Patents
Literature
424 results about "Process identifier" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
In computing, the process identifier (normally referred to as the process ID or PID) is a number used by most operating system kernels—such as those of UNIX, macOS and Microsoft Windows—to uniquely identify an active process. This number may be used as a parameter in various function calls, allowing processes to be manipulated, such as adjusting the process's priority or killing it altogether.
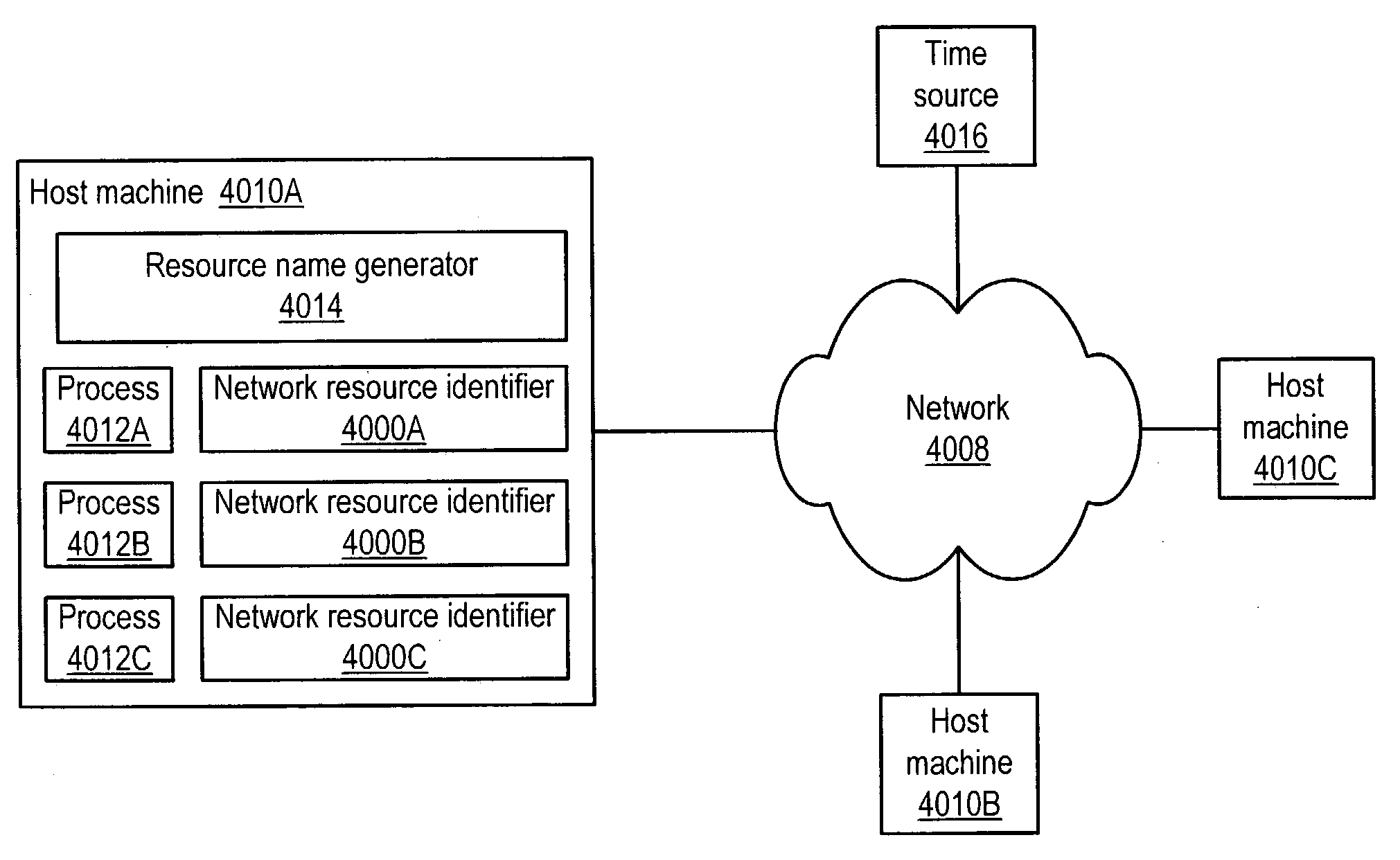
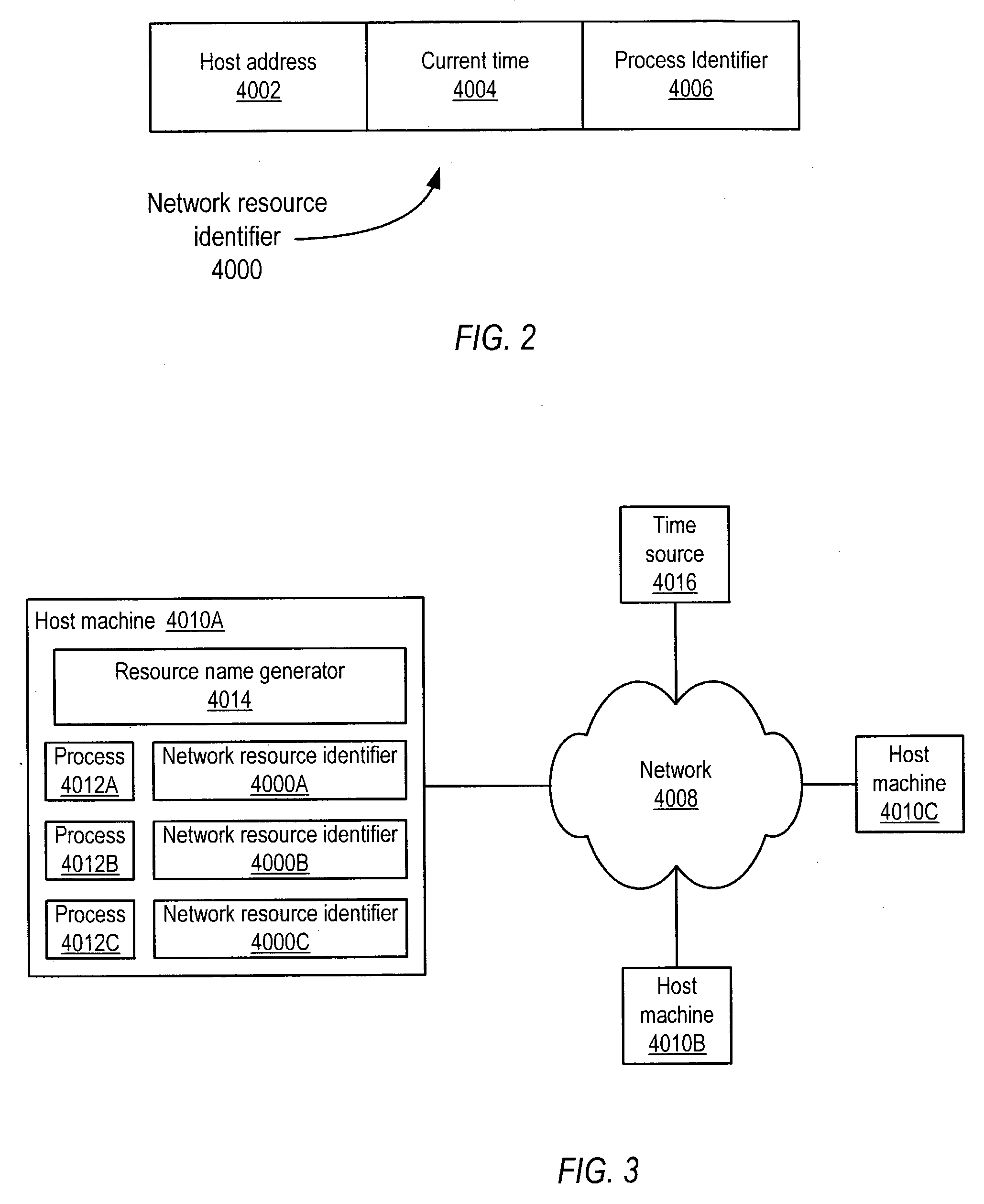
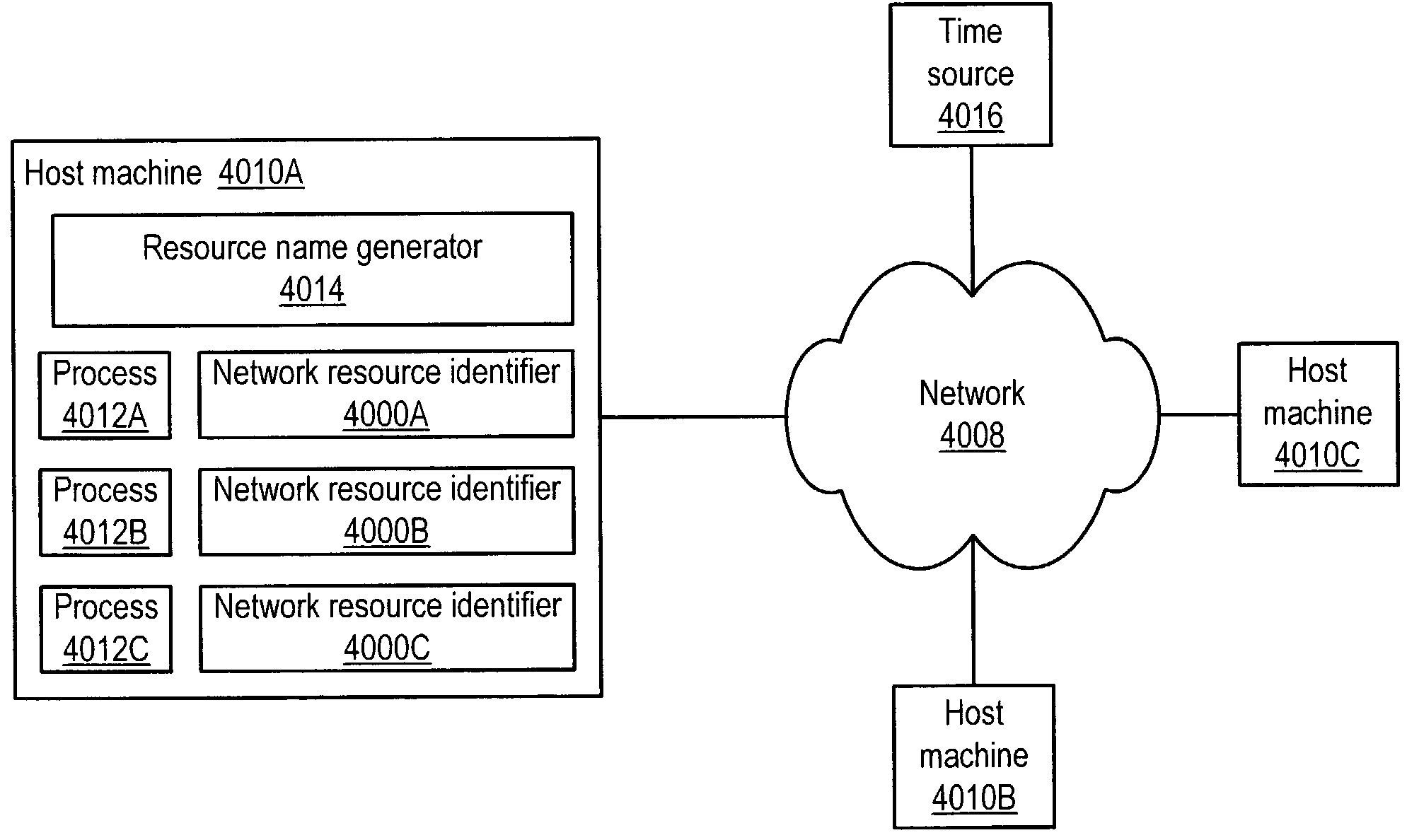
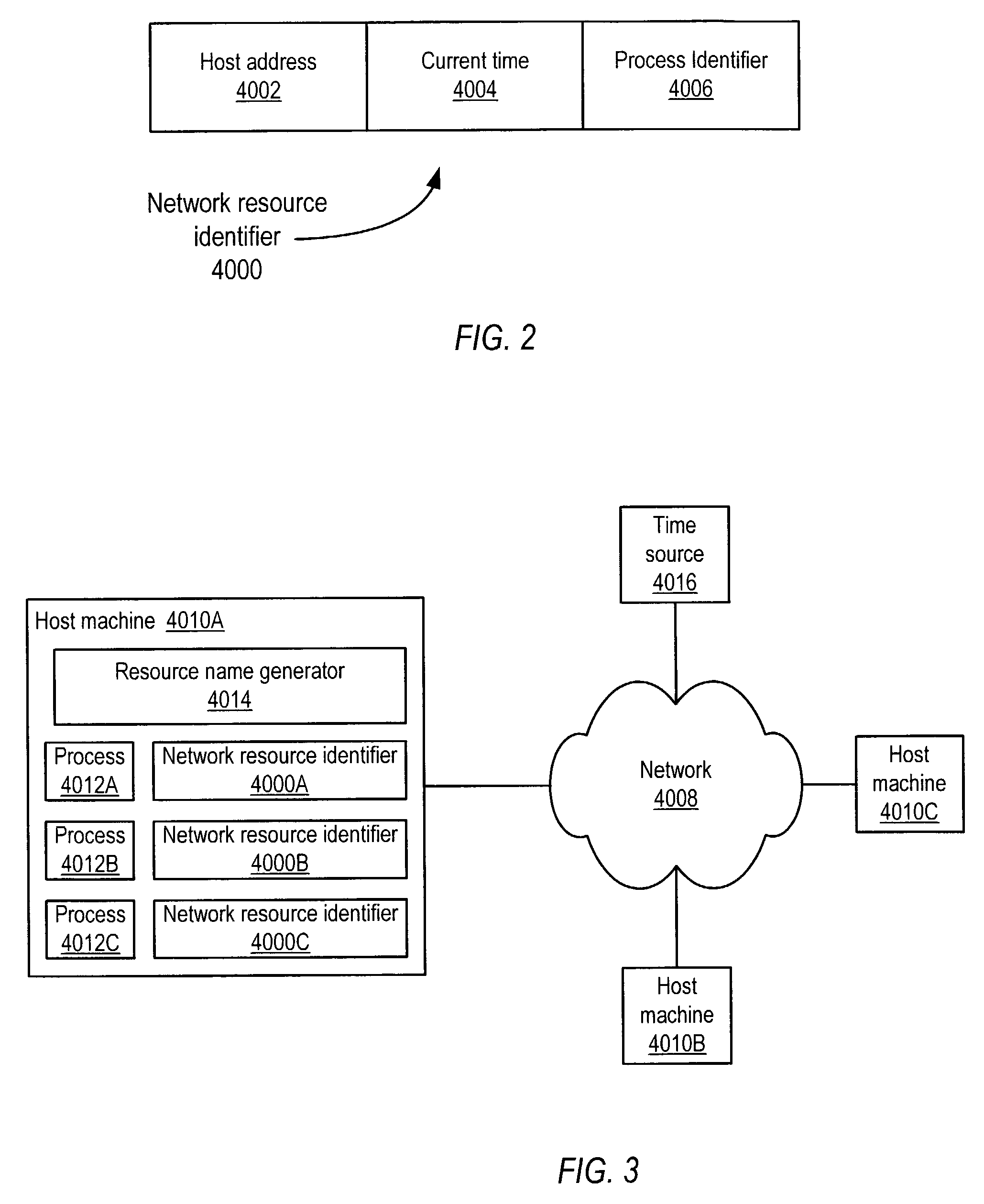
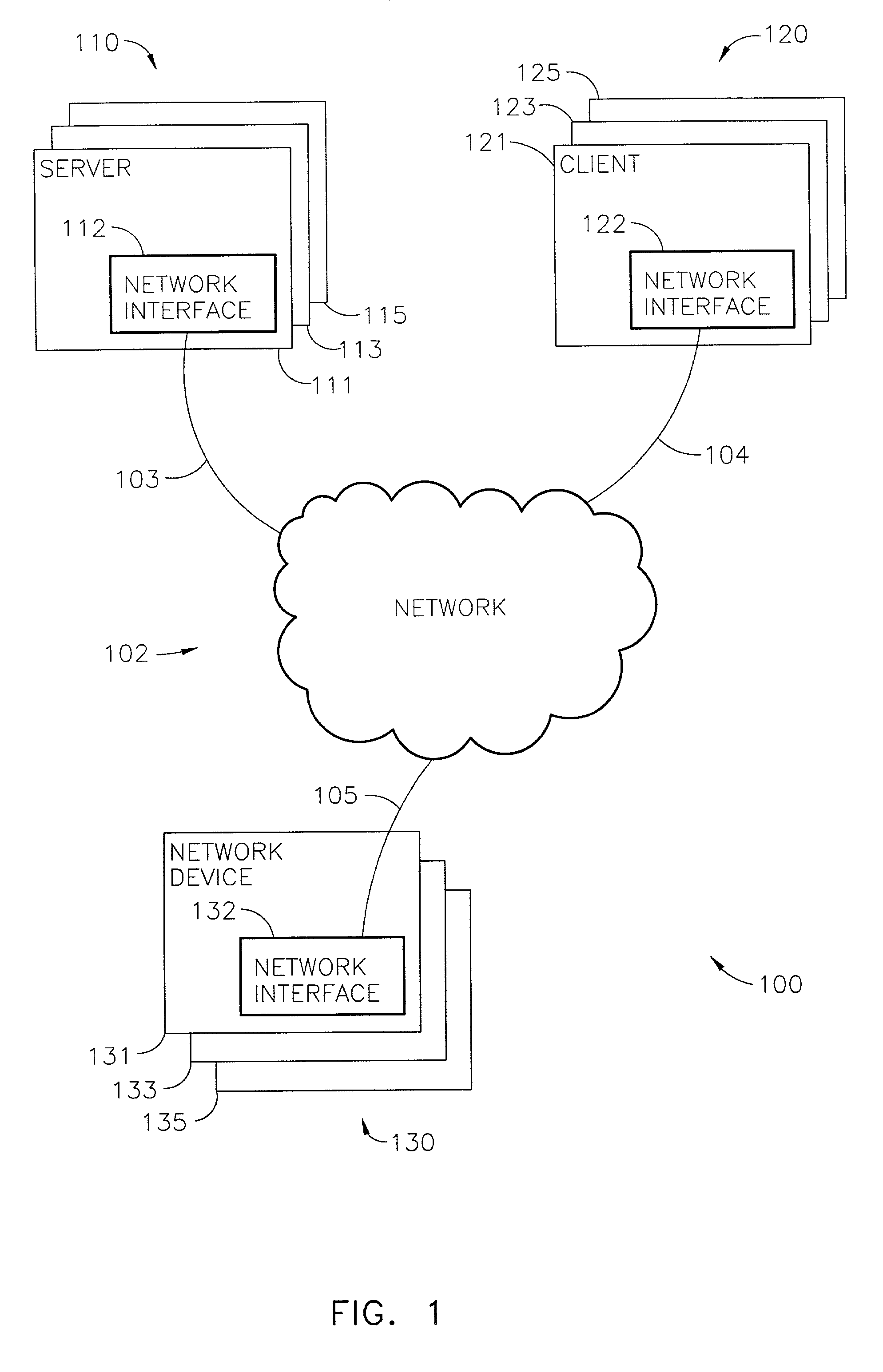
System and method for unique naming of resources in networked environments
ActiveUS20040148326A1Resource allocationData switching by path configurationName generatorUnique identifier
System and method for the unique naming of resources in networked environments including peer-to-peer network environments. Embodiments may be used to generate network resource identifiers that uniquely identify resources such as processes over time and across the networked environment. One embodiment may be implemented as a resource name generator that generates unique identifiers for resources in networked environments. One embodiment may generate unique network resource identifiers for processes from information including, but not limited to, a host address that uniquely identifies on the network the host machine of the resource for which the unique network resource identifier is being generated, a current time (e.g. obtained from the host machine or alternatively from an external source such as an atomic time server), and a process identifier of the process that uniquely identifies the process among current processes on the host machine.
Owner:ORACLE INT CORP
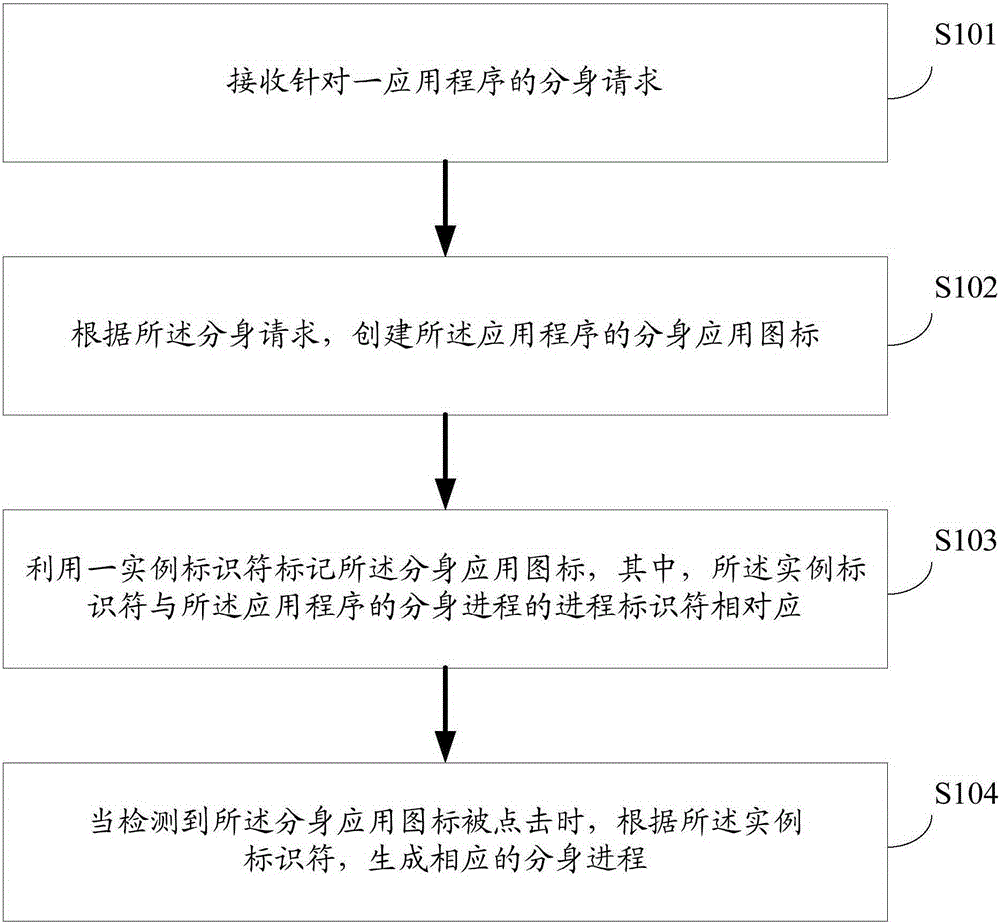
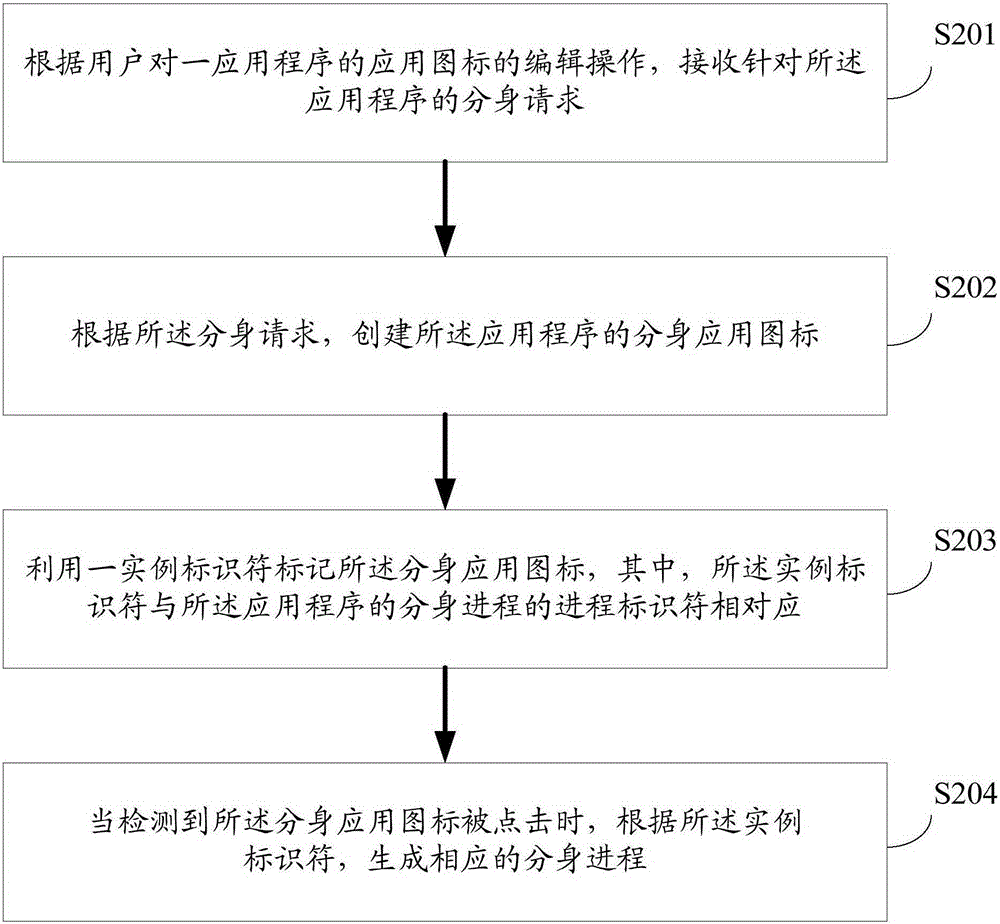
Multi-tasking method for application program and terminal
ActiveCN105224322ADouble realizationConvenient and Smart Twin ExperienceSpecific program execution arrangementsApplication softwareComputer engineering
The invention provides a multi-tasking method for application program. The multi-tasking method for application program comprises: receiving a multi-tasking request aimed at the application program; according to the multi-tasking request, establishing a multi-tasking application icon of the application program; using an instance identifier to mark the multi-tasking application icon, wherein the instance identifier is corresponding to a process identifier of a multi-tasking process of the application program; when the multi-tasking application icon is detected to be clicked, according to the instance identifier, generating a corresponding multi-tasking process. The invention also provides a corresponding terminal. The multi-tasking method for application program can realize multi-tasking of the application program, and operation is simple, so as to bring about convenient and intelligent application program multi-tasking experience.
Owner:VIVO MOBILE COMM CO LTD
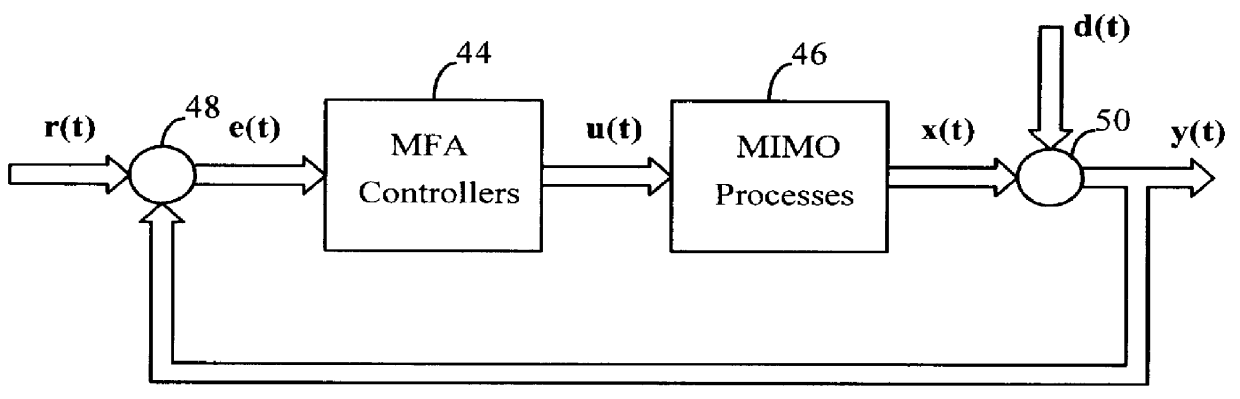
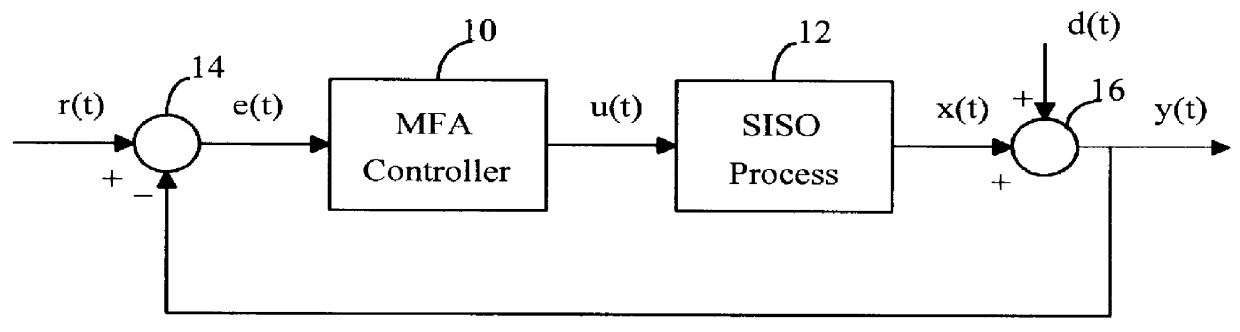
Model-free adaptive process control
InactiveUS6055524ALong response delayOvercome limitationsDigital computer detailsDigital dataData miningSelf adaptive
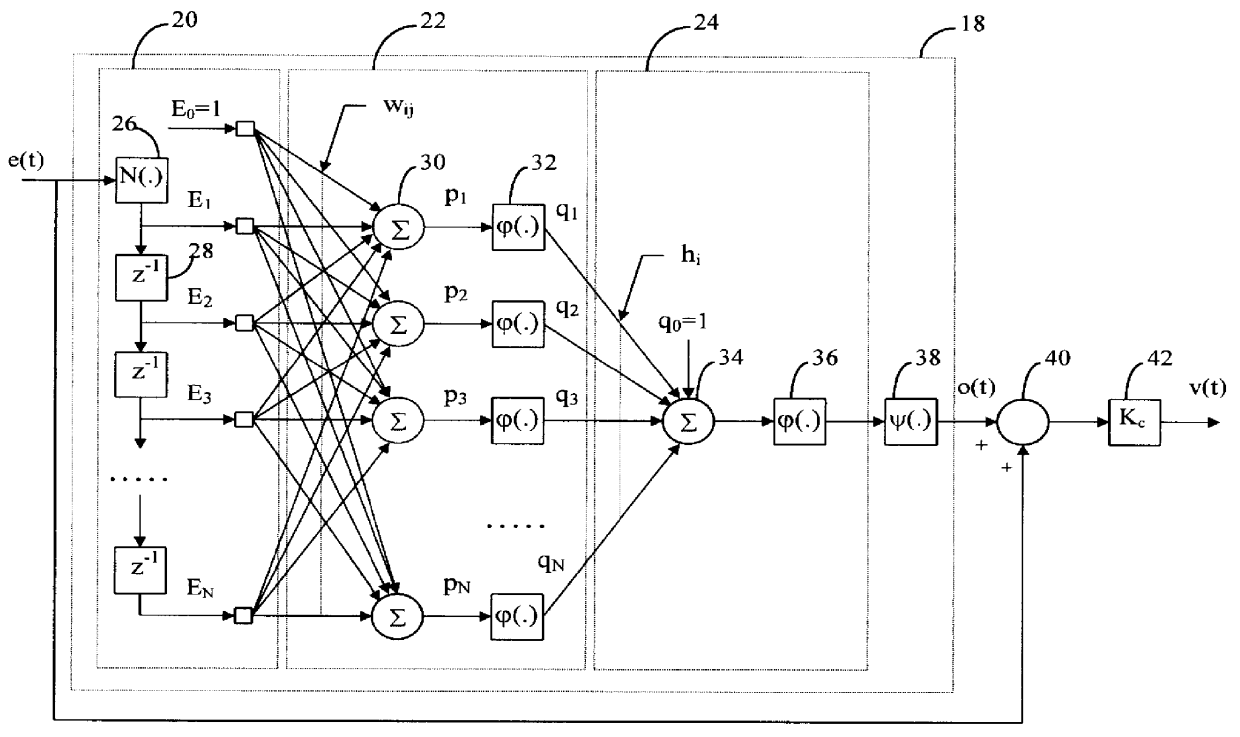
A model-free adaptive controller is disclosed, which uses a dynamic artificial neural network with a learning algorithm to control any single-variable or multivariable open-loop stable, controllable, and consistently direct-acting or reverse-acting industrial process without requiring any manual tuning, quantitative knowledge of the process, or process identifiers. The need for process knowledge is avoided by substituting 1 for the actual sensitivity function .differential.y(t) / .differential.u(t) of the process.
Owner:GEN CYBERNATION GROUP
Minimizing profiling-related perturbation using periodic contextual information
InactiveUS6662358B1Digital data information retrievalError detection/correctionCall stackProgram counter
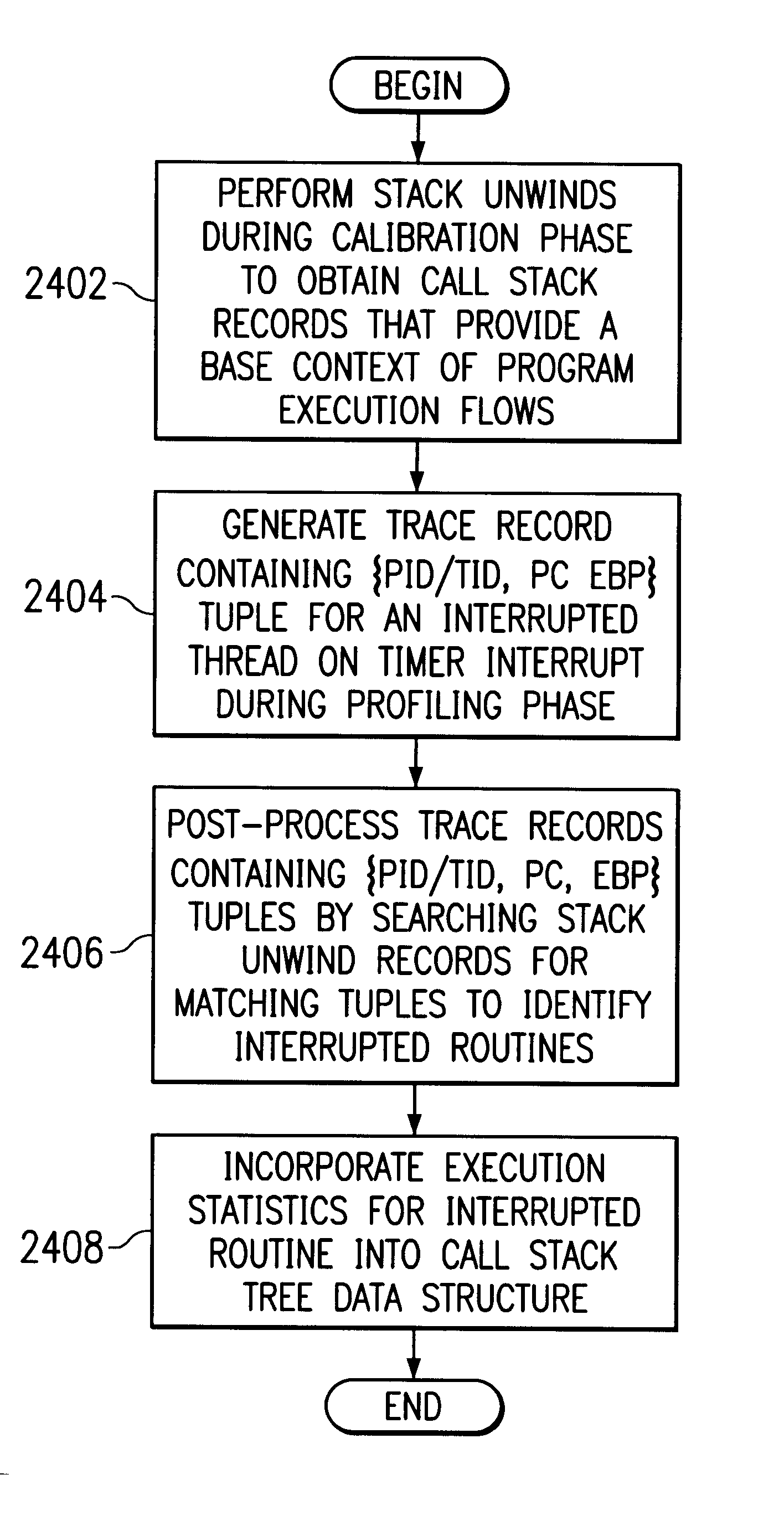
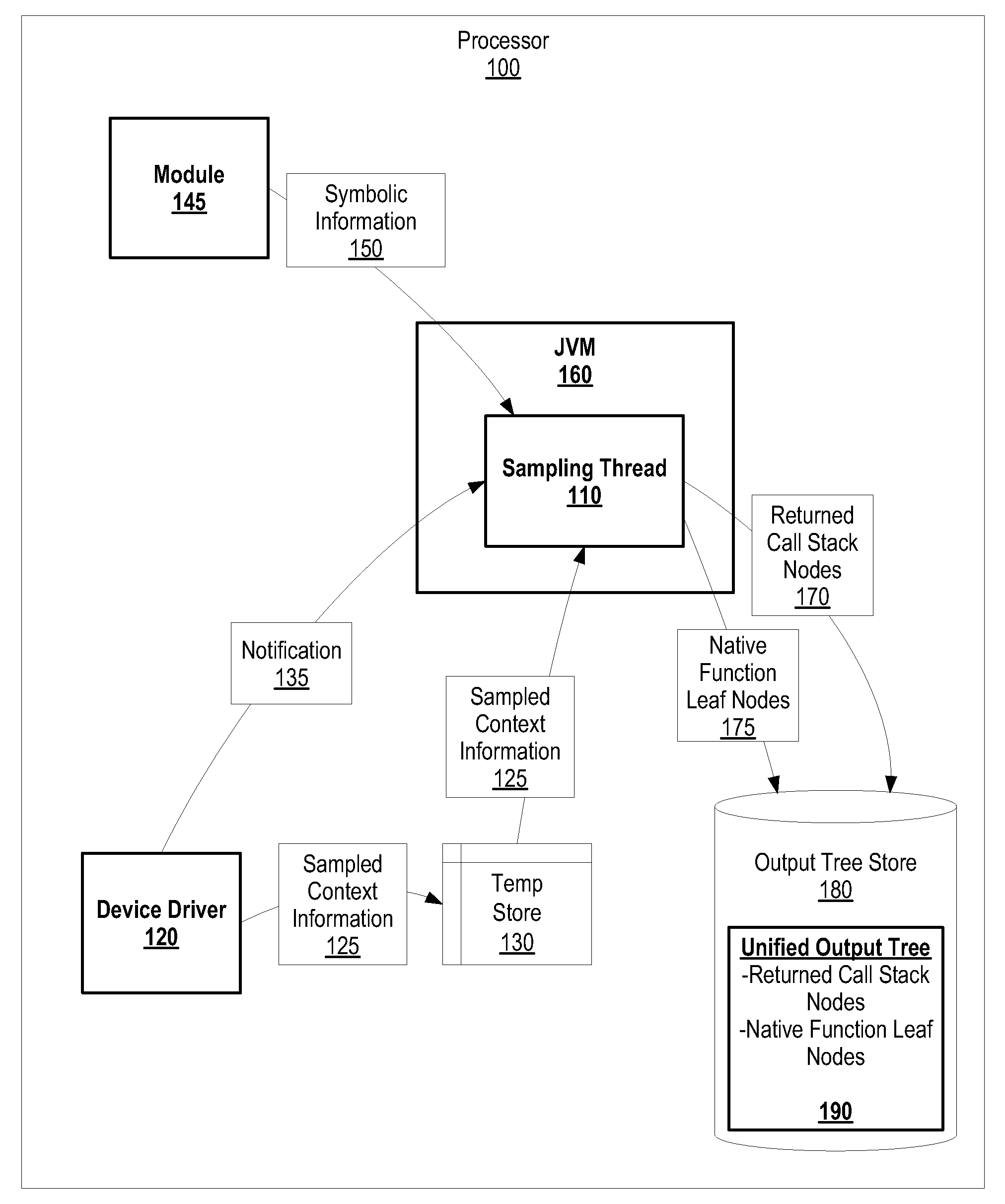
A method and system for monitoring performance of a program is provided. A trace record containing a call stack associated with the program is periodically generated. An occurrence of a selected event or a timer interrupt is detected, and in response, an execution context sample is obtained that contains a process identifier, a thread identifier, a program counter, and a stack pointer. A trace record containing the execution context sample data is generated. During post-processing, the execution context samples are compared with a call stack to identify the routine associated with the execution sample data.
Owner:IBM CORP
System and method for unique naming of resources in networked environments
ActiveUS7533141B2Resource allocationData switching by path configurationName generatorUnique identifier
Owner:ORACLE INT CORP
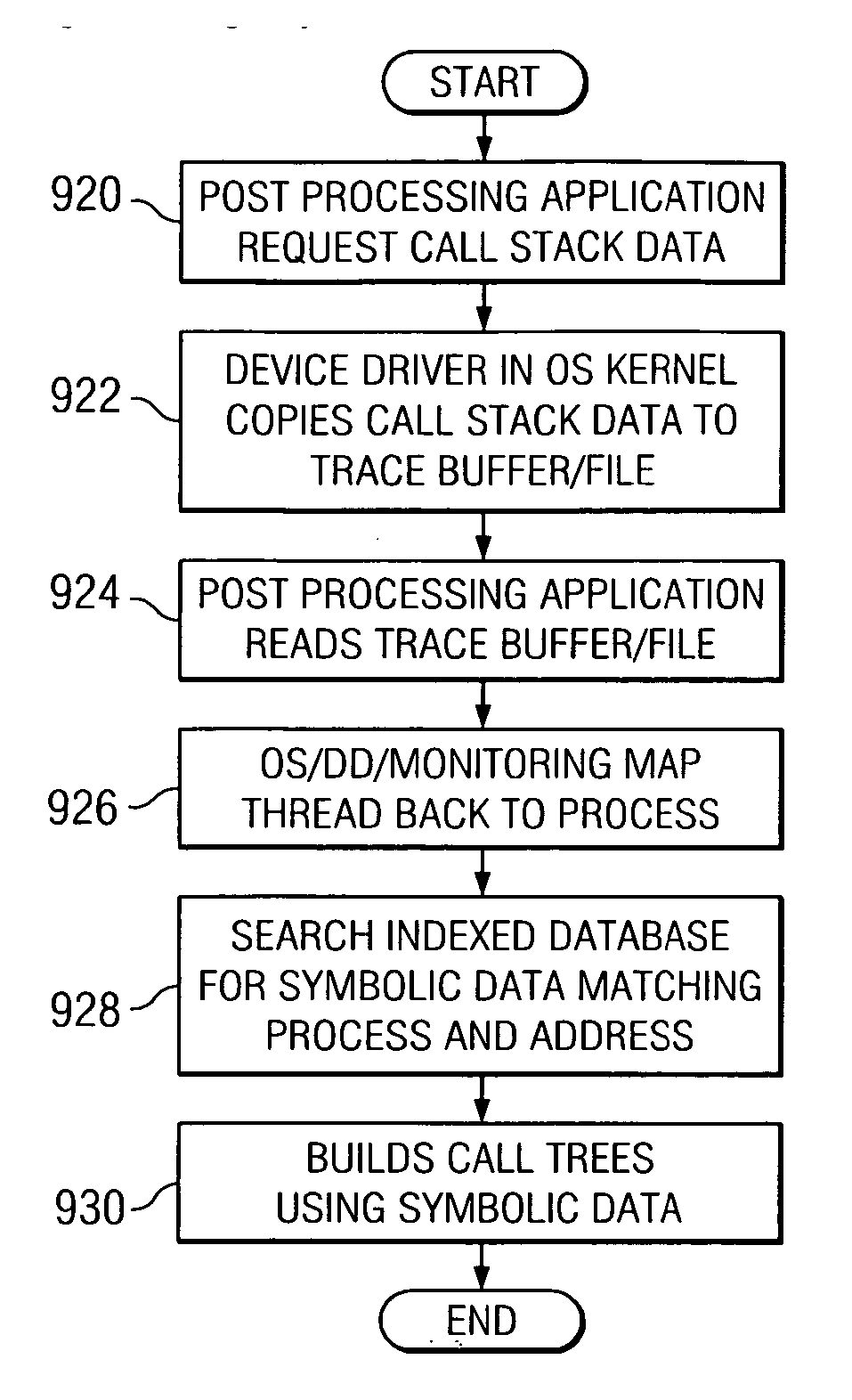
Method and apparatus for determining computer program flows autonomically using hardware assisted thread stack tracking and cataloged symbolic data
InactiveUS20050210454A1Error detection/correctionDigital computer detailsCall stackOperational system
A method, apparatus, and computer instructions for determining computer flows autonomically using hardware assisted thread stack and cataloged symbolic data. When a new thread is spawned during execution of a computer program, new thread work area is allocated by the operating system in memory for storage of call stack information for the new thread. Hardware registers are set with values corresponding to the new thread work area. Upon context switch, values of the registers are saved in a context save area for future restoration. When call stack data is post-processed, the operating system or a device driver copies call stack data from the thread work areas to a consolidated buffer and each thread is mapped to a process. Symbolic data may be obtained based on the process identifier and address of the method / routine that was called / returned in the thread. Corresponding program flow is determined using retrieved symbolic data and call stack data.
Owner:IBM CORP
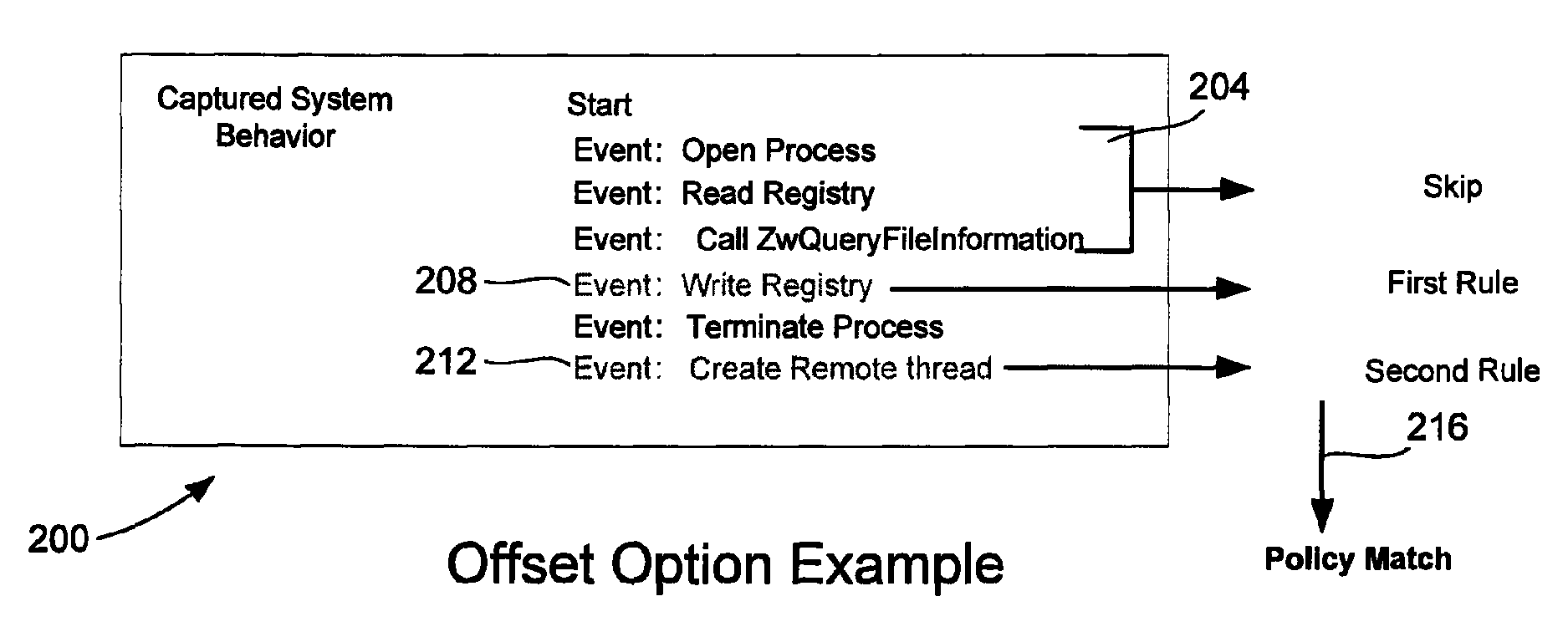
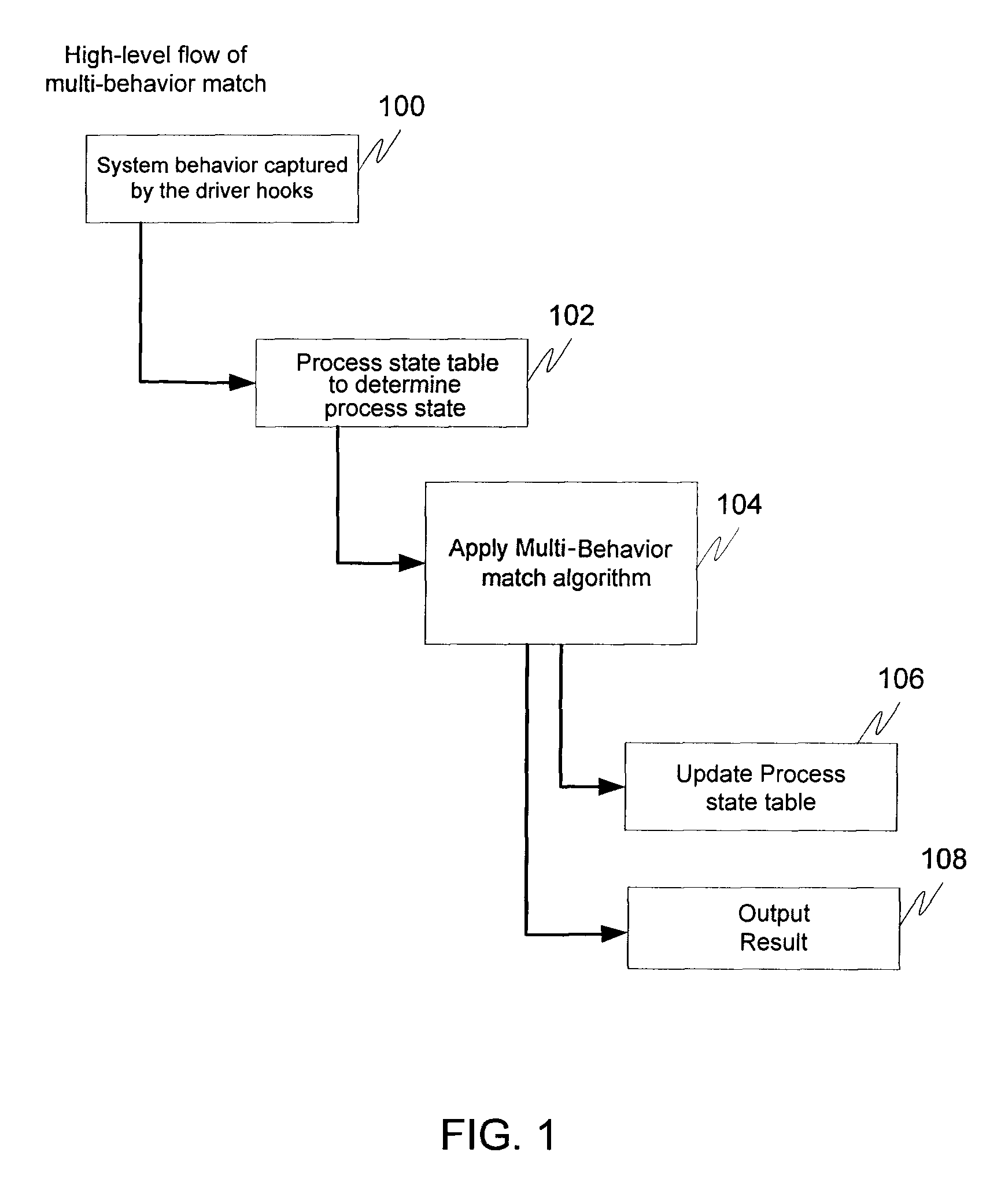
Multi-behavior policy matching for malware detection
ActiveUS8370931B1Avoid problemsPreventing inefficient searchMemory loss protectionDigital data processing detailsComputerized systemMalware
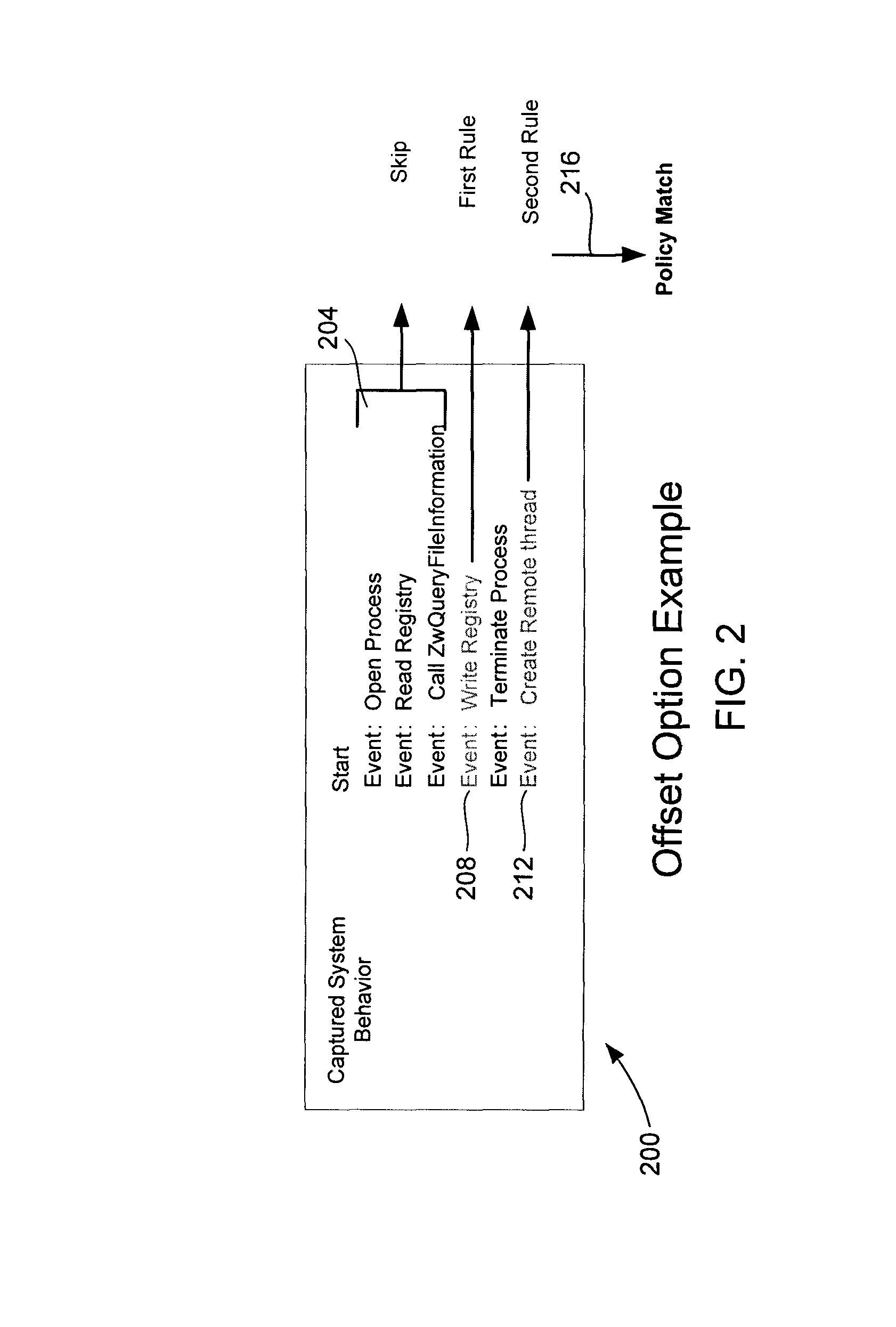
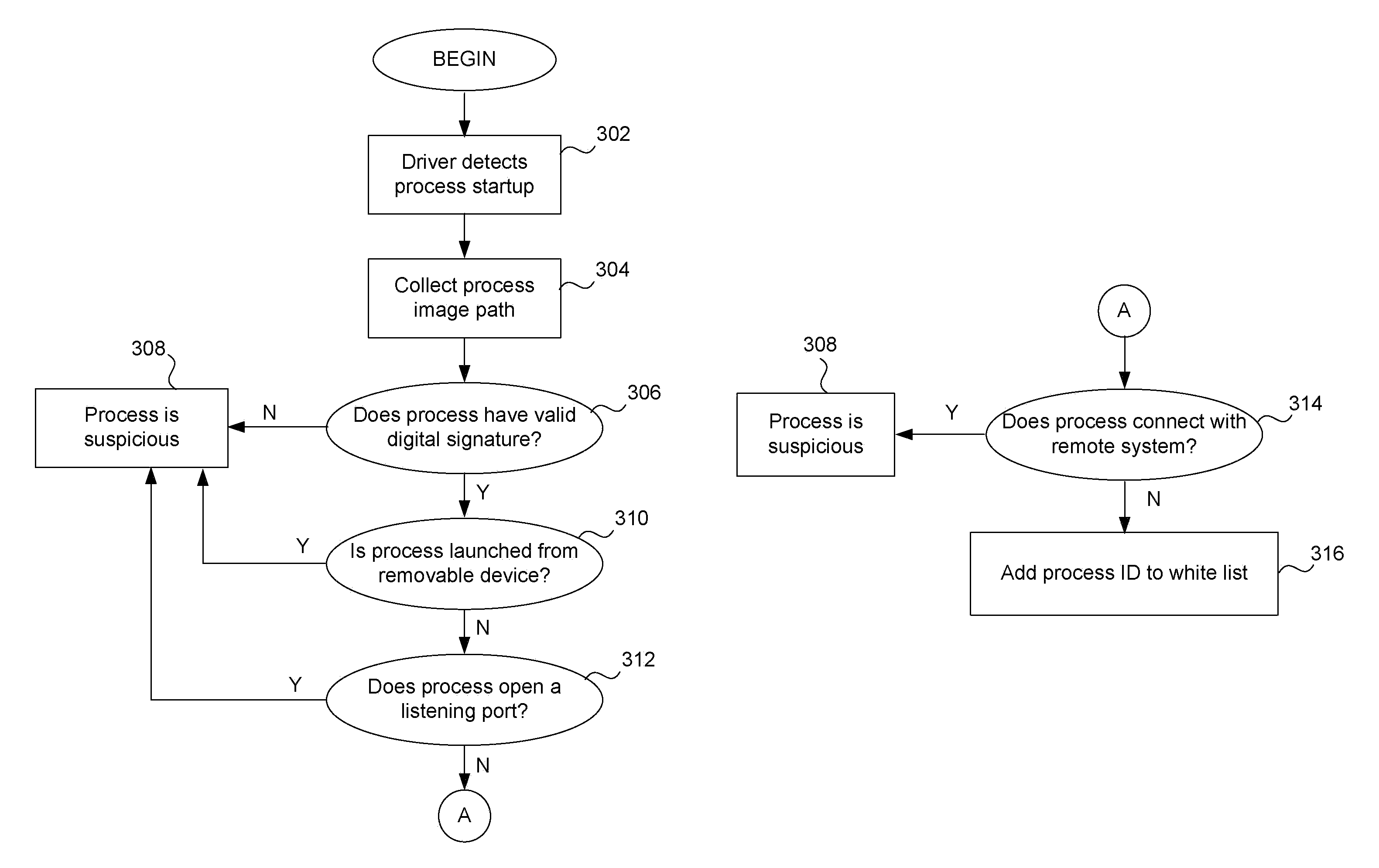
Multi-behavior matching in a computer system is performed in order to identify suspicious sequences of activities. System behavior is captured using driver hooks. A behavior monitoring system determines the process to which the system behavior belongs by processing a table. This includes using the process ID and thread ID of the system behavior as lookups into the table. A multi-behavior matching algorithm is applied to determine if there is any matching suspicious behavior by matching sets of rules (a policy) to system events caused by a particular process. A state machine is used to keep track of matching policies. Options to the rules and policies (such as “offset,”“depth,”“distance,”“within,”“ordered” and “occurrence / interval”) are used to refine when a rule or policy is allowed to produce a positive match, reducing false positives.
Owner:TREND MICRO INC
Android smart terminal based application multi-run management method and system
ActiveCN104199734ARealize multiple needsEliminate operating proceduresProgram initiation/switchingSoftware engineeringApplication software
The invention provides an Android smart terminal based application multi-run management method and system. The method includes: starting an application in an Android smart terminal; judging multi-run attribute, screening parameters and running processes via a control unit; according to judgment results, allowing the control unit to distribute PIDs (process identifiers) to create processes of the application and switch the running processes, or allowing the control unit to distribute new PIDs to recreate new processes of the application. The multi-run attribute is preset through a user interface for whether the application in the Android smart terminal can be multiply started along with processes created. The screening parameters are preset for the application meeting the multi-run attribute, through the user interface or by a manufacturer on delivery. The Android smart terminal based application multi-run management method and system has the advantages that a user can multiply run a certain application conveniently and quickly, and the multiply run application is more visual and convenient to use and manage.
Owner:山东智顺网络科技有限公司
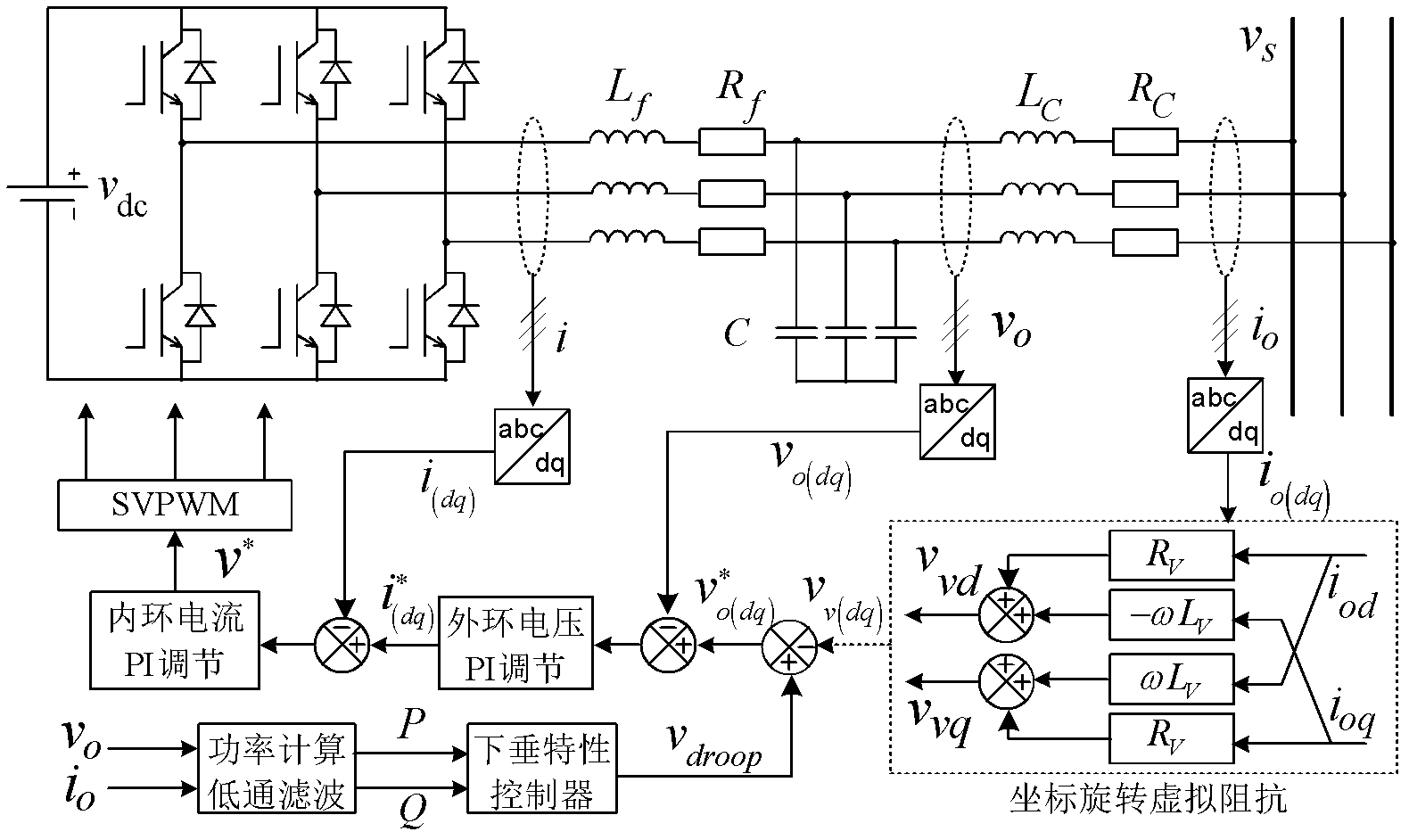
Method for islanding microgrid control and optimization based on rotating coordinate virtual impedance
InactiveCN102623992AImprove impedance characteristicsCompensation errorEnergy industrySingle network parallel feeding arrangementsMicrogridDynamic models
The invention discloses a method for islanding microgrid control and optimization based on rotating coordinate virtual impedance. Aiming to a fact that the actual microgrids have complicated impedance characteristics, the method for islanding microgrid control and optimization based on the rotating coordinate virtual impedance includes utilizing the coordinate rotation orthogonal transformation to design the coordinate rotation virtual impedance, improving the impedance characteristics of the microgrid, compensating errors of power distribution and improving power decoupling performance; establishing a complete small-signal dynamic model of the microgrid, wherein the small-signal dynamic model comprises distributed energy sources, power converters, loads and power grids, and guiding the selection of an optimal value on the basis of the small-signal dynamic analytical method; and simultaneously, providing a theoretical basis for the optimization selection of islanding microgrid control parameters by using the small-signal dynamic analytical method, wherein the islanding microgrid control parameters comprise droop control coefficients of the power distribution, process identifier (PI) parameters of a voltage current feedback controller, feedforward control coefficients and the like. The microgrid after being subjected to optimization design in an islanded operational mode is capable of effectively achieving power decoupling and improving the accuracy of the power distribution, the stability of the system and the dynamic performances.
Owner:SHANDONG UNIV
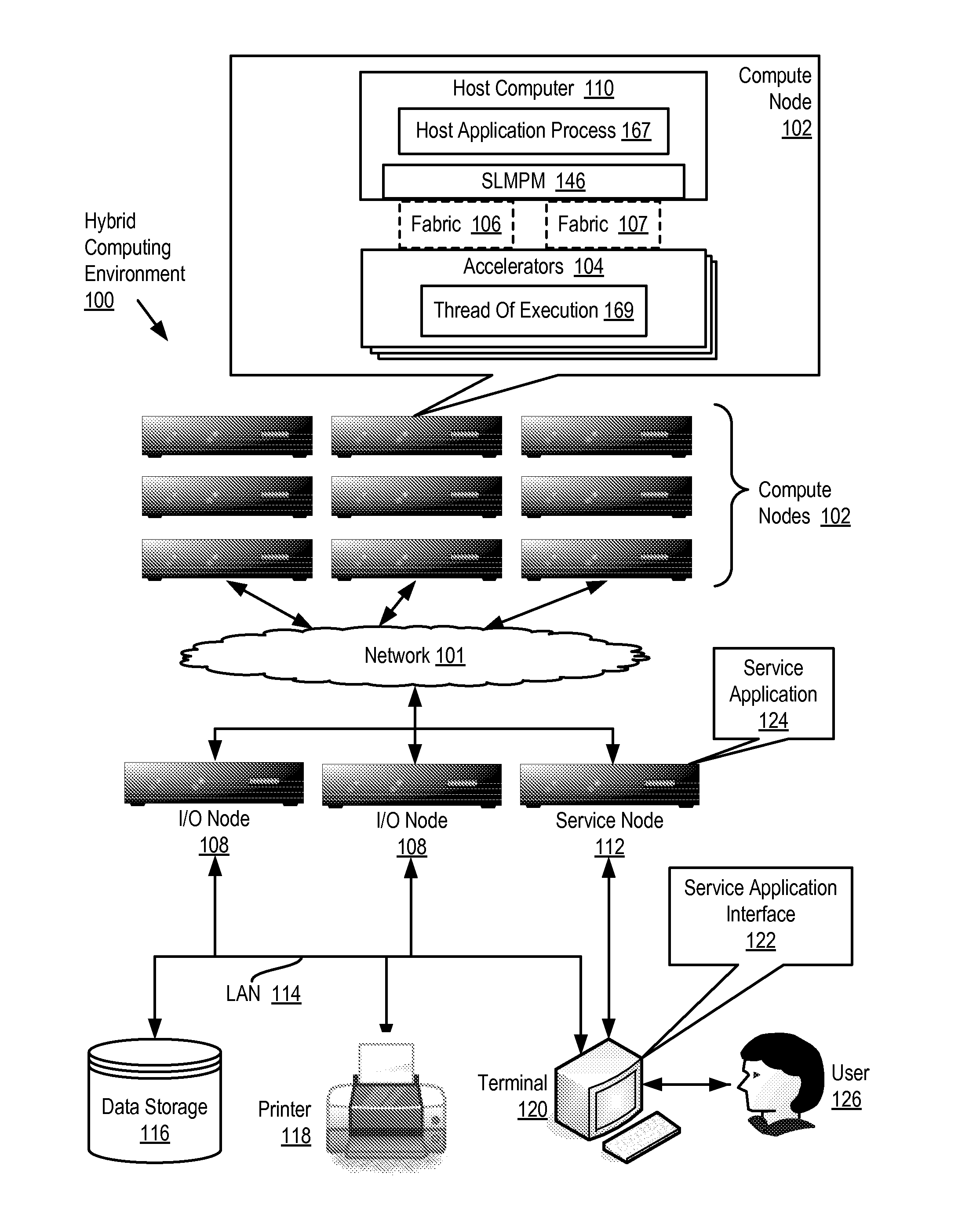
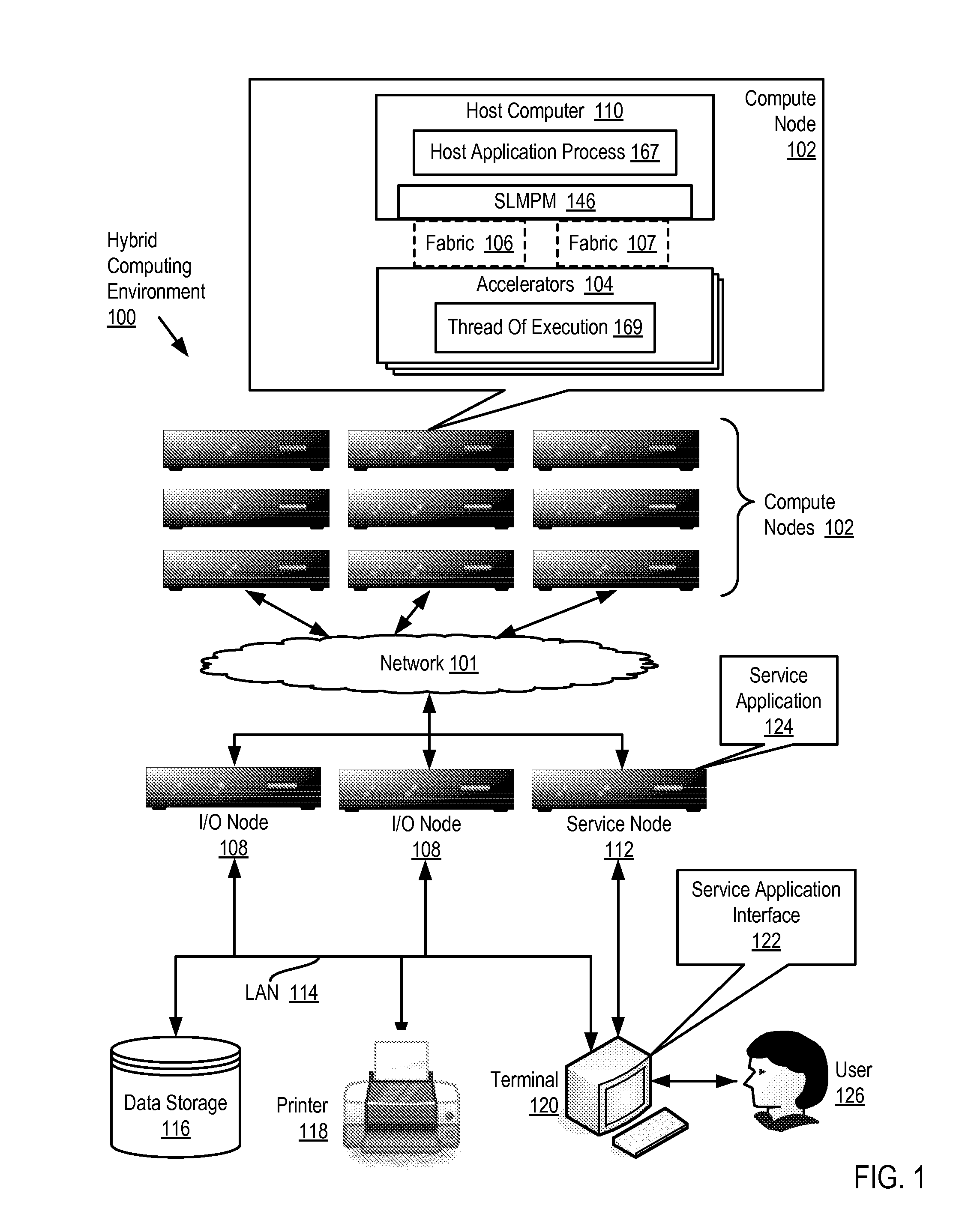
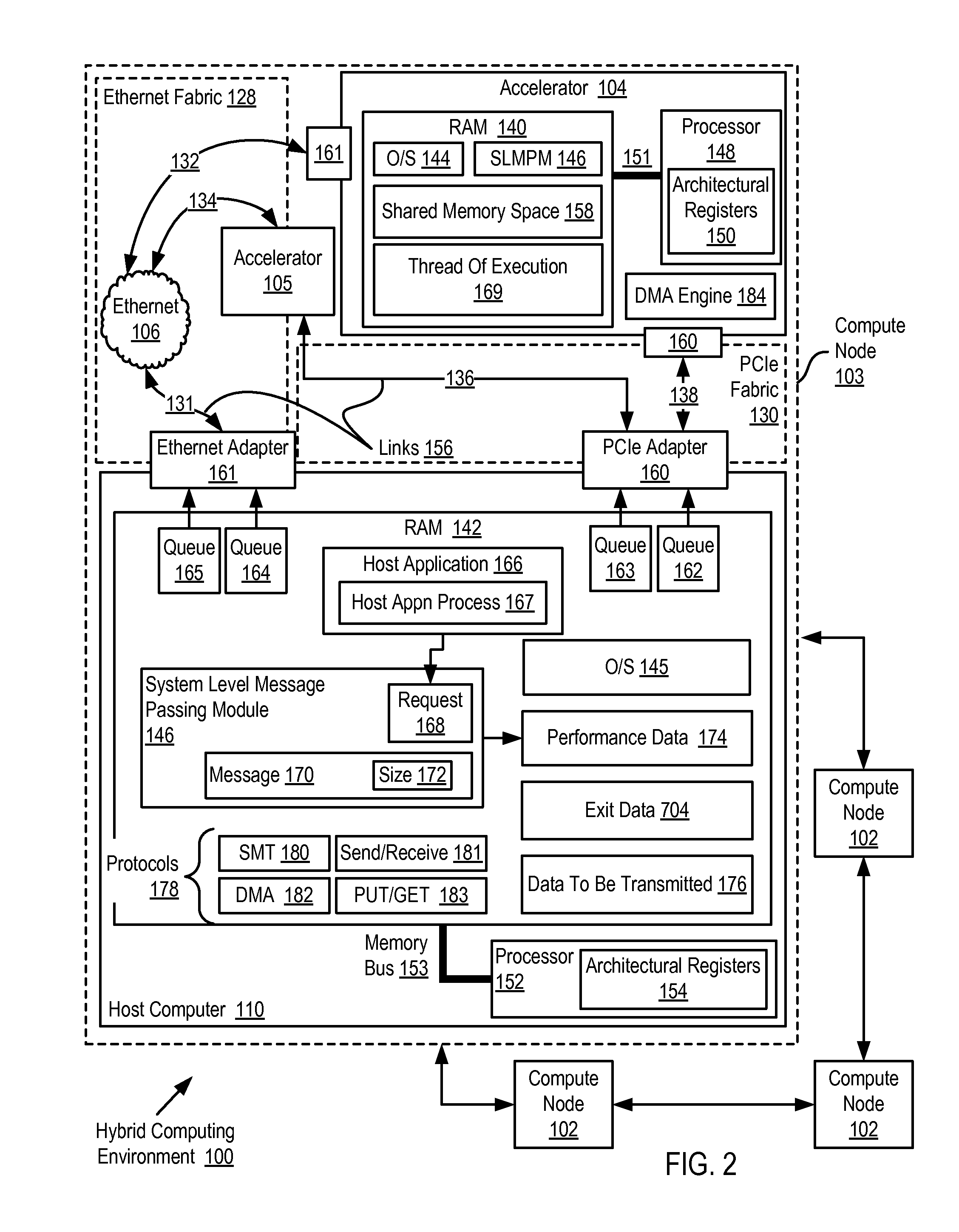
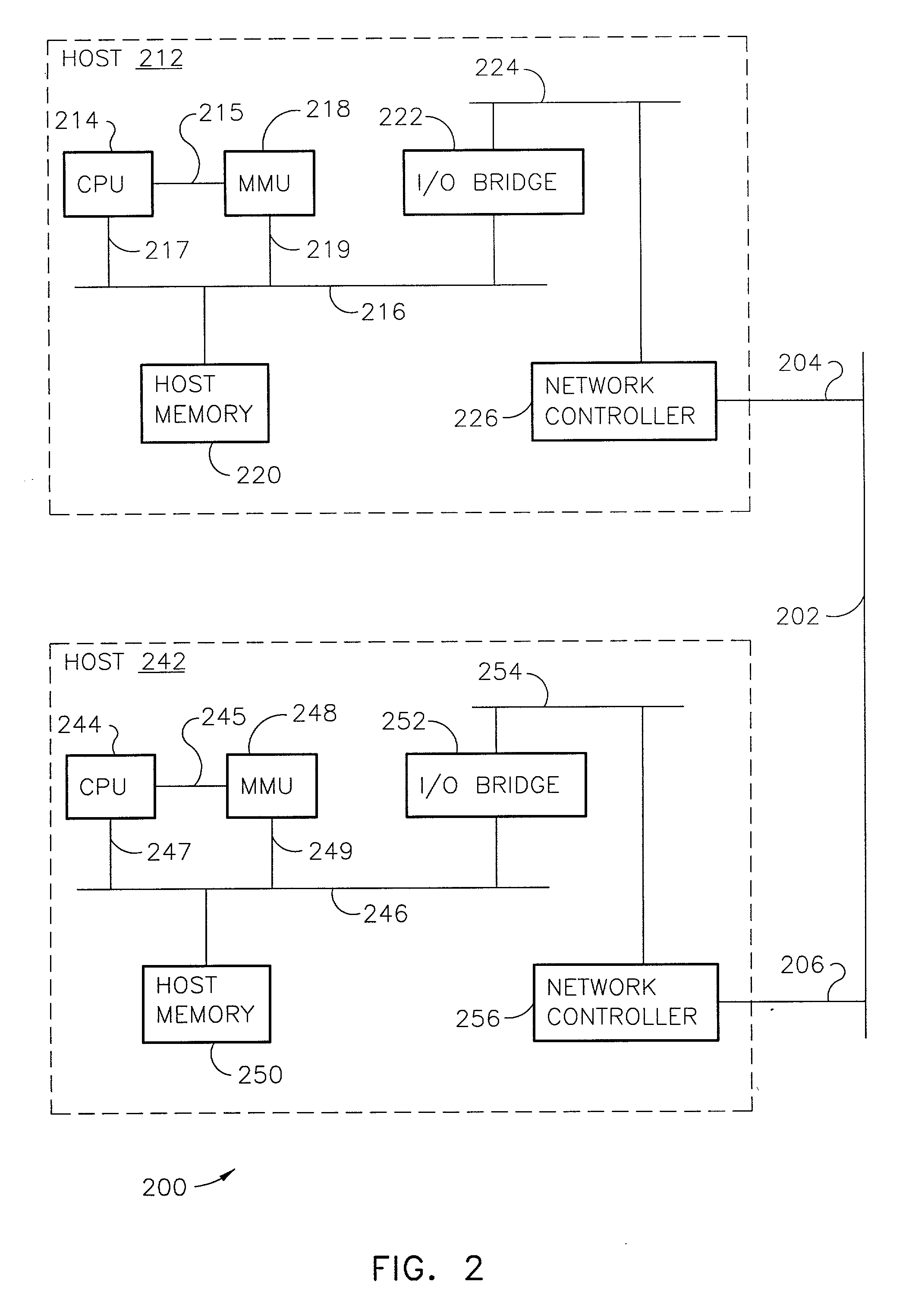
Data Processing In A Hybrid Computing Environment
ActiveUS20100058356A1General purpose stored program computerMultiprogramming arrangementsApplication softwareMessage passing
Data processing in a hybrid computing environment that includes a host computer having a host computer architecture; an accelerator having an accelerator architecture, the accelerator architecture optimized, with respect to the host computer architecture, for speed of execution of a particular class of computing functions; the host computer and the accelerator adapted to one another for data communications by a system level message passing module; and a host application process executing on the host computer. Data processing such a hybrid computing environment includes starting, at the behest of the host application process, a thread of execution on the accelerator; returning, by the system level message passing module to the host application process, a process identifier (‘PID’) for the thread of execution; and managing, by the host application process, the thread of execution on the accelerator as though the thread of execution were a thread of execution on the host computer.
Owner:IBM CORP
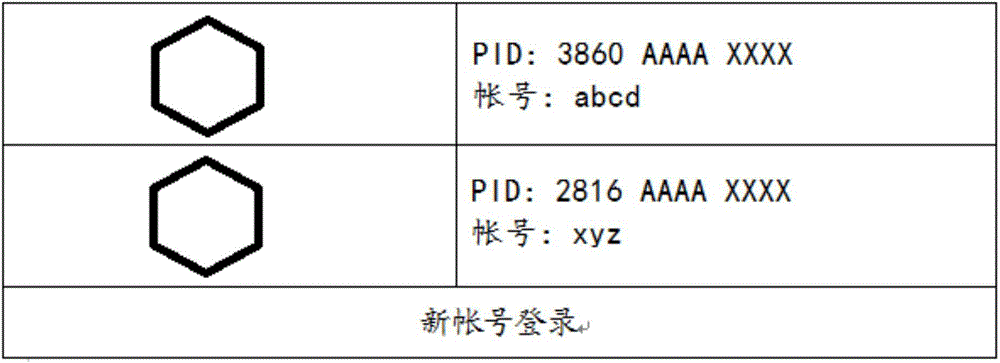
Method and device for simultaneously starting multiple same applications on intelligent terminal
InactiveCN104866342ASolve the problem that multiple identical applications cannot be opened at the same timeSave storage spaceProgram loading/initiatingApplication softwareComputer science
The application discloses a method and a device for simultaneously starting multiple same applications on an intelligent terminal. The method comprises following steps: receiving selecting operation of a user to applications of the intelligent terminal; determining whether activity instances of selected applications are present in the process of the intelligent terminal; distributing process identifiers for the applications if the activity instances do not exist and creating activity instances of applications based on process identifiers; and distributing process identifiers, having different process identifier values from the intelligent terminal, for the applications and recreating activity instances of the applications based on process identifiers or switching to activity instances of the selected applications of the intelligent terminal. By adoption of the above scheme, the problem that multiple same applications cannot be started on a conventional intelligent terminal is solved by distributing process identifiers, having different process identifier values from the intelligent terminal, for the applications and recreating activity instances of the applications.
Owner:北京数字天域科技有限责任公司
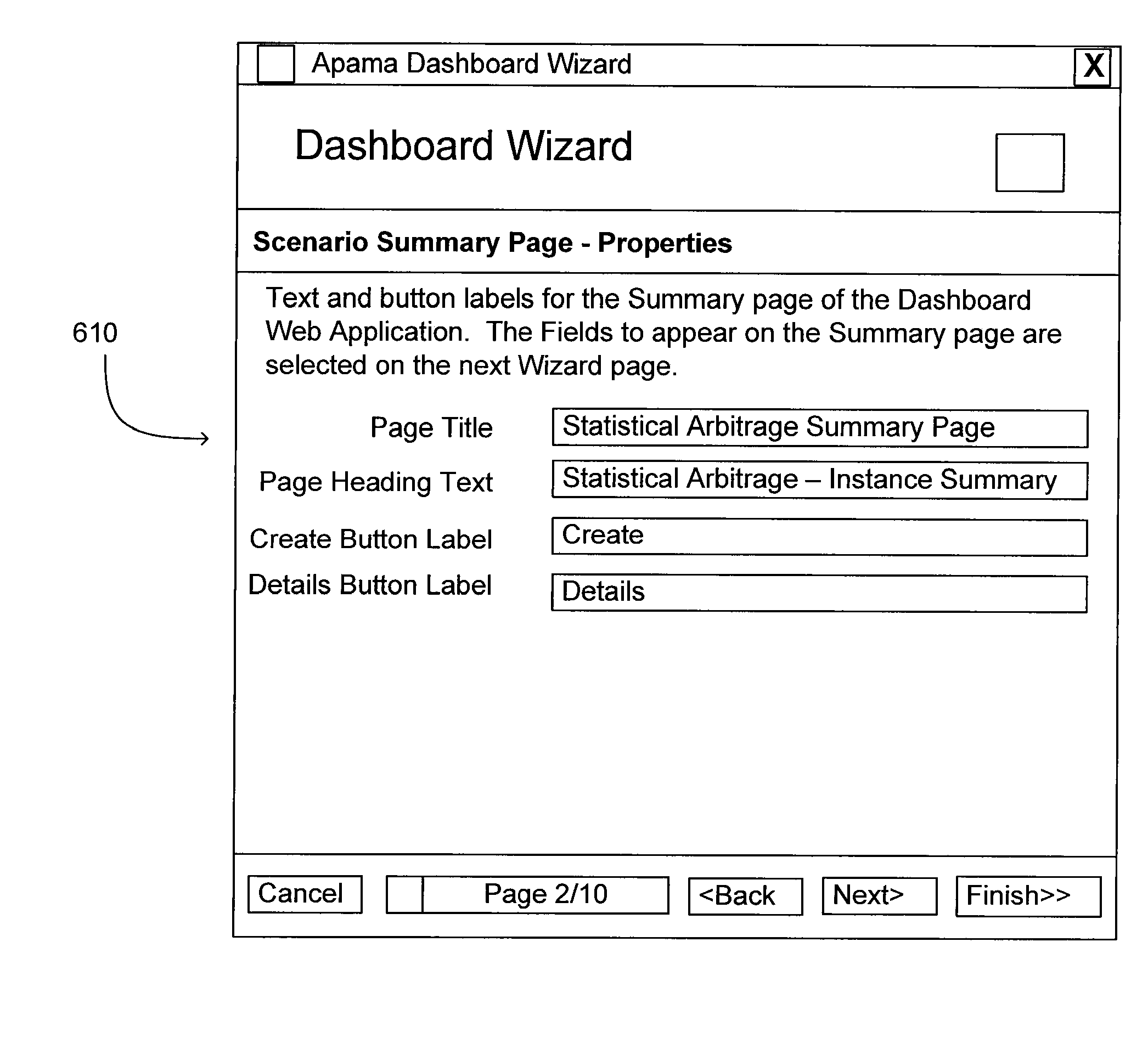
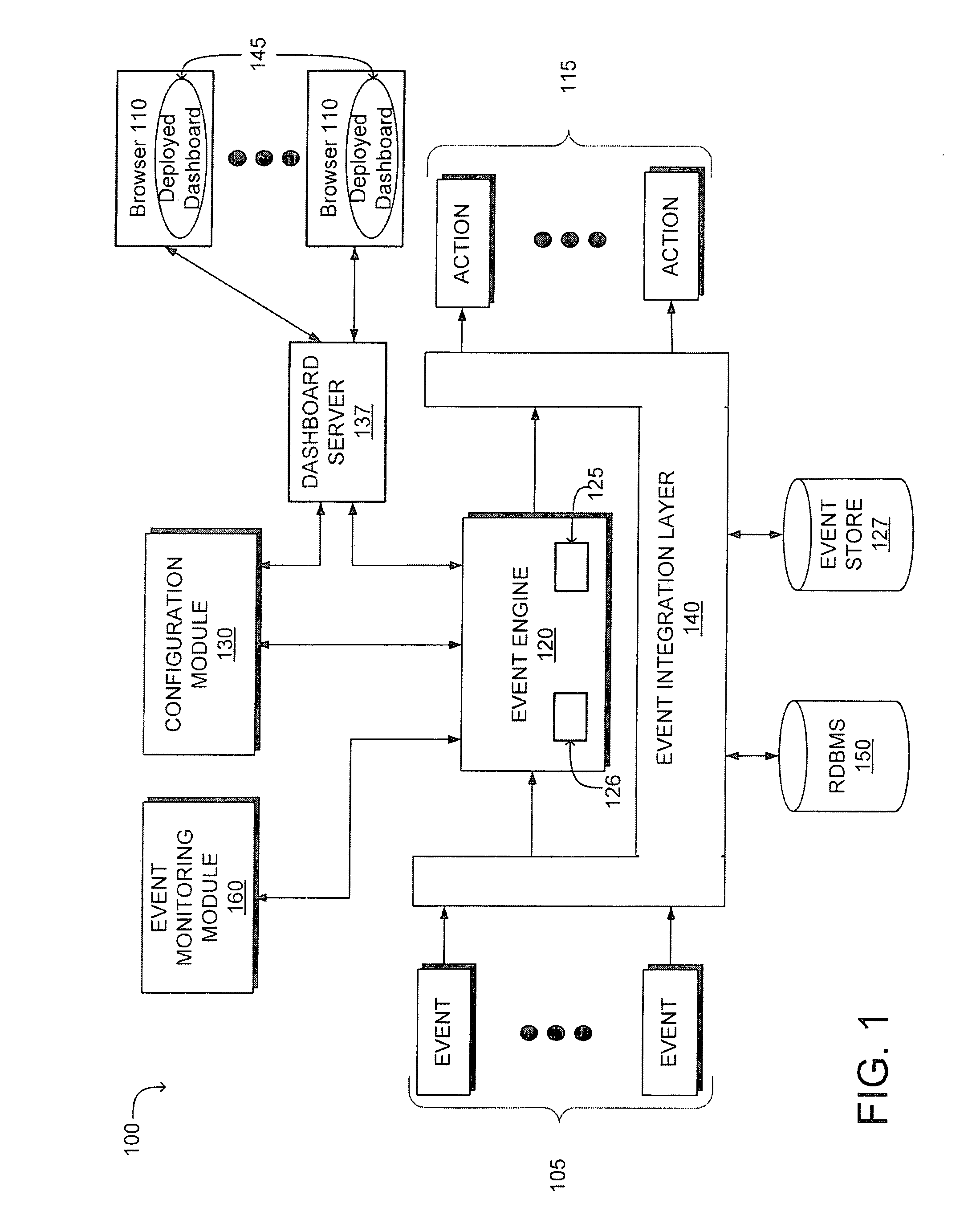
Automated construction and deployment of complex event processing applications and business activity monitoring dashboards
ActiveUS20080209078A1Simplified generationSpecific program execution arrangementsMemory systemsDashboardComplex event processing
A system and method for constructing and deploying a business activity monitoring (BAM) dashboard associated with an event-based process are disclosed. A configuration module receives an event-based process identifier for an event-based process and data, such as inputs or outputs, for the event-based process. A generation module then generates a dashboard description that includes the identifier and an associated dashboard template having one or more dashboard components. This dashboard description is used by a dashboard server to automatically generate a BAM dashboard for monitoring the event-based process by using the association between the dashboard template and the event-based process to display data associated with the event-based process using one or more dashboard components.
Owner:SOFTWARE AG
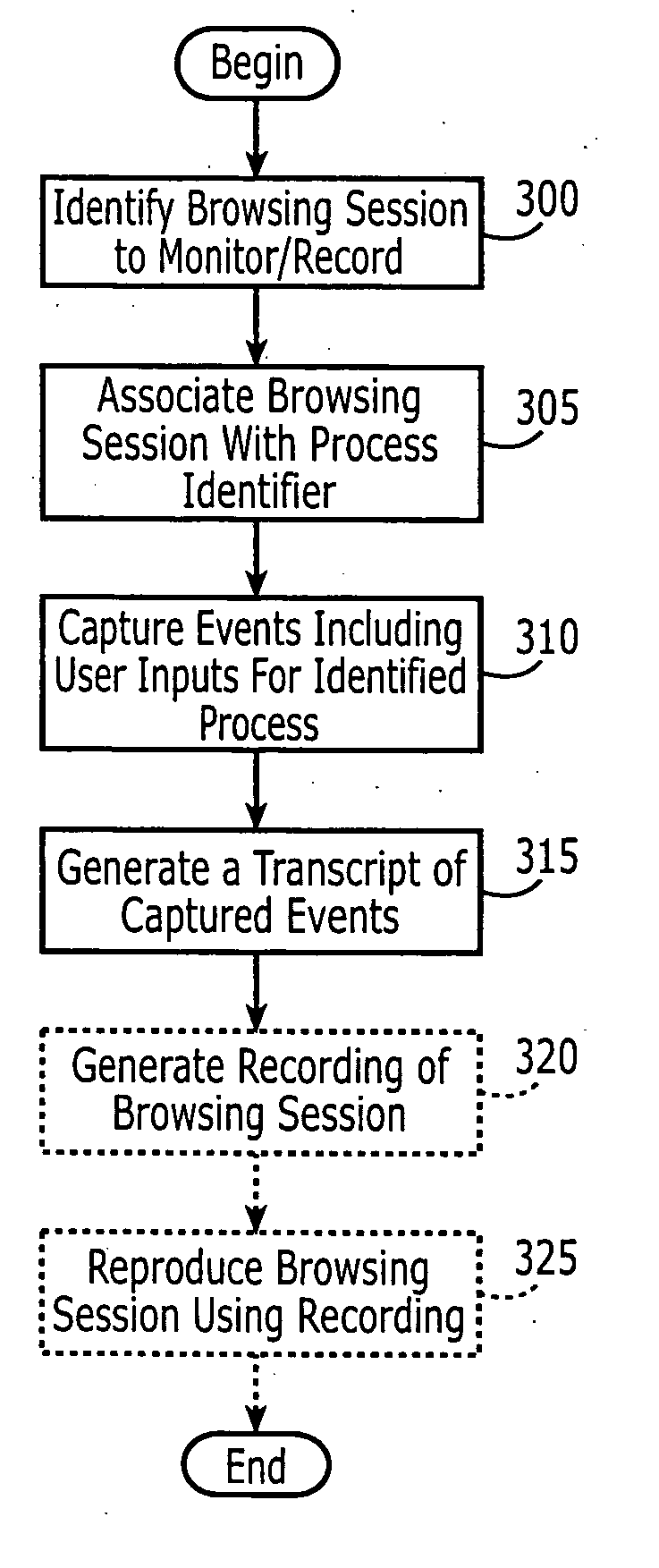
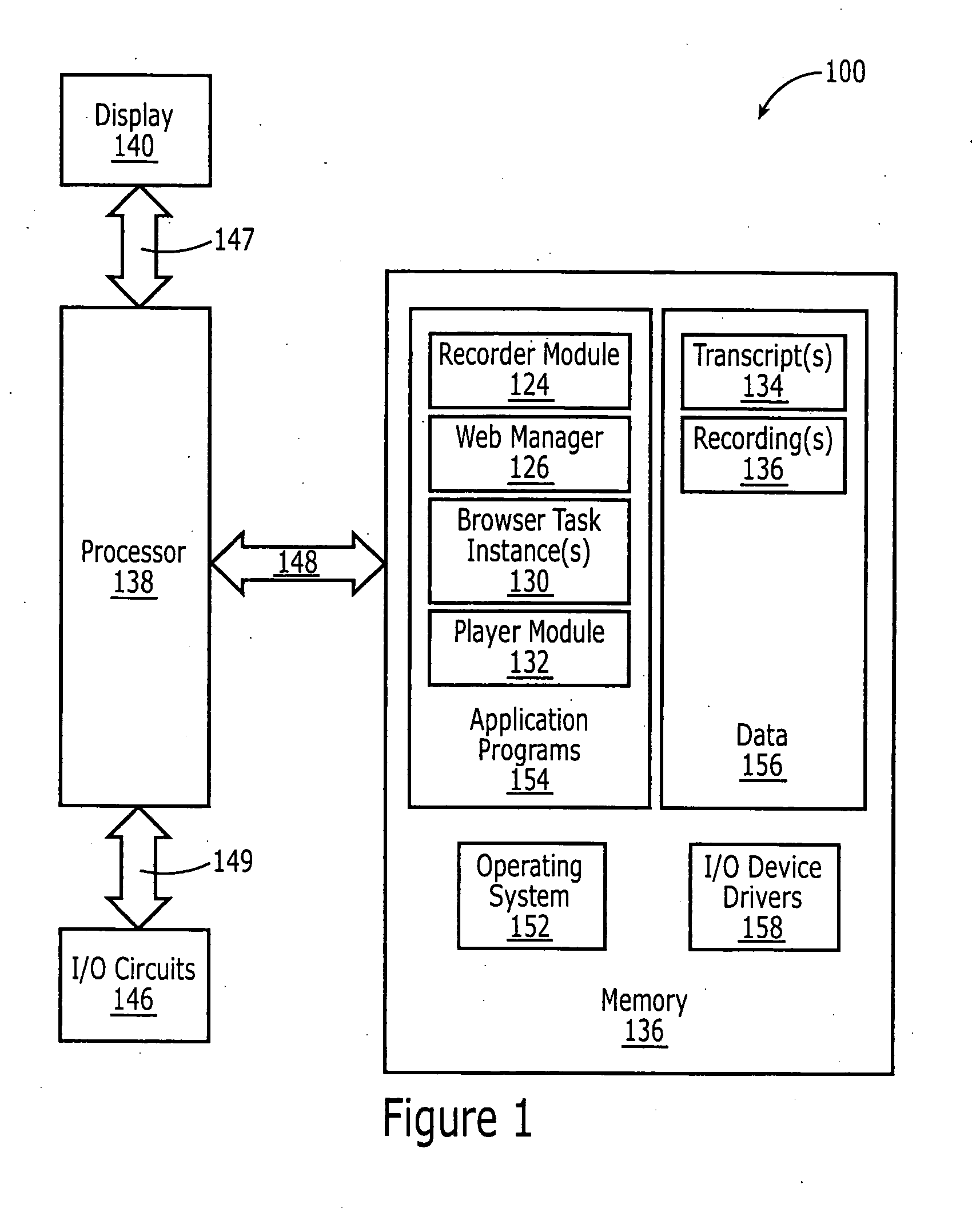
Methods, systems and computer program products for monitoring a browsing session
InactiveUS20070050844A1Error detection/correctionMultiple digital computer combinationsOperational systemUser input
Methods, systems and computer program products for monitoring a browsing session executing on a computer system having an operating system are provided. A browsing session to be monitored is identified. The browsing session is associated with a process identifier of the operating system. Events associated with the identified browsing session are captured, including capturing user input received through tasks executing on the operating system having the associated process identifier. At least one of the tasks is not a browser task instance. A transcript of the captured events is generated.
Owner:NETIQ
Method and system for authenticating application software of Android platform on mobile internet
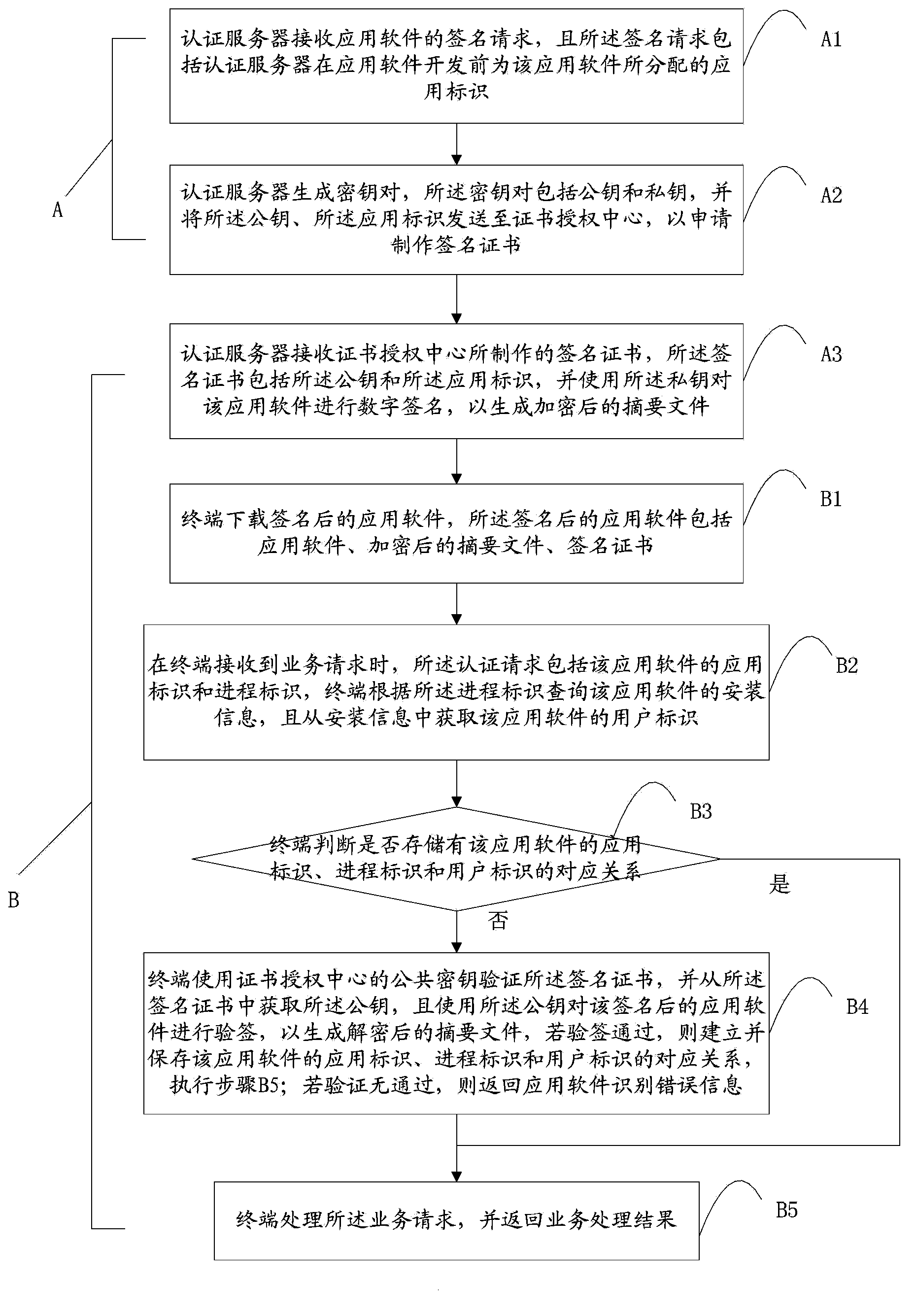
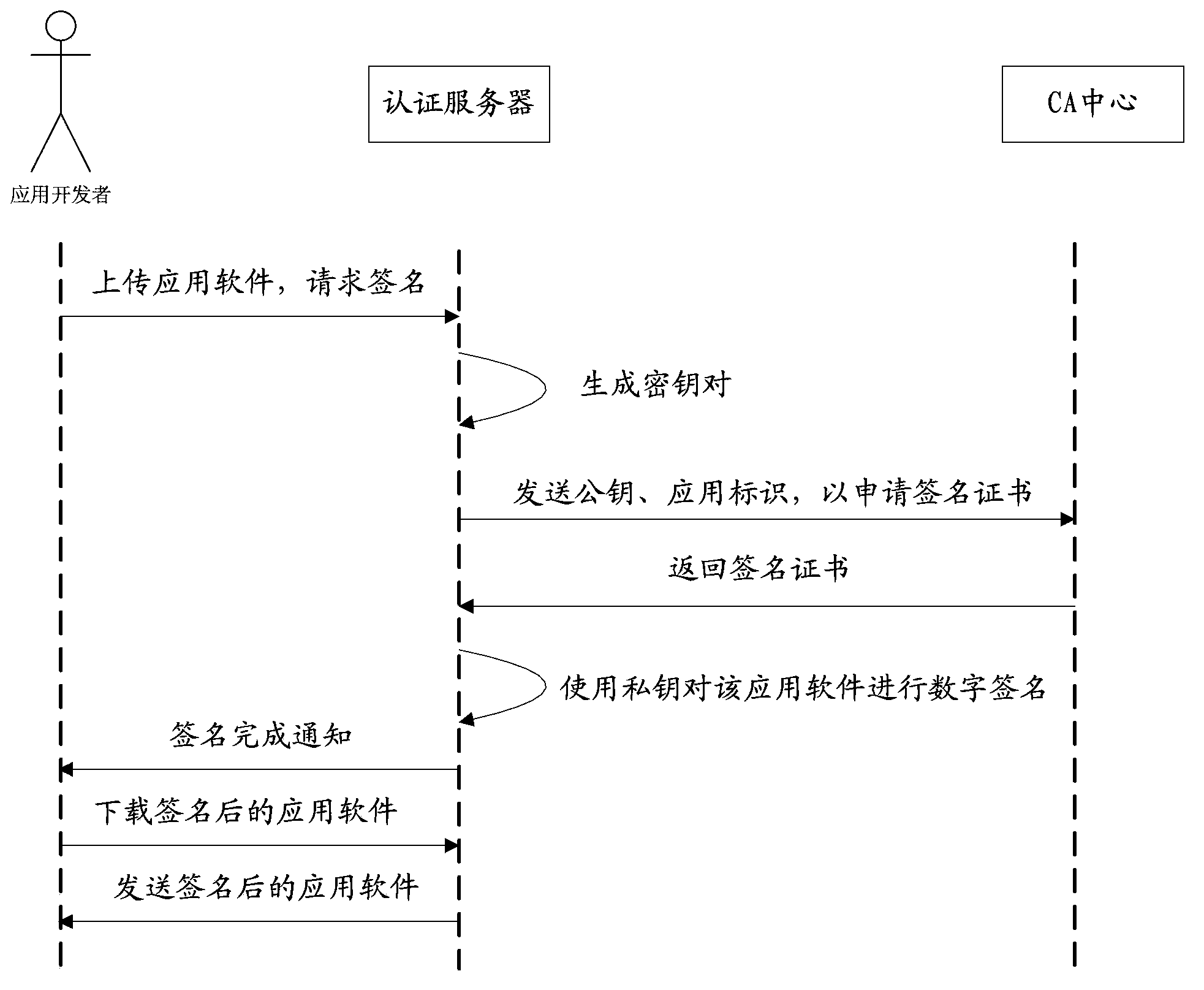
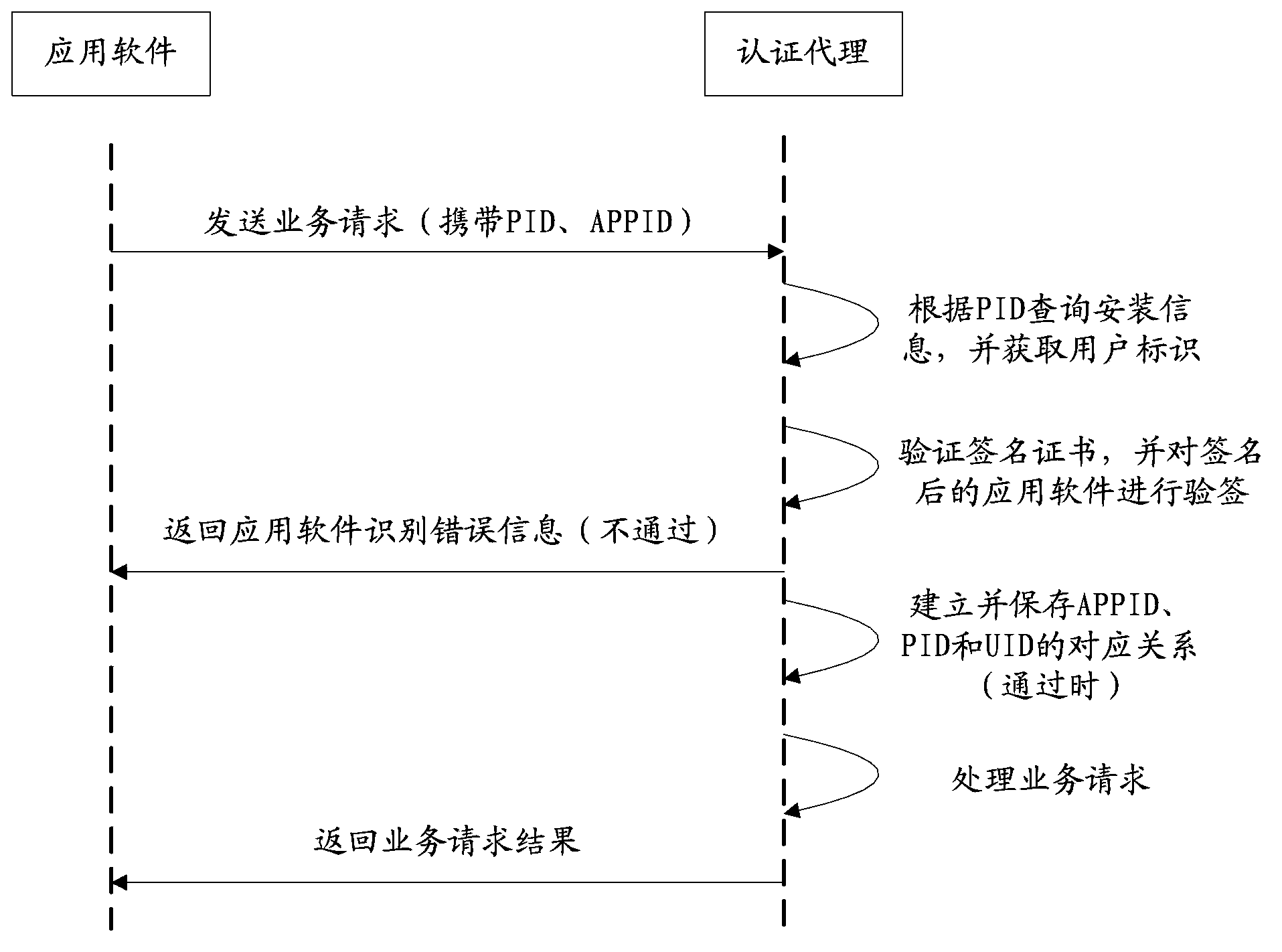
ActiveCN103685138AGuarantee the authenticity of the sourceIntegrity guaranteedPublic key for secure communicationUser identity/authority verificationDigital signatureAuthentication server
The invention discloses a method and a system for authenticating application software of an Android platform on the mobile internet. The authenticating method comprises receiving by an authentication server a signature request of the application software, generating a key pair and sending a public key and an application identifier to a certificate authority center, receiving a signature certificate, signing a digital signature on the application software by using a private key, downloading by a terminal the signed application software, inquiring the installation information of the application software according to a process identifier, acquiring a user identifier from the installation information, judging whether a corresponding relation of the application identifier, the process identifier and the user identifier of the application software is stored, if not, then verifying the signature certificate and using the public key to check, establishing and storing the corresponding relation of the application identifier, the process identifier and the user identifier of the application software when the checking is successful, processing the business request and returning the business processing result. When the technical scheme of the invention is implemented, the authenticity, the integrality and the anti-counterfeit property of the source of the application software are guaranteed.
Owner:卓望数码技术(深圳)有限公司
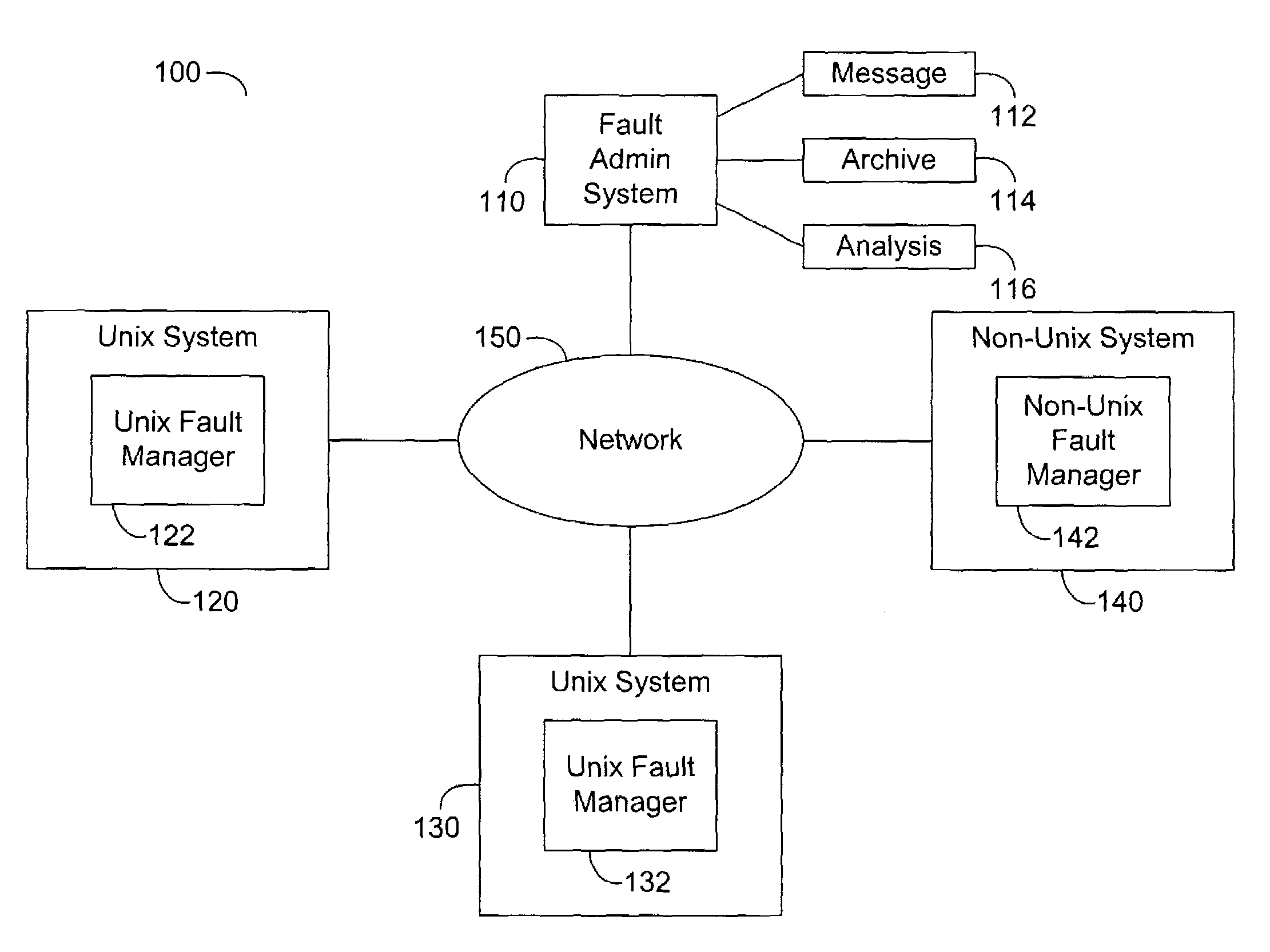
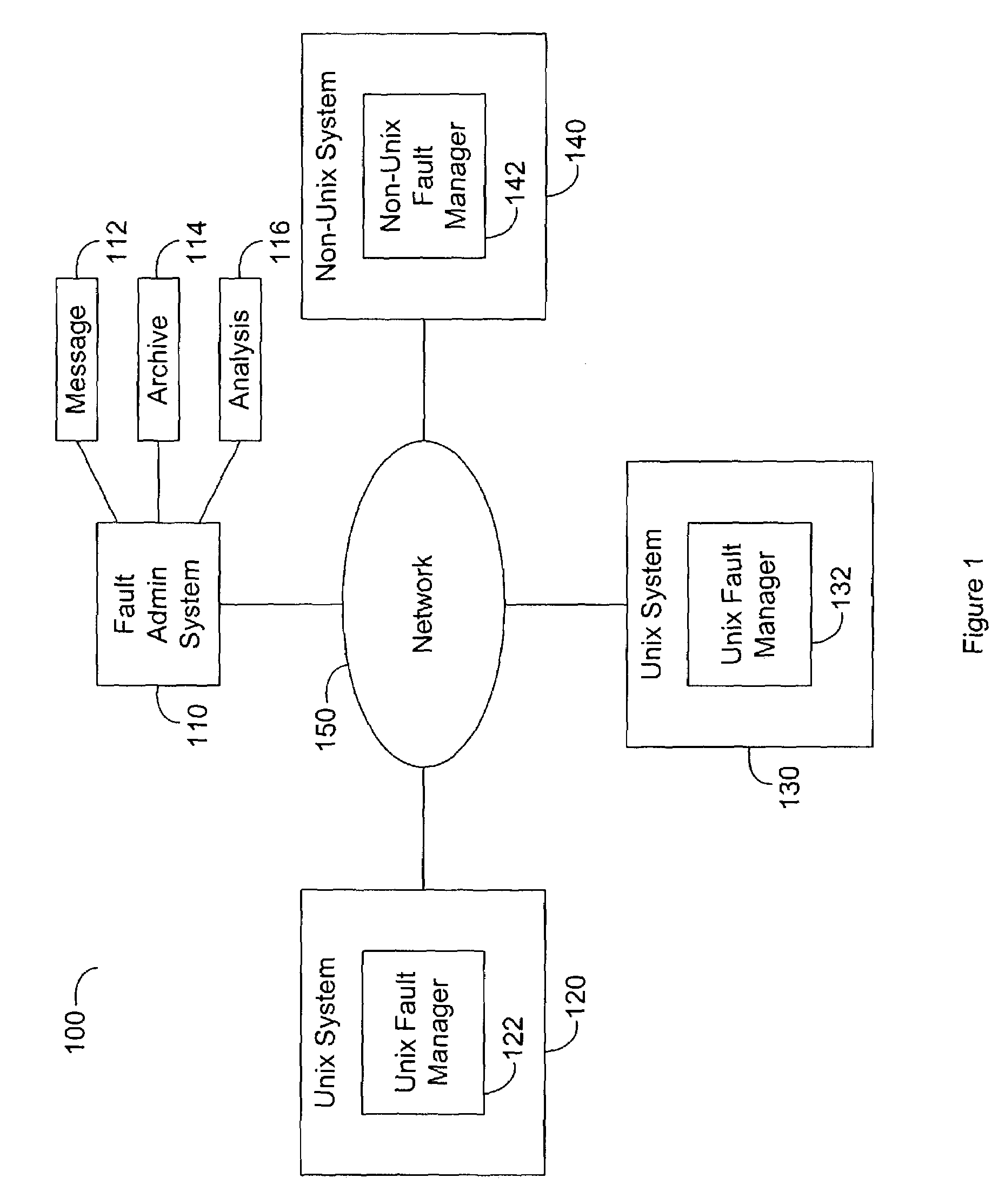
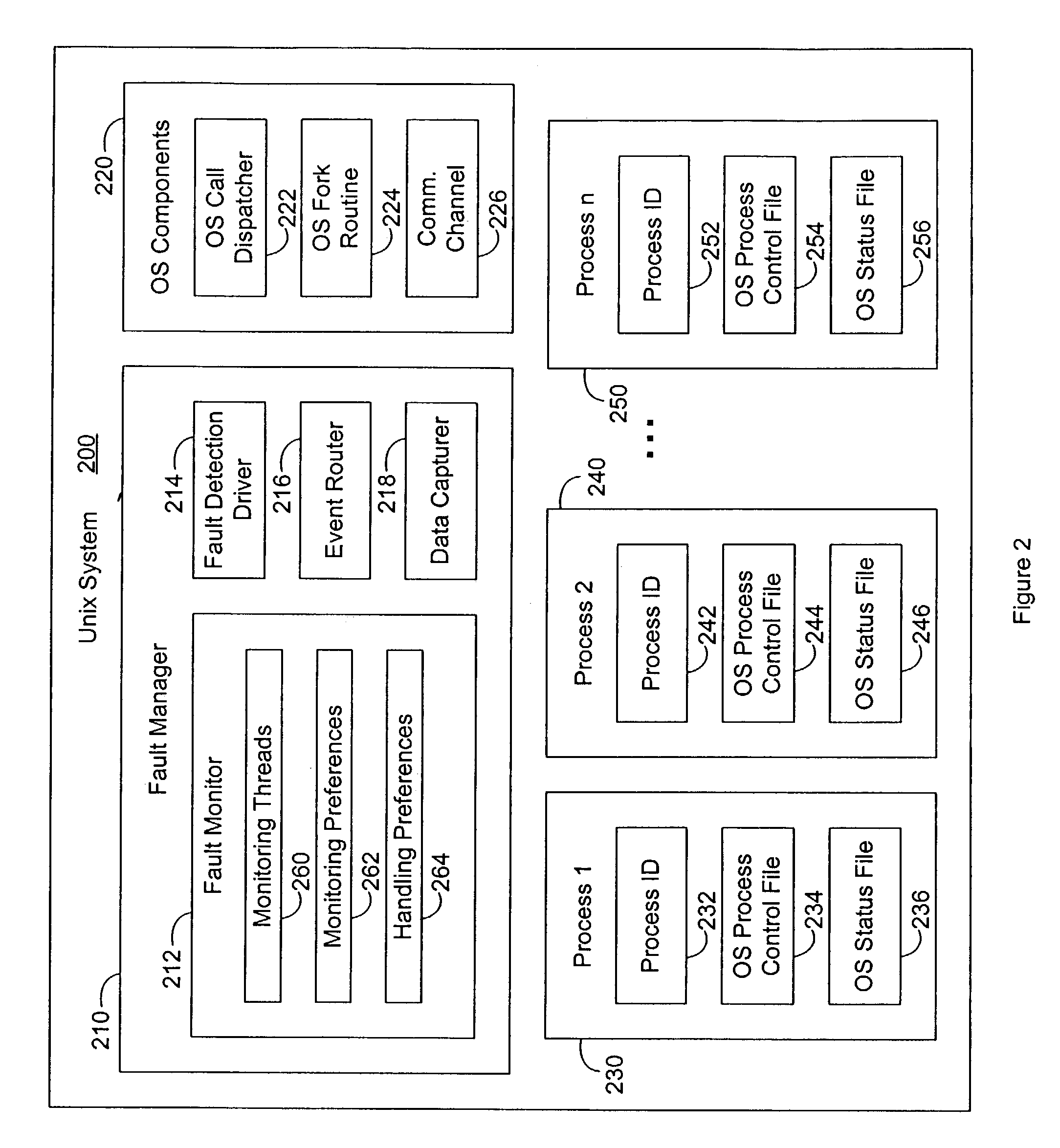
System and method of fault detection in a Unix environment
Systems and methods of fault detection in a Unix environment. A fault monitor uses process identifiers to access the process control file and status file maintained by the operating system. The fault monitor evaluates process interruptions indicated by the process control signals and selectively communicates information regarding detected interruptions through an event router. The fault monitor uses a fault detection driver that redirects fork requests in order to collect new process identifiers. The fault detection driver modifies the process table associated with the call dispatcher to insert itself between the call dispatcher and the fork routine.
Owner:BMC SOFTWARE
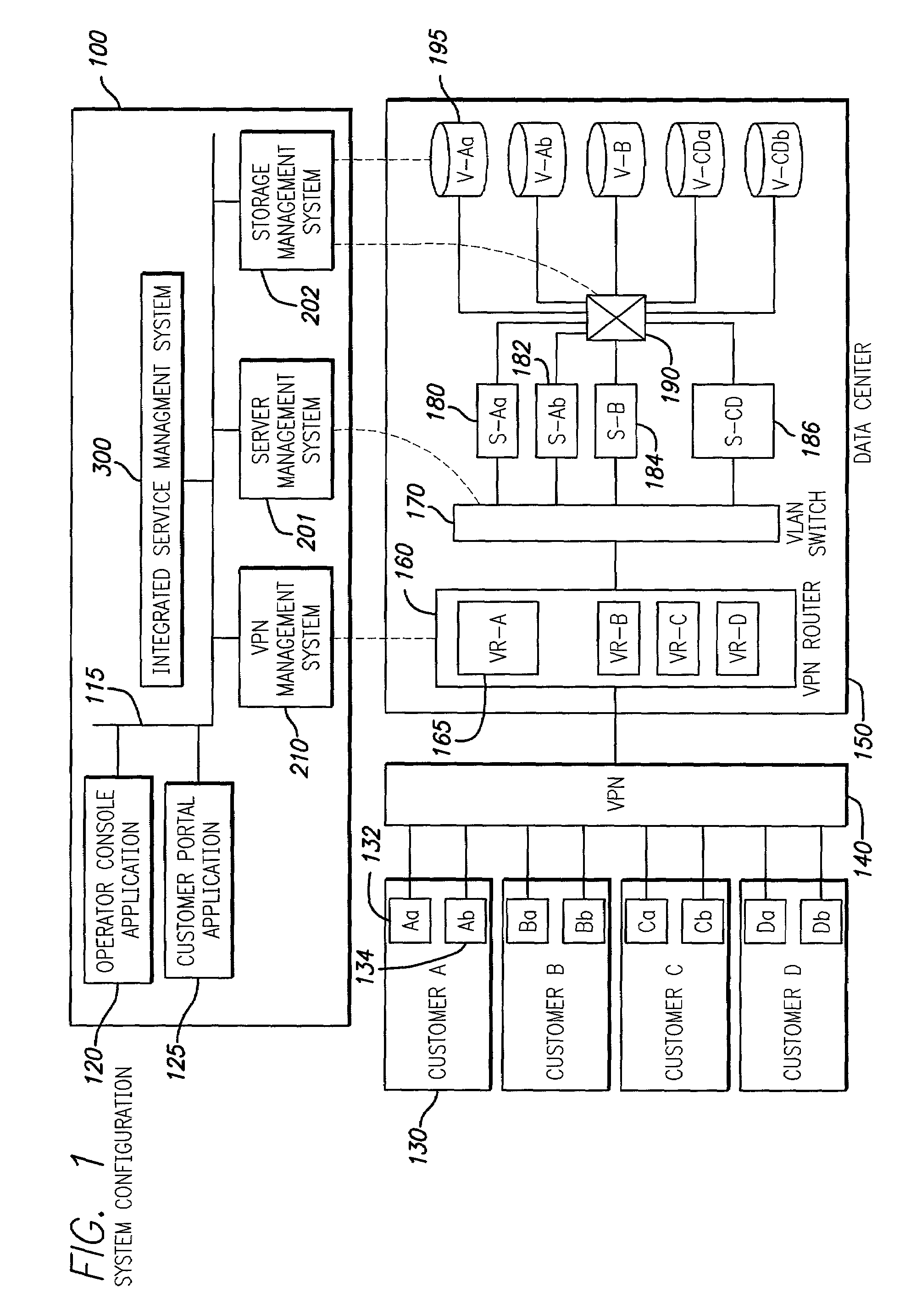
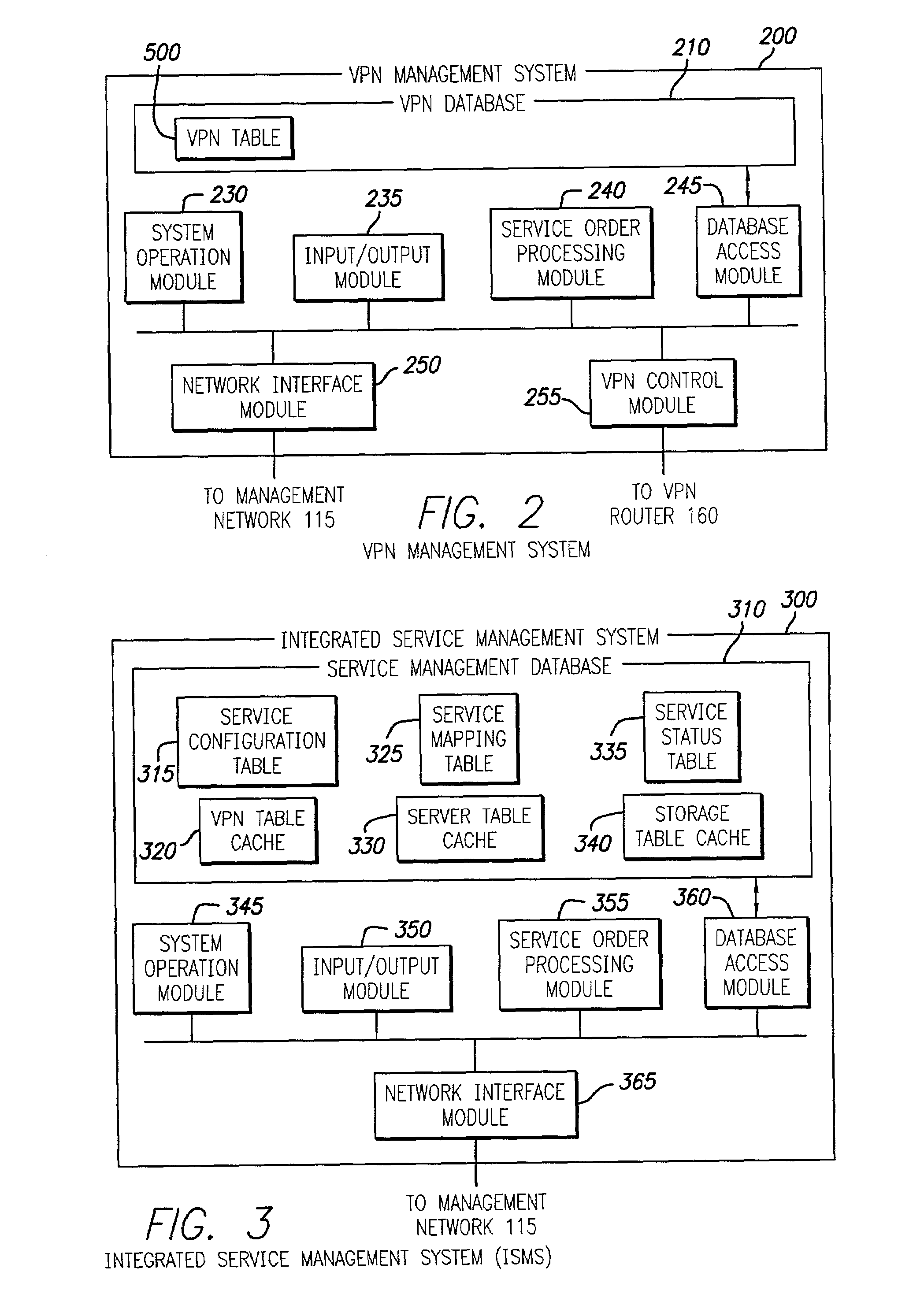
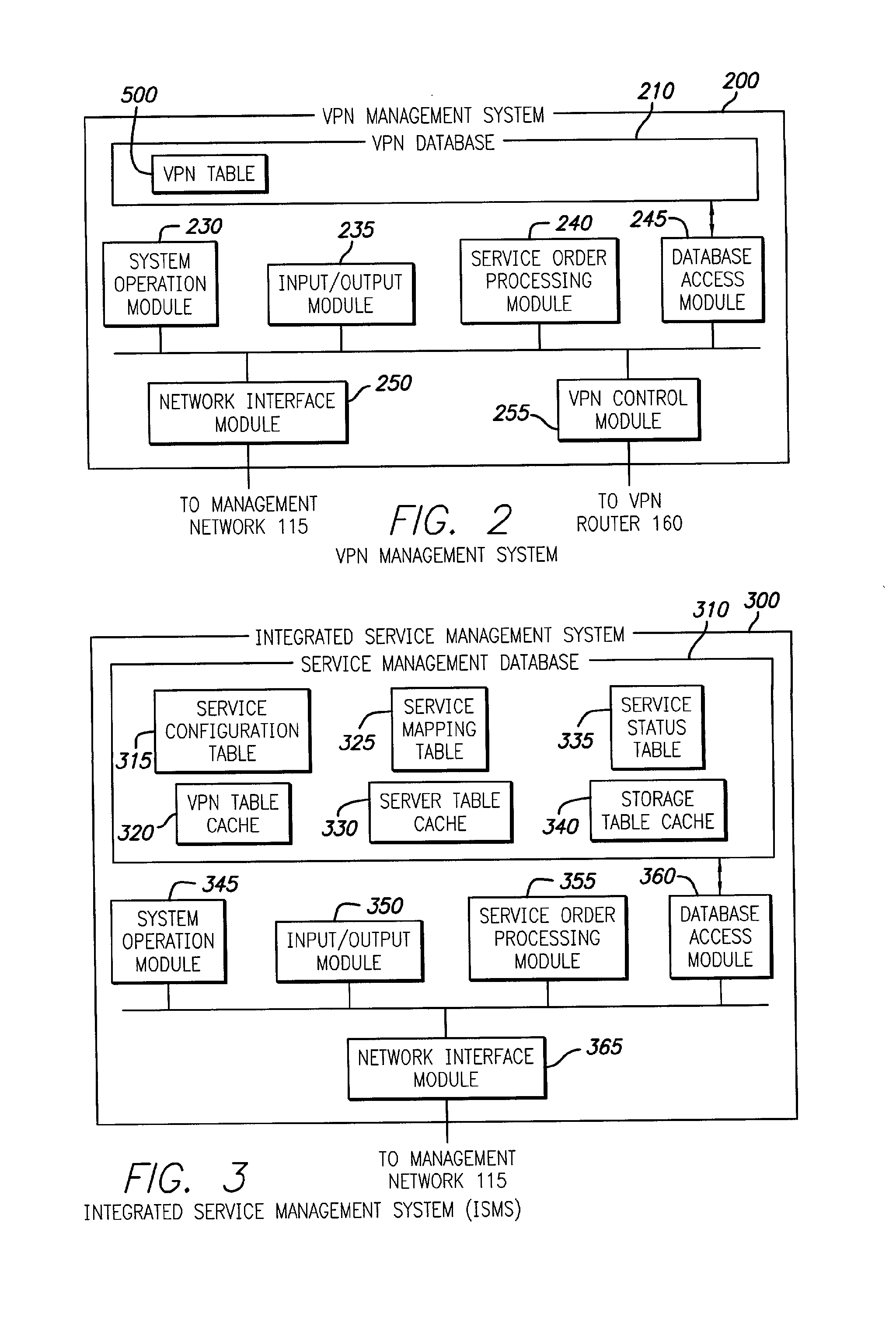
Integrated service management system for remote customer support
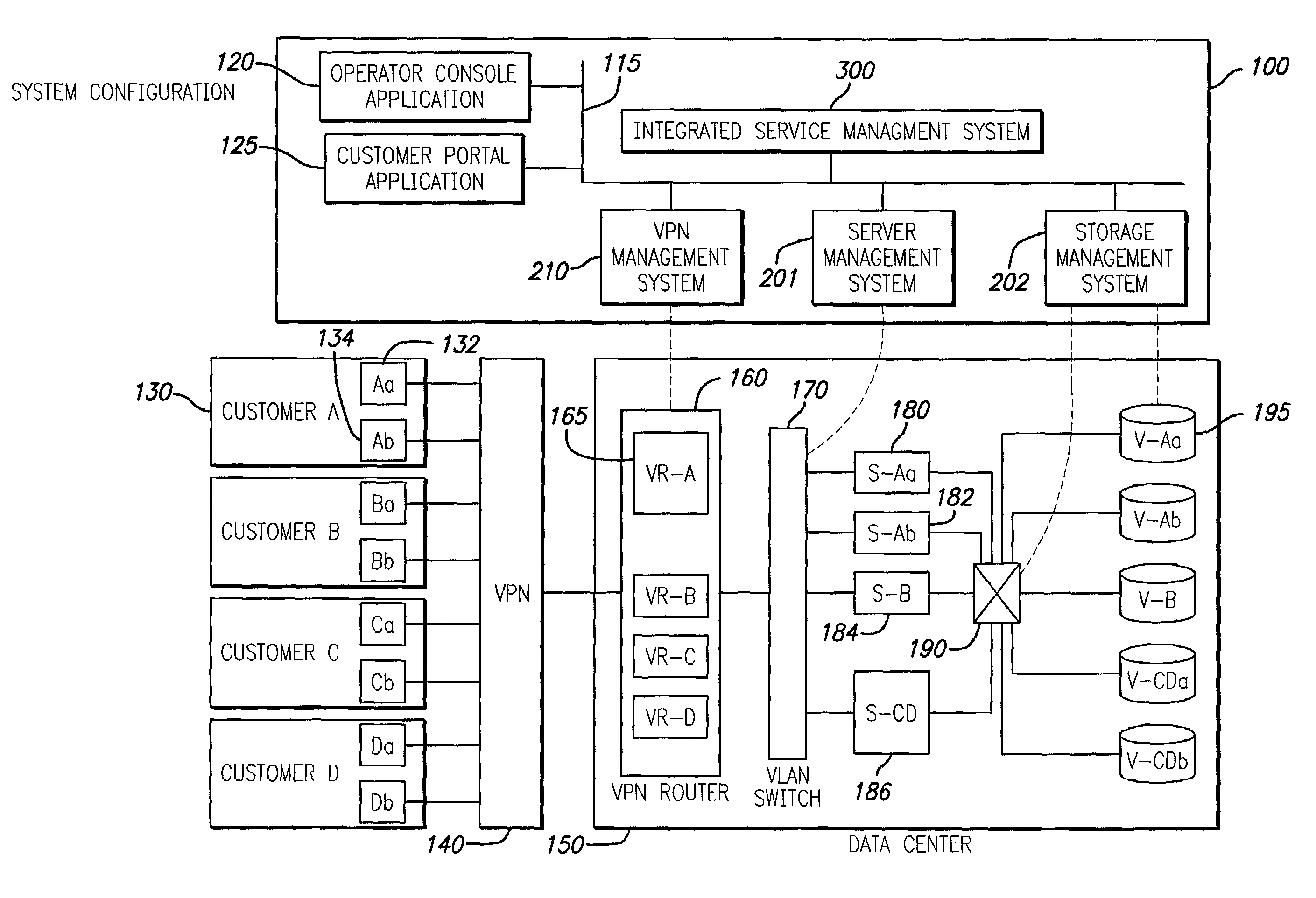
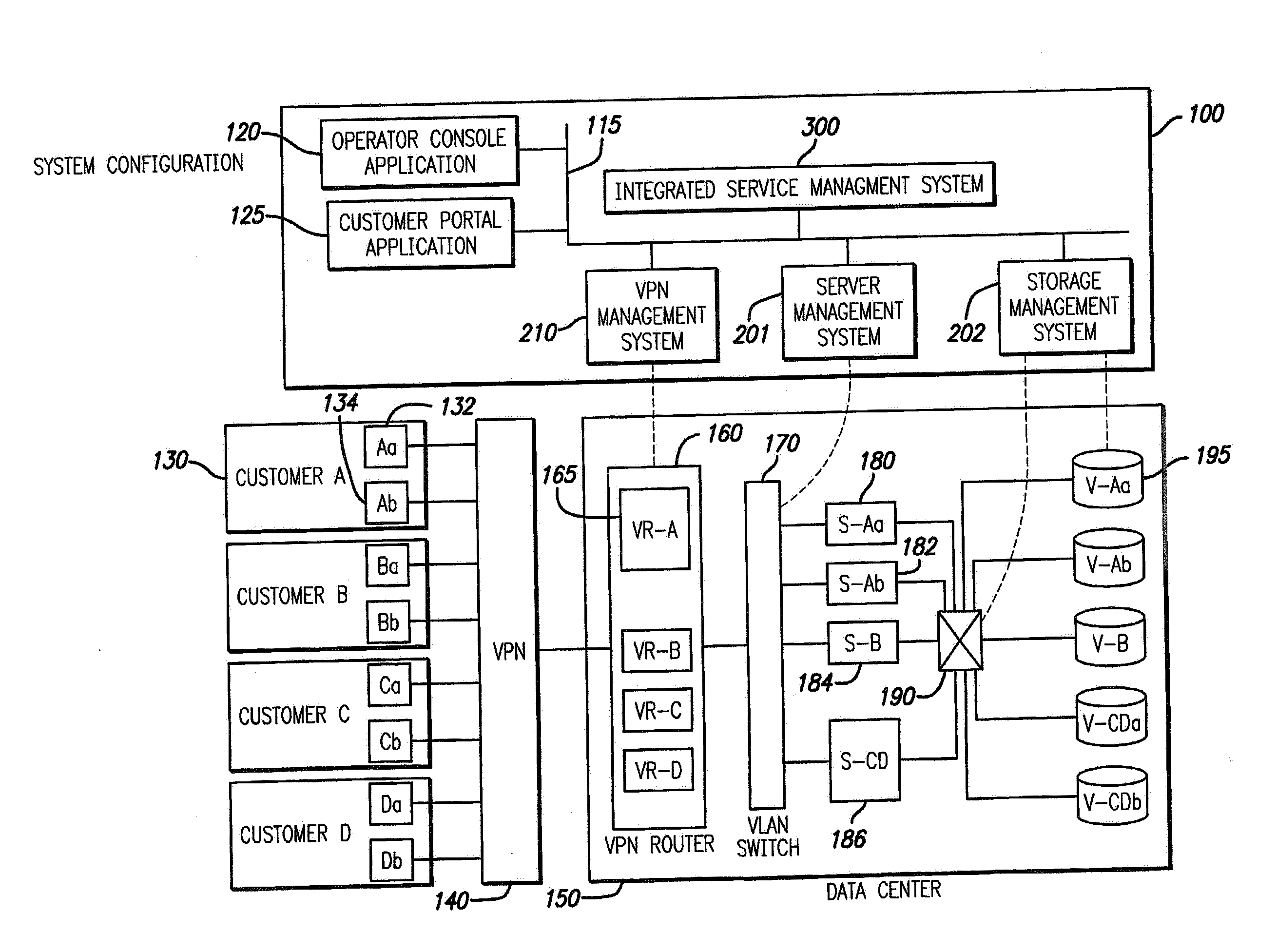
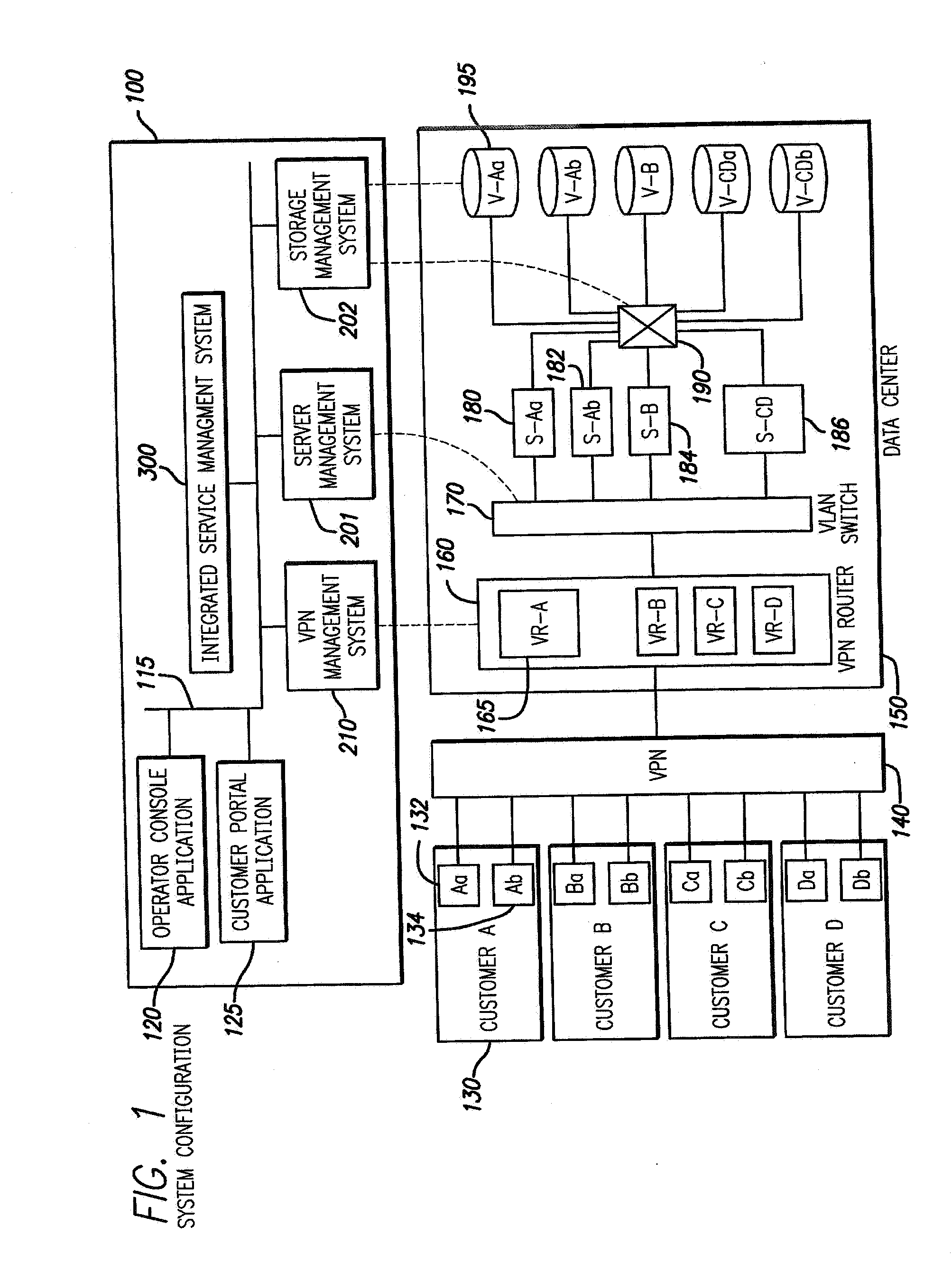
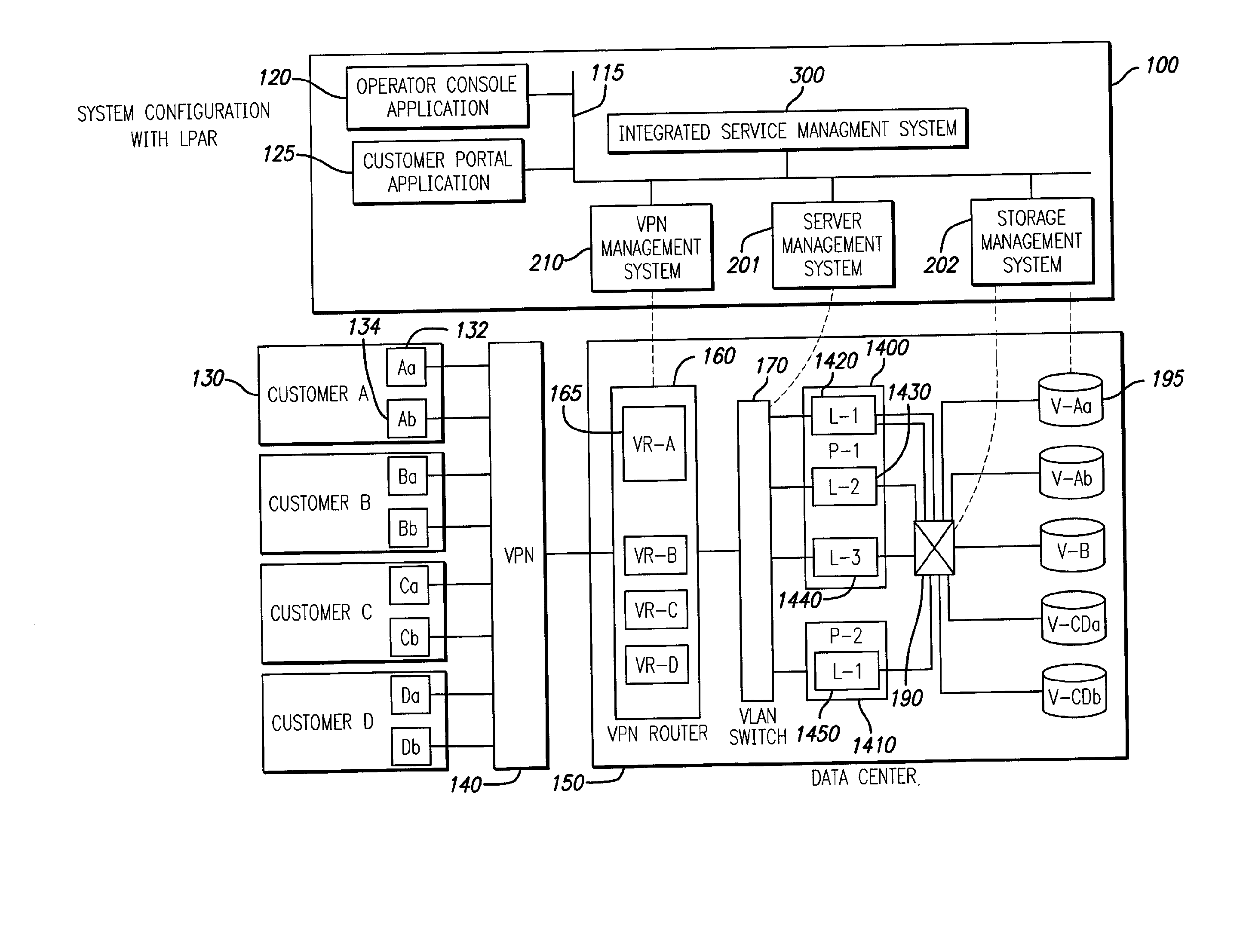
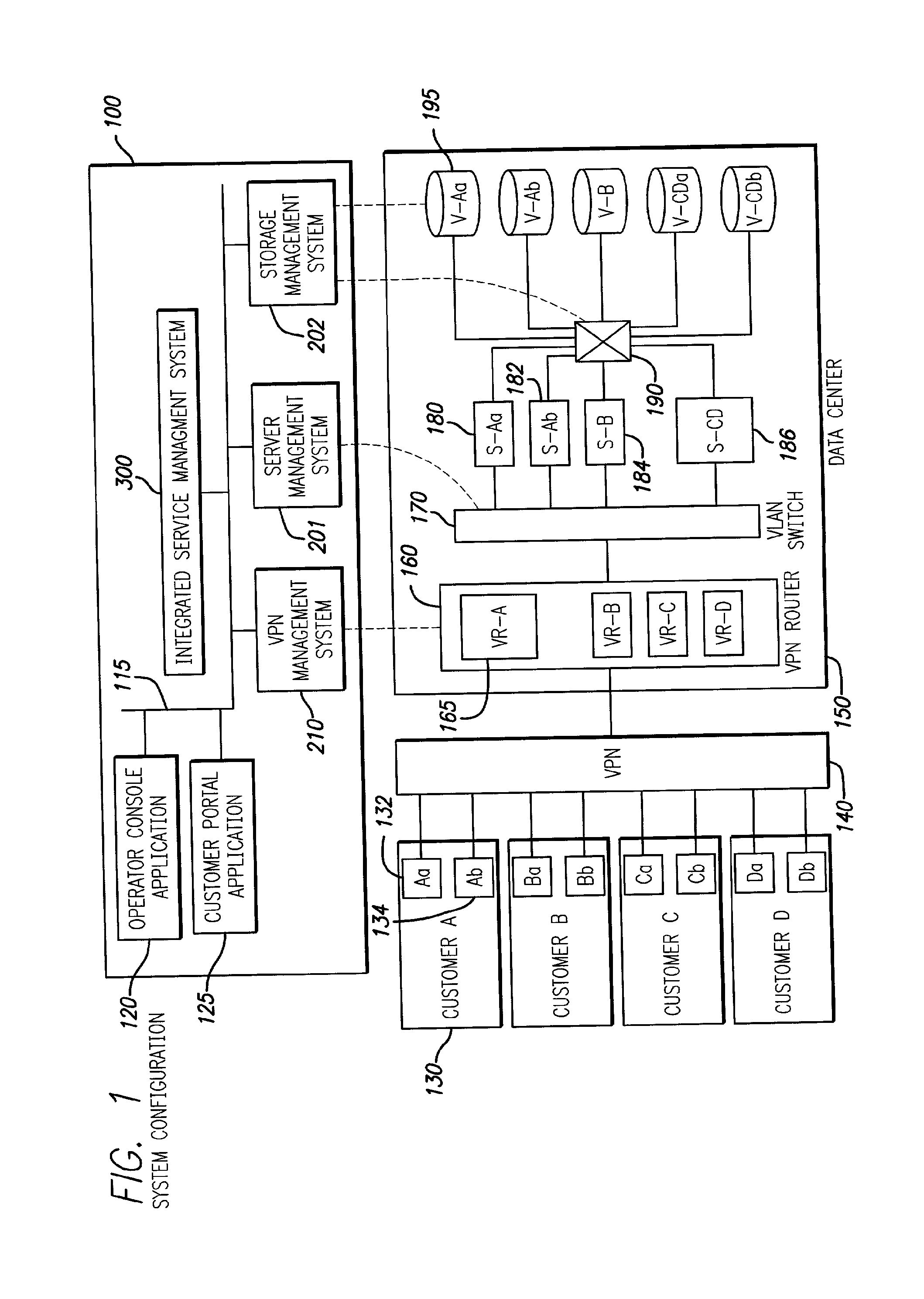
InactiveUS7085827B2Improve efficiencyDigital data processing detailsMultiple digital computer combinationsStorage area networkPrivate network
Techniques for creation, operation, management, and access control of network-based storage services are described. Specific embodiments provide improved efficiency of the service management tasks used for designing, operating and accounting the robust and profitable network services, for example. In representative embodiments, techniques for constructing integrated network and storage services are provided. In a specific embodiment, the service comprises of three major service components: virtual private networks (VPN), applications servers and storage area networks (SAN). Each of these service components has its own customer identification information, such as VPN identifier for VPN services, process identifier for application servers and logical unit number (LUN) for storage devices.
Owner:HITACHI LTD
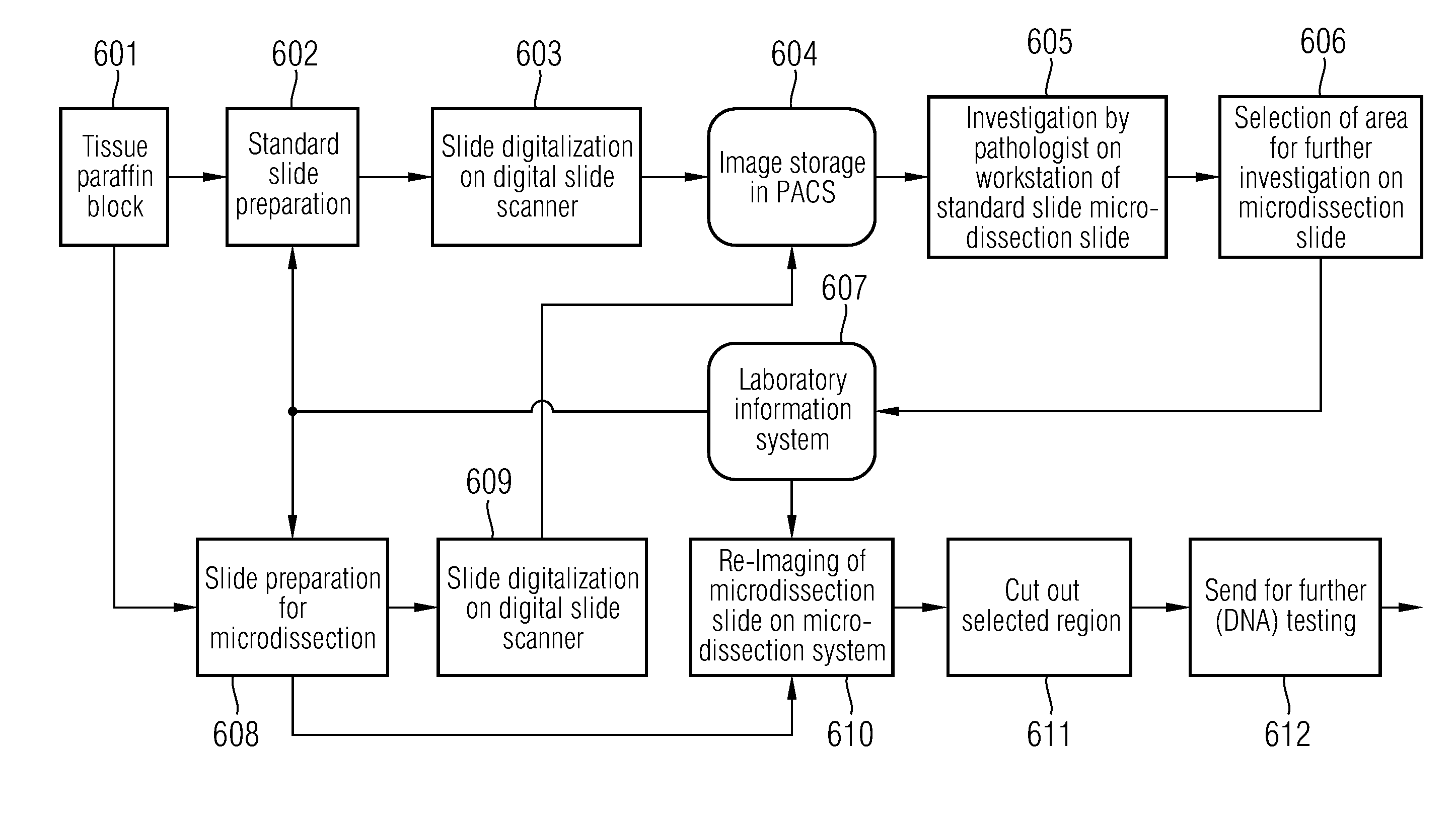
Microdissection method and information processing system
ActiveUS20120045790A1Easy to controlImage enhancementBioreactor/fermenter combinationsInformation processingBiological materials
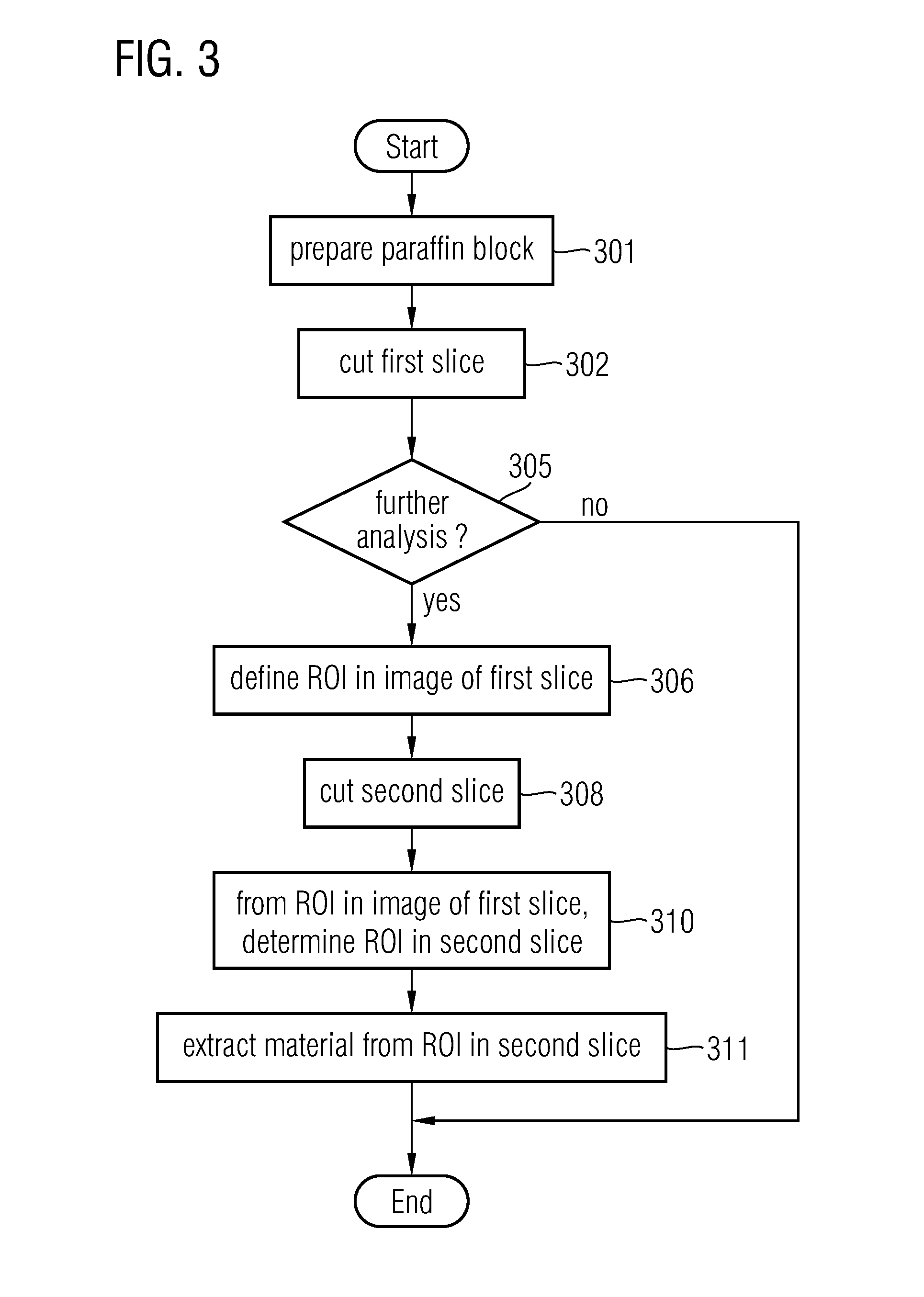
In a first aspect, a method for use in biology, histology, and pathology, comprises: providing a digital first image (44) of a first slice (12) of an object (10) comprising biological material; generating a digital second image (46) of a second slice (14) of the object; determining a region of interest (50) in the second image on the basis of a region of interest (48) in the first image; determining a region of interest in the second slice on the basis of the region of interest (50) in the second image; and extracting material from the region of interest in the second slice. In another aspect, an information processing system, for use in biology, histology and pathology, comprises: a predefined set of process identifiers (64); a set of data records (68, 70, 72) associated with an object (10) comprising biological material, wherein each of the data records comprises: a slice identifier identifying a slice (12; 14) of the object, and a process identifier selected from the set of process identifiers, the process identifier indicating a process to which the slice is intended to be subjected; a user interface (52, 56, 58, 60) for enabling a user to select a data record (68) from the set of data records.
Owner:KONINKLIJKE PHILIPS ELECTRONICS NV
Apparatus and method for displaying process operation
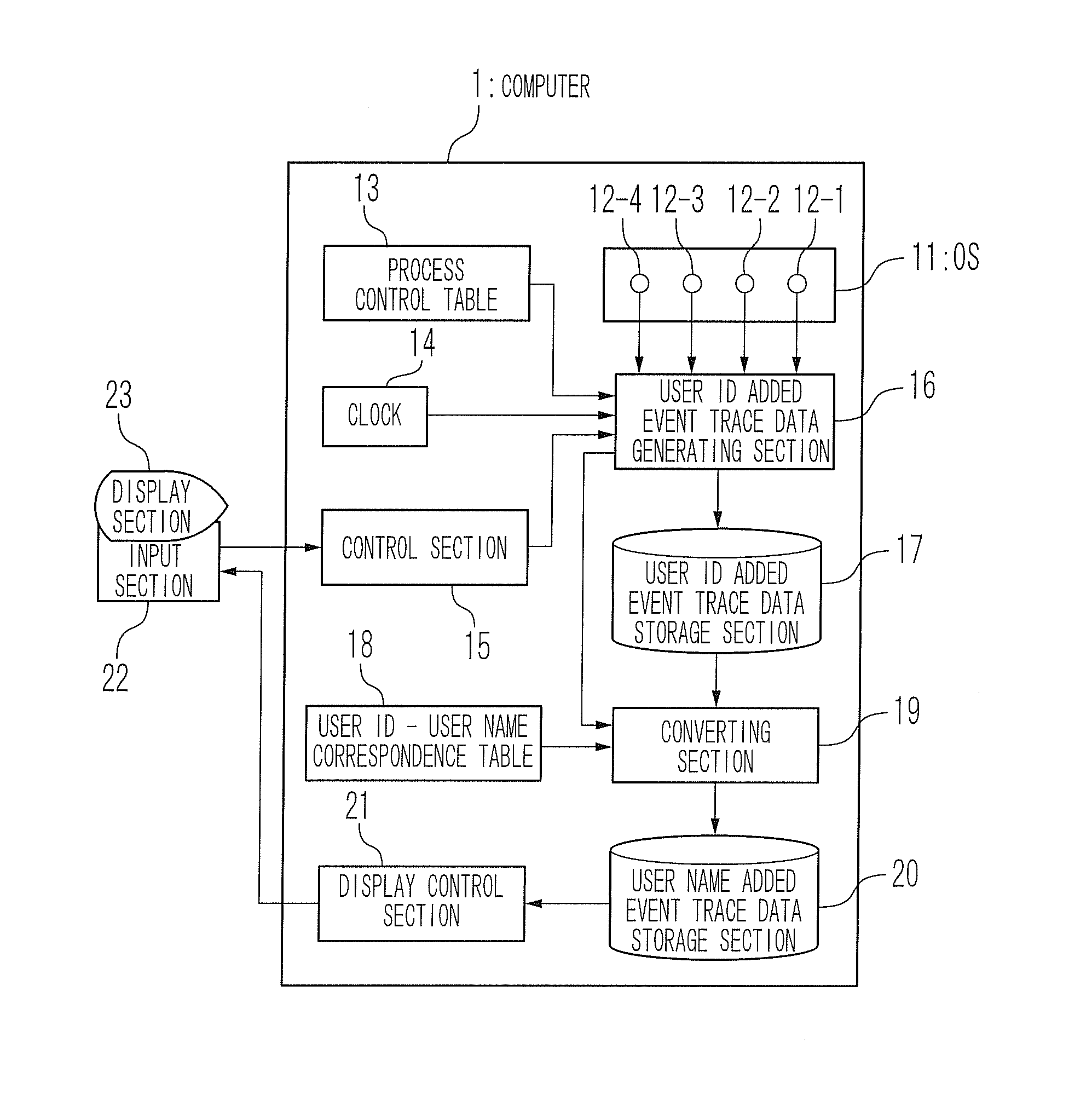
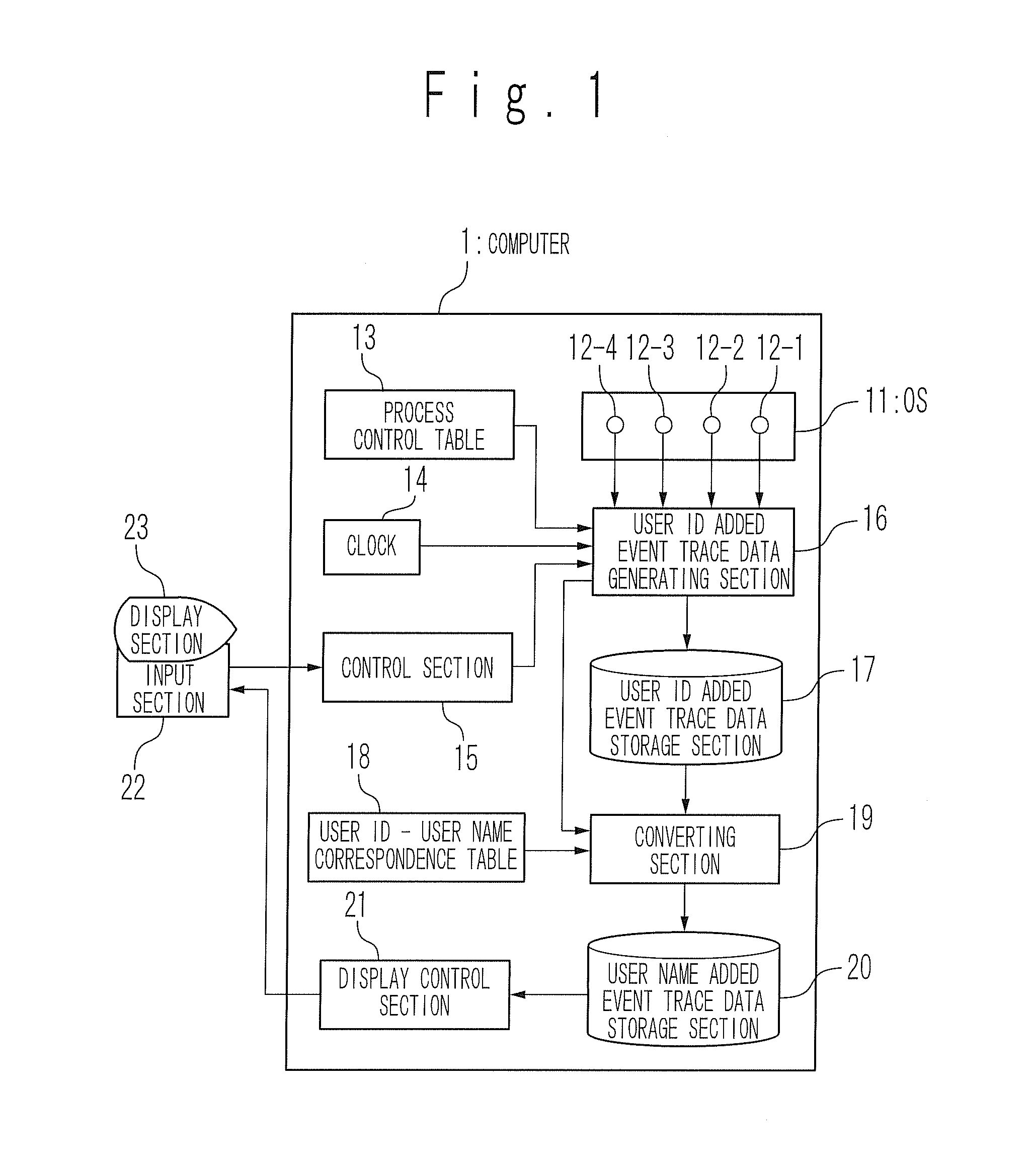
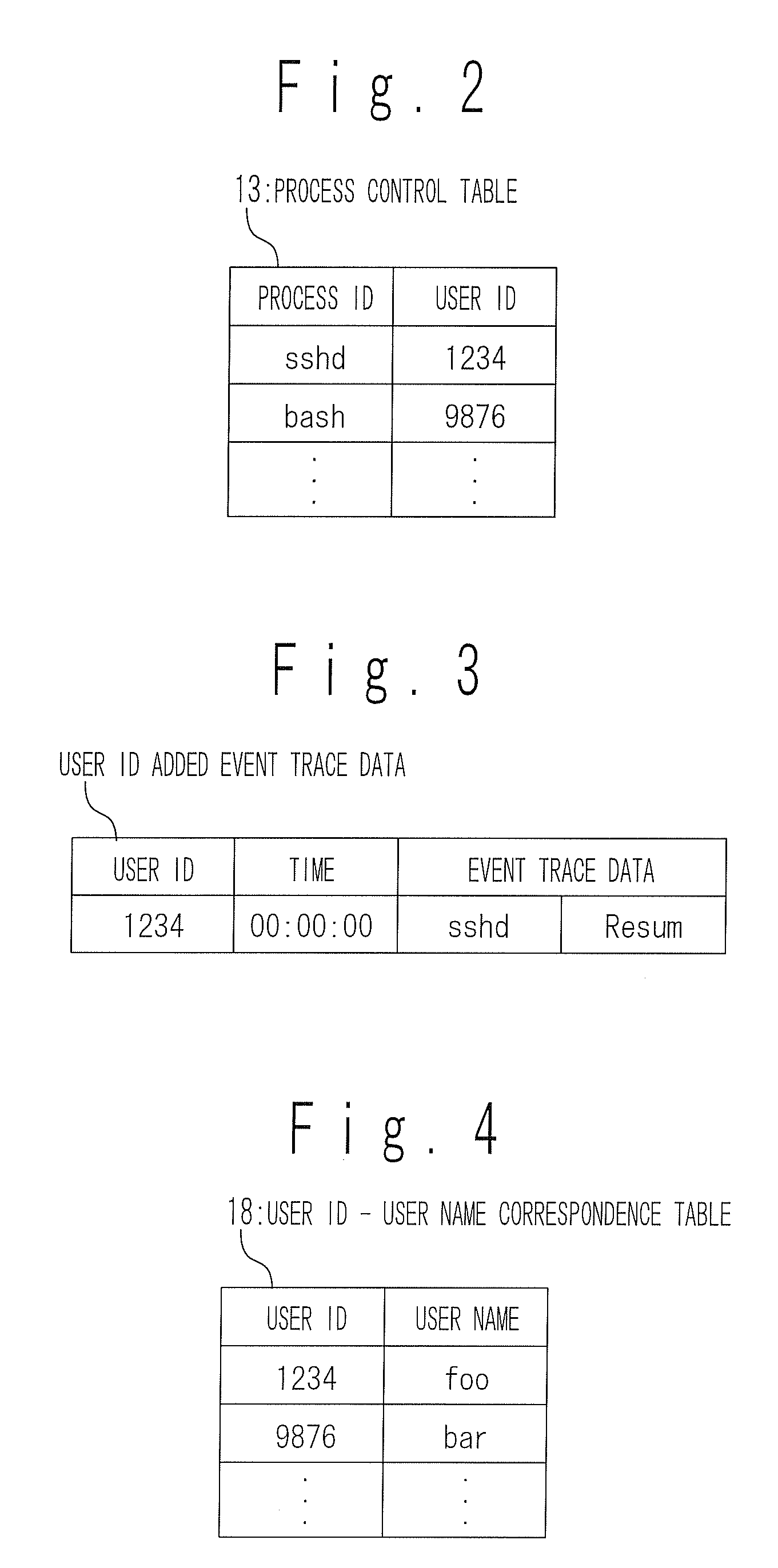
InactiveUS20080209443A1Sure easyError detection/correctionMultiprogramming arrangementsUser identifierEvent tracking
A process operation display apparatus includes a storage section configured to store a process control table in which a set of a process ID of a process and a user ID of a user is written. An event trace data outputting section detects events of about execution start and execution end of an executed process and generates an event trace data based on a process ID of the executed process and the detected events. A user ID added event trace data generating section generates a user ID added event trace data in which a set of the event trace data and the user ID corresponding to the process ID contained in the event trace data is written, by referring to the process control table based on the process ID. A display control section displays a set of the process ID of the executed process and the user ID of the user who instructed the execution of the executed process on a display unit based on the user ID added event trace data.
Owner:NEC CORP
Audio mixing control method and apparatus for Wince vehicle-mounted multimedia
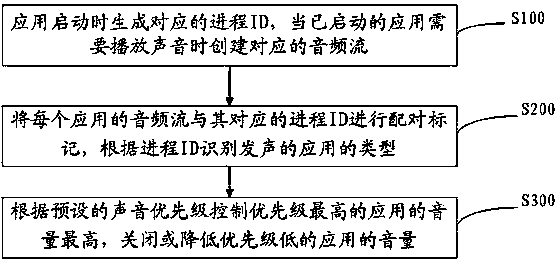
ActiveCN104023305ASolve the problem of inaudibleEasy to useStereophonic systemsComputer scienceLower priority
The invention discloses an audio mixing control method and apparatus for Wince vehicle-mounted multimedia. The audio mixing control method comprises: A, when supplications are started, generating corresponding process IDs, and when the already started applications need to play sound, creating corresponding audio streams; B, pairing the audio stream of each application and the corresponding process IDs for marking, and identifying the types of sounding applications according to the process IDs; and C, according to preset sound priorities, controlling the volume of an application whose priority is the highest to be highest, and closing or reducing the sound of an application whose priority is low. According to the invention, the volume of the application whose priority is the highest can be controlled to be highest according to the sound priorities, and the sound of the application whose priority is low can be reduced or closed, and such an automatic sound adjusting mode reduces the influence of other unnecessary sound, so that the problem can be solved that a user cannot listen clearly due to simultaneous playing of multiple sound at the same volume, manual operation by the user is unnecessary, the use of the user is greatly facilitated, and driving is not affected.
Owner:SHENZHEN APICAL TECH CO LTD
Processing trusted commands in trusted and untrusted environments
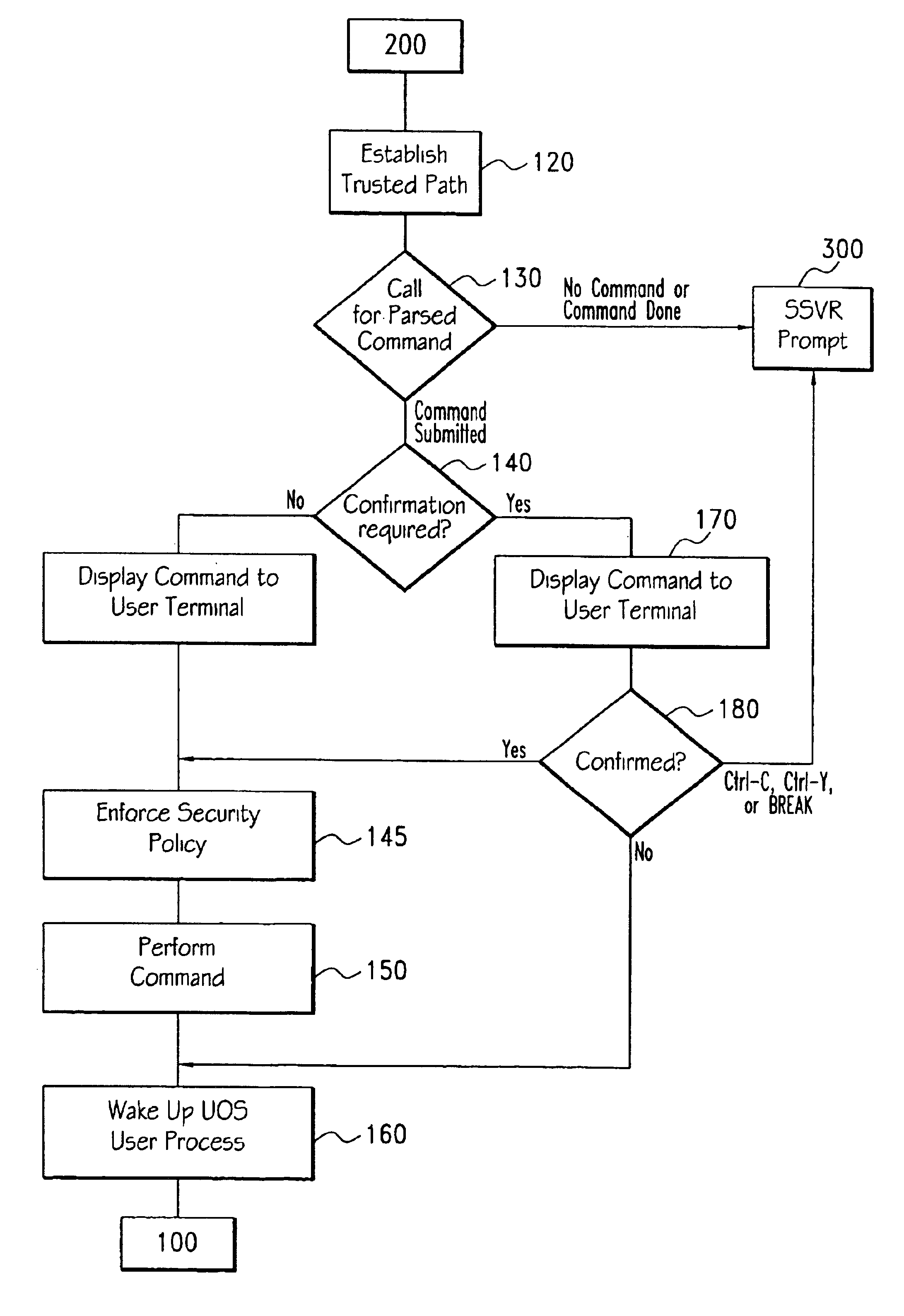
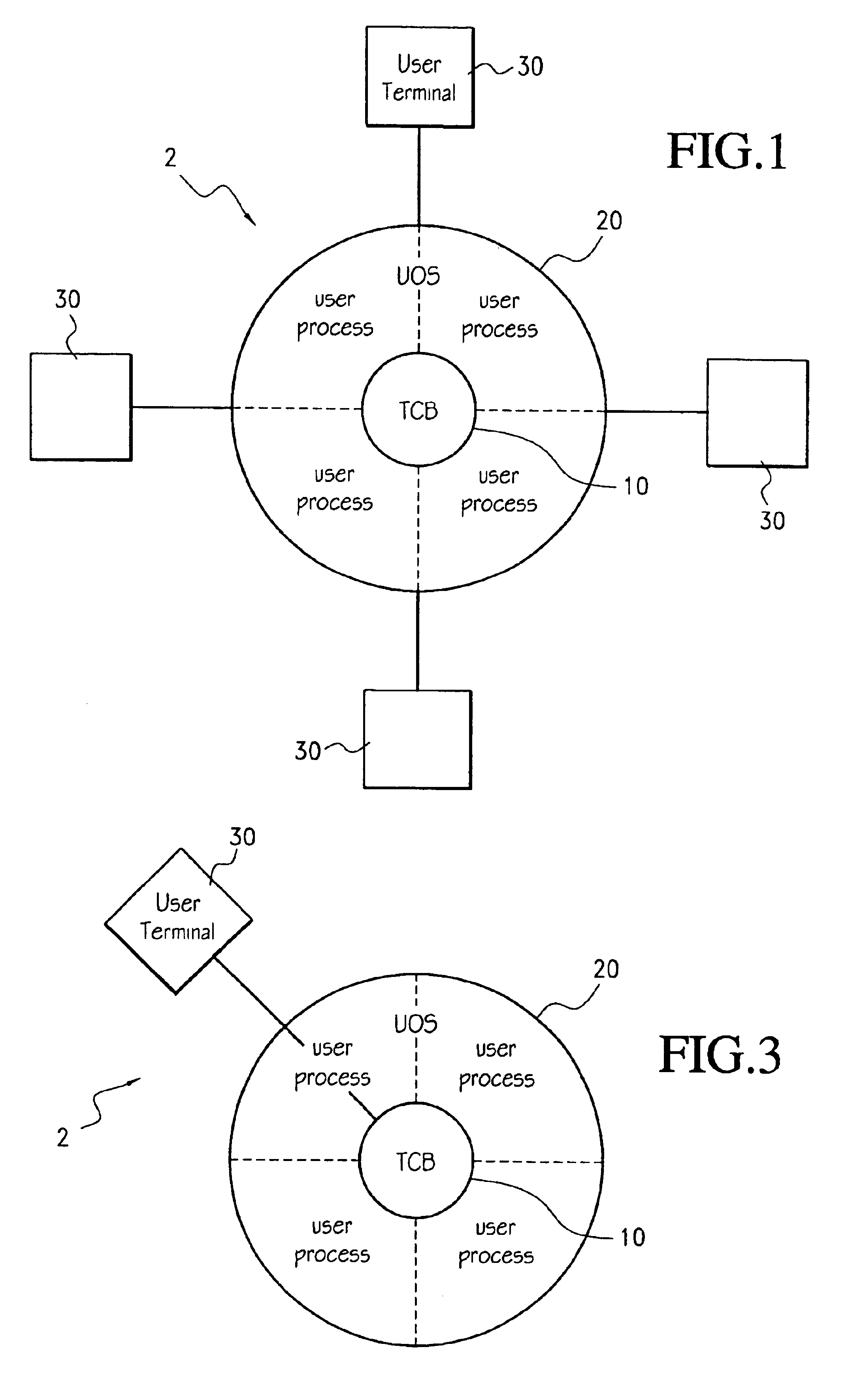
InactiveUS6871283B1Less codeQuantity minimizationDigital data processing detailsUser identity/authority verificationTrusted ComputingTrusted computing base
A method for executing trusted commands, in which a trusted command is first received from a user at a user terminal and parsed by untrusted code; then passed to a trusted computing base for execution. The trusted computing base displays some indication of what is to be done back to the user for confirmation. Confirmation of the commands prevents unauthorized modification of the commands and increases system confidence. A randomly (or pseudo-randomly) generated process identifier is employed to verify the existence of a trusted path.
Owner:HEWLETT PACKARD DEV CO LP
White list creation in behavior monitoring system
ActiveUS8161552B1Memory loss protectionDigital data processing detailsDigital signatureMonitoring system
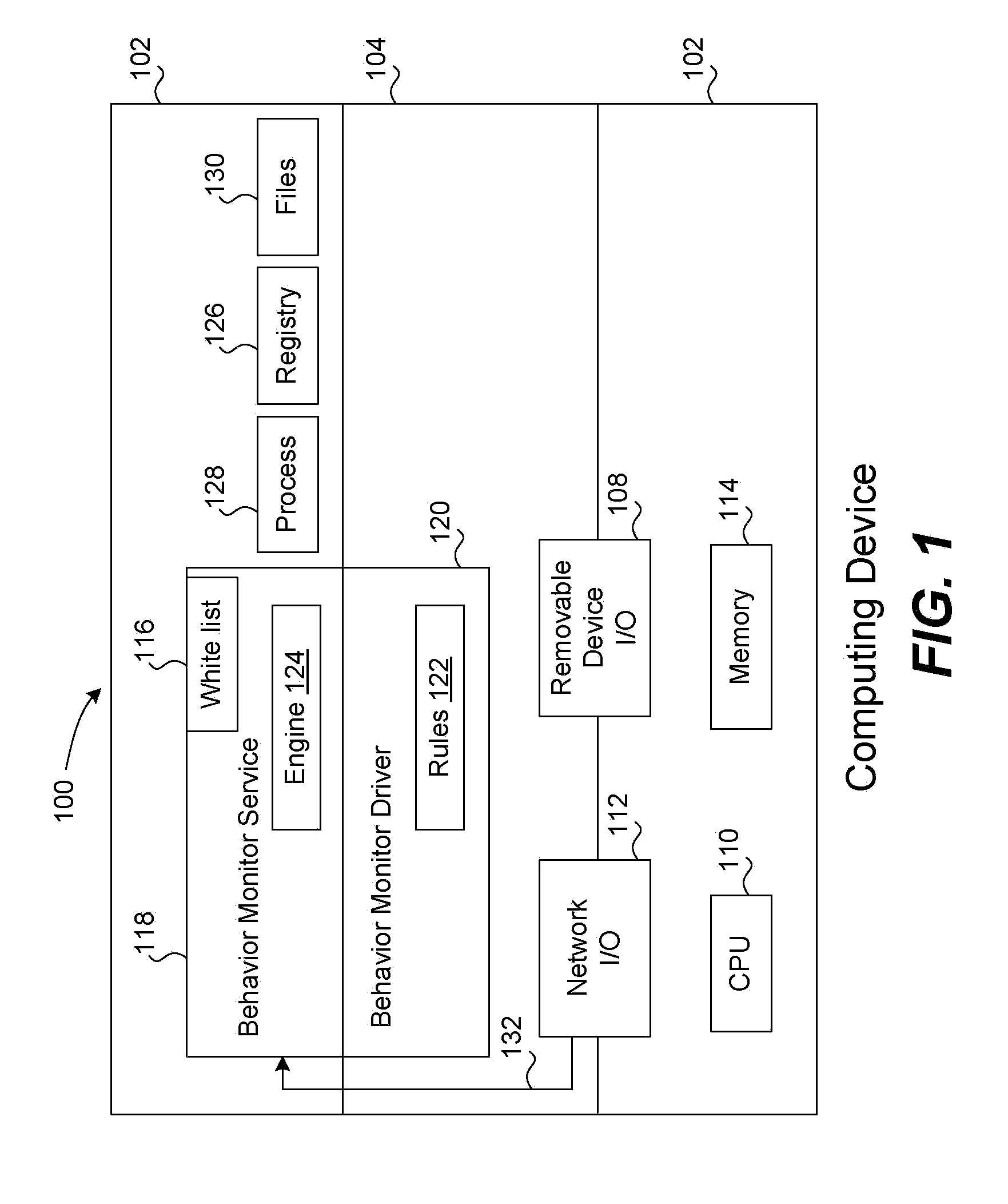
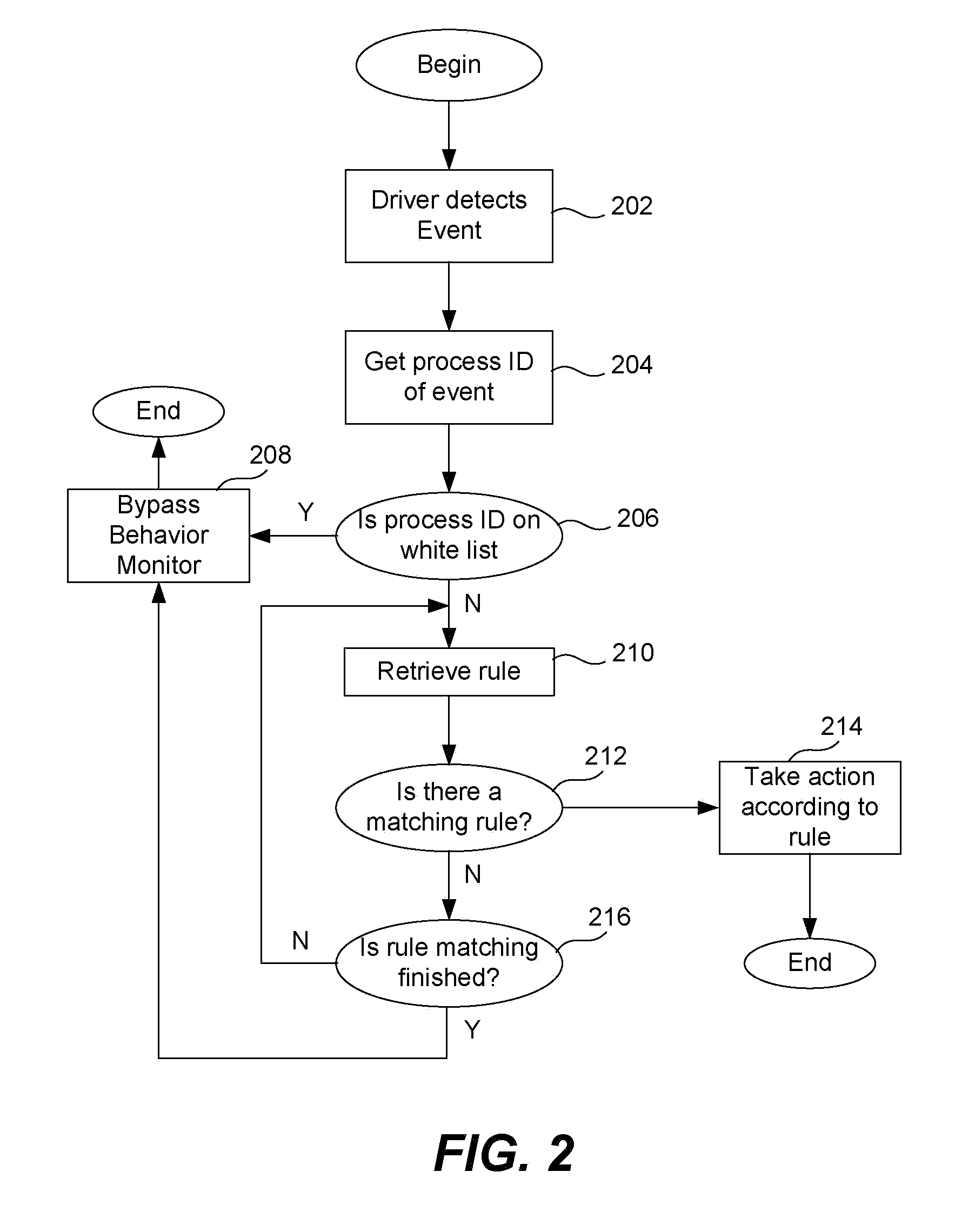
A white list (or exception list) for a behavior monitoring system for detecting unknown malware on a computing device is maintained automatically without human intervention. A white list contains process IDs and other data relating to processes that are determined to be (or very likely be) free of malware. If a process is on this list, the rule matching operations of a conventional behavior monitor are not performed, thereby saving processing resources on the computing device. When a process start up is detected, the behavior monitor performs a series of checks or tests. If the process has all valid digital signatures and is not launched from a removable storage device (such as a USB key) and is not enabled to make any inbound or outbound connections, it is eligible for being on the white list. The white list is also automatically maintained by removing process IDs for processes that have terminated or which attempt to make a new outbound or inbound connection, such as a TCP / UDP connection. Scheduled integrity checks on the white list are also performed by examining the process stack for each process to ensure that there are no abnormal files in the process stack.
Owner:TREND MICRO INC
System and Method for Call Stack Sampling Combined with Node and Instruction Tracing
InactiveUS20080307441A1Specific program execution arrangementsMemory systemsCall stackProgram counter
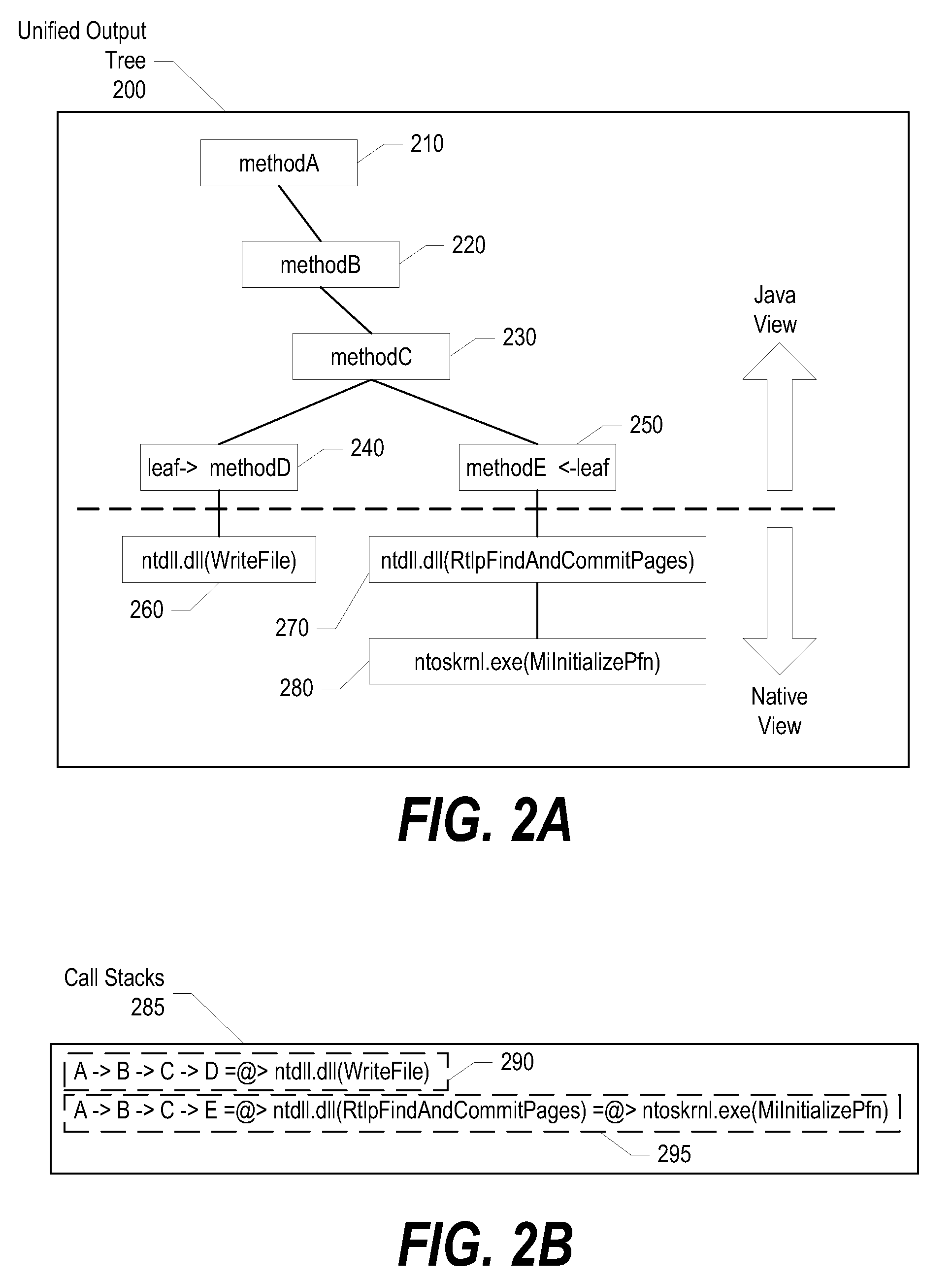
A system and method for Java™ call stack sampling combined with native sampling is presented. A kernel-mode device driver records and stores sampled context information that includes a program counter, a thread identifier, and a process identifier. The sampling thread receives a notification from the kernel-mode device driver, and proceeds to collect call stack information from a Java™ Virtual Machine. In turn, the sampling thread retrieves the sampled context information and harvests symbols corresponding to a loaded module. Once symbols are harvested, the sampling thread combines returned call stack nodes with native function leaf nodes into a unified output tree that provides the relationship between the two different node types. In one embodiment, the sampling thread may generate native function leaf nodes and the unified output tree in a post-processing manner.
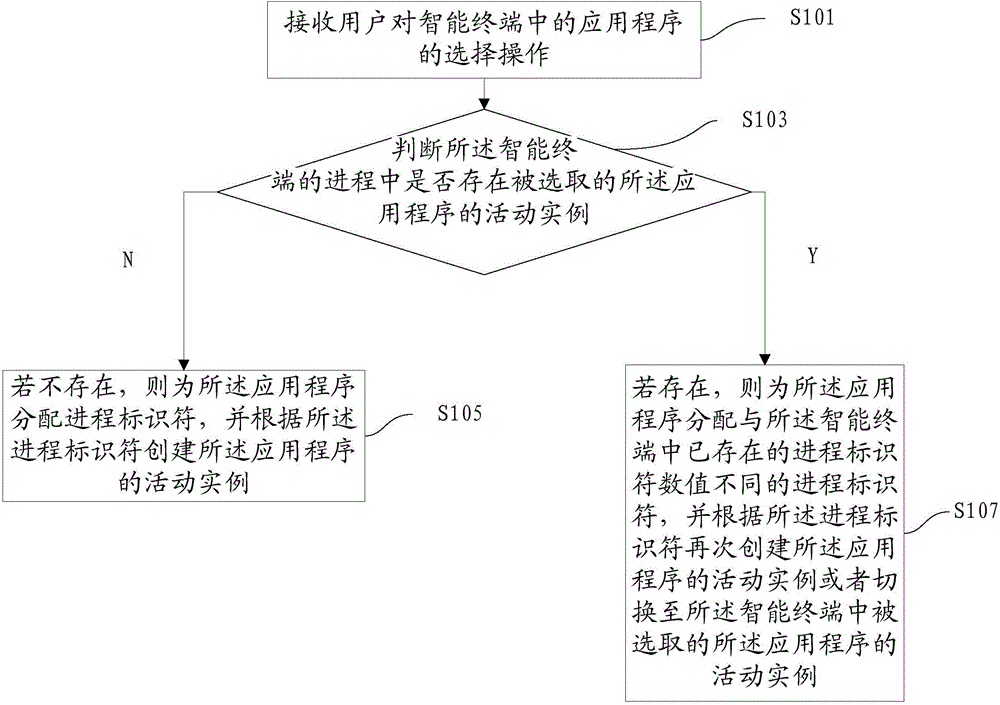
Owner:IBM CORP
Intergrated service management system
InactiveUS20100146098A1Improve efficiencyMultiple digital computer combinationsNetworks interconnectionStorage area networkPrivate network
Owner:HITACHI LTD
Integrated service management system
InactiveUS20080043764A1Improve efficiencyMultiple digital computer combinationsNetworks interconnectionStorage area networkPrivate network
The present invention provides techniques for creation, operation, management, and access control of network-based storage services. Specific embodiments provide improved efficiency of the service management tasks used for designing, operating and accounting the robust and profitable network services, for example. In representative embodiments, techniques for constructing integrated network and storage services are provided. In a specific embodiment, the service comprises of three major service components: virtual private networks (VPN), application servers and storage area networks (SAN). Each of these service components has its own customer identification information, such as VPN identifier for VPN services, process identifier for application servers and logical unit number (LUN) for storage devices.
Owner:HITACHI LTD
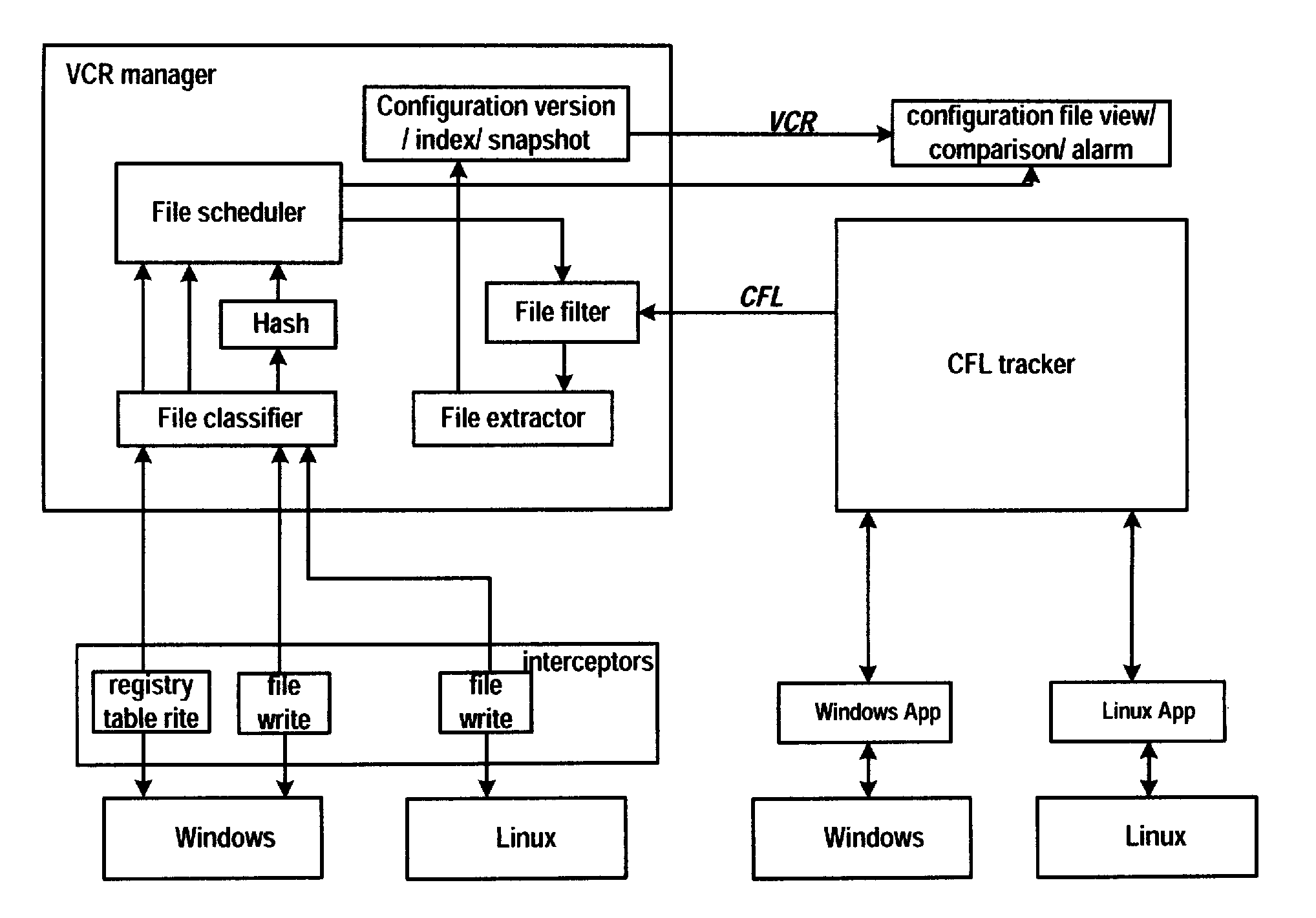
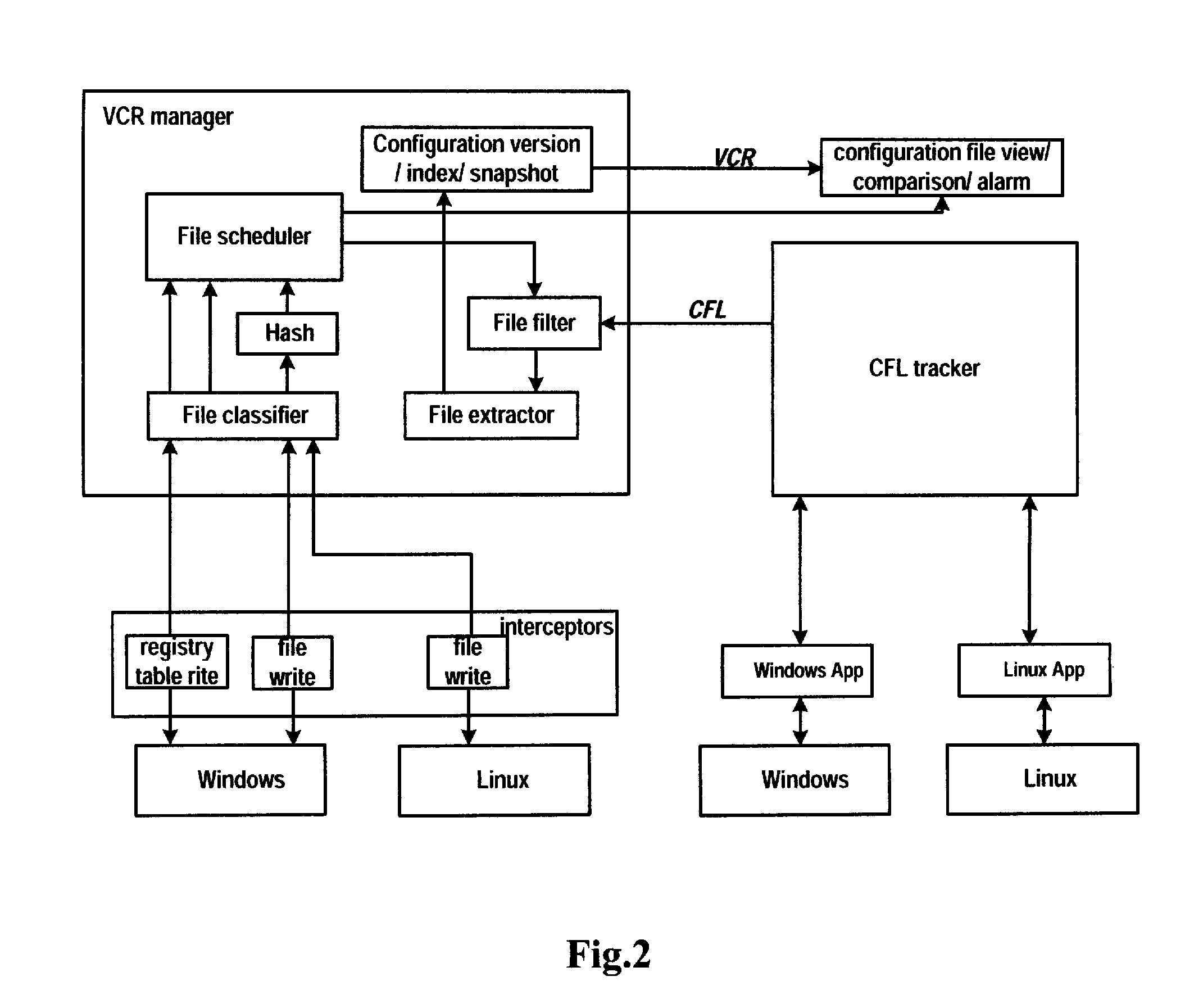
Method and apparatus for discovering application configuration files in a system
InactiveUS20100223306A1Precise changeFacilitate to quickly recoverDigital data processing detailsProgram controlOperational systemApplication software
A method and apparatus for discovering application configuration files in a system. The method includes the steps of: obtaining a process identifier of an application in concern; comparing the obtained process identifier with a process identifier of a process for operating configuration files in the system; and determining configuration files to be the configuration files of the application in concern if the obtained process identifier is identical to the process identifier of a process for operating the configuration files in the system. Application configuration files can be automatically discovered and thereby monitored, such that the change of the application configuration files can be effectively and accurately detected, so as to facilitate a user to perform various subsequent operations.
Owner:IBM CORP
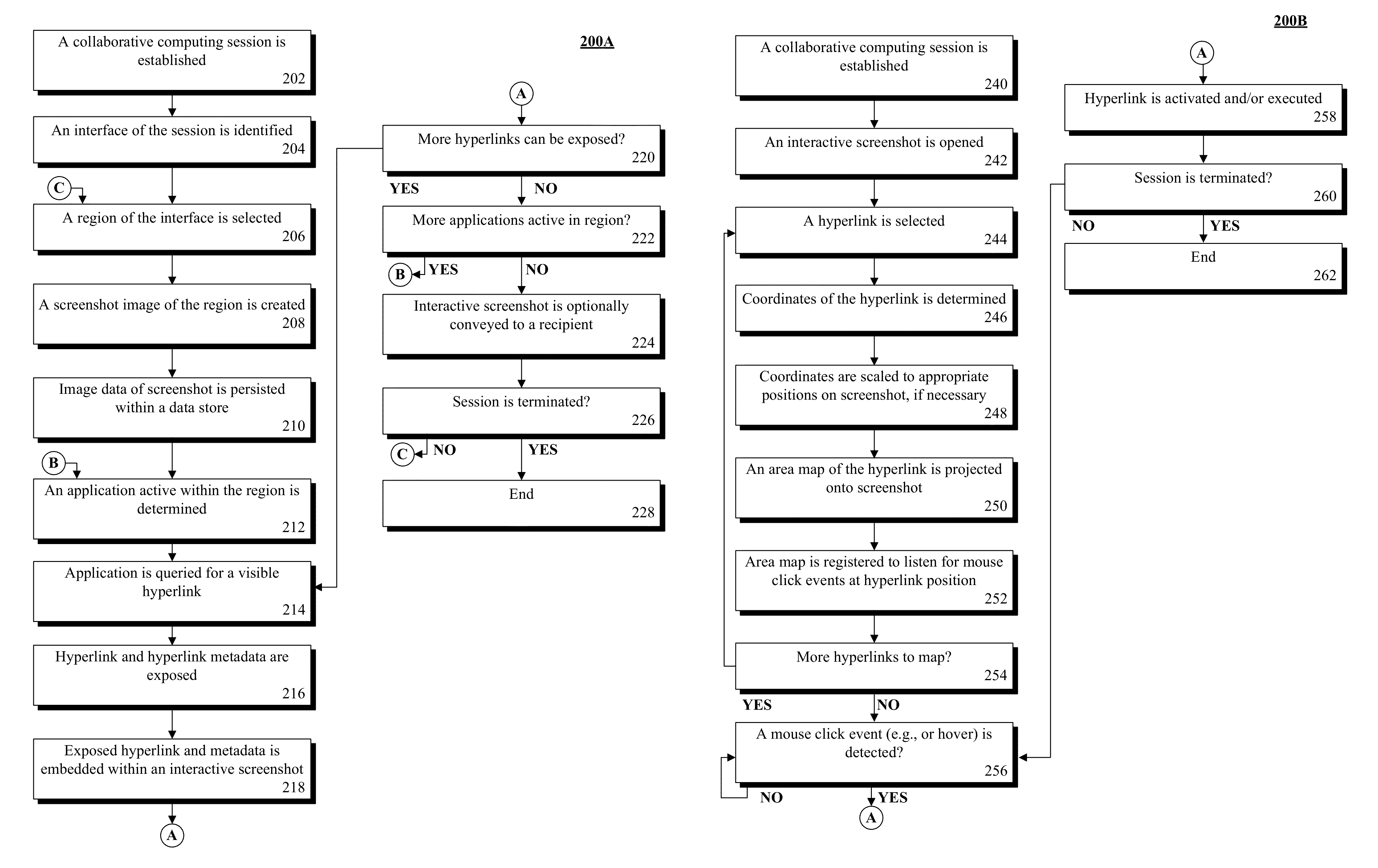
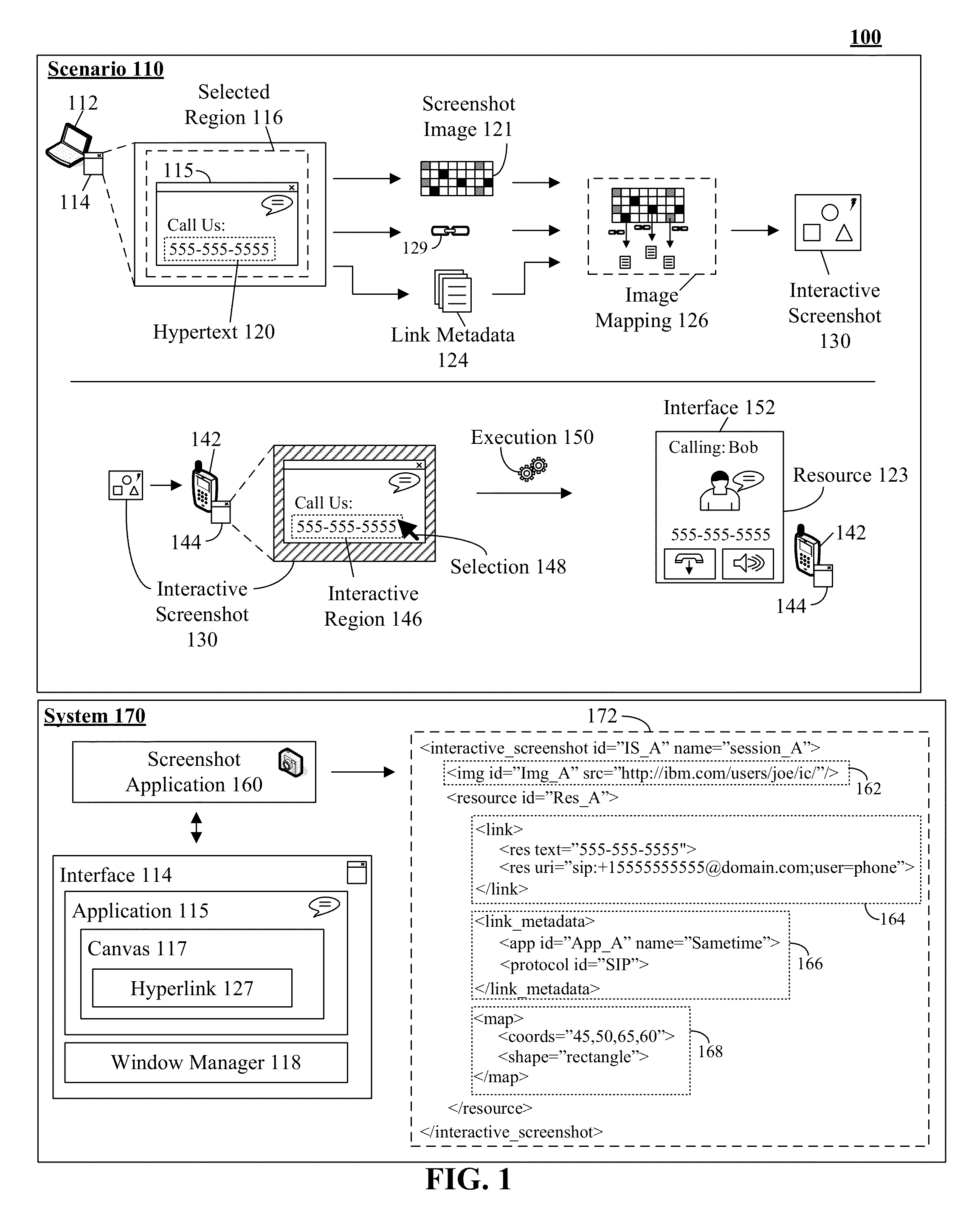
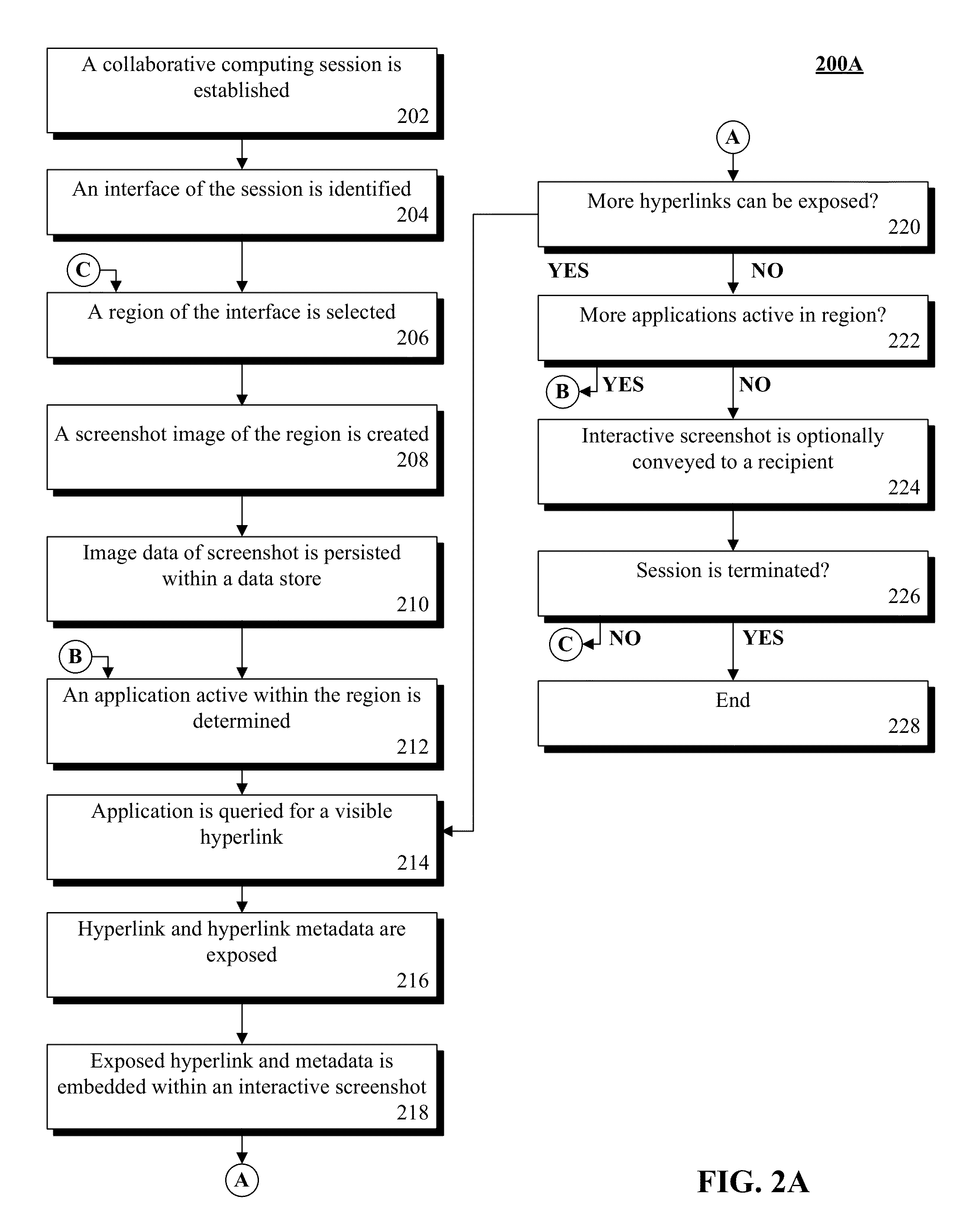
Enabling interactive screenshots within collaborative applications
InactiveUS20150128017A1Natural language data processingSpecial data processing applicationsUniform resource identifierApplication software
A resource link within a selected portion of an interface can be identified. The link can include a visible interface element and a non-visible reference to a resource. The reference can be a Uniform Resource Identifier. The identity of an application associated with the interface can be established. The identity can be an application or process identifier. The position / dimensions of the element within the selected portion can be determined. A screenshot image of the current state of the selected portion can be captured. The state can include a visual representation of the element. The position / dimensions of the element can be encoded within an image map. The encoding can map a bounded region surrounding the representation of the element within the screenshot corresponding to the element position / dimension of the link within the interface. The region can be associated with the identity of the application and the reference.
Owner:IBM CORP
Secure virtual interface
A network interface for secure virtual interface data communication includes a doorbell circuit, a processor, memory, and a bridge circuit. The doorbell circuit responds to physical I / O addresses of the host that are mapped by a memory management unit by a registration process. An application program seeking to use a channel of a virtual interface must register the virtual address of host memory where data for communication is or will be stored and register the virtual address of a page of I / O addresses. Access to the doorbell functions and to the host memory via the memory management unit are therefore denied when the requesting process identifier does not successfully compare with the process identifier for the process that performed the registrations. A password may be stored in the network interface in association with a virtual interface (VI) channel identifier and stored in association with the virtual to physical map used for VI communication. The network interface may abandon a requested or implied data communication function when passwords so not successfully compare. Methods for virtual interface (VI) communication performed by an application program may include one or more of the steps of (a) establishing a VI channel where physical I / O addresses of a network controller are secured; (b) registering host memory for use with a VI channel where physical memory addresses are secured; (c) describing blocks of host memory with reference to a memory handle; and (d) accomplishing data communication of a described block of host memory via an established VI channel where the data and controls of the VI channel are secured and the data and controls of other VI channels are secured. Security is provided against both erroneous operations and operations intentionally effected by rouge processes.
Owner:MARVELL ASIA PTE LTD
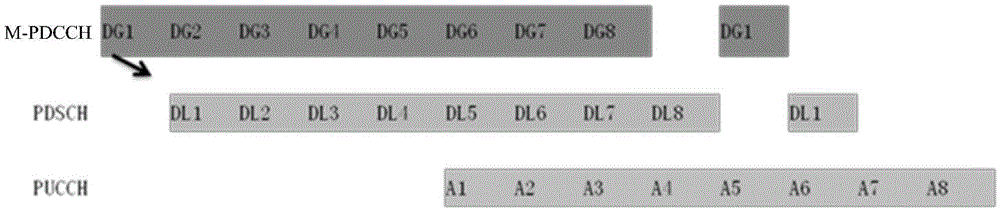
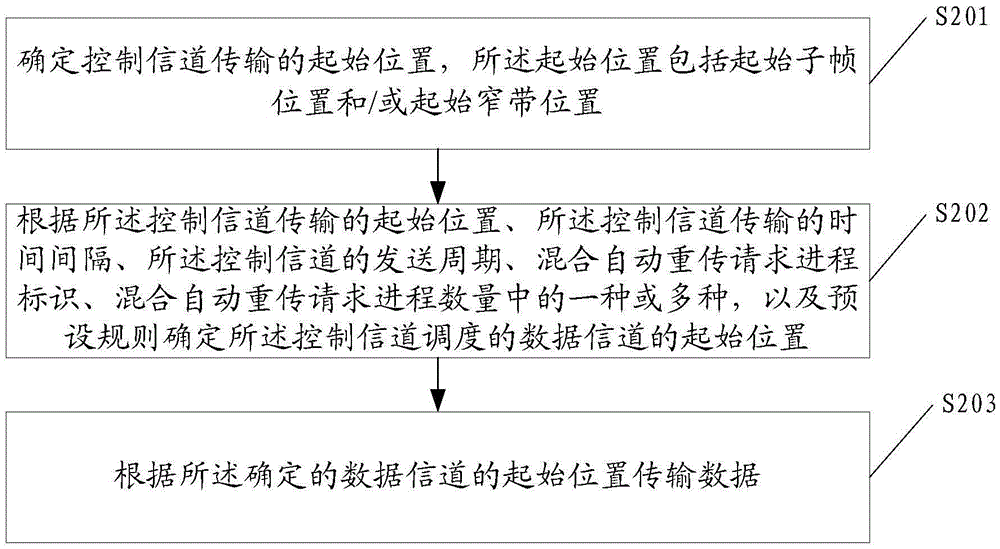
Method of data transmission and base station
ActiveCN106559188AGuaranteed to proceed normallyRetains the ability to flexibly schedule data narrowband locationsError prevention/detection by using return channelControl channelData transmission
The embodiment of the invention discloses a method of data transmission. The method comprises: determining starting positions, including a starting sub frame position and / starting narrow-band position, of control channel transmission; according to the starting positions of the control channel transmission, one or more of a time interval of the control channel transmission, a sending period of the control channel, a hybrid automatic repeat request process identifier, and the number of hybrid automatic repeat request processes, and a preset rule, a starting position of a data channel of control channel scheduling is determined; and on the basis of the determined starting position of the data channel, data are transmitted. In addition, the embodiment of the invention also discloses a base station. Therefore, when the terminal does not receive previous indication information, normal operation of follow-up data transmission can be guaranteed.
Owner:江苏赛鸥电气集团有限公司
Information processing apparatus and cache memory control method
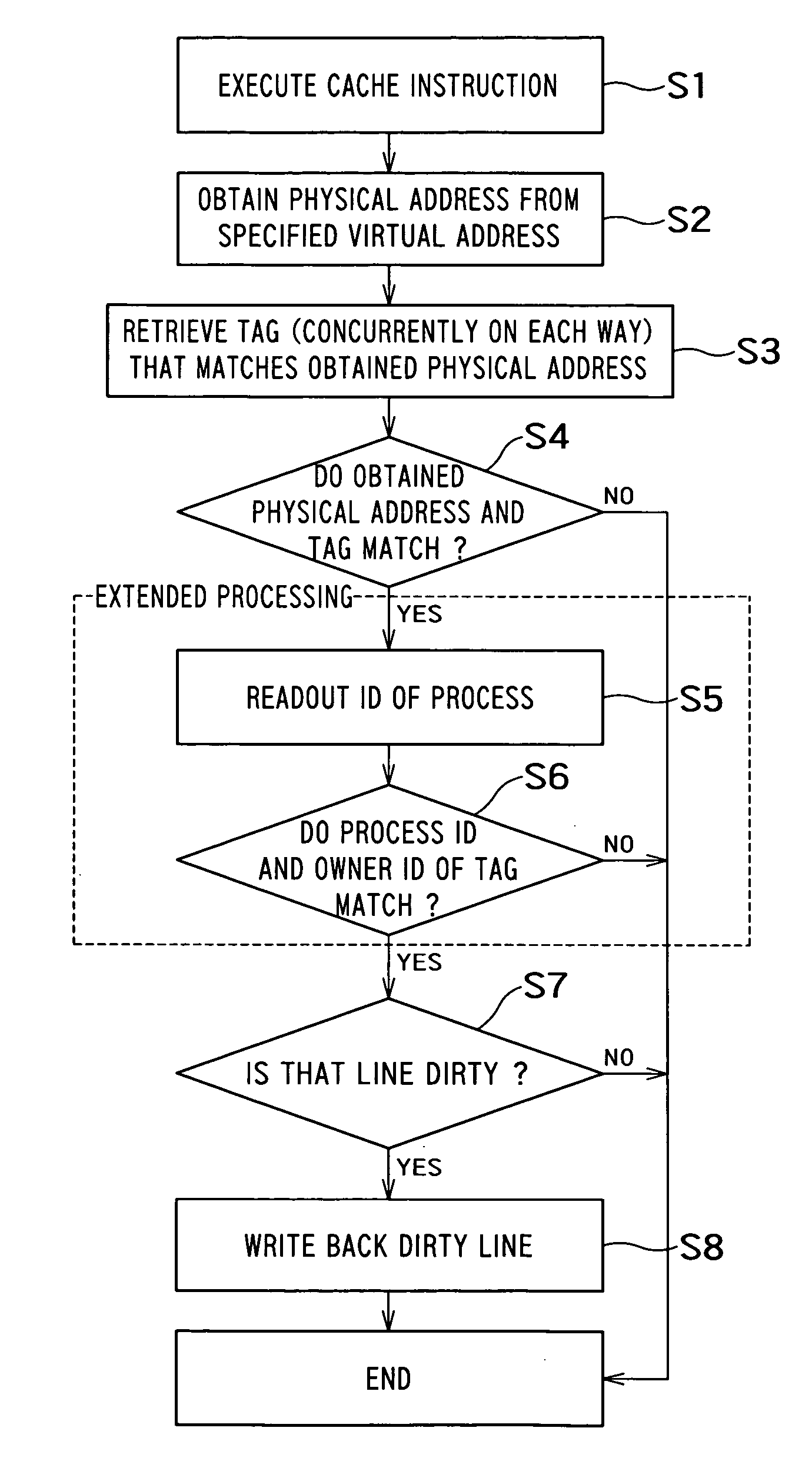
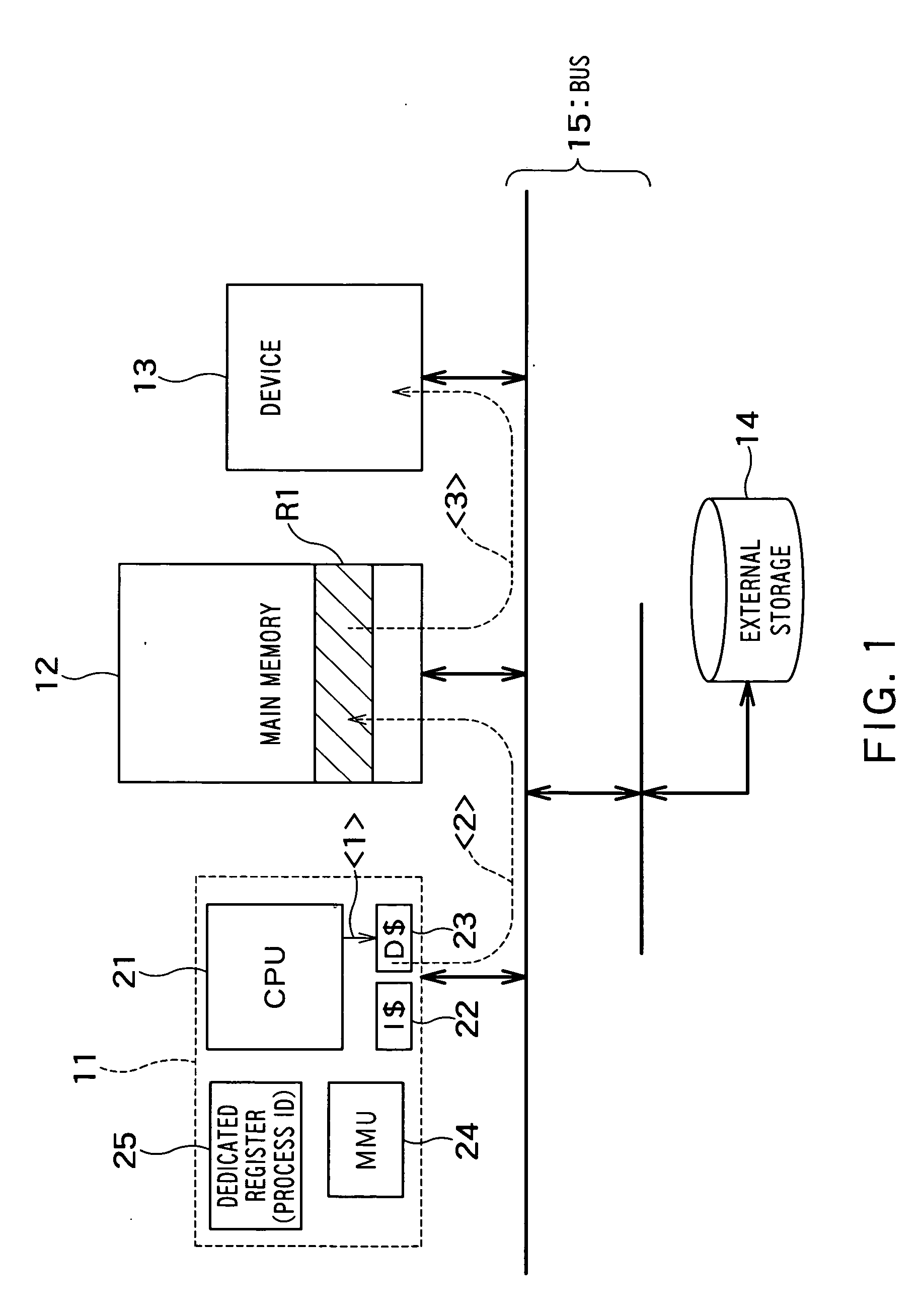
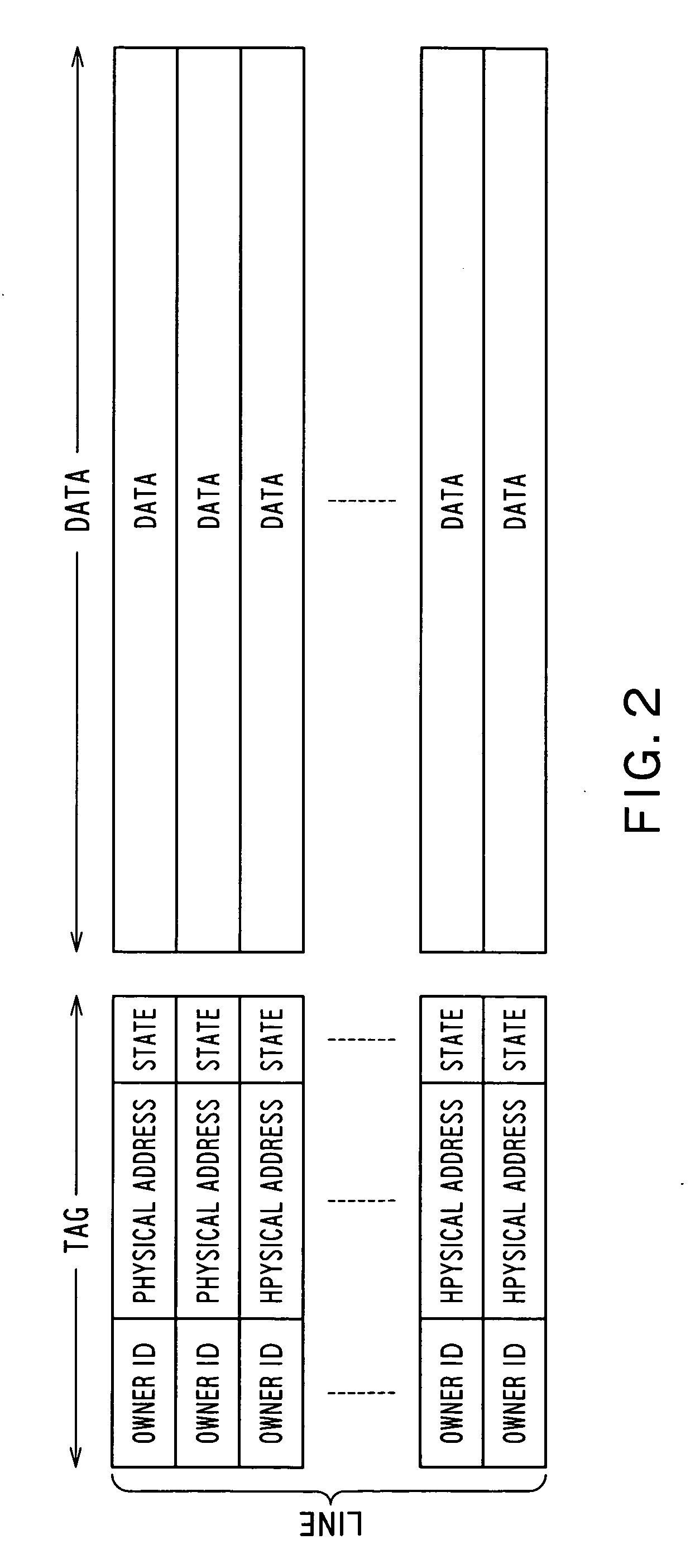
There is provided with an information processing apparatus, including: a CPU; a register that stores a task ID or a process ID that identifying a task or a process; and a cache memory that records data specified by the CPU on a cache line corresponding to a memory address specified by the CPU, and writes a task ID or a process ID stored in the register in one part of a tag that manages the cache line as an owner ID; wherein the CPU executes a cache control instruction instructing to write back only cache lines having an owner ID that is the same as a task ID or a process ID in the register.
Owner:KK TOSHIBA
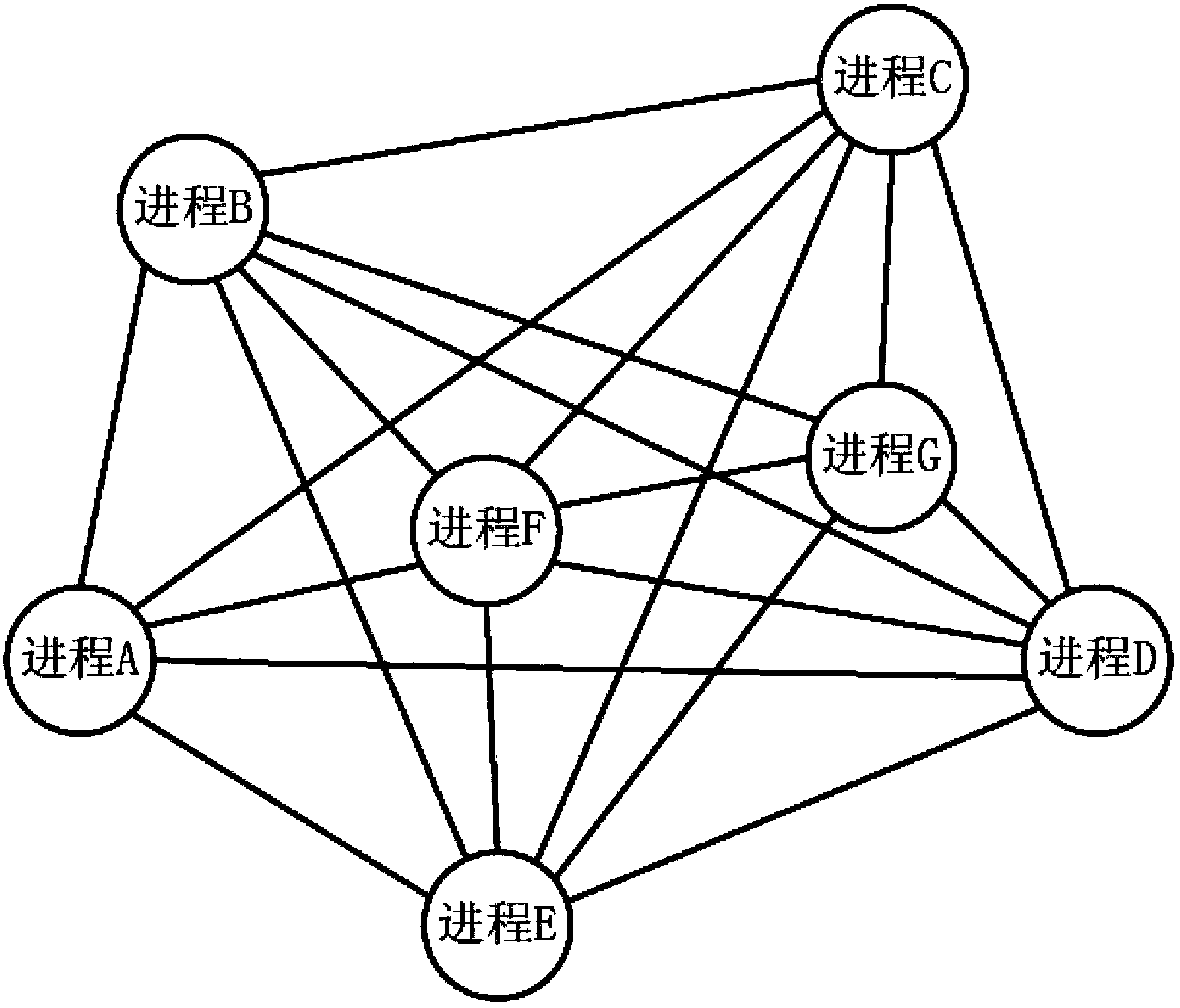
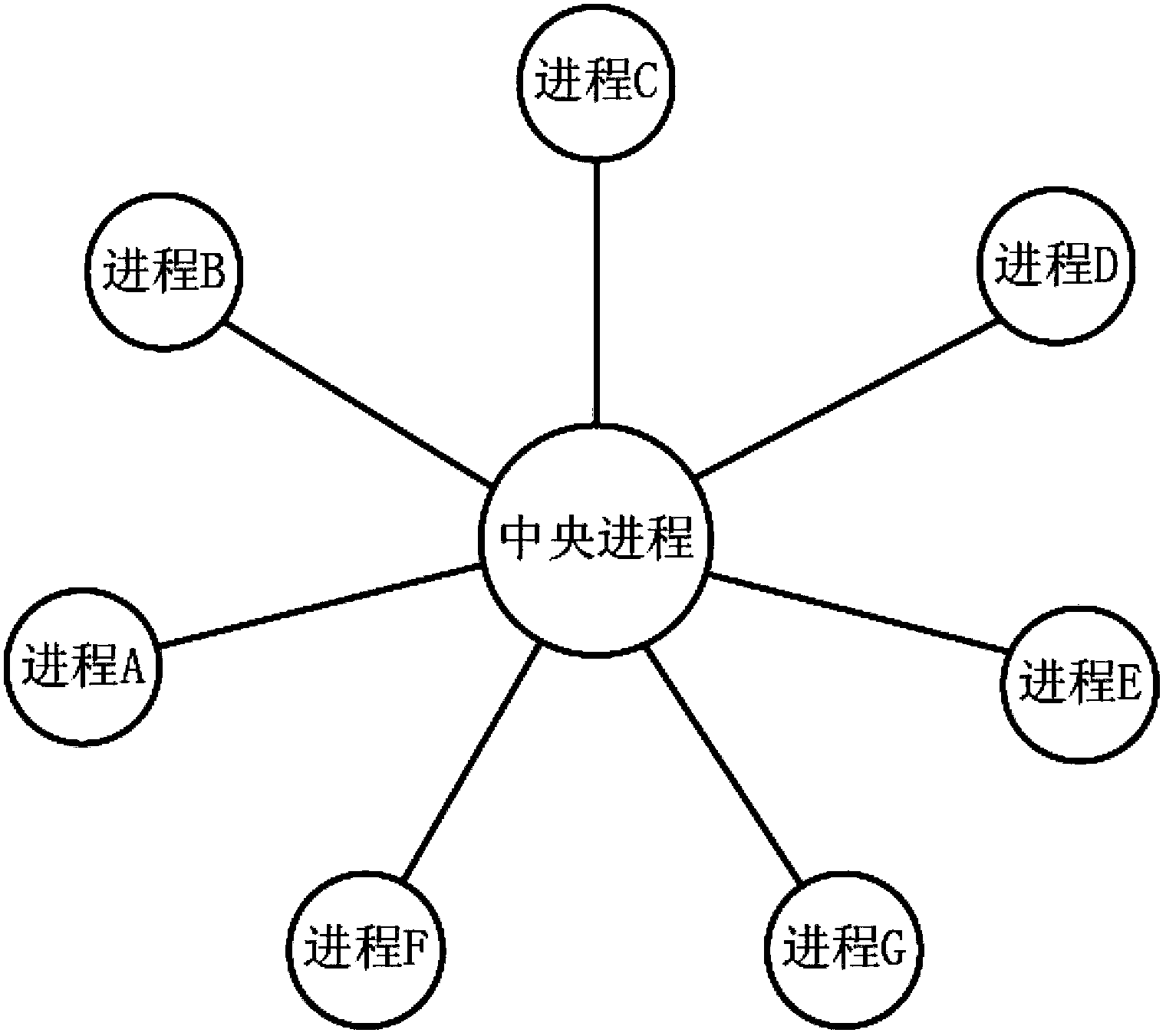
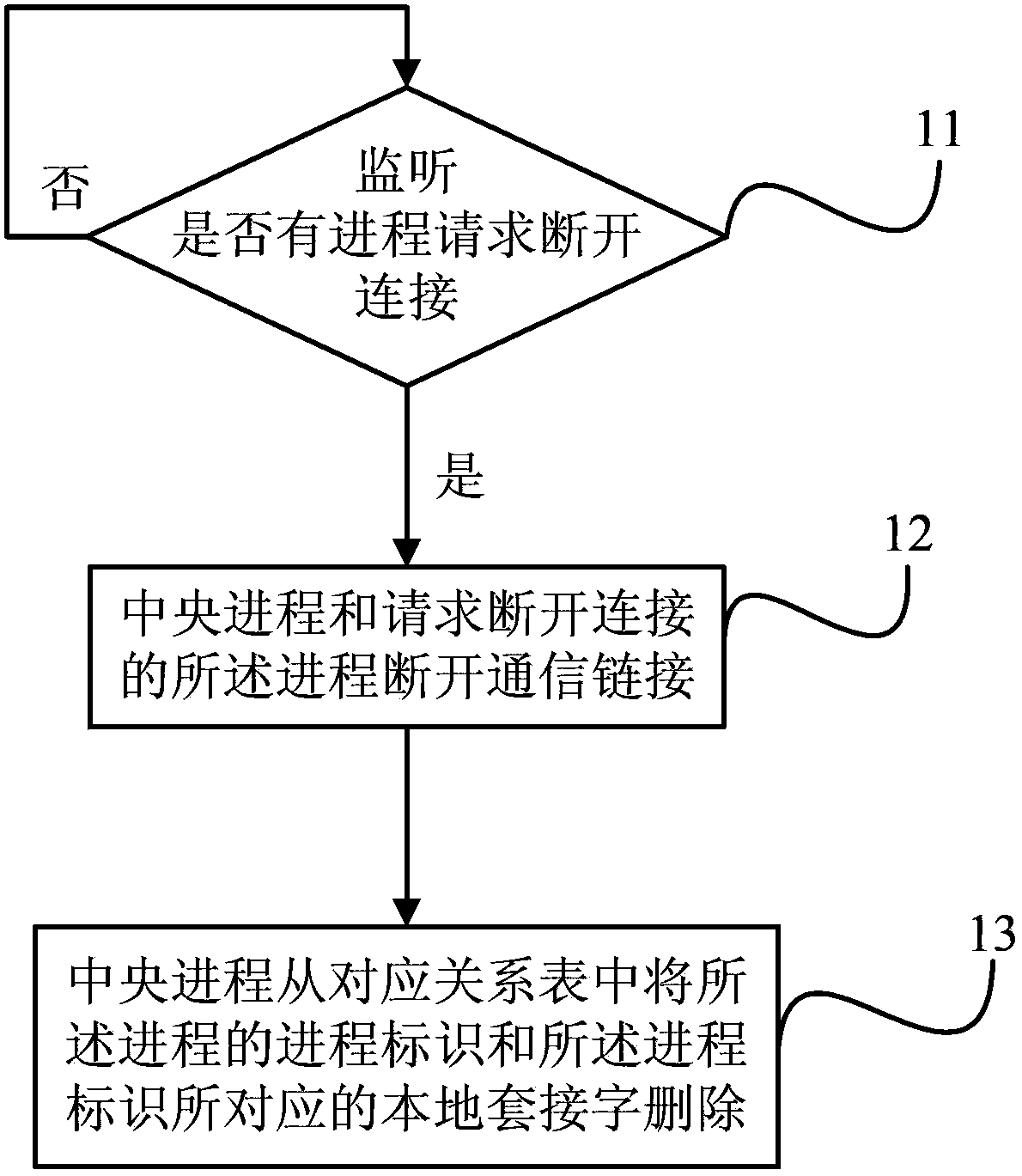
Multi-process communication system and establishment and communication method thereof
InactiveCN103455380AAchieve connectionMaintain effectivenessInterprogram communicationTelecommunicationsThe Internet
The invention discloses a multi-process communication system and an establishment and communication method thereof. The multi-process communication system comprises a central process and multiple processes. The processes are connected to the central process in an IPC (internet process connection) manner. The central process writes communication connecting identifiers and process identifiers of the processes into a correspondence table. When one optional process of the processes serves as a sending process, sends data to another process, serving as a receiving process, and is different with the sending process, of the processes; the central process receives the data, finds out the communication connecting identifier of the receiving process from the correspondence table according to the process identifier of the receiving process and sends the data to the receiving process according to the communication connecting identifier of the receiving process. An emanative communication connecting structure is established among the multiple processes, so that data communication among the processes can be implemented without establishing a large amount of IPC instances among the processes.
Owner:PHICOMM (SHANGHAI) CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com