Patents
Literature
124 results about "Attack surface" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
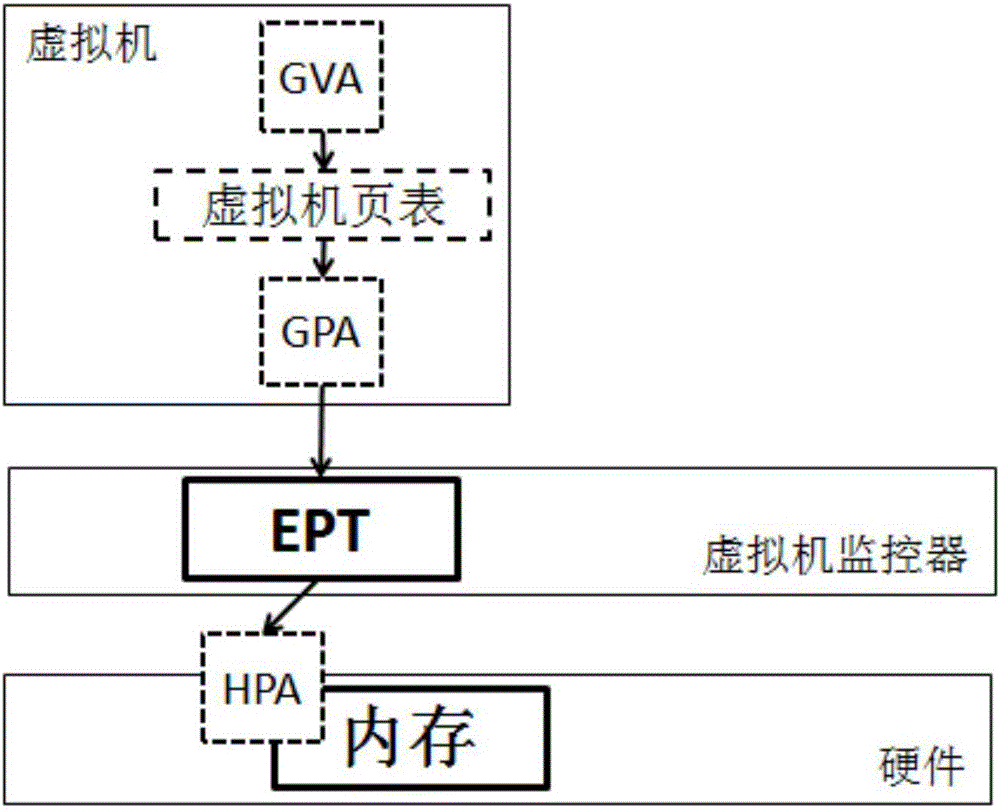
The attack surface of a software environment is the sum of the different points (the "attack vectors") where an unauthorized user (the "attacker") can try to enter data to or extract data from an environment. Keeping the attack surface as small as possible is a basic security measure.
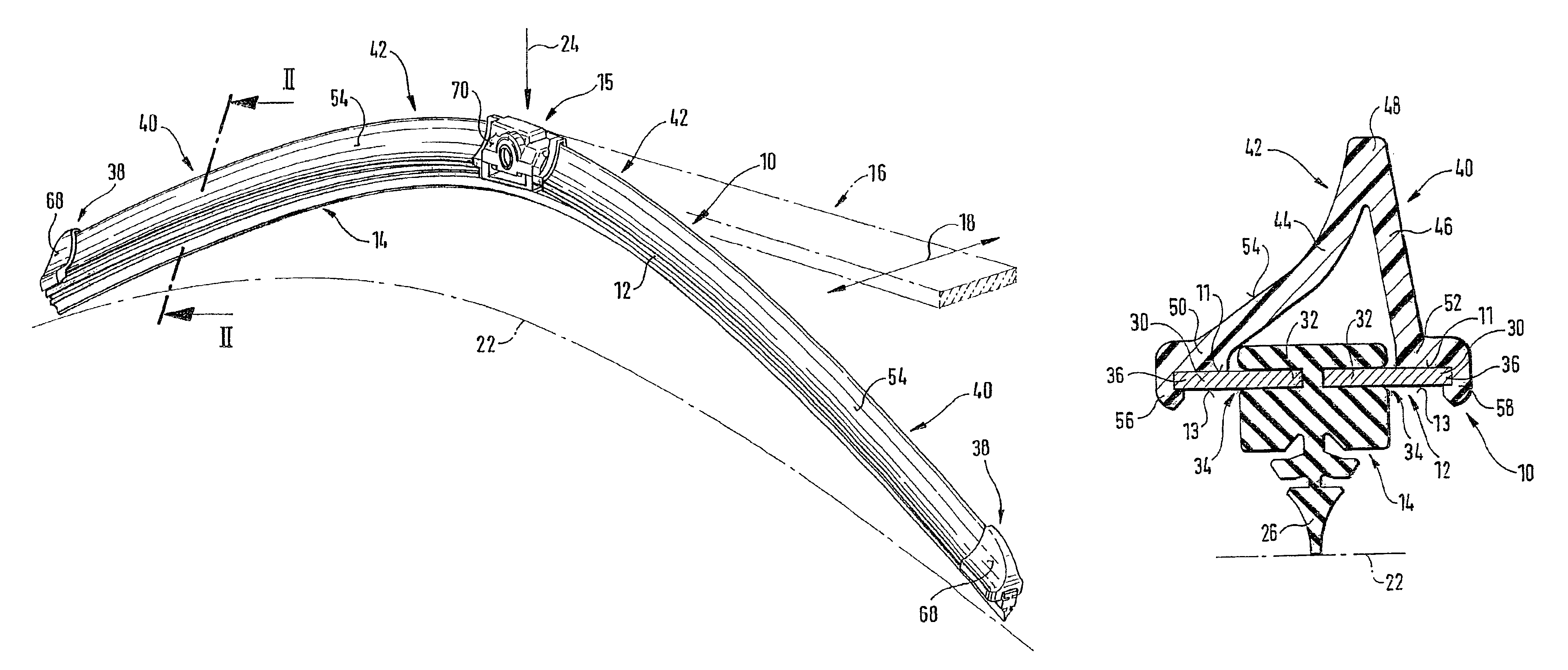
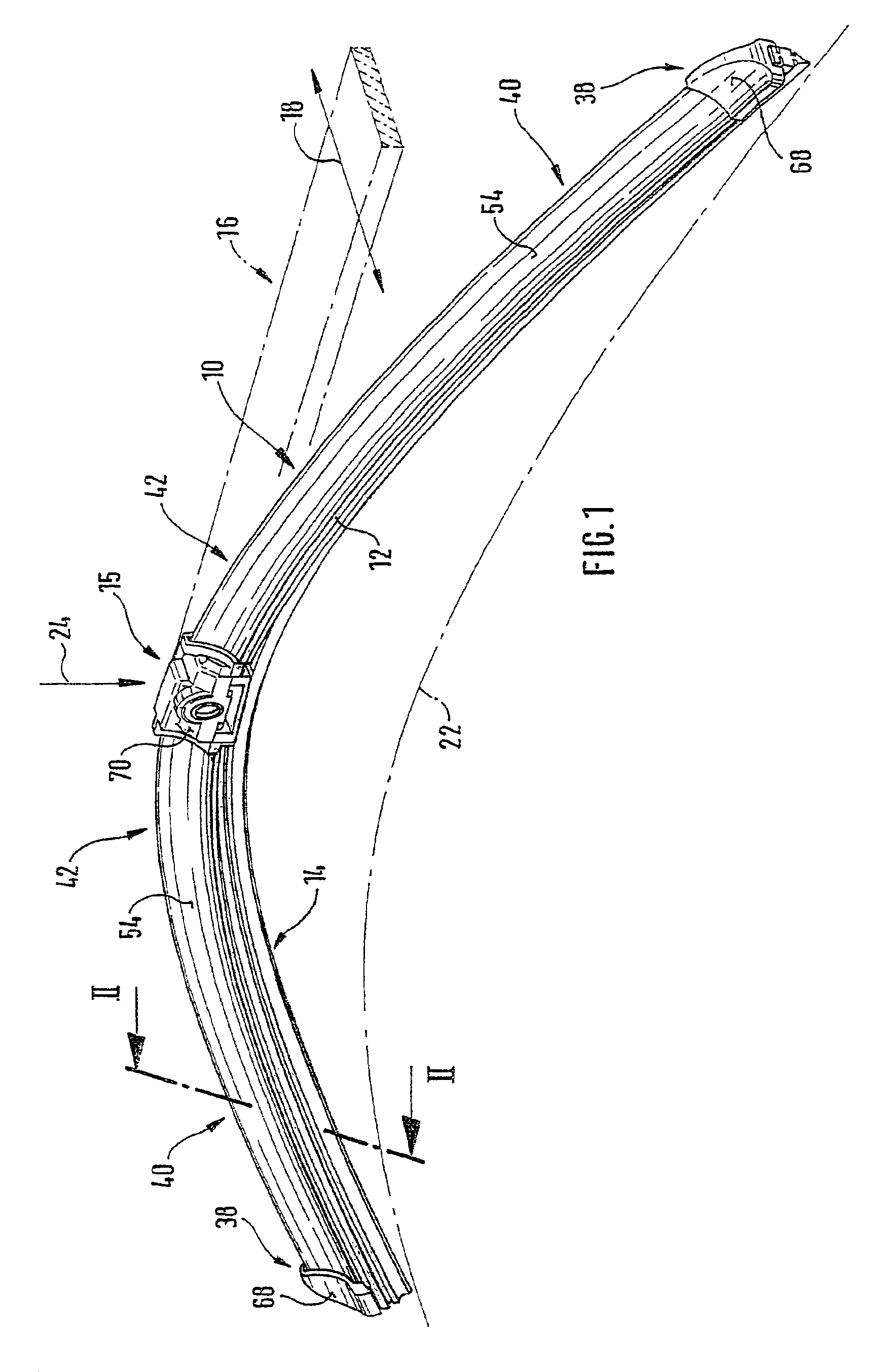
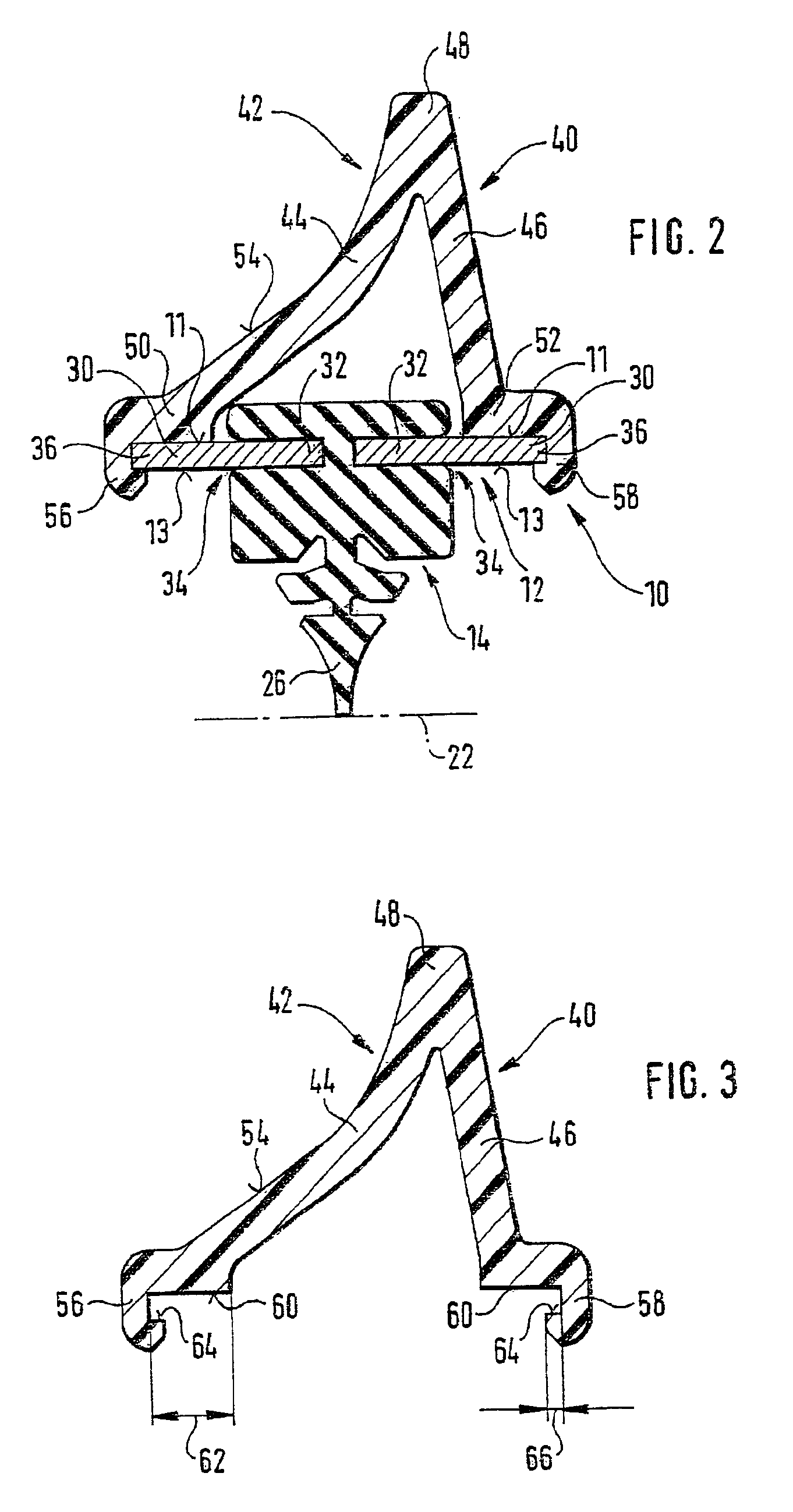
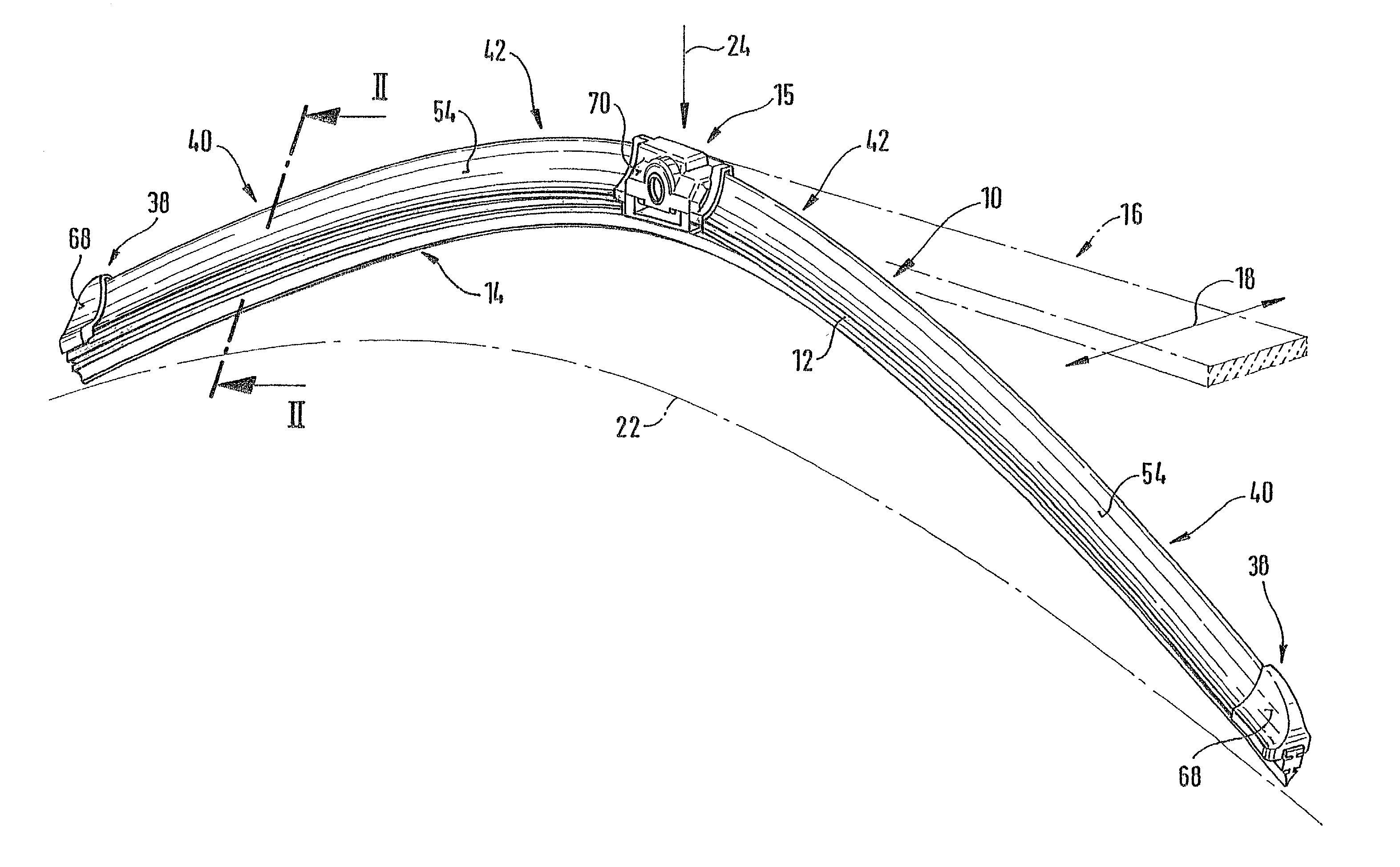
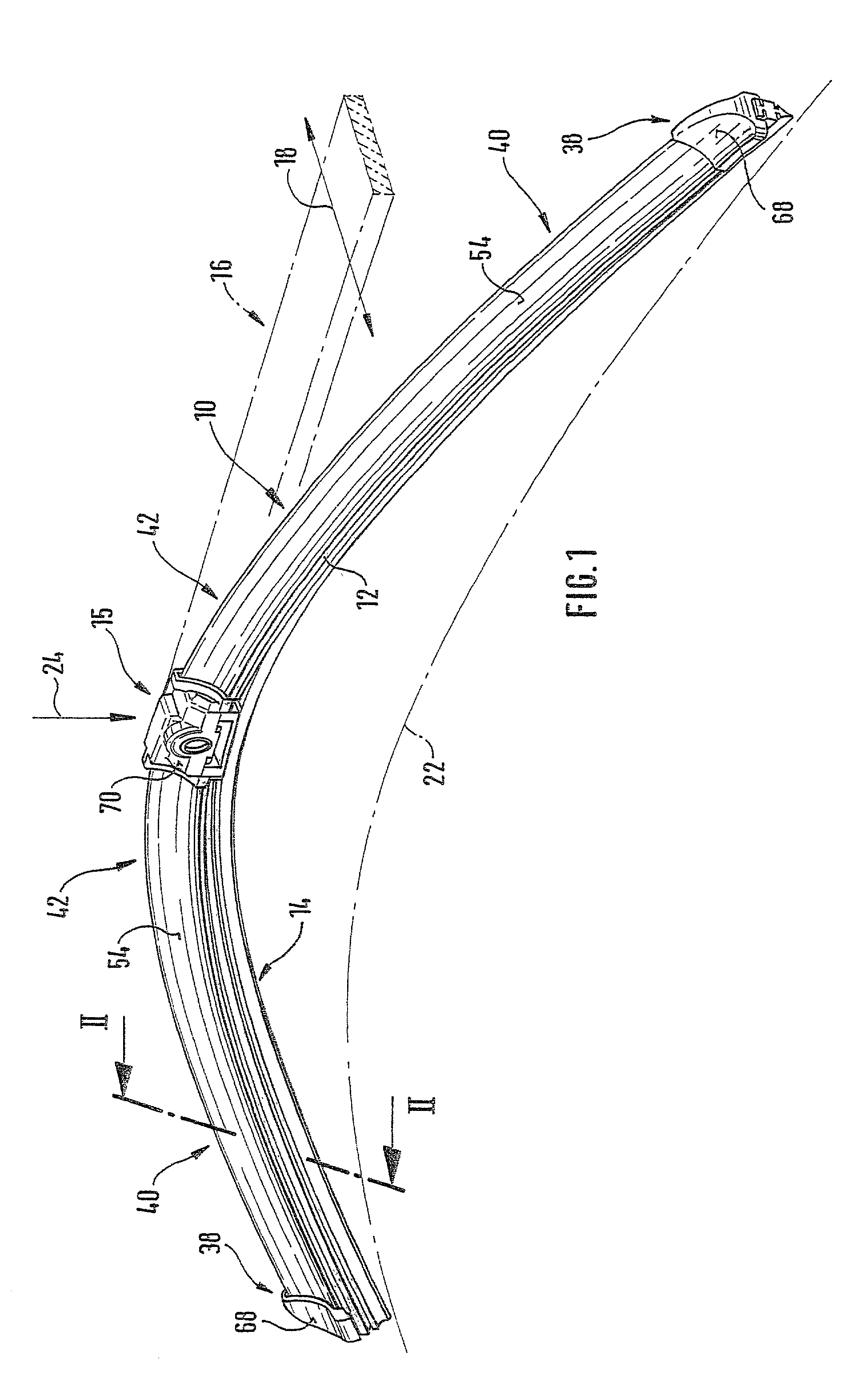
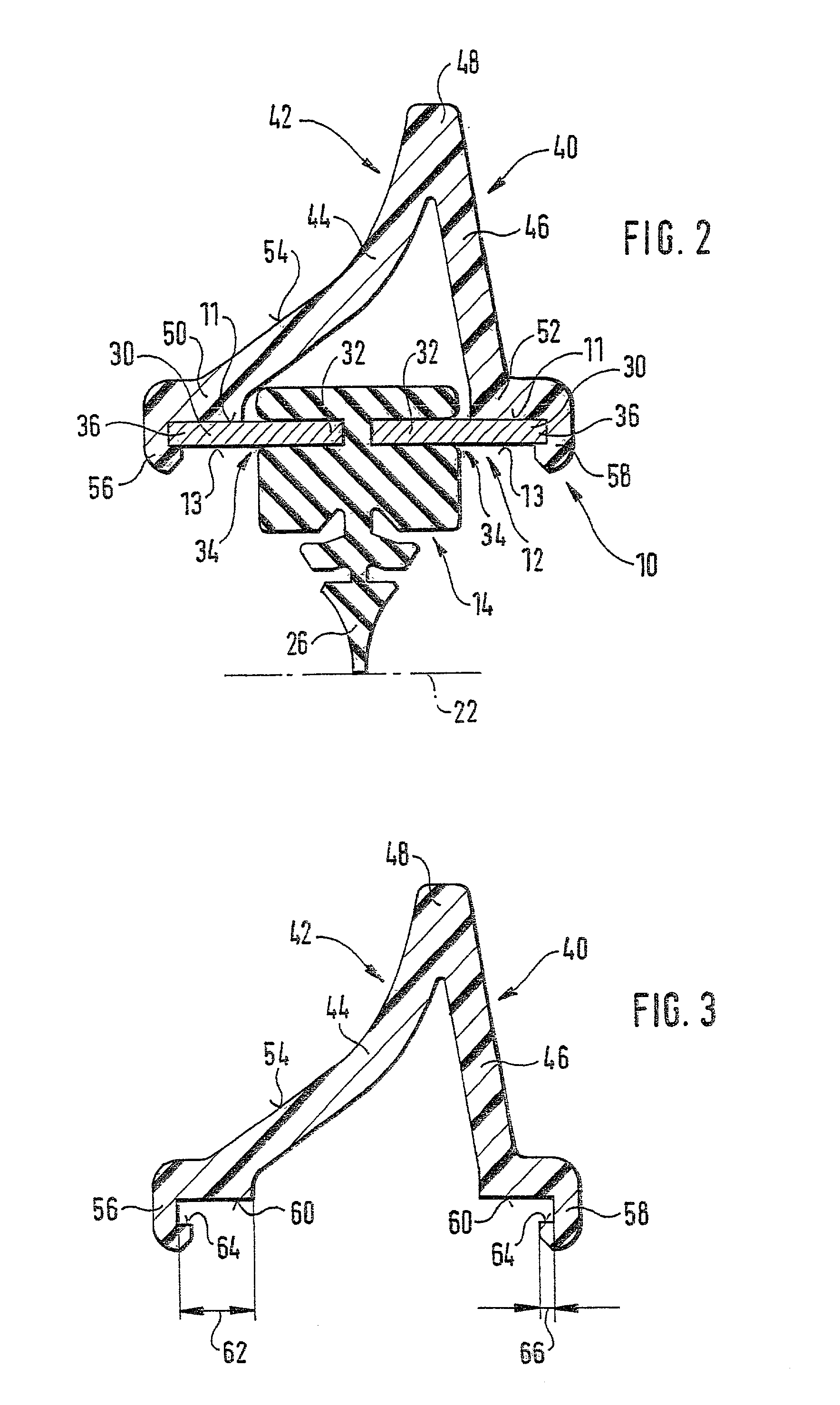
Wiper blade for cleaning screens in particular on motor vehicles
InactiveUS6944905B2Reduce weightSave materialWindow cleanersVehicle cleaningBand shapeMotorized vehicle
A wiper blade for cleaning motor vehicles is proposed, which is provided with a band-like, elongated, spring-elastic support element (12). The lower band surface (13) of the support element (12) oriented toward the window (22) has an elongated, rubber-elastic wiper strip (14), which can be placed against the window (22), disposed on it so that the longitudinal axes of these two parts are parallel and the upper band surface (11) of the support element (12) has a wind deflection strip (42) disposed on it, which extends in the longitudinal direction of the support element, is provided with an attack surface (54) oriented toward the main flow of the relative wind, and is comprised of an elastic material. A considerable weight savings for the wiper blade is achieved if the wind deflection strip (42, 142, or 242) has two diverging legs (44, 46), viewed in cross section, which are connected to each other at a common base (48) and whose free ends (50, 52) oriented toward the window (22) are supported on the wiper blade (10), and the attack surface (54) is embodied on the outside of the one leg (44).
Owner:ROBERT BOSCH CORP
Wiper blade for cleaning screens in particular on motor vehicles
InactiveUS20020133897A1Reduce weightSave materialWindow cleanersVehicle cleaningCommon baseMobile vehicle
A wiper blade for cleaning motor vehicles is proposed, which is provided with a band-like, elongated, spring-elastic support element (12). The lower band surface (13) of the support element (12) oriented toward the window (22) has an elongated, rubber-elastic wiper strip (14), which can be placed against the window (22), disposed on it so that the longitudinal axes of these two parts are parallel and the upper band surface (11) of the support element (12) has a wind deflection strip (42) disposed on it, which extends in the longitudinal direction of the support element, is provided with an attack surface (54) oriented toward the main flow of the relative wind, and is comprised of an elastic material. A considerable weight savings for the wiper blade is achieved if the wind deflection strip (42, 142, or 242) has two diverging legs (44, 46), viewed in cross section, which are connected to each other at a common base (48) and whose free ends (50, 52) oriented toward the window (22) are supported on the wiper blade (10), and the attack surface (54) is embodied on the outside of the one leg (44).
Owner:ROBERT BOSCH CORP
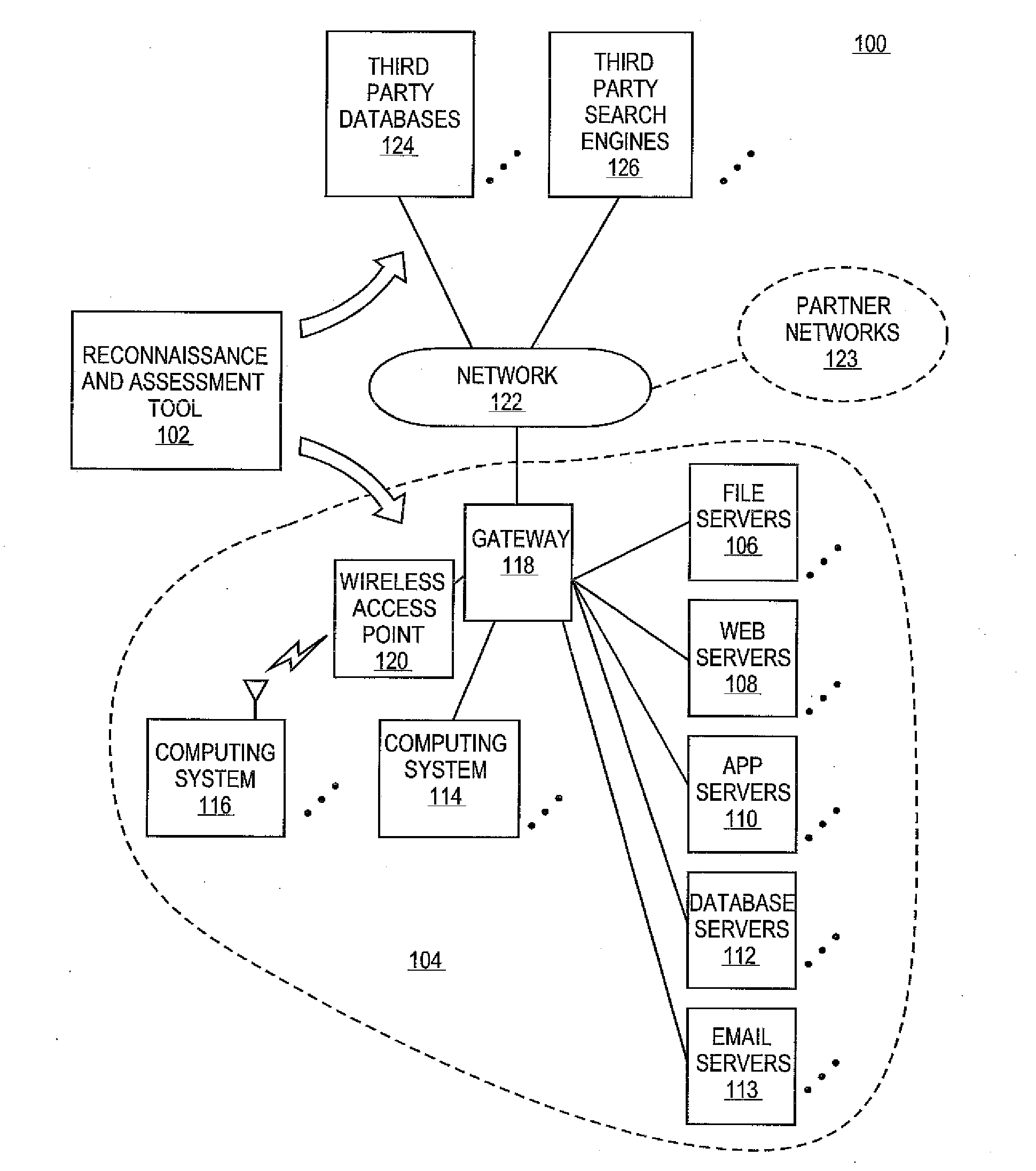
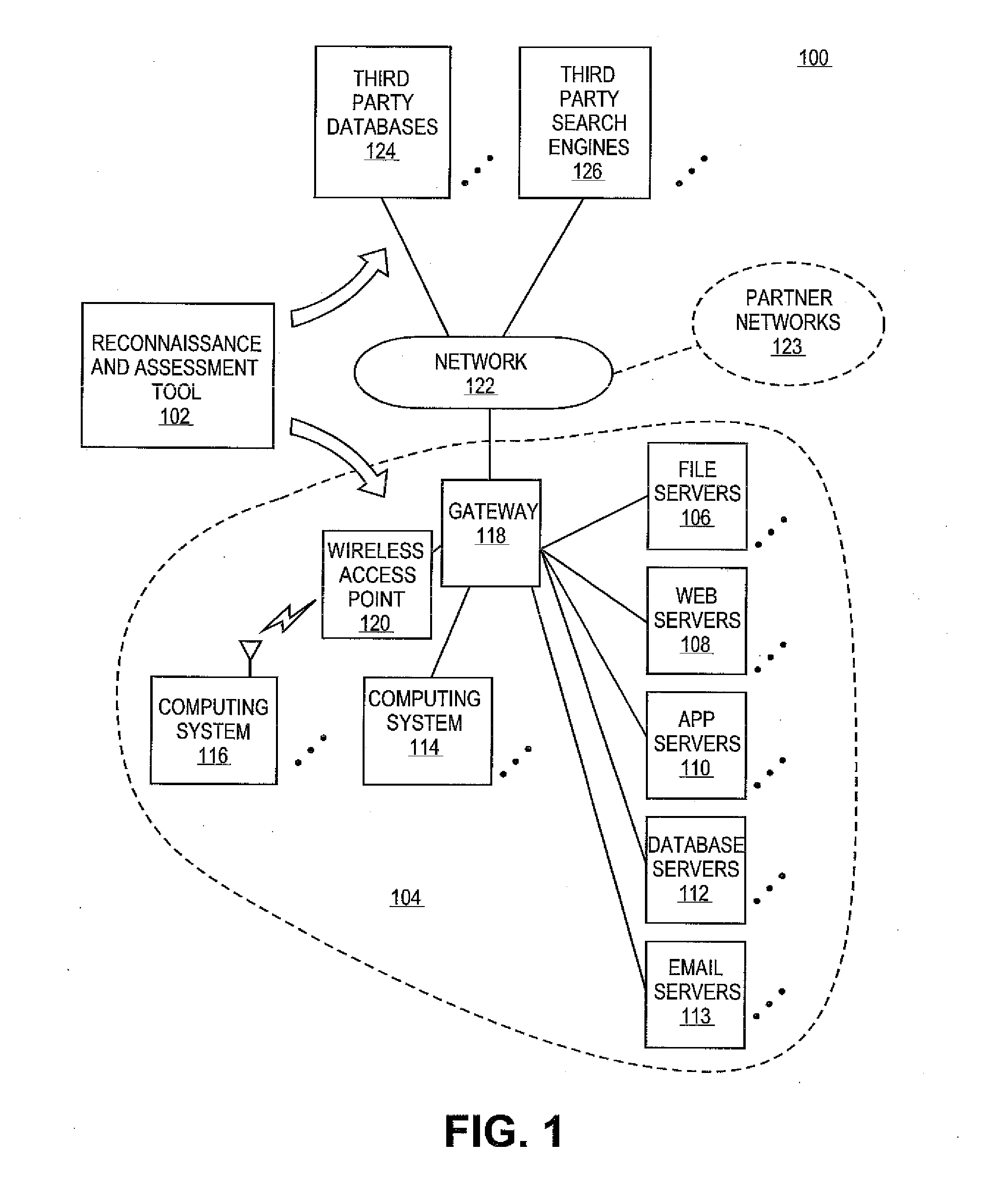
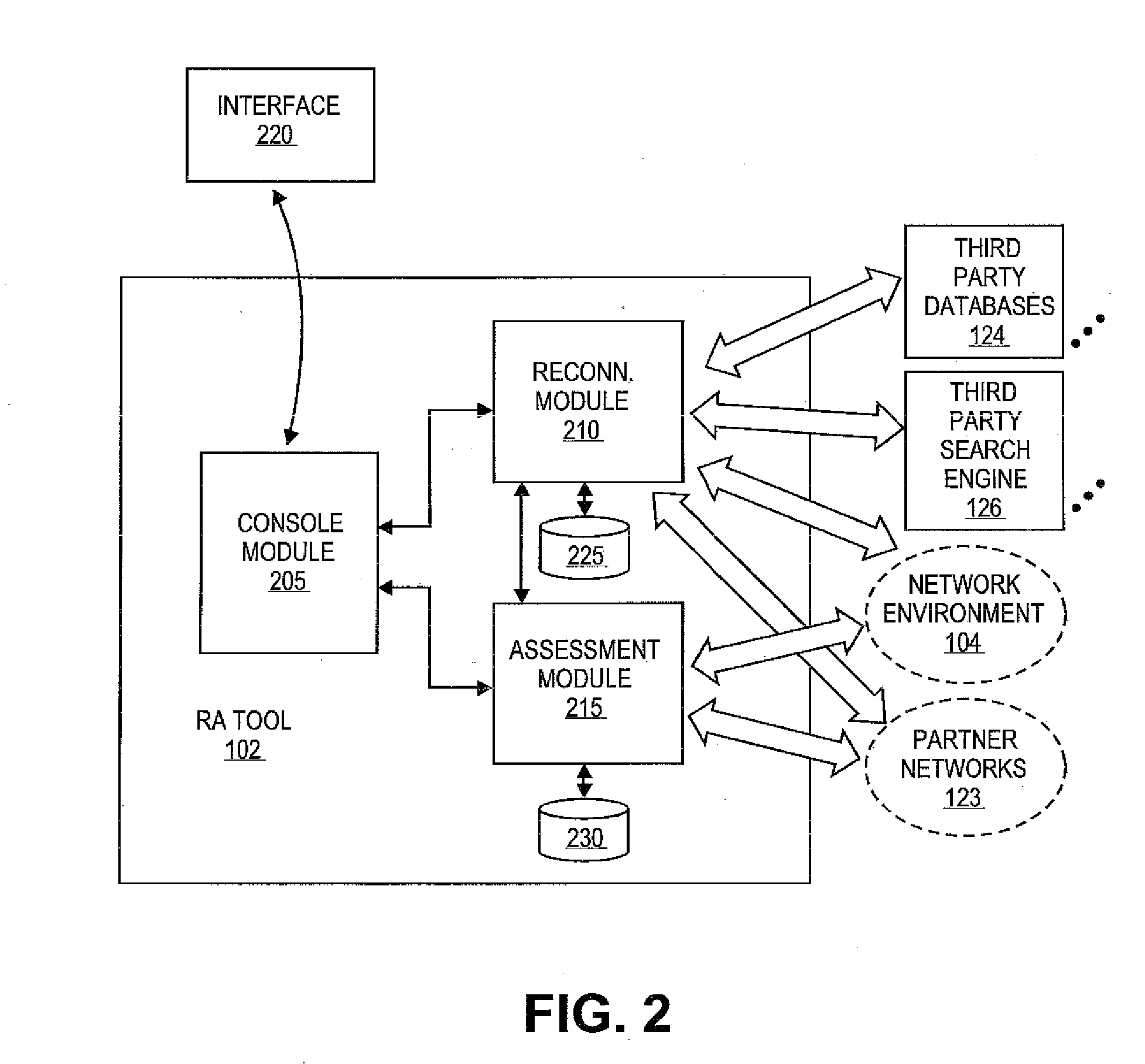
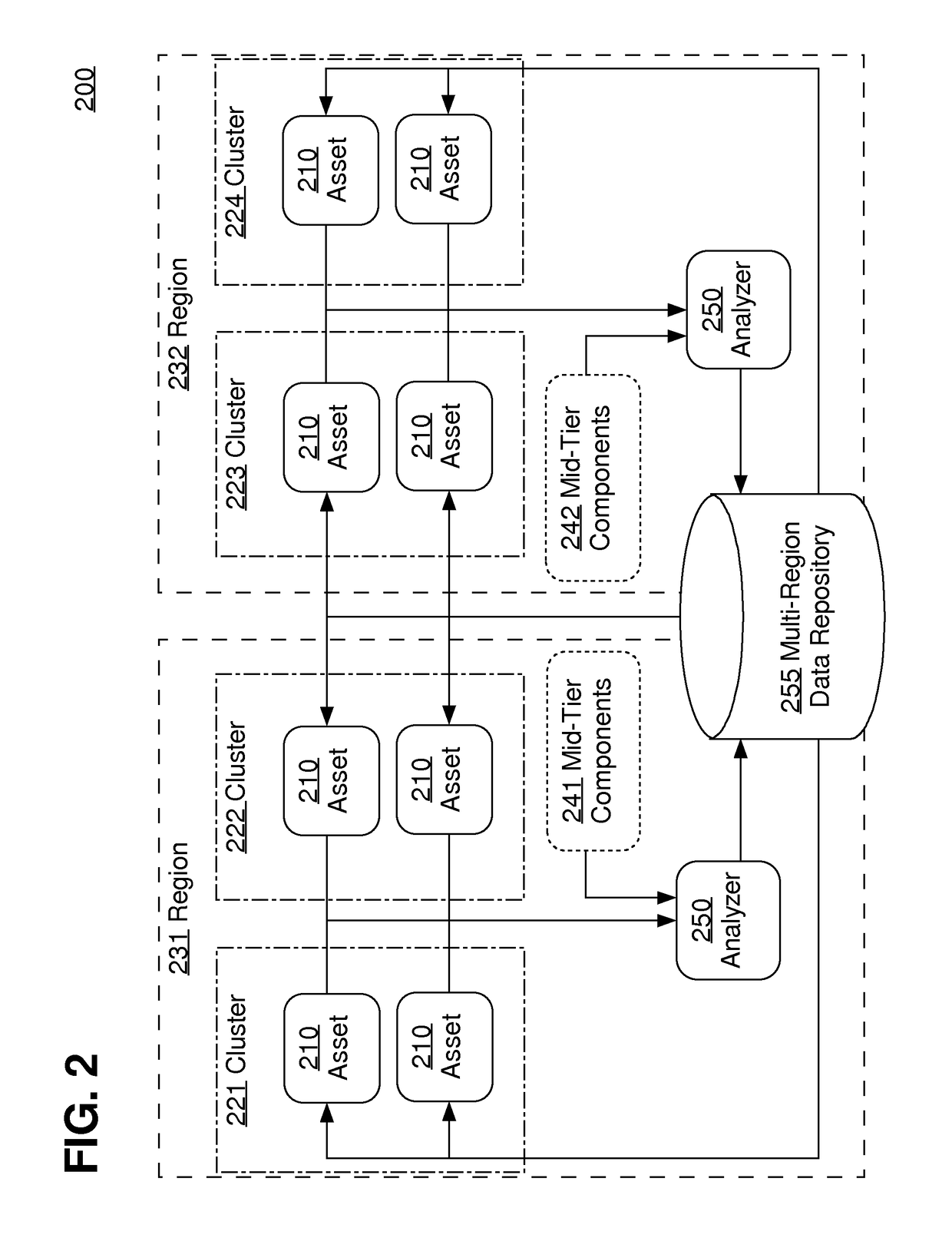
Methods and systems for integrating reconnaissance with security assessments for computing networks
A reconnaissance and assessment (RA) tool can receive base information about the network, such as basic network information and details about an entity and personnel associated with network. The RA tool can utilize the base information to perform reconnaissance procedures on the network to identify the attack surface of the network. The RA tool can perform reconnaissance on the network, itself, and on other external sources, such as third party databases, search engines, and partner networks. Once the attack surface is identified, the RA tool can automatically perform appropriate security assessments on the attack surface. Additionally, if additional information is determined about the network during the security assessments, the RA tool can perform additional reconnaissance and security assessments based on the additional information.
Owner:RAPID7
Distributed traffic management system and techniques
ActiveUS20160088020A1TransmissionSpecial data processing applicationsData synchronizationDecision taking
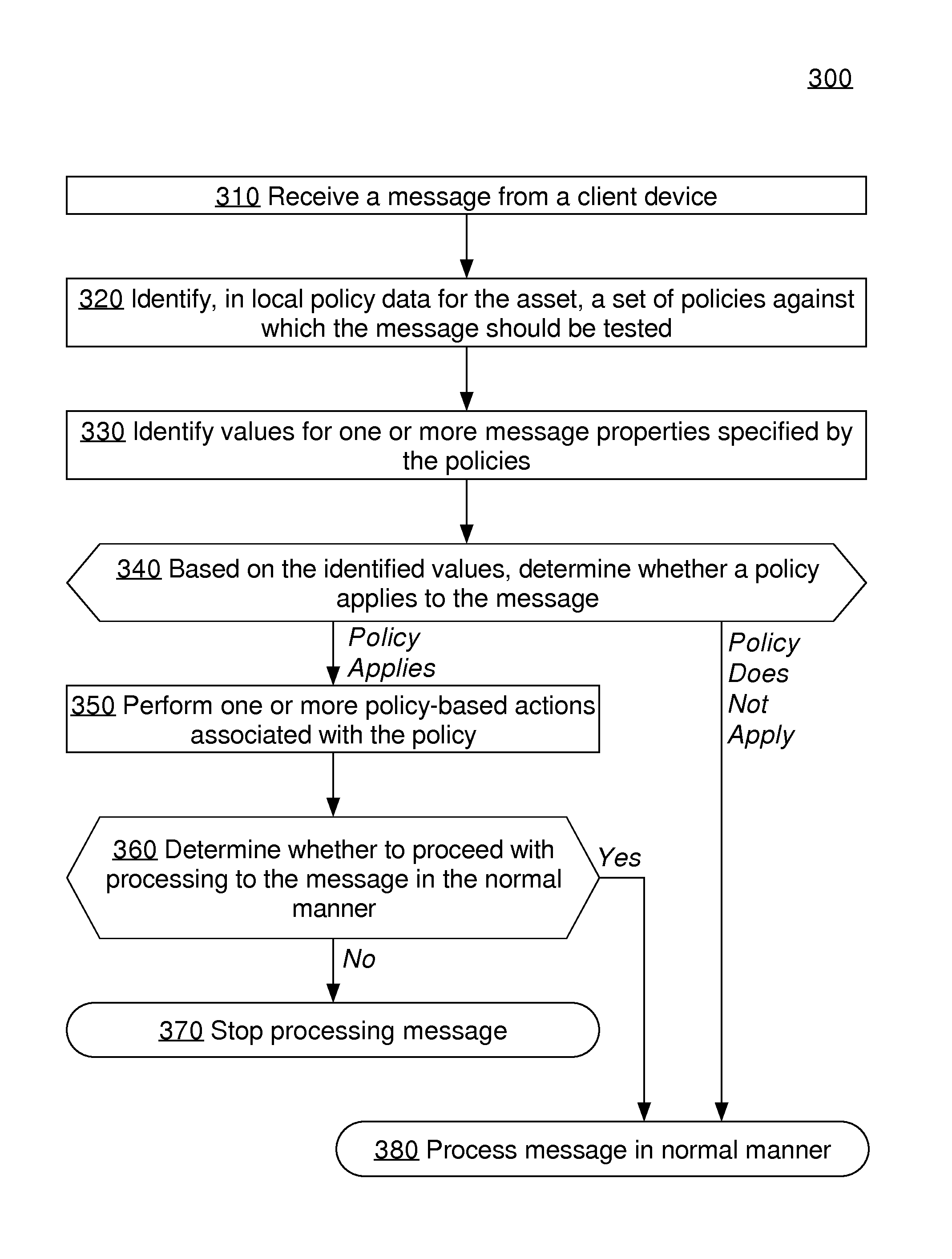
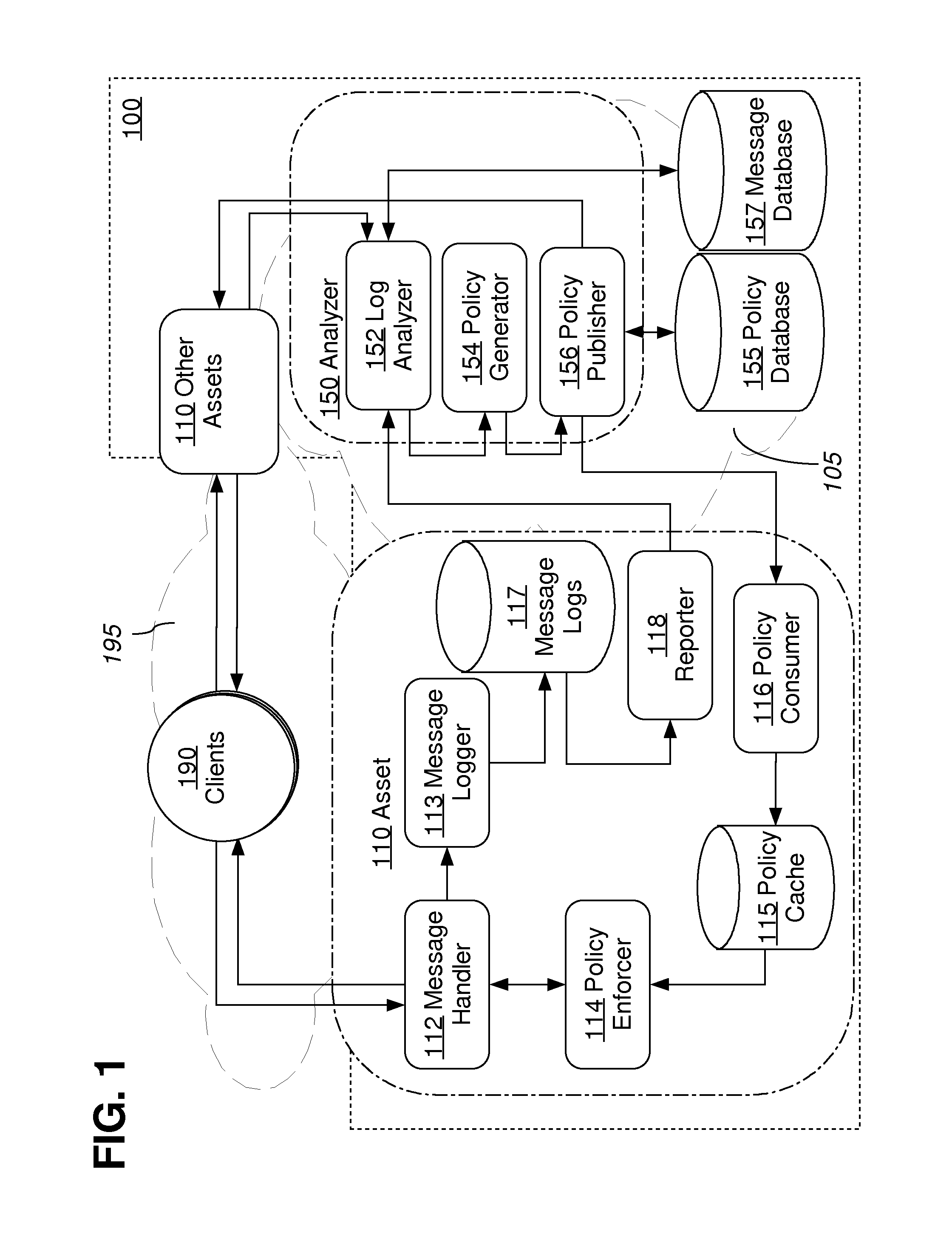
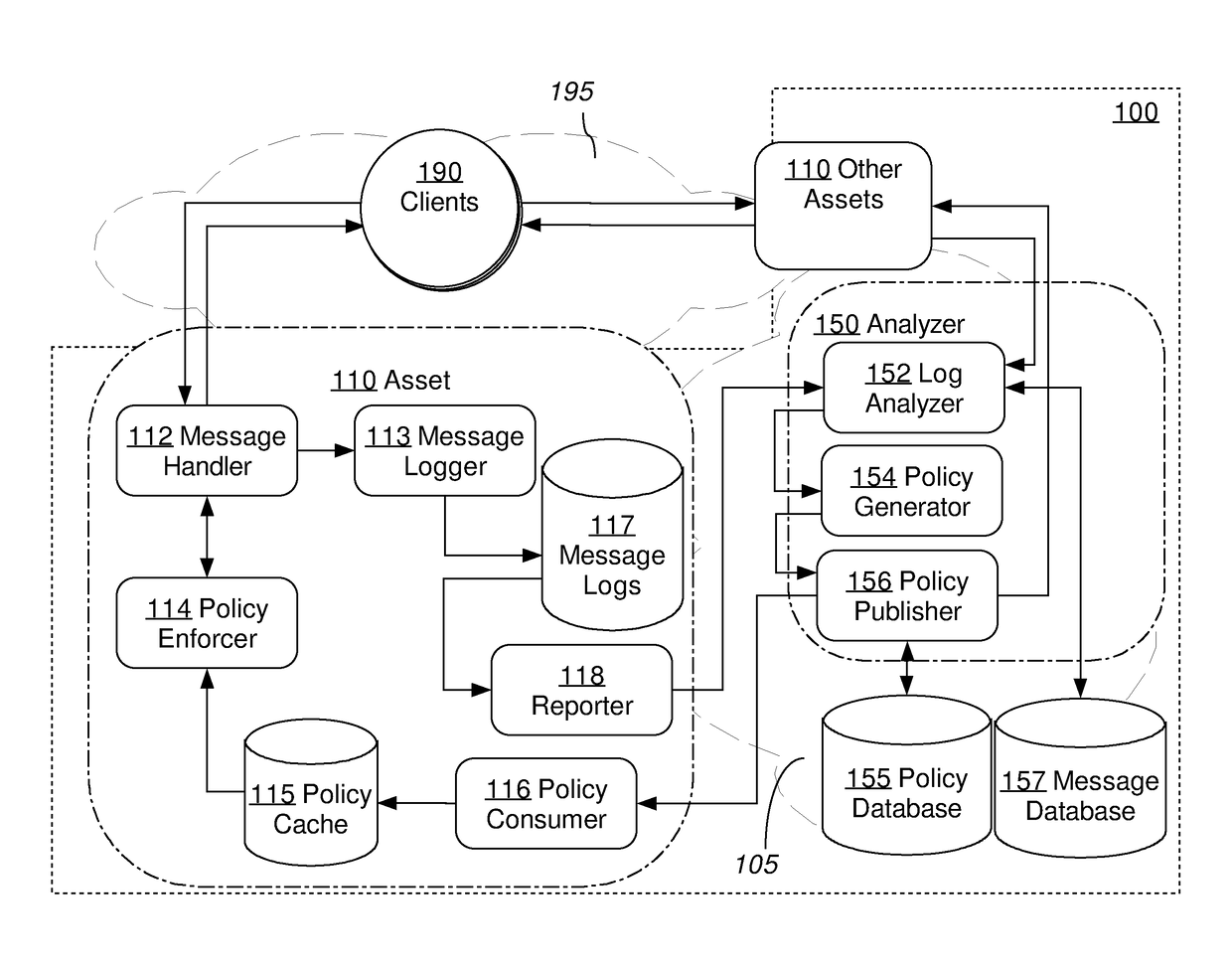
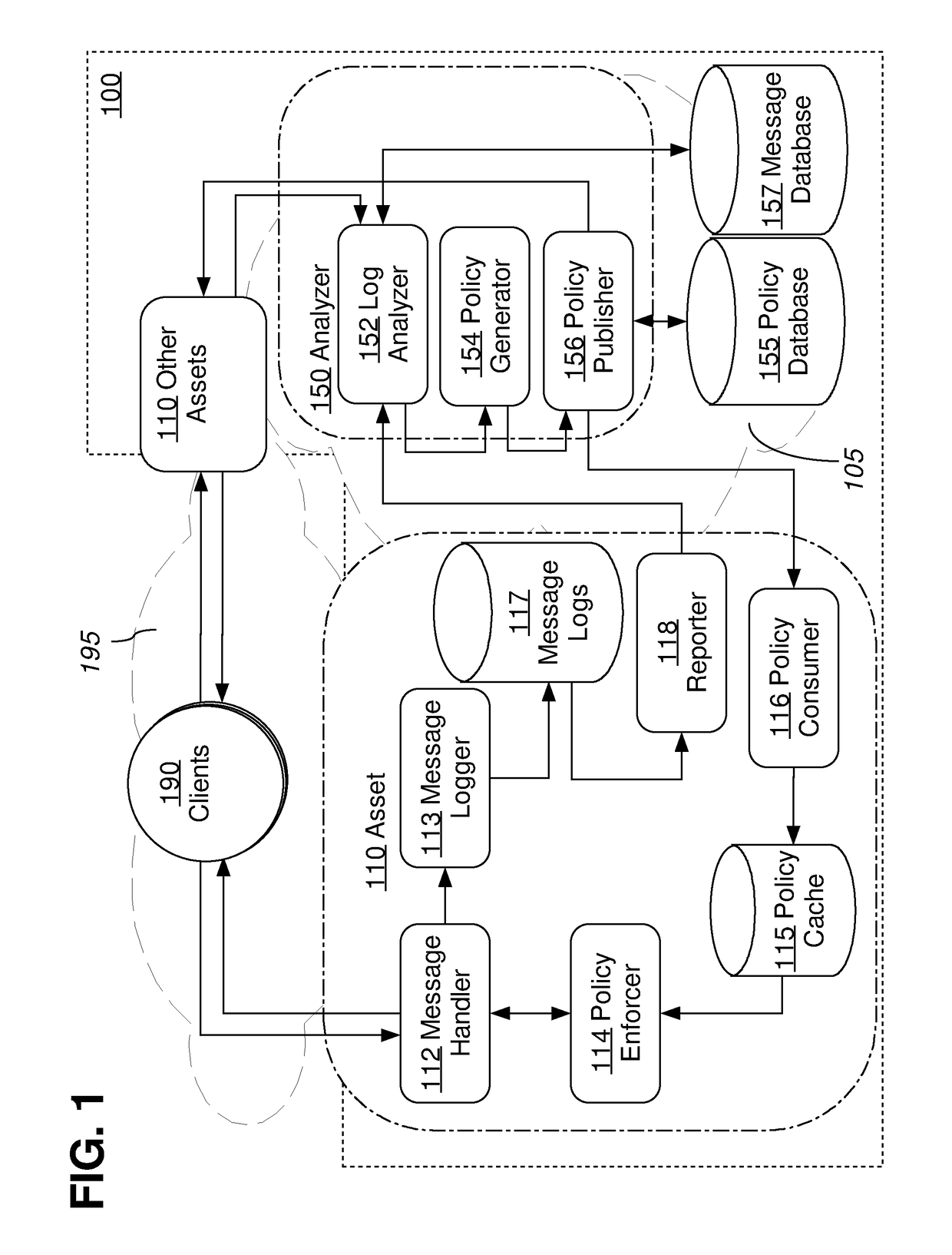
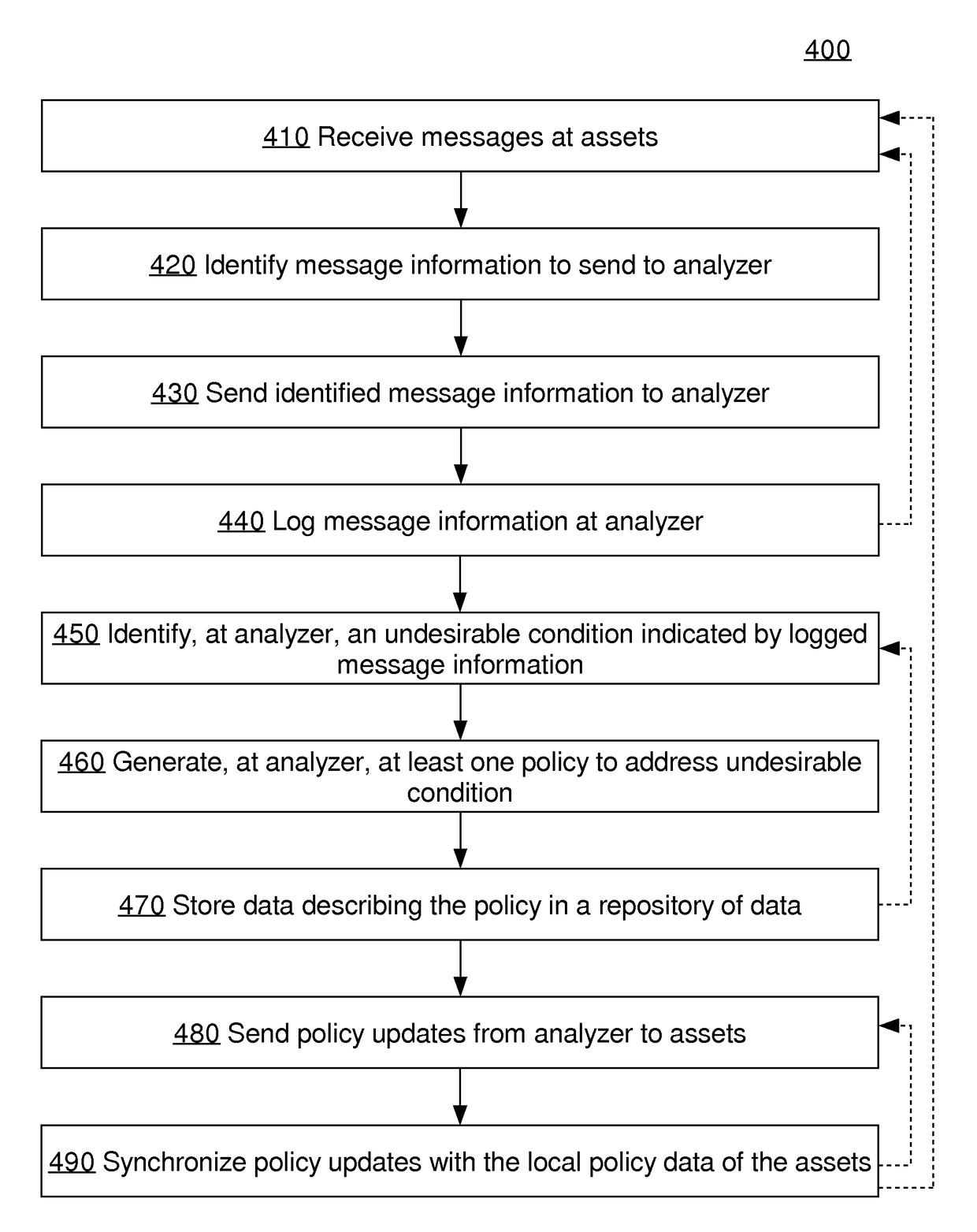
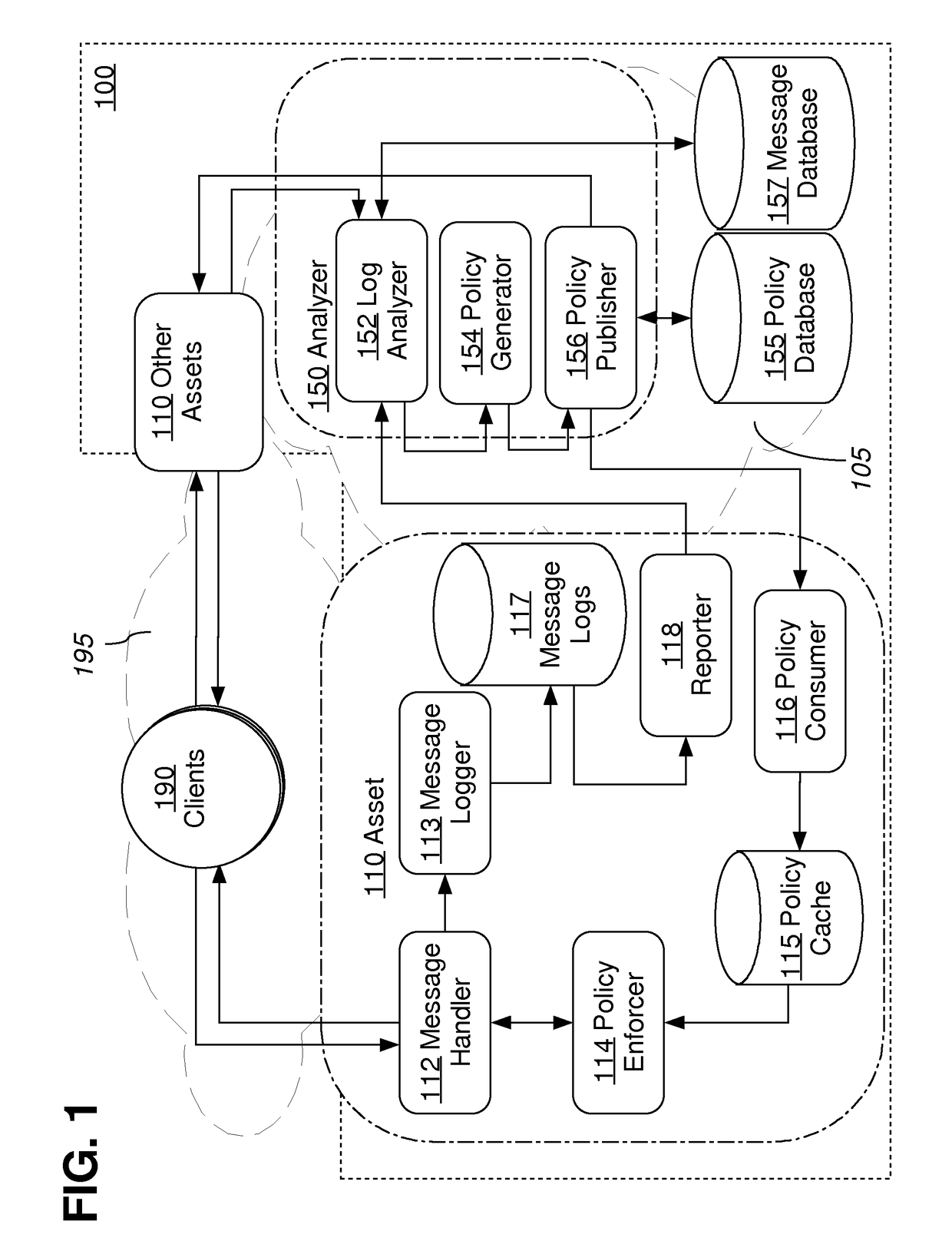
Approaches, techniques, and mechanisms are disclosed for implementing a distributed firewall. In an embodiment, many different computer assets police incoming messages based on local policy data. This local policy data is synchronized with global policy data. The global policy data is generated by one or more separate analyzers. Each analyzer has access to message logs, or information derived therefrom, for groups of computer assets, and is thus able to generate policies based on intelligence from an entire group as opposed to an isolated asset. Among other effects, some of the approaches, techniques, and mechanisms may be effective even in computing environments with limited supervision over the attack surface, and / or computing environments in which assets may need to make independent decisions with respect to how incoming messages should be handled, on account of latency and / or unreliability in connections to other system components.
Owner:NETFLIX
Virtual hardware characteristic-based system and method for efficiently isolating kernel modules
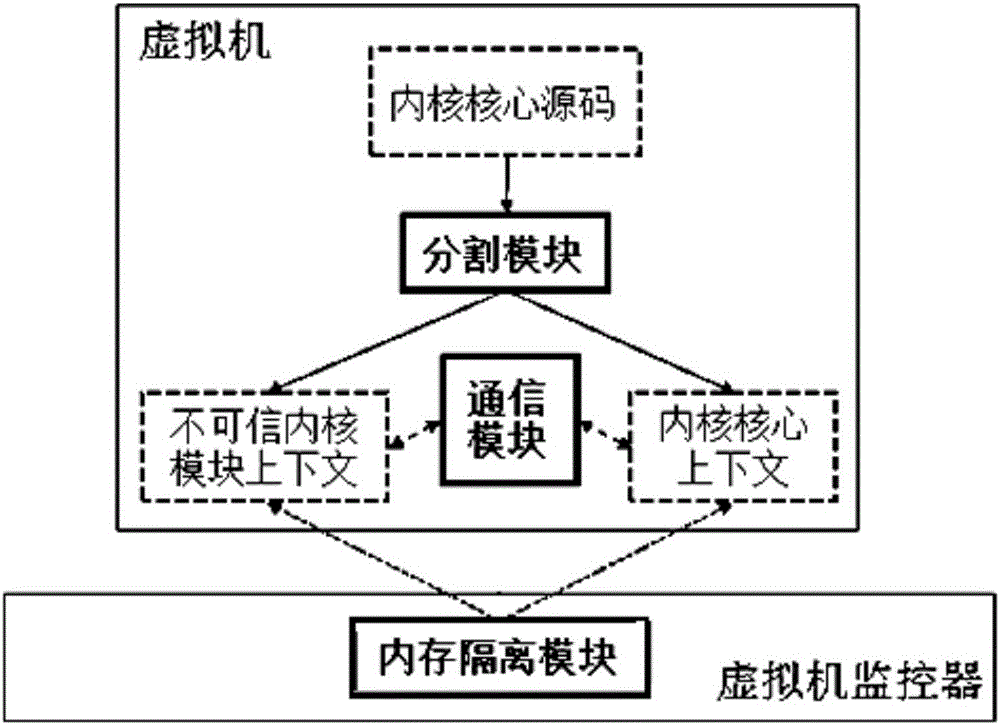
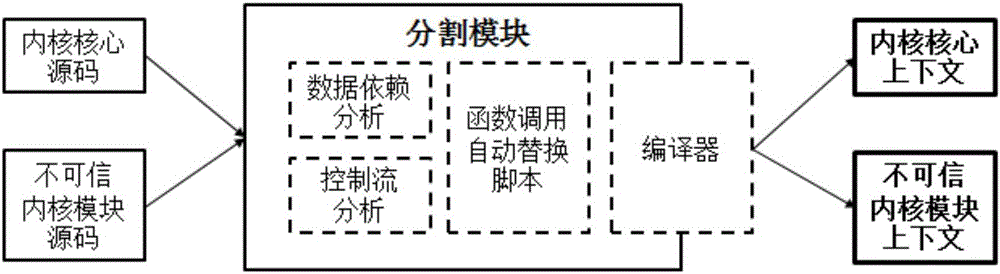
InactiveCN106203082AEffective segmentationEffective isolationInternal/peripheral component protectionPlatform integrity maintainanceVirtualizationControl flow
The invention provides a virtual hardware characteristic-based system and method for efficiently isolating kernel modules. According to the system and method, a secure and efficient strong isolation mechanism aiming at incredible kernel modules is designed, so that the present requirements for the security and functionality can be satisfied. Compared with the existing solutions, the system and method has better performance, stronger isolation and higher backward compatibility. The designed mechanism is easy to deploy in the present mainstream cloud computing platforms, so that considerable social benefit and economic benefit can be provided. In the mechanism, when the incredible kernel modules need to call functions of kernel cores or the kernel cores need to call functions in the incredible kernel modules, a secure and efficient virtual hardware characteristic-based control flow transformation mechanism is established, so that more attack surfaces are not exposed in the switching.
Owner:SHANGHAI JIAO TONG UNIV
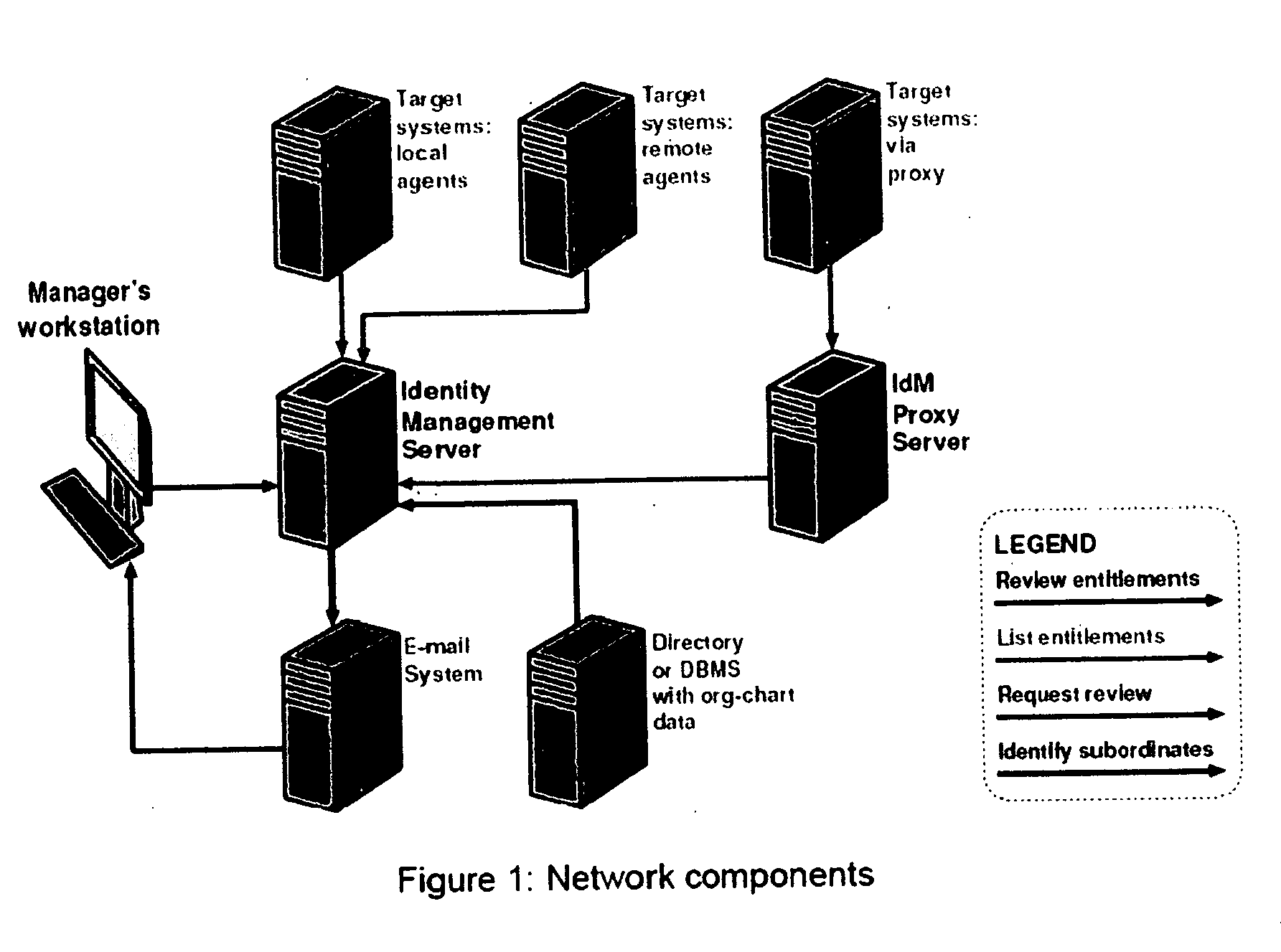
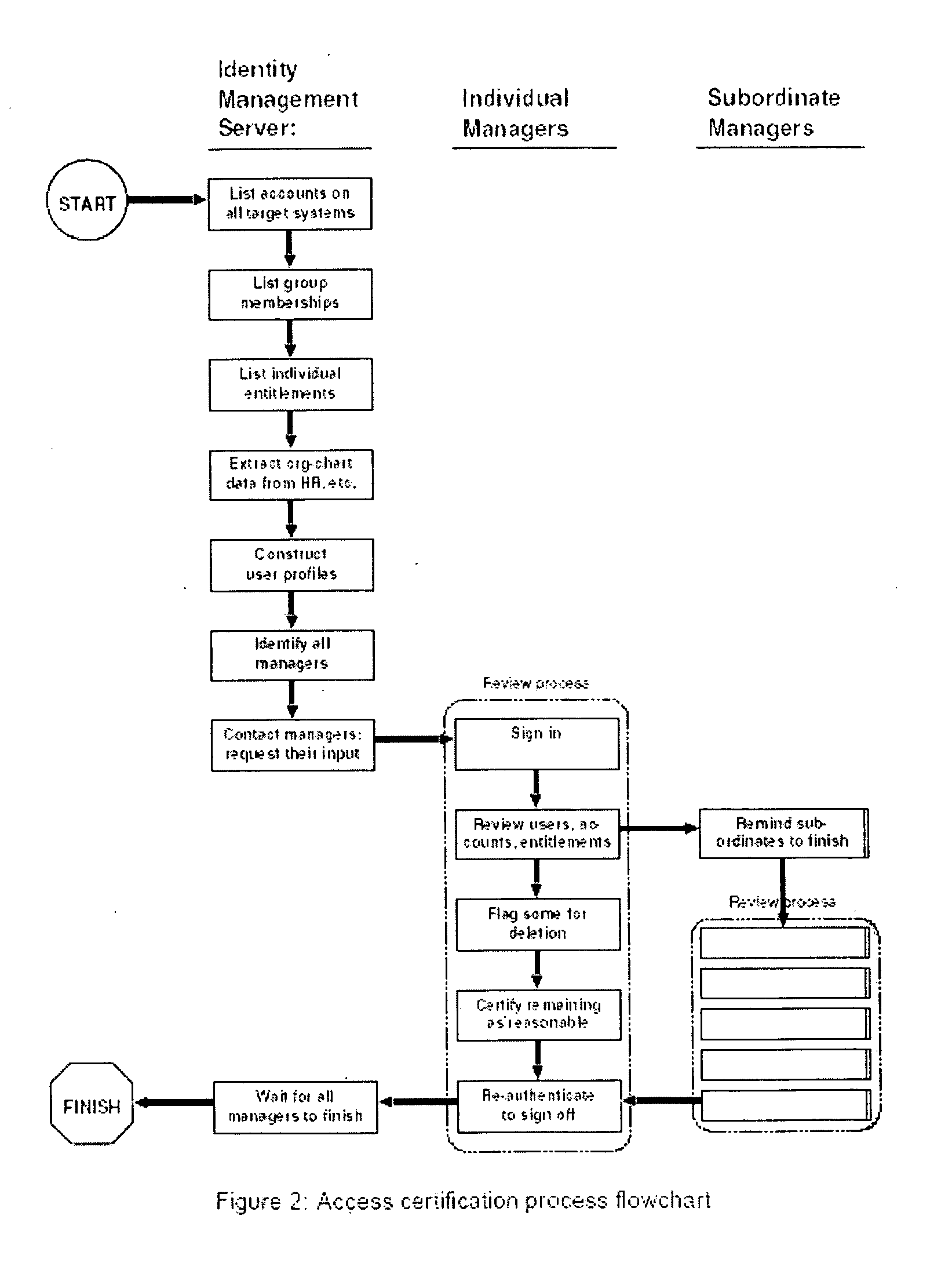
Process for removing stale users, accounts and entitlements from a networked computer environment
InactiveUS20060015930A1Reduce attack surfaceEffective internal controlDigital data processing detailsUser identity/authority verificationREMS StakeholderGood practice
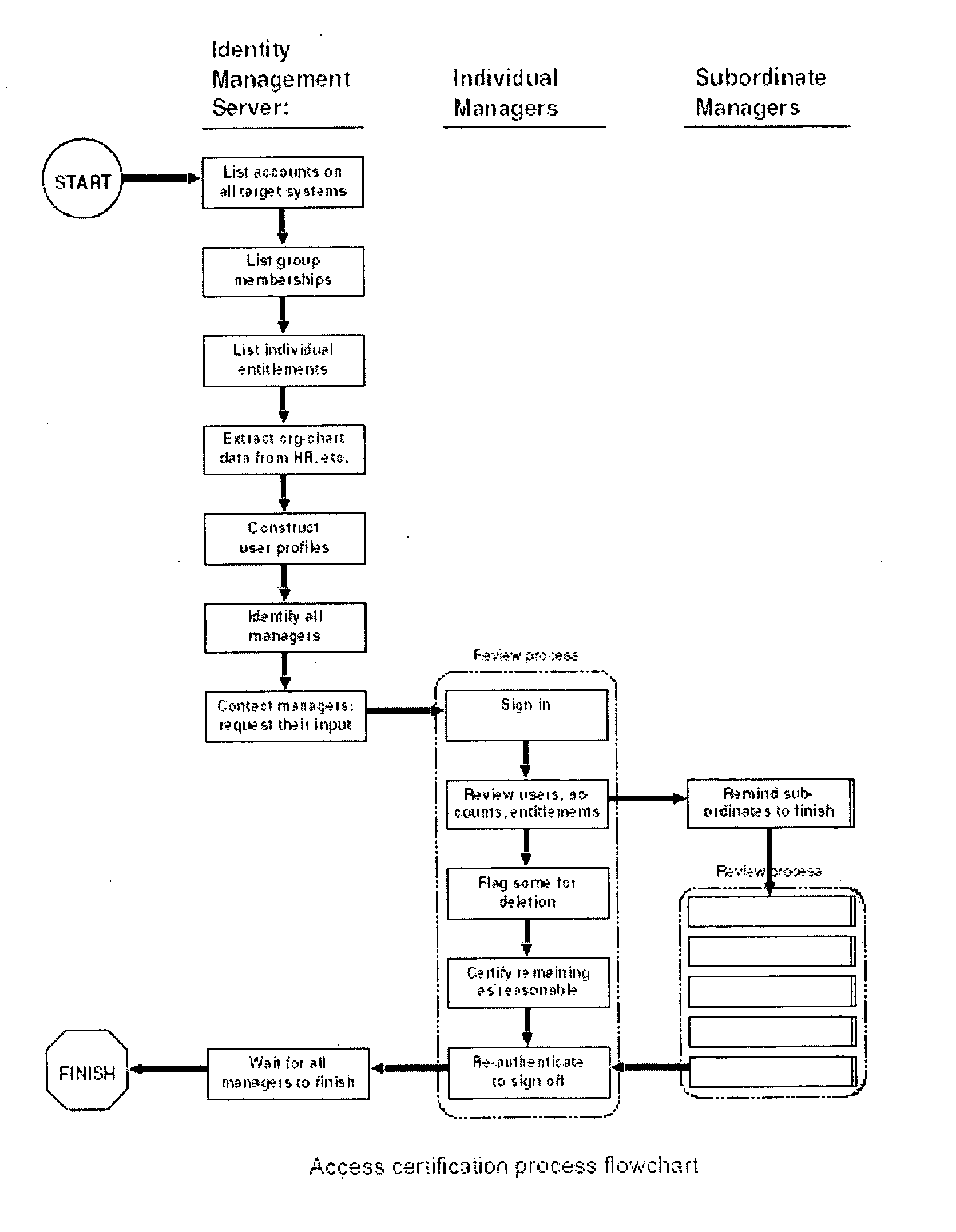
A method for collecting, presenting to stake-holders, reviewing and cleansing data about users and their entitlements in a networked computer environment, called access certification, is presented. This method begins with automated prompts sent to stake-holders, such as managers or application owners, asking them to review a list of their subordinates or users. Stake-holders are required to either certify or mark for later deletion each user. Next, stake-holders review the detailed security entitlements of each subordinate or user, again either certifying or flagging for deletion each item. Finally, stake-holders are asked to provide an electronic signature, indicating completion of their review process. To motivate stake-holder completion of the process, and to roll-up results across an organization, stake-holders are prevented from completing the signature step until all subordinate stake-holders have likewise completed. The present invention provides a feasible method for identifying and eliminating user accounts that are either no longer needed by their owners, or belong to owners who are no longer legitimate users of an organization's computer systems. The same method is used to identify and eliminate entitlements assigned to users who no longer need them. Removal of such stale, obsolete or incorrect users, login accounts, user objects, group memberships and security, entitlements is essential in order to reduce the security exposure (attack surface) posed by excessive privileges and unused accounts, and to comply with government and other regulations stipulating effective internal controls, especially over financial data, and computer security best practices.
Owner:M TECH INFORMATION TECH
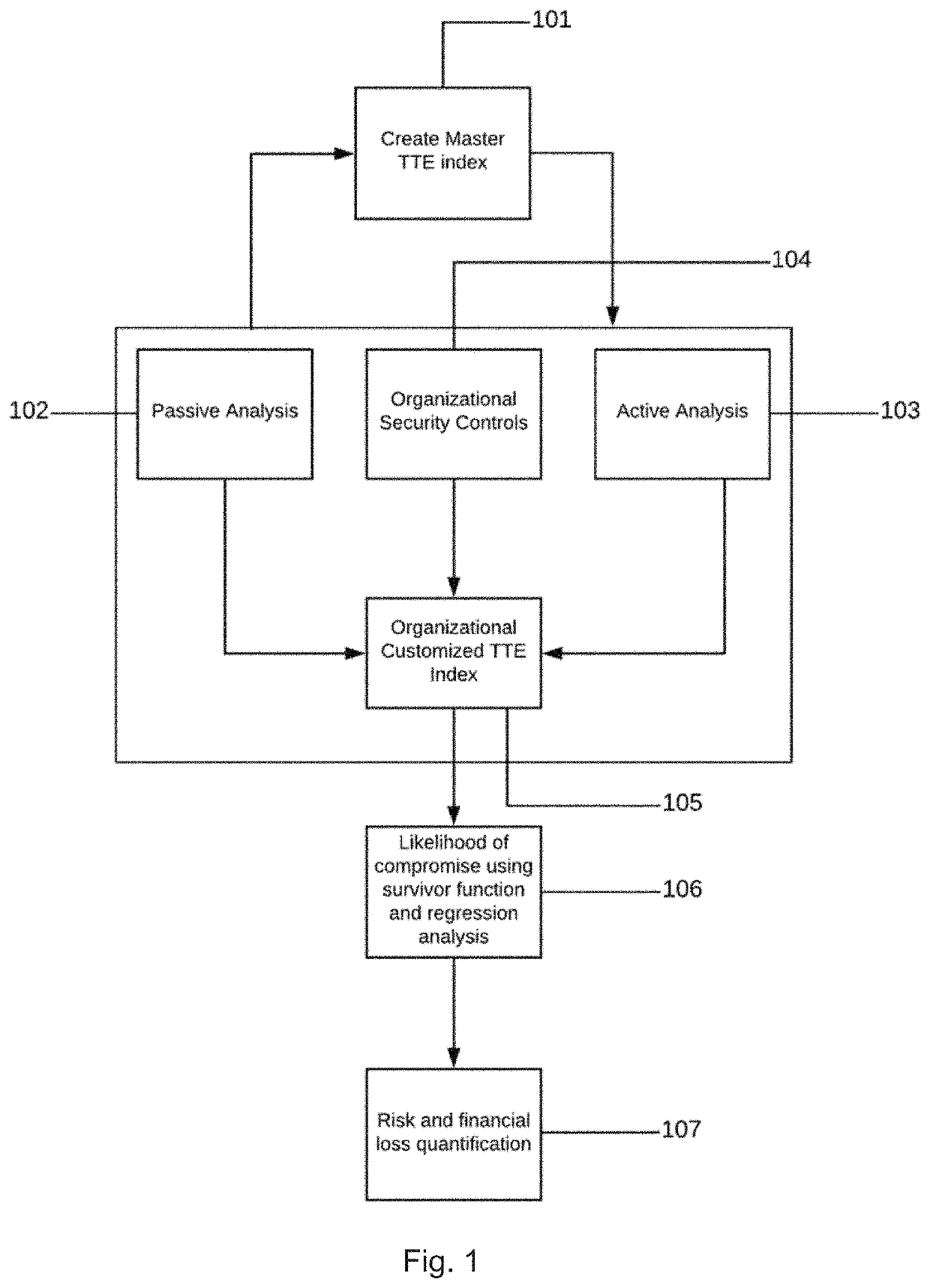
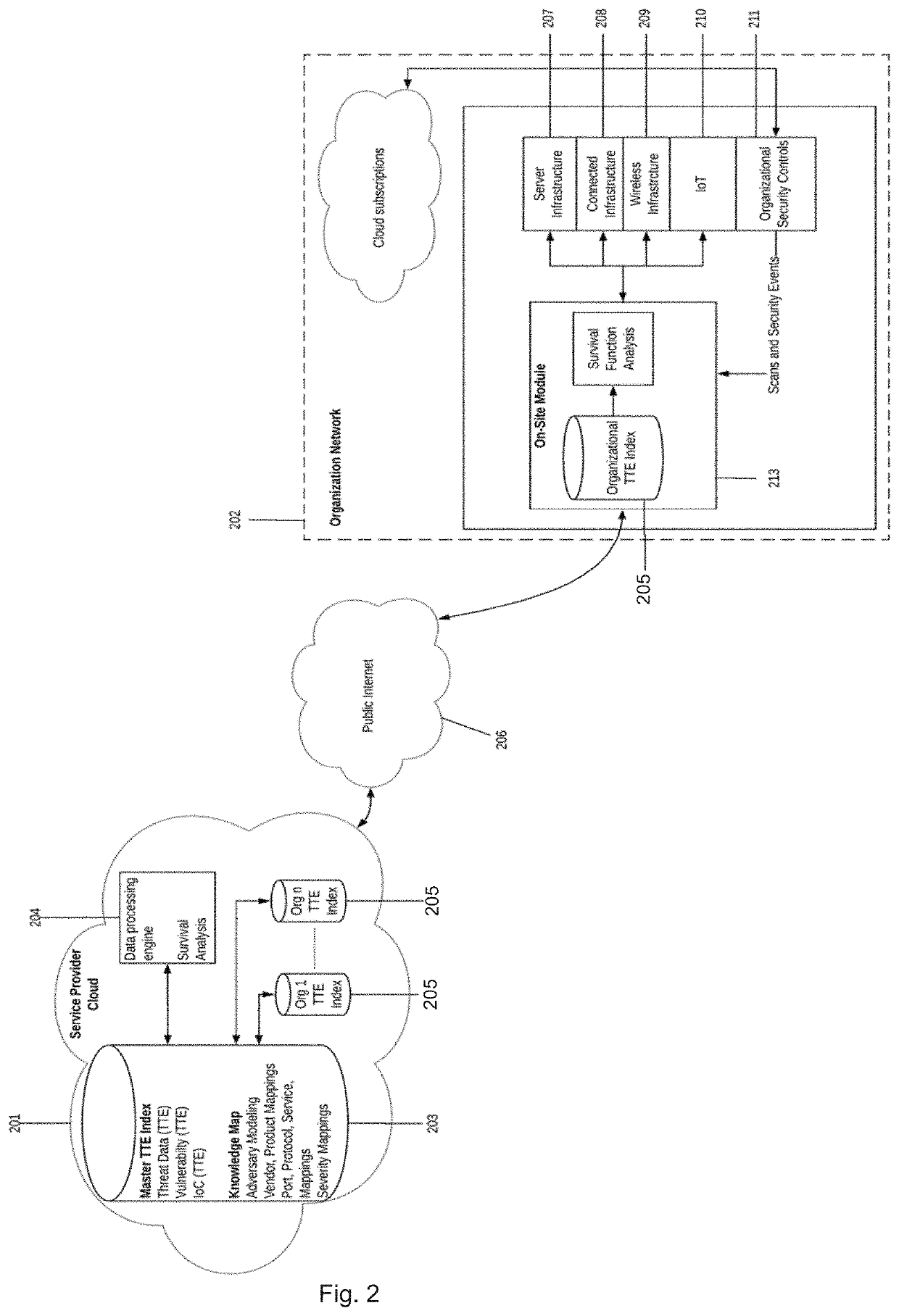
Complex Application Attack Quantification, Testing, Detection and Prevention
ActiveUS20200351298A1Avoid attackEasy to learnMathematical modelsOffice automationRisk quantificationAttack
An apparatus and method for cyber risk quantification calculated from the likelihood of a cyber-attack on the target enterprise and / or cyber ecosystem based on its security posture. The cyber-attack likelihood can be derived as a probability-based time-to-event (TTE) measure using survivor function analysis. The likelihood probability measure can also be passed to cyber risk frameworks to determine financial impacts of the cyber-attacks. Embodiments of the present invention also relate to an apparatus and method (1) to identify and validate application attack surfaces and protect web applications against business logic-based attacks, sensitive data leakage and privilege escalation attacks; and / or (2) that protects web applications against business logic-based attacks, sensitive data leakage and privilege escalation attacks. This can include implementing an intelligent learning loop using artificial intelligence that creates an ontology-based knowledge base from application request and response sequences. Stochastic probabilistic measures are preferably applied to a knowledge base for predicting malicious user actions in real time.
Owner:IVANTI INC
Balancing Malware Rootkit Detection with Power Consumption on Mobile Devices
InactiveUS20120291126A1Improve compromiseMemory loss protectionError detection/correctionOperational systemEnergy expenditure
The subject disclosure presents a novel technique for balancing the tradeoff between security monitoring and energy consumption on mobile devices. Security / energy tradeoffs for host-based detectors focusing on rootkits are analyzed along two axes: a scanning frequency, and a surface of attack. Experimental results are applied to a hypervisor-based framework, and a sweet spot is identified to minimize both energy consumption and a window of vulnerability for critical operating system objects such as code pages and kernel data.
Owner:AT&T INTPROP I L P +1
Vulnerability Detection in IT Assets by utilizing Crowdsourcing techniques
ActiveUS20180103054A1Preventing a potentially catastrophic falloutEnsemble learningTransmissionFeature vectorGoal system
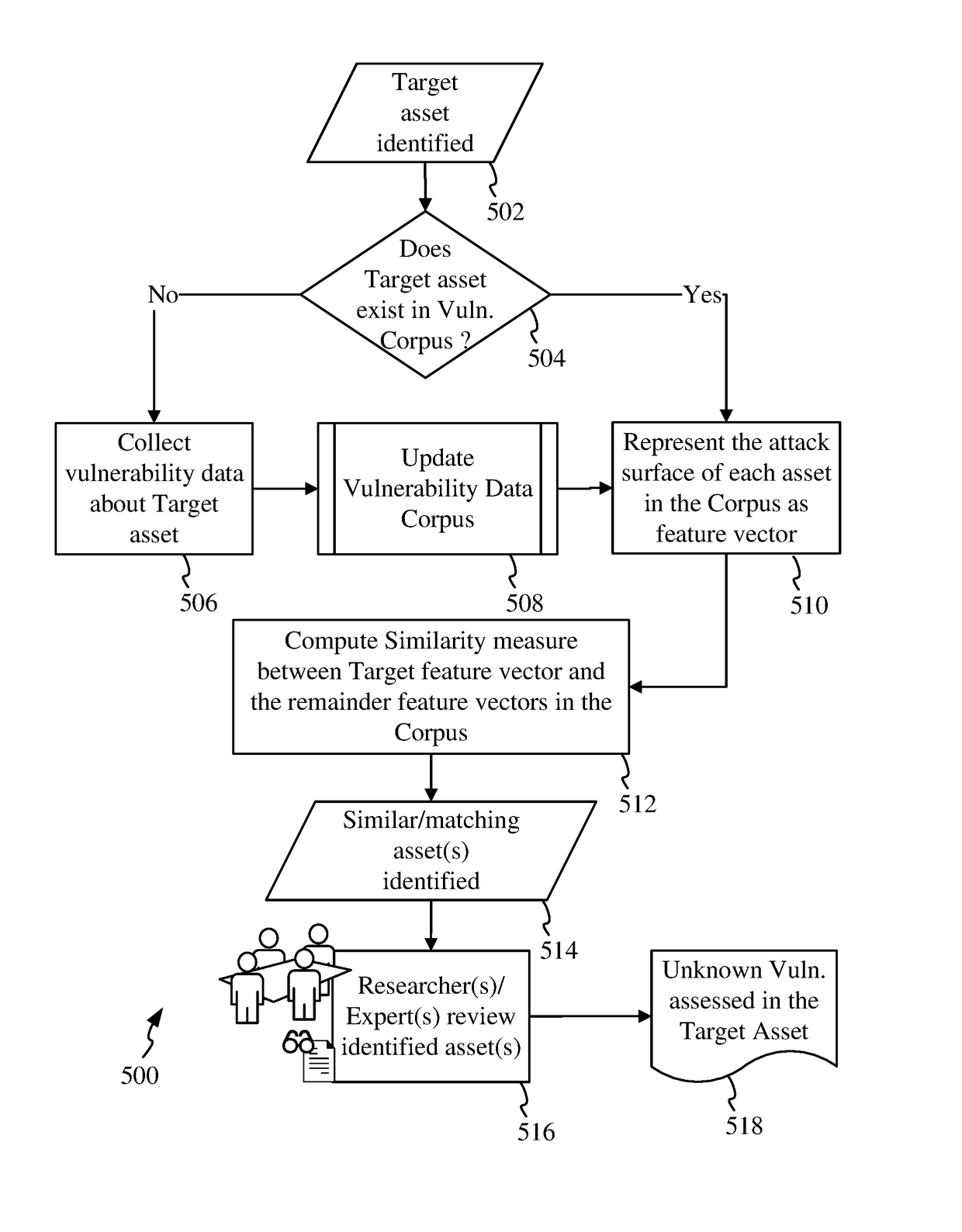
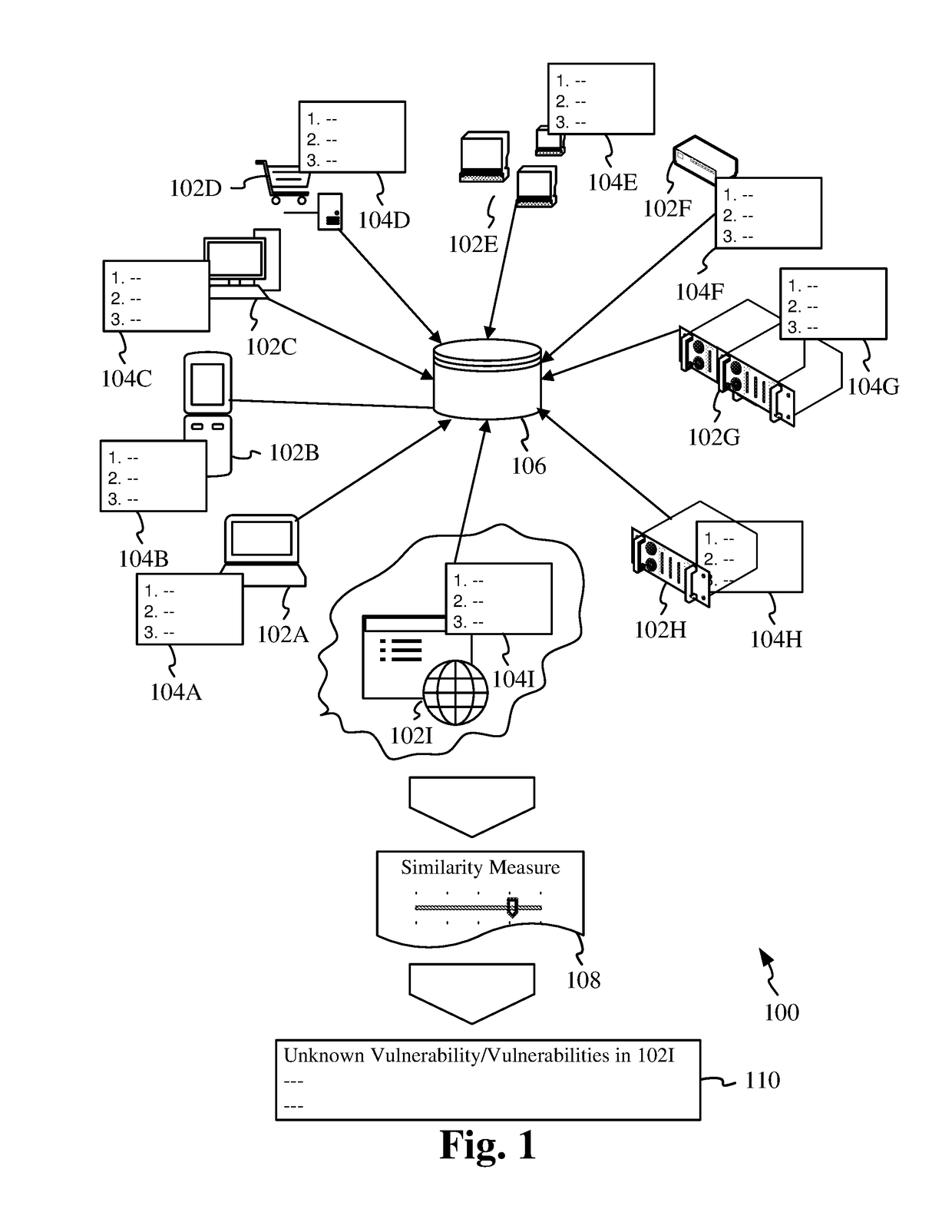
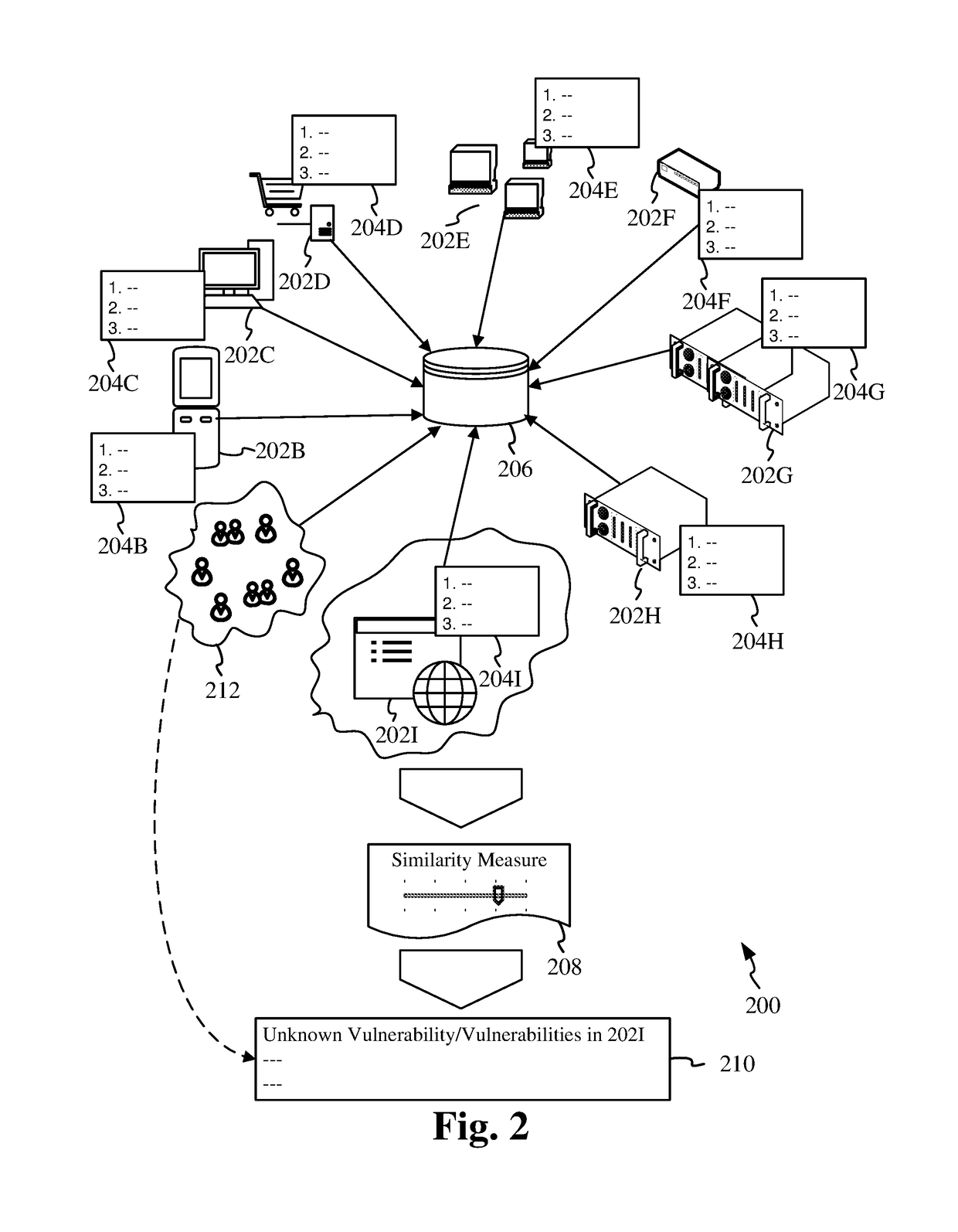
This invention discloses systems and methods for detecting vulnerabilities in IT assets by utilizing crowdsourcing techniques. A corpus containing vulnerability data of IT assets with known vulnerabilities is established. Vulnerability data in the corpus comprises security aspects or attributes related to the IT assets. The security aspects of an IT asset constitute its attack surface which is represented as a feature vector in a feature space. A determination is made as to how similar / close a target asset whose unknown vulnerabilities are to be detected, is to the rest of the IT assets in the corpus. This determination is made based on a measure of similarity / distance between the respective feature vectors in the feature space. Based on the review of similarity results by a community of researchers / experts, a determination of unknown vulnerabilities in the target system is made.
Owner:BUGCROWD INC
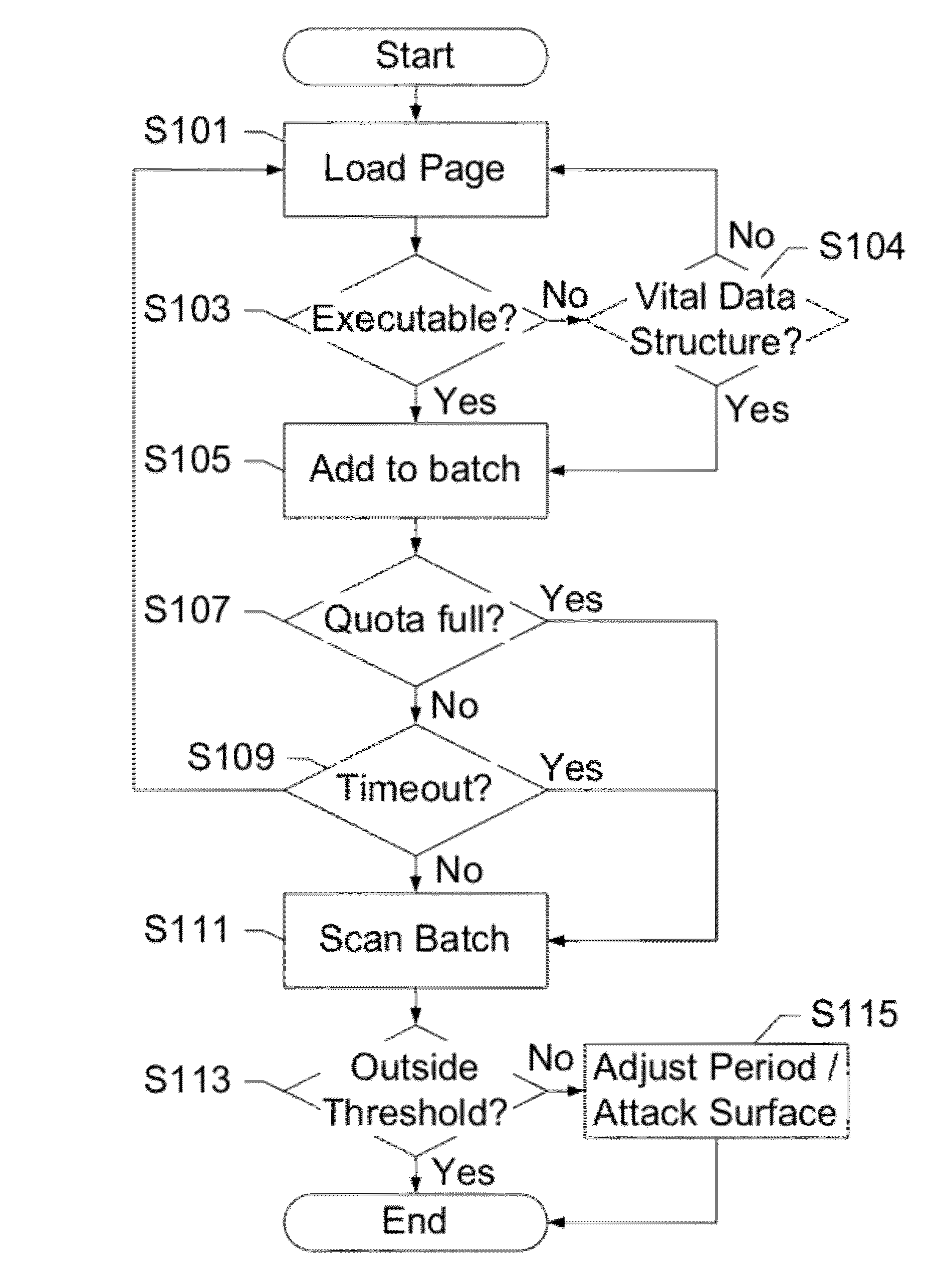
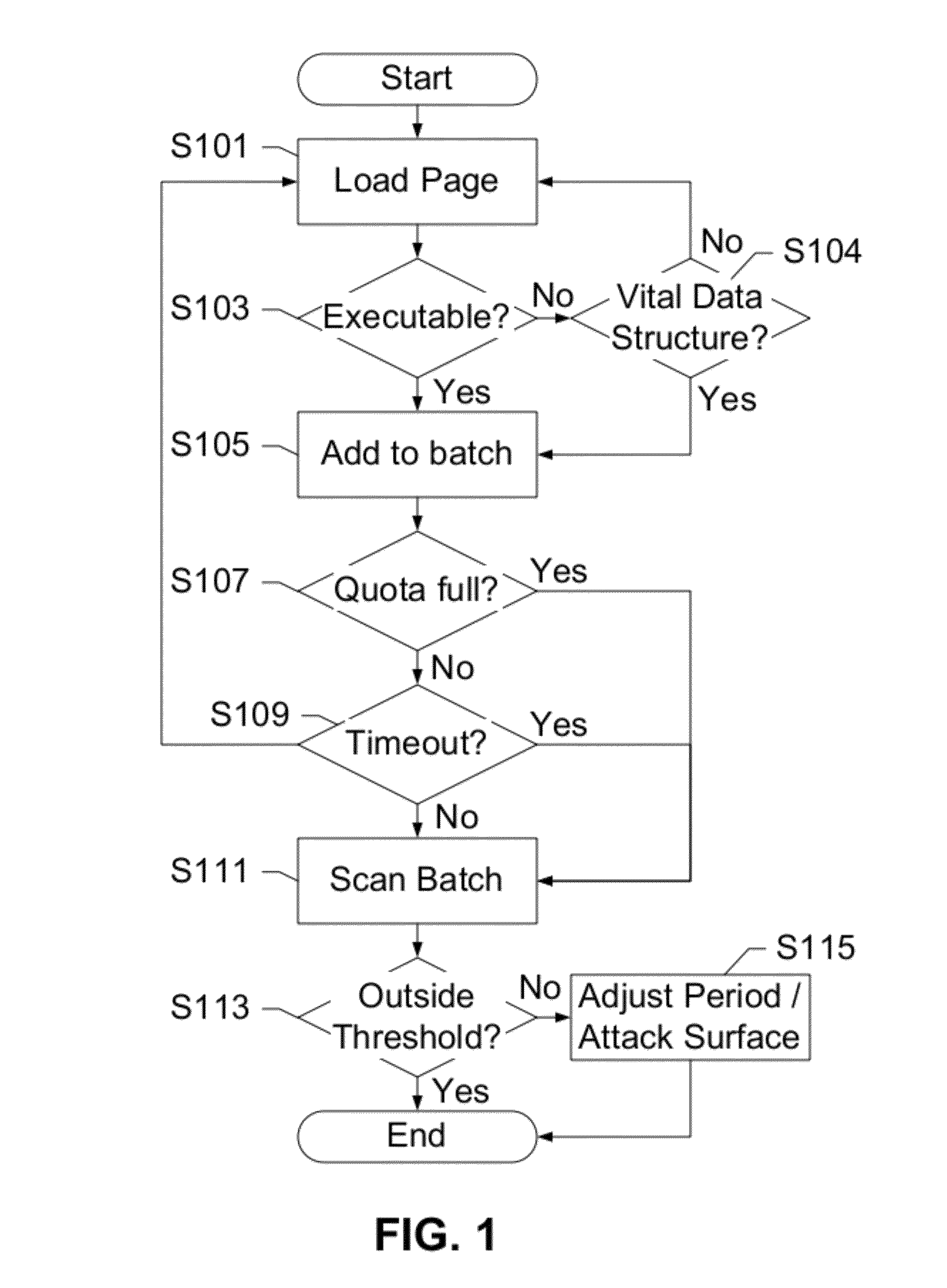
Method and System of Attack Surface Detection
ActiveUS20140344937A1Potential impactMemory loss protectionError detection/correctionAttack surfaceVulnerability
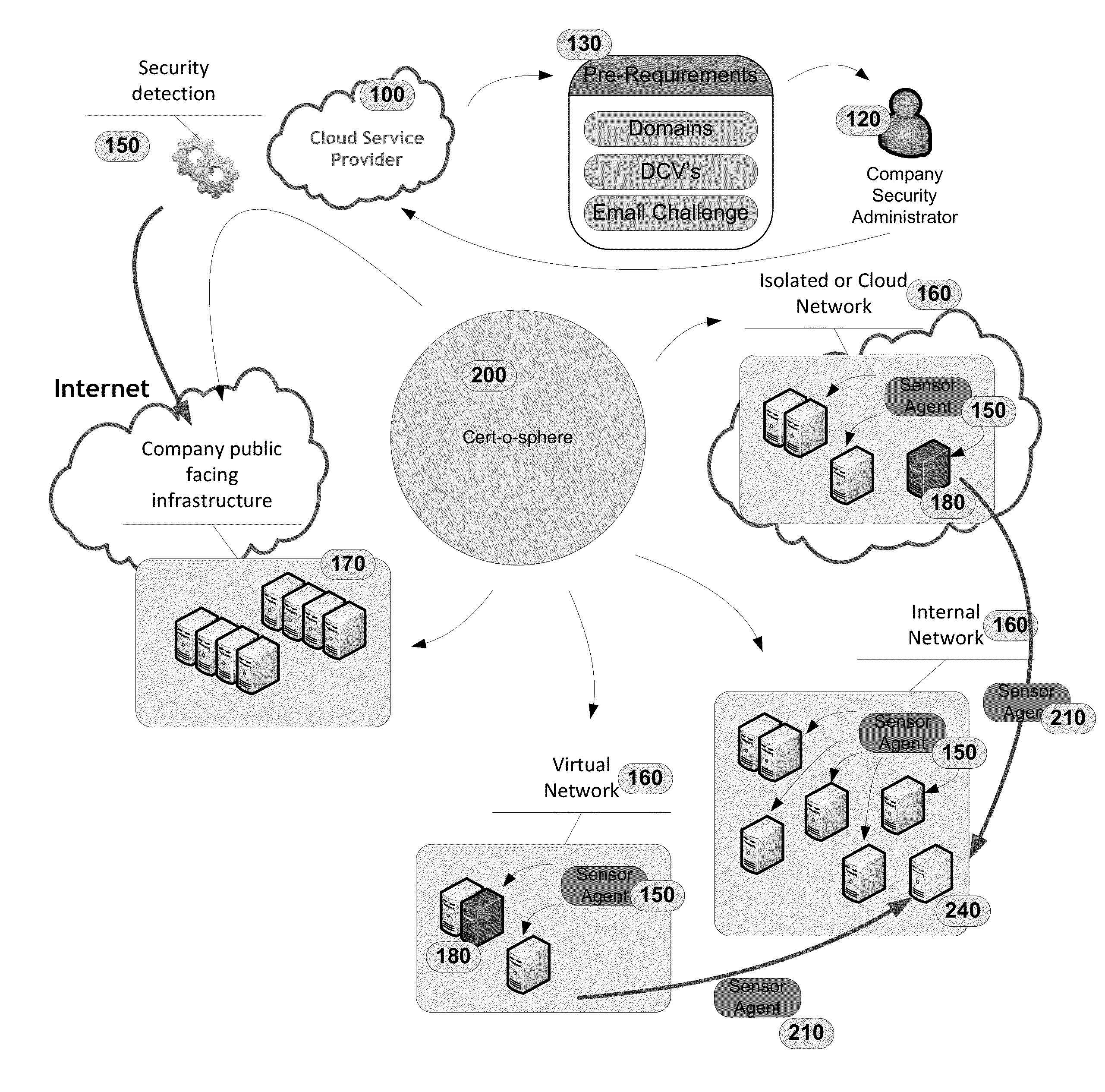
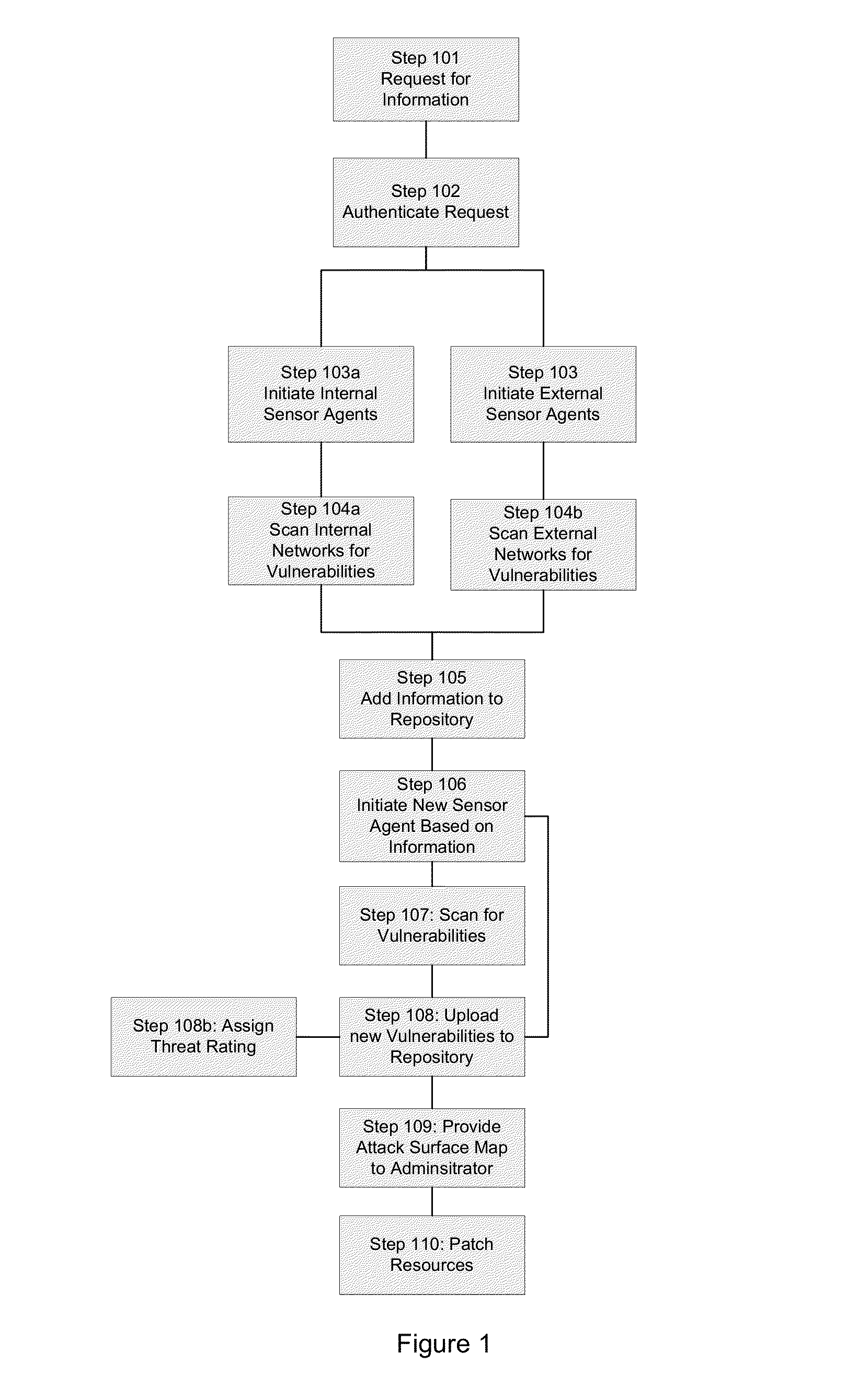
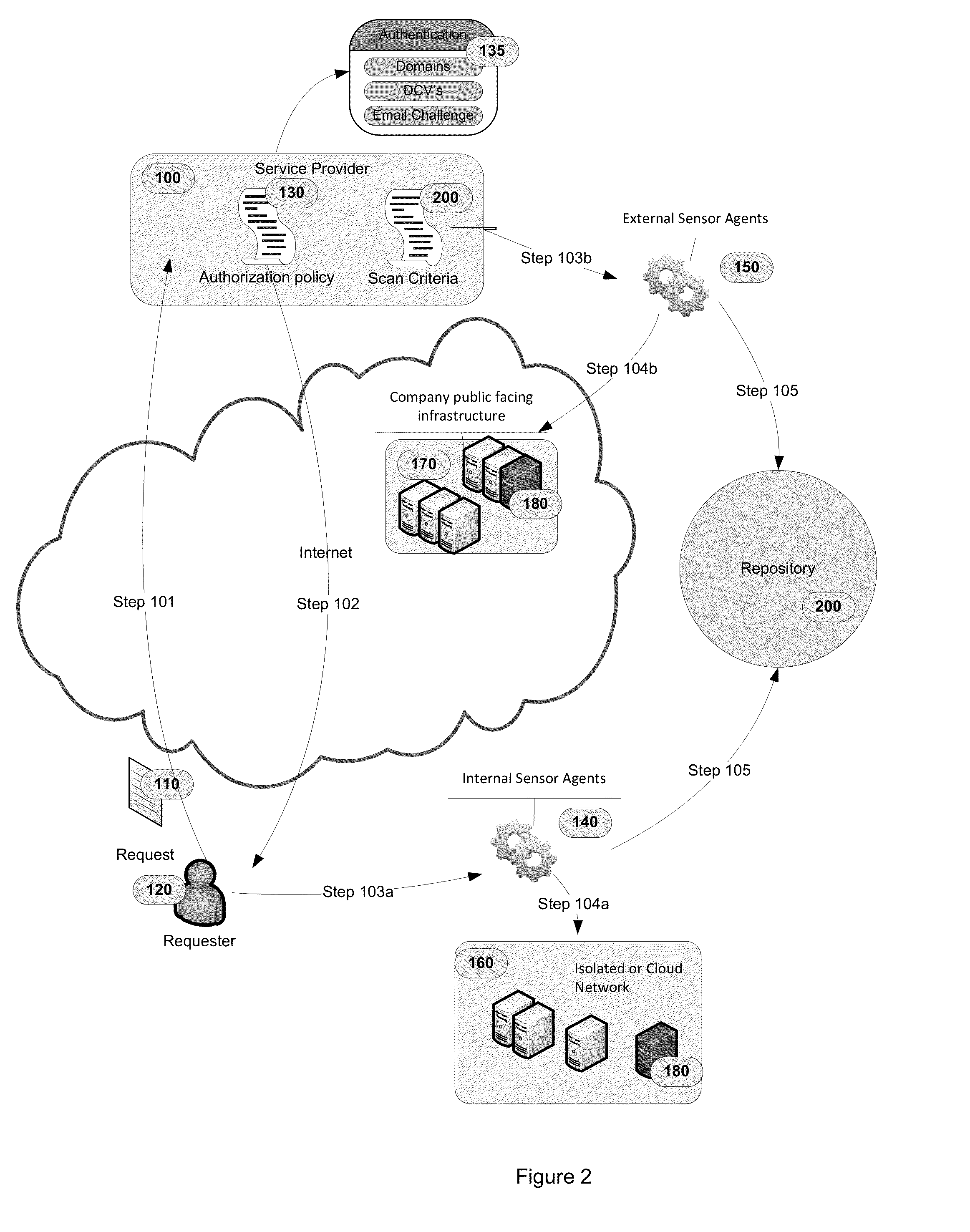
The invention comprises a method of using sensor agents to collect information in a central location to determine the entire attack surface of all certificate based resources, which includes vulnerable, insecure, or unknown resources but also includes where all the secure resources are located and the attack surface for each certificate resource. If a vulnerable resource is detected, the system may initiated additional sensor agents to determine the threat caused by the vulnerability. The system can also assign a rating to the overall security of the network based on vulnerabilities and display the attack surface as a topographic format for easy review by administrators.
Owner:DIGICERT
Multiple operating system rotation environment moving target defense
ActiveUS20160065612A1Memory loss protectionError detection/correctionOperational systemComputerized system
Systems and methods for providing a multiple operating system rotation environment (“MORE”) moving target defense (“MTD”) computing system are described. The MORE-MTD system provides enhanced computer system security through a rotation of multiple operating systems. The MORE-MTD system increases attacker uncertainty, increases the cost of attacking the system, reduces the likelihood of an attacker locating a vulnerability, and reduces the exposure time of any located vulnerability. The MORE-MTD environment is effectuated by rotation of the operating systems at a given interval. The rotating operating systems create a consistently changing attack surface for remote attackers.
Owner:UCHICAGO ARGONNE LLC
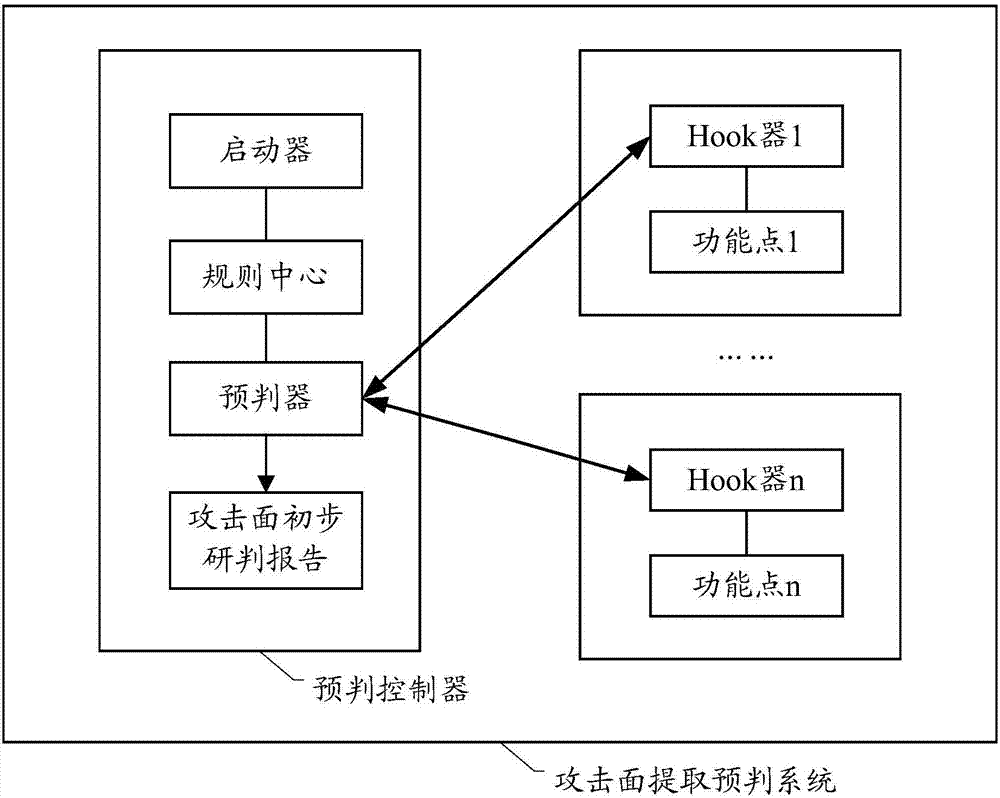
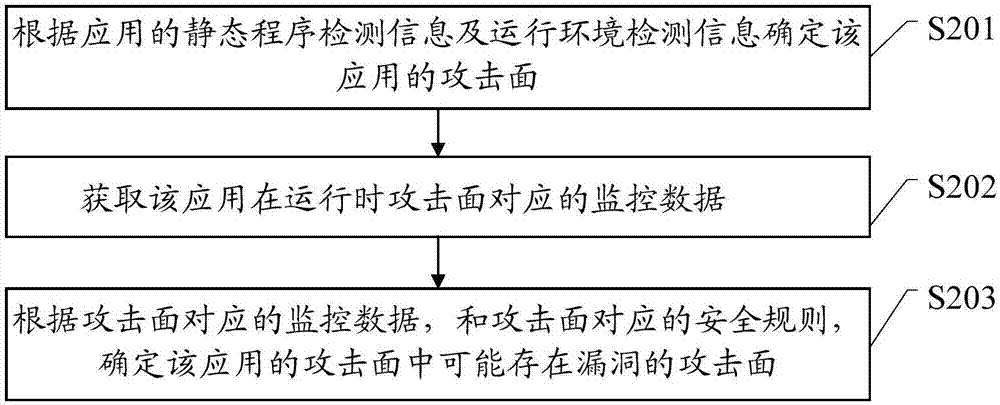
Method and device for searching application vulnerabilities, and system
ActiveCN107506648AImprove digging efficiencyPlatform integrity maintainanceAttack surfaceVulnerability
The embodiment of the invention discloses a method and a device for searching application vulnerabilities, and a system. The method comprises the following steps that: according to the static program detection information and the operation environment detection information of an application, determining the attack surface of the application; obtaining monitoring data corresponding to the attack surface when the application is operated; and according to the monitoring data corresponding to the attack surface and a network intrusion detection rule corresponding to the attack surface, determining the attack surface which may have vulnerabilities in the attack surface of the application, wherein the network intrusion detection rule of the attack surface is configured by aiming at the attack surface and is used for detecting network intrusion.
Owner:ADVANCED NEW TECH CO LTD
Fine-grained sandbox policy mining method for Linux container
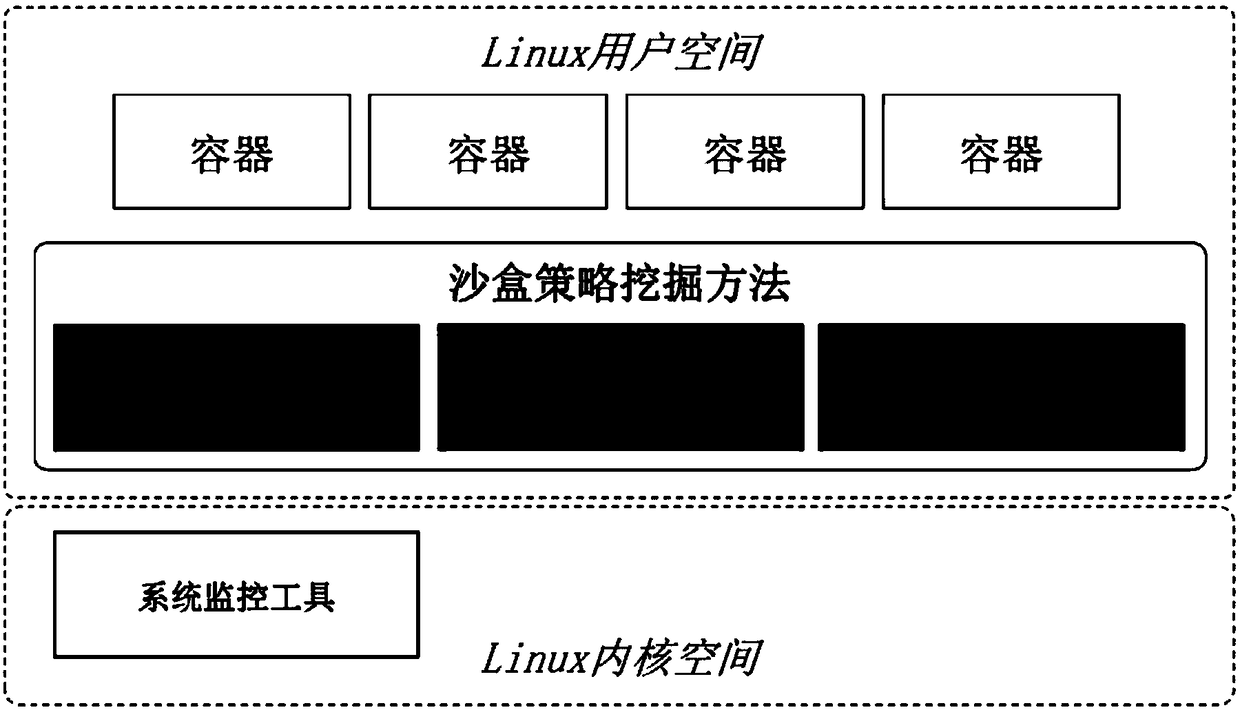
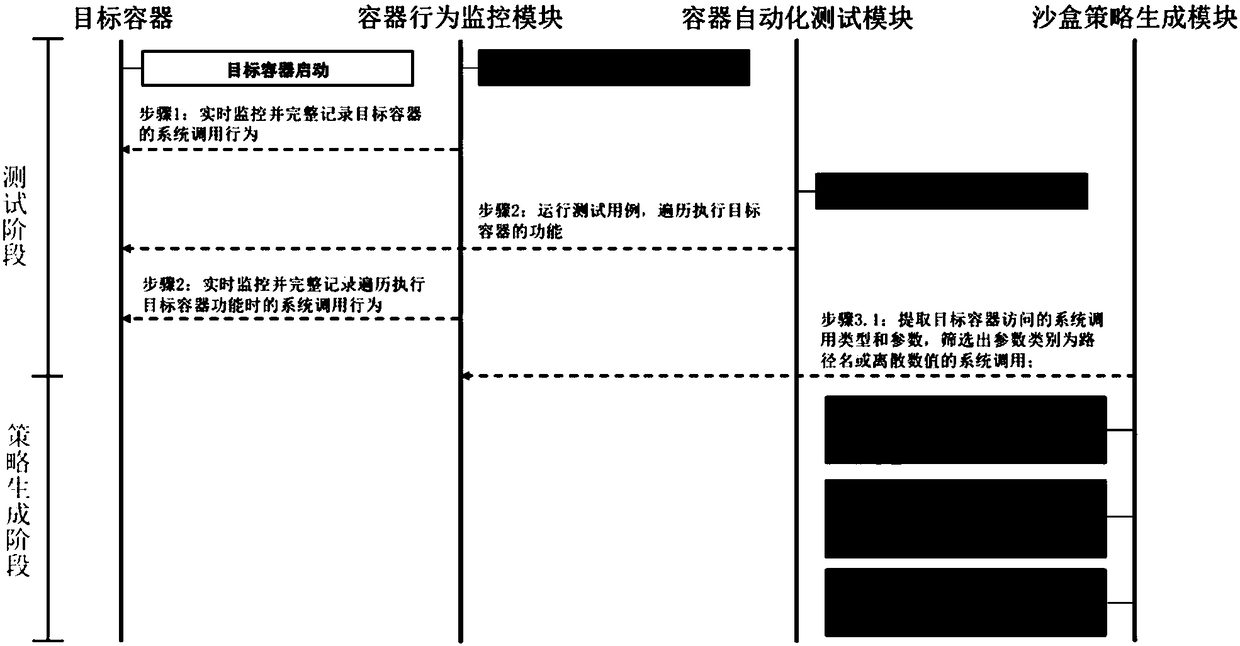
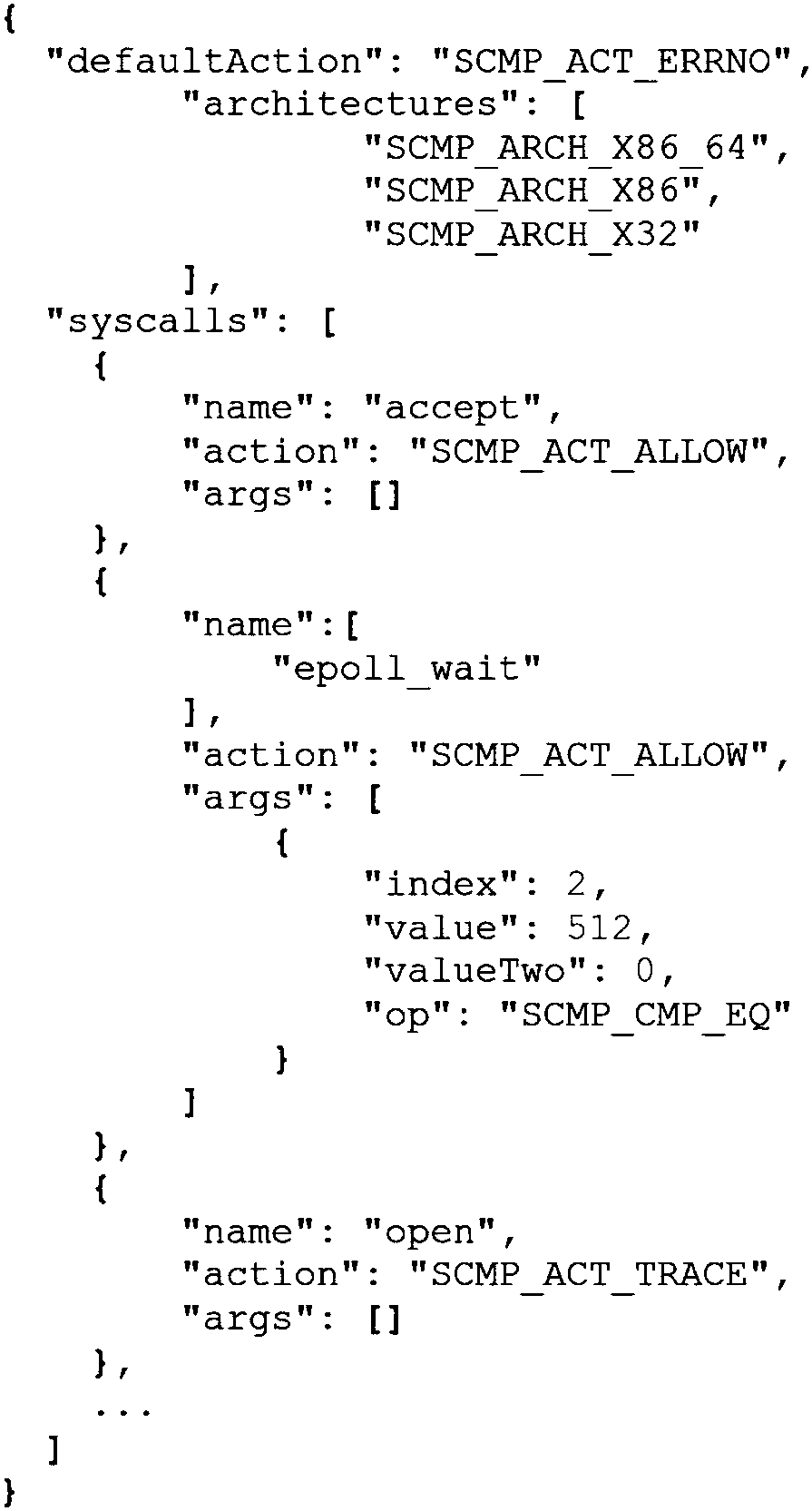
InactiveCN108171050AReduce attack surfacePlatform integrity maintainanceSoftware simulation/interpretation/emulationGNU/LinuxSystem call
The present invention provides a fine-grained sandbox policy mining method for a Linux container, which automatically mines and generates a customized sandbox policy of a target container. The policycomplies with the principle of least privilege, and reduces the attack surface by limiting the system call type and parameters of the target container. The method comprises that: a container behaviormonitoring control module starts a Linux system monitoring tool, and monitors and records the system call behavior of the target container in real time; a container automation test module runs a testcase of the target container, and traverses the function of executing the target container; and a sandbox policy generation module extracts system call behavior characteristics of the target containerfrom the recorded monitoring data, and converts the system call behavior characteristics of the target container into a sandbox policy.
Owner:ZHEJIANG UNIV
Mining method for built-in application vulnerability of Android system
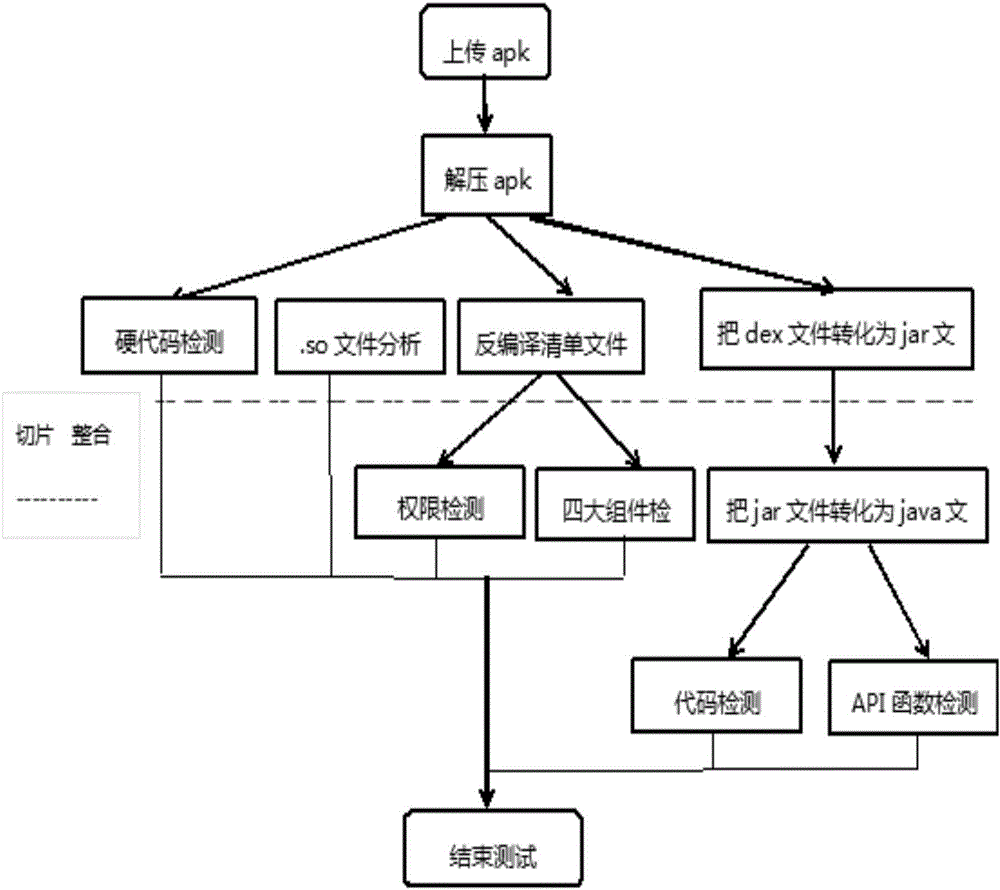
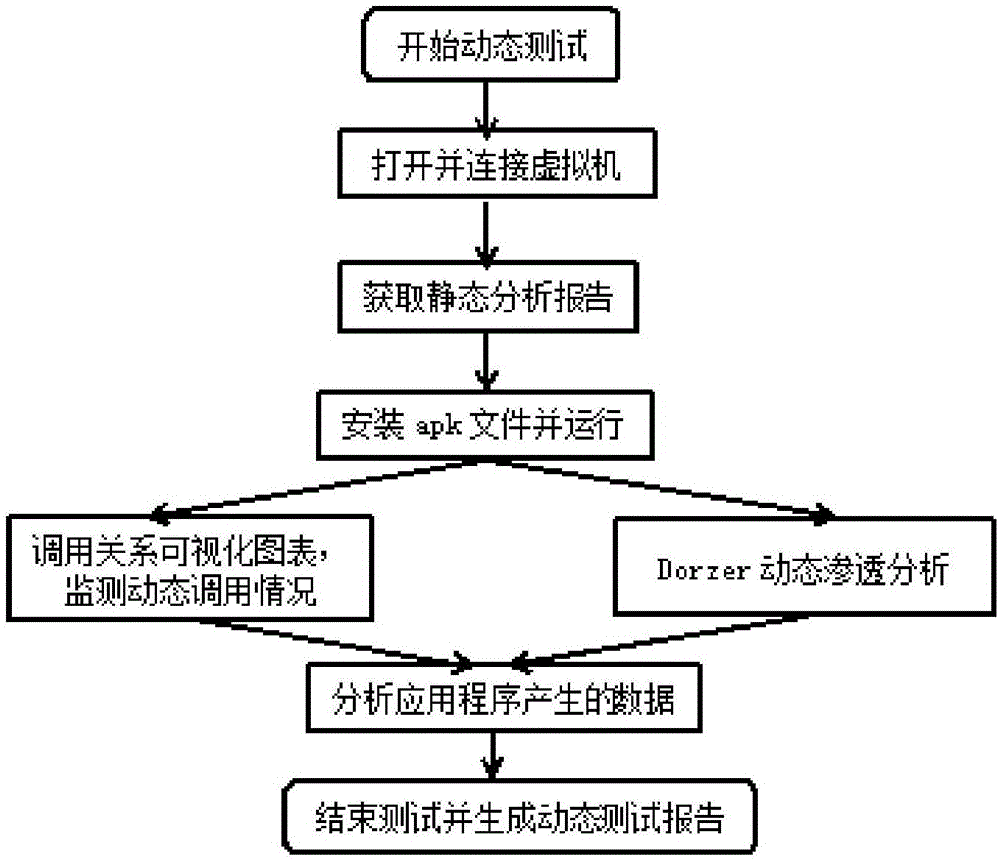
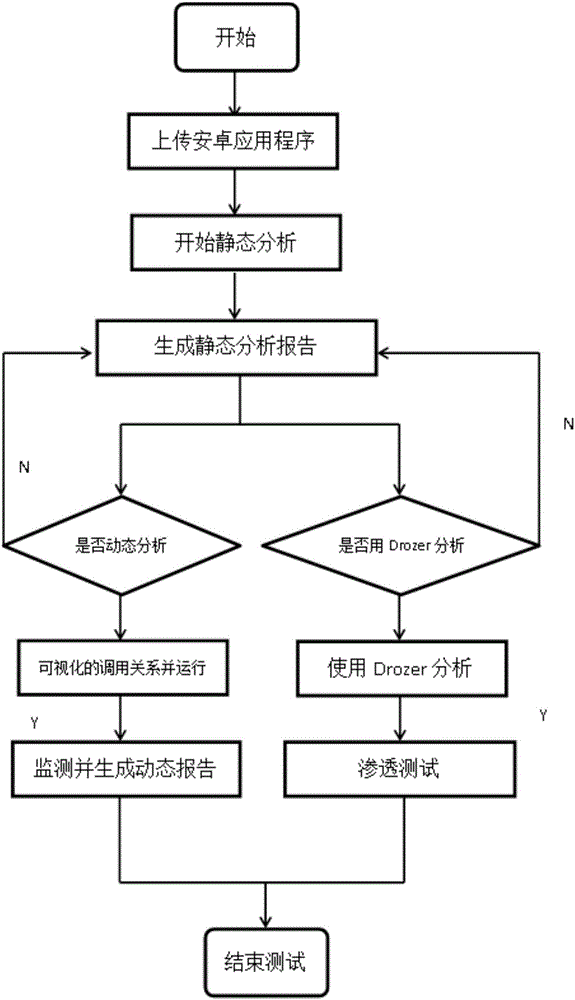
The invention belongs to the field of the information technology, and particularly relates to a mining method for the built-in application vulnerability of an Android system. The codes of each class of vulnerabilities are analyzed in detail, the class of vulnerability rule is sorted for each class of vulnerabilities, and different weights are attached according to the threat degree of each class of vulnerabilities; an APK (Android Package) file is decompiled, a corresponding executable file is disassembled, and a disassembling code is segmented; collected codes are generated into feature data, and an IDA (Interactive Disassembler) tool is imported to analyze a .so file; vulnerability matching is carried out; a .so file analysis result is combined to finally obtain a static weight report; before dynamic detection is started, an appointed APK file static report is obtained, the calling of an API (Application Program Interface) function is monitored; and through the integration of a Drozer dynamic analysis frame, various test commands are input in a command line, an attack surface is determined, and a test is carried out by aiming at an assaultable place. By use of the method, the safety of the developed APK can be quickly found, and the method has an important meaning for maintaining the stability and the business safety of the Android system.
Owner:BEIJING UNIV OF TECH
Balancing malware rootkit detection with power consumption on mobile devices
InactiveUS8566935B2Improve compromiseMemory loss protectionError detection/correctionOperational systemEnergy expenditure
Owner:AT&T INTPROP I LP +1
Organization attack surface management
ActiveUS20190334928A1Computer security arrangementsData switching networksReal-time dataSecurity rule
A system for sanitizing an organization's network against attacker breach, including a data collector, gathering information about network hosts, an analyzer constructing the organization's network topology, a machine learning engine categorizing the hosts into organizational units and identifying key assets of the organization, a security rules engine mapping real-time data, and inferring security rules that prescribe on which specific hosts which specific credentials are permitted to be stored, and a user interface including an analyst dashboard enabling an analyst to visualize in real-time activities within the organizations' network, to automatically infer security rules for the network, to activate the security rules in the network, and to eliminate potential attack vectors for which the activated security rules are violated, and an attacker view visualizing the organization's network, identifying security rule violations across the organization's network, and enabling removal of credential-based security rule violations by use of actions.
Owner:ILLUSIVE NETWORKS LTD
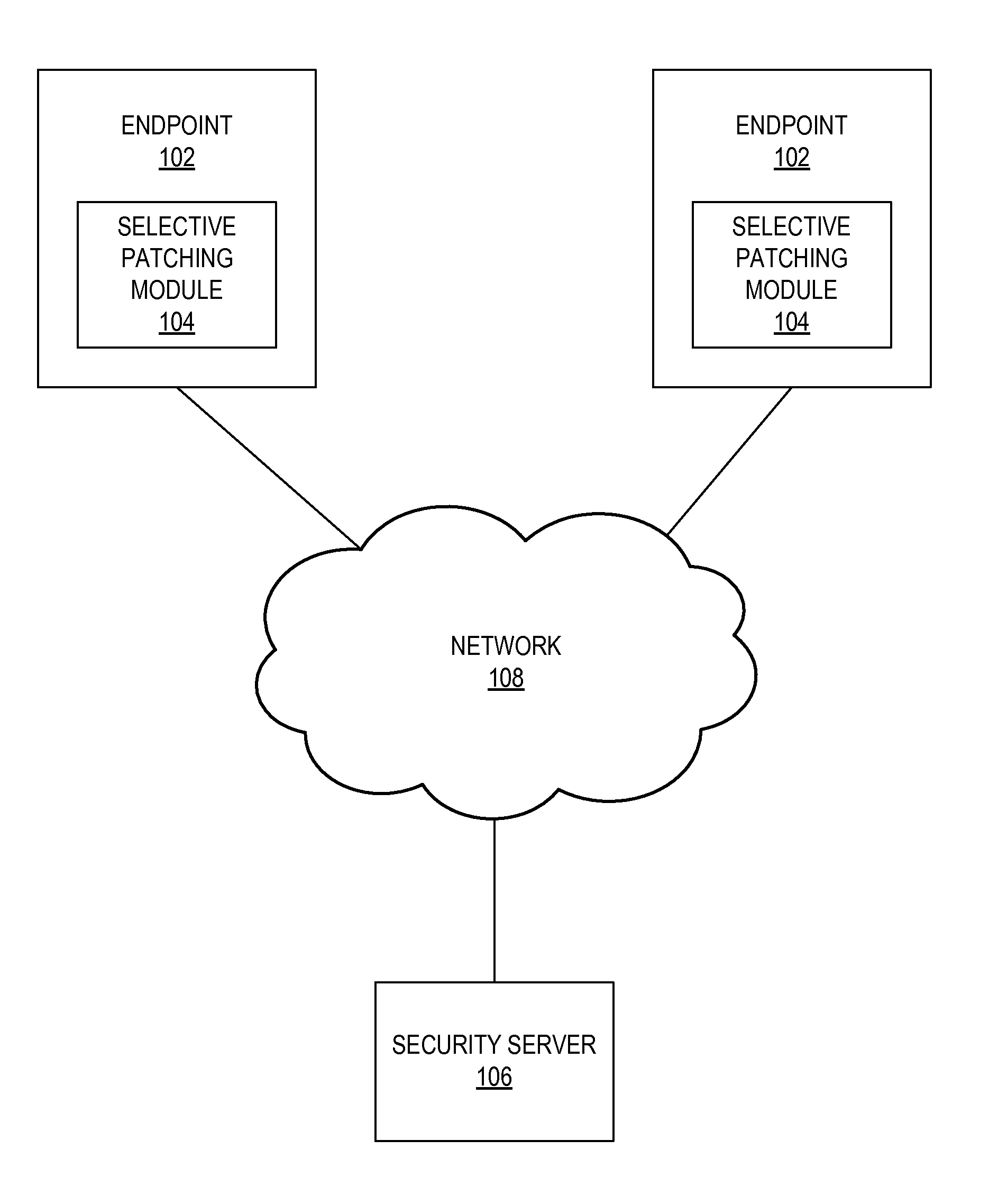
Safely Updating Latent Applications to Reduce Attack Surface
InactiveUS20120054729A1Specific program execution arrangementsMemory systemsApplication softwareAttack surface
Executable content on an endpoint is selectively patched based on the usage of the content. The usage of executable content on an endpoint is monitored. Based on the usage of the executable content, a usage score is calculated. The usage score indicates how often the executable content is used at the endpoint. Responsive to the usage score, a determination of whether to perform a patching action is made. If it is determined that a patching action is to be performed, a patching action is performed for the executable content.
Owner:NORTONLIFELOCK INC
Distributed traffic management system and techniques
ActiveUS20170201489A1TransmissionSpecial data processing applicationsData synchronizationAir traffic management
Approaches, techniques, and mechanisms are disclosed for implementing a distributed firewall. In an embodiment, many different computer assets police incoming messages based on local policy data. This local policy data is synchronized with global policy data. The global policy data is generated by one or more separate analyzers. Each analyzer has access to message logs, or information derived therefrom, for groups of computer assets, and is thus able to generate policies based on intelligence from an entire group as opposed to an isolated asset. Among other effects, some of the approaches, techniques, and mechanisms may be effective even in computing environments with limited supervision over the attack surface, and / or computing environments in which assets may need to make independent decisions with respect to how incoming messages should be handled, on account of latency and / or unreliability in connections to other system components.
Owner:NETFLIX
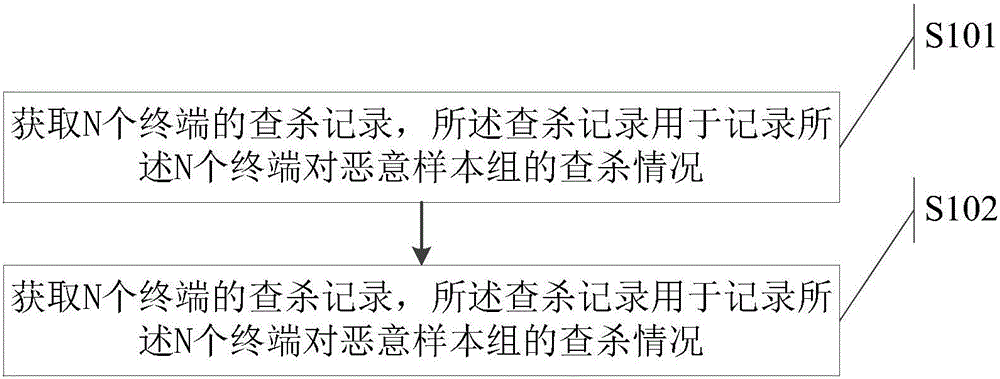
Method and equipment for determining attack surfaces of terminals
The invention discloses a method and equipment for determining attack surfaces of terminals. The method comprises the steps of acquiring checking and killing records of N terminals, wherein the checking and killing records are used for recording the checking and killing situations of the N terminals on a malicious sample group, and N is a positive integer; and determining an attack surface, attacked by the malicious sample group, of each terminal among the N terminals according to the checking and killing records, wherein the attack surface is used for characterizing the threatening degree of the malicious sample group on the terminal. The method and the equipment can solve the technical problem that a data determination method fitter to a personalized network environment of an enterprise lacks in malicious sample defense of the enterprise in the prior art so that more specific defensive measures are difficult to make. Provided is a data determination method capable of directly exposing the weak link attacked by malicious samples most easily.
Owner:BEIJING QIHOO TECH CO LTD +1
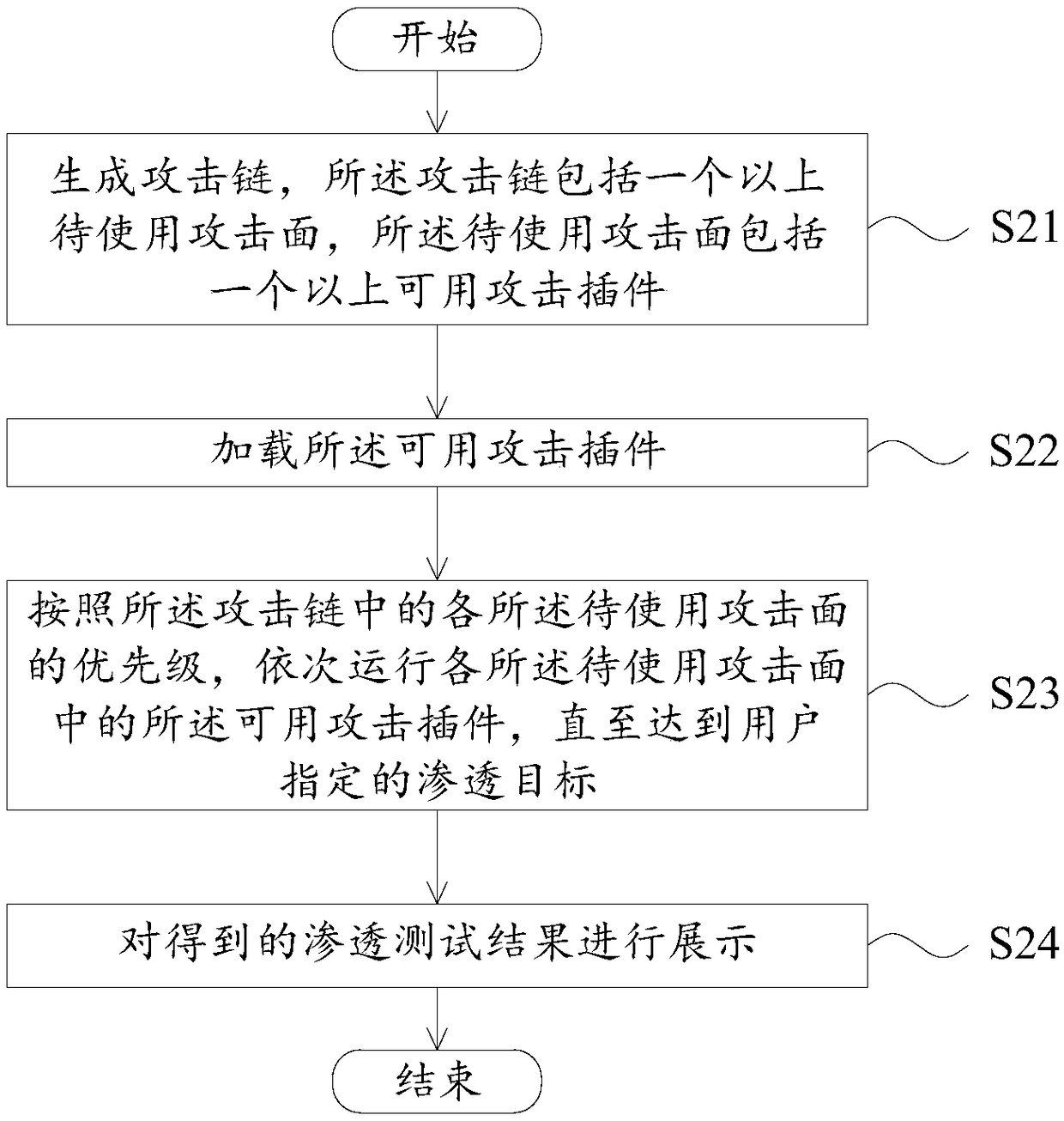
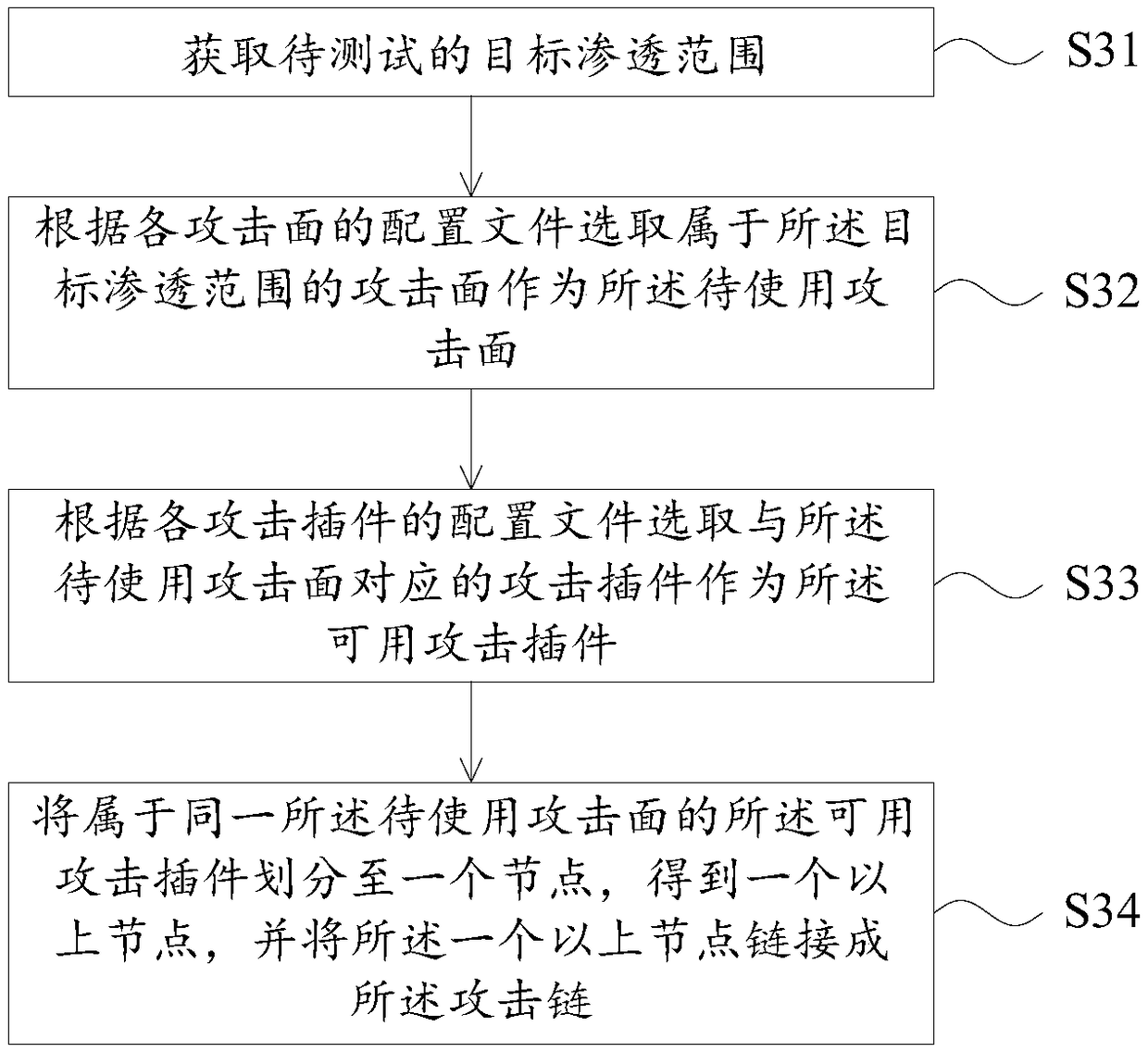
Penetration test method and device
ActiveCN109120643AAutomate Penetration TestingAvoid time costTransmissionAttack surfacePenetration test
The embodiment of the invention provides a penetration test method and device. According to the invention, a test terminal generates an attack chain, wherein the attack chain includes more than one attack surface to be used, and each attack surface to be used includes more than one available attack plug-in; the available attack plug-ins in the attack chain are loaded; the available attack plug-insin each attack surface to be used are sequentially put into operation according to the priority of each attack surface to be used in the attack chain until a penetration target specified by the useris reached; and the obtained penetration test result is displayed. According to the design, the automatic penetration test can be realized, and the time and labor cost required by the penetration testcan be reduced.
Owner:BEIJING KNOWNSEC INFORMATION TECH
Methods and apparatuses for improved network communication using a message integrity secure token
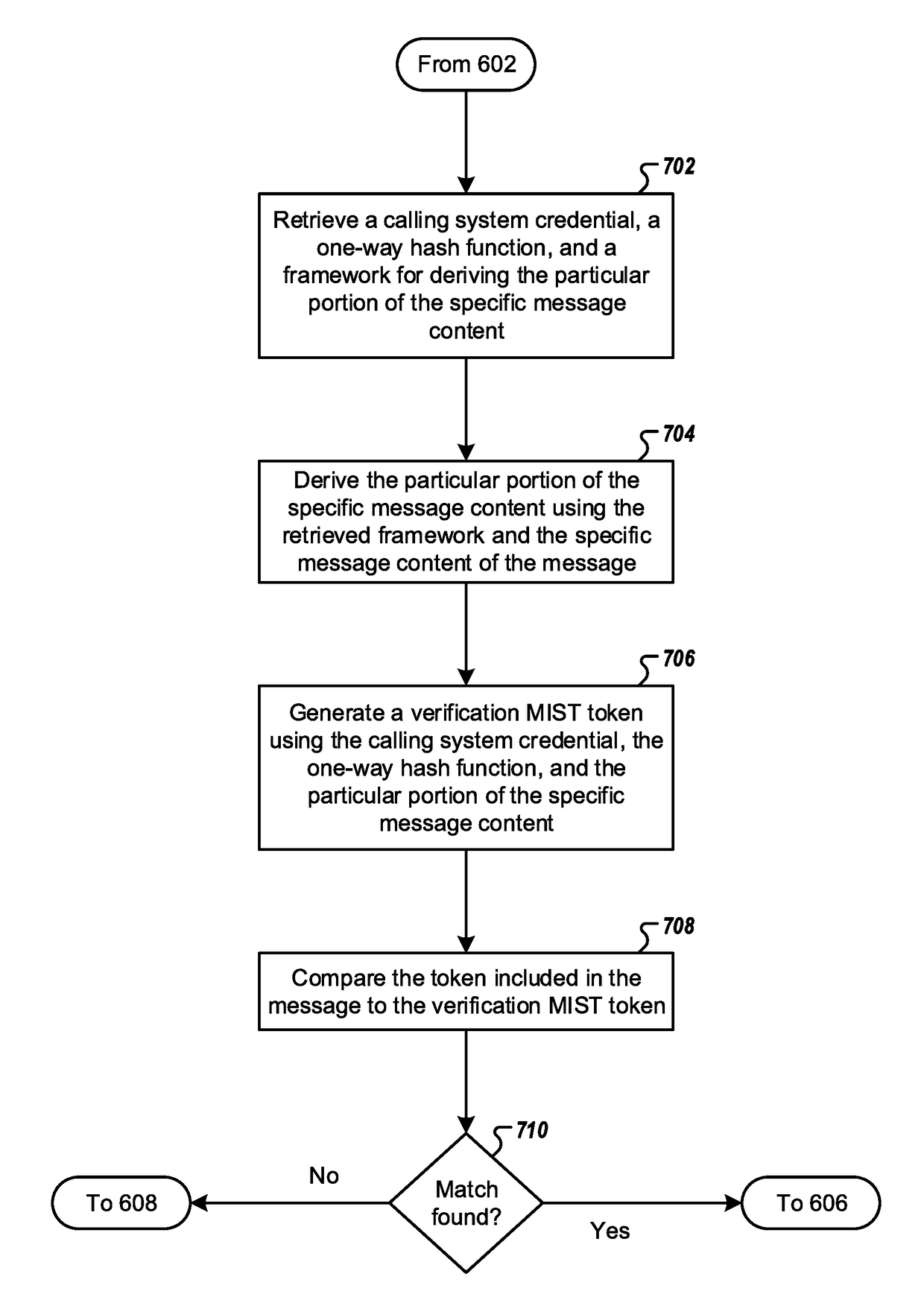
ActiveUS20180288068A1Prevents message tamperingShort response timeUser identity/authority verificationData switching networksEngineeringNetwork communication
Embodiments are disclosed for limiting an attack surface of a server application by enforcing integrity of a message transmitted to the server application. An example method includes receiving, by communications circuitry of a receiving system hosting the server application, a message including specific message content and a token. The example method further includes determining, by authentication circuitry of the receiving system and using the specific message content, whether the token comprises a valid message integrity secure token. If the token comprises a valid message integrity secure token, the example method further includes performing, by response circuitry of the receiving system, an operation in response to the message. If not, the method may include generating, by the authentication circuitry of the receiving system, an error message. Corresponding apparatuses and computer program products are also provided.
Owner:HYLAND SOFTWARE
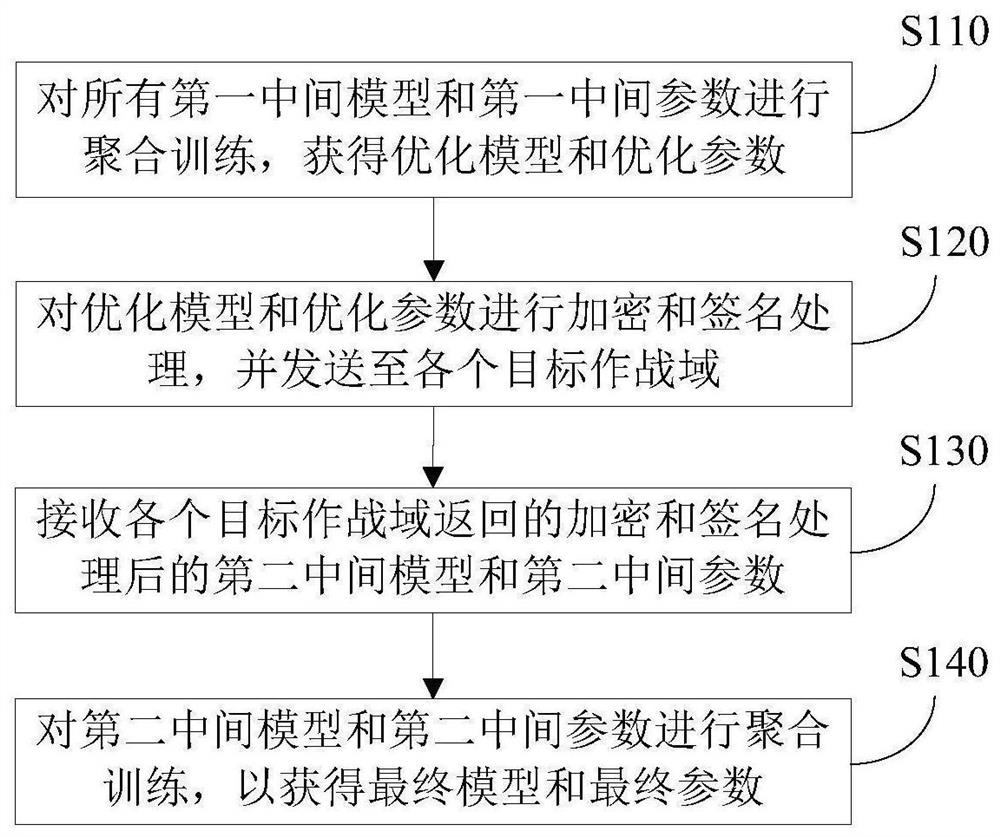
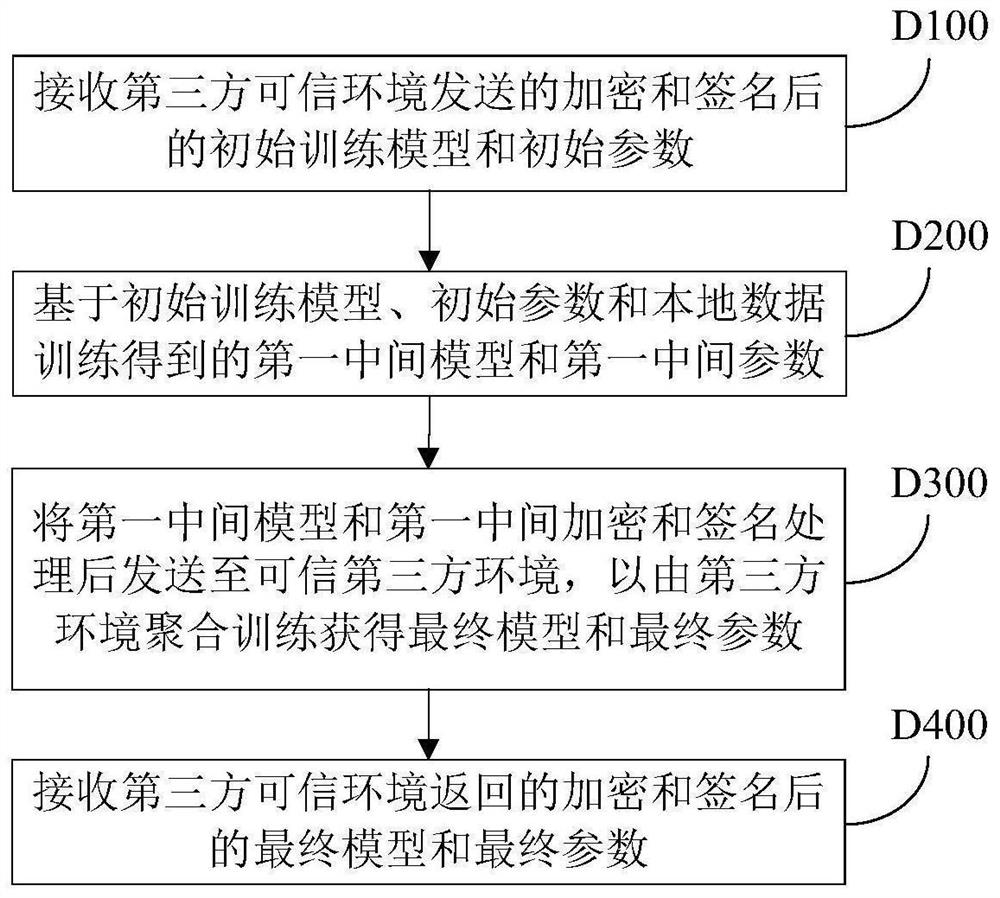
Cross-domain data security interconnection method and system based on federated learning
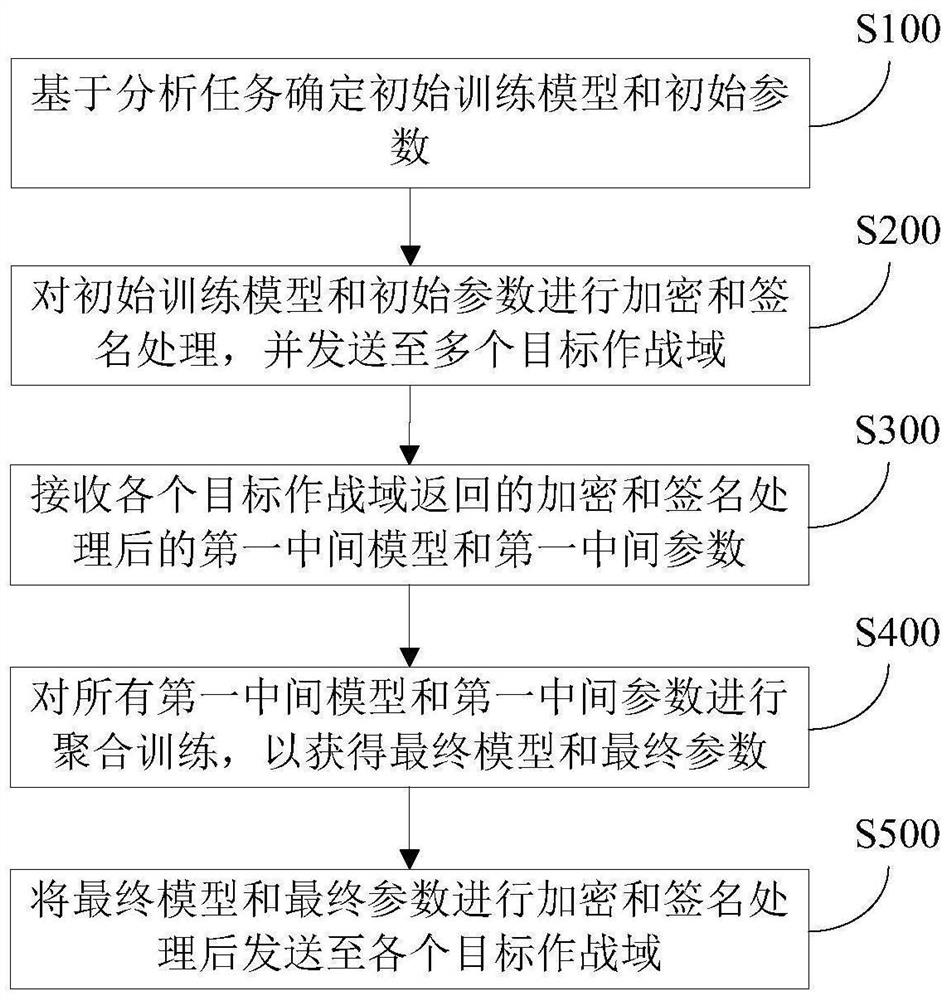
PendingCN111666987ARealization of secure interconnectionCharacter and pattern recognitionDigital data protectionInformation interoperabilityThird party
The invention provides a cross-domain data security interconnection method and system based on federated learning, being characterized in that a federated learning concept is expanded to the field ofcross-domain data sharing in joint operation; under the condition that effective transverse information intercommunication cannot be carried out in each combat domain, through coordination of the third party trusted environment, the cooperative analysis of the combat situation and the execution of related combat tasks are completed by efficiently cooperating with each combat domain, and then the purpose that the original data of each combat domain cannot be locally transmitted is achieved, and the data transmission service and the data security interconnection are minimized, and the attack surface, the exposed surface and the network bandwidth of the combat data are effectively reduced, and the systematic performance of the joint combat is ensured; moreover, the combat domains and the third-party trusted environment only interact with the encrypted and signed models and parameters, so that data security interconnection among the combat domains is realized while data barriers among thecombat domains are broken through, and effective support is provided for cross-domain data security sharing in a joint combat process.
Owner:CHINA ACADEMY OF ELECTRONICS & INFORMATION TECH OF CETC
Distributed traffic management system and techniques
ActiveUS9621588B2TransmissionSpecial data processing applicationsData synchronizationAir traffic management
Approaches, techniques, and mechanisms are disclosed for implementing a distributed firewall. In an embodiment, many different computer assets police incoming messages based on local policy data. This local policy data is synchronized with global policy data. The global policy data is generated by one or more separate analyzers. Each analyzer has access to message logs, or information derived therefrom, for groups of computer assets, and is thus able to generate policies based on intelligence from an entire group as opposed to an isolated asset. Among other effects, some of the approaches, techniques, and mechanisms may be effective even in computing environments with limited supervision over the attack surface, and / or computing environments in which assets may need to make independent decisions with respect to how incoming messages should be handled, on account of latency and / or unreliability in connections to other system components.
Owner:NETFLIX
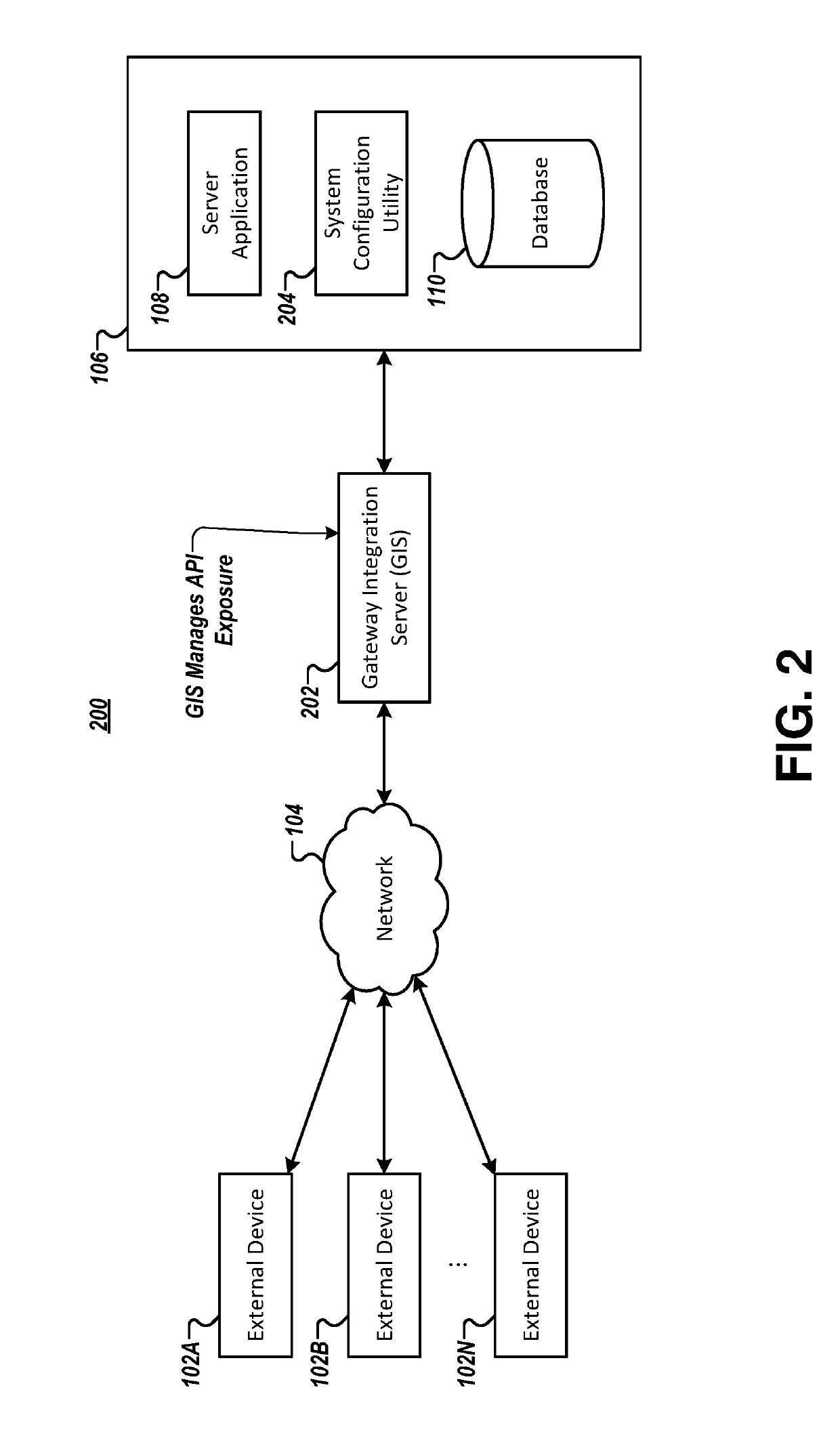
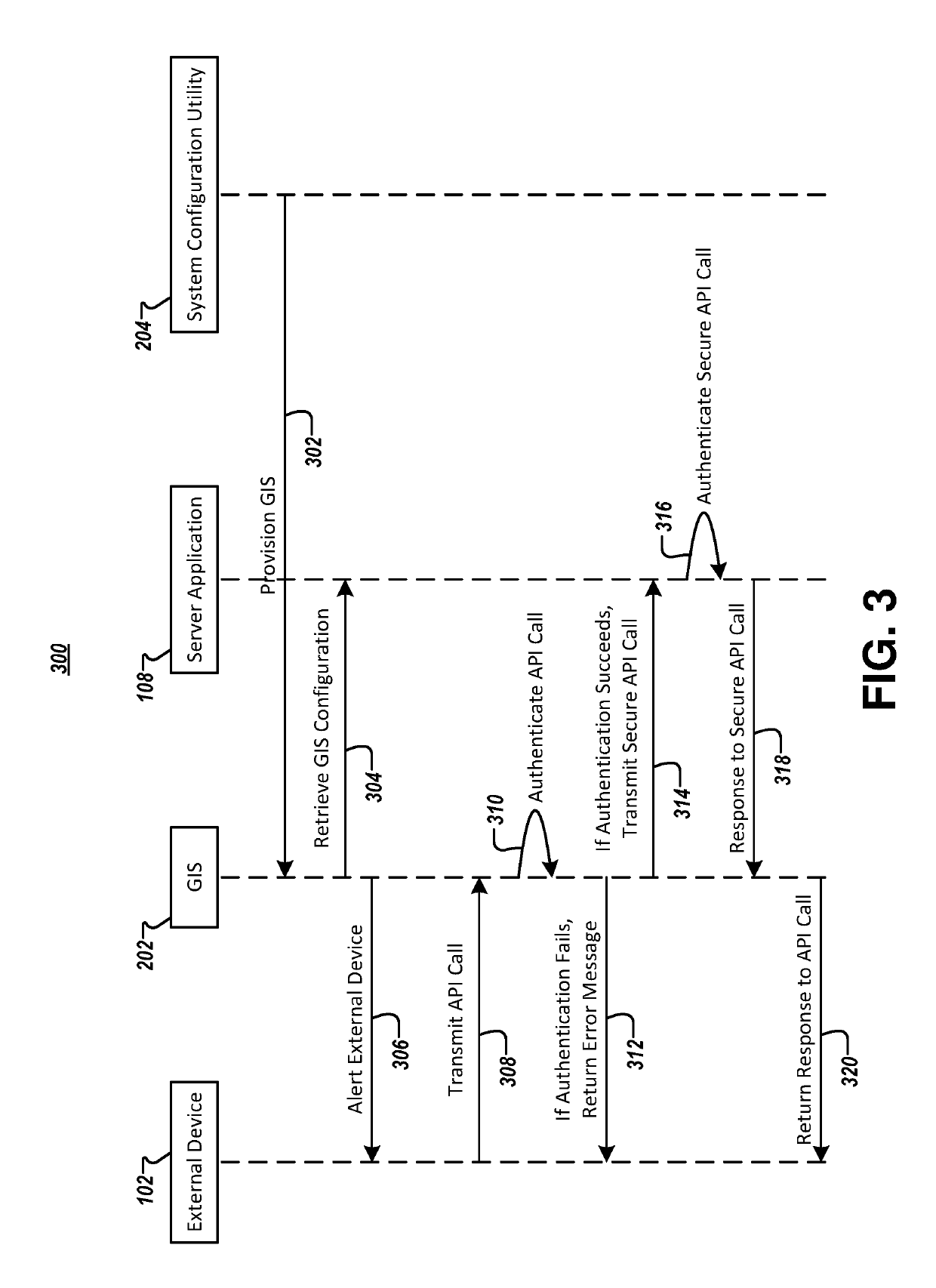
Methods and apparatuses for utilizing a gateway integration server to enhance application security
ActiveUS10511574B2Easy to useIncrease the user baseTransmissionApplication programming interfaceApplication security
Embodiments are disclosed for managing interactions between a server application and an external environment while limiting an attack surface of the server application. An example method includes receiving, by communications circuitry of a gateway integration server (GIS) and from a source device in the external environment, a message including an application programming interface (API) call. The example method further includes evaluating, by authentication circuitry of the GIS, whether the API call is authorized. If so, the example method further includes generating, by response circuitry of the GIS, a response to the API call, and transmitting, by the communications circuitry of the GIS and to the source device, the response to the API call. However, if not, the example method includes transmitting, by the communications circuitry of the GIS, an error message to the source device. Corresponding apparatuses and computer program products are also provided.
Owner:HYLAND SOFTWARE
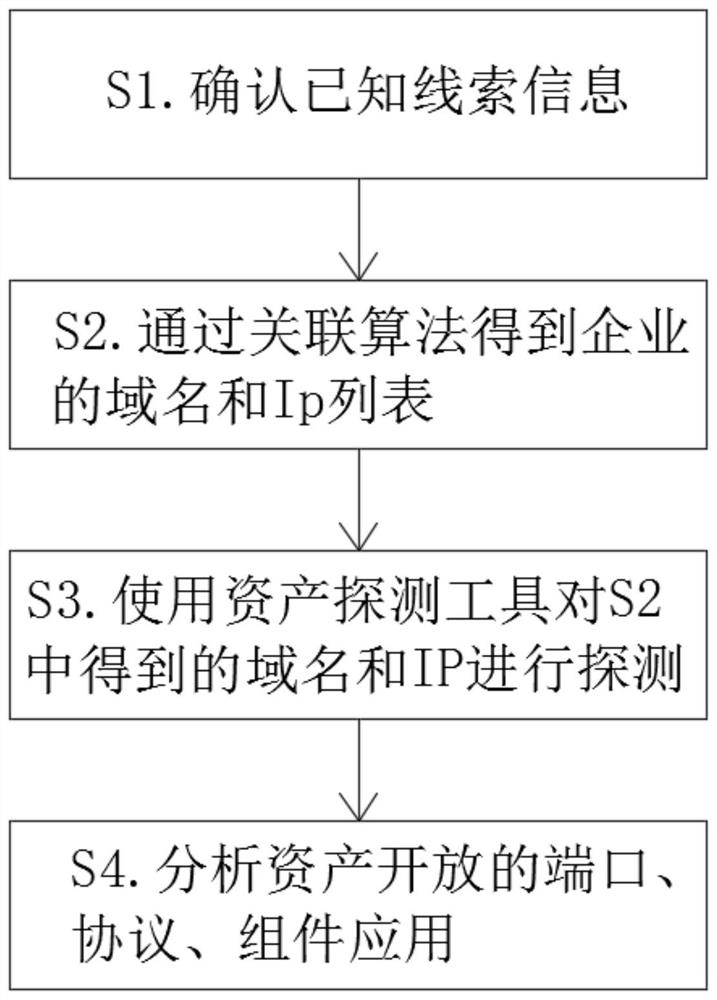
Internet asset exposure information checking method
PendingCN112926942AComprehensive exposure screeningReduce notificationFinanceOffice automationDomain nameInternal management
The invention discloses an internet asset exposure information checking method. The method comprises the following steps: S1, confirming known clue information; s2, obtaining a domain name and an Ip list of an enterprise through an association algorithm; s3, detecting the domain name and the IP obtained in the S2 by using an asset detection tool; and S4, analyzing ports, protocols and component applications of asset opening. The enterprise domain name and Ip list are obtained through association algorithms such as certificates, sub-domain name blasting, flow analysis, ICP information, domain name registration information, enterprise names, app, WeChat applets and the like, then the domain names and the IPs are detected by using an asset detection tool, open ports, protocols and component applications of assets are analyzed, comprehensive exposure surface investigation is carried out on enterprise internet assets. The method can converge the attack surface, reduce the attacked risk, improve the internal management of an enterprise, reduce the notification of a supervised unit, and lay a foundation for the subsequent safety risk assessment and monitoring.
Owner:北京华顺信安信息技术有限公司
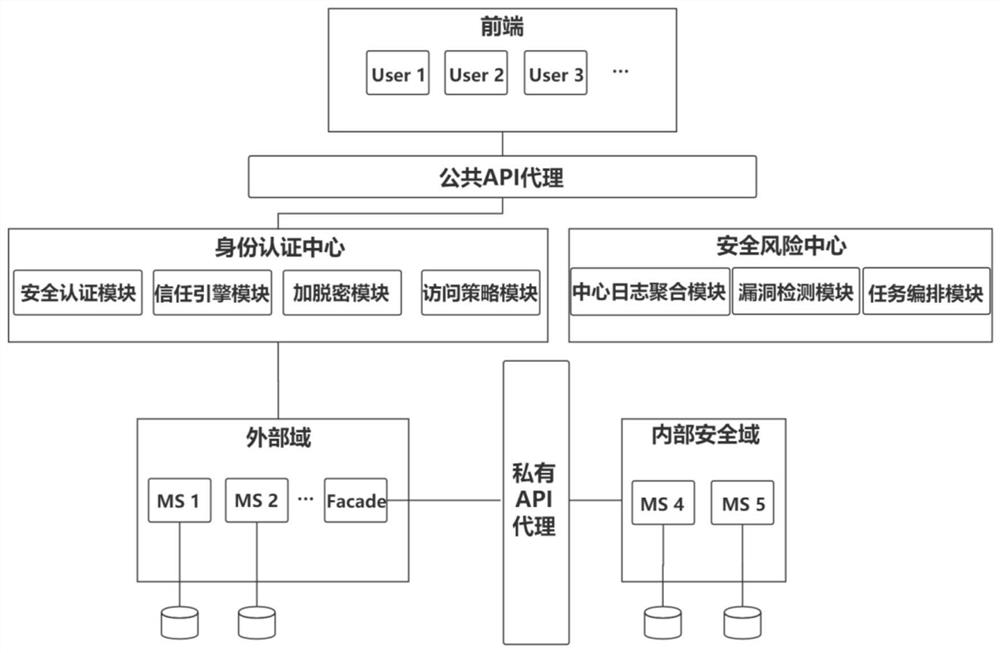
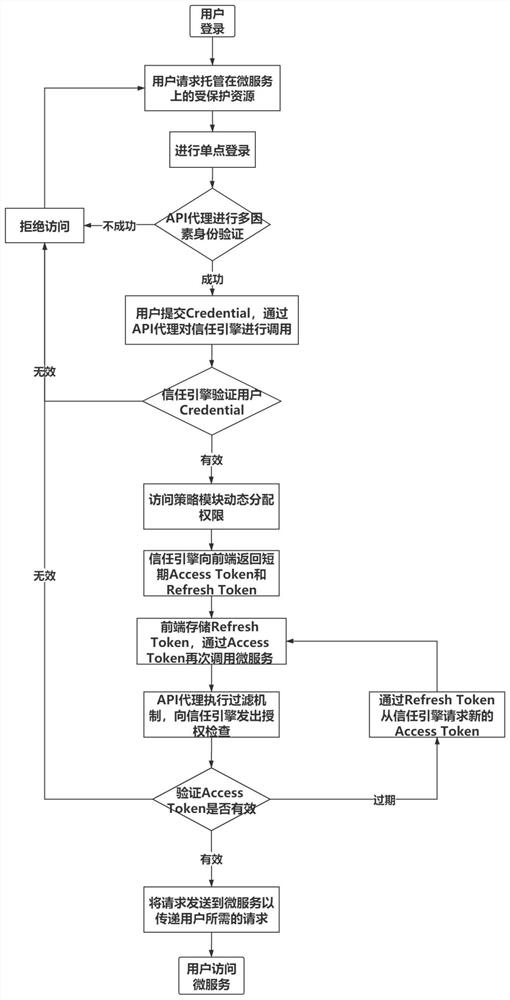
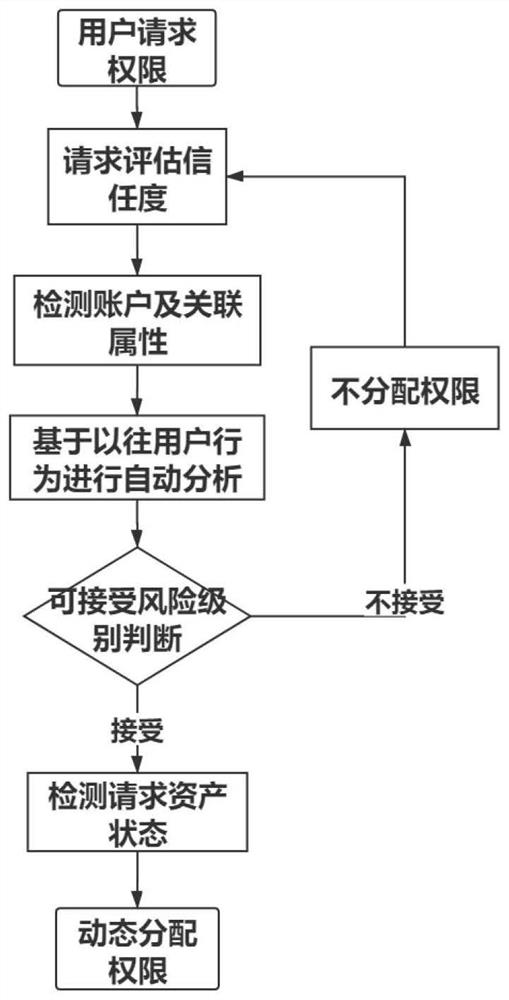
Security micro-service architecture based on zero-trust access strategy and implementation method
ActiveCN112765639AReduce attack surfaceEnsure data securityDigital data protectionDigital data authenticationService domainEnd system
The invention provides a security micro-service architecture based on a zero-trust access policy and an implementation method. The architecture comprises an identity authentication center, a micro-service domain, an internal security domain, a public API agent and a private API agent; the identity authentication center comprises an access policy module, an encryption and decryption module, a security production authentication module and a trust engine module; the trust engine module is used for executing identity verification and generating a short-term Access Token and a Refresh Token; the implementation process comprises the steps of requesting resources, performing single sign-on and identity verification, allocating permissions, returning Token, filtering and checking the validity of the Token to execute access. And when the calling party needs to arrive at the internal security domain, the private API agent is accessed through the Facade service, and the matched additional authorization level is transmitted. According to the method, the short-term Token is generated through identity verification and an authorization mechanism so as to protect the distributed micro-service isolated from the front-end system, the security priority level of the micro-service is adjusted in real time through the private API agent, the possible attack surface of the micro-service system is reduced, and a deep defense strategy is realized.
Owner:WUHAN UNIV
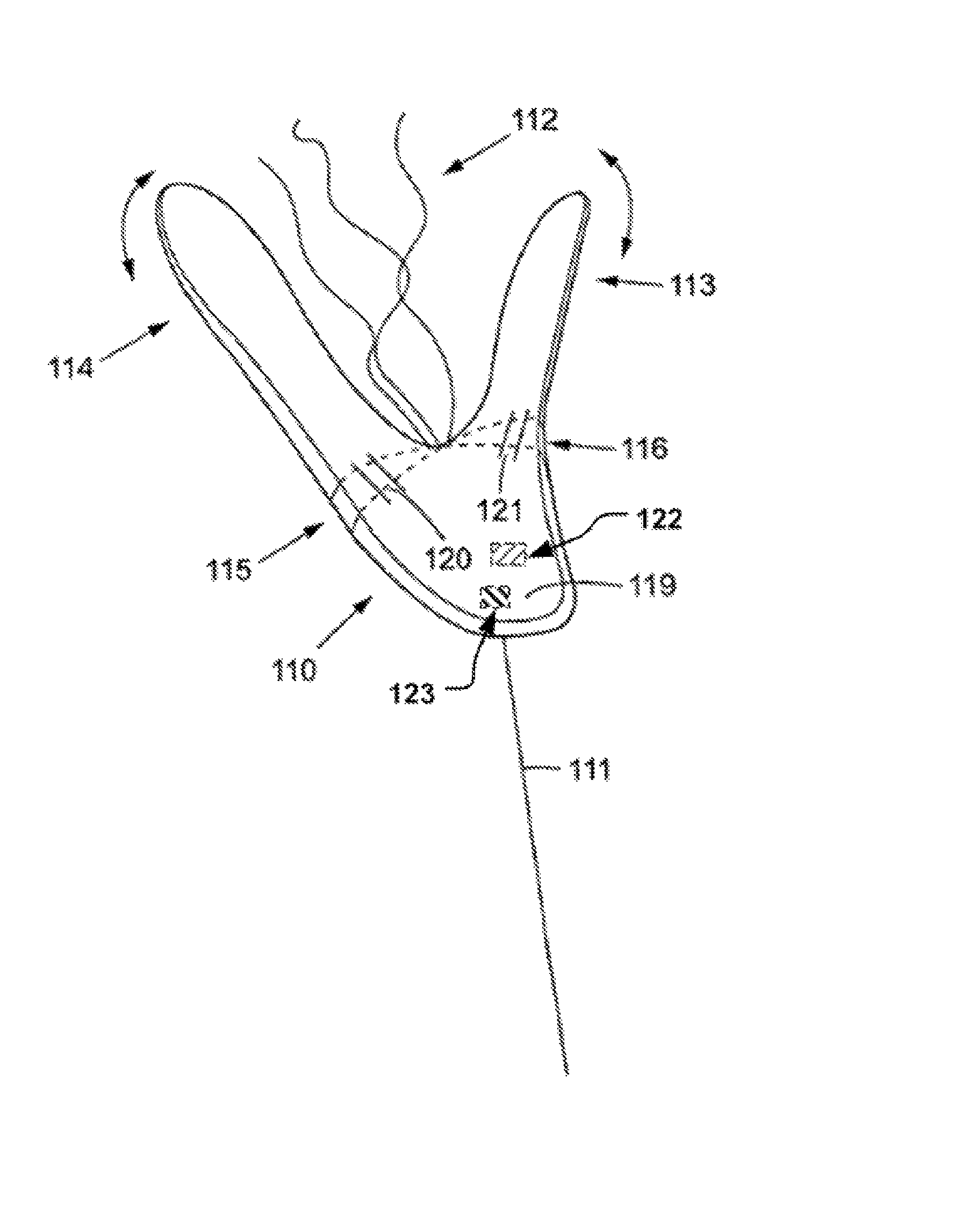
Location signaling device
InactiveUS8356569B2Effective surface is reducedReduce lifting forceVessel signalling devicesLife-savingLighter than airAirbag deployment
A location signalling device comprising a wing balloon for signalling a location. The wing balloon is fixed to a tether line that itself is fixed to the location to be signalled. The wing balloon has an inflatable aerodynamically shaped hollow body to be at least partly be filled with a lighter-than-air gas and having a wing attack surface for air flowing relative to said wing balloon. The floating aloft of said wing balloon is supported by said air flow. When the wing balloon is inflated, a flexible wing portion is passively variable. The stronger the wind, the less attack is given. Thus, the dragging force on the tether line is generally static.
Owner:SJOBLOM HANS
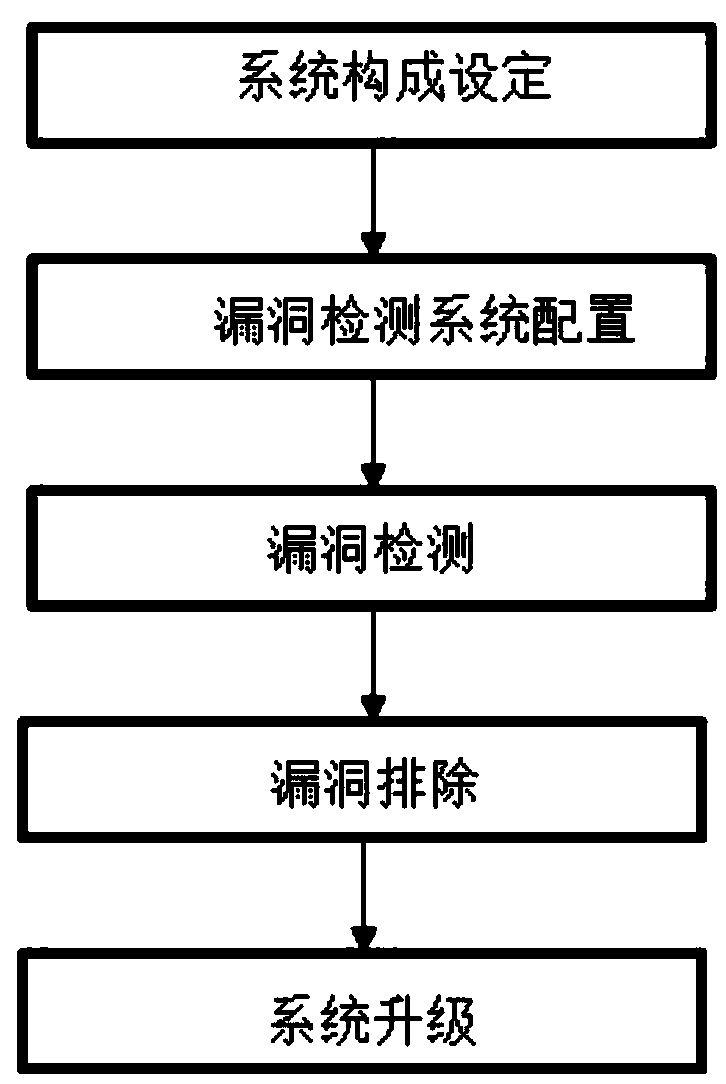
Loophole finding and emergency verification implementation method
ActiveCN109327471AEfficient detectionImprove efficiencyTransmissionSecurity arrangementNetworked systemSystem configuration
The invention relates to a loophole finding and emergency verification implementation method comprising the five steps of system formation setting, loophole detection system configuration, loophole detection, loophole elimination and system upgrade. On the one hand, the system is simple in formation, flexible in structure adjustment, and capable of effectively meeting the risk loophole detection,assessment and pre-warning of the different network systems and contents; on the other hand, the data compatibility capacity is strong, the data detection operation efficiency and accuracy are high, various vulnerability risks in the network can be efficiently detection all around, the professional and effective security analysis and repair advice are provided, auditing is performed on a repair result through fitting with the security management process, the attack surface is furthest reduced, and thus the efficiency and security of the network data management operation are greatly improved.
Owner:GUANGDONG POWER GRID CO LTD INFORMATION CENT
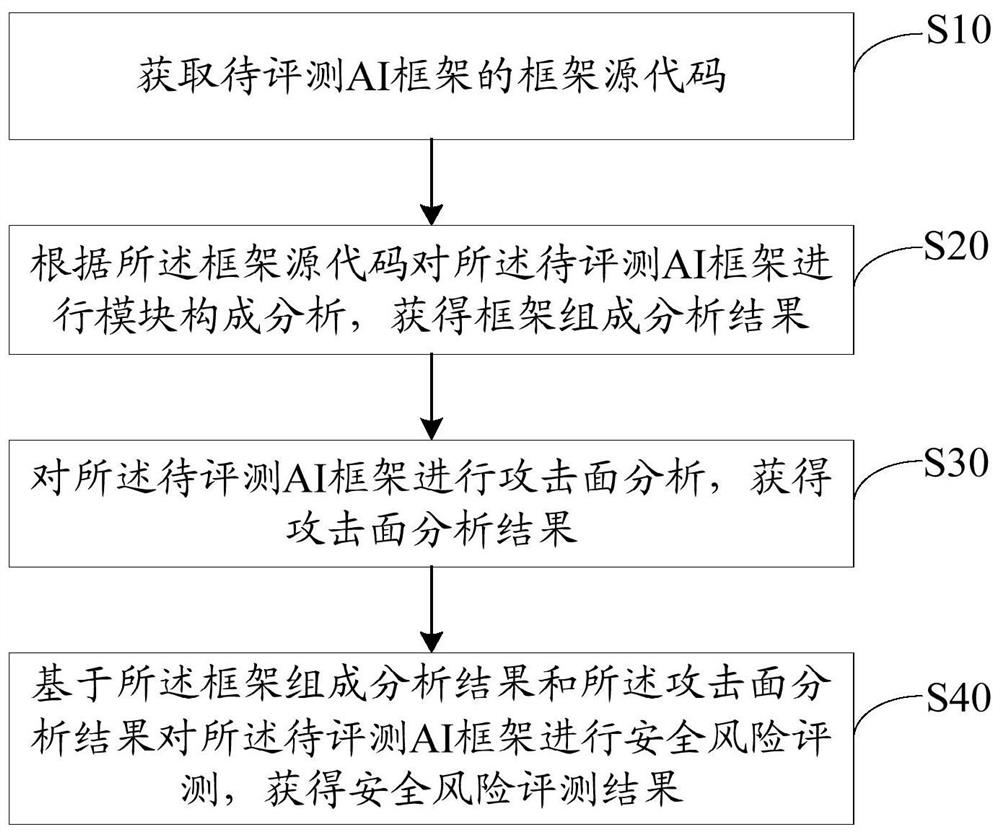
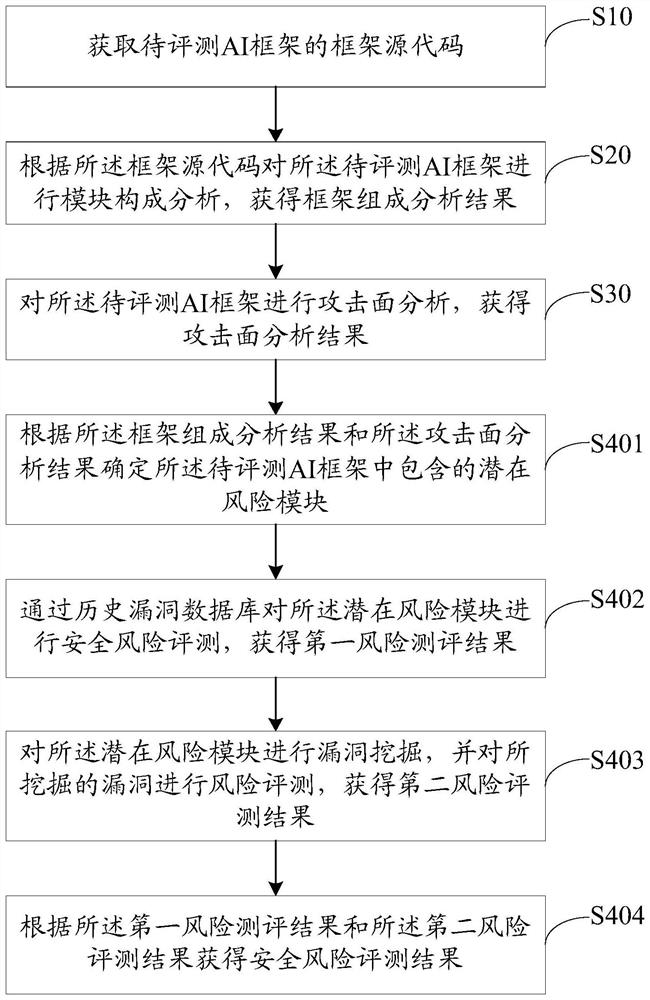
Safety evaluation method, device and equipment for AI framework and storage medium
ActiveCN112527674ADiversity guaranteedGuaranteed accuracySoftware testing/debuggingPlatform integrity maintainanceReverse analysisAlgorithm
The invention relates to the technical field of software security, and discloses an AI framework security evaluation method, device and equipment and a storage medium, and the method comprises the steps: obtaining a framework source code of a to-be-evaluated AI framework, carrying out the module composition analysis of the to-be-evaluated AI framework according to the framework source code, obtaining a framework composition analysis result, and carrying out the attack surface analysis of the to-be-evaluated AI framework; obtaining an attack surface analysis result, and performing security riskevaluation on the to-be-evaluated AI framework based on the framework composition analysis result and the attack surface analysis result to obtain a security risk evaluation result. According to themethod, the security risk evaluation is carried out on the AI framework by combining the component analysis of the module in the AI framework with the attack surface analysis of the module, so that compared with the existing traditional vulnerability mining technology and manual reverse analysis mode; on one hand, the comprehensiveness and accuracy of the risk evaluation can be ensured; on the other hand, the automation degree of risk evaluation and the perceptibility to safety risks can be improved.
Owner:苏州三六零智能安全科技有限公司
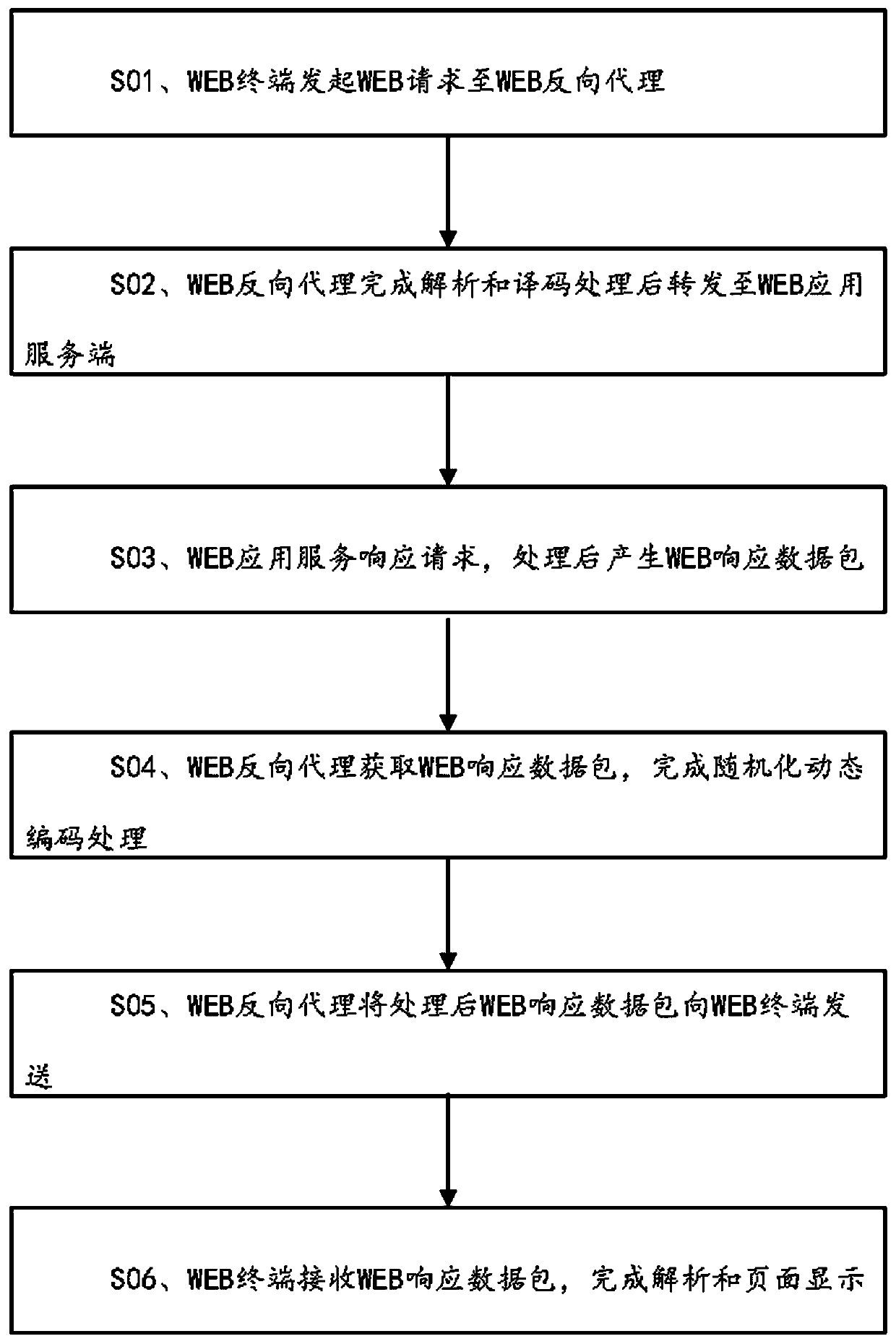
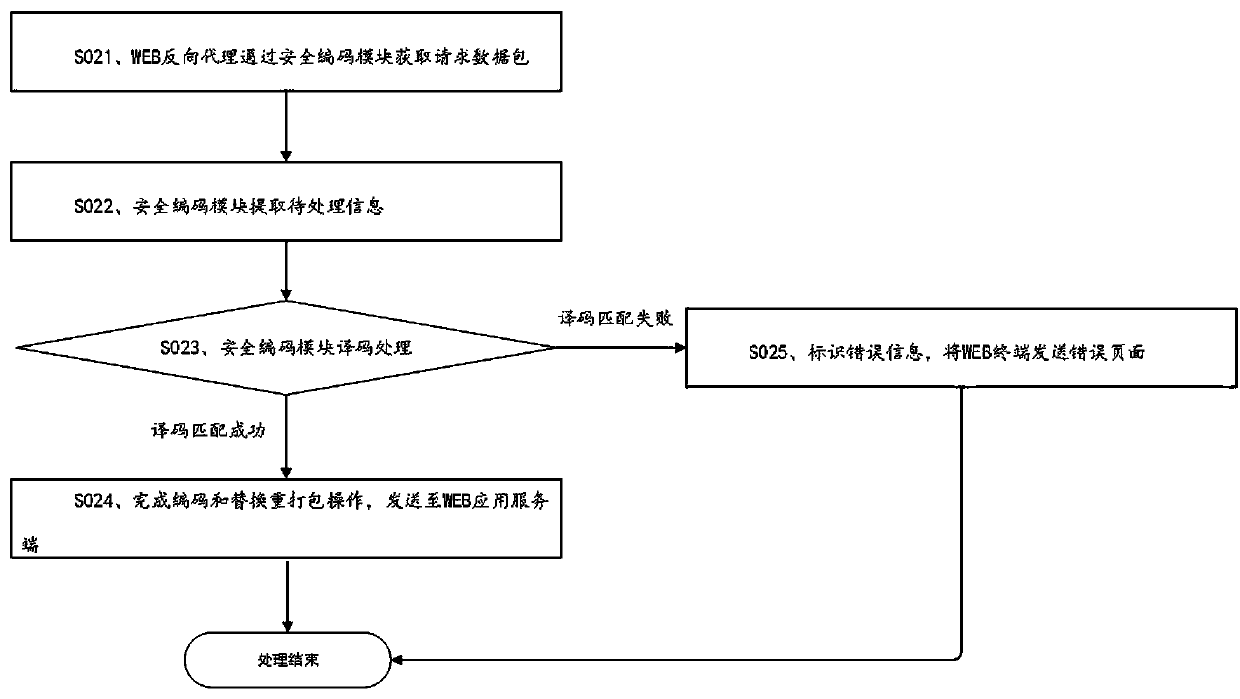
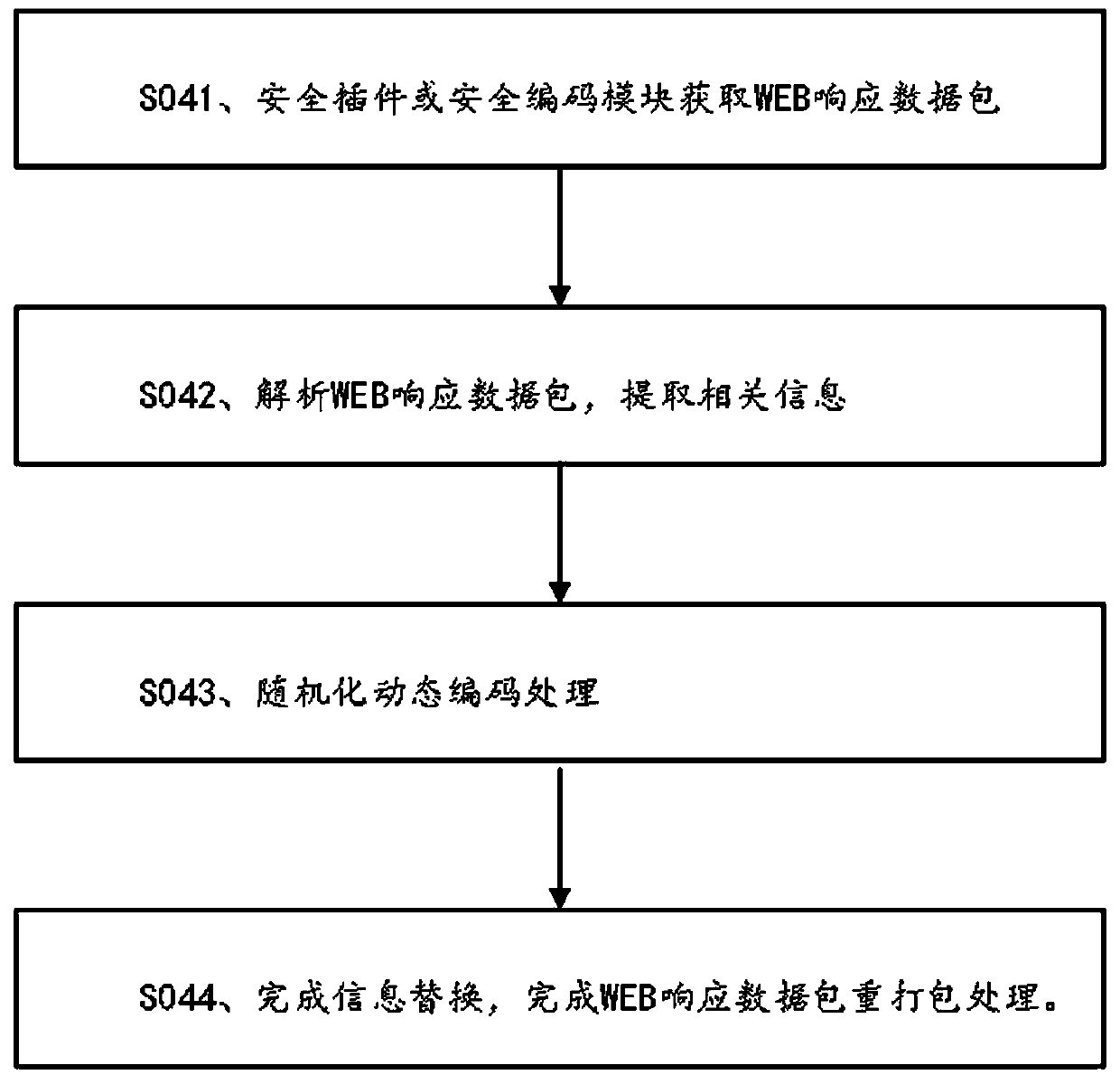
WEB dynamic security defense method and system
InactiveCN110381049AImplement virtualizationImplement one-shot transcodingTransmissionWeb applicationWeb service
The invention discloses a WEB dynamic security defense method and system. The method is based on a moving target defense technical thought. The invention provides an active dynamic defense mechanism for a WEB service system. When the protected WEB application service system is not attacked, the service entry or the resource address is actively transformed, so that the information of the backgroundof the server is effectively hidden and protected, the dynamics and uncertainty of the attacked surface of the system are realized in a randomized dynamic coding technical mode, the difficulty of network attack implementation is improved, and the anti-attack capability of the WEB application service system is effectively enhanced.
Owner:浙江智贝信息科技有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com