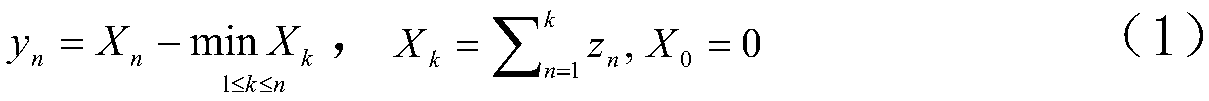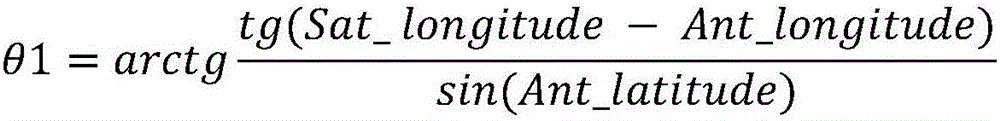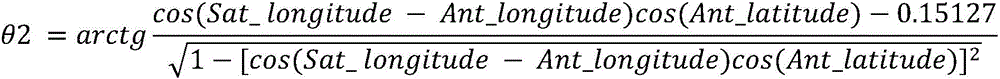Patents
Literature
132 results about "Physical level" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Method and apparatus for optimization of wireless multipoint electromagnetic communication networks
InactiveUS20040095907A1Improve signal qualityReduce interference energyPower managementSpatial transmit diversityGlobal optimizationDiversity scheme
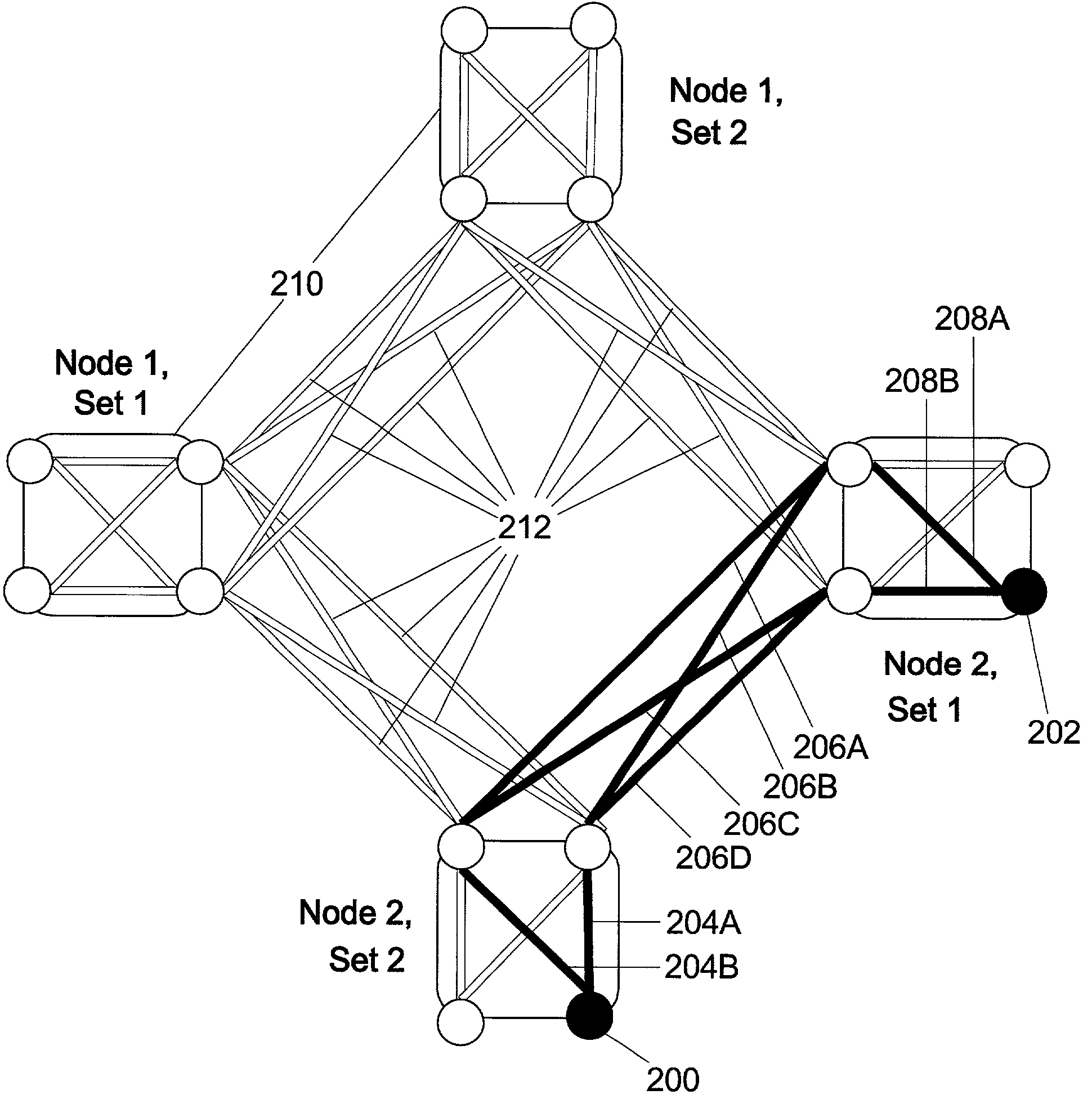
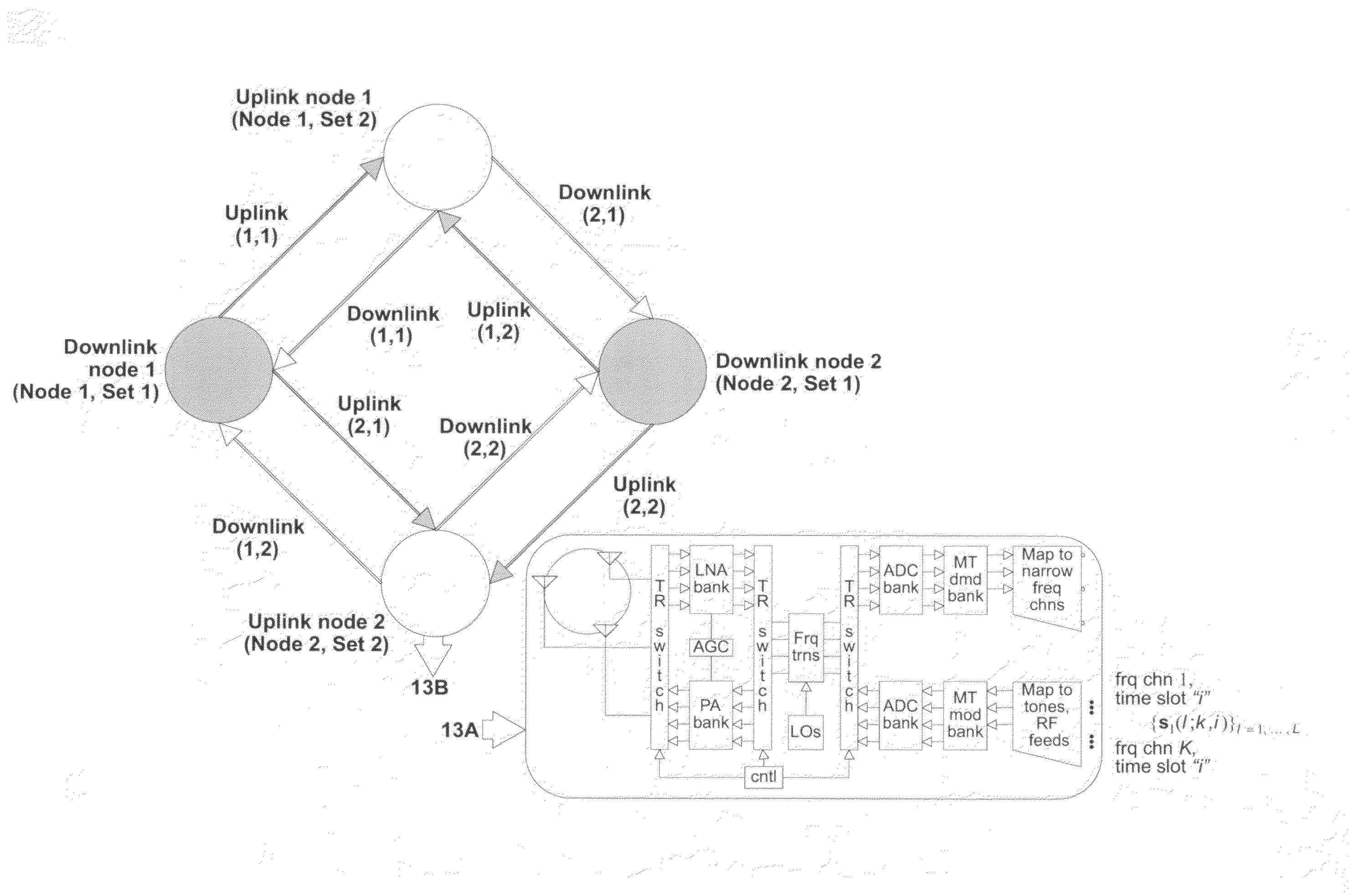
Exploiting the substantive reciprocity of internode channel responses through dynamic, adaptive modification of receive and transmit weights, enables locally enabled global optimization of a multipoint, wireless electromagnetic communications network of communication nodes. Each diversity-channel-capable node uses computationally efficient exploitation of pilot tone data and diversity-adaptive signal processing of the weightings and the signal to further convey optimization and channel information which promote local and thereby network-global efficiency. The preferred embodiment performs complex digital signal manipulation that includes a linear combining and linear distribution of the transmit and receive weights, the generation of piloting signals containing origination and destination node information, as well as interference-avoiding pseudorandom delay timing, and both symbol and multitione encoding, to gain the benefit of substantive orthogonality at the physical level without requiring actual substantive orthogonality at the physical level.
Owner:COMCAST CABLE COMM LLC
Method and apparatus for optimization of wireless multipoint electromagnetic communication networks
InactiveUS7248841B2Strong advantageReduced Power RequirementsPower managementSpatial transmit diversityGlobal optimizationRandom delay
Exploiting the substantive reciprocity of internode channel responses through dynamic, adaptive modification of receive and transmit weights, enables locally enabled global optimization of a multipoint, wireless electromagnetic communications network of communication nodes. Each diversity-channel-capable node uses computationally efficient exploitation of pilot tone data and diversity-adaptive signal processing of the weightings and the signal to further convey optimization and channel information which promote local and thereby network-global efficiency. The preferred embodiment performs complex digital signal manipulation that includes a linear combining and linear distribution of the transmit and receive weights, the generation of piloting signals containing origination and destination node information, as well as interference-avoiding pseudorandom delay timing, and both symbol and multitone encoding, to gain the benefit of substantive orthogonality at the physical level without requiring actual substantive orthogonality at the physical level.
Owner:COMCAST CABLE COMM LLC
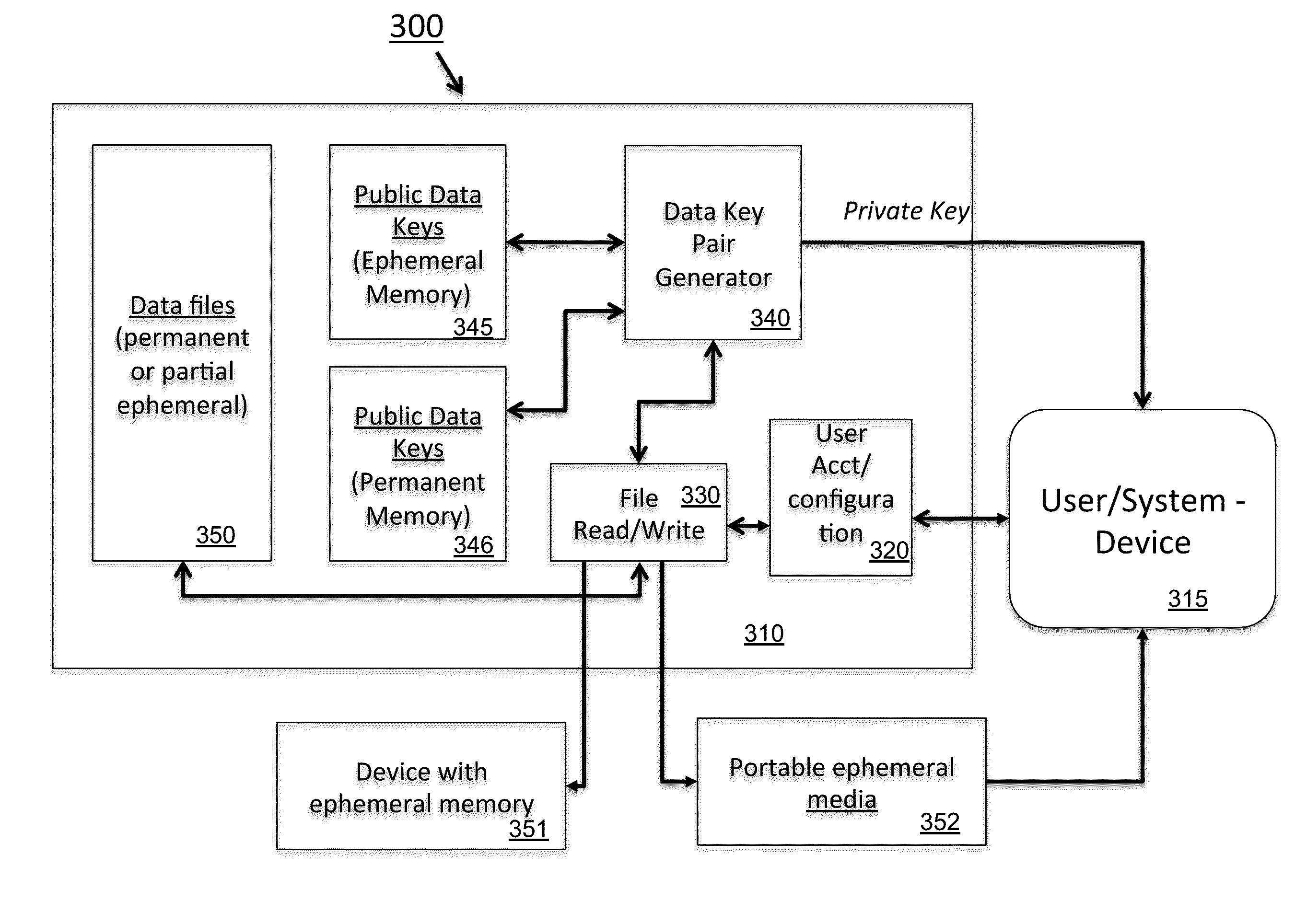
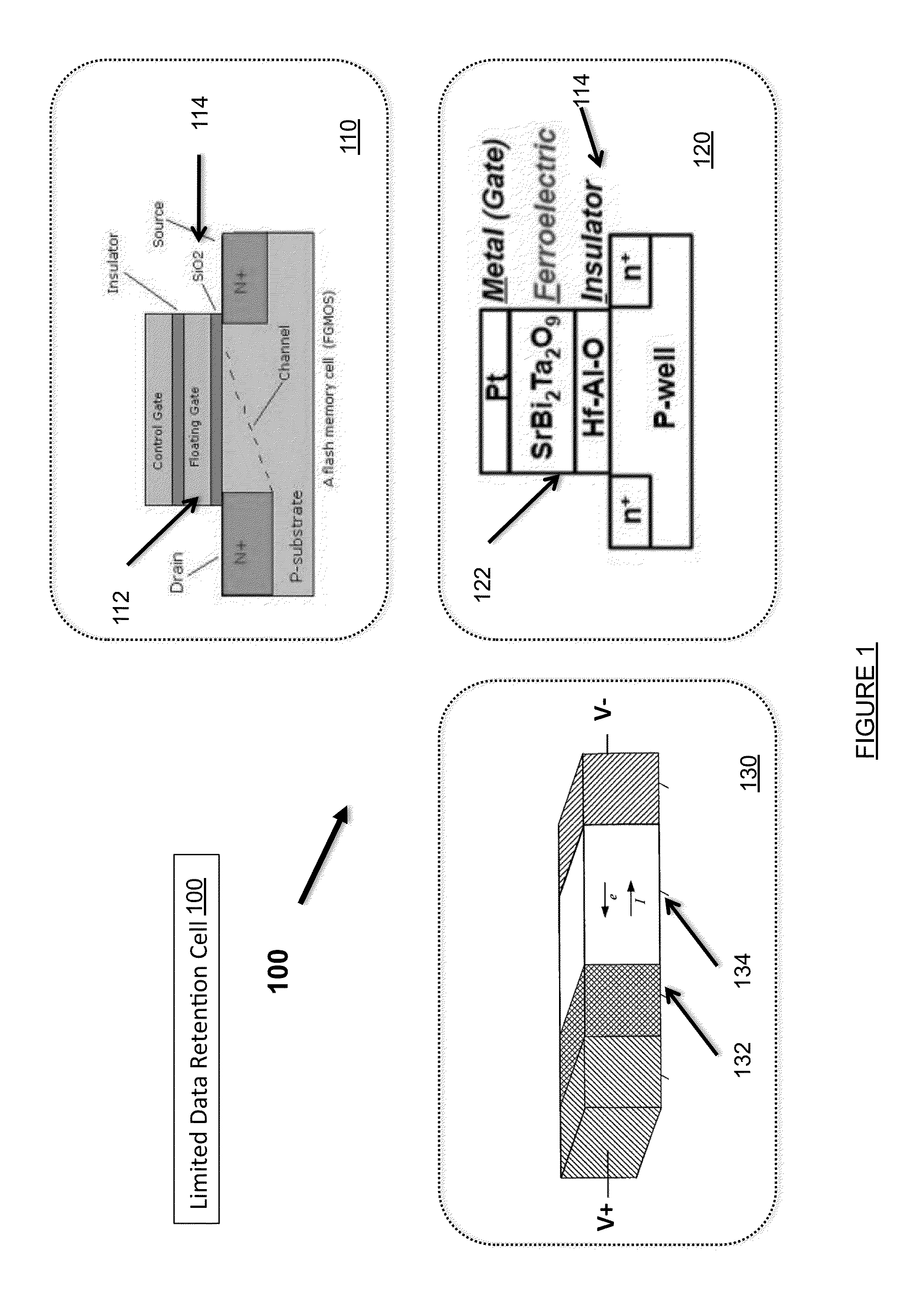
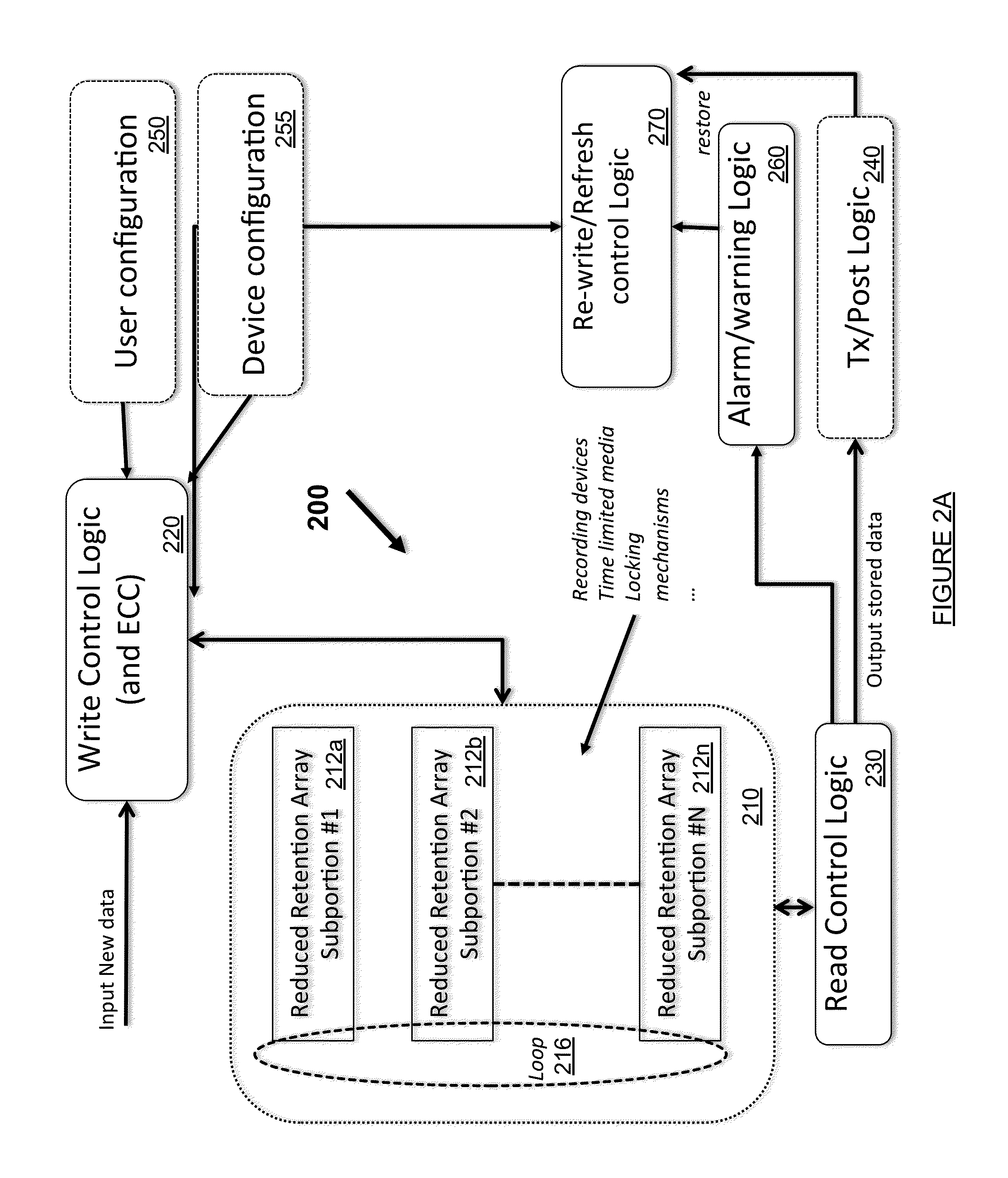
Ephemeral Storage Elements, Circuits, and Systems
An array of programmable non-volatile devices are is adapted such that their logic state is controllably altered over time by quiescent changes, slow controlled changes, scheduled changes, or some combination thereof imposed at a physical level. This allows for improved security and privacy for data to be permanently deleted. In some applications a data refresh and / or automatic backup can be implemented as well.
Owner:JONKER
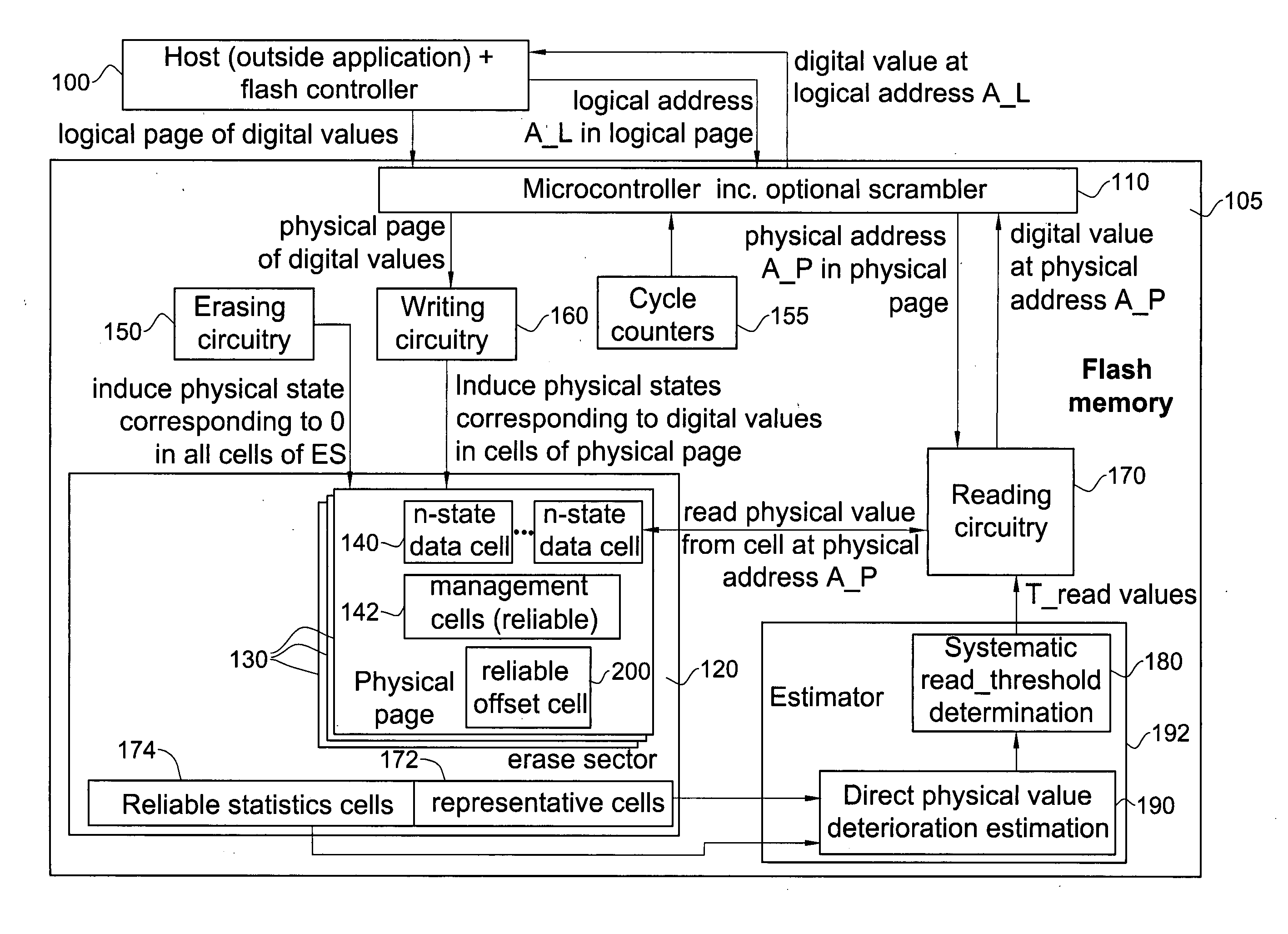
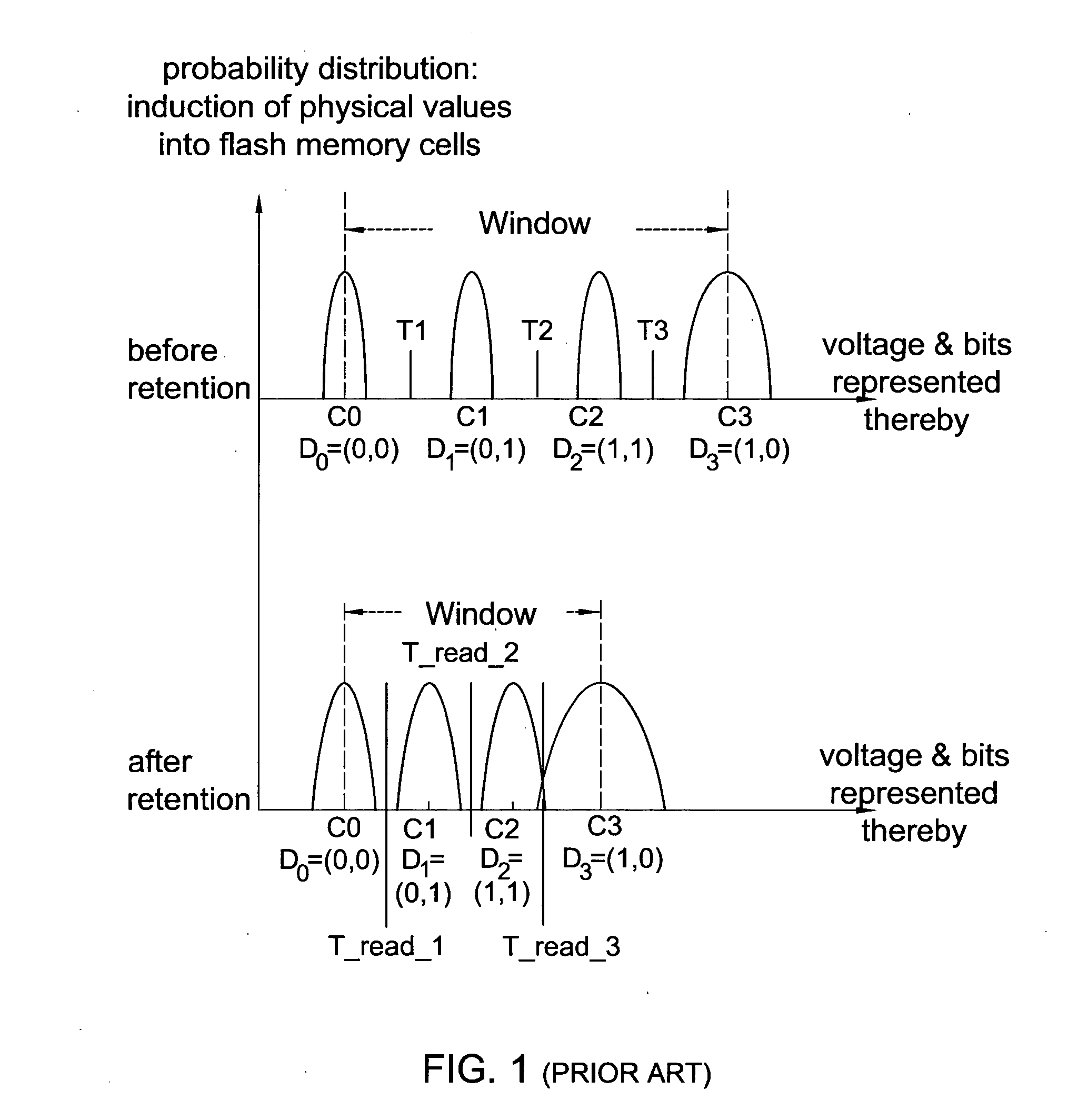
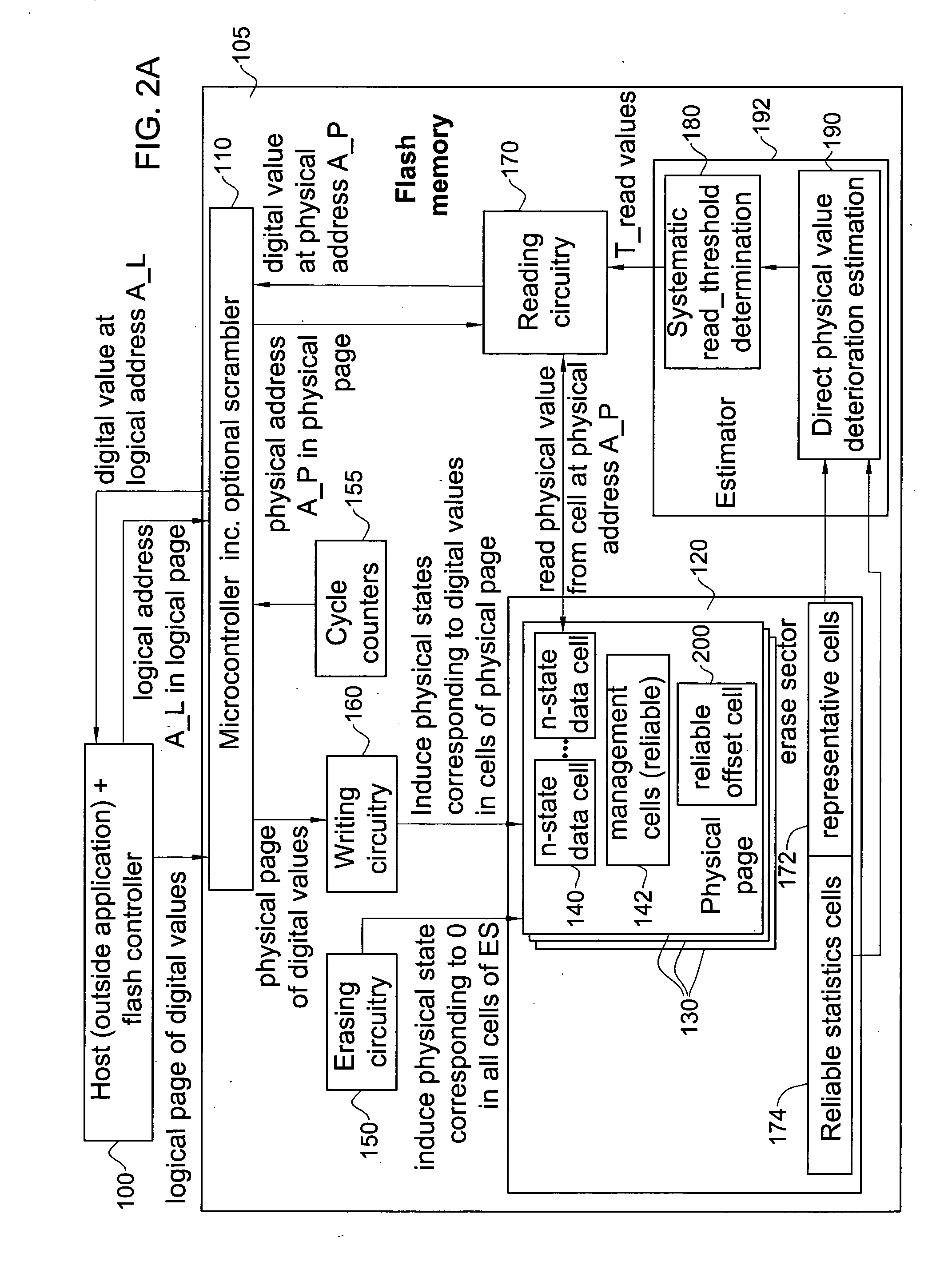
Flash memory device with physical cell value deterioration accommodation and methods useful in conjunction therewith
ActiveUS20100180073A1High densityGood effectMemory architecture accessing/allocationMemory adressing/allocation/relocationCombined useDigital storage
A method for determining thresholds useful for converting cell physical levels into cell logical values in an array of digital memory cells storing physical levels which diminish over time, the method comprising determining extent of deterioration of the physical levels and determining thresholds accordingly for at least an individual cell in said array; and reading the individual cell including reading a physical level in the cell and converting the physical level into a logical value using the thresholds, wherein the determining comprises storing predefined physical levels rather than data-determined physical levels in each of a plurality of cells and computing extent of deterioration by determining deterioration of the predefined physical levels.
Owner:AVAGO TECH INT SALES PTE LTD
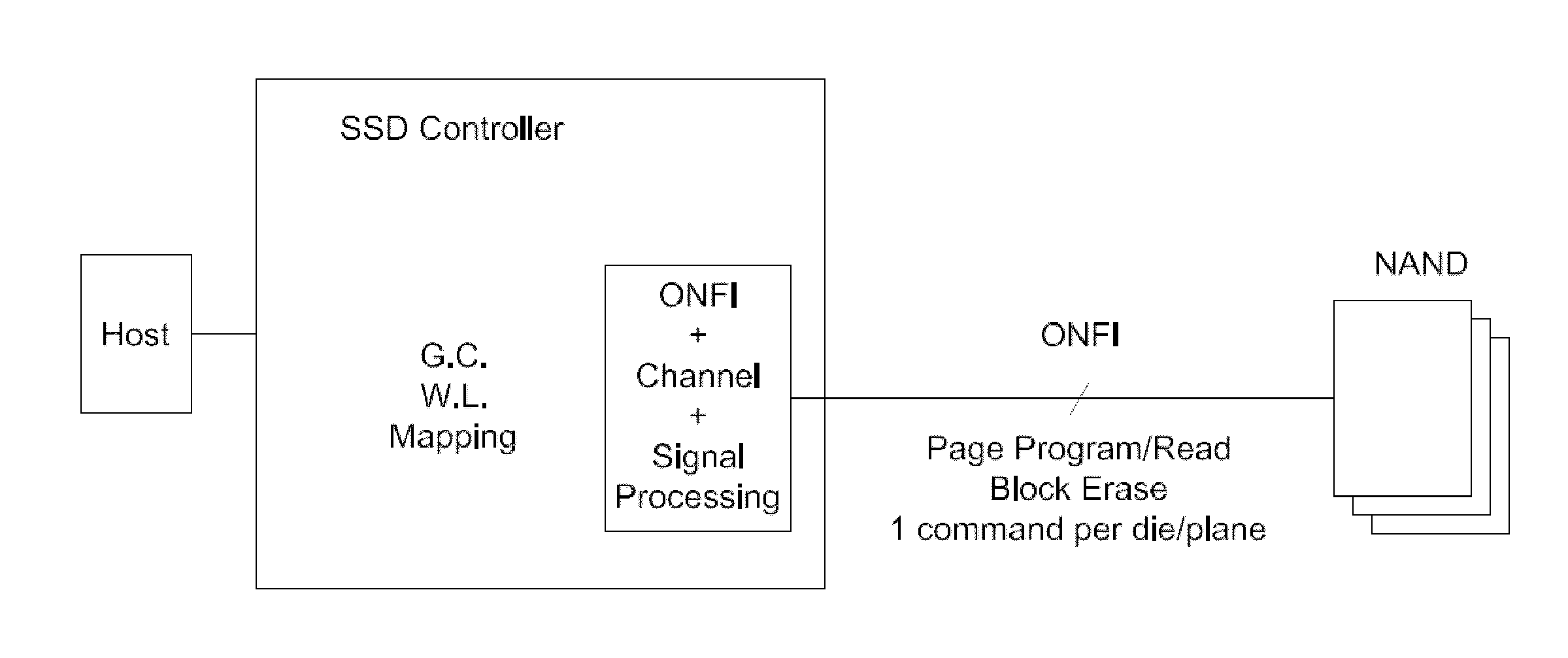
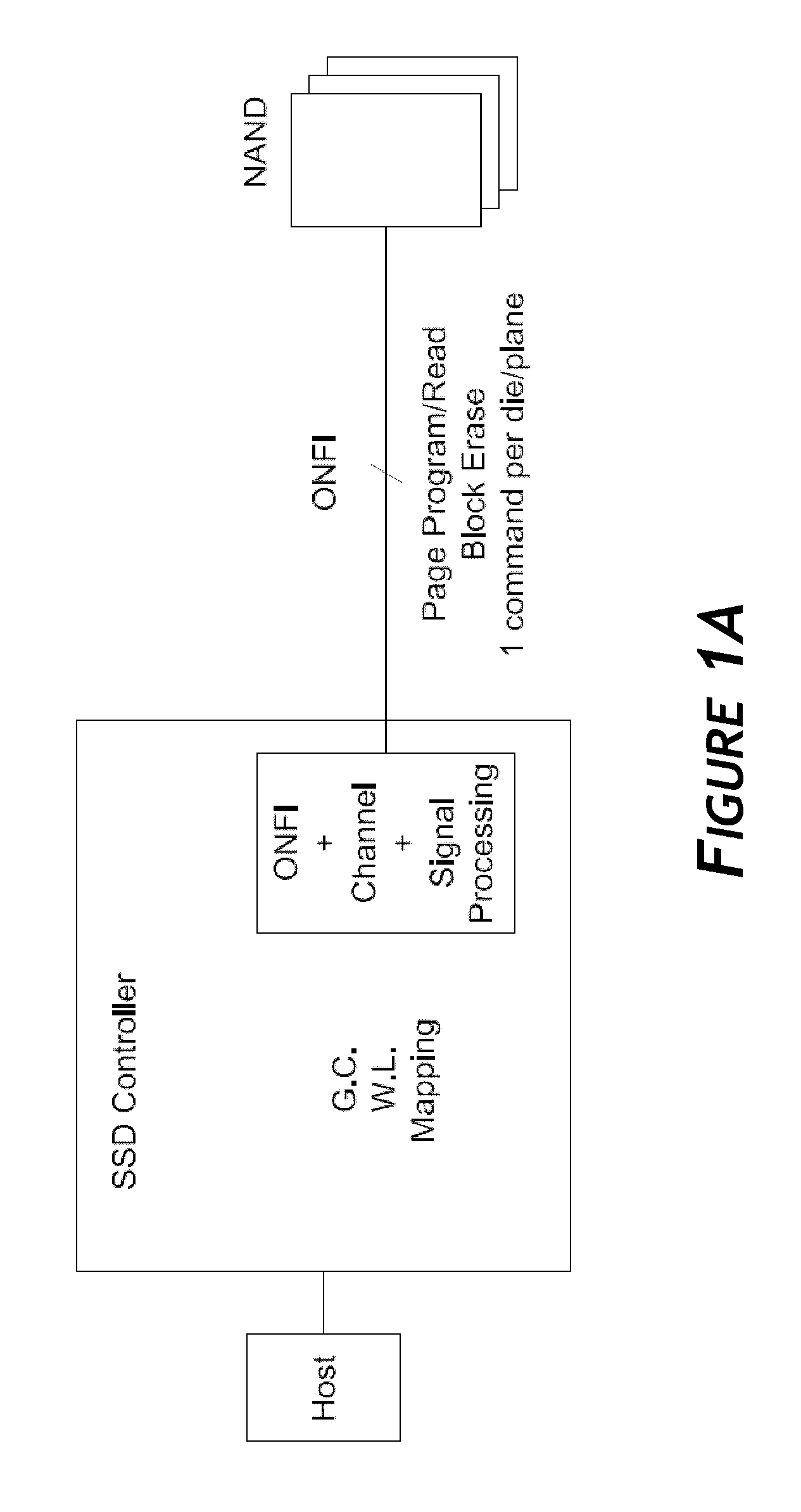
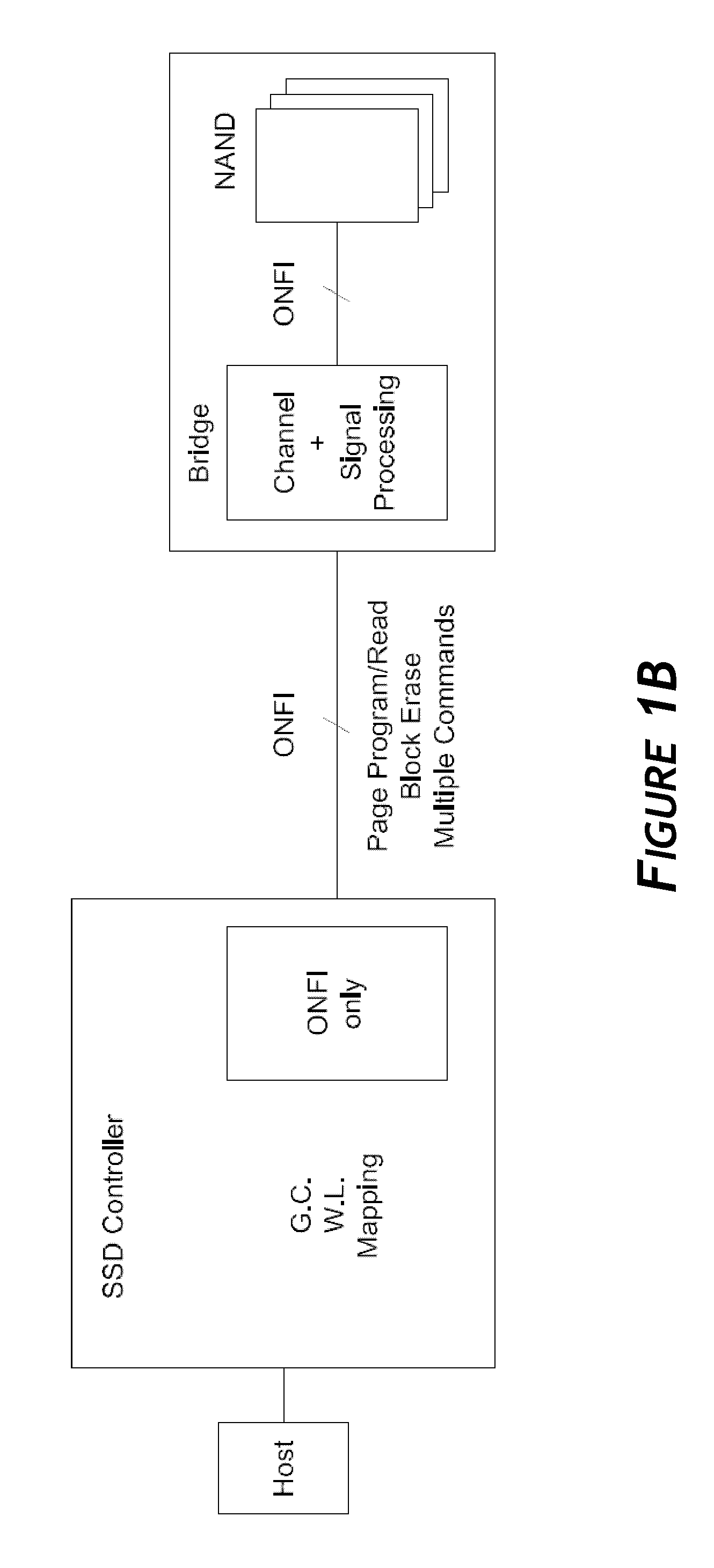
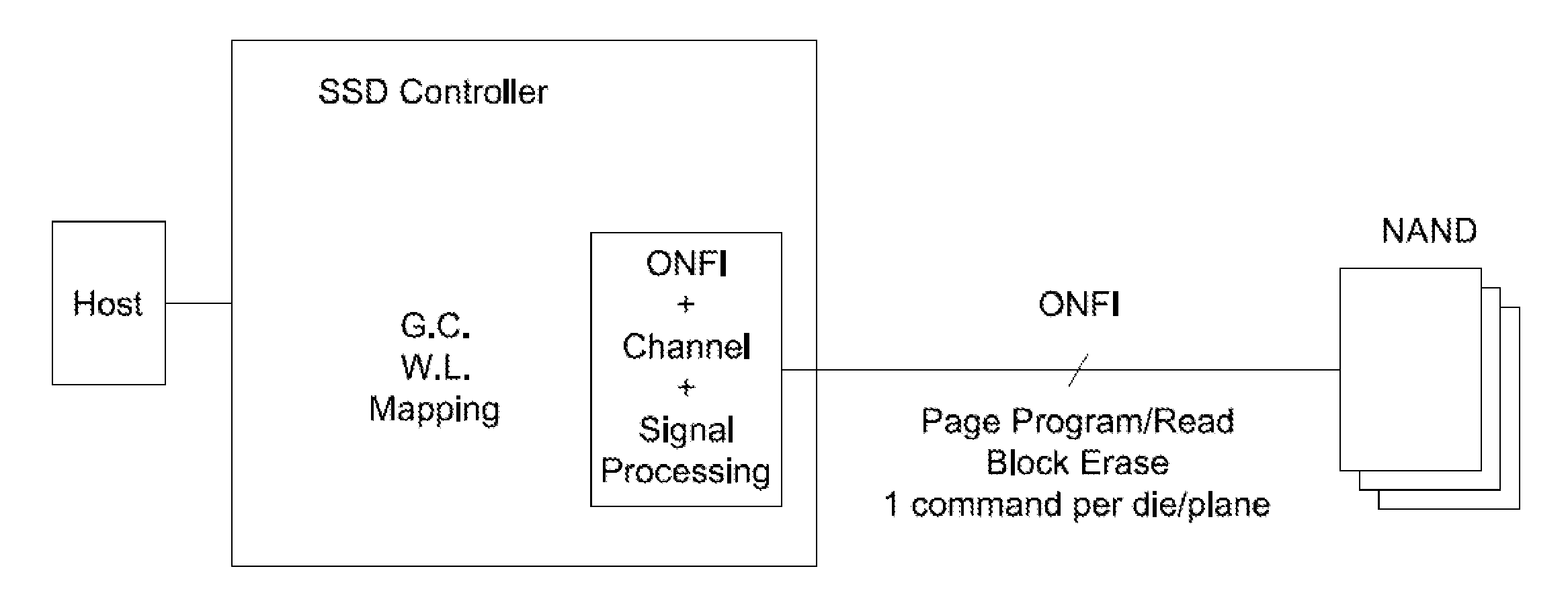
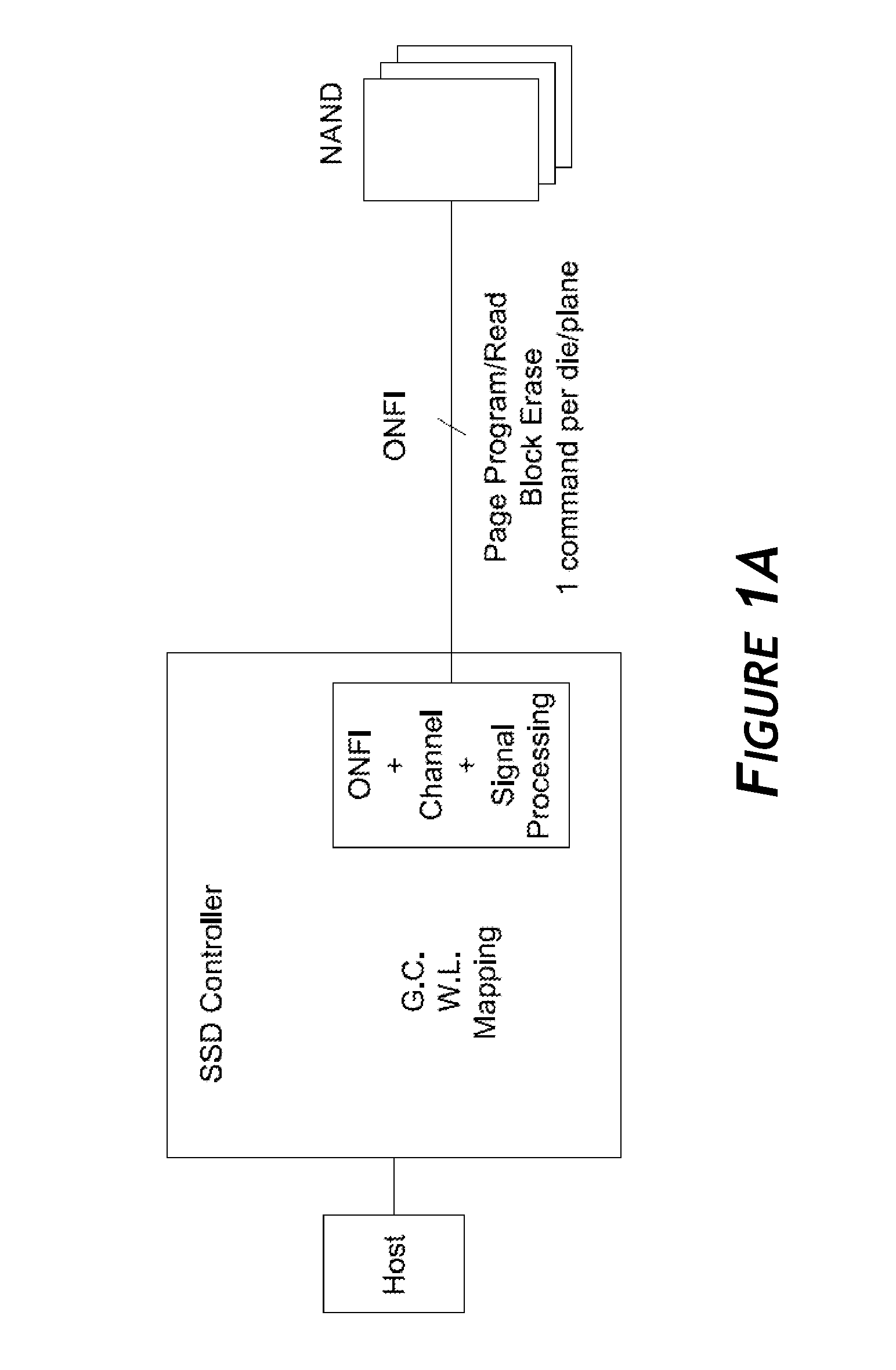
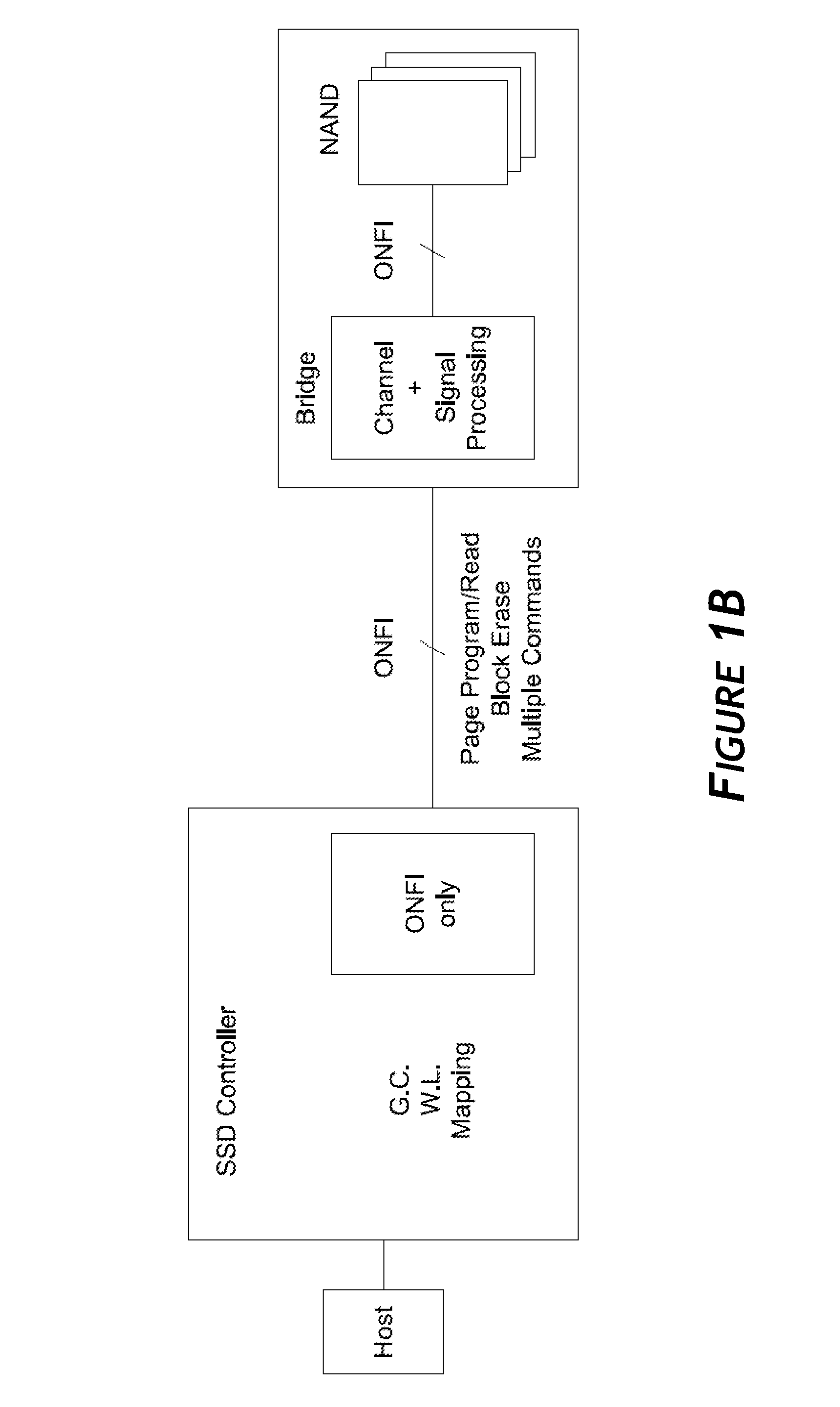
Systems and methods for an enhanced controller architecture in data storage systems
ActiveUS20130060981A1Memory adressing/allocation/relocationDigital computer detailsController architectureEngineering
Disclosed herein is a controller architecture that pairs a controller with a NVM (non-volatile memory) storage system over a high-level, high speed interface such as PCIe. In one embodiment, the NVM storage system includes a bridge that communicates with the controller via the high-level interface, and controls the NVM via an interface (e.g., ONFI). The controller is provided a rich set of physical level of controls over individual elements of the NVM. In one embodiment, the controller is implemented in a higher powered processor that supports advanced functions such as mapping, garbage collection, wear leveling, etc. In one embodiment, the bridge is implemented in a lower powered processor and performs basic signal processing, channel management, basic error correction functions, etc. This labor division provides the controller physical control of the NVM over a fast, high-level interface, resulting in the controller managing the NVM at both the page and block level.
Owner:WESTERN DIGITAL TECH INC
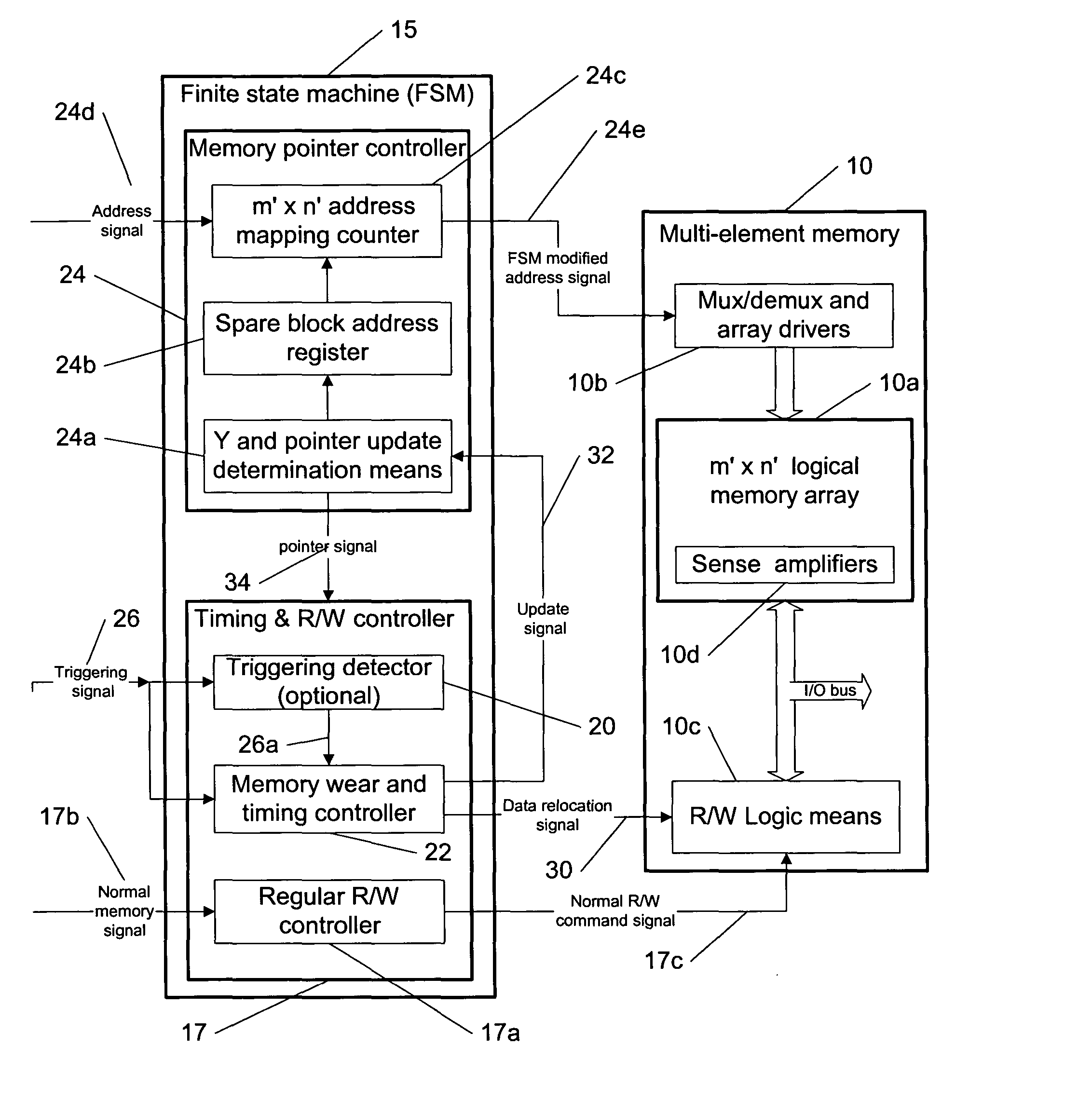
Memory wear leveling
InactiveUS20050055495A1Reduce wearMemory architecture accessing/allocationMemory loss protectionMemory typeComputer architecture
This invention describes a memory wear leveling for reducing wearing of hotspots (deteriorated memory blocks used more frequently) in all memory types by rotating the memory blocks on the physical level with the help of at least one spare memory block using predetermined criteria during both read and write operations. The invention can be implemented e.g. by using constant memory pointers at a logical level and dynamic memory pointers on the physical level. The rotation can be implemented as a combination of software and hardware functionalities or using hardware or software alone.
Owner:NOKIA SOLUTIONS & NETWORKS OY
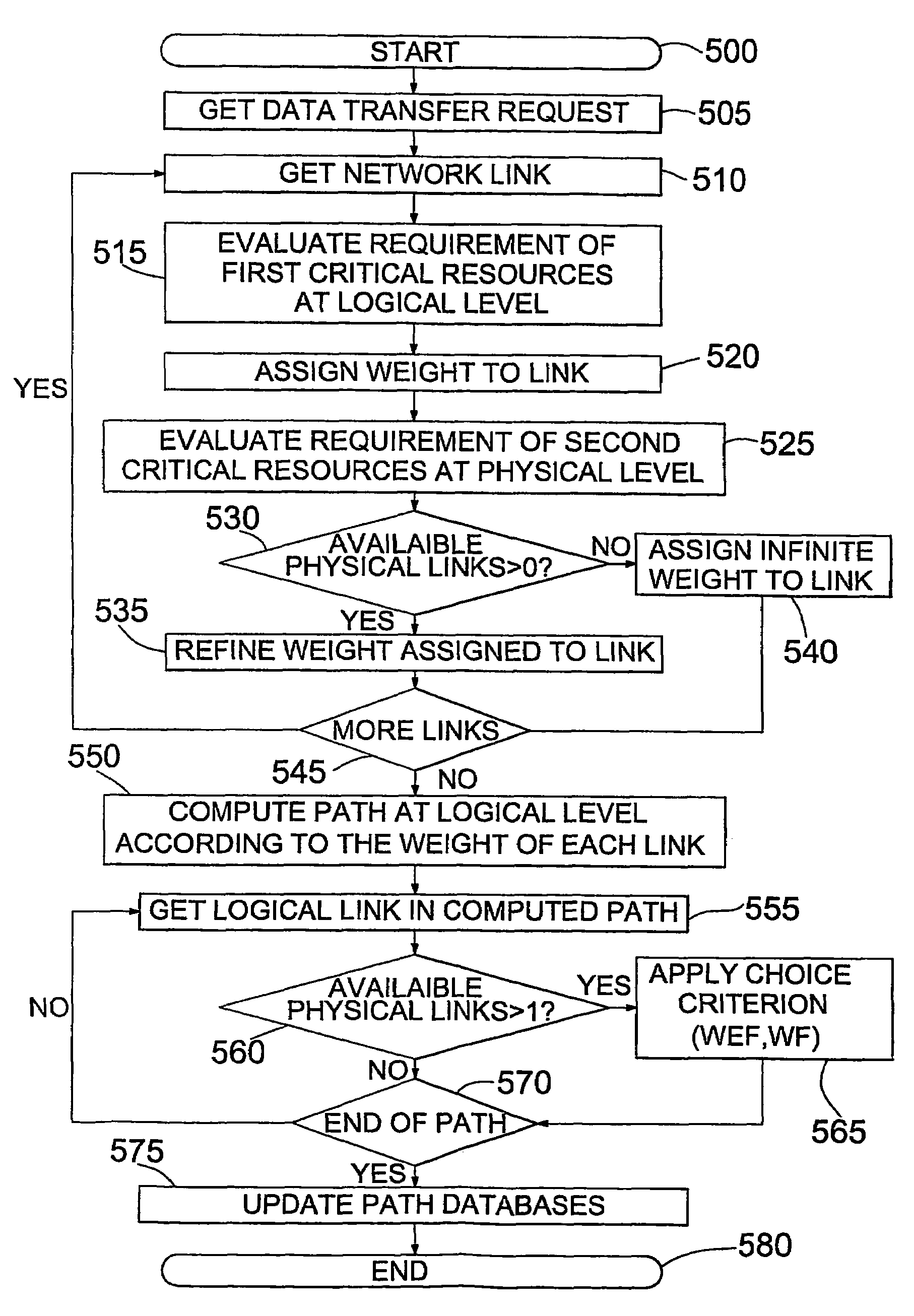
Dynamic routing in packet-switching multi-layer communications networks
InactiveUS20060209785A1Improve performanceImprove network performanceWavelength-division multiplex systemsNetworks interconnectionAdaptive routingPhysical level
A method is provided for routing data packets across a multi-layer network which includes a plurality of nodes, a logical level provided with a plurality of logical links and a physical level provided with a plurality of physical links, each of the logical links corresponding to at least one of the physical links, the method comprising the steps of assigning a weight to each logical link with respect to a first critical constraint in the logical level, refining the weight assigned to each logical link with respect to a second critical constraint in the physical level and, based on the weights assigned to each link, computing a path at the logical level connecting a start node to an end node for the transport of the data packets.
Owner:TELEFON AB LM ERICSSON (PUBL)
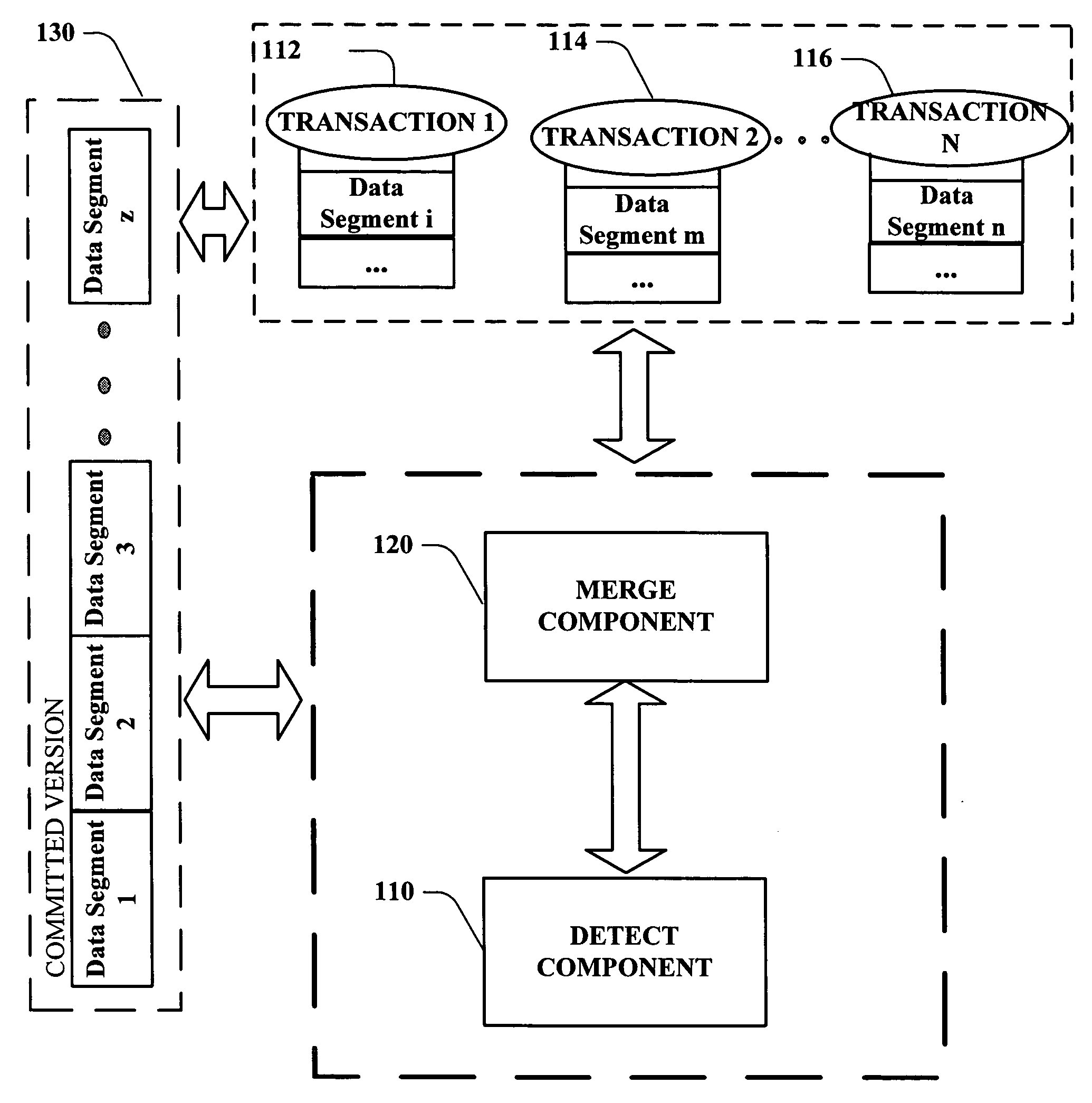
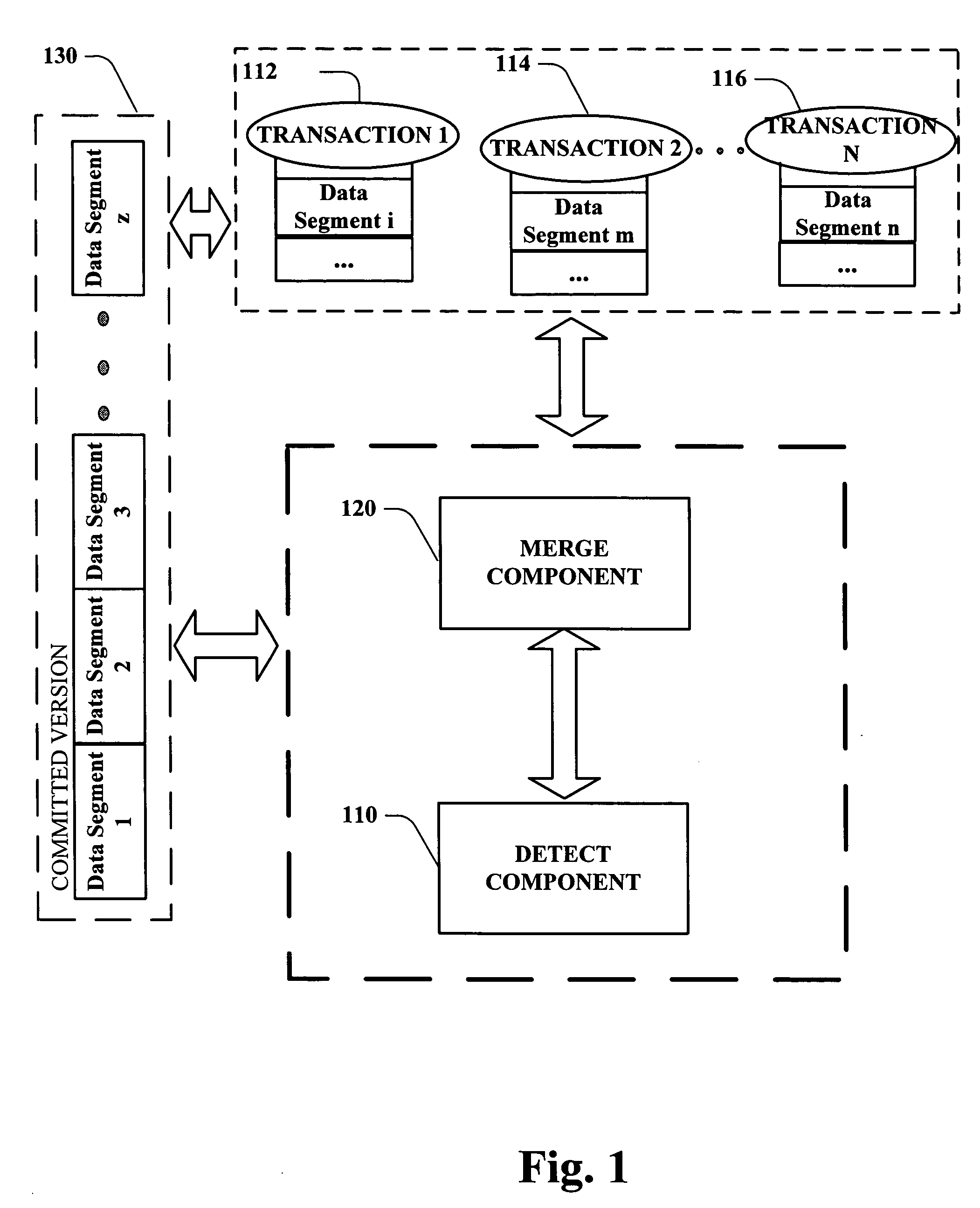
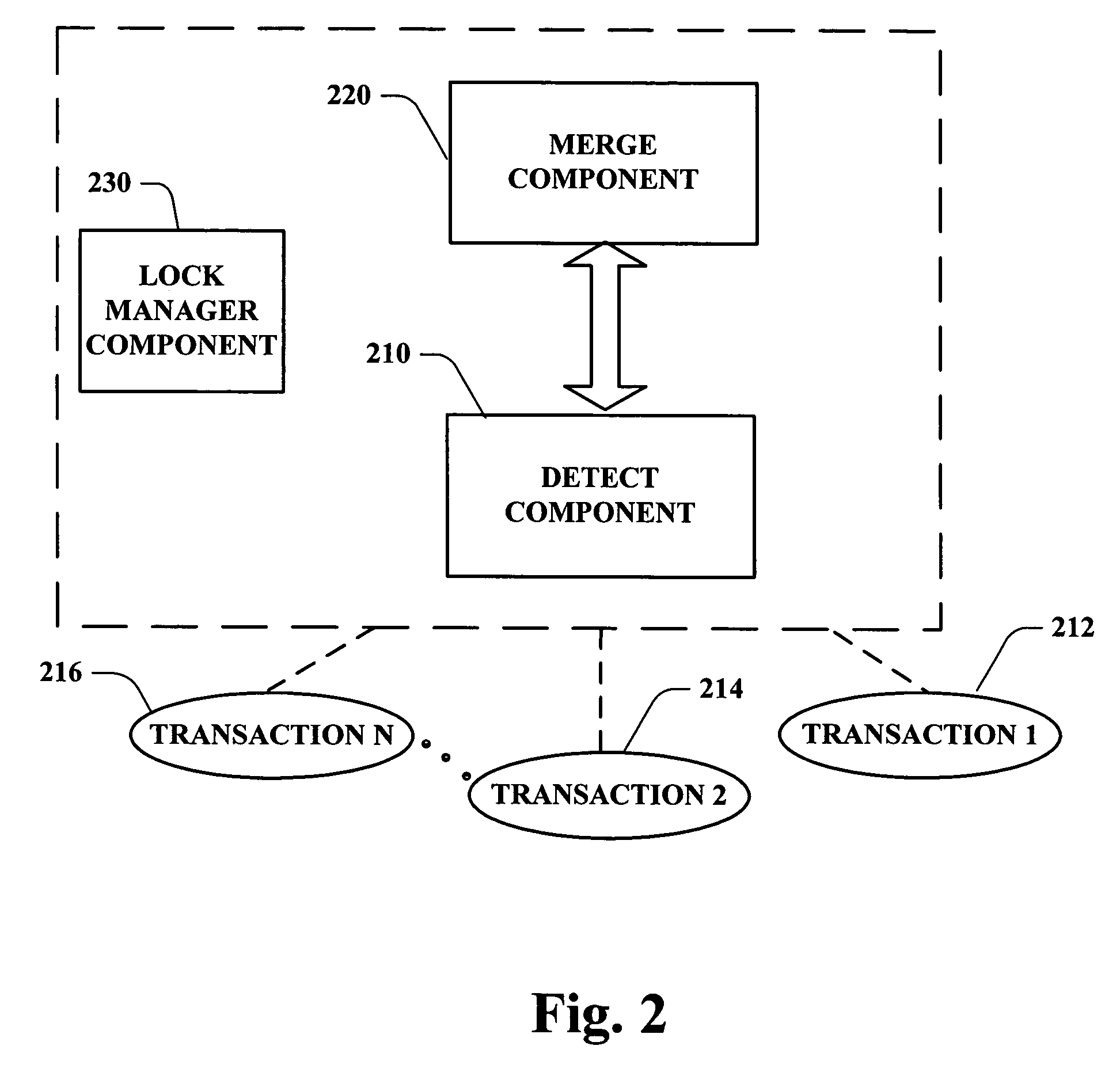
Concurrent transactions and page synchronization
ActiveUS20050289189A1Efficient executionSpace availability for particularDigital data information retrievalDigital data processing detailsData synchronizationFile synchronization
Systems and methodologies are provided for efficiently performing concurrent transactions by multiple users, and tracking data at a logical level beneath a physical level of the object being modified. Each transaction can copy a committed version of the data segment to be modified to its respective space, and can update such copy during modification. A detect component detects whether any data segment being operated upon requires updating as a result of other transactions committing, and a merge component synchronizes the data segment with its committed version. Various optimization procedures can also be incorporated as part of the commit stage, upon completion of the detect and merge process.
Owner:MICROSOFT TECH LICENSING LLC
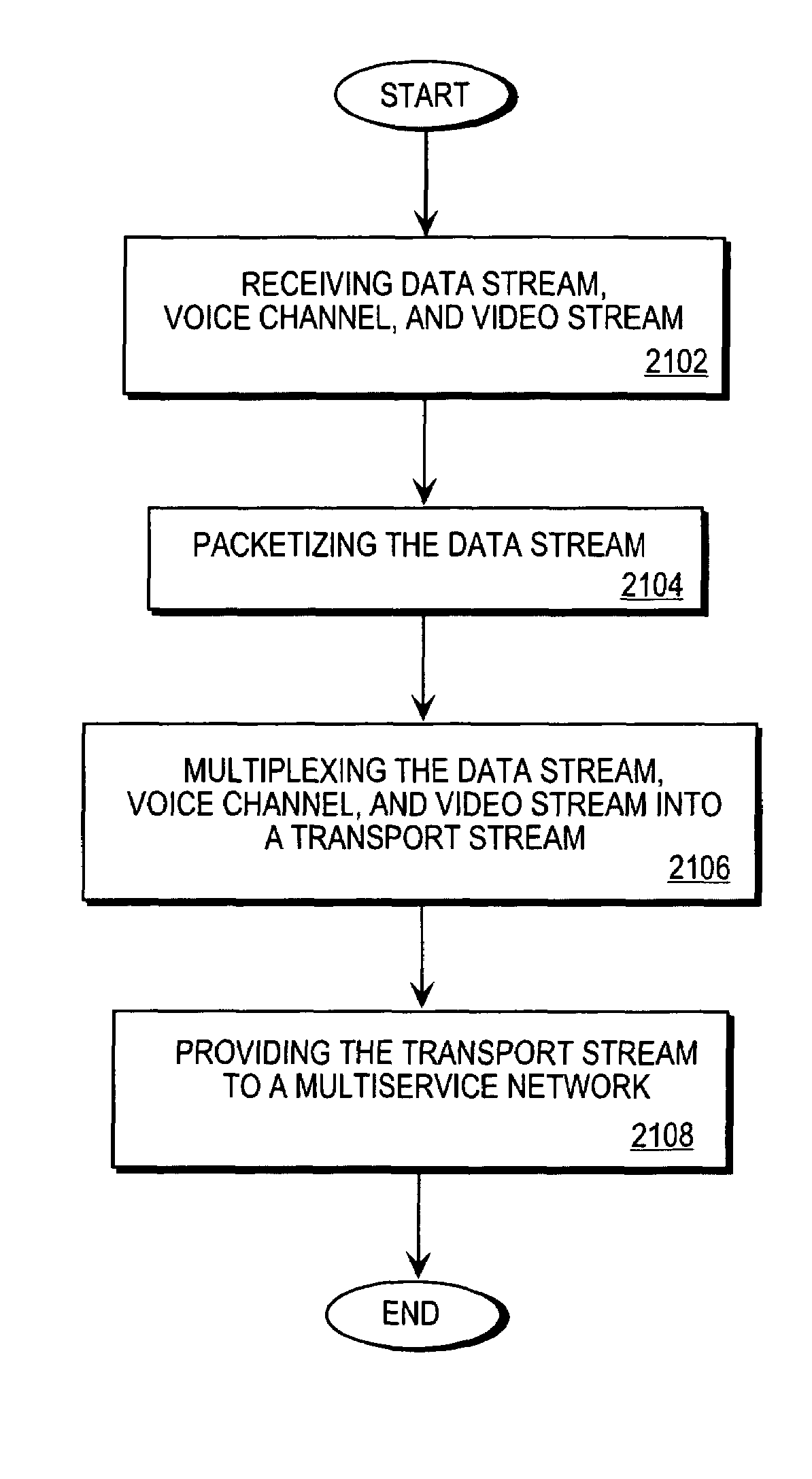
Method and apparatus for routing integrated data, voice, and video traffic
A Multiservice Access Concentrator (MAC) receives information comprising at least one data stream, at least one voice channel, at least one video stream, Local Area Network (LAN)-based traffic, and facsimile traffic. The received data stream is packetized, and the packetized data stream is multiplexed with the voice channel and the video stream to form an integrated transport stream. The voice channel comprises compressed and uncompressed voice information. The integrated transport stream is provided to at least one multi-service network using a software-configurable trunk. The multi-service network includes cell-based and packet-based networks comprising Asynchronous Transfer Mode (ATM), Frame Relay, High-level Data Link Control (HDLC), Internet Protocol (IP), and Time Division Multiplex (TDM) networks, as well as leased-line carrier services. The trunk is configured at a physical level and a protocol level using at least one trunk option.
Owner:CISCO TECH INC
Methods and systems for scalable interconnect
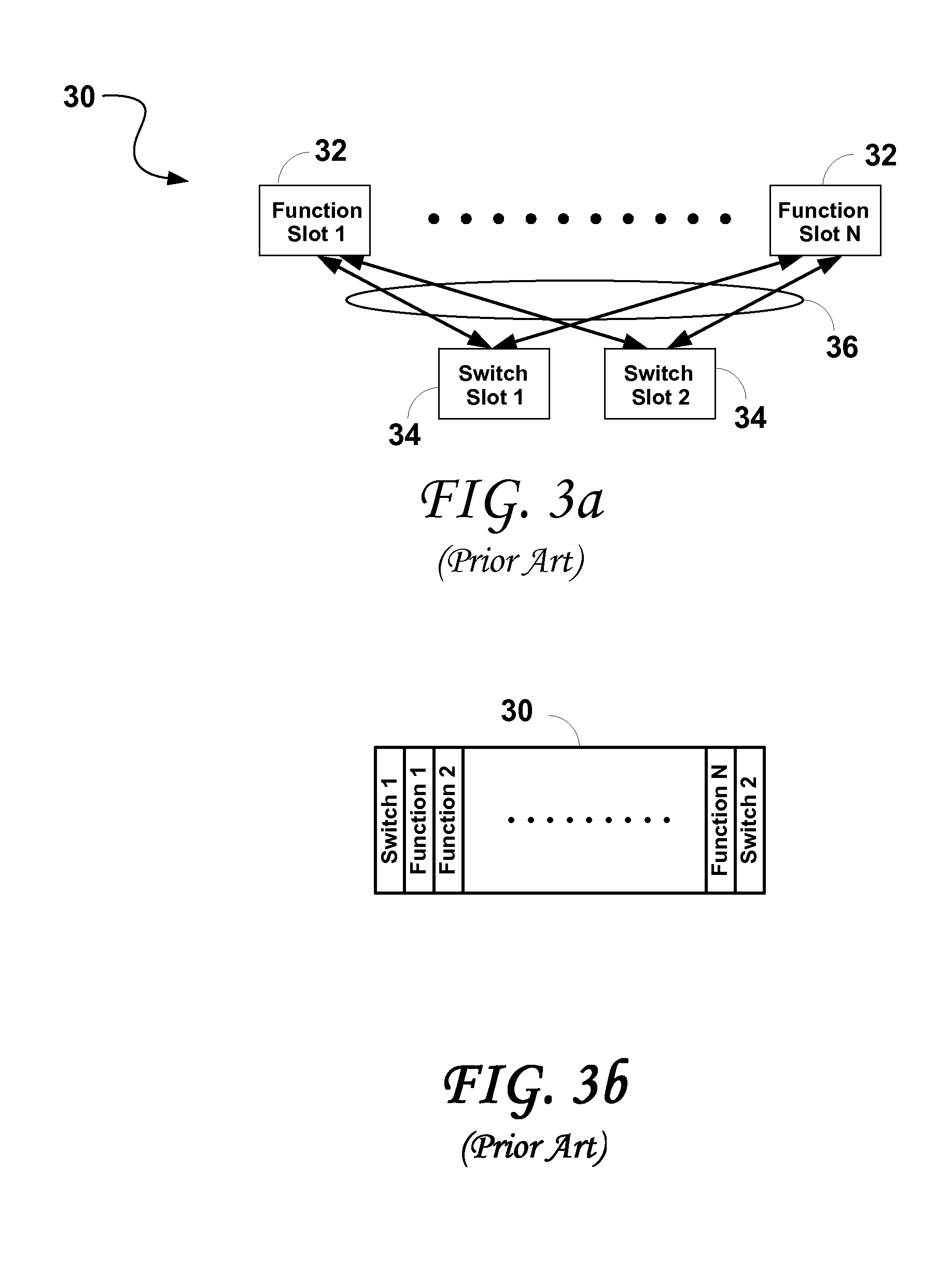
Embodiments of the present invention define a modular architecture that provides the physical level of interconnect that is used to cost effectively deploy high performance and high flexibility communication networks. Aspects of the physical communications are described to deliver scalable computer to computer communications as well as scalable computer to I / O communications, scalable I / O to I / O communications, and scalable function to function communications with a low cable count. Embodiments of the present invention focus on the physical switched communications layer, as the interconnect physical layer, functions, chassis; modules have been designed as an integrated solution.
Owner:LIQUID COMPUTING
Layer one switching in a packet, cell, or frame-based network
InactiveUS7324510B2Optimum advantage and efficiencyMultiplex system selection arrangementsTime-division multiplexQuality of serviceFrame based
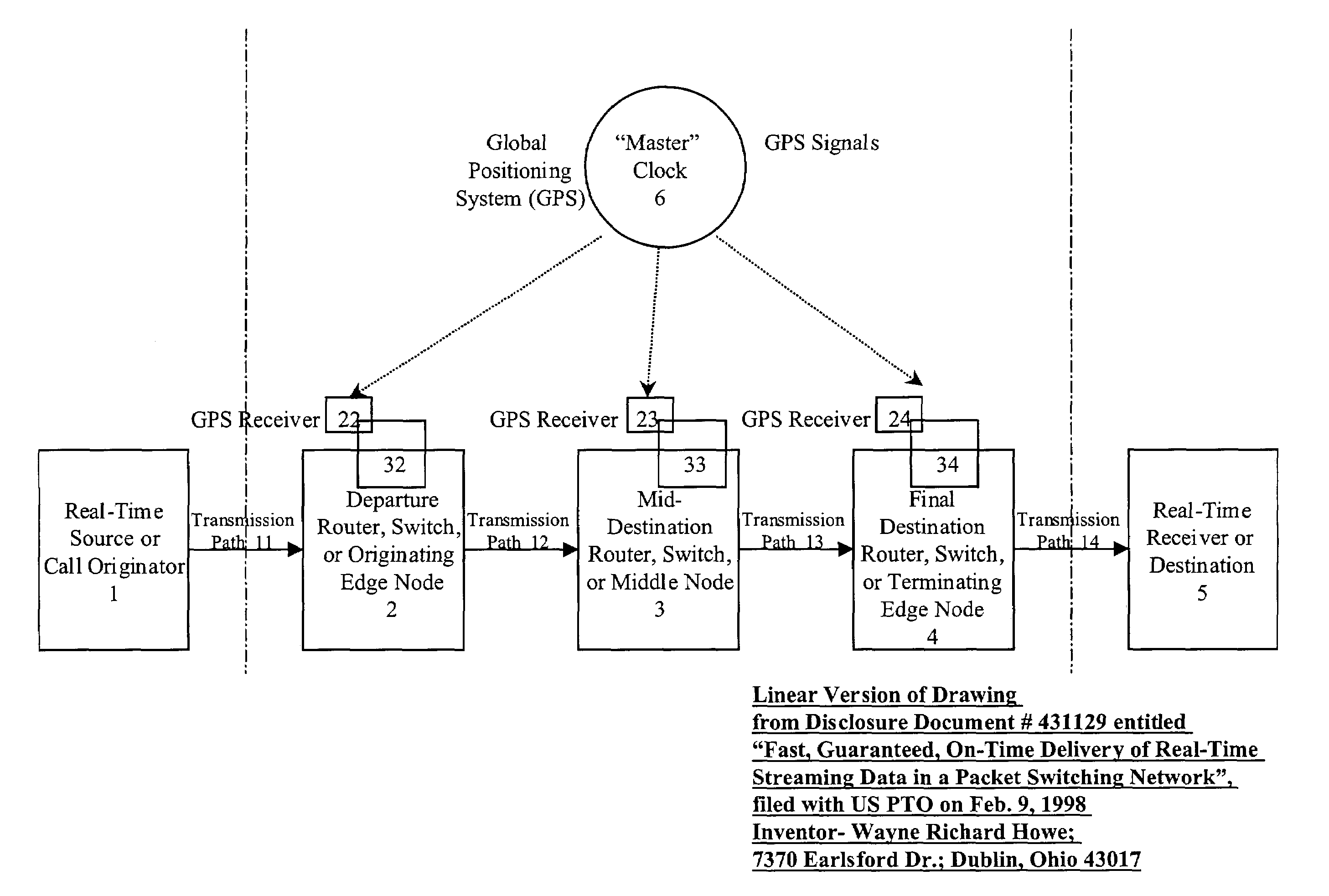
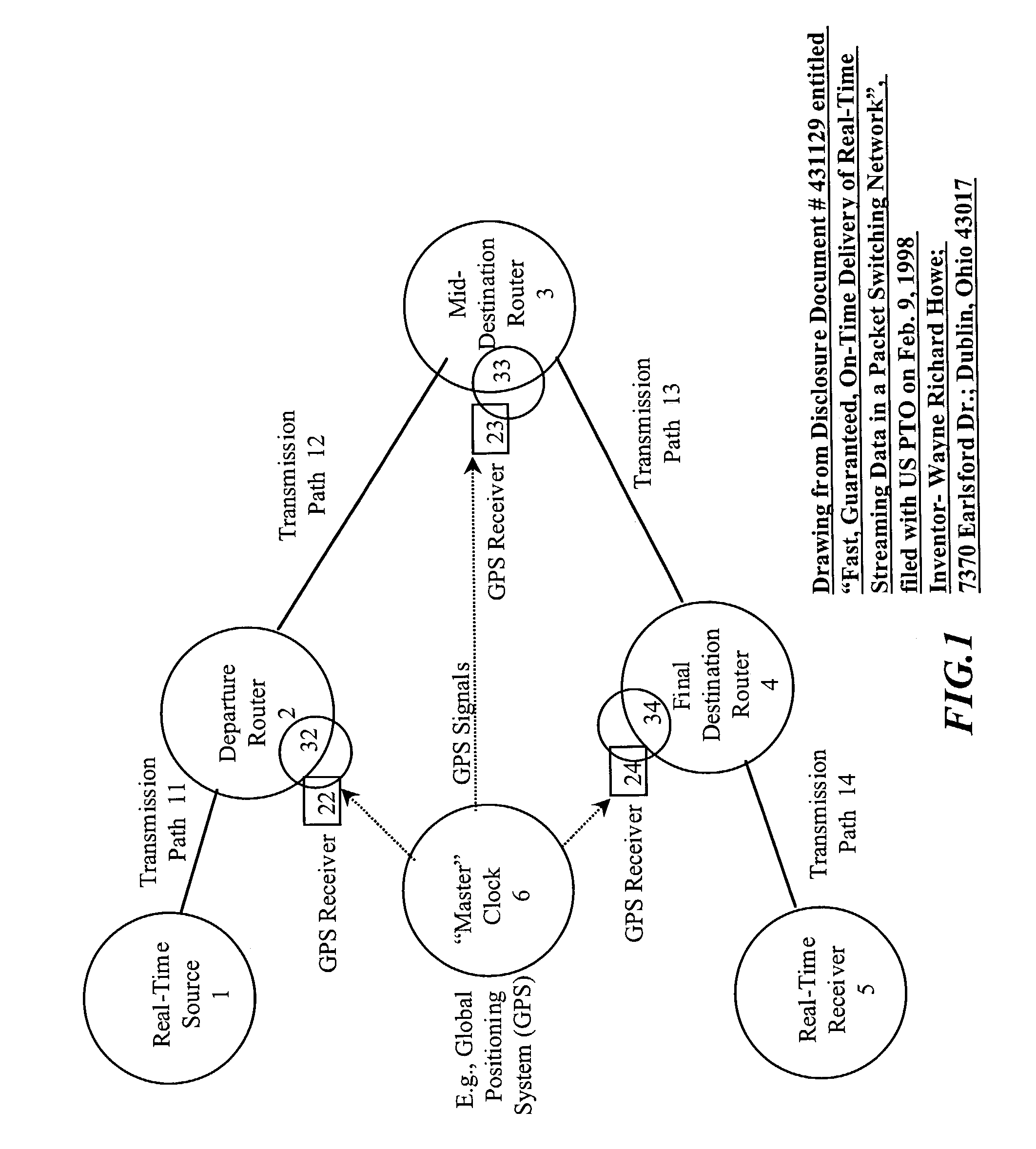
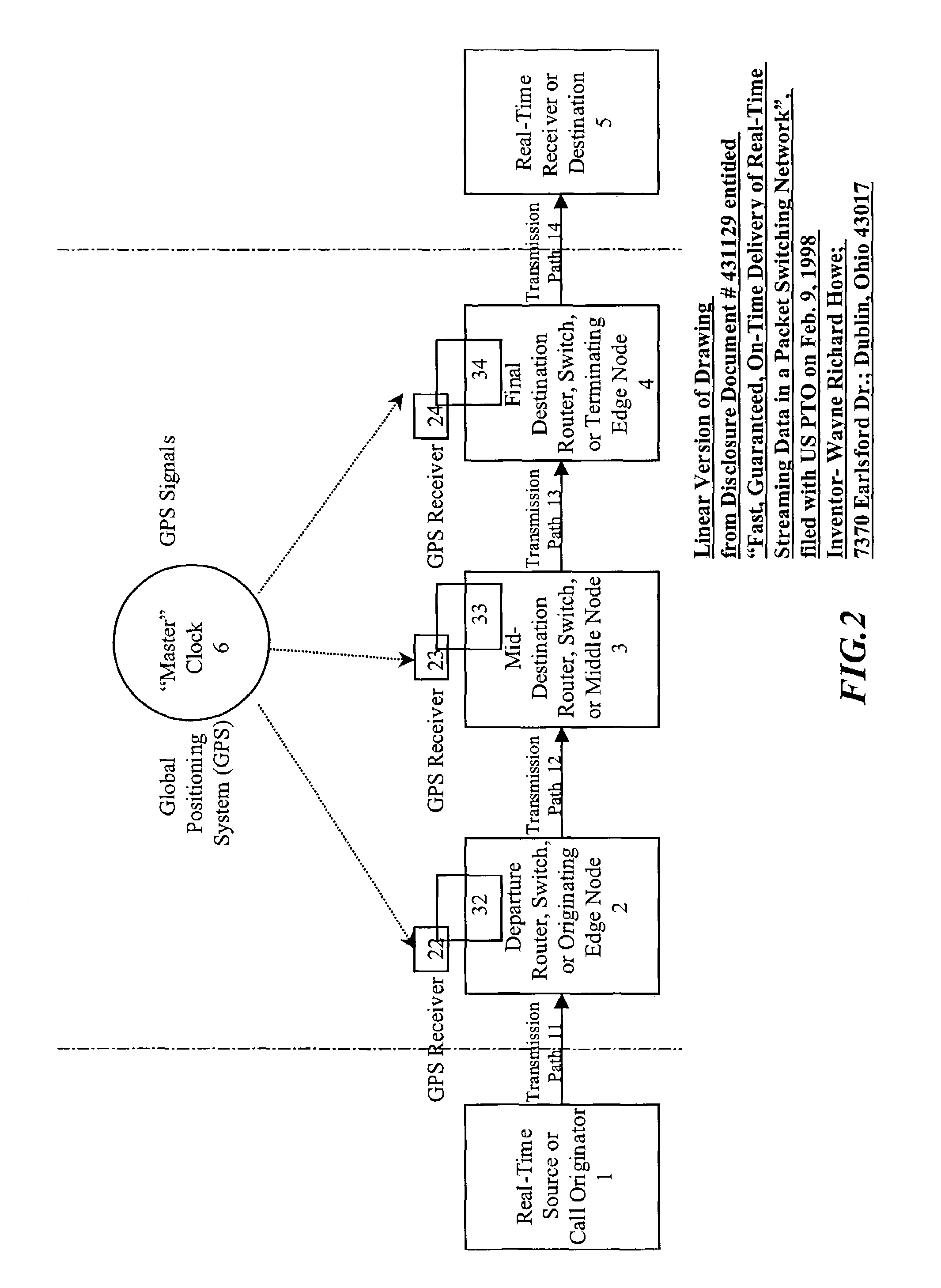
A system and method are described for synchronizing store-and-forward networks and for scheduling and transmitting continuous, periodic, predictable, time-sensitive, or urgent information such as real-time and high-priority messages over those networks. This enables packet-, cell-, and / or frame-based networks to thereby efficiently switch voice, video, streaming, and other real-time or high-priority data at the layer one or physical level, thus ensuring that the delivery of selected information can be made fast, on-time, immediate, non-blocked, non-congested, loss-less, jitter-free, and have guaranteed delivery, and guaranteed quality of service.
Owner:SWXTCH THE RULES
Relay physical layer safe transmission method
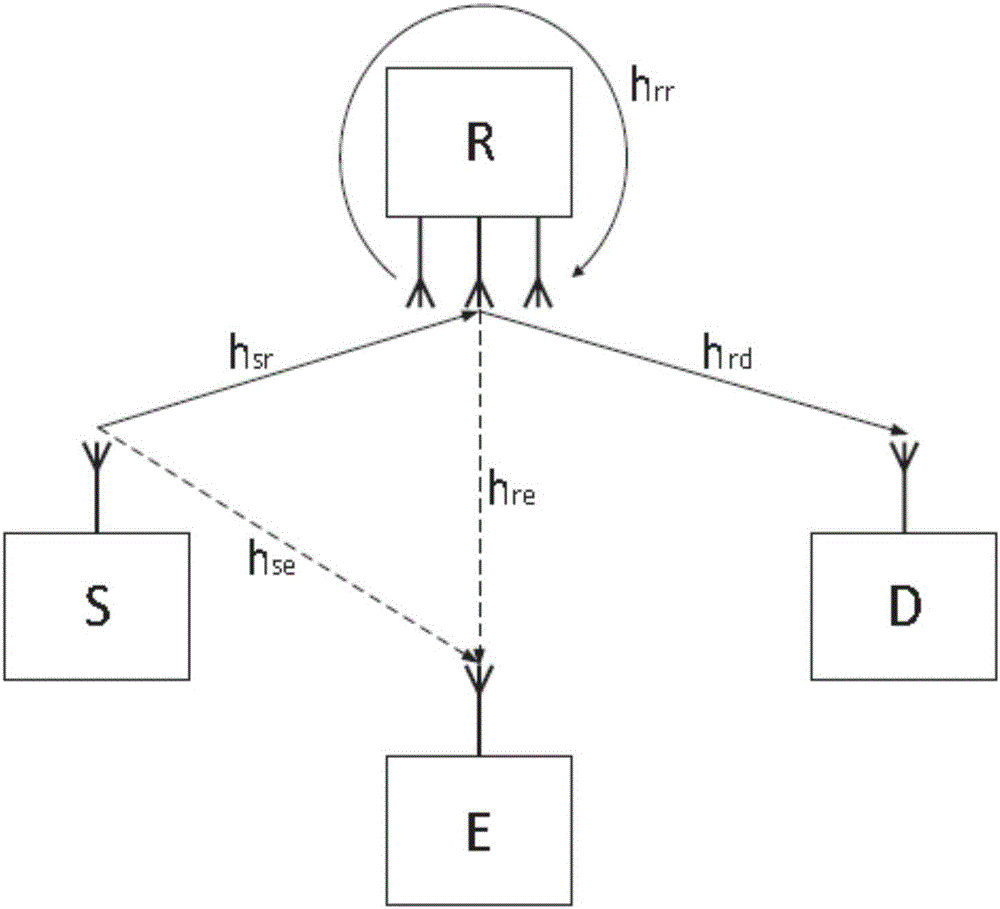
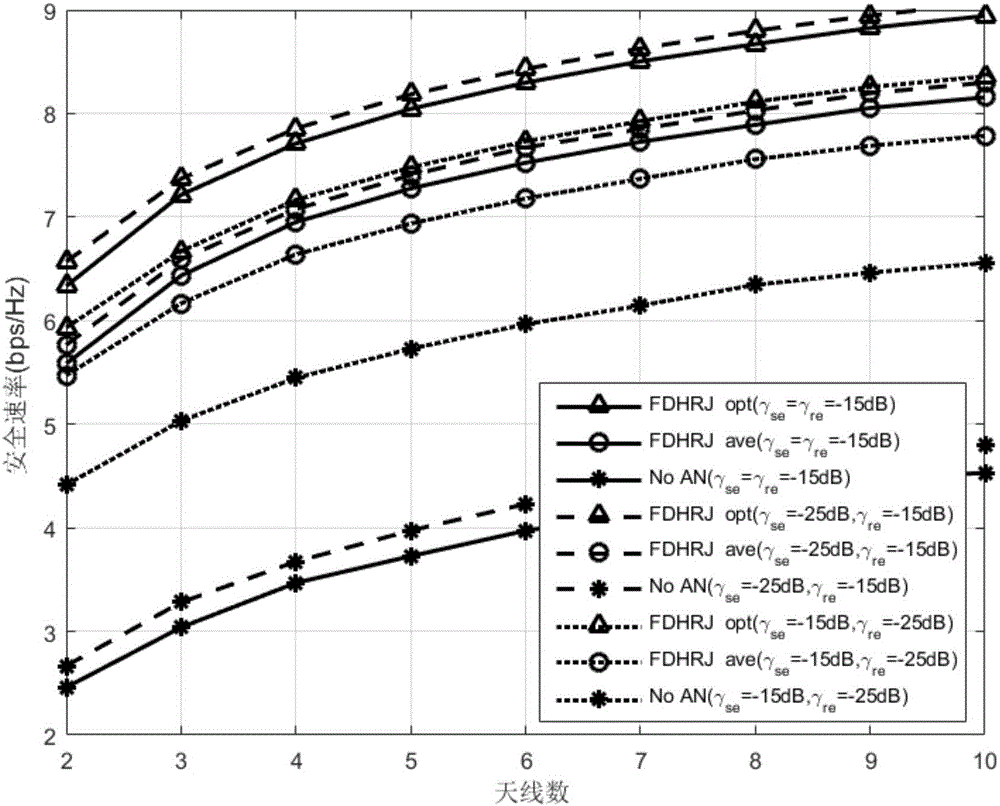
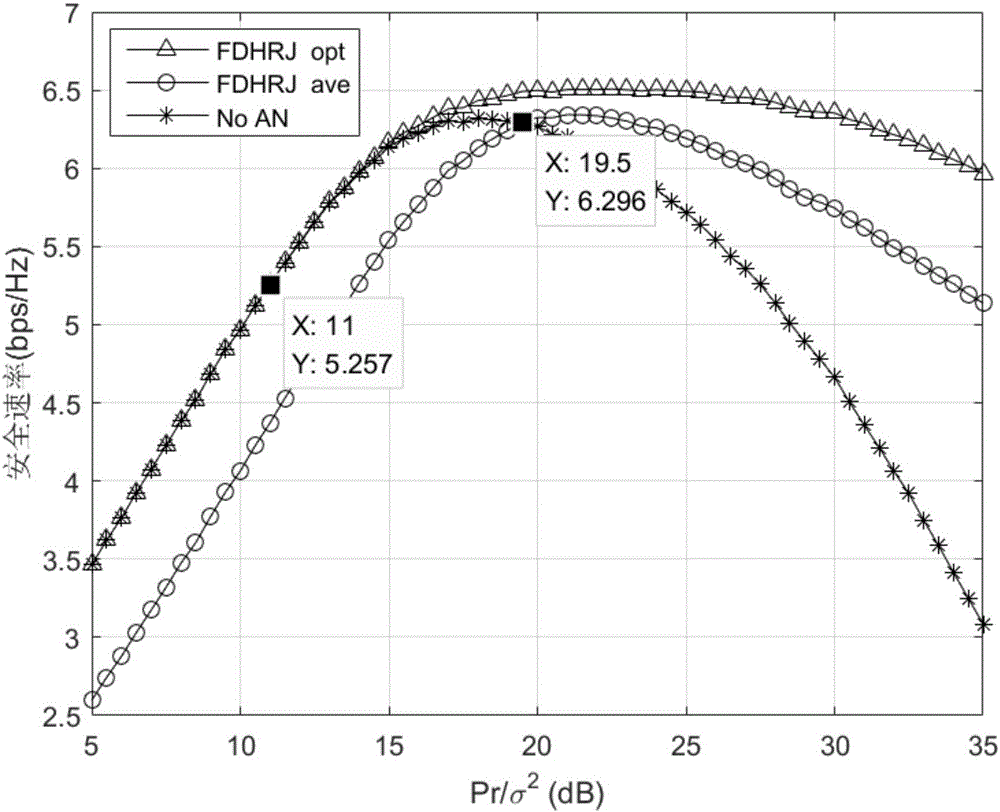
ActiveCN106059705AReduce adverse effectsImprove securityCommunication jammingSecurity arrangementPhysical levelPrecoding matrix
The invention provides a relay physical level safe transmission method and belongs to the field of communication. According to the invention, a relay node is, while under a full duplex working mode, is configured with a plurality of antennas, and adopts decode-and-forward protocol. The method designs a pre-coded array to be an artificial noise, and allows the relay node to transmit a hybrid signal of an expectation signal and the artificial noise to an object node at each time slot. A bugging node can bug the hybrid signal. The object node can eliminate the designed artificial noise from the hybrid signal so as to decode the expectation signal, while the bugging node fails to do the decoding. According to the invention, the method also derives and acquires the safety rate of the system, acquires the optimal power allocation polity between the expectation signal and the artificial noise. According to the invention, the method can effectively deal with bugging behavior and explicitly increase safety property of the system.
Owner:BEIJING UNIV OF POSTS & TELECOMM
Dynamic routing in packet-switching multi-layer communications networks
InactiveUS7539210B2Improve network performanceImprove performanceWavelength-division multiplex systemsTime-division multiplexAdaptive routingPhysical level
Owner:TELEFON AB LM ERICSSON (PUBL)
Cyber signal isolator
A cyber signal isolator system and a cyber signal isolator method for protecting a component of an Industrial Control System are described. The cyber signal isolator system includes one or more devices configured to monitor physical-level signal information to determine a cyber security threat or breach event based on activity occurring with physical signals present at one or more components of an Industrial Control System.
Owner:MISSION SECURE INC
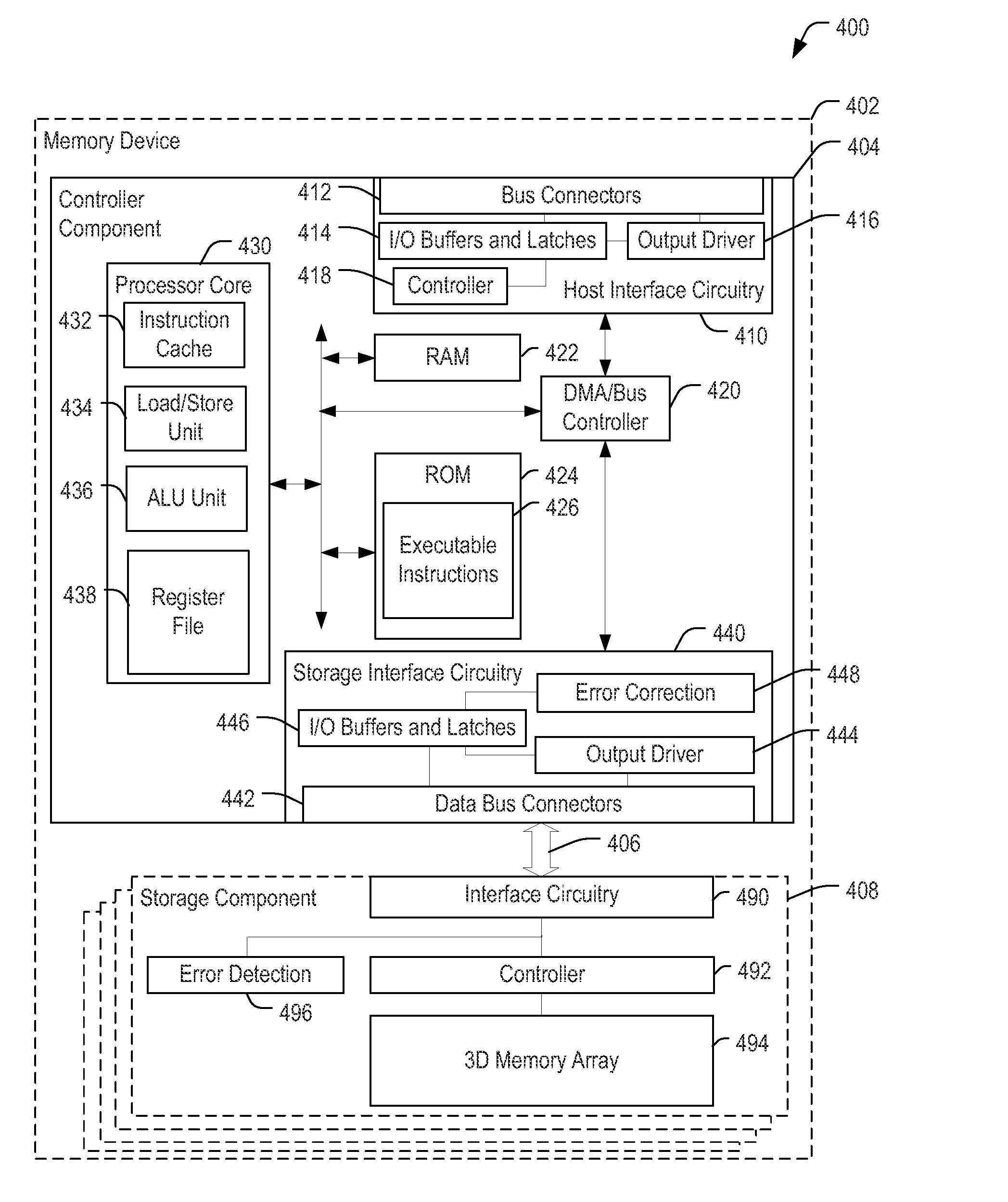
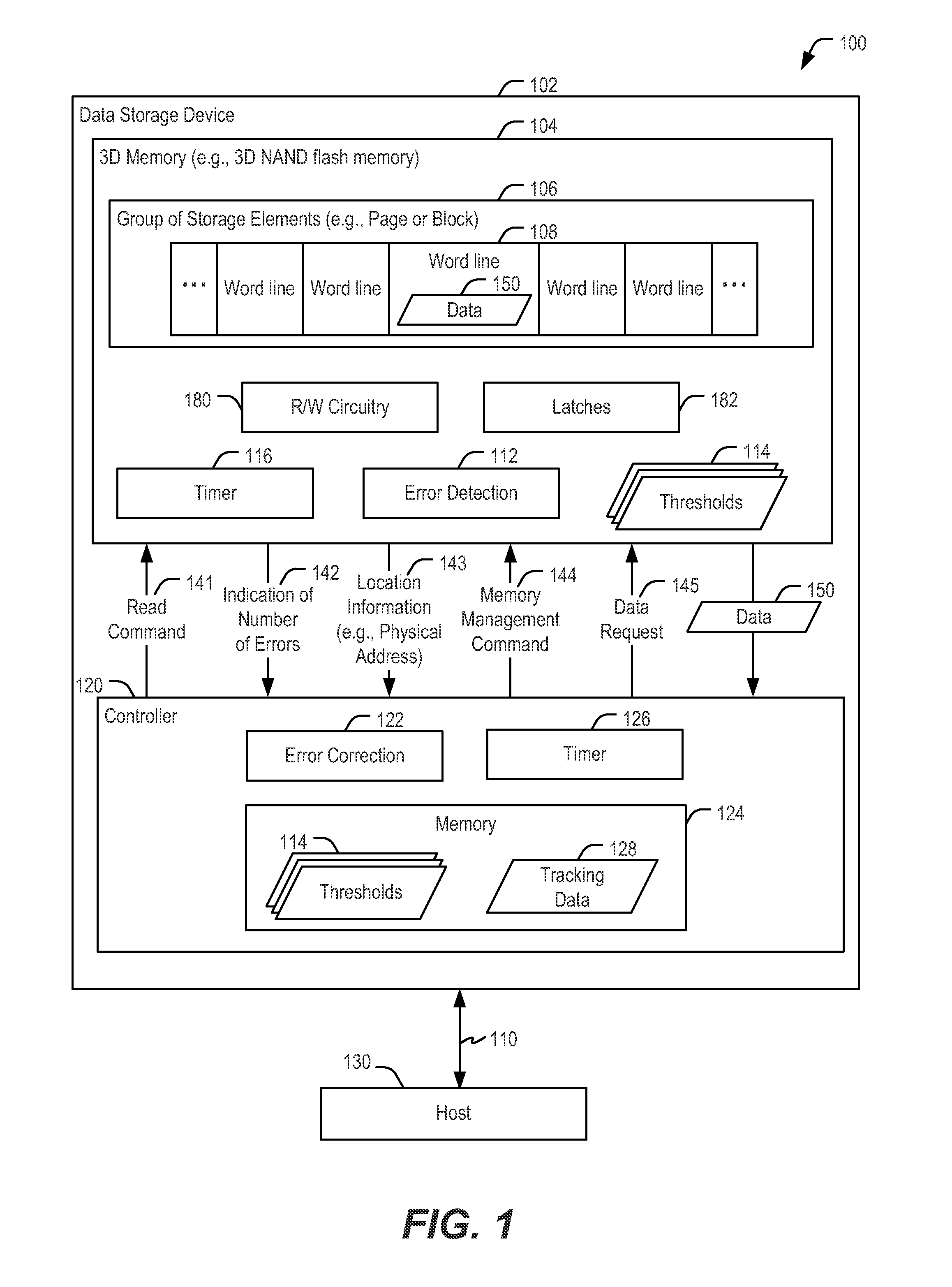
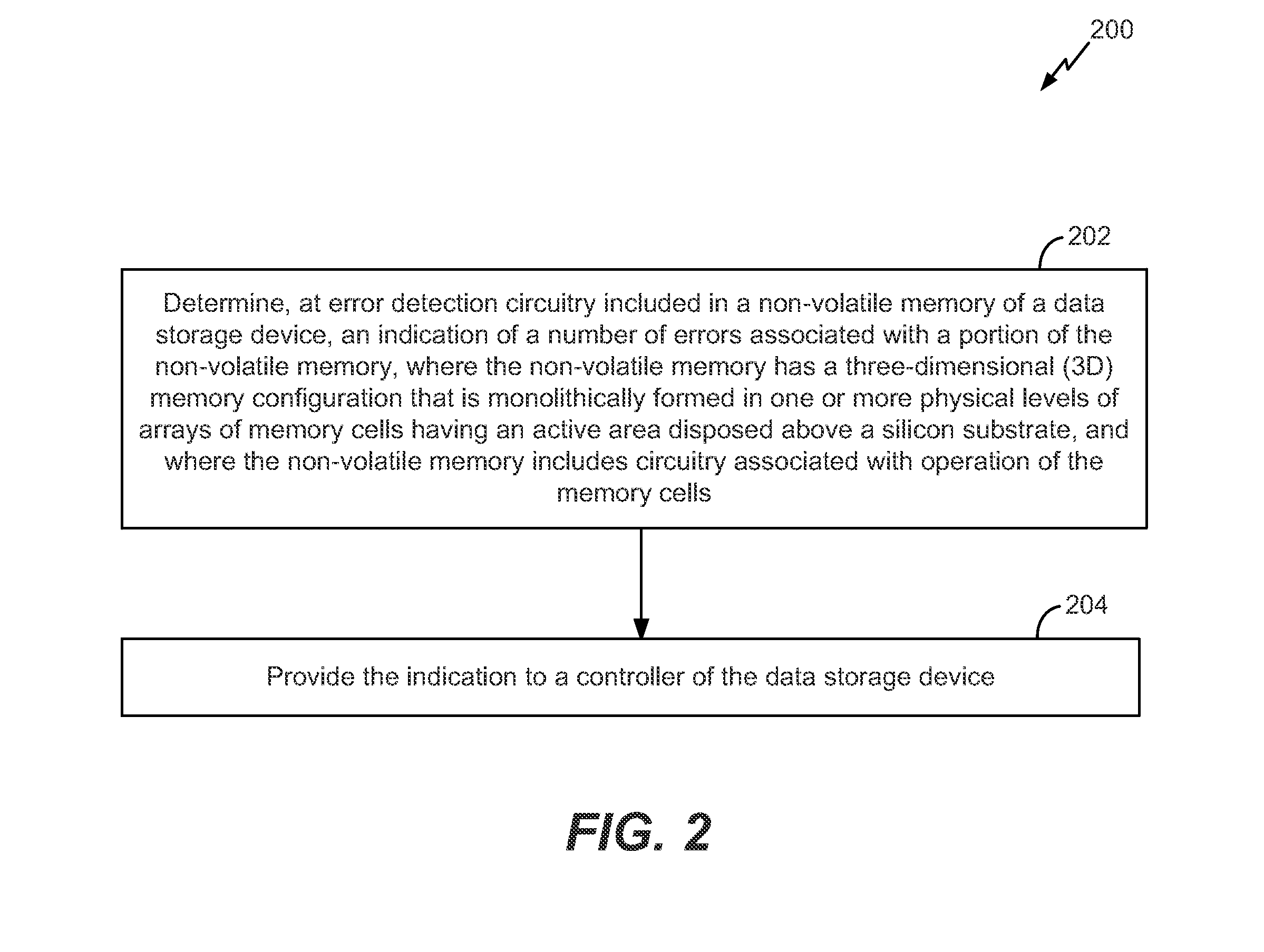
Three dimensional (3D) memory including error detection circuitry
ActiveUS20150363248A1Increase data trafficReduce bus trafficNon-redundant fault processingSiliconPhysical level
A method performed at a non-volatile memory of a data storage device includes determining, at error detection circuitry included in the non-volatile memory, an indication of a number of errors associated with a portion of the non-volatile memory. The method also includes providing the indication to a controller of the data storage device, where the controller includes error correction circuitry. The non-volatile memory has a 3D configuration that is monolithically formed in one or more physical levels of arrays of memory cells having an active area disposed above a silicon substrate. The non-volatile memory includes circuitry associated with operation of the memory cells.
Owner:SANDISK TECH LLC
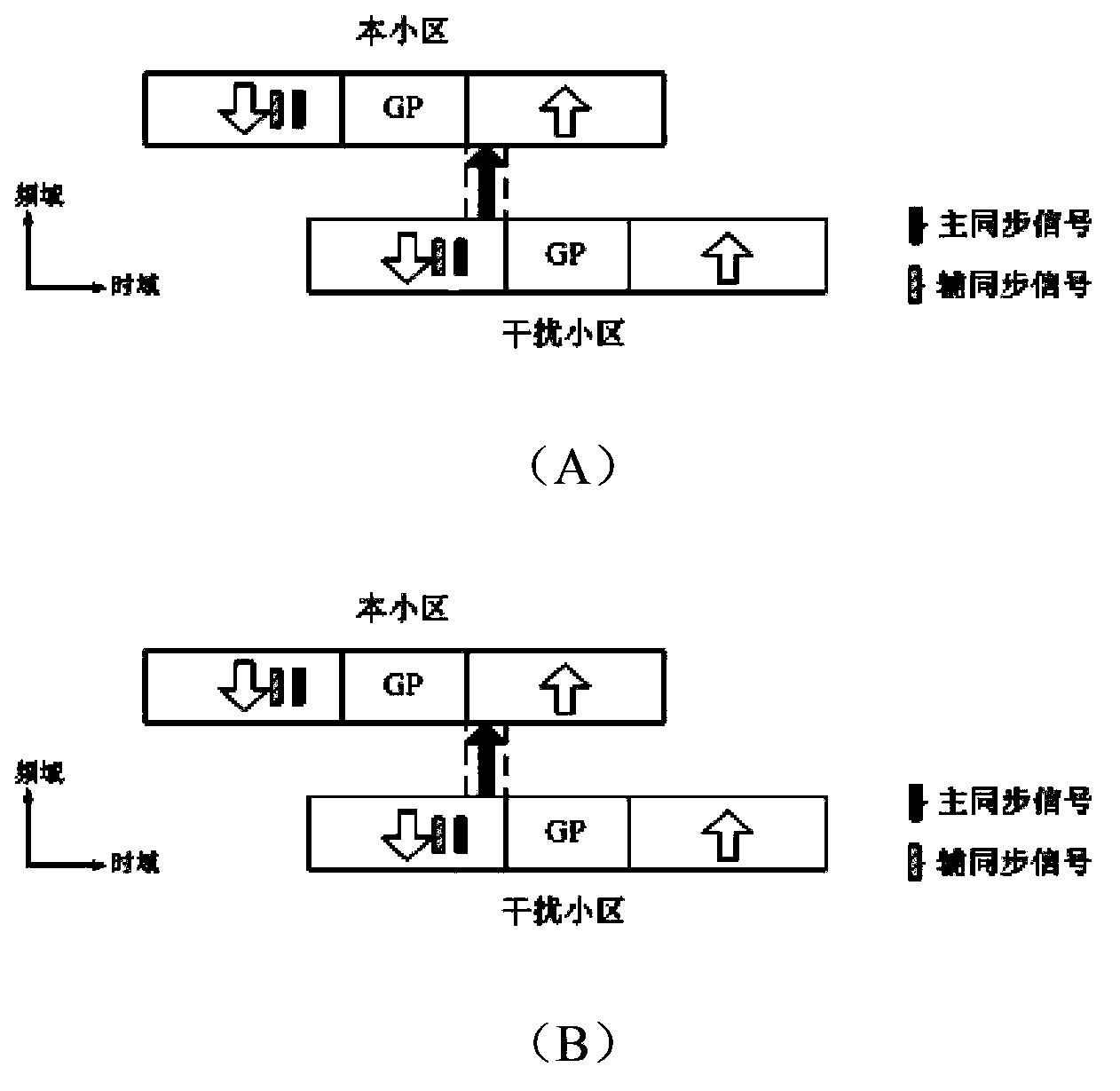
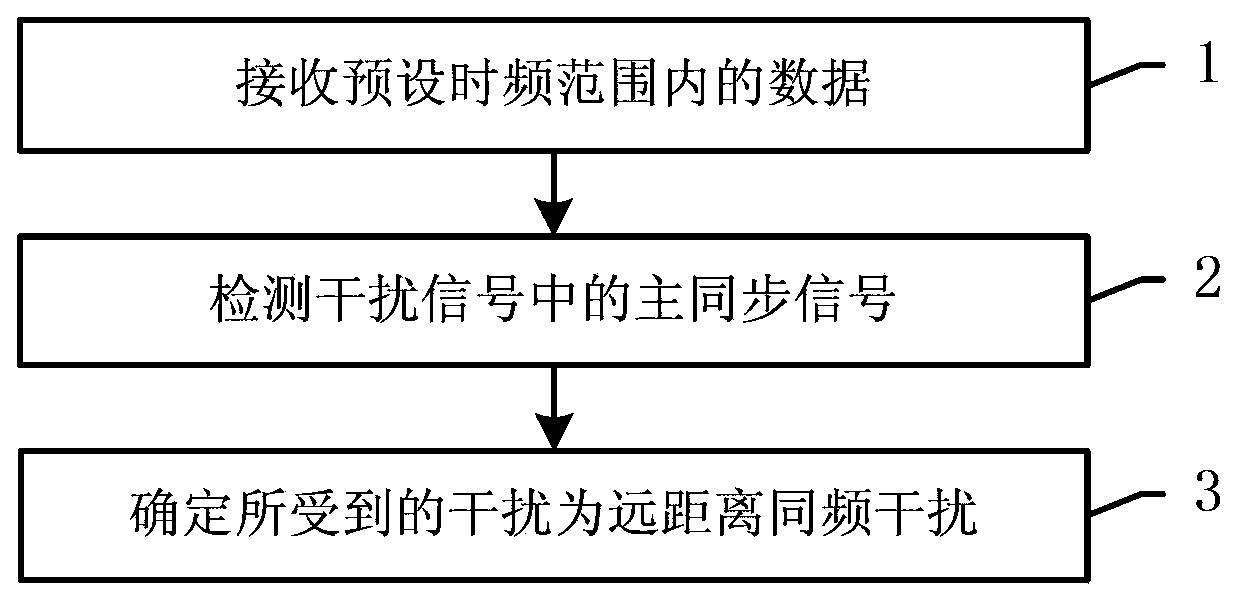
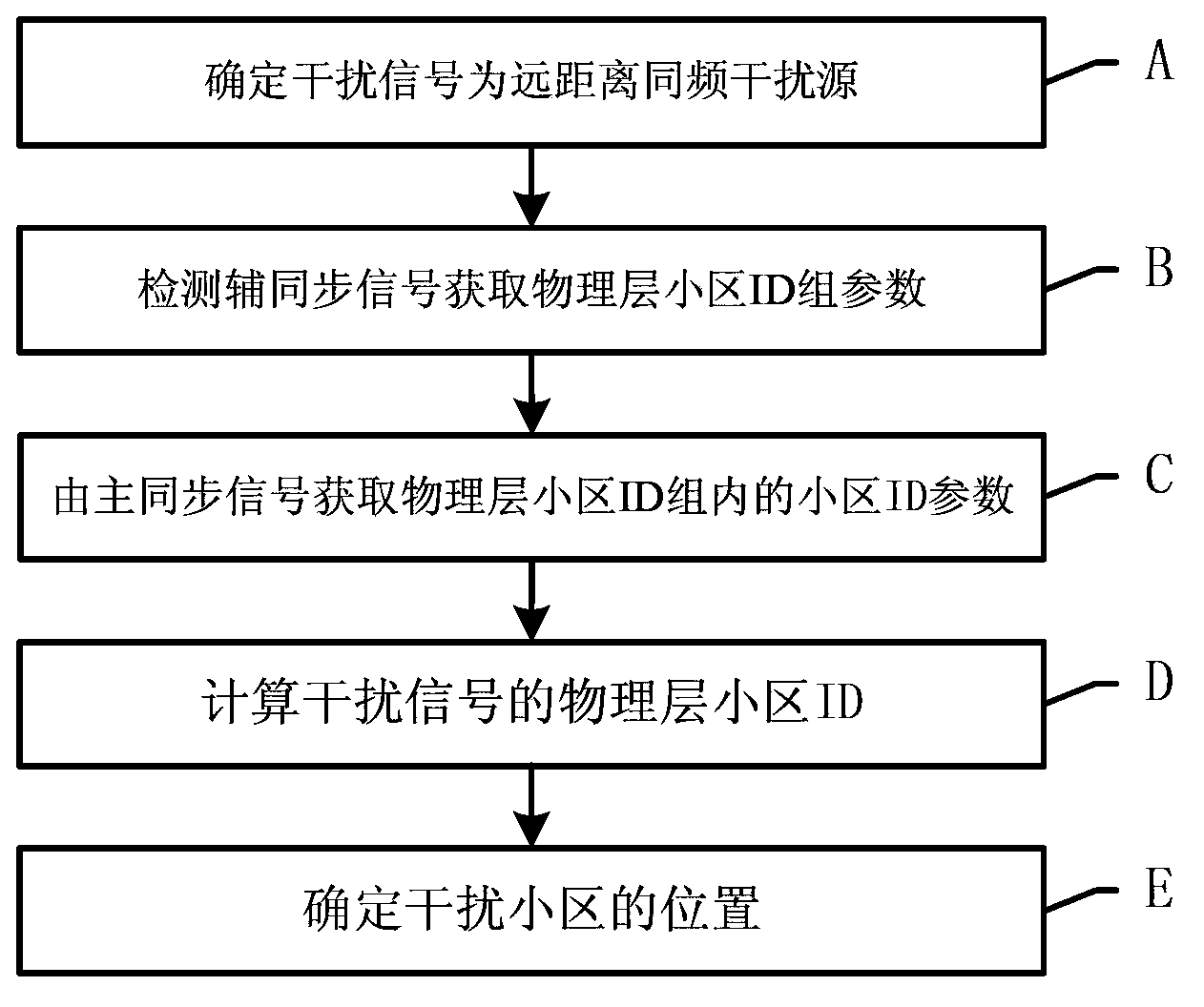
Long distance cofrequency interference source detection and positioning method for TD-LTE system
ActiveCN103796219ASave manpower and material resourcesImprove positioning efficiencyWireless communicationTime domainTime difference
The invention relates to a long distance cofrequency interference source detection and positioning method for a TD-LTE system. According to the detection method, a main synchronization signal of detected interference signals is compared with a main synchronization signal of local district signals in time domains, if time difference surpasses the threshold, the interference signals are a long distance cofrequency interference source; according to the positioning method, physical-level district ID parameters contained in the a secondary synchronization signal and in the main synchronization signal in the interference signals are utilized to acquire the signal district ID, and a position of the interference district is determined according to a signal district ID configuration table. Compared with the prior art, the method has advantages of high accuracy and high operation efficiency.
Owner:TONGJI UNIV
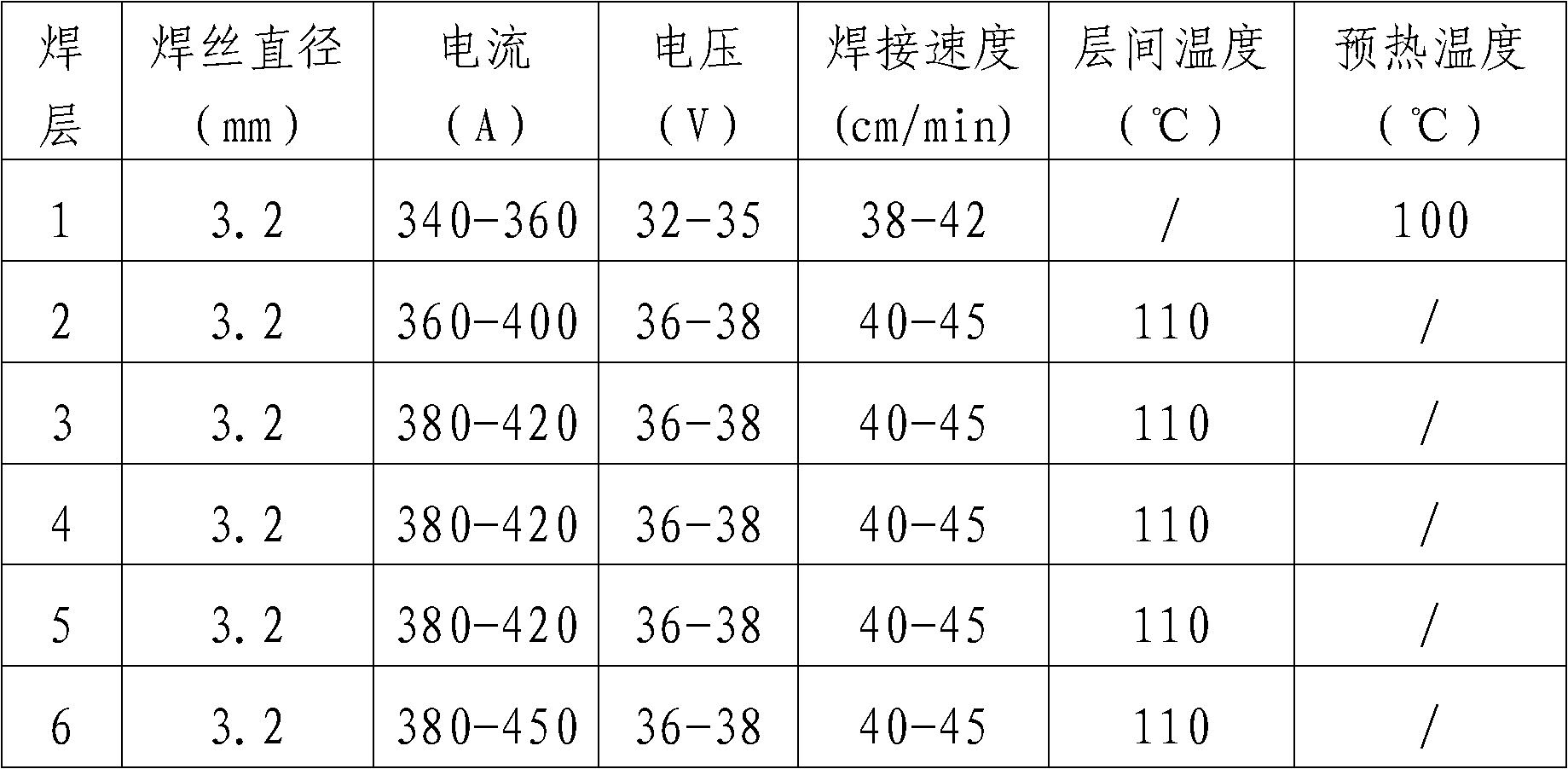
Domestic 08Ni3DR steel thin multi-pass welding process
ActiveCN102806405ARealize technological innovationAchieve upgradeArc welding apparatusFurnace typesCo2 absorptionDehydrogenation
The invention discloses a domestic 08Ni3DR steel thin multi-pass welding process, which is characterized by comprising the following steps of: machining a welding part into a single V-shaped or symmetrical double V-shaped groove, employing thin layer multi-pass welding, wherein on each layer, the weld pass thickness is less than 3mm, the diameter of a welding wire is 3.2mm, the welding current is 350 to 380A, the welding voltage is 34 to 38V and the welding speed is 36 to 45cm per minute, and controlling the interlayer and inter-pass temperature to be less than or equal to 150 DEG C; and performing dehydrogenation treatment and overall stress relief heat treatment after welding, and manufacturing a pressure container with the temperature level of 100 DEG C below zero such as main low temperature methanol wash equipment H2S and a CO2 absorption tower by employing the process, wherein the impact work kv2 of the welding joint of the equipment at the temperature of 101 DEG C below zero is more than or equal to 47J, and the mean value of the technical index and physical level is higher than American society of mechanical engineers (ASME) standard technical index.
Owner:WUHAN EAST PETROCHEM HEAVY EQUIP
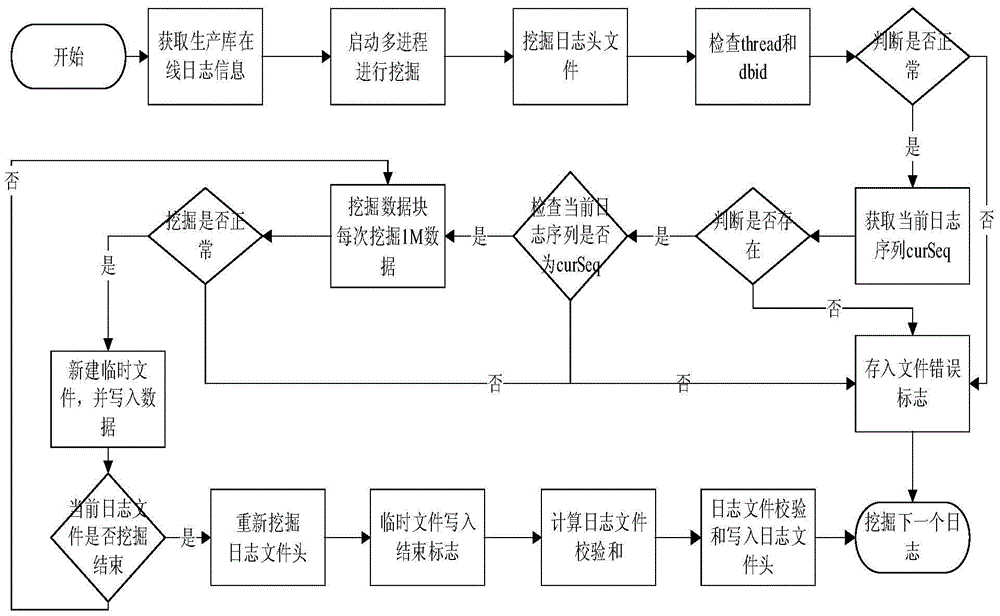
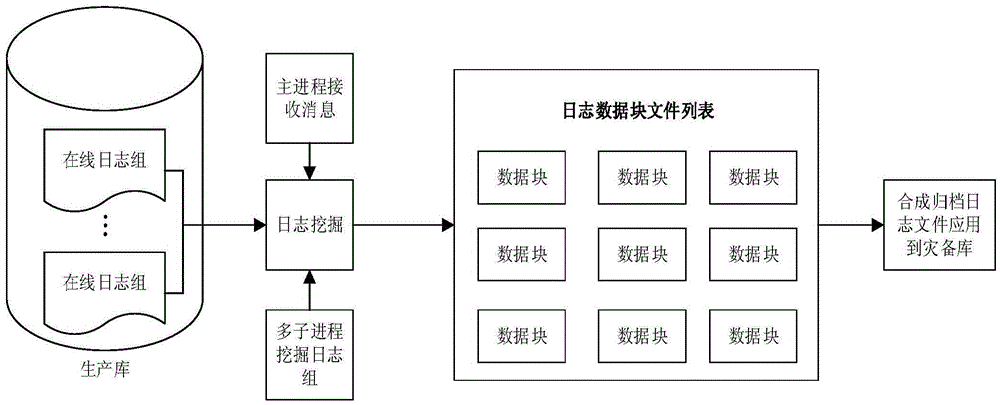
Method for log mining based on physical level database
ActiveCN105677876AImprove digging efficiencyEnsure consistencySpecial data processing applicationsLog miningFile system
The invention discloses a method for log mining based on a physical level database. The method comprises the following steps: (1) obtaining the size of a database system data block, an on-line log full path name and a log storage file system format; (2) obtaining current log group information from a database system view, and obtaining operating information; (3) mining log file header information, and obtaining current log series from a log file header; (4) mining a data block after the log file header, mining data of a fixed size each time and recording currently mined cut-off position indexes, and writing a data block content into a newly-built temporary file; (5) when an end mark of the file header is met, writing the end mark into a data block temporary file, ending current file mining, and staring next log file mining. According to the method, consistency and integrity of mined log information and a production library can be achieved fundamentally, and the performance influence on the production library caused by database log mining can be reduced.
Owner:STATE GRID CORP OF CHINA +3
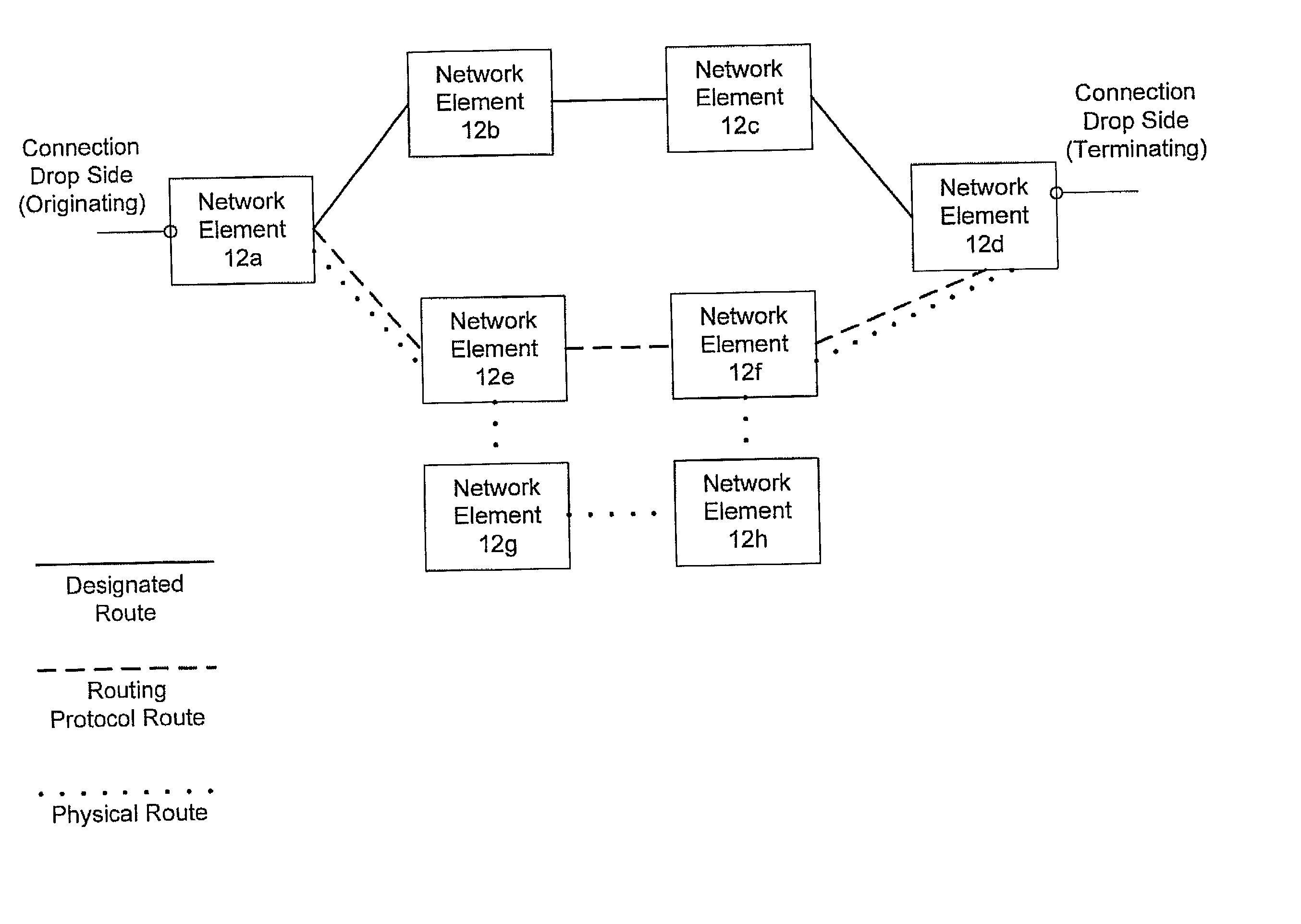
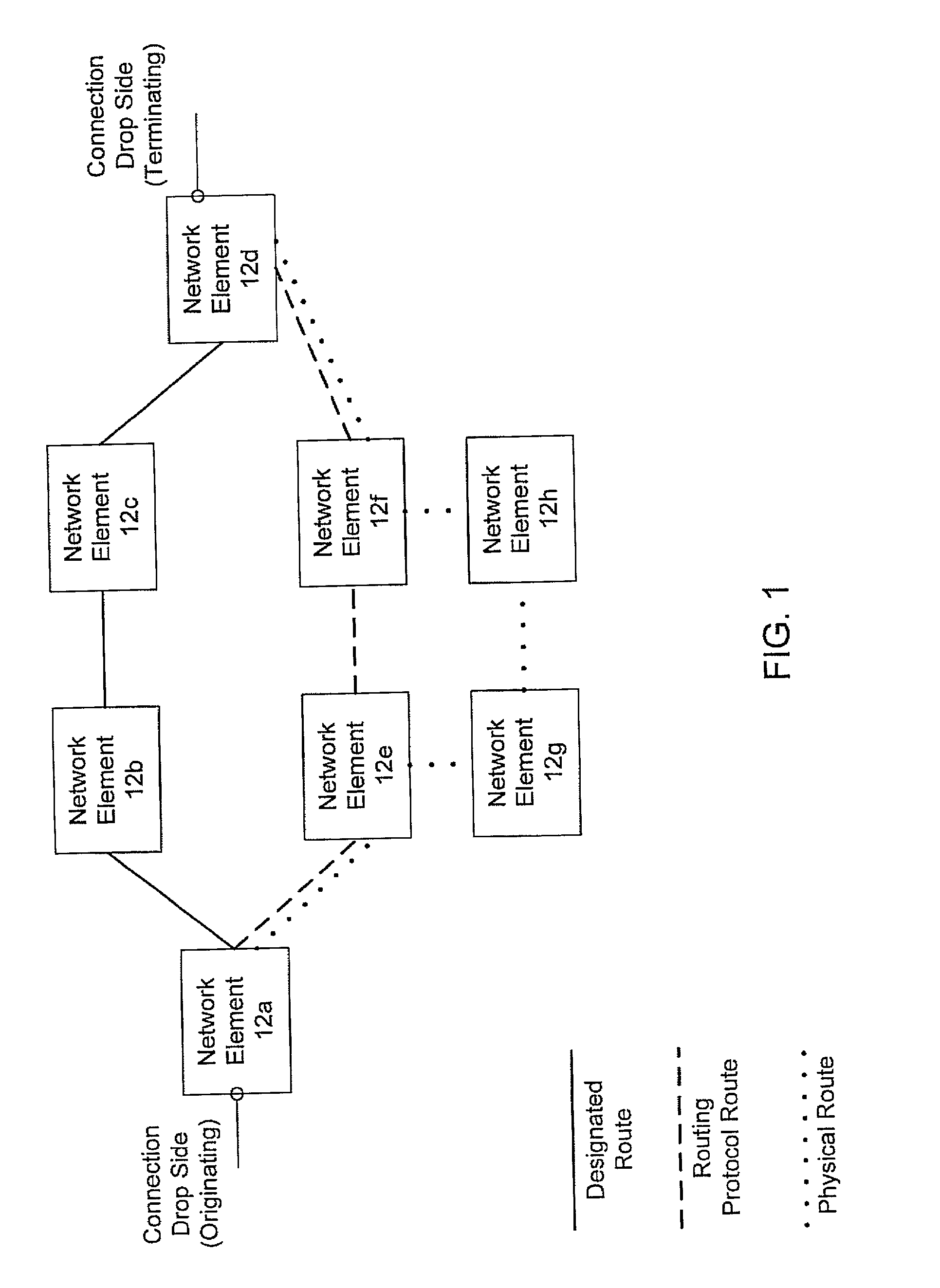
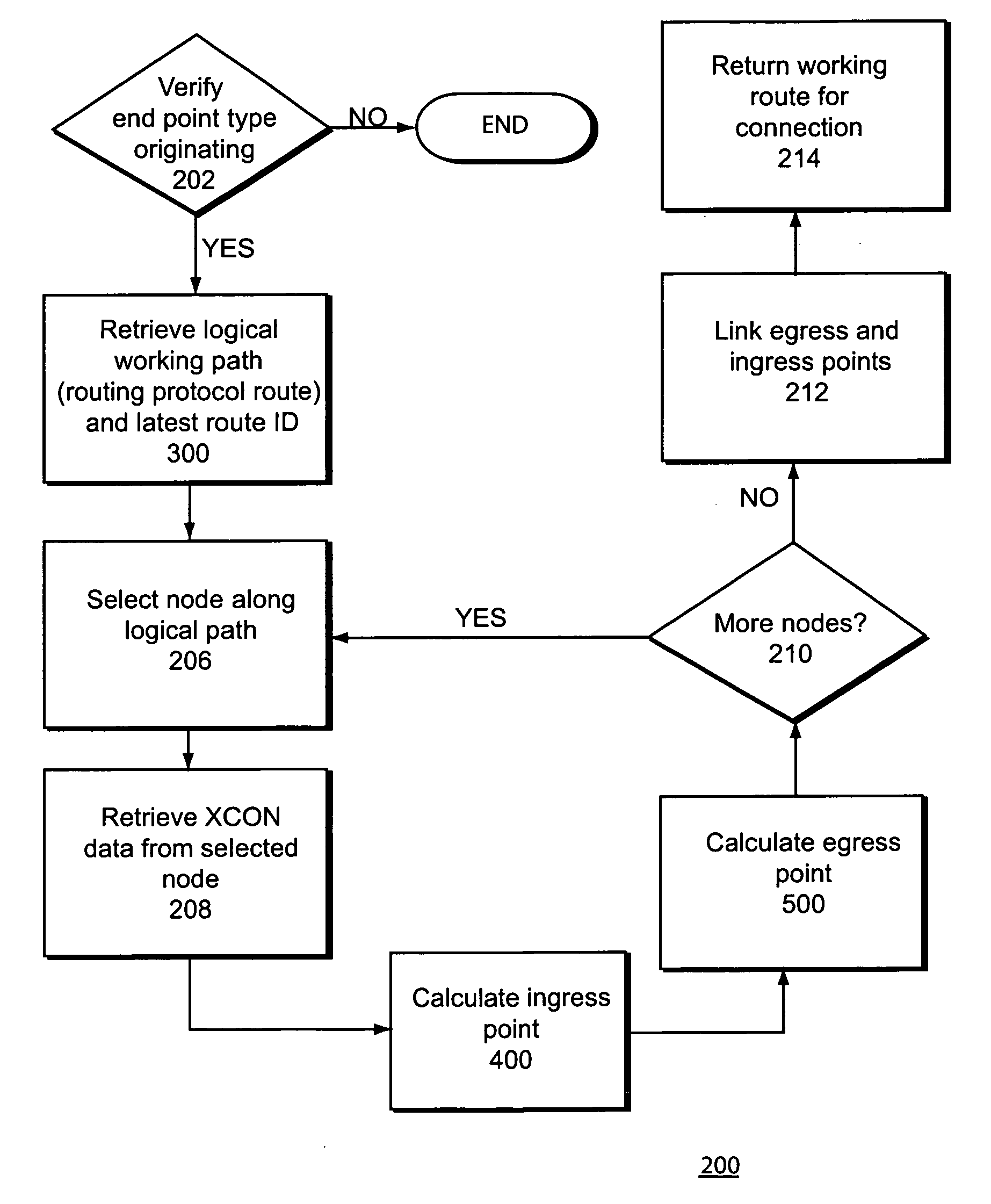
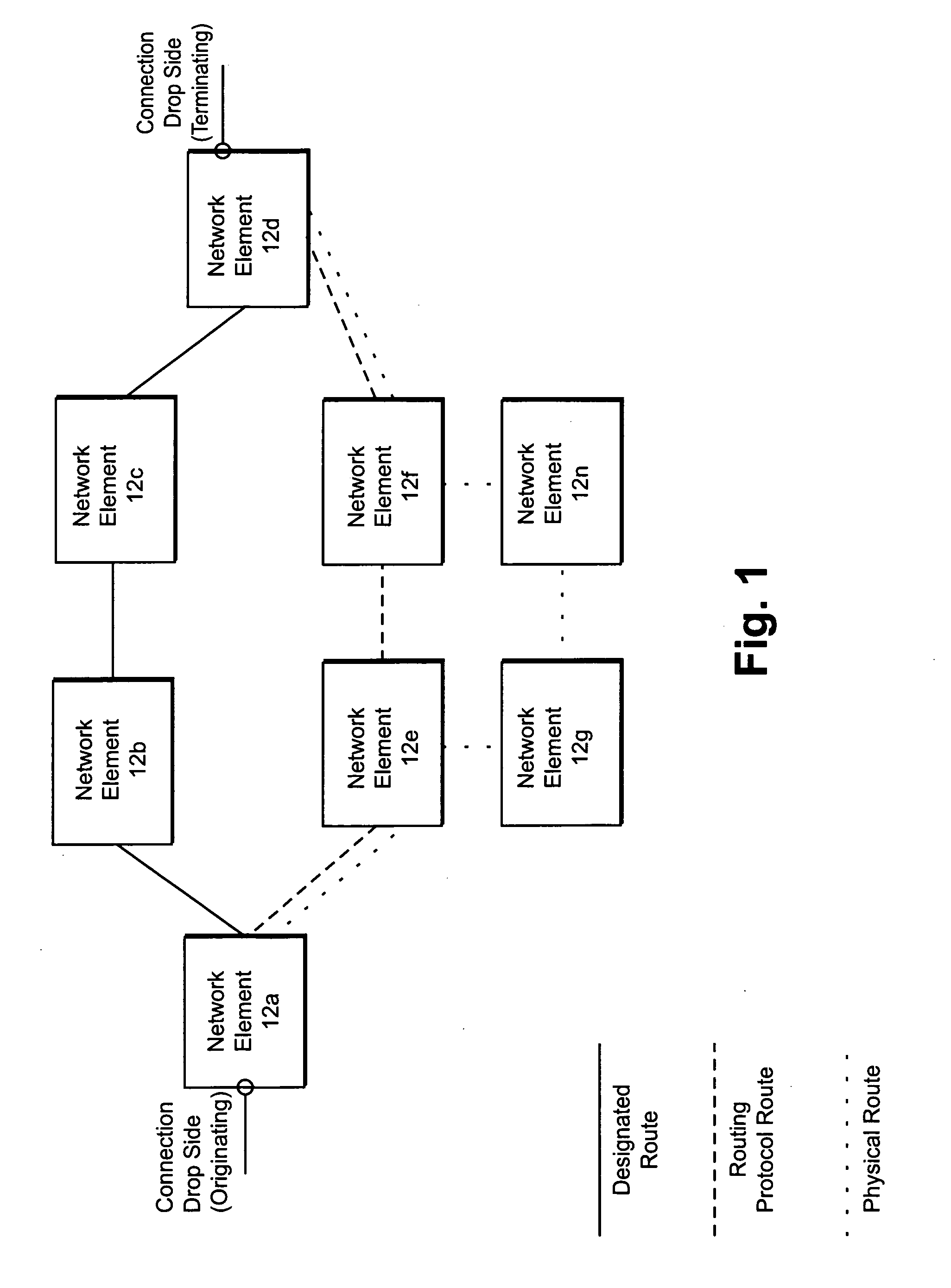
Calculating physical routes in a communication network
A system operating on a communication network for mapping service-level information comprising logical connections to physical-level information comprising working physical paths of the logical connections, where the physical-level information is obscured by activation of protect schemes within the communication network.
Owner:CIENA
A method and device for sharing encrypted cards in a virtual environment
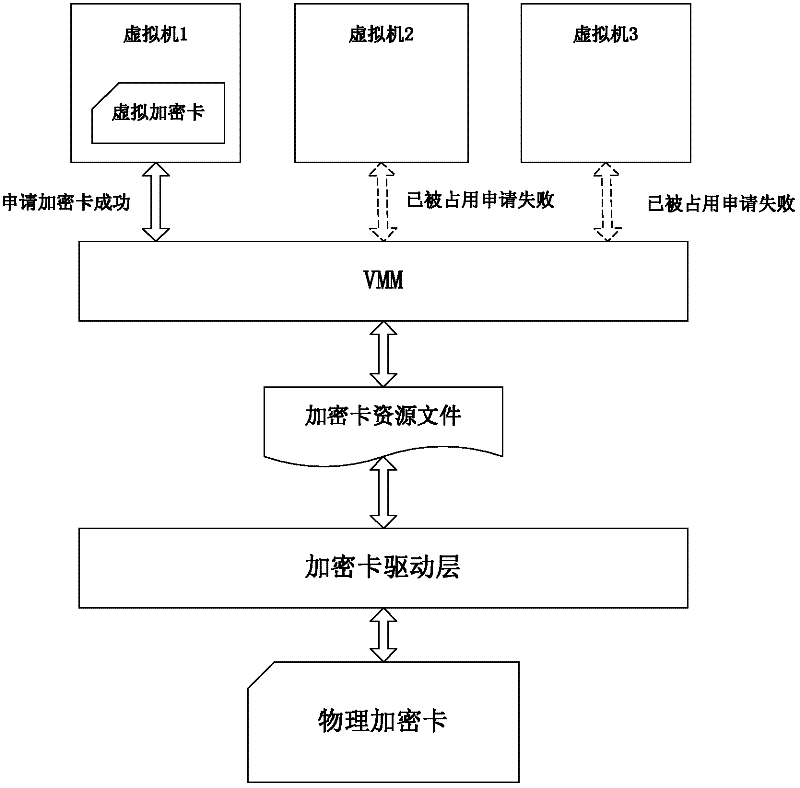
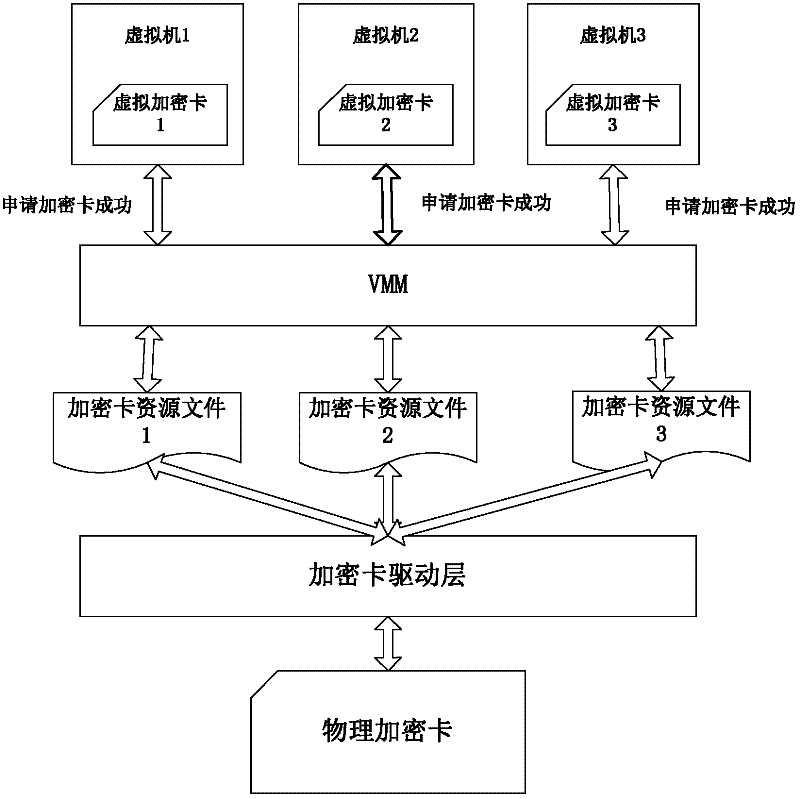
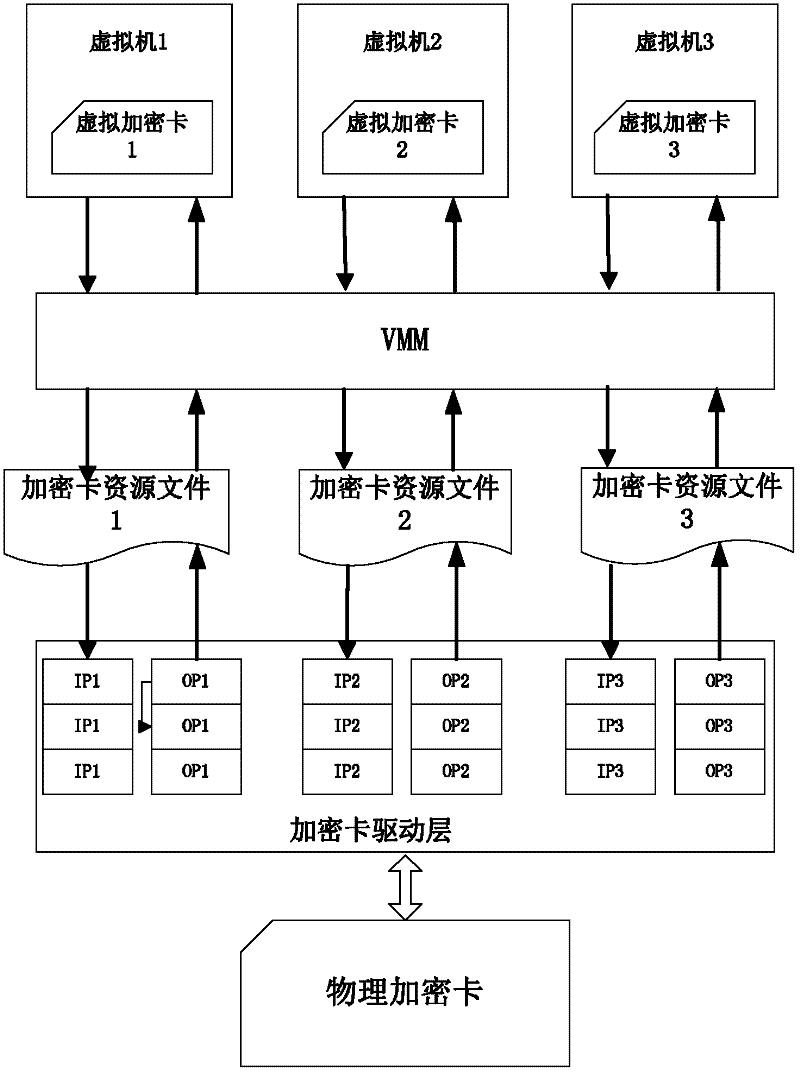
InactiveCN102270153AImprove efficiencyDigital data authenticationSoftware simulation/interpretation/emulationComputer hardwareResource allocation
The invention provides an encryption card sharing method in a virtual environment, which maps a hardware encryption card into an independent encryption card resource file; establishes a processing queue for each resource file and schedules processing requests. In the present invention, by mapping the same encryption card into multiple different resource files, multiple different encryption card resources can be allocated to each virtual machine for use, but each virtual machine still uses the same encryption card on the physical level , greatly improving the use efficiency of the encryption card.
Owner:DAWNING INFORMATION IND BEIJING
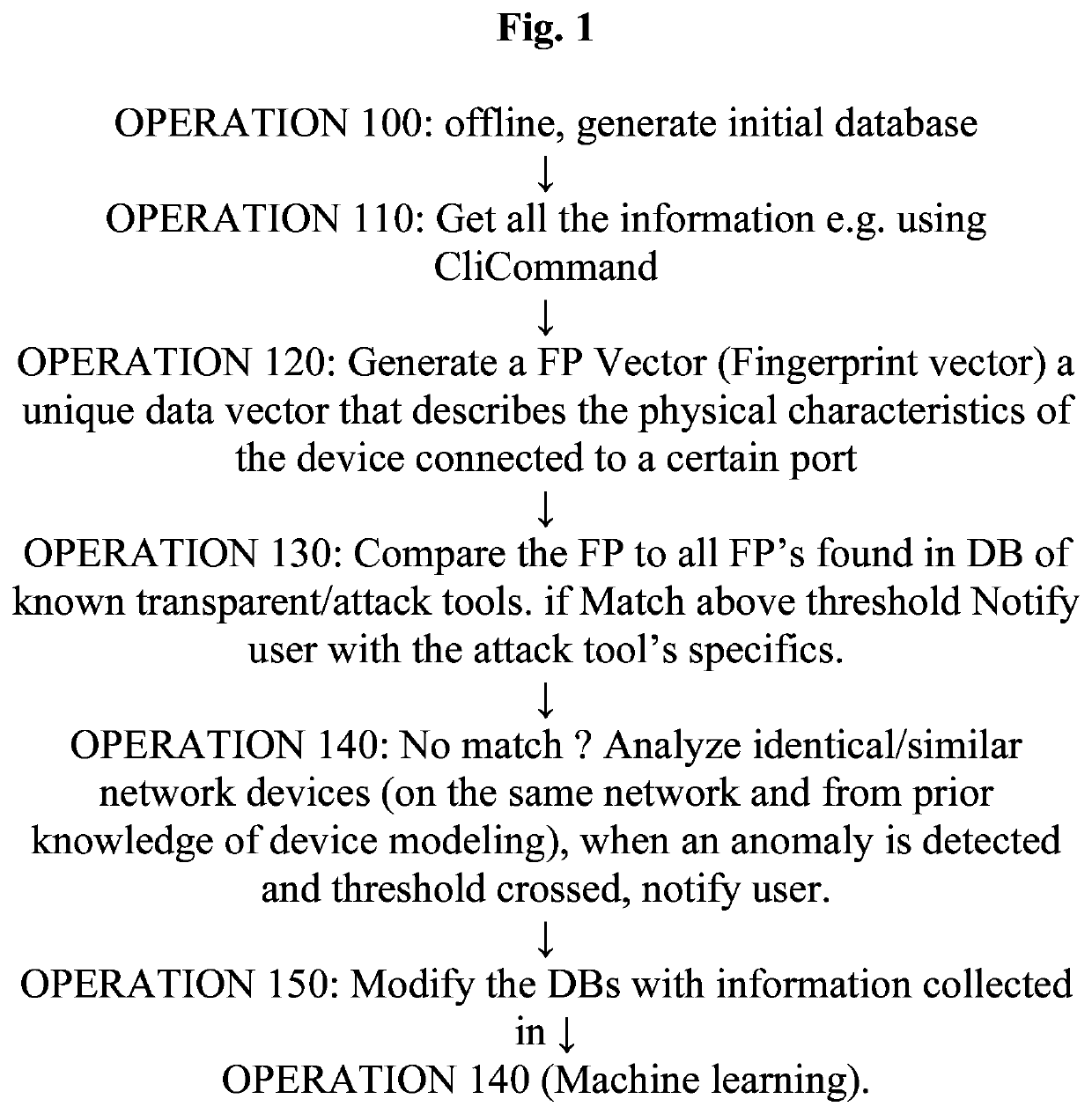
Improved system, method, and computer program product for securing a computer system from threats introduced by malicious transparent network devices
A network security system for detecting MAC'less / transparent devices, the system comprising a data repository aka DB, operative to accumulate “fingerprint” data indicative of expected physical level characteristics for each of plural types of switch-device links (aka link types) interconnecting a switch and a hardware device, wherein at least one pair of links of different types differ from one another at least with respect to the chipset residing in the respective device connected to the respective switch by each respective link; apparatus for reading physical level characteristics of links in at least one network to be protected; and an output device configured to generate alerts of possible presence of a transparent device along at least one link if the physical level characteristics of the at least one link, as read by the apparatus, is anomalous relative to the “fingerprint” data stored in the data repository.
Owner:CYBER SEPIO SYST LTD
MVB/USB adapter based on SOPC technology and communication method thereof
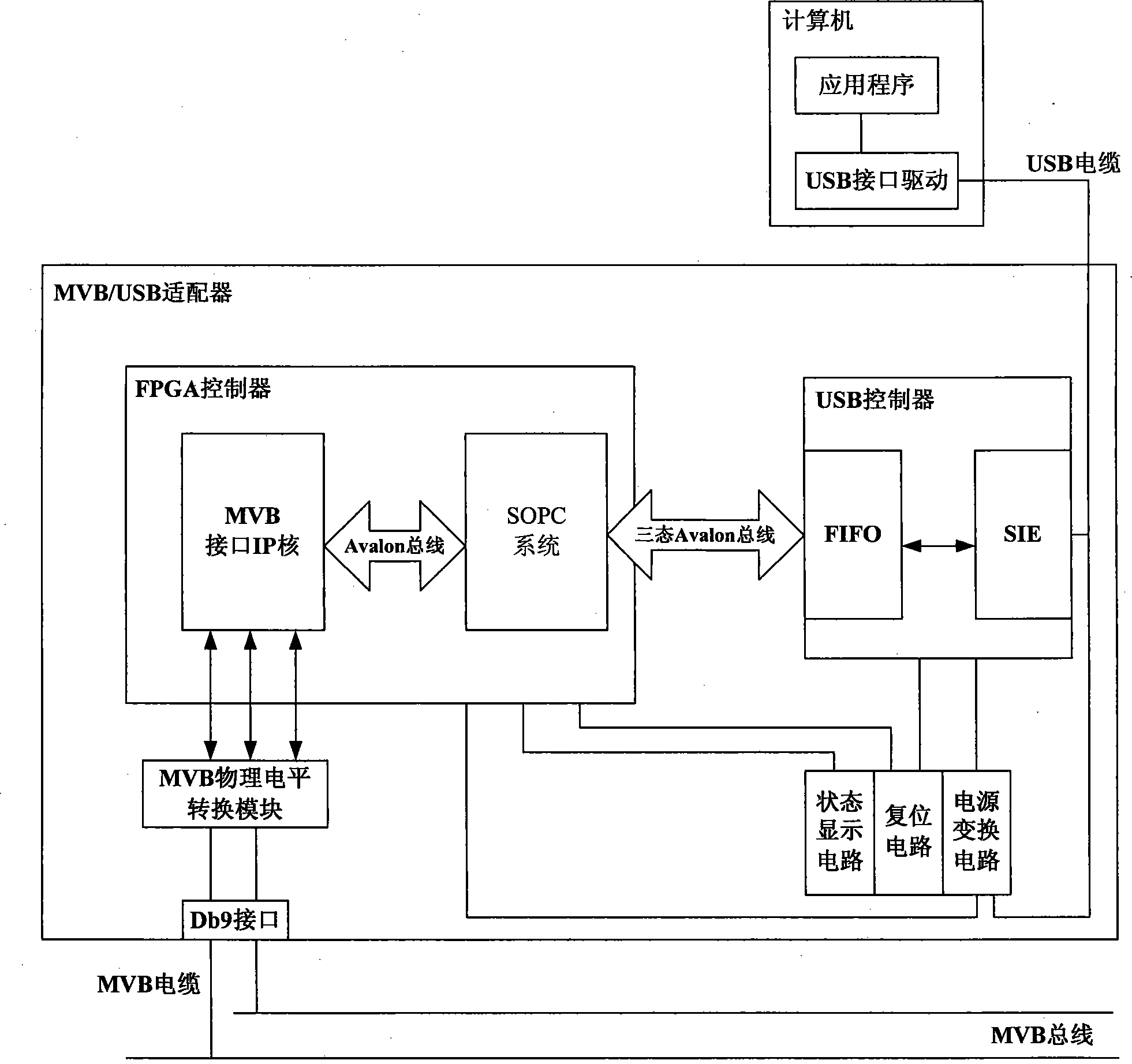
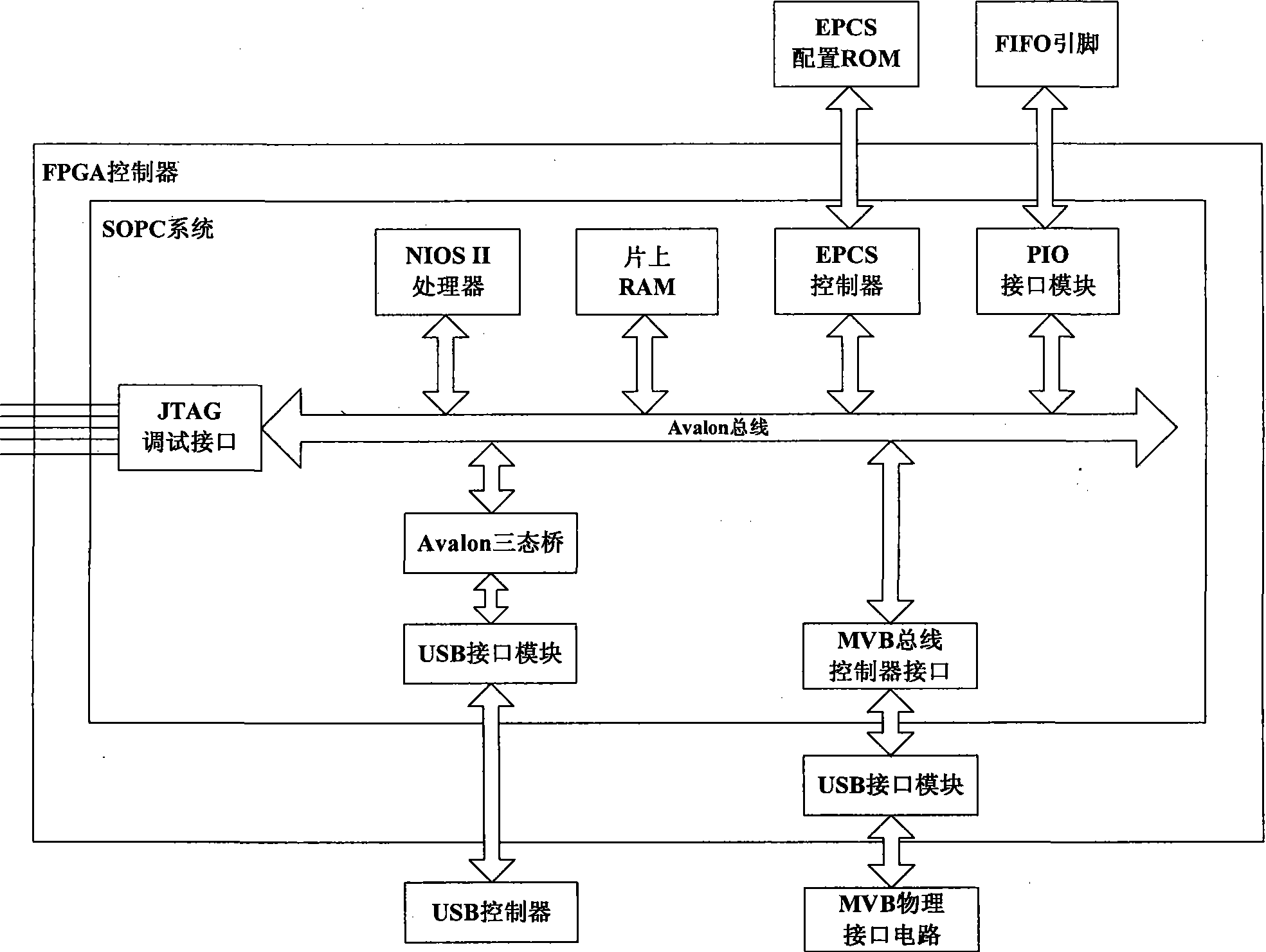
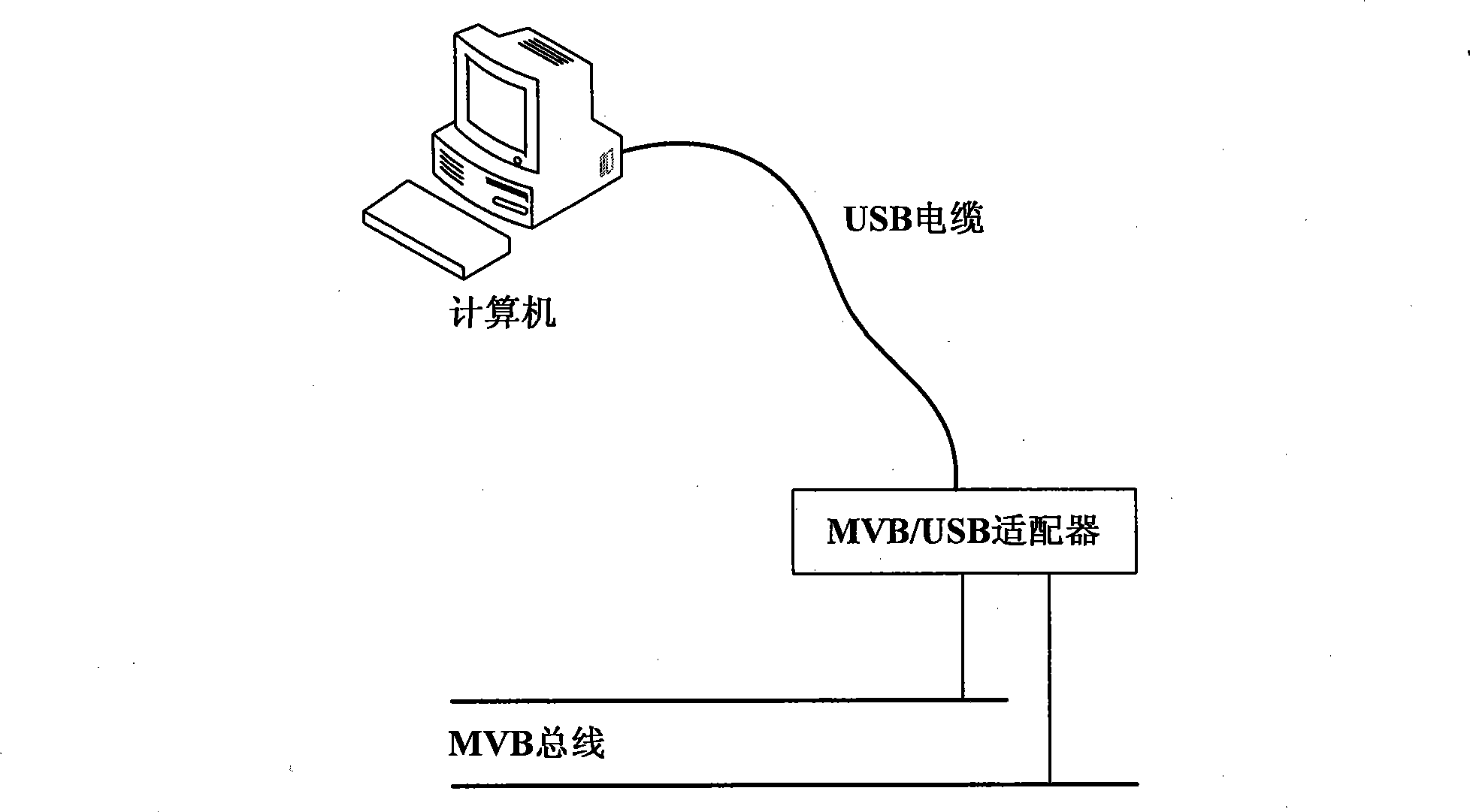
InactiveCN101419582AFirmly connectedFast transfer speedElectric digital data processingBus networksUSB adapterNetwork packet
The invention discloses an MVB / USB adapter based on the SOPC technology and a communication method thereof, belonging to the technical field of network communication. The technical proposal is as follows: the MVB / USB adapter comprises an FPGA controller, a USB controller, an MVB physical level conversion module, a power conversion circuit, a resetting circuit, a status lamp display circuit and a DB9 interface. The communication method of the MVB / USB adapter comprises the following steps: the MVB / USB adapter is respectively connected to a computer and an MVB bus; the computer sends data packet to the MVB / USB adapter; the MVB / USB adapter receives the data packet; the FPGA controller reads data from an FIFO module; required read-write operation is judged; and finally, data is sent to the computer or the MVB bus according the required read-write operation. The invention leads the connection of the MVB bus and the computer to be more convenient and the transmission speed to be faster.
Owner:BEIJING JIAOTONG UNIV
Method of optimising the performance of a computer and a main non-volatile memory unit optimised using specific-use sections
InactiveUS20050021501A1Good computing powerImprove securityEnergy efficient ICTInput/output to record carriersOperational systemCost effectiveness
A method is revealed for optimizing the performance of a computer by means of purpose-specific sections created in its main non-volatile storage medium. Such method creates a basic set of purpose-specific sections in order to separate, at a physical level and at a logical level, vital elements for equipment operation such as operating system, dynamic files, applications and user's files; and, optionally, creates an additional set of purpose-specific sections for storing non-vital elements separated in like manner. A secondary method, which supplements the previous one, in order to optimize quickly a unlimited number of identical computers, is also shown. Additionally, an optimized main non-volatile storage medium that results from using either one of the previous methods is presented. Applying this invention generates numerous advantages for the owner of the equipment being optimized. File fragmentation is minimized and several proven benefits are brought about, as the best possible performance obtained with less resources, an improved security scheme for the user's files, an optimized defragmentation of the main non-volatile storage medium, and an unsurpassed cost-benefit ratio. Such benefits are unattainable simultaneously by means of the traditional techniques or the optimization proposals published to date.
Owner:BUTRON MANUEL FERNANDO MEJIAS
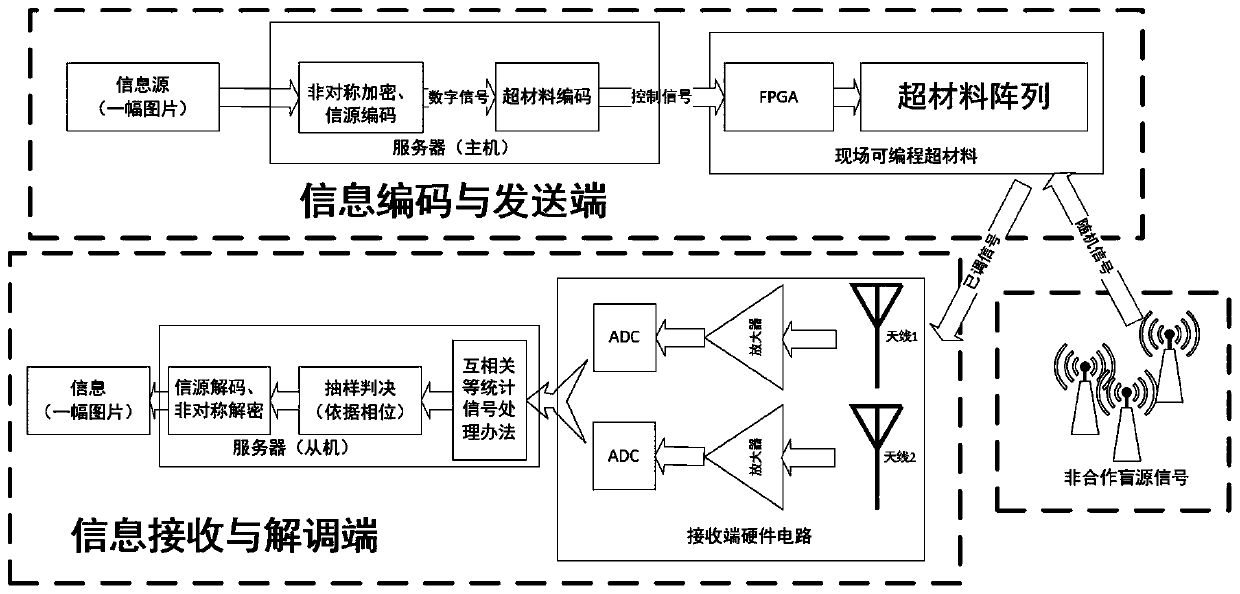
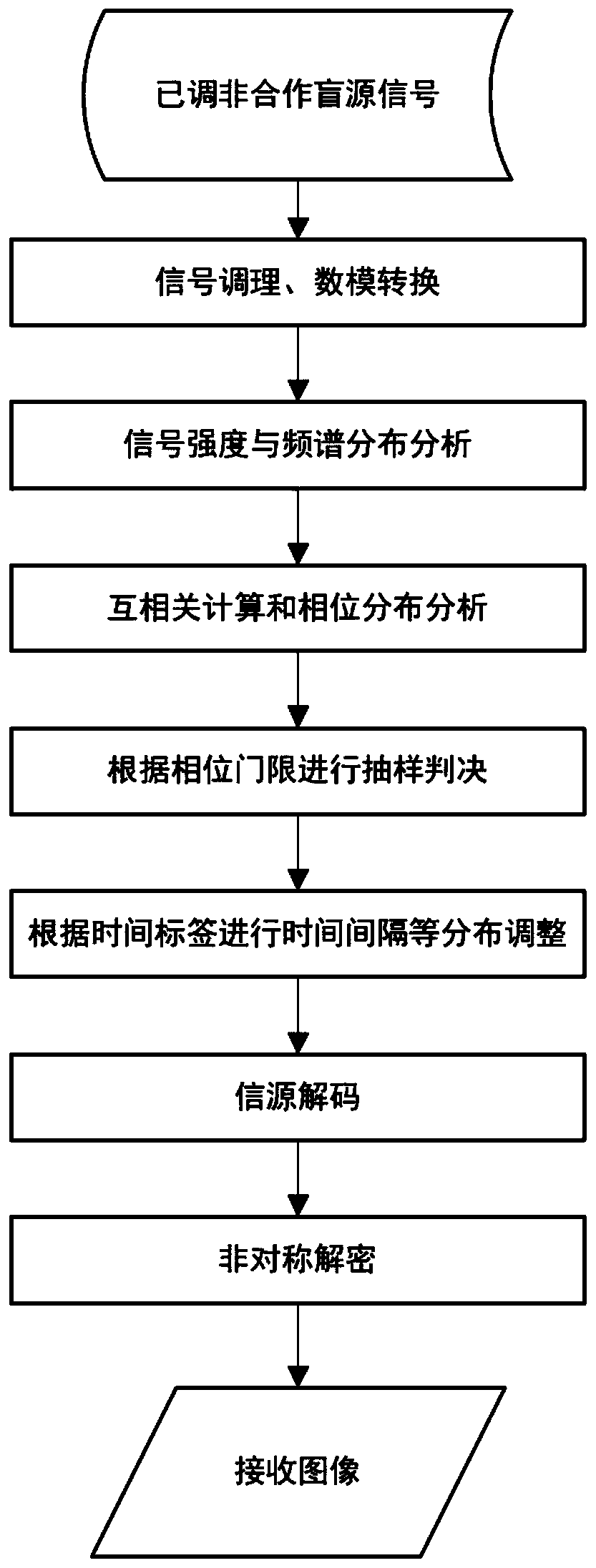
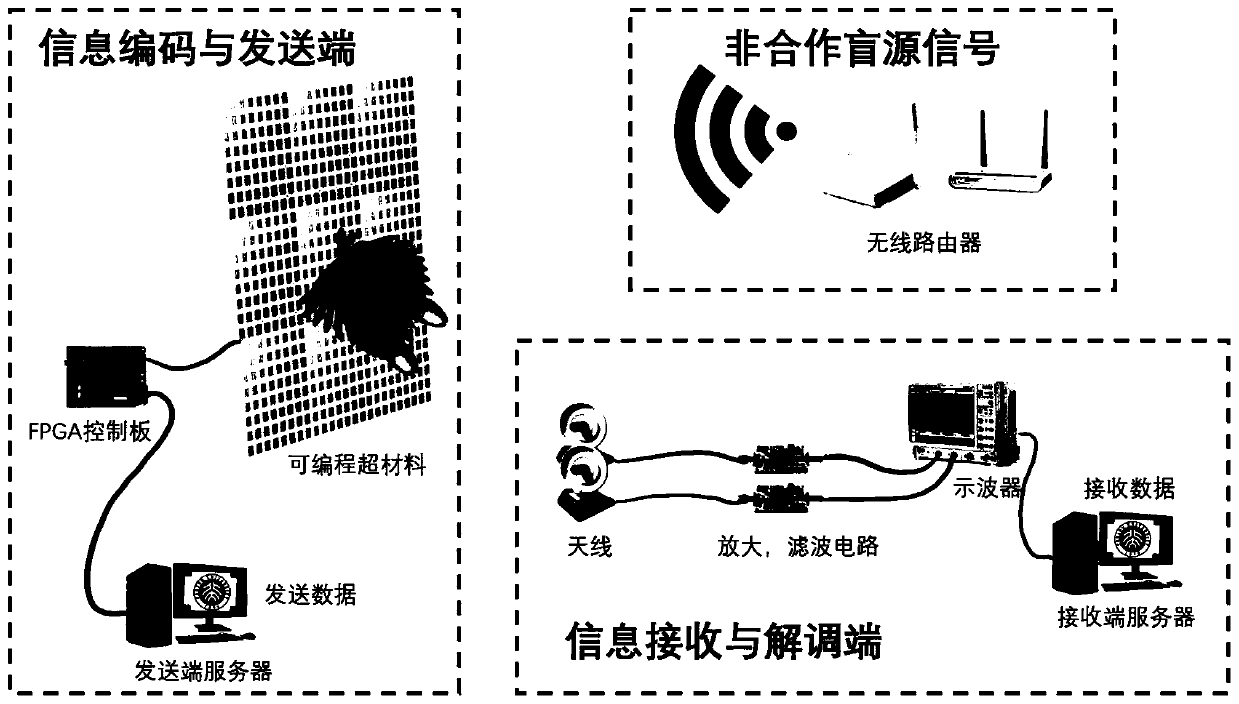
Latent communication system and method based on non-cooperative blind source signal
ActiveCN110190923ARealize indoor directional and fixed-point communicationSave carrier transmit powerSecret communicationSecurity arrangementFrequency spectrumCommunication quality
The invention discloses a latent communication system and method based on a non-cooperative blind source. The latent communication system comprises an information coding and transmitting end, an information receiving and demodulating end and a non-cooperative blind source signal, a non-cooperative blind source is used as a communication carrier wave, double antennas or multiple antennas are used as receiving ends, received electromagnetic waves are demodulated in a receiver, and therefore hidden transmission and passive transmission communication of information are achieved. By adopting the technical scheme of the invention, a signal emission source is not needed, the carrier emission power is saved, and new spectrum resources are not occupied; the circuit structure is simplified, and thehardware cost is reduced; concealed communication is guaranteed in the physical level, and indoor directional fixed-point communication can be achieved. Information can be sent to a sensor at a specific position in the Internet of Things, energy is provided for the radio frequency identification tag, and the wireless communication quality is improved.
Owner:PEKING UNIV
Systems and methods for providing inline parameter service in data storage devices
ActiveUS9053008B1Memory architecture accessing/allocationMemory adressing/allocation/relocationController architecturePhysical address
Disclosed herein is a controller architecture that pairs a controller with a NVM (non-volatile memory) storage system over a high-level, high speed interface such as PCIe. In one embodiment, the NVM storage system includes a bridge that communicates with the controller via the high-level interface, and controls the NVM via an interface. The controller is provided a rich set of physical level of controls over individual elements of the NVM. In one embodiment, the controller includes a volatile memory (e.g., DRAM) that stores parameters related to the operation of the NVM as provided by the bridge. The parameters may be related to optimizing use of the NVM and are automatically appended by the controller to appropriate data storage commands to the bridge. The parameters may be stored in a table format in which each entry is indexed by a physical address of the NVM.
Owner:WESTERN DIGITAL TECH INC
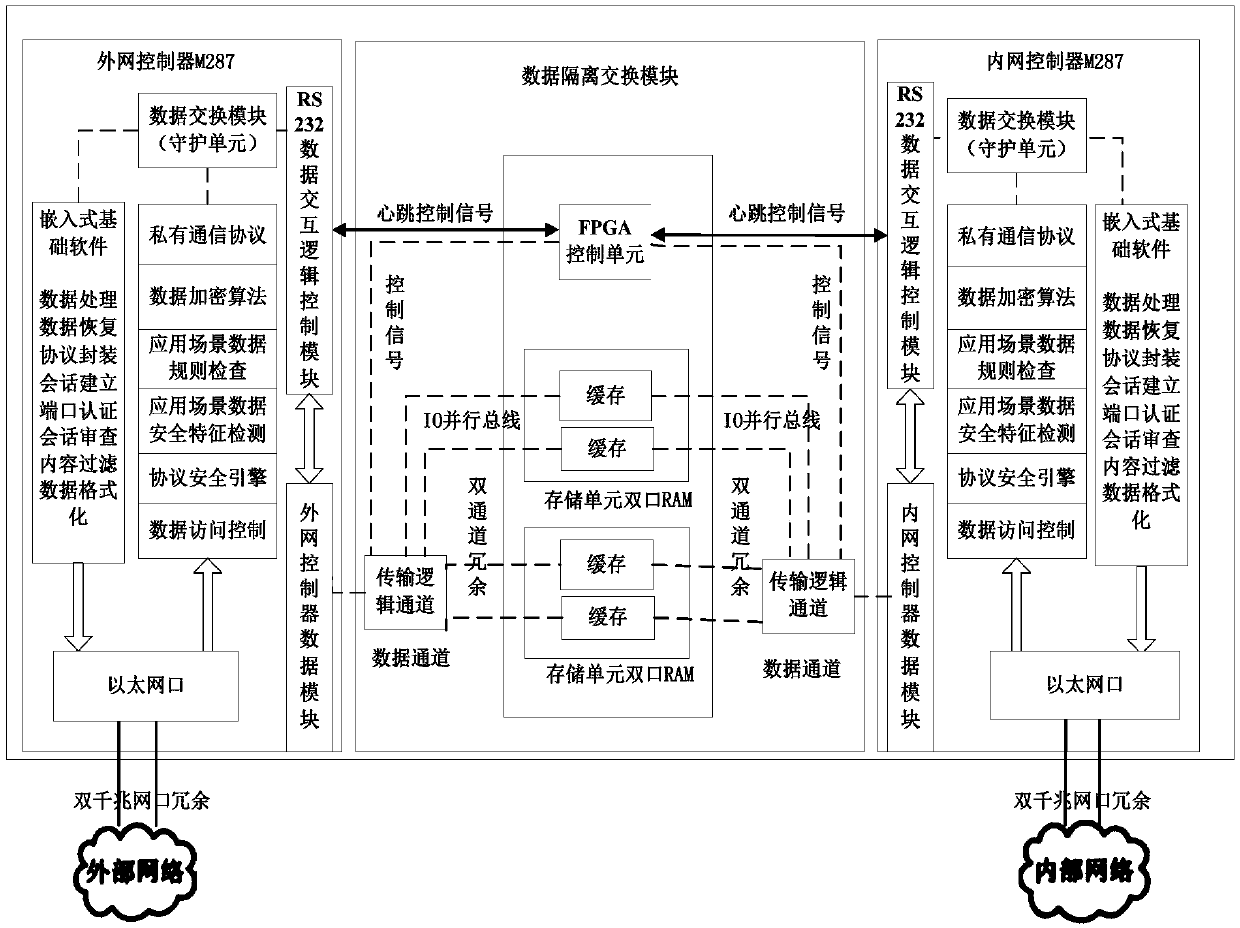
Network security protection system for civil air defense engineering
ActiveCN109561091AAchieve Logical IsolationPlatform integrity maintainanceData switching networksComputer moduleNetwork security policy
The invention discloses a network security protection system for civil air defense engineering, which belongs to the field of industrial control network security. The network security protection system comprises embedded hardware, embedded basic software and a business scenario application. The embedded hardware comprises a data isolation switching module, an internal network controller M287 and an external network controller M287. The data isolation switching module comprises a control unit FPGA, a storage unit dual-port RAM, and a data channel. The internal network controller M287 and the external network controller M287 are two sets of independent and high-performance embedded hardware, and each has an arithmetic unit, a storage unit and a switching unit which are independent. The internal network controller M287 is responsible for accessing a field end control network. The external network controller M287 is responsible for accessing an information end network. The internal networkcontroller M287 and the external network controller M287 are connected to the data isolation switching module composed of the storage unit dual-port RAM and the control unit FPGA respectively by means of an 8-bit IO parallel busbar, and isolate the TCP / IP communication at the physical level. The network security protection system has the advantage of solving the problems of relatively single protection capability and the like.
Owner:AUTOMATION RES & DESIGN INST OF METALLURGICAL IND
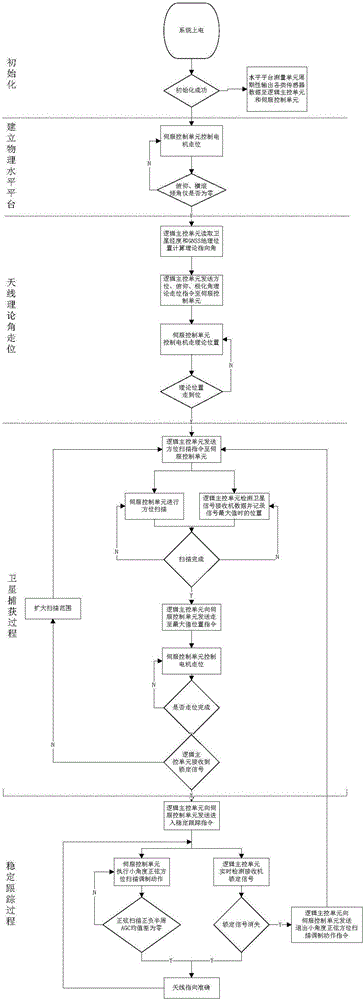
Satellite capturing and tracking method for VSAT (Very Small Aperture Terminal) antenna system with physical level platform
The invention proposes a satellite capturing and tracking method for a VSAT (Very Small Aperture Terminal) antenna system with a physical level platform. The method is applicable to a control object such as an antenna system in a direction, pitching and rolling three-axis (A-E-C) pedestal form. The physical level platform is built in the antenna system, a local geographic coordinate system is also built on the physical level platform, thus, the theoretical direction and the pitching angle of an antenna points relative to a fixed local geographic coordinate system are consistent with the direction and the pitching angle of the antenna points relative to a mobile local geographic coordinate system on the physical level platform; and an electric shaft of the antenna is controlled to accurately point a satellite by a mode similar to a fixed antenna on the basis, and the satellite is automatically tracked when a carrier moves. According to the method provided by the invention, heading attitude participation operation is not needed to perform by the carrier in real time during the capturing and tracking process, thus, a shipborne compass system is not needed to install on the carrier, the environment condition requirement of the carrier is reduced, and the method is beneficial for promotion and application in a small-tonnage civil ship or a water carrier with limited equipment budge and equipment resource.
Owner:西安坤蓝电子技术有限公司
Group broadcast cipher key managing method based on physical layer
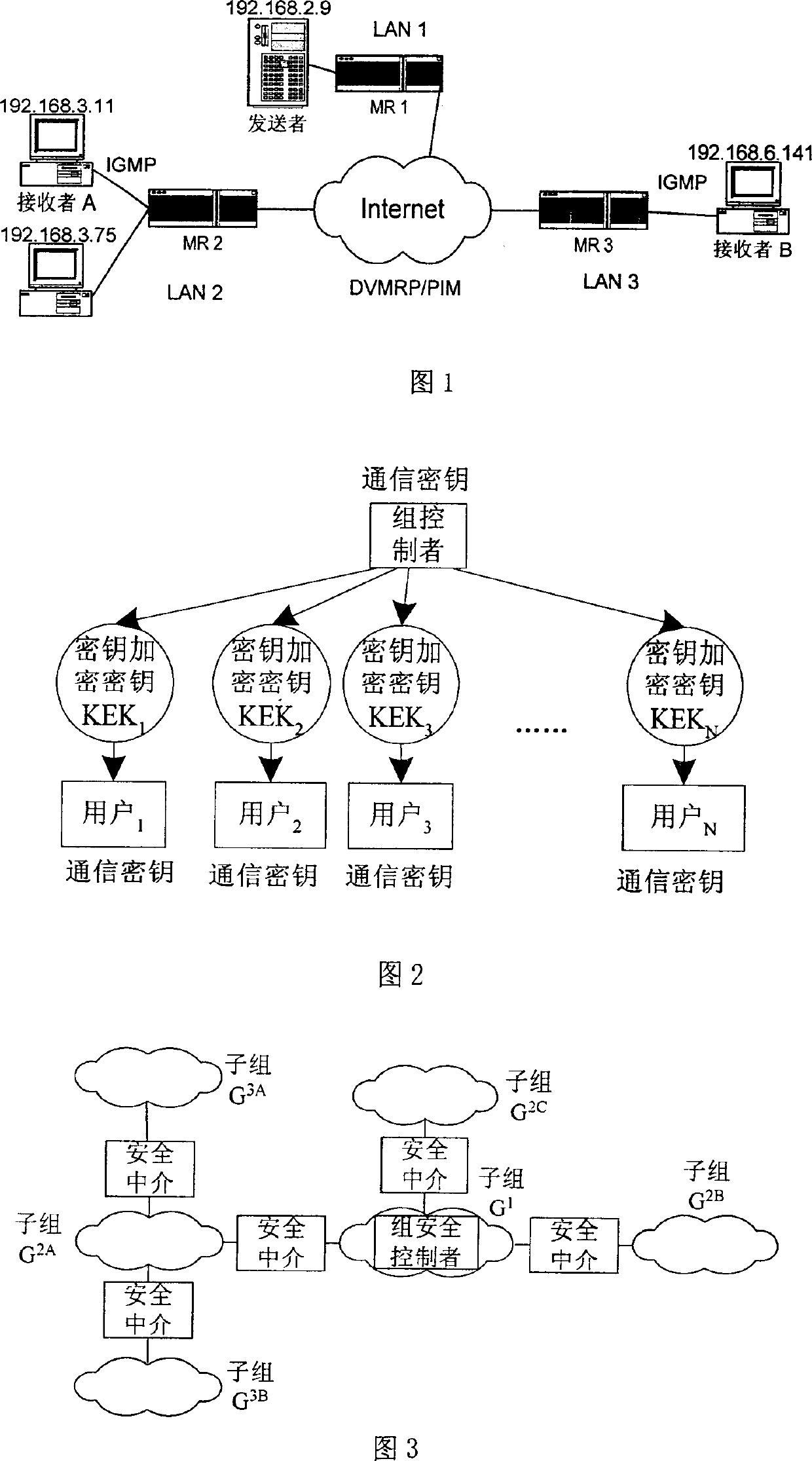
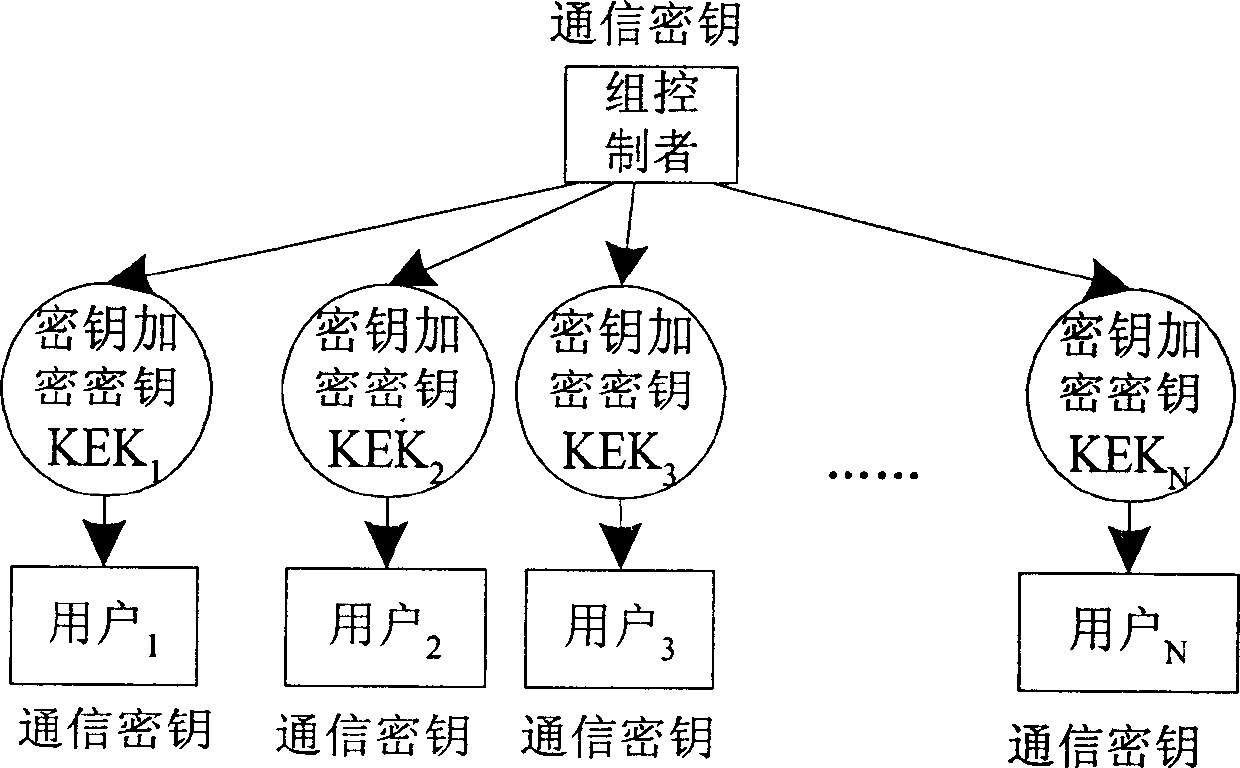
InactiveCN1716853AReduce overheadEfficient managementSpecial service provision for substationMultiple keys/algorithms usageExtensibilityMulticast network
The present invention discloses a kind of managing method for group transmission key secret code based on the physical levels of group transmission network. It relates to internet safety group transmission field, which is used as a means for graduating subgroup, group transmission key secret code administration and group transmission communication in the group transmission service, thus reducing the expenses for the renewal of the group key secret code. The source of group transmission uses the local subgroup communication key secret code with the SEK data, transmit it to the physical subgroup; and after the local physical subgroup of the group safety agent has received, deciphered it, then it uses the communication key secret code with enciphered data of the logical subgroup to transmit it to other physical subgroups, and the other physical subgroups of the group safety agents, having received it, use the logical subgroup communication key secret code with encryption group to transmit it to the group transmitting receivers of the physical subgroup. The group transmitting receivers use the local transmission key secret code to obtain data through decryption. The invention can effectively divide the subgroups and resolve the problem of the key secret code administration of the safety group transmission, thus reducing the expenses for the renewal of the group transmission key secret code without limitation to scope and with favorable expansion.
Owner:UNIV OF SCI & TECH OF CHINA
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com