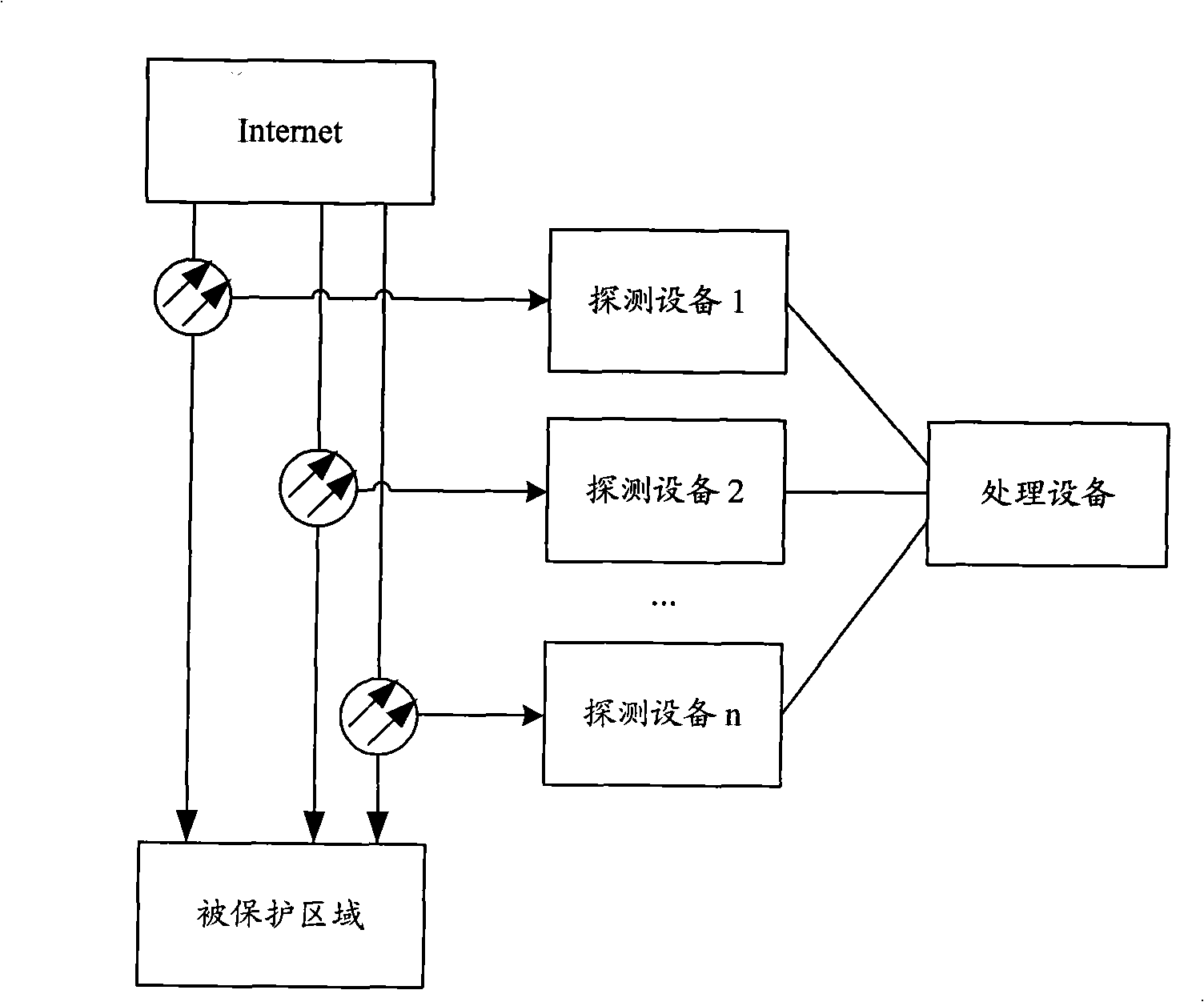
Patents
Literature
58 results about "Defensive measure" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
• DEFENSIVE MEASURE (noun) The noun DEFENSIVE MEASURE has 1 sense: 1. military action or resources protecting a country against potential enemies. Familiarity information: DEFENSIVE MEASURE used as a noun is very rare.
System and methods relating to autonomous tracking and surveillance
ActiveUS20100042269A1Low costReduce riskDigital data processing detailsNavigation instrumentsProximateDefensive measure
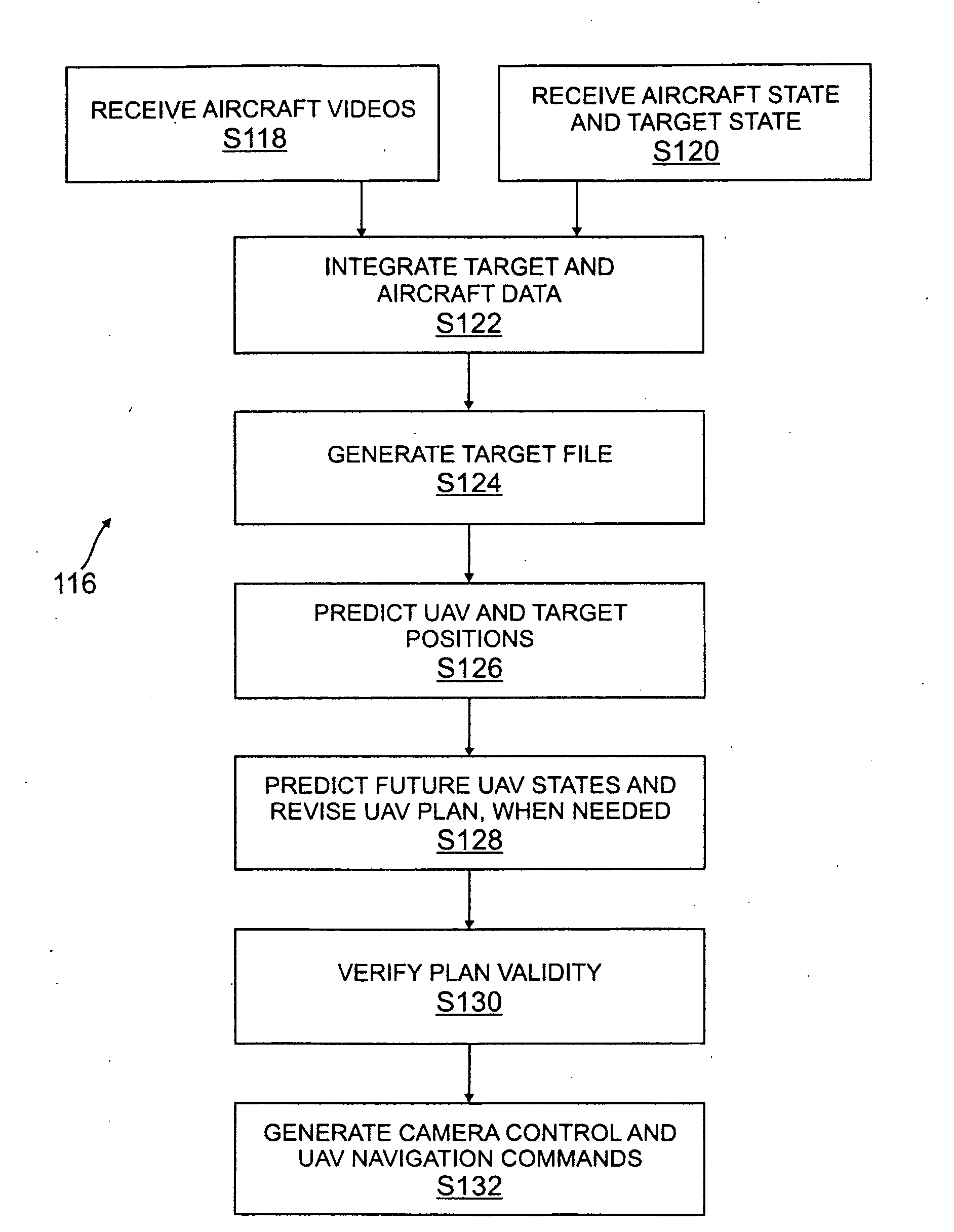
A method of protecting an asset using at least one unmanned vehicle. The method includes establishing a plurality of boundaries around the asset. The boundaries define edges of zones. The method further includes observing a target in a first one of the zones. The method further includes deploying the unmanned vehicle to a location in a vicinity of the asset and tasking the vehicle to perform a first defensive measure as long as the target remains in the first zone. If the target crosses a boundary from the first zone into a second one of the zones, where the second zone is more proximate to the asset than the first zone, the method further includes tasking the vehicle to perform a second defensive measure.
Owner:THE BOEING CO
Computerized system and method for securely distributing and exchanging cyber-threat information in a standardized format
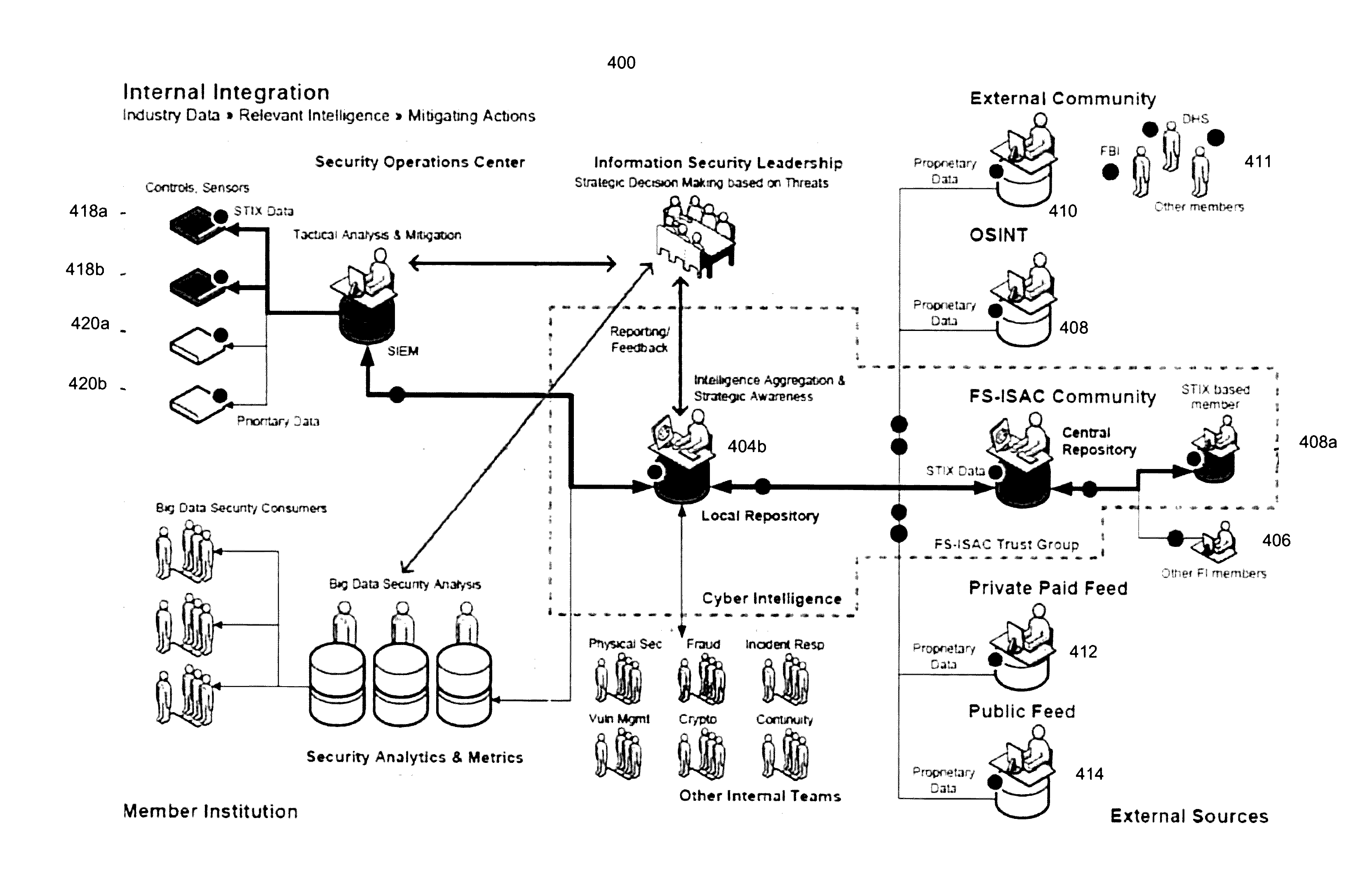
Computerized systems and methods for sharing identified cyber-threat information in a standardized and secure format. The sharing of cyber-threat information assists in preventing malicious actors from replicating successful cyber-attacks by informing potential targets of the methods employed by the malicious actors, and the defensive measures that those targets should to implement to prevent those methods from succeeding. By distributing cyber-threat information in a standardized format, the systems and methods enable participating entities to automatically analyze and implement defensive measures for cyber-threat information shared by any other participating entities. The systems and methods also permit an entity to control which threat information it shares and which other entities it shares it with in a secure manner in order to preserve that entity's security and reputation.
Owner:CELERIUM INC
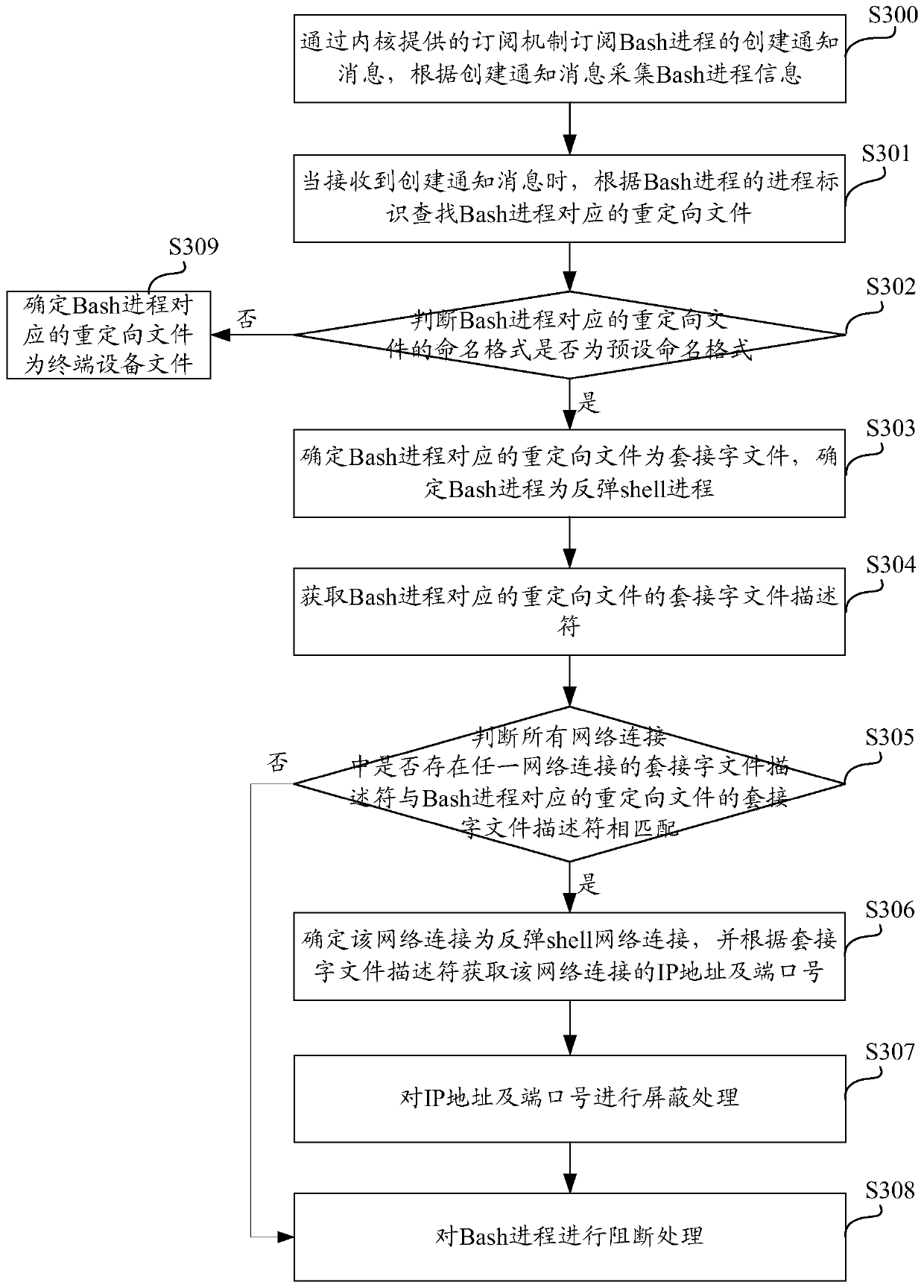
A DDoS attack detection and defense method and system in a software-defined network
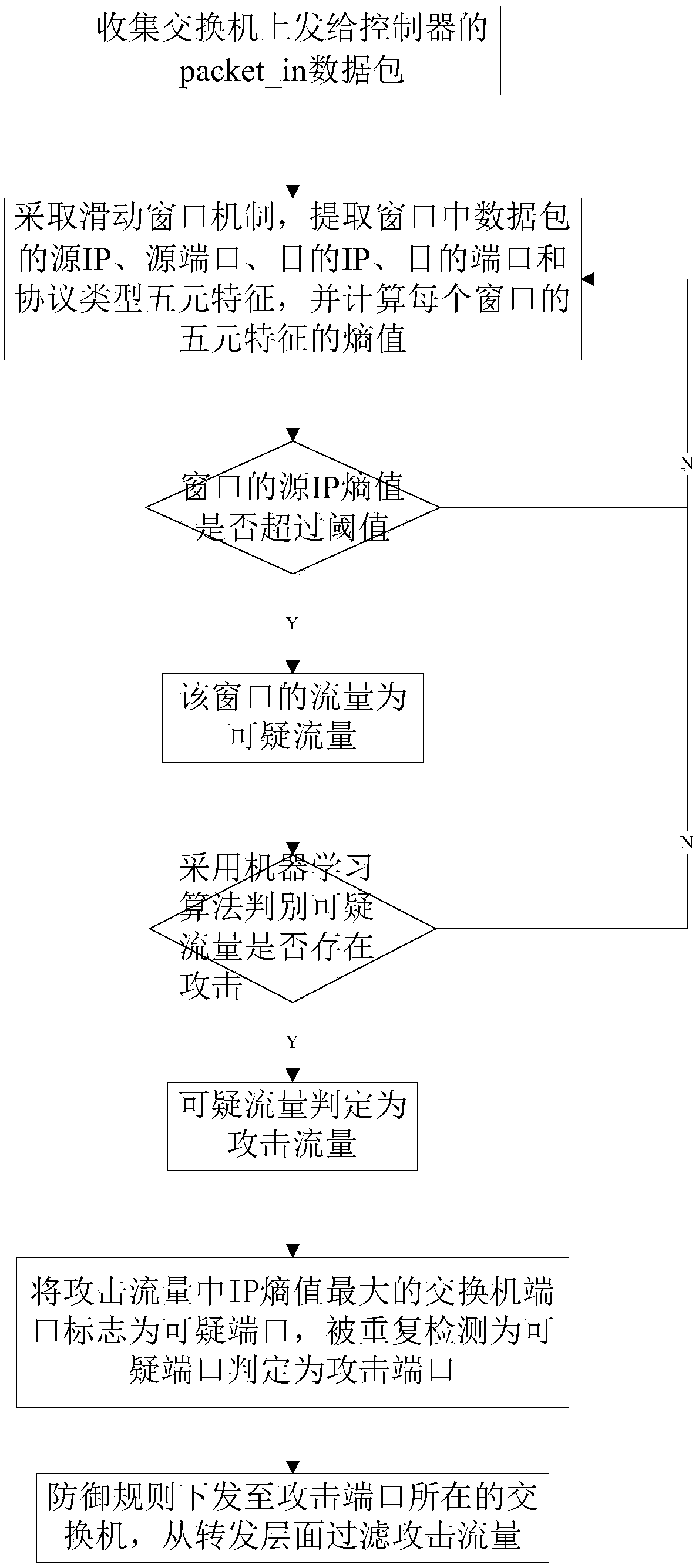
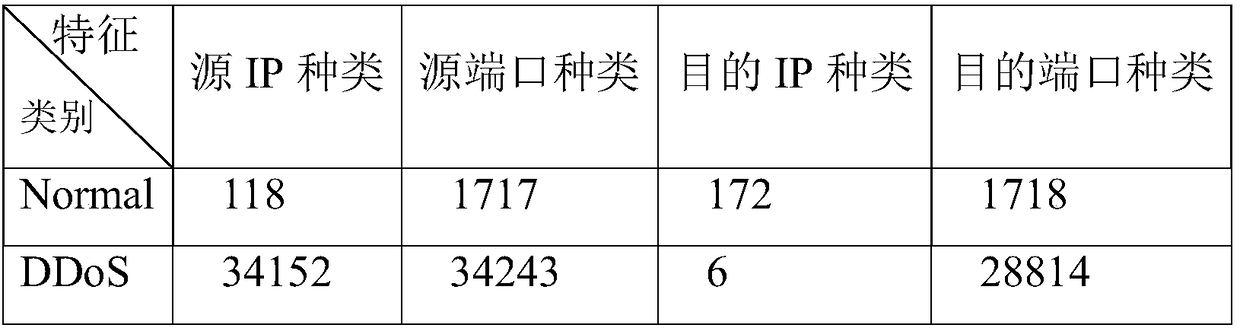
The invention discloses a DDoS attack detection and defense method and system in a software-defined network. The method comprises:the quintuple features of source IP, source port, destination IP, destination port and protocol type are extracted and the quintuple feature entropy is calculated; whether the IP entropy value of the window source exceeds the threshold value is judged, if yes, it is determined that the window source IP entropy value is suspicious traffic, otherwise, the window traffic is filtered; machine learning is used to judge whether the suspicious traffic exists attack, if yes, it is judged as attack traffic, otherwise, the suspicious traffic is filtered; the switch port with the largest IP entropy value in the attack traffic is marked as a suspicious port, which is repeatedly detected as a suspicious port and is judged as an attack port; defense rules are issued to the switch where the attack port is located and attack traffic is filtered from the forwarding layer. The invention combines quintuple characteristic entropy value and machine learning algorithm to detect DDoS attack, locates and takes defensive measures in time, filters a large amount of malicious traffic from the forwarding layer, and protects the controller and the switch.
Owner:HUAZHONG UNIV OF SCI & TECH
Method, system and equipment for judging network attack
ActiveCN101355463AAddresses prone attack false positivesSolve the defects of false negativesData switching networksDefensive measureNetwork attack
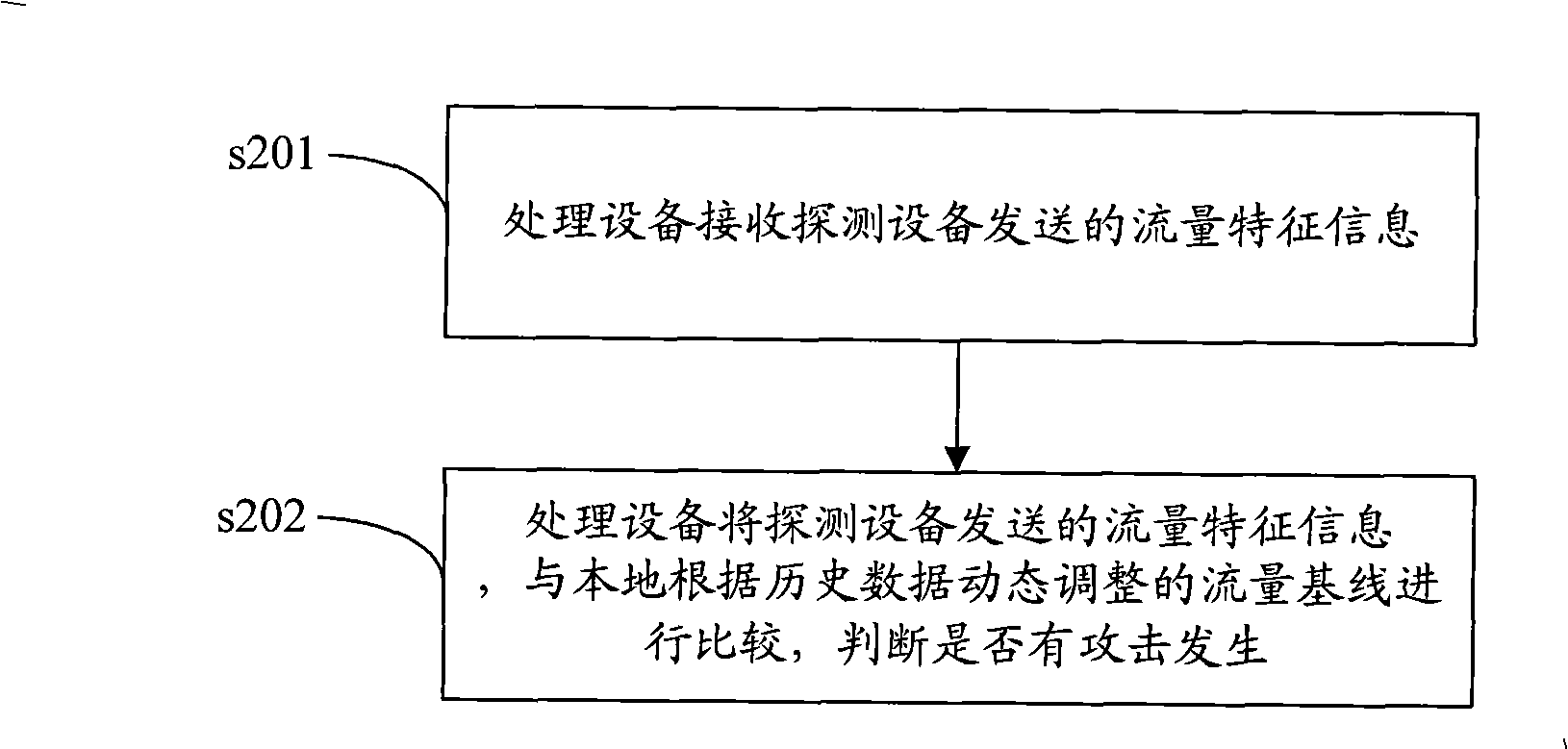
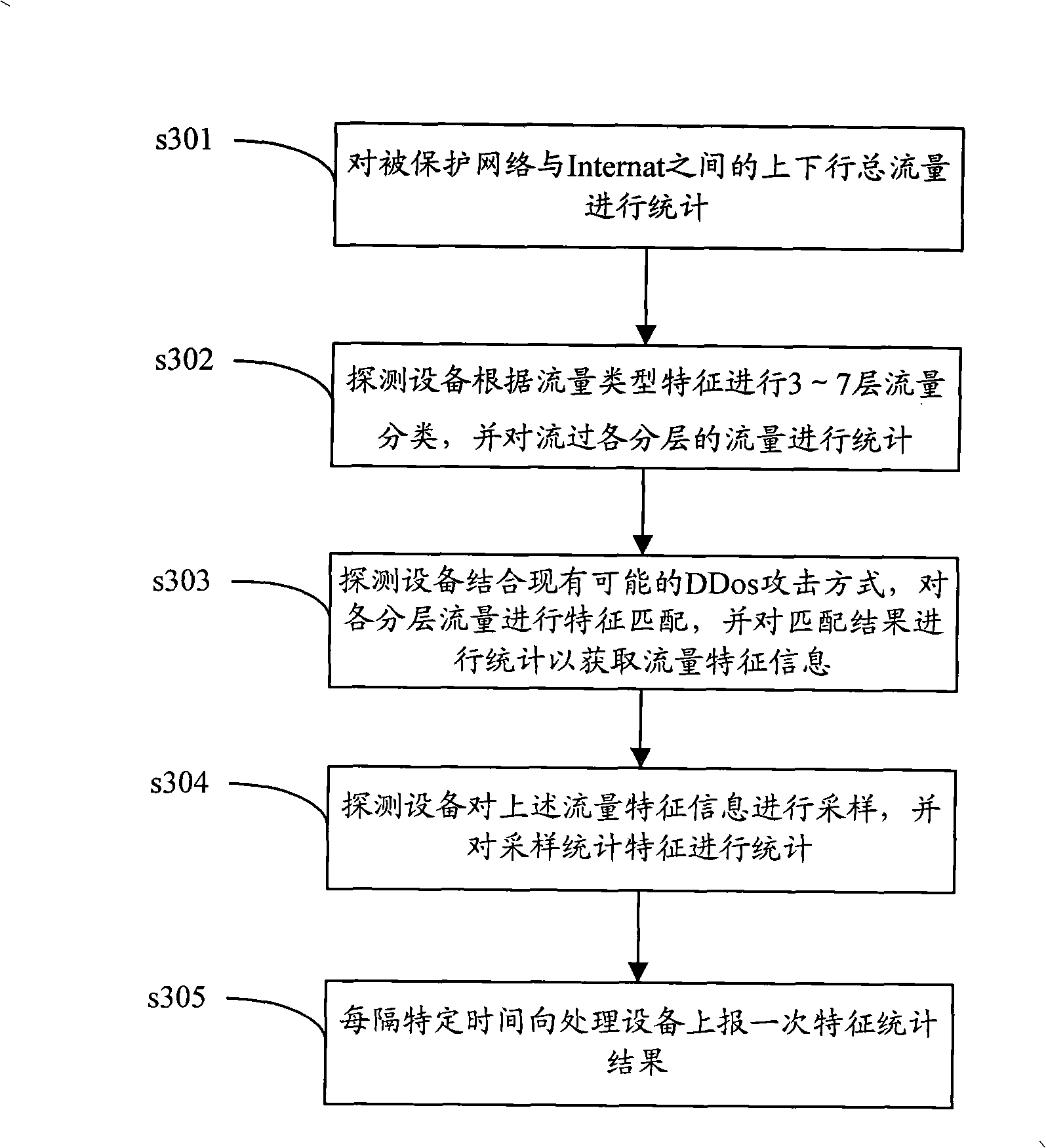
The embodiment of the invention discloses a judgment method for network attack, which comprises the following steps: flow characteristic information sent by detection equipment is received; and whether the attack appears is judged by comparing the flow characteristic information sent by detection equipment with a local flow baseline which is dynamically adjusted according to history data. The embodiment of the invention also discloses a judgment system and judgment equipment for the network attack. With the embodiment of the invention, whether the attack appears is judged through the flow baseline which is dynamically adjusted, whether a host group in a large range is attacked can be promptly and effectively judged, and the timely alarm is performed to start corresponding defensive measures. The judgment method for the network attack overcomes the defect that the misreporting and the missing report of the attack are easy to appear when a unified static benchmark value is adopted for alarm protection of the network attack.
Owner:HUAWEI TECH CO LTD
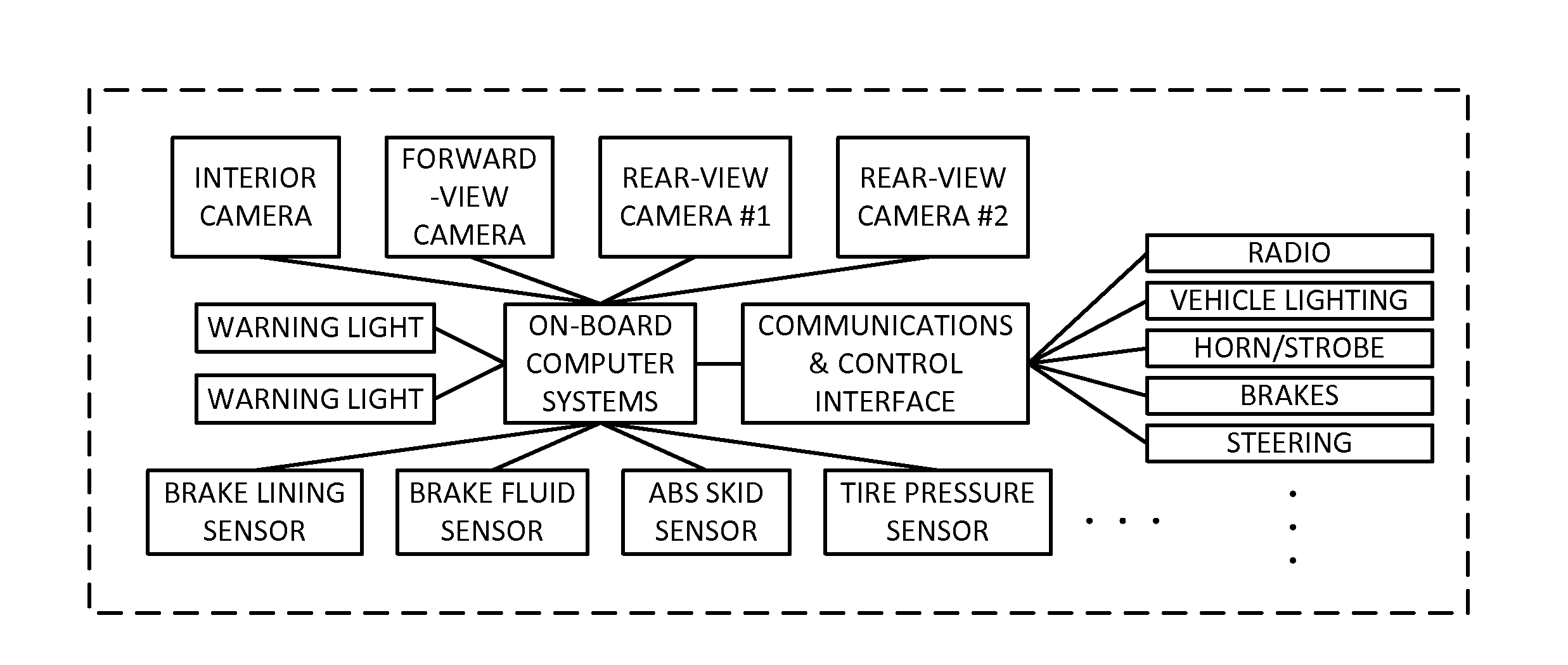
Vehicular safety methods and arrangements
InactiveUS20140375810A1Acoustic signal devicesRoad vehicles traffic controlDefensive measureMechanical engineering
Owner:DIGIMARC CORP
Active defense method for network trick and counter attack
InactiveCN103457931AGuaranteed dynamic performanceReduce the chance of attackData switching networksNetwork communicationDefensive measure
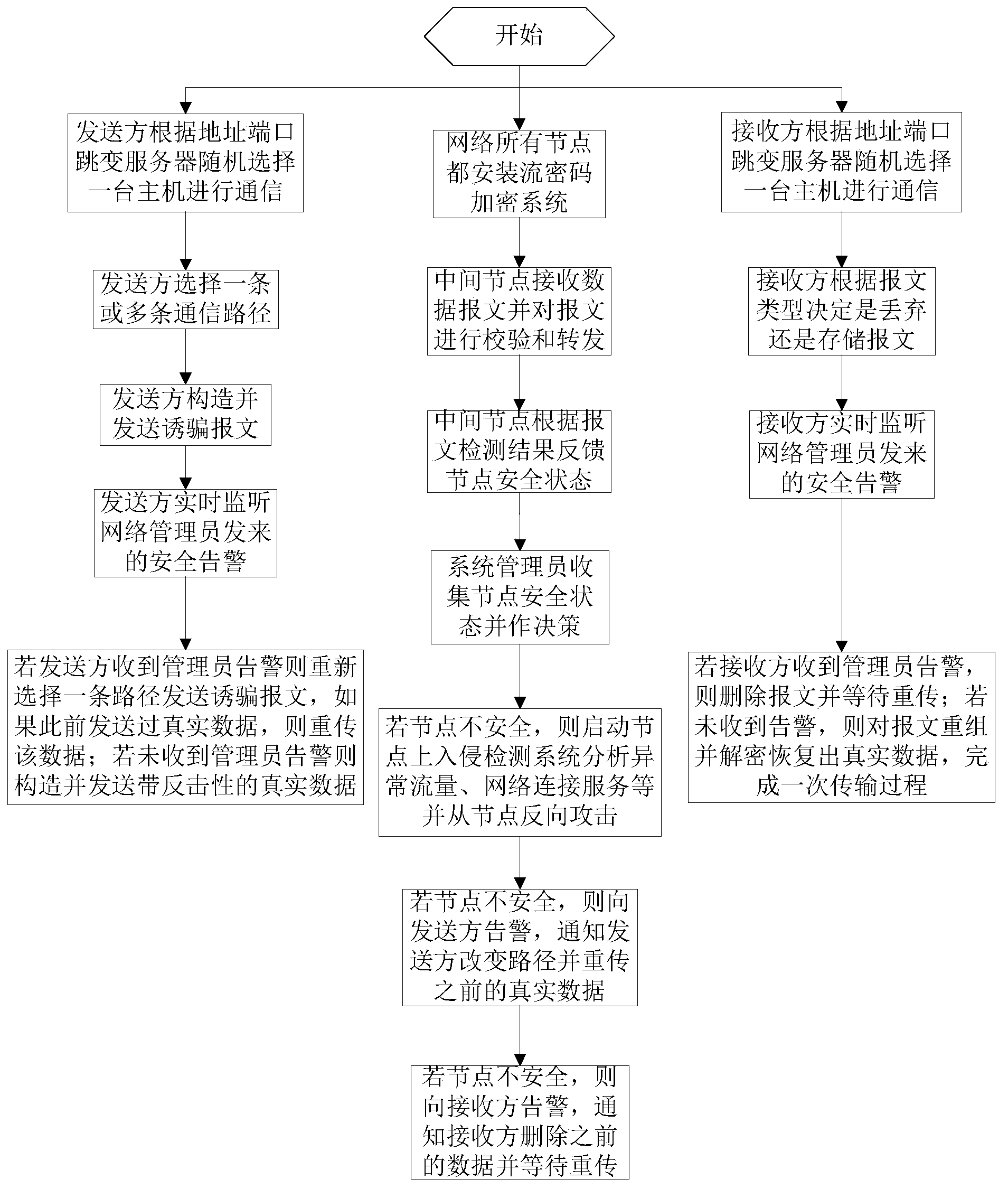
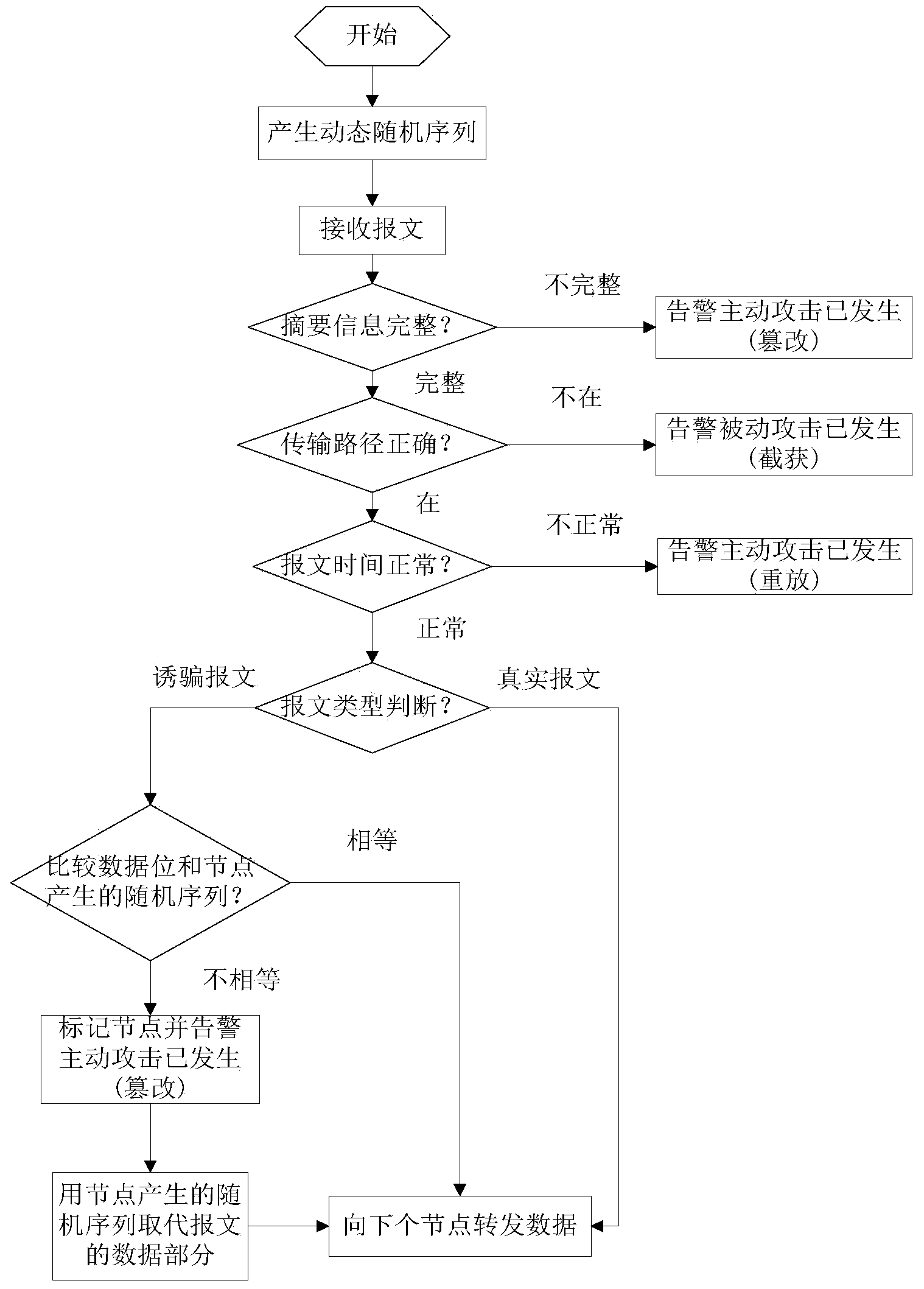
The invention discloses an active defense method for a network trick and a counter attack. The method comprises the following steps that two communication sides set a plurality of host computers for data sending and receiving, and one host computer is dynamically and randomly selected as a communication host computer through an address and port hopping server; a sender selects one or more transmission links to send a trick message to detect the safety and the channel quality of the transmission links, wherein if the links are safe, true data with the counter attack are constructed and sent, and meanwhile the sender continues to send the trick message to detect the links; an intermediate node takes in charge of detecting and feeding the safety situation of the transmission links back to a network administrator; the network administrator updates a transmission path according to the safety situation of the node and takes the defensive measure. The active defense method can effectively prevent and detect common safety attack in the network communication and carry out certain counter attack on an attacker.
Owner:HUAZHONG UNIV OF SCI & TECH
Detecting web browser based attacks using browser digest compute tests launched from a remote source
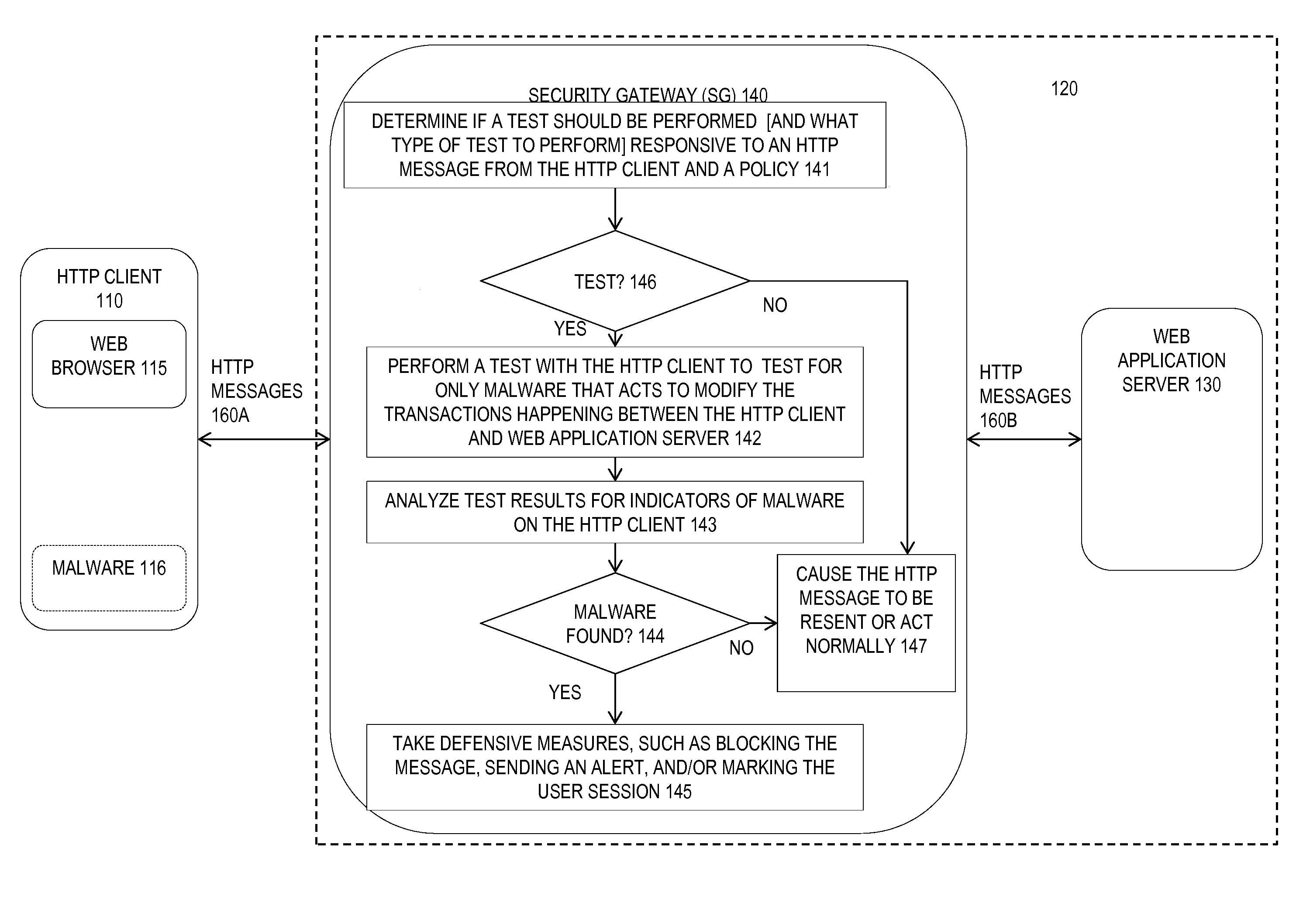
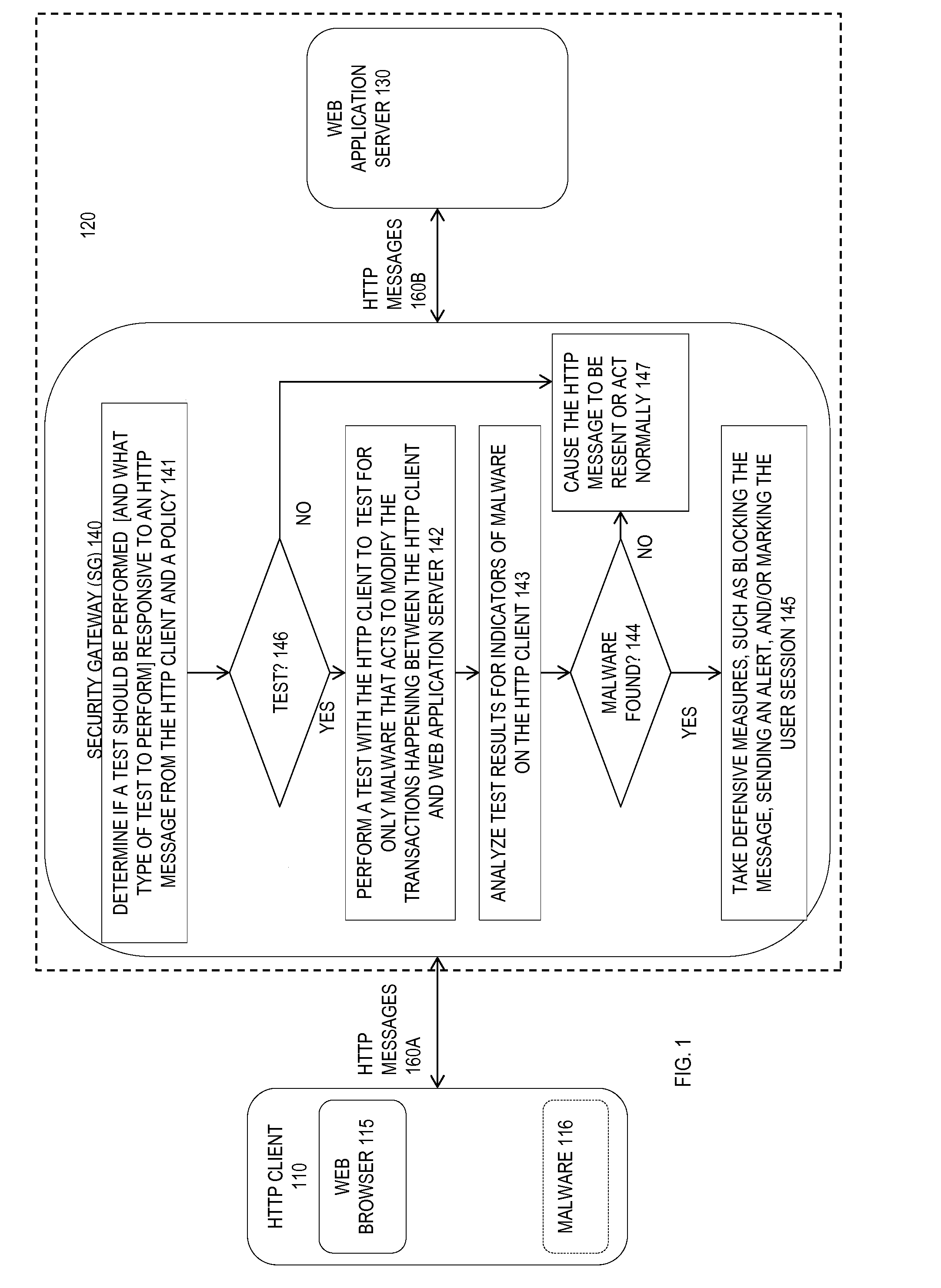
The detection of web browser-based attacks using browser tests launched from a remote source is described. In one example, a digest is computed based on the content of an HTTP response message. The message is modified and sent to a client device that also computes a digest. The digests are compared to determine whether content has been modified by malware on the HTTP client. The results of the test are analyzed and defensive measures are taken.
Owner:IMPERVA
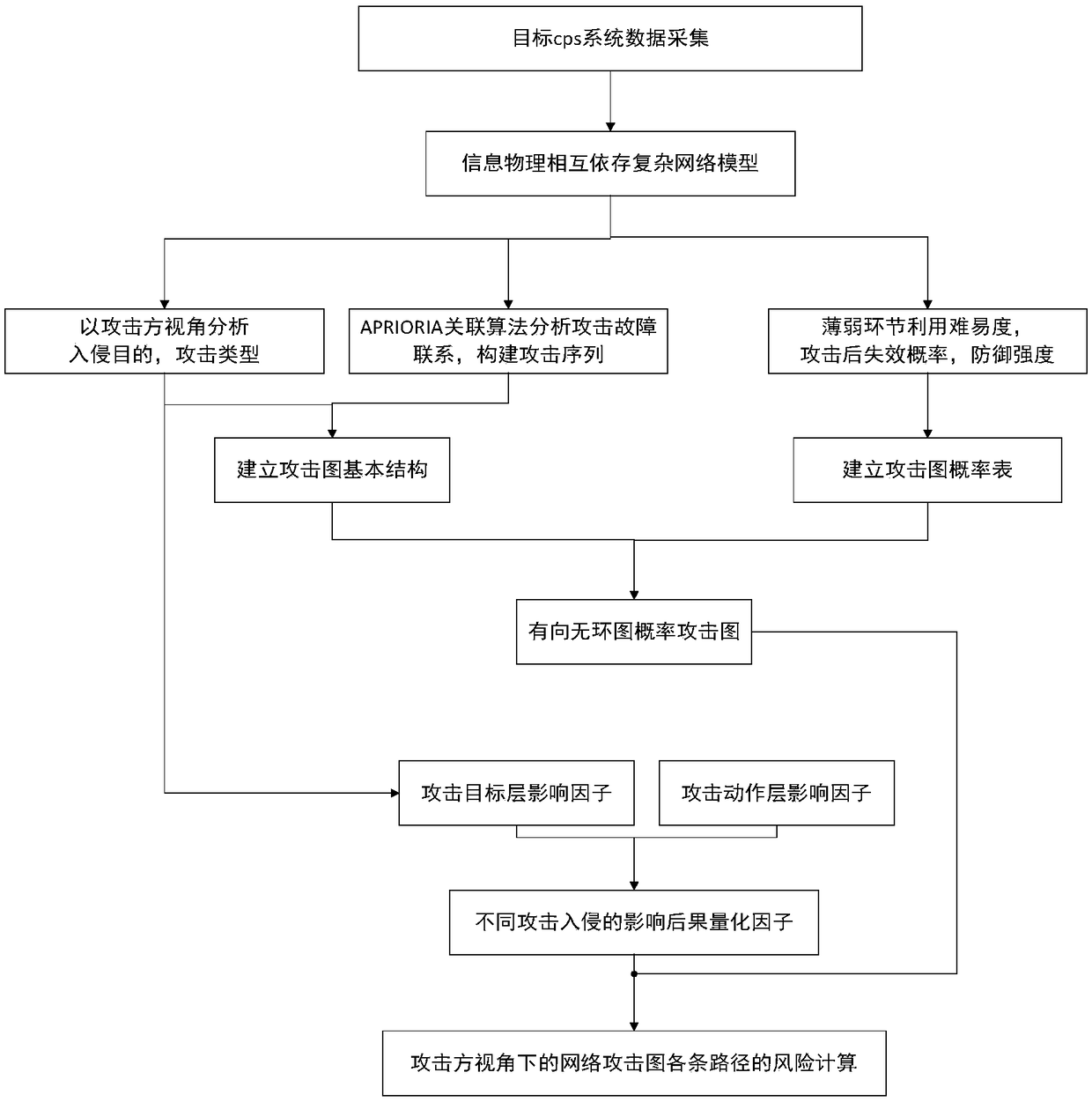
Network attack risk assessment method of distribution network CPS dependent system based on attacker perspective
ActiveCN109191326ADesign optimisation/simulationPlatform integrity maintainanceRisk levelGrid operator
The invention provides a network attack risk assessment method of a distribution network CPS dependent system based on an attacker perspective. From an attacker perspective, the risk level caused bypower grid cps system attack is analyzed based on different attack and invasion aims and the risk situation of potential attack paths is analyzed, so that the method provides a new perspective for thestudy of cps security analysis and protection methods, and provides an accurate basis for grid operators to formulate defensive measures.
Owner:NORTHEASTERN UNIV
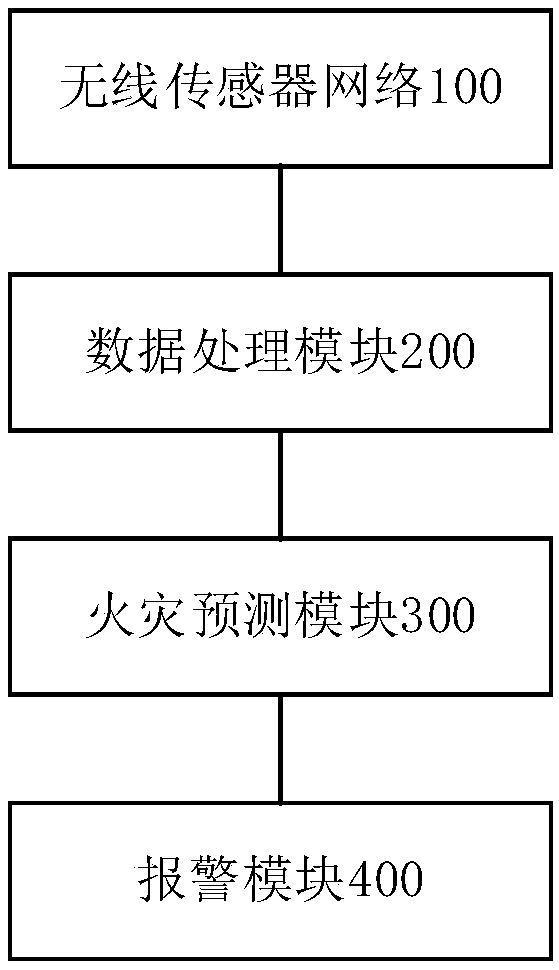
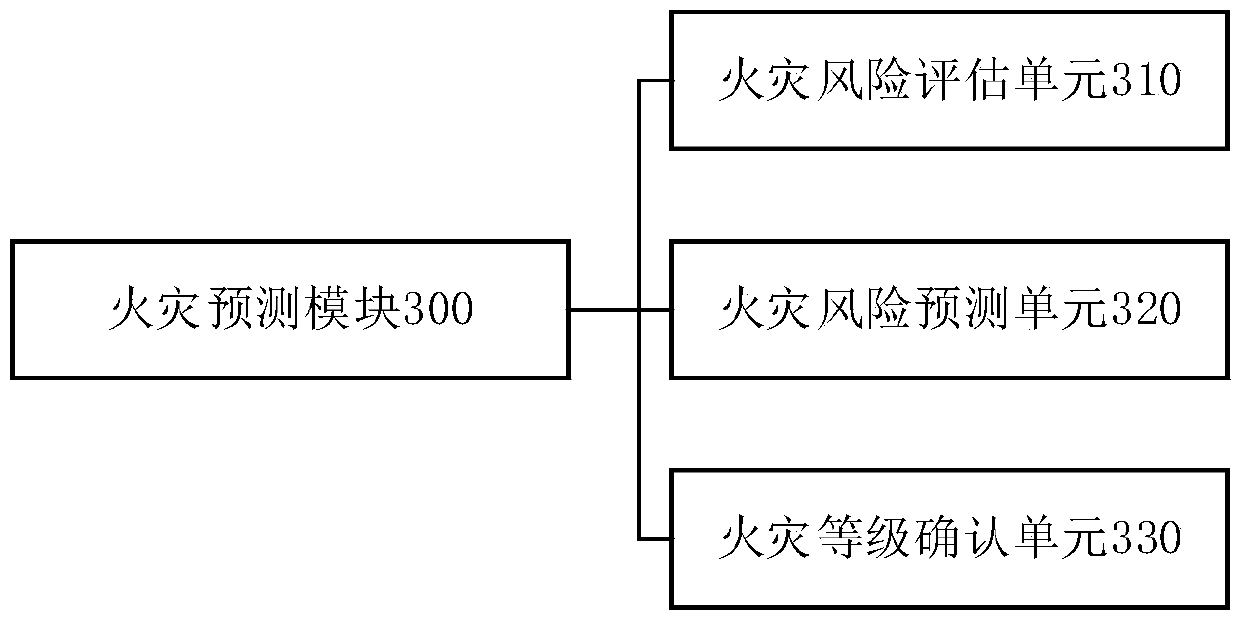
Forest fire early warning system based on wireless sensor network
InactiveCN108765836ARealize monitoringTimely and accurate early warningParticular environment based servicesNetwork topologiesEarly warning systemWireless mesh network
The invention provides a forest fire early warning system based on a wireless sensor network. The system comprises a wireless sensor network for acquiring environmental impact factor data in a forest;a data processing module for processing the acquired data to generate a situation information capable of describing a forest fire situation; a fire prediction module for predicting the fire risk of the forest according to the obtained situation information, and determining a corresponding fire risk level; and an alarm module for giving a corresponding alarm according to the obtained fire risk level. The forest fire early warning system can effectively and quickly predict the future development trend of the forest fire through the wireless sensor network, and timely and accurately gives earlywarning on the forest fire and determines the fire risk level, and contributes to workers to take corresponding defensive measures timely.
Owner:深圳源广安智能科技有限公司
Vulnerable line identification method and system of power system
InactiveCN106253270AImprove effectivenessImprove accuracyAc network circuit arrangementsNODALState dependent
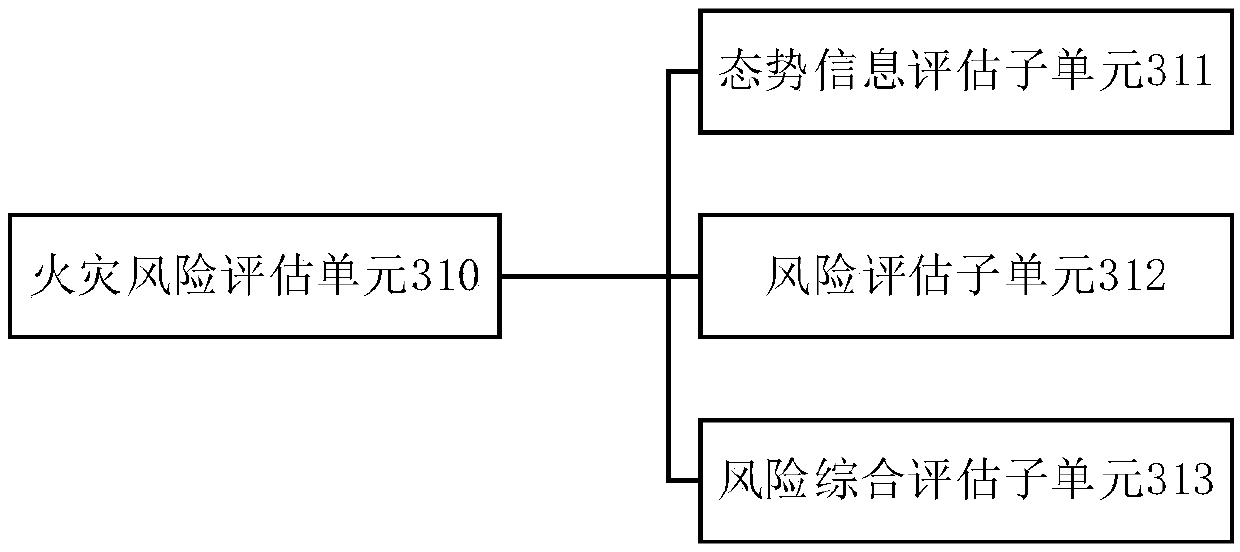
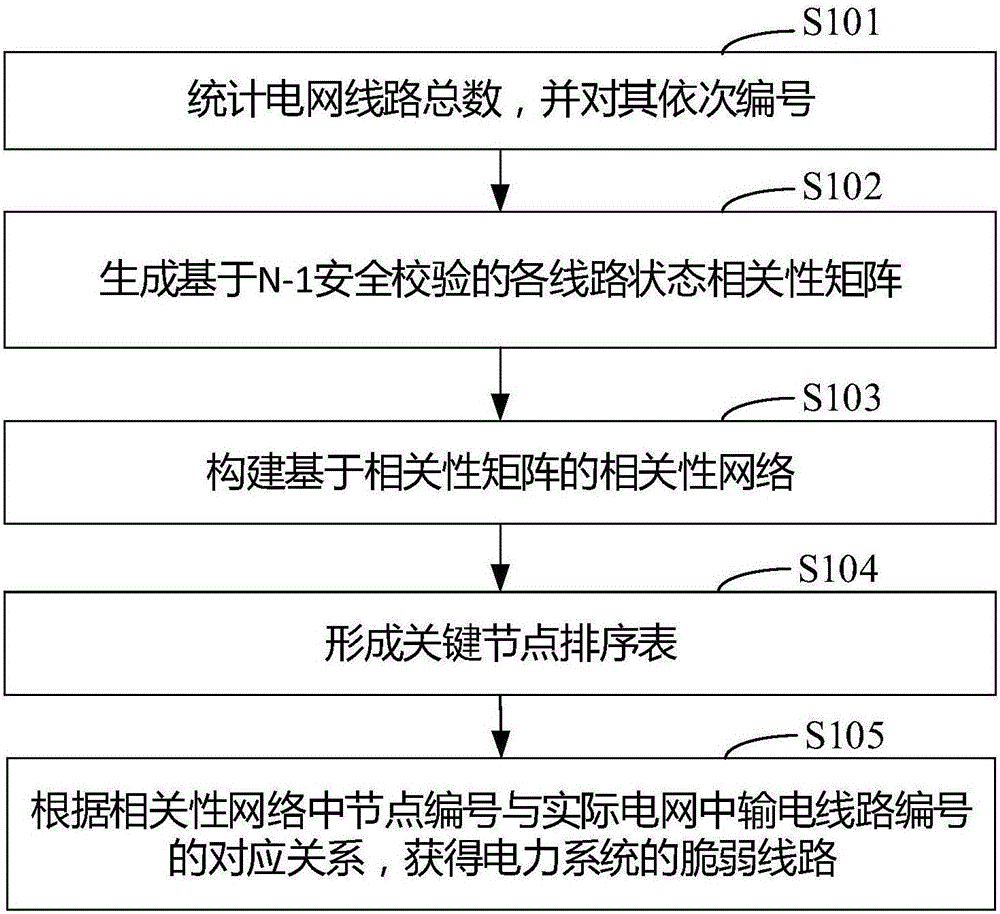
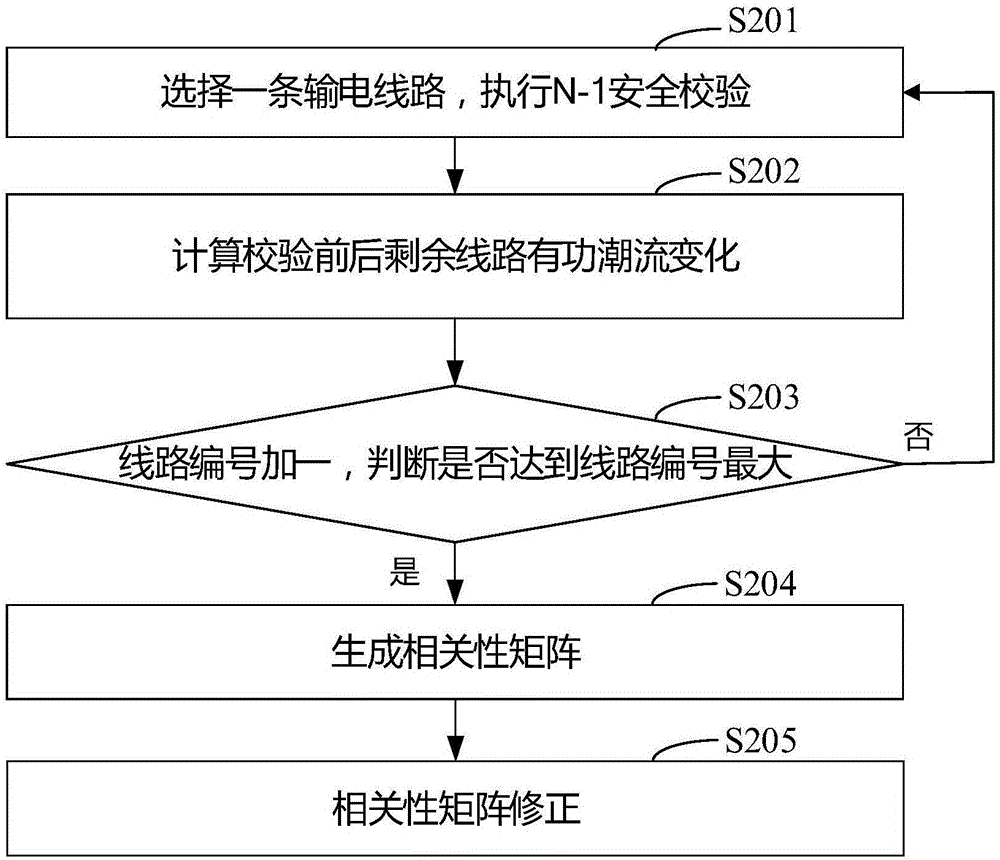
The invention discloses a vulnerable line identification method and system of a power system. The method comprises the following steps of counting the total number of power grid circuits, and sequentially numbering the power grid circuits; generating (N-1) safety verification based correlation matrix of each circuit state; building a correlation network based on the correlation matrix; estimating key nodes in the correlation network according to a preset identification method, and forming a sorting list of the key nodes; and acquiring a vulnerable line of the power system according to a node number in the correlation network and a corresponding relation of the number of a power transmission line in an actual power grid. The system comprises a numbering module, a verification module, a processing module and a sequencing module. By the method and the system, the vulnerable line affecting safe and stable running of the power grid is effectively and accurately identified, a positive and defensive measure is taken afterwards, and a power-off risk brought by a blackout accident is reduced to the greatest extent.
Owner:SOUTHWEST JIAOTONG UNIV
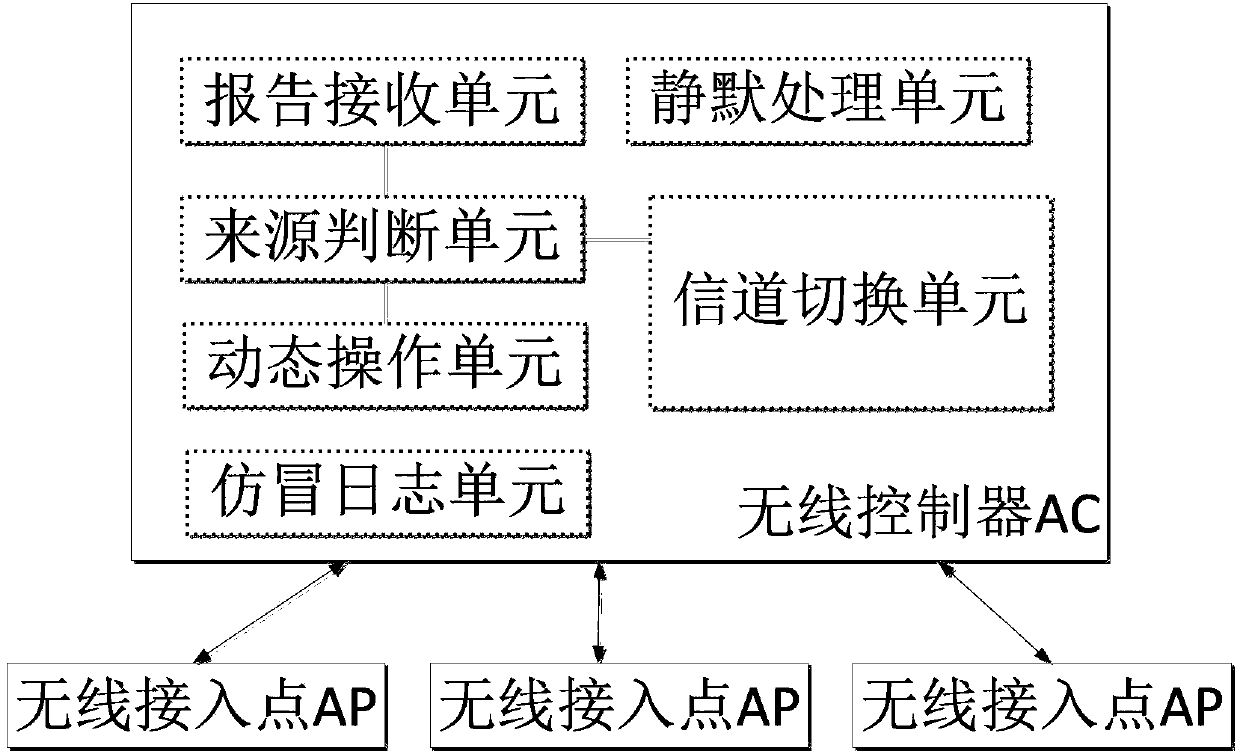
Wireless attack detection and defense device and method thereof
ActiveCN103391546AAvoid accidental injuryTransmissionSecurity arrangementDefensive measureClient-side
The invention provides a wireless attack detection and defense device. The device is applied to a wireless access controller (AC) which is applied to management of wireless access points (APs). The device comprises a report receiving unit, a source determining unit and a dynamic operation unit. The report receiving unit is used for receiving attack reports reported by the wireless APs, reporting and determining source MAC addresses of attackers in the reports. The source determining unit is used for determining whether the APs corresponding to the source MAC addresses of the attackers are wireless APs associated with legal clients. The dynamic operation unit is used for sending the source MAC addresses used by the attackers to dynamic blacklists of the wireless APs which send the attack reports when the wireless APs corresponding to the source MAC addresses of the attackers are not wireless APs associated with legal clients. By means of the wireless attack detection and defense device, whether legal clients or counterfeiting persons send the attacks can be recognized, and corresponding defensive measures can be adopted, so that legal clients can be prevented from being accidentally injured.
Owner:NEW H3C TECH CO LTD
Device and method for transmitting data in an encrypted manner
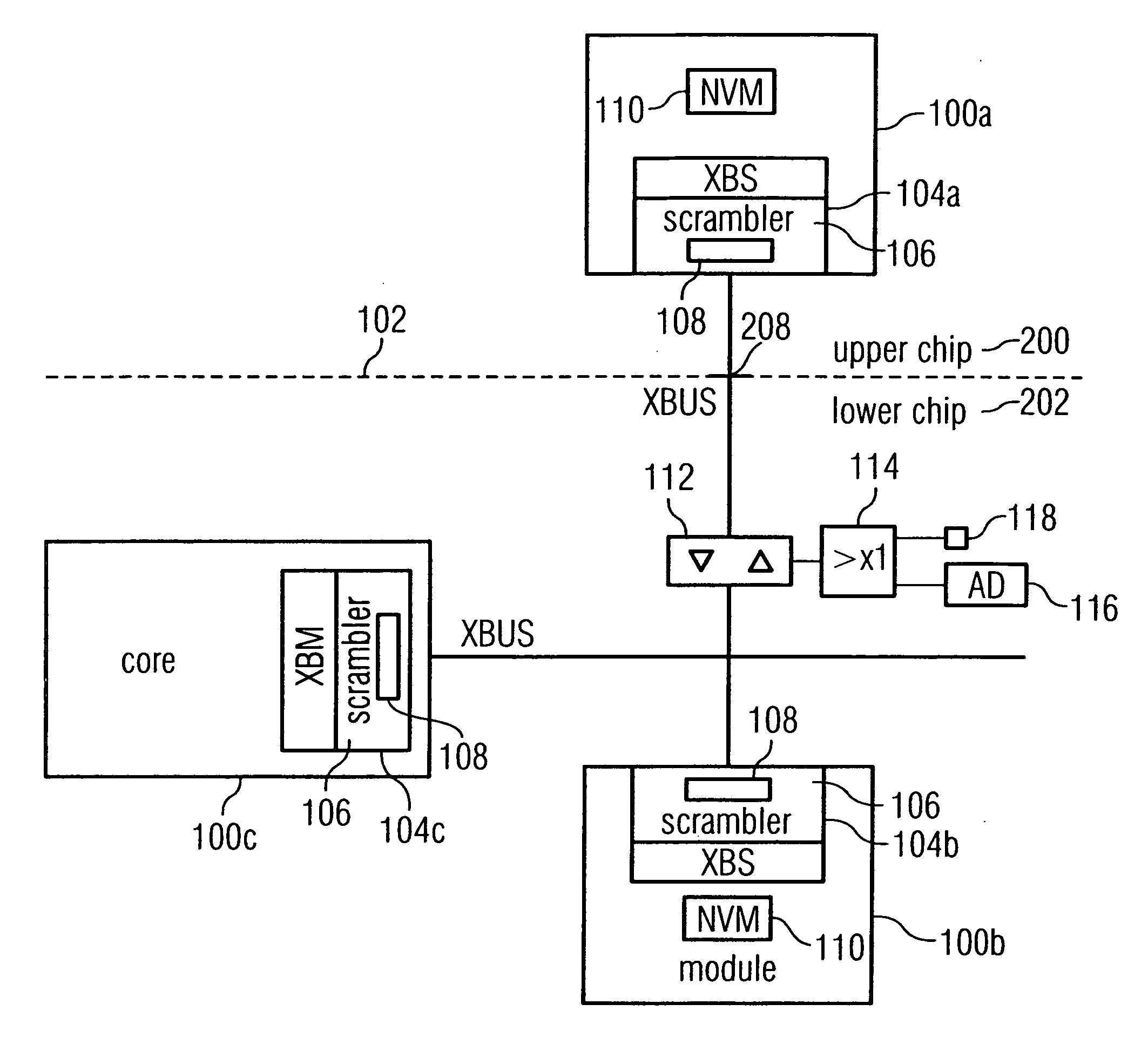
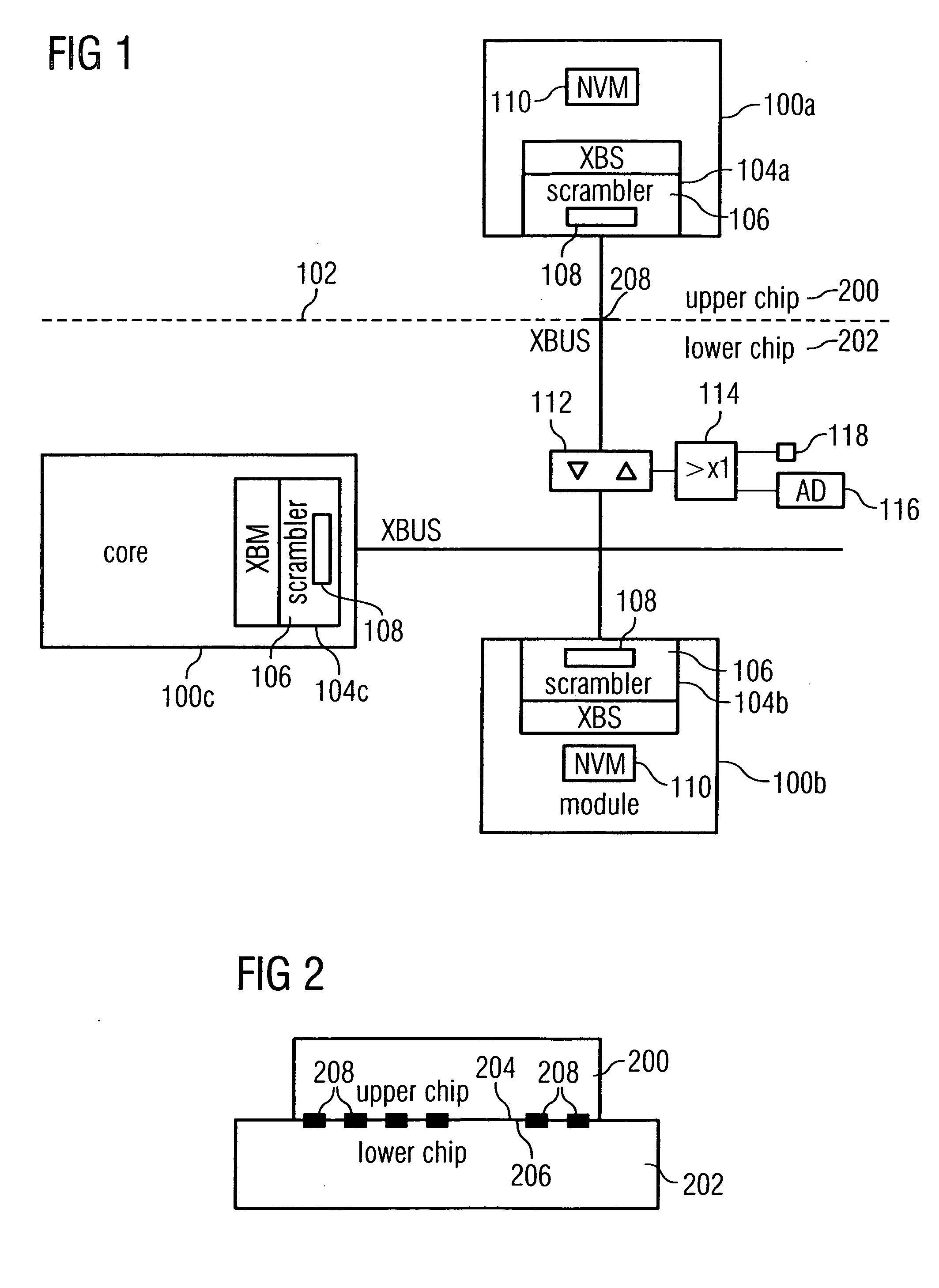
ActiveUS20060233360A1Flexible partitioningGood effectData stream serial/continuous modificationInternal/peripheral component protectionData streamSemiconductor chip
A device according to the present invention is configured for transmitting data between two semiconductor chips of a data processor in an encrypted manner, wherein a first semiconductor chip is connected to a second semiconductor chip. The device includes a non-volatile memory element in each of the two semiconductor chips, wherein an encryption initial value for an encryption rule is stored in the memory element of the first semiconductor chip and a decryption initial value associated to the encryption initial value for a decryption rule associated to the encryption rule is stored in the memory element of the second semiconductor chip. Additionally, the first semiconductor chip has a first data transmission interface formed to generate an encryption data stream from an input data stream using the encryption initial value according to the encryption rule. Also, the second semiconductor chip has a second data transmission interface formed to receive the encryption data stream and to generate a decryption data stream from the encryption data stream using the decryption initial value according to the decryption rule and to compare the decryption data stream generated to an expected data stream, wherein the second data transmission interface is also formed to perform a defensive measure against transmitting data from the second data transmission interface to the first data transmission interface when the decryption data stream does not correspond to the expected data stream.
Owner:INFINEON TECH AG
Method for quantitative evaluation on information safety vulnerability of SCADA system
The invention relates to a method for quantitative evaluation on the information safety vulnerability of an SCADA system, provides a method for evaluating the information safety vulnerability of the SCADA system based on analytic hierarchy process empowerment and an attack defense tree model and aims to utilize an analytic hierarchy process to scientifically endow weight values for calculation indexes of leaf nodes, then calculate leaf nodes and attack sequences of attack defense trees, the overall vulnerability of the system and the vulnerability sensitivity of the leaf nodes and thus determine key leaf nodes affecting the information safety vulnerability of the SCADA system. A quantified reference basis specific to adoption of defensive measures for weak links of the SCADA system is provided for technicians.
Owner:SOUTHWEST JIAOTONG UNIV
Power network information security active defense system based on big data
InactiveCN108848069AMeet the needs of security protectionStrong real-timeTransmissionData acquisitionPower grid
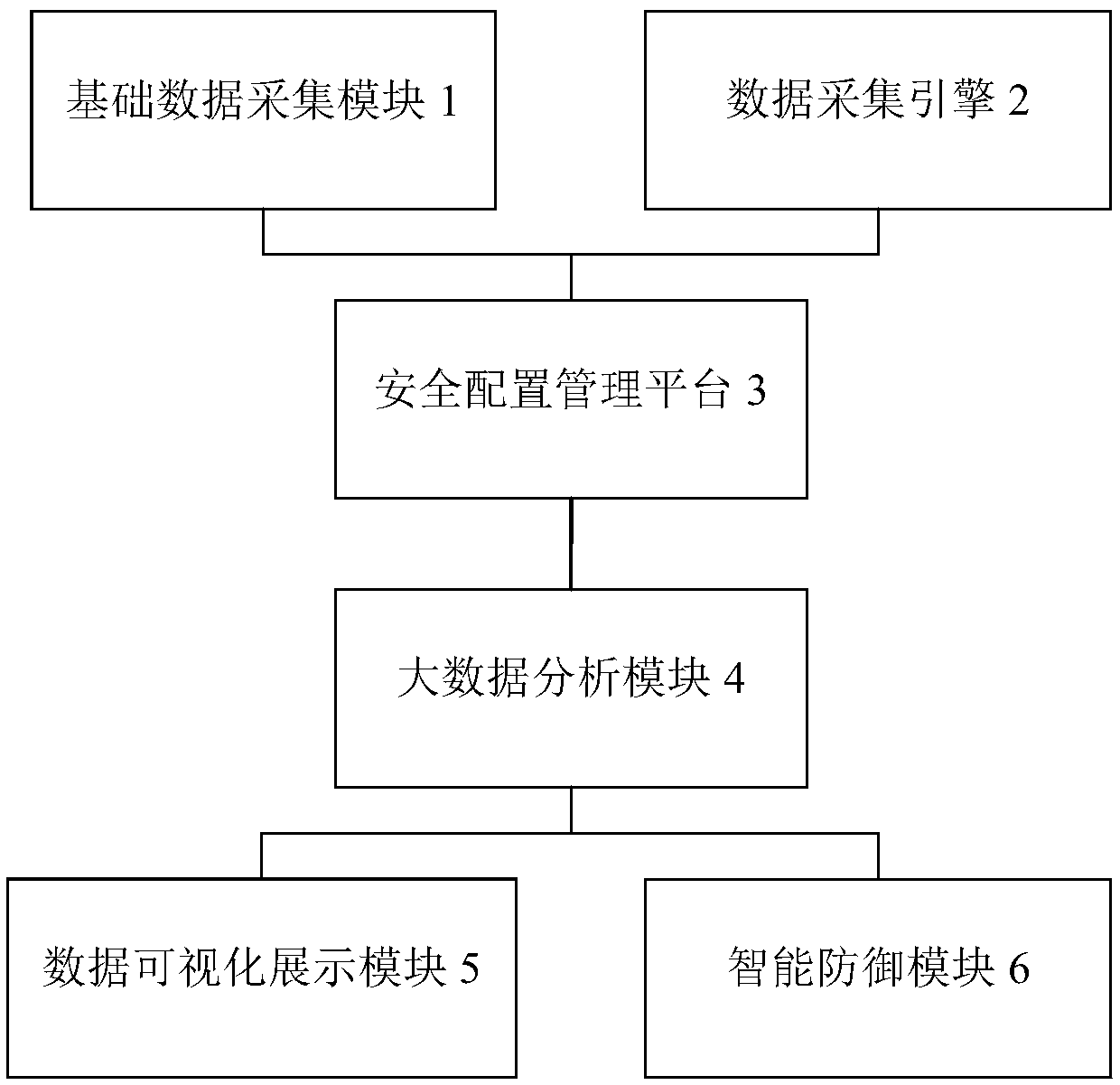
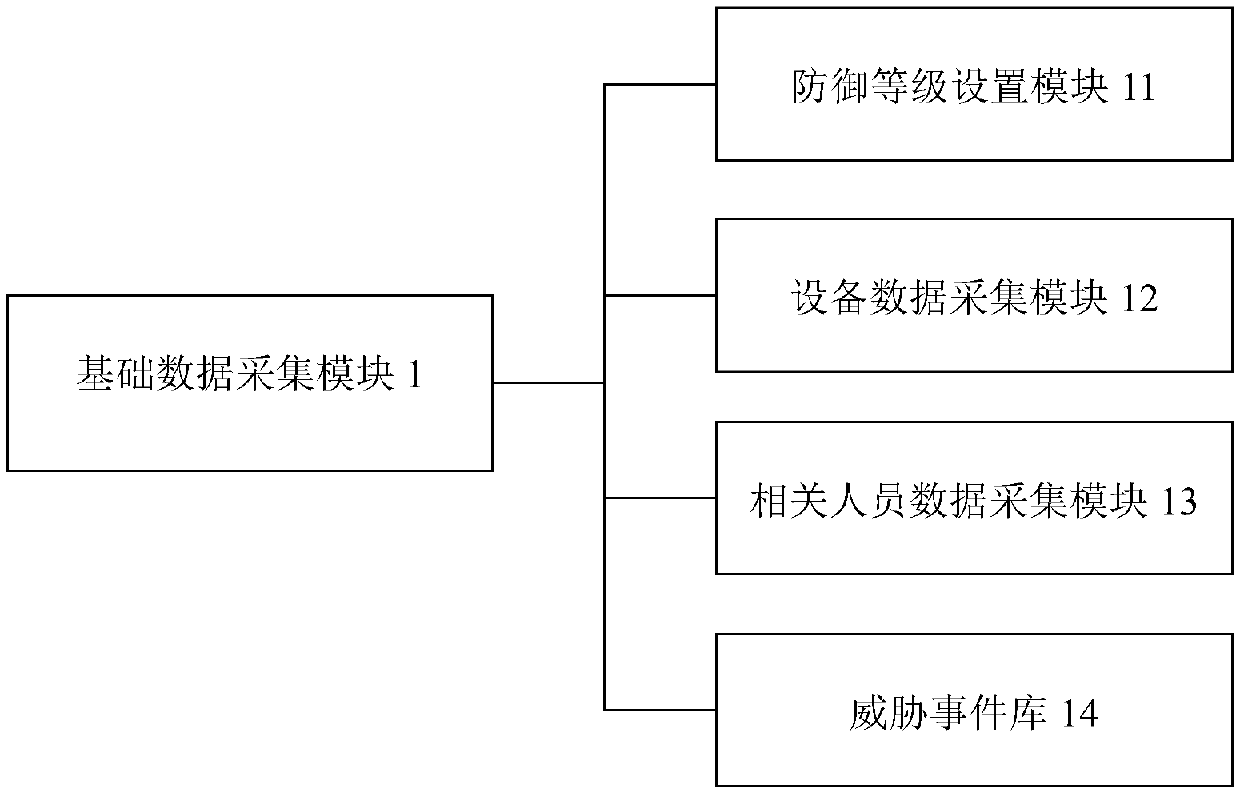
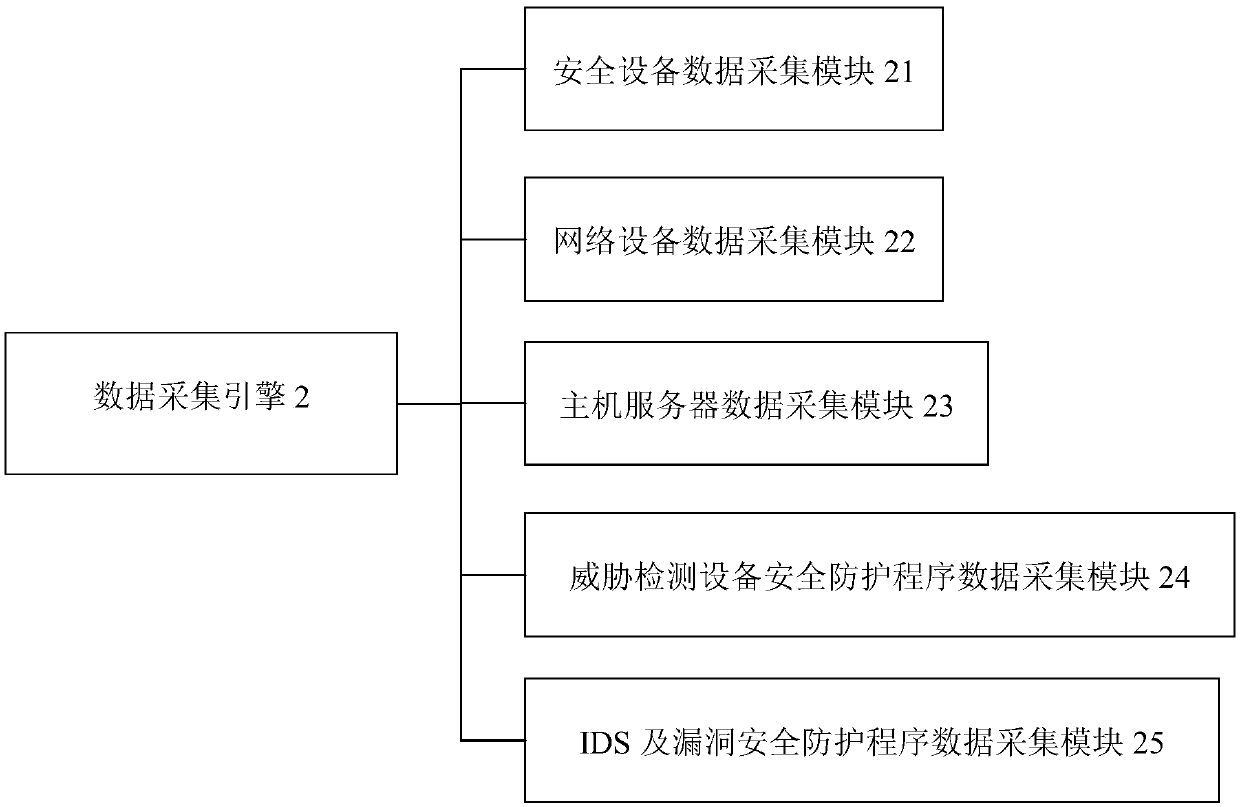
The invention provides a power network information security active defense system based on big data. The system comprises the following parts: a basic data collection module, configured to collect device data and related personnel data in the power network and provide protection levels and threat events; a data collection engine, configured to perform centralized operation status monitoring on devices in the power network; a security configuration management platform, configured to receive data collected by the basic data collection module and the data collection engine, and perform performance and operation status monitoring on all devices according to the collected data; a big data analysis module, configured to process and analyze the monitored data of the security configuration management platform, and perform security situational awareness and prediction to sense the threat situation; and an intelligent defense module, configured to match appropriate defense measures for executionfrom a defensive measures library according to the threat situation acquired by the big data analysis module. The invention adapts to the current needs of the power network for information security protection.
Owner:广州智达机械技术有限公司
Method and equipment for determining attack surfaces of terminals
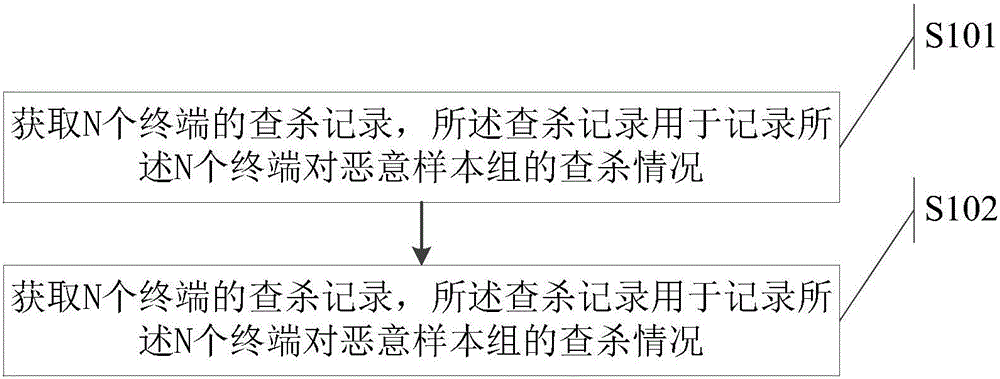
The invention discloses a method and equipment for determining attack surfaces of terminals. The method comprises the steps of acquiring checking and killing records of N terminals, wherein the checking and killing records are used for recording the checking and killing situations of the N terminals on a malicious sample group, and N is a positive integer; and determining an attack surface, attacked by the malicious sample group, of each terminal among the N terminals according to the checking and killing records, wherein the attack surface is used for characterizing the threatening degree of the malicious sample group on the terminal. The method and the equipment can solve the technical problem that a data determination method fitter to a personalized network environment of an enterprise lacks in malicious sample defense of the enterprise in the prior art so that more specific defensive measures are difficult to make. Provided is a data determination method capable of directly exposing the weak link attacked by malicious samples most easily.
Owner:BEIJING QIHOO TECH CO LTD +1
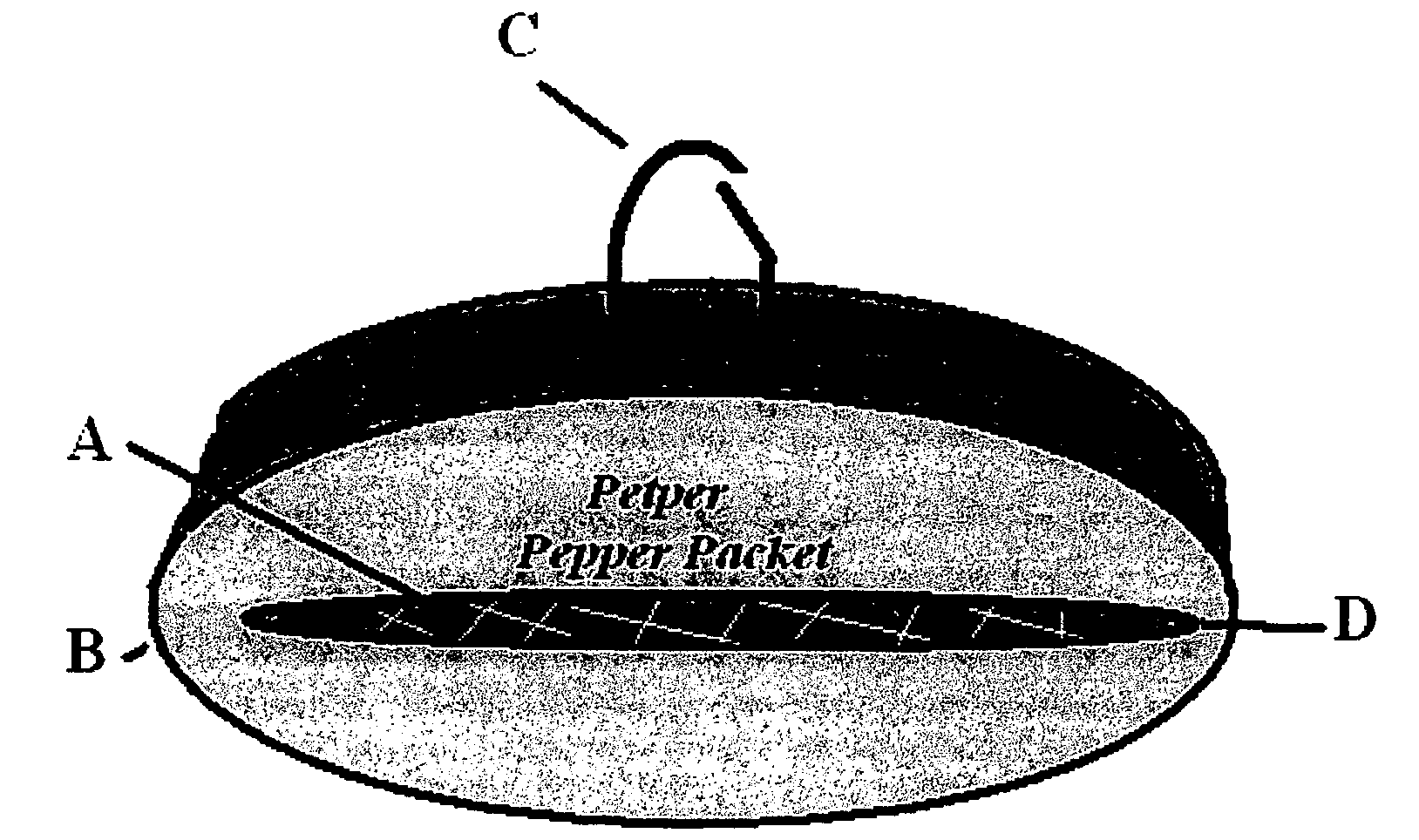
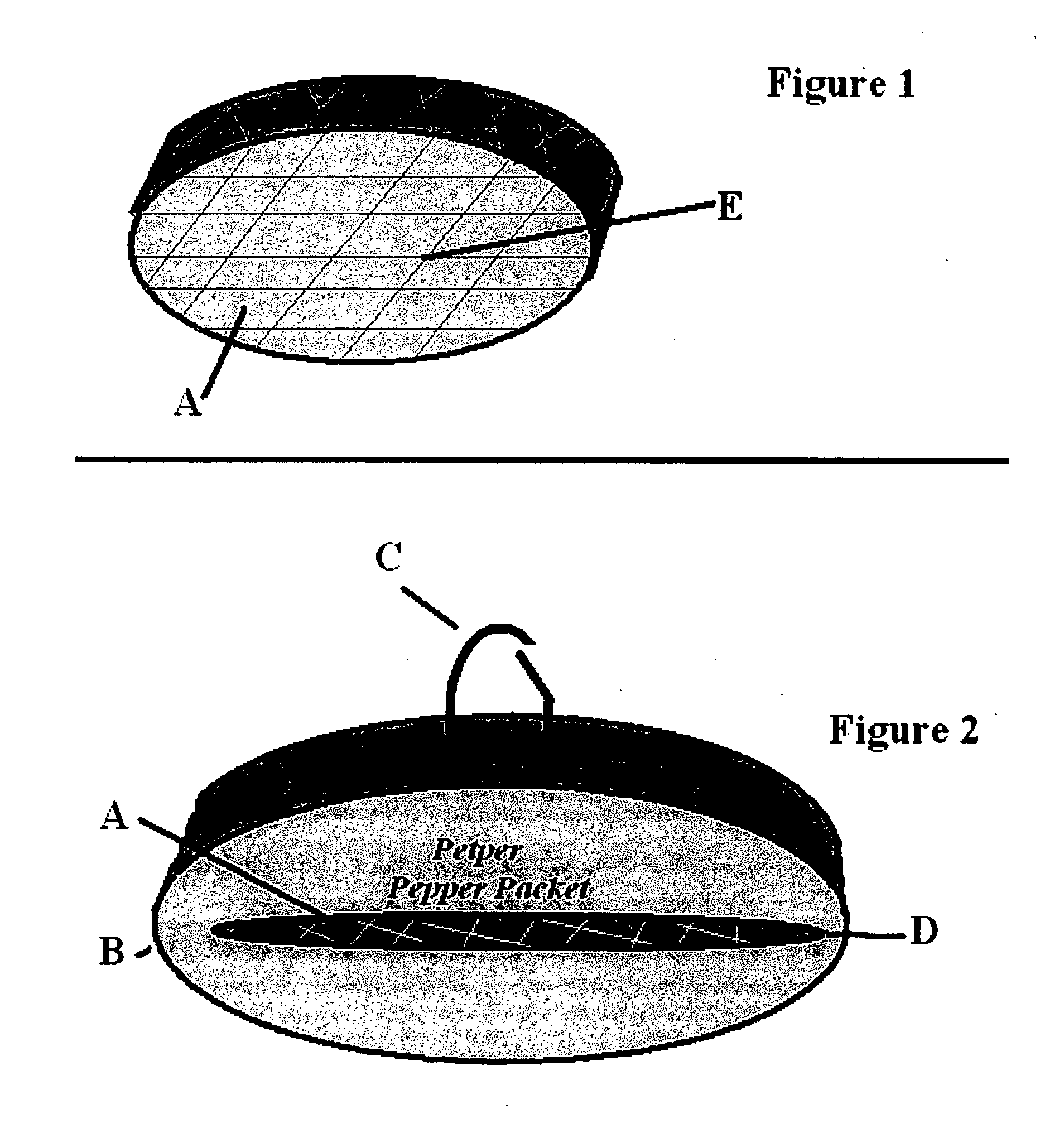
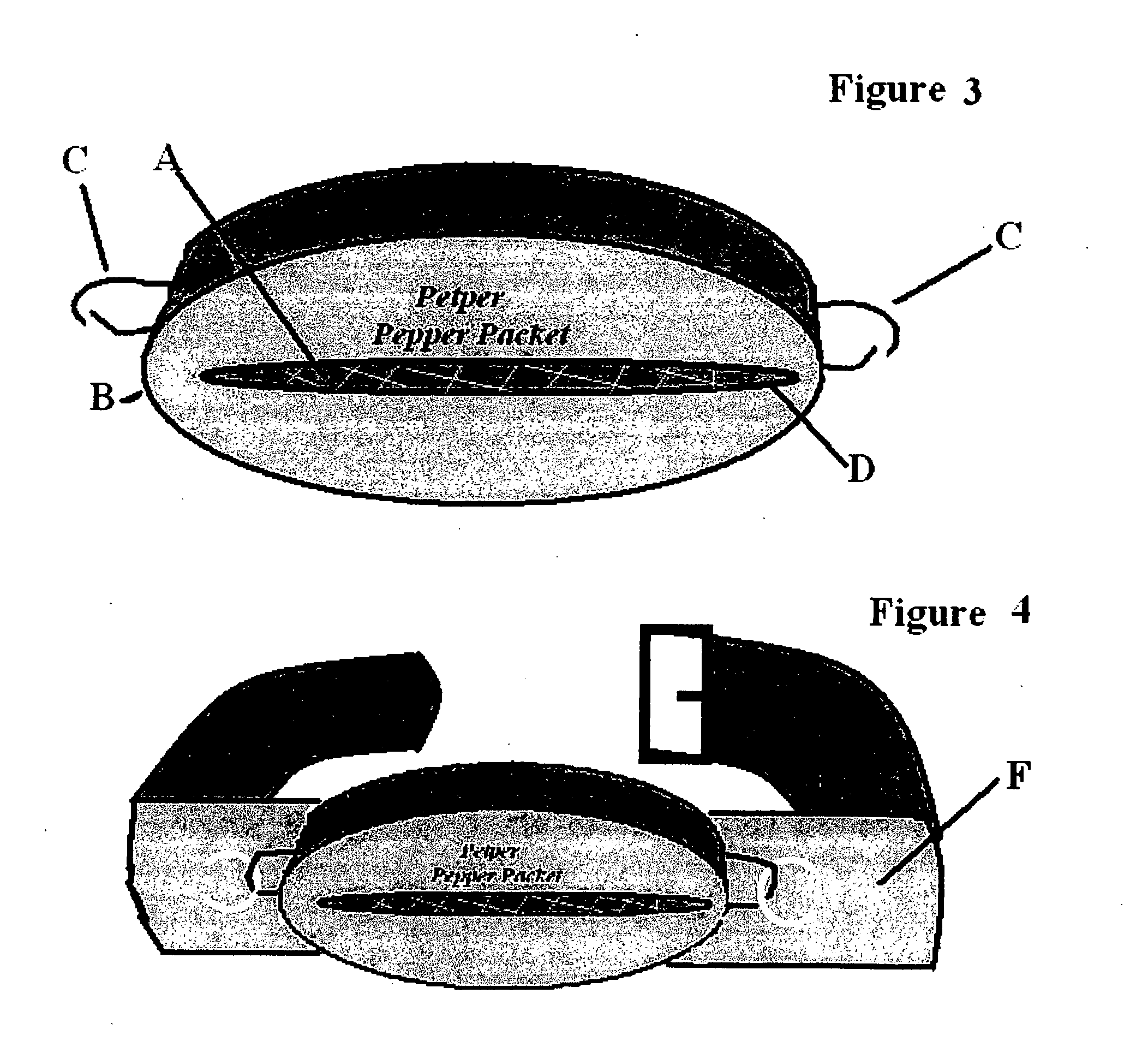
Passive chemical irritant release system for personal and pet defense
InactiveUS20080098966A1Little effectImproved oddsRepellant gas/chemical self-defence devicesTaming and training devicesEngineeringDefensive measure
A dormant pressurized or non-pressurized pouch, canister or bag containing a debilitating substance, such as a pepper mace, that deploys when bitten, clawed or otherwise punctured or squeezed. Attached or imbedded on a pet's collar, on a hiker's clothing or on a rancher's animal, the victim does not need to activate any defensive measure when attacked; the attack itself releases the chemicals. The chemical defense system not only curtails any immediate attack due to instant disbursement of debilitating chemical agents, but also allows some protection over time as the victim is temporarily coated with noxious chemicals, and able to escape the attack.
Owner:KNOBLACH JOHN
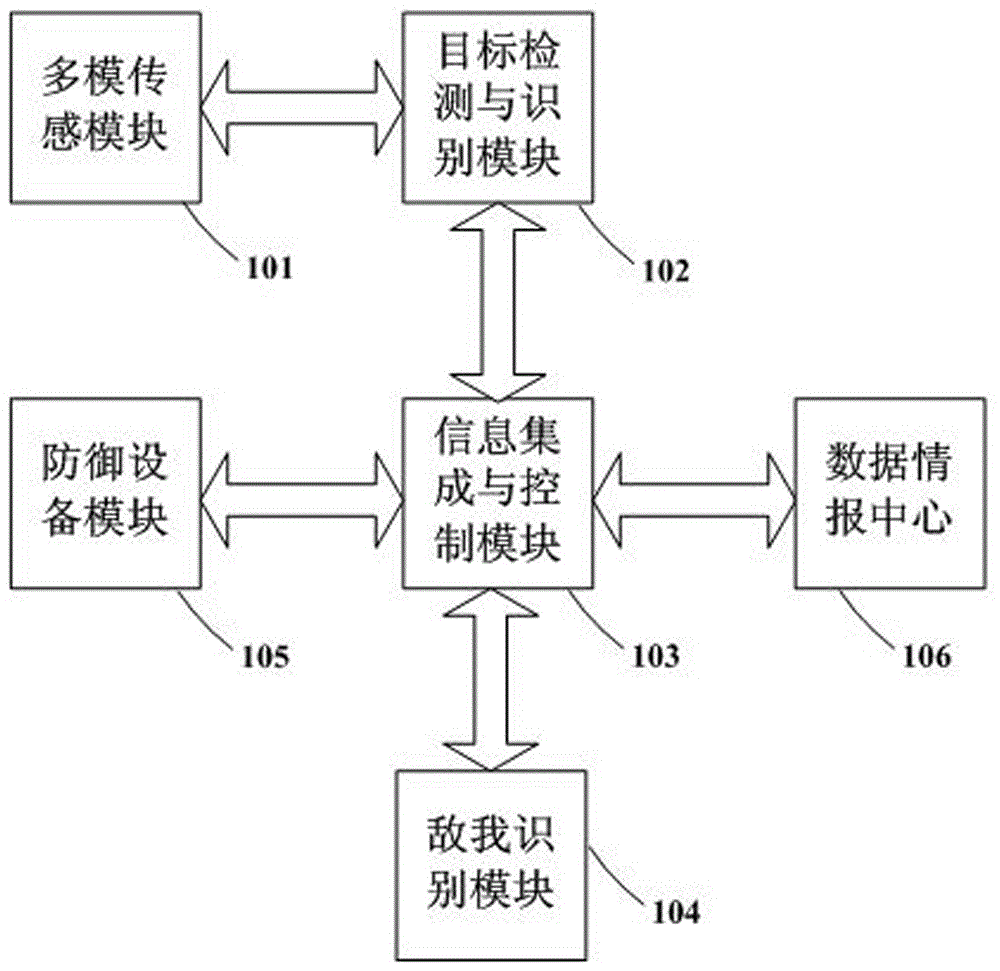
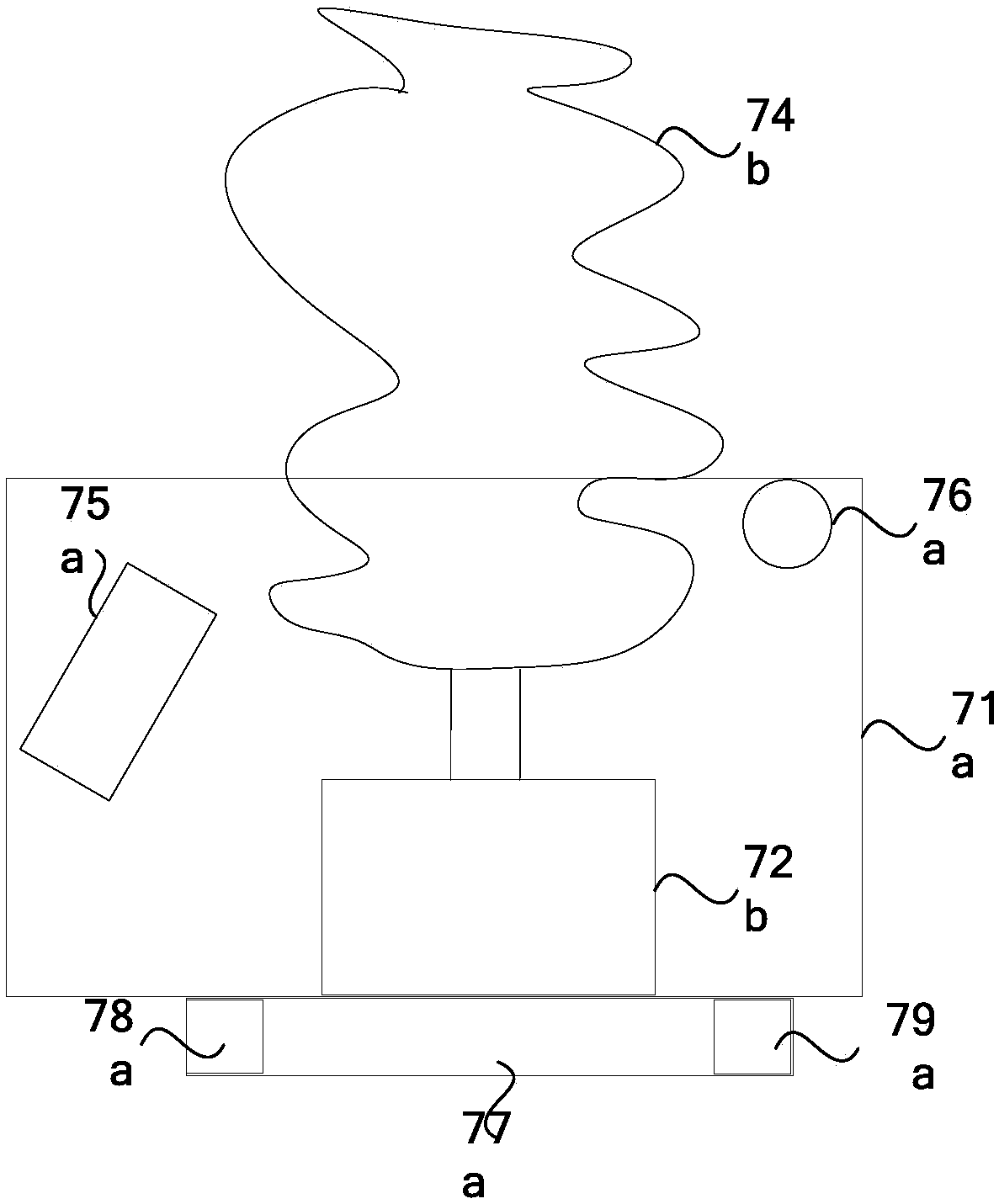
Region monitoring and defending system based on multimode compound sensing mechanism
ActiveCN106643303APortable and convenientQuick Arming CapabilitiesWeapons typesData centerEngineering
The invention relates to a region monitoring and defending system based on a multimode compound sensing mechanism. A result obtained by conducting multi-source sourcing information collection on an open space target through a multimode sensing module is sent to a target detection and identification module for information fusion and analysis; when an analysis result indicates that a target exists in a region, a friend or foe identification module receives target information and feeds a judged result on a target threat level back to an information integration and control module, the information integration and control module can send a control instruction to a defense equipment module in an automatic or manual intervention mode on the basis of pre-designed or set defensive strategies, and corresponding defensive measures are automatically adopted for a ground or aerial target according to the characteristics of comprehensive defense equipment and target properties. By means of an information data center connected to an information integration and control module, a human intervention control interface is provided, and on the basis of multidimensional sensing information collected by the multimode sensing module, continuous updating and property optimization are conducted on the system.
Owner:SHANGHAI RADIO EQUIP RES INST
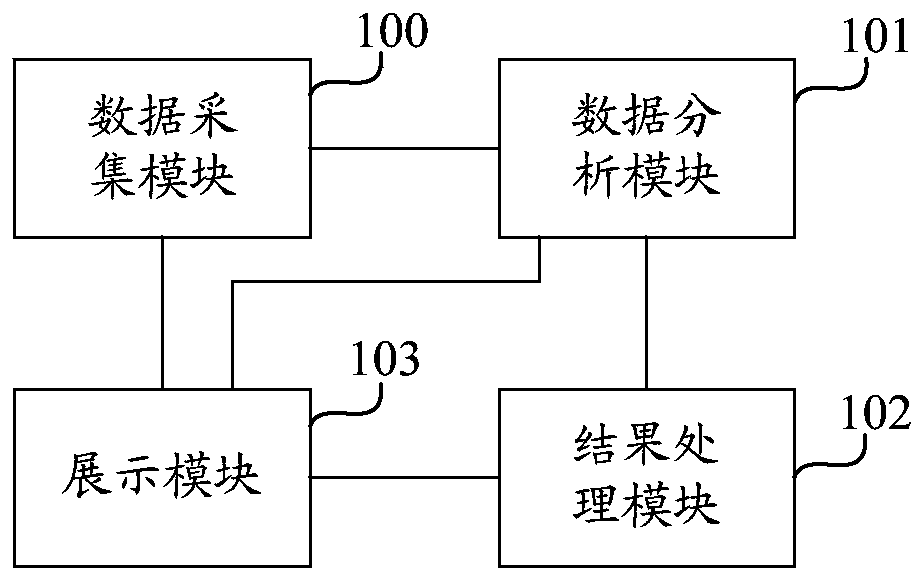
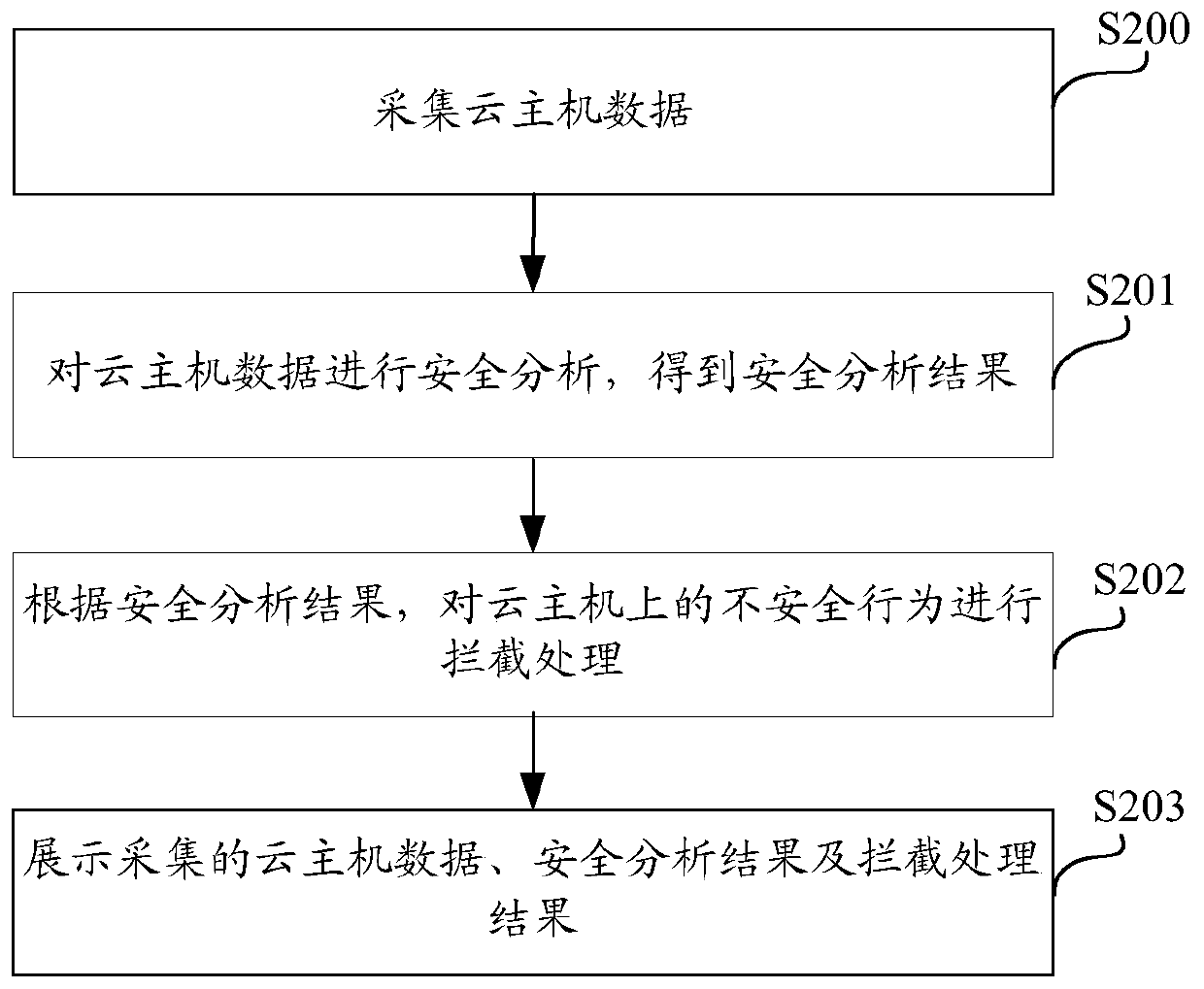
Cloud host security detection system and method
InactiveCN110099044AClear understanding of operation dynamicsAddress Cybersecurity RisksTransmissionCyber-attackData acquisition
The invention discloses a cloud host security detection system and method. The system comprises: a data acquisition module, which is suitable for acquiring cloud host data; a data analysis module which is suitable for carrying out security analysis on the cloud host data to obtain a security analysis result; a result processing module which is suitable for intercepting unsafe behaviors on the cloud host according to the safety analysis result; and a display module which is suitable for displaying the acquired cloud host data, the security analysis result and the interception processing result.The cloud host security detection system is based on the host. Cloud host data generated on a protected cloud host are continuously collected and analyzed; according to the security analysis result,corresponding defensive measures are taken to immediately terminate the occurrence of malicious behaviors, the attack behaviors of attackers are thoroughly blocked, the network security risk faced bythe cloud host in the cloud environment is solved, an enterprise is helped to construct a cloud host security protection system, and the cloud host is prevented from being attacked by the network.
Owner:JIANGSU PAYEGIS INFORMATION SECURITY TECH CO LTD
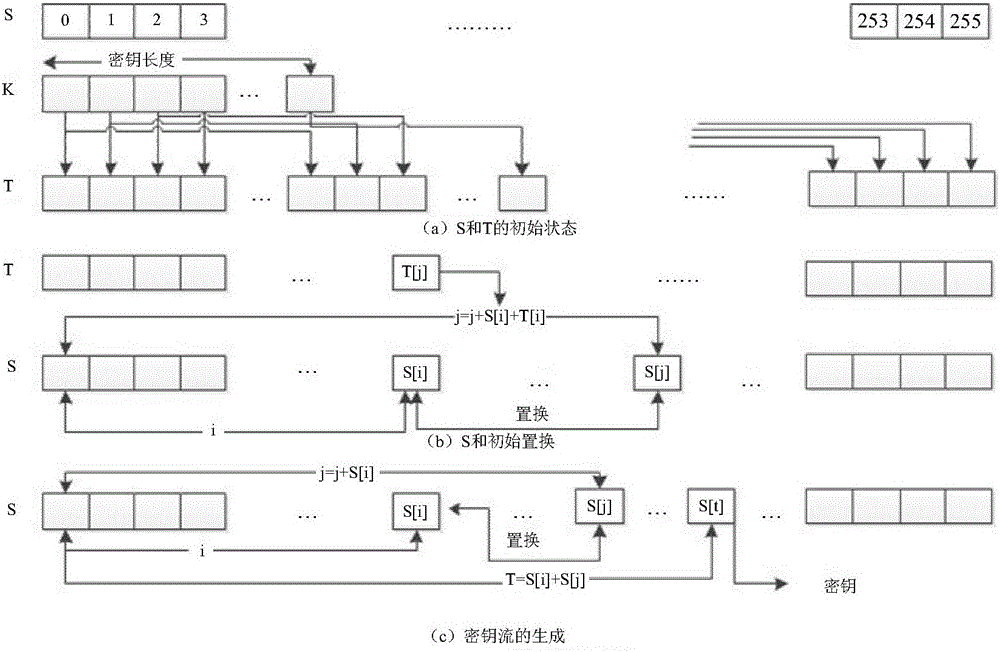
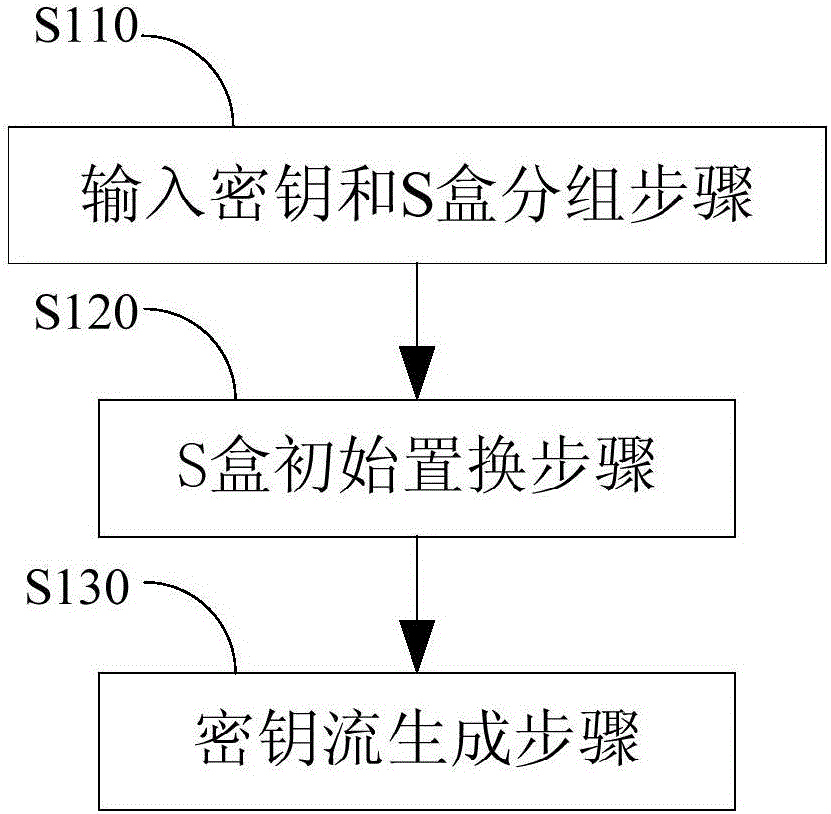
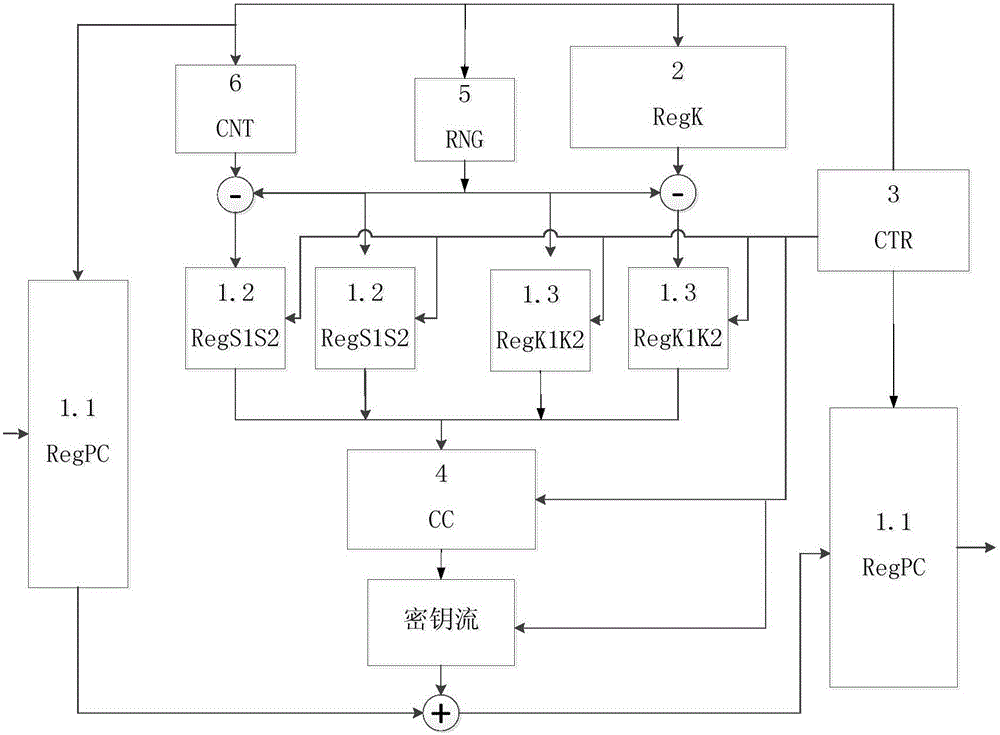
RC4 hardware circuit mark protection method and system
InactiveCN106411499AAchieve resistance to power consumption attacksData stream serial/continuous modificationRC4S-box
The present invention provides a RC4 hardware circuit mark protection method and system. The method comprises: the secret key inputting and S box grouping step: performing grouping with the same number of the inputted secret keys and the S boxes, introducing random numbers to the inputted secret keys and the S boxes at the same time, wherein the inputted secret keys and the S boxes are subjected to grouping, the sum of each part is the same as the content of the inputted secret keys and the S boxes which don't have protection; the S box initial permutation step: performing initial permutation of the grouping S boxes according to the grouping inputted secret keys; and the secret key stream generation step: performing permutation once again of the grouping S boxes after the initial permutation, and taking the sum of the grouping S boxes after the permutation once again as a new index, wherein the content of the X boxes pointed by the new index is an output secret key stream. Through adoption of the algorithm level defensive measure, the RC4 hardware circuit mark protection method and system quote random numbers to take as masks to resist to the power consumption attack, especially the template attack aiming at the RC4.
Owner:TSINGHUA UNIV
Threat degree ordering method for server attack sources
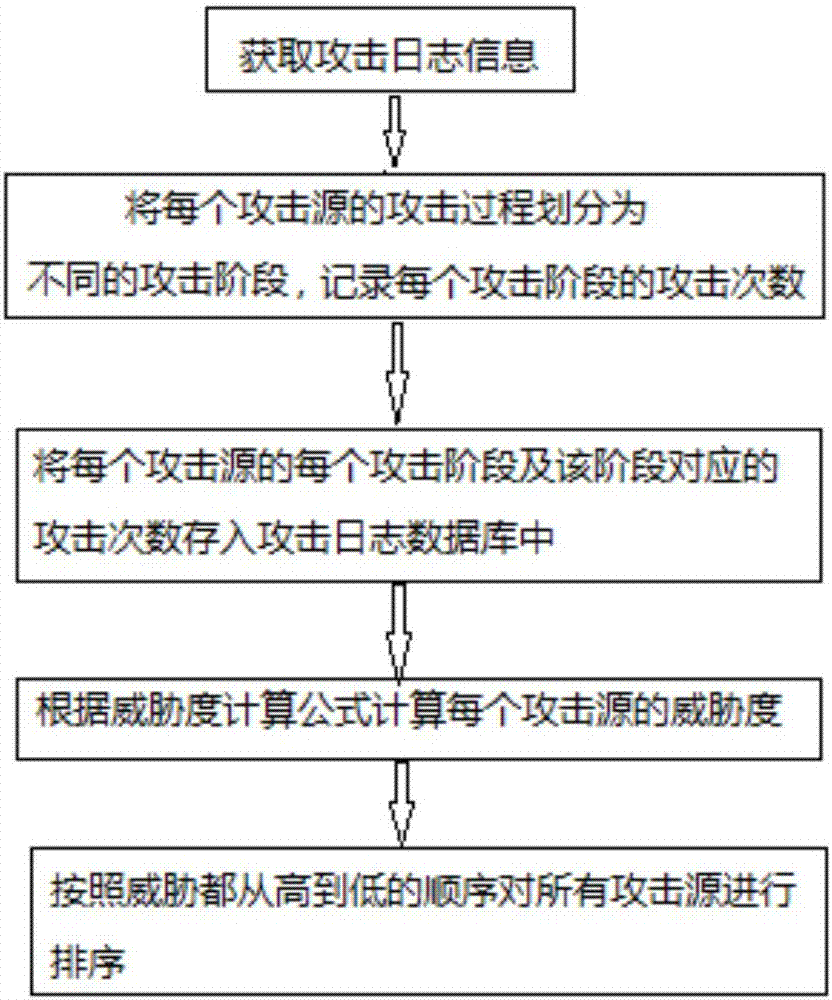
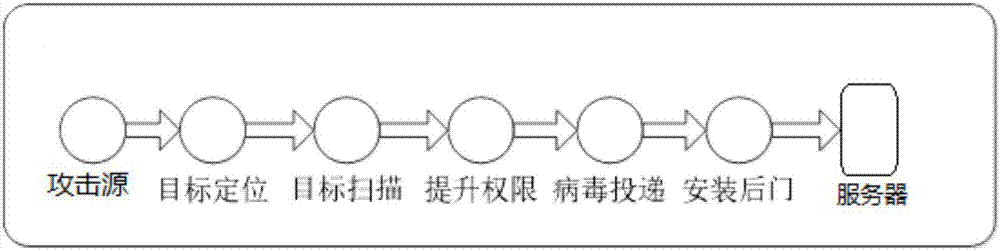
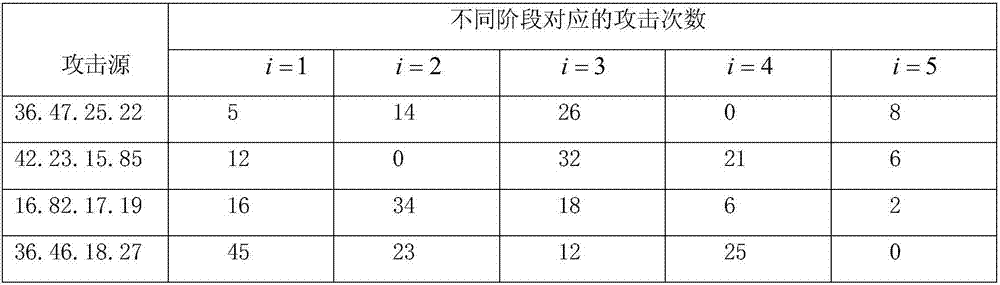
ActiveCN107294971AHigh threatImprove detection efficiencyTransmissionDefensive measureIntrusion detection system
The embodiment of the invention discloses a threat degree ordering method for server attack sources. The threat degree ordering method for server attack sources includes the steps: acquiring the log information generated in an intrusion detection system of a server; according to the log information, dividing the process of attacking the server by each attack source into a plurality of attack phases, counting the attack number of each attack phase, and according to the threat degree weight given by each attack phase, determining the threat degree of each attack source to the server; and at last, according to the threat degree of each attack source to the server, ordering the threat degree. The threat degree ordering method for server attack sources enables the user to visually obtain the attack source having the highest threat degree to the own server to make corresponding defensive measures timely, thus effectively improving the detection efficiency of the invasion detection system.
Owner:西安交大捷普网络科技有限公司
Method for sensing a threat
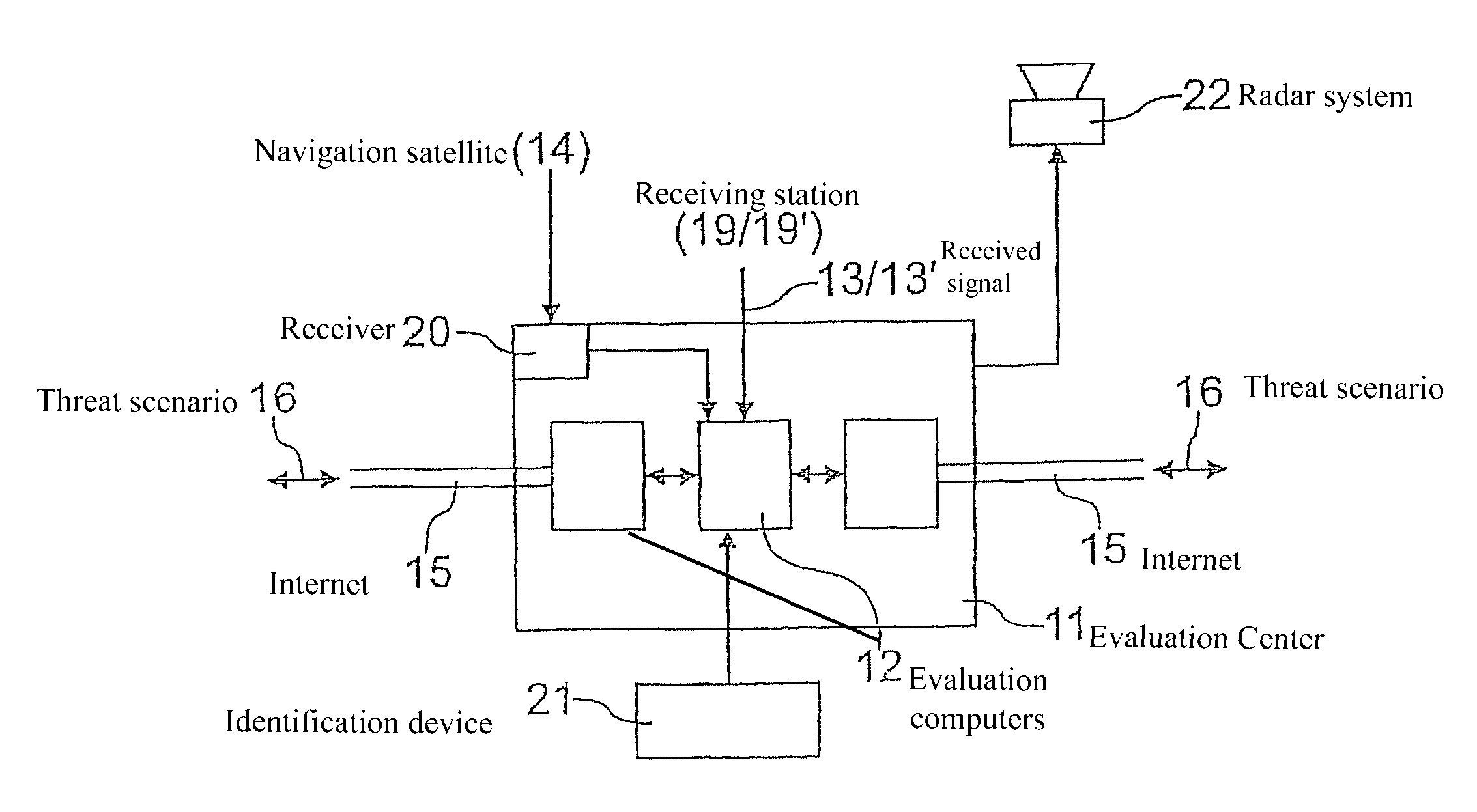
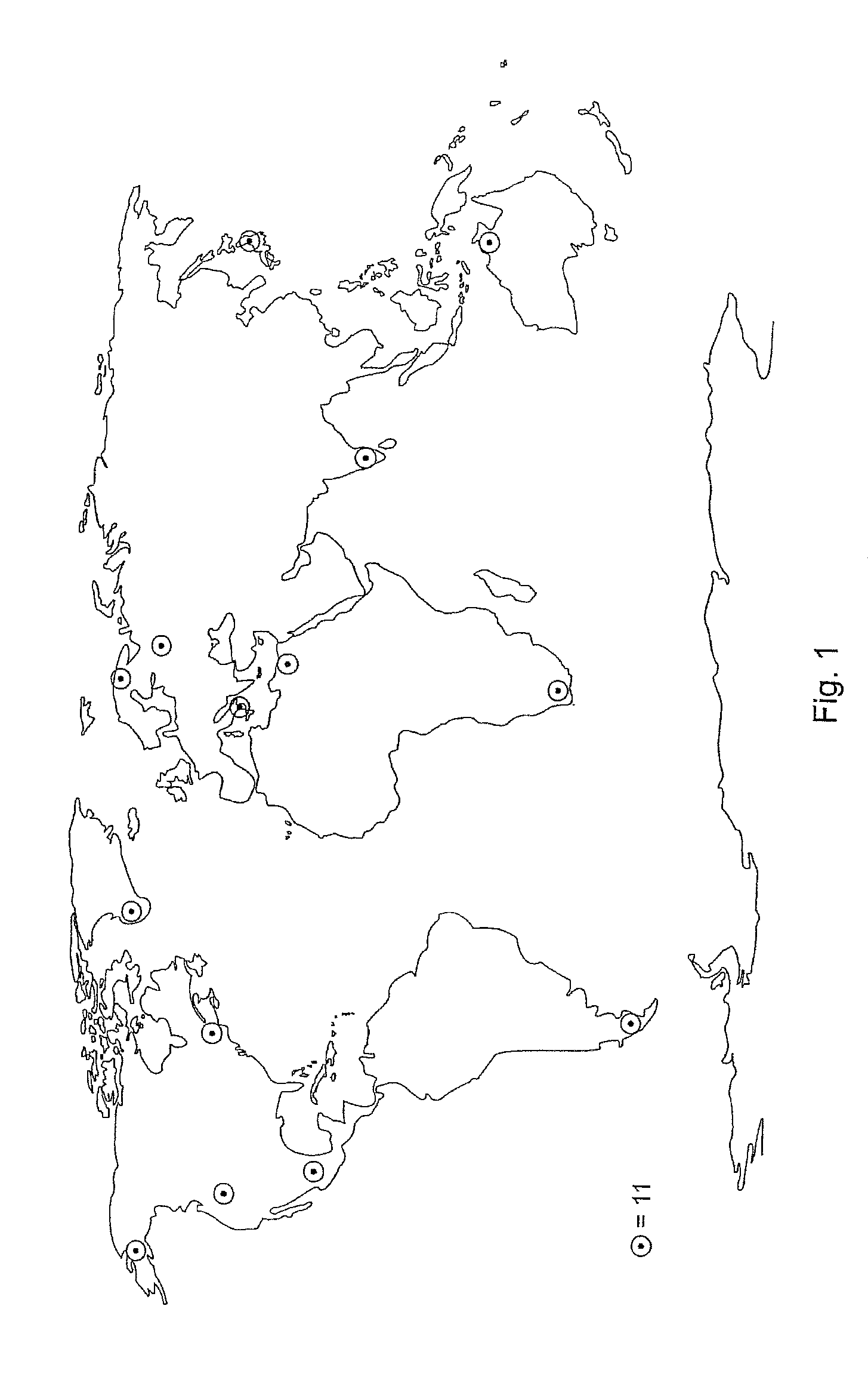
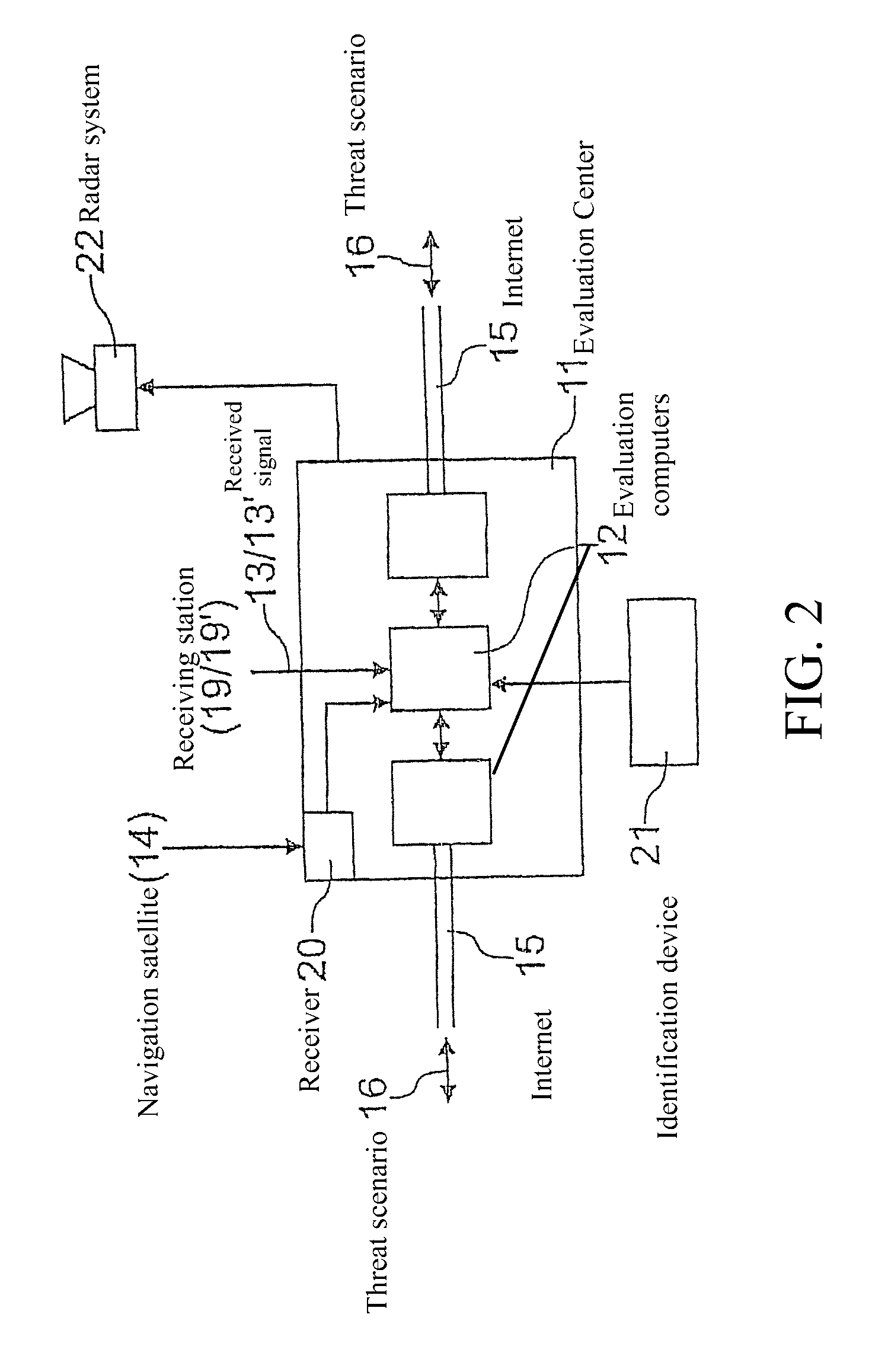
ActiveUS8179310B2Accurate imagingFound more accuratelySatellite radio beaconingRadio wave reradiation/reflectionRadar systemsPassive radar
A method employed for threat analysis based on the passive-radar principle, using the transmitter in navigation satellites, a plurality of receiving stations, which are operated distributed over wide regions, and at least one evaluation center. The receiving stations act as wake-up sensors, transmit their received signals to at least one evaluation center for comparison with expected signals from each navigation satellite and sensing of a threat. Depending on the result, radar systems are operated on a stationary or mobile basis, can then be used with their higher-quality antenna systems on a three-dimensional basis to obtain more precise details relating to a conspicuous entity and the threat which may possibly originate from it in a possible target region or to a mobile or stationary threatened object, and then to make it possible to decide on any currently required protective or defensive measures.
Owner:DIEHL STIFTUNG
Traffic data collection and processing system and control method thereof
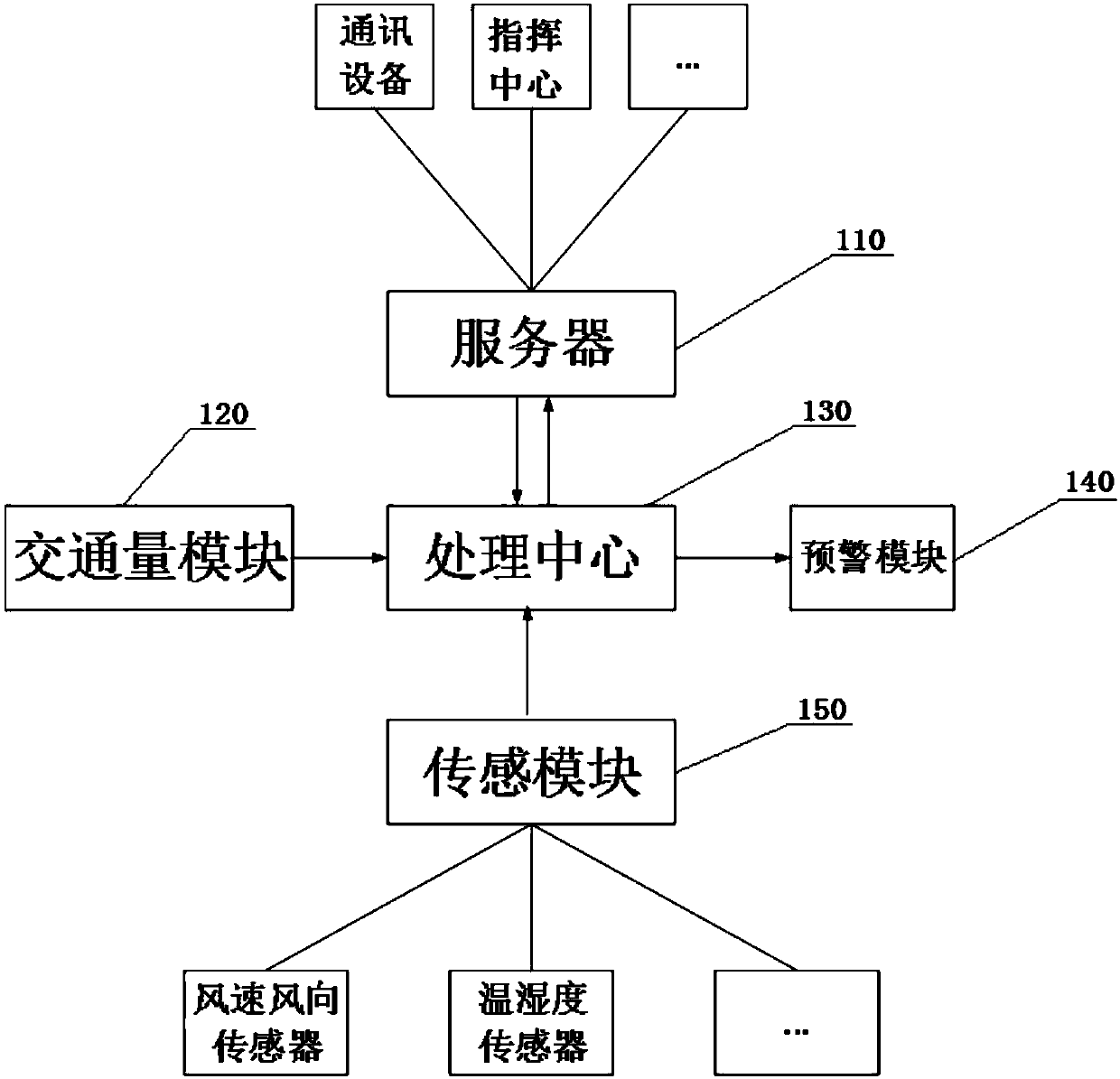
InactiveCN108492554AAvoid in timeAvoid excessive trafficDetection of traffic movementData acquisitionDefensive measure
The present invention discloses a traffic data collection and processing system. The system comprises: a sensing module distributed on a measured road and capable of measuring road meteorological information; a processing center capable of receiving measurement data transmitted by the sensing module and a traffic volume module; and a server connected with the processing center to each other and capable of receiving traffic data transmitted from the processing center, distinguishing the data, transmitting the early warning information to an early warning module through the processing center andtransmitting real-time road conditions to a command center and a communication device. The traffic data collection and processing system and the control method thereof can perform timely understanding of the road capacity, can allow travelers to timely plan a traveling path and can avoid excessive traffic jamming, and moreover, the traffic command center understands the road capacity to timely perform avoidance of some emergency circumstances, timely adopt defensive measures and command means and reduce the disasters caused by traffic inconvenience.
Owner:LIAONING UNIVERSITY OF TECHNOLOGY
Social engineering attack defense method and device
ActiveCN110290155AMeet security protection requirementsTransmissionInternet privacySocial engineering (security)
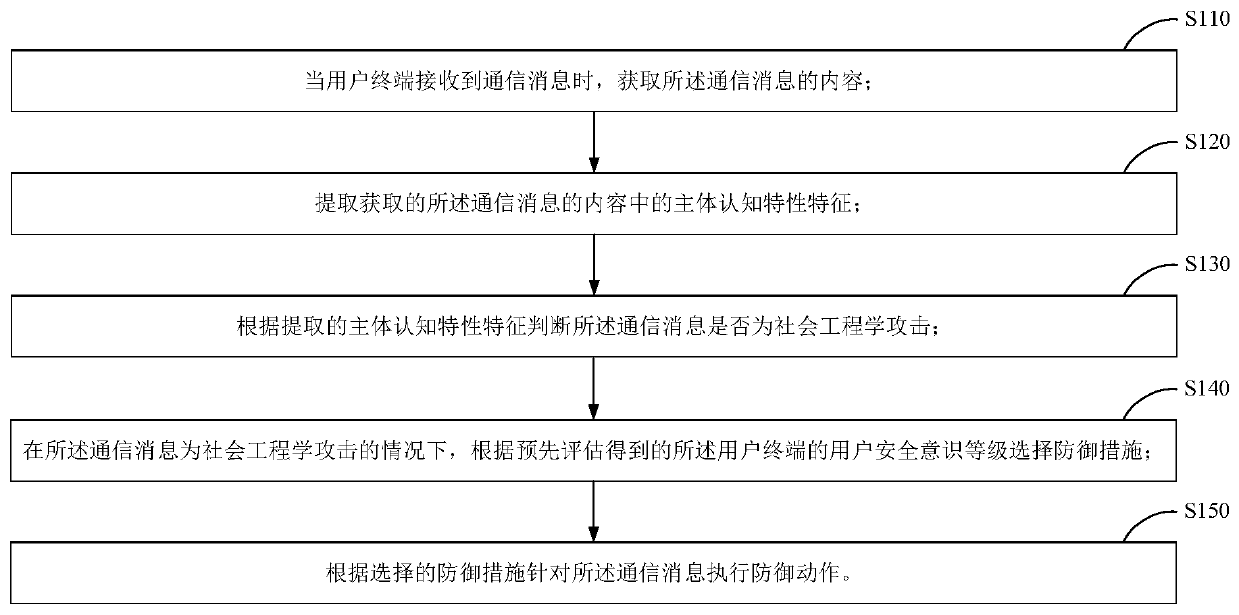
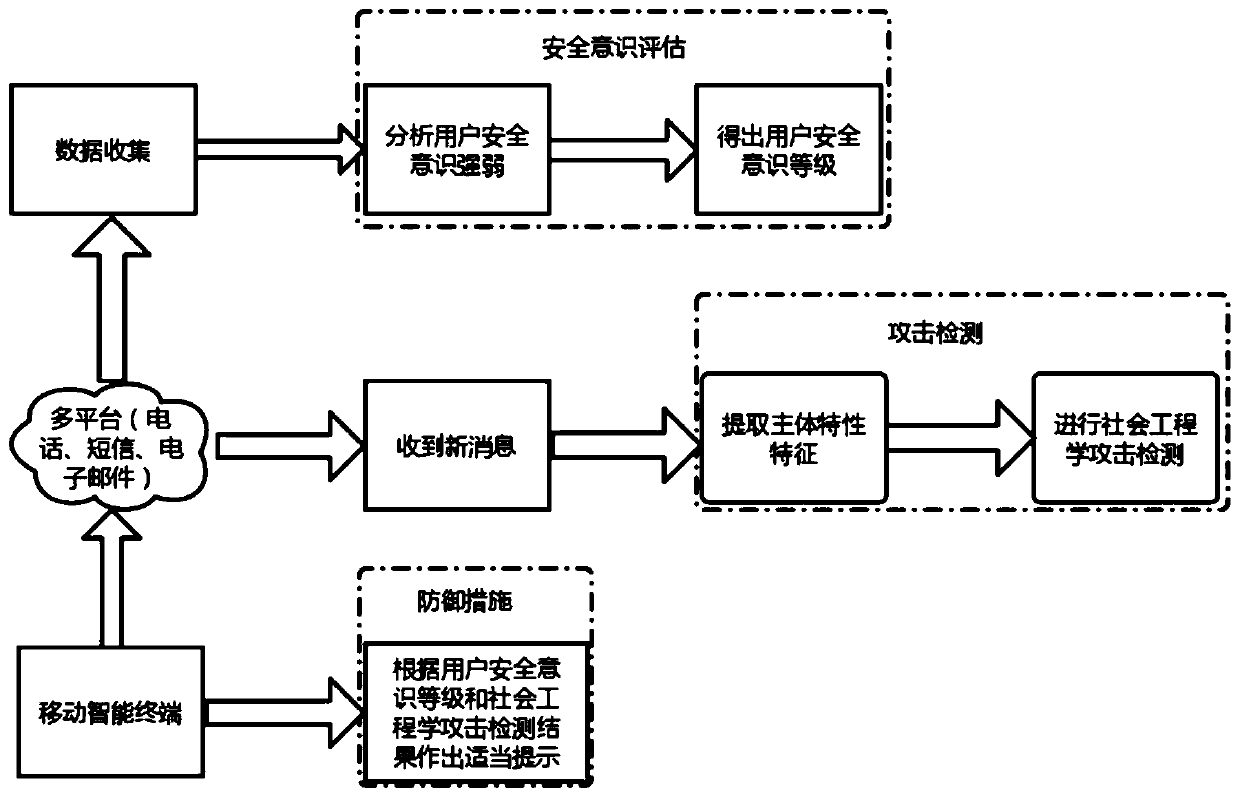
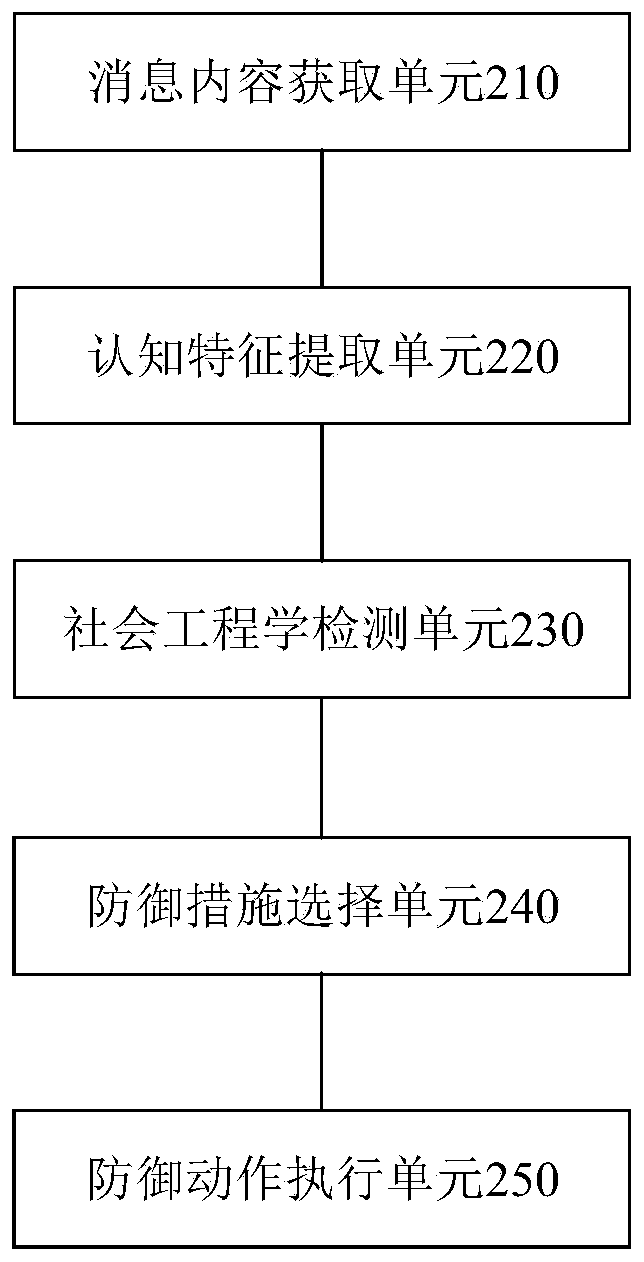
The invention provides a social engineering attack defense method and device, and the method comprises the steps: obtaining the content of a communication message when a user terminal receives the communication message; extracting subject cognitive characteristic characteristics in the acquired content of the communication message; judging whether the communication message is a social engineering attack or not according to the extracted subject cognitive characteristic characteristics; under the condition that the communication message is a social engineering attack, selecting a defense measure according to the pre-evaluated user security awareness level of the user terminal; and executing a defense action on the communication message according to the selected defense measure. According to the scheme, adaptive safety protection is provided for the user, and all-around safety protection requirements of the user are met.
Owner:BEIJING UNIV OF POSTS & TELECOMM
Method and equipment for detecting man-in-the-middle attack by user equipment
ActiveCN108769086AShorten the timeAccurate attack identificationTransmissionMan-in-the-middle attackIp address
The purpose of the invention is to provide a method for detecting man-in-the-middle attack by user equipment. The method comprises the following steps: transmitting a plurality of corresponding TCP (Transmission Control Protocol) handshake requests to a plurality of random IP (Internet Protocol) addresses; determining TCP handshake success count corresponding to the corresponding TCP handshake requests according to whether the corresponding TCP handshake requests succeed in preset time; and determining whether man-in-the-middle attack does not exist or not in a current network of the user equipment if the TCP handshake success count is less than or equal to a TCP handshake success threshold. According to the method disclosed by the invention, SSLSniff man-in-the-middle attack, SSLStrip man-in-the-middle attack and website distortion man-in-the-middle attack in the man-in-the-middle attack can be actively detected, the coverage area is wide, the man-in-the-middle attack is rapidly recognized, the user waiting time is greatly shortened, and the user side can conveniently take corresponding defensive measures in the shortest time.
Owner:上海尚往网络科技有限公司
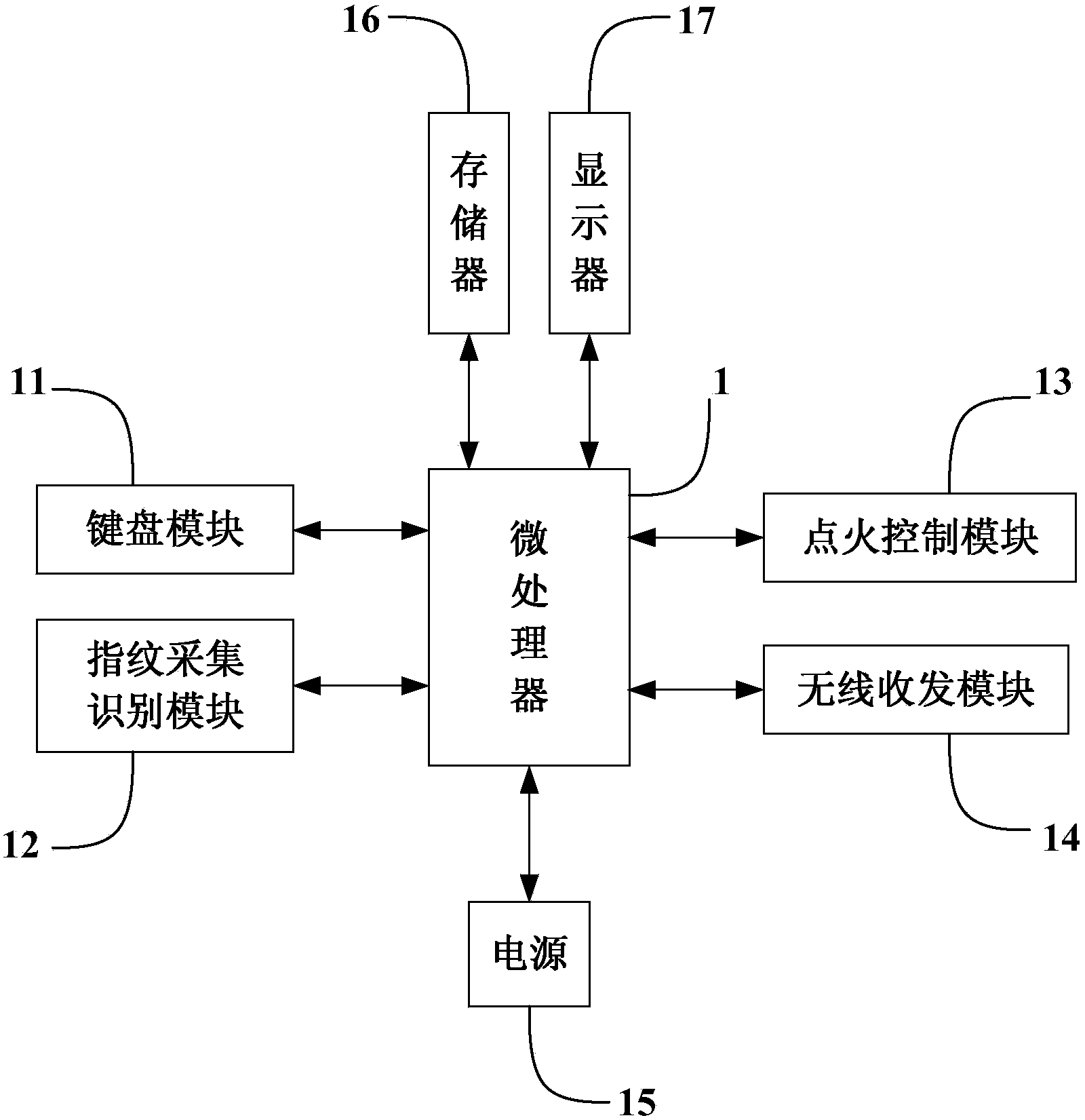
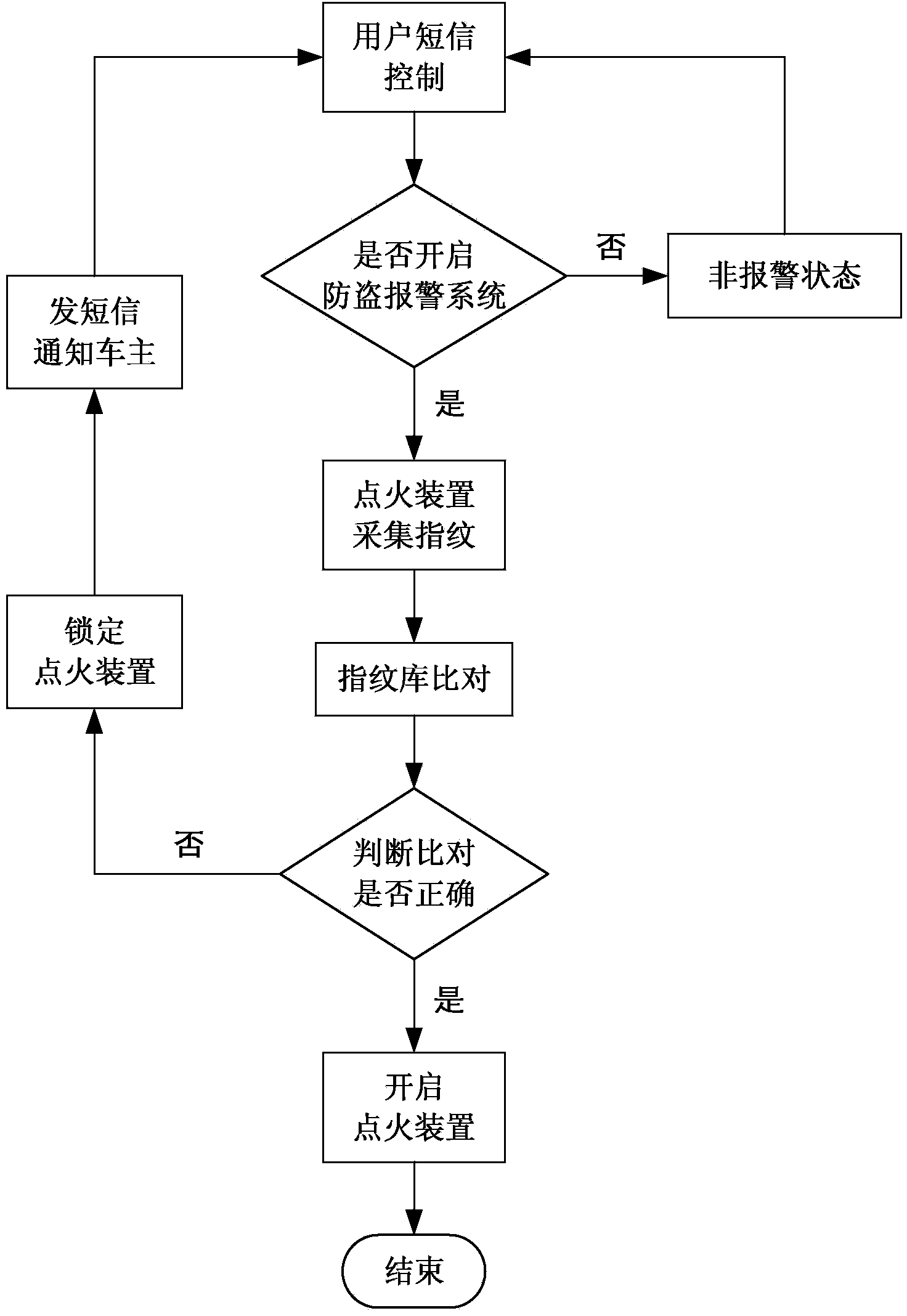
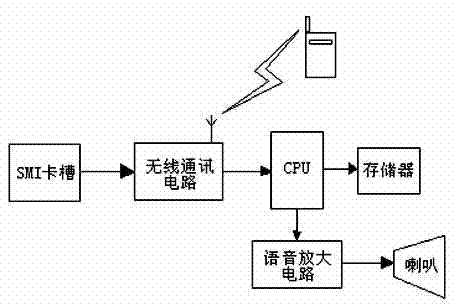
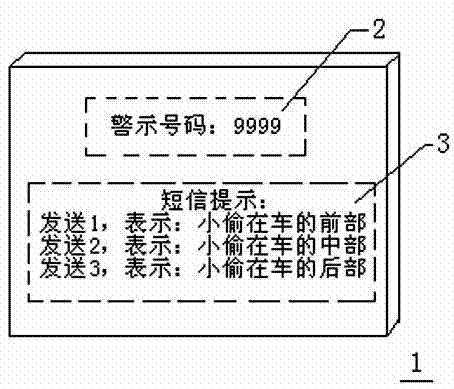
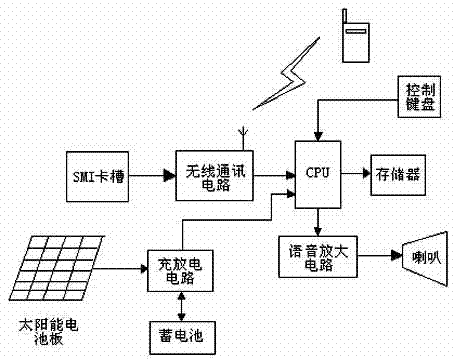
Automobile anti-theft alarm system based on fingerprint recognition and GSM
The invention discloses an automobile anti-theft alarm system based on fingerprint recognition and GSM. The automobile anti-theft alarm system comprises a keyboard module, a fingerprint acquisition recognition module, an ignition control module, a wireless transceiving module, a power supply, a memorizer and a display. When the anti-theft system is powered on, the ignition device can be powered on only when fingerprint recognition is qualified; if the fingerprint recognition does not succeed, a short message is immediately sent to an automobile owner, and then the automobile owner can take defensive measures. The automobile owner can also control the anti-theft alarm system to be powered on or powered off through short messages. By adopting the automobile anti-theft alarm system, the security and the reliability of the automobile anti-theft alarm system are effectively improved.
Owner:WUXI GANGWAN NETWORK TECH
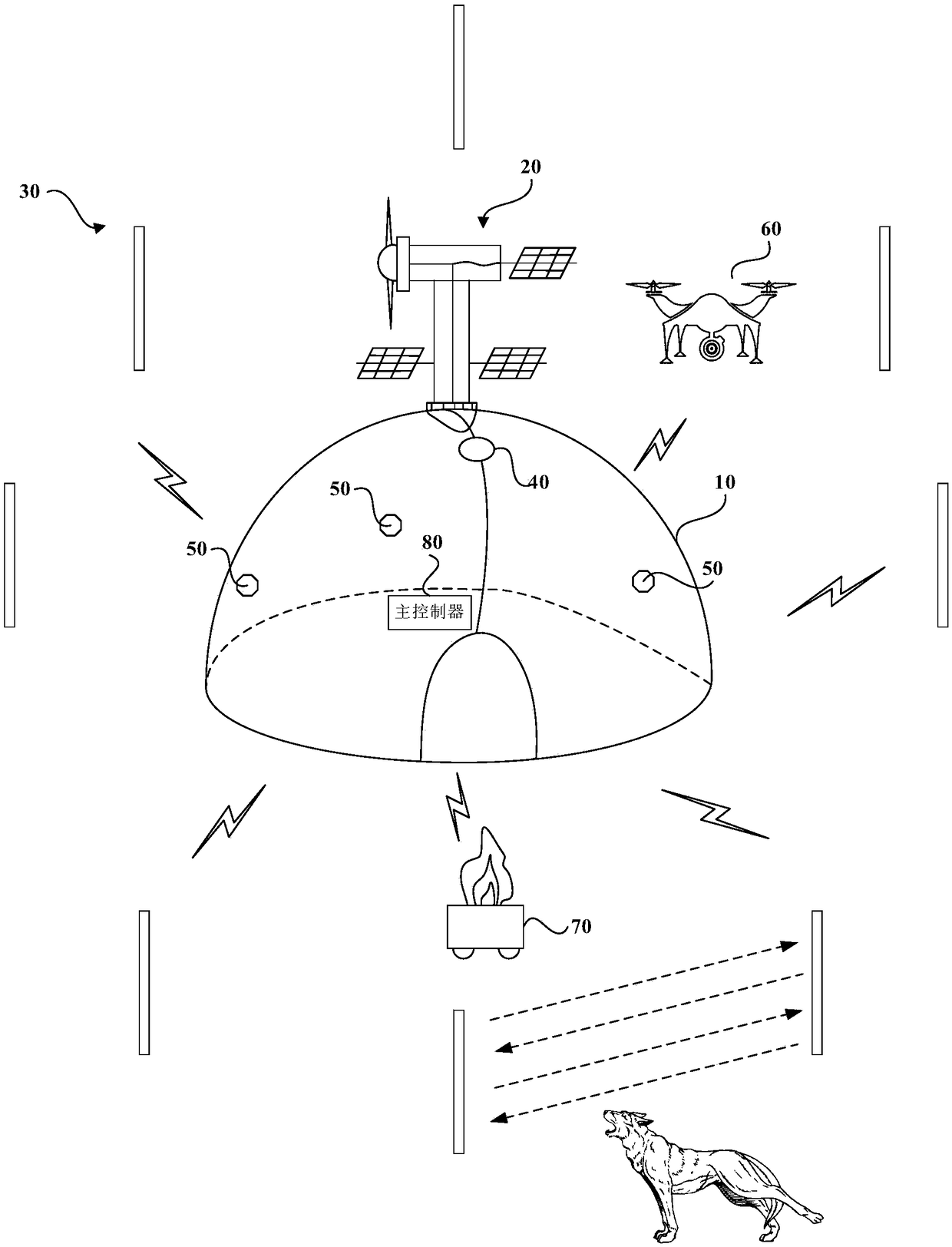
Outdoor intelligent tent system based on clean energy sources and unmanned aerial vehicle
The embodiment of the invention provides an outdoor intelligent tent system based on clean energy sources and an unmanned aerial vehicle. The outdoor intelligent tent system comprises a tent, clean energy source power generation equipment, a plurality of infrared curtain walls, passive type infrared detectors, a plurality of wireless proximity sensors, the unmanned aerial vehicle, electronic bonfire equipment and a main controller. Four early warning and defensive measures are constructed, as for the first early warning and defensive measure, the unmanned aerial vehicle is controlled to achieve patrol in an area with the distance to the tent being about 1000 m or more; as for the second early warning and defensive measure, the infrared curtain walls are constructed around the tent by 100 m, and various complex types of joint driving-away operation is conducted by utilizing the unmanned aerial vehicle; as for the third early warning and defensive measure, the passive type infrared alarmmeans is arranged around the tent by 10 m, and further driving-away operation is conducted on invading wild animals by matching with starting of an electronic bonfire device; as for the fourth earlywarning and defensive measure, the proximity sensors with the detection range being 0.01 m and a low-strength defensive power grid cover are arranged on a tent body; and the camping safety of field expedition personnel is ensured though the four early warning and defensive measures.
Owner:郭树军
Method for realizing anti-theft warning on buses
InactiveCN102339509AGood practical valueDeter criminal activityTelephonic communicationMessaging/mailboxes/announcementsDefensive measureEngineering
Owner:程勇
Method and Circuit Arrangement for Protecting Against Scanning of an Address Space
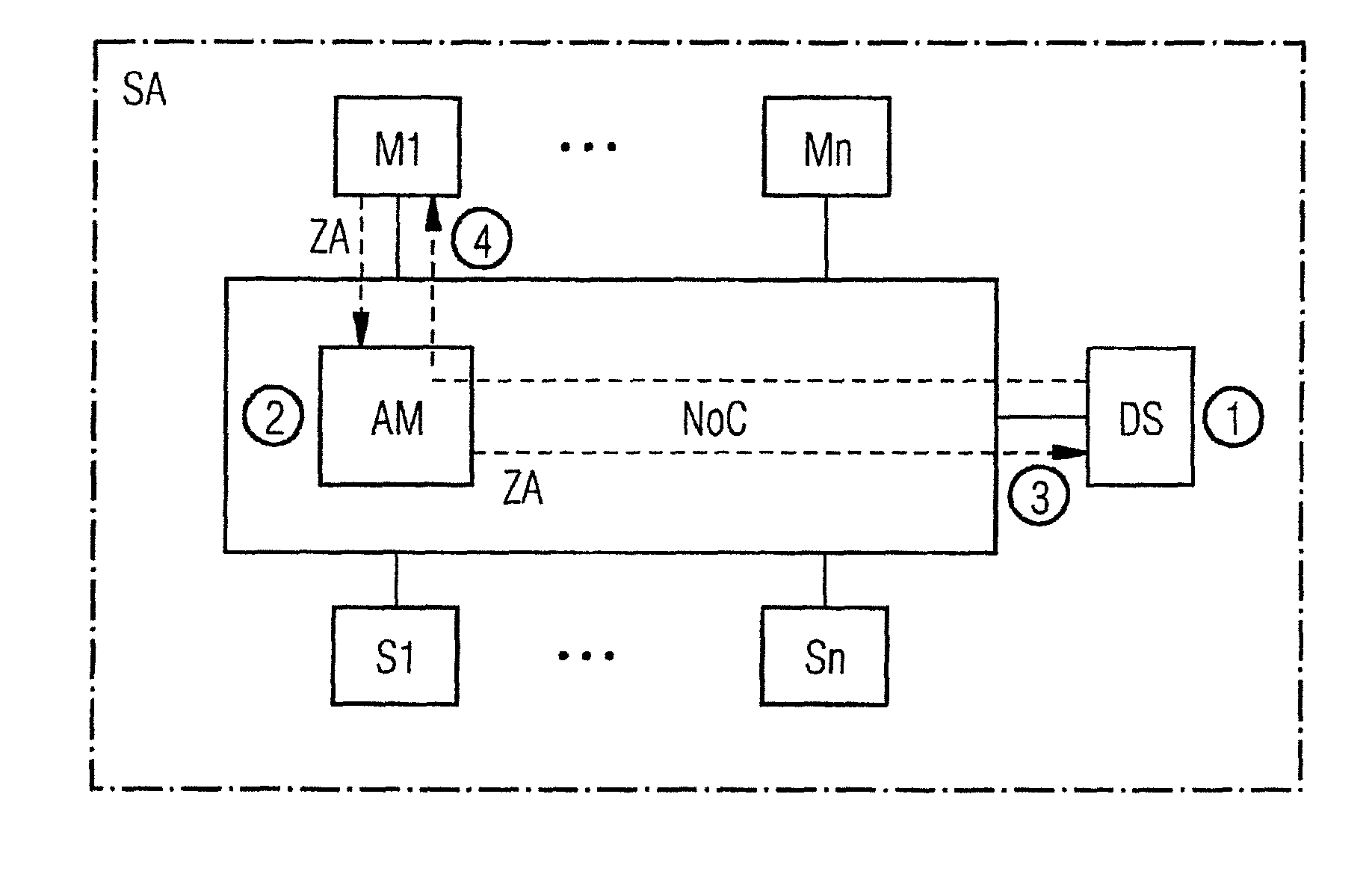
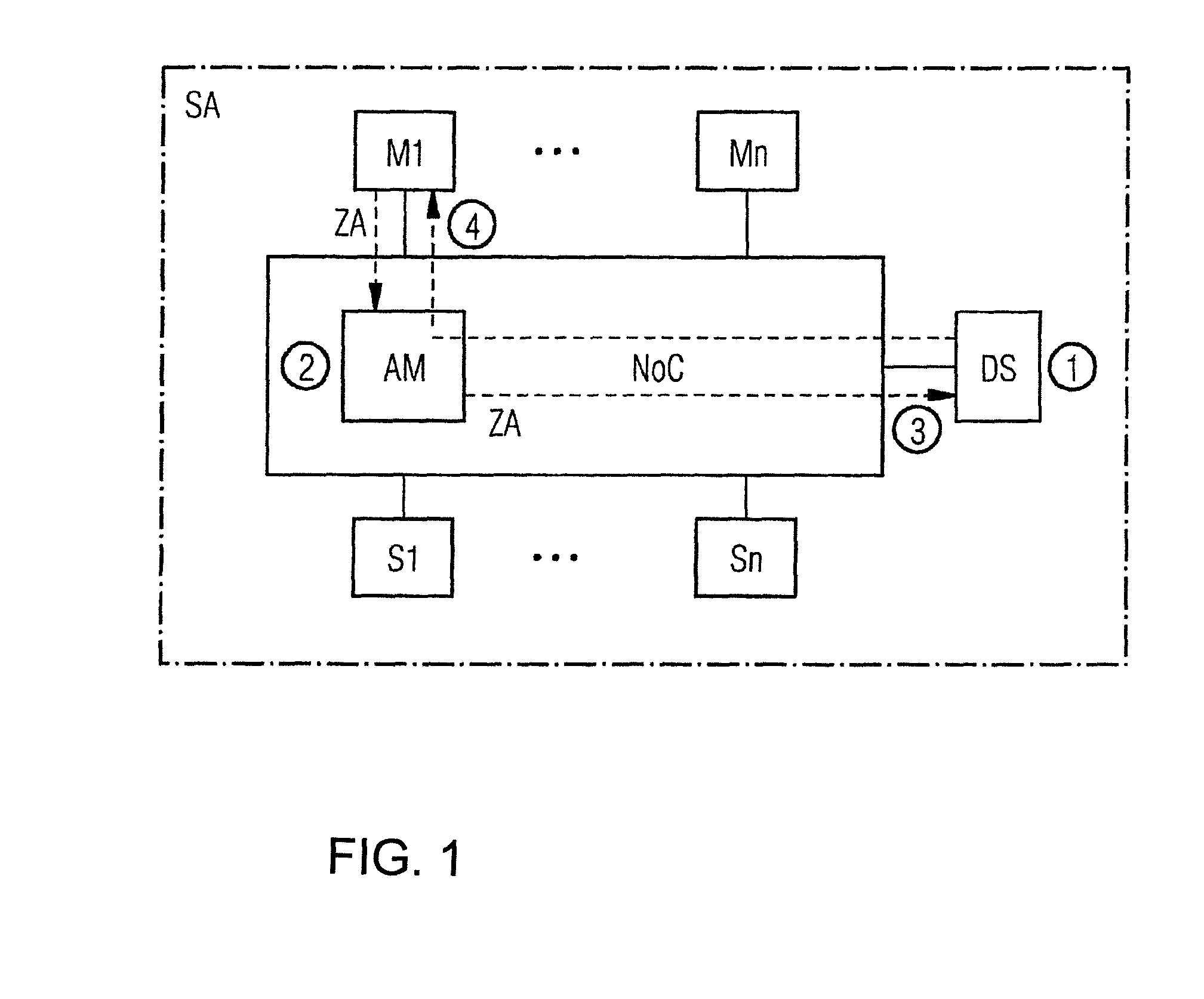
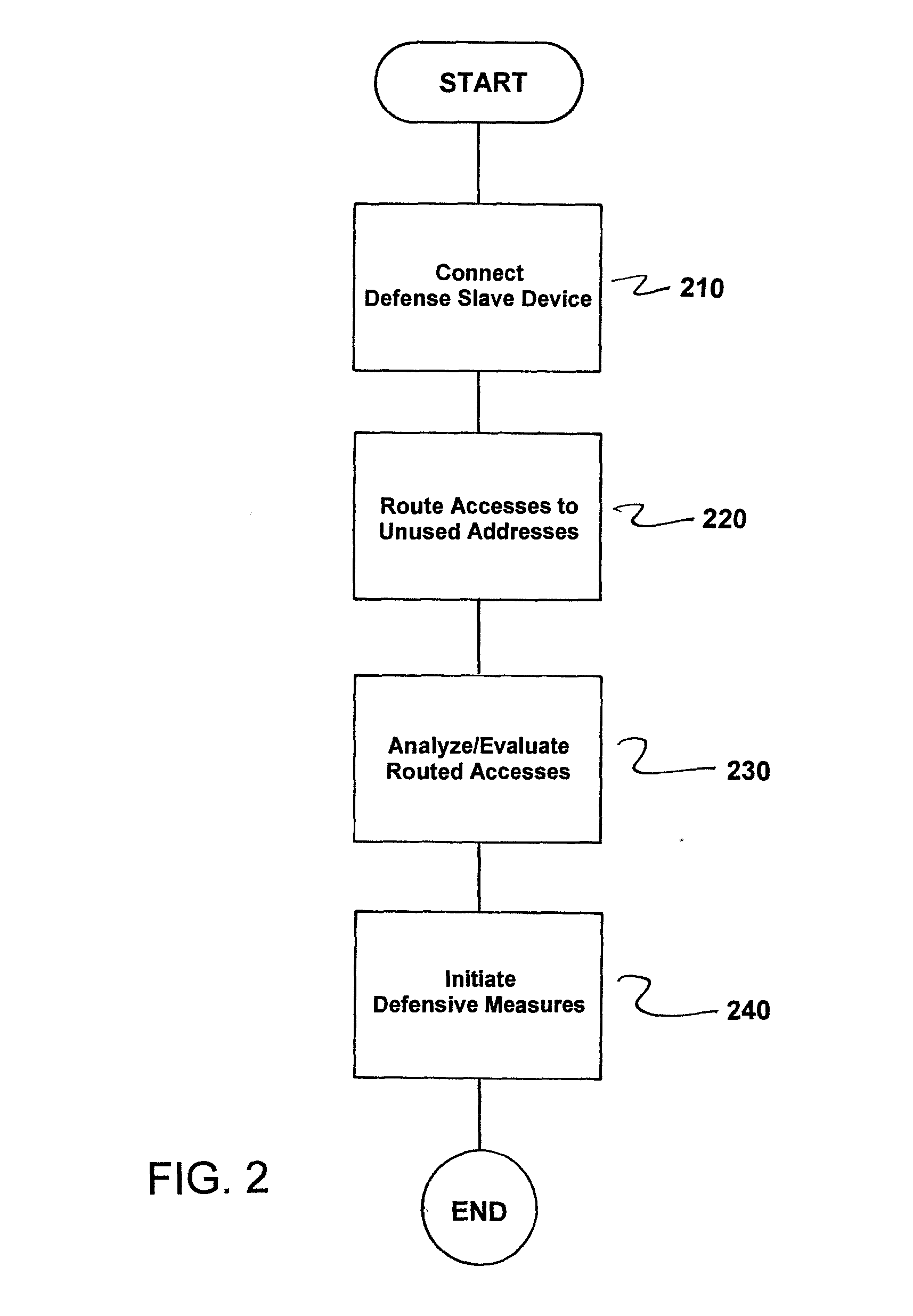
ActiveUS20160203341A1Avoid scanningMemory loss protectionError detection/correctionEngineeringDefensive measure
A circuit arrangement and method for securing an integrated electronic circuit against scans of an address space, wherein the circuit arrangement has at least one master unit and at least one slave unit interconnected via a bus system for access of the master unit to the slave unit, and addresses are used from an address space that is allocated and used in accordance with functionalities of the integrated electronic circuit, where a defense slave unit is connected to the bus system, access to unused address regions of the address space are forwarded to the defense slave unit, the access is analyzed and evaluated by the defense slave unit and depending on an analysis result and the respective access type, defensive measures are triggered, such that address space scans are interrupted or a potential scan result is rendered useless in a simple manner.
Owner:SIEMENS AG OESTERR
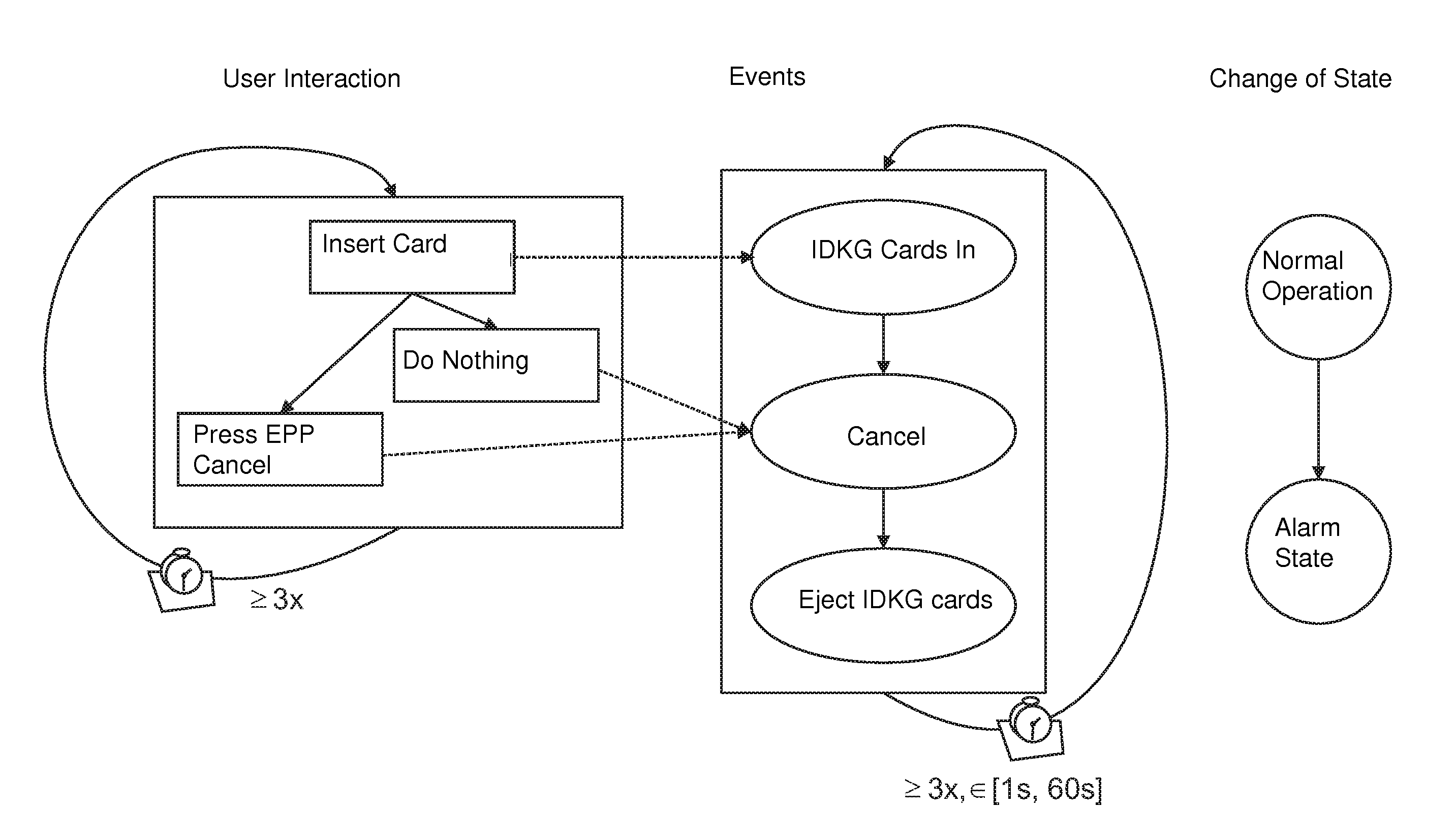
Method and device for recognizing attacks on a self-service machine
ActiveUS20110179485A1High accuracy rateIncrease chanceComplete banking machinesMemory loss protectionDefensive measureSelf-service
The invention relates to a method for recognizing attacks on at least one interface of a computer system, particularly a self-service machine, comprising: monitoring the interface in order to detect changes to the interface; if changes occur, the probability of an impermissible attack on the interface is determined based on the nature of the change; if the probability is above a defined threshold value, defensive measures are taken.
Owner:DIEBOLD NIXDORF SYST GMBH
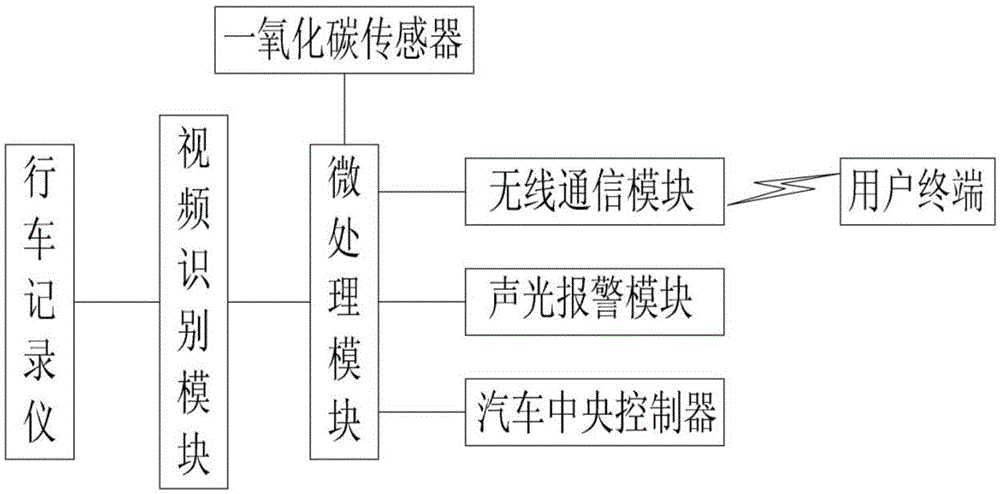
Automobile alarm system based on video identification
InactiveCN105416233AReduce property damageAvoid poisoningAnti-theft devicesDefensive measureComputer terminal
The invention discloses an automobile alarm system based on video identification. The automobile alarm system comprises an automobile data recorder, a video identification module, a micro-processing module, a wireless communication module and a sound-light alarm module. The automobile data recorder is used for recording video information in real time. The input end of the video identification module is connected with the output end of the automobile data recorder and the video identification module is used for analyzing and processing data output by the automobile data recorder and meanwhile inputting the processed result into the micro-processing module. The output end of the micro-processing module is connected with the wireless communication module and the sound-light alarm module and the micro-processing module is used for controlling communication of the wireless communication module and a user terminal according to the processed result of the video identification module or controlling the sound-light alarm module to give out an alarm signal. According to the automobile alarm system, the video information surrounding an automobile is analyzed through the video identification function, effective identification and predication can be conducted on abnormal conditions so that corresponding defensive measures can be made by an owner of the automobile in time, and the property loss is reduced to the maximum for the owner of the automobile.
Owner:CHONGQING HORSE SHIELD TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com