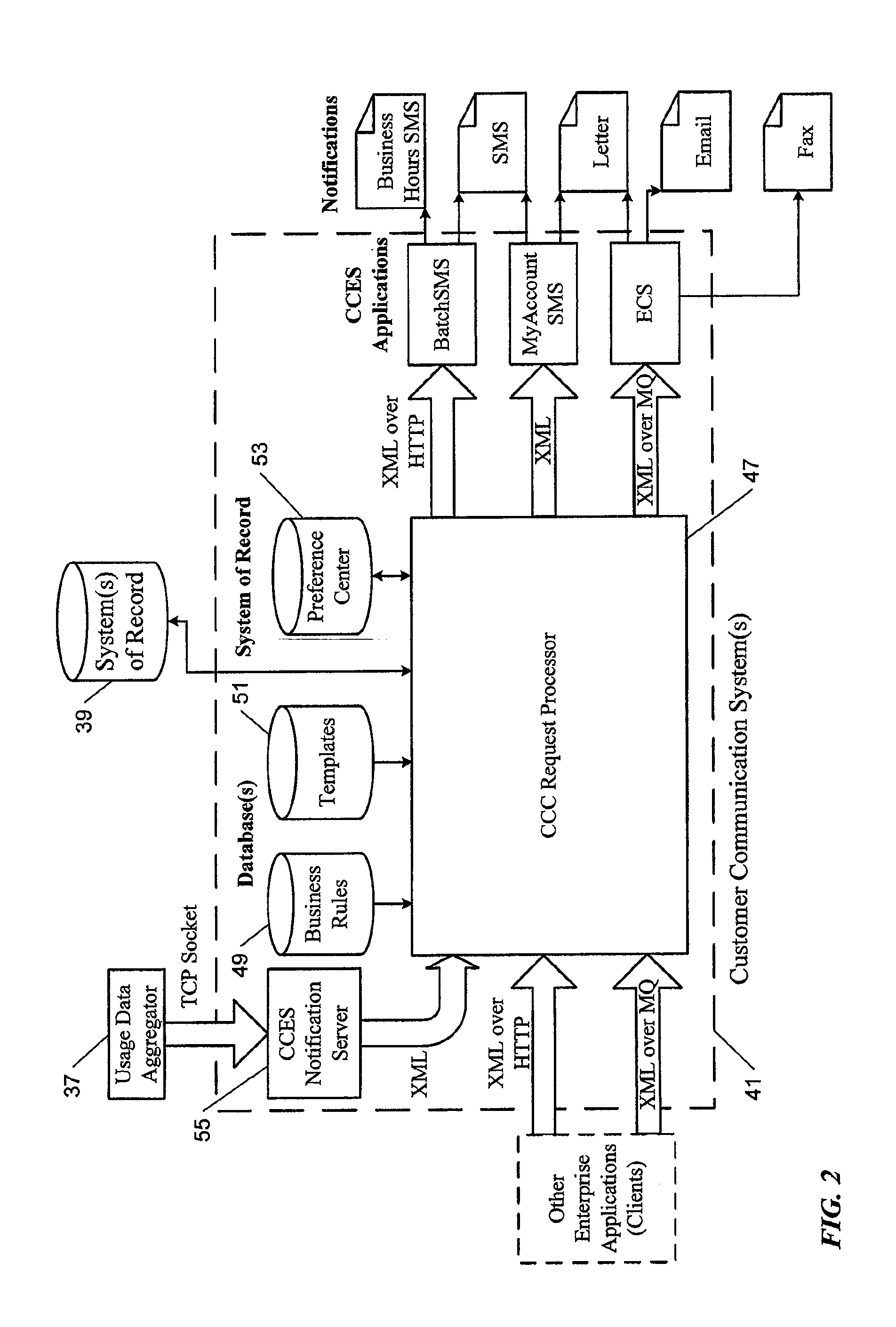
Patents
Literature
14983 results about "Current time" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
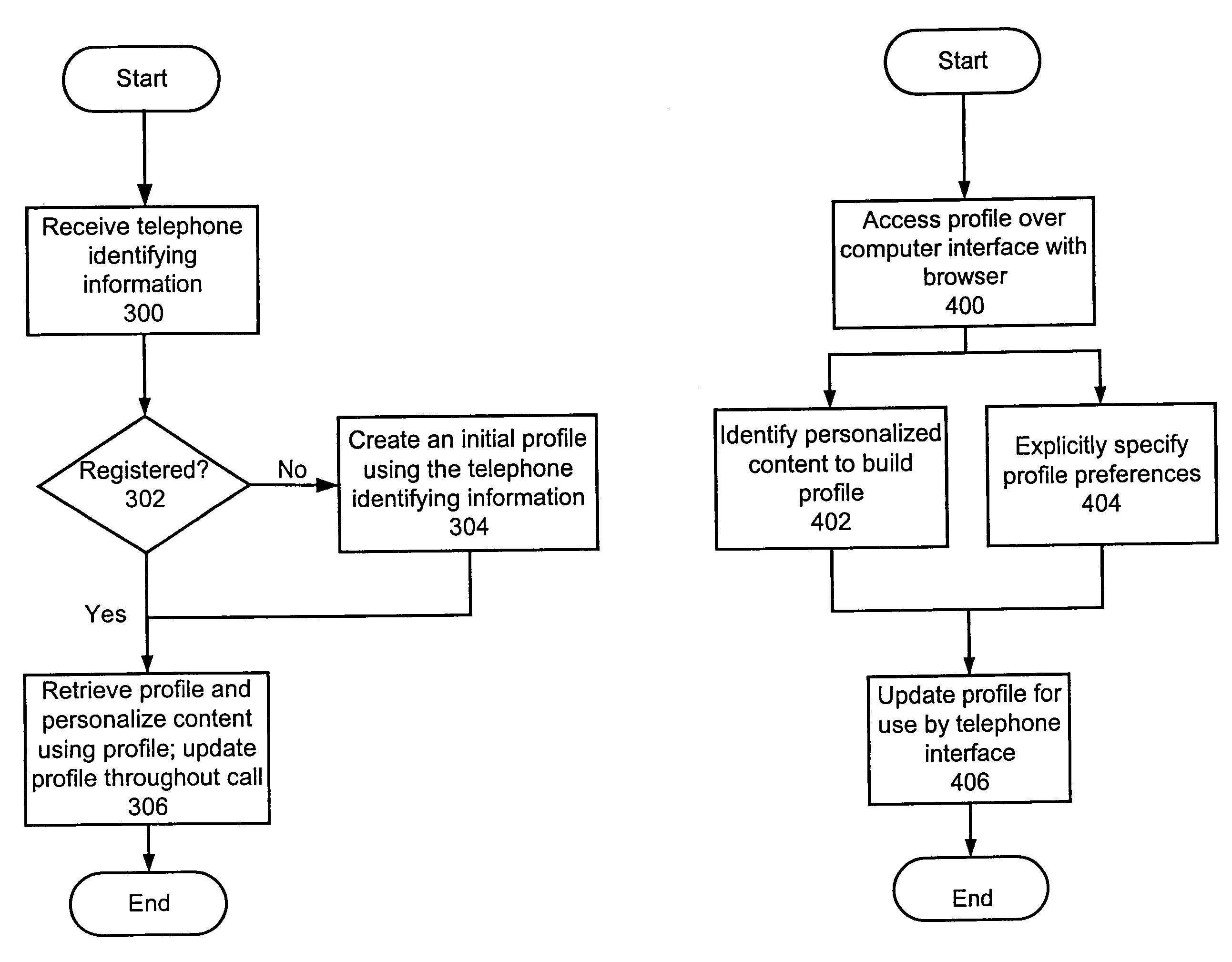
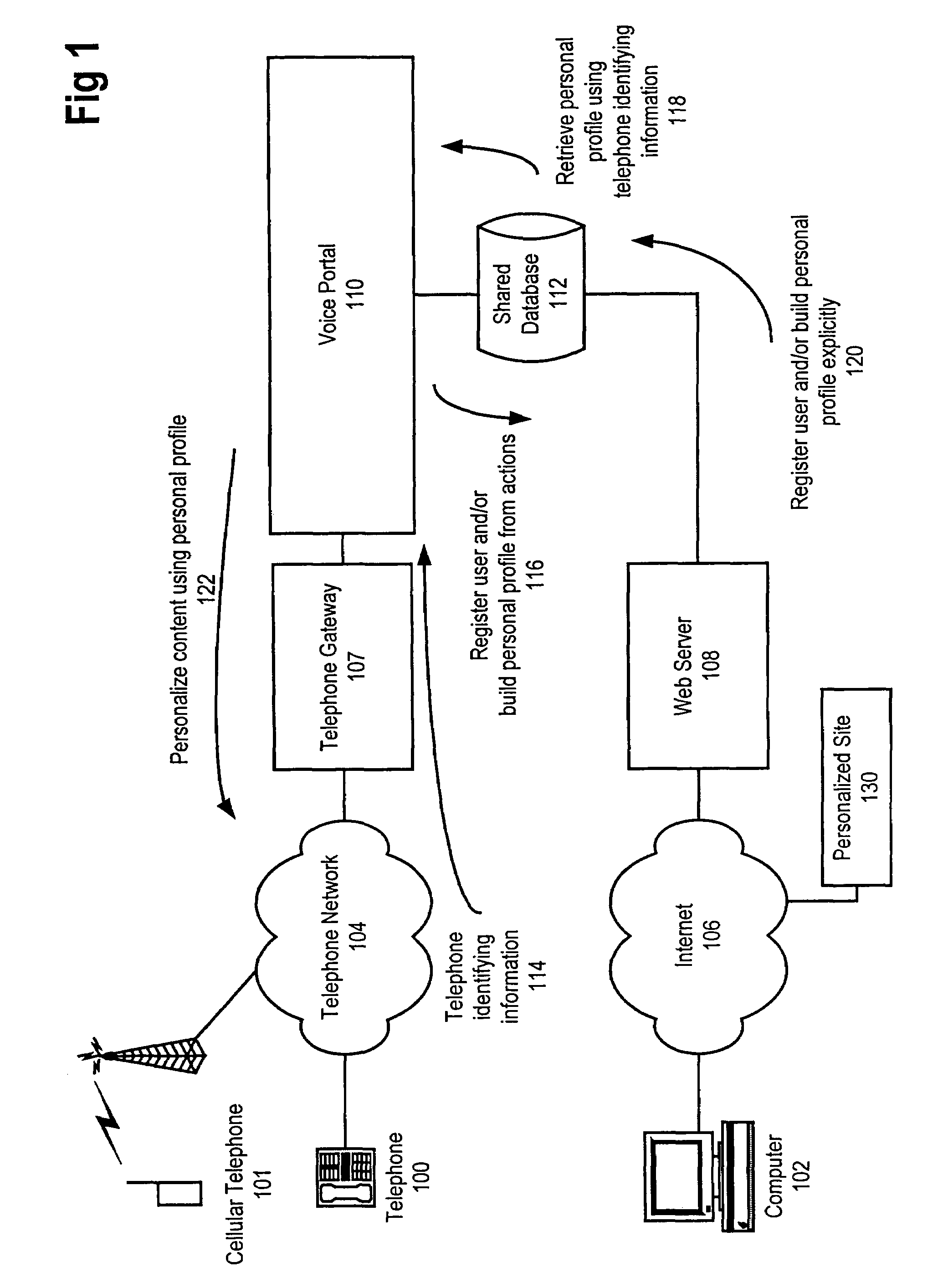
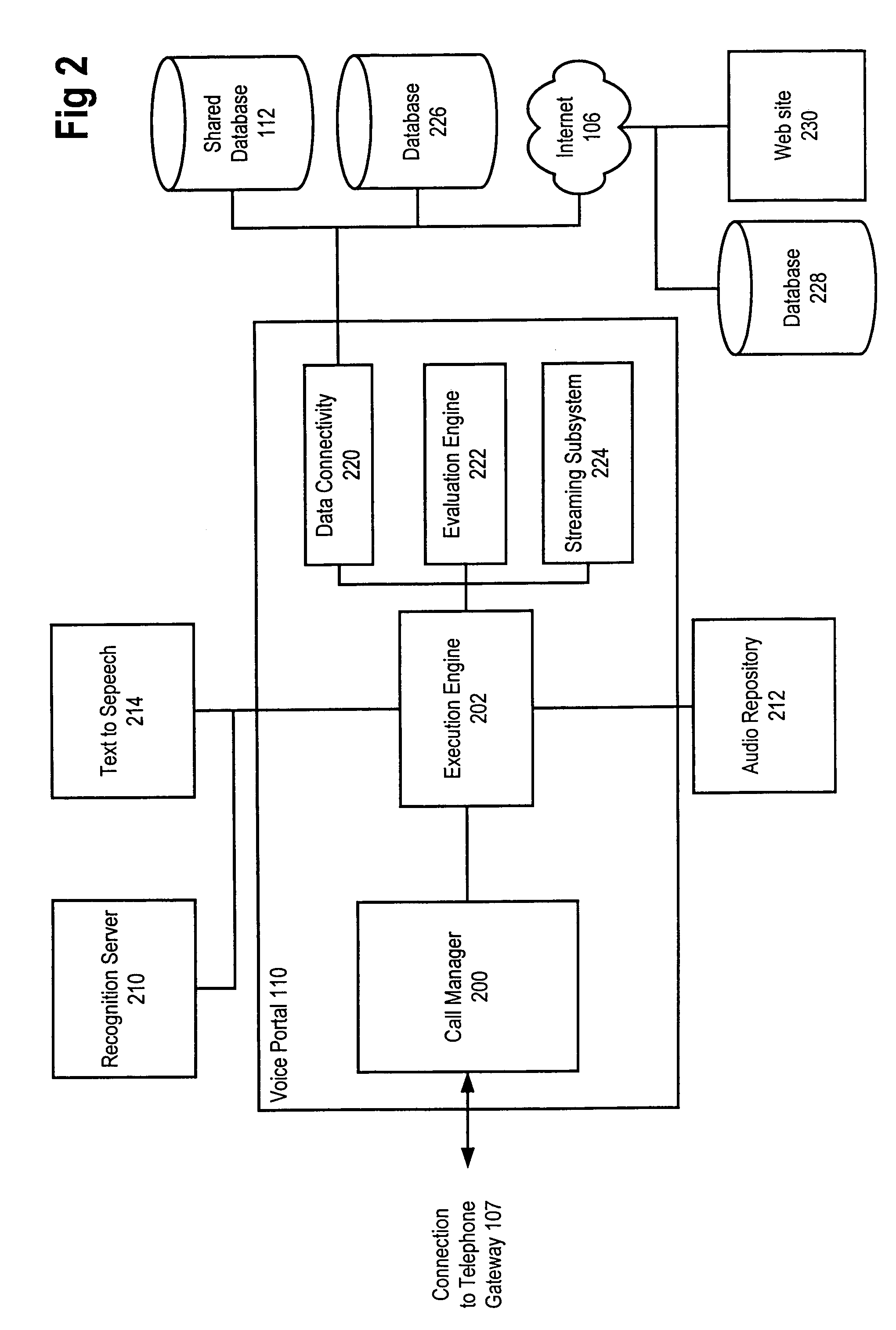
Method and apparatus for content personalization over a telephone interface with adaptive personalization
InactiveUS6842767B1Shorten speedIncrease volumeMultiple digital computer combinationsAutomatic exchangesPersonalizationHuman language
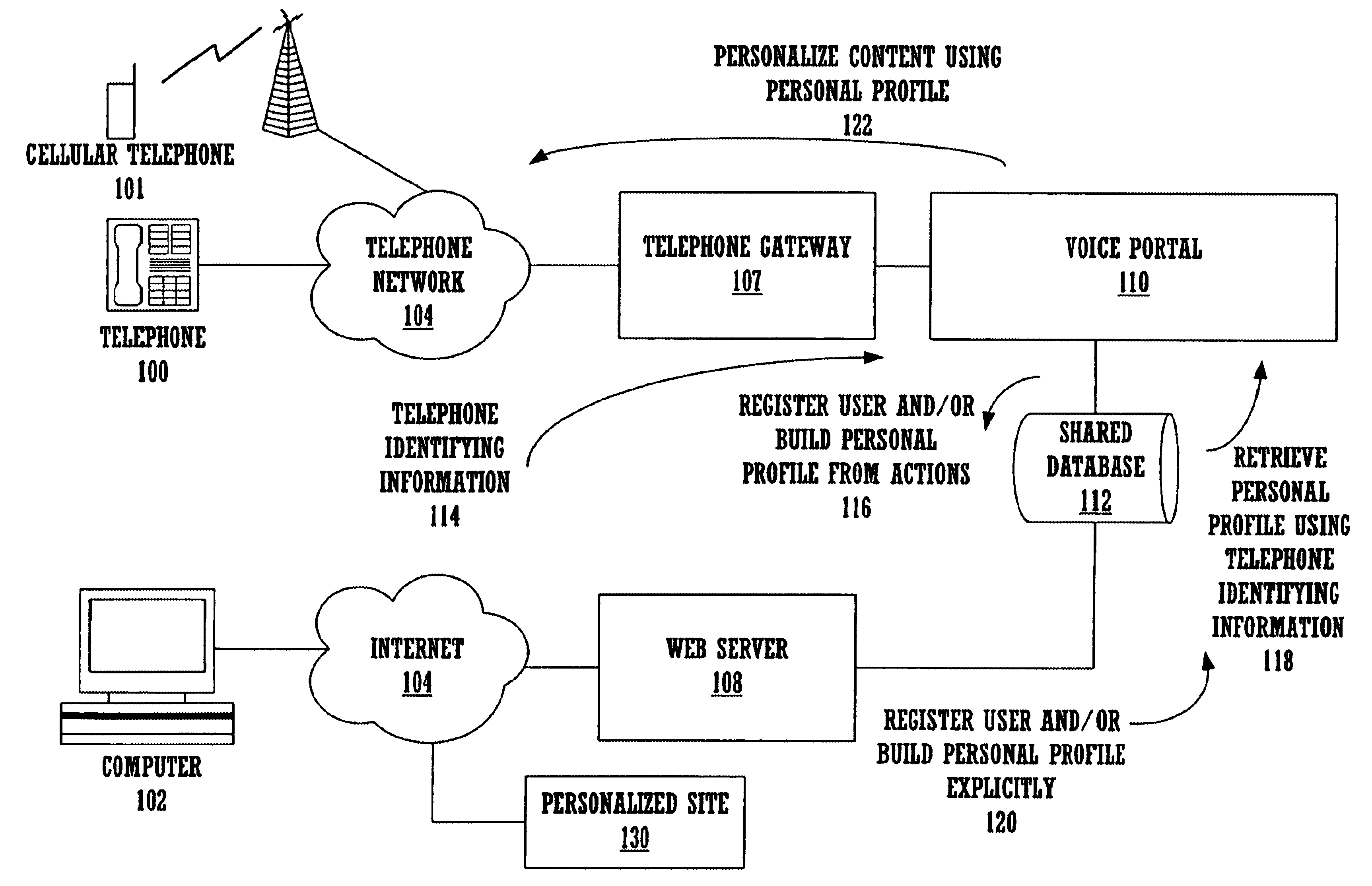
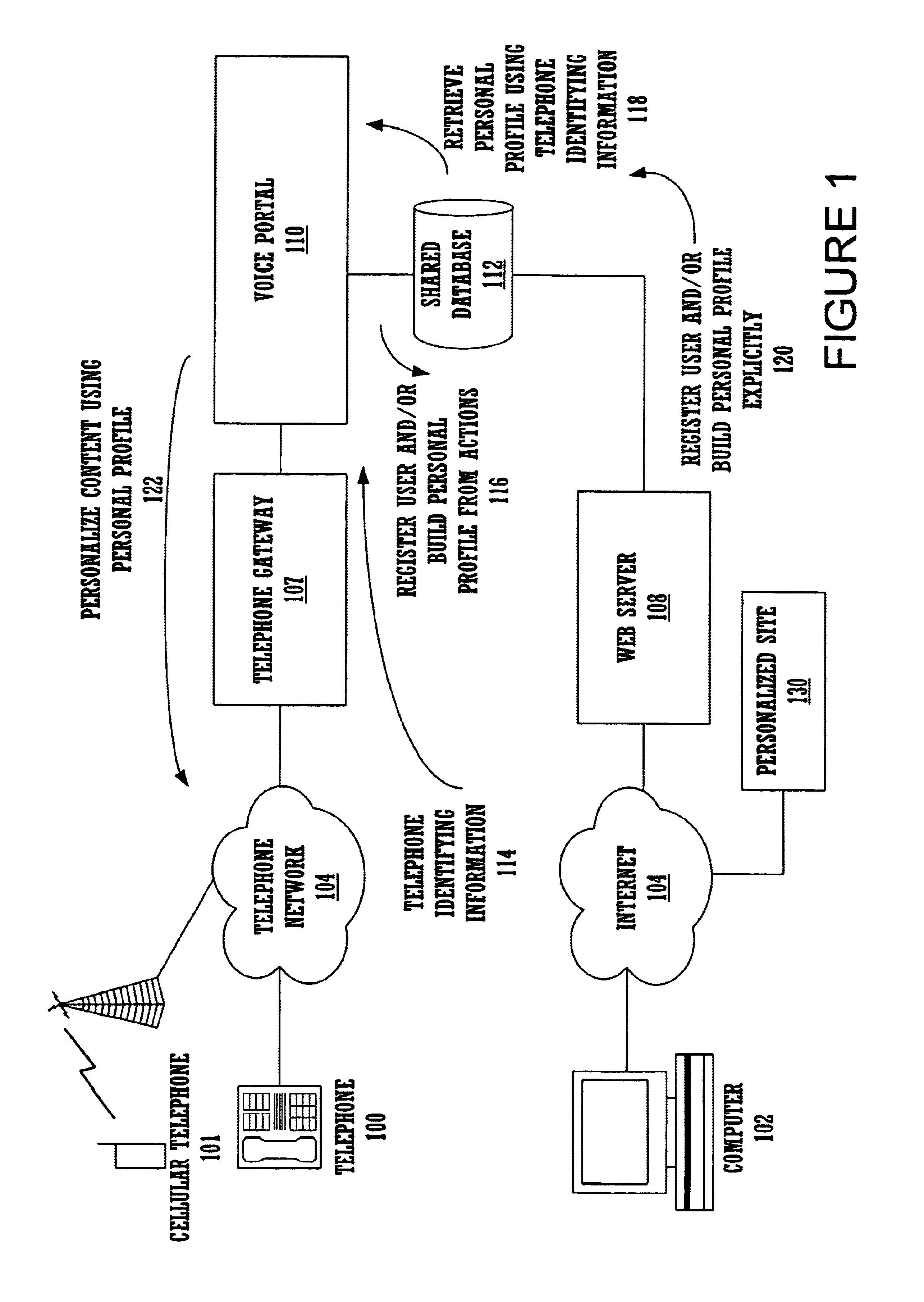
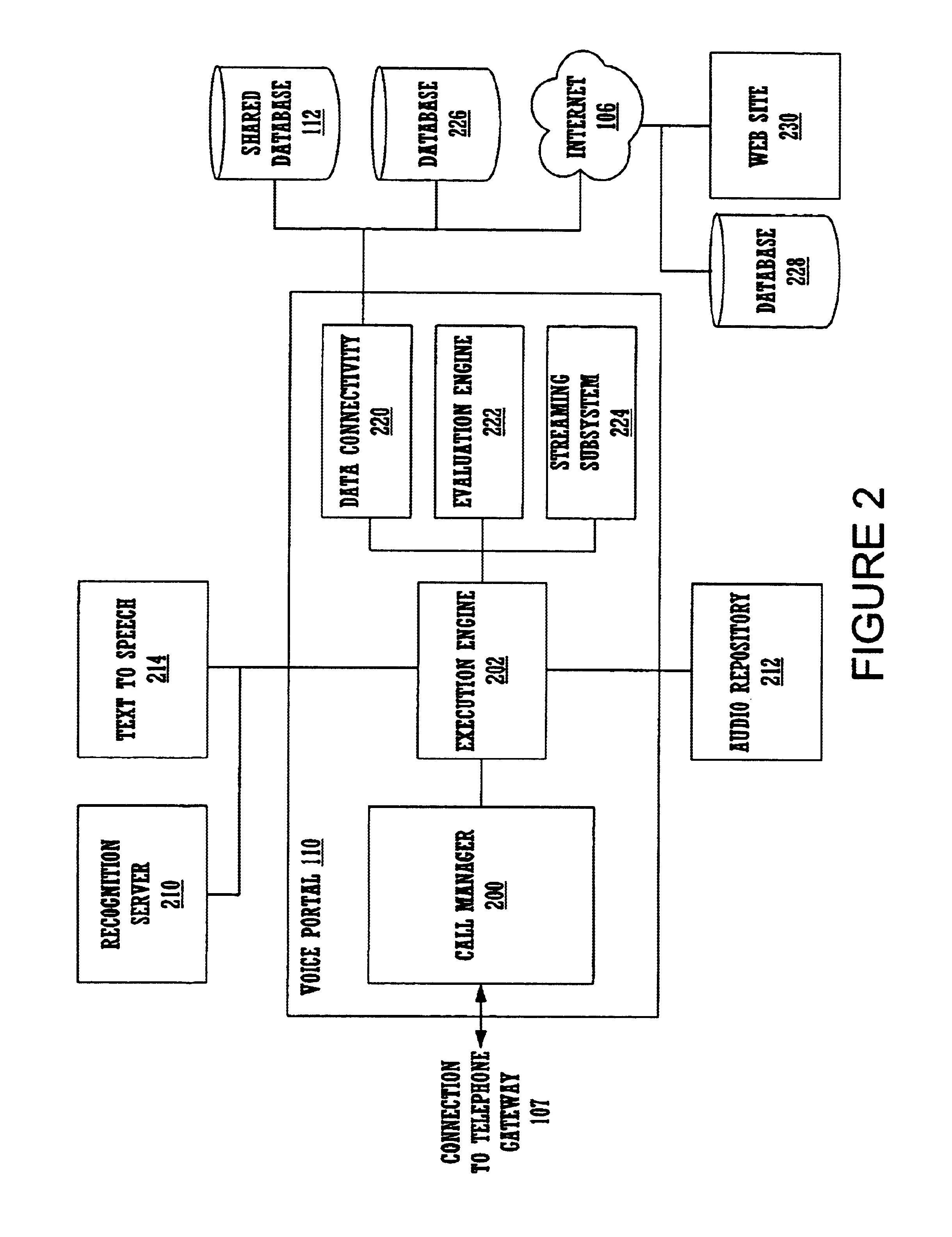
A method and apparatus for providing personalized information content over telephones is described. The creation of a voice portal is supported by the invention. Embodiments of the invention use telephone identifying information such as the calling party's number to identify, or create, user profiles for customization. The personalized content is specific to that user based on her / his telephone identifying information and may be further customized based on the current time, current date, the calling party's locales, and / or the calling party's dialect and speech patterns. Also, the telephone identifying information may support targeted advertising, content, and purchasing recommendations specific to that user. The system may use a voice password and / or touch-tone login system when appropriate to distinguish the caller or verify the caller's identity for specific activities. Typically, embodiments of the invention will immediately present a caller personalized content based on her / his profile using the appropriate dialect as well as the caller's preferred content. Profiles can be constructed as the caller uses embodiments of the invention as well as through explicit designation of preferences. For example, as the user selects topics, as well as particular content, a record of actions can be maintained. This record of actions can be used to provide suggestions and direct the personalization of the system for the user.
Owner:MICROSOFT TECH LICENSING LLC
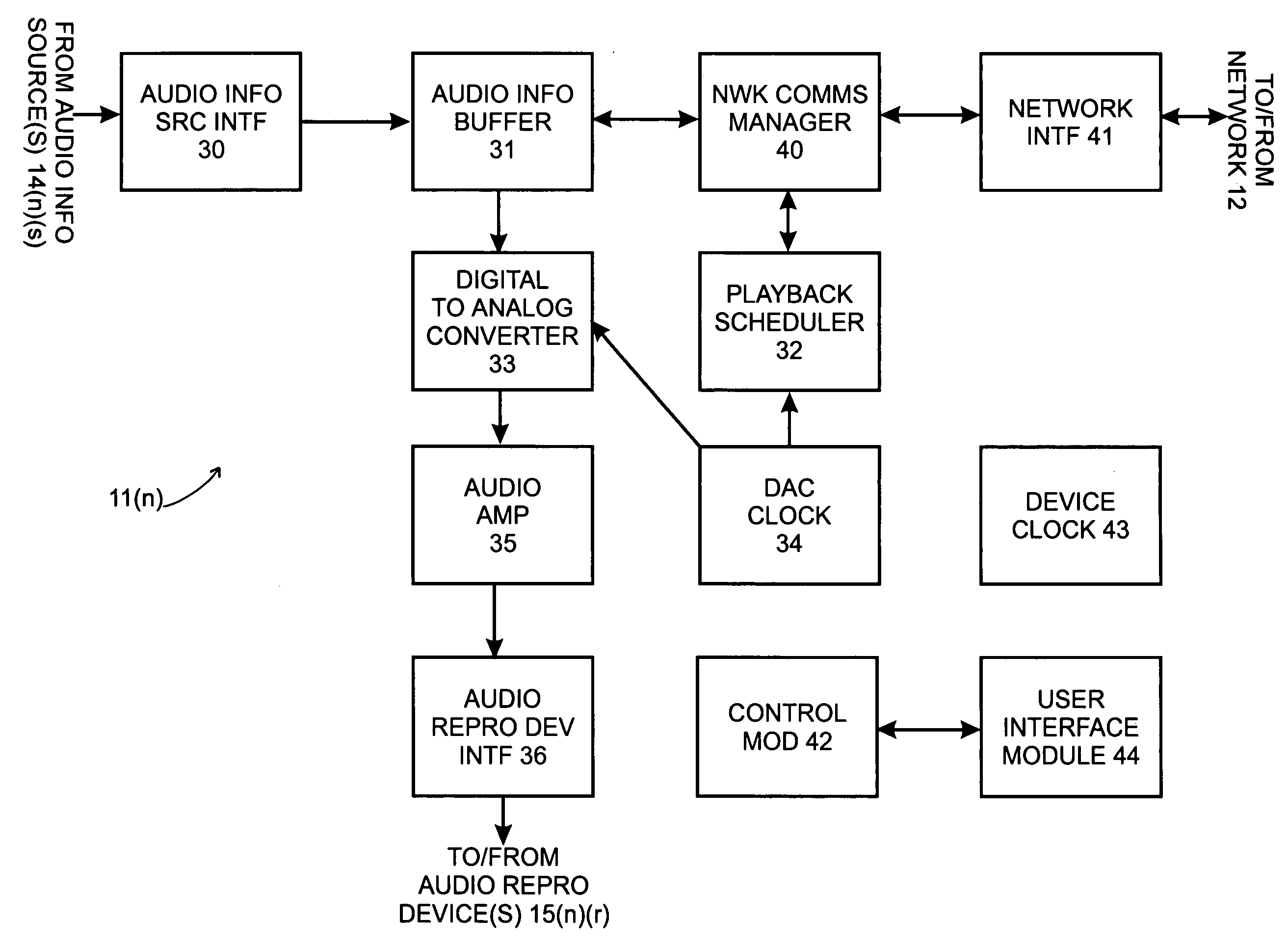
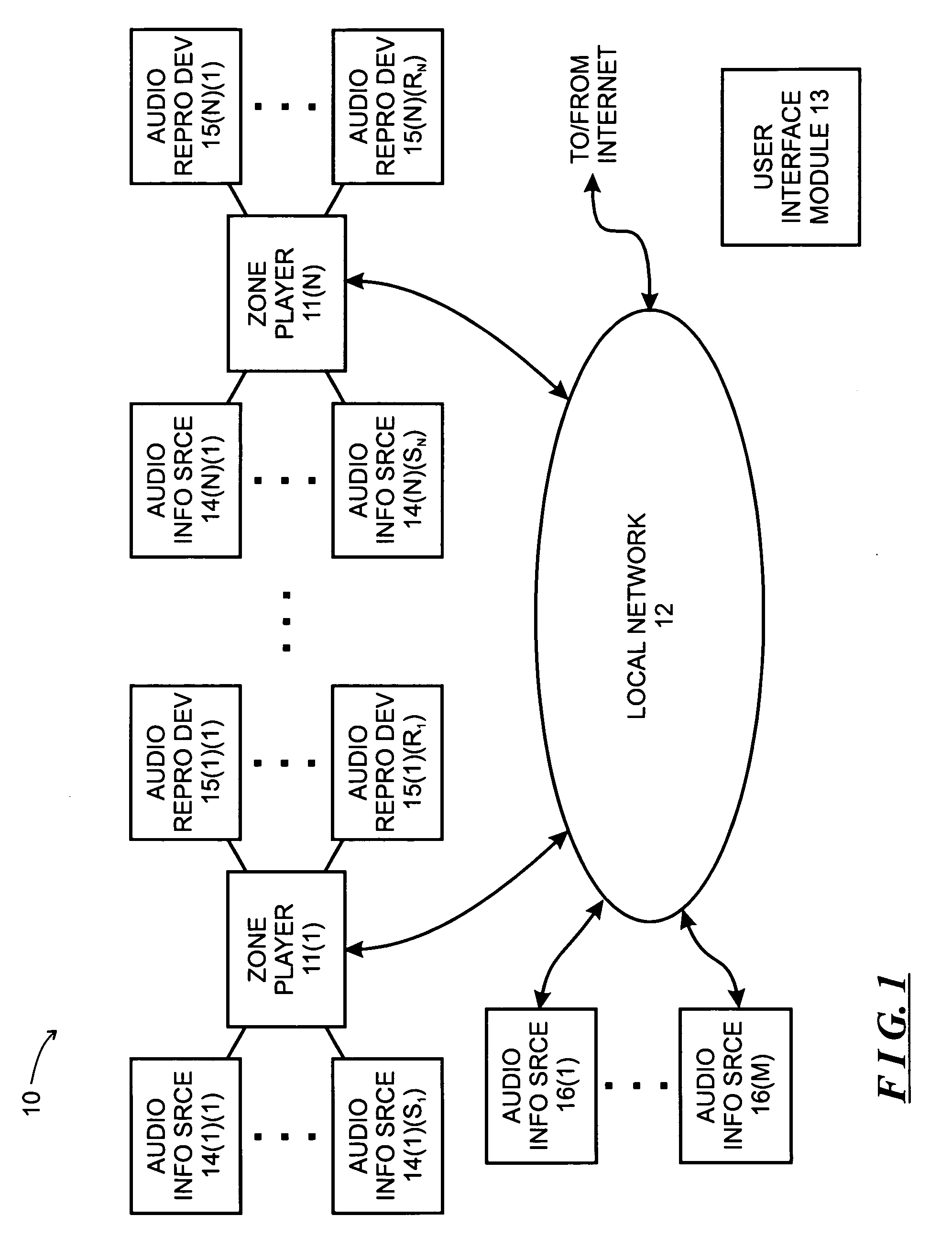
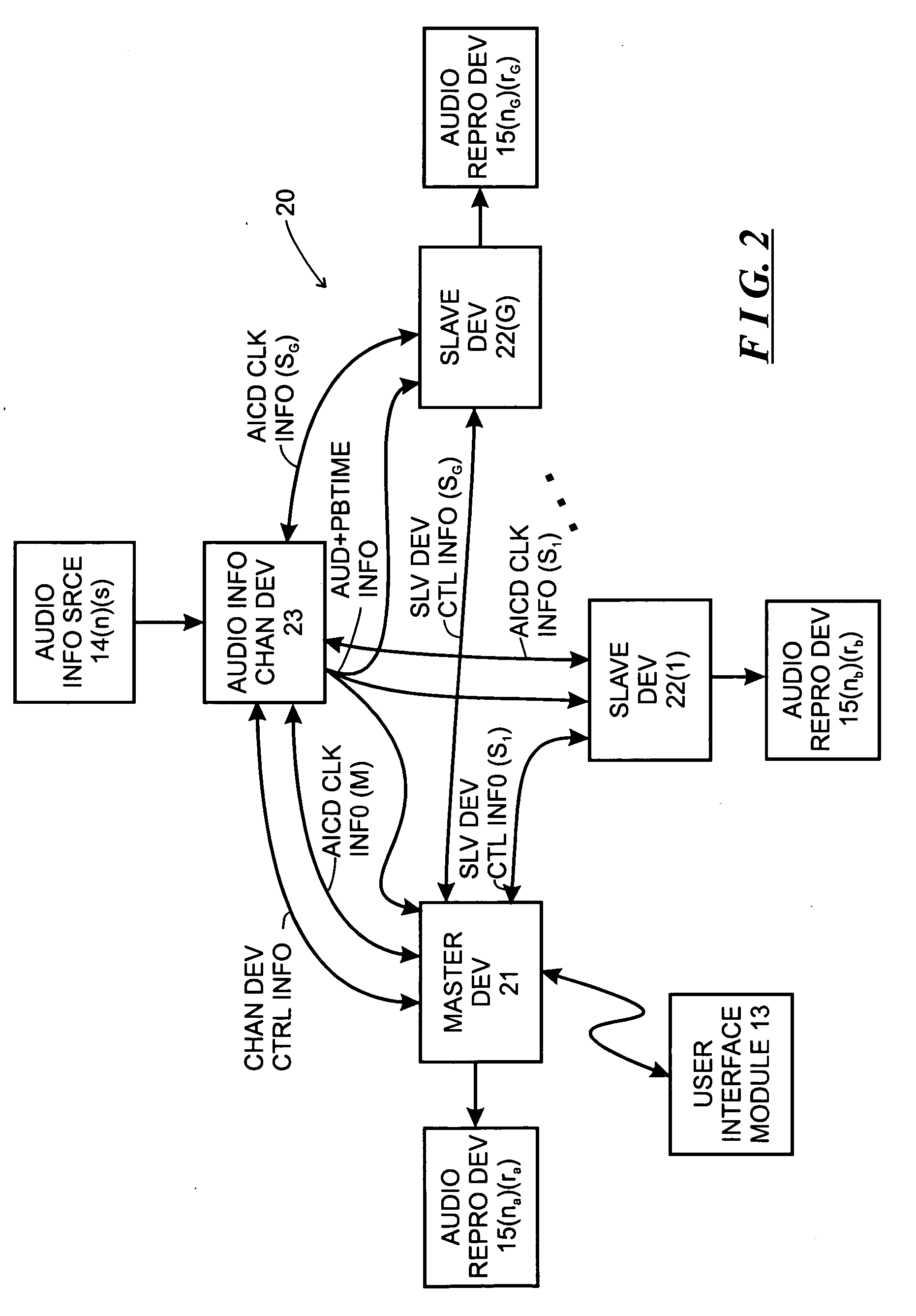
System and method for synchronizing operations among a plurality of independently clocked digital data processing devices
ActiveUS20070038999A1Maintenance operationTelevision system detailsGain controlElectronic data processingIndependent clock
A system is described for maintaining synchrony of operations among a plurality of devices that have independent clocking arrangements. The system includes a task distribution device that distributes tasks to a synchrony group comprising a plurality of devices that are to perform the tasks distributed by the task distribution device in synchrony. The task distribution device distributes each task to the members of the synchrony group over a network. Each task is associated with a time stamp that indicates a time, relative to a clock maintained by the task distribution device, at which the members of the synchrony group are to execute the task. Each member of the synchrony group periodically obtains from the task distribution device an indication of the current time indicated by its clock, determines a time differential between the task distribution device's clock and its respective clock and determines therefrom a time at which, according to its respective clock, the time stamp indicates that it is to execute the task.
Owner:SONOS
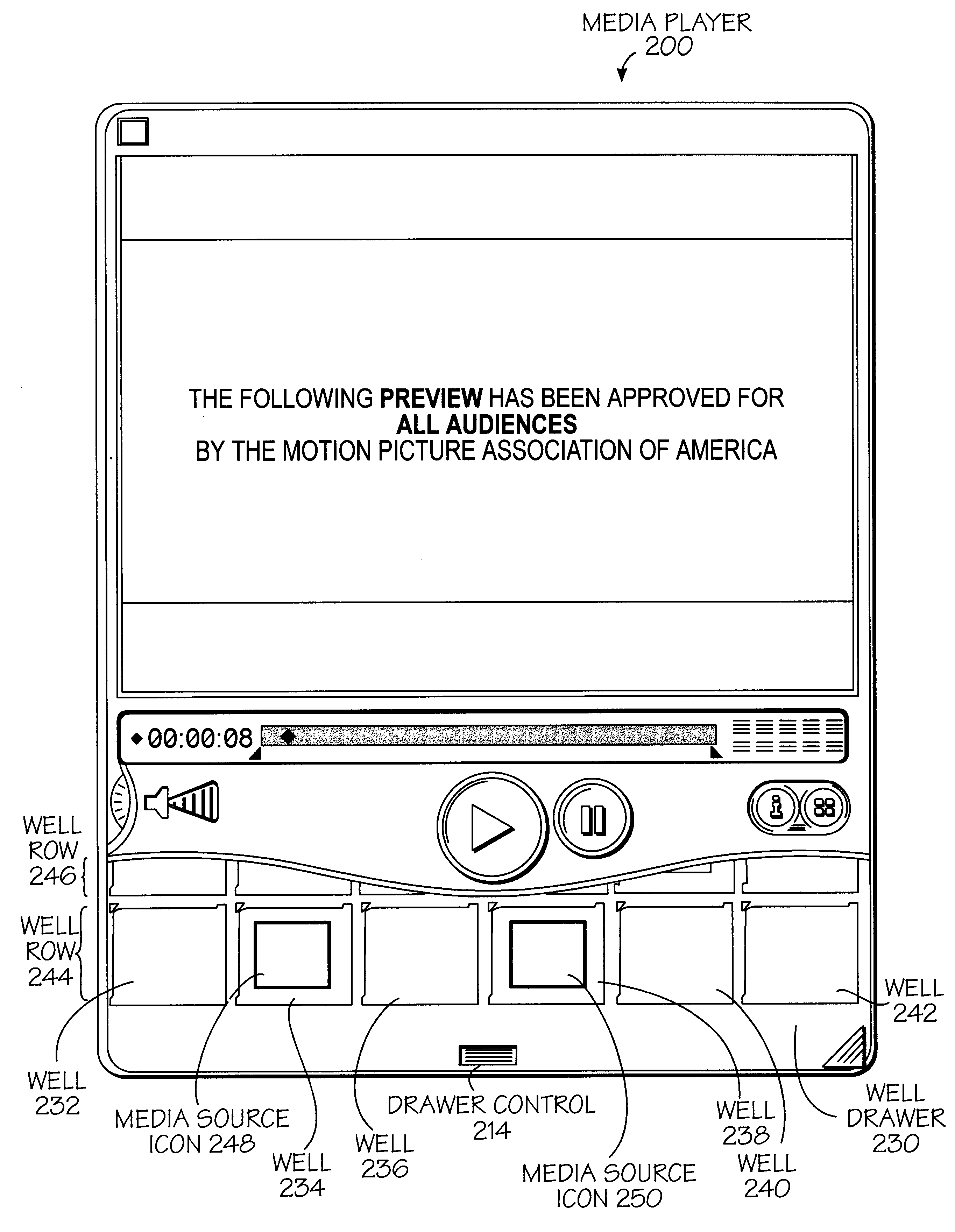
User interface for presenting media information
A user interface and methods for using a user interface for controlling processing of time-based media files. In one exemplary method, a graphical representation of a time line for a time-based media is displayed along with a graphical representation of a current time along the graphical representation of the time line. A start graphical indicator and a stop graphical indicator is also displayed along the graphical representation of the time line. A portion of the time-based media may be selected for presentation by dragging or positioning at least one of the start graphical indicator and the stop graphical indicator along the graphical representation of the time line. In another aspect of the invention, an exemplary method allows for the adaptive control of a portion of the interface which indicates time relating to a time-based media. An input speed is determined where this input is to change the portion and the rate at which the change to this portion occurs is dependent upon the input speed. Other aspects of the present invention relating to the interface for controlling the processing of time-based media files are also described.
Owner:APPLE INC
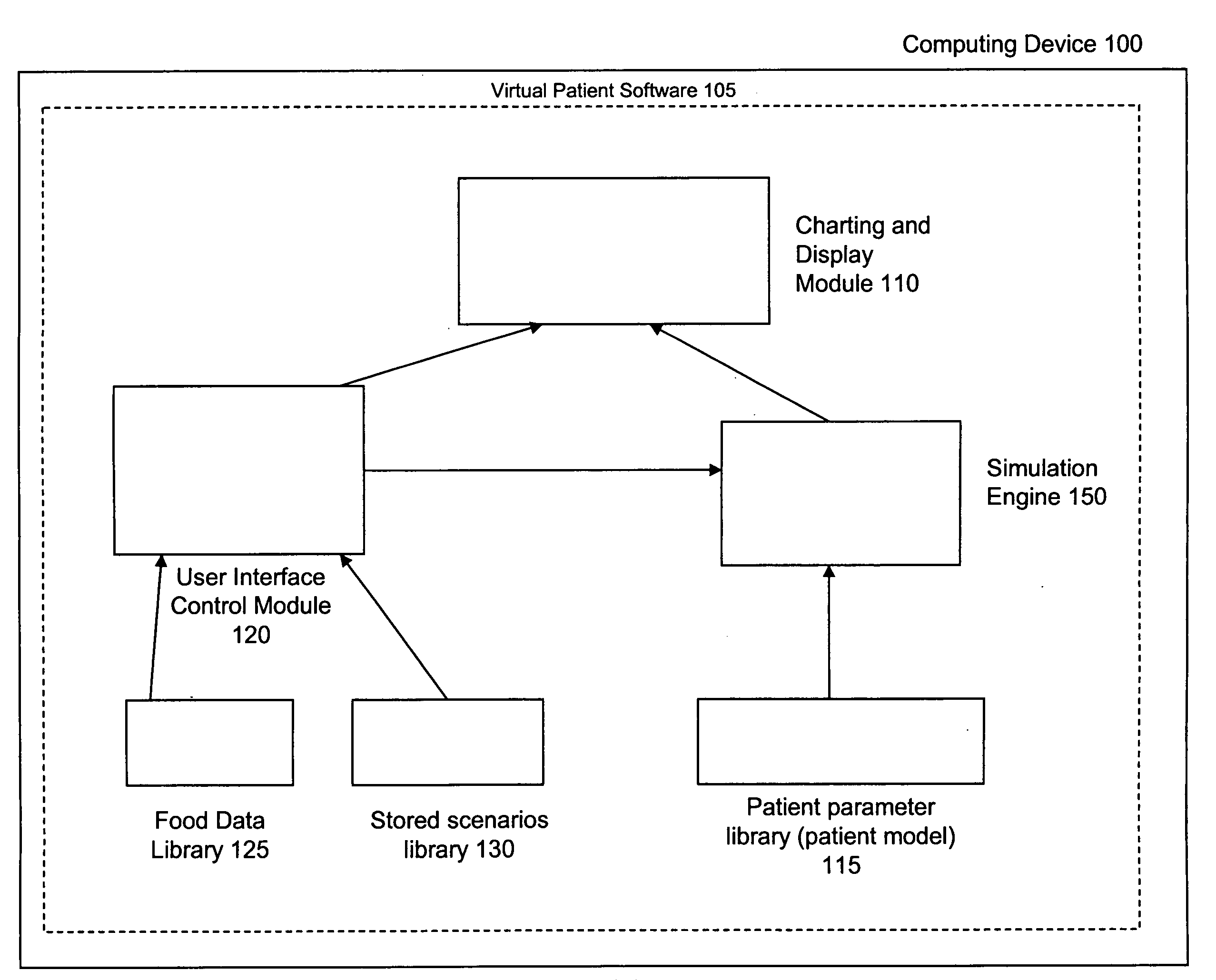
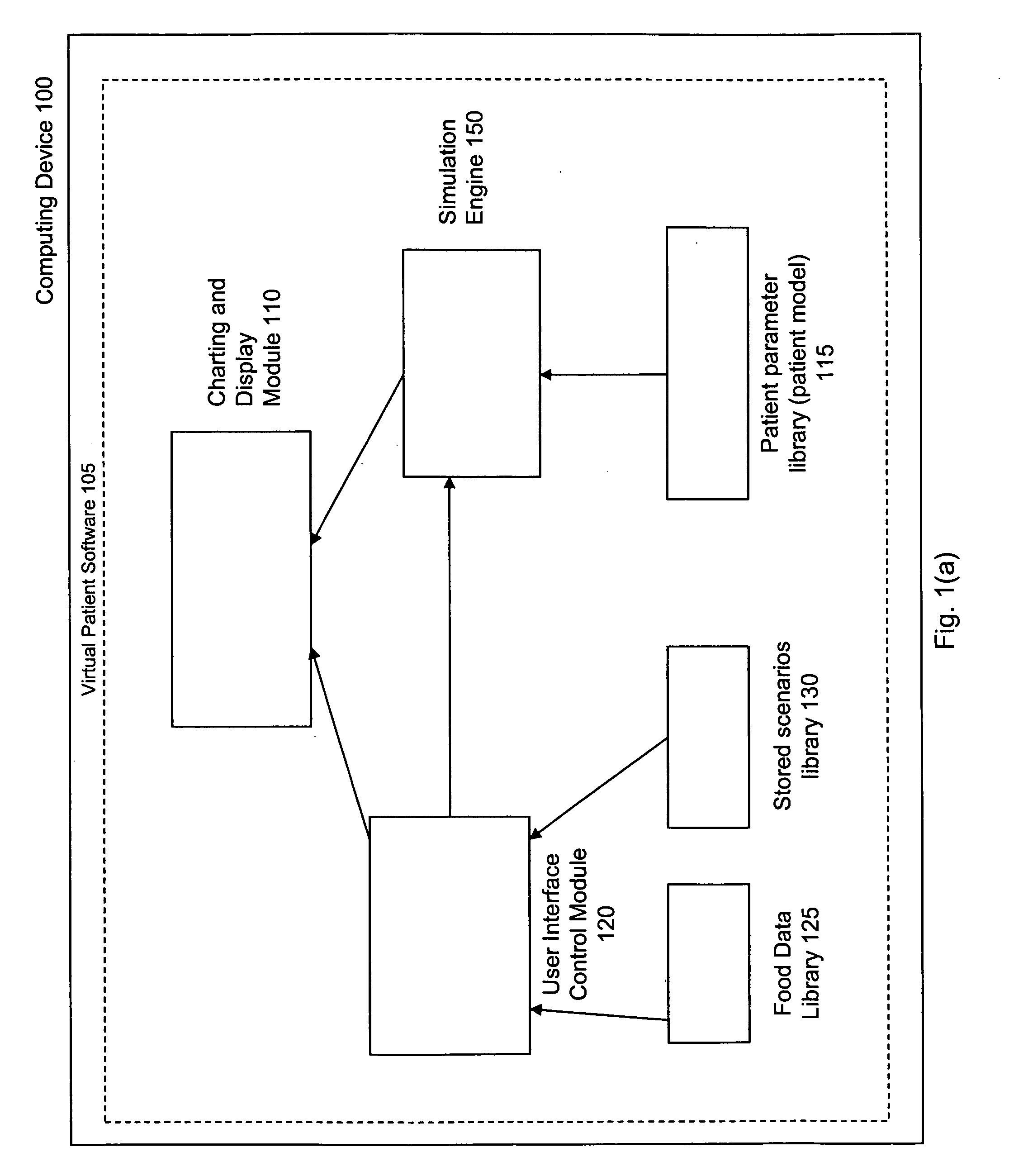
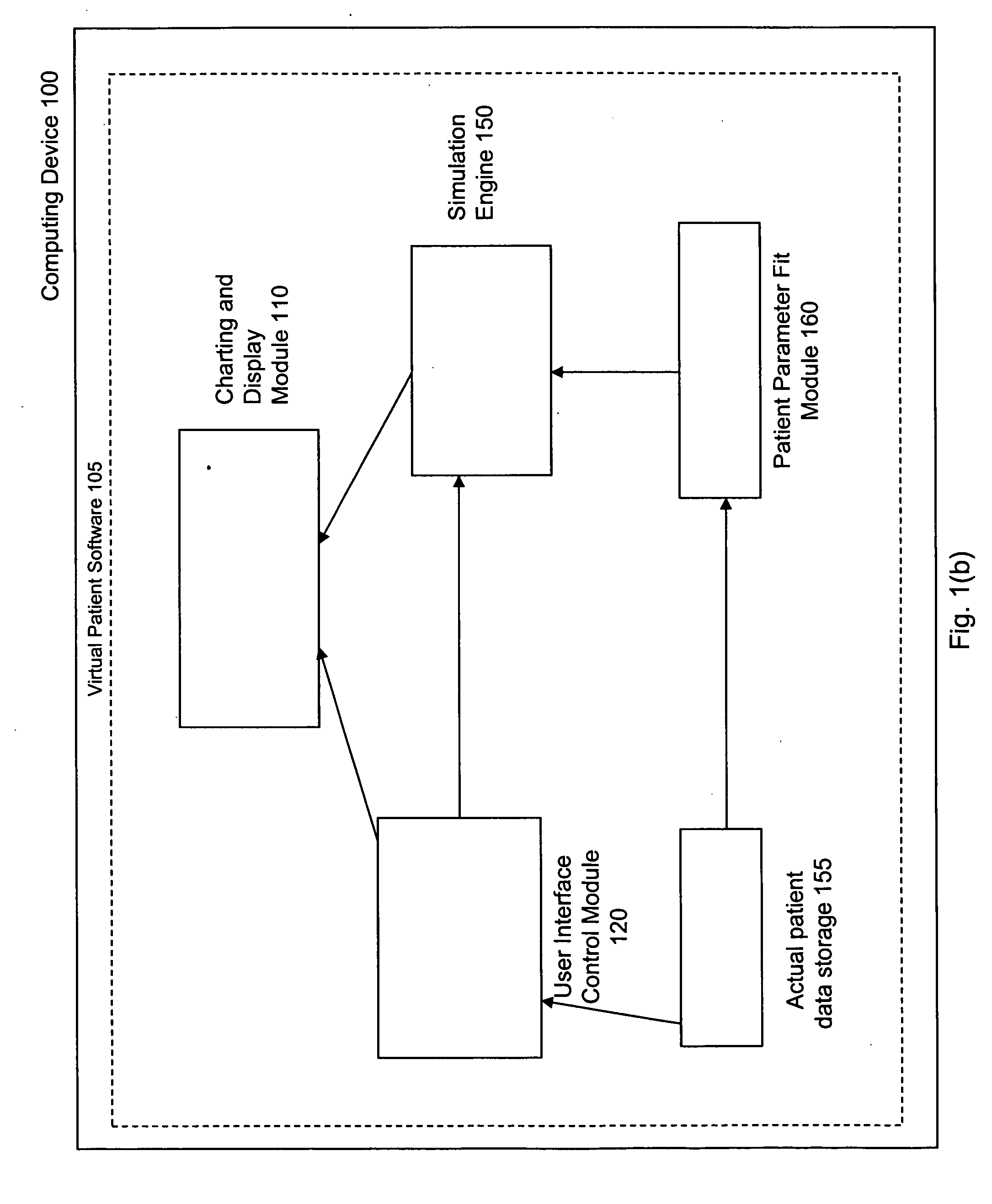
Virtual patient software system for educating and treating individuals with diabetes
A system to assist an individual in developing a therapy in diabetes treatment of a patient includes a user interface control module, a simulation engine, a charting and display module. The user interface control module receives an input related to the patient and captures a current time of the simulation. The simulation engine receives the input, generates a plurality of blood glucose readings for the patient up to the current time of the simulation based on the input, and to transfers the plurality of blood glucose readings. The charting and display module receives the plurality of blood glucose readings and display the plurality of blood glucose readings. The simulation engine receives patient parameters from a patient parameter library based on a selected patient model.
Owner:MEDTRONIC MIMIMED INC
System for providing personalized content over a telephone interface to a user according to the corresponding personalization profile including the record of user actions or the record of user behavior
InactiveUS7330890B1Shorten speedIncrease volumeMultiple digital computer combinationsAutomatic exchangesPersonalizationPassword
Owner:MICROSOFT TECH LICENSING LLC
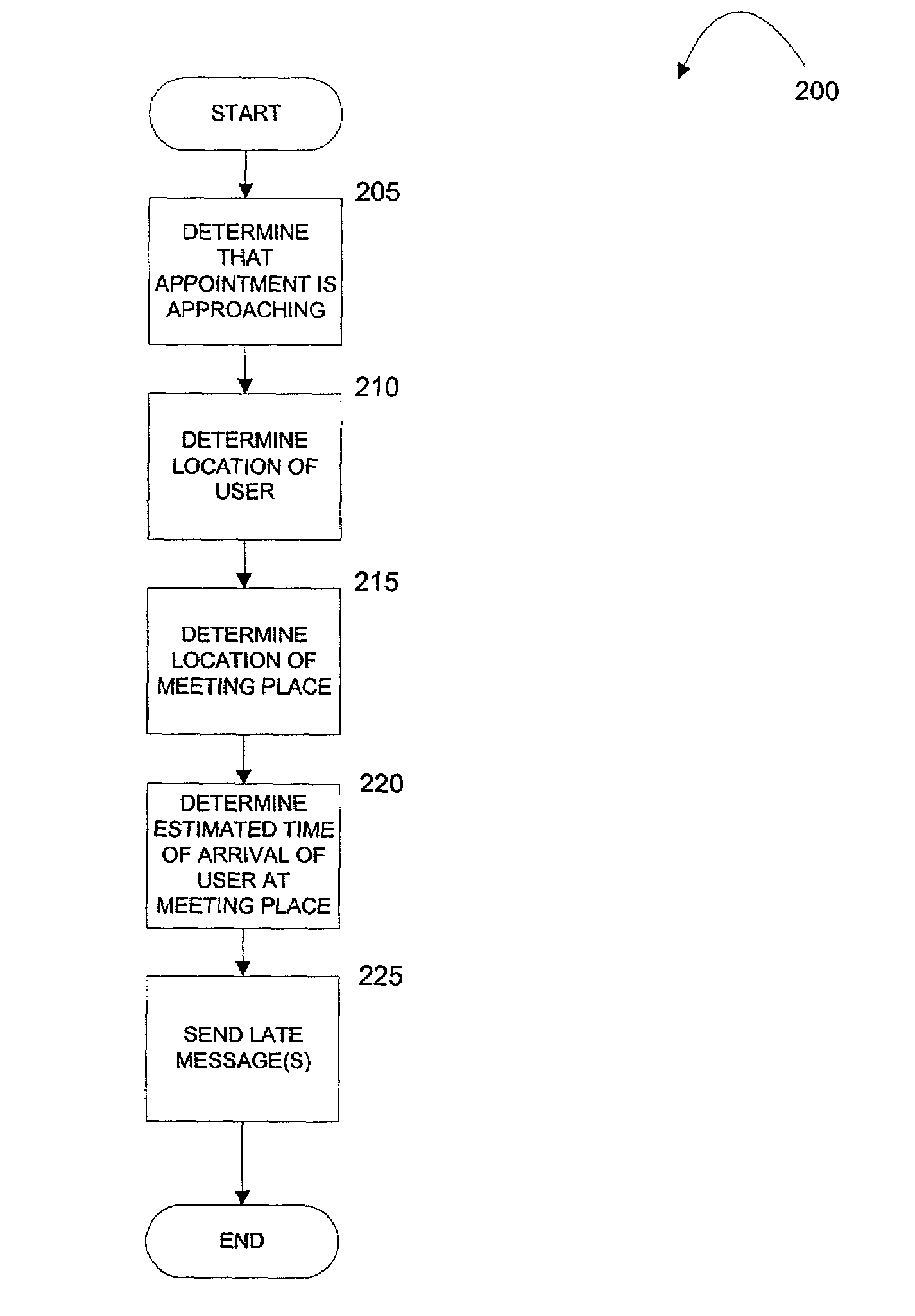
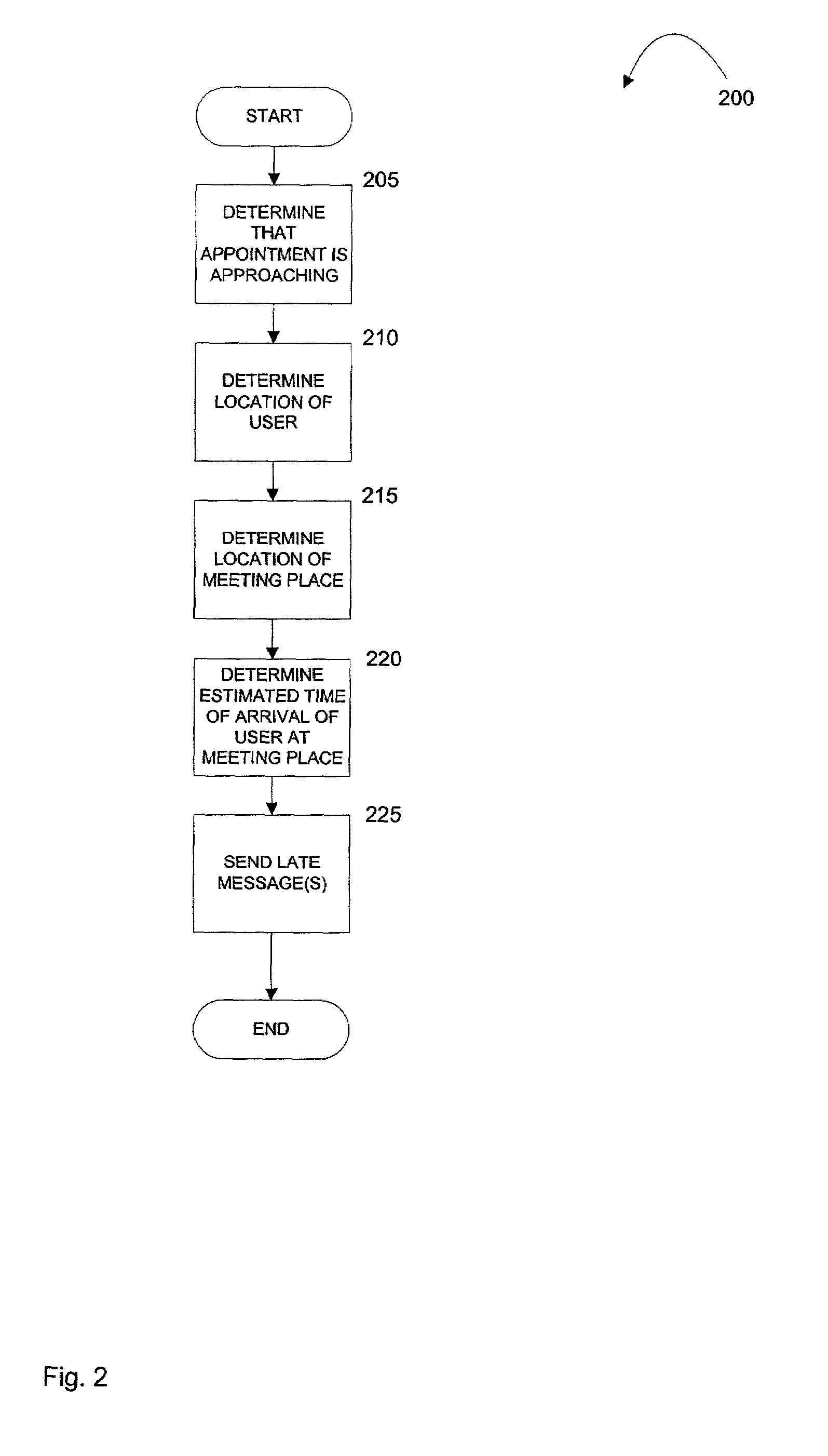
Location and time sensitive wireless calendaring
ActiveUS7139722B2Instruments for road network navigationRoad vehicles traffic controlStart timePager
A computer-implemented method provides location-sensitive and time-sensitive calendaring to a wireless device, such as a cellphone, pager, PDA, etc. A user's calendar is maintained with a number of appointments, start times and end times for the appointments, meeting place and a list of attendees for the appointments. When the present time reading is within a predetermined minimum of a meeting start time of an appointment of a calendar of a user, the location of the user is determined based on the location of the wireless device. The location of the meeting place is also determined. Using historical data (of the user or others), the estimated time of arrival of the user at the meeting place is determined. If the estimated time of arrival is after the meeting start time, then a late message may be sent to the user and / or to the other meeting attendees.
Owner:BELLSOUTH INTPROP COR +1
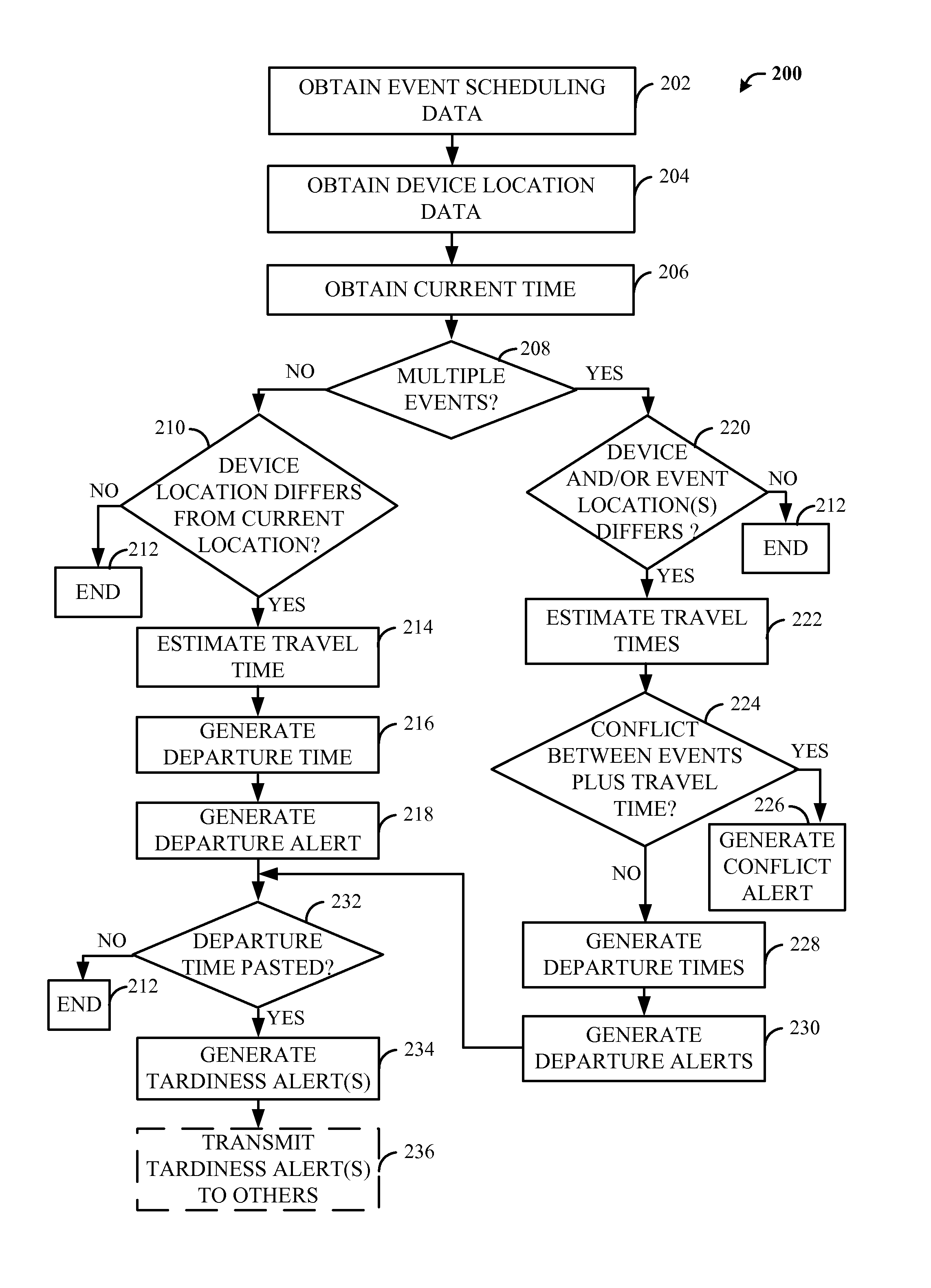
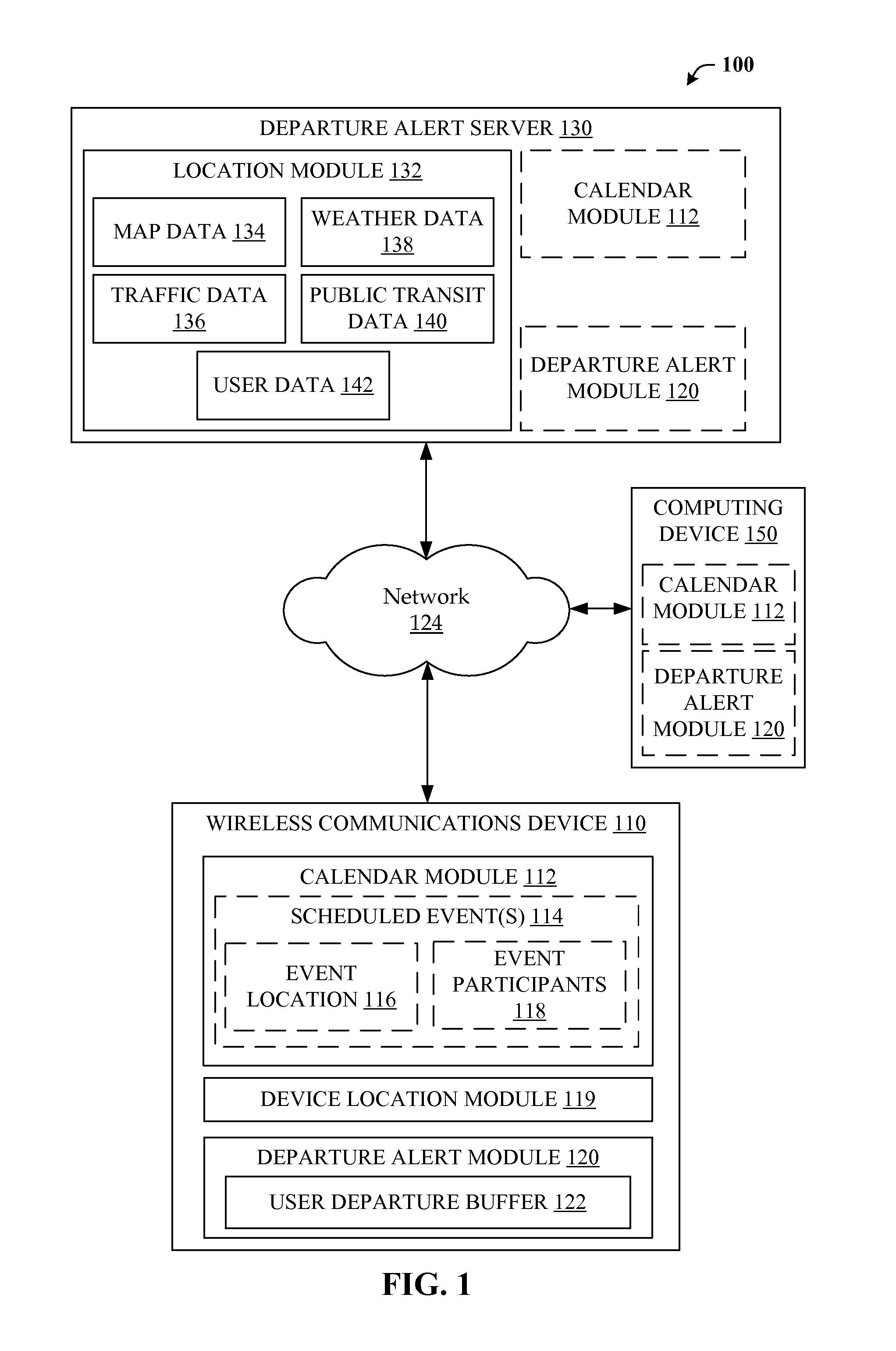
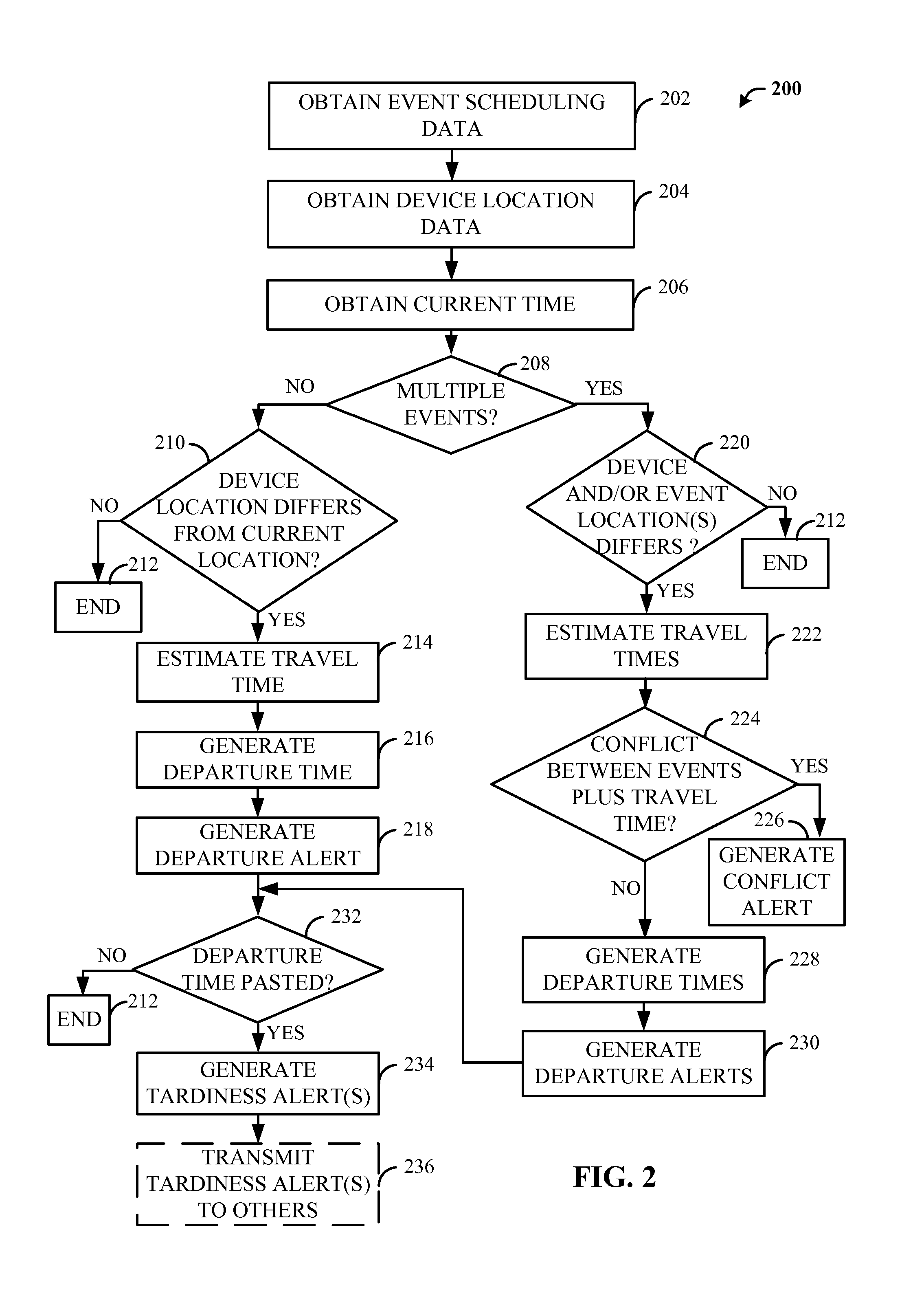
Methods and Apparatus for Estimating Departure Time Based on Known Calendar Events
ActiveUS20110090078A1Arrangements for variable traffic instructionsNavigation instrumentsEvent schedulingReal-time computing
A method and apparatus generating a departure alert for an event based on a current location. The method may comprises: obtaining scheduling data associated with a first event, wherein the first event scheduling data includes a first event time value and a first event location value, obtaining a device location value, obtaining a current time value, determining if the first event location value and the device location value differ by more than a event location threshold, upon a determination that the first event location value and the device location value differ by more than the event location threshold, estimating a first travel time value from the device location and the first event location, generating a departure time value by comparing the first event time value and the estimated first travel time value, and generating a departure alert by comparing the departure time value and the current time value.
Owner:QUALCOMM INC
Systems for communicating current and future activity information among mobile internet users and methods therefor
InactiveUS7284033B2Multiple digital computer combinationsMarketingInternet usersMobile Internet device
A computer-implemented method implemented via the Internet for coordinating a current or future event between a user of a mobile Internet device and other users communicating through the Internet. The method includes receiving the current or future activity information pertaining to the future event from the user via the mobile Internet device. The current activity pertains to an activity occurring at a current time relative to a time the future activity information is received. The future activity pertains to an activity occurring at a future time relative to a time the future activity information is received. The method further includes transmitting the current or future activity information to a backend database coupled to the Internet, the backend database being remote from the mobile Internet device. The method further includes rendering the current or future activity information accessible to at least one recipient via the Internet. The recipient represents a subset of the users coupled to the Internet and having access privilege to information pertaining to the current or future event involving the user.
Owner:META PLATFORMS INC
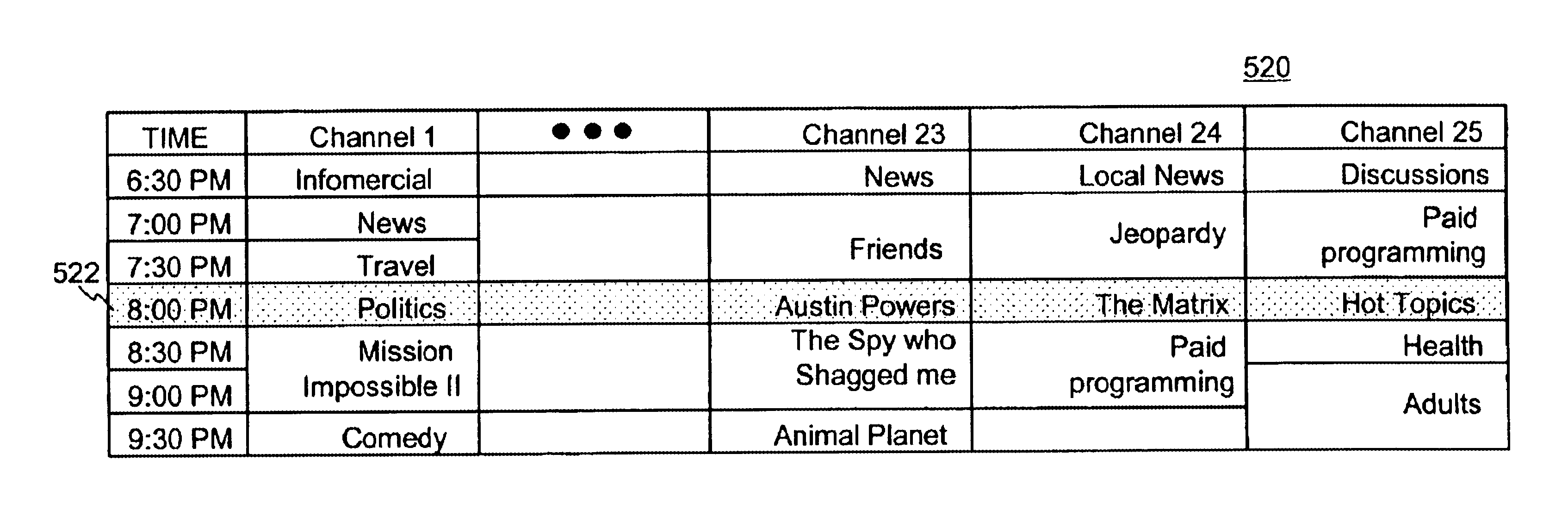
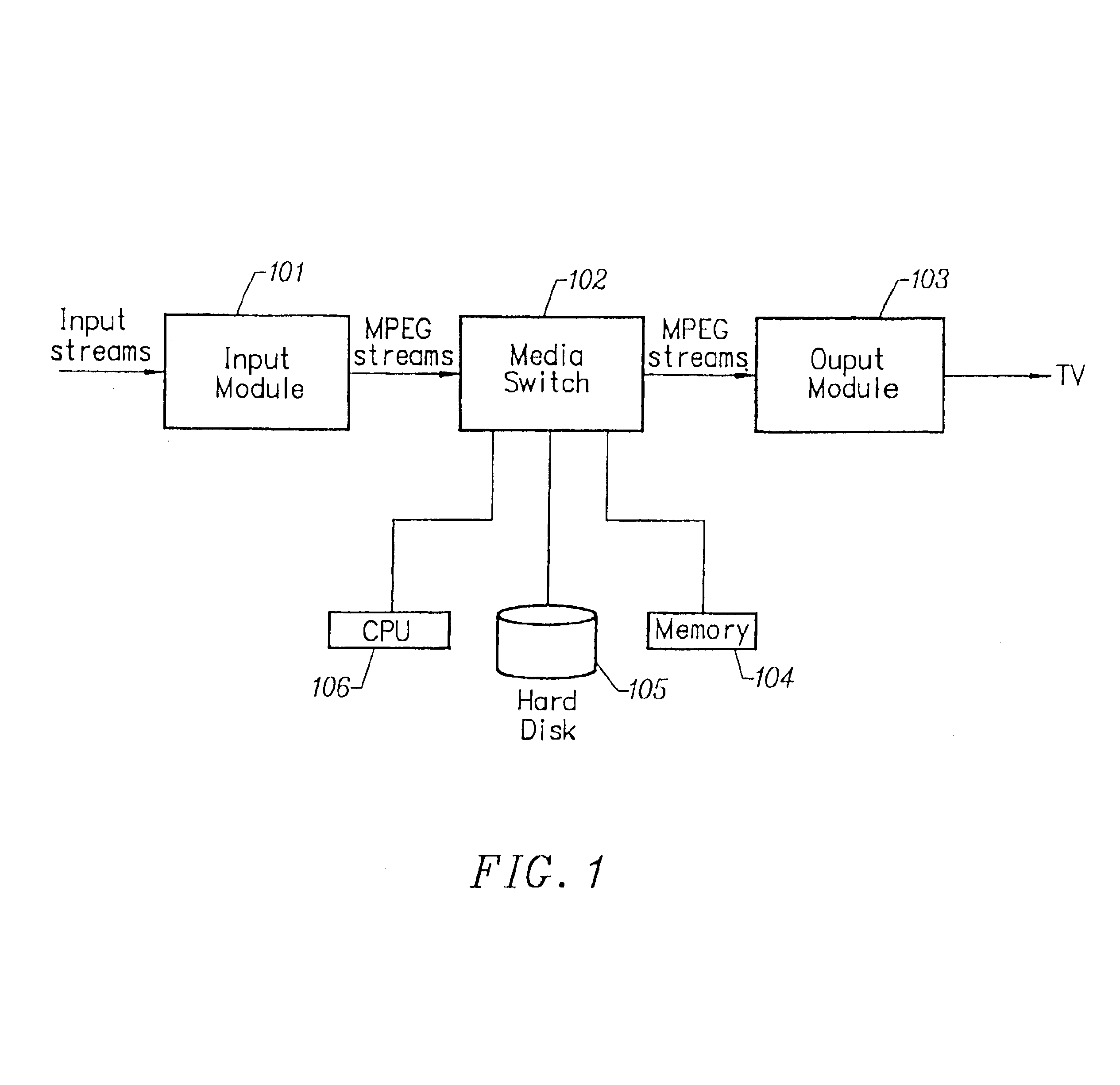
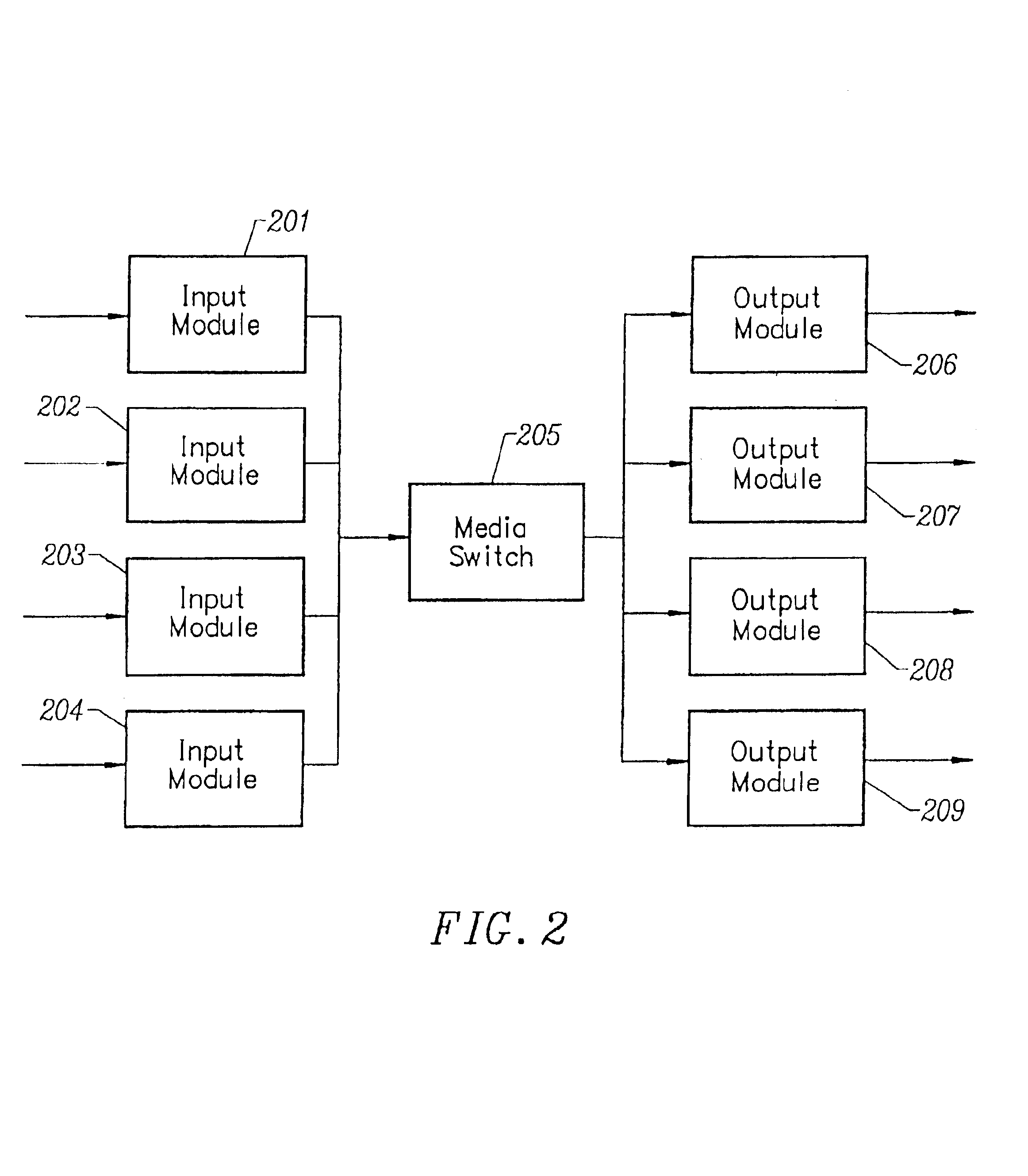
Program guide with a current-time bar
Improved approaches for configuration, management and operation of a media delivery system are disclosed. The media delivery system centrally manages and stores media content and also controls the delivery of media content to subscribers. According to one embodiment, a method for providing a program guide to subscribers of the media delivery system is disclosed. The media delivery system delivers programs to the subscribers in accordance with the program guide. The program guide can be customized for subscribers. The customization can be implemented in a variety of ways. One example of customization is to provide the program guide with a time bar.
Owner:MINERVA NETWORKS
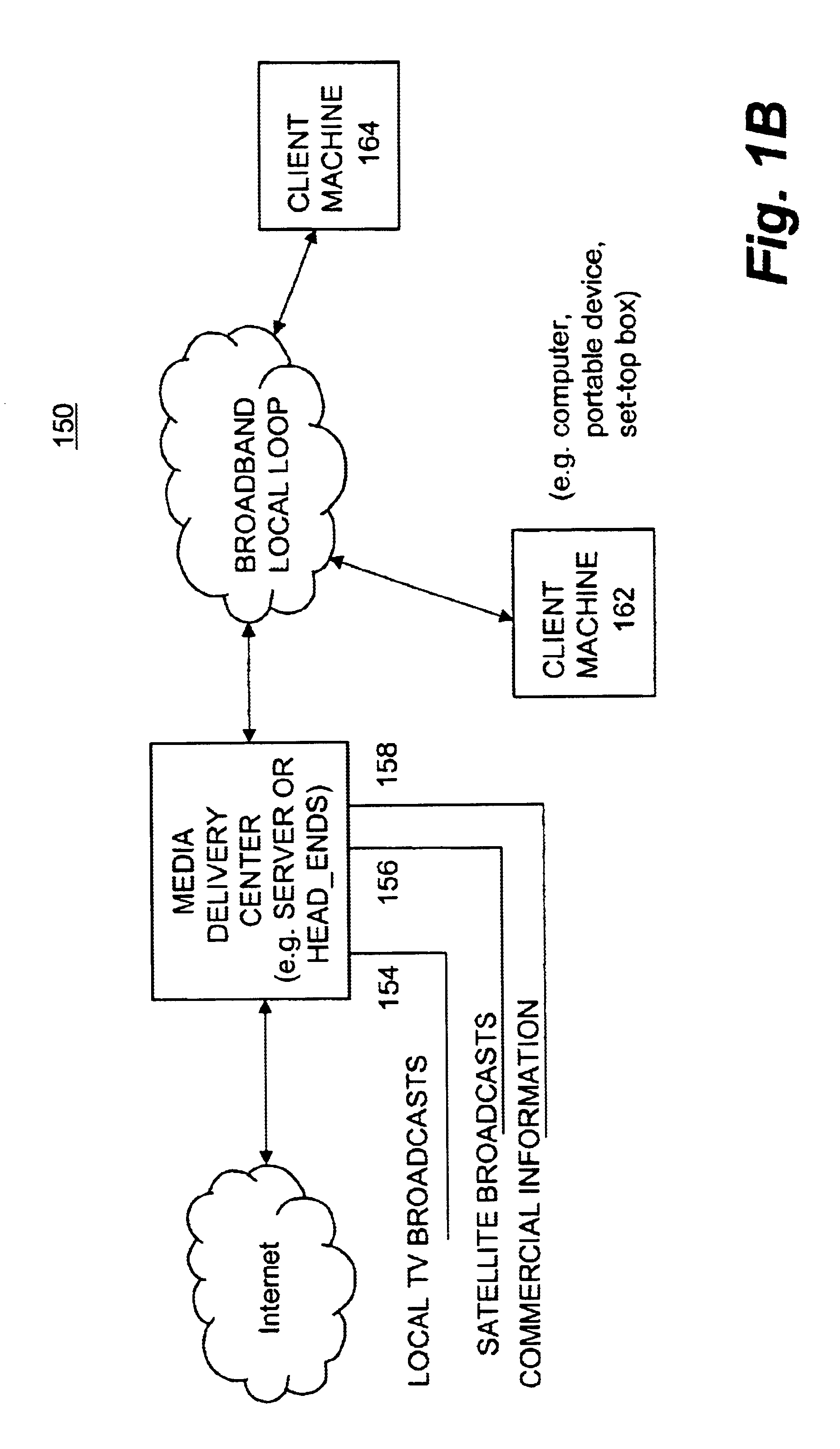
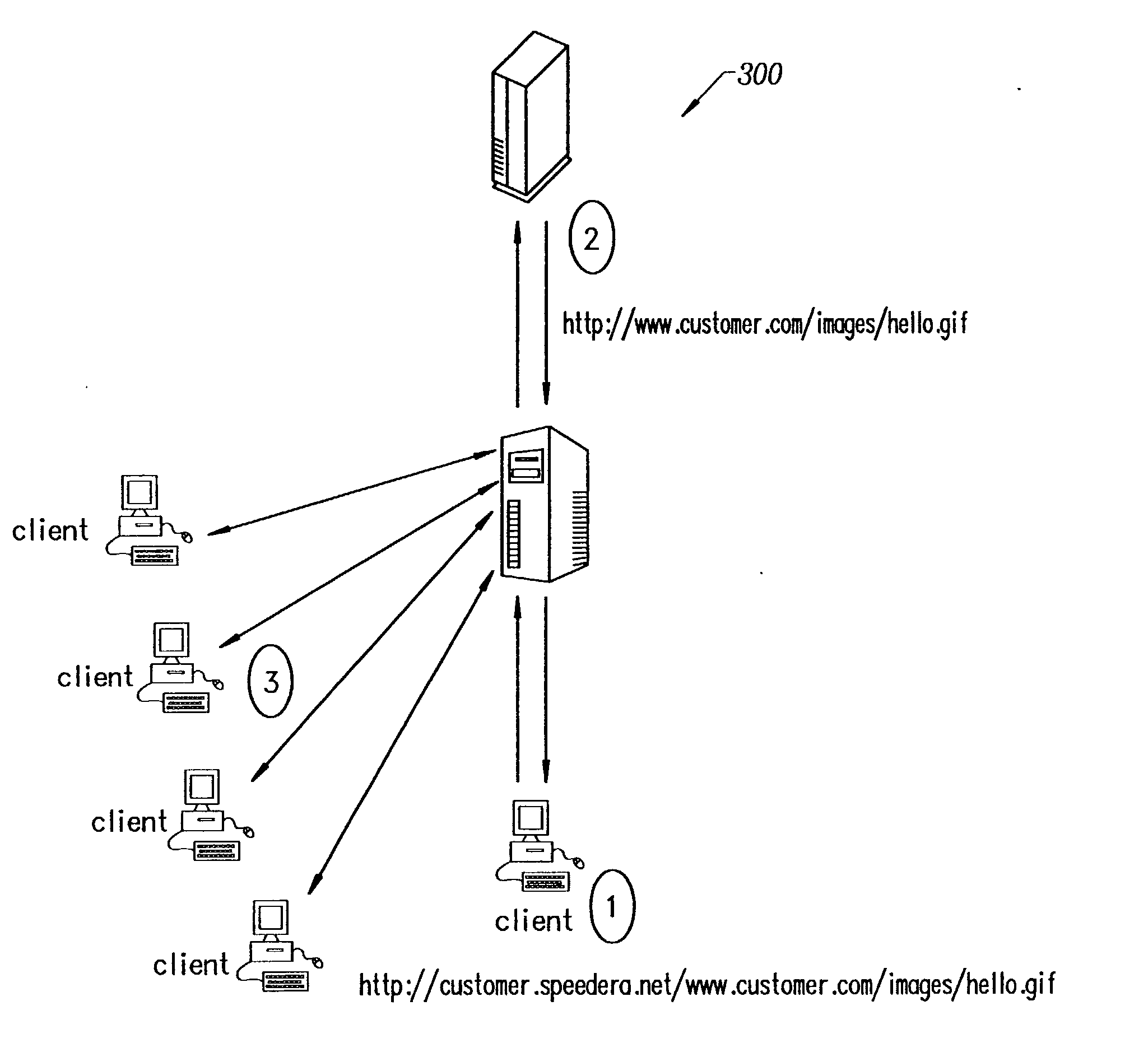
Secure content delivery system
InactiveUS20030097564A1Metering/charging/biilling arrangementsUser identity/authority verificationExpiration TimeRelevant information
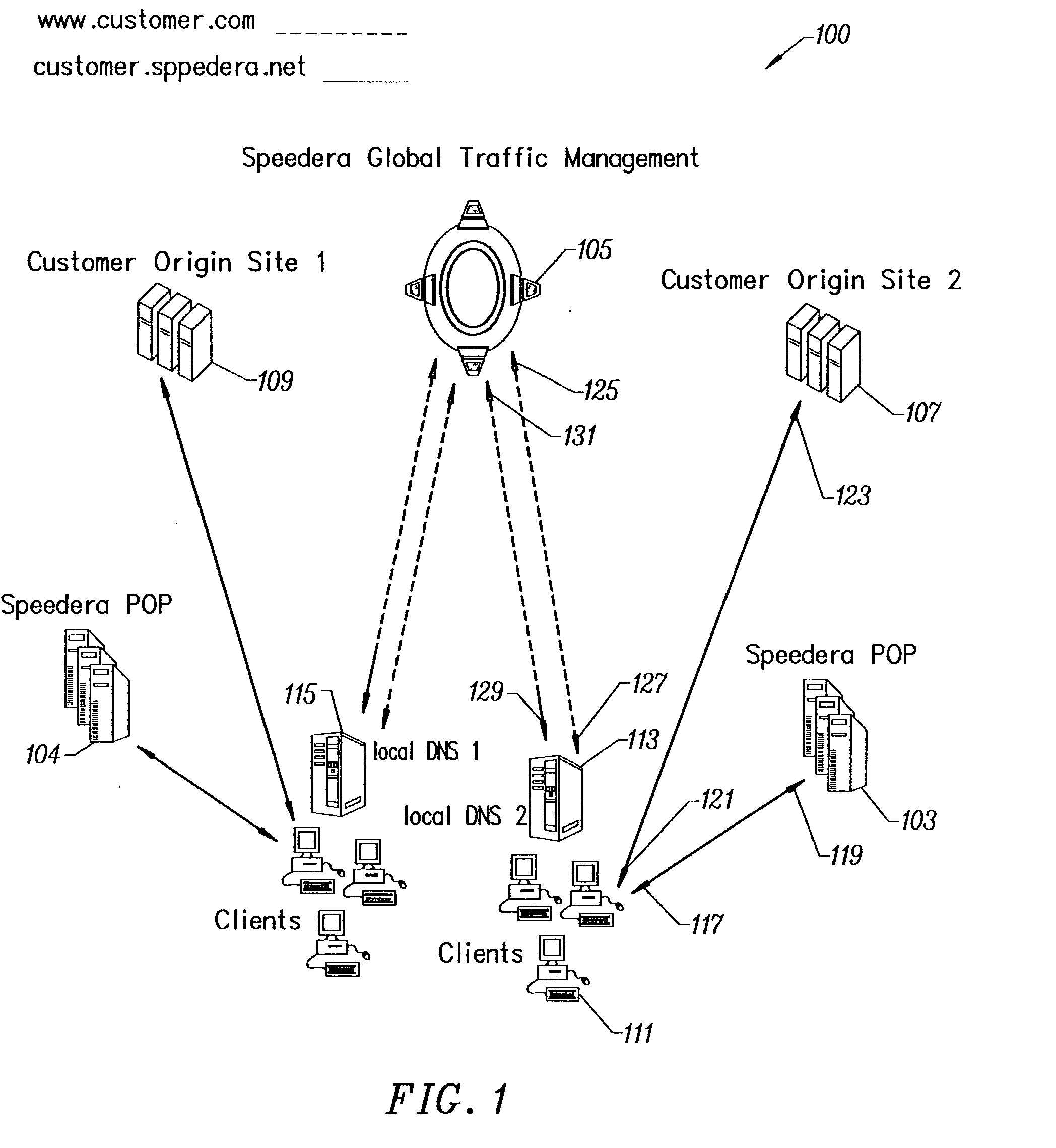
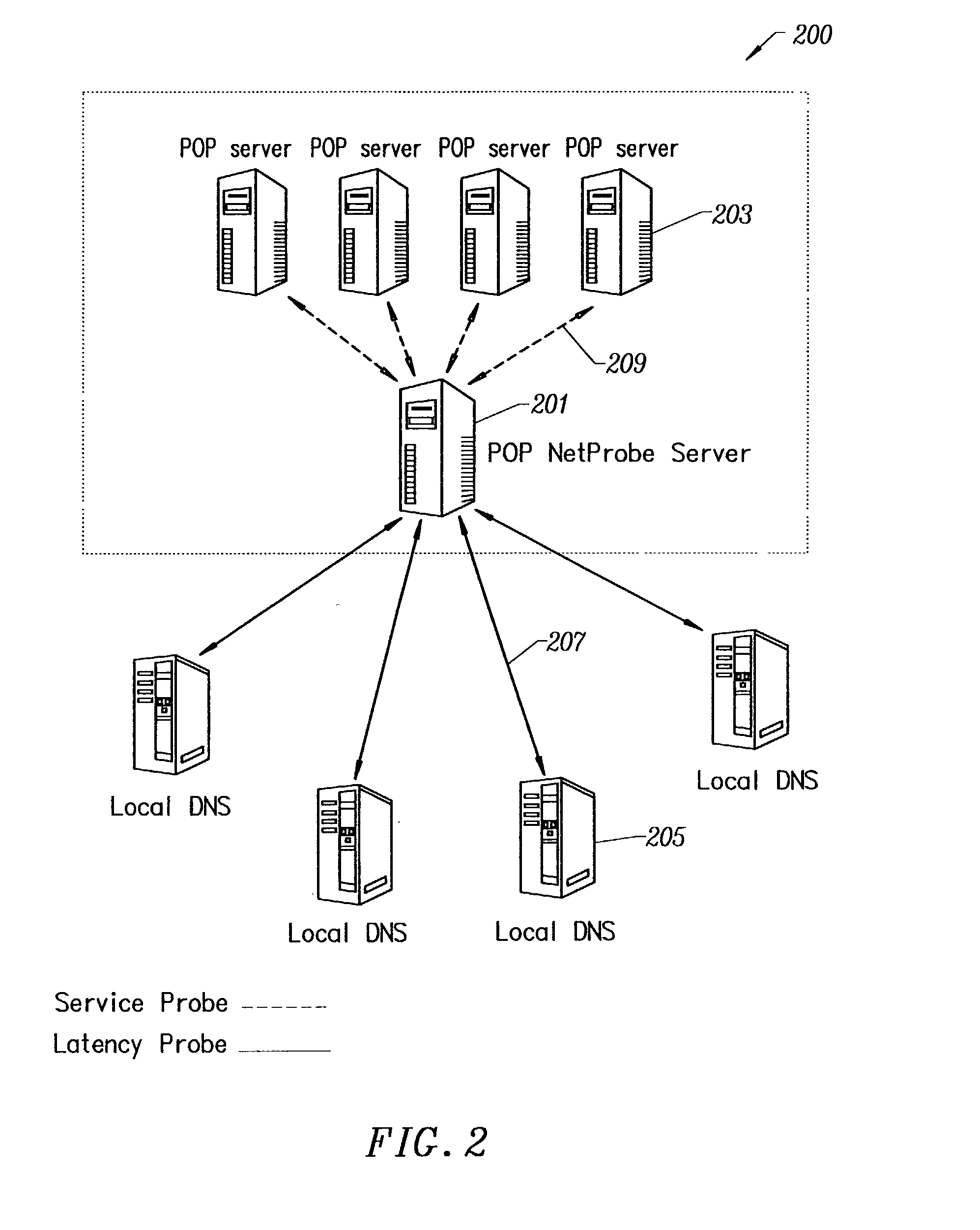
A secure streaming content delivery system provides a plurality of content servers connected to a network that host customer content that can be cached and / or stored, e.g., images, video, text, and / or software. The content servers respond to requests for customer content from users. The invention load balances user requests for cached customer content to the appropriate content server. A user makes a request to a customer's server / authorization server for delivery of the customer's content. The authorization server checks if the user is authorized to view the requested content. If the user is authorized, then the authorization server generates a hash value using the authorization server's secret key, the current time, a time-to-live value, and any other information that the customer has configured, and embeds it into the URL which is passed to the user. A content server receives a URL request from the user for customer content cached on the content server. The request is verified by the content server creating its own hash value using the customer server's secret key, the current time, a time-to-live value, and any other related information configured for the customer. If the hash value from the URL matches the content server's generated hash value, then the user's request is valid and within the expiration time period and the content server delivers the requested content to the user.
Owner:AKAMAI TECH INC
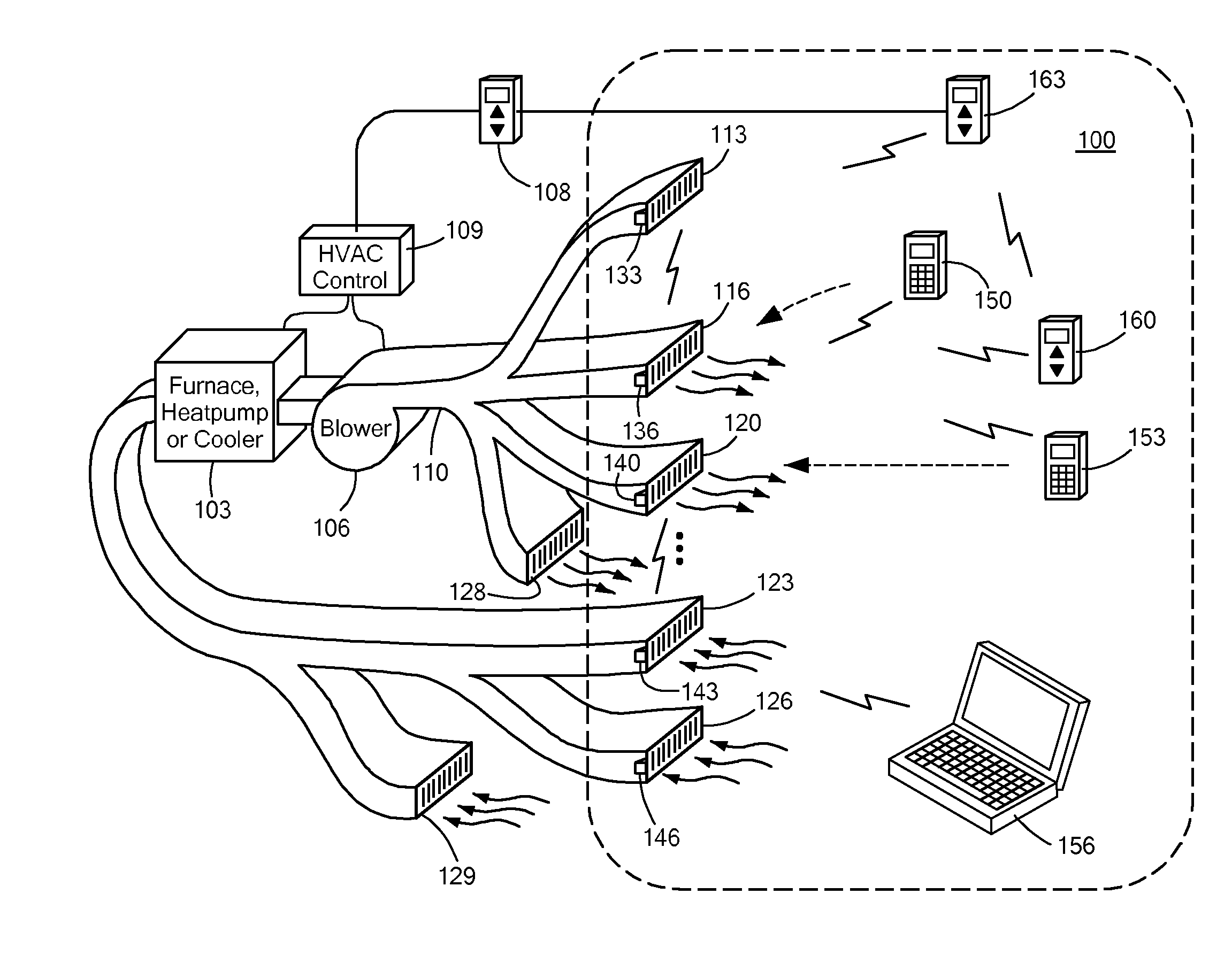
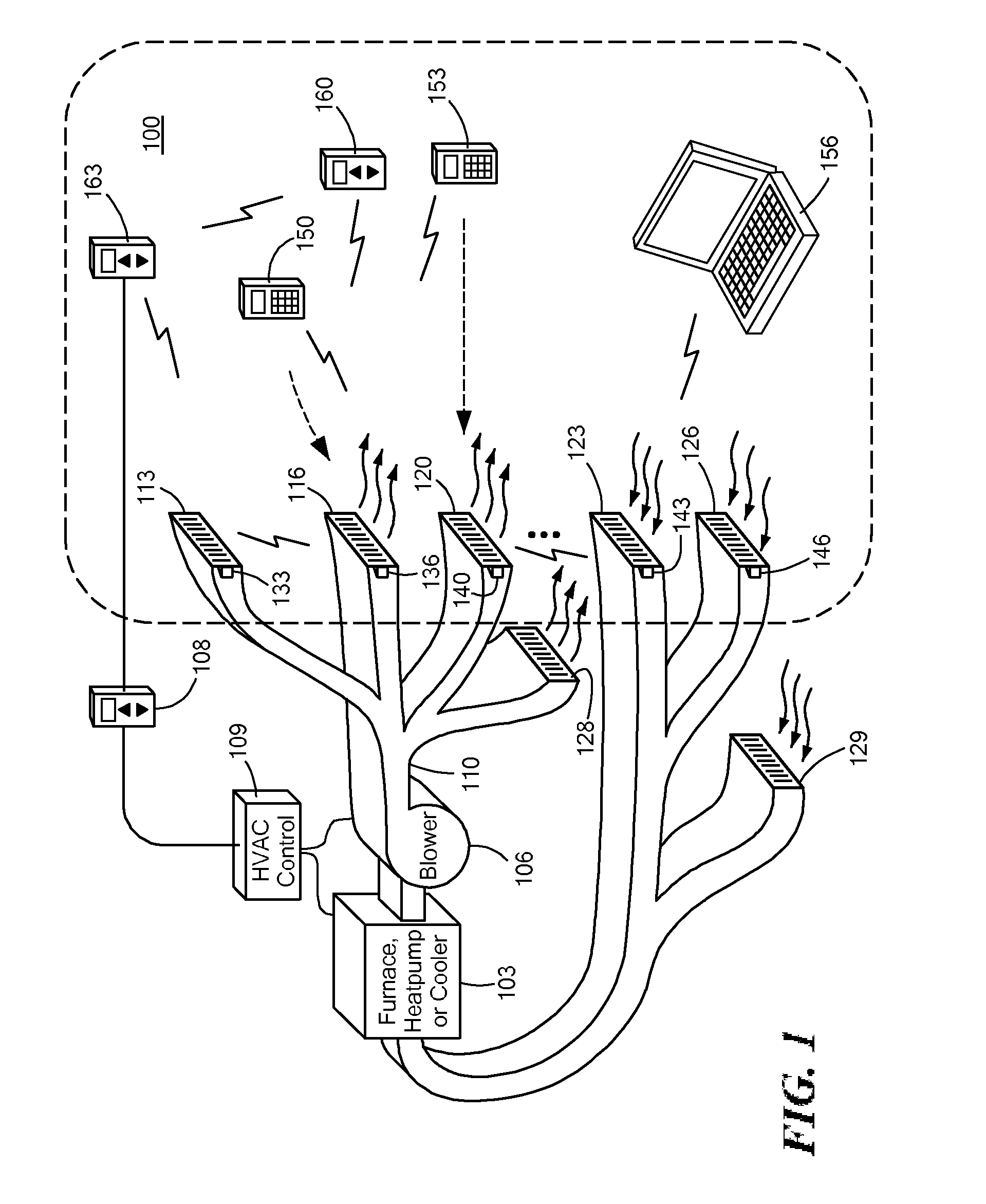
Automatically Balancing Register for HVAC Systems
Distributed nodes, such as intelligent register controllers, of a heating, ventilating and / or air conditioning (HVAC) system wirelessly communicate with each other on a peer-to-peer basis, forming a network, and collectively control the HVAC system, without a central controller. The intelligent register controllers collectively control the amount of conditioned air introduced into each region. Each node may base its operation at least in part on information about one or more (ideally all) of the other nodes. Each intelligent register controller automatically determines how much conditioned air to allow into its region, or how much return air to allow to be withdrawn from its region, based on information collected by the register controller, such as: current temperature of the region; desired temperature of the region; calculated amount of conditioned air required to change the region's temperature to the desired temperature; temperature of conditioned air begin supplied by a duct to the register; current time, day of week, vacation or other schedule data; temperatures of other regions and their respective desired temperatures; calculated amounts of air required to be supplied or withdrawn by the other controlled registers to change their respective regions' temperatures to their desired temperatures; or combinations thereof. Each register controller automatically determines when and to what extent to operate its respective controllable damper.
Owner:ZONER
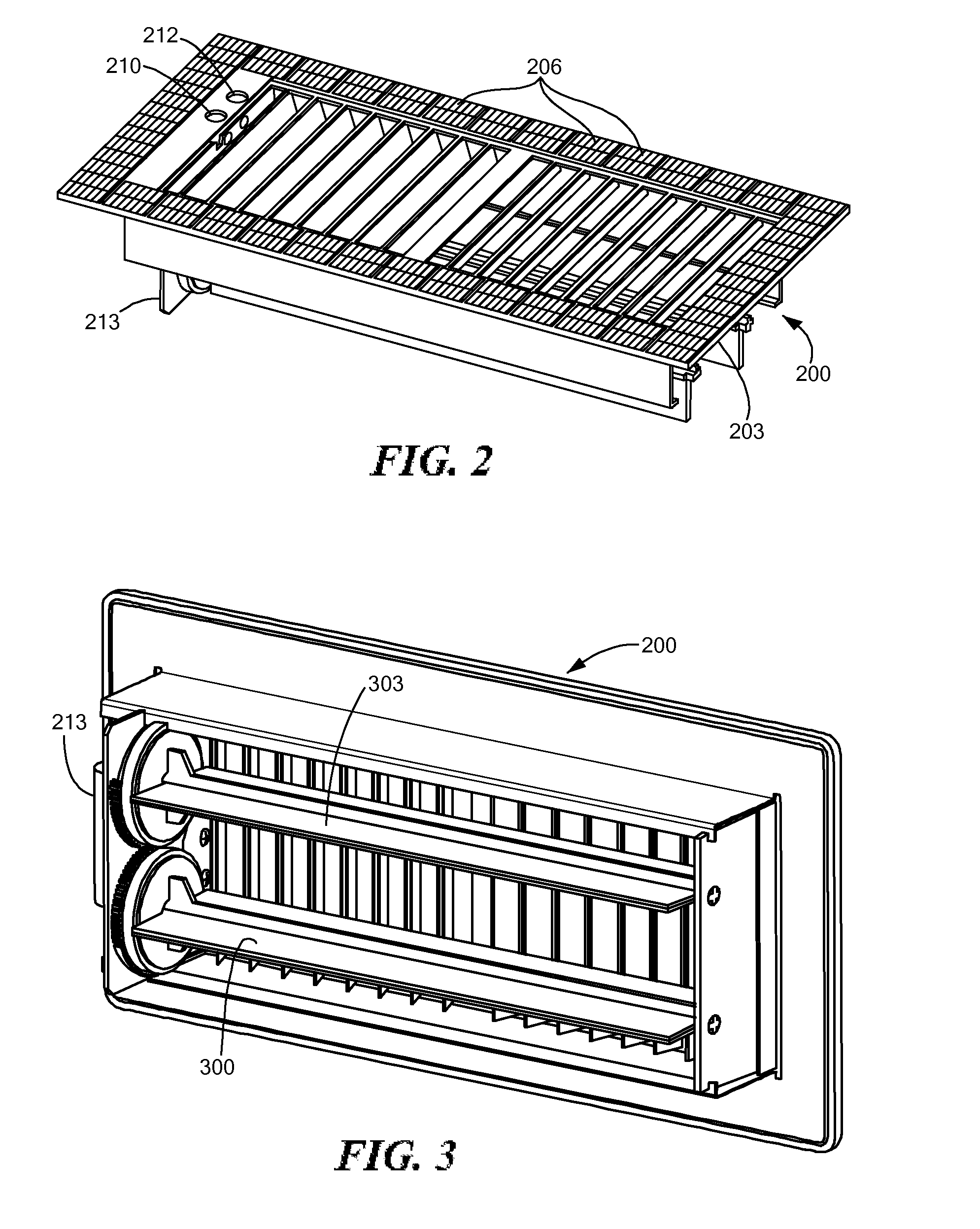
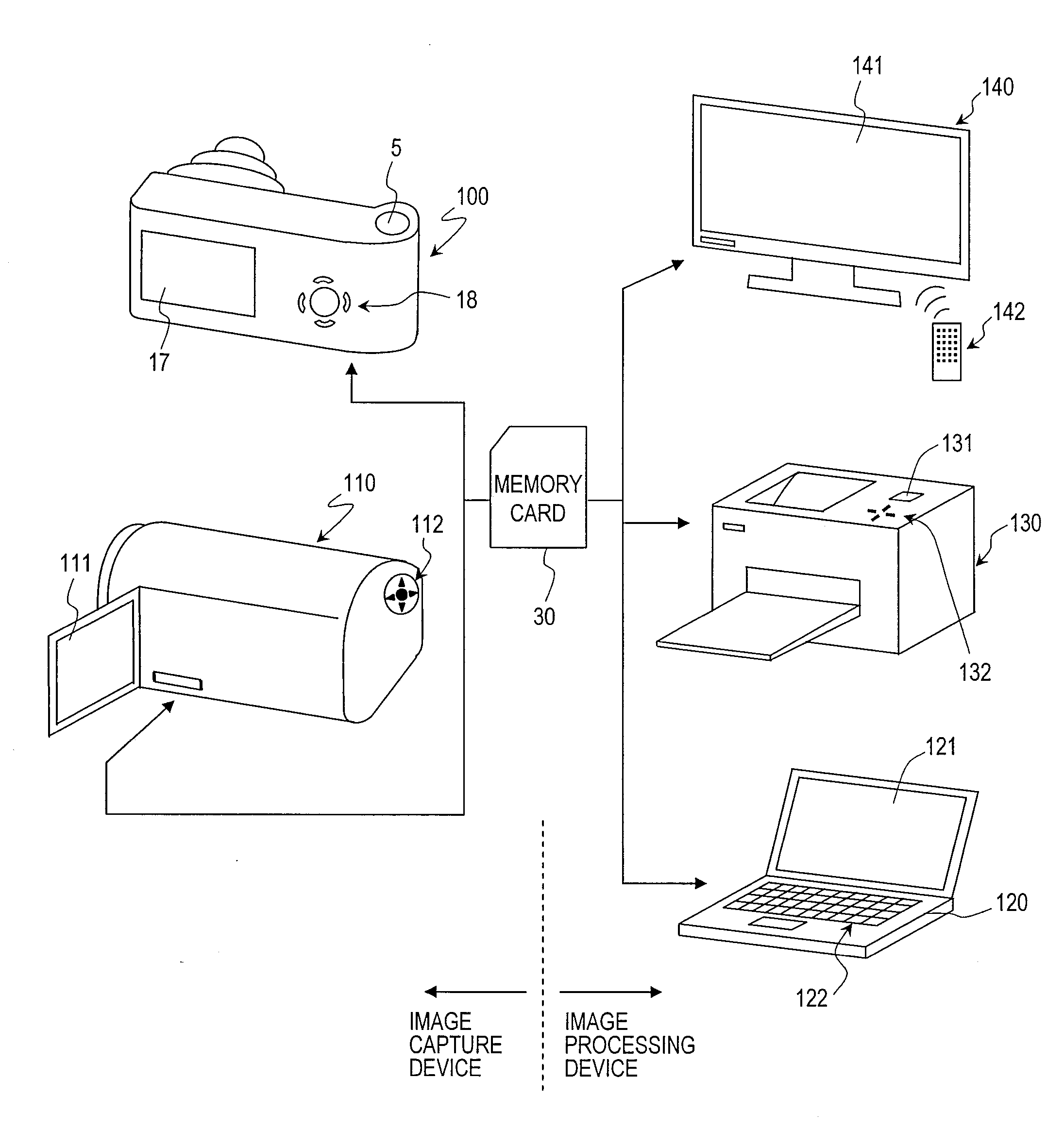
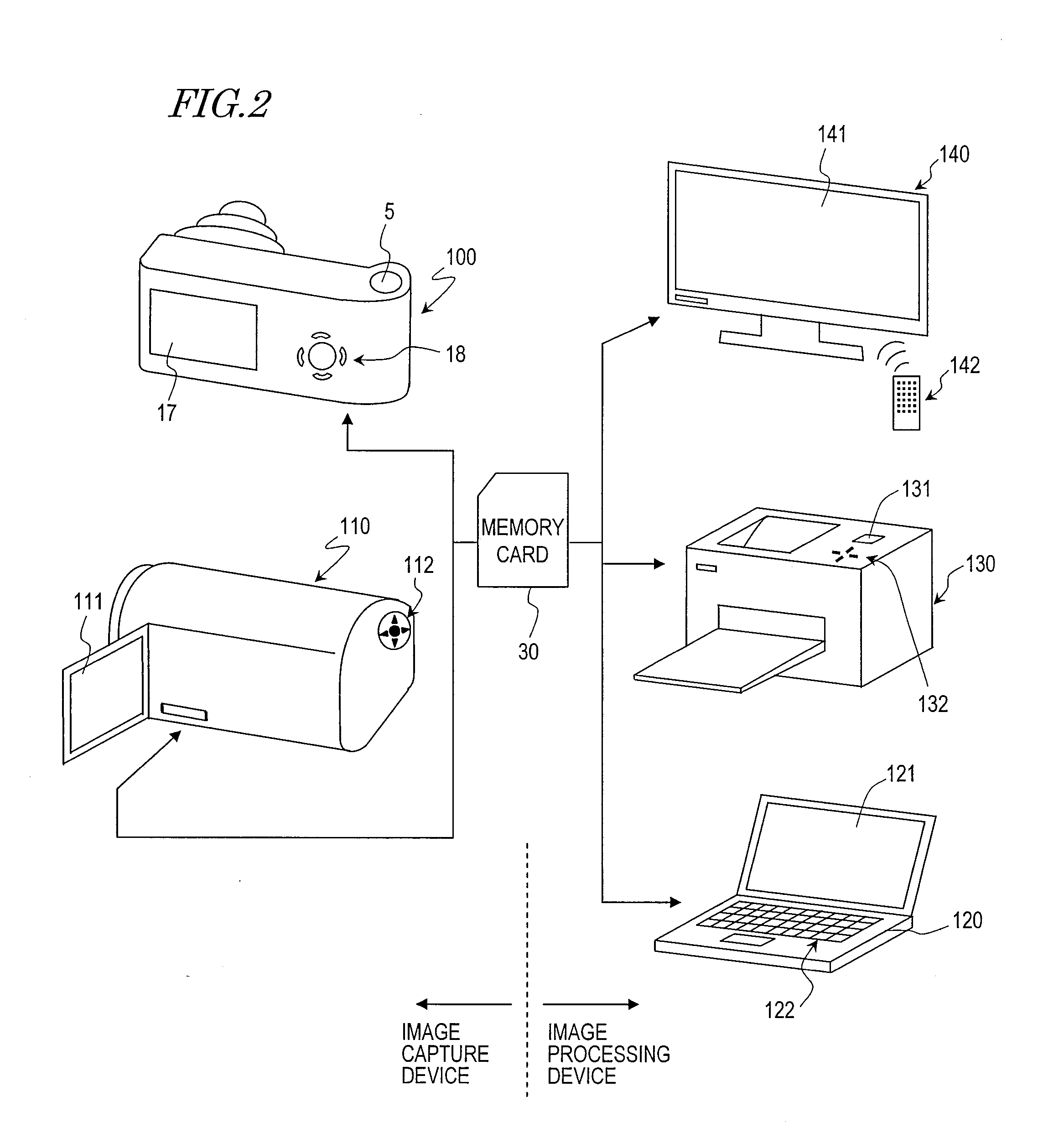
Image capture device and image processing device
ActiveUS20080266421A1Simple processReduce the burden onTelevision system detailsColor television detailsImaging processingComputer science
An image capture device includes: an imager for imaging an object and generating image data; an image file generator for generating an image file by adding, to the image data generated by the imager, a header portion which stores at least one type of information concerning shooting circumstances; a timer for outputting information indicating a current time; and a manipulation section which is used to set period information specifying a period. The image file generator changes the type of information to be stored in the header portion depending on whether a time of imaging as indicated by the information which is output from the timer at the time of the imaging falls within the period specified by the period information.
Owner:PANASONIC CORP
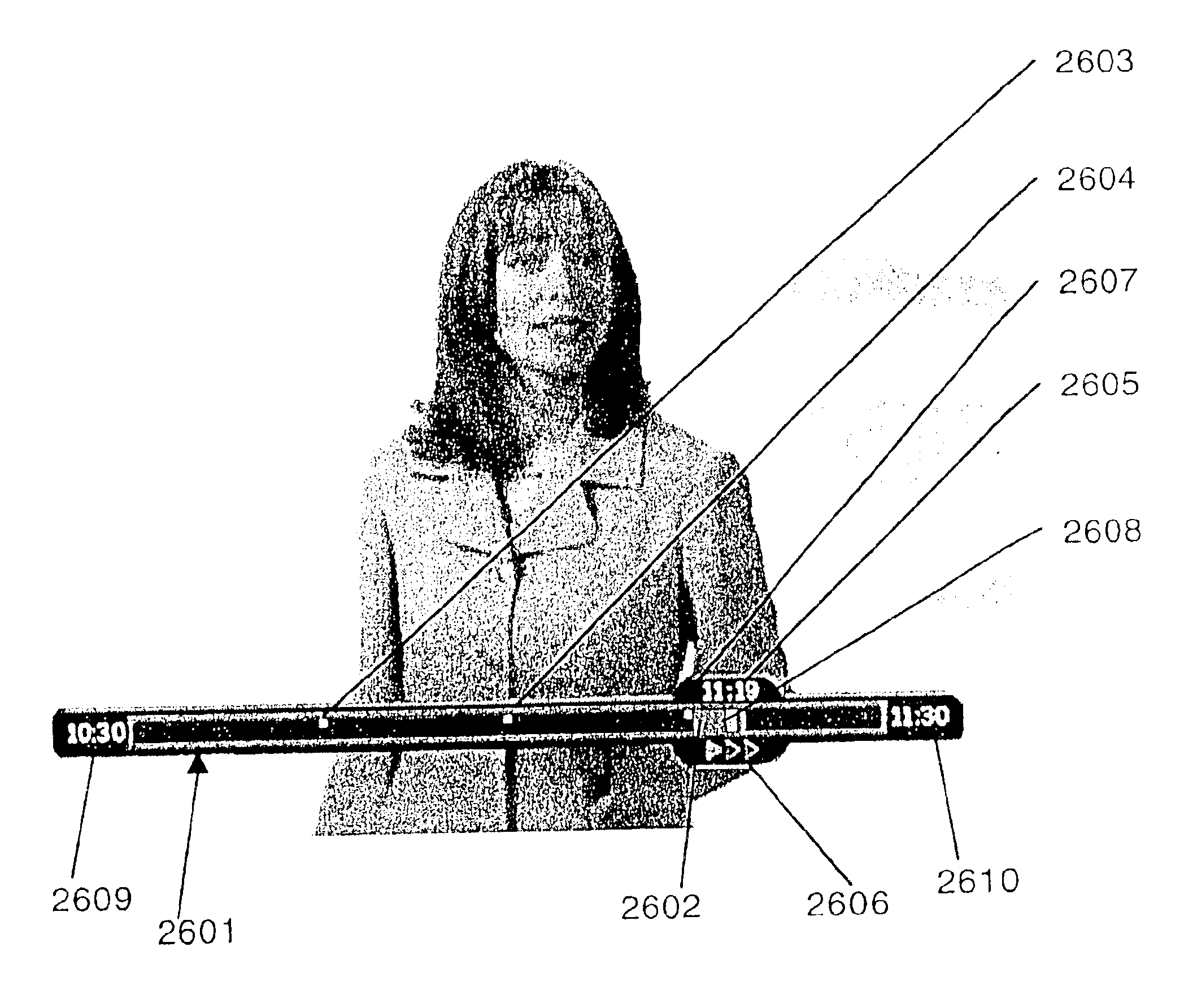
Multimedia visual progress indication system
InactiveUS6847778B1Enhanced interactionTelevision system detailsDisc-shaped record carriersTime markComputer graphics (images)
A multimedia visual progress indication system that provides a trick play bar that is overlaid onto the program material or displayed on a dedicated display. A cache bar inside of the trick play bar indicates the length of a recording session or the length of stored program material and expands to the right when material is being recorded. Every half hour (or selected increment), the cache bar slides to the left. Time marks are displayed inside the trick play bar giving the user a visual reference point from which to judge the current time and visual time reference points. The time marks are in any increment of time needed. The total length of the stored program material or next time or counter increment in the recording cycle is displayed on the right hand end of the trick play bar. A position indicator moves within the trick play bar and tells the user visually where his current position is within the program material. A slider moves along the trick play bar and on top of the cache bar and is linked to the position indicator and can be moved anywhere within the cache bar by the user. The slider displays the numeric time or counter mark of the current position. A mode indicator is positioned below the slider and follows the slider's movement and displays whether the user is in play, record, pause, slow play, fast play, fast forward (1×, 2×, and 3×), slow reverse play, slow reverse, and fast reverse (1×, 2×, and 3×) modes. The 1×, 2×, and 3× speeds are adjustable by the system to be any variable desired (e.g., 2×, 16×, and 32×). The trick play bar and its associated components are displayed for a predetermined time period when overlaid onto the program material.
Owner:TIVO SOLUTIONS INC
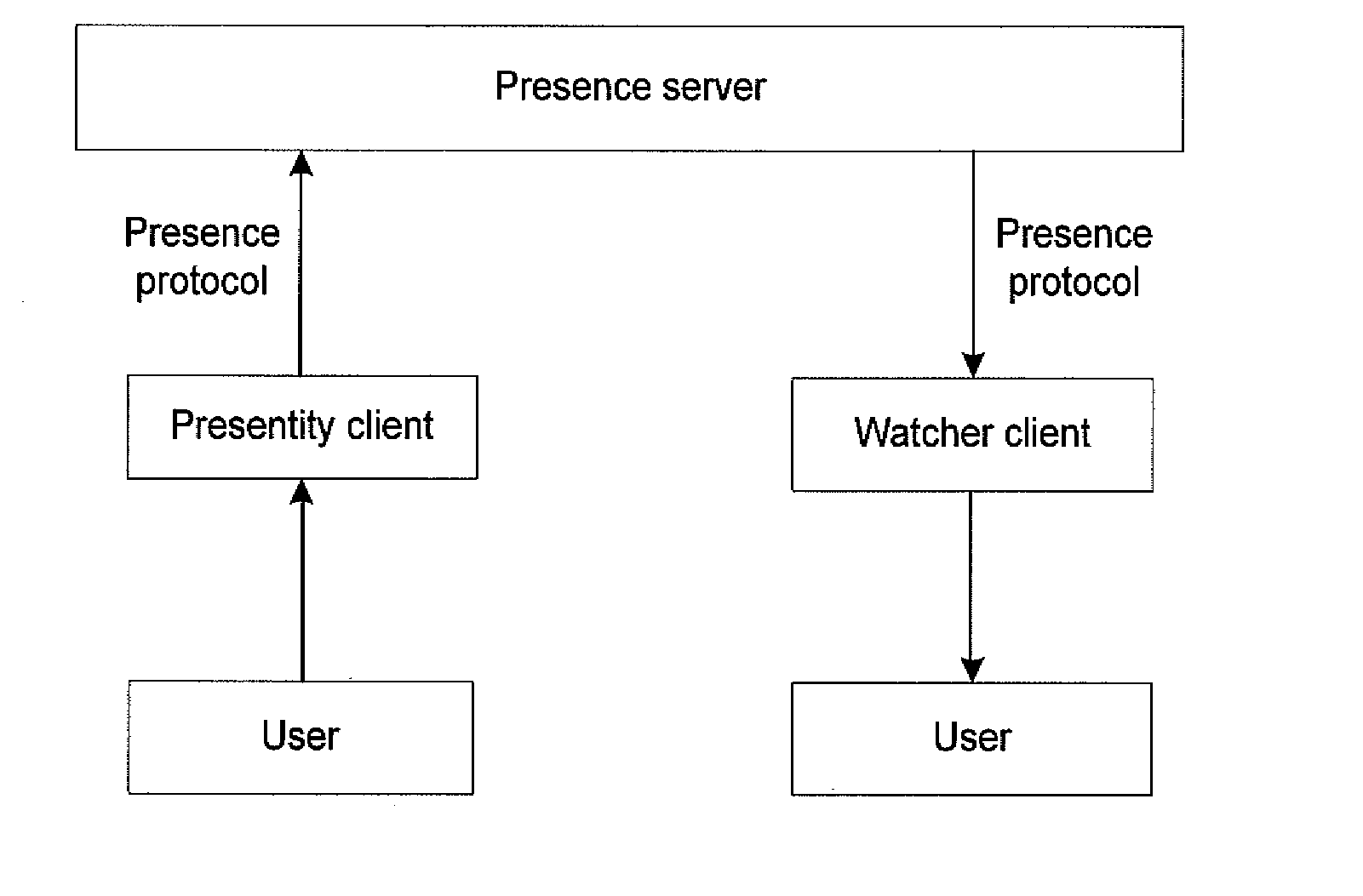
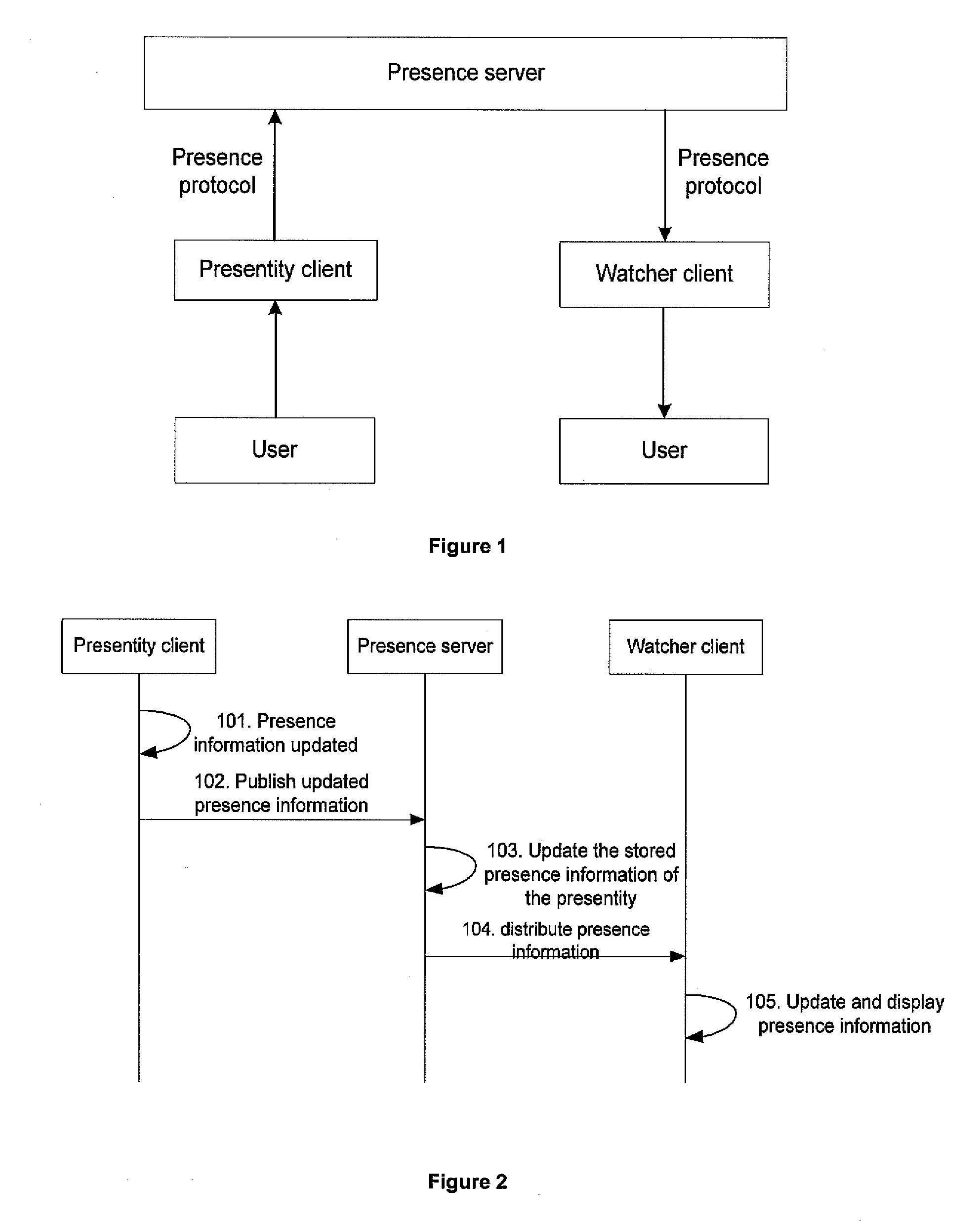
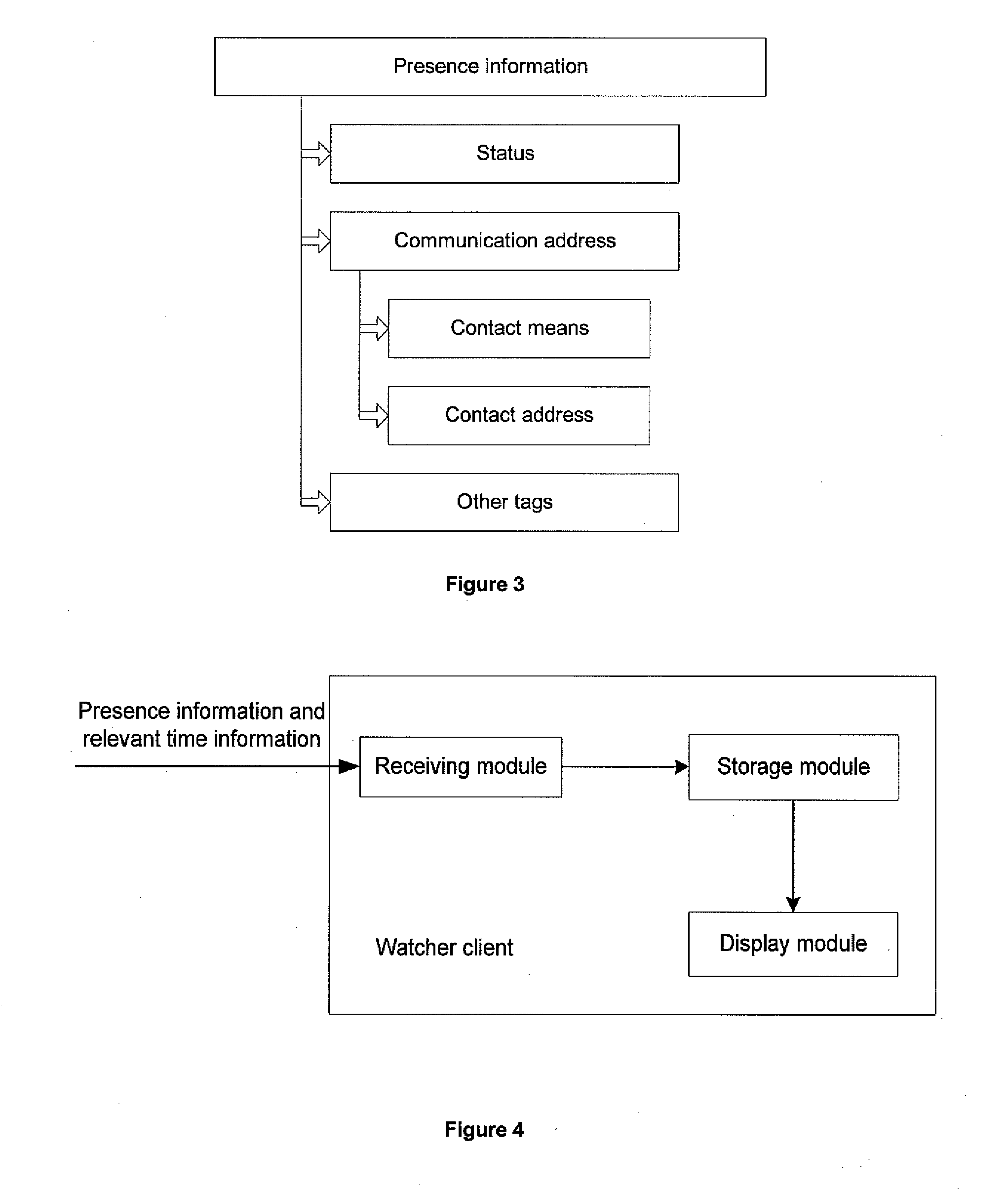
Method and apparatus for providing presence information
InactiveUS20070233859A1Digital computer detailsData switching networksTemporal informationState of art
The present invention discloses a method for providing presence information, a watcher, a presence server, a presence system and a presentity. It enables the provisioning of history and future presence information, while the prior arts can provide only presence information corresponding to the current time. The method provided by the present invention includes: setting time elements of presence information; recording relevant time information of presence information in the time elements; providing the watcher with presence information together with relevant time information.
Owner:HUAWEI TECH CO LTD
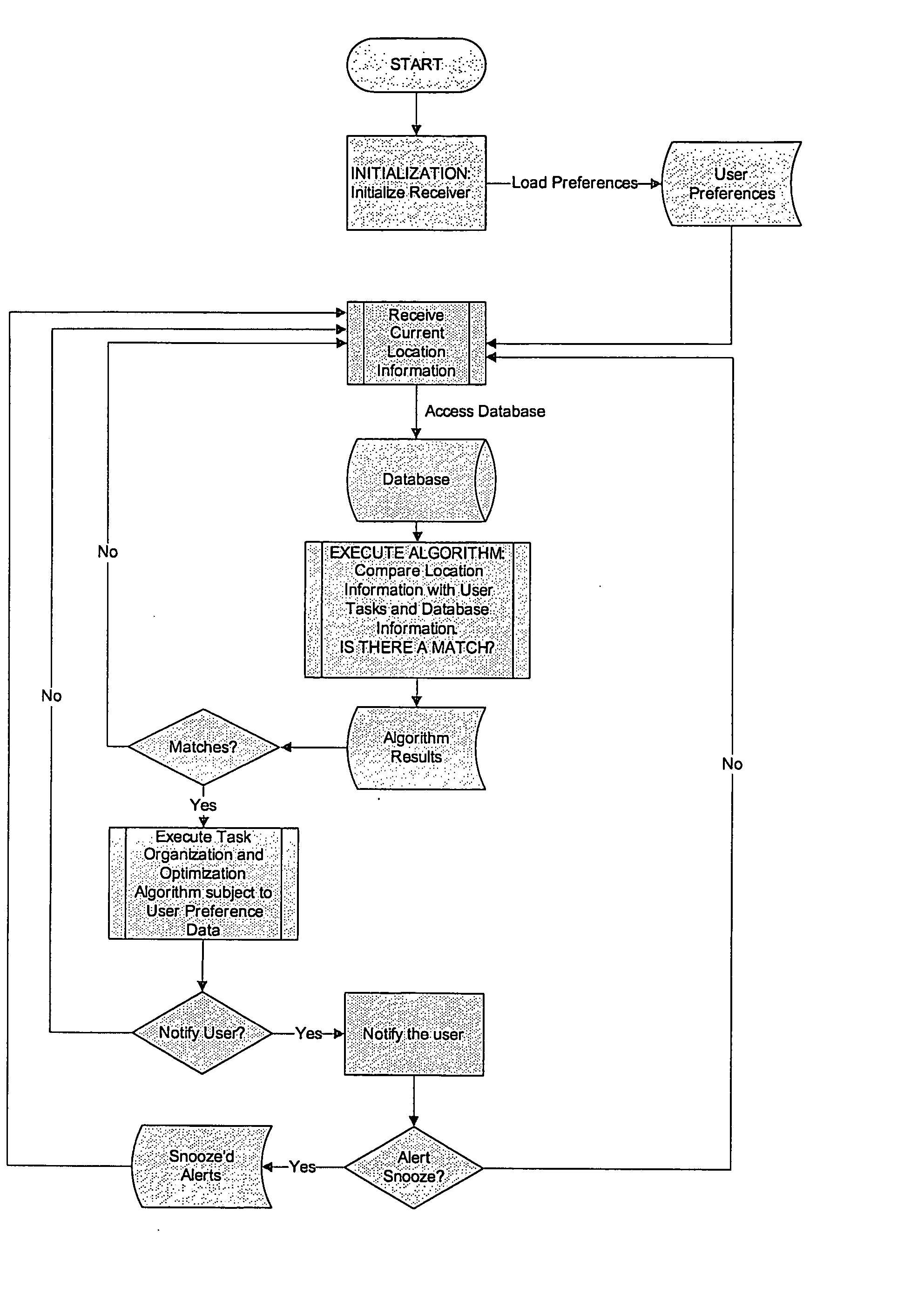
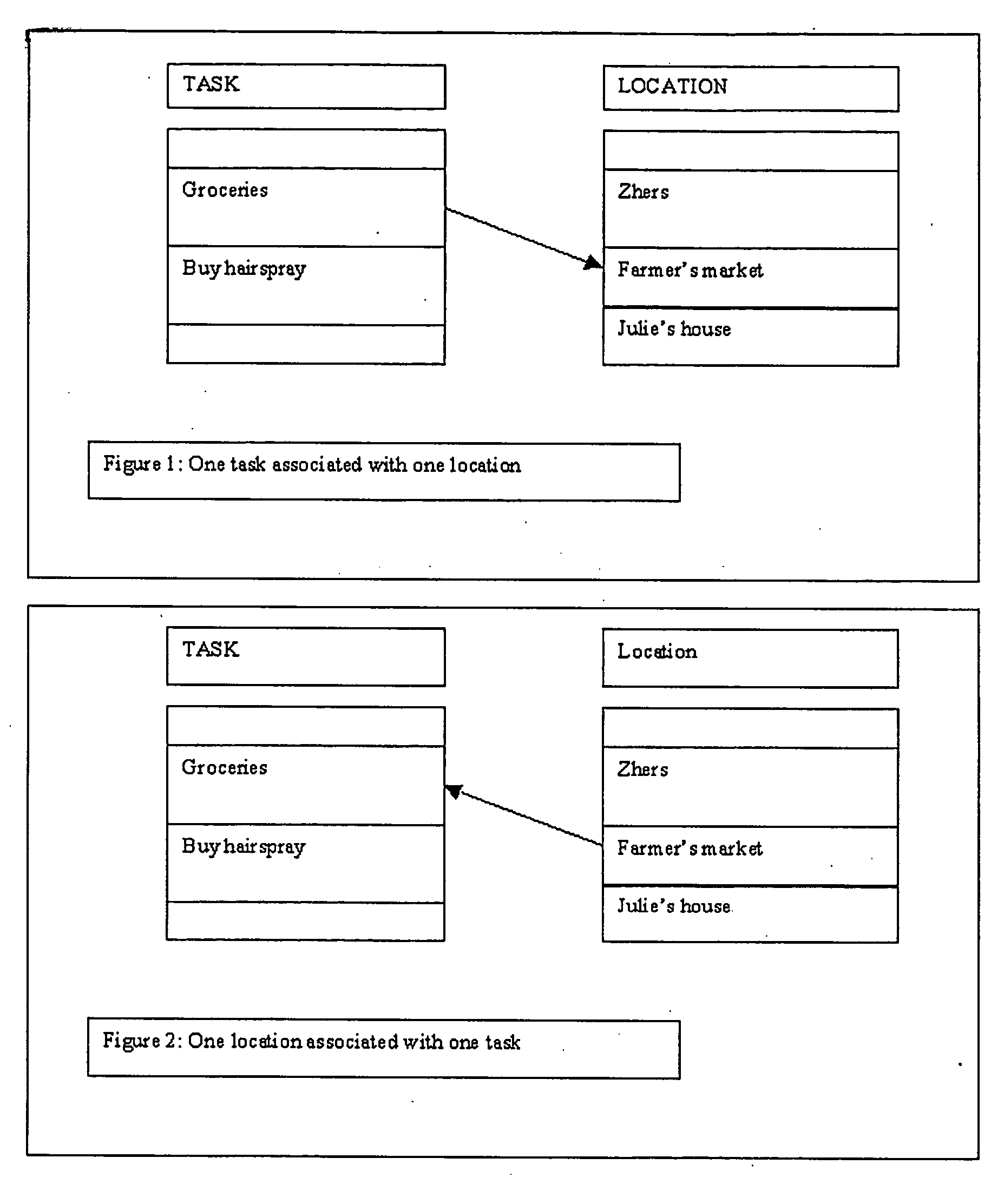
Recordable location-based reminder system organizer
An organization system using location information, possibly in conjunction with time based information for tasks, with the purpose of optimizing user travel distance and / or time to complete specified tasks. Task organization may include alternate criteria such as importance, or sharing and assigning of tasks over groups to optimize in terms of the time / location / schedule of other members of the group. The mobile system may alert users of some tasks based on the user proximity to those tasks, alert of other tasks based on both time and location, or others based solely on the current time and the time of the task. The system can provide a dynamic schedule, changing based on time estimates of the user tasks as well as actual time to complete user tasks, estimates of travel time between tasks, as well as other criteria.
Owner:BLASS MELANIE MAGDOLNA
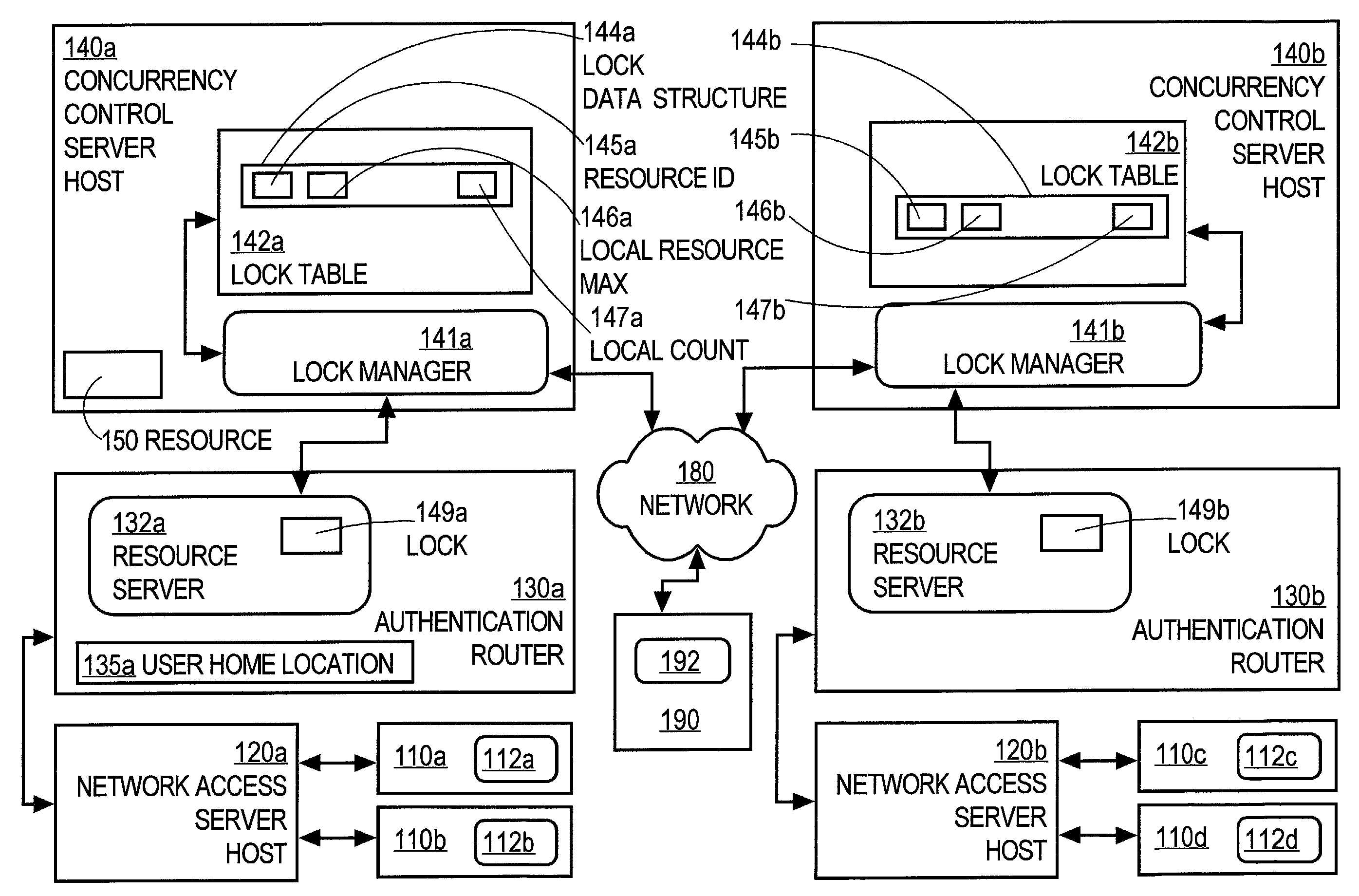
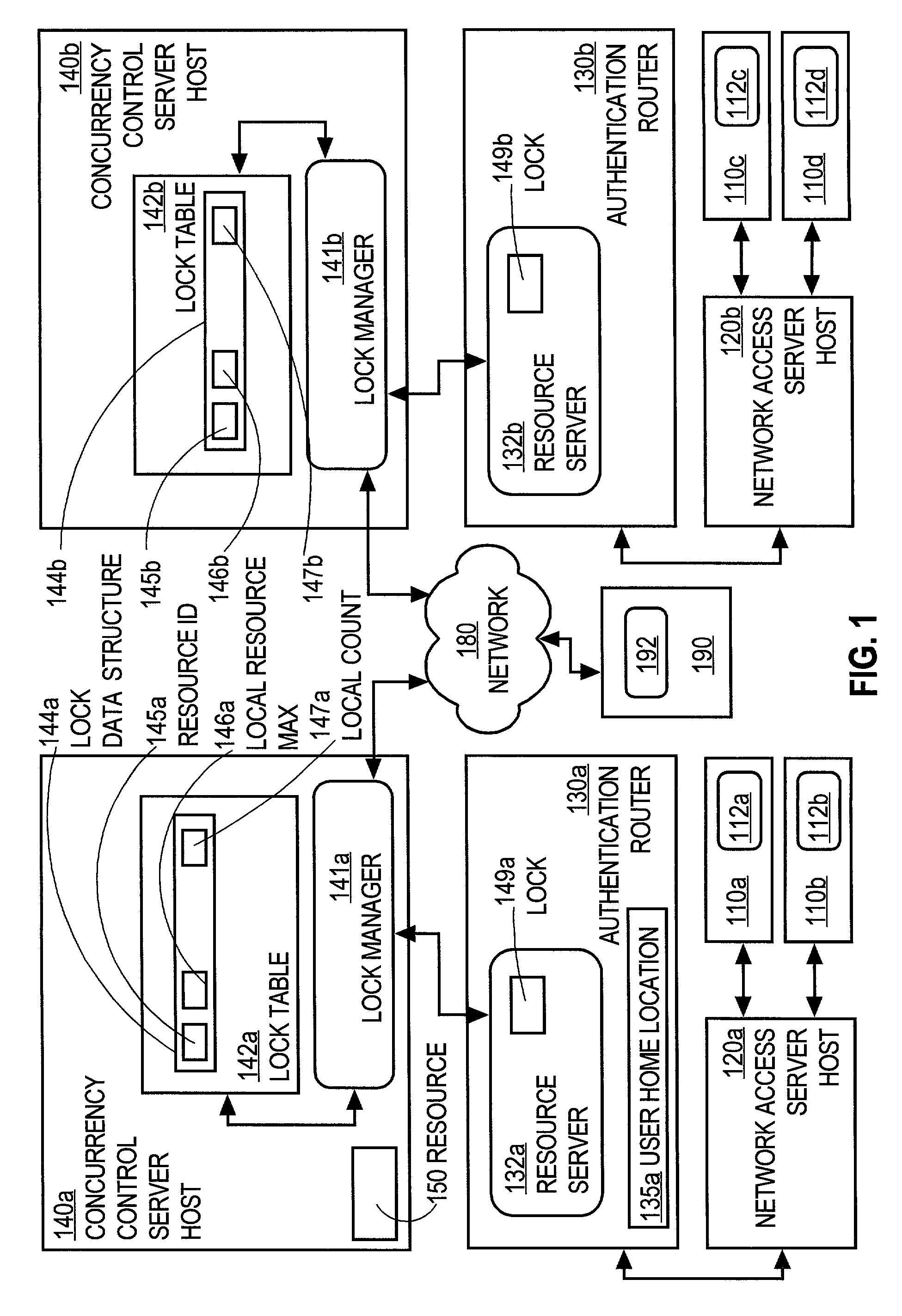
Controlling access of concurrent users of computer resources in a distributed system using an improved semaphore counting approach
ActiveUS7328263B1Data processing applicationsUnauthorized memory use protectionLimited resourcesComputer resources
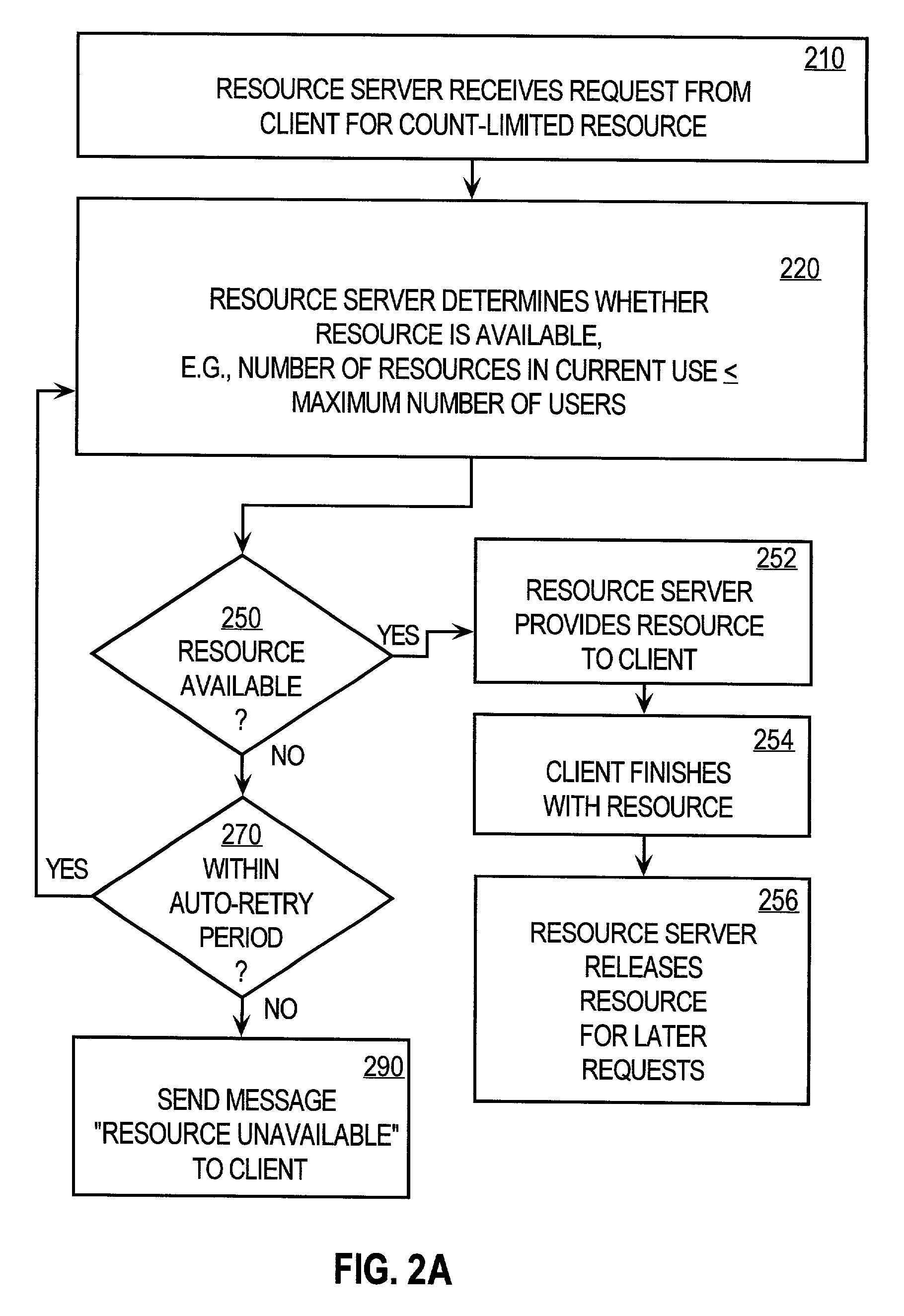
A method of controlling concurrent users of a distributed resource on a network is disclosed. In one aspect, there are one or more local lock managers executing on corresponding hosts and cooperating as a distributed lock manager. The resource is limited to a maximum number of concurrent users. A user identification for each user is associated with one host. In response to a request associated with a particular user associated with a first host, a lock is requested from a first local lock manager process executing on the first host. A related method of handling a request for a count-limited resource includes receiving a request from a client process for the computer resource. If it is determined that the request exceeds a maximum count for the resource, then it is determined whether a current time is within a retry time period of the client's first request. If it is determined the current time is within the retry time period, then it is automatically determined again whether the request exceeds the maximum count for the resource. If it is determined that the request does not exceed the maximum count, then the resource is provided to the client process.
Owner:CISCO TECH INC
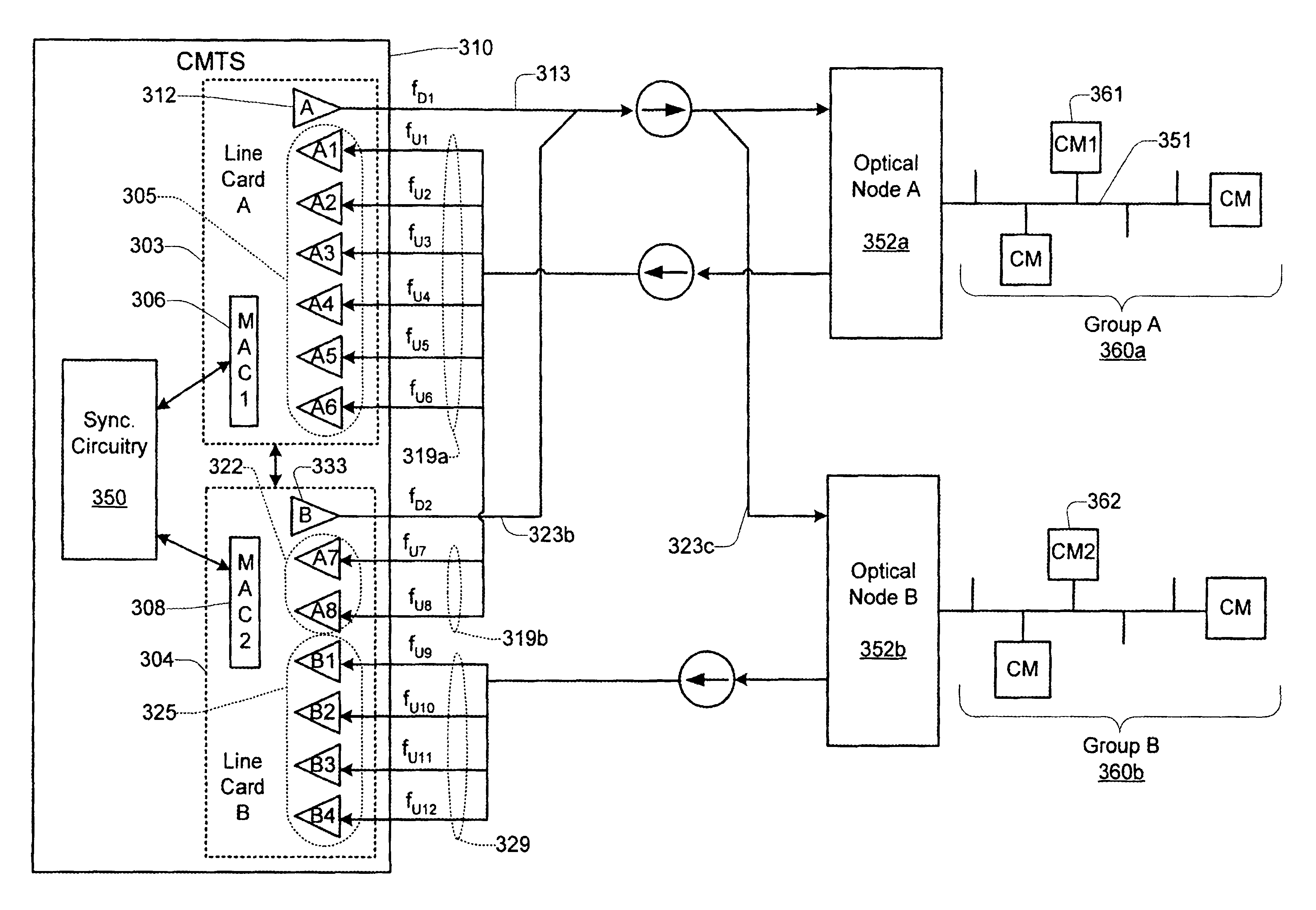
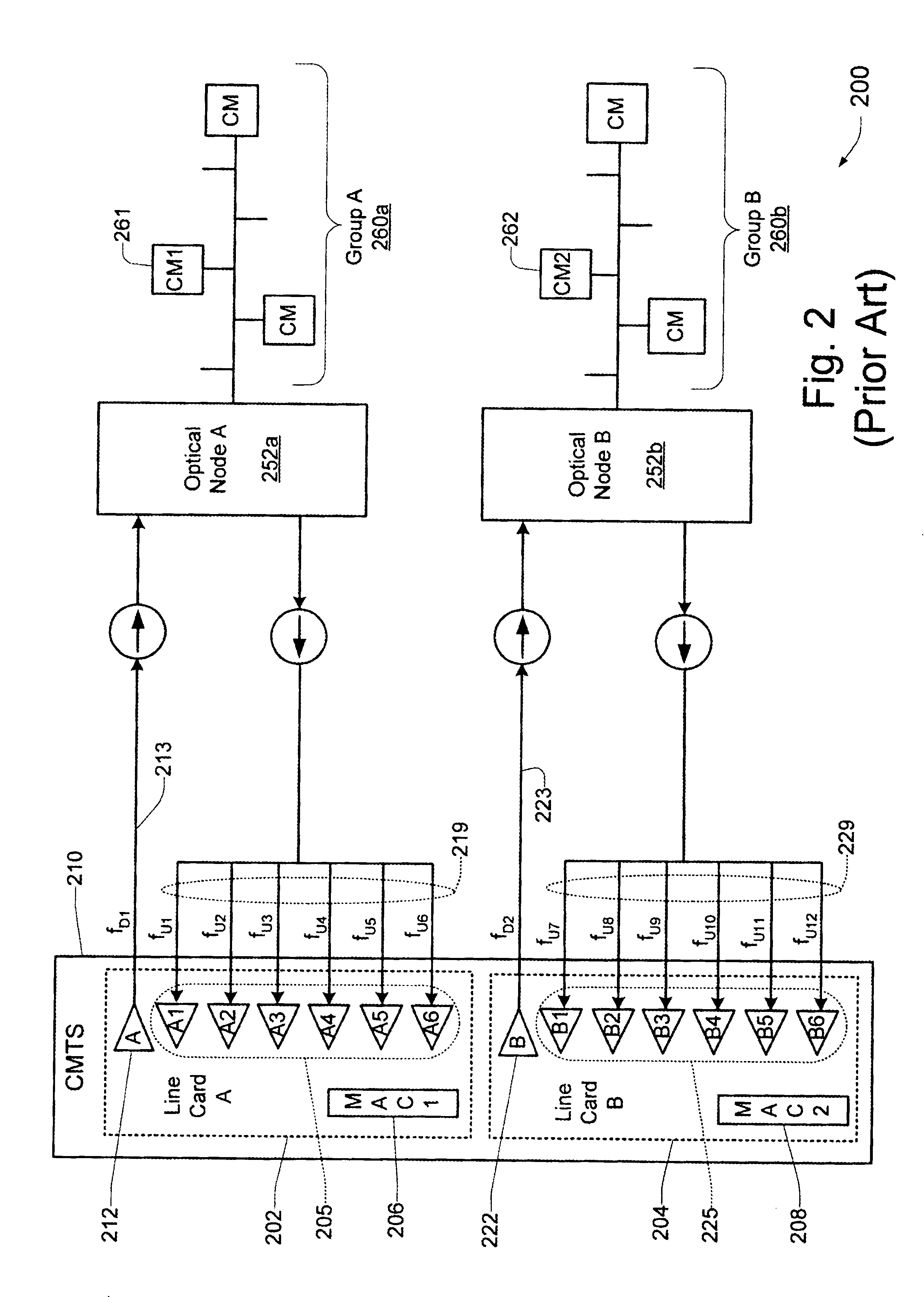
Technique for synchronizing multiple access controllers at the head end of an access network
InactiveUS7065779B1Broadband local area networksAnalogue secracy/subscription systemsAccess networkTimestamp
A technique is described which may be used to synchronize a plurality of different access controllers which control a plurality of distinct ports at the Head End of an access network. In the context of a cable network, the technique of the present invention may be used to synchronize desired upstream and / or downstream channels across different line cards within a Cable Modem Termination System (CMTS). The technique involves utilizing a master time reference device which maintains and updates a current time reference, and periodically distributes synchronization signals to desired line cards in the system in order to synchronize these line cards. In a specific embodiment, the synchronization signals include current timestamp data generated from the master time reference device and distributed to all (or selected) line cards in the system. A slave time reference device on each of the line cards receives the periodic synchronization updates and uses the synchronization data to remain synchronized with the master time reference device. There are also provisions in this protocol to allow for hot insertion and removal of line cards, software reset or loading of the master and / or slave time reference devices, and redundant master time reference devices, including master time reference device fault detection and automatic fail over.
Owner:CISCO TECH INC
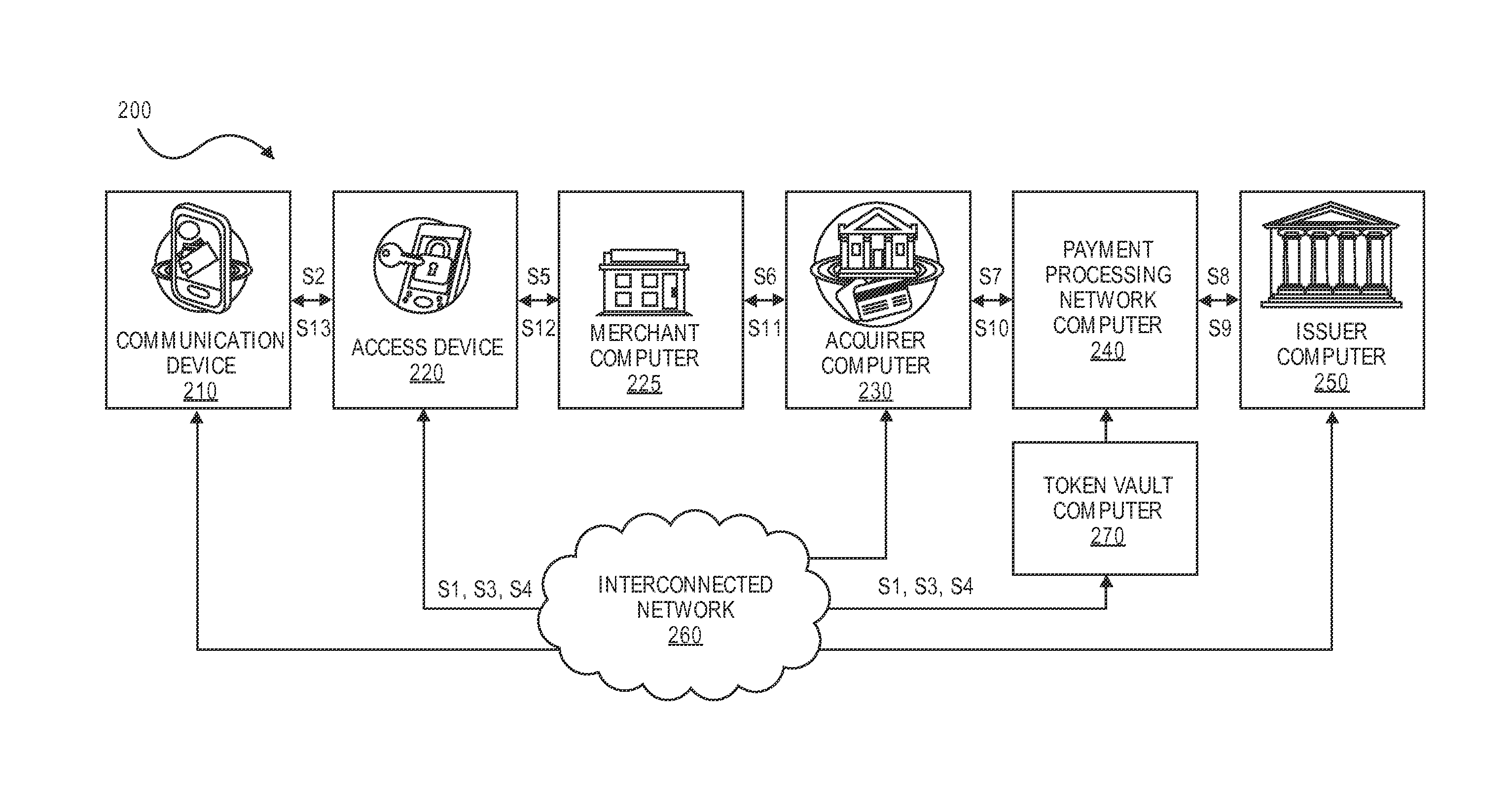
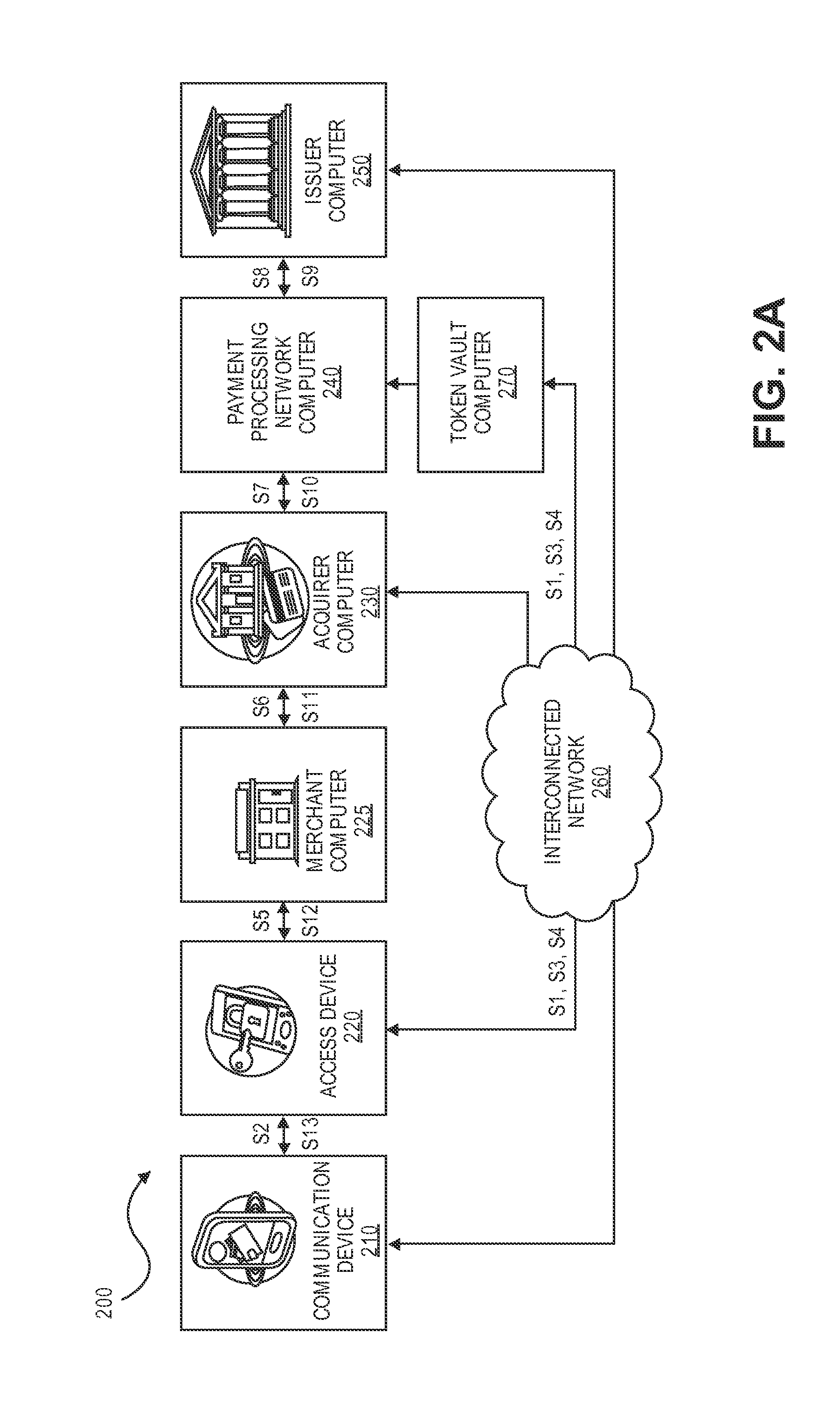
Systems and methods for locally derived tokens
Systems and methods for generating a token are provided. An access device may receive, from a token vault computer, an encryption key and a credential identifier. The access device may generate a token using the encryption key and a current time. The access device may then transmit the token, the current time, and the credential identifier to the token vault computer. The token vault computer may receive the token, a current time, and a credential identifier. The token vault computer may retrieve an encryption key associated with the received credential identifier. The token vault computer may then validate the token based at least in part on the received current time and the retrieved encryption key.
Owner:VISA INT SERVICE ASSOC
Intelligent automated data usage upgrade recommendation
A method of notifying a mobile station regarding data usage with a plan limit includes tracking an amount of data usage consumed by the mobile station. A first data usage limit and a first data usage time frame are determined from a user account. A comparison is made of the data usage to the first data usage limit and a present time to the first data usage time frame. From this comparison, a projected data usage amount is determined and whether the projected data usage exceeds the first data usage limit. If exceeded, the system analyzes a second data usage limit to determine if it is greater than the projected data usage amount. If greater, the server provides a message to the mobile station notifying the user of the projected overage and suggestions to change to a new plan offering the second data usage limit.
Owner:CELLCO PARTNERSHIP INC
Information providing method and information providing device
InactiveUS20040128066A1Instruments for road network navigationRoad vehicles traffic controlInformation acquisitionAction prediction
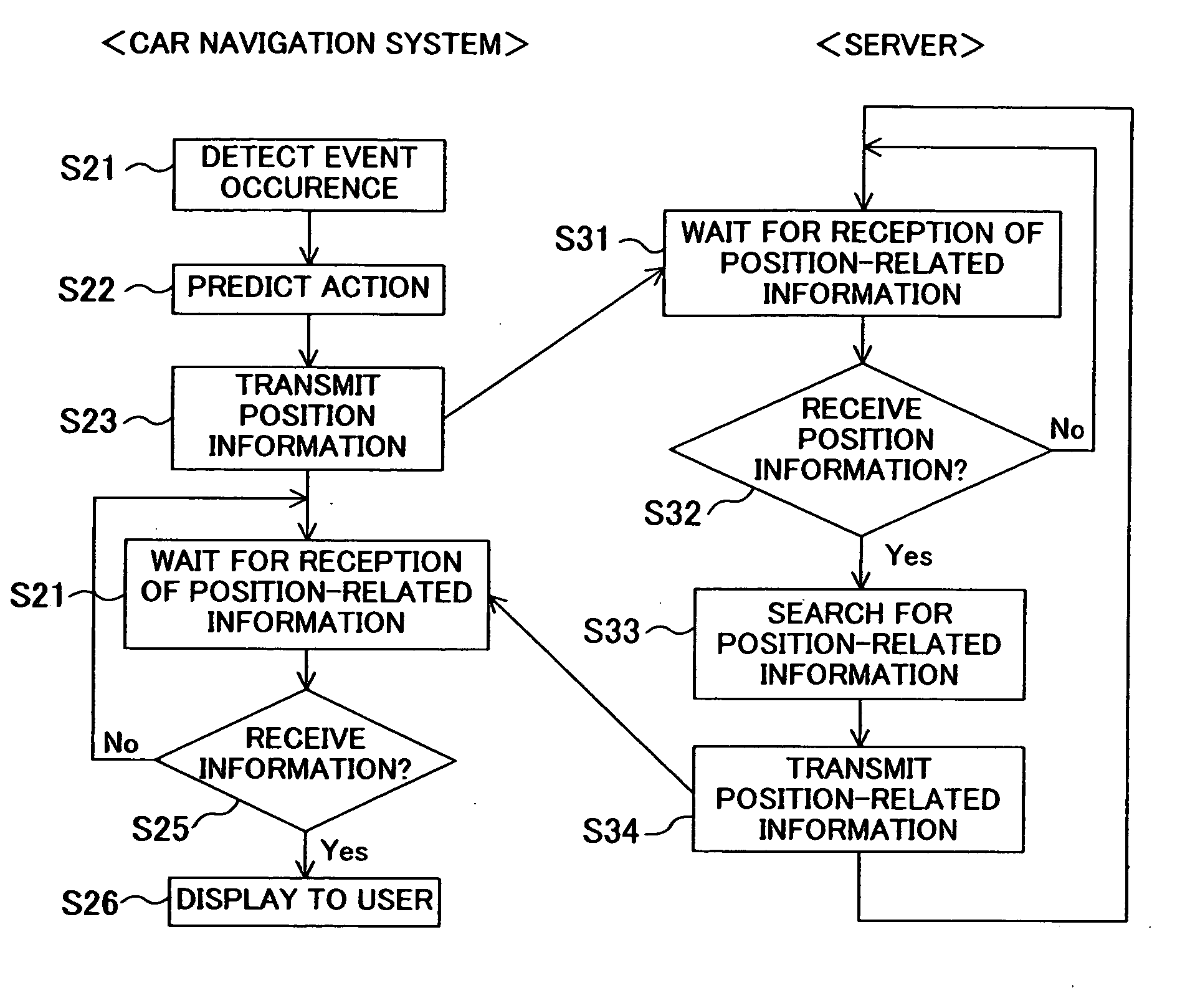
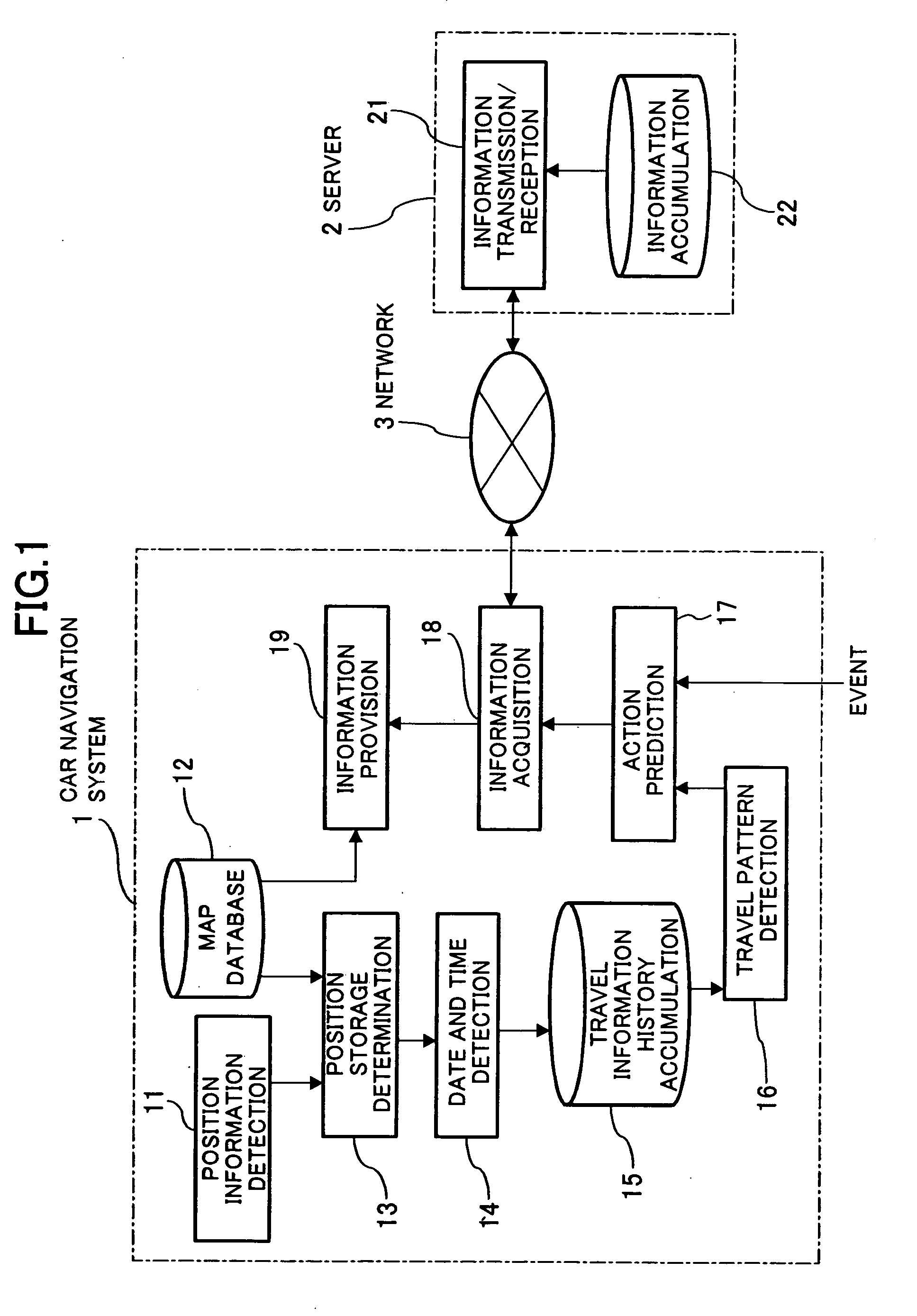
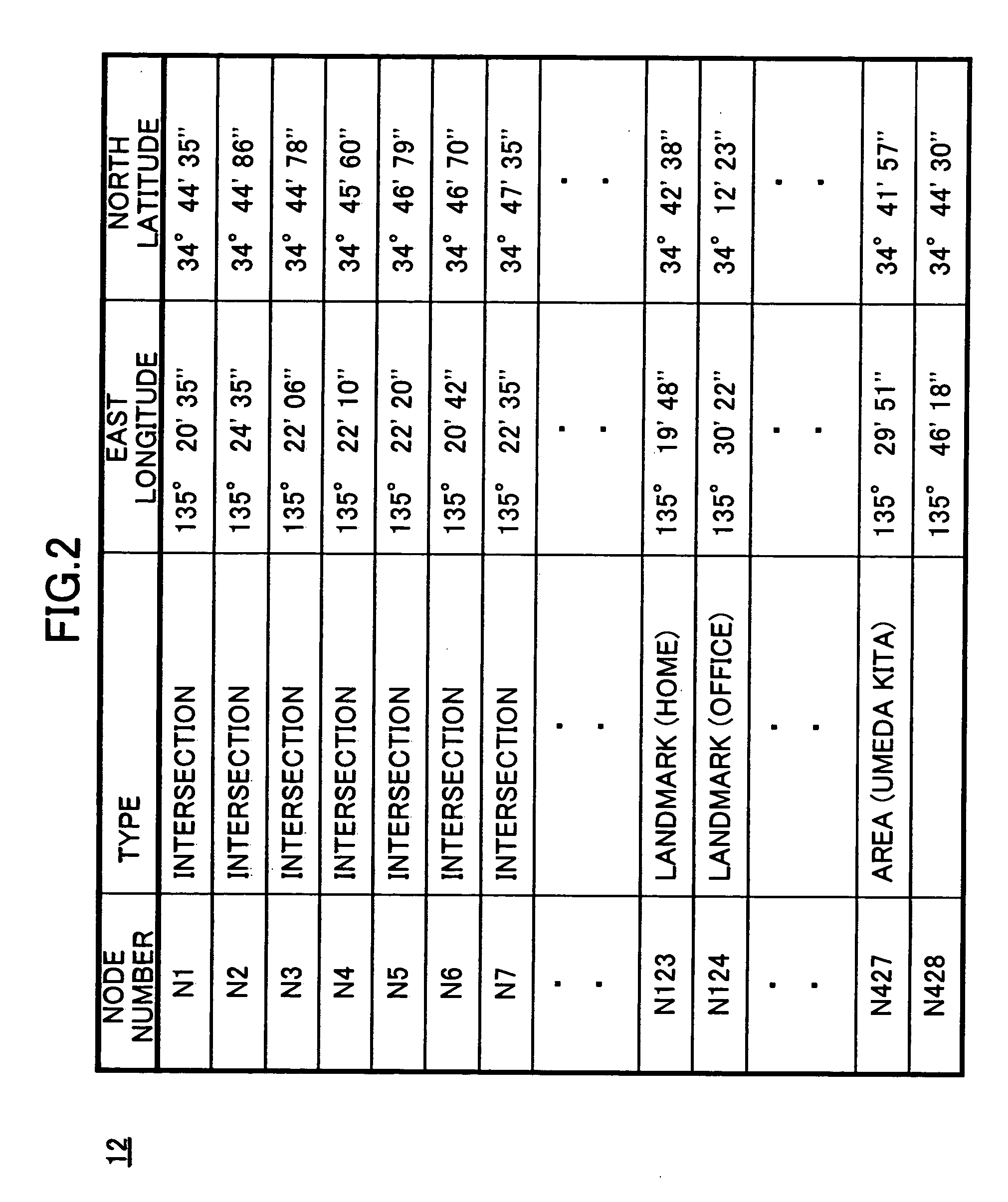
In a car navigation system (1), a position information detection means (11) detects position information on a vehicle using, for example, a GPS. A travel information history of the vehicle obtained based on the detected position information is accumulated in a travel information history means (15). When detecting an event such as start of an engine, an action prediction means (17) predicts a destination of the vehicle by referring to a route to the current time and to the accumulated travel information history. Commercial or traffic information regarding the predicted destination is acquired by an information acquisition means (18) from a server (2), and then is displayed on a screen, for example, by an information provision means (19).
Owner:PANASONIC INTELLECTUAL PROPERTY CORP OF AMERICA
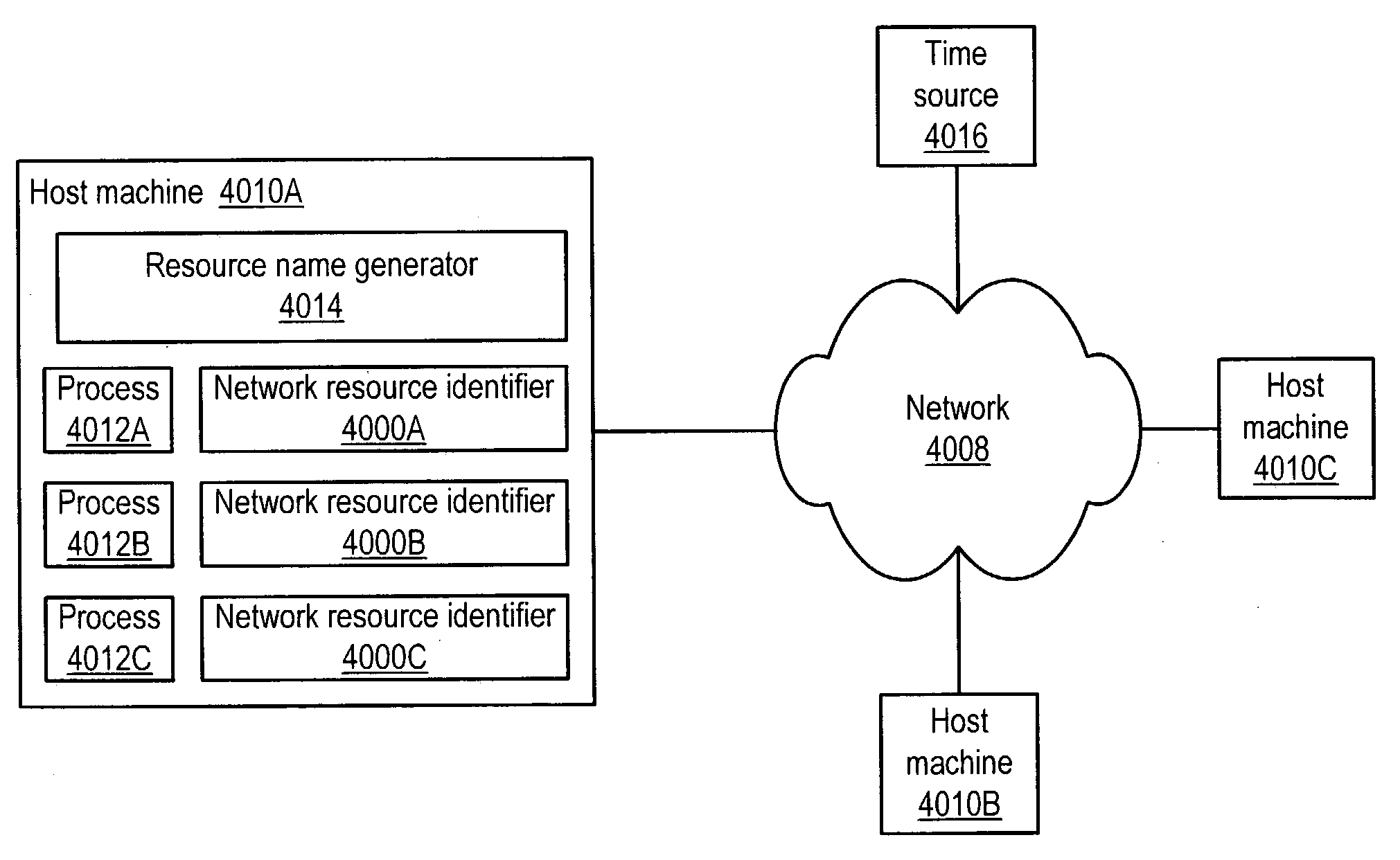
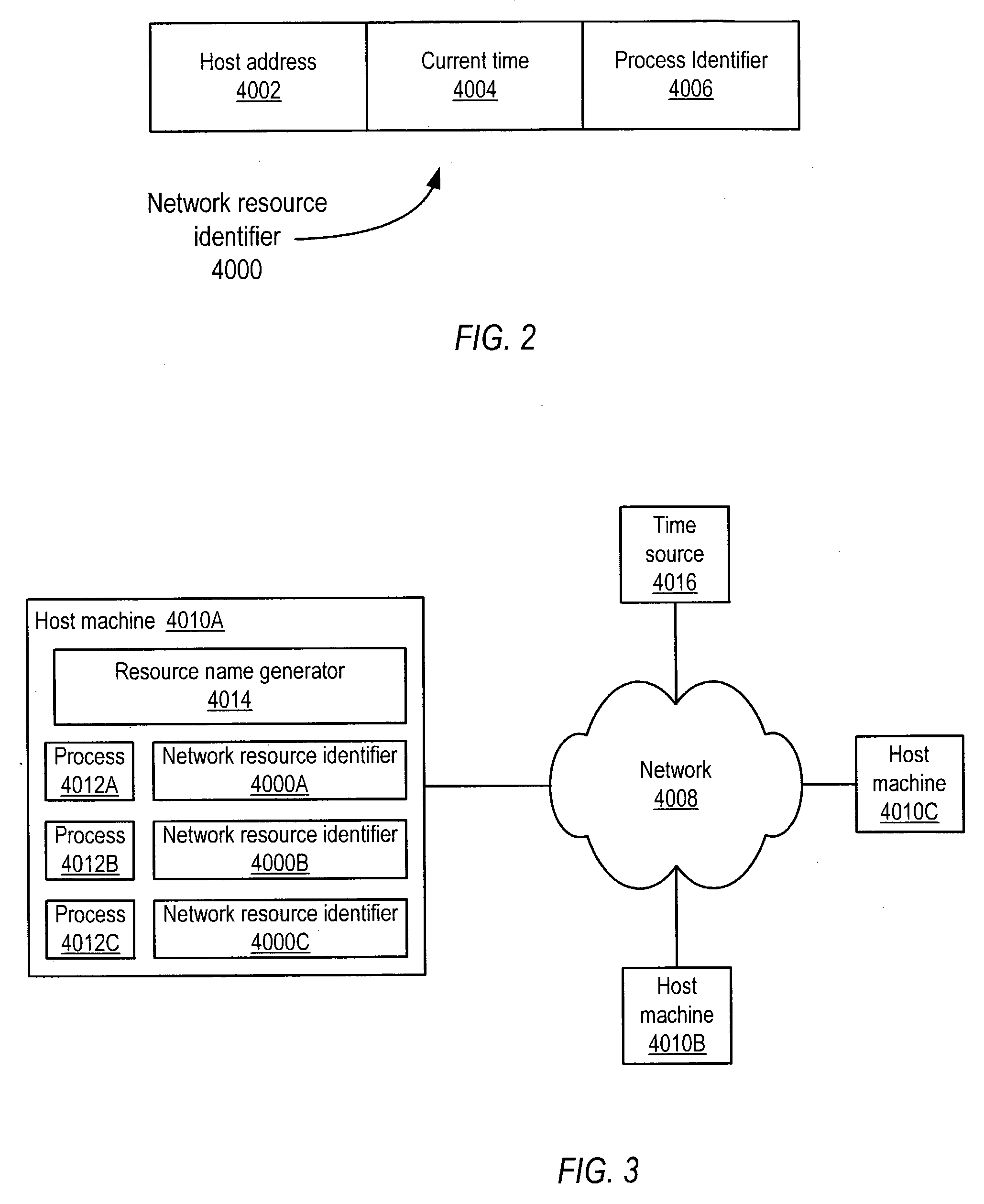
System and method for unique naming of resources in networked environments
ActiveUS20040148326A1Resource allocationData switching by path configurationName generatorUnique identifier
System and method for the unique naming of resources in networked environments including peer-to-peer network environments. Embodiments may be used to generate network resource identifiers that uniquely identify resources such as processes over time and across the networked environment. One embodiment may be implemented as a resource name generator that generates unique identifiers for resources in networked environments. One embodiment may generate unique network resource identifiers for processes from information including, but not limited to, a host address that uniquely identifies on the network the host machine of the resource for which the unique network resource identifier is being generated, a current time (e.g. obtained from the host machine or alternatively from an external source such as an atomic time server), and a process identifier of the process that uniquely identifies the process among current processes on the host machine.
Owner:ORACLE INT CORP
Visual communications system and method of controlling the same
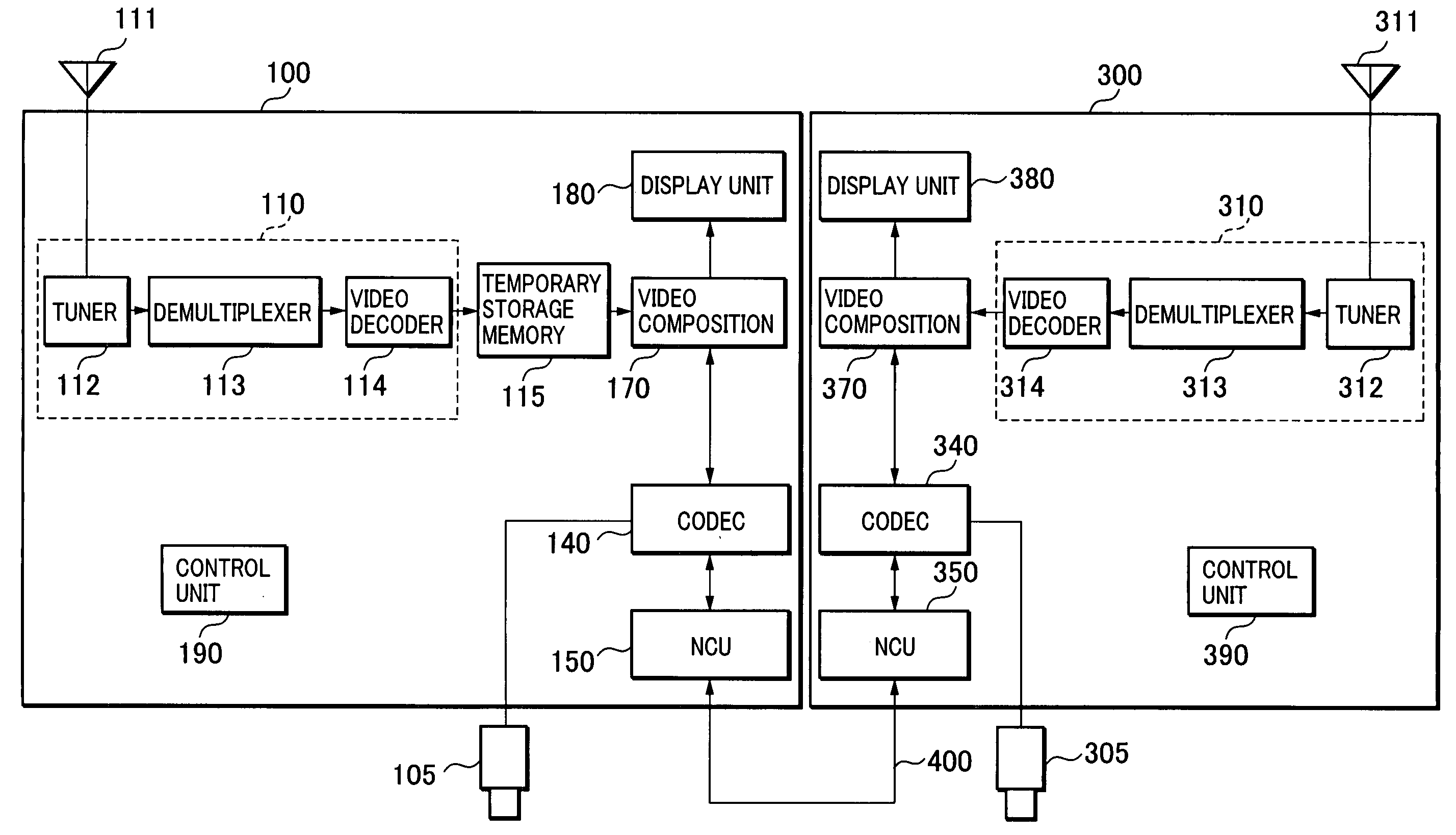
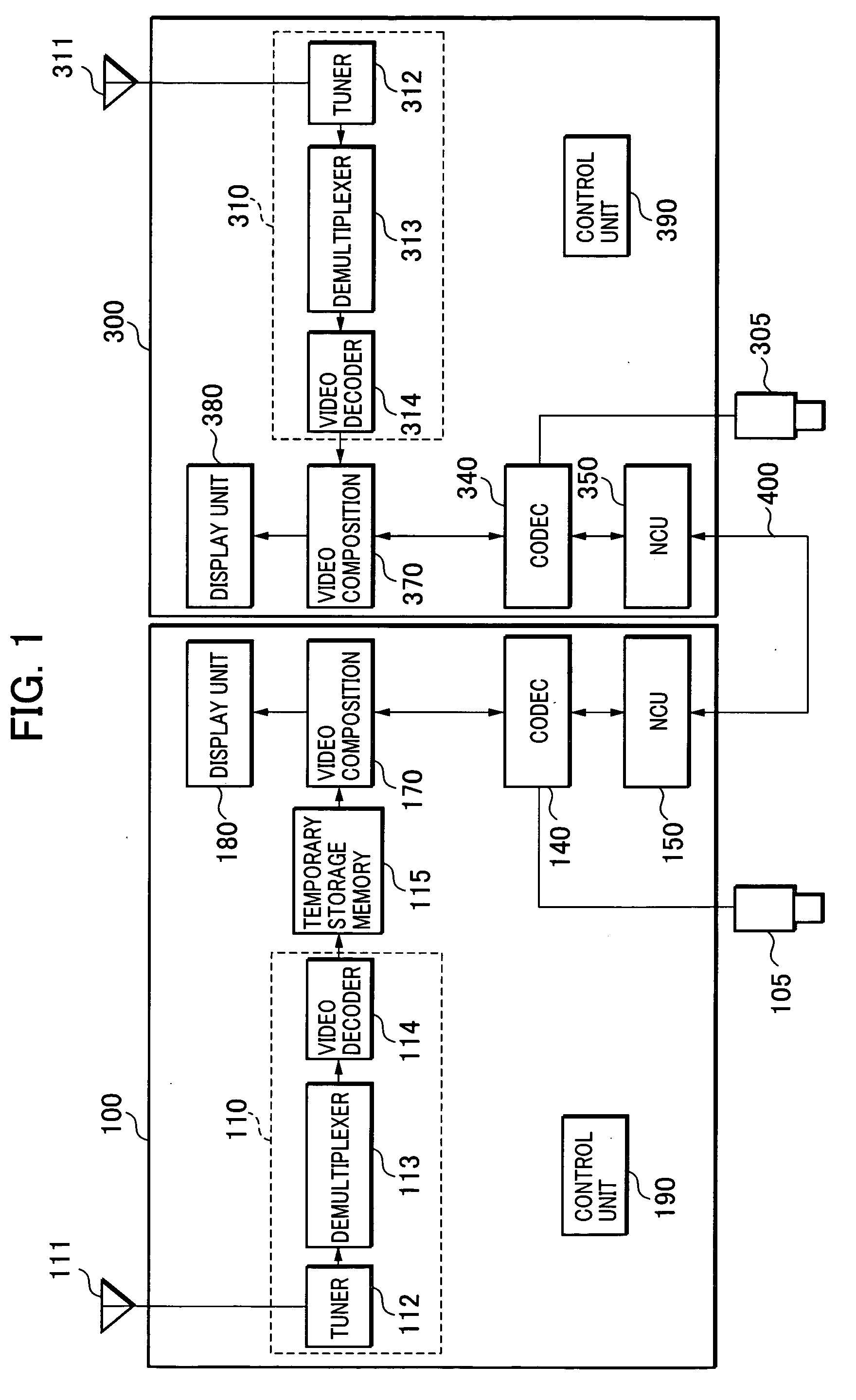
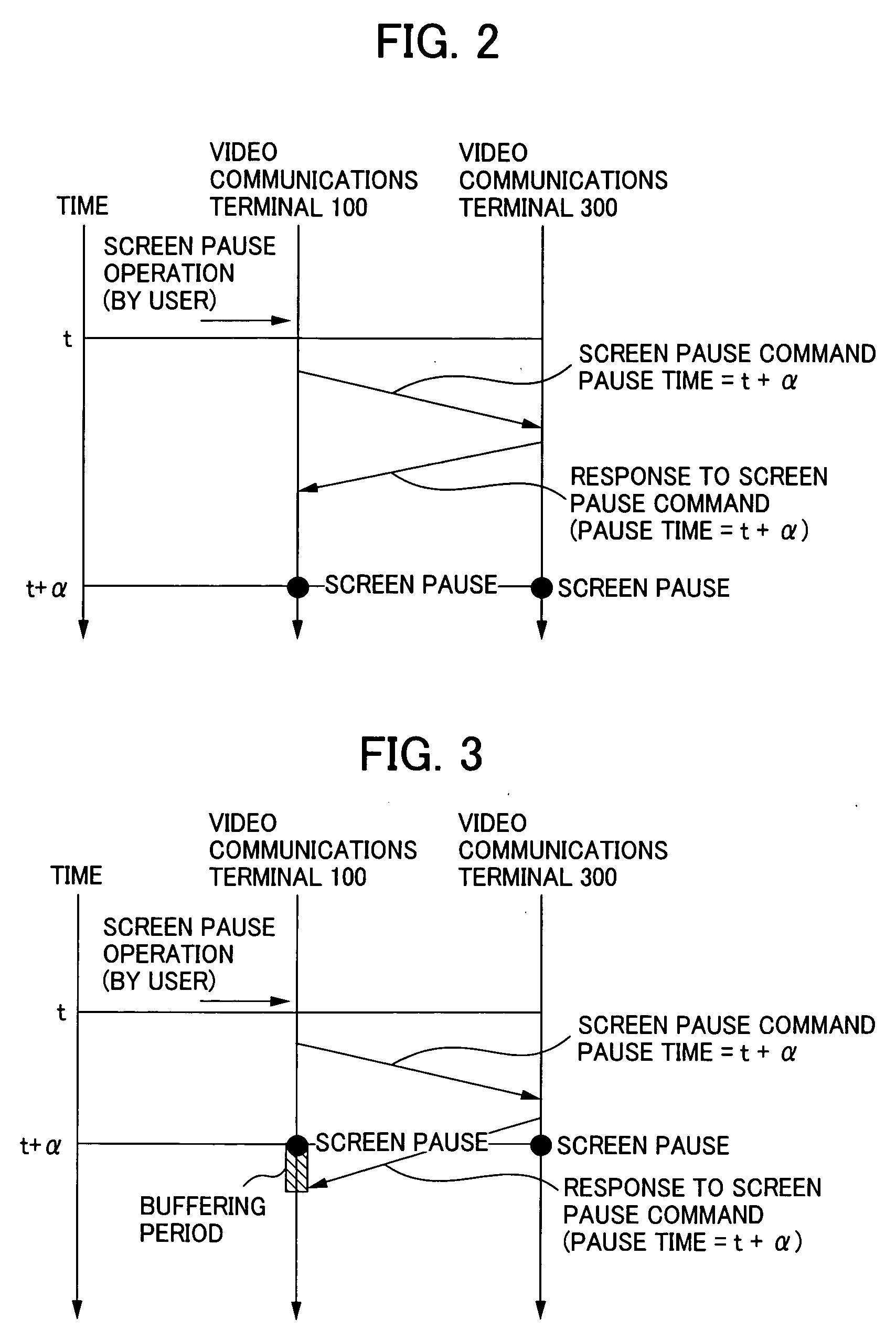
InactiveUS20050166242A1Television system detailsAnalogue secracy/subscription systemsCommunications systemComputer science
A visual communications system and a method of controlling the same for pausing the screens of two terminals at quite the same image. Video communications terminals receive the same channel in their respective broadcast program receiving units. A first video communications terminal temporarily stores the video of the received channel in the temporary storage memory. When a user pauses operation of the first terminal, it temporarily stores a screen pause time obtained by adding a predetermined time to the current time, and transmits a screen pause command and the screen pause time to a second video communications terminal. The second terminal pauses the video at the screen pause time if possible in time. Otherwise, it pauses the video immediately, and transmits a response with its own image pause time to the first terminal. The first terminal displays an image corresponding to the image pause time of the second terminal memory.
Owner:CANON KK
Methods for display, notification, and interaction with prioritized messages
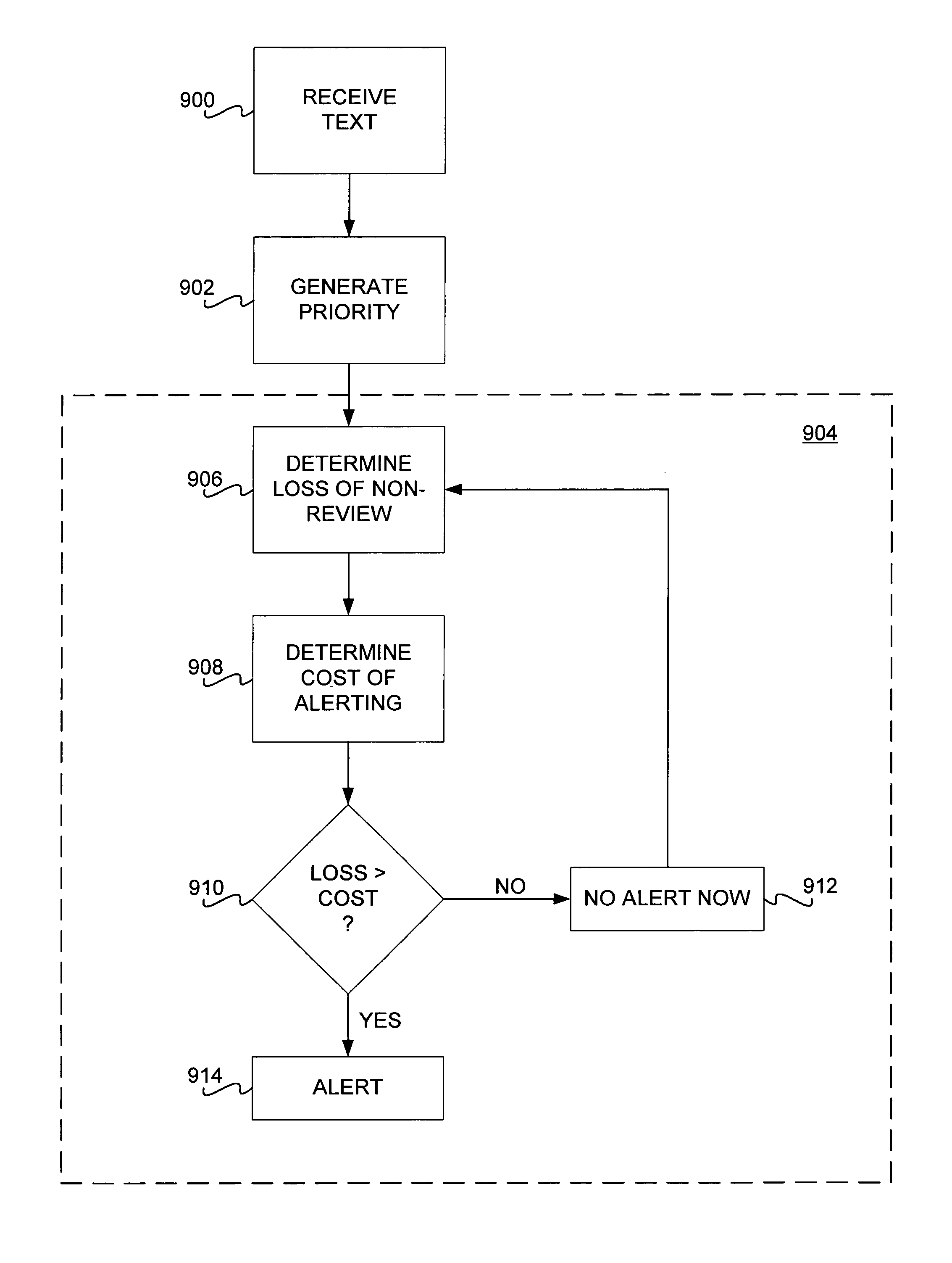
InactiveUS7120865B1Digital computer detailsTransmissionLevel of detailSupport vector machine classifier
Prioritization of document, such as email messages, is disclosed. In one embodiment, a computer-implemented method first receives a document. The method generates a priority of the document, based on a document classifier such as a Bayesian classifier or a support-vector machine classifier. The method then outputs the priority. In one embodiment, the method includes alerting the user based on an expected loss of now-review of the document as compared to an expected cost of alerting the user of the document, at a current time. Several methods are reviewed for display and interaction that leverage the assignment of priorities to documents, including a means for guiding visual and auditory actions by priority of incoming messages. Other aspects of the machinery include a special viewer that allows users to scope a list of email sorted by priority so that it can include varying histories of time, to annotate a list of messages with color or icons based on the automatically assigned priority, to harness the priority to control the level of detail provided in a summarization of a document, and to use a priority threshold to invoke an interaction context that lasts for some period of time that can be dictated by the priority of the incoming message.
Owner:MICROSOFT TECH LICENSING LLC
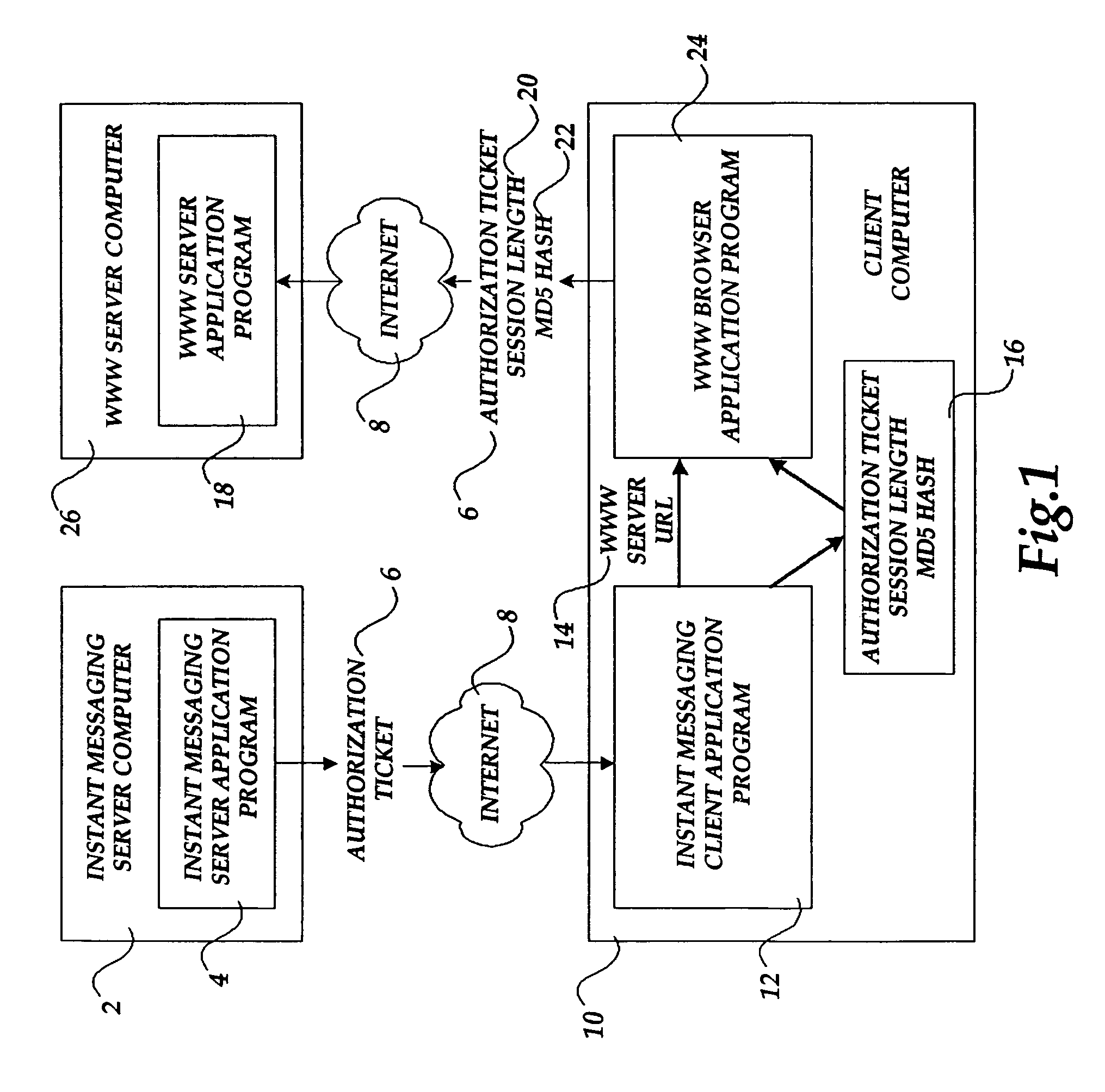
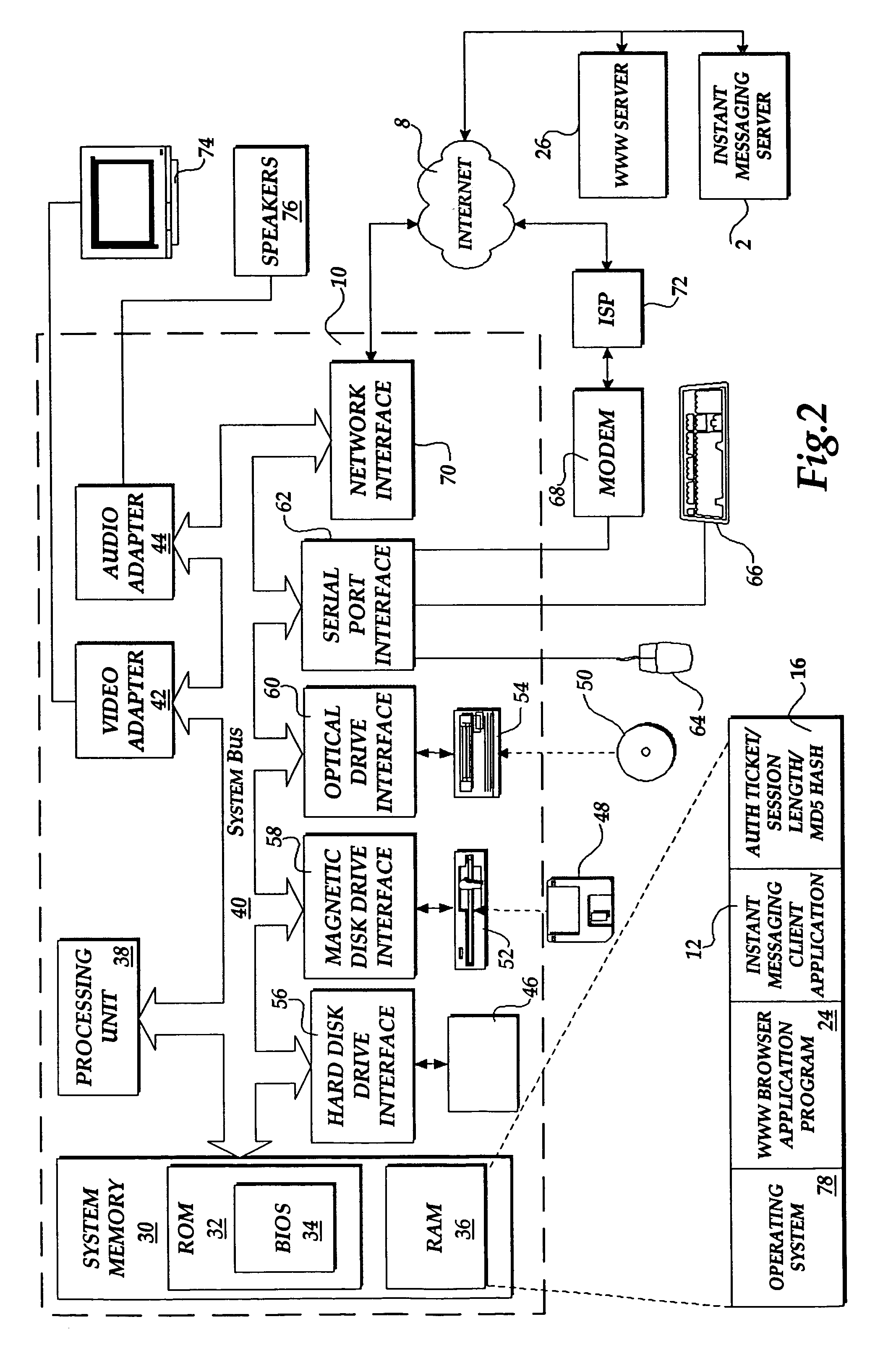
Method and system for authorizing a client computer to access a server computer
InactiveUS7089585B1Key distribution for secure communicationDigital data processing detailsAuthorization certificateHash function
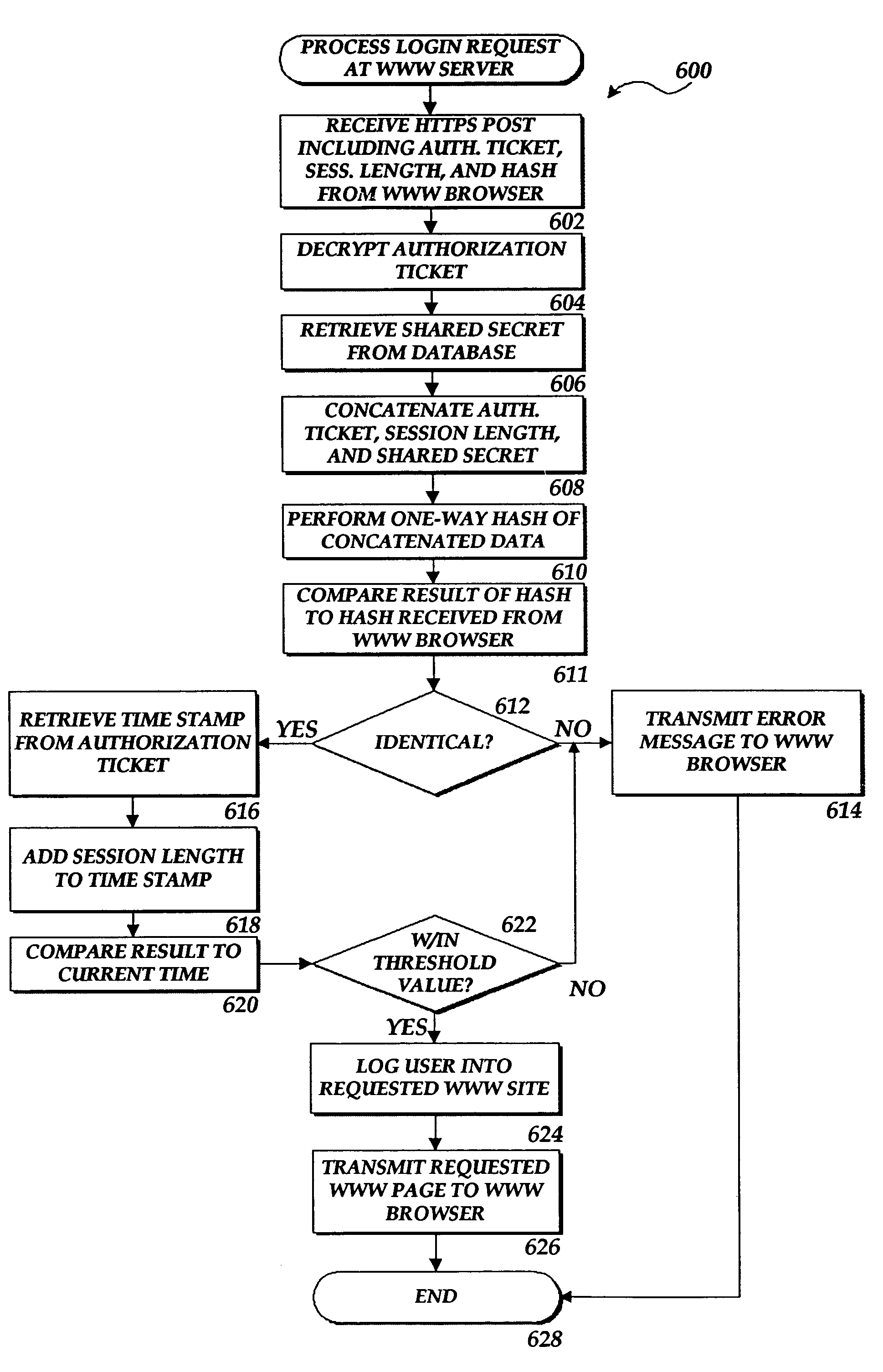
The present invention includes a client computer, a first server computer, and a second server computer. The first server provides an authorization ticket containing a time stamp to the client computer when the client computer is authorized to access the first server. An elapsed time counter is started at the client computer when access is provided to the first server. When a request is received at the client computer to access the second server, the client computer determines the session length based upon the elapsed time counter. The client computer calculates a hash value for the authorization ticket, the session length, and a secret shared with the second server computer. The client computer transmits a login request to the second server including the authorization ticket, the session length, and the hash. The second server decrypts the authorization ticket and retrieves a copy of the shared secret. The second server executes a hash function on the authorization ticket, the session length, and the shared secret. The second server then compares the computed hash to the hash value received from the second client application. If the two hash values are identical, the second server retrieves the time stamp from the authorization ticket and adds the session length to the time stamp. The second server then compares the resulting value to the current time. If the resulting value and the current time are within a preset threshold value, the client computer is provided.
Owner:MICROSOFT TECH LICENSING LLC
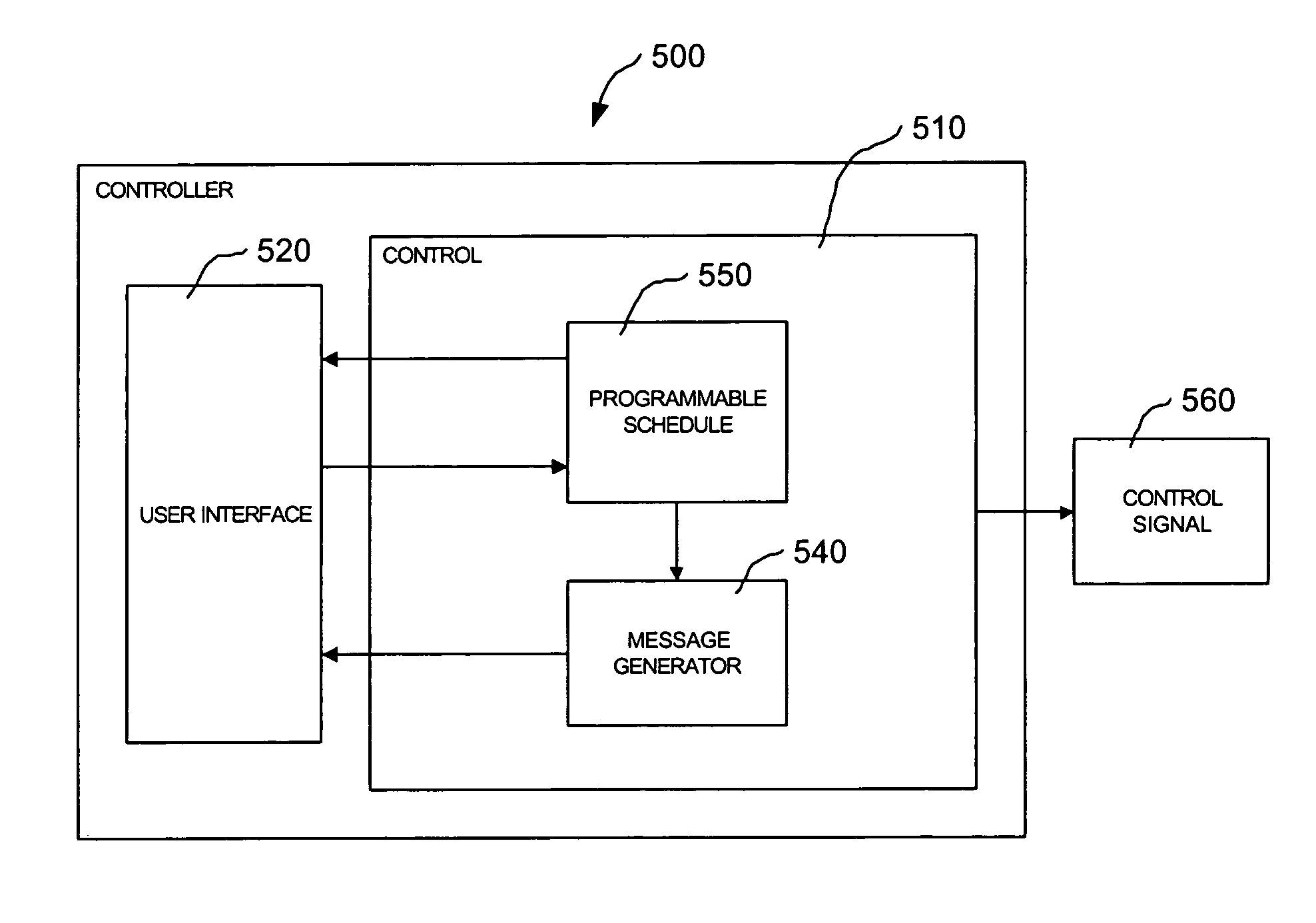
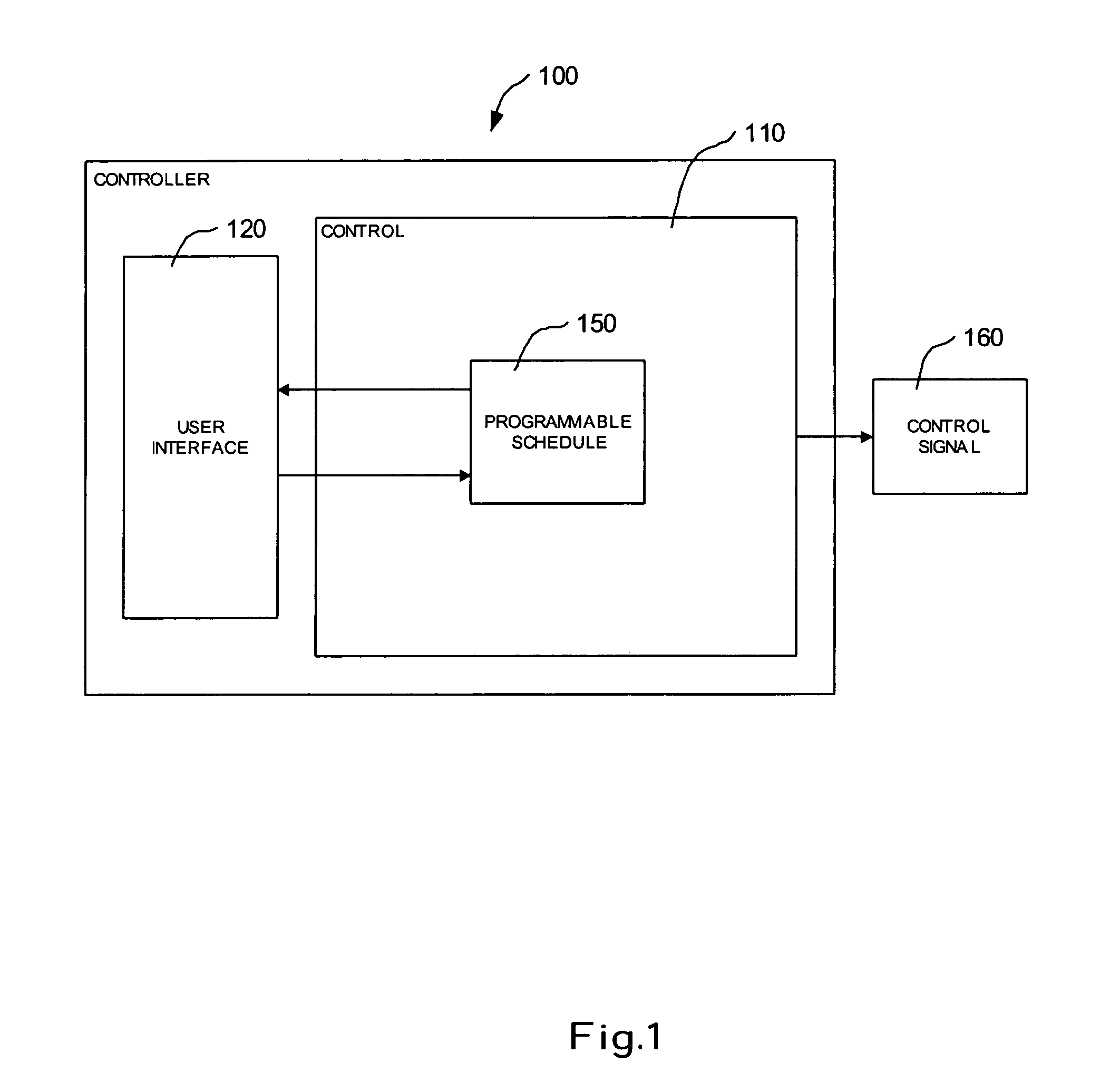
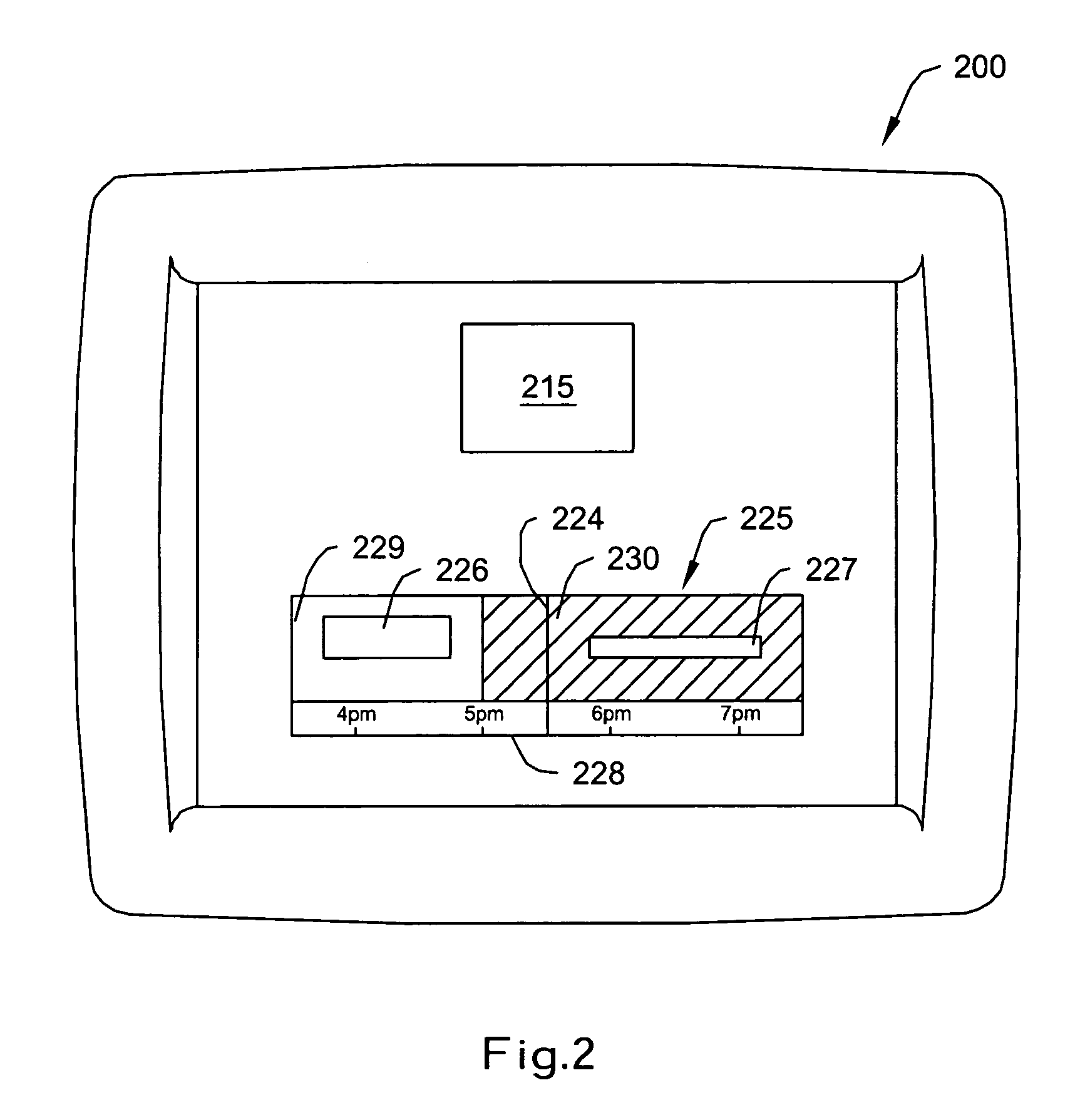
Controller interface with dynamic schedule display
ActiveUS7142948B2Temperature control with auxillary non-electric powerLighting and heating apparatusTime scheduleSet point
A controller includes a programmable schedule and a user interface, adapted and configured to illustratively display at least a portion of the programmable schedule along a time axis and a current time indicator positioned to indicate the current time along the time axis. A method is also described including the steps of: operating a programmable controller having a scheduled current set point and a scheduled future set point; and providing a message indicating a time of the scheduled future set point change.
Owner:ADEMCO INC
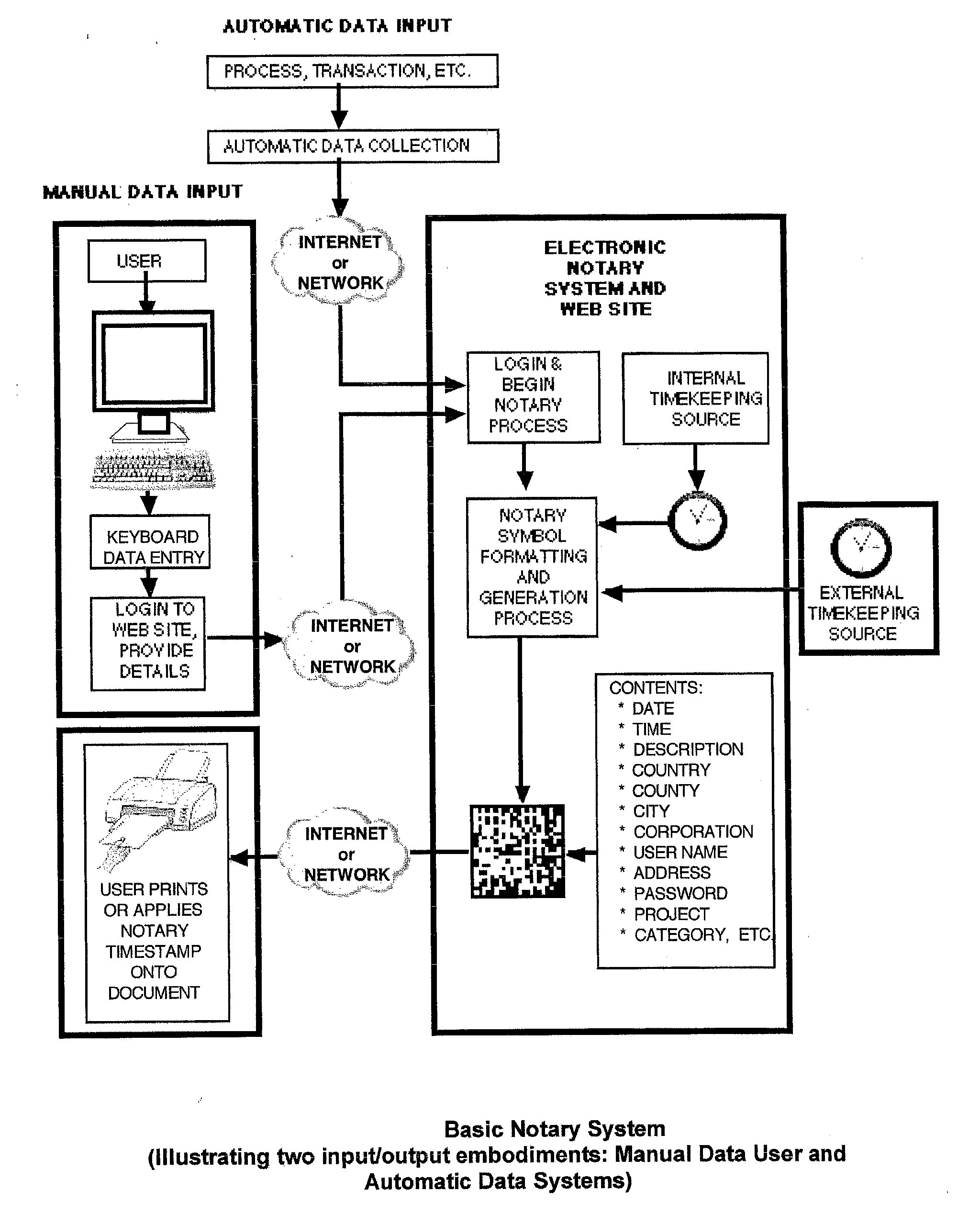
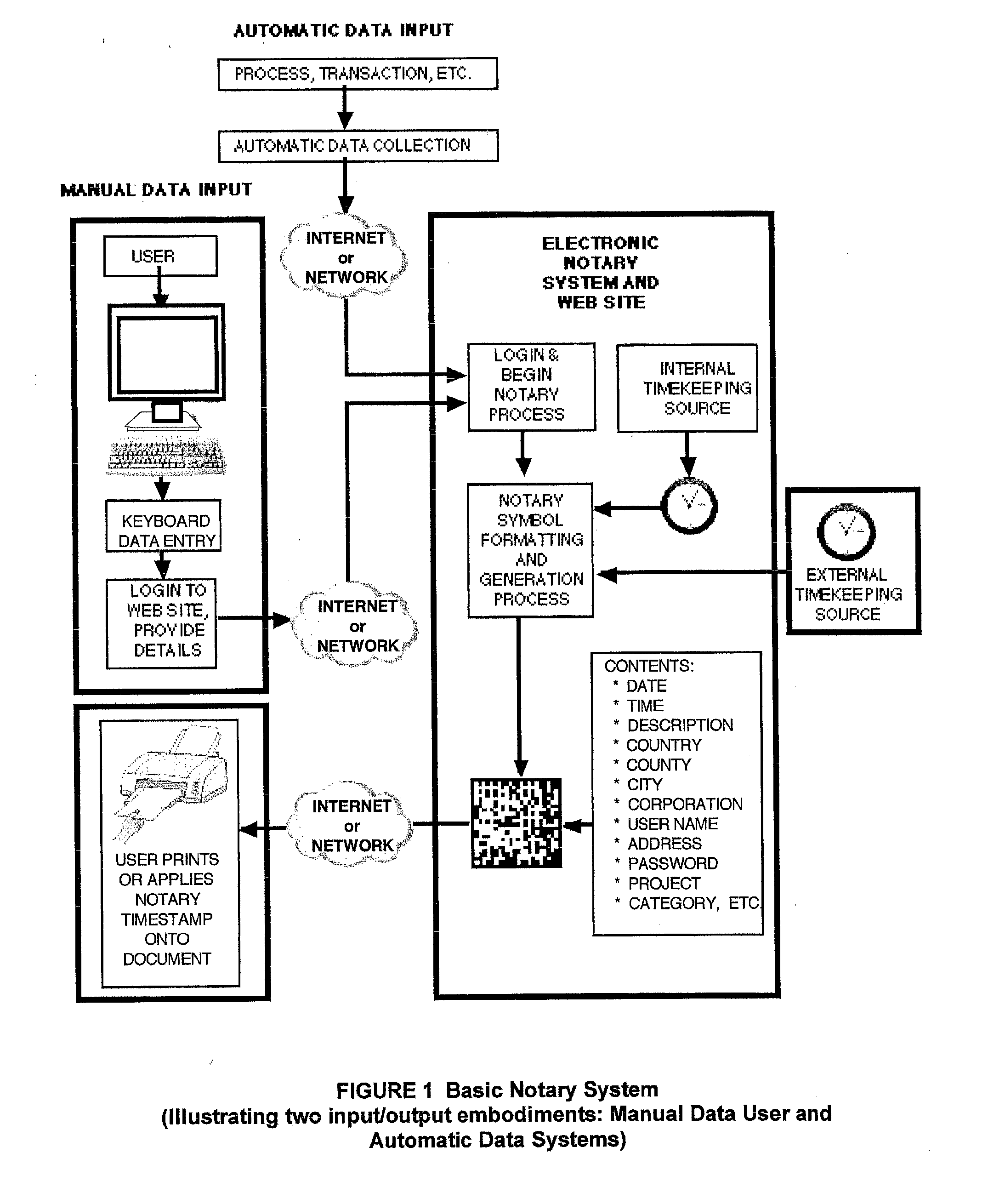
Electronic notary system, method and computer-readable medium
A system includes a computer having a time retrieval unit to connect to an official time provider via a network and to retrieve an official current time, a data acceptance unit to receive information regarding a target object entered via a data input interface, an encoding unit to create and encode a machine readable identifier representing the official current time and the information regarding the target object, a marking unit to mark the target object by marking the machine readable identifier to the target object and a storage unit to store data associated with the machine readable identifier in a storage in a server.
Owner:SANTANSELMO ROBERT
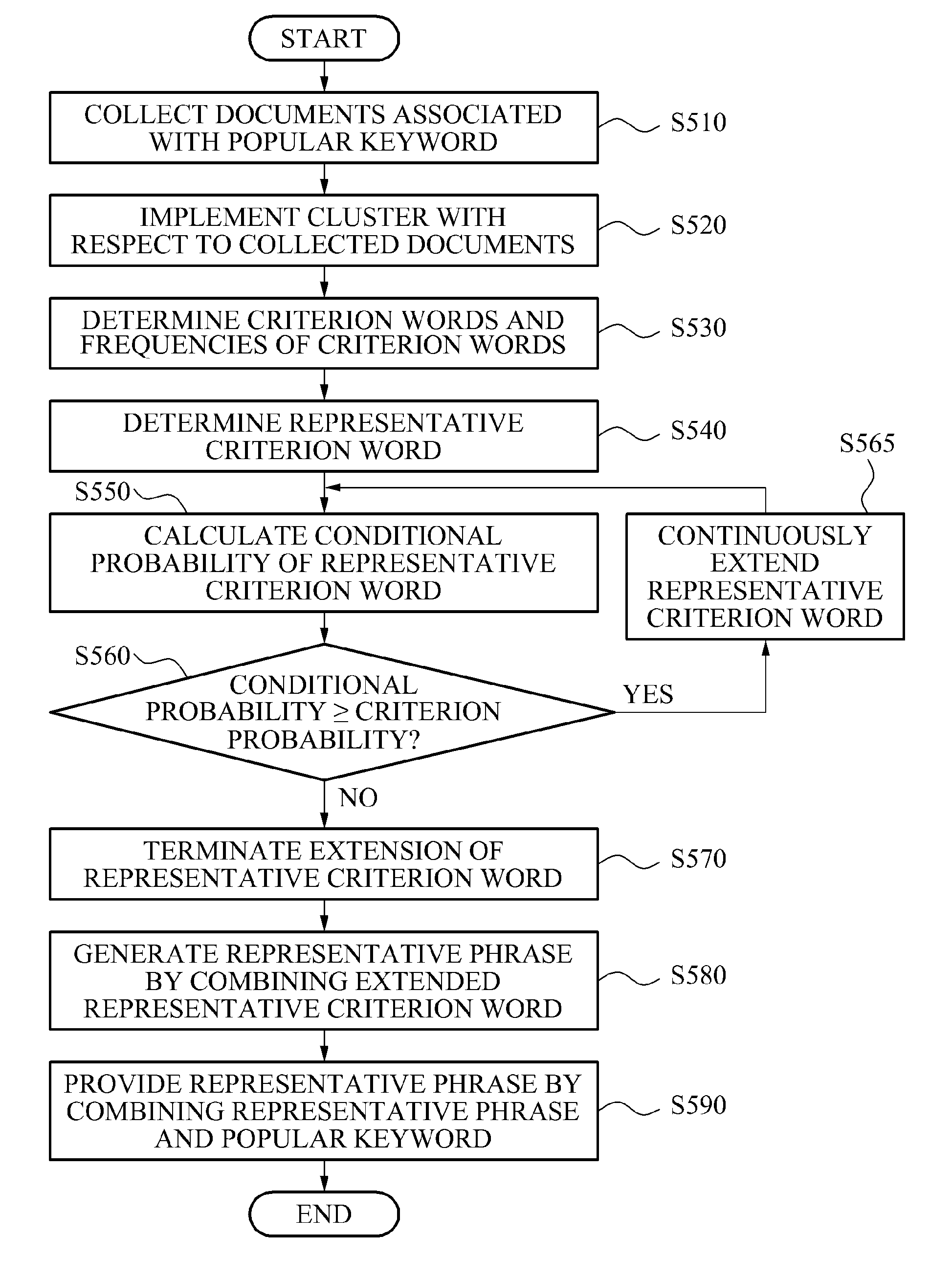
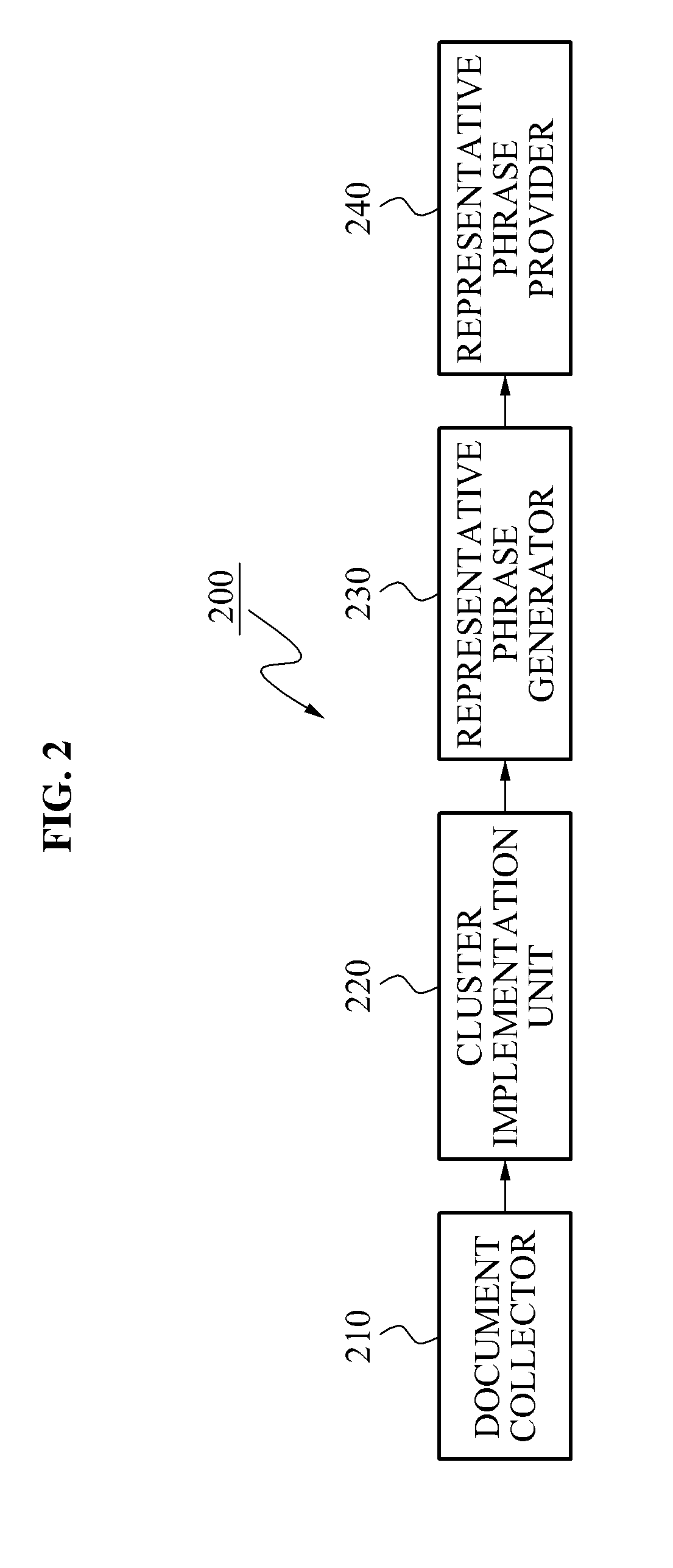
Method and system for providing representative phrase
ActiveUS20120004904A1Natural language data processingSpecial data processing applicationsMorphemeDocument preparation
A method and system for providing a representative phrase corresponding to a real time (current time) popular keyword. The method and system may extend a representative criterion word, determined by analyzing morphemes of words in documents grouped into a cluster, and may combine the extended representative criterion word and the popular keyword, thereby providing the representative phrases. The method and system may display the popular keyword and the representative phrases on a web page, or the like.
Owner:NHN CORP
Scheduling threads in a multi-threaded computer
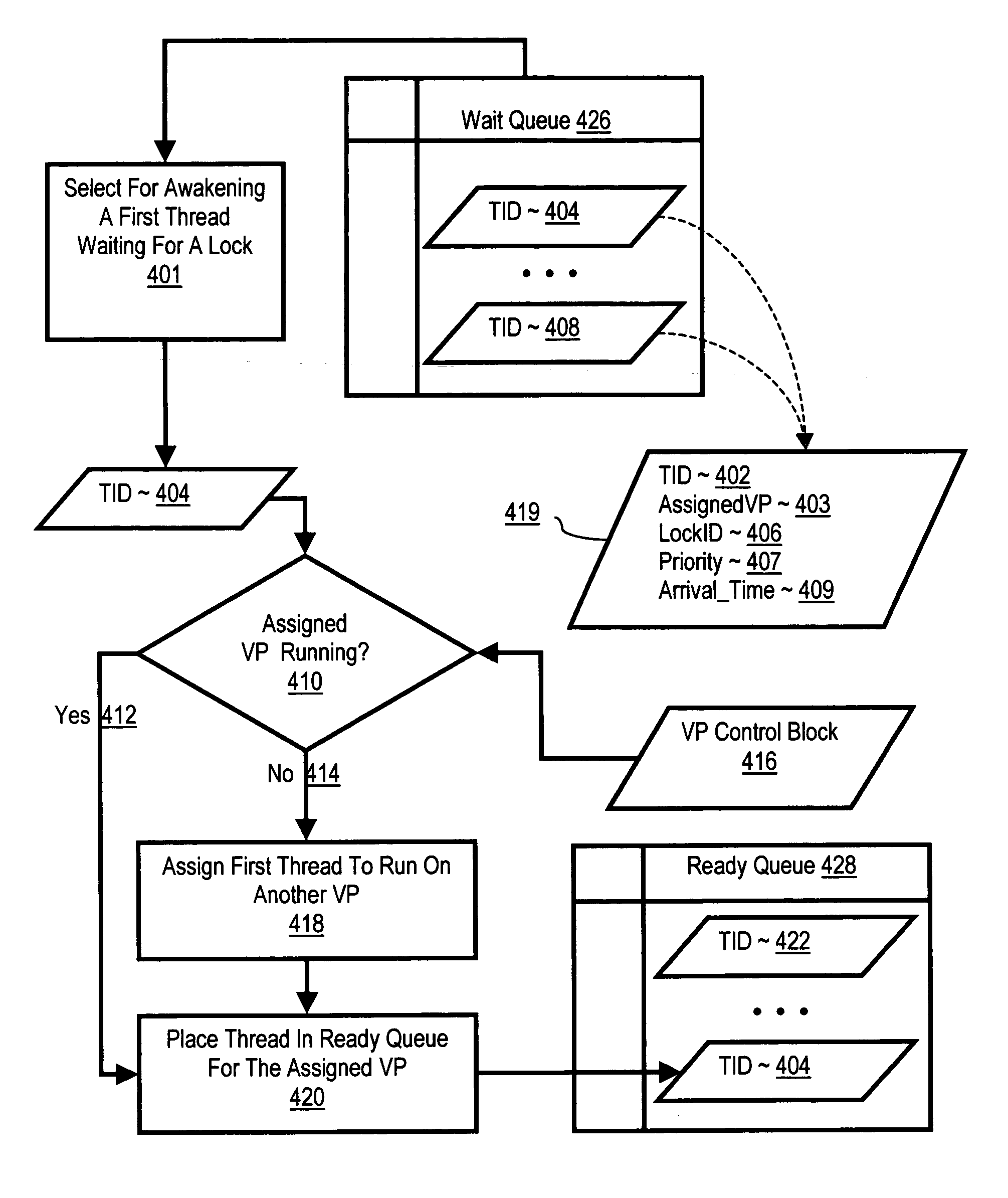
InactiveUS20060130062A1Reduce riskImprove utilization efficiencyMultiprogramming arrangementsMemory systemsVirtual ProcessorReal-time computing
Scheduling threads in a multi-threaded computer including selecting for awakening a thread that is waiting for a lock, the thread having an assigned virtual processor; determining whether the assigned virtual processor is running; and if the assigned virtual processor is not running, assigning the thread to run on another virtual processor. Selecting a thread may include selecting the thread according to thread priority or selecting the thread according to sequence of thread arrival in a wait queue. Selecting a thread may include selecting a thread having an assigned virtual processor that is running. Selecting a thread may include selecting a thread having an assigned virtual processor that is running and has at least a predetermined amount of time remaining in its current time slice.
Owner:IBM CORP
Method and apparatus for time and frequency transfer in communication networks
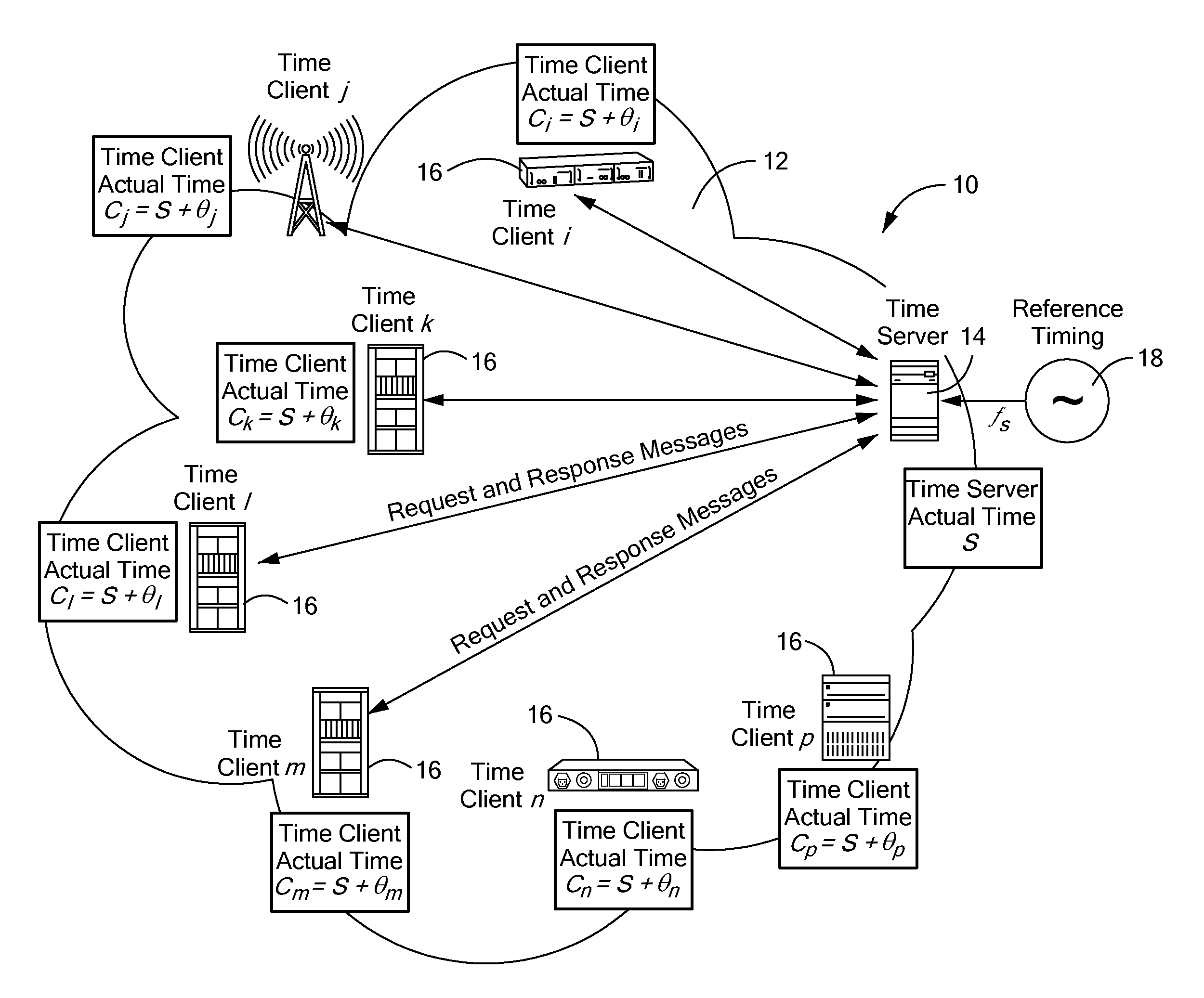
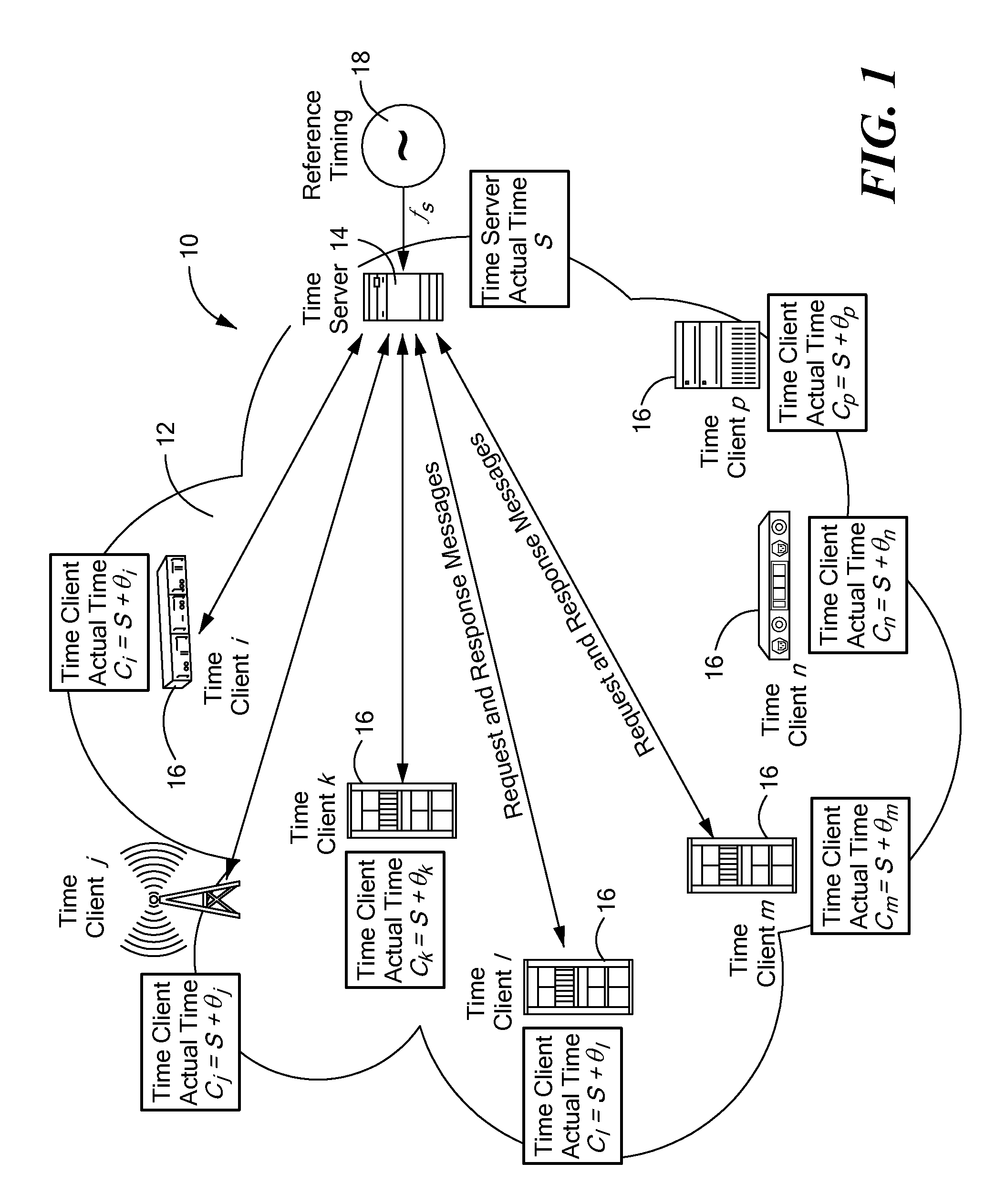
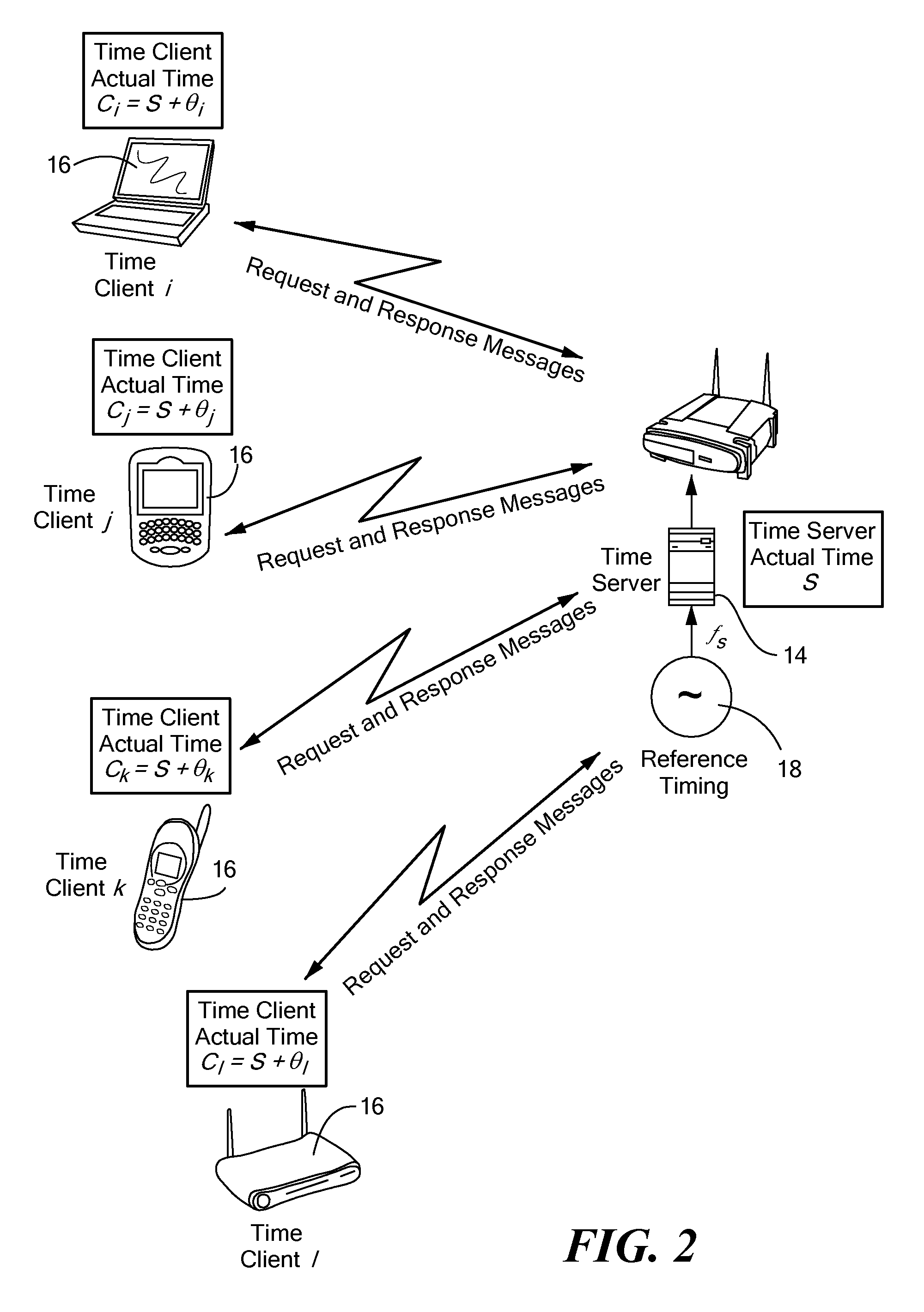
A timing system for time synchronization between a time server and a time client over a packet network. The timing system includes a time server for generating current timestamp information and a time client having a phase-locked loop driven client clock counter. The time client periodically exchanges time transfer protocol messages with the time server over the packet network, and calculates an estimated client time based on the timestamp information. The phase-locked loop in the time client receives periodic signals representing the estimated server time as its input and calculates a signal which represents the error difference between the estimated server time and the time indicated by the time client clock counter. The error difference eventually converges to zero or a given error range indicating the time presented by the client clock counter, which is driven by the phase-locked loop having locked onto the time of the time server.
Owner:RPX CLEARINGHOUSE +1
Technologies and methods for security access
ActiveUS20140375422A1Verify authenticityWell formedProgramme controlElectric signal transmission systemsStart timeRemote computer
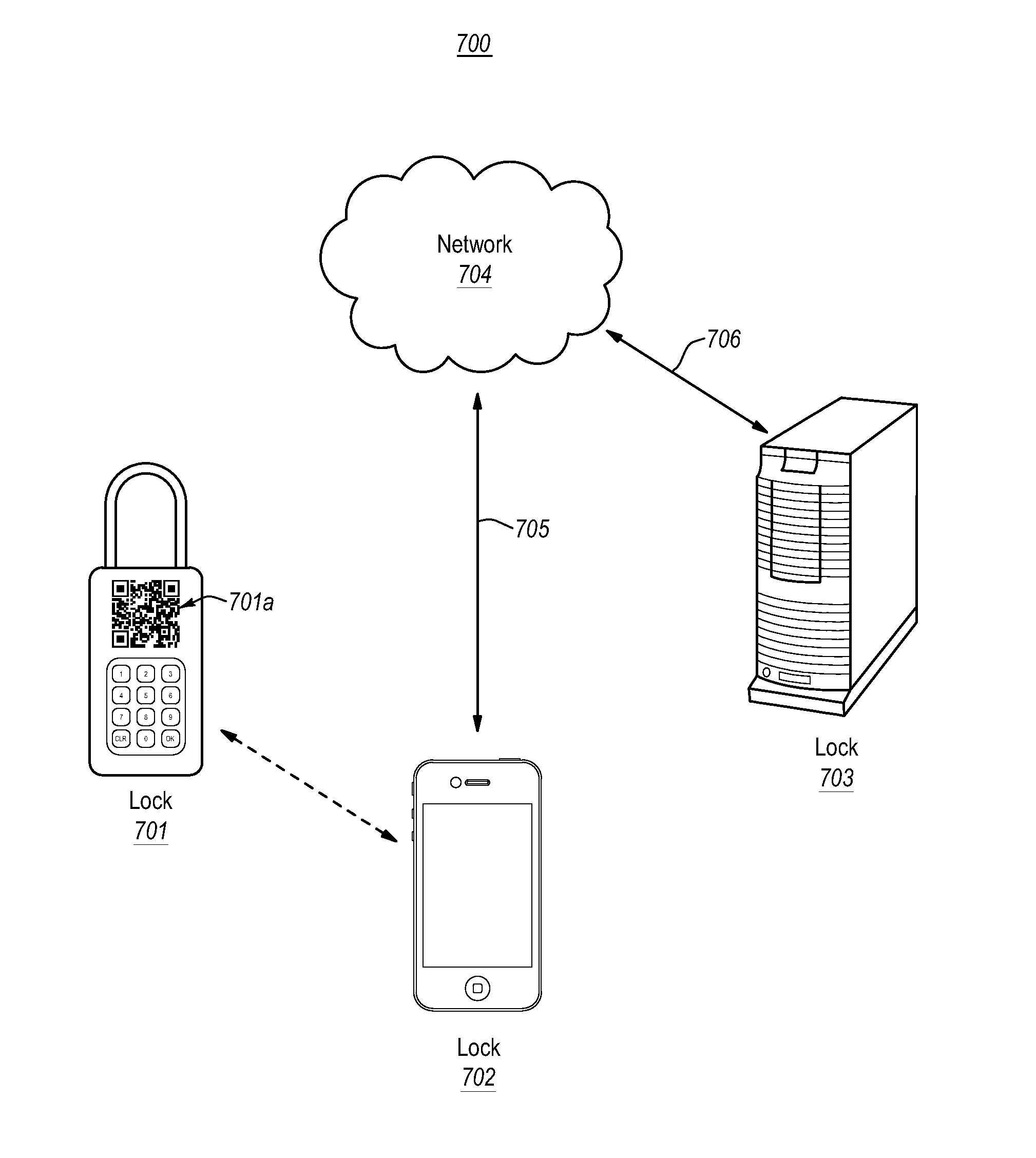
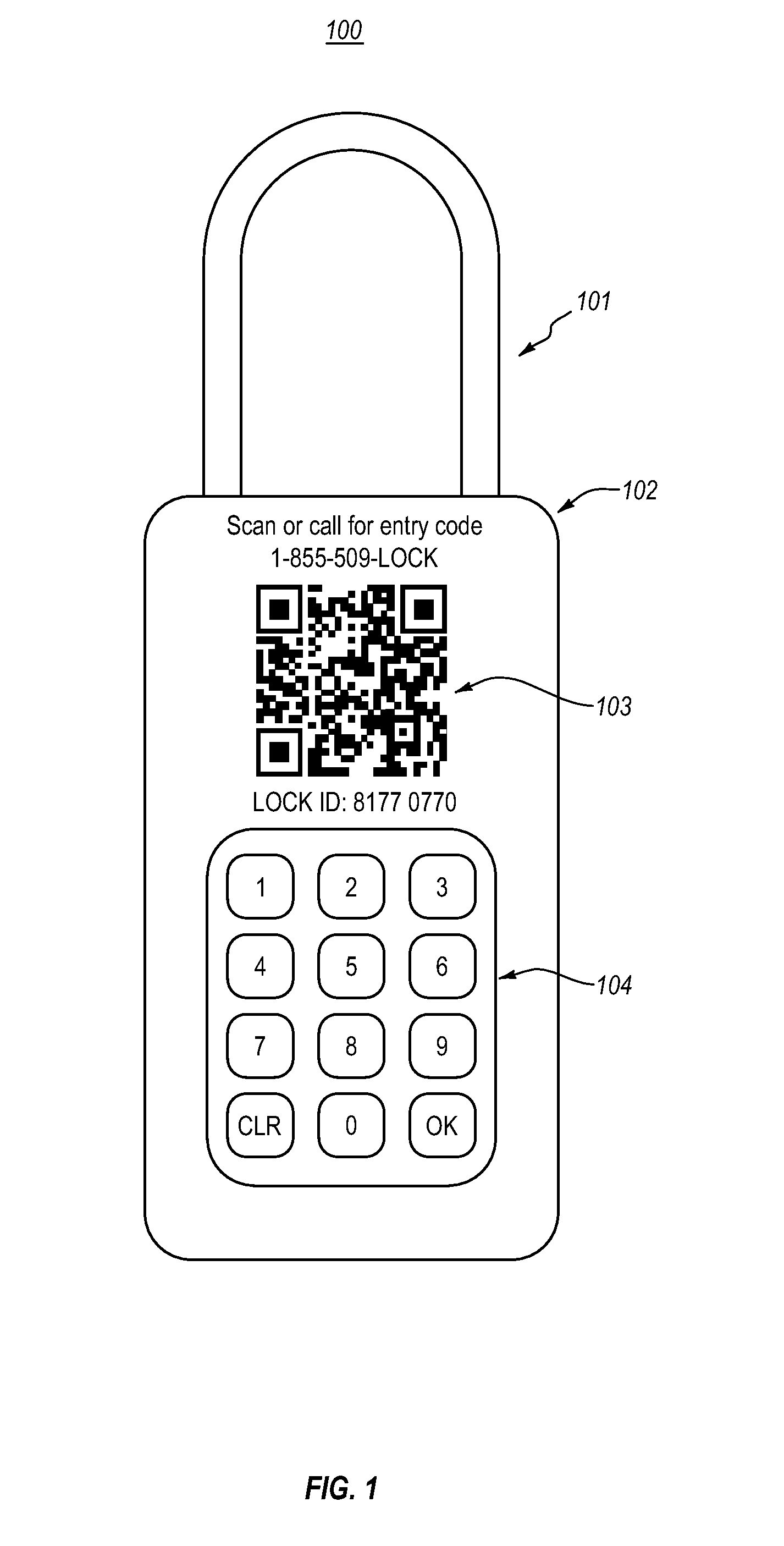
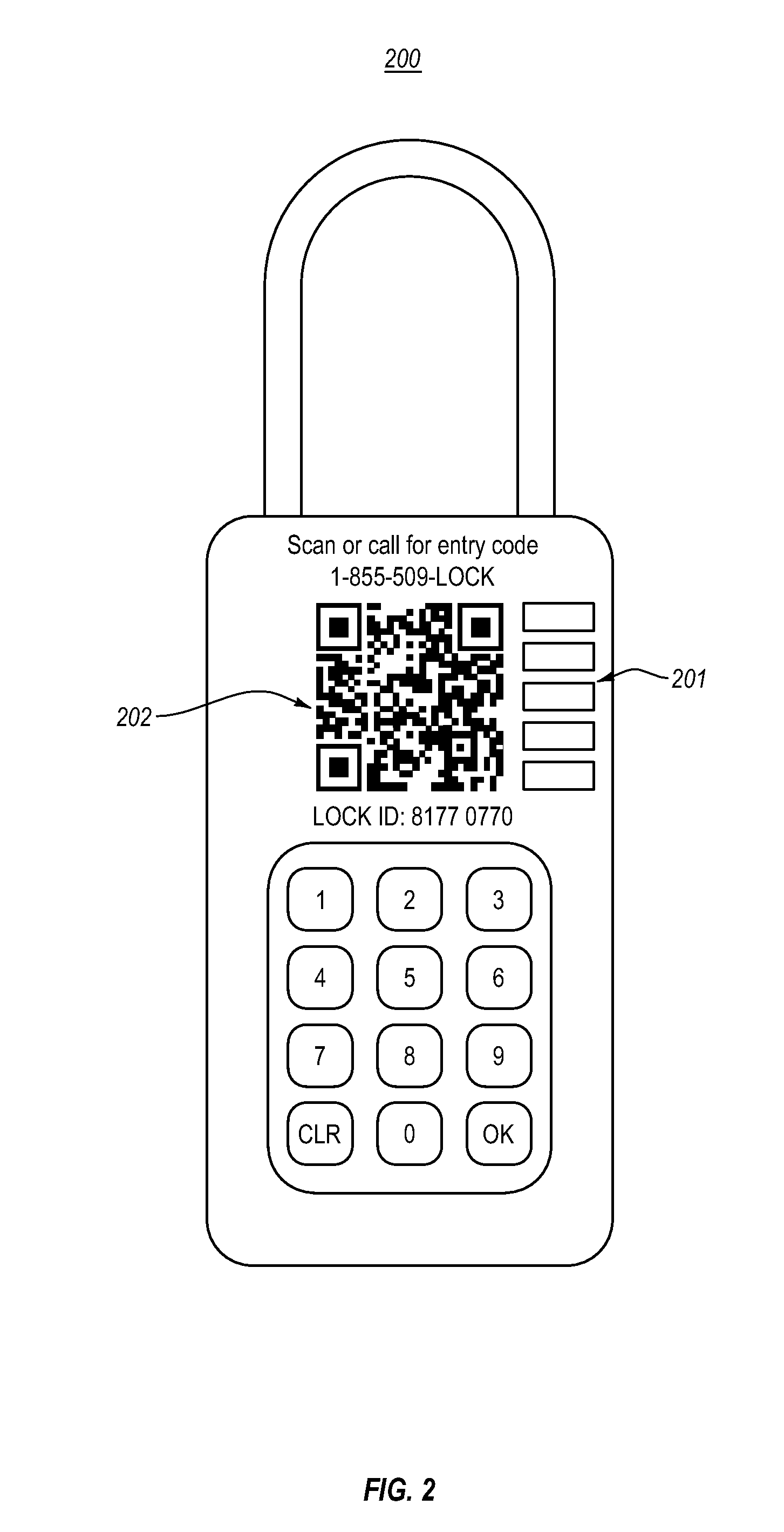
Embodiments herein are directed security access. Embodiments include an electronic lock that executes a time-based cryptographic algorithm to compute a time-based access code. The electronic lock compares the time-based access code with a received access code, and grants access to one or more lock features when the time-based access code matches the received access code. Embodiments also include providing an unlock code, including receiving a lock identifier and a user identifier. The lock identifier and the user identifier are sent to a remote computer system, and an access code for the lock is received from the remote computer system. Embodiments also include an electronic lock that receives and verifies an access code that includes a validity start time and a validity end time. When the current time is within the validity start time and the validity end time, the electronic lock grants access to one or more lock features.
Owner:BRIVO SYST LLC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com