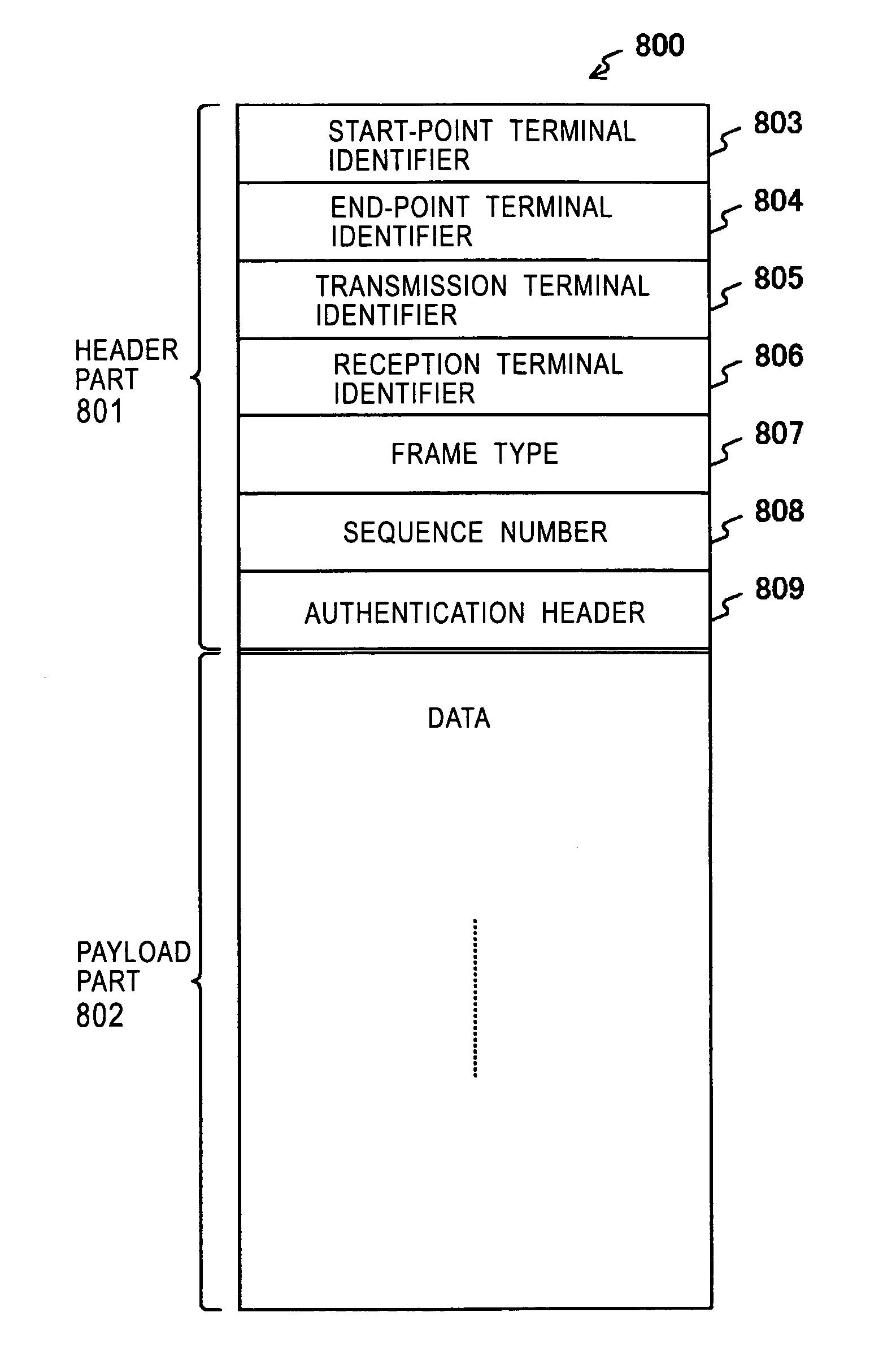
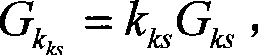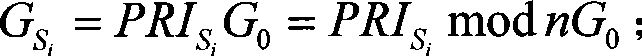Patents
Literature
90 results about "Source authentication" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
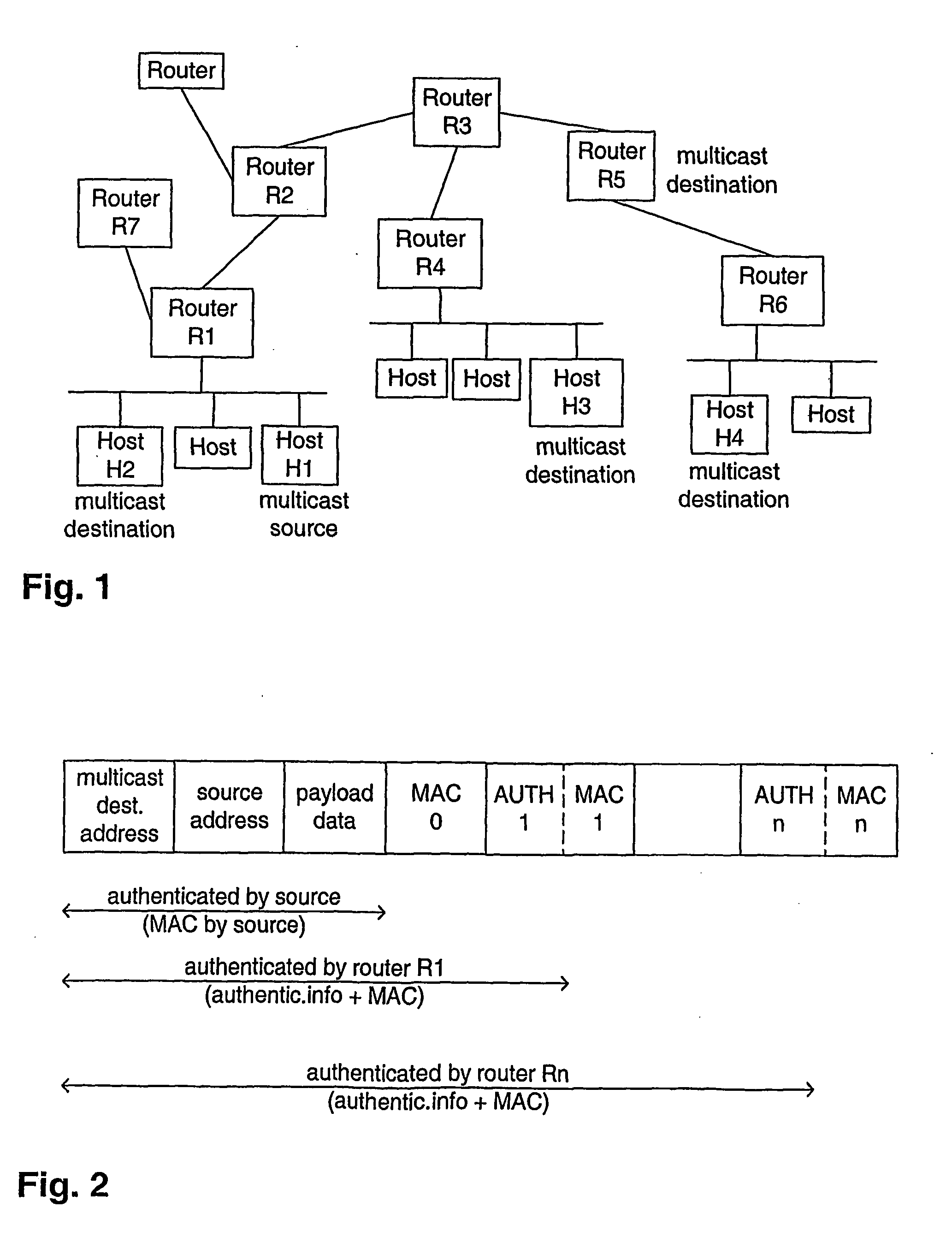
Message identification with confidentiality, integrity, and source authentication
InactiveUS7095855B1Encryption apparatus with shift registers/memoriesDigital data processing detailsComputer hardwareConfidentiality
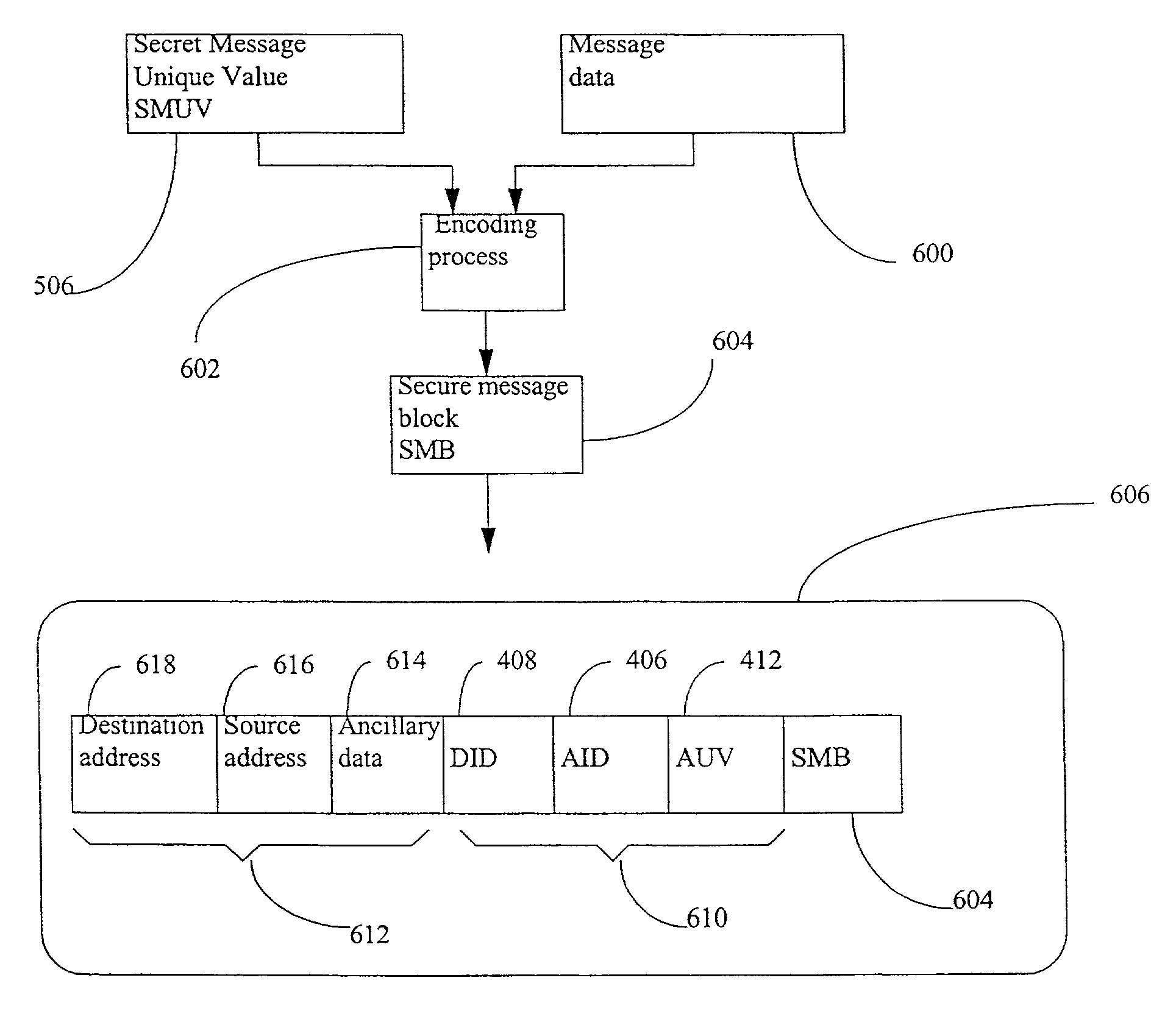
A method for securely encoding and transmitting a message by an originating device to one of a plurality of recipient devices, said message being associated with a particular one of a plurality of application running on the originating device. Transmission is generated by using a device identifier, an application identifier and an application value, of a message value; combining the message value with one or more first secret values, said secret values being known substantially only to the originating device and one or more intended recipient device of the message, to establish a secret message value; applying the secret message value and the message to an encoding process to form a secure message block, and combining an address with a device identifier, the application identifier, the application value and the secure message block, to form a secure message for transmission which is decodable by the one or more of said intended recipient devices which thereby recover the message, the address, the device identifier, the application identifier and the application value.
Owner:COLLINS LYAL SIDNEY
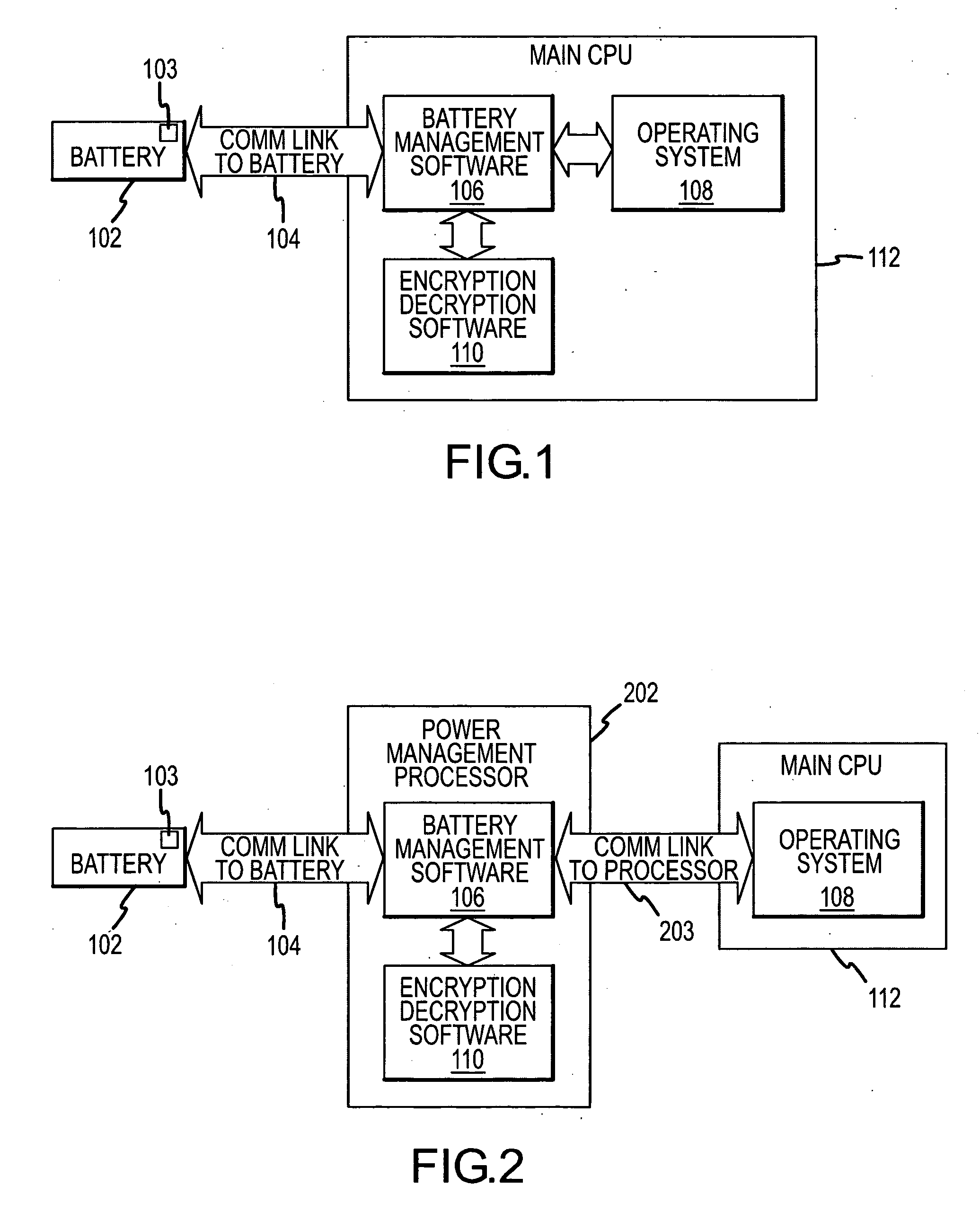
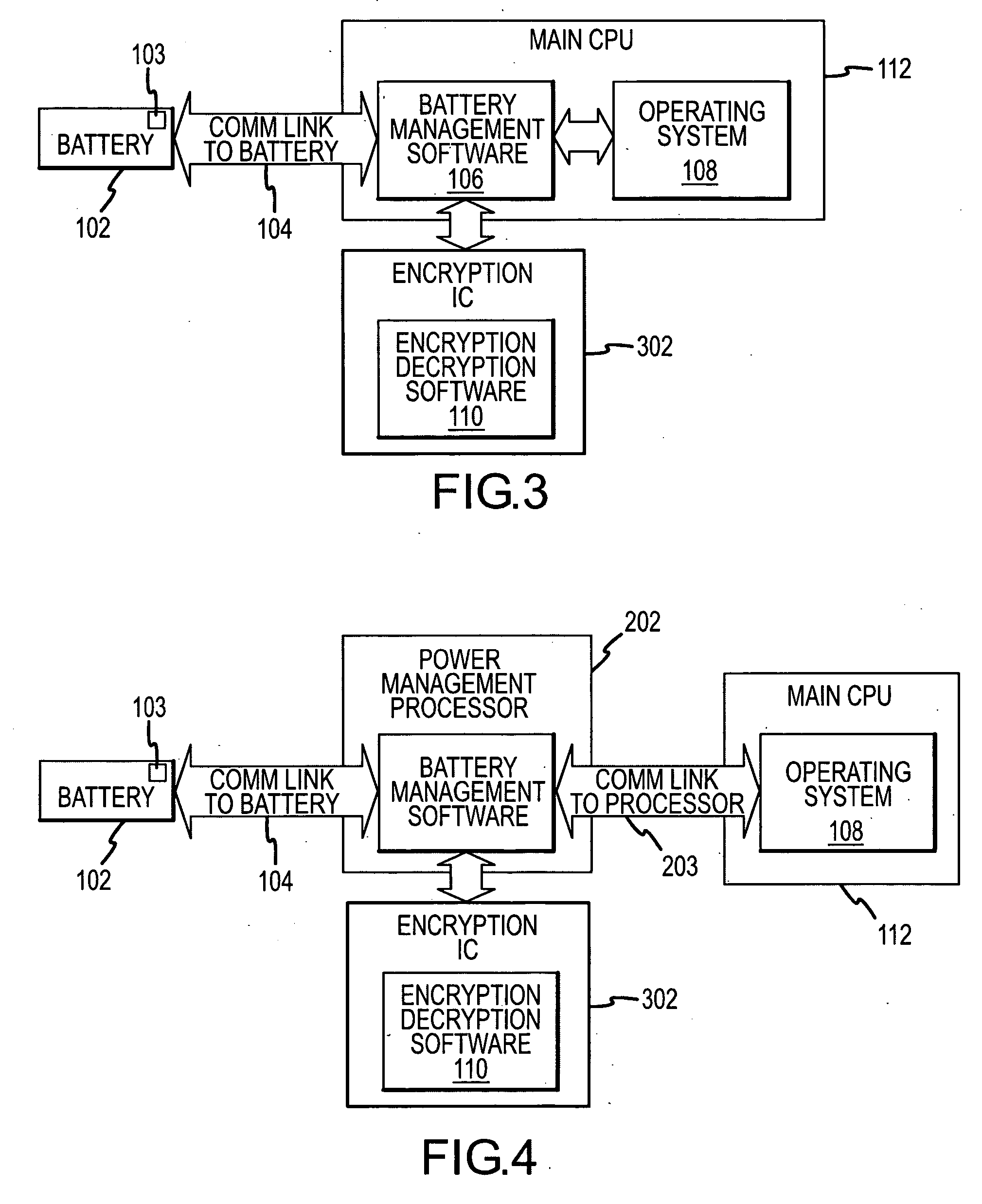
Methods and apparatus for power source authentication
InactiveUS20070143864A1Reduce usageBatteries circuit arrangementsError detection/correctionChallenge responseManagement system
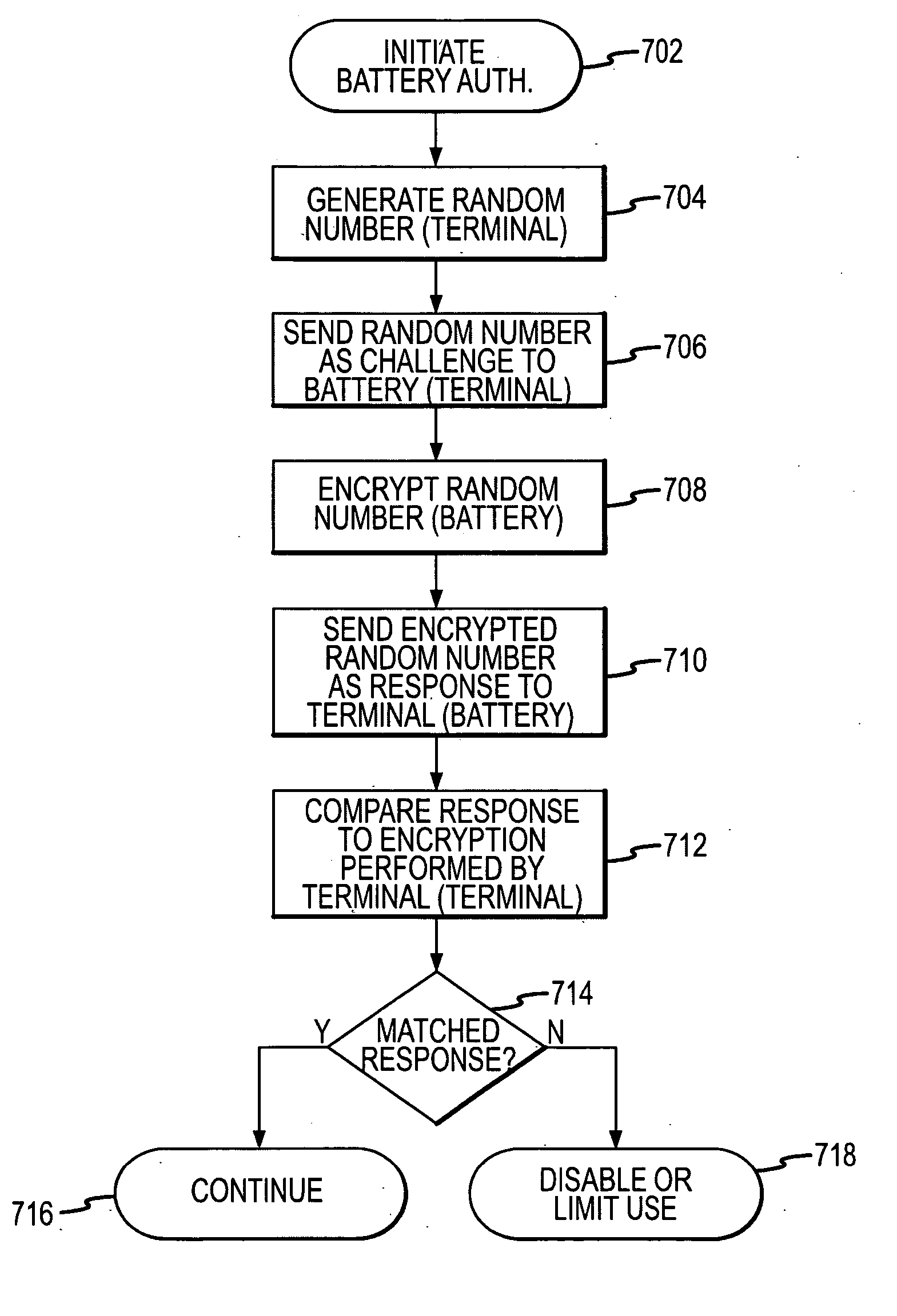
A power source management system disposed within a device is configured to communicate with a power source and perform an authentication procedure to determine whether the power source is an approved power source. The authentication procedure may involve the use of a challenge-response procedure using keys resident in the device and the power source. If it is determined that the power source is not an approved power source, the power source management system prevents use of or disables certain functionality of the device.
Owner:SYMBOL TECH INC
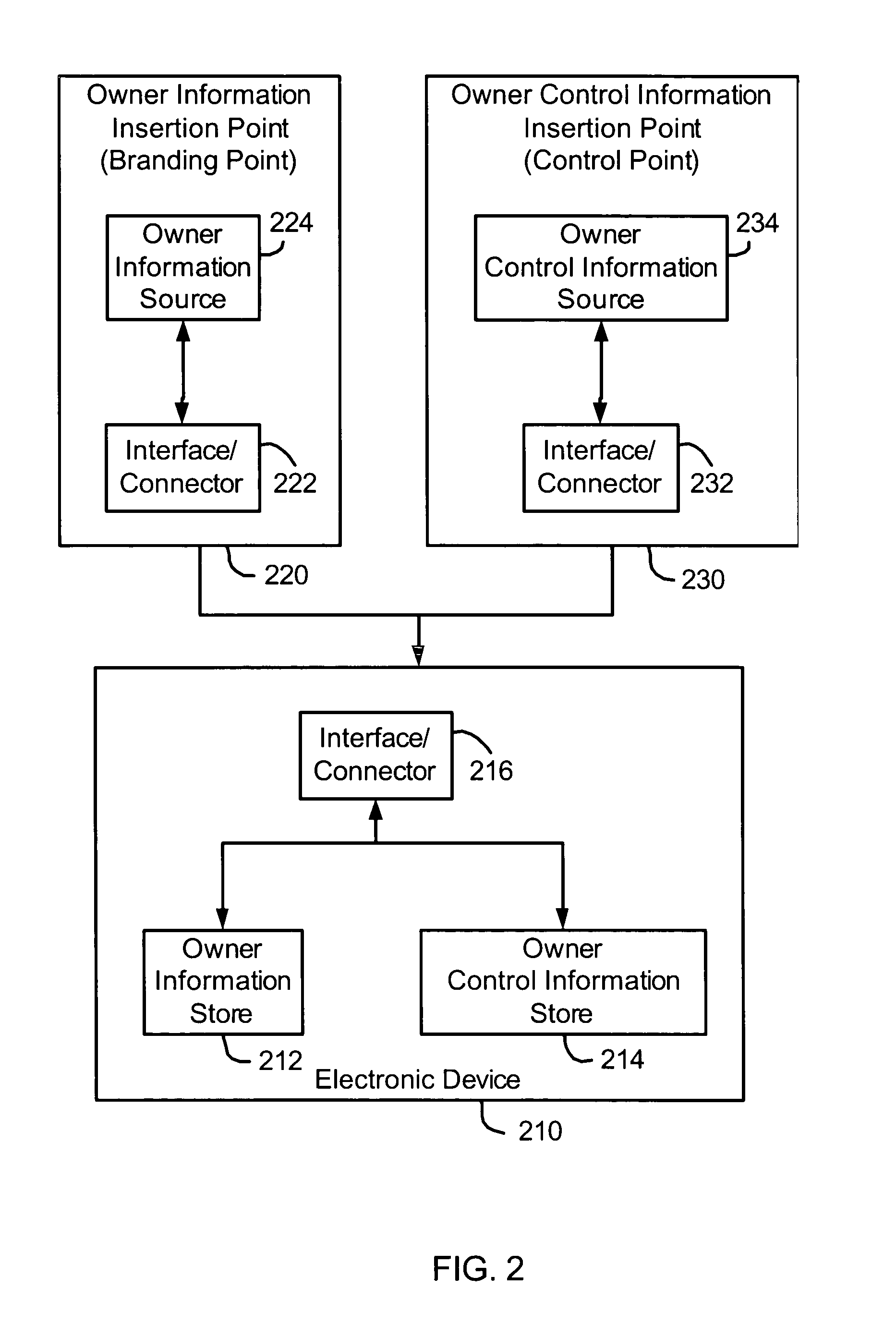
System and method of owner control of electronic devices
ActiveUS7793355B2Error detection/correctionVolume/mass flow measurementData integritySource authentication
A system and method of owner control of an electronic device are provided. Owner identification information, such as data integrity and source authentication information, is stored on the electronic device. Received owner control information is stored on the electronic device where the integrity of the received owner control information is verified and / or the source is authenticated using the owner identification information. In one embodiment, owner identification information comprises an owner signature private key.
Owner:MALIKIE INNOVATIONS LTD
Method and apparatus for source authentication in a communications network
ActiveUS20050286511A1Time-division multiplexData switching by path configurationComputer networkSource authentication
Owner:ORACLE INT CORP
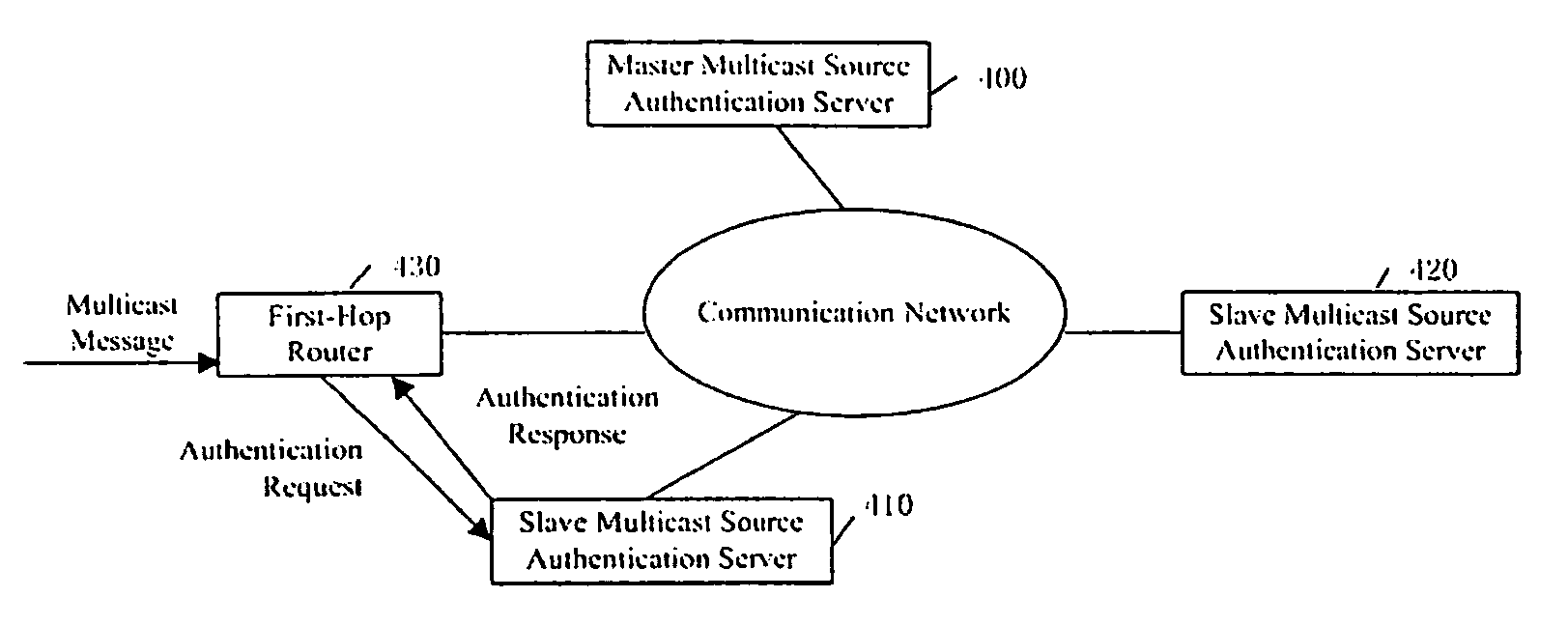
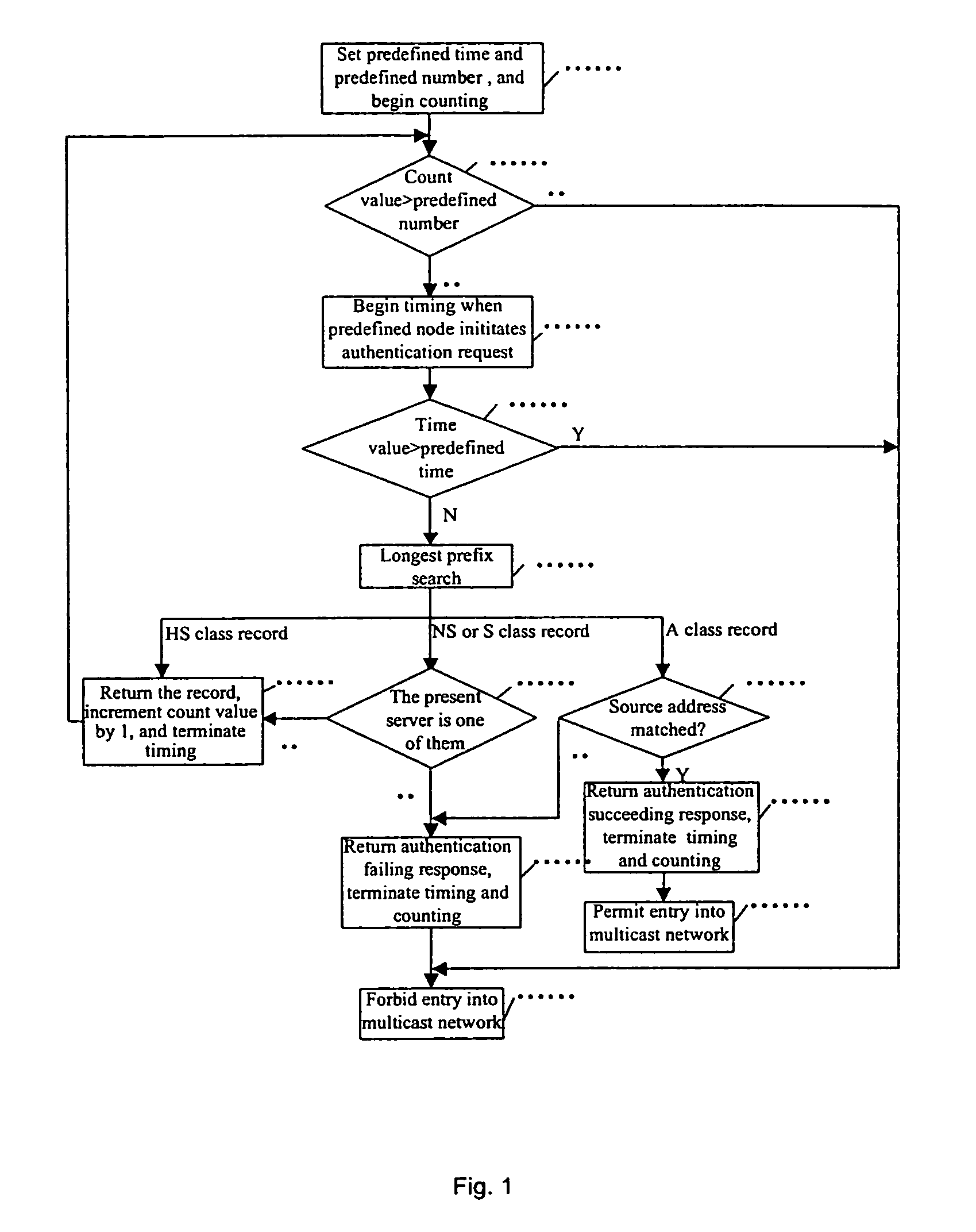
Method and system for controlling the multicast source
ActiveUS20070115975A1Reduce managementReduce maintenance costsSpecial service provision for substationError preventionNetwork terminationControl system
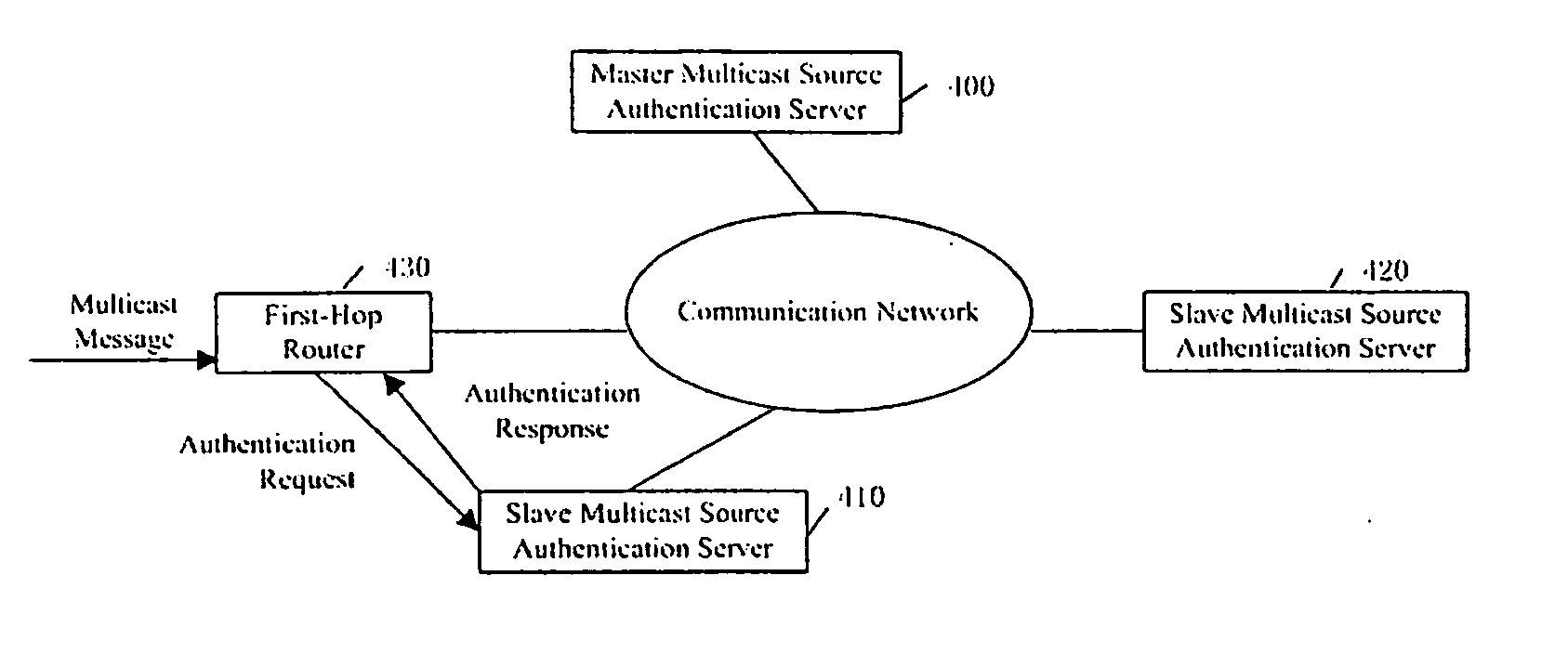
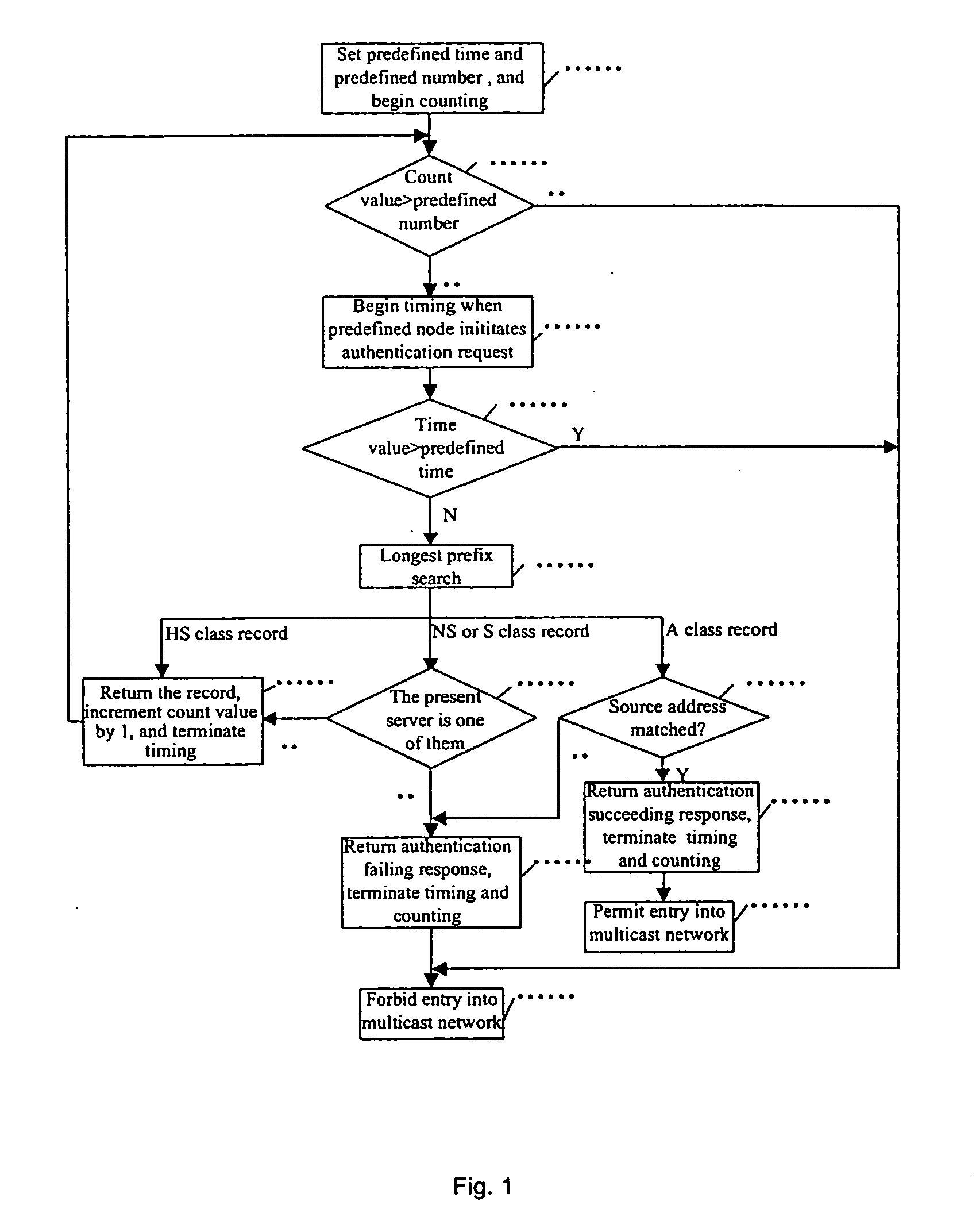
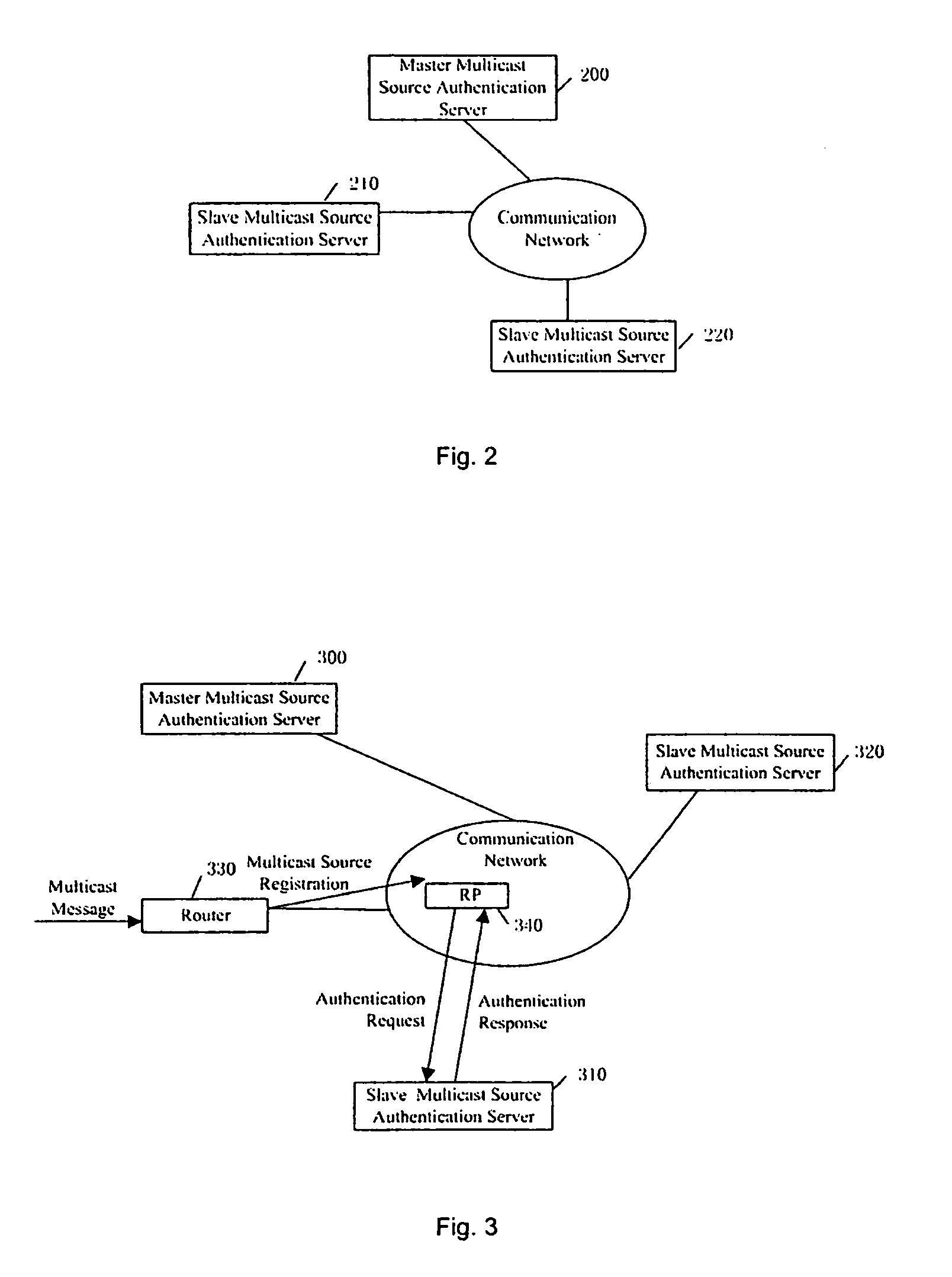
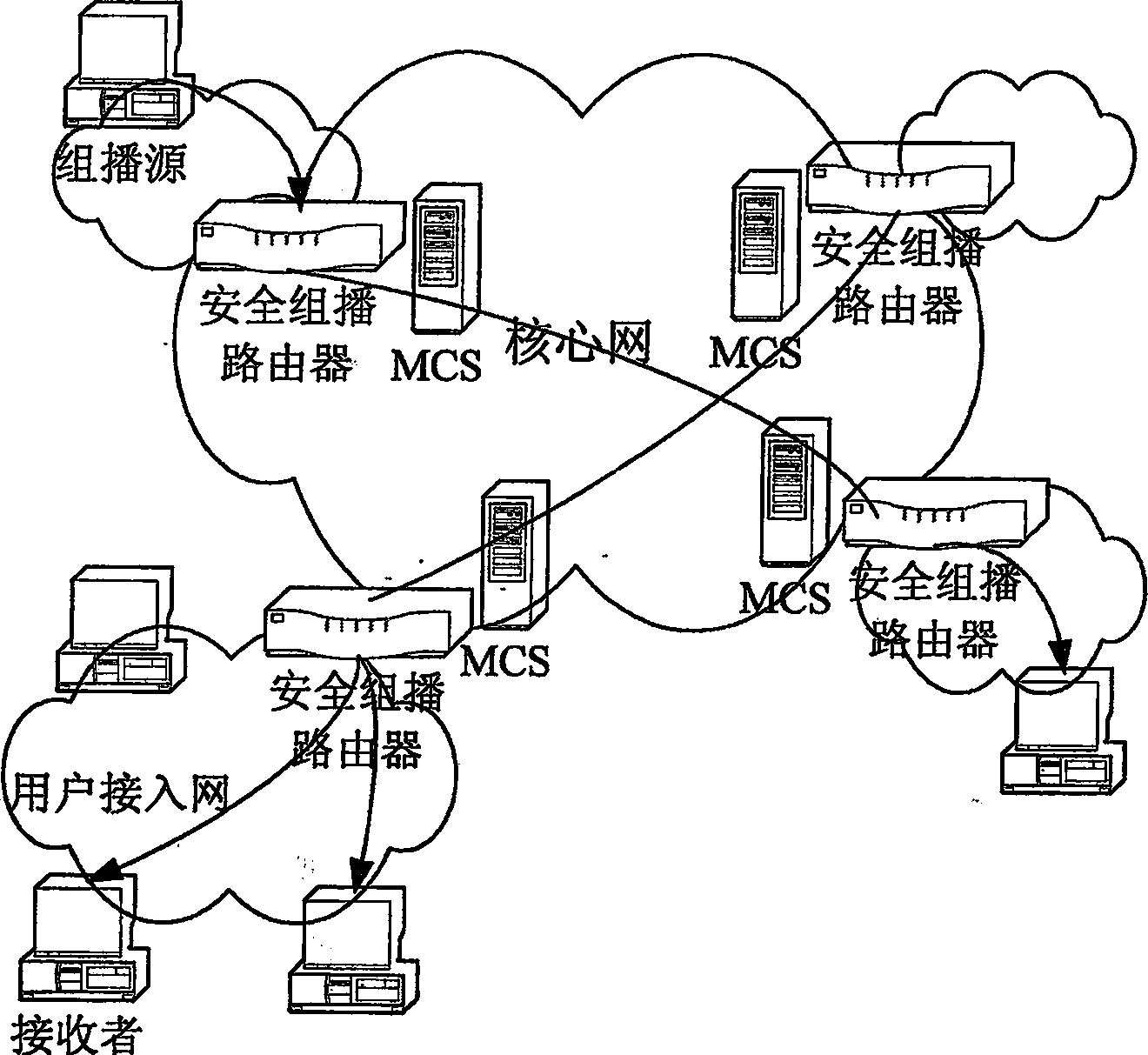
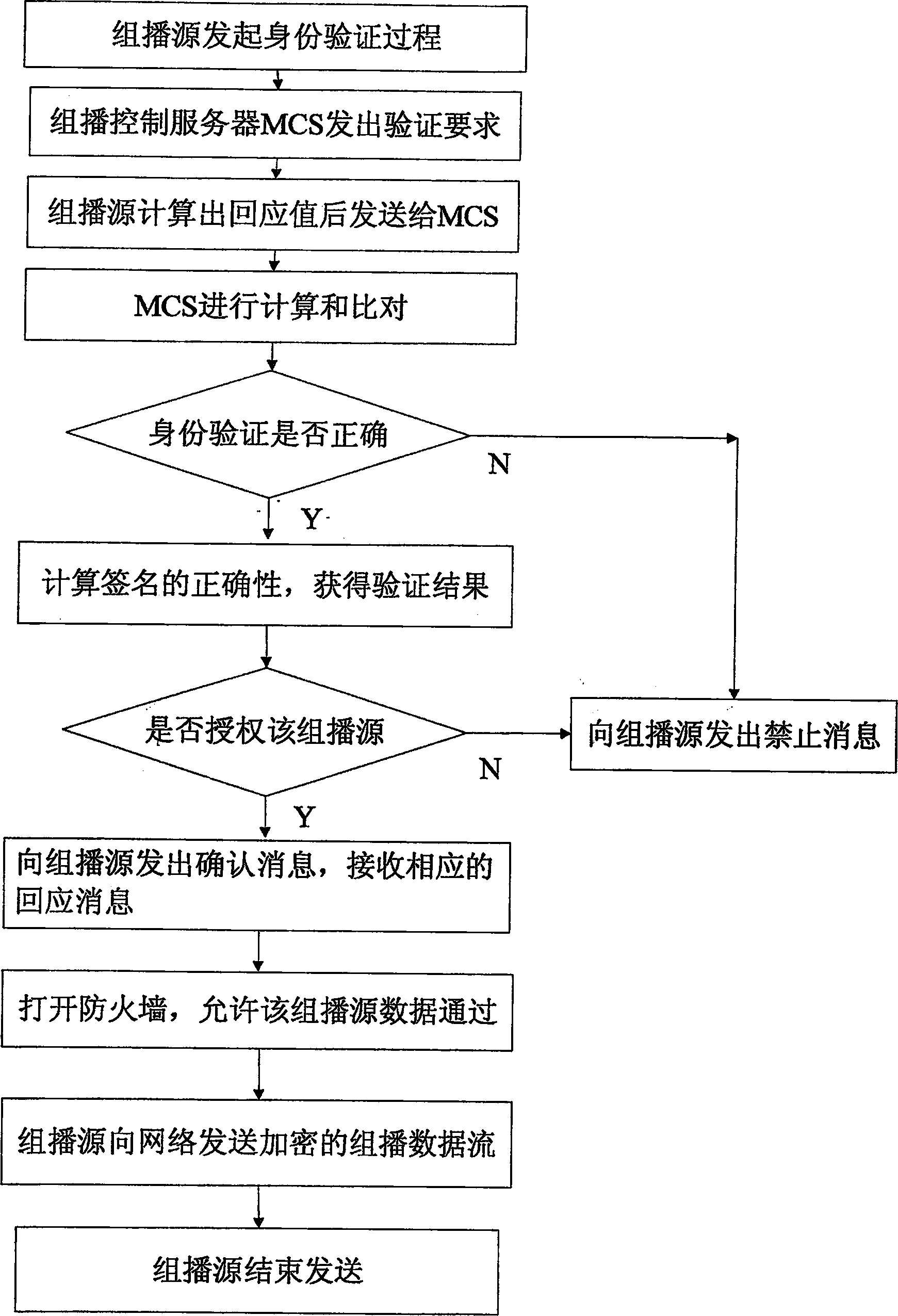
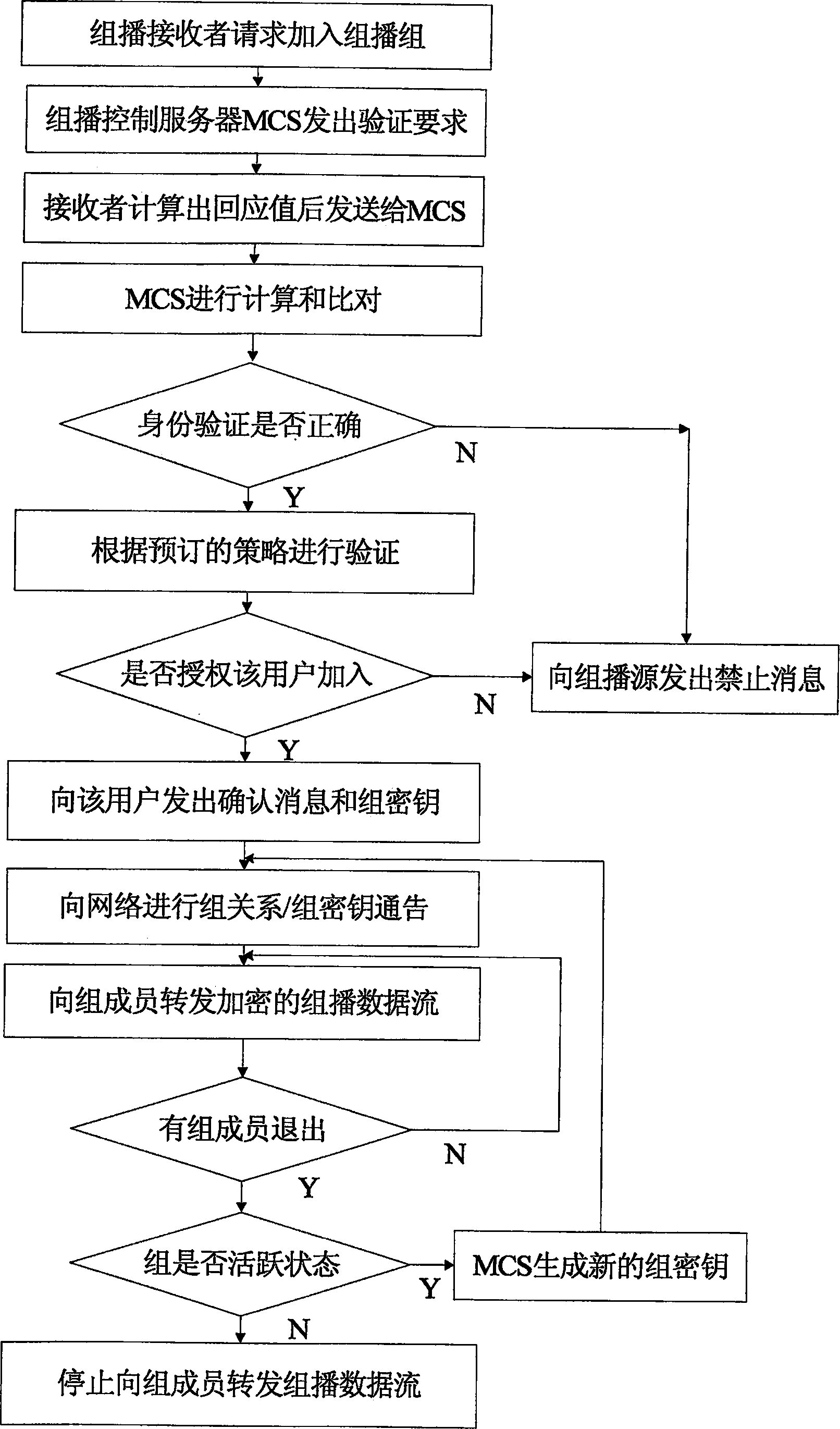
The present invention provides a multicast source control method, which comprises: creating multicast source authentication information; a management platform of the multicast source authentication information dynamically updating said multicast source authentication information in accordance with restriction on multicast source; controlling multicast message sent from the multicast source in accordance with said multicast source authentication information. The present invention also provides a multicast source control system comprising a master multicast source authentication server, a group of slave multicast source authentication servers, and a predefined node. With the present invention, multicast sources can be performed a control management at the earliest time through initiating authentication requests for multicast sources by the predefined node; the network terminal resources are saved through deploying hierarchical distributed multicast source authentication servers to manage different multicast address fields; without manual intervention, the master and slave multicast source authentication servers interact for authentication information periodically and in real time, such that automatic and real time management of multicast sources can be implemented; and thereby the object of reducing management and maintenance cost as well as improving manageability and operability of the multicast network is attained.
Owner:CHENGDU HUAWEI TECH
Dynamic source authentication and encryption cryptographic scheme for a group-based secure communication environment
InactiveUS20050111668A1Key distribution for secure communicationMultiple keys/algorithms usageSecure communicationAdemetionine
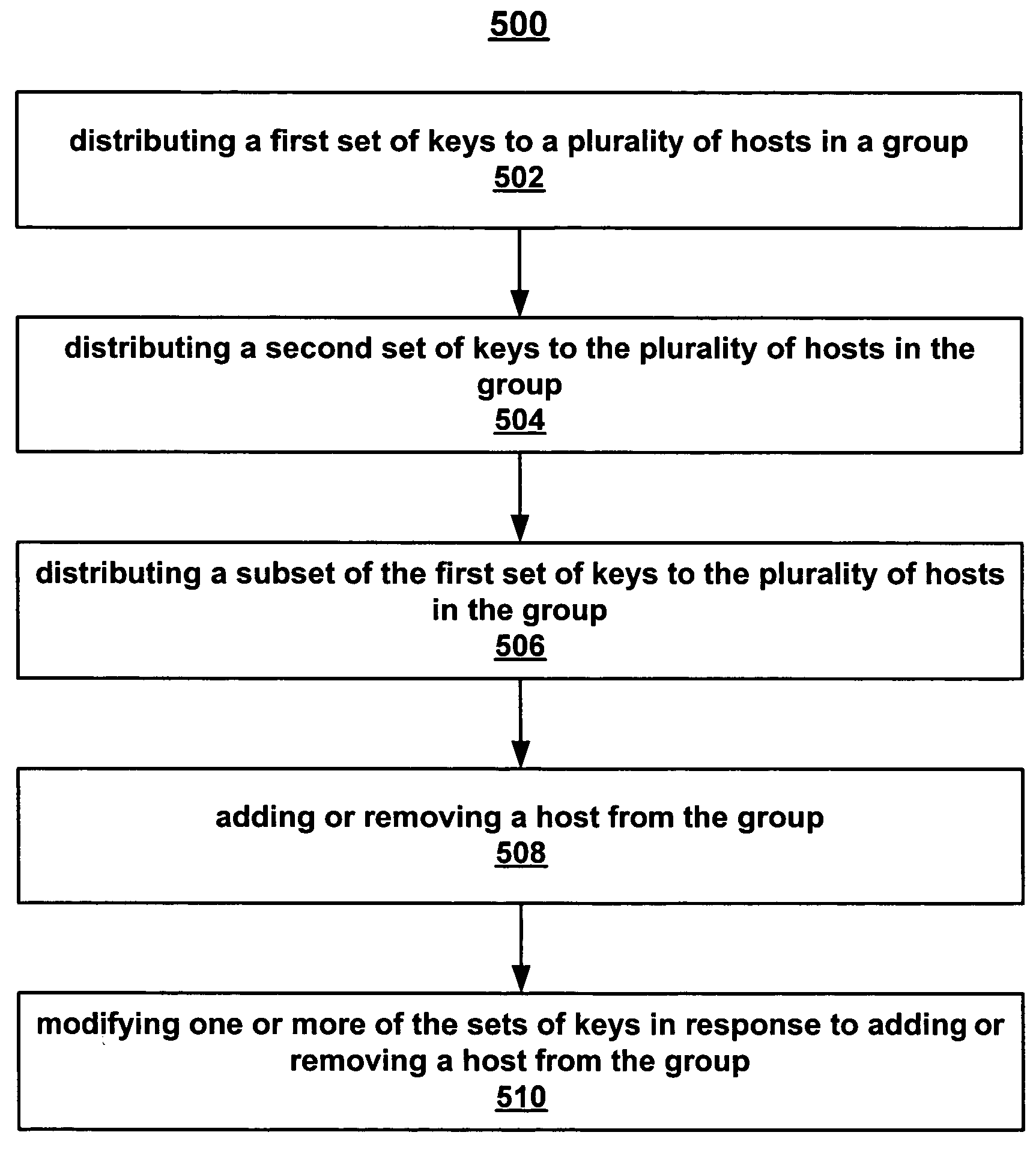
Embodiments of the present invention include a method for establishing secure group-based communication comprising: distributing a first set of keys to a plurality of hosts for encrypting communication and for source authentication of group-based communication between the plurality of hosts. The method further includes distributing a second set of keys to the plurality of hosts for dynamically modifying the first set of keys as also any other keys used (encryption keys or seed variables) when required (viz. for periodic re-keying or for adjusting to a change in group membership).
Owner:HEWLETT PACKARD DEV CO LP
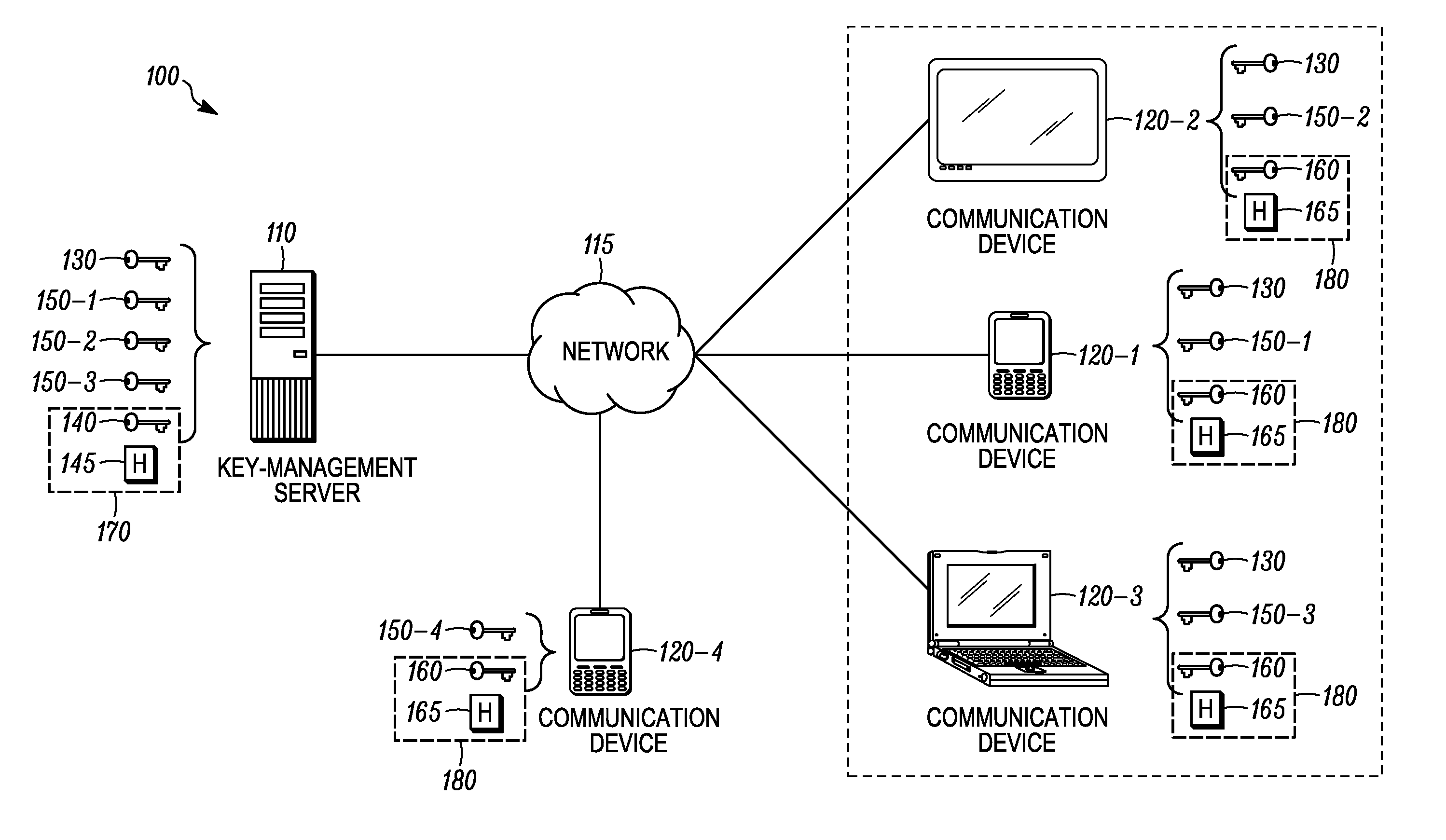
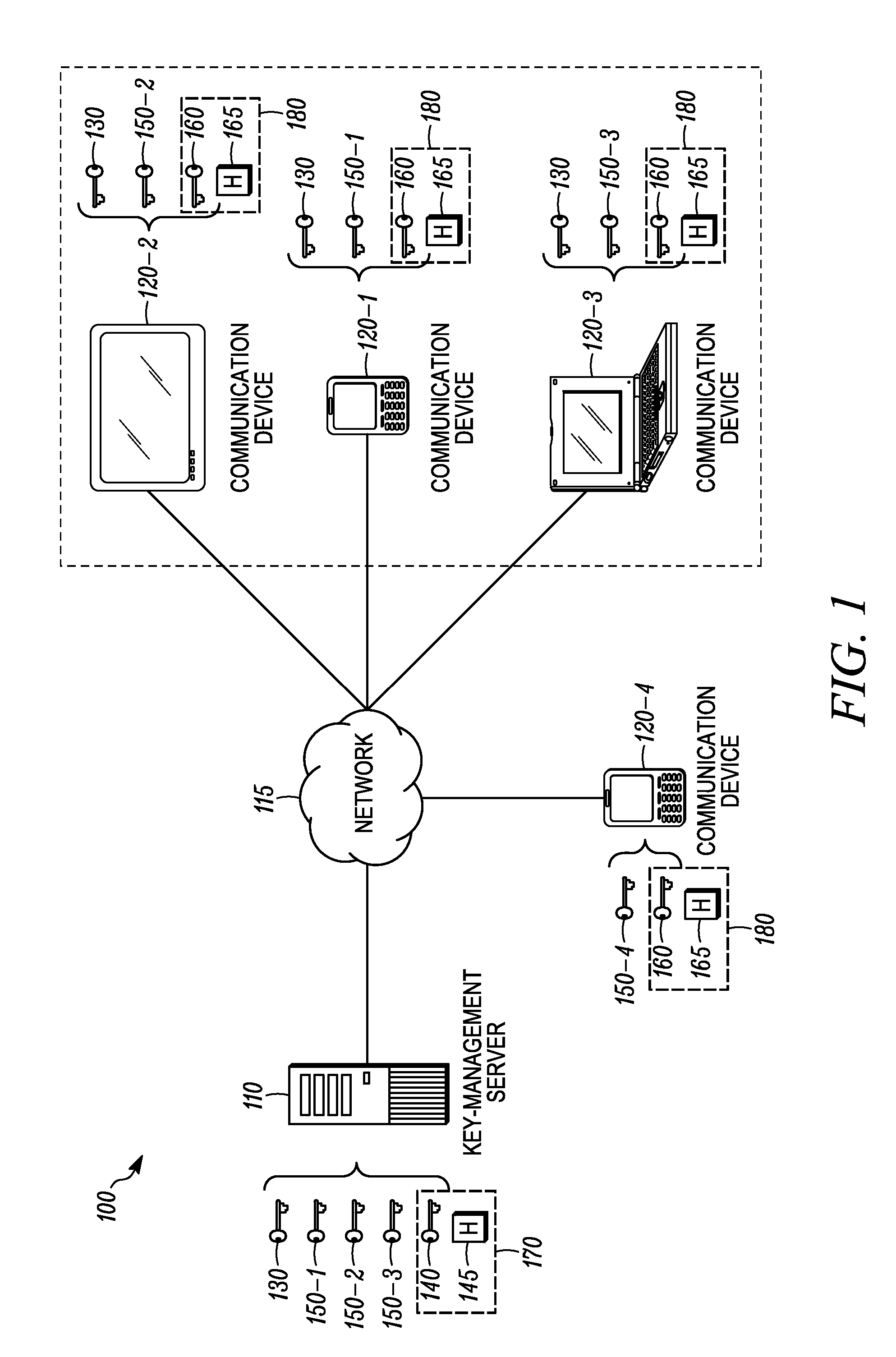
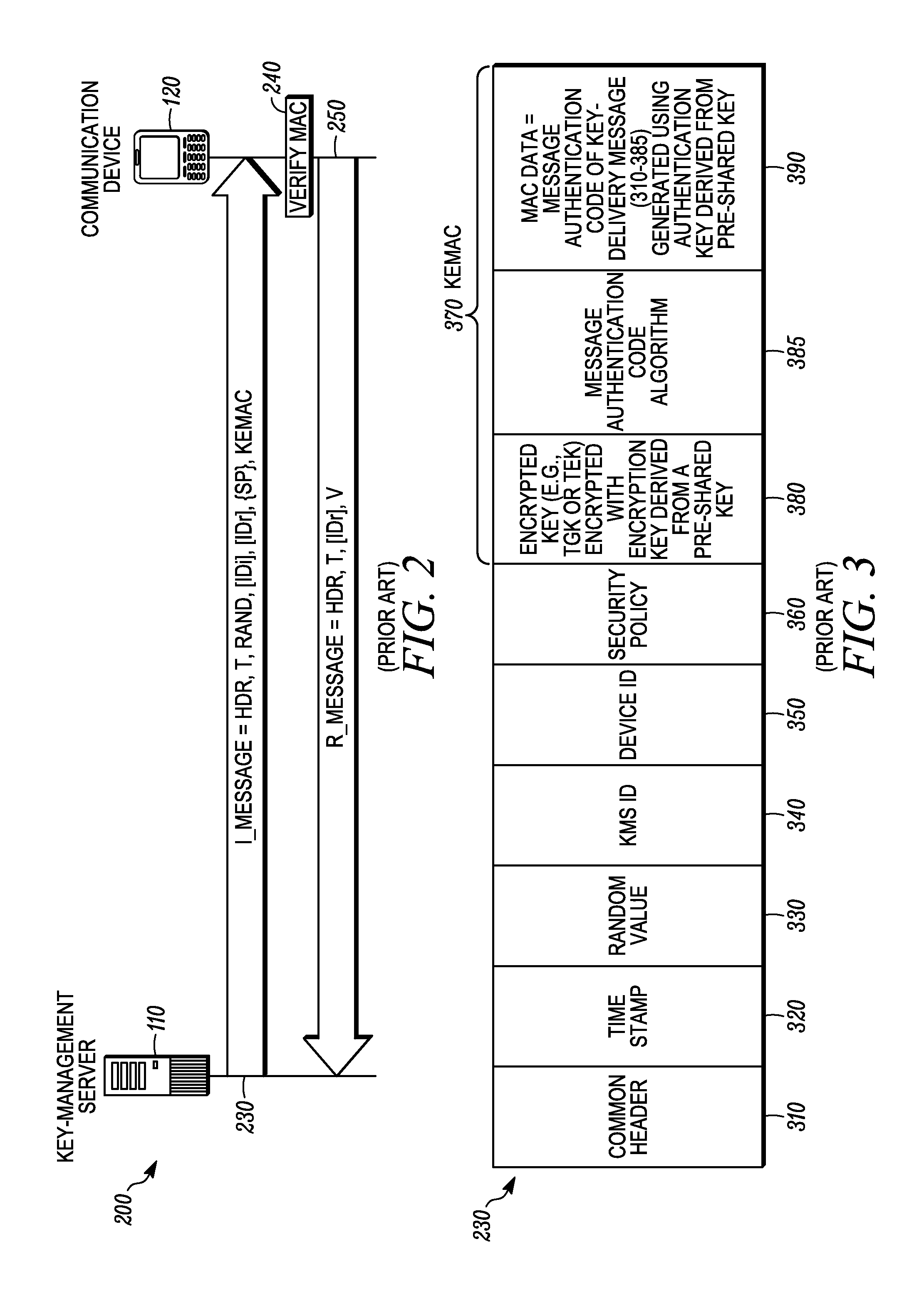
Methods and apparatus for source authentication of messages that are secured with a group key
Methods, systems and apparatus are provided for source authentication. In accordance with the disclosed embodiments, a key-management server generates a key-delivery message that includes a key data transport payload secured with a group key, and a source authentication payload. Upon receiving the key-delivery message at a communication device, the communication device may verify whether the source authentication payload of the key-delivery message is valid. When the source authentication payload is determined to be valid, the communication device thereby authenticates that the key-delivery message was transmitted by the key-management server.
Owner:MOTOROLA SOLUTIONS INC
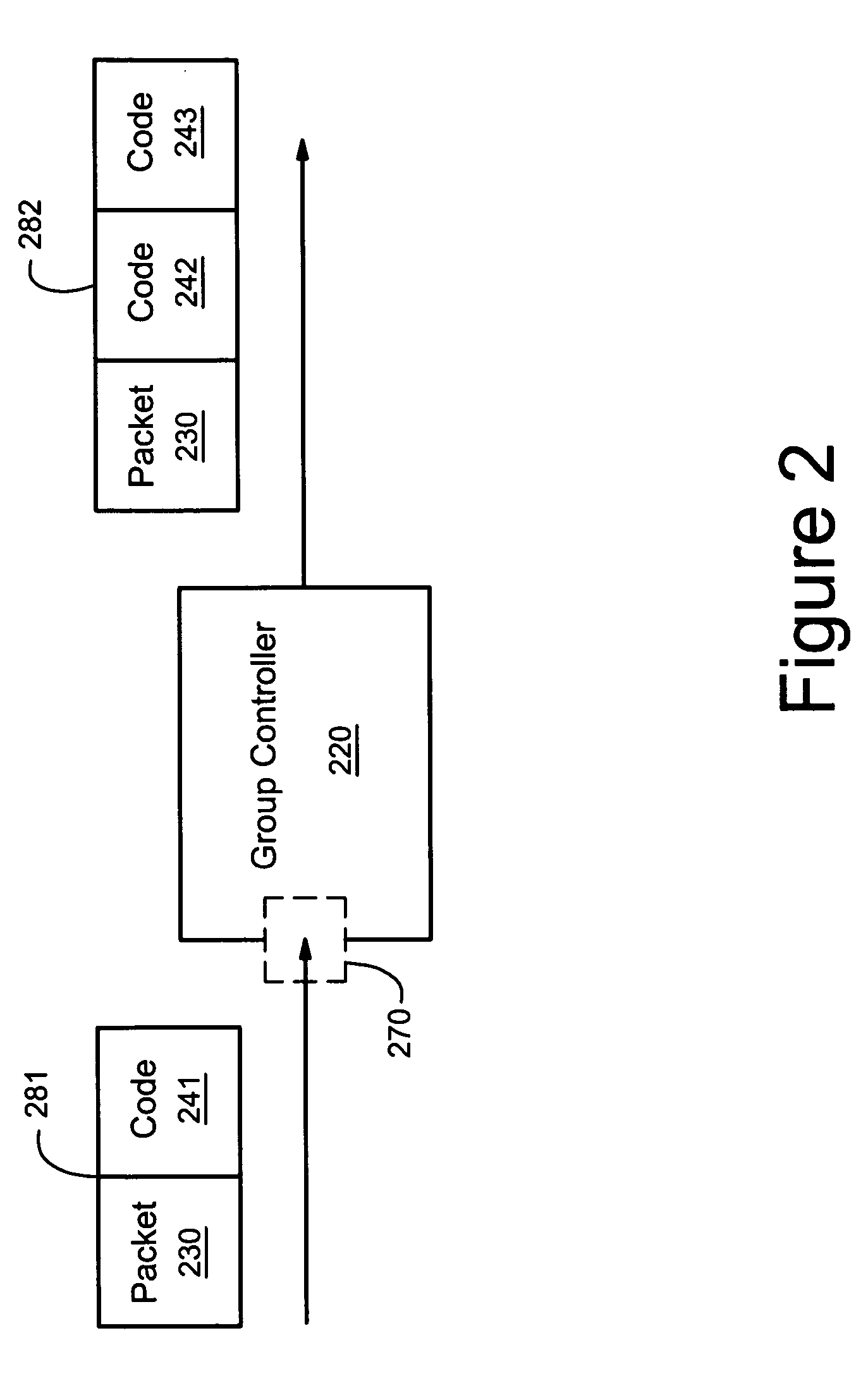
Apparatus and method for data source authentication for multicast security
A method and apparatus for data source authentication in multicast communications is provided. Multicasting a packet may be divided into two actions. The first action includes unicasting the packet from a sending member to a group controller. The second action includes multicasting the packet from the group controller to the multicast group. The packet may be unicast to the group controller with a message authentication code (MAC) that may be generated by encrypting the packet with a symmetric key that is intended to be known only to the sending member and the group controller. After authenticating the MAC, the group controller multicasts the packet to the multicast group. The group controller includes with the packet a separate MAC for substantially each receiving member of the multicast group, each encrypted by a separate symmetric key. Each symmetric key may be intended to be known only by the receiving member and the group controller.
Owner:NOKIA SOLUTIONS & NETWORKS OY
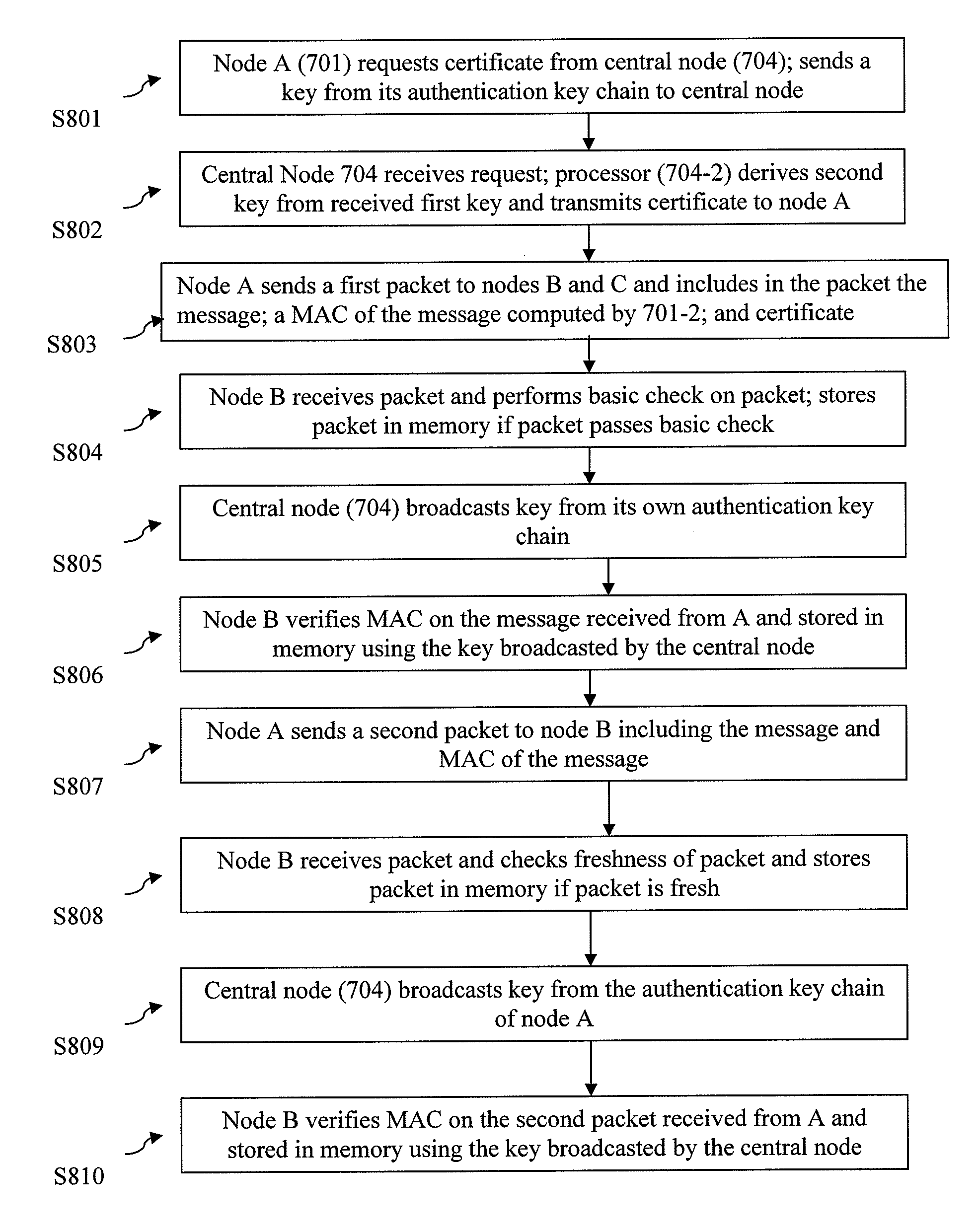
Method and System for Source Authentication in Group Communications
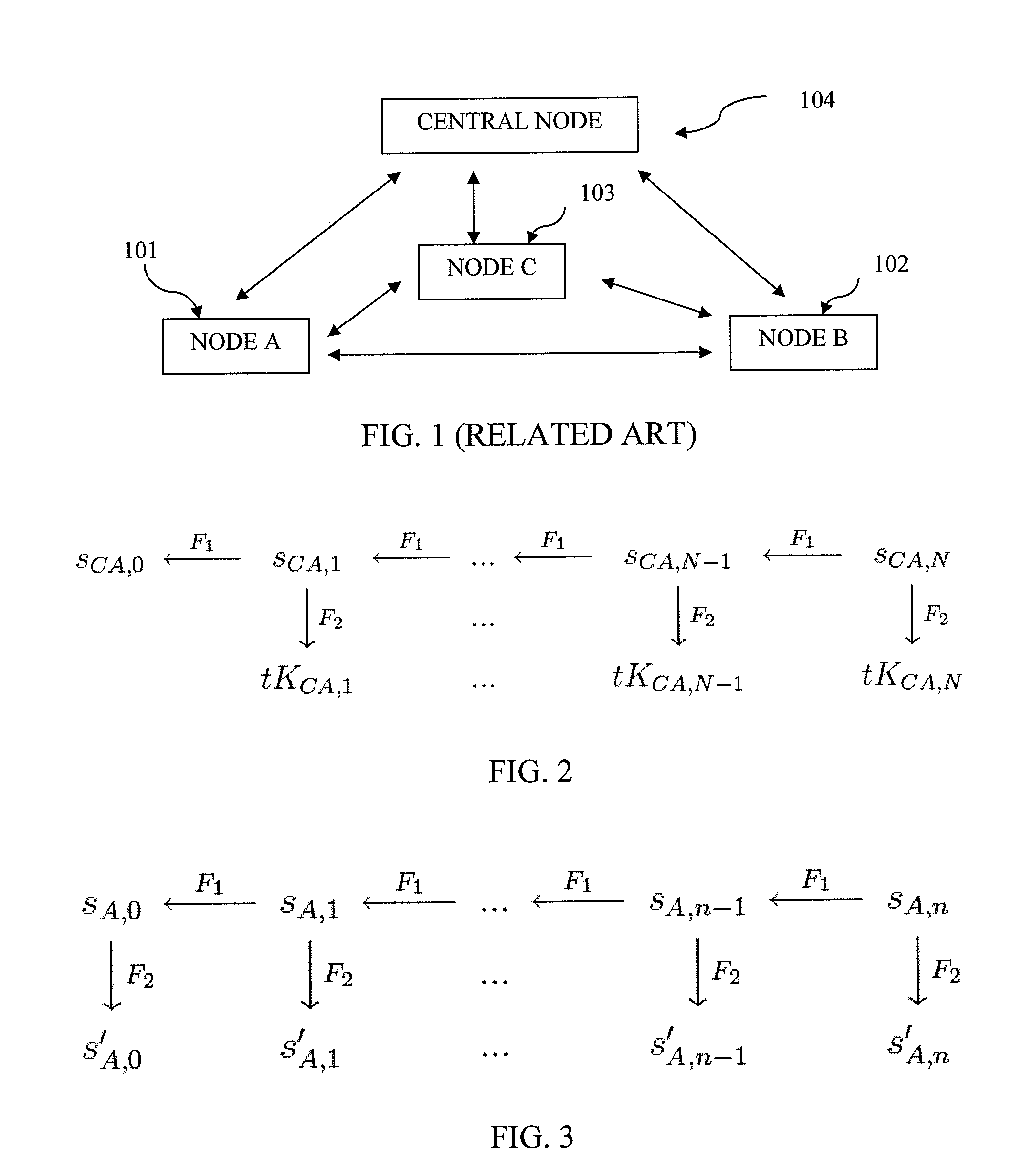
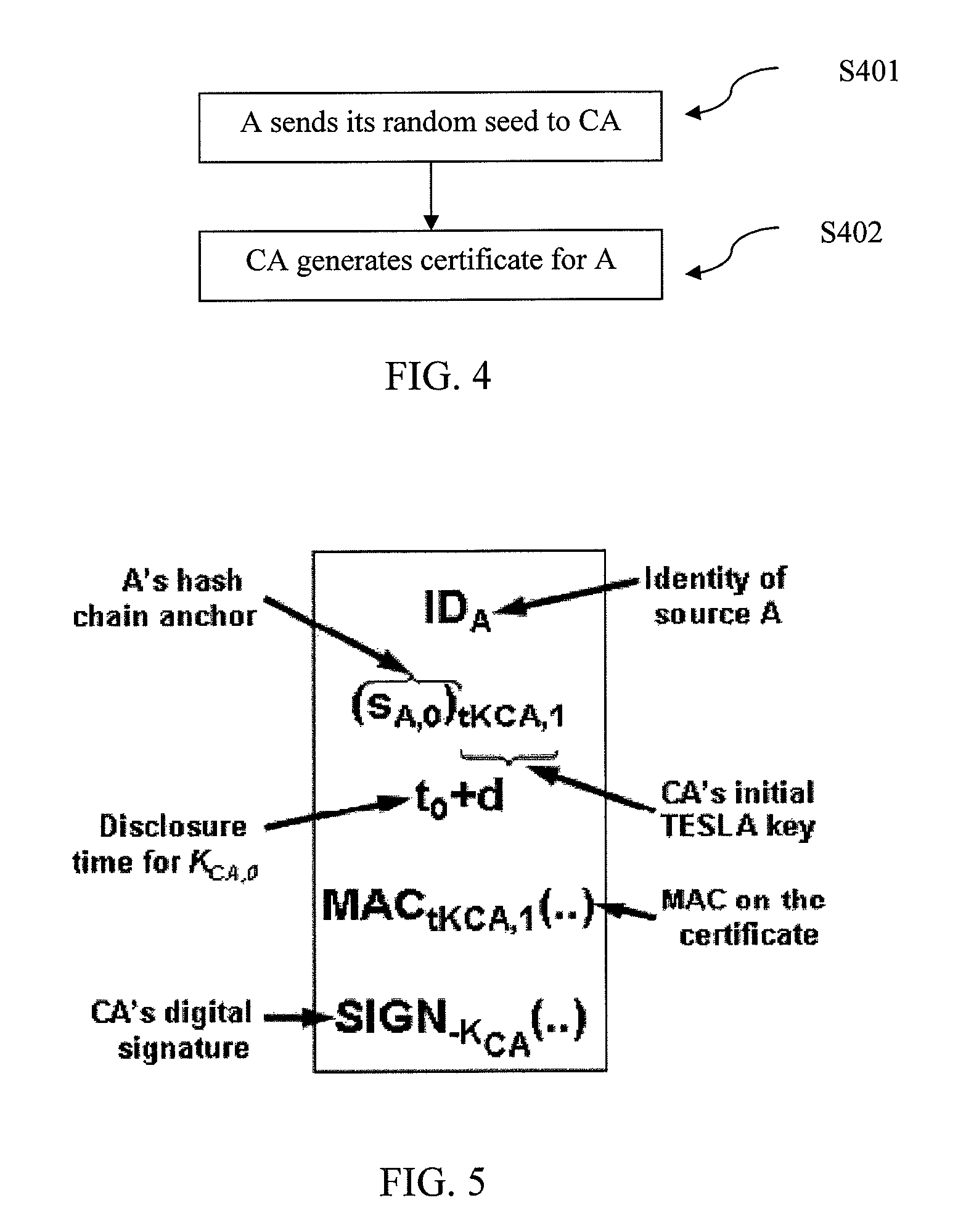
ActiveUS20100268943A1Efficient implementationMultiple keys/algorithms usageUser identity/authority verificationKey generationSource authentication
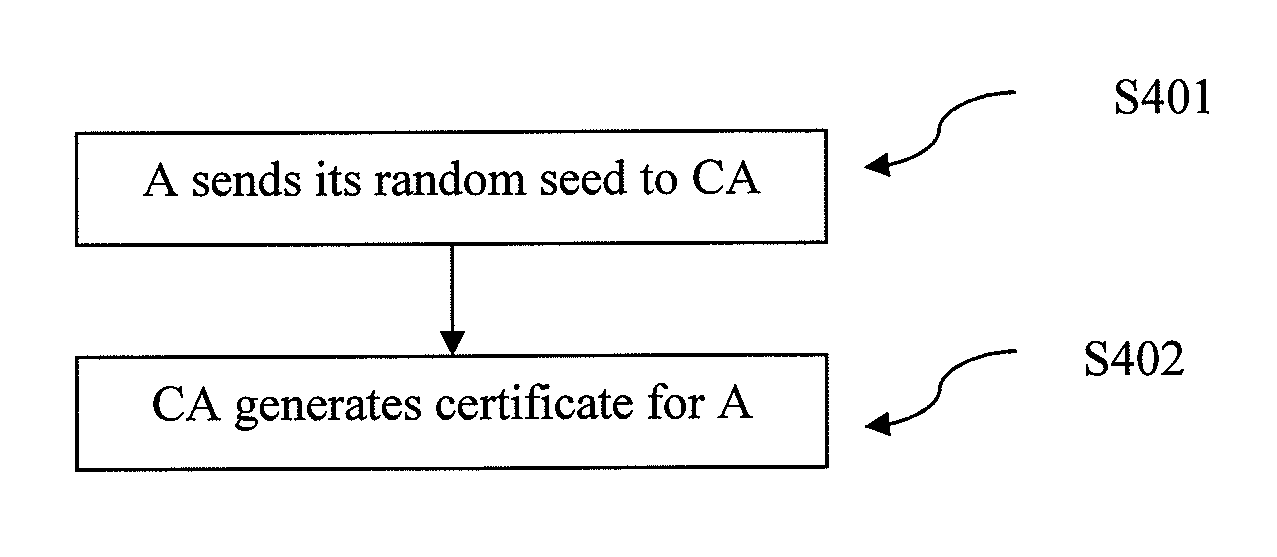
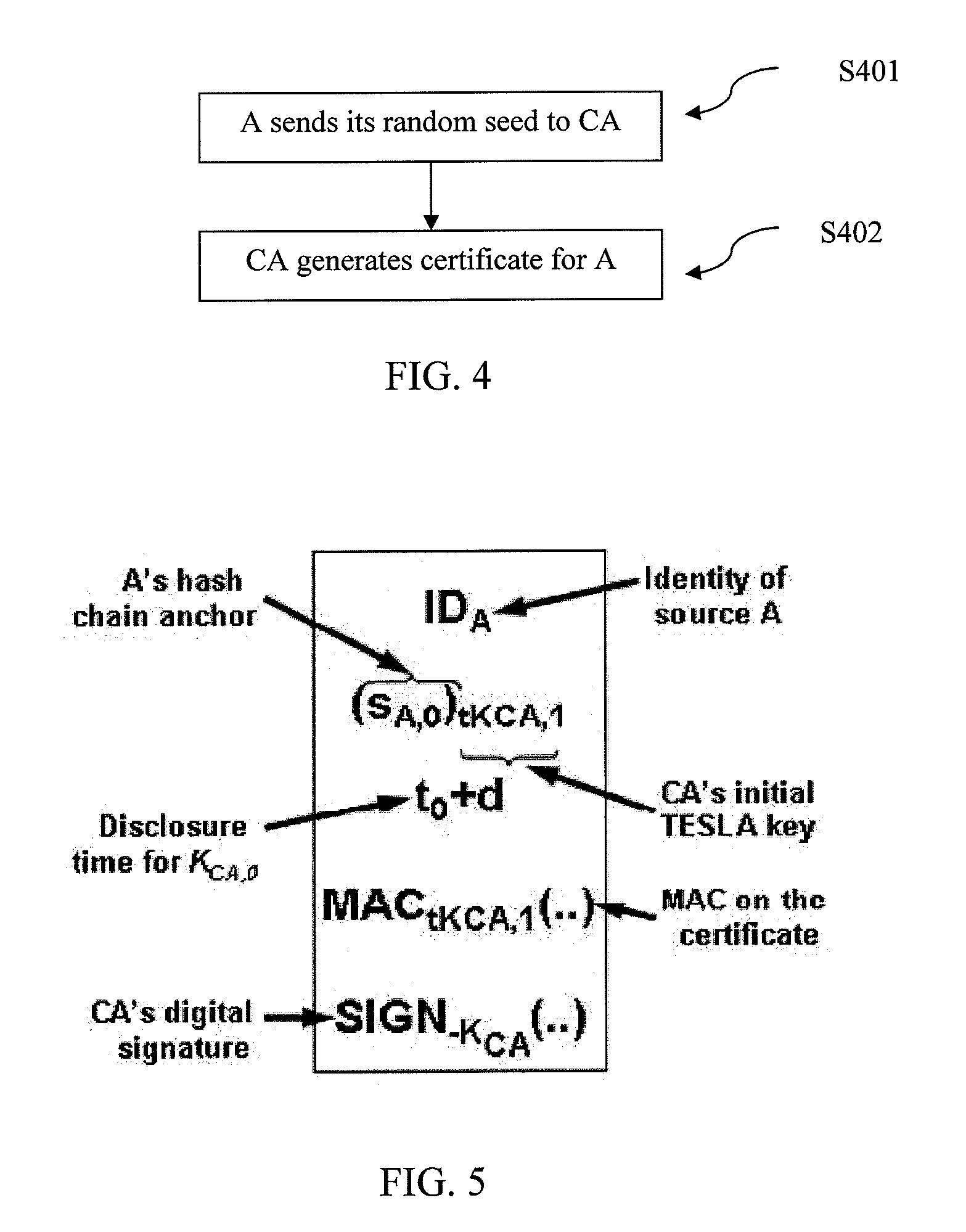
A method and system for authentication is provided. A central node for issuing certificates to a plurality of nodes associated with the central node in a network is also provided. The central node receives a first key from at least one node from among the plurality of nodes and generates a second key based on the received first key and generates a certificate for the at least one node. The generated certificate is transmitted to the at least one node.
Owner:UNIV OF MARYLAND
Method and system for performing authentication on access request
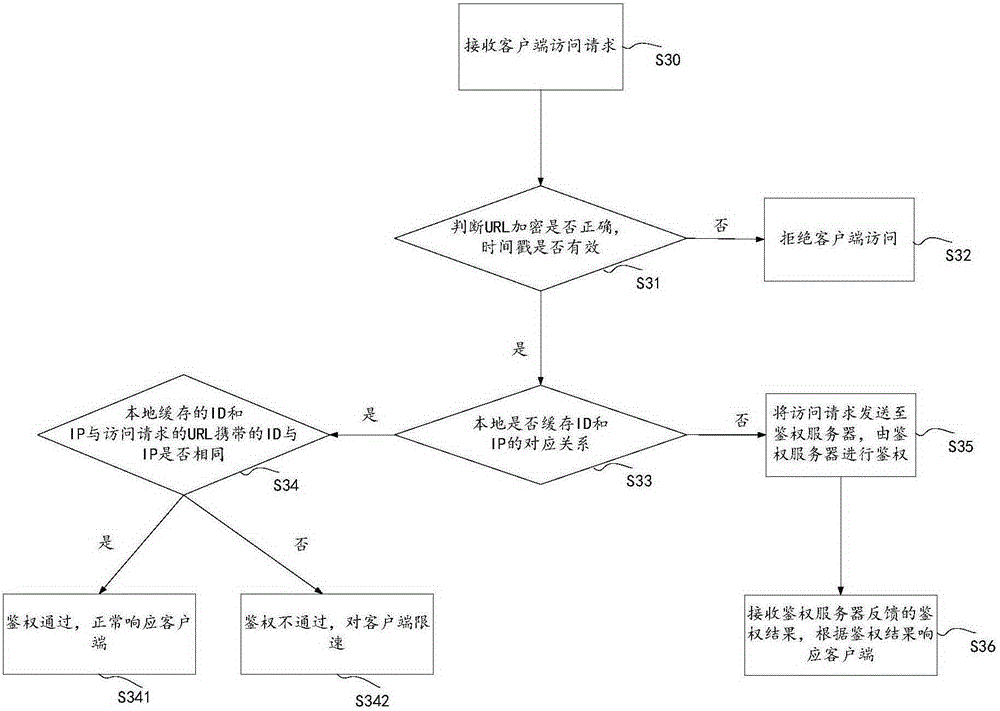
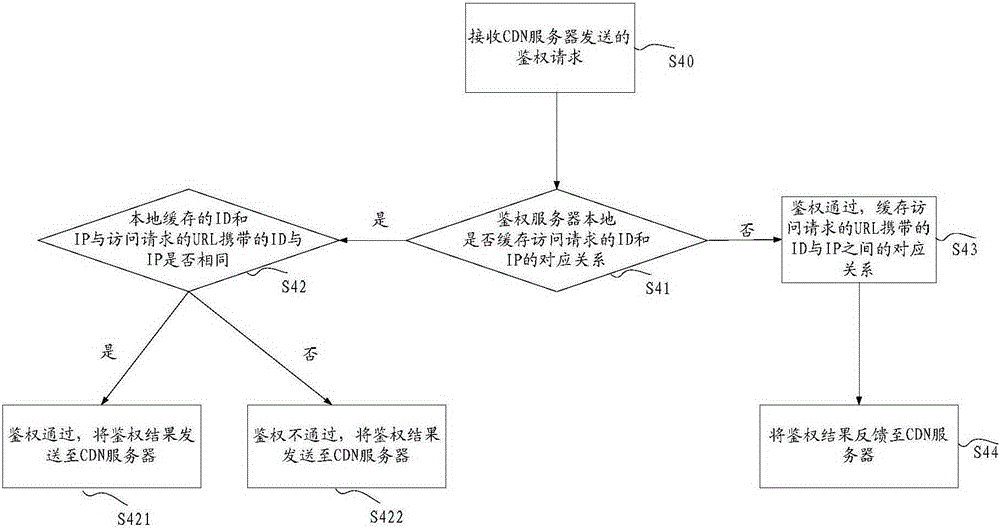
ActiveCN105357190ATroubleshoot technical issues with overloadTransmissionContent distributionAuthentication server
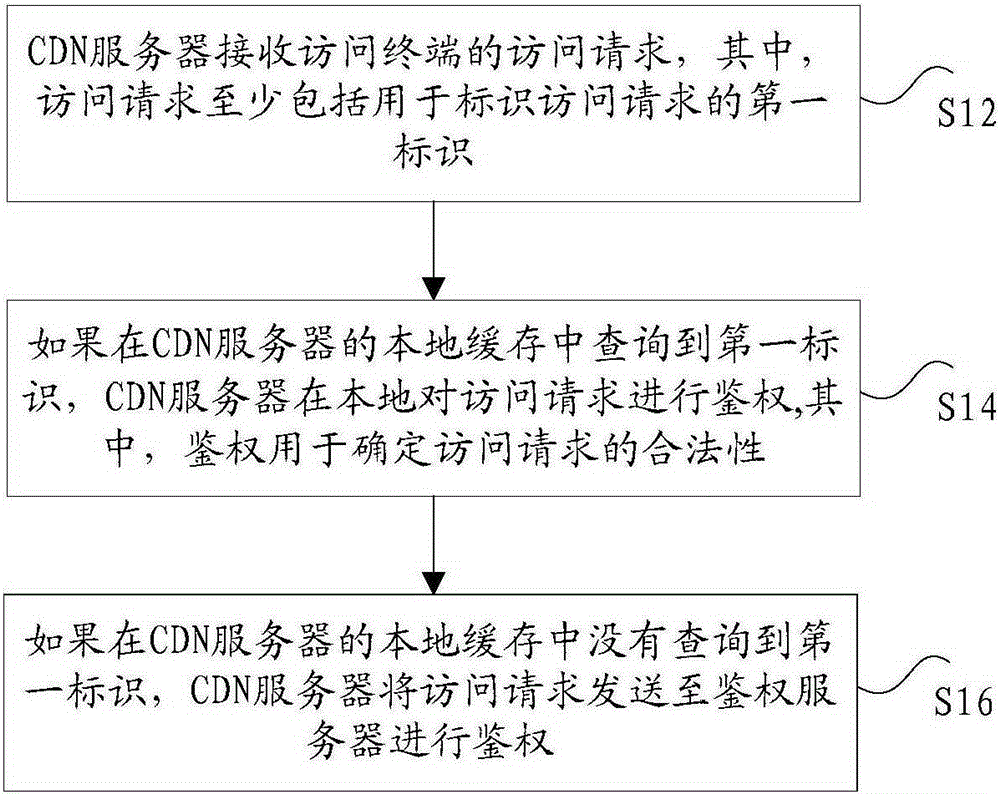
The invention discloses a method and system for performing authentication on an access request. The method comprises the following steps: receiving an access request of an access terminal by a CDN (Content Distribution Network) server, wherein the access request at least comprises a first identification used for identifying the access request; if the first identification is inquired in a local cache of the CDN server, then performing authentication on the access request locally by the CDN server, wherein authentication is used for determining the legality of the access request; and if the first identification is not inquired in the local cache of the CDN server, then transmitting the access request to an authentication server to perform authentication by the CDN server. The method and system for performing authentication on the access request provided by the invention solve the technical problem that an anti-stealing link method of the existing back to the source authentication only depends on the authentication server to recognize a hotlinking request in any case, so that the load of the authentication server is excessive.
Owner:CHINANETCENT TECH
SYN Cookie source authentication method and device for preventing DDOS attack
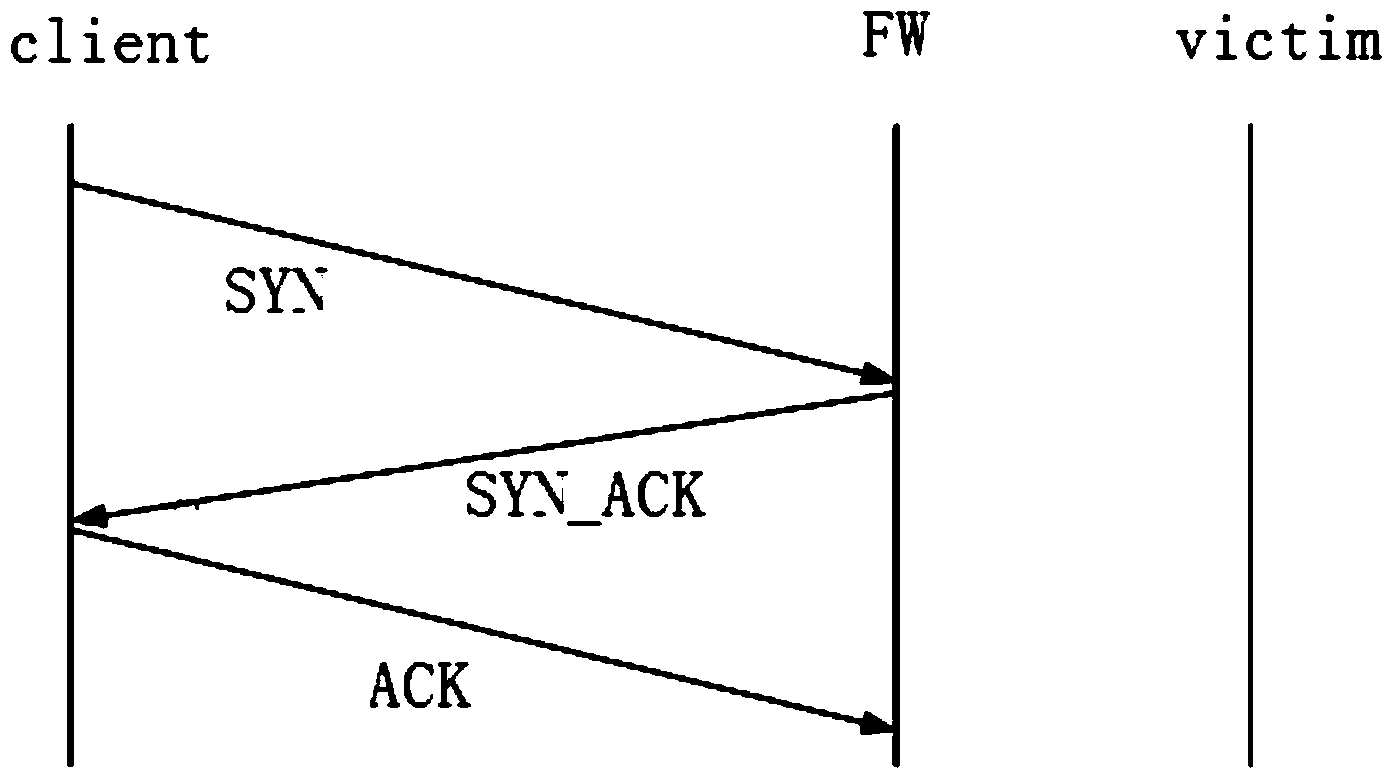
InactiveCN103546486AEffective protectionAccurately and quickly find outTransmissionSerial codeSource authentication
The invention discloses a SYN Cookie source authentication method for preventing a DDOS attack. The SYN Cookie source authentication method is characterized in that after a SYN message received by an attacked server Victim exceeds a set threshold, a DDOS attack preventing device generates SYN Cookie according to the SYN message, the SYN Cookie serves as the TCP serial number to be packaged, the SYN_ACK message is sent to a SYN message sending source, and after the SYN Cookie is verified by the ACK message of the DDOS attack preventing device, a follow-up message of the SYN message sending source is transmitted to the Victim through the DDOS attack preventing device. The invention further provides a SYN cookie source authentication device for preventing the DDOS attack. The DDOS attack is prevented through the method.
Owner:UNITED ELECTRONICS
Anti-disclosure mail safe card and method for detecting disclosure mail
InactiveCN101257378ASolve security and confidentiality issuesImprove information security defense capabilitiesData switching networksSecuring communicationInternal memoryNetwork control
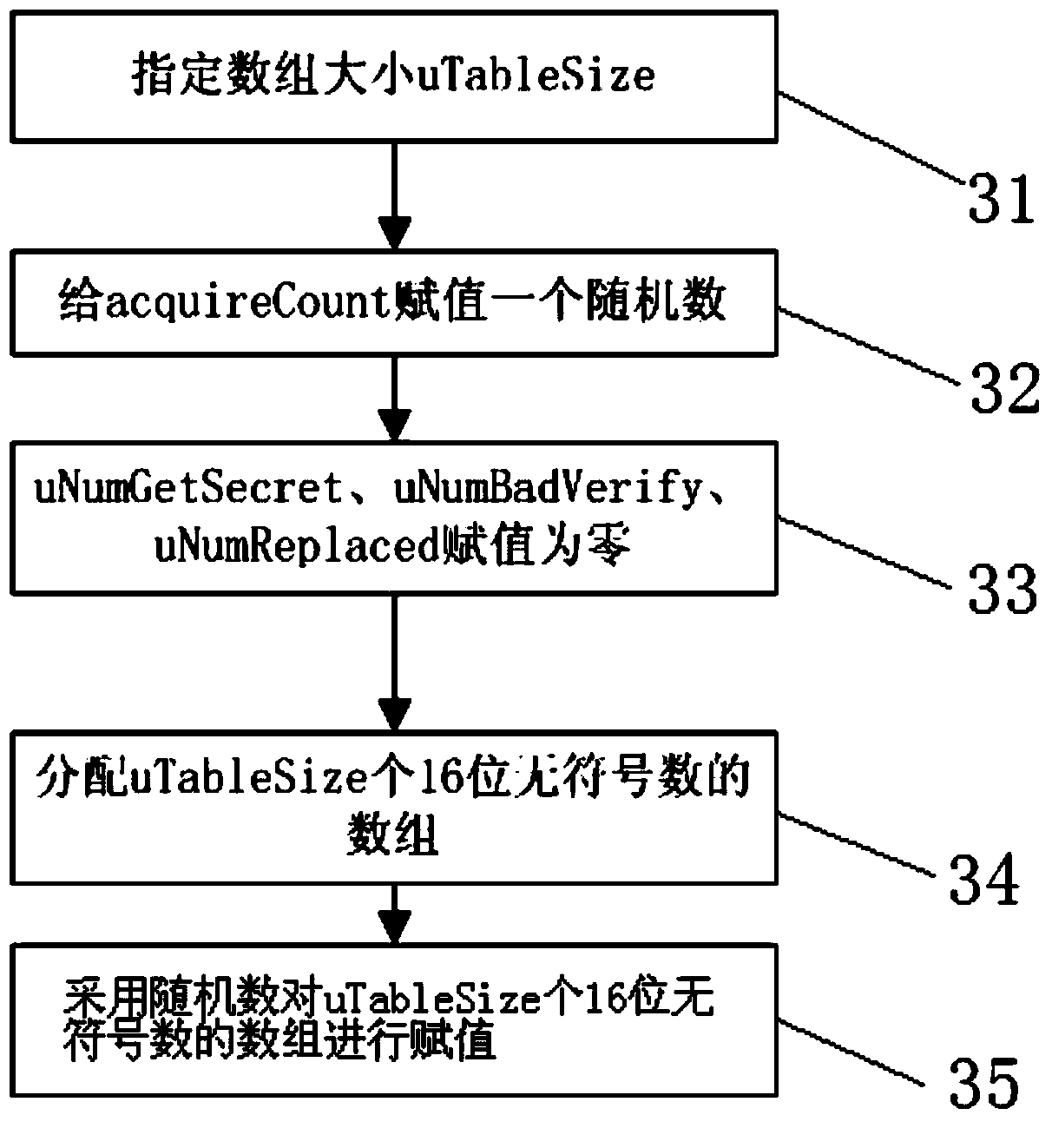
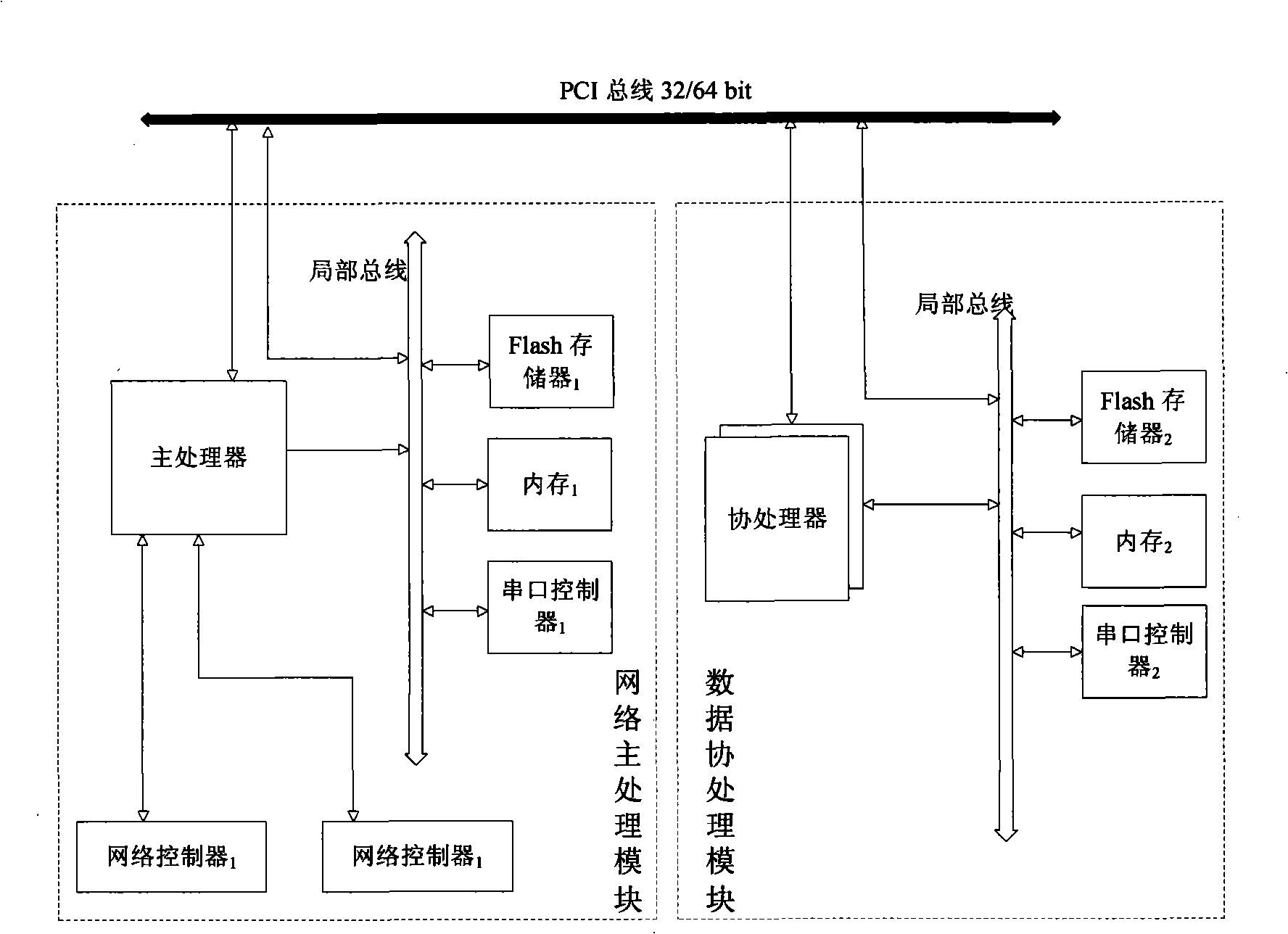
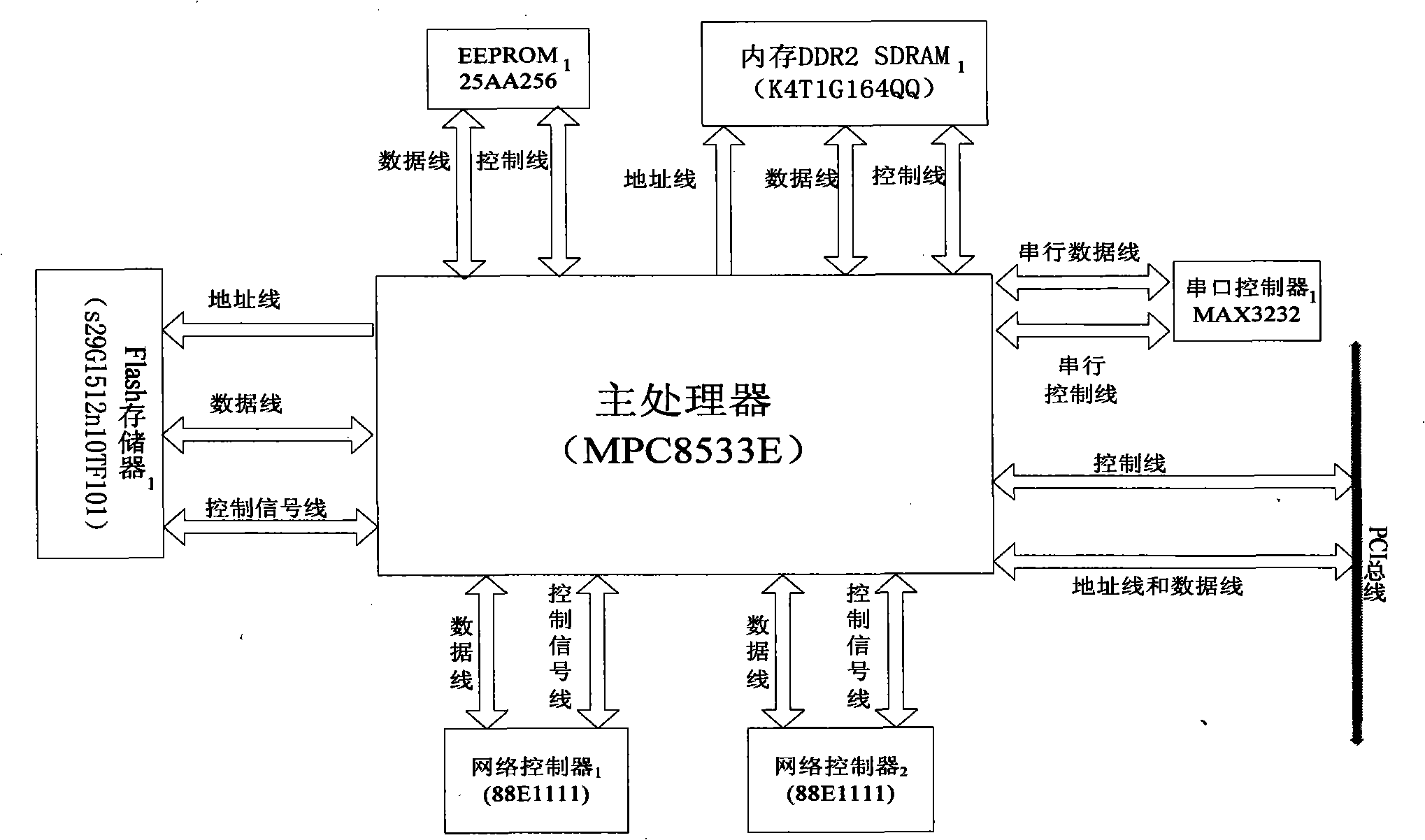
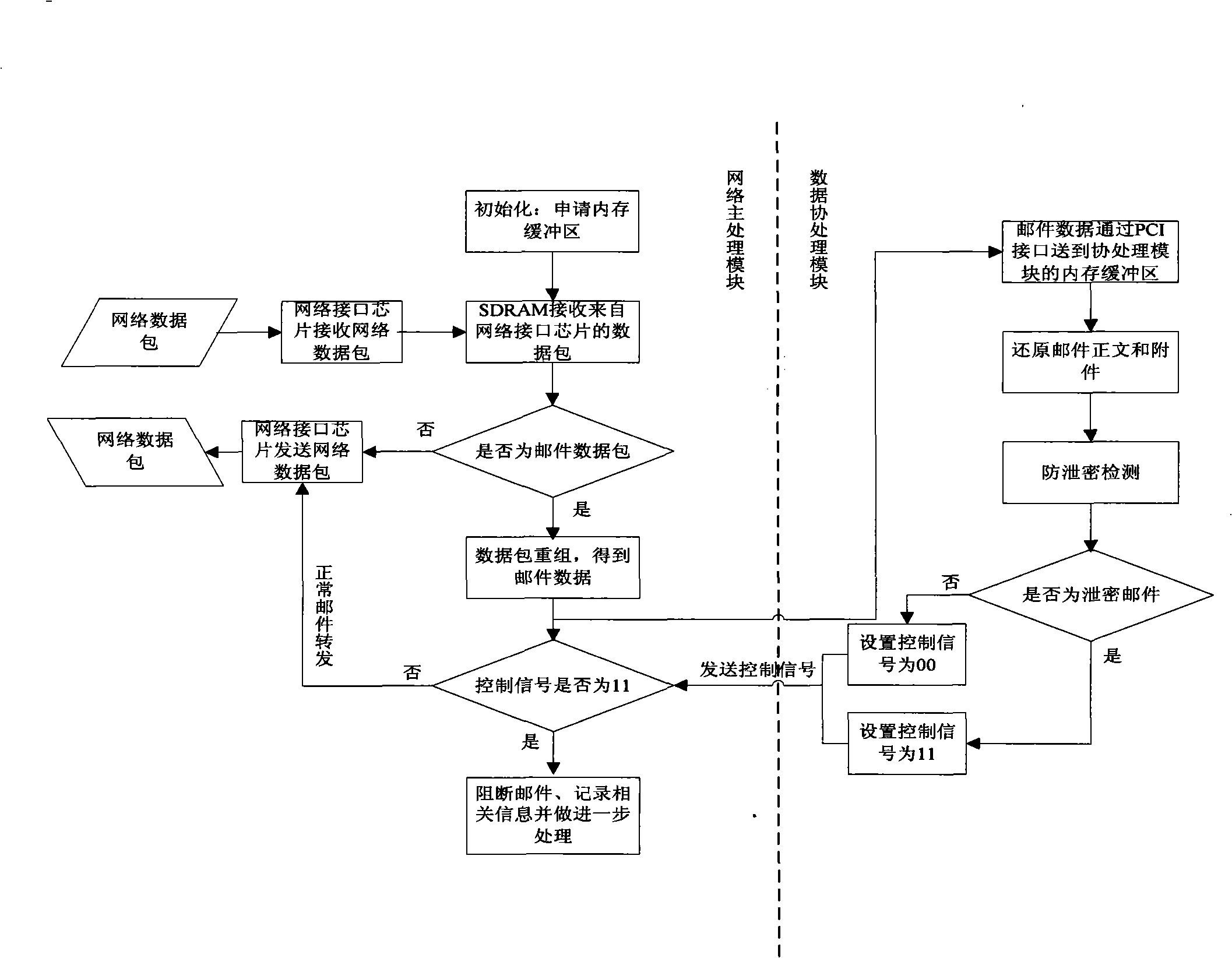
An anti-leakage mail security card and its leakage mail detecting method belong to the computer network information security technology. The security card comprises a network host processing module and a data assistant processing module. The network host processing module comprises a main processor, a first Flash memory, a first internal memory, a first serial controller, a first network controller and a second network controller. The data assistant processing module comprises a first assistant processor, a second assistant processor, a second Flash memory, a second internal memory, a second serial controller. The detecting method comprises: recovering and analyzing the text and the accessory of the read mail; judging the mail information security classification; detecting the mail path security; anti-leakage detecting based on the regulation and the algorithm; actively blocking the leakage mail and the suspected leakage mail; manual audit; sending alarm information to the leakage mail and automatically generating evidence. The invention has security, anti-leakage performance, reliability, source authentication and non-repudiation.
Owner:NANJING UNIV OF AERONAUTICS & ASTRONAUTICS
Wireless adhoc communication system, terminal, authentication method for use in terminal, encryption method, terminal management method, and program for enabling terminal to perform those methods
InactiveUS7292842B2Secrecy of the payloadSecrecy of the payload can be ensuredKey distribution for secure communicationUnauthorised/fraudulent call preventionComputer hardwareCommunications system
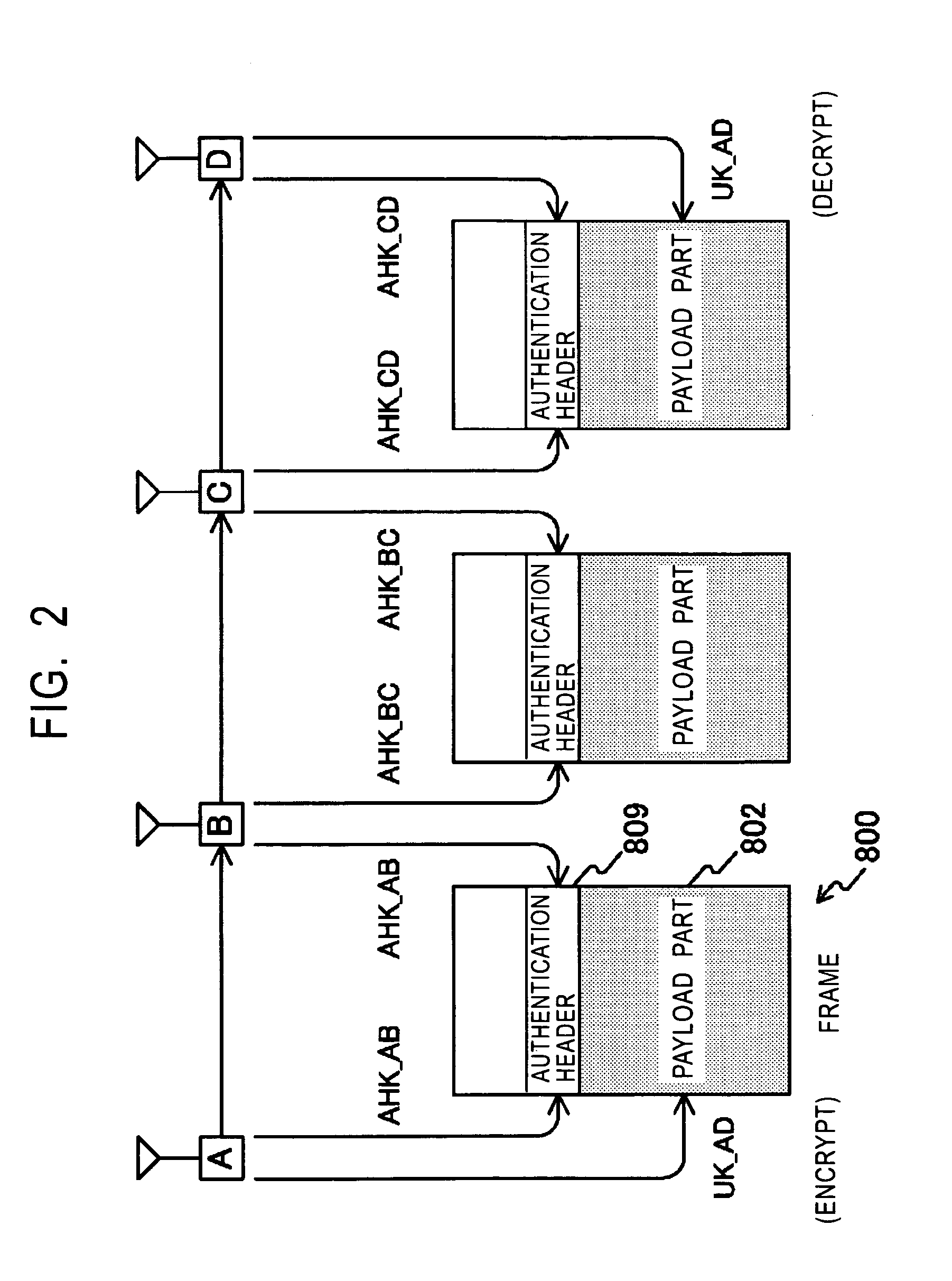
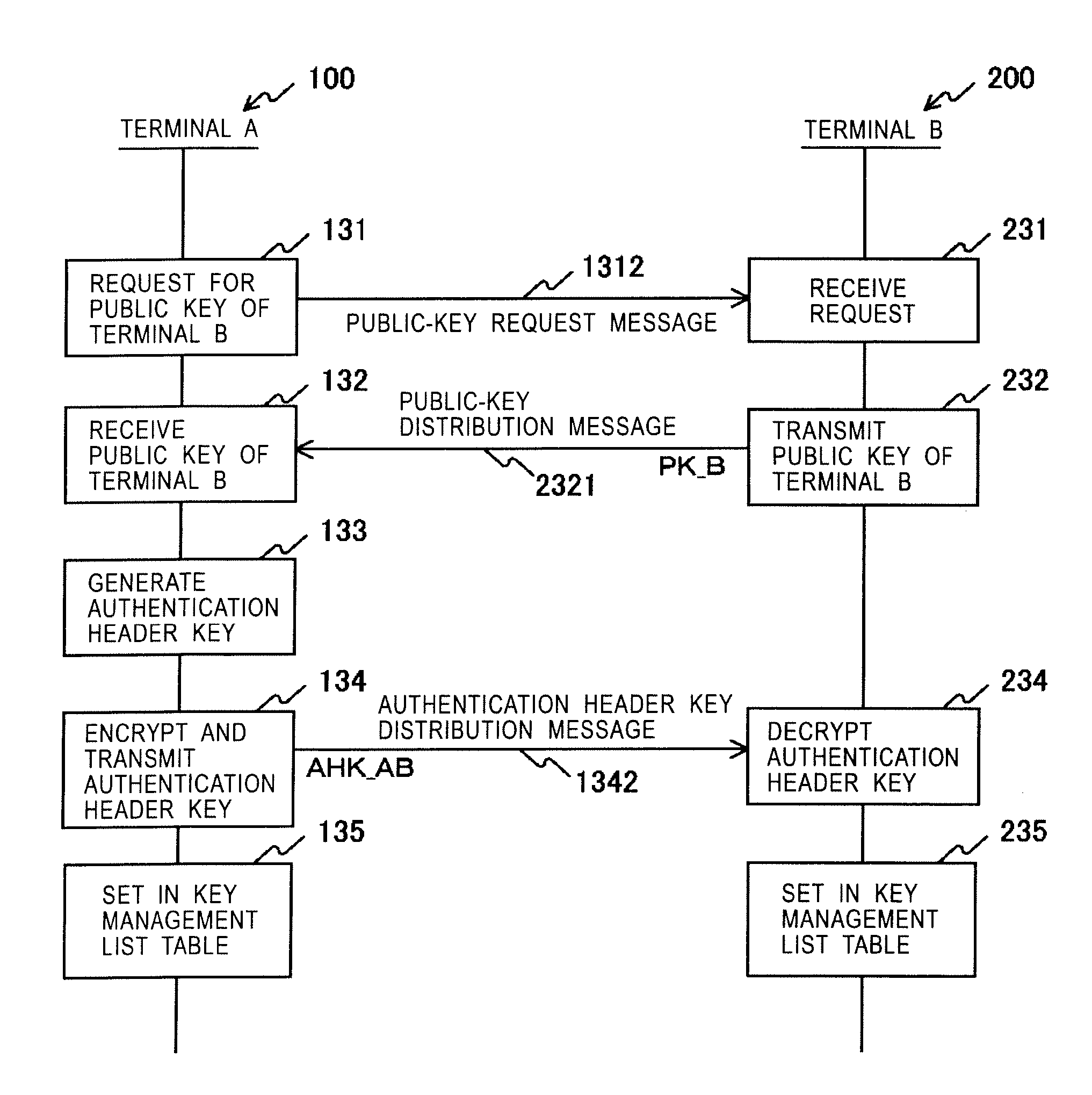
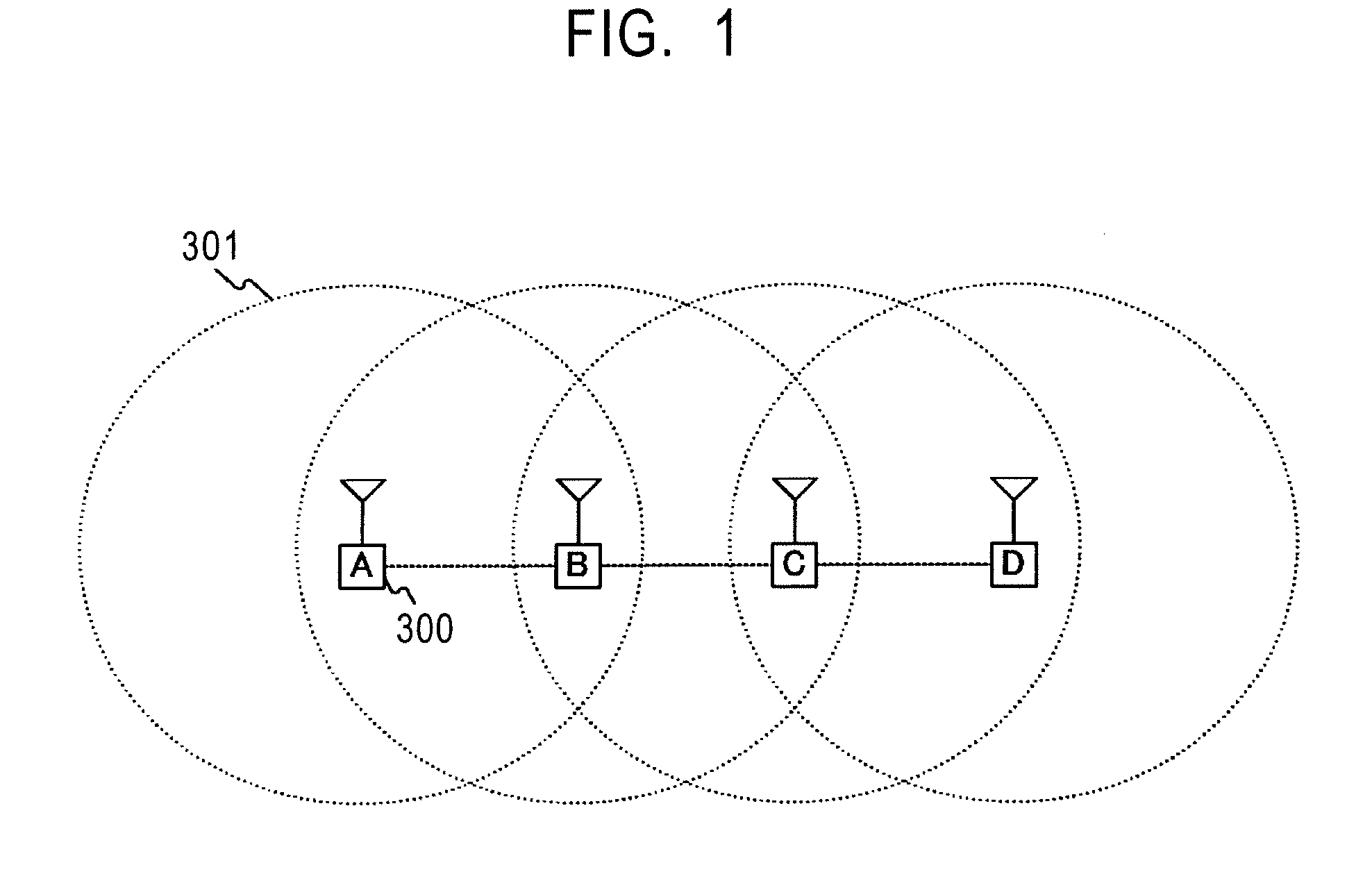
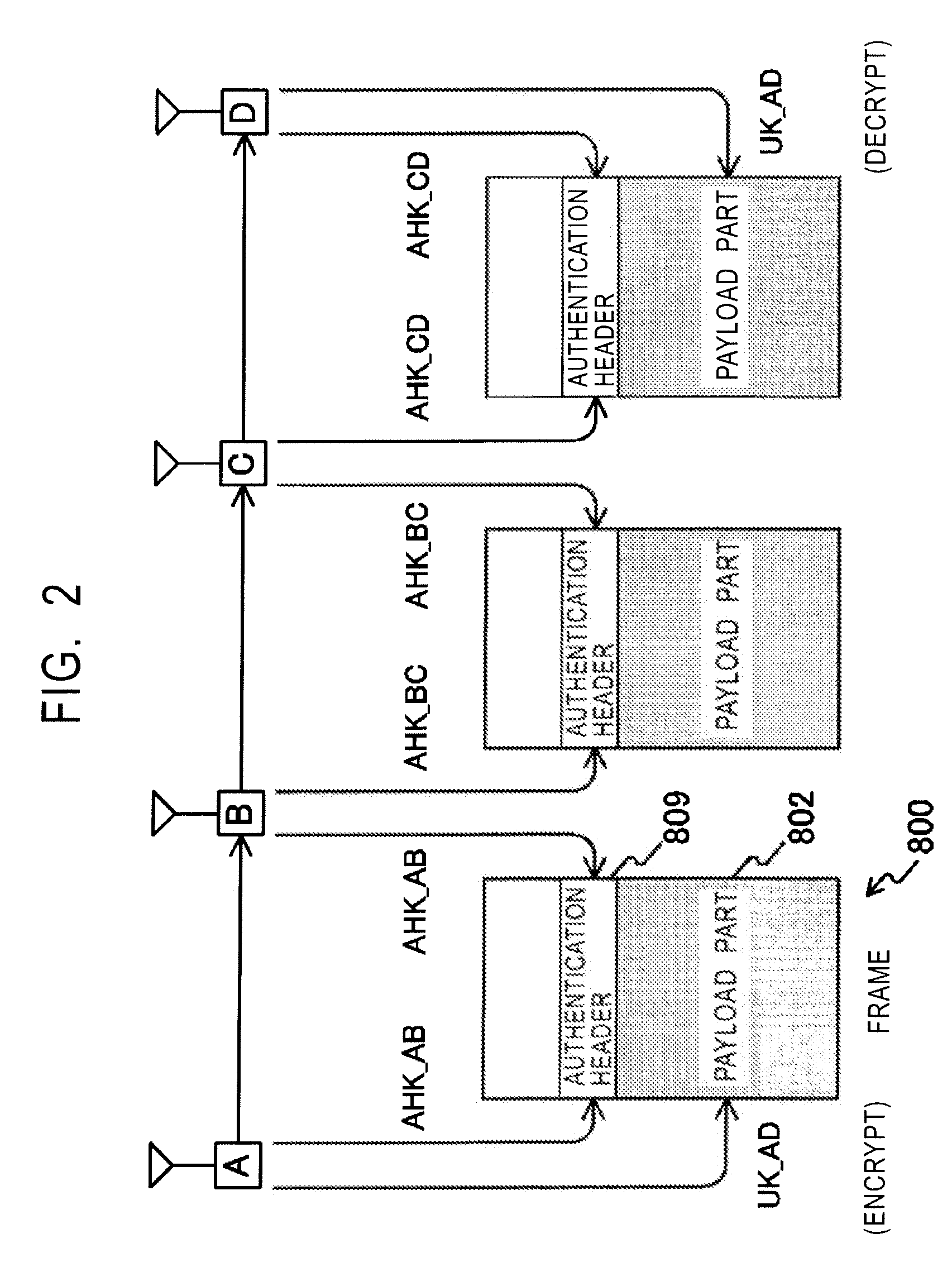
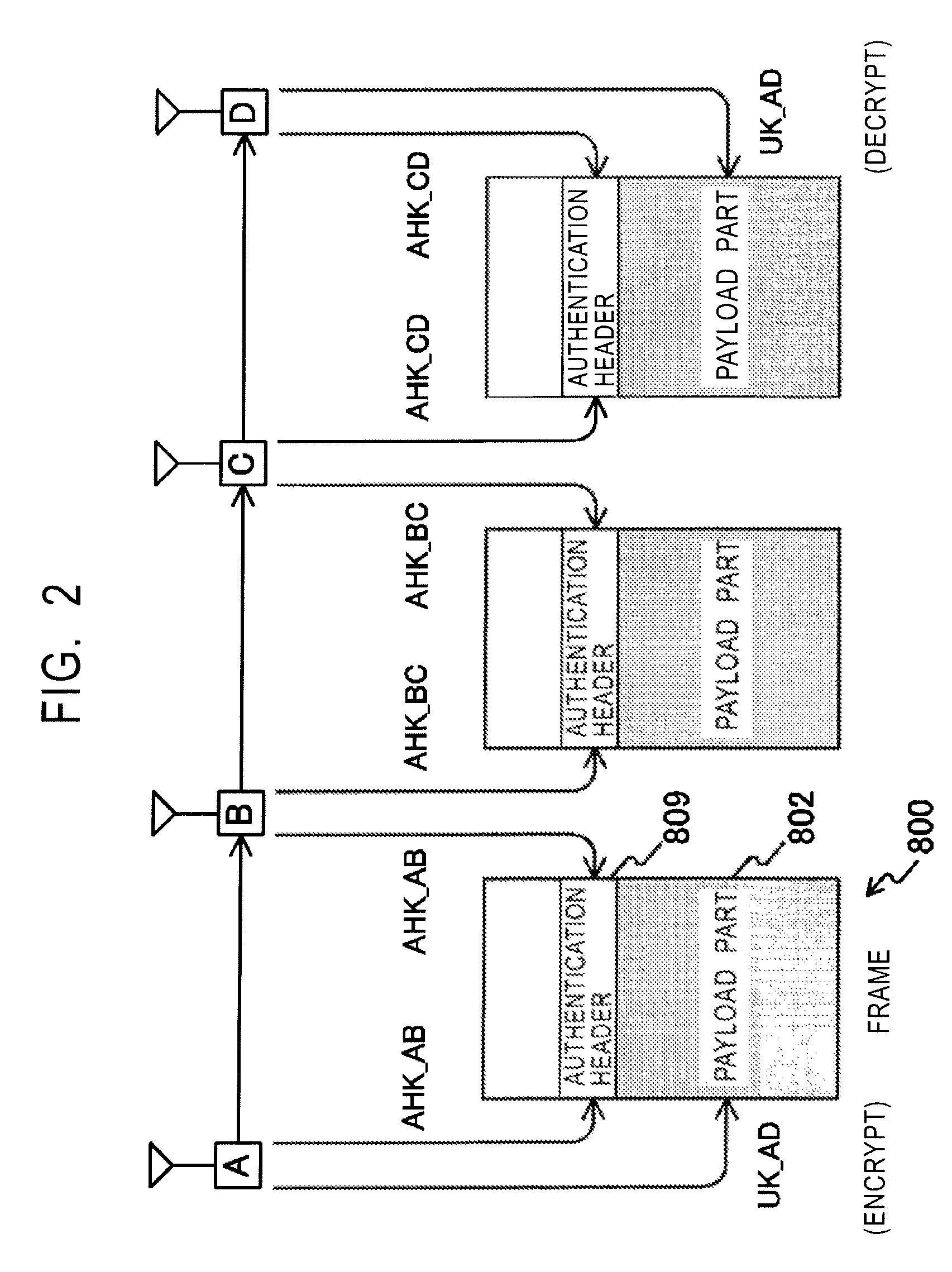
Frame transmission source authentication is performed among terminals involved in delivery in a wireless adhoc communication system. A first terminal generates a keyed hashed value by using an authentication header key determined with respect to a second terminal, and gives it to an authentication header of a frame. The second terminal generates a keyed hashed value by using the authentication header key determined with respect to the first terminal, and compares it with the authentication header given to the frame. If the keyed hashed value generated at the second terminal matches the authentication header, it is confirmed that the frame has been transmitted from the first authenticated valid terminal. The first terminal encrypts a payload part by using a unicast encryption key determined with respect to a third terminal. This encrypted payload part can be decrypted only by the third terminal having the unicast encryption key.
Owner:SONY CORP
Method of authenticating multicast messages
InactiveUS20070260879A1Data switching networksSecuring communicationMulticast packetsSource authentication
A method of message authentication in communication networks with multicast-enabled routers or switches is disclosed. The latter are tasked to support the packet source authentication: On reception of a multicast packet, the router attests the authenticity of the sender of the packet, and adds corresponding authentication information to the packet, before forwarding it in the normal multicast manner. Any receiver of the multicast packet then uses the authentication information collected by the packet while traversing the network to verify the original packet source.
Owner:ABB RES LTD
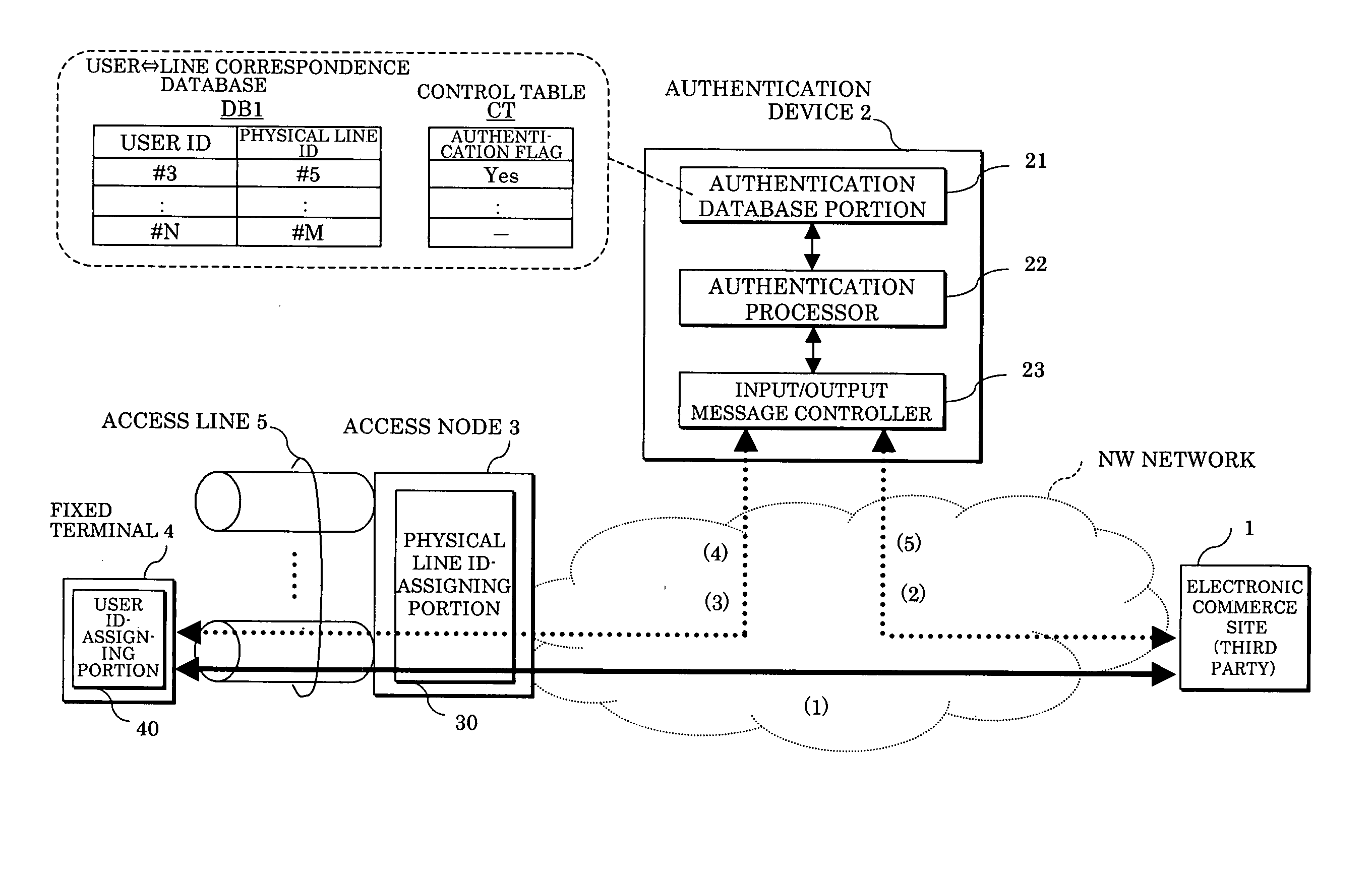
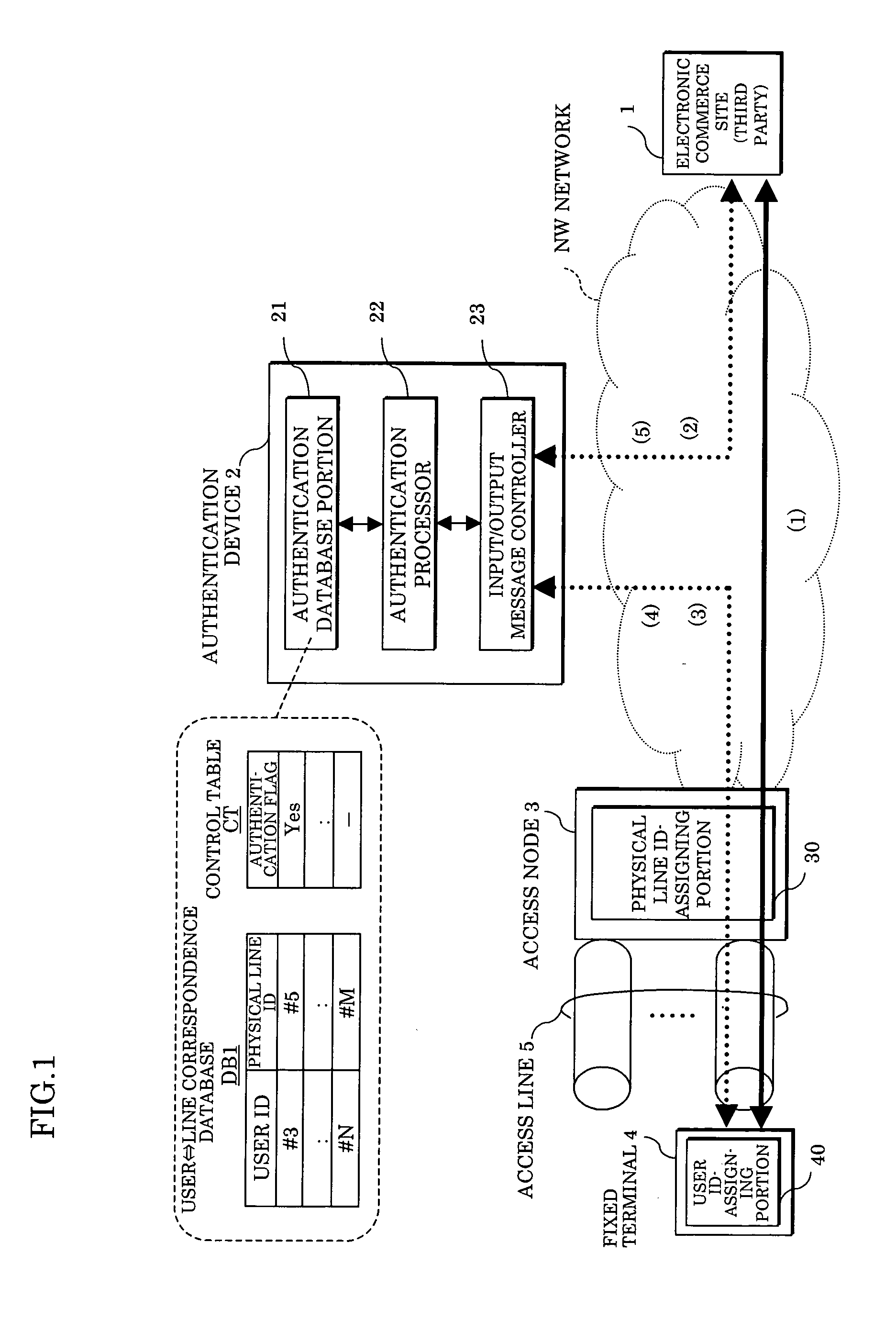
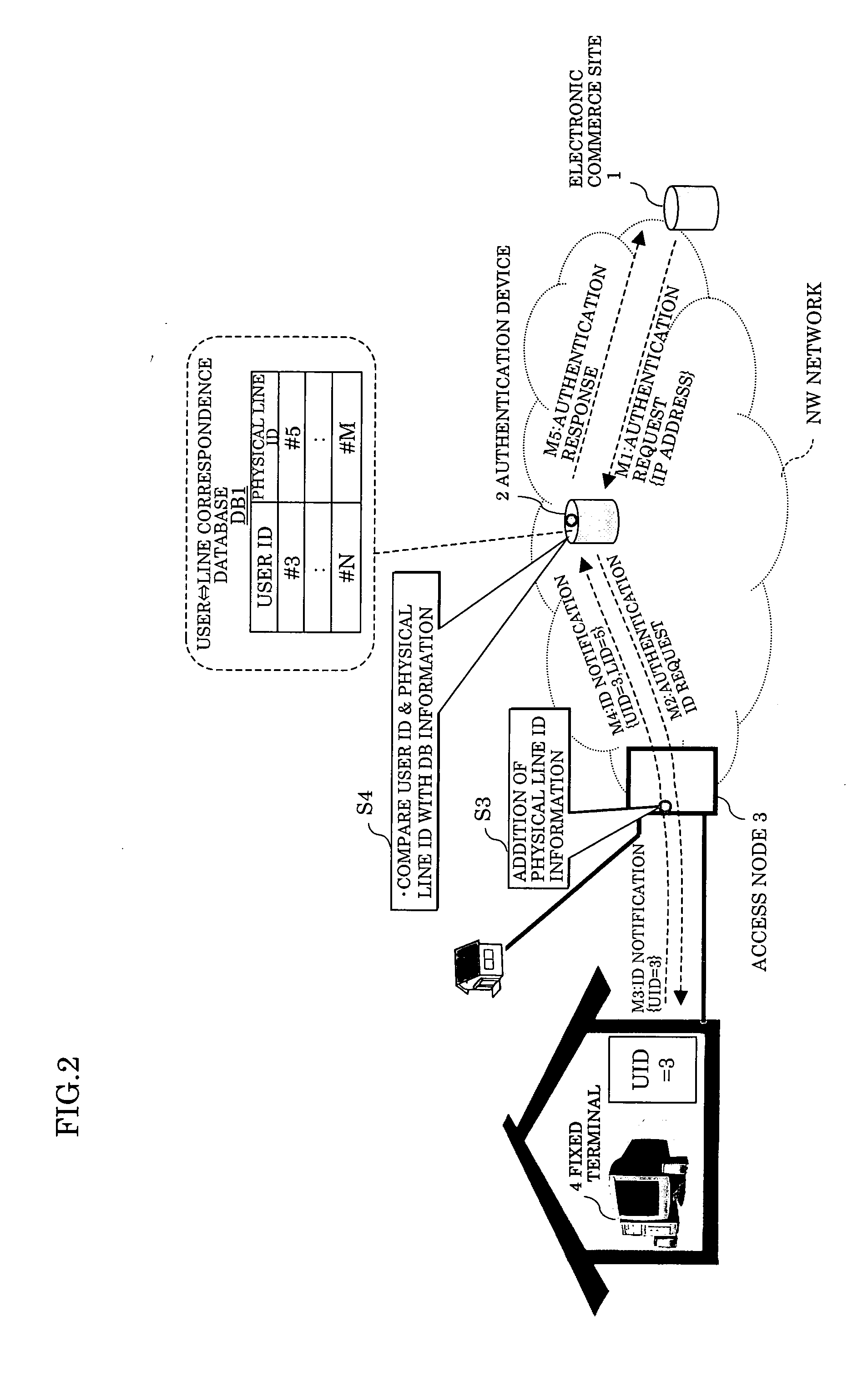
Access source authentication method and system
InactiveUS20050216769A1Data taking preventionDigital data processing detailsUser authenticationComputer science
In an access source authentication method and system, an access node adds an ID of a physical line, through which a message has passed, to the message including a user ID from a fixed terminal of a user to be transferred to au authentication device through the physical line, and the authentication device manages a relationship between a user ID and a physical line ID by a database, receives the user ID and the physical line ID transferred from the node and performs a user authentication by comparing the user ID and the physical line ID received with those in the database. Also, the authentication device generates an authentication ID in which the user ID and the physical line ID are encrypted, transmits the authentication ID to a request source of the authentication ID, an electronic commerce site through a request destination of the authentication ID, the fixed terminal and obtains the user ID and the physical line ID by decrypting the authentication ID when an authentication request including the authentication ID is received from the electronic commerce site, thereby enabling the user authentication to be performed.
Owner:FUJITSU LTD
Method for identification authentication of IPv6 broadcast source and inhibiting attack of malice/non-malice service
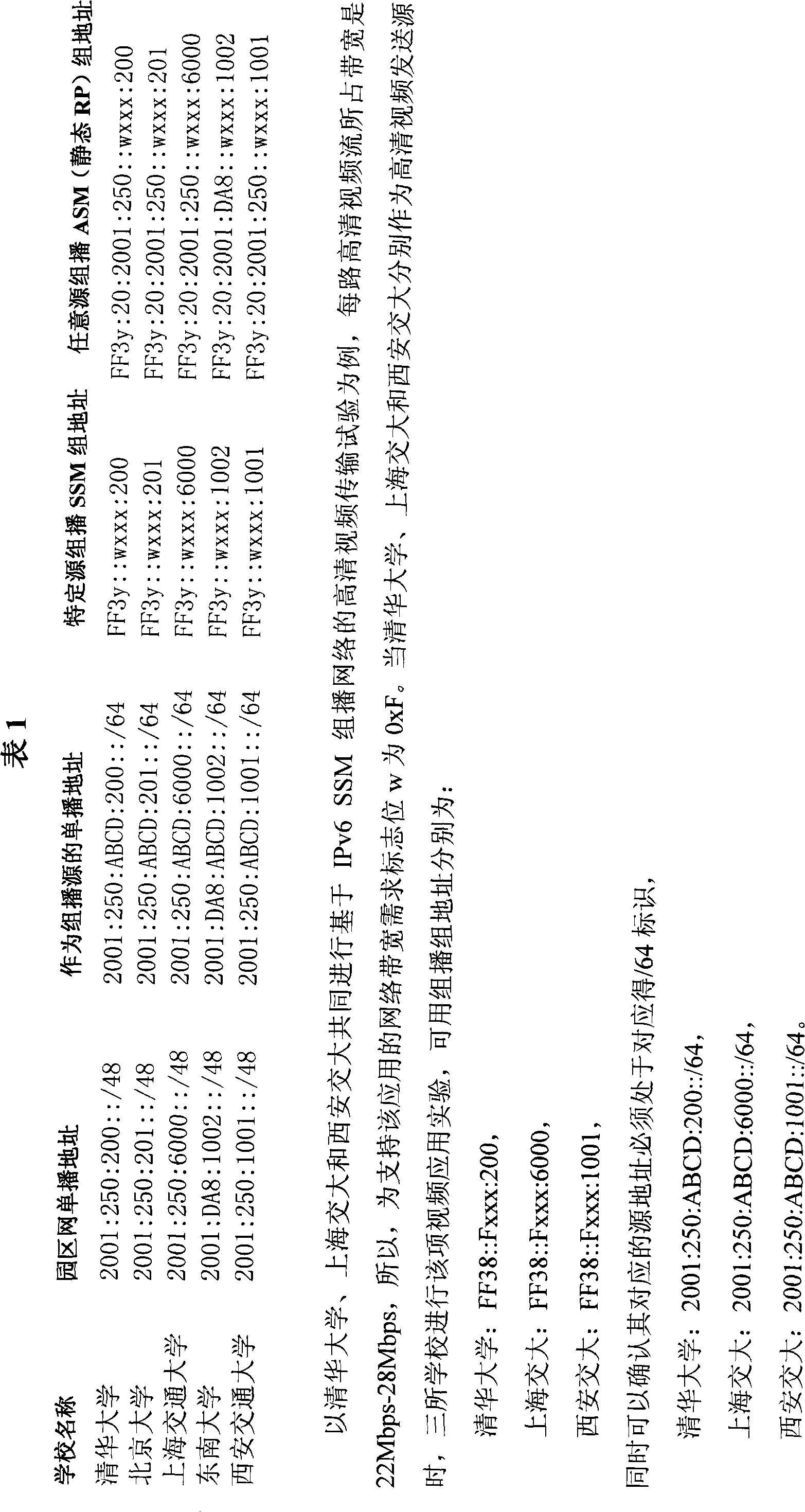
IPv6 multicast source identity authentication and method of restraining malicious / non- malicious service attack belong to the technical field of computer network communication; the present invention is characterized in, on the basis of following RFC about IPv6 multicast group address format definition and distributing principle, independently distributing a block / 48 IPv6 address for the multicast source, distributing block / 64 for each park network, the identifier is corresponding to the identifier of each park network; embedding the unicast address of eth special group multicast source and bandwidth demand identifier needed for supporting the multicast into the reserved 20 bit through finely defining 32-bit user self-definition and forming multicast group new definition formation facing to the special source multicast SSM and any source multicast ASM and other protocols. The combination of ACL enactment about flow control, source address control, etc. configured in the router effectively resolves the safety problem of multicast source authentication and anti-DOS attack, laying the first stone of better implementing the operation and management of large-scale IPv6 non-tunnel multicast network.
Owner:TSINGHUA UNIV
Remote video source authentication protocol
InactiveUS20120297458A1Avoid connectionDigital data processing detailsNetwork topologiesApplication softwareProtocol for Carrying Authentication for Network Access
A method and system of enabling slave software applications from a portable device via a vehicle interface system. The vehicle includes a first communication channel for exchanging data communications between the portable device and the vehicle interface system and a second communication channel configured to transmit video to the vehicle interface system. A mutual authentication is performed between the portable device and the vehicle interface system using the first communication channel based on identifying the portable device as an entity authorized to execute approved slave software applications. The portable device is authenticated over the second communication channel for verifying that the portable device is the authorized entity to transmit video over the second communication channel. The video is transmitted to the vehicle interface system over the second communication channel conditioned upon a successful authentication of the portable device over the second communication channel.
Owner:GM GLOBAL TECH OPERATIONS LLC
Safety multicast method based on protocol of conversation initialization
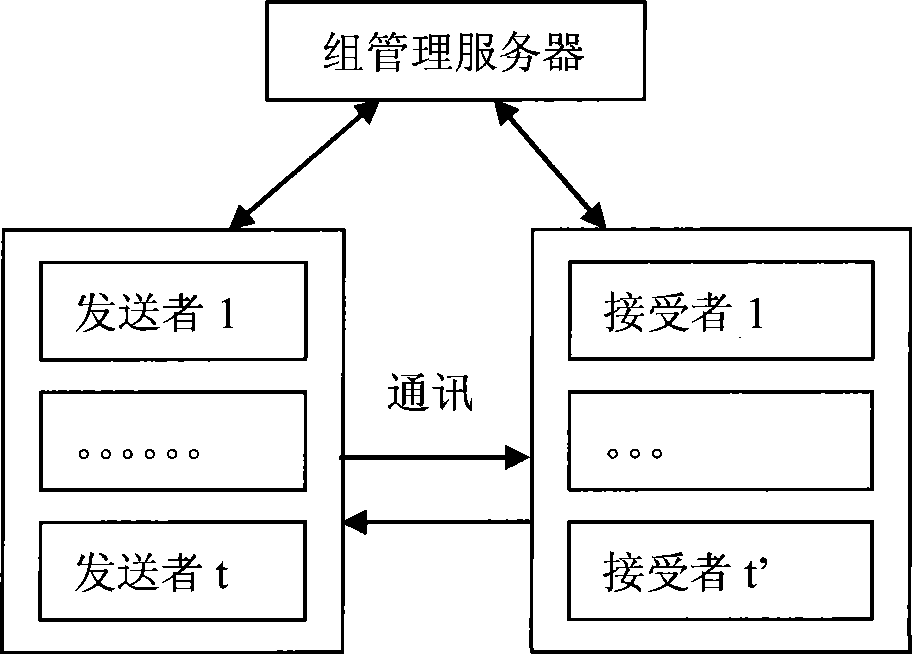
InactiveCN1874224ASolve the requestSolve the statistical billing abilityUser identity/authority verificationSecure communicationMethod selection
The safe multicast method is a first method of using the protocol of conversation initialization to implement operation of safe multicast. The method presents a set of scheme for solving issue of safe multicast including access control of multicast source, access control for receiver, management of group key, authentication of multicast source, service statistics, and charging capability. The method includes procedures: using route in network to encrypt data of multicast to guarantee access control of service, and safe comm.; method for authenticating multicast source in two stages is adopted; when IGMP / MLD adapter layer implements the method, working mode of traditional multicast route system does not need to be changed; three expansion techniques including cluster of regional multicast control server, regional physical and logical segmentations. The expansibility is suitable to large-scale network environment, and concurrent use. The invention does not change core network.
Owner:SOUTHEAST UNIV
Wireless adhoc communication system, terminal, authentication method for use in terminal, encryption method, terminal management method, and program for enabling terminal to perform those methods
InactiveUS20070101142A1Guaranteed StrengthAuthentication can be performedKey distribution for secure communicationUnauthorised/fraudulent call preventionComputer hardwareCommunications system
Owner:DIGIMARC ID SYST
Self-representation secure routing authorization method based on identity, namely, public key
ActiveCN105141597AThe principle is simpleThe deployment method remains unchangedData switching networksAuthorization certificateSecurity parameter
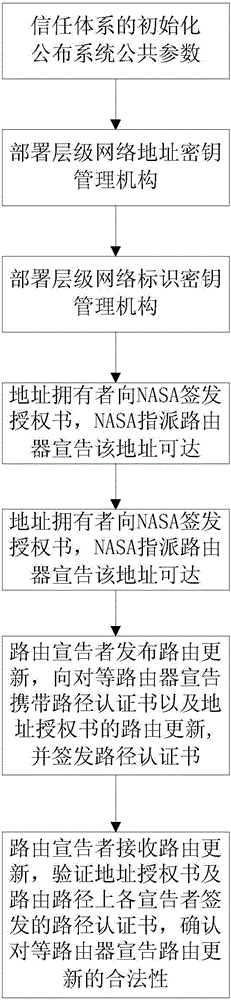
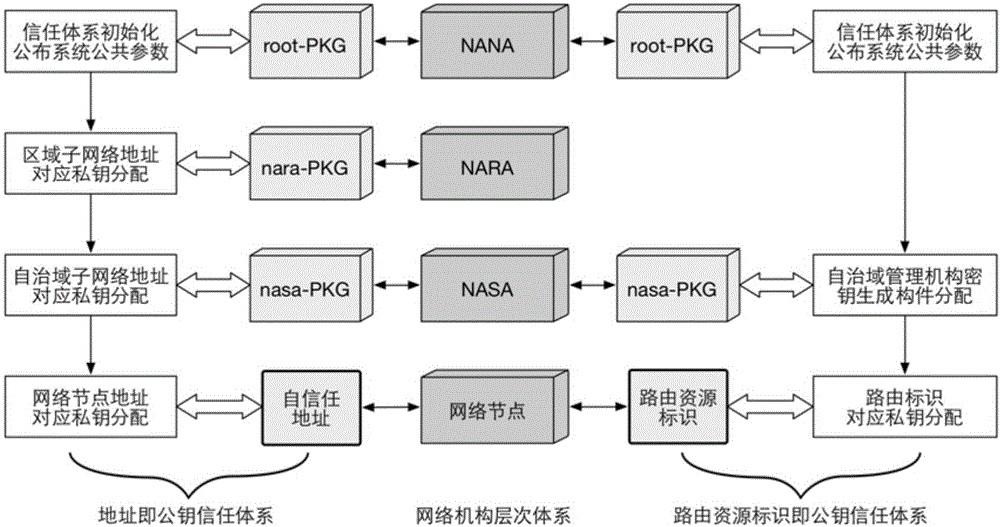
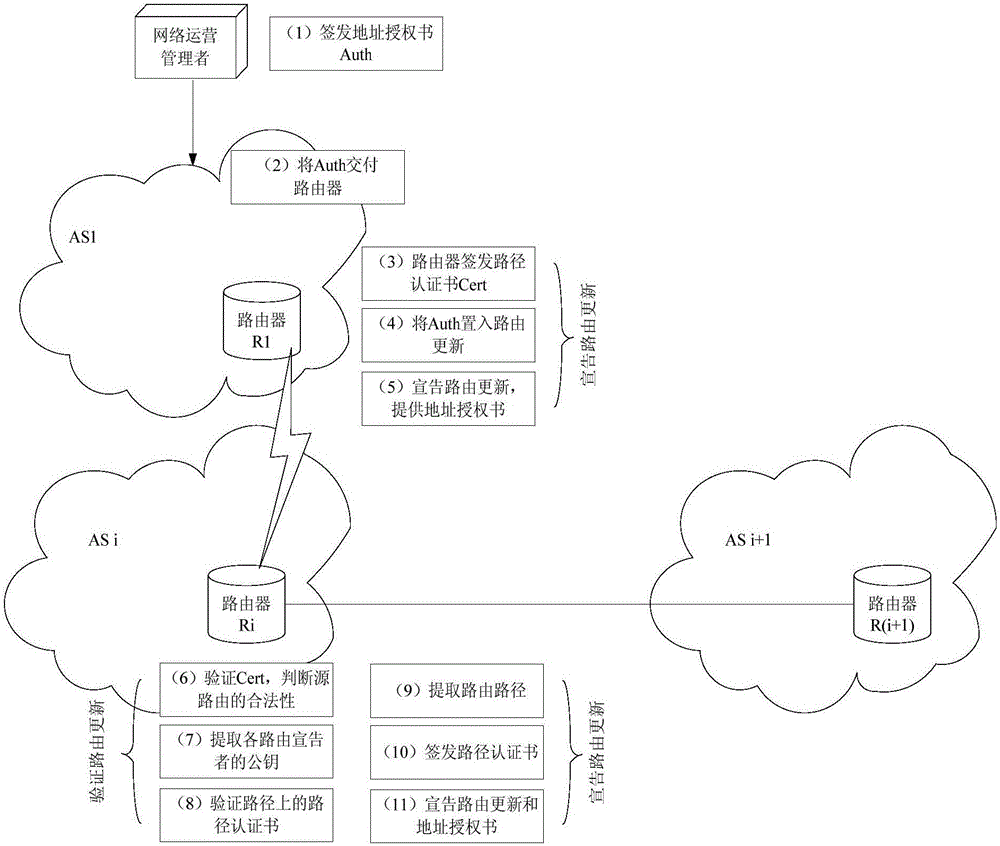
The invention discloses a self-representation secure routing authorization method based on an identity, namely, a public key. The method comprises the following steps: S1, publishing a public security parameter, and starting a trusted root; S2, constructing a self-trusted address system; S3, constructing a self-trusted routing identity system; S4, signing and issuing an address authorization certificate to an NASA (Network Autonomous System Authority) by an address owner, and assigning a deployed routing announcer to announce address reachable information by the NASA; S5, signing and issuing a path authentication certificate by the routing announcer, and announcing routing update carrying the path authentication certificate and the address authorization certificate to a peer route; and S6, receiving the routing update by a peer routing announcer, verifying the address authorization certificate and the path authentication certificate issued and signed by each announcer on a routing path, and determining the validity of the routing update. The self-representation secure routing authorization method is simple in principle and easy for deployment; source authentication and path authentication of inter-domain routing can be realized; and the problem of inevitable prefix hijacking in a conventional inter-domain routing mechanism can be solved effectively.
Owner:NAT UNIV OF DEFENSE TECH
Methods and apparatuses for distributing keys for ptp protocol
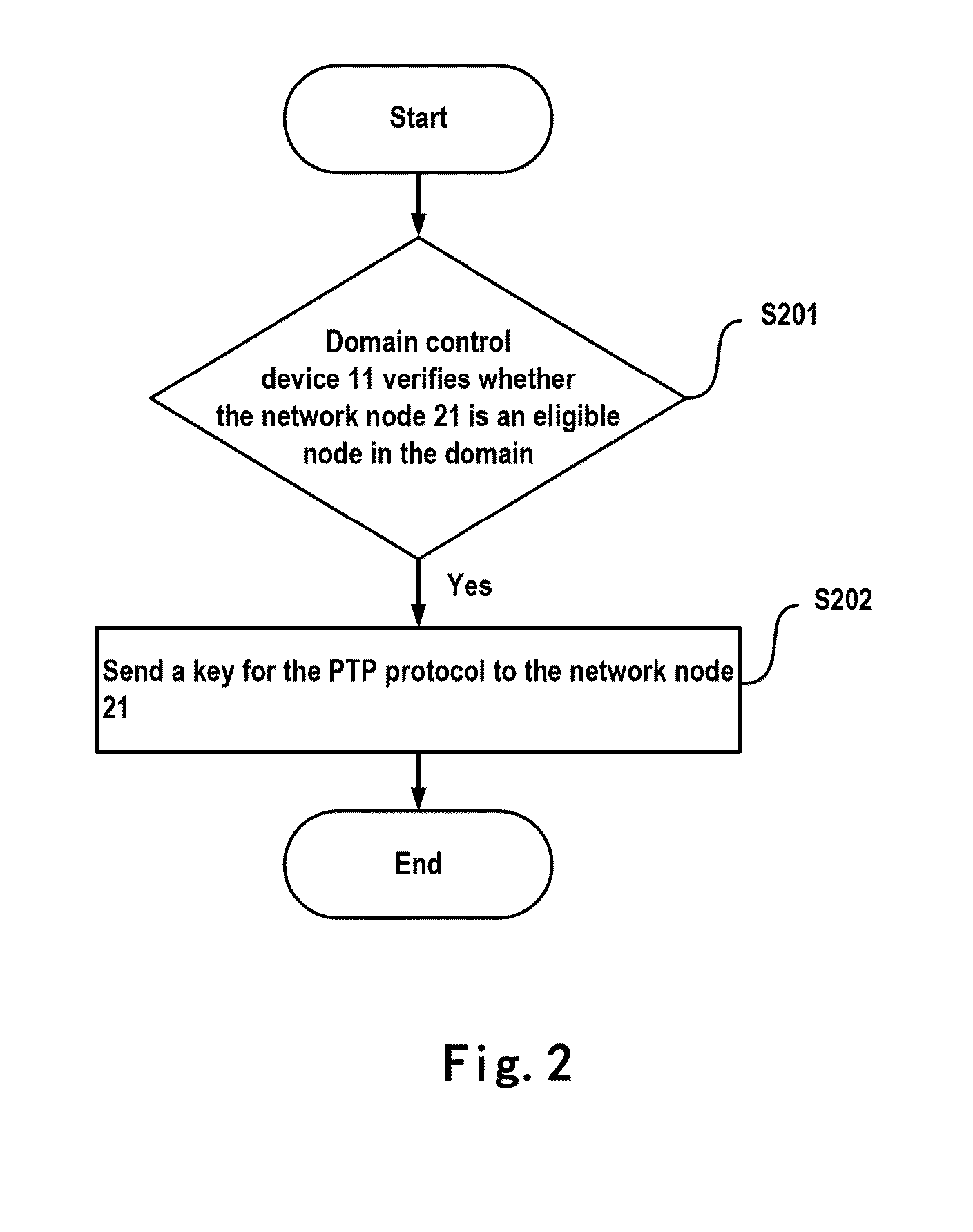
InactiveUS20130305048A1Improve securityKey distribution for secure communicationUser identity/authority verificationAuto-configurationConfidentiality
The present invention provides a solution of automatically distributing PIP keys, and on that basis, provides a new encryption method. A domain control device is proposed to verify whether a network node is an eligible node in the domain; if the network node is an eligible node in the domain, then a key for the PTP protocol is sent to the network node. The methods and apparatuses according to the present invention enable access authentication of various forms of PTP network nodes, as well as the automatic configuration and dynamic sending of PTP keys, such that the security of the keys are significantly increased. Additionally, by means of SignCryption encryption algorithm, it is enabled that for each PTP message, not only message source authentication, message integrity authentication, message confidentiality, and replay protection can be provided, but also its sending network node can be tracked. Thus, the security is significantly increased.
Owner:ALCATEL LUCENT SAS
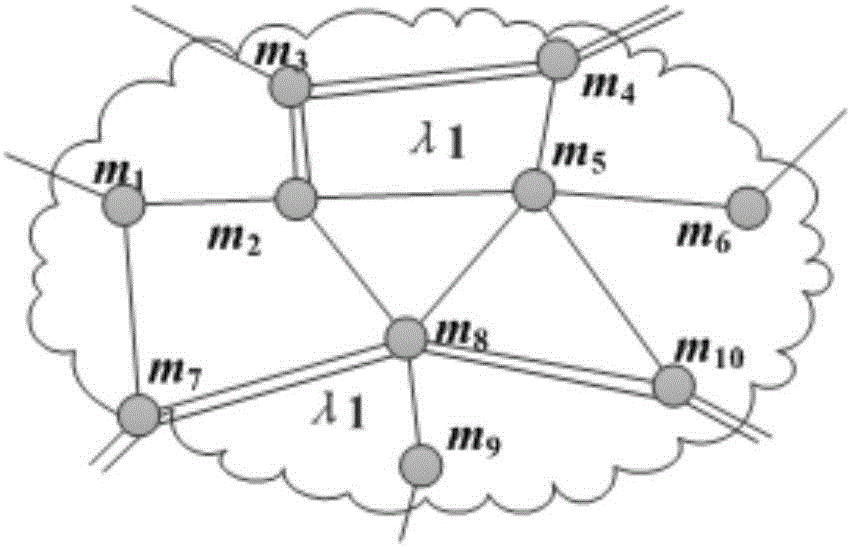
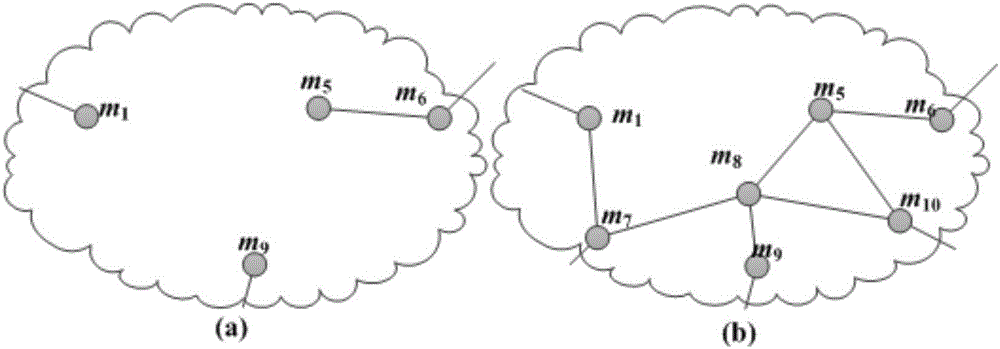
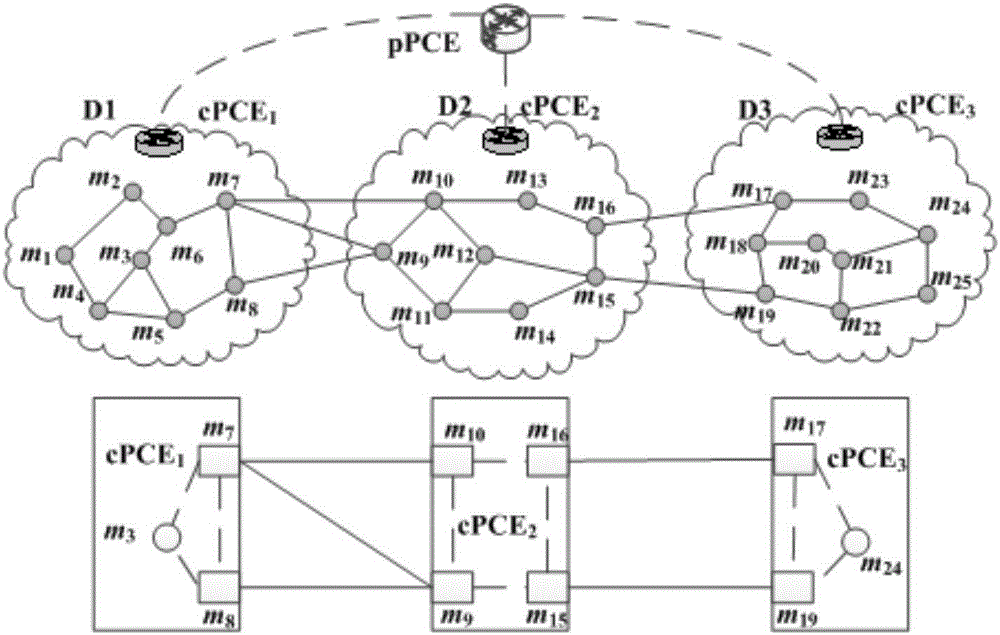
Layered PCE based multi-domain optical network secure light path establishment protocol
ActiveCN106851441AShort setup delaySatisfy confidentialityMultiplex system selection arrangementsUser identity/authority verificationConfidentialityPrivacy protection
The invention discloses a layered PCE based multi-domain optical network secure light path establishment protocol. Aiming at the problems of security problem and comprehensive efficiency existing in a multi-domain optical network light path establishment process, a new GO-PCE (Global Optimizing secure light-path protocol based PCE in multi-domain optical network) is designed by combining with a trust model and a key management scheme, adopting a globally optimized multi-domain trusted path selection, usable wavelength calculation and wavelength distribution strategy, and utilizing a TLS based bidirectional identity authentication, TCP-AO based source authentication, identity cryptography based encryption and digital signature technology and a Path-Key based privacy protection mechanism. The secure service requirements such as confidentiality, completeness, authenticity, non-repudiation, freshness and privacy can be met; compared with an SD-PCE and pH-PCE light path establishment protocols, the layered PCE based multi-domain optical network secure light path establishment protocol has relatively low blocking rate and relatively short light path establishment time delay.
Owner:ENG UNIV OF THE CHINESE PEOPLES ARMED POLICE FORCE
Large cluster safe real-time communication method executed by using elliptical curve
InactiveCN101488958AImprove efficiencySave storage spaceKey distribution for secure communicationPublic key for secure communicationTrunkingComputer science
This invention discloses a method of using elliptical curve to perform large trunking safety real-time communication, belonging to the field of network real-time communication and including following steps: initializing a communication group, a register protocol, a group key management protocol, a re-registration protocol and a source authentication protocol. The communication group referred in this method is composed of a set of controllers / main servers, a receiver and a sender. The method is a new type which is designed based on the elliptical curve theory and used for the group key management and the source authentication protocol for the real-time communication, and supports the re-distribution of the key and the rescinding level process. In the level and the rescinding process, a group management server sends the key materials based on the elliptical curve to the sender and the receiver. In the next group key building process, the sender and the receiver can uses these key materials to build a shared group key without consulting with the group management server. This invention capable of saving the storage space is safer and with higher efficiency.
Owner:SOUTHEAST UNIV
Wireless adhoc communication system, terminal, authentication method for use in terminal, encryption method, terminal management method, and program for enabling terminal to perform those methods
InactiveUS7499443B2Secrecy of the payloadSecrecy of the payload can be ensuredKey distribution for secure communicationInterconnection arrangementsComputer hardwareCommunications system
Frame transmission source authentication is performed among terminals involved in delivery in a wireless adhoc communication system. A first terminal generates a keyed hashed value by using an authentication header key determined with respect to a second terminal, and gives it to an authentication header of a frame. The second terminal generates a keyed hashed value by using the authentication header key determined with respect to the first terminal, and compares it with the authentication header given to the frame. If the keyed hashed value generated at the second terminal matches the authentication header, it is confirmed that the frame has been transmitted from the first authenticated valid terminal. The first terminal encrypts a payload part by using a unicast encryption key determined with respect to a third terminal. This encrypted payload part can be decrypted only by the third terminal having the unicast encryption key.
Owner:DIGIMARC ID SYST
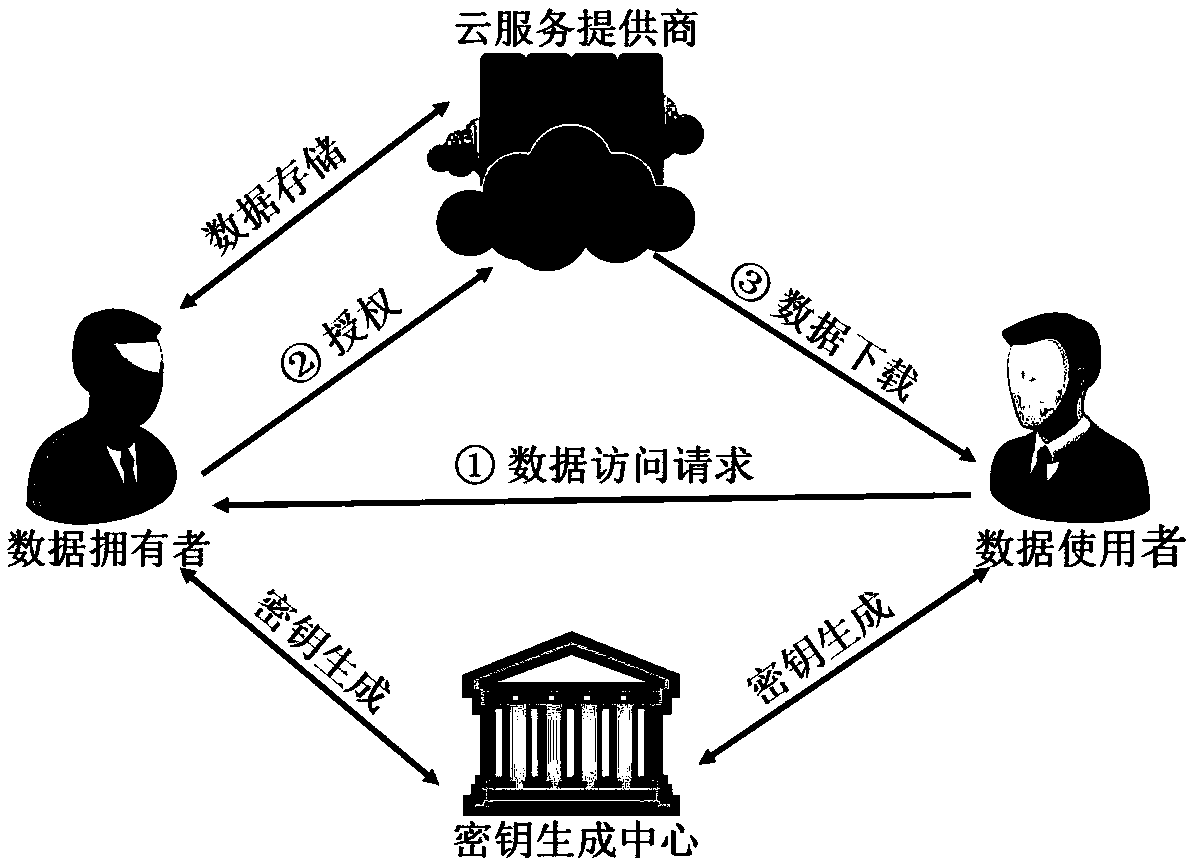
Access control method of convertible data cloud storage with data source authentication function
ActiveCN109547413AKey distribution for secure communicationEncryption apparatus with shift registers/memoriesCiphertextData cloud
The invention belongs to the technical field of cloud computing, and discloses an access control method of convertible data cloud storage with a data source authentication function. The control methodcomprises system parameter initialization, user key generation, data encryption storage, data downloading decryption, data access control and ciphertext data conversion. By adoption of the access control method disclosed by the invention, the problems of how to ensure data source authentication in the existing cloud data access control and how to determine the responsibility of a cloud service provider and the public convertibility of the ciphertext data when the data are damaged on a cloud server are solved, the access control method disclosed by the invention is constructed based on a certificate-free public key system, thereby having no certificate management problem in PKI or key escrow problem based on an identity public key system, and the access control method of convertible data cloud storage with the data source authentication function is proposed.
Owner:福建中信网安信息科技有限公司
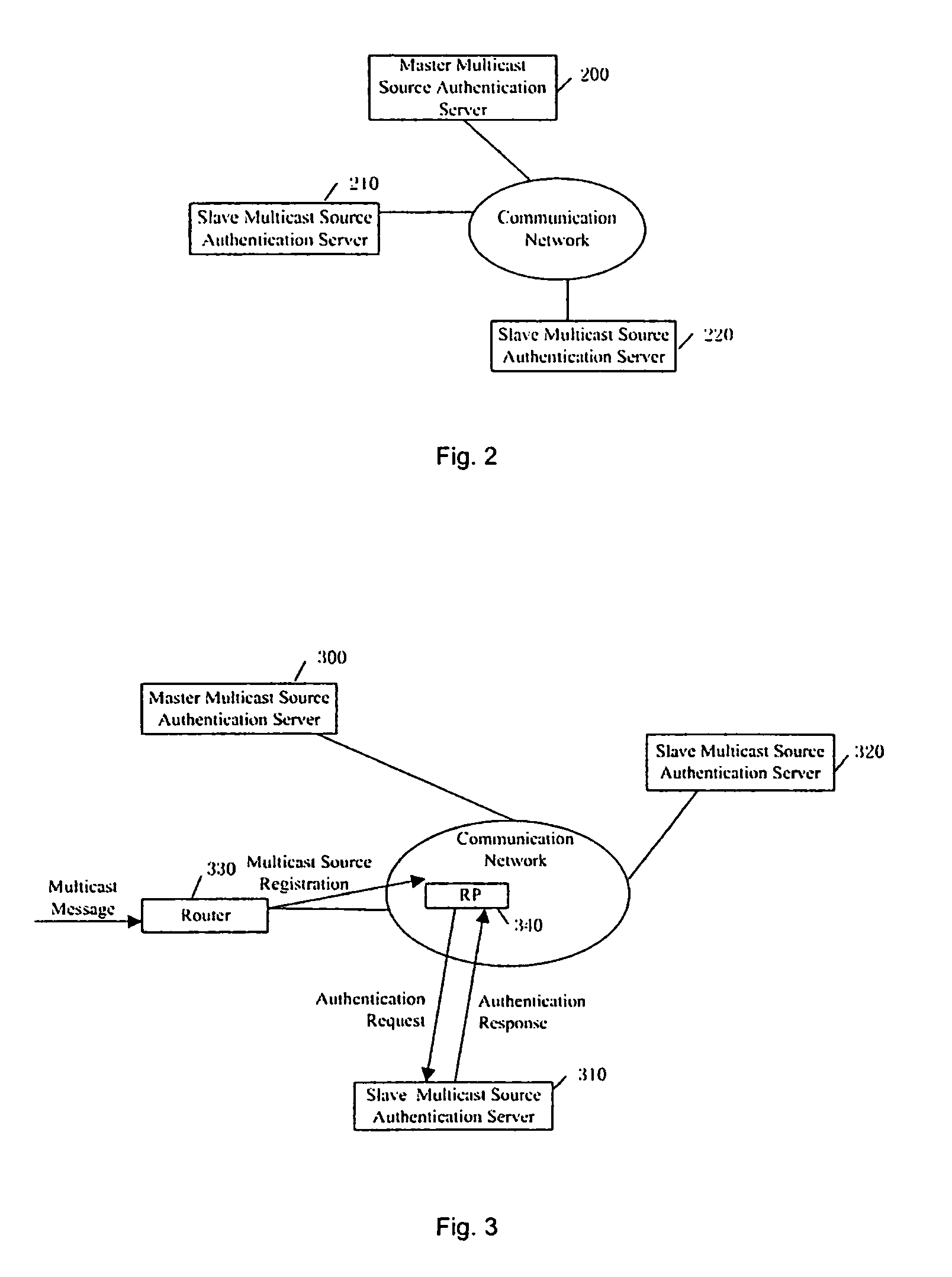
Method and system for controlling the multicast source
ActiveUS7855956B2Improve manageabilityEasy to operateSpecial service provision for substationError preventionNetwork terminationTime control
The invention provides a method on the source of the multicast control, including: establish the source of the multicast authentication message; the source of the multicast authentication message controlling terminal updates the said the source of the multicast authentication message dynamic according to the limit of the multicast source; control the multicast message transmitted by the multicast source according to the said multicast source authentication message; the invention also provides a system on the source of the multicast control, including: master multicast source authentication server, a group of slave multicast source authentication server preset point; by this invention, the preset point request the multicast source authentication application so as to control managing the multicast source at the first time; manage different multicast addresser by setting the multicast source authentication server layer distribution, saving the resource of the net terminal; without human operation, master and slave multicast source authentication server interactive authentication message periodically and in time, so as to manage the multicast source automatically and in time; thereby realize the purpose which reduce managing and maintenance cost of the multicast internet, improve the administrating and the running ability.
Owner:CHENGDU HUAWEI TECH
Method and system for source authentication in group communications
ActiveUS8397062B2Efficient implementationMultiple keys/algorithms usageDigital data processing detailsComputer scienceSource authentication
A method and system for authentication is provided. A central node for issuing certificates to a plurality of nodes associated with the central node in a network is also provided. The central node receives a first key from at least one node from among the plurality of nodes and generates a second key based on the received first key and generates a certificate for the at least one node. The generated certificate is transmitted to the at least one node.
Owner:UNIV OF MARYLAND
Packet source authentication method using single-buffered hash in multicast environment and apparatus for the same
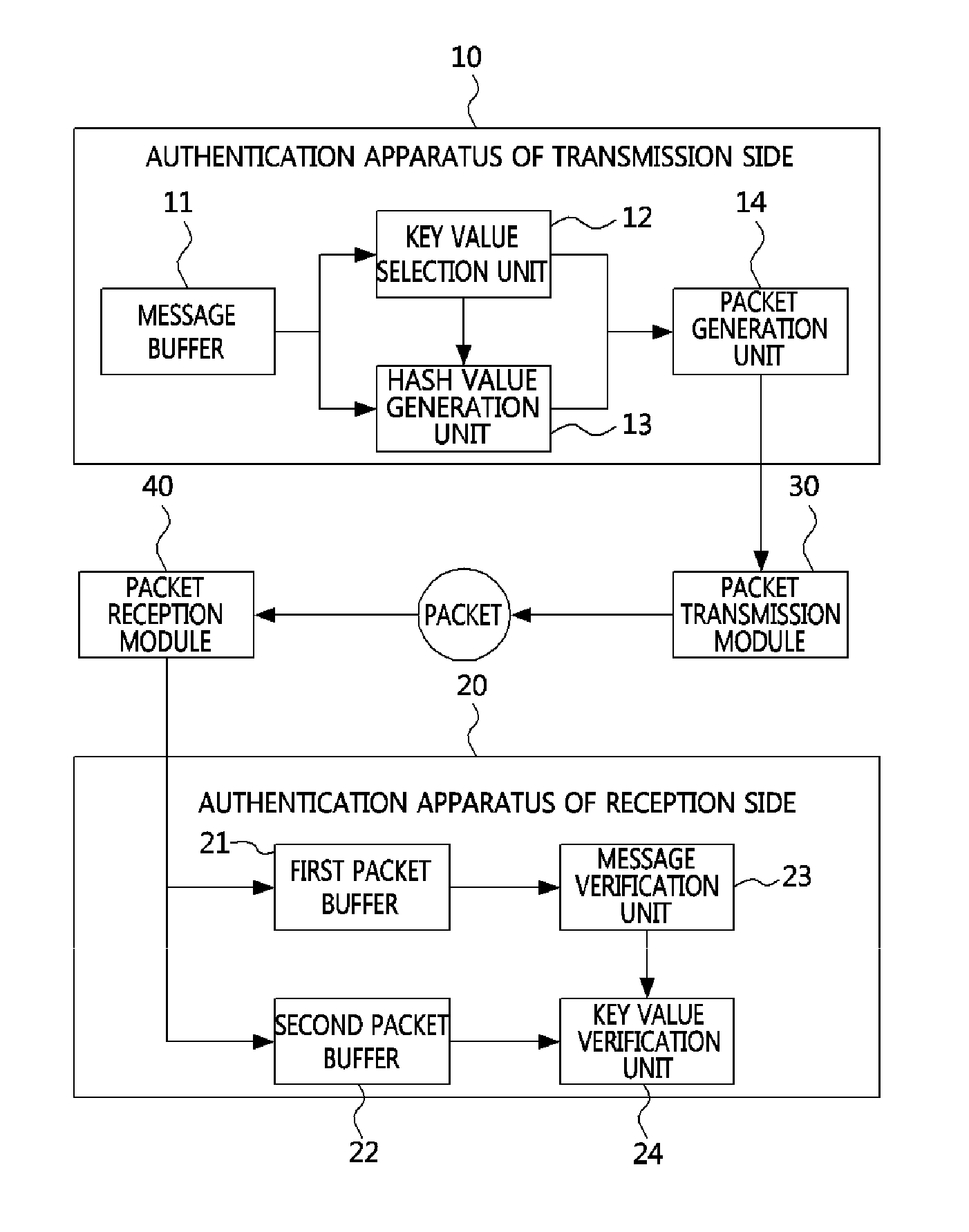
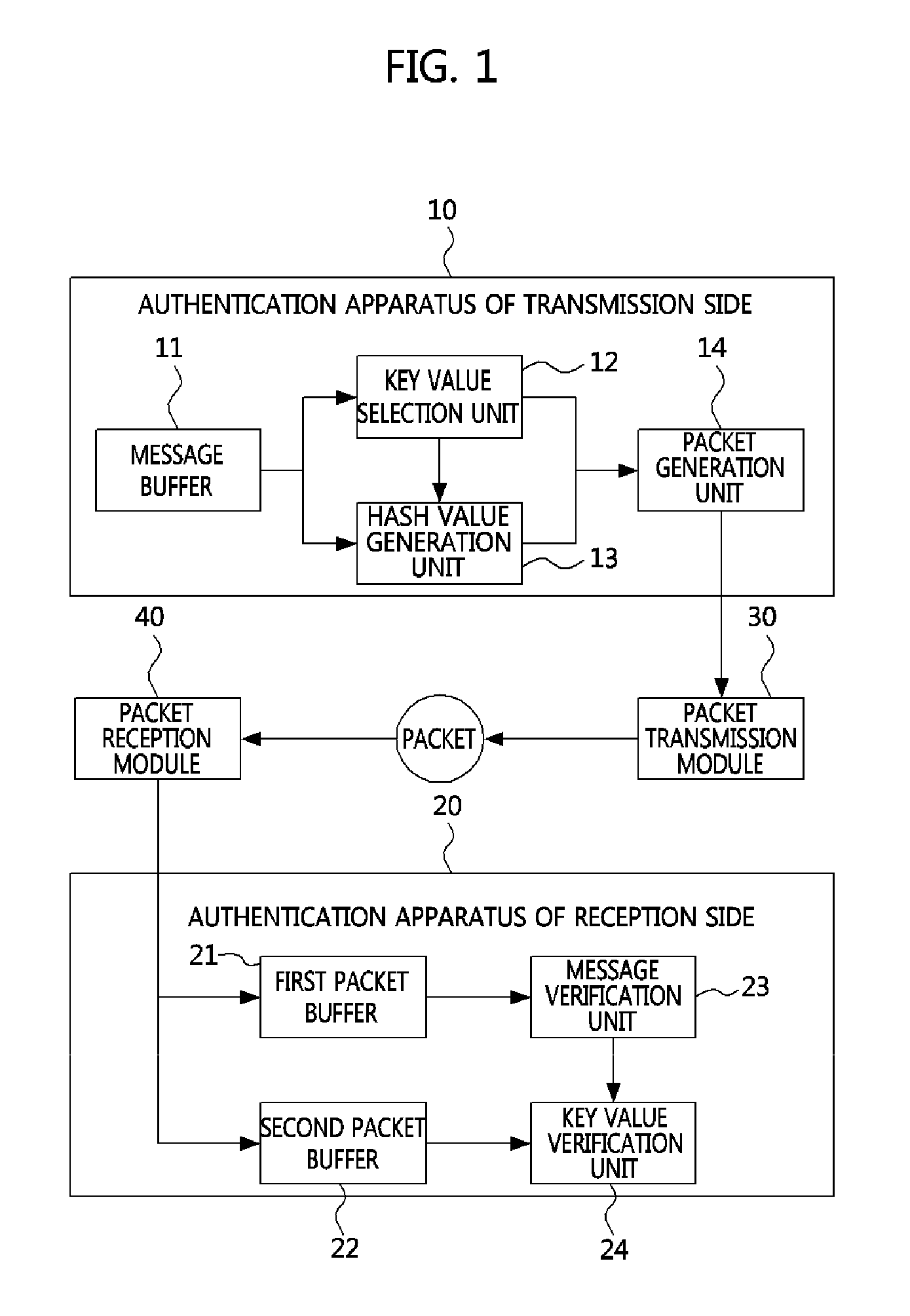
InactiveUS20130054974A1Efficient executionMinimizing buffering loadUser identity/authority verificationHash tableSource authentication
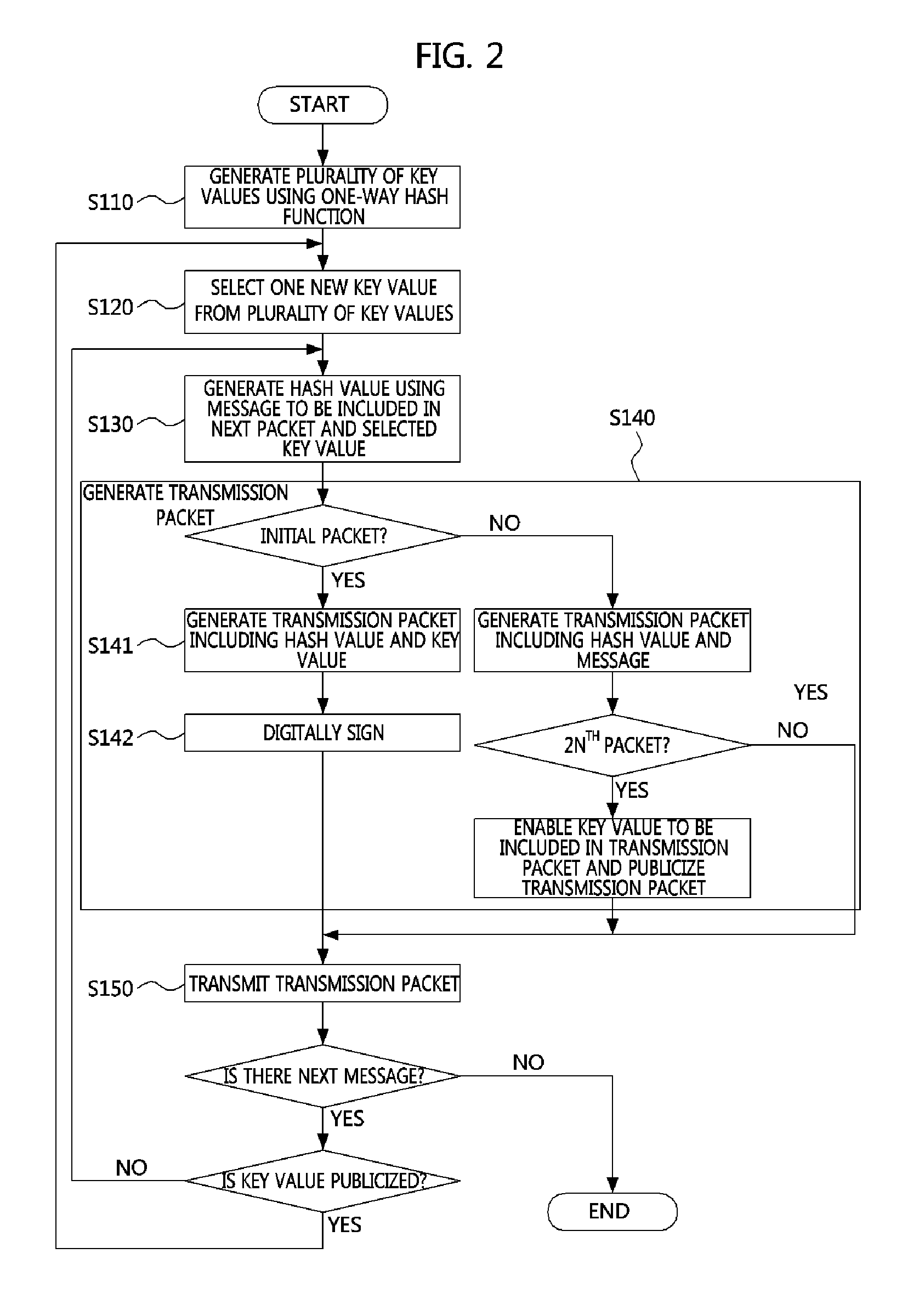
A source authentication method and apparatus according to the present invention are disclosed. The source authentication method is performed with respect to a transmission packet on a message transmission side, and includes generating a first hash value to which a first hash function is applied using a message to be included in a next packet and a key value, and generating the transmission packet including the first hash value, wherein the key value is one of at least one key value generated in advance by applying a second hash function. Meanwhile, according to the present invention, effective low-cost multicast authentication may be performed by reducing a variety of loads such as buffer management, key calculation costs, and the like.
Owner:ELECTRONICS & TELECOMM RES INST
Security certification method for accessing extended function module into network mobile terminal
InactiveCN102149090AImprove compatibilityEasy to deploySecurity arrangementComputer hardwareOperational system
The invention provides a method for performing security certification on an extended function module of a network mobile terminal. The method comprises the following steps that: a plug-in extended module a for updating application functions is accessed into the network mobile terminal; a plug-in manager transmits an identification request to an application program manager; the application program manager acquires a digital watermark on the plug-in extended module a, and an operating system driving layer generates an additional key; the additional key is transmitted to a security chip to verify source authentication and authority authentication; if the verification succeeds, an operation request is transmitted to the application program manager, and the application program manager permits the plug-in extended module a to be loaded and installed; and if the verification fails, the permission of the application program manager cannot be acquired, and the plug-in extended module a cannot be loaded and installed.
Owner:苏州汉辰数字科技有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com