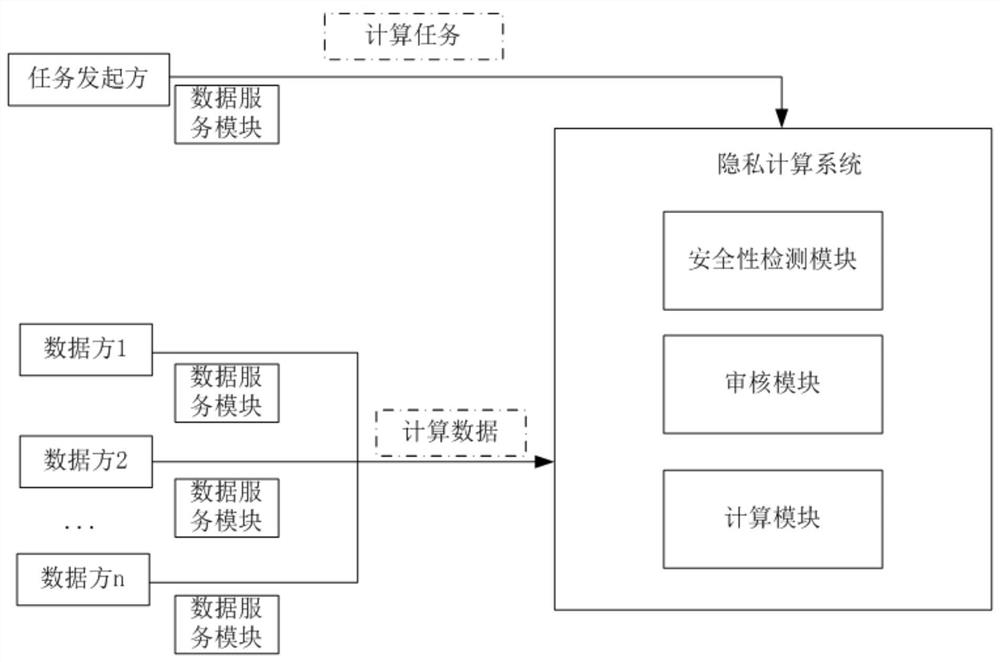
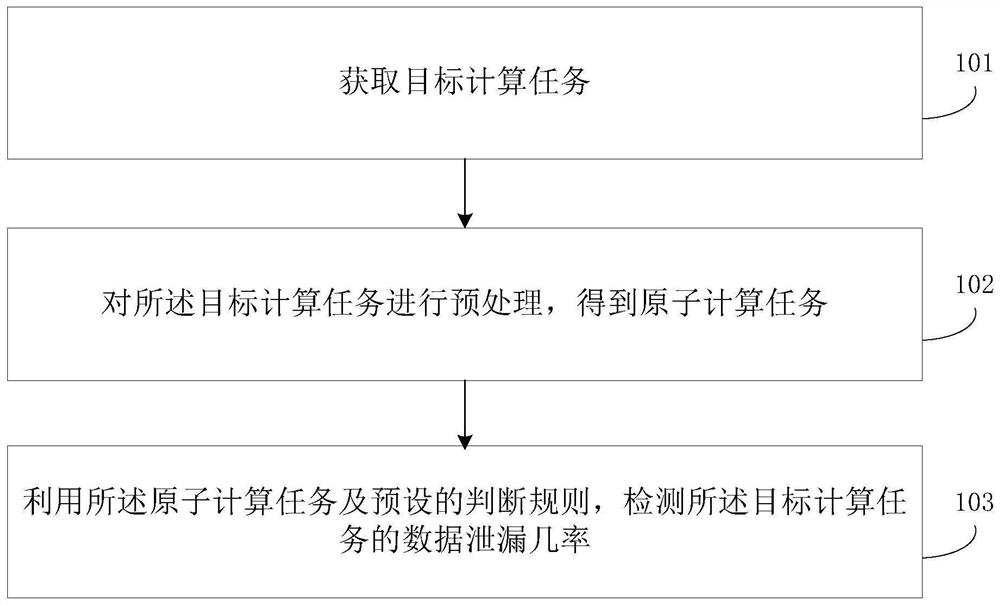
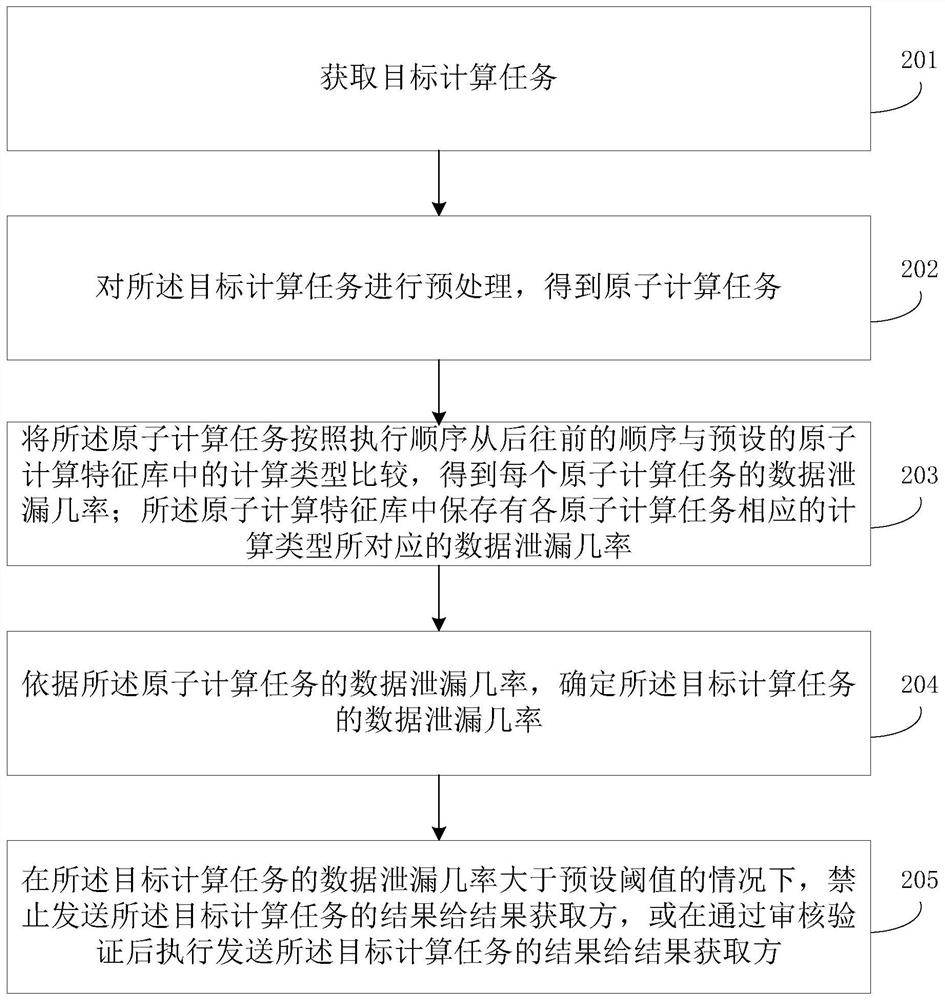
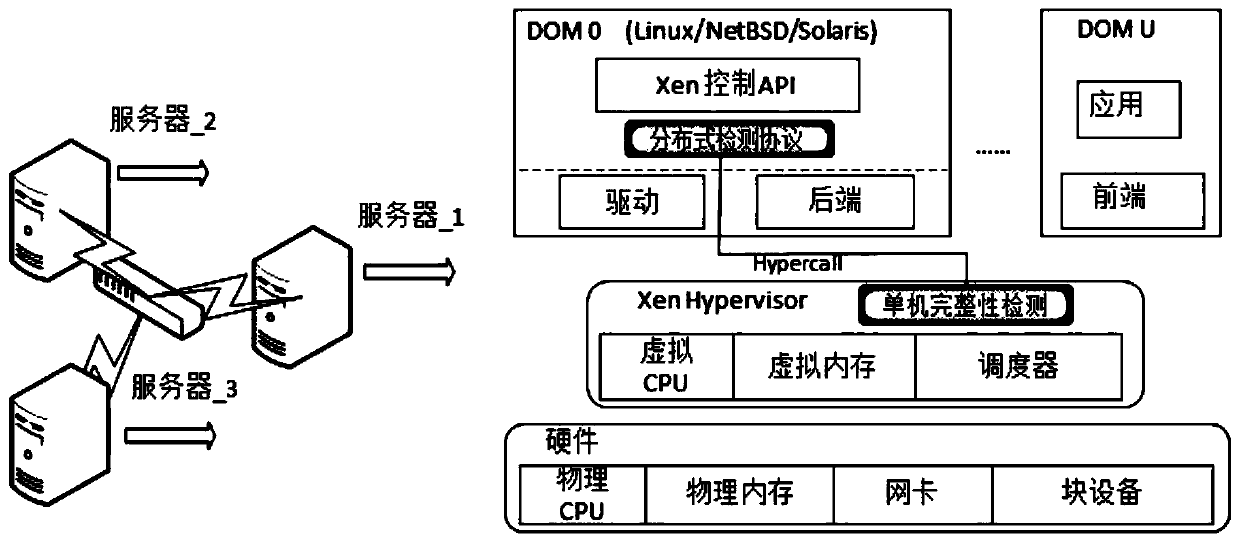
Patents
Literature
82 results about "Safety property" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
In distributed computing, safety properties informally require that "something bad will never happen" in a distributed system or distributed algorithm. Unlike liveness properties, safety properties can be violated by a finite execution of a distributed system. In a database system, a promise to never return data with null fields is an example of a safety guarantee. All properties can be expressed as the intersection of safety and liveness properties.
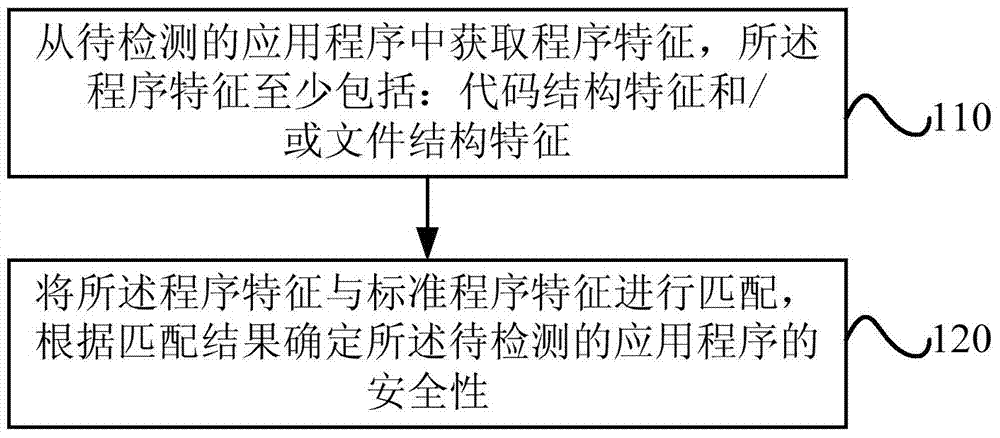
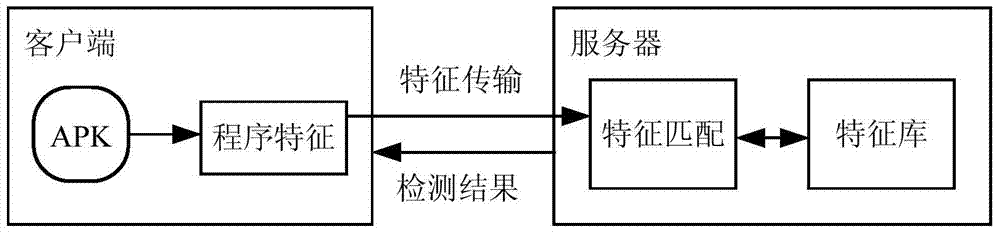
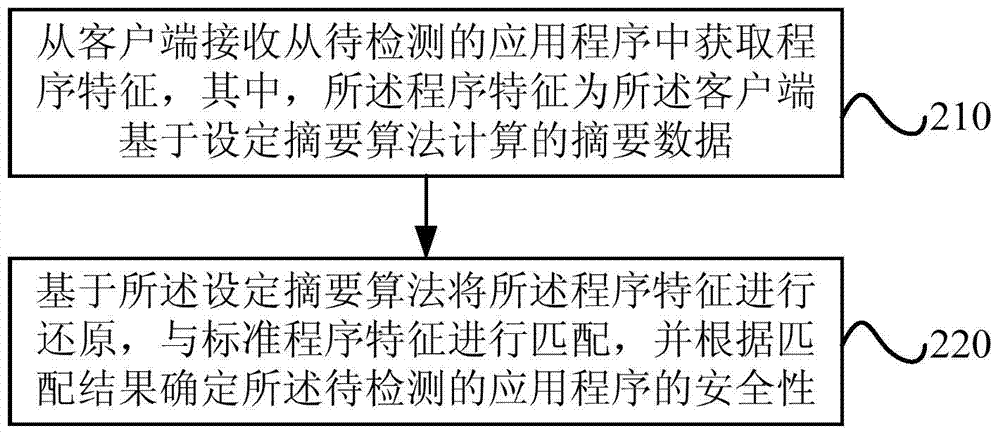
Method and device for detecting safety performance of application program
ActiveCN104123493ASecurity testingSecurity determinedPlatform integrity maintainanceProgram/content distribution protectionProgramming languageStandard program
The embodiment of the invention provides a method and device for detecting the safety performance of an application program. The method includes the steps of obtaining program characteristics from the application program to be detected, wherein the program characteristics at least include the code structure characteristics and / or the file structure characteristics; matching the program characteristics with standard program characteristics, and determining the safety performance of the application program according to the matching result. By means of the scheme, the program characteristics are obtained from the application program to be detected, the important characteristics including the code structure characteristics and / or the file structure characteristics can be obtained, the program characteristics and the standard program characteristics are matched, the safety performance of the application program to be detected can be determined according to the matching result including successful matching, failed matching or the characteristic contact ratio and the like, whether codes are changed or not or whether malicious codes are added or not and whether files are replaced or not can be detected by matching the program characteristics, and therefore whether the application program to be detected is piratical or not can be fundamentally detected through the code structure characteristics and / or the file structure characteristics.
Owner:BAIDU ONLINE NETWORK TECH (BEIJIBG) CO LTD
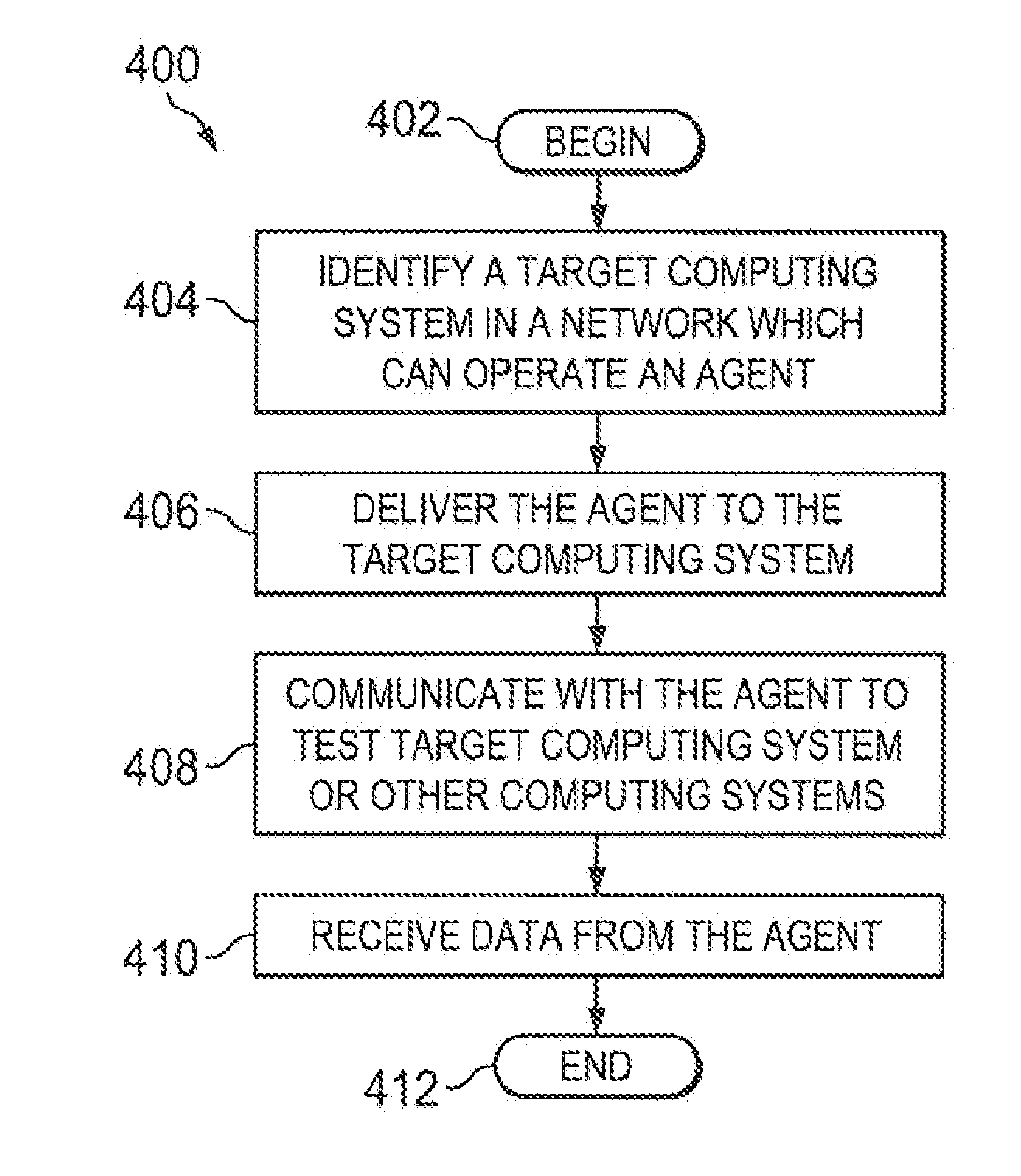
Methods and systems for providing a framework to test the security of computing system over a network
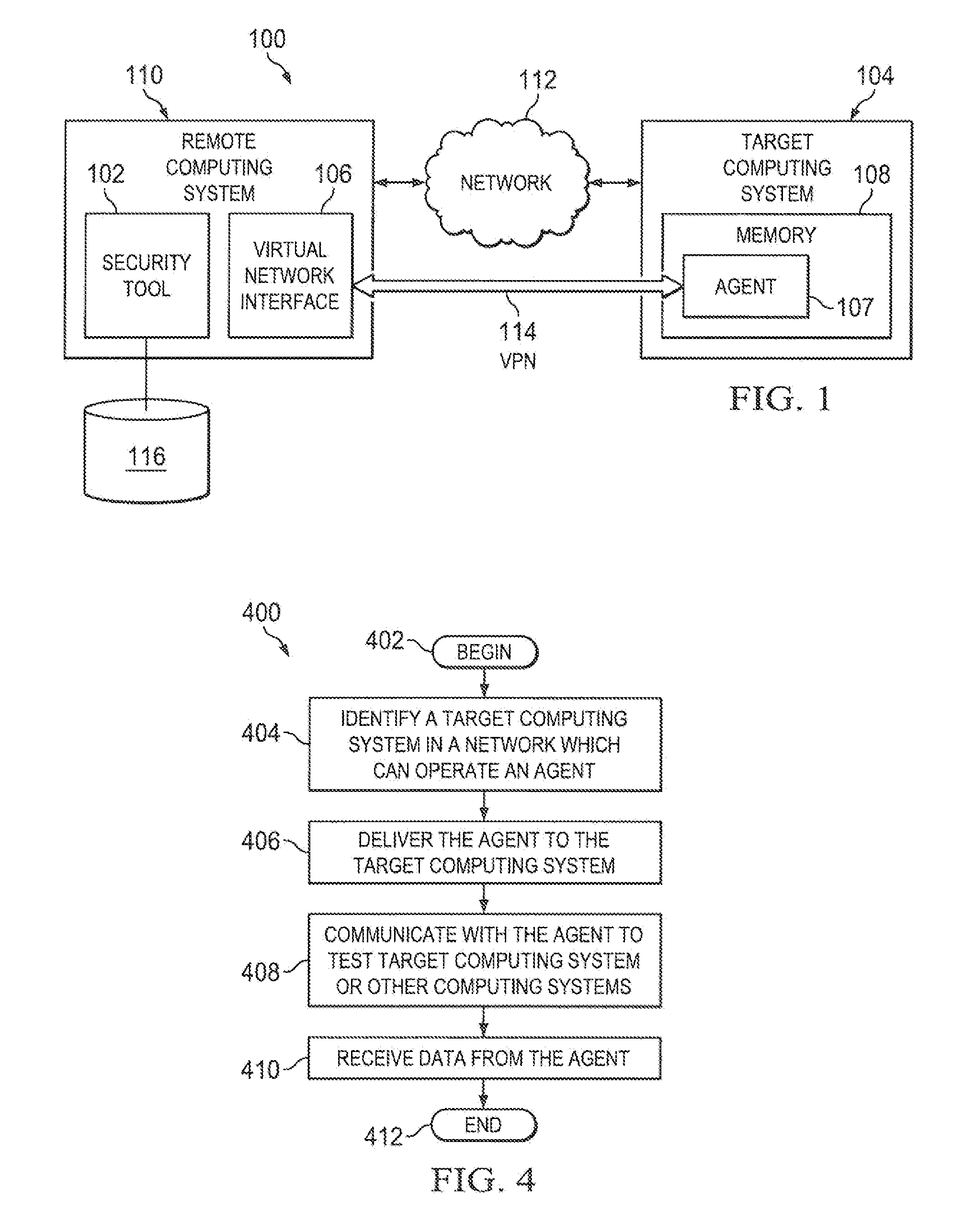
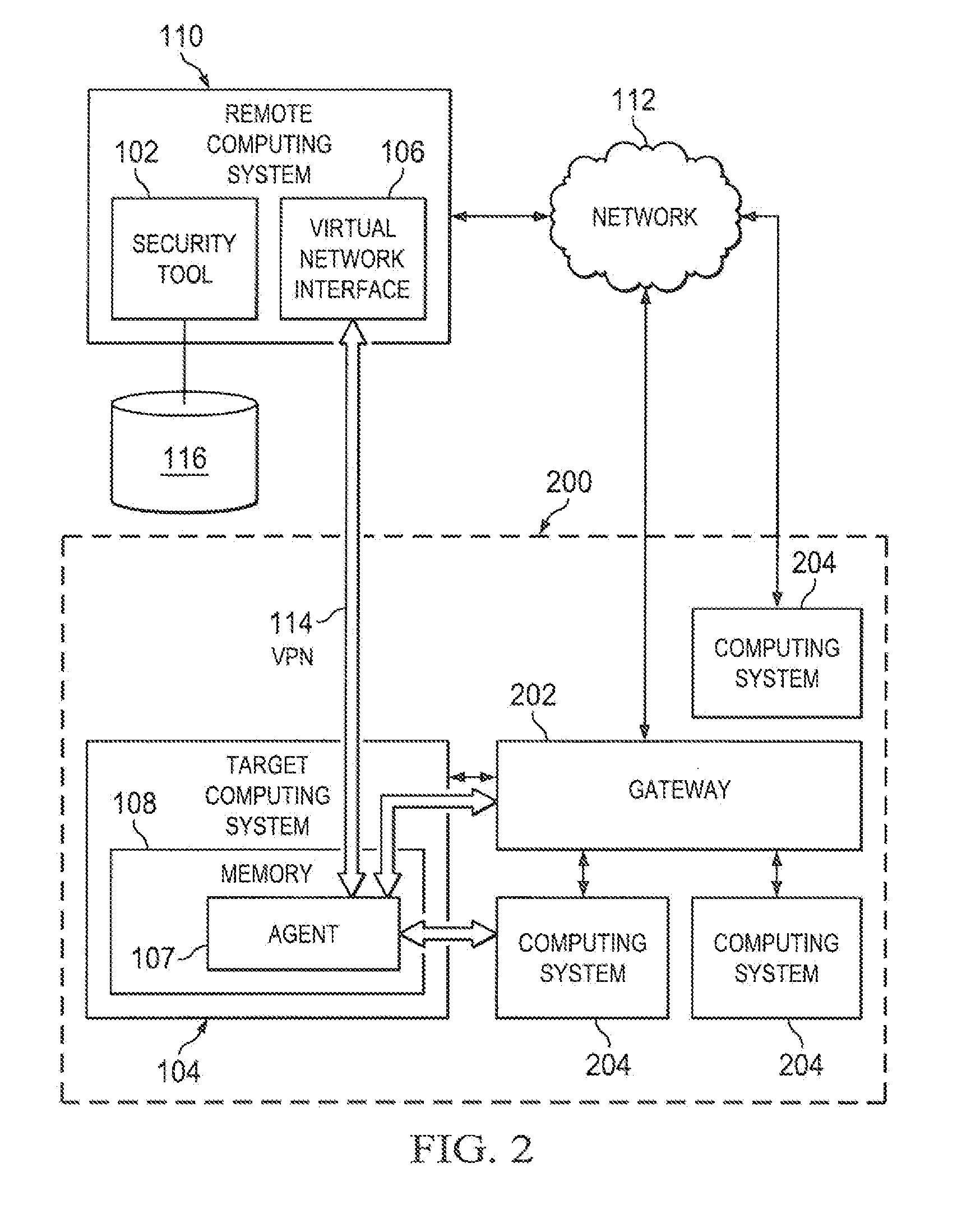
A security tool can utilize a vulnerability in a computing system or credentials for the computing system to gain access to the computing system. Once access is gained, the security tool can deliver an agent to the computing system. The agent can execute, detected or undetected, on the computing system in order to establish a network link between the computing system and the security tool. Once established, the security tool creates a virtual network interface on the computing system on which it is running and instructs the agent to relay network traffic between the virtual network interface of the computing system executing the security tool and the existing network interfaces of computing system executing the agent.
Owner:RAPID7
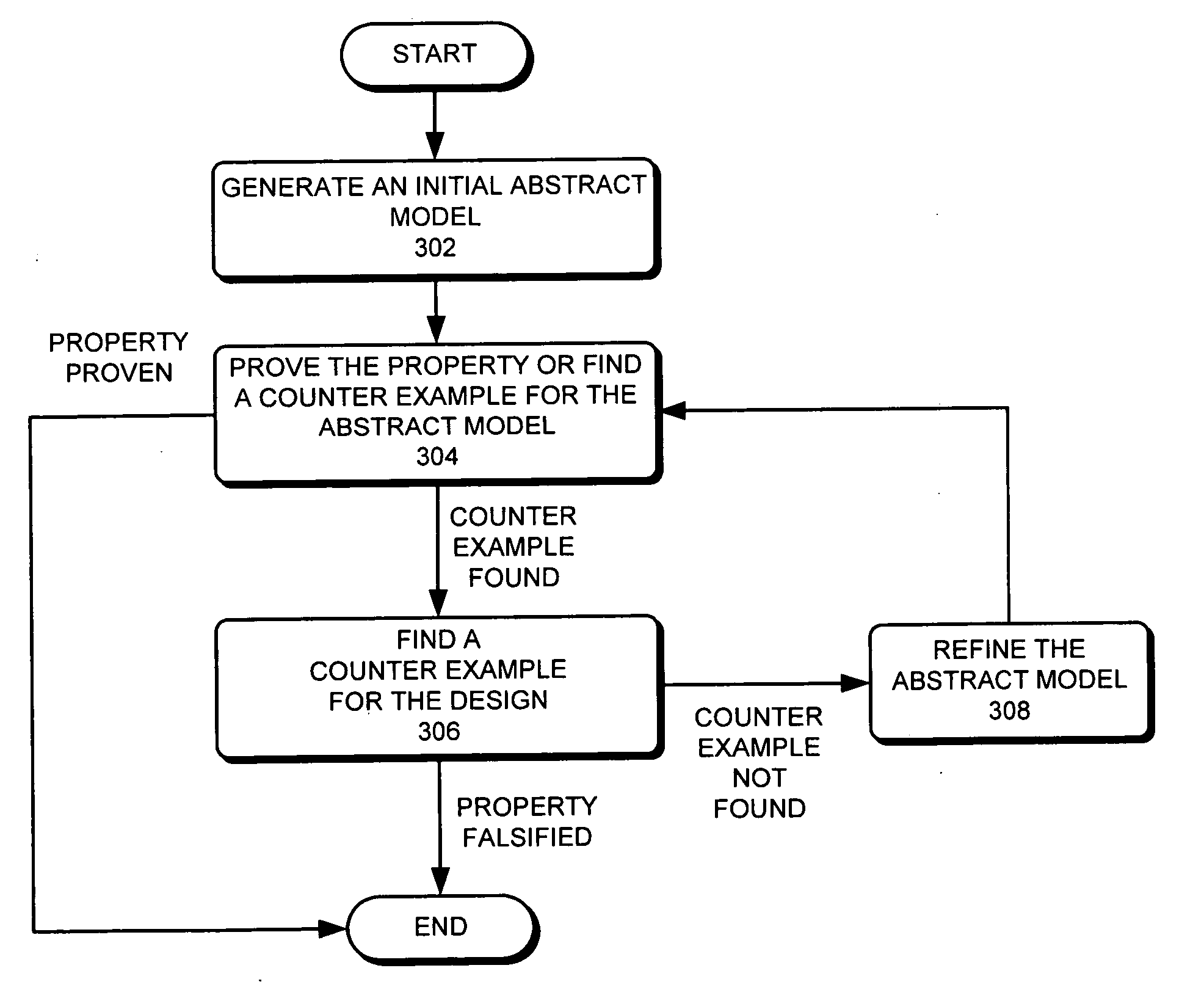
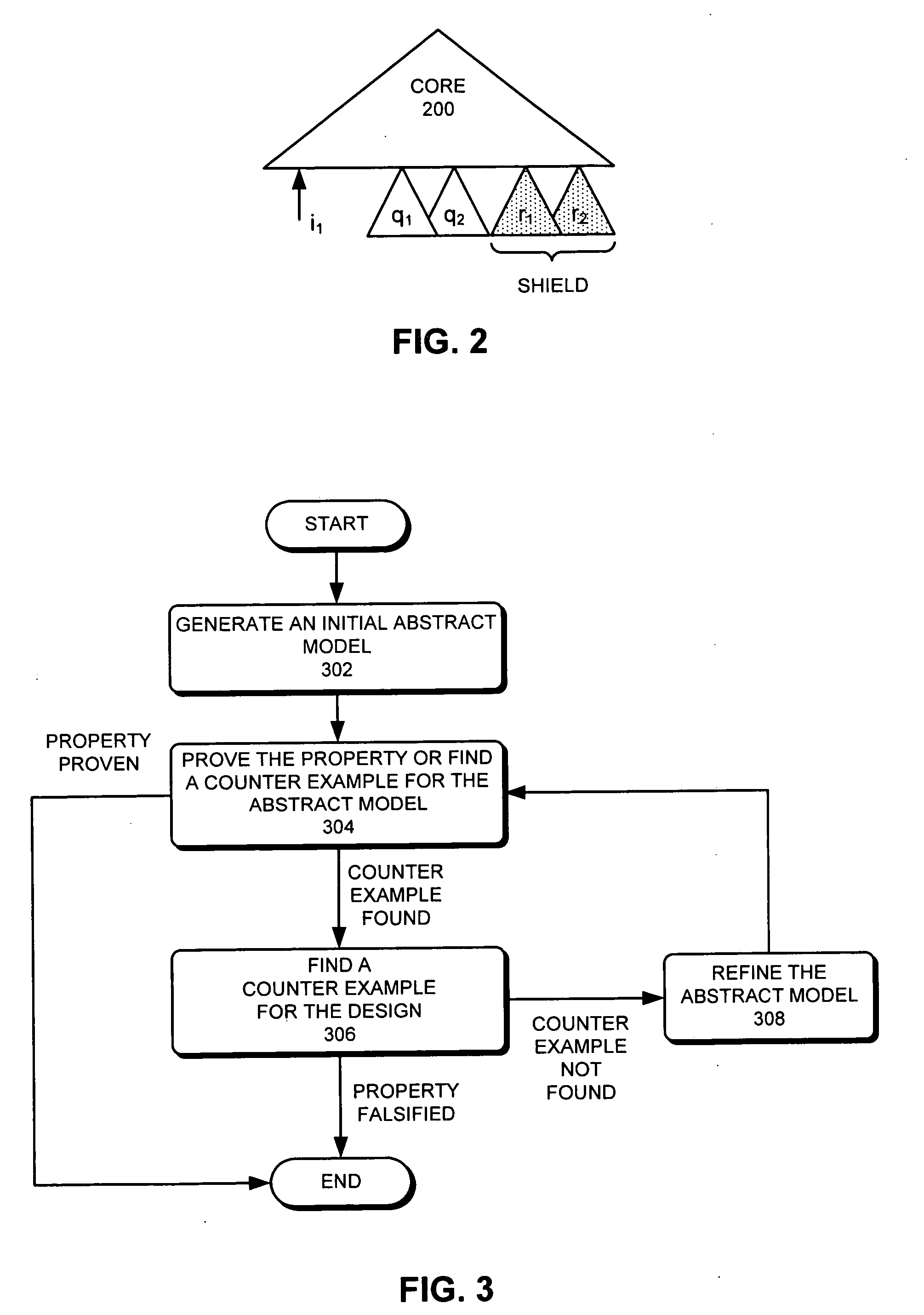
Abstraction refinement using controllability and cooperativeness analysis
InactiveUS20060129959A1Analogue computers for electric apparatusComputer aided designTheoretical computer scienceSecurity properties
One embodiment of the present invention provides a system that refines an abstract model. Note that abstraction refinement is commonly used in formal property verification. During operation, the system receives an abstract model which is a subset of a logic design which can be represented using a set of variables and a set of Boolean functions. Next, the system receives a safety property for the logic design which is desired to be proven. The system also receives a set of counter-examples. A counter-example is a sequence of states that violates the safety property. Note that a state is an assignment of values to the variables, which are determined using the set of Boolean functions and the variable values in the previous state. The system then determines a set of cooperative variables using the set of counter-examples. A cooperative variable is a variable that can help invalidate all counter-examples. The system then refines the abstract model using the set of cooperative variables.
Owner:SYNOPSYS INC
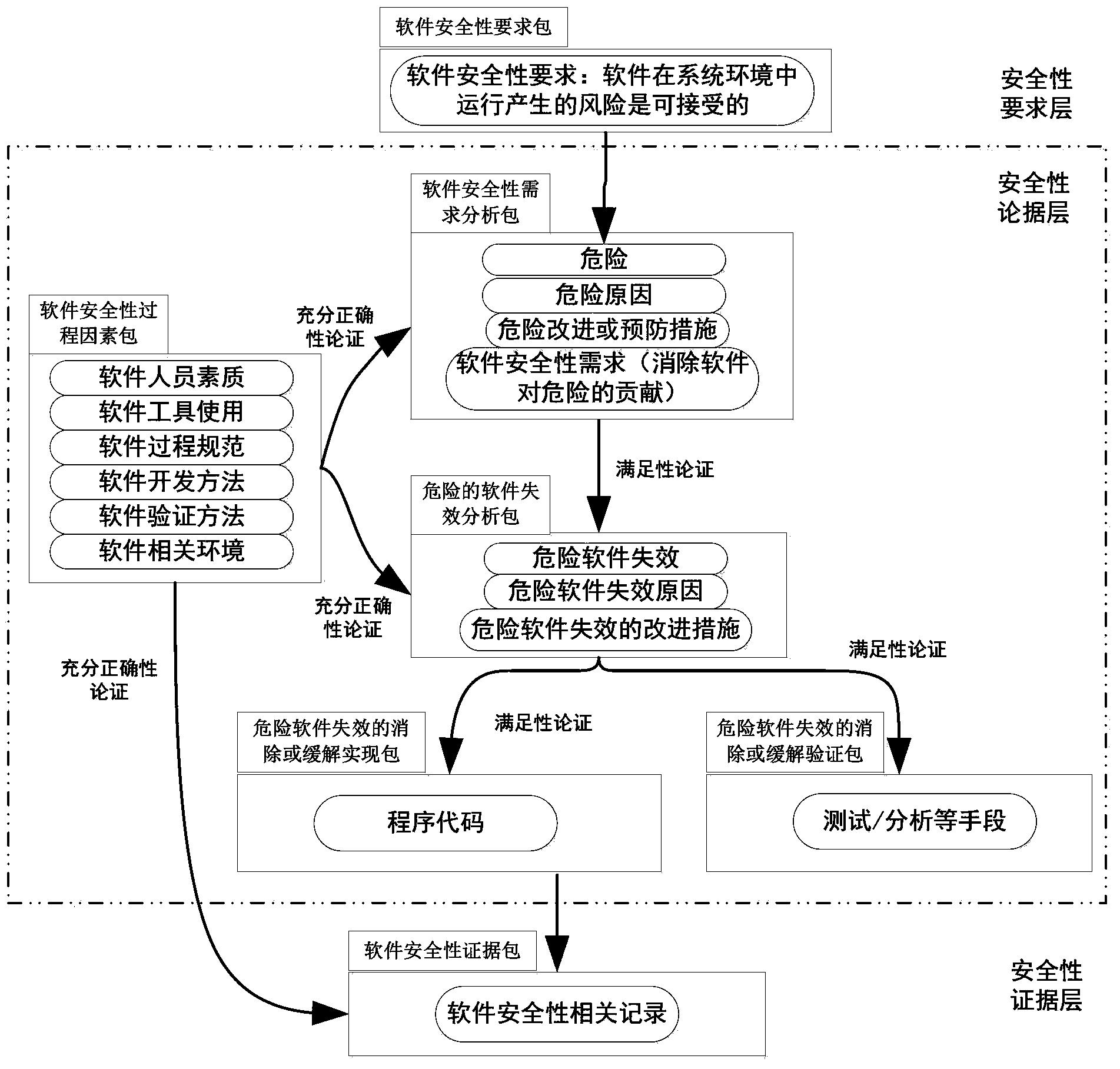
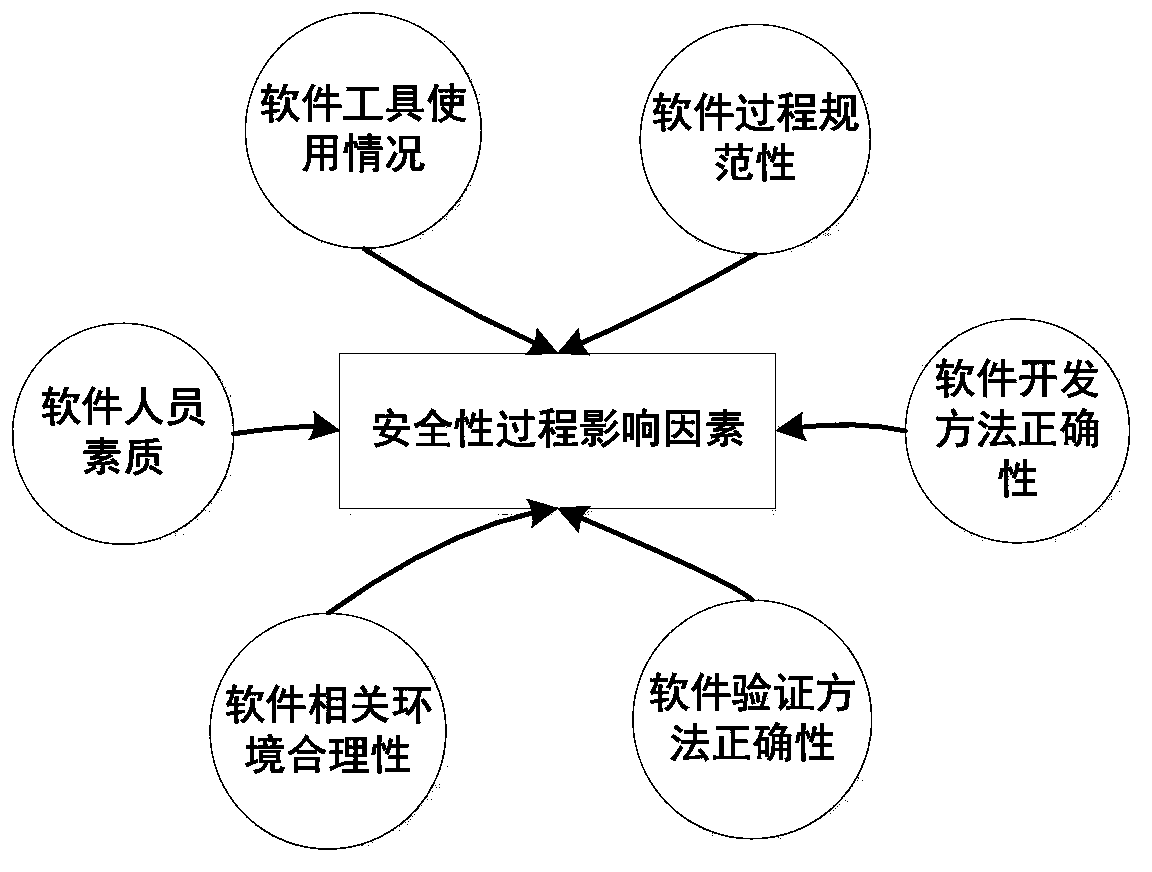
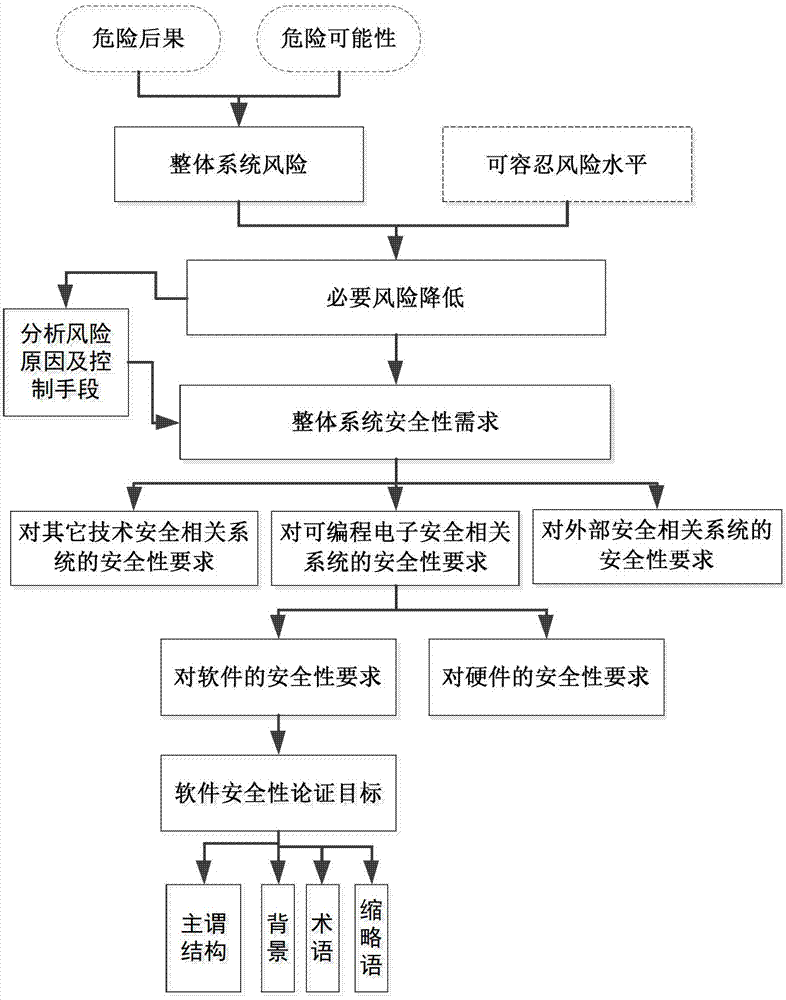
Software safety proof development method combining product and process
ActiveCN103383722AConfidenceOvercoming the Shortcomings of Software Security EvidenceSoftware testing/debuggingProgram/content distribution protectionSoftware engineeringSatisfiability
The invention discloses a software safety proof development method combining a product and a process. The method takes danger or danger control as the core, realizes risk management of system safety from the aspect of software, and launches proofing of two aspects including satisfiability and full correctness surrounding the top target. The purpose of satisfiability proofing is to prove that proofed objects are realized and satisfied, so as to perform proofing from the aspects of danger, danger control, and danger control realization, all based on the product method which serves as a main line. The purpose of full correctness is to prove that the objects are complete and correct, so as to enhance the realization confidence based on process method and through the factors such as 'process standardization, personnel quality and development method'. The software safety proof development method overcomes the deficiency of software safety proofing only through product or only through process, can effectively guide the development of software safety proofing, and provide a more effective method for a software-related party to check the safety and other related situation.
Owner:天航长鹰(江苏)科技有限公司
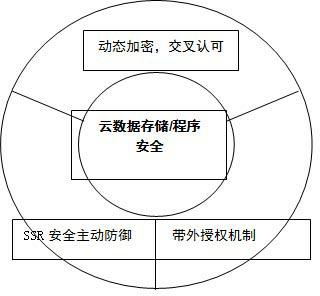
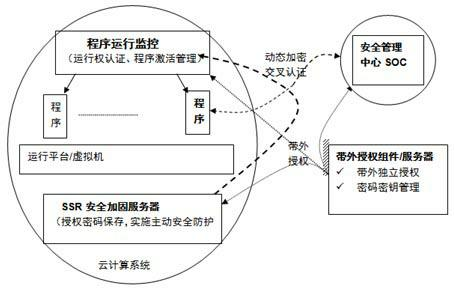
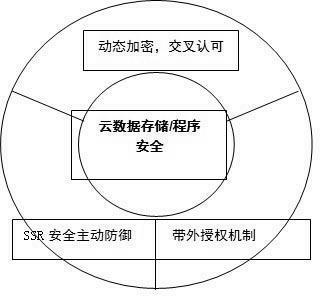
Out-of-band authorization safety reinforcement method for cloud computing platform
The invention provides a safety reinforcement method for a cloud computing platform. The method is characterized in that: programs on the cloud computing platform are subjected to out-of-band encryption authorization by adopting an active defense technology based on server system reinforcement (SSR) and the out-of-band encryption authorization, and the legitimacy of running a cloud computing program and the security of related data access are ensured under the support of the SSR by dynamic cross authorization between a cloud platform operation monitoring and management system and an external security management center. Therefore, a program running right is prevented from being illegally stolen and controlled by a super hacker Trojan, critical data is prevented from being illegally accessed, and the security of the cloud platform program running and the critical data can be greatly improved.
Owner:INSPUR TIANYUAN COMM INFORMATION SYST CO LTD
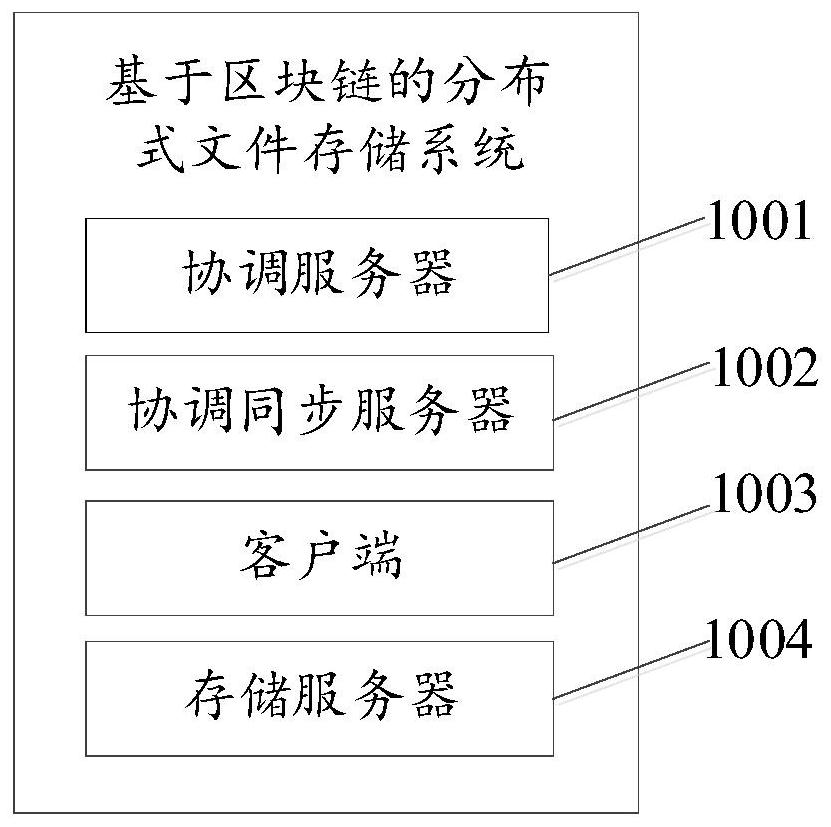
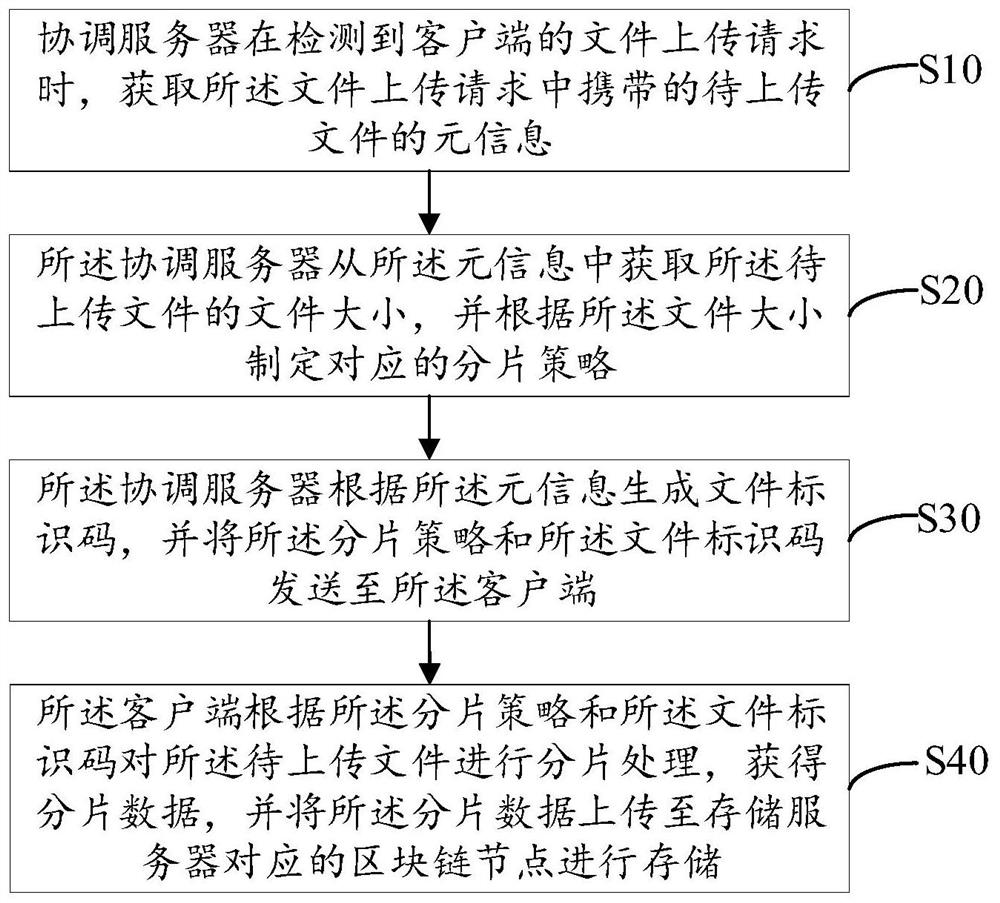
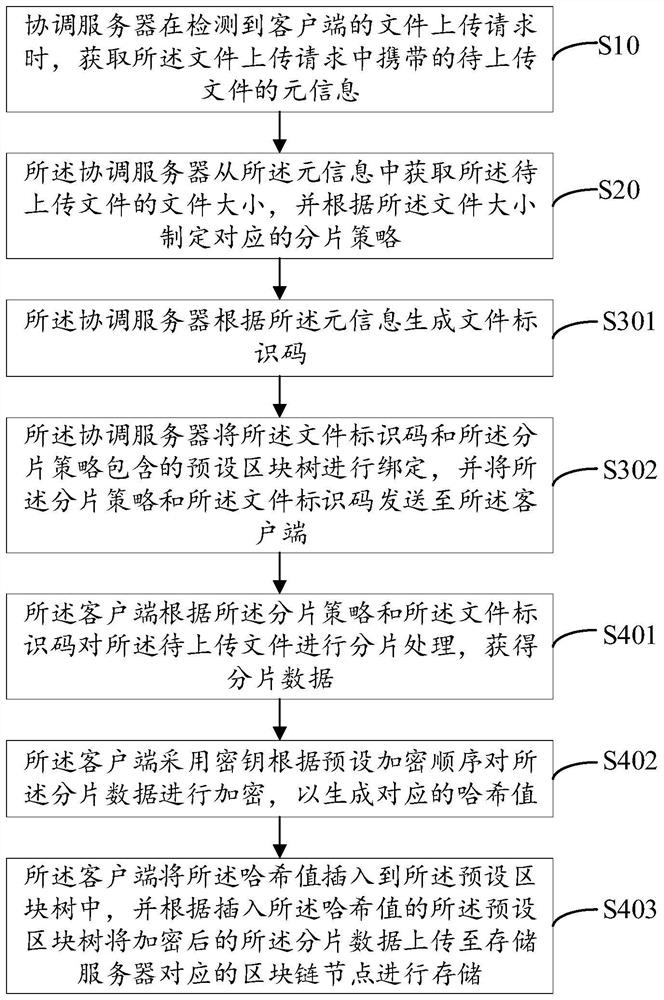
Distributed file storage method and system based on block chain
PendingCN112256663AImprove storage efficiencyImprove storage securityDigital data protectionFile access structuresThird partyStorage security
The invention relates to the technical field of block chains, and discloses a distributed file storage method and system based on a block chain, and the method comprises the steps: meta-information ofa to-be-uploaded file carried in a file uploading request is acquired when a coordination server detects the file uploading request of a client, a coordination server obtains the file size of the to-be-uploaded file from the meta-information, formulates a corresponding fragmentation strategy according to the file size, generates a file identification code according to the meta-information, and sends the fragmentation strategy and the file identification code to a client; and the client performs fragmentation processing on the to-be-uploaded file according to the fragmentation strategy and thefile identification code to obtain fragmentation data, and uploads the fragmentation data to a block chain node corresponding to the storage server for storage so as to realize distributed storage ofthe file. Potential safety hazards caused by the fact that the to-be-uploaded file is stored in the third-party server in the prior art are avoided, the storage pressure of the storage server is reduced, and the file storage efficiency and the storage safety are improved.
Owner:ONE CONNECT SMART TECH CO LTD SHENZHEN
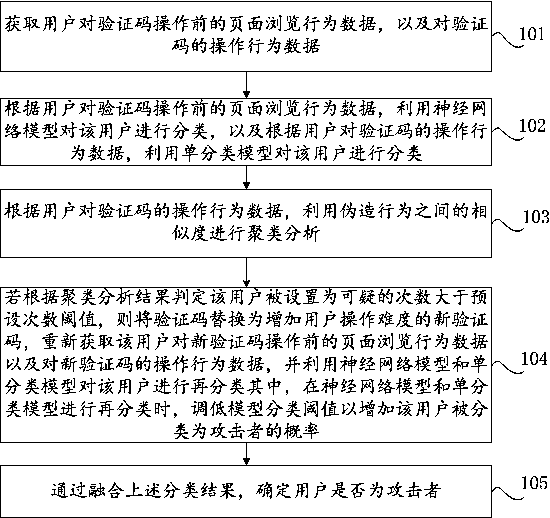
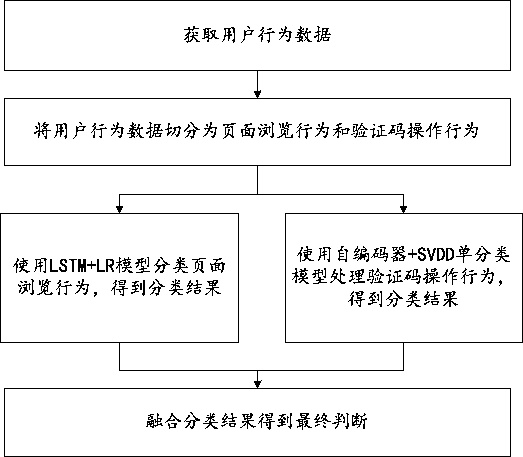
Safety processing method, device and equipment based on user behaviors
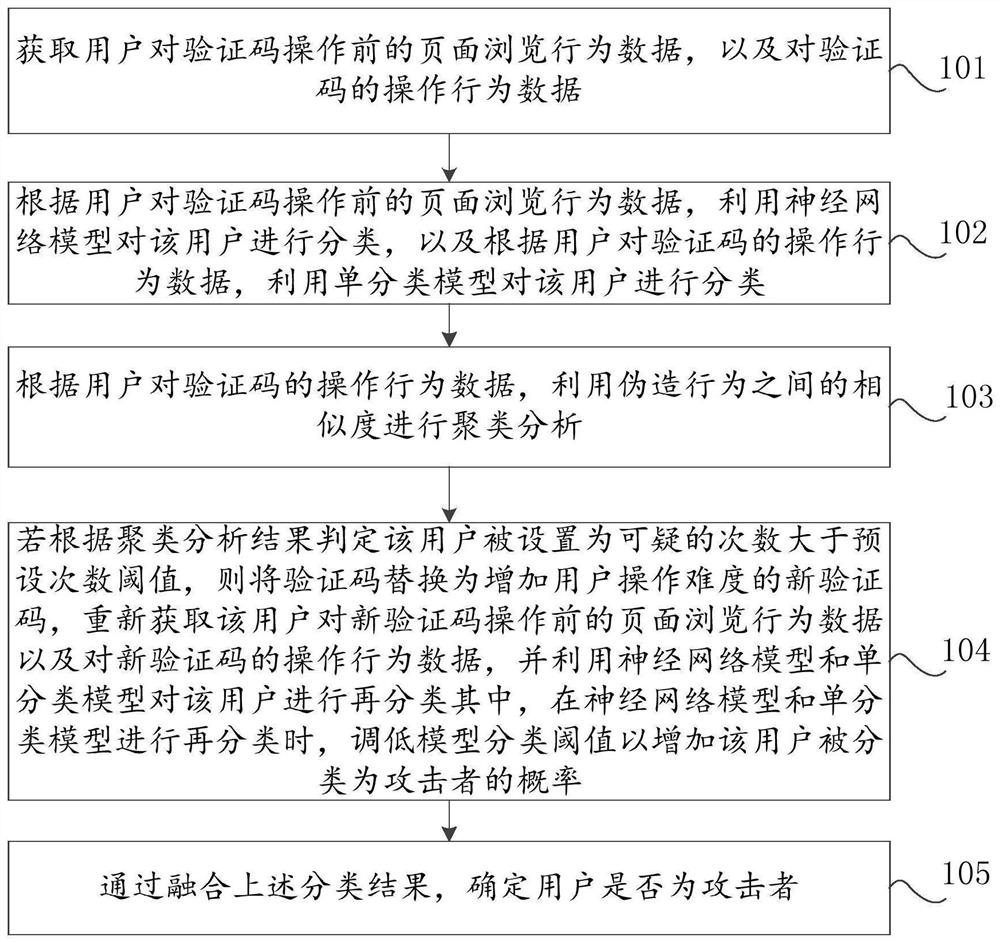
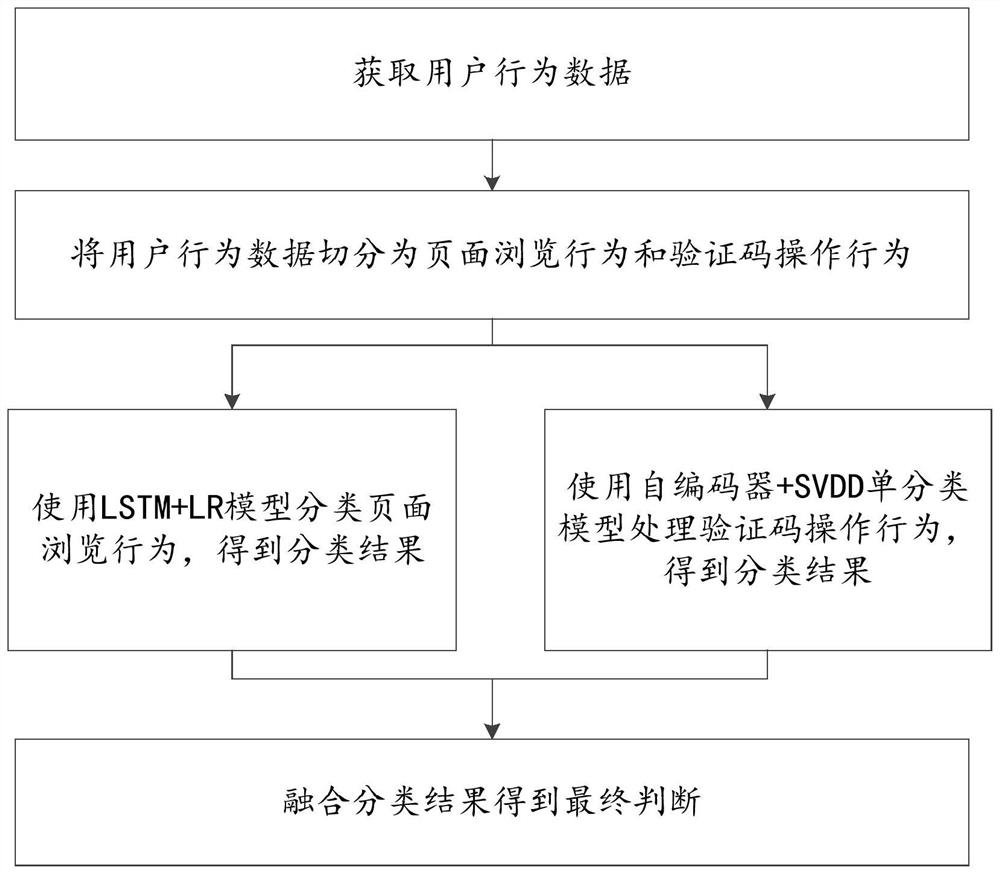
ActiveCN111428231AIncrease operational difficultyEnsure safetyCharacter and pattern recognitionDigital data authenticationWeb siteAttack
The invention discloses a safety processing method, device and equipment based on user behaviors, and relates to the technical field of data safety. The method comprises the following steps: judging whether a user is an attacker or not according to page browsing behavior data of the user before operating a verification code and operation behavior data of the verification code; if it is judged thatthe operation behavior data of the user is behavior data of a real user, based on the operation behavior data of the user, carrying out clustering analysis by utilizing the similarity between forgedbehaviors, and if the number of times that the user is set to be suspicious is greater than the preset number of times threshold, increasing the verification difficulty, increasing the probability that a model is classified as an attacker, and re-classifying behavior data re-collected by the user; and finally, determining whether the user is an attacker or not by fusing classification results. According to the invention, stricter black product attack defense can be realized based on the user behavior data of the operation verification code, and the website security is ensured.
Owner:BEIJING PERFECT WORLD SOFTWARE TECH DEV CO LTD
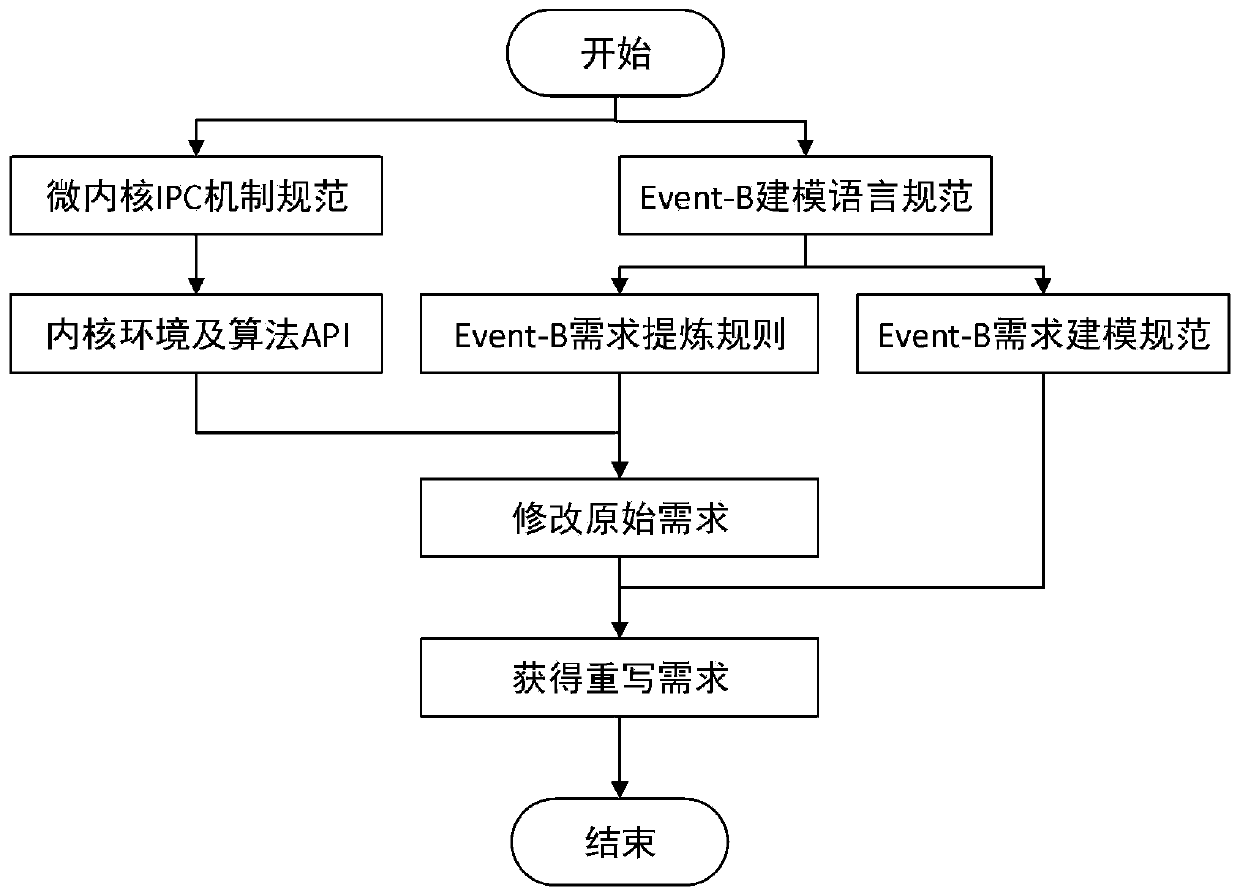
Formal modeling and verification method for inter-process communication mechanism of microkernel operating system based on Event-B method
ActiveCN110968436AProof of feasibilityProve securityProgram synchronisationInterprogram communicationOperational systemSafety property
The invention discloses a formal modeling and verification method for an inter-process communication mechanism of a microkernel operating system based on an Event-B method. The method comprises the steps that demand design analysis is conducted, specifically, according to a microkernel operating system inter-process communication mechanism based on an Event-B method, in combination with a subscriber publisher mode, design analysis is conducted to meet the original demand of Event-B modeling; according to the inter-process communication mechanism of the microkernel operating system based on theEvent-B method and the result of the original demand, designing and analyzing meet the rewriting demand of Event-B modeling; and modeling and refining verification: a model for verifying the inter-process communication mechanism of the microkernel operating system is designed and created based on the Event-B method according to a rewriting demand. Proving obligations needing to be verified by themodel comprise a model functional invariant, a model property invariant and a safety property related invariant.
Owner:EAST CHINA NORMAL UNIV
Safety processing method, device and apparatus based on user behaviors
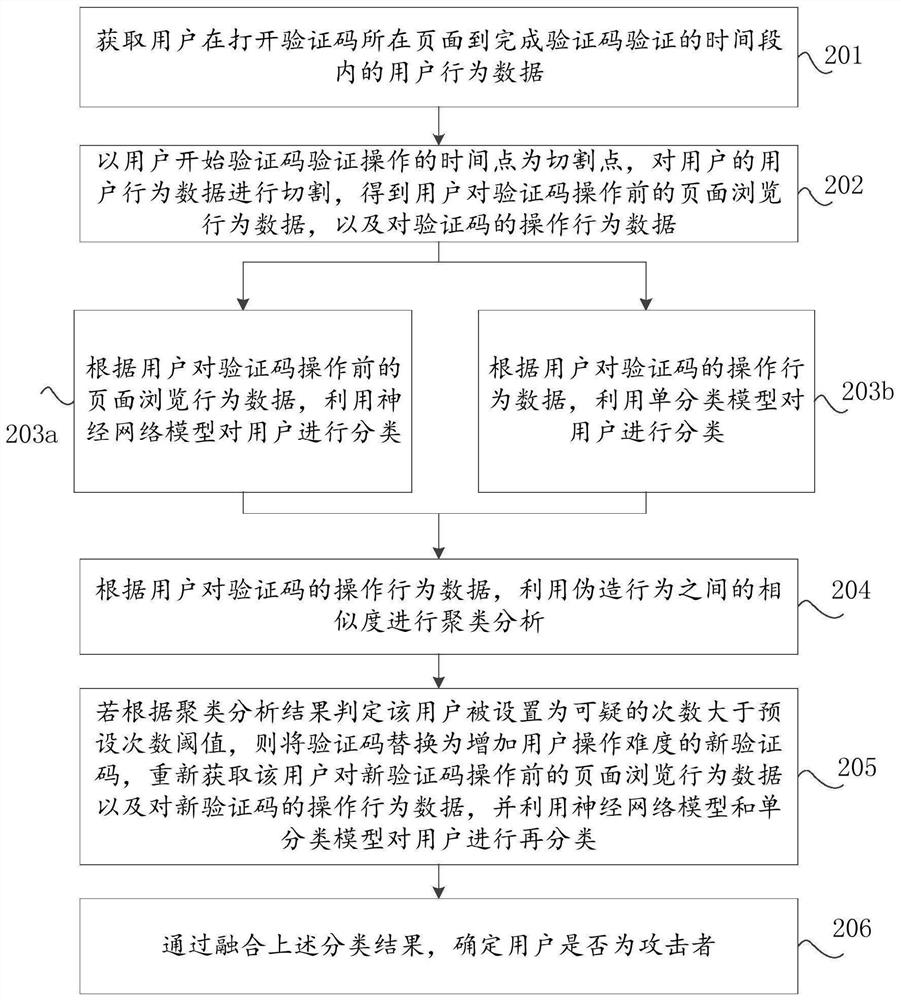
PendingCN112069485AIncrease operational difficultyEnsure safetyCharacter and pattern recognitionDigital data authenticationAttackSafety property
The invention discloses a safety processing method, device and apparatus based on user behaviors, and relates to the technical field of data safety. The method comprises the following steps: judging whether a user is an attacker or not according to page browsing behavior data of the user before operating a verification code and operation behavior data of the verification code; and if judging the operation behavior data of the user is behavior data of a real user, performing clustering analysis by using similarity between counterfeit behaviors based on the operation behavior data of the user, and if the suspicious frequency of the user is set to be greater than a preset frequency threshold, performing clustering analysis by using similarity between counterfeit behaviors; If not, increasingthe verification difficulty, and the probability that the model is classified as an attacker, and re-classifying behavior data re-collected by the user by using the model; and finally, determining whether the user is an attacker or not by fusing classification results. Stricter black product attack defense can be realized based on the user behavior data of the operation verification code, and thewebsite security is ensured.
Owner:BEIJING PERFECT WORLD SOFTWARE TECH DEV CO LTD
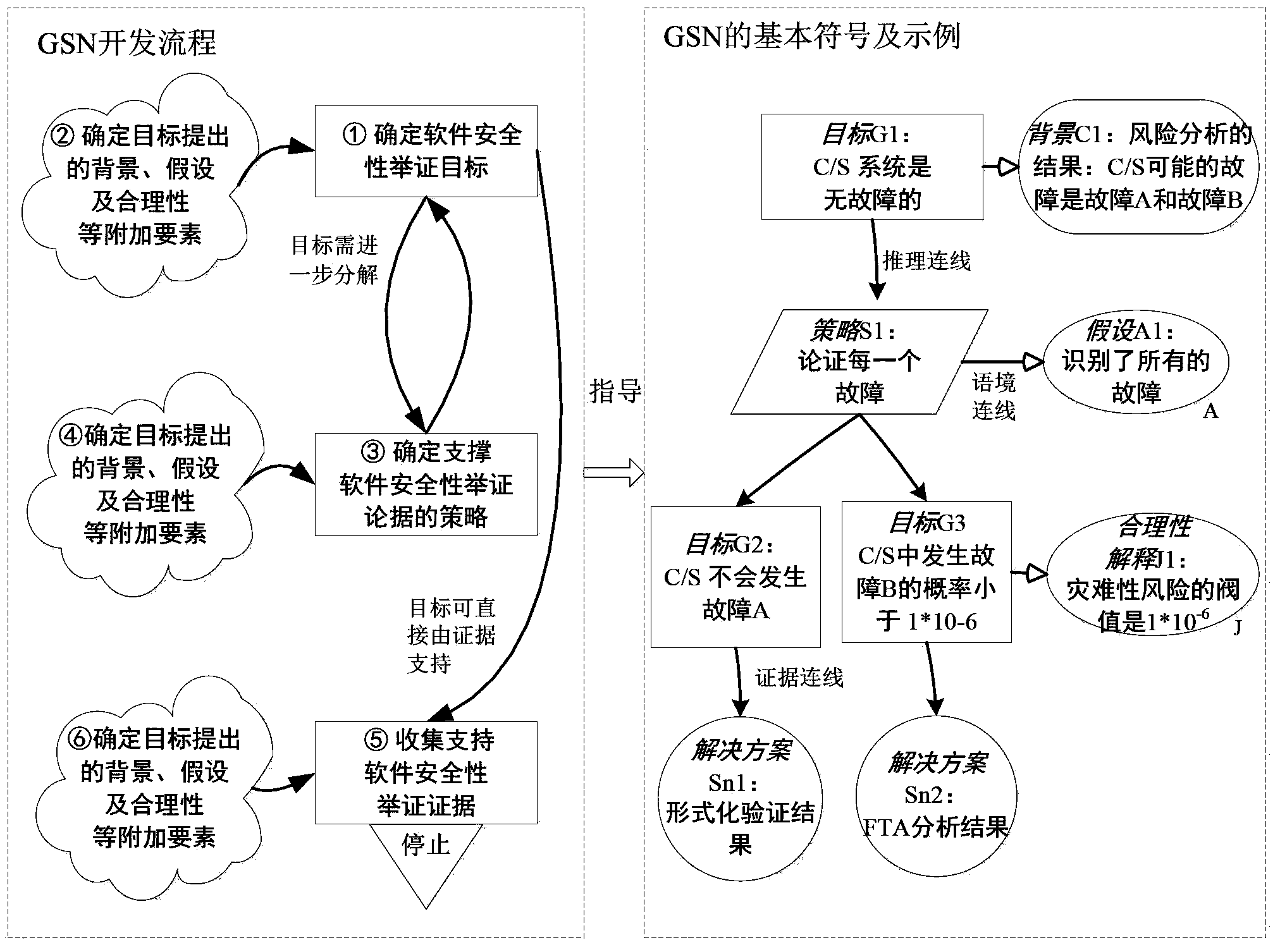
Software safety argumentation method based on Toulmin model
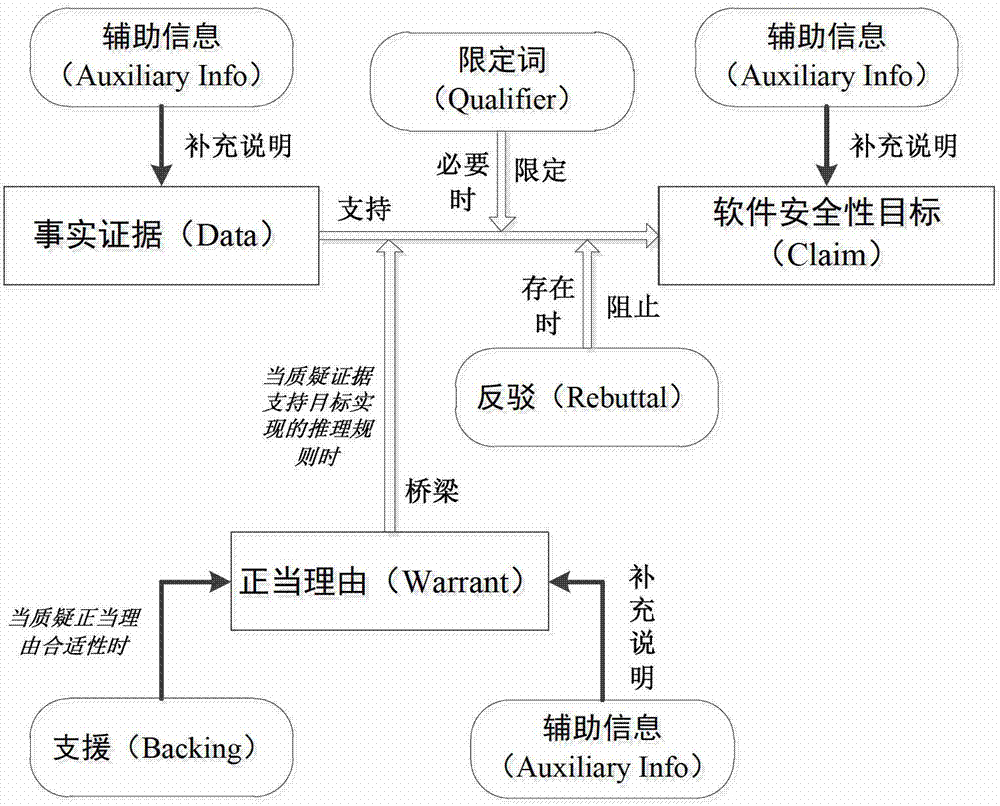
InactiveCN102779253ADirect implementationDirect and clearer implementationComputer security arrangementsSoftware engineeringSoftware
The invention discloses a software safety argumentation method based on a Toulmin model. The software safety argumentation method comprises the following steps of: using a software safety target required to be performed argumentation as a core; providing factual evidence supporting the target; for doubts, giving a right reason to provide the factual evidence for supporting the target and support for strengthening the authoritative statement of the right reason; determining determiners for target achievement degree if the target is not completely a fact; and giving refutation that prevents authenticating the target reasonable based on the right reason, so as to achieve the safety argumentation method using the software safety target as the core. The software safety argumentation method is more free and extensible, capable of directly and more clearly indicating how the software safety target is satisfied, and simultaneously promoting the development to actively carry out safety security work in a more effective manner, thereby improving the software safety in a more active manner.
Owner:BEIHANG UNIV
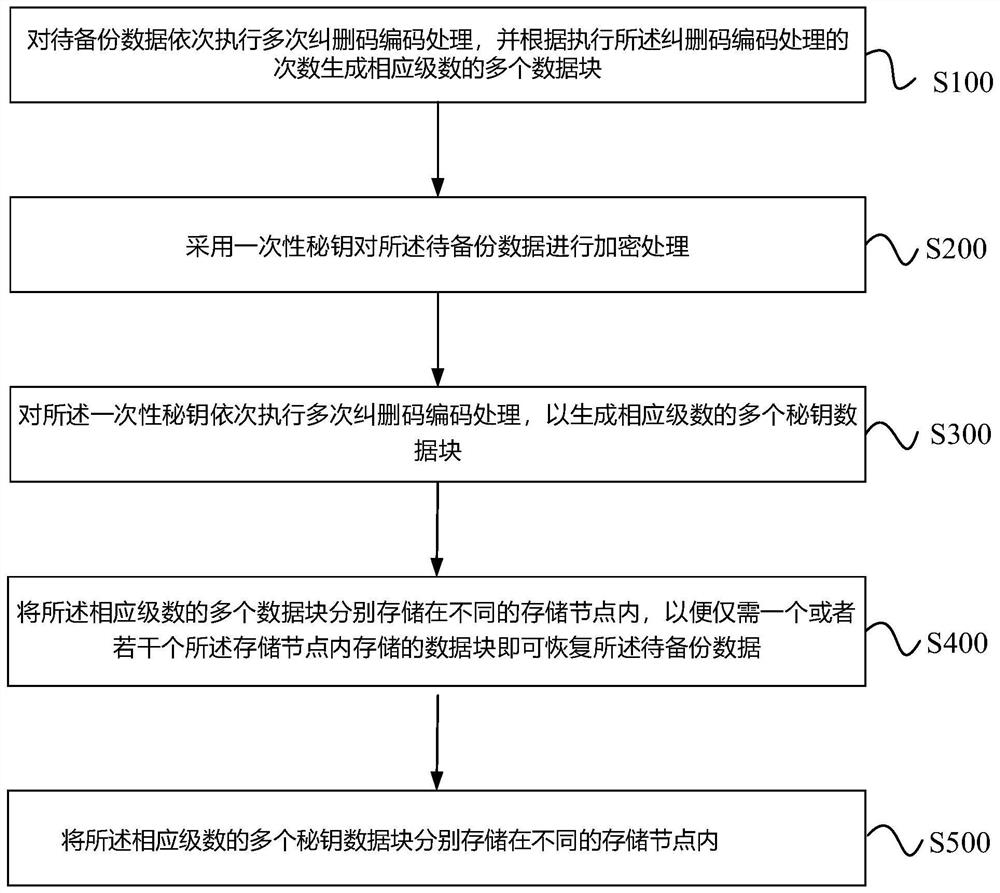
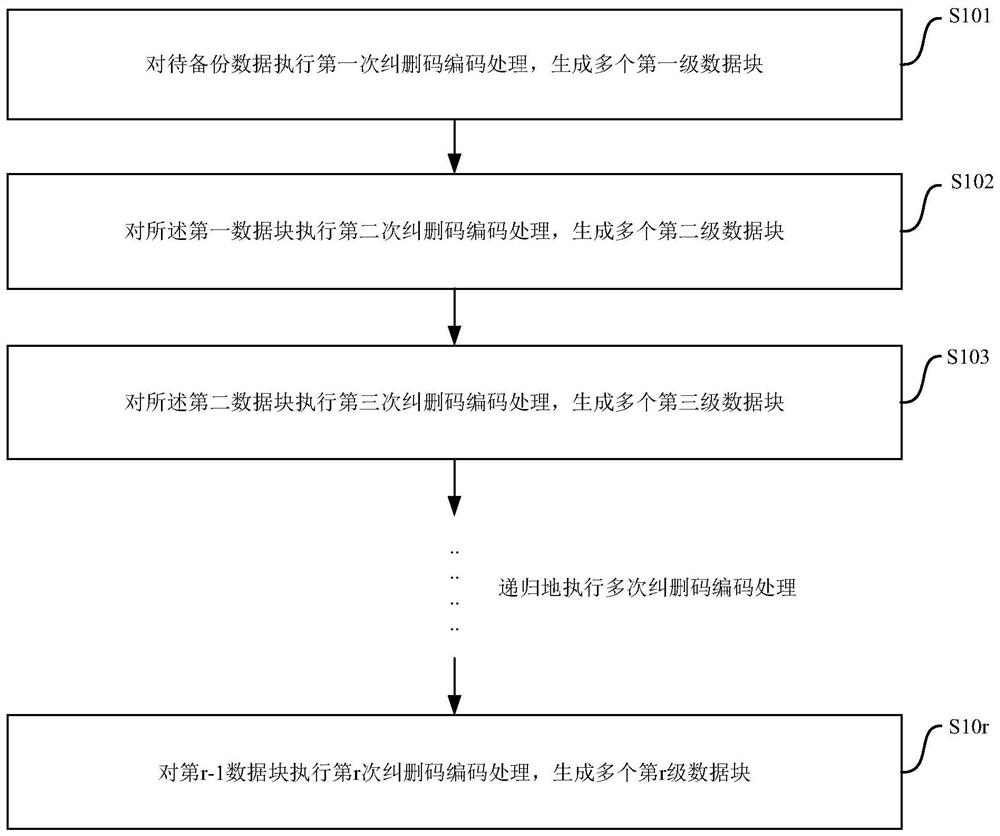
Data backup method and system
PendingCN111679939AReduce storage costsImprove securityInternal/peripheral component protectionRedundant data error correctionConfidentialitySafety property
The invention relates to the field of data disaster tolerance and cloud storage, and provides a data backup method and system. The method comprises the steps: sequentially carrying out the repeated erasure code coding of to-be-backed-up data, and generating a plurality of data blocks with corresponding levels according to the frequency of the erasure code coding; respectively storing the pluralityof data blocks in different storage nodes; wherein an erasure code matrix adopted during erasure code encoding processing is a column full-rank matrix, and the erasure code matrix is stored in the storage node so as to be called when the to-be-backed-up data needs to be recovered. According to the method and the system, the erasure code encoding processing is sequentially executed on the to-be-backed-up data for multiple times, so that the storage resource expenditure of the storage node can be reduced; and moreover, the plurality of data blocks are separately stored in different storage nodes, so that the storage space expenditure required by a single storage node is reduced, and the disaster tolerance safety and confidentiality safety of data storage are improved.
Owner:JIANGSU SUPERFLUIDITY INFORMATION TECH CO LTD
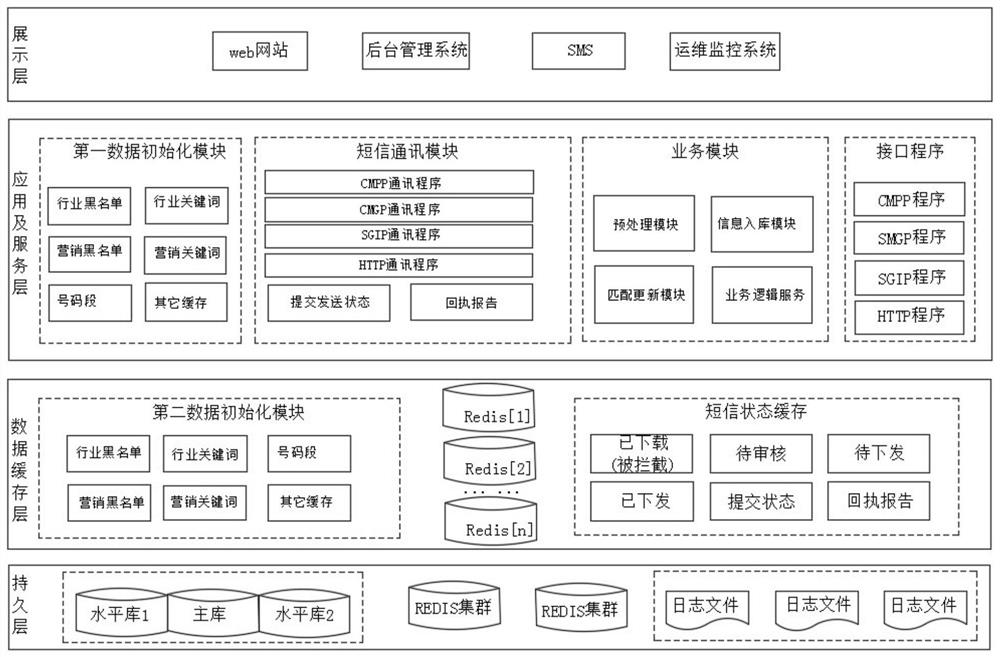
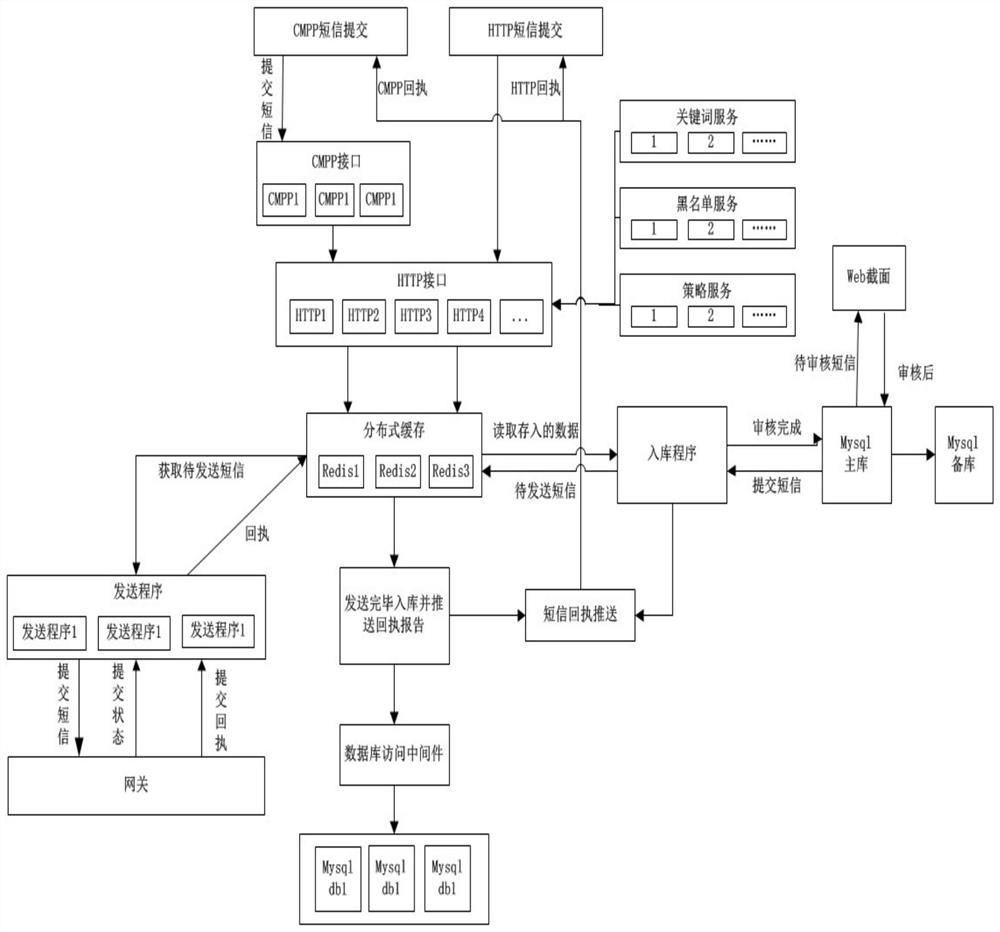
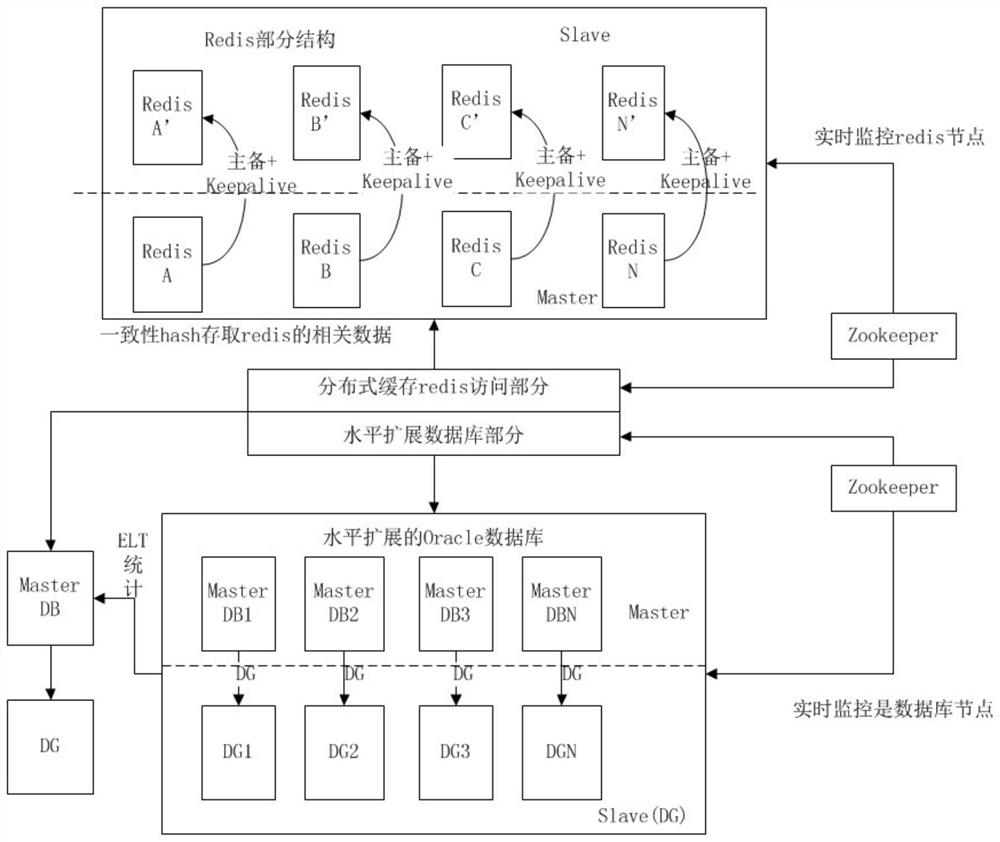
Short message management system and method based on distributed storage
ActiveCN112040429ASolve capacity problemsSolve concurrencyMessaging/mailboxes/announcementsTransmissionSafety propertyEngineering
The invention provides a short message management system and method based on distributed storage. The method comprises the steps that an application service layer receives first short message data through short message interface modules based on different types of operators, carries out the safety verification based on a preset strategy management model, forms second short message data and corresponding channel data, and sends the data to a data cache layer; the data cache layer caches the second short message data and the channel data, and schedules the second short message data to a corresponding channel based on a scheduling strategy; a persistent layer correspondingly stores the short messages scheduled to a distributed database in a master-slave synchronization mode; and a display layer is used for displaying the short message data to the user based on a query request of the user. Through added database middleware, a group of data is connected in series to form the distributed database so that problems of a capacity, concurrency and horizontal expansion are effectively solved, and the performance and stability of the system are greatly improved.
Owner:南京云中云信息技术有限公司
Security detection method and device for computing task
PendingCN112487415AReduce complexityReduce difficultyProgram initiation/switchingPlatform integrity maintainanceAlgorithmSafety property
Owner:HUAKONG TSINGJIAO INFORMATION SCI BEIJING LTD
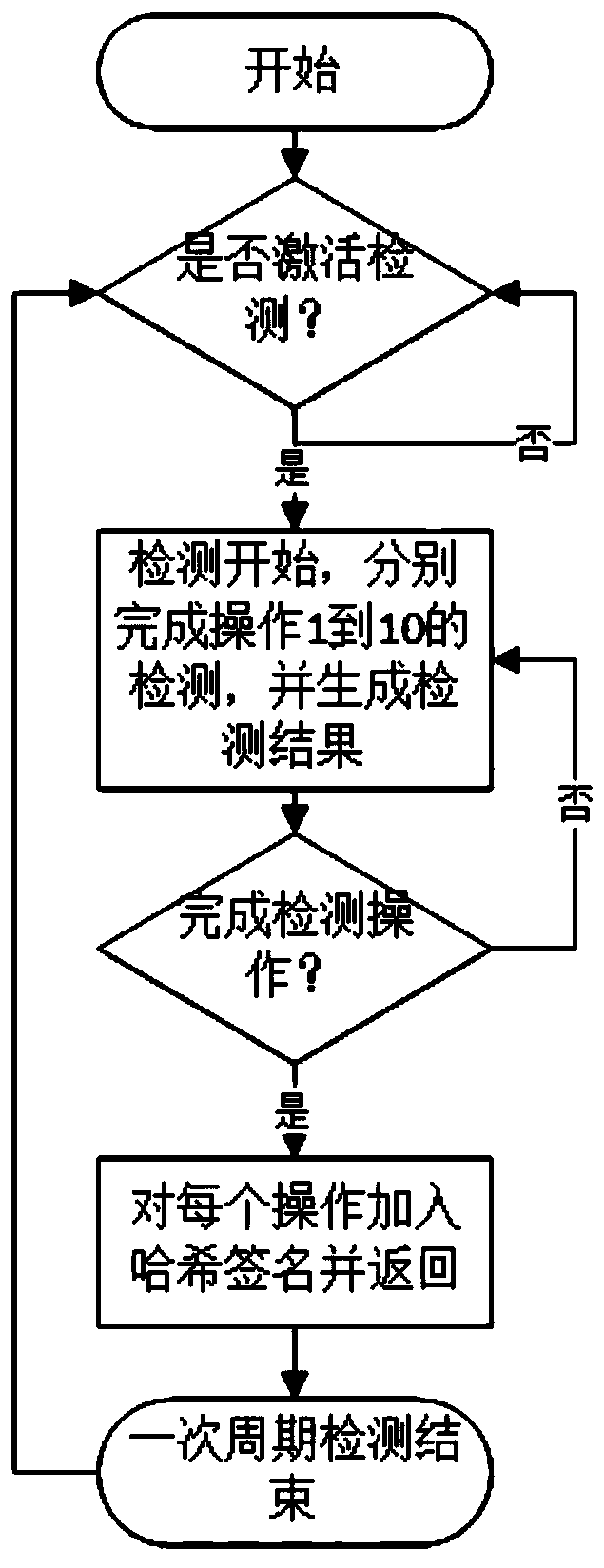
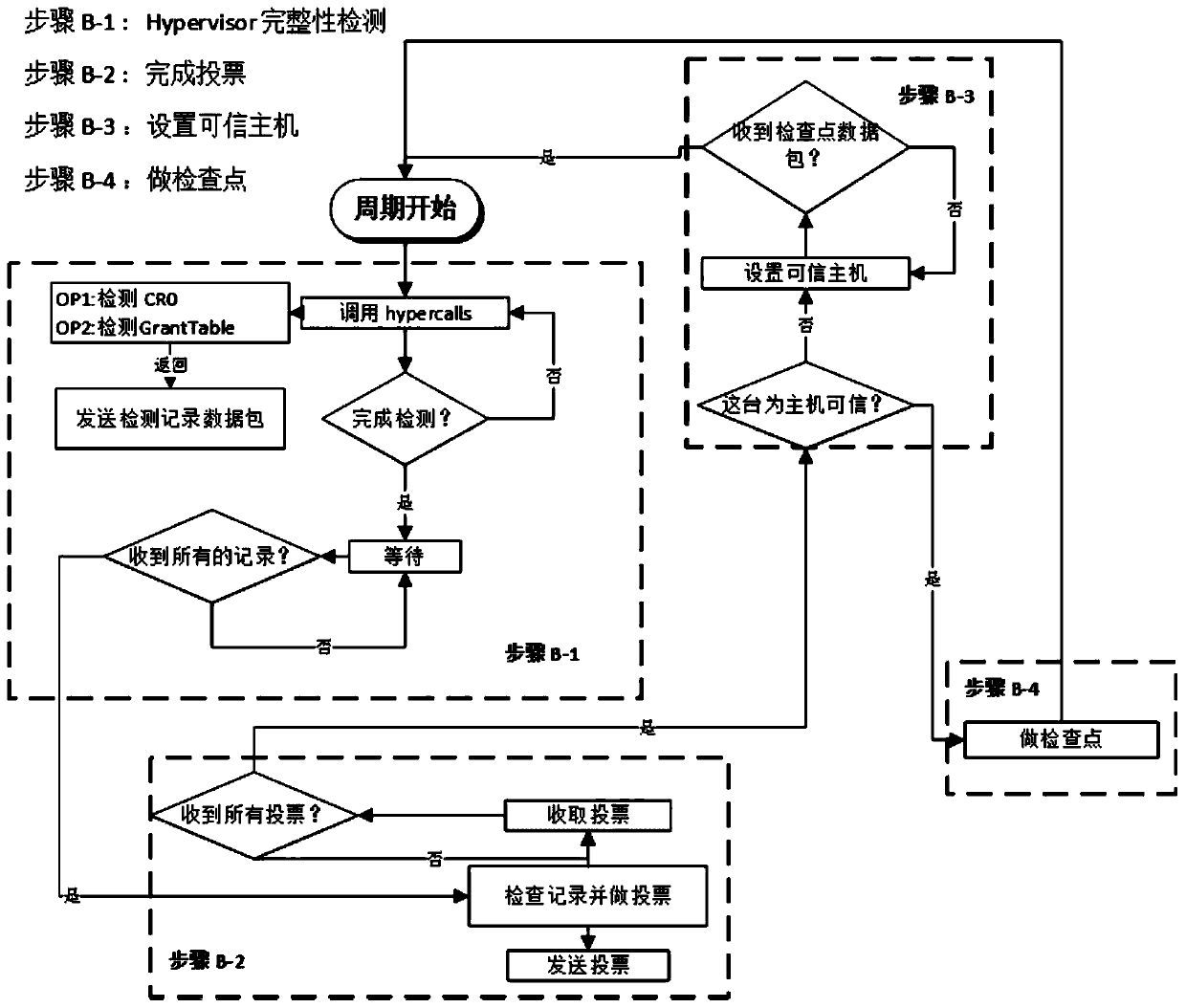
Hypervisor integrity detection method for virtualization system
ActiveCN109951527AReduce insecurityImprove securityData switching networksSafety propertyMultitenancy
The invention aims to provide a hypervisor integrity detection method for a virtualization system. The safety of the hypervisor is improved by utilizing a distributed hypervisor integrity detection framework, and the technical scheme can be summarized as follows: integrity detection is divided into a single-machine integrity detection part and a distributed detection protocol part. According to the method and the system, the probability that the multi-tenant cloud environment is unsafe due to the fact that the integrity of the hypervisor is damaged in the virtualization technology is greatly reduced, the security and the reliability of the virtualization technology are improved, and the method and the system are suitable for any multi-tenant cloud platform built by using the virtualizationtechnology.
Owner:EAST CHINA NORMAL UNIV
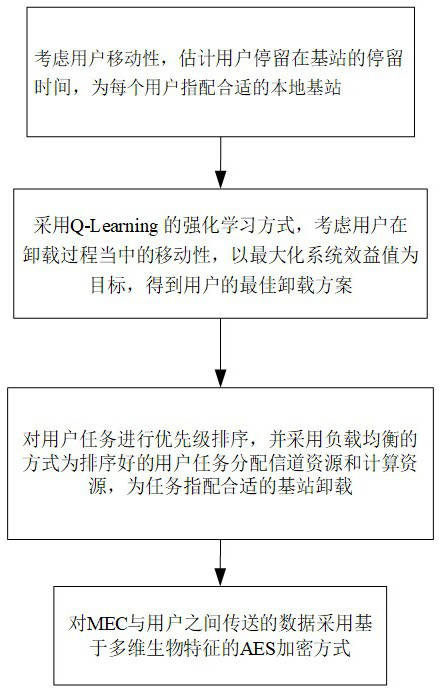
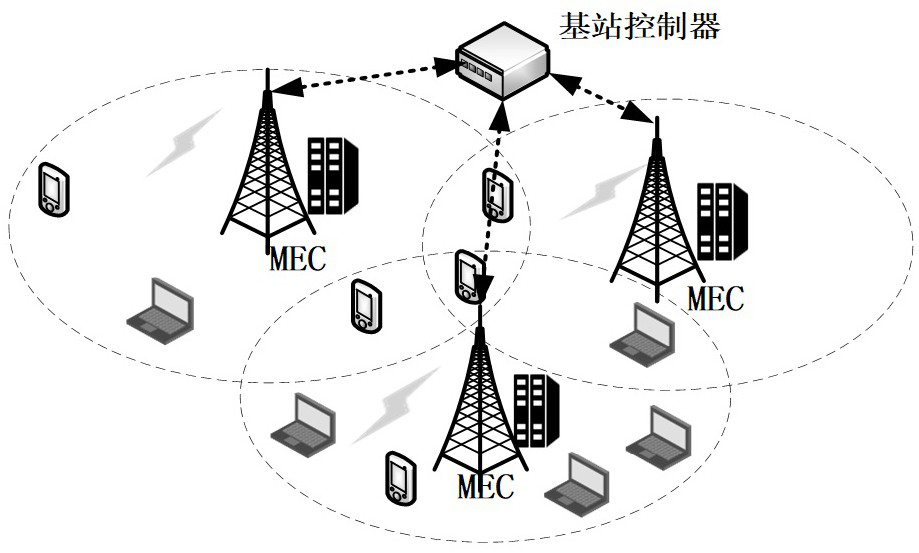
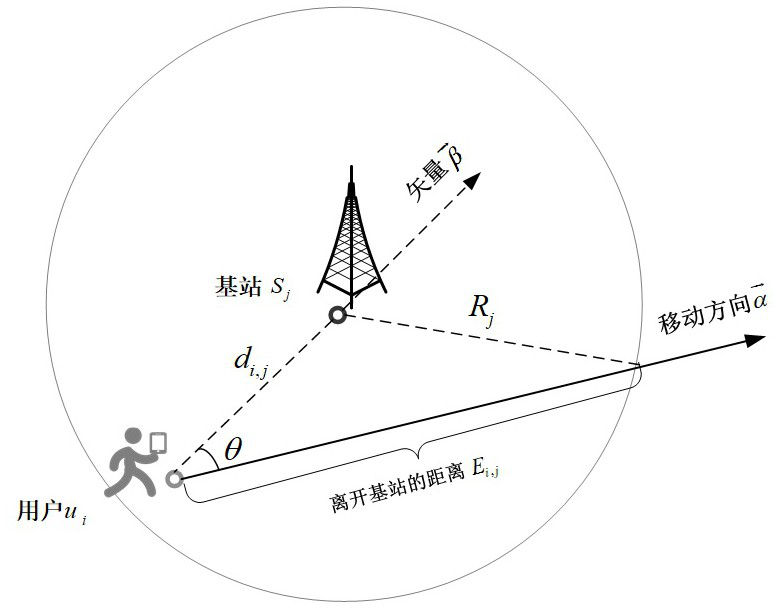
Computing task intelligent unloading and safety guarantee method in 5G edge computing environment
ActiveCN113377547ABest uninstall strategyEfficient use ofResource allocationEncryption apparatus with shift registers/memoriesSafety propertyTime delays
The invention discloses a computing task intelligent unloading and safety guarantee method in a 5G edge computing environment. The method comprises the following steps: firstly, considering the mobility of a user in an unloading process, estimating the residence time of the user in a base station, considering the mobility, consumed time delay and energy of the user in the unloading process and the cost paid to an MEC (Mobile Edge Computing) server by the user, taking maximization of system benefits as a target, and acquiring an unloading scheme of a user by adopting Q-Learning; secondly, considering load balance among the base stations, performing priority ranking on user tasks, and assigning appropriate base station unloading to the tasks, so that computing resources of an MEC server and channel resources of the base stations are utilized more effectively; and in addition, considering the security of a user task during unloading too, and adopting AES encryption based on multi-dimensional biological characteristics for data transmitted between the MEC and the user.
Owner:NANJING UNIV OF POSTS & TELECOMM +1
Safety compiling method and device based on HiWing SylixOS operating system
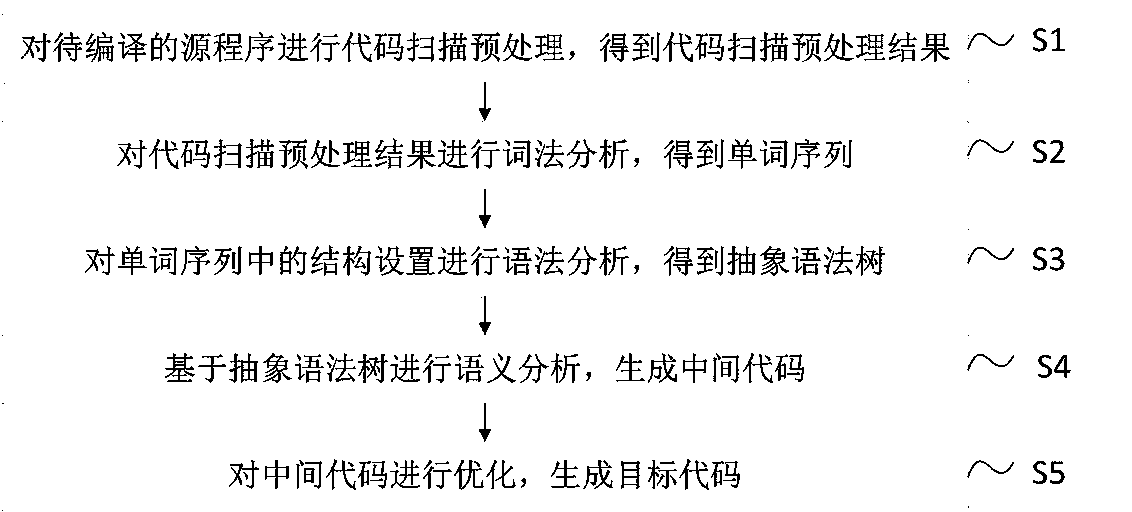
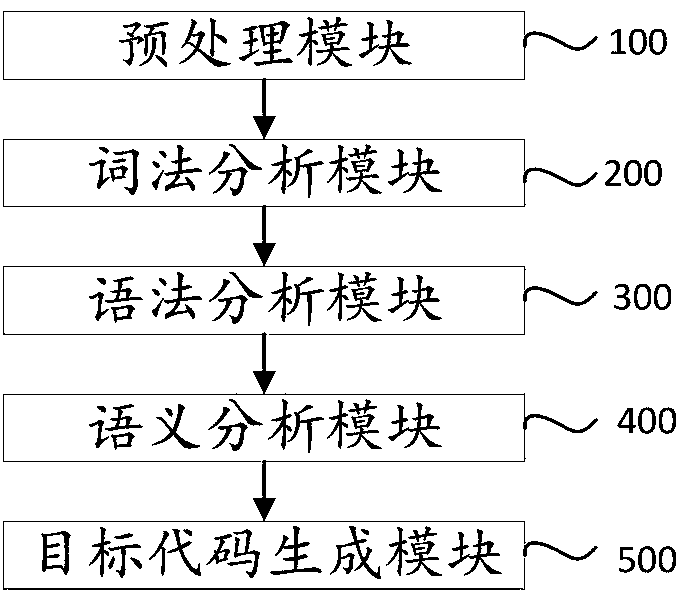
InactiveCN111459500AImplementation checkQuality improvementCode compilationOperational systemLexical analysis
The invention relates to a safe compiling method and device based on a HiWing SylixOS operating system, and belongs to the technical field of embedded operating systems. The problems that an existingcompiling method is difficult to realize high safety, high quality and the like of the HiWing SylixOS operating system are solved. The method comprises the following steps: carrying out code scanningpreprocessing on a source program to be compiled to obtain a code scanning preprocessing result; performing lexical analysis on the code scanning preprocessing result to obtain a word sequence; carrying out syntax analysis on structure settings in the word sequence to obtain an abstract syntax tree, wherein the structure settings comprise a control structure, a data type, a function statement anda parameter table; performing semantic analysis based on the abstract syntax tree to generate an intermediate code; and optimizing the intermediate code to generate a target code. Inspection of code formats, annotation styles, character set legality and conditional compilation is achieved, and safety and quality of compilation software are improved.
Owner:BEIJING RES INST OF MECHANICAL & ELECTRICAL TECH
Method for detecting security of Java open source component
The invention discloses a method for detecting security of a Java open source component, which comprises the following steps: establishing a private warehouse by using Maven, marking security risk levels for open source components stored in the private warehouse, and storing the open source components as first open source components; uploading a system engineering file, configuring a maven dependency package information extraction plug-in in a maven engineering pom file to analyze the system engineering file, and obtaining a list of second open source components on which the engineering file depends; finding third open source components corresponding to the second open source components from the first open source assemblies, comparing the second open source components with the third open source components, and generating a safety report. According to the method, an open source component library is defined, the open source components are subjected to security labeling through the four security dimensions, the open source components quoted by the uploaded system engineering file are detected, the open source components with security risks are found, and the security of the system engineering file is improved.
Owner:SICHUAN CHANGHONG ELECTRIC CO LTD
Hybrid consensus method combining POW and POS
PendingCN111445241ACheating can'tSolve the single point of failure problemDatabase distribution/replicationPayment protocolsSafety propertyLogisim
The invention discloses a hybrid consensus method combining POW and POS. The consensus method comprises two block chains, a first chain adopts a POW consensus output block, a second chain adopts a POSconsensus output block based on historical data of the first chain and operates business logic, and the consensus process comprises three parts of address mapping, computing power mapping and competition output block. According to the method, the characteristics of high safety and addition without auditing of the POW algorithm are combined; the method also has the characteristics of short POS algorithm block output interval and less computing resource occupation, and can bear more business logics and provide quicker response service; on the premise of ensuring the security of the blockchain,the high efficiency of the blockchain can be ensured.
Owner:杭州泛链科技有限公司
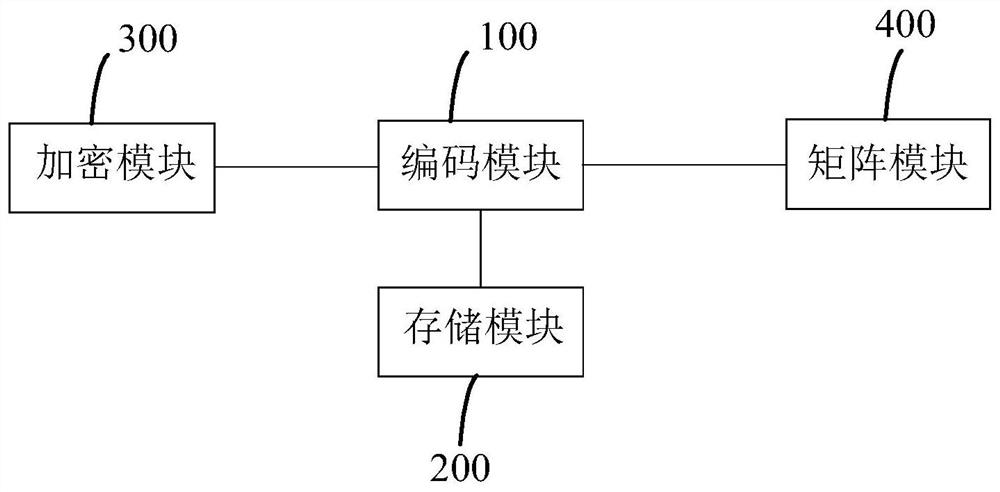
High-safety equipment coding method and system and train
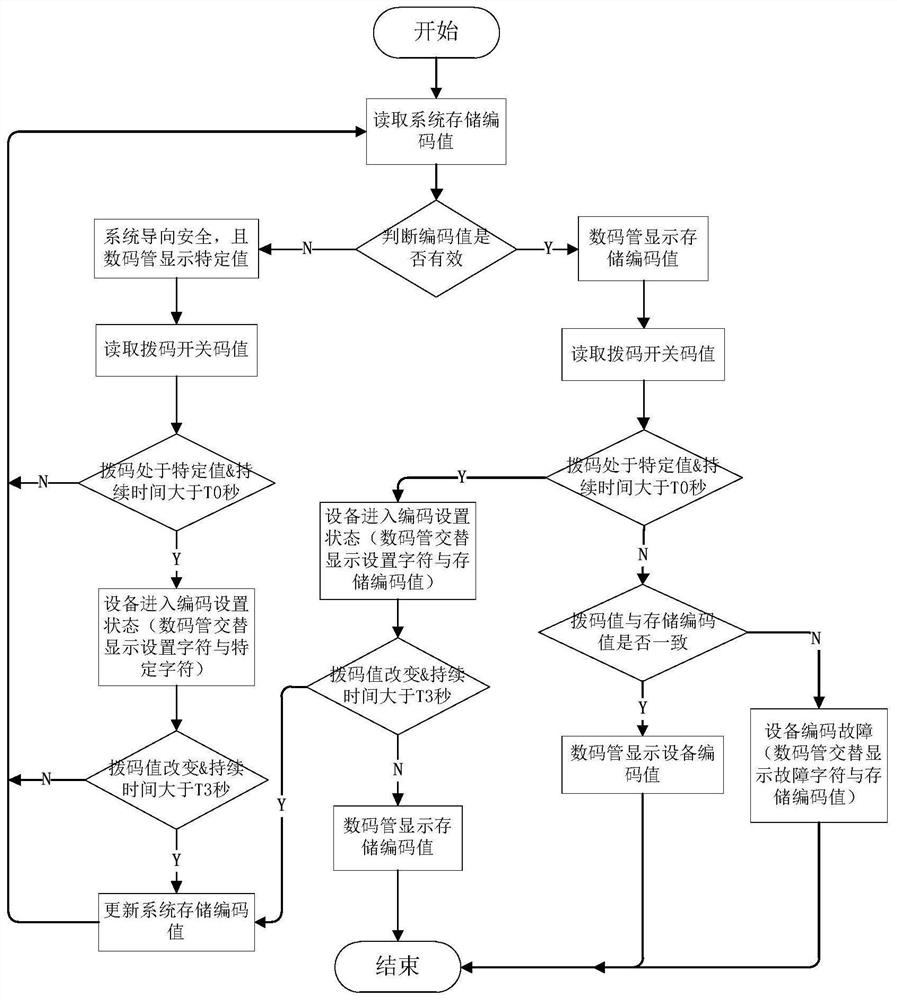
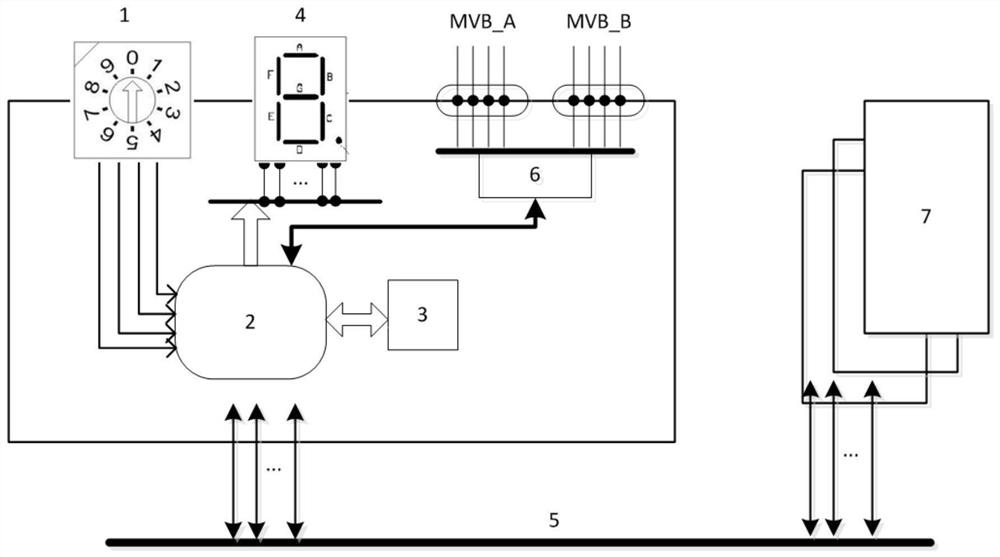
ActiveCN113010343AImprove securityImprove usabilityRedundant data error correctionFault toleranceSafety property
The invention discloses a high-safety equipment coding method and system and a train, and the high-safety equipment coding method comprises the following steps: S1, when equipment is powered on, reading a storage coding value stored by the equipment during the previous work; S2, judging whether the stored code value is valid or not, skipping to a step S31 when the stored code value is invalid, and skipping to a step S32 when the stored code value is valid; s31, guiding safety operation is carried out on the equipment; and S32, displaying, outputting and storing the coded value. The invention has the coding fault detection and prompt function, the fault tolerance processing function and the coding false dialing prevention function; according to the invention, the security of equipment coding is improved, errors of same equipment coding can be avoided, network abnormity caused by same equipment coding faults is avoided, the equipment maintenance efficiency is improved, and the security and availability of distributed network equipment and a communication network are improved.
Owner:ZHUZHOU ELECTRIC LOCOMOTIVE CO
Bug wormhole attack method aiming at safe, high-efficiency distance vector routing protocol
InactiveCN101772126AStrong targetingHarmfulAssess restrictionWireless network protocolsDistance-vector routing protocolAttack
The invention relates to a bug wormhole attack method aiming at safe, high-efficiency distance vector routing protocol based on distance vector routing protocol with wide application, the safety is improved; the bugs in the protocol are researched to institutively know the safety problems in other safety routing protocols in an Ad Hoc network, in particular to the safety of the distance vector routing protocol; the attack protocol in the invention is generated by researching the routing construction process of the SEAD protocol, the hash chain spreading and the verification mode of the hash chain value; based on multi-node combined attack, the invention has strong hidden property, compared with the normal node in the network, the attack node does not show special abnormal behavior and has strong camouflage capacity.
Owner:NANJING UNIV OF POSTS & TELECOMM
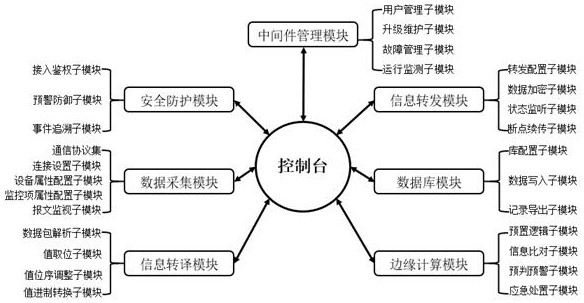
Edge computing Internet of Things middleware oriented to multiple communication protocols
InactiveCN112118303AWide compatibilityQuickly identify anomaliesData switching networksComputer networkSafety property
Edge computing Internet of Things middleware oriented to multiple communication protocols comprises seven functional modules, specifically including a middleware management module, a safety protectionmodule, a data acquisition module, an information translation module, an edge computing module, a database module and an information forwarding module. By the method, the technical problem of interconnection and intercommunication and resource sharing among heterogeneous networks in the Internet of Things industry can be solved, the safety of the Internet of Things is improved, meanwhile, the pre-judgment capability and the real-time response capability of the equipment side are improved, cloud computing and network bandwidth pressure are shared, and the congenital defects of cloud computingand network transmission delay are overcome.
Owner:HUNAN CONSTR ENG GRP COR +1
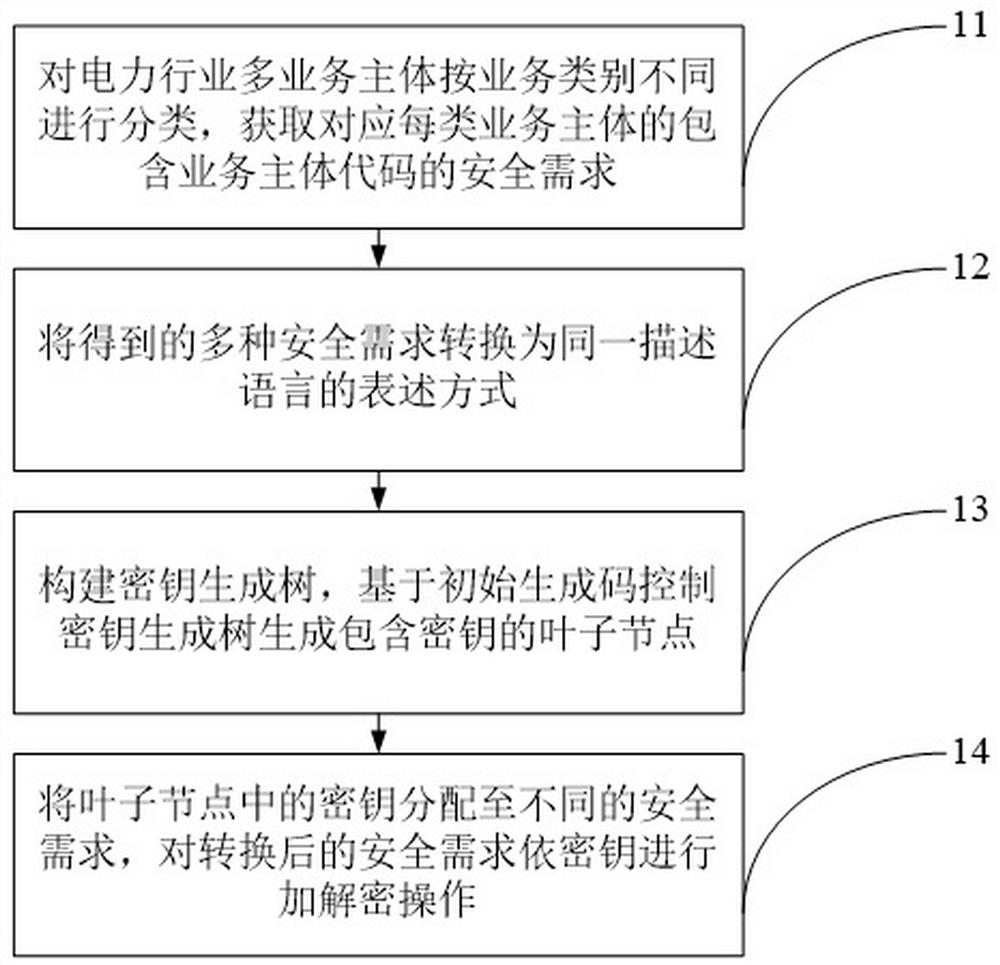
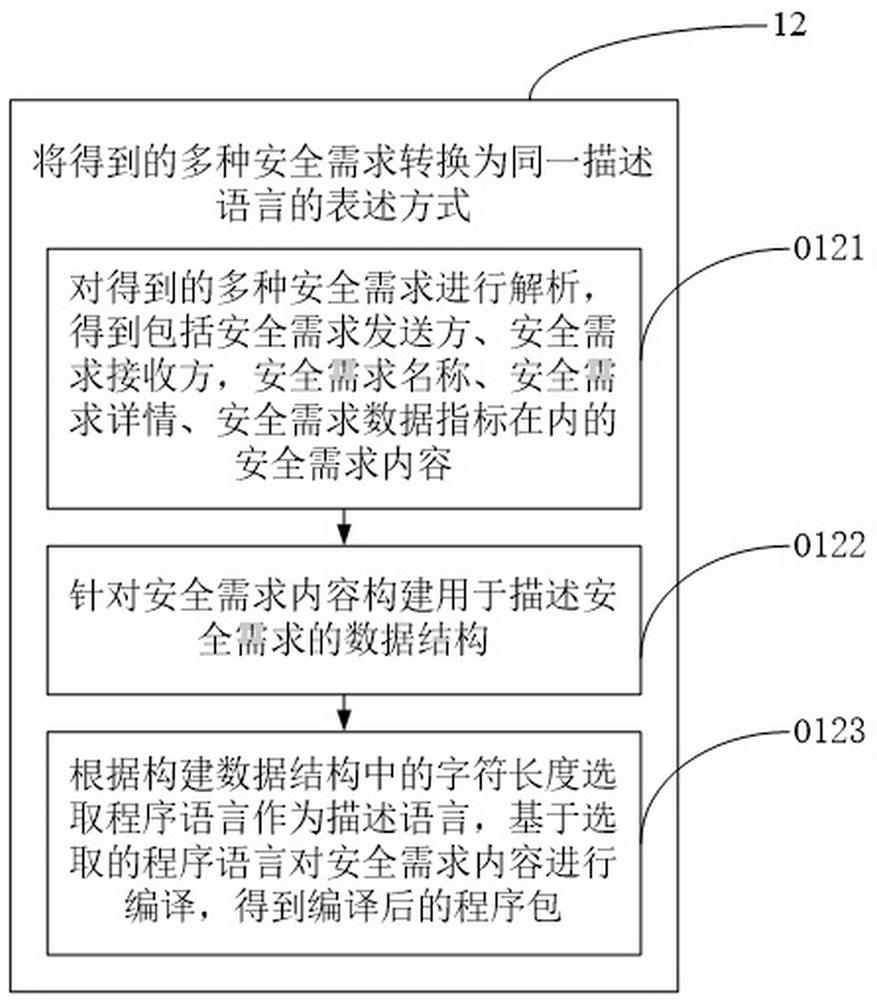
Information safety sharing method for power industry multi-service subjects
ActiveCN111680316AIncrease randomnessIncreased complexityData processing applicationsDigital data protectionInformation transmissionSafety property
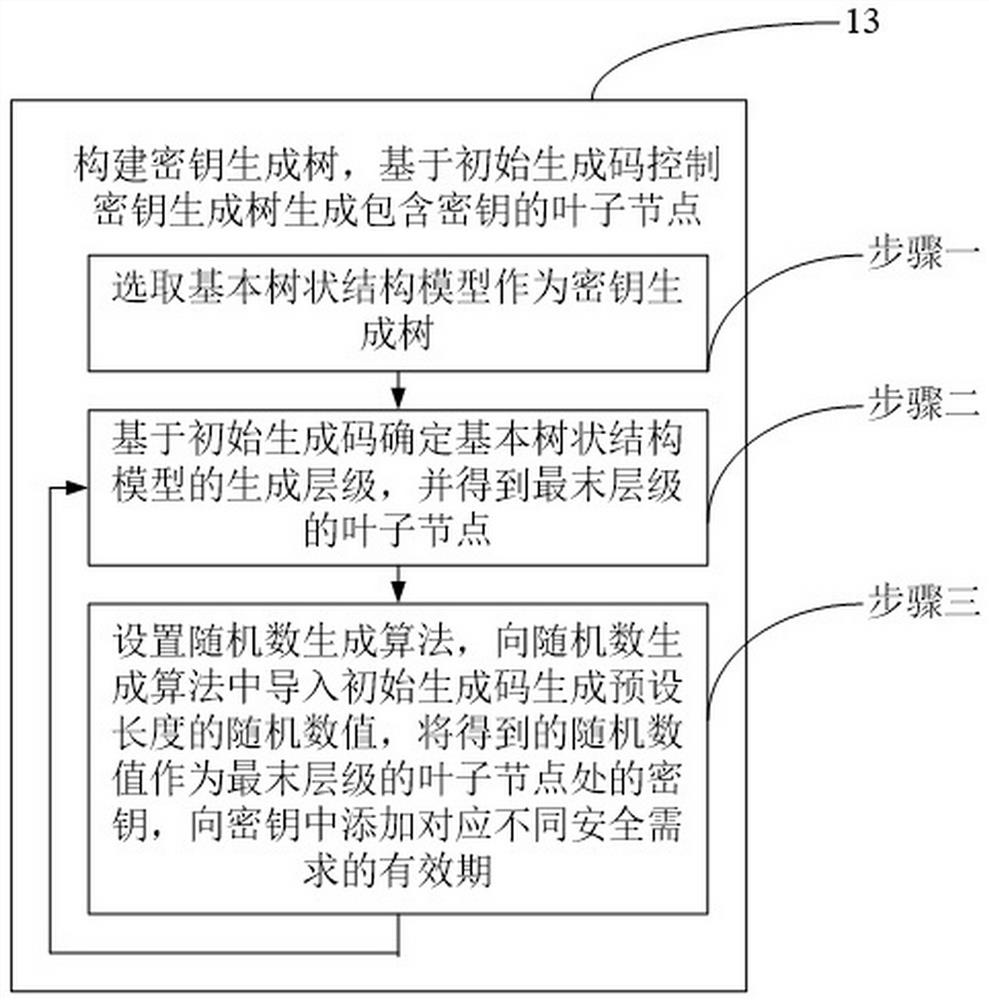
The information safety sharing method for the power industry multi-service main bodies provided by the embodiment of the invention comprises the following steps: classifying the power industry multi-service main bodies according to different service categories, and obtaining safety requirements containing service main body codes and corresponding to each type of service main bodies; converting theobtained multiple safety requirements into an expression mode of the same description language; constructing a key generation tree, and controlling the key generation tree to generate a leaf node containing a key based on the initial generation code; the secret keys in the leaf nodes are distributed to different safety requirements; encryption and decryption operations are carried out on the converted safety requirements according to a secret key; the randomness of the secret key is improved by randomly generating the leaf nodes in the secret key generation tree. Meanwhile, the attribute limitation of the validity period of the secret key is increased, it is ensured that the secret key can be used for encryption and decryption only within the validity period, and the complexity of the secret key is increased based on the two dimensions, so that the safety of information transmission is ensured.
Owner:STATE GRID ZHEJIANG ELECTRIC POWER CO MARKETING SERVICE CENT +1
Information generation method based on threat perception big data, and artificial intelligence perception system
InactiveCN113434868ACharacter and pattern recognitionPlatform integrity maintainanceSafety propertyEngineering
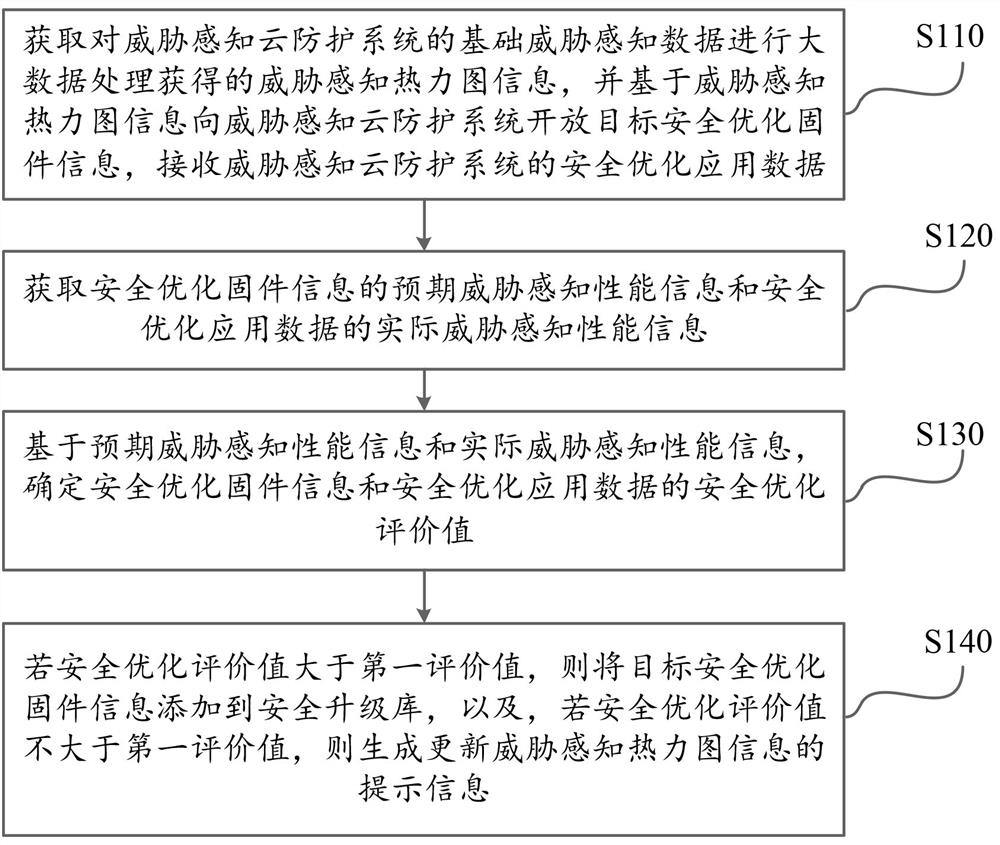
An embodiment of the invention provides an information generation method based on threat perception big data, and an artificial intelligence perception system. According to the information generation method based on the threat perception big data, and the artificial intelligence perception system provided by the embodiment of the invention, after the security optimization application data is obtained, the security optimization performance evaluation is performed on the security optimization firmware information and the security optimization application data, whether the safety optimization application data are matched with the optimization performance of the safety optimization firmware information is judged by judging whether the safety optimization application data is matched with the optimization performance of the safety optimization firmware information, so that whether the safety performance optimization meets the safety performance optimization condition can be determined, and if yes, the target safety optimization firmware information can be added to a safety upgrading library to carry out upgrading basic resource recording. Therefore, high-reliability security upgrade library resources are continuously formed, and prompt information for updating the threat perception thermodynamic diagram information of a security optimization firmware information pushing basis is generated when the security upgrade library resources do not accord with the threat perception thermodynamic diagram information so as to prompt that the current threat perception thermodynamic diagram information needs to be updated.
Owner:广州天悦科技信息有限公司
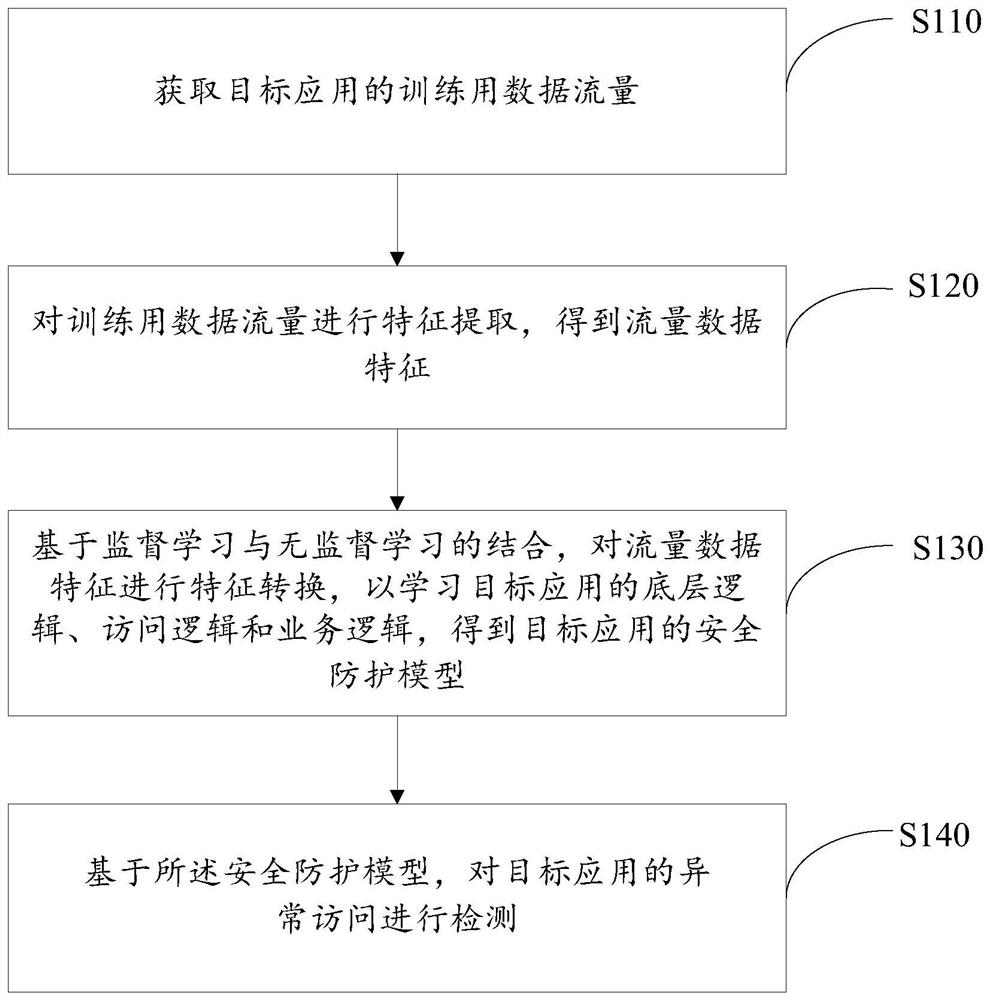
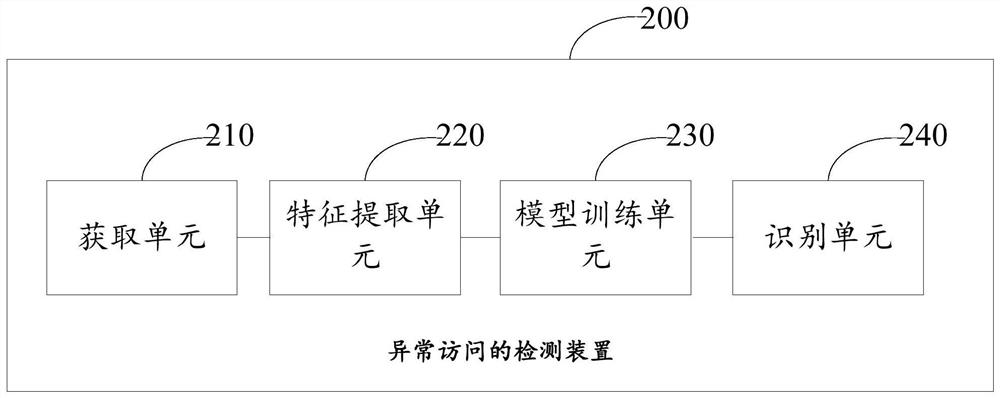
Abnormal access detection method and device, electronic equipment and readable storage medium
PendingCN113949527AImprove securityEfficient identificationSecuring communicationFeature extractionAttack
The invention discloses an abnormal access detection method and apparatus, an electronic equipment and a readable storage medium. The method comprises the steps of obtaining training data traffic of a target application; performing feature extraction on the data traffic for training to obtain flow data features; based on combination of supervised learning and unsupervised learning, performing feature conversion on the flow data features to learn underlying logic, access logic and service logic of the target application, and obtaining a safety protection model of the target application; and recognizing abnormal access of a target application based on the safety protection model. On the basis of an artificial intelligence method, the attack behaviors, especially the attack behaviors of 0-day vulnerabilities, can be intelligently recognized efficiently and accurately; the safety of an internet application system is remarkably improved, the applicability is wide, and the accuracy is high.
Owner:ZHONGYUNWANGAN TECHNOLOGY (BEIJING) CO LTD
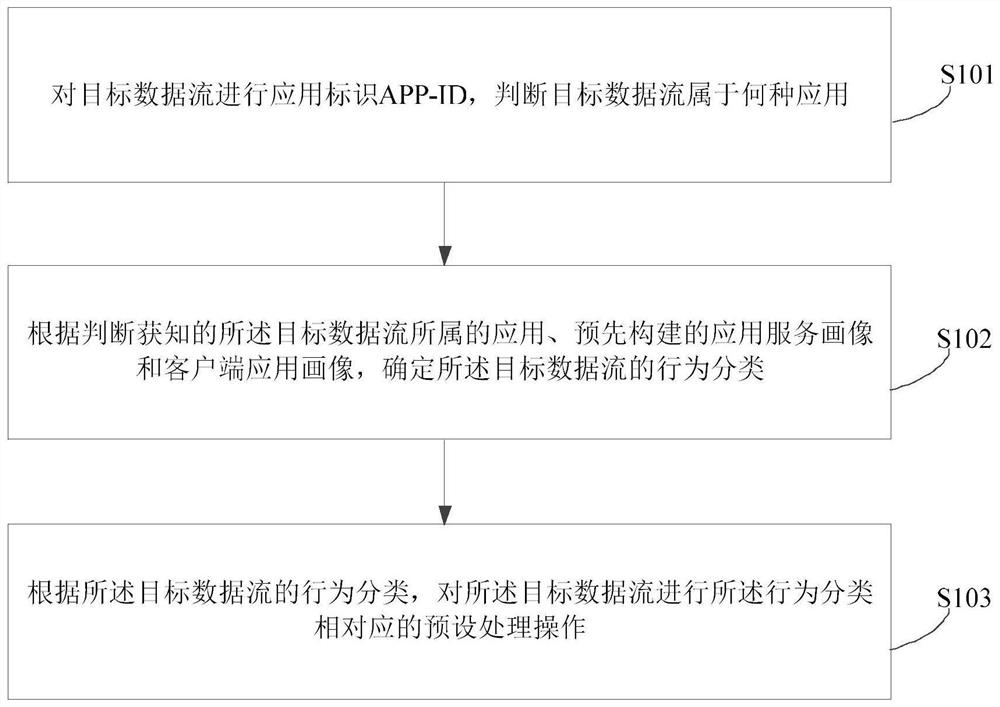
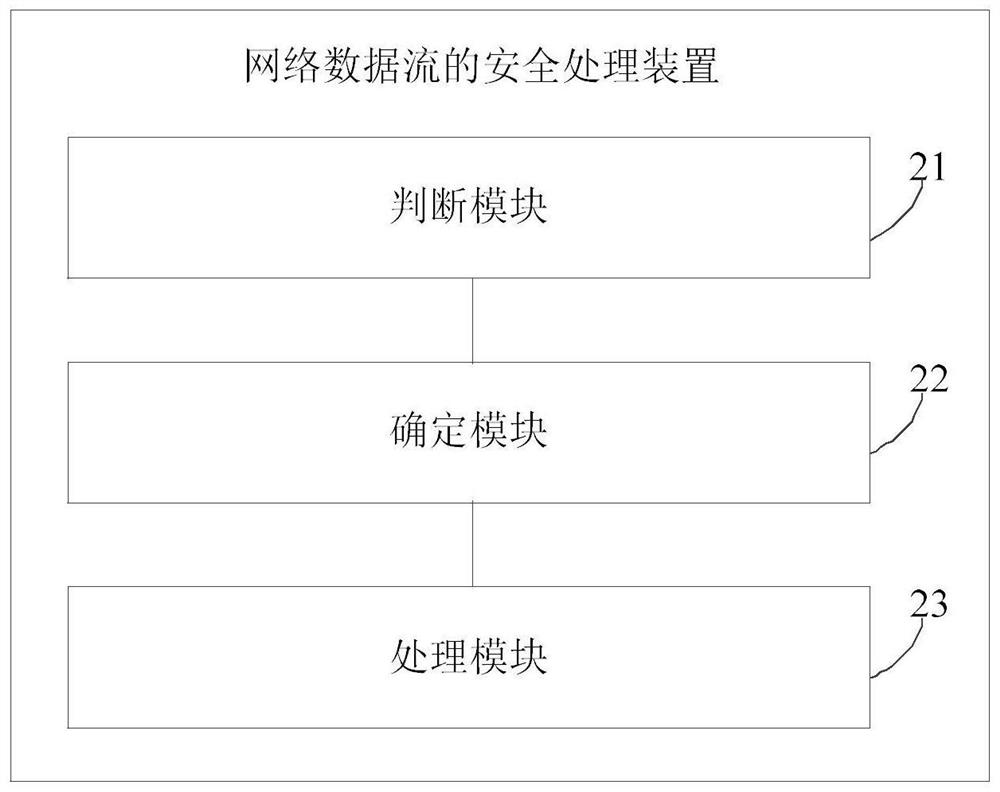
A method and device for securely processing network data streams
ActiveCN107579993BImprove securityResolving static identitiesData switching networksSafety propertyDynamic update client
The embodiment of the invention discloses a safety processing method and a safety processing device for a network dataflow. The method comprises the steps of performing application identification APP-ID on the target dataflow to judge that the target dataflow belongs to which application; determining behavior classification of the target dataflow according to the application to which the learned target dataflow belongs, a pre-built application service portrait and a client application portrait; and performing preset processing operation corresponding to the behavior classification on the target dataflow according to the behavior classification of the target dataflow. According to the method and the device provided by the embodiment of the invention, security of a network can be improved, static identification of the App-ID on traffic is achieved, reaction response time is reduced, and warning information can be sent out in advance; an APT is continuously tracked by dynamically updatingthe client application portrait; visualization can be further improved, and what the network dataflow do not just the network dataflow belongs to which application can be learned.
Owner:北京云杉世纪网络科技有限公司
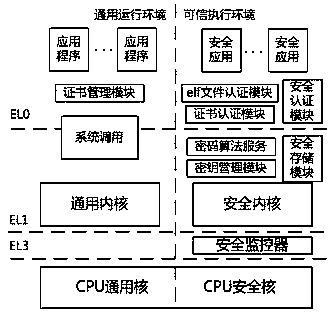
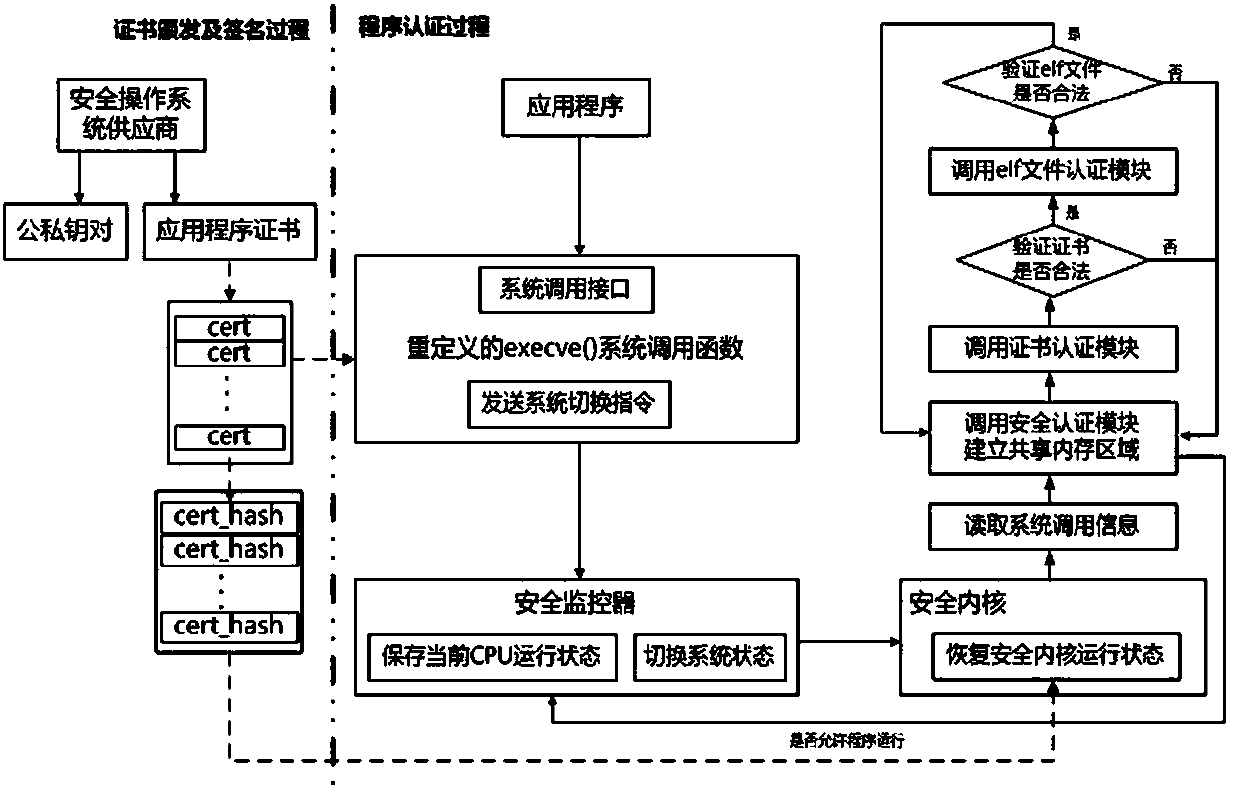
A method for implementing security authentication of application program based on cpu space-time isolation mechanism
ActiveCN106815494BGuaranteed validityImprove the isolation effectPlatform integrity maintainanceProgram/content distribution protectionSafety propertySecurity kernel
The invention discloses a method for realizing application program safety certification based on a CPU space-time isolating mechanism. The method comprises the following steps: firstly, establishing a credible executing environment with an application program certification component, namely, a safety kernel; secondly, establishing a general running environment for executing an application program; lastly, constructing a safety monitor, switching context between two running environments and running in the CPU safety kernel. The method has the advantages that the hardware-level credible safety certification is supplied through an executing flow of a starting process of a safety enhancing application program; the problems of secret key falsifying and poor timeliness can be effectively solved; the safety of the computer terminal in an application program loading process is promoted within limited time consumption.
Owner:中软信息系统工程有限公司
Safety protection method and system, computer equipment and computer readable storage medium
ActiveCN111177799AGuarantee authorityImprove the protective effectDigital data protectionPlatform integrity maintainanceSecurity kernelSafety property
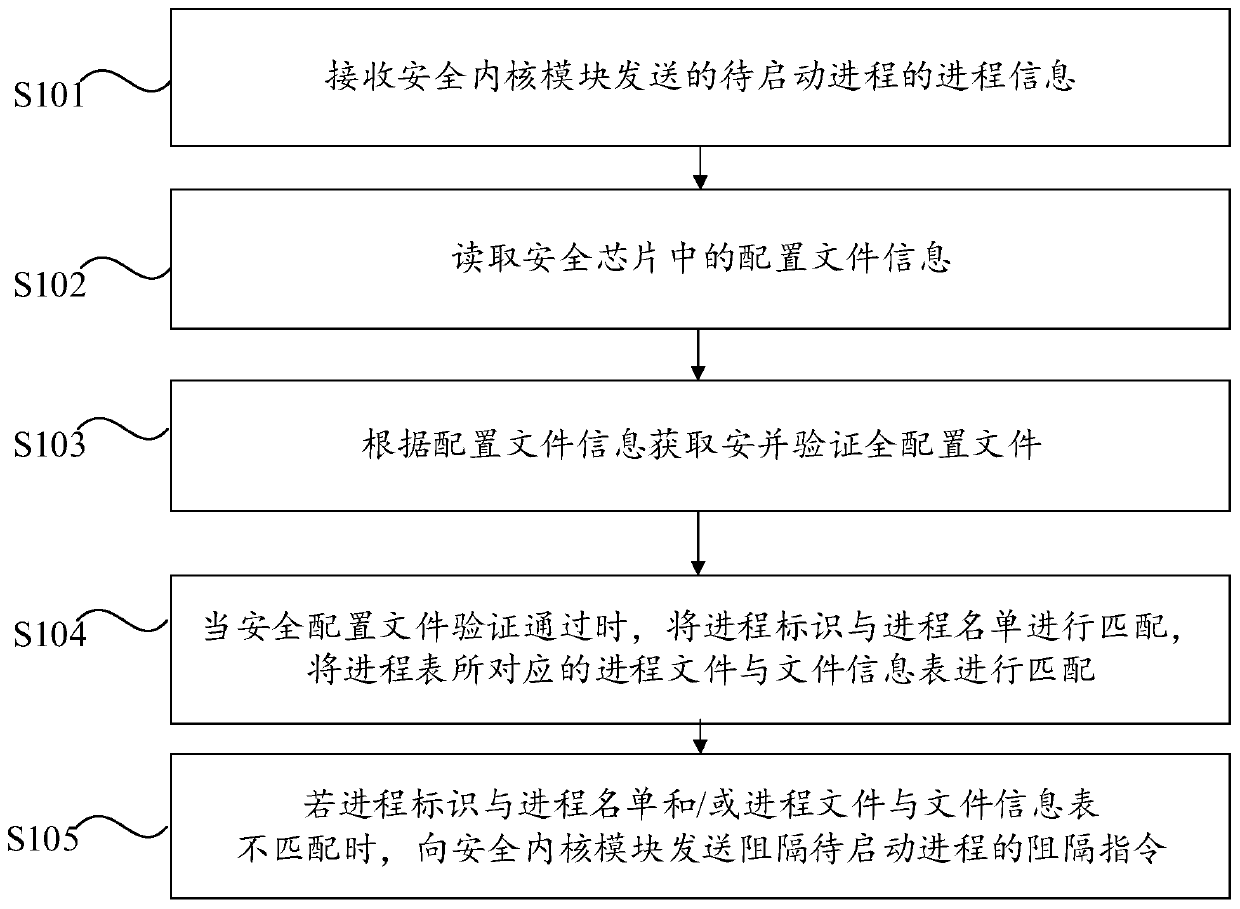
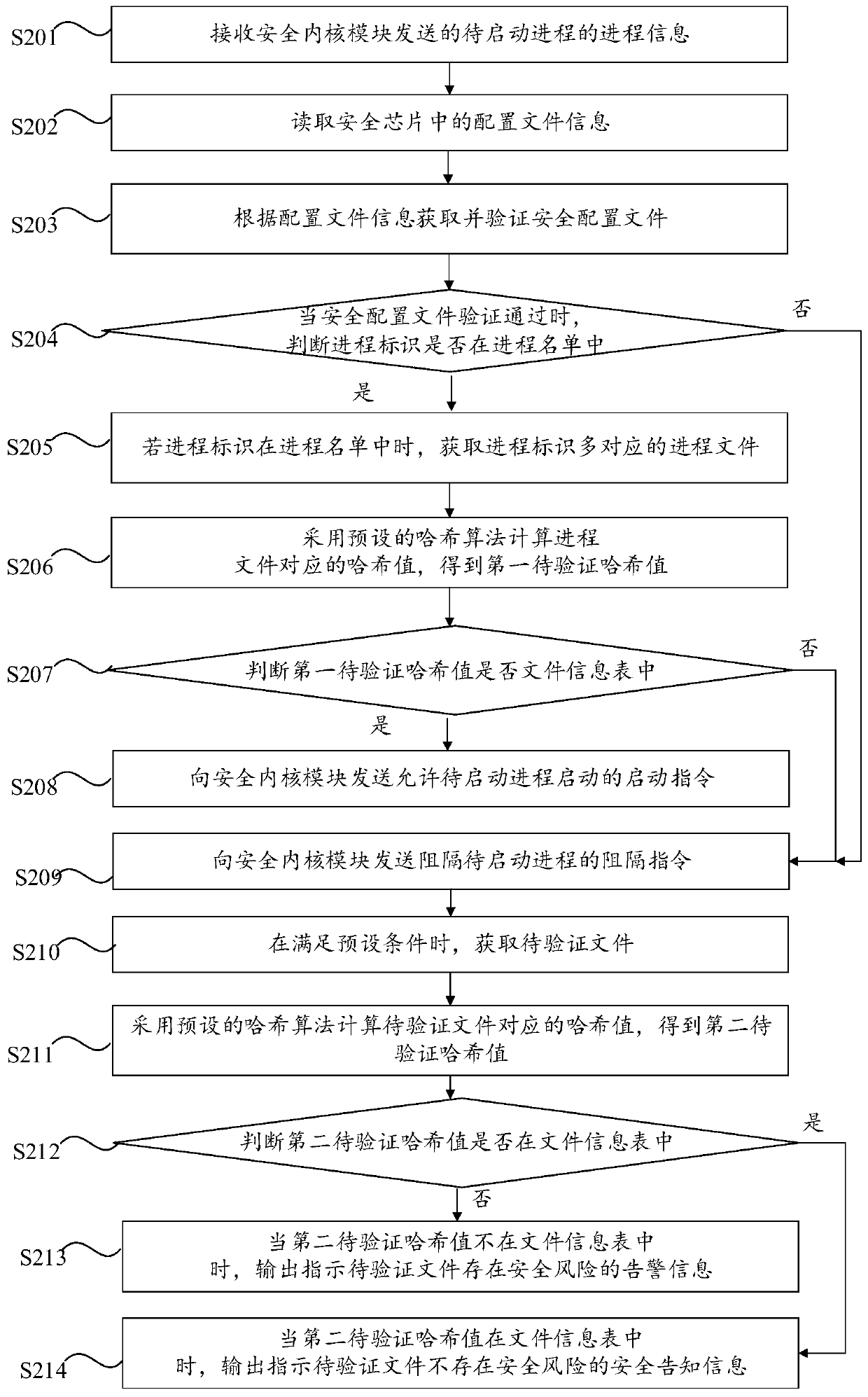
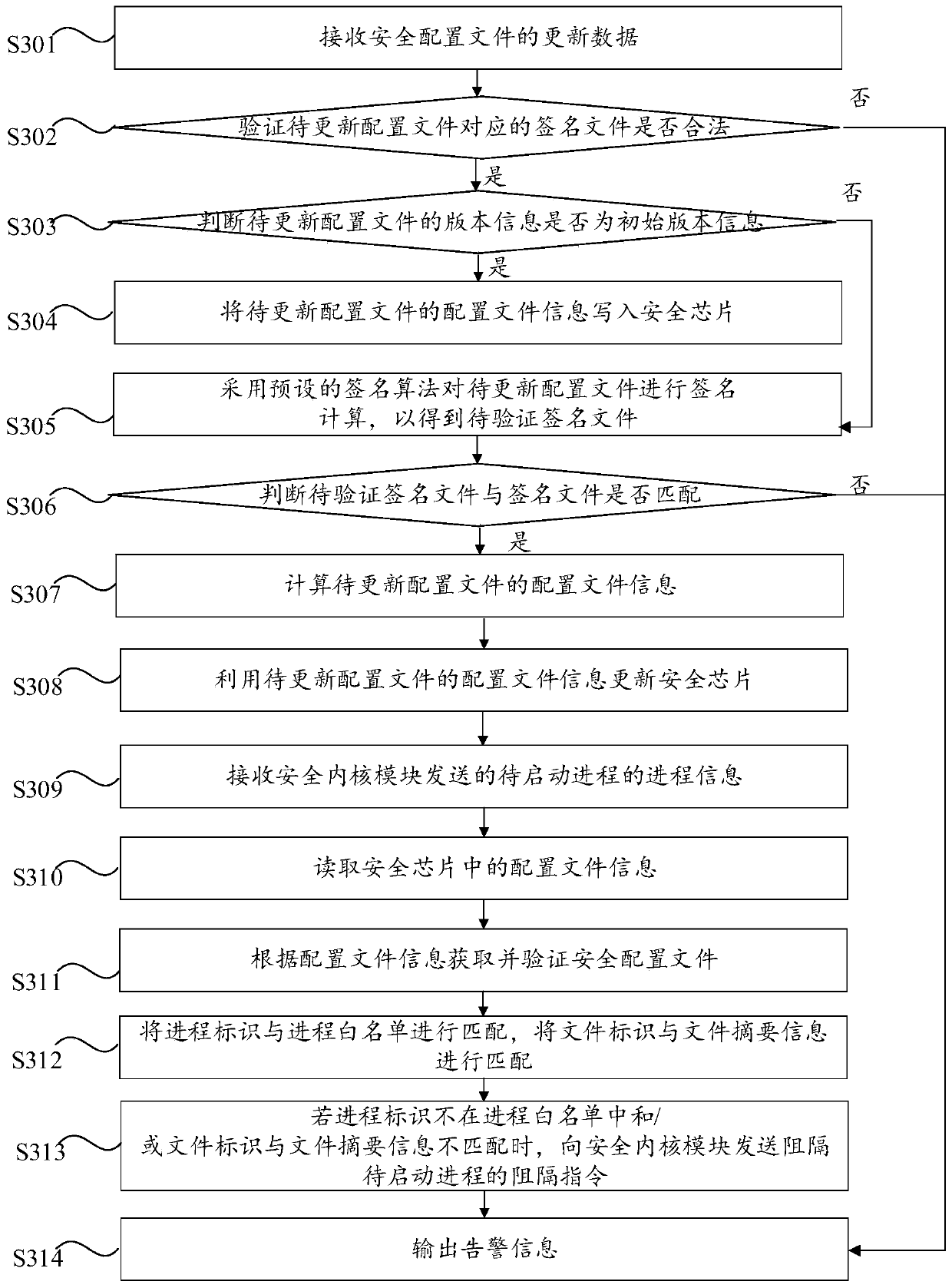
The invention provides a safety protection method and a system, computer equipment and a computer readable storage medium. The method comprises the steps of receiving process information of a to-be-started process sent by a security kernel module; reading configuration file information in the security chip, and when the security configuration file is modified, changing the configuration file information; acquiring and verifying a security configuration file according to the configuration file information; when the security configuration file passes the verification, matching the process identifier with the process list, and matching the process corresponding to the process file with the file information table; and if the process identifier is not matched with the process list and / or the process file is not matched with the file information table, sending an obstruction instruction for obstructing the to-be-started process to a security kernel module, the security kernel module being used for obstructing the to-be-started process when receiving the obstruction instruction. According to the method, the safety performance of the safety protection system can be improved.
Owner:BEIJING QIANXIN TECH +1
Safety control method of distributed heterogeneous processing system based on workflow
PendingCN113836544AEfficient analysis of operational potentialEfficient processing meansDatabase updatingData processing applicationsIp addressSafety property
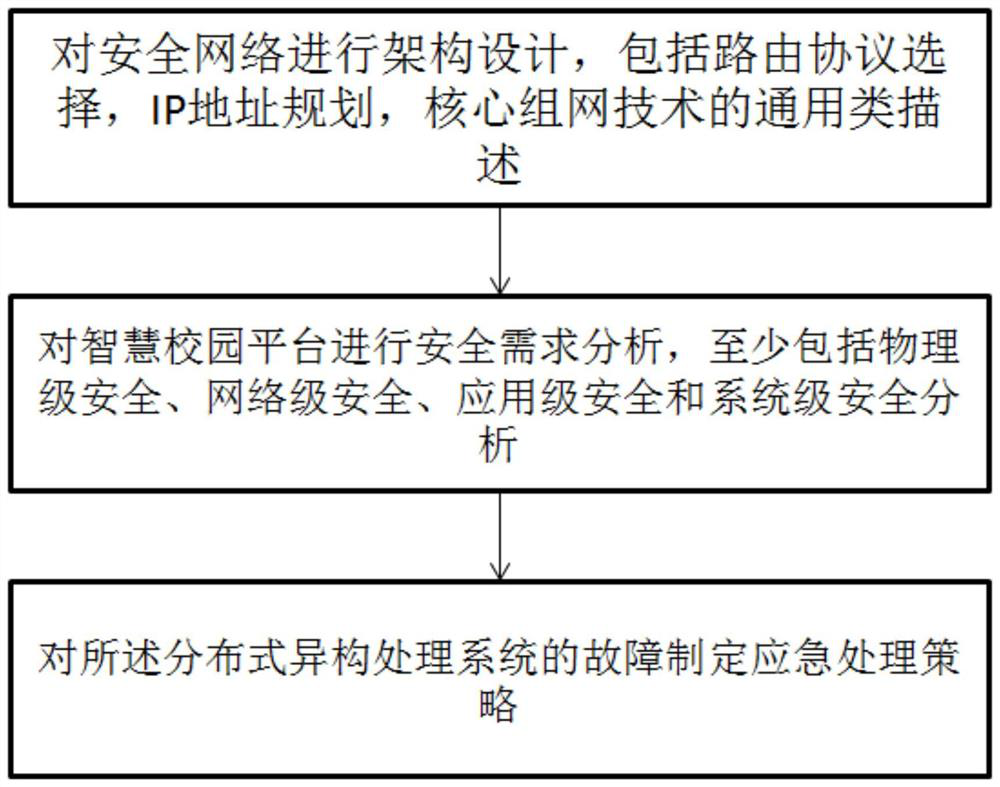
The invention relates to a safety control method of a distributed heterogeneous processing system based on workflow, and the method comprises the steps: carrying out the architecture design of a safety network, including routing protocol selection, IP address planning, and general description of a core networking technology, and carrying out the security demand analysis of a smart campus platform, at least including physical-level security analysis, network-level security analysis, application-level security analysis and system-level security analysis; and formulating an emergency processing strategy for the fault of the distributed heterogeneous processing system. The method is an important reference guide for emergency work when the smart campus platform breaks down, the operation potential of the platform system is effectively analyzed by comprehensively considering multi-dimensional indexes such as network architecture, safety analysis and fault processing strategies, instructive strategies are provided for operation and maintenance of the platform system, the processing means are efficient, and the robustness and robustness of the platform system during operation are effectively ensured.
Owner:李登峻
Safety algorithm configuration method, control plane center node and terminal
ActiveCN112399422AAvoid safety hazardsImprove securitySecurity arrangementSecuring communicationAlgorithm configurationSafety property
Provided are a safety algorithm configuration method, a control plane center node and a terminal. The method comprises the steps of sending safety algorithm information corresponding to a user plane center node CUUP to the terminal, implementing a negotiation process of the safety algorithm information corresponding to the CUUP, implementing that the CUUP can correspond to its own safety algorithminformation, and implementing the negotiation process of the safety algorithm information corresponding to the CUUP. The safety of the CUUP service is improved.
Owner:DATANG MOBILE COMM EQUIP CO LTD
Method for analyzing and verifying software for safety and security
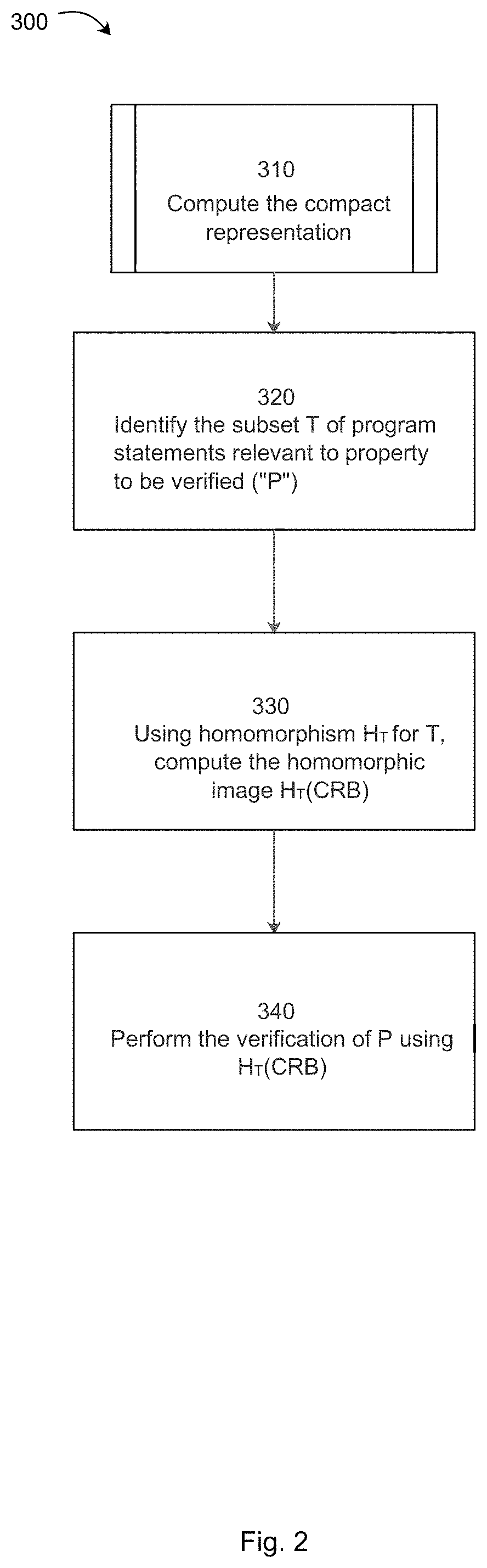
ActiveUS20210374236A1Compact representationAchieve reductionComputation using non-contact making devicesPlatform integrity maintainanceSafety propertySoftware engineering
A computer implemented method for analyzing and verifying software for safety and security. A software program comprising a sequence of program statements to be executed is provided. A compact representation of the program is computed, and the subset of program statements that are relevant to a property of the software to be verified is identified. A homomorphism that maps non-relevant program statements to an identity is computed, and the property is verified using the homomorphism.
Owner:ENSOFT CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com