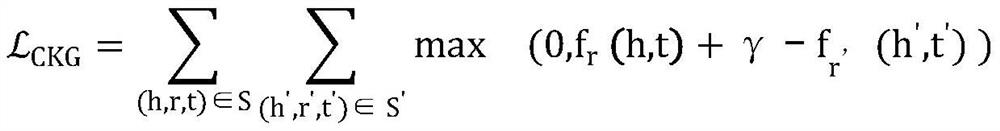Patents
Literature
2202 results about "Behavioral data" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
System and method for an electronic product advisor
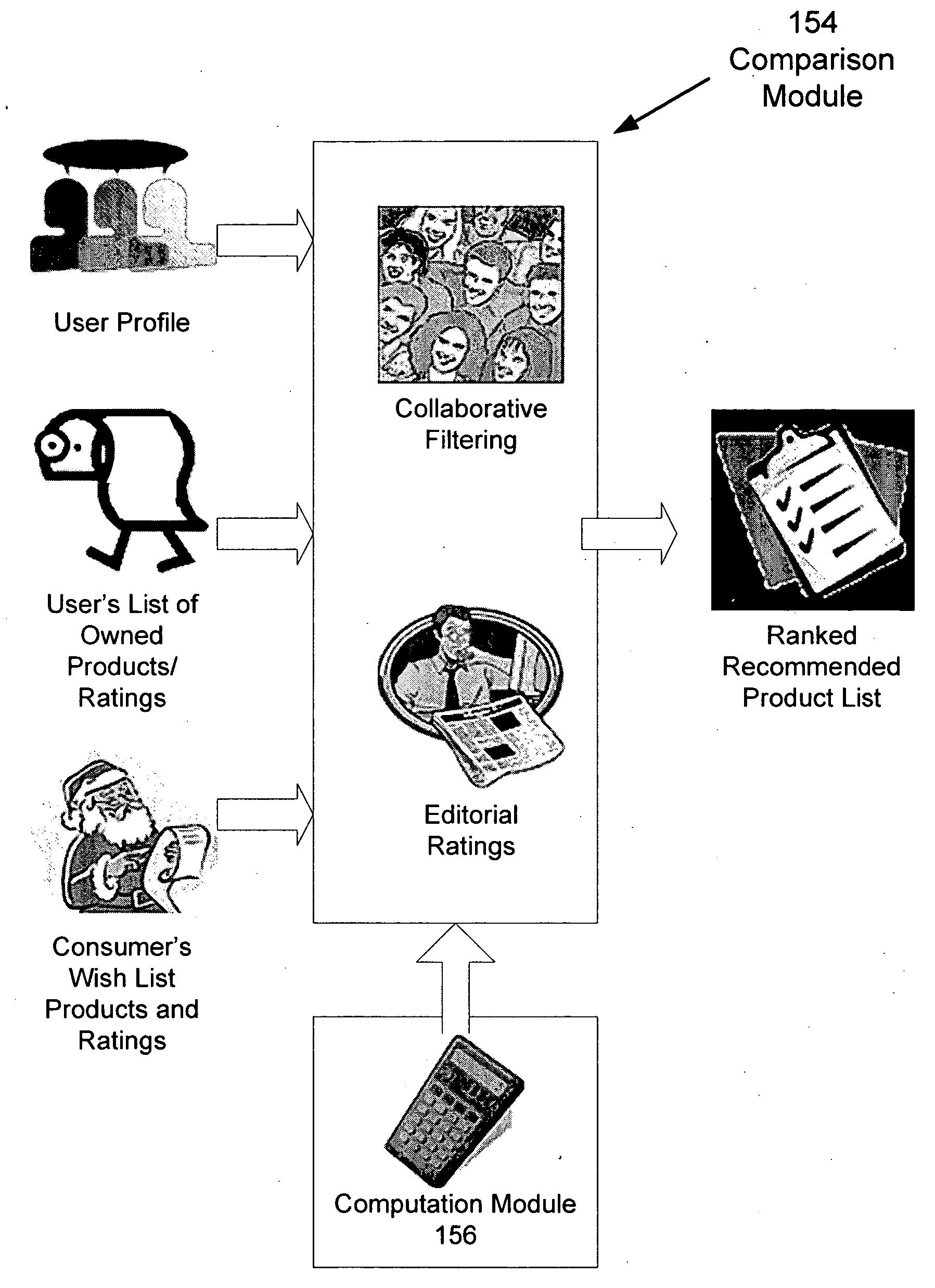
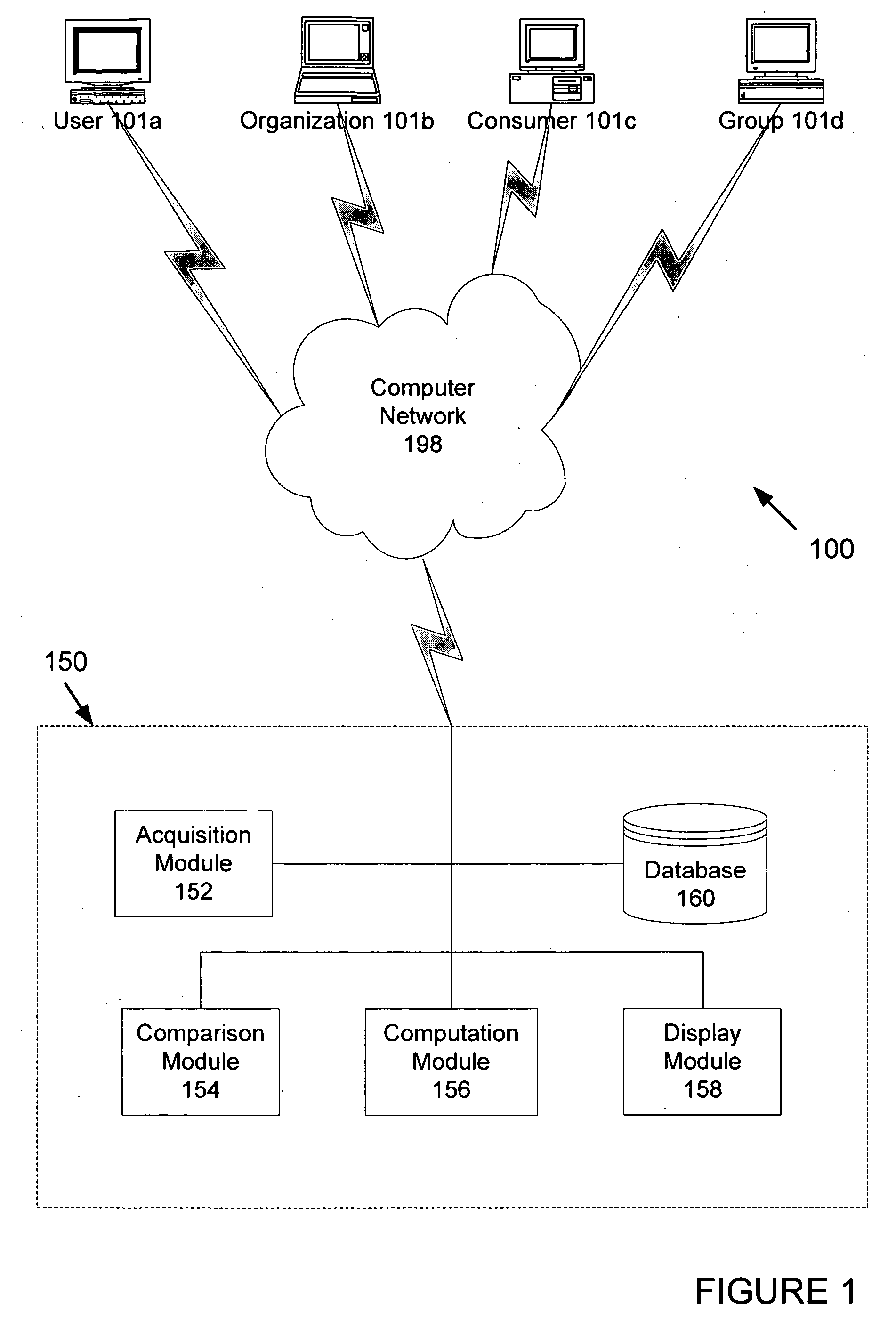
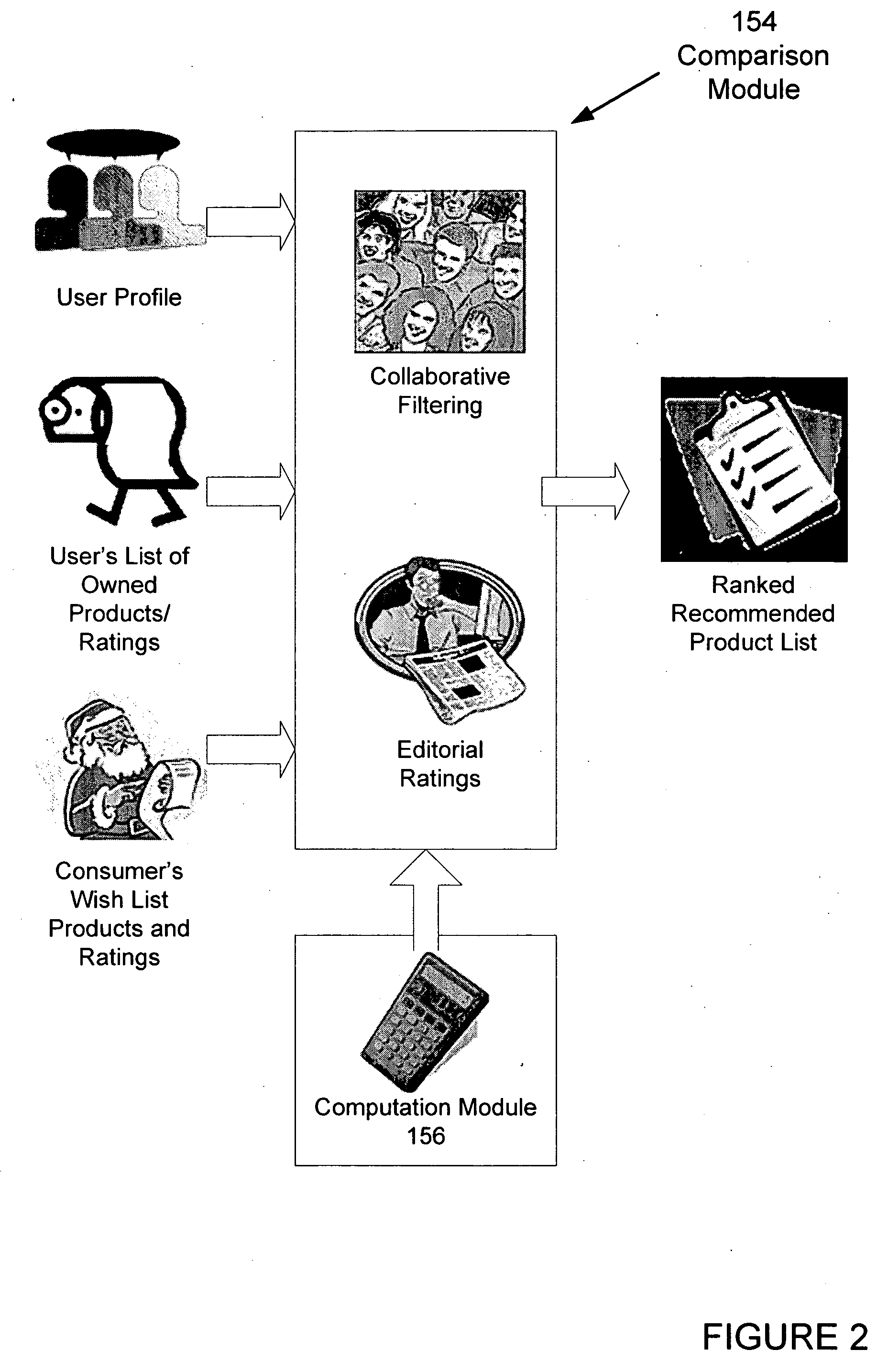
A system and method operates on a client device and acquires a suspect list of user products based on information derived from the client device. The system normalizes the list, and the user confirms the accuracy of the product list. The user product list is sent to a server where the user product list is compared to other lists using collaborative filtering techniques. The collaborative filtering techniques determine products of interest for the use and the level of interest of the user. The system computes a similarity measure based upon the number of similar products that match the user's product list and rankings provided by the user and others. Demographic and behavioral data may also be used in performing the comparison and the similarity measure. The system acquires editorial rankings of products from other users and provides a ranked list of recommended products based upon the editorial rankings.
Owner:CBS INTERACTIVE INC
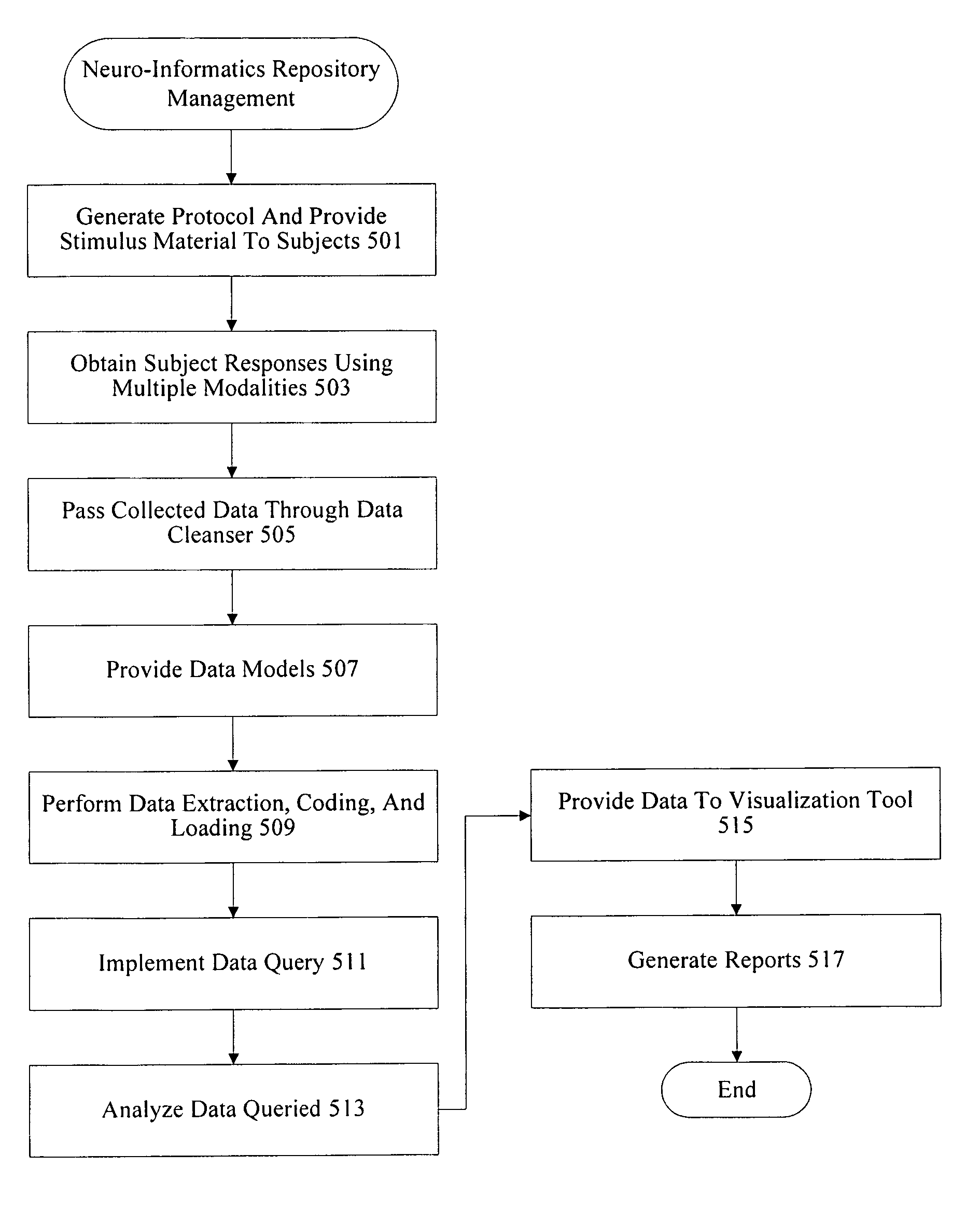
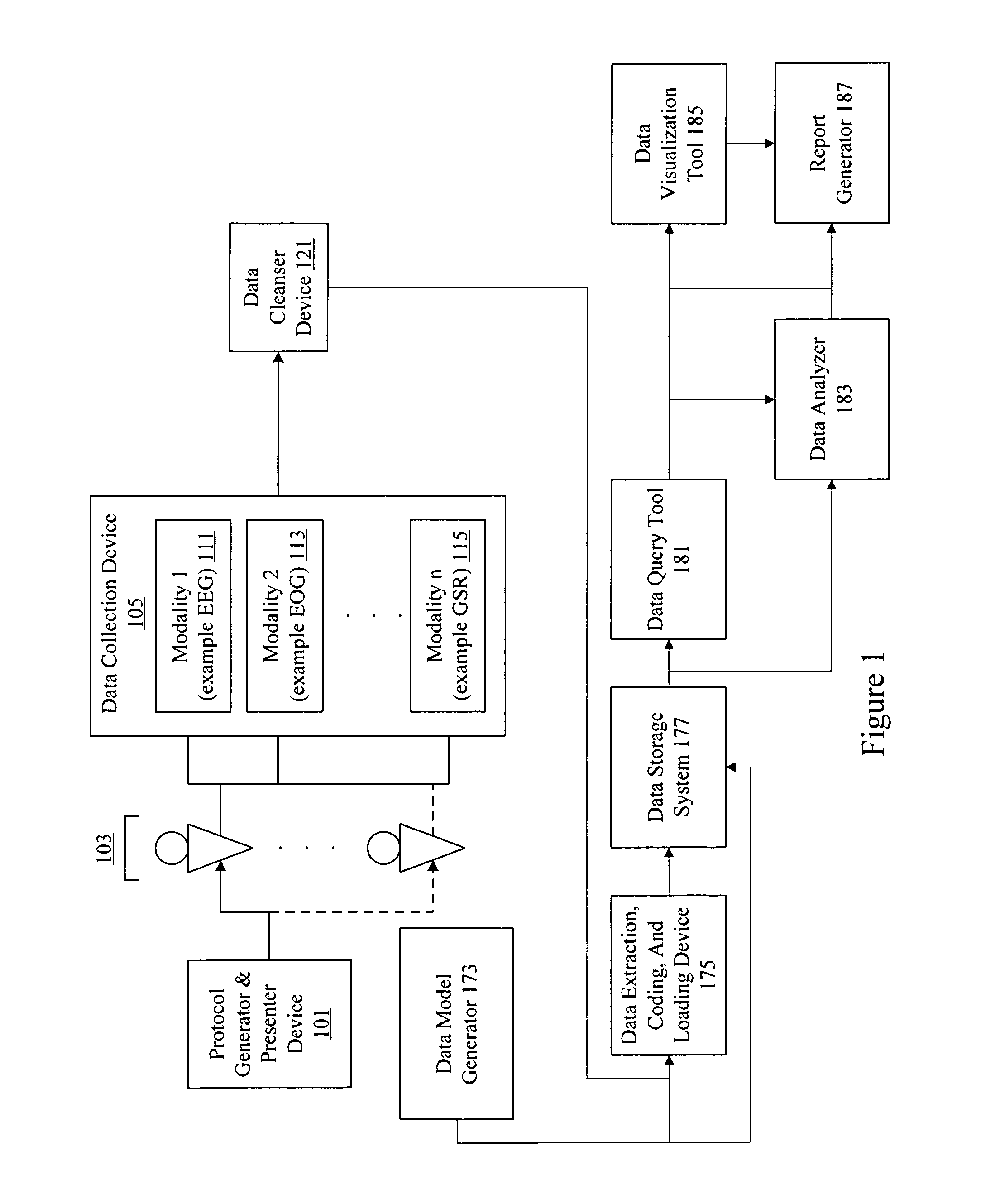
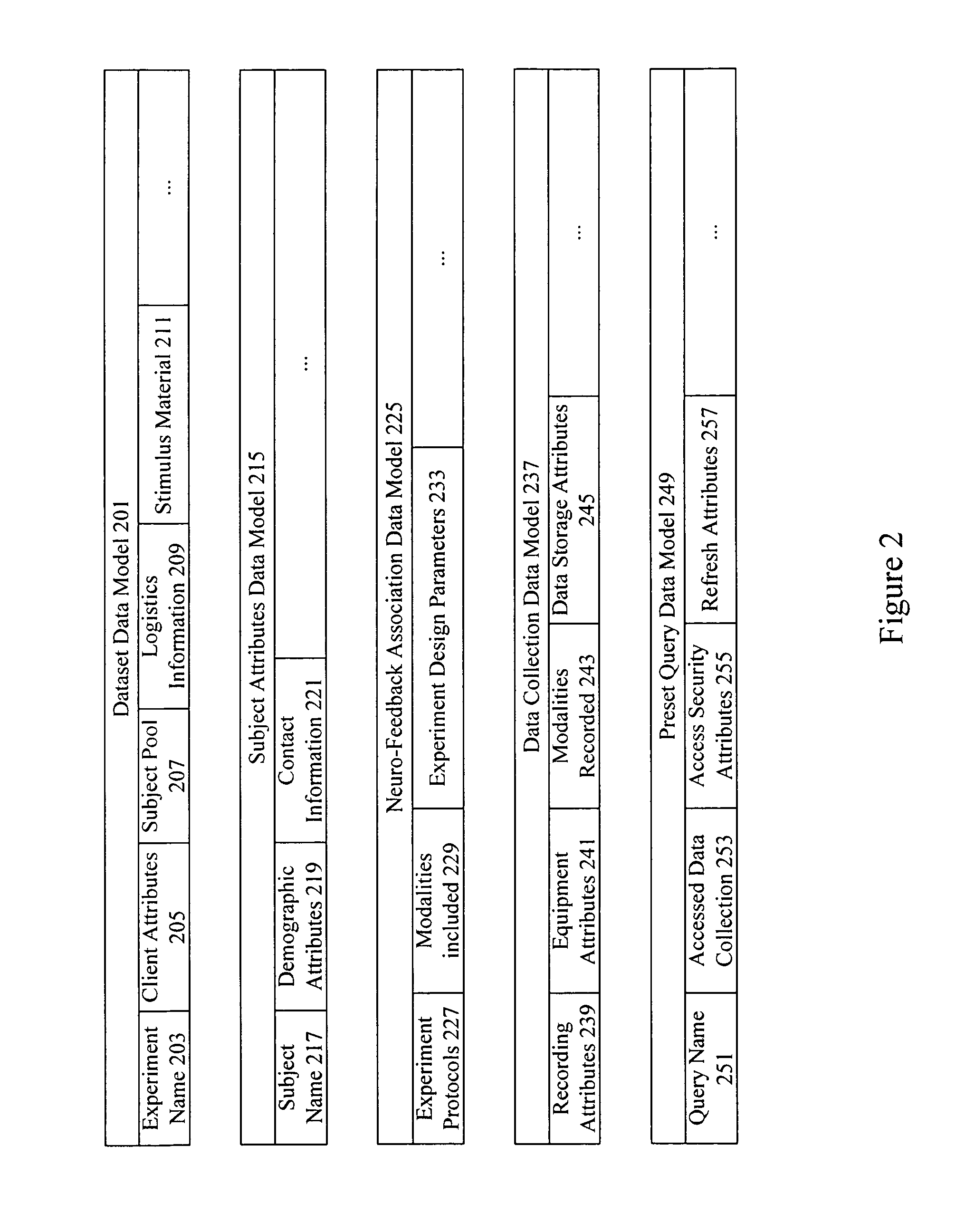
Neuro-informatics repository system
ActiveUS20090030930A1ElectroencephalographyMedical simulationDiagnostic Radiology ModalityInformation repository
A neuro-informatics repository system is provided to allow efficient generation, management, and access to central nervous system, autonomic nervous system, effector data, and behavioral data obtained from subjects exposed to stimulus material. Data collected using multiple modalities such as Electroencephalography (EEG), Electrooculography (EOG), Galvanic Skin Response (GSR), Event Related Potential (ERP), surveys, etc., is stored using a variety of data models to allow efficient querying, report generation, analysis and / or visualization.
Owner:NIELSEN CONSUMER LLC
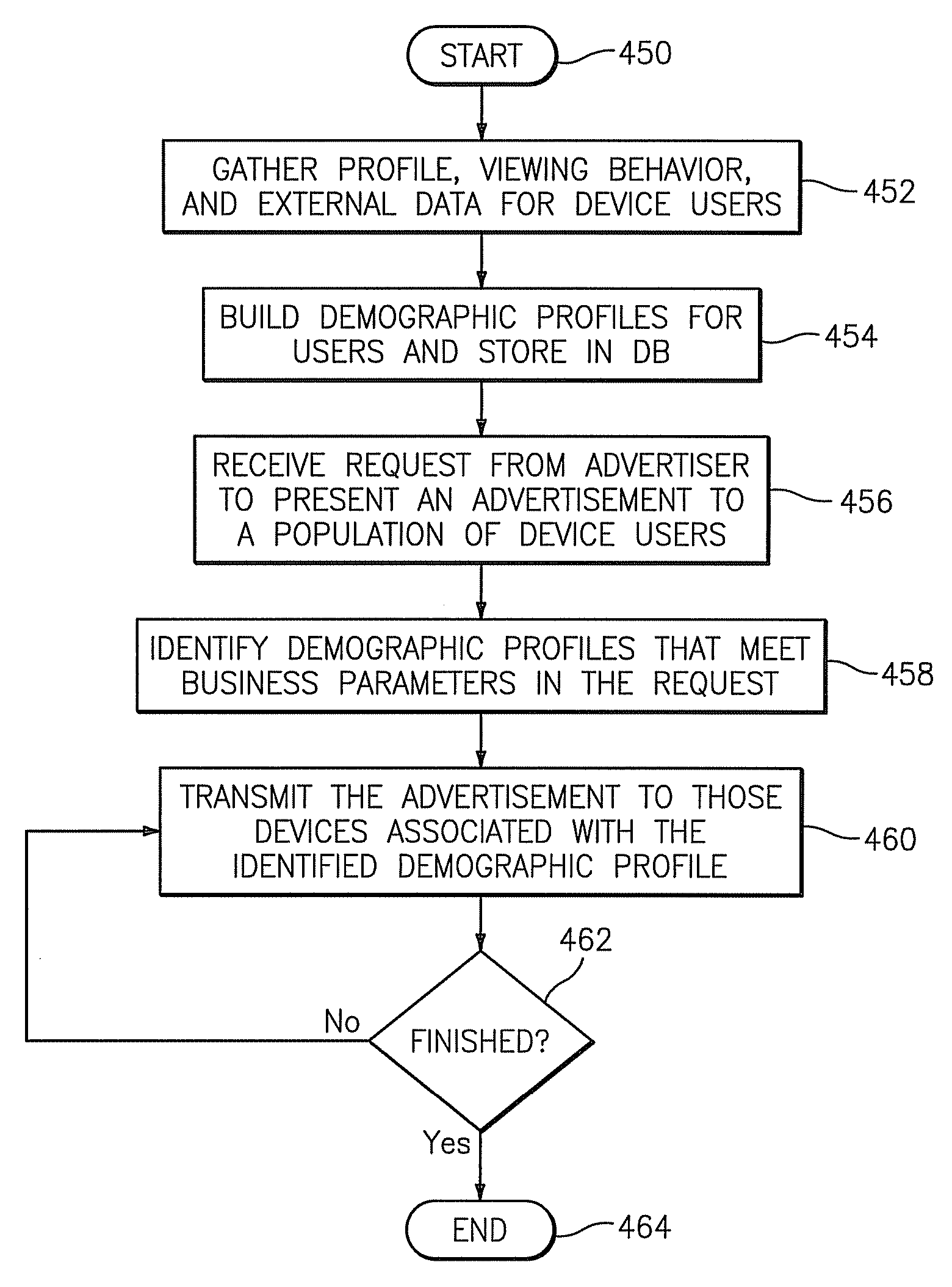
Methods, systems, and computer program products for providing targeted advertising to communications devices
InactiveUS20070208619A1Selective content distributionElectrical cable transmission adaptationExternal dataDemographic data
A method, system, and computer program product for providing targeted advertising services are provided. The method includes gathering profile data, behavior data, and external data for users of communications devices accessing content over a network. The method also includes creating a database of demographic profiles based on the gathered data, receiving a request from an advertising entity to present an advertisement to a population of the communications devices based upon a set of business parameters, and identifying a demographic profile in the database that satisfies criteria set forth in the business parameters. The method further includes transmitting the advertisement to the communications devices associated with the demographic profile that satisfies the criteria set forth in the business parameters.
Owner:BELLSOUTH INTPROP COR
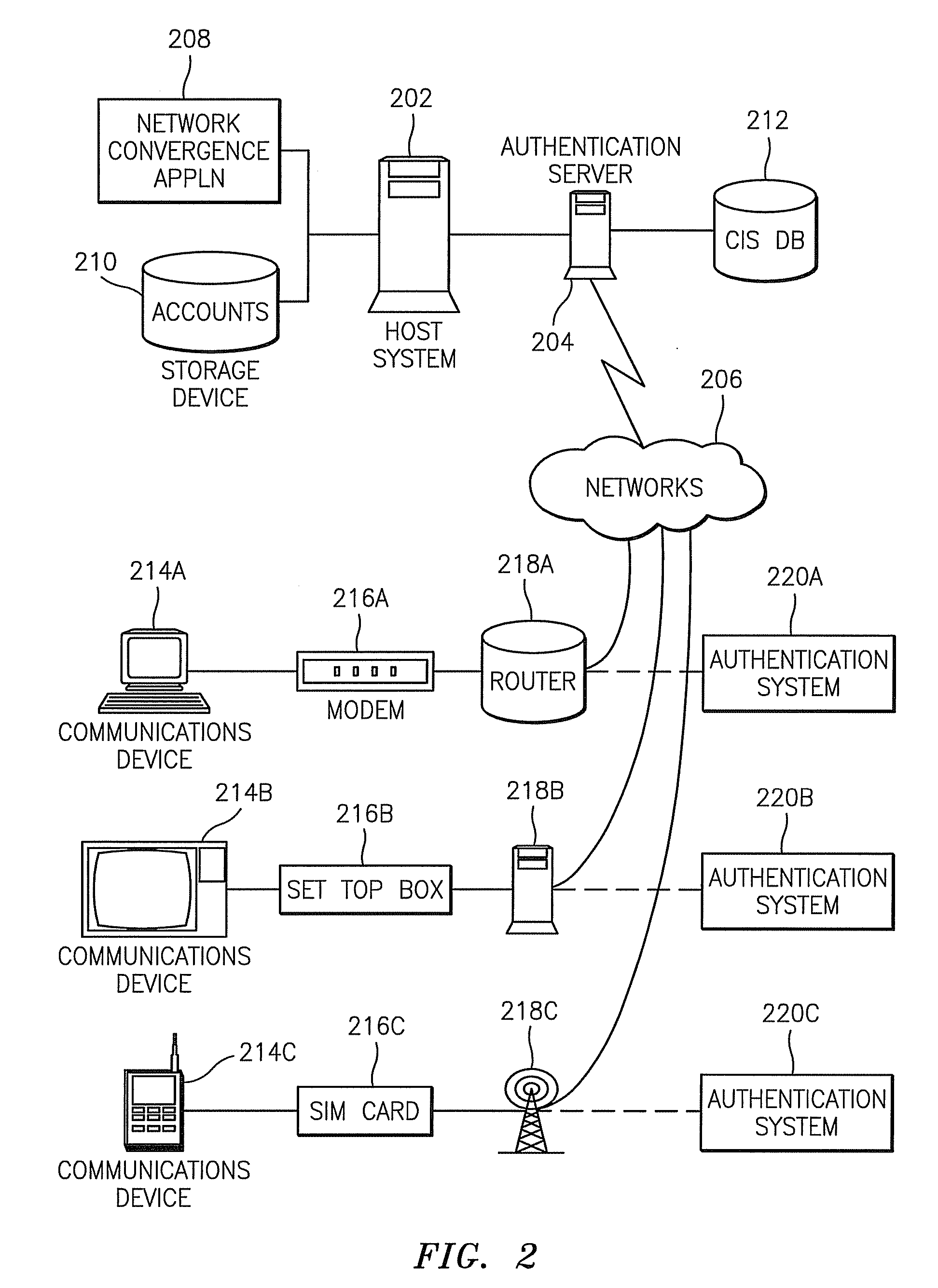
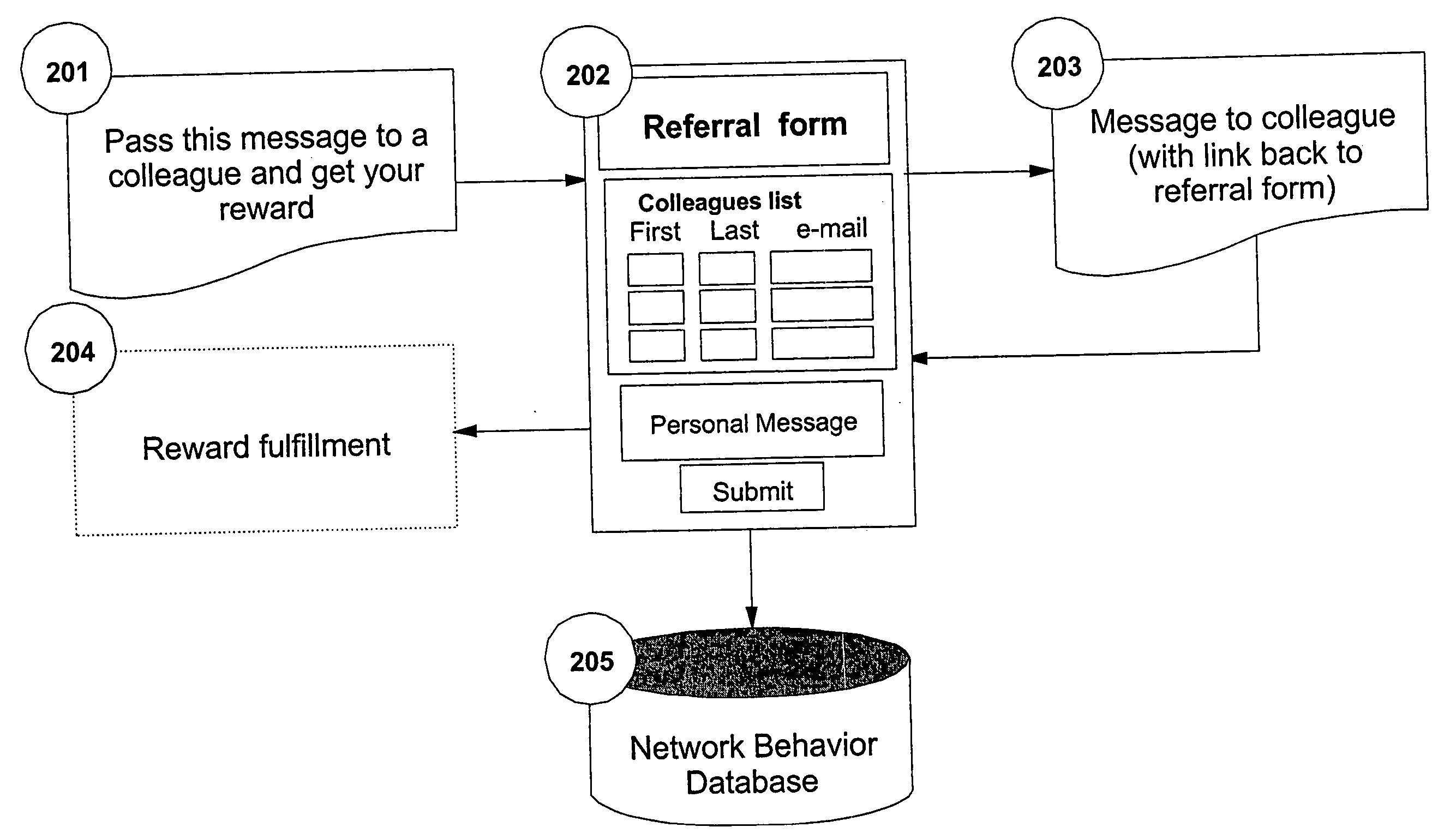
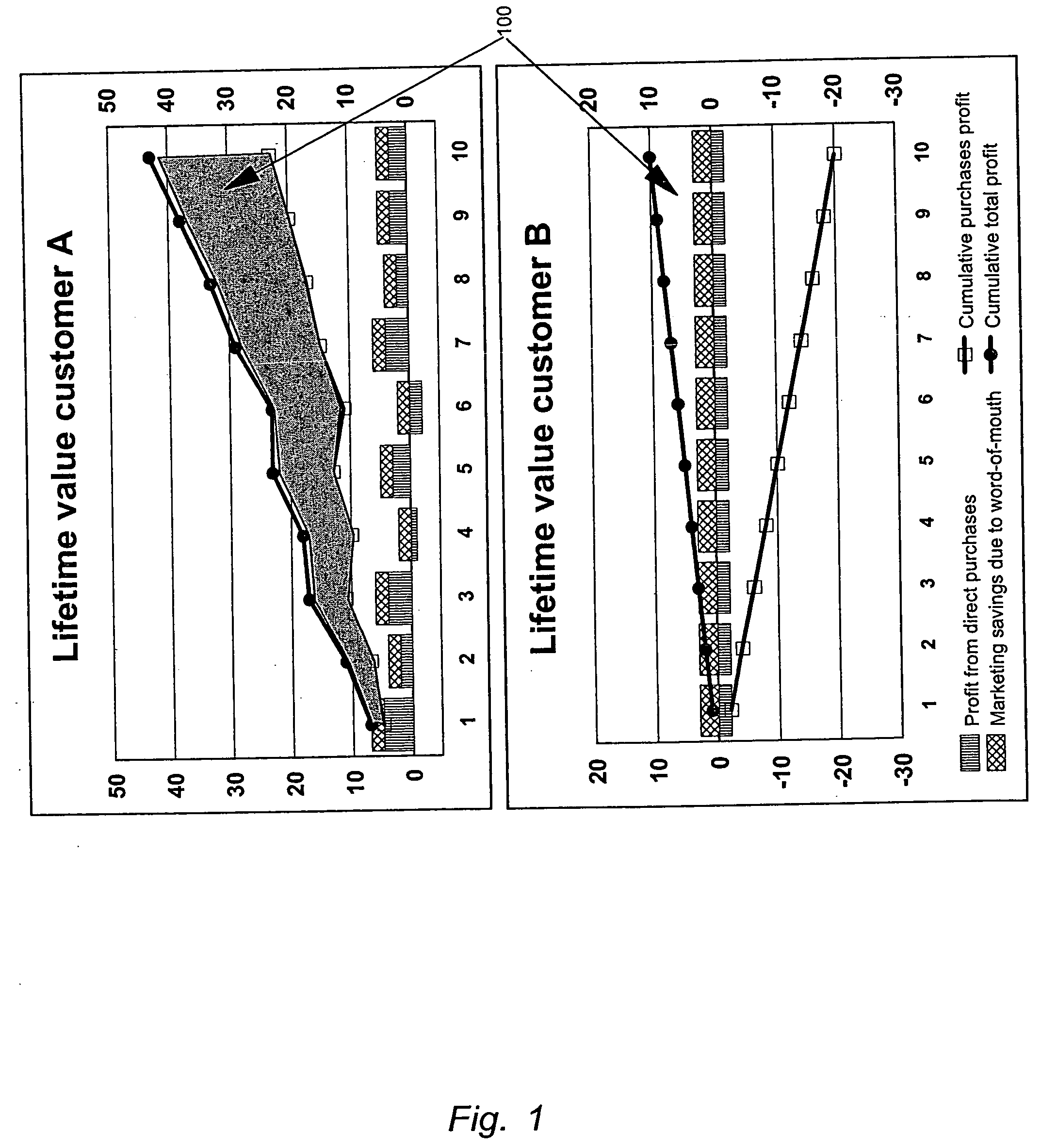
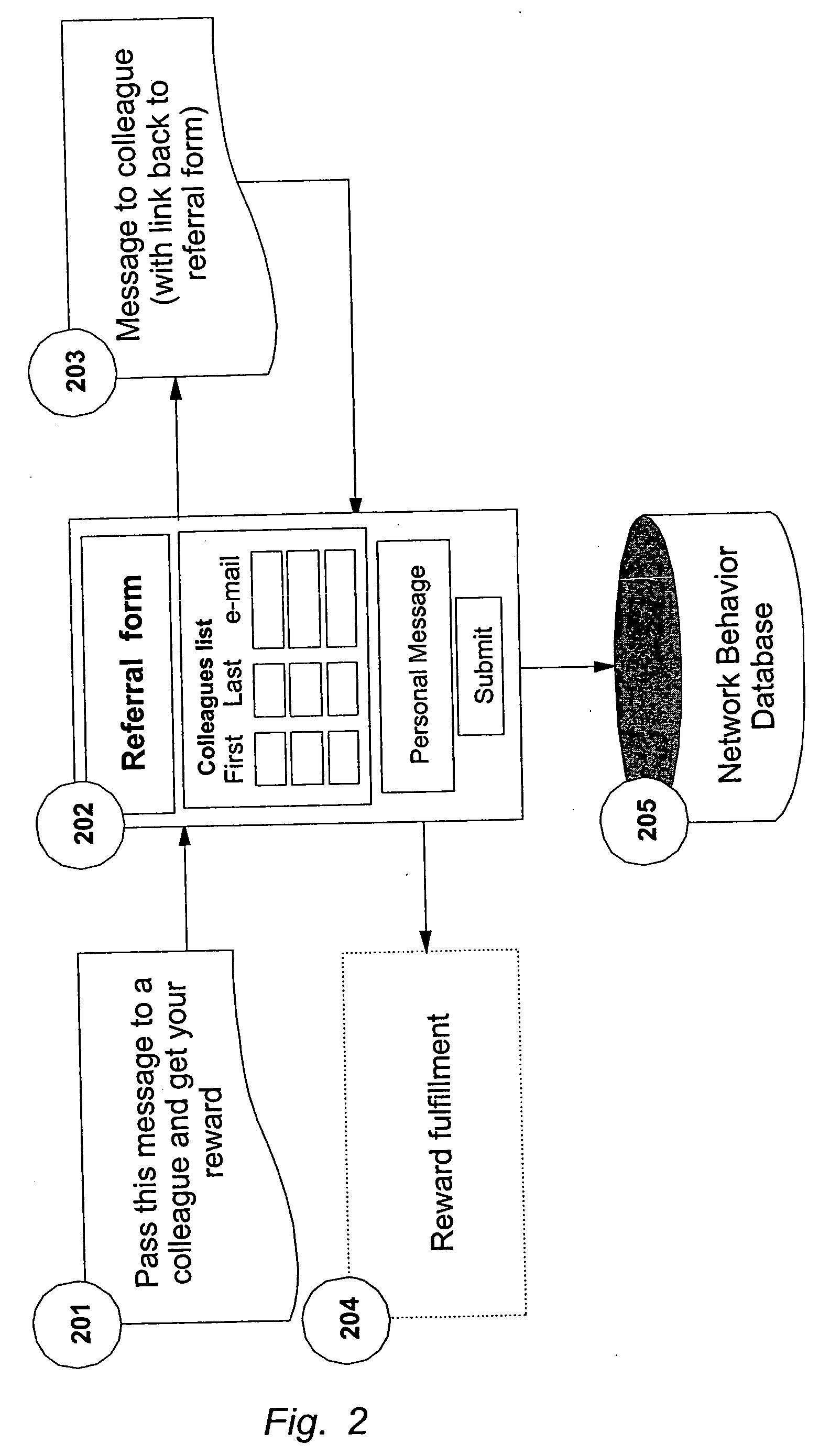
Method and system for managing customer network value
A method, system and computer program product are disclosed for evaluating a customer network value of a set of customers for a given marketing campaign, said method comprising the steps of storing for each customer static information, collecting for each customer, historical and time cumulative network behavior data, building a customer network map from network behavior data said map describing network relation between nodes, one node representing one customer, computing the social network parameters for the nodes of the network map, selecting the most relevant social network parameters according to the objectives of the given marketing campaign, and, computing for each customer a Customer Network Value Index (NVI) by combining the most relevant social network parameters and static information. When a static information profile is defined for an extended customer population, applying data mining techniques on this population allows estimating a probabilistic NVI for each customer in the extended customer population for which no NVI has been computed.
Owner:RAKUTEN GRP INC
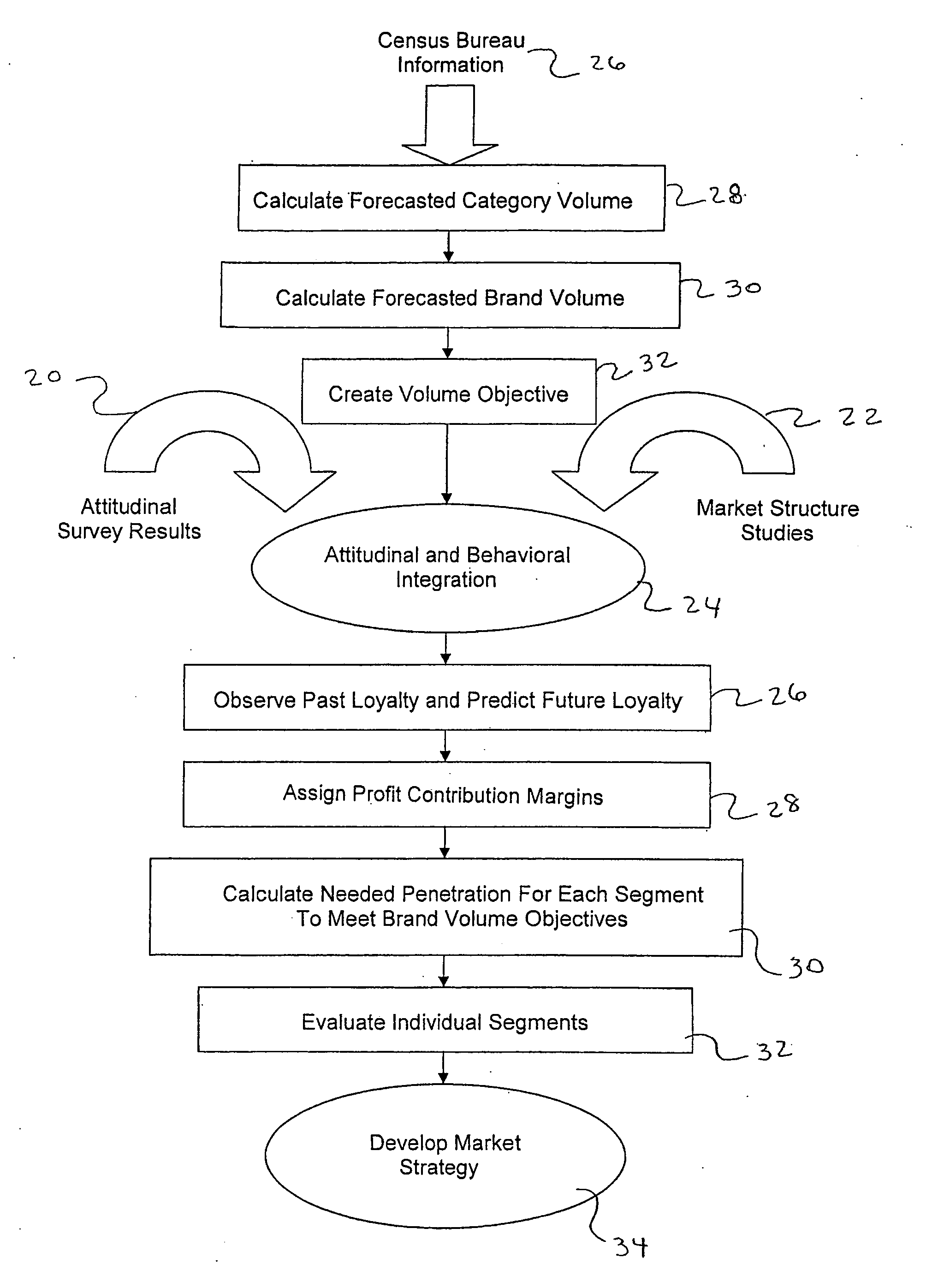
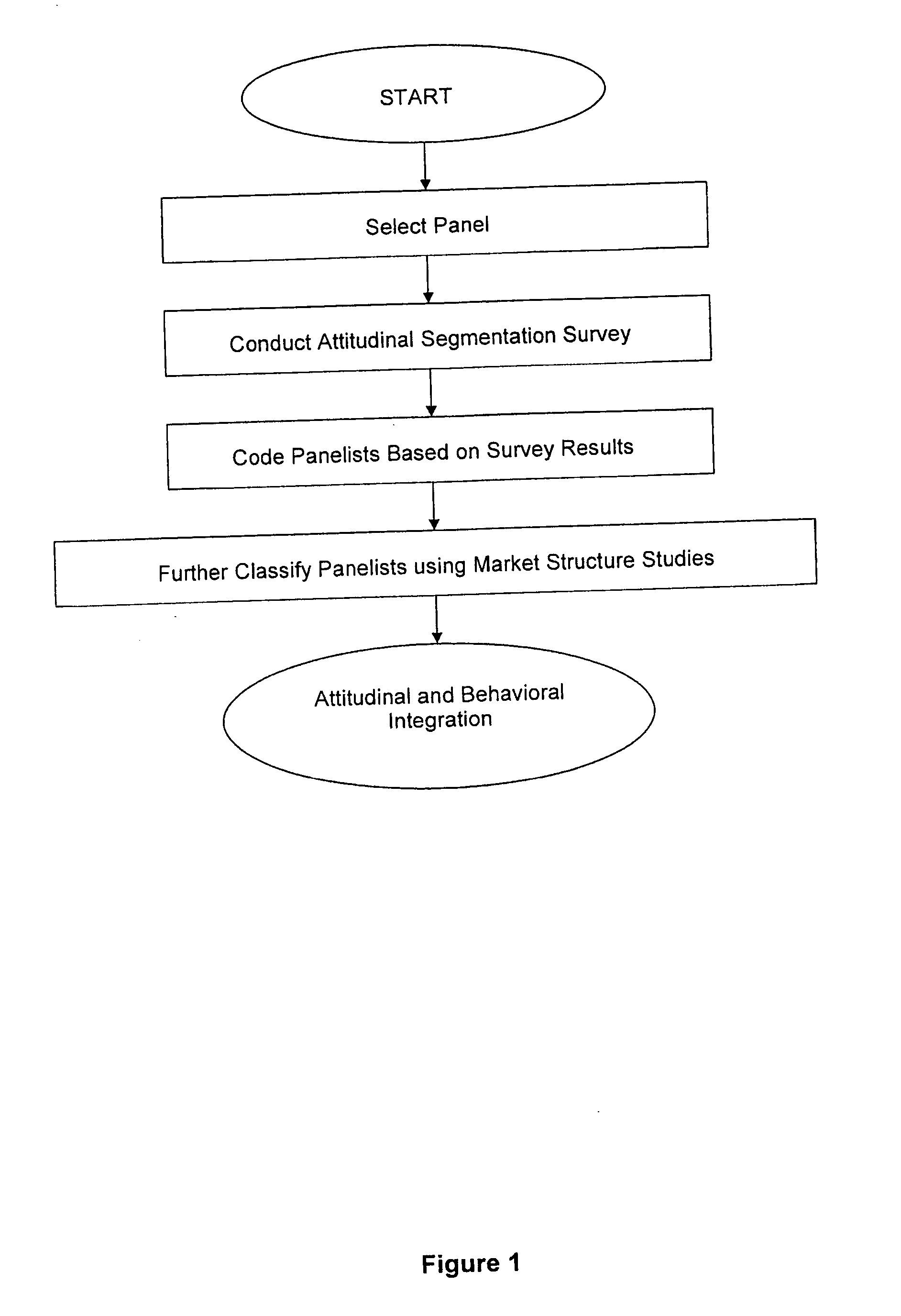
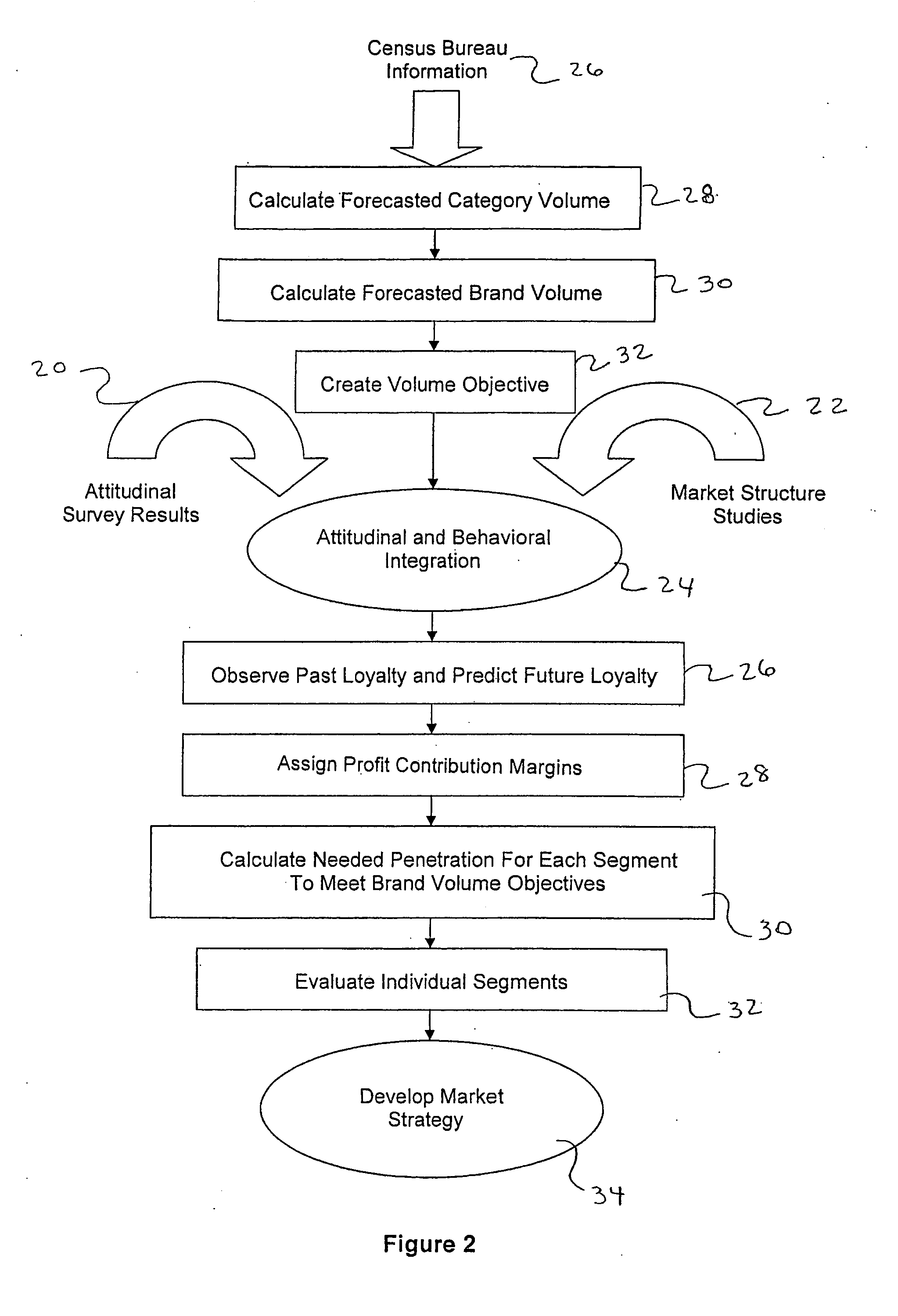
Method for integrating attitudinal and behavioral data for marketing consumer products
A method and system for marketing a consumer product is disclosed. According to the method, attitudinal information and purchase behavioral information is obtained from a plurality of consumers. For instance, consumers may be surveyed regarding their attitudes about purchasing a product category and about the amount of product contained in the product category that they purchase over a given length of time. The attitudinal data and the purchase behavioral data is then integrated together creating a plurality of consumer segments. The consumer segments are grouped together based upon commonalities. Based upon loyalty to a particular brand and a volume sales objective for the brand, increased penetration into the consumer segments may be calculated in order to meet the volume objectives. One of the consumer segments may then be targeted for marketing purposes.
Owner:KIMBERLY-CLARK WORLDWIDE INC
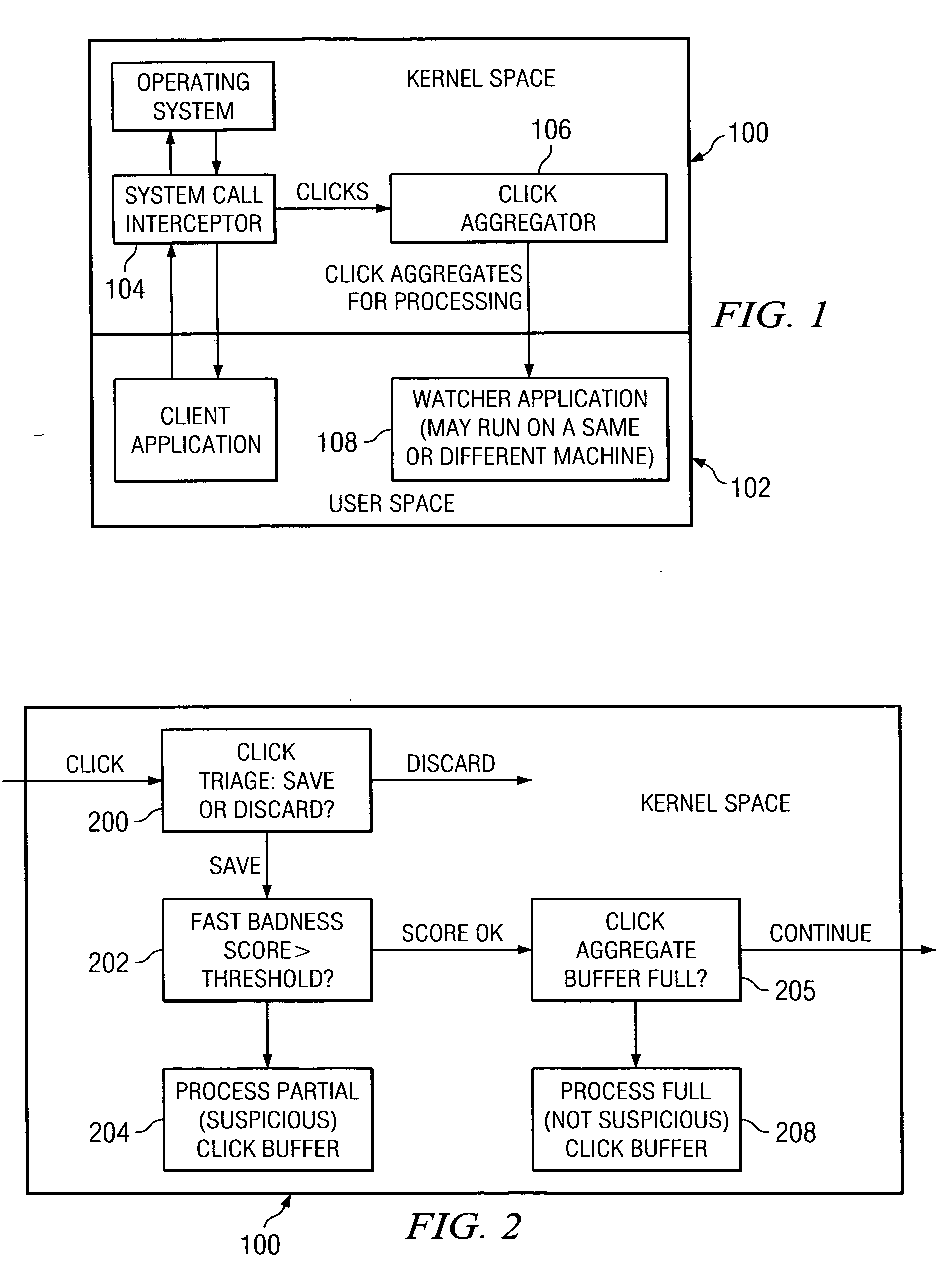
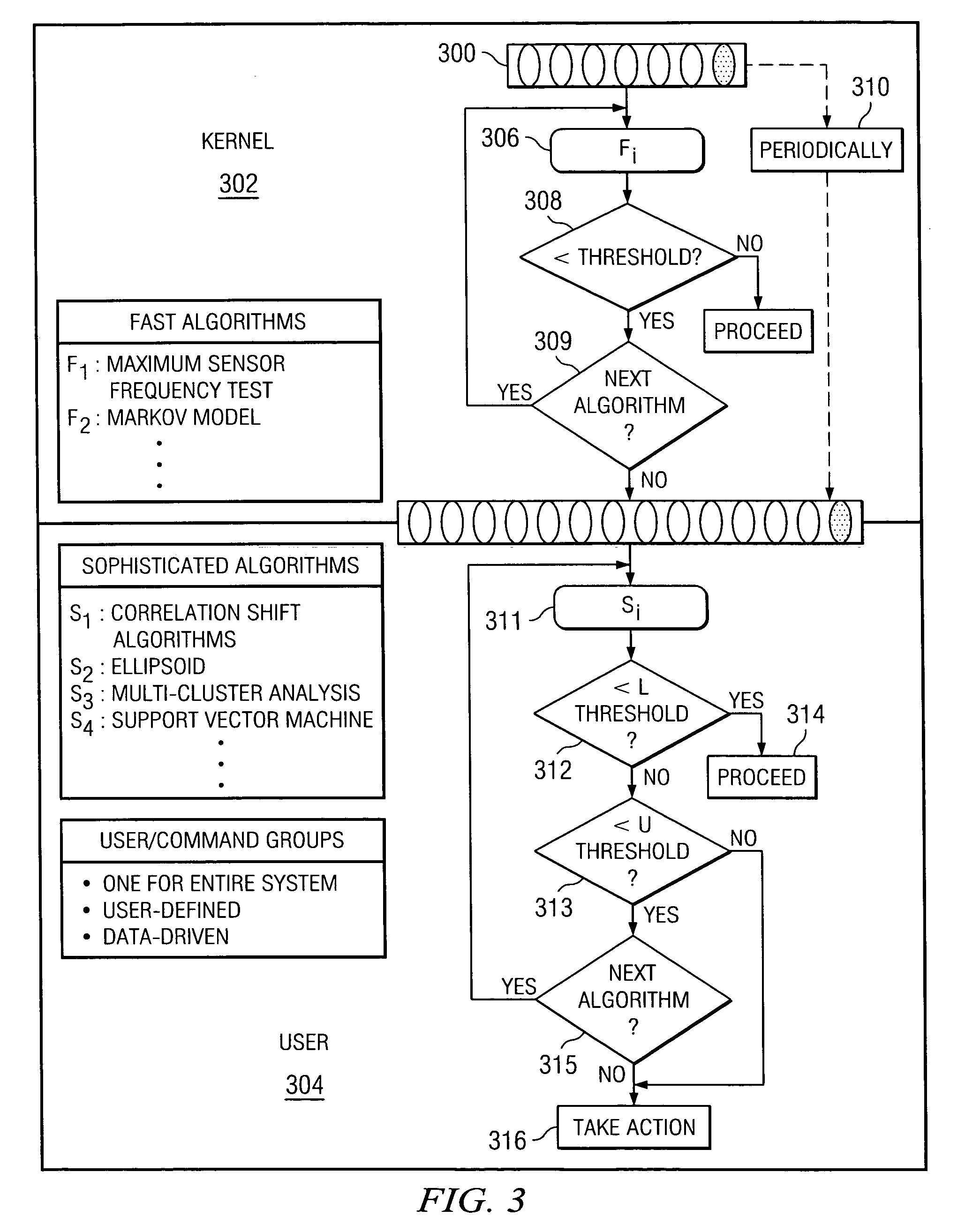
Method and system for detecting intrusive anomalous use of a software system using multiple detection algorithms
InactiveUS20060085854A1Improve detection accuracyAccurate detectionMemory loss protectionDetecting faulty computer hardwareCountermeasureSoftware system
A method of detecting an intrusion into (or an anomaly in a behavior of) a target software system begins by instrumenting the target software system to generate behavior data representing a current observation or observation aggregate. The method then determines whether the current observation or observation aggregate warrants a second level examination; preferably, this determination is made by processing the current observation or observation aggregate through a first level detection algorithm that provides a first, provisional indication of a possible intrusion. If a result of executing the first level detection algorithm indicates that the current observation or observation aggregate warrants a second level examination, the method continues by processing the current observation or observation aggregate through at least one or more second level detection algorithms to provide a second, more definite, fine grain indication of a possible intrusion. The observation aggregates used by the first and second level detection algorithms may be the same or different. The first and second level detection algorithms may be executed in the same or different systems, machines or processors. The target software system operation may be suspended as the current observation or observation aggregate is processed through the one or more second level detection algorithms. A given action (e.g., sending an alert, logging the event, activating a countermeasure, or the like) may be taken if the result of the second level examination indicates a possible intrusion. Multiple algorithms may be executed together within a single examination level, with the individual results then analyzed to obtain a composite result or output indicative of intrusive or anomalous behavior.
Owner:STRATACLOUD
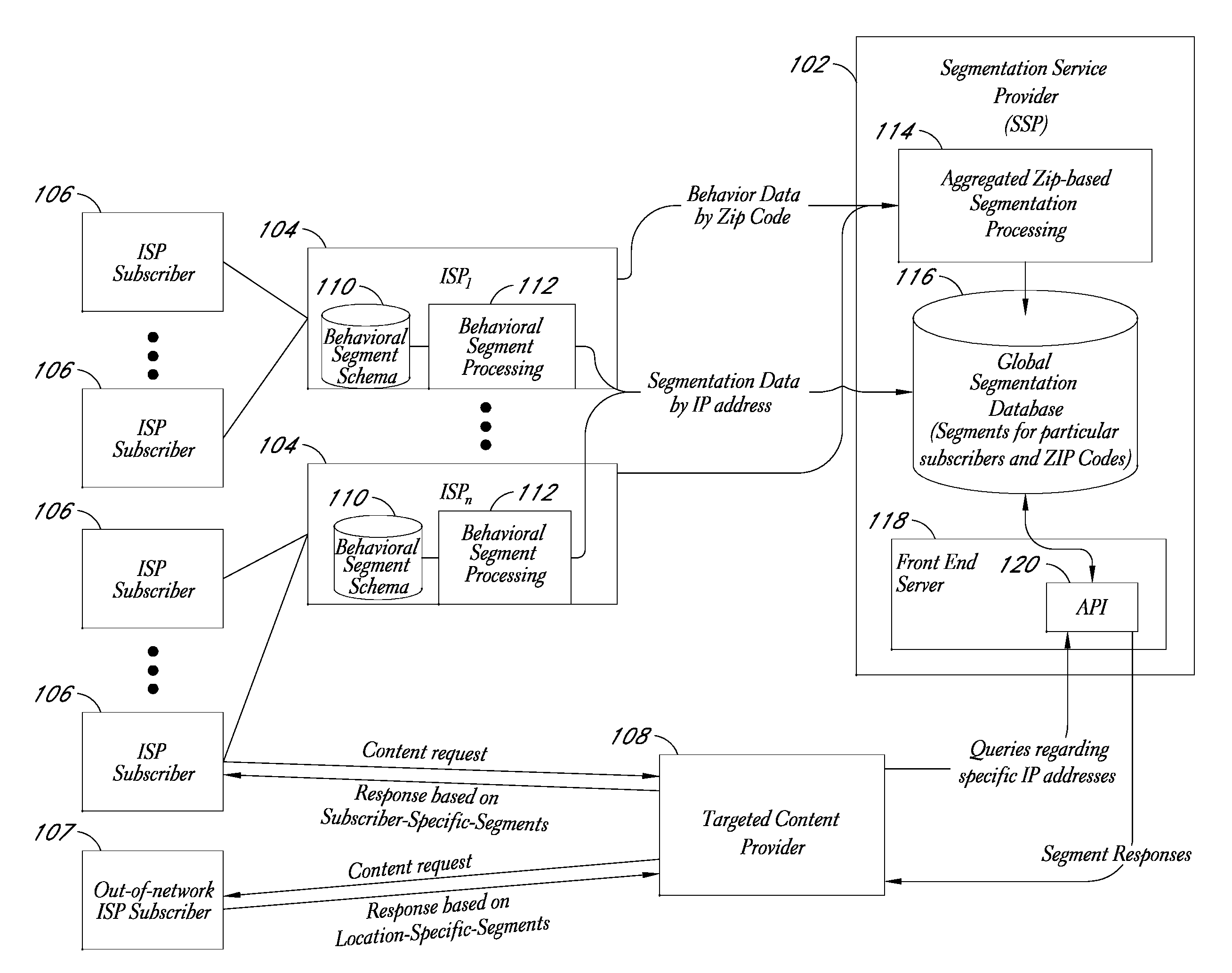
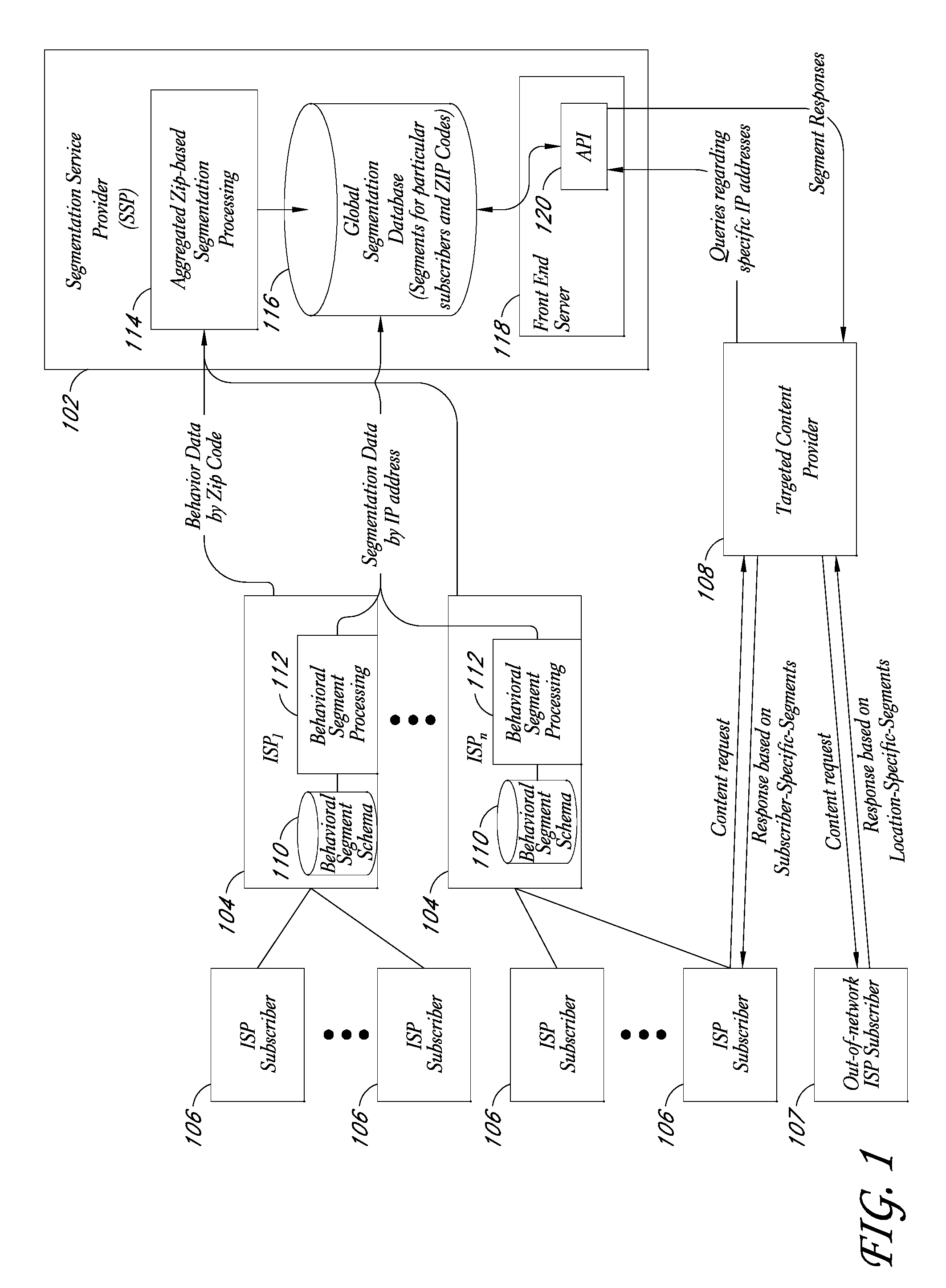
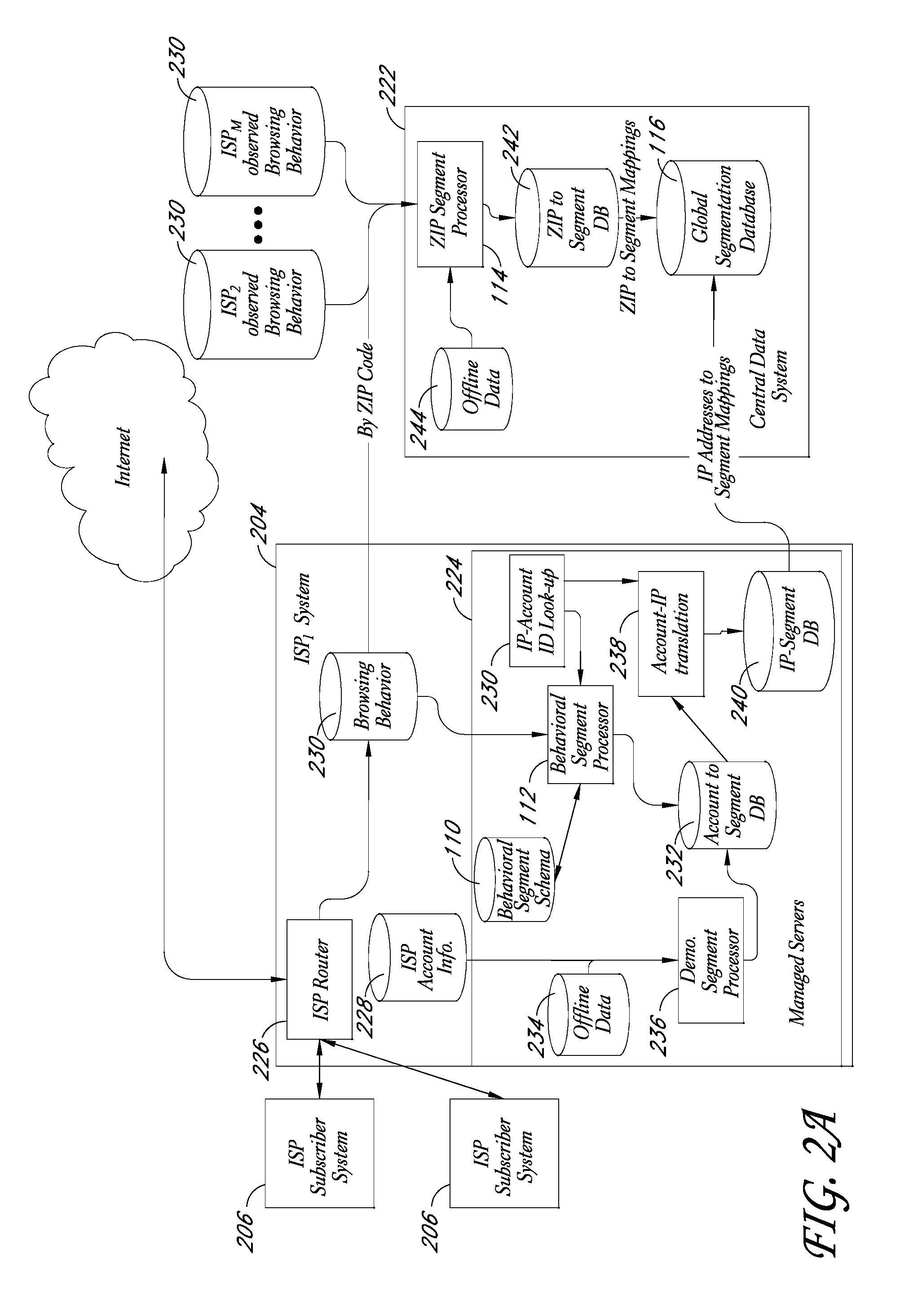
Behavioral segmentation using isp-collected behavioral data
InactiveUS20090132559A1Highly relevantExpand coverageDigital data processing detailsSpecial data processing applicationsWeb siteInternet searching
A system is disclosed that uses behavioral data collected by ISPs to categorize particular ISP subscribers. The behavioral data may, for example, include the identities of particular web sites and / or web pages accessed by particular subscribers, the search queries used by the subscribers to conduct Internet searches, and / or other types of behavioral information. The ISP subscribers are assigned to particular behavioral categories or “segments” using a behavioral segmentation schema that maps particular subscriber behaviors to particular behavioral segments. The ISP subscribers may also be mapped to other segment types, such as demographic segments derived from off-line data about the subscribers. The subscriber-to-segment mappings are made available to content targeting entities via a query interface that, for example, supports queries of the form “what are the segments associated with IP address X?”
Owner:EXPERIAN MARKETING SOLUTIONS
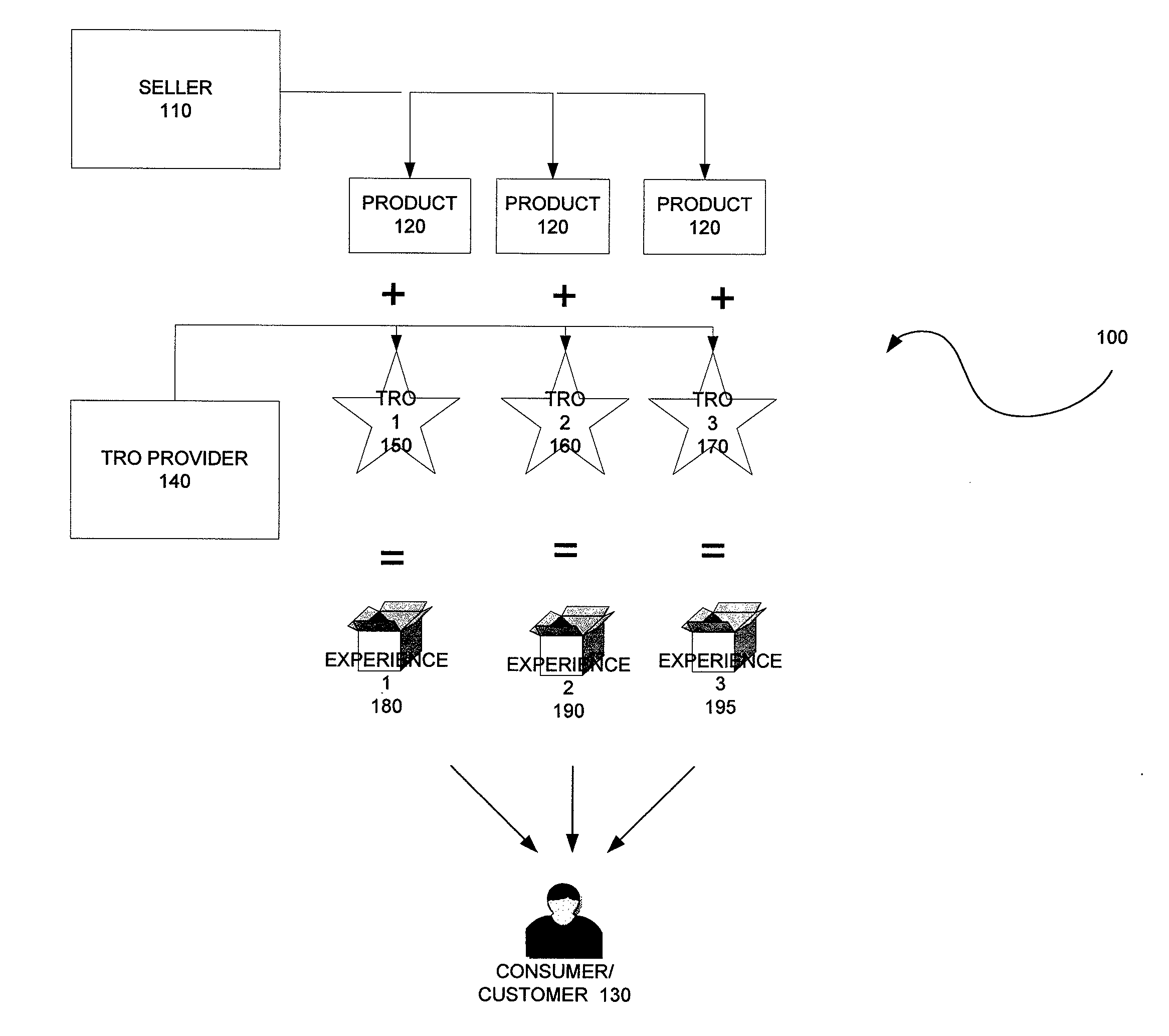
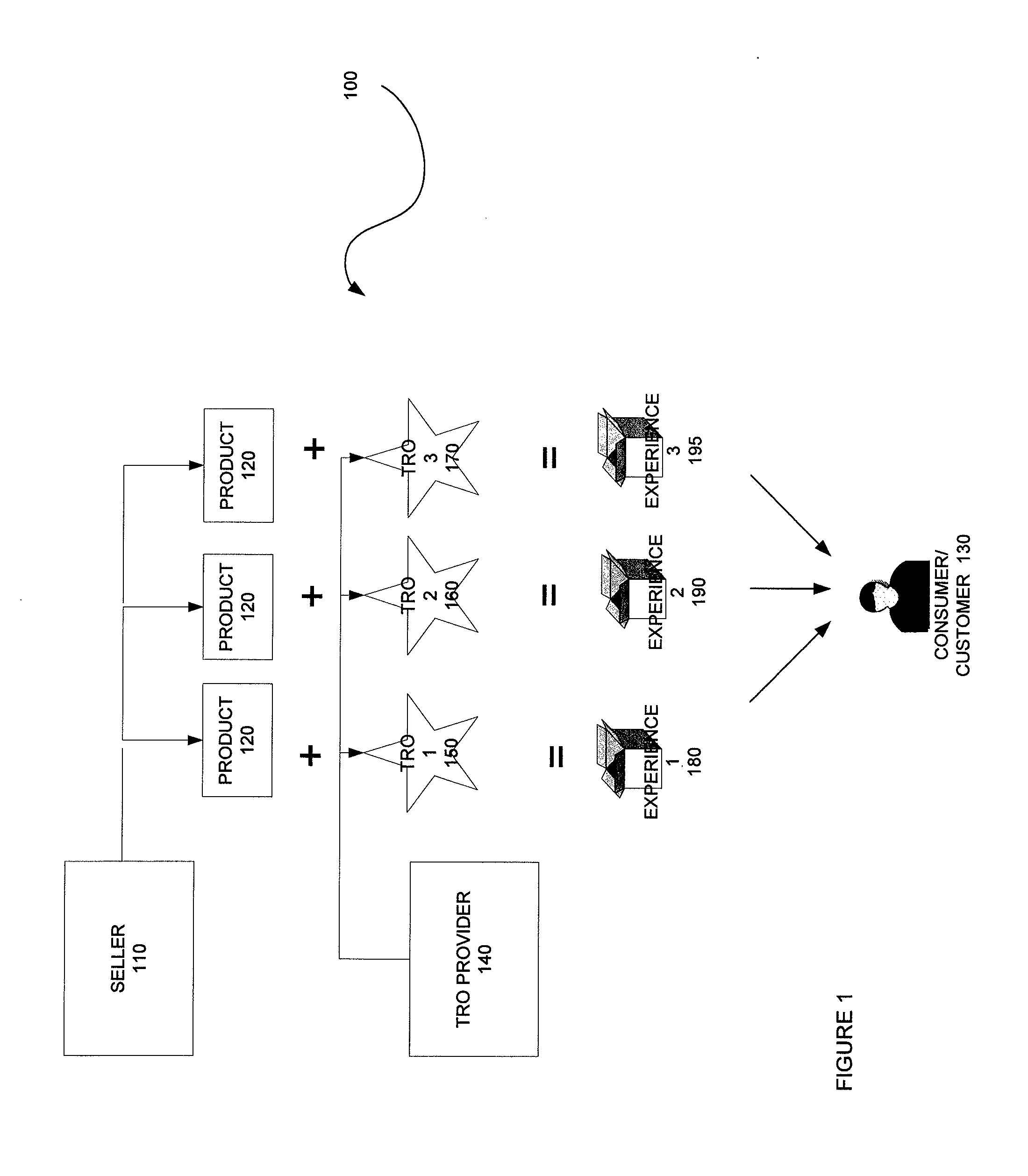
Method, system and components for obtaining, evaluating and/or utilizing seller, buyer and transaction data
ActiveUS20090119160A1Discounts/incentivesSpecial data processing applicationsDecision modelWeb analytics
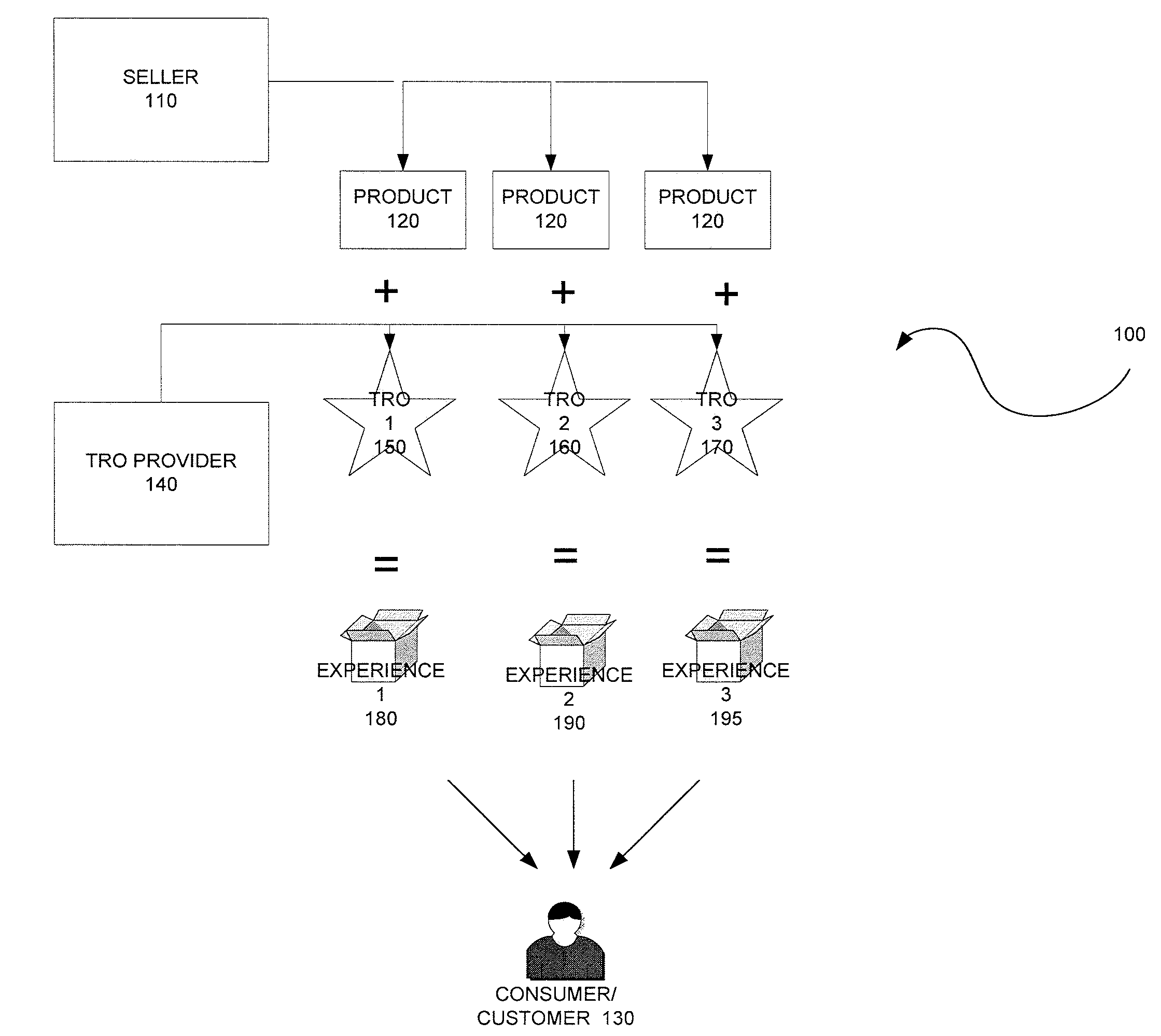
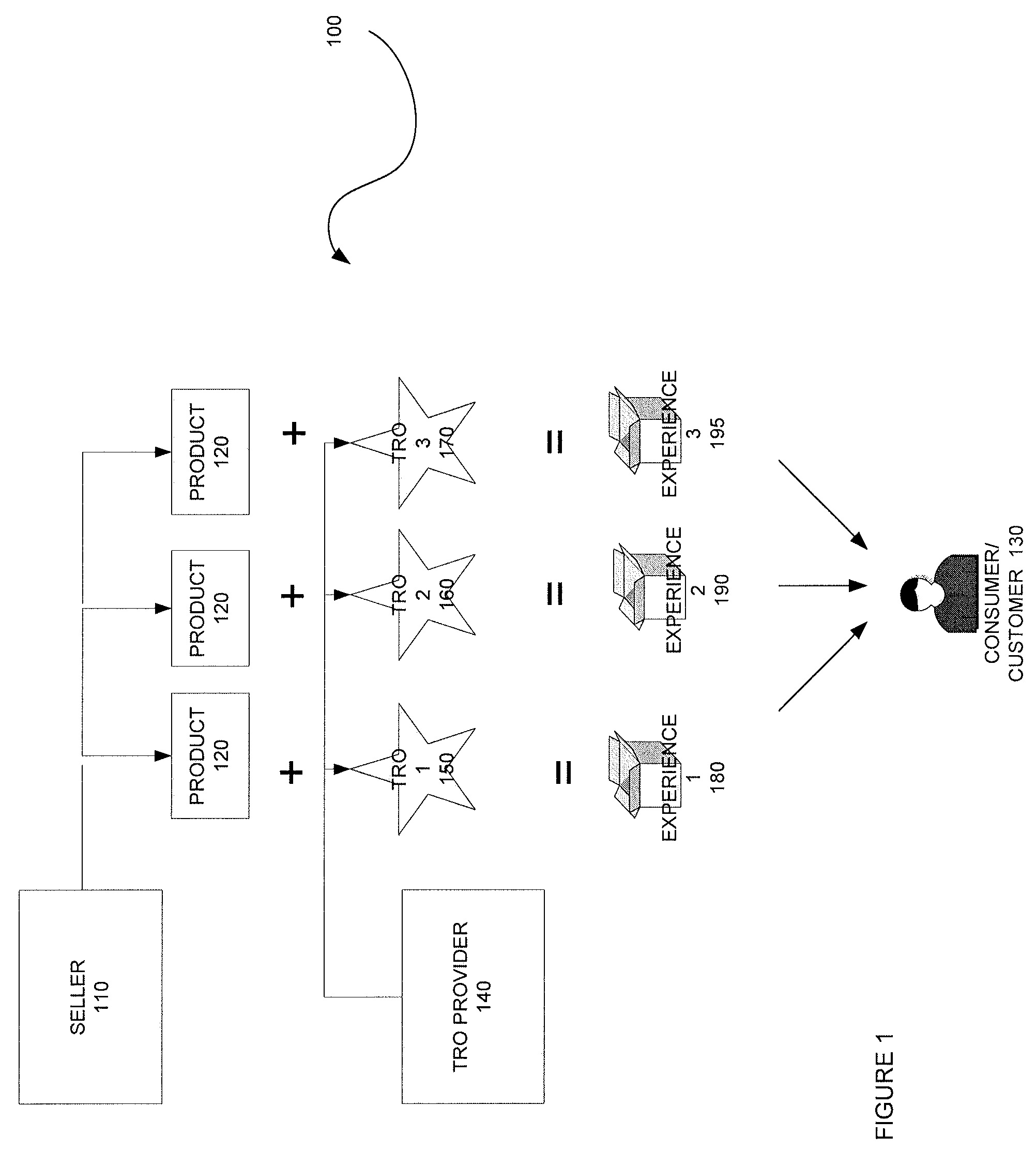
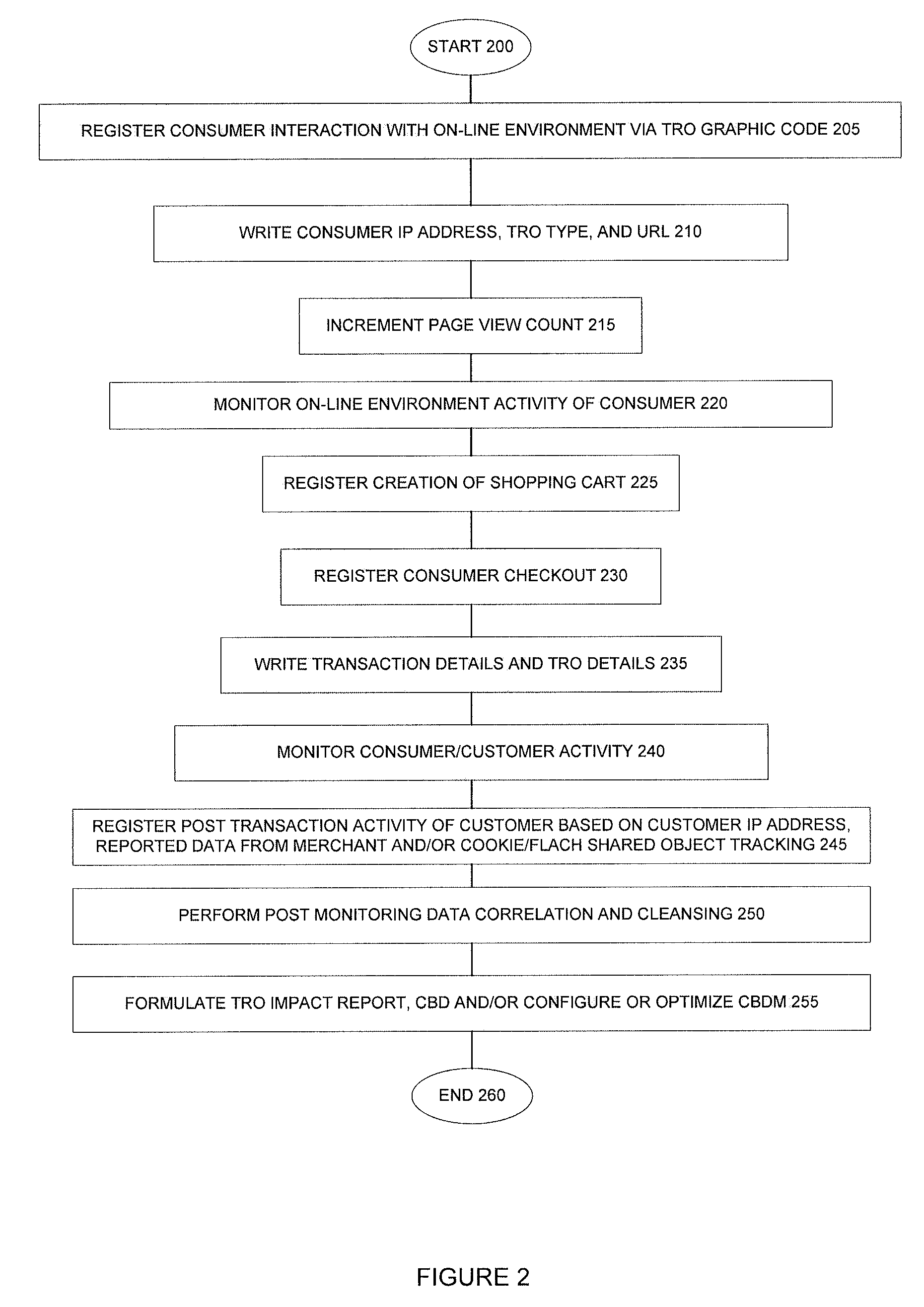
Methodologies, systems, components and software are provided that perform web analytics to measure visitor to consumer conversion continuously throughout surfing, through conversion and past completion of a purchase on-line. In accordance with at least one embodiment, such methodologies, systems, components and software may be utilized to determine efficacy of a plurality of parameters relating to one or more Transaction Related Offerings (TROs). In accordance with at least one embodiment of the invention, such methodologies, systems, components and software may be utilized to configure one or more Consumer Behavior Decision Models (CBDMs) and / or generate consumer behavior data.
Owner:BUYSAFE
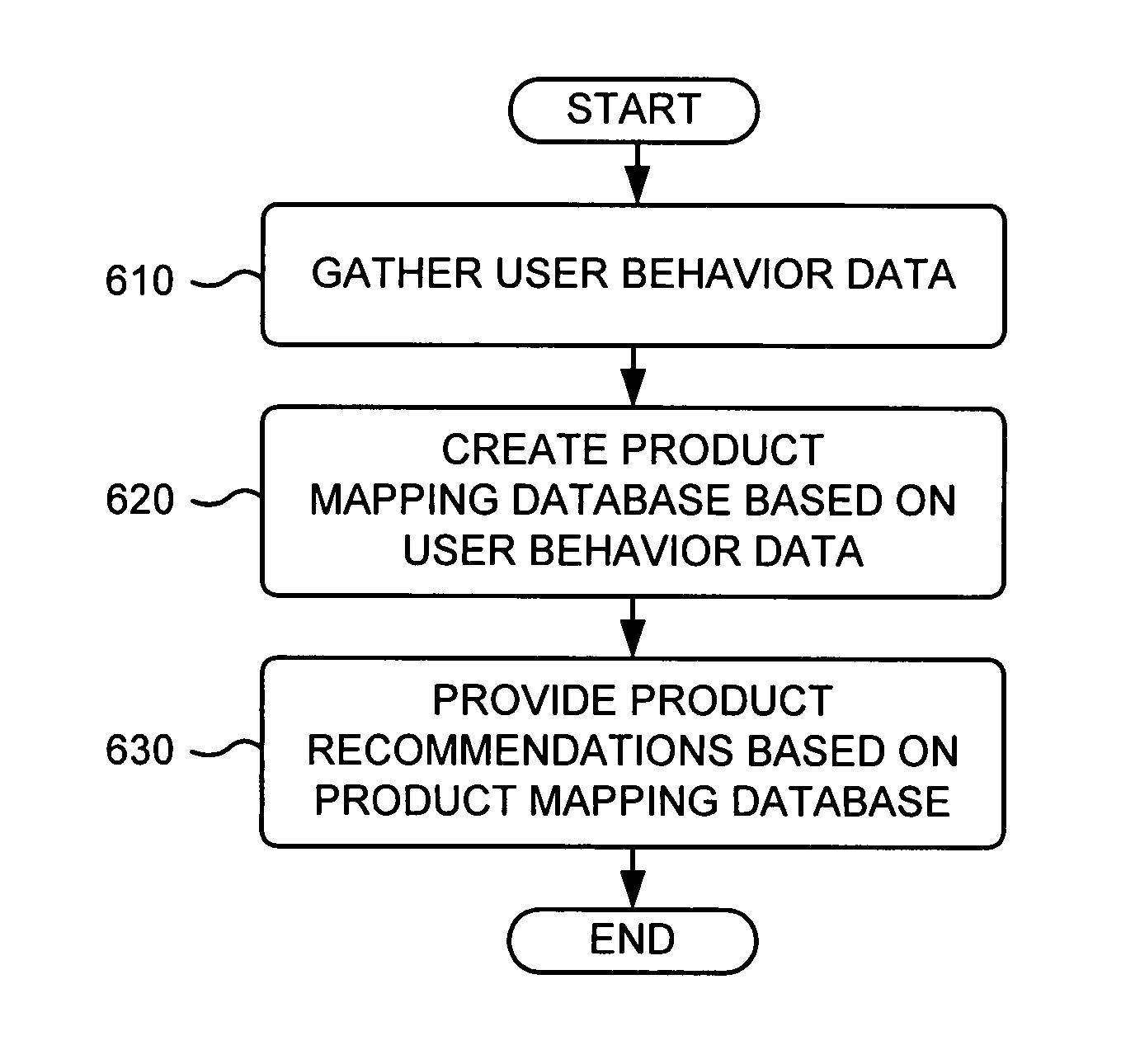
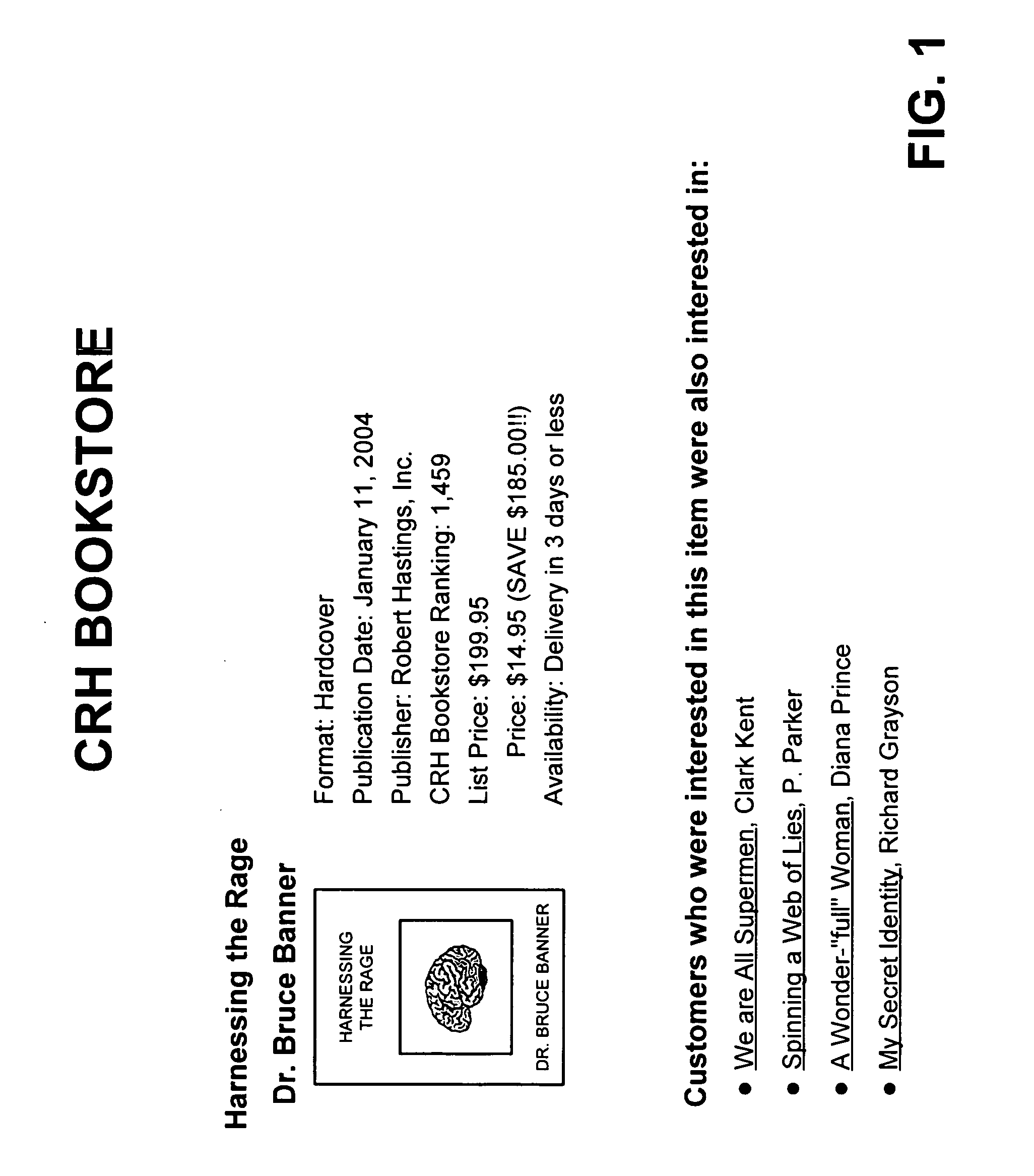
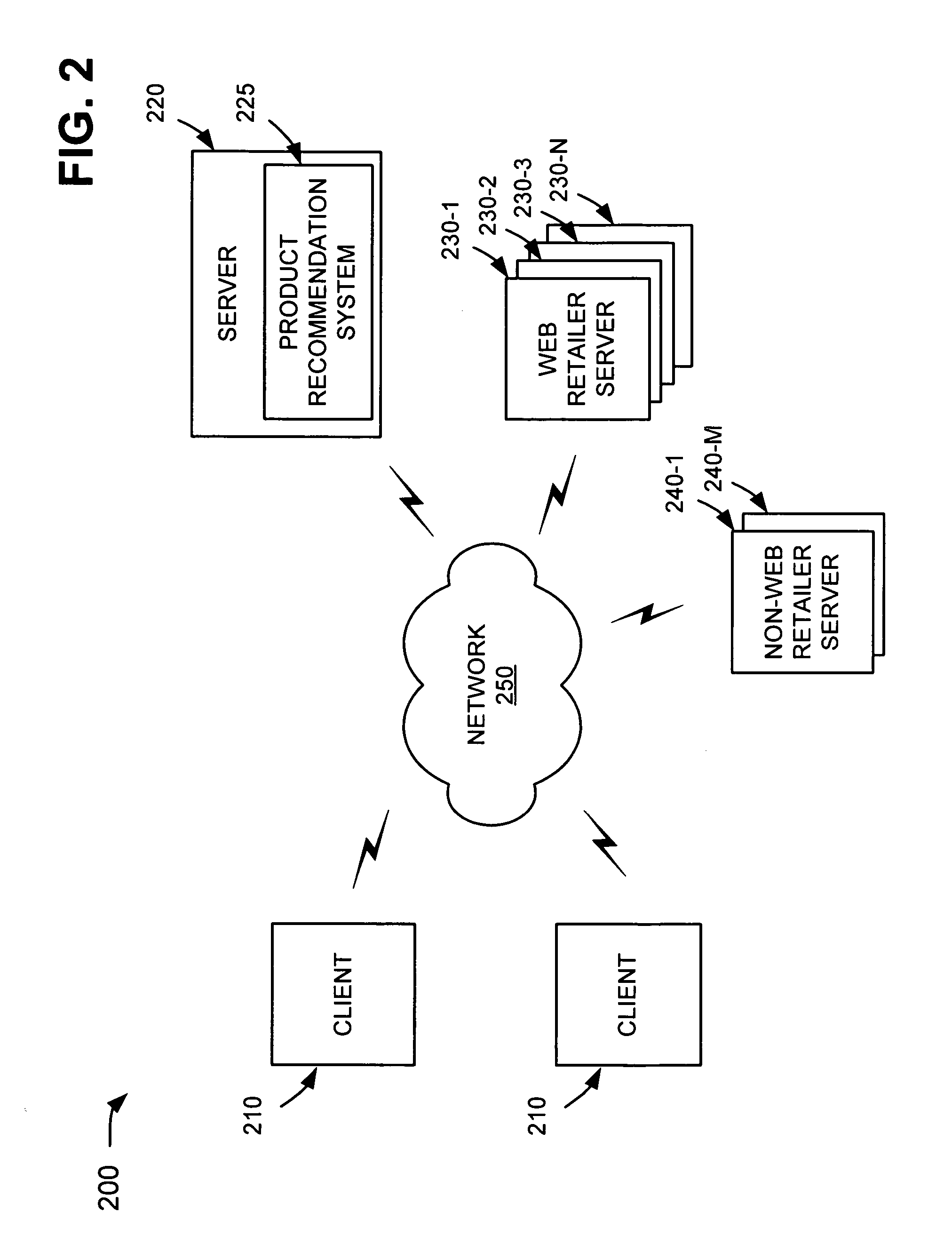
Product recommendations based on collaborative filtering of user data
ActiveUS20070005437A1Other databases browsing/visualisationSpecial data processing applicationsBehavioral dataWorld Wide Web
A system gathers user behavior data from a group of web retailers and / or non-web retailers, analyzes the user behavior data to identify product recommendations for products offered by the web retailers, and provides one of the identified product recommendations in connection with a product page associated with one of the web retailers.
Owner:GOOGLE LLC
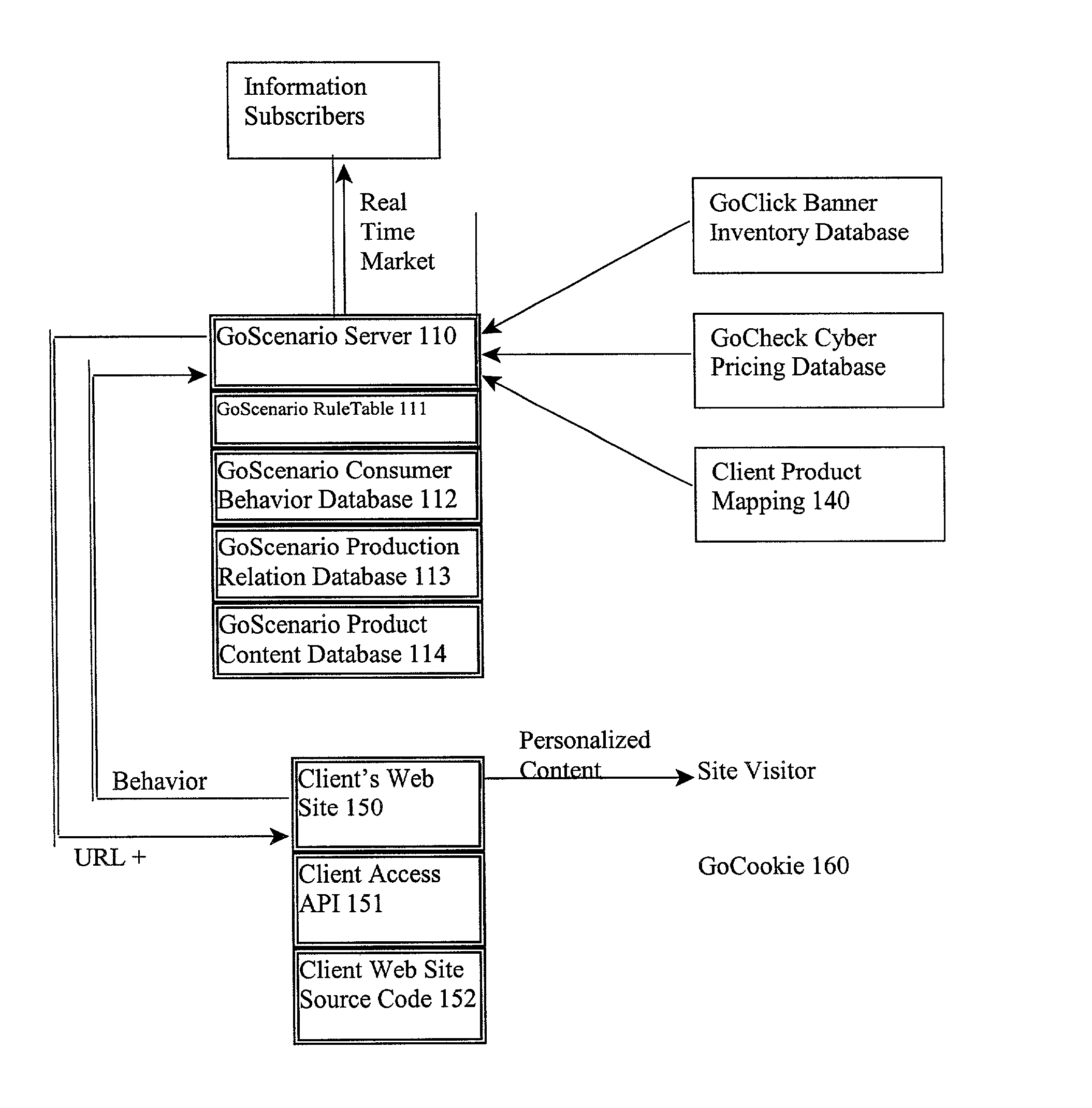
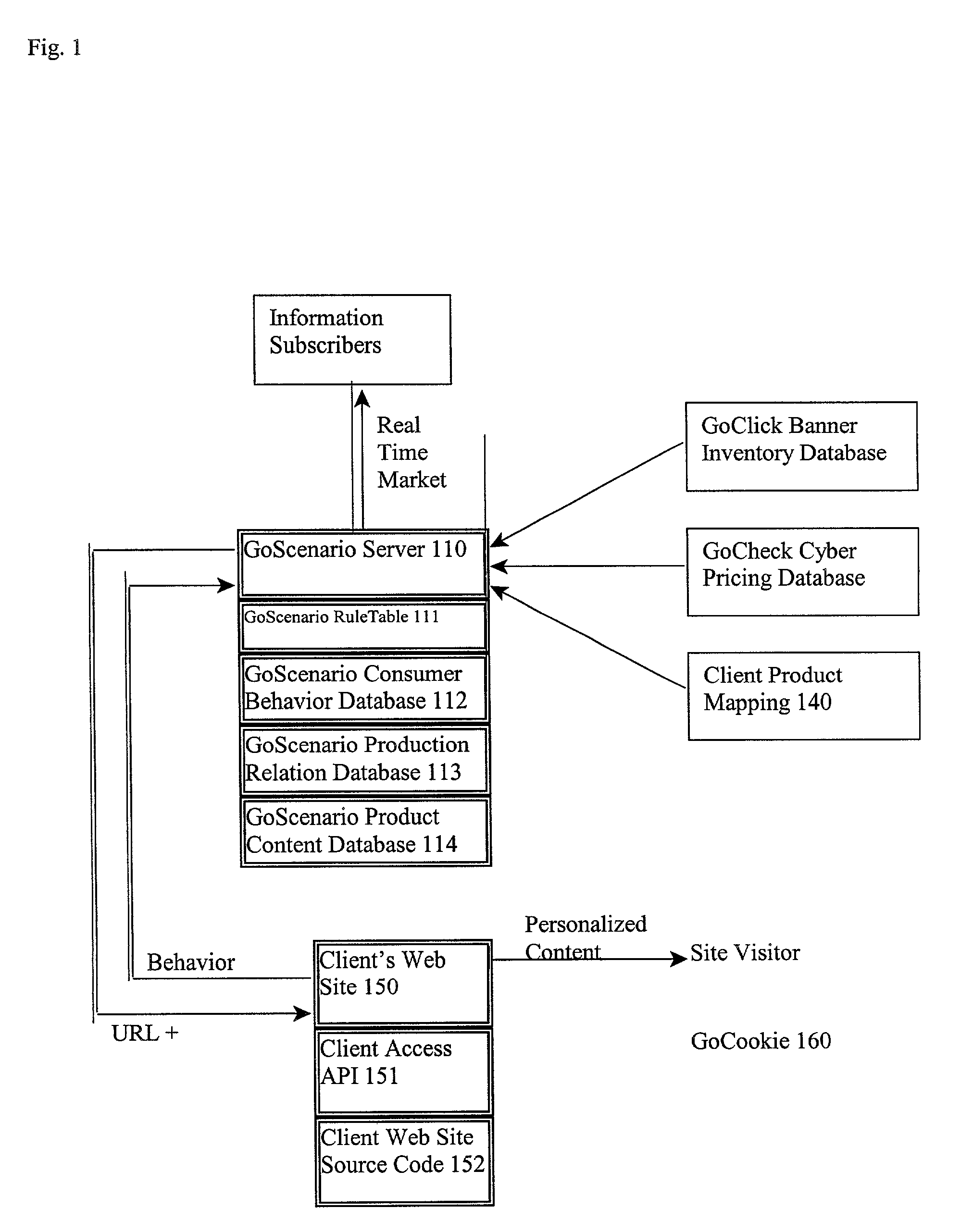
Knowledge by go business model
InactiveUS20020178166A1Digital data processing detailsWebsite content managementCustomer relationship managementField analysis
KnowledgeByGo is a knowledge based Internet application service provider system (ASP), that tracks and analyzes browser behavior in real-time. Data analysis is delivered to the website owner or marketing agent to decide if a real time response or off line campaign needs to be initiated. KnowledgeByGo allows real-time behavioral tracking and prediction; customer relation management; one-to-one banner manager; site analysis reporting service; industry wide marketing research reports; product management; order processing; secure payment system; and customer contact manager. Subscribers get the immediate benefits of: collaborative filtering; real-time behavioral prediction; up-selling and / or cross-sell selling; banner advertisement income; Customer Relation Management (CRM); one-to-one banner management; site analysis reporting server; network-wide sales and marketing reports; product content and online pricing spidering; site management, backend product management, backend order processing, RMA processing, secured payment system, customer contact manager, price-search engine utility, and consolidated participation purchasing.
Owner:DIRECT411 COM
Hierarchical behavioral profile
InactiveUS20130166494A1Reduce storage requirementsFuzzy logic based systemsCommerceData aggregatorBehavioral data
In a hierarchical profile, each node represents at least one feature of behavioral data collected about an entity profiled, with the topmost node selected as the “statistically most informative” feature of the data. A profile can cover numerous domains and be predictively very powerful in each domain. A number of observations can be “aggregated” together into a single datapoint. In use, the structure of the profile is compared against current information associated with the entity to produce a recommendation or prediction. If the profile represents at least some data aggregation, then new observations are folded into the profile based on statistical weights of the aggregations. Because of the way the profile is created and updated, its hierarchical structure maps the collected observations. Therefore, as new observations are incorporated, if the new observations change the profile's structure significantly, then it can be hypothesized that something “interesting” has happened to the entity.
Owner:GOOGLE TECH HLDG LLC
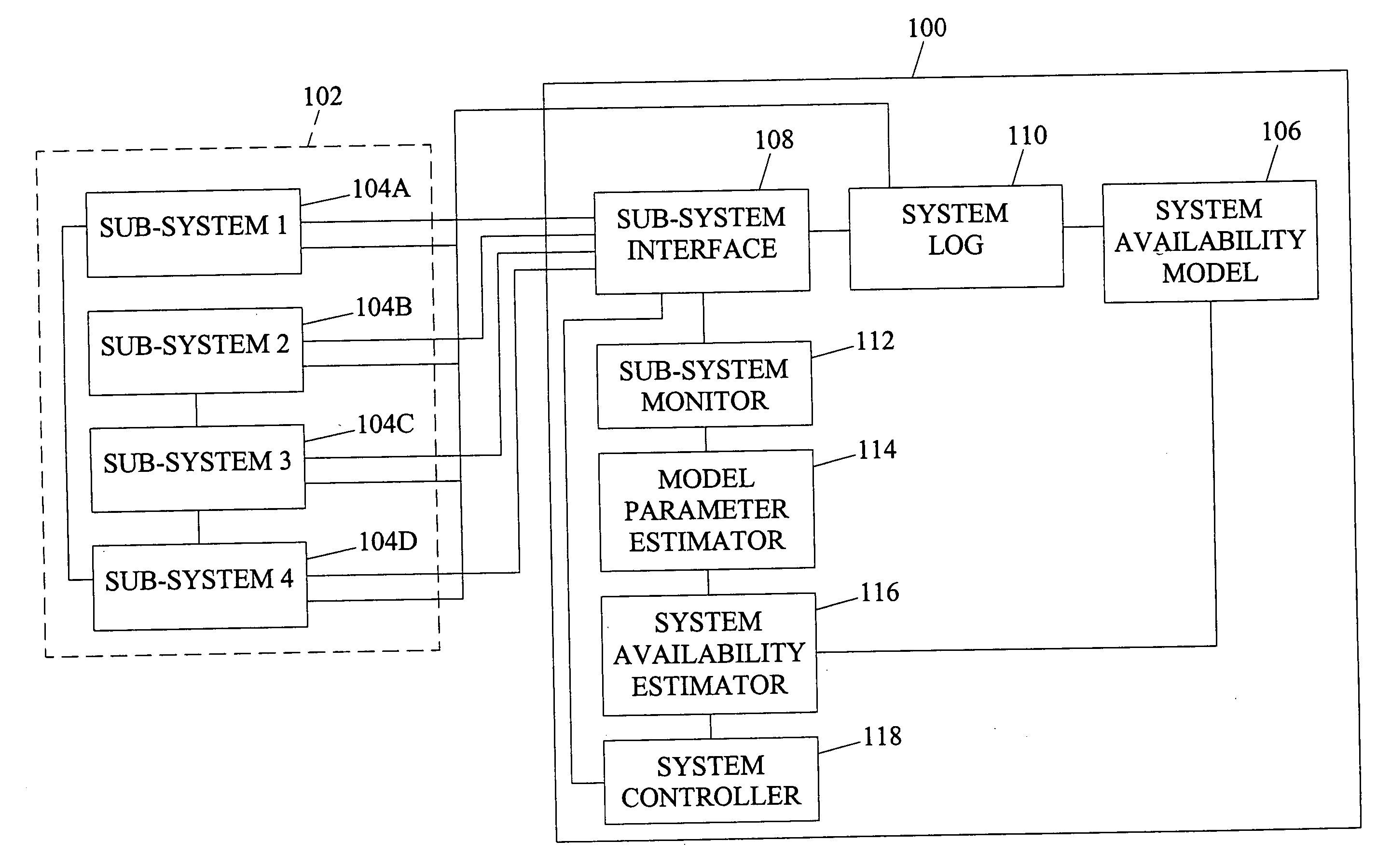
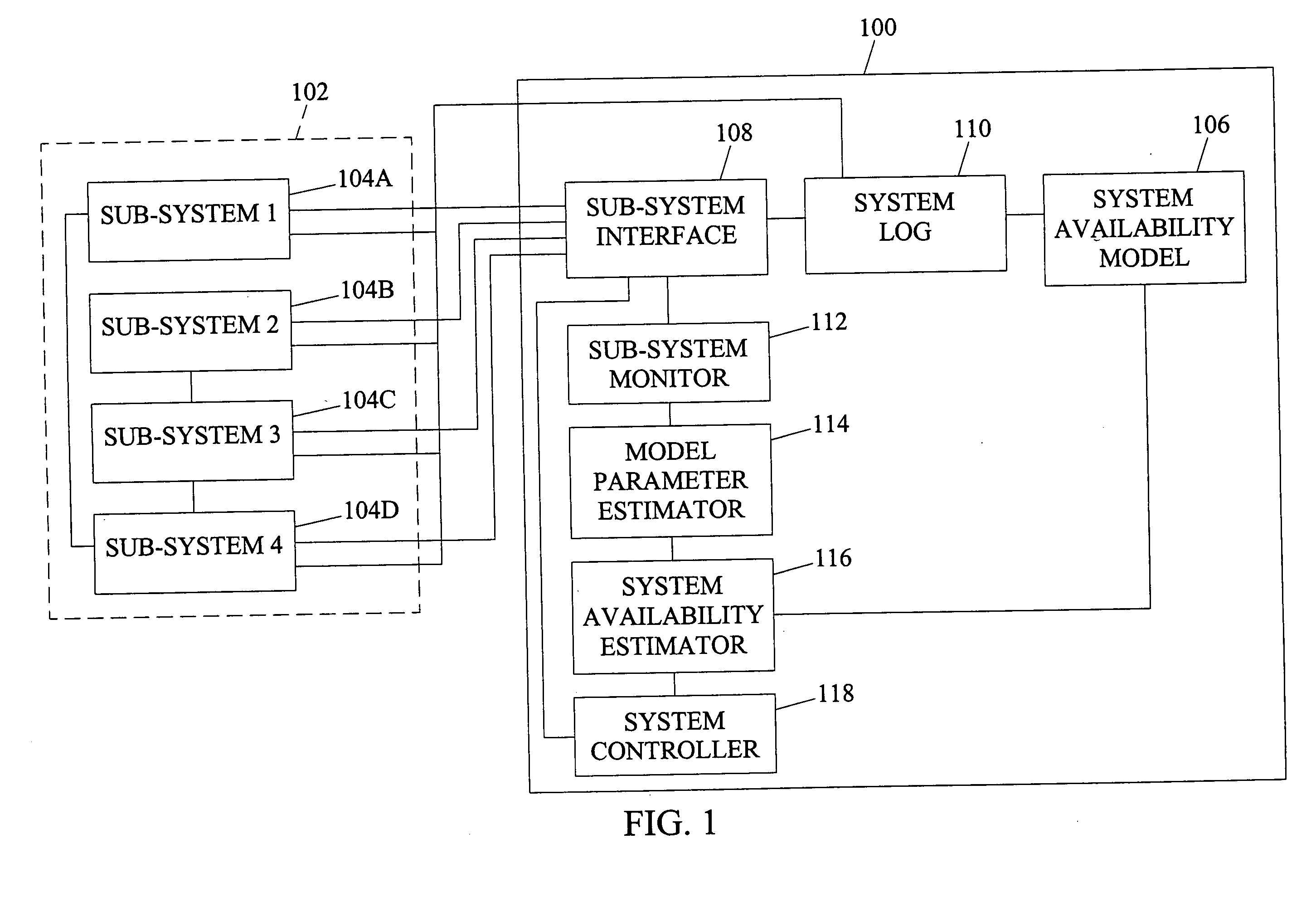
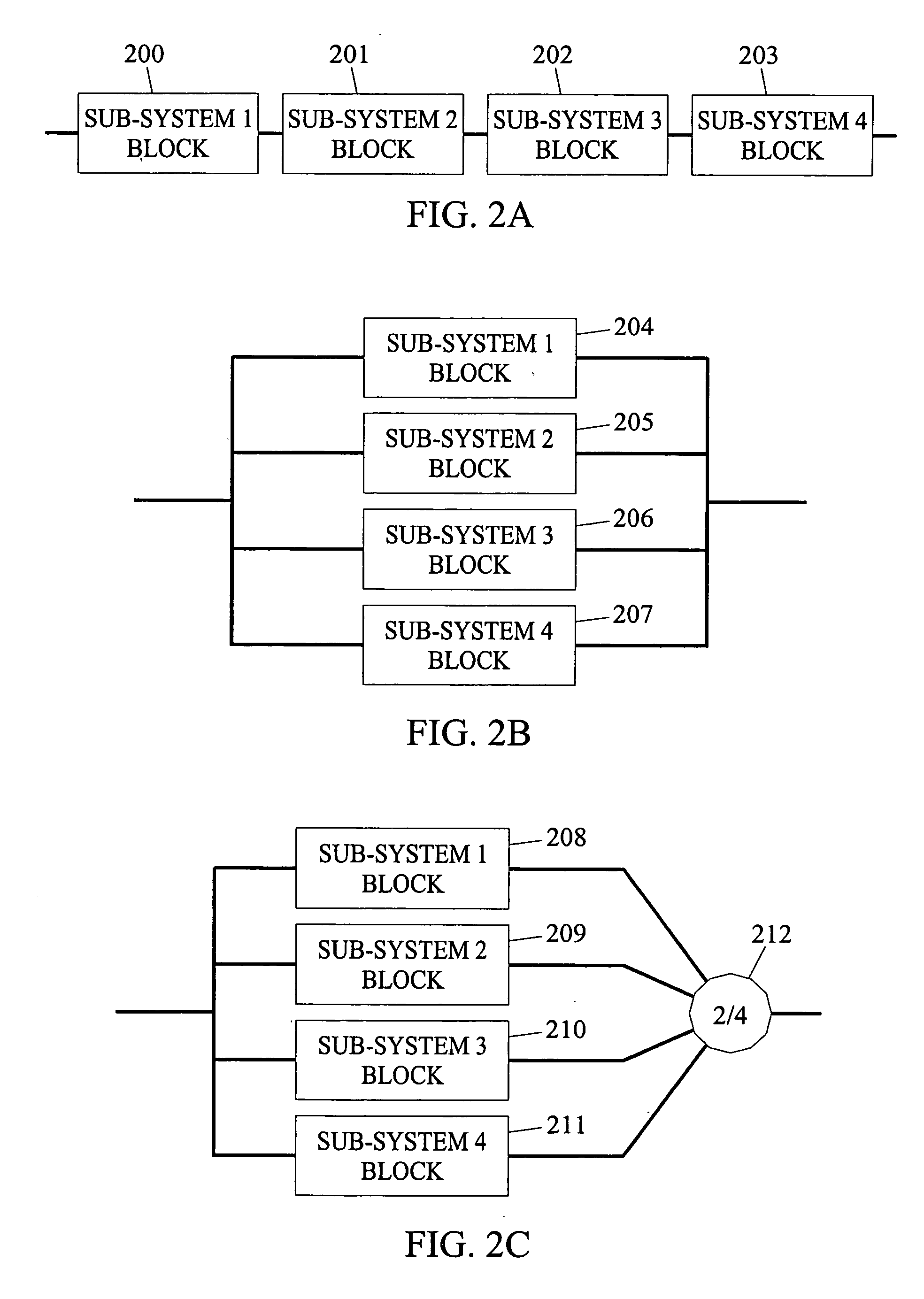
Systems, methods, and computer program products for system online availability estimation
InactiveUS20060129367A1Analogue computers for electric apparatusTransmissionConfidence intervalStatistical Confidence
Systems, methods, and computer program products for system online availability estimation. A method according to one embodiment can include a step for providing an availability model of a system. The method can also include a step for receiving behavior data of the system. In addition, the method can include estimating a plurality of parameters for the availability model based on the behavior data. The method can also include determining individual confidence intervals for each of the parameters. Further, the method can include determining an overall confidence interval for the system based on the individual distributions of the estimated parameters. The method can also include determining control actions based on the estimated overall availability or inferred parameter values.
Owner:DUKE UNIV
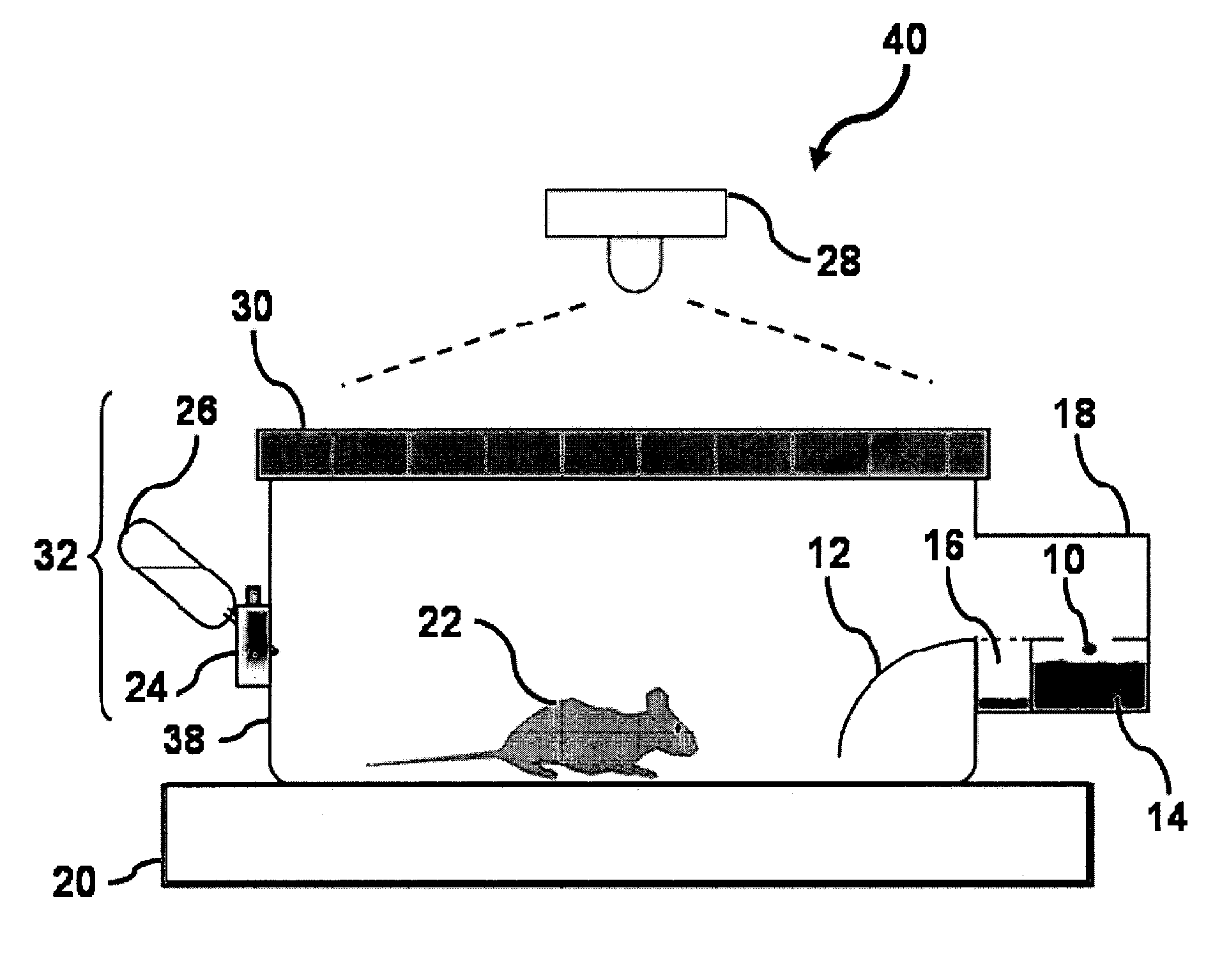
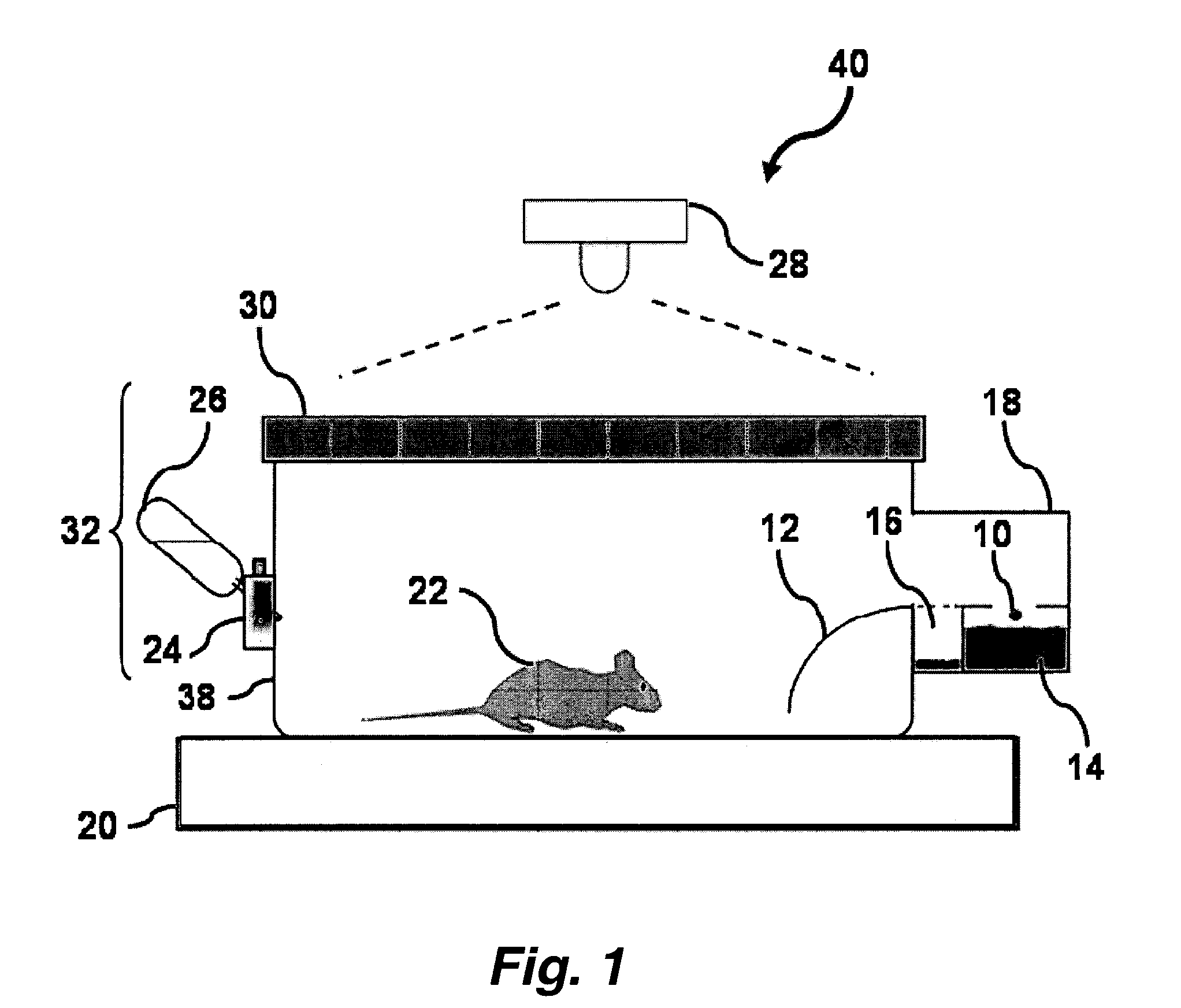
Animal cage behavior system
InactiveUS7086350B2Facilitates automated analysis and generationHigh resolutionAnimal housingOther apparatusAnimal behaviorTemporal resolution
A behavioral monitoring system useful for the analysis of complex behaviors in a number of animal species. The monitoring systems of this invention allow continuous monitoring of feeding, drinking and movement of animals with high temporal and spatial resolution. In certain embodiments, the system comprises an enclosure comprising: an animal position indicator; a food consumption indicator; and a fluid consumption indicator, where the system reports behavioral data at a temporal resolution of 20 seconds or lower.
Owner:RGT UNIV OF CALIFORNIA
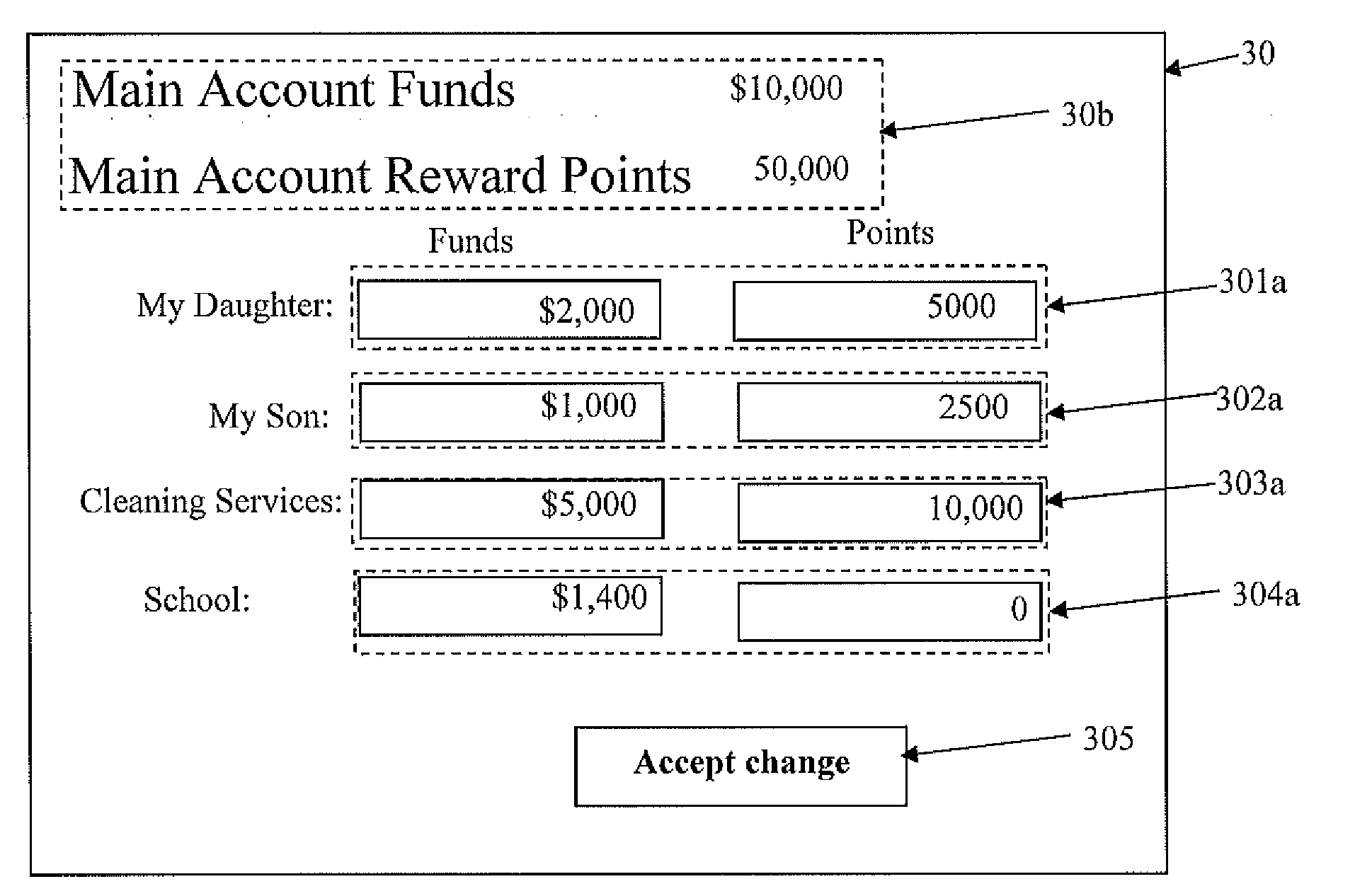
Apparatus and Method for Managing Bank Account Services, Advertisement Delivery and Reward Points
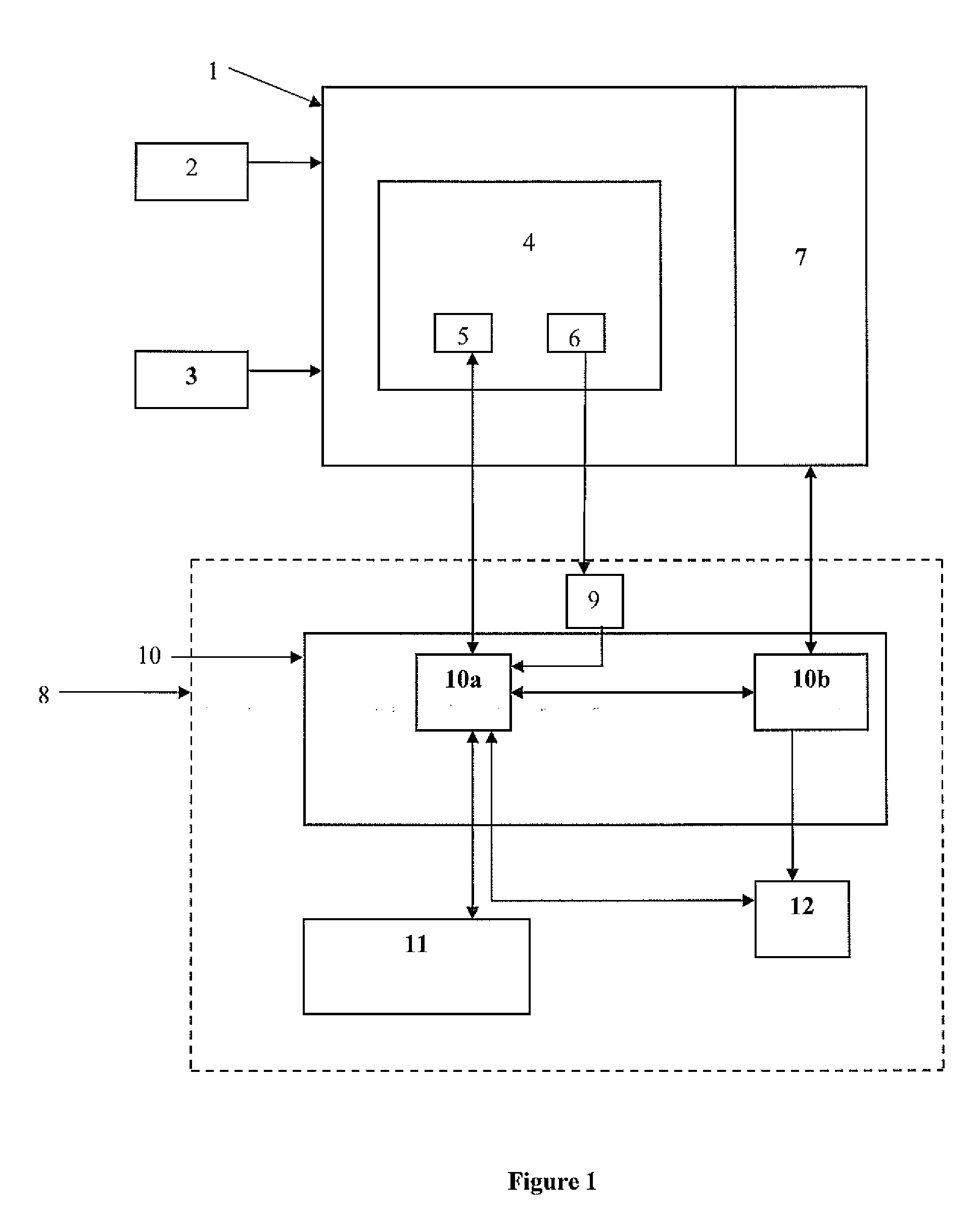
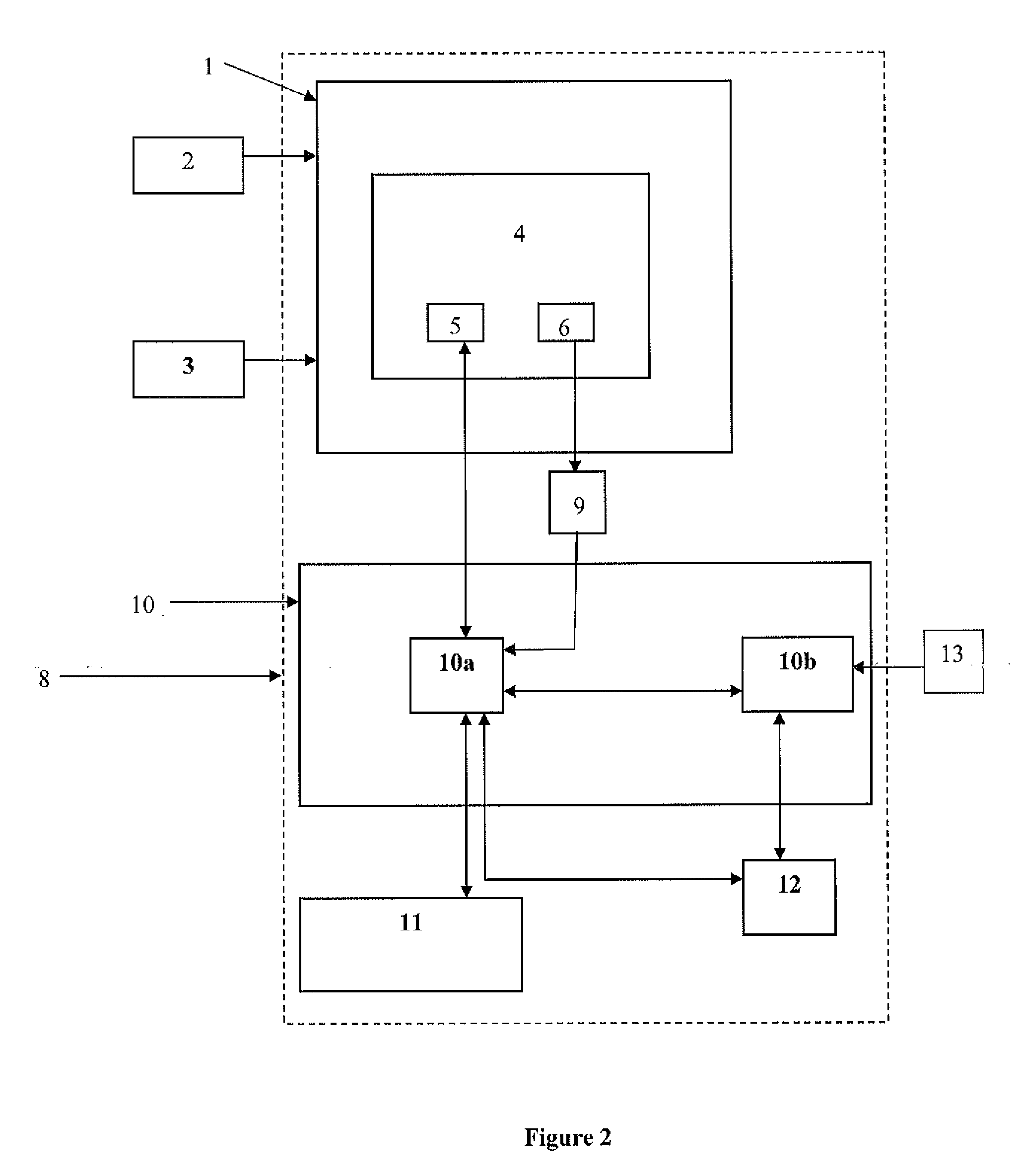
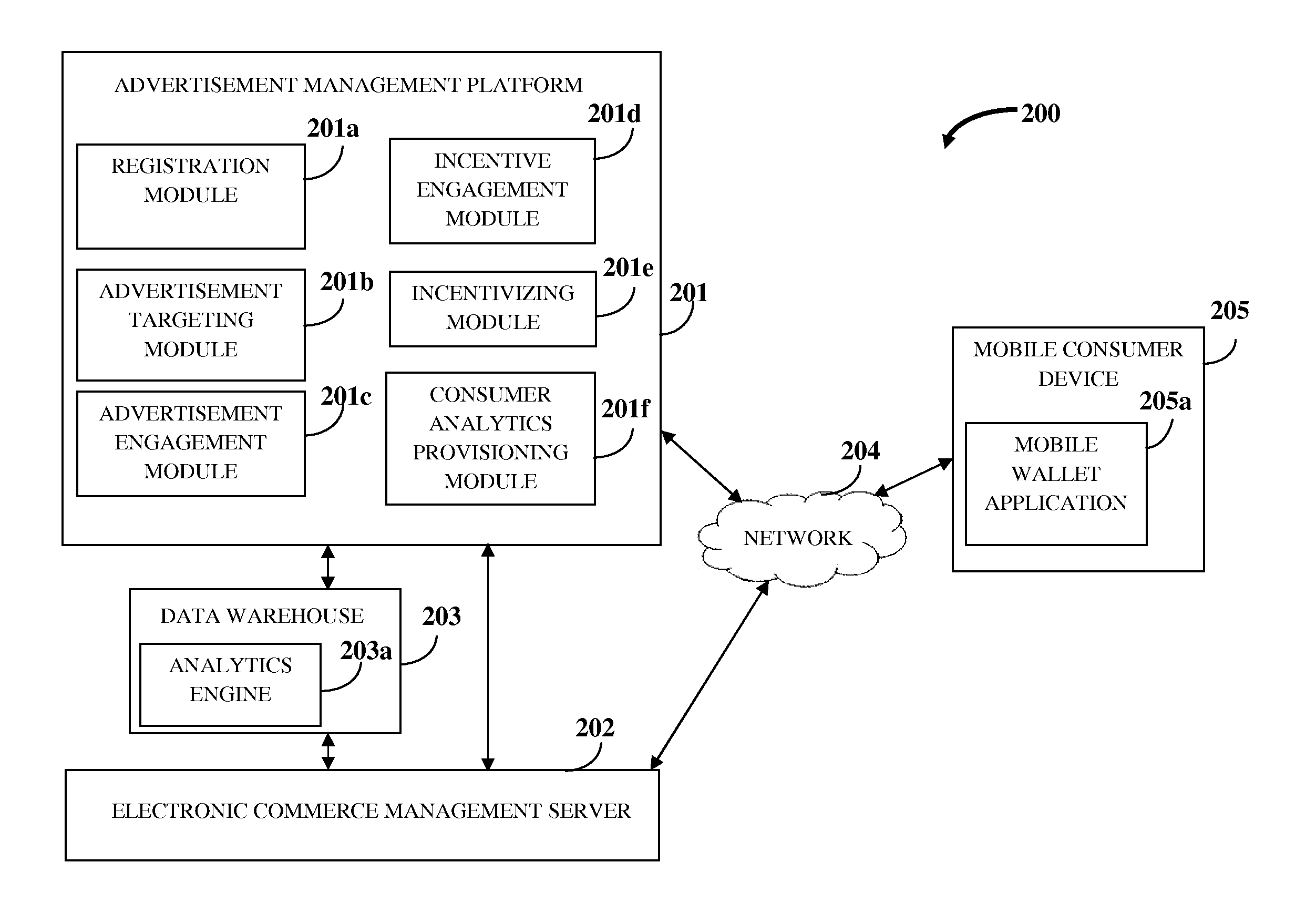
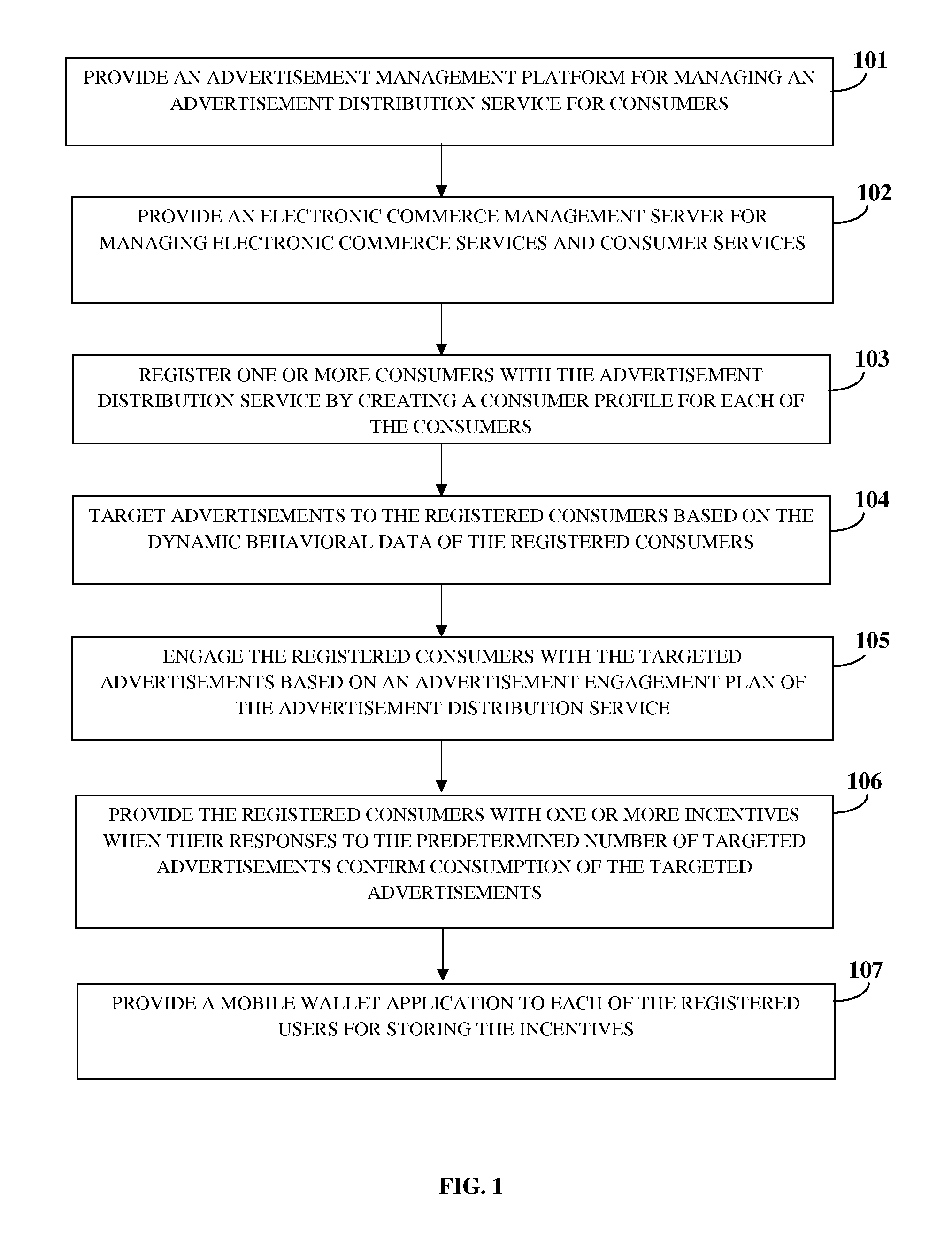
A system to securely and effectively control, process and manage financial services, targeted advertisement delivery, multiple account cards and reward points comprising a web portal or financial institution internet banking portal, offering financial services comprising a secure and effective on-line apparatus and method to manage bank account services, reward points, account cards and advertisement by matching users with advertisers wherein accurate information, such as current personally identifiable financial and transactional information as well as on-line behavioral data, is employed by means to securely process, control and manage financial information located within the premises of the financial institution providing the financial services as one of the criteria for matching advertisers with users.
Owner:EVERTEC GRP LLC
Management Of Advertisements, Electronic Commerce, And Consumer Services
Owner:YUROW A PIERRE
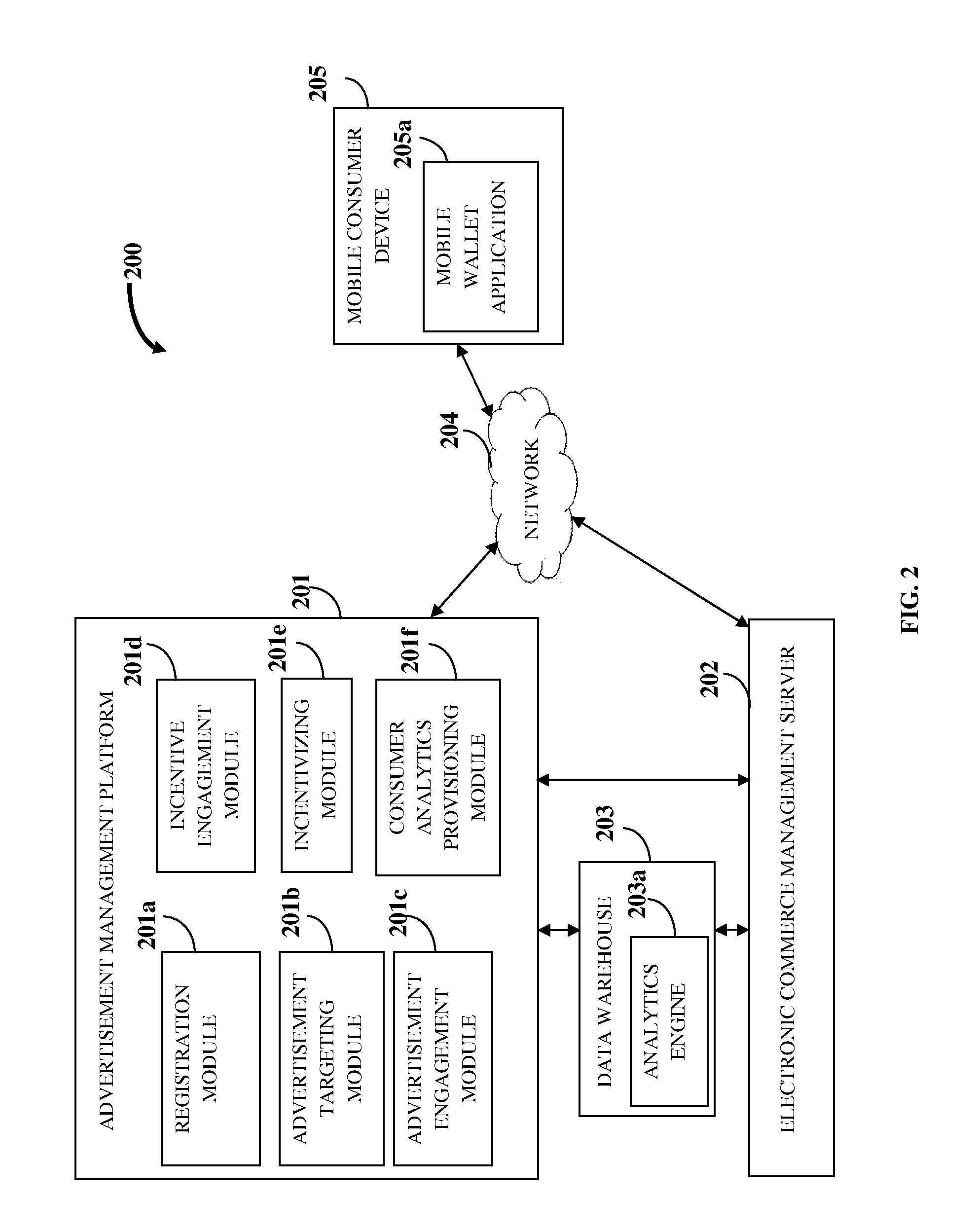
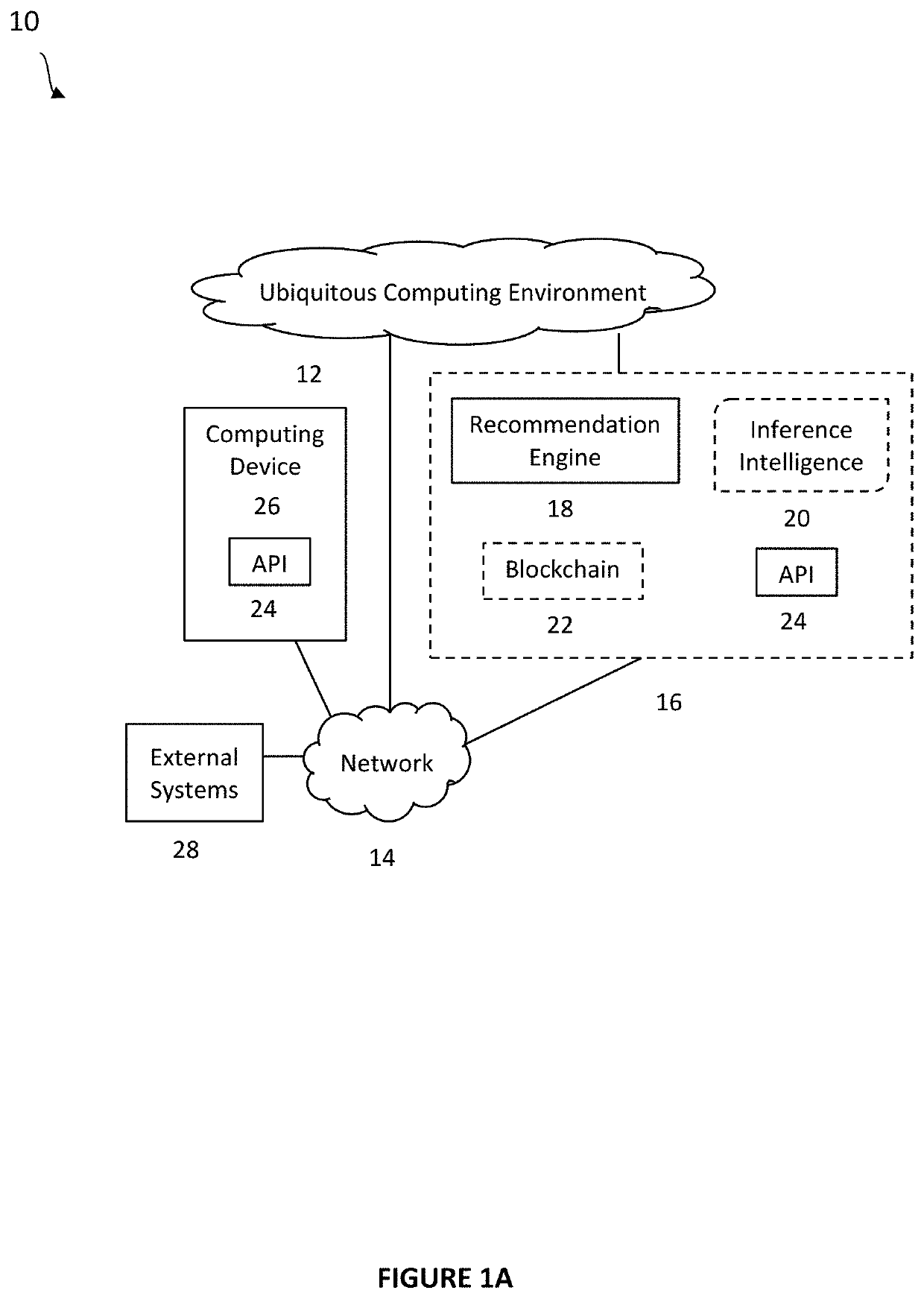
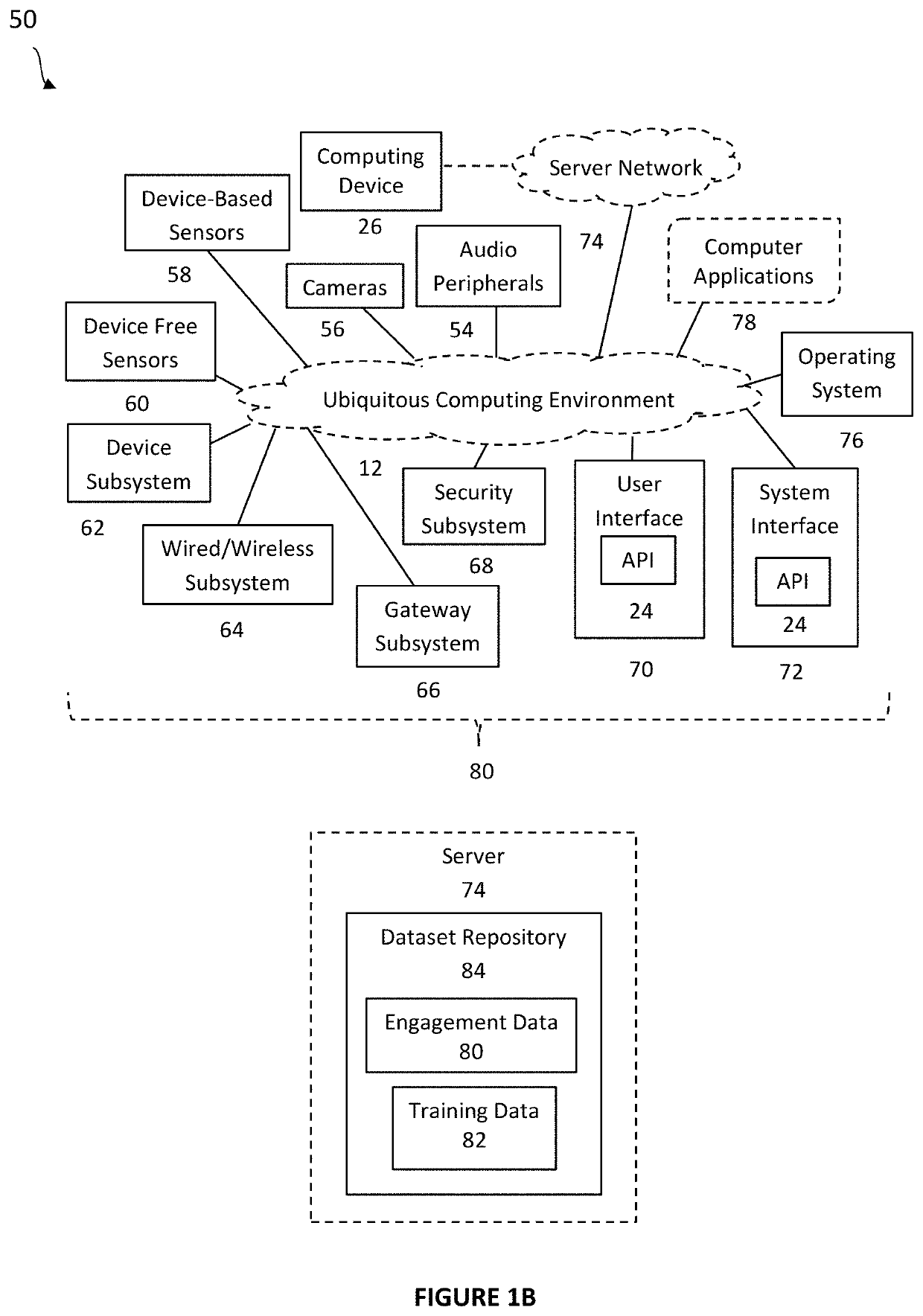
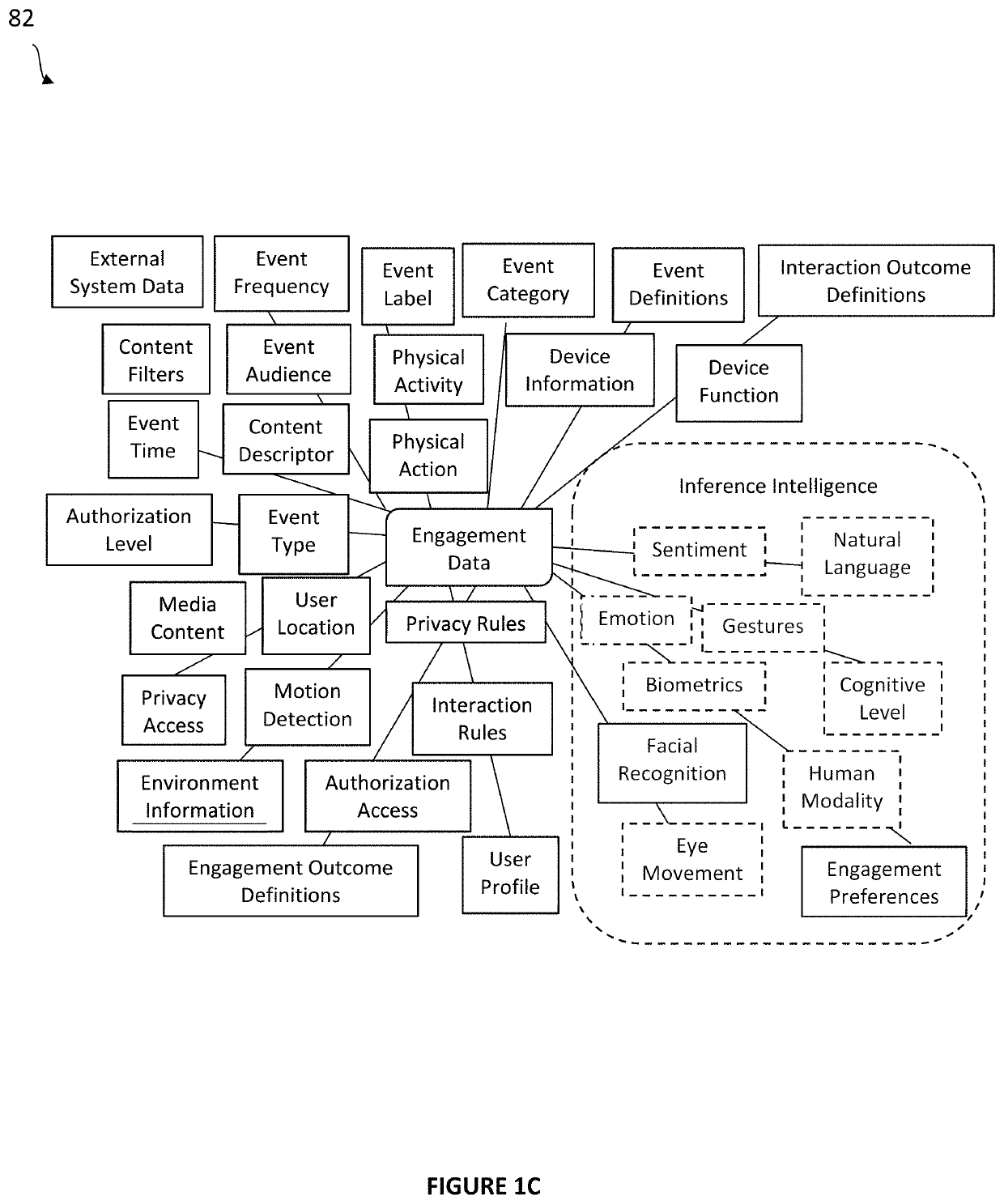
System and method for recommendations in ubiquituous computing environments
ActiveUS20200364588A1Particular environment based servicesCharacter and pattern recognitionEngineeringBehavioral data
Systems and methods for creating an ad hoc pervasive computing environment comprised of an inference recommendation engine coupled to commodity devices and sensors that passively collect human activity and behavioral data. Methods include machine learning and deep learning applications that analyze data to generate preference based recommendations to assist, inform, and guide subjects interacting with a connected living space and their connected social network.
Owner:KNOX GREGORY
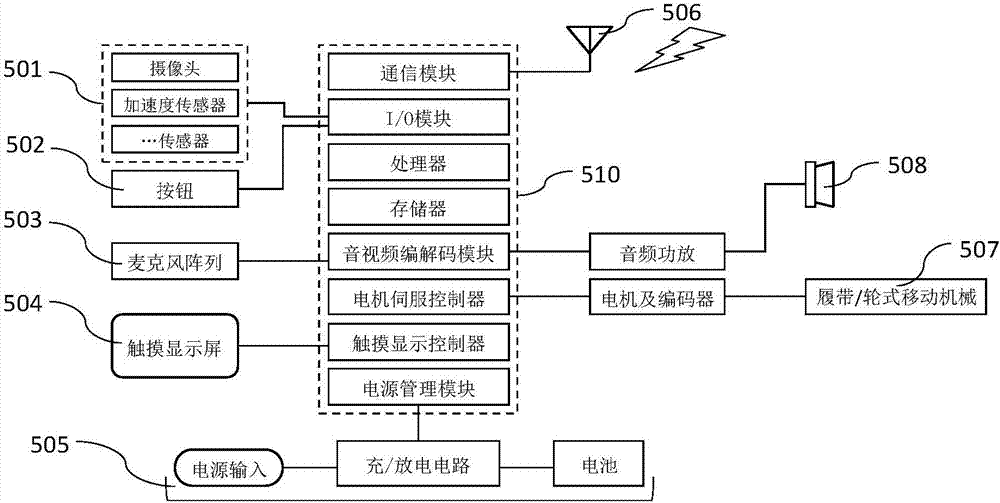
Robot, server and human-computer interaction method
ActiveCN107053191AFunctionalSmart companion functionInput/output for user-computer interactionProgramme-controlled manipulatorPhysical medicine and rehabilitationBehavioral data
The embodiment of the invention provides a human-computer interaction method. The method comprises the following steps: detecting and acquiring the sensing information of an accompanying object of a target object and the emotion information of the target object which interacts with the accompanying object through the robot; extracting emotion characteristic vectors through the robot based on the emotion information; determining the emotion mode of the target object during interacting with the accompanying object according to the emotion characteristic vectors, and determining the interestingness of the target object to the accompanying object according to the emotion mode; extracting the behavior data of the accompanying object from the sensing information according to the interestingness, and screening the behavior data to obtain simulating object data; and simulating the accompanying object through the robot based on the simulating object data.
Owner:HUAWEI TECH CO LTD
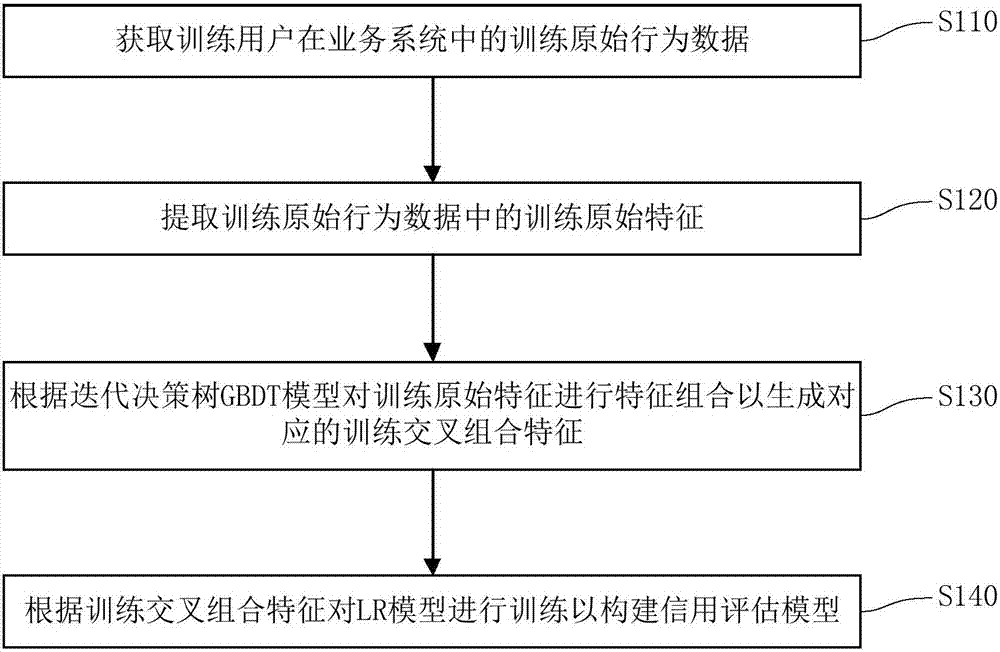
Credit assessment model training method, and credit assessment method and apparatus
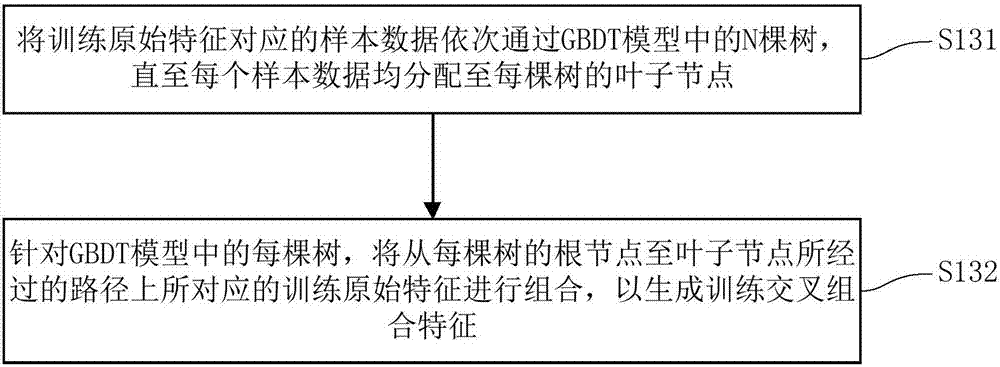
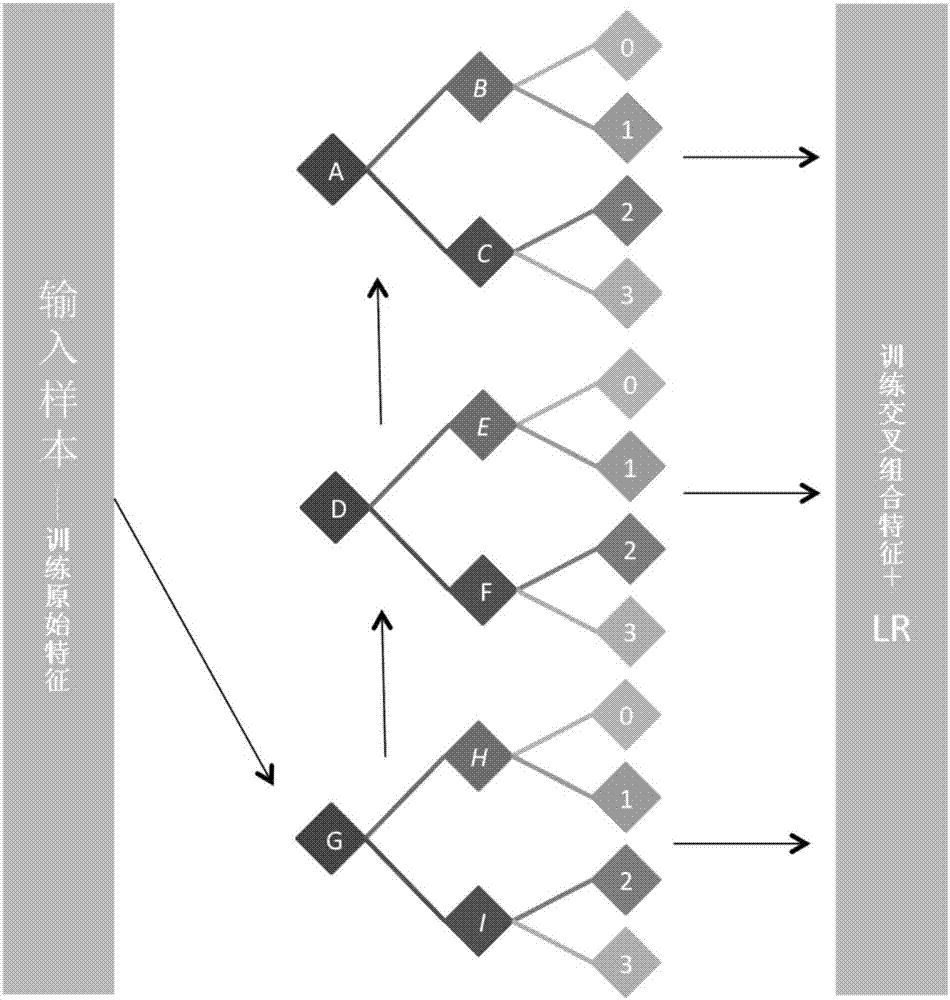
InactiveCN107301577AImprove performanceInterpretableBuying/selling/leasing transactionsNonlinear modelLinear model
The invention discloses a credit assessment model training method, and a credit assessment method and apparatus. The training method comprises the steps of obtaining original training behavior data of a training user in a business system; extracting original training features in the original training behavior data; performing feature combination on the original training features according to a GBDT model to generate corresponding training cross combination features; and performing training on a logistic regression model according to the training cross combination features to build a credit assessment model. According to the method, the original training features are trained through the nonlinear GBDT model to generate the corresponding training cross combination features, and the linear LR model is trained through the training cross combination features to build the credit assessment model, so that the credit assessment model has not only high performance of the nonlinear model but also interpretability of the linear model.
Owner:ALIBABA GRP HLDG LTD
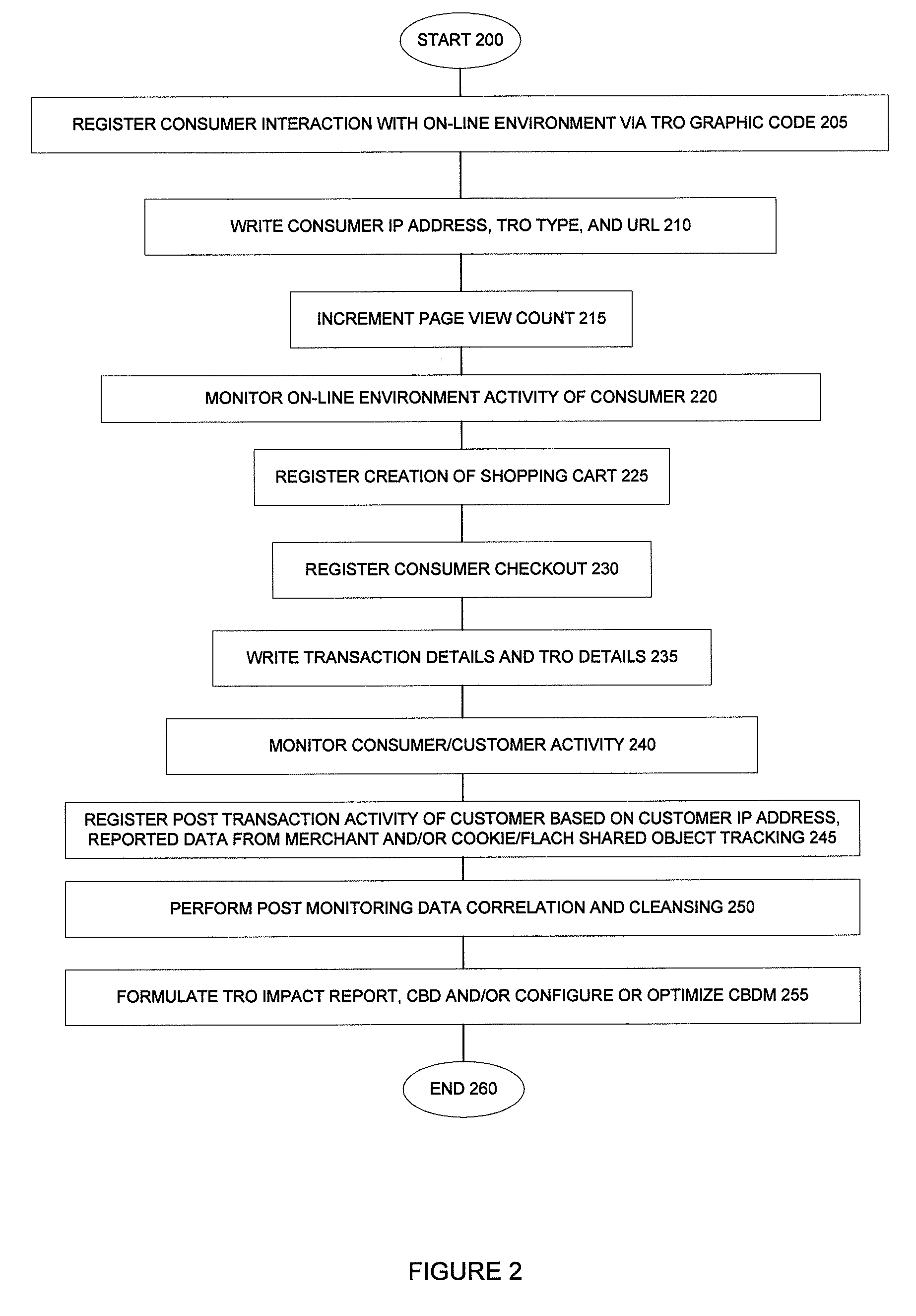
Method, system and components for obtaining, evaluating and/or utilizing seller, buyer and transaction data
Methodologies, systems, components and software are provided that perform web analytics to measure visitor to consumer conversion continuously throughout surfing, through conversion and past completion of a purchase on-line. In accordance with at least one embodiment, such methodologies, systems, components and software may be utilized to determine efficacy of a plurality of parameters relating to one or more Transaction Related Offerings (TROs). In accordance with at least one embodiment of the invention, such methodologies, systems, components and software may be utilized to configure one or more Consumer Behavior Decision Models (CBDMS) and / or generate consumer behavior data.
Owner:BUYSAFE
Method for carrying out personalized recommendation on commodities by fusing knowledge graph
PendingCN112232925ACapture potential interestRecommended results are accurateWeb data retrievalBuying/selling/leasing transactionsPersonalizationEngineering
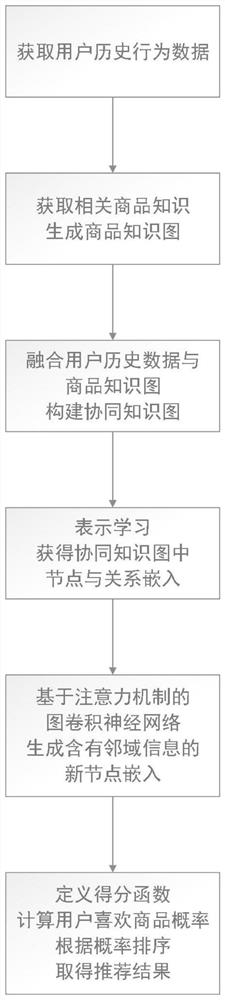
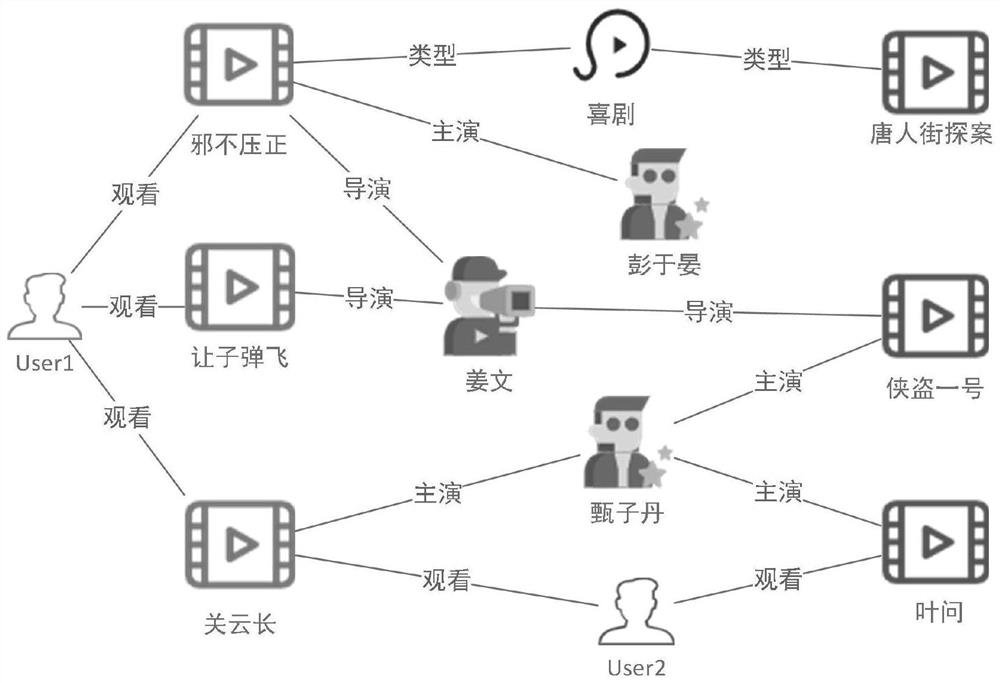
The invention relates to a method for carrying out personalized recommendation on commodities by fusing a knowledge graph. The invention relates to the technical field of machine learning for personalized recommendation of commodities, and the method comprises the steps: obtaining the historical behavior data of a user, and generating a commodity knowledge graph; fusing the historical behavior data of the user with the commodity knowledge graph to construct a collaborative knowledge graph; adopting a representation learning method in machine learning to obtain vector embedding representation of nodes and relationships in the collaborative knowledge graph; embedding vectors of nodes and relations in the collaborative knowledge graph and inputting historical behavior data of the user into agraph convolutional neural network model based on an attention mechanism to form vector embedding representation of new nodes and relations containing neighborhood information; and defining a score function, calculating the probability that the user likes the commodity through the user and commodity vector embedding representation of the fused neighborhood information output by the graph convolutional neural network model, and performing sorting according to a prediction result to obtain a recommendation list.
Owner:HARBIN ENG UNIV
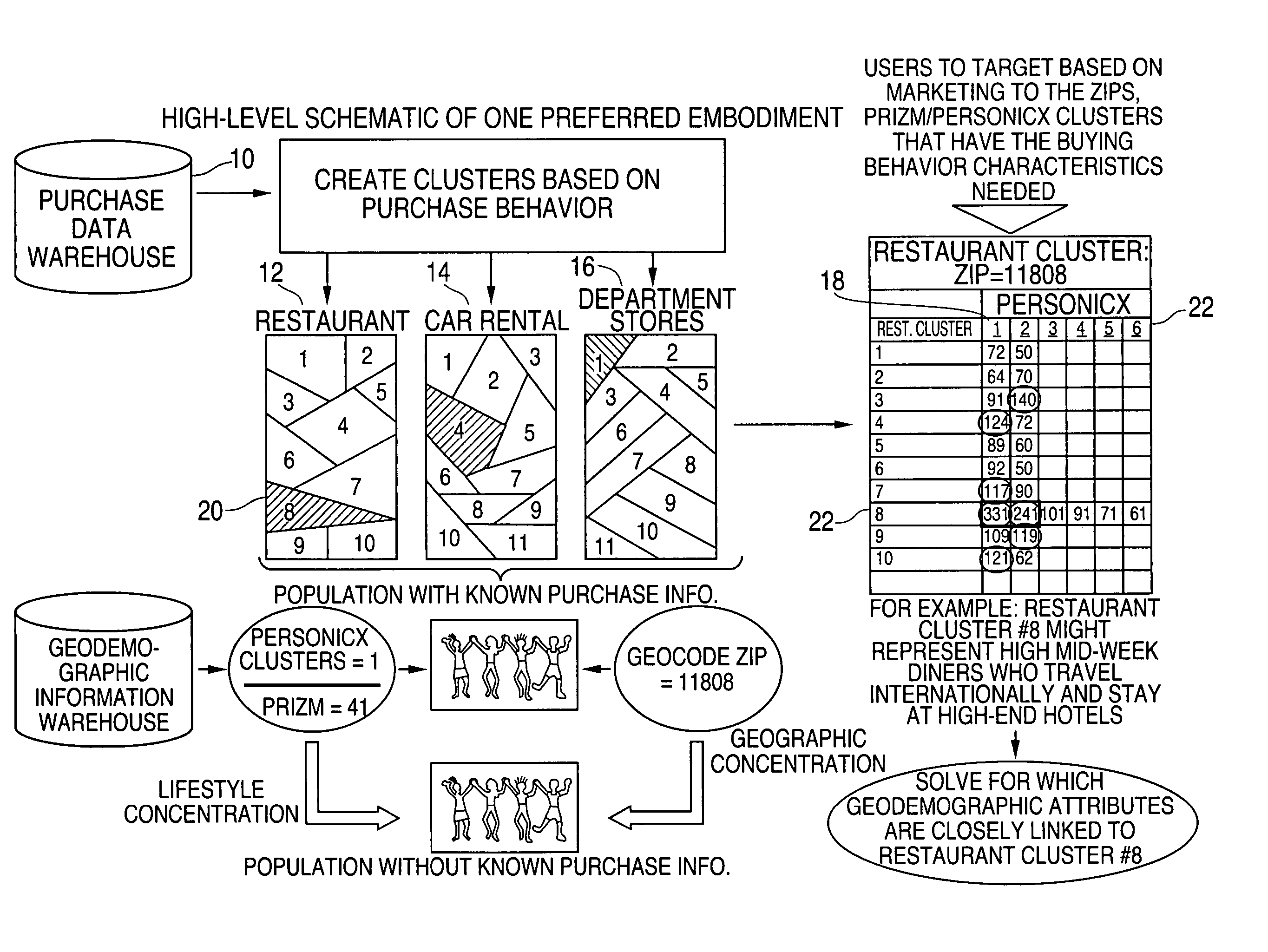
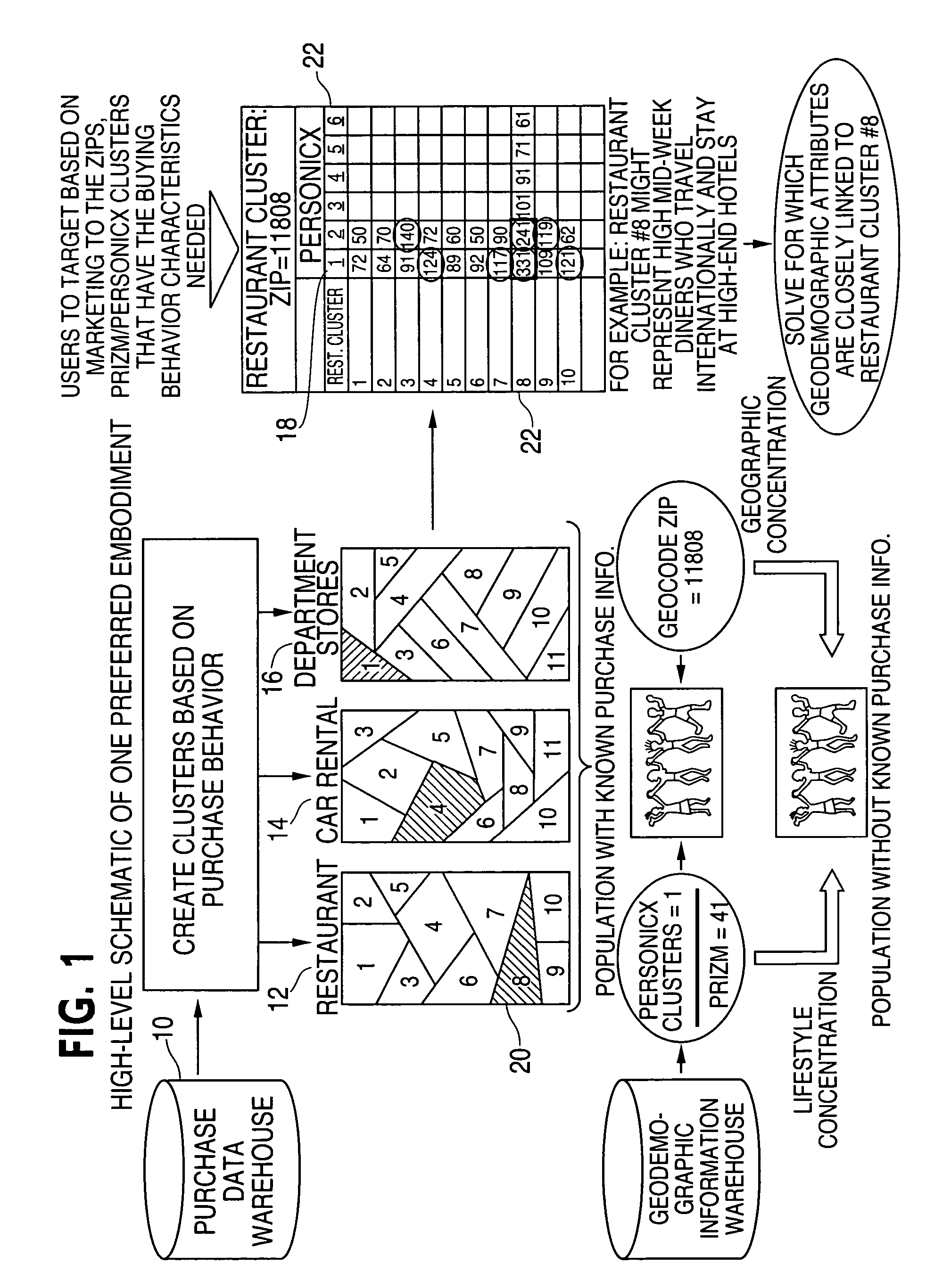
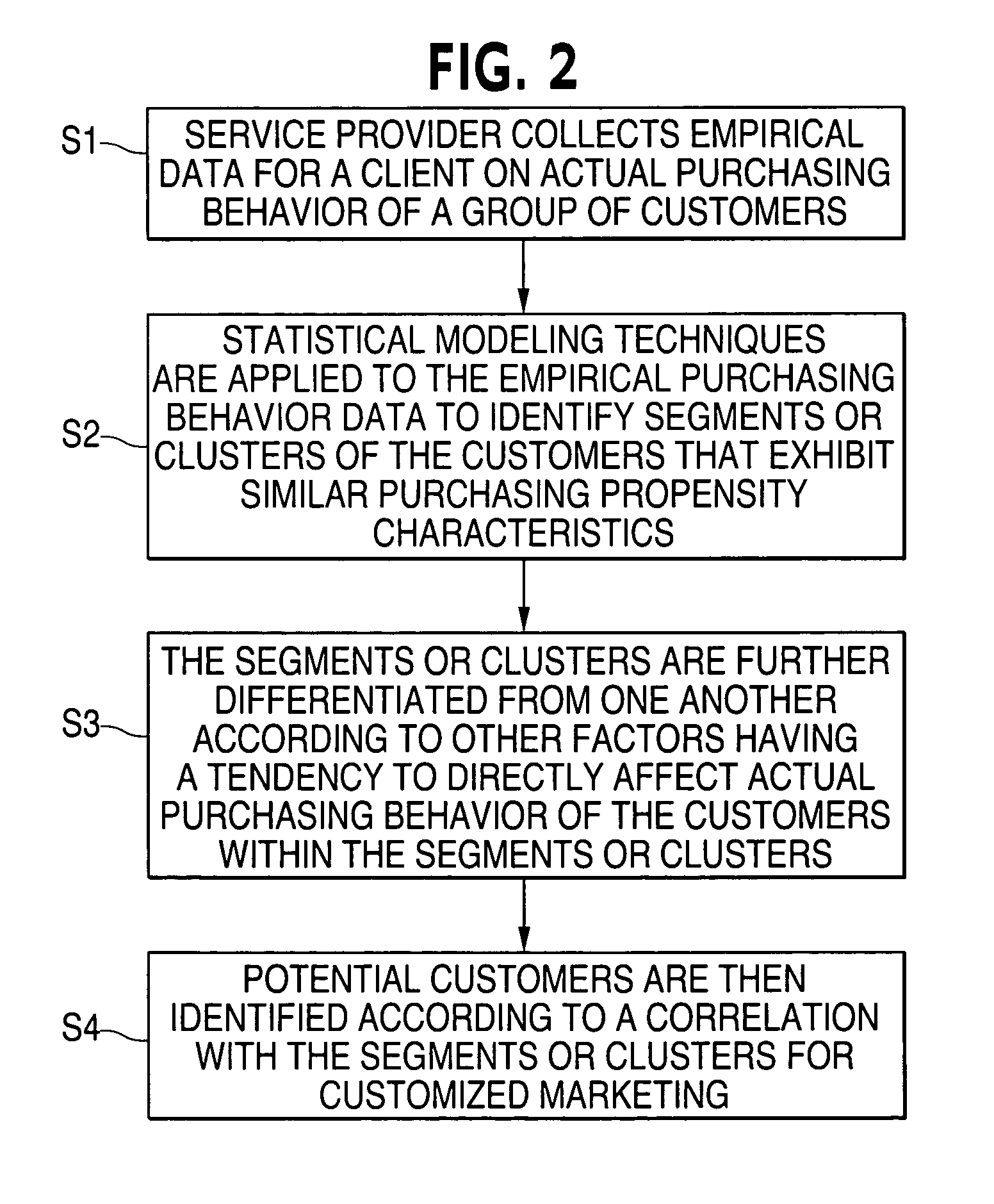
Method and system for purchase-based segmentation
ActiveUS20050177449A1Improve accuracyImprove Segmentation AccuracyMarket predictionsDigital computer detailsBehavioral dataArtificial intelligence
A method and system for purchased-based segmentation of potential customers employs the use of actual, observed purchases instead of presumptions and correlations to improve the accuracy of segmentation and involves collecting empirical data for a client on actual purchasing behavior of a group of customers and applying statistical modeling techniques to the empirical purchasing behavior data to identify segments or clusters of the customers that exhibit similar purchasing propensity characteristics. Thereafter, the segments or clusters are further differentiated from one another according to other factors having a tendency to directly affect actual purchasing behavior of the customers within the segments or clusters, and potential customers are then identified according to a correlation with the segments or clusters for customized marketing.
Owner:CITICORP CREDIT SERVICES INC (USA)
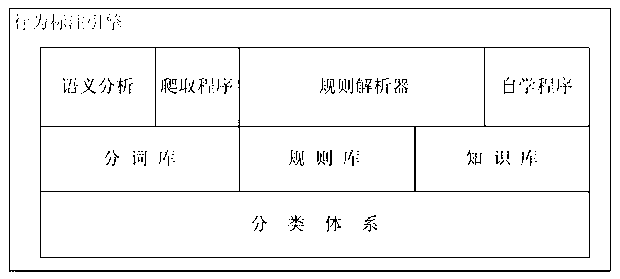
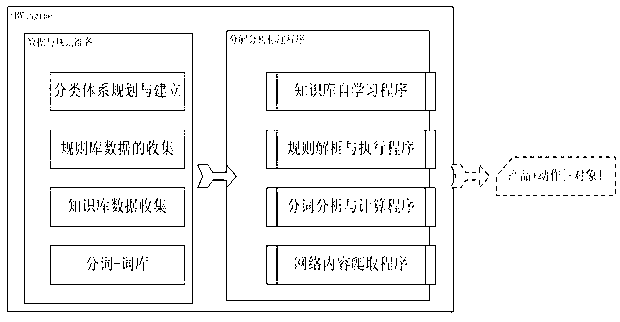
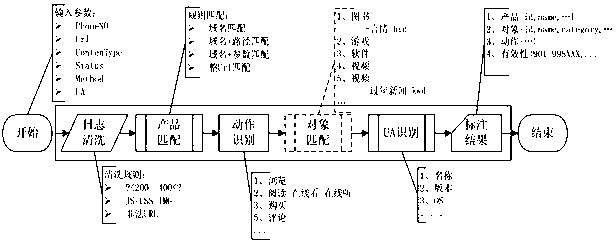
Internet behavior markup engine and behavior markup method corresponding to same
The invention discloses an internet behavior markup engine and a behavior markup method corresponding to the same, and belongs to the technical field of user internet behavior data collection and analysis. The markup engine comprises a classification system module, a word segmentation base module, a semantic analysis module, a crawling program module, a rule base module, a knowledge base module, a rule parser module and a self-learning program module. The internet behavior markup method provides a basic logical structure that user behavior=behavior agent + behavior identification + behavior state. By the engine and the method, classification efficiency and accuracy are improved, description particle size of internet user behavior data is thinned, action, object and environmental conditions of one-time user behaviors are integrally recognized, and internet user behaviors are restored integrally. User behavior data outputted according to IUBML (internet universal behavior markup language) rules directly provide accurate advertising services based on user behaviors and demand understanding, and marketing requirements of corporate clients are met.
Owner:北京宽连十方数字技术有限公司
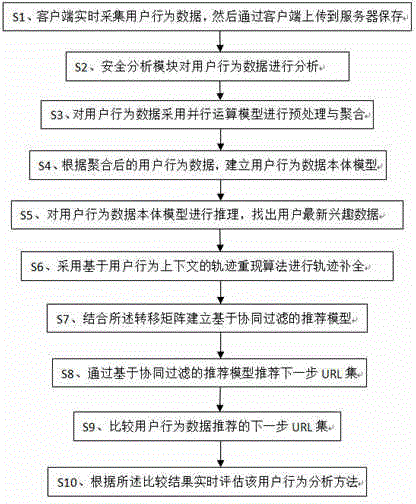
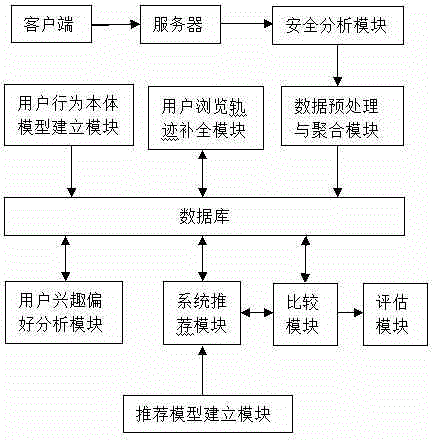
User behavior analysis method and system based on big data
InactiveCN104462213AGain interest in timeEffective and accurate pushWebsite content managementSpecial data processing applicationsEngineeringContext data
The invention discloses a user behavior analysis method and system based on big data. According to the method, user behavior data are collected through a client side in real time, user behaviors and contextual information of a page URL are combined, the real scene that a user browses Web pages is reproduced to the greatest extent, comprehensive user behavior tracks are extracted, and effective data assurance is provided for analyzing the user behaviors; security assurance is provided for the user behavior data through a safety analysis module, and a user behavior data body model is used for modeling the user behaviors, so that behavior information semantic levels are shared and reused, and the interoperability and the reliability of the model are improved; the user behavior and context data are collected in real time for analysis, so that a result is more reliable; body and behavior information is stored through a column storage database, and therefore the foundation of massive data management is laid; the powerful processing capacity and the large-scale data storage capacity of the cloud computing technology, the body and a reasoning and knowledge discovery method of the body are combined, the massive user behavior data are analyzed in real time to obtain user interest in time, and then effective and accurate user push is achieved.
Owner:成都逸动无限网络科技有限公司
Application recommendation method and device and server equipment
InactiveCN103593434AImprove user experienceRealize personalized recommendationSpecial data processing applicationsPersonalizationTerminal equipment
The invention discloses an application recommendation method and device and server equipment. The method comprises the steps that according to a behavior data list of application acquisition terminal equipment recently browsed and downloaded by terminal equipment, the list comprises a plurality of first application identifications and nearest behavior time of first applications; according to the degree of association between the first applications and second applications in a preset application bank, multiple corresponding second applications are obtained from the preset application bank to form an alternative application assembly; according to current time, the nearest behavior time of the first applications is unified to obtain initial weighted values of the first applications; according to the degree of association of the second applications, the first application identifications corresponding to the degree of the associations and the initial weighted values of the first applications, an application recommendation list is generated, the application recommendation list is sent to the terminal equipment to allow the terminal equipment to show the application recommendation list. According to the technical scheme, individualized recommendation can be achieved, and recommendation efficiency of the applications is effectively improved.
Owner:BEIJING QIHOO TECH CO LTD +1
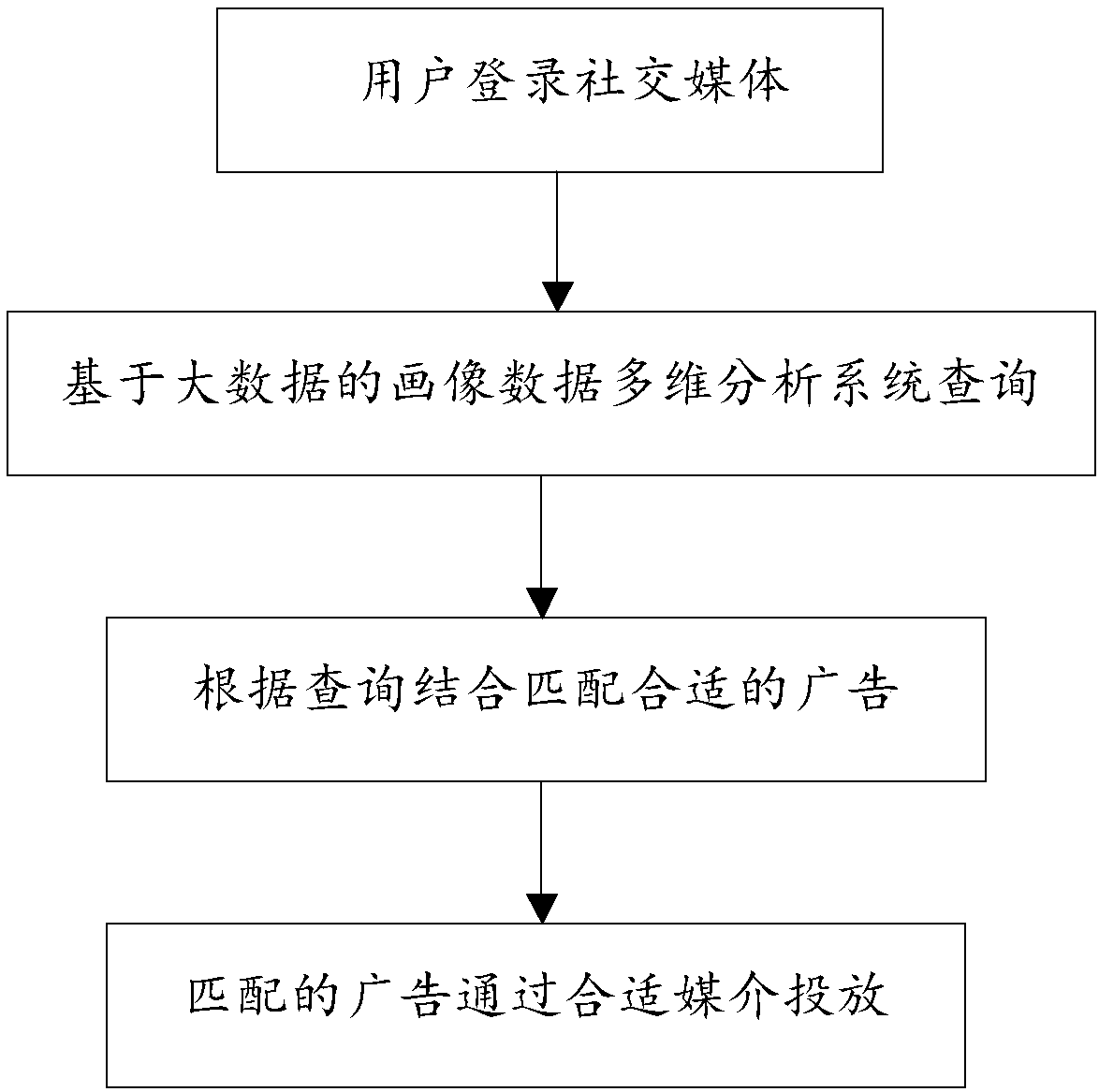
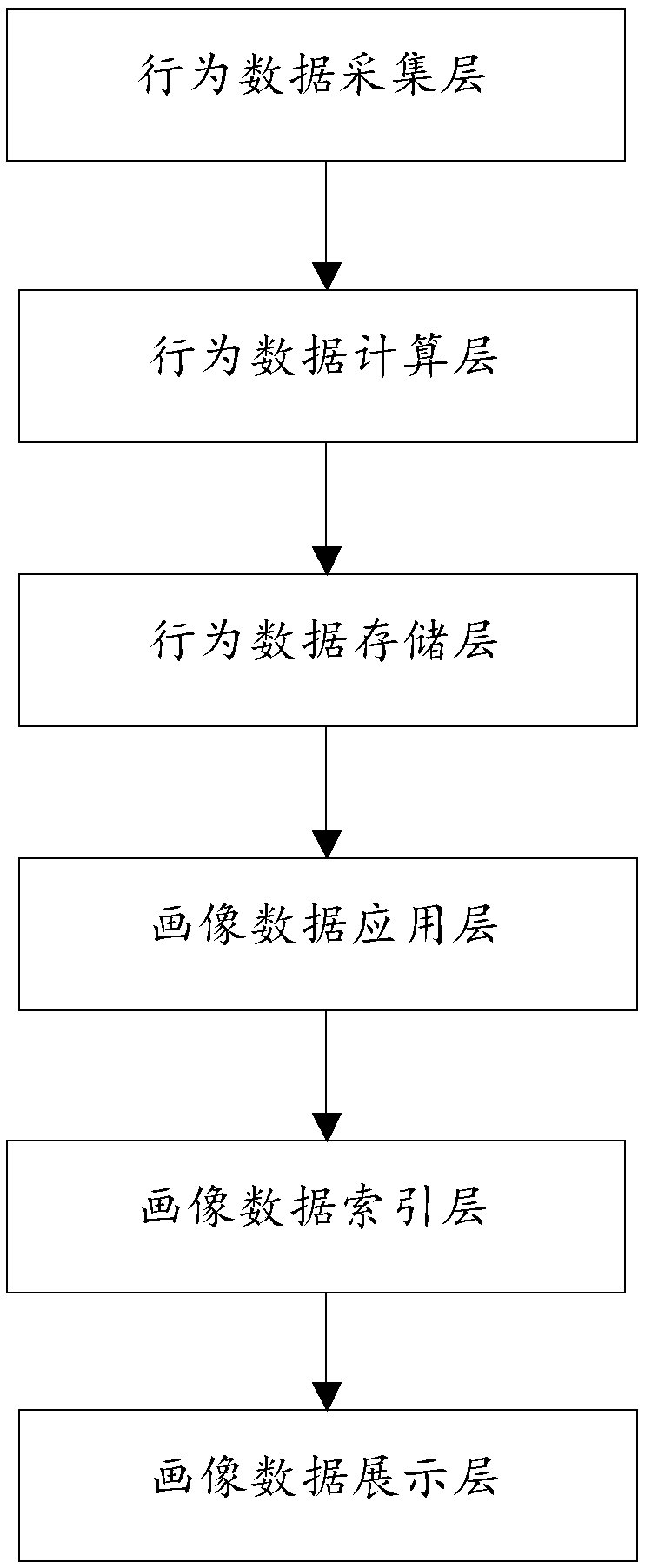
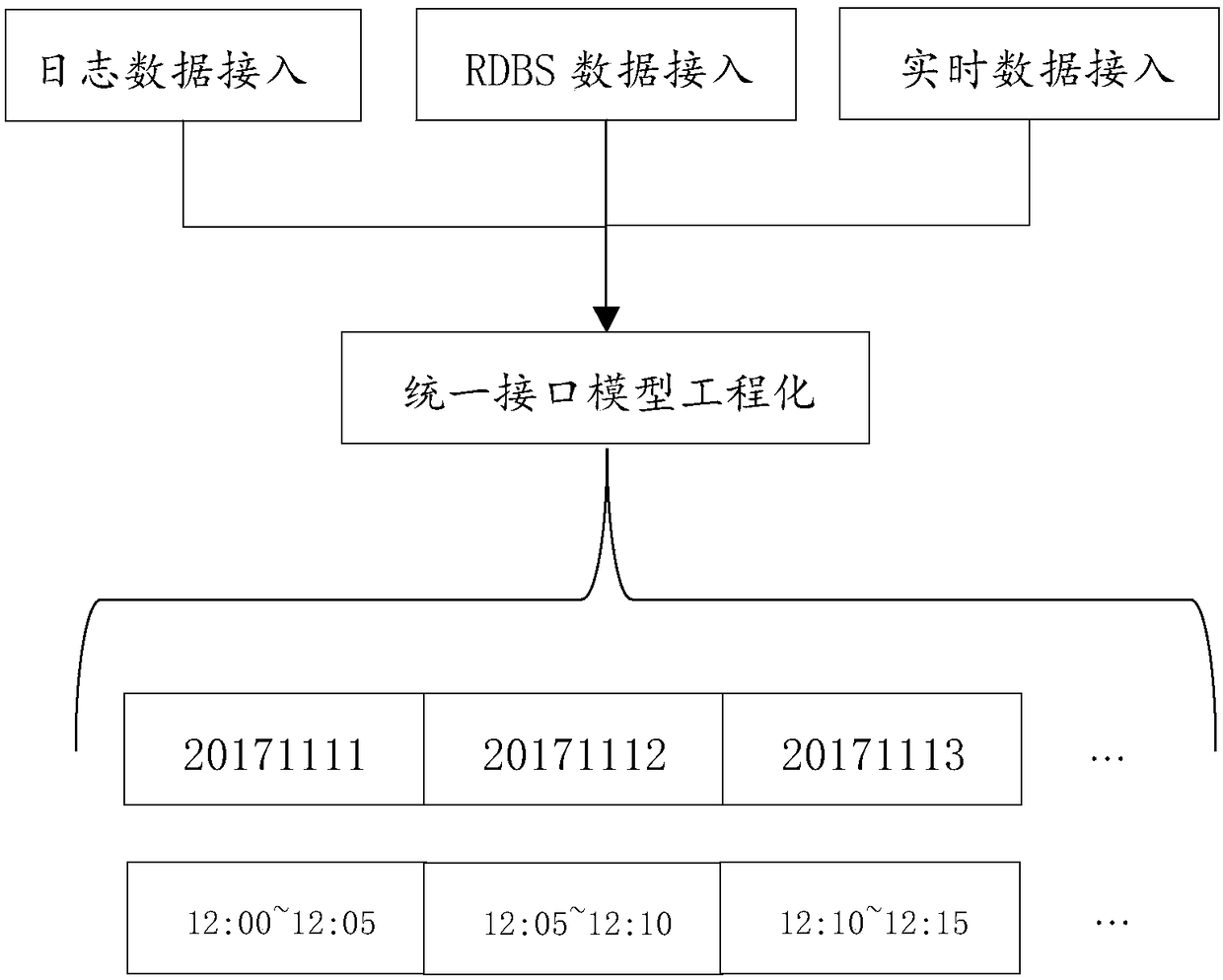
Intelligent social advertisement release platform based on portrait data of big data
ActiveCN108416620ATargetedBeyond Business IntelligenceSpecial data processing applicationsMarketingInverted indexOrganizational form
The invention provides an intelligent social advertisement release platform based on portrait data of big data. Real-time and offline behavior data of a user can be collected by a single interface (based on a dataflow model); integration and calculation are performed through a big data component; a calculation result is user portrait data; and a data organization form is a wide-table taking tags as fields. The portrait data is organized in a reverse index mode; and indexes of the data are stored in a big data warehouse. A Web platform takes multiple specific tags as input conditions and outputs statistical and aggregation results. During use, data specifically used for interests, hobbies and the like is analyzed, and advertisement release is performed according to specific hobbies of the user, so that the intelligent social advertisement release platform is formed, the advertisement release randomness and blindness are reduced, and the pertinence is achieved.
Owner:HANGZHOU FUYUN NETWORK TECHNOLOGY CO LTD
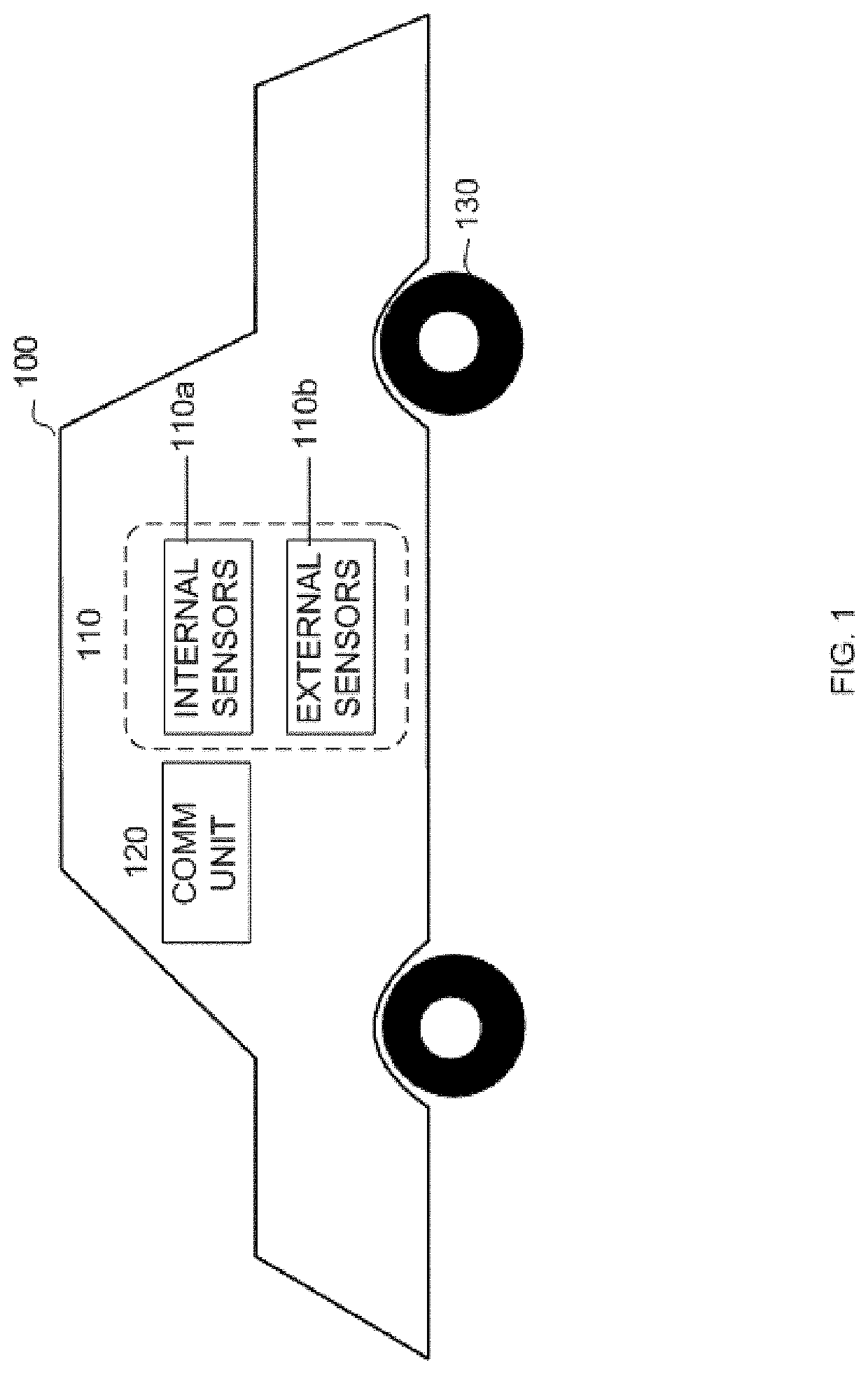
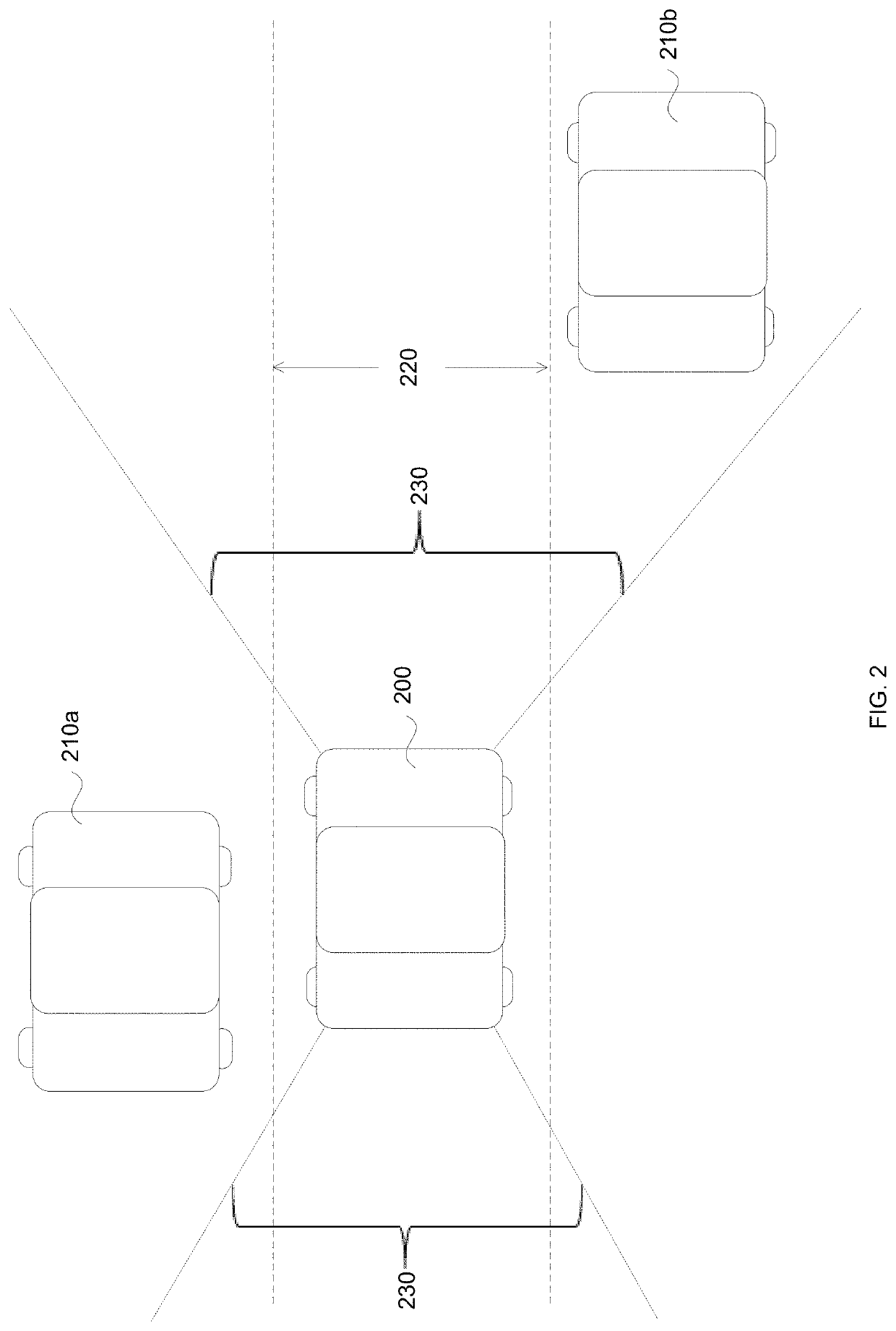
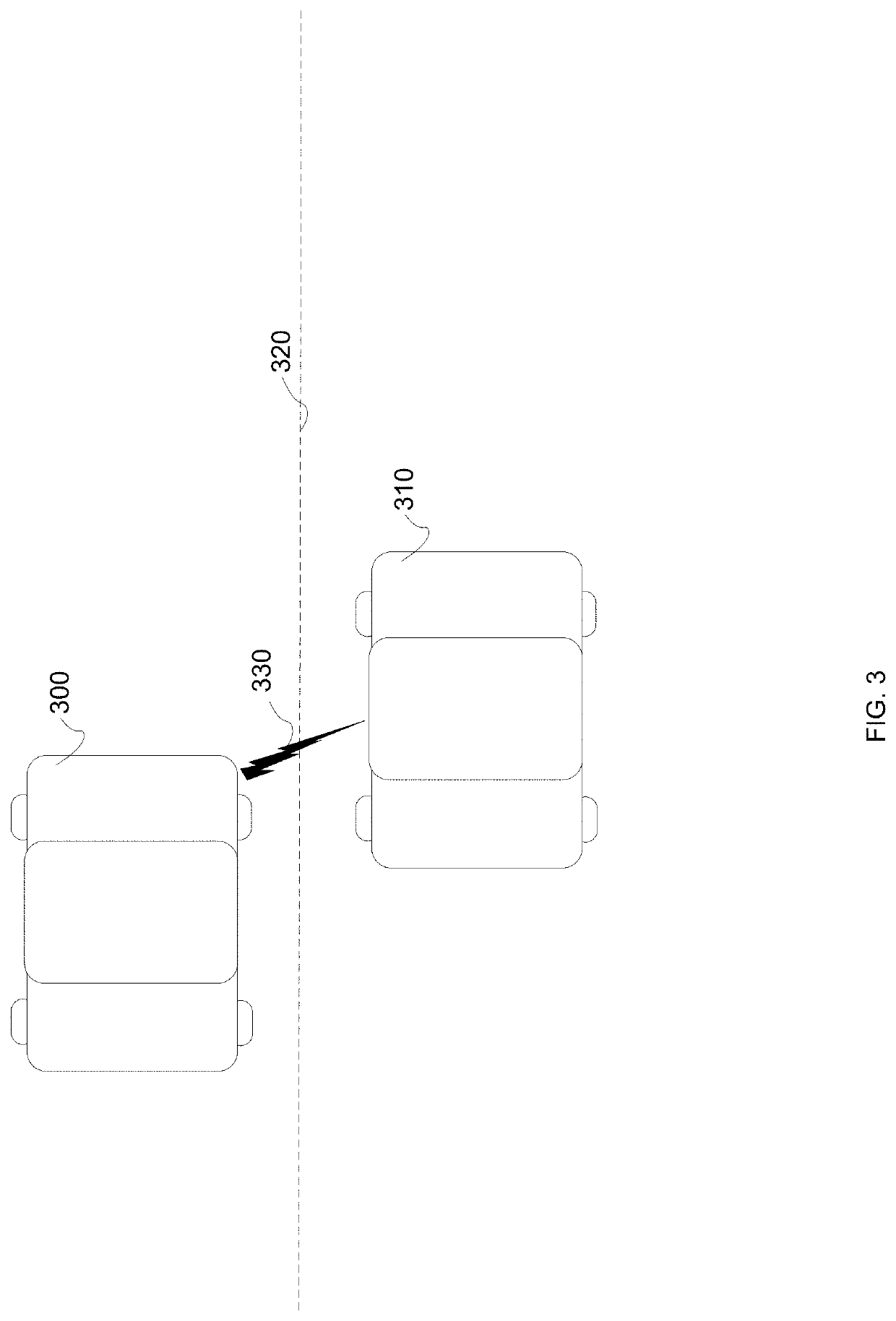
Vehicle behavior monitoring systems and methods
InactiveUS20200008028A1FinanceRegistering/indicating working of vehiclesVehicle behaviorMonitoring system
A method of analyzing vehicle data includes collecting behavior data of one or more surrounding vehicles with aid of one or more sensors on-board a sensing vehicle and analyzing the behavior data of the one or more surrounding vehicles with aid of one or more processors to determine a safe driving index for each of the one or more surrounding vehicles.
Owner:SZ DJI TECH CO LTD
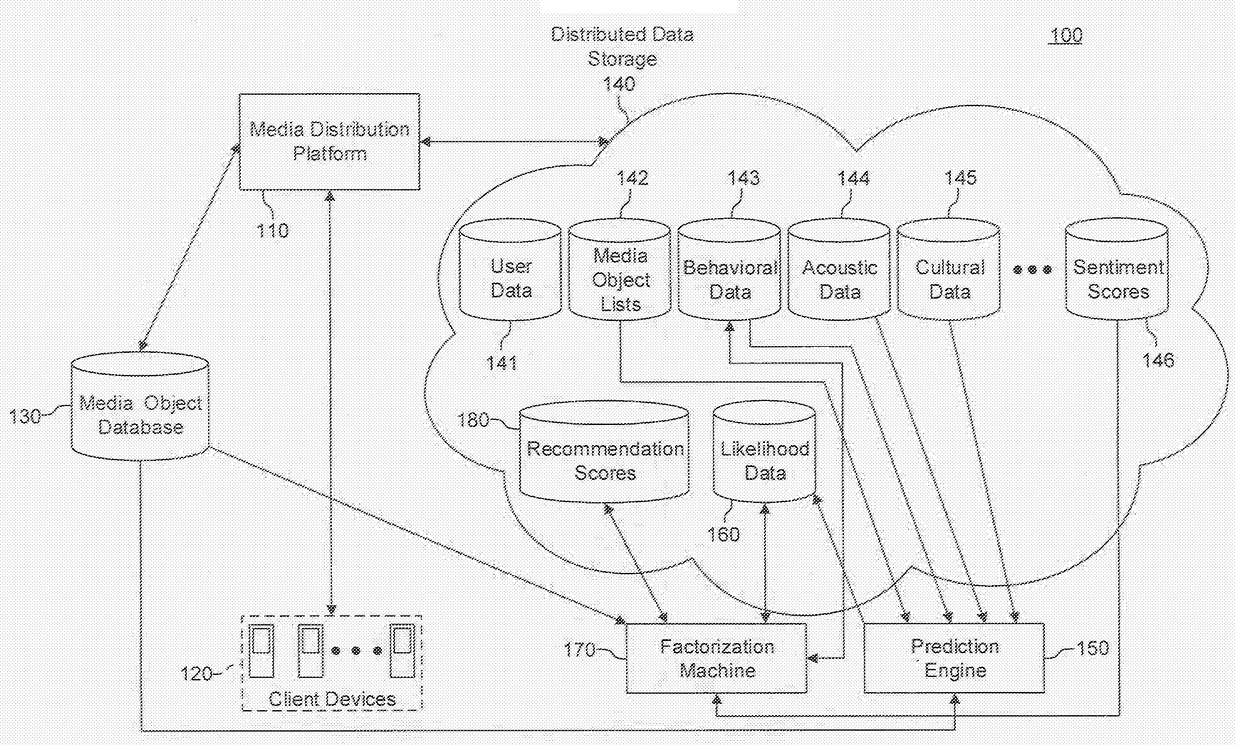
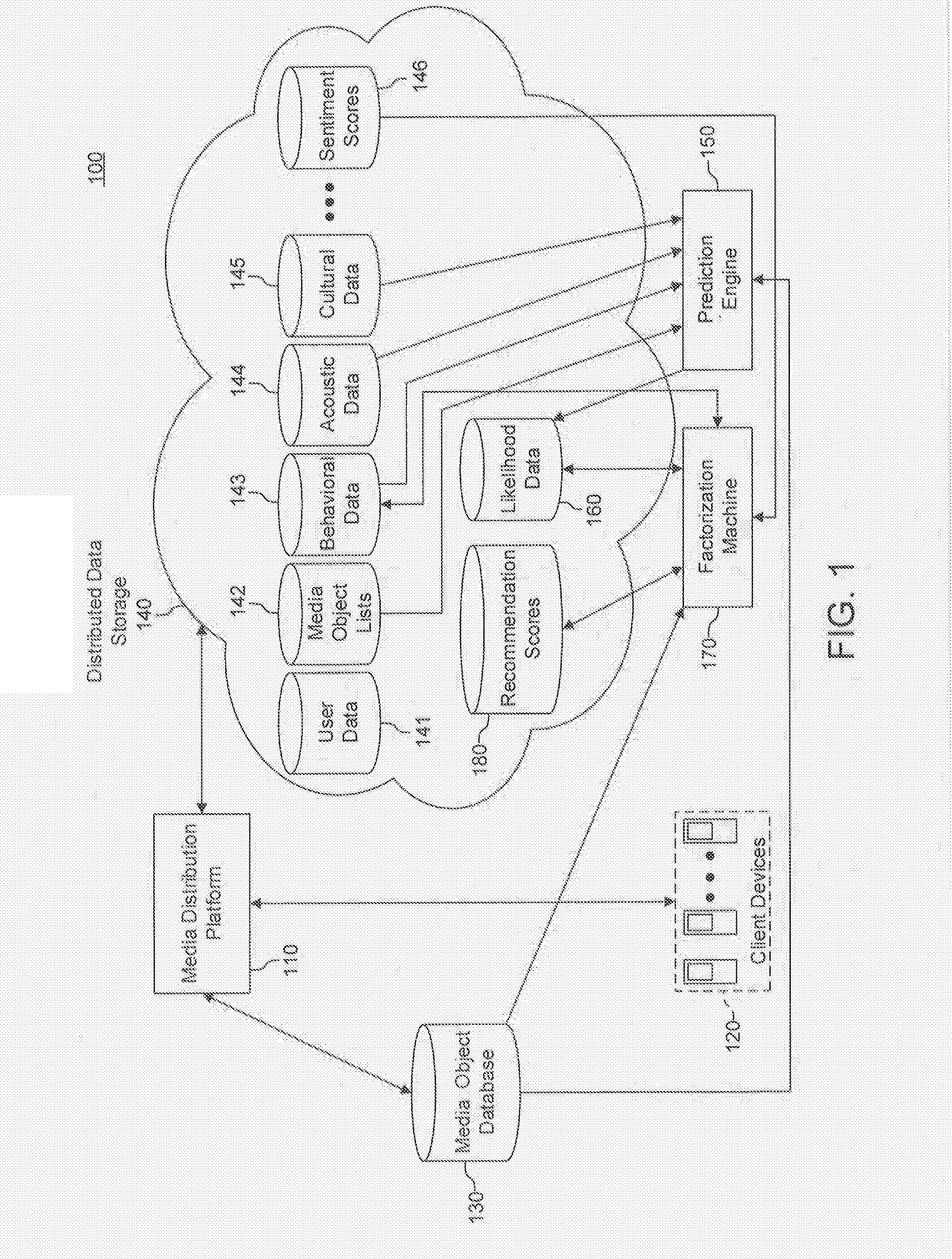
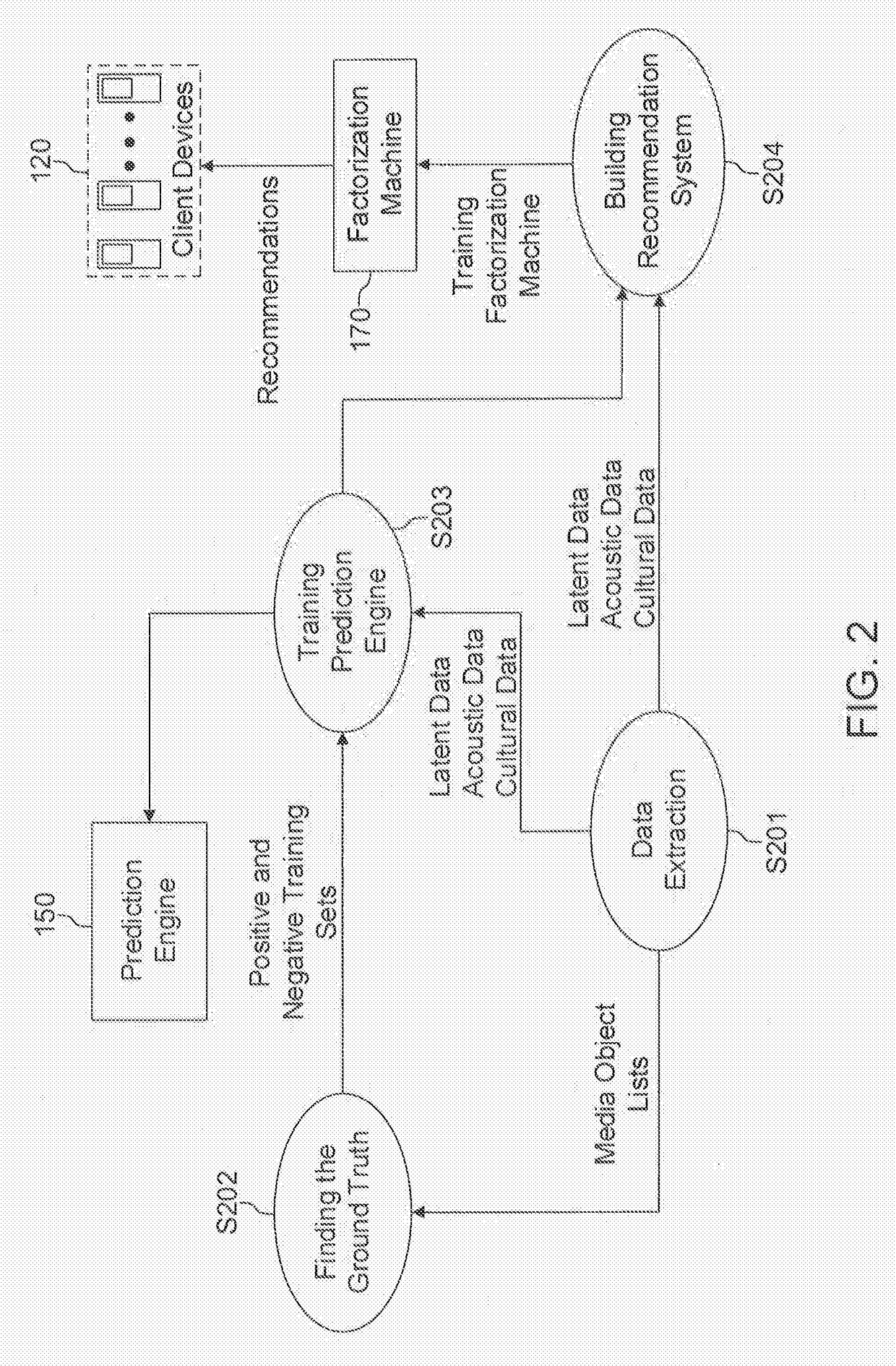
Systems, methods, and computer products for recommending media suitable for a designated style of use
Media suitable for a designated style of use are recommended from among a database of media objects. A prediction engine is trained using a plurality of media object lists, each of the media object lists containing metadata associated with a plurality of media objects, the media object lists corresponding to the designated style of use, and the prediction engine being trained to calculate the likelihood that a media object is suitable for the designated style of use. The prediction engine includes a binomial classification model trained with feature vectors that include behavioral data, acoustic data and cultural data for the plurality of media objects. The trained prediction engine is applied to media objects in the database of media objects so as to calculate likelihoods that the media objects are suitable for the designated style of use. One or more media objects are recommended using the calculated likelihoods.
Owner:SPOTIFY
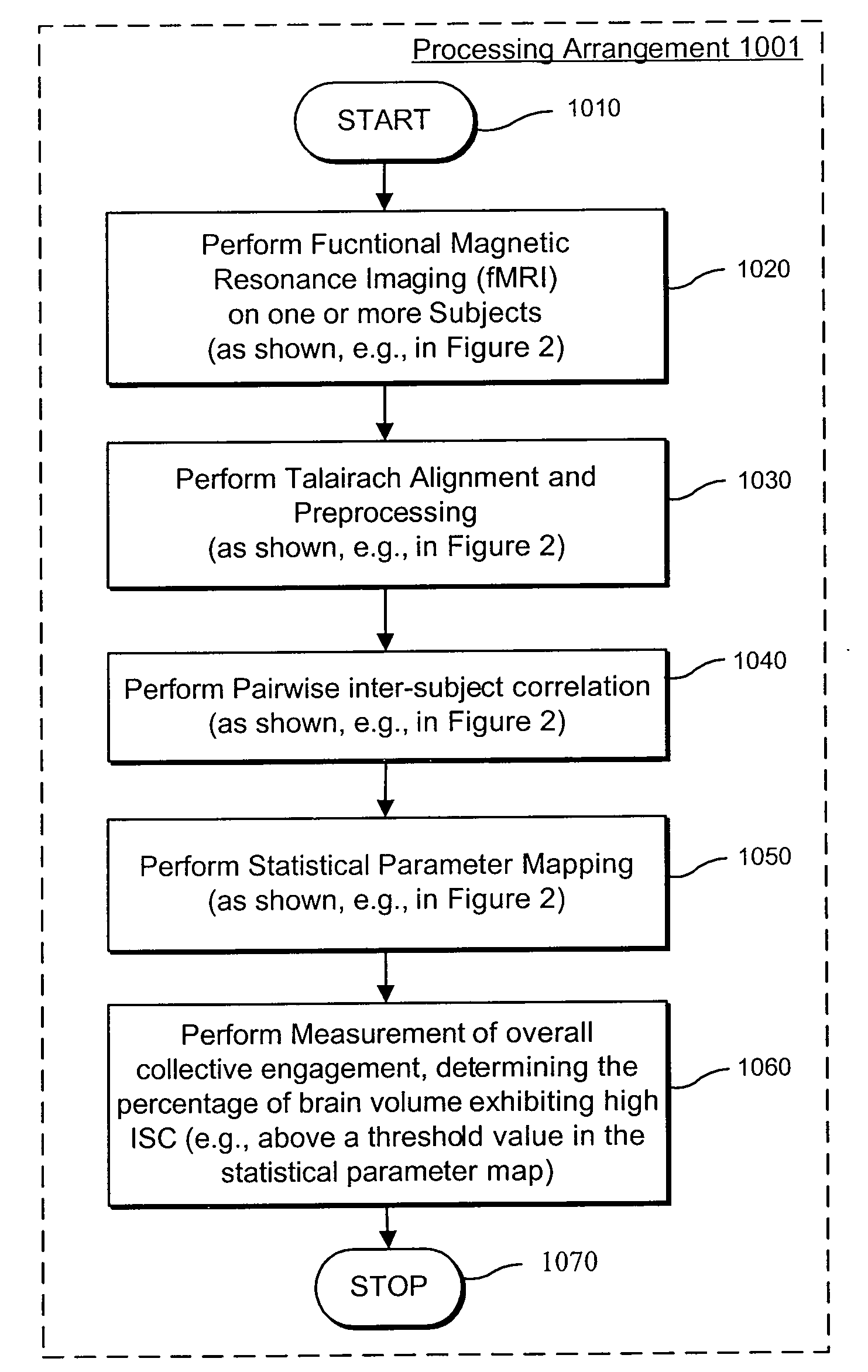
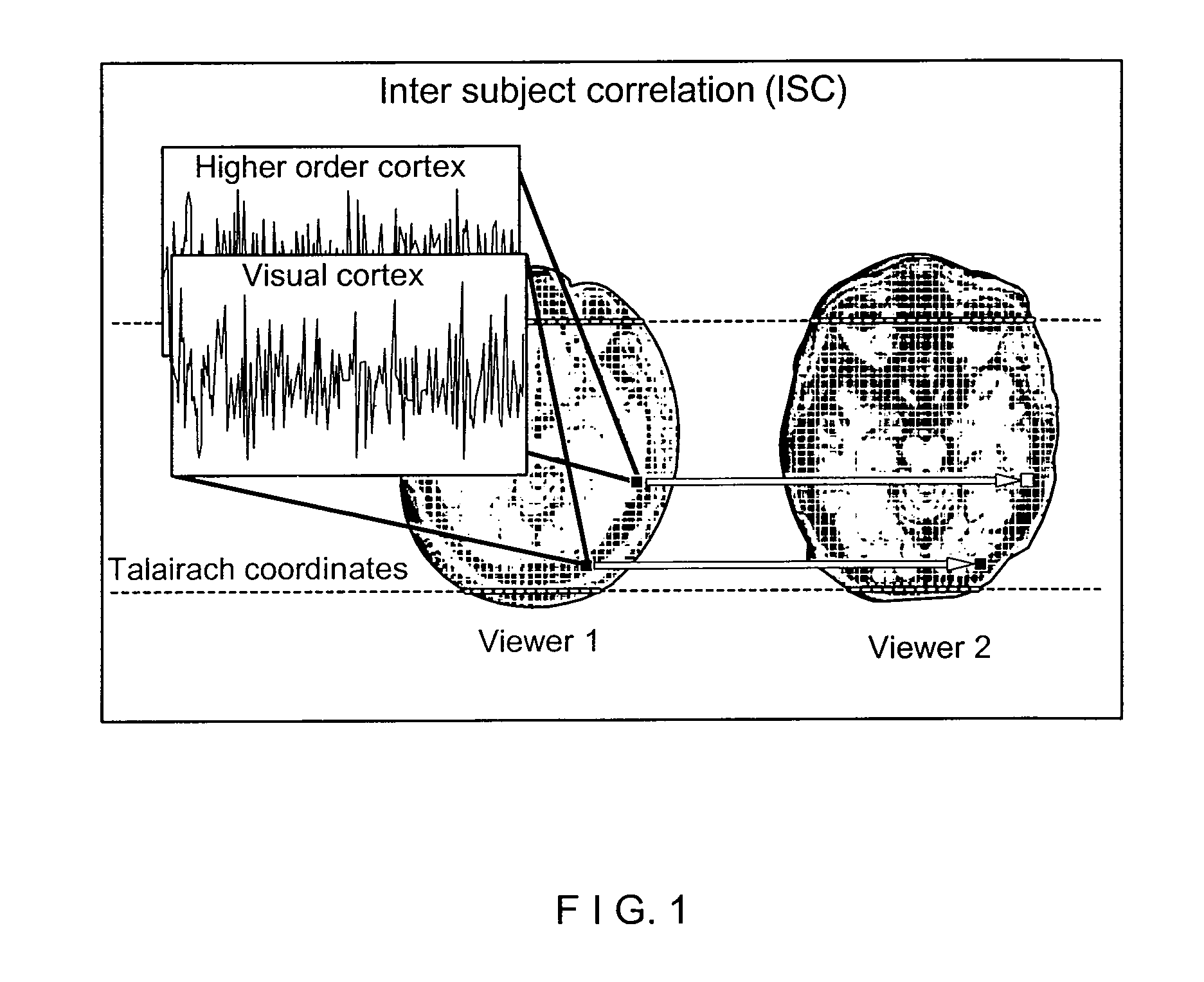
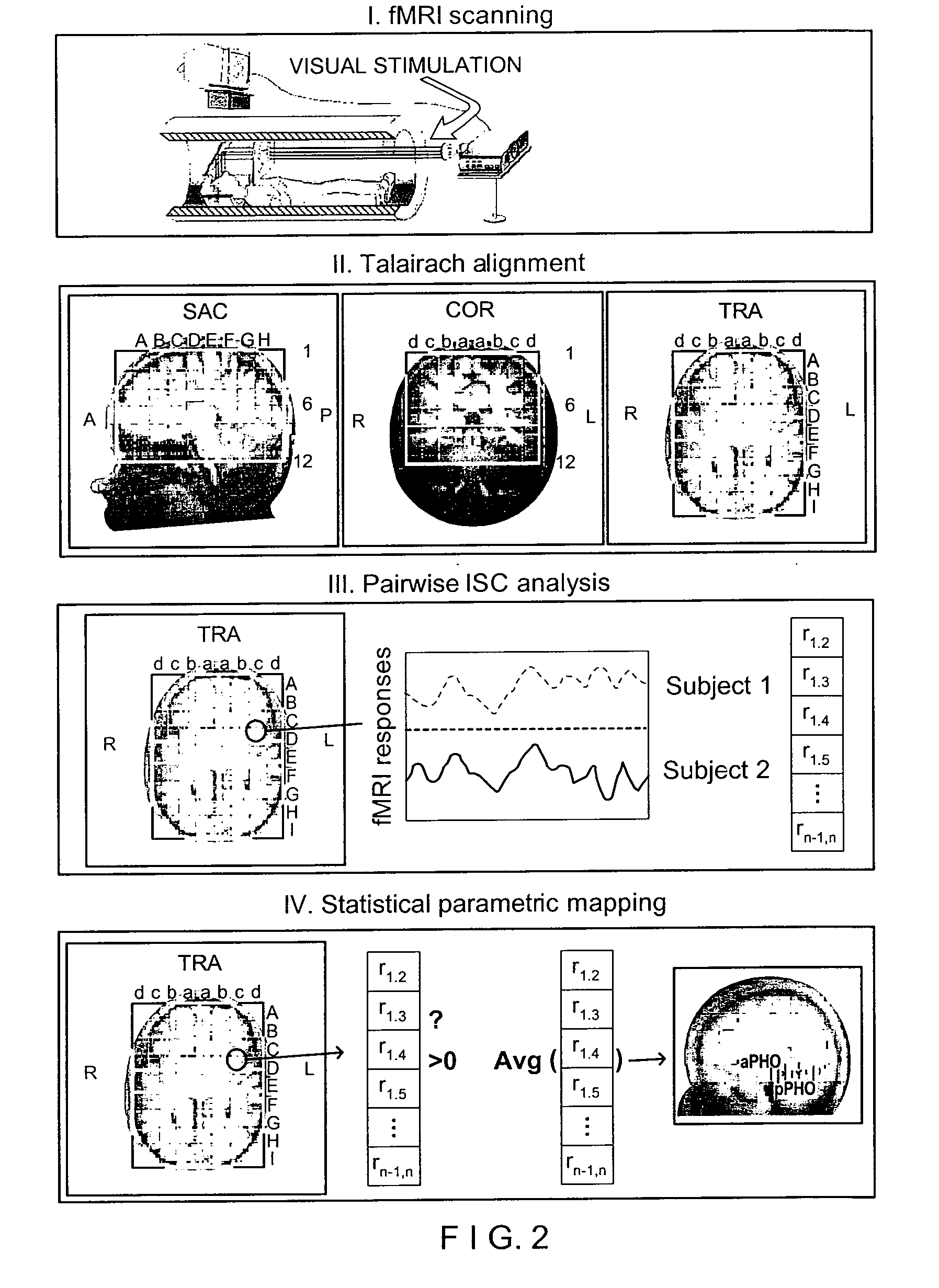
Computer-accessible medium, system and method for assessing effect of a stimulus using intersubject correlation
Exemplary embodiments of a system and method can be provided for measuring a level and / or details of how engaging, effective or memorable a stimulus that may be based on information associated with one or more subjects' neuronal, physiological and / or behavioral responses to the stimulus. In addition, an exemplary embodiment of a computer-accessible medium containing executable instructions thereon can also be provided which can be executed by a processing arrangement. For example, when the processing arrangement executes the instructions, the processing arrangement can be configured to, e.g., receive neuronal, physiological and / or behavioral data one or more subjects being presented with stimuli, determine further data associated with a measure of inter-subject similarity of the neuronal, physiological and / or behavioral data, and identify particular portions of the stimuli that meet a pre-determined criteria relating to the further data associated with the measure of inter-subject similarity. In addition, the processing arrangement can be further configured to display and / or store identifiers of the particular portions of the stimuli in a storage arrangement in a user-accessible format and / or a user-readable format.
Owner:NEW YORK UNIV +1
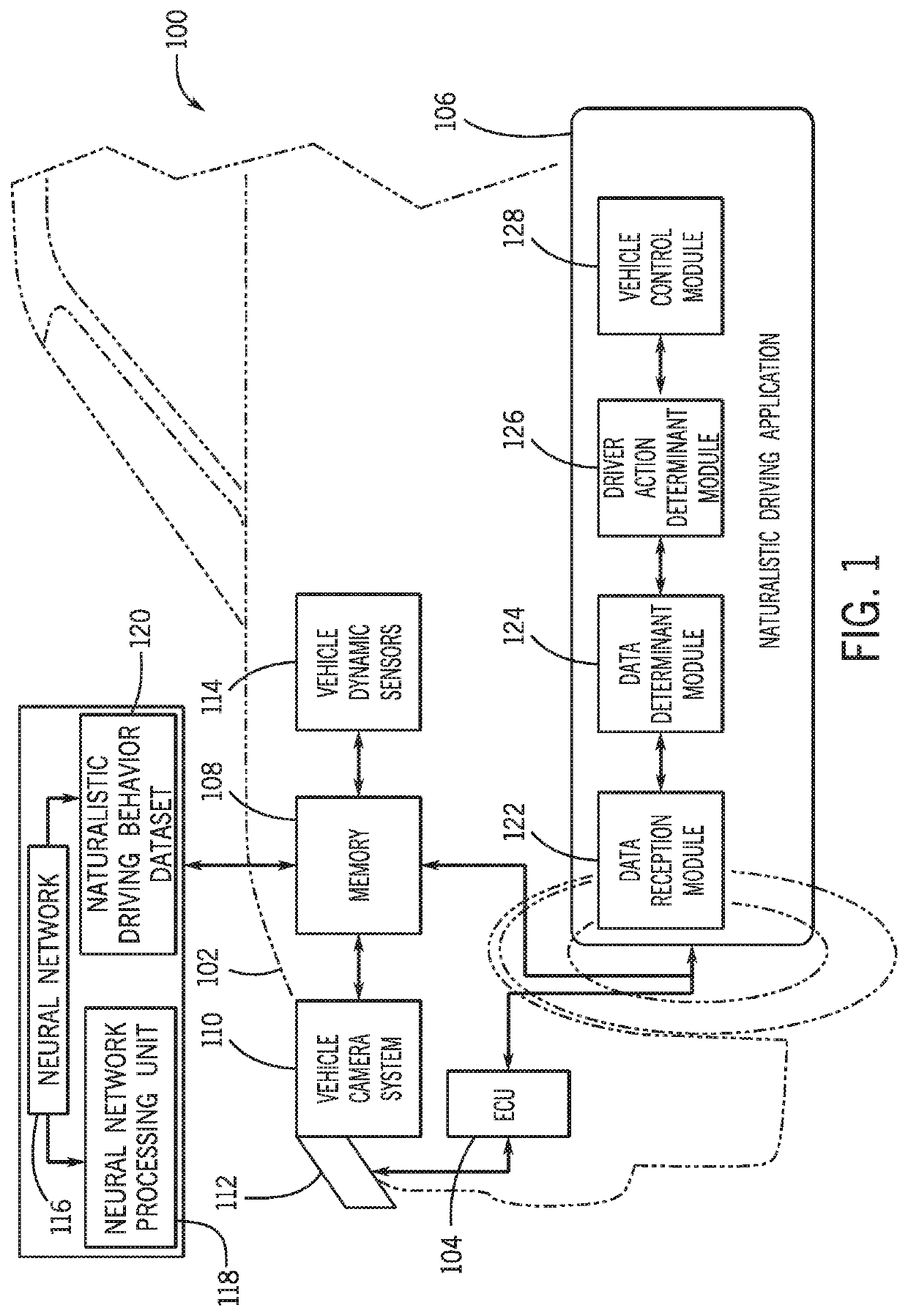
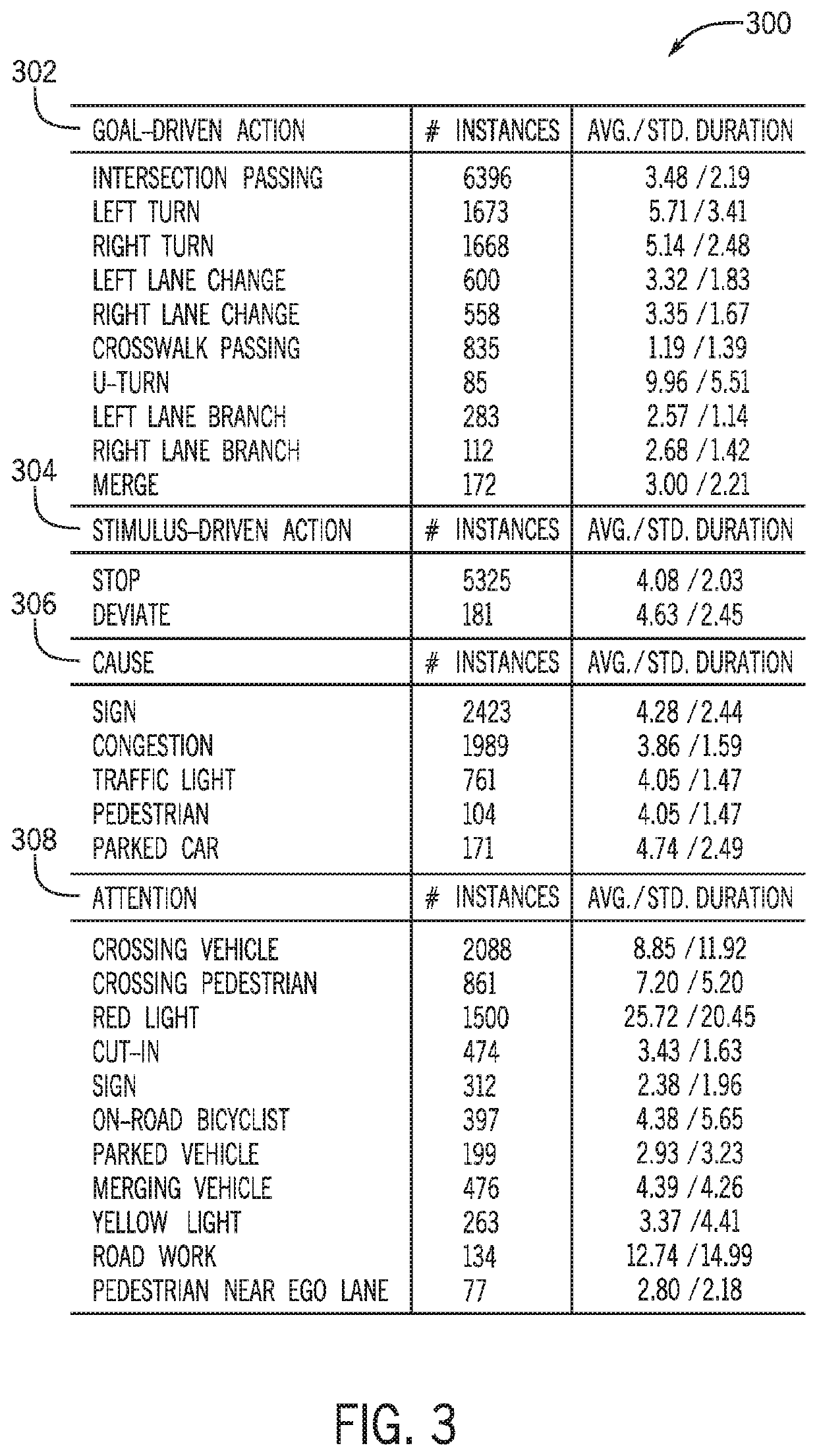
System and method for learning naturalistic driving behavior based on vehicle dynamic data
A system and method for learning naturalistic driving behavior based on vehicle dynamic data that include receiving vehicle dynamic data and image data and analyzing the vehicle dynamic data and the image data to detect a plurality of behavioral events. The system and method also include classifying at least one behavioral event as a stimulus-driven action and building a naturalistic driving behavior data set that includes annotations that are based on the at least one behavioral event that is classified as the stimulus-driven action. The system and method further include controlling a vehicle to be autonomously driven based on the naturalistic driving behavior data set.
Owner:HONDA MOTOR CO LTD
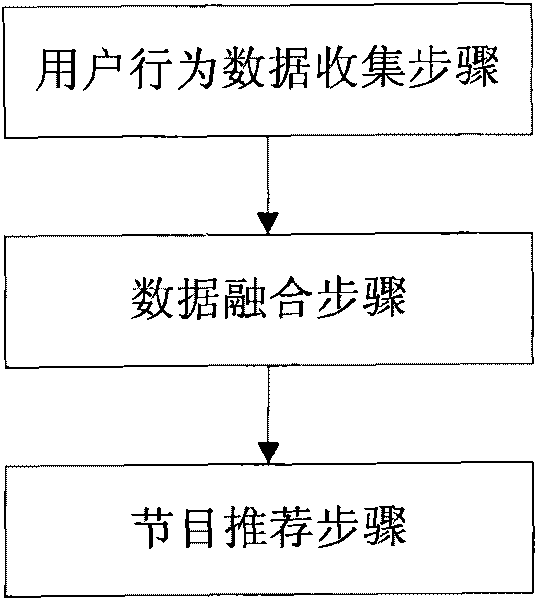
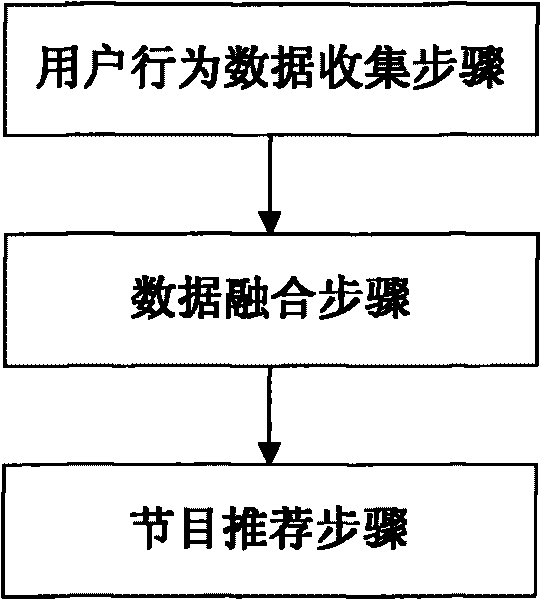
Data fusion based video program recommendation method
InactiveCN101763351AAvoid cold start problemsAccurate recommendationSpecial data processing applicationsMarketingWeb siteComputer science
A data fusion based video program recommendation method comprises the following steps: 1) collection of behavioral data of users: collecting the behavioral data of the users in browsing video websites and storing the behavioral data in a database; 2) data fusion: converting the behavioral data of a user in browsing a video program into the interest value of the user in the video program; and 3) program recommendation: according to the interest value of the user in a few programs, recommending the programs in which the user has high interest value to other users having the same favorites, wherein the behavioral data in browsing comprise behavioral data in playing. The duration ratio r is obtained by dividing the duration of the programs played by the users by the total duration of the programs. The higher the duration ratio r is, the higher the interest value is. As long as the users play the programs and other behavioral data of the users related to the interest value are fused, the program lists to be recommended can be generated more accurately and the degree of satisfaction of the users with the recommended programs is greatly improved.
Owner:RESHUFFLE TECH SHANGHAI
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com