Method and device for detecting safety performance of application program
An application program and security technology, applied in computer security devices, program/content distribution protection, platform integrity maintenance, etc., can solve the problems of genuine application developers not being able to make profits, stealing user privacy information, infection, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
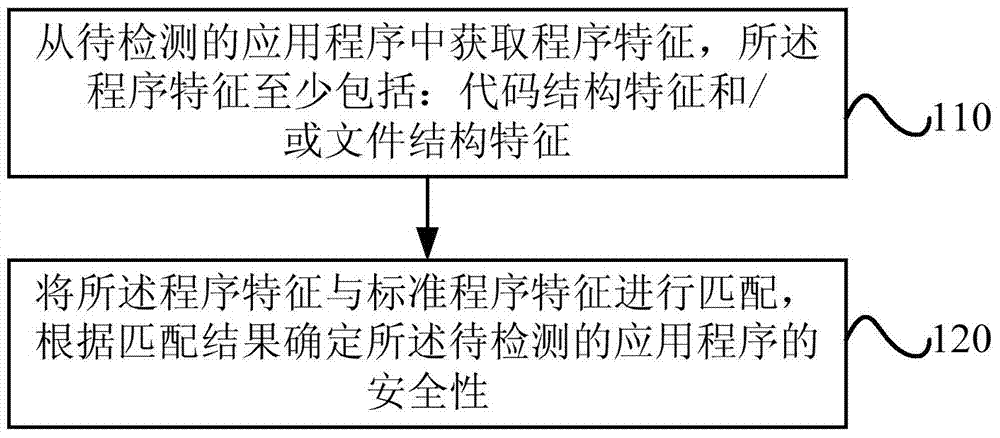
[0023] see Figure 1a , which is a flow chart of a method for detecting the security of an application program provided in Embodiment 1 of the present invention. The method in the embodiment of the present invention may be executed by a hardware and / or software implemented application program security detection device, and the implementation device is typically configured in a server capable of providing application program security detection services.
[0024] Such as Figure 1a As shown, the method includes:
[0025] 110. Obtain program features from the application program to be detected, where the program features at least include: code structure features and / or file structure features;
[0026] This operation is specifically to obtain the program characteristics of the application program to be detected. Specifically, only the code structure characteristics of the application program to be detected may be obtained, or only the file structure characteristics of the applic...
Embodiment 2
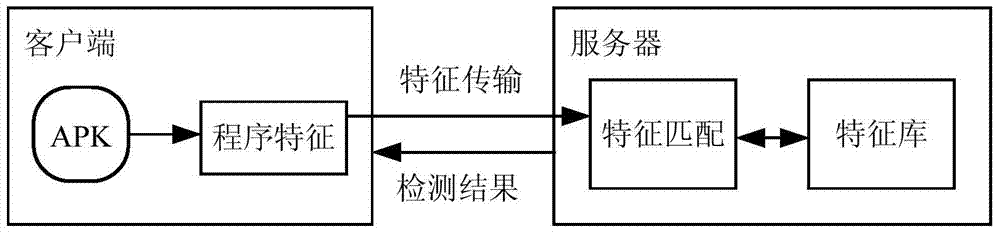
[0064] see Figure 2a , is a flow chart of a method for detecting the security of an application program provided by Embodiment 2 of the present invention.
[0065] Such as Figure 2a As shown, the method includes:
[0066] 210. Receive program features obtained from the application program to be detected from the client, wherein the program features are summary data calculated by the client based on a set summary algorithm;
[0067] In this operation, the program features at least include: code structure features and / or file structure features.
[0068] This operation is specifically to acquire the summary data of the code structure characteristics and / or the summary data of the file structure characteristics of the application program to be detected.
[0069] Among them, the digest algorithm is an algorithm that generates a fixed-length smaller binary output from an arbitrary-length binary input. For example, the program feature of the application program to be detected ...
Embodiment approach
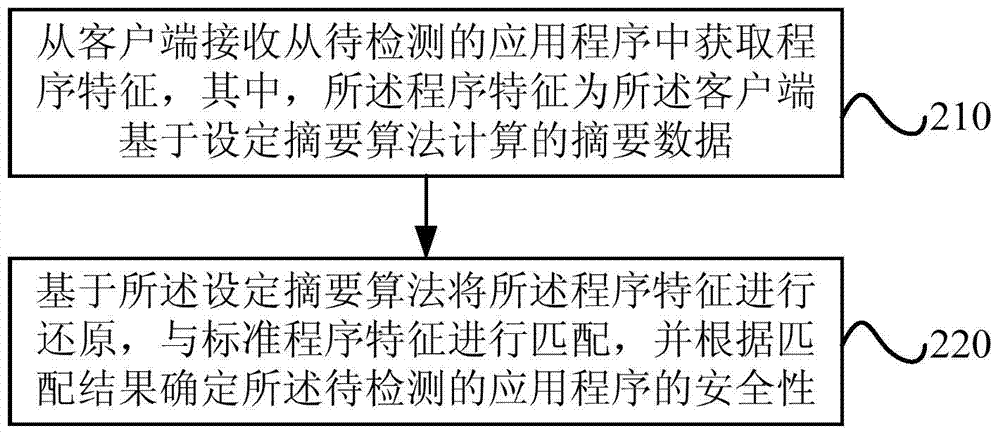
[0082] see Figure 2b , as a preferred implementation of this embodiment, the preferred method includes:
[0083] 210. Receive program features obtained from the application program to be detected from the client, wherein the program features are summary data calculated by the client based on a set summary algorithm;
[0084] In this operation, the program features at least include: code structure features and / or file structure features.
[0085] 230. Match the program feature with a standard program feature, and determine the security of the application program to be detected according to the matching result, where the standard program feature is summary data calculated based on a set summary algorithm.
[0086] This operation specifically matches the summary data of the program features of the application to be tested with the summary data of the standard program features of the genuine application, and determines the security of the application to be tested based on the ma...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com