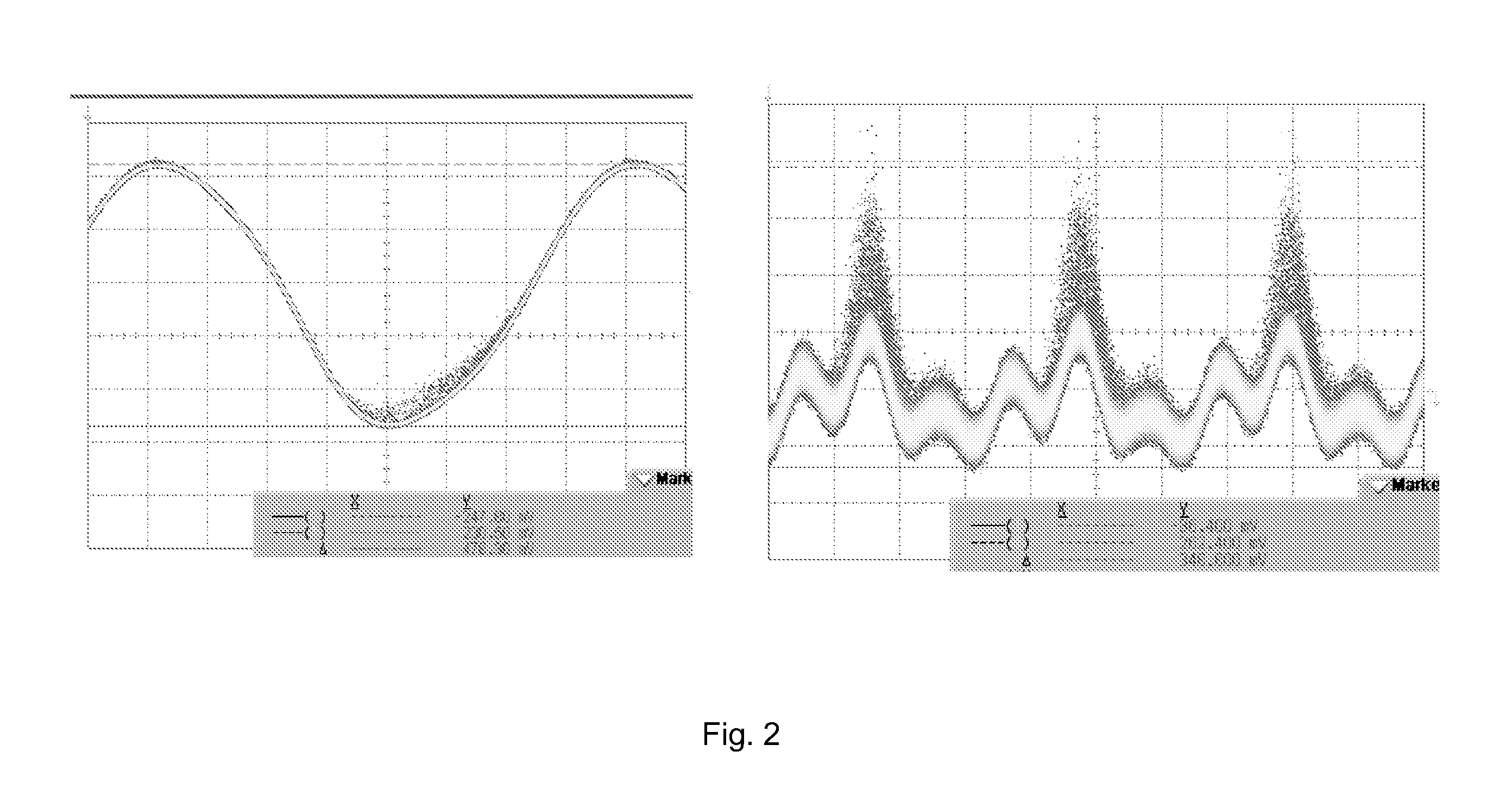
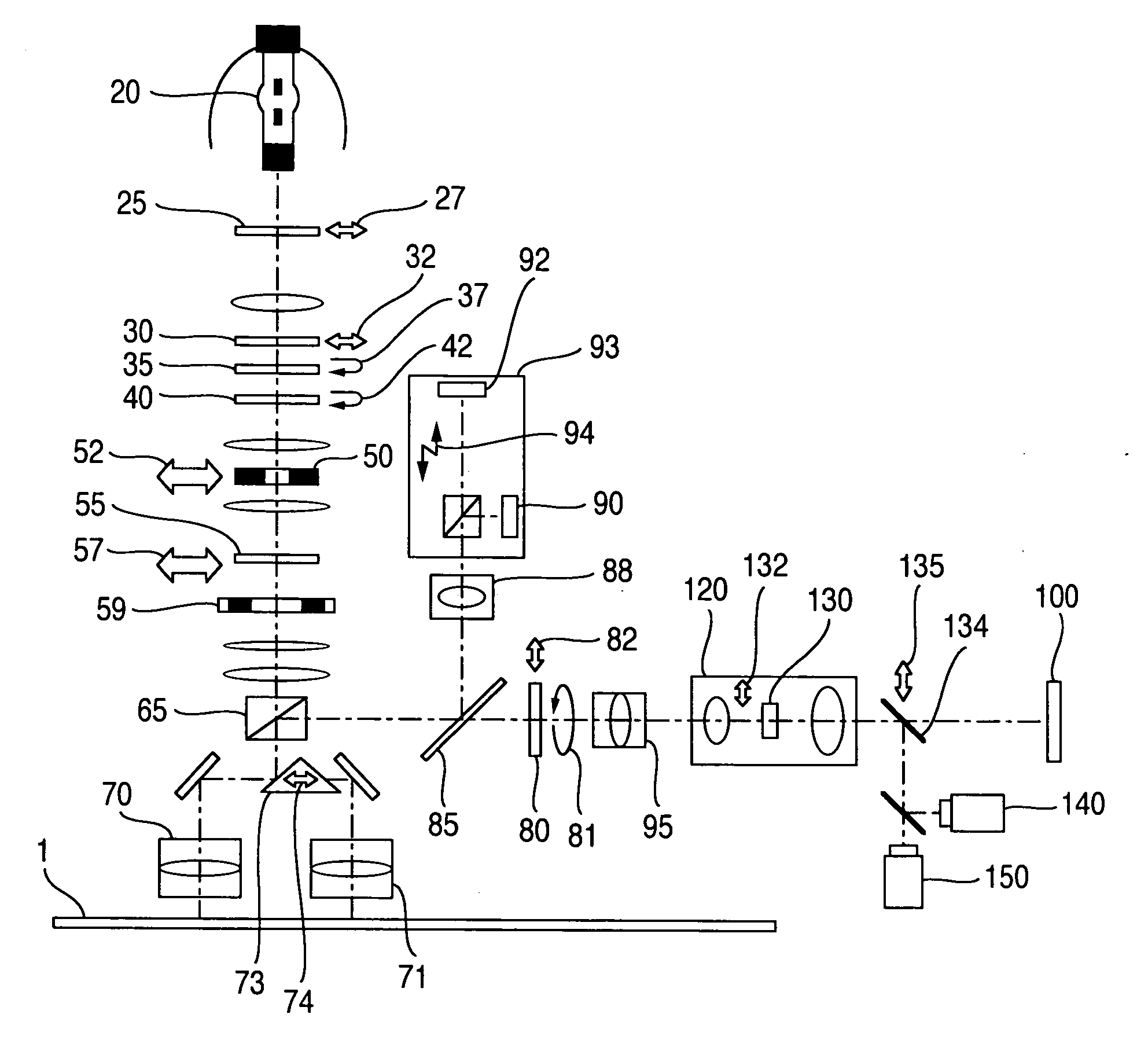
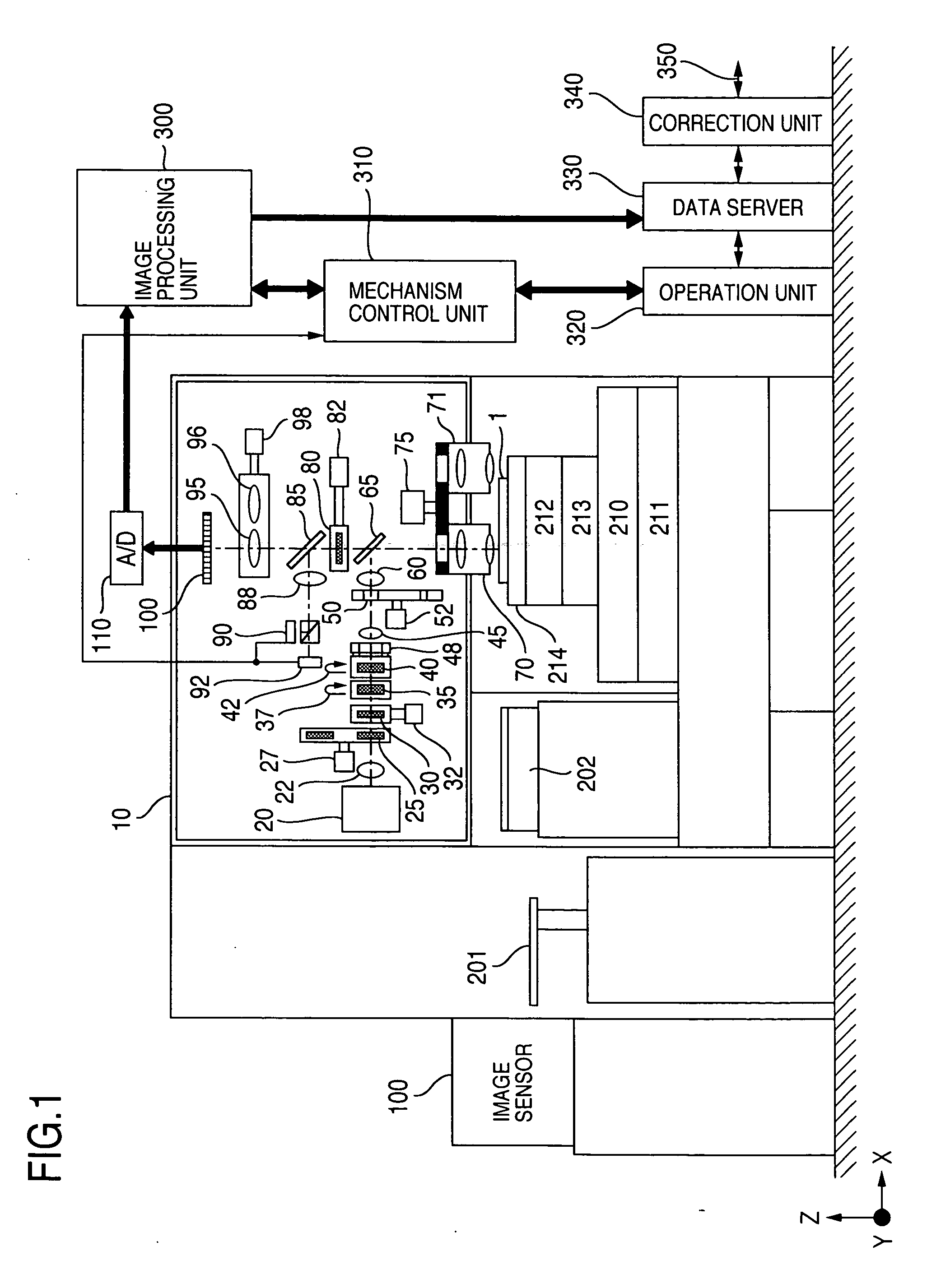
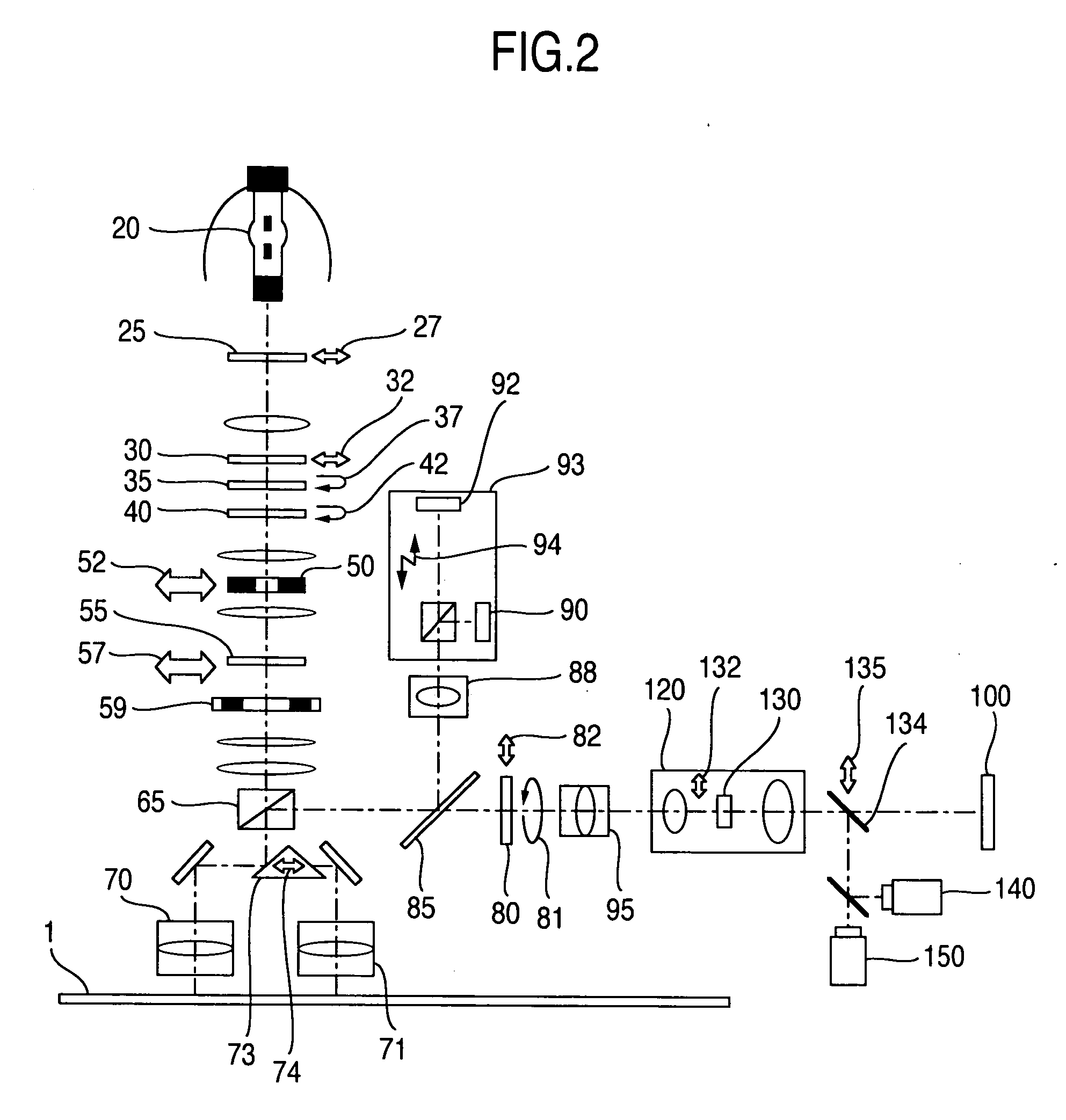
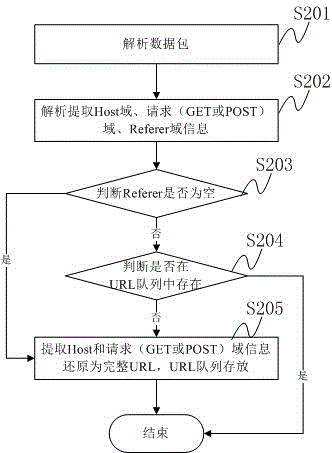
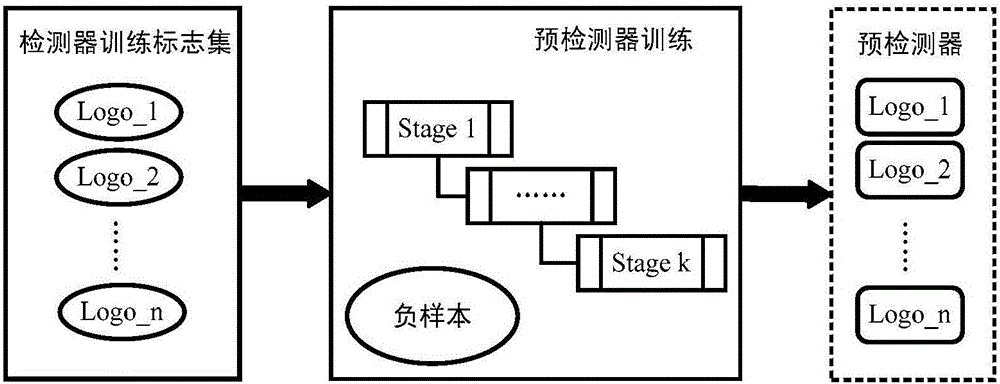
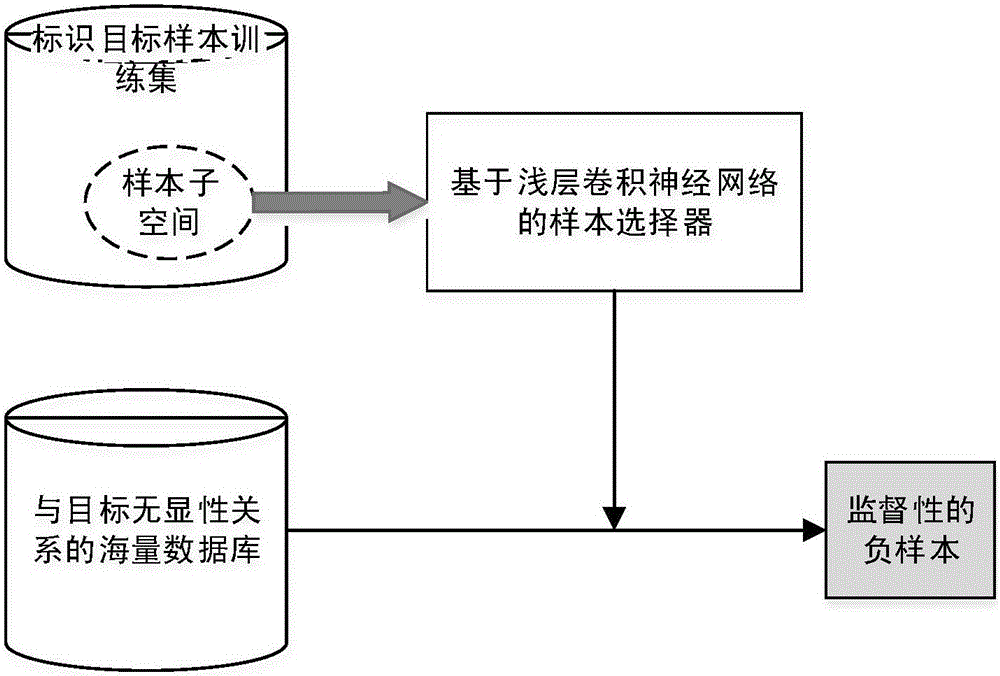
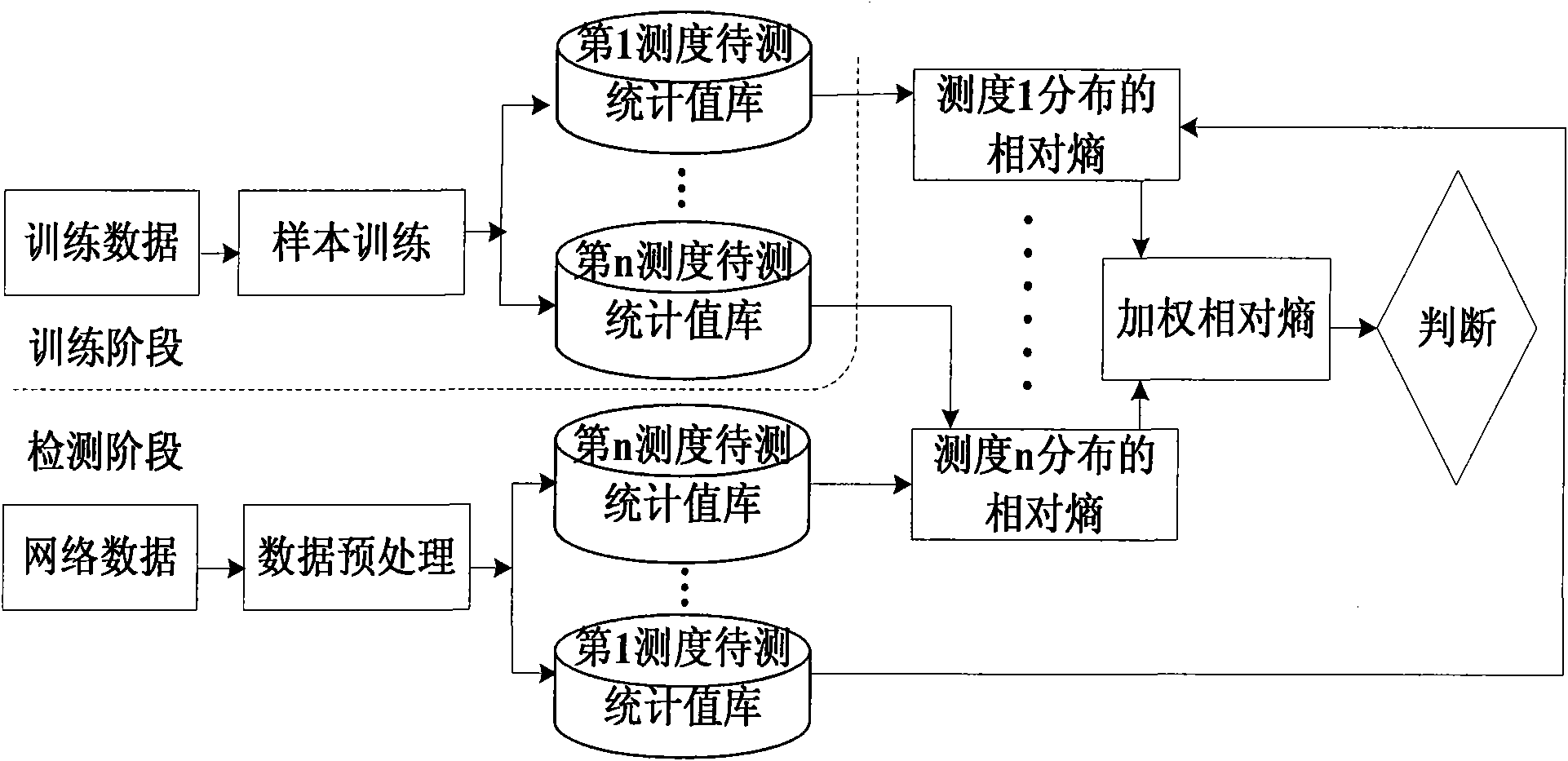
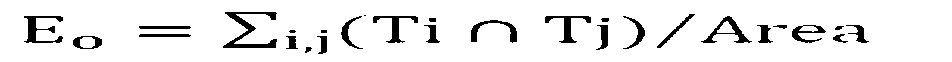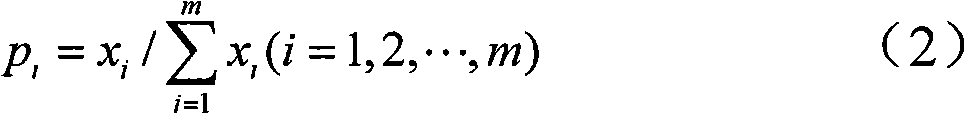Patents
Literature
2568 results about "Detection rate" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Detection rate. The proportion of individuals with a particular condition who test positive for that condition when measured by a gold-standard methodology.
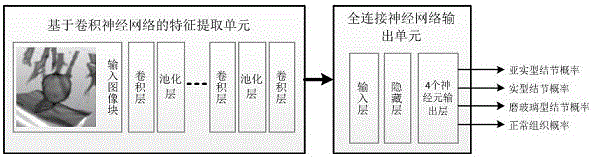
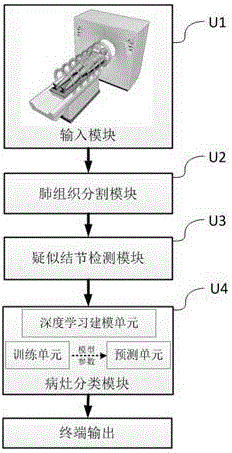
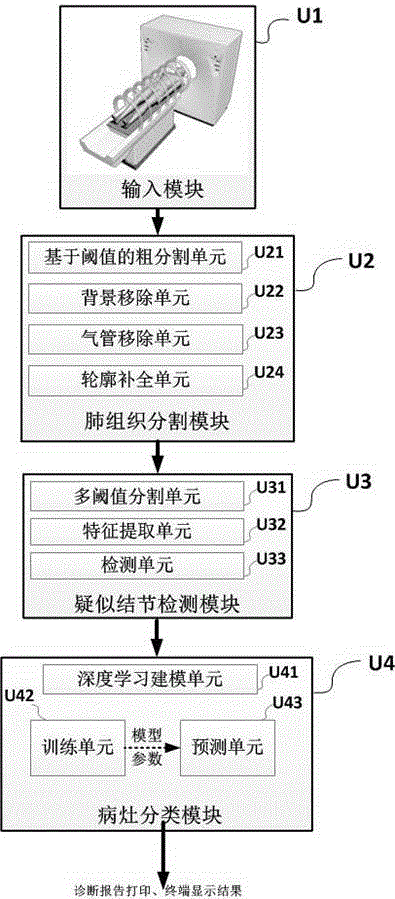
Automatic detection system for pulmonary nodule in chest CT (Computed Tomography) image
ActiveCN106780460AAvoid nodulesImplement classificationImage enhancementImage analysisPulmonary nodulePrediction probability
The invention relates to an automatic detection system for a pulmonary nodule in a chest CT (Computed Tomography) image. The system provides improvements for the problems of large calculated amount of computer aided software, inaccurate prediction and few prediction varieties. The improvement of the invention comprises the steps of acquiring a CT image; segmenting a pulmonary tissue; detecting a suspected nodular lesion area in the pulmonary tissue; classifying nidi based on a nidus classification model of deep learning; and outputting an image mark and a diagnosis report. The system has high nodule detection rate and relatively low false positive rate, acquires an accurate locating, quantitative and qualitative result of a nodular lesion and a prediction probability thereof. The end-to-end (from a CT machine end to a doctor end) nodular lesion screening is truly realized, the accuracy and operability demands of doctors are satisfied and the system has wide mar5ket application prospects.
Owner:杭州健培科技有限公司
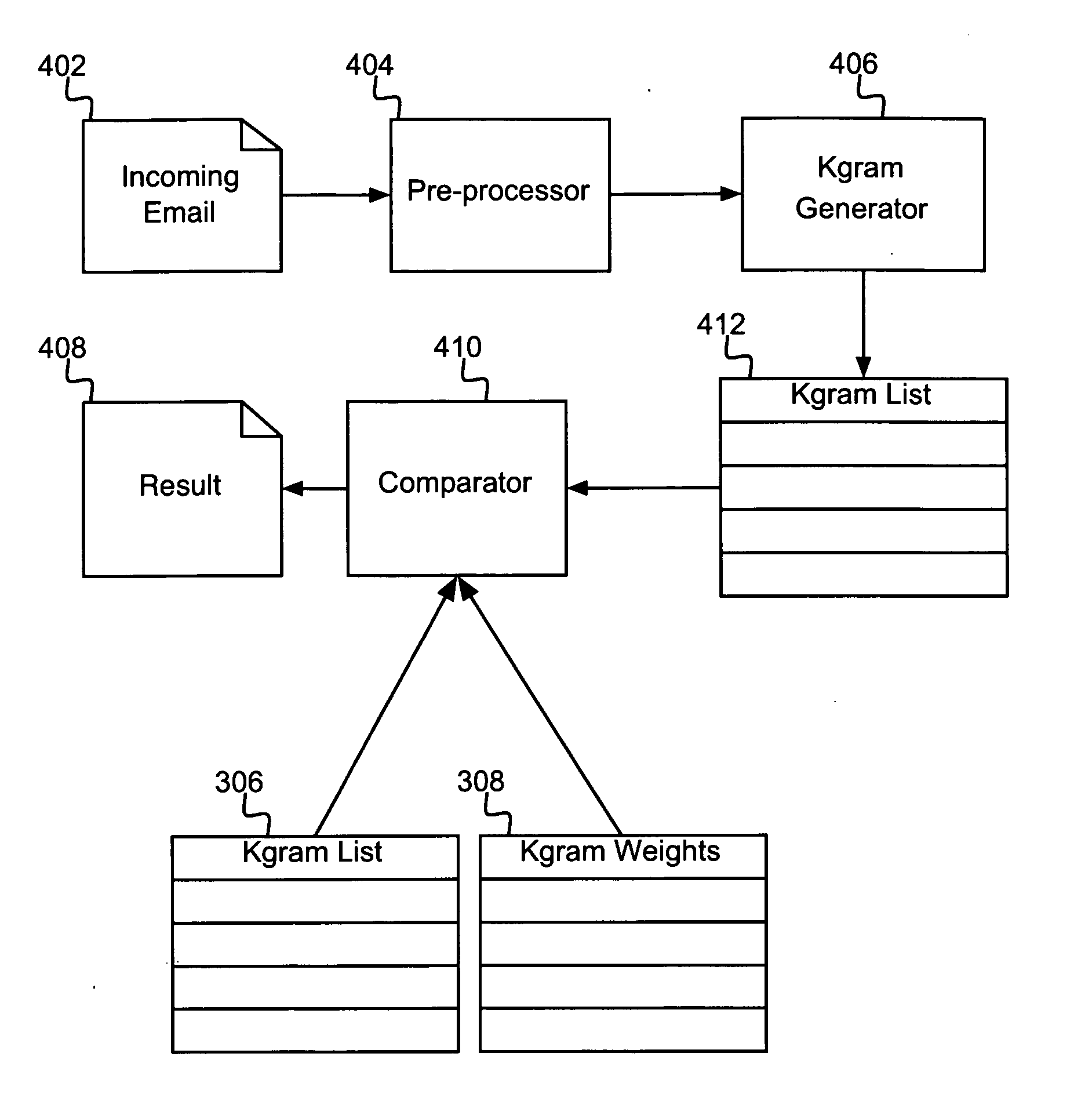
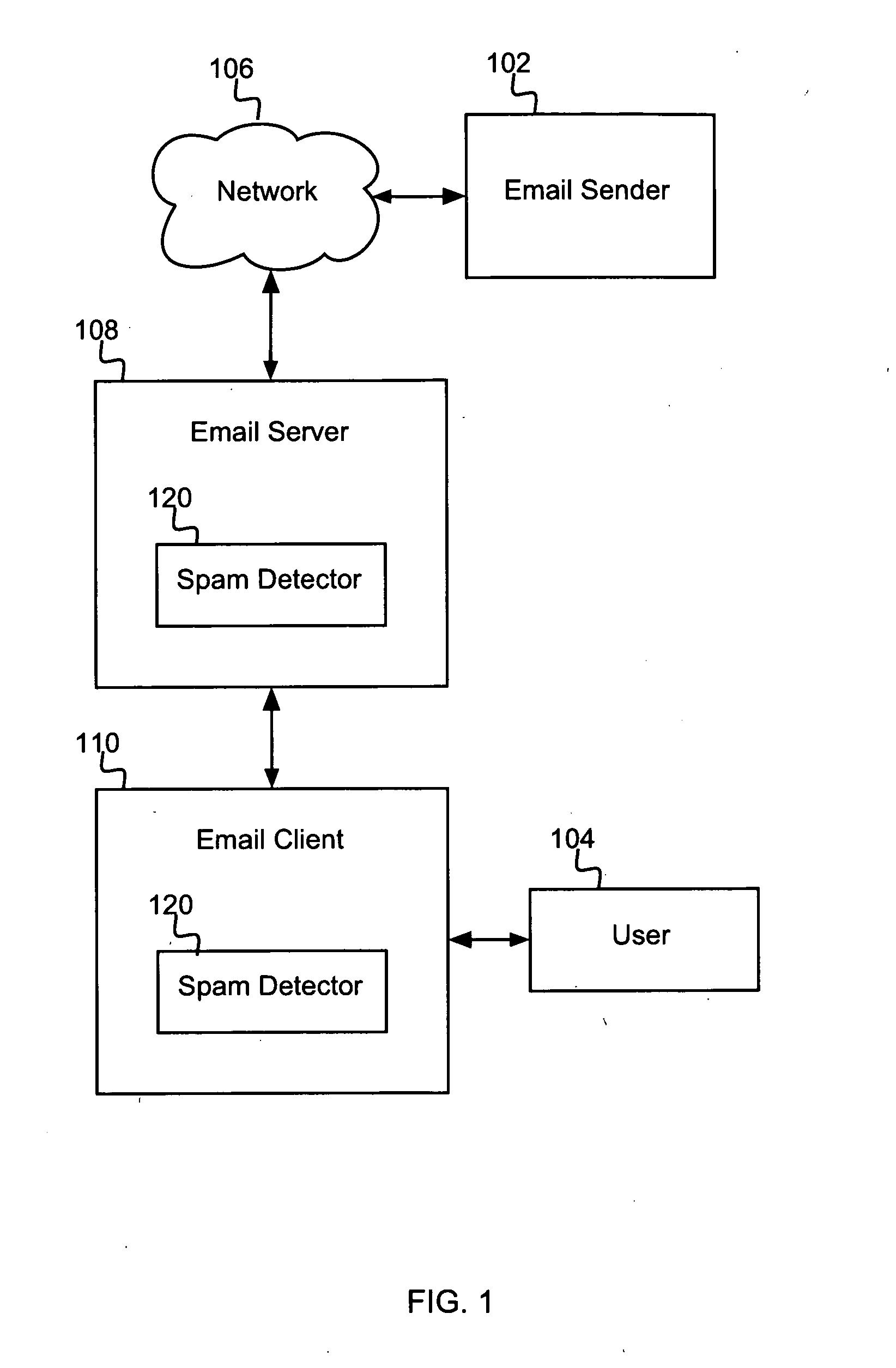
Detecting spam email using multiple spam classifiers
InactiveUS20060149821A1Multiple digital computer combinationsData switching networksSpammingData mining
A method for detecting undesirable emails is disclosed. The method combines input from two or more spam classifiers to provide improved classification effectiveness and robustness. The method's effectiveness is improved over that of any one constituent classifier in the sense that the detection rate is increased and / or the false positive rate is decreased. The method's robustness is improved in the sense that, if spammers temporarily elude any one constituent classifier, the other constituent classifiers will still be likely to catch the spam. The method includes obtaining a score from each of a plurality of constituent spam classifiers by applying them to a given input email. The method further includes obtaining a combined spam score from a combined spam classifier that takes as input the plurality of constituent spam classifier scores, the combined spam classifier being computed automatically in accordance with a specified false-positive vs. false-negative tradeoff. The method further includes identifying the given input email as an undesirable email if the combined spam score indicates that the input e-mail is undesirable.
Owner:IBM CORP
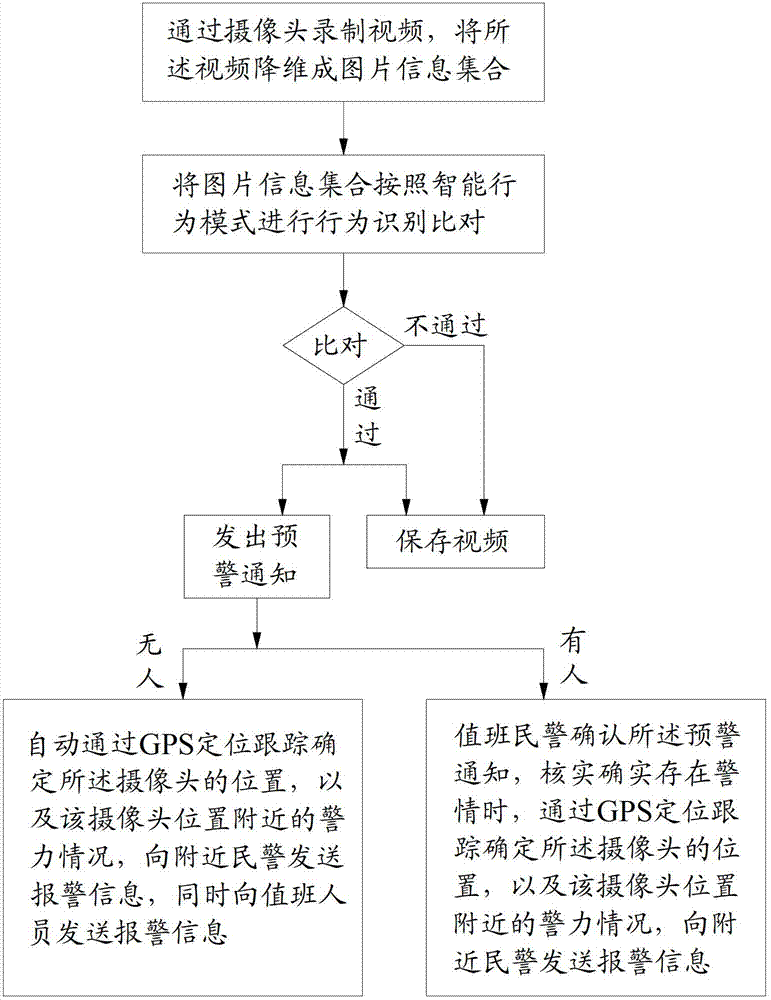
Crime monitoring method based on face recognition technology and behavior and sound recognition
ActiveCN103246869ALock in timeInhibit deteriorationCharacter and pattern recognitionSpeech recognitionSound recognitionGps positioning
The invention provides a crime monitoring method based on the face recognition technology and behavior and sound recognition, which includes the following steps: Step 1, recoding a video through a camera, reducing dimensions of the video to form a picture message ensemble; Step 2, performing the recognition comparison to the picture message ensemble as per an intelligent behavior pattern, and issuing an early warning and storing the video if the comparison is successful; and Step 3, verifying the crime situation by a police on duty, confirming the position of the camera through a GPS for positioning and tracking and confirming the police strength nearby, and sending crime situation to polices nearby by the police on duty, and if no police is on duty, confirming the position of the camera automatically through the GPS for positioning and tracking and confirming the police strength nearby, and sending crime situation to polices nearby and staff on duty. According to the invention, different intelligent behavior patterns are set as per the monitoring requirements of different situations, targeted monitoring is introduced, early warning prevention in advance is realized, the case is prevented from further worsening, the time in solving a criminal case is shortened, and the detection rate is improved.
Owner:FUJIAN YIRONG INFORMATION TECH
Remote obstacle detection method based on laser radar multi-frame point cloud fusion
ActiveCN110221603ASolve the problem of inability to effectively detect long-distance obstaclesPrecision FusionElectromagnetic wave reradiationPosition/course control in two dimensionsPoint cloudMultiple frame
The invention discloses a remote obstacle detection method based on laser radar multi-frame point cloud fusion. A local coordinate system and a world coordinate system are established, an extraction feature point of each laser point is calculated on an annular scanning line of the laser radar according to the original point cloud data under the local coordinate system, and the global pose of the current position relative to the initial position and the de-distortion point cloud in the world coordinate system are obtained through inter-frame feature point matching and map feature point matching; the de-distortion point clouds of the current frame and the previous frame are fused to obtain more compact de-distortion point cloud data, which is unified to the local coordinate system, then projection is performed on two-dimensional grids, and an obstacle is screened according to the height change features of each two-dimensional grid. According to the method in the invention, the problem that the detection rate of the remote barrier caused by sparse laser point clouds is low is solved, the remote barriers can be effectively detected, the error detection rate and the leak detection rateare low, and the system cost can be greatly reduced.
Owner:ZHEJIANG UNIV
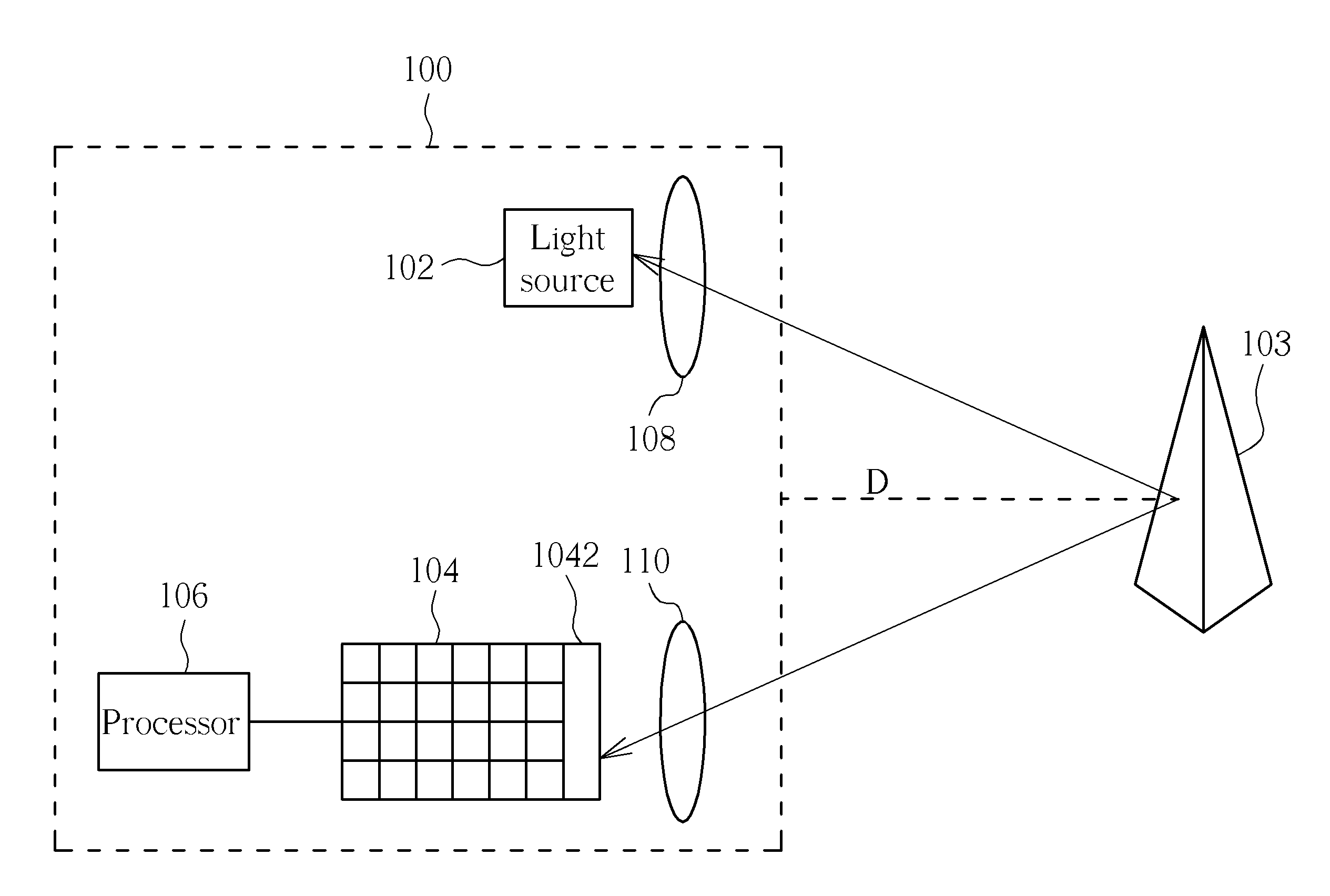
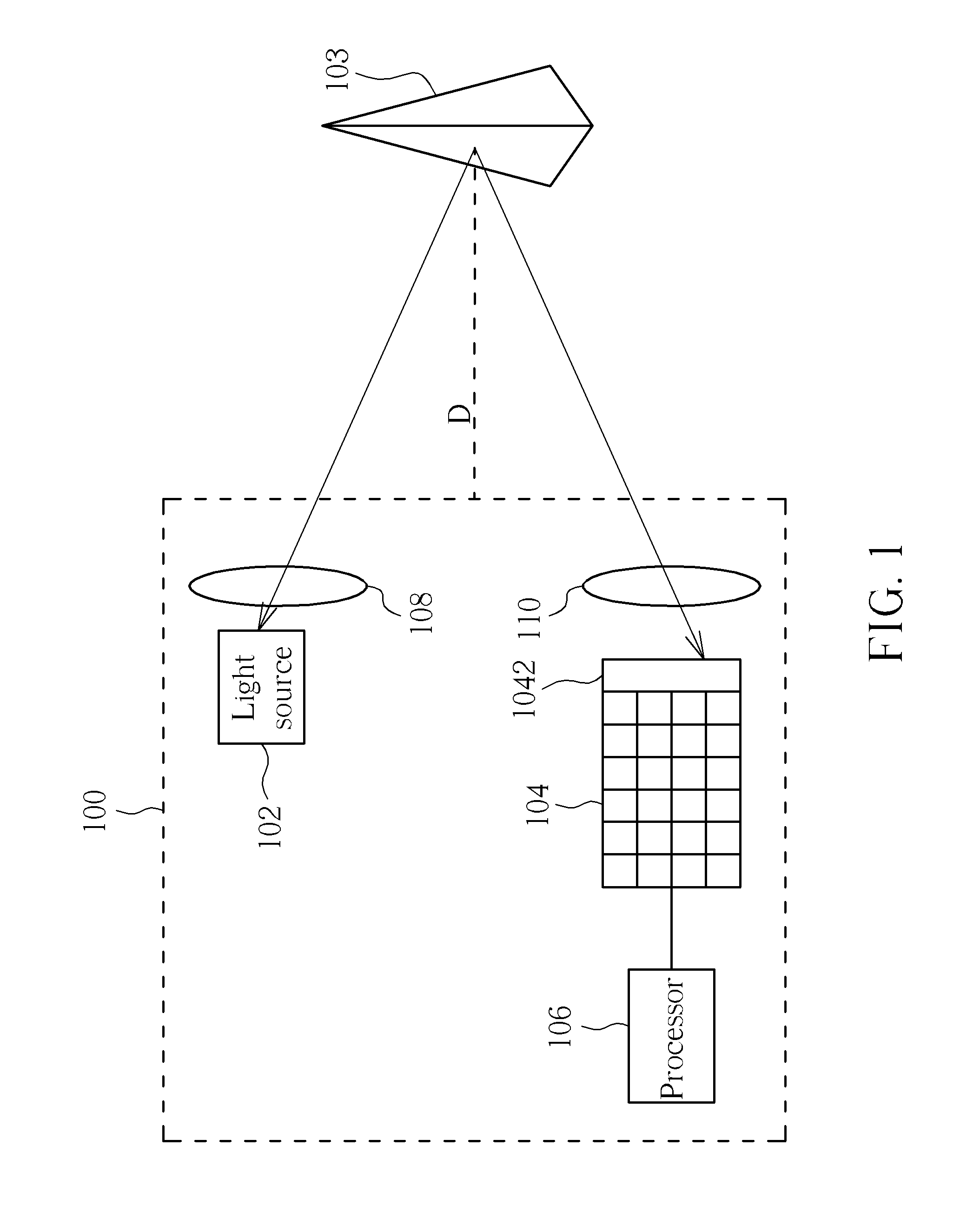
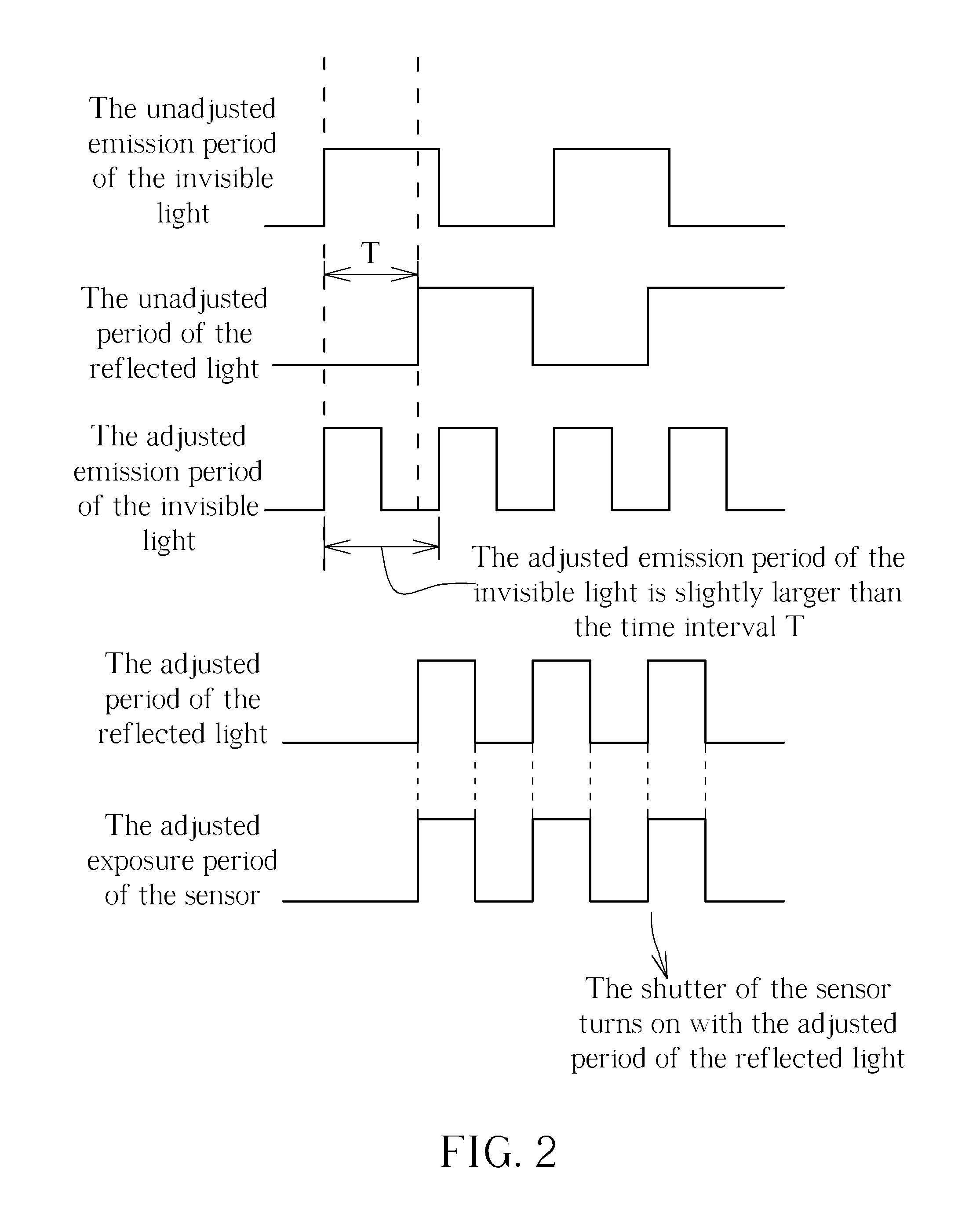
Time of flight system capable of increasing measurement accuracy, saving power and/or increasing motion detection rate and method thereof
ActiveUS20110304842A1High measurement accuracySave powerOptical rangefindersElectrical apparatusExposure periodUltimate tensile strength
A light source is used for emitting an invisible light toward an object. The object reflects the invisible light and reflected light is formed, and a sensor is used for receiving the reflected light. A processor is coupled to the sensor for recording a time interval of the invisible light traveling from the light source to the object and reflected from the object to the sensor. Then, the processor estimates a measurement distance of the object according to the time interval, and adjusts an emission period of the light source, an exposure period of the sensor, intensity of the invisible light, and / or main sensing range of the sensor according to the measurement distance.
Owner:SAMSUNG ELECTRONICS CO LTD
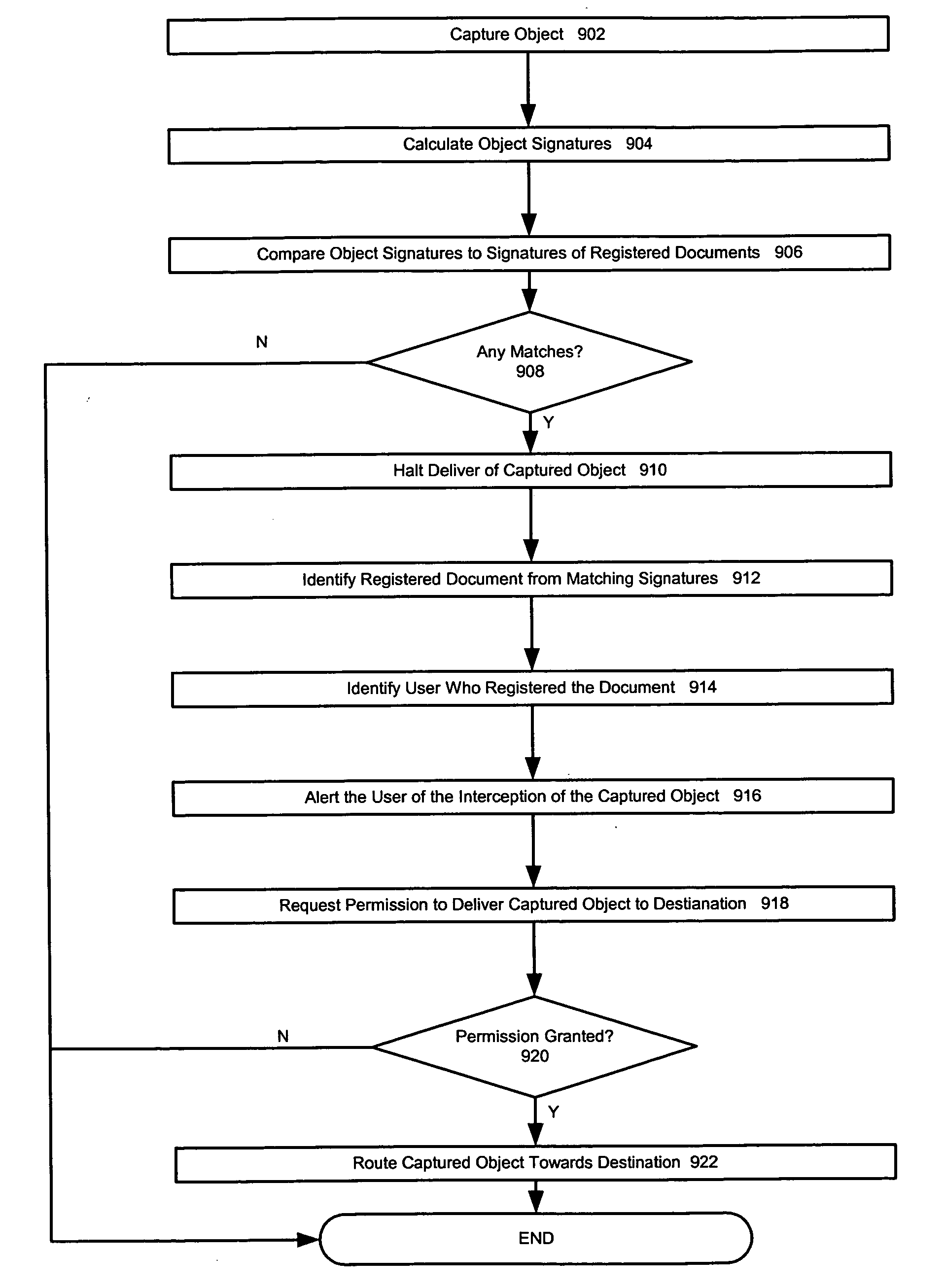
Document de-registration
ActiveUS20050132198A1Memory loss protectionError detection/correctionPaper documentDocument preparation
A document accessible over a network can be registered. A registered document, and the content contained therein, cannot be transmitted undetected over and off of the network. In one embodiment, the invention includes maintaining a plurality of stored signatures in a signature database, each signature being associated with one of a plurality of registered documents. In one embodiment, the invention further includes maintaining the signature database by de-registering documents by removing the signatures associated with de-registered documents. In one embodiment, the invention further includes maintaining the database by removing redundant and high detection rate signatures. In one embodiment, the invention also includes maintaining the signature database by removing signatures based on the source text used to generate the signature.
Owner:MCAFEE LLC
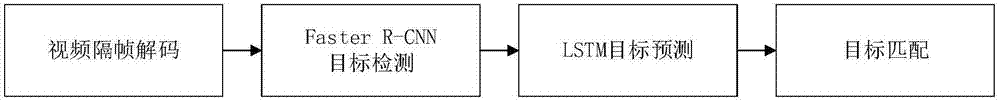
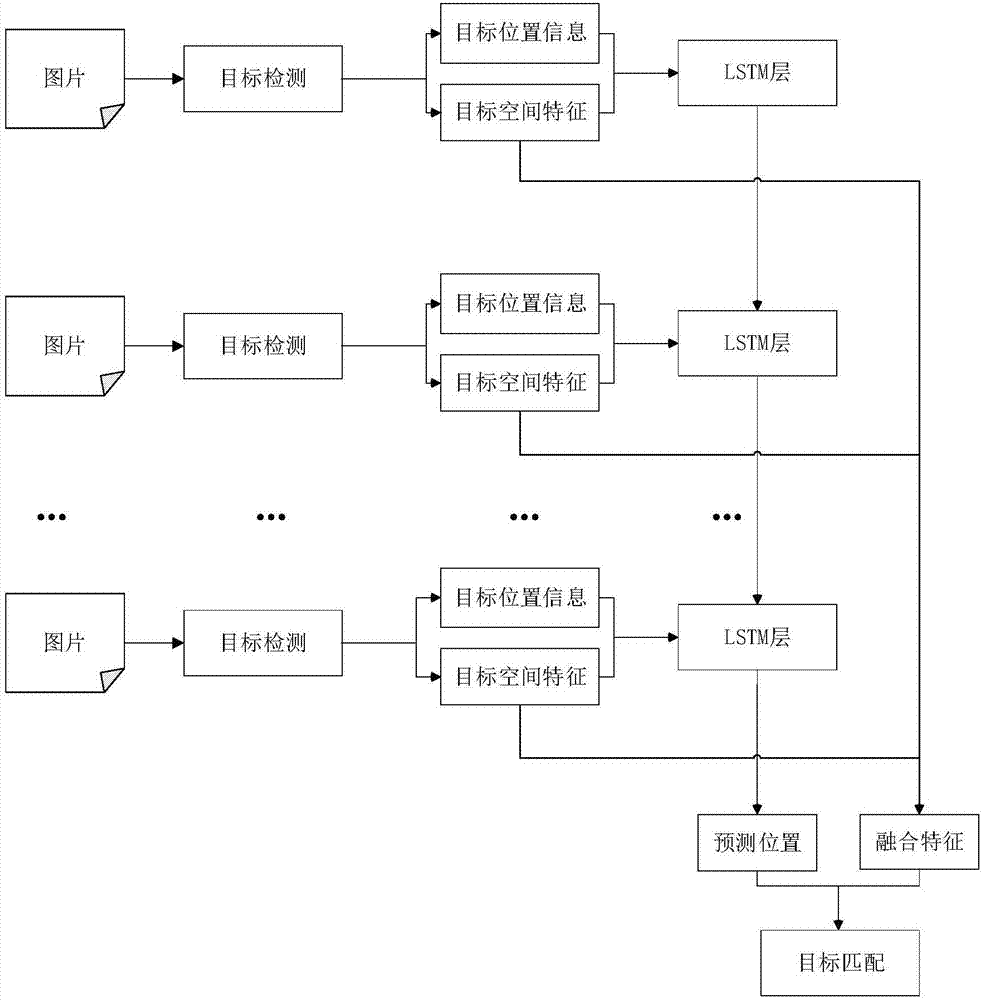
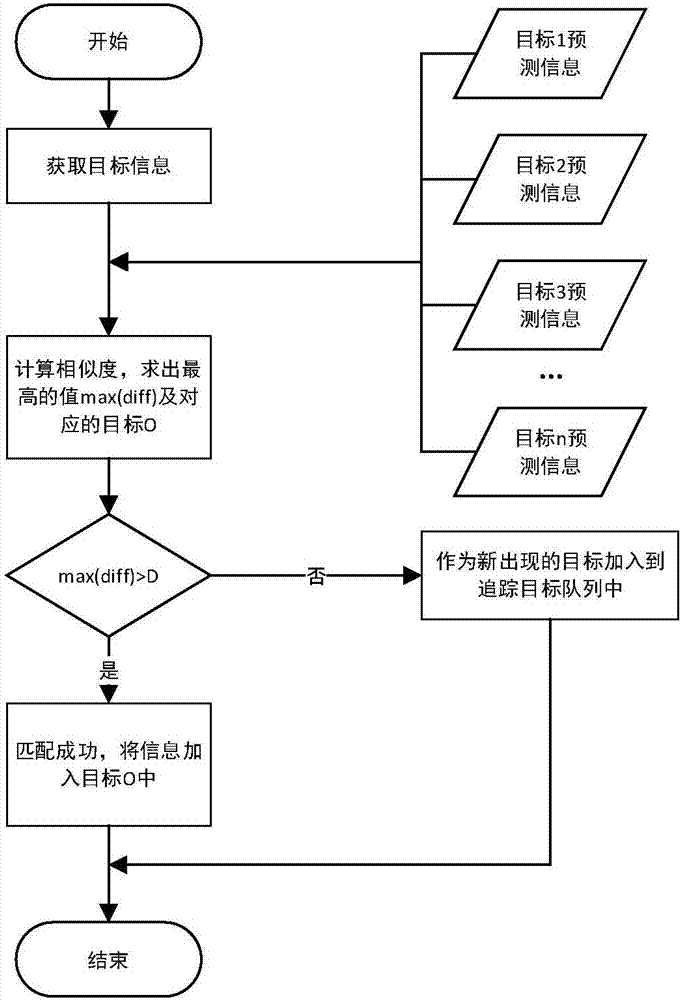
Monitoring video multi-target tracking method based on deep learning
ActiveCN107330920AEnhance expressive abilityHigh similarityImage enhancementImage analysisPattern recognitionMulti target tracking
The invention discloses a monitoring video multi-target tracking method based on deep learning. The method includes the steps of firstly encoding a video, extracting an image sequence from the encoded video, then preprocessing and inputting images into a trained Faster R-CNN network model, the Faster R-CNN network model extracting target location information and target spatial features from corresponding layers of the network; inputting the target location information and the target spatial features into an LSTM network, and predicting locations of targets at a next moment; and subjecting the spatial features of the targets to a fusion method to obtain fusion features of the targets at the next moment, adding different weights through the location similarity and spatial feature similarity to obtain the final similarity, and then judging the corresponding relationship of the multiple targets detected at the current moment and the multiple targets in a tracking state at the previous moment. By target tracking, the method of the invention can reduce the missed detection rate of multi-target tracking, improve the accuracy of multi-target tracking, and solve the target occlusion problem in a short time in the tracking process.
Owner:HUAZHONG UNIV OF SCI & TECH
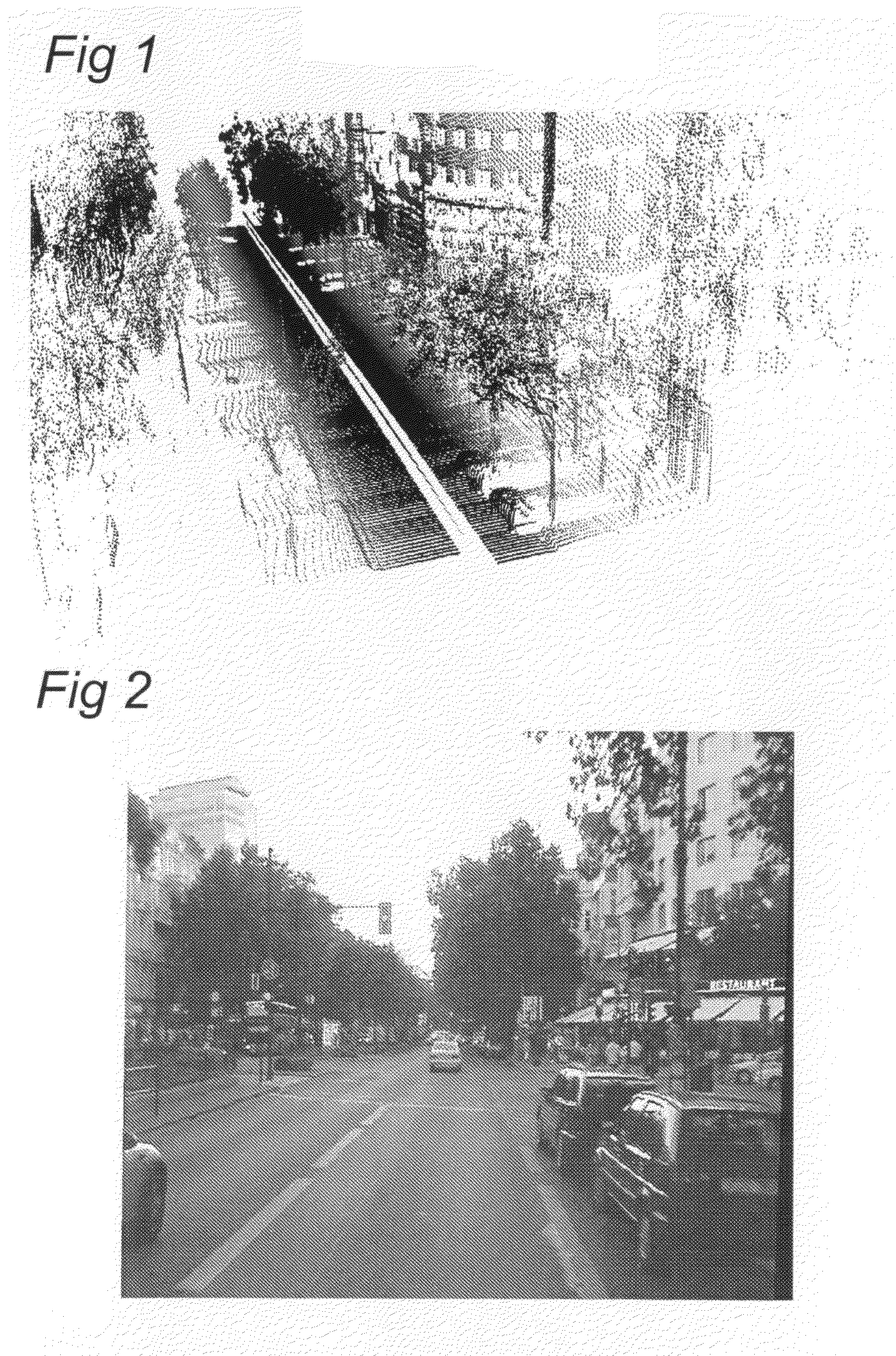
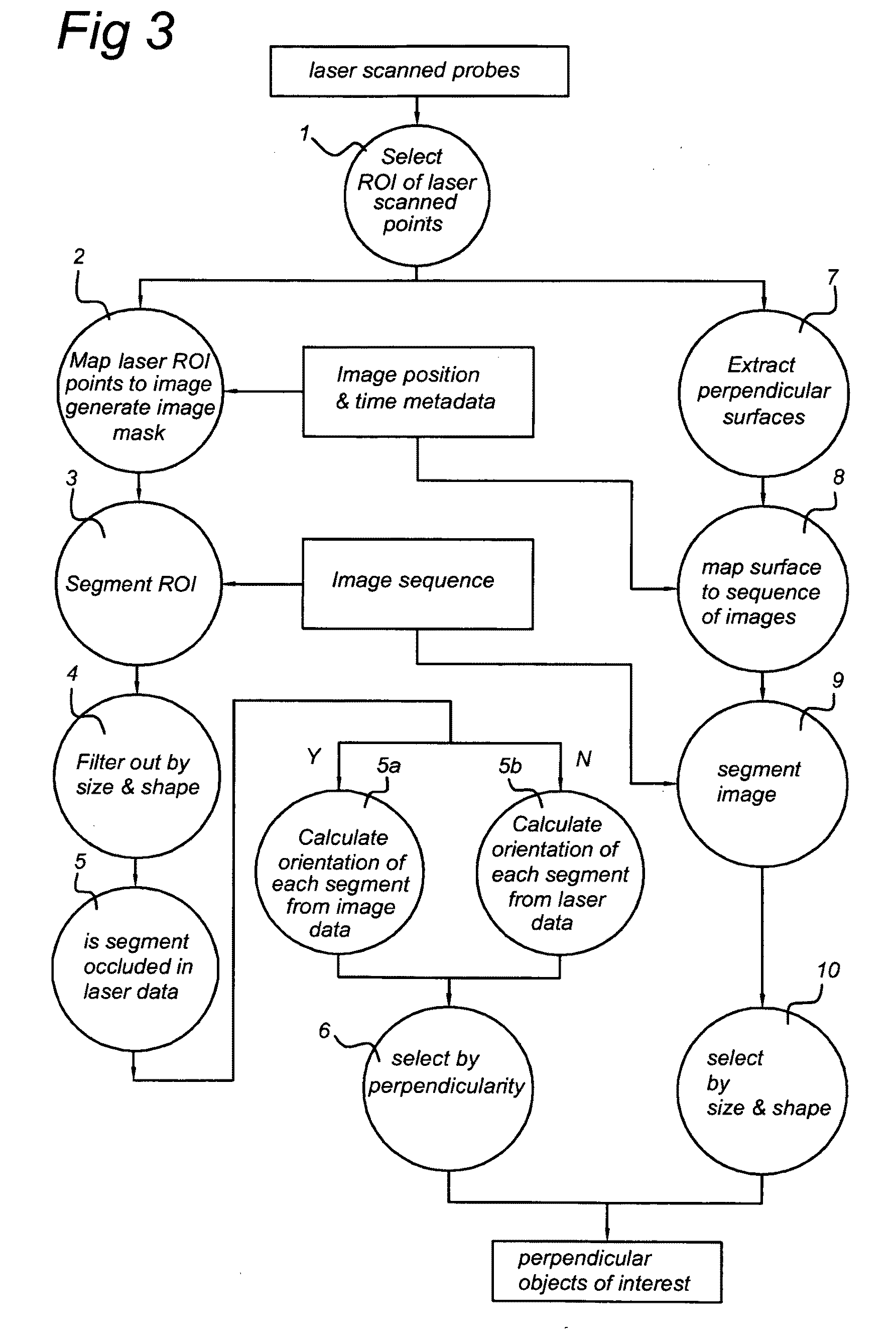
Method and apparatus for detecting objects from terrestrial based mobile mapping data
ActiveUS20100020074A1Efficient processingEffectively scaledImage enhancementInstruments for road network navigationMobile mapping3d image
A method of detecting objects from terrestrial based mobile mapping data is disclosed, wherein the terrestrial based mobile mapping data has been captured by way of a terrestrial based mobile mapping vehicle driving on a road having a driving direction, the mobile mapping data including laser scanner data, source images obtained by at least one camera and position and orientation data of the vehicle, wherein the laser scanner data includes laser points, each laser point having associated position and orientation data, and each source image comprises associated position and orientation data. In at least one embodiment, the method includes: retrieving a position and orientation of the vehicle; filtering the laser scanner data in dependence of the position and orientation of the vehicle to obtain laser points corresponding to regions of interest; retrieving a source image associated with the position and orientation of the vehicle; mapping the laser points corresponding to regions of interest to image coordinates of the source image to generate a recognition mask; combining the recognition mask and the source image to obtain candidate 3D images representative of possible objects within the regions of interest; and, detecting a group of objects from the candidate 3D images. By combining image recognition and laser scanner recognition the detection rate can be increased to a very high percentage, thereby substantially reducing human effort. Furthermore, the generating of regions of interest in the laser data, enables a significant reduction of the processing power and / or the processing time needed to detect the objects in the images.
Owner:TOMTOM GLOBAL CONTENT
Small target rapid detection method based on deep convolution neural network
InactiveCN106599827AIncrease the number ofReduce computational complexityBiological neural network modelsScene recognitionNerve networkComputation complexity
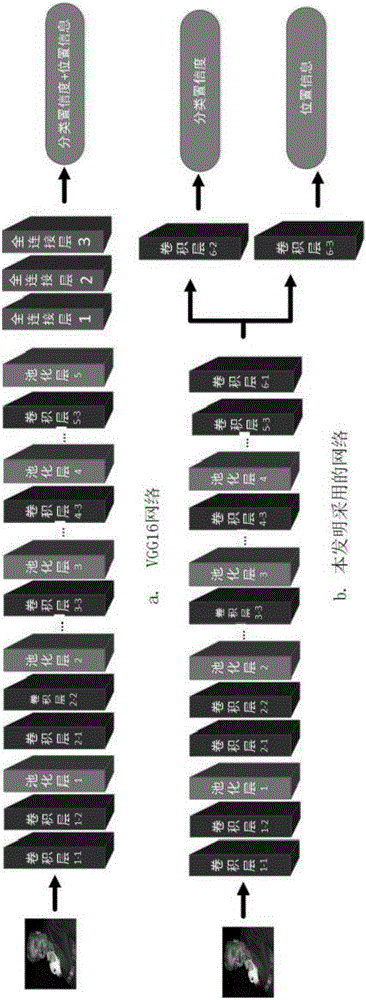
The invention discloses a small target rapid detection method based on a deep convolution neural network. The deep convolution neural network is improved by the following steps: selecting the sliding windows on the convolution feature map of the last shared convolution layer of a VGG16 network as candidate boxes, wherein the sliding windows adopted are half-pixel precision sliding window; deleting a fifth pooling layer, and retaining other convolution layers and pooling layers; adding a convolution layer with a 3*3 convolution kernel; and using two convolution layers with 1*1 convolution kernels to replace all full-connection layers in the network to get the network adopted in the invention, training the network using collected data to get a small target classification model, and using the model to detect small targets. By using the method, the computational complexity is reduced, and the detection rate of small targets is improved.
Owner:ZHEJIANG GONGSHANG UNIVERSITY +1
Moving target detecting method based on differential fusion and image edge information
InactiveCN102184552AReliable detectionExcellent recognitionImage enhancementImage analysisBackground imageVideo image
The invention relates to a moving target detecting method based on differential fusion and image edge information. The method comprises the following steps of: extracting a video image for preprocessing, and extracting the edge of the image to acquire continuous edge images; performing inter-frame differential operation on the continuous edge images respectively in a unit 8 data format, and performing background differential operation on the image in an intermediate frame; and fusing the detecting results of two differences to primarily extract a moving pedestrian target. In a background difference, a background automatic extracting method is improved, and a continuous-edge-image-based background image extracting and updating method is provided. A moving target area in the image is extracted by using an adaptive-background-model-based dynamic threshold value, and morphologic filtering and connectivity detection are performed, so that the foreground target of a moving pedestrian is acquired. Under the complex condition of sudden light variation, a moving target can be accurately and reliably detected, and the method is superior to the three traditional methods in the two aspects ofan identification rate and an error detection rate.
Owner:UNIV OF SHANGHAI FOR SCI & TECH
Rapid detection method of face in color image under complex background
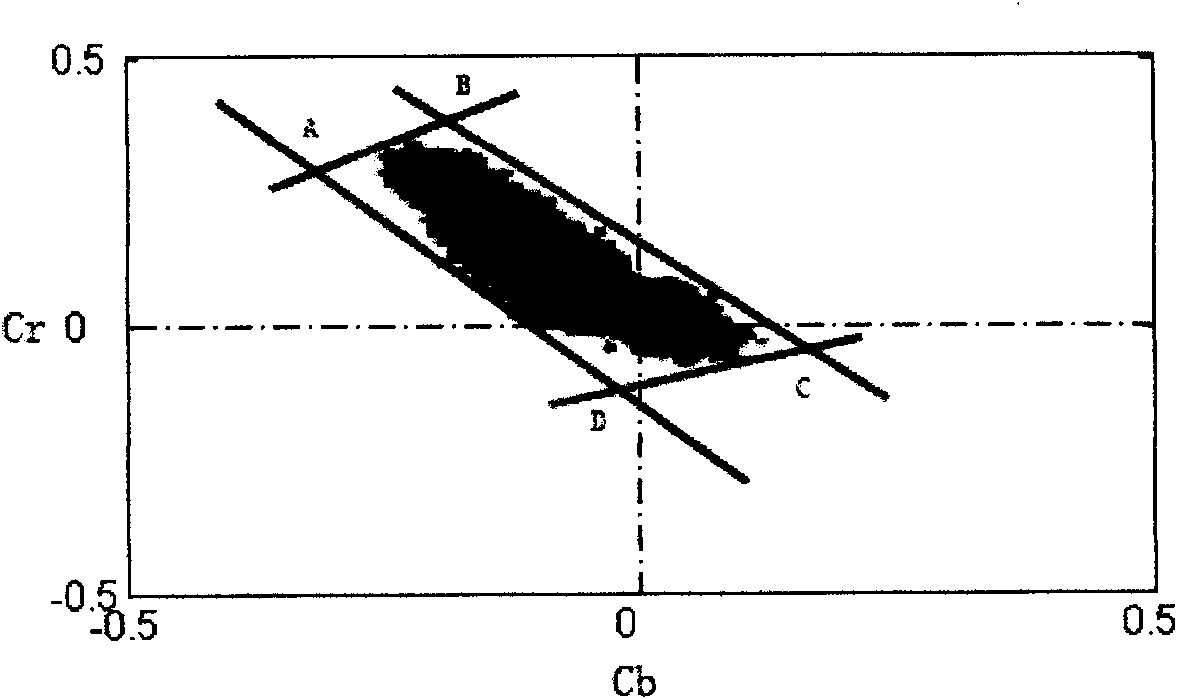
InactiveCN101630363ADetection speedReduce skin tone segmentation timeCharacter and pattern recognitionColor imageFace detection
The invention relates to the technical field of face recognition, in particular to a rapid detection method of a face in a high-resolution color image under a complex background. The invention comprises the following steps: building a face skin color mixed model which is composed of two color space restrictions of RGB and YCbCr according to a large amount of acquired skin color sample data to determine the skin color pixel; rapidly skipping non-face regions by adopting a whole skin color pixel ratio to improve the location efficiency of a face candidate region; then using the improved face rapid detection algorithm which is based on forward characteristic selection to realize face preliminary judging of the face candidate region; and finally utilizing a false alarm restraining method which is based on space restriction and geometric restriction to further lower false detection rate and complete face detection. The invention can realize rapid location of a plurality of frontal faces in images at a high detection rate under the condition of low false alarm rate; the good performances of the invention are proved by the results of the test set of Bao open database and a plurality of video frequencies and high resolution color images.
Owner:NO 709 RES INST OF CHINA SHIPBUILDING IND CORP
Method and apparatus for regaining watermark data that were embedded in an original signal by modifying sections of said original signal in relation to at least two different reference data sequences
Every watermarking processing needs a detection metric to decide at decoder side whether audio signal content is marked, and which symbol is embedded inside the audio signal content. The invention provides a new detection metric that achieves a reliable detection of watermarks in the presence of additional noise and echoes. This is performed by taking into account the information contained in the echoes of the received audio signal in the decision metric and comparing it with the corresponding metric obtained from decoding a non-marked audio signal, based on calculating the false positive detection rates of the reference sequences for multiple peaks. The watermark symbol corresponding to the reference sequence having the lowest false positive error is selected as the embedded one.
Owner:MAGNOLIA LICENSING LLC
System for controling and calibrating single photon detection devices
ActiveUS20110127415A1Minimizing measurement timeOptimal measurementMaterial analysis by optical meansCalibration apparatusElectricityDark count rate
A single photon detection system and method are disclosed which have a control block for helping to monitor and optimize performance, especially at high detection rates. The system is based on photon detectors constructed with avalanche photodiodes (APD) gated in time to operate in the Geiger mode. An electrical reference frequency is generated which is subtracted from the APD output in order to better isolate the breakdown event. The resulting signal is sampled and analyzed to allow the control unit to optimize the magnitude and phase of the electrical reference frequency. The control unit may also change the gate pulse shape and phase, including by the use of a digital-to-analog converter. The gate pulse can be shifted off an input optical pulse so as to estimate dark count rate, or shifted to measure a reference input signal to estimate detection efficiency.
Owner:NUCRYPT
Method and apparatus for detecting defects
InactiveUS20070058164A1Quick selectionImproves grayscale depthOptically investigating flaws/contaminationUsing optical meansLength waveLight filter
This invention provides a defect inspection method and apparatus that can easily and quickly determine, from among a plurality of inspection conditions, a condition that allows for an inspection with high sensitivity. The inspection apparatus has a variety of optical functions to cover a variety of kinds of defects to be inspected (shape, material, nearby pattern, etc.). For each optical function, grayscale depths of defects that the operator wants detected and of pseudo defects that he or she wants undetected are accumulated for future use, so that conditions conducive to a higher sensitivity and a lower pseudo defect detection rate can be selected efficiently. Conditions that can be selected for optical systems include a bright-field illumination, a dark-field illumination and a bright- / dark-field composite illumination, illumination wavelength bands, polarization filters and spatial filters.
Owner:HITACHI HIGH-TECH CORP
Real-time detection method and system of phishing website
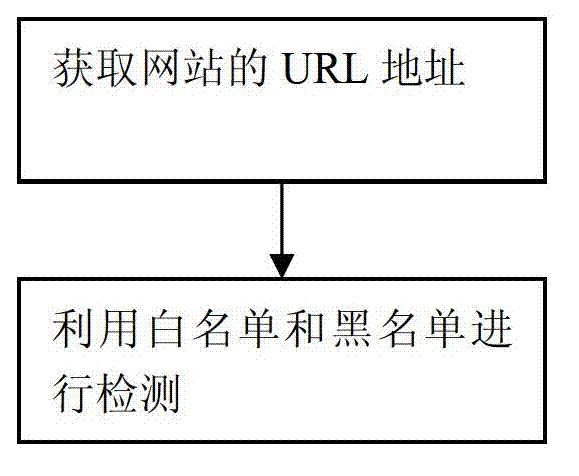
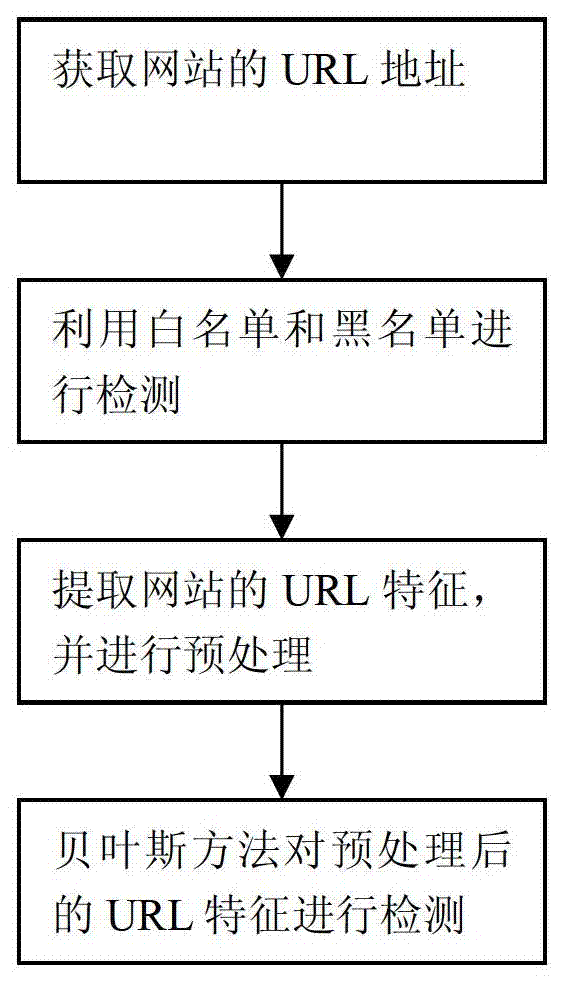
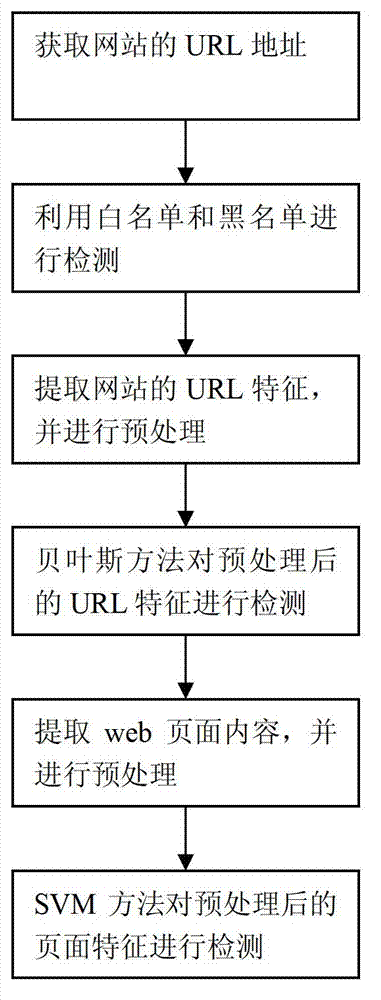
InactiveCN102932348AEasy extractionMeet the requirements for rapid classificationData switching networksLeast squares support vector machineClient-side
The invention relates to a real-time detection method and system of a phishing website. The method comprises the following steps of: obtaining the URL (uniform resource locator) address of the current website; detecting the URL address of the website by use of a white list and a black list; extracting the URL features of the website URL not in the white list and the black list, and performing pretreatment; detecting the URL features after the pretreatment by a Bayesian method, and judging whether the website is a phishing website; if the website can not be clearly determined, determining the website to be a suspicious website; extracting the web page content of the suspicious website, and performing pretreatment; and detecting the page features after the pretreatment by a least square support vector machine method, and judging whether the website is a phishing website. The system consists of a system server and a system client, wherein the system server comprises a white list and black list module and the like; and the system client comprises a URL fingerprint list and the like. Compared with the prior art, the method and system provided by the invention improve the detection rate and the accuracy.
Owner:CHANGZHOU UNIV
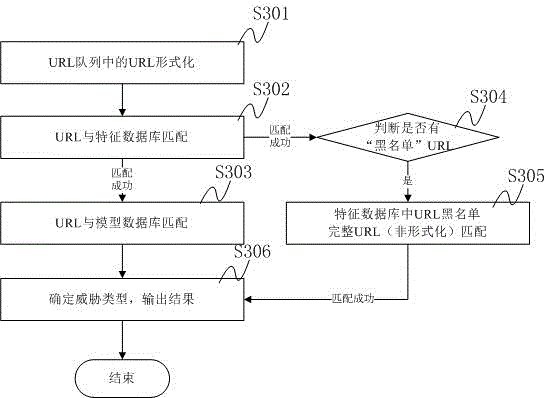
Malicious code detection method and system based on plurality of URLs (Uniform Resource Locator)
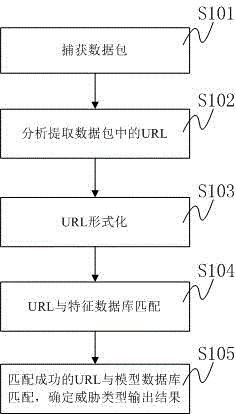
ActiveCN102801697AImprove the detection effectAvoid variable problemsComputer security arrangementsTransmissionAnti virusNetwork packet
The invention discloses a malicious code detection method based on a plurality of URLs (Uniform Resource Locator), comprising the following steps of: capturing all network communication data packets within appointed time intervals; sequentially analyzing all the network communication data packets and extracting the URL in each data packet; carrying out formalization treatment on all the extracted URLs; matching the URLs (which are subjected to the formalization treatment) as URLs to be detected with a characteristic database; and if the matching is successful, carrying out matching with a data model base, determining threat types and outputting corresponding detection results. The invention further discloses a malicious code detection device based on the plurality of URLs. According to the malicious code detection method and system disclosed by the invention, the disadvantages and the limitation of current anti-virus software characteristic code matching and URL filtering are solved; and the detectable rate of a malicious Trojan program is greatly improved.
Owner:BEIJING ANTIY NETWORK SAFETY TECH CO LTD
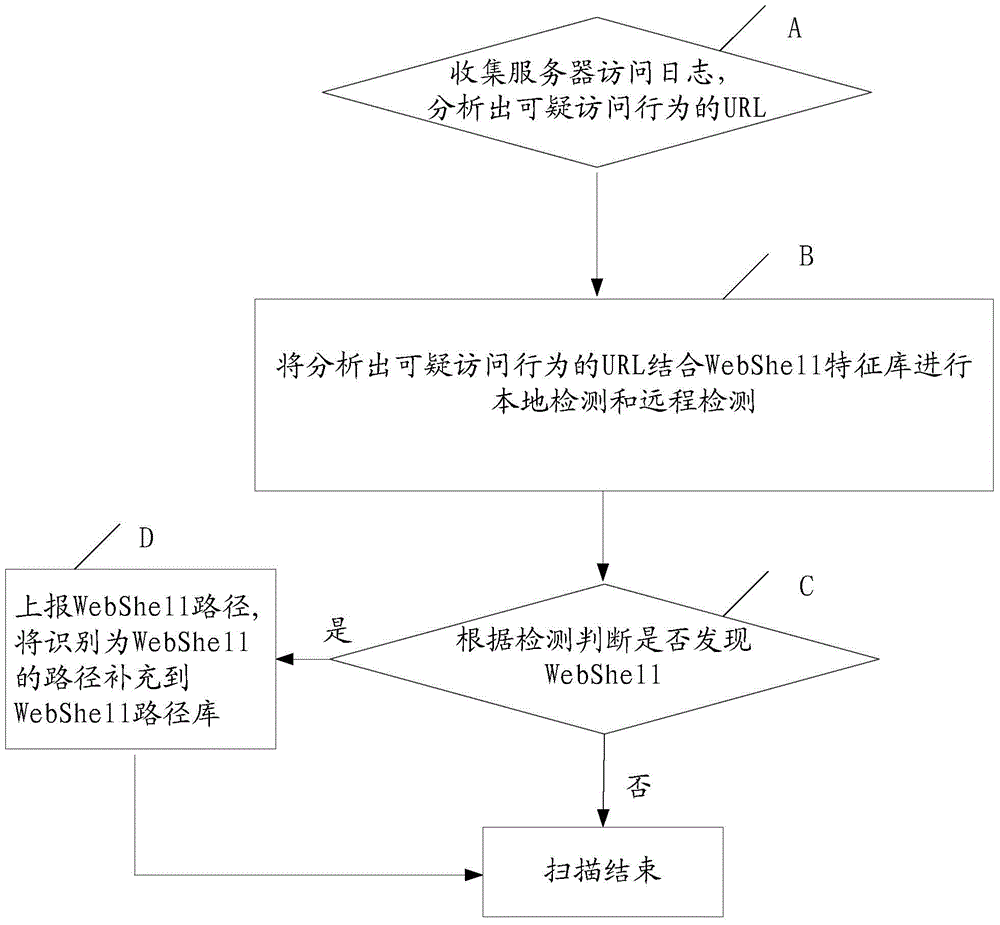
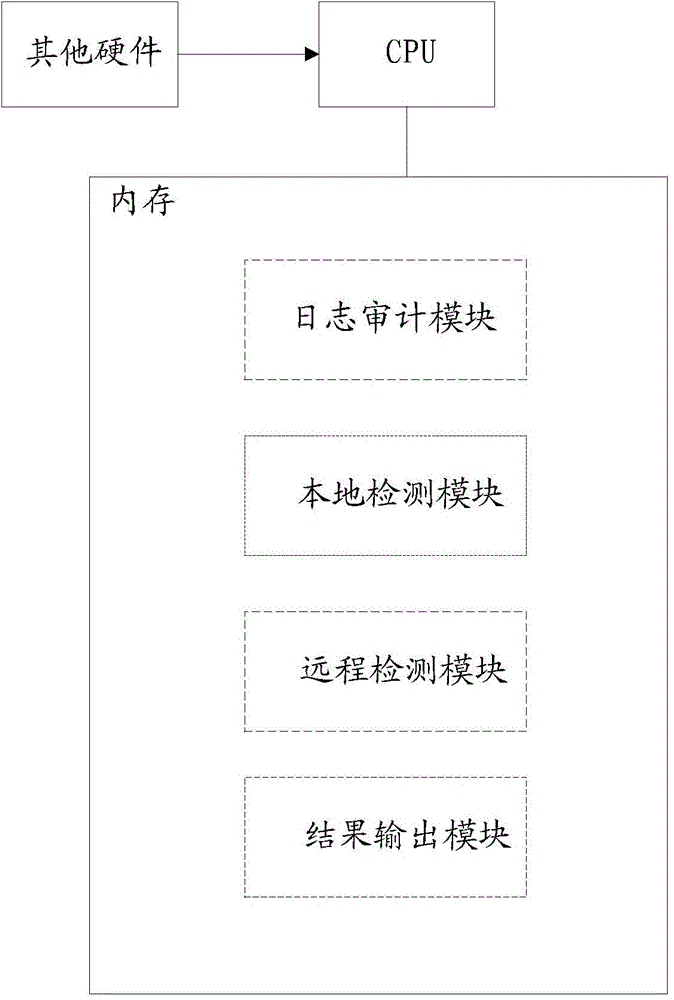
WebShell detection method and system
ActiveCN104468477AImprove accuracyImprove the detection rateTransmissionWeb applicationUniform resource locator
The invention provides a WebShell detection method and system. The system comprises a log auditing module, a local detection module, a remote detection module and a result output module. The system executes the following processing flow: A, collecting a server access log, and analyzing a URL (Uniform Resource Locator) with suspicious access behaviors; B, performing local detection and remote detection on the analyzed URL with suspicious access behaviors in combination with a WebShell feature library; C, and performing judgment according to the detection, reporting a WebShell path if WebShell is found, and meanwhile adding the path identified as WebShell into a WebShell path library. Through adoption of the method and the system, the detection rate and detection efficiency of WebShell detection in network Web application are increased, and the missing report rate and false report rate are lowered.
Owner:杭州迪普信息技术有限公司
Vehicle-mounted video target detection method based on deep learning
ActiveCN109977812AAdditional detailsRich image featuresCharacter and pattern recognitionPattern recognitionColor image
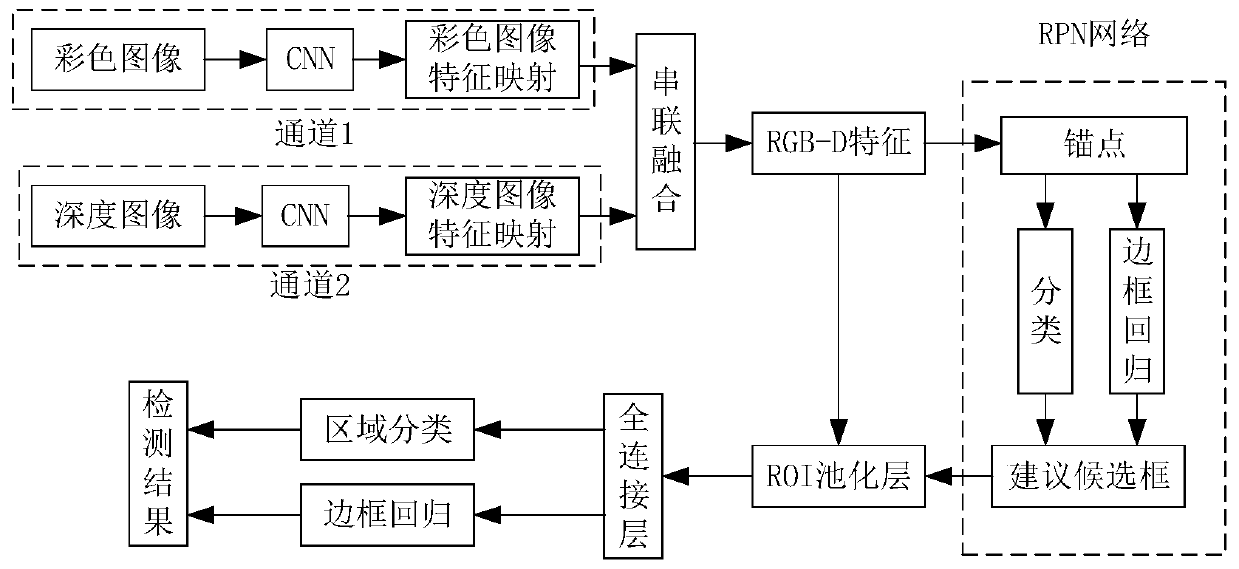
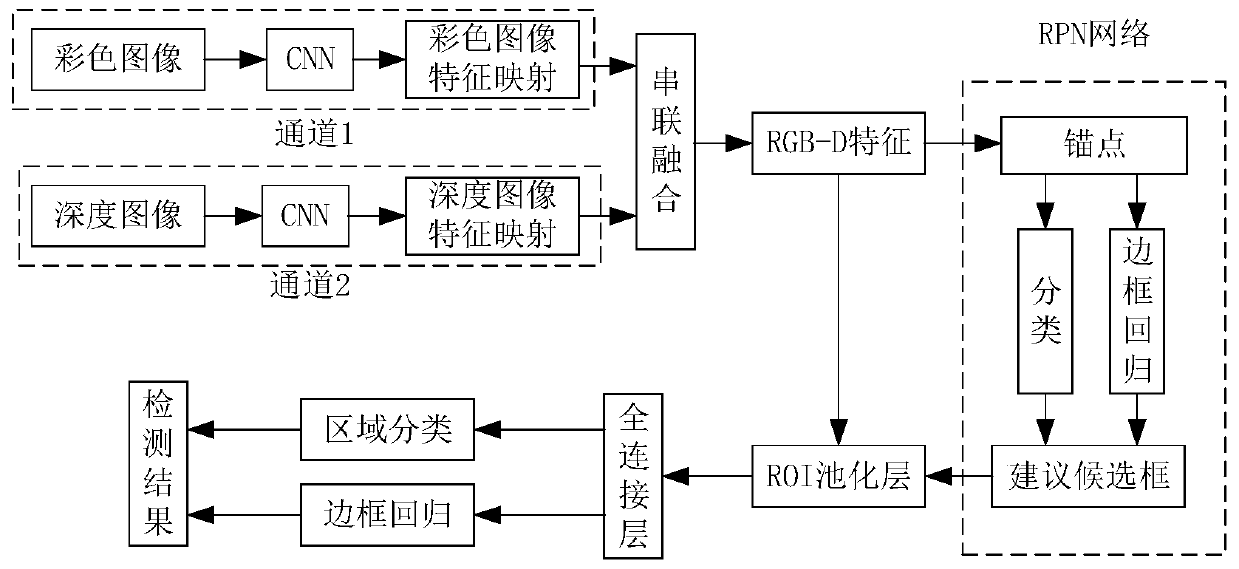
The invention discloses a vehicle-mounted video target detection method based on deep learning, and the method comprises the steps: employing an improved Faster R-CNN algorithm to realize target detection in a complex traffic environment, to provide a driving safety auxiliary function. An existing target tracking algorithm has a serious problem of small target missed detection. The depth information channel is added, the depth information channel is connected with an original color image channel in parallel, fusion is carried out in the channel dimension, candidate frame extraction and targetdetection are carried out on the fused feature image, the detection rate of a small target is improved, in addition, training of a difficult sample is added in training, and the overall target recognition rate of the algorithm is improved. According to the method, a problem of small target missed detection by using the Faster R-CNN algorithm is fully considered. The accuracy of vehicle recognitionin a complex traffic scene is improved through depth image feature fusion and a difficult sample mining method.
Owner:NANJING UNIV OF POSTS & TELECOMM
Adaboost arithmetic improved robust human ear detection method
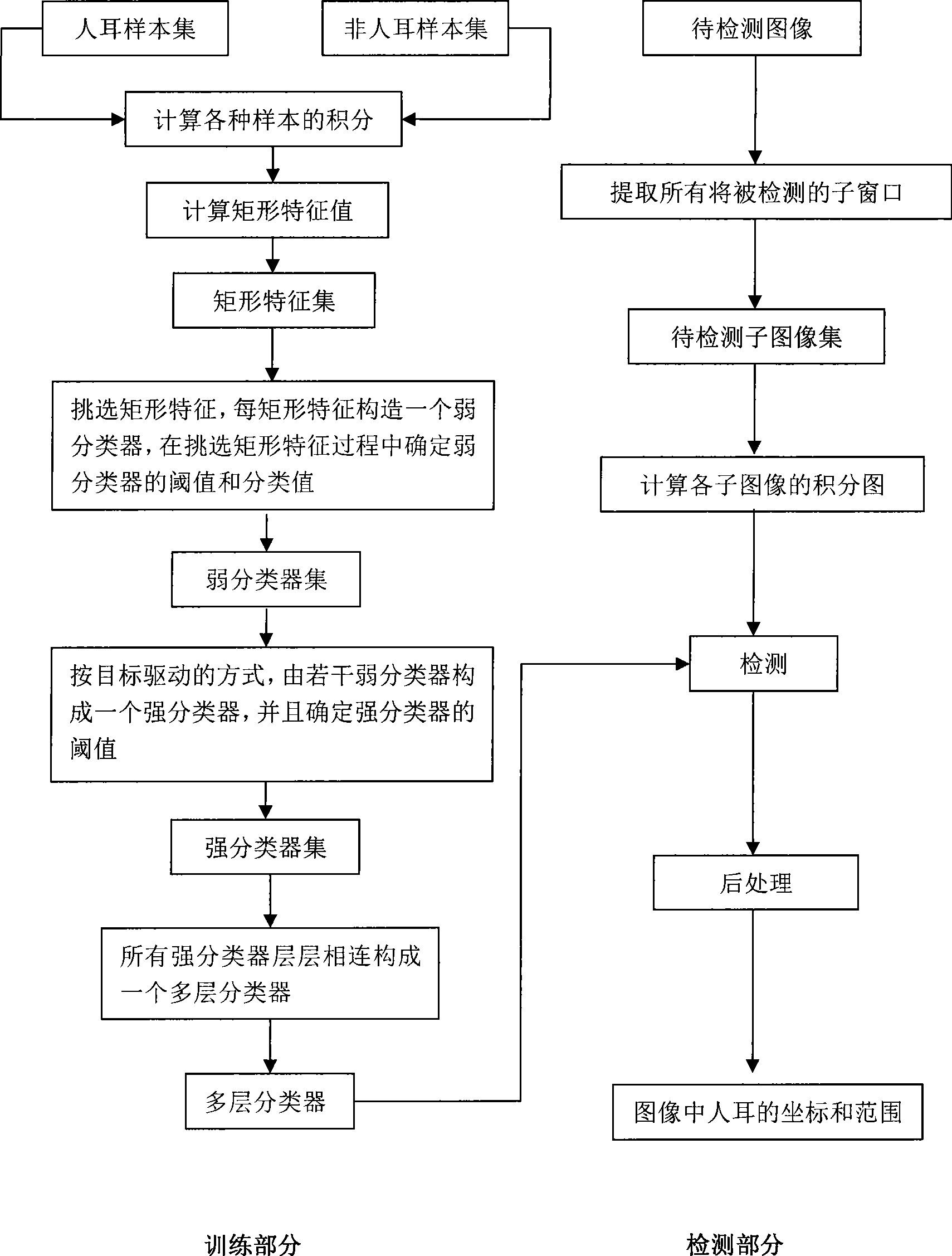
InactiveCN101398893ASimple structureReduce training timeCharacter and pattern recognitionHuman earAdaboost algorithm
The invention relates to a robust ear detection method which improves an AdaBoost arithmetic and belongs to the technical field of image mode identifying. The invention is characterized by proposing an ear detection method with excellent performances under a complex underground. The invention proposes four anisomerous Haar-like corner characteristics which are used for describing the grayscale changes on the partial areas of the ears; a policy of subsection selection is adopted for selecting the best sorting threshold of the Haar-like characteristics, thus reducing the sample training time; the weight of a weak sorter is modified for reducing the mistaken detection rate of the sorter; the threshold HW is set and eliminated according to the distribution change of the sample weight in the training, thereby preventing an over-studying phenomenon from being generated and leading the miss-detection rate and the mistaken direction rate of the ear detection to be reduced; besides, the invention also provides a single-ear detection policy for leading both the defection efficiency and the detection effect to be improved. The excellent performances of the robust ear detection method are shown on a PC machine and a DSP.
Owner:UNIV OF SCI & TECH BEIJING
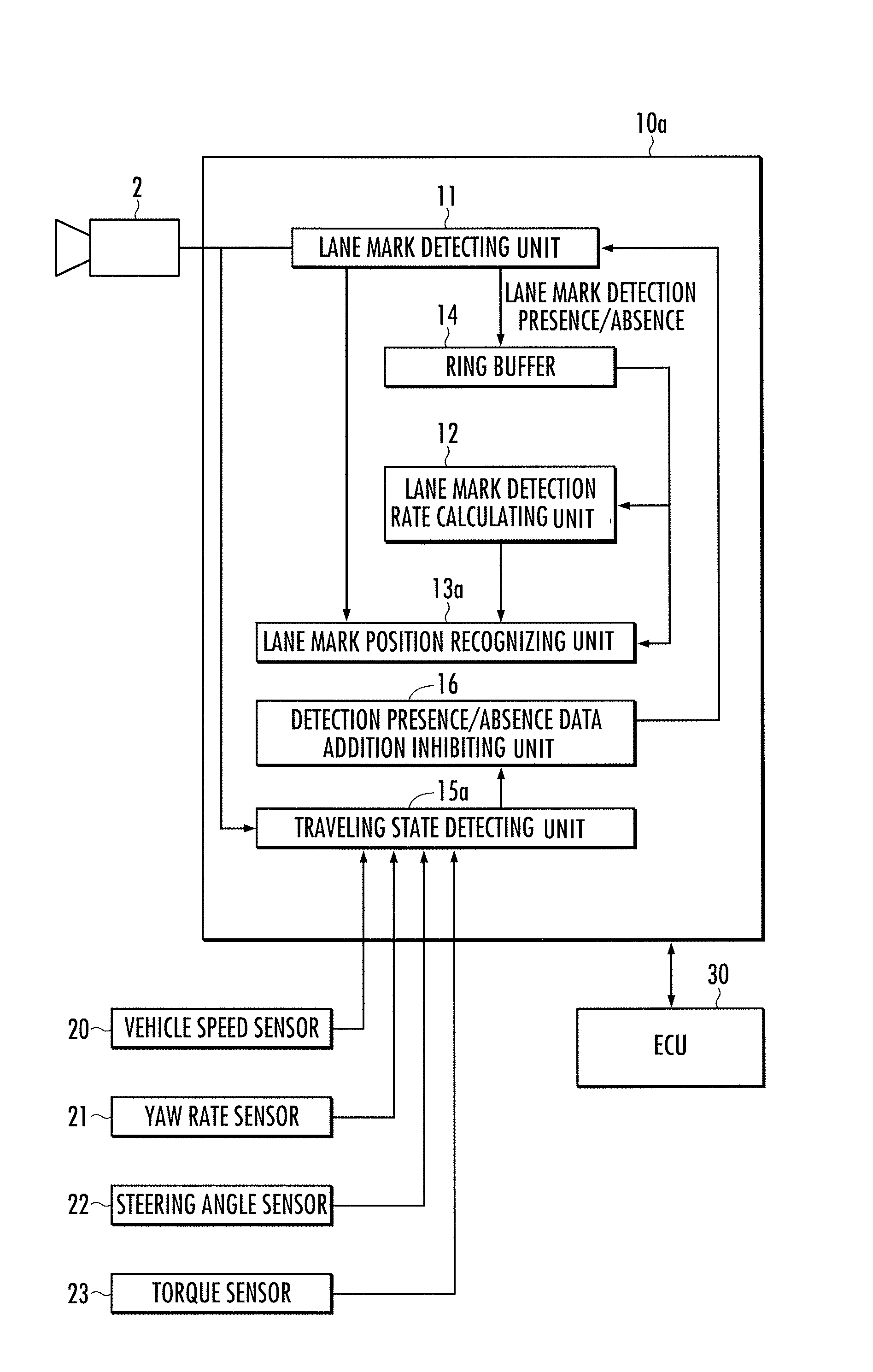
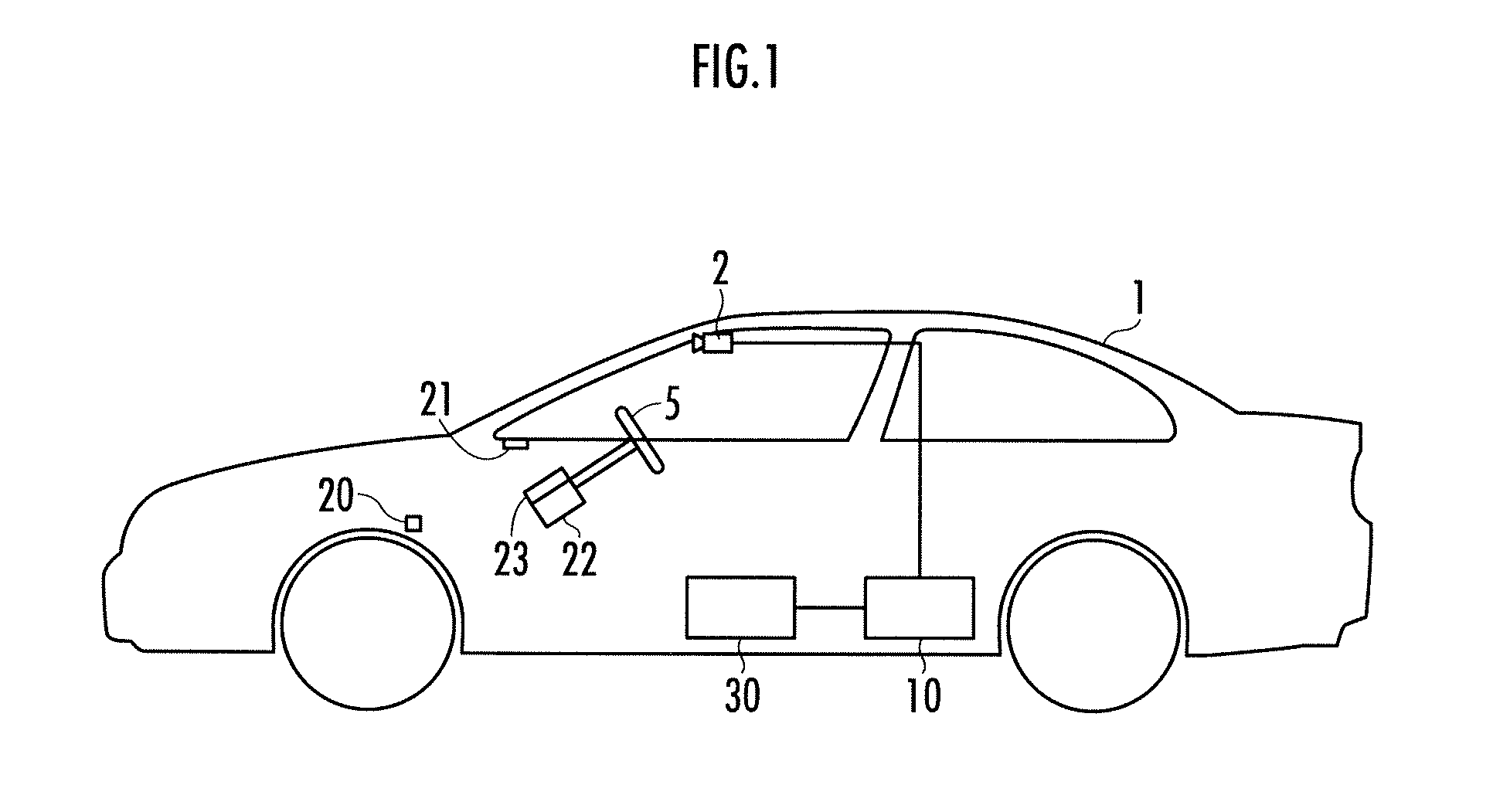
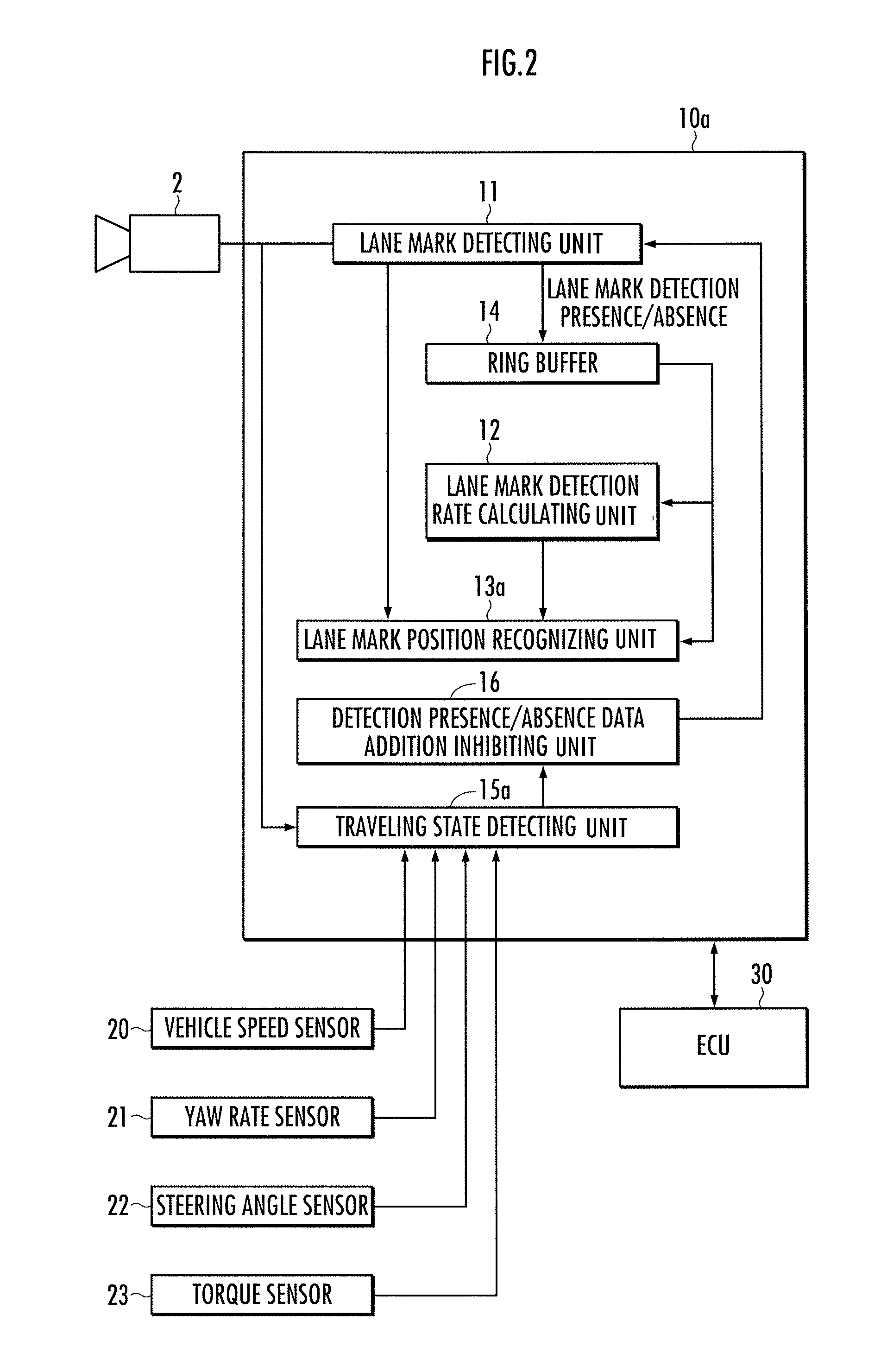
Lane recognition device
ActiveUS20100231718A1Improve reliabilityShorten the overall cycleComputer controlSimulator controlSimulationDetection rate
The lane mark recognition device is equipped with a lane mark detecting unit which executes a lane mark detection process in each predetermined control cycle, and adds a detection presence / absence data to a ring buffer, a detection presence / absence data addition inhibiting unit which inhibits addition of the detection presence / absence data to the ring buffer when the vehicle is traveling in the intersection, and a lane mark position recognizing unit which recognizes a relative position of the vehicle and the lane mark, when the lane mark is detected in the situation where a lane mark detection rate calculated from the data of the ring buffer is higher than a reliability threshold value.
Owner:HONDA MOTOR CO LTD
Method and device for detecting tumbling
ActiveCN102302370AReduce complexityEffective filteringDiagnostic recording/measuringSensorsFeature vectorCharacteristic space
The invention provides a method and device for detecting tumbling. The method provided by the invention comprises the steps of: firstly, collecting behavioral data of a user; secondly, identifying behavior of the user according to the behavioral data of the user; thirdly, segmenting out behavioral switching data from the collected data according to a behavioral identification result, and warping the behavioral switching data into equilong characteristic vectors; and fourthly, performing tumbling detection according to the warped characteristic vectors. According to the method and device provided by the invention, tumbling detection is performed on the basis of behavioral switching, a great amount of normal behavioral data can be filtered, the complexity of a feature space is reduced, the separating capacity of models is enhanced, and the model detection rate is improved.
Owner:INST OF COMPUTING TECH CHINESE ACAD OF SCI
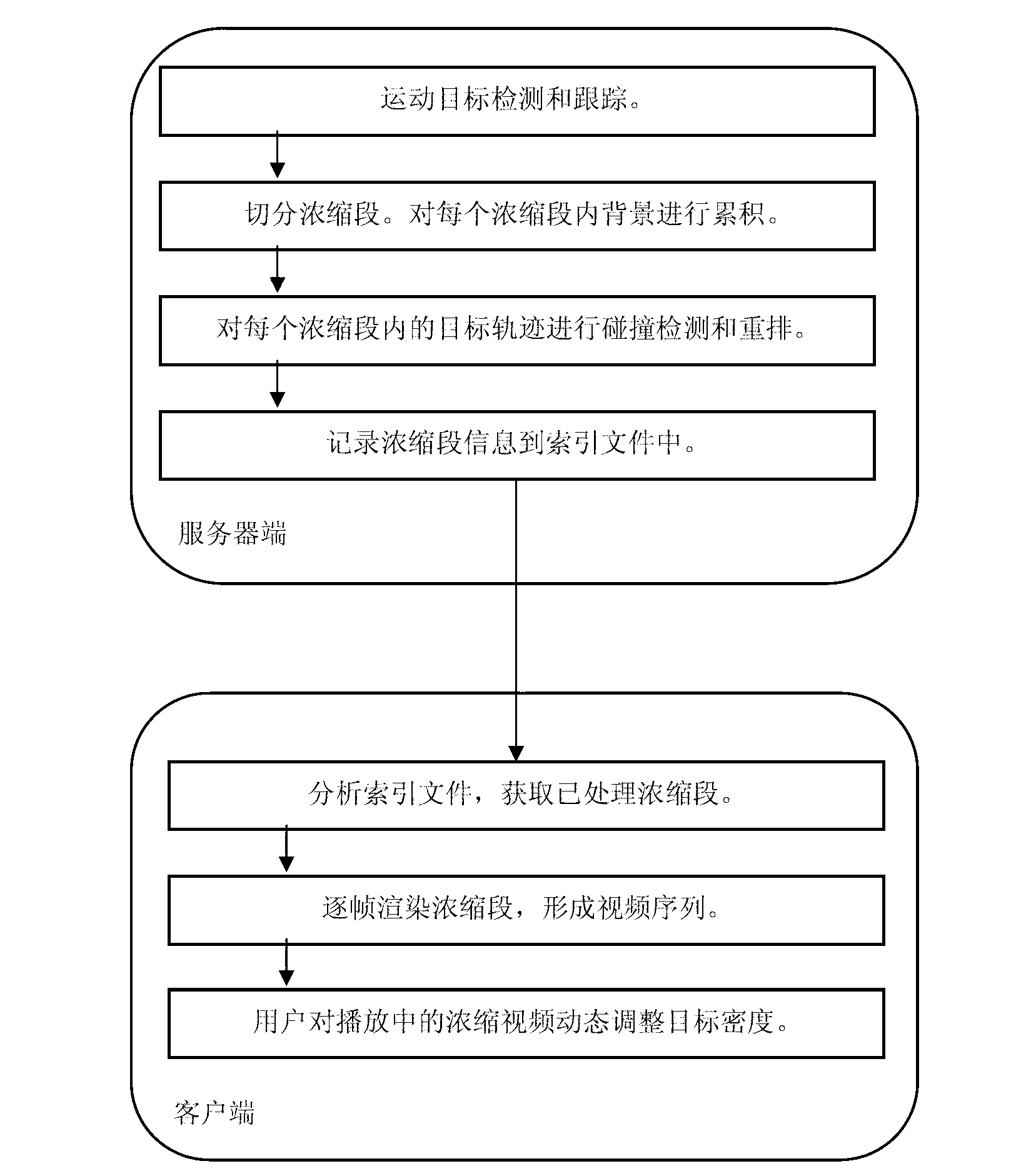
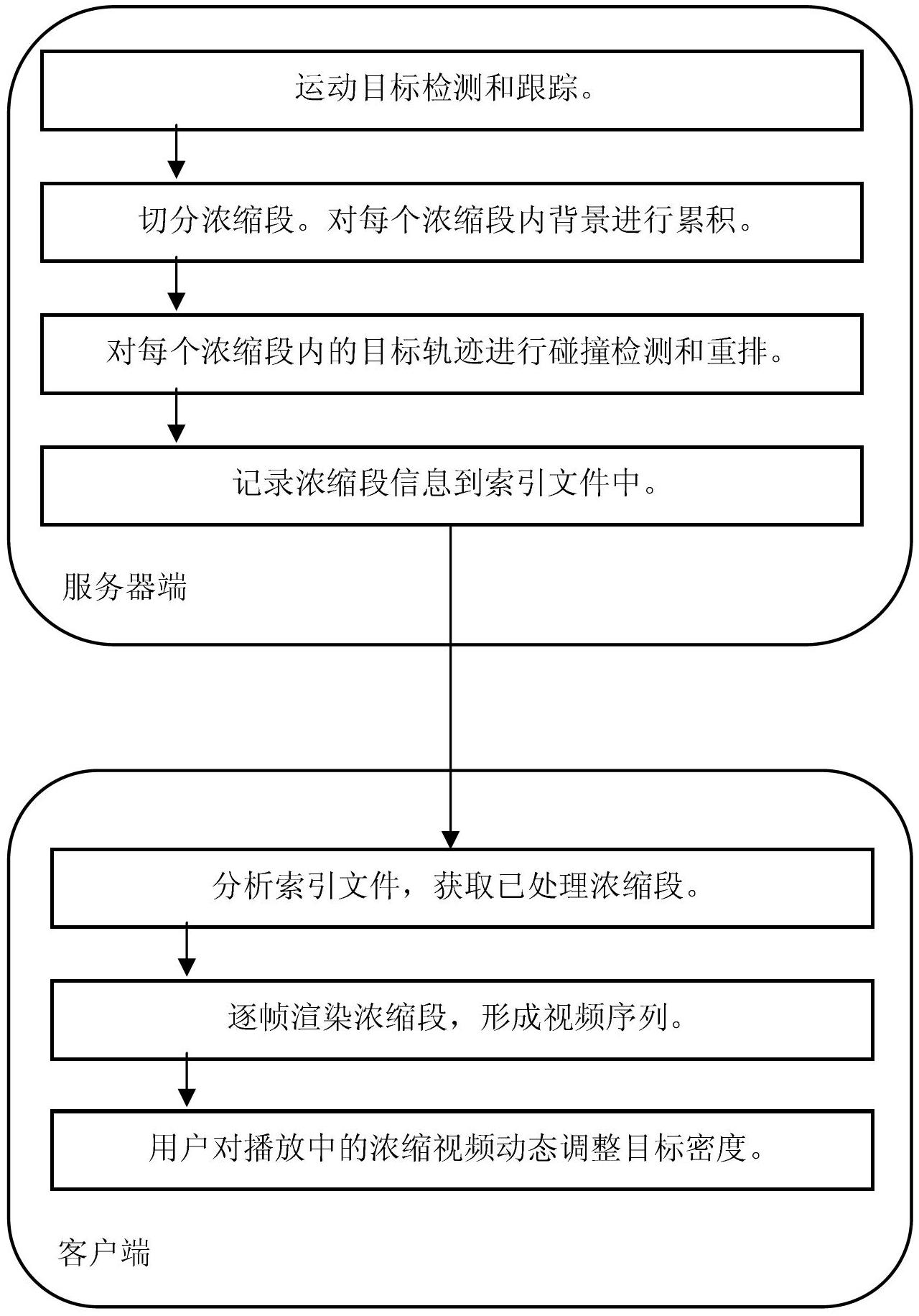
Rapid video concentration abstracting method
ActiveCN102708182AGood tracking target continuityContour area completeSpecial data processing applicationsCollision detectionVideo sequence
The invention relates to a rapid video concentration abstracting method. The conventional video concentration technology is poor in detection rate and tracking rate to a moving target, and cannot effectively concentrate the video length. The rapid video concentration abstracting method is characterized in that a server side detects and tracks the moving target in a pretreatment video, judges according to the length of the video or the number of the detection targets in the video, cuts the video into multiple concentration segments, performs collision detection and rearrangement on the target tracks in each concentration segment, and then, records the concentration segment information and enters in an index file; and a client side analyzes the index file stored in the server side, obtains the treated concentration segments, renders the concentration segments frame by frame to form a video sequence, and dynamically regulates the target density in the played concentrated video. According to the method, the target tracking continuity is excellent, profile region is complete, the detection rate is high, the false detecting rate is low, and the target density at each time point of the concentrated video is substantially consistent.
Owner:ZHEJIANG ICARE VISION TECH
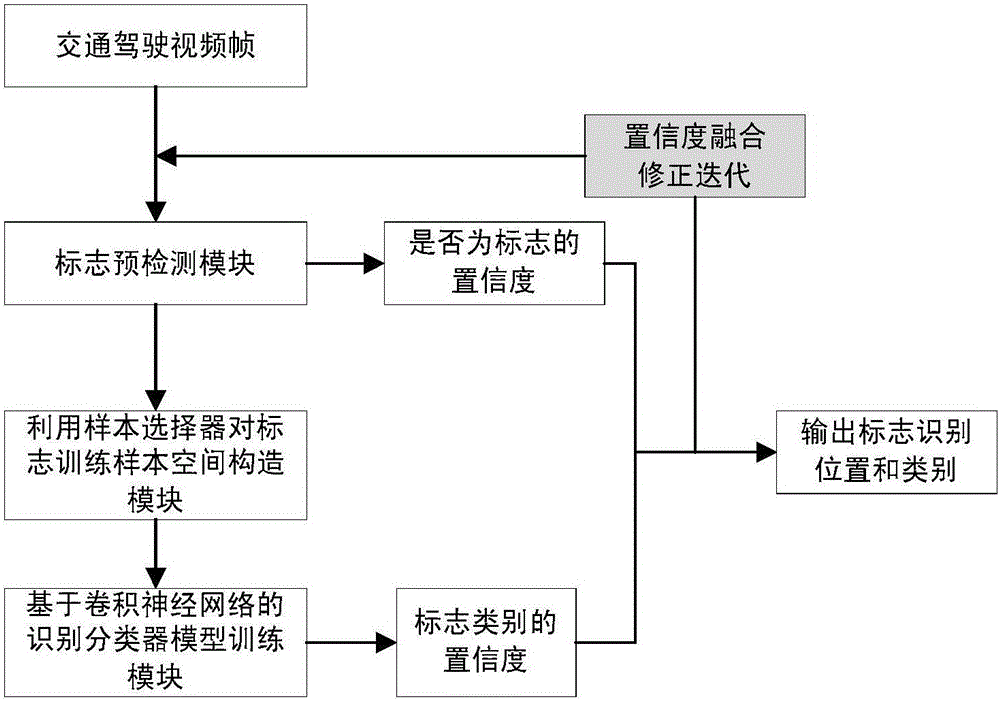
Traffic sign identifying method and traffic sign identifying system based on cascading deep learning
ActiveCN106022300AMake up for the shortcomings of insufficient supervisionImprove detection accuracyCharacter and pattern recognitionTraffic sign recognitionNerve network
The invention provides a traffic sign identifying method and a traffic sign identifying system based on cascading deep learning. By introducing a cascading convolutional neural network idea, expanding target sign sample space, and adding more samples having supervision functions, identification of traffic signs is additionally provided with more apriori information, and then sample space used for training of an identification device has the higher supervision function. The traffic sign identifying method is advantageous in that by fully using the various characteristic information of the signs, the deficiency of the conventional traffic sign identification based on the neural networks is remedied, and therefore the detection rate and the identification rate of the signs are improved.
Owner:INST OF INFORMATION ENG CAS
Multi-measure network abnormity detection method based on relative entropy theory
InactiveCN101645884ASolution rangeResolve detectionData switching networksAnomaly detectionSingle measure
The invention discloses a multi-measure network abnormity detection method based on a relative entropy theory. In the detection method, an integrative relative entropy is obtained by weighting the relative entropy of a plurality of measures to judge network abnormity, thereby avoiding the problem of single-point malfunction of single-measure detection under a certain specific attack; simultaneously, abnormity detection based on the relative entropy is different from the abnormity detection of the flow rate, and the abnormity of the measures can be accurately reflected. The method is concretelyactualized according to the following steps: step 1, selecting and quantifying the measures for abnormity detection; step 2, preprocessing data; step 3, training a sample; step 4, detecting the single-measure relative entropy; step 5, calculating the multi-measure weighting relative entropy; and step 6, displaying an alarm mechanism and a detection result. The technical scheme provided by the method is beneficial to solving the problems of insufficient attack detection range and contravention between the detection rate and the misinformation lowering rate existing in the prior network abnormity detection technique and can provide various network environments, such as a host machine, a local area network, a wide area network and the like, to carry out network circuit abnormity detection.
Owner:XIAN UNIV OF TECH
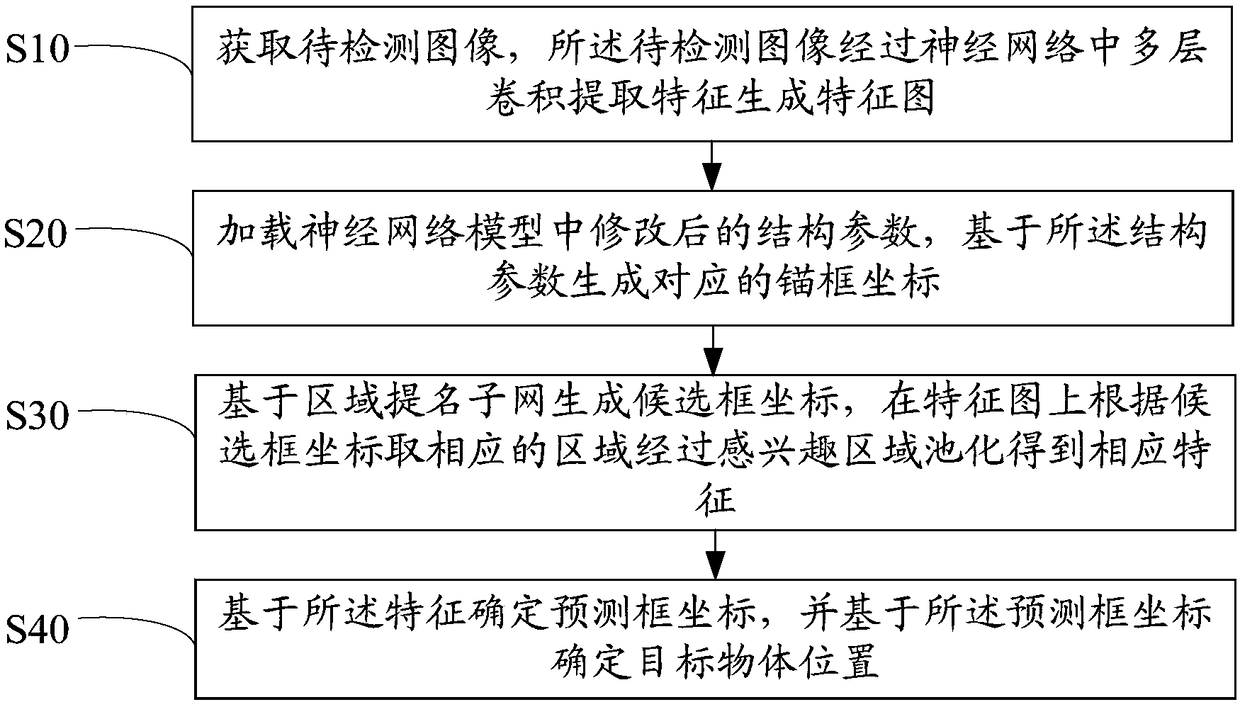
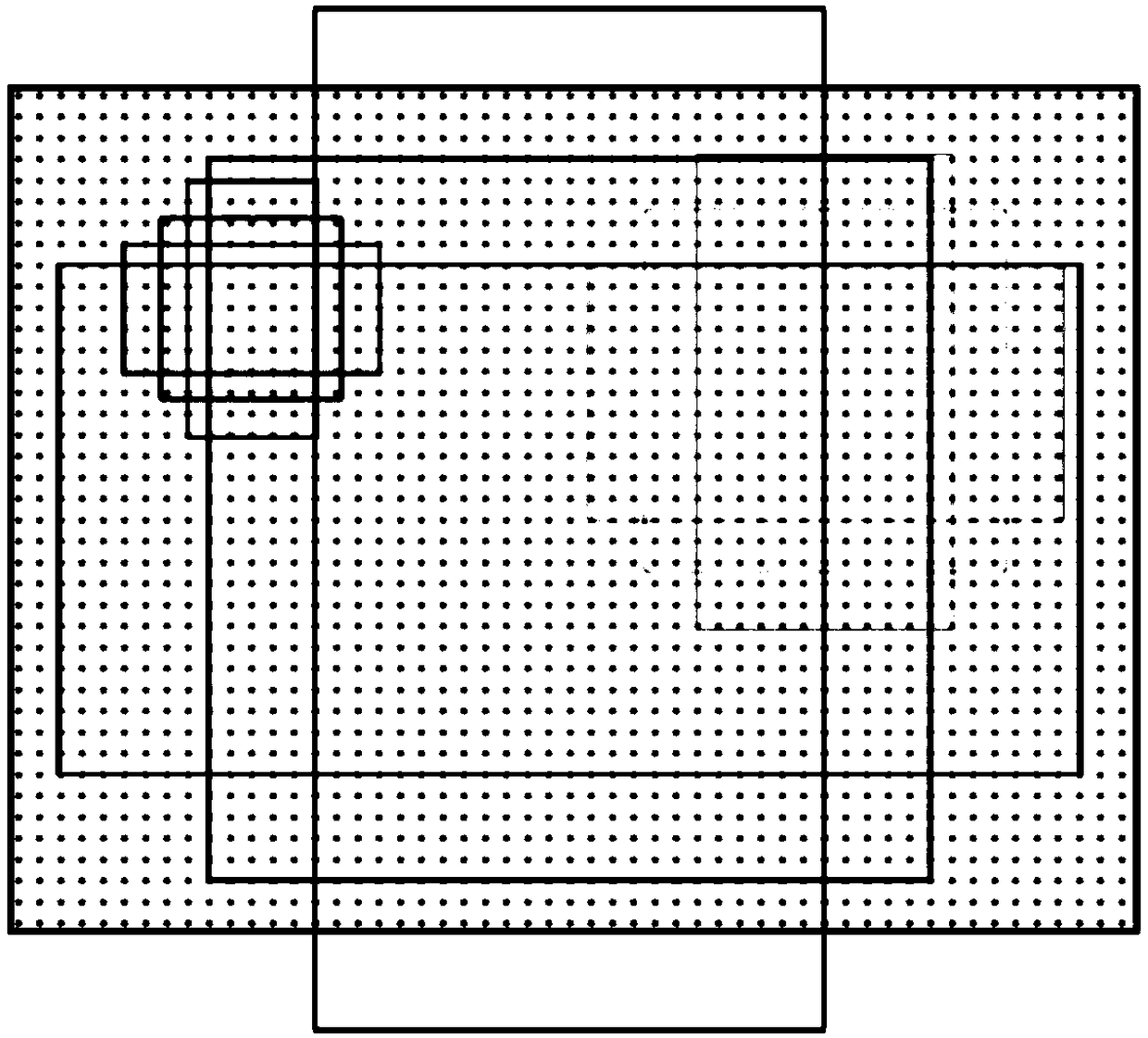
Target detection method and device and computer readable storage medium
InactiveCN108875577AImprove detection rateCharacter and pattern recognitionNeural architecturesNetwork modelSmall target
The invention discloses a target detection method which comprises the following steps of: acquiring a to-be-detected image, wherein the to-be-detected image is subjected to multi-layer convolution extraction of features in a neural network to generate a feature map; loading modified structural parameters in a neural network model, and generating corresponding anchor box coordinates on the basis ofthe structural parameters, wherein the preset structural parameters comprise a reference dimension of an anchor box, an anchor box scale and a length-width ratio of the anchor box; generating candidate box coordinates on the basis of a region nomination subnet, taking a corresponding region on the feature map according to the candidate coordinates, and by pooling of a ROI (Region Of Interest), obtaining corresponding features; and on the basis of the features, determining prediction box coordinates, and on the basis of the prediction box coordinates, determining a target object position. Theinvention further discloses a target detection device and a computer readable storage medium. According to the invention, a case of generating an optimized prediction box to determine a target objectis implemented, a small target can be detected, and a detection rate for the target is improved.
Owner:SHENZHEN ECHIEV AUTONOMOUS DRIVING TECH CO LTD
Pedestrian detection method based on video monitoring
ActiveCN101887524AThe detection process is fastImprove detection accuracyImage enhancementCharacter and pattern recognitionVideo monitoringSupport vector machine
The invention discloses a pedestrian detection method based on video monitoring, which comprises the following steps of: rapidly detecting a pedestrian by utilizing an expanded gradient histogram characteristic and an Adaboost algorithm, and then further identifying and verifying the detected pedestrian by utilizing the gradient histogram characteristic and a support vector machine. In the invention, experiments based on a standard pedestrian database indicate that the method not only can greatly reduce the detection time, but also markedly improves the detection rate. As one of key technologies of target detection, pedestrian detection has broad application prospect in the fields of video monitoring safety, intelligent traffic management and the like.
Owner:HUNAN CHUANGHE FUTURE TECH CO LTD
Target space knowledge and two-stage prediction learning-based target detection method
ActiveCN107871119AIncrease the number ofIncrease diversityScene recognitionVisual perceptionFalse alarm
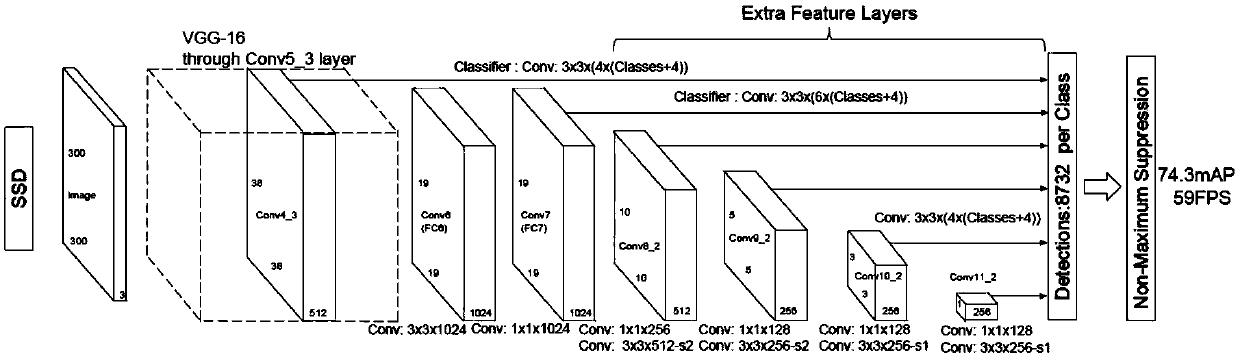
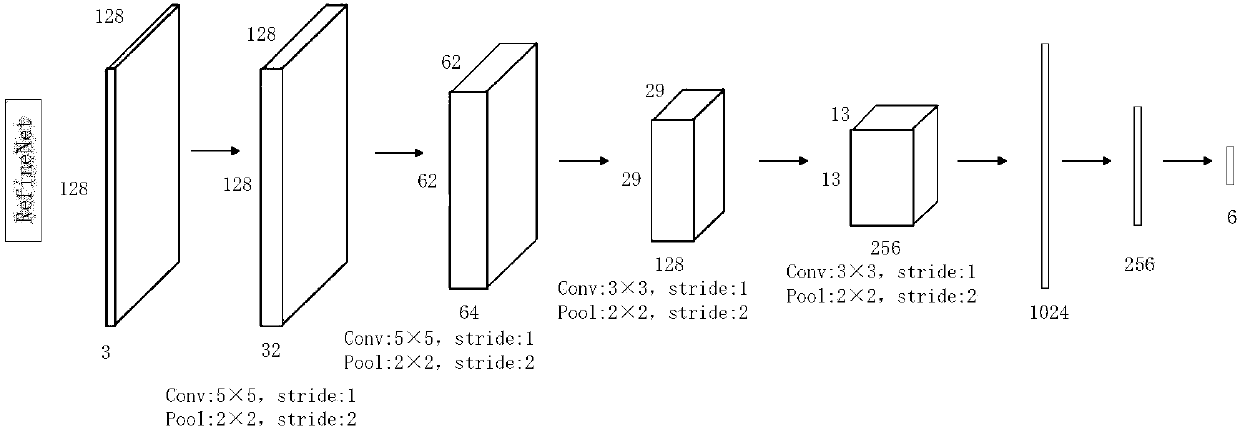
The invention discloses a target space knowledge and two-stage prediction learning-based target detection method. By utilizing various data conversion methods, a sample number is increased and samplediversity is improved; two deep neural networks including SSD and newly designed RefineNet are trained; for a prediction target with a relatively high probability in a primary prediction result of theSSD, the accuracy of judgment is further improved through the RefineNet; and by establishing peculiar spatial structure constraint rules of the target, the wrong prediction is reduced, thereby obtaining a final detection result. Compared with a few existing methods, the method provided by the invention has the advantages that visual and spatial characteristics of a remote sensing target are considered at the same time; and end-to-end target candidate selection, feature extraction and classified locating are realized by utilizing the deep networks with excellent feature extraction capabilities, so that the detection rate of the remote sensing target is remarkably increased and the false alarm rate is reduced.
Owner:XIDIAN UNIV
Marker for detecting colon and rectum cancer as well as detection method, kit and biological chip thereof
InactiveCN101988060AEasy to storeWide detection rangeMicrobiological testing/measurementDNA/RNA fragmentationBULK ACTIVE INGREDIENTBlood plasma
The invention relates to a marker for detecting colon and rectum cancer by utilizing 86 specific ribonucleic acids stably existing in the serum / plasma of a human body, as well as a method, a relevant kit and a biological chip for detecting the marker. The method can be used in the aspects of diagnosing and differentially diagnosing the colon and rectum cancer and predicting the generation and the recurrence of the complications of diseases, evaluating the curative effect, screening the active ingredients in drugs, evaluating the drug effect and the like, and has the advantages of wide detection pedigree, high sensitivity and low detection cost, material is convenient for obtainment, samples are easy to store and the like. The method can be widely used for generally surveying the colon and rectum cancer and relevant work and improving low specificity and low sensitivity which are brought by the individual difference difficultly and are difficult to overcome by the single marker, thereby obviously enhancing the clinical detection rate of the colon and rectum cancer and becoming an effective means for early diagnosing the colon and rectum cancer.
Owner:JIANGSU MICROMEDMARK BIOTECH
Semi-supervised anomaly intrusion detection method
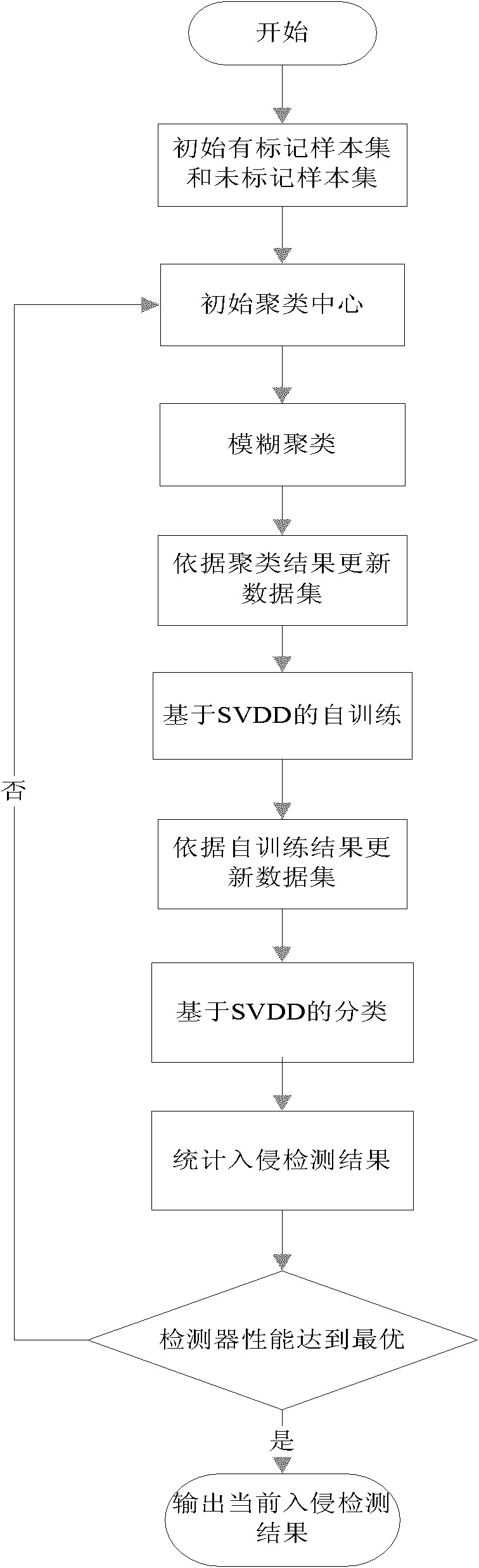
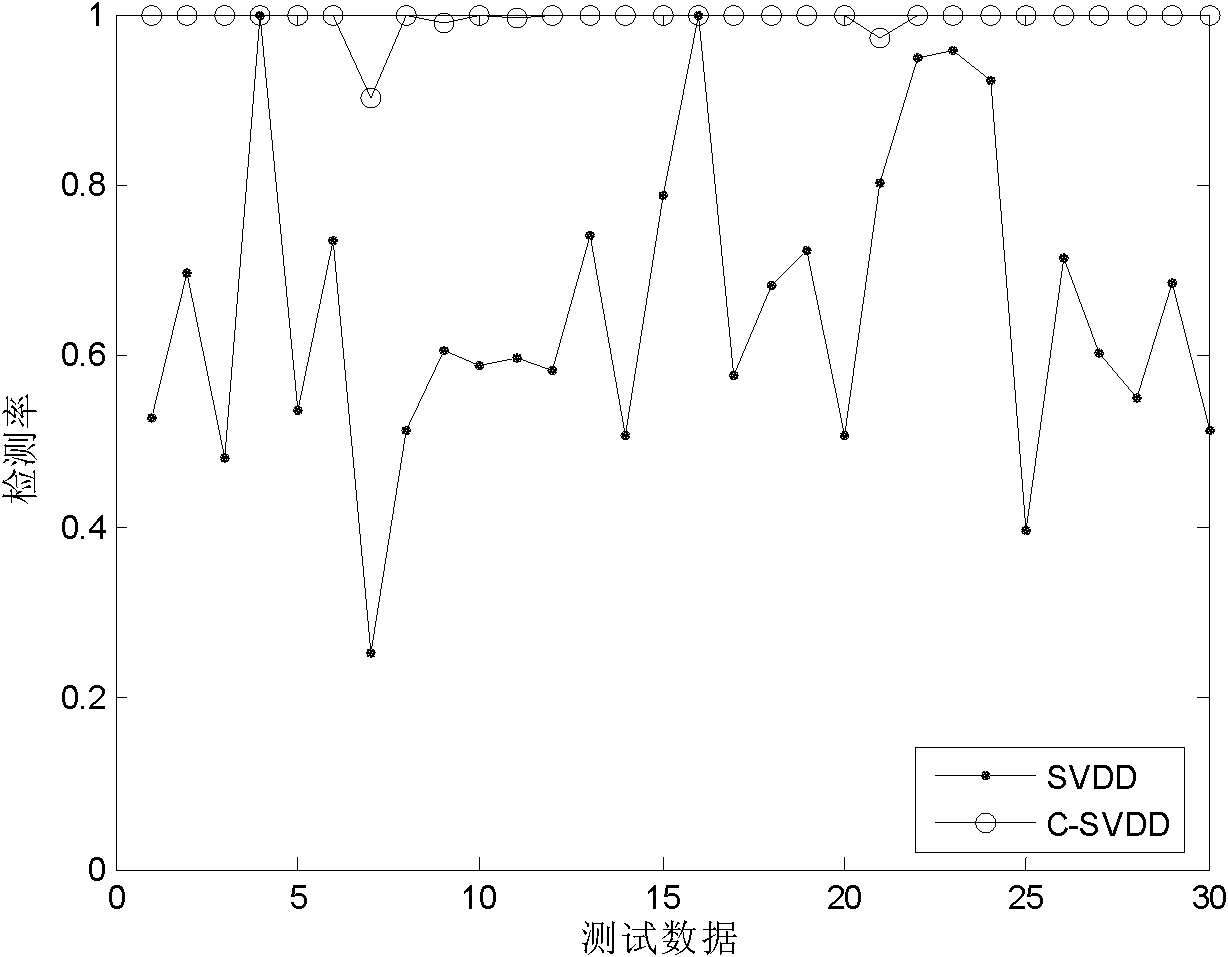
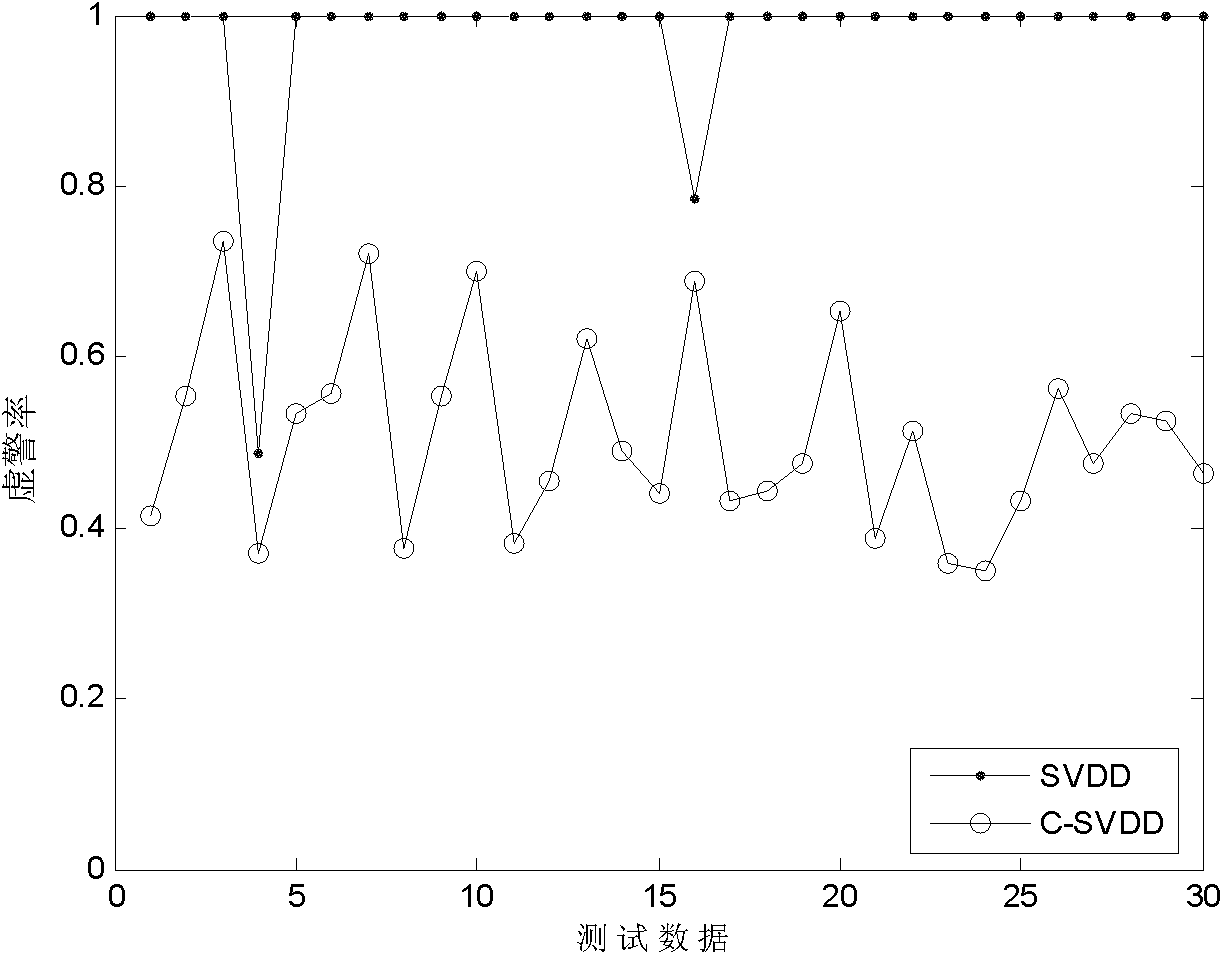
InactiveCN101980480AReduce troubleImprove detection rateData switching networksSelf trainingFuzzy clustering
The invention discloses a fuzzy clustering and support vector domain description-based (SVDD) semi-supervised anomaly intrusion detection method, which is mainly used for solving the problems of low intrusion detection data detection rate and high false alarm rate in the prior art. The method comprises the following steps of: (1) initializing a labeled sample set and an unlabeled sample set; (2) initializing a clustering center; (3) carrying out fuzzy C-mean clustering; (4) updating the labeled sample set and the unlabeled sample set according to a clustering result; (5) carrying out SVDD-based self-training; (6) updating the labeled sample set and the unlabeled sample set according to a self-training result; (7) carrying out SVVD-based classification; and (8) evaluating and outputting anintrusion detection result. The method improves the detection rate and reduces the false alarm rate at the same time, and can be used for a real-time intrusion detection system in which training dataonly contains less normal data.
Owner:XIDIAN UNIV
Telcom phone phishing-resistant method and system based on discrimination and identification content analysis
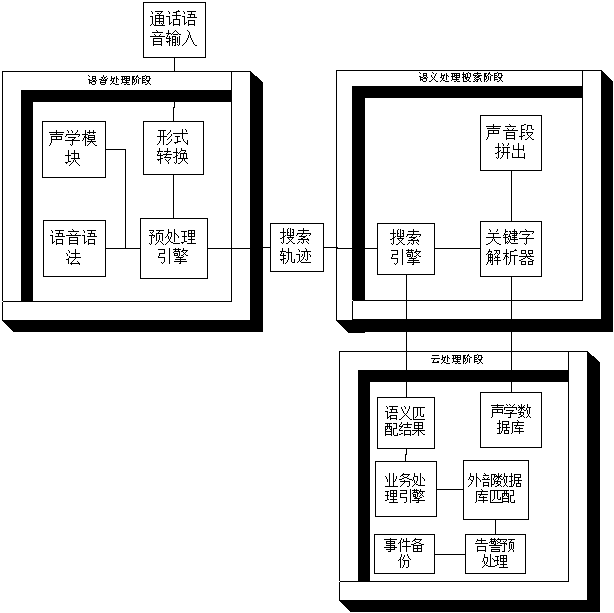
InactiveCN103179122ARealize identificationTransmissionSecurity arrangementInformation miningPhishing
The invention relates to a telcom phone phishing-resistant method and a telcom phone phishing-resistant system based on discrimination and identification content analysis. By improving the efficiency and the accuracy rate of the voice and semanteme identification during calling, and using a Chinese semanteme determining technology, the cold call transmitter is determined whether or not to be a phishing call. The method specifically comprises the following steps of: analyzing the voice by large vocabulary provided by the invention and the large vocabulary continuous speech recognition (LVCSR) of nonspecific person during calling between two parts, determining the analyzed key words or key numbers, constructing a strategy engine by an algorithm, analyzing and classifying the semanteme of a calling party at a cloud service side by the algorithm, analyzing key information in the voice, synchronously matching the information of the bank to which the calling person belongs, and determining whether or not the call is the phishing call. Generally speaking, according to the method, the happening of the phone phishing can be effectively avoided particularly, the user safety can be protected through the discrimination and identification identifying and determining mode and the cloud platform information mining and matching mode, and the voice identification and the suspicious call relevance ratio can meet the normal use as well.
Owner:马博
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com