Cipher key setting system, access point, and cipher key setting method
a technology of access points and cipher keys, applied in wireless communication, digital transmission, transportation and packaging, etc., can solve the problems that the security environment cannot be optimized between wireless lan devices participating in the network, and achieve the effect of relieve the troublesomeness of performing notifications, and prevent the effect of lowering security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
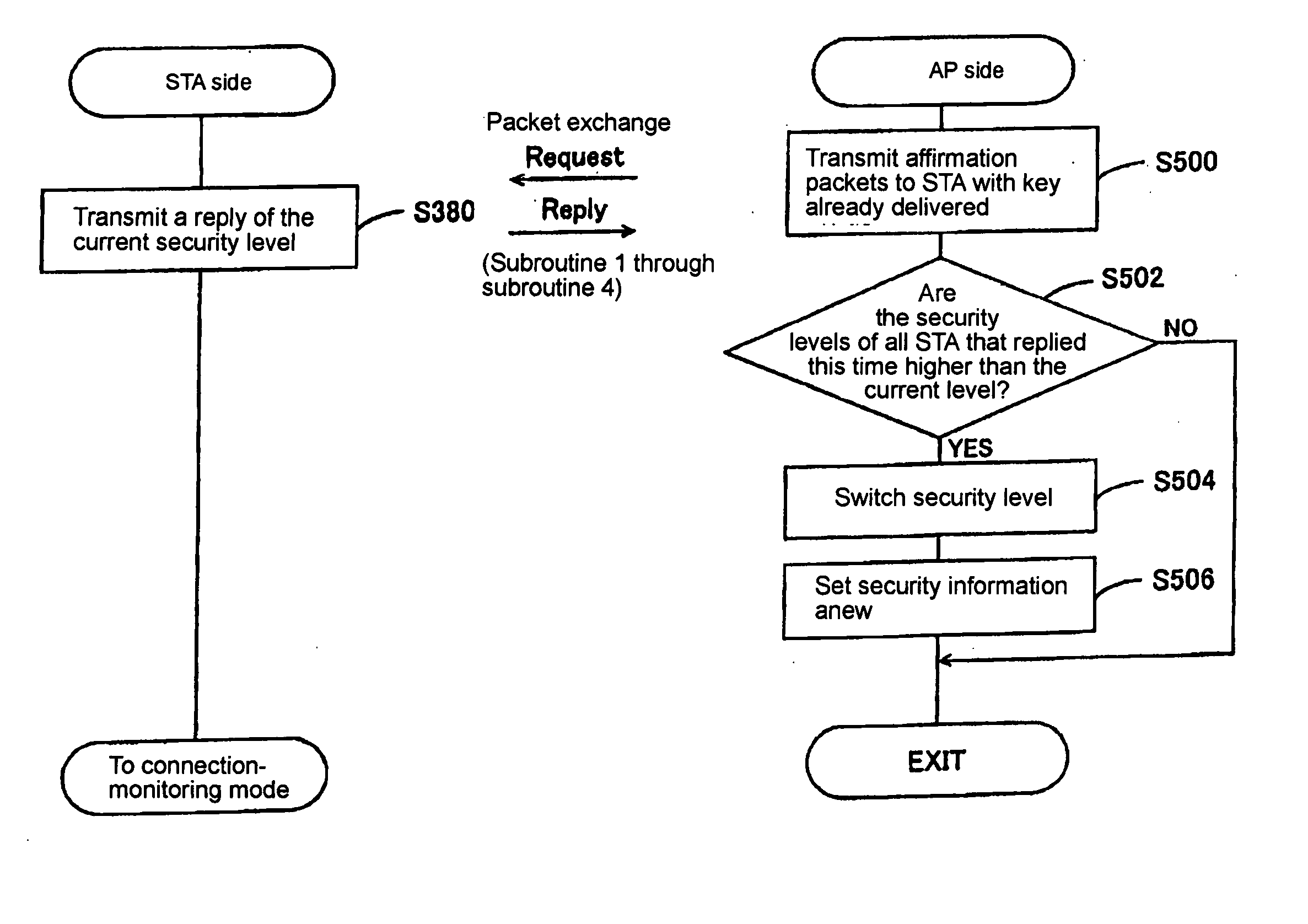
[0050] The preferred embodiments of the invention will be described in the following order. [0051] 1. Schematic construction for implementing the cipher key setting system [0052] 2. Concrete contents of the cipher key setting system
[0053] 2-1. case of increasing the terminal number
[0054] 2-2 case of decreasing the terminal number [0055] 3. Modified examples [0056] 4. Conclusion
1. Schematic Construction for Implementing the Cipher Key Setting System
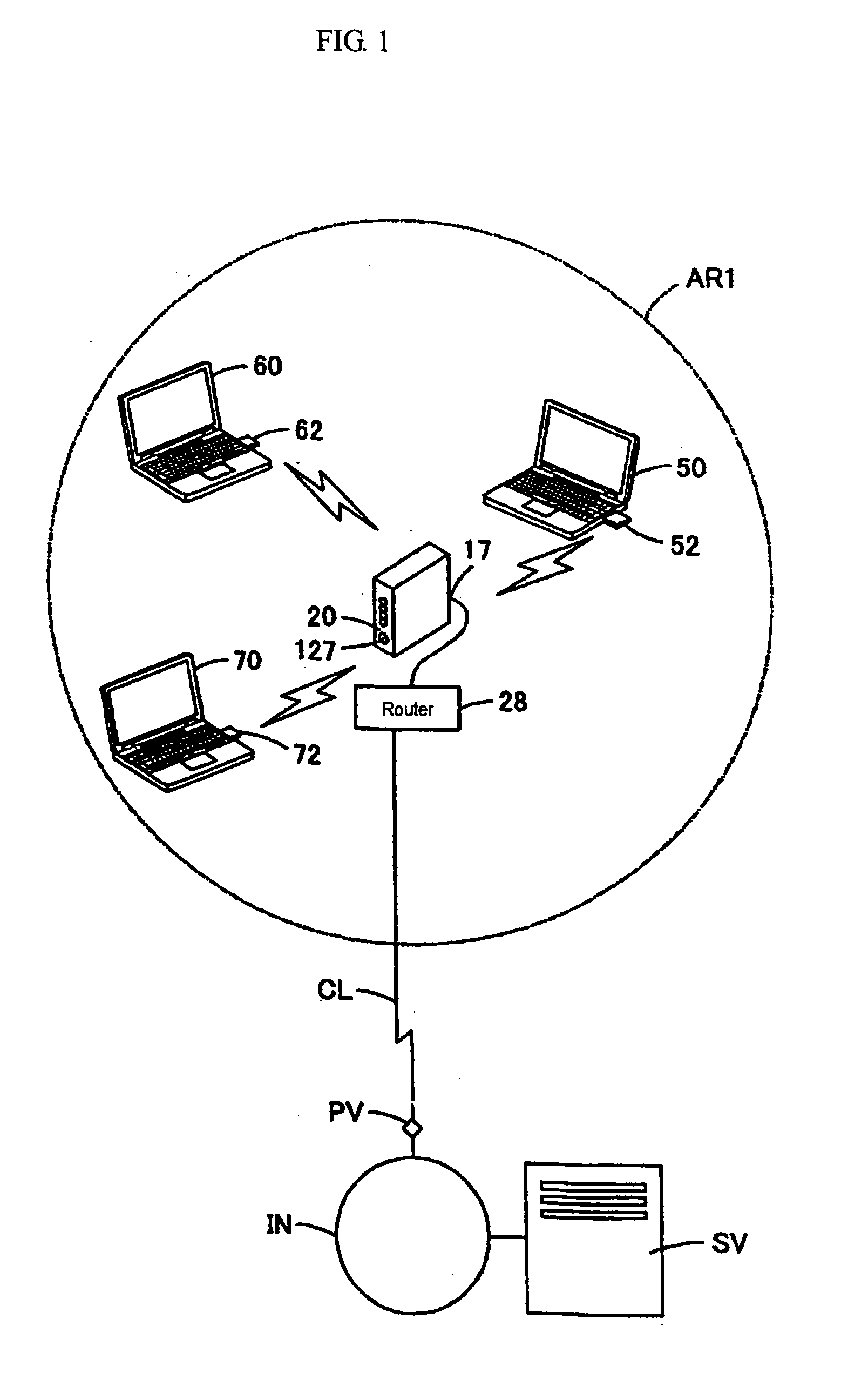
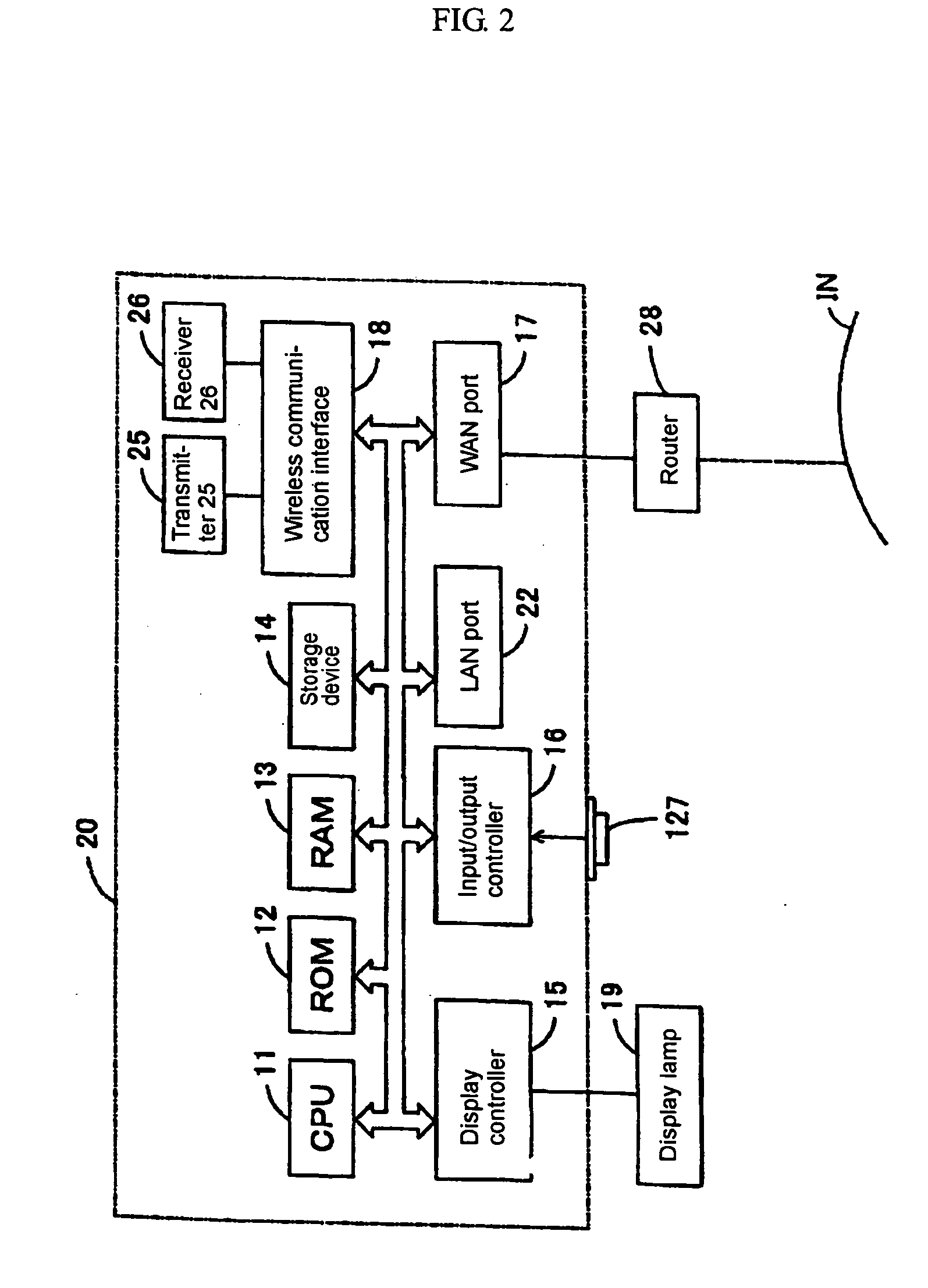
[0057]FIG. 1 illustrates a construction of hardware that implements the cipher key setting system relating to the invention. FIG. 2 illustrates a construction of an access point 20.
[0058] The cipher key setting system performs a wireless communication between a specified terminal and the access point 20 in a wireless LAN communication area AR1, in which the cipher key data representing the contents of the cipher key are superposed on a radio wave; and thereby, the system sets the cipher key used in the wireless communication between ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com