Patents
Literature
151results about How to "Secure delivery" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
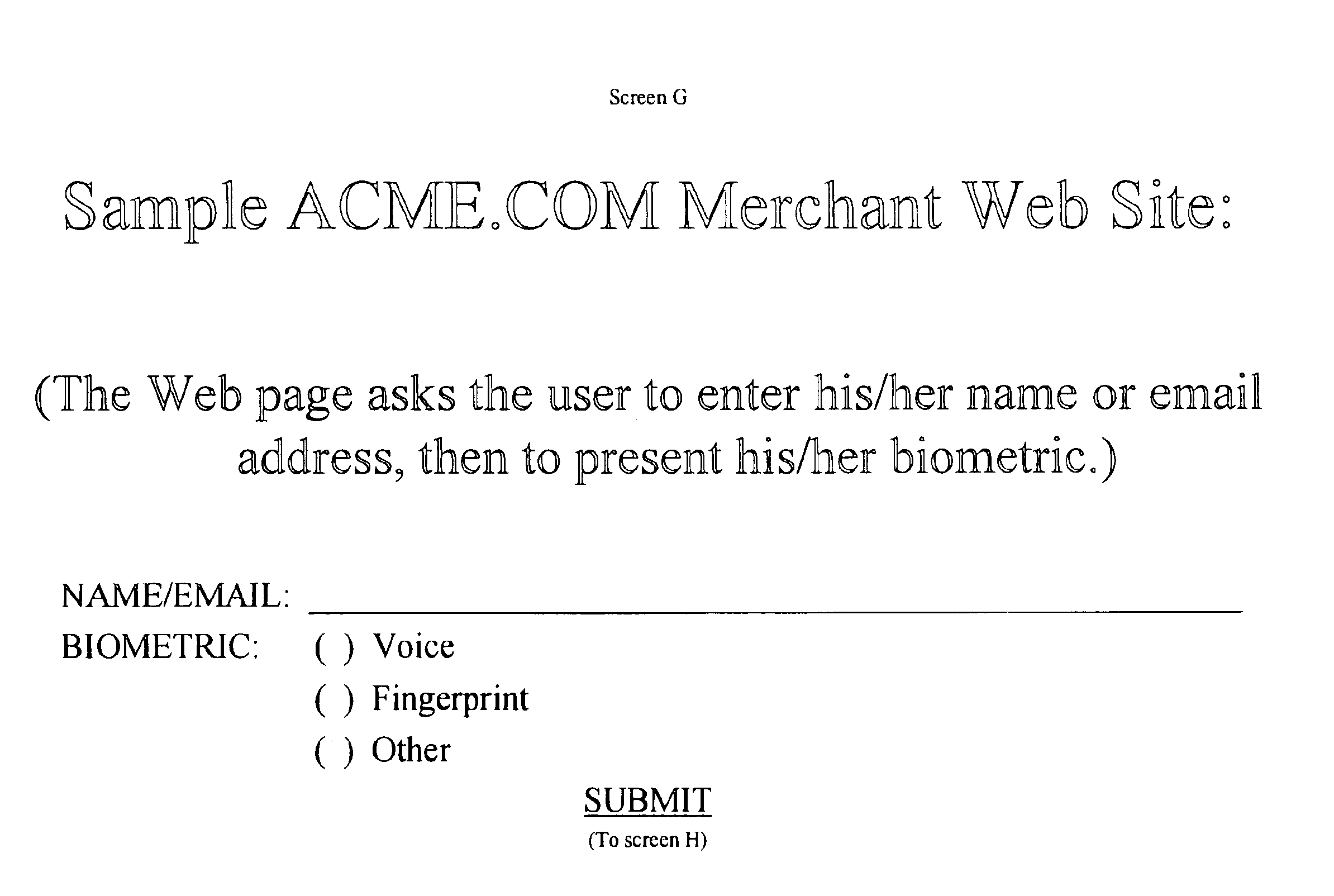
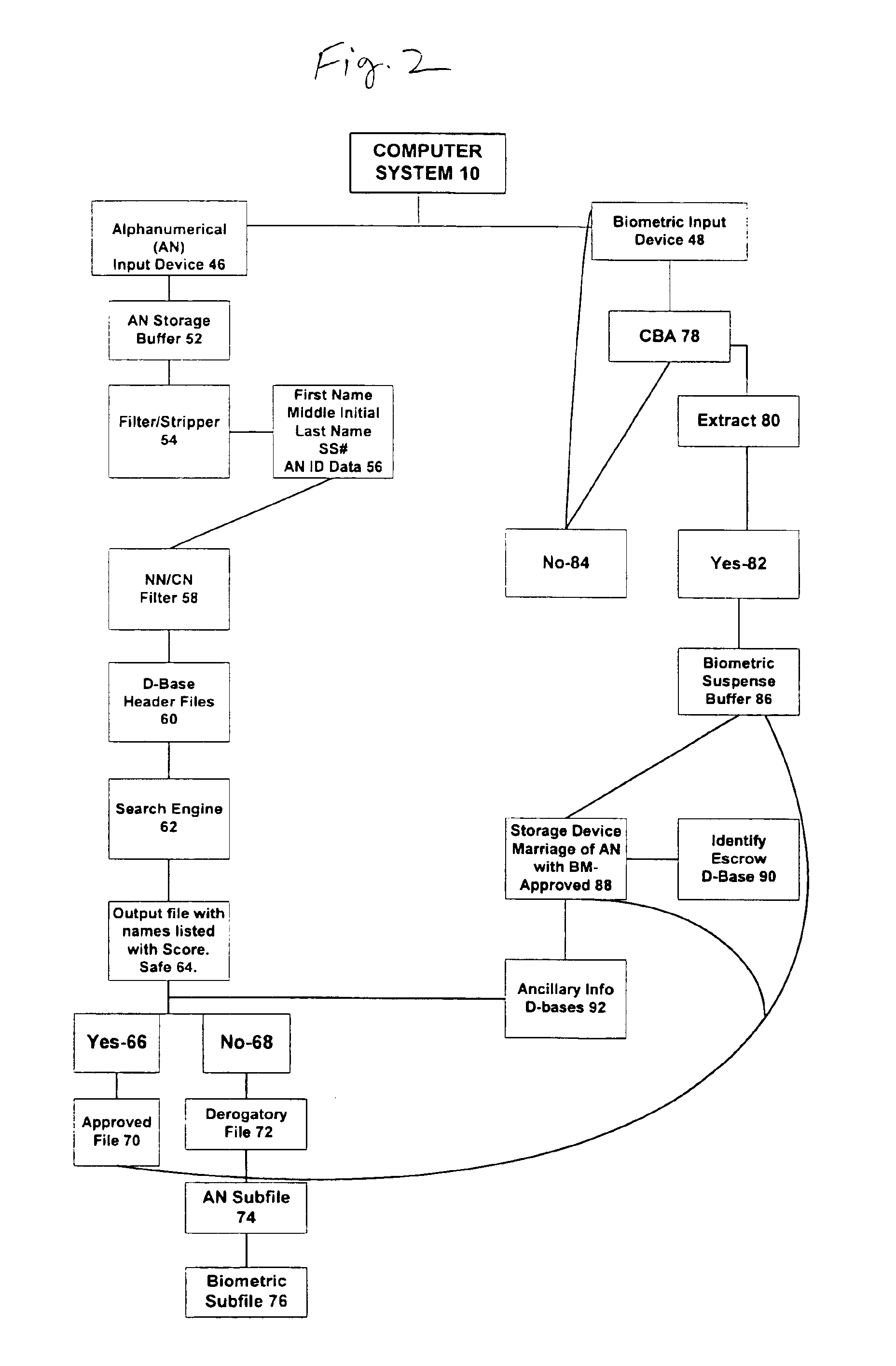
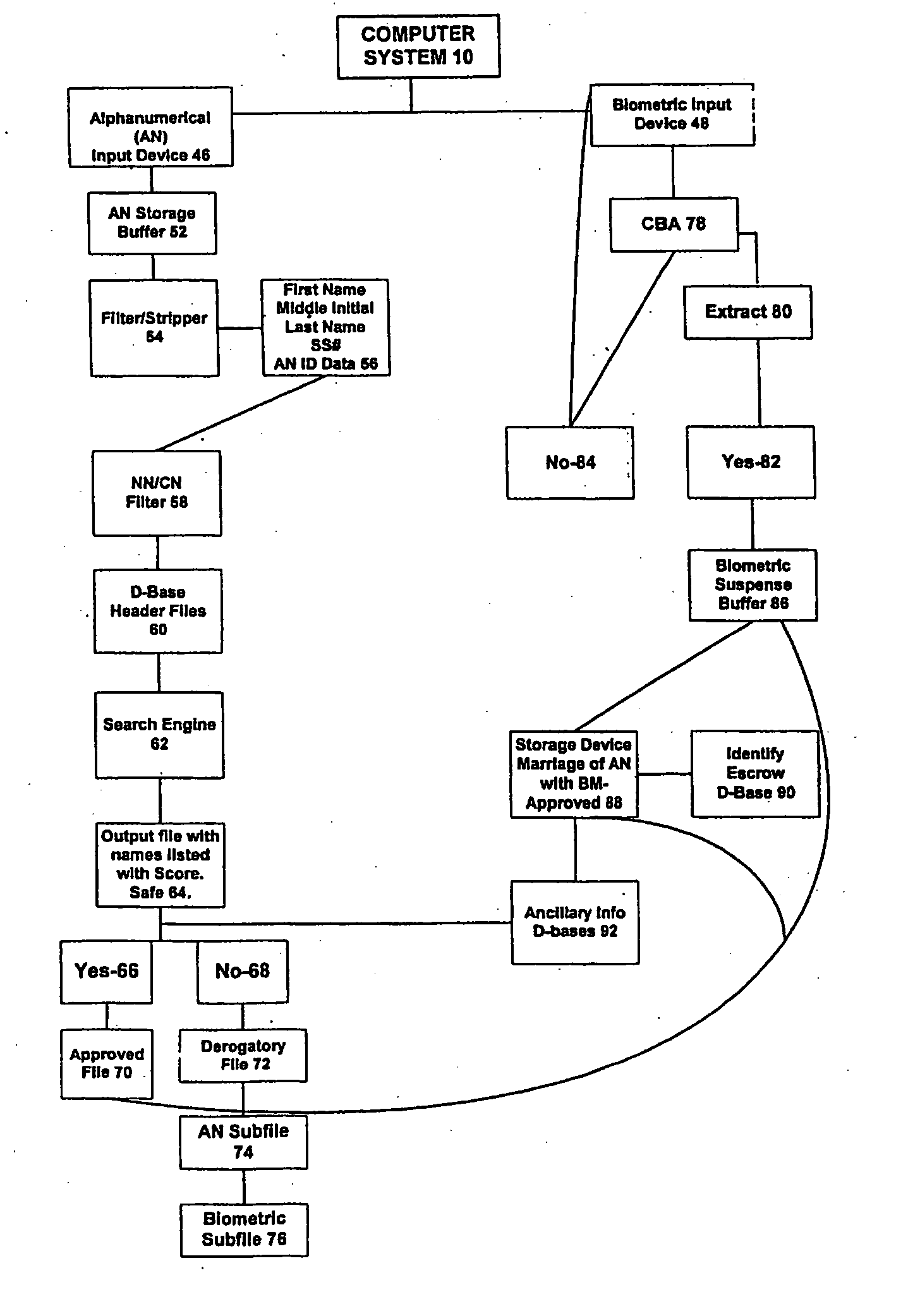
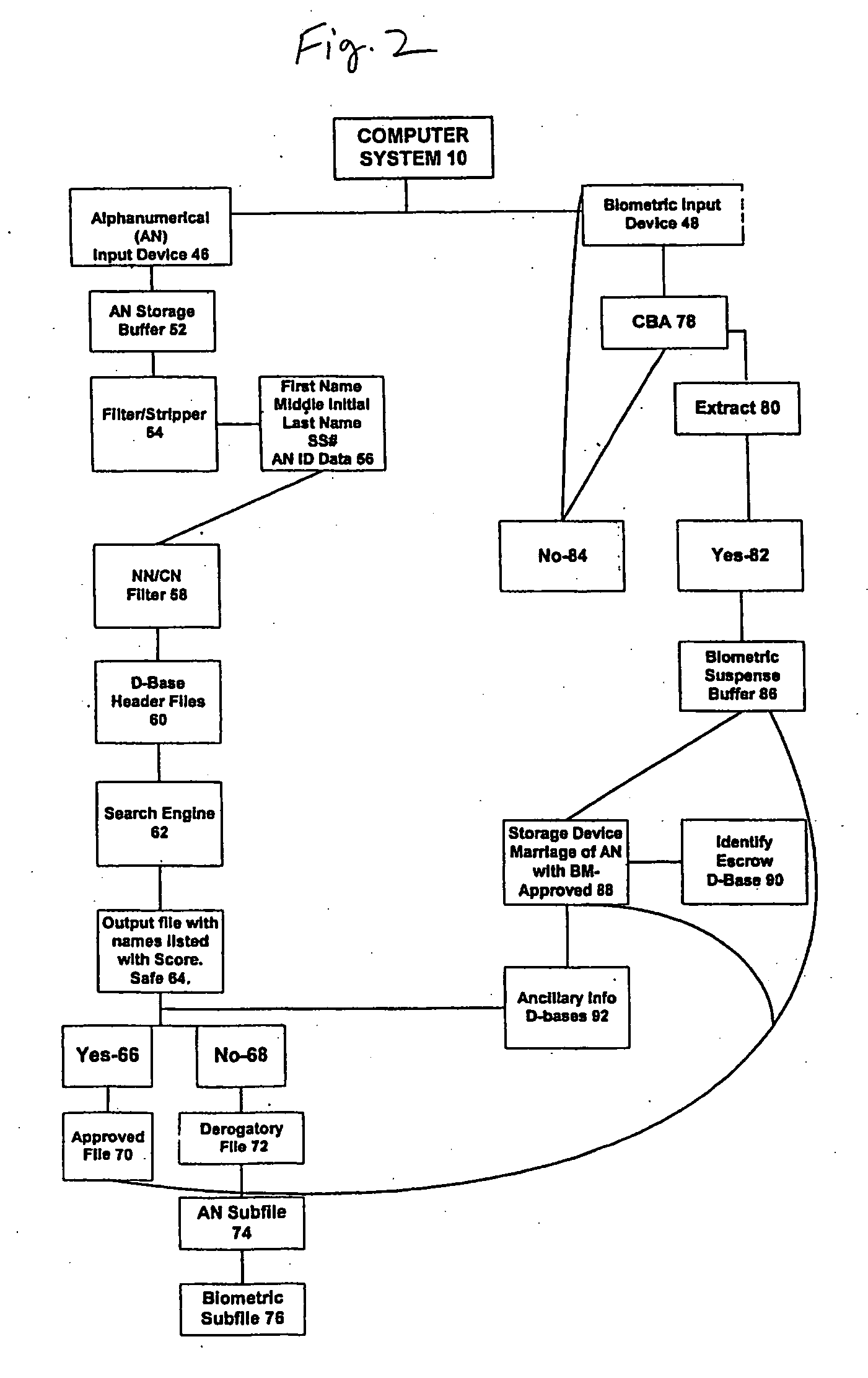
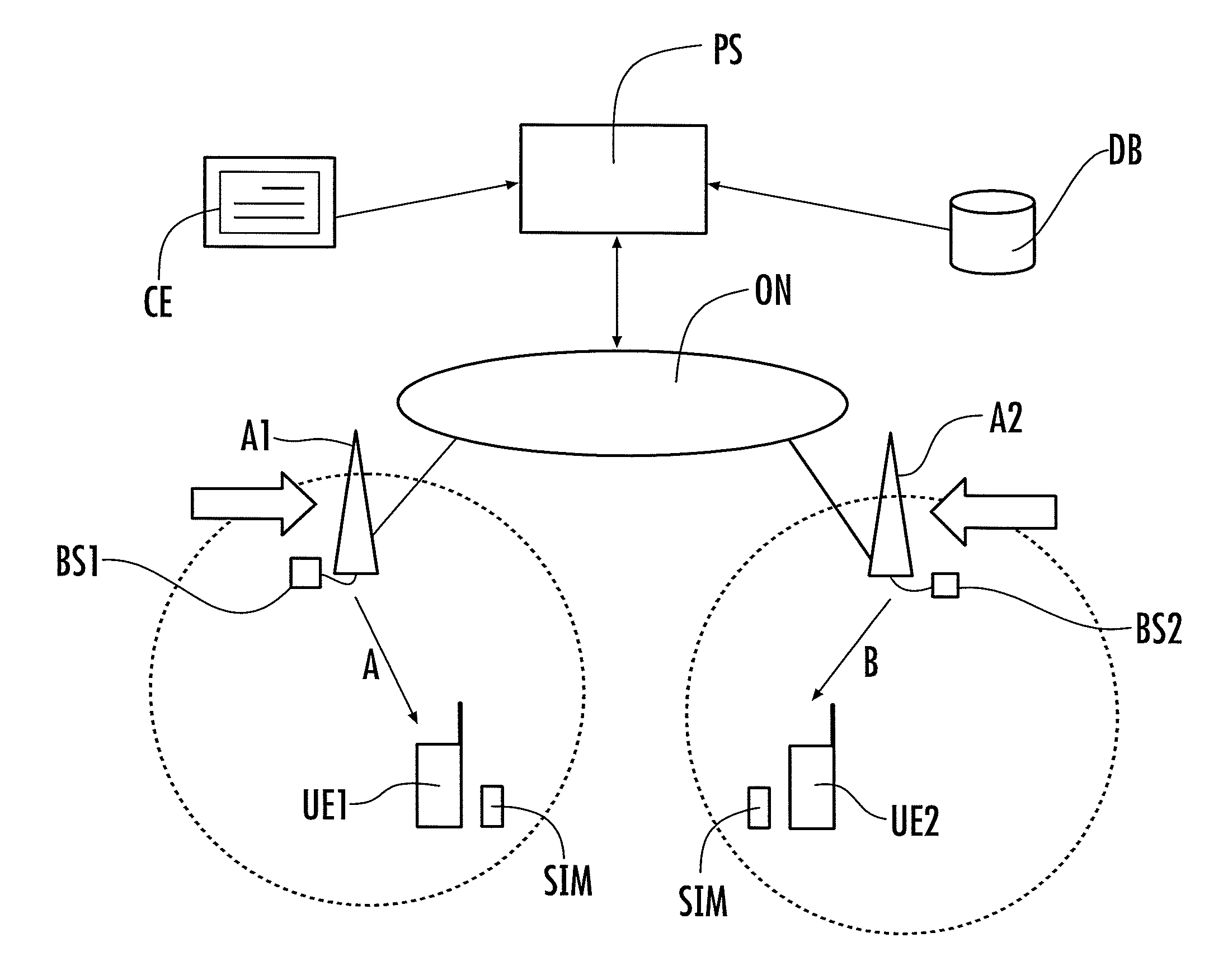
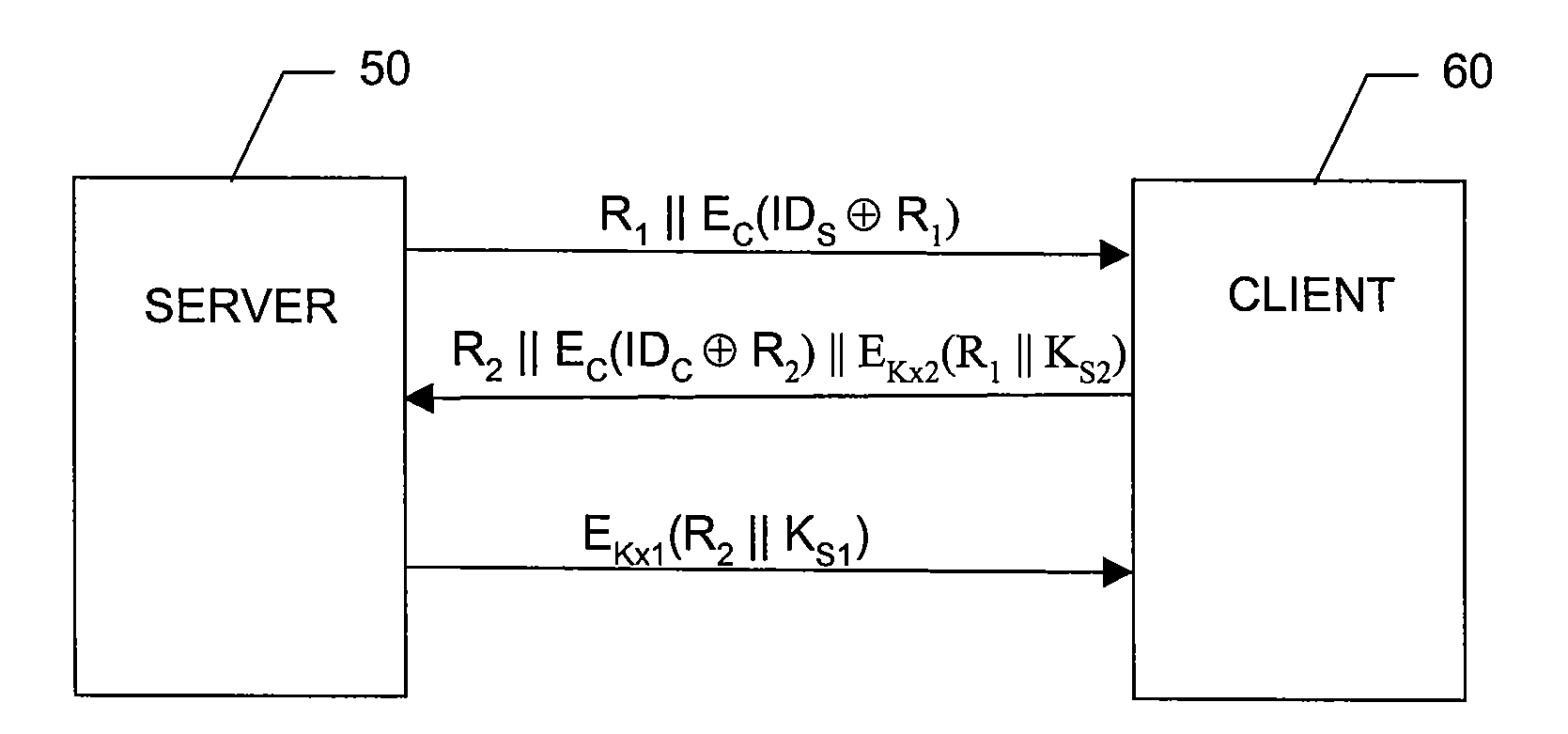
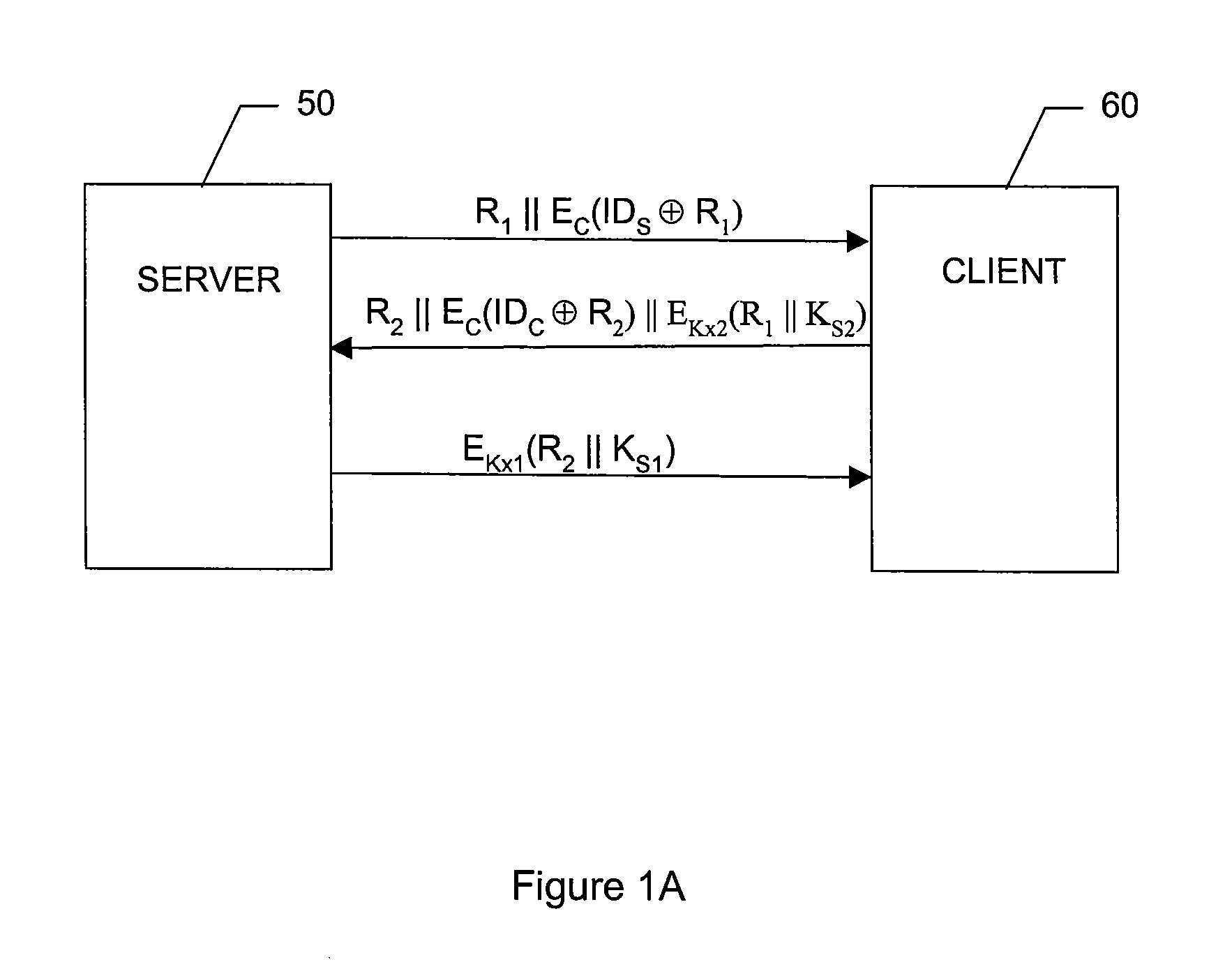
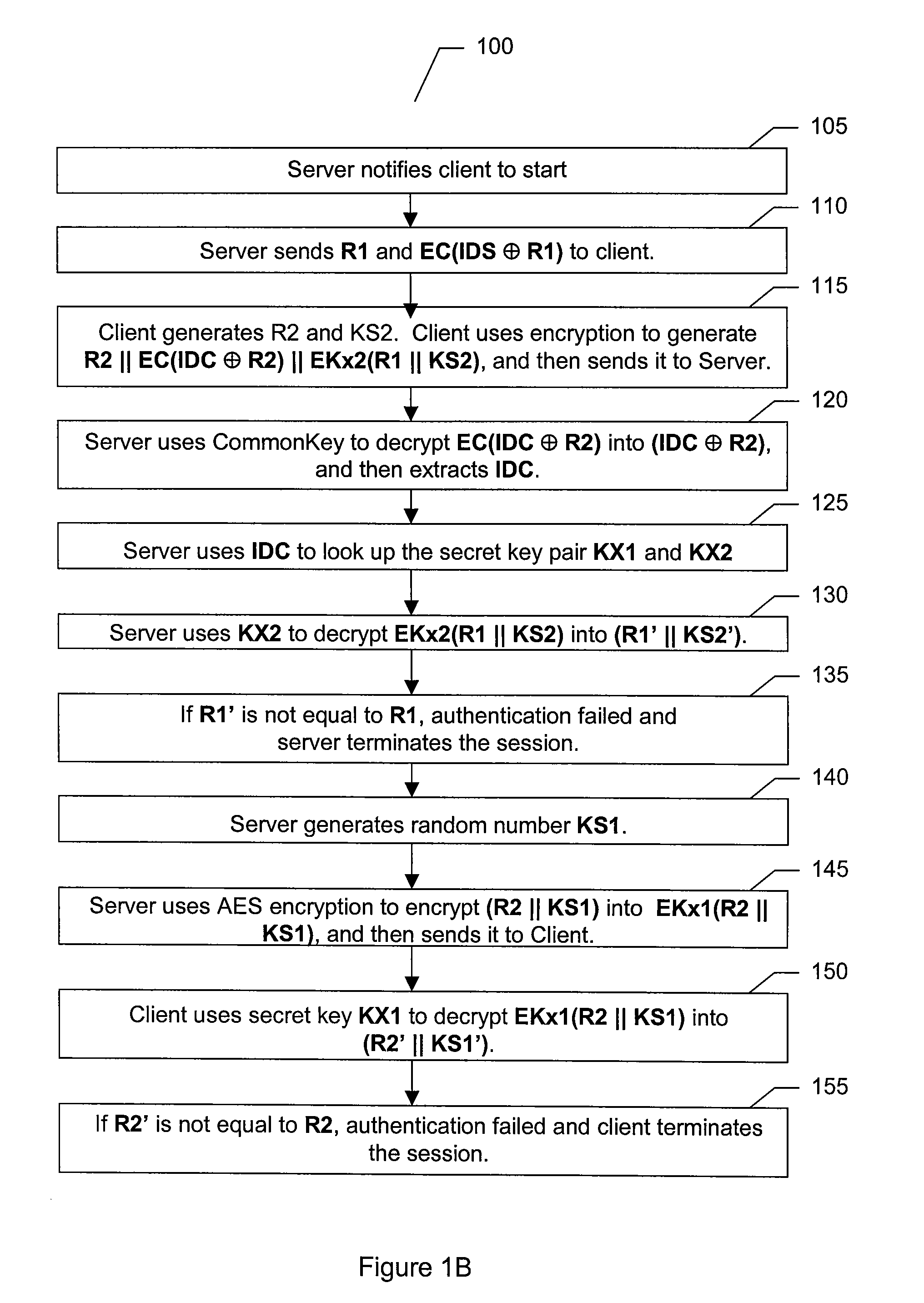
System and method for verification of identity
InactiveUS6871287B1Secure deliverySafe handlingFinanceDigital data processing detailsBiometric dataUser input
A system and method for the identification and verification of a user is provided. The disclosed invention has an enrollment system which includes (i) an alphanumeric input device; (ii) a biometric input device; (iii) a header file database having a plurality of identities; (iv) a search engine in communication with the header file database that searches the database for identifies that match alphanumeric data input by a user according to a predetermined first set of criteria; (v) a processor to score the set of identities matched by the search engine according to a predetermined second set of criteria, and determine that the user's input alphanumeric data based on the score is not suspicious; and (vi) an identity escrow database which receives an approved identity data signal based on the acceptability of the score, and is capable of receiving a biometric identity data signal input by the user to the biometric input device, the escrow database further capable of creating at least one subfile within the escrow database for each user comprising the approved identity data signal and the biometric data signal.
Owner:EDENTIFY INC
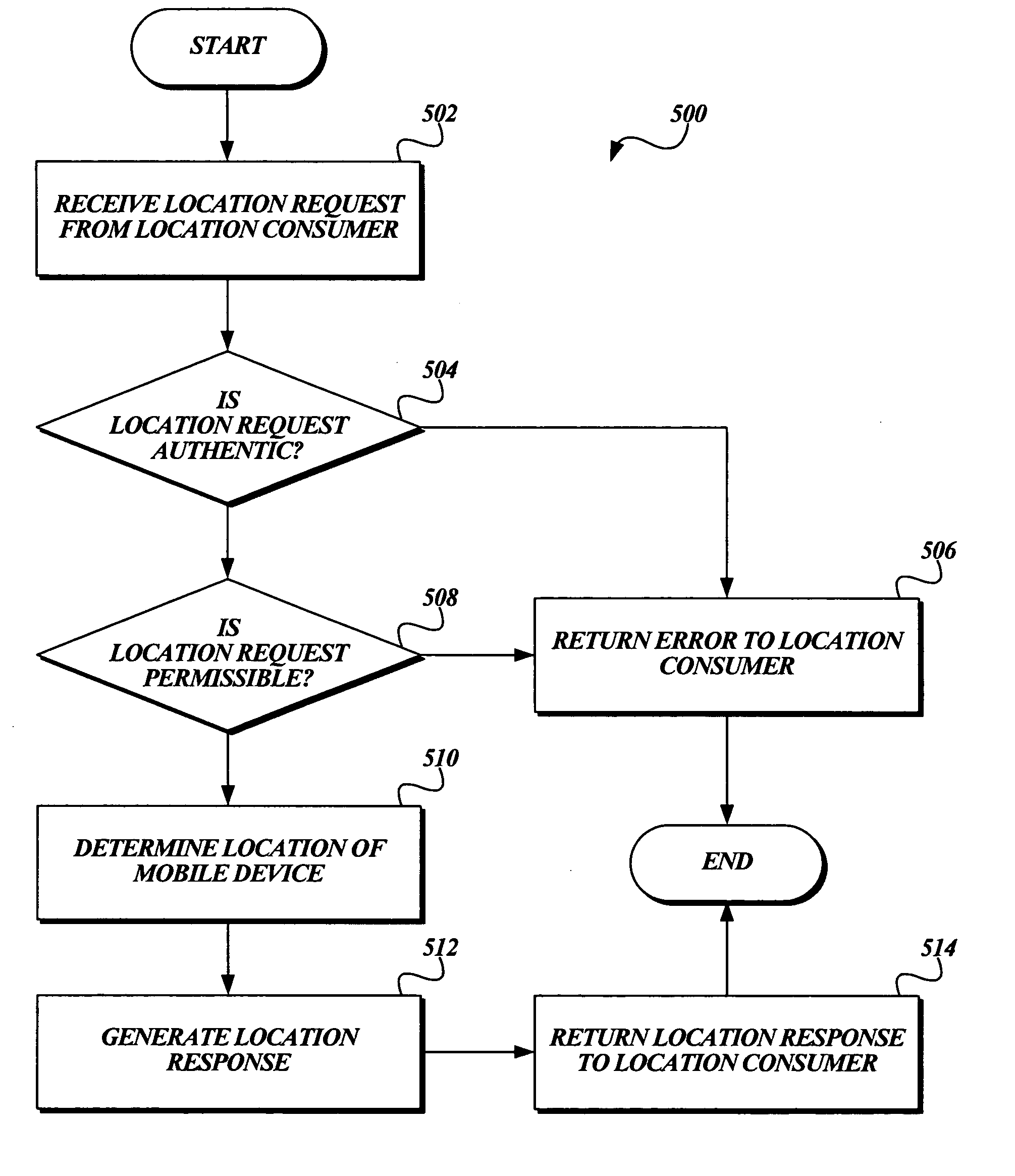
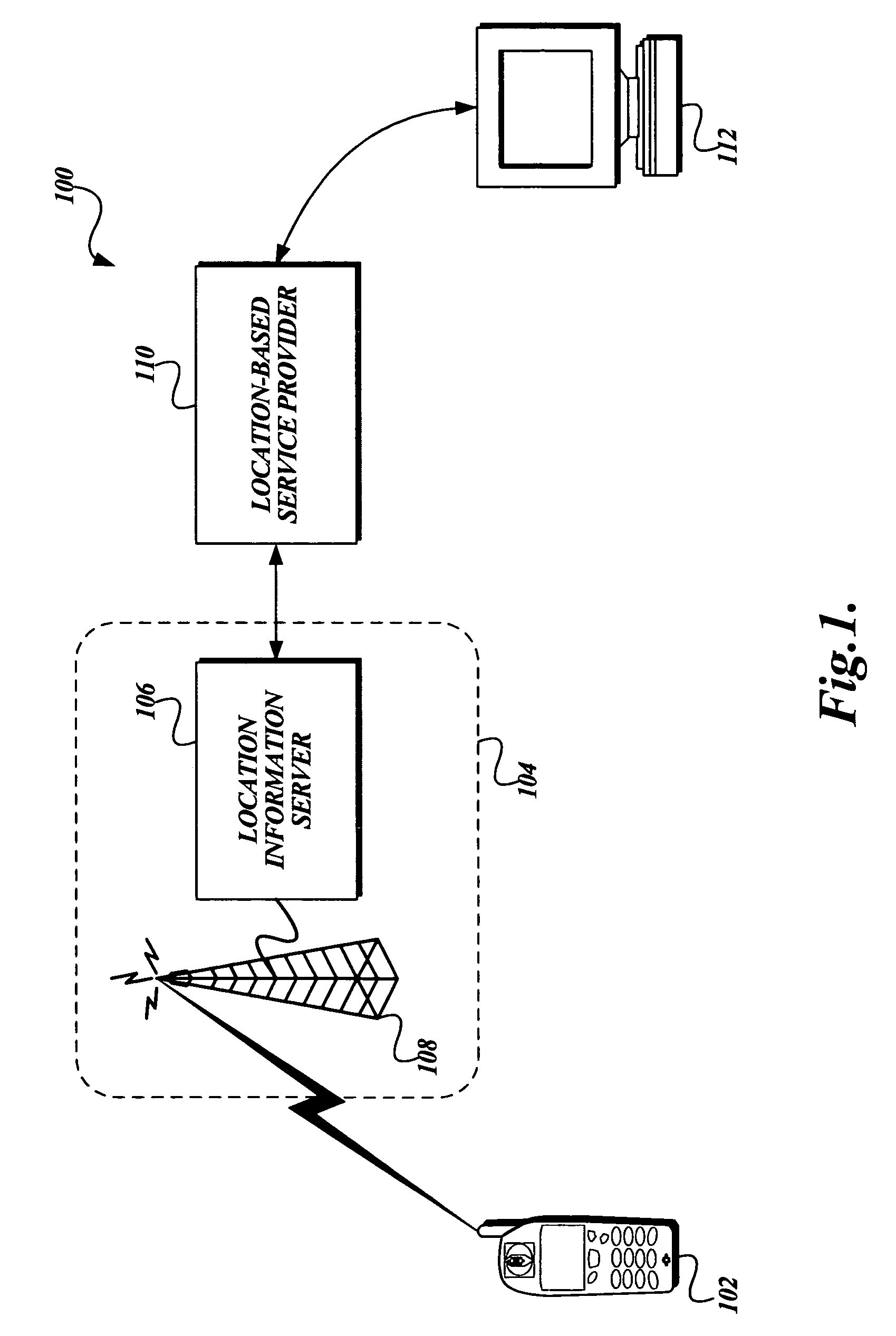
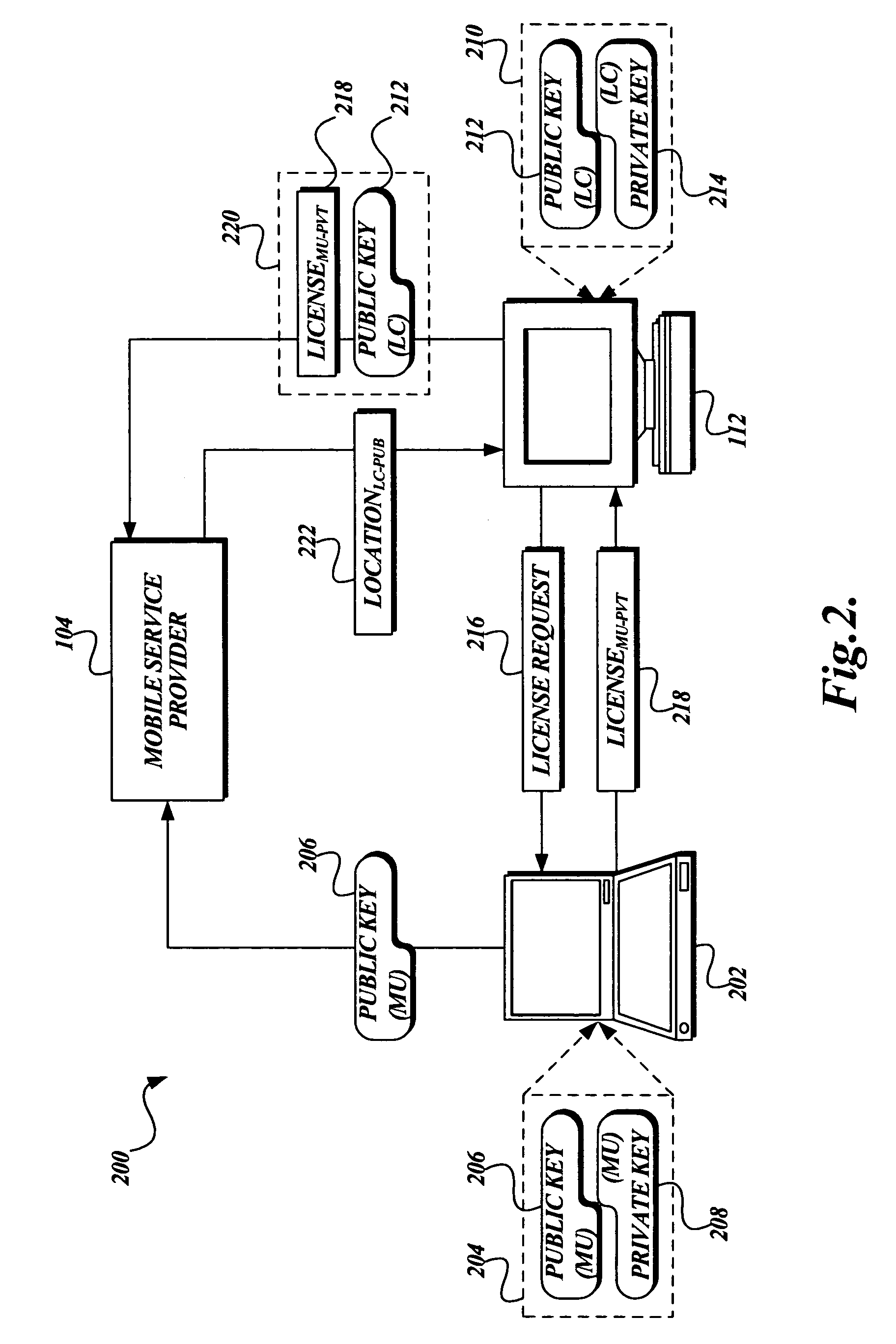
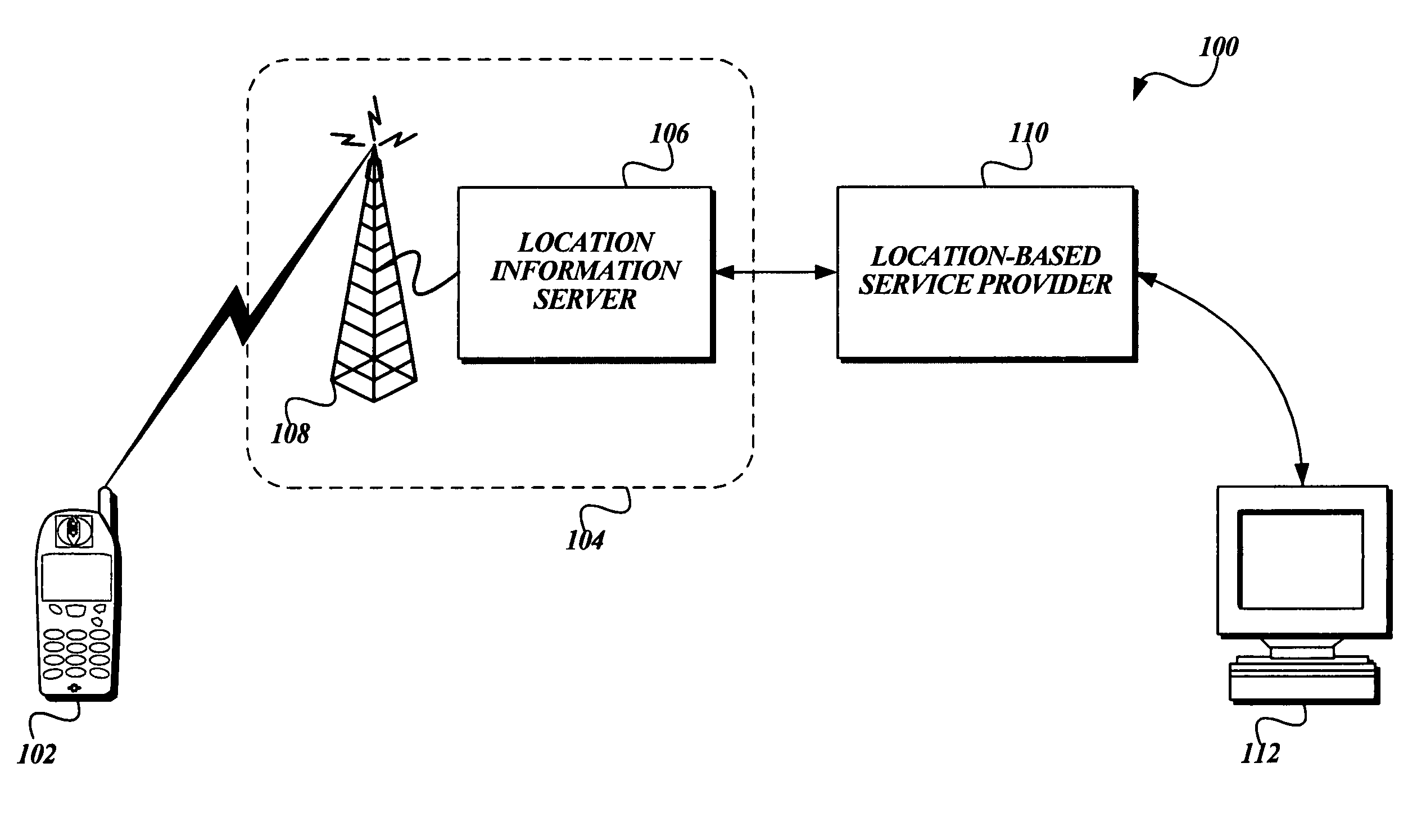
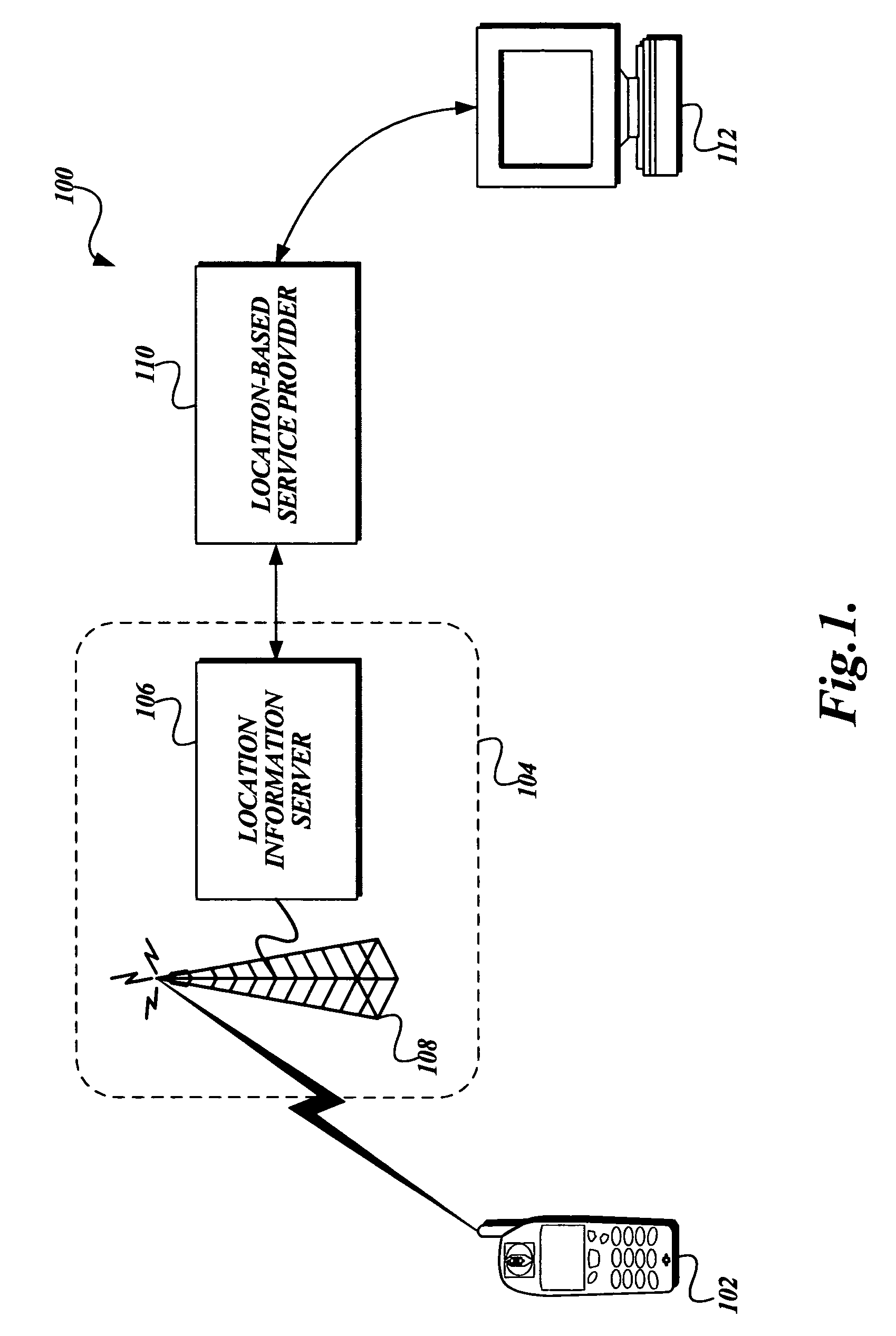
System and method for enforcing location privacy using rights management
InactiveUS20060046744A1Secure deliveryData processing applicationsUser identity/authority verificationRights managementMobile device
A system and method for securely delivering the location information of a mobile device to a location consumer is presented. In operation, the mobile device user issues a license to a location consumer. The license identifies the location consumer and any conditions the mobile device user places on the license. The license is encrypted such that it cannot be modified without invalidating the license. The license is submitted in a location request by the location consumer. A location information server receives the request, validates that the license was issued to the location consumer and that the location request conforms to the conditions of the license. If so, the location information server obtains the mobile device's location information, generates a location response, encrypts some of the location response, and returns the location response to the location consumer.
Owner:MICROSOFT TECH LICENSING LLC
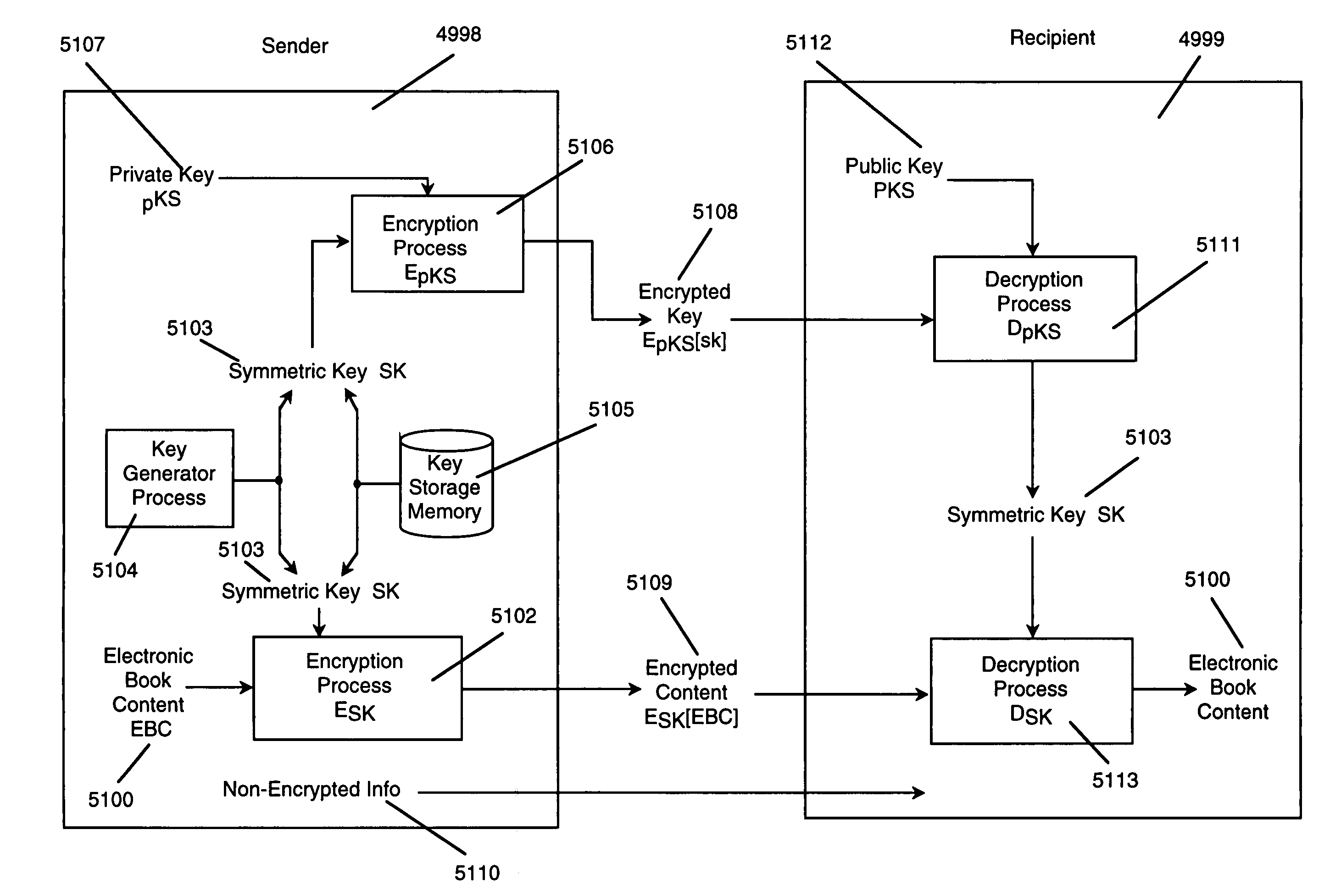
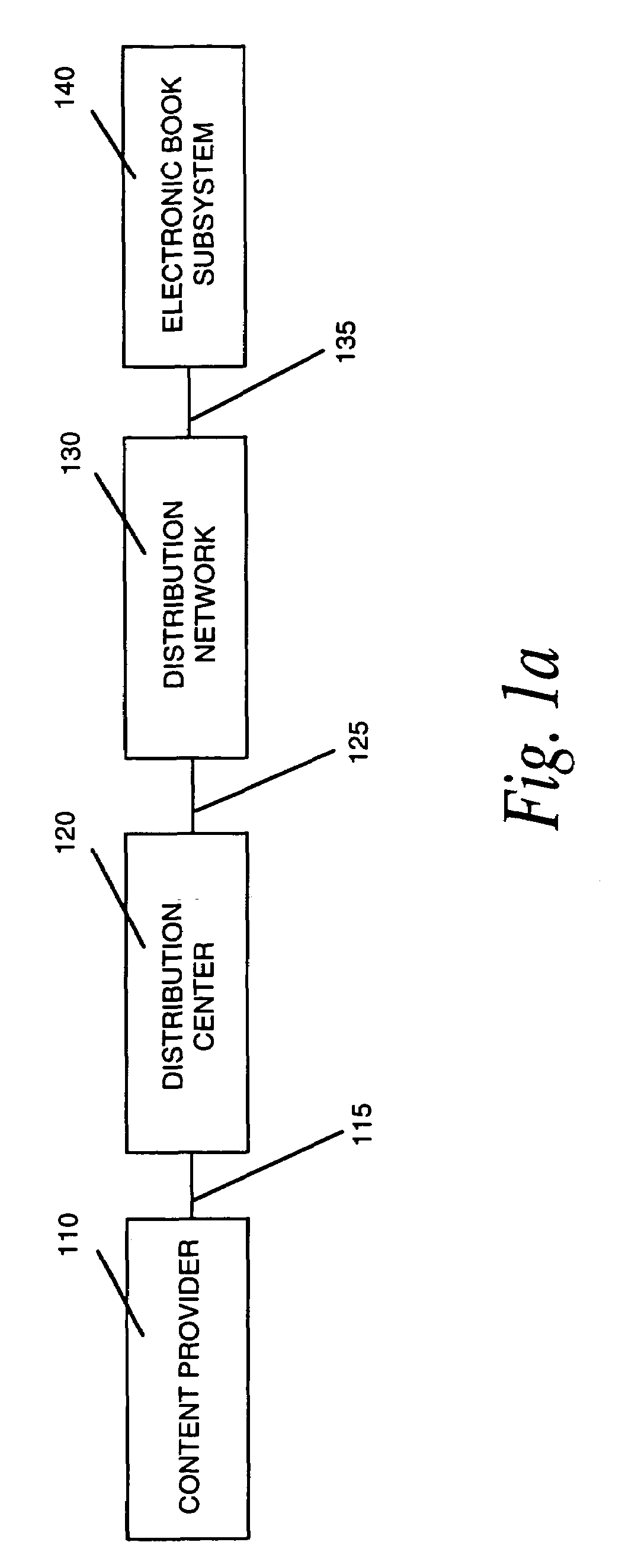
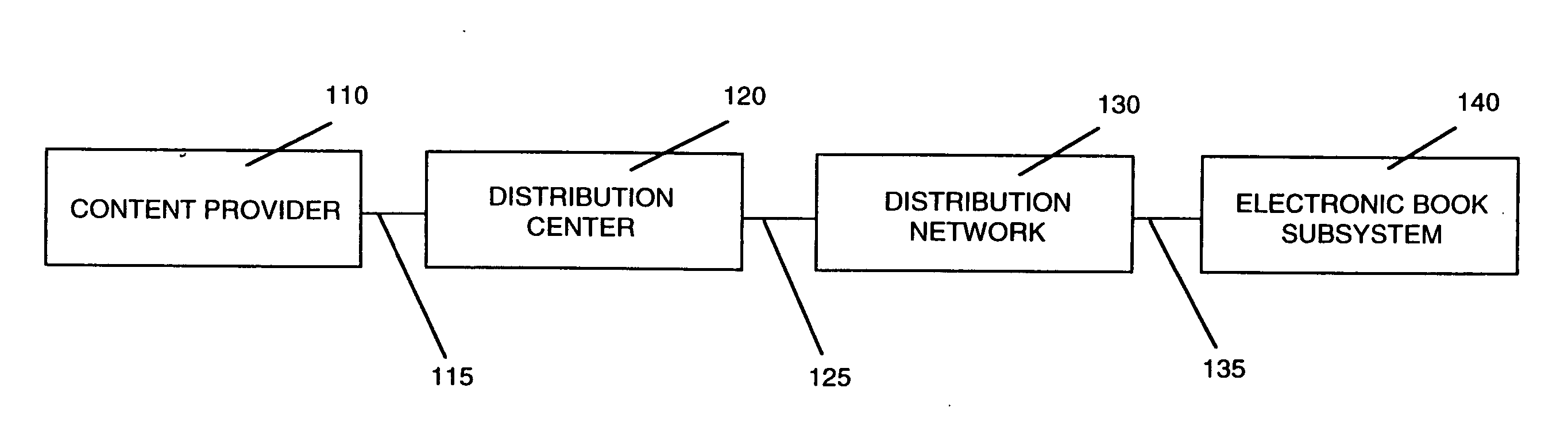
Electronic book security and copyright protection system
InactiveUS7298851B1High tech auraEasy to useKey distribution for secure communicationDigital data processing detailsGraphicsPayment
Owner:ADREA LLC
Portable high speed internet access device with encryption
InactiveUS6928461B2Low costSecure deliveryDigital data information retrievalMultiple digital computer combinationsThe InternetSound file
Owner:TULI RAJA SINGH MR
System and method for verification of identity
InactiveUS20050216953A1Secure deliverySafe handlingDigital data processing detailsCharacter and pattern recognitionThird partyBiometric data
A system for verifying identities comprising an enrollment system having: (i) at least one alphanumeric input device; (ii) at least one biometric input device; (iii) at least one header file database having a plurality of identities; (iv) at least one search engine, said search engine in communication with said header file database such that said search engine first receives an alphanumeric data signal which has been input into said alphanumeric input device by the user, and then searches said database for identities that match the alphanumeric data according to a predetermined first set of criteria; (v) a processor to score the set of identities matched by said search engine according to a predetermined second set of criteria, said processor capable of determining the acceptability or unacceptability of said user's input alphanumeric data based on said score; and (vi) an identity escrow database which is in communication with said processor and receives from said unit an approved identity data signal based on the acceptability of the score, said escrow database additionally in communication with said biometric input device capable of receiving at least one biometric identity data signal input by the user to said biometric input device, said escrow database further comprising means for coupling the approved identity data signal and the biometric identity data signal to create at least one subfile within the escrow database for each user comprising the approved identity data signal and the biometric data signal. The present invention further comprises a verification system for verifying the identity of said user after the user has enrolled in the enrollment system. The verification system has means for processing a second input biometric data signal input by the user to the biometric input device to match the user's preexisting biometric data in said escrow database according to a predetermined third set of criteria. The verification system has an output device for transmitting to a third party whether or not a match was located within said escrow database for said user. The present invention further relates to a method and system for providing a warranty against the theft of a user's identity.
Owner:ELLINGSON JOHN F
Electronic book security and copyright protection system
InactiveUS20070201702A1High tech auraEasy to useKey distribution for secure communicationProgram/content distribution protectionGraphicsPayment
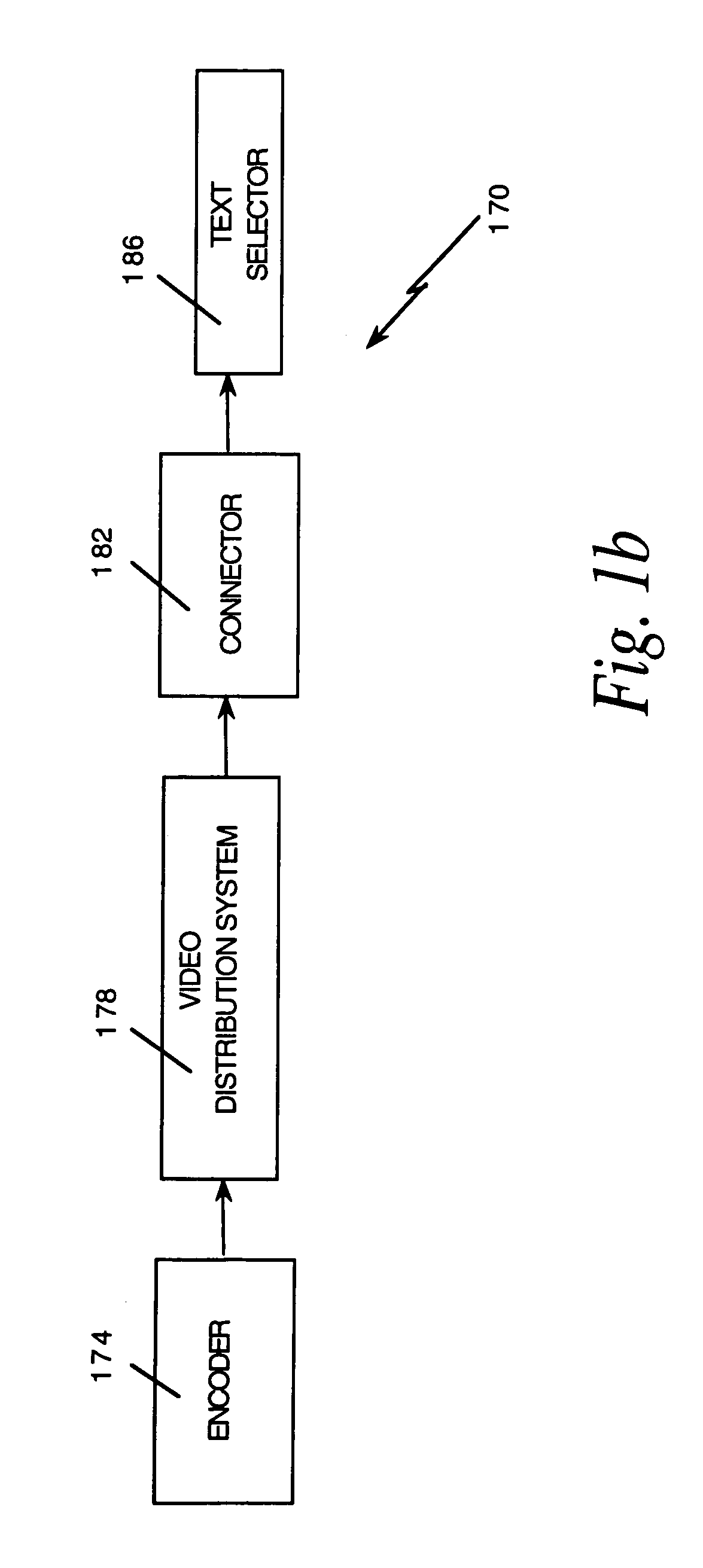
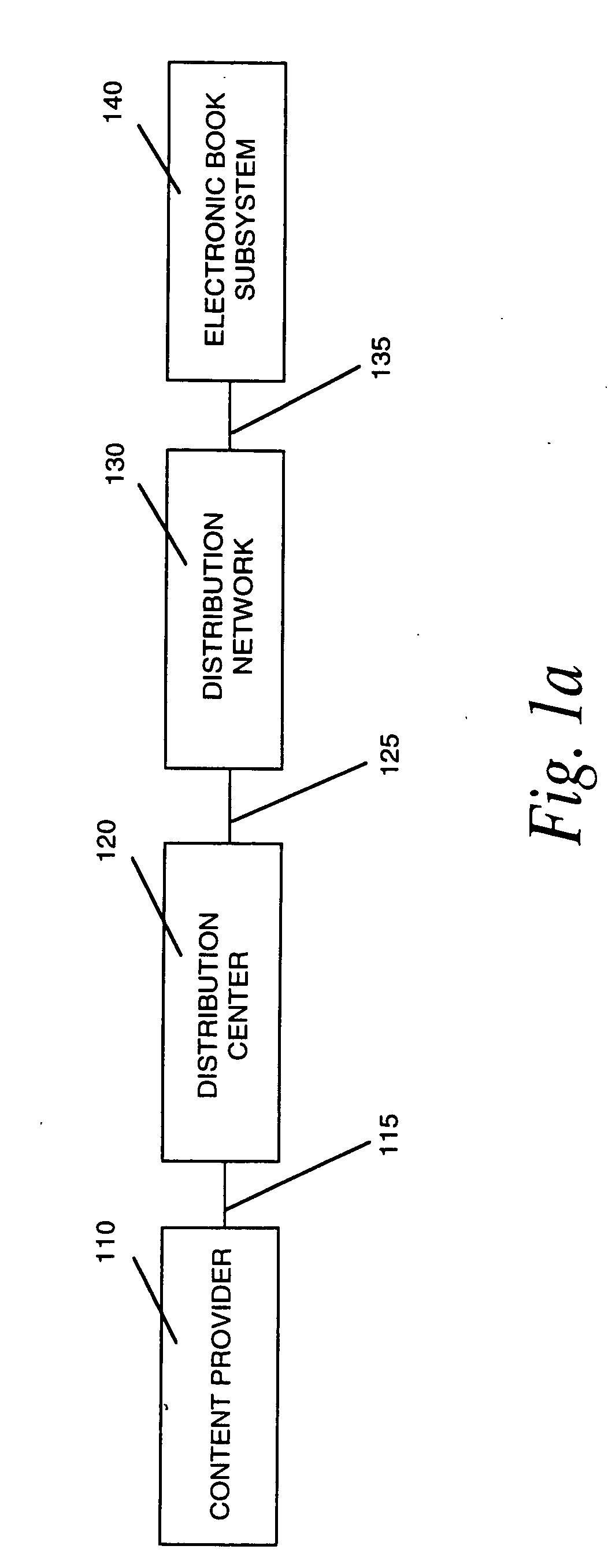
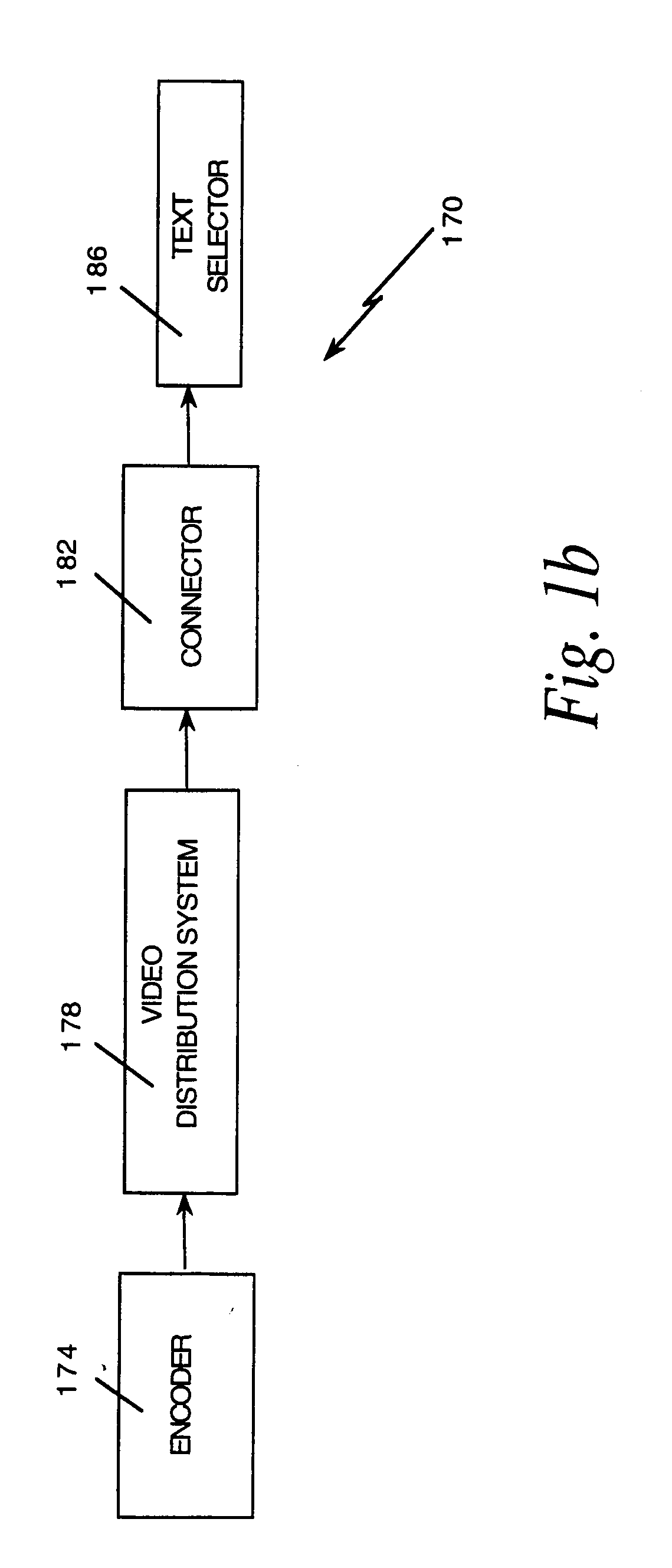
The invention, electronic book security and copyright protection system, provides for secure distribution of electronic text and graphics to subscribers and secure storage. The method may be executed at a content provider's site, at an operations center, over a video distribution system or over a variety of alternative distribution systems, at a home subsystem, and at a billing and collection system. The content provider or operations center and / or other distribution points perform the functions of manipulation and secure storage of text data, security encryption and coding of text, cataloging of books, message center, and secure delivery functions. The home subsystem connects to a secure video distribution system or variety of alternative secure distribution systems, generates menus and stores text, and transacts through communicating mechanisms. A portable book-shaped viewer is used for secure viewing of the text. A billing system performs the transaction, management, authorization, collection and payments utilizing the telephone system or a variety of alternative communication systems using secure techniques.
Owner:ADREA LLC
Resource supply management system and method
InactiveUS20110288905A1Avoid the needSecure deliveryTechnology managementResourcesElectricityEngineering
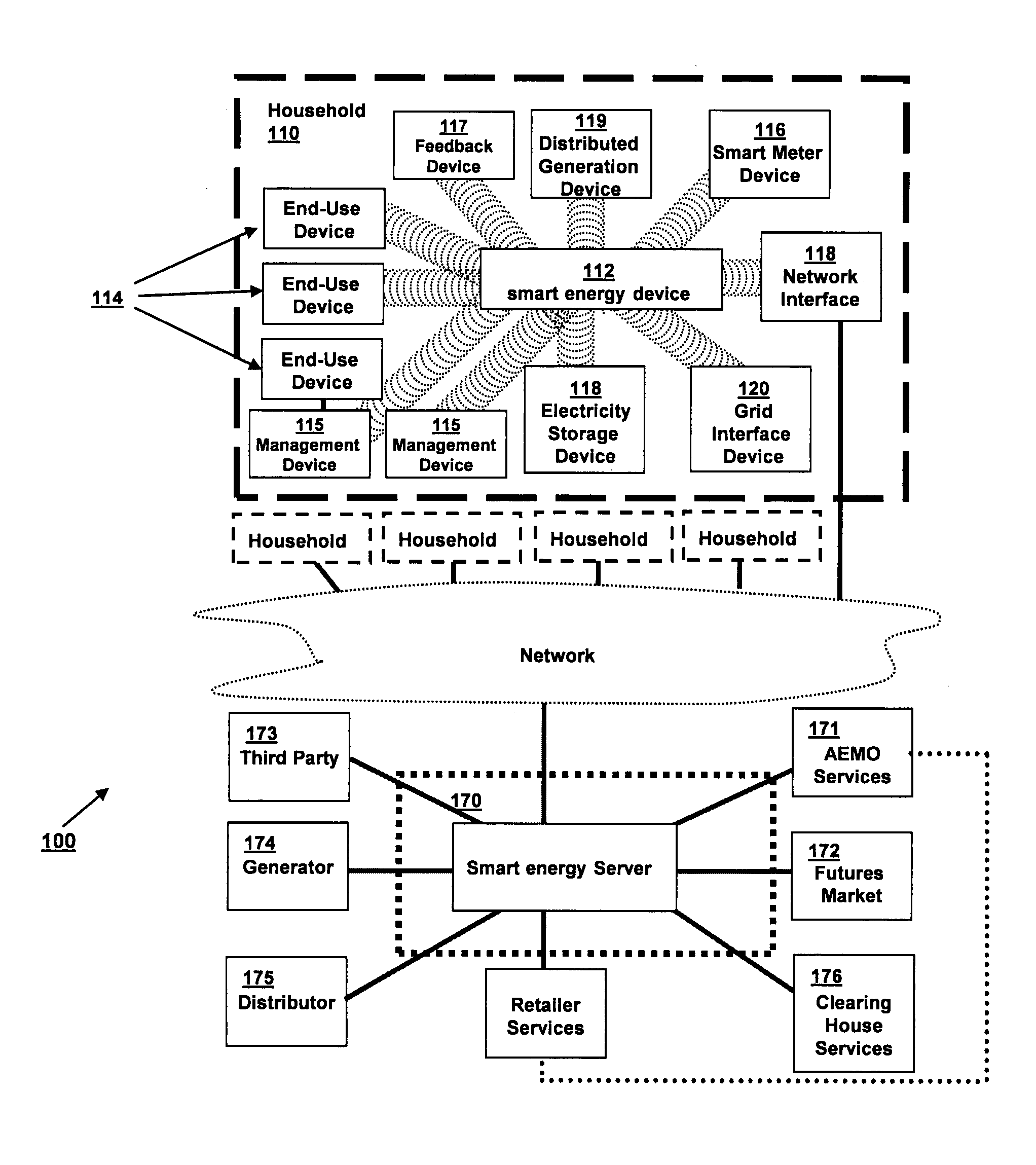
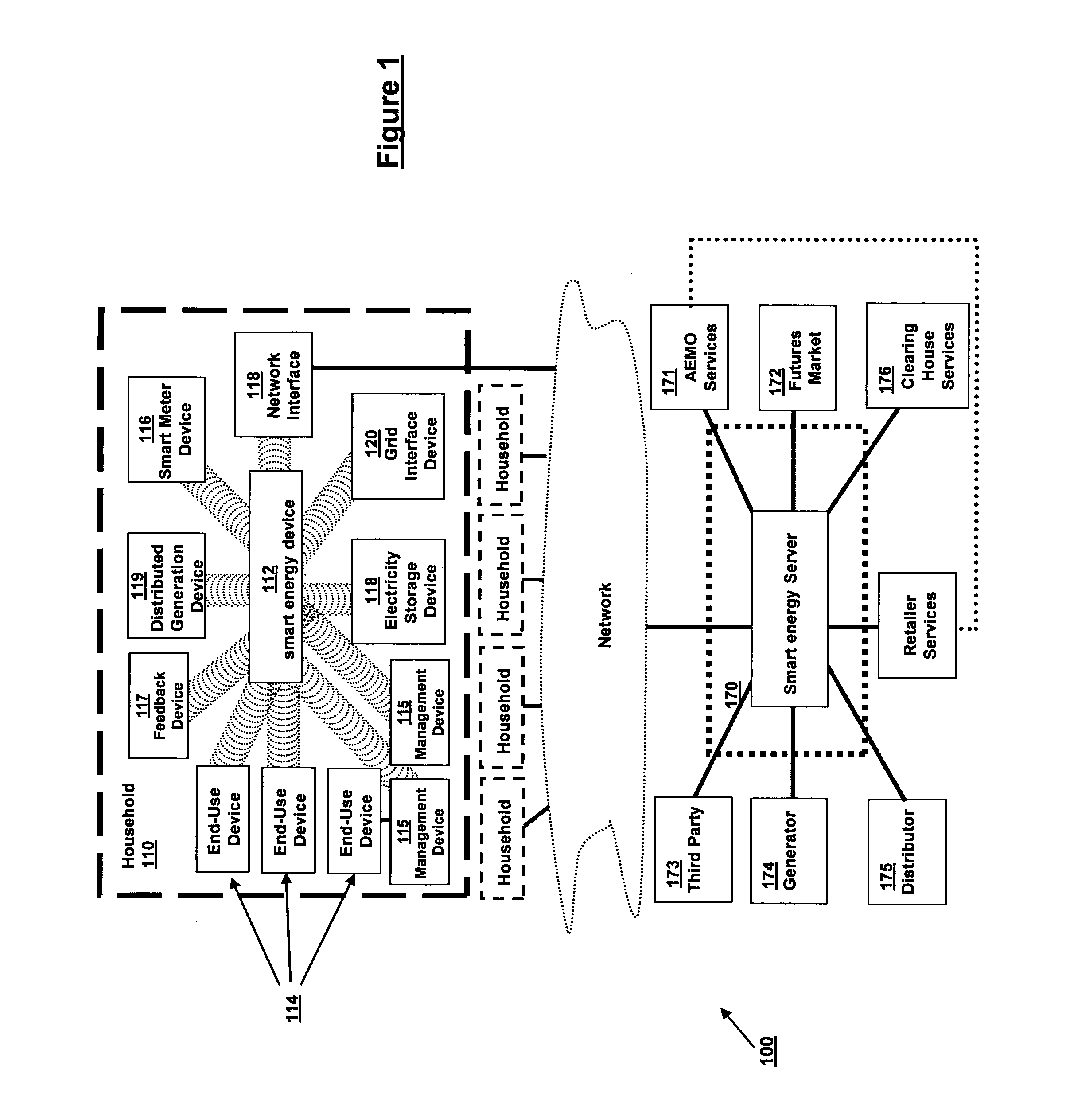
This system is for efficient consumption of a consumable or resource such as electricity, gas or the like. Each consumer site, such as a household or business, has a consumer node. The consumer node gathers consumption data from one or more consumer devices consuming the consumable. A central node is in communication with the consumer nodes and determines a collective consumption of the consumable across the plurality of consumer sites. The central node participates in live markets in order to secure delivery of the consumable as required collectively across the plurality of consumer sites. The central node communicates market data conveying substantially live market effects to the consumer nodes, and the consumer nodes process the market data in a manner to influence consumption of the consumable, for example by deactivating devices during market peaks.
Owner:GREENBOX IP
Methods and systems for ensuring secure delivery of parcels using internet-enabled storage receptacle
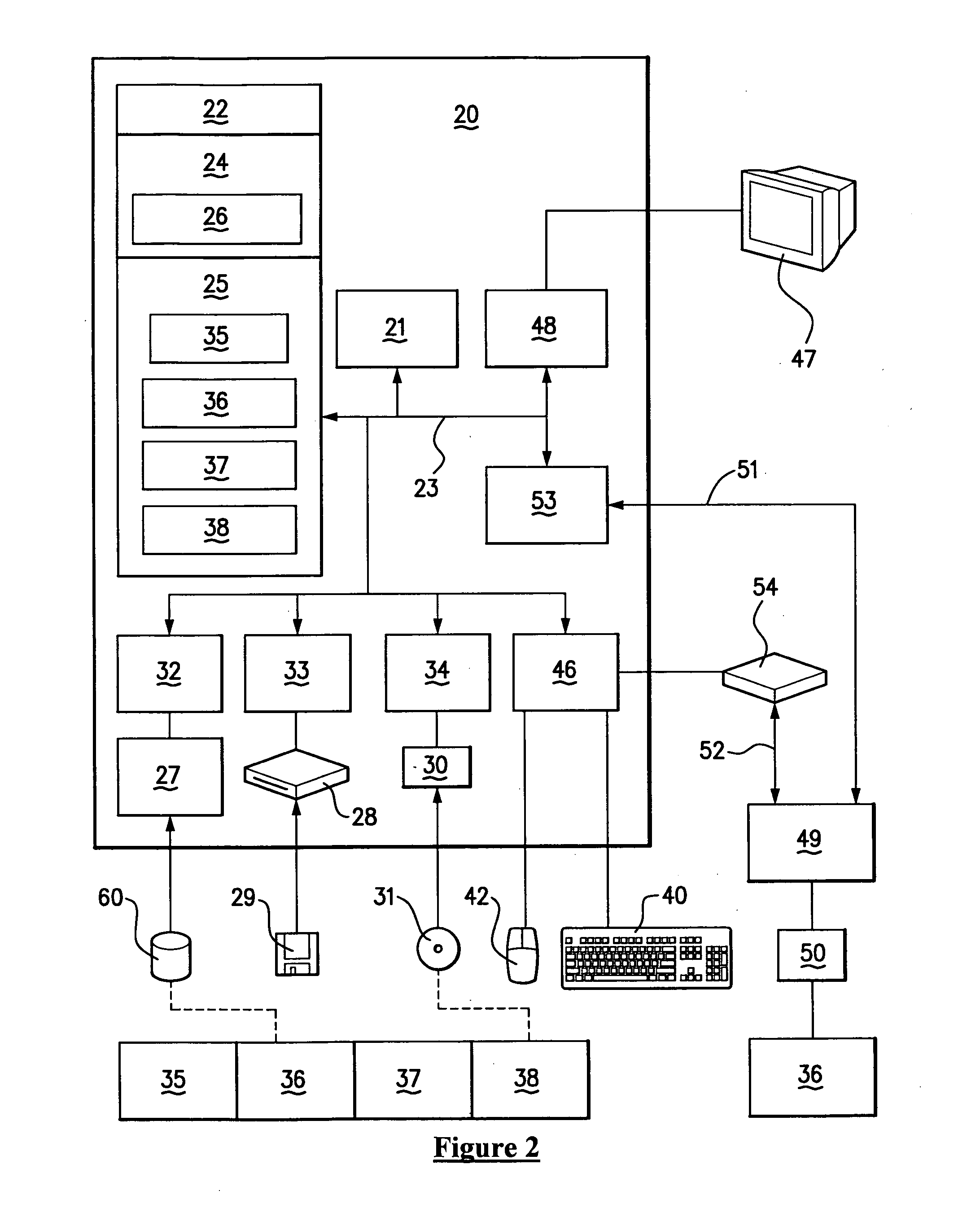
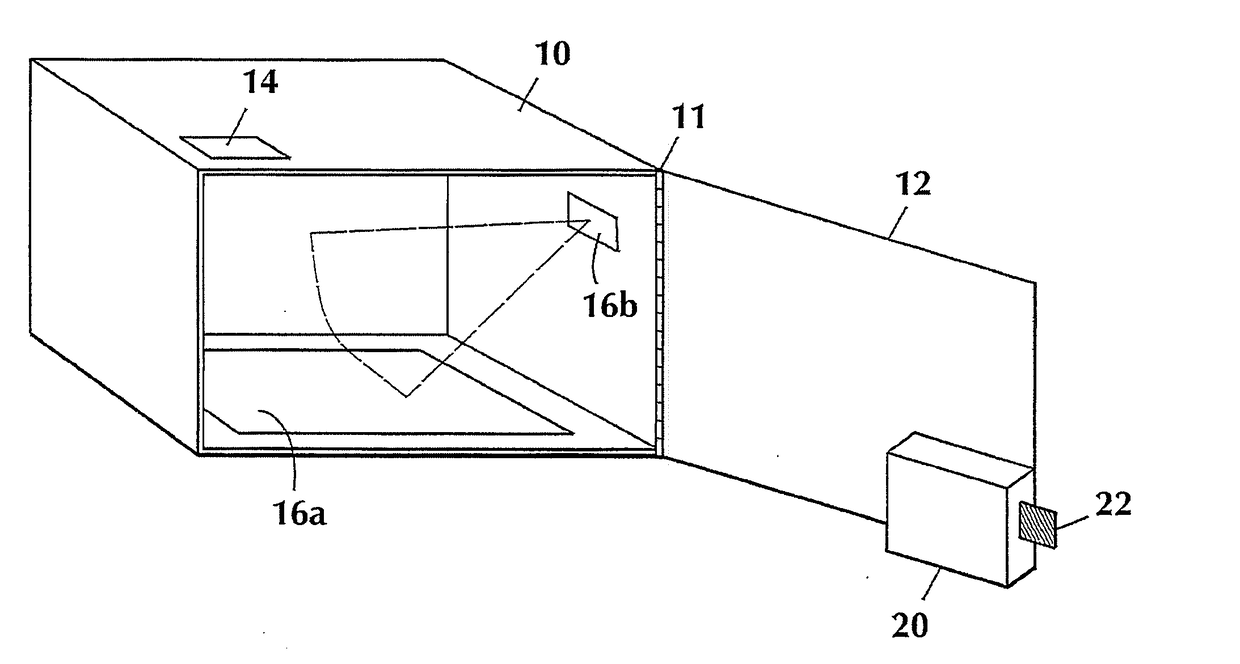
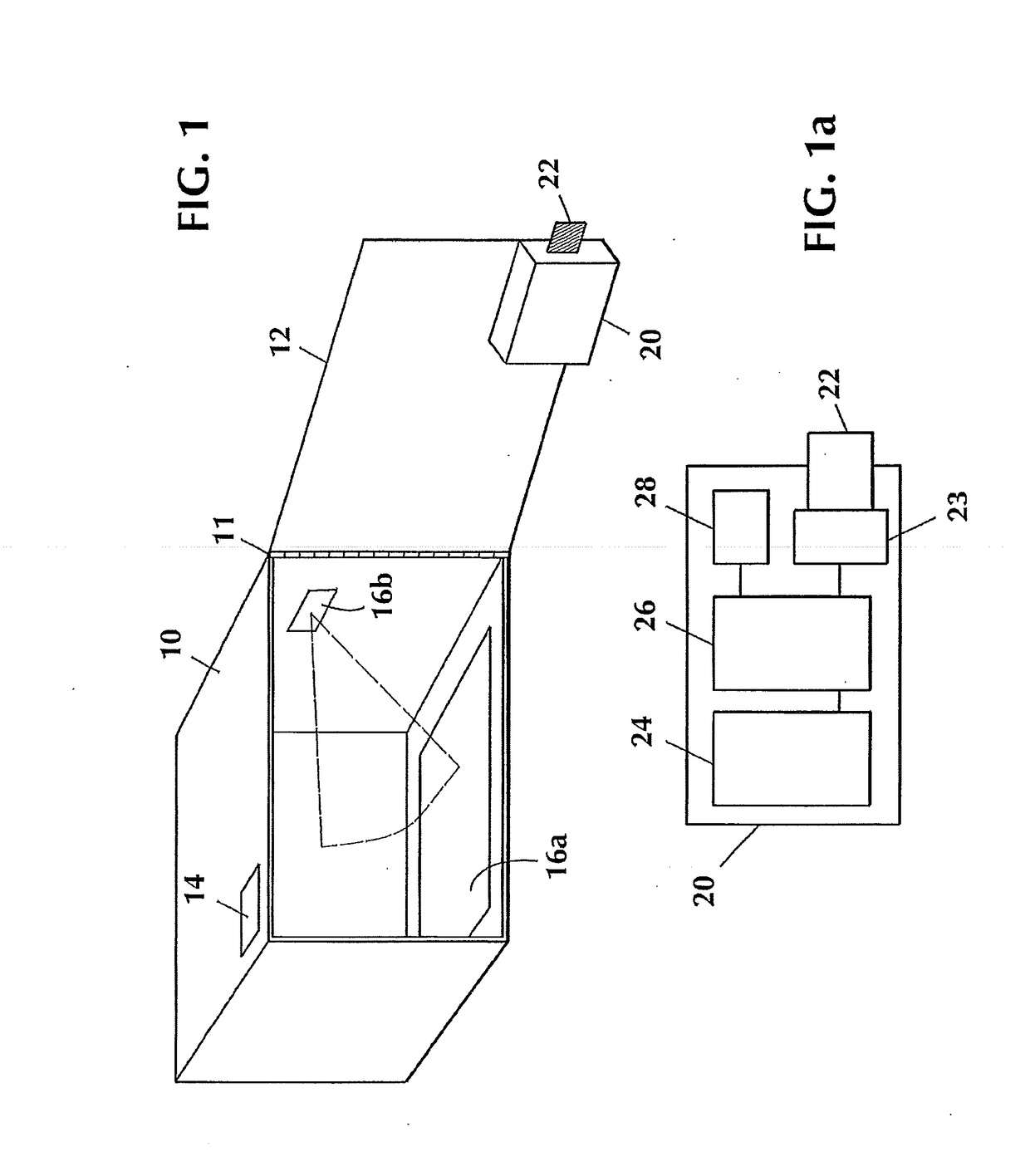
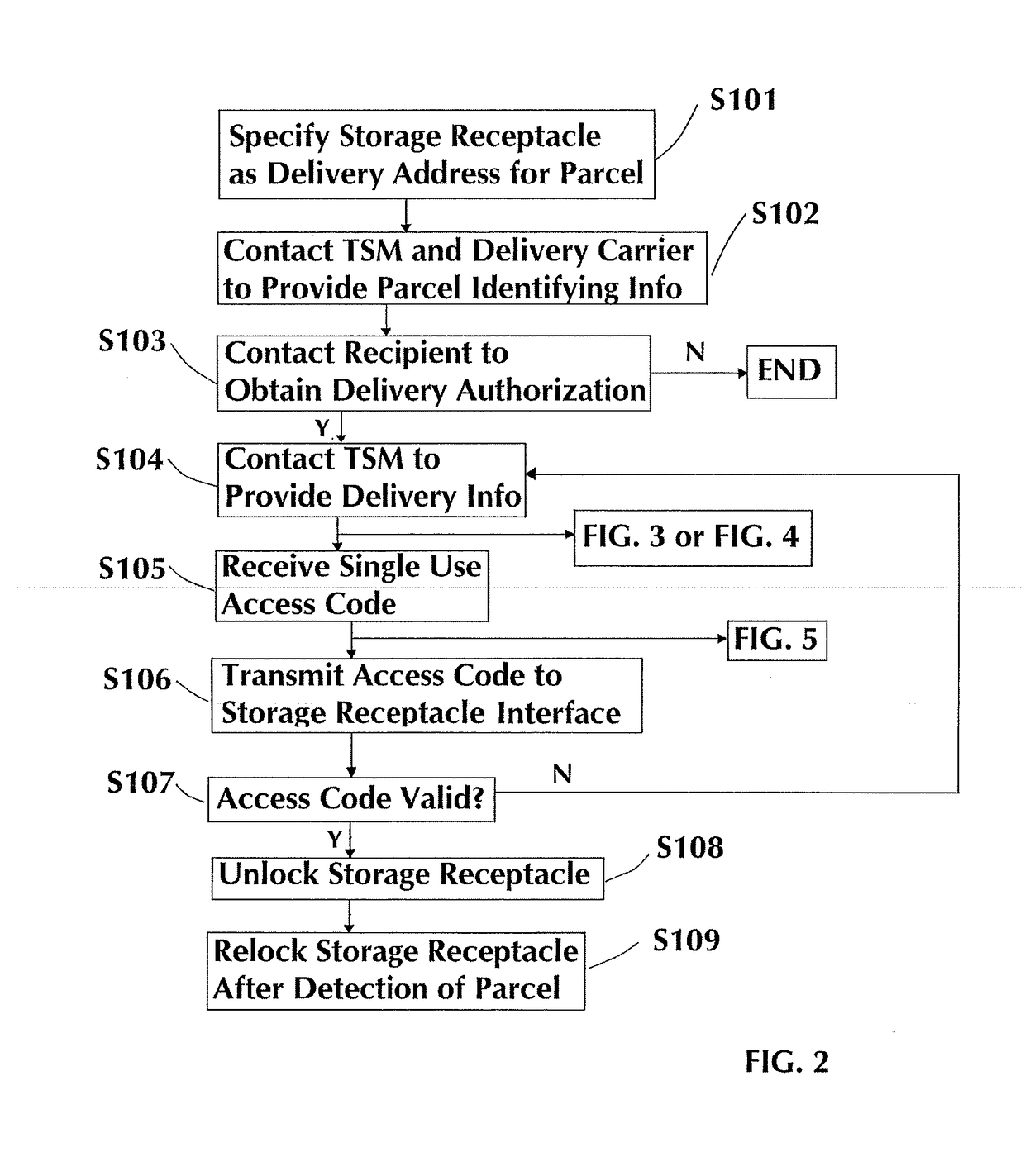
ActiveUS20170124510A1Secure deliveryEasy to unlockOffice automationIndividual entry/exit registersComputer hardwareLocking mechanism
Methods and system for securing delivery of a parcel when an intended recipient is unavailable, comprising at least one storage receptacle having an electronically controlled locking mechanism, the storage receptacle comprising an interface for receiving an access code for facilitating unlocking of the storage receptacle, a wireless communication radio, and a processor. The system further comprises a remote service manager comprising an access code generator and a wireless communication radio for transmitting an access code to a mobile computing device operated by a delivery carrier. The mobile computing device includes a wireless communication radio, one or more processors, and a memory comprising instructions which, when executed by the one or more processors, cause the one or more processors to: receive, via the wireless communication radio, from the remote service manager, a single use access code for facilitating unlocking of the storage receptacle, and transmit the access code to the storage receptacle interface. The storage receptacle processor confirms the validity of the access code and causes the storage receptacle to first unlock and then lock after detection of the parcel within the storage receptacle.
Owner:SARGENT MANUFACTURING CO INC
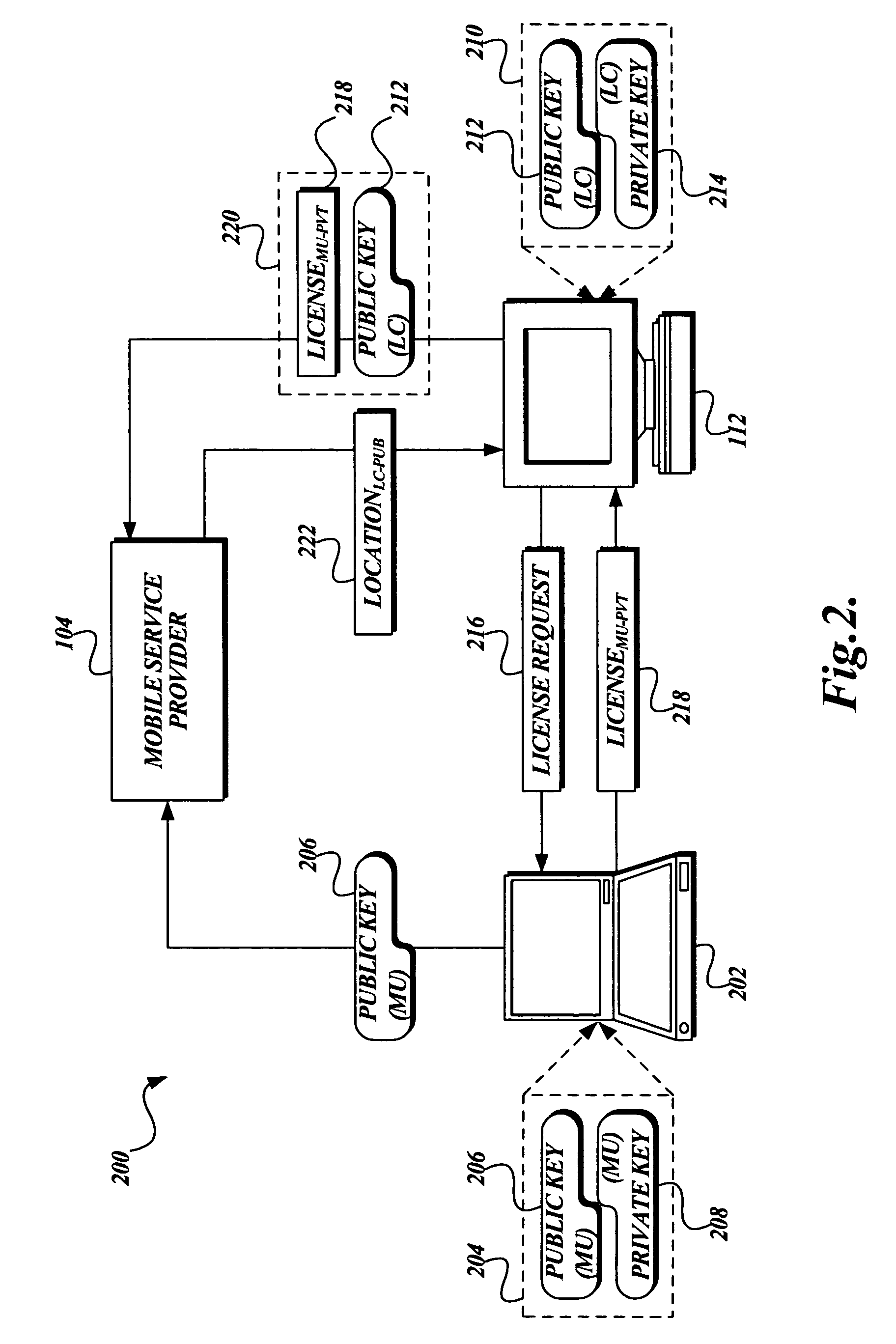
System and method for enforcing location privacy using rights management
InactiveUS7503074B2Secure deliveryData processing applicationsDigital data processing detailsRights managementMobile device
A system and method for securely delivering the location information of a mobile device to a location consumer is presented. In operation, the mobile device user issues a license to a location consumer. The license identifies the location consumer and any conditions the mobile device user places on the license. The license is encrypted such that it cannot be modified without invalidating the license. The license is submitted in a location request by the location consumer. A location information server receives the request, validates that the license was issued to the location consumer and that the location request conforms to the conditions of the license. If so, the location information server obtains the mobile device's location information, generates a location response, encrypts some of the location response, and returns the location response to the location consumer.
Owner:MICROSOFT TECH LICENSING LLC
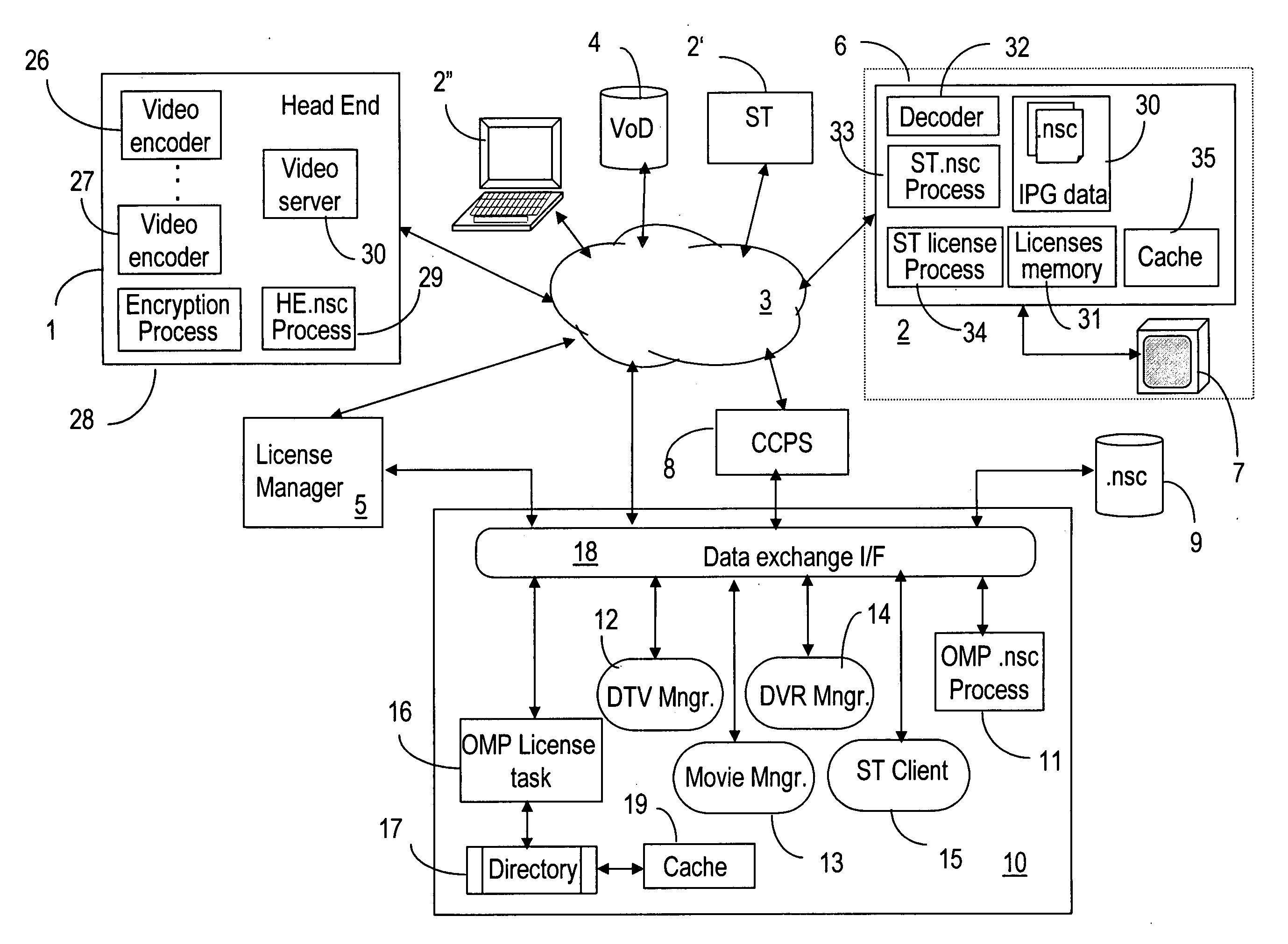
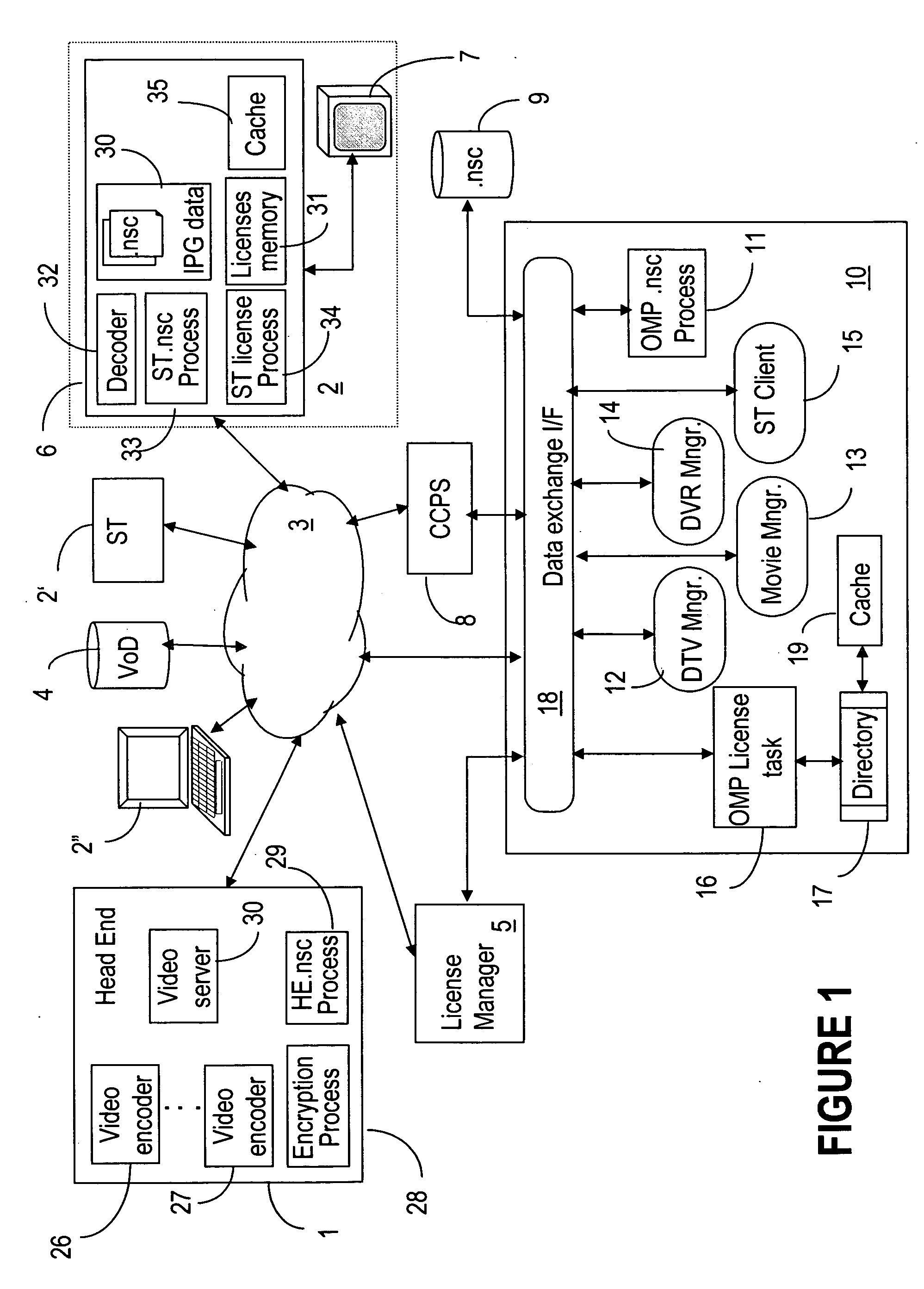
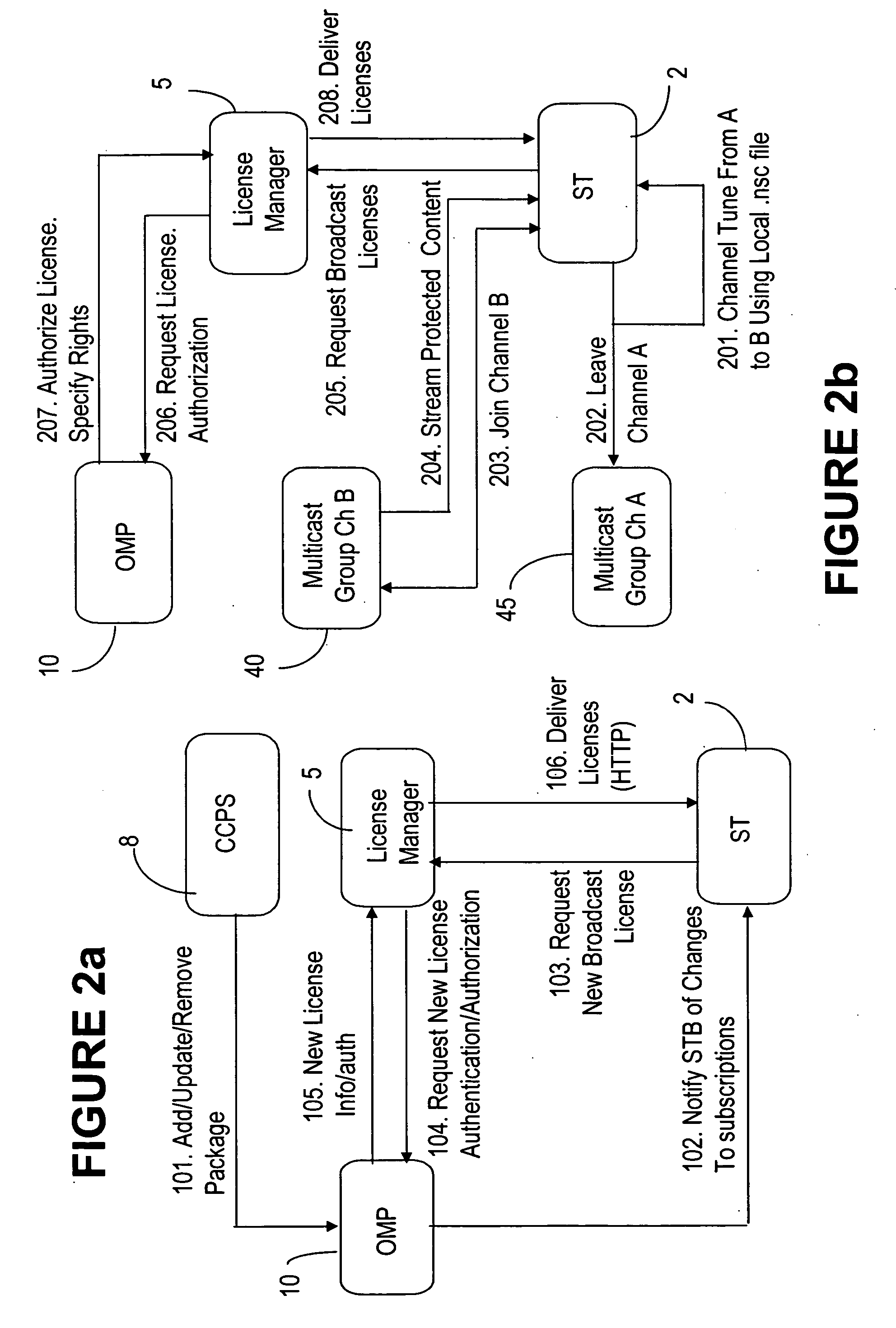
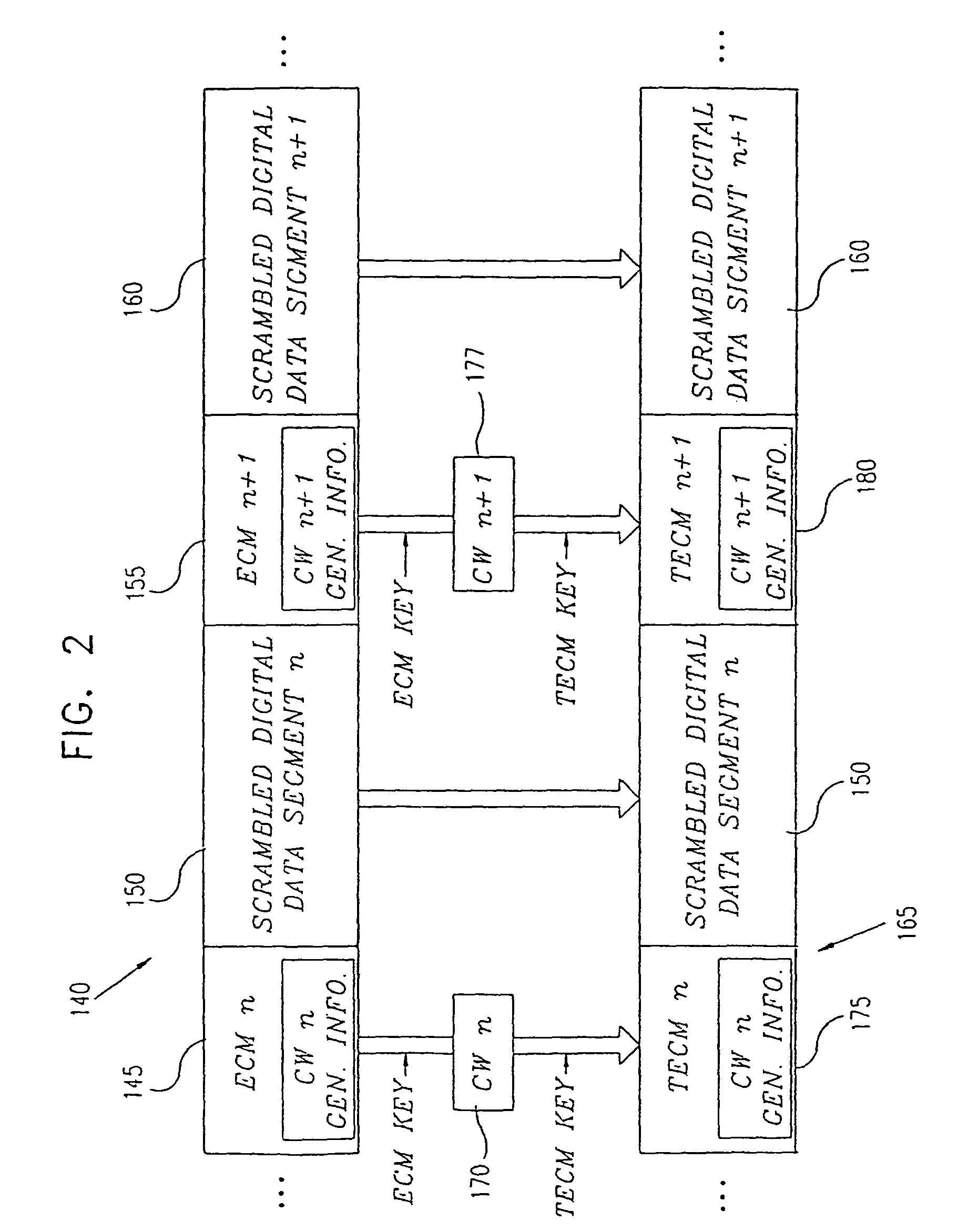
Digital rights management for media streaming systems
InactiveUS20060235800A1Effective limitSecure deliveryComputer security arrangementsTransmissionPersonalizationDigital rights management
An open media platform (OMP) notifies the subscriber terminals (ST) that the services it provides have changed and that the updated licenses should be retrieved. The STs then initiate a request to a license manager for the new licenses that are required. In response, the license manager requests from the OMP authentication / authorization of the ST and the license terms for the appropriate channels. The OMP authenticates the ST and determines the content ID's associated with the licenses that need to be issued. If authentication is successful, the appropriate C-ID's and terms are returned to the license server. When authorization and the license information are received from the OMP, the license manager generates the personalized licenses and delivers them to the originating ST to enable viewing of the protected content.
Owner:WSOU INVESTMENTS LLC
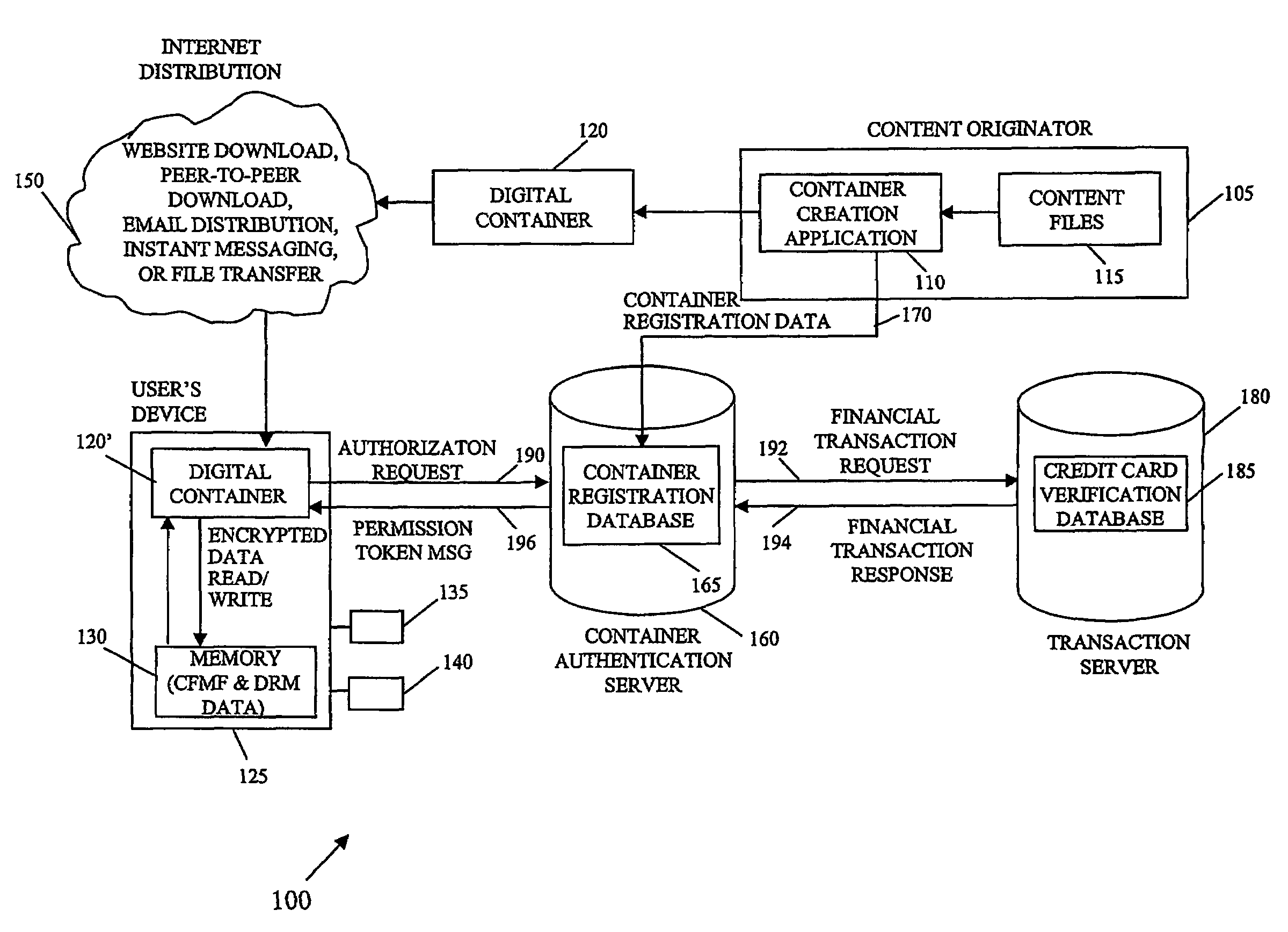
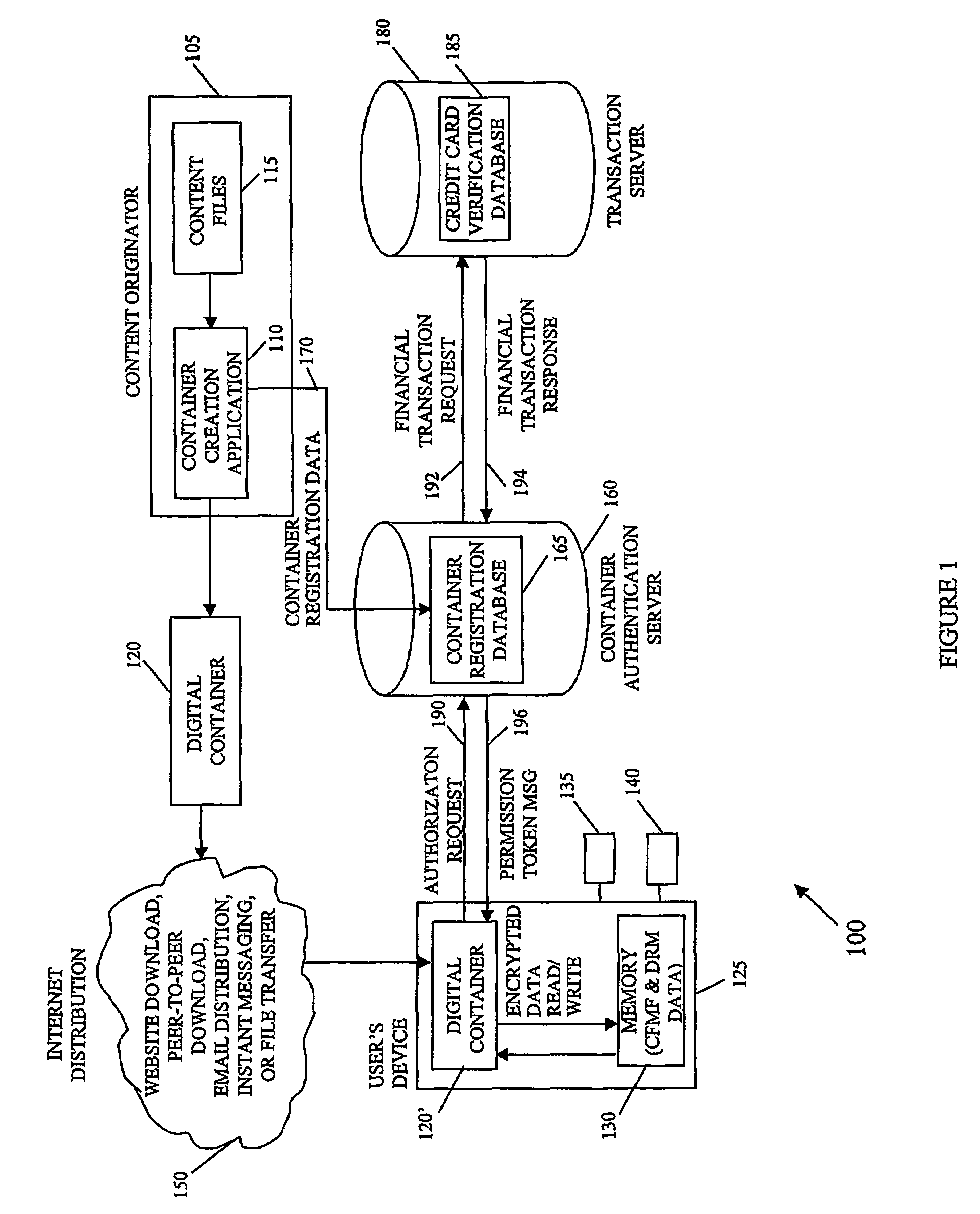
Securing digital content system and method
InactiveUS7421741B2Secure deliveryKey distribution for secure communicationPublic key for secure communicationDigital contentContent security
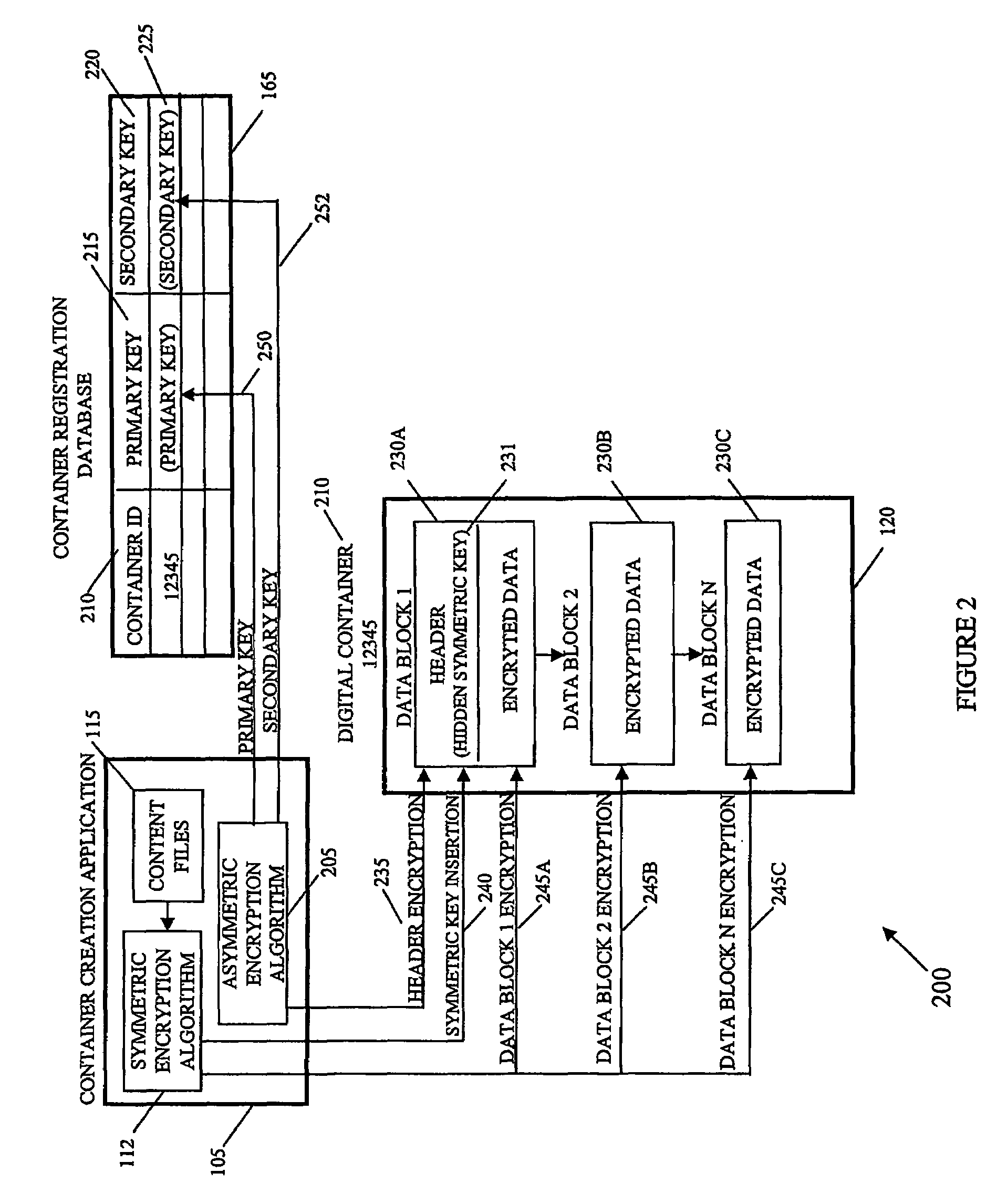
A system and method of encrypting digital content in a digital container and securely locking the encrypted content to a particular user and / or computer or other computing device is provided. The system uses a token-based authentication and authorization procedure and involves the use of an authentication / authorization server. This system provides a high level of encryption security equivalent to that provided by public key / asymmetric cryptography without the complexity and expense of the associated PKI infrastructure. The system enjoys the simplicity and ease of use of single key / symmetric cryptography without the risk inherent in passing unsecured hidden keys. The secured digital container when locked to a user or user's device may not open or permit access to the contents if the digital container is transferred to another user's device. The digital container provides a secure technique of distributing electronic content such as videos, text, data, photos, financial data, sales solicitations, or the like.
Owner:DIGITAL REG OF TEXAS
Method and system for secured transport and storage of data on a network
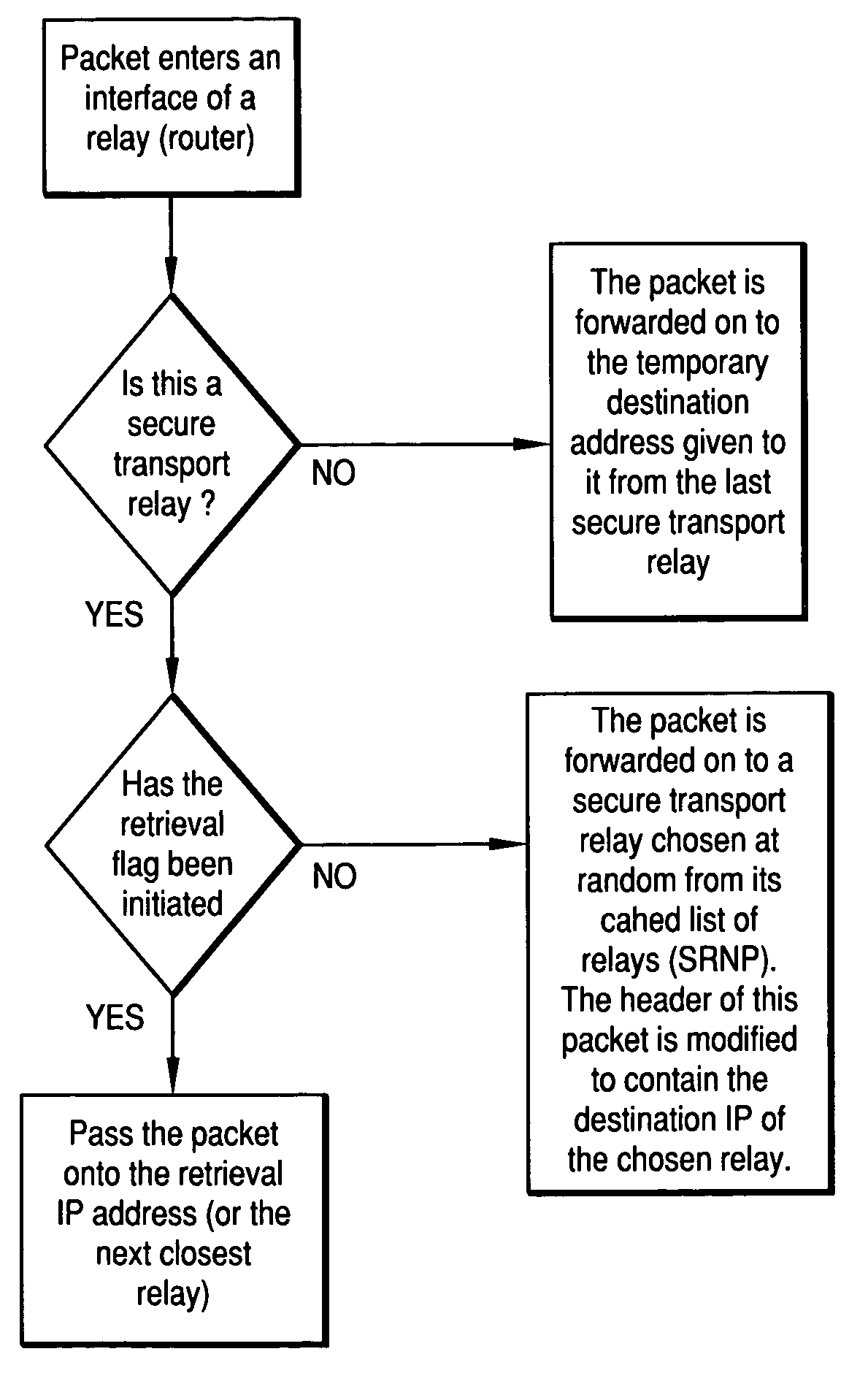
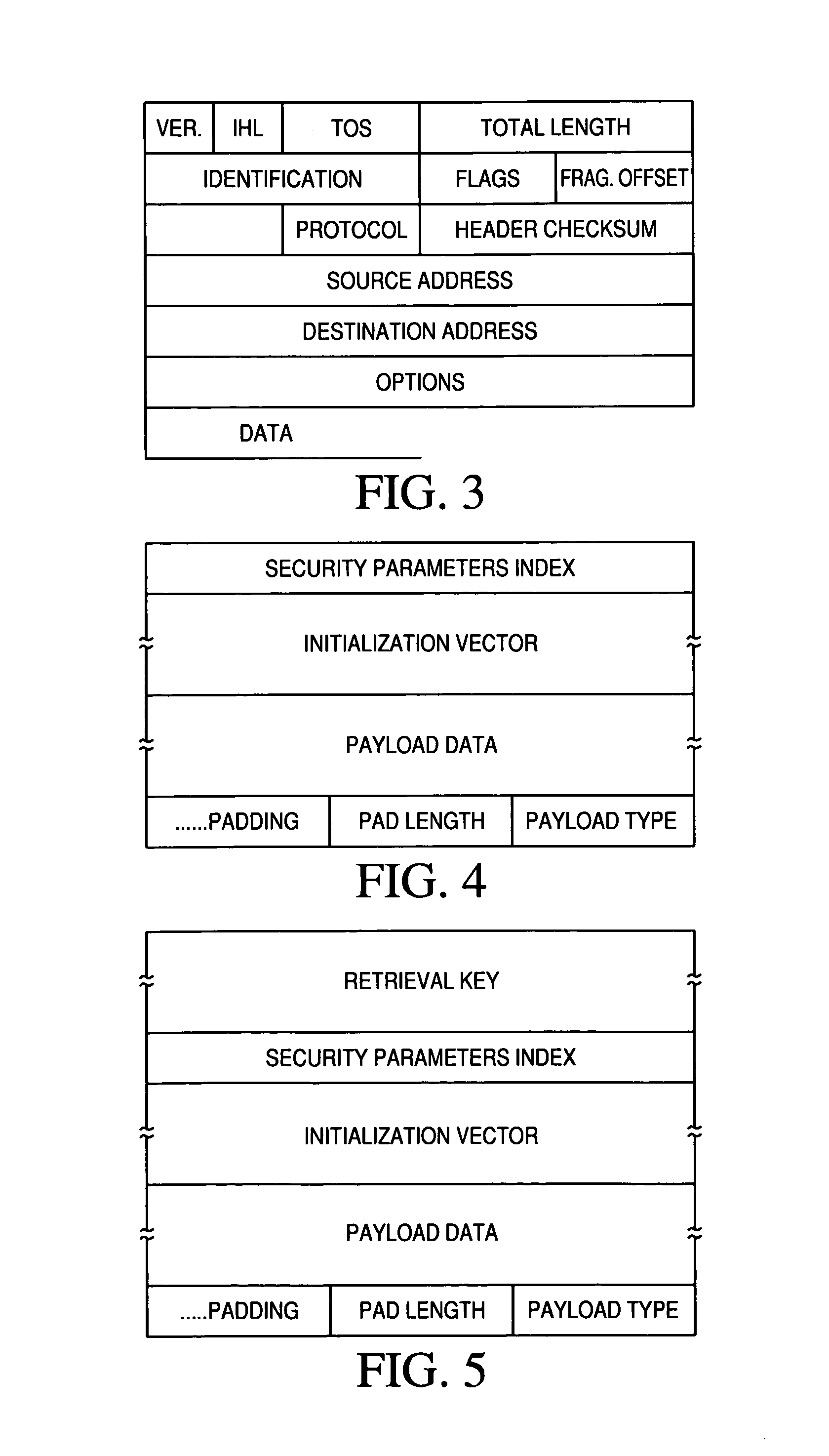
InactiveUS7113996B2Improve securityEfficient deliveryDigital data processing detailsUnauthorized memory use protectionDistribution systemPacket forwarding
A secure transport system and a secure distribution system for transporting secure packets from a first node to a second node, comprising: a first node that creates secure packets; a first secure relay that receives secure packets and non secure packets from multiple nodes, wherein the secure relay forward each secure packet to a different secure relay and forwards non-secure packets to destination relays, and wherein the secure relay forwards each secure packet to the second node when a retrieval condition has been indicated; and a second node that creates a relay condition and receives the secure packets.
Owner:ELIA DATA OF TEXAS
Method and system for dynamic spectrum allocation, and computer program product therefor
ActiveUS8000715B2Precise definitionEfficient use ofAssess restrictionWireless commuication servicesFrequency spectrumBroadcasting
A communication network such as a cellular network or a WLAN includes a set of user terminals. Within the communication network, a system dynamically controls spectrum usage. The system includes a functionality sensor for sensing spectrum usage within the area covered by the communication network, and a policy server for producing, as a function of the sensed spectrum usage, spectrum usage policies for the communication network. A broadcasting arrangement broadcasts the spectrum usage policies to the user terminals. The system is applicable to cognitive radio systems.
Owner:STMICROELECTRONICS SRL
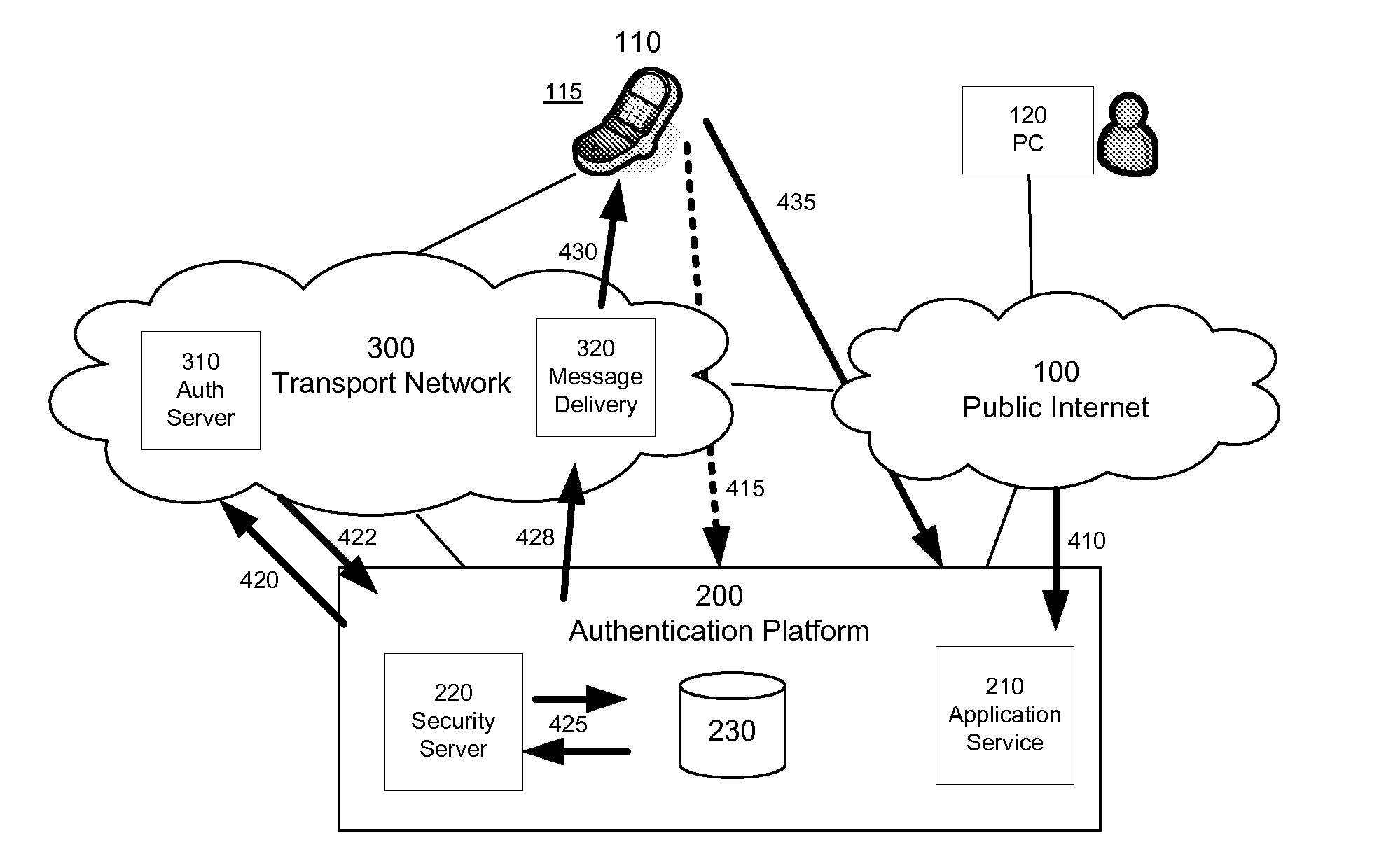
Automated Authentication Process for Application Clients
InactiveUS20080178273A1Enhanced authenticationSecure deliveryKey distribution for secure communicationDigital data processing detailsIPsecThe Internet
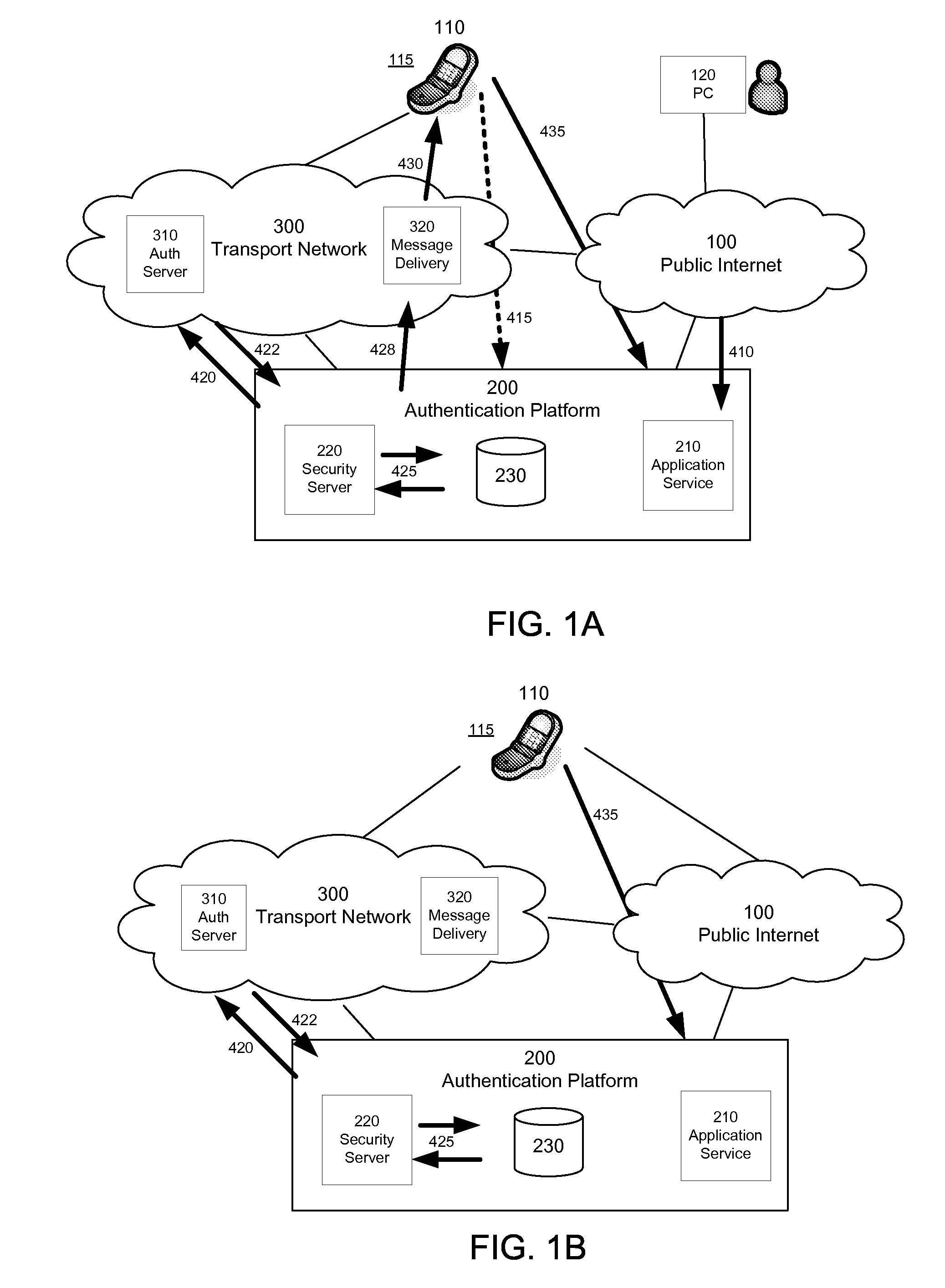
One aspect of the invention defines a process which allows application providers to remotely activate and authenticate logins from an application client. In one implementation, this is achieved through a three step approach. First, the application client notifies the application service of its successful installation (e.g. by accessing a unique URL). Second, it leverages the built-in security features of a mobile network (e.g. security mechanisms of GSM or IMS access security) to securely deliver a message containing authentication information to the application client. Examples of message transports are SMS or SIP with IPsec as specified by IMS. Third, this information is used to authenticate the application client when accessing the remote application service (e.g. via the Internet).
Owner:JIBE MOBILE
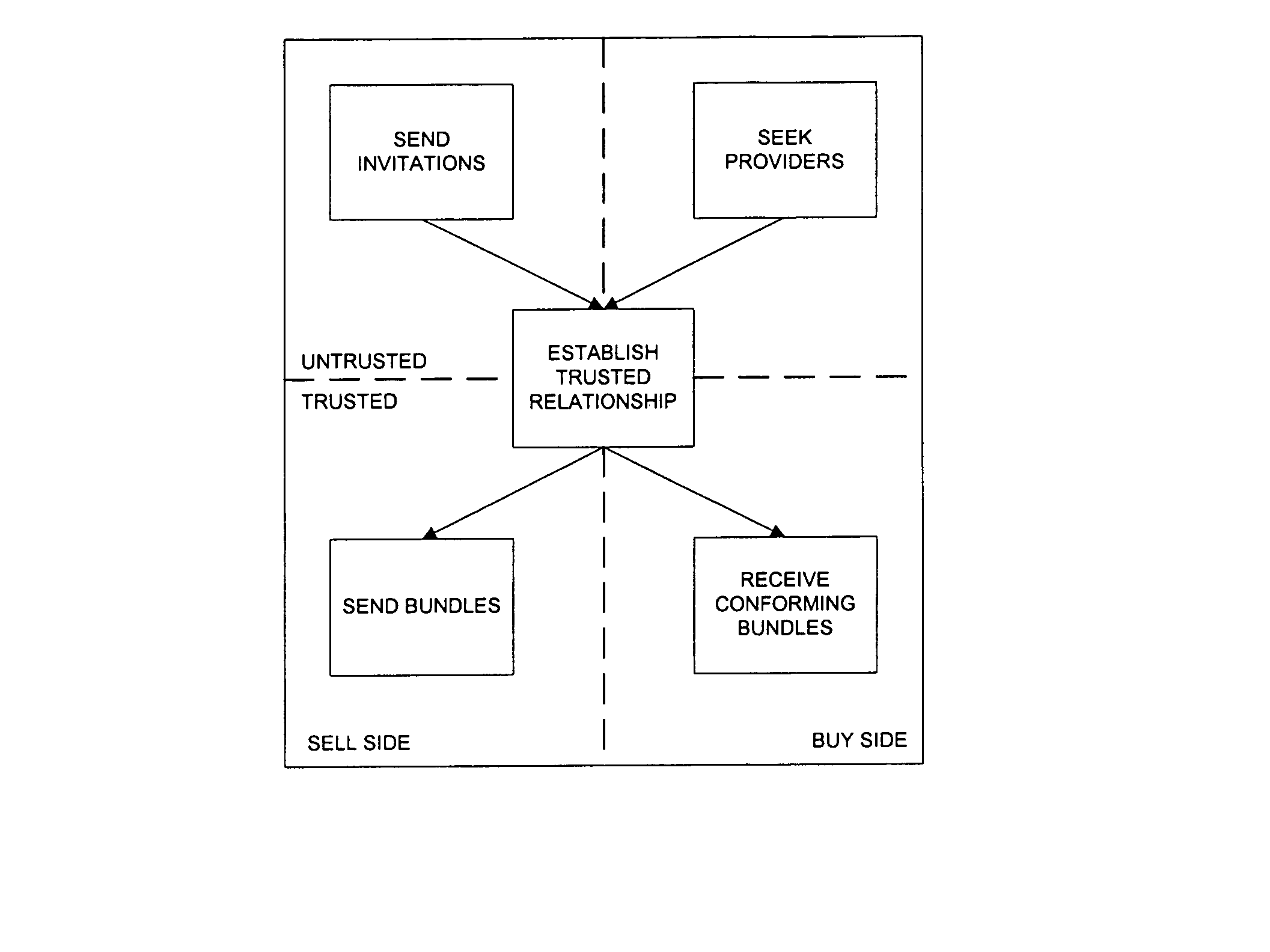
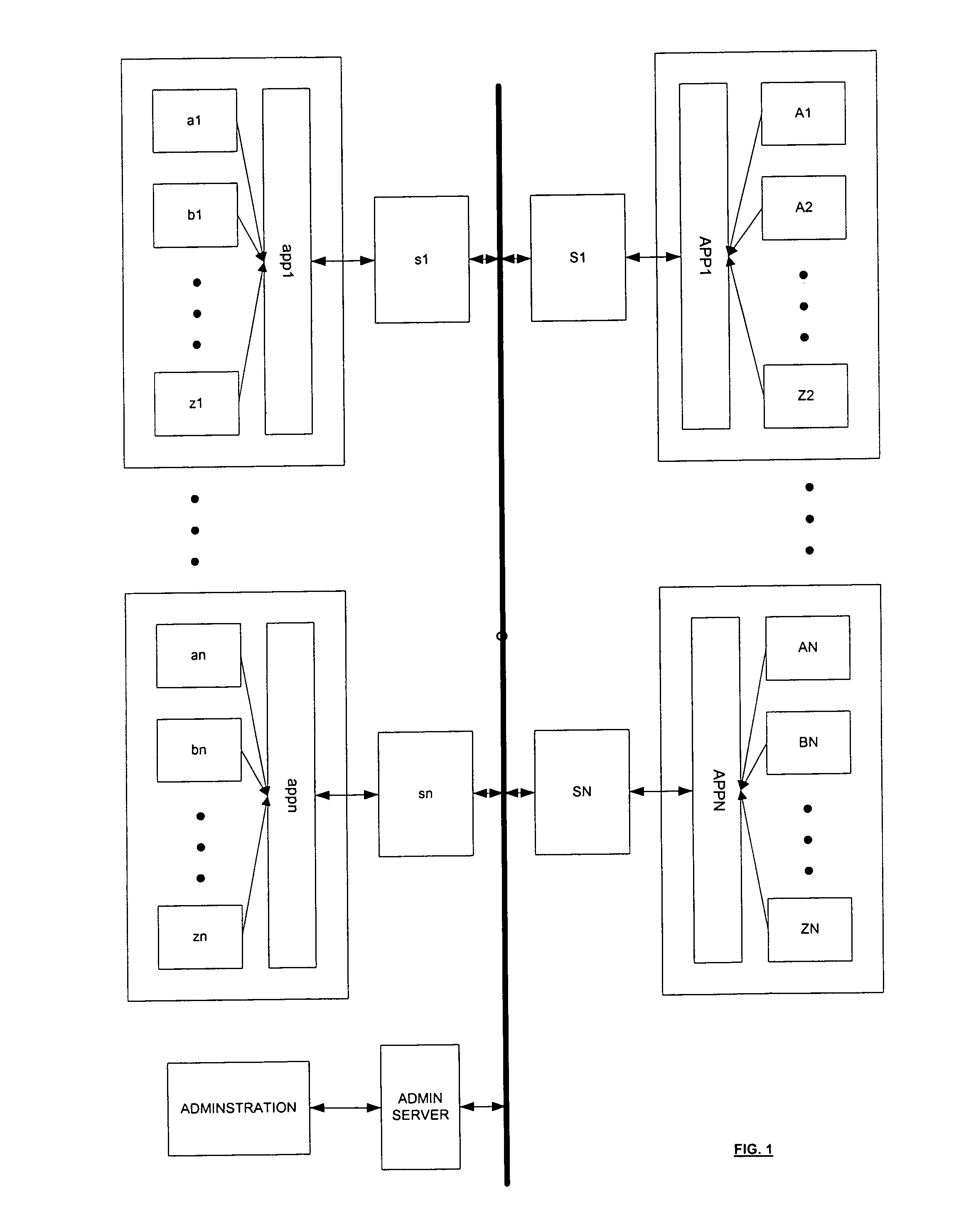
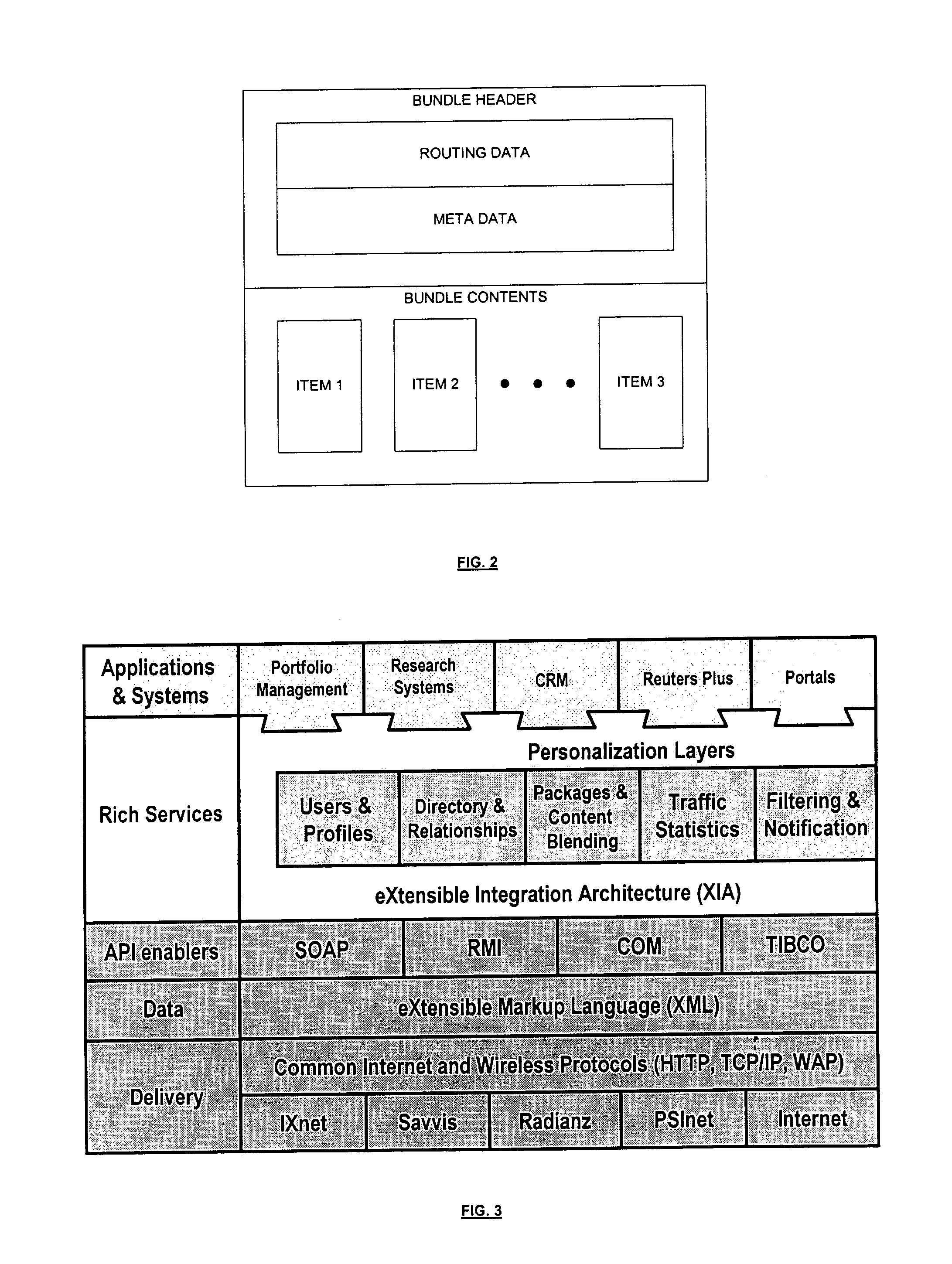
Electronic commerce infrastructure system
ActiveUS7287089B1Retain controlEasy to useDigital computer detailsBuying/selling/leasing transactionsE-commerceInteraction management
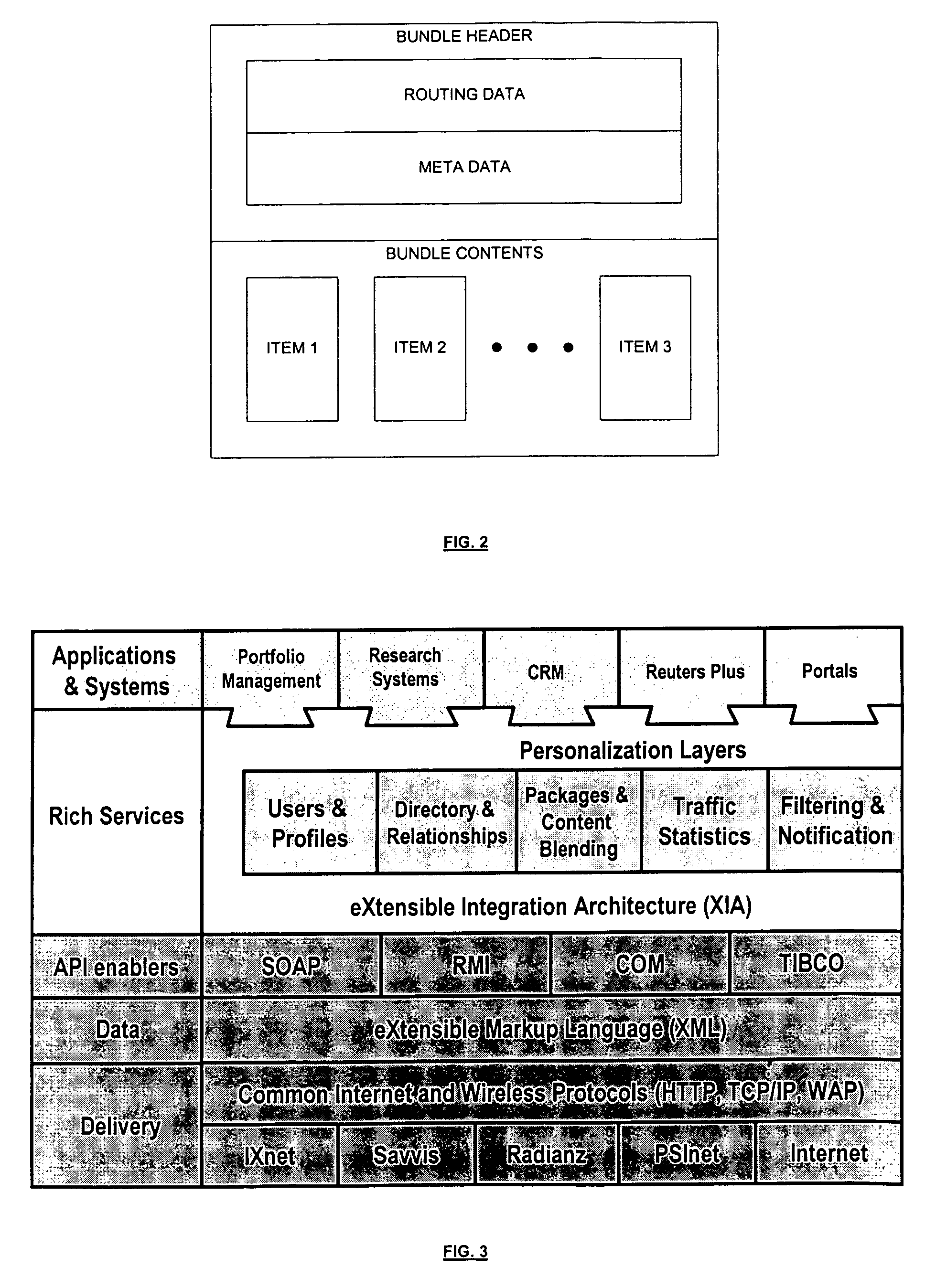
A networked commercial interaction management method assembles information into bundles that include a data element reference and meta data describing the data element. The method distributes the meta data and the data element reference from the bundles through the network, and distributes copies of the data elements in the bundles from the network node of their respective data owners to the network nodes of accessors using the meta data and the data element reference distributed through the network. In at least one embodiment, the method periodically issues bundle version identifying signals to different nodes of the network. The bundle version identifying signals indicate changes to the data elements to the network nodes of accessors.
Owner:REFINITIV US ORG LLC
Method and system for dynamic spectrum allocation, and computer program product therefor
ActiveUS20100238868A1Precise definitionEfficient use ofAssess restrictionWireless commuication servicesComputer hardwareFrequency spectrum
A communication network such as a cellular network or a WLAN includes a set of user terminals. Within the communication network, a system dynamically controls spectrum usage. The system includes a functionality sensor for sensing spectrum usage within the area covered by the communication network, and a policy server for producing, as a function of the sensed spectrum usage, spectrum usage policies for the communication network. A broadcasting arrangement broadcasts the spectrum usage policies to the user terminals. The system is applicable to cognitive radio systems.
Owner:STMICROELECTRONICS SRL
Secure handling of stored-value data objects
ActiveUS7315944B2Prevent them be reuseSecure deliveryTicket-issuing apparatusUser identity/authority verificationComputer securityData objects
An approach to managing stored-value data objects, such as electronic tickets, comprises secure systems and procedures for ticket issuing, storage, and redemption. With these systems and procedures in place, stored-value data objects may be securely transferred to remote systems, such as a user's personal electronic device, for subsequent secure redemption, thus allowing the user to gain access to the desired goods or service upon redeeming the data object. Techniques provide secure delivery of the requested data object to the requesting device, and provide secure redemption and disposal of the data object. Ticket issuing systems may be Internet-accessible systems, and users may purchase and redeem tickets using mobile terminals or other devices adapted for wireless communication. Standardized WPKI and Internet access procedures may be employed in ticket issuance and redemption. Techniques further provide temporary and rapid verification data objects useful where rapid ticket verification is essential, such as mass transit systems.
Owner:ERICSSON INC
Secure digital content delivery system and method over a broadcast network
ActiveUS7995603B2Eliminate needSecure deliveryKey distribution for secure communicationUser identity/authority verificationKey exchangeDigital content
A system and a method for secure distribution of digital media content through a packet-based network such as the Internet. The security of the present invention does not require one-to-one key exchange, but rather enables keys, and / or information required in order to build the key, to be broadcast through the packet-based network. The digital media content is then also preferably broadcast, but cannot be accessed without the proper key. However, preferably only authorized end-user devices are able to access the digital media content, by receiving and / or being able to access the proper key. Thus, the present invention is useful for other types of networks in which digital media content is more easily broadcast rather than unicast, in addition to packet-based networks.
Owner:SYNAMEDIA LTD
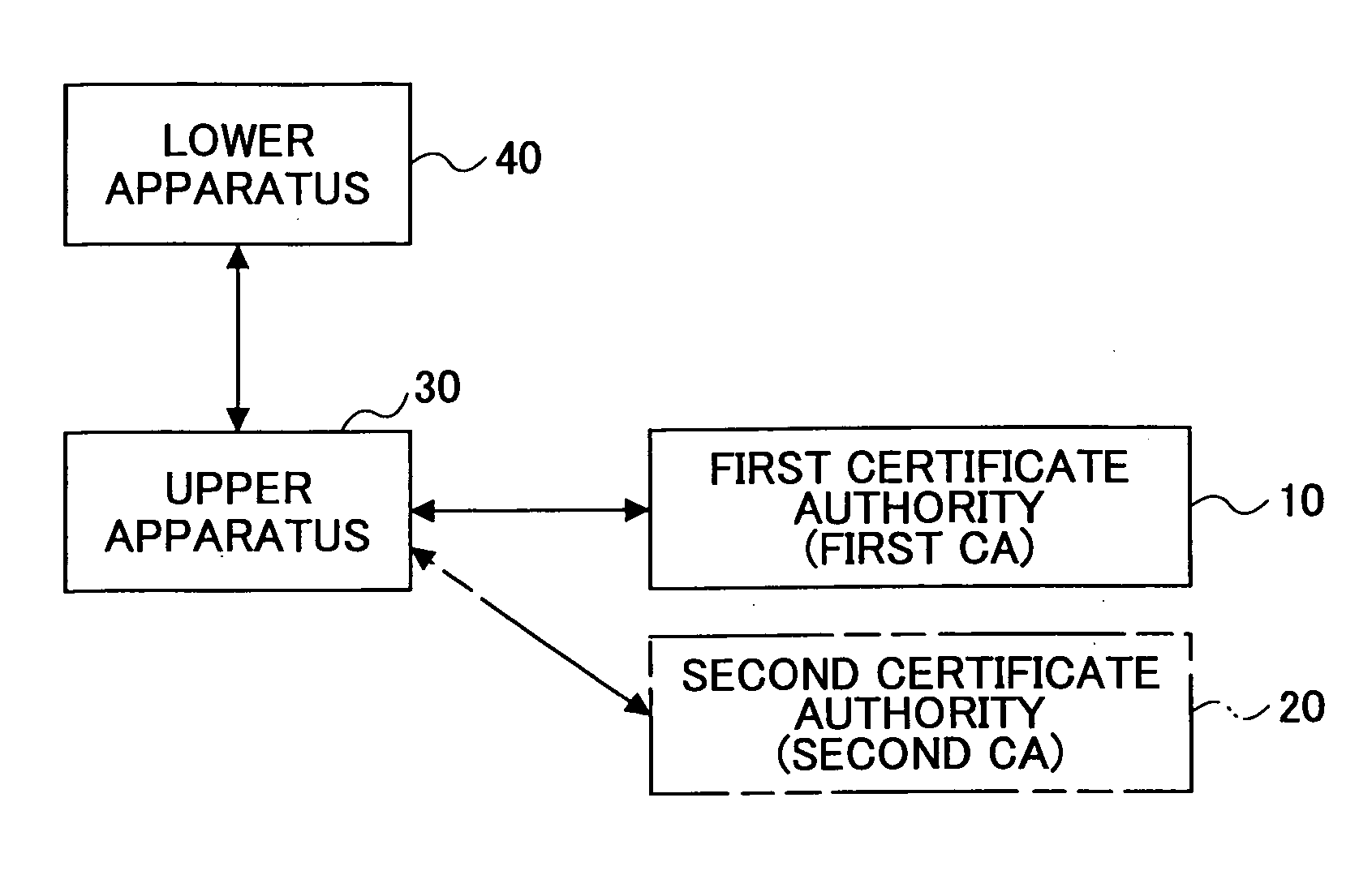
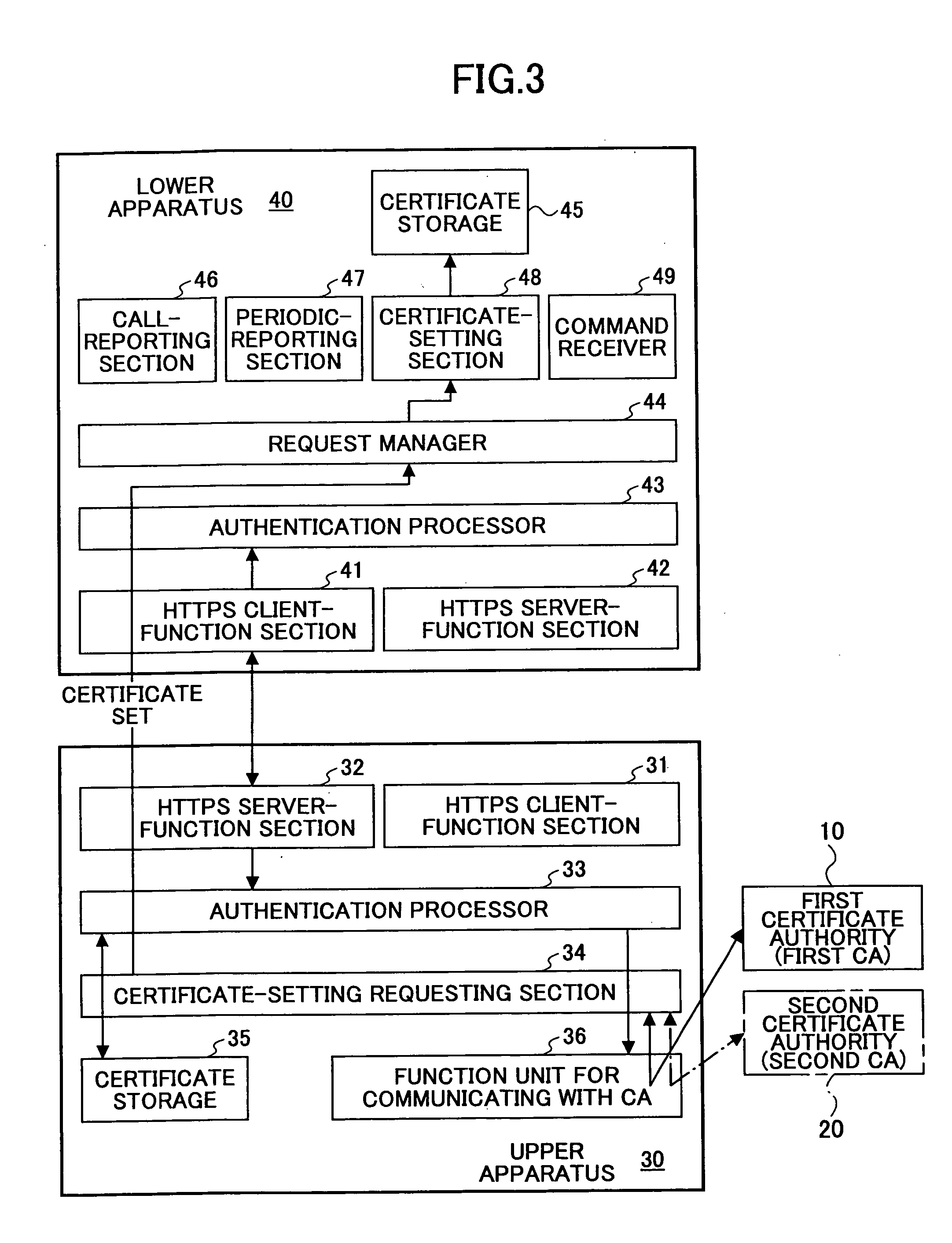
Method of transferring digital certificate,apparatus for transferring digital certificate, and system, program, and recording medium for transferring digital certificate
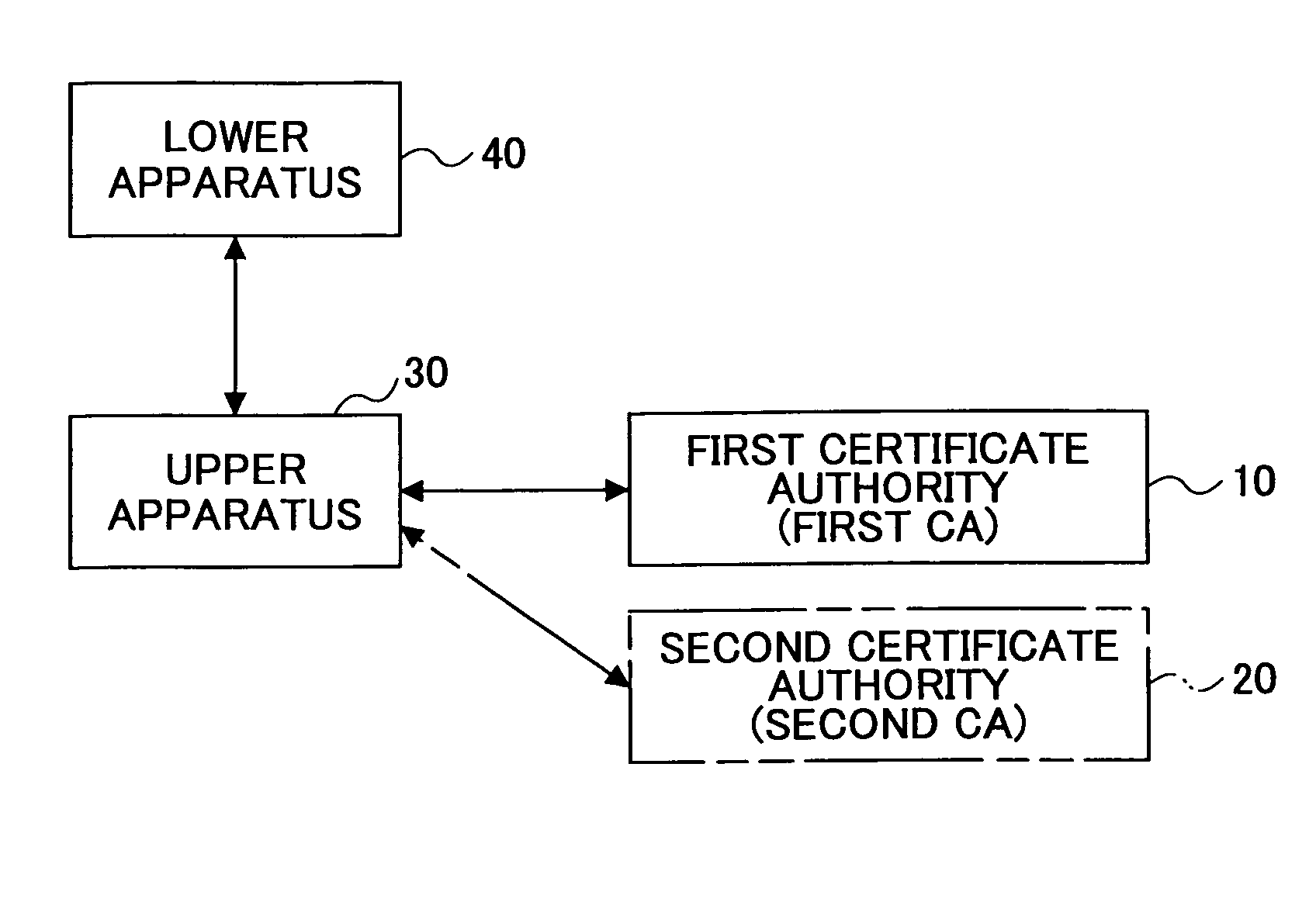
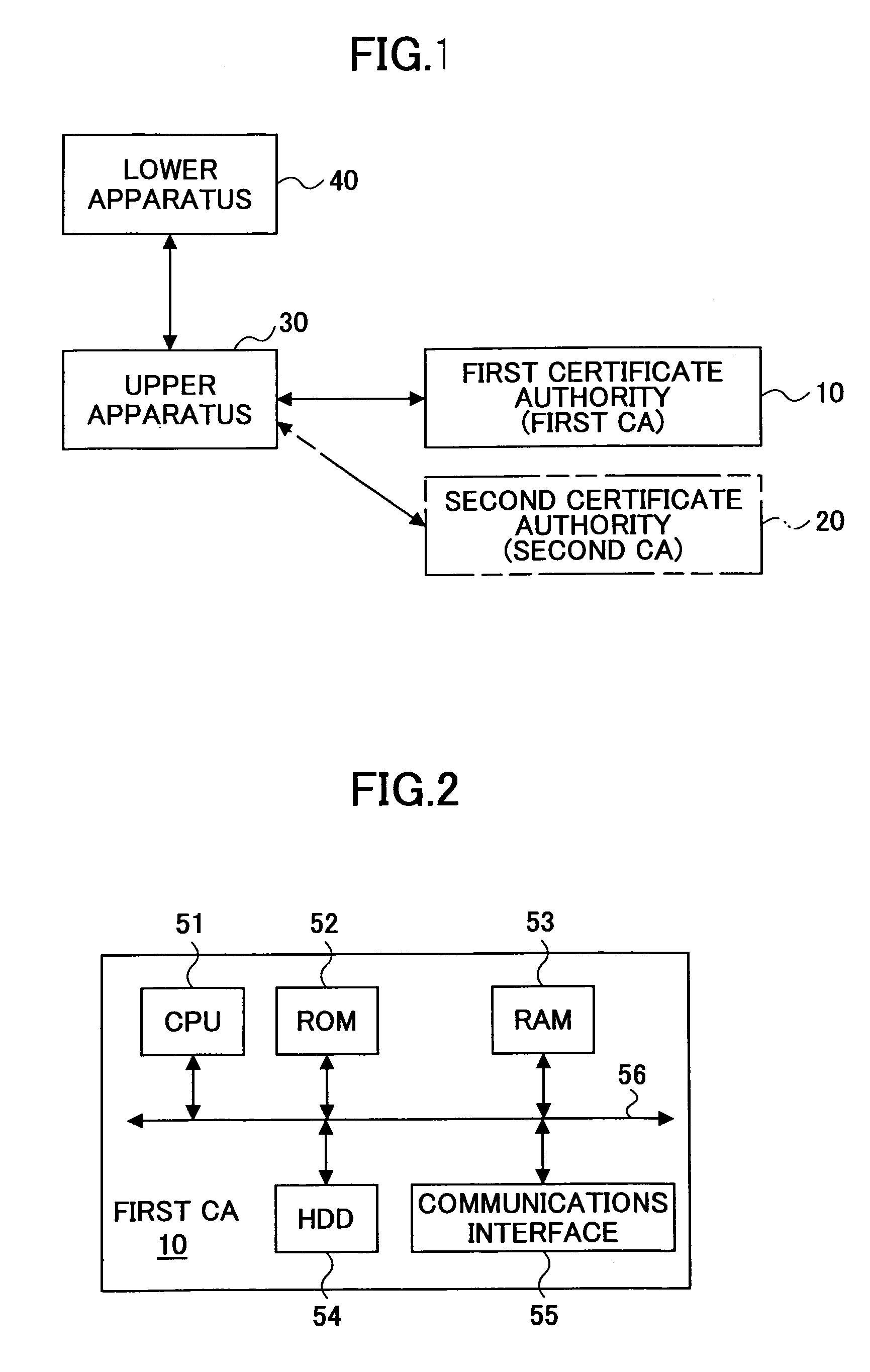
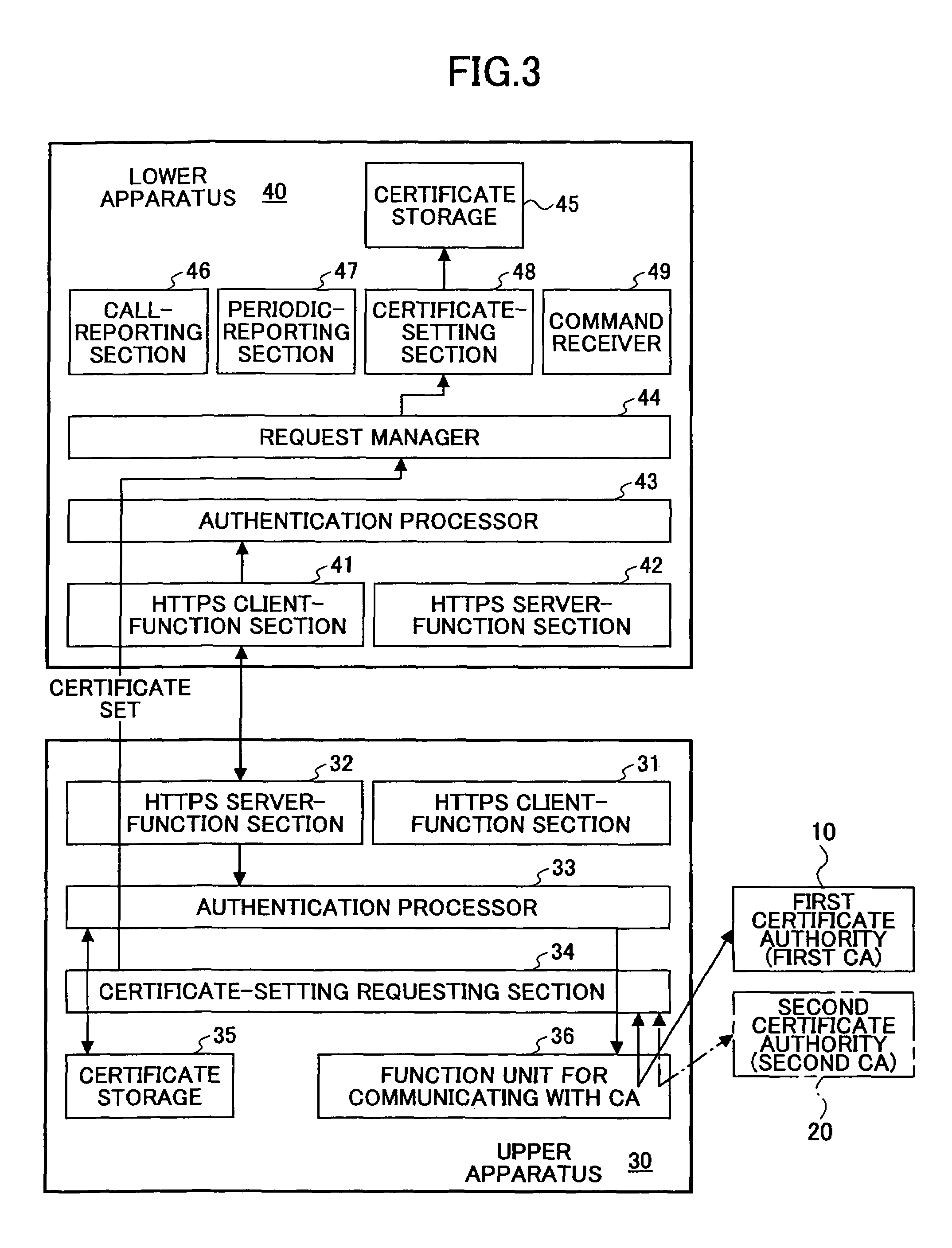
ActiveUS20050204164A1Secure deliveryPrecise deliveryKey distribution for secure communicationDigital data processing detailsCommunication deviceRecording media
A method of transferring digital certificates for transferring, by means of a digital-certificate transferring apparatus, a digital certificate to a communications apparatus to be its communications counterpart is disclosed. The method includes the step of causing the digital-certificate transferring apparatus to execute; a first transferring procedure of using a common certificate being a digital certificate without apparatus-identifying information so as to authenticate the communications counterpart, and transferring a normal certificate being a digital certificate with information identifying the communications counterpart to the communications counterpart when the authenticating succeeds; and a second transferring procedure of receiving a first normal certificate from the communications counterpart, and when, based on the received first normal certificate, transferring a second normal certificate, with the information identifying the communications counterpart, and being different from the first normal certificate, is determined to be necessary, transferring the second normal certificate to the communications counterpart.
Owner:RICOH KK
Glass substrate position correcting device and method
ActiveCN102897507AAvoid breakingReduce defective rateControl devices for conveyorsCharge manipulationEngineeringElectrical and Electronics engineering
Owner:SHENZHEN CHINA STAR OPTOELECTRONICS TECH CO LTD
Content protection system
InactiveUS20080046731A1Secure deliveryCommunication is interceptedUser identity/authority verificationTelevision systemsClient-sideComputer security
A content protection system for securely delivering audio / video data from a content server to a content client through an unsecured channel is disclosed. For each session, the content protection system comprises two phases. The first phase is client-server mutual authentication and session key establishment. In this phase, the content server and the content client verify each other's legitimacy, and at the same time exchange information so that both server and client can calculate or derive the same session key. In the second phase, audio / video data is encrypted with the session key in the content server, and then decrypted with the session key in the content client. If a version of server or client is found to be compromised, its ID will be put into a blacklist.
Owner:COREL CORP
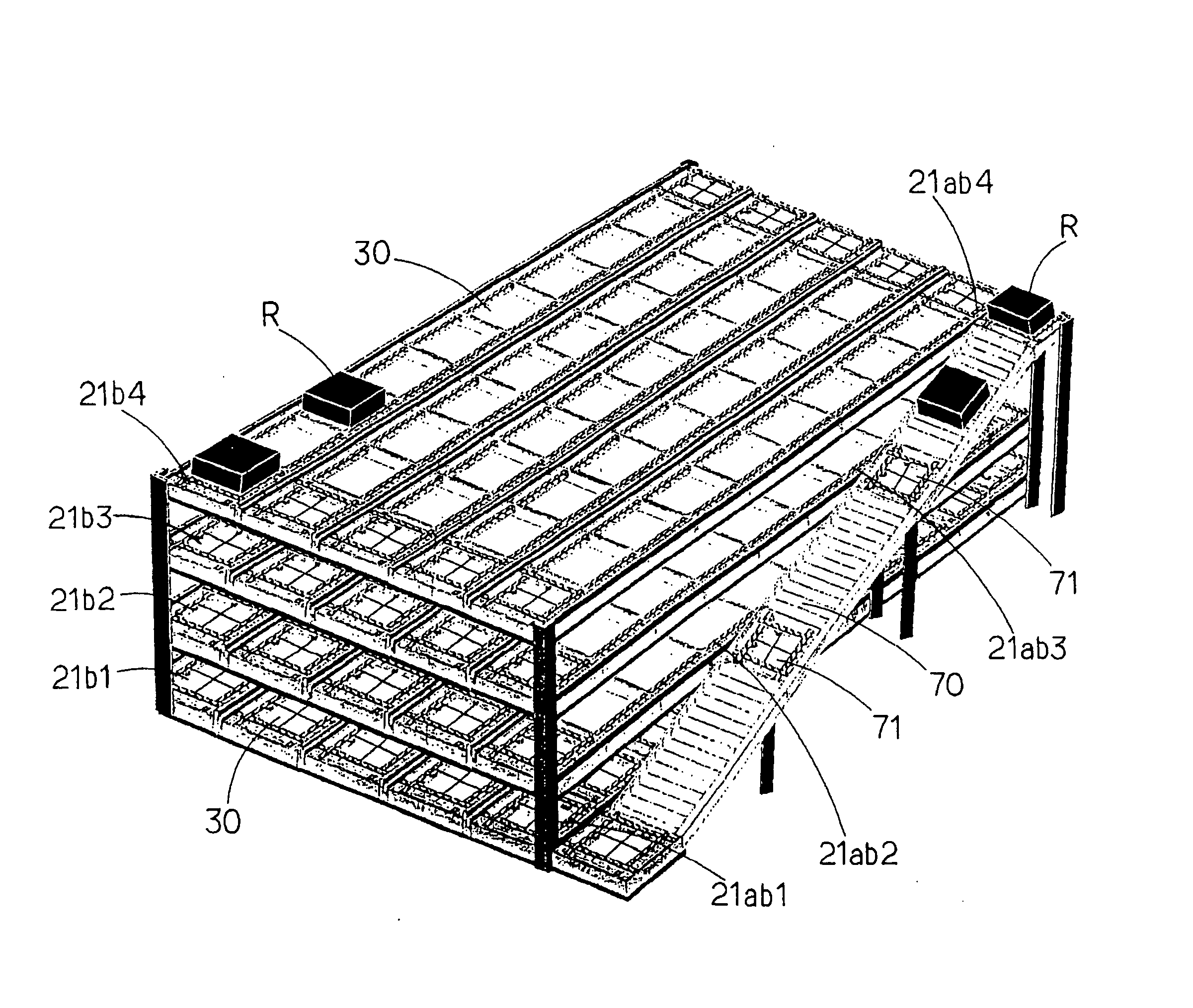
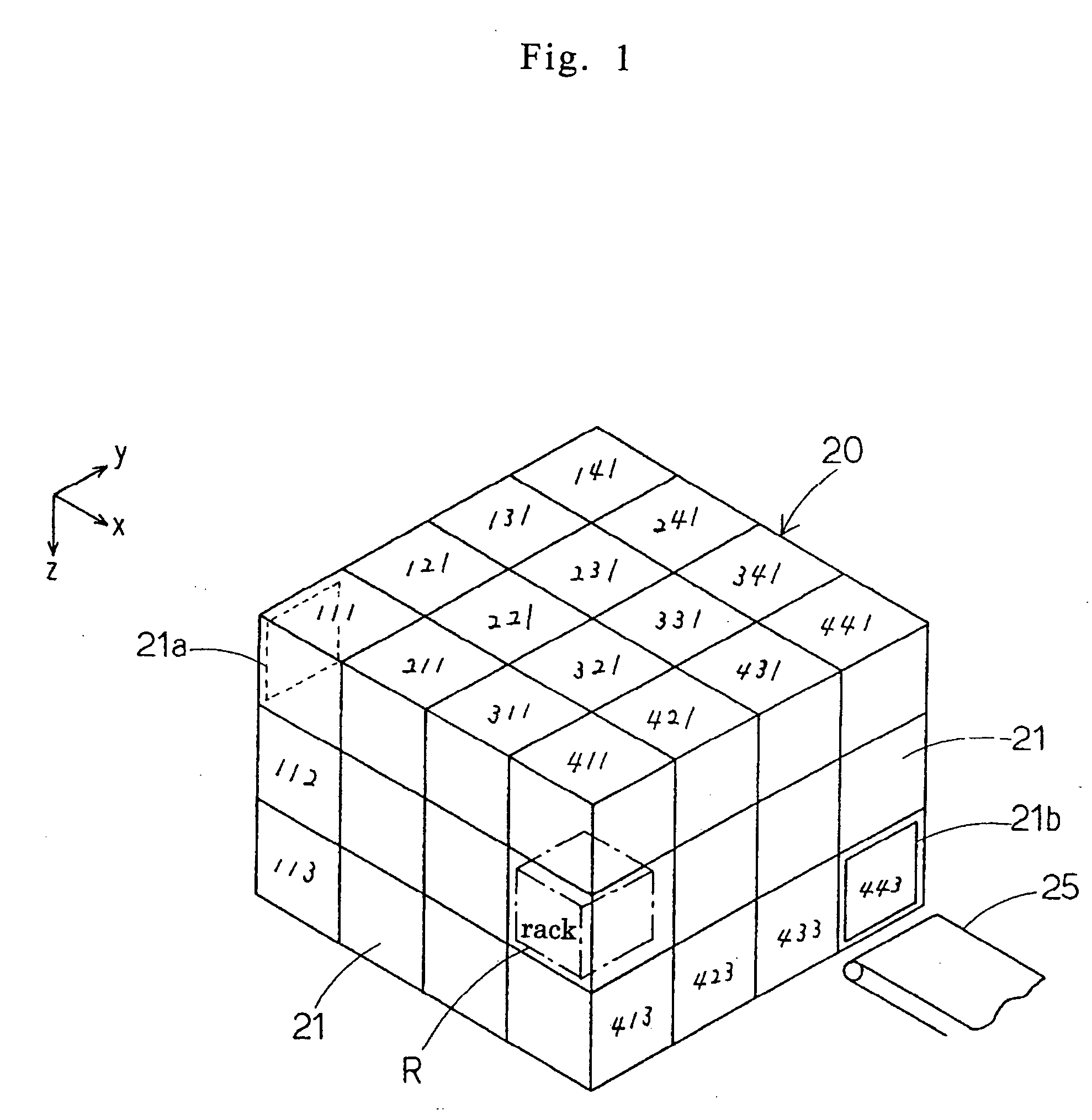
Automatic storage and retrieval system
An automatic storage and retrieval system comprises at least one entrance opening, at least one delivery opening, a goods storage section having at least one storage layer in which unit goods storage sections are disposed in row and column, a goods conveyance section for selecting a stored good (rack) freely in direction and for accepting and sending out the stored good, the goods conveyance section being provided at each of the unit goods storage sections, and a conveyance control section for guiding the stored good to the delivery opening by the delivering date and time of the stored good upon reception of the stored good through the entrance opening.
Owner:ITO DENKI KK
Electronic sales system
InactiveUS7305360B1Retain controlEasy to useComplete banking machinesTelephonic communicationInternet privacyTrust relationship
Owner:REFINITIV US ORG LLC
Method of transferring digital certificate,apparatus for transferring digital certificate, and system, program, and recording medium for transferring digital certificate
ActiveUS7584351B2Accurately delivering such digital certificateSecure deliveryKey distribution for secure communicationDigital data processing detailsComputer networkRecording media
A method of transferring digital certificates from a digital-certificate transferring apparatus to a communications counterpart. The method includes authenticating the communications counterpart using a common certificate and transferring a normal certificate to the communications counterpart when the authenticating succeeds. The method further includes receiving a first normal certificate at an address from said communications counterpart, and when, it is determined to be necessary, transferring to the communications counterpart a second normal certificate along with the information identifying the communications counterpart and an address corresponding to a second normal certificate. The second normal certificate is of a different type than the first normal certificate.
Owner:RICOH KK
Global resource locator
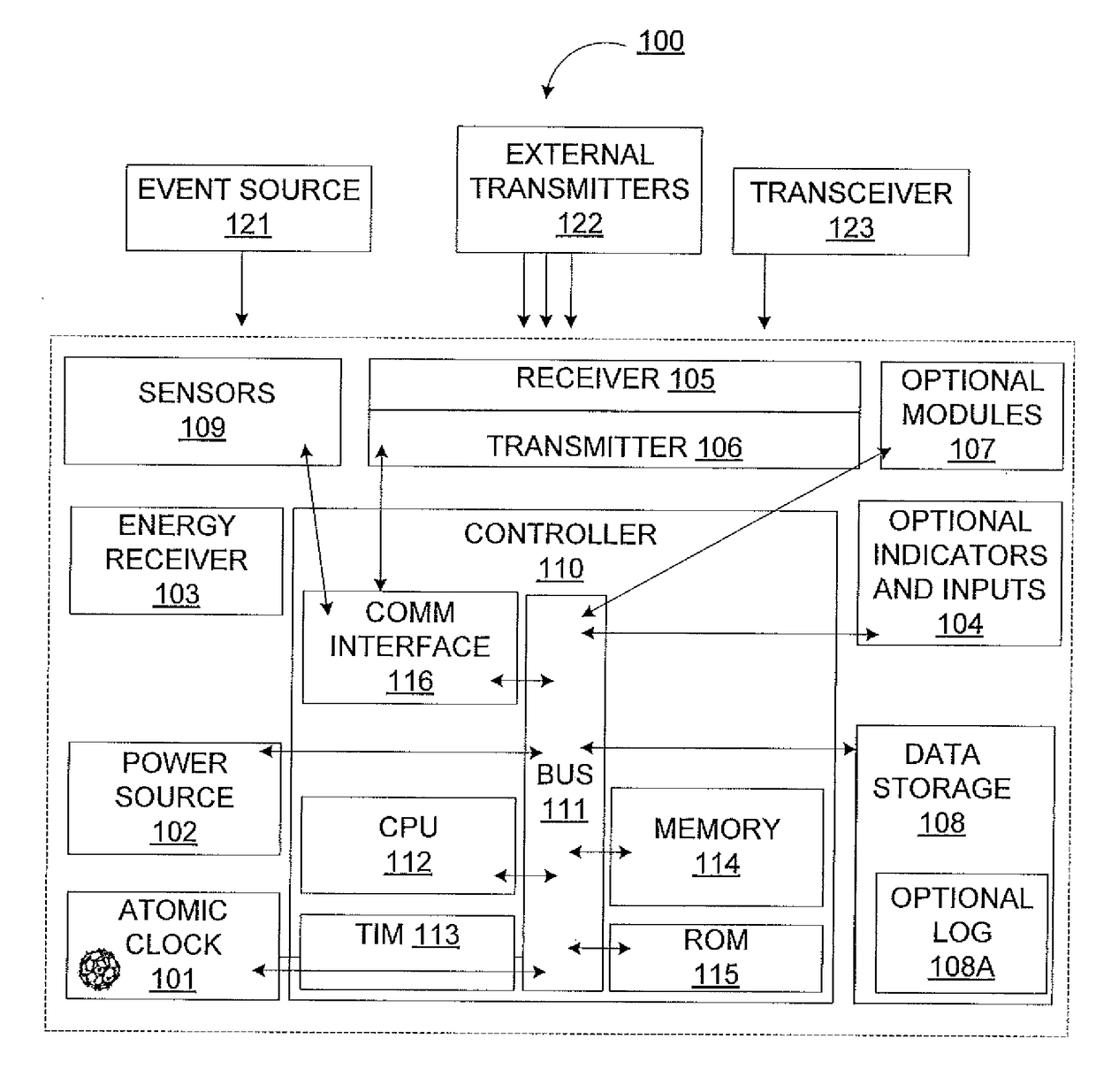
ActiveUS20180052218A1Easy to operateAccurate locationPosition fixationComputer security arrangementsLogistics managementMarket based
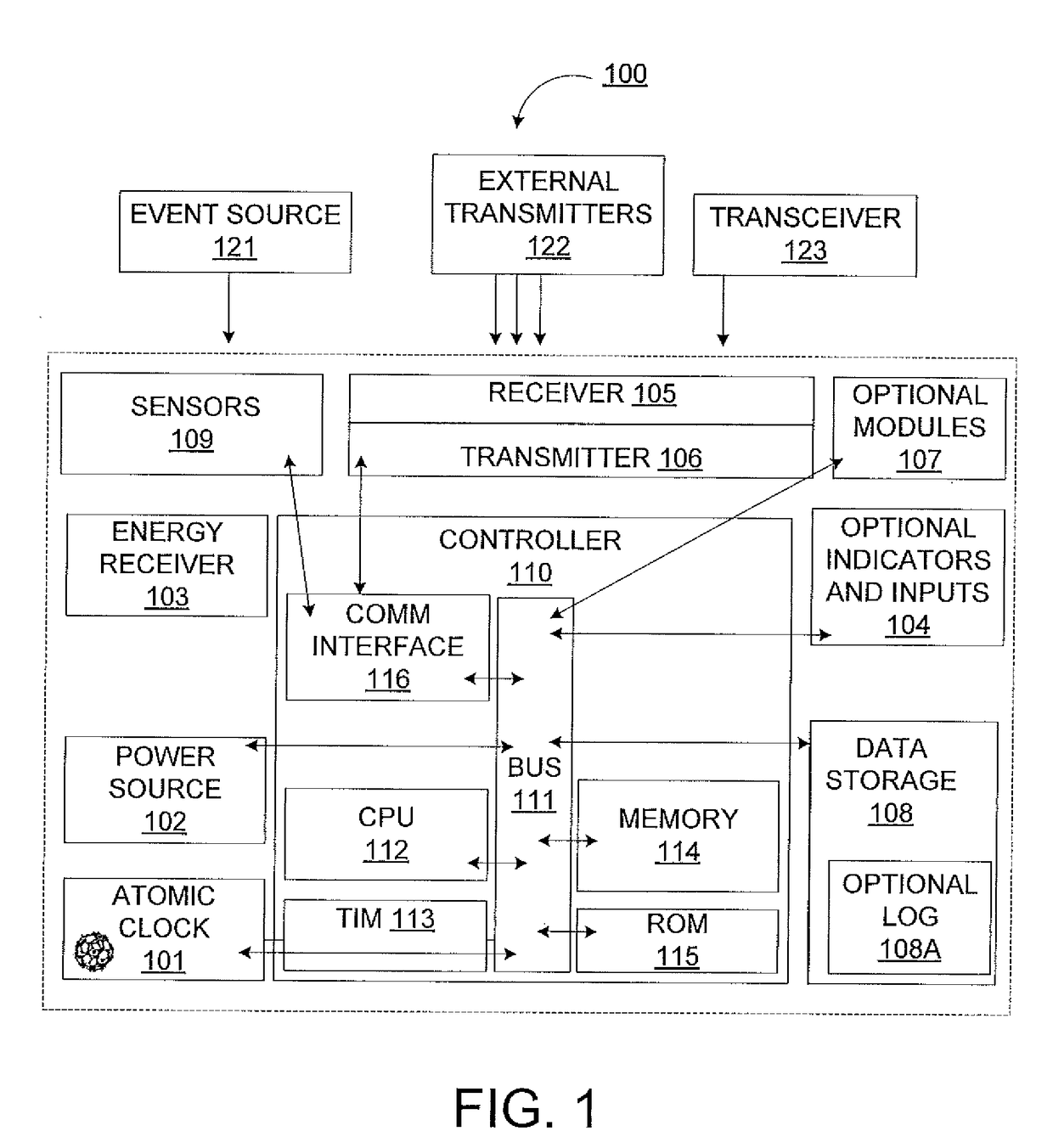
The present disclosure relates to methods and apparatus for accurately calculating time with a Miniature Atomic Clock along with other components that can receive process and communicate information to enable locating, identifying, and tracking physical Assets and data contained within the Assets. More specifically, the present disclosure presents a Global Resource Locating (GRL) device and service that may be adhered or inserted in the Asset, which may be built in or attached to a second Asset, wherein the device may comprise a receiver and a trilateration mechanism. In some aspects, the Asset may comprise a product, organism, produce, or component of a logistics based operational process and marketing based Asset movement and usage analysis.
Owner:LOCATORX INC
System, apparatus and method for secure deliveries of items to a residence with control of delivery authorizations and storage temperatures, and communications with delivery services
InactiveUS20190130348A1Prevent theftSecure deliveryLighting and heating apparatusKitchen equipmentResidenceComputer module
A container appliance for secure receiving and storing of delivered items at a residence of a final recipient may include a storage compartment, securing mechanism, thermal conditioning system and appliance management module configured to control the securing mechanism to provide authorized delivery events and to control the thermal conditioning system to establish a temperature in a thermal conditioned region.
Owner:SDSC LLC
System, method and software based medium for providing a safe and secure delivery platform for a drone including real time data communication incorporating any of video, RFID and process step notification
ActiveUS20190039751A1Secure deliveryUnmanned aerial vehiclesDwelling equipmentReal-time dataControl system
An assembly for accomplishing package transfer to and from a drone. The assembly includes a base supporting at least one extendable member. A package receiving platform is secured atop the member and a control system interfaces the assembly with the drone for issuing a set of command instructions for guiding and positioning the drone relative to the platform and for accomplishing package transfer between the drone and the platform. The command instructions include at least an instruction to elevate the platform at any point prior to package exchange and a subsequent instruction to retract the platform at any point following package exchange. Additional command instructions provide for managing each of pre-exchange and post-exchange of the package, such as for providing secure retention and post-exchange access by the recipient in the instance of a drone delivered and securely retained package.
Owner:JANSSEN BRIAN
Apparatus, system and method for implementing business for transmitting as soon as shooting
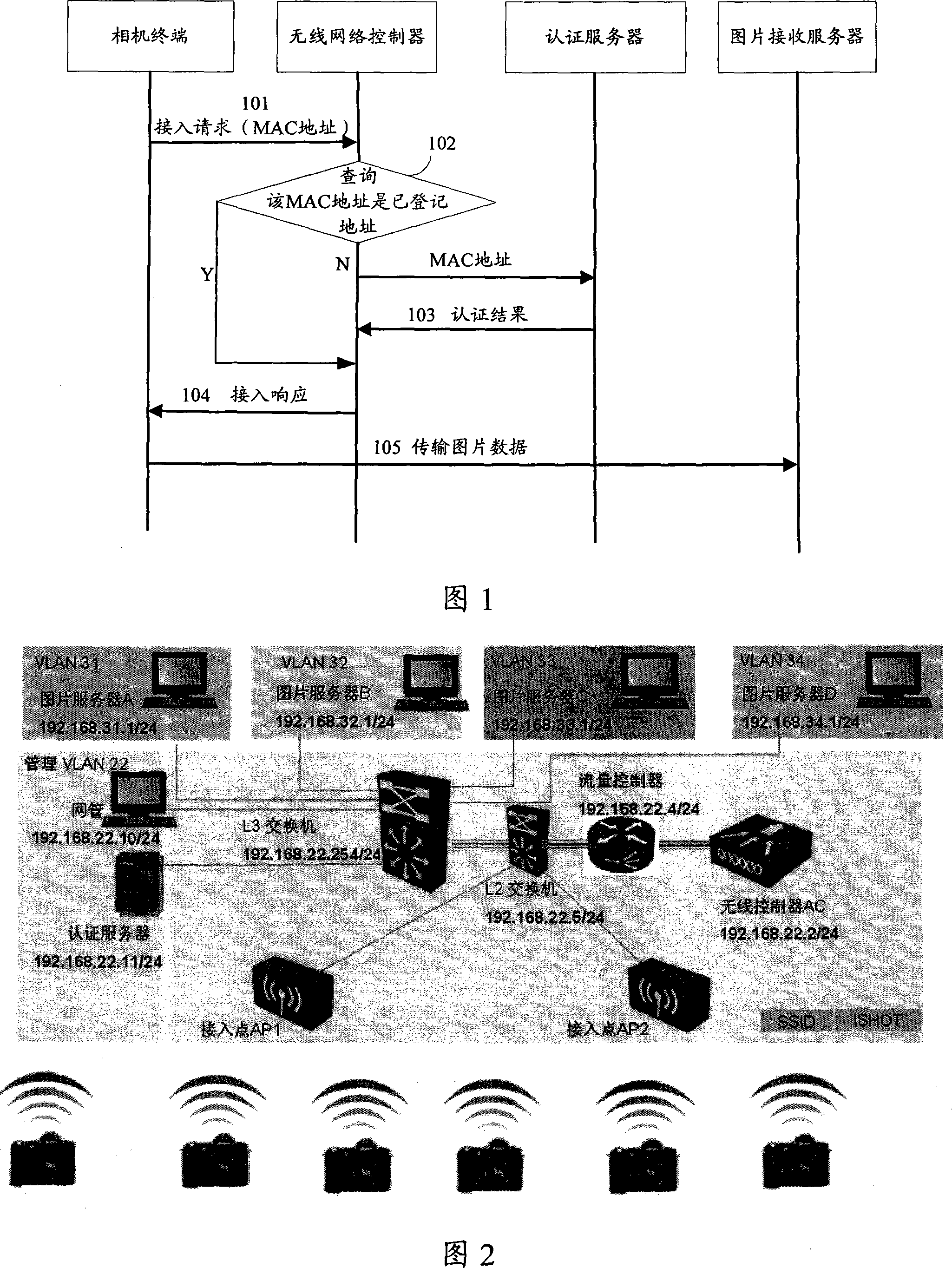
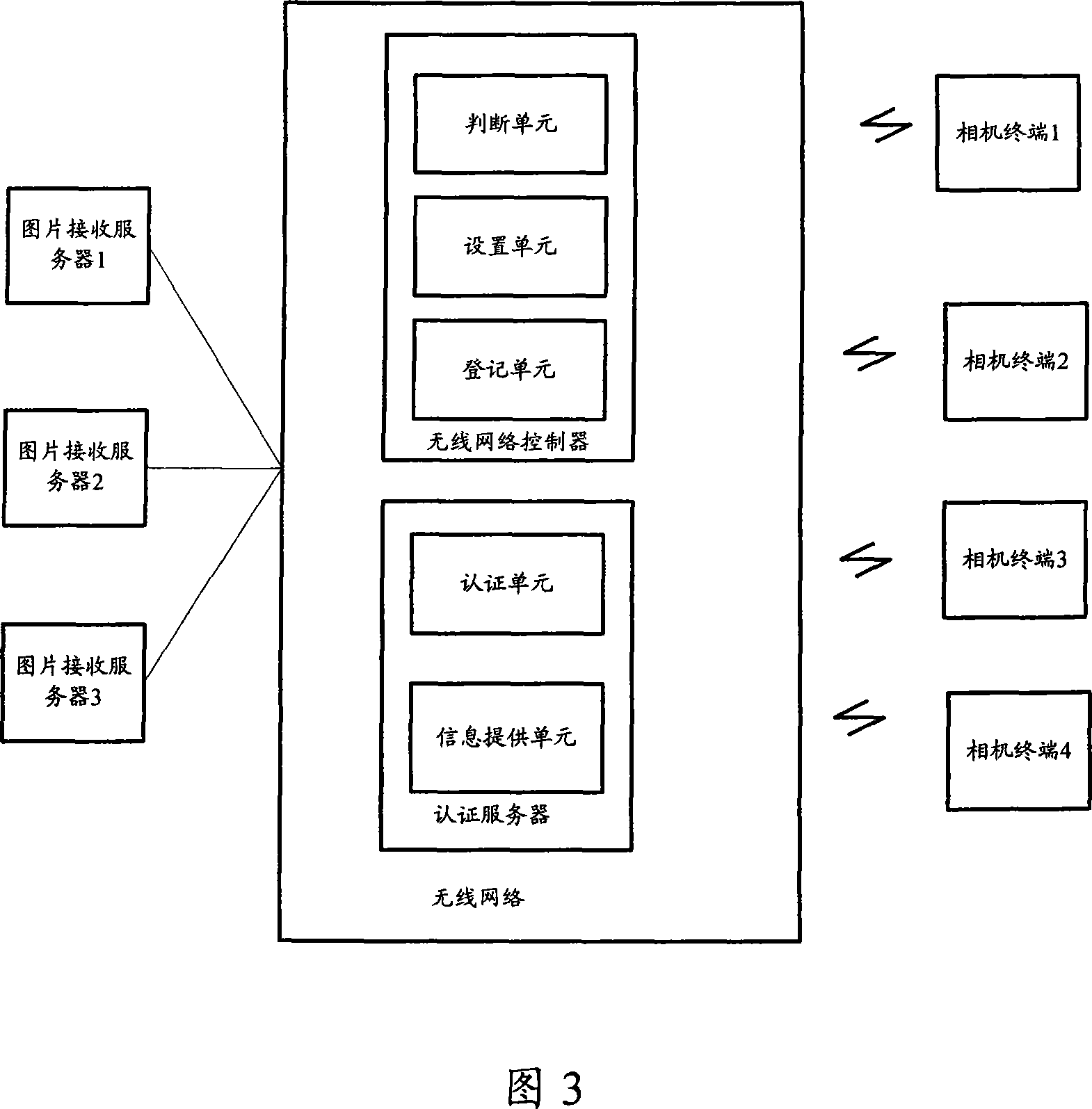
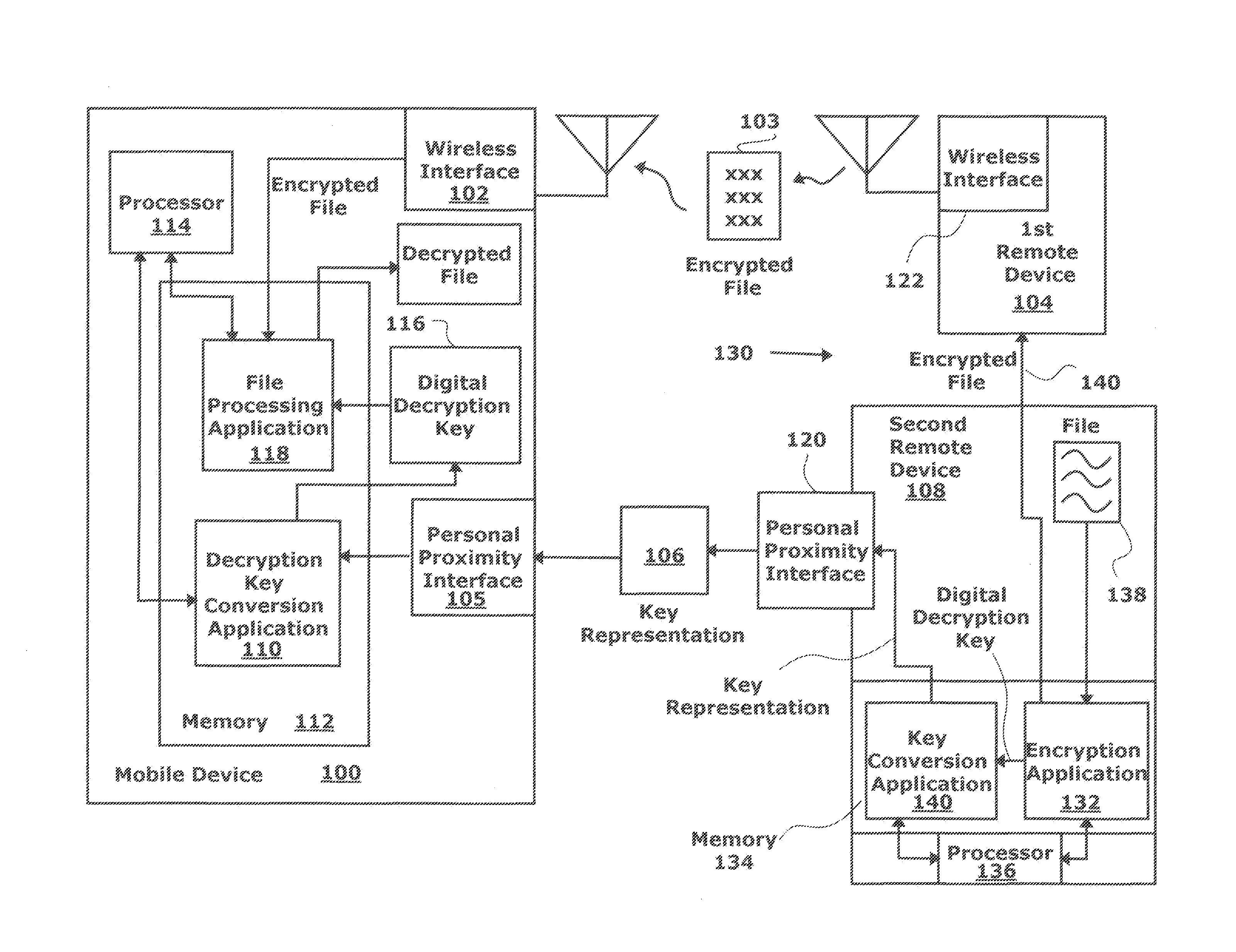
ActiveCN101227374ASecure deliveryTelevision system detailsColor television detailsVirtual LANMedia access control
The invention discloses a method, a system and a device for achieving transmitting the shot immediately, which is used to solve security problem that a terminal end of a camera achieves the business of transmitting the shot immediately. The method comprises dividing wireless network into more than one virtual local area network (VLAN), leading wireless network to utilize medium access control (MAC) address on the terminal end of the camera to identify the terminal end of the camera, if the identification is passed, setting the MAC address to be a legal user, and registering the MAC address to the belonged VLAN, transmitting register data which is shot to a picture receiving server in the belonged VLAN after wireless network is accessed on the terminal end of the camera.
Owner:CHINA MOBILE GRP BEIJING
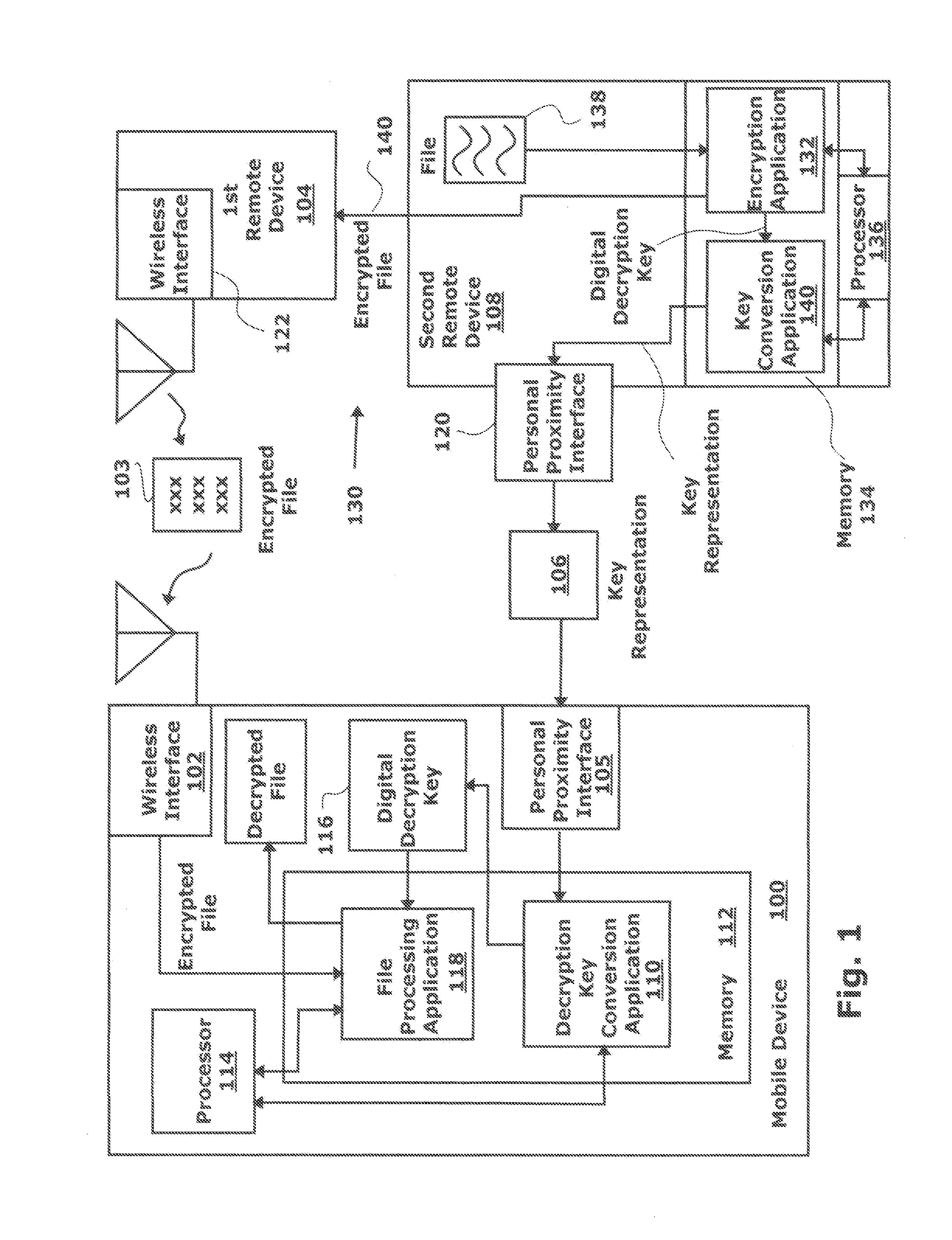
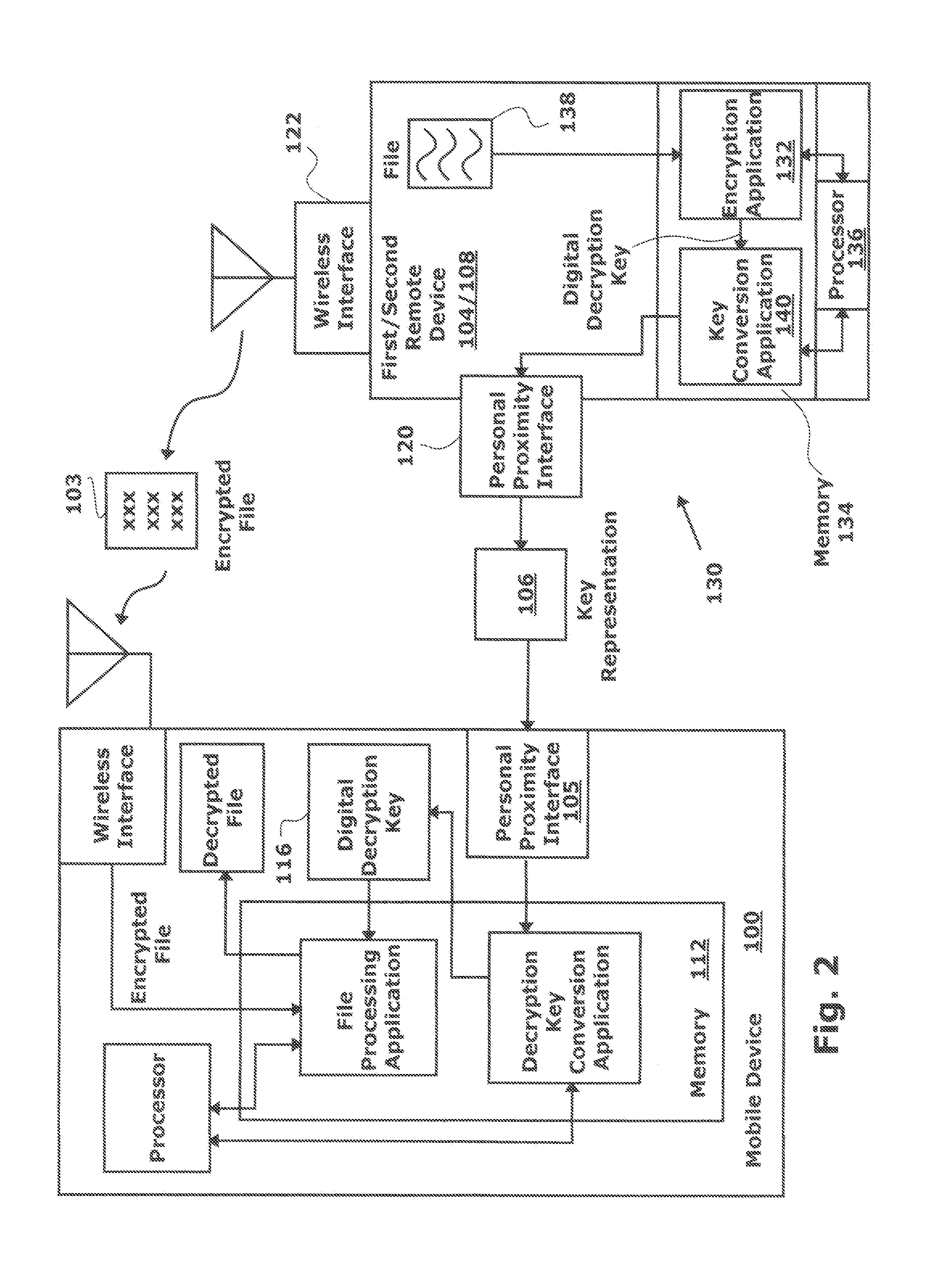
System and Method for Securely Decrypting Files Wirelessly Transmitted to a Mobile Device
InactiveUS20120278616A1Capability and ease of useSecure deliverySecuring communicationRadio frequencyMicrophone
A method is provided for securely decrypting files that are wirelessly sent to a mobile device. A mobile device typically has a wireless interface, such as a cellular telephone or WiFi interface that can be used to accept an encrypted file from a first remote device. A decryption key representation is accepted from a second remote device via a personal proximity interface which can be a camera, microphone, or near-field radio frequency (RF) detector. In one aspect, the first device can, for example, be a multi-functional peripheral (MFP), a network server, or a computer. In another aspect, the first and second devices can be the same device, such as an MFP or a computer. A mobile device conversional application converts the decryption key representation to a digital decryption key, and the digital decryption key is then used to decrypt the encrypted file.
Owner:SHARP LAB OF AMERICA INC SLA
User authentication
InactiveUS20110289316A1Reduce the possibilityAvoid interferenceUser identity/authority verificationDigital data authenticationUser authenticationEmail authentication
Owner:AFILIAS TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com