Patents
Literature
63335results about "Wireless commuication services" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
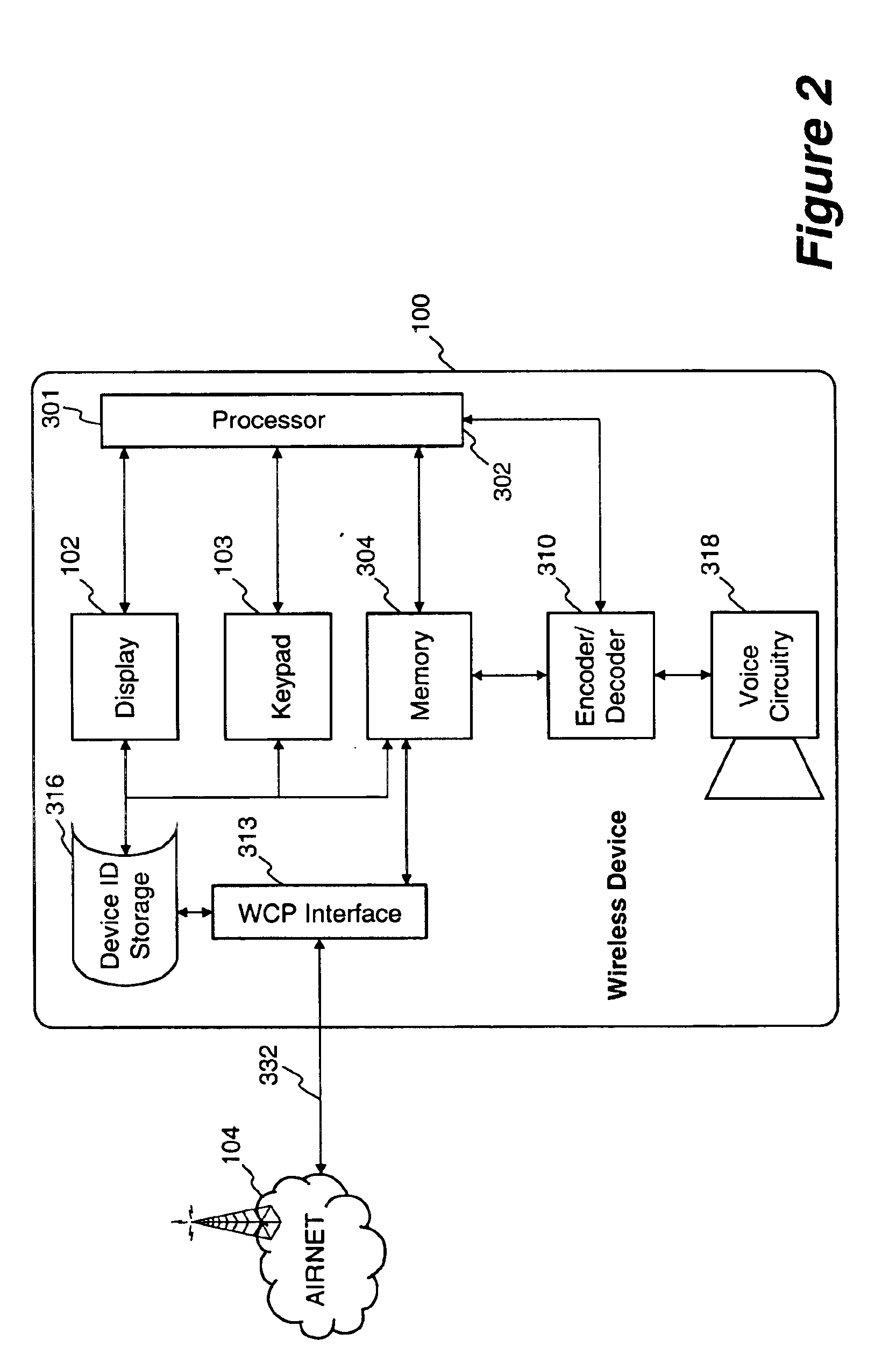
Information distribution and processing system
InactiveUS7508789B2Reduce loadSufficient amountTelevision system detailsTimetable based automatic information retrievalDigital dataHandling system
An information distribution and processing system contains a remote site, a sender and a receiving apparatus. The remote site contains a first set of digital data. The sender delivers a second set of digital data to the receiving device. In one embodiment of the present invention, the receiving device contain a timing device for automatically receiving the second set of digital data at predetermined times. The second set of digital data contains a first set of displayable data, a second set of displayable data, at least one non-displayable symbol, and at least one linking reference associated with the second set of displayable data. If desired, a user can select the second set of displayable data. The associated linking reference is sent to the remote site. The associated linking reference is used by the remote site to search for the additional information, and returns the requested information to the user.
Owner:ONLINE NEWS LINK
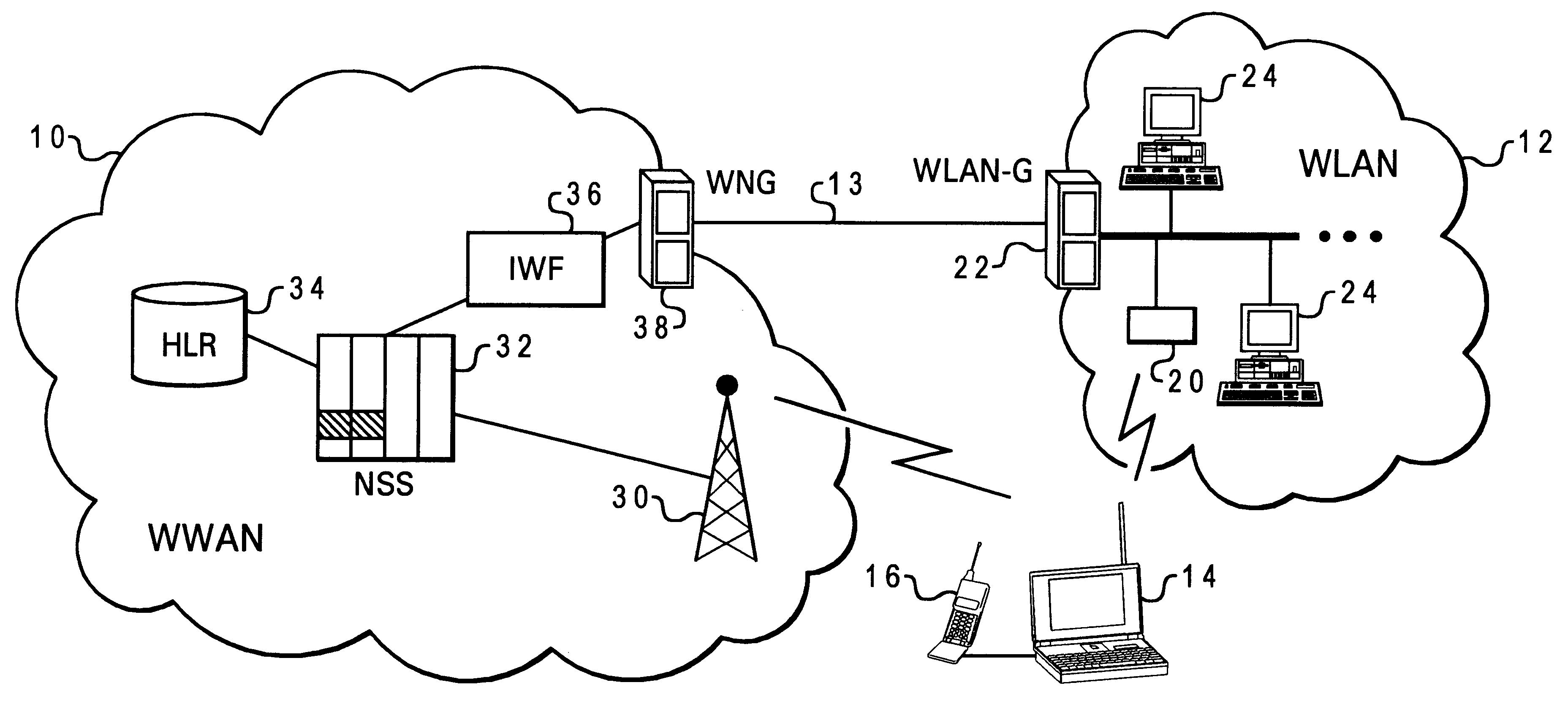
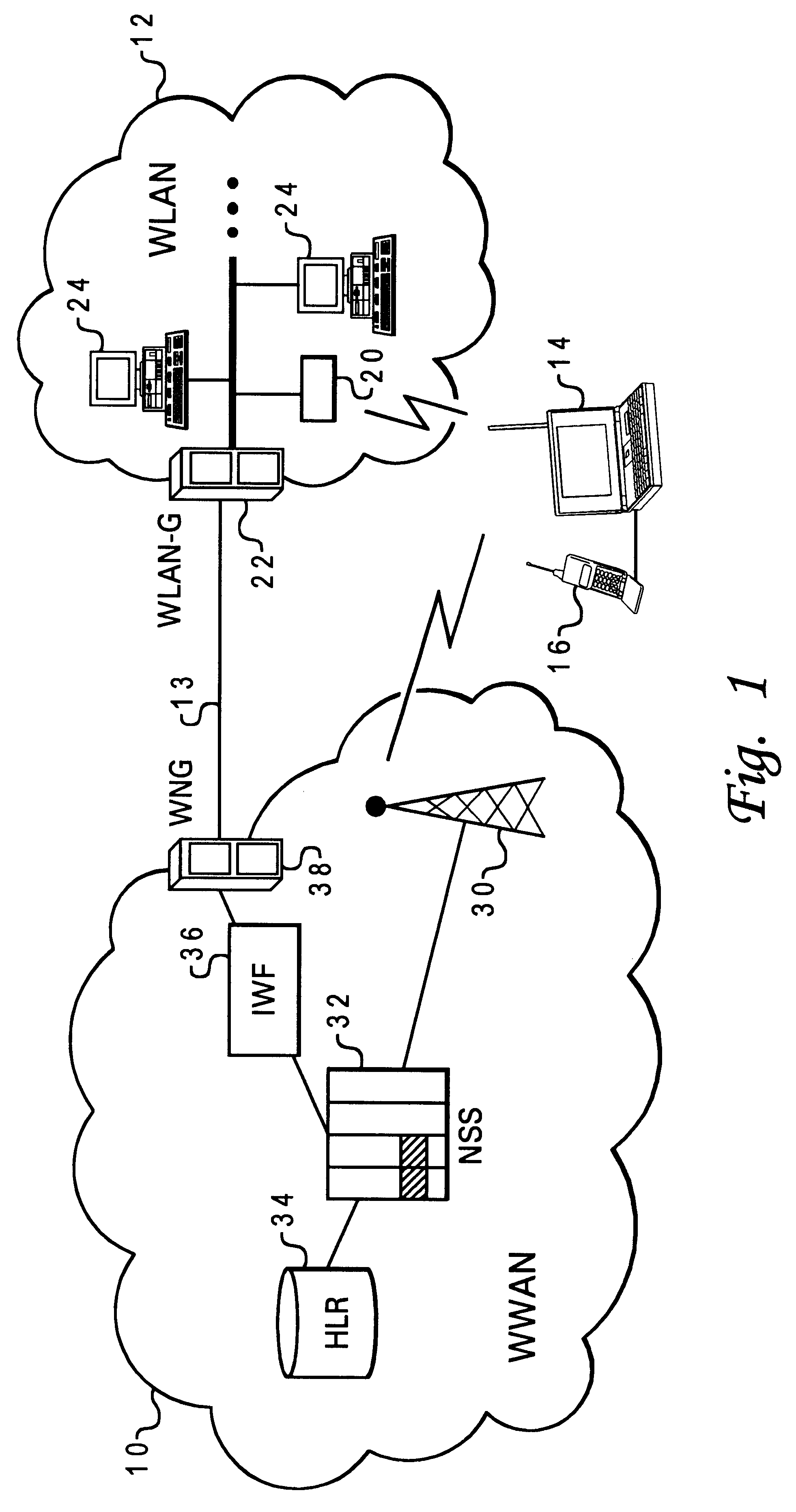
Automatic and seamless vertical roaming between wireless local area network (WLAN) and wireless wide area network (WWAN) while maintaining an active voice or streaming data connection: systems, methods and program products
ActiveUS20020085516A1Data switching by path configurationRadio/inductive link selection arrangementsData connectionUser verification
A Mobile Station (MS) is able to vertically roam in either direction between two different network, i.e. WWAN and WLAN. The MS is equipped with a dual mode Radio for WWAN and WLAN transmissions. The WLAN Radio is linked to a WLAN Enterprise Gateway Controller (EGC) via a first air link and the WWAN Radio is linked to a WWAN Base Transceiver Station (BTS) via a second air link. The EGC is connected to a Mobile Switching Center (MSC) which is in turn connected to the BTS. An outgoing VoIP call from the WLAN Radio to a remote party on the WWAN will transition or seamlessly switch over to a WWAN connection when the MS detects packet error rates, frequent scale back or consistent signal degradation. Upon such conditions, the WLAN Radio requests the EGC to request an Explicit Call Transfer via the MSC to the MS integrated WWAN Radio portion which automatically accepts the call based on referenced information stored in the user's subscriber identification module (SIM). Once the WWAN Radio is confirmed connected to the remote party on the WWAN, the WLAN Radio drops the WLAN connection. An incoming call between the MS and a remote user via the WWAN will transition to the WLAN Radio when the MS enters WLAN coverage. The MS issues an ECT to the WLAN. After user verification by the WLAN Radio and the EGC signals acceptance of the call, the WWAN Radio connection is dropped and the call is now established between the WLAN Radio and the remote party on the WWAN.
Owner:SYMBOL TECH LLC
Method and apparatus for optimization of wireless multipoint electromagnetic communication networks
InactiveUS20040095907A1Improve signal qualityReduce interference energyPower managementSpatial transmit diversityGlobal optimizationDiversity scheme
Exploiting the substantive reciprocity of internode channel responses through dynamic, adaptive modification of receive and transmit weights, enables locally enabled global optimization of a multipoint, wireless electromagnetic communications network of communication nodes. Each diversity-channel-capable node uses computationally efficient exploitation of pilot tone data and diversity-adaptive signal processing of the weightings and the signal to further convey optimization and channel information which promote local and thereby network-global efficiency. The preferred embodiment performs complex digital signal manipulation that includes a linear combining and linear distribution of the transmit and receive weights, the generation of piloting signals containing origination and destination node information, as well as interference-avoiding pseudorandom delay timing, and both symbol and multitione encoding, to gain the benefit of substantive orthogonality at the physical level without requiring actual substantive orthogonality at the physical level.
Owner:COMCAST CABLE COMM LLC
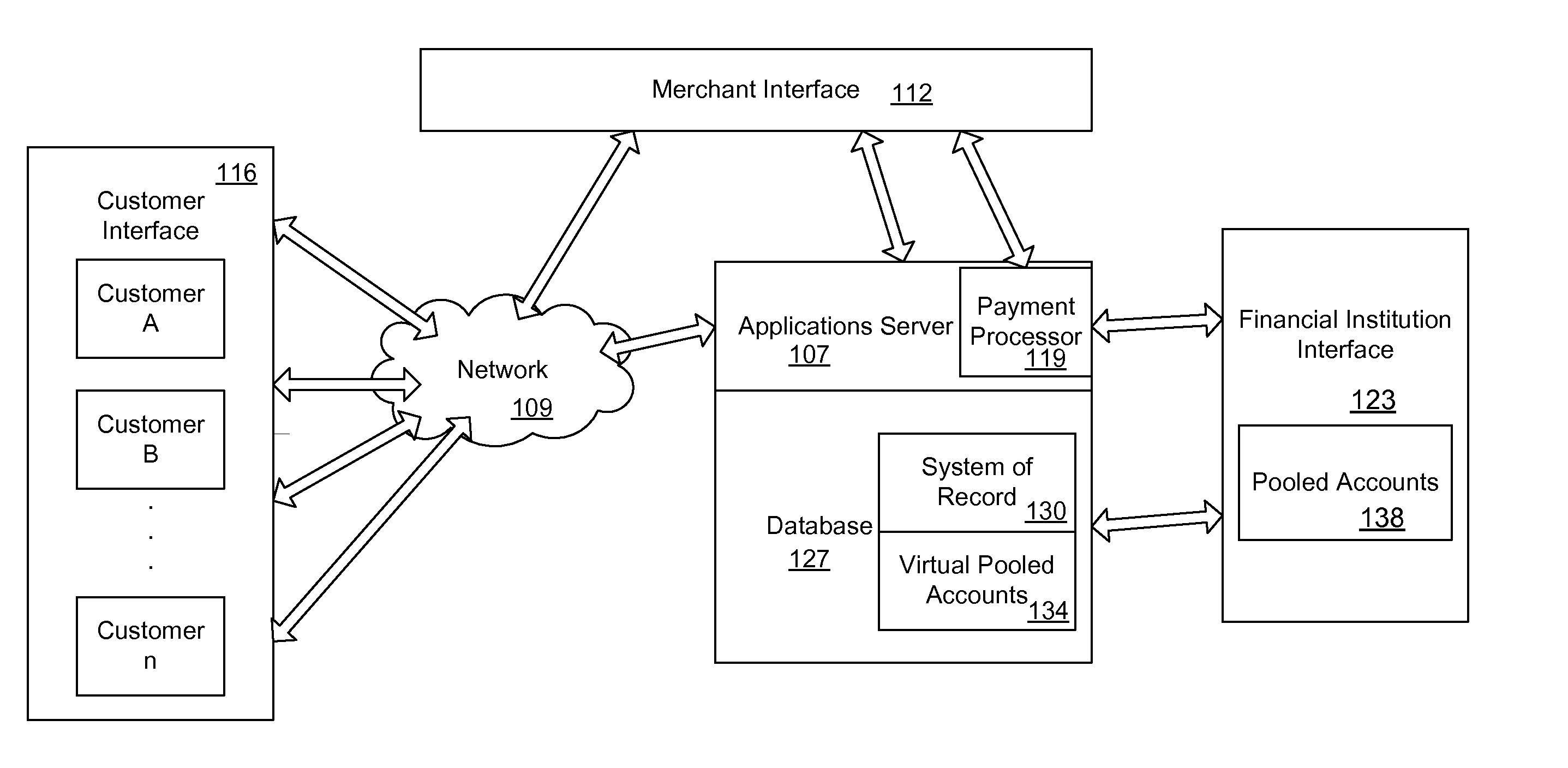
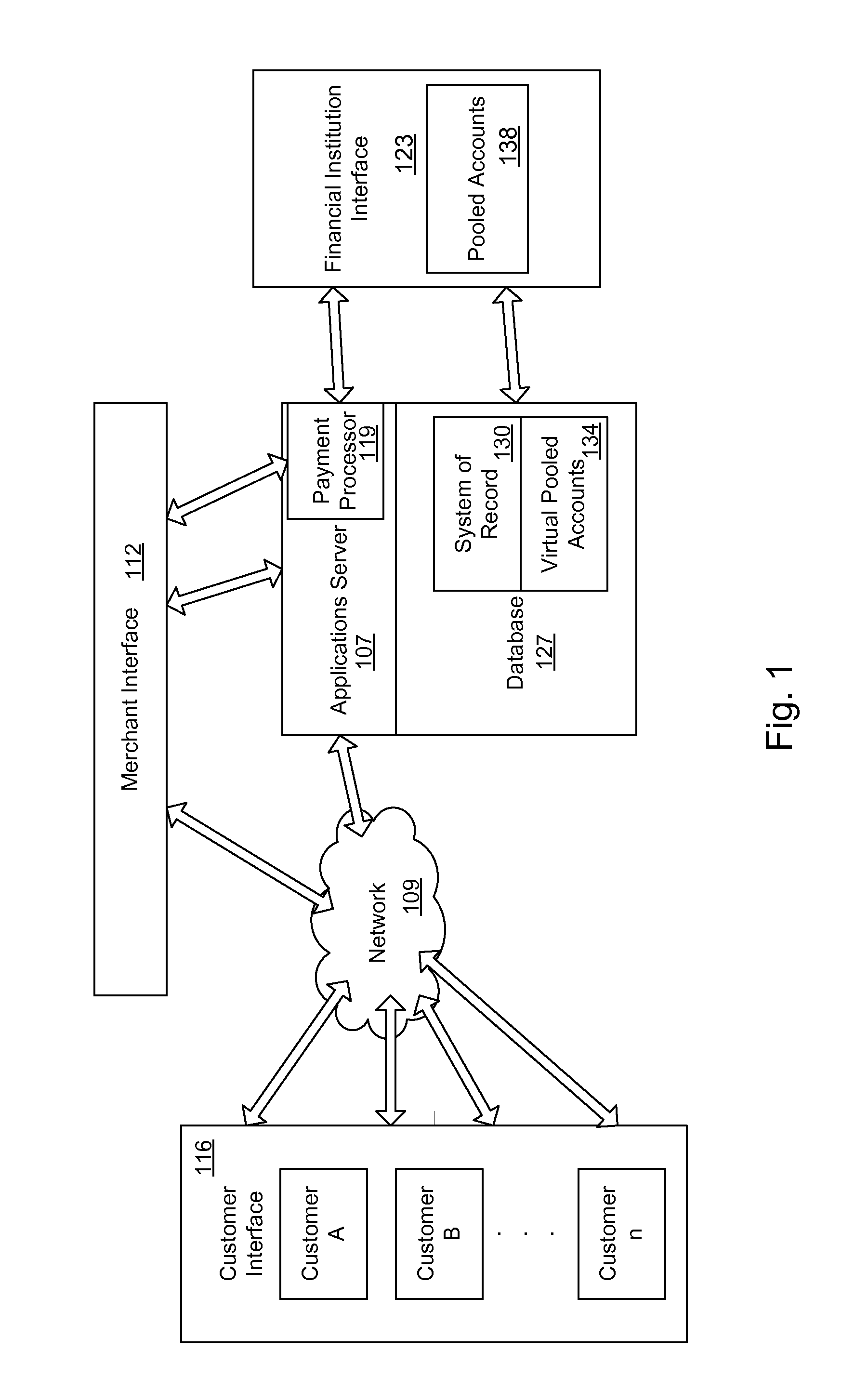
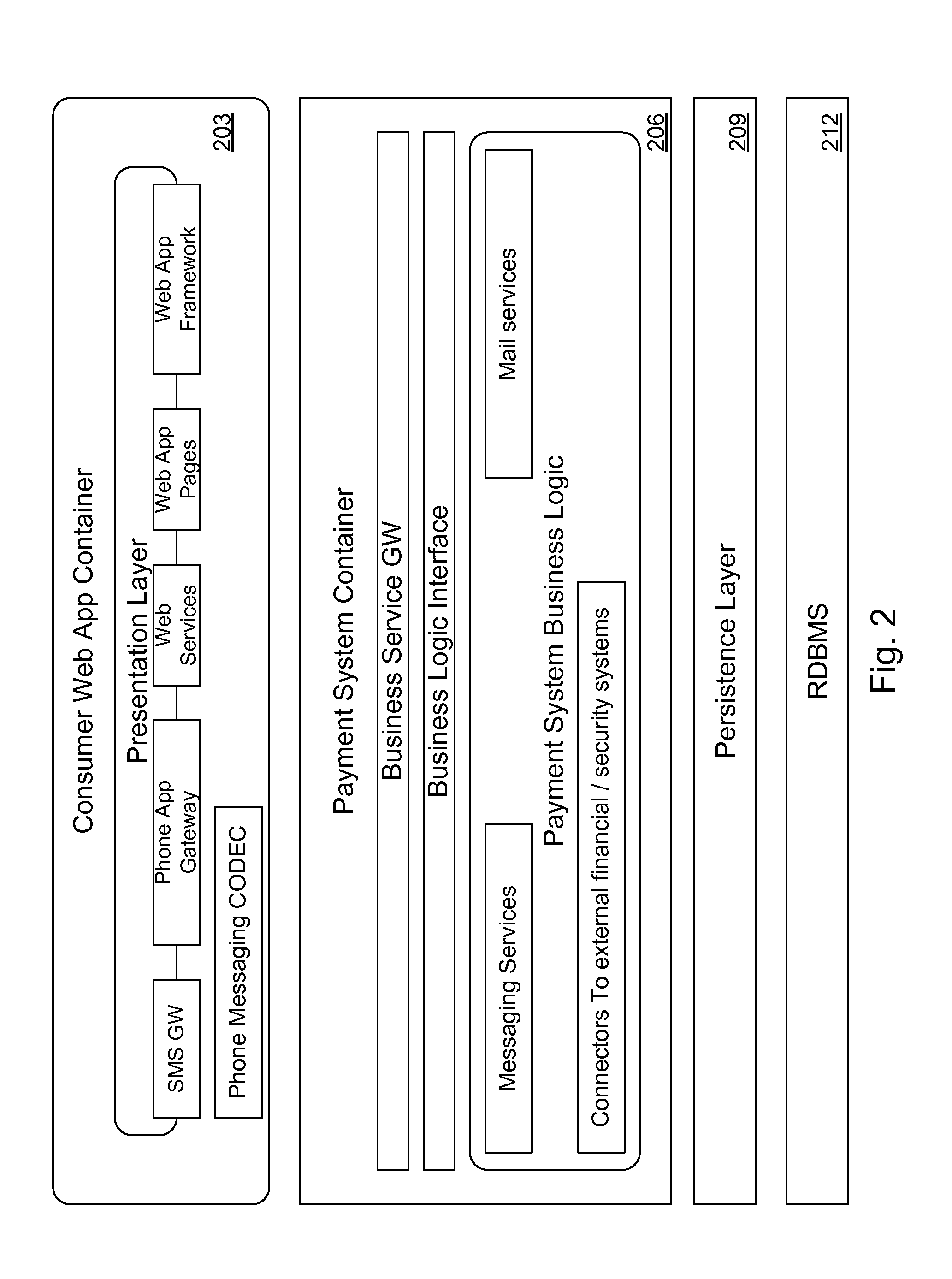
Mobile Person-to-Person Payment System
InactiveUS20070255653A1Easy to useFraudulent transaction is minimizedFinancePayment architectureBarcodeFinancial transaction
A mobile payment platform and service provides a fast, easy way to make payments by users of mobile devices. The platform also interfaces with nonmobile channels and devices such as e-mail, instant messenger, and Web. In an implementation, funds are accessed from an account holder's mobile device such as a mobile phone or a personal digital assistant to make or receive payments. Financial transactions can be conducted on a person-to-person (P2P) or person-to-merchant (P2M) basis where each party is identified by a unique indicator such as a telephone number or bar code. Transactions can be requested through any number of means including SMS messaging, Web, e-mail, instant messenger, a mobile client application, an instant messaging plug-in application or “widget.” The mobile client application, resident on the mobile device, simplifies access and performing financial transactions in a fast, secure manner.
Owner:OBOPAY MOBILE TECH INDIA PTE LTD
Portable communications device and method of use
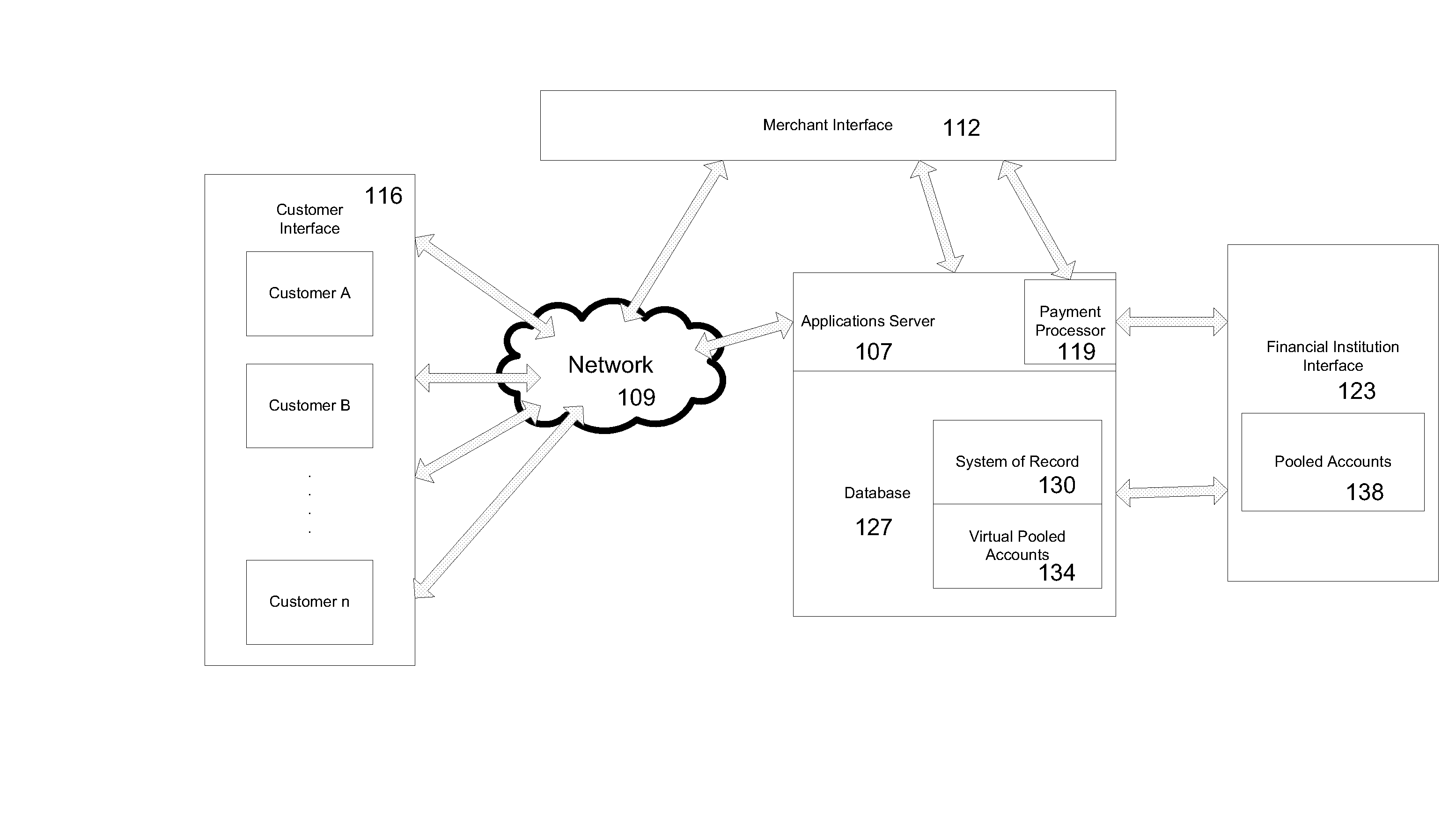
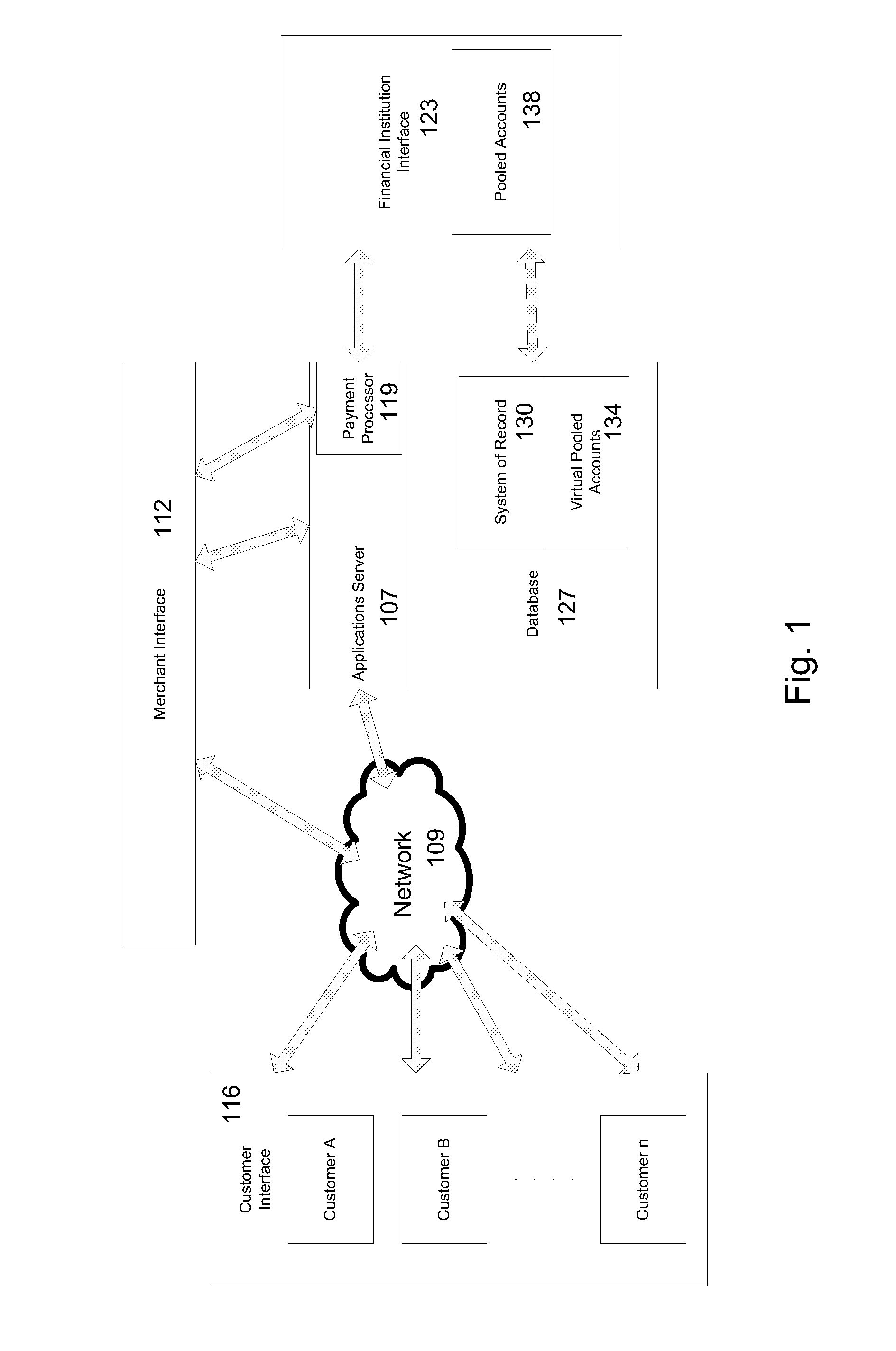
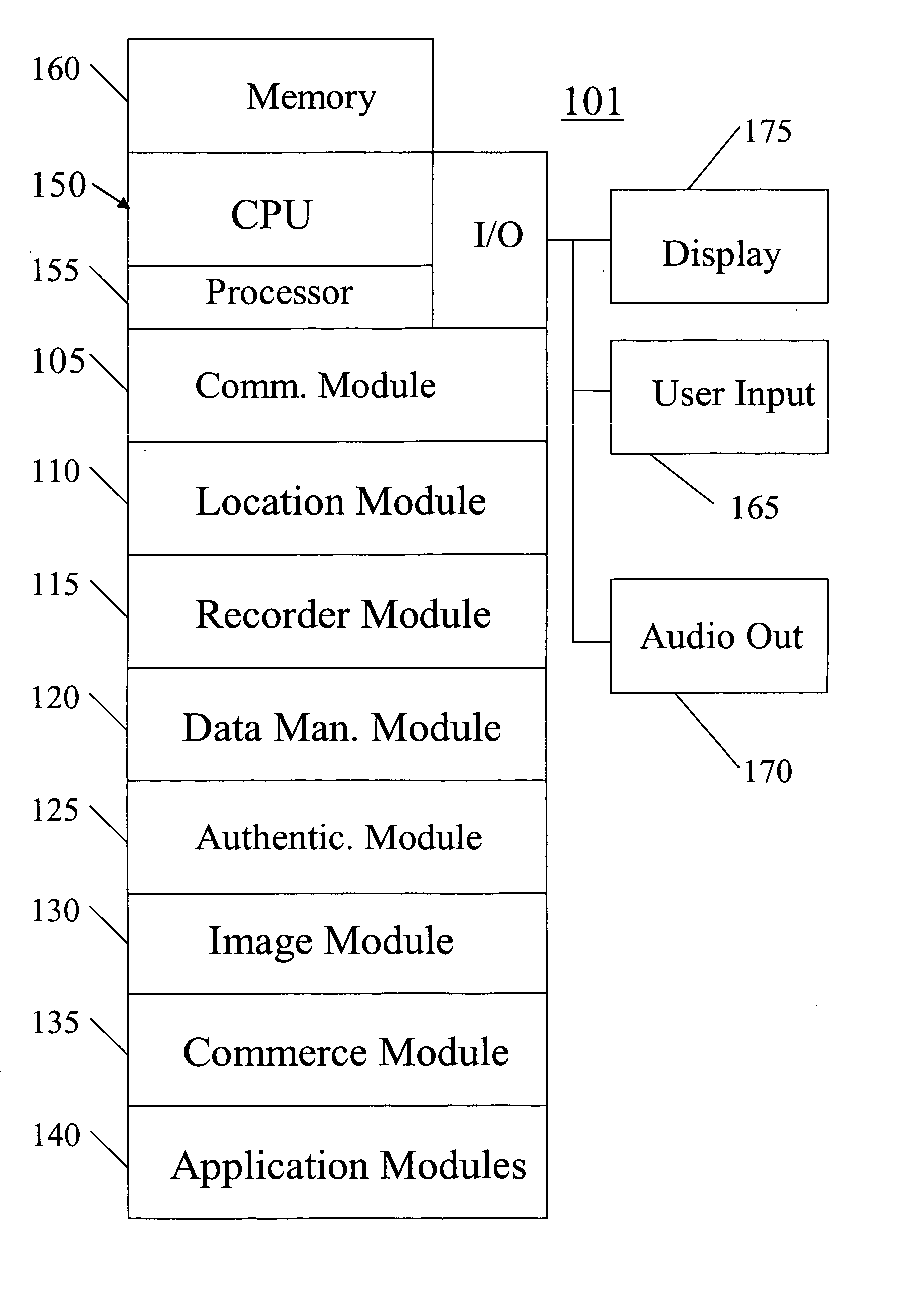
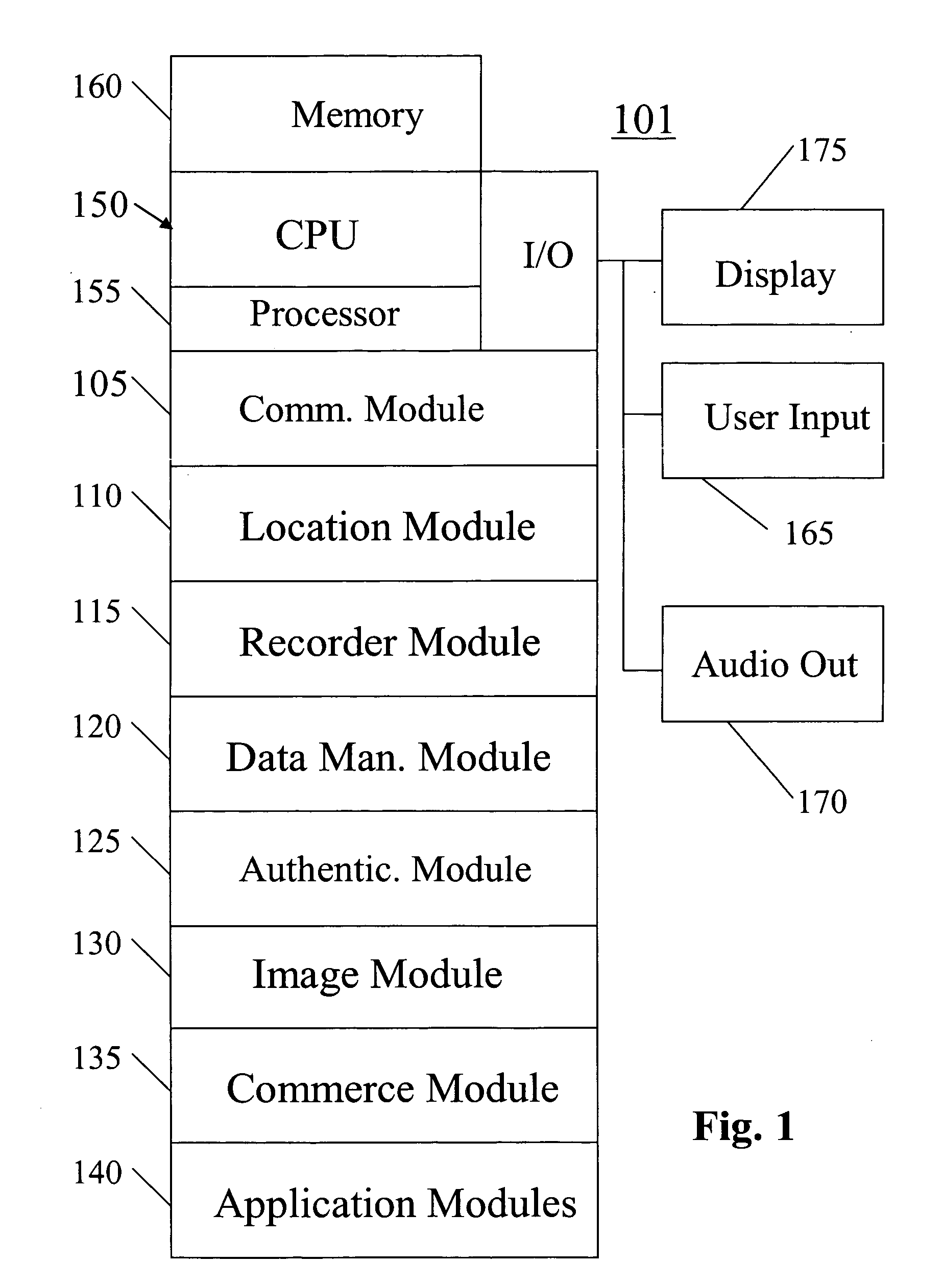
A system, method, apparatus and computer program product for providing location based functions and mobile e-commerce comprising a central processing unit including a processor, a storage device, and programming stored in the storage device, a display device, an audio input device, an audio output device, a communications module, a commerce module, an image module, and a location module. The programming controls the operation of the present invention to provide functions based on location data, to facilitate commercial exchanges by wirelessly exchanging payment and product information with venders, to identify services such as venders meeting selection criteria, to wirelessly exchange select information with other users and systems, to restrict and / or monitor the use of the device based on authorized user parameters, to select one of a plurality networks through which to communicate, to detect a trigger for performing an action based on a change in location and sensed data, to store a voice annotation with a computer data file, to determine service providers and associated communication parameters, to contemporaneously maintain a wireless voice and data link, to provide a system for selecting mobile advertisements, and many other functions and services that are described herein.
Owner:WOUNDER
Integrating public and private network resources for optimized broadband wireless access and method
InactiveUS20020075844A1Network traffic/resource managementNetwork topologiesNetwork access serverPrivate network
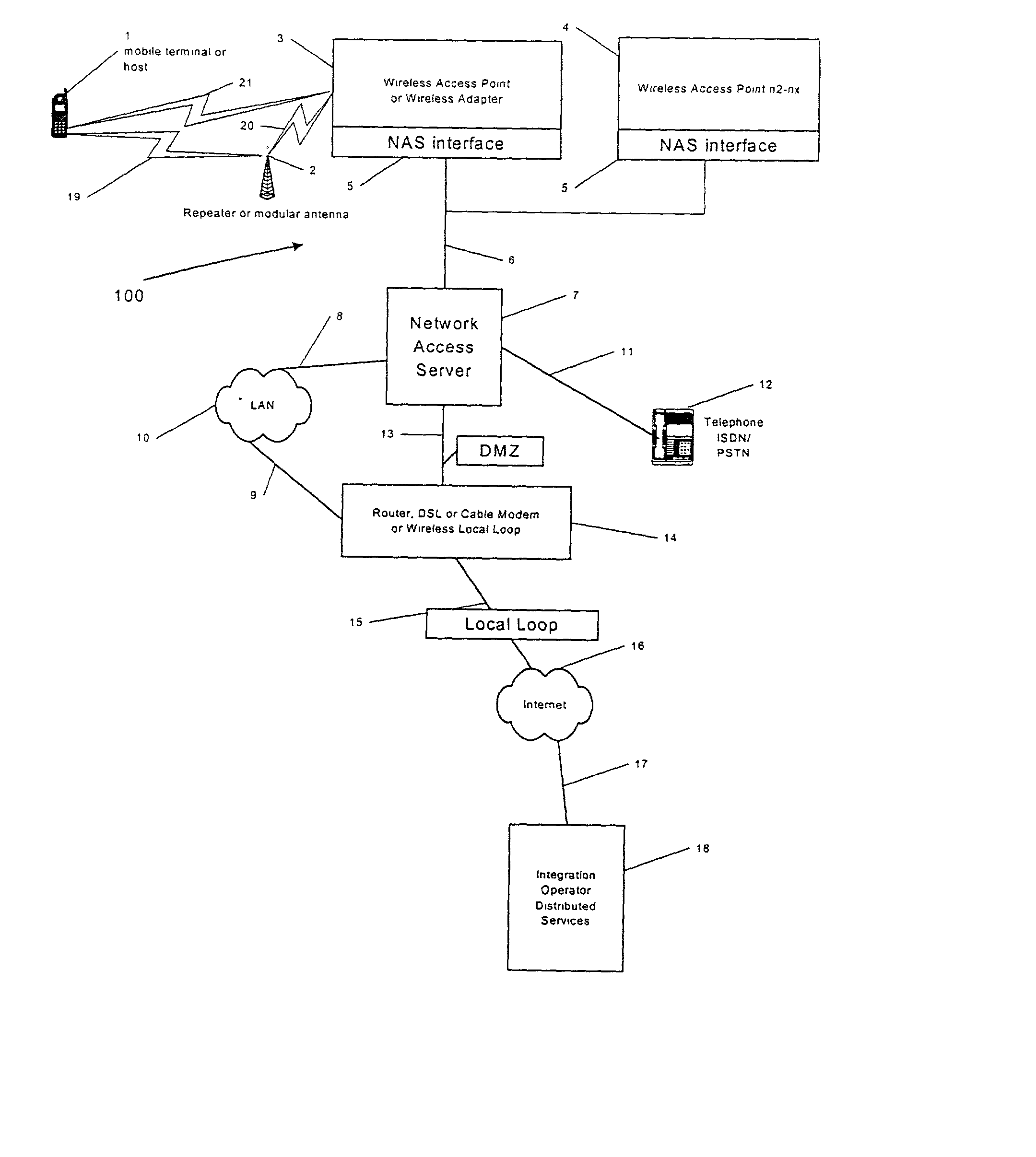
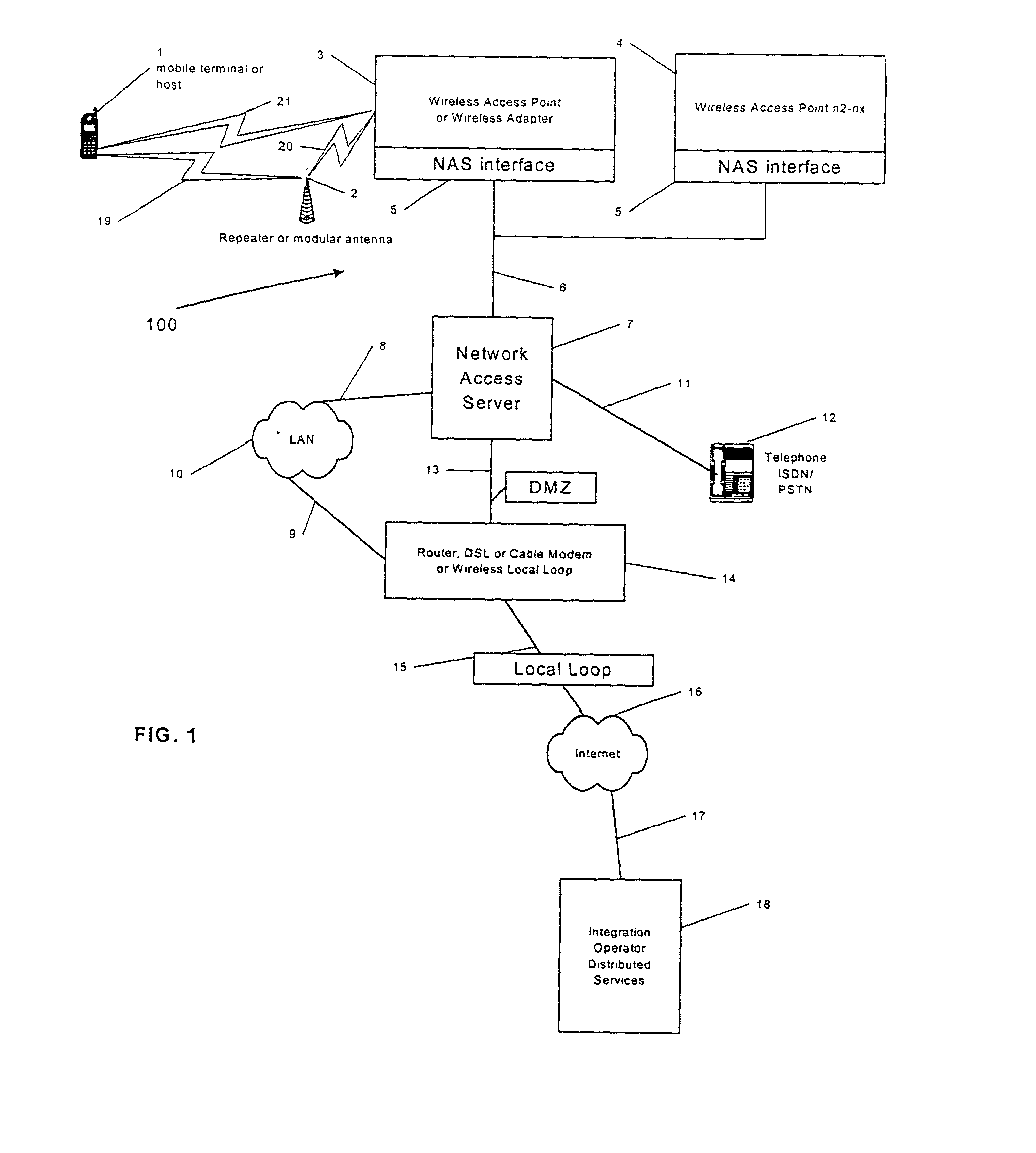
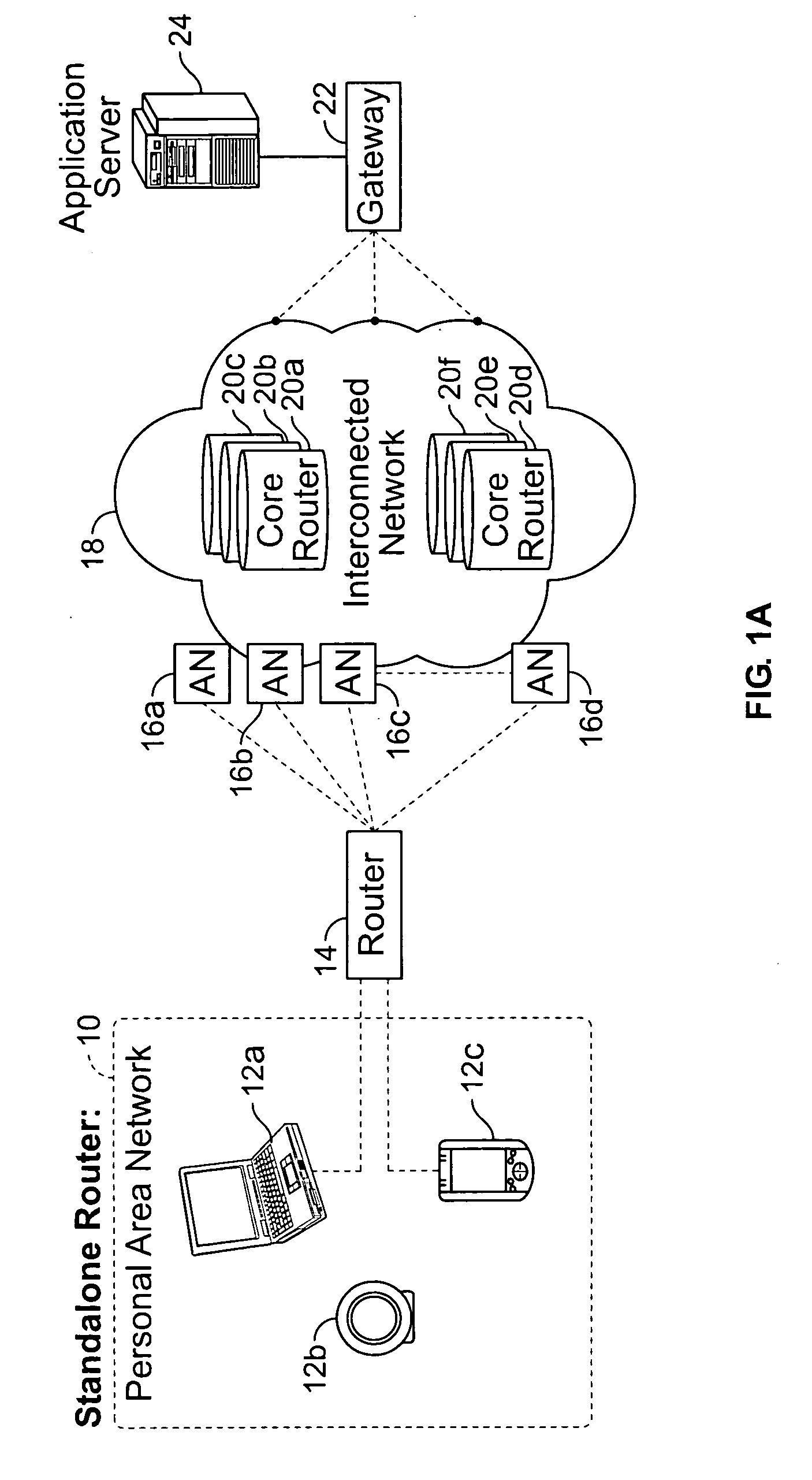
A system and method are disclosed for providing ubiquitous public network access to wireless, mobile terminals using private networks having private network access points and connections with the public network. The wireless, mobile terminals are permitted to use wireless, radio frequency communication devices comprising private network access points. A network access server (NAS) is associated with each wireless, radio frequency communication device and provides an interface between the wireless, mobile terminals and the private network. The NAS controls registration of wireless, mobile terminals as subscribers, and provides public network access to the mobile terminals through the private network's access point and public network connection. The NAS also restricts access by the mobile terminals to the private network, meters network useage by the mobile terminals, and controls use of bandwidth by the mobile terminals. The NAS also interfaces with integration operator distributed services over the public network. The integration operator services include databases and servers for storing and providing subscriber and network provider information for subscriber registration, network access and useage control, and accounting purposes. The NAS may be provided as a standalone element embodied in a computer, or may be integrated with the wireless radio frequency device and / or a network adaptor device for the private network.
Owner:NTT DOCOMO DCMR COMM LAB USA
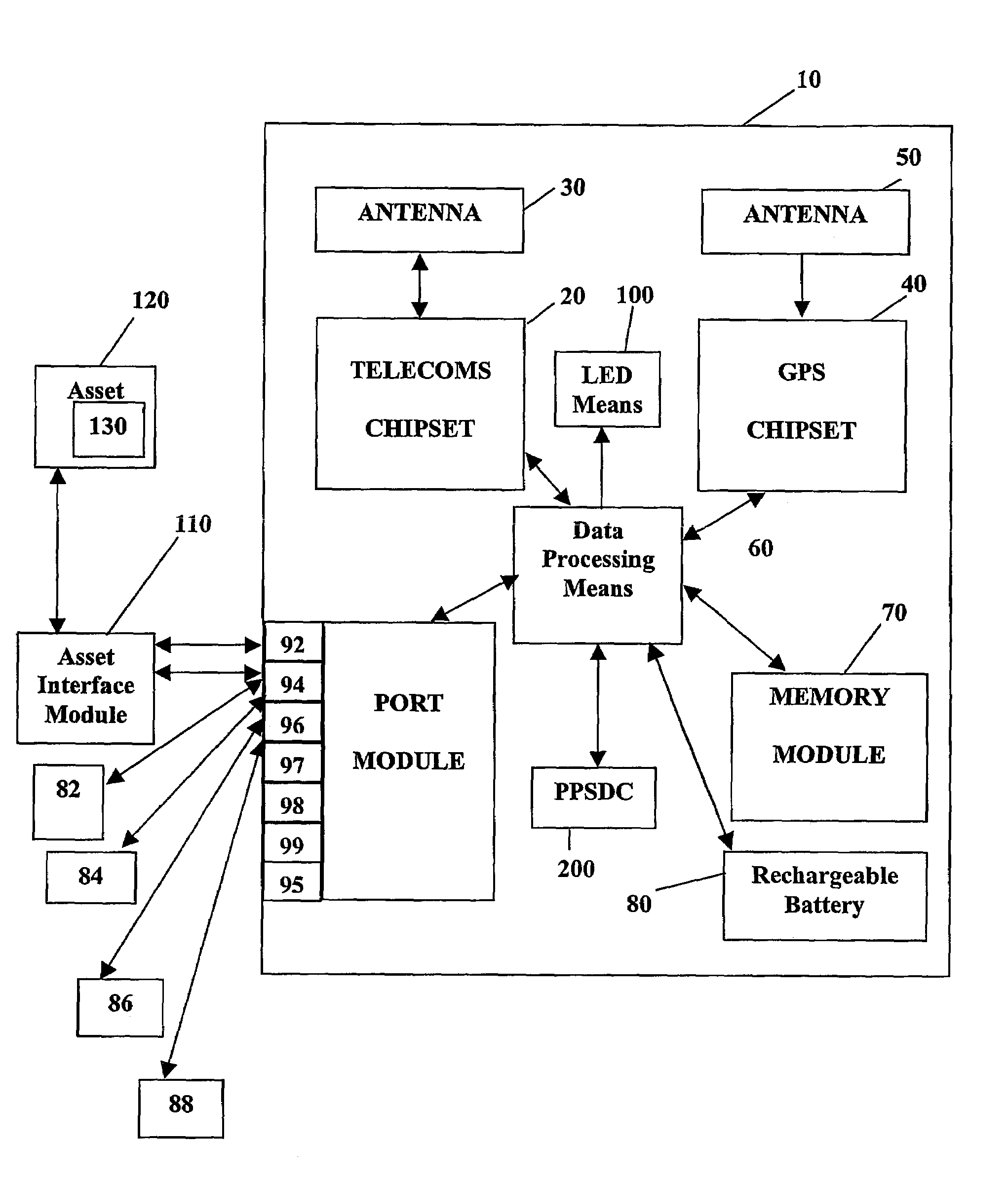
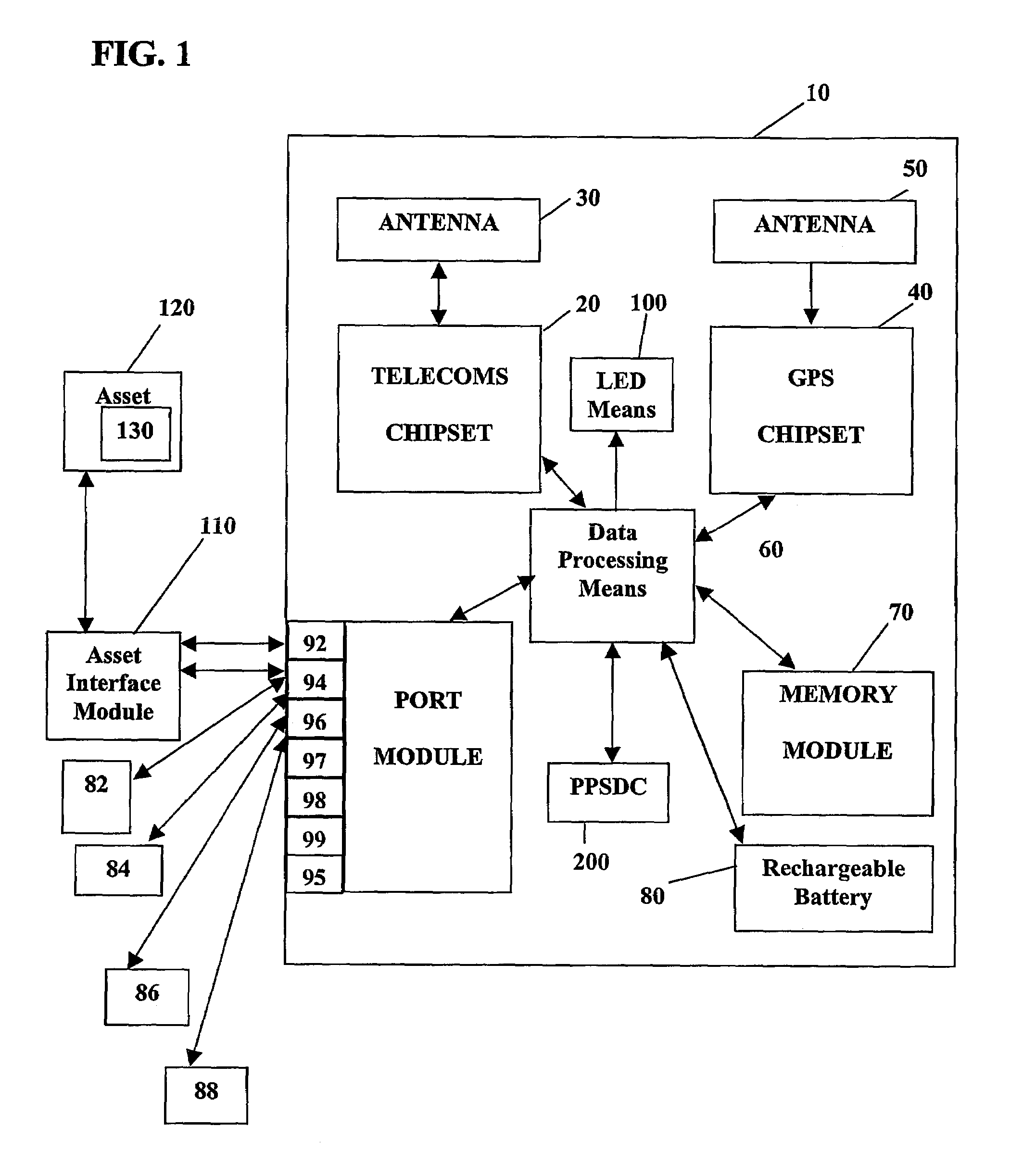
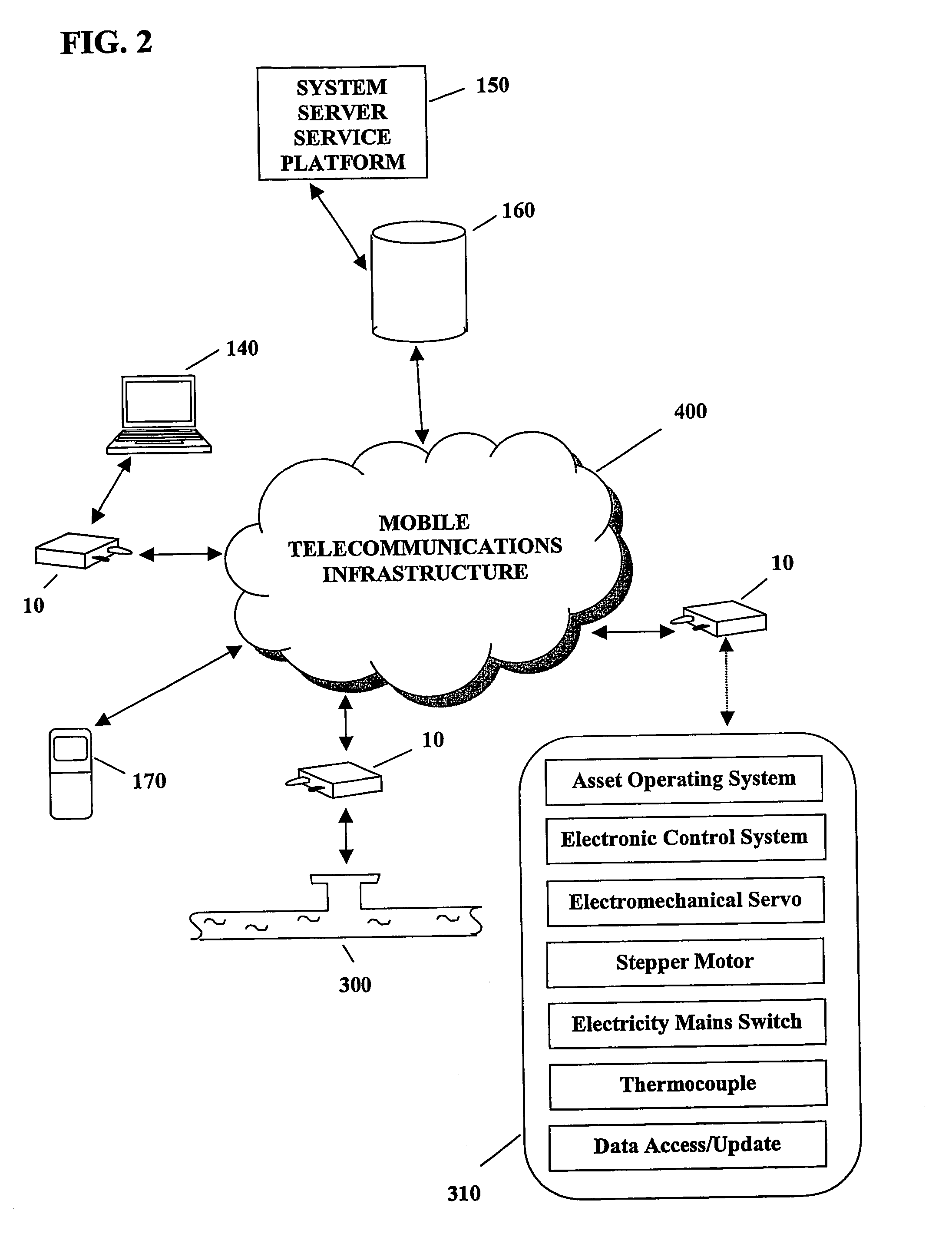
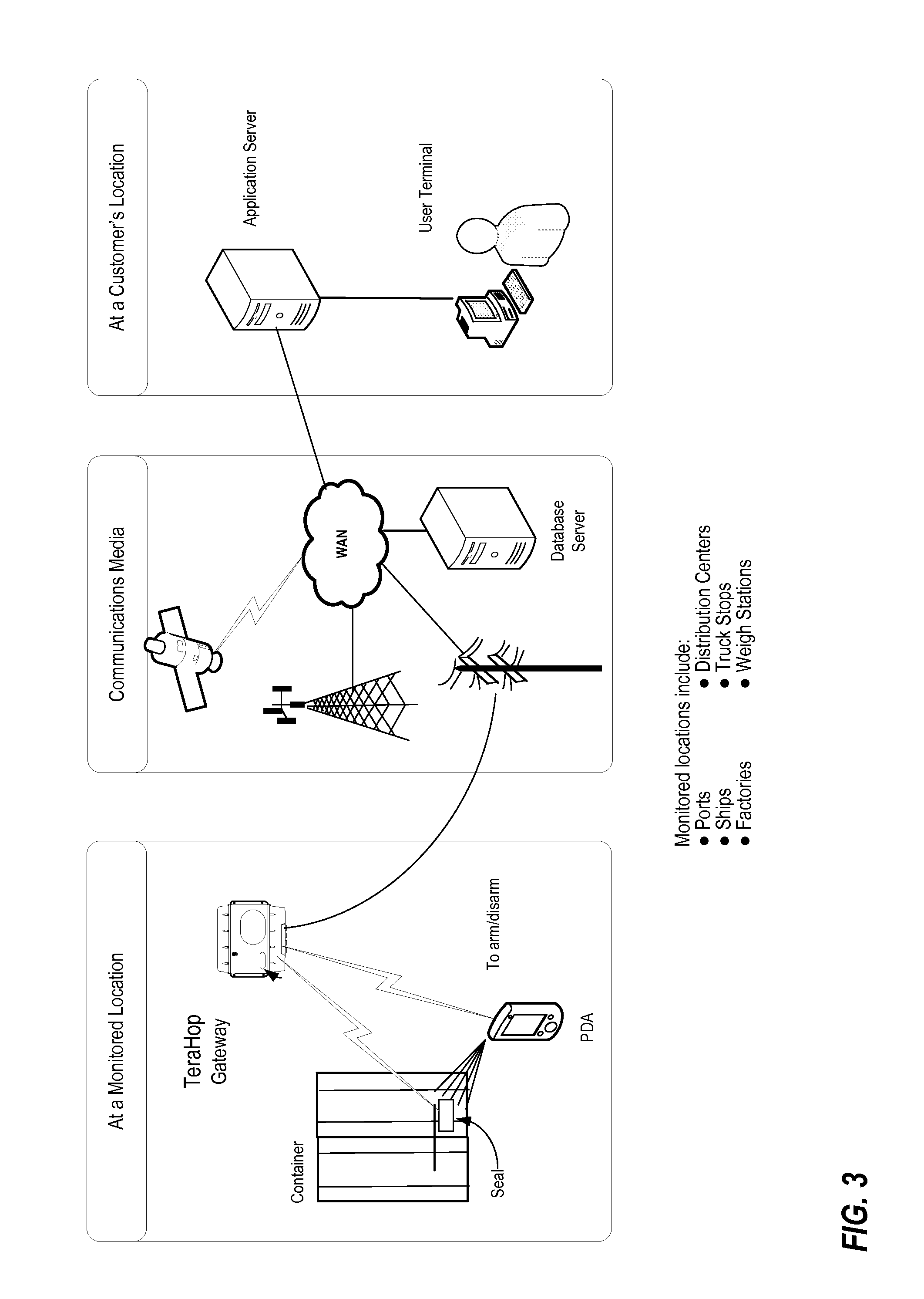
System and method for monitoring and control of wireless modules linked to assets
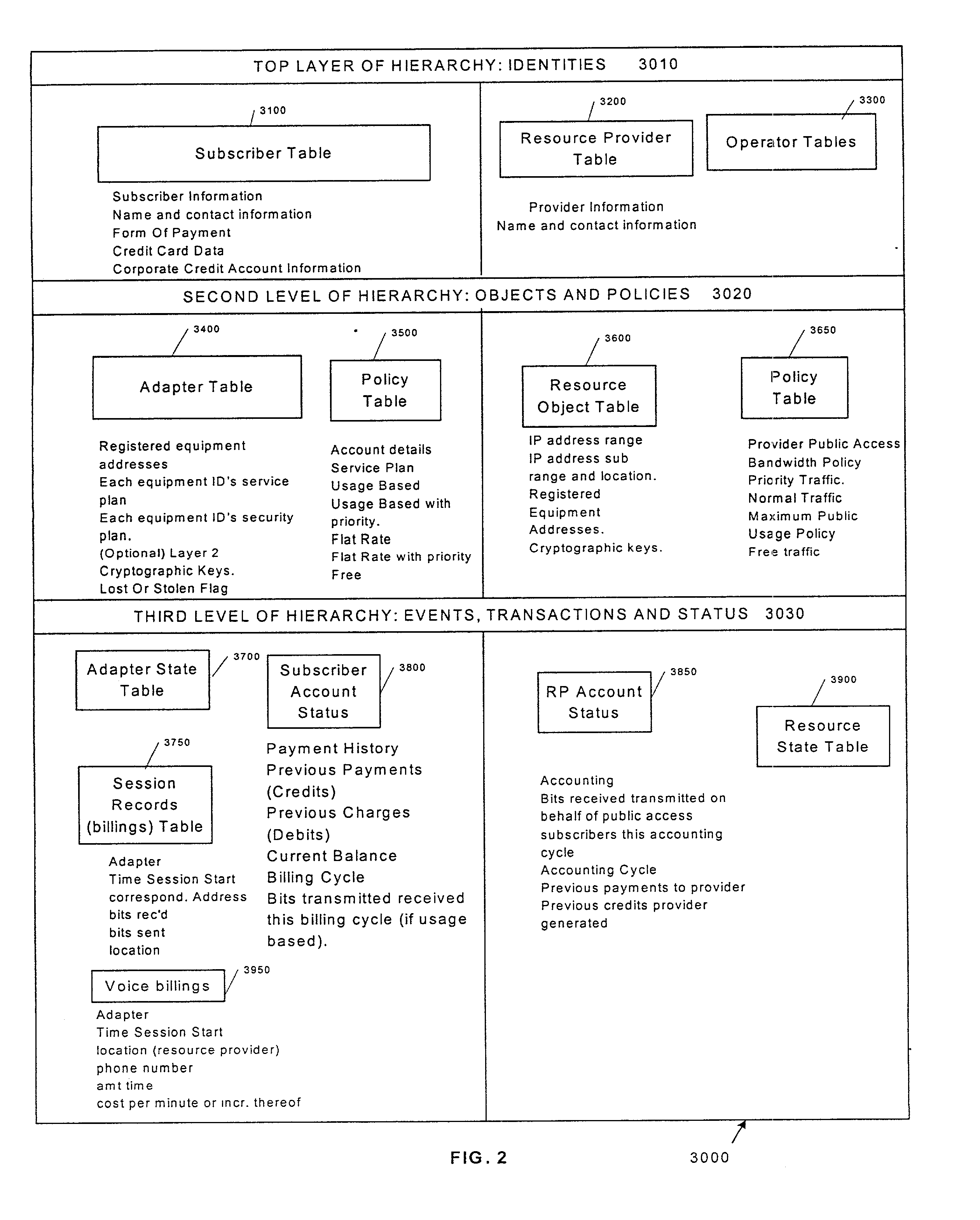
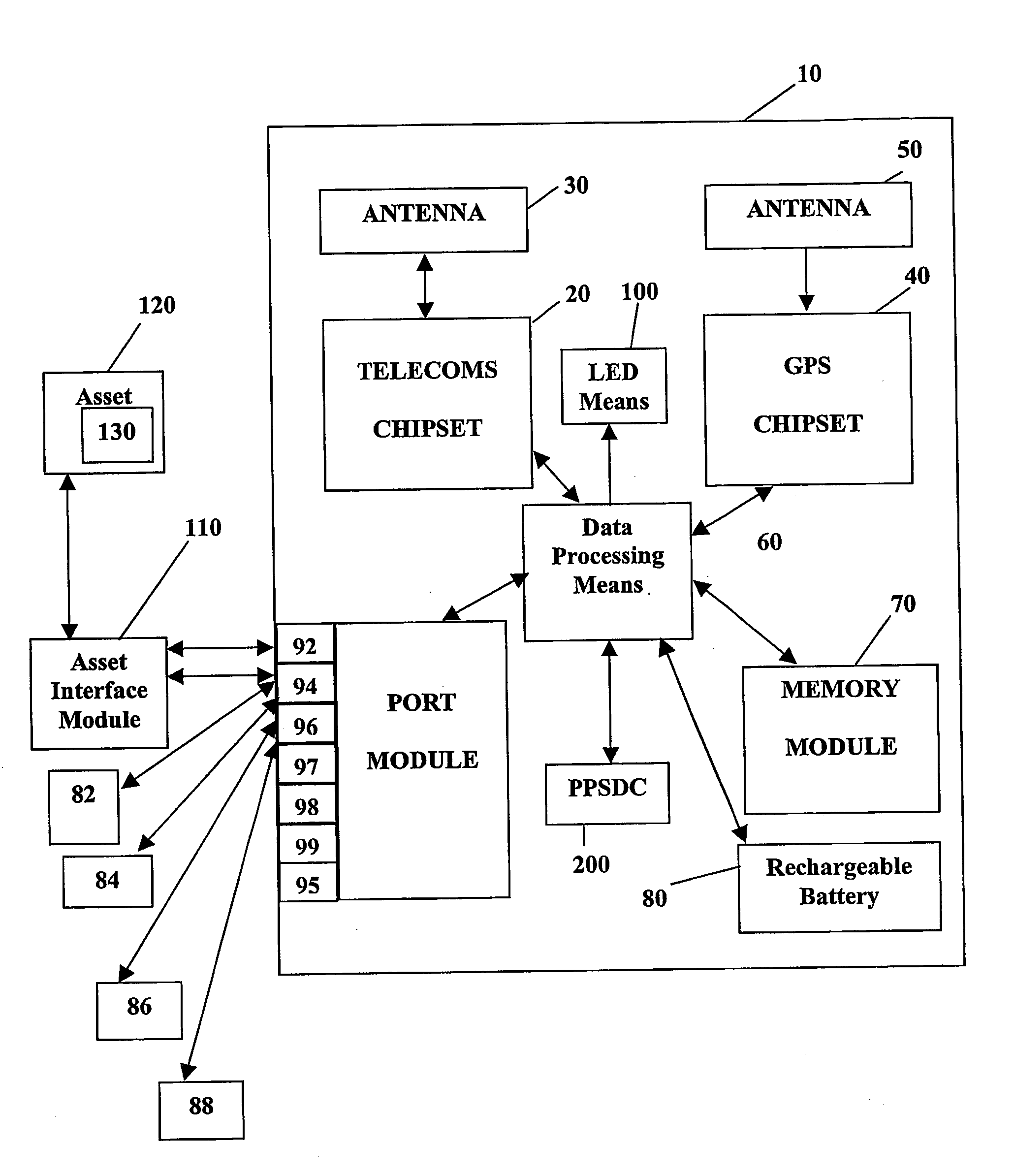
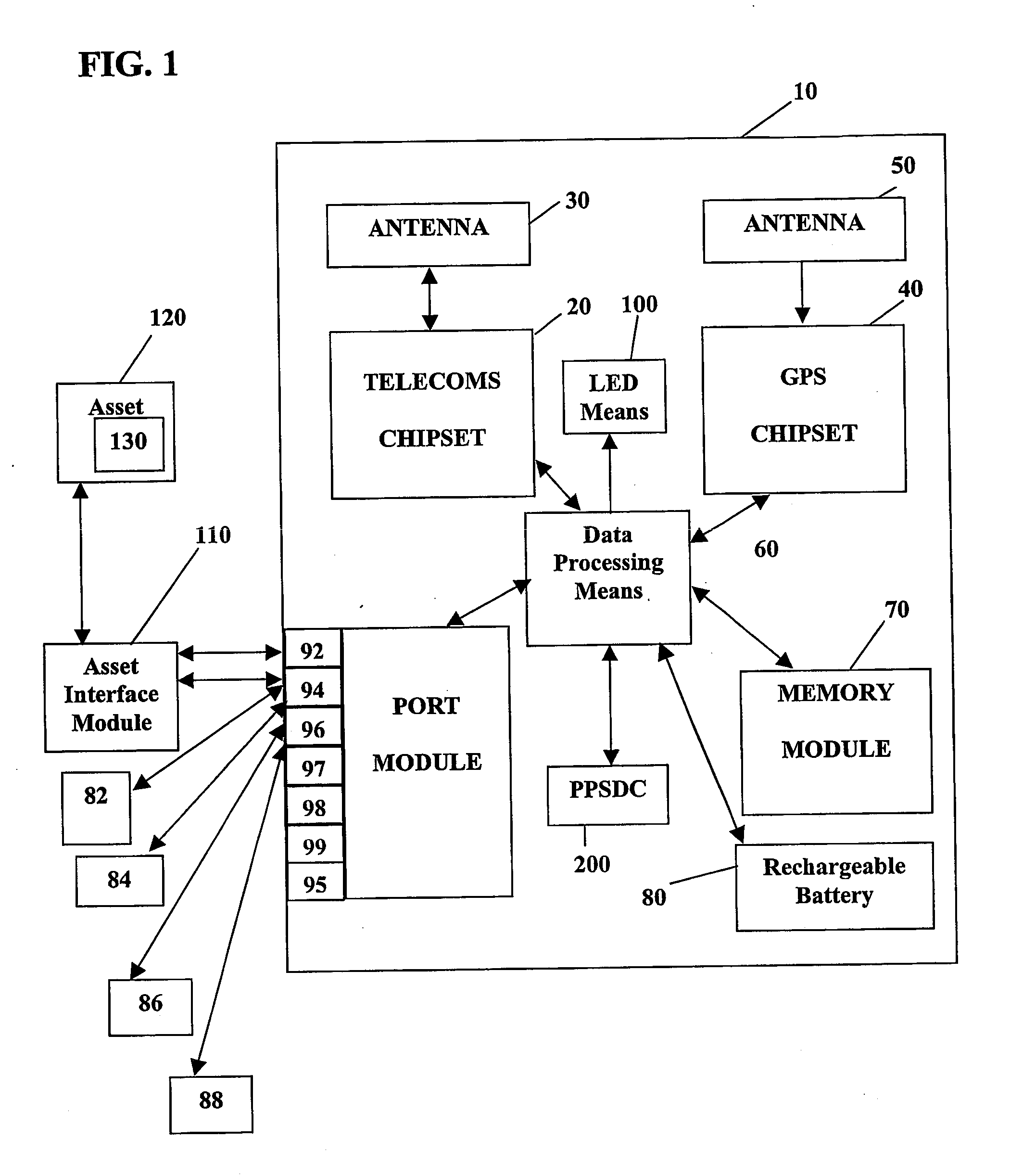
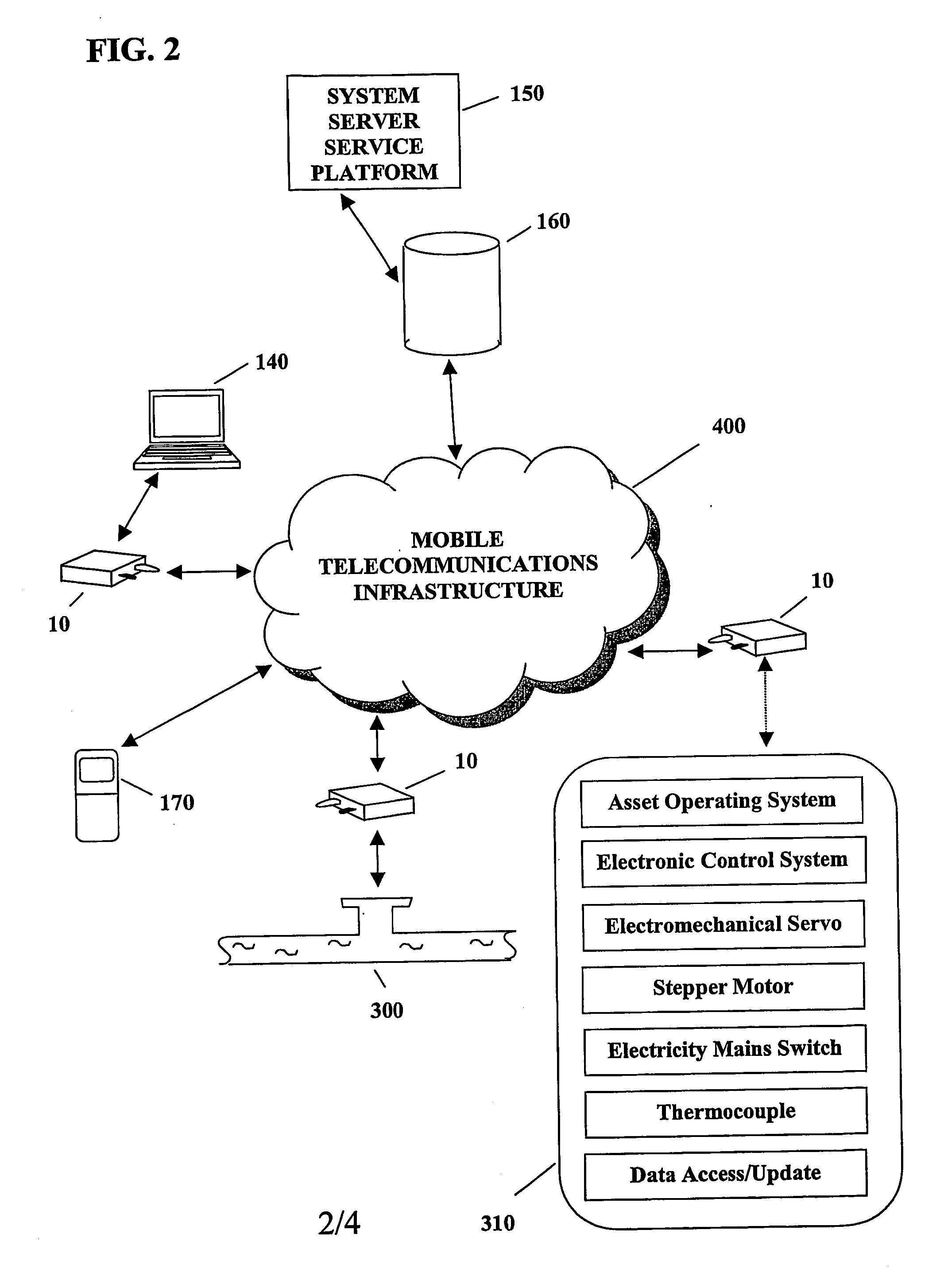
A system and method for remote asset management is described which can provide the basis for a diverse product group including an improved remote location monitoring system, a means for communicating with and for monitoring the status and or location of a plurality of diverse assets, as well as the means for communicating with said assets for the purpose of modifying the operational status of one or more of said assets according to one or more stored data parameters such as location, use, battery power, and such like. The remote asset management system comprise a wireless module, which is associated with at least one of the plurality of assets and which is interfaced with the operating system of said asset and or with an electromechanical control means, which may control one or more features of the operation of said assets. A supporting network-based, or internet-based service platform controls and manages the status of each of the plurality of assets, either automatically, or in response to received messages from fixed or wireless communication devices, and which is capable of selectively communicating data to said assets for changing the operational status of said assets according to pre-programmed conditions.
Owner:M2M SOLUTIONS
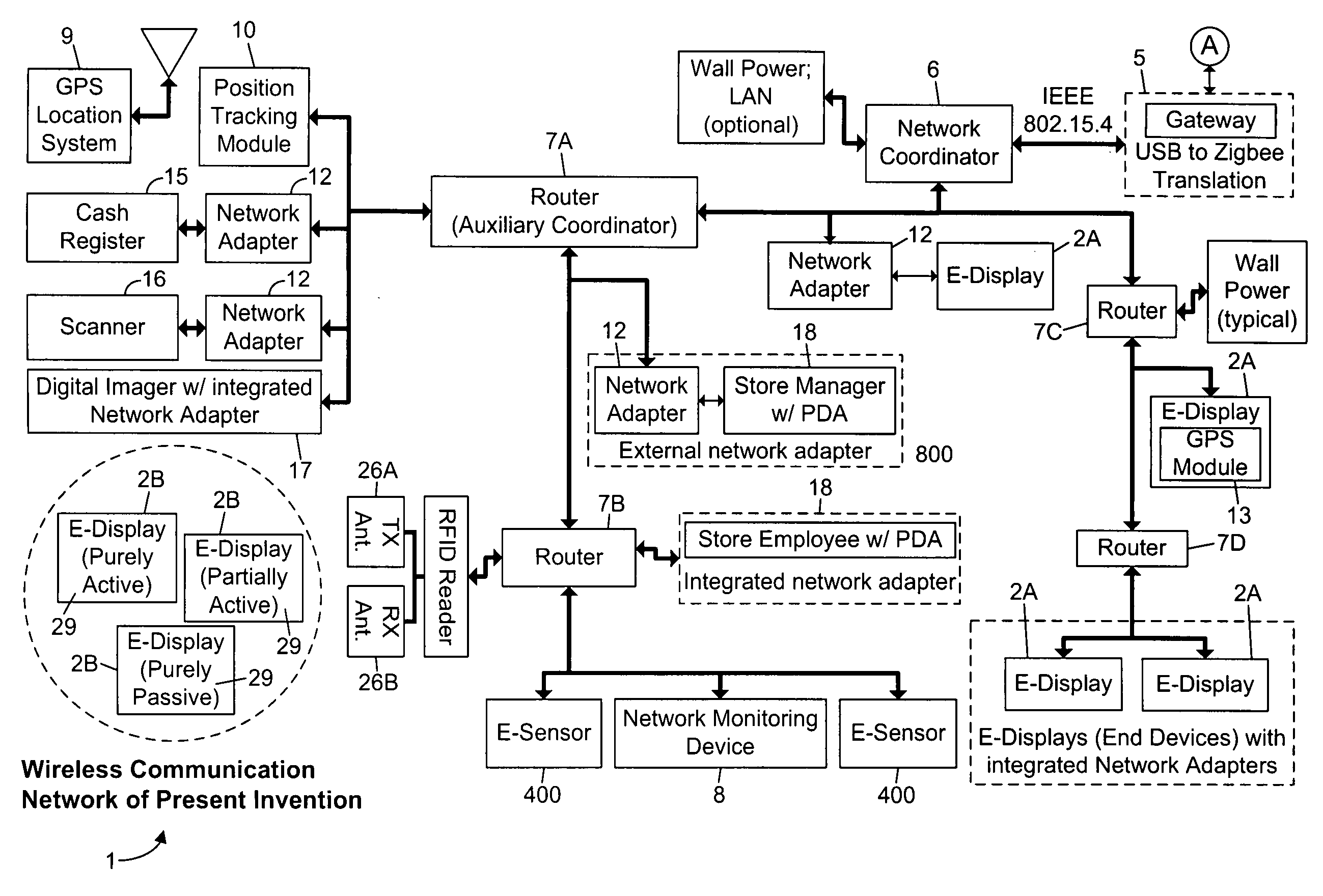
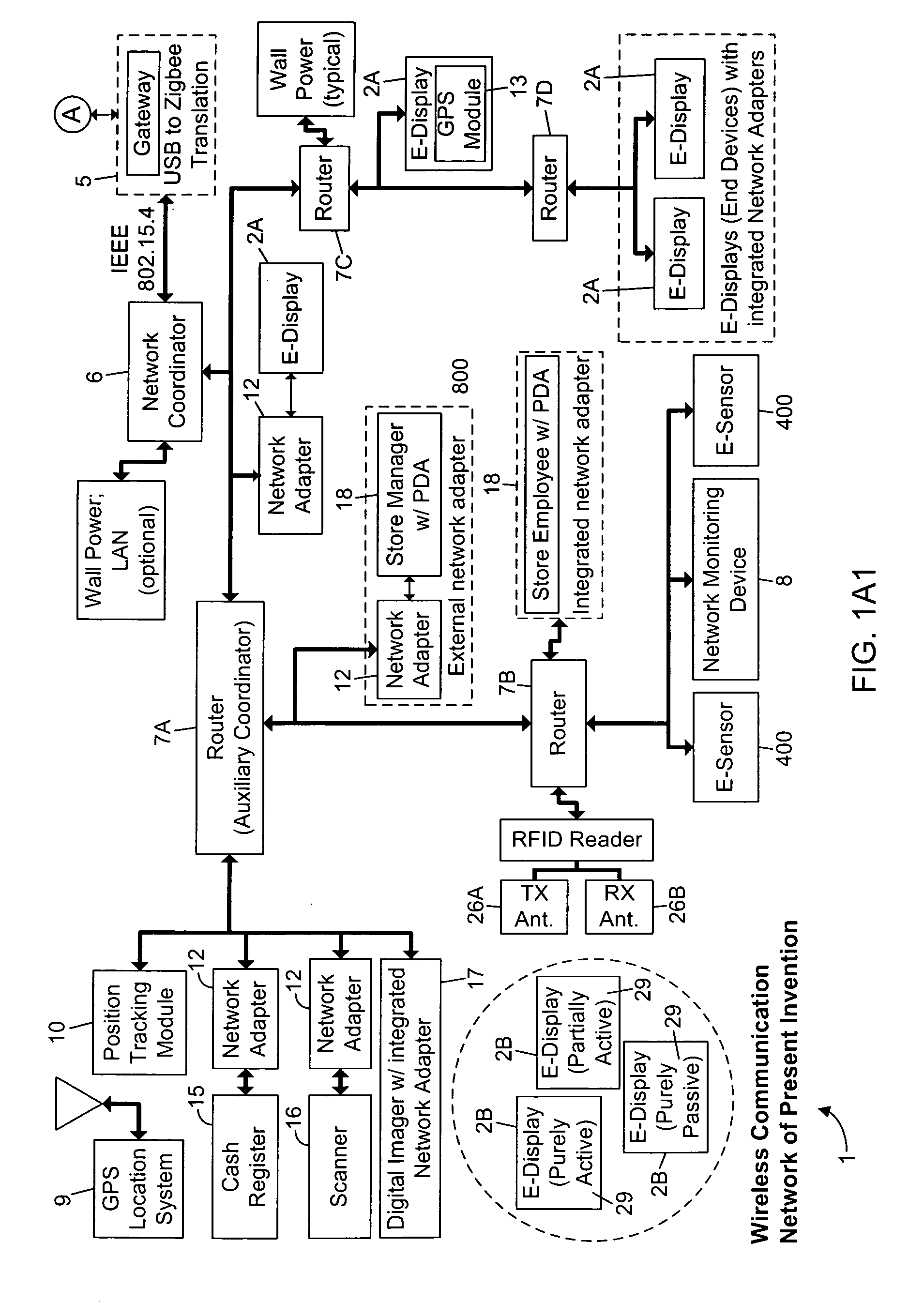
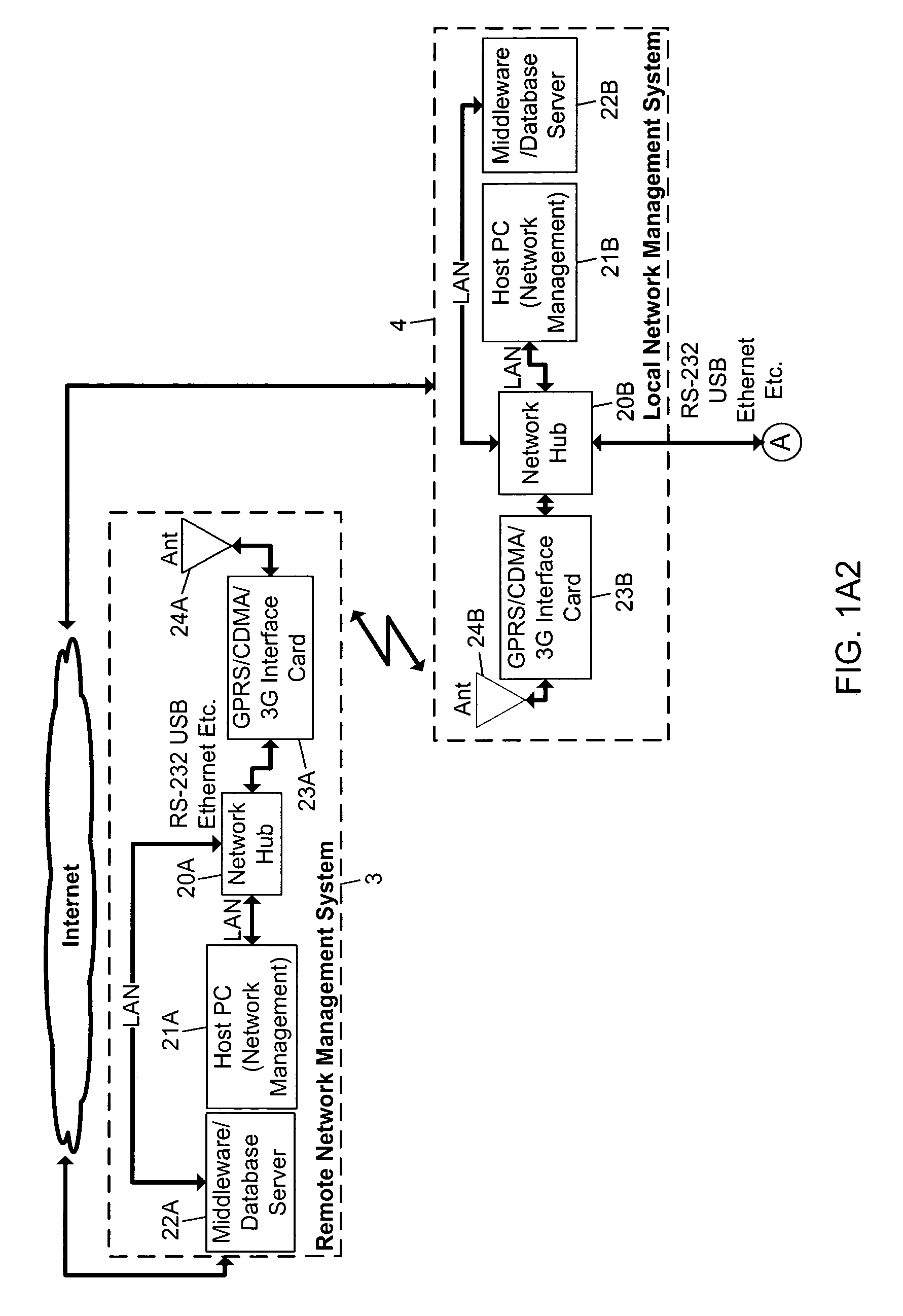
Methods of and apparatus for programming and managing diverse network components, including electronic-ink based display devices, in a mesh-type wireless communication network
InactiveUS20100177749A1Static indicating devicesDigital data processing detailsLogistics managementDisplay device
A wireless communication network for programming and monitoring a plurality of network-managed devices, including electronic-ink based display devices, comprising a network management computer system, a network gateway device, one or more wireless network routers, a plurality of network-managed devices, and a network coordinator. The wireless communication network of the present invention bridges the gap between wireless display networks, wireless sensor networks, and the worlds of passive, active and partially-active RFID and real-time locating systems. The wireless communication network of the present invention allows conventional communication network protocols to operate in more flexible ways in dynamic, diverse, and heterogeneous application environments, in fields including retail, healthcare, transport, logistics, manufacturing, education, etc. At the same time, the wireless communication network of the present invention is preferably based on the IEEE 802.15.4 network layer standard, which offers low-cost wireless network communication between a large number of wireless network end-devices.
Owner:METROLOGIC INSTR
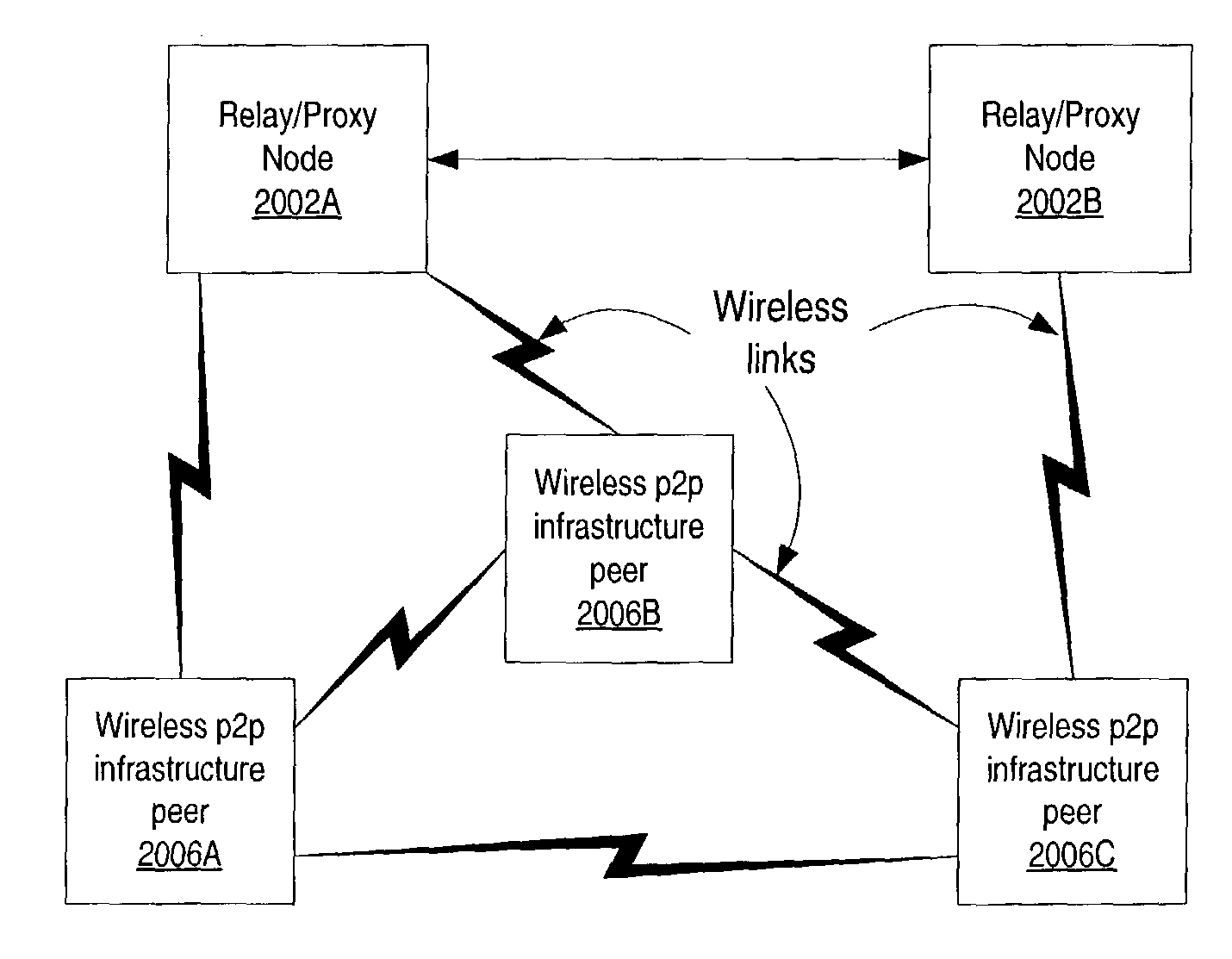
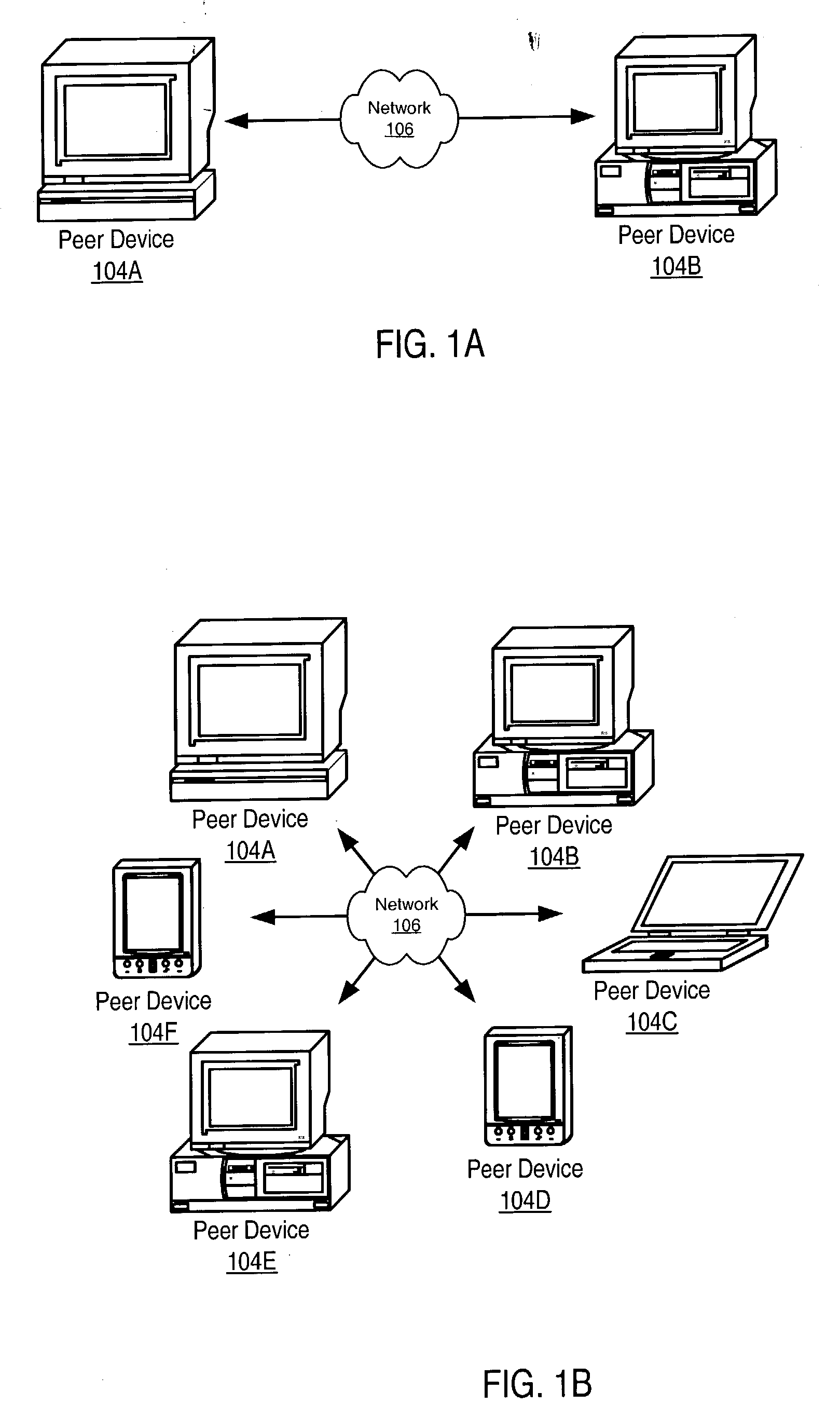
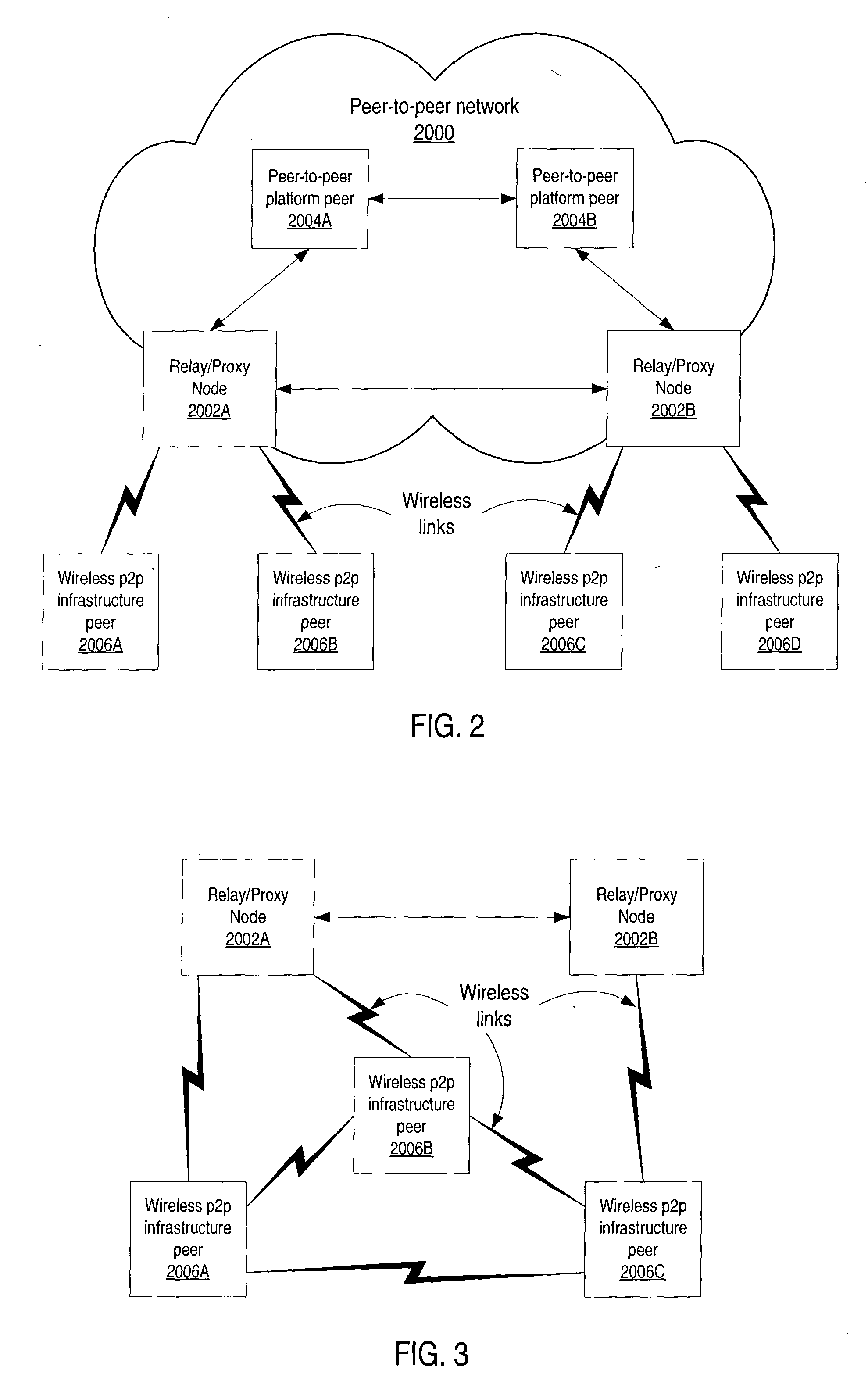
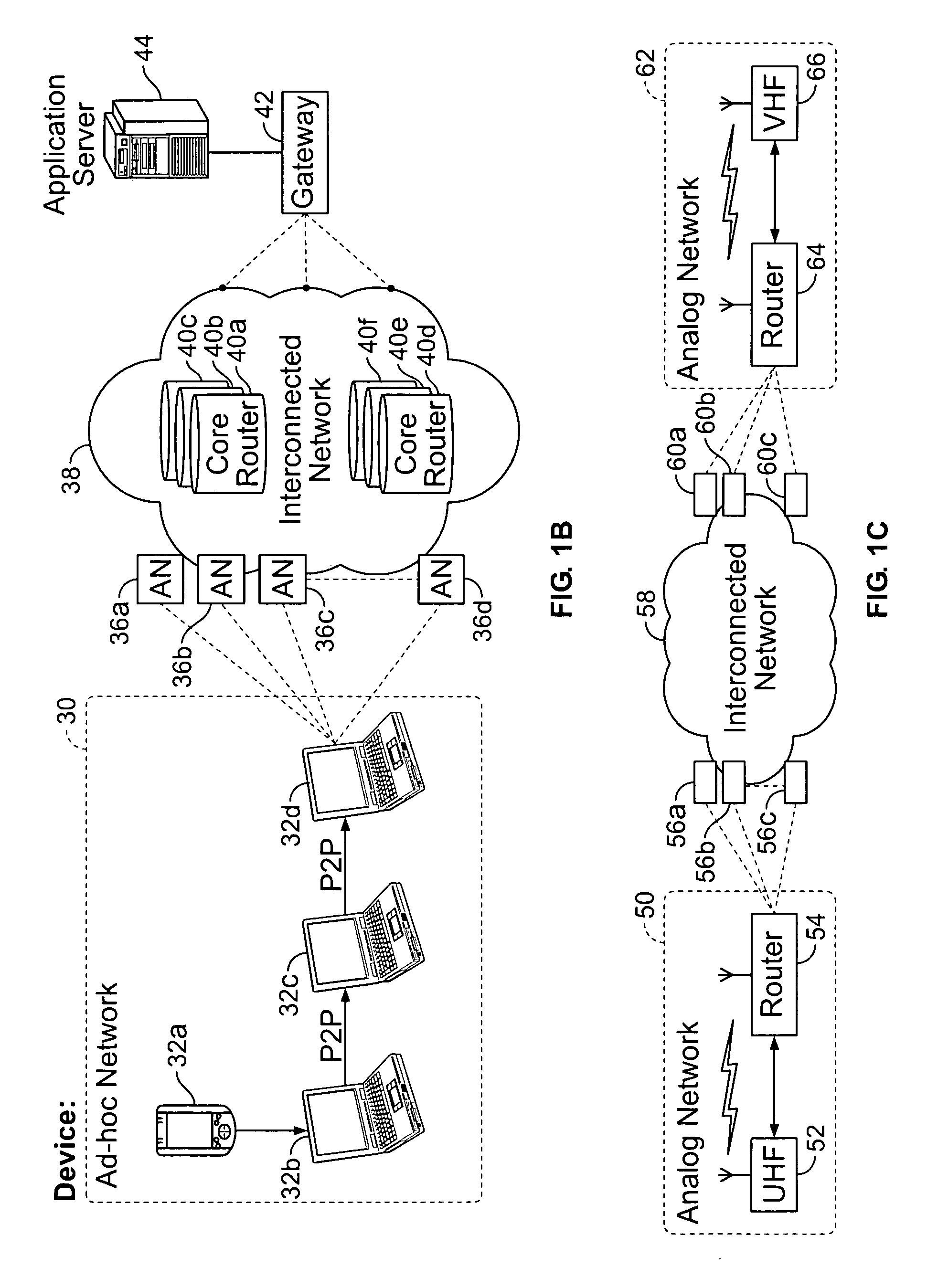
Infrastructure for accessing a peer-to-peer network environment
ActiveUS20040162871A1Multiple digital computer combinationsBroadcast service distributionLimited resourcesWireless connectivity
Embodiments of a system and method for providing peer-to-peer (p2p) capabilities to devices with limited resources (e.g. wireless devices). A mechanism is described that allows the devices to participate as peer nodes in p2p network environments through wired or wireless connections. In one embodiment, the p2p network environment may be implemented according to a p2p platform, and the mechanism may be interoperable with p2p platform devices in the p2p network environment. A relay / proxy node on the network may serve as an interface to the p2p environment for devices using the mechanism to participate as peers in the p2p network. The relay / proxy node may be accessed using the mechanism to perform one or more p2p network environment functions on behalf of the devices.
Owner:ORACLE INT CORP
System for providing mobile VoIP
ActiveUS20050286466A1Preserve battery lifeLow power capabilityPower managementNetwork topologiesMobile deviceHandover
A system for providing handoff for a mobile devices comprising a mobile phone programmed to automatically handover between differing data bearers and to optimally detect those bearers in a roaming environment keeping power consumption to a minimum. Repeating means for these mobile devices to extend the range of coverage and the protocol for that coverage.
Owner:TRUPHONE
Wireless communications apparatus and method
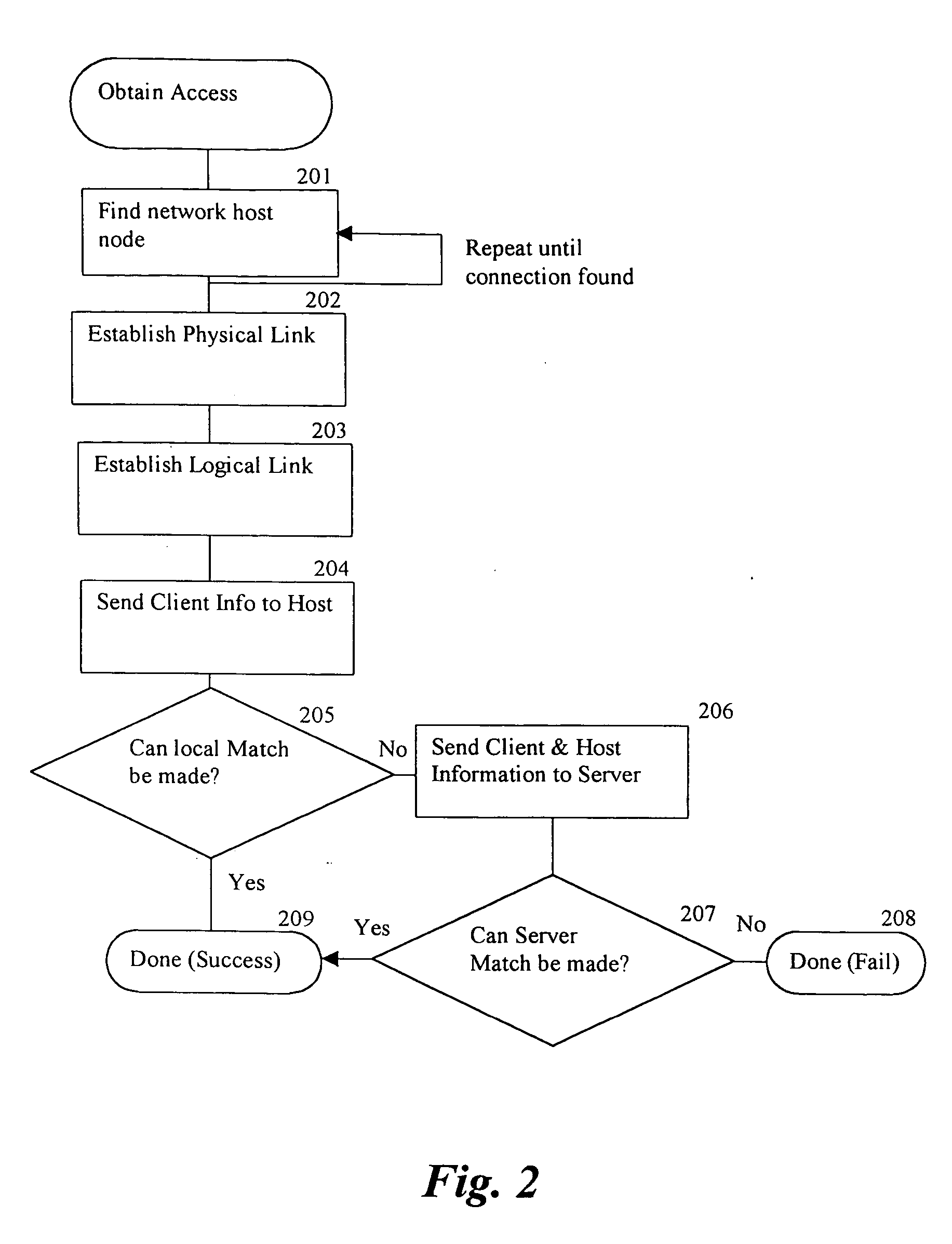
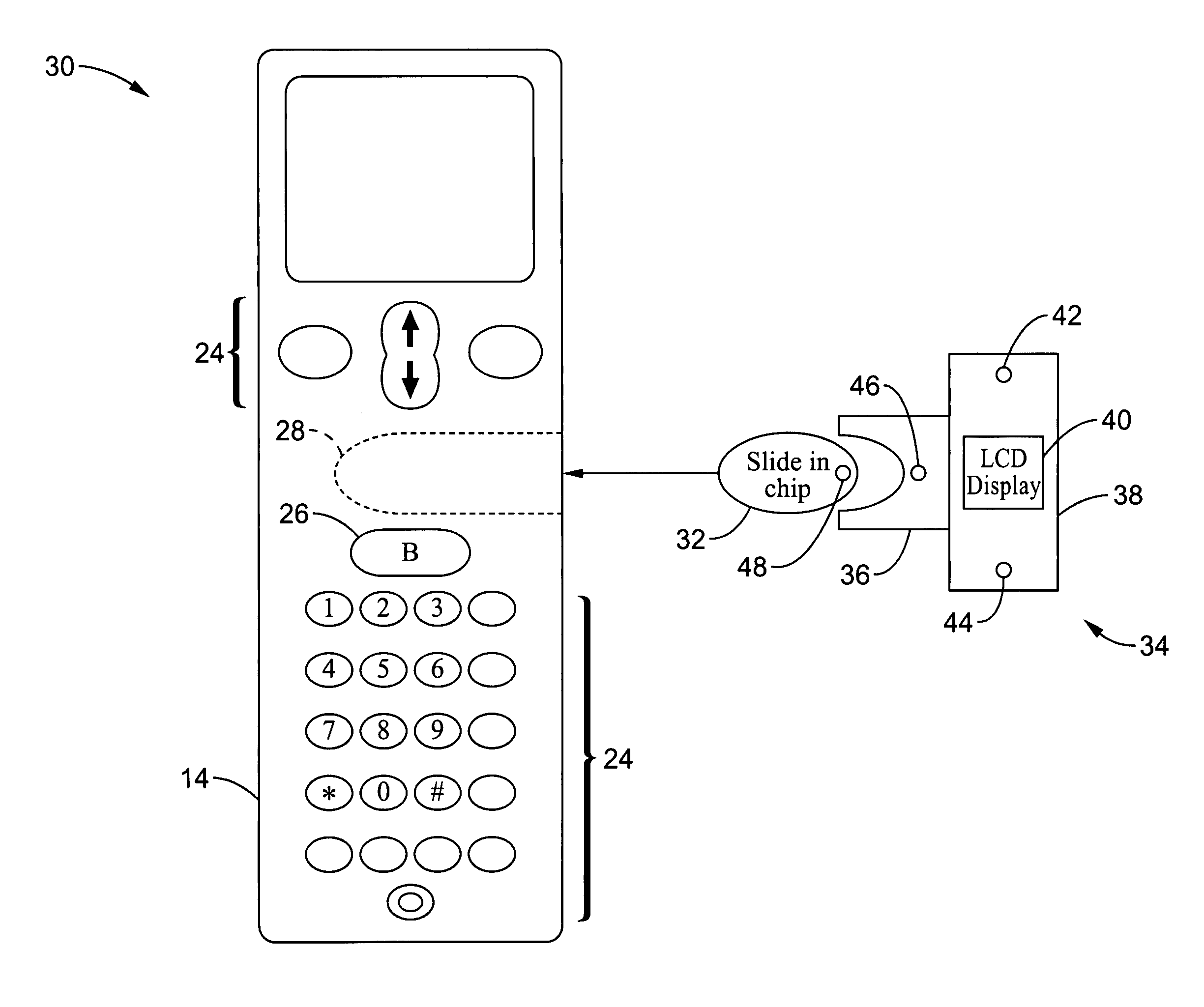
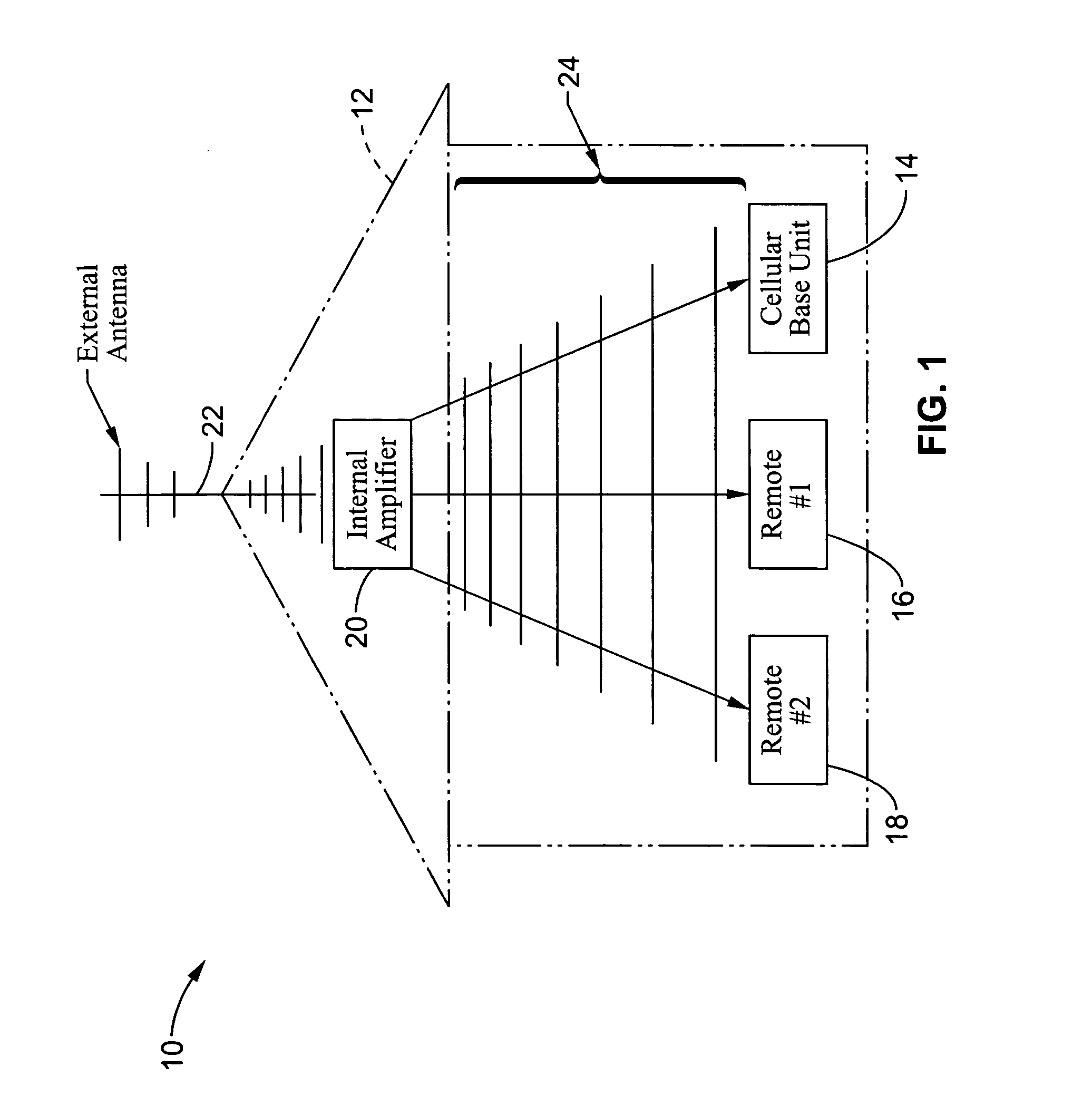
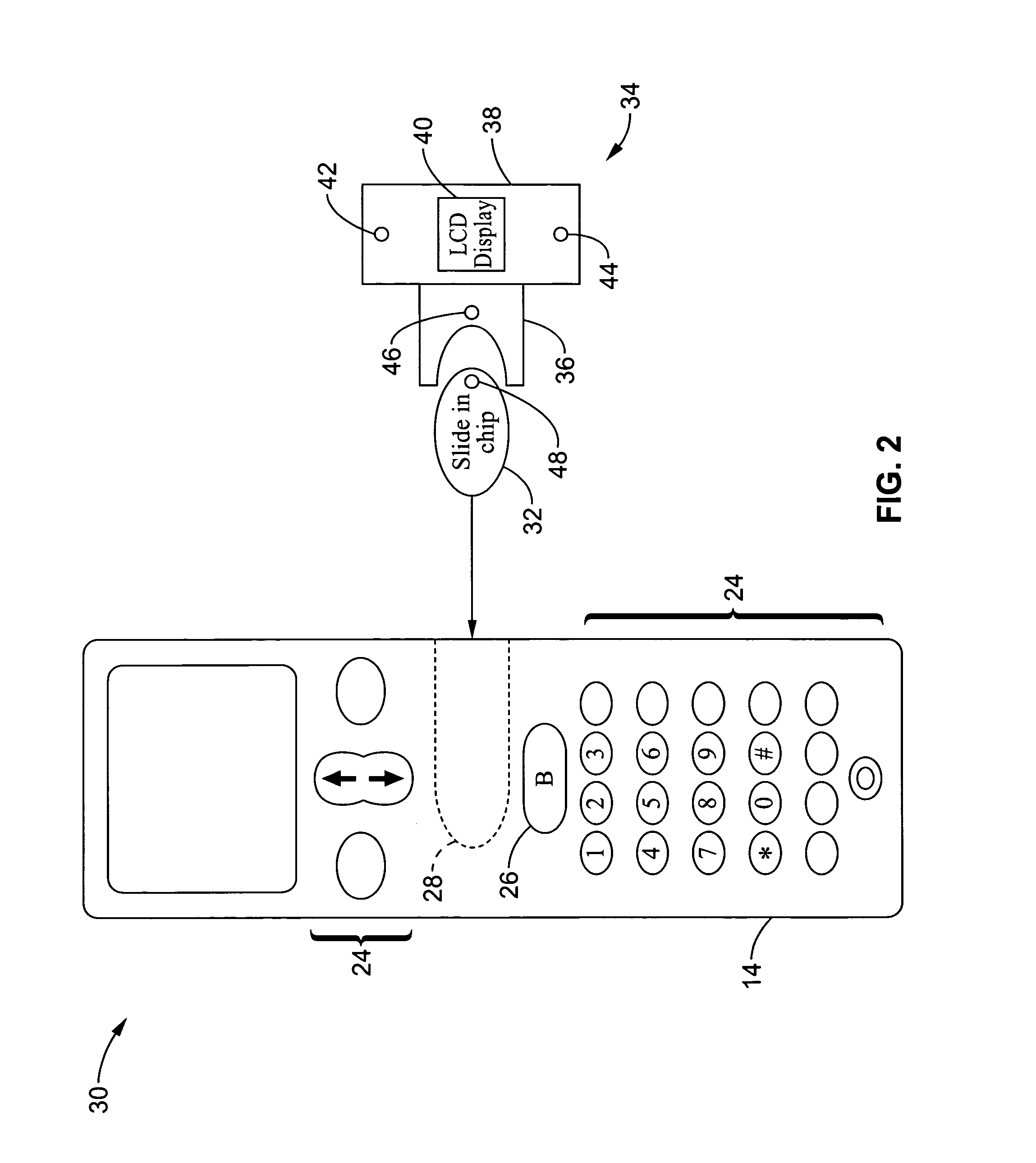
InactiveUS7146191B2Easy to be stolenProcess safetyUnauthorised/fraudulent call preventionEavesdropping prevention circuitsInterconnectivityDisplay device
A wireless communication method and apparatus are described for increasing security for communication devices utilizing identification chips for accessing wireless networks and the associated billing for services. One aspect of the invention is an enhanced phone chip and a communications device adapted to engage the enhanced phone chip, which then cannot be installed or removed from the wireless communications device by unauthorized users. In one embodiment a security key mates to the identification chip and is utilized for installing and removing the enhanced phone chip. The security key preferably has a display upon which information about the communication device is displayed prior to removing the security key after installing the enhanced phone chip. Other aspects of the invention include wireless base station communication devices which support wired (dedicated and non-dedicated), and more preferably wireless extensions, while providing sharing of wireless network resources and interconnectivity between base station and extensions.
Owner:US THERMOELECTRIC CONSORTIUM
Apparatus and method for delivering information to an individual based on location and/or time
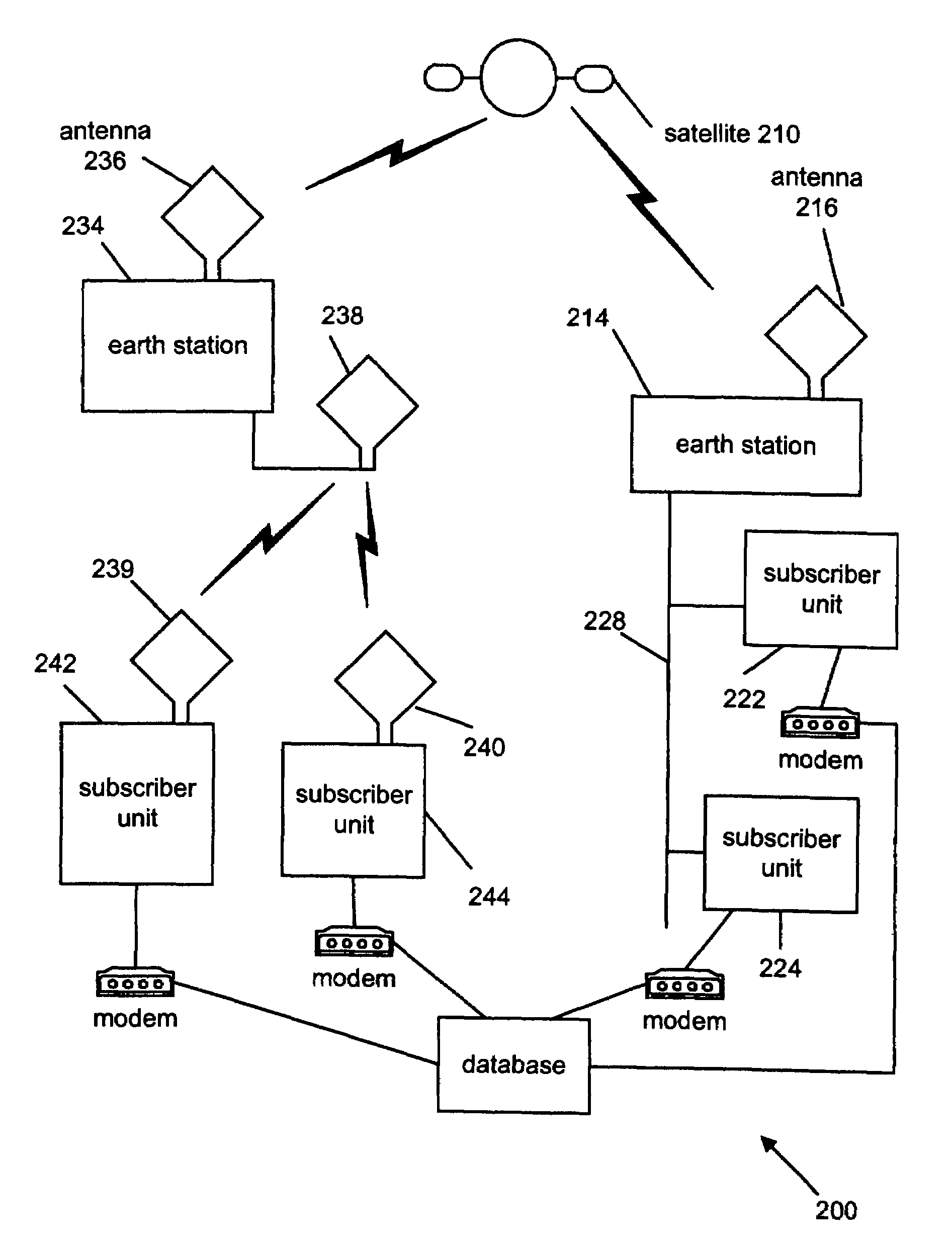
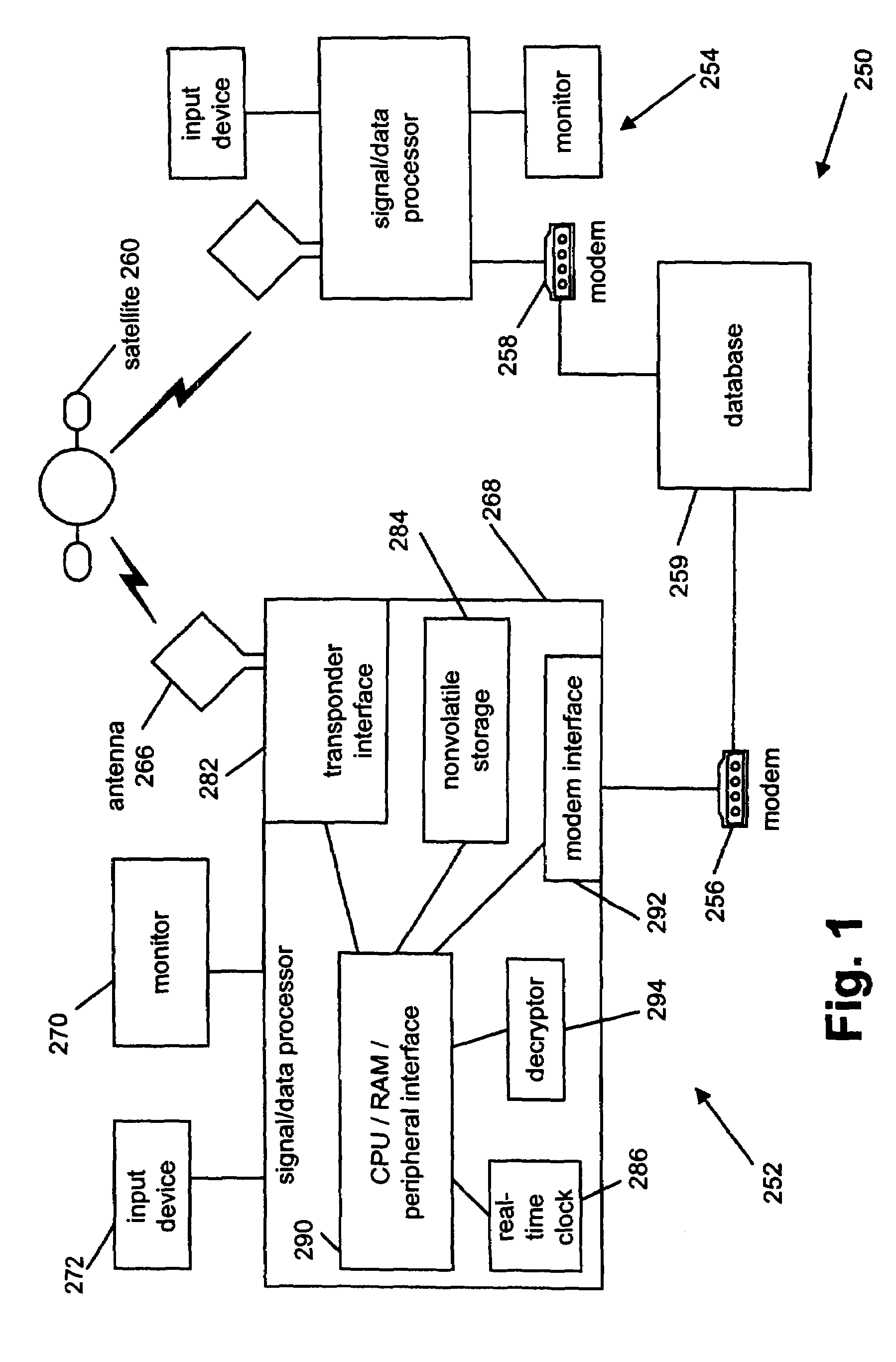
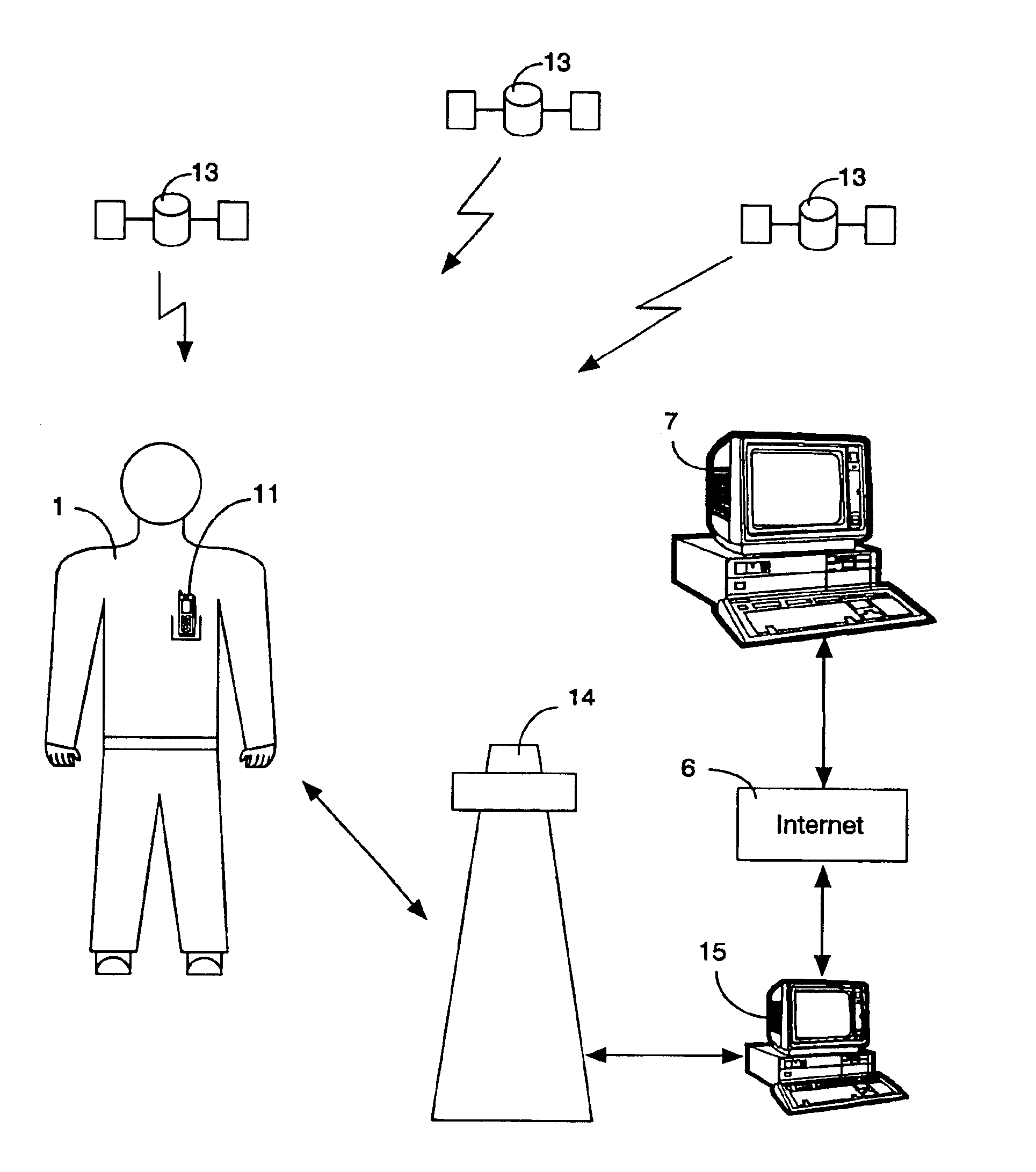
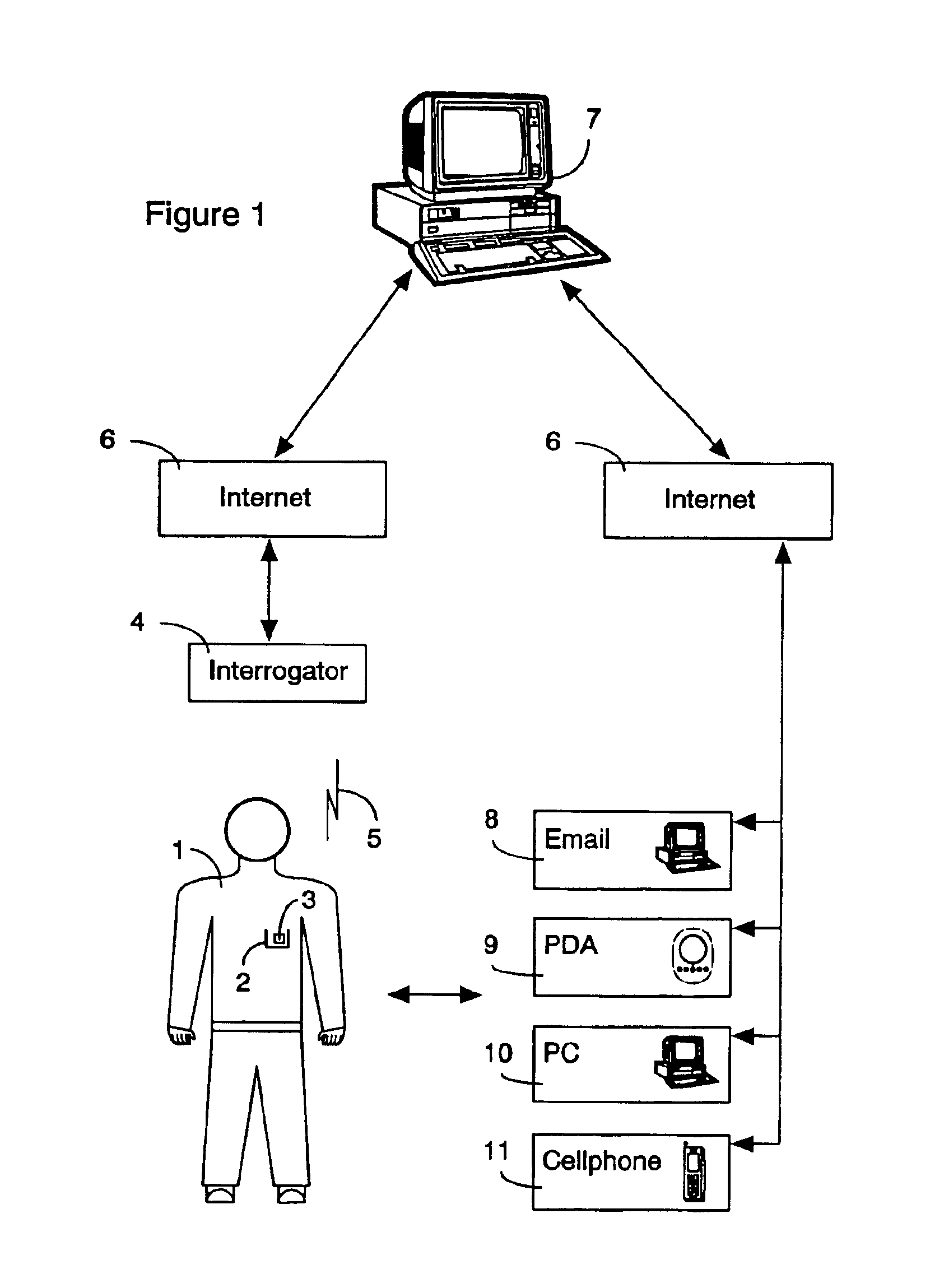
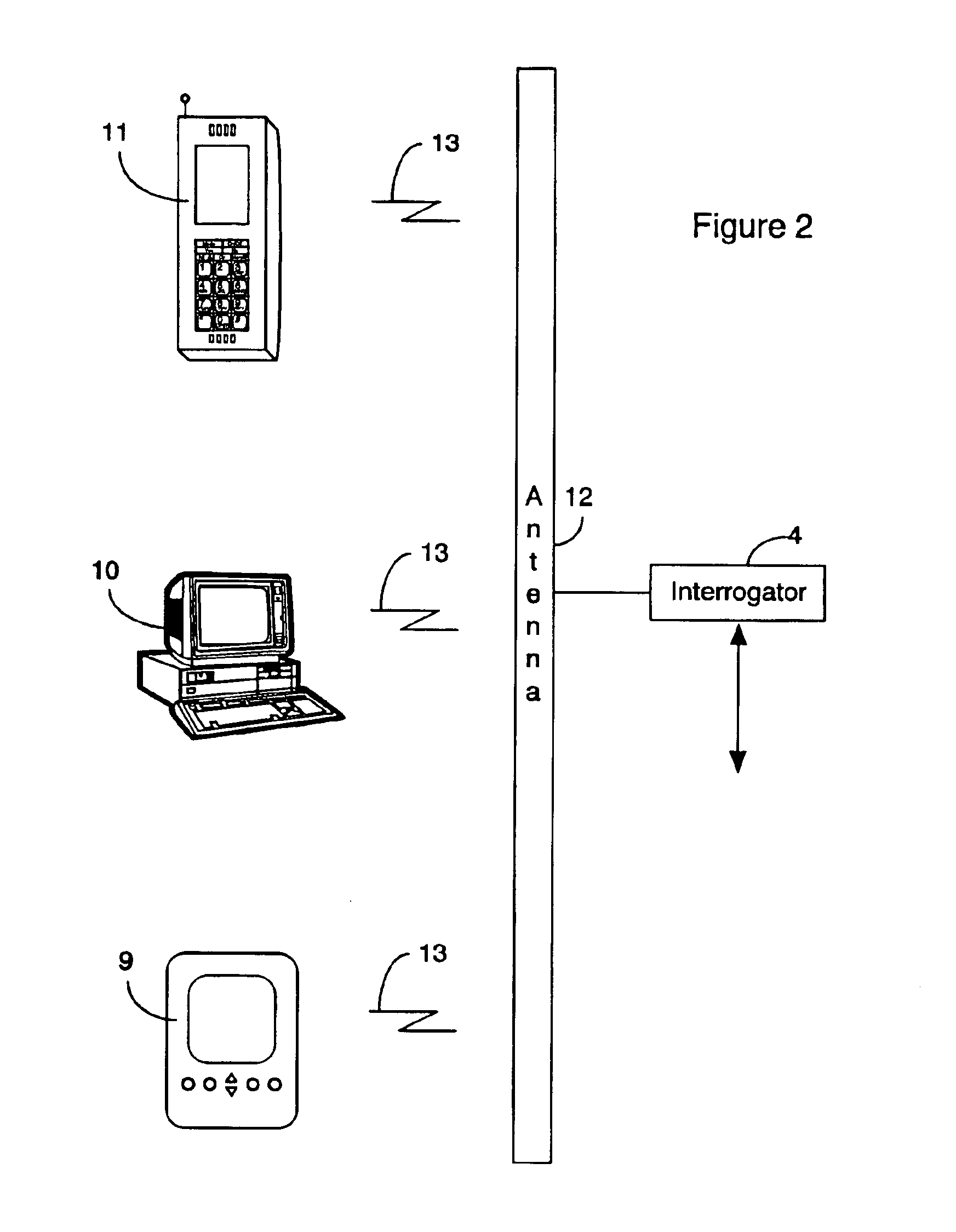
InactiveUS6912398B1The location information is accurateWireless commuication servicesMarketingPagerThe Internet
A time / location information delivery system that provides focused advertising and / or other information to individuals based on the time and their location. A wireless identification device is carried by an individual and can be read from or written to when the individual passes by interrogators in a specific geographic location. The detectors read ID information embedded in the wireless identification device. A computer uses the ID and location information to select, from a list of information providers, those information providers which provide information content identifiable or correlated to a location and / or time, and is of interest to the individual. The information content can be forwarded to the individual by a variety of information channels. One channel uses conventional Internet email to deliver advertisements and other information to the individual's Internet mailbox. The email can be delivered to a conventional PC, a portable computer, a PDA, an intelligent telephone, pager or other suitable device. For ease of discussion, a pager and a PDA will be referred to collectively as a PDA. The wireless identification device can be an RFID tag embedded in a card, or even a wireless telephone. The RFID tag is read or written to by fixed interrogators and the location of the wireless telephone is detected by triangulating information from cell towers or by embedding the GPS receiver in the wireless telephone thereby providing the location information directly from the telephone. Of course, other nearly identical location determination means, such as quadrangulation could also be used. The location determination can be performed through similar means with other devices such as PDAs, laptops, pagers, etc.
Owner:CDN INNOVATIONS LLC +1
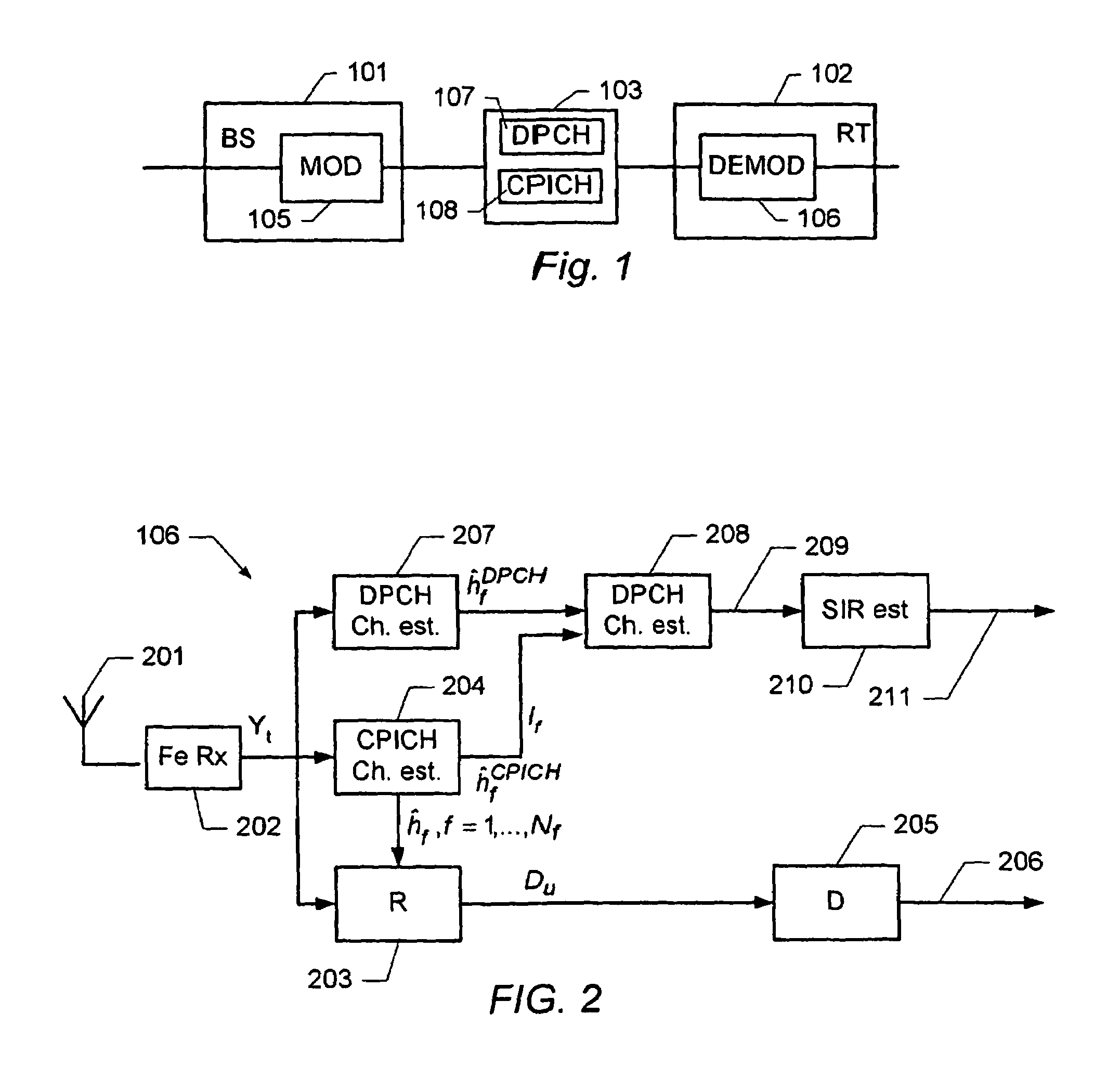
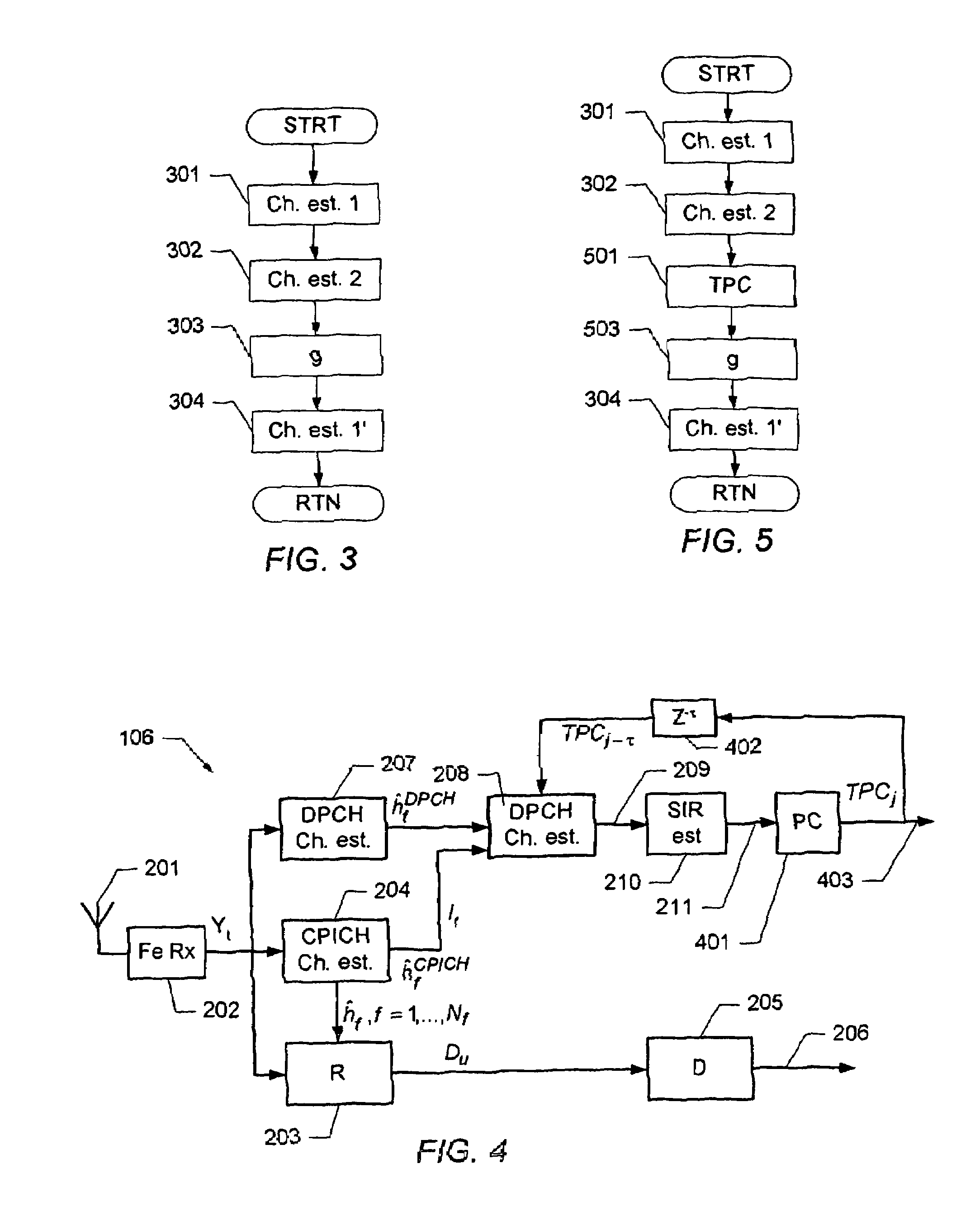
Determination of a channel estimate of a transmission channel
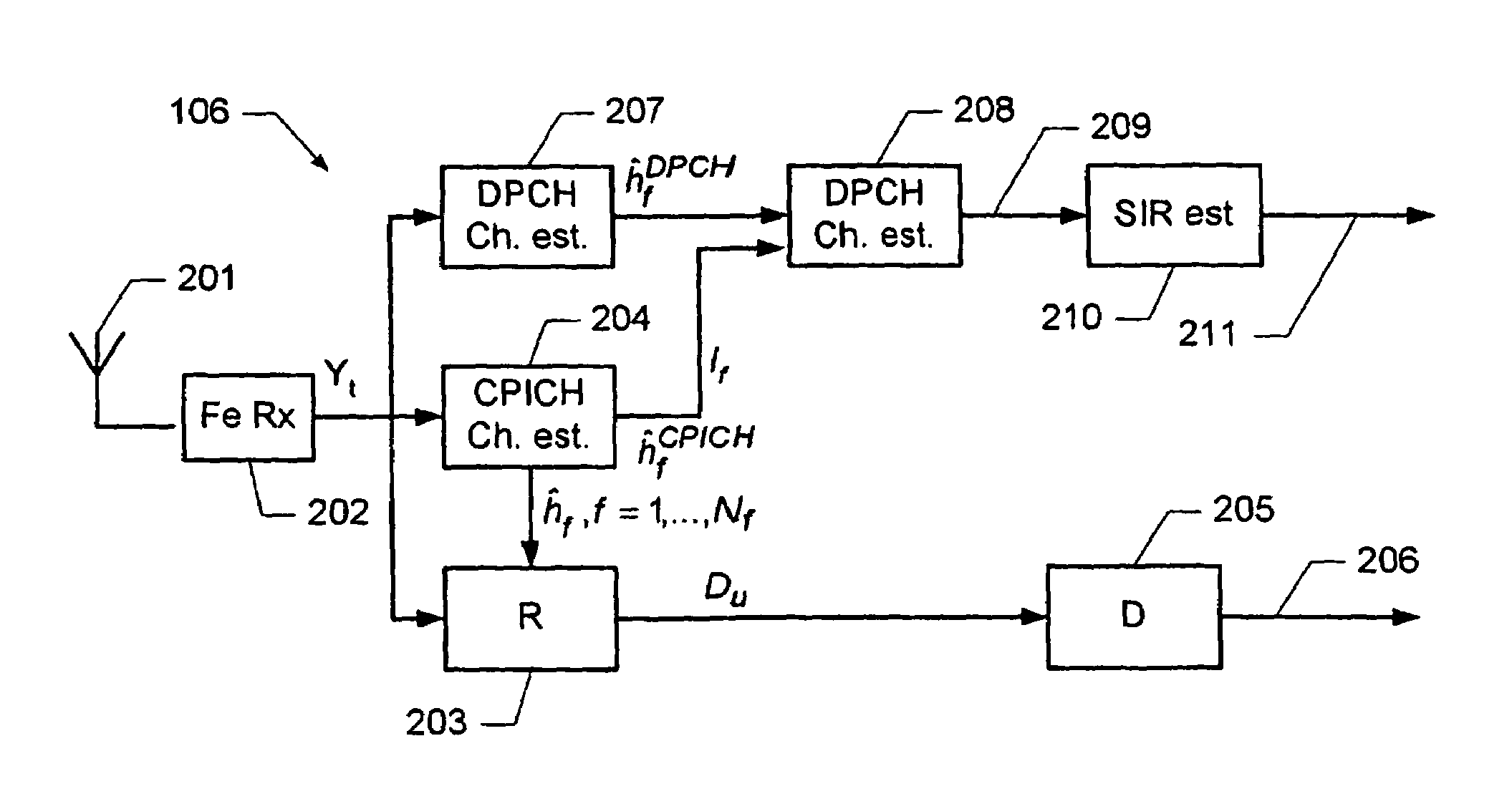
ActiveUS7561637B2Good estimateChannel estimate for one of the channels is improvedMultiplex system selection arrangementsSpecial service provision for substationCommunications systemTransmission channel
A method of determining a channel estimate of a first transmission channel in a communications system. The method comprises deriving a first set of channel estimates from symbols received through said first transmission channel; deriving a second set of channel estimates from symbols received through a second transmission channel in the communications system; determining a scale factor between the first and second sets of channel estimates from a least squares error criterion; and determining the channel estimate of the first transmission channel as a channel estimate of the second transmission channel scaled by the determined scale factor.
Owner:TELEFON AB LM ERICSSON (PUBL)
Method and system for seamless roaming between wireless communication networks with a mobile terminal
A mobile computer system capable of seamless roaming between wireless communication networks includes data processing resources for executing software, a plurality of wireless interfaces that supports simultaneous wireless connections with first and second wireless communication networks, and a network access arbitrator that routes data communicated between the software executed by the data processing resources and the first and second wireless communication networks. To permit seamless roaming, the network access arbitrator routes the data to the first wireless communication network via a first wireless interface and then seamlessly reroutes the data to a second wireless communication network via a second wireless interface. According to one embodiment, the network access arbitrator reroutes the data in response to the data bandwidths of the connections with the first and second wireless communication networks.
Owner:NORTEL NETWORKS LTD
System and method for providing communication services to mobile device users incorporating proximity determination
InactiveUS20070030824A1Disadvantages can be reduced eliminatedWeb data retrievalTelephonic communicationComputer networkMobile device
In certain embodiments, a method for proximity determination includes receiving one or more network identifiers, each associated with a corresponding network, from a first mobile device. The method further includes receiving one or more network identifiers, each associated with a corresponding network, from a second mobile device. The method further includes processing the network identifiers received from the first and second mobile devices to determine whether the first mobile device and the second mobile device are in proximity to one another.
Owner:JAMBO NETWORKS
Authenticating Wireless Person-to-Person Money Transfers
InactiveUS20070255662A1Facilitates manualFacilitates automated load functionalityDebit schemesLock-out/secrecy provisionWireless transmissionComputer science
A technique is used to ensure the authenticity of a wireless transmission source which is requesting a transaction to be performed by a system. The transaction may be a person-to-person money transfer or other value exchange transaction. The wireless transmission source may be a mobile phone or other similar device. The wireless transmission source transmits a key with the transaction request. The system will determine the authenticity of the transmission based on the transmitted key. If the transmission is determined to be authentic, the transaction will be acted upon. Various approaches for determining authenticity are discussed. The technique may also be used to prevent acting upon duplicate transmissions.
Owner:OBOPAY MOBILE TECH INDIA PTE LTD
Multi-access terminal with capability for simultaneous connectivity to multiple communication channels
ActiveUS20060193295A1Improve reliabilityImprove behaviorNetwork traffic/resource managementTime-division multiplexTransceiverOperational system
An apparatus is disclosed for permitting a mobile terminal having multiple, heterogeneous network connections (e.g., multiple wired or wireless transceivers of various types) to set up and maintain virtual connections over multiple networks to either the same or to multiple destinations. The mobile terminal can “load-share” traffic, i.e., it can distribute segments of traffic over a full set of heterogeneous networks, significantly improving the reliability and availability of communications. In a first embodiment, a mobile terminal is configured with multiple radio frequency (RF) transceivers. Operating system software is provided for dynamically establishing and maintaining traffic flow for user applications over multiple communications paths, and for automatically adapting to variations in the networking environment, application traffic flow requirements, end user preferences, or mobility. In a second embodiment, a software-defined radio is used to implement the physical layer protocols for each desired network, eliminating the need for multiple transceivers.
Owner:TRUSTEES OF STEVENS INST OF TECH THE
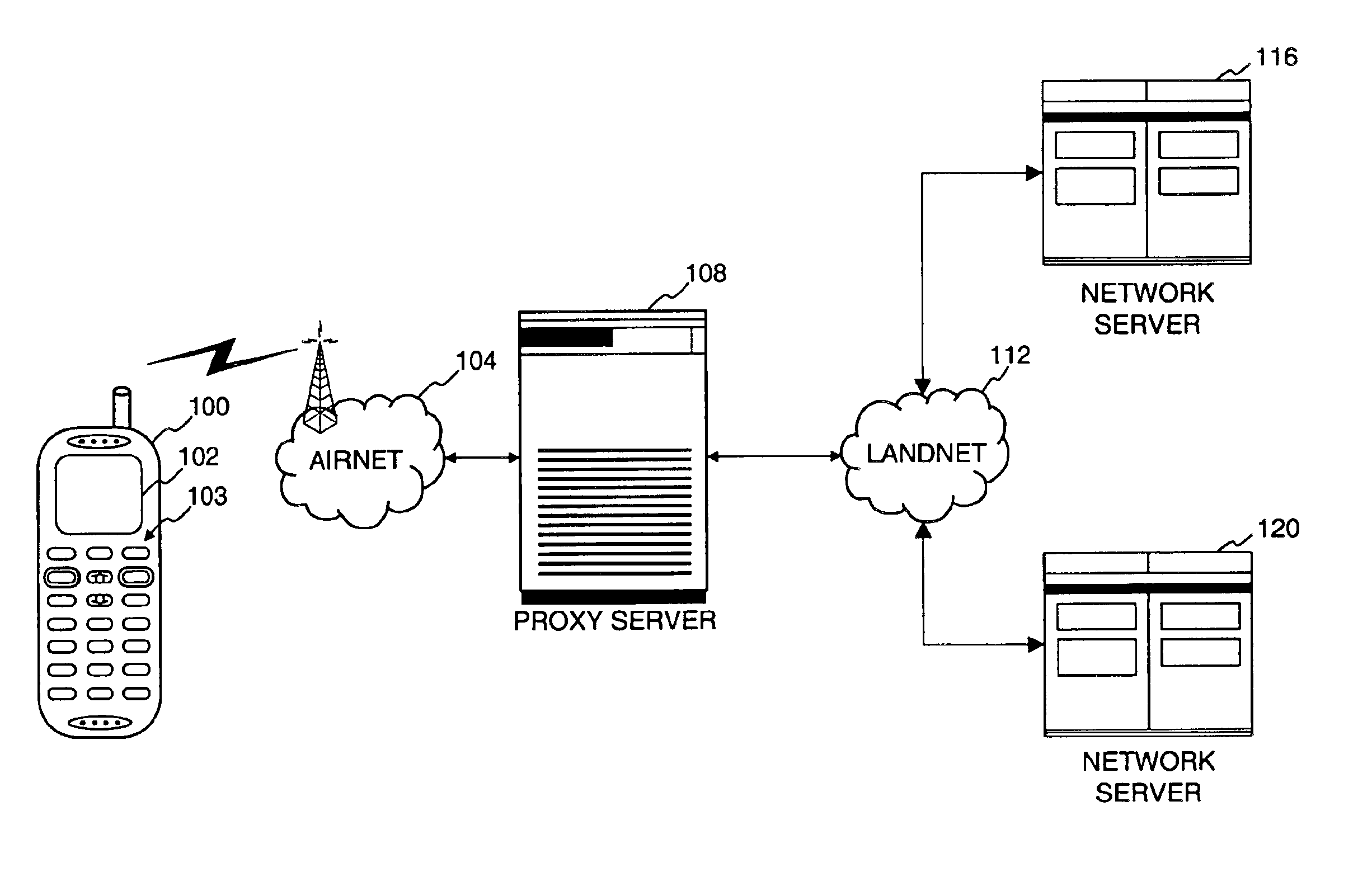
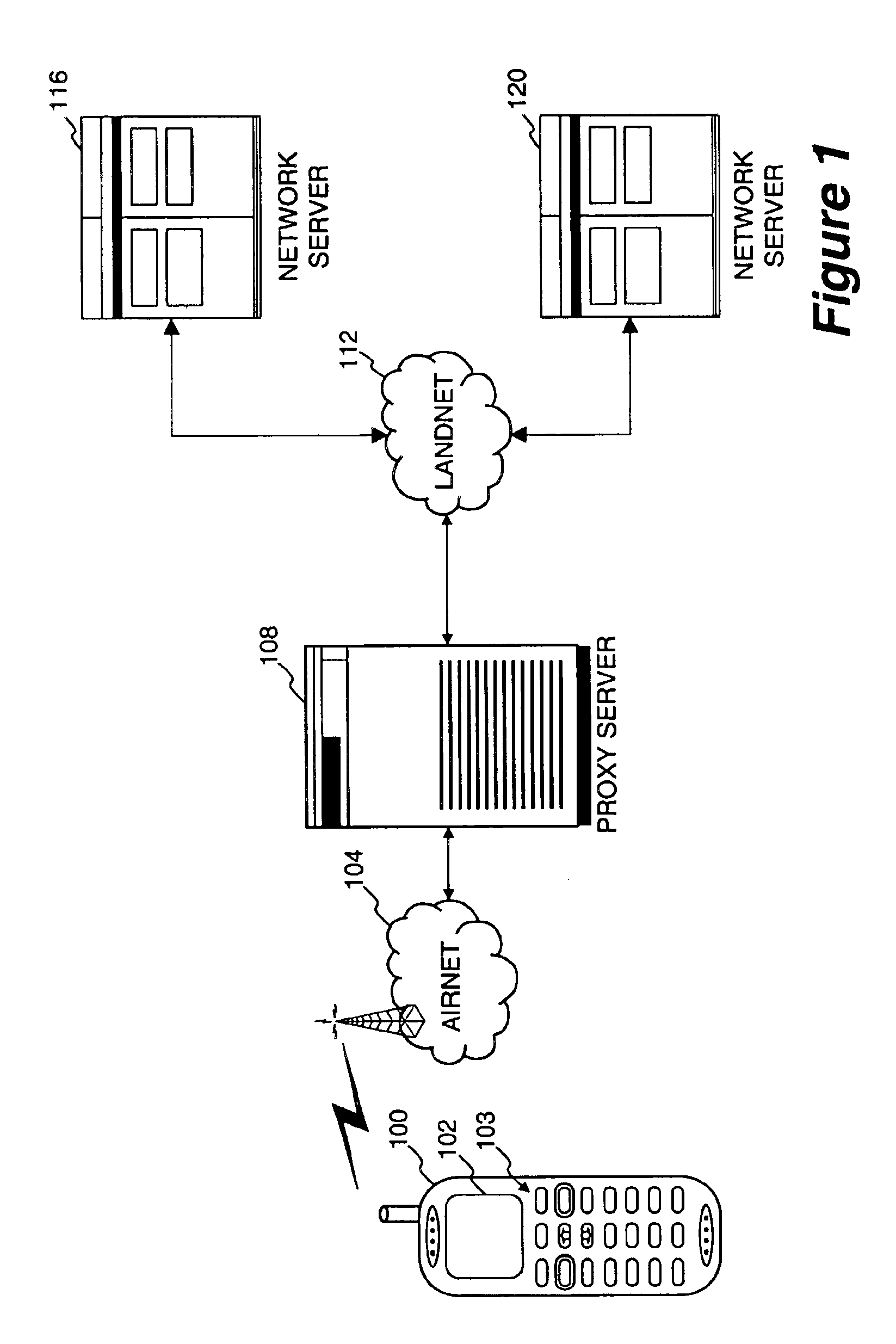
Method and apparatus for providing internet content to SMS-based wireless devices
A method and apparatus for providing hypermedia content maintained remotely on a network to a wireless device without a browser are described. A Short Message Service (SMS) request for Internet-based content is received from the wireless device at a proxy server, via an SMS Center (SMSC). The SMS request is transmitted to the SMSC on a wireless network. The proxy server transcodes the SMS request from a character set of the SMSC to a character set of an application and extracts a keyword from the trancoded request. The proxy server maintains a mapping of keywords to URLs. The proxy server looks up the extracted keyword in the keyword-to-URL mapping to identify the URL of an application associated with the keyword. The proxy server constructs an HTTP POST operation containing the keyword and the URL, and submits the HTTP POST operation to the application over a wireline network such as the Internet. Upon receiving an HTTP response containing the requested content from the application in response to the POST operation, the proxy server extracts the content from the HTTP response. The proxy server then translates the content from the content-type used by the application to the content-type used by the SMSC and transcodes the content from the character set used by the application to the character set used by the SMSC. The proxy server then sends the translated and transcoded content in an SMS response to the SMSC, for subsequent delivery to wireless device as an SMS message.
Owner:UNWIRED PLANET
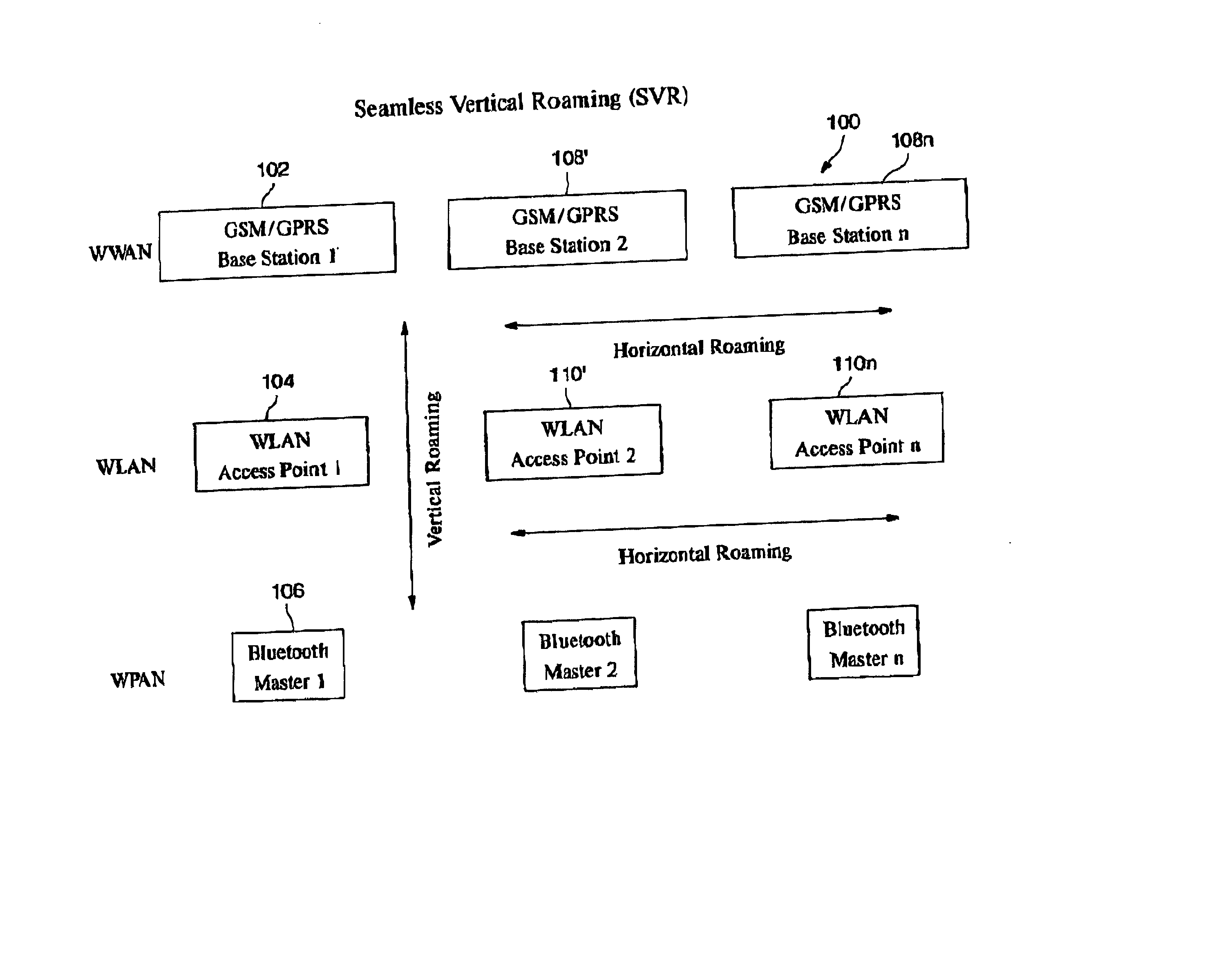
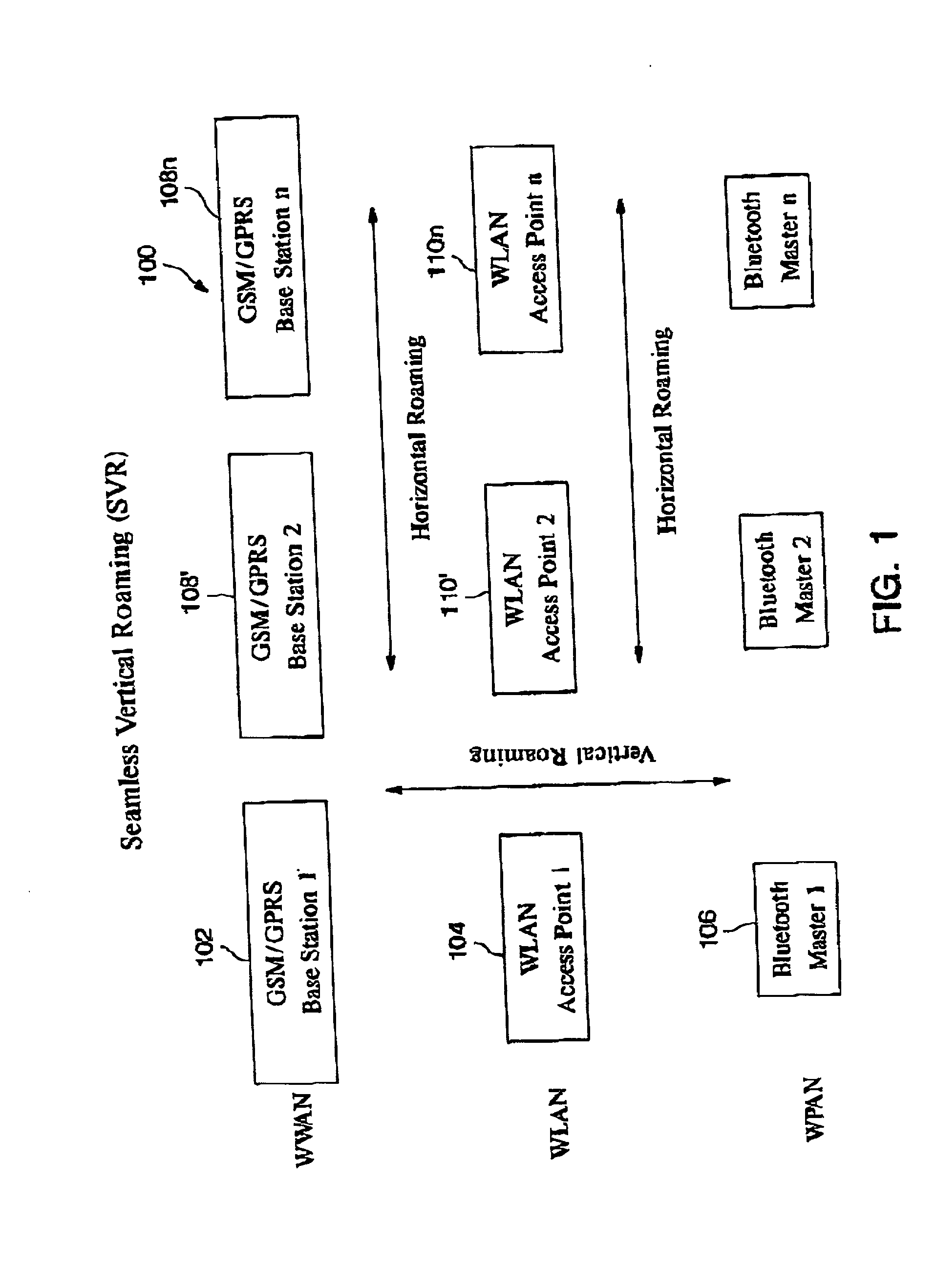
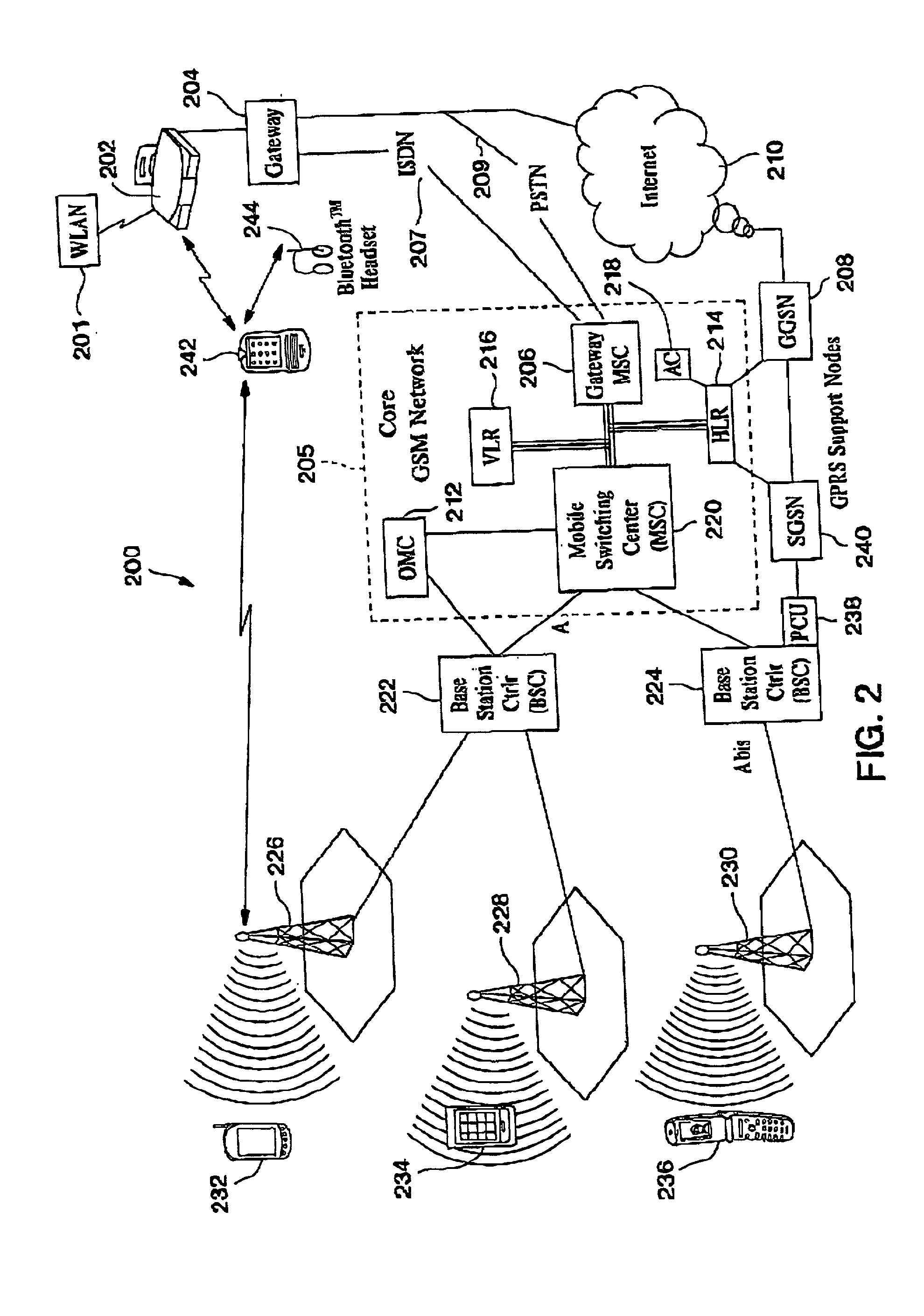
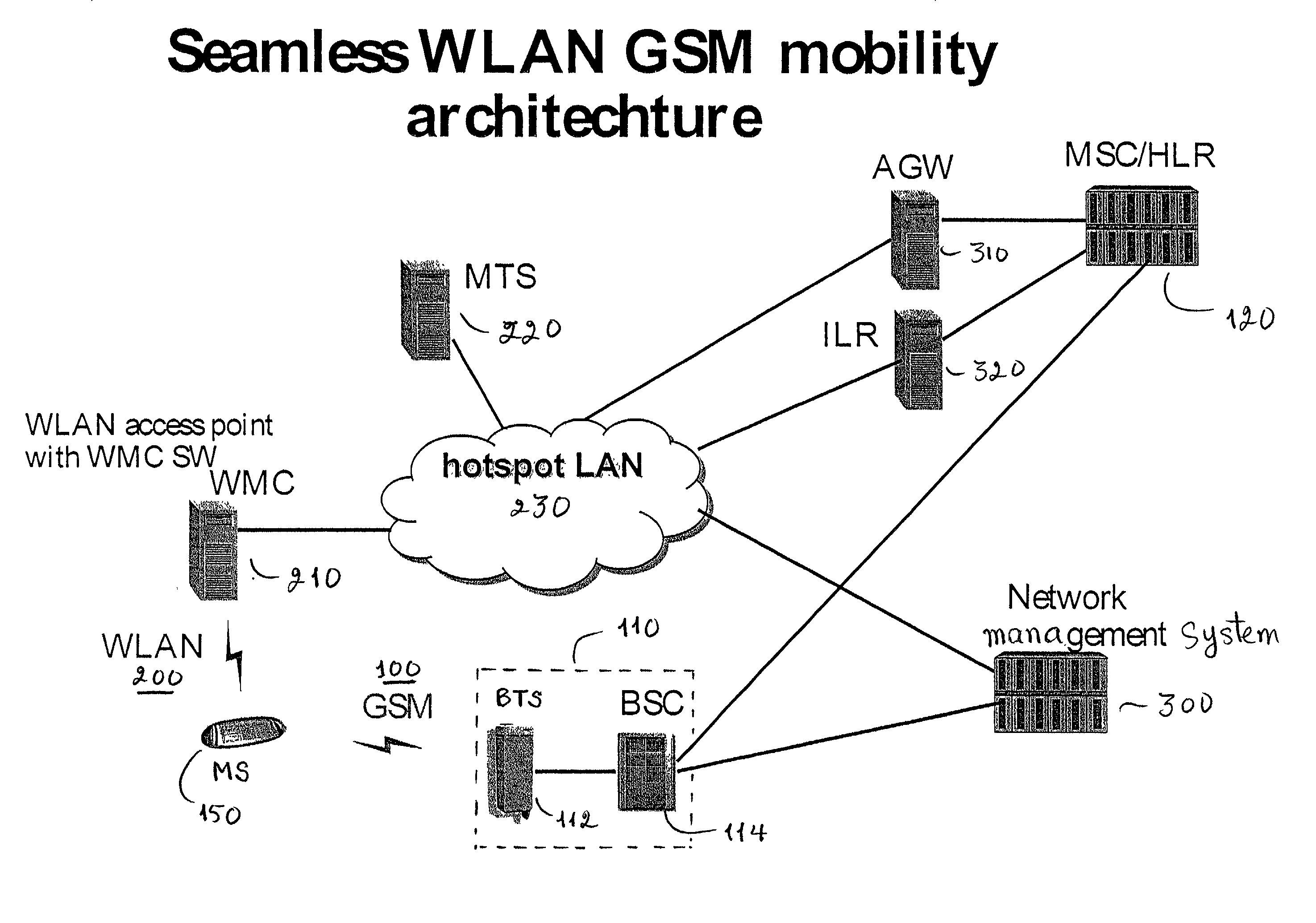
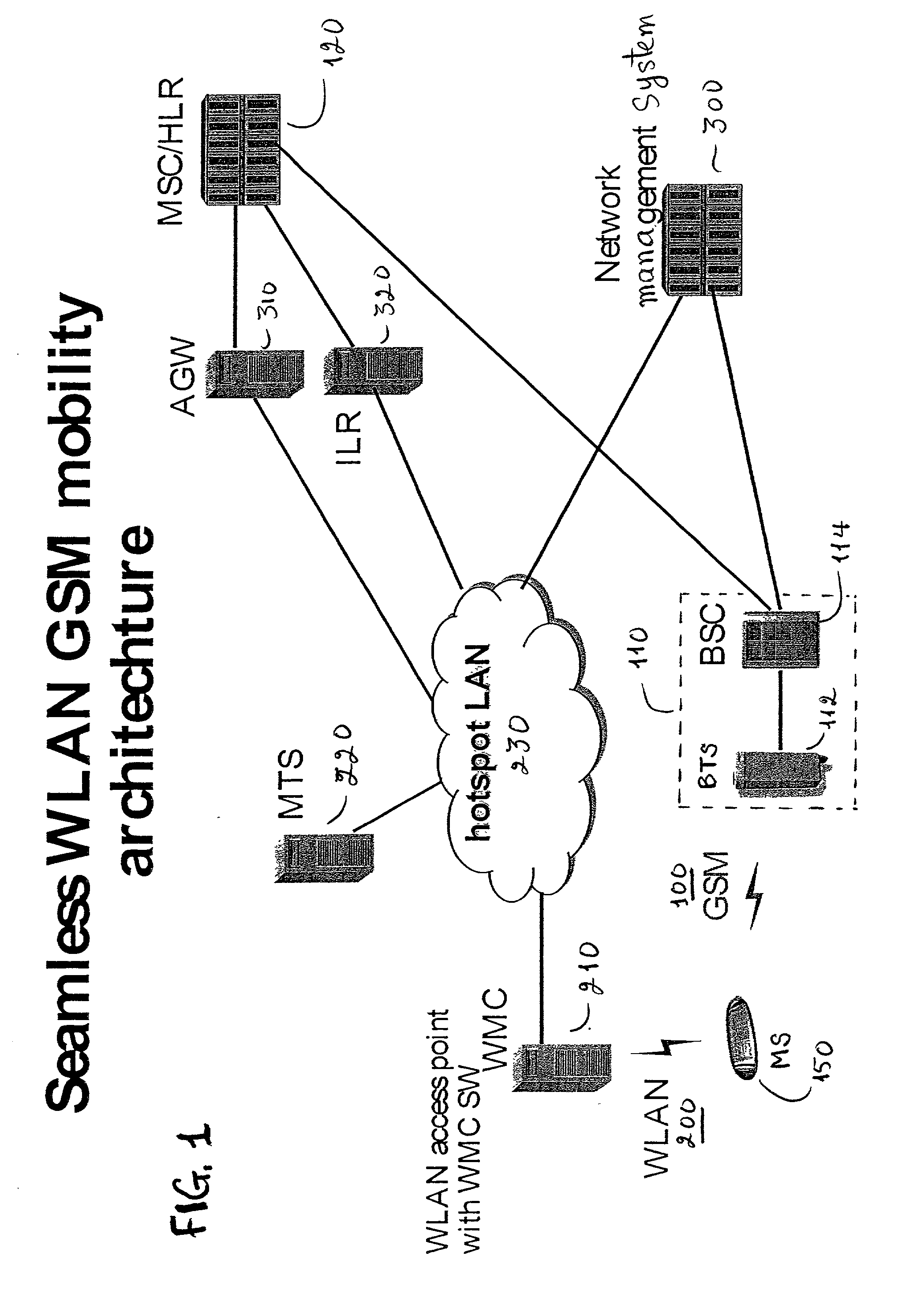
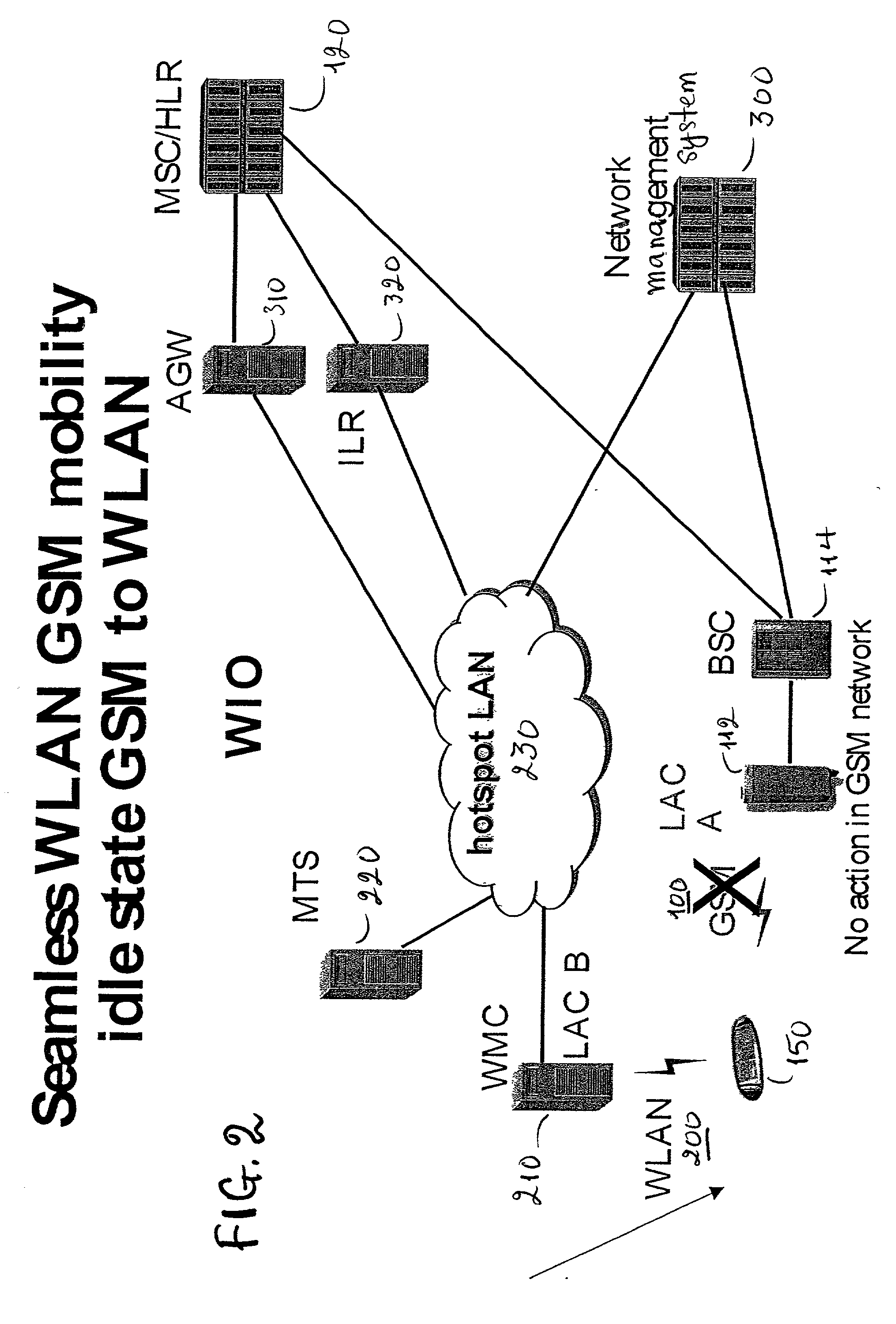
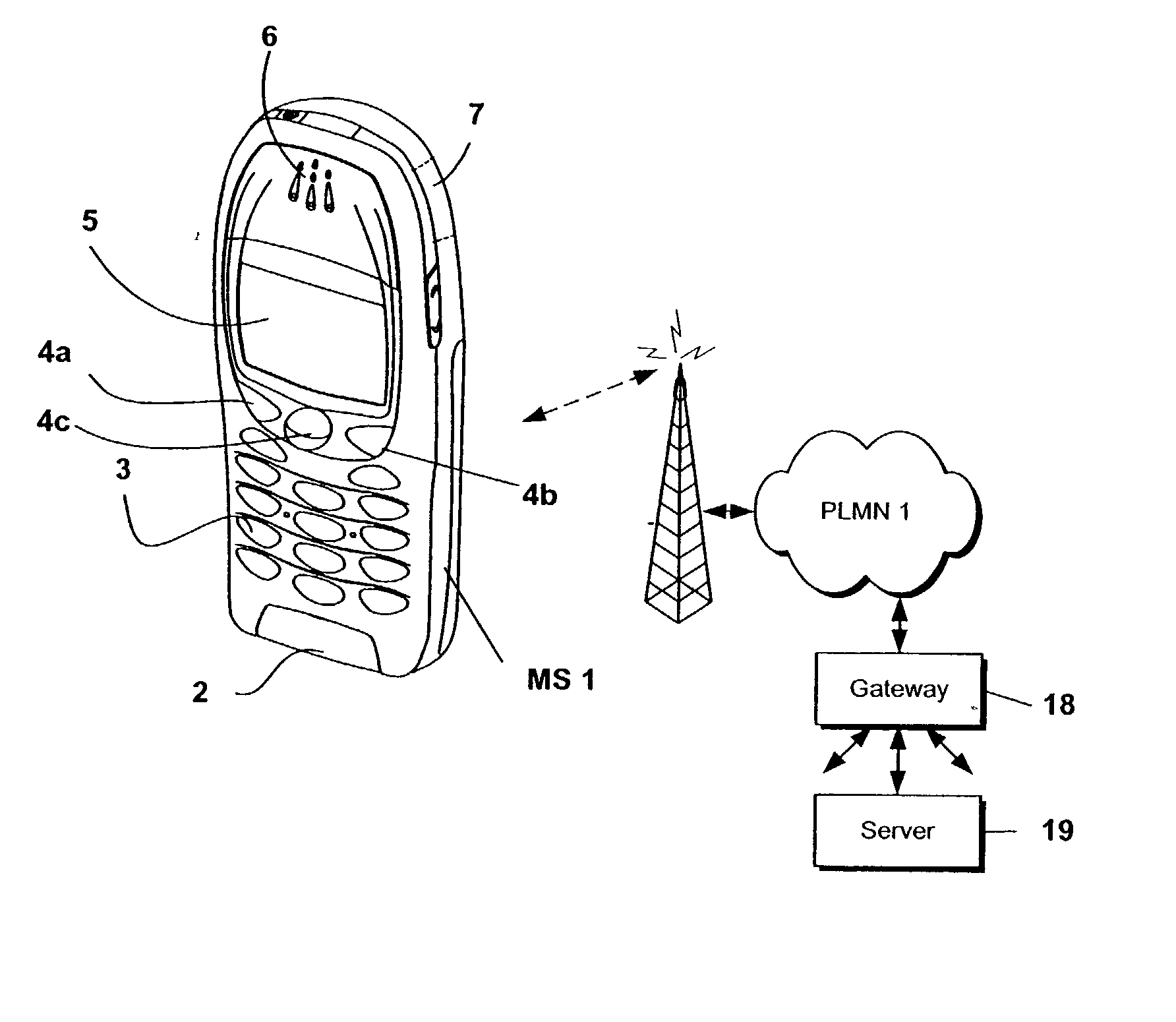
GSM Networks and solutions for providing seamless mobility between GSM Networks and different radio networks
InactiveUS20020147008A1Data switching by path configurationSubstation equipmentRadio networksDual mode
A network architecture for Wireless Intranet Office (WIO) applications including a local radio network such as a wireless local area network (WLAN) which comprises a Wireless Mobile Center (WMC) arranged to serve as a WLAN access point; a GSM network which comprises a Mobile Station (MS) in a form of a dual-mode cellular phone to access both WLAN and GSM radio technologies, a Base Station (BS) arranged to convert a radio signal from the Mobile Station (MS) for communication, a Mobile Switching Center (MSC) arranged to establish call connection; and a Handover Module implemented in either the Mobile Station (MS) or the Wireless Mobile Center (WMC) for providing seamless mobility between the GSM network and the wireless LAN, when the Mobile Station (MS) roams between the GSM network and the wireless LAN.
Owner:RPX CORP
Method of interference management for interference/collision avoidance and spatial reuse enhancement
InactiveUS20050058151A1Improve rendering capabilitiesImprove channel utilizationEnergy efficient ICTPower managementDifferentiated servicesDifferentiated service
A method called the evolvable interference management (EIM) method is disclosed in this patent for avoiding interference and collision and increasing network throughput and energy efficiency in wireless networks. EIM employs sensitive CSMA / CA, patching approaches, interference engineering, differentiated multichannel, detached dialogues, and / or spread spectrum techniques to solve the interference and QoS problems. EIM-based protocols can considerably increase network throughput and QoS differentiation capability as compared to IEEE 802.11e in multihop networking environments. Due to the improvements achievable by EIM, the techniques and mechanisms presented in this application may be applied to obtain an extension to IEEE 802.11 to better support differentiated service and power control in ad hoc networks and multihop wireless LANs. New protocols may also be designed based on EIM.
Owner:YEH CHIHSIANG
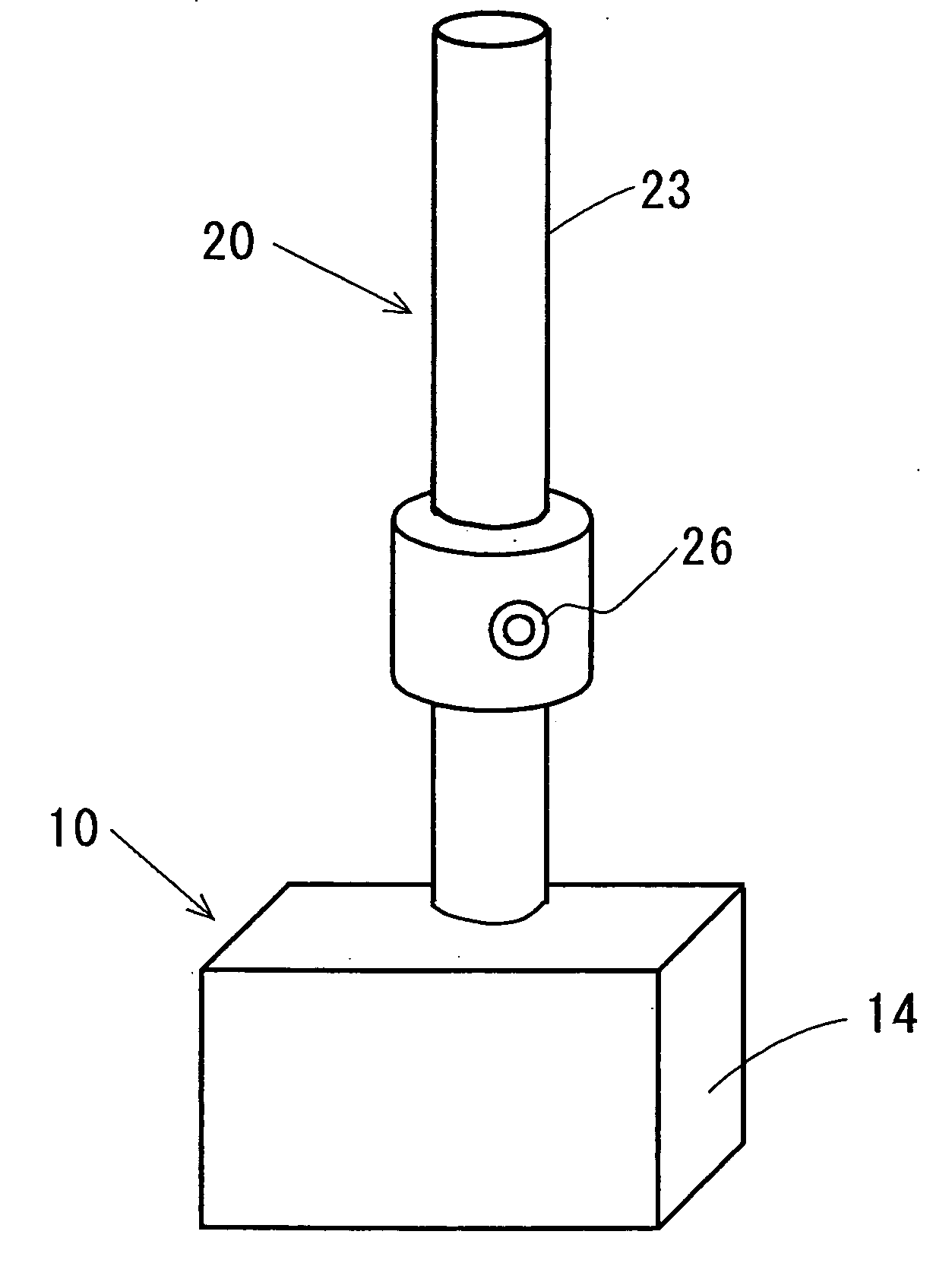
Cordless device system
InactiveUS20050130682A1Fast chargingSolution to short lifeBatteries circuit arrangementsRadio/inductive link selection arrangementsEngineeringControl circuit
A cordless instrument (20, 40) detachable from a charger (10, 30, 31) is attached to the charger (10, 30, 31), and is charged. A first storage part (12, 33) chargeable from a direct current source (11, 32) included in the charger (10, 30, 31), a first charge and discharge control circuit (13, 50) to control charge and discharge of the first storage part (12, 33), a second storage part (21, 43) included in the cordless instrument (20, 40), and a second charge and discharge control circuit (22, 45) to control charge and discharge of the second storage part (21, 43) are provided. Further, a third storage part (28) chargeable from the direct current source (11, 32) may be provided. Also to the cordless instrument (20, 40), a fourth storage part (44) may be provided. Upon attaching the cordless instrument, the second storage part (21, 43) is charged at least from the first storage part (12, 33). In comparison with charging time to conventional secondary batteries, it is capable of rapid charge, long life use, resulting in such merits as to realize the compact size of a charger and low cost.
Owner:SUN BRIDGE CORP
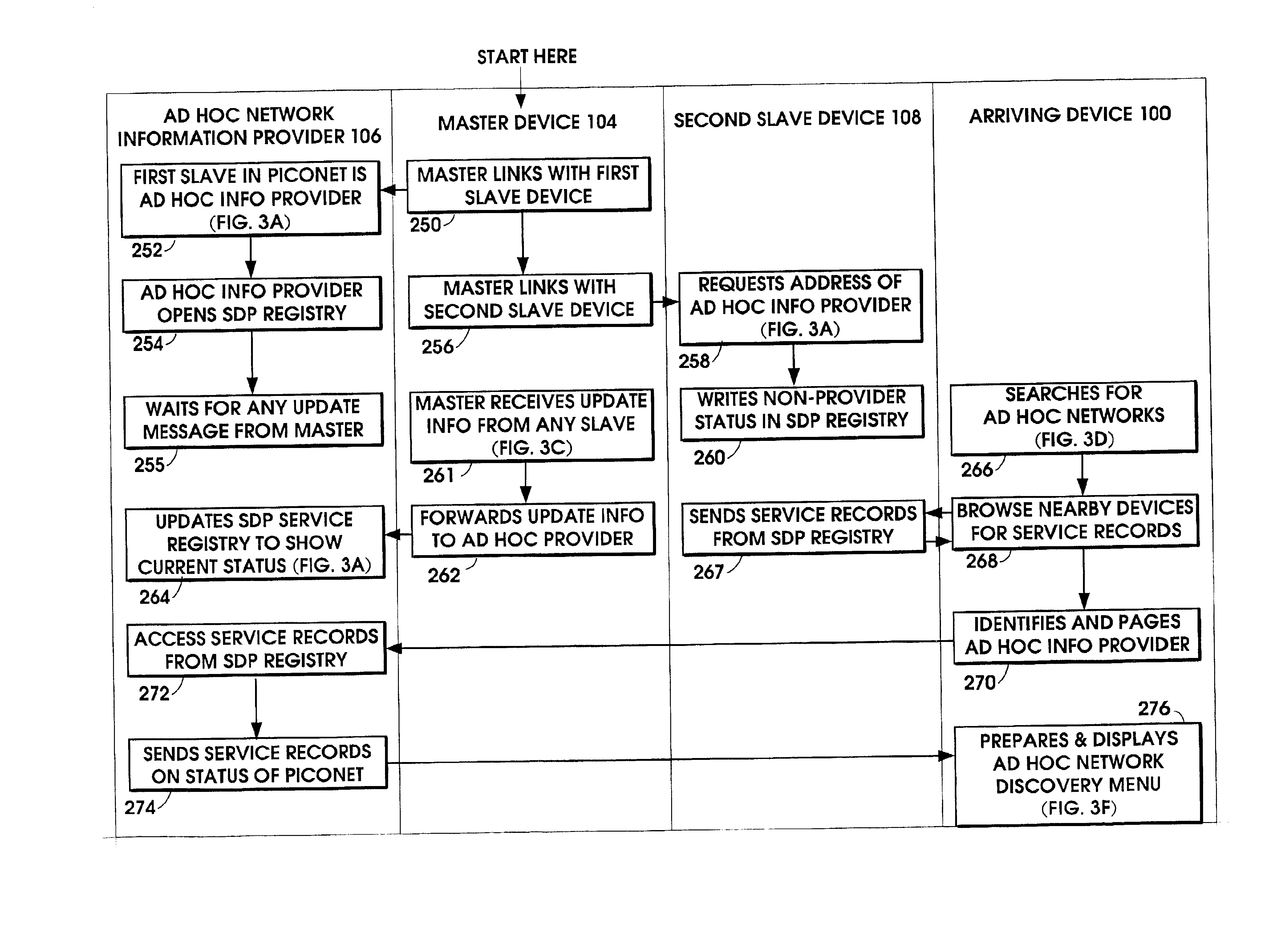
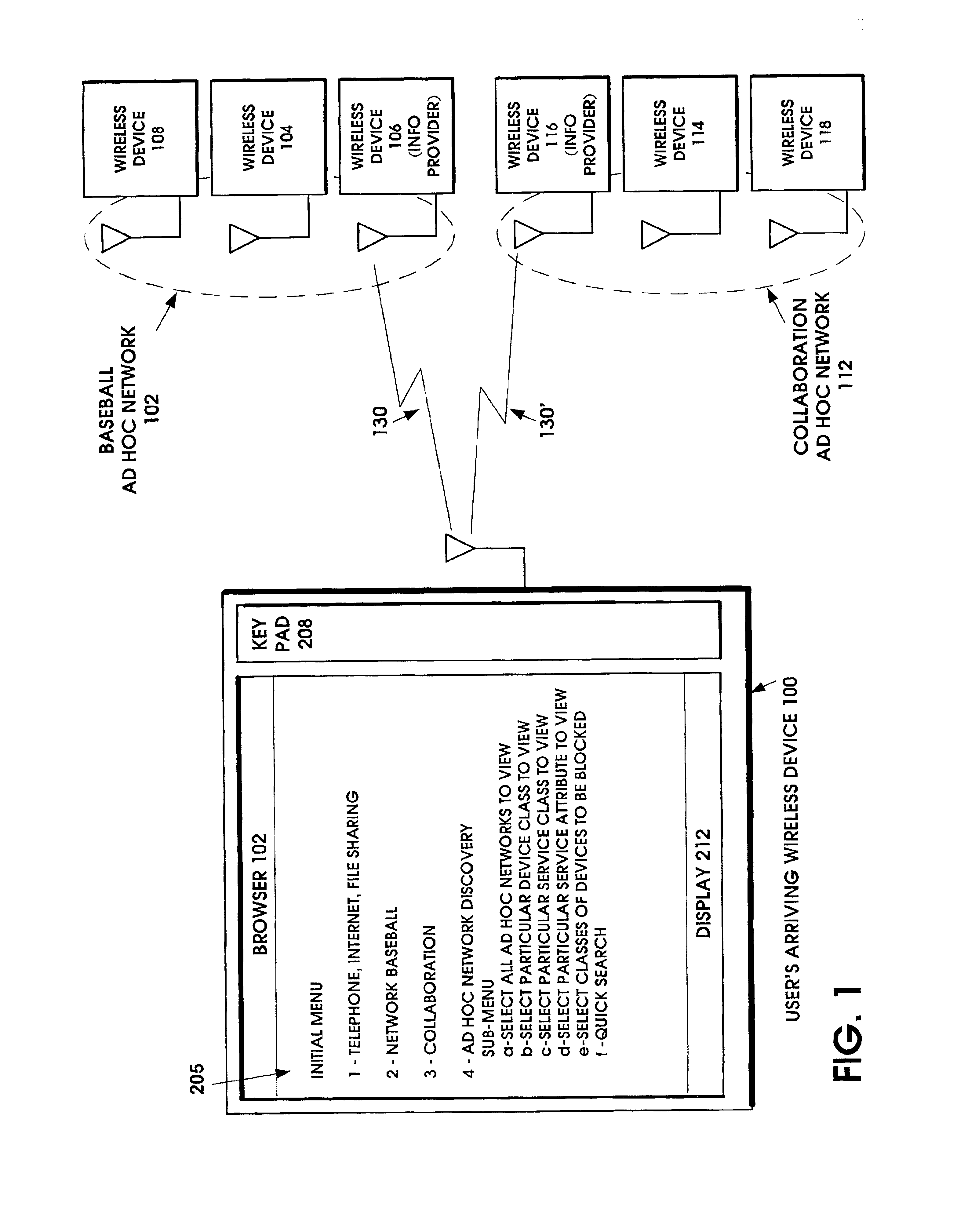
Ad hoc network discovery menu
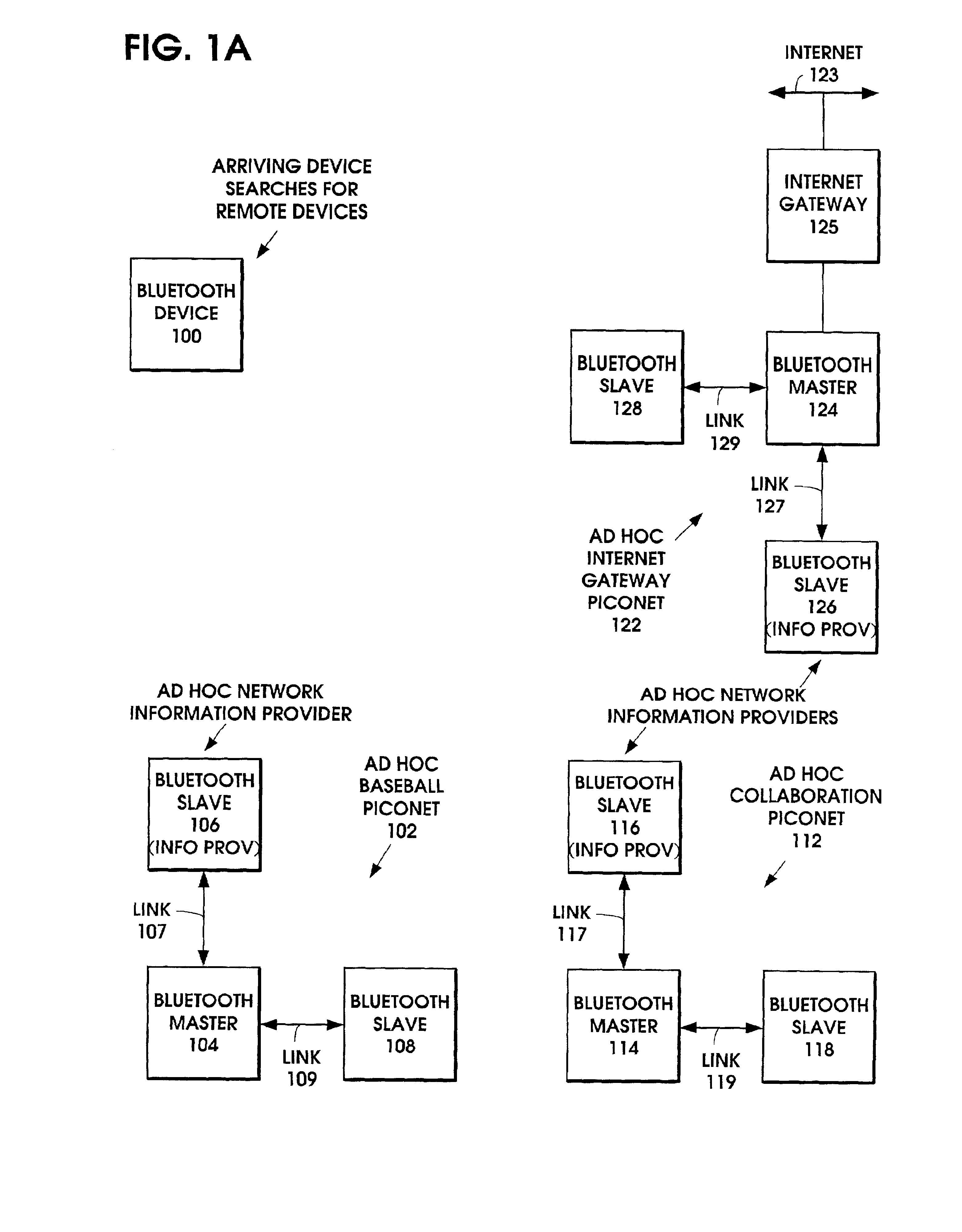
When an ad hoc network is formed between short range wireless devices, at least one device assumes the role of an ad hoc network information provider for the new piconet. In this role, the device allocates a browsing hierarchy of service classes in its service registry. The service classes will provide a record to characterize the ad hoc network. When a new wireless device arrives within the communication range of any member of the ad hoc network, its inquiry signals are answered by the first member detecting the inquiry. If that first member is an ad hoc network information provider, it responds with information accessed from its service registry characterizing the ad hoc network. If, instead, an ordinary device in the ad hoc network is the first to respond to the inquiry signals of the arriving device, the device responds with the address of the ad hoc network information provider. The arriving device then pages the ad hoc network information provider to obtain information characterizing the ad hoc network.
Owner:NOKIA TECHNOLOGLES OY
System and method for monitoring and control of wireless modules linked to assets
InactiveUS7027808B2Wireless commuication servicesElectric/magnetic detectionOperational systemComputer module
A system and method for remote asset management is described which can provide the basis for a diverse product group including an improved remote location monitoring system, a means for communicating with and for monitoring the status and or location of a plurality of diverse assets, as well as the means for communicating with said assets for the purpose of modifying the operational status of one or more of said assets according to one or more stored data parameters such as location, use, battery power, and such like. The remote asset management system comprises a wireless module, which is associated with at least one of the plurality of asset and which is interfaced with the operating system of said assert and or with an electromechanical control means, which may control one or more features of the operation of said assets. A supporting network-based, or internet-based service platform, controls and manages the status of each of the plurality of assets, either automatically, or in response to received messages from fixed or wireless communication devices, and which is capable of selectively communicating data to said assets for changing the operational status of said assets according to pre-programmed conditions.
Owner:M2M SOLUTIONS
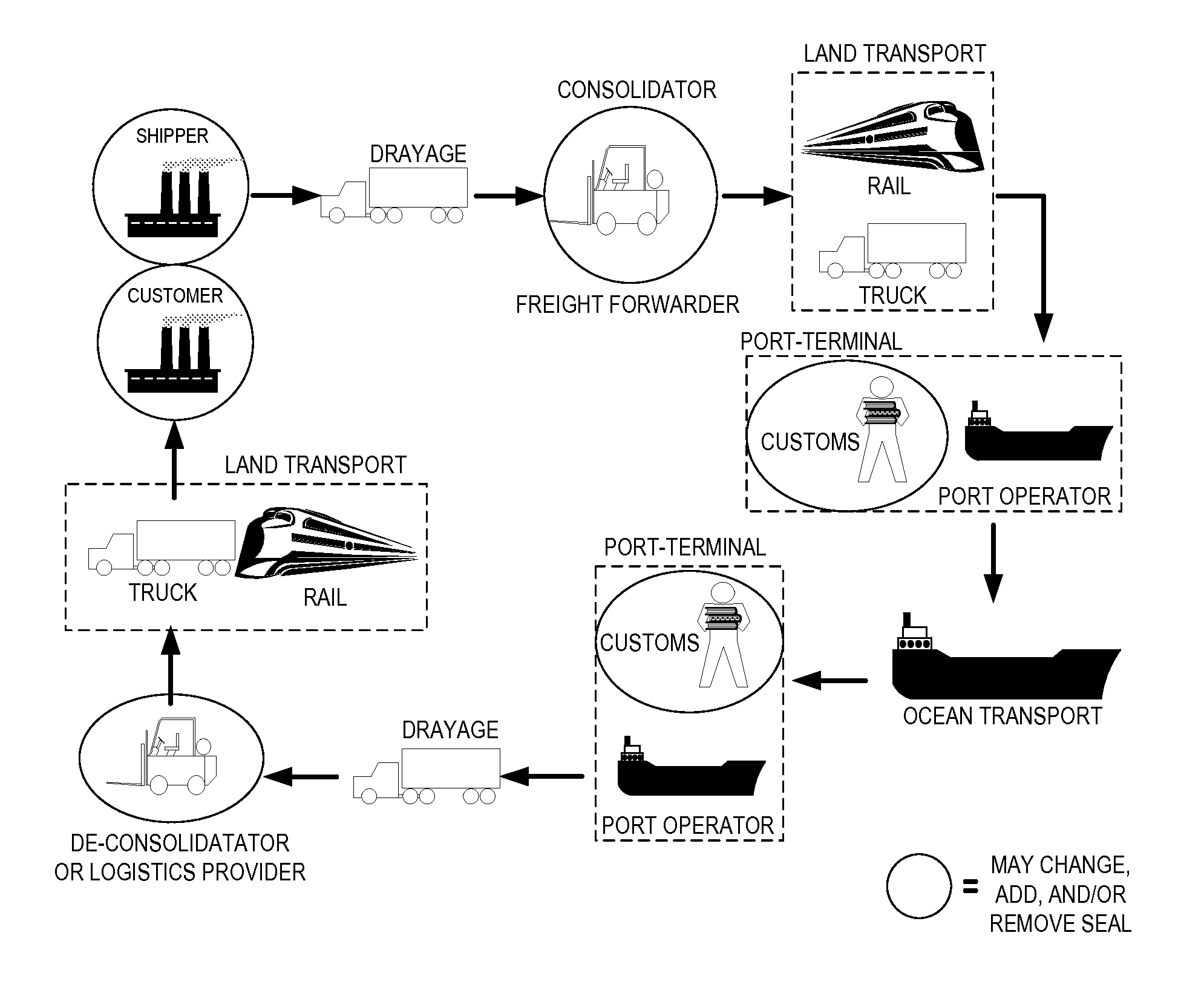
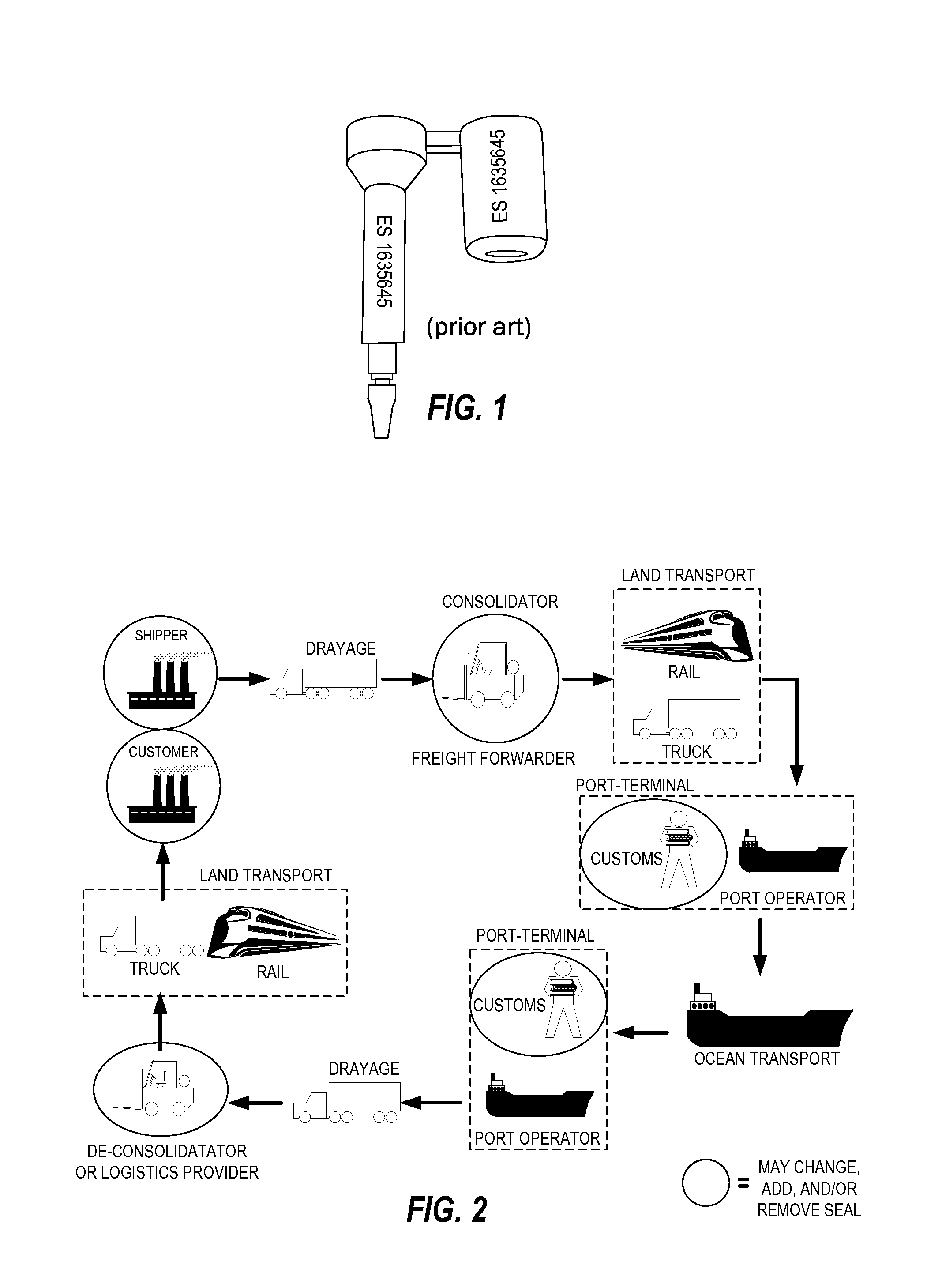
Securing, monitoring and tracking shipping containers
InactiveUS20090322510A1Data switching by path configurationWireless commuication servicesBarcodeEngineering
A method of securing a container includes inserting, into a seal device at a container, an electronic bolt; reading, by the seal device, a serial number stored in the electronic bolt; communicating, from the seal device, to a user application, insertion of the bolt; scanning, by the user via a handheld device, a barcode on the seal device representative of an identification of the seal device; communicating, from the handheld device to the user application, the identification of the seal device; inputting, by a user at the container via the handheld device, information associated with the container; communicating, from the handheld device to the user application, the information associated with the container; associating, in a database by the user application, the information associated with the container with the bolt serial number and the identification of the seal device; communicating, by the user application, a confirmation to the seal device.
Owner:GOOGLE LLC
System and method for providing context sensitive recommendations to digital services
ActiveUS20040043758A1Reducing or minimizing the processing load and memoryReduces privacy concernInterconnection arrangementsDigital data information retrievalComputer networkRelevant information
A system and method is disclosed to provide recommendations to a wireless device, based on stored bookmark / short-cut data. When a wireless device accesses services, data pertaining to the service access, along with any context related information is transmitted within the wireless device, or to a remote server. The data is processed in conjunction with bookmarks / short-cuts specified within the device, and are organized and presented to the wireless device in accordance with preference instructions specified within the wireless device.
Owner:NOKIA TECHNOLOGLES OY
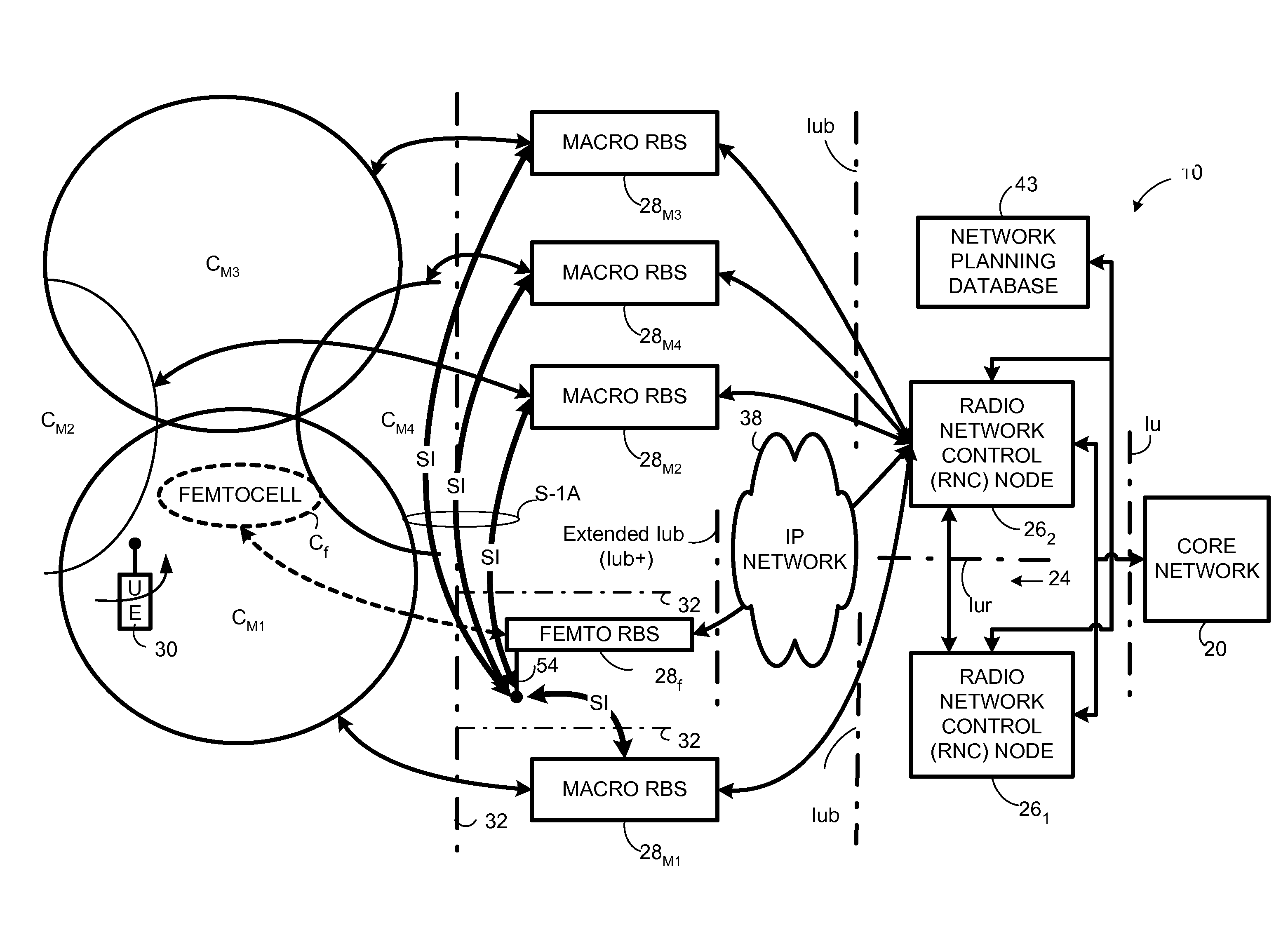
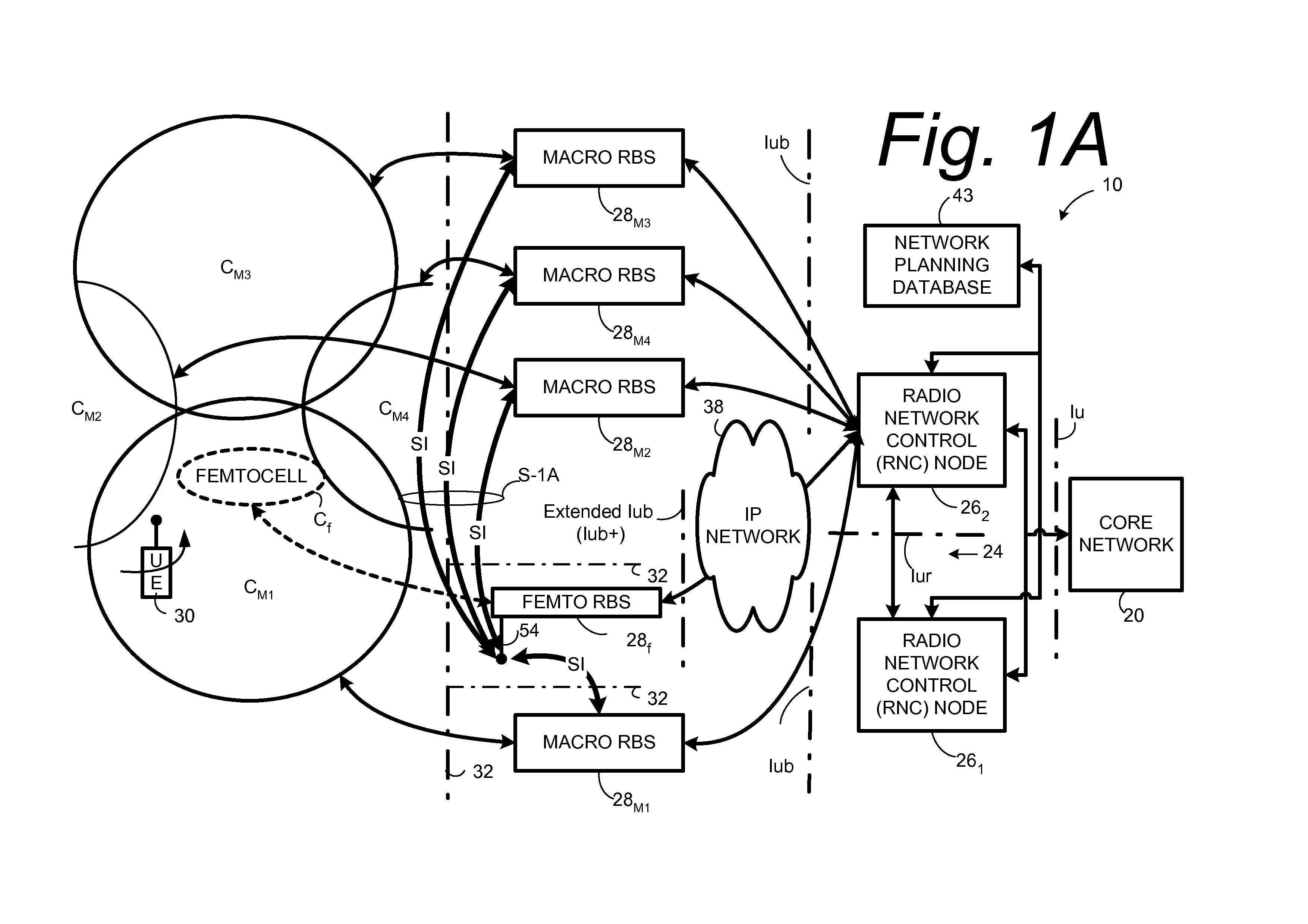
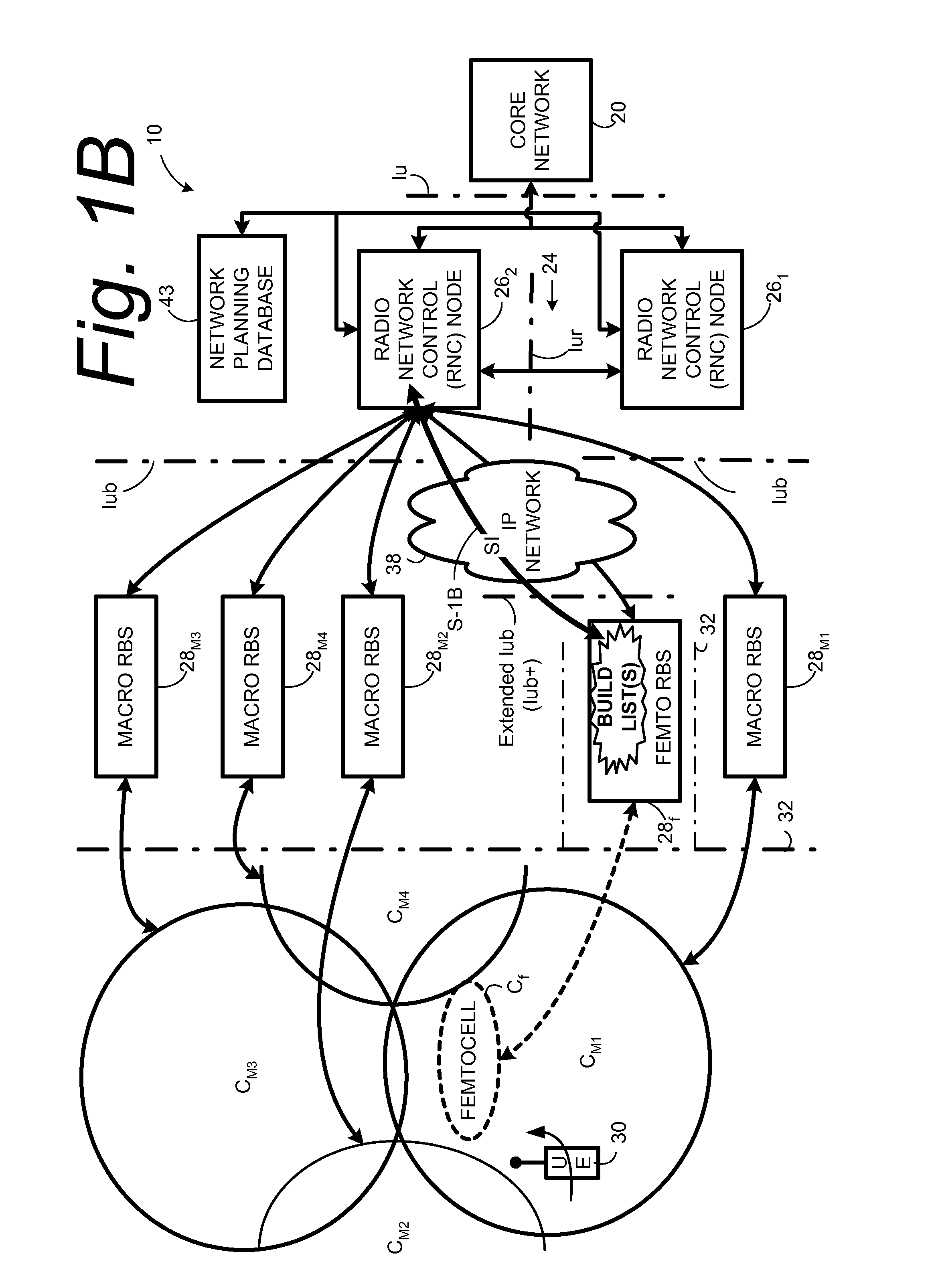
Automatic configuration of pico radio base station
Methods and apparatus configure a femto radio base station ( 28 f). A macro receiver of the femto radio base station ( 28 f) is used to acquire detected coverage information of a radio access network ( 24 ). The detected coverage information is used to determine an operation parameter for use by the macro transceiver ( 52 ) of the femto radio base station ( 28 f). In one embodiment, the detected coverage information is transmitted to a control node ( 26 ) of the radio access network. The control node ( 26 ) determines the operation parameter and communicates the operation parameter to the femto radio base station ( 28 f). The femto radio base station ( 28 f) is accordingly configured using the operation parameter for further operation towards UEs ( 30 ) accessing the femto radio base station ( 28 f).
Owner:TELEFON AB LM ERICSSON (PUBL)
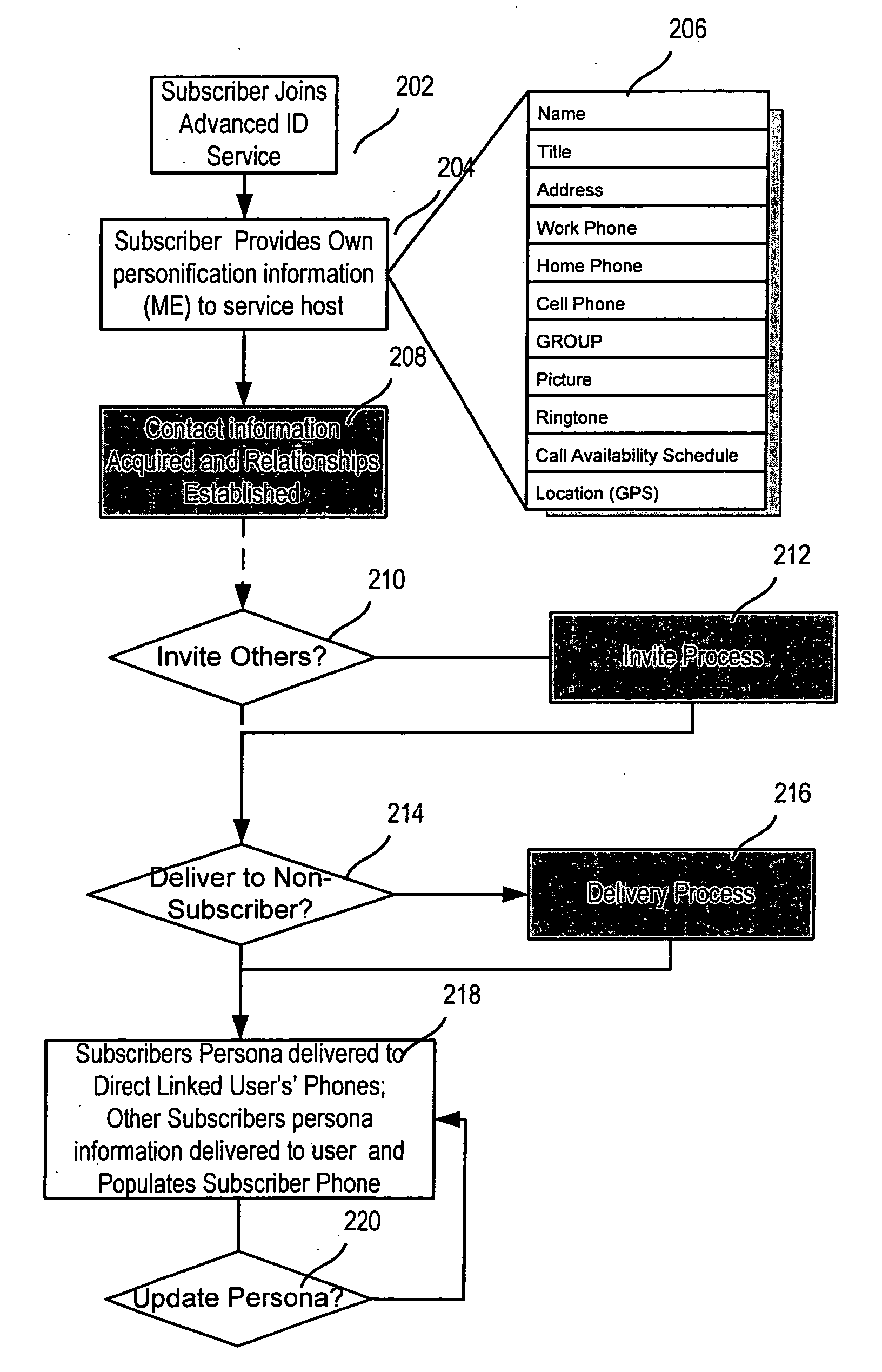
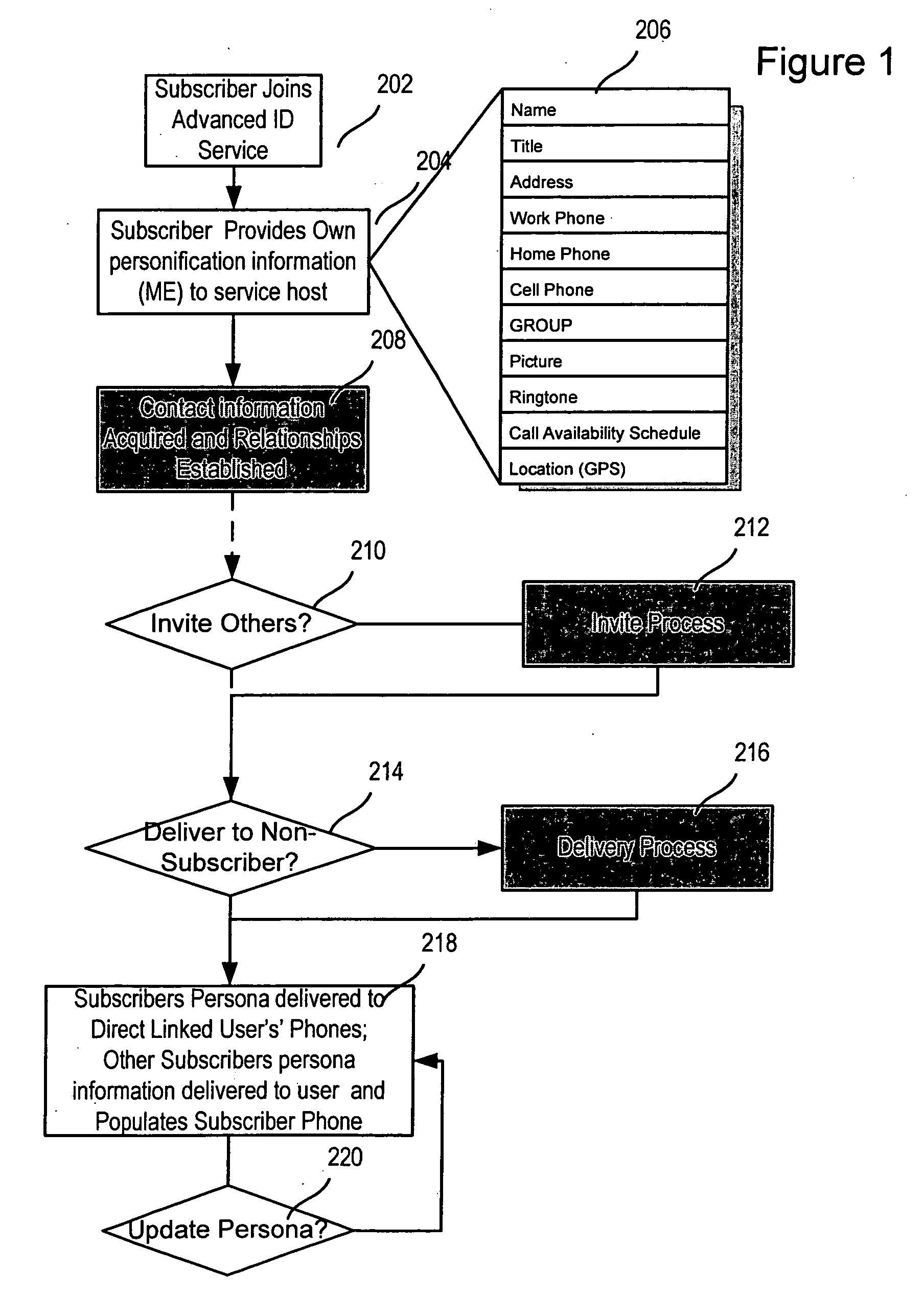
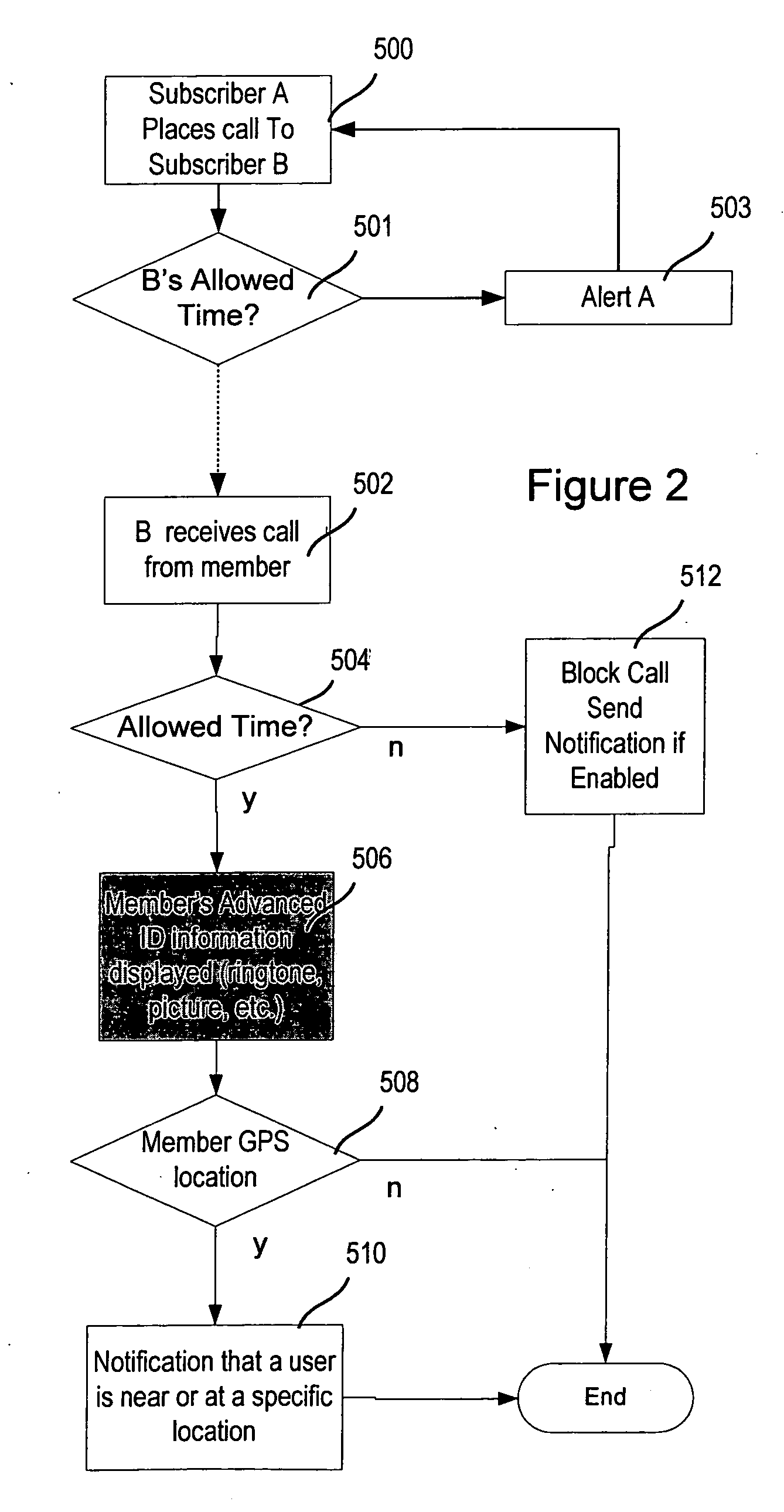
Advanced contact identification system
ActiveUS20060052091A1Special service for subscribersServices signallingAddress bookCommunication device
A system and method of advanced identification information to be created and distributed to users of wireless communication devices, such as mobile phones. Subscribers can define their own personas as collections of information which define the users. Subscribers can then publish their persona(s) to their friends' and associates' mobile phones, and update the others' address books with the subscriber's contact information. Users can specify different personas to be presented to different users.
Owner:SYNCHRONOSS TECH
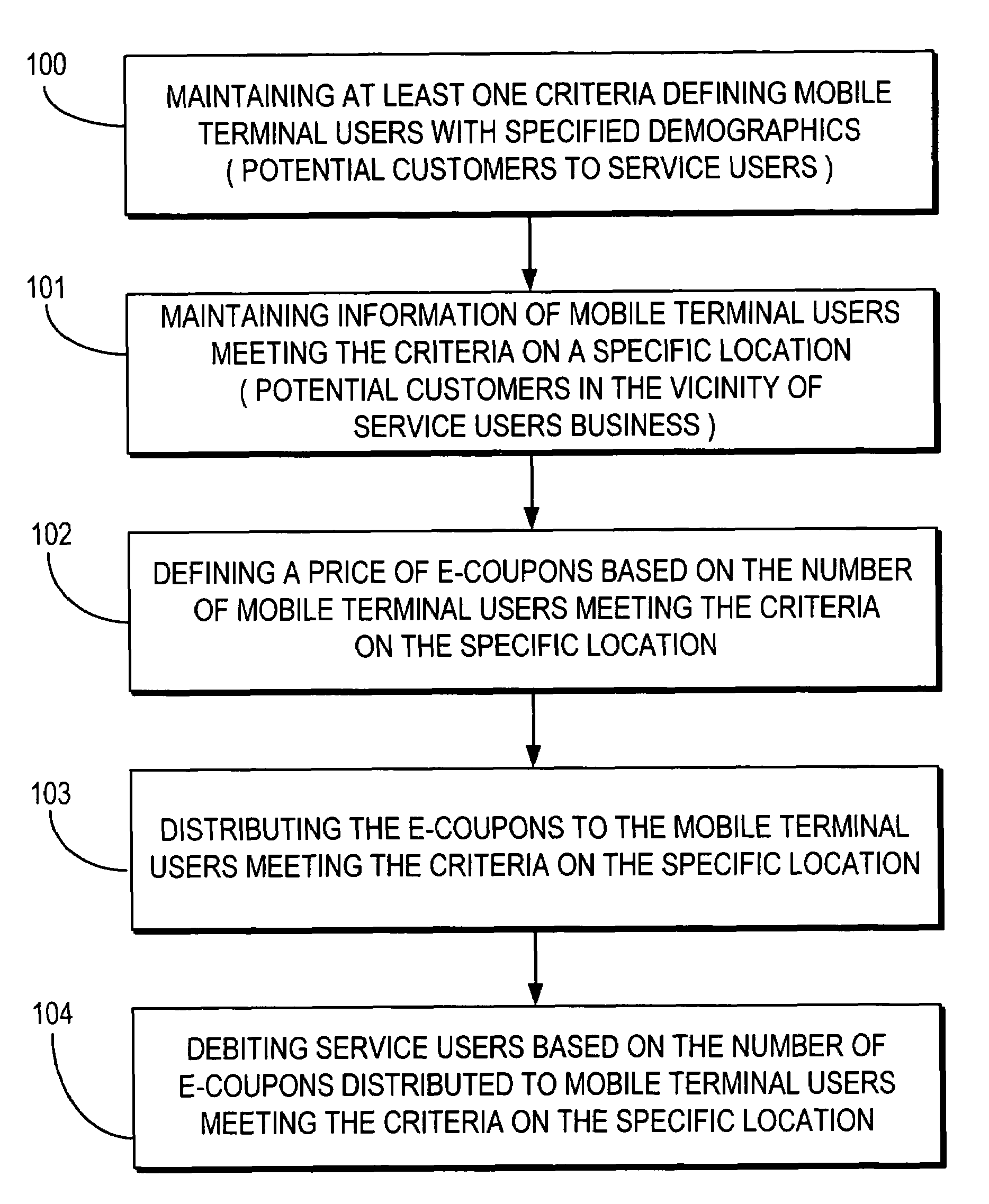
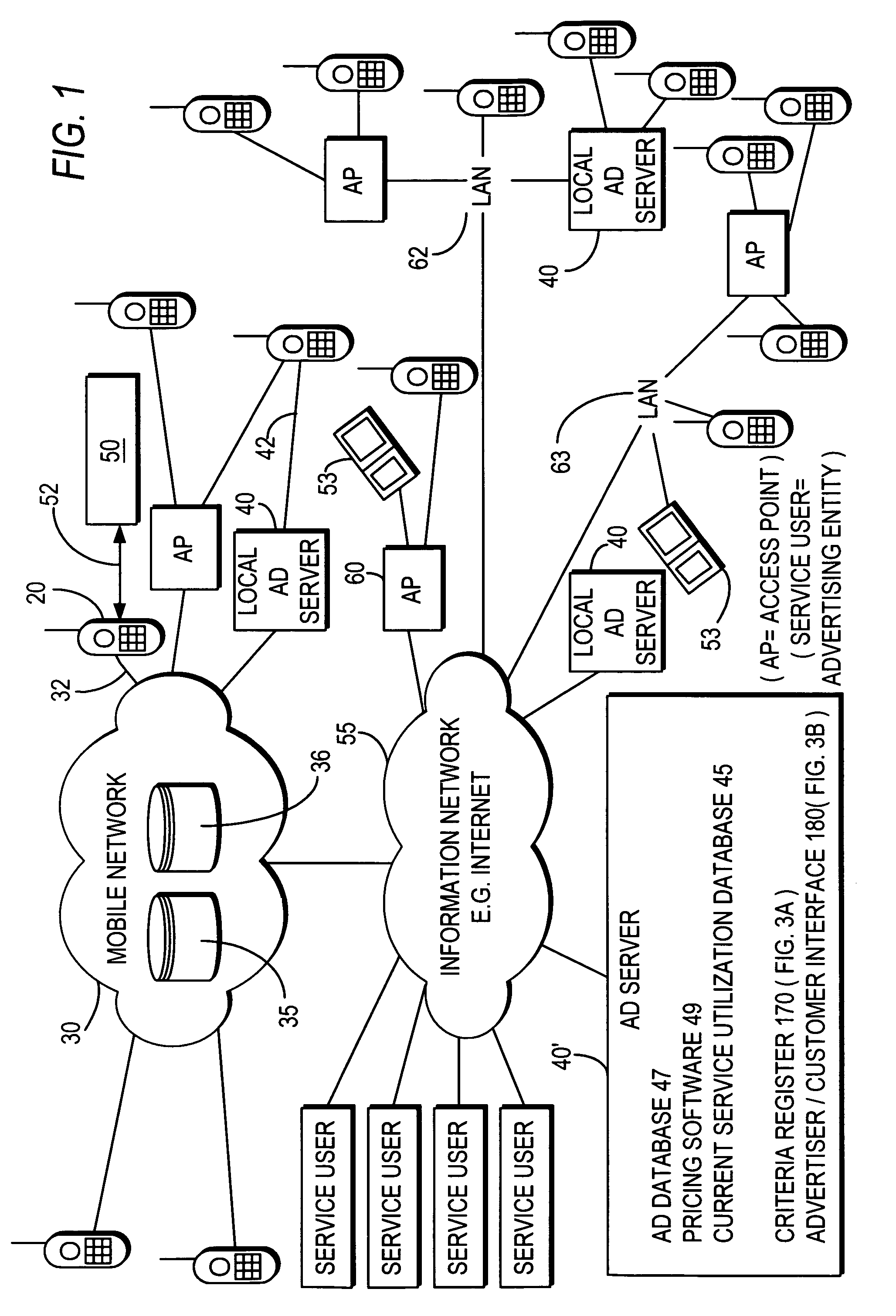
Real-time wireless e-coupon (promotion) definition based on available segment
Advertising messages are provided to mobile terminals of those users identified by user information as meeting certain criteria, such as users fitting particular user profiles and / or users located in a particular desired location. The content of the advertising messages is dynamically generated based on the number of mobile terminals to whom the advertising message is to be sent and the advertising message is sent to the identified mobile terminals over a mobile network or a short range communication signal. In the latter case, location information may be sent to the mobile terminal along with an advertising message. Where the content of an advertising message comprises an electronic coupon, the value of the coupon depends on the number of mobile terminals to whom the advertising message is to be sent. A mobile terminal user can redeem an electronic coupon by transmitting it from his mobile terminal to a coupon redemption terminal.
Owner:NOKIA TECH OY
Method and apparatus for optimization of wireless multipoint electromagnetic communication networks
InactiveUS7248841B2Strong advantageReduced Power RequirementsPower managementSpatial transmit diversityGlobal optimizationRandom delay
Exploiting the substantive reciprocity of internode channel responses through dynamic, adaptive modification of receive and transmit weights, enables locally enabled global optimization of a multipoint, wireless electromagnetic communications network of communication nodes. Each diversity-channel-capable node uses computationally efficient exploitation of pilot tone data and diversity-adaptive signal processing of the weightings and the signal to further convey optimization and channel information which promote local and thereby network-global efficiency. The preferred embodiment performs complex digital signal manipulation that includes a linear combining and linear distribution of the transmit and receive weights, the generation of piloting signals containing origination and destination node information, as well as interference-avoiding pseudorandom delay timing, and both symbol and multitone encoding, to gain the benefit of substantive orthogonality at the physical level without requiring actual substantive orthogonality at the physical level.
Owner:COMCAST CABLE COMM LLC
Method and system for managing data traffic in wireless networks
ActiveUS7042988B2Facilitate secure integrationExtensive controlError preventionUnauthorised/fraudulent call preventionWireless mesh networkNetwork architecture
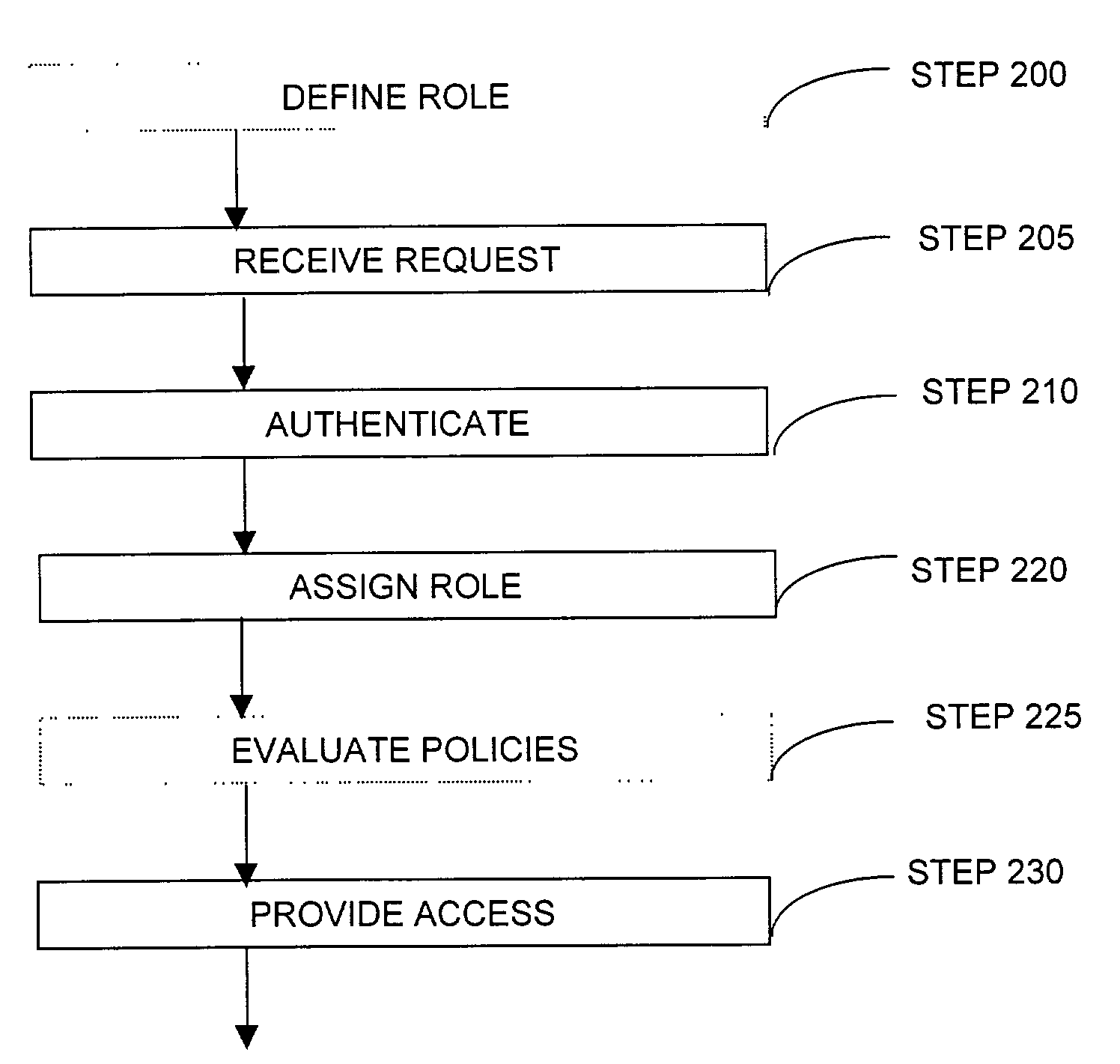
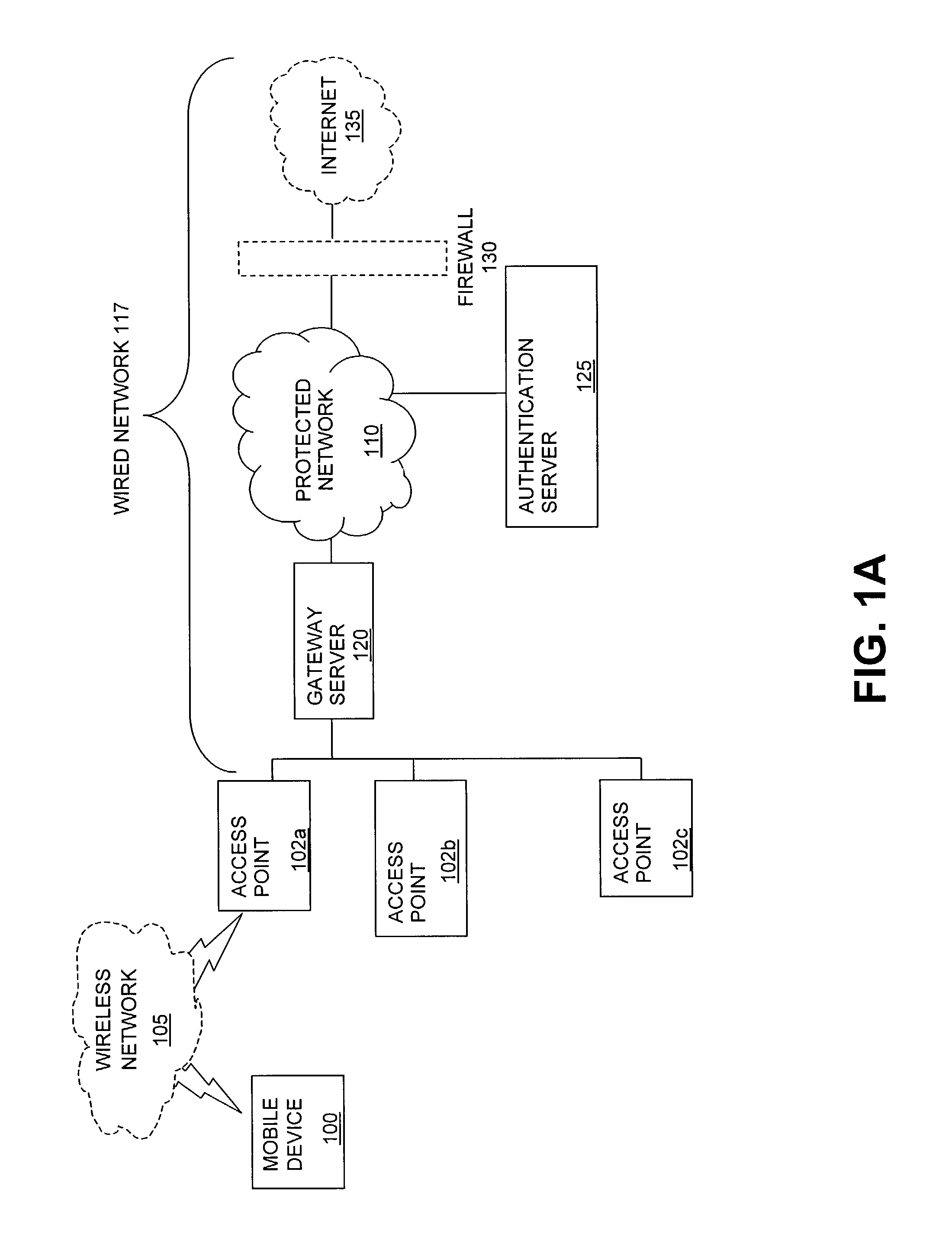
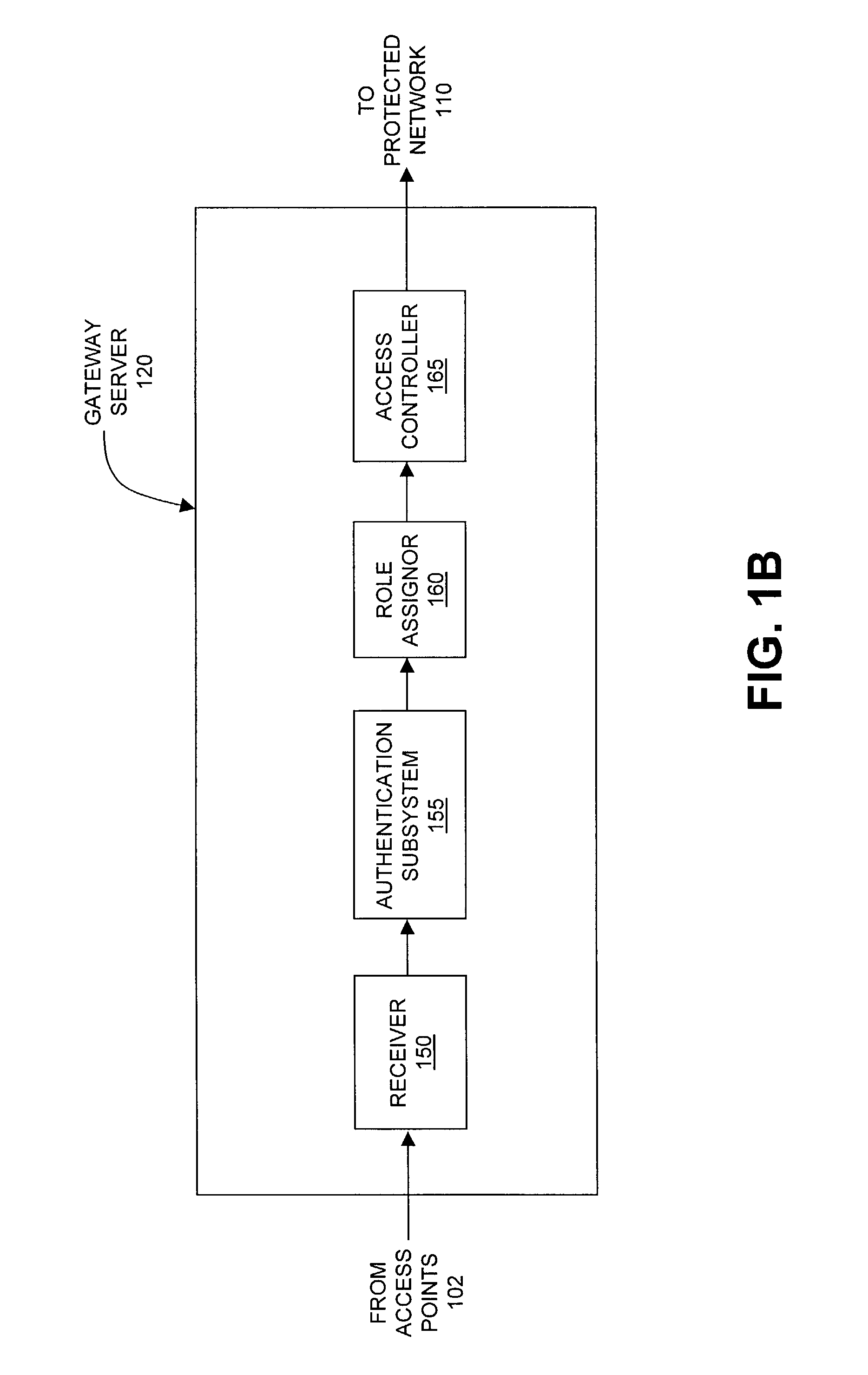
The present invention can be used to facilitate the integration of wireless capability provided by wireless access points into an enterprise computer network. A gateway server is interposed between wireless access points and protected networks to provide security and integration functions, for example, authentication, access control, link privacy, link integrity, and bandwidth metering in various embodiments. Use of such a gateway server allows substantial control to be gained over network access even with the use of relatively simple access points. In general, such a gateway server receives a request to access the protected network. An authentication subsystem of the gateway server authenticates the user, preferably by accessing an external authentication server and returns a role to the authenticated user. An access controller in the gateway server provides differential access to the protected network based on the user's assigned role. A multiple gateway servers can be connected together to form a mesh network architecture.
Owner:BLUESOCKET
Popular searches
Frequency-division multiplex details GHz frequency transmission Broadcast transmission systems Accumulation-type receiver broadcast Color television details Two-way working systems Broadcast information update Broadcast receiving circuits Electrical cable transmission adaptation Distribution switching arrangements
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com