tag
InactiveUS6898489B1Reduce stepsVehicle testingRegistering/indicating working of vehiclesMobile vehicleOperational system
A radio frequency identification system for a motor vehicle, in which RFID tags having unique alphanumeric codes are encapsulated and mounted to selected vehicle components, such as the vehicle chassis, body, or engine parts. The RFID tags are operably interconnected with a computer in the motor vehicle. The computer is operably interconnected with a vehicle operating system, such as the ignition system. The alphanumeric codes are read and transmitted to the computer, which compares the read codes with stored alphanumeric codes, and based on the comparison, controls the operation of the vehicle. Removal or destruction of an RFID tag or removal of a component in which an RFID tag is molded will cause the computer to deactivate the vehicle operating system, preventing operation of the vehicle.
Owner:CASCADE ENG
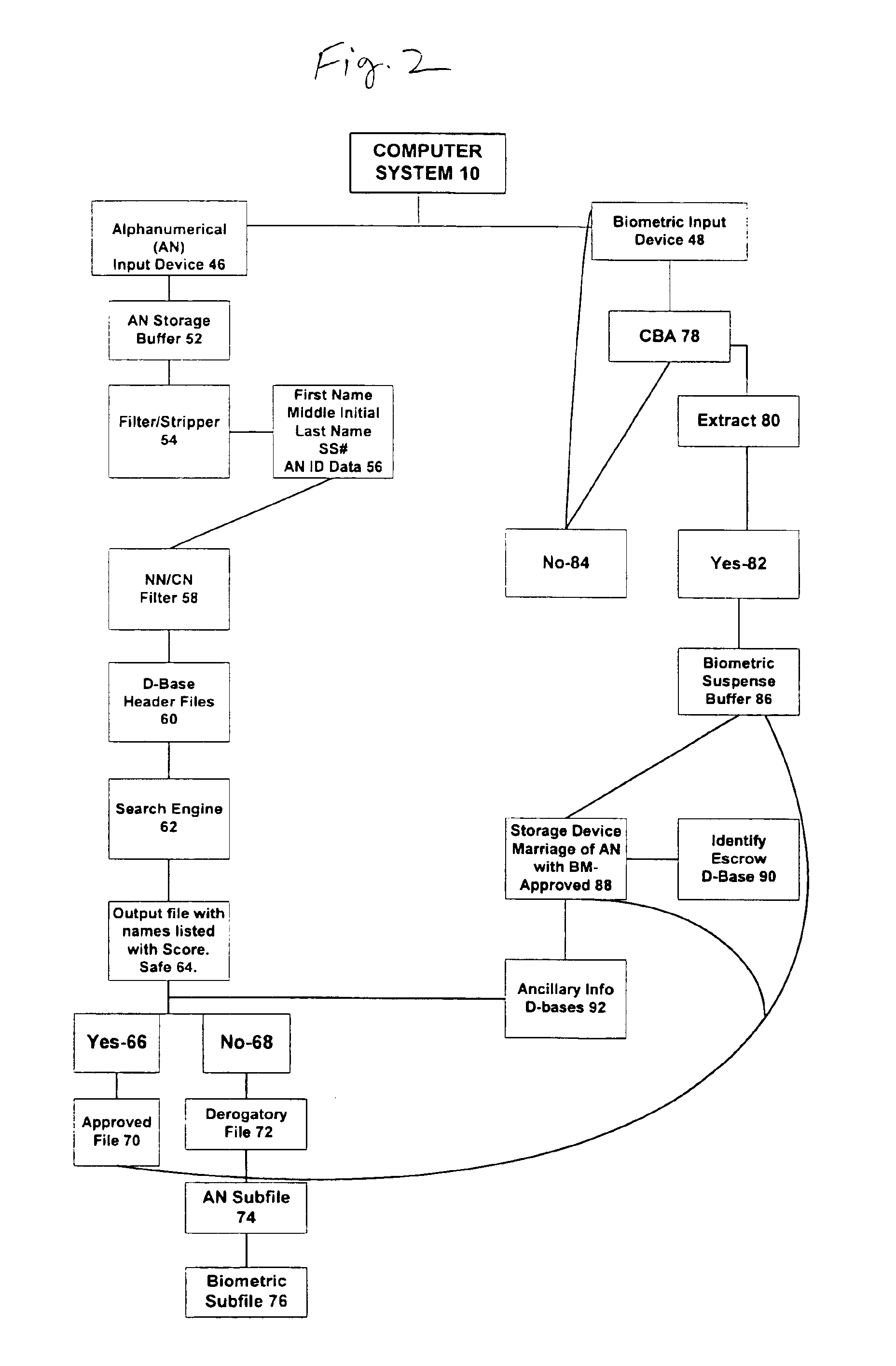
System and method for verification of identity
InactiveUS20050216953A1Secure deliverySafe handlingDigital data processing detailsCharacter and pattern recognitionThird partyBiometric data
A system for verifying identities comprising an enrollment system having: (i) at least one alphanumeric input device; (ii) at least one biometric input device; (iii) at least one header file database having a plurality of identities; (iv) at least one search engine, said search engine in communication with said header file database such that said search engine first receives an alphanumeric data signal which has been input into said alphanumeric input device by the user, and then searches said database for identities that match the alphanumeric data according to a predetermined first set of criteria; (v) a processor to score the set of identities matched by said search engine according to a predetermined second set of criteria, said processor capable of determining the acceptability or unacceptability of said user's input alphanumeric data based on said score; and (vi) an identity escrow database which is in communication with said processor and receives from said unit an approved identity data signal based on the acceptability of the score, said escrow database additionally in communication with said biometric input device capable of receiving at least one biometric identity data signal input by the user to said biometric input device, said escrow database further comprising means for coupling the approved identity data signal and the biometric identity data signal to create at least one subfile within the escrow database for each user comprising the approved identity data signal and the biometric data signal. The present invention further comprises a verification system for verifying the identity of said user after the user has enrolled in the enrollment system. The verification system has means for processing a second input biometric data signal input by the user to the biometric input device to match the user's preexisting biometric data in said escrow database according to a predetermined third set of criteria. The verification system has an output device for transmitting to a third party whether or not a match was located within said escrow database for said user. The present invention further relates to a method and system for providing a warranty against the theft of a user's identity.
Owner:ELLINGSON JOHN F
System and method to automatically discriminate between a signature and a barcode
The invention features a system and method for automatically discriminating between different types of data, such as a barcode and a signature, with an image reader. In brief overview of one embodiment, the automatic discrimination feature of the present image reader allows a human operator to aim a hand-held image reader at a target containing a dataform, a signature, or another data type and actuate the trigger on the image reader. An autodriscrimination module in the image reader in one embodiment analyzes image data representative of the target and determines whether the target contains a dataform, a signature, or another type of data. If the target contains a dataform, the image reader decodes the dataform and outputs decoded dataform data, such as the alphanumeric sequence encoded by a barcode. If the target contains a signature, the image reader captures or stores a representation of the signature.
Owner:HAND HELD PRODS
Method of formatting documents
ActiveUS7272789B2Flexible designFlexible presentationNatural language data processingSpecial data processing applicationsGraphicsRating system
Owner:TYPEFI SYST PTY LTD
A method and apparatus for searching large databases via limited query symbol sets
InactiveUS20050192944A1Digital data information retrievalSpecial data processing applicationsOutput deviceVery large database
Methods and systems for searching a database that includes a plurality of records. Each record includes one or more tokens. The one or more tokens include one or more letters, numbers, or symbols. The system includes a user interface that when activated by a user generates at least one of a query symbol or a string of query symbols. A processing device compares the generated query symbol or string of query symbols to the stored records. An output device presents the record or records having tokens that match the generated query symbol or a string of query symbols based on the comparison. The user interface includes two or more input keys. Each input key is associated with a query symbol and the number of input keys is less than the number of distinct letters, characters, and symbols.
Owner:MELODEO
Mobile phone
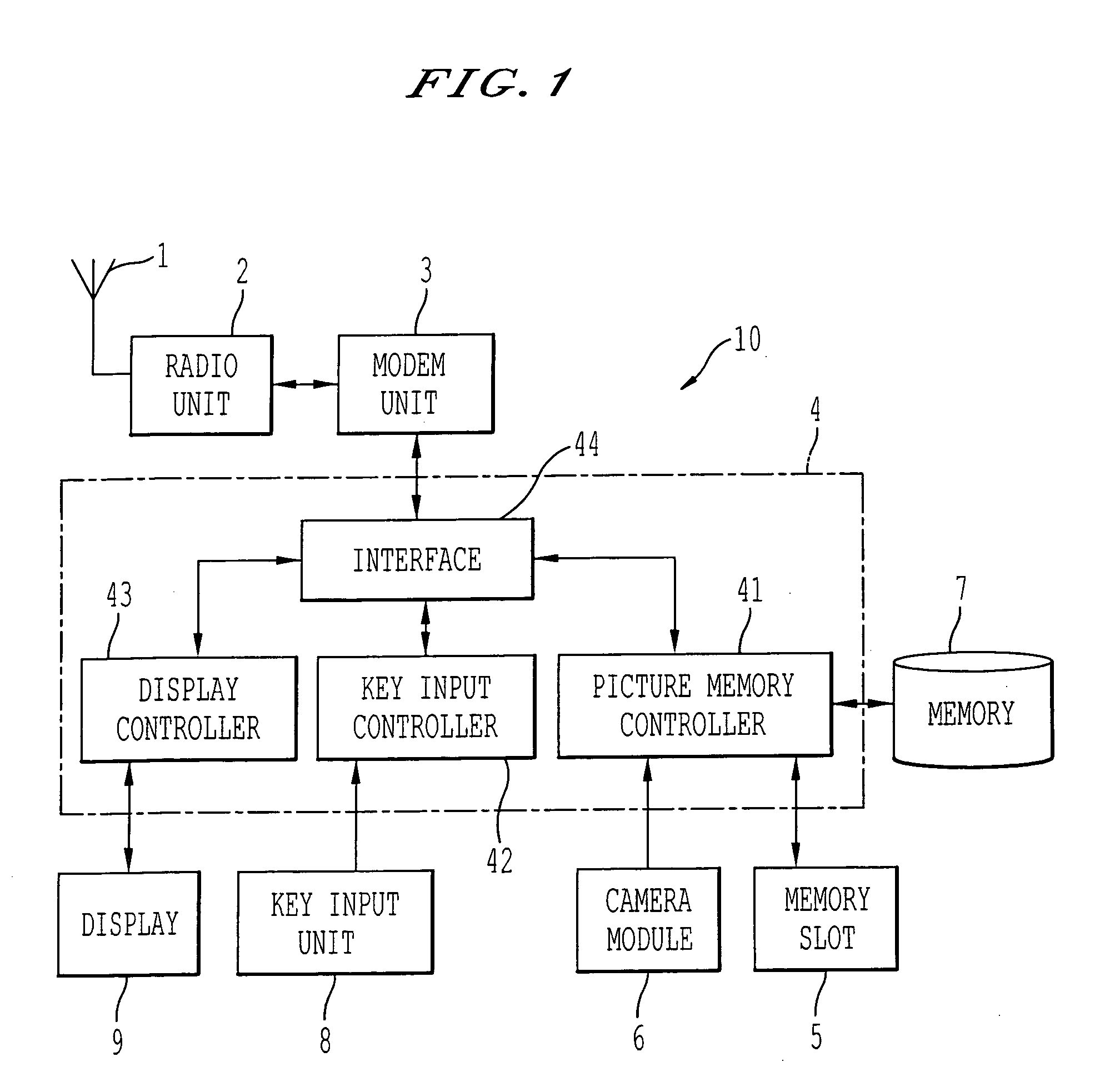
InactiveUS20070021160A1Interconnection arrangementsAutomatic exchangesLiquid-crystal displayDisplay device
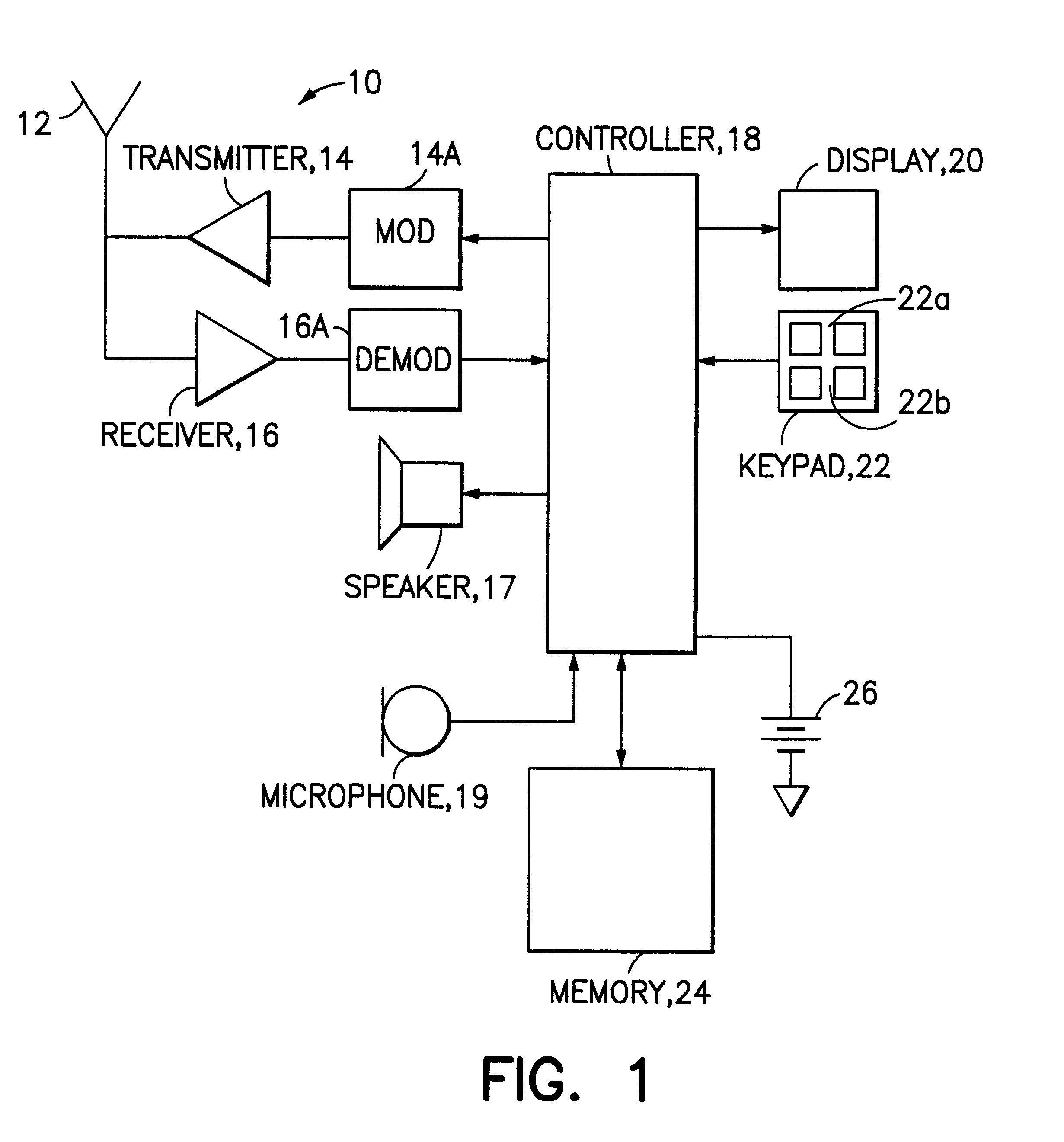
The present invention is to provide a mobile phone comprising a body and a housing. A hollow is formed within the housing and the body is slidably disposed in the hollow. The hollow has an opening in an end of the housing and the other end terminated at a closed end of the housing distal the opening. A display (e.g., LCD (liquid crystal display)) is disposed on a front surface of the housing. The body comprises a circuit board and an input device. The circuit board is installed within the body and comprises electronic circuits and devices for controlling the components of the mobile phone. The input device (e.g., alphanumeric keypad) is disposed on a front surface of the body for operating the mobile phone. The body is capable of being engaged with the housing and being slid towards outside of the hollow through the opening to expose the input device for a user to make a phone call.
Owner:INVENTEC APPLIANCES CORP
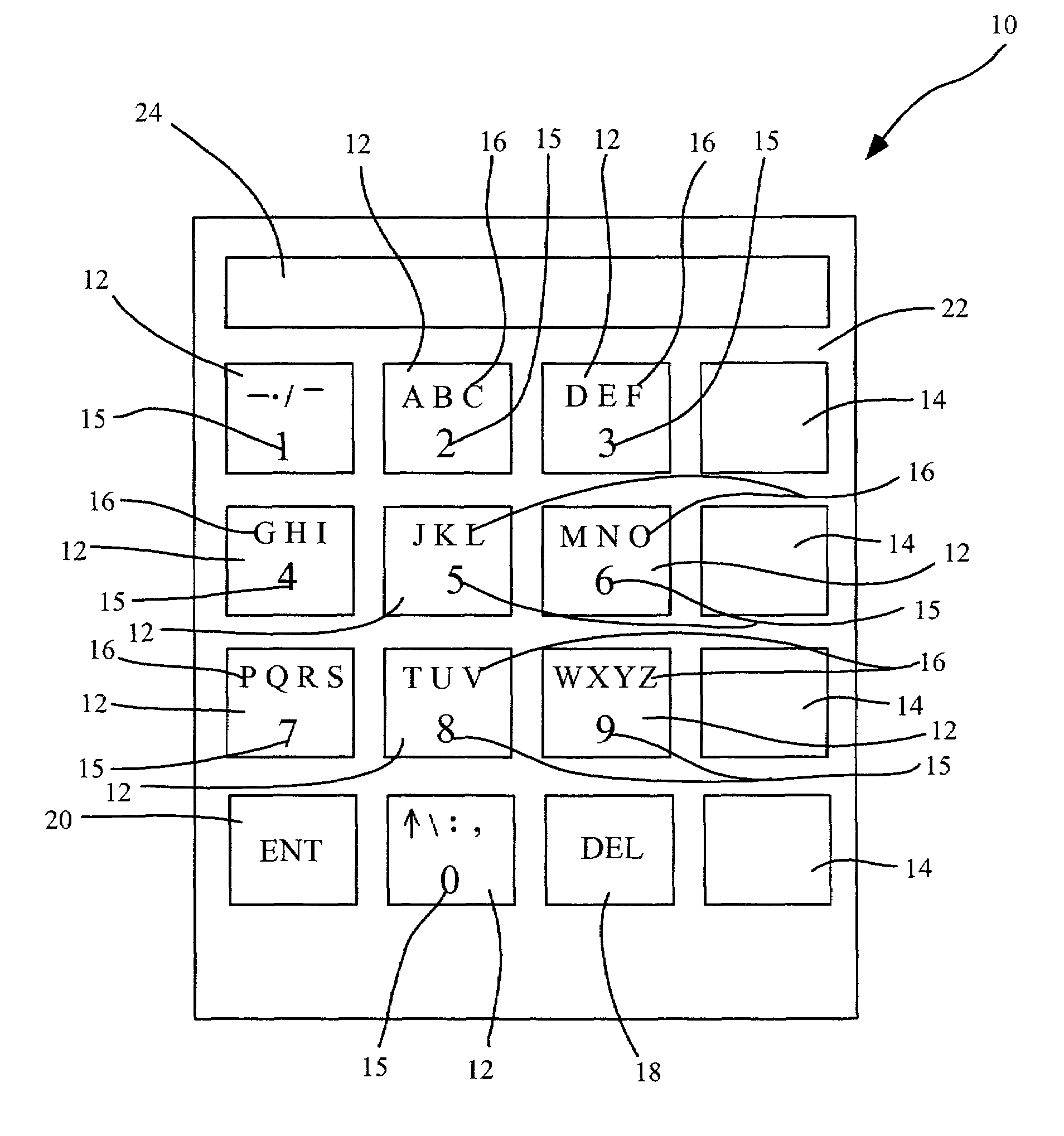
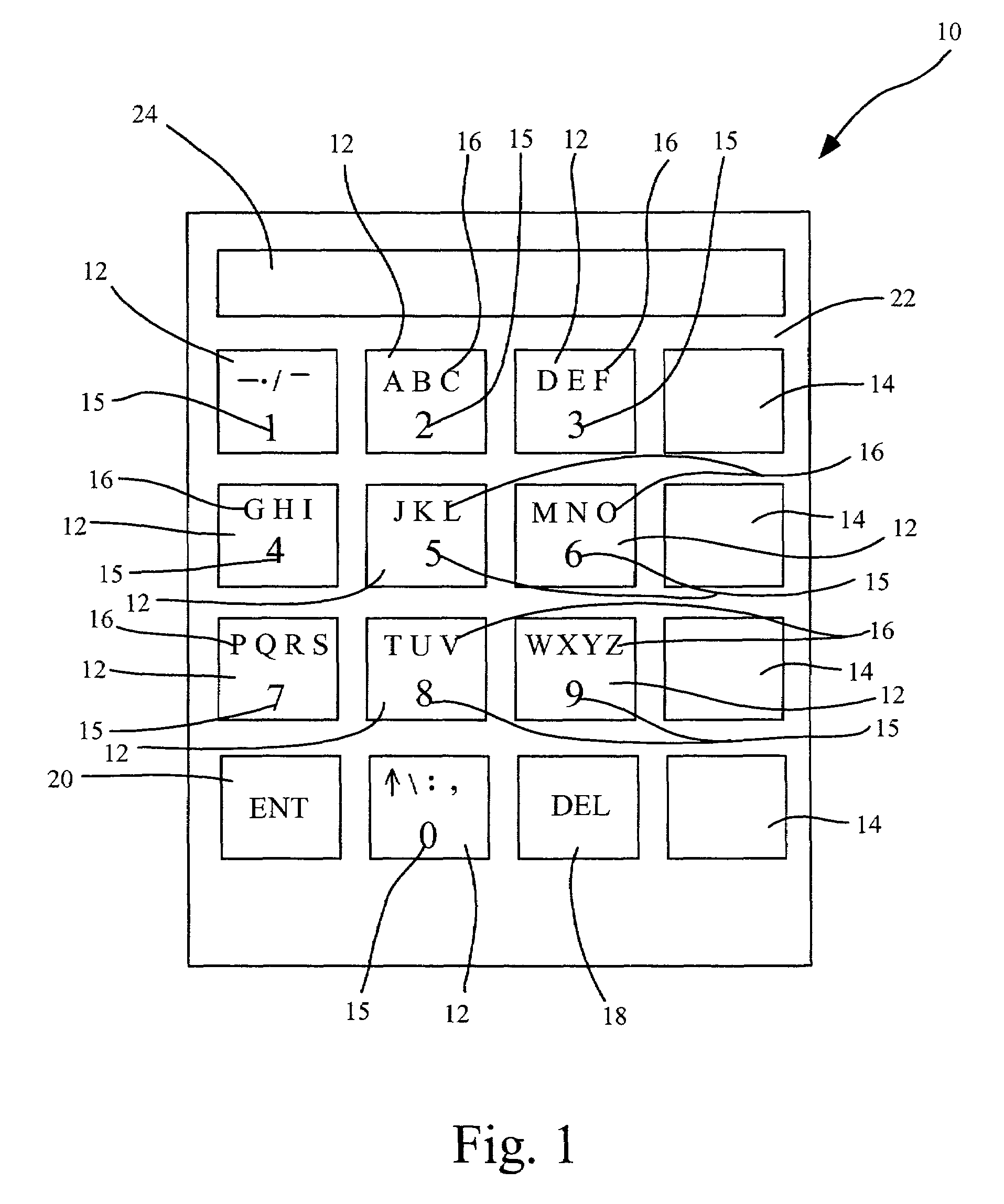
Alphanumeric keypad and display system and method
InactiveUS7113172B2Input/output for user-computer interactionElectronic switchingDisplay deviceData treatment
Owner:LIFESCAN IP HLDG LLC
Alphanumeric keypad and display system and method
InactiveUS20050140659A1Input/output for user-computer interactionCathode-ray tube indicatorsDisplay deviceTouchscreen
Data entry and display apparatus and methods that provide greater efficiency in data processing devices. The apparatus comprises a keypad with a plurality of first keys and plurality of secondary keys, the first keys each having at least one primary alphanumeric symbol and at least one of the first keys having a secondary alphanumeric symbol associated therewith, the first key with the secondary symbol being operable to selectively display the secondary alphanumeric symbols in association with the second keys. The apparatus may further comprise a display, which may be embodied in a common touch screen user interface with the keypad. The methods comprise actuating one of the first keys on the keypad and displaying a set of secondary alphanumeric symbols in association with the secondary keys, and selecting the primary alphanumeric symbol associated with the first key or selecting one of the set of secondary alphanumeric symbols by actuating one of the second keys. Selection and actuation of appropriate combinations of first and second keys allows entry of any character string.
Owner:LIFESCAN IP HLDG LLC
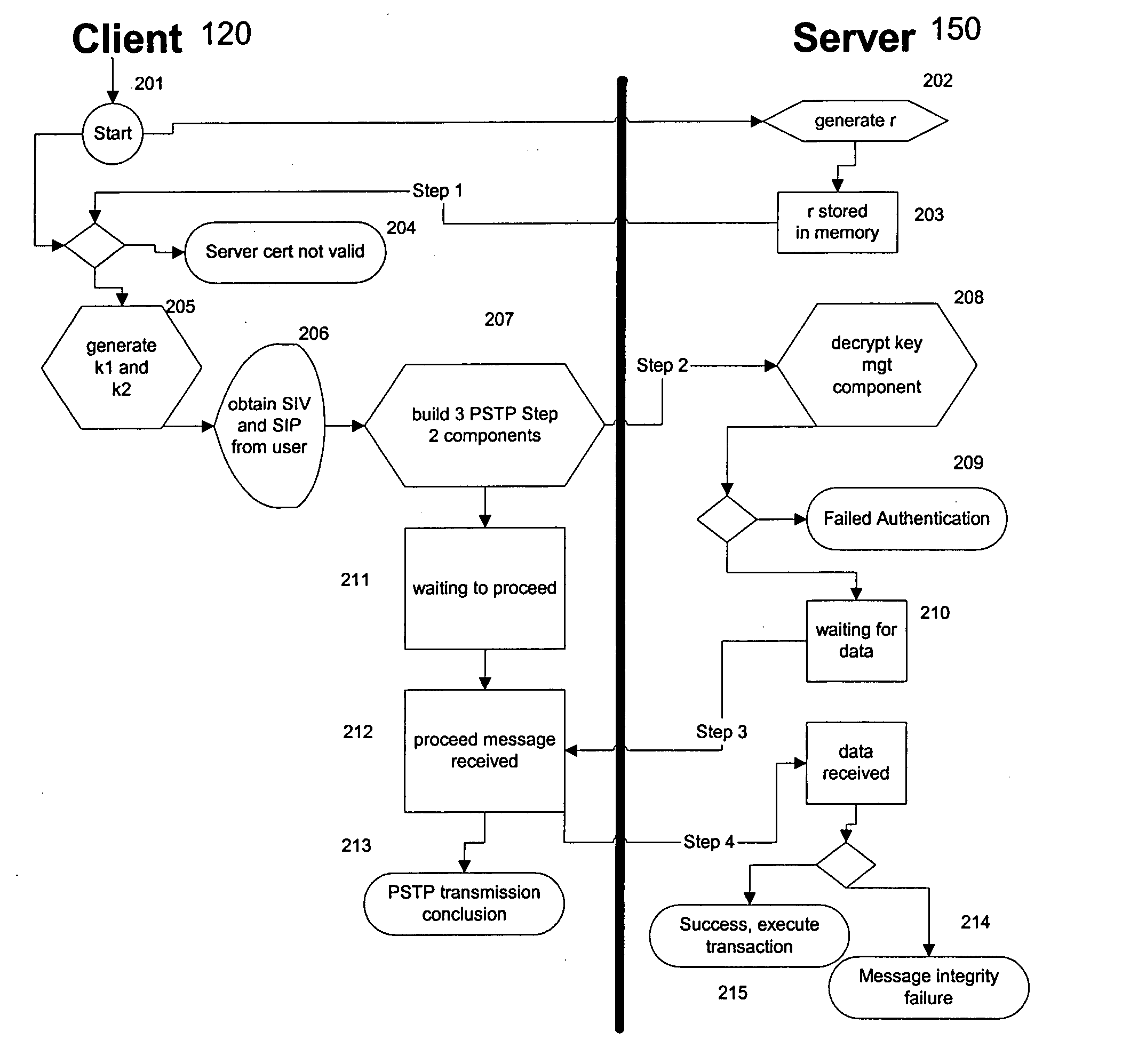
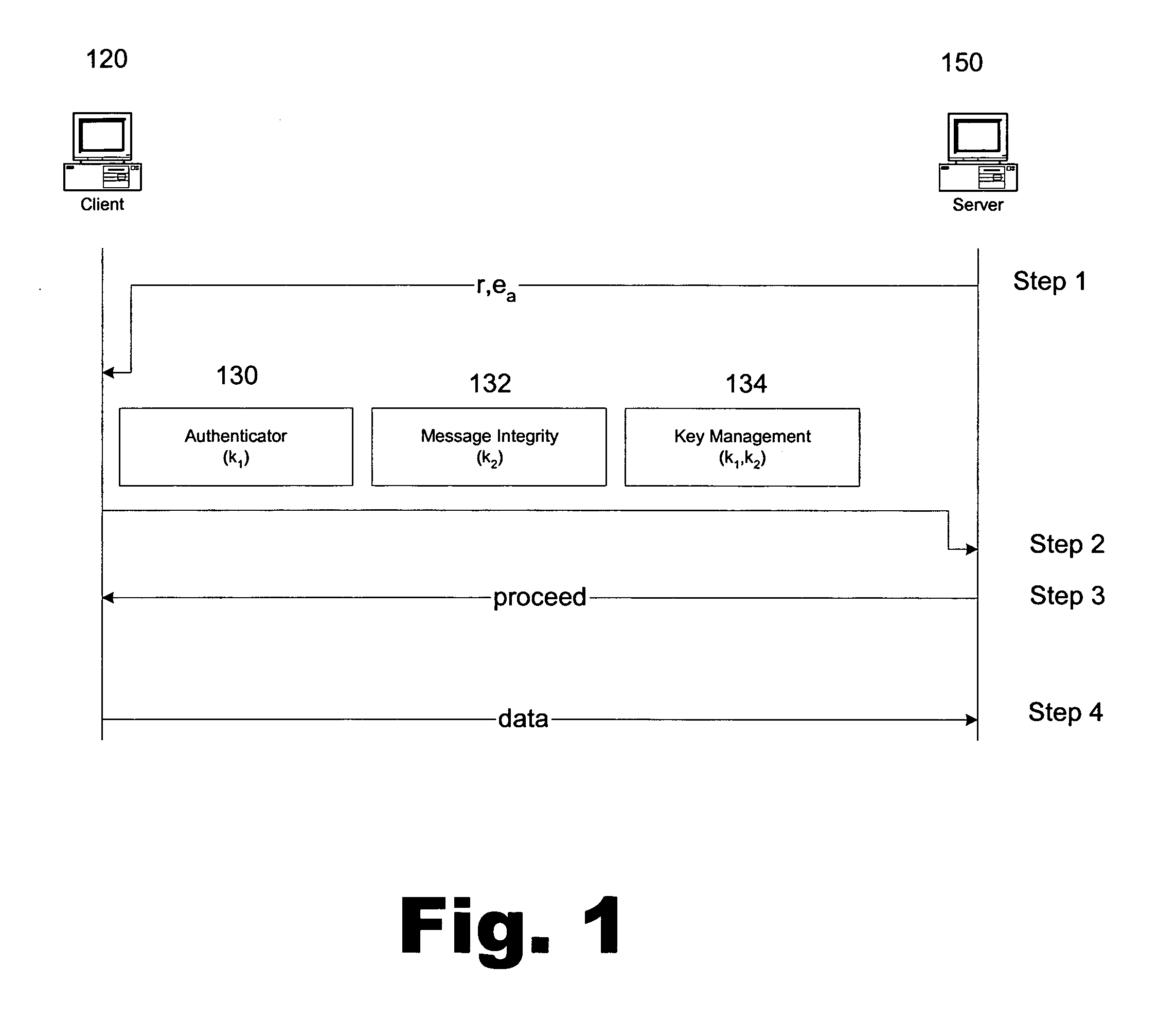
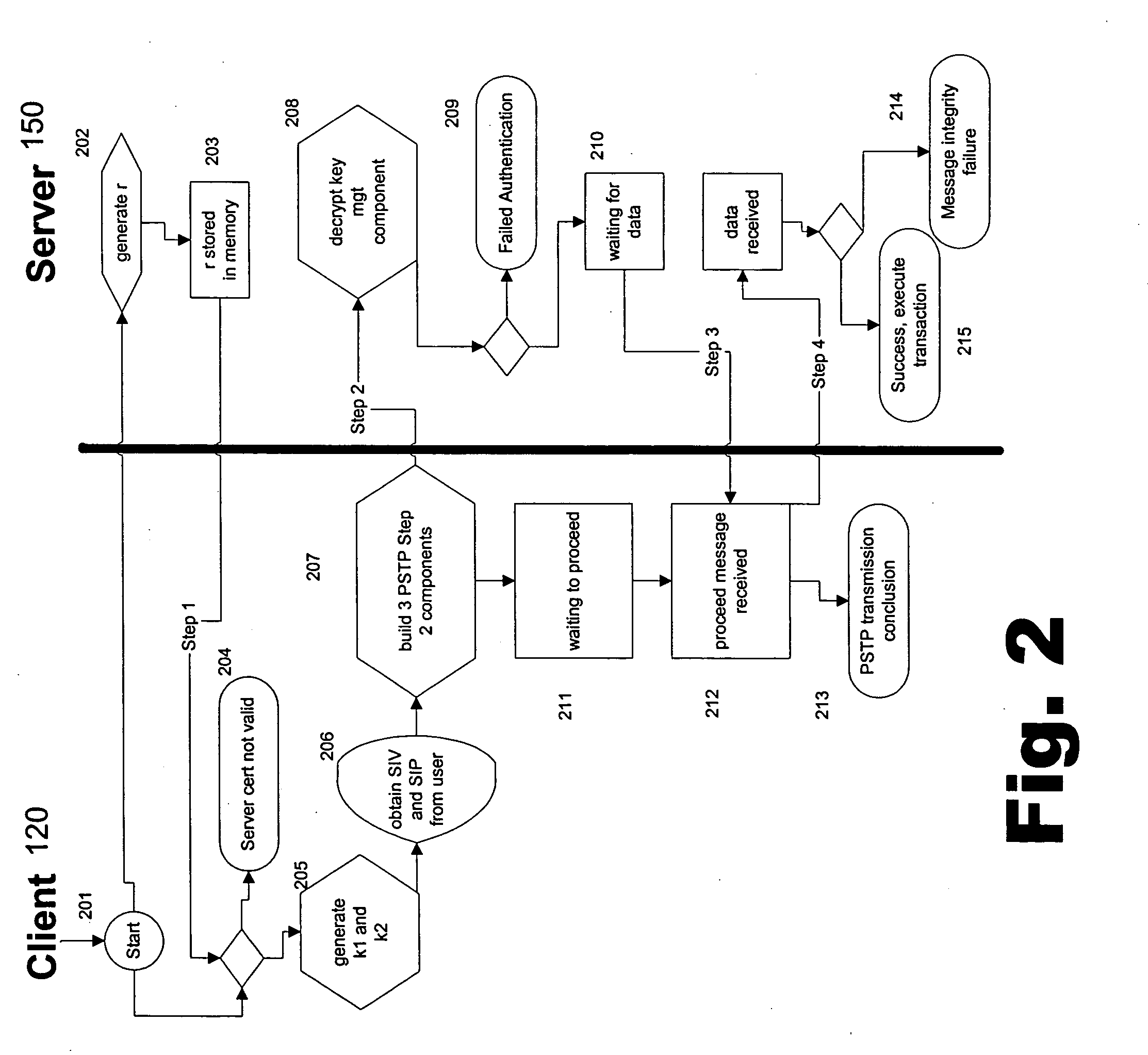
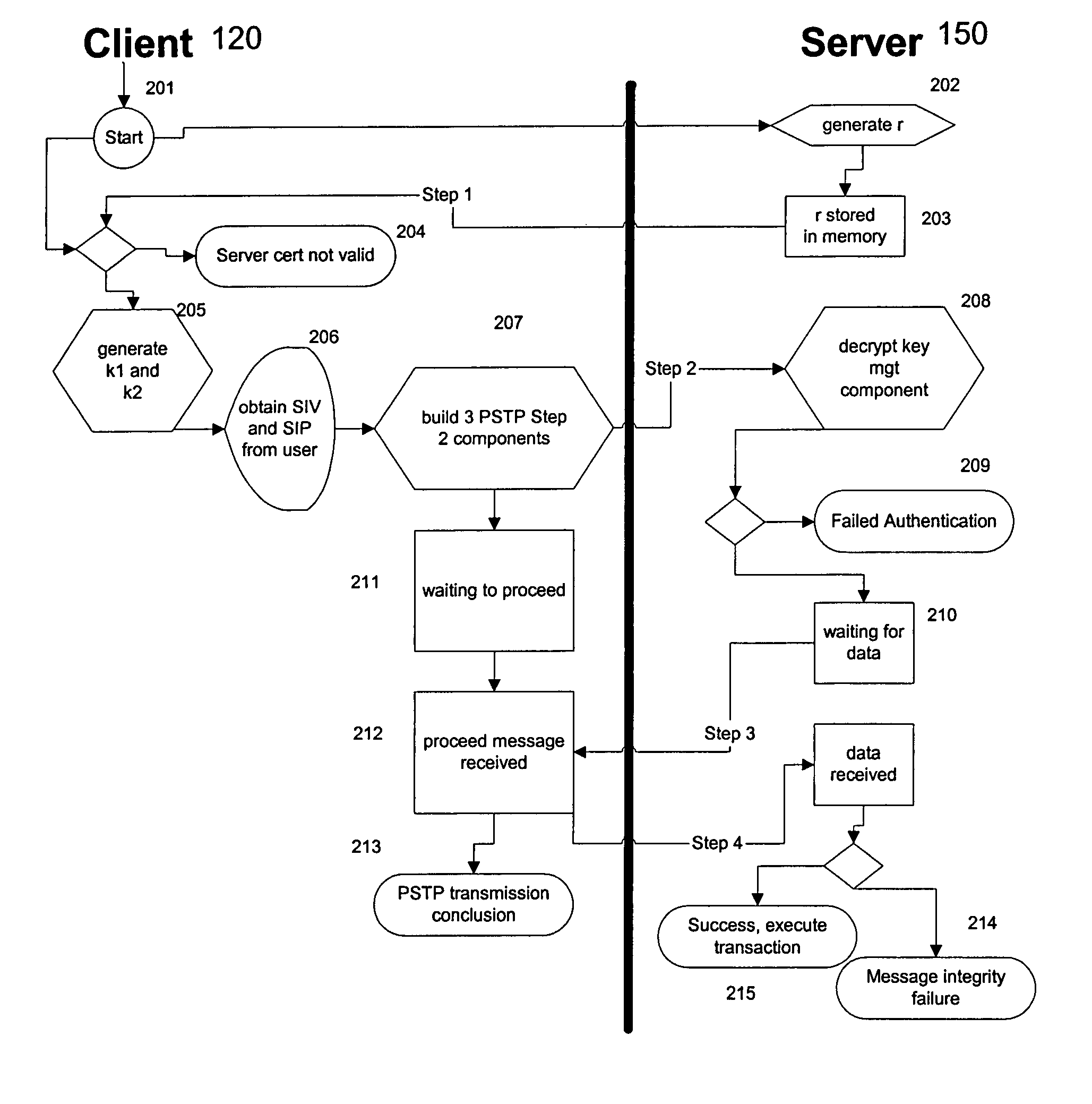
Portable security transaction protocol
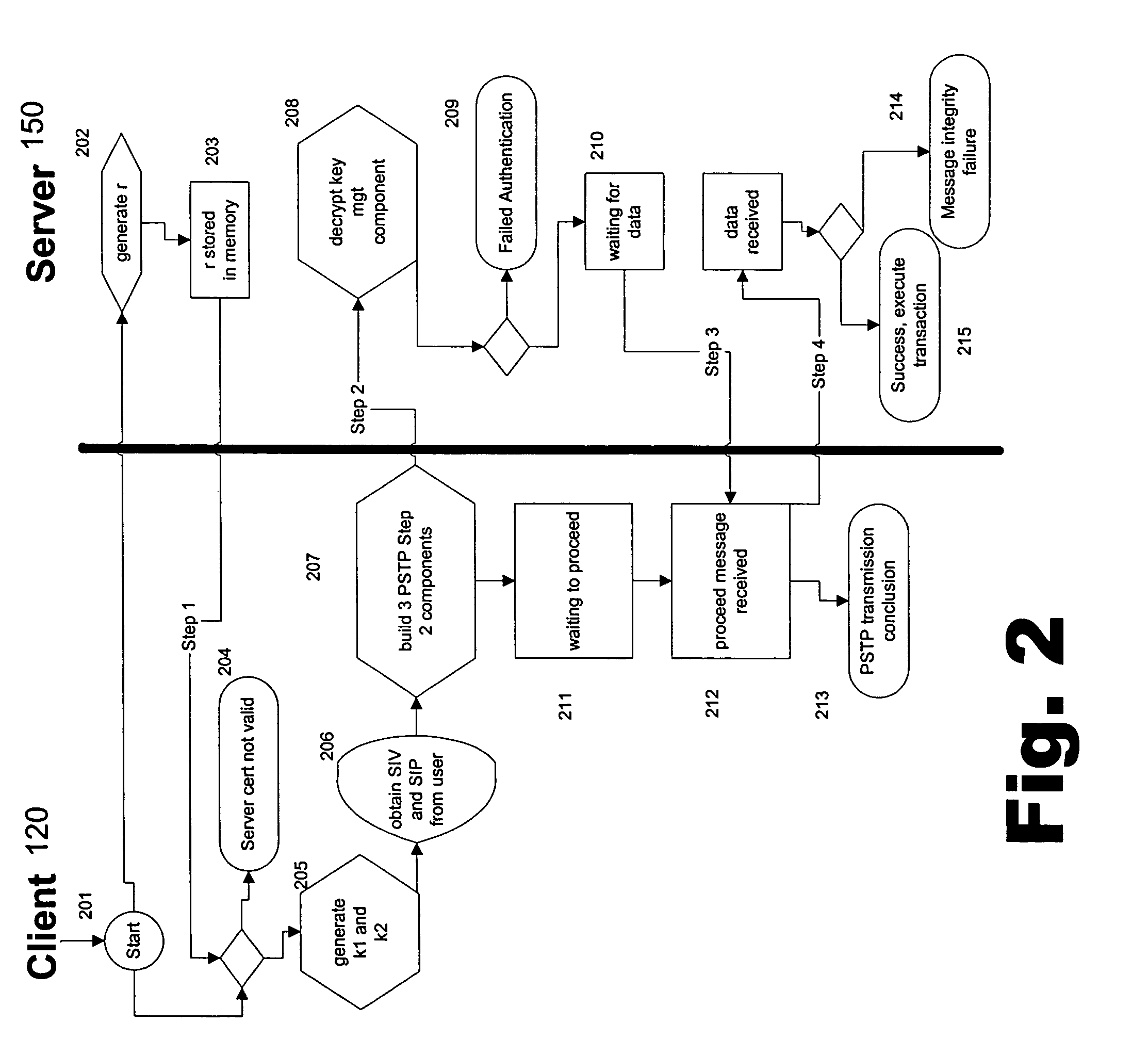
ActiveUS20050091492A1Provide authenticityUser identity/authority verificationPayment circuitsThird partyCredit card
A technique for providing message authenticity includes accepting transaction information, accepting a first data item used for authenticating an originating user, cryptographically processing the transaction information using only a second data item, wherein the entropy of the first data item is less than the entropy of the second data item, and authenticating the originating user using the first data item. The first data item can be a sequence of digits corresponding to those displayed on an external device, such as, for example, an RSA authorization token, credit card, etc. In general, the first data item will be a short alphanumeric string and the second data item will generally be much larger, e.g., a 128 bit sequence to be used principally for data authentication. According to another aspect of the present invention, consequential evidence of the transaction may be secured to provide after-the-fact evidence of the transaction. This evidence can include a message written to a tamper-resistant log record, the message including the transaction information, the first data item, the second item, and an identifier for the originating user, as well as other information. At a subsequent point, the transaction can be shown to have been sent by the originating user and received by the intended recipient, by consulting the log record. Preferably, the validity of the transaction would be ascertained by an independent, mutually trusted third party.
Owner:JPMORGAN CHASE BANK NA
Portable security transaction protocol
ActiveUS8190893B2Digital data processing detailsUser identity/authority verificationCredit cardThird party
A technique for providing message authenticity includes accepting transaction information, accepting a first data item used for authenticating an originating user, cryptographically processing the transaction information using only a second data item, wherein the entropy of the first data item is less than the entropy of the second data item, and authenticating the originating user using the first data item. The first data item can be a sequence of digits corresponding to those displayed on an external device, such as, for example, an RSA authorization token, credit card, etc. In general, the first data item will be a short alphanumeric string and the second data item will generally be much larger, e.g., a 128 bit sequence to be used principally for data authentication. According to another aspect of the present invention, consequential evidence of the transaction may be secured to provide after-the-fact evidence of the transaction. This evidence can include a message written to a tamper-resistant log record, the message including the transaction information, the first data item, the second item, and an identifier for the originating user, as well as other information. At a subsequent point, the transaction can be shown to have been sent by the originating user and received by the intended recipient, by consulting the log record. Preferably, the validity of the transaction would be ascertained by an independent, mutually trusted third party.
Owner:JPMORGAN CHASE BANK NA
Mobile station and network having hierarchical index for cell broadcast service
InactiveUS6370391B1Easy to useEmergency connection handlingTime-division multiplexBroadcast domainMobile station
This invention provides for the use of an index message in a Cell Broadcast Service. An index message is considered to be a special type of Cell Broadcast message which contains general information about actual broadcast messages. The index message is transmitted in a predetermined logical S-BCCH subchannel, and contains information elements such as (a) message overviews or summaries for each cell broadcast message, (b) information concerning emergency messages, (c) information concerning the language used in different broadcast messages, (d) an alphanumeric broadcast domain operator name and a specific operator greeting, (e) information concerning changes in broadcast messages, and (f) information concerning subchannels.
Owner:NOKIA MOBILE PHONES LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com