Patents
Literature
2622 results about "Hash function" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
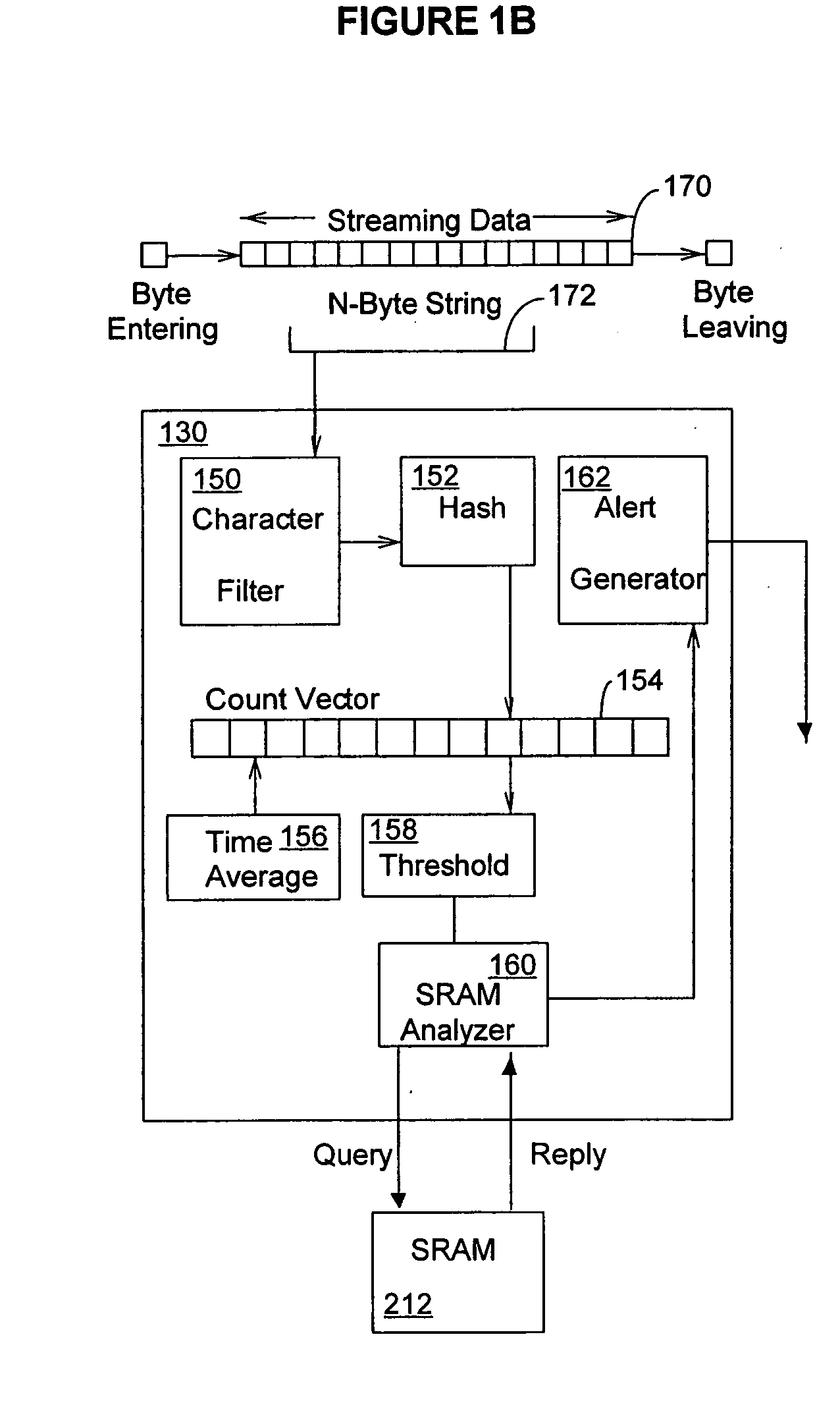
A hash function is any function that can be used to map data of arbitrary size to fixed-size values. The values returned by a hash function are called hash values, hash codes, digests, or simply hashes. The values are used to index a fixed-size table called a hash table. Use of a hash function to index a hash table is called hashing or scatter storage addressing.
Peer-to-Peer Redundant File Server System and Methods
InactiveUS20090271412A1Digital data information retrievalMultiple digital computer combinationsHash functionFile system
Peer-to-peer redundant file server system and methods include clients that determine a target storage provider to contact for a particular storage transaction based on a pathname provided by the filesystem and a predetermined scheme such as a hash function applied to a portion of the pathname. Servers use the same scheme to determine where to store relevant file information so that the clients can locate the file information. The target storage provider may store the file itself and / or may store metadata that identifies one or more other storage providers where the file is stored. A file may be replicated in multiple storage providers, and the metadata may include a list of storage providers from which the clients can select (e.g., randomly) in order to access the file.
Owner:OVERLAND STORAGE
Identifying and requesting data in network using identifiers which are based on contents of data
InactiveUS6415280B1Improve efficiencyImprove integrityData processing applicationsDigital data processing detailsHash functionData content
In a system in which a set of data items are distributed across a network of servers, at least some of the data items being cached versions of data items from a source server, a content delivery method includes determining a data identifier for a particular data item, the data identifier being determined using a given function of the data comprising the particular data item; and responsive to a request for the particular data item, the request including at least the data identifier of the particular data item, providing the particular data item from a given one of the servers of the network of servers. The request for the particular data item may be resolved based on a measure of availability of at least one of the servers, where the measure of availability may be a measurement of bandwidth to the server; a measurement of a cost of a connection to the server, and / or a measurement of a reliability of a connection to the server. The function used to determine the identifier may be a message digest function or a hash function.
Owner:LEVEL 3 COMM LLC +1
Internet database system
InactiveUS6523036B1Data processing applicationsDigital data processing detailsApplication serverHash function
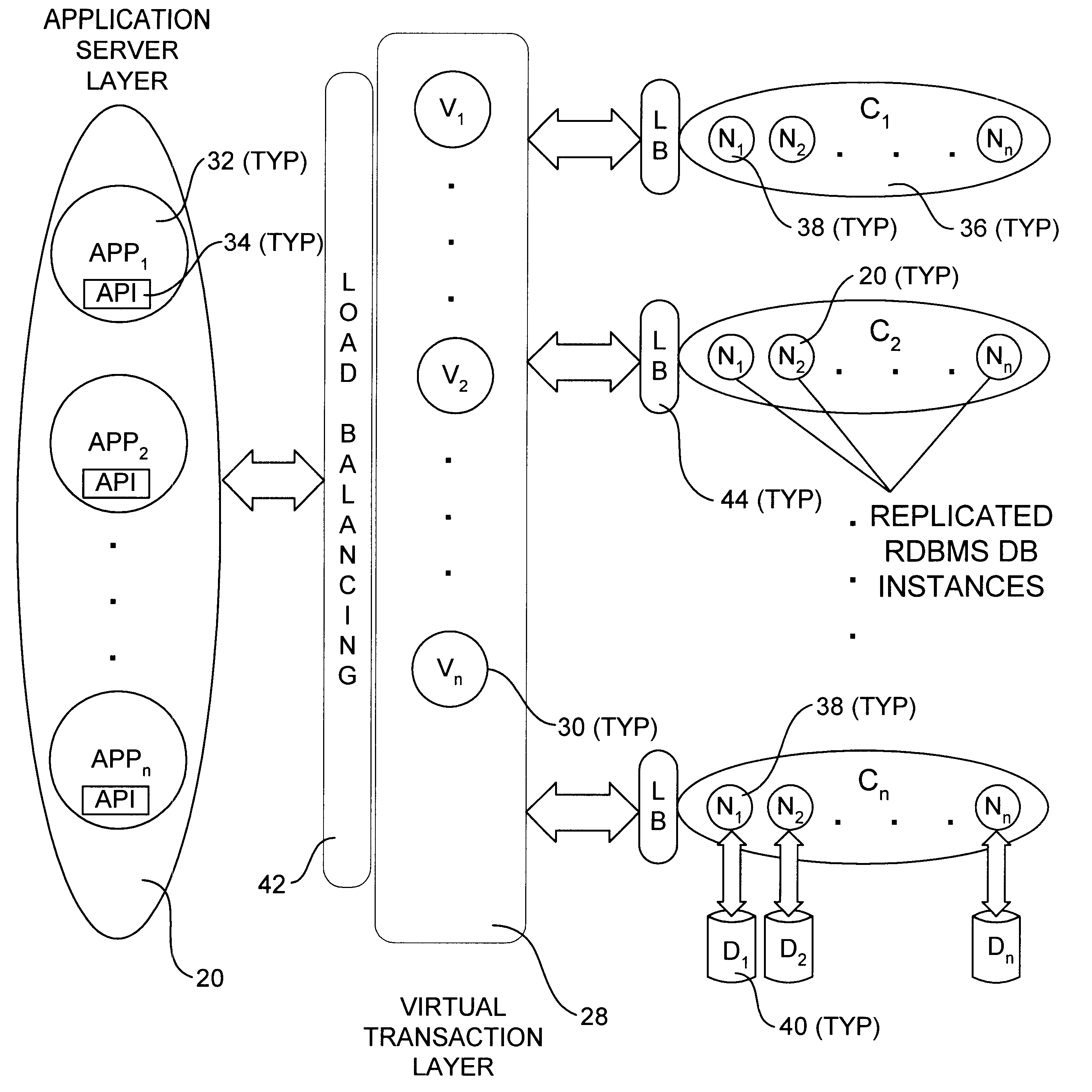
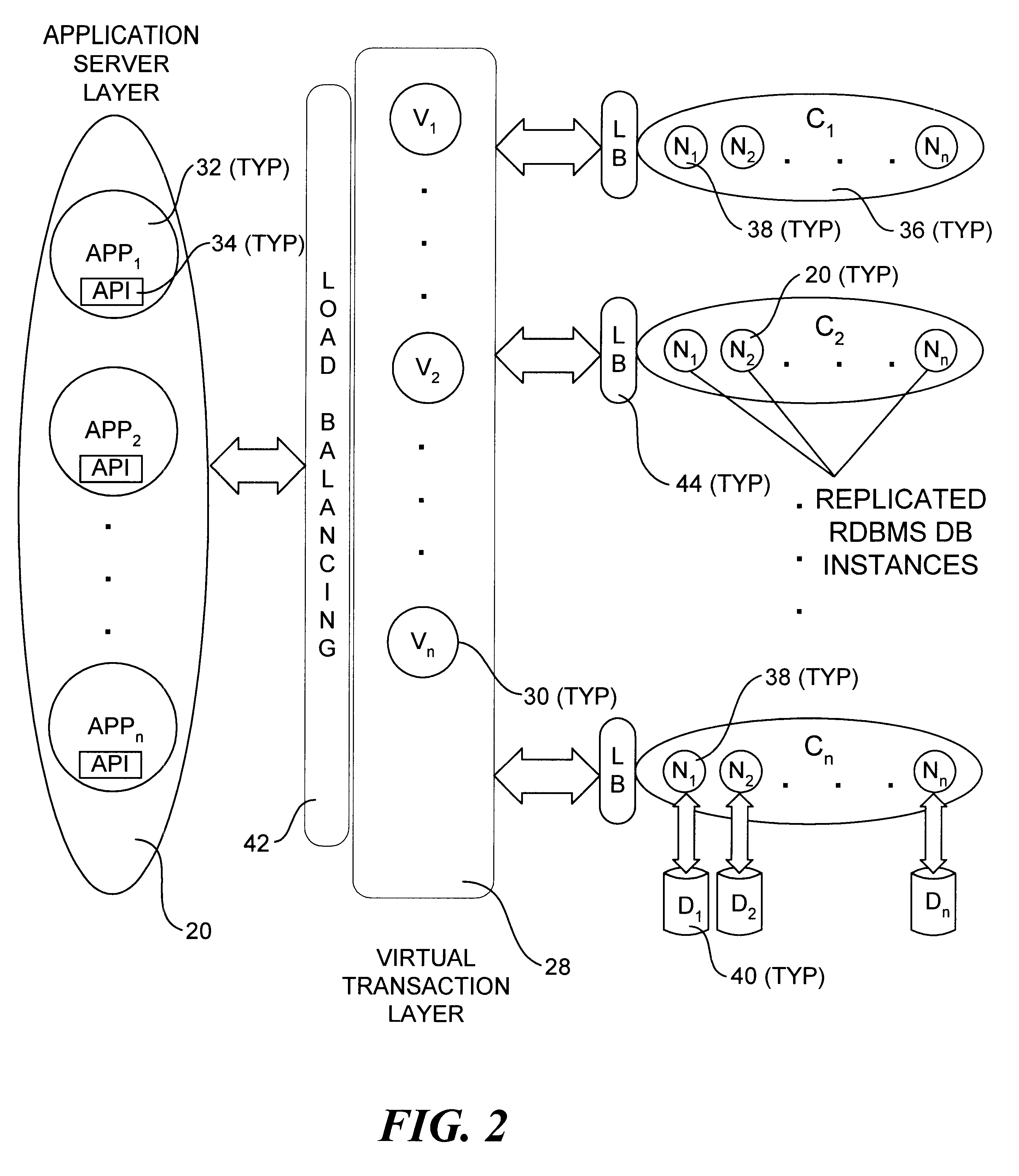
An incrementally-scalable database system and method. The system architecture enables database servers to be scaled by adding resources, such as additional servers, without requiring that the system be taken offline. Such scaling includes both adding one or more computer servers to a given server cluster, which enables an increase in database read transaction throughput, and adding one or more server clusters to the system configuration, which provides for increased read and write transaction throughput. The system also provides for load balancing read transactions across each server cluster, and load balancing write transactions across a plurality of server clusters. The system architecture includes an application server layer including one or more computers on which an application program(s) is running, a database server layer comprising two or more server clusters that each include two or more computer servers with replicated data, and an intermediate "virtual transaction" layer that includes at least two computers that facilitate database transactions with one or more databases operating in the database server layer. Data in the database(s) are evenly distributed across the server clusters in fragmented mutually exclusive subsets of data based on a hashing function. An application program interface is provided so as to enable application programs to perform a full range of database transactions without regard for where data is stored, or what database(s) is operating in the database server layer.
Owner:EMC IP HLDG CO LLC
Use of hashing function to distinguish random and repeat errors in a memory system
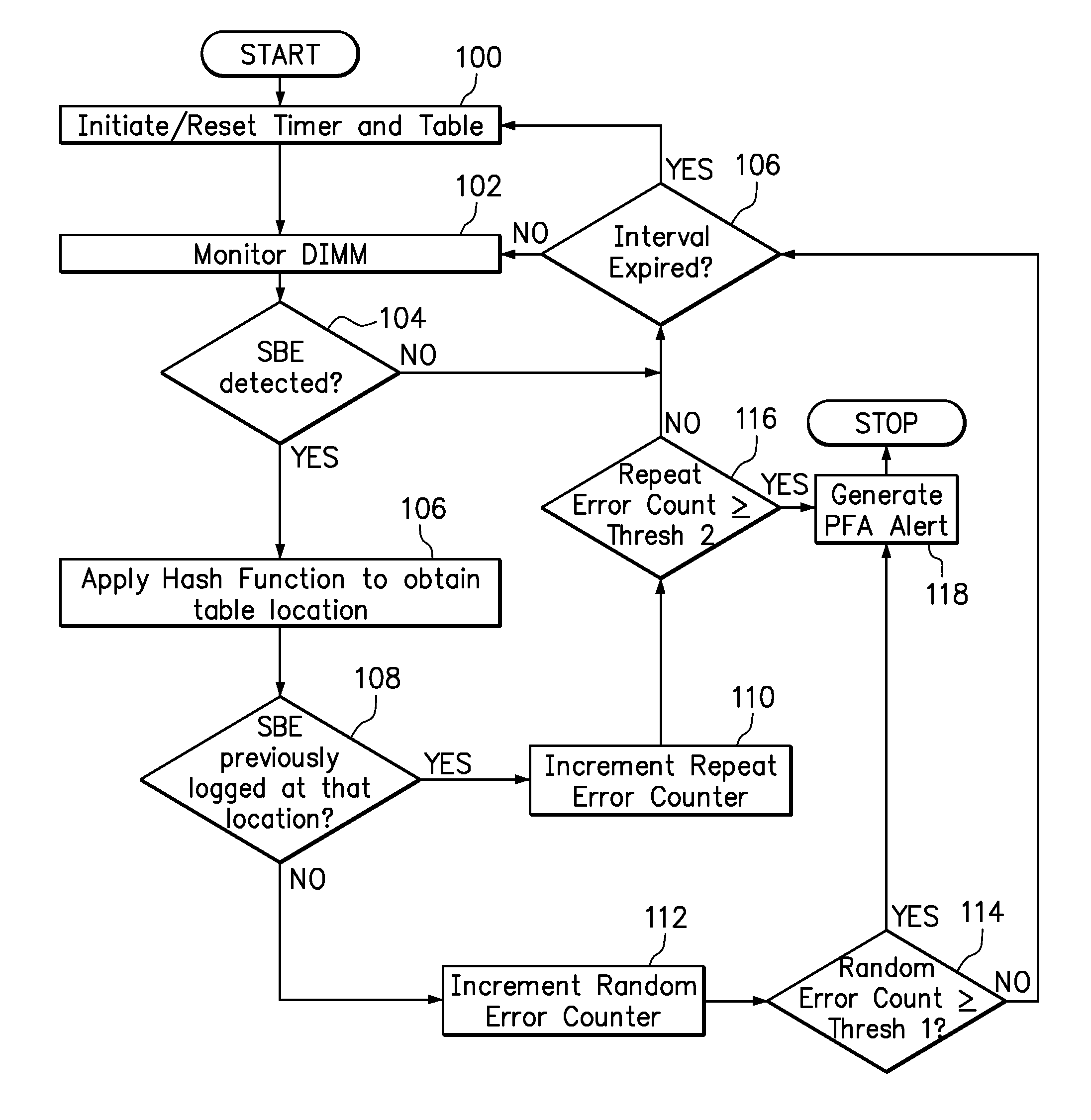
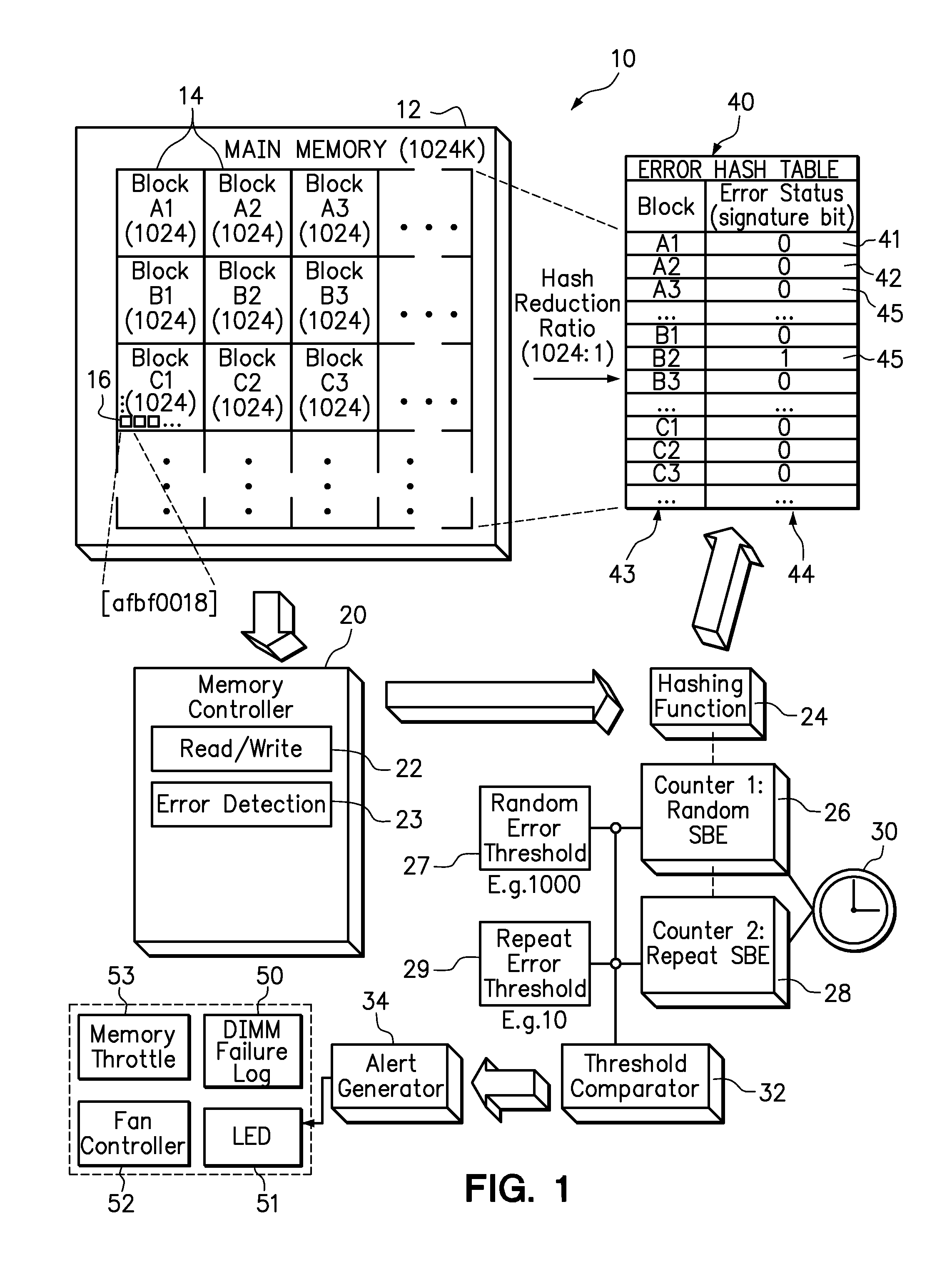
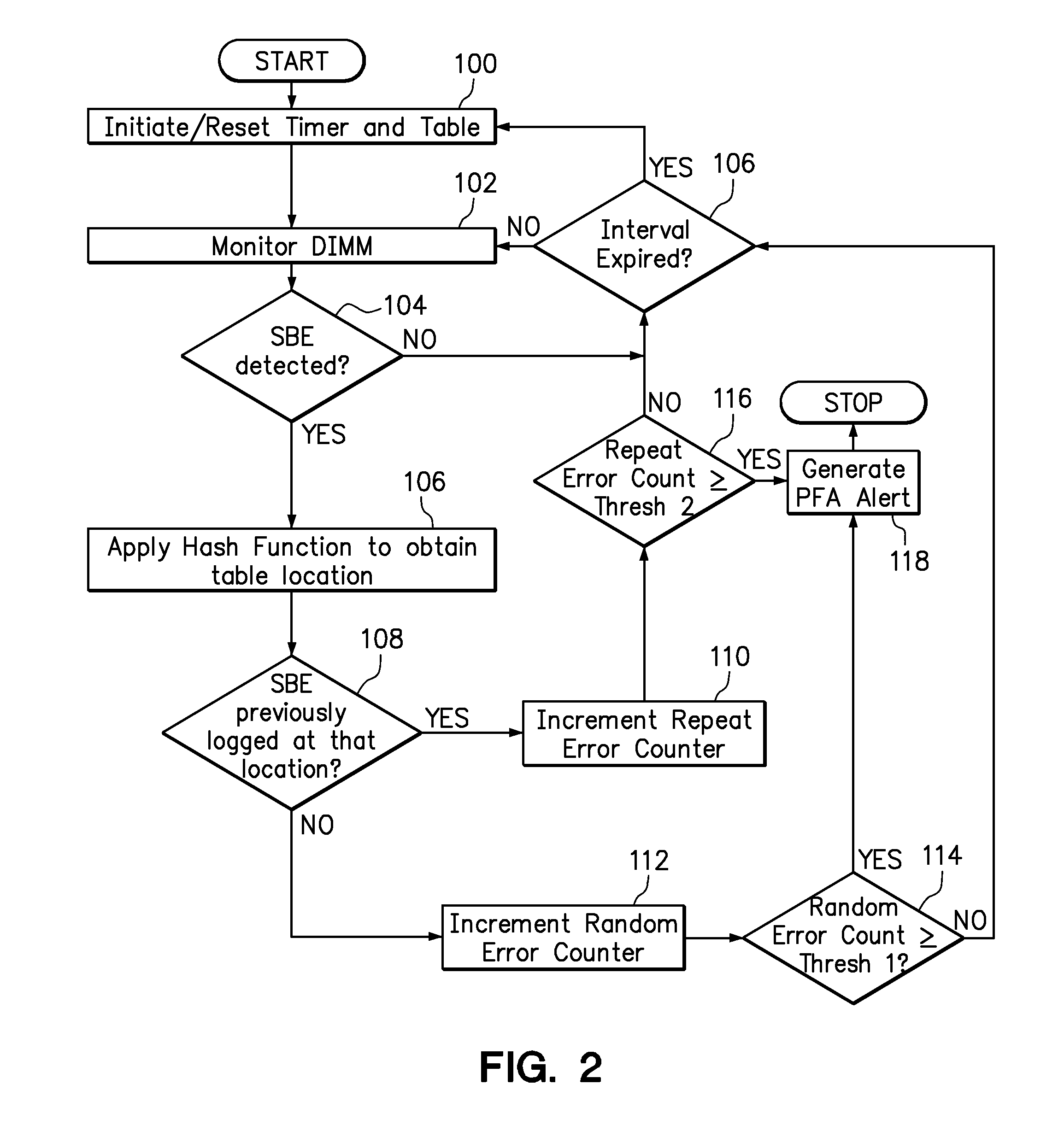
One embodiment provides an error detection method wherein single-bit errors in a memory module are detected and identified as being a random error or a repeat error. Each identified random error and each identified repeat error occurring in a time interval is counted. An alert is generated in response to a number of identified random errors reaching a random-error threshold or a number of identified repeat errors reaching a repeat-error threshold during the predefined interval. The repeat-error threshold is set lower than the random-error threshold. A hashing process may be applied to the memory address of each detected error to map the location of the error in the memory system to a corresponding location in an electronic table.
Owner:LENOVO GLOBAL TECH INT LTD
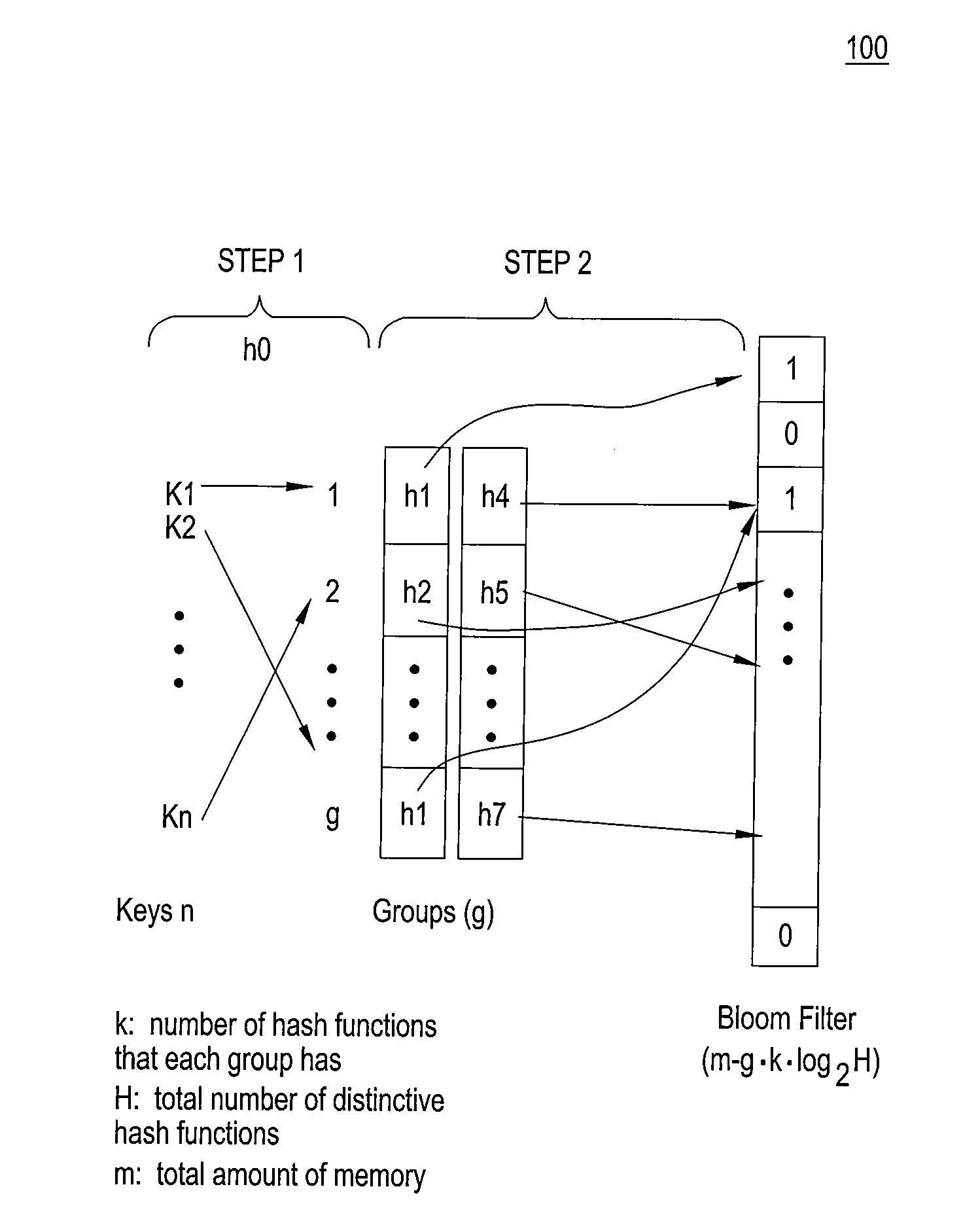
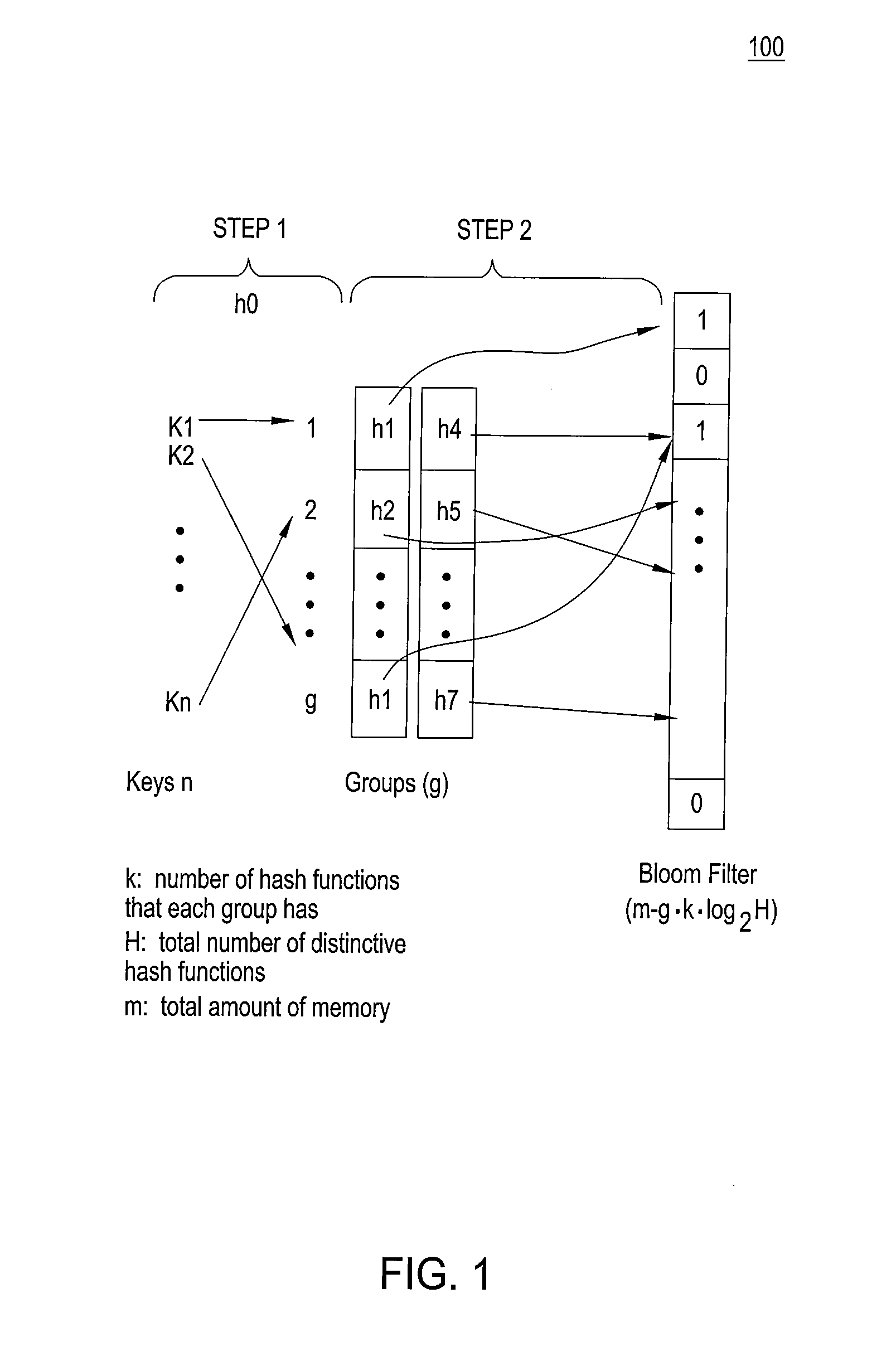
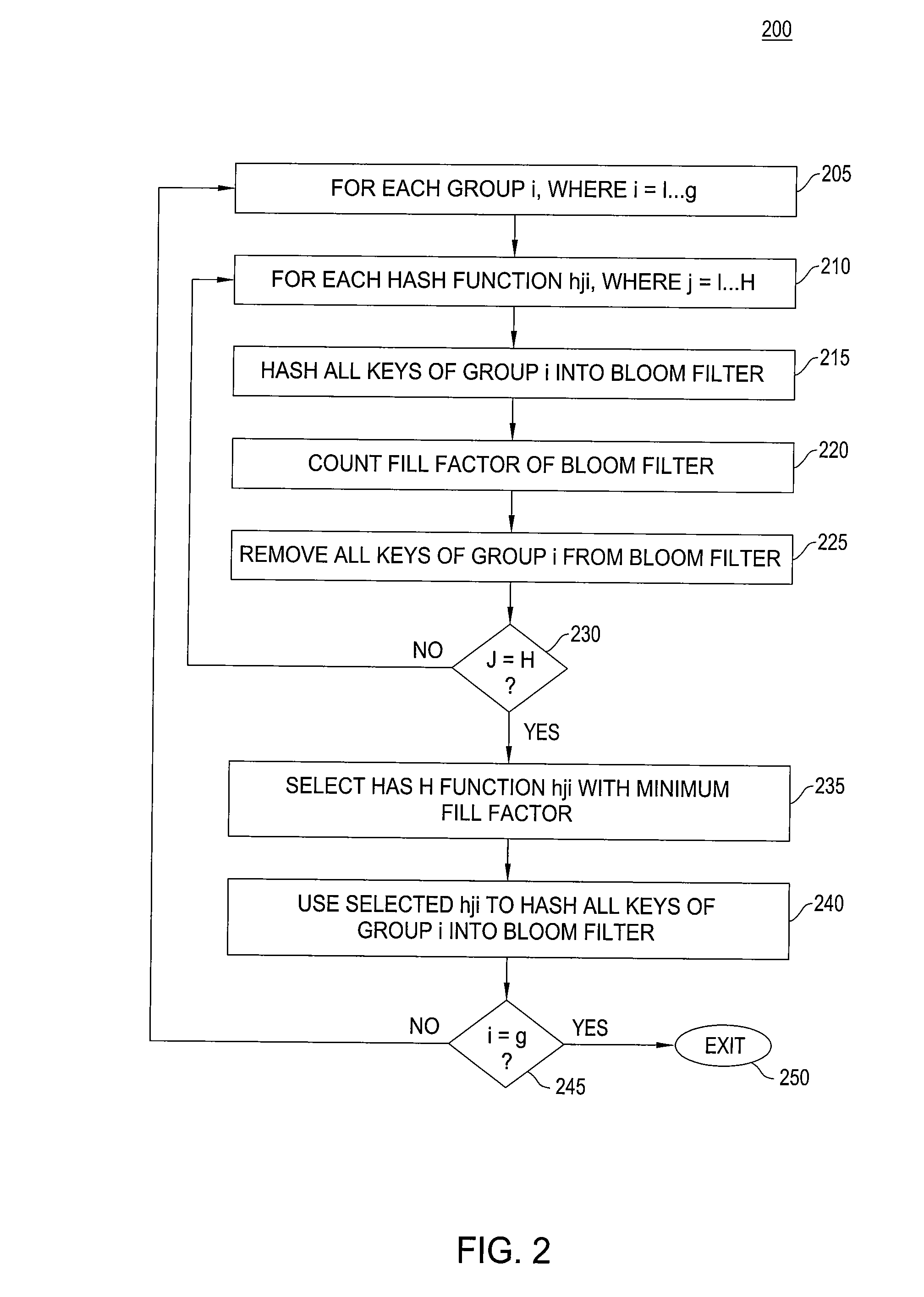
High accuracy bloom filter using partitioned hashing
ActiveUS20080313132A1Reduce false alarm rateReduce the probability of false positivesTransmissionSpecial data processing applicationsHash functionTheoretical computer science
A method and system for generating a bloom filter by mapping into respective groups each of a plurality of initial keys according to a first hash function and mapping each group hashed key into a bloom filter using k respective hash functions.
Owner:ALCATEL-LUCENT USA INC
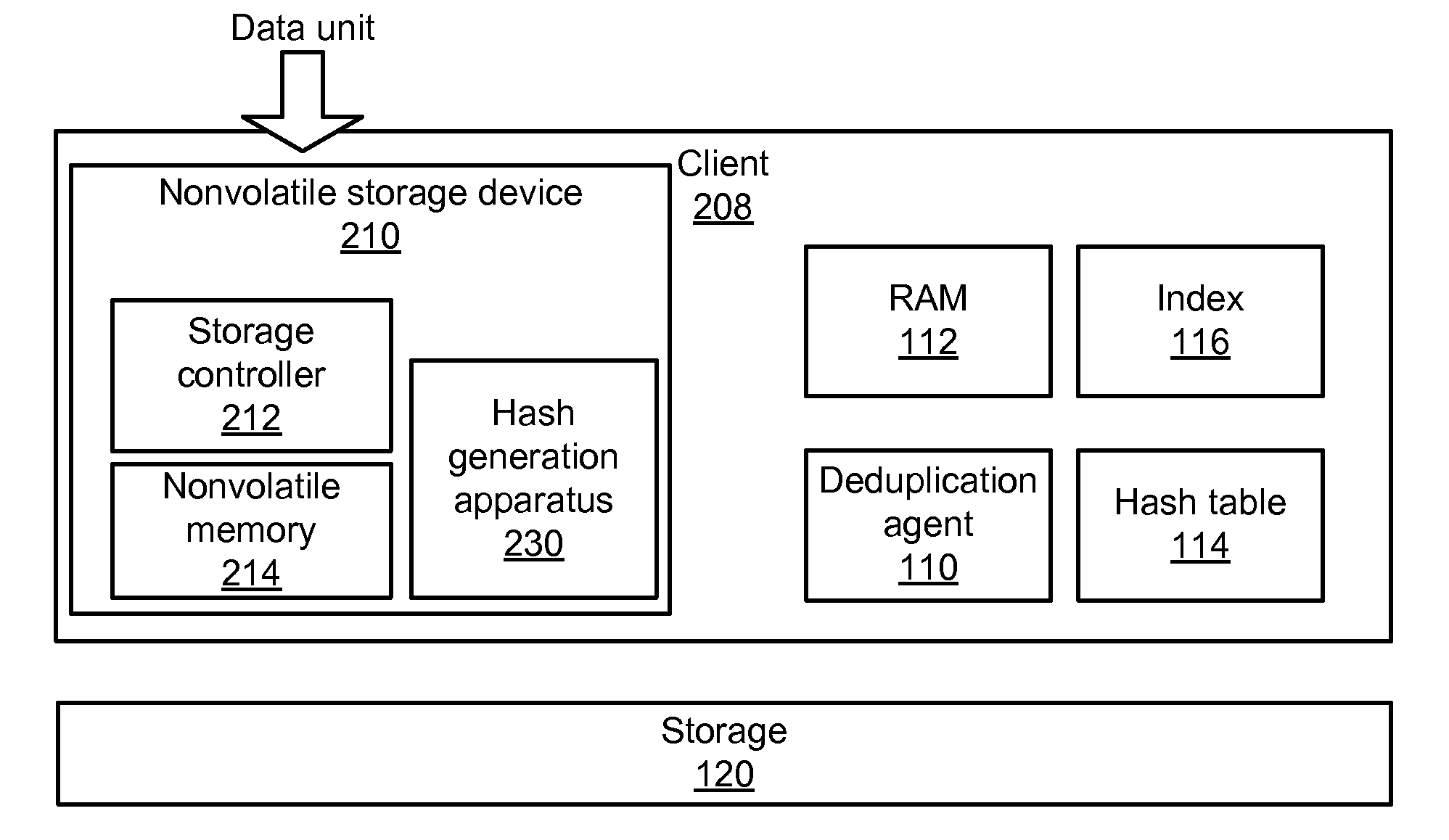
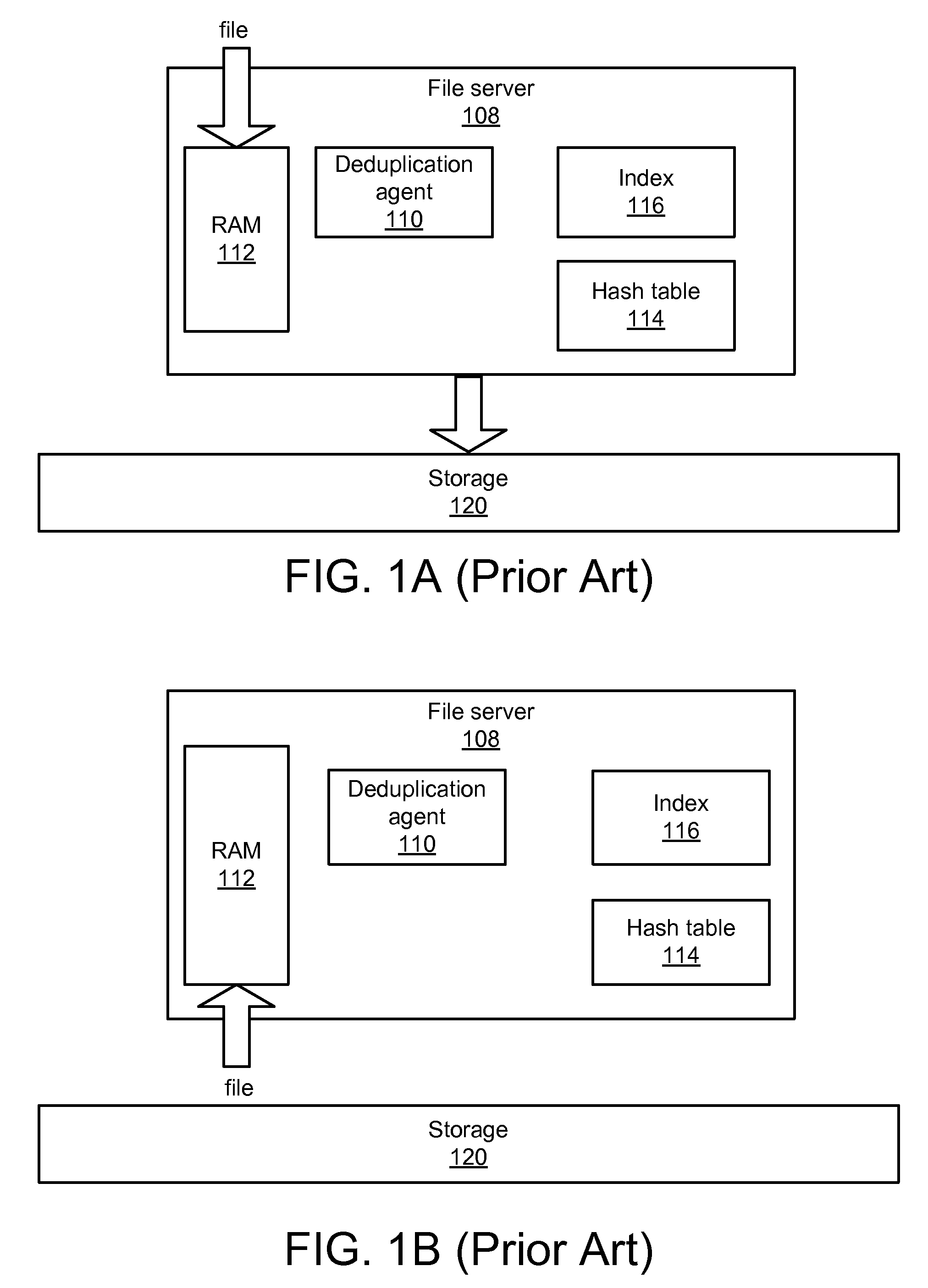
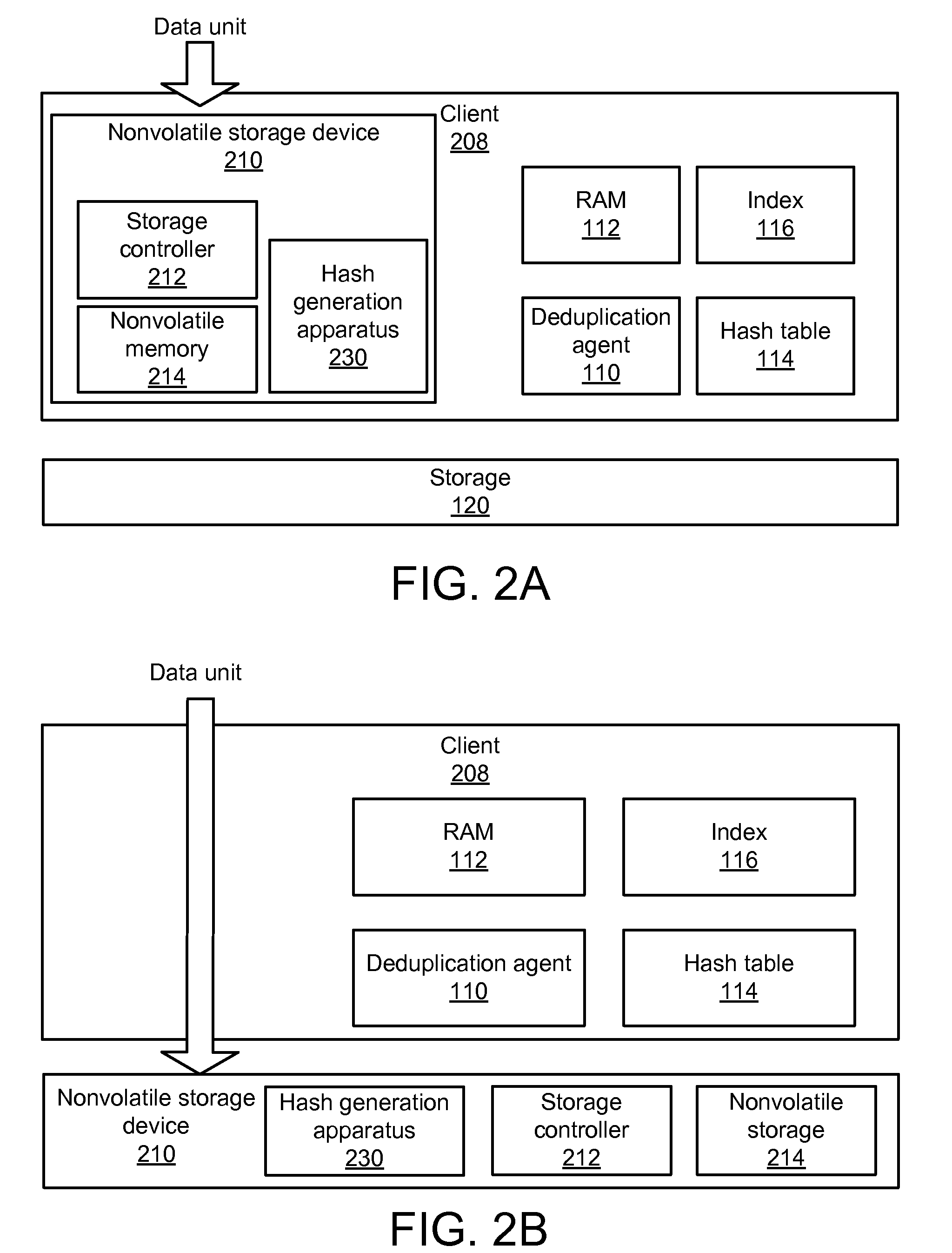
Apparatus, system, and method for improved data deduplication
InactiveUS20110055471A1Memory architecture accessing/allocationMemory systemsComputer hardwareHash function
An apparatus, system, and method are disclosed for improved deduplication. The apparatus includes an input module, a hash module, and a transmission module that are implemented in a nonvolatile storage device. The input module receives hash requests from requesting entities that may be internal or external to the nonvolatile storage device; the hash requests include a data unit identifier that identifies the data unit for which the hash is requested. The hash module generates a hash for the data unit using a hash function. The hash is generated using the computing resources of the nonvolatile storage device. The transmission module sends the hash to a receiving entity when the input module receives the hash request. A deduplication agent uses the hash to determine whether or not the data unit is a duplicate of a data unit already stored in the storage system that includes the nonvolatile storage device.
Owner:SANDISK TECH LLC
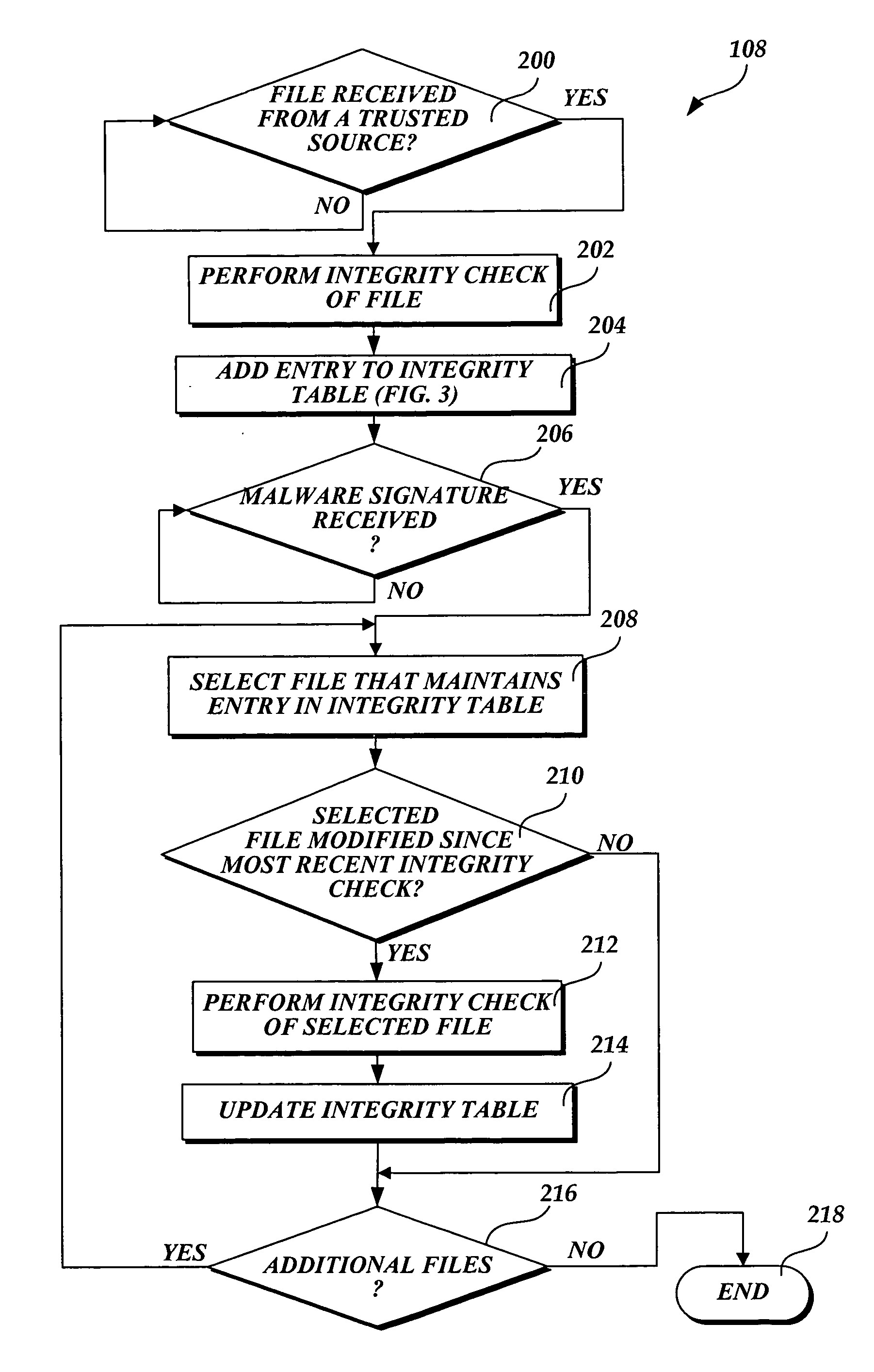
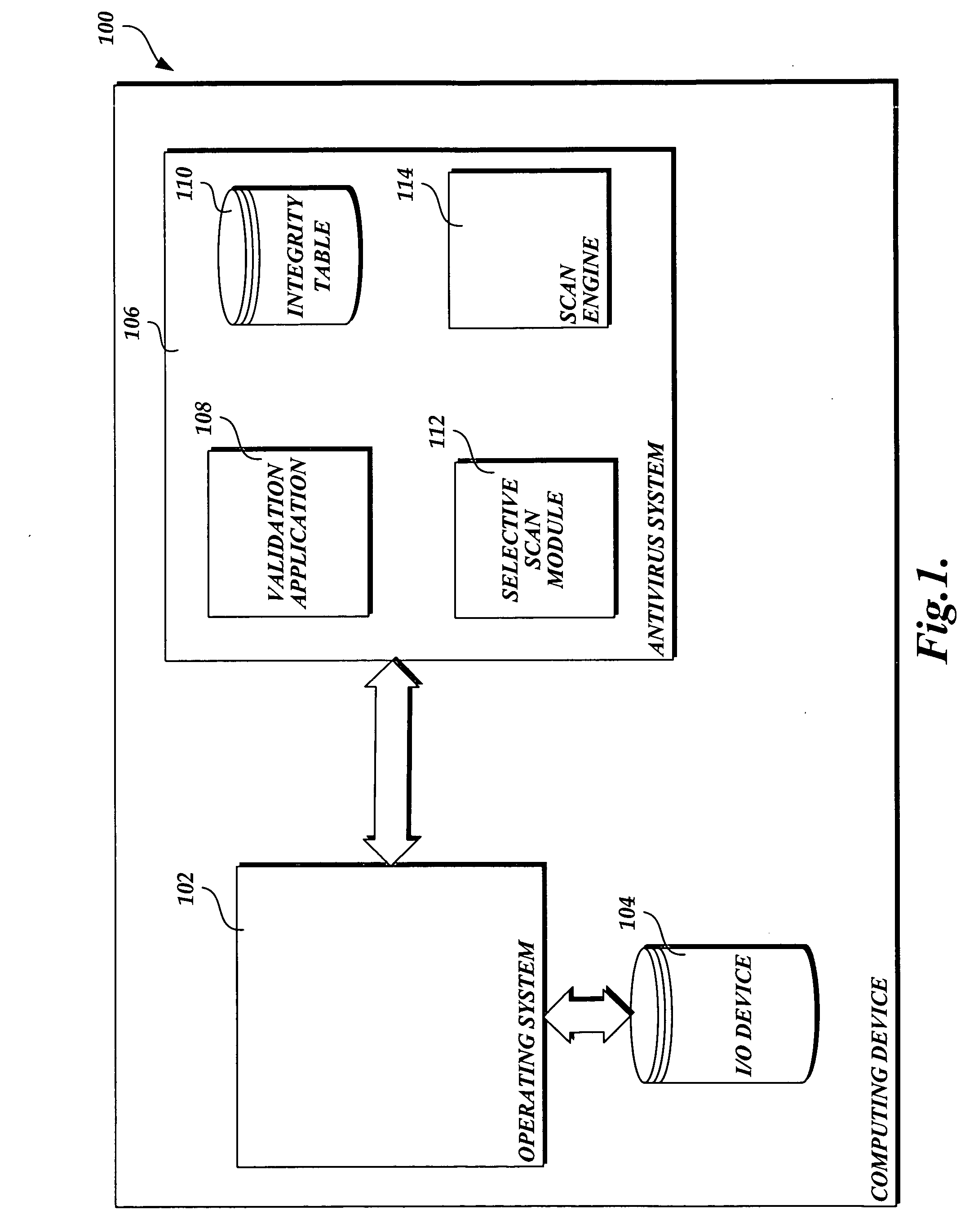
System and method of selectively scanning a file on a computing device for malware
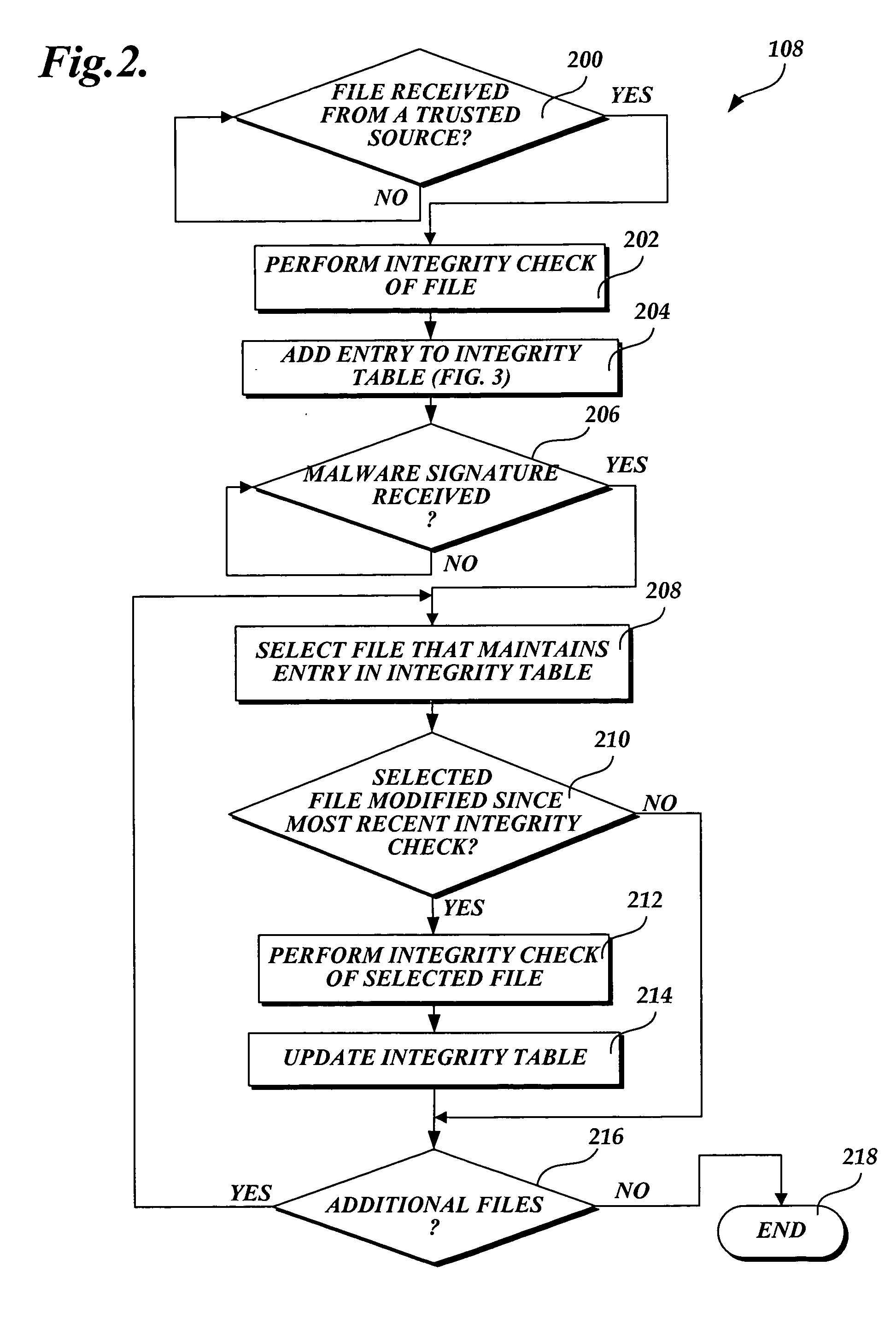
ActiveUS20060218637A1Improve computing powerMemory loss protectionDigital data processing detailsOperational systemHash function
In accordance with this invention, a system, method, and computer-readable medium that selectively scans files stored on a computing device for malware is provided. One or more files may be sent from a trusted source to a computing device that implements the present invention. The integrity of the files that originate from a trusted source is validated using a signature-based hashing function. Any modifications made to files stored on the computing device are tracked by a component of the operating system. In instances when the file is not modified after being validated, an aspect of the present invention prevents the file from being scanned for malware when a scanning event is directed to the file. As a result, the performance of the computing device is improved as static files from trusted sources are not repeatedly scanned for malware.
Owner:MICROSOFT TECH LICENSING LLC
Peer-to-peer name resolution protocol (PNRP) and multilevel cache for use therewith
InactiveUS7065587B2Fast convergenceError preventionFrequency-division multiplex detailsDomain nameAddress Resolution Protocol
A serverless name resolution protocol ensures convergence despite the size of the network, without requiring an ever-increasing cache and with a reasonable numbers of hops. This convergence is ensured through a multi-level cache and a proactive cache initialization strategy. The multi-level cache is built based on a circular number space. Each level contains information from different levels of slivers of the circular space. A mechanism is included to add a level to the multi-level cache when the node determines that the last level is full. A peer-to-peer name resolution protocol (PNRP) includes a mechanism to allow resolution of names which are mapped onto the circular number space through a hash function. Further, the PNRP may also operate with the domain name system by providing each node with an identification consisting of a domain name service (DNS) component and a unique number.
Owner:MICROSOFT TECH LICENSING LLC
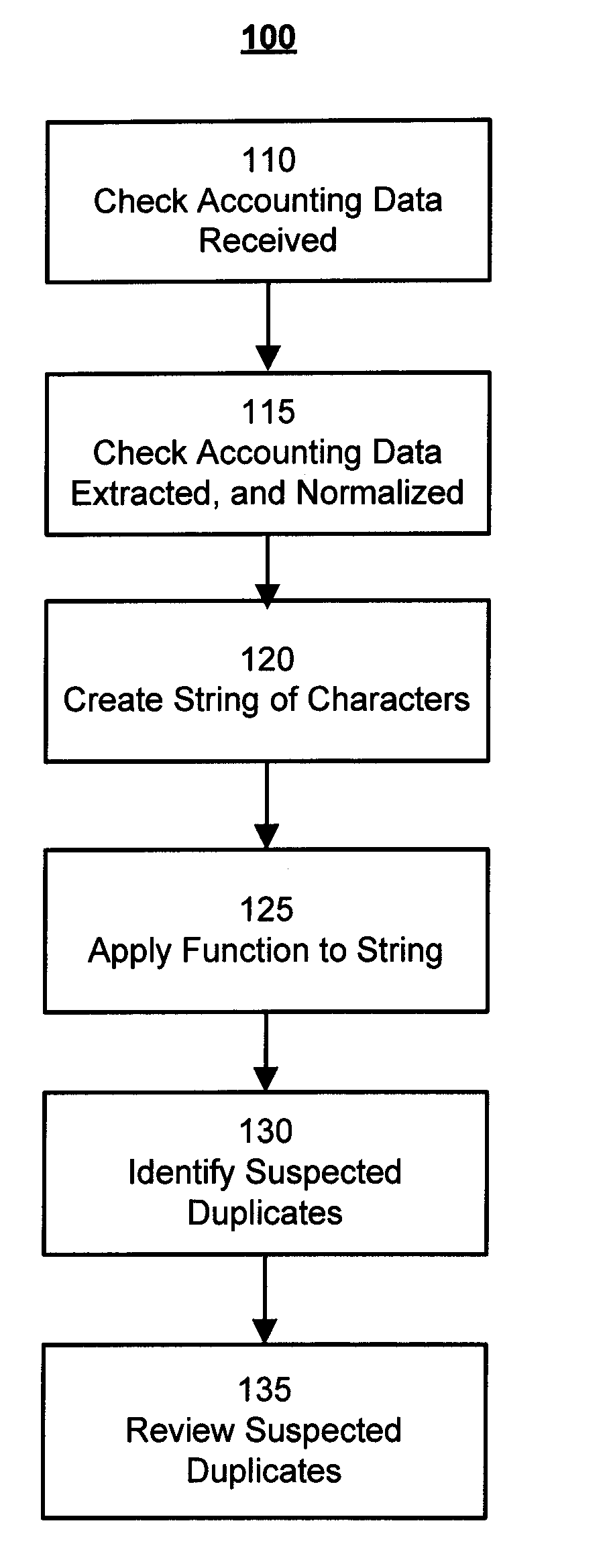
Method and System for Duplicate Check Detection
ActiveUS20100098318A1Reduce false positive rateMinimize table sizeComplete banking machinesFinanceHash functionBloom filter
A system and method for detecting duplicate checks during processing. The duplicate detection may be performed by a financial institution, such as a bank. The method may be implemented on a computer based system. The duplicate detection method may be automated. The method may be applied to incoming check files prior to processing of the check data to prevent processing of duplicate checks. The system and method may use a function, such as a hash function, to perform the duplicate detection. Other functions, such as a Bloom filter which may use multiple hash functions, may be used to perform the duplicate detection.
Owner:JPMORGAN CHASE BANK NA
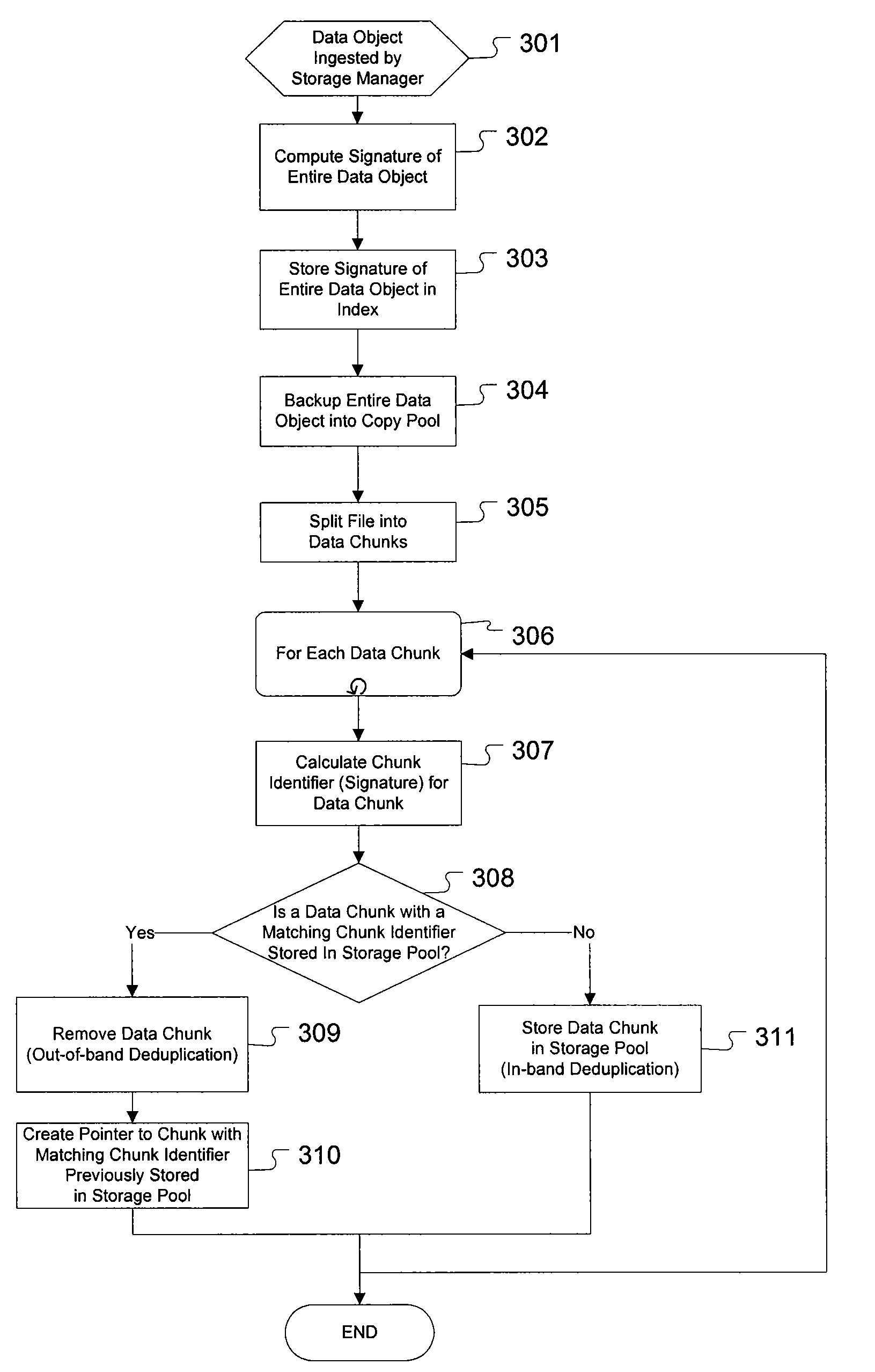
Enhanced method and system for assuring integrity of deduplicated data
ActiveUS20090271454A1Access latencyDigital data information retrievalDigital data processing detailsHash functionDigital signature
The present invention provides for an enhanced method and system for assuring integrity of deduplicated data objects stored within a storage system. A digital signature of the data object is generated to determine if the data object reassembled from a deduplicated state is identical to its pre-deduplication state. In one embodiment, generating the object signature of a data object before deduplication comprises generating an object signature from intermediate hash values computed from a hash function operating on each data chunk within the data object, the hash function also used to determine duplicate data chunks. In an alternative embodiment, generating the object signature of a data object before deduplication comprises generating an object signature on a portion of each data chunk of the data object.
Owner:DROPBOX
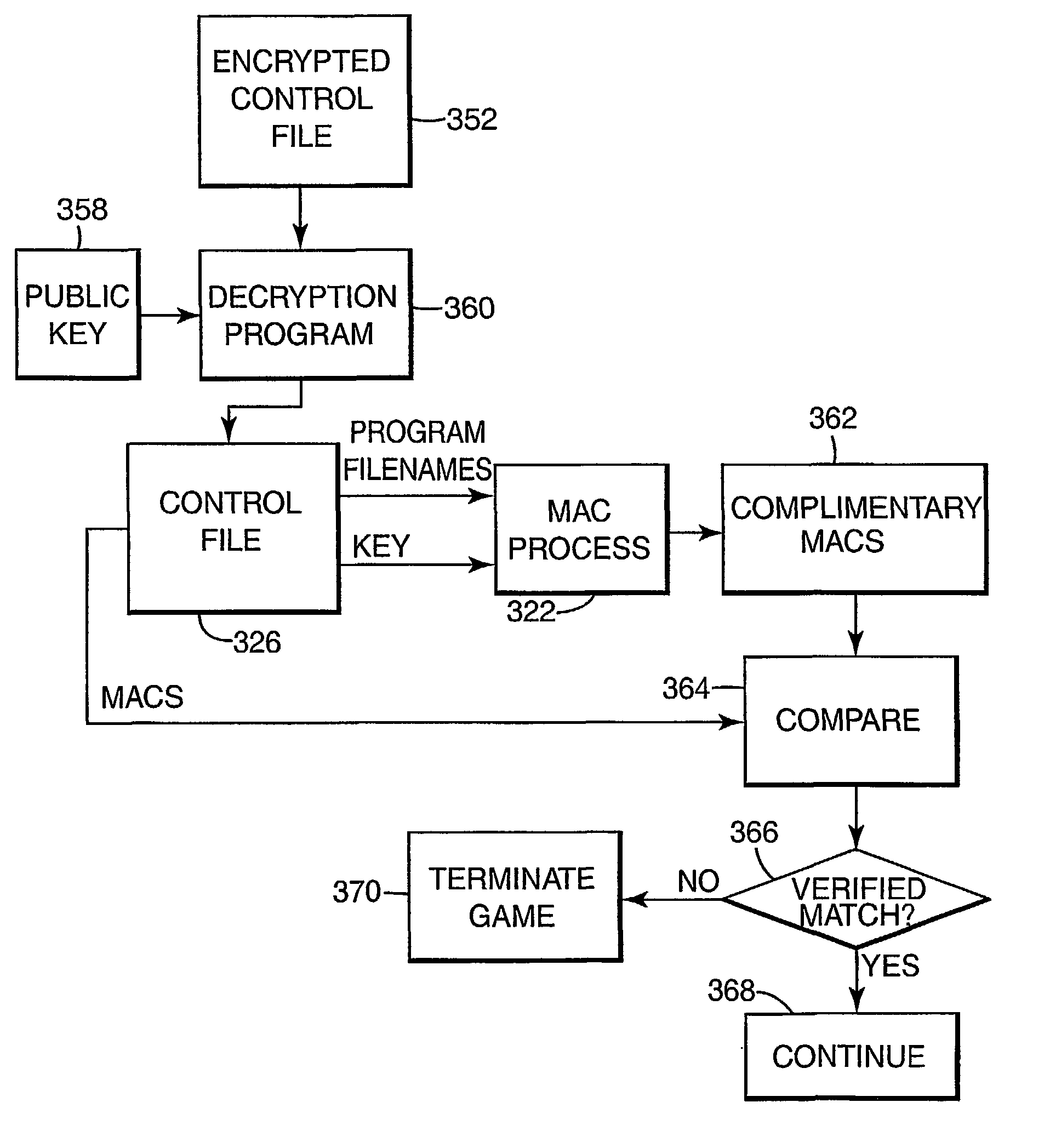
Encryption in a secure computerized gaming system
InactiveUS7043641B1Straightforward and easy to manageUser identity/authority verificationUnauthorized memory use protectionHash functionDigital signature
An architecture and method for a gaming-specific platform are disclosed that features secure storage and verification of game code and other data, provides the ability to securely exchange data with a computerized wagering gaming system, and does so in a manner that is straightforward and easy to manage. Some embodiments provide the ability to identify game program code as certified or approved, such as by the Nevada Gaming Regulations Commission or other regulatory agency. These and other functions make use of encryption, including digital signatures and hash functions as well as other encryption methods.
Owner:IGT
Method and apparatus for web caching
InactiveUS6990526B1Reduced activityAvoid delayDigital data information retrievalMultiple digital computer combinationsHash functionData access
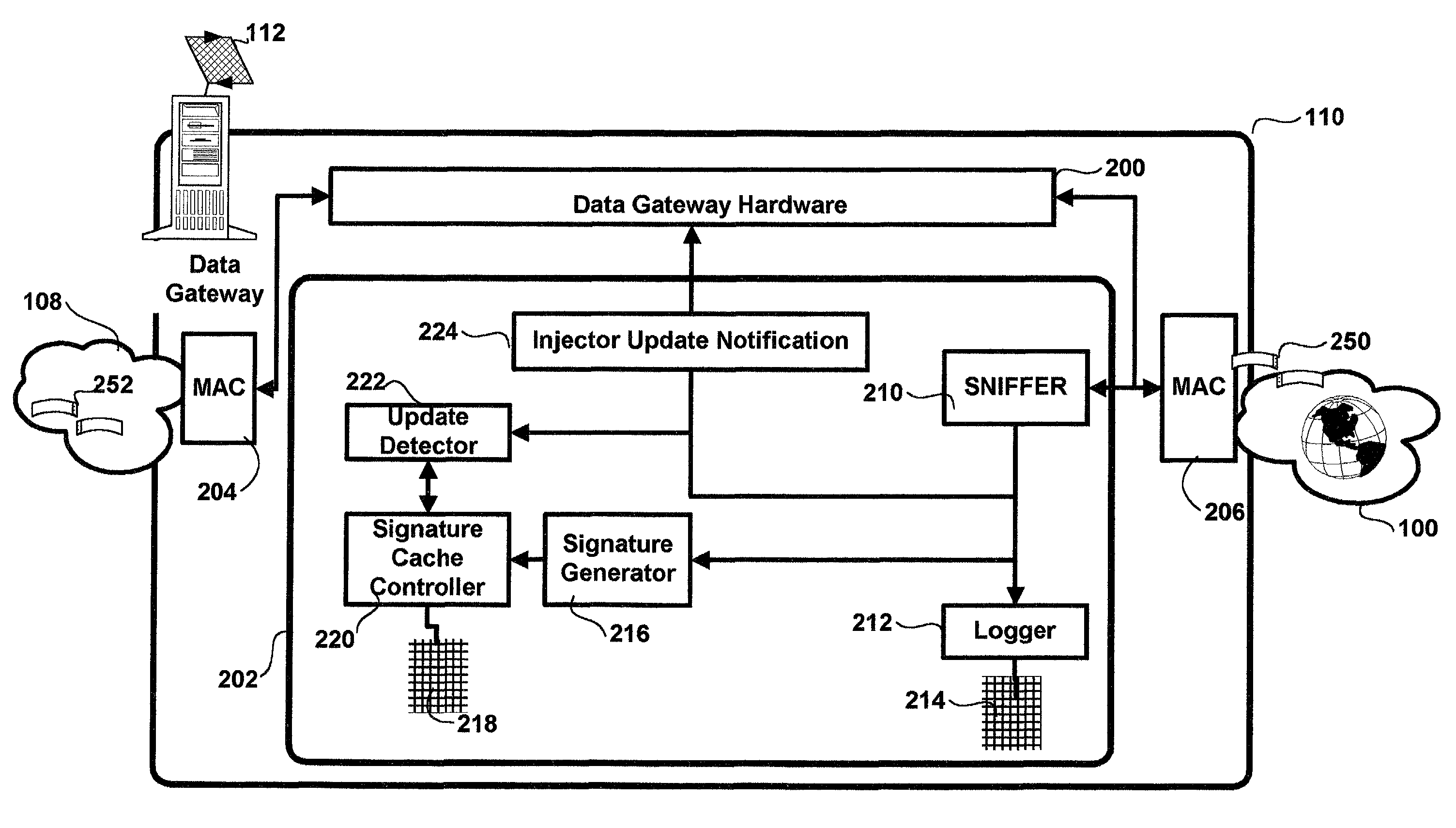
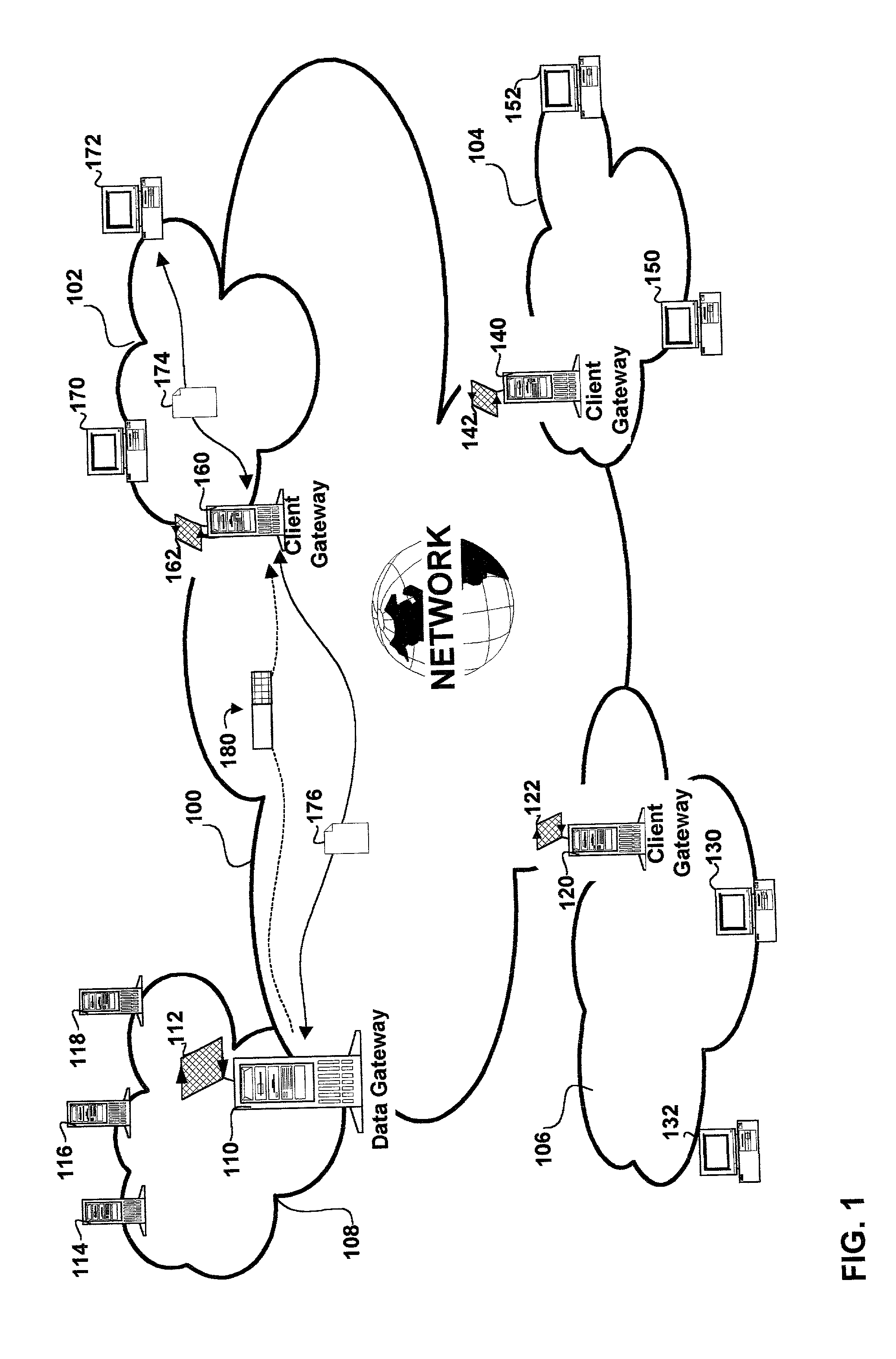
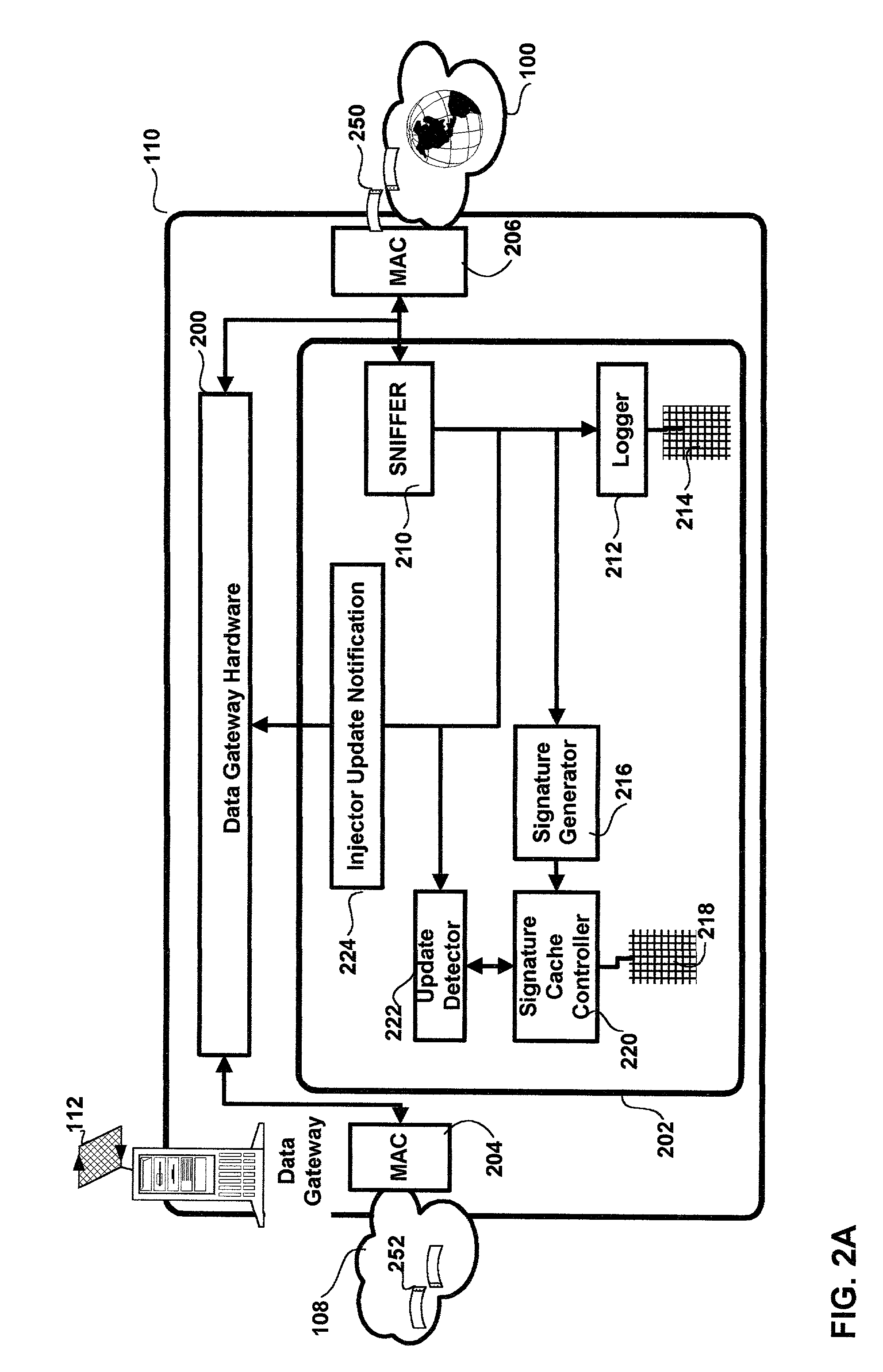
A method and apparatus for web caching is disclosed. The method and apparatus may be implemented in hardware, software or firmware. Complementary cache management modules, a coherency module and a cache module(s) are installed complementary gateways for data and for clients respectively. The coherency management module monitors data access requests and or response and determines for each: the uniform resource locator (URL) of the requested web page, the URL of the requestor and a signature. The signature is computed using cryptographic techniques and in particular a hash function for which the input is the corresponding web page for which a signature is to be generated. The coherency management module caches these signatures and the corresponding URL and uses the signatures to determine when a page has been updated. When, on the basis of signature comparisons it is determined that a page has been updated the coherency management module sends a notification to all complementary cache modules. Each cache module caches web pages requested by the associated client(s) to which it is coupled. The notification from the cache management module results in the cache module(s) which are the recipient of a given notice updating their tag table with a stale bit for the associated web page. The cache module(s) use this information in the associated tag tables to determine which pages they need to update. The cache modules initiate this update during intervals of reduced activity in the servers, gateways, routers, or switches of which they are a part. All clients requesting data through the system of which each cache module is a part are provided by the associated cache module with cached copies of requested web pages.
Owner:POINTRED TECH
Peer-to-peer name resolution protocol (PNRP) and multilevel cache for use therewith
InactiveUS20050267993A1Fast convergenceMultiple digital computer combinationsData switching networksDomain nameHash function
A serverless name resolution protocol ensures convergence despite the size of the network, without requiring an ever-increasing cache and with a reasonable numbers of hops. This convergence is ensured through a multi-level cache and a proactive cache initialization strategy. The multi-level cache is built based on a circular number space. Each level contains information from different levels of slivers of the circular space. A mechanism is included to add a level to the multi-level cache when the node determines that the last level is full. A peer-to-peer name resolution protocol (PNRP) includes a mechanism to allow resolution of names which are mapped onto the circular number space through a hash function. Further, the PNRP may also operate with the domain name system by providing each node with an identification consisting of a domain name service (DNS) component and a unique number.
Owner:MICROSOFT TECH LICENSING LLC
Peer-to-peer name resolution protocol (PNRP) and multilevel cache for use therewith
InactiveUS20050267992A1Fast convergenceMultiple digital computer combinationsData switching networksDomain nameHash function
A serverless name resolution protocol ensures convergence despite the size of the network, without requiring an ever-increasing cache and with a reasonable numbers of hops. This convergence is ensured through a multi-level cache and a proactive cache initialization strategy. The multi-level cache is built based on a circular number space. Each level contains information from different levels of slivers of the circular space. A mechanism is included to add a level to the multi-level cache when the node determines that the last level is full. A peer-to-peer name resolution protocol (PNRP) includes a mechanism to allow resolution of names which are mapped onto the circular number space through a hash function. Further, the PNRP may also operate with the domain name system by providing each node with an identification consisting of a domain name service (DNS) component and a unique number.
Owner:MICROSOFT TECH LICENSING LLC
Peer-to-peer name resolution protocol (PNRP) and multilevel cache for use therewith
InactiveUS20050267991A1Fast convergenceMultiple digital computer combinationsData switching networksDomain nameHash function
A serverless name resolution protocol ensures convergence despite the size of the network, without requiring an ever-increasing cache and with a reasonable numbers of hops. This convergence is ensured through a multi-level cache and a proactive cache initialization strategy. The multi-level cache is built based on a circular number space. Each level contains information from different levels of slivers of the circular space. A mechanism is included to add a level to the multi-level cache when the node determines that the last level is full. A peer-to-peer name resolution protocol (PNRP) includes a mechanism to allow resolution of names which are mapped onto the circular number space through a hash function. Further, the PNRP may also operate with the domain name system by providing each node with an identification consisting of a domain name service (DNS) component and a unique number.
Owner:MICROSOFT TECH LICENSING LLC
System and method providing disconnected authentication
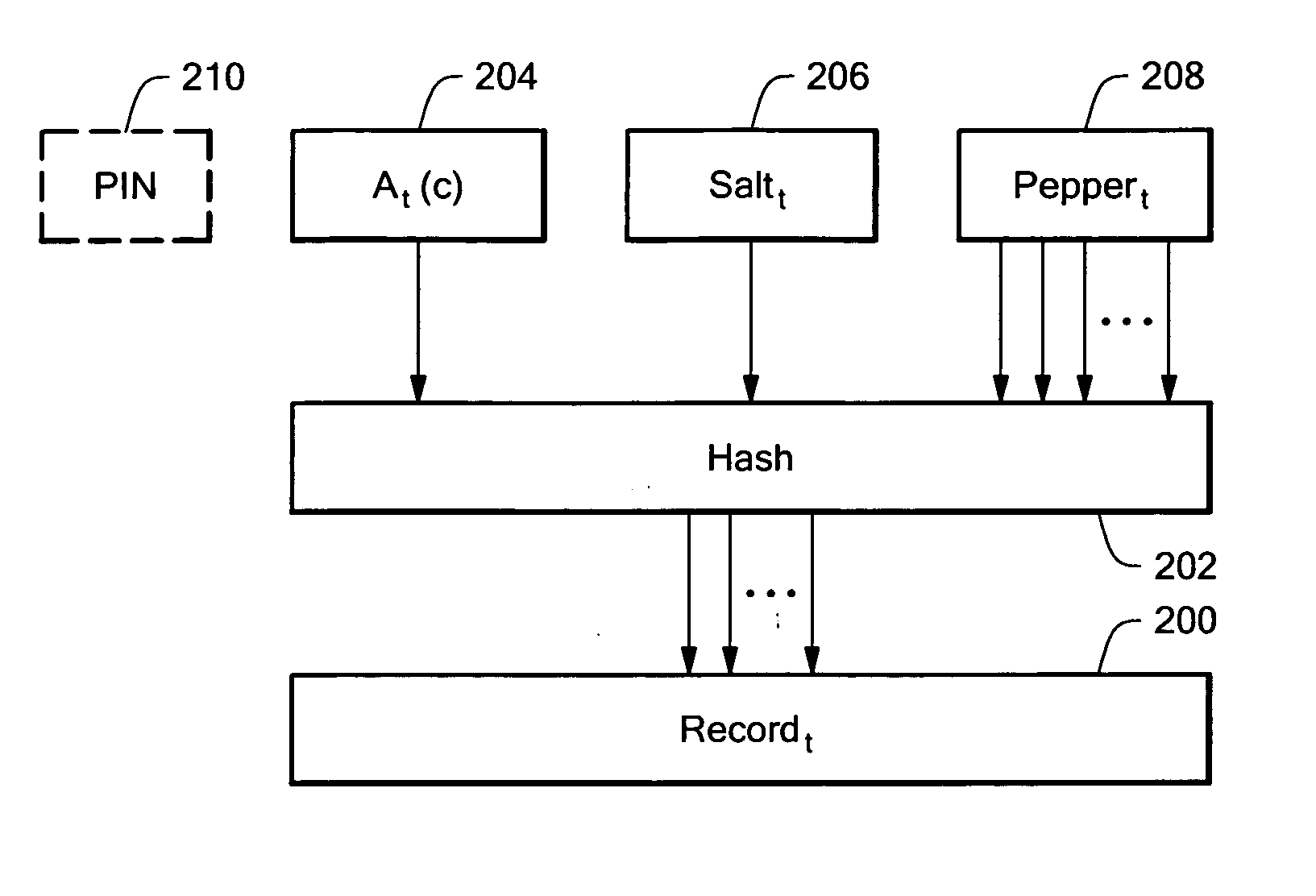
ActiveUS20050166263A1Minimize the possibilityDigital data processing detailsUser identity/authority verificationHash functionPassword
In a system for disconnected authentication, verification records corresponding to given authentication token outputs over a predetermined period of time, sequence of events, and / or set of challenges are downloaded to a verifier. The records include encrypted or hashed information for the given authentication token outputs. In one embodiment using time intervals, for each time interval, token output data, a salt value, and a pepper value, are hashed and compared with the verification record for the time interval. After a successful comparison, a user can access the computer. A PIN value can also be provided as an input the hash function. A portion of the hash function output can be used as a key to decrypt an encrypted (Windows) password, or other sensitive information.
Owner:EMC IP HLDG CO LLC
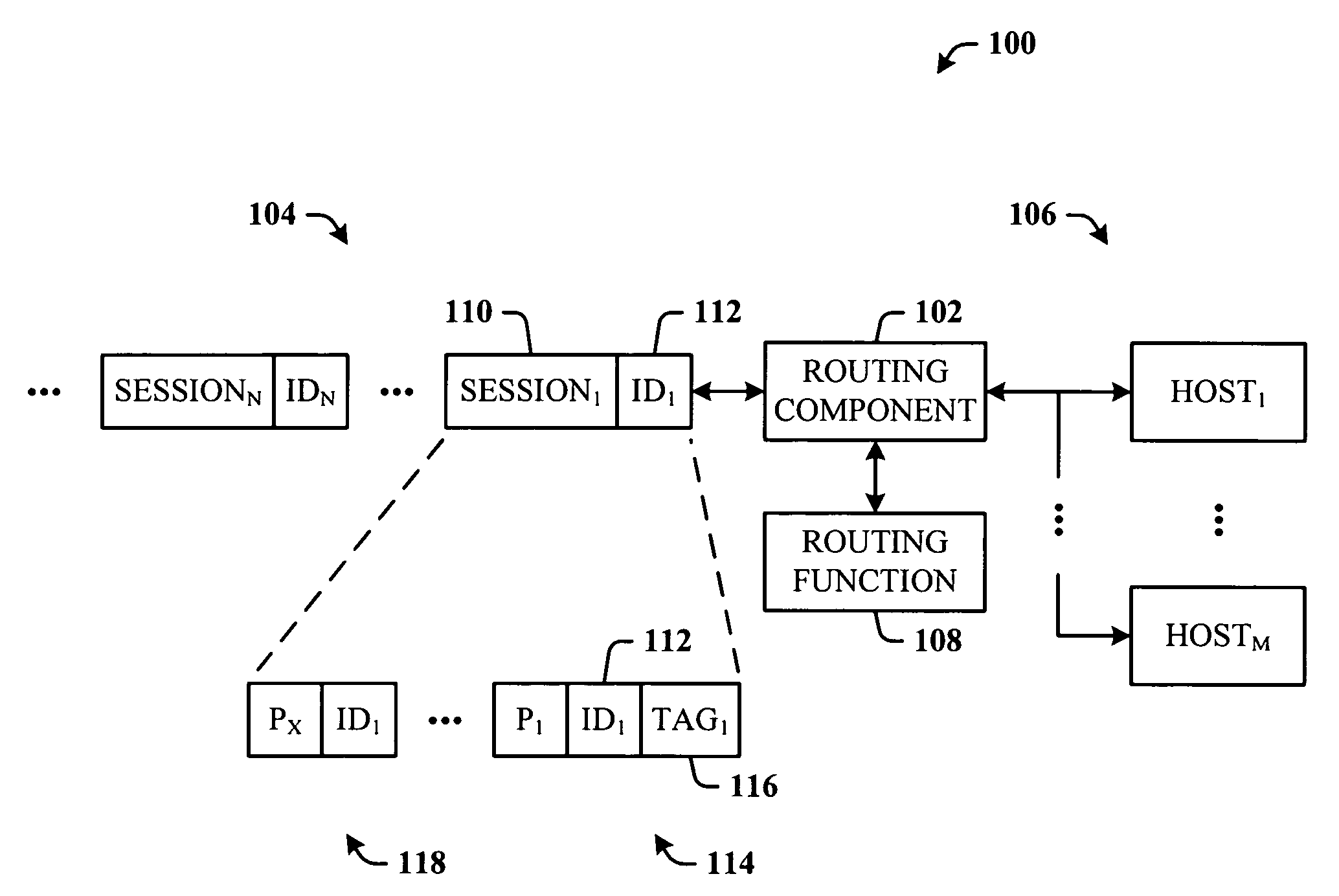
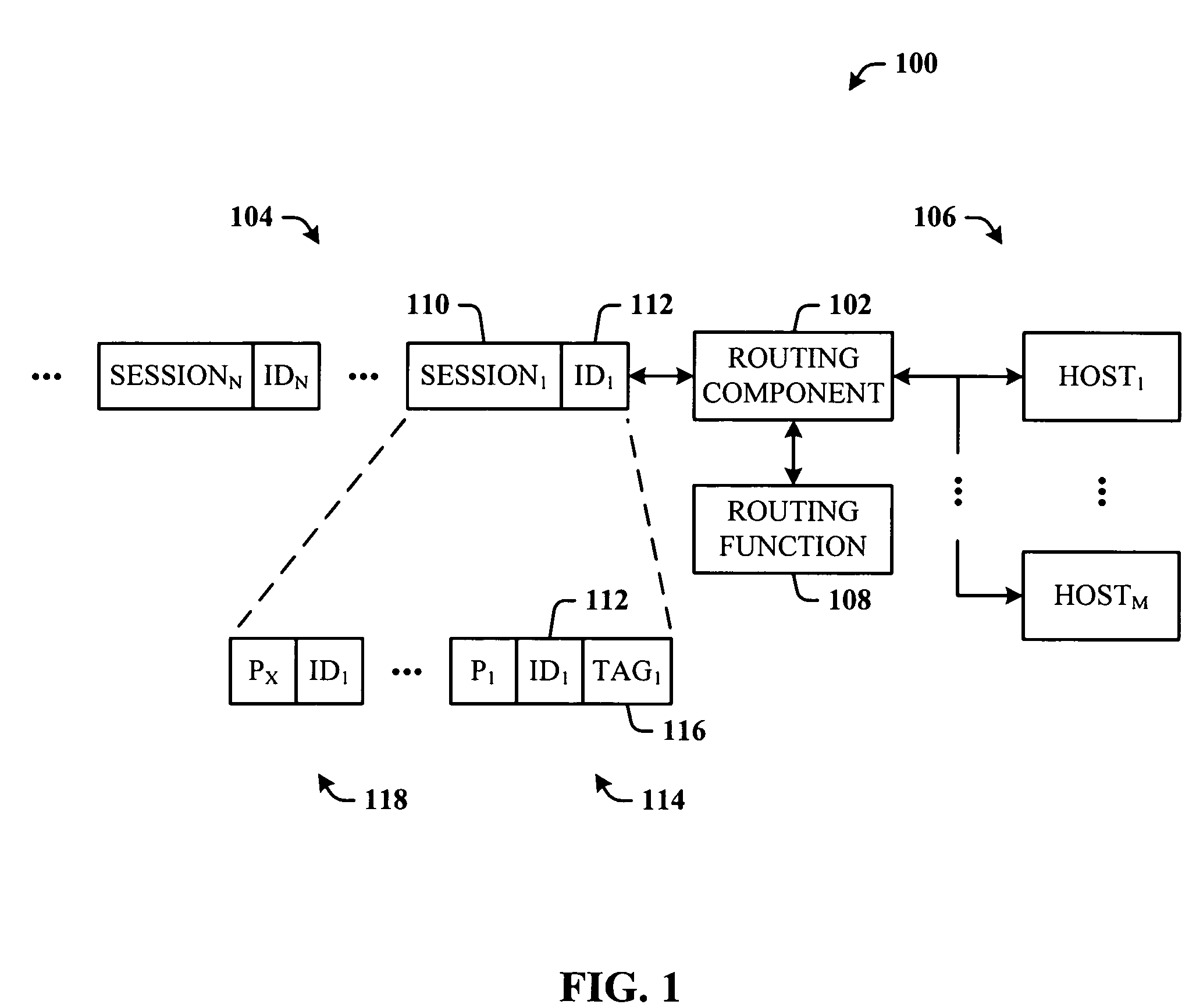
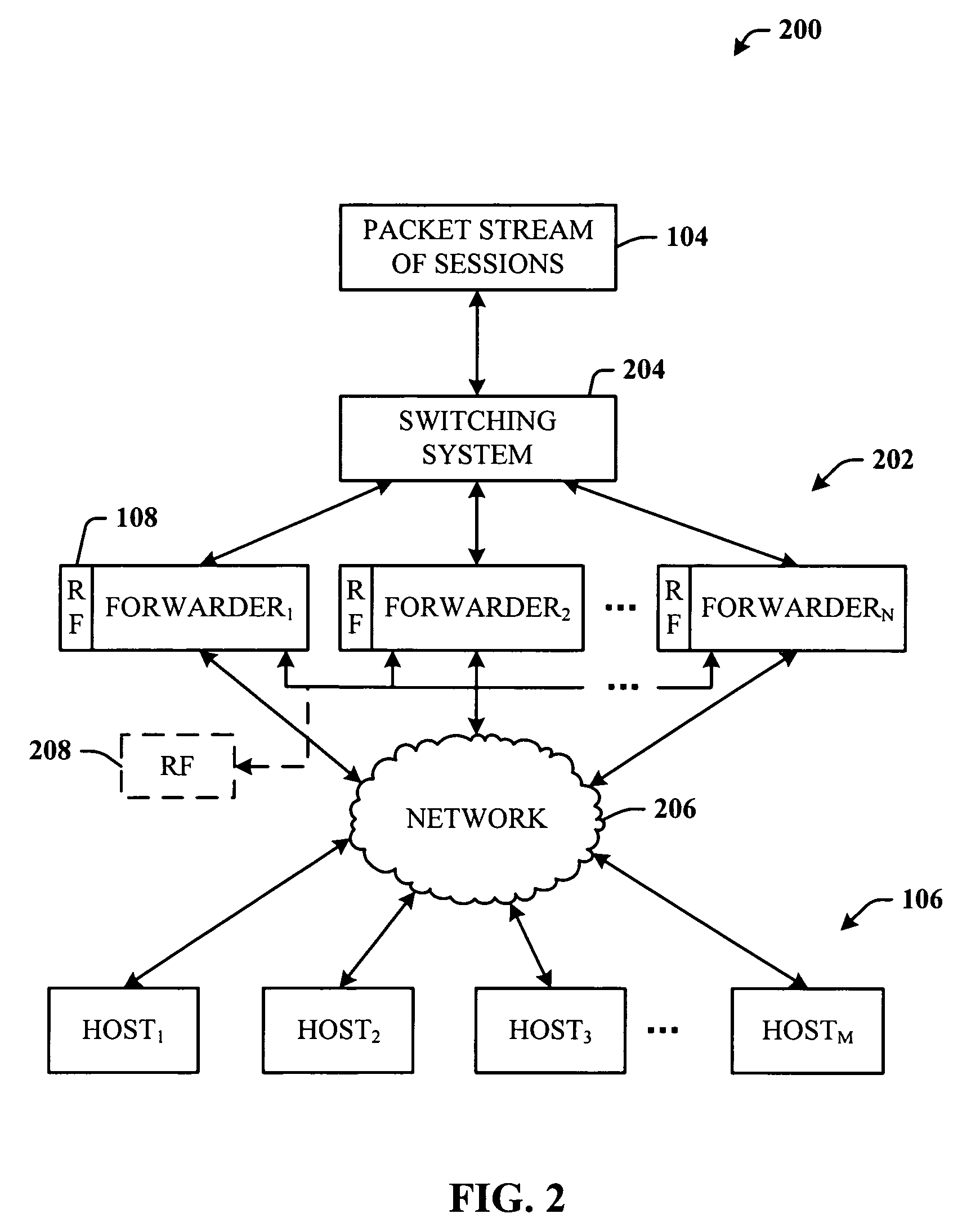
Stateless, affinity-preserving load balancing
ActiveUS20060233106A1Flexible scaling optionFacilitates maintaining constant steady-state per-host bandwidthError preventionTransmission systemsLoad SheddingData pack
The invention relates to an architecture that facilitates load balancing among a plurality of hosts and preserve session affinity to a given host. An incoming stream of data packets that include packet sessions is input to one or more forwarding mechanisms for forwarding to one or more hosts. The forwarders generate a routing function that takes into consideration host availability, and distributes session packets according to the routing function. A session is distributed to the same host to preserve session affinity. When host availability changes, a new routing function is generated, such that any new session is routed according to the new routing function and existing sessions are routed according to the old routing function. When the old routing function becomes irrelevant, it is phased out. An optimization utilizes a maximally backward compatible hash function to minimize the differences between the old and new routing functions.
Owner:MICROSOFT TECH LICENSING LLC
Encryption in a secure computerized gaming system
InactiveUS7203841B2Straightforward and easy to manageUser identity/authority verificationUnauthorized memory use protectionComputer hardwareHash function
The present invention provides an architecture and method for a gaming-specific platform that features secure storage (354) and verification (366) of game code and other data, provides the ability to securely exchange data with a computerized wagering gaming system, and does so in a manner that is straightforward and easy to manage. Some embodiments of the invention provide the ability to identify game program code as certified or approved, such as by the Nevada Gaming Regulations Commission or other regulatory agency. The invention provides these and other functions by use of encryption (216), including digital signatures (220) and hash functions (210) as well as other encryption methods.
Owner:IGT
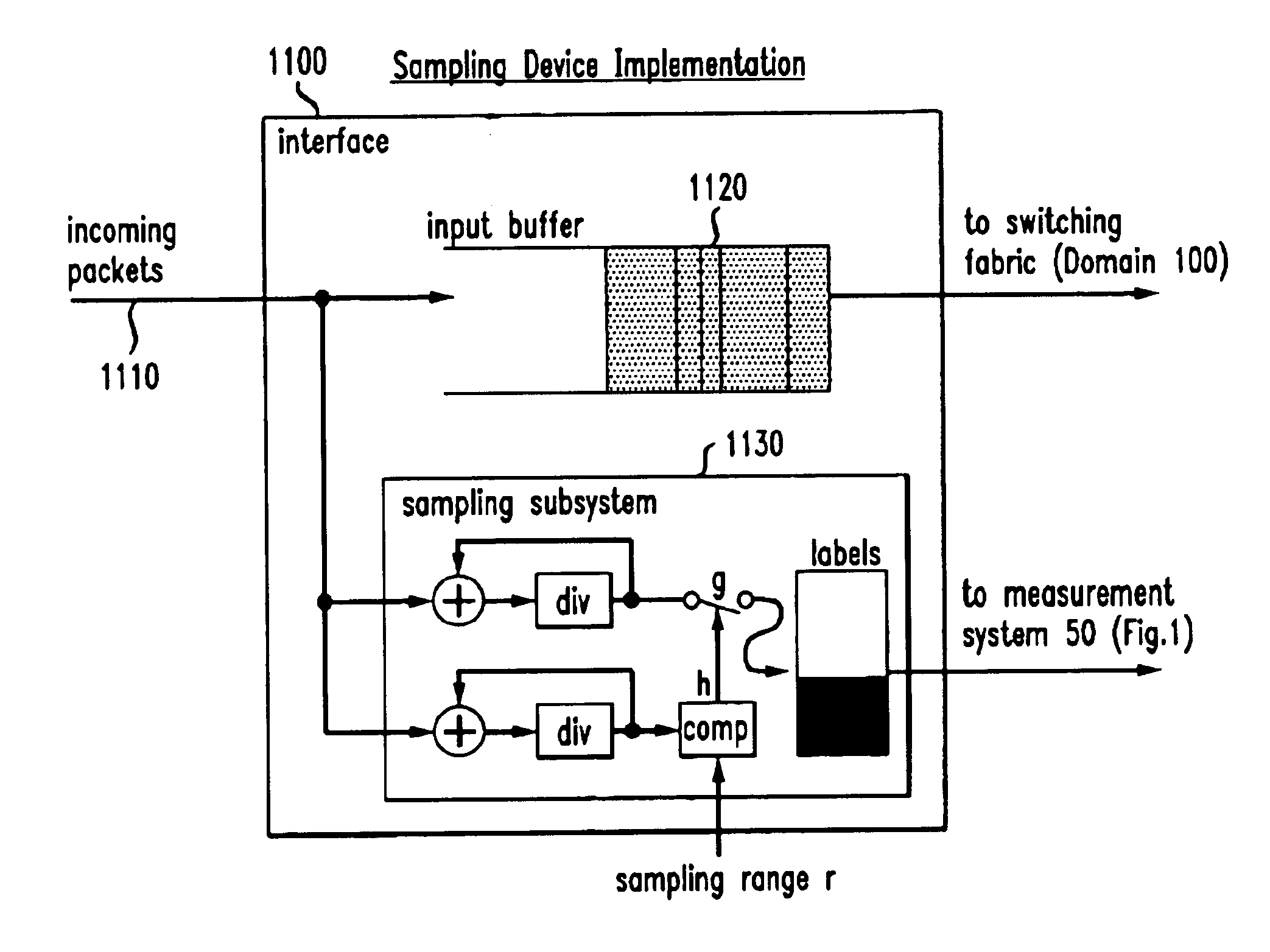
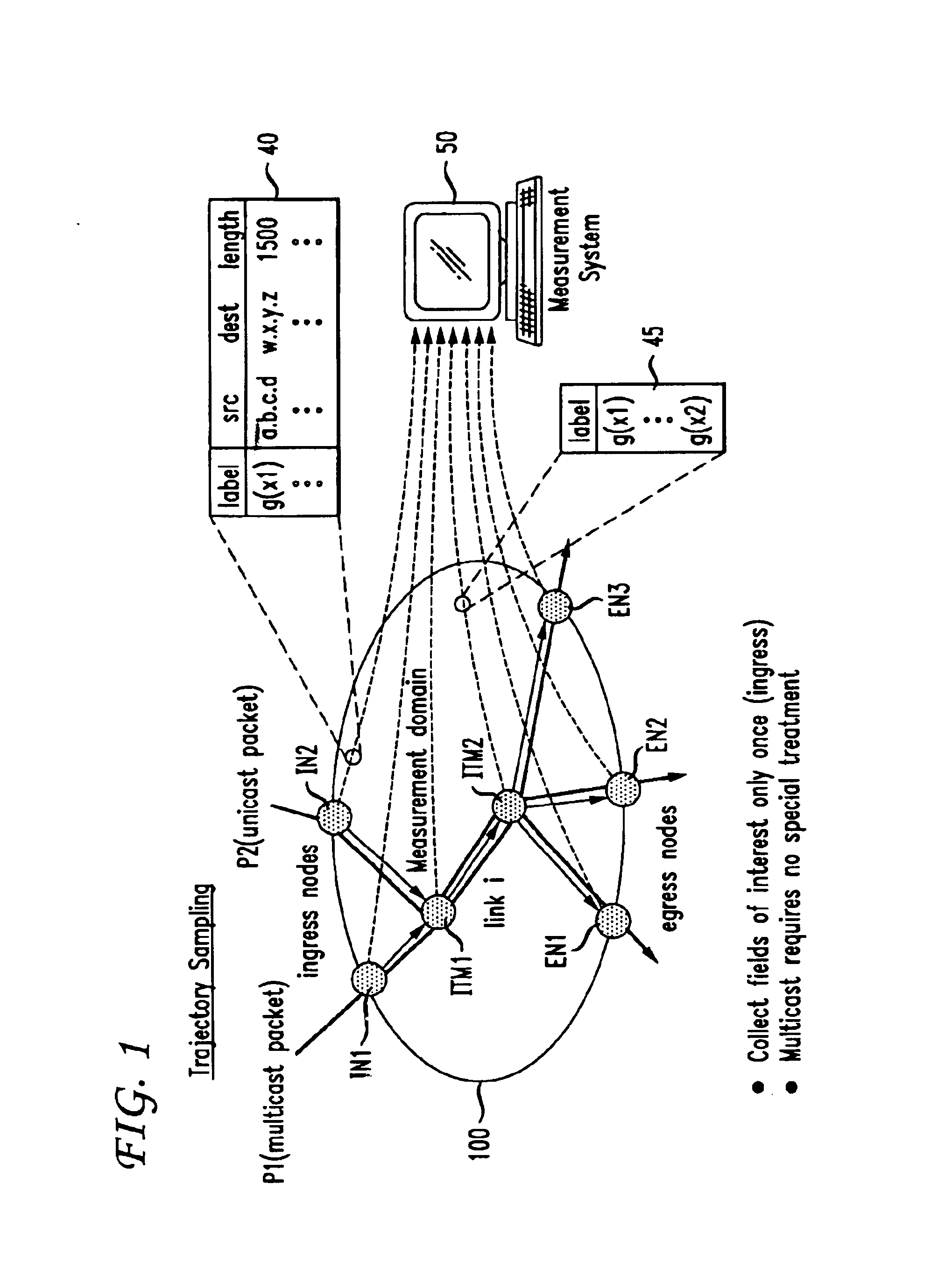
Consistent sampling for network traffic measurement
InactiveUS6873600B1Reduce ambiguityIncrease choiceError preventionFrequency-division multiplex detailsHash functionNetwork measurement
Traffic measurement should make it possible to obtain the spatial flow of traffic through the domain, i.e., the paths or trajectories followed by packets between any ingress and egress point of the domain. A method of sampling packet trajectories in a packet switching network allows the direct inference of traffic flows through a measurement domain by observing the trajectories of a subset of all packets traversing the network. A method which assumes that the measurement domain does not change comprises the steps of selecting packets for sampling in accordance with a sampling function of the packet content and generating a practically unique label for each sampled packet. The method does not rely on routing state, its implementation cost is small, and the measurement reporting traffic is modest and can be controlled precisely. Using the same hash function will yield the same sample set of packets in the entire domain, and enables us to reconstruct packet trajectories. An alternate embodiment which assumes no constraints and that the measurement domain may change comprises the steps of applying a sampling function and altering an invariant bit position as a signaling flag in each packet selected for sampling.
Owner:AMERICAN TELEPHONE & TELEGRAPH CO
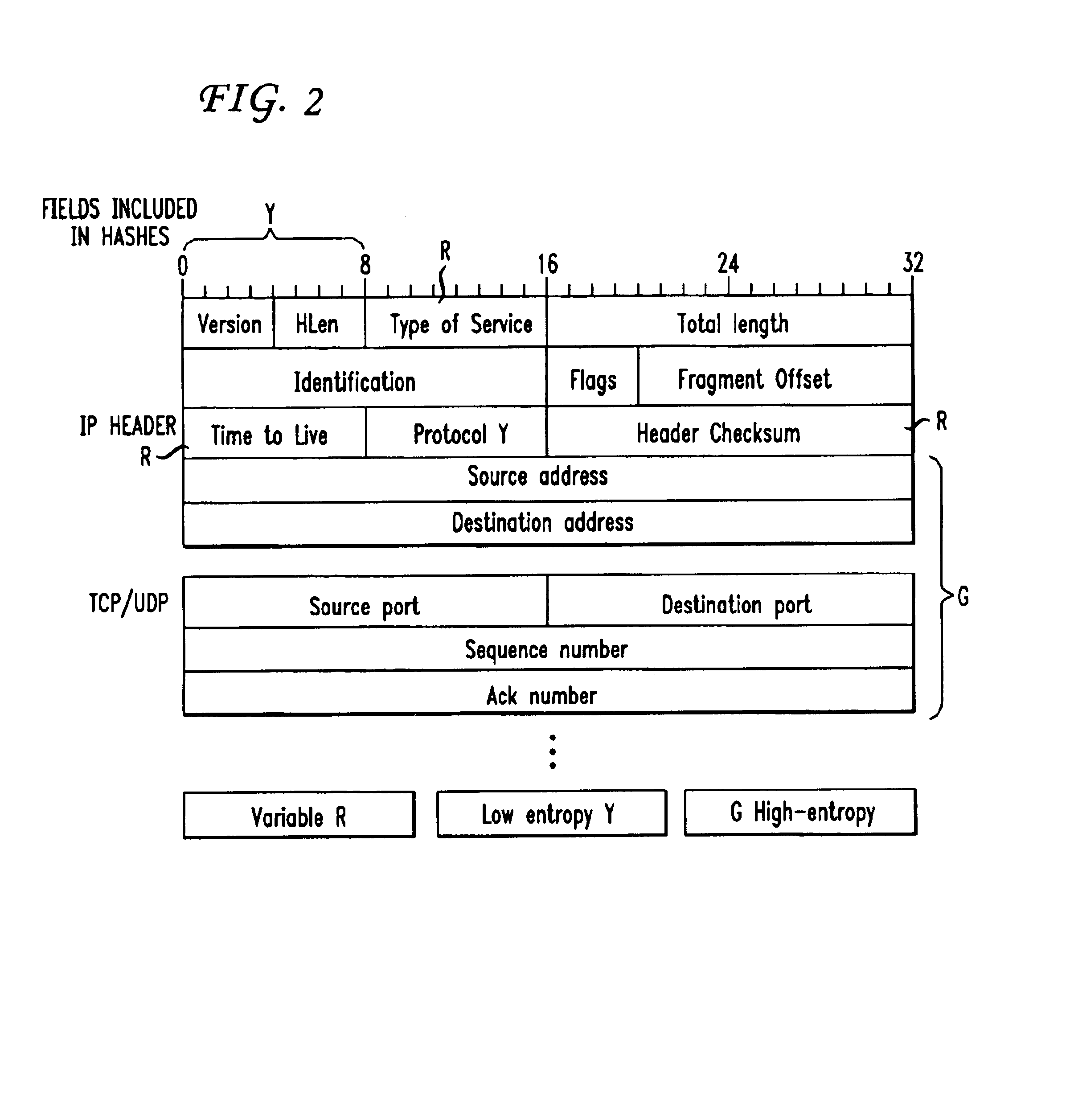
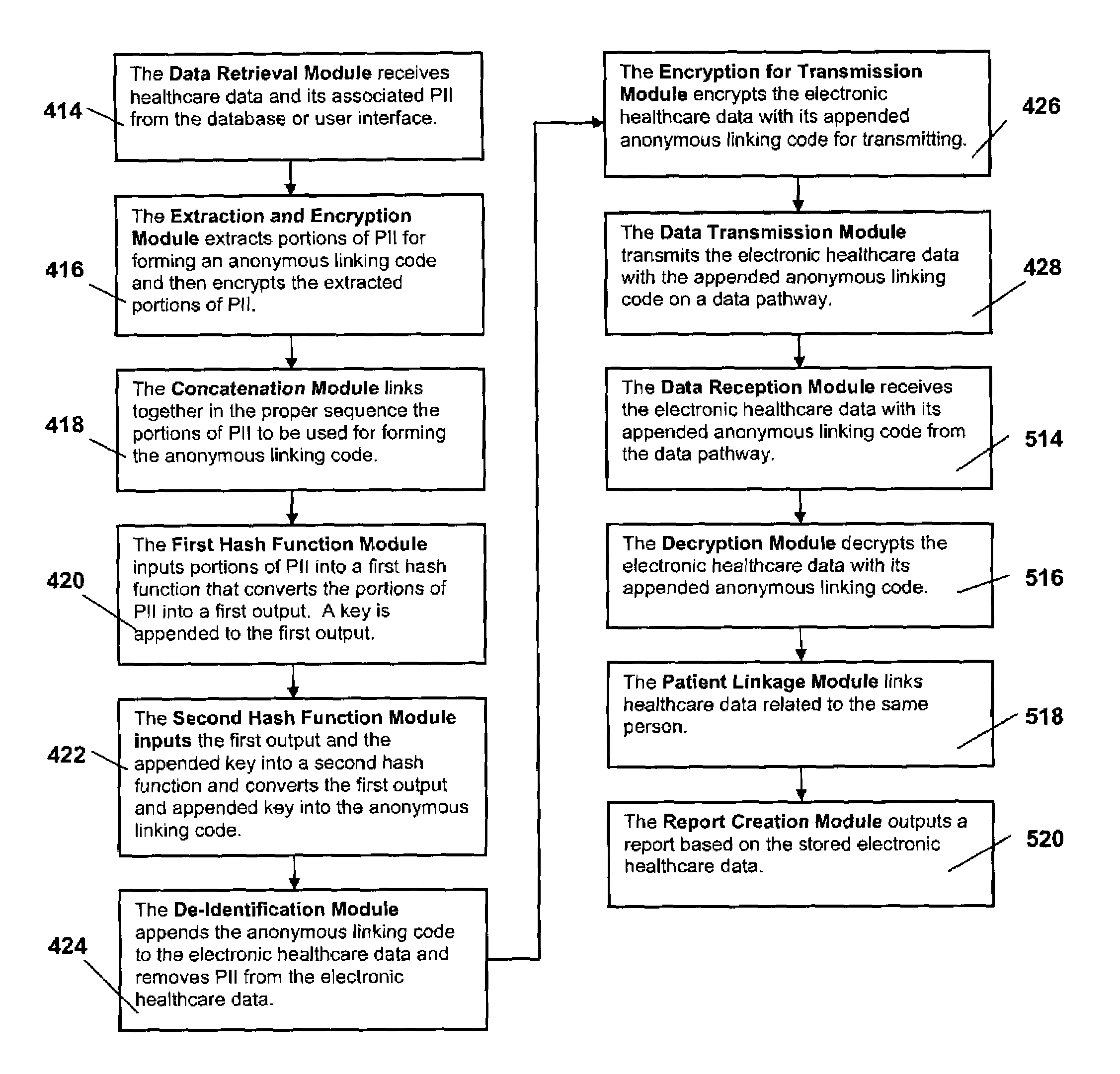
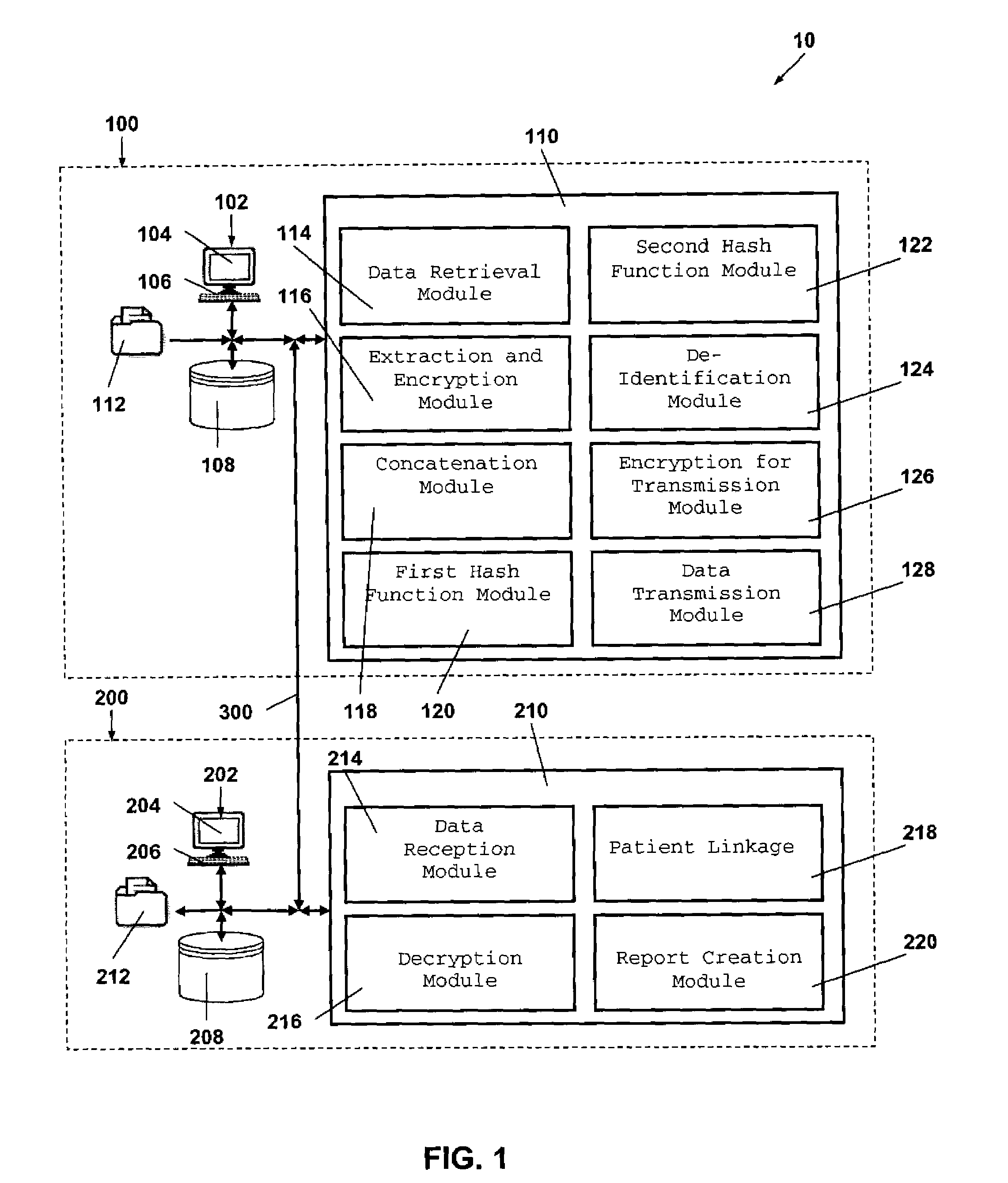
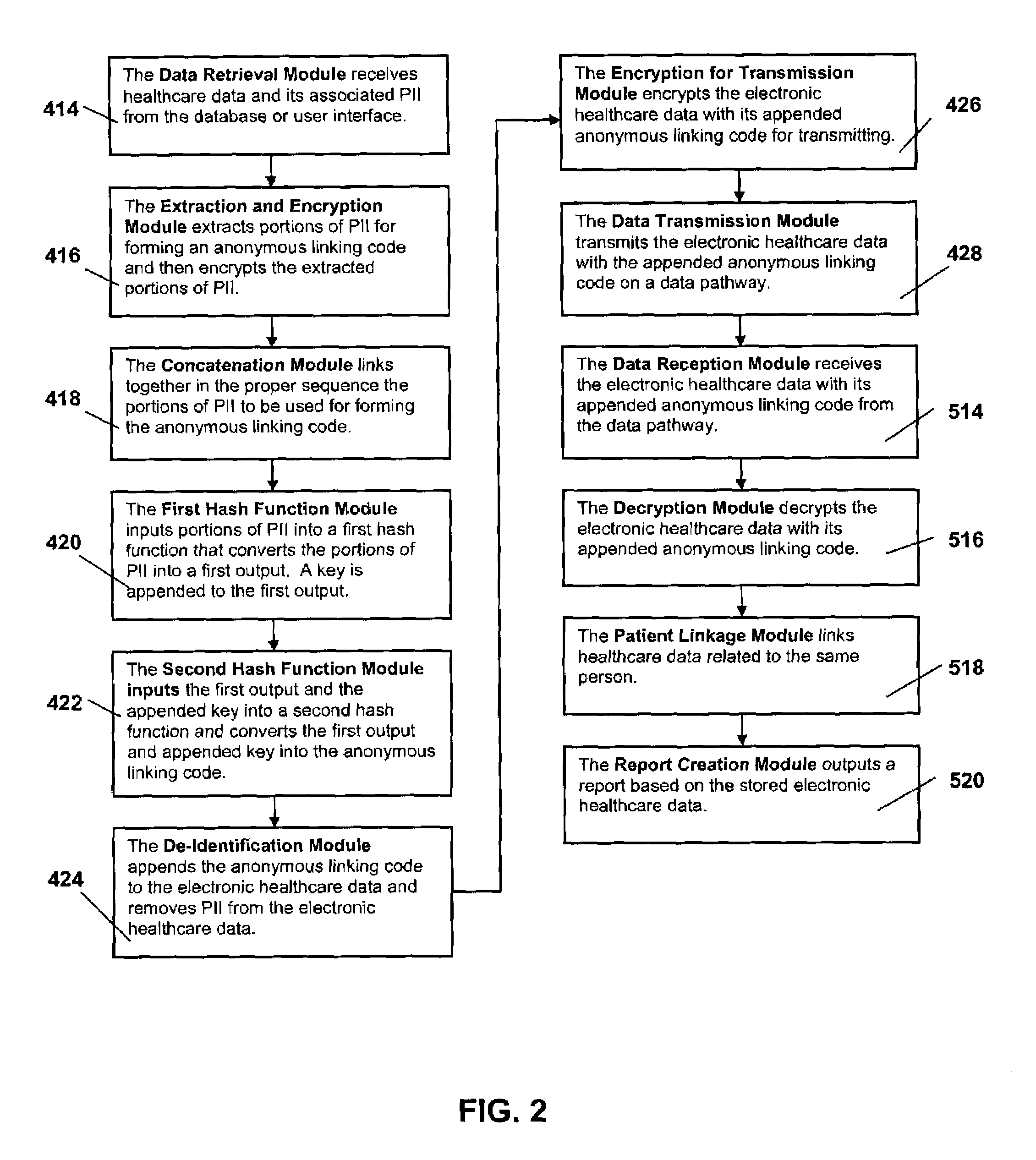
System and method for the protection and de-identification of health care data
ActiveUS20080147554A1Computer security arrangementsPatient personal data managementHash functionInternet privacy
A system for protecting and de-identifying healthcare data includes a storage device for storing the healthcare data and personally identifiable information for a person and a processor in communication with the database. The processor generates an anonymous linking code using a keyed hash function and a second hash function. The anonymous linking code is based at least in part on a portion of the personally identifiable information. The processor further appends the anonymous linking code to the healthcare data for the person.
Owner:IQVIA INC
High-Performance Distributed Data Storage System with Implicit Content Routing and Data Deduplication
InactiveUS20150039645A1Digital data information retrievalDigital data processing detailsHash functionData location
A write request that includes a data object is processed. A hash function is executed on the data object, thereby generating a hash value that includes a first portion and a second portion. A data location table is queried with the first portion, thereby obtaining a storage node identifier. The data object is sent to a storage node associated with the storage node identifier. A write request that includes a data object and a pending data object identification (DOID) is processed, wherein the pending DOID comprises a hash value of the data object. The pending DOID is finalized, thereby generating a finalized data object identification (DOID). The data object is stored at a storage location. A storage manager catalog is updated by adding an entry mapping the finalized DOID to the storage location. The finalized DOID is output.
Owner:EBAY INC
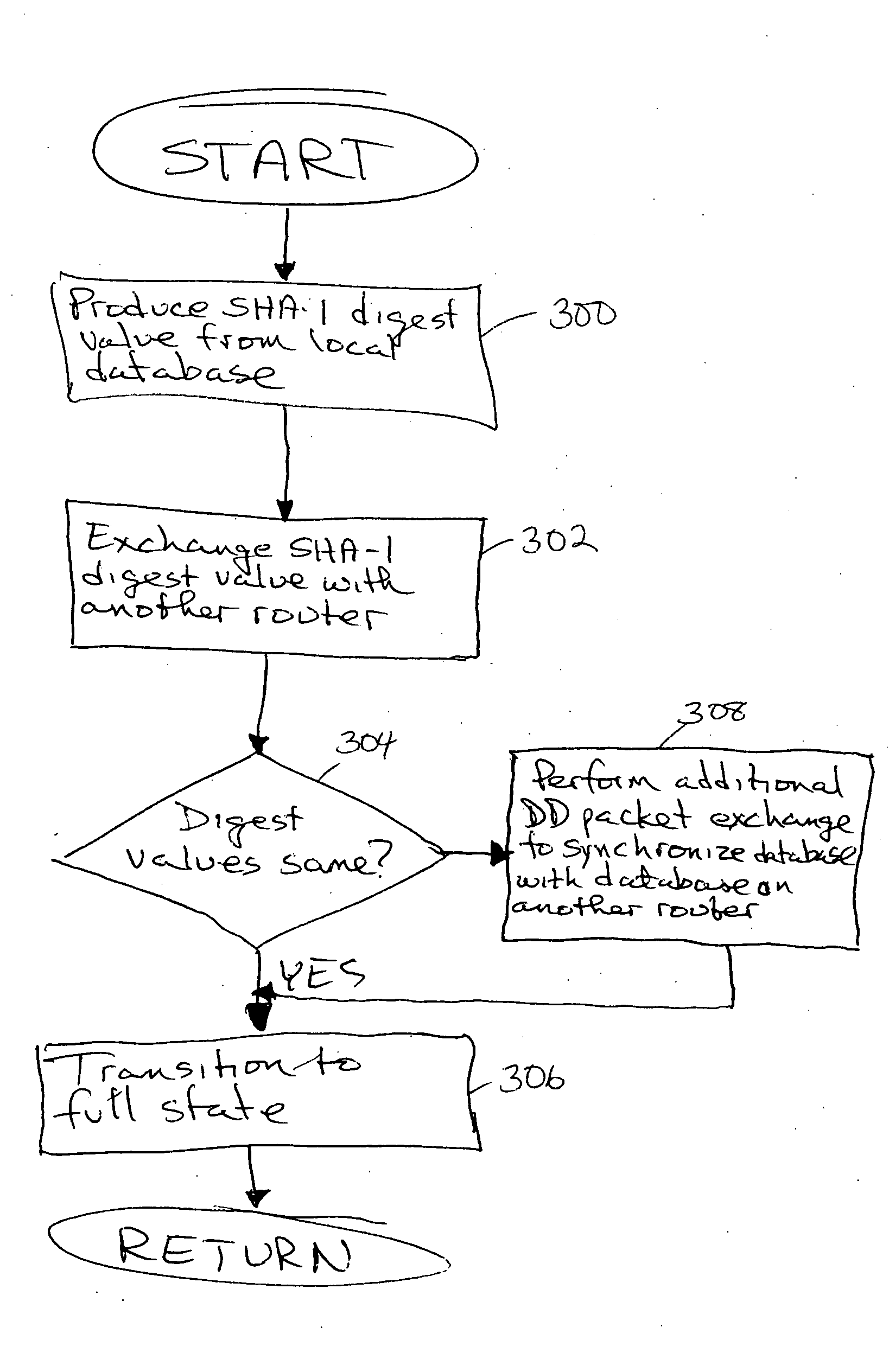
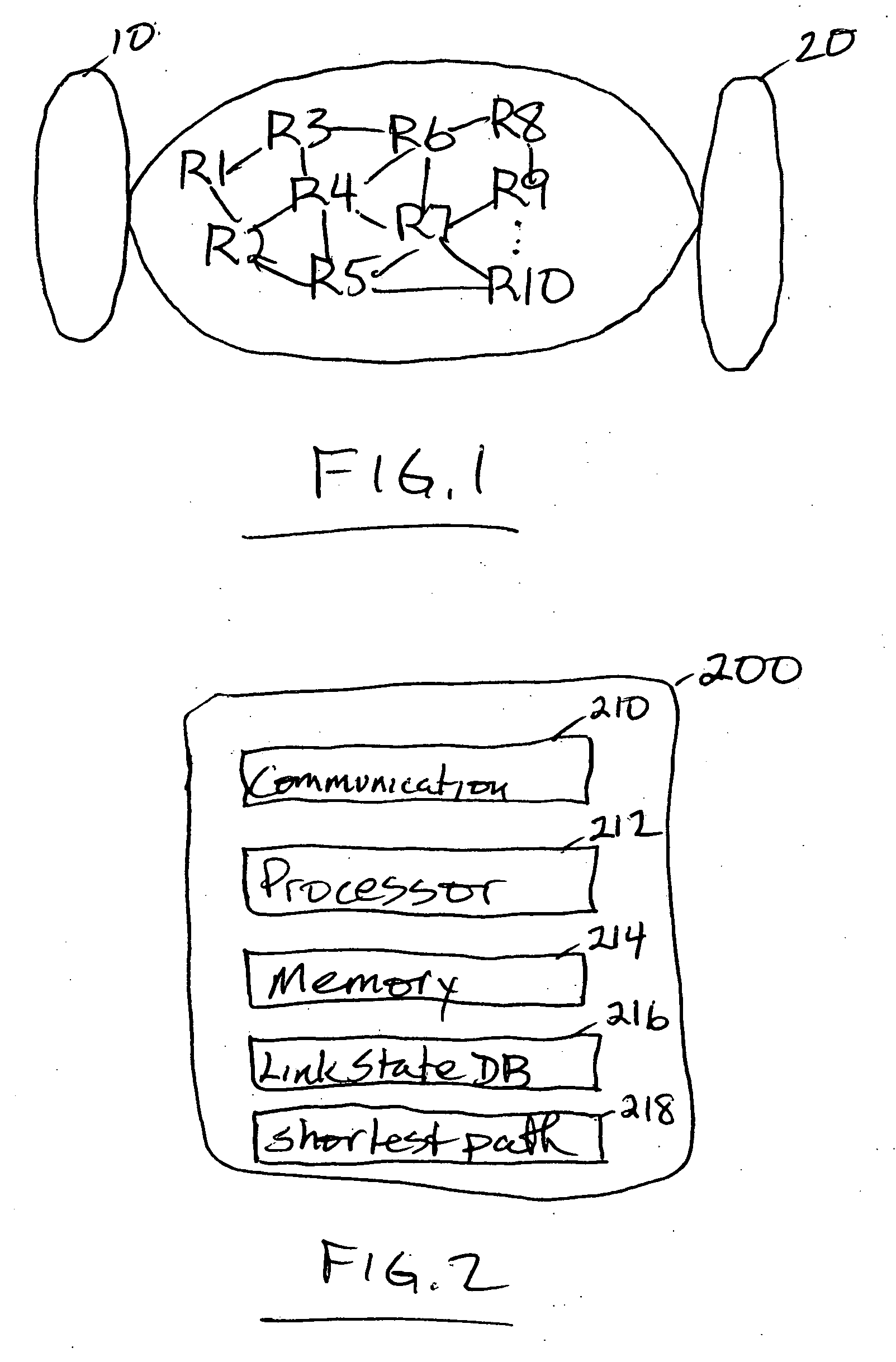
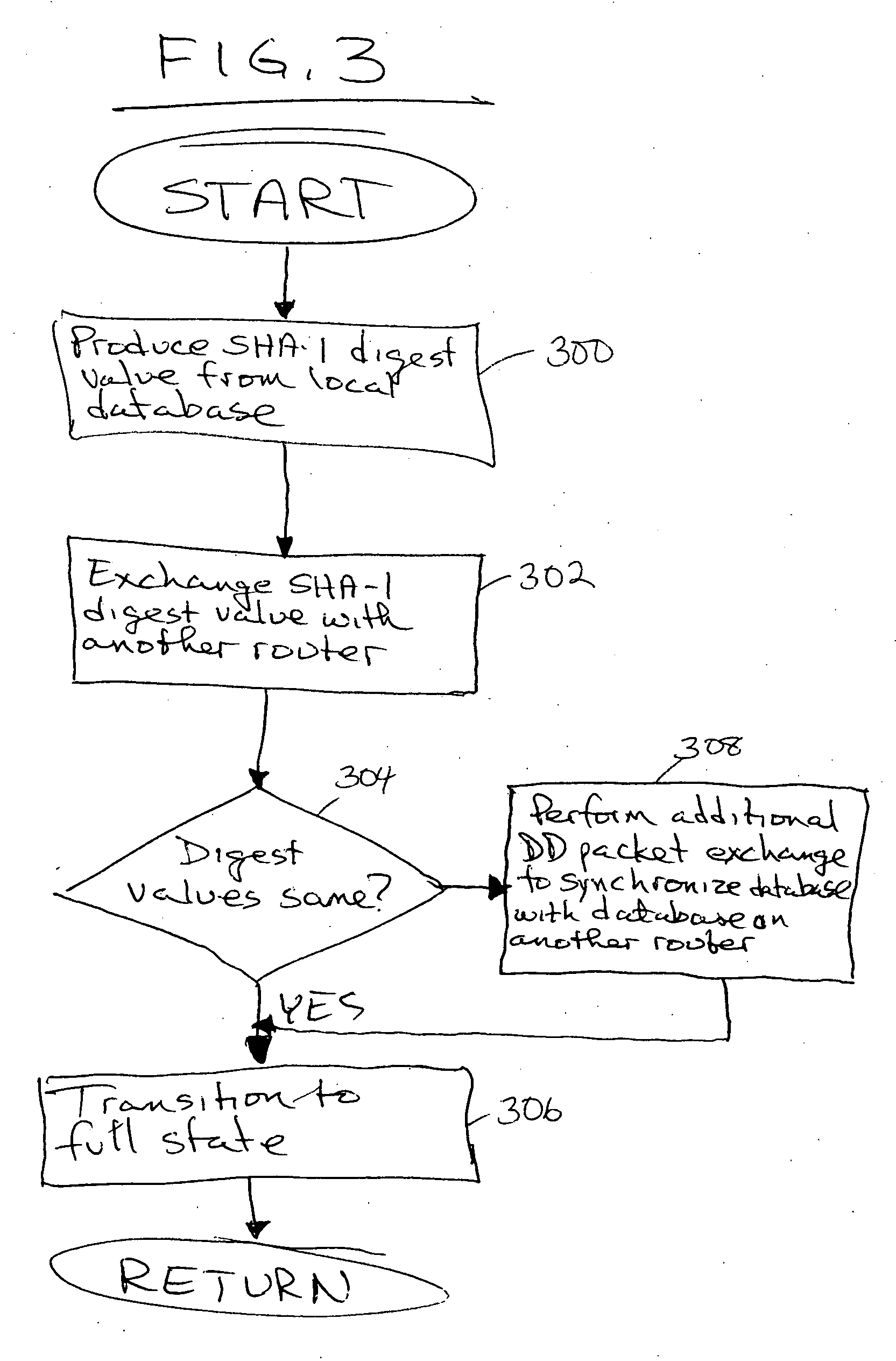
Method and apparatus to minimize database exchange in OSPF by using a SHA-1 digest value
The present invention provides a method of determining whether database located on a first router is synchronized with the database located on a second router by performing a hash function on the values contained in a link state database to derive a SHA-1 digest value. In an embodiment, the digest value is based on LSA type. The digest value is exchanged initially during a database description packet swap between the first router and second router. If the digest values are the same, the databases are already synchronized. The routers thus skip the database description packet exchange of LSAs in the database and go directly to FULL state, indicating full synchronization between databases on the first and second router and announcing adjacency to each other. If the digest differs, normal database description packet exchange is performed as specified in OSPF.
Owner:CISCO TECH INC
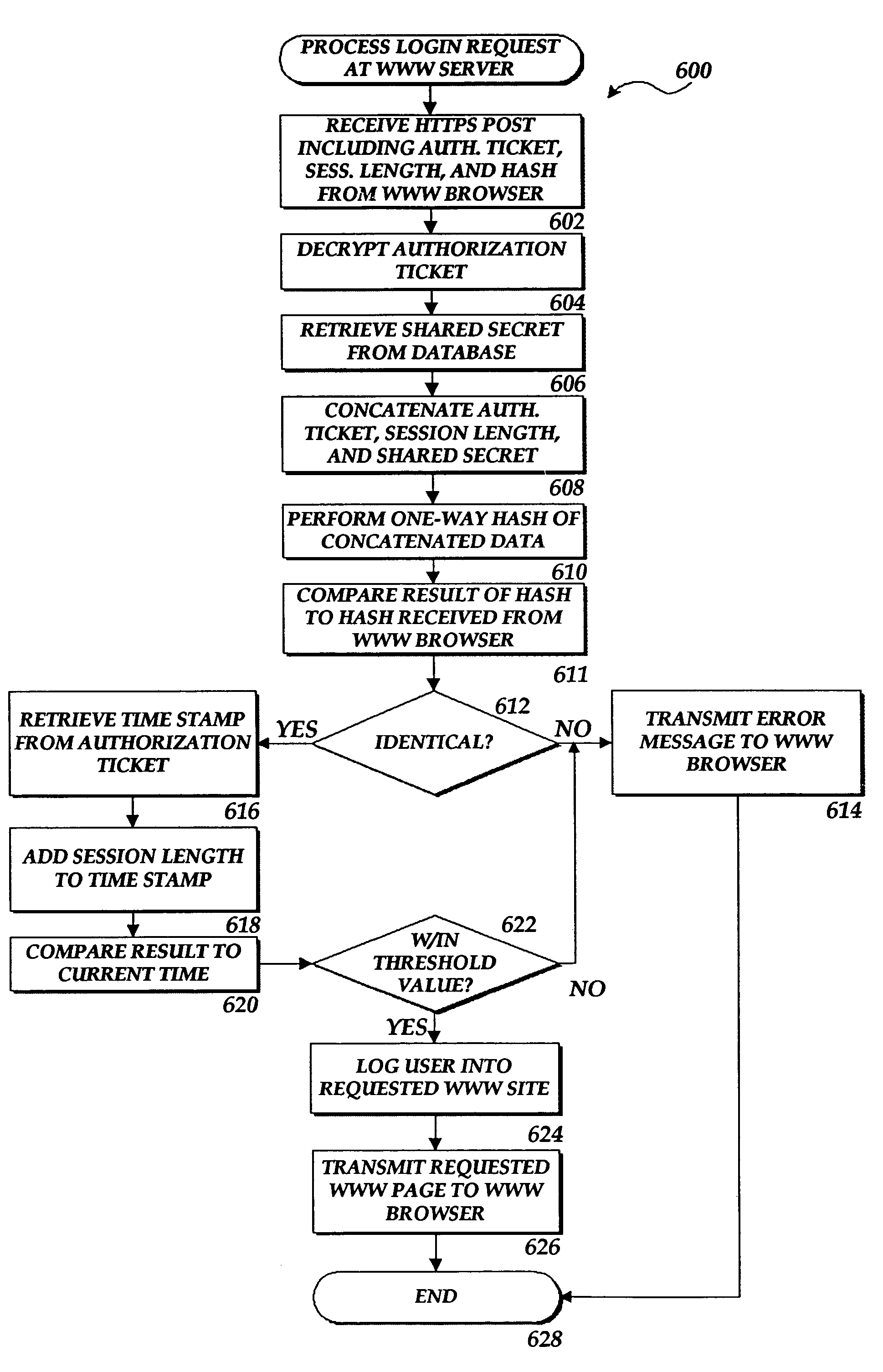
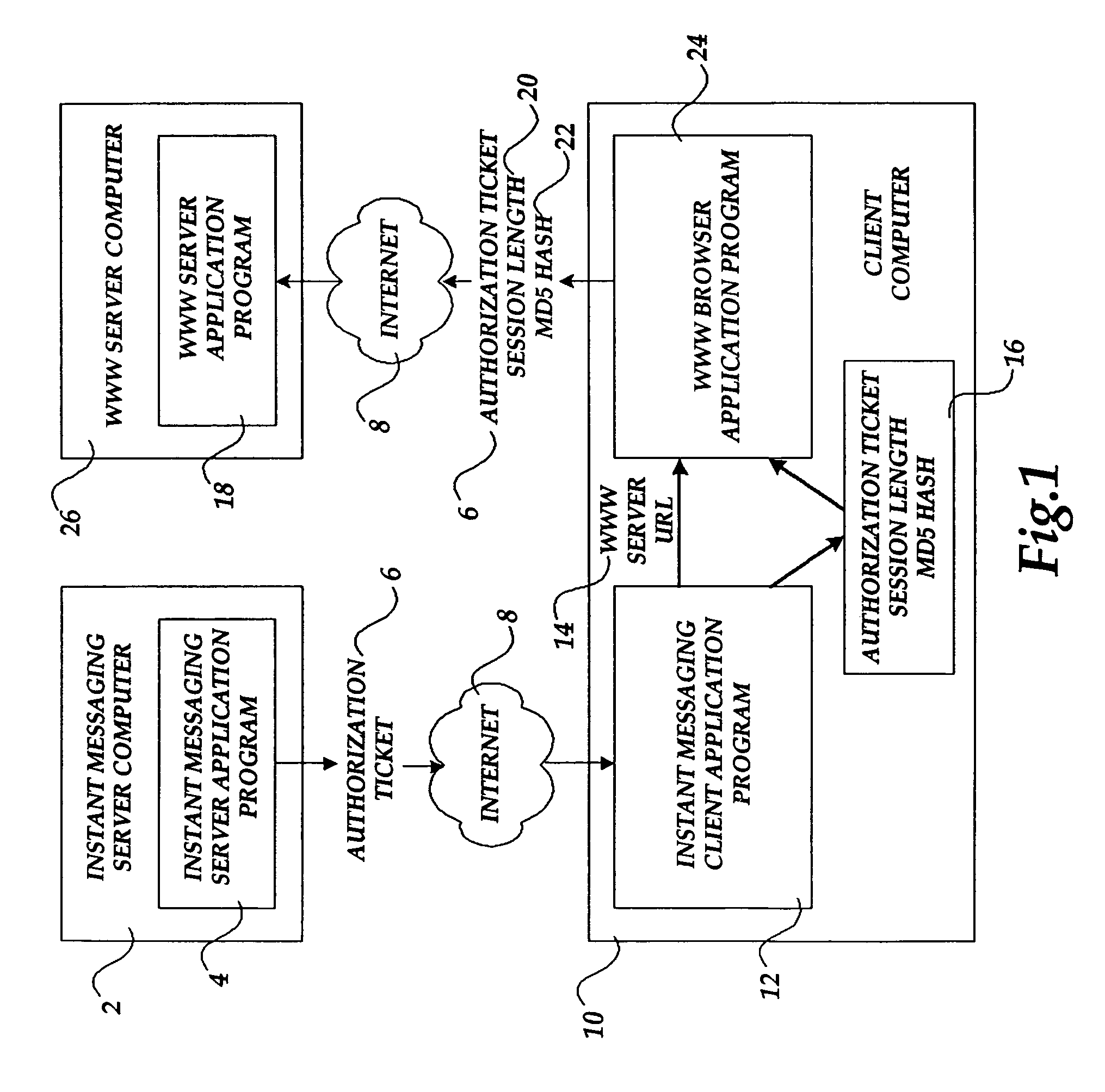
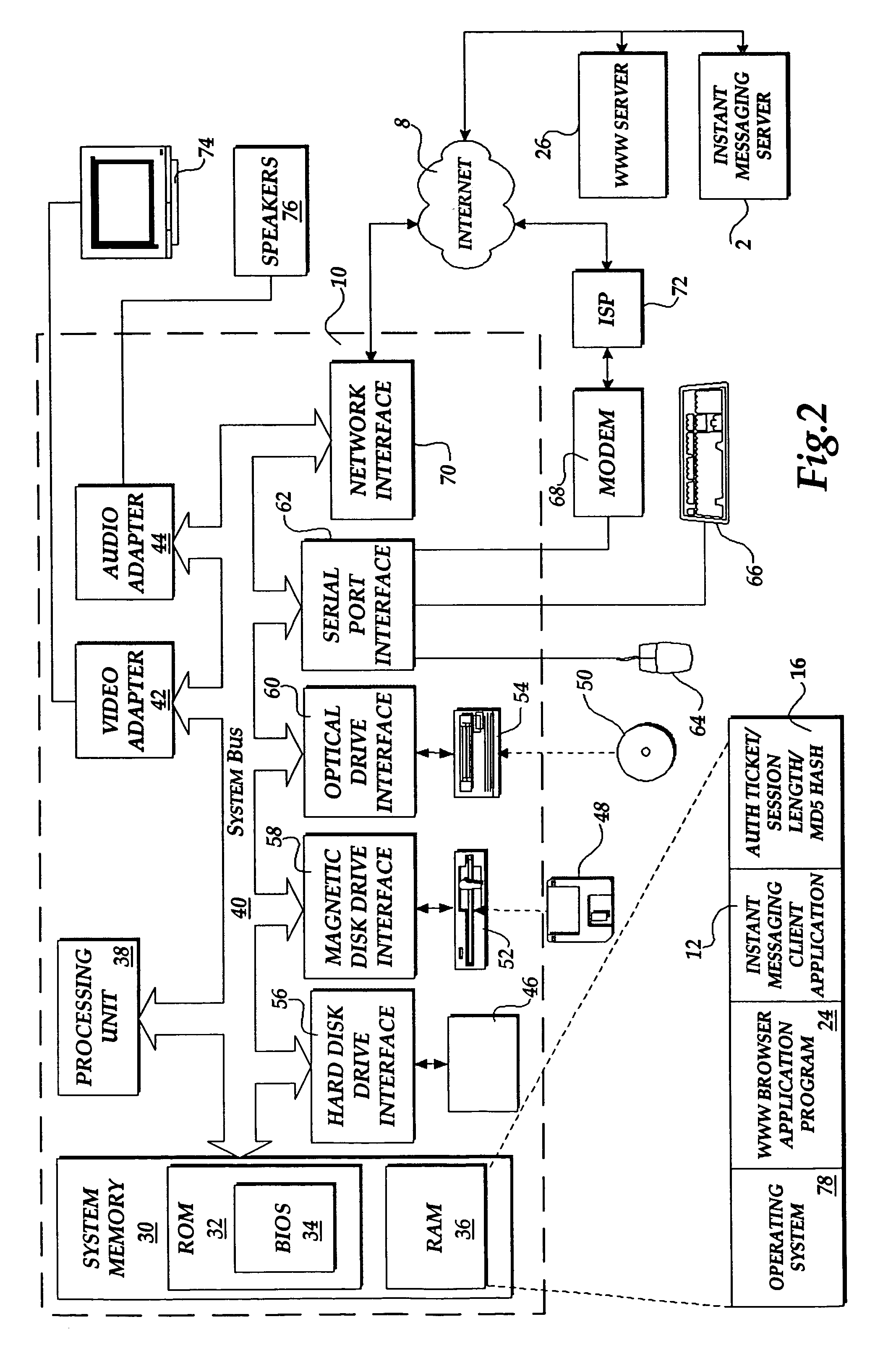
Method and system for authorizing a client computer to access a server computer
InactiveUS7089585B1Key distribution for secure communicationDigital data processing detailsAuthorization certificateHash function
The present invention includes a client computer, a first server computer, and a second server computer. The first server provides an authorization ticket containing a time stamp to the client computer when the client computer is authorized to access the first server. An elapsed time counter is started at the client computer when access is provided to the first server. When a request is received at the client computer to access the second server, the client computer determines the session length based upon the elapsed time counter. The client computer calculates a hash value for the authorization ticket, the session length, and a secret shared with the second server computer. The client computer transmits a login request to the second server including the authorization ticket, the session length, and the hash. The second server decrypts the authorization ticket and retrieves a copy of the shared secret. The second server executes a hash function on the authorization ticket, the session length, and the shared secret. The second server then compares the computed hash to the hash value received from the second client application. If the two hash values are identical, the second server retrieves the time stamp from the authorization ticket and adds the session length to the time stamp. The second server then compares the resulting value to the current time. If the resulting value and the current time are within a preset threshold value, the client computer is provided.
Owner:MICROSOFT TECH LICENSING LLC
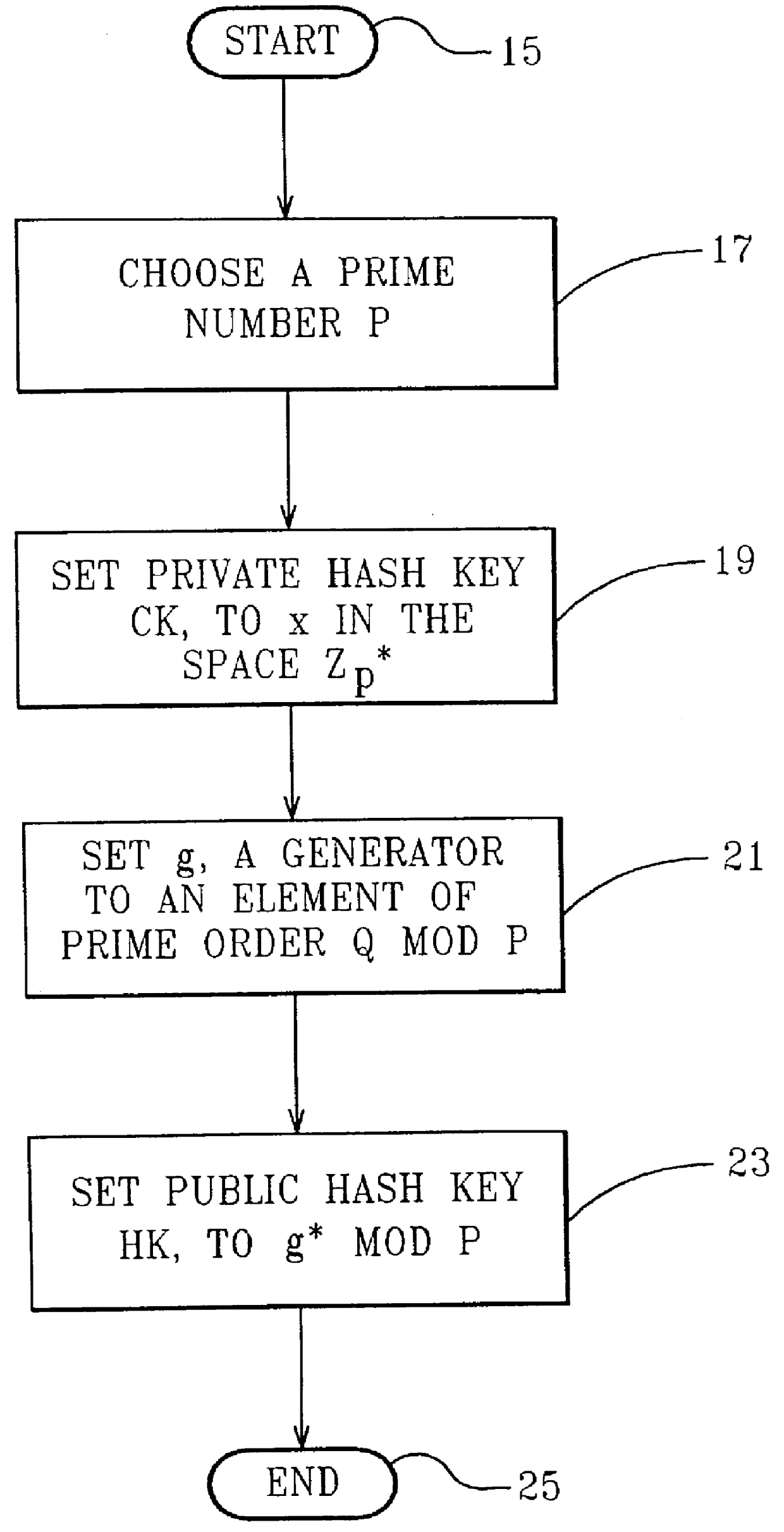
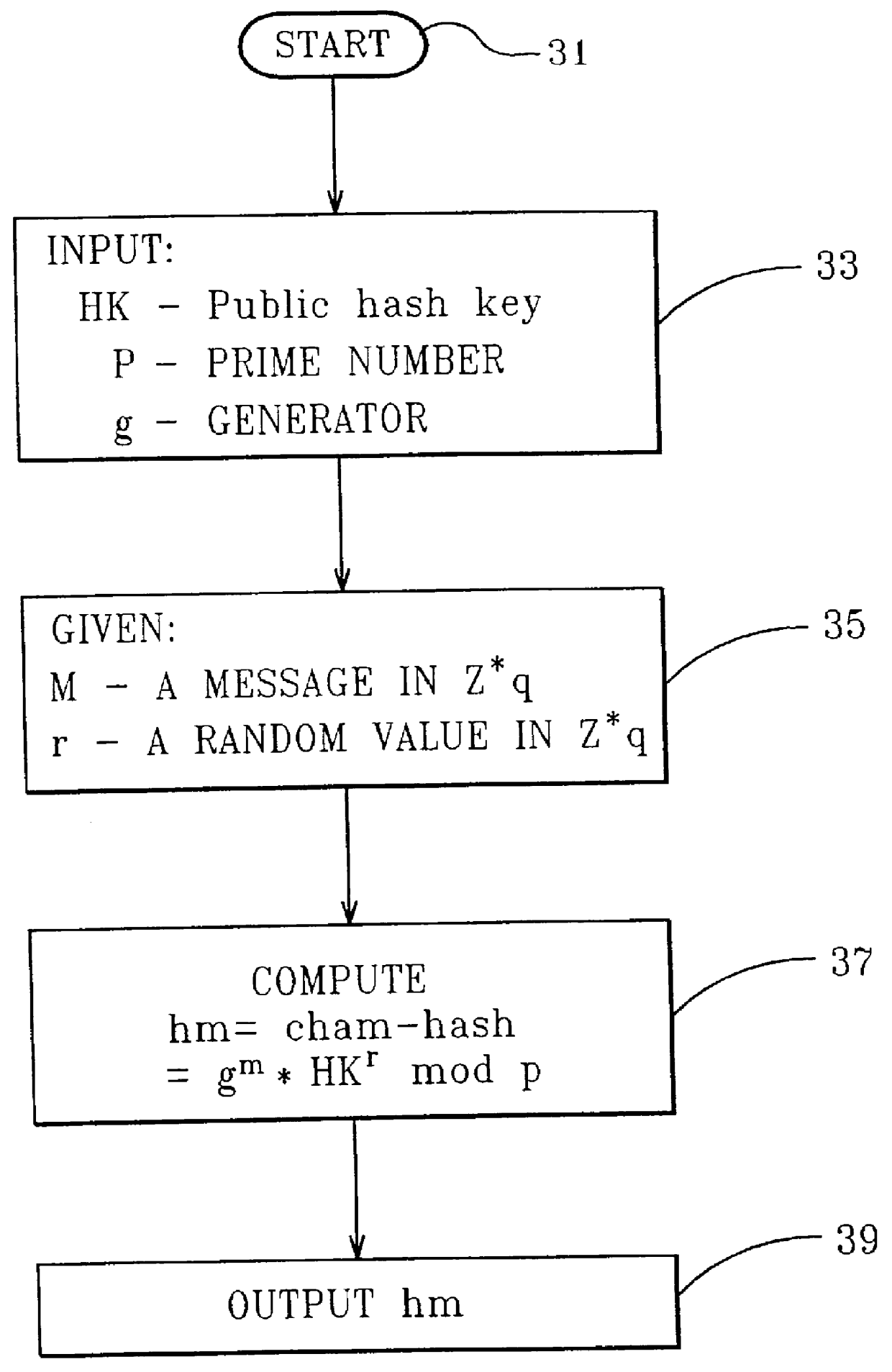
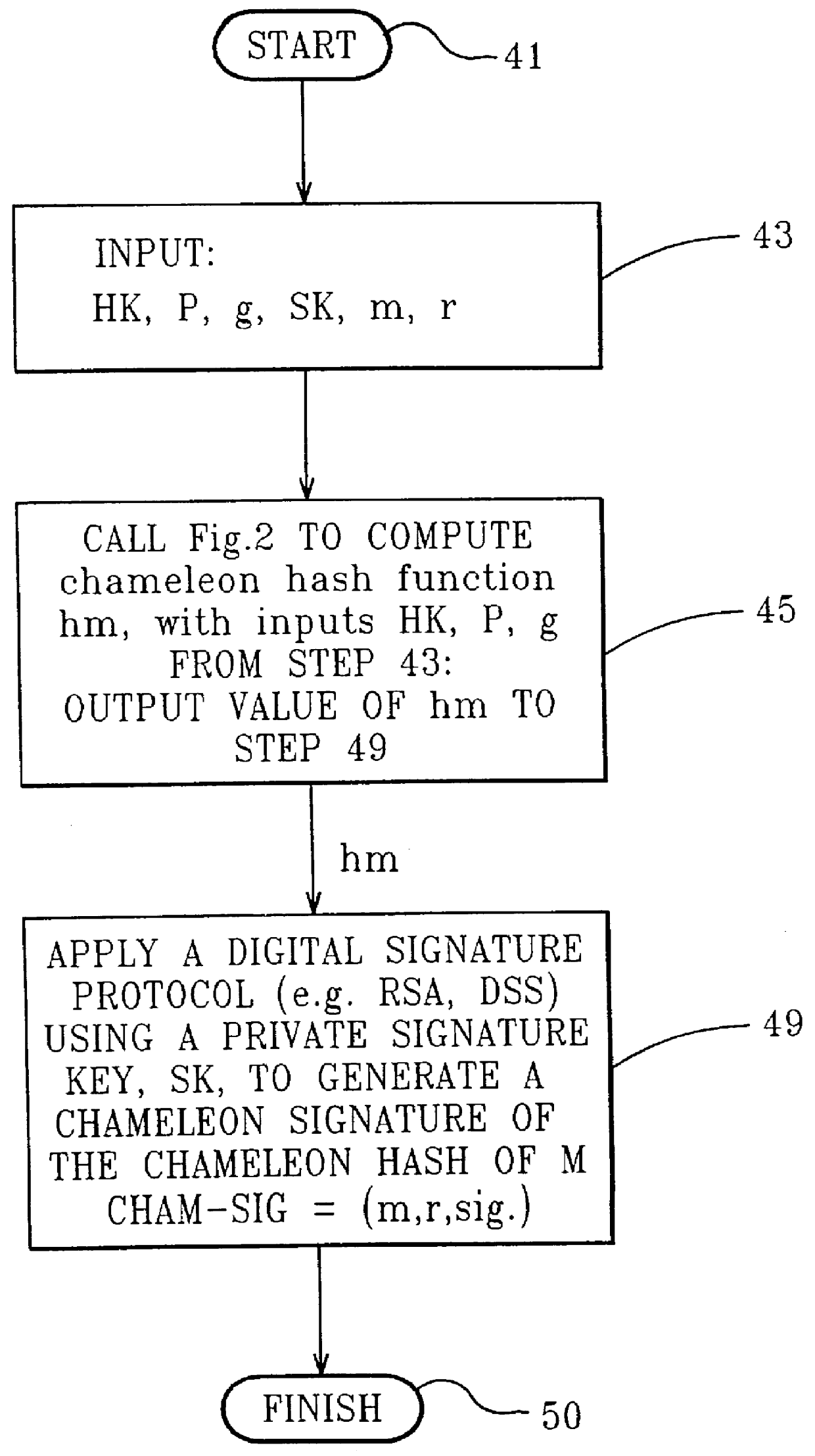
Chameleon hashing and signatures
InactiveUS6108783AImprove performanceSimple and cost-effective constructionPublic key for secure communicationUser identity/authority verificationThird partyHash function
A method for providing a digital signature, "chameleon signatures", which provide the signer of a digital signature exclusive control to disclose the contents of the signed information to third parties. The signatures are closely related to "undeniable signatures", but allow for simpler and more efficient realizations. The method is essentially non-interactive requiring no communication between sender and receiver and do not involve the design and complexity of zero knowledge proofs on which traditional undeniable signatures are based. The method employs a combination of standard digital signing methods with a unique hash functions. These hash functions are characterized by the non-standard property of being collision resistant for the signer but collision tractable for the recipient.
Owner:IBM CORP
Traffic distribution control device
InactiveUS20050276263A1Process stabilityHigh bandwidthError preventionTransmission systemsTraffic capacityHash function
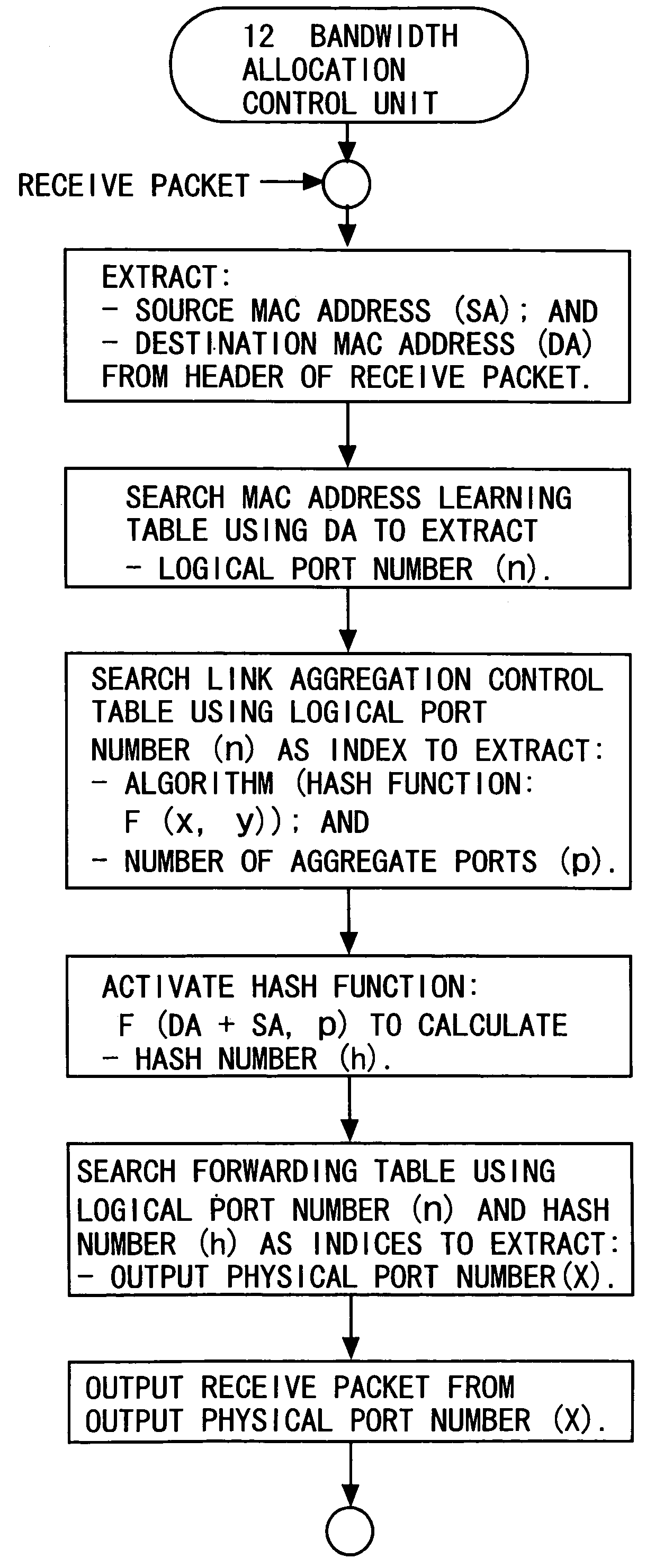
A data transmission device 10 serving as a traffic distribution control device is a device which, in order to distribute traffic across a plurality of physical ports composing a logical port for link aggregation, uses a hash function to calculate a hash value from a destination address and a source address of a receive packet, and determines a destination physical port. The traffic distribution control device includes a measuring unit 13 that measures an output flow rate of a packet outputted from each of the plurality of physical ports; a calculating unit 14 that calculates a flow rate ratio between the plurality of physical ports with respect to the measured output flow rates; and a first control unit 12 that feeds the calculated flow rate ratio back to a bandwidth distribution ratio between the plurality of physical ports to change numerical allocation of hash values for determining the destination physical port.
Owner:FUJITSU LTD
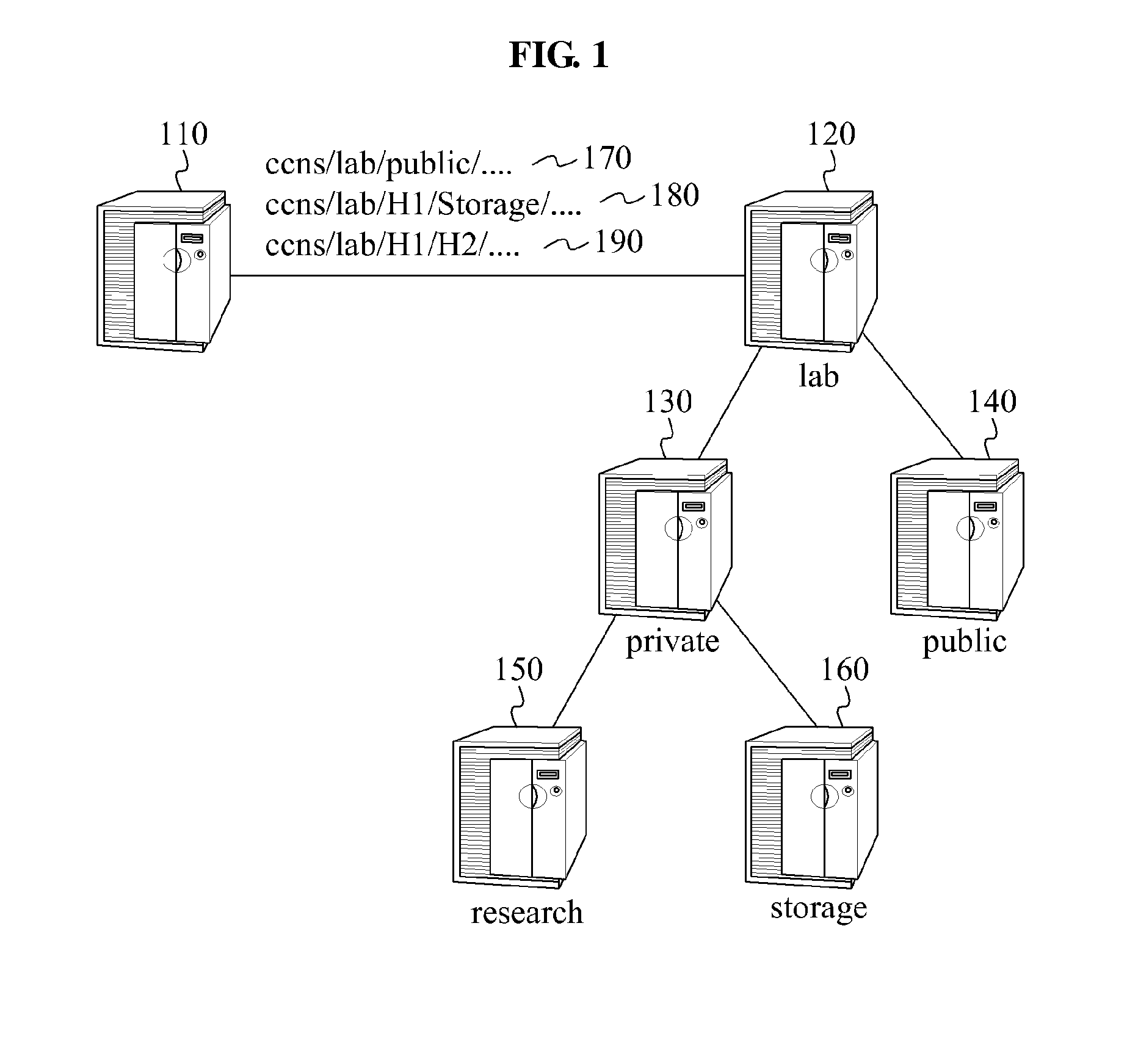
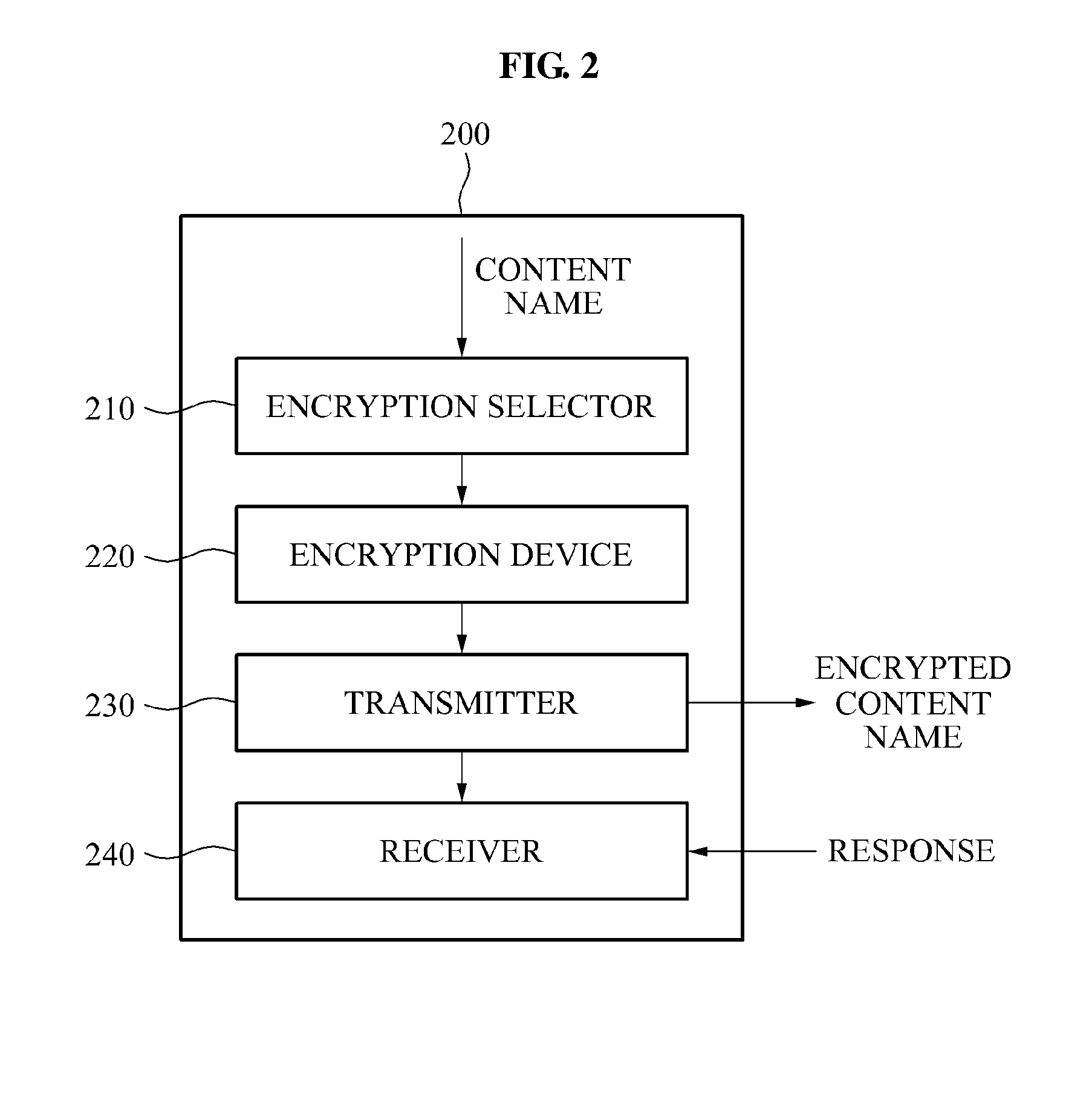
System for encrypting content name
InactiveUS20140149733A1Well formedEncryption apparatus with shift registers/memoriesComputer networkHash function
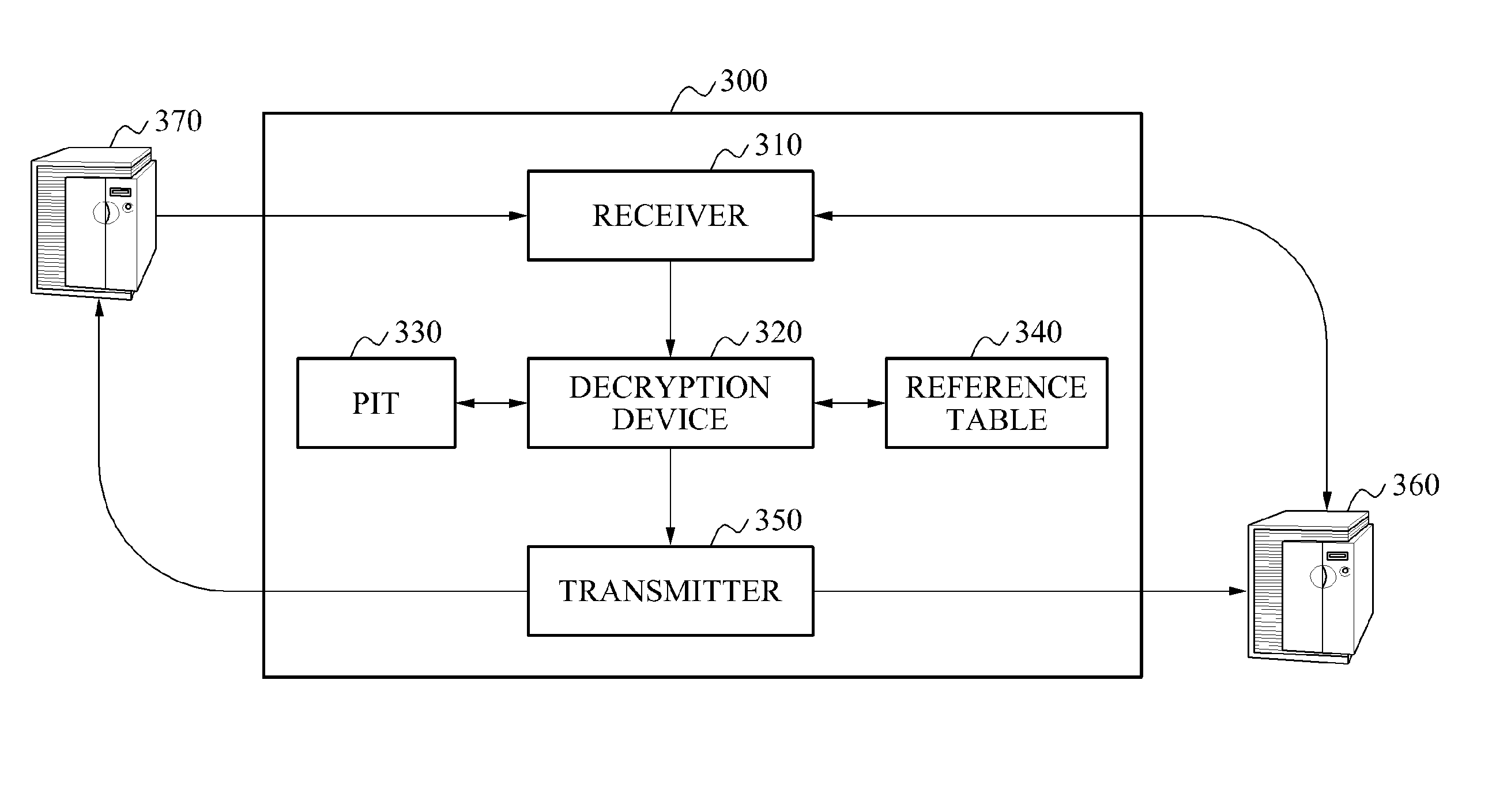
A system encrypts a name of content stored in a node of a hierarchical structure. A content receiving node encrypts a name of a predetermined node among names of nodes included in a content name, such as by using a hash function, and transmits the encrypted content name to receive the stored content. A relay node receives the content name including the encrypted name of the node and decrypts the encrypted name of the node, such as by using a reference table. The relay node uses the decrypted node name to relay the content request to the content storage node. Since the content name is encrypted, content routing may be performed without disclosing information associated with a hierarchical structure in which the content is stored.
Owner:SAMSUNG ELECTRONICS CO LTD
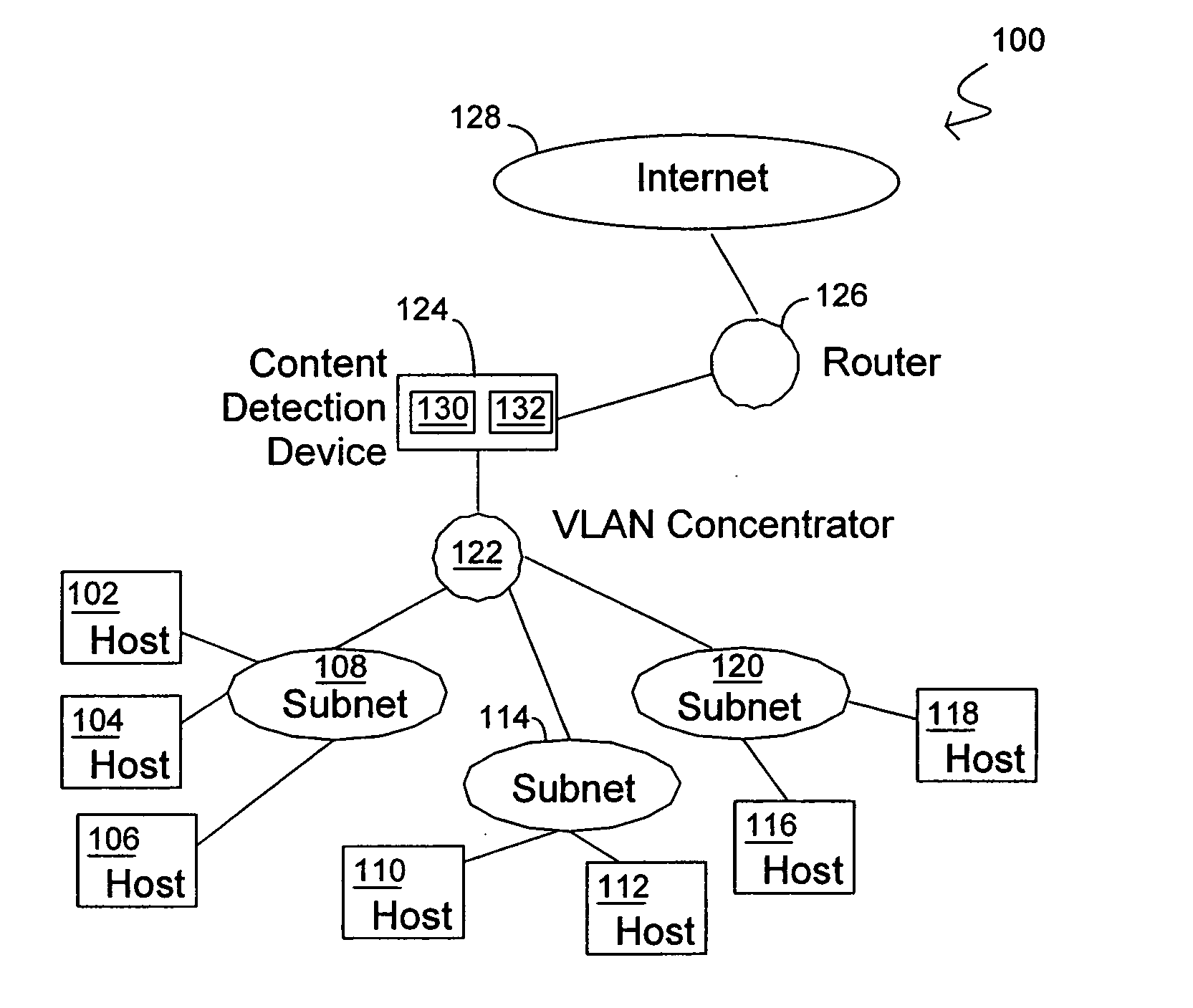
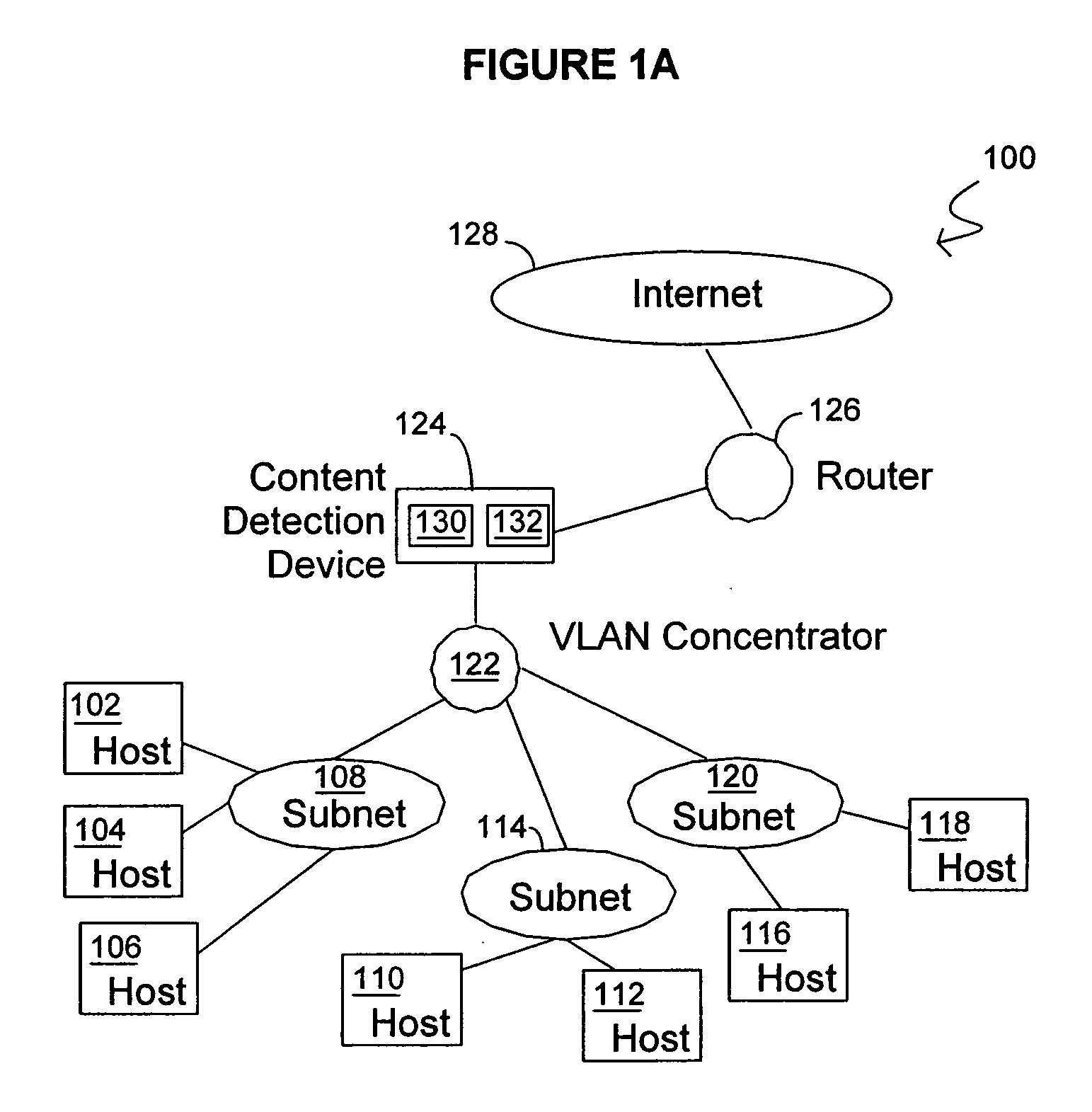
Methods and systems for content detection in a reconfigurable hardware
InactiveUS20060053295A1Improve throughputMaintain throughputMemory loss protectionPublic key for secure communicationDuplicate contentHash function
Methods and systems consistent with the present invention identify a repeating content in a data stream. A hash function is computed for at least one portion of a plurality of portions of the data stream. The at least one portion of the data stream has benign characters removed therefrom to prevent the identification of a benign string as the repeating content. At least one counter of a plurality of counters is incremented responsive to the computed hash function result. Each counter corresponds to a respective computed hash function result. The repeating content is identified when the at least one of the plurality of counters exceeds a count value. It is verified that the identified repeating content is not a benign string.
Owner:WASHINGTON UNIV IN SAINT LOUIS
Shared dictionary between devices
ActiveUS20130318051A1Digital data information retrievalDigital data processing detailsComputer hardwareHash function
In one embodiment, a system and method for managing a network deduplication dictionary is disclosed. According to the method, the dictionary is divided between available deduplication engines (DDE) in deduplication devices that support shared dictionaries. The fingerprints are distributed to different DDEs based on a hash function. The hash function takes the fingerprint and hashes it and based on the hash result, it selects one of the DDEs. The hash function could select a few bits from the fingerprint and use those bits to select a DDE.
Owner:AVAGO TECH INT SALES PTE LTD
Method and device for inserting and authenticating a digital signature in digital data
InactiveUS7216232B1Reduce storageReduce bandwidth requirementsUser identity/authority verificationUnauthorized memory use protectionDigital dataHash function
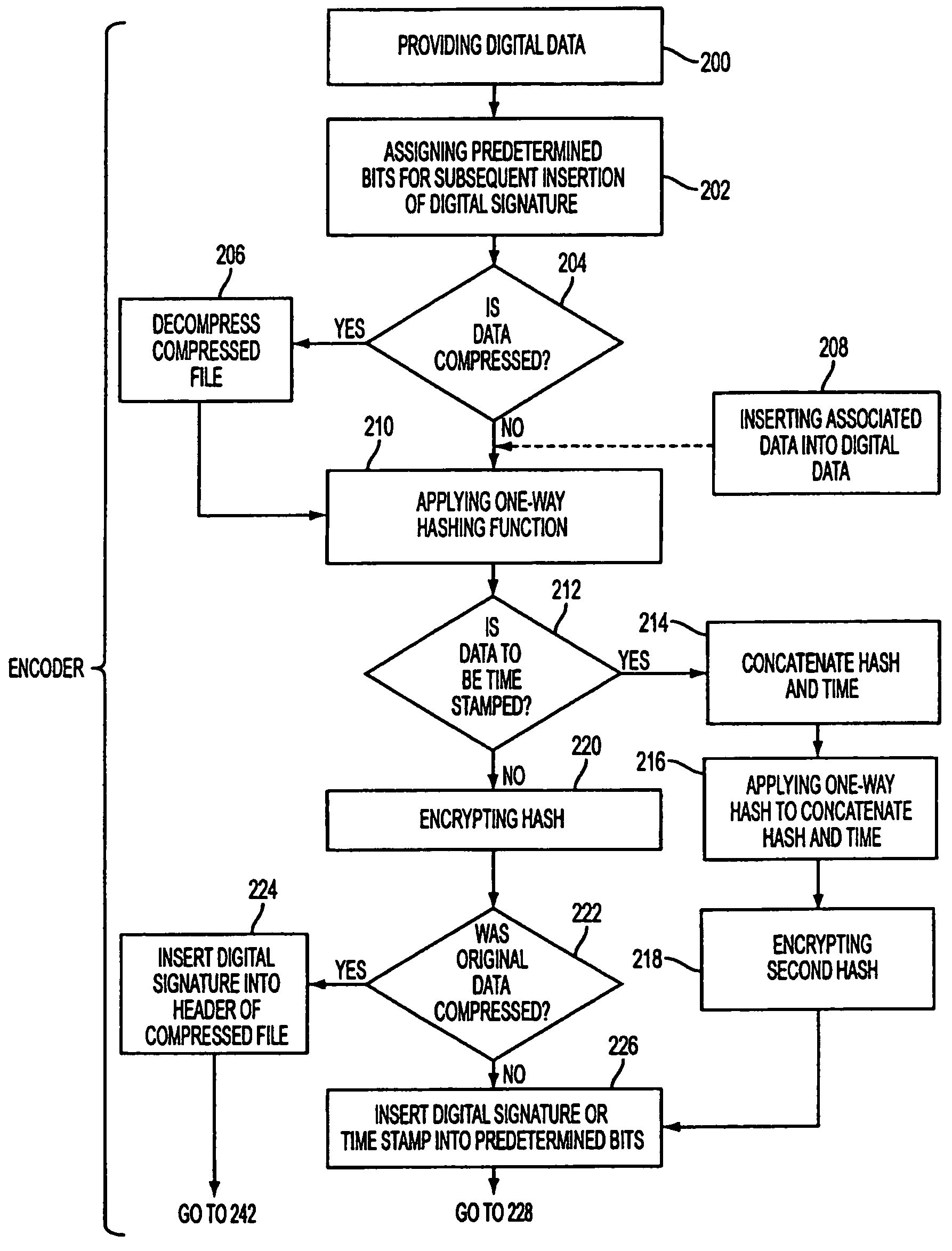
A method for inserting a digital signature into digital data is provided. The digital data has bits and the method includes the steps of: assigning predetermined bits of the digital data for receiving the digital signature; signing the digital data excluding the predetermined bits resulting in the digital signature; and inserting the digital signature into the predetermined bits of the digital data for subsequent authentication of the digital data. Also provided is a method for authenticating digital data having the embedded digital signature in the predetermined bits of the digital data including the steps of: extracting the digital signature from the predetermined bits; decrypting the digital signature from the digital data resulting in a first hash; applying a known one-way hashing function used by an encoder of the digital data to the digital data excluding the predetermined bits resulting in a second hash; and comparing the first hash to the second hash wherein if the first hash matches the second hash the digital data is authentic. In a preferred version of the methods of the present invention, the method further includes the step of inserting associated data into the digital data prior to the signing step such that the digital signature authenticates both the associated data as well as the digital data. Preferably, the associated data is inserted into the bits of the digital data excluding the predetermined bits.
Owner:NEC CORPOATION OF AMERICA
System and method for data deduplication for disk storage subsystems
ActiveUS20120016845A1Low costShorten the timeDigital data processing detailsError detection/correctionData setData segment
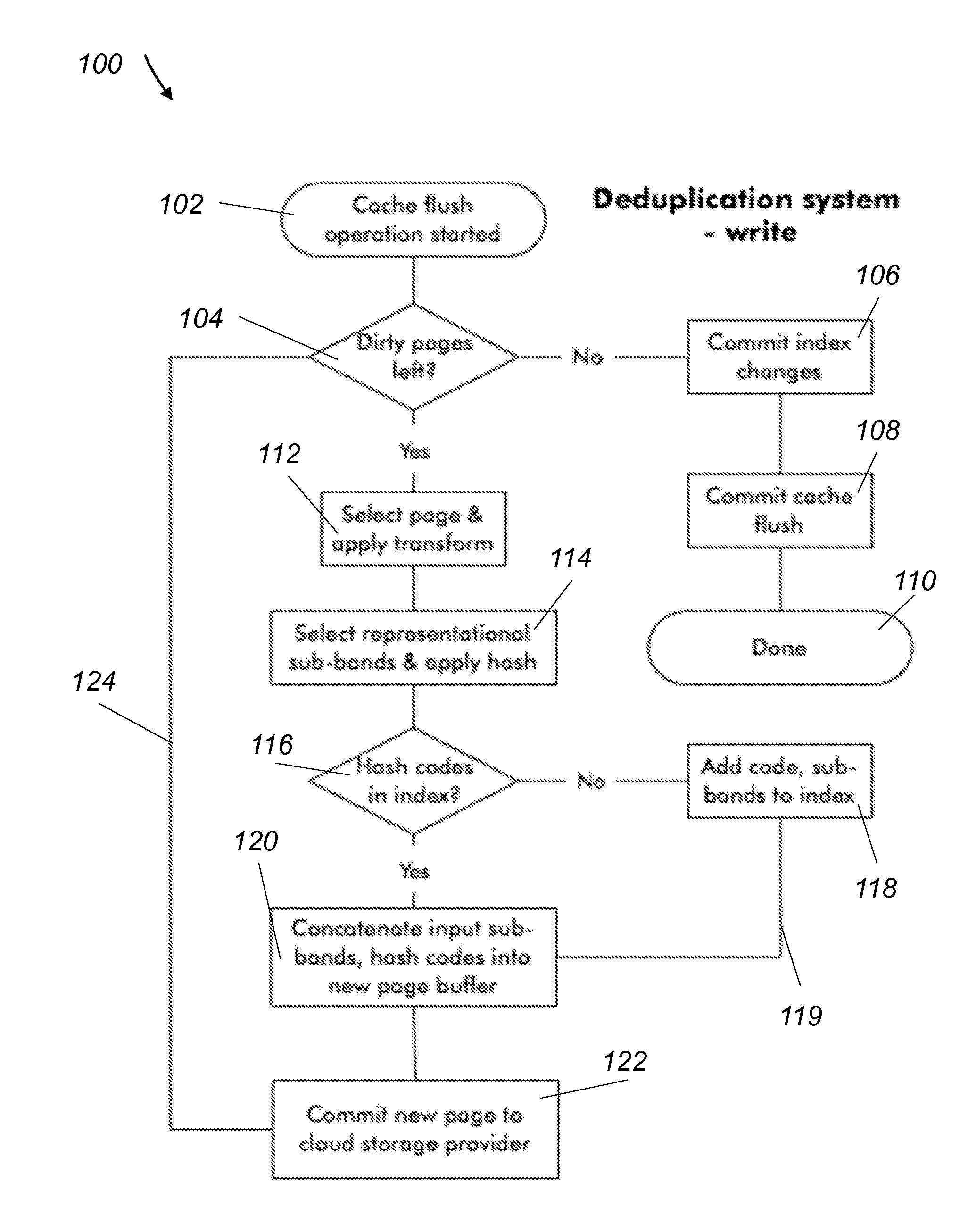
A method for data deduplication includes the following steps. First, segmenting an original data set into a plurality of data segments. Next, transforming the data in each data segment into a transformed data representation that has a band-type structure for each data segment. The band-type structure includes a plurality of bands. Next, selecting a first set of bands, grouping them together and storing them with the original data set. The first set of bands includes non-identical transformed data for each data segment. Next, selecting a second set of bands and grouping them together. The second set of bands includes identical transformed data for each data segment. Next, applying a hash function onto the transformed data of the second set of bands and thereby generating transformed data segments indexed by hash function indices. Finally, storing the hash function indices and the transformed data representation of one representative data segment in a deduplication database.
Owner:EMC IP HLDG CO LLC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com