Patents
Literature
261 results about "Duplicate detection" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
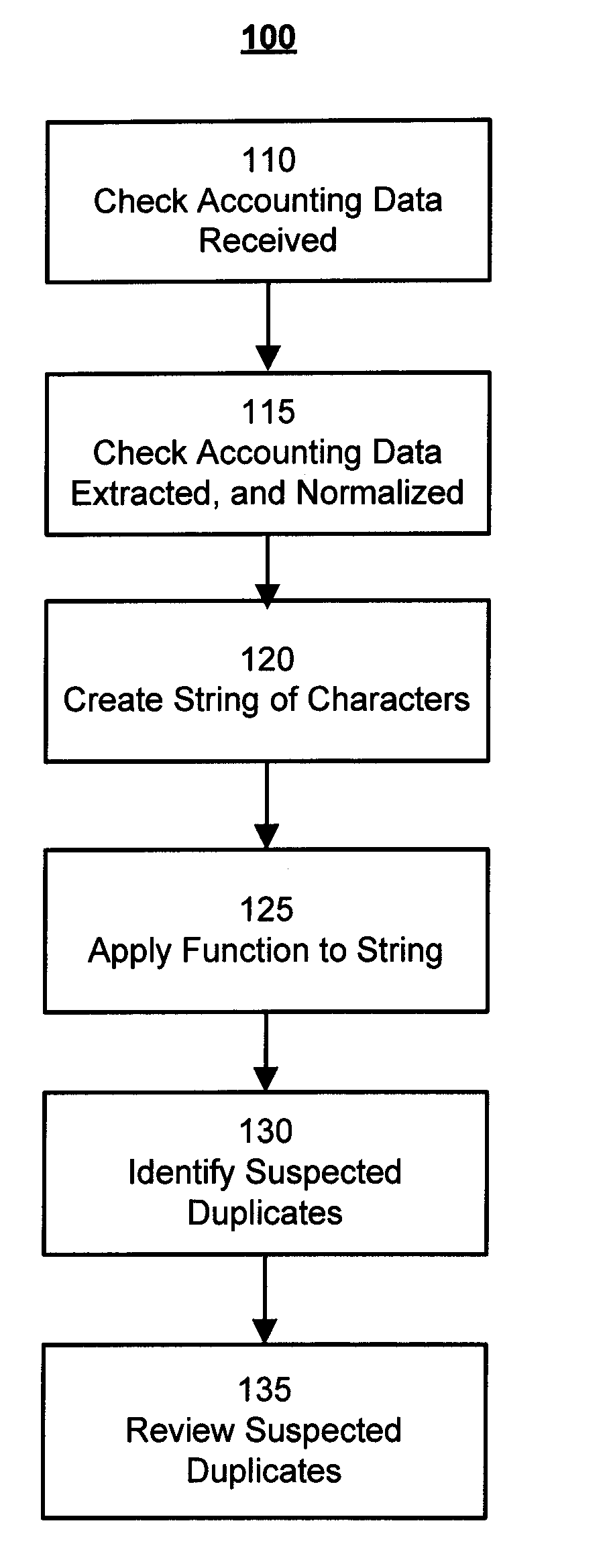
Duplicate Detector is smart enough to find duplicate or similar records in many situations. Duplicate Detector for SugarCRM works on any existing or custom field of type varchar, name or phone. It prompts the user if the value has already been used while they are creating records in the edit view or quick create mode.
Method and System for Duplicate Check Detection
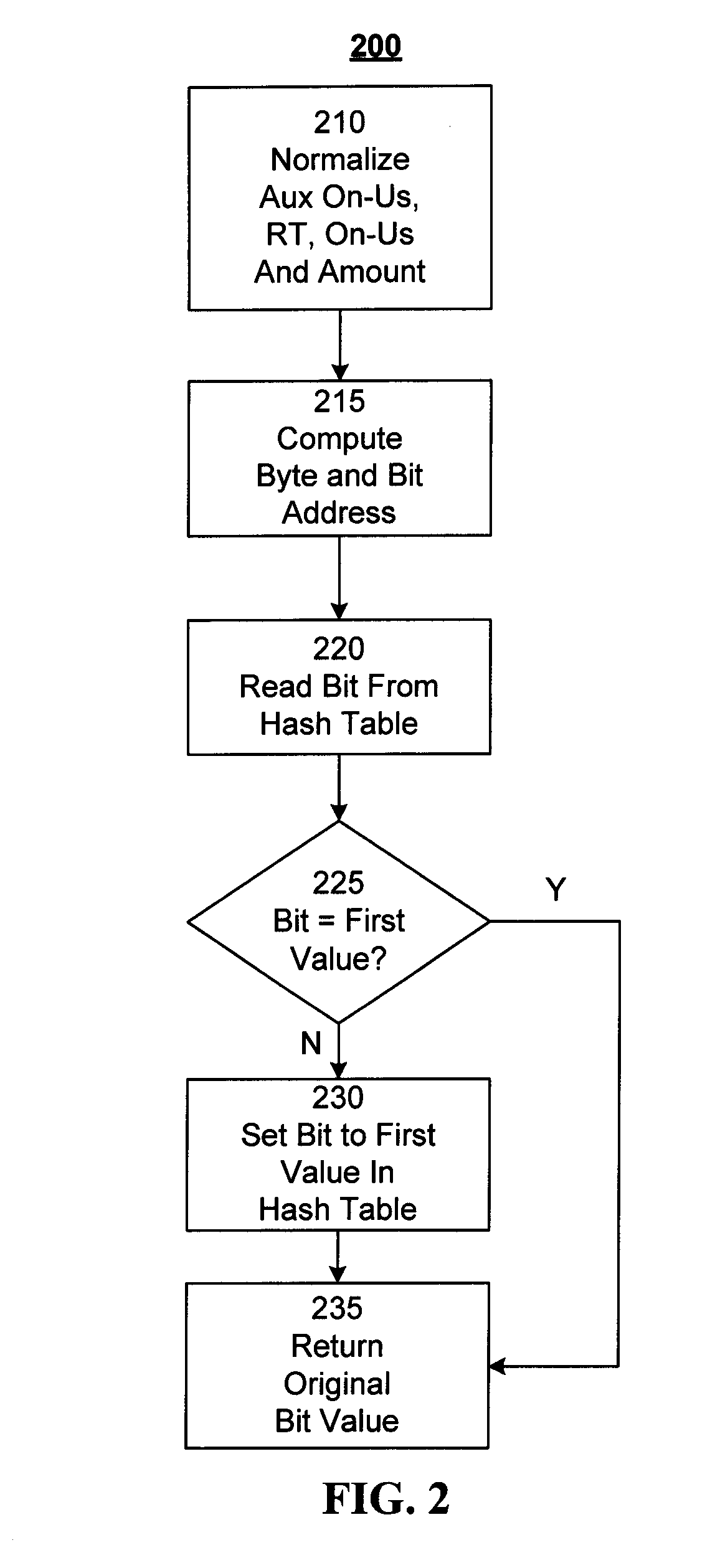
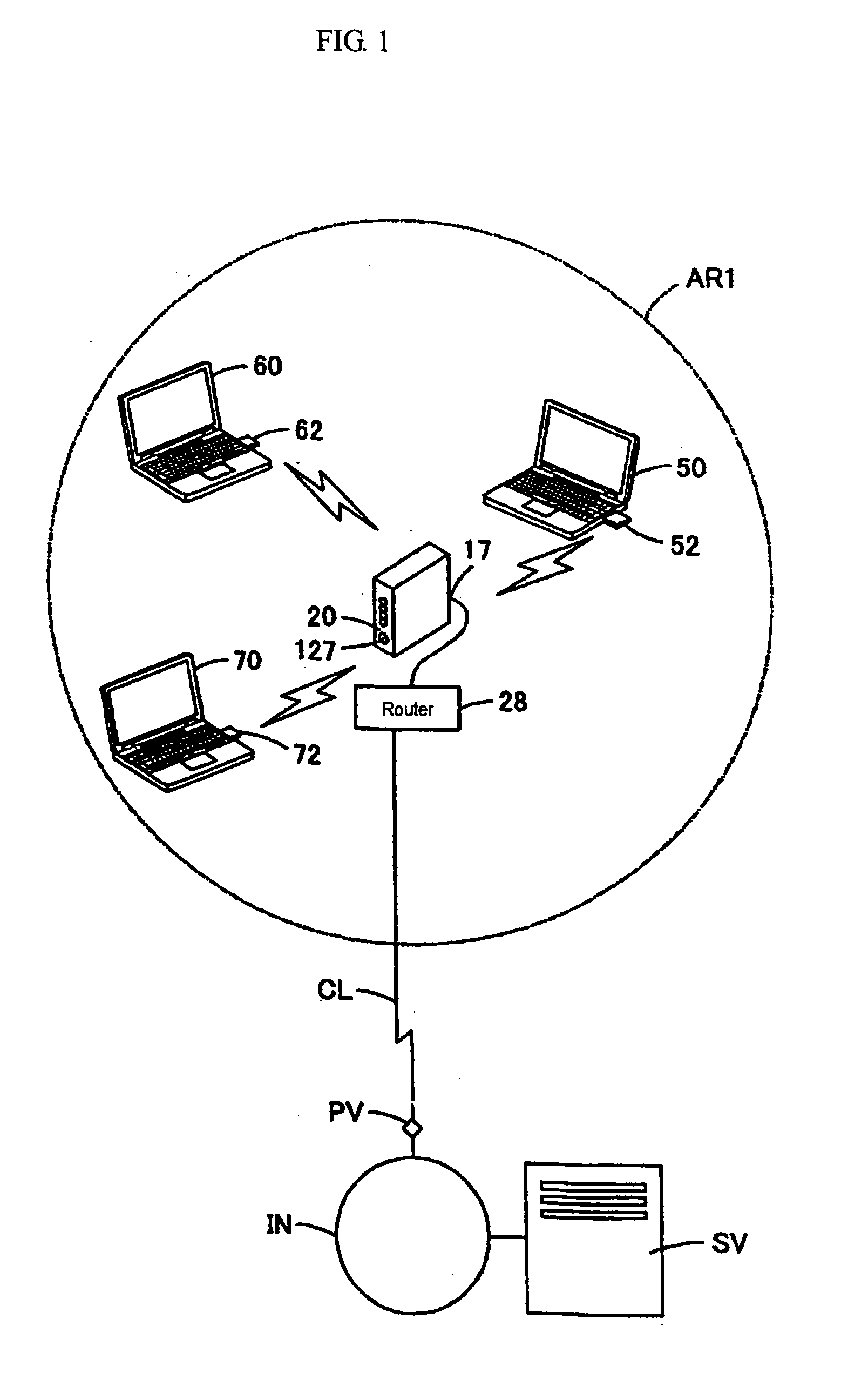
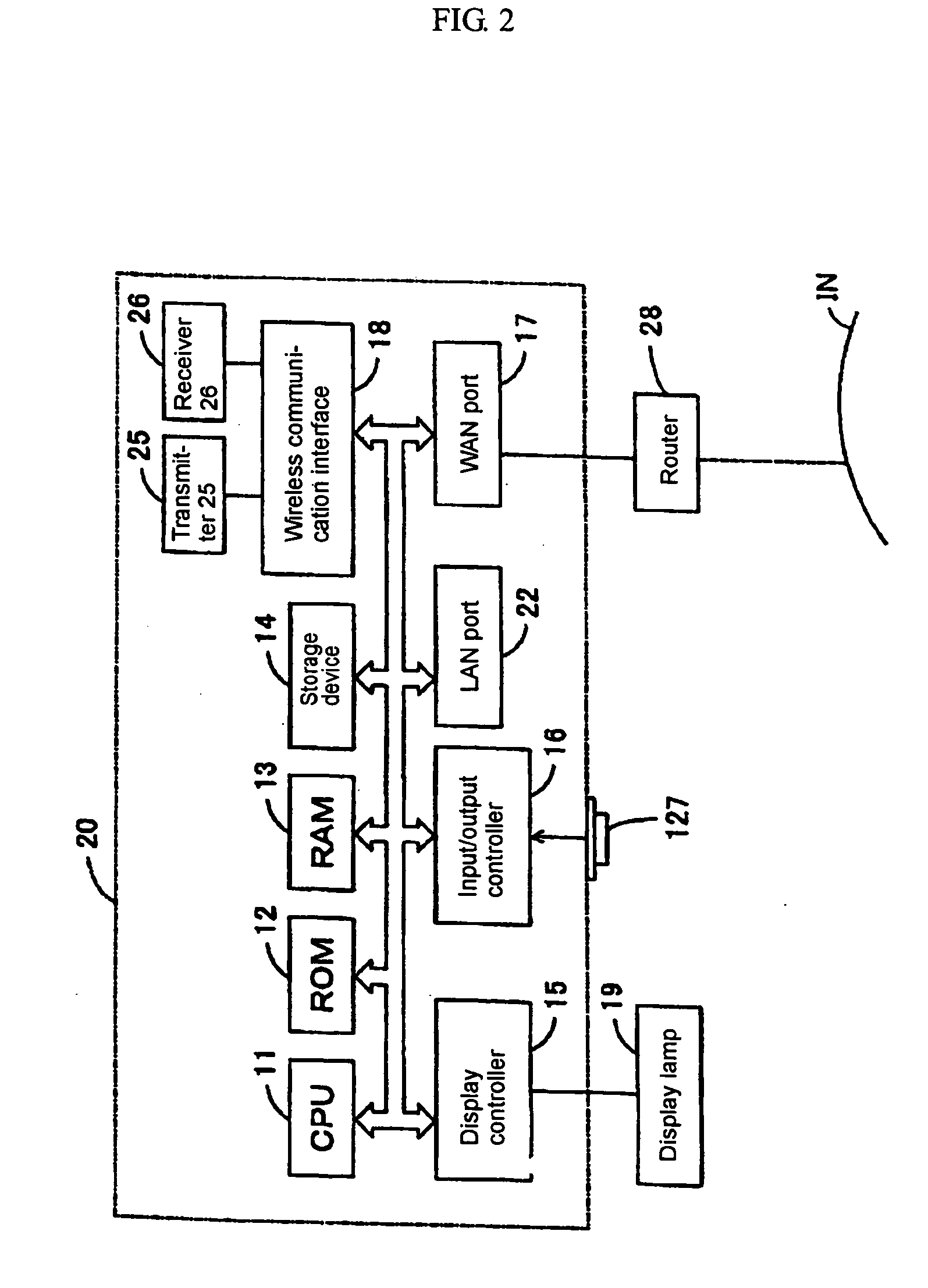
ActiveUS20100098318A1Reduce false positive rateMinimize table sizeComplete banking machinesFinanceHash functionBloom filter
A system and method for detecting duplicate checks during processing. The duplicate detection may be performed by a financial institution, such as a bank. The method may be implemented on a computer based system. The duplicate detection method may be automated. The method may be applied to incoming check files prior to processing of the check data to prevent processing of duplicate checks. The system and method may use a function, such as a hash function, to perform the duplicate detection. Other functions, such as a Bloom filter which may use multiple hash functions, may be used to perform the duplicate detection.
Owner:JPMORGAN CHASE BANK NA
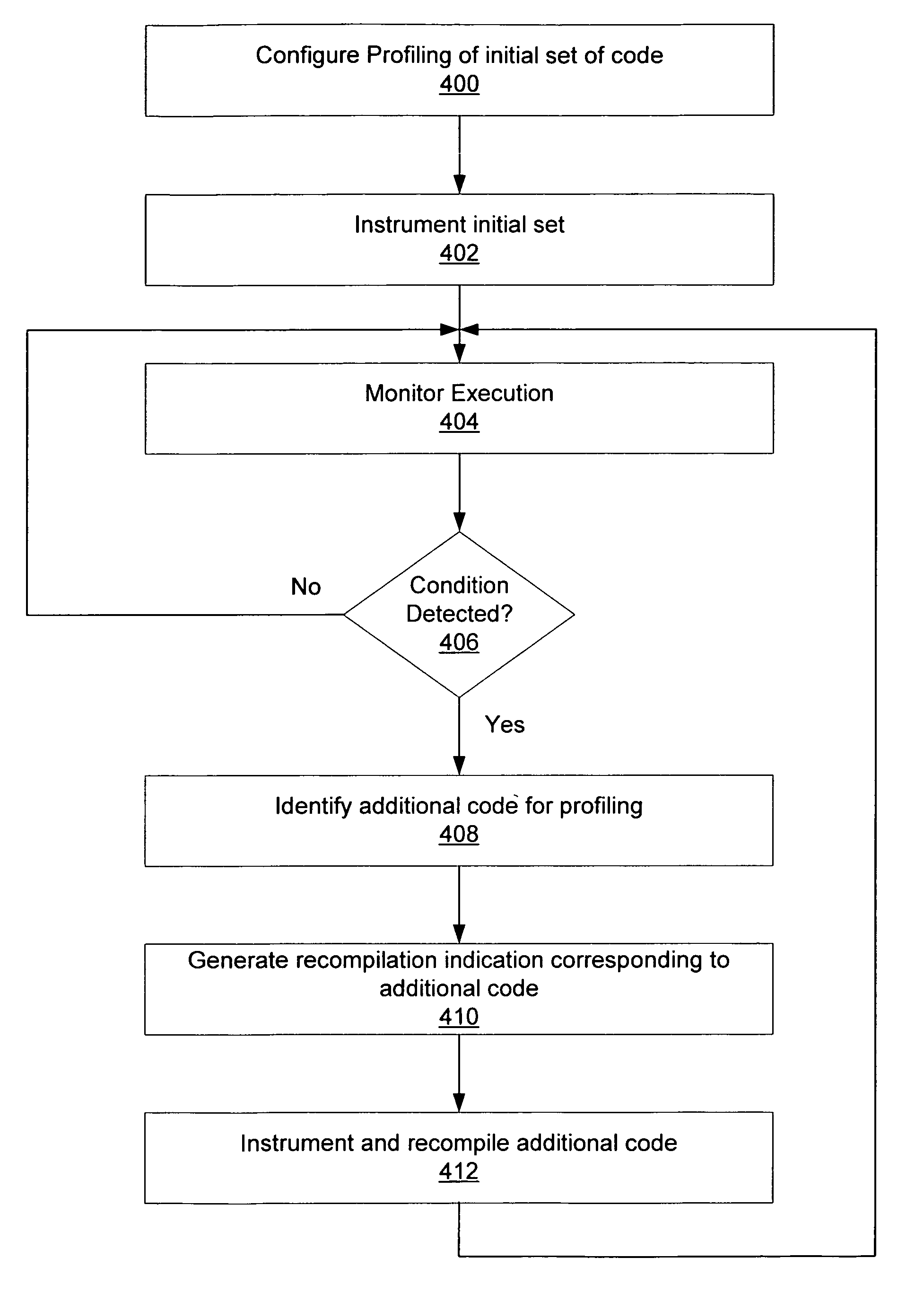
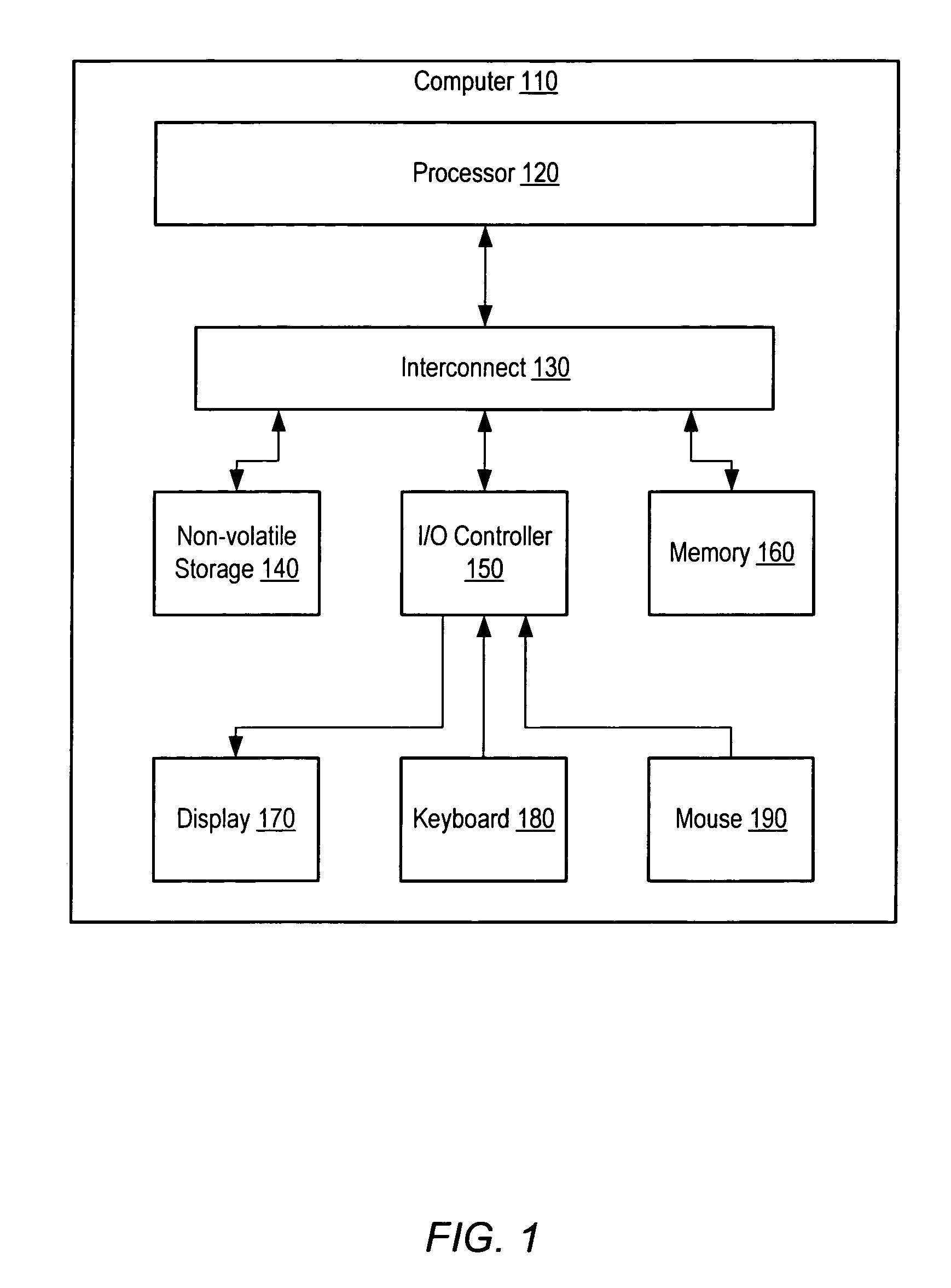
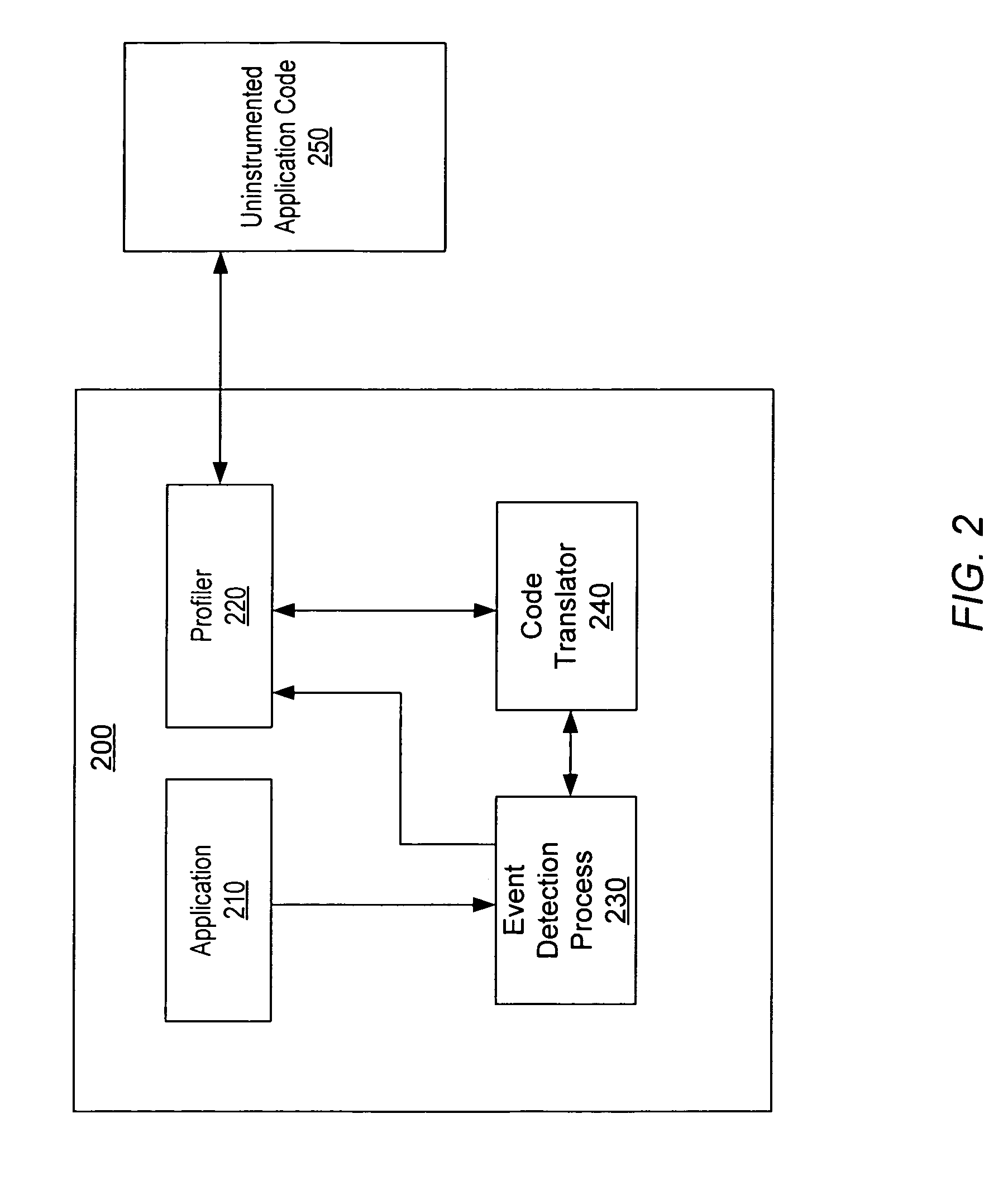
Adaptive instrumentation through dynamic recompilation
ActiveUS8176480B1Long performance latencySoftware engineeringSpecific program execution arrangementsProgram instructionParallel computing
A system and method for instrumenting program instructions. A processing system includes a compiler and a profiler. The profiler is configured to instrument an application by inserting one or more instrumentation instructions in the application. During execution of the application, execution is monitored and a particular condition is detected. Responsive to the condition, a portion of the code which corresponds to the detected condition is identified. A request is conveyed for recompilation of code which corresponds to code. Prior to recompilation of the code, the profiler instruments the portion of code. Execution and monitoring of the execution continue, and instrumentation / recompilation may be repeated. Initially, relatively little of the application code may be instrumented. As execution and monitoring continues, more and more of the application code may be dynamically instrumented during execution.
Owner:SYMANTEC OPERATING CORP
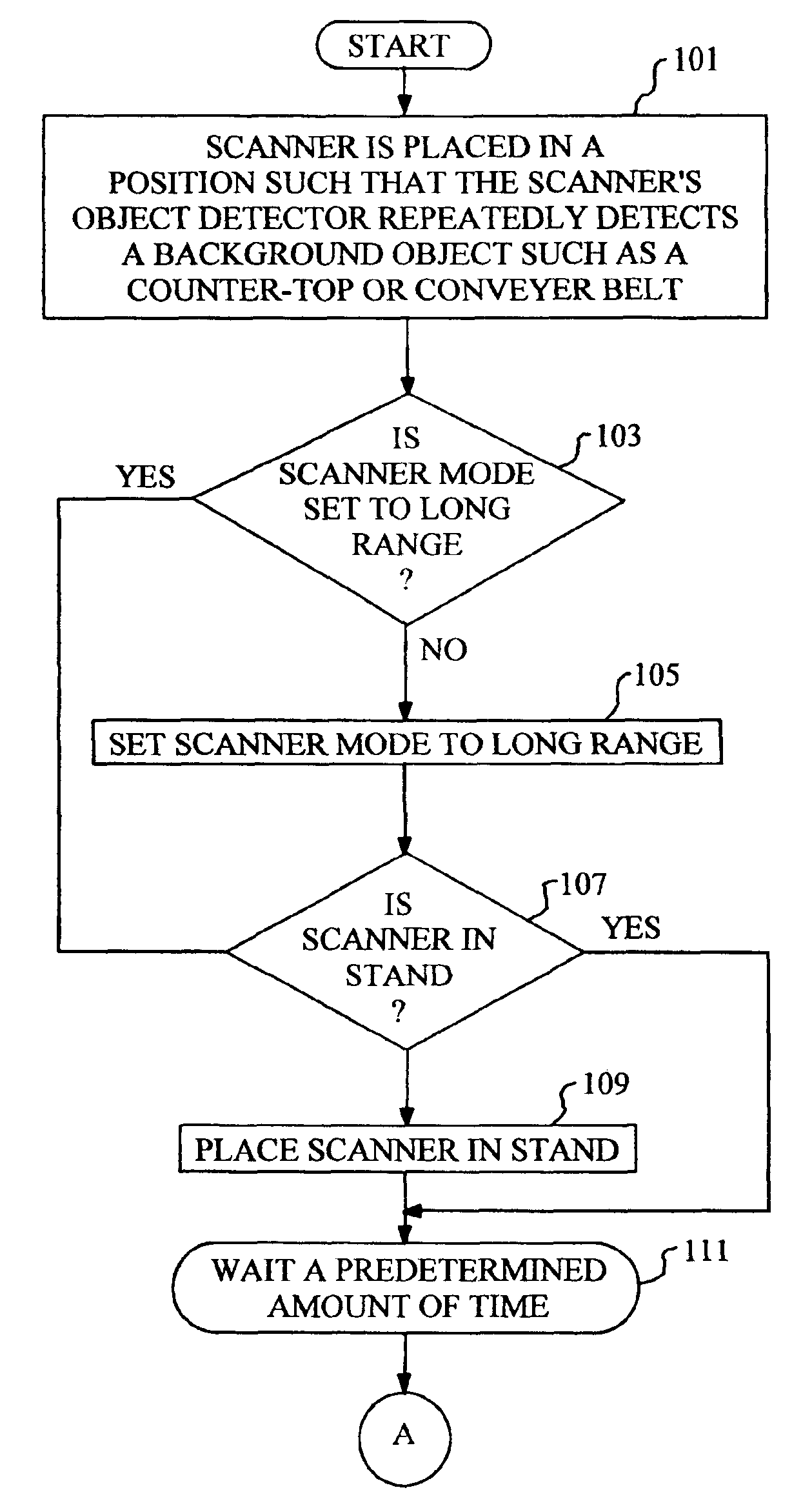
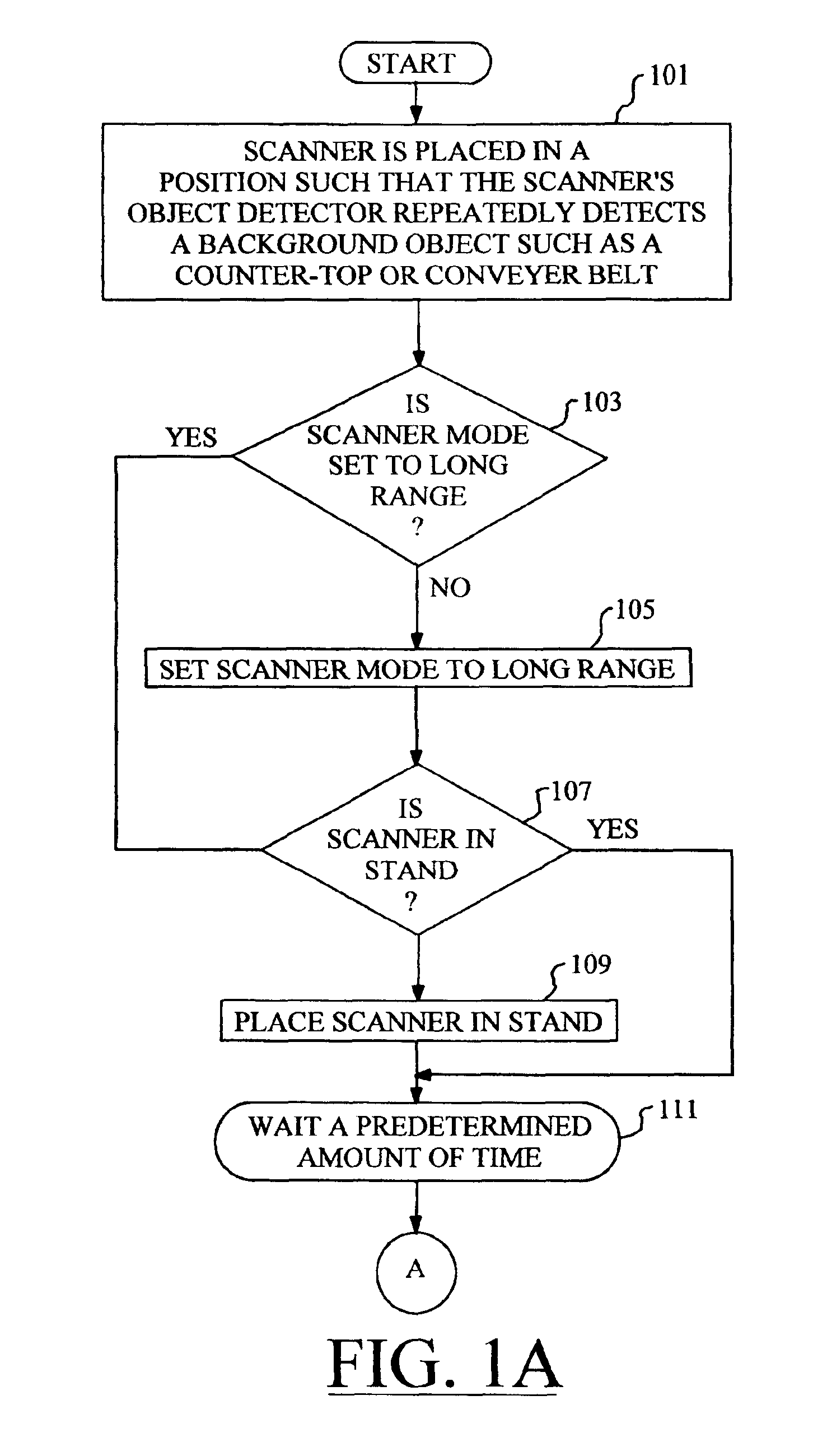
Automatic range adjustment techniques for stand-mountable bar code scanners
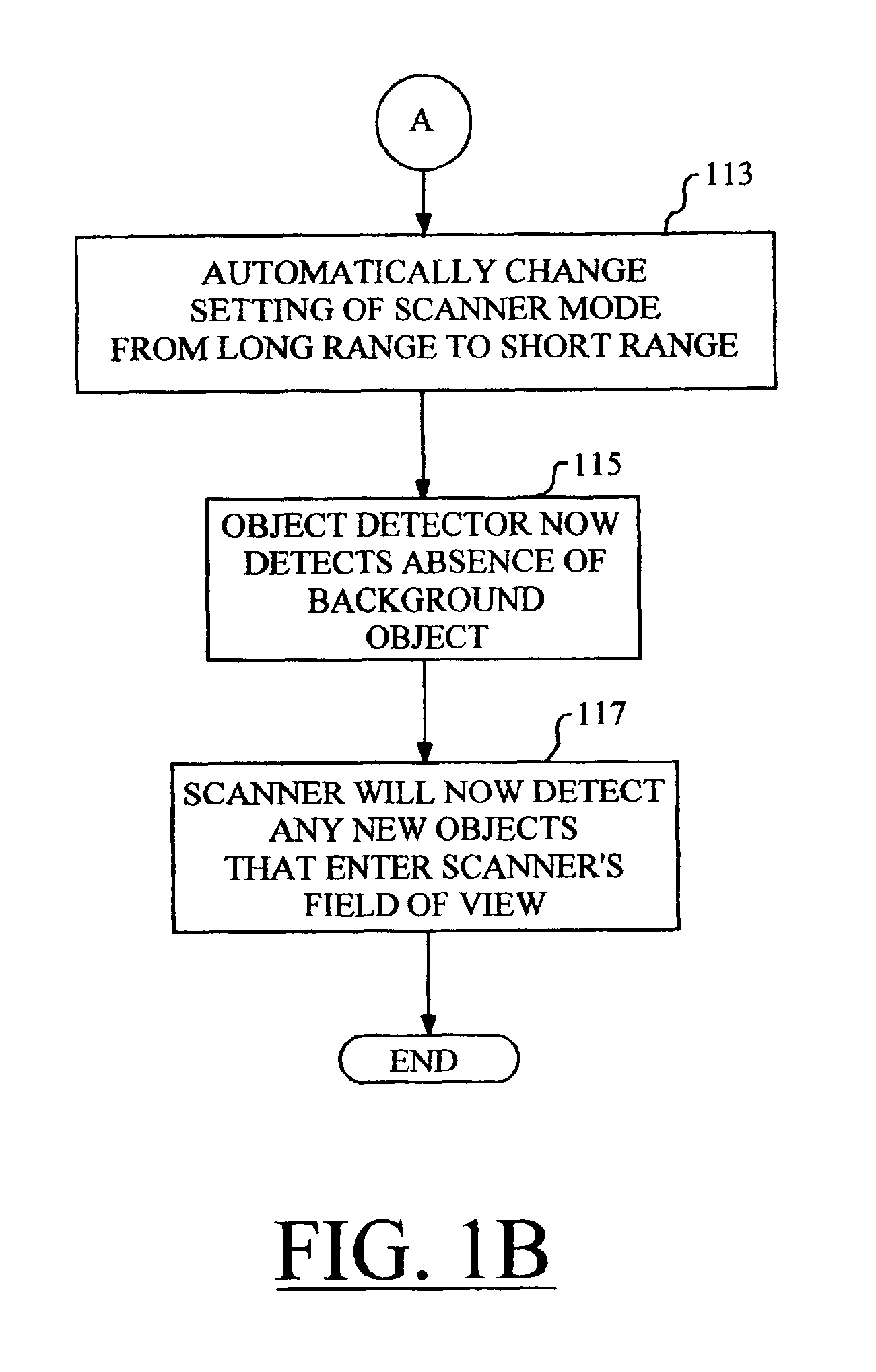
By automatically adjusting the object detection mechanism of a bar code scanner from a long range mode of operation to a short range mode of operation, the scanner will remain capable of detecting and decoding bar codes even if the object detection mechanism repeatedly detects the presence of a background object. The techniques of the present invention commence when the bar code scanner is placed in a position such that the scanner's object detection mechanism repeatedly detects a background object such as a counter top or conveyer belt. The object detection mechanism is set to the long range mode of operation if it is not already so set. In the case of a stand-mounted scanner, a test is performed to ascertain whether or not the scanner is in its stand, and the method will only proceed once the scanner is resting in the stand. Next, the scanner is programmed to wait for a predetermined amount of time, after which the operational mode of the object detection mechanism is changed from the long range mode to the short range mode. At this time, the object detection mechanism no longer detects the presence of the background object. The scanner will now detect any new objects that enter the field of view of the object detection mechanism, and attempt to read any bar codes which may be present
Owner:METROLOGIC INSTR
System and method for duplicate detection
Owner:BANK OF AMERICA CORP
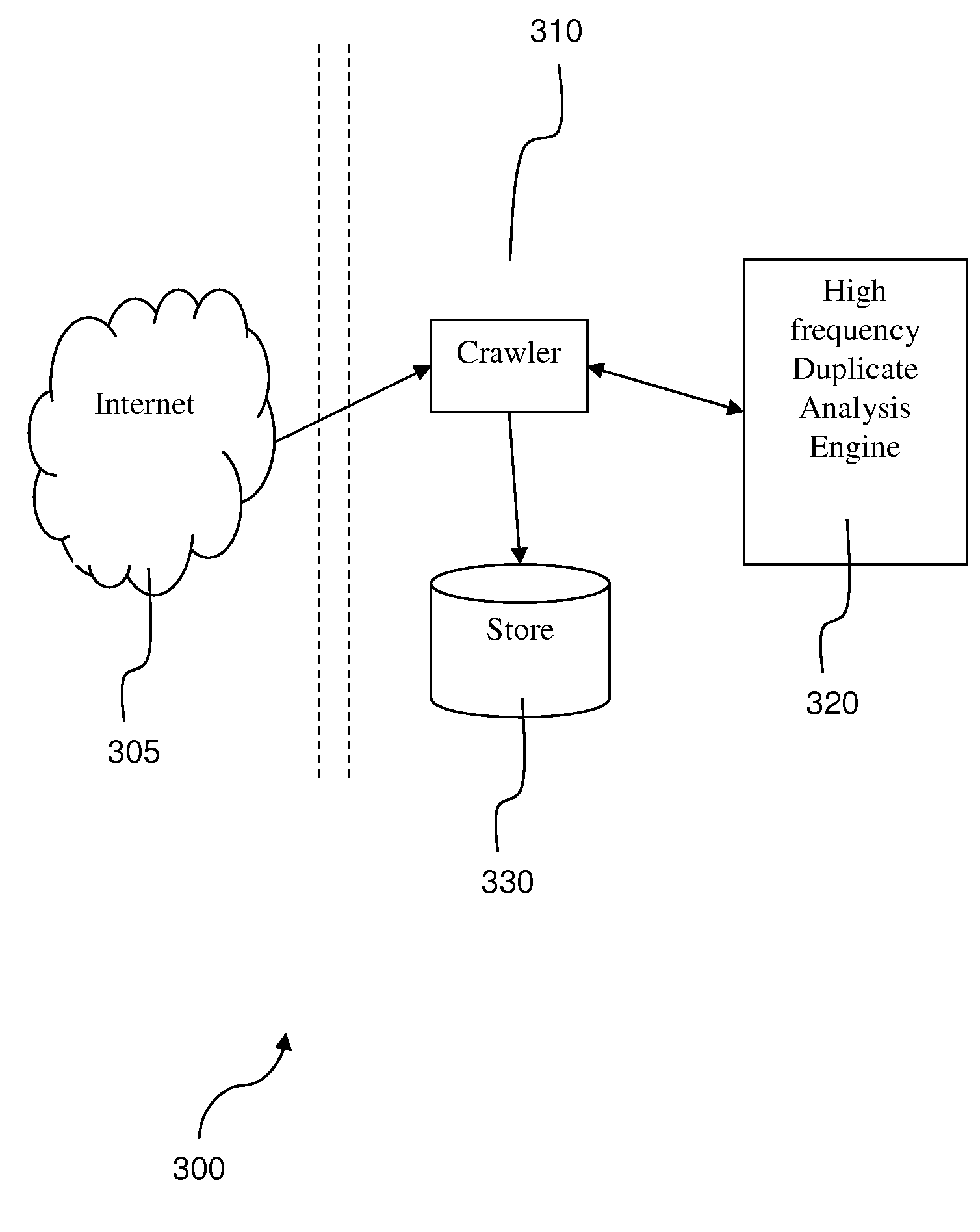
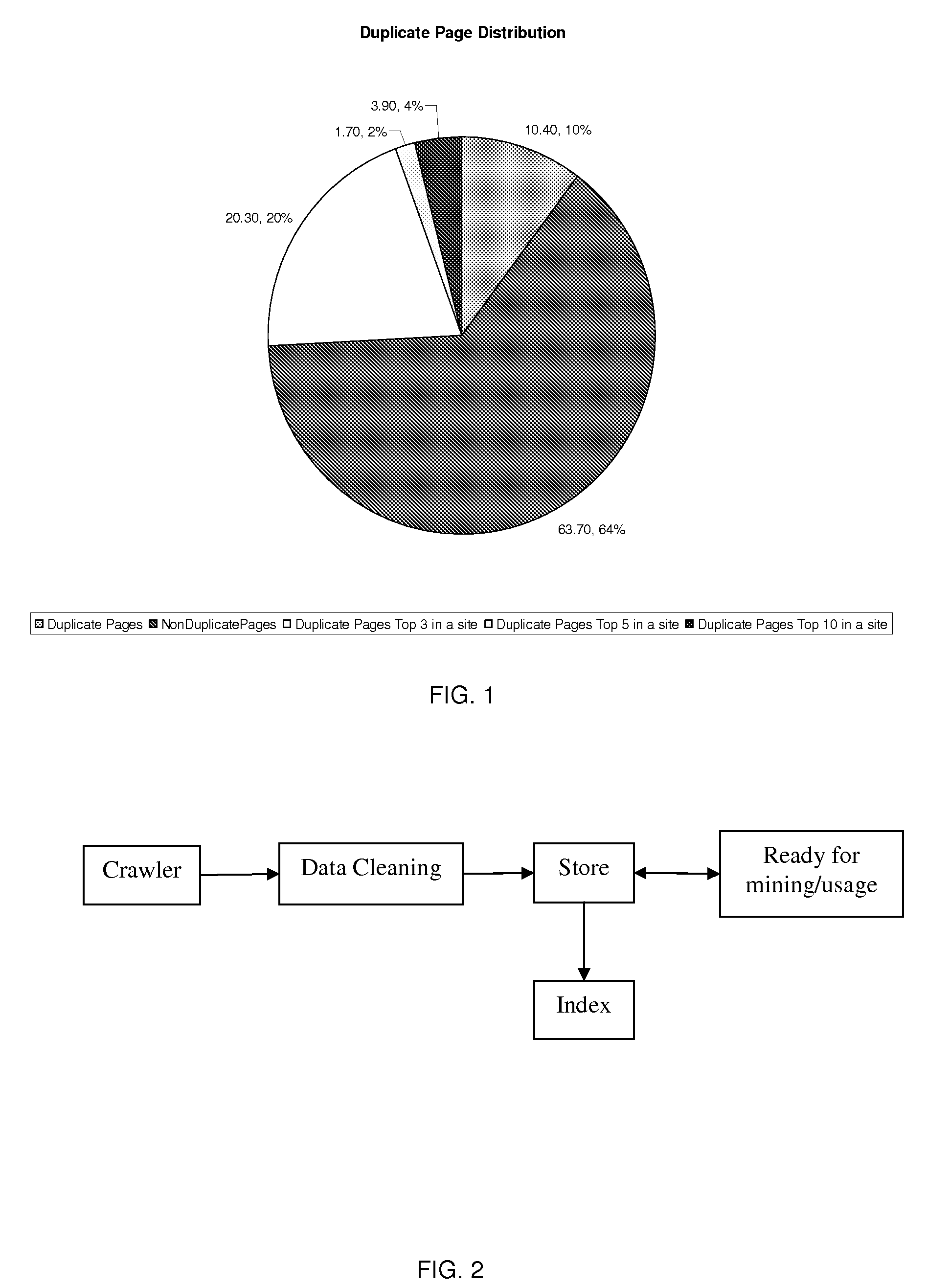
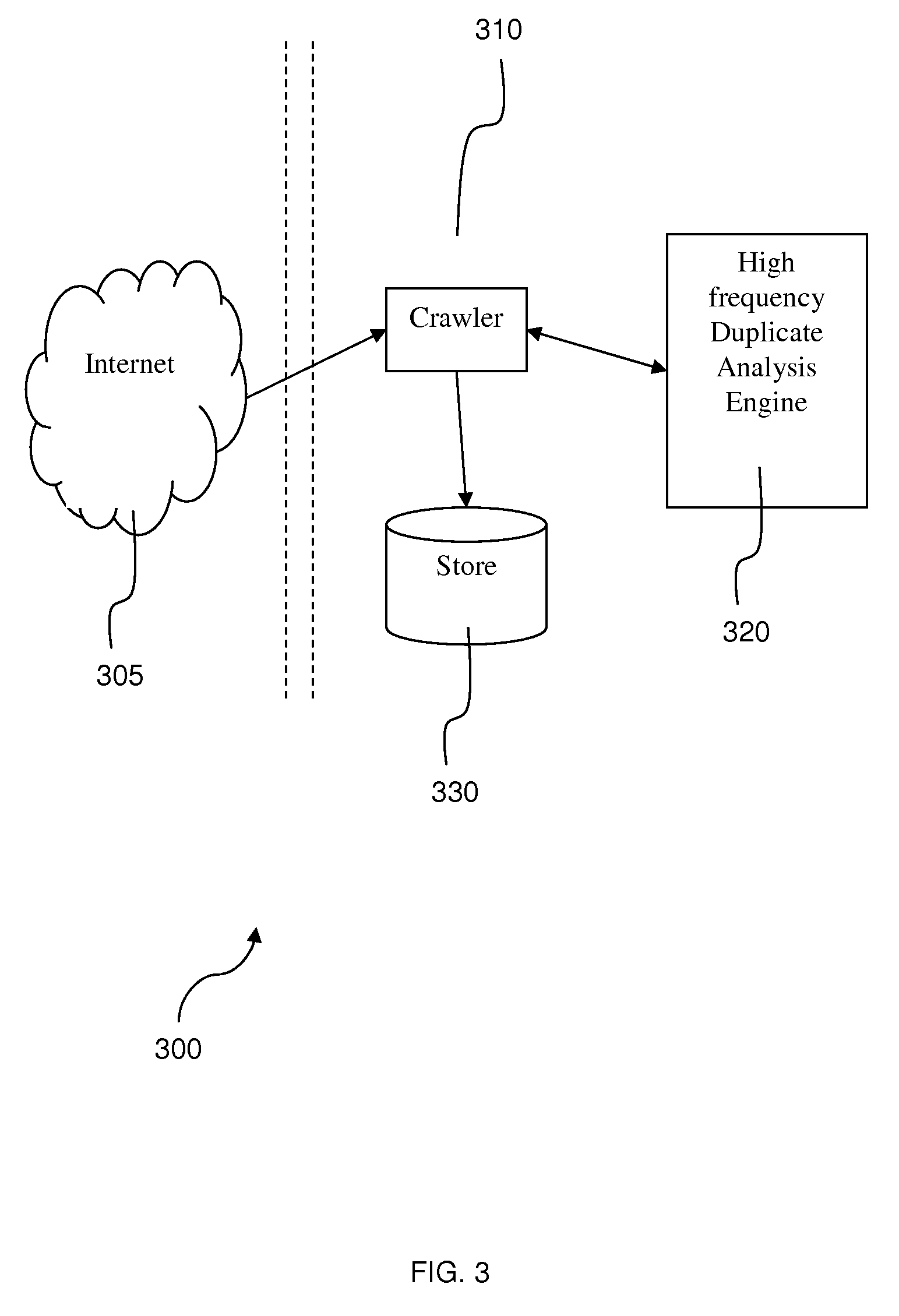
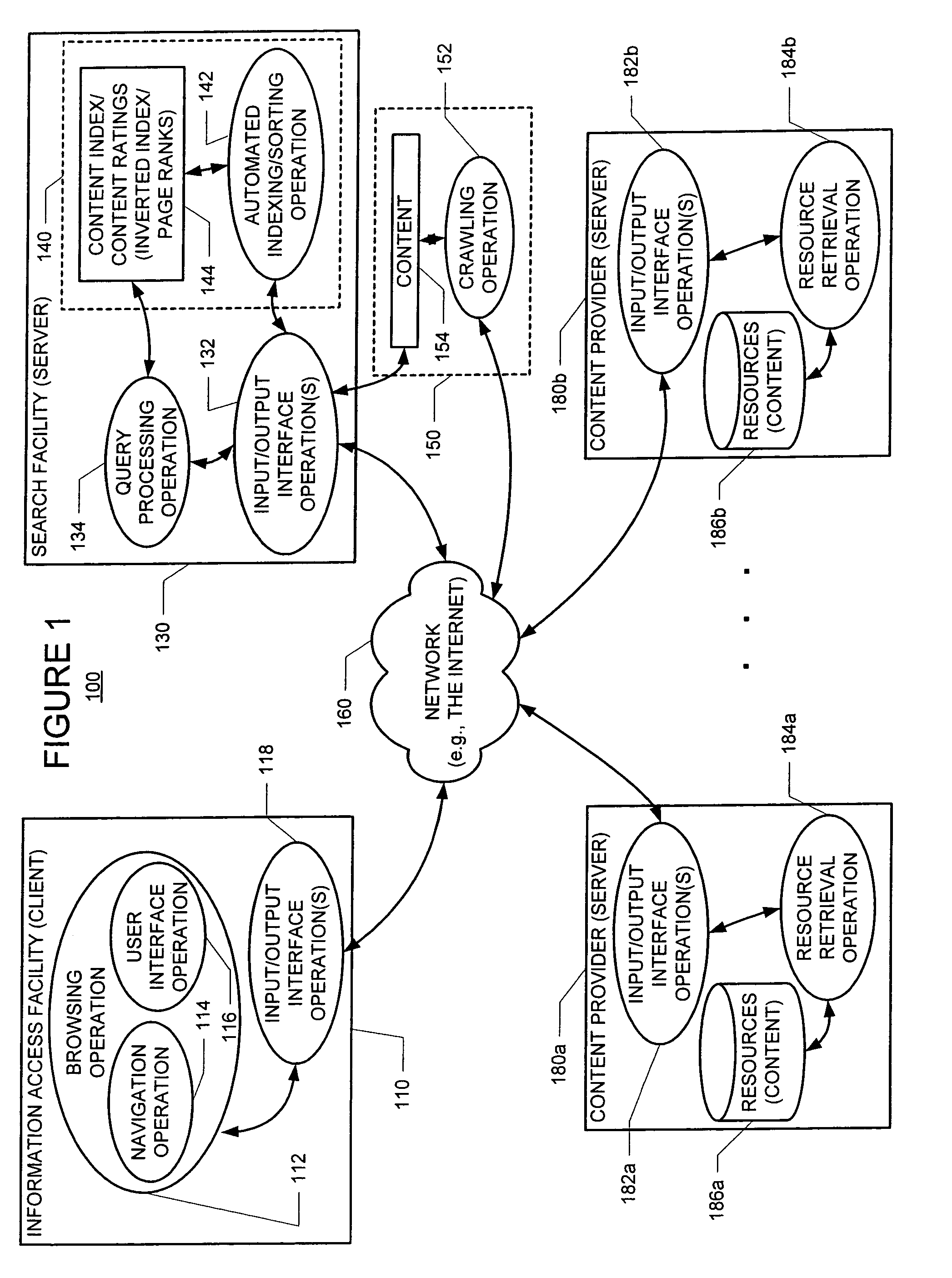
System and method for online duplicate detection and elimination in a web crawler
InactiveUS20080235163A1Eliminate duplicationWeb data indexingDigital computer detailsUniform resource locatorWeb crawler
As part of the normal crawling process, a crawler parses a page and computes a de-tagged hash, called a fingerprint, of the page content. A lookup structure consisting of the host hash (hash of the host portion of the URL) and the fingerprint of the page is maintained. Before the crawler writes a page to a store, this lookup structure is consulted. If the lookup structure already contains the tuple (i.e., host hash and fingerprint), then the page is not written to the store. Thus, a lot of duplicates are eliminated at the crawler itself, saving CPU and disk cycles which would otherwise be needed during current duplicate elimination processes.
Owner:IBM CORP
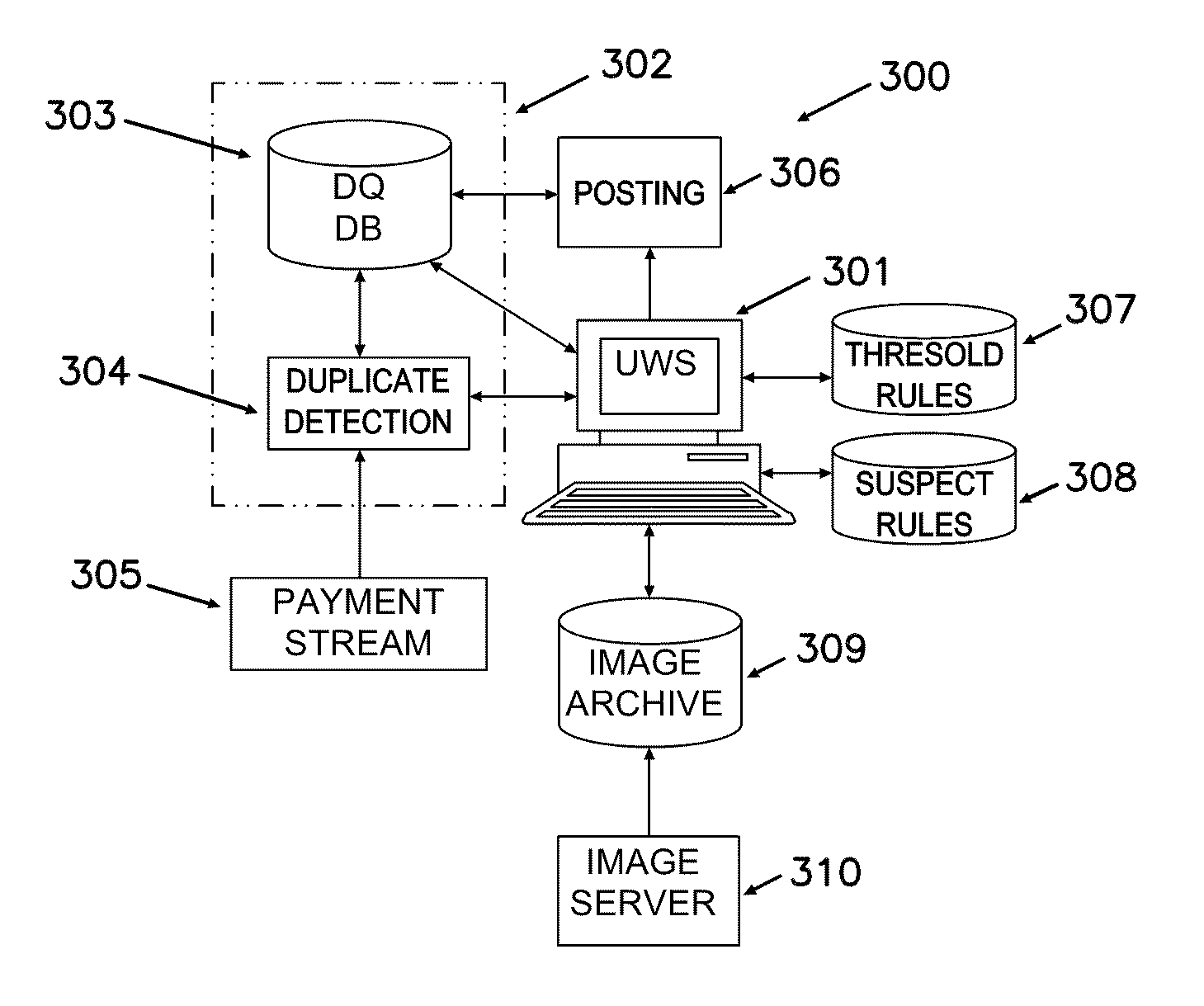
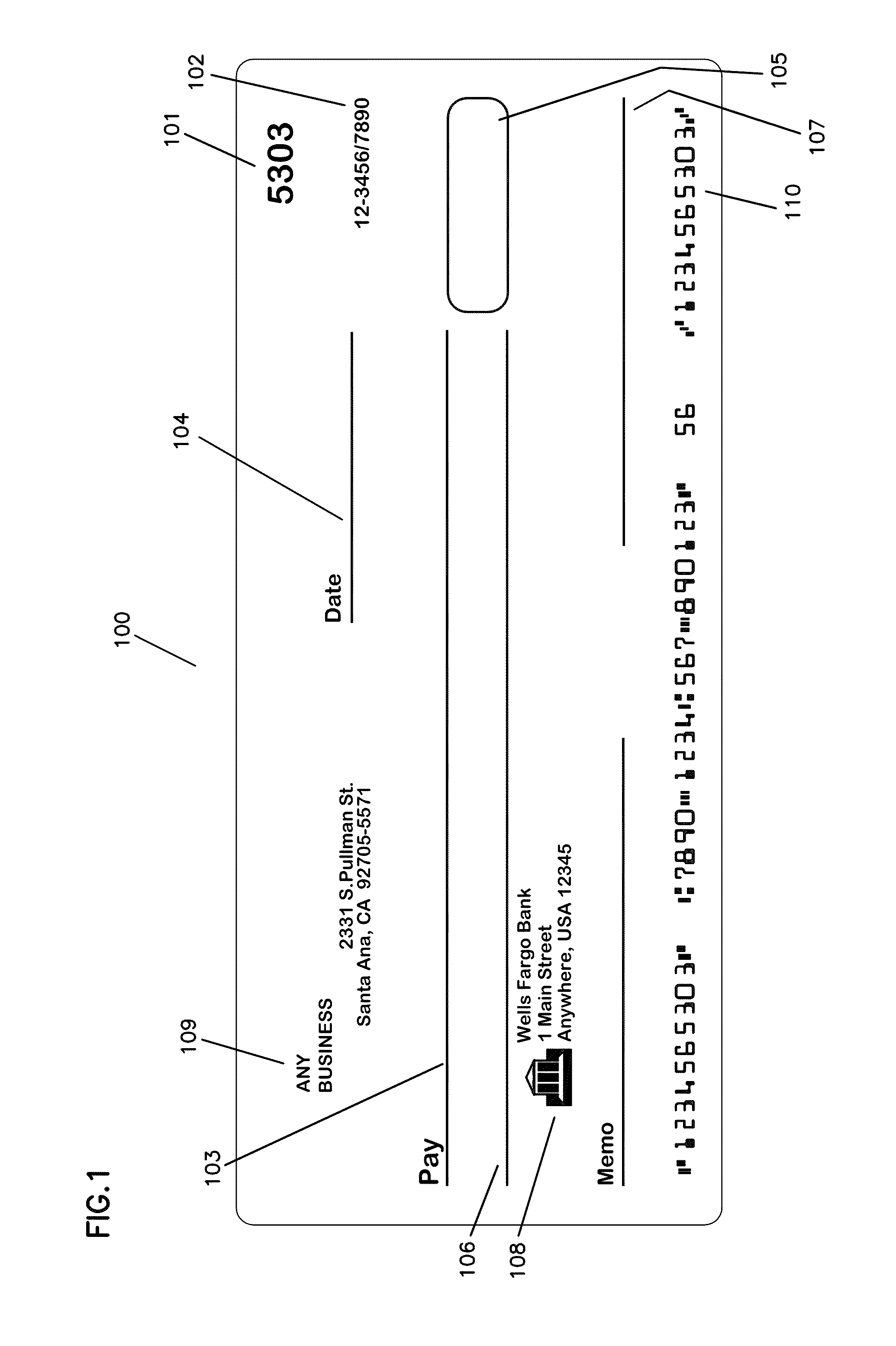
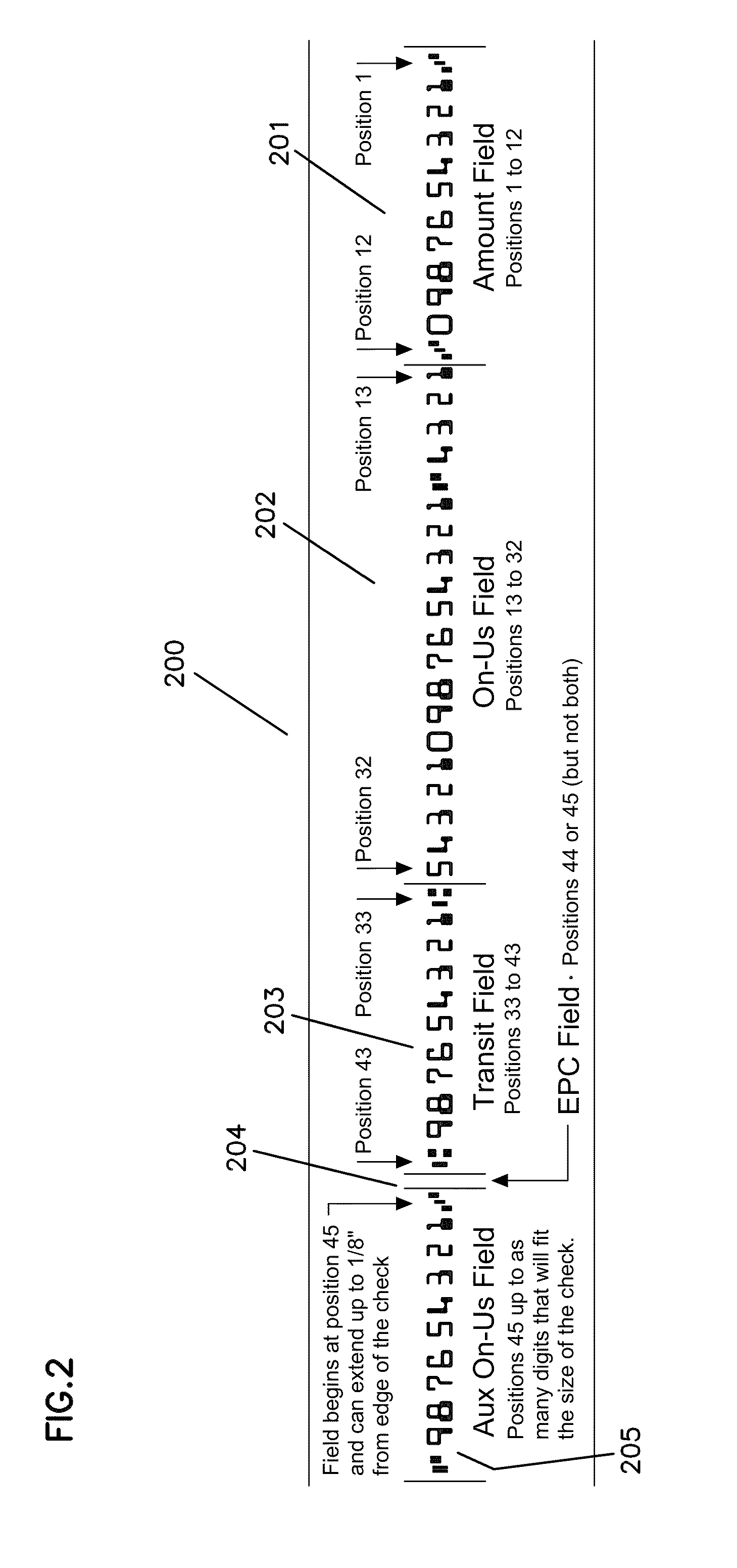
System and method for MICR-based duplicate detection and management
A system and method for MICR-based duplicate detection and management identifies duplicate presented items on day one across a plurality of payment channels, prior to posting, preventing them from impacting financial institution customers by rerouting to an adjustments team. Inquiry files containing MICR data for a plurality of presented items are evaluated by a duplicate detection module. Each item presented is evaluated against all previous items based on its MICR line. Unique items are processed in the usual manner. Duplicate suspects undergo further processing. Suspects having identical MICR data, but that are not duplicates, such as NSF (non-sufficient funds) checks being re-deposited, are identified and posted. The remaining suspects go in the suspect queue of a universal workstation. After being researched, suspects found not to be duplicates are posted. The remaining suspects are flagged as duplicates and routed to an adjustor for further action.
Owner:WELLS FARGO BANK NA
Detecting duplicate and near-duplicate files
InactiveUS7366718B1Eliminate duplicate documentsStorage requirements is greatly reducedData processing applicationsWeb data indexingDocument preparationDocumentation
Owner:GOOGLE LLC
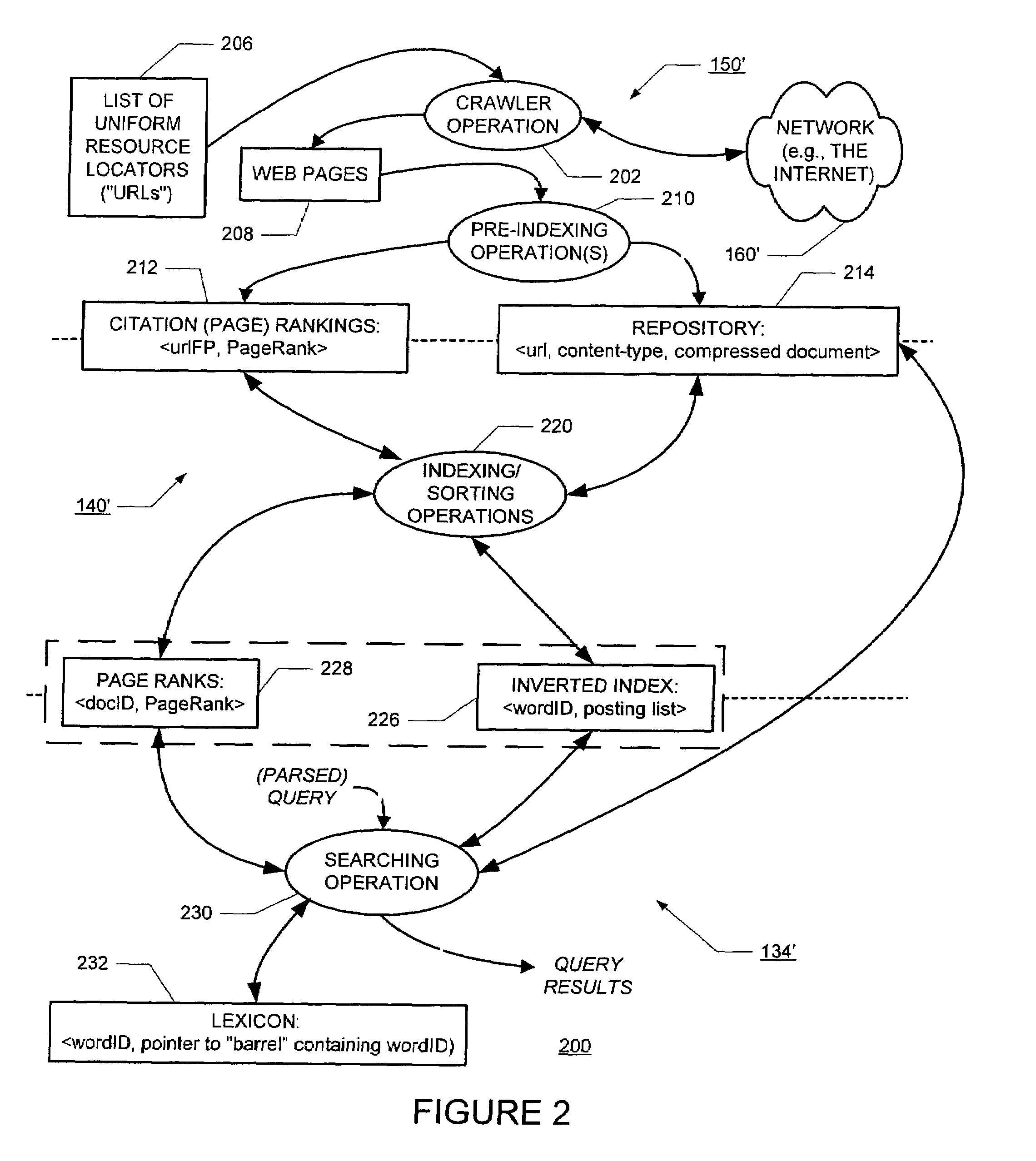
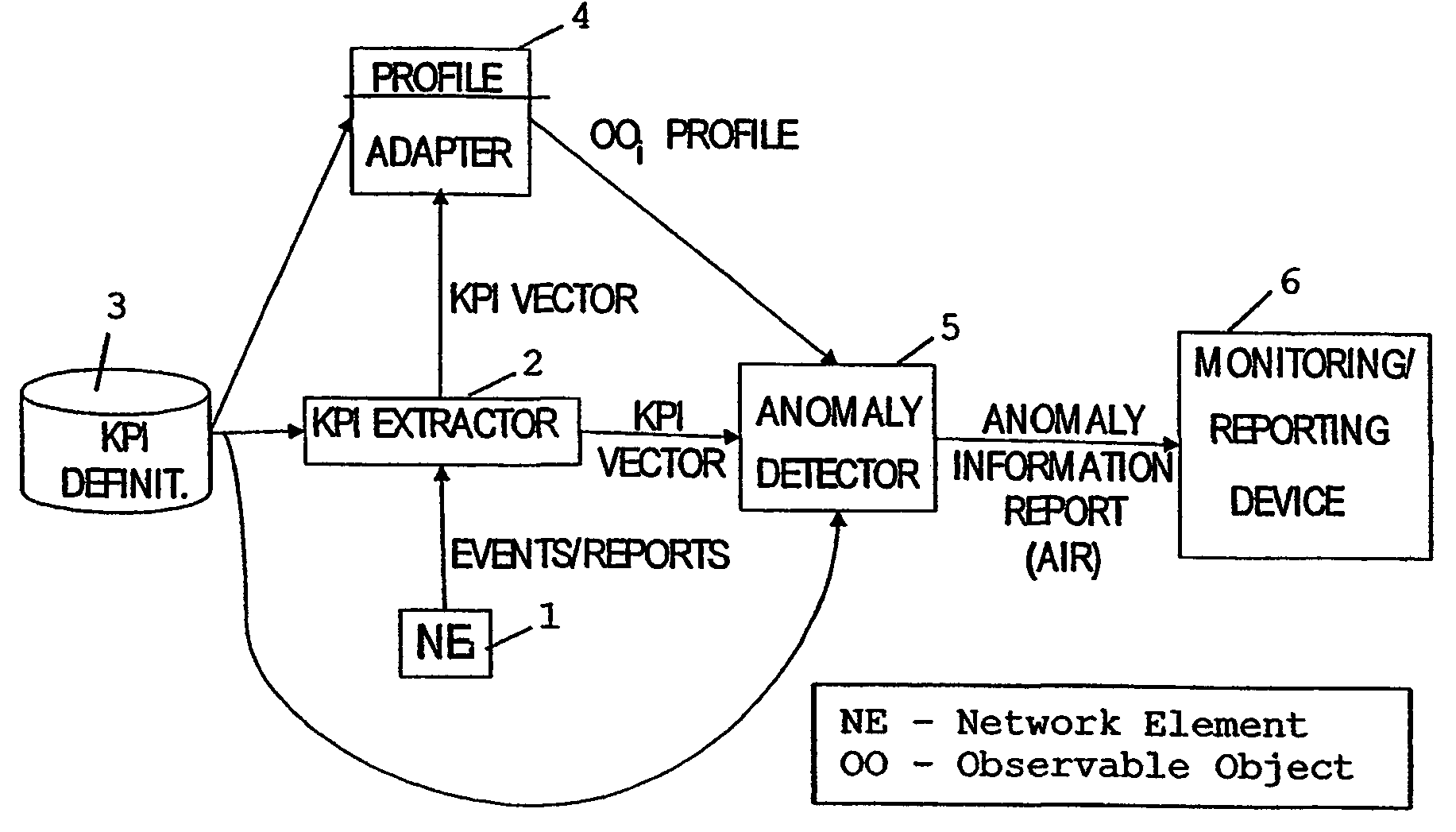
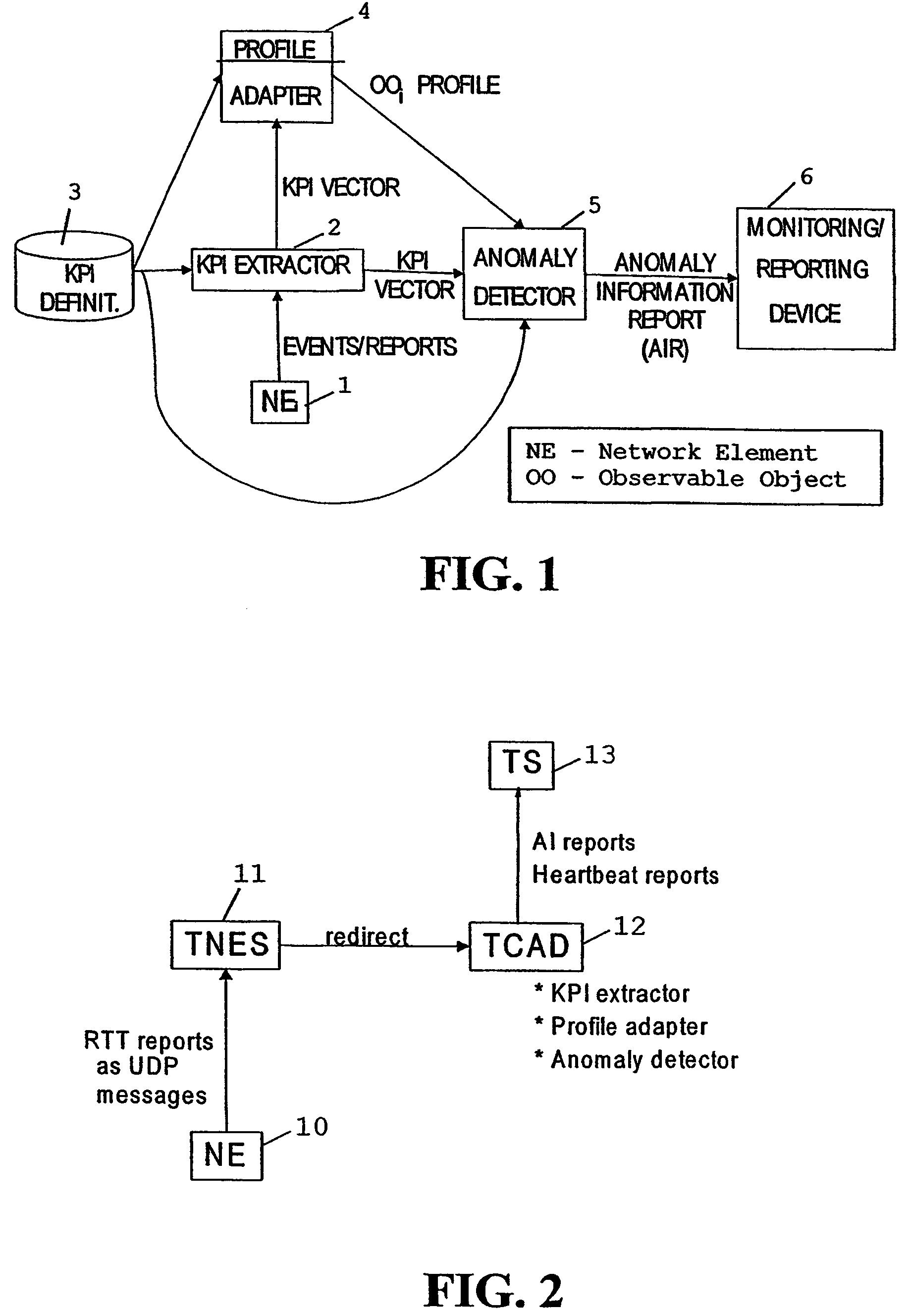
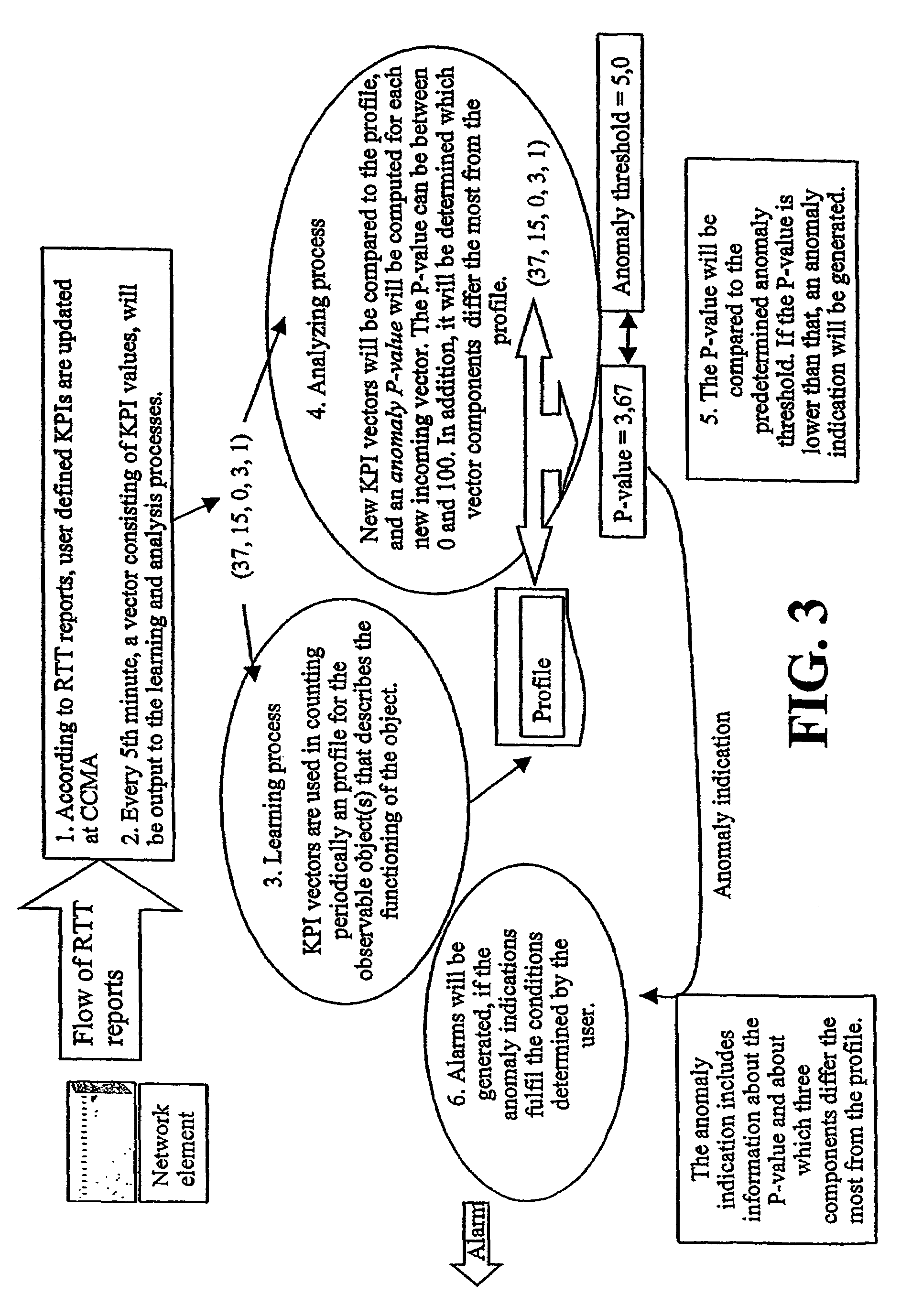
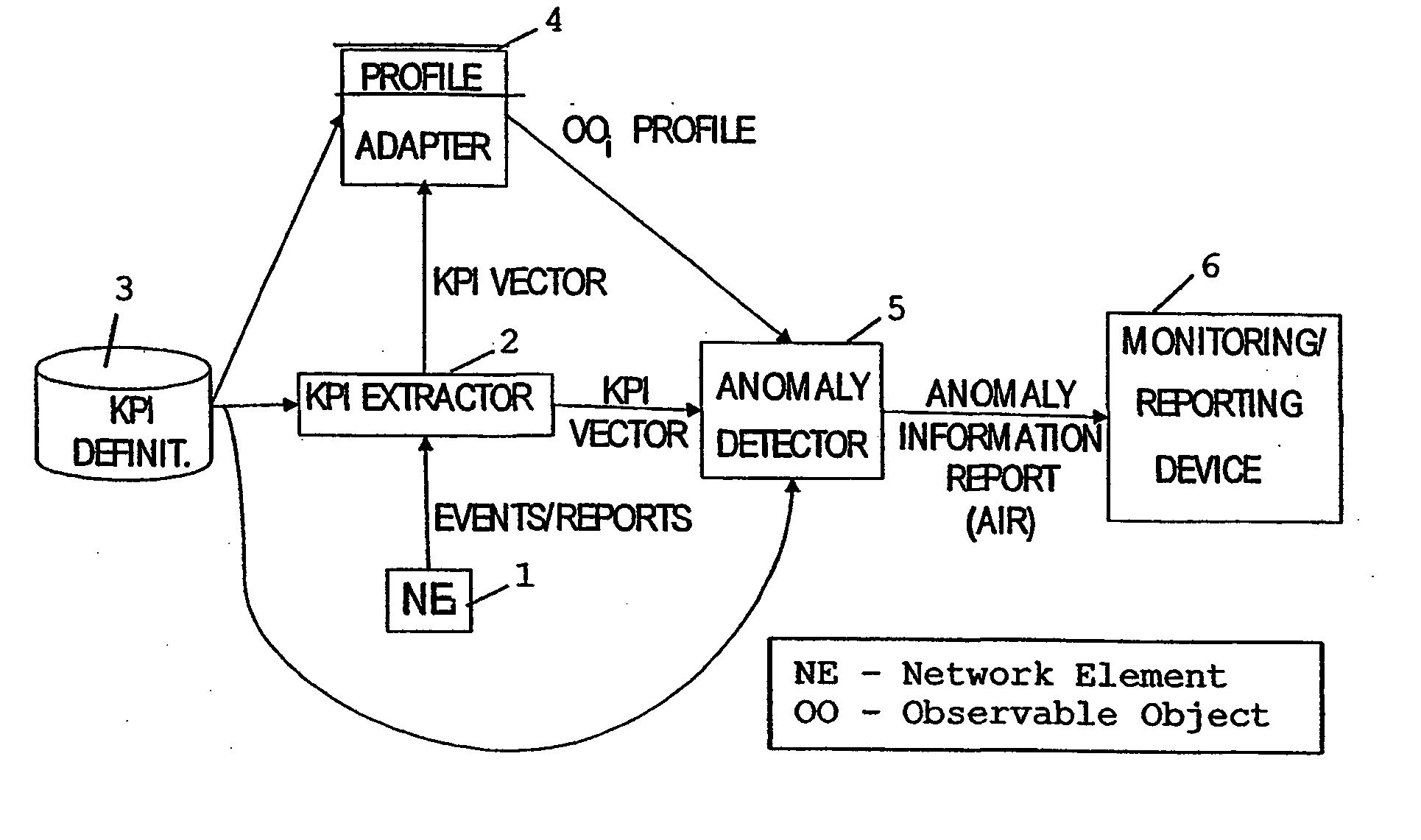
System, device and method for automatic anomaly detection
InactiveUS7519860B2Easy to introduceEasy to monitorMemory loss protectionError detection/correctionAnomaly detectionDuplicate detection
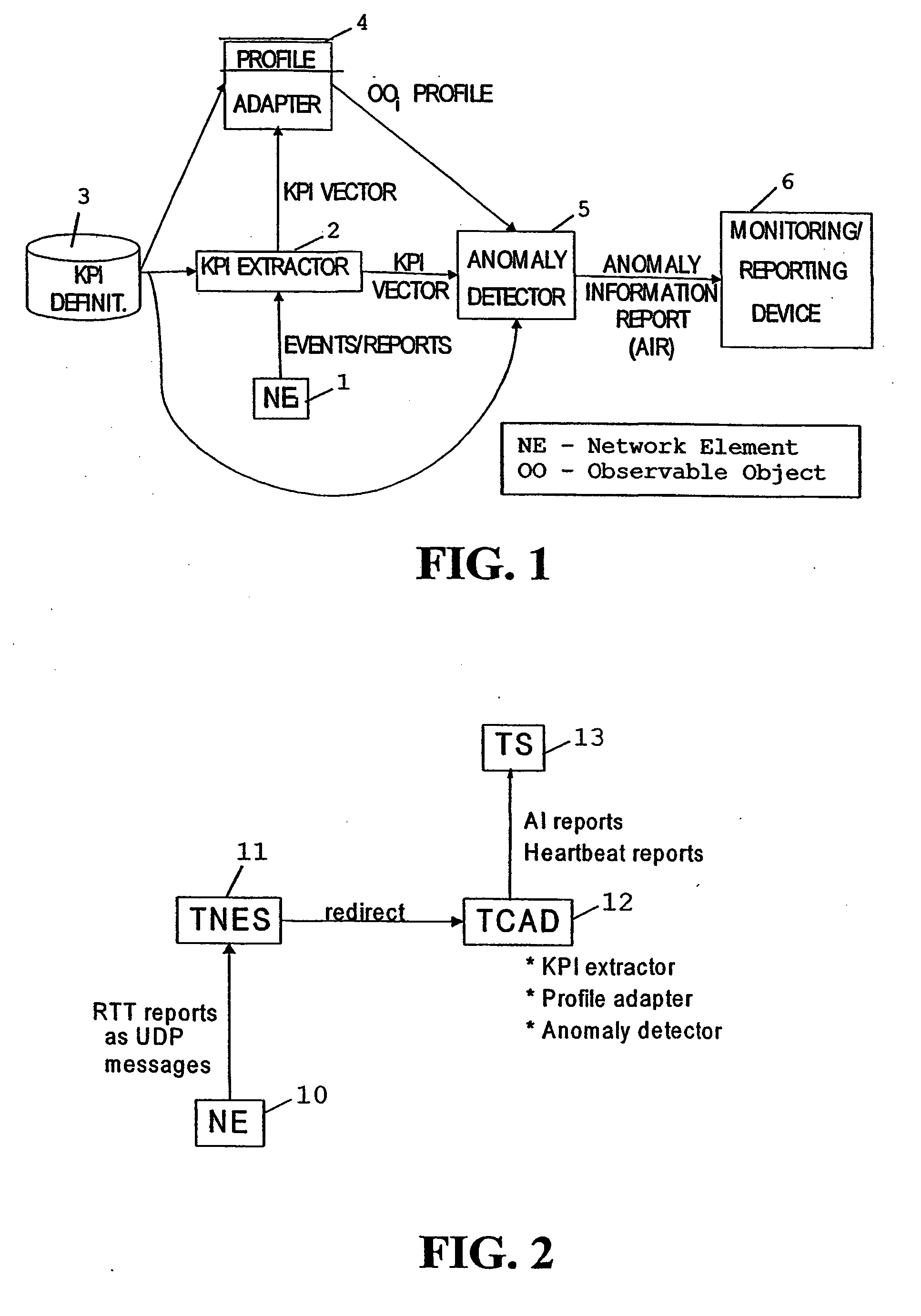
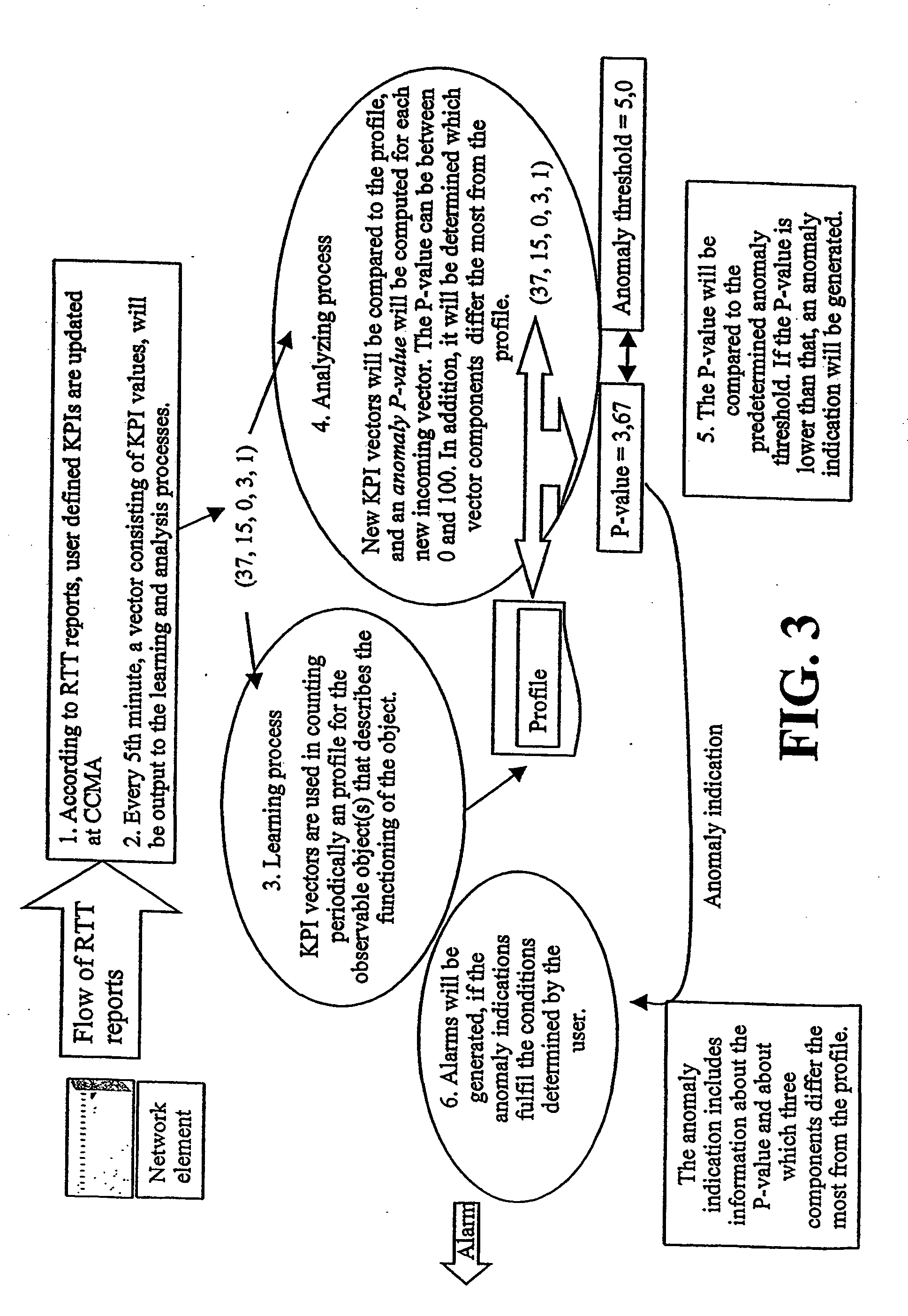
A method and system for monitoring the behavior of at least one observable object, e.g. a network element, of a network, wherein at least one parameter of the observable object is repeatedly detected. An actually detected parameter is input to a learning process and to an analyzing process, wherein the learning process forms a reference, based on at least two detected parameter values, for describing the behavior of the observable object. The analyzing process compares the input parameter and the reference for detecting an anomal behavior. The parameter preferably is a vector which includes several values describing properties or functioning of the observable object, and is formed based on events and / or reports from the object.
Owner:NOKIA CORP
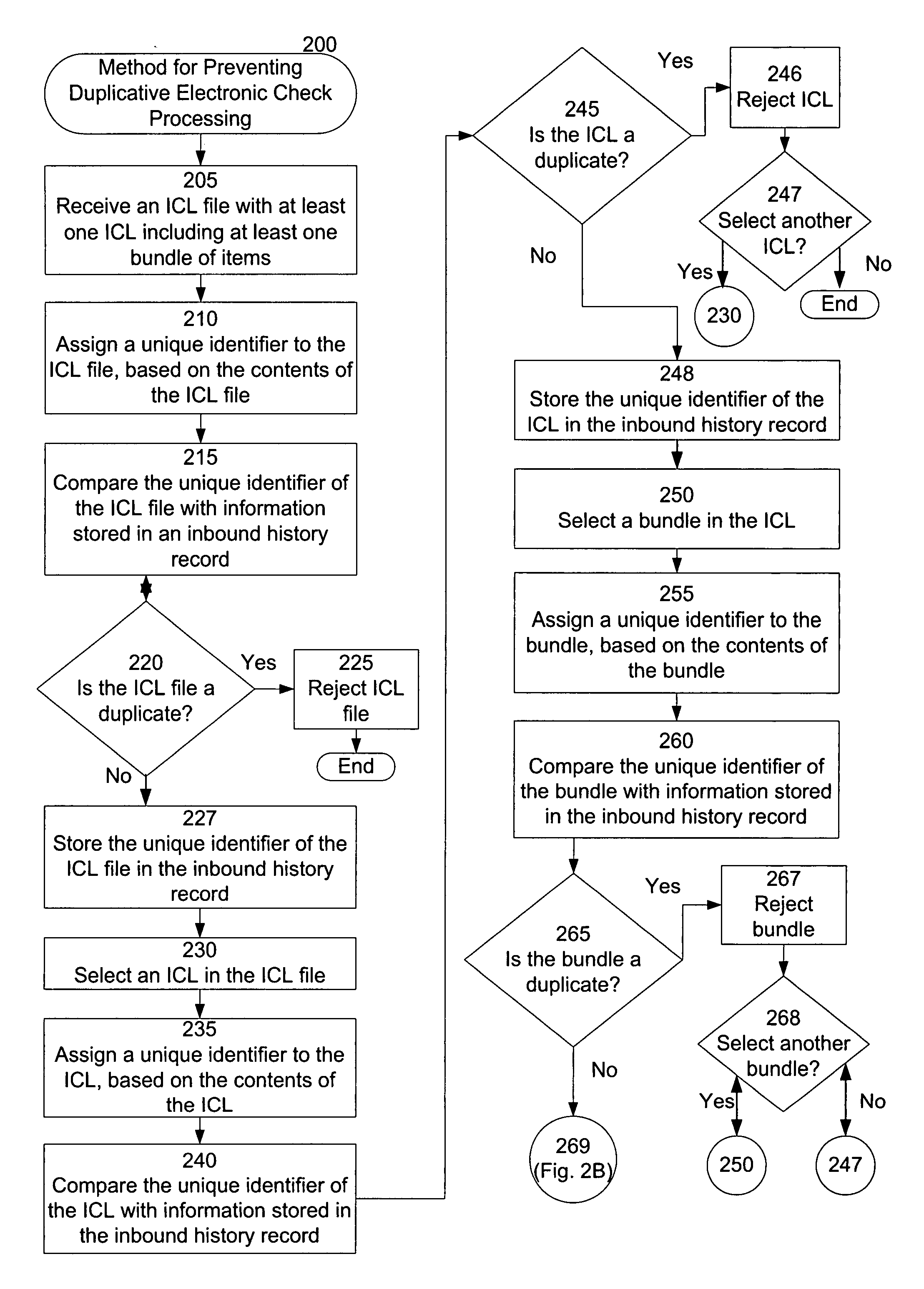
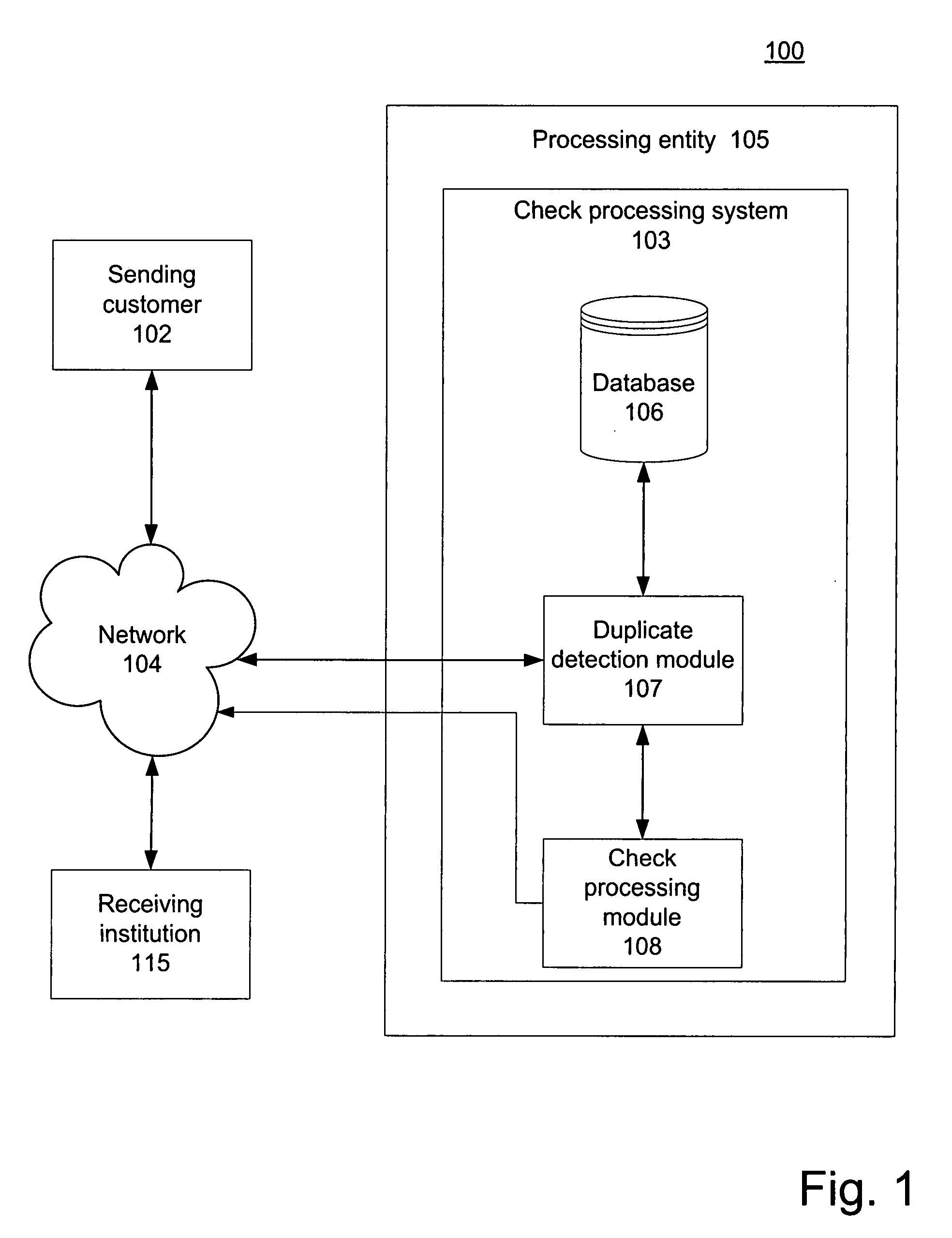
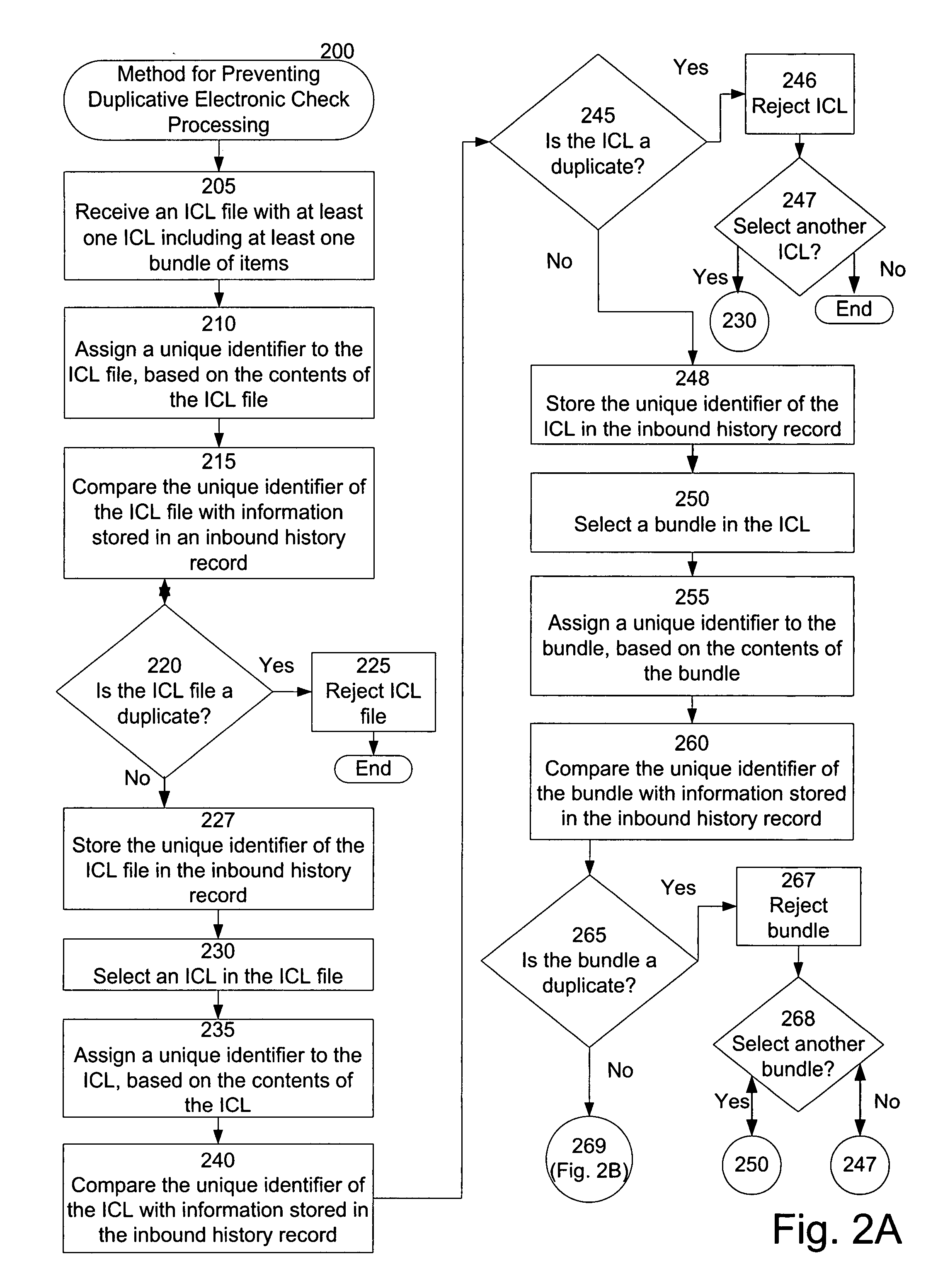
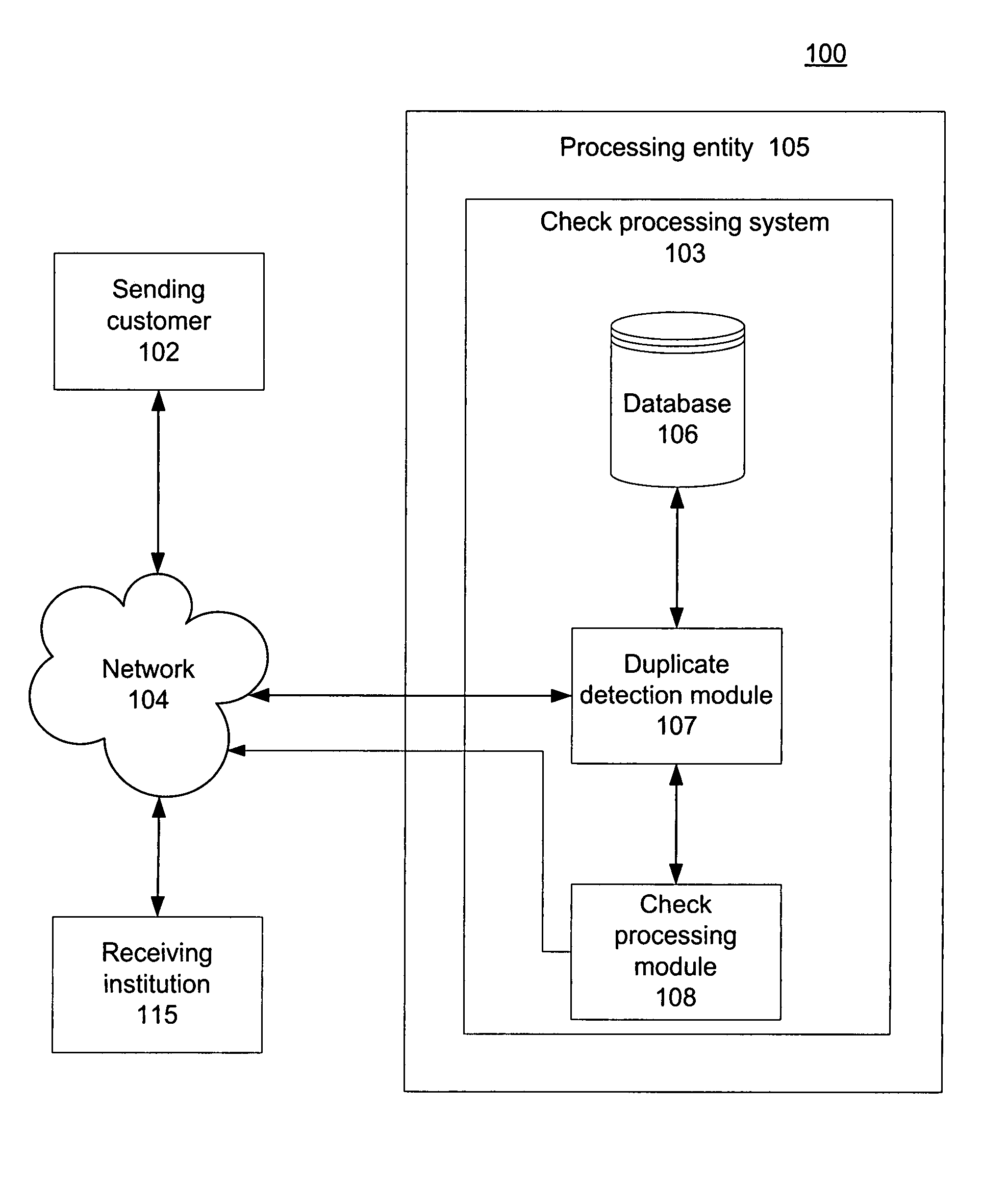
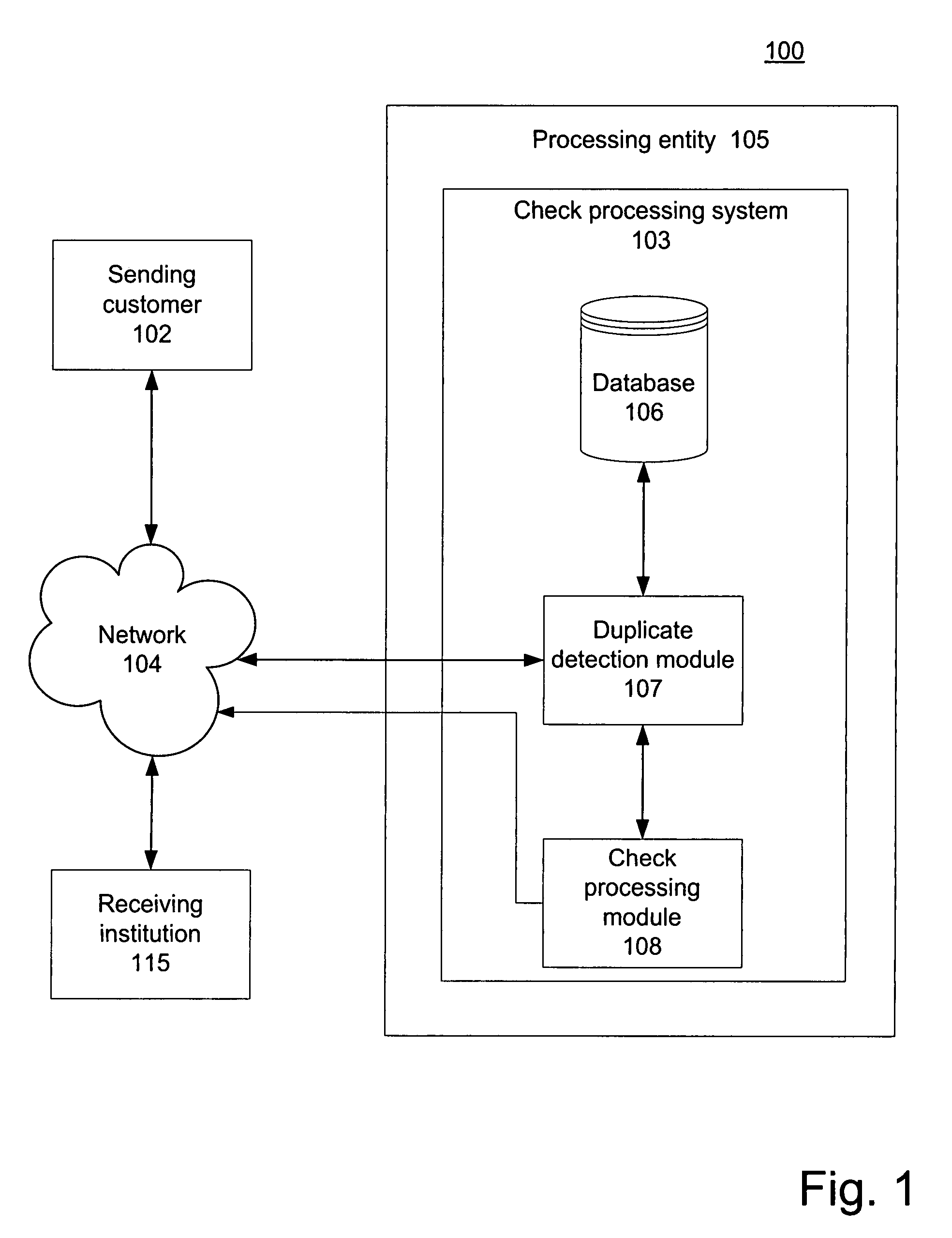
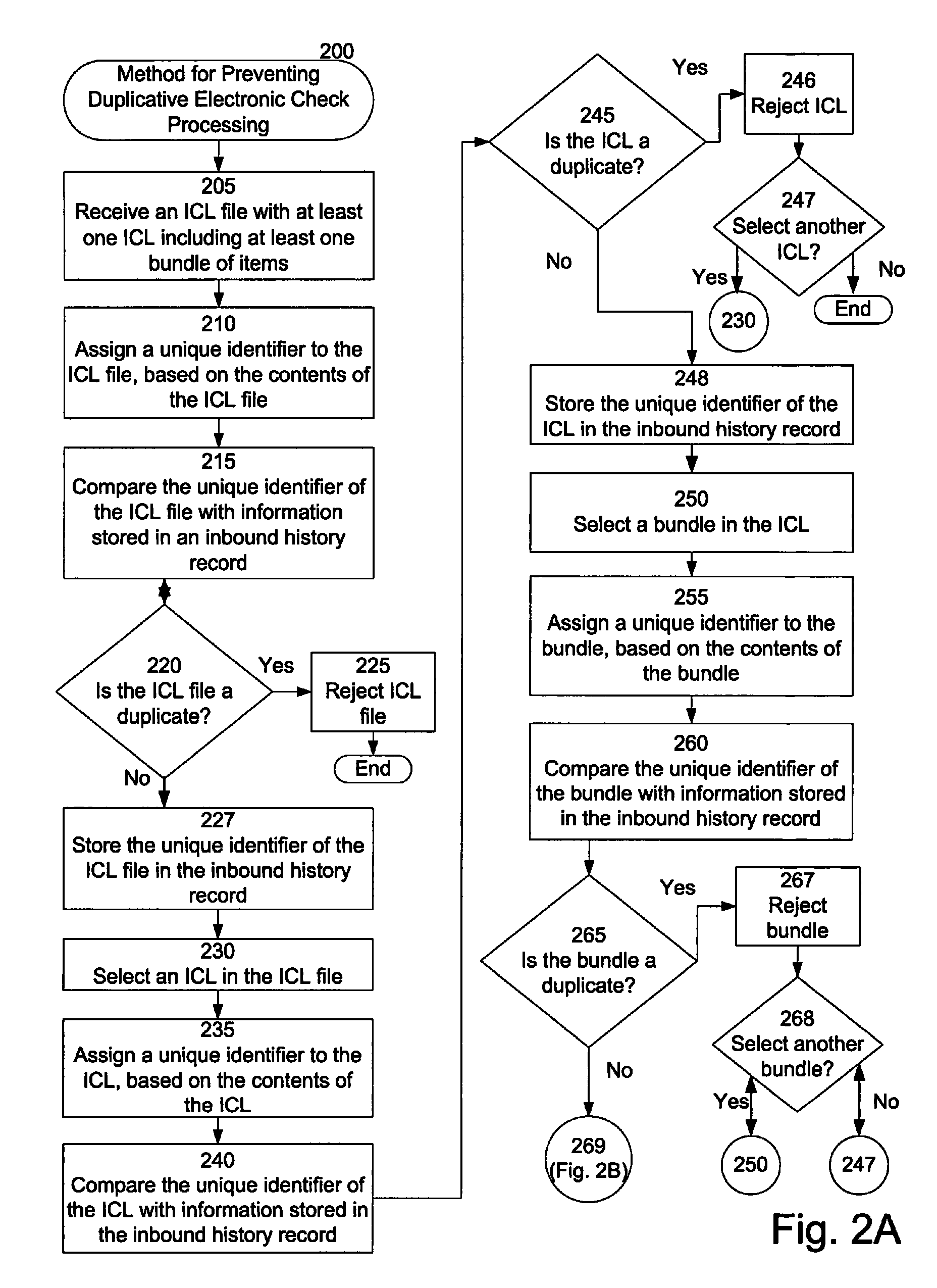
Systems and methods for preventing duplicative electronic check processing
Preventing duplicate ICL files and / or ICL file elements, including duplicate ICLs, items, and item bundles, from being processed for payment and / or presentment. A duplicate detection module can assign a predictable and repeatable unique identifier to each ICL file and / or ICL file element. The duplicate detection module can determine whether each ICL file and / or element is a duplicate by comparing the identifier associated with the ICL file and / or element with information stored in a record of already processed files / elements. In response to determining that an ICL file and / or element is a duplicate, the duplicate detection module can determine not to process the file / element for payment and / or presentment. In response to determining that the ICL file and / or element is not a duplicate, the duplicate detection module can store information regarding the file / element in the record. For example, the stored information can include the unique identifier associated with the file / element.
Owner:US FEDERAL RESERVE BANK OF ATLANTA +2
System, device and method for automatic anomally detection
InactiveUS20040039968A1Easy to introduceEasy to monitorMemory loss protectionError detection/correctionAnomaly detectionSimulation
The invention relates to a method and system for monitoring the behaviour of at least one observable object, e.g. a network element, of a network, wherein at least one parameter of the observable object is repeatedly detected. An actually detected parameter is input to a learning process and to an analyzing process, wherein the learning process forms a reference, based on at least two detected parameter values, for describing the behaviour of the observable object. The analyzing process compares the input parameter and the reference for detecting an anomal behaviour. The parameter preferably is a vector which comprises several values describing properties or functioning of the observable object, and is formed based on events and / or reports from the object.
Owner:NOKIA CORP
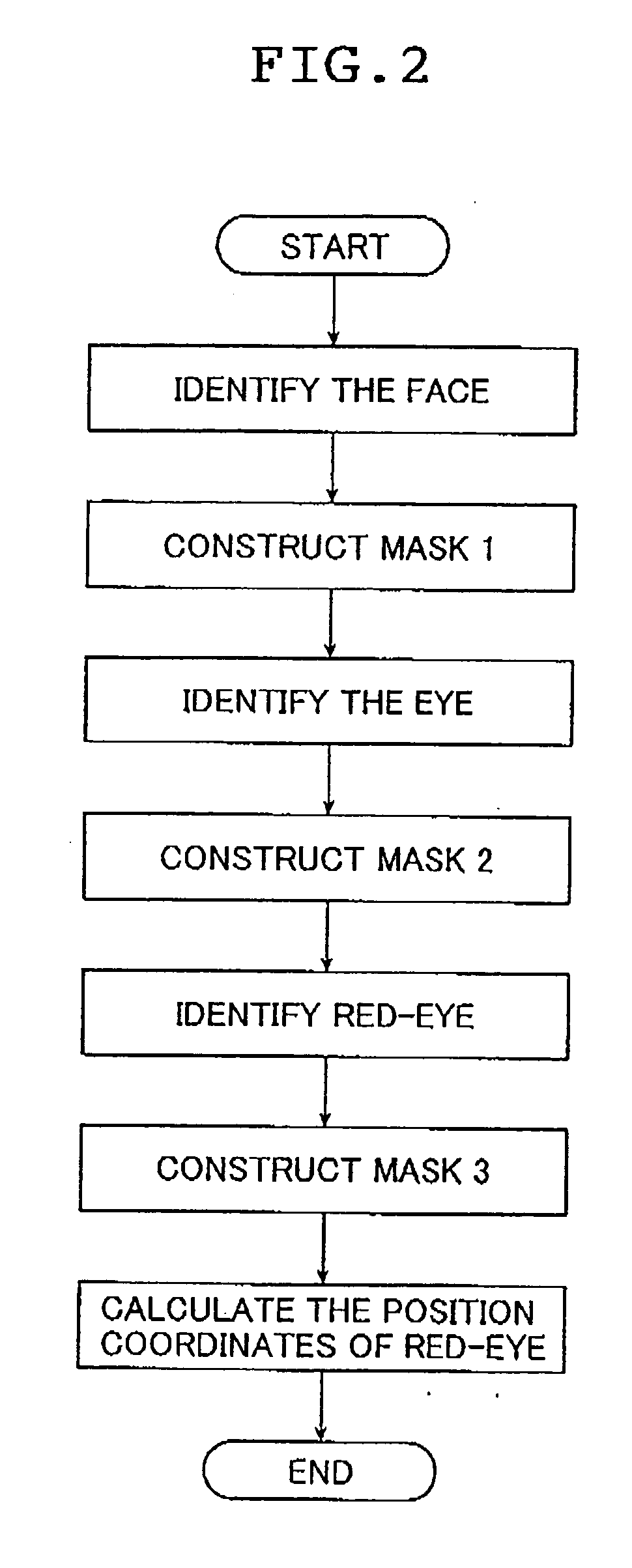
Image processing apparatus and method, red-eye detection method, as well as programs for executing the image processing method and the red-eye detection method
ActiveUS20050074164A1Quick checkAppropriate detectionImage analysisCharacter and pattern recognitionImaging processingDuplicate detection
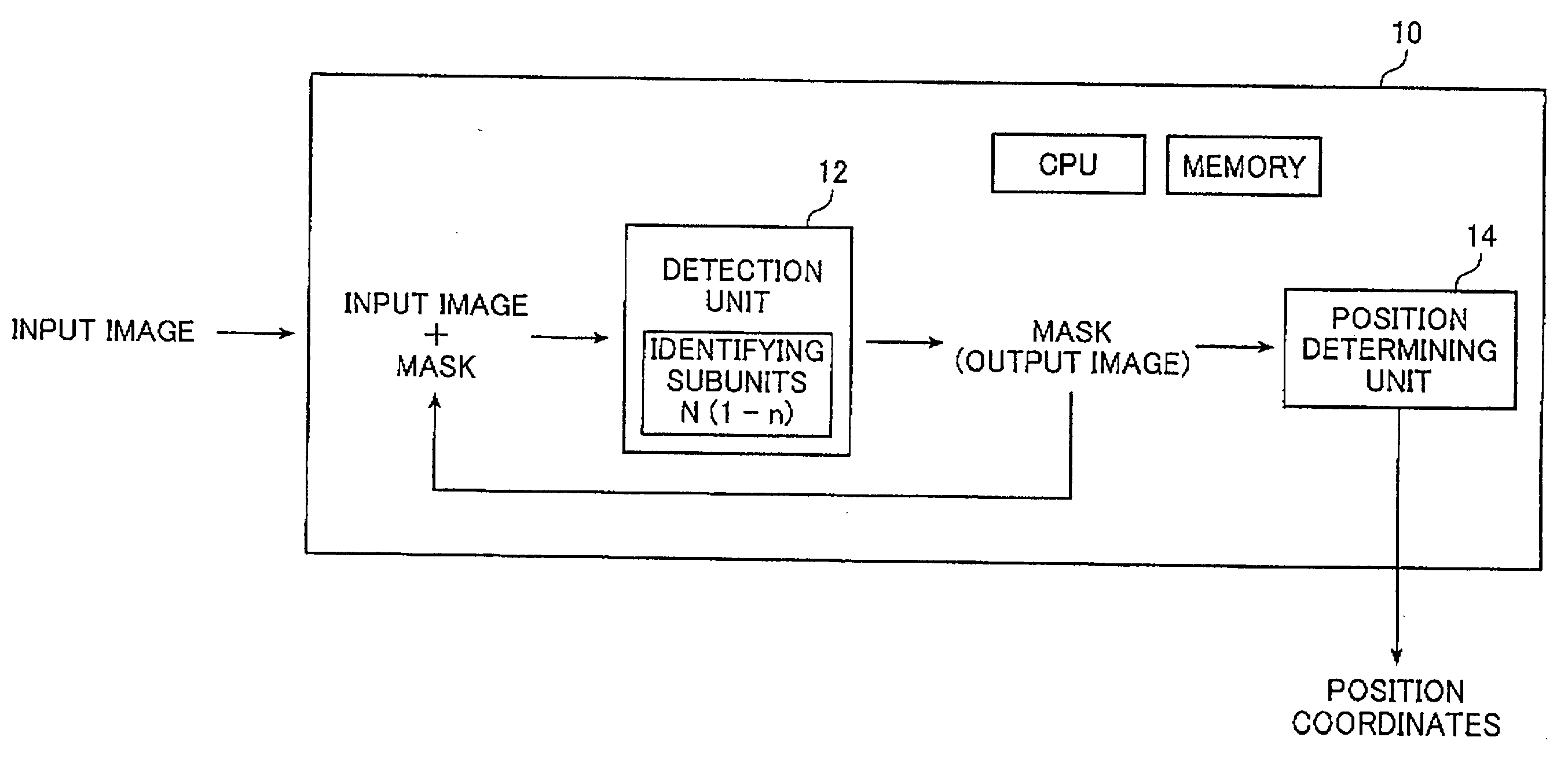
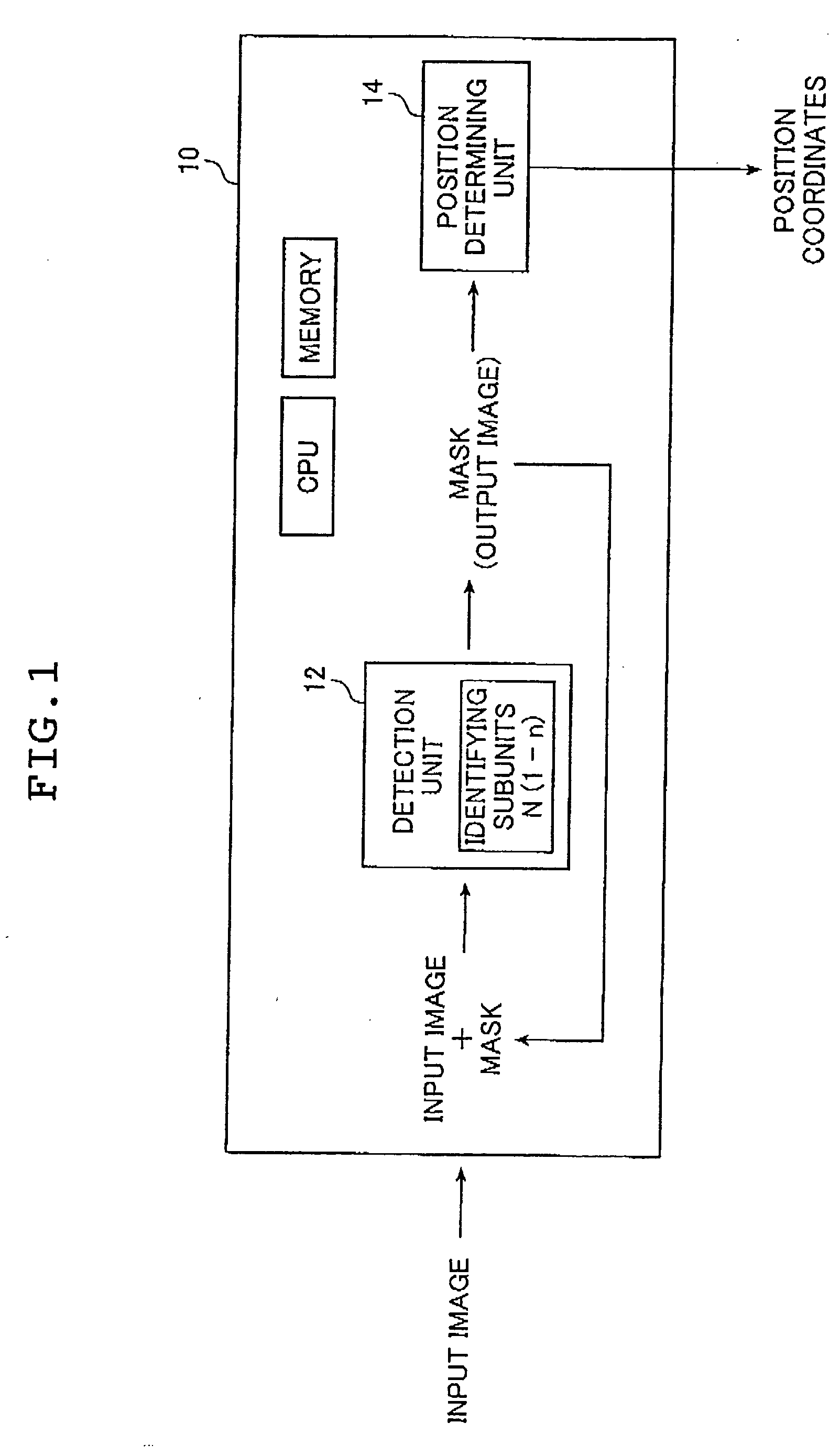
An image processing apparatus which processes an input image to detect a specified object of interest that is recorded in the input image is provided. The apparatus has a detection unit and a position determining unit. The detection unit has a plurality of identifying subunits each of which identifies an object from the input image under a different condition. The detection unit detects a region of the identified object. The position determining unit calculates the position coordinates of the object of interest in the input image from the region of the identified object. The detection unit performs the identification and the detection repeatedly and the detection unit performs the identification and the detection by using a detected region of an identified object in the previous identification. The detection unit detects the specified object of interest using the repeatedly detected regions.
Owner:FUJIFILM CORP +1
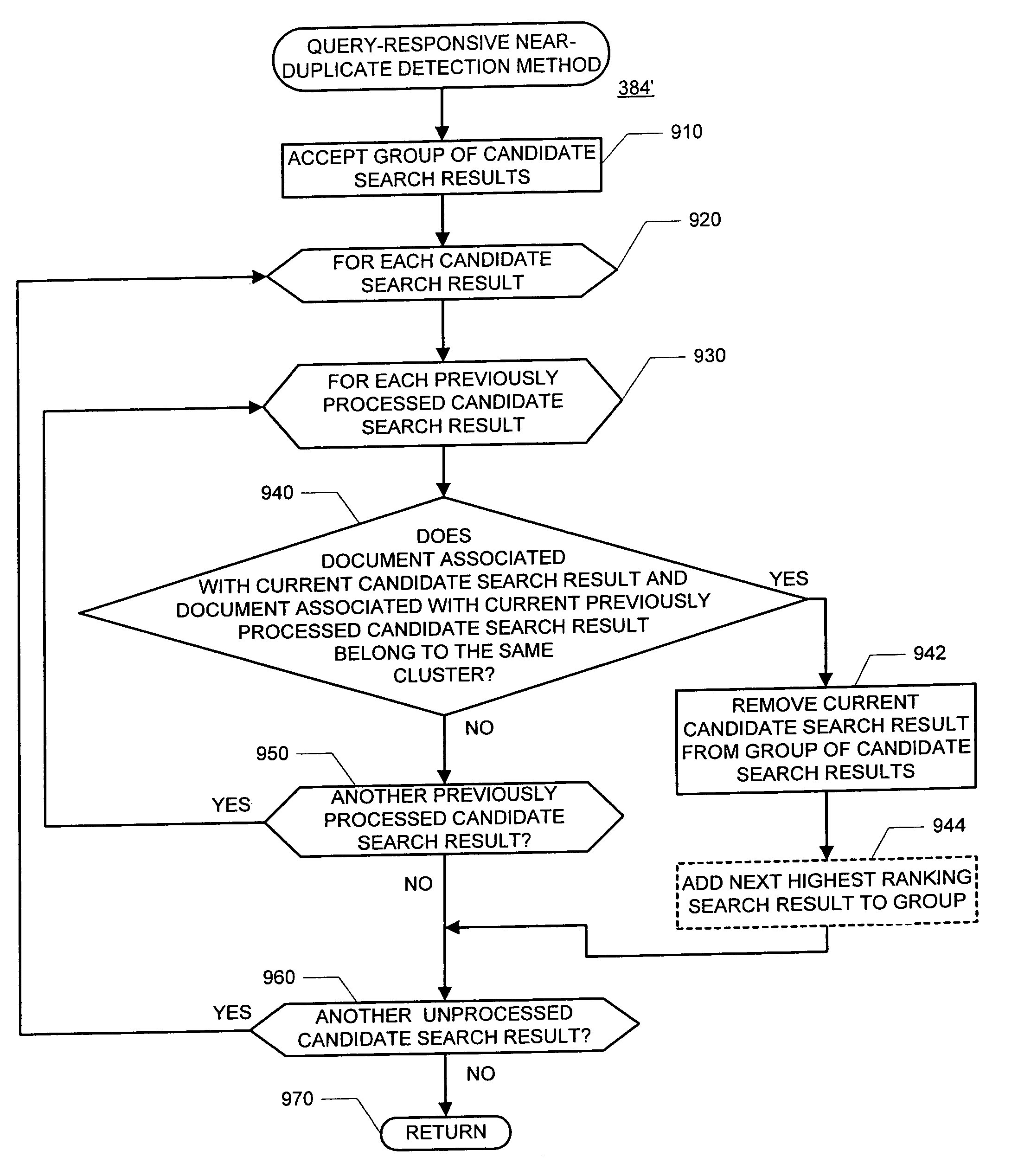
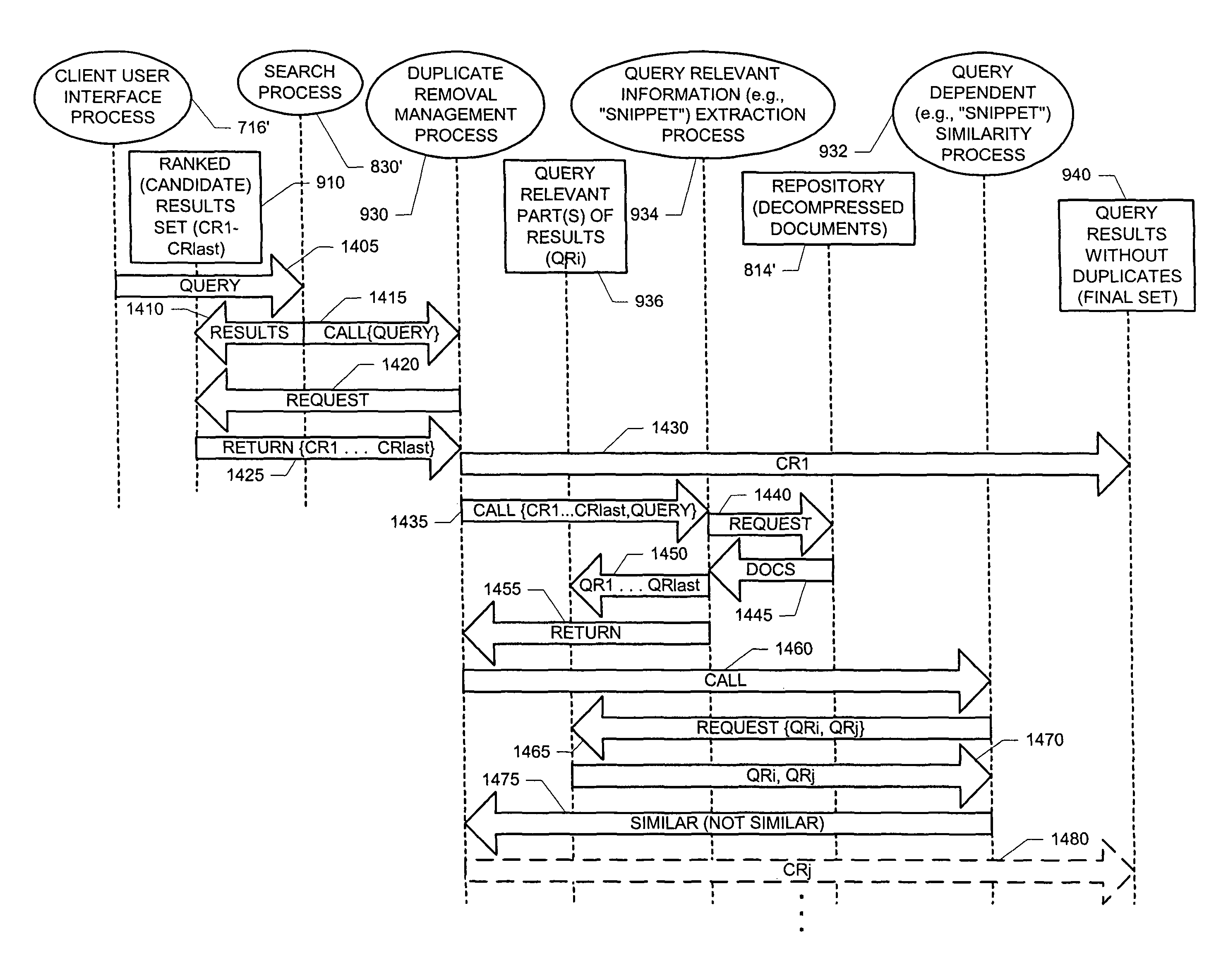
Detecting query-specific duplicate documents
InactiveUS7779002B1Reduce in quantityNot set it lowMetadata text retrievalData processing applicationsRelevant informationDocument preparation
An improved duplicate detection technique that uses query-relevant information to limit the portion(s) of documents to be compared for similarity is described. Before comparing two documents for similarity, the content of these documents may be condensed based on the query. In one embodiment, query-relevant information or text (also referred to as “snippets”) is extracted from the documents and only the extracted snippets, rather than the entire documents, are compared for purposes of determining similarity.
Owner:GOOGLE LLC
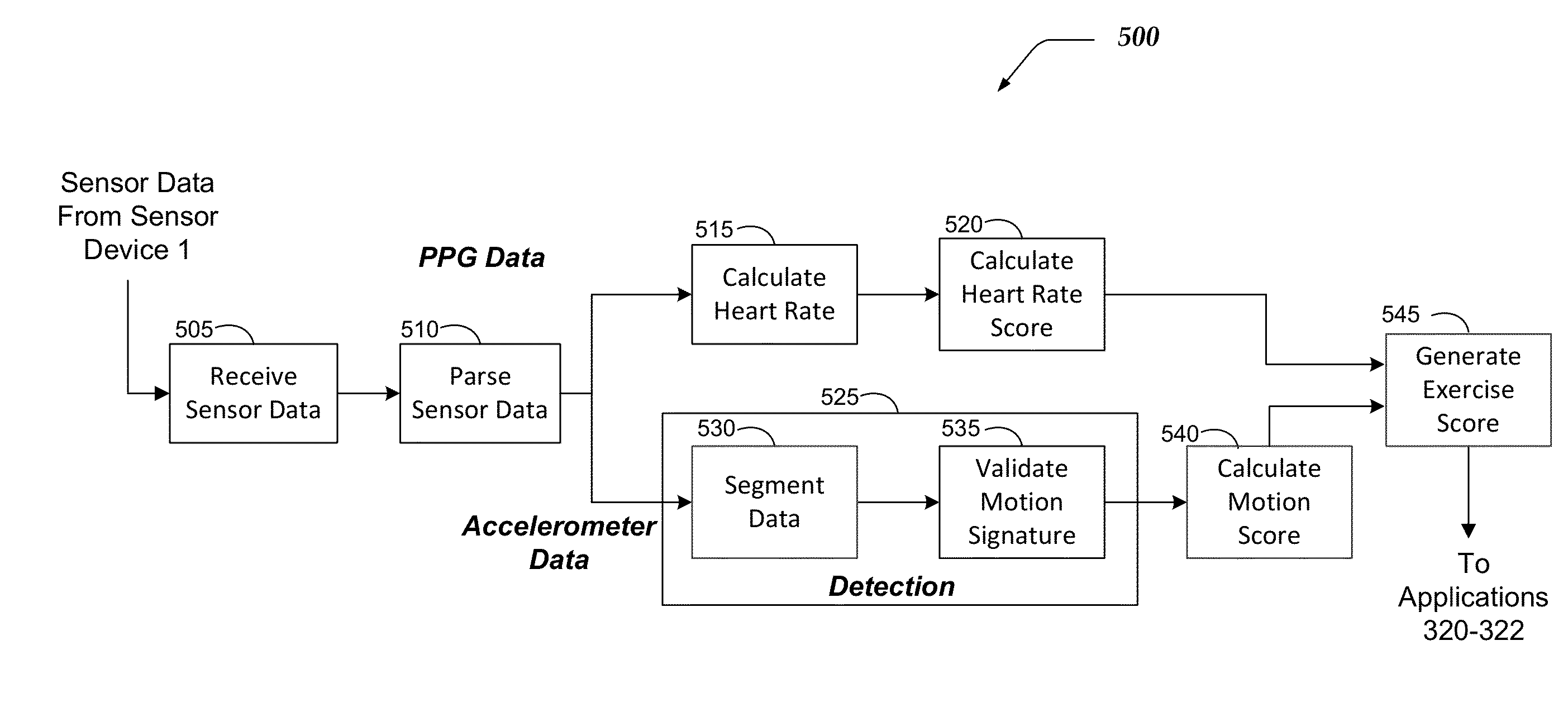
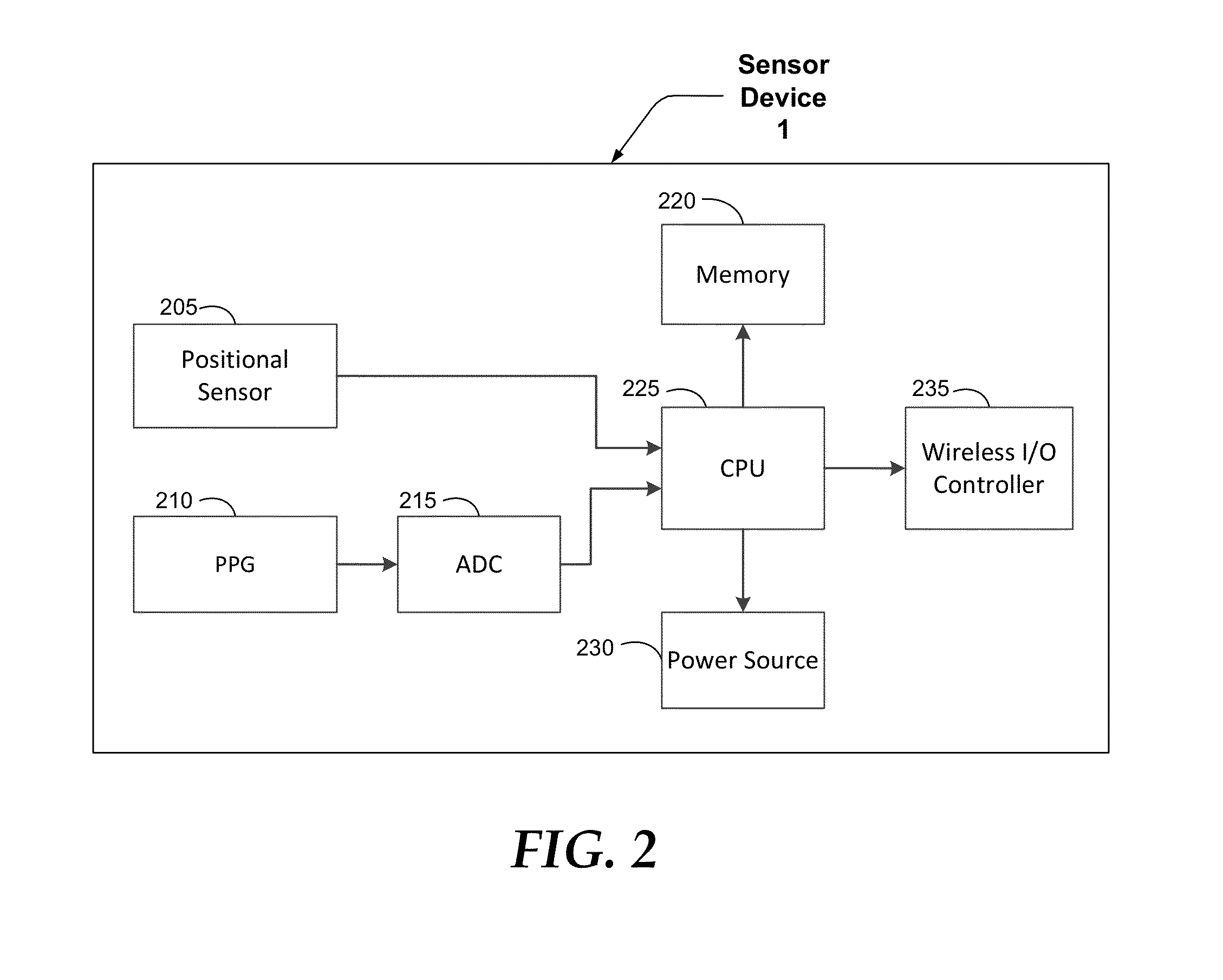
Head Worn Sensor Device and System for Exercise Tracking and Scoring
InactiveUS20150100141A1Physical therapies and activitiesInertial sensorsAccelerometer dataRating system
The subject invention is directed to a computer-implemented method, a device and a system for detecting and scoring exercises, including maintaining, by a mobile device, a library of motion signatures, in which a motion signature for an exercise is a sequence of characteristic features and a characteristic feature is a movement in the exercise; receiving, by a mobile device, a time series of data from a sensor device, the sensor device attached to the head or torso of a user, the data comprising accelerometer data from an accelerometer included in the sensor device, detecting a single repetition of a designated exercise performed by the user and calculating a motion score for the single repetition of the detected exercise.
Owner:ZINC SOFTWARE
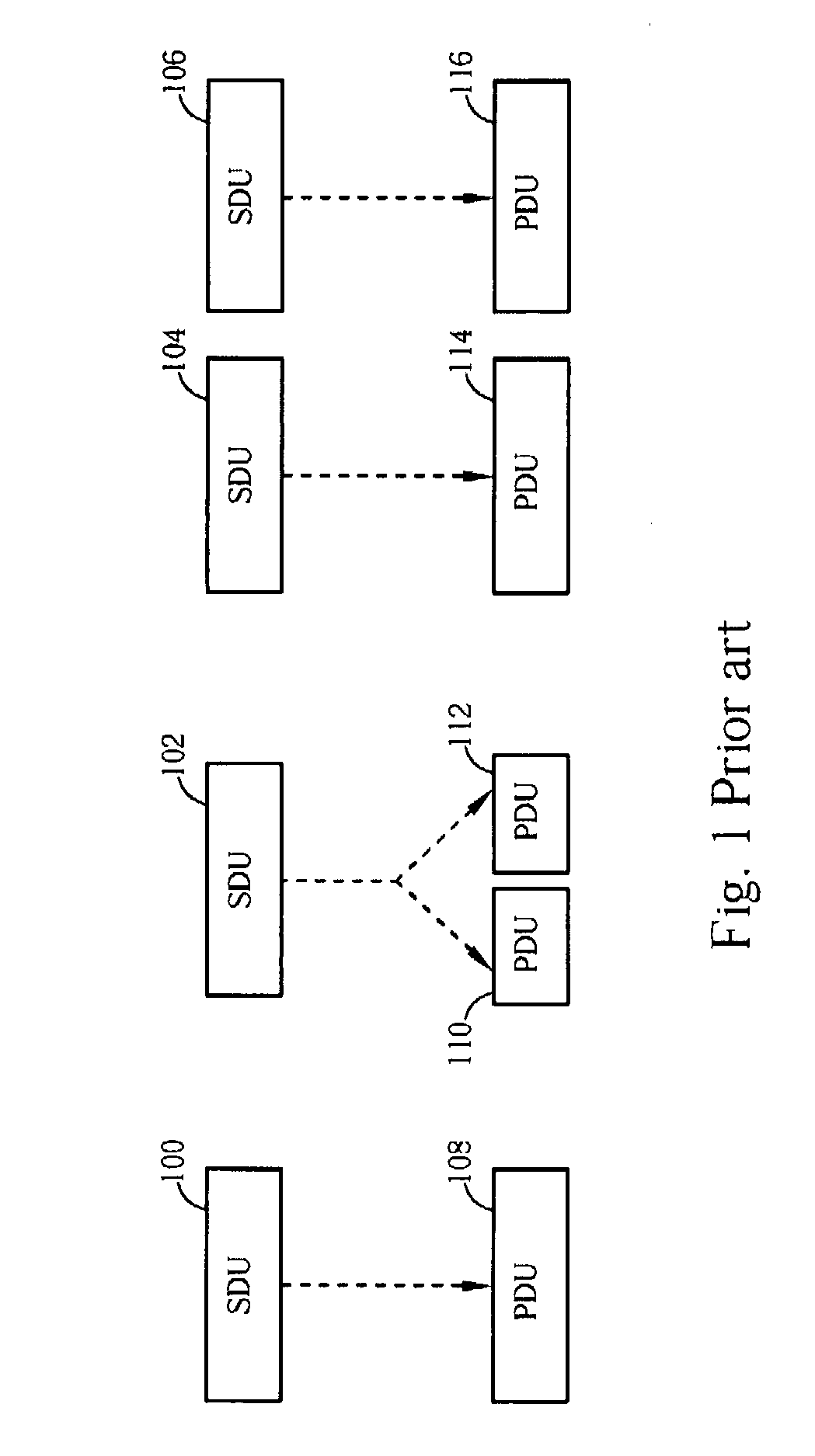
Methods and apparatus for handling segmentation and numbering of SDUs in wireless communication systems
InactiveUS20070253447A1Shorten the lengthError preventionNetwork traffic/resource managementCommunications systemAutomatic repeat request
A method for handling segmentation and numbering of protocol data units (PDUs) in a radio link control (RLC) entity of a wireless communications system includes handling a plurality of service data units (SDUs), an SDU of the plurality of SDUs comprising at least a first sequence number (SN) field and a first data field, a PDU of the RLC entity comprising a second data field storing all or segmented data of the first data field, the PDU further comprising a second SN field at least storing a value of the first SN field, and the RLC entity using the second SN field for performing an automatic repeat request, duplicate detection, a sequence number check, in-sequence delivery, etc.
Owner:INNOVATIVE SONIC
Detecting duplicate records in databases
InactiveUS20050262044A1Reduce in quantityData processing applicationsDigital data information retrievalSnowflake schemaData warehouse
The invention concerns a detection of duplicate tuples in a database. Previous domain independent detection of duplicated tuples relied on standard similarity functions (e.g., edit distance, cosine metric) between multi-attribute tuples. However, such prior art approaches result in large numbers of false positives if they are used to identify domain-specific abbreviations and conventions. In accordance with the invention a process for duplicate detection is implemented based on interpreting records from multiple dimensional tables in a data warehouse, which are associated with hierarchies specified through key-foreign key relationships in a snowflake schema. The invention exploits the extra knowledge available from the table hierarchy to develop a high quality, scalable duplicate detection process.
Owner:MICROSOFT TECH LICENSING LLC
Duplicate detection method for ad hoc network
InactiveUS20080247355A1Frequency-division multiplex detailsNetwork topologiesContent IdentifierSelf-organizing network
A duplicate detection method is disclosed for reducing redundant traffic in an ad hoc network. The duplicate detection method of the present invention includes receiving a first packet having a content identifier and a subcontent identifier, storing the content identifier and the subcontent identifier of the first packet, receiving a second packet, extracting a content identifier from the second packet, determining whether the content identifiers of the first and second packets are identical, extracting, when the content identifiers are identical, a subcontent identifier from the second packet, determining whether the subcontent identifiers of the first and second packets are identical, determining, when the subcontent identifiers of the first and second packets are identical, the second packet is a duplicate of the first packet.
Owner:SAMSUNG ELECTRONICS CO LTD
Detection of objects in an image using self similarities
InactiveUS20130058535A1Easy to classifyImage enhancementImage analysisComputer visionDuplicate detection
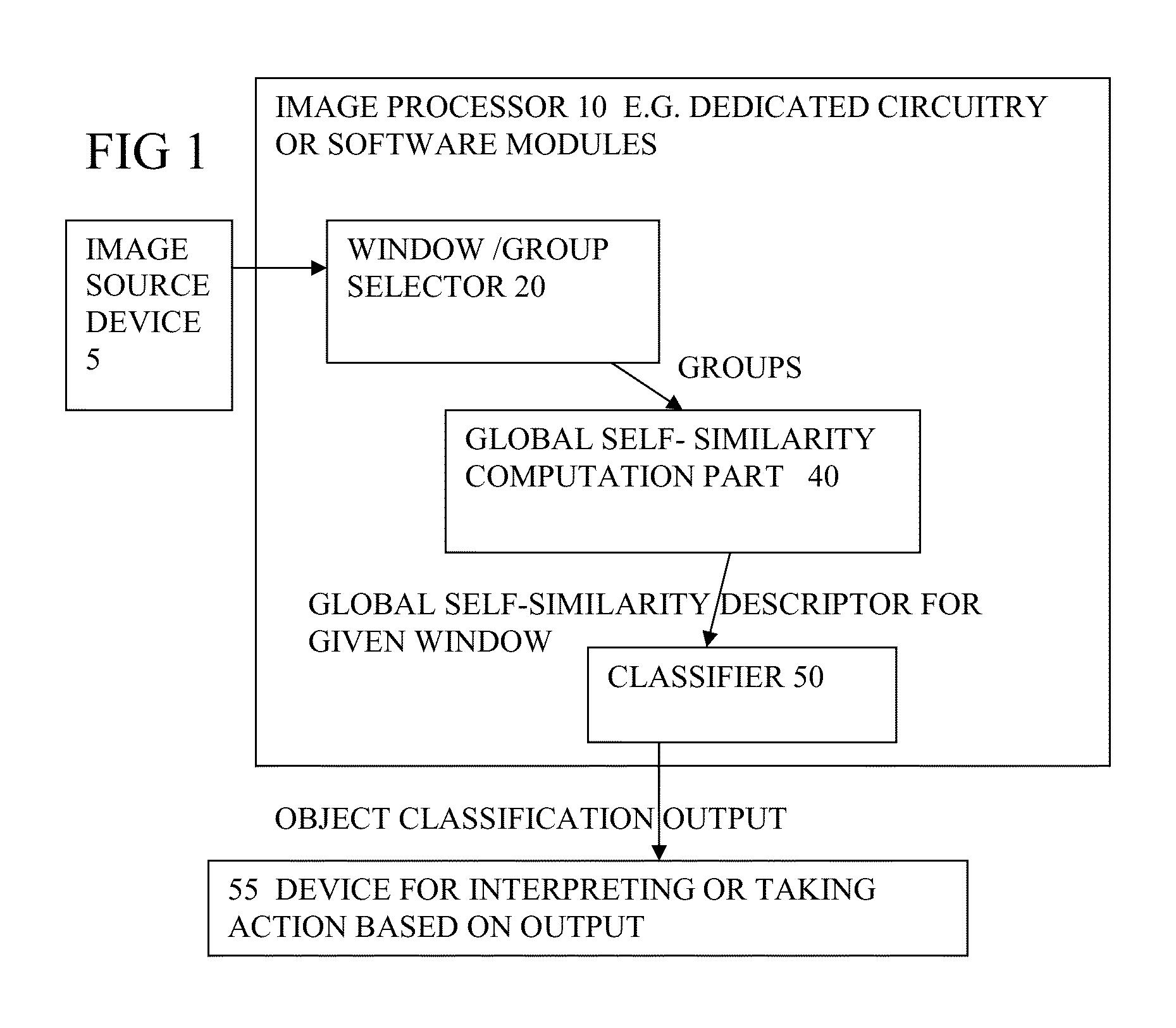
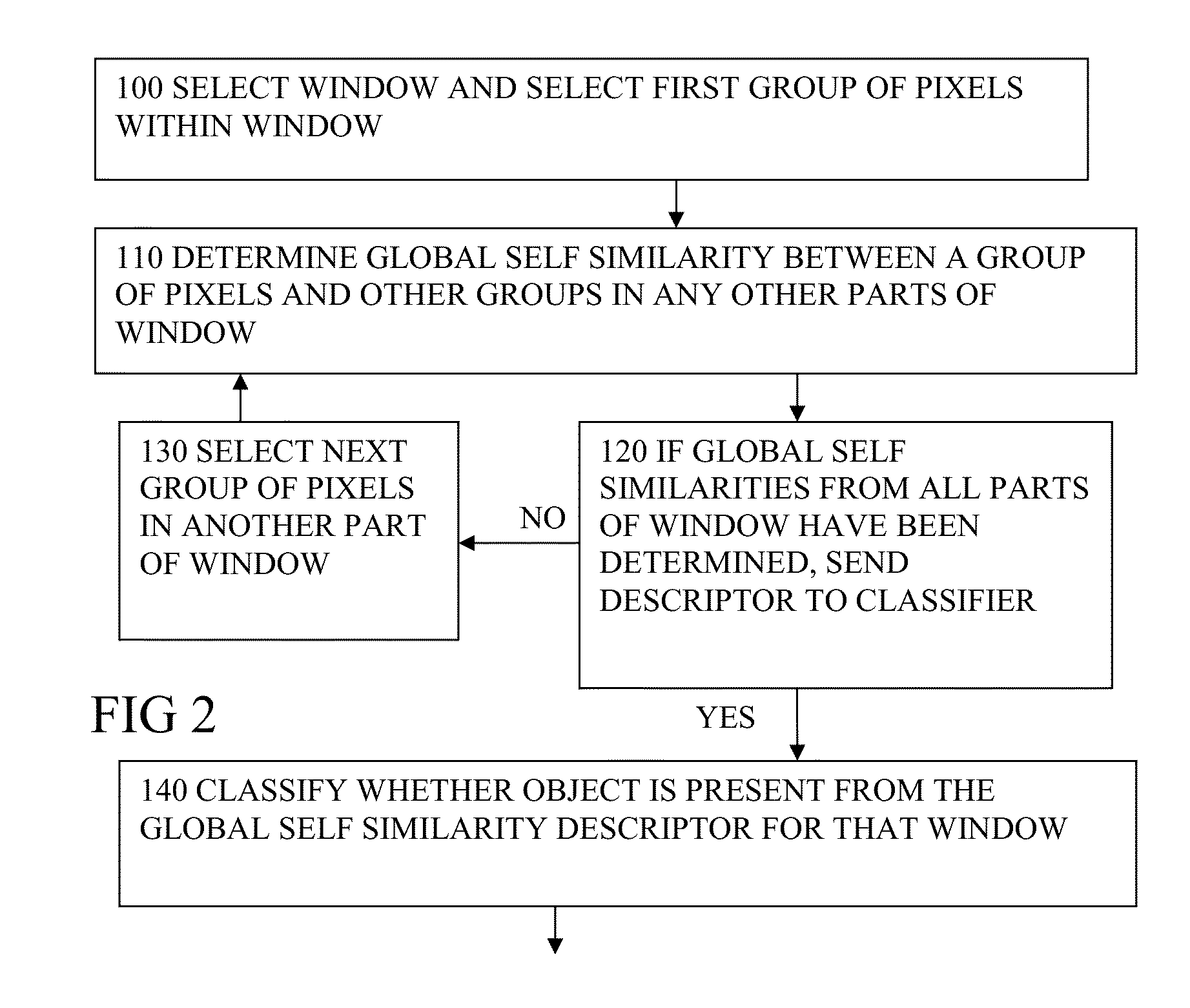
An image processor (10) has a window selector for choosing a detection window within the image, and a self similarity computation part (40) for determining self-similarity information for a group of the pixels in any part of the detection window, to represent an amount of self-similarity of that group to other groups in any other part of the detector window, and for repeating the determination for groups in all parts of the detection window, to generate a global self similarity descriptor for the detection window. A classifier (50) is used for classifying whether an object is present based on the global self-similarity descriptor. By using global self-similarity rather than local similarities more information is captured which can lead to better classification. In particular, it helps enable recognition of more distant self-similarities inherent in the object, and self-similarities present at any scale.
Owner:TECH UNIV DARMSTADT +1
Deep convolutional neural network-based human face occlusion detection method
ActiveCN106485215AAccurate occlusion detectionJudging the occlusionCharacter and pattern recognitionNoseMultilayer perceptron
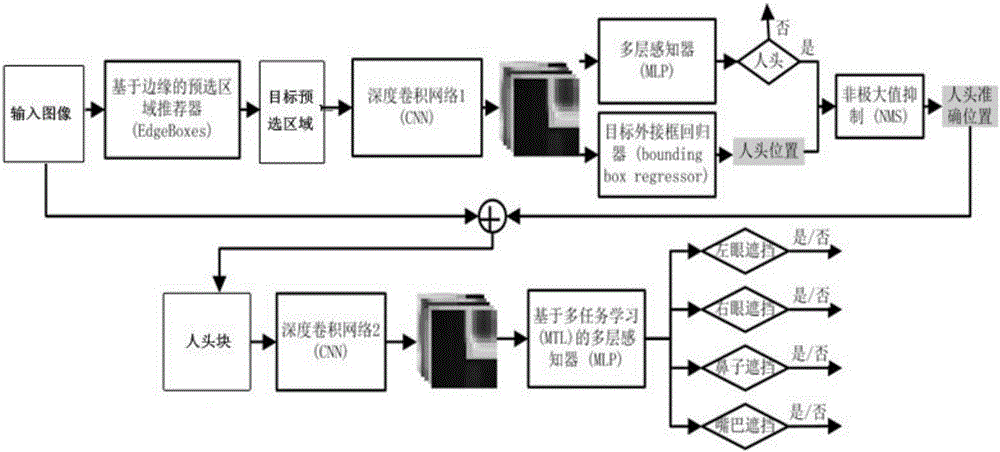
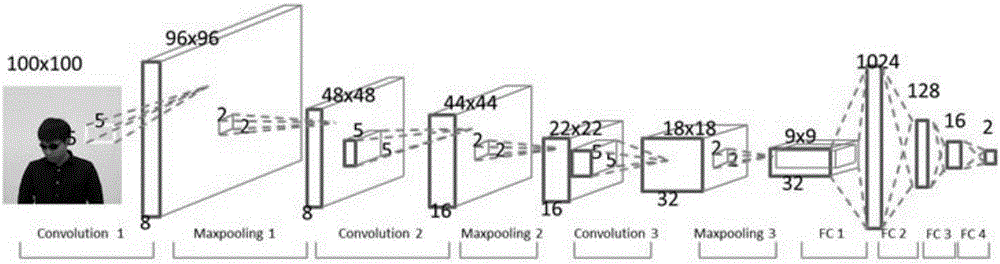
The invention discloses a deep convolutional neural network-based human face occlusion detection method. The method comprises the steps of performing block segmentation on an input image to obtain a target pre-selected region; constructing a first deep convolutional neural network, training the first deep convolutional neural network comprising a first deep convolutional network and a first multilayer perceptron connected with the first deep convolutional neural network to obtain required parameters, extracting features of the target pre-selected region, and performing classification; predicting the position of a human head through a second multilayer perceptron according to the extracted features; filtering the credibility of a classification type which is the human head and the predicted position of the human head through non-maximum suppression to remove an overlapped duplicate detection box; and obtaining a human head block in combination with original image segmentation, constructing a multi-task learning policy-based second deep convolutional neural network, and judging whether the left eye, the right eye, the nose and the mouth of the human head block are occluded or not. According to the method, the occluded human face can be accurately detected and the specific occluded part of the human face can be judged; and the method is mainly used for crime pre-warning of videos of a camera in front of an automatic teller machine.
Owner:XIAN JIAOTONG LIVERPOOL UNIV
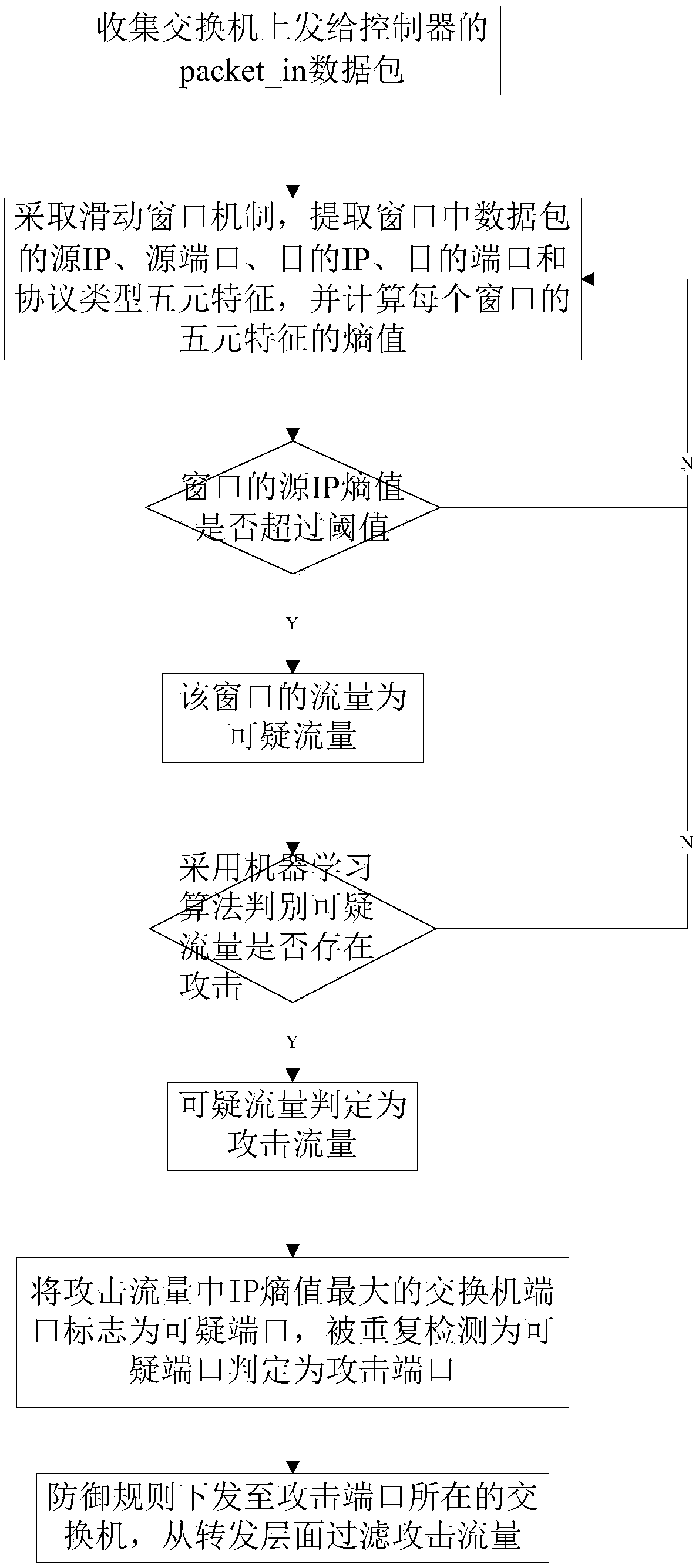
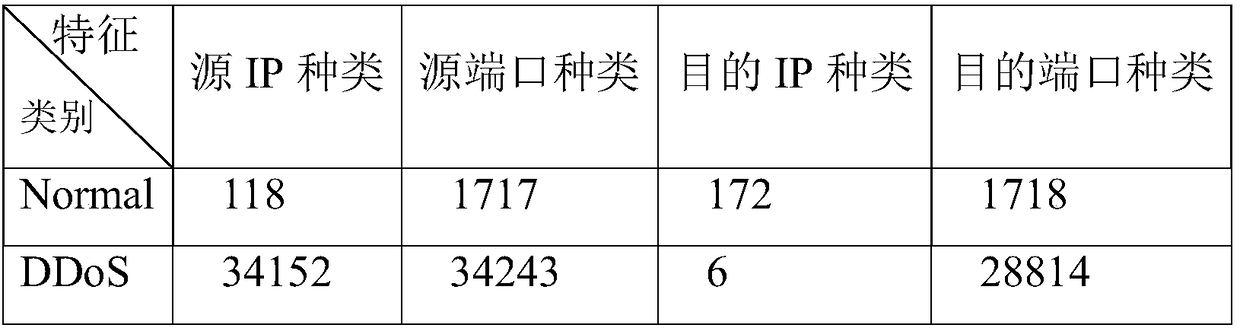
A DDoS attack detection and defense method and system in a software-defined network
The invention discloses a DDoS attack detection and defense method and system in a software-defined network. The method comprises:the quintuple features of source IP, source port, destination IP, destination port and protocol type are extracted and the quintuple feature entropy is calculated; whether the IP entropy value of the window source exceeds the threshold value is judged, if yes, it is determined that the window source IP entropy value is suspicious traffic, otherwise, the window traffic is filtered; machine learning is used to judge whether the suspicious traffic exists attack, if yes, it is judged as attack traffic, otherwise, the suspicious traffic is filtered; the switch port with the largest IP entropy value in the attack traffic is marked as a suspicious port, which is repeatedly detected as a suspicious port and is judged as an attack port; defense rules are issued to the switch where the attack port is located and attack traffic is filtered from the forwarding layer. The invention combines quintuple characteristic entropy value and machine learning algorithm to detect DDoS attack, locates and takes defensive measures in time, filters a large amount of malicious traffic from the forwarding layer, and protects the controller and the switch.
Owner:HUAZHONG UNIV OF SCI & TECH
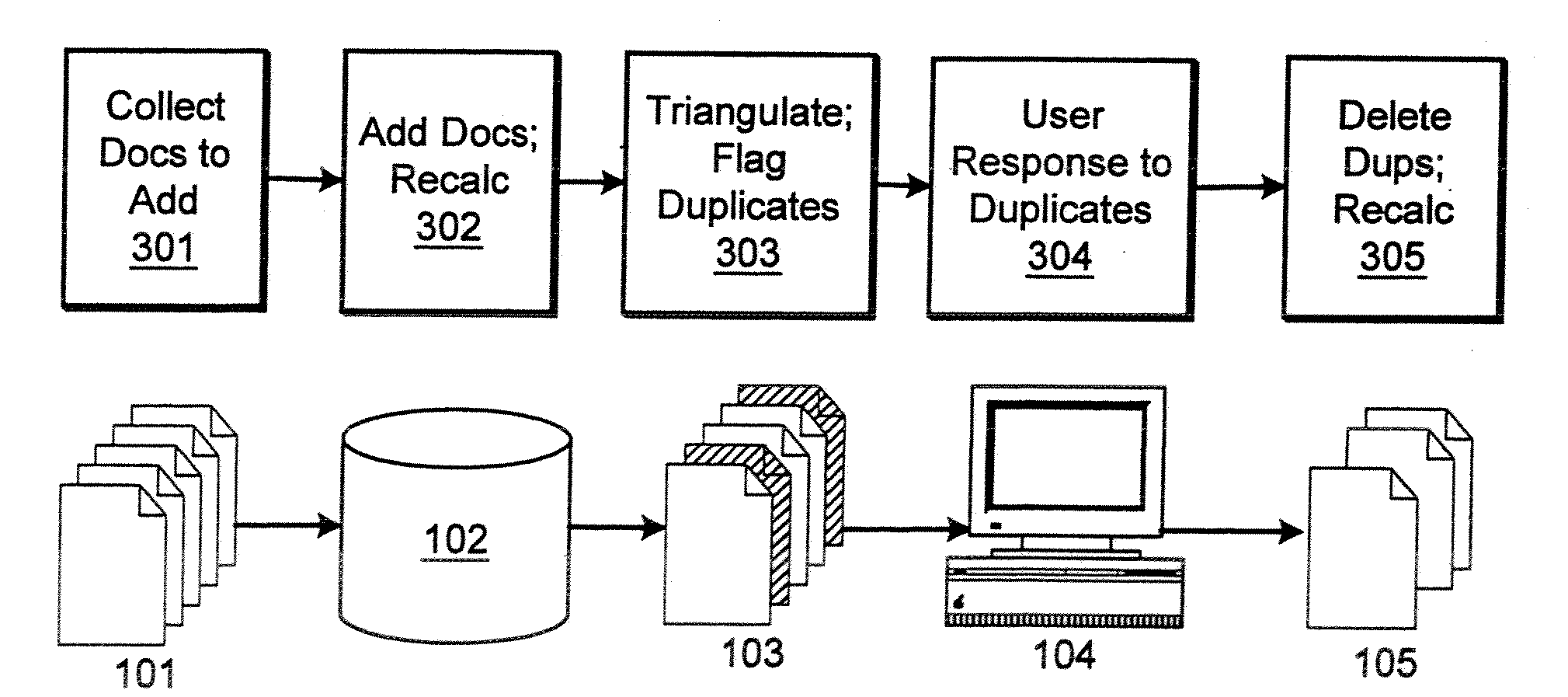
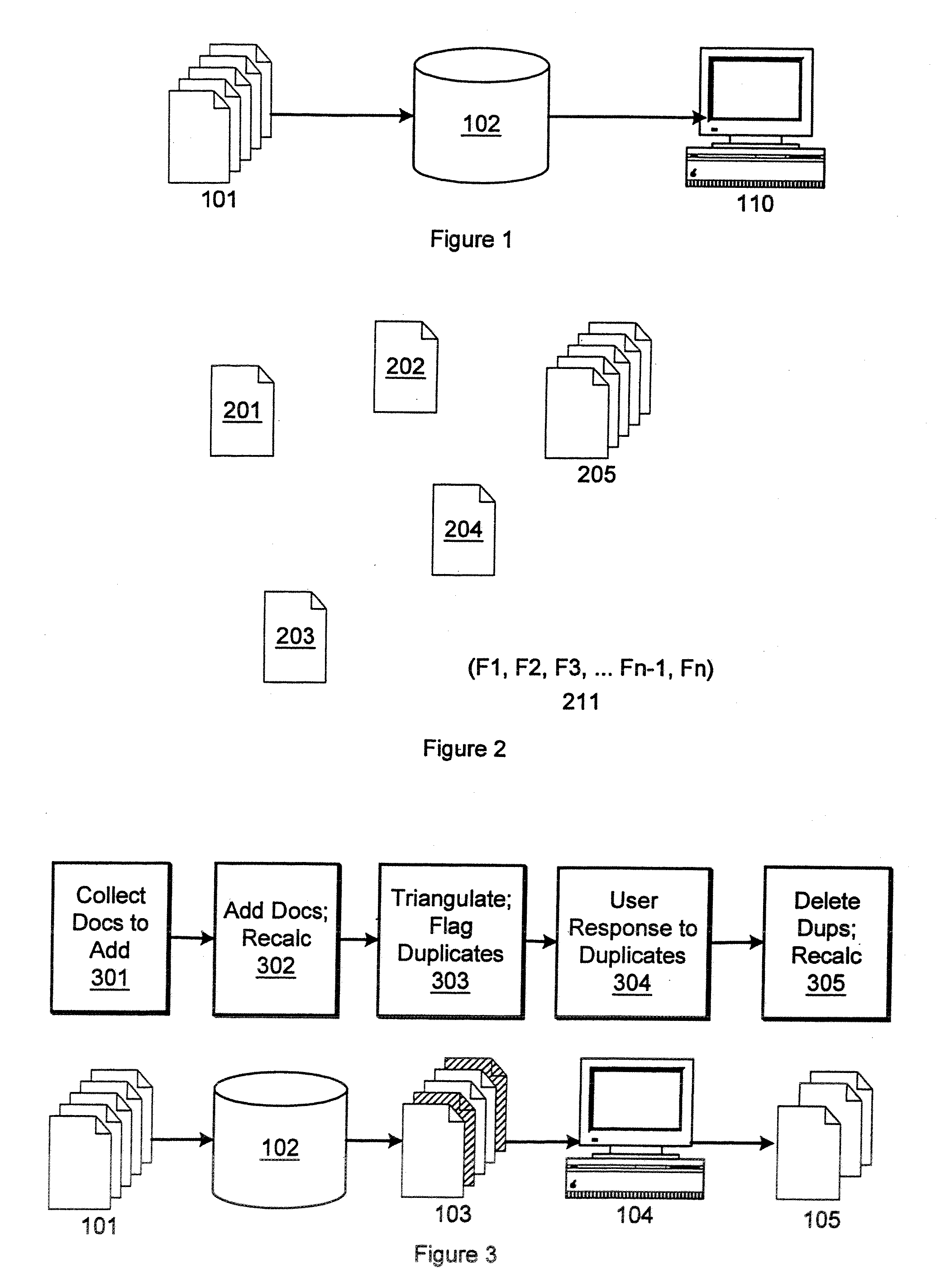
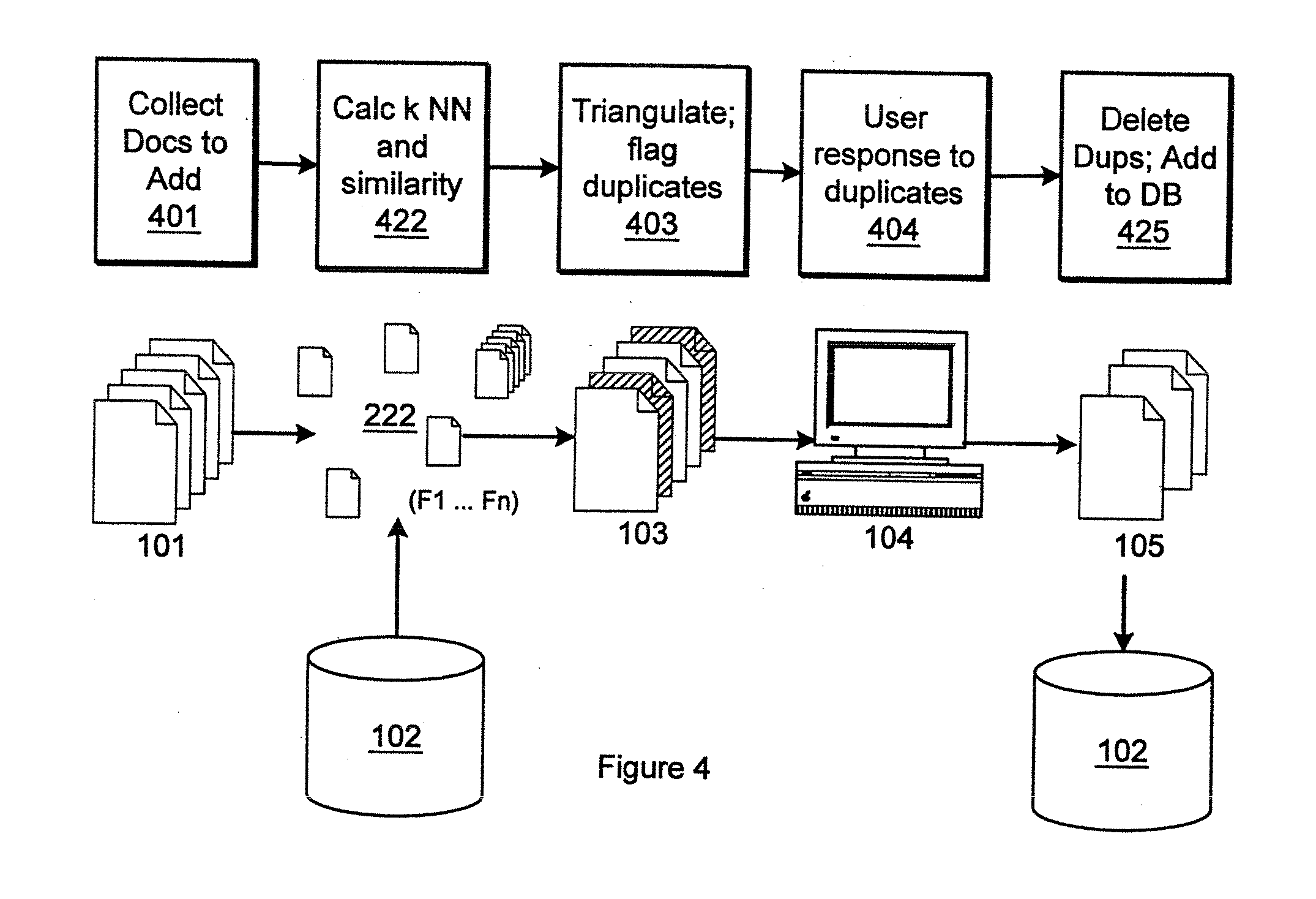
Method and apparatus for duplicate detection
InactiveUS20080243837A1Digital data processing detailsSpecial data processing applicationsTriangulationDuplicate detection
The present invention includes a method and device for detecting duplicate documents by triangulation. Particular aspects of the present invention are described in the claims, specification and drawings.
Owner:BUSINESS OBJECTS AMERICAS
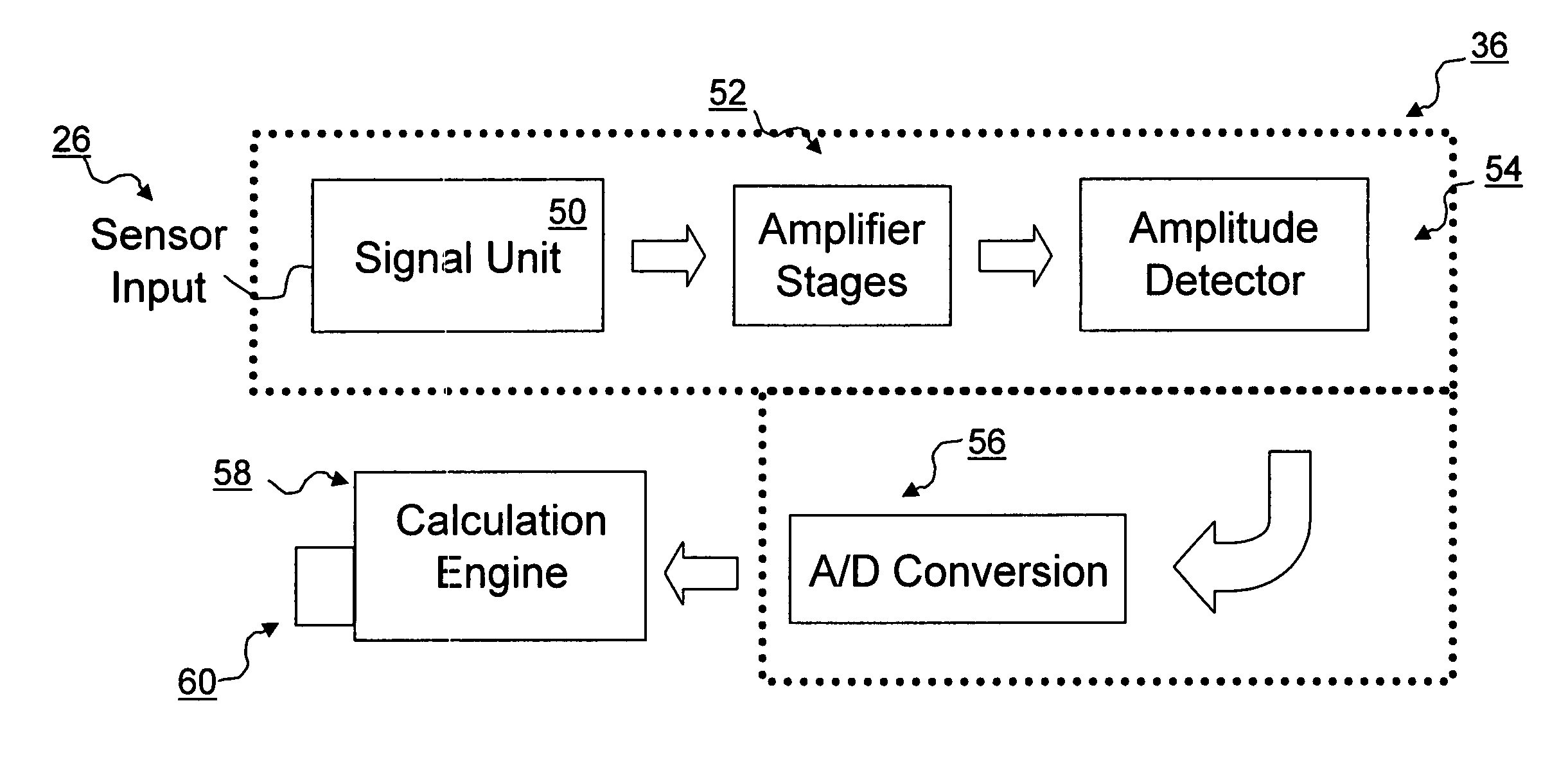
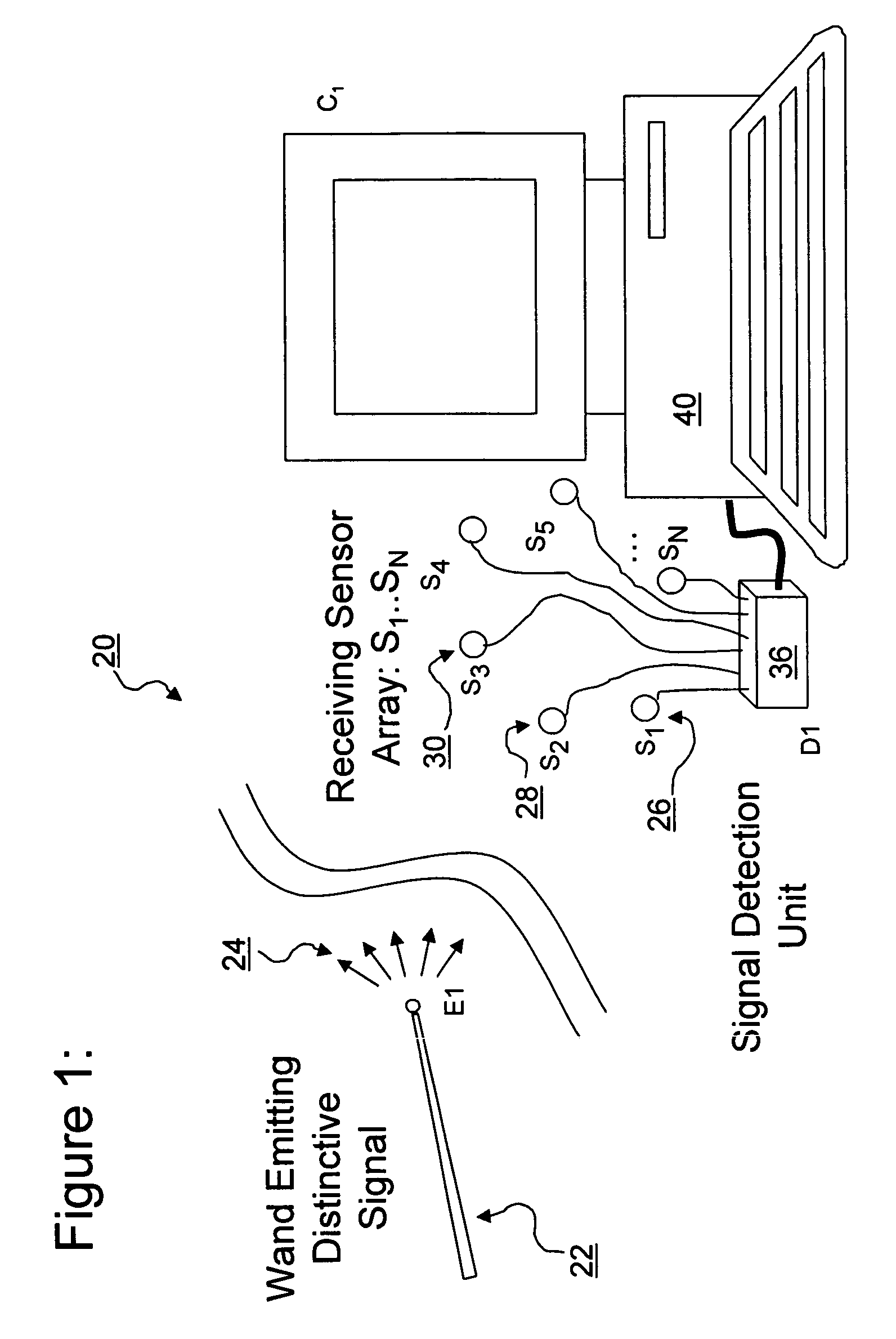
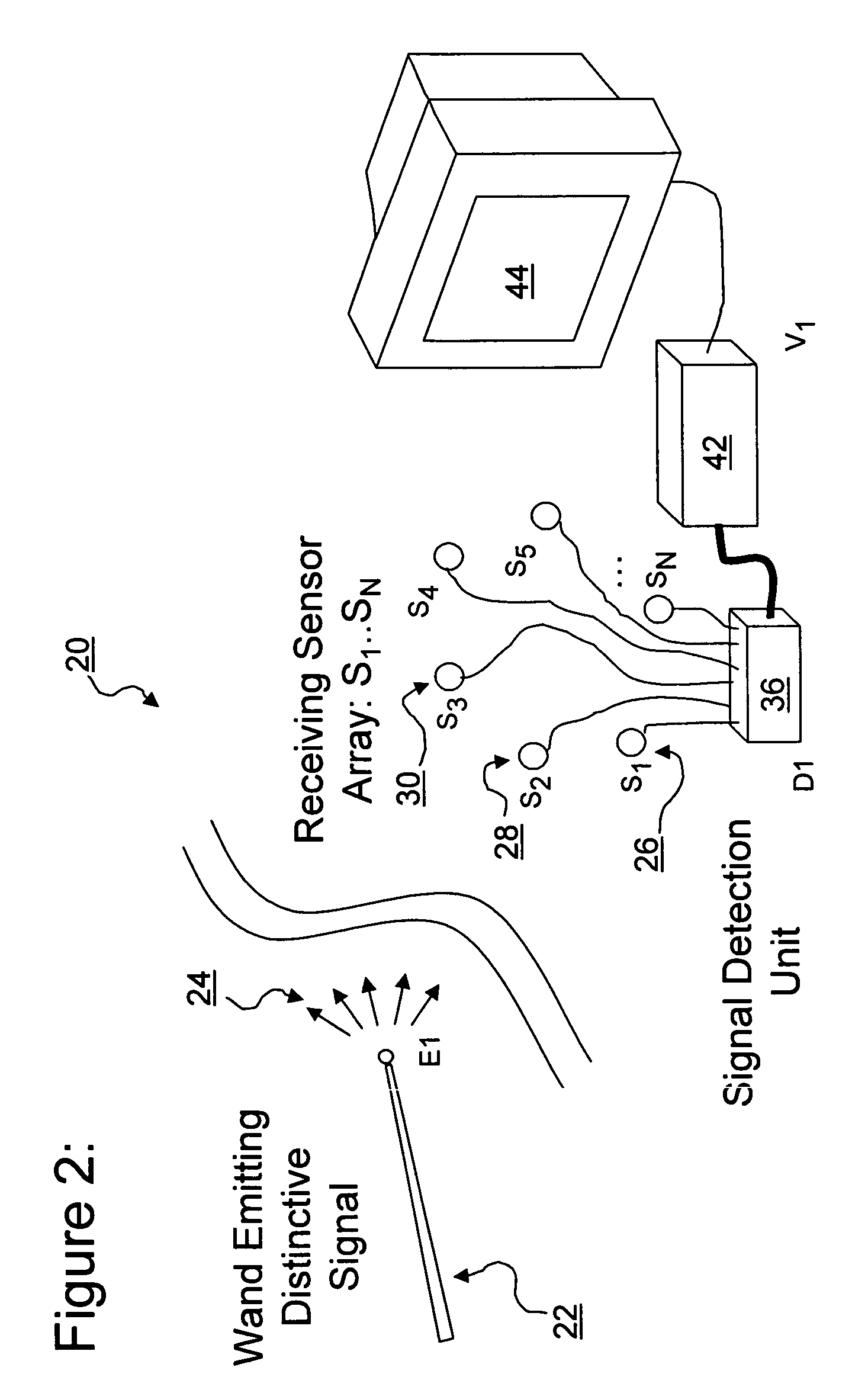
Three-dimensional position and motion telemetry input
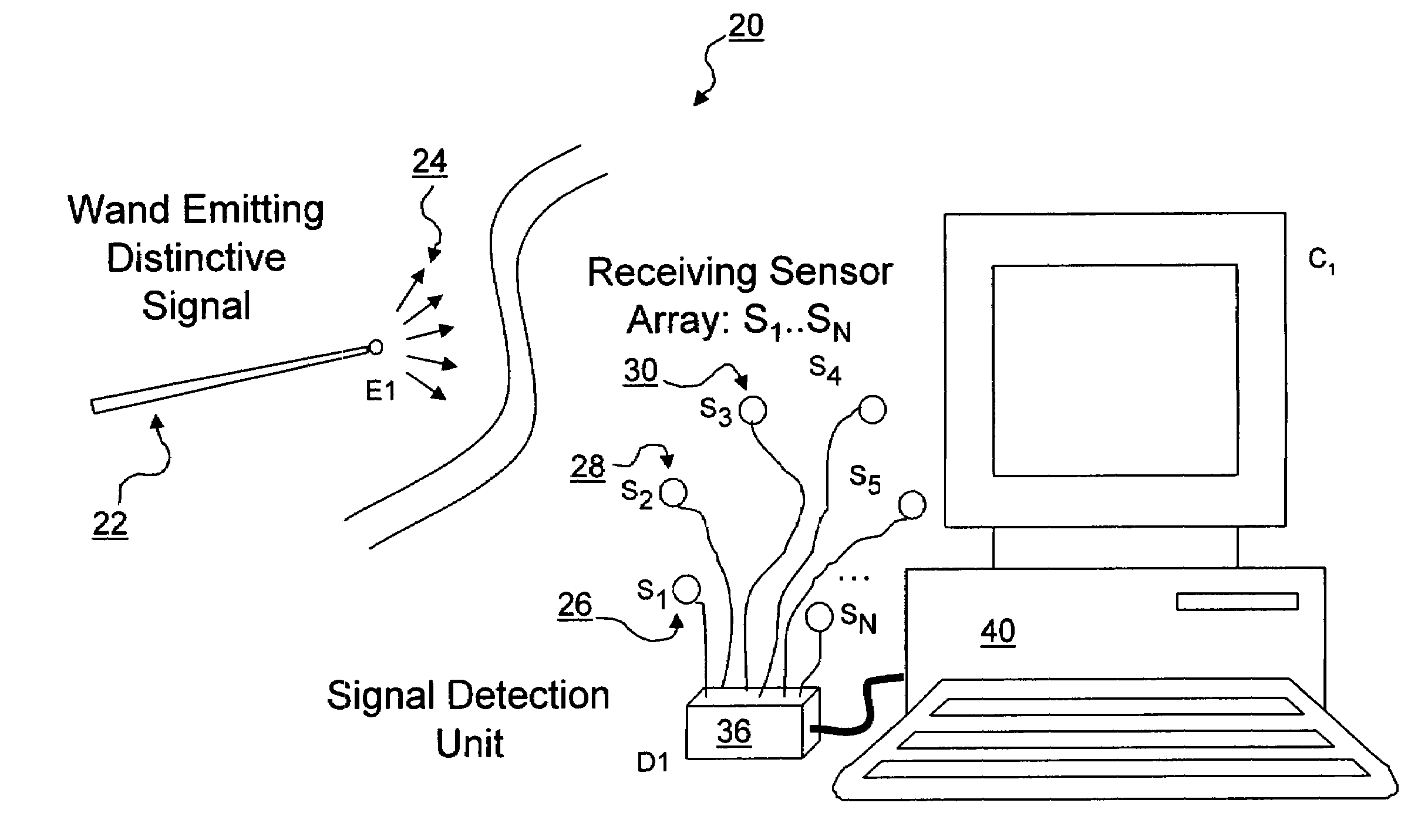
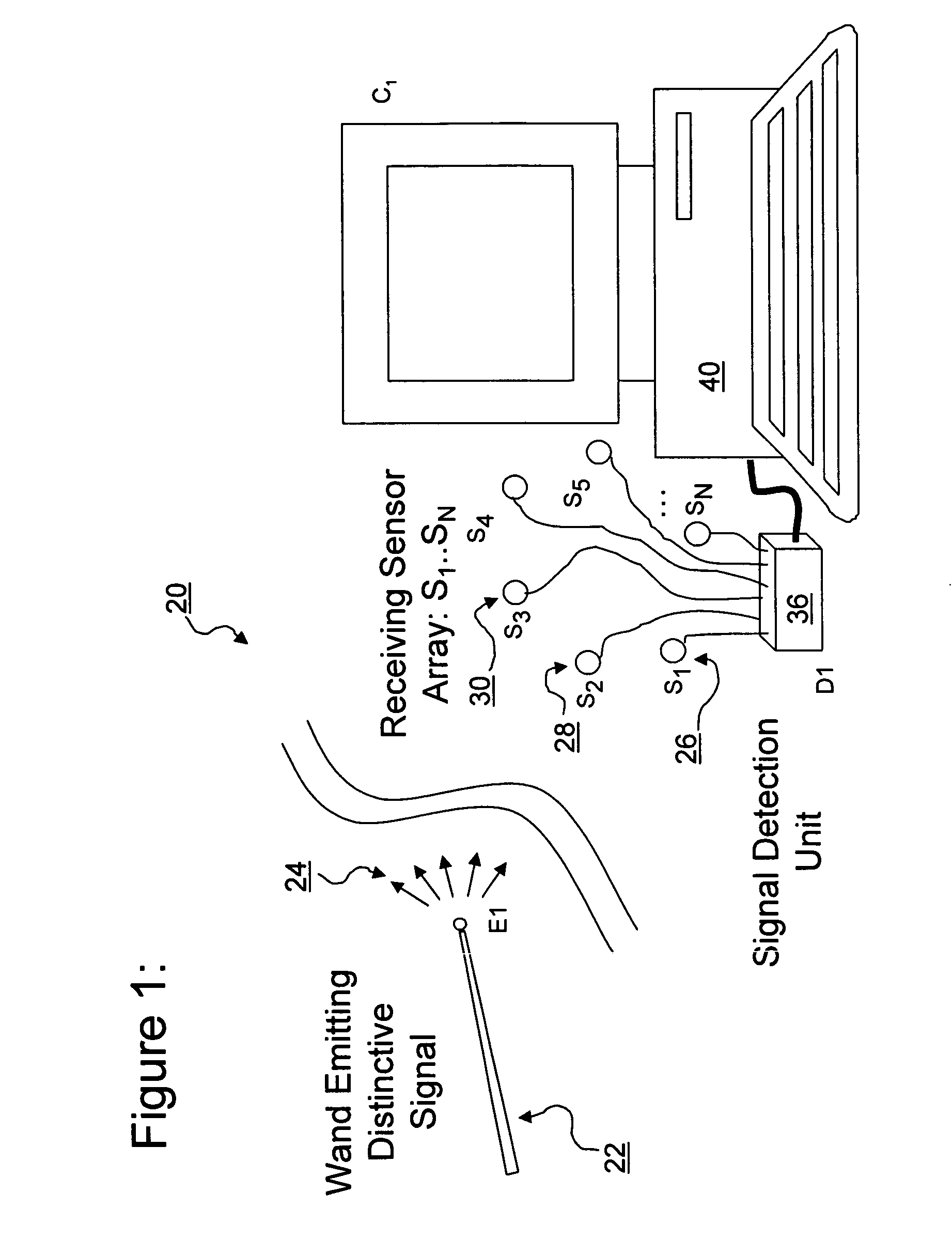
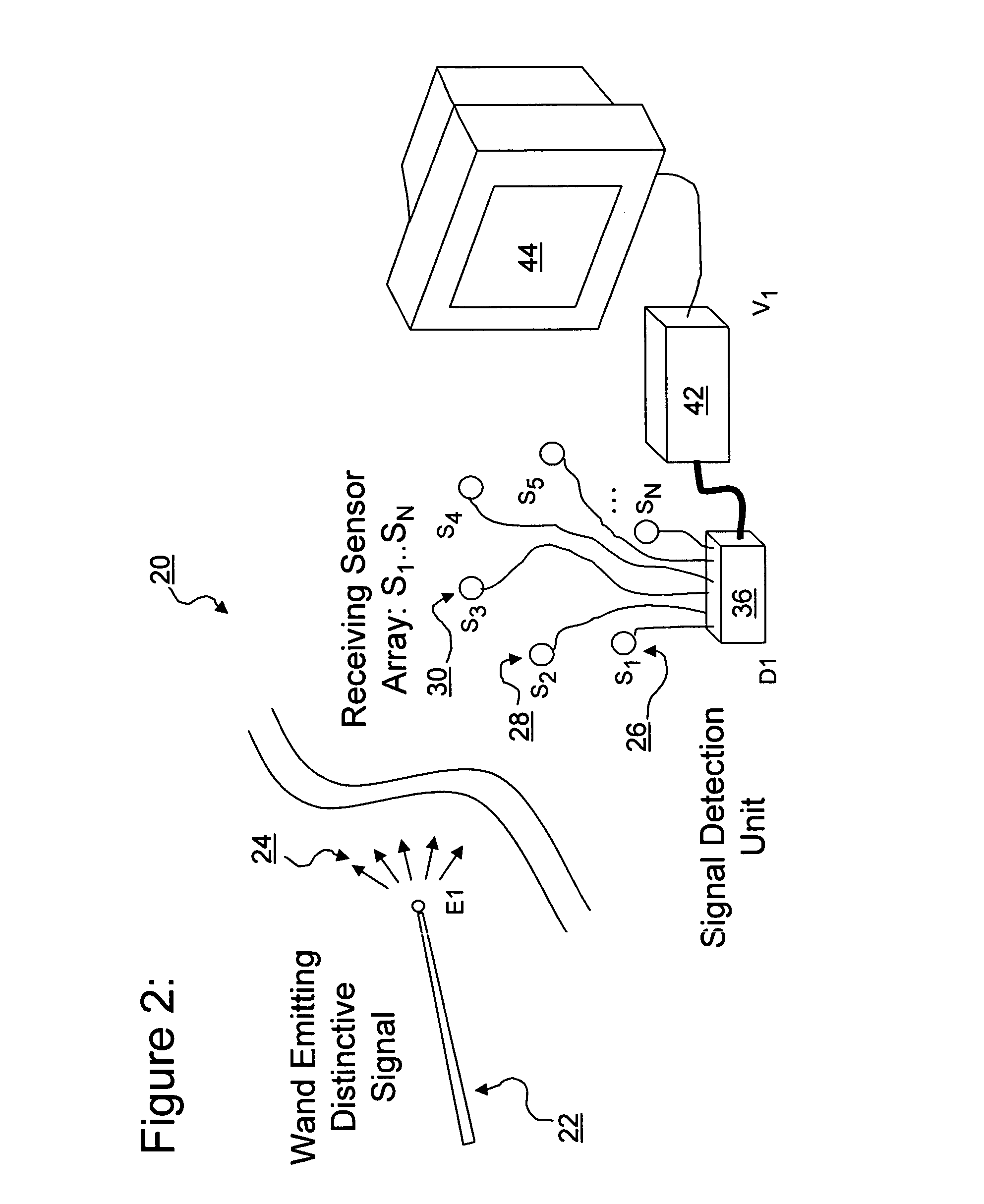
ActiveUS7353134B2Digital computer detailsSpeed measurement using gyroscopic effectsEngineeringSignal detector
A three-dimensional position and motion telemetry computer input apparatus includes a wireless movable element configured to repeatedly transmit encoded signals in at least three mutually distinct directions. A set of at least three unidimensional signal detectors are disposed in spaced relation to one another and configured to repeatedly detect in real-time, the amplitude of the encoded signals incident thereon. A controller is configured to repeatedly capture data corresponding to the signal amplitude, in real-time. A calculation engine repeatedly determines the 3-D position of the movable element using the captured data. At least one output port coupled to the calculation engine, repeatedly transmits the 3-D position of the movable element to a data consumer in real time.
Owner:CIRIELLI DEAN A
Systems and methods for preventing duplicative electronic check processing
Preventing duplicate ICL files and / or ICL file elements, including duplicate ICLs, items, and item bundles, from being processed for payment and / or presentment. A duplicate detection module can assign a predictable and repeatable unique identifier to each ICL file and / or ICL file element. The duplicate detection module can determine whether each ICL file and / or element is a duplicate by comparing the identifier associated with the ICL file and / or element with information stored in a record of already processed files / elements. In response to determining that an ICL file and / or element is a duplicate, the duplicate detection module can determine not to process the file / element for payment and / or presentment. In response to determining that the ICL file and / or element is not a duplicate, the duplicate detection module can store information regarding the file / element in the record. For example, the stored information can include the unique identifier associated with the file / element.
Owner:US FEDERAL RESERVE BANK OF ATLANTA +2
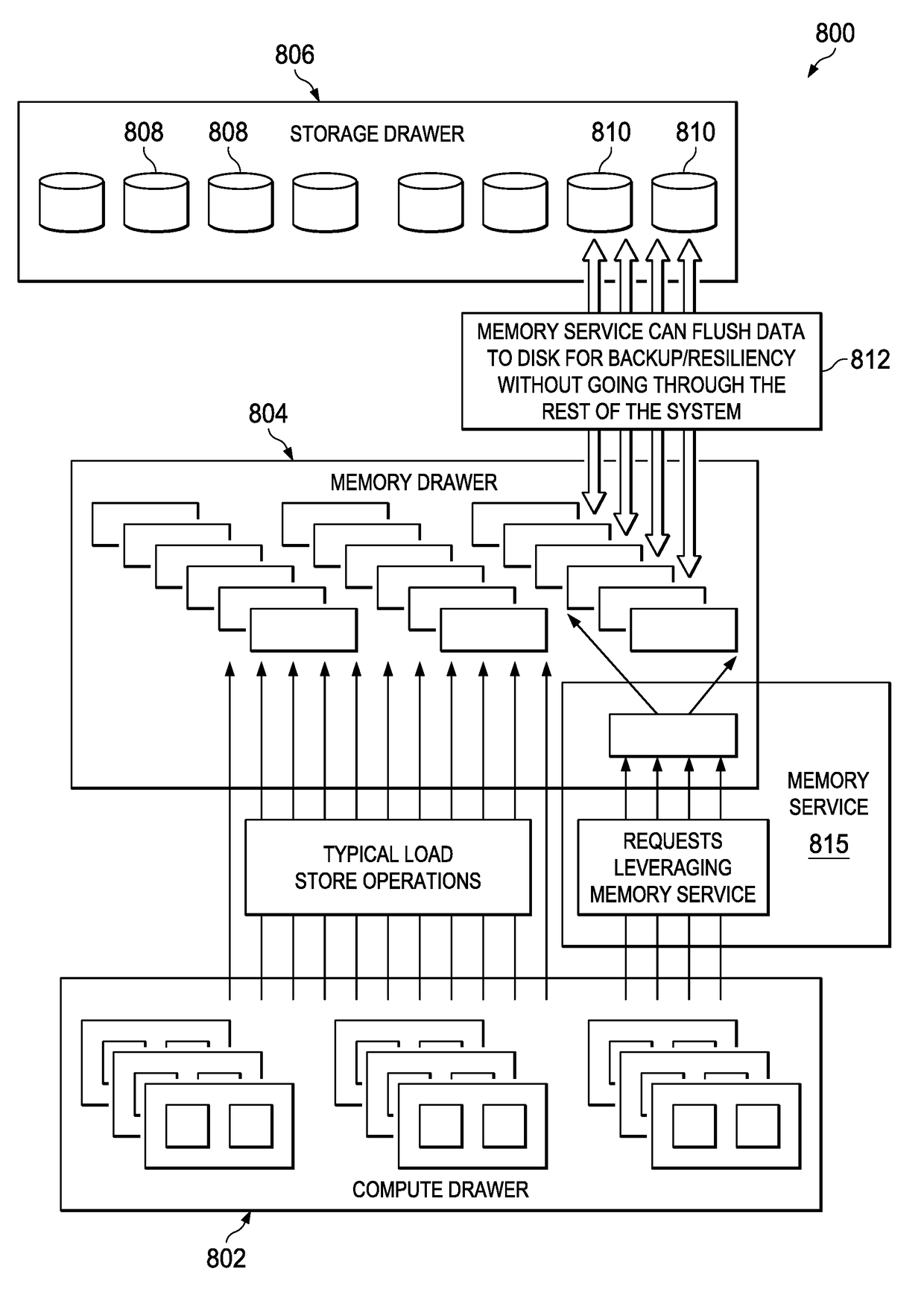
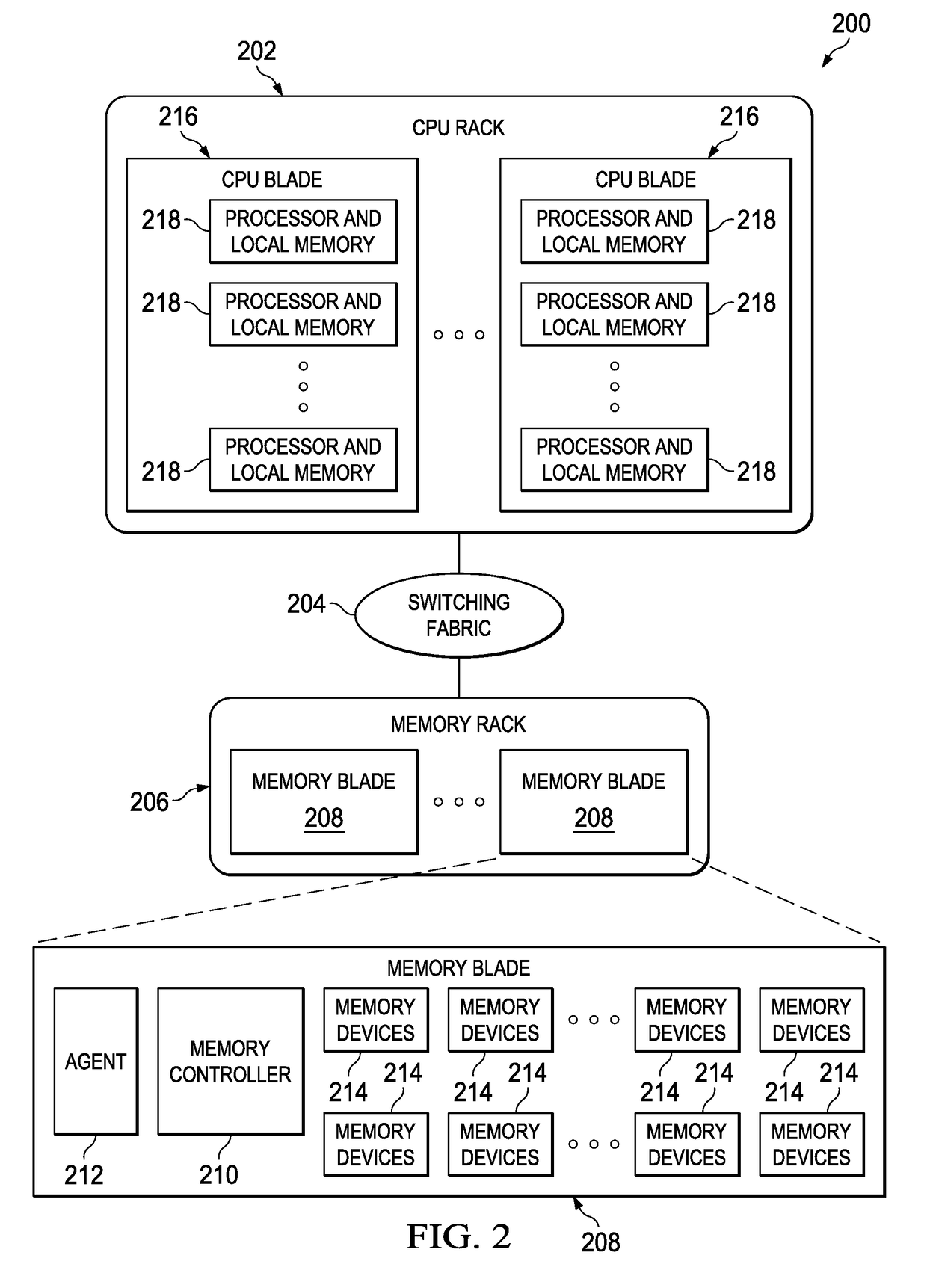
Multi-tenant memory service for memory pool architectures
ActiveUS20170293447A1High resource utilizationSignificant comprehensive benefitsMemory architecture accessing/allocationInput/output to record carriersDistribution patternMemory architecture
A memory management service occupies a configurable portion of an overall memory system in a disaggregate compute environment. The service provides optimized data organization capabilities over the pool of real memory accessible to the system. The service enables various types of data stores to be implemented in hardware, including at a data structure level. Storage capacity conservation is enabled through the creation and management of high-performance, re-usable data structure implementations across the memory pool, and then using analytics (e.g., multi-tenant similarity and duplicate detection) to determine when data organizations should be used. The service also may re-align memory to different data structures that may be more efficient given data usage and distribution patterns. The service also advantageously manages automated backups efficiently.
Owner:IBM CORP
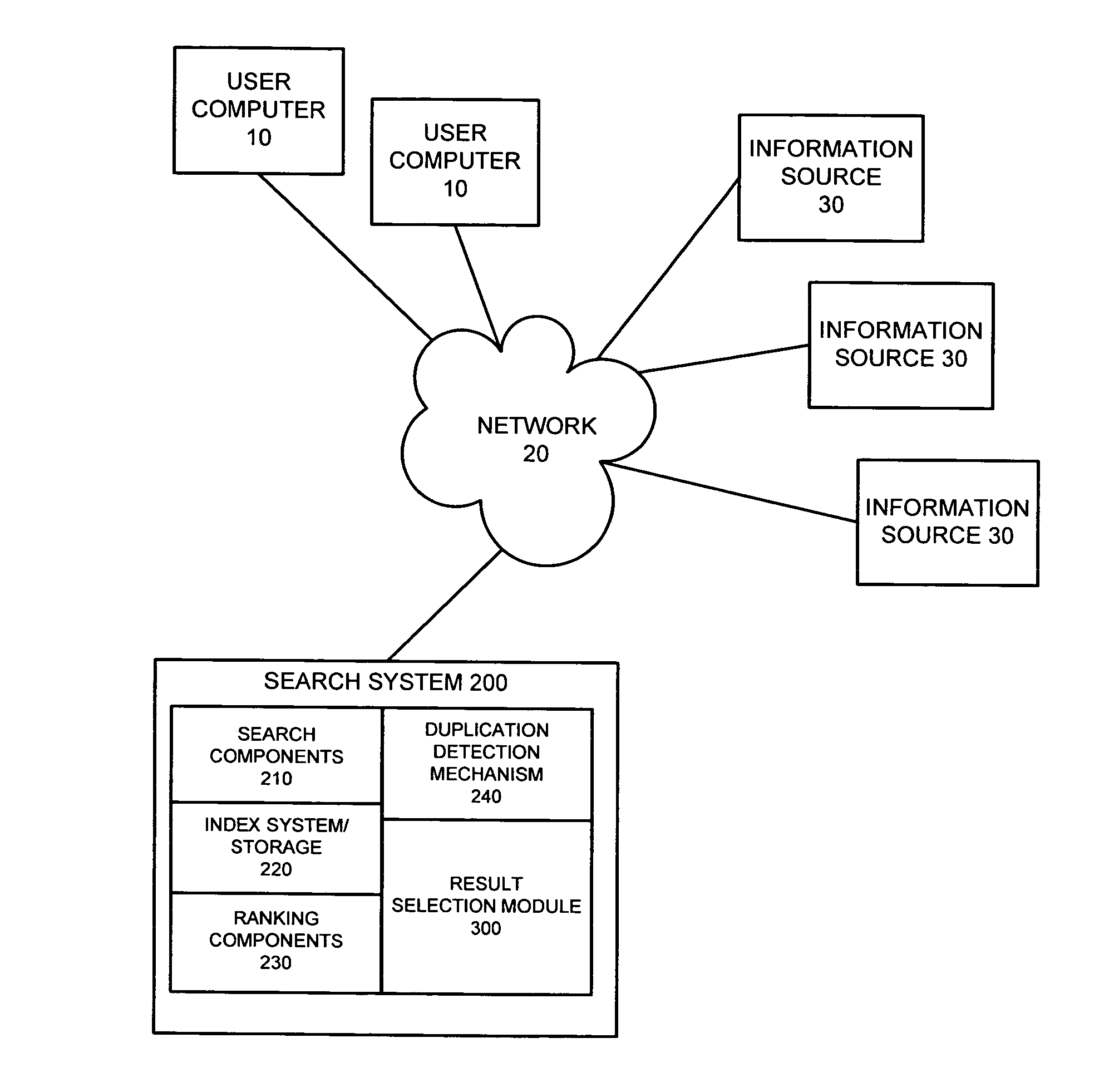
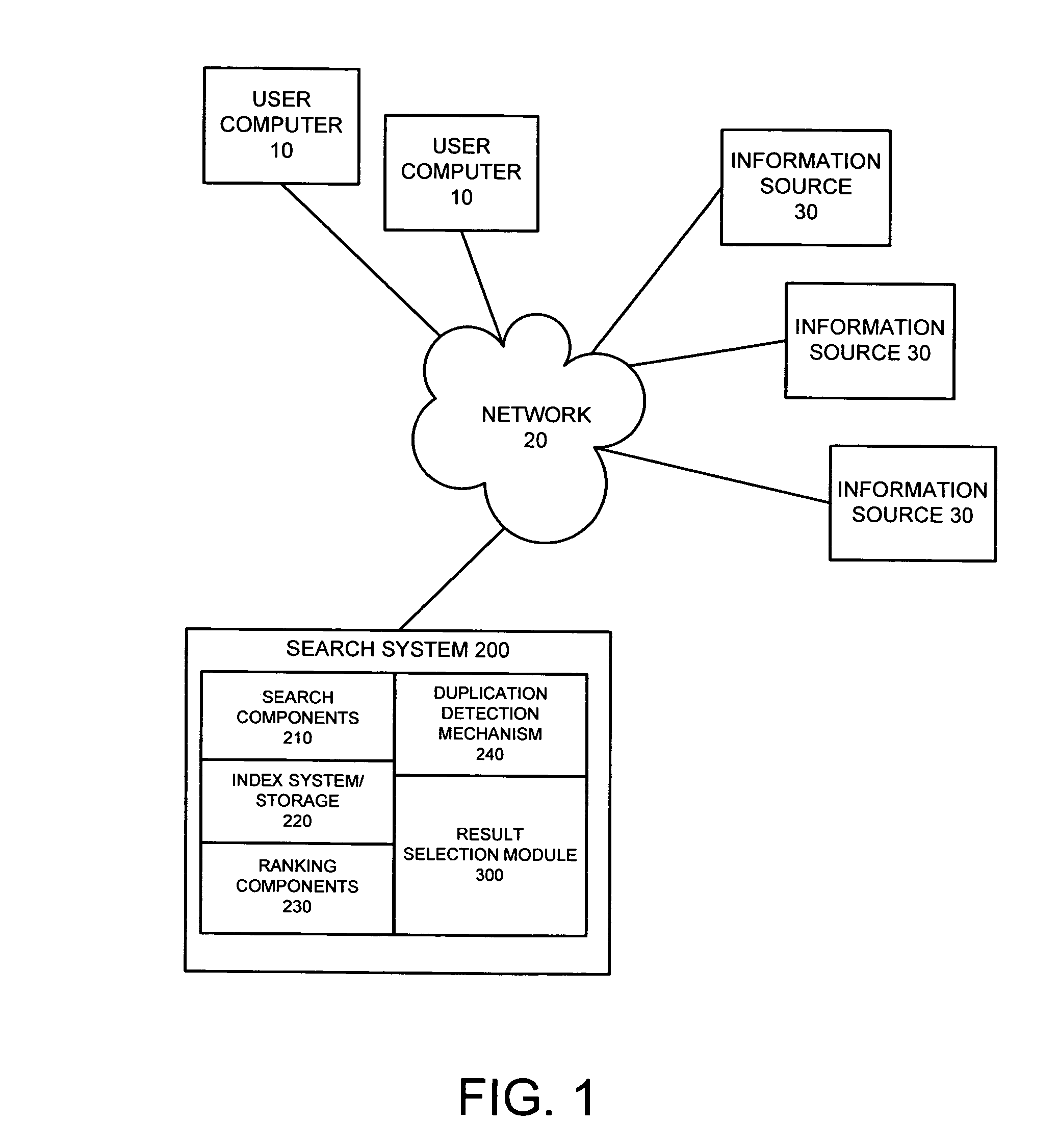
System and method for optimizing search results through equivalent results collapsing
InactiveUS20060248066A1Digital data information retrievalSpecial data processing applicationsDuplicate detection
A system and method are provided for optimizing a set of search results typically produced in response to a query. The method may include detecting whether two or more results access equivalent content and selecting a single user-preferred result from the two or more results that access equivalent content. The method may additionally include creating a set of search results for display to a user, the set of search results including the single user-preferred result and excluding any other result that accesses the equivalent content. The system may include a duplication detection mechanism for detecting any results that access equivalent content and a user-preferred result selection mechanism for selecting one of the results that accesses the equivalent content as a user-preferred result.
Owner:MICROSOFT TECH LICENSING LLC
Method for duplicate detection and suppression
InactiveUS20050210043A1Reduce memory requirementsFalse detectionData processing applicationsWebsite content managementWeb search enginePaper document
A method detects similar objects in a collection of such objects by modification of a previous method in such a way that per-object memory requirements are reduced while false detections are avoided approximately as well as in the previous method. The modification includes (i) combining k samples of features into s supersamples, the value of k being reduced from the corresponding value used in the previous method; (ii) recording each supersample to b bits of precision, the value of b being reduced from the corresponding value used in the previous method; and (iii) requiring l matching supersamples in order to conclude that the two objects are sufficiently similar, the value of l being greater than the corresponding value required in the previous method. One application of the invention is in association with a web search engine query service to determine clusters of query results that are near-duplicate documents.
Owner:MICROSOFT TECH LICENSING LLC
Three-dimensional position and motion telemetry input
ActiveUS20070213952A1Measurement arrangements for variableDigital computer detailsEngineeringSignal detector
A three-dimensional position and motion telemetry computer input apparatus includes a wireless movable element configured to repeatedly transmit encoded signals in at least three mutually distinct directions. A set of at least three unidimensional signal detectors are disposed in spaced relation to one another and configured to repeatedly detect in real-time, the amplitude of the encoded signals incident thereon. A controller is configured to repeatedly capture data corresponding to the signal amplitude, in real-time. A calculation engine repeatedly determines the 3-D position of the movable element using the captured data. At least one output port coupled to the calculation engine, repeatedly transmits the 3-D position of the movable element to a data consumer in real time.
Owner:CIRIELLI DEAN A
Cipher key setting system, access point, and cipher key setting method
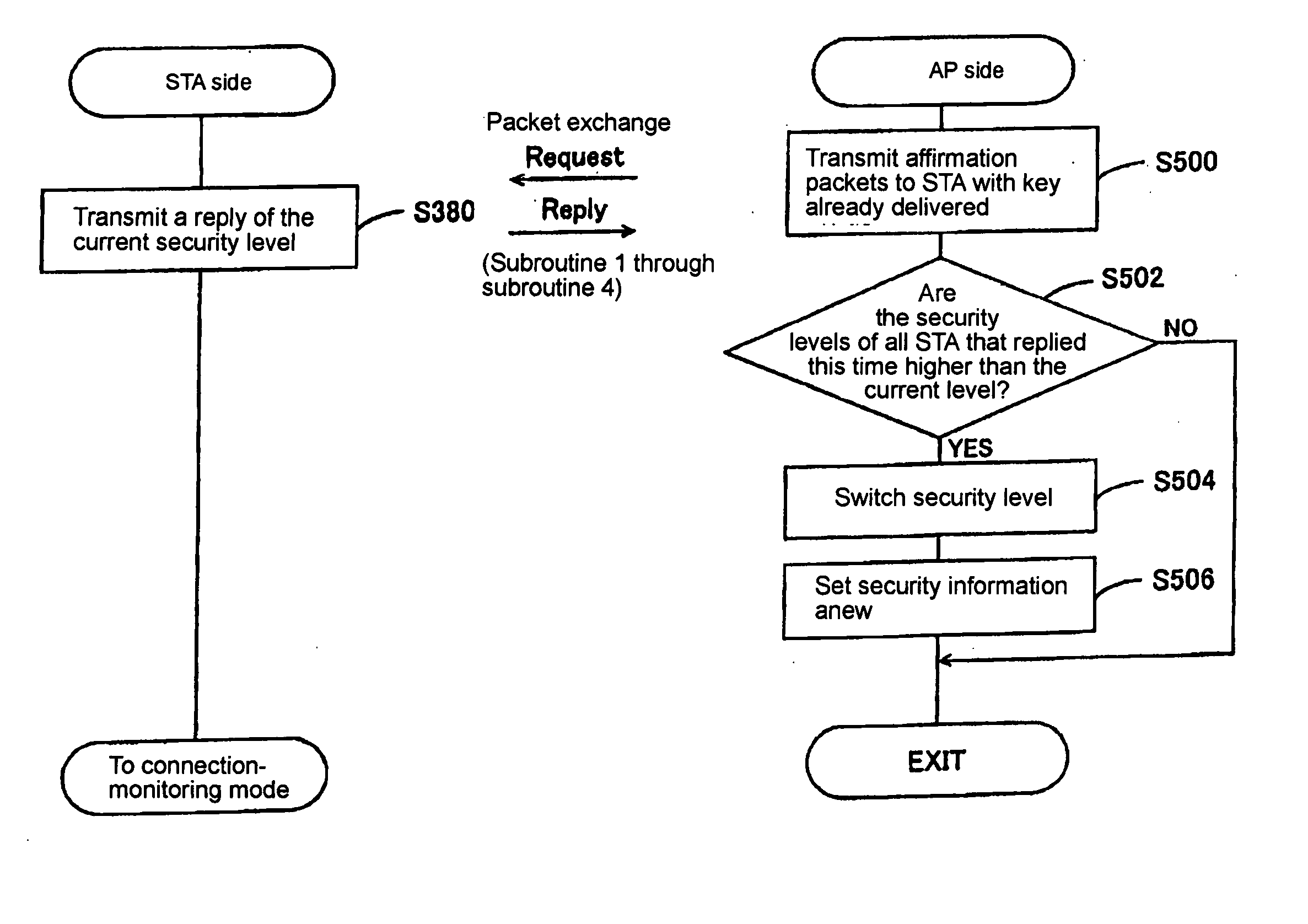
InactiveUS20050238172A1Relieve troublesImprove securityKey distribution for secure communicationConveyorsGuidelineWireless lan
Disclosed is a cipher key setting system wherein the access point detects the terminals connected to the wireless LAN through the access point itself repeatedly at each predetermined time, reviews the adopted cipher systems when there are replacements of the terminals participating in the wireless LAN and a decrease in the number of the terminals, and adopts a cipher system according to the guideline ‘selecting the cipher system of the highest security level among the cipher systems that the devices building up the network can commonly adopt’. The system prevents the security setting from being maintained at a needlessly low level, after a certain terminal withdrew from the network or after some terminals were replaced.
Owner:BUFFALO CORP LTD
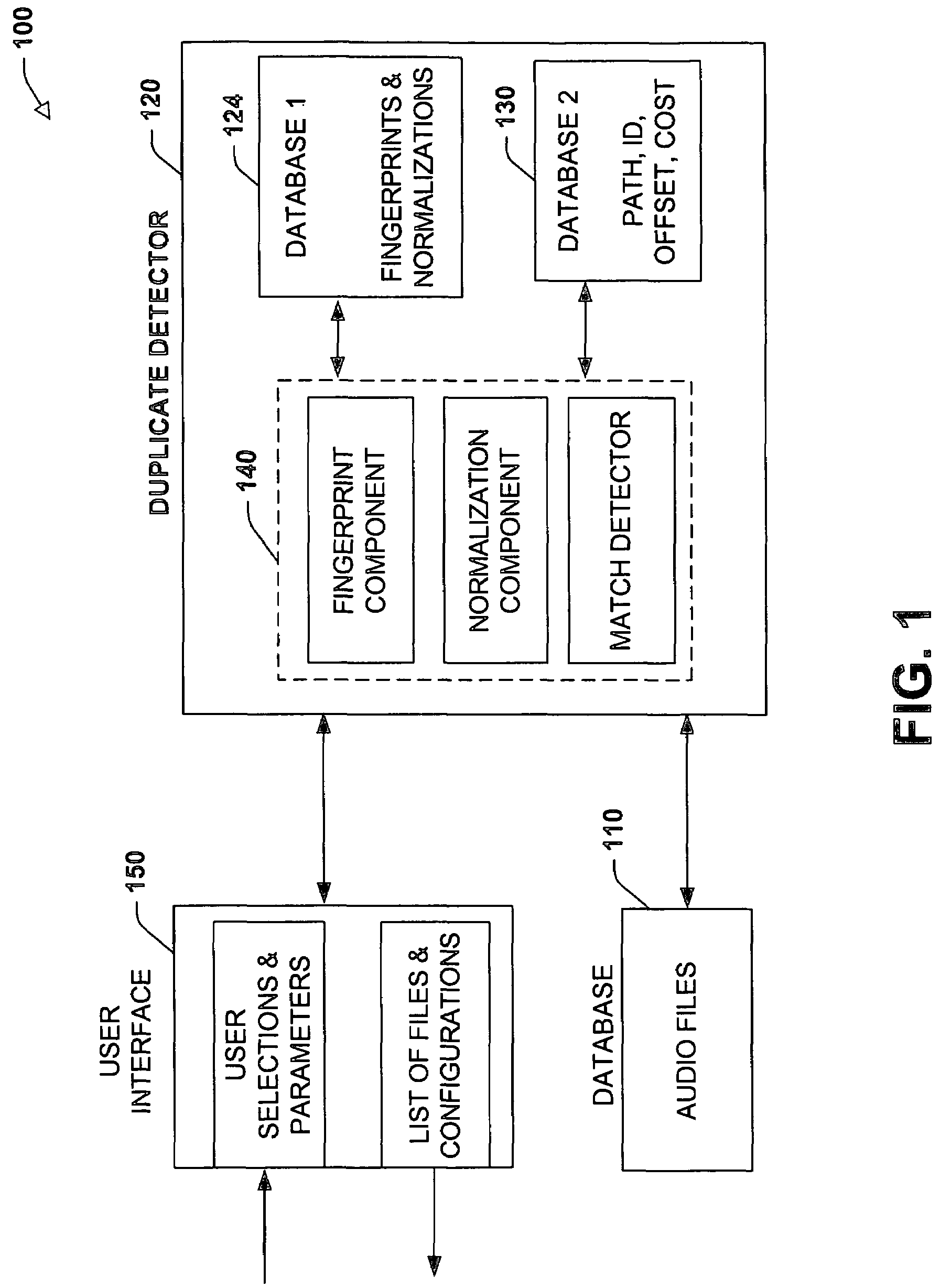
Audio duplicate detector
ActiveUS7421305B2Facilitate management and removalExtensive managementElectrophonic musical instrumentsMultimedia data retrievalApplication softwareDuplicate detection
The present invention relates to a system and methodology to facilitate automatic management and pruning of audio files residing in a database. Audio fingerprinting is a powerful tool for identifying streaming or file-based audio, using a database of fingerprints. Duplicate detection identifies duplicate audio clips in a set, even if the clips differ in compression quality or duration. The present invention can be provided as a self-contained application that it does not require an external database of fingerprints. Also, a user interface provides various options for managing and pruning the audio files.
Owner:MICROSOFT TECH LICENSING LLC
System and method for differential document analysis and storage
InactiveUS20190236102A1Natural language analysisOther databases indexingDocument analysisDocumentation procedure
Systems and methods for differential document analysis and storage are provided. Specifically, the system can be configured to perform one or more differential analyses on a set of documents to detect and measure changes in language across entire sets of documents of a similar type, as well as changes in language in the specific objects (e.g., document sections, paragraphs, clauses) of the documents. The system comprises three primary components: document parsing, textual near-duplicate detection, and morphological analysis. The document parsing component breaks documents down into objects and creates indexes for each full document and components of the document. These indexes enable documents and objects to be compared for similarity using the near-duplicate detection component, which implements various similarity analysis algorithms. The morphological analyses component is configured to search the documents for particular language or sections and compare documents in which the searched language is present.
Owner:PLANET DATA SOLUTIONS INC
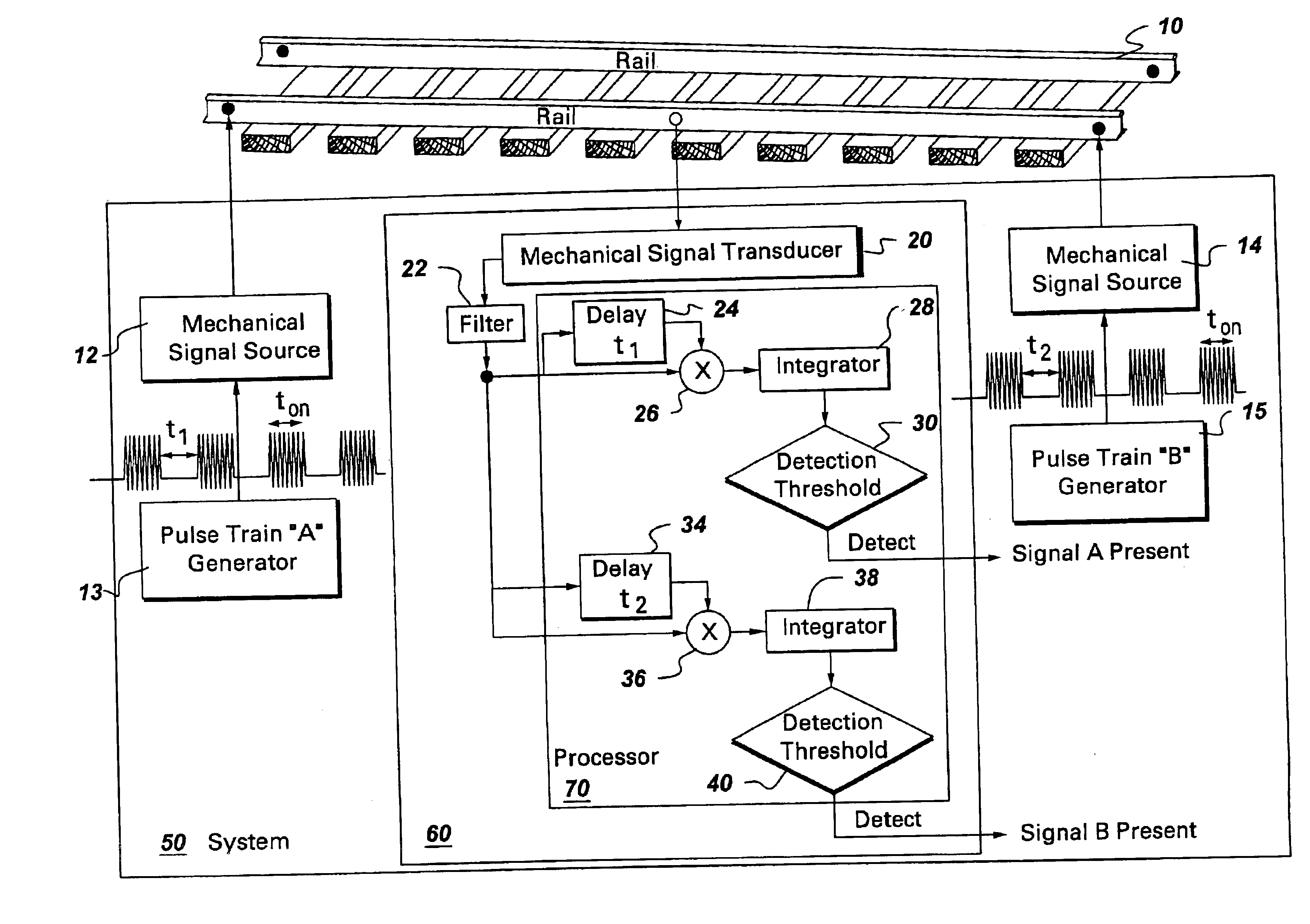
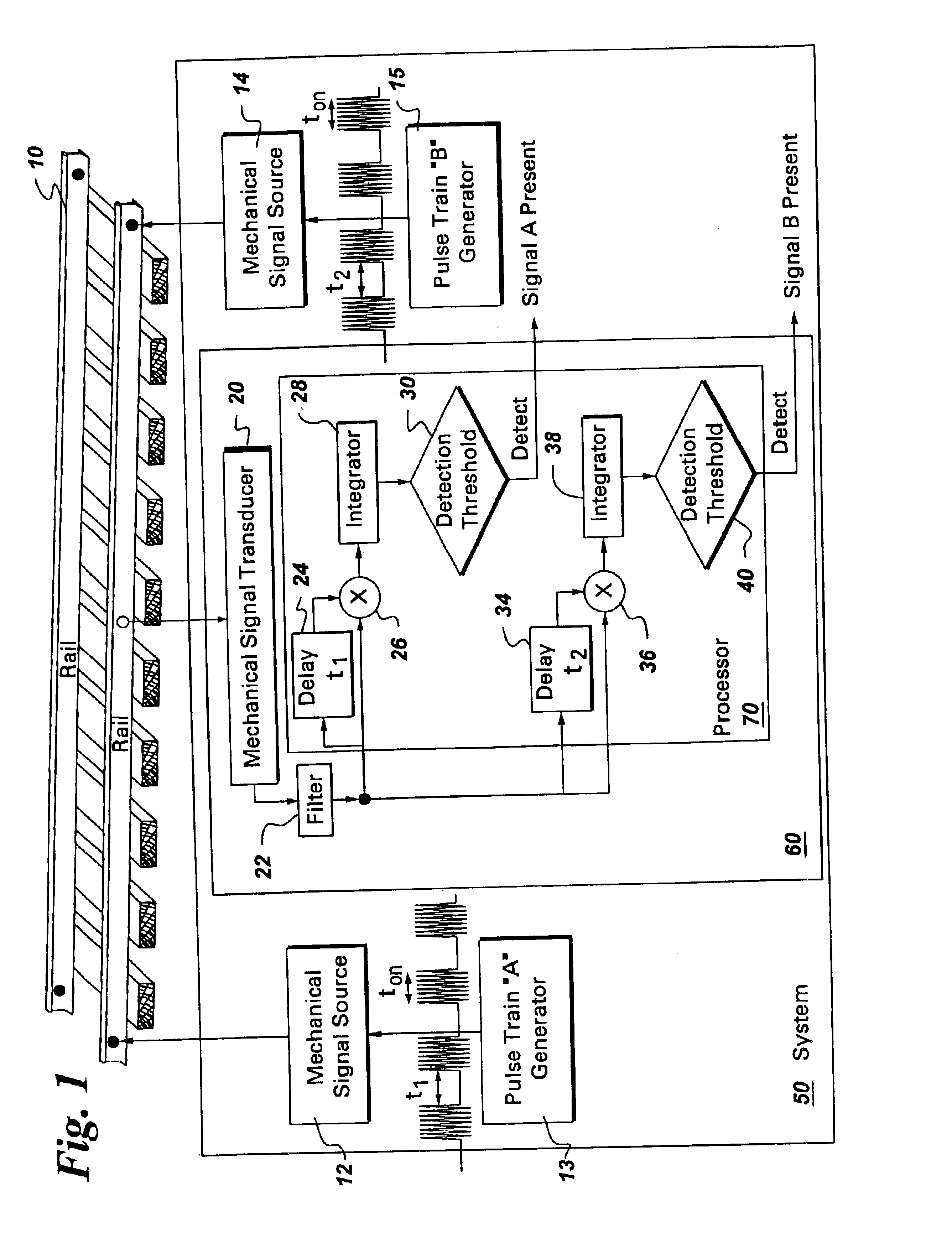
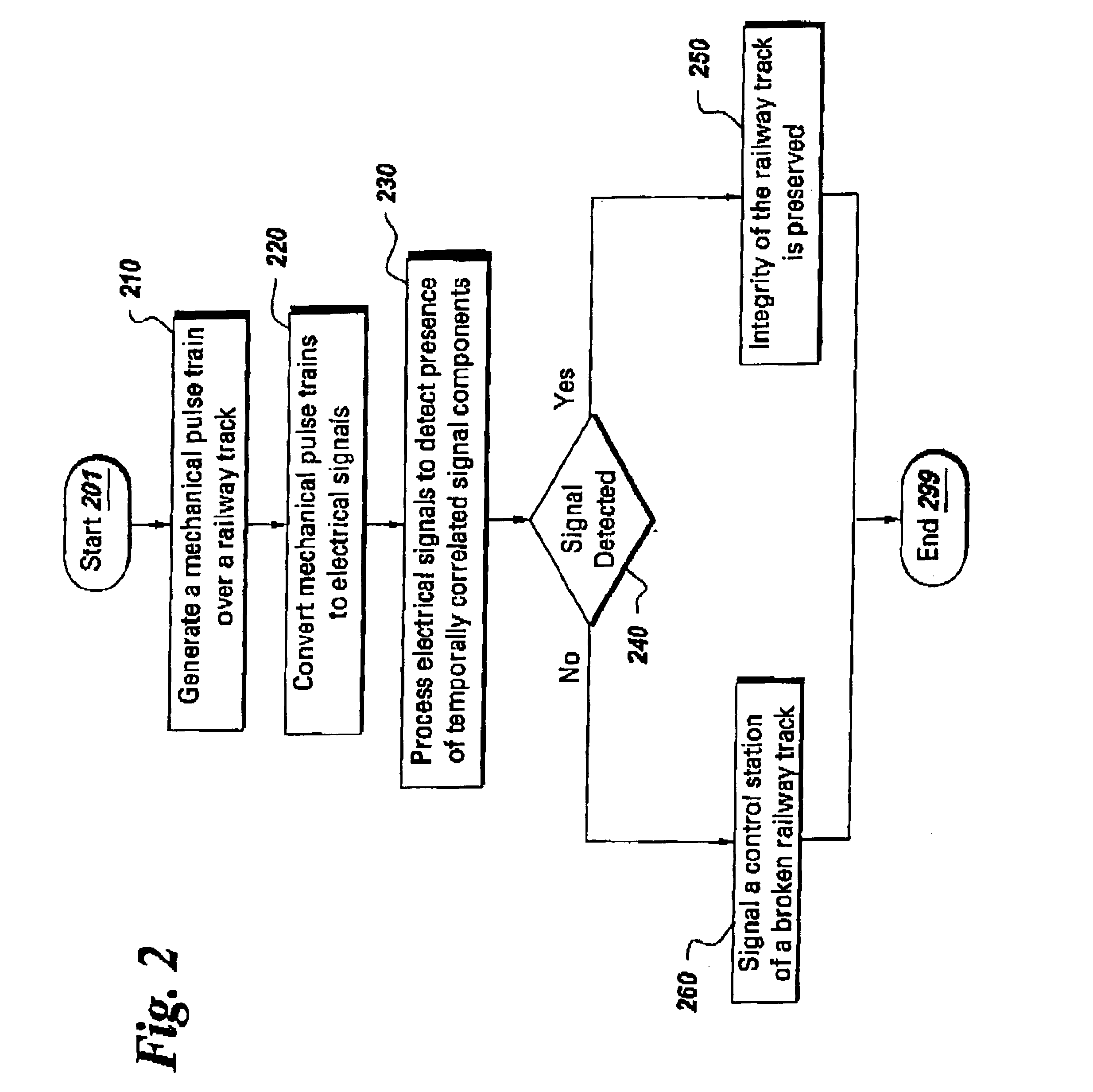
Active broken rail detection system and method
A system to monitor the integrity of a railway track is provided. The system comprises a mechanical signal source and a correlation detector. The mechanical signal source coupled to the railway track and is configured for generating a mechanical signal pulse train over the railway track. The correlation detector monitors the integrity of the railway track by observing the pulse trains transmitted by the mechanical signal sources. If the railway track is intact, then the pulse train will travel to the correlation detector and afford the opportunity for repeatable detection.
Owner:GE GLOBAL SOURCING LLC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com