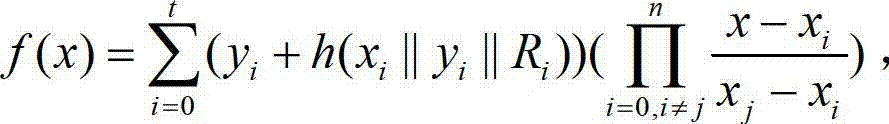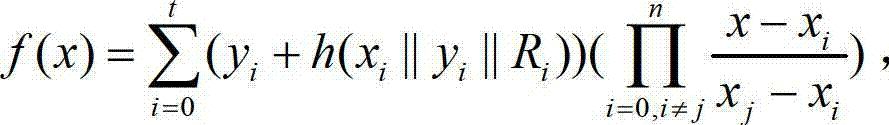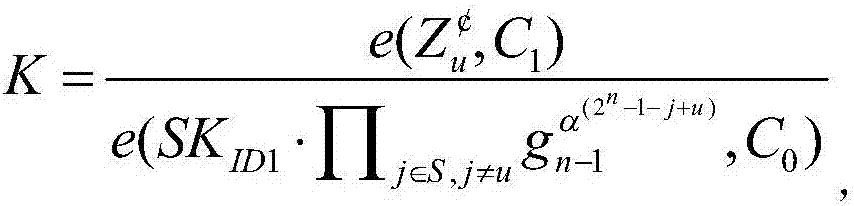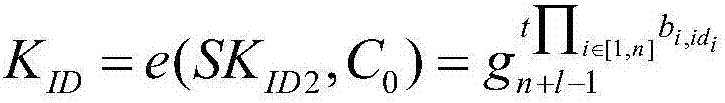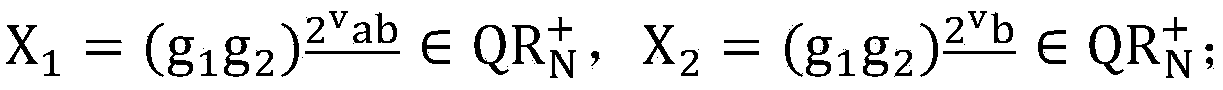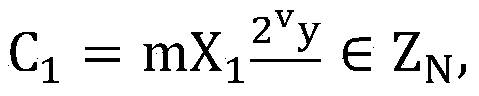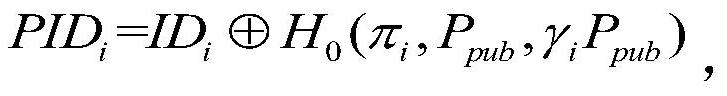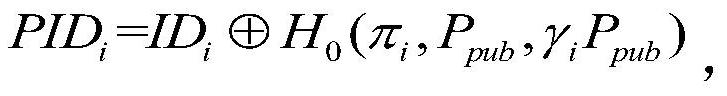Patents
Literature
42results about How to "Satisfy confidentiality" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
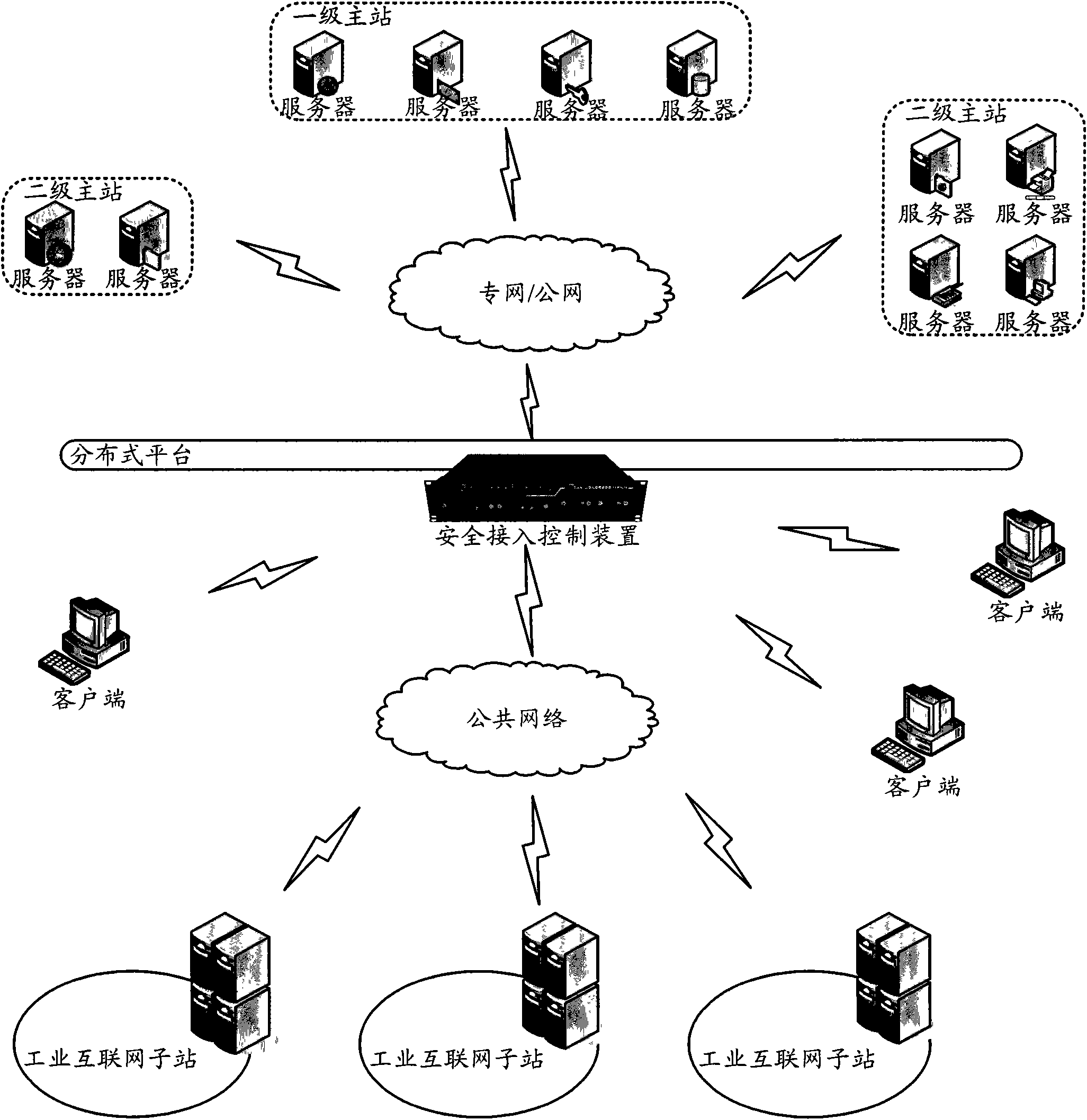
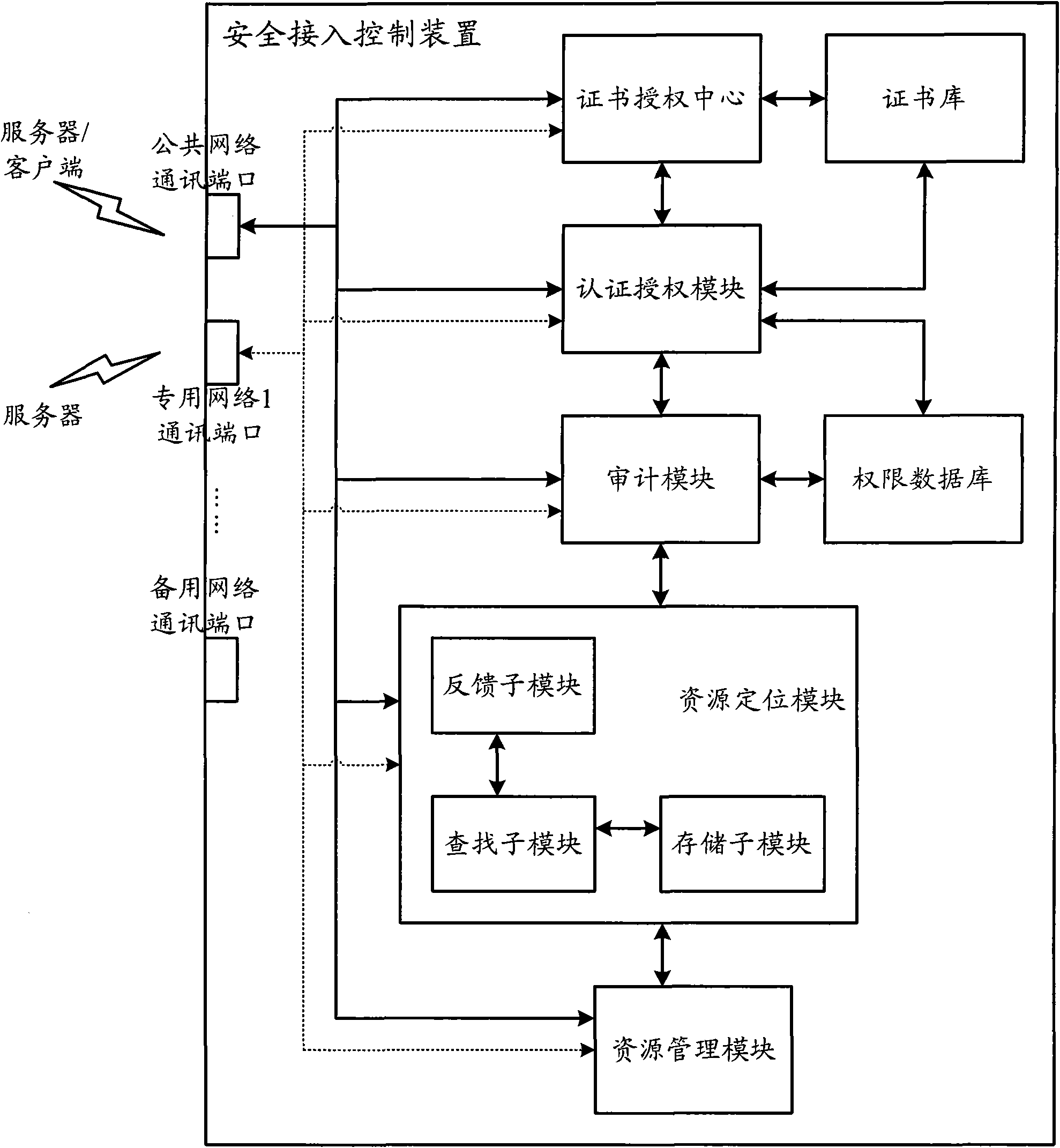
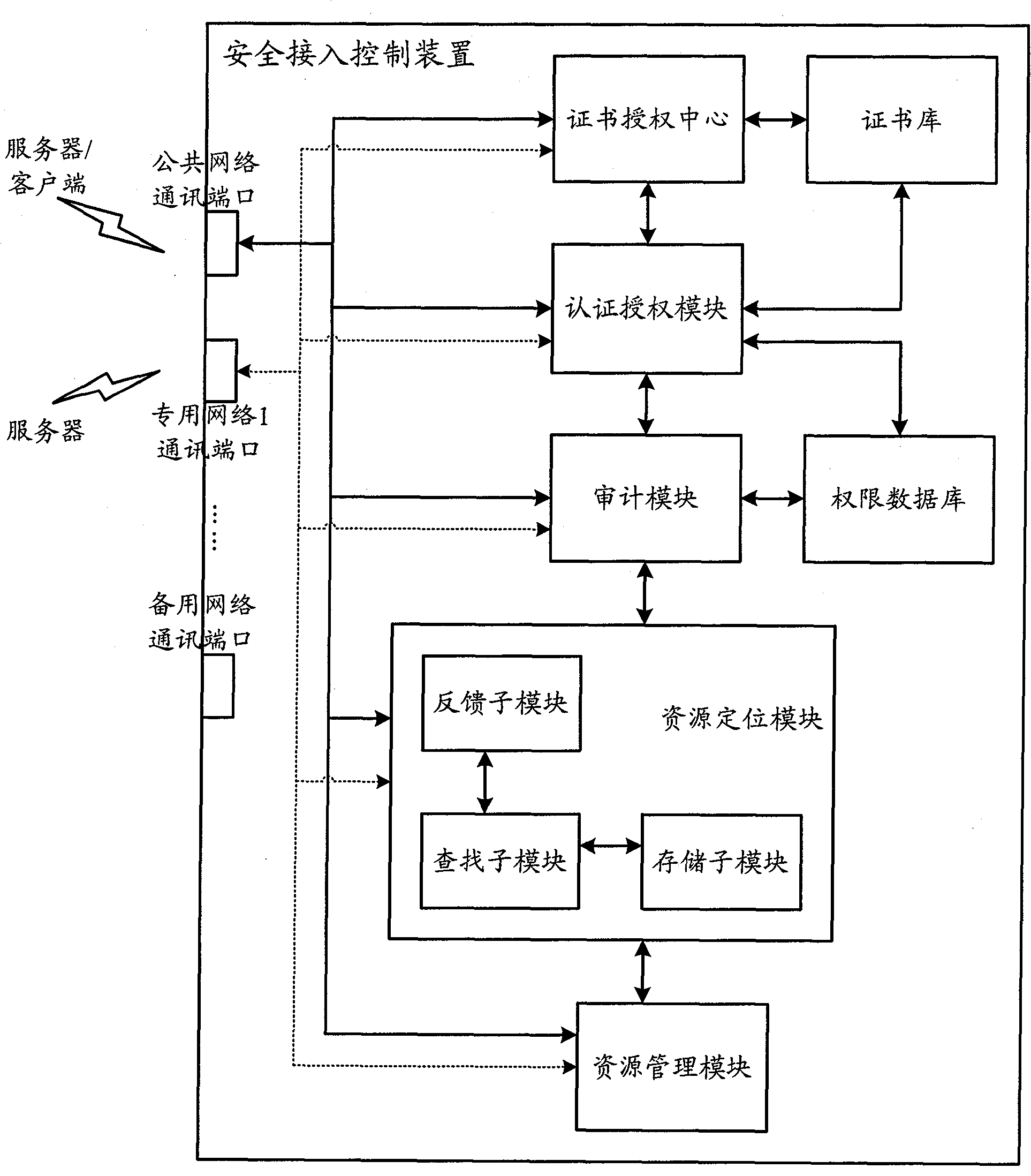
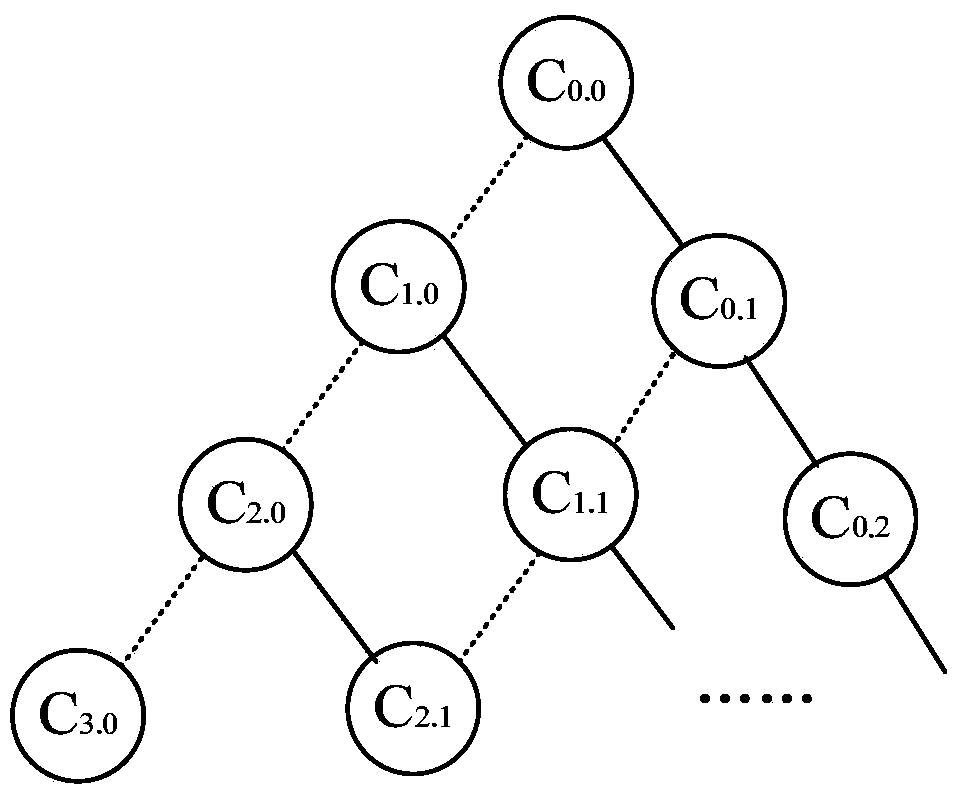
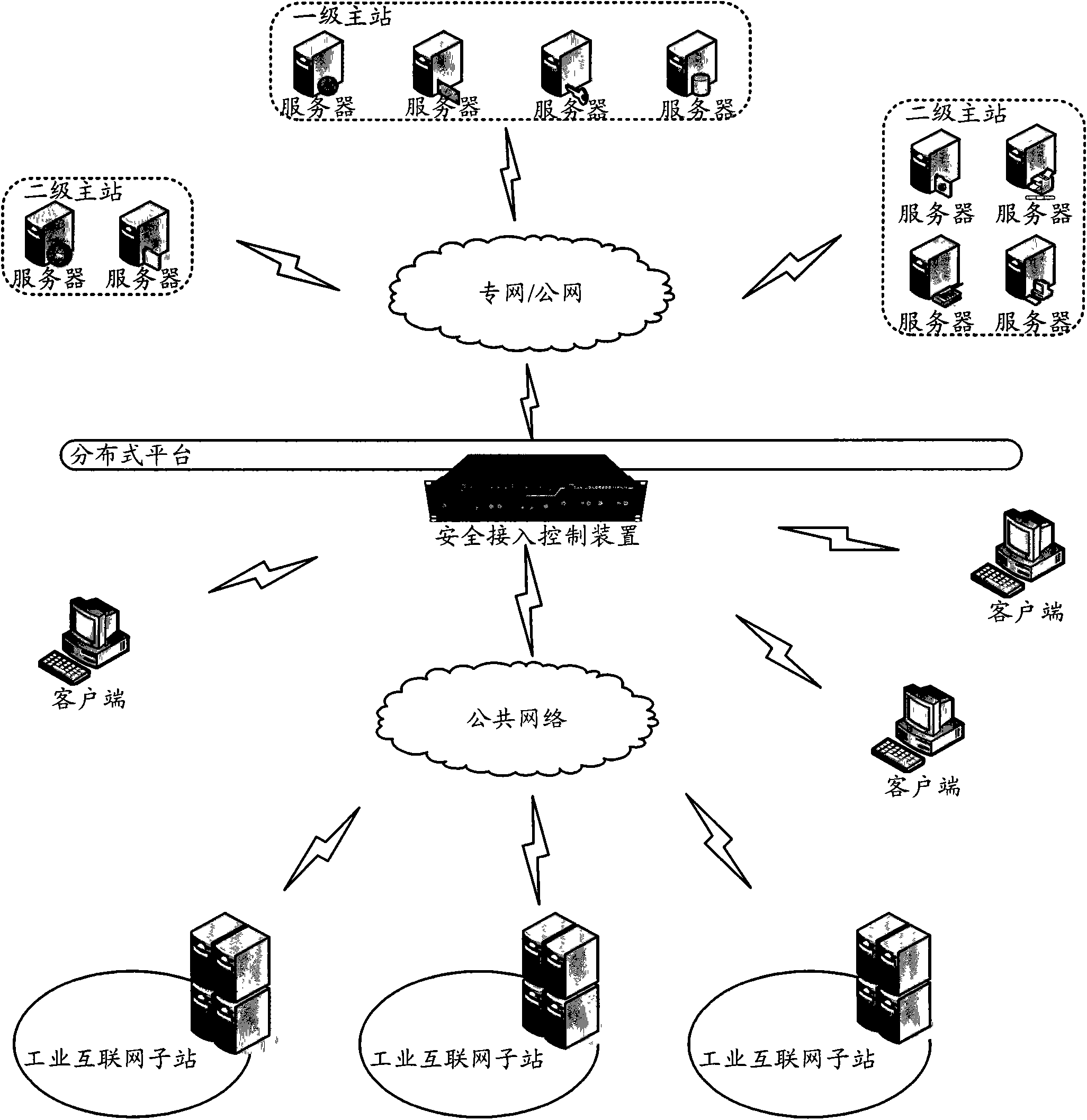
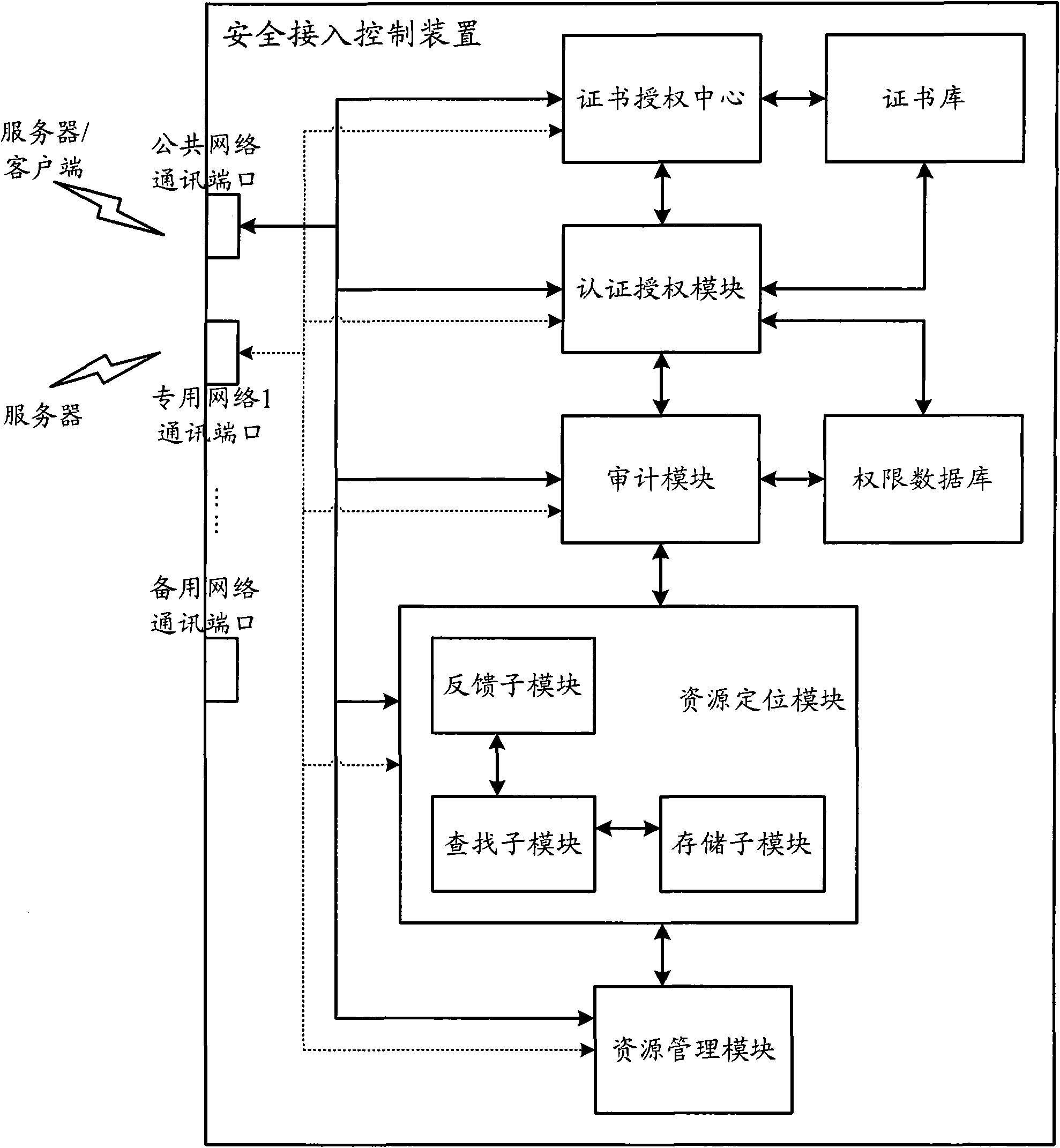
Industrial Internet distributed system safety access control device
ActiveCN102487383AGuaranteed legalityPrevent theftUser identity/authority verificationThe InternetIndustrial Internet
The invention discloses an industrial Internet distributed system safety access control device. The device integrates a module which is used to carry out authentication and authorization to identities and access operations of a user and a server, the module which is used to audit the access operations of the user and the server and the module which is used to carry out uniform resource positioning to object resources accessed by the user and the server. Identity security and authority validity of the user or the server which access to the industrial Internet distributed system and acquire information / service can be effectively ensured. In addition, the user and the server in the industrial Internet do not need to know an actual storage position of the needed object resources. Through a uniform resource positioning platform of the distributed system, the corresponding server can be positioned and the needed object resources can be acquired. A demand in a distributed environment can be rapidly and conveniently satisfied.
Owner:ASAT CHINA TECH
Multiple uncertainty encryption system with misleading function
The invention discloses a multiple uncertainty encryption system with a misleading function, which aims at attacks such as rubber-hose attacks, key stealing, brute force attacks and the like. Multiple encryption is performed, and an algorithm and encryption multiplicity are uncertain, so the system has multiple uncertainty, a password analyzer cannot perform analysis, and even though the brute force attacks are adopted, a plaintext obtained only by incomplete single decryption is meaningless. The encryption multiplicity of the algorithm, encryption algorithms of each layer and keys of each layer are all uncertain, and are all included in a structural master key. The multiple uncertainty makes securer the algorithm. The system is required to comprise an improved one-time pad mechanism, and one-time pad has high reversibility, so the encryption system can obtain pseudo keys in two ways to mislead and confuse the password analyzer, and has high value in military affairs and special occasions.
Owner:桂林轻鸿科技有限公司
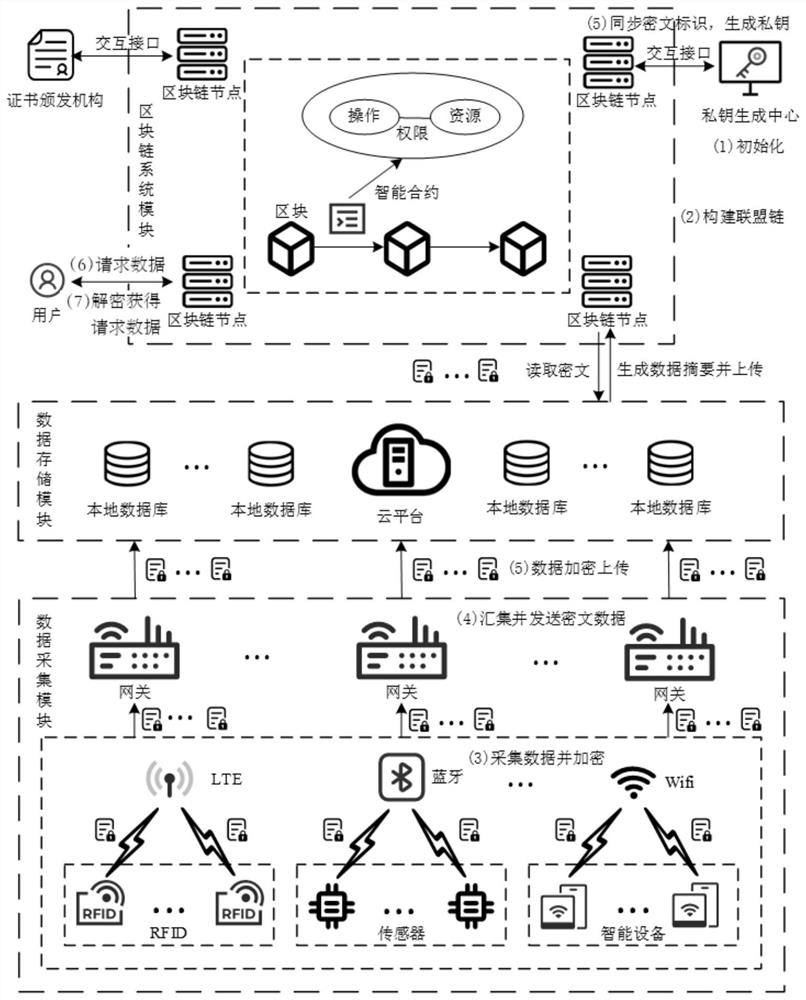
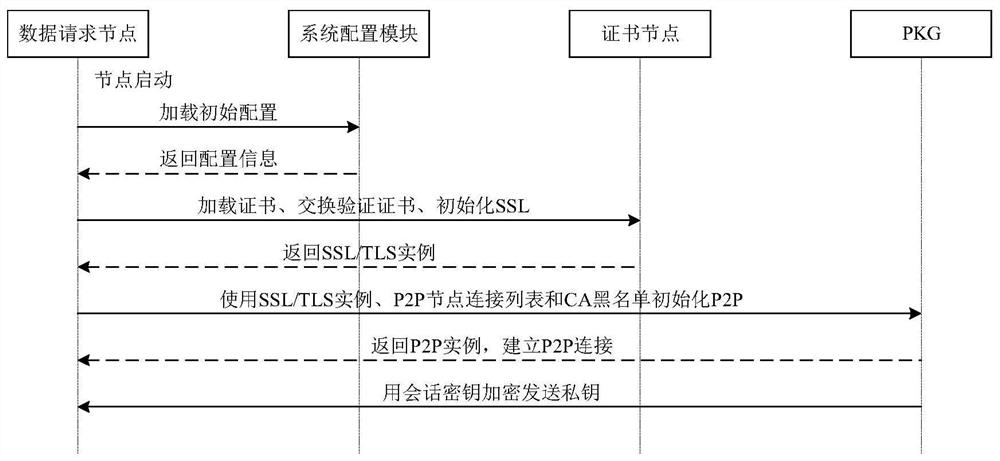
Internet of Things data access control method and system based on block chain and IBE algorithm
ActiveCN113783836AAvoid single point of failure problemsEffectively prevent node replication attacksKey distribution for secure communicationUser identity/authority verificationIot gatewayAlgorithm
The invention discloses an Internet of Things data access control method and system based on a block chain and an IBE algorithm. A private key generation center PKG carries out system initialization, and constructs an alliance chain; Internet of Things equipment acquires data, encrypts the data to obtain a ciphertext, and sends the ciphertext to the Internet of Things gateway; the Internet of Things gateway sends the ciphertext to an Internet of Things system cloud platform or a local database for storage; a hash value corresponding to the ciphertext is generated, and the ciphertext identifier and a key value pair corresponding to the hash value are stored in the block chain; the PKG generates a private key; a data requester initiates a data request transaction on a block chain, an access control contract deployed on the block chain verifies validity of a data request, the PKG establishes a secure connection with the data requester to share a private key after verification is passed, and the data requester decrypts encrypted data by applying an IBE decryption algorithm to obtain request data. According to the invention, safe and credible fine-grained access control in an Internet of Things environment can be realized, and confidentiality, integrity and availability are satisfied.
Owner:NANJING UNIV OF POSTS & TELECOMM
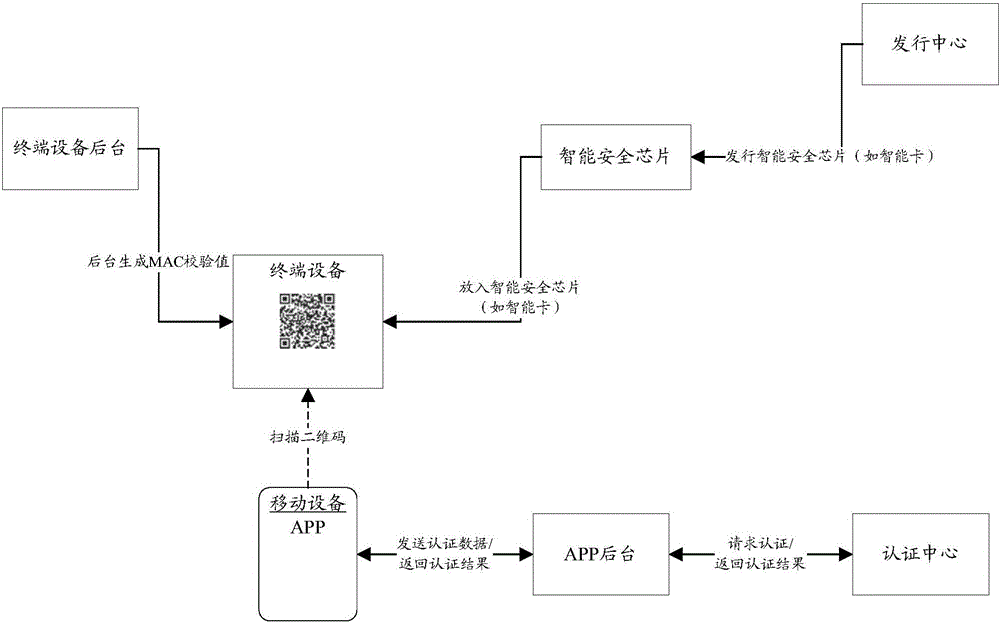
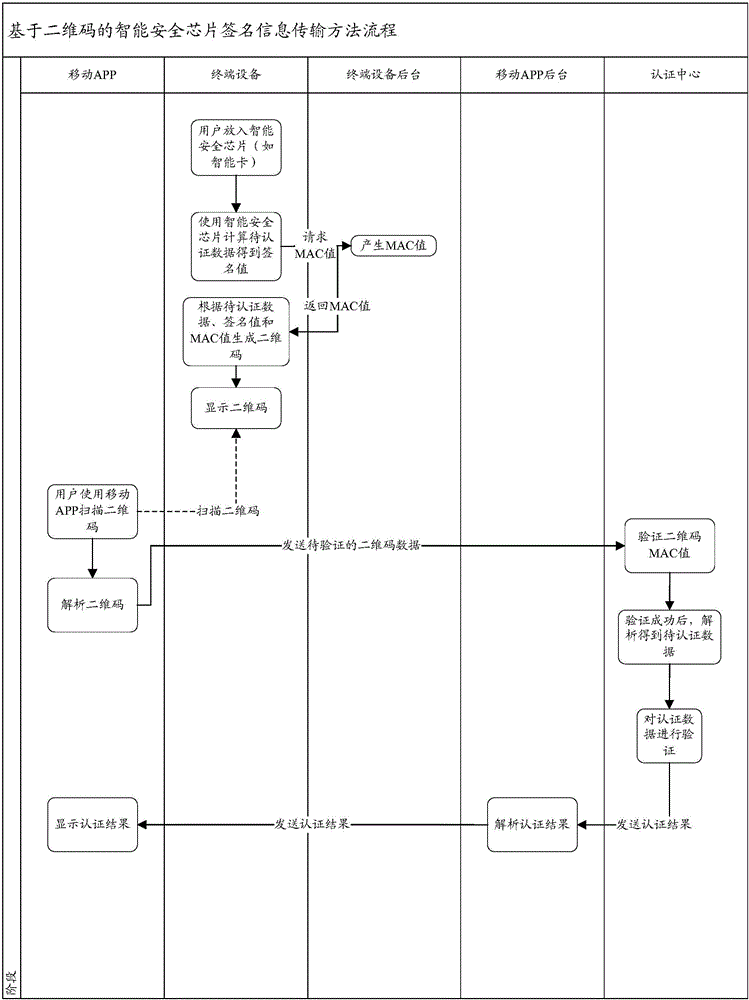
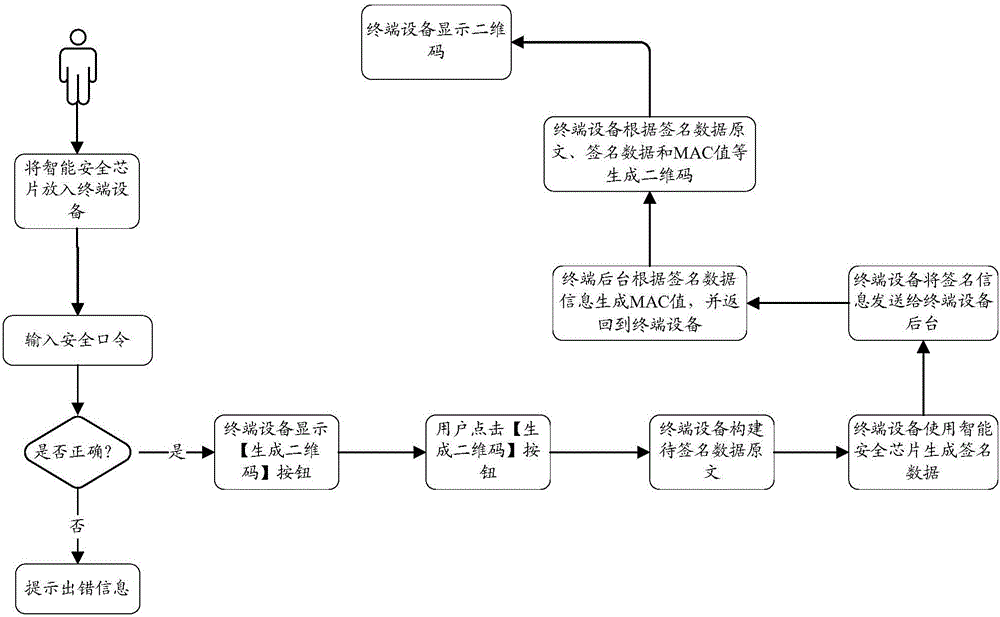
Intelligent security chip signature information transmission method and system based on 2-dimensional bar code
ActiveCN106100850AImprove securitySatisfy confidentialityEncryption apparatus with shift registers/memoriesUser identity/authority verificationInformation transmissionOriginal data
The invention relates to an intelligent security chip signature information transmission method and system based on a 2-dimensional bar code. The 2-dimensional bar code is generated by the following steps: an intelligent security chip is inserted into a terminal device; the intelligent security chip is used to put a signature on the original data and thus signature value information is obtained; and the terminal device assemblies the original data, the signature value information and a message verification code to generate a 2-dimensional bar code, and displays the 2-dimensional bar code. Scanning authentication of the 2-dimensional bar code comprises the following steps: an application scans the 2-dimensional bar code, parses the data of the 2-dimensional bar code so as to obtain the to-be-authenticated data, and then sends the to-be-authenticated data to an application background; an authentication center verifies the to-be-authenticated data, and sends a verification result back to the application through the application background. With application of the intelligence security chip signature information transmission method and system based on a 2-dimensional bar code, in an intelligent card identity authentication application system, the problem of poor data communication between an intelligent card and a background system due to unavailable card reading devices is solved, so that comparative transmission of the signature information of the intelligent card is fulfilled without using a particular intelligent card reading device.
Owner:THE THIRD RES INST OF MIN OF PUBLIC SECURITY
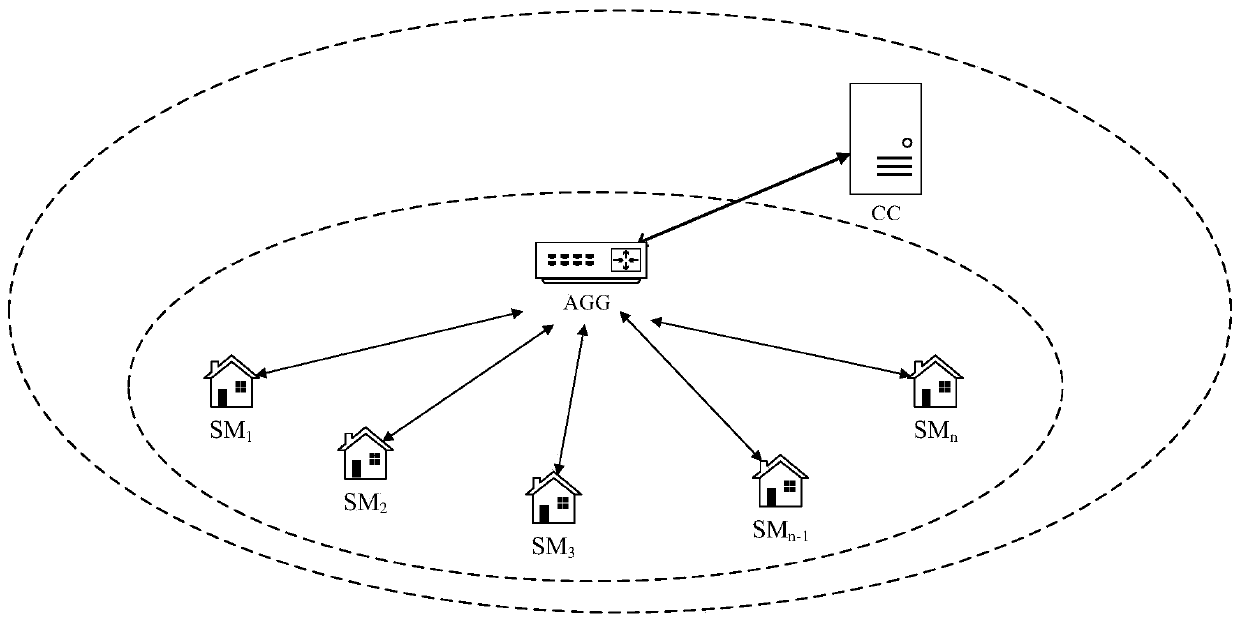
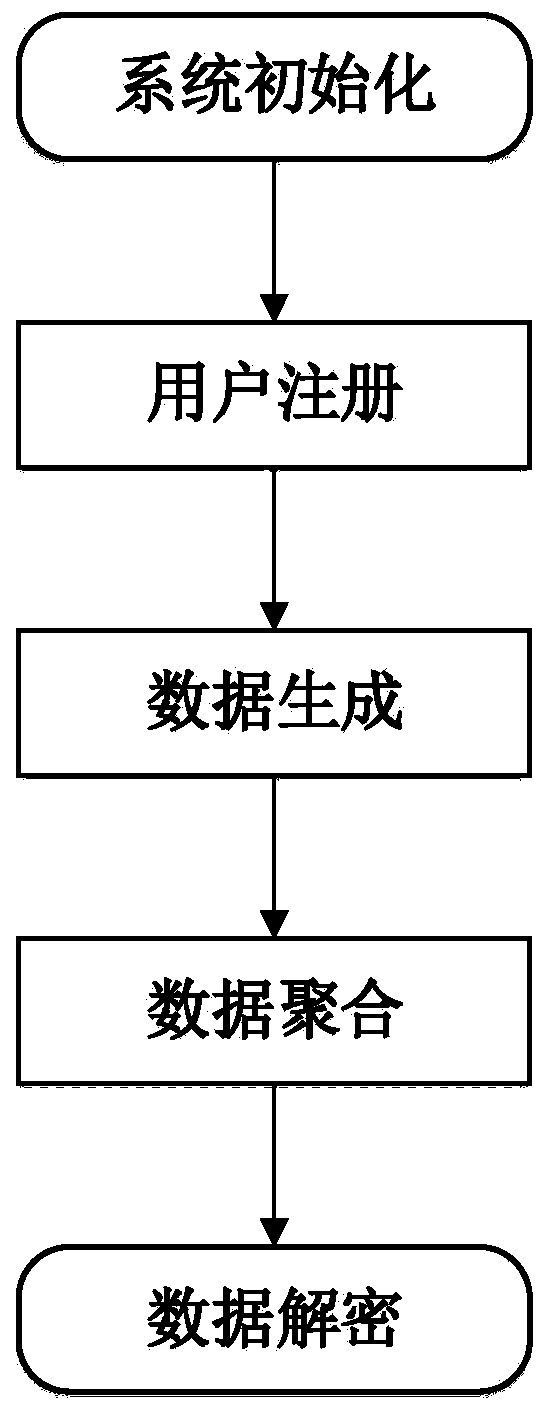
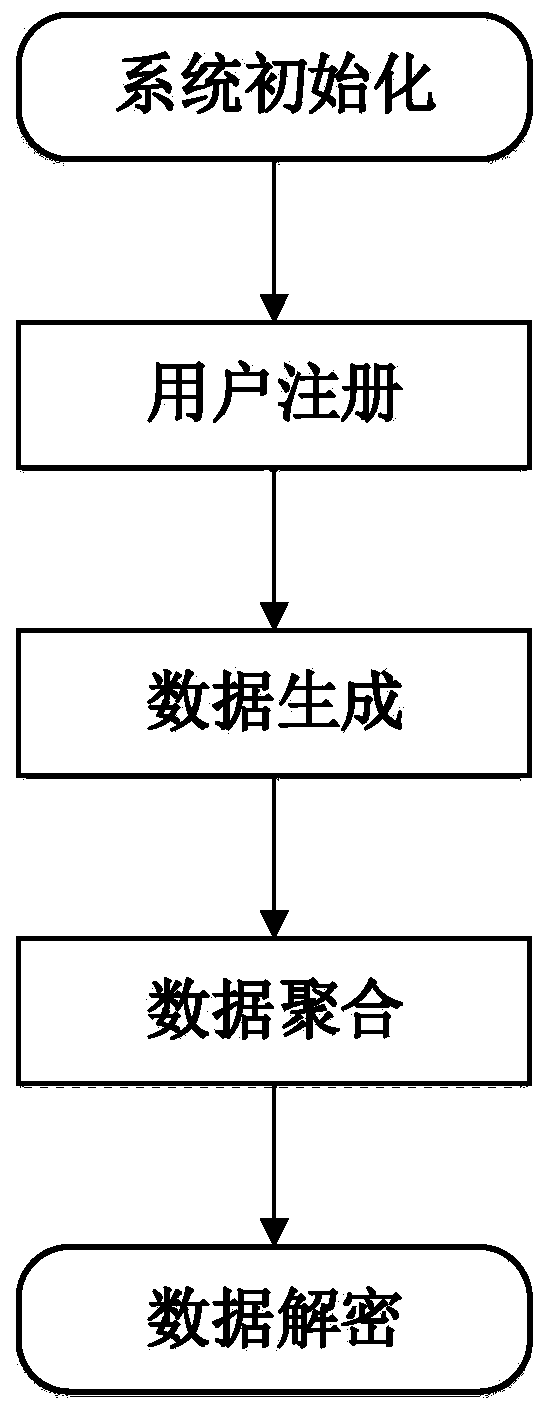
Privacy protection data aggregation method and system for smart power grid
ActiveCN111131148AImprove reliabilitySatisfy confidentialityKey distribution for secure communicationPublic key for secure communicationThird partyConfidentiality
The invention requests to protect a privacy protection data aggregation method and system for a smart power grid. The method and system can protect the data privacy of a single user from being leakedand aggregates the sum of data in a certain area, and only a control center can read an aggregation result. The method comprises a system initialization step, a user registration step, an encrypted data generation step, a data aggregation step and a data decryption step. According to the invention, an intelligent electric meter and an aggregator negotiate a session key, and a BGN encryption algorithm based on an elliptic curve is used to encrypt the data. The method does not depend on a trusted third party, the system can still operate normally when the intelligent electric meter is missing, so that better reliability is achieved, the identity of the user is anonymous, and an attacker cannot obtain the real identity of the user. According to the method, the calculation efficiency is improved, the corresponding security requirements of confidentiality, integrity, certification and the like are met, and the security can be proved.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
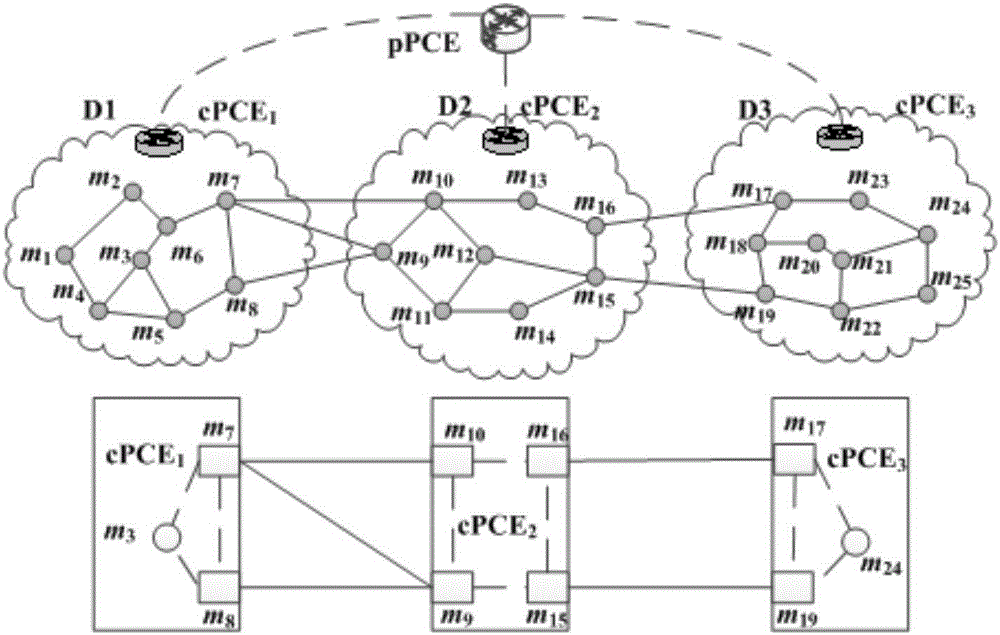
Layered PCE based multi-domain optical network secure light path establishment protocol
ActiveCN106851441AShort setup delaySatisfy confidentialityMultiplex system selection arrangementsUser identity/authority verificationConfidentialityPrivacy protection
The invention discloses a layered PCE based multi-domain optical network secure light path establishment protocol. Aiming at the problems of security problem and comprehensive efficiency existing in a multi-domain optical network light path establishment process, a new GO-PCE (Global Optimizing secure light-path protocol based PCE in multi-domain optical network) is designed by combining with a trust model and a key management scheme, adopting a globally optimized multi-domain trusted path selection, usable wavelength calculation and wavelength distribution strategy, and utilizing a TLS based bidirectional identity authentication, TCP-AO based source authentication, identity cryptography based encryption and digital signature technology and a Path-Key based privacy protection mechanism. The secure service requirements such as confidentiality, completeness, authenticity, non-repudiation, freshness and privacy can be met; compared with an SD-PCE and pH-PCE light path establishment protocols, the layered PCE based multi-domain optical network secure light path establishment protocol has relatively low blocking rate and relatively short light path establishment time delay.
Owner:ENG UNIV OF THE CHINESE PEOPLES ARMED POLICE FORCE
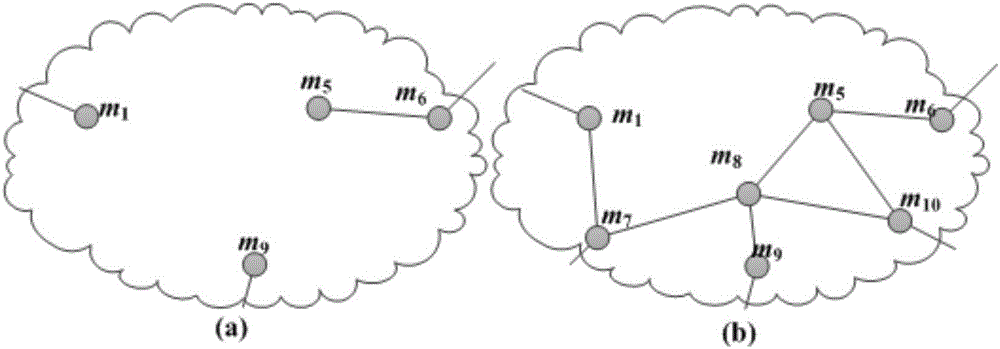
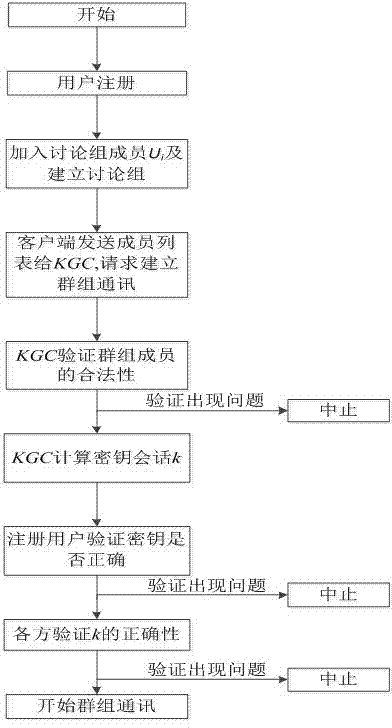
Method for establishing safety communication of network groups
InactiveCN103051457AEnsure safetyPrevent attack and stealSpecial service provision for substationUser identity/authority verificationSecure communicationHash function
The invention discloses a method for establishing safety communication of network groups. The method comprises the following steps of: processing long-term secret data and authentication information of group communication members by using an SHA (Secure Hash Algorithm) safety hash function which is 512 bits in length; and distributing a key by using an interpolation polynomial according to a secret partition threshold scheme of Shamir to keep a group key fresh, confidential and authenticable and effectively resist external attacks and internal attacks. According to the invention, all information is transmitted on a public channel, so that the method has the characteristics of low calculation amount, high running speed and high server calculation efficiency.
Owner:GUILIN UNIV OF ELECTRONIC TECH
Information security method of industrial control network and security function block
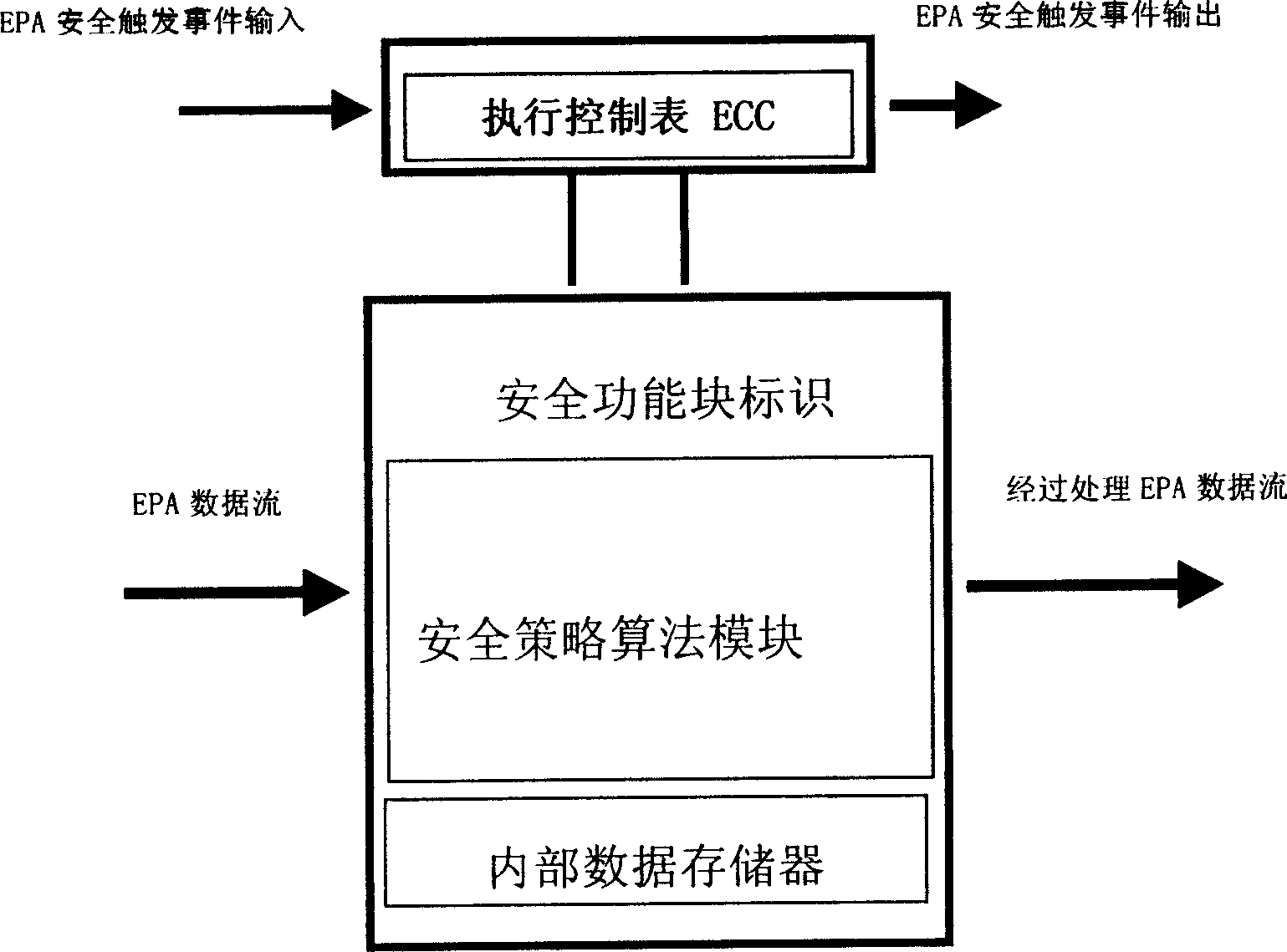
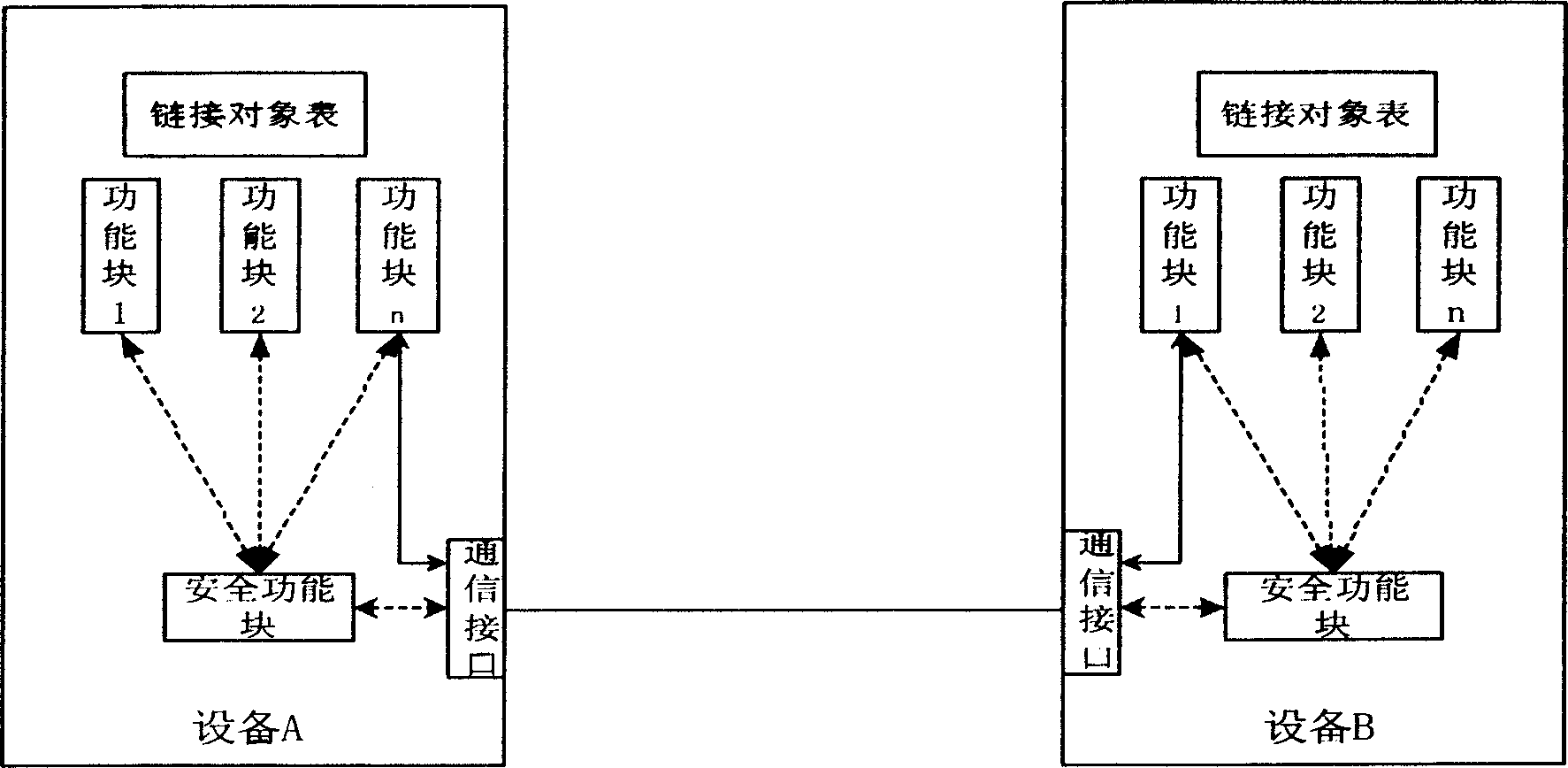
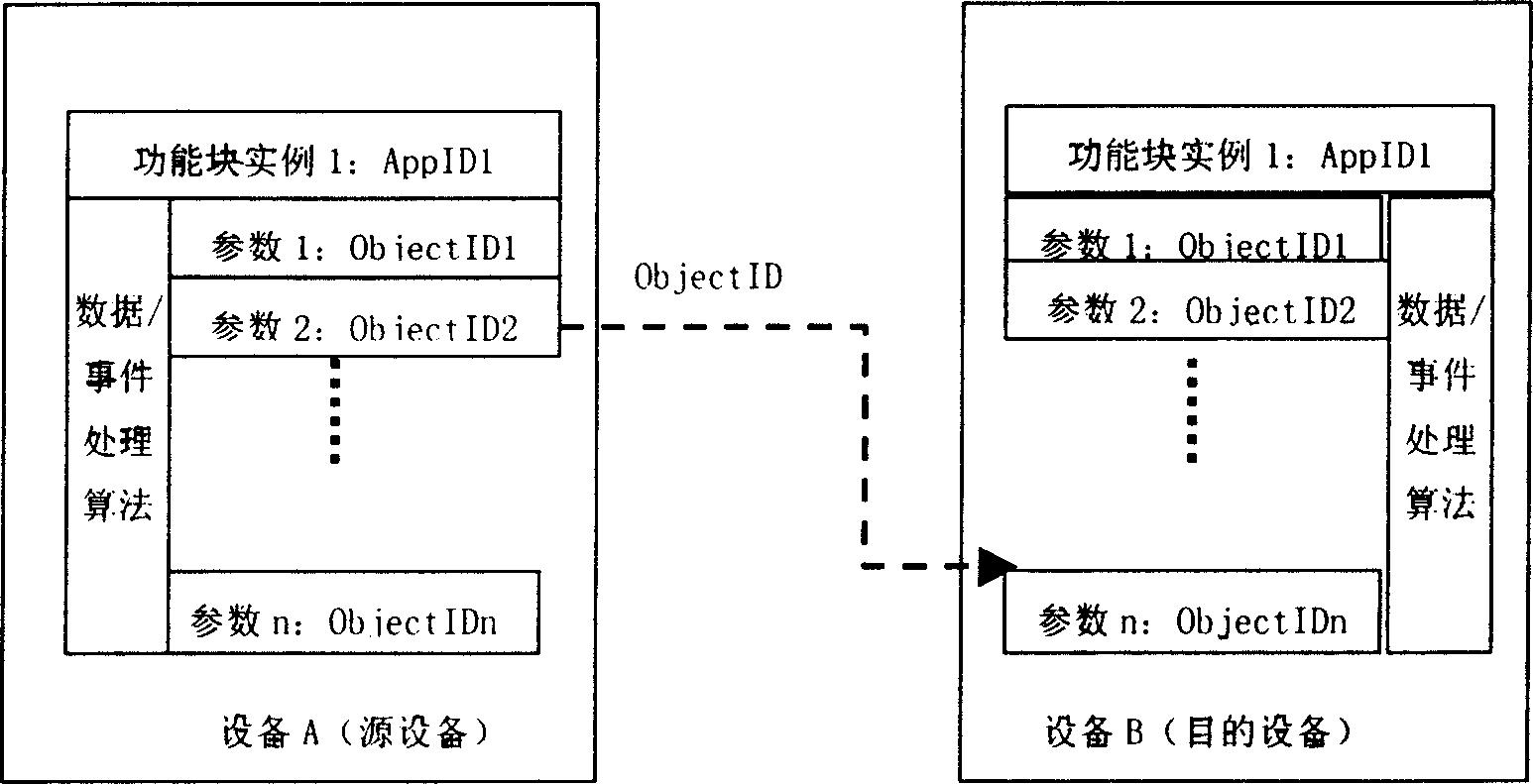
InactiveCN1703046AEnsure confidentialityEnsure integrityData switching networksSecuring communicationExecution controlInformation security
This invention relates to one information safety method and its function module based on industry controlled network and to the safety management method, which comprises the following steps: establishing safety function module in the net; defining safety function module input interface and outputting interface and safety affairs and executing control form dispatching formula when the affairs arrive; processing the input unsigned char to fulfill the data coding and buffer the results in the output interface; finally executing the control form to send one affair signal and completing the coding formula in the key dispatching system.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
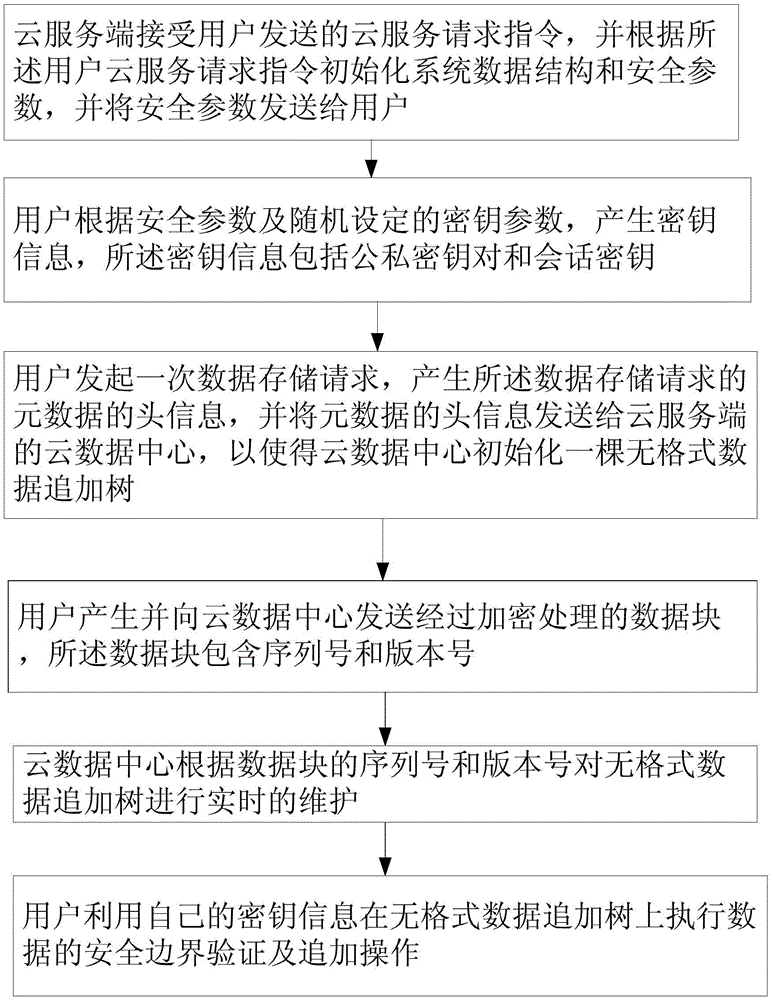
Cloud computing data security boundary protection method
InactiveCN103618703ASatisfy data confidentialityGood universalityUser identity/authority verificationData securityMetadata
The invention discloses a cloud computing data security boundary protection method. The cloud computing data security boundary protection method comprises the steps that a cloud service request instruction sent by a user is received, and a data structure and safety parameters of a system are initialized and sent to the user; the user generates a secret key message; the user sends a data storage request, the header information of the metadata of the data storage request is generated, and a cloud data center initializes a plain data append tree; the user generates and sends an encrypted data block to the cloud data center; the cloud data center maintains the plain data append tree in real time according to the serial number and version number of the data block; the user executes security boundary verification and append operation of data on the plain data append tree by utilizing the secret key information of the user. The cloud computing data center of a cloud server terminal not only provides the encryption, fault tolerance and security boundary maintenance functions for the data of the user, but also meets the confidentiality, integrity and survivability of the data.
Owner:ENG UNIV OF THE CHINESE PEOPLES ARMED POLICE FORCE
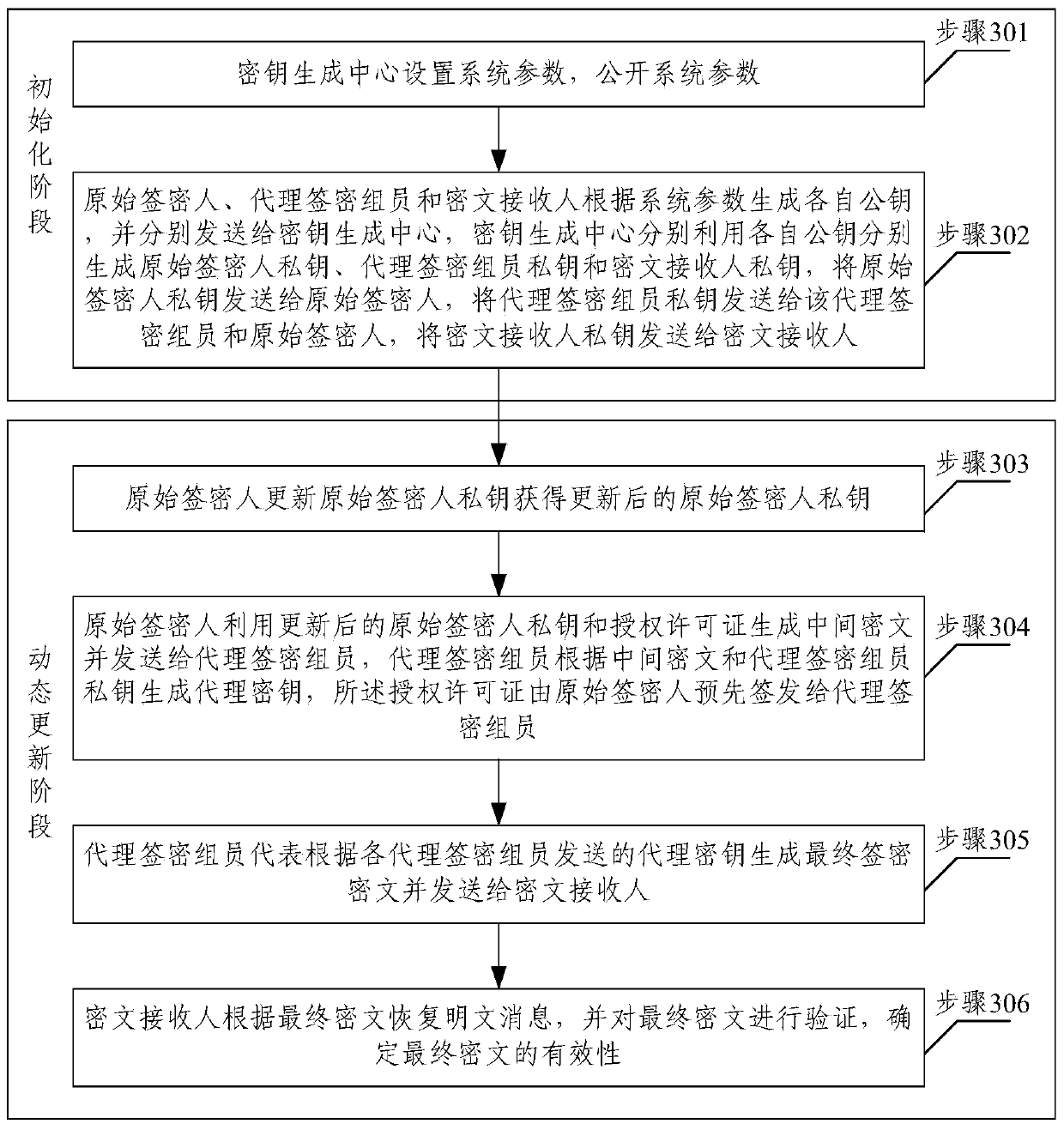
Certificateless multi-proxy signcryption method with forward secrecy
InactiveCN103634788AReduce system overheadImprove securitySecurity arrangementCryptosystemForward secrecy
The invention belongs to the fields of communication data authentication and privacy in a wireless network and provides a certificateless multi-proxy signcryption method with forward secrecy. An original signcrypter private key is constantly updated in a dynamic updating stage, and a proxy secret key is constantly updated too, a signcryption public key is unchanged in a whole process; furthermore, the private key is updated through a secrete key updating algorithm which is an one-way function; therefore, system overhead under a condition of higher security is reduced due to addition of a certificateless cryptosystem, thus meeting requirements of an original multi-proxy signcryption system on security, strong identifiability, public verification, strong non-repudiation and abuse resistance; in addition, the method can meet higher requirements on forward secrecy and strong unforgeability.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
Wireless sensor network security routing method based on IPv6 addressing
ActiveCN104811934AWith data collectionWith wireless communication moduleTransmissionSecurity arrangementTimestampRouting table
The invention discloses a wireless sensor network security routing method based on IPv6 addressing. Network IP addressing and network joining and leaving rules of nodes based on a tree topological structure are provided by aiming at the practical requirement that data require security transmission in a wireless sensor network so that storage space of IP addresses and routing tables is greatly saved, and time and space utilization efficiency is enhanced. Meanwhile, a message security routing transmission strategy based on unicast and multicast is designed, and the network is enabled to resist attack means like replaying and capturing by the characteristic of combination of encryption and decryption, hash algorithm and timestamps.
Owner:张北数据港信息科技有限公司
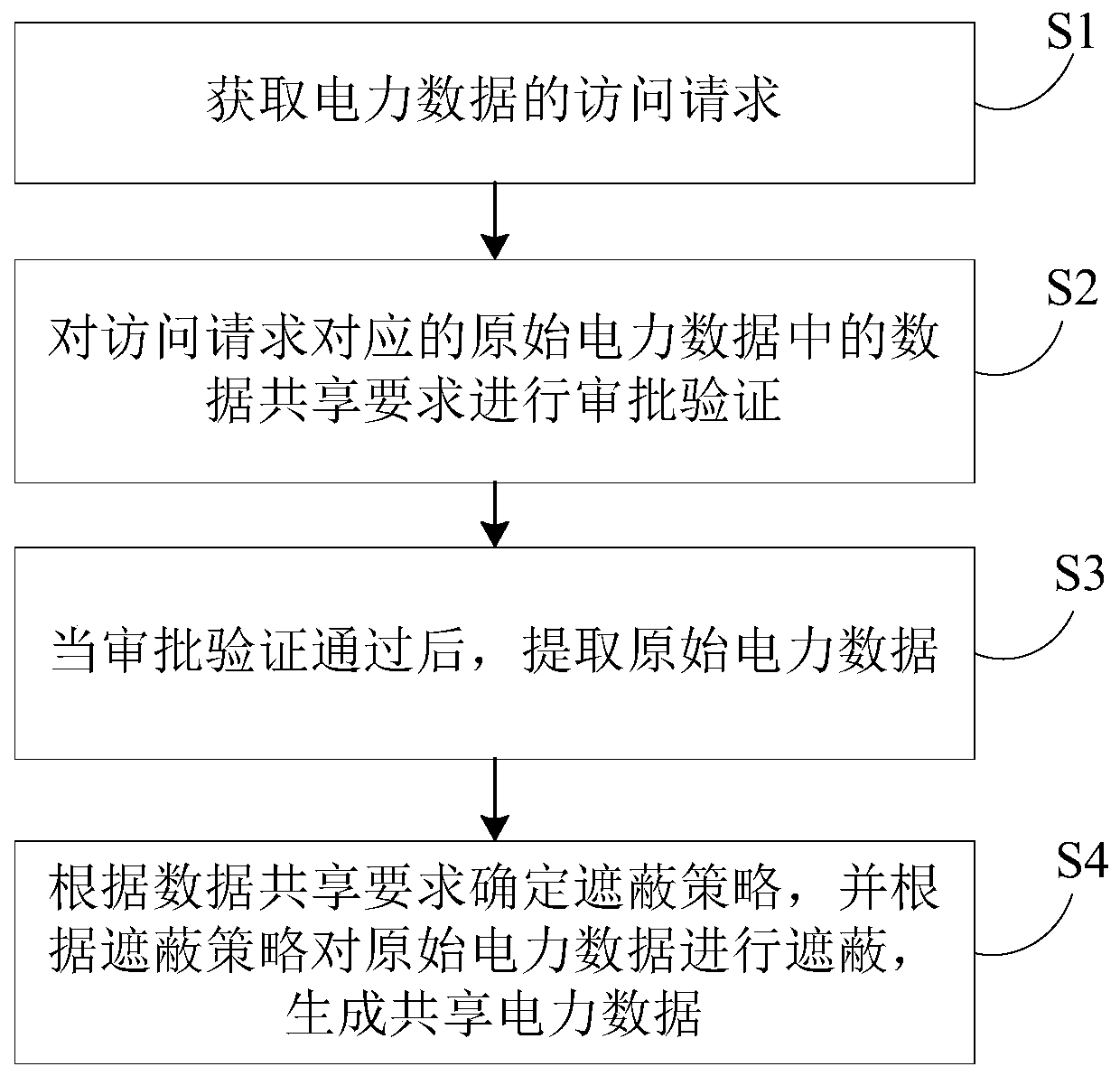
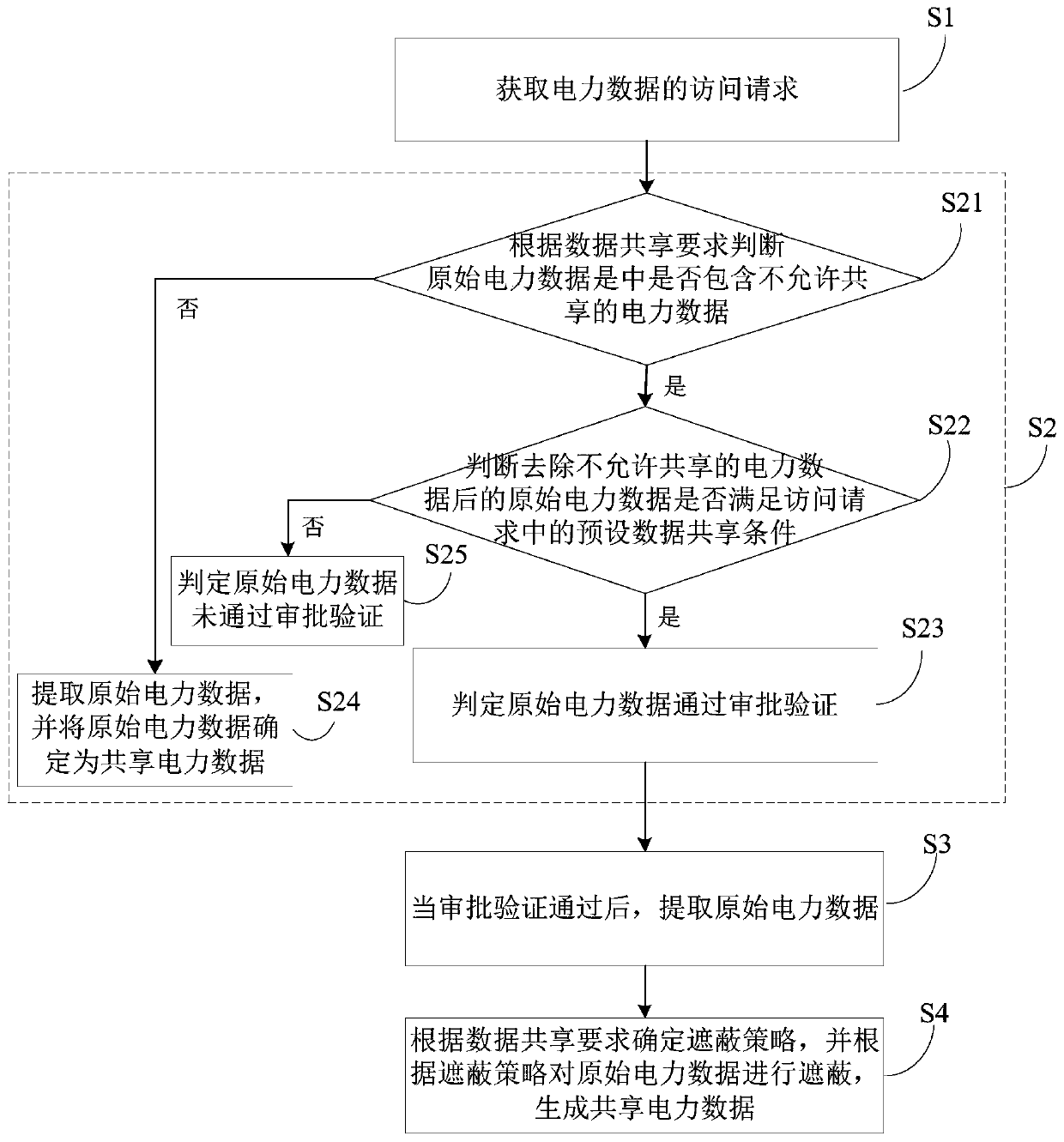
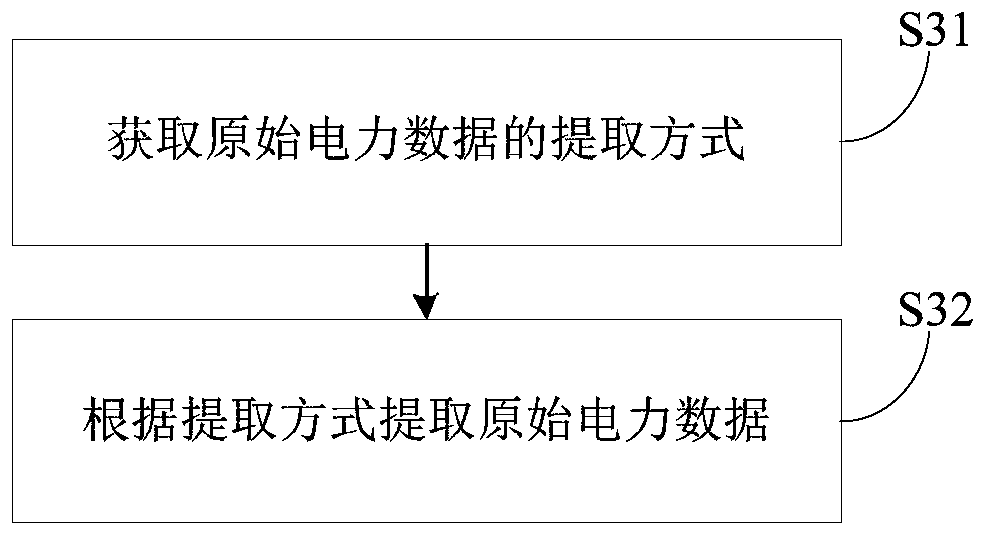
Power data sharing method and system
InactiveCN109800595ASatisfy confidentialitySatisfy securityDigital data protectionElectric power systemConfidentiality
The invention provides an electric power data sharing method and system. The method comprises the steps of obtaining an access request of electric power data; carrying out approval verification on a data sharing requirement in the original power data corresponding to the access request; after the approval verification is passed, extracting original power data; and determining a shielding strategyaccording to the data sharing requirement, shielding the original power data according to the shielding strategy, and generating shared power data. By implementing the method and the device, the shared electric power data is generated by executing approval verification and setting the shielding strategy corresponding to the original electric power data, so that the requirements on confidentiality,security and privacy of the electric power data are met, the resource sharing of the electric power data is realized, and the utilization rate of the electric power data is further improved.
Owner:GLOBAL ENERGY INTERCONNECTION RES INST CO LTD +1
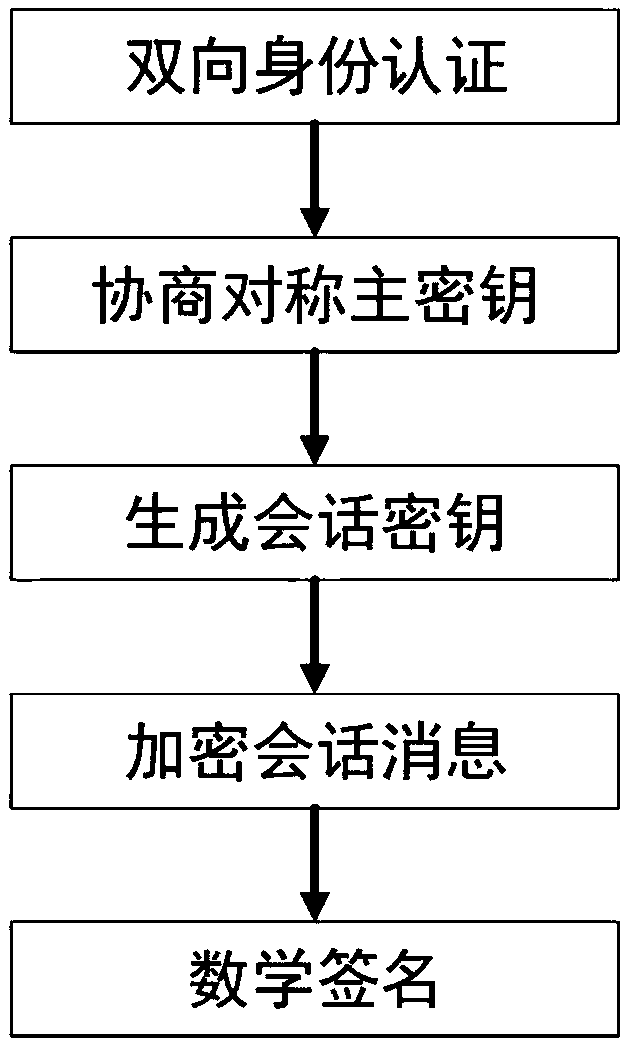
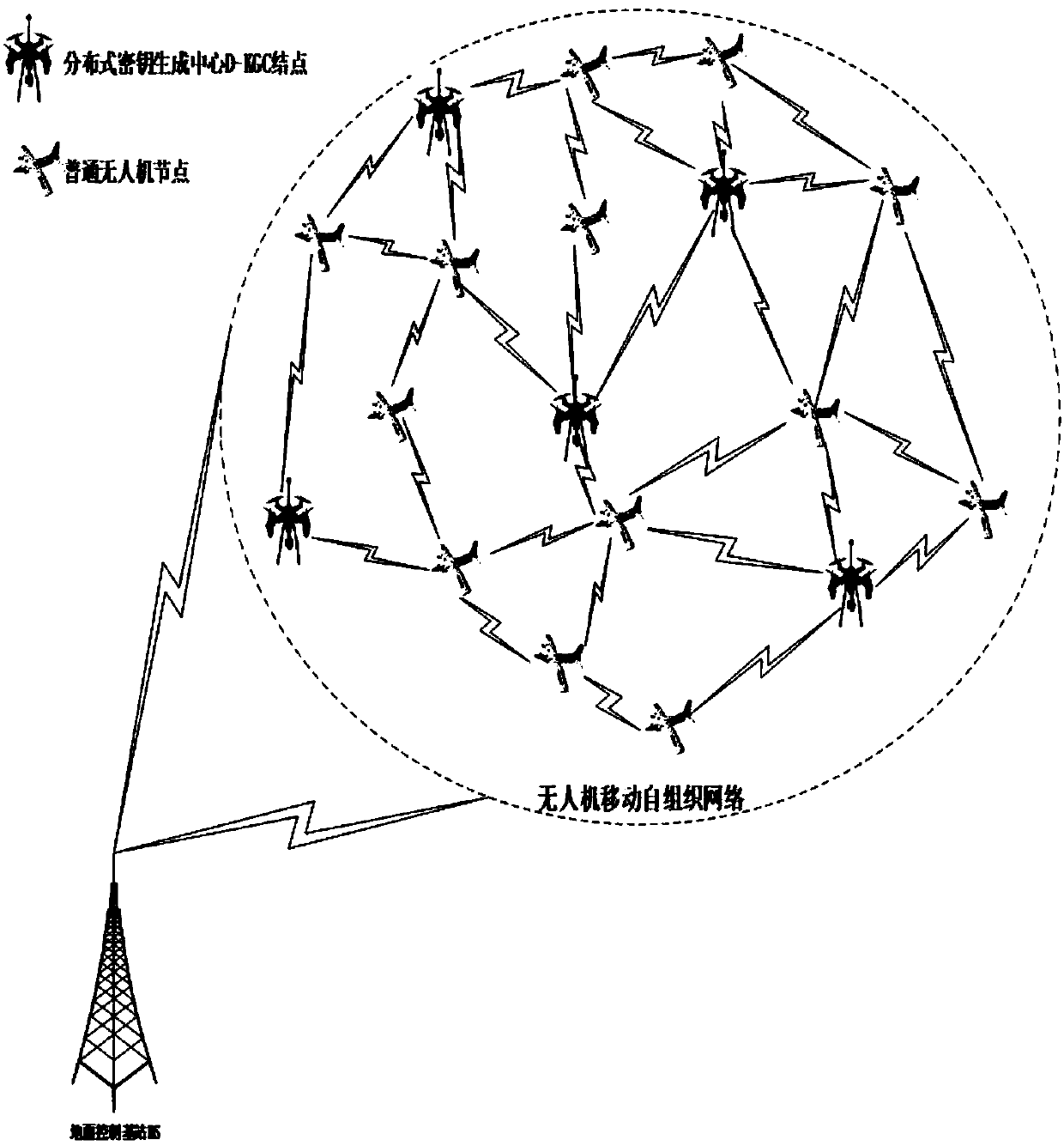
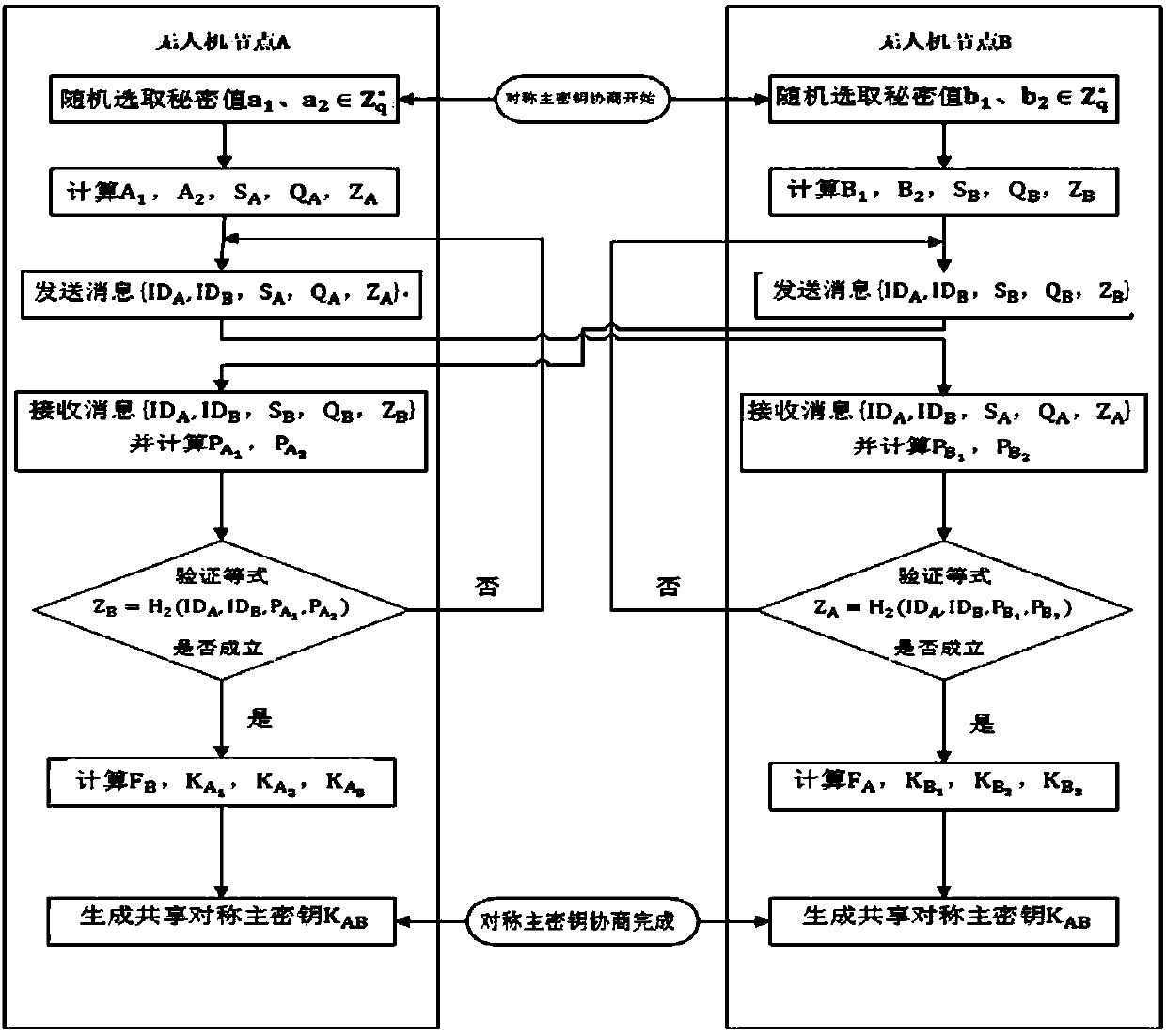
Method of enhancing UVA (Unmanned Aerial Vehicle) MANET network security
ActiveCN108521401AImprove the efficiency of secure communicationsReduce operational complexityKey distribution for secure communicationPublic key for secure communicationDigital signatureUncrewed vehicle
The invention discloses a method of enhancing UVA (Unmanned Aerial Vehicle) MANET network security in the field of wireless communication technology. The method of enhancing UVA MANET network securitycomprises the specific steps as follows: S1, performing bidirectional identity authentication between UVA nodes, to be specific, S1.1, sending an identity authentication request to a UVA node A by aUVA node B, S1.2, responding to the identity authentication request of the UVA node A by the UVA node B, and S1.3, sending the identity authentication request to the UVA node A by the UVA B, and S1.4,responding to the identity authentication request of the UVA node B by the UVA node A; S2, negotiating symmetric master keys; S3, generating a session key; and S4, generating a digital signature, tobe specific, signing a message M and then sending the message signature sigma and the message M to the UVA node B by the UVA node A, and verifying the correctness of the signature by the node B. By adoption of a form of double keys, a key trusteeship problem and possibility of revealing a system private key due to inverse derivation of a malicious node can be well overcome through a negligible calculated amount.
Owner:XIDIAN UNIV
Certificateless parallel key isolation signcryption method
InactiveCN109660332AAvoid managementSatisfy confidentialityKey distribution for secure communicationEncryption apparatus with shift registers/memoriesPlaintextConfidentiality
The invention discloses a certificateless parallel key isolation signcryption method. Two different and independent assistors are imported in the configuration, the two assistors help a signcryption user and an unsigncryption user to generate initial private keys, temporary private keys can be alternately updated without affecting each other, and even the frequent update of the temporary private key of the signcryption user does not increase the leakage risk of the key of the assistor. The signcryption user performs signcryption on a plaintext by using his own private key and a public key of the unsigncryption user to generate a signcryption ciphertext; and after receiving the signcryption ciphertext, the unsigncryption user performs unsigncryption on the signcryption ciphertext by using his own private key and the public key of the signcryption user to restore the plaintext. According to the certificateless parallel key isolation signcryption method disclosed by the invention, a key isolation mechanism is imported into a certificateless signcryption scheme, which not only reduces the computation and communication costs, but also satisfies the characteristics of confidentiality, non-repudiation, parallelism and strong key isolation and the like, and also supports frequent key update without increasing the key leakage risk.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
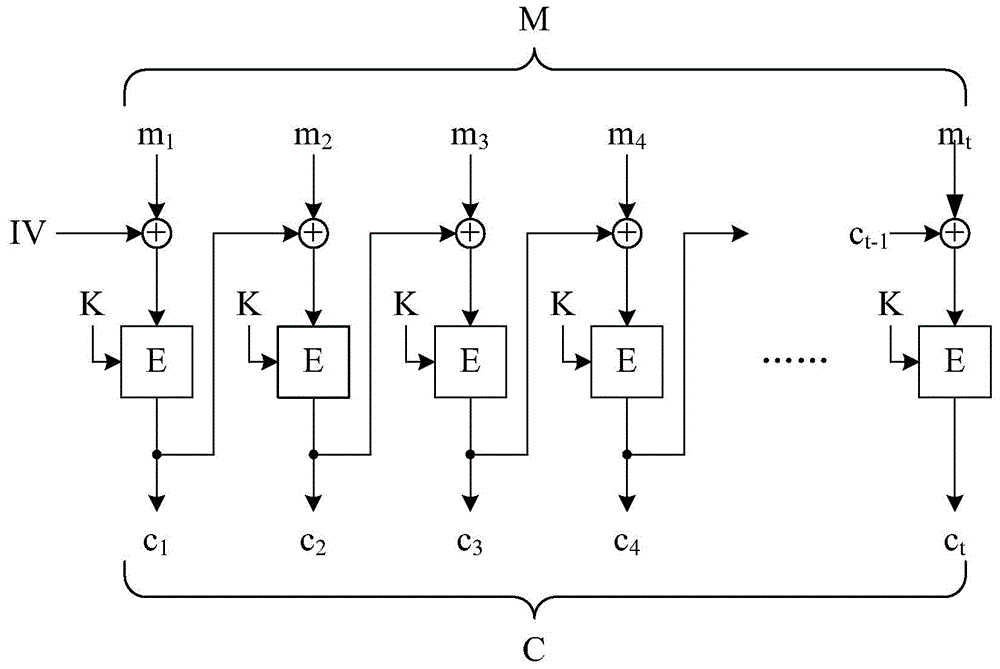
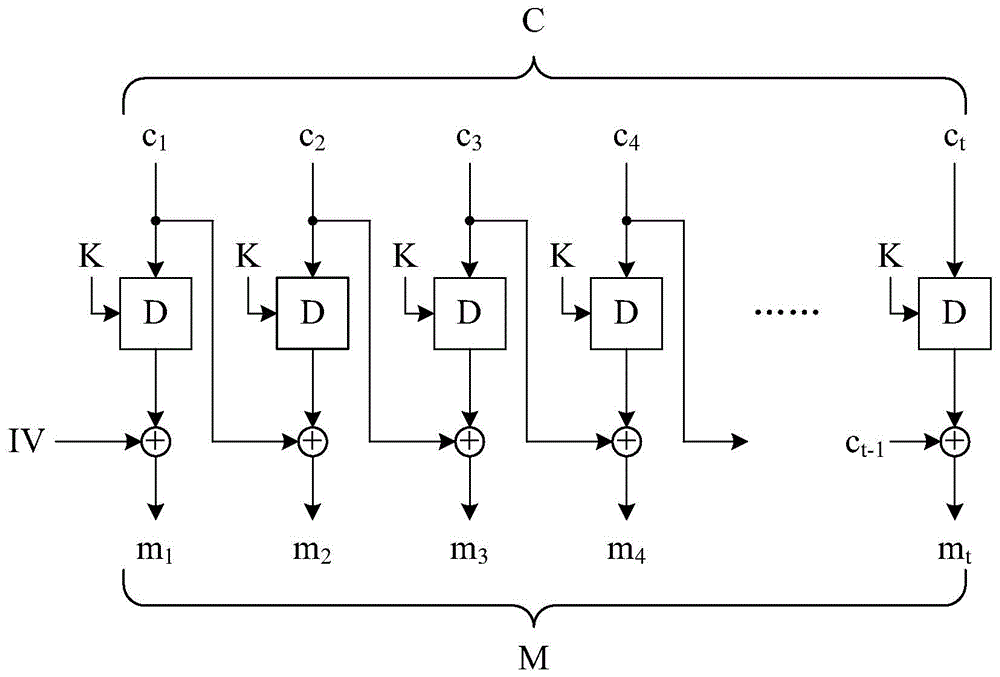
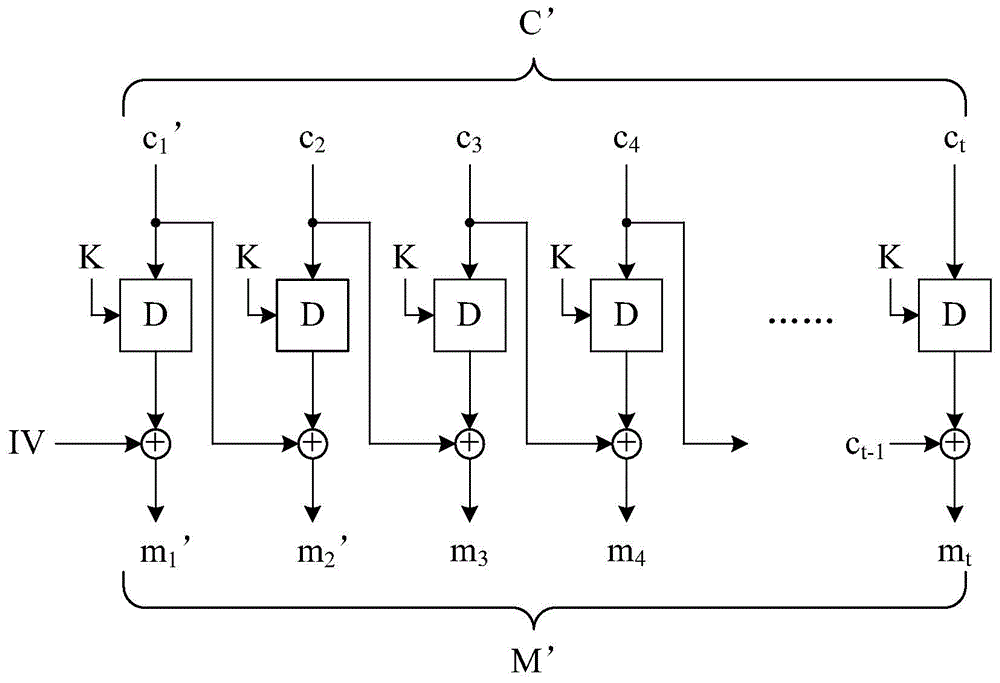
Block encryption device, block encryption method, block decryption device and block decryption method considering integrity verification
ActiveCN104683093ASatisfy IntegritySatisfy confidentialityEncryption apparatus with shift registers/memoriesUser identity/authority verificationComputer hardwareCiphertext
An encryption method and decryption method are provided. The encryption method divides an electronic file into a plurality of message blocks, wherein the message blocks have a sequence. The encryption method sets a checking vector as the last message block. The encryption method performs the following steps on each message block according to the sequence: generating an input block, deriving an output block by encrypting the input block by an encryption key, and deriving an encrypted block by applying XOR operation to the output block and the previous message block, wherein the input block is equivalent to applying XOR operation to the message block, the output block corresponding to the previous message block, and the message block before the previous one. The encryption method generates an electronic encrypted file by concatenating the encrypted blocks. The decryption method performs a series of operations corresponding to the above operations.
Owner:INSTITUTE FOR INFORMATION INDUSTRY
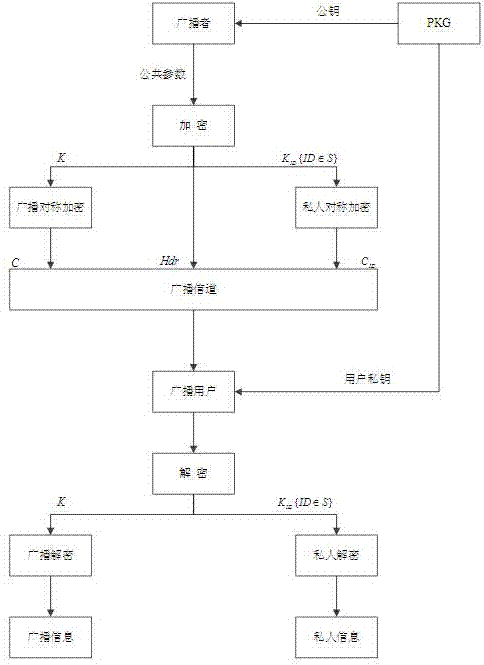
Broadcast encryption method capable of sending private information
InactiveCN107317675AReduce storage overheadImprove computing efficiencySpecial service provision for substationKey distribution for secure communicationChosen-plaintext attackBroadcast domain
The invention belongs to the technical field of the computer network secret communication, and specifically relates to a broadcast encryption method capable of sending private information. The method comprises the following steps: 1, setting a broadcast encryption system parameter, establishing a user set space, generating a public key and a main private key required by the broadcast system; 2, generating the private key for each use by a PKG and secretly sending the private key to the user; 3, encrypting the broadcasted information by using a symmetric encryption algorithm with key as K, and encrypting the communication information of the broadcaster and each user by using the symmetric encryption algorithm with the key as shown in description, and then broadcasting the generated ciphertext; and 4, after the user receives the ciphertext information, if the user belongs to the authorized user set, recovering the key K and the formula as shown in description by using the self private key and the broadcast ciphertext header Hdr, and respectively decrypting the corresponding encryption information to recover the plaintext information. By using the method disclosed by the invention, the confidentiality, the collusion attack resistance and the chosen plaintext attack security are satisfied at the same time; the method has the advantages of being low in expenditure and capable of sending the private information.
Owner:ENG UNIV OF THE CHINESE PEOPLES ARMED POLICE FORCE
Network safety verification method of distributed system
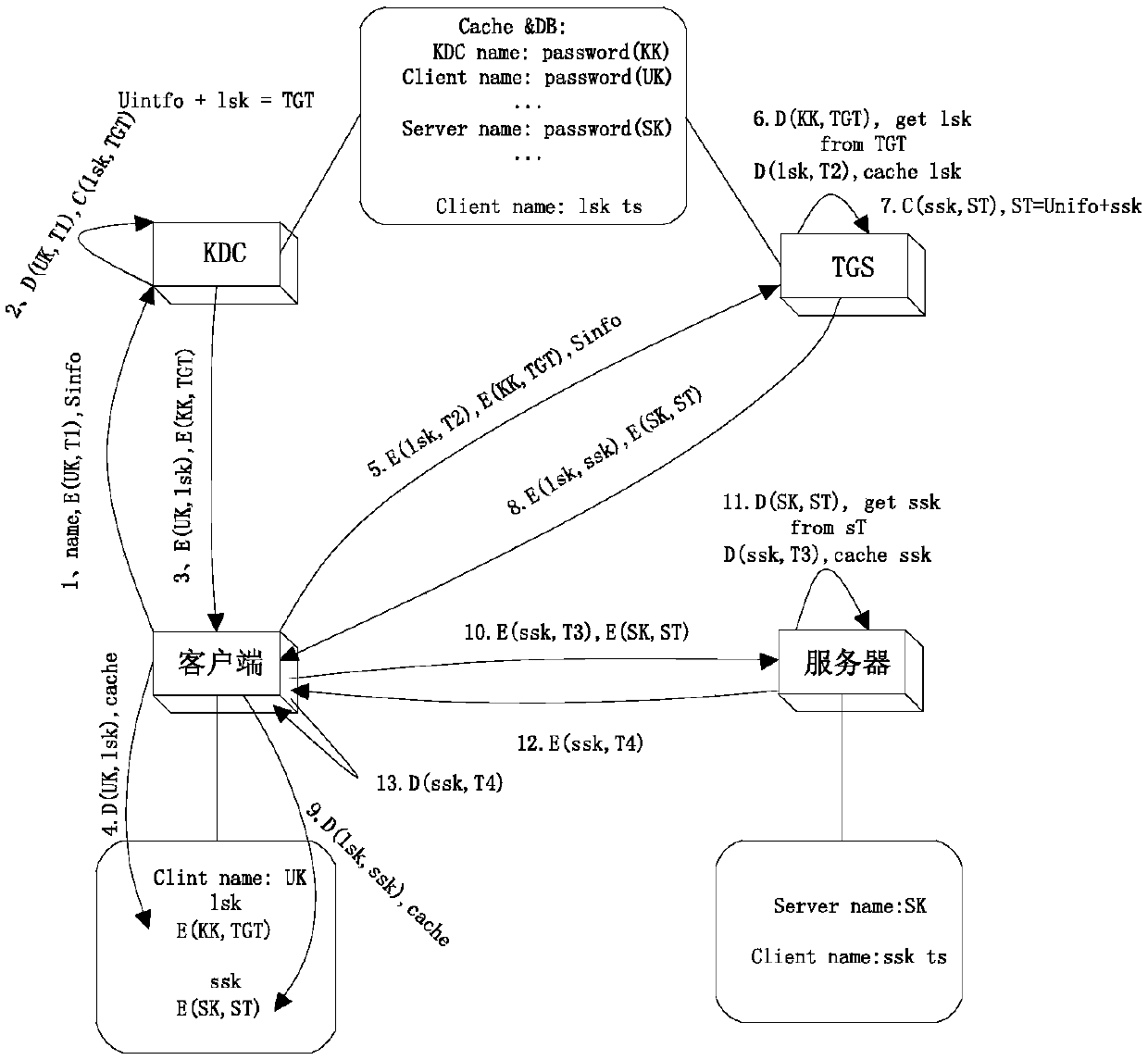
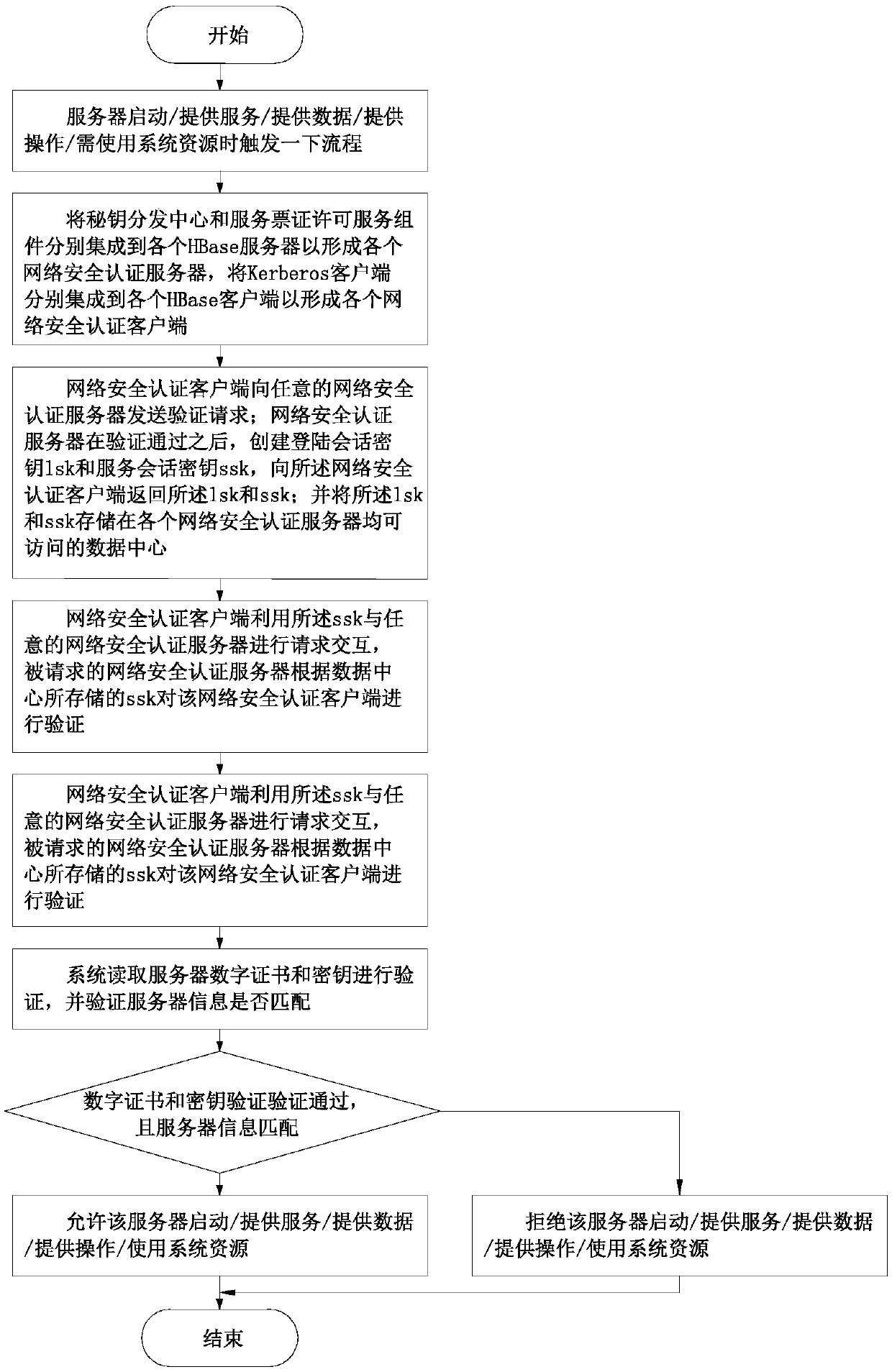
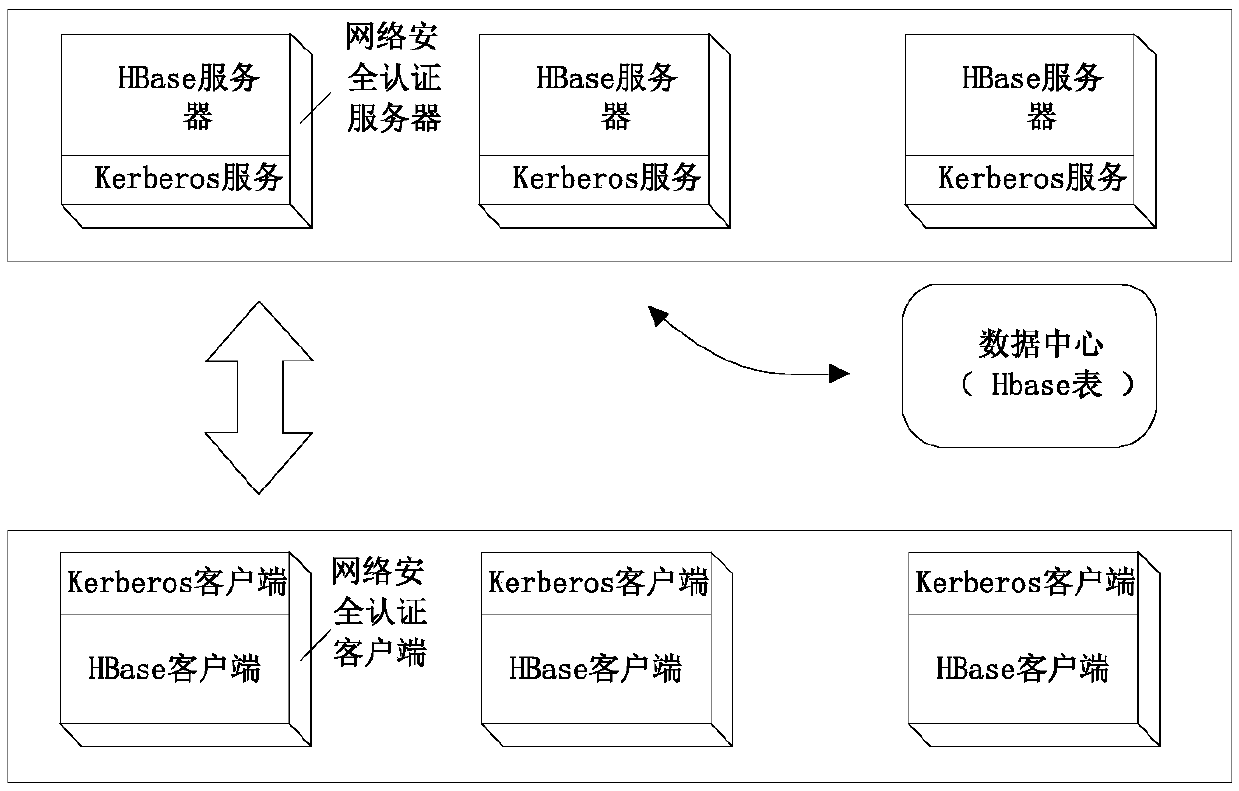
InactiveCN110620750AReduce the number of transfersEasy to expand and maintainKey distribution for secure communicationUser identity/authority verificationData centerAuthentication server
The invention discloses a network safety verification method of a distributed system. The method comprises the following steps: 1, when a server in the distributed network has a behavior, performing identity authentication on the server; respectively integrating a key distribution center KDC and a service ticket permission service component KDC-TGS to each HBase server to form each network safetyauthentication server, and respectively integrating a Kerberos client to each HBase client to form each network safety authentication client; the network safety authentication client performing request interaction with any network safety authentication server by utilizing the ssk, and the requested network safety authentication server verifies the network safety authentication client according tothe ssk stored in the data center; the digital certificate and the secret key of the server being bound with the server information, so that one server can only correspond to one fixed digital certificate and secret key, and the effectiveness and the integrity of server identity authentication are further ensured.
Owner:NINGDE NORMAL UNIV
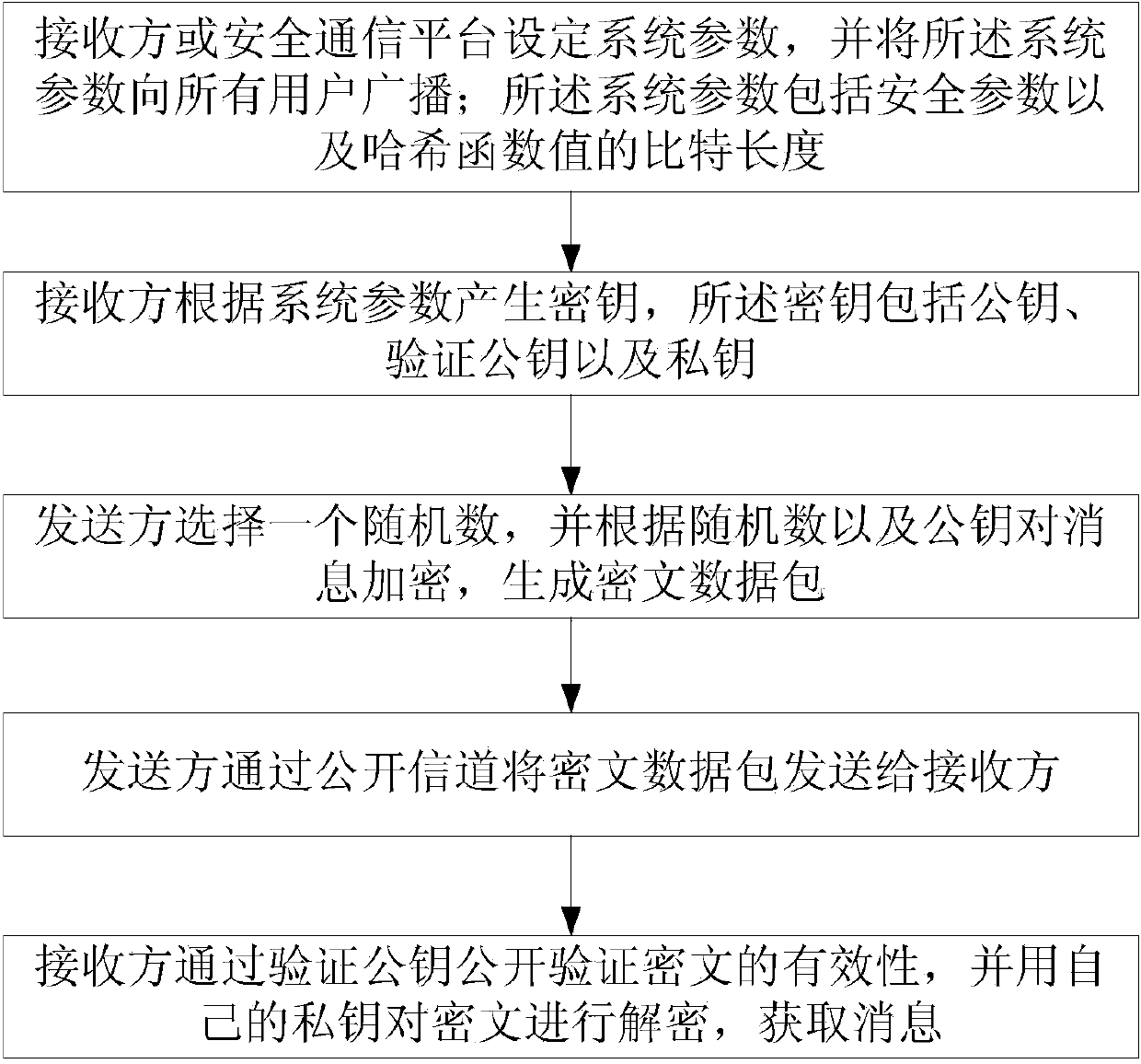
Method for encrypting public key in signed quadratic residue class group
InactiveCN104184581AMake it publicly verifiableSatisfy confidentialityPublic key for secure communicationNetwork packetConfidentiality
The invention discloses a method for encrypting a public key in a signed quadratic residue class group. The method comprises the steps of 1, setting system parameters; 2, generating a secret key; 3, selecting a random number by a sender, carrying out encryption on a message, and generating a ciphertext data packet; 4, sending the ciphertext data packet to a receiver by the sender through a public channel; and 5, verifying the effectiveness of the ciphertext after the receiver receives the ciphertext data packet, decrypting the ciphertext data packet by using a private key, and acquiring the message. The method disclosed by the invention satisfies the confidentiality, the integrity and the chosen-ciphertext attack security simultaneously, and realizes public verification of the ciphertext legitimacy; the method does not use bilinear pairings and one-time signatures which are time-consuming, so that defects of other public key encryption methods in which the ciphertext legitimacy is verified by using the bilinear pairings and the one-time signatures are overcome, thereby having higher computational efficiency and higher practical values.
Owner:ENG UNIV OF THE CHINESE PEOPLES ARMED POLICE FORCE
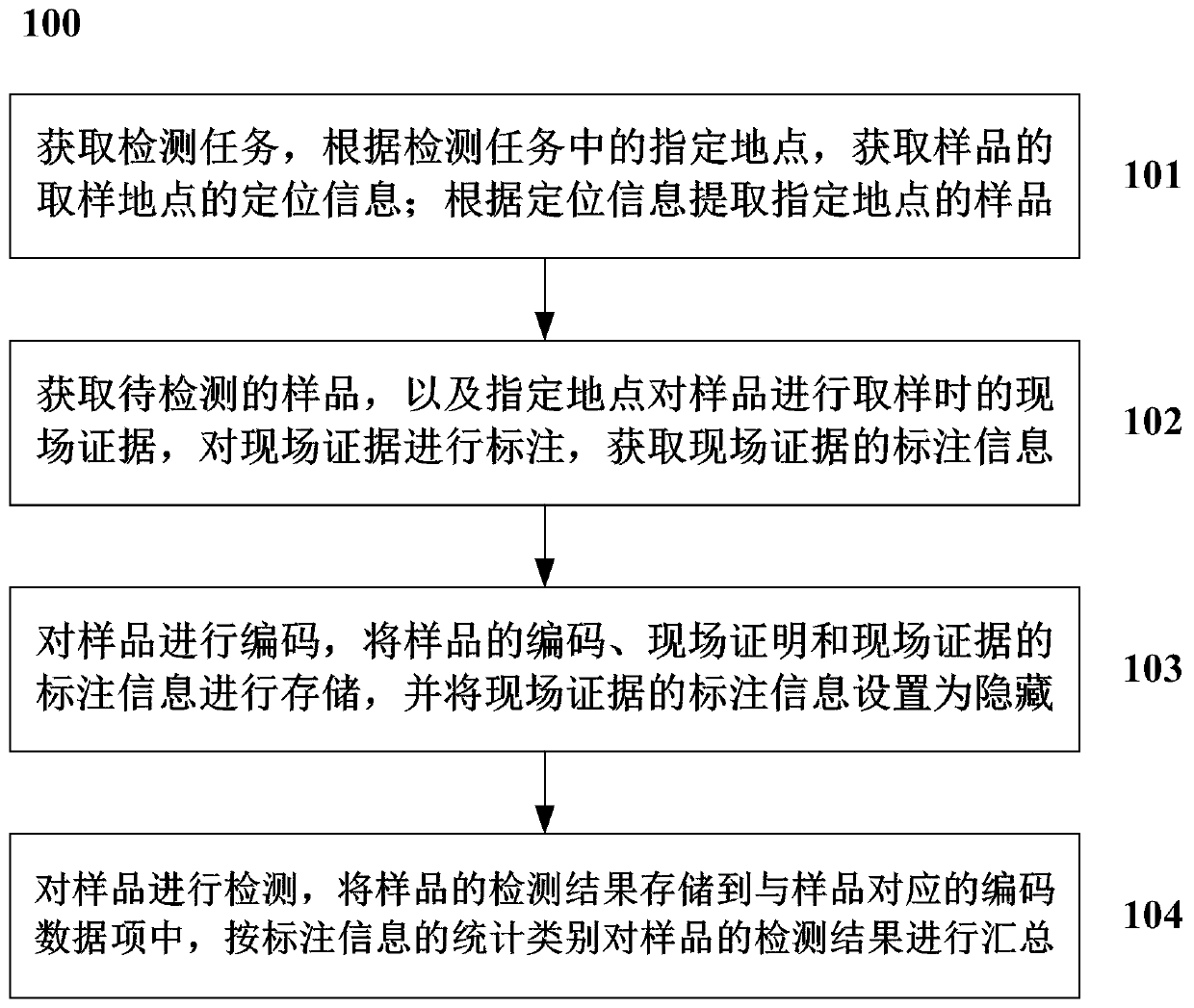
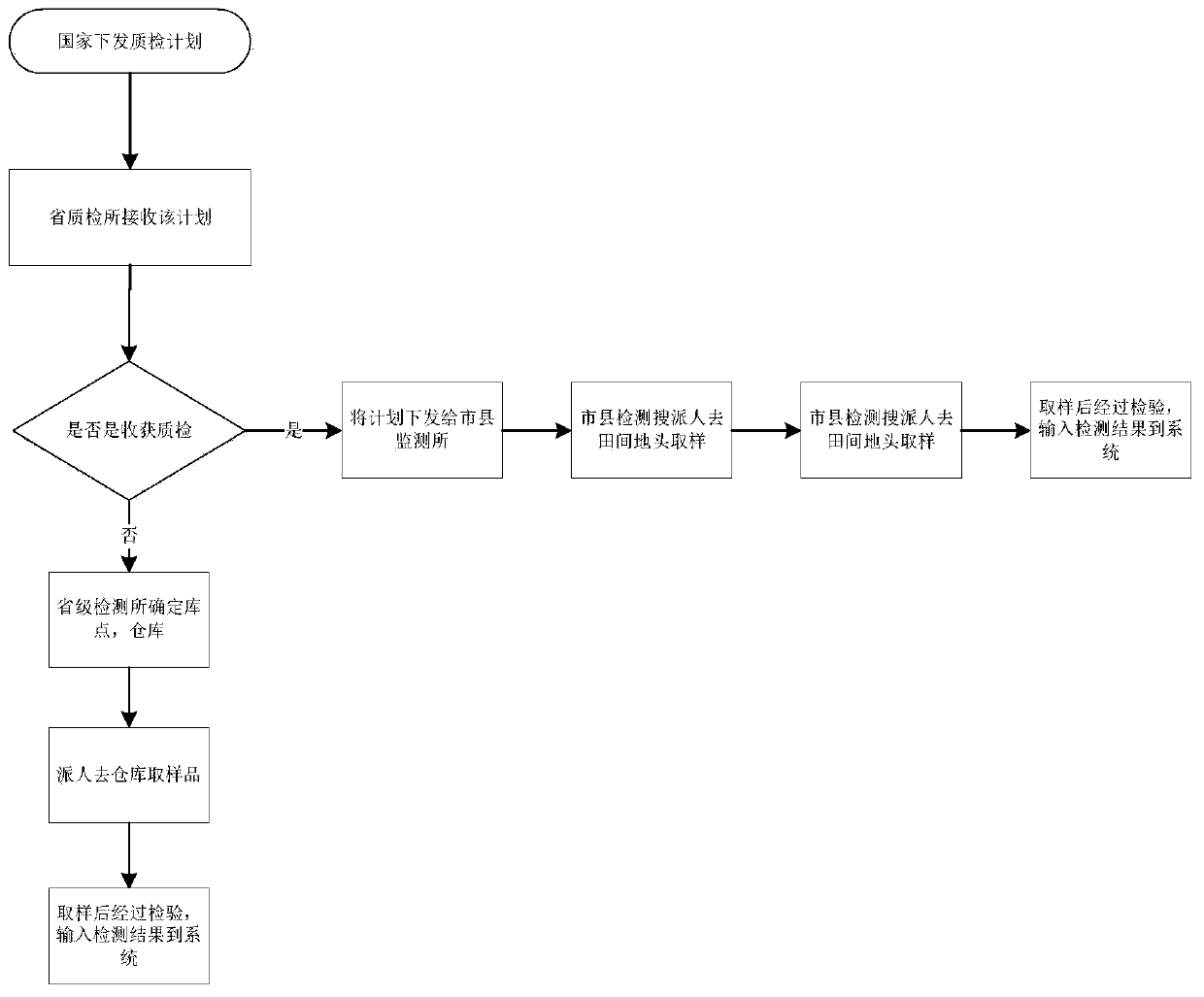
Method and system for detecting fixed-point sample
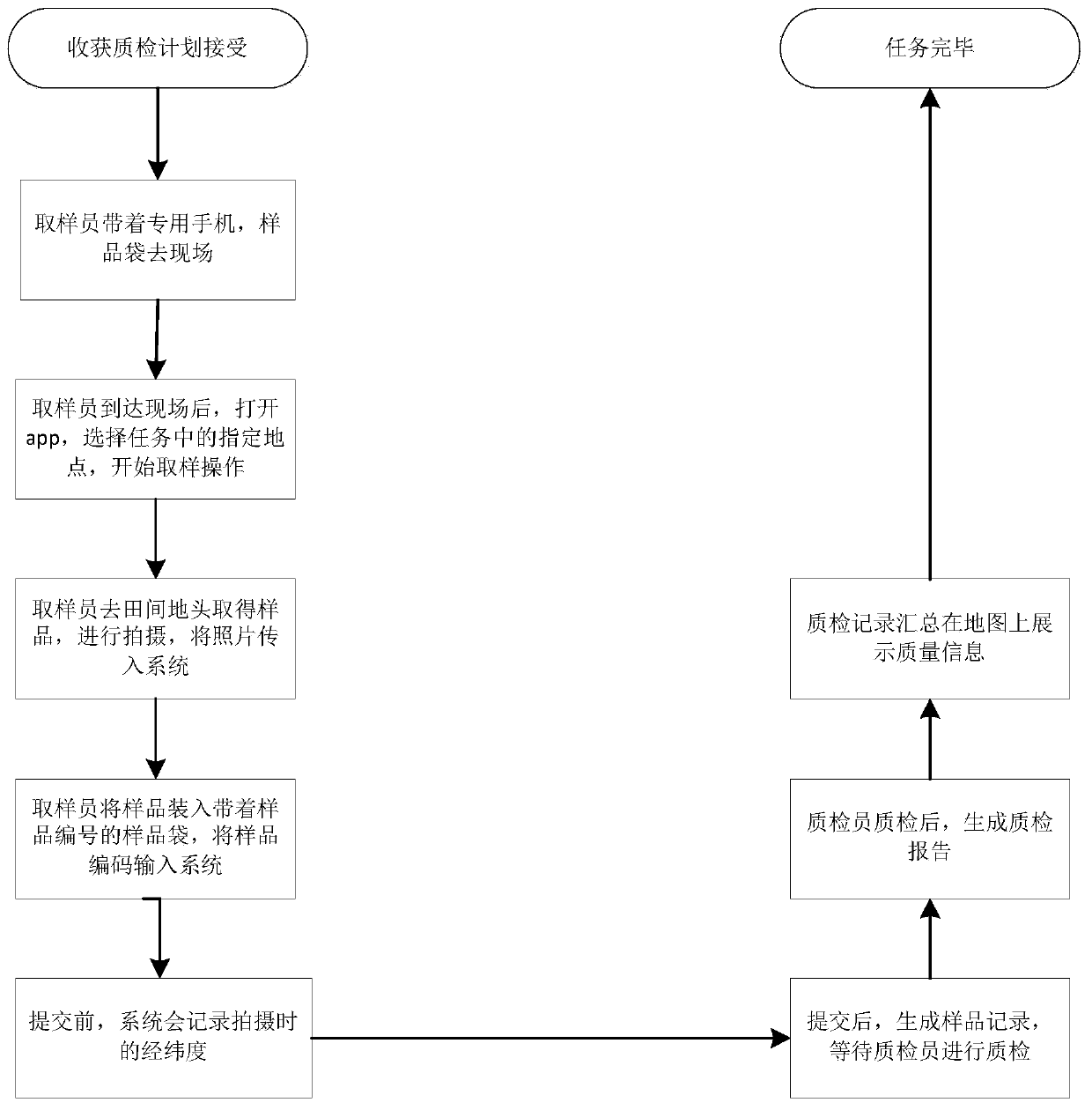
PendingCN111198249AReduce workloadSatisfy confidentialityWithdrawing sample devicesSatellite radio beaconingMedicineData mining
The invention discloses a method and system for detecting a fixed-point sample, and the method comprises the steps: obtaining a detection task, and obtaining the positioning information of a samplingplace of a sample according to a specified place in the detection task; extracting a sample of the designated place according to the positioning information; acquiring a to-be-detected sample and field evidences when the sample is sampled at the designated place, labeling the field evidences, and acquiring labeling information of the field evidences; encoding the sample, storing the code of the sample, the on-site evidence and the labeling information of the on-site evidence, and setting the labeling information of the on-site evidence to be in a hidden state; and detecting the sample, storingthe detection result of the sample into the coded data item corresponding to the sample, and summarizing the detection result of the sample according to the statistical category of the labeling information.
Owner:AEROSPACE INFORMATION
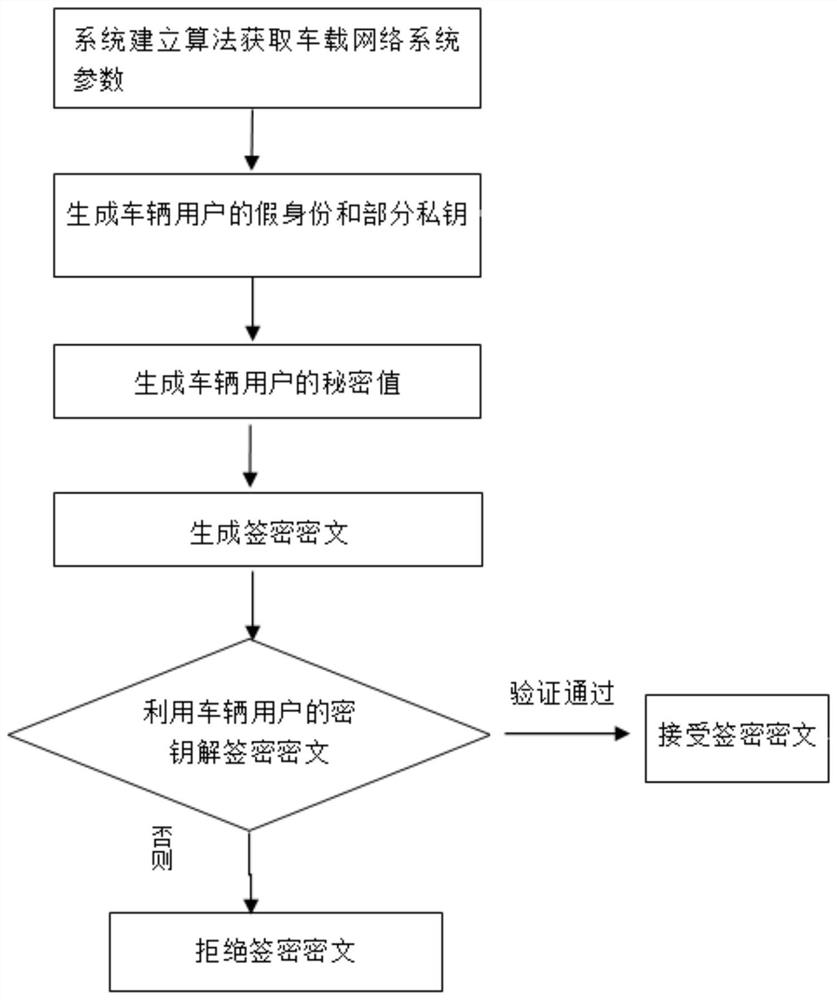
Certificateless signcryption algorithm suitable for VANETs
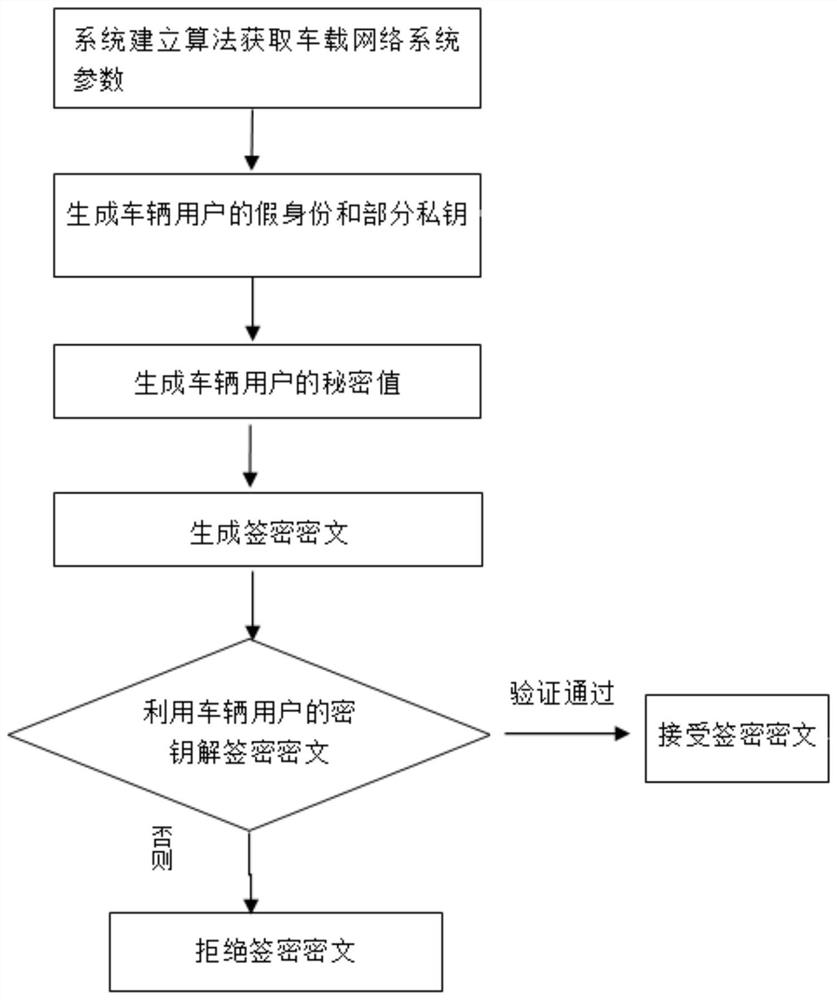
ActiveCN112565375AResistance to leak attacksImprove securityKey distribution for secure communicationPublic key for secure communicationAlgorithmCiphertext
The invention provides a certificateless signcryption method suitable for VANETs, and the method comprises the following steps: S1, obtaining vehicle-mounted network system parameters from a vehicle-mounted network system by employing a system building algorithm, and building a vehicle user IDi; adopting a false identity generation algorithm and a partial private key generation algorithm to generate a vehicle user false identity, the validity period of the false identity and a partial private key; generating a vehicle user secret value by adopting a vehicle user secret key generation algorithm; a vehicle user sender generating a user message, generating a signcryption ciphertext based on the partial private key, the user public key and the secret value, and sending the signcryption ciphertext to a vehicle user receiver; and decrypting the signcryption ciphertext through a verification equation to obtain a decrypted user message, and finally judging whether the decryption is valid or not. The method is an efficient and safe certificateless signcryption algorithm, confidentiality, authentication, integrity, non-repudiation and privacy protection can be provided for information transmitted between vehicle communication units, and safety guarantee is provided for vehicle-mounted self-organizing network safety communication.
Owner:BAOJI UNIV OF ARTS & SCI
Sensor device for electric power measurement and control method
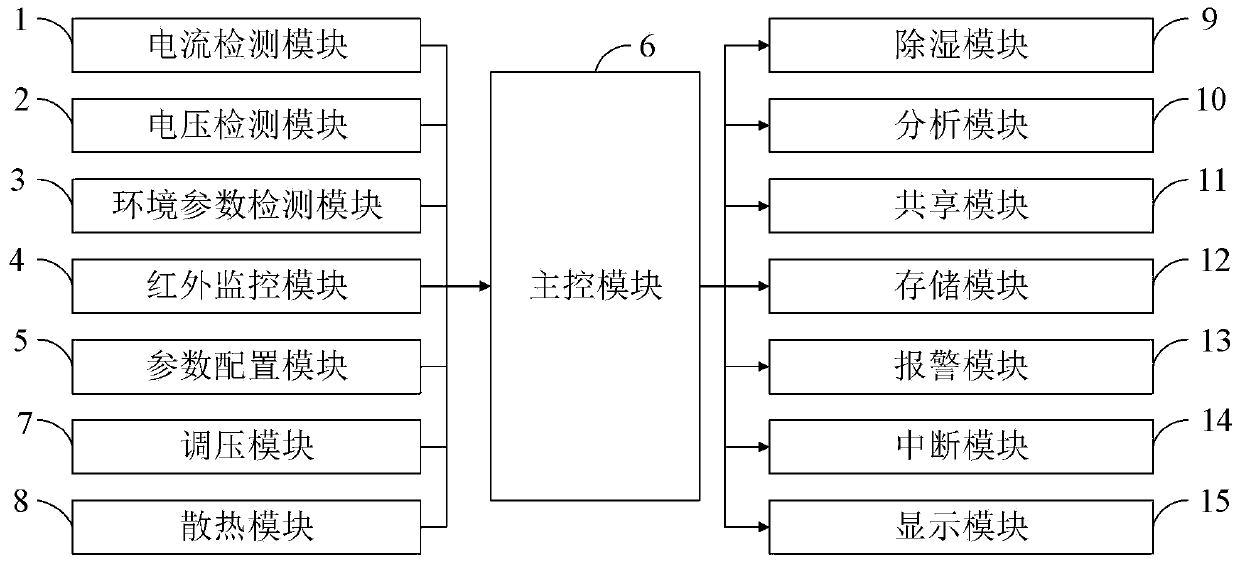
InactiveCN111044100AReal-time monitoring of environmental dataAvoid exceptionProgramme controlMeasurement devicesEngineeringElectric power
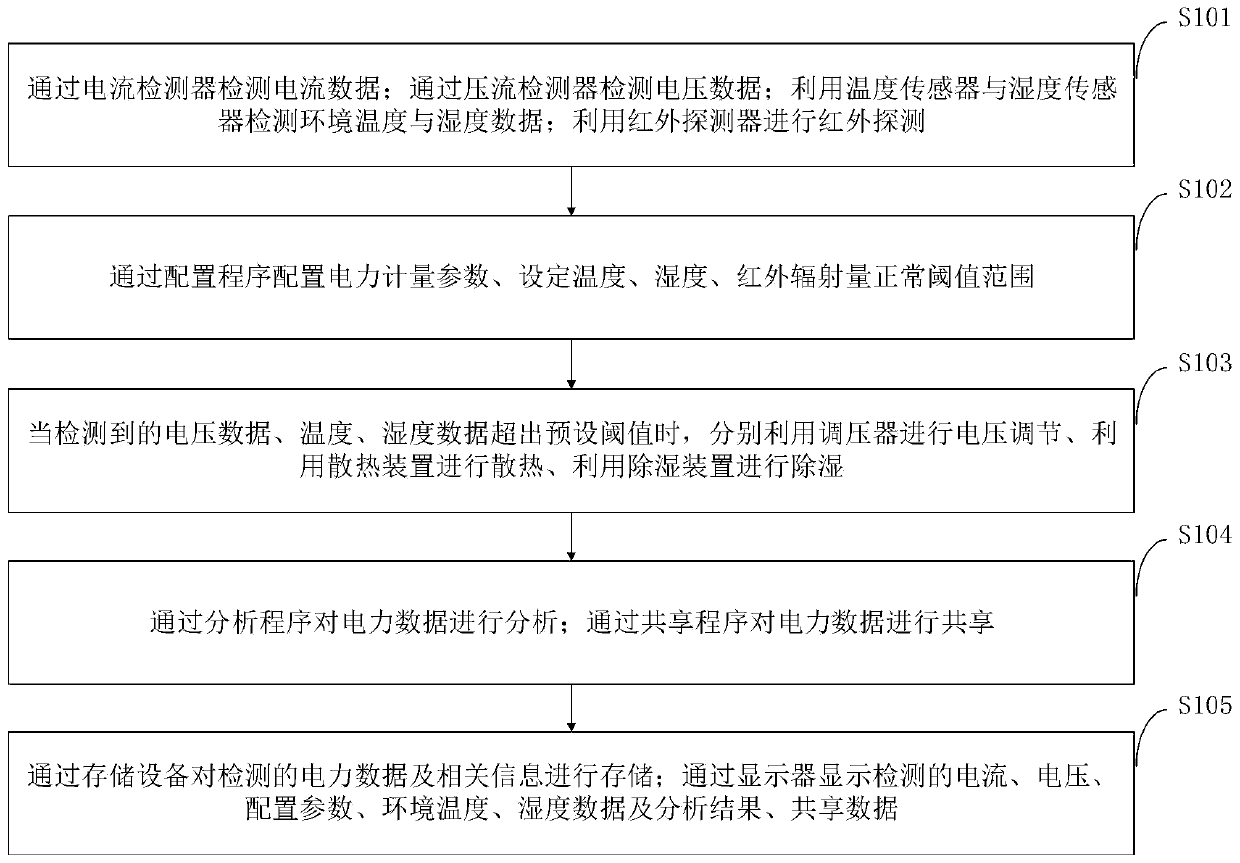
The invention belongs to the technical field of electric power measurement, and discloses a sensor device for electric power measurement and a control method. The control method comprises the steps of: detecting current and voltage data by means of current and voltage detectors; detecting temperature and humidity data by means of temperature and humidity sensors; performing infrared detection by using an infrared detector; setting electric power metering parameters, and setting normal threshold ranges of temperature, humidity and infrared radiation quantity; when the temperature, humidity andinfrared radiation quantity exceeds preset threshold values, performing corresponding adjustment by means of a pressure regulator, a heat dissipation device and a dehumidification device; analyzing power data by using an analysis program; and sharing the power data by means of a sharing program. The sensor device can monitor environmental data of the device in real time, avoids abnormality of thedevice caused by over-high temperature and humidity, can automatically adjust the environmental temperature and humidity data to ensure stable operation of the device, and can automatically alarm andinterrupt when encountering abnormality, and guarantees the operation safety of the device.
Owner:STATE GRID SHANDONG ELECTRIC POWER CO TAOXIAN POWER SUPPLY CO
Cave depot doorsill-free protection airtight door
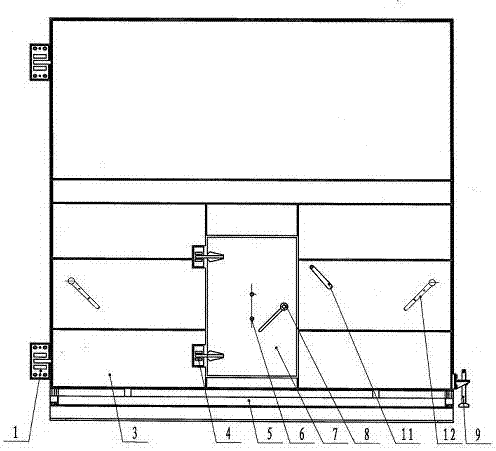
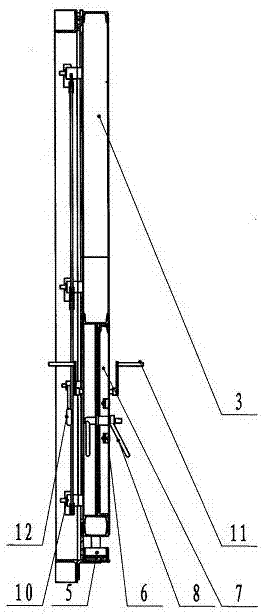
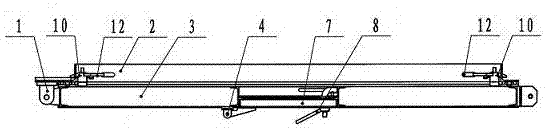
InactiveCN106948730AA wide variety of solutionsSolve space problemsServing doorsWing arrangementsReinforced concreteConfidentiality
The invention relates to a non-threshold protective airtight door of a cavern, which is characterized in that: a sealing beam operating handle and a door locking operating handle are arranged on the large door leaf, the door hinges and ground locks are respectively arranged on both sides of the large door leaf, and the small door leaf It is arranged at the lower part of the large door leaf, and the small door leaf is equipped with a key lock device and a small door lock; the large door leaf is provided with a sealing beam operating handle and a small door hinge, and the left side of the large leaf is provided with a large door hinge. There are door lock operation handles and door locks on both sides of the back, and a sealing beam device is installed at the bottom of the door leaf, and the door frame is pre-buried in the reinforced concrete wall. The present invention is a multi-functional protective airtight door integrating protective airtightness and two built-in locks. It adopts double doors and double locks. The two locks are opened by two different keys respectively, and the door can be opened. confidentiality. It solves the problems of various types of military material cavern doors, large space occupation, large number of doors, cumbersome opening and high cost.
Owner:ANSHAN HONGTUO MACHINERY MFG
Block encryption device, block encryption method, block decryption device, and block decryption method capable of integrity verification
ActiveCN104683093BSatisfy IntegritySatisfy confidentialityEncryption apparatus with shift registers/memoriesUser identity/authority verificationComputer hardwareCiphertext
The invention provides a block encryption device, a block encryption method, a block decryption device and a block decryption method with integrity verification. The encryption device divides an electronic file into several message blocks, and the message blocks have a sequence. The encryption device uses a check vector as the last of the message blocks. The encryption device performs the following operations on each of the message blocks in this order: generate an input block, encrypt the input block into an output block with a key, and compare the output block with the previous message block An XOR operation is performed to obtain a ciphertext block, and the value of the input block is equal to the value after XOR operation of the message block, the output block corresponding to the previous message block, and the previous message block. The encryption device concatenates the ciphertext blocks in sequence to generate an electronic ciphertext. The decryption device operates correspondingly to the encryption device.
Owner:INSTITUTE FOR INFORMATION INDUSTRY
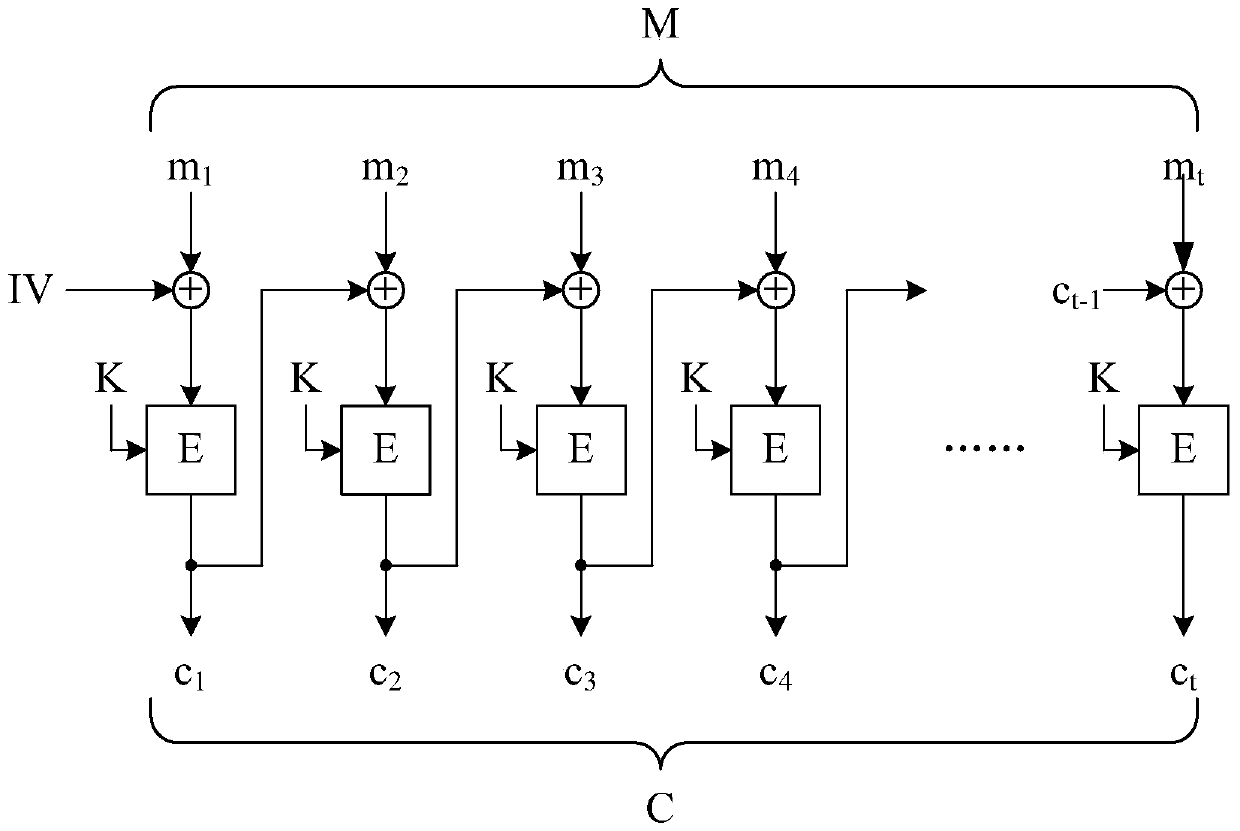
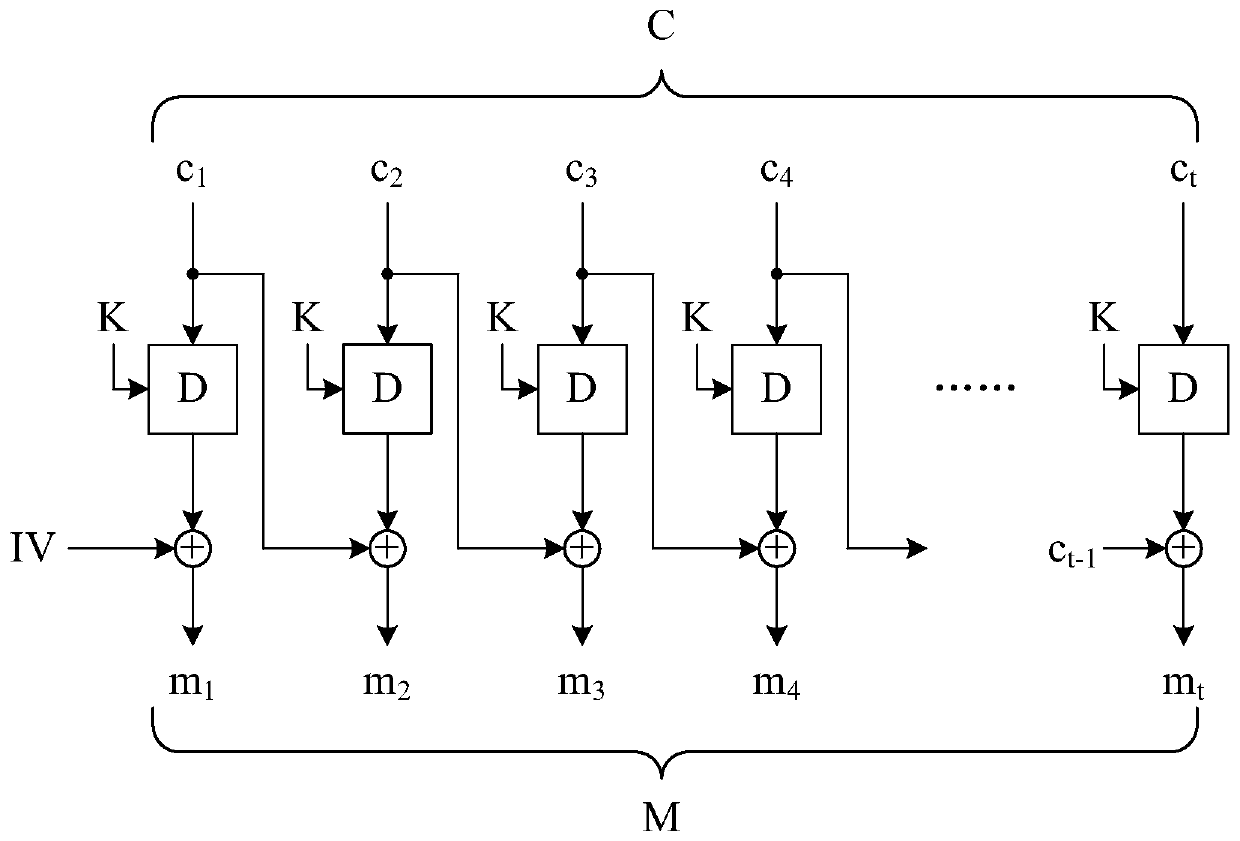
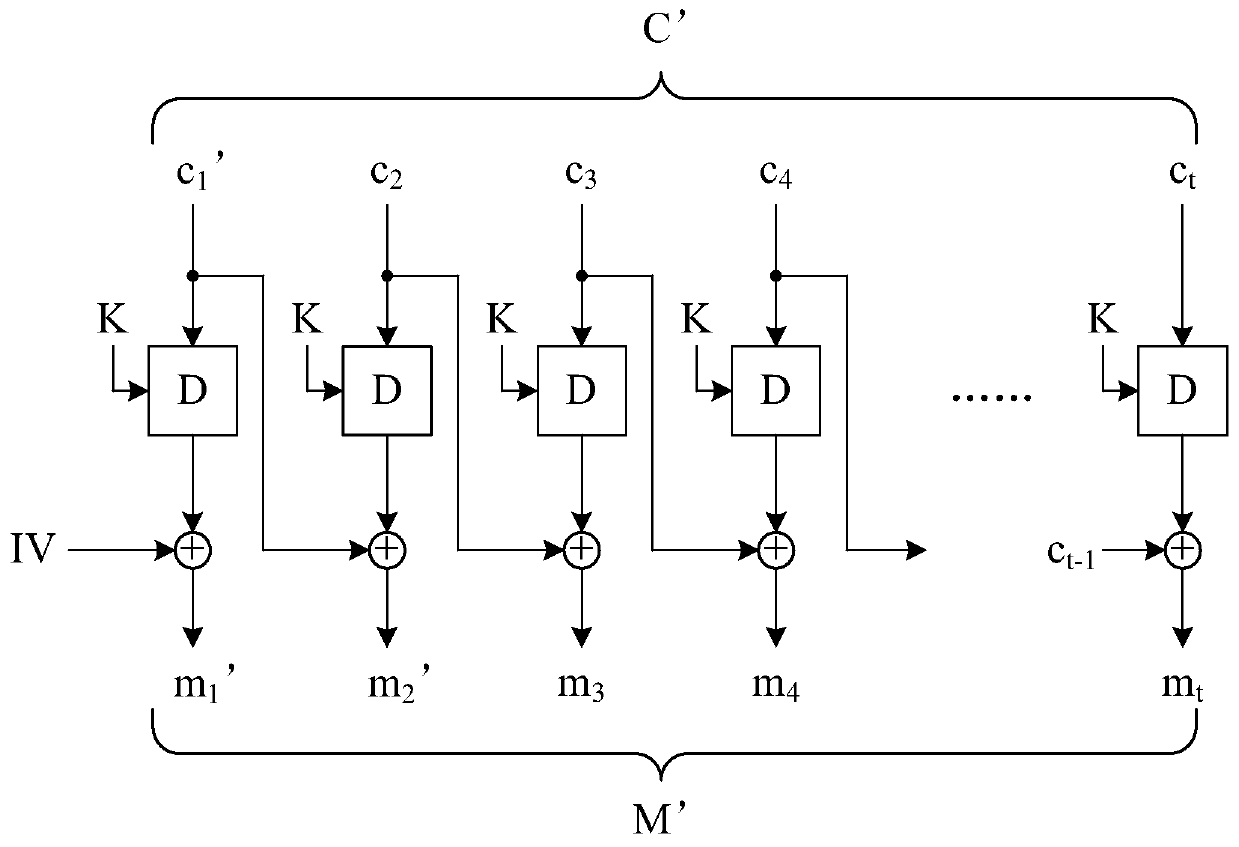
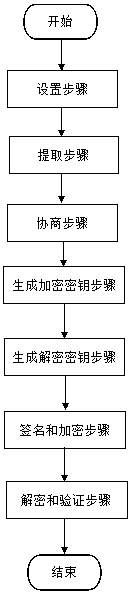
Sender Authenticated Asymmetric Group Key Agreement Method
ActiveCN106357397BSatisfy confidentialitySatisfy forward securityKey distribution for secure communicationConfidentialityGroup key
The invention discloses a sender-authenticated asymmetric group key negotiation method, which comprises the following steps: a setting step, an extracting step, a negotiation step, an encryption key generating step, a decryption key generating step, a signature and encryption step, and a decryption and verification step. The method provided by the invention has the following characteristics of satisfying the confidentiality of messages, the forward security, the sender authenticity and privacy, and the sender dynamism; the calculation cost is reduced because the general transformation is not used.
Owner:EAST CHINA NORMAL UNIV
A Certificateless Signcryption Algorithm Suitable for Vanets
ActiveCN112565375BResistance to leak attacksImprove securityKey distribution for secure communicationPublic key for secure communicationAlgorithmCiphertext
The present invention proposes a certificateless signcryption method suitable for VANETs, comprising the following steps: S1, adopting a system establishment algorithm to obtain vehicle network system parameters from the vehicle network system, and establishing a vehicle user ID i ;Use the fake identity generation algorithm and partial private key generation algorithm to generate the vehicle user fake identity, the validity period of the fake identity and part of the private key; use the vehicle user key generation algorithm to generate the vehicle user secret value; the vehicle user sender generates the user message, Based on the partial private key, user public key and secret value, a signcrypted ciphertext is generated and sent to the vehicle user receiver; the signcrypted ciphertext is decrypted by the verification equation to obtain the decrypted user message, and finally it is judged whether the decryption is valid. The invention is an efficient and safe certificateless signcryption algorithm, which can provide confidentiality, authentication, integrity, non-repudiation and privacy protection for information transmitted between vehicle communication units, and provide security guarantee for vehicle self-organizing network security communication .
Owner:BAOJI UNIV OF ARTS & SCI
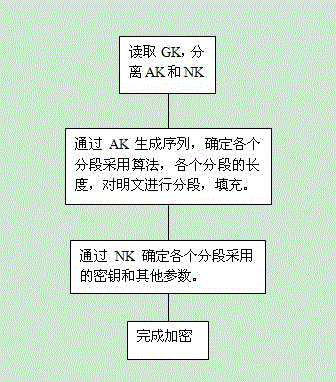
A Fractional Encryption Method Using Uncertain Encryption Algorithm
ActiveCN102404111BImprove securityIncrease uncertaintyMultiple keys/algorithms usageAlgorithmTheoretical computer science
The invention belongs to a new type of encryption method, and relates to a segmented encryption method using an uncertain encryption algorithm, which encrypts plaintext in segments, and the algorithm used in each segment encryption is uncertain and confidential, and is defined by a generalized key to make sure. It determines the length of each segment, the encryption algorithm of the segment, and various keys and parameters through the generalized key. Due to the uncertain algorithm, it is impossible for the cryptanalyst to decipher it. Even if some information is obtained, it is difficult to crack other segments. It doesn't make sense either.
Owner:GUILIN UNIV OF ELECTRONIC TECH
A cloud computing data security boundary protection method
InactiveCN103618703BSatisfy confidentialityConvenient verificationUser identity/authority verificationFault toleranceSurvivability
Owner:ENG UNIV OF THE CHINESE PEOPLES ARMED POLICE FORCE
Industrial Internet distributed system safety access control device
ActiveCN102487383BGuaranteed legalityPrevent theftUser identity/authority verificationThe InternetIndustrial Internet
The invention discloses an industrial Internet distributed system safety access control device. The device integrates a module which is used to carry out authentication and authorization to identities and access operations of a user and a server, the module which is used to audit the access operations of the user and the server and the module which is used to carry out uniform resource positioning to object resources accessed by the user and the server. Identity security and authority validity of the user or the server which access to the industrial Internet distributed system and acquire information / service can be effectively ensured. In addition, the user and the server in the industrial Internet do not need to know an actual storage position of the needed object resources. Through a uniform resource positioning platform of the distributed system, the corresponding server can be positioned and the needed object resources can be acquired. A demand in a distributed environment can be rapidly and conveniently satisfied.
Owner:ASAT CHINA TECH +1
A secure routing method for wireless sensor networks based on IPv6 addressing
ActiveCN104811934BSatisfy confidentialityMeet authenticityTransmissionSecurity arrangementRouting tableIp address
The invention discloses a wireless sensor network security routing method based on IPv6 addressing, aiming at the actual demand for safe transmission of data in the wireless sensor network, it proposes network IP addressing based on a tree topology and nodes joining and leaving the network The rules save a lot of storage space for IP addresses and routing tables, and improve the efficiency of time and space utilization; at the same time, a message security routing and transmission strategy based on unicast and multicast is designed, in which encryption and decryption, hash operations and timestamp The combination of features can enable the network to resist attacks such as replay and capture.
Owner:张北数据港信息科技有限公司
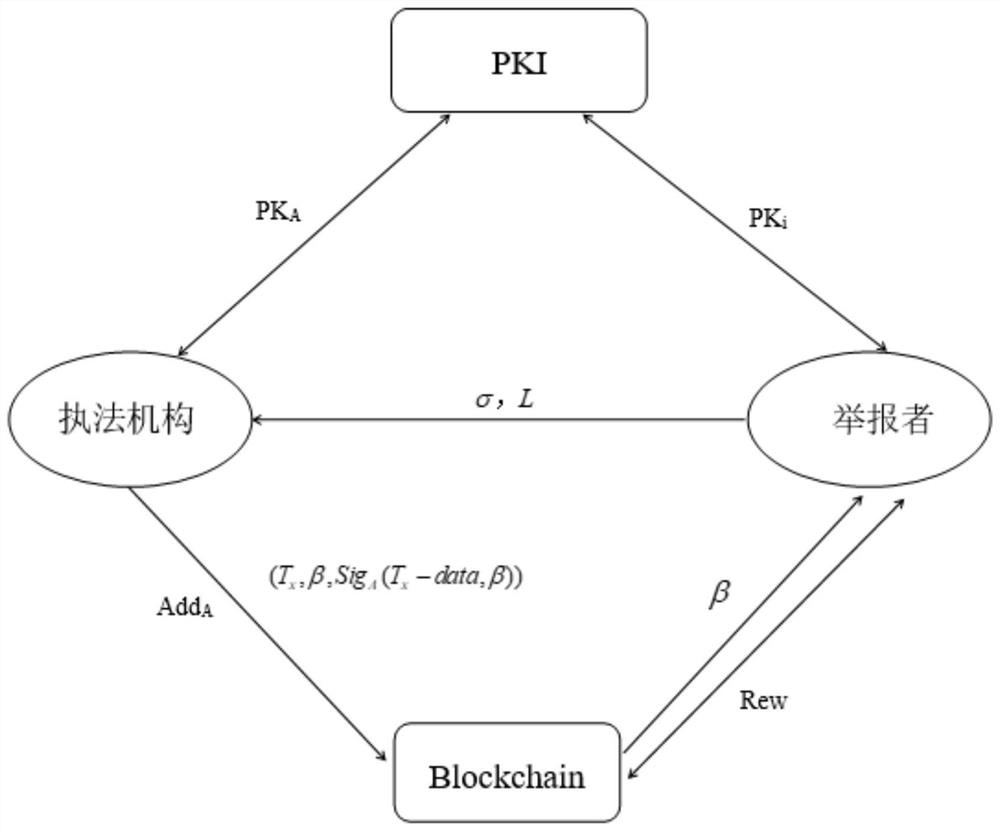
Anonymous reporting method based on block chain technology
InactiveCN114448675AImprove computing efficiencyMeet identity anonymityPublic key for secure communicationMarketingInformation transmissionCiphertext
The invention discloses an anonymous reporting method based on a block chain technology, and the method comprises the steps: generating public keys and private keys of all reporters and a law enforcement agency, and generating a block chain public key address and a corresponding private key of the law enforcement agency; processing the reporting information of the reporter based on a ring signcryption algorithm, generating a signcryption ciphertext, and sending the signcryption ciphertext to a law enforcement agency; the law enforcement agency carries out resolving after receiving the signcryption ciphertext, obtains and verifies the report information, and receives the report information if the verification is passed; and if the report information is valid, the law enforcement agency transfers the bonus to the public key address of the reporter on the block chain based on an anonymous reward algorithm, and the reporter obtains the bonus based on the private key. According to the method, confidentiality, non-repudiation and privacy protection of the identity of a reporter are provided for reporting information transmission, enough safety service is provided for the reporter, and crimes are safely reported.
Owner:BAOJI UNIV OF ARTS & SCI
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com