Patents
Literature
54 results about "Trusted path" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
A trusted path or trusted channel is a mechanism that provides confidence that the user is communicating with what the user intended to communicate with, ensuring that attackers can't intercept or modify whatever information is being communicated.
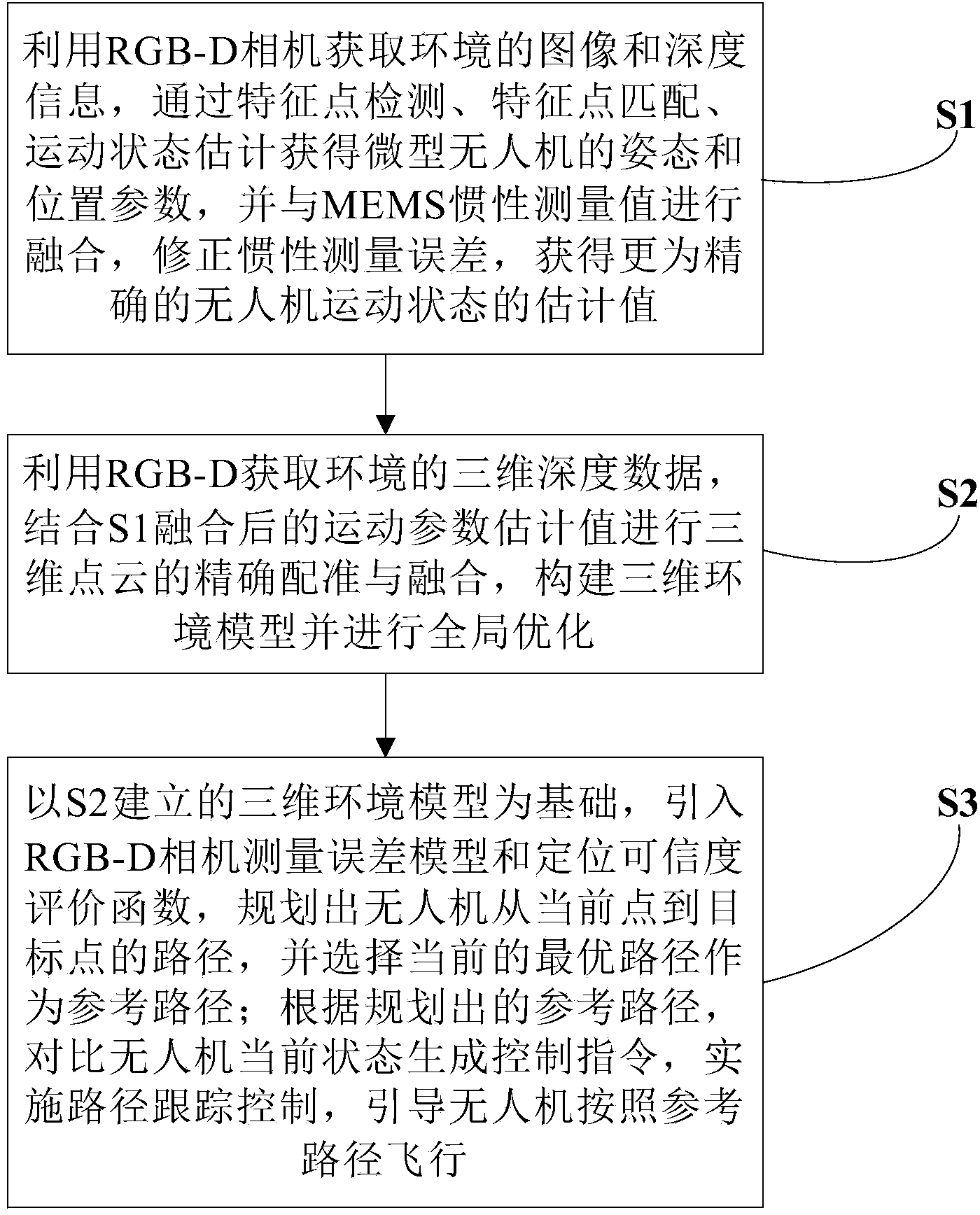
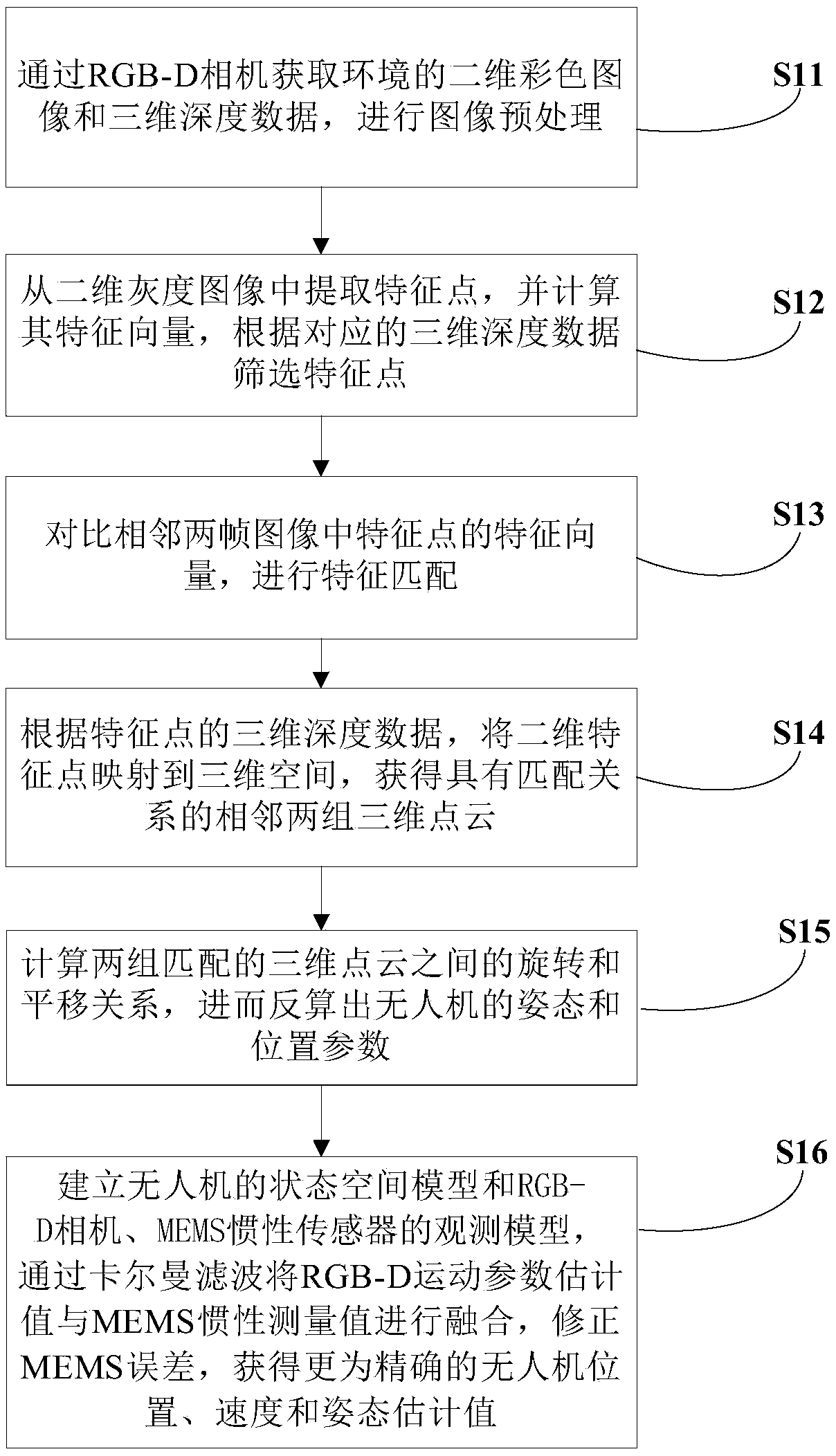
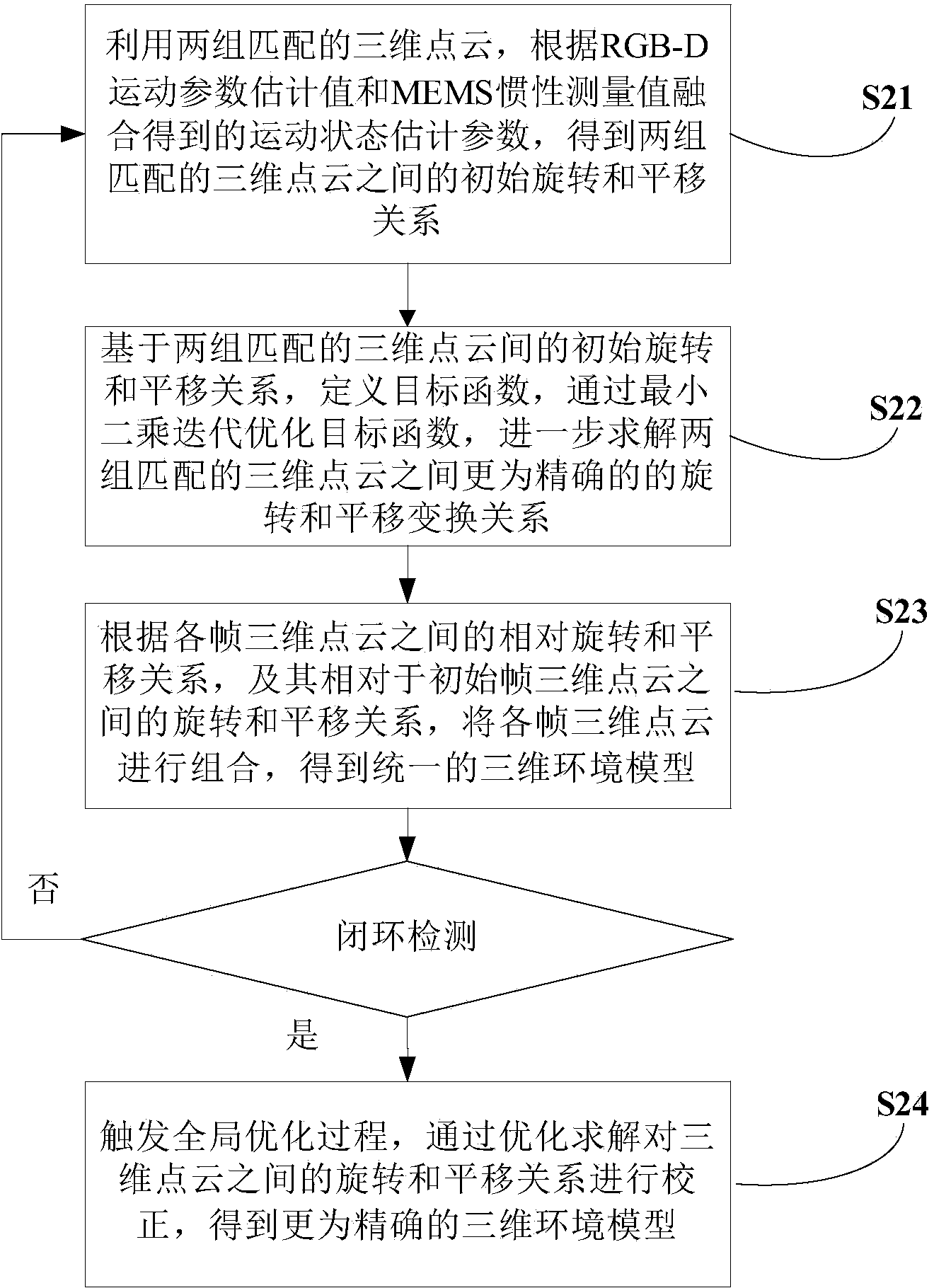
Indoor autonomous navigation method for micro unmanned aerial vehicle
ActiveCN104236548ACorrection error accumulationHigh precisionNavigation by speed/acceleration measurementsAttitude controlUncrewed vehicle
The invention relates to an indoor autonomous navigation method for a micro unmanned aerial vehicle, belonging to the technical field of autonomous navigation of micro unmanned aerial vehicles. The method comprises the following steps: estimating the motion state of the micro unmanned aerial vehicle based on an RGB-D camera and an MEMS inertial sensor; performing real-time three-dimensional environment modeling based on fusion of the RGB-D camera and the MEMS inertial sensor; and performing real-time trusted path planning and path tracking control, implementing position control and attitude control through the three steps, and guiding the unmanned aerial vehicle to track the preset path to fly. According to the method, the unmanned aerial vehicle positioning accuracy and the motion state estimation accuracy are improved; the indoor autonomous environmental perception capability of the micro unmanned aerial vehicle is improved; according to the generated path, the positioning accuracy can be effectively guaranteed on the basis that the path feasibility is met; and the autonomy capability of the micro unmanned aerial vehicle is effectively improved.
Owner:TSINGHUA UNIV
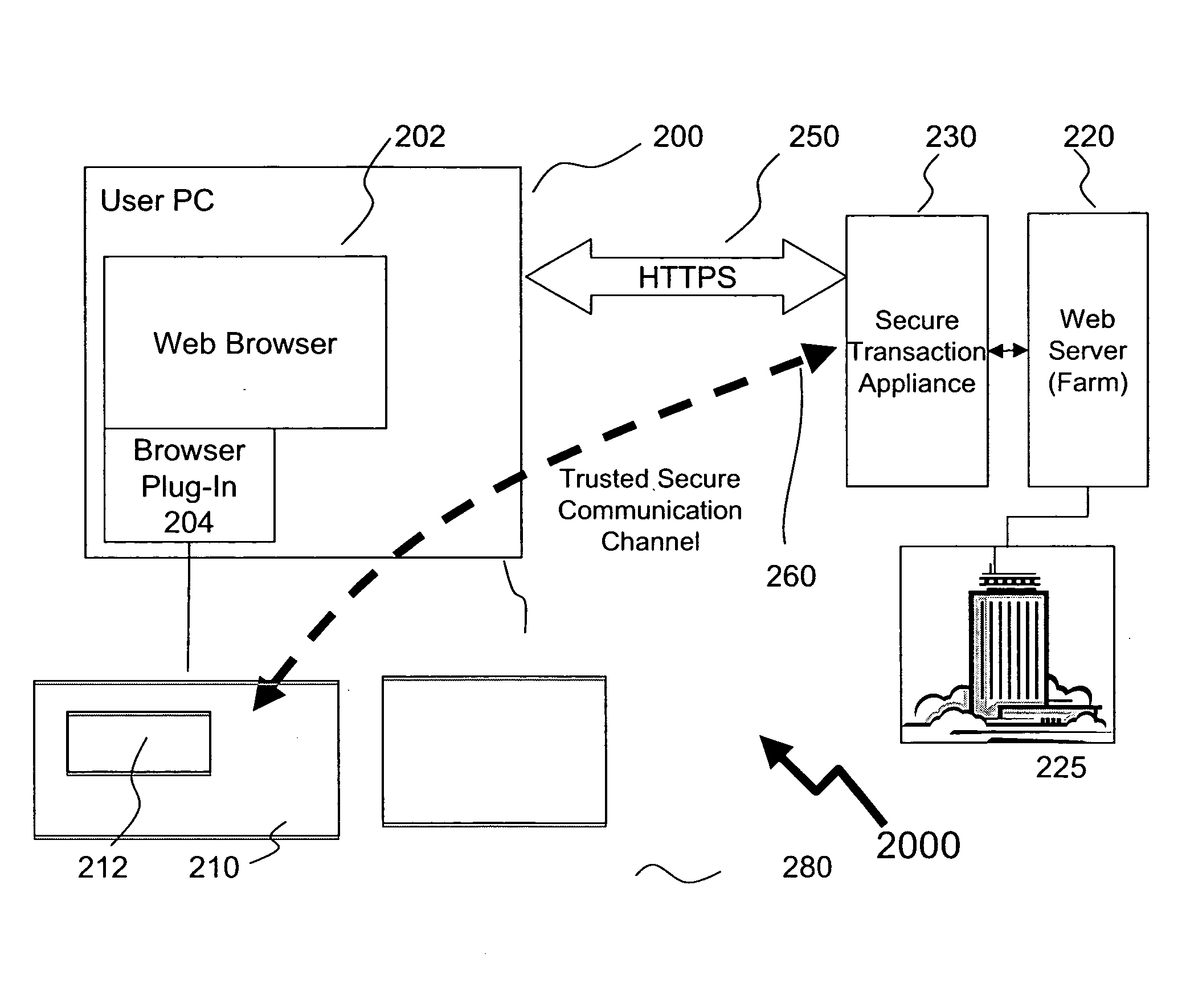
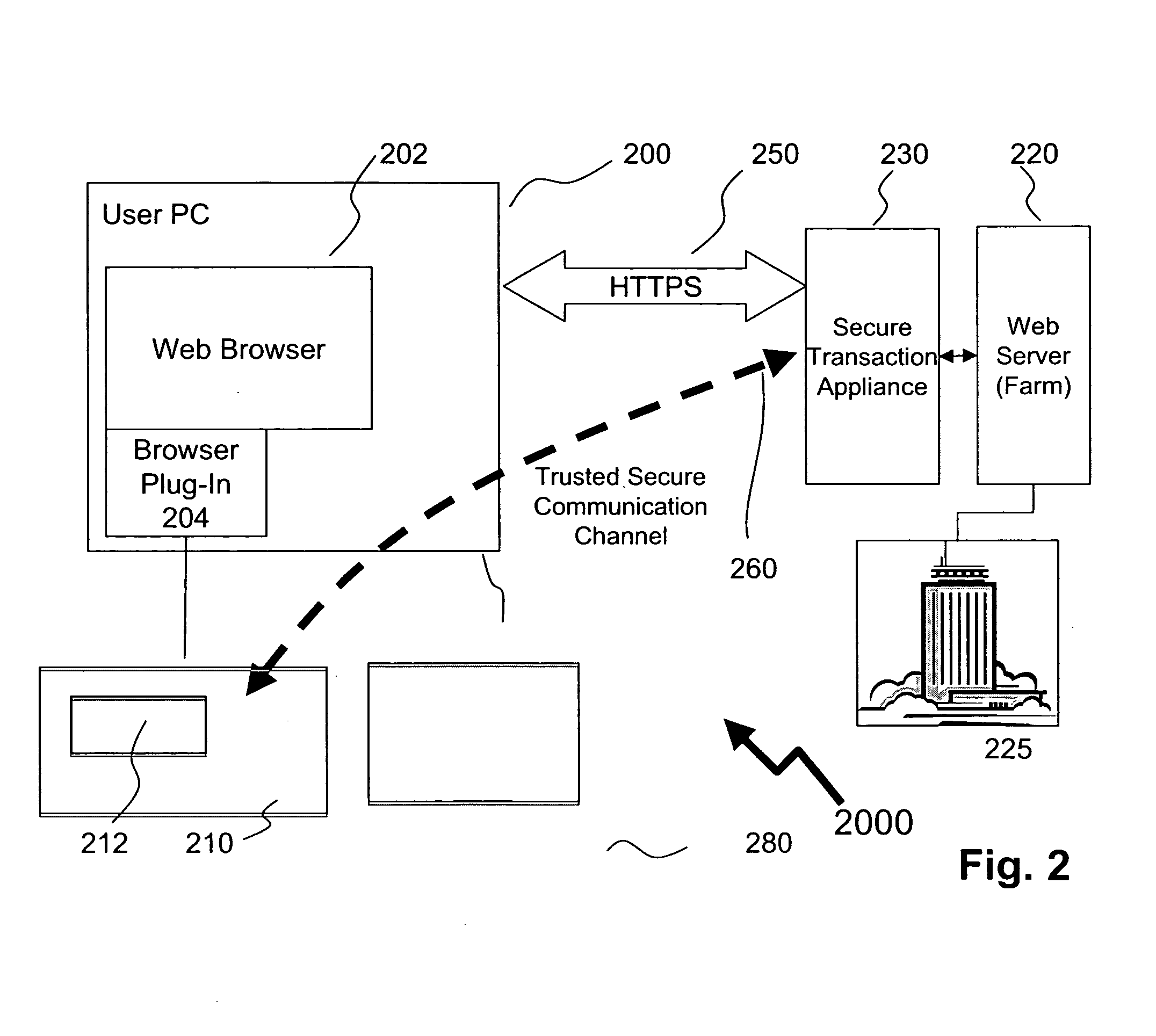
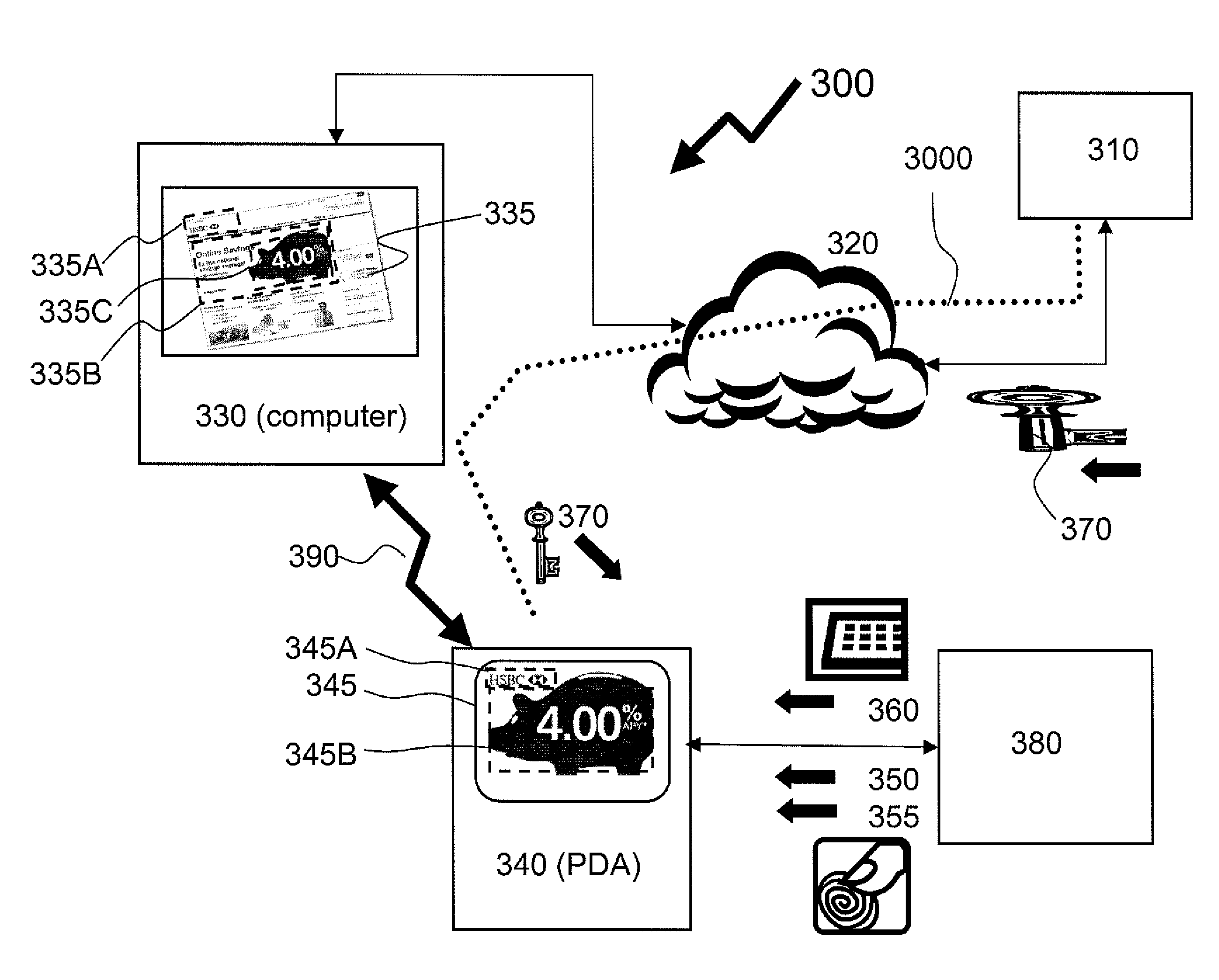
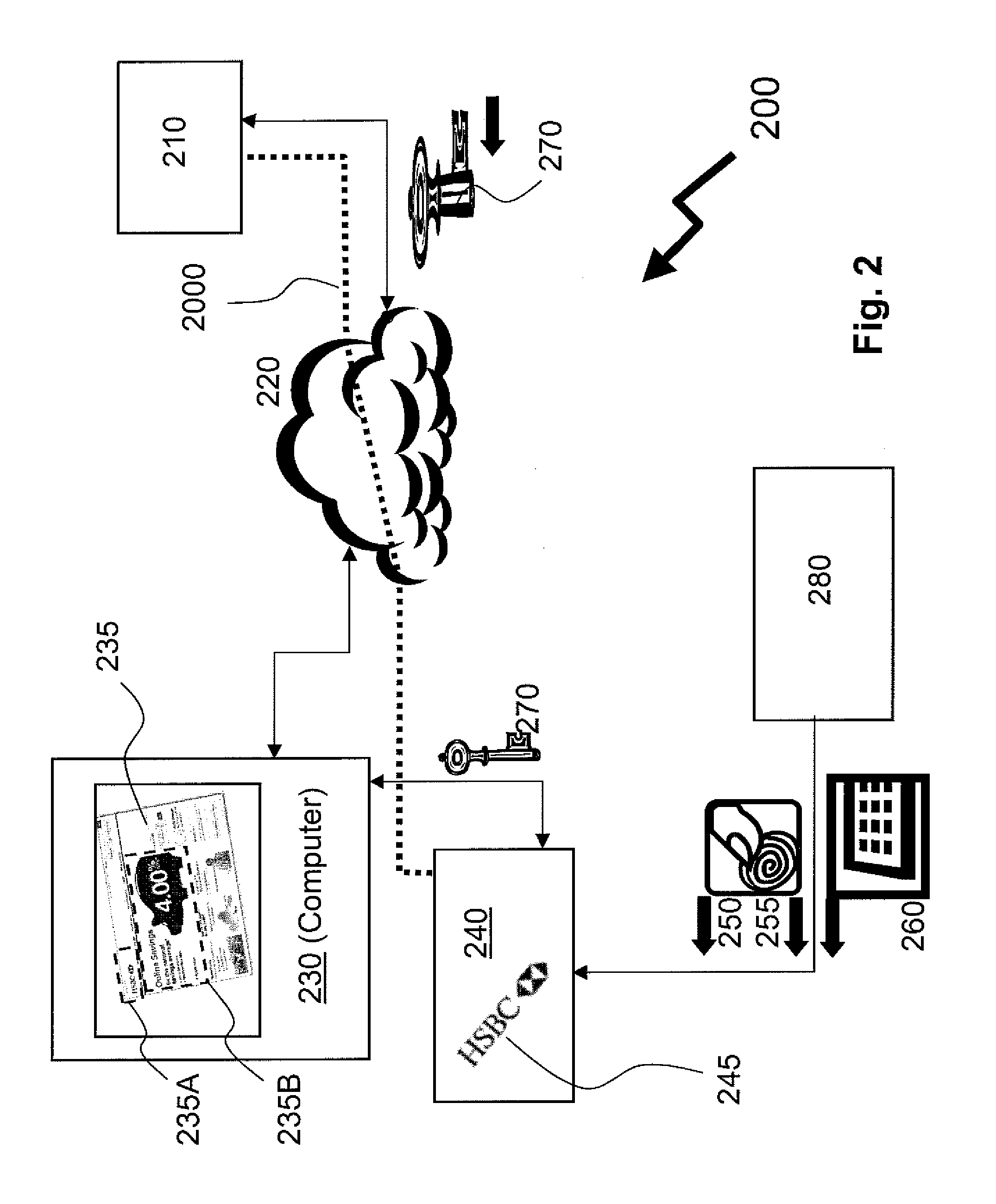
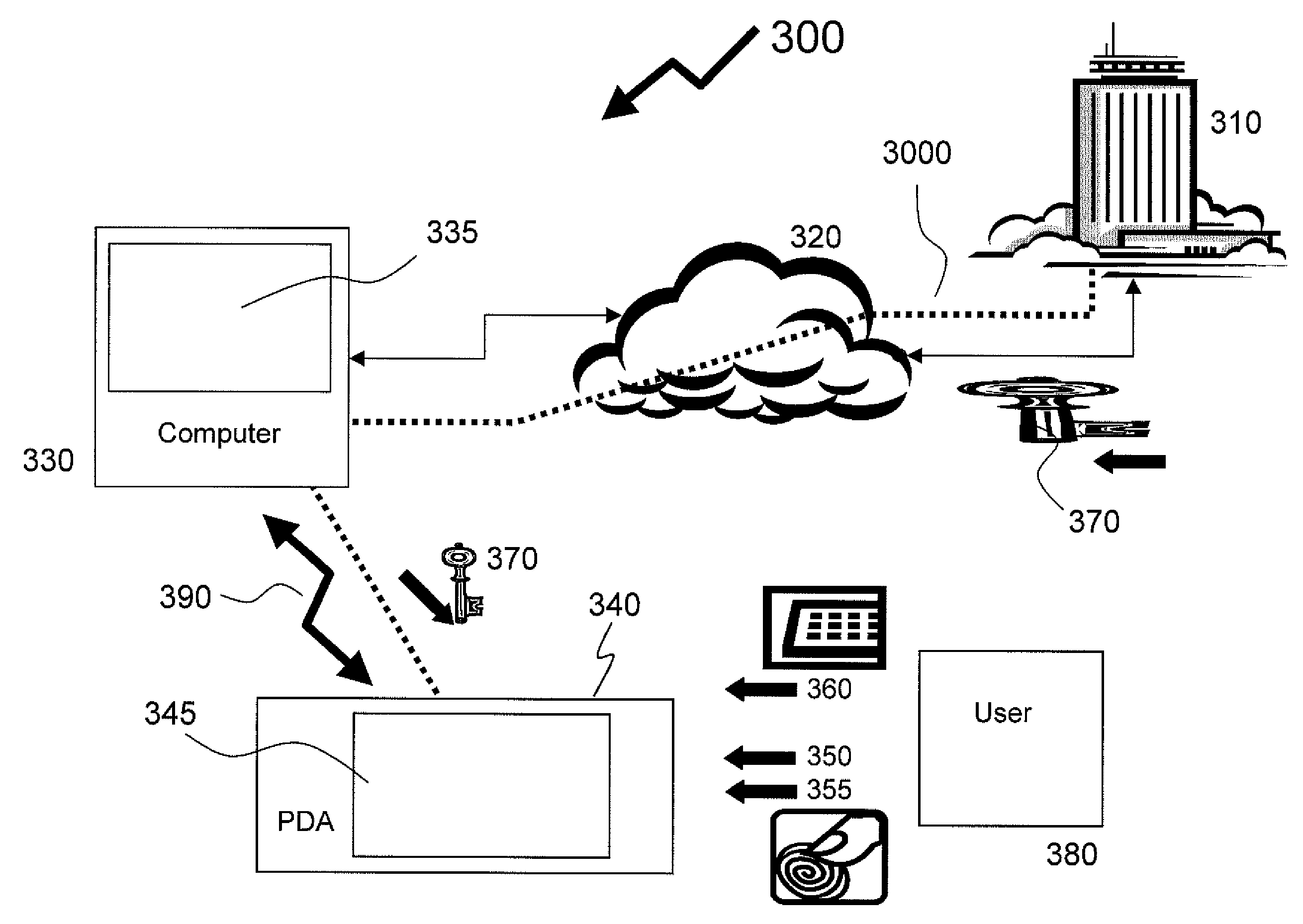
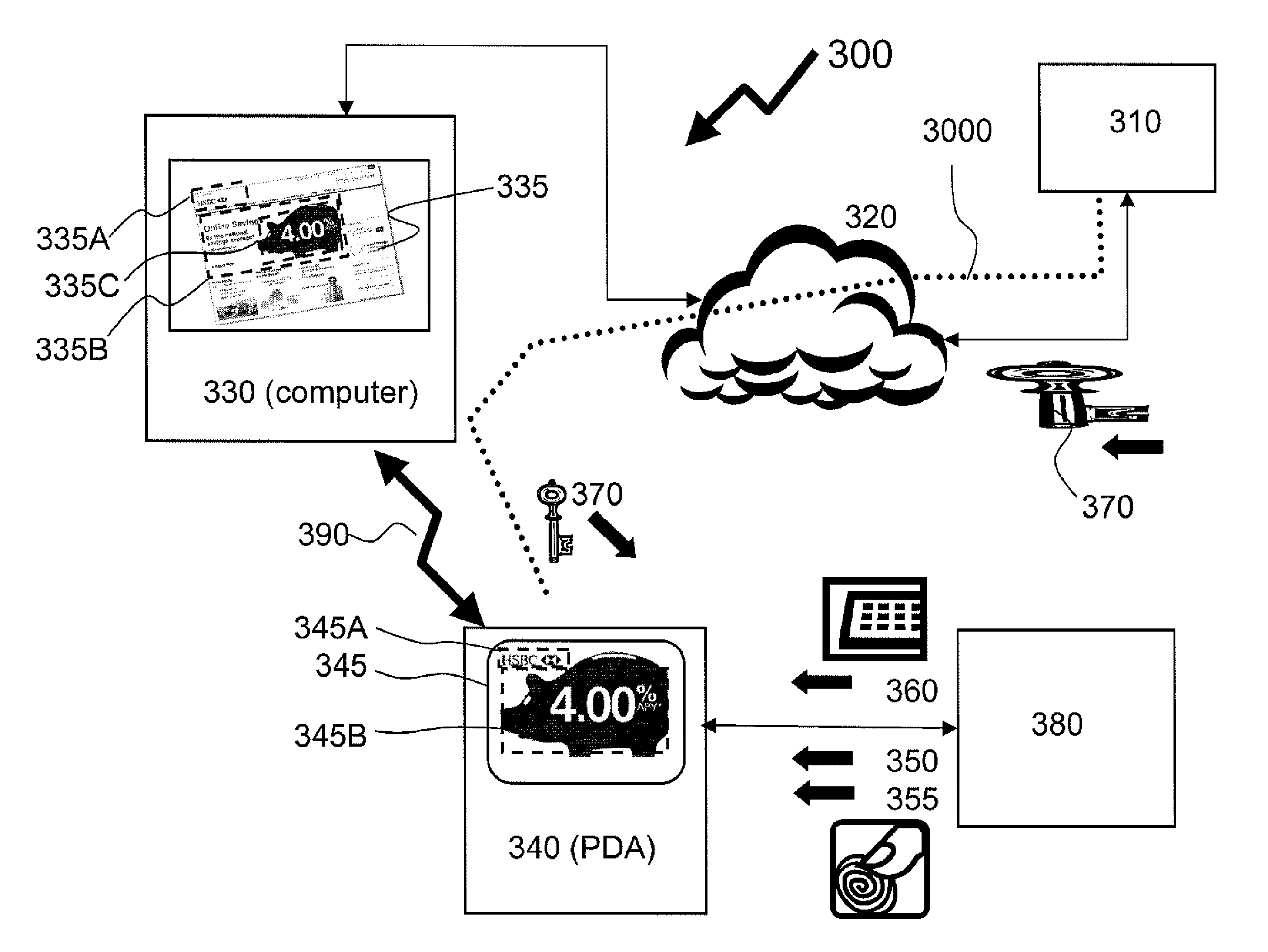
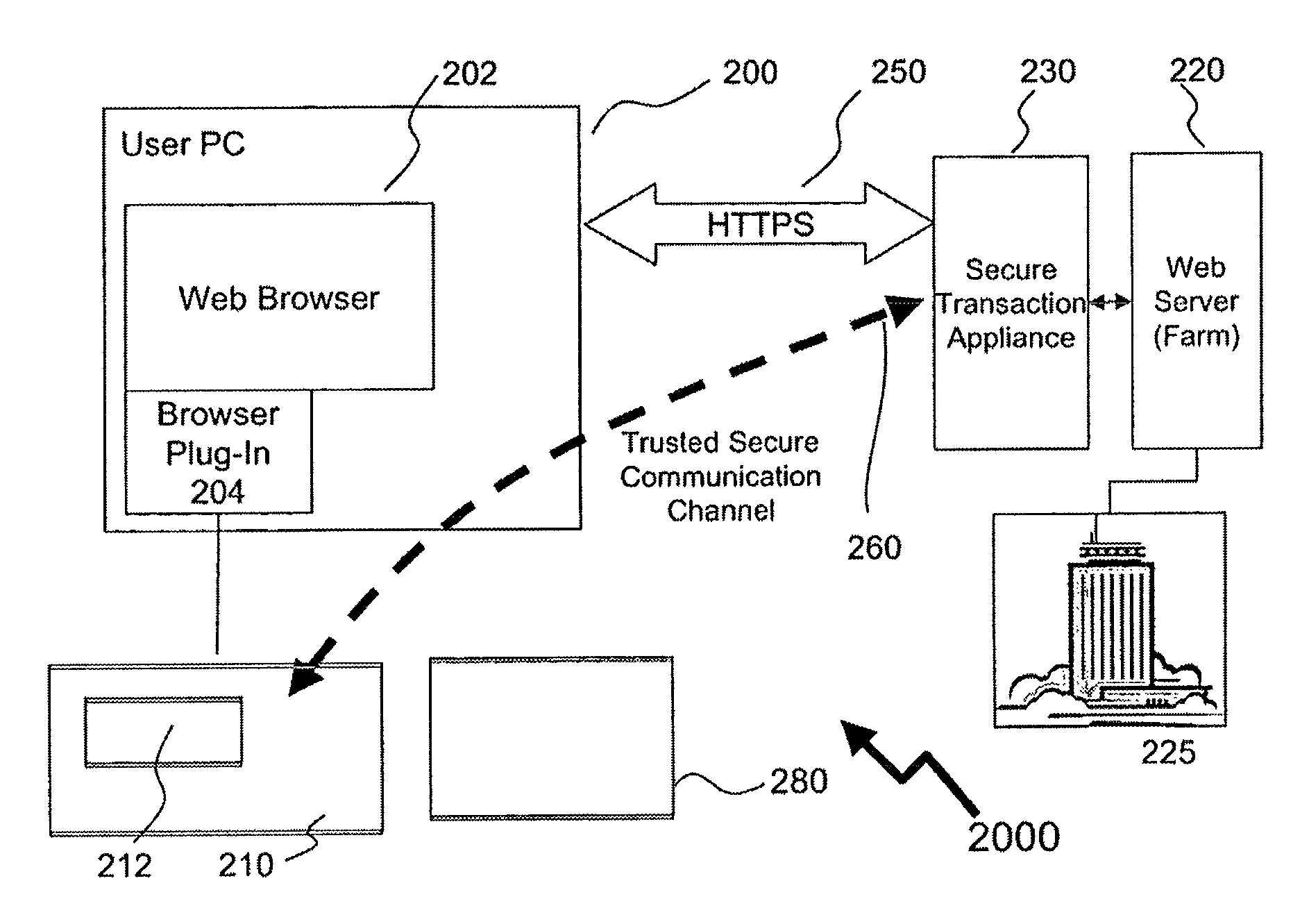
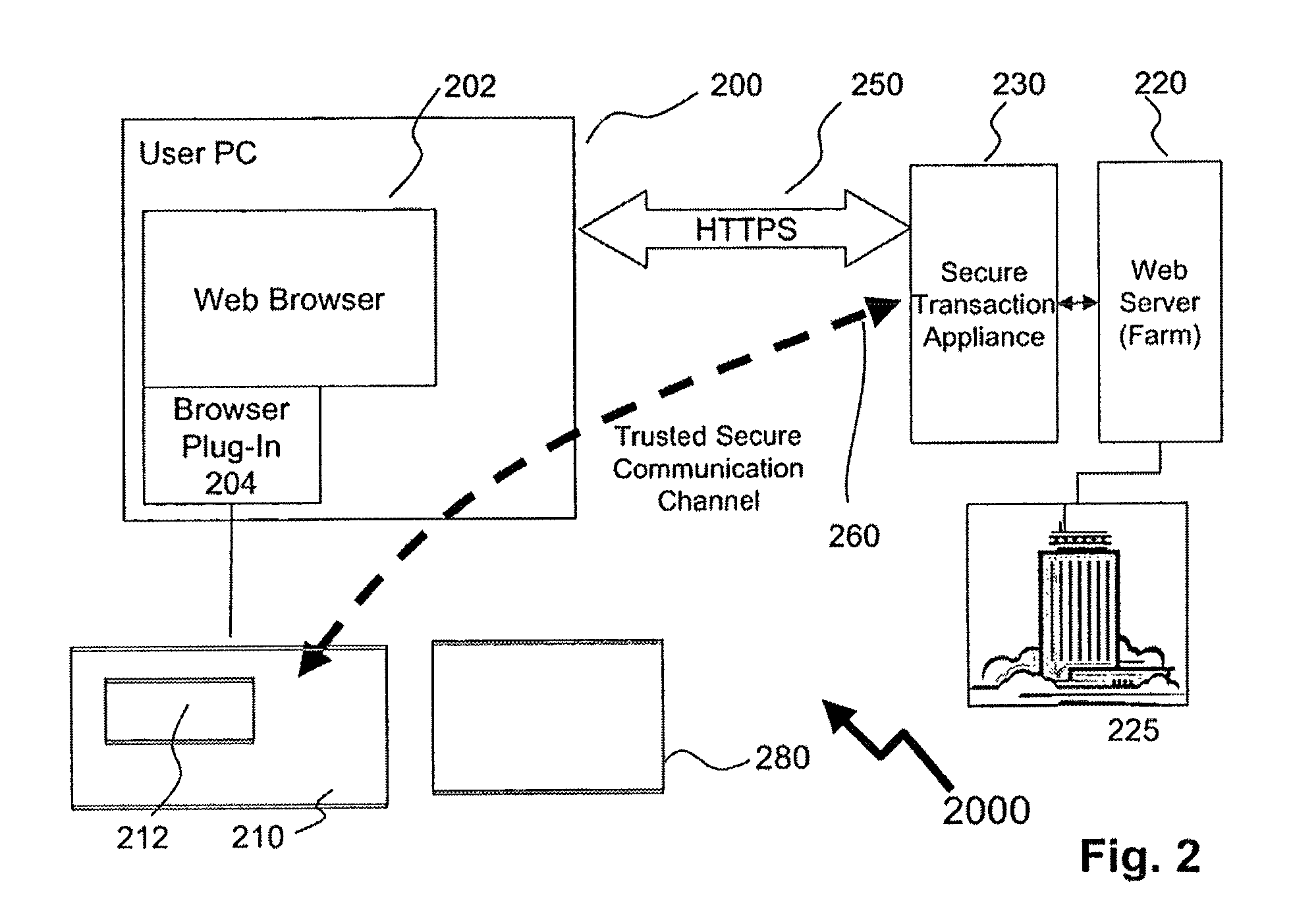
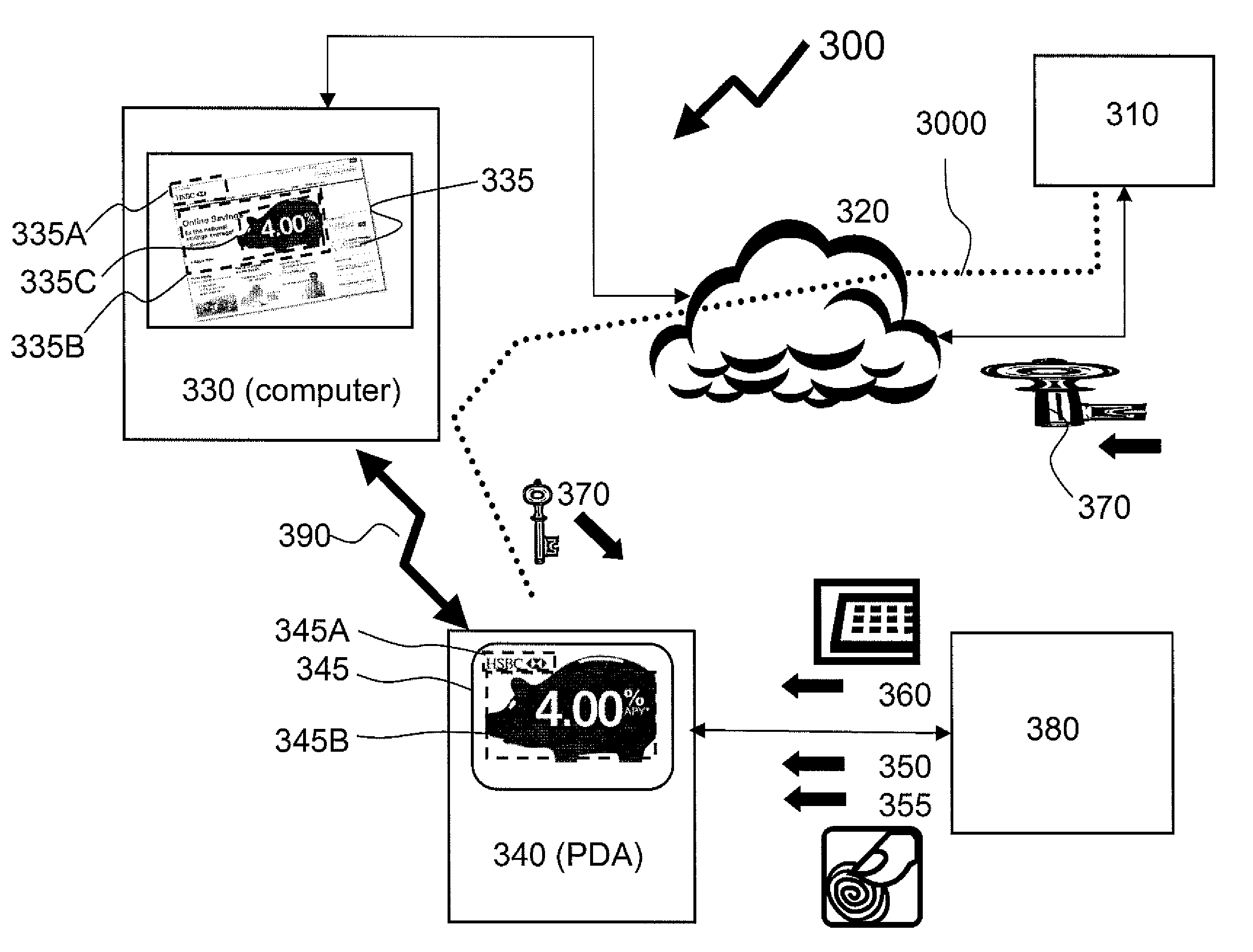
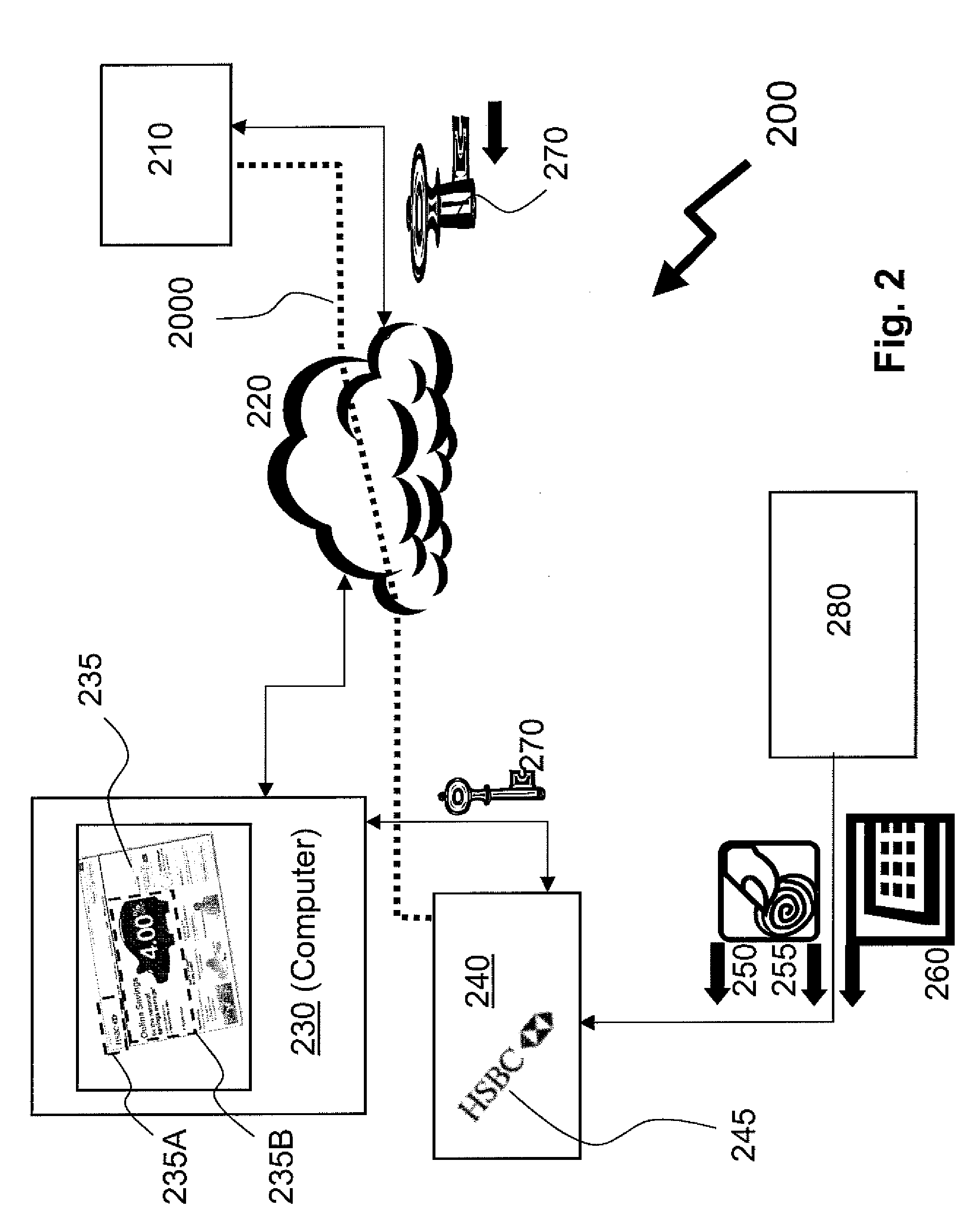
Method of providing assured transactions using secure transaction appliance and watermark verification
ActiveUS20090106556A1User identity/authority verificationComputer security arrangementsPersonalizationElectronic security
Disclosed is a method of improving electronic security by establishing a path between a user and a secure transaction appliance. The secure transaction appliance receiving information destined for the user which includes a tagged portion, said tagged portion triggering the secure transaction appliance to forward the information to the computer from which the request was issued, and to seeking an electronic signature to verify the content or transaction by transmitting a watermark, tagged portion of the content, or similar electronic content. The secure trusted path providing the user with the tagged portion incorporating additional elements such as a watermark, or in some embodiments only the additional elements, upon a personalized security device associated with the user making interception or manipulation more complex and difficult.
Owner:DATA LOCKER INC
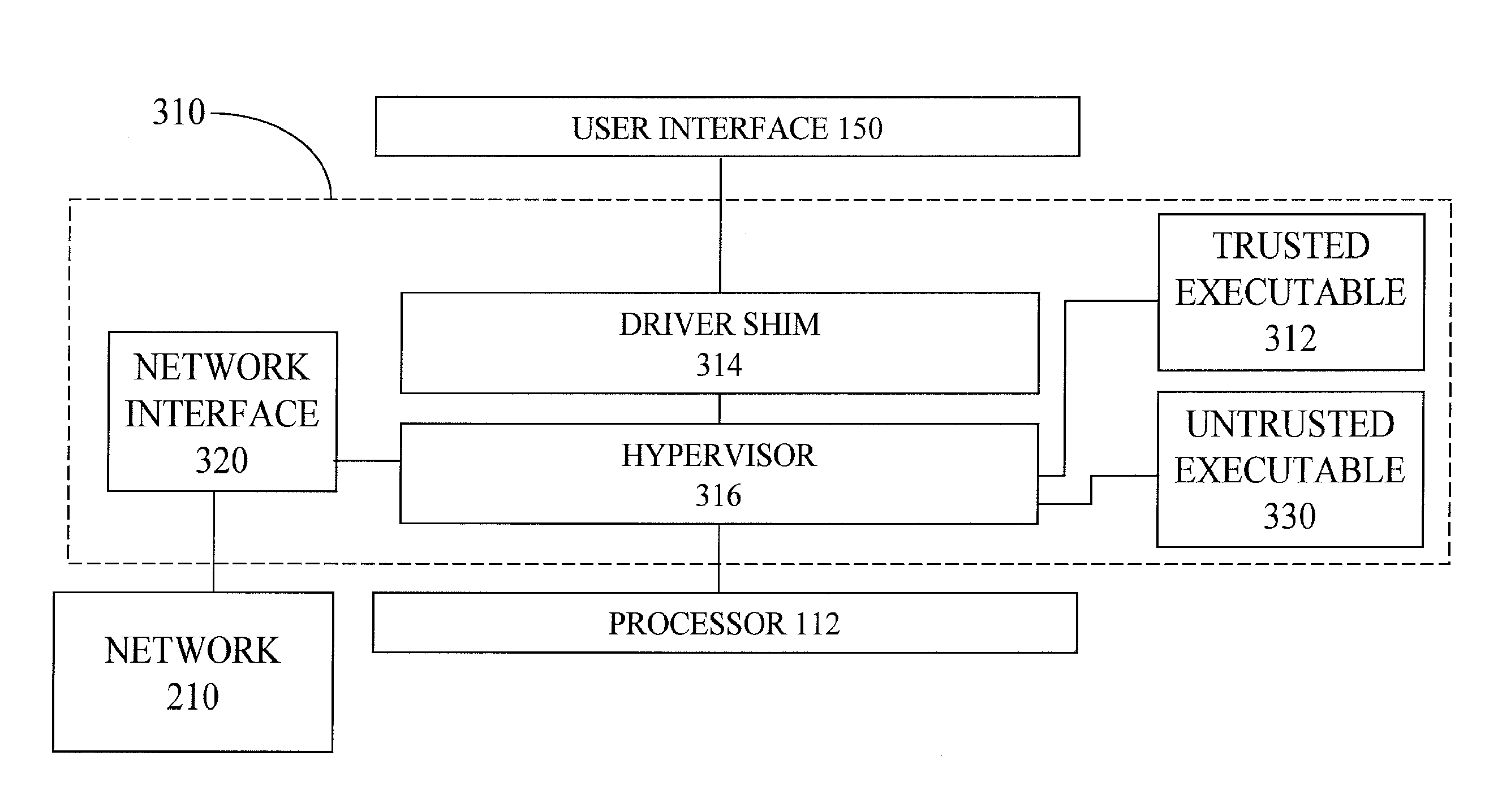
Methods and Apparatuses for User-Verifiable Trusted Path in the Presence of Malware
ActiveUS20120198514A1Improve the immunityInternal/peripheral component protectionPlatform integrity maintainanceDriver/operatorInternet privacy
An apparatus and method for establishing a trusted path between a user interface and a trusted executable, wherein the trusted path includes a hypervisor and a driver shim. The method includes measuring an identity of the hypervisor; comparing the measurement of the identity of the hypervisor with a policy for the hypervisor; measuring an identity of the driver shim; comparing the measurement of the identity of the driver shim with a policy for the driver shim; measuring an identity of the user interface; comparing the measurement of the identity of the user interface with a policy for the user interface; and providing a human-perceptible indication of whether the identity of the hypervisor, the identity of the driver shim, and the identity of the user interface correspond with the policy for the hypervisor, the policy for the driver shim, and the policy for the user interface, respectively.
Owner:CARNEGIE MELLON UNIV
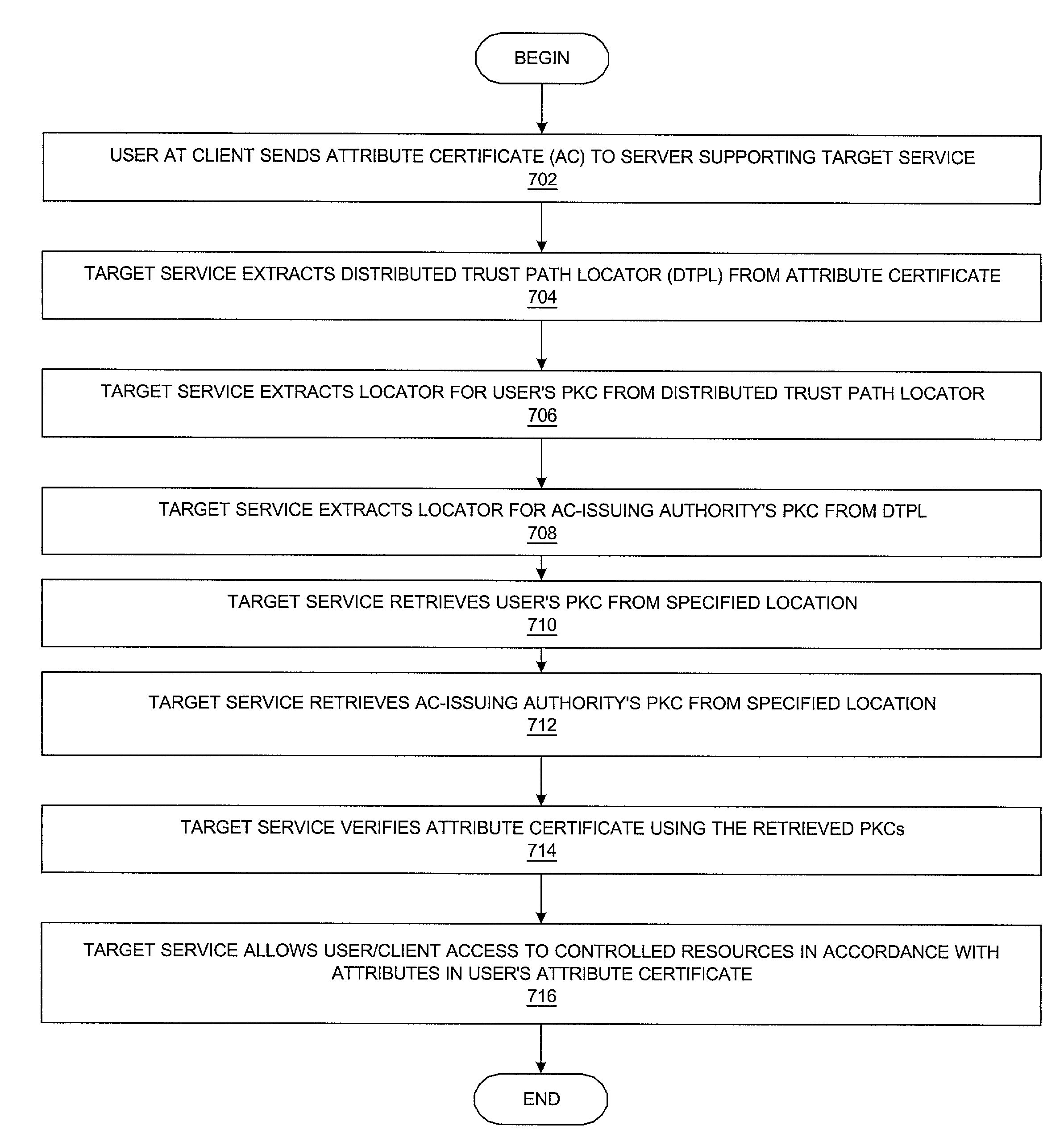
Method and system for managing a distributed trust path locator for public key certificates relating to the trust path of an X.509 attribute certificate
InactiveUS7356690B2Data processing applicationsDigital data processing detailsPublic key certificatePKCS
A method and a system is presented for managing attribute certificates. An extension within an attribute certificate, called a distributed trust path locator, allows an attribute certificate to be physically disassociated from its supporting public key certificates while remaining logically associated with its supporting public key certificates. The user's attribute certificate and its supporting PKCs allows any server using an attribute certificate to locate and retrieve the PKC of the user and of the AC-issuing authority. The user is not required to communicate his / her PKC to a target service. In addition, configuring the target service to accept attribute certificates does not require the deployment of a PKC for every AC-issuing authority.
Owner:IBM CORP
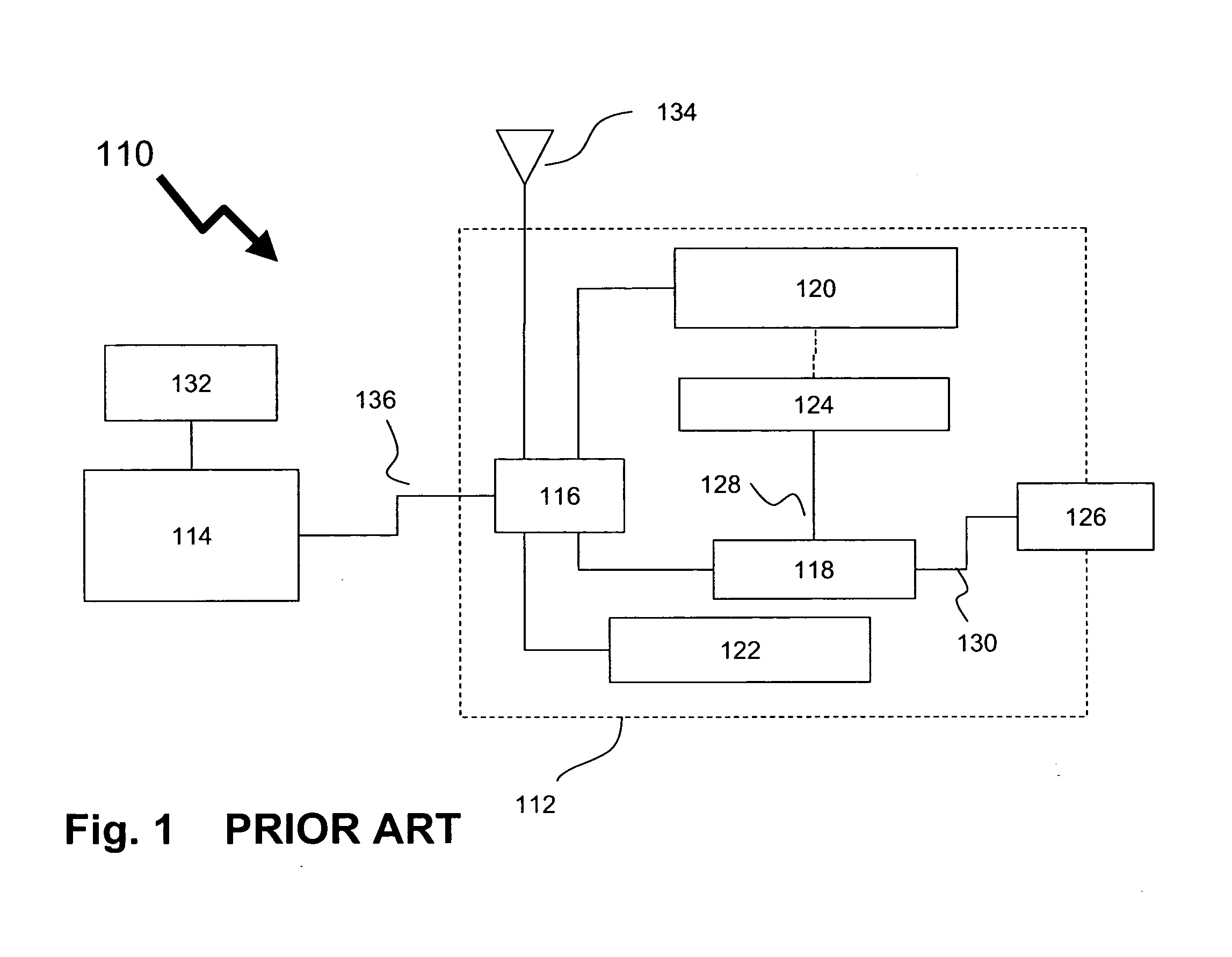
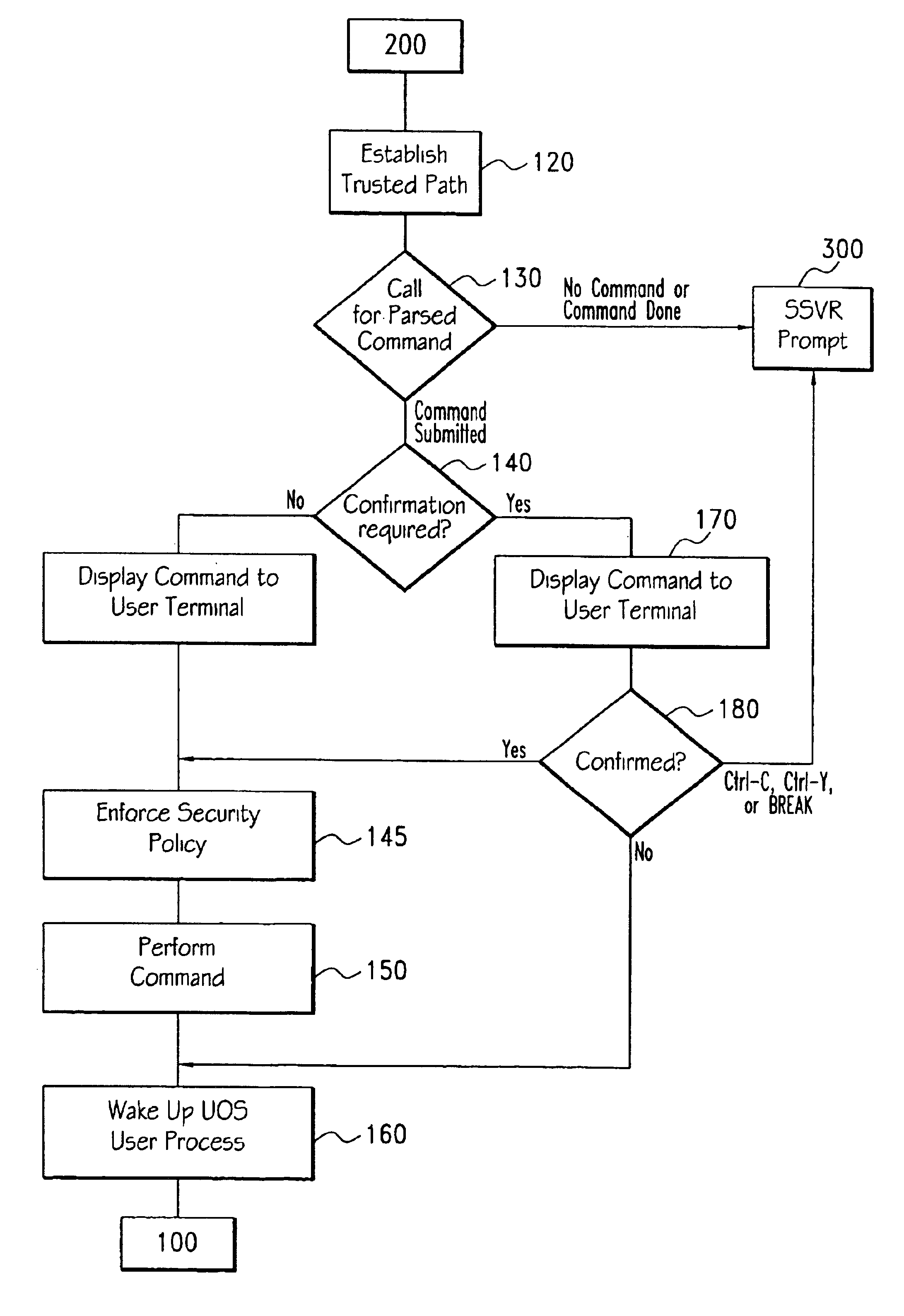
Processing trusted commands in trusted and untrusted environments
InactiveUS6871283B1Less codeQuantity minimizationDigital data processing detailsUser identity/authority verificationTrusted ComputingTrusted computing base
A method for executing trusted commands, in which a trusted command is first received from a user at a user terminal and parsed by untrusted code; then passed to a trusted computing base for execution. The trusted computing base displays some indication of what is to be done back to the user for confirmation. Confirmation of the commands prevents unauthorized modification of the commands and increases system confidence. A randomly (or pseudo-randomly) generated process identifier is employed to verify the existence of a trusted path.
Owner:HEWLETT PACKARD DEV CO LP
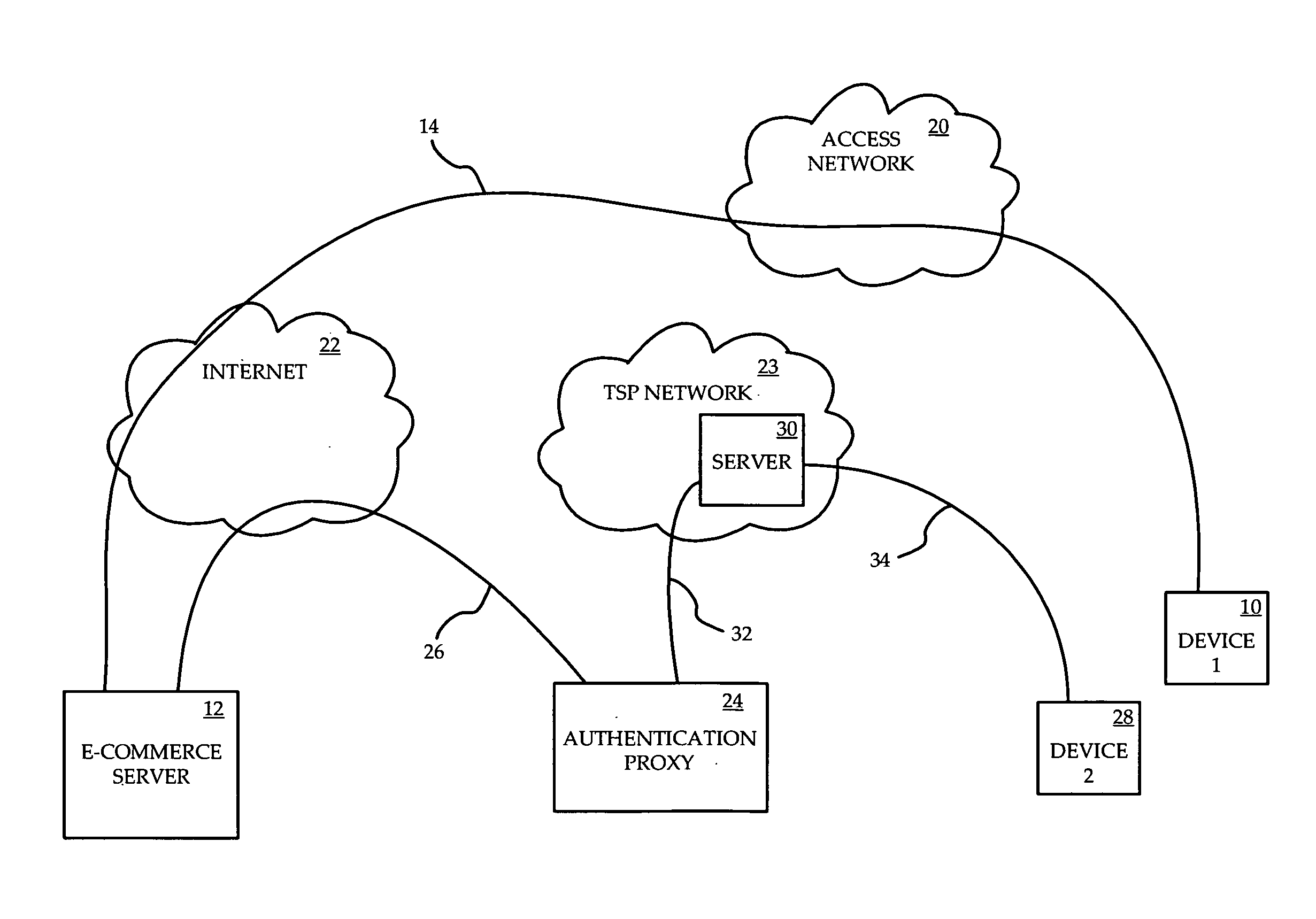
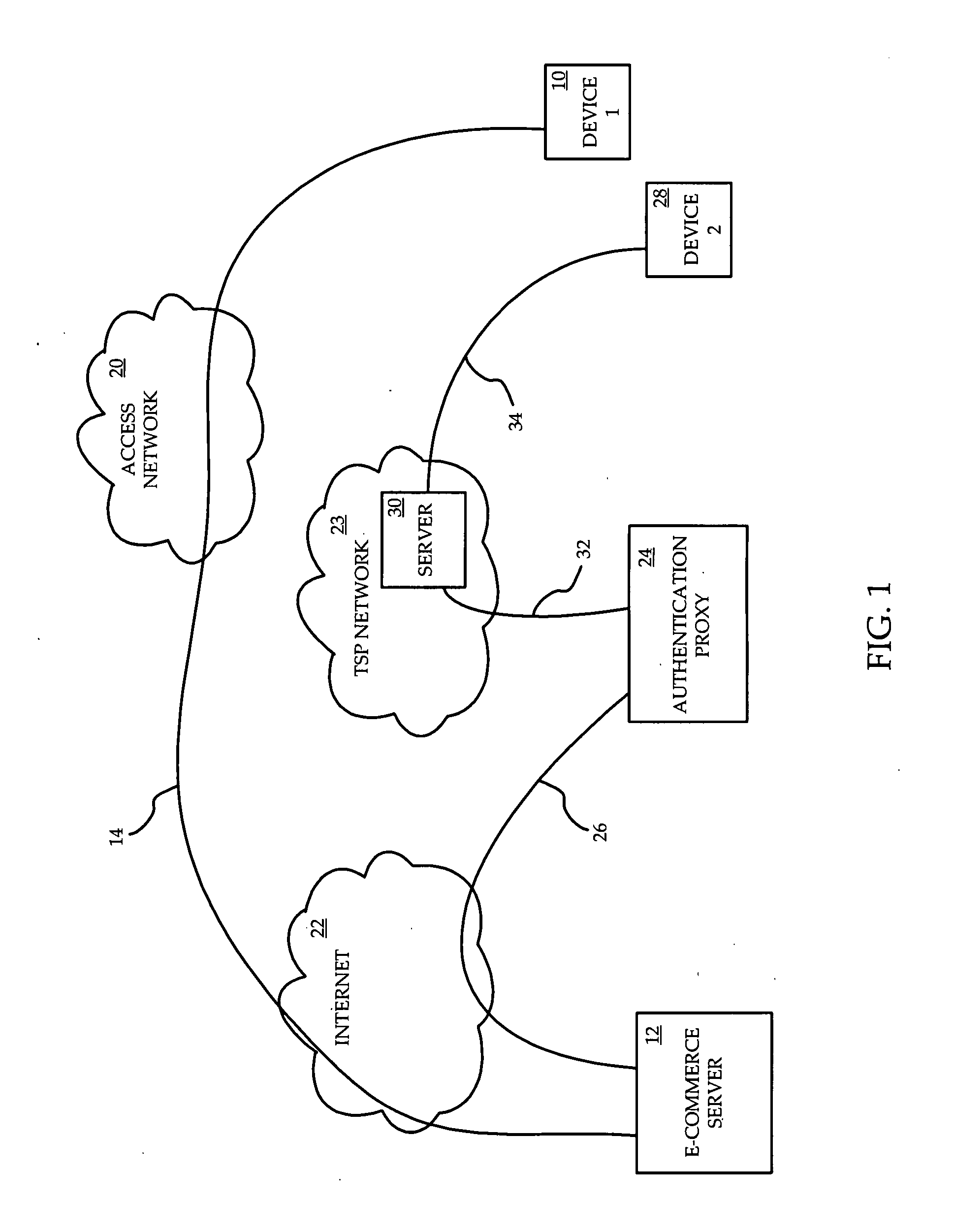
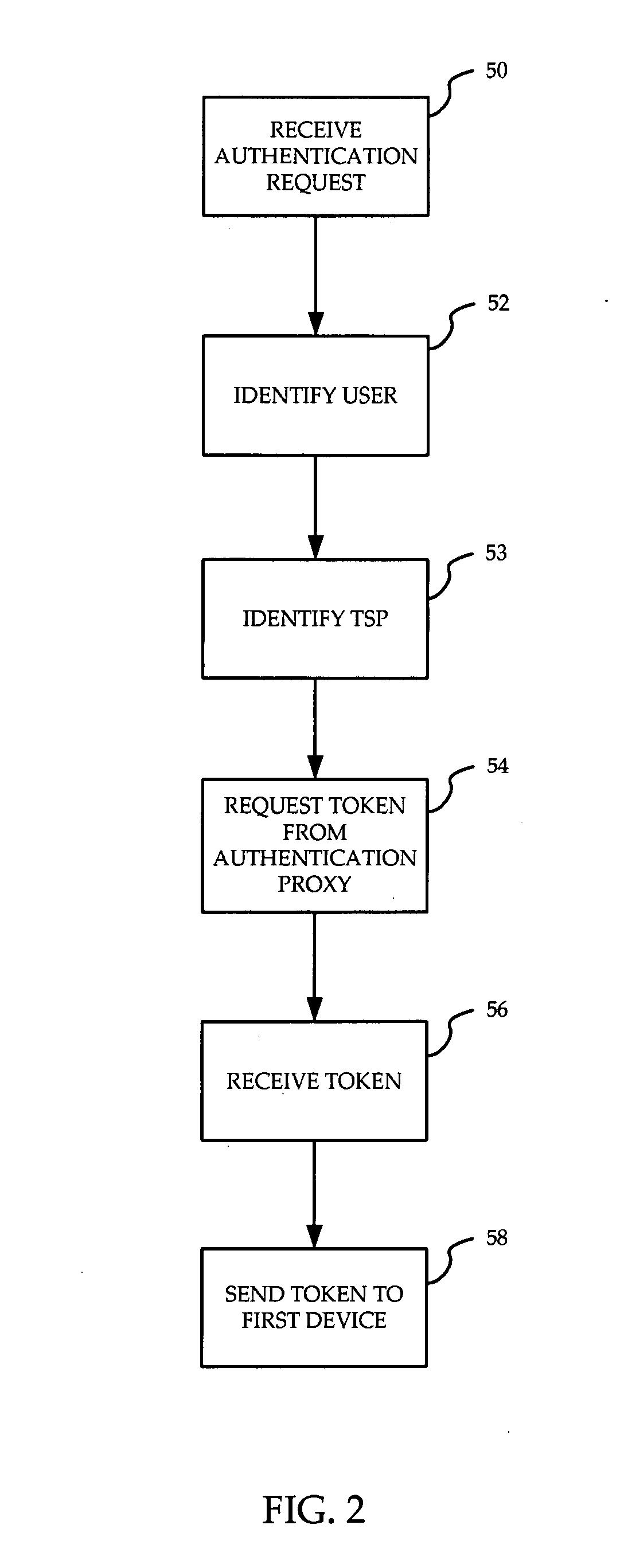
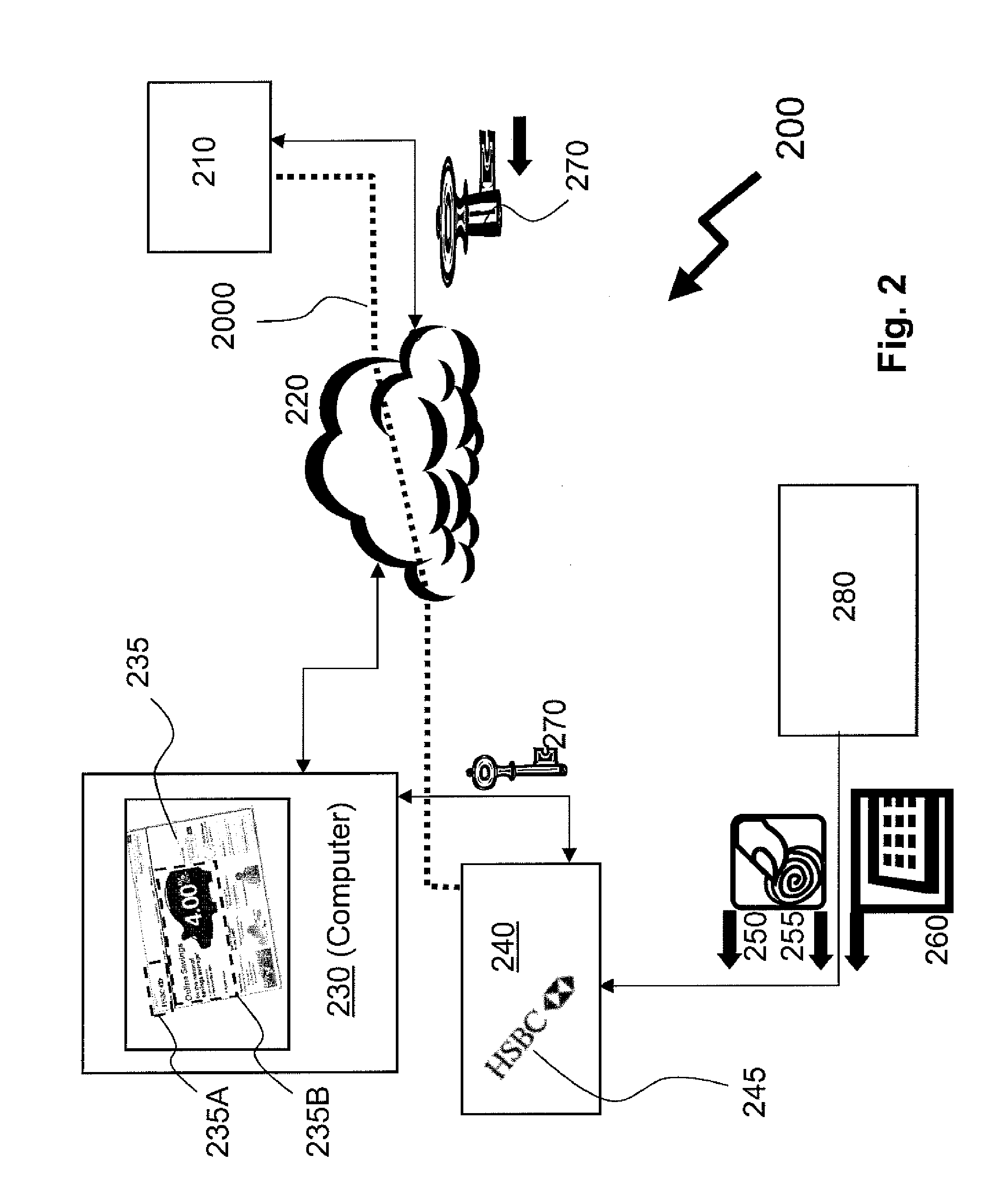
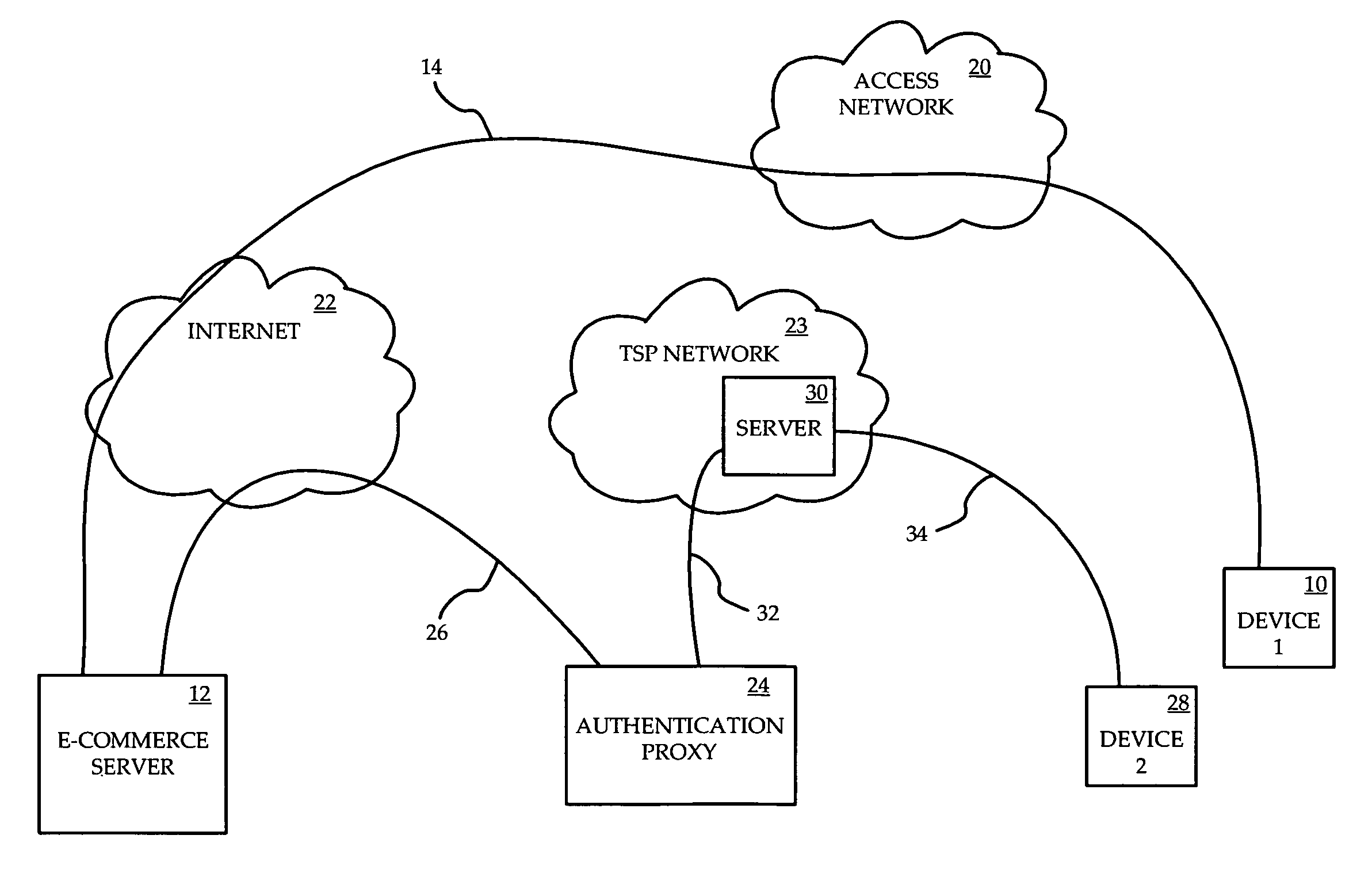
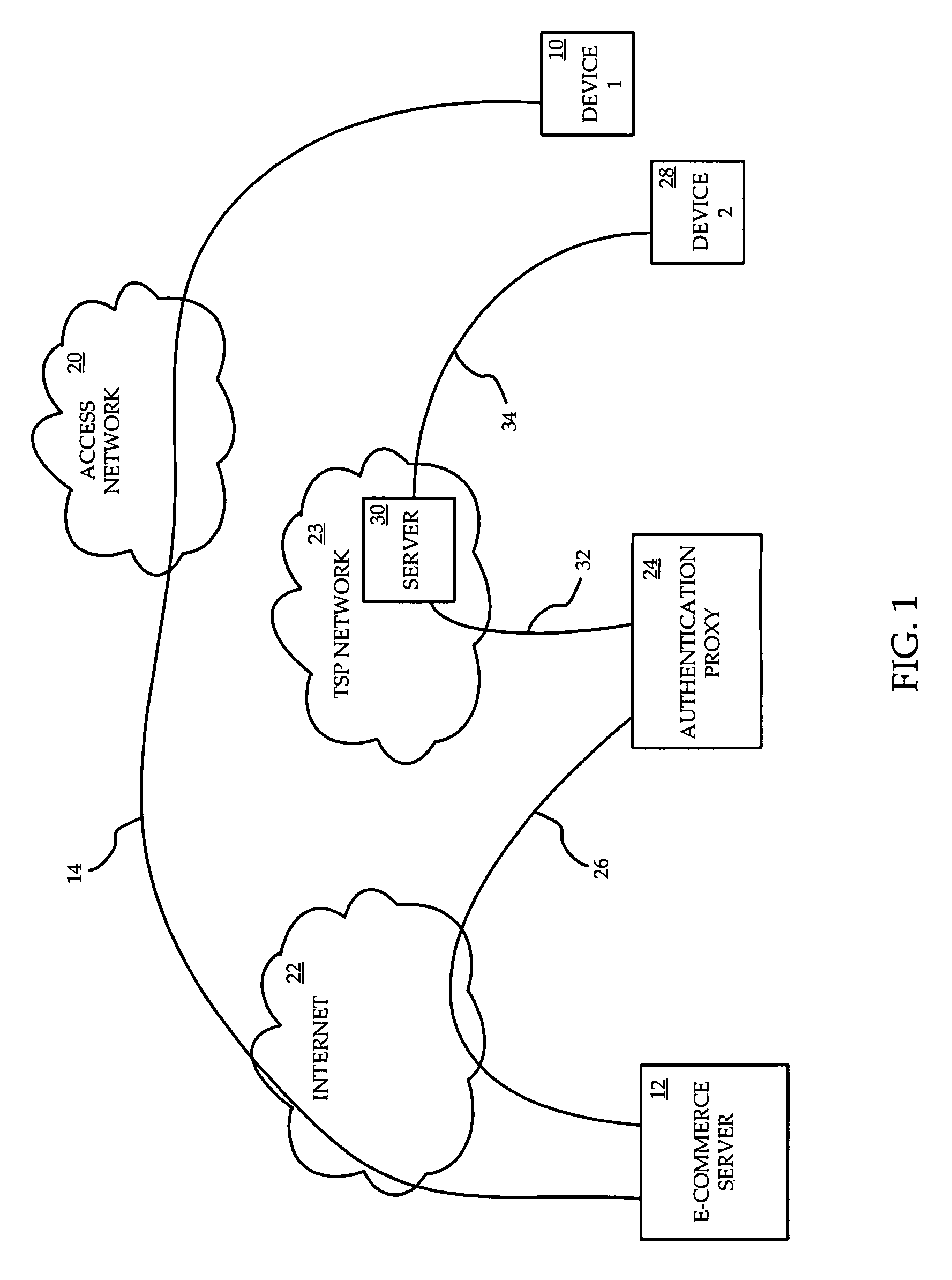
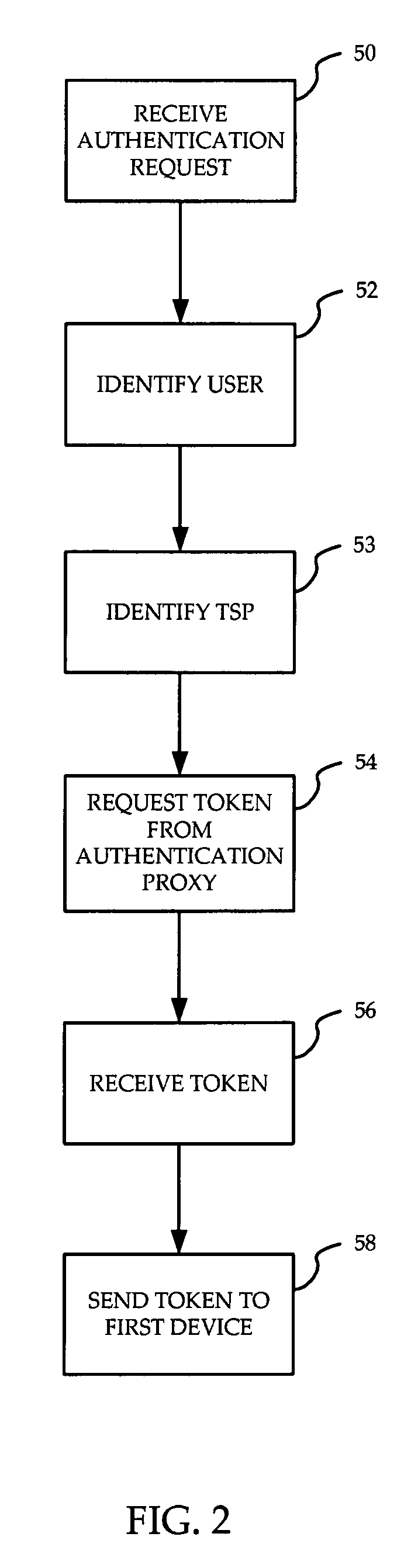
Identity verification for secure e-commerce transactions
ActiveUS20090119182A1Expand the scope of servicesIdentity of with easeFinanceDigital data processing detailsInternet privacyE-commerce
A method and apparatus are provided for providing authentication of an e-commerce server to a user engaging in e-commerce transactions. When the user begins an e-commerce session, the e-commerce server requests an authentication token from an authentication proxy with which it has registered. If the authentication proxy recognizes the e-commerce server, the authentication proxy generates an authentication token in the form of a simple image, and sends the authentication token to the e-commerce server over a trusted path. The e-commerce server sends the authentication token to the user. The authentication proxy also sends a copy of the authentication token to the user over a second trusted path to a second device or application accessible by the user. The user can then see that the authentication token presented by the e-commerce server matches the authentication token presented by the authentication proxy. Since the user has received the two authentication proxies over separate channels, one of which is typically secure, the user can be assured that the e-commerce server has been authenticated by the authentication proxy, and that the e-commerce server is therefore legitimate.
Owner:WSOU INVESTMENTS LLC
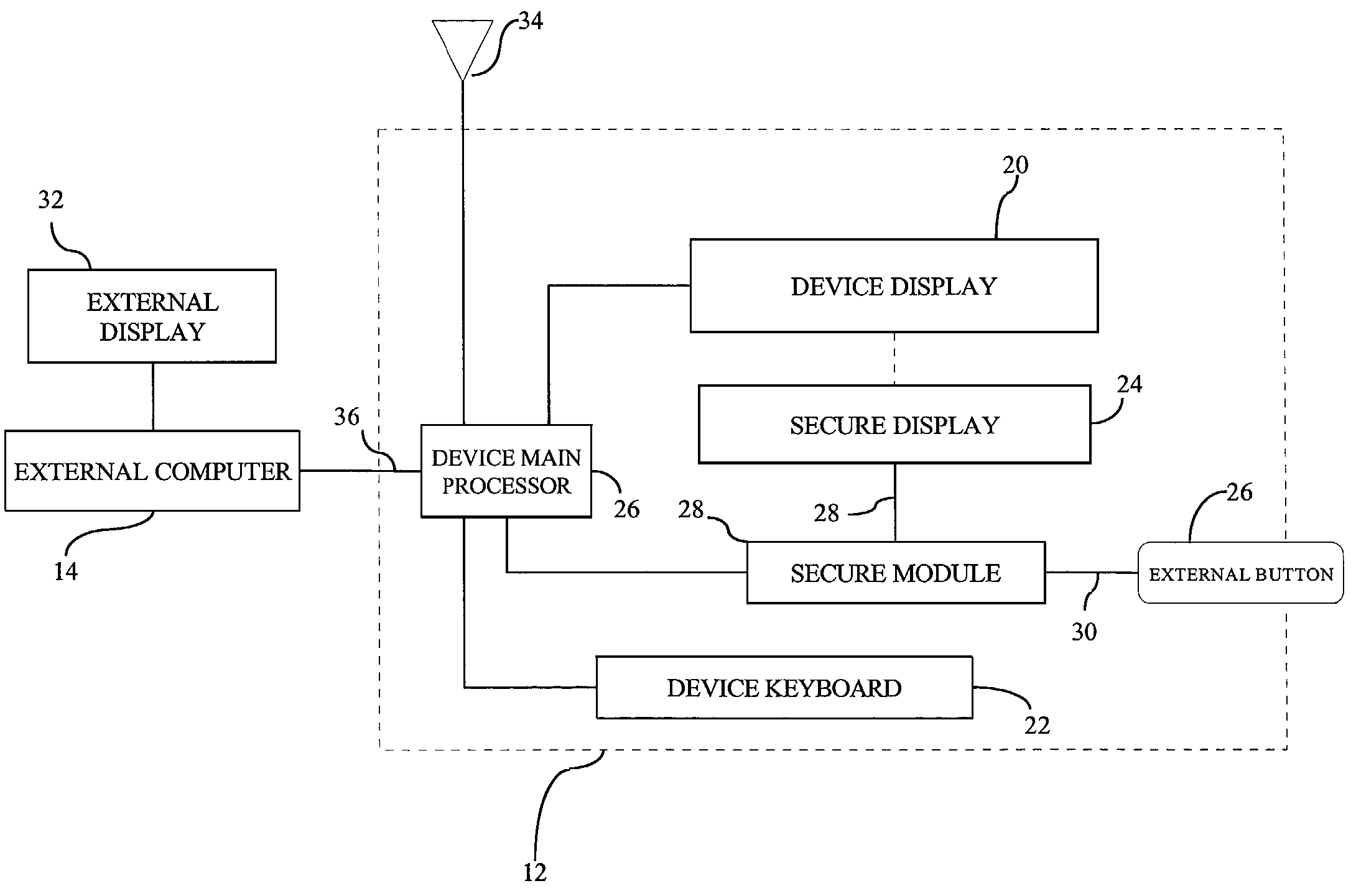
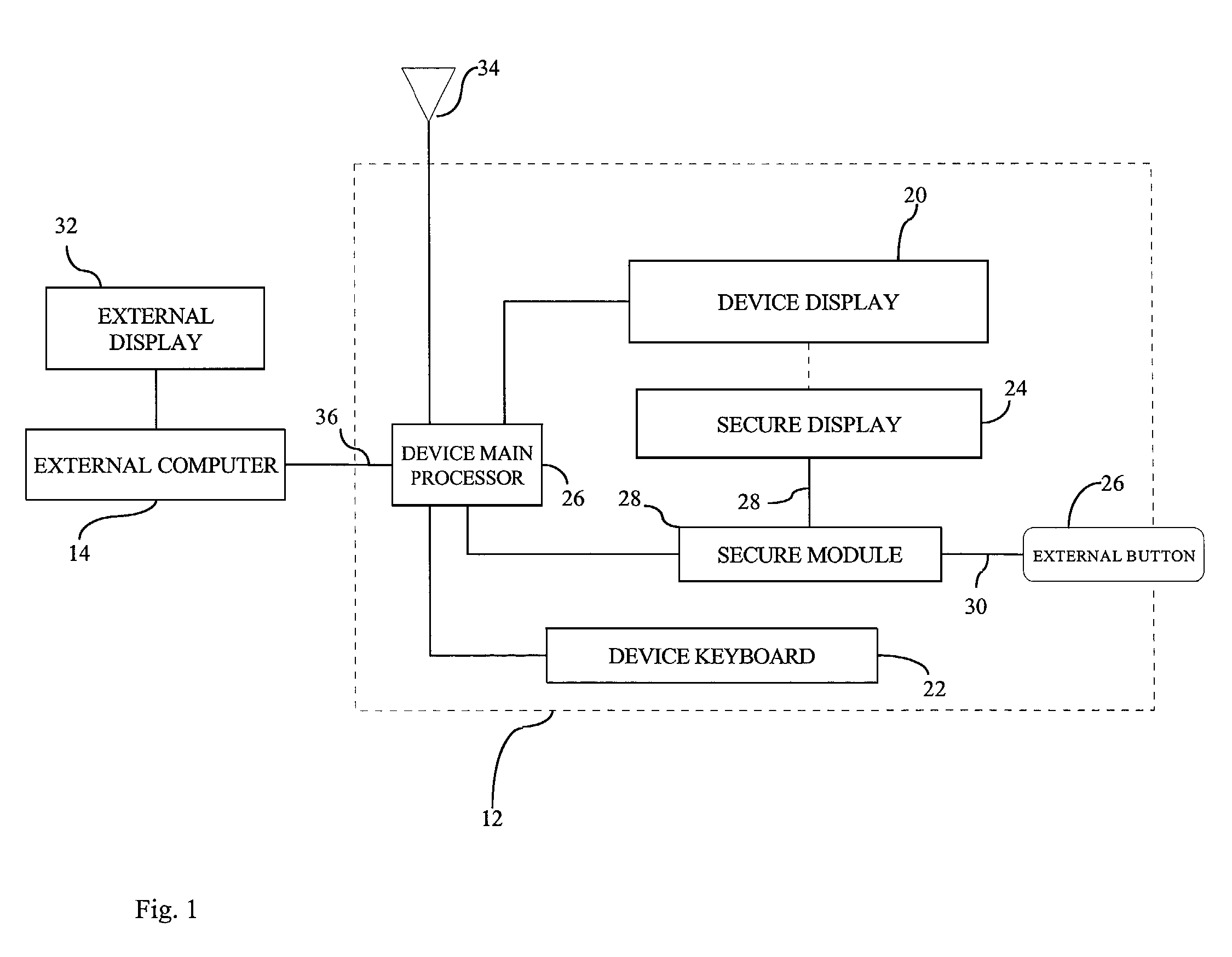
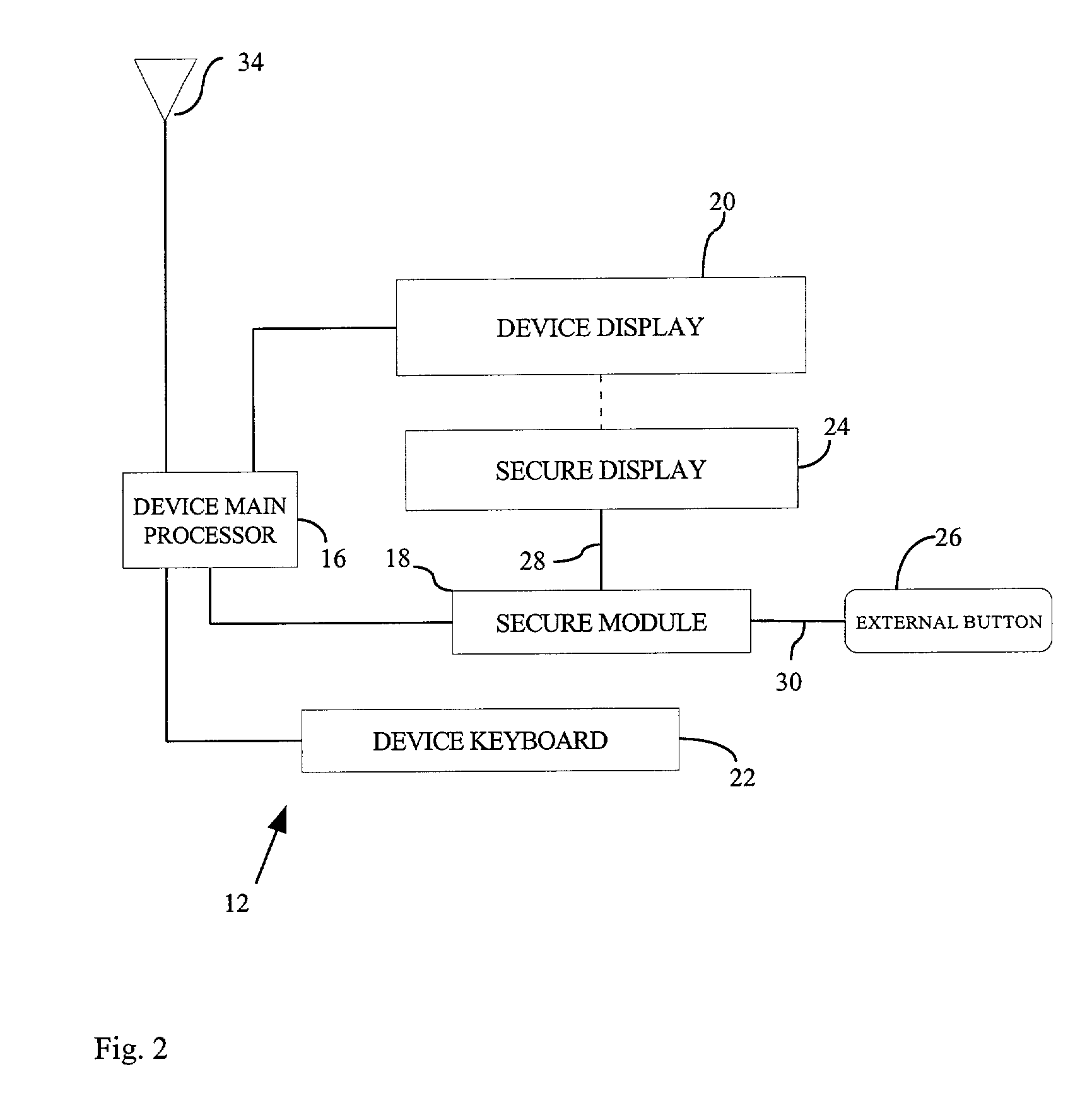
System and method for trusted communication
ActiveUS7216237B2Mitigate such drawbackEasy inputDigital data processing detailsUser identity/authority verificationPersonalizationData integrity
A method of establishing a trusted path of data and a method of verifying the integrity of data presented for signing to a user of the personalized device in a public-key cryptographic scheme. The method comprises establishing a trusted path between the user and secure module residing on the personalized device. The secure module holds the user's private key, displays information about the data message directly to the user, and generates the signature only when instructed to do so. The decision whether or not to sign the data message is determined by the user.
Owner:MALIKIE INNOVATIONS LTD
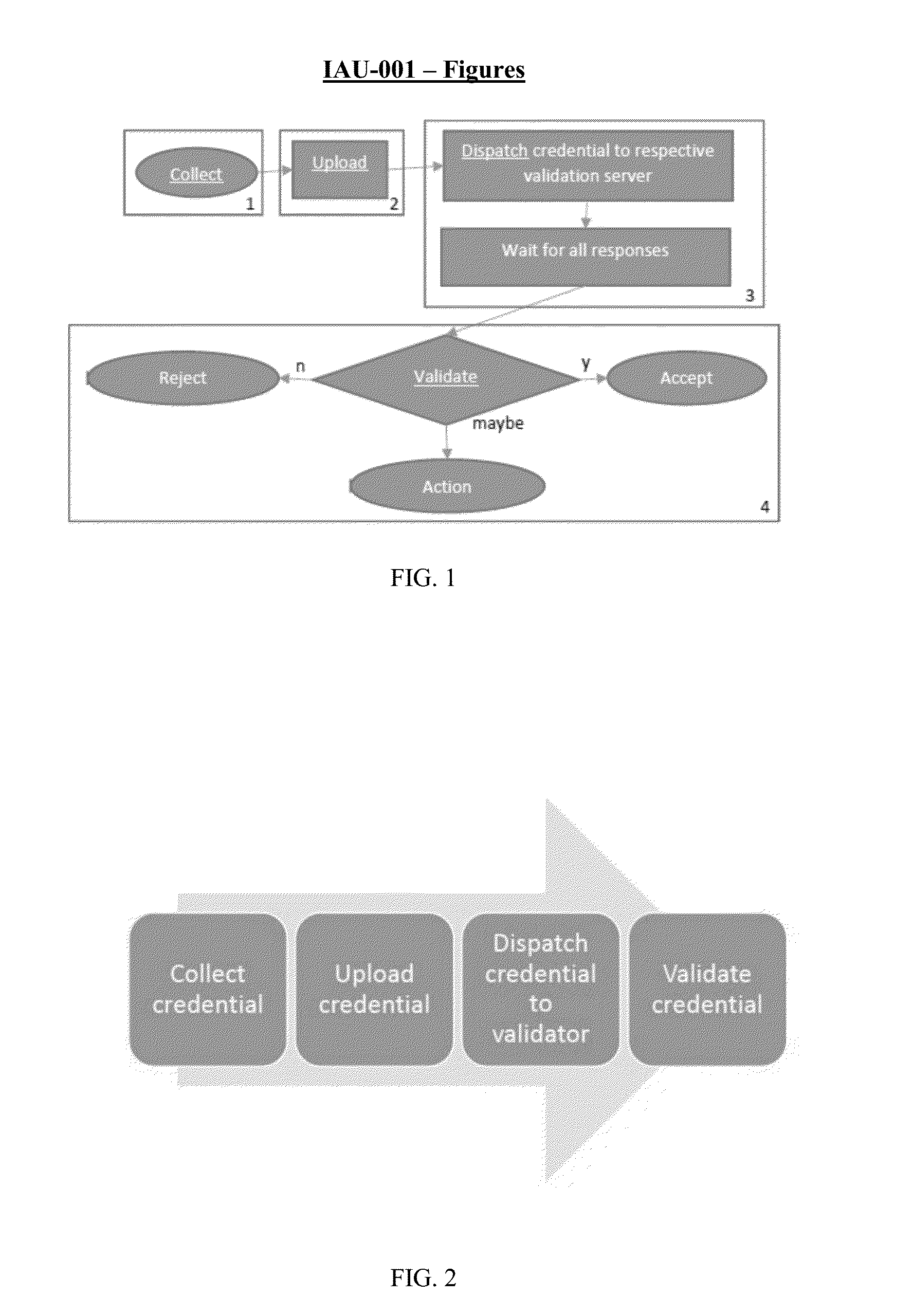
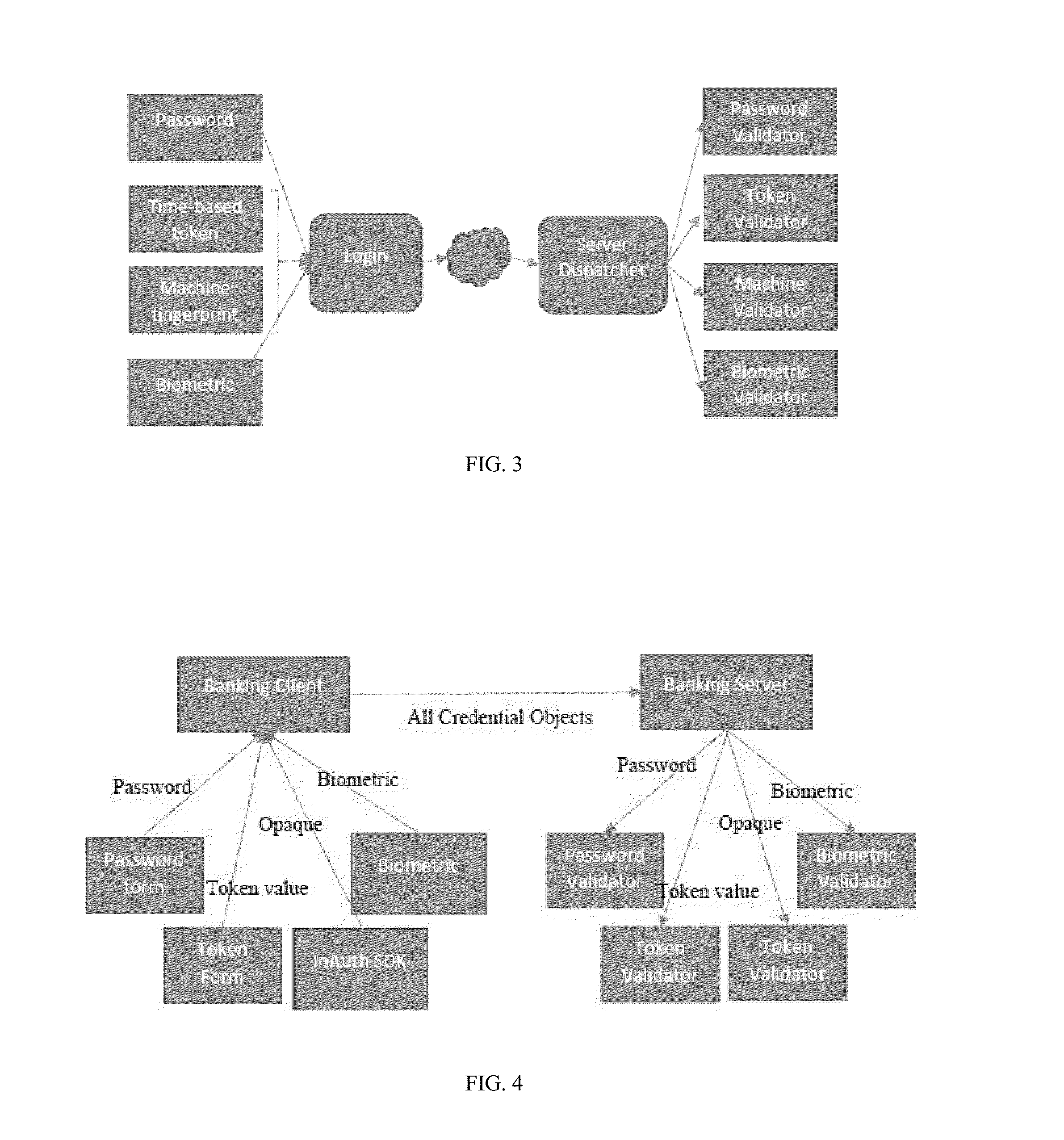
Systems and methods for trusted path secure communication
ActiveUS20160248590A1Connection securityUser identity/authority verificationDigital data protectionConfidentialityMessage delivery
A system for establishing a trusted path for secure communication between client devices and server devices, such as between an account holder and a financial institution, can provide the core security attributes of confidentiality (of the parties), integrity (of the information), anti-replay (protection against replay fraud) and / or anti-tampering (protection against unauthorized changes to information being exchanged and / or modules that generate and communicate such information). A messaging layer implementation in favor of a transport layer implementation can provide a trusted path. This infrastructure features secure cryptographic key storage, and implementation of a trusted path built using the cryptographic infrastructure. The trusted path protects against unauthorized information disclosure, modification, or replays. These services can effectively protect against Man-in-the-Middle, Man-in-the-Application, and other attacks.
Owner:INAUTH
Method of Providing Transactions Employing Advertising Based Verification
ActiveUS20090235081A1Prevent tamperingEncryption apparatus with shift registers/memoriesUser identity/authority verificationPersonalizationMalware
A method of improving electronic security establishes a secure trusted path between a user and an institution seeking an electronic signature to verify a transaction before any request for signature and completing electronic transaction activities occurs. The secure trusted path providing the user with a first predetermined portion of a branded watermark, for instance an advertisement, provided from the institution in conjunction with the request, and a second predetermined portion of the branded watermark being provided upon a personalized device that cannot be intercepted or manipulated by malware, allowing the user to verify that the request as displayed upon the user's primary computing device is valid.
Owner:DATA LOCKER INC
Method of Providing Assured Transactions by Watermarked File Display Verification
ActiveUS20090049301A1Prevent tamperingEncryption apparatus with shift registers/memoriesUser identity/authority verificationPersonalizationMalware
Electronic transactions employing prior art approaches of digital certificates and authentification are subject to attacks resulting in fraudulent transactions and abuse of identity information. Disclosed is a method of improving electronic security by establishing a secure trusted path between a user and an institution seeking an electronic signature to verify a transaction before any request for signature and completing electronic transaction activities occurs. The secure trusted path providing the user with a predetermined portion of the request from the institution for a signature upon a personalized device that cannot be intercepted or manipulated by malware to verify that the request as displayed upon the user's primary computing device is valid.
Owner:DATA LOCKER INC
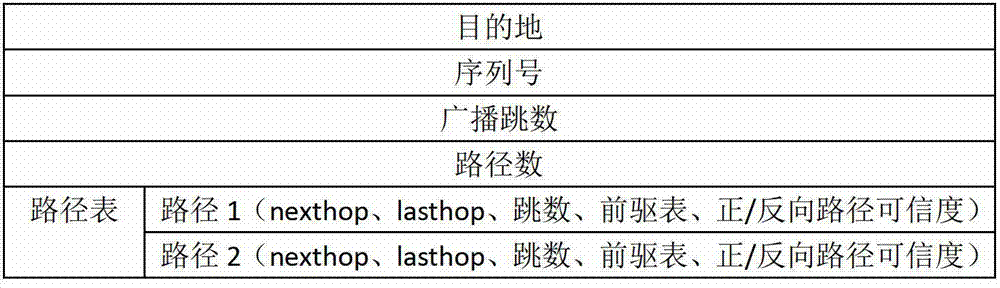
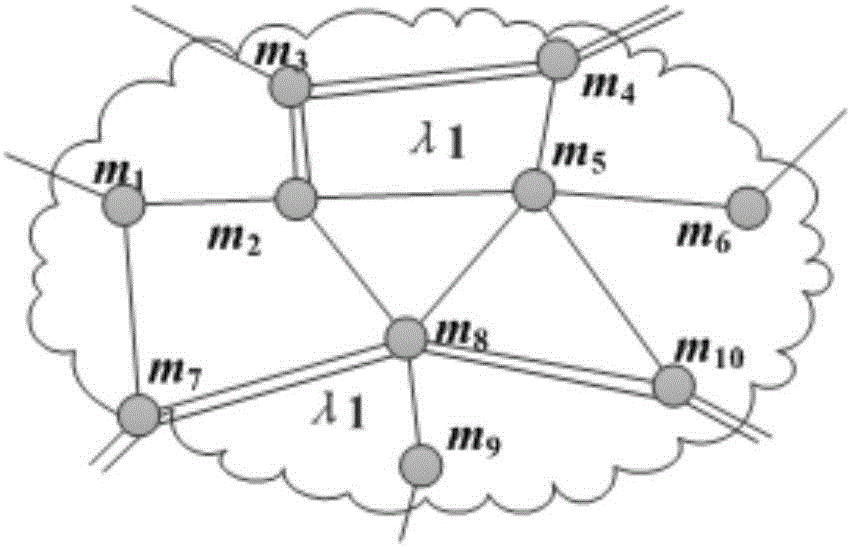
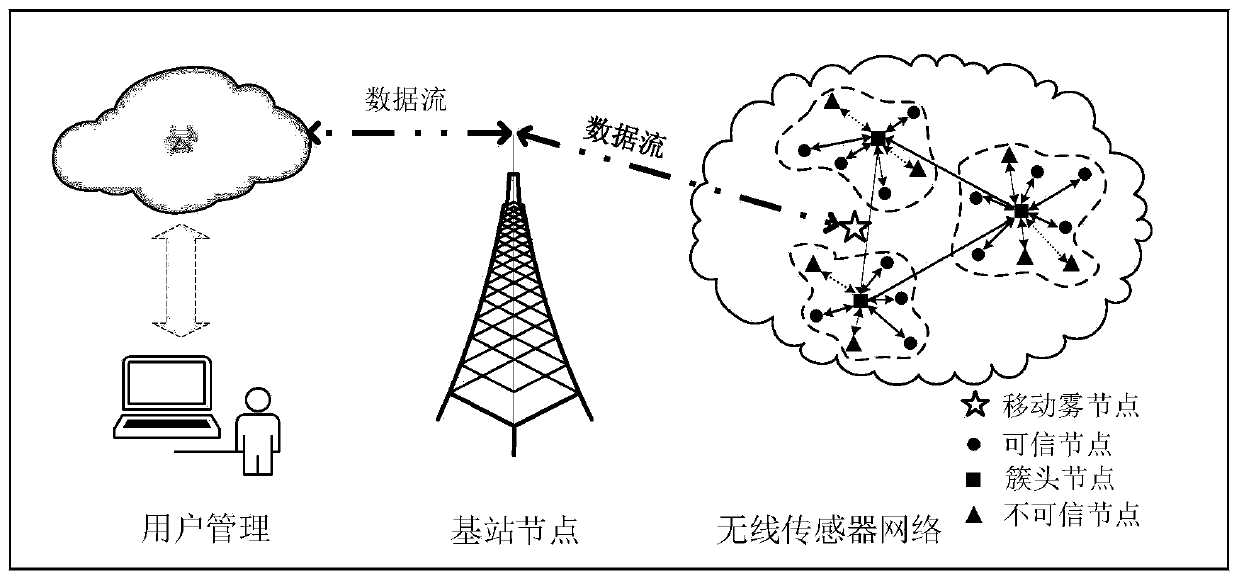
Trust-based on-demand multipath vector routing algorithm of Ad Hoc network
InactiveCN103118412AReduce computational overheadEasy assessment processWireless communicationQuality of serviceTrusted path
The invention discloses a trust-based on-demand multipath vector routing algorithm of an Ad Hoc network The trust-based on-demand multipath vector algorithm of the Ad Hoc network includes that simple and practical credible theories are utilized to improve and expand an AOMDV (Ad Hoc On-demand Multipath Distance Vector) routing protocol, and the packet loss rate is used as a measurement of credibility to establish a credible multipath, so that the data transfer rate is greatly increased. Meanwhile, the path maintenance system is added based on the original route maintenance, and the original route error broadcast is changed to the wrong path unicast, so that the maintenance overhead of trusted paths is reduced. According to the Ad Hoc network trust-based on-demand multipath vector routing algorithm, a balance is found between the transmission rate and the network overhead, and the quality of service is substantially improved due to the fact that the trust-based on-demand multipath vector routing algorithm of the Ad Hoc network is verified by an NS2 simulation testing and a field testing.
Owner:SHANDONG UNIV
Method of Providing Transactions Employing Advertising Based Verification
A method of improving electronic security establishes a secure trusted path between a user and an institution seeking an electronic signature to verify a transaction before any request for signature and completing electronic transaction activities occurs. The secure trusted path providing the user with a first predetermined portion of a branded watermark, for instance an advertisement, provided from the institution in conjunction with the request, and a second predetermined portion of the branded watermark being provided upon a personalized device that cannot be intercepted or manipulated by malware, allowing the user to verify that the request as displayed upon the user's primary computing device is valid.
Owner:DATA LOCKER INC
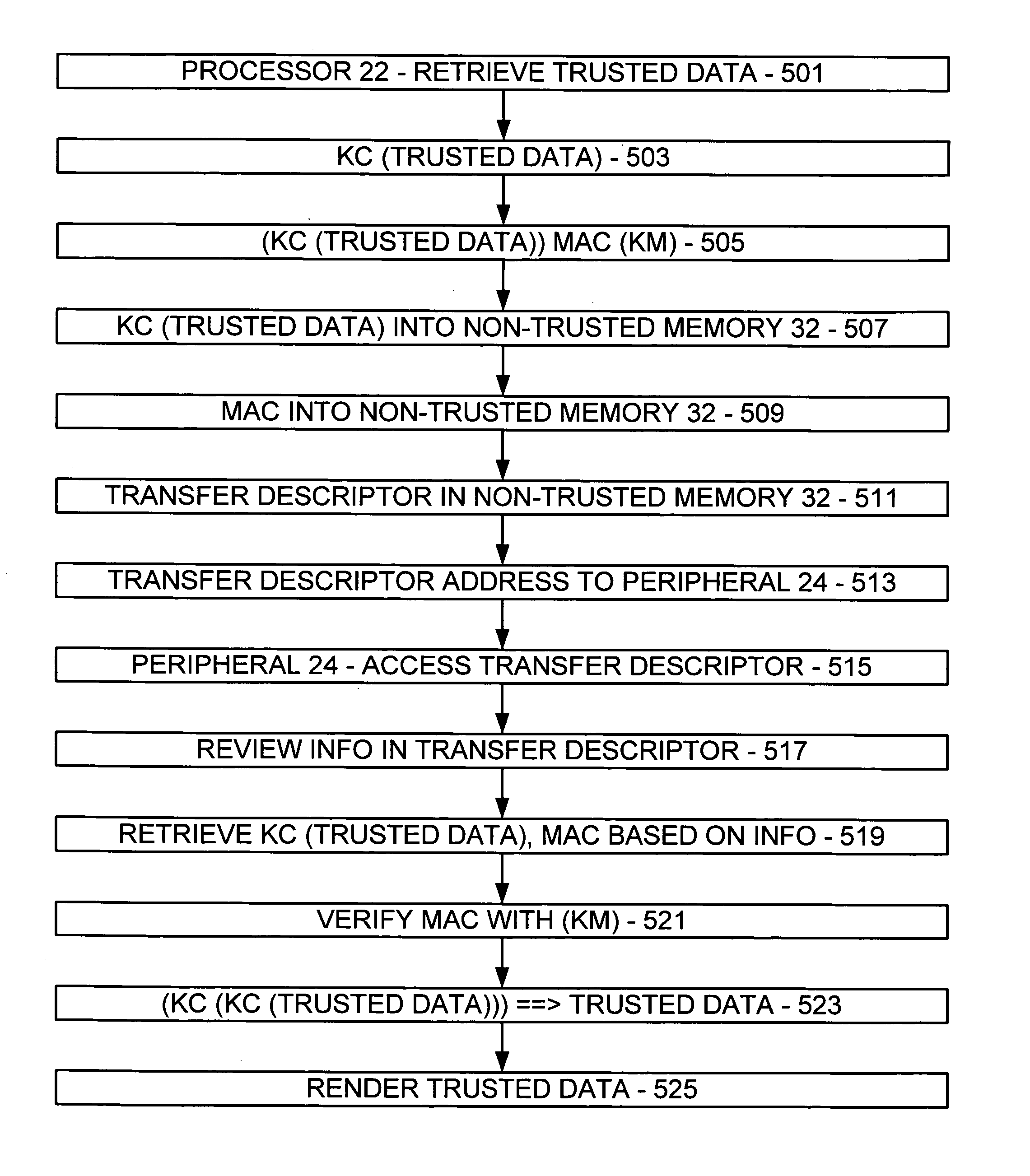
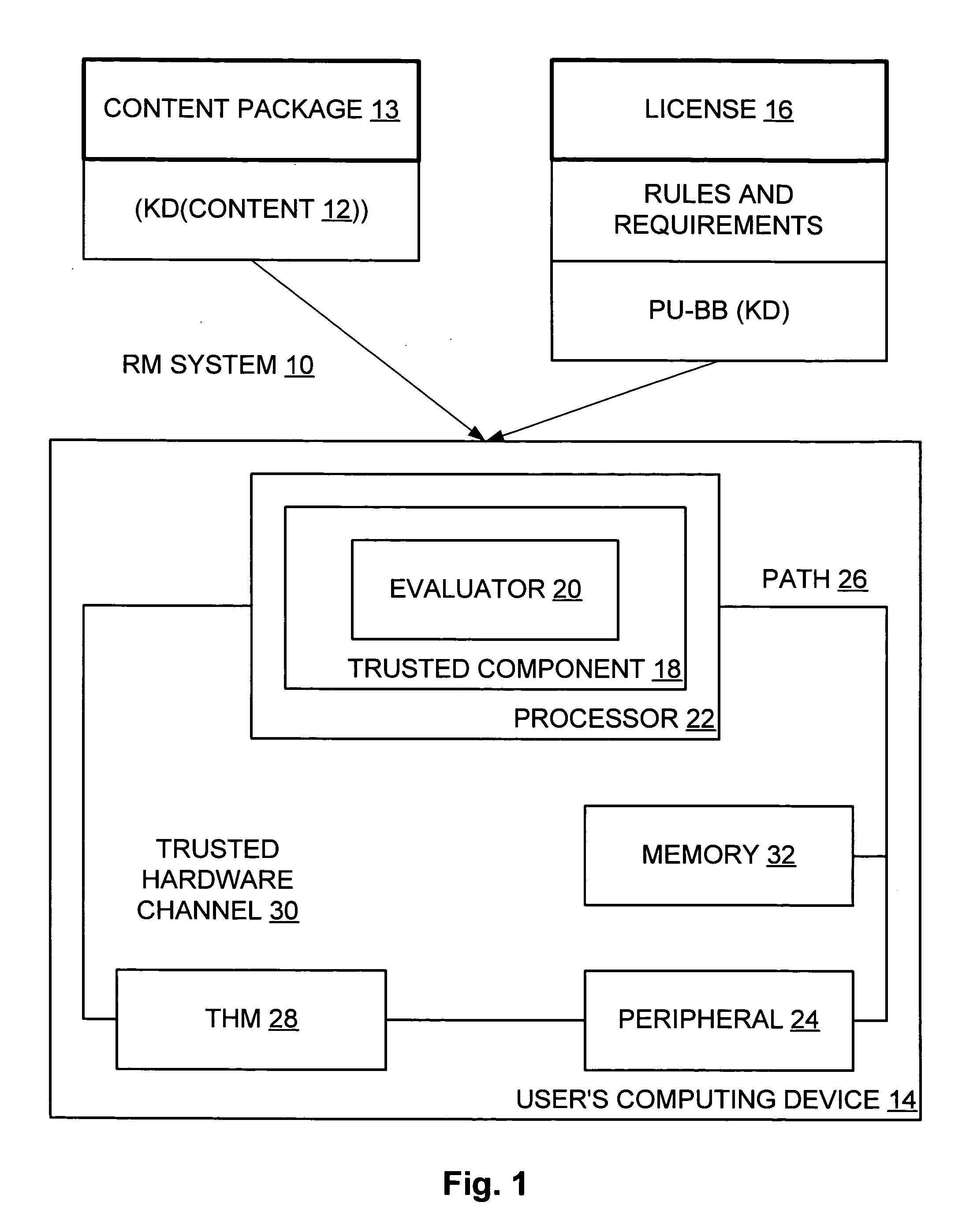
Trusted path for transmitting content thereon
InactiveUS20050172134A1Satisfies needDigital data processing detailsAnalogue secracy/subscription systemsComputer hardwareTrusted path
A method is provided for a processor of a computing device to obtain a trusted identification of a hardware peripheral of the computing device, for the computing device and the peripheral to derive a set of shared keys, and for the processor to send trusted data to the peripheral.
Owner:MICROSOFT TECH LICENSING LLC
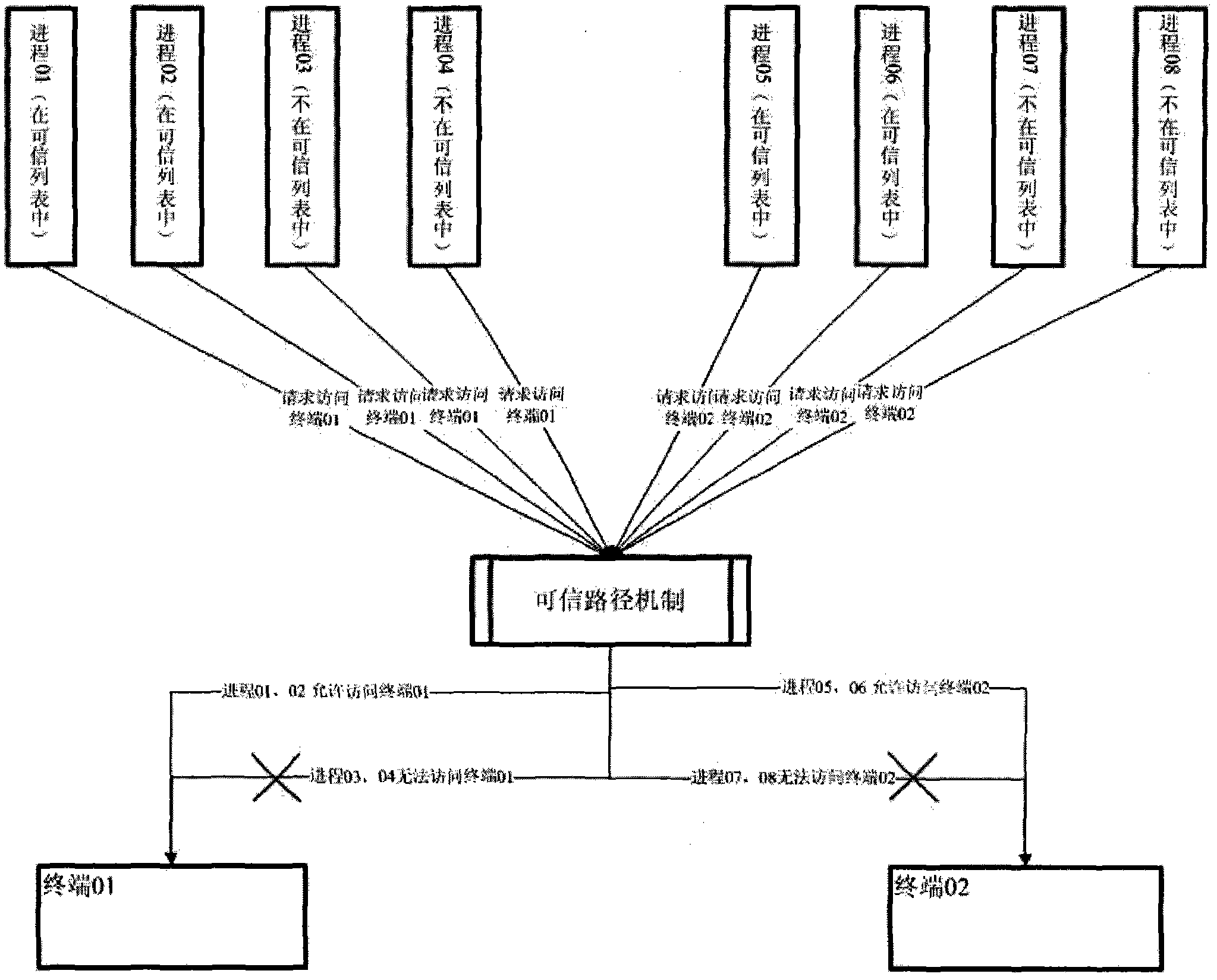
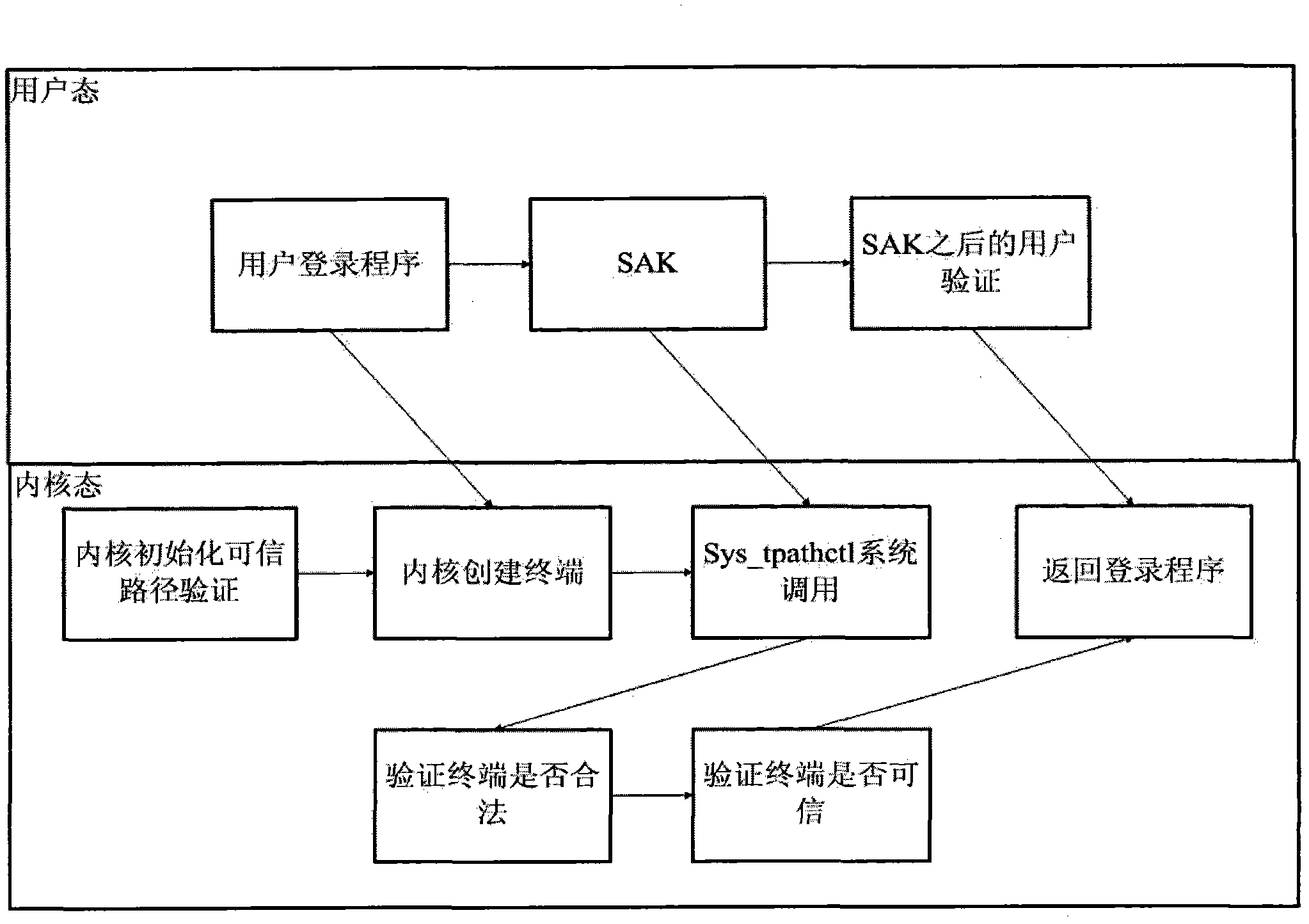
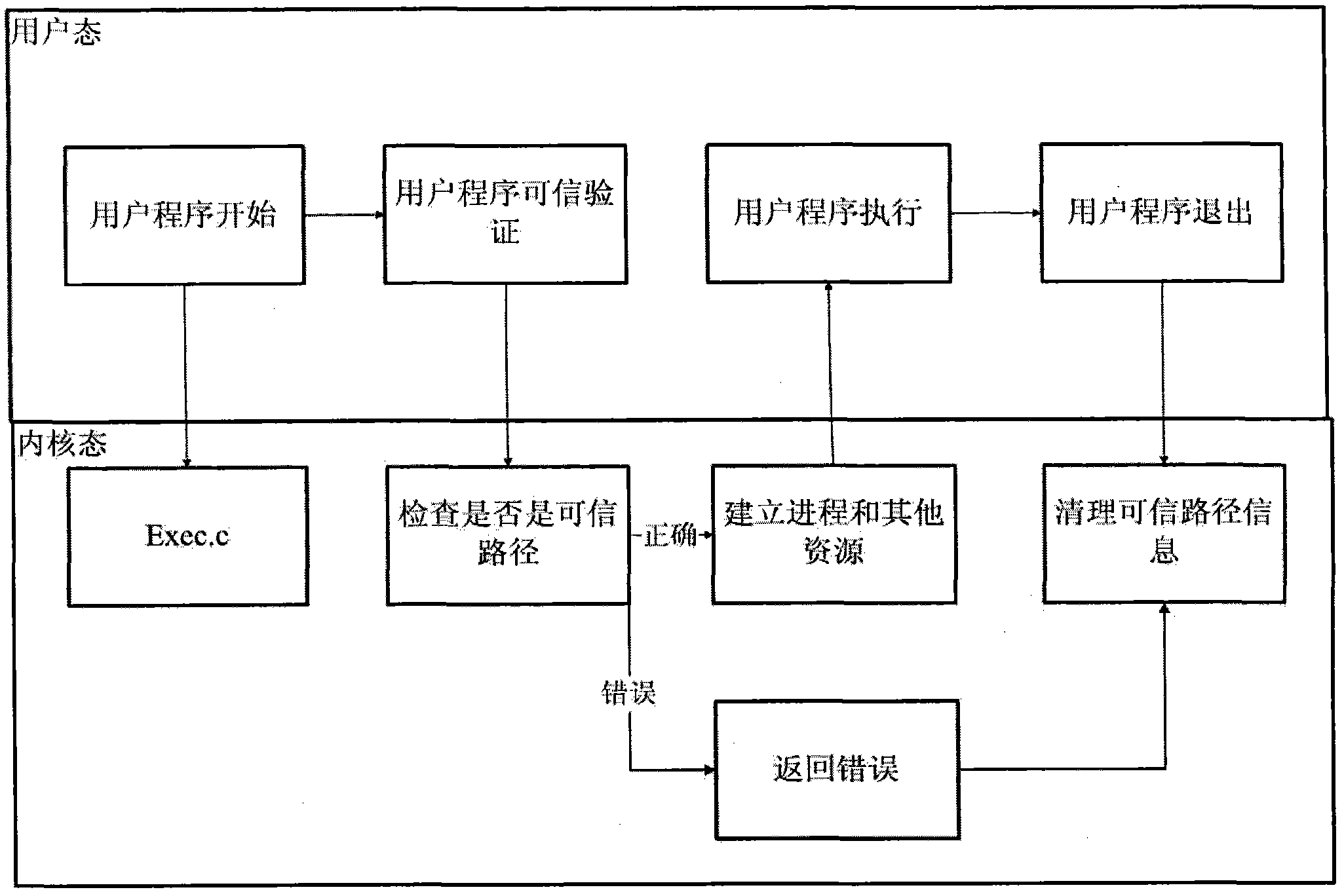
Method for establishing trusted path in secure operating system
InactiveCN102831355AAvoid destructionProtection securityComputer security arrangementsOperational systemComputer terminal
The invention relates to a method for establishing a trusted path in a secure operating system. The access of any course to a terminal requires arbitration of a trusted path system; the design core of the trusted path system is a trusted program list and a trusted course list; and the terminal can be operated by the course only when access is allowed after the two lists of the trusted path system are verified.
Owner:INST OF SOFTWARE - CHINESE ACAD OF SCI +1
Methods and apparatuses for user-verifiable trusted path in the presence of malware
ActiveUS8832778B2Digital data processing detailsInternal/peripheral component protectionInternet privacyMalware
An apparatus and method for establishing a trusted path between a user interface and a trusted executable, wherein the trusted path includes a hypervisor and a driver shim. The method includes measuring an identity of the hypervisor; comparing the measurement of the identity of the hypervisor with a policy for the hypervisor; measuring an identity of the driver shim; comparing the measurement of the identity of the driver shim with a policy for the driver shim; measuring an identity of the user interface; comparing the measurement of the identity of the user interface with a policy for the user interface; and providing a human-perceptible indication of whether the identity of the hypervisor, the identity of the driver shim, and the identity of the user interface correspond with the policy for the hypervisor, the policy for the driver shim, and the policy for the user interface, respectively.
Owner:CARNEGIE MELLON UNIV
Method and system for evaluating trustworthiness
InactiveUS8566252B2Optimize networkReduce riskFinanceWeb data indexingTrust relationshipComputer science
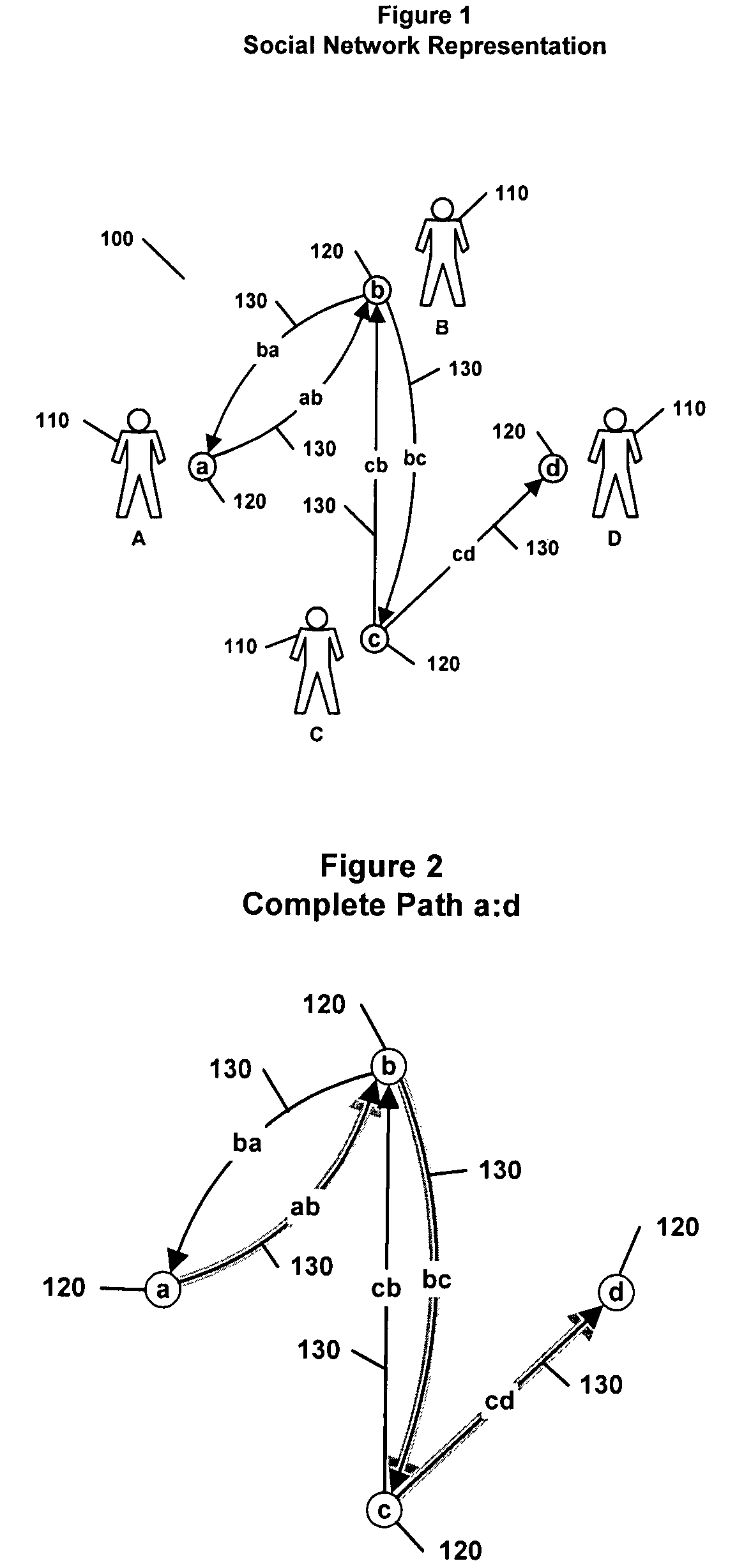
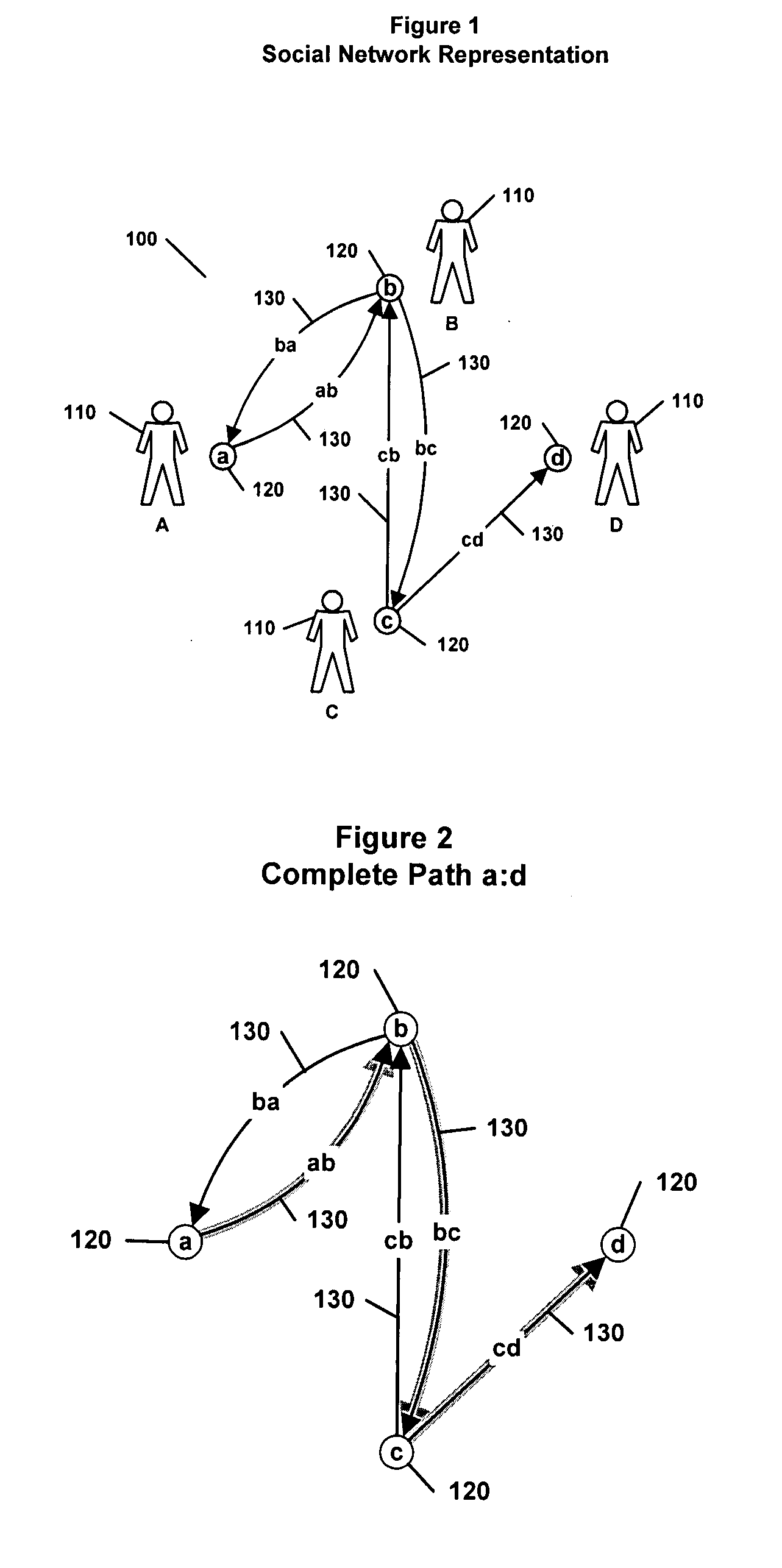
Disclosed are a method and system for evaluating the trustworthiness of a target person by a user. The method and system include providing a network comprising a plurality of nodes connected by a plurality of directed links, wherein each node in the plurality of nodes is associated with a person and each link in the plurality of links connects from a first node to a second node. The link is associated with a trusting relationship from a first person associated with the first node to a second person associated with the second node, and wherein the user is associated with at least one node in the plurality of nodes. A continuous path from the user to the target person is identified, wherein the continuous path begins at a node in the network that is associated with the user and ends at a node in the network that is associated with the target person, the continuous path traversing links from their first node to their second node, the continuous path termed a trust path, thereby providing an indication of the trustworthiness of the target person.
Owner:HARDING BENJAMIN L
Software-defined Internet of Things network topology data transmission security management method and system
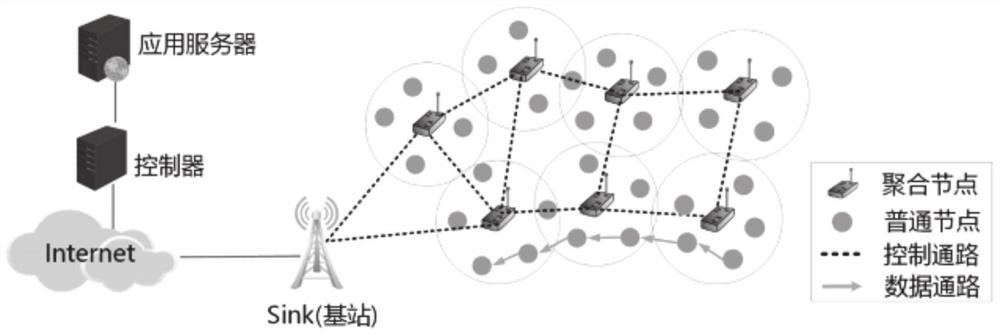
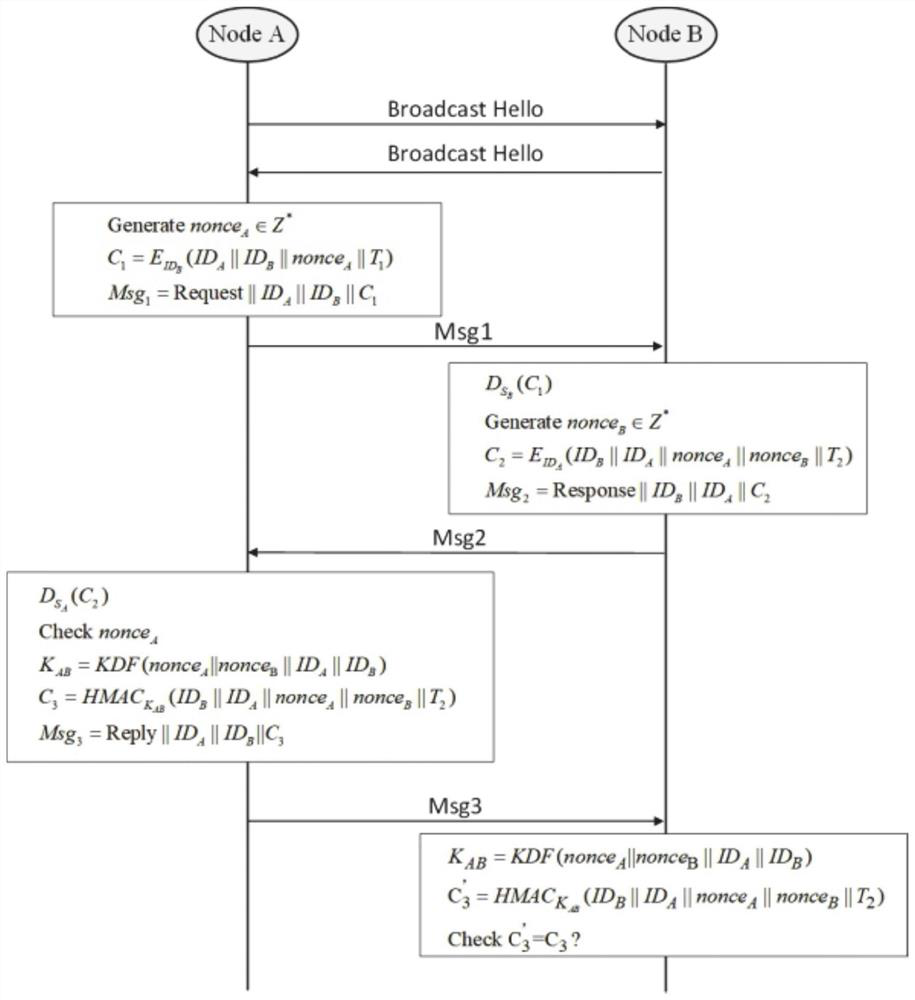
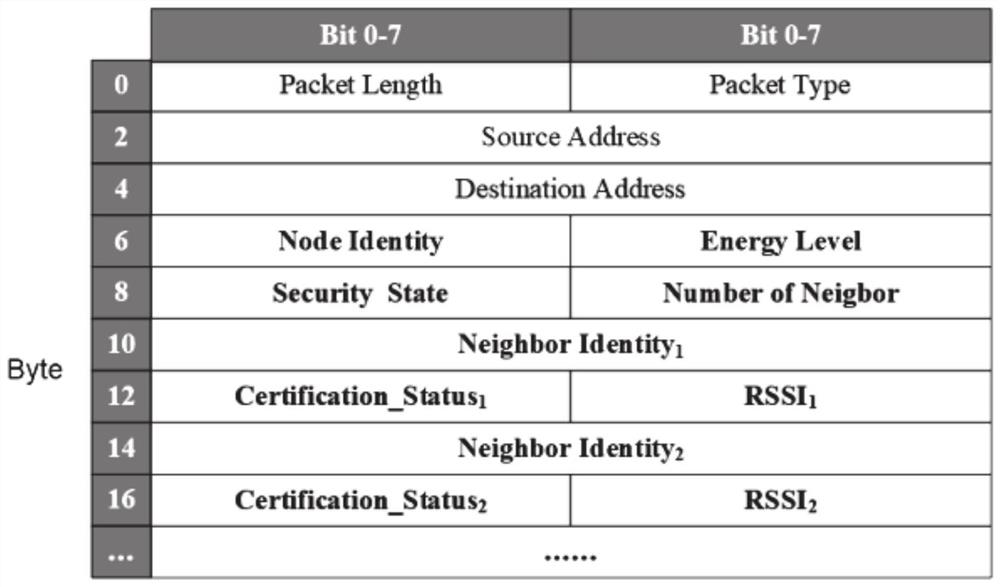
ActiveCN112565230AReduce control overheadGuaranteed safe transmissionKey distribution for secure communicationUser identity/authority verificationGlobal topologyTopology information
The invention provides a software-defined Internet of Things network topology data transmission security management method and system, and the method comprises the steps: deploying common nodes and aggregation nodes at Internet of Things network nodes, and enabling the nodes to communicate with each other; performing encryption algorithm configuration on common nodes and aggregation nodes; each adjacent node performing bidirectional identity authentication and key agreement, and each node recording credible nodes passing authentication around itself and suspicious nodes failing to be authenticated; periodically executing topology discovery, collecting topology information of common nodes by the aggregation nodes, forwarding messages of trusted nodes among the aggregation nodes, establishing a trusted path, and constructing a global topology view; sequentially forwarding and aggregating the topology state messages according to the determined trusted path; and determining newly added nodes and malicious nodes based on the global topology view, broadcasting, and updating the network topology structure of the Internet of Things. According to the invention, the security and reliabilityof data transmission can be effectively improved.
Owner:ELECTRIC POWER RESEARCH INSTITUTE OF STATE GRID SHANDONG ELECTRIC POWER COMPANY +1
Layered PCE based multi-domain optical network secure light path establishment protocol
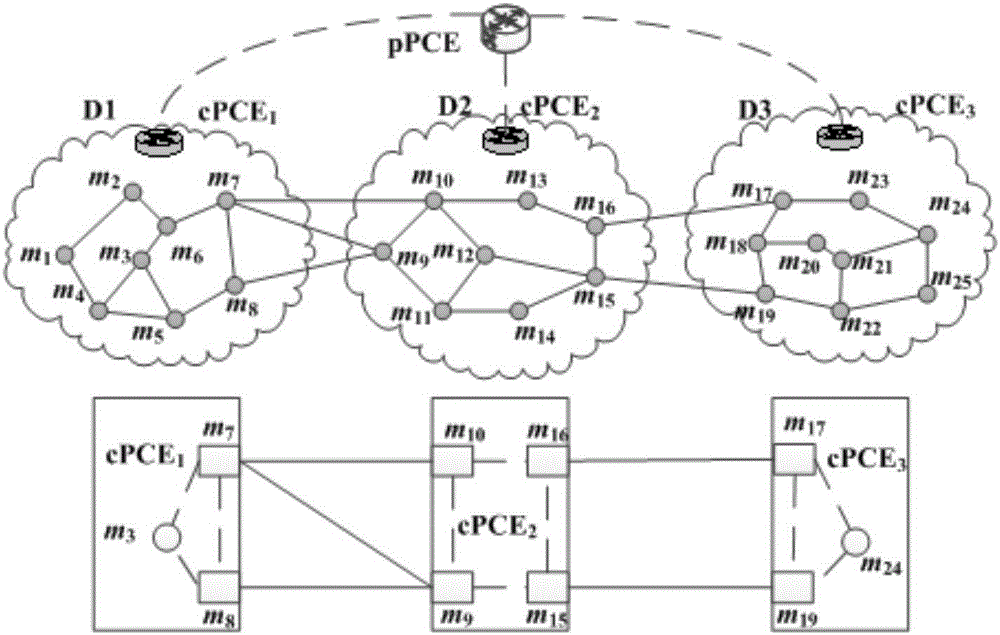
ActiveCN106851441AShort setup delaySatisfy confidentialityMultiplex system selection arrangementsUser identity/authority verificationConfidentialityPrivacy protection
The invention discloses a layered PCE based multi-domain optical network secure light path establishment protocol. Aiming at the problems of security problem and comprehensive efficiency existing in a multi-domain optical network light path establishment process, a new GO-PCE (Global Optimizing secure light-path protocol based PCE in multi-domain optical network) is designed by combining with a trust model and a key management scheme, adopting a globally optimized multi-domain trusted path selection, usable wavelength calculation and wavelength distribution strategy, and utilizing a TLS based bidirectional identity authentication, TCP-AO based source authentication, identity cryptography based encryption and digital signature technology and a Path-Key based privacy protection mechanism. The secure service requirements such as confidentiality, completeness, authenticity, non-repudiation, freshness and privacy can be met; compared with an SD-PCE and pH-PCE light path establishment protocols, the layered PCE based multi-domain optical network secure light path establishment protocol has relatively low blocking rate and relatively short light path establishment time delay.
Owner:ENG UNIV OF THE CHINESE PEOPLES ARMED POLICE FORCE
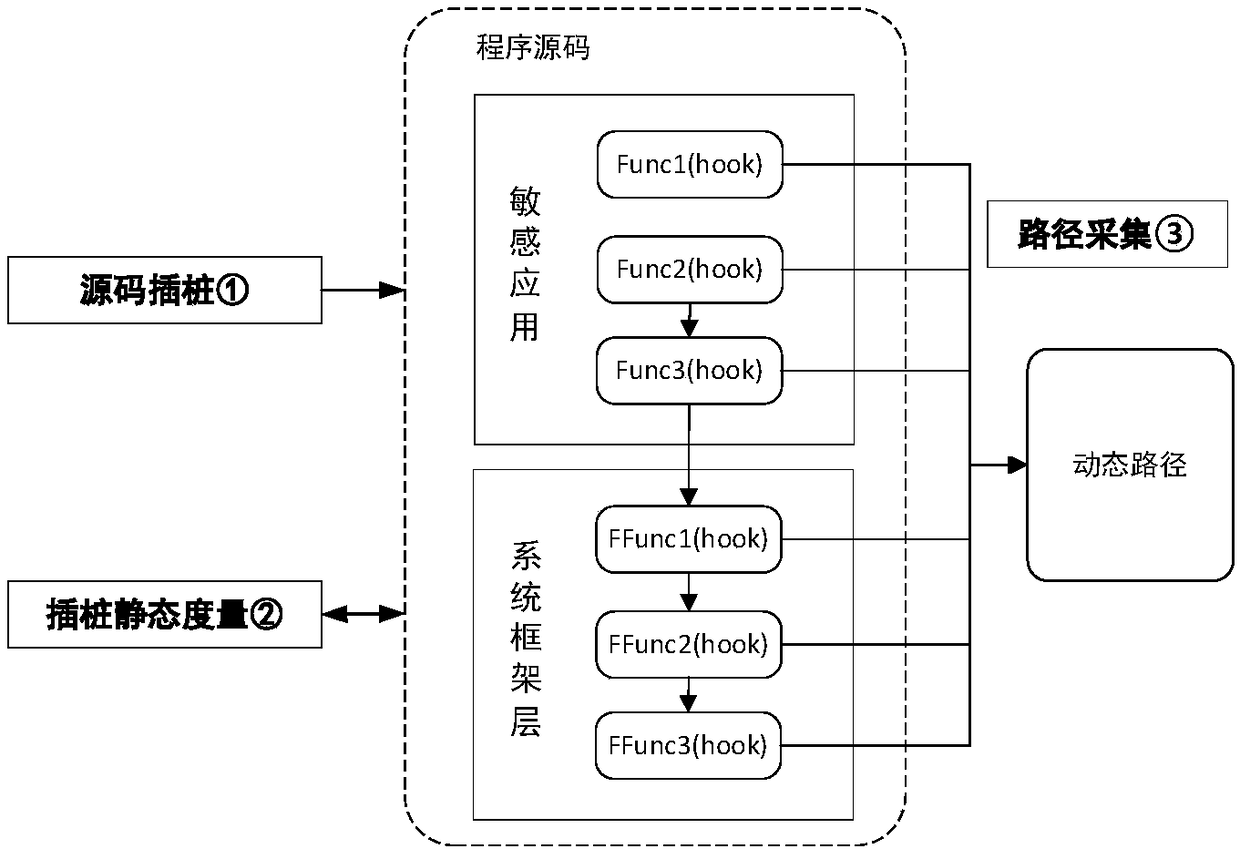
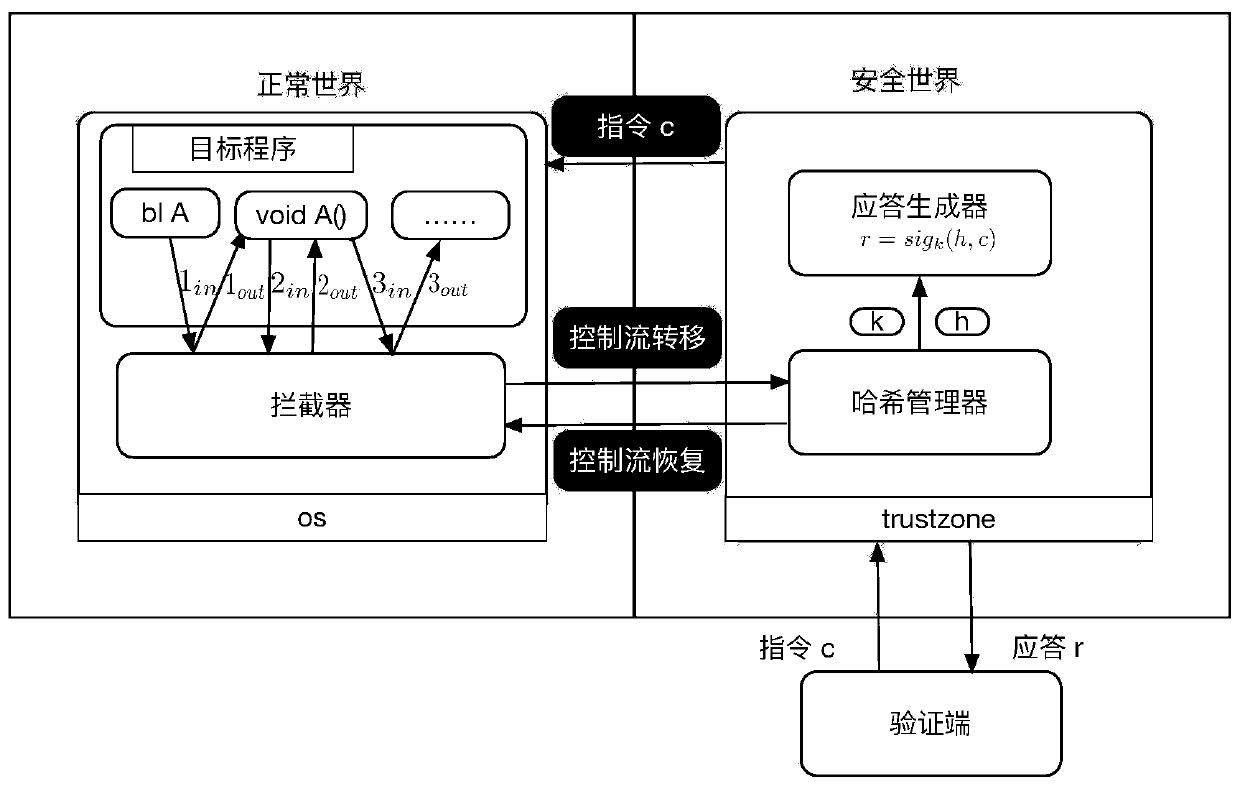
Dynamic measurement method and system for sensitive application in multiple secure environments
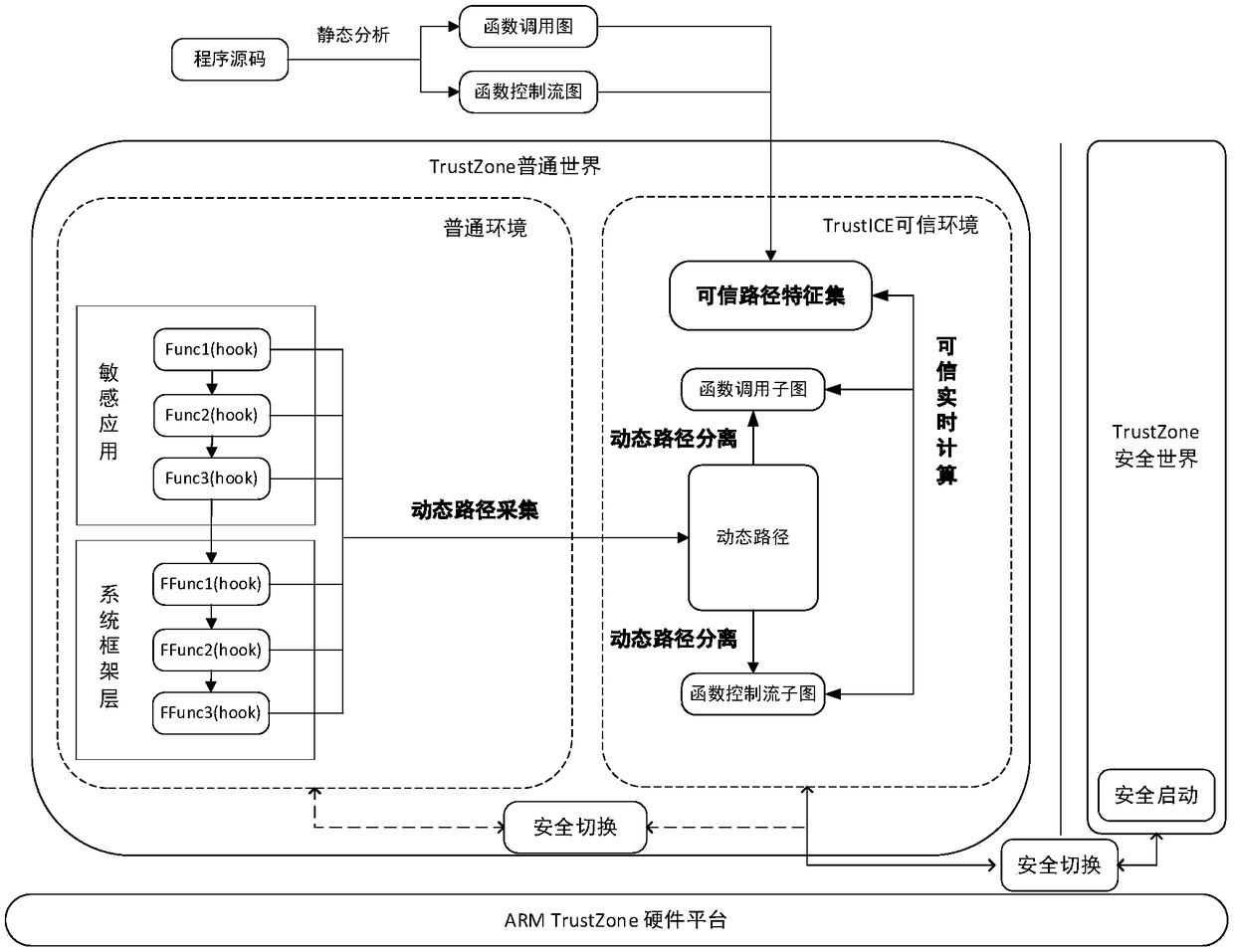
InactiveCN108694320AImprove securityEnsure safetyPlatform integrity maintainanceControl flowFeature set
The invention relates to a dynamic measurement method and system for sensitive application in multiple secure environments. According to the method, program source code is subjected to static analysisto generate a function calling graph and each function control flow graph so as to build a trusted path feature set; the program source code is subjected to pile pitching preprocessing; the obtaineddynamic path is separated in a security domain; a function calling sub graph and a function control flow sub graph are obtained; the security domain is used for matching the function calling sub graphwith the function calling graph; the function calling sub graph is enabled to be a sub graph of the function calling graph; and then, the security domain is used for matching the function control flow sub graph with the function control flow graph. The dynamic measurement is performed on the execution completeness of the sensitive application in the trusted path execution process, and the programis enabled to be executed on the trusted path in sequence.
Owner:INST OF INFORMATION ENG CAS
Method of providing assured transactions using secure transaction appliance and watermark verification
ActiveUS9083746B2User identity/authority verificationDigital data protectionPersonalizationElectronic security
Disclosed is a method of improving electronic security by establishing a path between a user and a secure transaction appliance. The secure transaction appliance receiving information destined for the user which includes a tagged portion, said tagged portion triggering the secure transaction appliance to forward the information to the computer from which the request was issued, and to seeking an electronic signature to verify the content or transaction by transmitting a watermark, tagged portion of the content, or similar electronic content. The secure trusted path providing the user with the tagged portion incorporating additional elements such as a watermark, or in some embodiments only the additional elements, upon a personalized security device associated with the user making interception or manipulation more complex and difficult.
Owner:DATA LOCKER INC
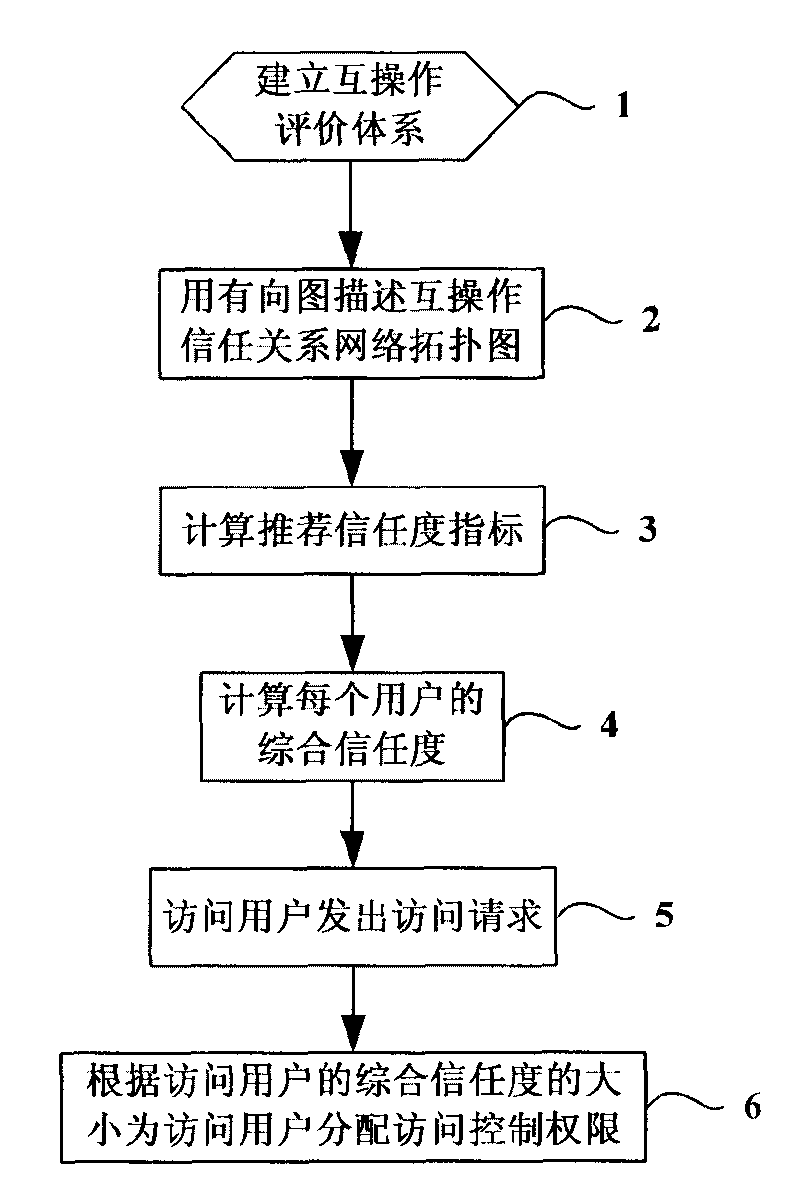
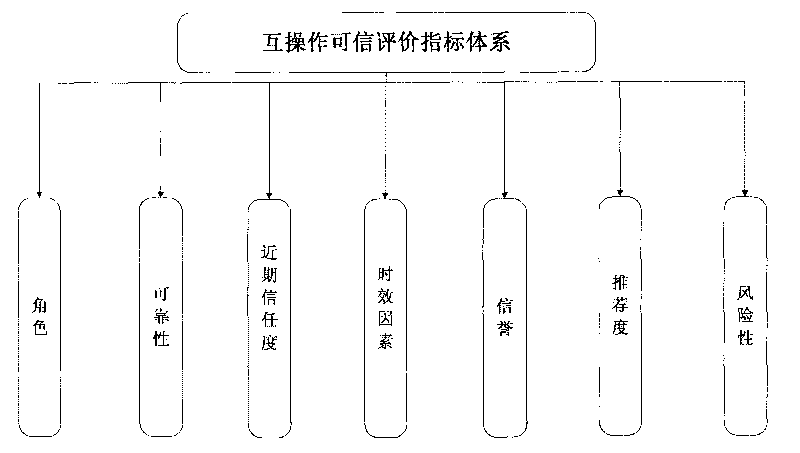
Dynamic trust management-based interoperation security guaranteeing method
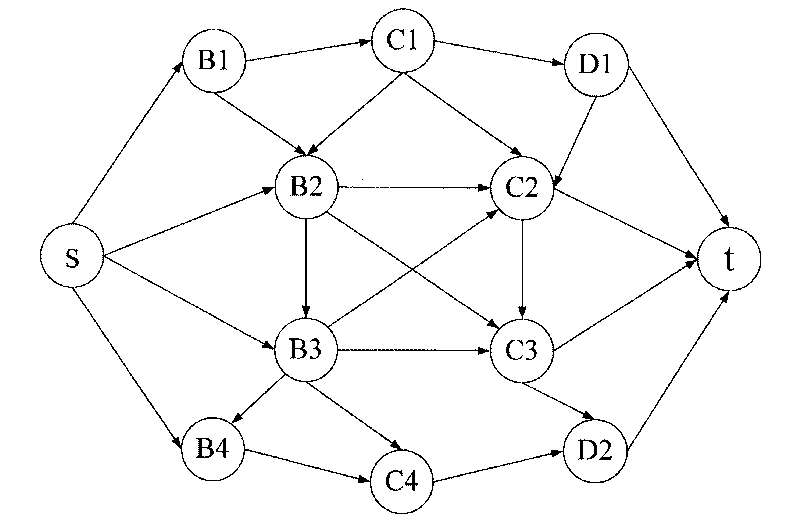
InactiveCN101719202ARealize dynamic conversionOvercome permission conflictsBiological modelsPlatform integrity maintainanceTrust relationshipOperation safety
The invention discloses a dynamic trust management-based interoperation security guaranteeing method in the technical field of interoperation management control, which comprises the following steps: establishing an interoperation evaluation system; describing an interoperation trust relationship network topological diagram with directed graphs; calculating a recommended trust index based on an interoperation trust path searching algorithm of a max-min ant colony system; substituting the obtained recommended trust index into a fuzzy variable weighting theory-based interoperation dynamic trust comprehensive evaluation method to calculate the comprehensive trust of each user; issuing an access request by an access user; and allocating access control authority to the access user according to the comprehensive trust of the access user. The method has the advantages of solving the problem that conventional trust management only has a single evaluation index, being adapted to dynamic security environmental change and also solving the problem of authority confliction caused by a conventional role-based access control model.
Owner:BEIJING JIAOTONG UNIV
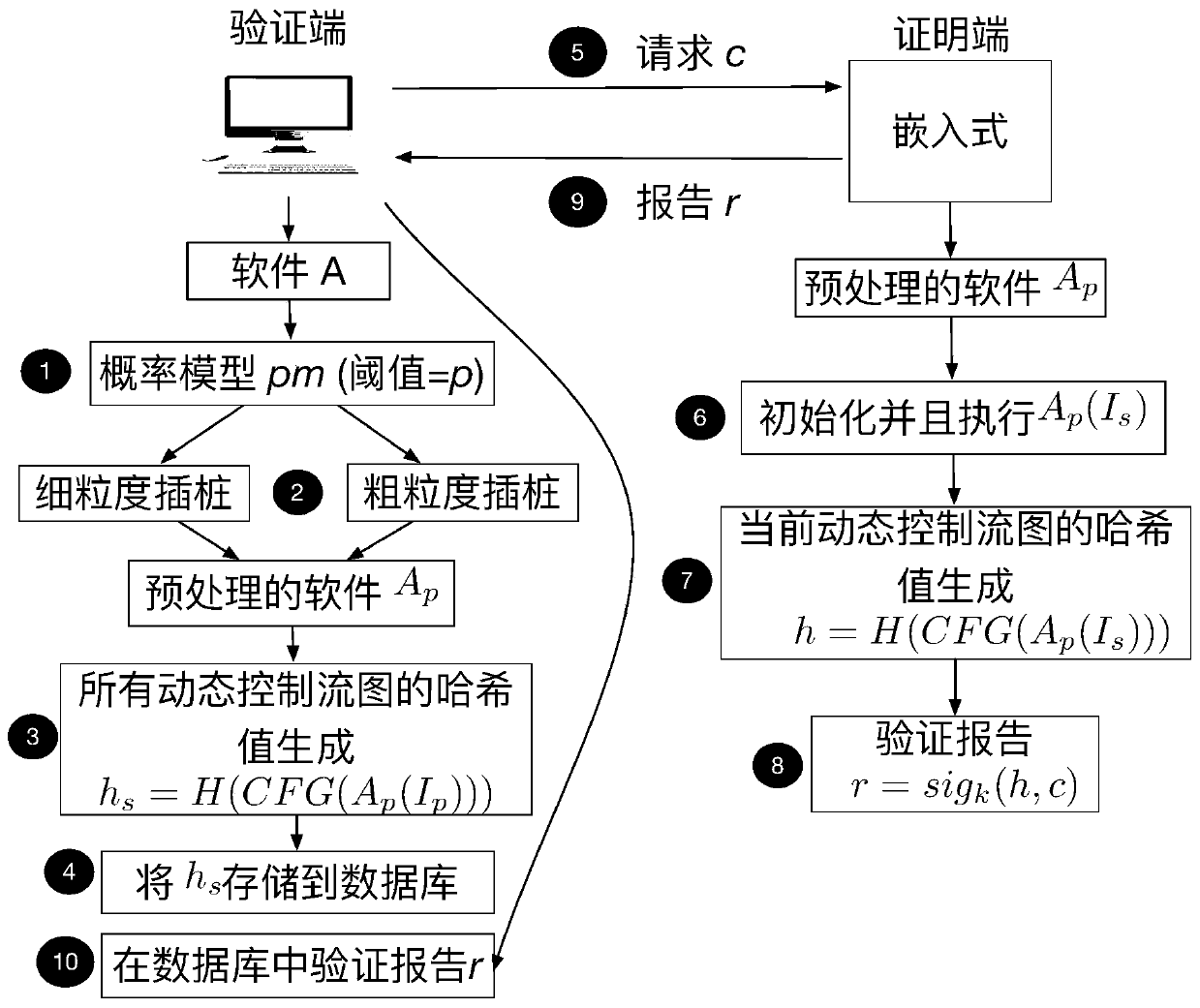
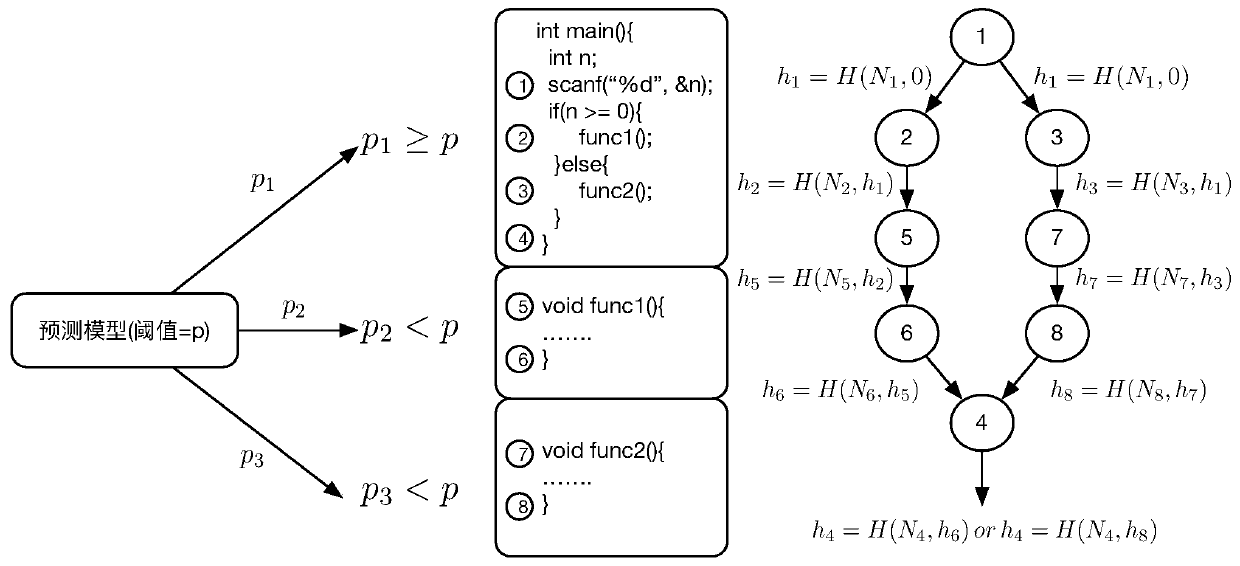
Embedded variable-granularity control flow verification method and system based on probability prediction
InactiveCN110276198ADetect attackBalance efficiencyPlatform integrity maintainanceComputer hardwareFeature set
The invention relates to an embedded variable-granularity control flow verification method and system based on probability prediction. The embedded variable-granularity control flow verification method is divided into a verification end and a certification end. The method comprise: constructing a trusted path feature set, carrying out vulnerability probability prediction on each function in the target source program, carrying out coarse-fine granularity instrumentation preprocessing on the functions, obtaining all possible dynamic control flow graphs of the target program by using different inputs in a verification end, and replacing and storing the control flow graphs in a database by using Hash values; collecting a dynamic path, the proving end running the processed target program after receiving the request sent by the verification end, and calculating the hash value of the control flow graph in the security world and signing; when the dynamic path is checked, the proving end sending a signature to the verifying end, the verifying end matching a Hash value obtained by decrypting the signature in a database, if the Hash value can be matched, the control flow running at the time being complete, and otherwise, the integrity of the control flow being damaged.
Owner:INST OF INFORMATION ENG CAS
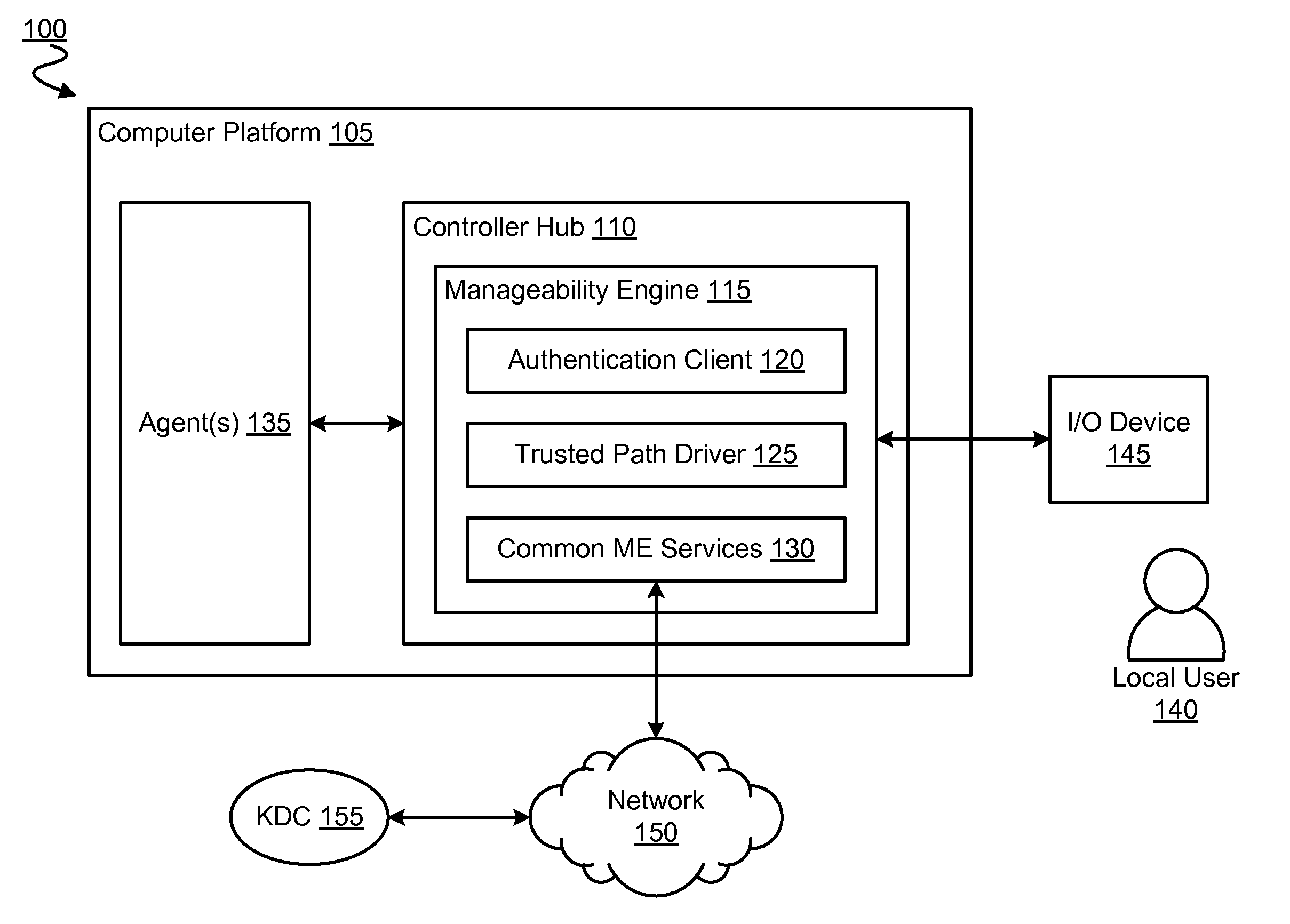
Method, apparatus and system for controlling access to computer platform resources
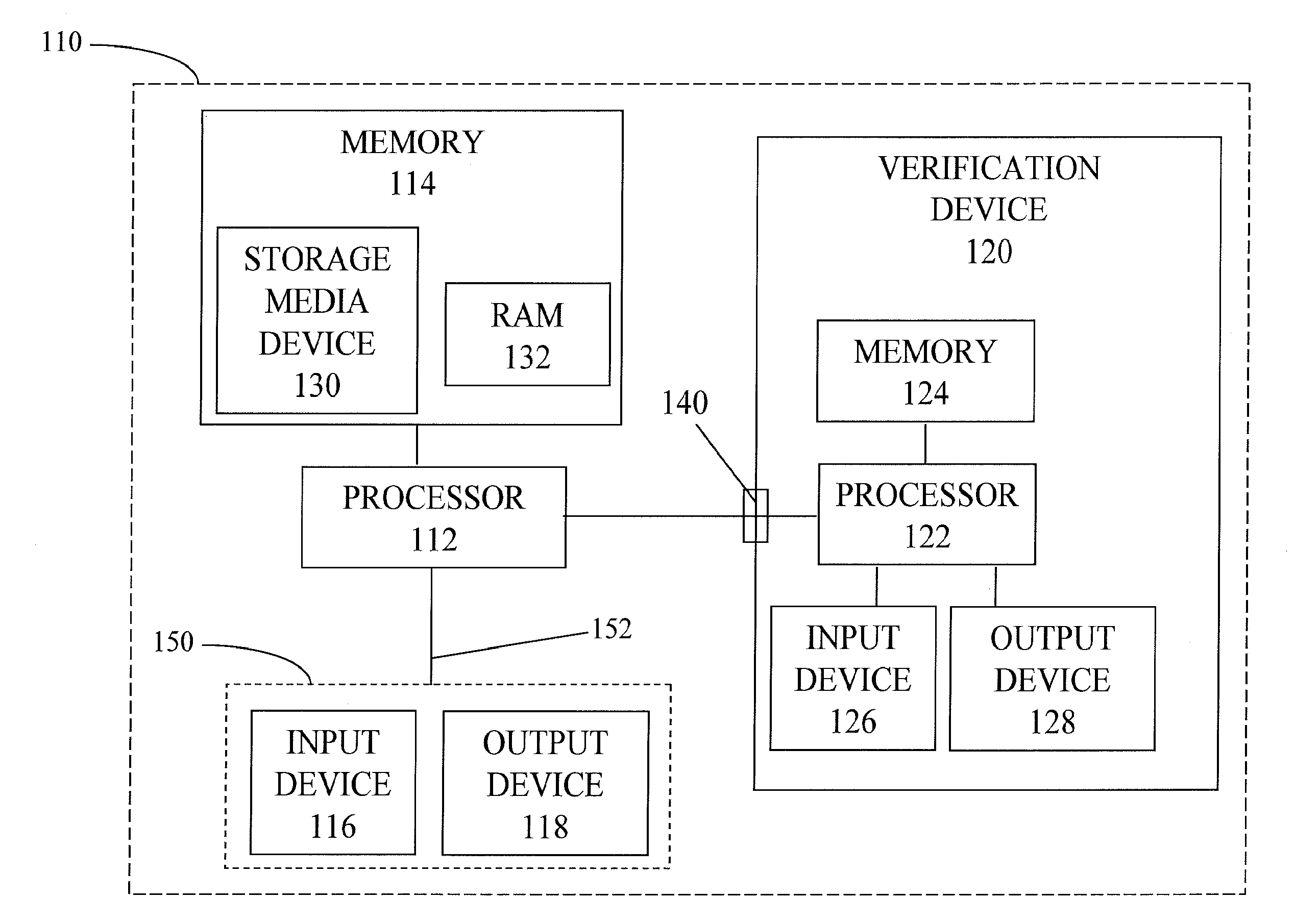
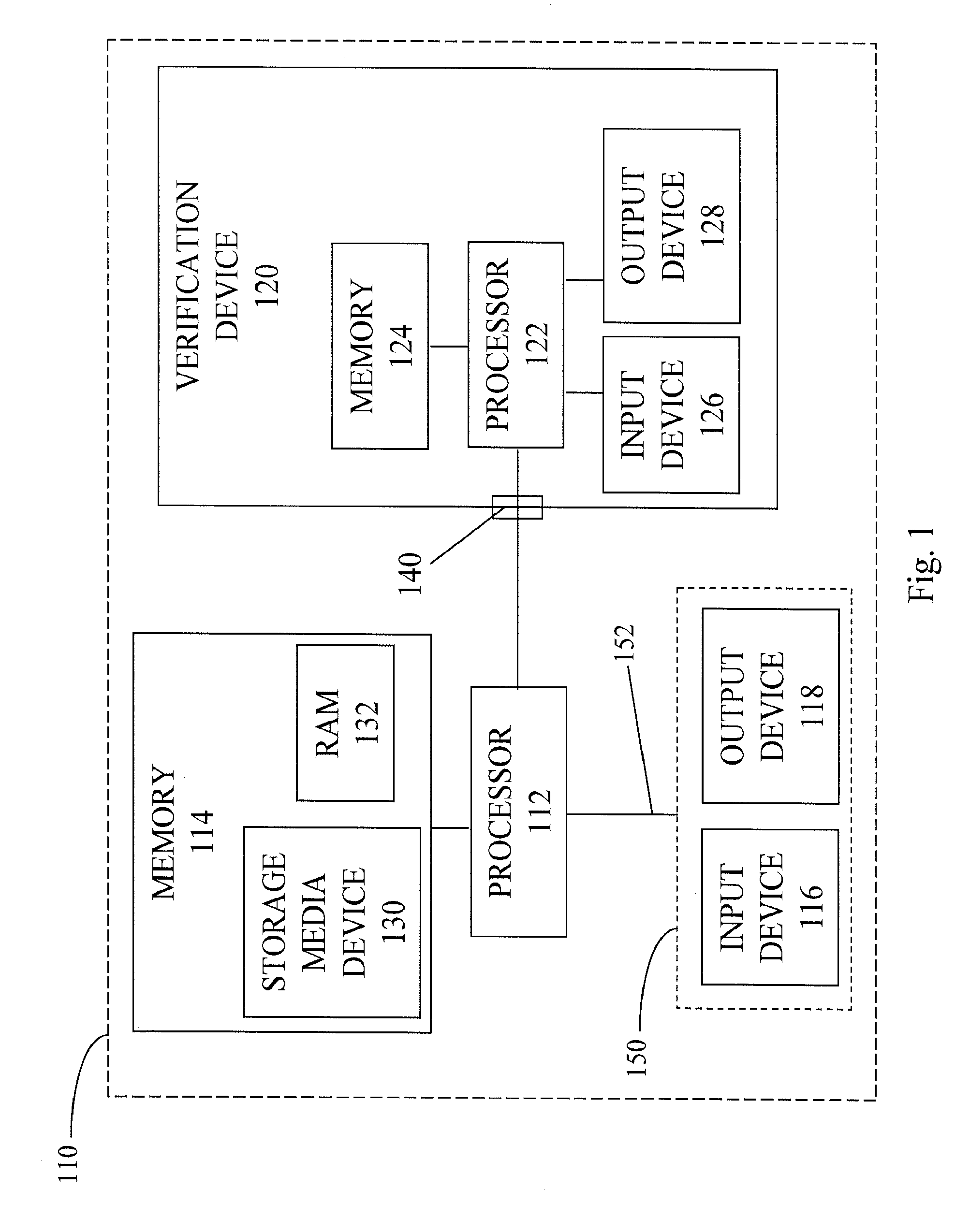
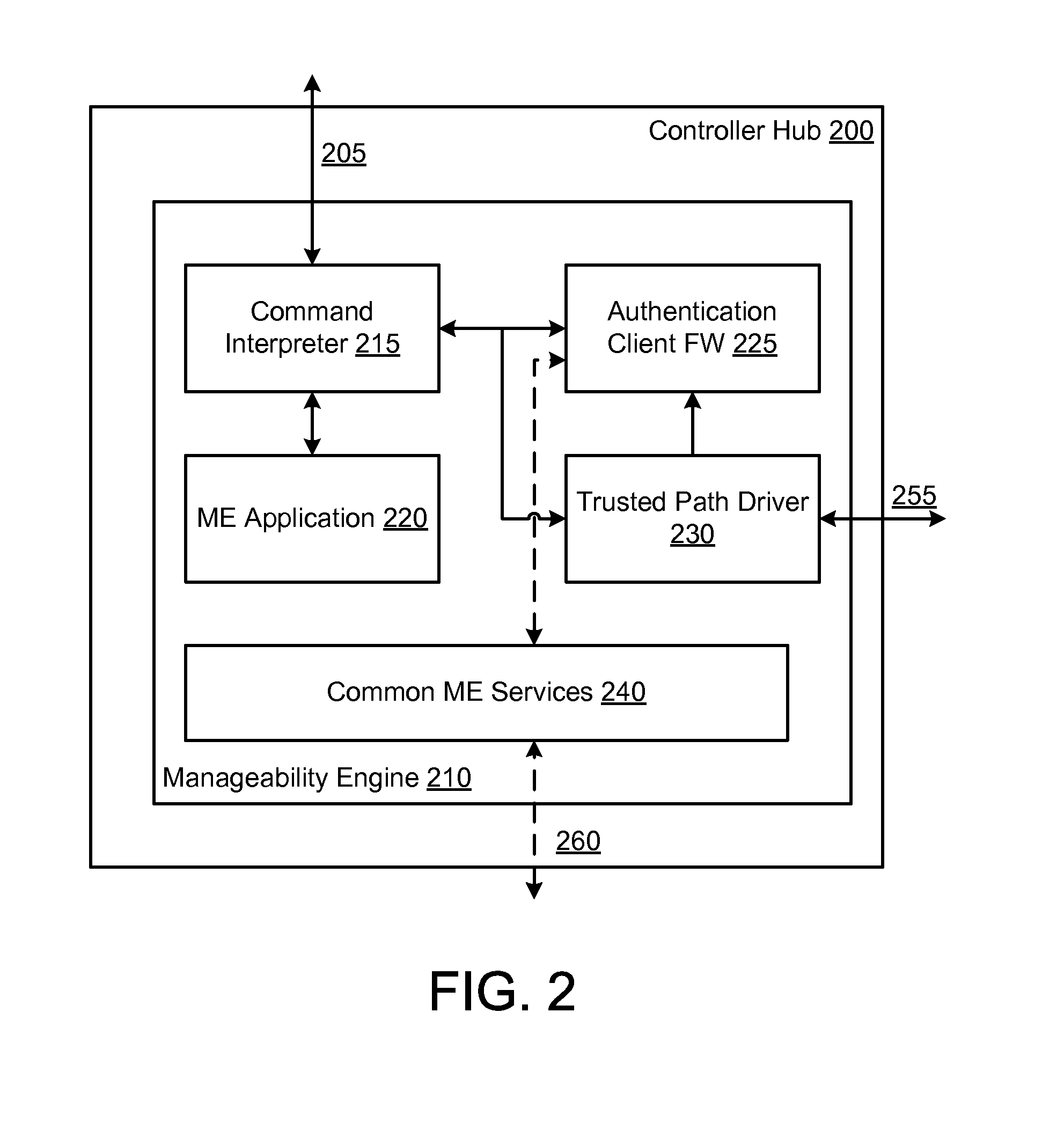
ActiveUS20120167187A1Digital data processing detailsUser identity/authority verificationOutput deviceTrusted path
A manageability engine, and / or operations thereof, for controlling access to one or more resources of a computer device. In an embodiment, the manageability engine executes an authentication agent to perform authentication of a local user of a computer platform which includes the manageability engine. In another embodiment, the manageability engine includes a device driver to control an input / output device for the local user to exchange an authentication factor via a trusted path between the input / output device and the manageability engine.
Owner:INTEL CORP
Method and system for evaluating trustworthiness
InactiveUS20080109451A1Reduce the impactOptimize networkFinanceWeb data indexingTrust relationshipComputer science
Disclosed are a method and system for evaluating the trustworthiness of a target person by a user. The method and system include providing a network comprising a plurality of nodes connected by a plurality of directed links, wherein each node in the plurality of nodes is associated with a person and each link in the plurality of links connects from a first node to a second node. The link is associated with a trusting relationship from a first person associated with the first node to a second person associated with the second node, and wherein the user is associated with at least one node in the plurality of nodes. A continuous path from the user to the target person is identified, wherein the continuous path begins at a node in the network that is associated with the user and ends at a node in the network that is associated with the target person, the continuous path traversing links from their first node to their second node, the continuous path termed a trust path, thereby providing an indication of the trustworthiness of the target person.
Owner:HARDING BENJAMIN L
Method of providing transactions employing advertising based verification
ActiveUS8060447B2User identity/authority verificationComputer security arrangementsPersonalizationMalware
A method of improving electronic security establishes a secure trusted path between a user and an institution seeking an electronic signature to verify a transaction before any request for signature and completing electronic transaction activities occurs. The secure trusted path providing the user with a first predetermined portion of a branded watermark, for instance an advertisement, provided from the institution in conjunction with the request, and a second predetermined portion of the branded watermark being provided upon a personalized device that cannot be intercepted or manipulated by malware, allowing the user to verify that the request as displayed upon the user's primary computing device is valid.
Owner:DATA LOCKER INC
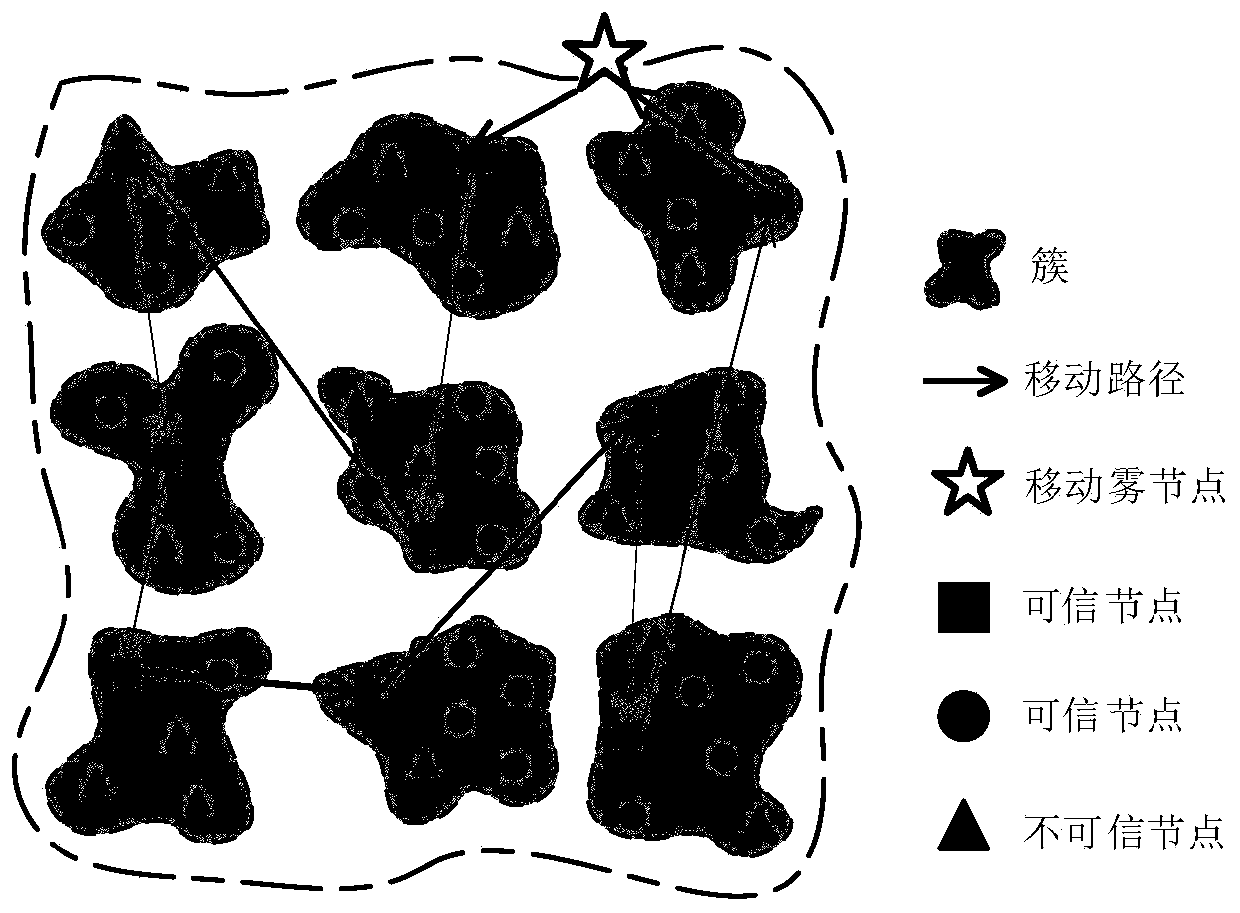
Mobile trusted data collection method based on trust value utility in sensor network
ActiveCN110049528AHigh trust utilityLarge trust value utilityTransmission systemsNetwork topologiesData miningEuclidean distance
The invention relates to a mobile trusted data collection method based on trust value utility in a sensor network, which comprises the following steps of: designing a node trust evaluation algorithm (such as a direct trust value and an indirect trust value) according to the relationship between nodes in the application of wireless sensor data collection, and obtaining a quantized trust value of anode by an existing algorithm; and according to the obtained trust value, generating a trusted cluster head node in the subsequent cluster head node election; finally, calculating the next cluster head node with the maximum trust utility value according to the Euclidean distance between the cluster head nodes and the trust value of the related next hop cluster head node, thereby generating a trusted path with the maximum trust utility value.
Owner:HUAQIAO UNIVERSITY
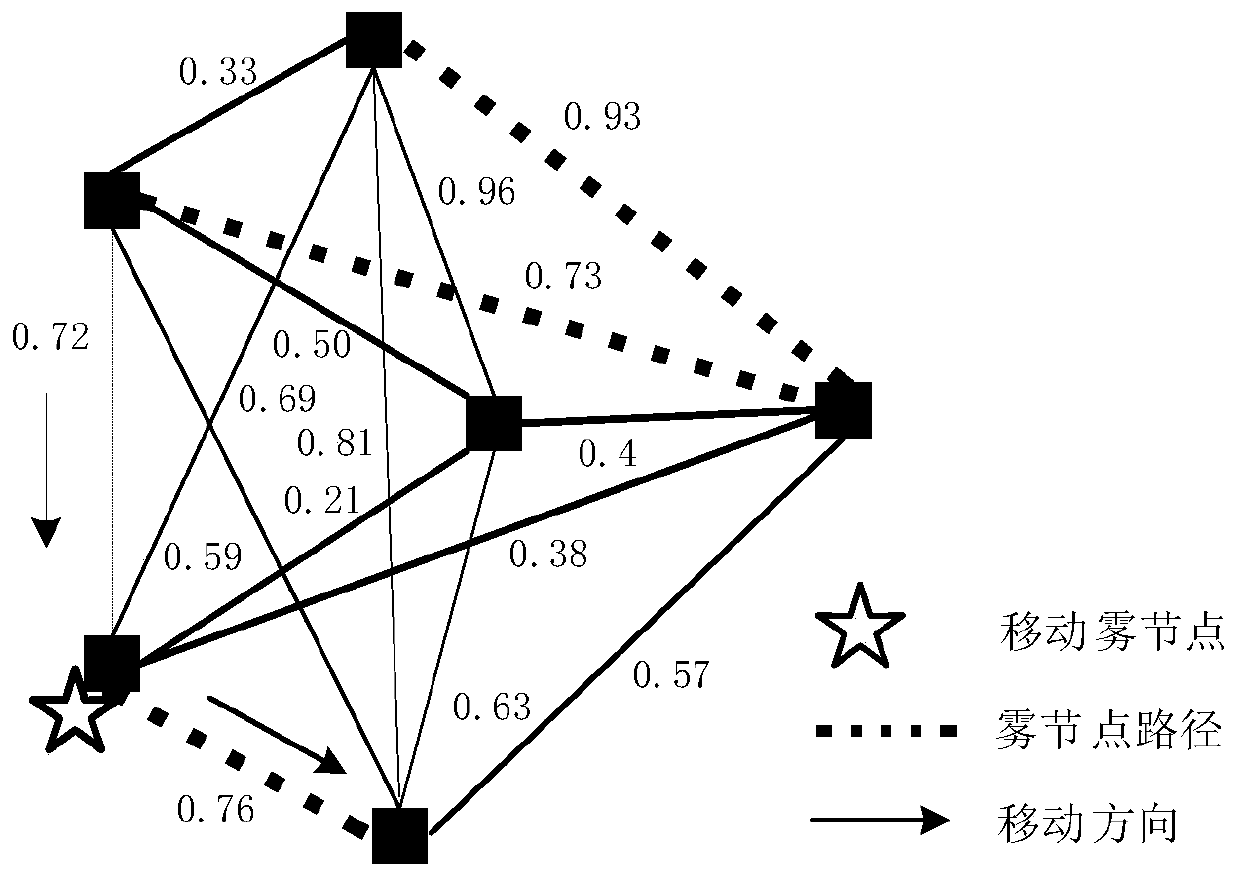
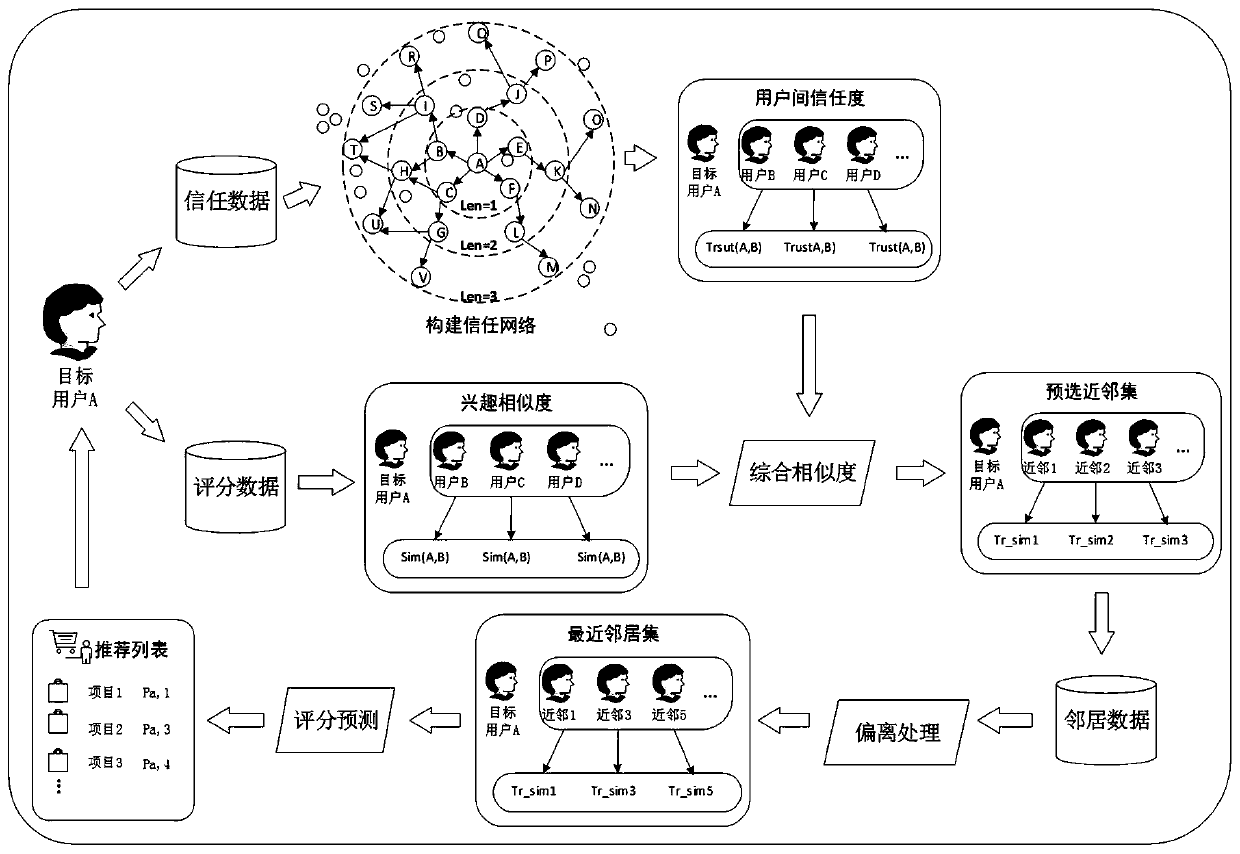
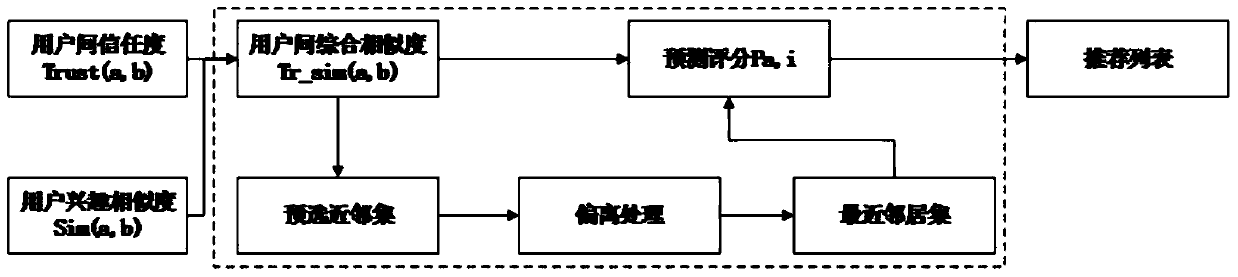
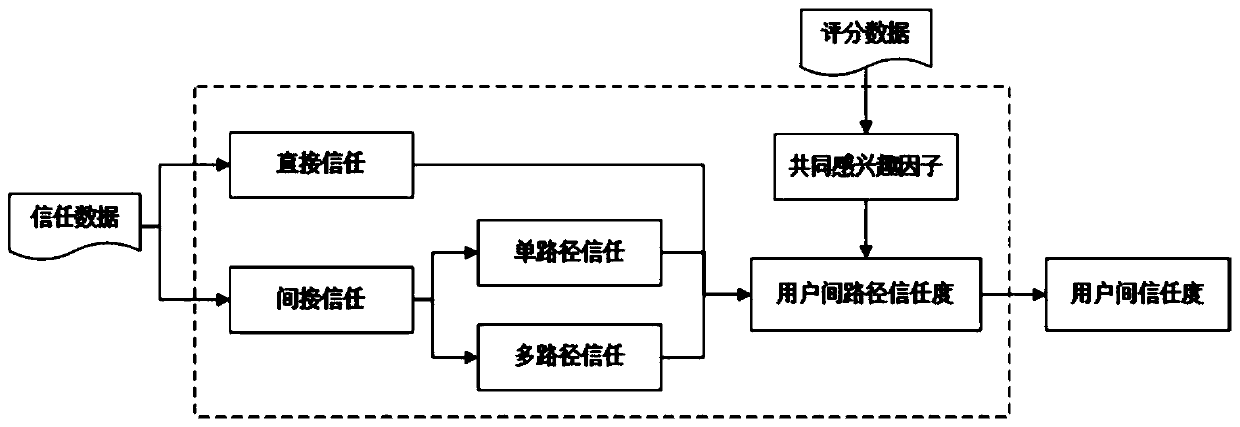
Collaborative filtering recommendation method based on optimal trust path
ActiveCN110990713AImprove operational efficiencyImprove recommendation accuracyDigital data information retrievalBuying/selling/leasing transactionsTheoretical computer scienceNear neighbor
The invention discloses a collaborative filtering recommendation method based on an optimal trust path, which is improved by aiming at a traditional collaborative filtering algorithm and a trust fusion collaborative filtering algorithm, and comprises the following steps of: firstly, constructing a trust network of users, calculating trust degrees among the users, and calculating interest similarity among the users; calculating the comprehensive similarity among the users by combining the trust degree among the users and the interest similarity among the users; obtaining a nearest neighbor setaccording to the comprehensive similarity among the users; and finally predicting the score of the target user to the project to obtain a project recommendation result. According to the method, a global user is considered during calculation; a multi-path trust degree algorithm is provided on the basis of the fused trust recommendation algorithm; the optimal path is selected from multiple trust paths to represent the path trust degree between two users, the trust weight relationship contained in the path is considered, the recommendation accuracy and the operation efficiency of the algorithm are improved, and the operation time of the algorithm is about 1 / 4 of the operation time of the existing fusion trust recommendation algorithm.
Owner:GUANGDONG POLYTECHNIC NORMAL UNIV
Identity verification for secure e-commerce transactions
ActiveUS8315951B2Convenient verificationIdentity of with easeFinanceDigital data processing detailsInternet privacyE-commerce
Owner:WSOU INVESTMENTS LLC
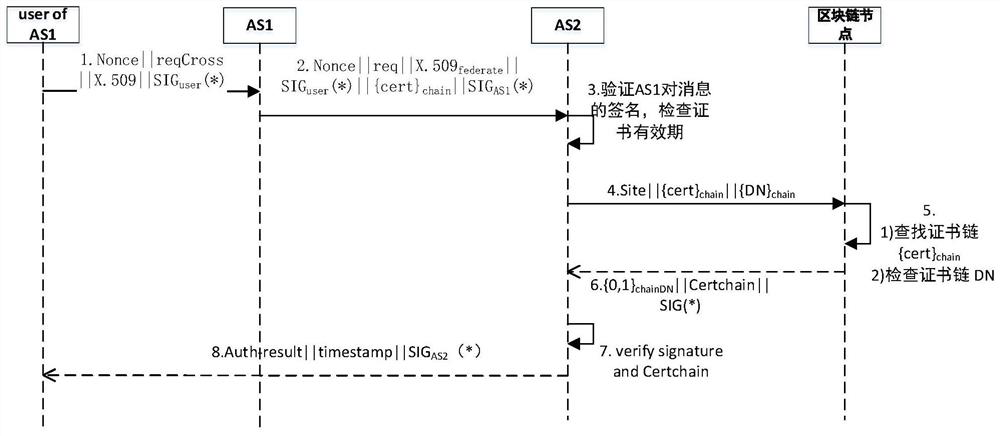
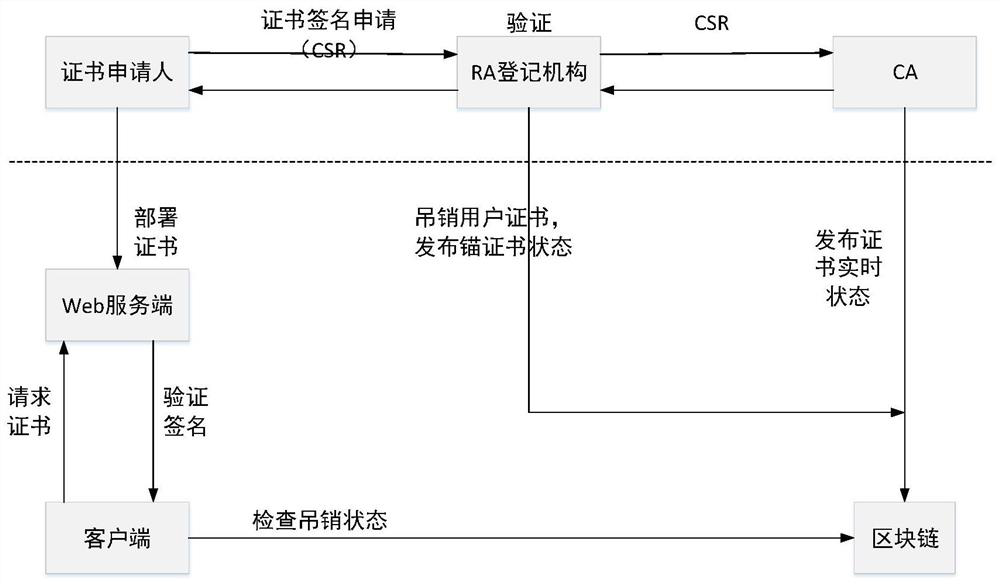
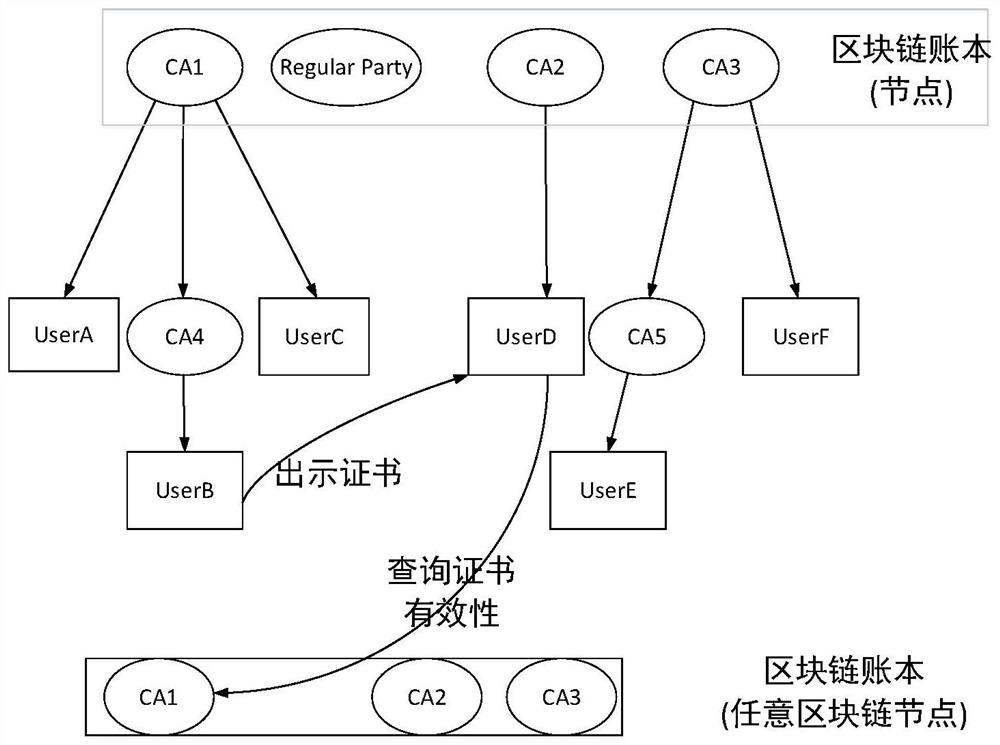
PKI certificate cross-domain authentication method based on blockchain
ActiveCN113672942AImprove real-time performanceImprove securityDigital data protectionRoot certificateInternet privacy
The invention discloses a PKI certificate cross-domain authentication method based on a blockchain. The method comprises the following steps: when a user initiates a cross-domain access request through a client end, a certificate is shown to an authentication server; the authentication server initiates a request to the blockchain for verifying whether each certificate in a certificate chain is revoked or not according to attribute fields of the shown certificate; a smart contract searches whether each certificate is valid in a BCRL (blockchain certificate revocation list), obtains a whole certificate chain, verifies whether the certificate chain is valid step by step from a root-of-trust certificate of a relying party, and signs and issues a user access token if each certificate is not revoked and the certificate chain verification is passed. Through the method provided by the invention, a complex topological structure in cross authentication is solved, a certificate chain trust path can be quickly constructed based on a multi-node tampering-free trust anchor of the blockchain, and the security of PKI certificate cross-domain authentication is improved.
Owner:NO 30 INST OF CHINA ELECTRONIC TECH GRP CORP
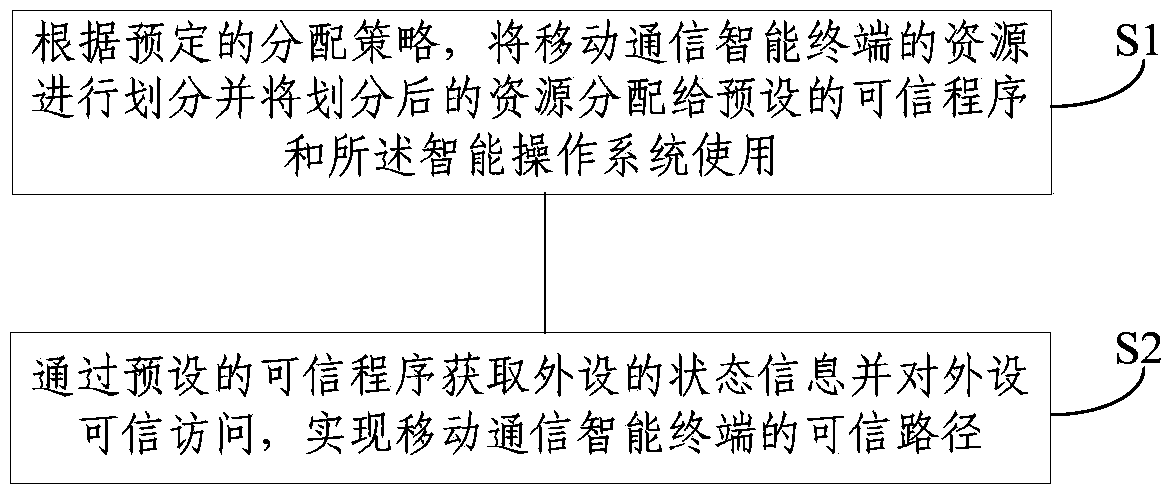
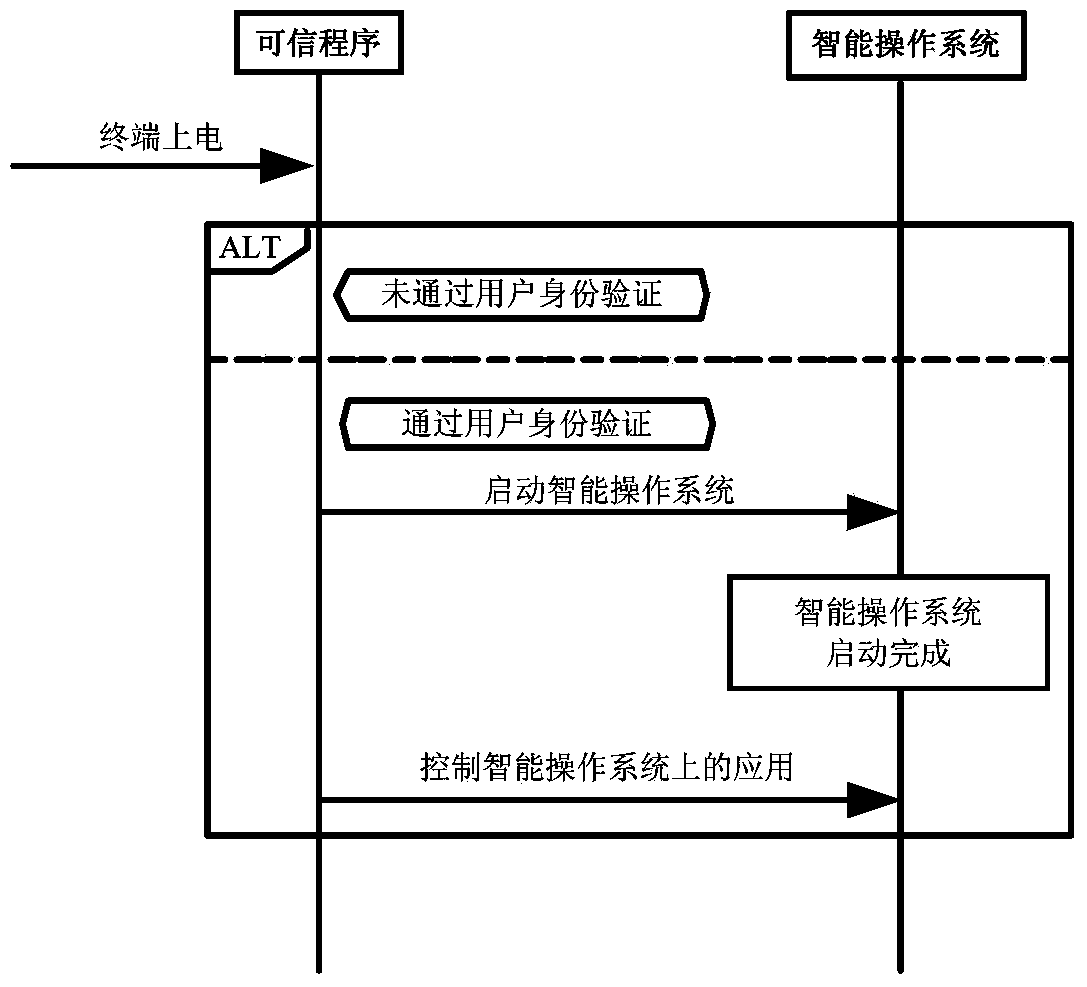
Implement method and system of trusted path of mobile communication intelligent terminal
ActiveCN103971057AMonitor System StatusAccurate graspInternal/peripheral component protectionPlatform integrity maintainanceComputer hardwareOperational system
The invention discloses an implement method and system of a trusted path of a mobile communication intelligent terminal. The method includes the steps that S1, according to a predetermined allocation strategy, resources of the mobile communication intelligent terminal are divided, the divided resources are allocated to a preset trusted program and an intelligent operating system for use, and accordingly resource isolation of the mobile communication intelligent terminal can be achieved; S2, peripheral state information is acquired through the preset trusted program, trust access is performed on the peripheral, and thus the trusted path of the mobile communication intelligent terminal can be obtained.
Owner:XINGTANG TELECOMM TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com