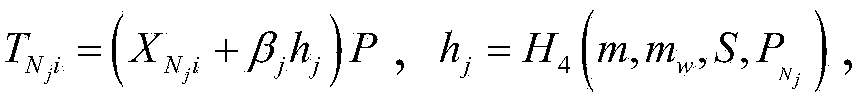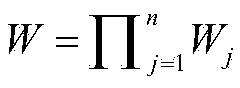Certificateless multi-proxy signcryption method with forward secrecy
A forward security, certificateless technology, applied in the forward security certificateless multi-agent signcryption field, can solve the problems of not taking into account the loss of the private key and the agent key, and the security cannot be guaranteed, reducing the The effect of system overhead
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
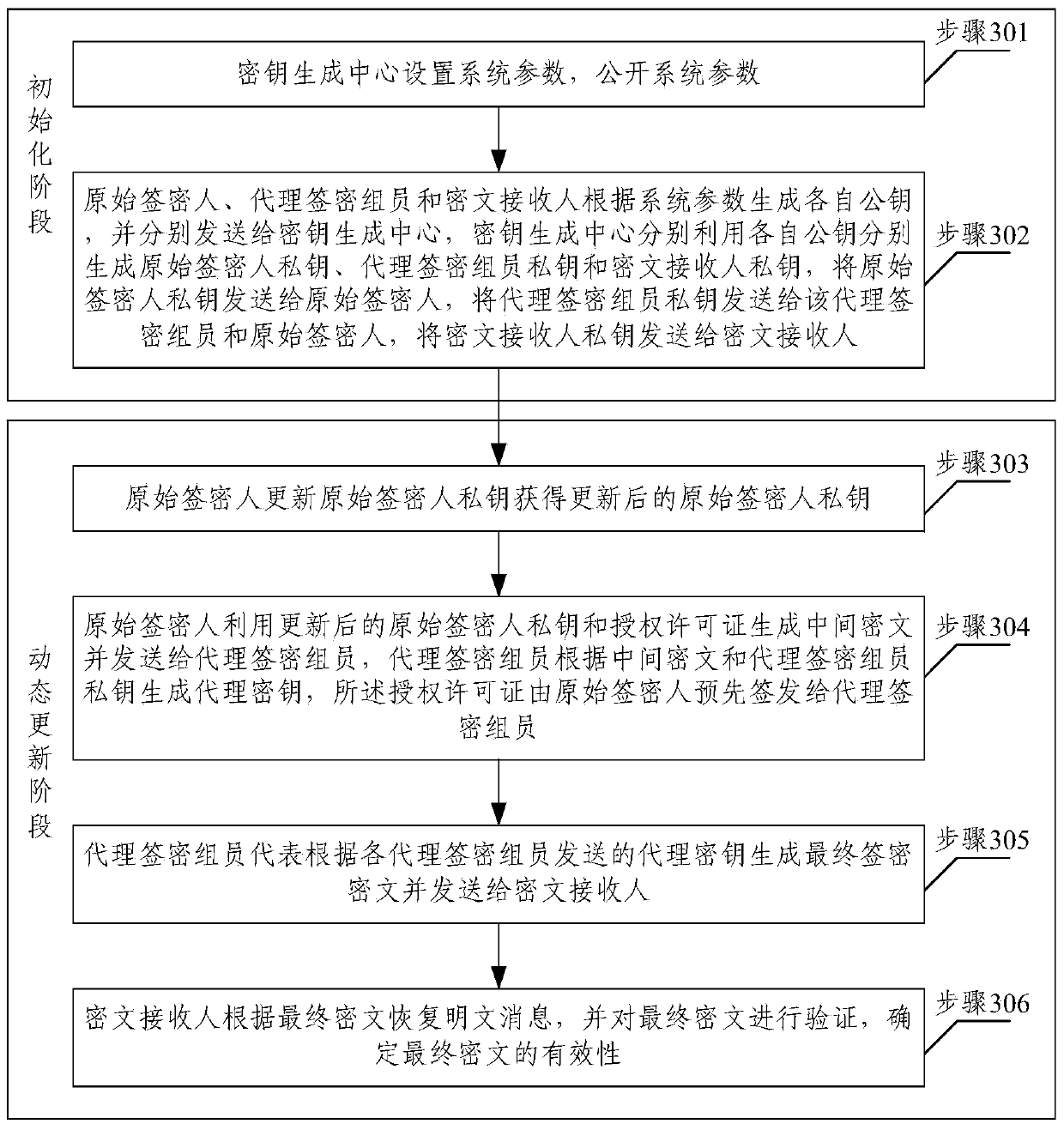
[0018] In order to make the purpose, technical solution and advantages of the present invention more clear, the present invention will be further described in detail below in conjunction with the accompanying drawings and embodiments.
[0019] For ease of understanding, relevant parameters or representation symbols of the present invention are described:
[0020] m and c indicate text message and ciphertext respectively; H, H 1 ,H 2 ,H 3 ,H 4 respectively refer to five different safe monomial functions; H t (a,b), 1≤t≤4 means: the function operation of this single item contains elements a, b; H t (a□b), 1≤t≤4 means: this single hash function operation includes the result of the connection operation of elements a and b. point to Z q The set of all modular multiplication invertible elements in , Z q Refers to the residual class ring, q is any prime number; {0,1} n Refers to the collection of all strings of length n bits composed of 0 and 1; {0,1} * Refers to the set of...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com